Canaux
108470 éléments (108470 non lus) dans 10 canaux
 Actualités
(48730 non lus)
Actualités
(48730 non lus)
 Hoax
(65 non lus)
Hoax
(65 non lus)
 Logiciels
(39066 non lus)
Logiciels
(39066 non lus)
 Sécurité
(1668 non lus)
Sécurité
(1668 non lus)
 Referencement
(18941 non lus)
Referencement
(18941 non lus)
éléments par Mark Wilson
BetaNews.Com
-

Apple apologizes for having contractors listen to Siri recordings and announces privacy changes
Publié: août 28, 2019, 7:19pm CEST par Mark Wyciślik-Wilson
Following outcry over human "grading" of Siri recordings, Apple has issued an apology and promised that it will no longer retain recordings of interaction with the digital assistant unless given explicit permission. The company says that "we haven't been fully living up to our high ideals, and for that we apologize". Having suspended the human grading of Siri requests, Apple is now making fundamental changes to its privacy policy saying that only Apple employees will be able to listen to recordings, as opposed to contractors, and users will have to opt in for this to happen. See also: Apple puts… [Continue Reading] -

Fairphone 3: the ethical, environmentally friendly, modular phone 'that cares'
Publié: août 28, 2019, 11:41am CEST par Mark Wyciślik-Wilson
Fairphone is not a new name in the smartphone market, but it's not one that everyone is aware of. The company has a strong ethical and environmental stance, producing handsets that are gentle on the environment, the people producing them, and are easily repaired. Now the company has announced the Fairphone 3. Due for release next month, the Android handset is a decent mid-ranger which is likely to attract more interest than its two predecessors. So what's all the fuss about? The Fairphone 3 is billed as "the phone that cares for people and planet", and not without good reason.… [Continue Reading] -

Libra Bug Bounty Program seeks to strengthen the security of Facebook's blockchain
Publié: août 28, 2019, 10:24am CEST par Mark Wyciślik-Wilson
Facebook's plans to venture into the world of cryptocurrencies has proved highly controversial, but the social media giant is plowing on regardless. The company and the partners it is working with on Libra have launched a public bug bounty program, offering pay-outs of up to $10,000 per bug. Announced by the Libra Association, the aim of the Libra Bug Bounty Program is to "strengthen the security of the blockchain". The association wants to track down " security and privacy issues and vulnerabilities". See also: Facebook ups its privacy game (a bit) with new tool for users to control data shared… [Continue Reading] -

Microsoft faces another European investigation over Windows 10 privacy concerns
Publié: août 28, 2019, 9:44am CEST par Mark Wyciślik-Wilson
Worries about privacy in Windows 10 show no signs of abating, with Europe expressing ongoing concerns about Microsoft's data gathering and telemetry. Having already asked Microsoft to make modifications to Windows, the Dutch data protection agency (DPA) has since looked into what changes the company has implemented. Having found "new, potentially unlawful, instances of personal data processing", the agency is calling for an investigation by the Irish Data Protection Commission (DPC), Microsoft's lead EU privacy regulator. See also: Google seeks to make the web more private for Chromium users with Privacy Sandbox Got Bluetooth problems in Windows 10? KB4505903 update… [Continue Reading] -

Just ask auntie: BBC to launch its own digital assistant called Beeb
Publié: août 27, 2019, 10:48am CEST par Mark Wyciślik-Wilson
The BBC is working on a digital assistant to rival the likes of Siri and Alexa. Due to launch in 2020, the system goes by the name Beeb, and is being developed to handle regional accents better than current assistants. The corporation has no plans -- for now at least -- to release a physical product along the lines of Google Home, as Beeb is destined to be used to allow people to use their voices to interact with online services and search for shows. See also: How to opt out of Amazon listening to what you say to Alexa… [Continue Reading] -

Apple puts the kibosh on vulnerability that let iPhone users jailbreak iOS 12.4
Publié: août 27, 2019, 10:23am CEST par Mark Wyciślik-Wilson
Apple has released an update to iOS 12.4, plugging a vulnerability that had been reintroduced which allowed for jailbreaking. iOS 12.4.1 repatches a security flaw which Apple previously fixed and then, inexplicably or accidentally, unpatched. iPhone owners now face a dilemma: upgrade to iOS 12.4.1 and have the most up-to-date, secure operating system, or stick with iOS 12.4 and retain jailbreak. See also: Now you can jailbreak iOS 12.4 -- or hack it Apple Card is now available to everyone in the US Trump says Tim Cook makes a 'compelling' argument against Apple paying tariffs In releasing this update Apple… [Continue Reading] -

How to access Google's secret Wizard of Oz Easter egg
Publié: août 26, 2019, 11:23am CEST par Mark Wyciślik-Wilson
Yesterday was the 80th anniversary of the theatrical debut of the seminal movie The Wizard of Oz. To celebrate the release of the 1939 classic, Google has hidden a movie-related secret in its search engine. Whether you're a friend of Dorothy, a lover of the cowardly lion, or just a hater of the Wicked Witch of the West, it's a cool little Easter egg that's well worth checking out. Repeat after me: "There's no place like home!" See also: Google Calendar spam is a thing; here's how to protect yourself Google seeks to make the web more private for Chromium… [Continue Reading] -

Google Calendar spam is a thing; here's how to protect yourself
Publié: août 26, 2019, 10:51am CEST par Mark Wyciślik-Wilson
Spam is something we've become used to in our email inboxes as well as via SMS, but it's certainly not the only way we can be pestered, harangued and irritated. Even Google Calendar can be used to spam you with ads. The phenomenon is not entirely new, but it has been in the spotlight recently. Google Calendar spam takes advantage of a default setting that Google puts in place. By disabling this, you can protect yourself against unwanted intrusions... but there are side-effects to consider. See also: Google seeks to make the web more private for Chromium users with Privacy… [Continue Reading] -

Web host Hostinger resets 14 million customer passwords following data breach
Publié: août 26, 2019, 9:58am CEST par Mark Wyciślik-Wilson
Hosting company Hostinger has reset passwords for all of its customers after a data breach in which a database containing information about 14 million users was accessed "by an unauthorized third party". Hostinger says that the password reset is a "precautionary measure" and explains that the security incident occurred when hackers used an authorization token found on one of the company's servers to access an internal system API. While no financial data is thought to have been accessed, hackers were able to access "client usernames, emails, hashed passwords, first names and IP addresses". See also: Over 3,800 data breaches reported… [Continue Reading] -

Got Bluetooth problems in Windows 10? KB4505903 update could be to blame
Publié: août 25, 2019, 1:10pm CEST par Mark Wyciślik-Wilson
We are frequently advised to ensure that all of the latest Windows updates are installed in the name of security, as well as to ensure that we have access to all of the latest features. But sometimes things go wrong, as the KB4505903 update for Windows 10 illustrates. This cumulative update was released a little while back -- July 26, to be precise -- but over the intervening weeks, problems have emerged with Bluetooth. You may find that you're not able to connect your Bluetooth speaker, or that audio quality is terrible. Microsoft has a workaround. See also: Microsoft and… [Continue Reading] -

Google seeks to make the web more private for Chromium users with Privacy Sandbox
Publié: août 23, 2019, 12:01pm CEST par Mark Wyciślik-Wilson
Google is not a company synonymous with privacy, but the company increasingly recognizes the importance people place on it. With this in mind, it has launched a new initiative called Privacy Sandbox which aims to increase online privacy. The bold goal is to "develop a set of open standards to fundamentally enhance privacy on the web", and one of the first proposals seeks to limit online track of users. It will limit fingerprinting, change the way targeted advertising works, and more. See also: Google reveals Android Q will be called Android 10 as it undergoes an evolutionary rebrand Google pulls… [Continue Reading] -

Google reveals Android Q will be called Android 10 as it undergoes an evolutionary rebrand
Publié: août 22, 2019, 4:26pm CEST par Mark Wyciślik-Wilson
Google has famously named each version of Android after a dessert or confectionery. With Android Q this changes. As well as introducing a new naming scheme, Google is also updating the branding for Android. Android Q is to be called Android 10 -- bringing Google's mobile operating system in line with Microsoft's Windows 10, and Apple's iPhone X. The new name is accompanied by a new logo and a new color scheme. See also: Google pulls out its death hammer once again -- YouTube messaging is the next victim Google no longer lets you turn off status lights on Nest… [Continue Reading] -

Microsoft and others join the Linux Foundation's Confidential Computing Consortium
Publié: août 22, 2019, 1:25pm CEST par Mark Wyciślik-Wilson
Microsoft, Google, Red Hat, IBM and Intel are among those to join the newly formed Confidential Computing Consortium (CCC). The new organization will be hosted at the Linux Foundation, having been established to help define and accelerate the adoption of confidential computing. The company explains that, "confidential computing technologies offer the opportunity for organizations to collaborate on their data sets without giving access to that data, to gain shared insights and to innovate for the common good". Microsoft will be contributing the Open Enclave SDK that allows developers to build Trusted Execution Environment (TEE) applications using a single enclaving abstraction.… [Continue Reading] -

Microsoft contractors have been listening to audio captured via Xbox consoles
Publié: août 22, 2019, 11:21am CEST par Mark Wyciślik-Wilson
There have been lots of exposés over the last few weeks about the fact that numerous companies -- including Apple, Microsoft, Facebook, Amazon and Google -- have been listening to recordings of interactions between customers and digital assistants. The latest revelation is that Microsoft contractors have been listening to Xbox users. A new report says that contractors working for Microsoft listened to audio clips recorded when Xbox users interacted with Kinect and Cortana on their consoles. See also: Facebook has been paying people to listen to your Messenger conversations Microsoft is at it too: workers are listening to your Skype… [Continue Reading] -

Google pulls out its death hammer once again -- YouTube messaging is the next victim
Publié: août 22, 2019, 10:38am CEST par Mark Wyciślik-Wilson
Google has announced that it is killing off yet another of its messaging tools. This time rather than terminating a standalone messaging tool, it is the direct messaging feature of YouTube that is for the chop. The cut-off date is less than a month away, but Google warns that some messaging elements -- including the sharing of videos through messages -- may vanish before the ultimate end date of September 18. See also: Nest owners can finally migrate to a Google account Google no longer lets you turn off status lights on Nest cameras Privacy: Google stops transcribing Assistant recordings… [Continue Reading] -

Beta bug hunters can bag up to $30k in the Microsoft Edge Insider Bounty program
Publié: août 21, 2019, 7:14pm CEST par Mark Wyciślik-Wilson
With a new beta of the Chromium-based version of Edge now available, Microsoft has unveiled details of a new bug bounty program for the browser. Through the Microsoft Edge Insider Bounty it is possible to earn a maximum payout of $30,000 for discovering vulnerabilities in the Dev and Beta builds of Edge. Microsoft says that it intends to complement the Chrome Vulnerability Reward Program, meaning that any report that affects the latest version of Microsoft Edge but not Chrome will be eligible. See also: Microsoft Edge Beta available to download now for Windows and macOS Chromium-based Microsoft Edge has more… [Continue Reading] -

Now you can jailbreak iOS 12.4 -- or hack it
Publié: août 21, 2019, 12:02pm CEST par Mark Wyciślik-Wilson
Hackers have taken advantage of a vulnerability in iOS 12.4 to release a jailbreaking tool. This is the first time in many years that it has been possible to jailbreak iPhones running the most recent version of iOS. Security researchers discovered that in iOS 12.4, Apple has unpatched a vulnerability it previously fixed and it didn't take long for hacker Pwn20wnd to release a free jailbreak tool. See also: Apple Card is now available to everyone in the US Trump says Tim Cook makes a 'compelling' argument against Apple paying tariffs Privacy: Apple now treats WebKit tracking circumvention as a… [Continue Reading] -

Facebook ups its privacy game (a bit) with new tool for users to control data shared by websites
Publié: août 21, 2019, 11:46am CEST par Mark Wyciślik-Wilson
Facebook has launched a new privacy tool, giving users the chance to see and control the data the social network collects about them from other websites. Called Off-Facebook Activity, the new tool lets users restrict what is shared to Facebook by apps and websites. More than this, it enables Facebook users to sever ties between websites and the social network, with a view to limiting the personalization of ads on Facebook. See also: Facebook has been paying people to listen to your Messenger conversations Facebook is renaming WhatsApp and Instagram EU says that websites with Facebook Like buttons are liable… [Continue Reading] -

Apple Card is now available to everyone in the US
Publié: août 20, 2019, 4:24pm CEST par Mark Wyciślik-Wilson
Following an initially limited launch earlier this month, Apple's take on the credit card -- the Apple Card -- is now available to everyone in the US. For now, it is just the US that is being treated to the card. The rest of the world will almost certainly get a look-in at some point in the future, but for now Apple is focusing its attention on Americans. See also: Trump says Tim Cook makes a 'compelling' argument against Apple paying tariffs These are the Apple Card restrictions you need to know about Apple Card: The Apple credit card is… [Continue Reading] -

Trump says Tim Cook makes a 'compelling' argument against Apple paying tariffs
Publié: août 19, 2019, 11:15am CEST par Mark Wyciślik-Wilson
At a weekend meeting with Donald Trump, Tim Cook made a "compelling" argument for Apple to be exempt from tariffs. Cook is said to have argued if Apple was forced to pay tariffs, it made it difficult to compete with other companies, such as Samsung. Trump acknowledged that it was "tough" for Apple to be paying tariffs on its China-made products when Samsung was not subject to them, but made no indication that exemption for Apple was on the cards. See also: Privacy: Apple now treats WebKit tracking circumvention as a security issue Apple widens the scope of its bug… [Continue Reading] -

Minecraft is getting better graphics thanks to real-time ray tracing by Nvidia
Publié: août 19, 2019, 10:15am CEST par Mark Wyciślik-Wilson
Microsoft may have canceled the Super Duper Graphics Pack update for Minecraft, but the blocky game is still due for a graphical improvement... for some people, at least. At Gamescon in Germany today, Nvidia and Microsoft announced that a real-time ray tracing technique called path tracing will be coming to the Windows 10 version of Minecraft -- but only for systems with NVIDIA GeForce RTX GPUs. The graphic improvements will give Minecrafters better lighting, colors and shadows, and will be delivered by a free update to the game. See also: Microsoft cancels major Super Duper Graphics Pack update for Minecraft… [Continue Reading] -

Microsoft is working to fix error 0x80073701 in Windows 10
Publié: août 18, 2019, 5:21pm CEST par Mark Wyciślik-Wilson
Microsoft is investigating a problem that has struck many users installing KB4512508 Cumulative Update for Windows 10 1903. People whose systems are affected by the problem complain that updates do not install, and Error 0x80073701 is displayed. The issue affects both Windows 10 and Windows Server 1903. See also: Microsoft releases action-packed Windows 10 20H1 Build 18963 Microsoft Surface Pro 6 and Surface Book 2 hit with CPU throttling issues Chromium-based Microsoft Edge has more natural-sounding Read Aloud voices thanks to the cloud At the moment,the cause of the problem is not known, and Microsoft is investigating it to determine… [Continue Reading] -

Google no longer lets you turn off status lights on Nest cameras
Publié: août 16, 2019, 2:48pm CEST par Mark Wyciślik-Wilson
Google is rolling out updates to its Nest Cam, Dropcam and Nest Hello cameras that removes the option to disable status indicator lights. Citing privacy, Google says that users should "always see a clear visual indicator when your Nest cameras are on and sending video and audio". The company might be introducing the change in the name of privacy, but owners of the devices are far from happy about it. See also: Privacy: Google stops transcribing Assistant recordings and Apple stops listening to Siri recordings Google to let Android users in Europe choose their default search engine -- and will… [Continue Reading] -

Microsoft Surface Pro 6 and Surface Book 2 hit with CPU throttling issues
Publié: août 16, 2019, 2:06pm CEST par Mark Wyciślik-Wilson
Microsoft is trying to fix a mysterious issue with Surface Pro 6 and Surface Book 2 devices which is causing CPU speeds to be throttled to a painfully slow 400 MHz. At the moment it is not clear what is causing the problem, but it appears to be related to an Intel CPU flag -- BD PROCHOT which throttles processor speeds in a bid to reduce temperature. See also: Chromium-based Microsoft Edge has more natural-sounding Read Aloud voices thanks to the cloud. Microsoft cancels major Super Duper Graphics Pack update for Minecraft Microsoft is at it too: workers are listening… [Continue Reading] -

Privacy: Apple now treats WebKit tracking circumvention as a security issue
Publié: août 16, 2019, 1:48pm CEST par Mark Wyciślik-Wilson
Apple has updated its WebKit policy, increasing the company's focus on privacy. The new WebKit Tracking Prevention Policy now states that any circumvention of its anti-tracking feature is treated in the same way, and as seriously, as security issues. The aim is to prevent web tracking completely because "these practices are harmful to users because they infringe on a user's privacy without giving users the ability to identify, understand, consent to, or control them". Apple says it wants "to see a healthy web ecosystem, with privacy by design". See also: Privacy: Google stops transcribing Assistant recordings and Apple stops listening… [Continue Reading] -

Chromium-based Microsoft Edge has more natural-sounding Read Aloud voices thanks to the cloud
Publié: août 15, 2019, 11:04am CEST par Mark Wyciślik-Wilson
Having your browser read web pages to you is a great accessibility feature, and it also allows for multi-tasking. There's just one problem -- the computerized voices used are little short of terrible... often to the point of being distracting. With the Dev and Canary builds of Chromium-based versions of Microsoft Edge, however, this changes. Embracing the power of the cloud, Edge now features 24 more natural-sounding voices driven by Microsoft Cognitive Services. See also: Microsoft cancels major Super Duper Graphics Pack update for Minecraft Microsoft is at it too: workers are listening to your Skype and Cortana conversations Microsoft… [Continue Reading] -

Facebook has been paying people to listen to your Messenger conversations
Publié: août 14, 2019, 10:12am CEST par Mark Wyciślik-Wilson
It probably comes as absolutely no surprise to anyone, but Facebook is just the same as Google, Amazon and Apple when it comes to listening in on your conversations -- the ones you thought (or at least hoped) were private. Following a report from Bloomberg News, Facebook has confirmed that paid contractors have been listening to audio of conversations. The company says, however, that it has put the brakes on the practice -- for now, at least. See also: How to opt out of Amazon listening to what you say to Alexa Yes, Google really is listening in on what… [Continue Reading] -

Microsoft cancels major Super Duper Graphics Pack update for Minecraft
Publié: août 13, 2019, 10:21am CEST par Mark Wyciślik-Wilson
It is now two years since Microsoft announced the Super Duper Graphics Pack for Minecraft, a major upgrade and new look for the game, but now the update has been canceled. The company says that the "ambitious initiative" has "proved too technically demanding to implement as planned". Performance is cited as a reason for ditching the update, but Microsoft promises that it will work on developing a new look for Minecraft in other ways. See also: Microsoft is at it too: workers are listening to your Skype and Cortana conversations Microsoft announces Windows 10 20H1 Build 18956 with network and… [Continue Reading] -

Verizon sells Tumblr to WordPress owner, Automattic
Publié: août 13, 2019, 9:32am CEST par Mark Wyciślik-Wilson
A mere two years after acquiring it, Verizon is selling Tumblr. Full details of the deal have not yet been revealed, but the micro-blogging service is being bought by Automattic, the company behind WordPress. Tumblr came into the spotlight last year when it introduced a ban on all adult content, and anyone hoping for this to change is going to be disappointed. Automattic says the ban will remain in place. See also: Tumblr turns family-friendly and bans ALL adult content Et tu, Tumblr? Blogging site says it was used by Russia to spread fake news in 2016 Verizon is splitting… [Continue Reading] -

Apple widens the scope of its bug bounty program, and increases top payout to $1 million
Publié: août 9, 2019, 3:40pm CEST par Mark Wyciślik-Wilson
Bug bounty programs are a common way for companies to learn about problems with their hardware and software, while giving people the chance to get paid for finding them. Apple is one of the big names to run such a program, and it has at long last expanded it to included macOS. The iPhone-maker made the announcement at the Black Hat security conference, where it also revealed that not only will its bug bounty program spread to tvOS, watchOS and iCloud as well, but also that the maximum reward is increasing to a cool $1 million. See also: Apple is… [Continue Reading] -

Microsoft is at it too: workers are listening to your Skype and Cortana conversations
Publié: août 9, 2019, 3:02pm CEST par Mark Wyciślik-Wilson
The idea that conversations you have with or via your computer are confidential has been completely dispelled over the last couple of weeks. We've learned that not only were Google workers listening to recordings of people using Google Assistant, Apple workers were listening in on Siri commands, and Amazon workers could hear what you're saying to Alexa. If you thought Microsoft would not engage in such activity, think again. A new report reveals evidence that contractors working for Microsoft are listening to Skype calls made via the translation feature. Privacy: Google stops transcribing Assistant recordings and Apple stops listening to… [Continue Reading] -

Apple is discouraging the installation of third party batteries by displaying Battery Health warnings
Publié: août 9, 2019, 11:33am CEST par Mark Wyciślik-Wilson
In a move that is going to prove more than a little controversial, Apple is using the Battery Health feature of iOS to strongly discourage people from using cheaper third-party batteries rather than official Apple units. Now, if you install a non-official battery in an iPhone XS, XR or XS Max, Battery Health will display a "Service" notification that is usually used to indicate that there is a problem. Click through, and you'll see a message that reads: "Unable to verify this iPhone has a genuine Apple battery. Health information not available for this battery". See also: These are the… [Continue Reading] -

Linux is rubbish when RAM runs low
Publié: août 7, 2019, 5:49pm CEST par Mark Wyciślik-Wilson
A developer has pointed out what many people have been complaining about for some time: Linux is terrible when memory runs low. Writing in a message to the Linux kernel mailing list, developer Artem S Tashkinov says that the problem has been "bugging people for many years" and is still present in version 5.2.6 of the Linux kernel. He says that non-technically minded users could be prompted to ditch Linux-based OSes if they encounter the issue which he points out is "is reproducible in less than a few minutes under the latest and greatest kernel". See also: NordVPN brings WireGuard-based… [Continue Reading] -

Microsoft quietly fixes SWAPGS processor vulnerability to protect Windows users
Publié: août 7, 2019, 8:05am CEST par Mark Wyciślik-Wilson
It has been revealed that Microsoft silently pushed out a patch to Windows users to fix a vulnerability that affected Intel CPUs produced since 2012 -- which means everything post Ivy Bridge chips. The SWAPGS vulnerability is similar to the now-famous Spectre and Meltdown chip flaws, and was discovered by security firm Bitdefender a year ago; the fact that it has now been patched was only revealed at the BlackHat security conference. Red Hat says that an update to the Linux kernel is needed to protect against the flaw which it says affects both Intel and AMD chips, although Bitdefender… [Continue Reading] -

These are the Apple Card restrictions you need to know about
Publié: août 5, 2019, 12:12pm CEST par Mark Wyciślik-Wilson
Apple Card is due to launch later this month and there are a few restrictions associated with Apple's predictably-named credit card. The Apple Card Customer Agreement document drawn up by backing creditor Goldman Sachs shows that it cannot be used to buy cryptocurrencies. Additionally, the iPhone-based digital version of the credit card cannot be used on jailbroken devices. See also: Privacy: Google stops transcribing Assistant recordings and Apple stops listening to Siri recordings Apple Card: The Apple credit card is coming in August Privacy: Apple workers may well hear all of your sordid secrets via Siri Goldman Sachs' agreement document… [Continue Reading] -

Cloudflare terminates 8chan over links to mass shootings
Publié: août 5, 2019, 10:48am CEST par Mark Wyciślik-Wilson
Cloudflare has announced that it is terminating its services with controversial site 8chan. The move comes after the mass shootings in El Paso, Texas and Dayton, Ohio. There have been numerous calls for 8chan to be taken offline in the past, and Cloudflare has previously considered removing its protective services from the site. What has now tipped the company's decision is the fact that the shooter at El Paso "appears to have been inspired" by 8chan, and even posted a racist manifesto on the site. Cloudflare CEO Matthew Prince explains that the links between 8chan and the recent mass shootings… [Continue Reading] -

Facebook is renaming WhatsApp and Instagram
Publié: août 4, 2019, 1:46pm CEST par Mark Wyciślik-Wilson
Being such globally recognized names, you would think that a rebranding of WhatsApp and Instagram would be a crazy exercise... but that's precisely what Facebook is doing. In a move that is more than a little surprising -- and, many would argue, somewhat pointless -- the social networking giant is to rename the two products Instagram from Facebook and WhatsApp from Facebook. The renaming will make it clear that the company people love to hate is behind the chat and social networking tools. See also: EU says that websites with Facebook Like buttons are liable for private data sharing FTC… [Continue Reading] -

How to opt out of Amazon listening to what you say to Alexa
Publié: août 4, 2019, 1:22pm CEST par Mark Wyciślik-Wilson
There have been privacy concerns about digital assistants for just about as long as there have been digital assistants, and the recent confirmation that Google and Apple were listening to Assistant and Siri conversations has done nothing to allay fears. The 'were' in that last sentence is important, as both companies have agreed -- at least temporarily -- to cease the practice. Not wanting to miss out on an opportunity for good PR, Amazon is getting in on the action, giving Alexa users the chance to opt out of having their conversations with its digital assistant listened to -- or… [Continue Reading] -

Leaked: download the Microsoft Edge for Mac beta
Publié: août 3, 2019, 3:32pm CEST par Mark Wyciślik-Wilson
Microsoft continues with the development of Edge, and a new leak gives Mac users a chance to see what the company is doing with the web browser for their preferred operating system. Renowned leaker WalkingCat has provided a download link to an unreleased beta version of the Mac build of Microsoft Edge. As it's a beta that hasn't been released to official channels, there are possible stability issues, but it serves as a chance to try out the latest Chromium-base version of Edge for Mac. The build number for the leaked version is 76.0.182.22, and it's not clear when --… [Continue Reading] -

Amazon Dash buttons get chucked on the scrap heap this month
Publié: août 2, 2019, 12:12pm CEST par Mark Wyciślik-Wilson
The much-maligned Dash button from Amazon is being killed off for good. Having previously announced that they were being discontinued, Amazon has announced that as of the end of this month, it will no longer be possible to place orders via a physical Dash button. This does not mean that the Dash ordering service is ceasing completely -- it will continue to exist in the form of virtual Dash button that can be accessed from a range of devices. In fact, it is the success of virtual Dash buttons that negates the need for physical buttons, prompting Amazon to discontinue… [Continue Reading] -

Users complain that Windows 10 is stuck in S mode
Publié: août 2, 2019, 11:55am CEST par Mark Wyciślik-Wilson
Windows 10 S mode is proving problematic for some people, with a number of users complaining that they are unable to get their computers out of the limited mode. A number of laptops -- including the Surface Go and Surface Laptop -- come pre-configured to run in Windows 10 S mode, preventing users from changing their search engine in Edge, or from installing software from outside of the Microsoft Store. It is supposed to be possible to exit S mode, but the option has been broken for a number of days. See also: Microsoft releases Windows 10 20H1 Build 18950… [Continue Reading] -

Privacy: Google stops transcribing Assistant recordings and Apple stops listening to Siri recordings
Publié: août 2, 2019, 11:24am CEST par Mark Wyciślik-Wilson
Following the revelations that Apple contractors are listening to recordings of things people say to Siri, and Google workers are manually transcribing Assistant recordings, both companies have said they will cease the practice -- at least temporarily. Both Apple and Google were "listening in" on recordings with a view to improving their respective digital assistants, but privacy concerns have forced them to take action. But while Apple is suspending its "grading" program worldwide, Google is only changing the way it operates in Europe. See also: Yes, Google really is listening in on what you say to Google Assistant Privacy: Apple… [Continue Reading] -

Google to let Android users in Europe choose their default search engine -- and will make money in doing so
Publié: août 2, 2019, 11:00am CEST par Mark Wyciślik-Wilson
In response to a $5 billion fine for antitrust violations in Europe, Google has announced that it will introduce a new "search engine choice" option next year. It's an idea that is similar to the Browser Choice screen Microsoft introduced following anti-competition complaints about Internet Explorer. Google will "introduce a new way for Android users to select a search provider to power a search box on their home screen and as the default in Chrome (if installed)" in Europe starting in 2020. The search engines that appear in the list will be determined by auctions. Google rivals will have to… [Continue Reading] -

Cisco to pay $8.6 million for supplying the US government with software known to be insecure
Publié: août 1, 2019, 11:10am CEST par Mark Wyciślik-Wilson
Cisco has agreed to pay $8.6 million to settle a claim that it sold video surveillance software to the American government even though it was aware it contained security vulnerabilities. A total of fifteen US states filed a case under the False Claims Act after Homeland Security, the Secret Service, the Army, the Navy, the Marines, the Air Force and the Federal Emergency Management Agency all purchased flawed software from Cisco. Rather than improving security as desired, the complainants said that Cisco's software actually made systems less secure. See also: Apple pushes out another emergency security update to fix videoconferencing… [Continue Reading] -

NordVPN brings WireGuard-based NordLynx to Linux users
Publié: juillet 31, 2019, 2:19pm CEST par Mark Wyciślik-Wilson
NordVPN has announced an important new option for users of the Linux version of its eponymous VPN tool. The company is introducing a new technology called NordLynx which is based on the WireGuard protocol. The company says that it successfully combines the highspeed connection offered by WireGuard with NordVPN's own privacy-protecting double NAT system. The change is NordVPN's recognition of the fact that the relatively new WireGuard protocol is outperforming existing favorites such as OpenVPN and IPSec in many ways. One of the key advantages of it is that WireGuard comprises a mere 4,000 lines of code (one hundredth of… [Continue Reading] -

Chrome 76 arrives, blocking Flash and making paywalls easier to bypass
Publié: juillet 31, 2019, 12:59pm CEST par Mark Wyciślik-Wilson
Google has released Chrome 76 for Windows, macOS and Linux. As expected from the preview releases, this version of the browser brings a couple of important changes: Flash is now blocked by default, and Incognito mode detection is also blocked. The blocking of Flash will be welcomed by many, and -- once word spreads about what the implications are (namely that it makes it far easier to get around paywalls) -- the same is likely to be true of the changes to the detection of Incognito mode. The changes have been welcomed by privacy and security advocates. See also: Google… [Continue Reading] -

Microsoft announces that Skype for Business Online will be retired
Publié: juillet 31, 2019, 10:00am CEST par Mark Wyciślik-Wilson
As Microsoft continue to push Teams, the company has announced that Skype for Business Online will be retired in 2021. While this is far from surprising, this is the first time a date has been mentioned so users can prepare to transition away. With the retirement date set at July 31, 2021, users have two years to get ready for a move to Teams. See also: Microsoft releases Windows 10 20H1 Build 18945 -- on purpose! -- with improvements to Cortana, Windows Subsystem for Linux and File Explorer Microsoft's web-based Outlook 365 is leaking users' IP addresses in emails Privacy… [Continue Reading] -

Apple Card: The Apple credit card is coming in August
Publié: juillet 31, 2019, 9:37am CEST par Mark Wyciślik-Wilson
You might well be waiting for news of the new iPhone line-up, and we'll know more about that soon. In the meantime, however, Apple has a new product for its loyal fanbase. A credit card. The Apple Card has been talked about for some time, and now Tim Cook has revealed that it will be launching in August. The news came from the Apple CEO during an earnings call yesterday, and he said that the company's employees have been beta testing the Apple Card, which comes in both digital and physical forms. See also: Privacy: Apple workers may well hear… [Continue Reading] -

EU says that websites with Facebook Like buttons are liable for private data sharing
Publié: juillet 30, 2019, 9:54am CEST par Mark Wyciślik-Wilson
The fingers of Facebook have spread like a cancer across the internet. Even people who have made the conscious decision to boycott the network find it near-impossible to completely avoid its reach thanks to the prevalence of Like buttons. Now the Court of Justice of the European Union has ruled that websites with embedded Like buttons can be held responsible for the transmission of data to Facebook. This is a particularly important ruling due to the fact that Like buttons can be used to share information about site visitors without the need for the button to be clicked. See also:… [Continue Reading] -

Personal details of 106 million Americans and Canadians stolen in huge Capital One data breach
Publié: juillet 30, 2019, 9:14am CEST par Mark Wyciślik-Wilson
A hacker has been arrested following a massive data breach at Capital One. The attacker -- Paige A Thompson, also known as "erratic" -- was able to access the credit applications of 100 million Americans and 6 million Canadians after exploiting a "configuration vulnerability". In most cases, personal details such as name, date of birth, address and phone number were exposed by Thompson, but for tens of thousands of individuals, she also gained access to credit scores, Social Security numbers and account balances. See also: Microsoft warns thousands that they are victims of state-sponsored hacking You need to update your… [Continue Reading] -

Windows 10's WSL 2 now lets you add a custom Linux kernel and enjoy localhost access
Publié: juillet 28, 2019, 3:47pm CEST par Mark Wyciślik-Wilson
For Windows 10 users looking to install a Linux-based operating system within Windows, WSL -- Windows Subsystem for Linux -- was a blessing from Redmond. And things are just getting better and better. The latest Insider build of Windows 10, Windows 10 20H1 build 18945 includes Windows Subsystem for Linux 2 (WSL 2) with a couple of key enhancements. Not only are you now able to gain localhost access to network resources, you can also make use of your preferred Linux kernel. See also: Microsoft releases Windows 10 20H1 Build 18945 -- on purpose! -- with improvements to Cortana, Windows… [Continue Reading] -

Hate the new-look Twitter? Here's how to get the old version back
Publié: juillet 28, 2019, 3:08pm CEST par Mark Wyciślik-Wilson
People are often resistant to change, particularly when it feels like change for the sake of change -- and this is certainly the feeling that abounds with the recent redesign of Twitter. While some Twitter users have been working with the new look for some time, it only rolled out globally a couple of weeks ago. Predictably, the reaction has been mixed, but the redesign has certainly not been met with universal praise. If you're one of the many who hate the way things are now, you'll be frustrated to learn that Twitter does not give you a way to… [Continue Reading] -

Privacy: Apple workers may well hear all of your sordid secrets via Siri
Publié: juillet 27, 2019, 4:19pm CEST par Mark Wyciślik-Wilson
It's only a couple of weeks since we learned, for certain, that Google is listening to what people say to Google Assistant. Now -- and perhaps surprising no one -- it transpires that Siri is just as much of a privacy invasion. Just as with Amazon and Google with Alexa and Google Assistant, Apple shares some of the recordings made via Siri with contractors with a view to improving the service. But while it may mean that Siri gets better at responding to queries, it also means that the contractors charged with "grading" Siri's performance "regularly hear confidential details" --… [Continue Reading] -

Microsoft's web-based Outlook 365 is leaking users' IP addresses in emails
Publié: juillet 26, 2019, 10:01am CEST par Mark Wyciślik-Wilson
Anyone using Office 365's webmail component to send emails is unwittingly sharing their IP address with the people they communicate with. The web-based Outlook 365 inserts the sender's IP address into the header of an email, which makes it stand apart from other webmail services such as Gmail -- and even Microsoft's own Outlook.com. While the injected IP address serves something of a purpose, it's also a privacy and security risk that many users may not be aware of. See also: Privacy concerns raised that SmartScreen in Edge shares browsing history with Microsoft German schools ban Microsoft Office 365 because… [Continue Reading] -

Alleged critical VLC flaw is nothing to worry about -- and is nothing to do with VLC
Publié: juillet 25, 2019, 11:32am CEST par Mark Wyciślik-Wilson
There has been a degree of confusion over the last few days after news spread of a supposed vulnerability in the media player VLC. Despite being labelled by security experts as "critical", VLC's developers, VideoLAN, denied there was a problem at all. And they were right. While there is a vulnerability, it was in a third-party library, not VLC itself. On top of this, it is nowhere near as severe as first suggested. Oh -- and it was fixed over a year ago. An older version of Ubuntu Linux was to blame for the confusion. See also: 'Critical' vulnerability discovered… [Continue Reading] -

Department of Justice's Antitrust Division launches big tech investigation
Publié: juillet 24, 2019, 11:42am CEST par Mark Wyciślik-Wilson
Without naming any names, the Department of Justice has announced today that its Antitrust Division is to launch an investigation into the practices of "market-leading online platforms". The probe comes amid concerns that the big names in technology are "engaging in practices that have reduced competition, stifled innovation, or otherwise harmed consumers". While the DoJ has not officially named any of the companies it is planning to look into as part of its investigation, the likes of Facebook, Google (or Alphabet) and Amazon are likely to feature prominently. The Department says that the investigation -- or "review" as it calls… [Continue Reading] -

'Critical' vulnerability discovered in VLC on Linux and Windows -- but VideoLAN says it is not reproducible
Publié: juillet 24, 2019, 11:11am CEST par Mark Wyciślik-Wilson
Reports have emerged of a security bug in the Windows and Linux versions of VLC, making it vulnerable to remote-code execution via malicious videos. But although German and American security experts have branded the flaw as "critical", VLC-maker VideoLAN is downplaying things. In fact, more than downplaying the vulnerability, VideoLAN is flat-out denying that it exists, with the software developer dismissing it as "fake news". The alleged vulnerability has been assigned a 9.8 critical score on NIST and a similar warning has been issued by CERT. The flaw supposedly means that malicious MKV files could be used to compromise VLC.… [Continue Reading] -

Privacy concerns raised that SmartScreen in Edge shares browsing history with Microsoft
Publié: juillet 23, 2019, 12:57pm CEST par Mark Wyciślik-Wilson
A security researcher has revealed that the SmartScreen feature of Microsoft Edge is sharing full URLs of pages visited with the Windows-maker. Also shared are users' account IDs, raising concerns about privacy-invading tracking of browsing history. SmartScreen is a security feature that Microsoft uses to identify phishing and malware websites, but the lack of obfuscation or anonymization of URLs shared with the company opens ups the potential for invasions of privacy and the revealing of sensitive information. See also: Microsoft to pay $26 million to settle claims of violating the Foreign Corrupt Practices Act Microsoft plows $1 billion into OpenAI… [Continue Reading] -

Apple may buy Intel's modem business for $1 billion as early as next week
Publié: juillet 23, 2019, 11:59am CEST par Mark Wyciślik-Wilson
Apple is said to be in advanced talks with Intel with a view to buying the company's 5G modem business for a figure upwards of $1 billion. Following legal wrangles and fallings out with Qualcomm, Apple eventually came to an agreement with the firm, but now it seems that the iPhone-maker is turning its attention to Intel. The deal is said to include a portfolio of patents and staff. See also: Apple pushes out another emergency security update to fix videoconferencing vulnerabilities Apple's 2019 MacBook Air is significantly slower than last year's model Apple updates MacBook Pro and MacBook Air… [Continue Reading] -

Microsoft to pay $26 million to settle claims of violating the Foreign Corrupt Practices Act
Publié: juillet 22, 2019, 6:07pm CEST par Mark Wyciślik-Wilson
Microsoft has come to an agreement with the US Justice Department and the SEC because of employee misconduct in Hungary. The company was to face a probe over violations of the Foreign Corrupt Practices Act. In agreeing to pay this money, Microsoft is neither really admitting guilt nor denying the claims made against it, and company President and Chief Legal Officer Brad Smith has written to all employees saying: "There is no room for compromise when it comes to ethical business practices". See also: Microsoft plows $1 billion into OpenAI partnership Microsoft is ripping SMS Connect from Skype... Again Microsoft… [Continue Reading] -

Microsoft plows $1 billion into OpenAI partnership
Publié: juillet 22, 2019, 4:02pm CEST par Mark Wyciślik-Wilson
Microsoft is investing $1 billion in a multi-year partnership with OpenAI-- a company co-founded by Elon Musk three years ago. The partnership will see Microsoft and OpenAI working together to build new Azure AI supercomputing technologies. Microsoft says that it will focus on building a platform to create new AI technologies and deliver on the promise of artificial general intelligence (AGI). See also: Microsoft releases Windows 10 20H1 Build 18941, but warns the installation may fail or cause your PC to get stuck in a boot loop Microsoft is ripping SMS Connect from Skype... Again Microsoft warns thousands that they… [Continue Reading] -

European Commission rules that UK dwelling EU citizens can still hold .eu domains after Brexit
Publié: juillet 21, 2019, 2:59pm CEST par Mark Wyciślik-Wilson
What Brexit really means for the UK -- whenever it may end up happening -- still remains to be seen. But a new ruling by the European Commission means that even after leaving Europe, UK citizens will still be able to hold .eu top-level domains after leaving the European Union. The ruling is a reversal of a decision taken earlier in the year that EU citizens living in the UK post-Brexit would not be able to own such domains. It comes as the Commission becomes increasingly concerned about the "uncertainties surrounding the ratification of the Withdrawal Agreement", and what the… [Continue Reading] -

Wizz Air sends out password reset emails to millions of customers following 'technical irregularity'
Publié: juillet 20, 2019, 2:08pm CEST par Mark Wyciślik-Wilson
Hungarian airline Wizz Air has emailed millions of customers informing them that their passwords have been reset. While the company is at pains to stress that it has not been the victim of hacking, nor is any personal information at risk, the email took many customers by surprise and raised concerns about a possible data breach. See also: Scotland Yard Twitter account and website hacked Microsoft warns thousands that they are victims of state-sponsored hacking Apple pushes out another emergency security update to fix videoconferencing vulnerabilities Wizz Air has not really given any details about what has happened, simply referring… [Continue Reading] -

Scotland Yard Twitter account and website hacked
Publié: juillet 20, 2019, 12:00pm CEST par Mark Wyciślik-Wilson
The Twitter account of Scotland Yard has been hit by hackers, resulting in a series of strange and offensive tweets being sent to hundreds of thousands of followers. The website for the Metropolitan Police was also hacked. Tweets sent by the hackers made references to Keemstar as well as drill artist Digga D, calling for the rapper to be freed from prison. The attack by hackers also resulted in a series of emails being sent out to journalists via the Metropolitan Police's official email address. See also: Microsoft warns thousands that they are victims of state-sponsored hacking You need to… [Continue Reading] -

Google boosts Chrome bug bounties
Publié: juillet 19, 2019, 10:07am CEST par Mark Wyciślik-Wilson
Bug bounty programs have become a popular way for companies to unearth security issues in software and address them quickly. Google is no stranger to such programs, and it has just announced massive increases to the payouts made for finding vulnerabilities in Chrome. Some rewards have doubled while others have tripled, taking the maximum compensation for reporting a security flaw in Google's web browser -- and other Chromium-based browsers -- to an impressive $30,000. See also: Google is closing a Chrome API loophole to make Incognito Mode more secure and private Google kills off its censored Chinese search engine, Project… [Continue Reading] -

Slack resets hundreds of thousands of passwords following data breach
Publié: juillet 19, 2019, 9:25am CEST par Mark Wyciślik-Wilson
Slack has just been made aware of additional information about a security breach that took place back in 2015, forcing the company to reset the passwords of around 1 percent of its users. The company announced earlier this year that it has a daily userbase of over 10 million people, so this means that a huge number of users are affected by the incident no matter how much Slack tries to downplay it. See also: Microsoft Teams is more popular than Slack Leaked: Microsoft bans employees from using Slack, Kaspersky… even GitHub use is discouraged How the smartest companies use… [Continue Reading] -

Google is closing a Chrome API loophole to make Incognito Mode more secure and private
Publié: juillet 19, 2019, 9:02am CEST par Mark Wyciślik-Wilson
Following increasing awareness that using Incognito Mode in Chrome can be detected, and it is still possible for sites to track your online behavior when you're using it, Google has announced upcoming changes that will close a loophole. The update is due at the end of this month and it addresses a chink in the FileSystem API. Google says the change are coming in Chrome 76, and will also make it harder for publishers to determine when people are trying to bypass paywalls. See also: Google kills off its censored Chinese search engine, Project Dragonfly Yes, Google really is listening… [Continue Reading] -

Microsoft is ripping SMS Connect from Skype... Again
Publié: juillet 18, 2019, 12:10pm CEST par Mark Wyciślik-Wilson
Microsoft has announced that it is cutting the SMS Connect feature from Skype at the end of August. The feature -- which makes it possible for Android users to send and receive text messages via Skype on their computers -- has been dropped in the past but made a reappearance last year. But now Microsoft is trying to push people into using the Your Phone app instead. See also: Microsoft warns thousands that they are victims of state-sponsored hacking German schools ban Microsoft Office 365 because of privacy concerns Microsoft blocks Surface Book 2 owners from upgrading to Windows 10… [Continue Reading] -

Microsoft warns thousands that they are victims of state-sponsored hacking
Publié: juillet 18, 2019, 11:39am CEST par Mark Wyciślik-Wilson
Microsoft has revealed that it has issued warnings to nearly 10,000 people that they are the targets or victims of state-sponsored hacking. The announcement comes as Microsoft showcases election systems running Microsoft ElectionGuard which not only helps to increase security, but also makes voting more accessible. Microsoft reveals that the vast majority of the state-sponsored attacks targeted enterprise customers, but there were still a significant number of regular consumers affected. See also: German schools ban Microsoft Office 365 because of privacy concerns Microsoft blocks Surface Book 2 owners from upgrading to Windows 10 1903 Microsoft backtracks on plans to scrap… [Continue Reading] -

F-Secure's Data Discovery Portal reveals what the big tech companies know about you
Publié: juillet 18, 2019, 10:12am CEST par Mark Wyciślik-Wilson
In an age where people want -- even expect -- everything for free, particularly online, the price we pay for using various services is our privacy. Social networks are obvious collectors of personal data, but it doesn't end there... and who really knows what information has been collected about them over the years? This is what F-Secure hopes to cast a light on with its new Data Discovery Portal which aims to "expose the true cost of using some of the web's most popular free services". It covers Amazon, Apple, Facebook, Google, Snapchat and Twitter. See also: German schools ban… [Continue Reading] -

Apple pushes out another emergency security update to fix videoconferencing vulnerabilities
Publié: juillet 17, 2019, 4:07pm CEST par Mark Wyciślik-Wilson
Having released a silent update last week to protect Zoom users from webcam hijacking, Apple has now pushed out a second security patch that is silently installed in the background. This second patch addresses issues with the RingCentral and Zhumu videoconferencing tools. These apps suffered from a very similar vulnerability, putting users at risk, so Apple has stepped in once again to neutralize the problem. See also: Apple and Zoom push out updates to remove potentially privacy-invading web server Zoom for Mac has a security hole that means your webcam could be turned on without permission Apple's 2019 MacBook Air… [Continue Reading] -

Google kills off its censored Chinese search engine, Project Dragonfly
Publié: juillet 17, 2019, 2:21pm CEST par Mark Wyciślik-Wilson
Google has decided to close down its controversial Project Dragonfly which would have seen the company launching a censored version of its search engine in China. The company's vice president of public policy, Karan Bhatia, made the revelation speaking at a Senate Judiciary Committee hearing yesterday. She said simply: "We have terminated Project Dragonfly". See also: Yes, Google really is listening in on what you say to Google Assistant There will be no more tablets from Google Google confirms that second-hand Nest Cams could have been used to spy on people Google has never said anything publicly about Project Dragonfly,… [Continue Reading] -

Apple's 2019 MacBook Air is significantly slower than last year's model
Publié: juillet 16, 2019, 2:16pm CEST par Mark Wyciślik-Wilson
When Apple announced the 2019 refresh of its MacBook Pro and MacBook Air, attention was focused on the reduction in price and a boost to hardware. But while much was made of the addition of True Tone to the Retina Display and the lower starting figure, it seems that the price cut comes at the price of performance. Tests show that the 2019 MacBook Air's SSD is actually slower, significantly slower, than last year's model. See also: Apple Watch eavesdropping vulnerability forces Apple to disable Walkie-Talkie app Apple and Zoom push out updates to remove potentially privacy-invading web server Apple… [Continue Reading] -

You need to update your Logitech wireless dongle to avoid falling victim to MouseJack hacking
Publié: juillet 16, 2019, 9:19am CEST par Mark Wyciślik-Wilson
If the word MouseJack seems familiar, it's because it as been around for a while. It is a remote access hack that emerged a few years back that took advantage of a vulnerability in some Logitech wireless dongles, as well as hardware from other manufacturers. Being at least three years old, you would expect that patches would have been addressed -- and they were. But a large number of devices are still at risk because Logitech failed to recall the affect units that were on sale so there's a chance that if you bought a Logitech wireless keyboard, mouse or… [Continue Reading] -

Twitter redesign rolls out on the web
Publié: juillet 15, 2019, 7:58pm CEST par Mark Wyciślik-Wilson
Twitter is rolling out a faster, redesigned version of its website, bringing not only a new look to the desktop, but also a range of new features. It's now possible to bookmark tweets -- something users have been asking for for a very long time -- there is a darker dark mode, and the Explore feature from Twitter's mobile apps makes its way to the web. There's certainly a lot to like, but the fact that the new look is not optional is likely to grate with some users. The redesign has been in the pipeline for some time now,… [Continue Reading] -

German schools ban Microsoft Office 365 because of privacy concerns
Publié: juillet 15, 2019, 12:34pm CEST par Mark Wyciślik-Wilson
The German state of Hesse has banned schools from using Microsoft Office 365 because it fears the software opens up student and teachers' private information to the risk of "potential access by US authorities". The Hesse Commissioner for Data Protection and Freedom of Information (HBDI) believes that Office 365 is in contravention of GDPR legislation, and also expressed concerns about the collection of telemetry data by Windows 10. The commissioner voices concerns that data stored in the cloud through Office 365 could be access by US authorities. The ruling says that "public institutions in Germany have a special responsibility regarding… [Continue Reading] -

Europe relies on American GPS as its own Galileo system suffers massive outage
Publié: juillet 15, 2019, 9:51am CEST par Mark Wyciślik-Wilson
Europe's Galileo satellite network -- used by satnavs, financial institutions and more -- is in the throes of a huge outage. The system has been down since Friday meaning that travelers (and others) in Europe have instead had to fall back on the American Global Positioning System (GPS) -- or even Russia or Chinese systems. Galileo has been struck by what is being described as a "technical incident related to its ground infrastructure", and it's not clear when the situation will be remedied. The European GNSS Agency (Global Navigation Satellite Systems Agency, or GSA) says that the incident affects only… [Continue Reading] -

Microsoft blocks Surface Book 2 owners from upgrading to Windows 10 1903
Publié: juillet 14, 2019, 10:30am CEST par Mark Wyciślik-Wilson
Having just removed some of the blocks that were preventing people from installing Windows 10 May 2019 Update (Windows 10 version 1903), the company has now introduced a couple more obstacles -- including for its own devices. One of the new blocks prevents Surface Book 2 owners from installing the update, while another affects systems with Intel 4 series chipset integrated GPUs. See also: Microsoft fixes some problems that blocked upgrades to Windows 10 version 1903 Microsoft Teams is more popular than Slack Microsoft backtracks on plans to scrap free software licenses for partners The Surface Book 2 issue lies… [Continue Reading] -

AMD Ryzen 3000 causes boot problems for some newer Linux distros
Publié: juillet 13, 2019, 12:35pm CEST par Mark Wyciślik-Wilson
Just last week AMD launched its latest Ryzen 3000 series of CPUs. The third-generation Ryzen chips are the first to be based on 7nm technology, but there is a problem for users of some Linux-based systems. For distributions based on newer versions of the Linux kernel, an issue renders systems unable to boot. Some users have managed to patch the systemd component with an older version to allow successful booting, but a BIOS update from AMD is what's needed. See also: IBM officially acquires Red Hat for $34 billion -- Linux distros are unaffected Kali Linux arrives on Raspberry Pi… [Continue Reading] -

Microsoft backtracks on plans to scrap free software licenses for partners
Publié: juillet 13, 2019, 11:35am CEST par Mark Wyciślik-Wilson
When Microsoft announced that it was going to start charging its partners for software licenses that had previously been free, there was an understandable backlash. Now the company has announced that it is putting these plans on hold, and free software licenses will still be available to Microsoft Partners. On the eve of its Inspire conference, Microsoft's Gavriella Schuster revealed that the decision to revoke internal use rights (IURs) has now been reversed. See also: Microsoft fixes some problems that blocked upgrades to Windows 10 version 1903 Microsoft Teams is more popular than Slack Microsoft sneaks telemetry into Windows 7… [Continue Reading] -

FTC to fine Facebook $5 billion for Cambridge Analytica privacy violations
Publié: juillet 13, 2019, 10:51am CEST par Mark Wyciślik-Wilson
The Federal Trade Commission has voted to hit Facebook with a $5 billion fine for privacy violations relating to the Cambridge Analytica scandal. While this is the largest fine ever handed out by the FTC, the impact on Facebook's coffers is going to be minimal; this is how much revenue the company generates in a month. Although the fine has not been officially confirmed -- and neither the FTC nor Facebook are commenting on the matter -- a Friday vote on the fine is said to have gone 3-2 in favor of approving it. The size of the penalty has… [Continue Reading] -

Microsoft fixes some problems that blocked upgrades to Windows 10 version 1903
Publié: juillet 12, 2019, 4:14pm CEST par Mark Wyciślik-Wilson
Installation rates for Windows 10 May 2019 Update (version 1903) remain low, and this is at least in part because Microsoft has blocked updates for many people because of a series of problems with hardware and software compatibility. Now installation numbers may start to increase as Microsoft has removed some of these blocks -- although the company warns that it could take a little while for the update to appear to those who were previously unable to install it. See also: Compatibility issues stand in the way of installing Windows 10 May 2019 Update on some Macs Only a tiny… [Continue Reading] -

Microsoft Teams is more popular than Slack
Publié: juillet 12, 2019, 12:04pm CEST par Mark Wyciślik-Wilson
Microsoft has shared usage numbers for its group chat tool, Teams. The company has revealed the number of daily and weekly users for the first time, and they reveal that Microsoft Teams has overtaken Slack in popularity. The number of daily users of Microsoft Teams stands at 13 million, while the weekly figure is 19 million. Considering the service is just two years old, to have surpassed the behemoth that is Slack is an impressive achievement. See also: Microsoft sneaks telemetry into Windows 7 via security update Microsoft is retiring its 3D model repository Remix 3D Microsoft releases public preview… [Continue Reading] -

Yes, Google really is listening in on what you say to Google Assistant
Publié: juillet 12, 2019, 10:56am CEST par Mark Wyciślik-Wilson
You may well have suspected it, but now Google has confirmed it -- contractors for the company are able to listen to what you say to Google Assistant. The revelation came after recordings of people using the AI-powered digital assistant were leaked. Belgian broadcaster VRT News obtained a large number of Dutch language recordings and was able to hear highly personal information about users -- even if they had not used the "OK Google" trigger words. See also: Google confirms that second-hand Nest Cams could have been used to spy on people Is Google Safe Browsing falling short on mobile?… [Continue Reading] -

Microsoft sneaks telemetry into Windows 7 via security update
Publié: juillet 11, 2019, 8:07pm CEST par Mark Wyciślik-Wilson
Microsoft appears to be at it again, adding telemetry components into its operating system. This time around it is Windows 7 that gets the telemetry treatment, and Microsoft seems to have gone about things in a rather sneaky fashion. The latest "security-only" update for Windows 7 includes a Compatibility Appraiser element (KB2952664) which performs checks to see whether a system can be updated to Windows 10. Hardly what most people would consider a security-only update. So what's going on? See also: Microsoft is retiring its 3D model repository Remix 3D Microsoft releases Windows 10 20H1 Build 18936 with passwordless sign-ins… [Continue Reading] -

Ditch the HDMI cables with IOGEAR's Share Pro Mini Wireless HD Video Transmitter and Receiver [Review]
Publié: juillet 11, 2019, 3:16pm CEST par Mark Wyciślik-Wilson
The humble HDMI cable is simultaneously brilliant, and a massive pain in the ass. Great for delivering HD video from your computer to a TV or projector, but a serious downside is the fact that, well, it's a cable. Who hasn't yearned for a wireless HDMI cable? This is, effectively, what the Share Pro Mini Wireless HD Video Transmitter and Receiver Kit from IOGEAR is (GWHD2DKIT). It's a two-part piece of equipment that lets you stream audio and video up to 12m (40 feet) wirelessly. Best of all, there's no software involved, and no need for Wi-Fi. The kit comprises… [Continue Reading] -

Easily share large files with Dropbox Transfer
Publié: juillet 11, 2019, 12:14pm CEST par Mark Wyciślik-Wilson
Dropbox has revealed a new file sharing service that makes it possible to send files of up to 100GB. The company says the service has been designed as a quick and easy alternative to configuring sharing and permissions, and it means that it is possible to share large files even with people who do not have Dropbox accounts. Dropbox Transfer is currently undergoing beta testing, and there's a waiting list to join if you want to take part. But if you're able to get signed up, you'll find that you have a handy alternative to email attachments. There are some… [Continue Reading] -

Apple Watch eavesdropping vulnerability forces Apple to disable Walkie-Talkie app
Publié: juillet 11, 2019, 11:53am CEST par Mark Wyciślik-Wilson
Apple has disabled the Walkie-Talkie app for Apple Watch after a vulnerability that potentially allows for eavesdropping on iPhone conversations emerged. The company says that it is not aware of any incidents of the vulnerability being exploited, and it has not shared any details of the security issue. Apple's short-term solution is to simply disable the app while it works on a fix. See also: Apple and Zoom push out updates to remove potentially privacy-invading web server Apple updates MacBook Pro and MacBook Air -- hardware bumped, prices dropped Apple ditching the wonderful MacBook butterfly keyboard is a huge mistake… [Continue Reading] -

Microsoft is retiring its 3D model repository Remix 3D
Publié: juillet 11, 2019, 11:19am CEST par Mark Wyciślik-Wilson
Microsoft has emailed users of Remix3D.com to warn them that the site is to be retired in six months' time. The site is a repository of free 3D models designed to be used in the likes of Paint3D, PowerPoint and the Windows 10 Photos app. The move is not entirely surprising as the writing has been on the wall for some time -- references to Remix3D were removed from Paint3D some time ago, for instance. See also: Microsoft releases Windows 10 20H1 Build 18936 with passwordless sign-ins Microsoft releases public preview of Desktop Analytics to help with Windows 10 update… [Continue Reading] -

Apple and Zoom push out updates to remove potentially privacy-invading web server
Publié: juillet 11, 2019, 10:50am CEST par Mark Wyciślik-Wilson
A few days ago, a security issue with the Zoom chat tool came to light -- a flaw that made it possible for Mac webcams to be switched on without permission. Despite seemingly suggesting that the flaw was in fact not a flaw, Zoom issued an update that grants users more control over the software. Apple has also produced an update of its own which nukes the security hole. The silent update has been pushed out to users and is installed without the need for confirmation or user interaction. See also: Zoom for Mac has a security hole that means… [Continue Reading] -

IBM officially acquires Red Hat for $34 billion -- Linux distros are unaffected
Publié: juillet 9, 2019, 5:44pm CEST par Mark Wyciślik-Wilson
IBM has closed its acquisition of Red Hat following the statement of intent back in October. Following the $34 billion deal, Red Hat will operate as a distinct unit within IBM -- and will be reported as part of IBM's Cloud and Cognitive Software segment. For IBM, the deal means fully embracing open source as it looks to accelerate its business model within the enterprise. For Red Hat, it means expanding its client base and working with a big player in the enterprise cloud business. Red Hat CTO Chris Wright says: "We are coming together to build upon a firm… [Continue Reading] -

US Court of Appeals says Trump can't block people on Twitter
Publié: juillet 9, 2019, 5:12pm CEST par Mark Wyciślik-Wilson
Donald Trump's love of Twitter is legendary and often ridiculed; it is also the source of frequent controversy. The US president is huge fan of ranting, raving and venting steam in tweet storms, but his famed love of sycophants also comes to the fore. Many people who have responded to his tweets critically have found themselves blocked. Now the US Court of Appeal says this is a violation of their First Amendment rights. See also: Banned from social media? Feeling persecuted and censored? Report it to Donald Trump! The Twitter app is returning to macOS Twitter looks into whether white… [Continue Reading] -

Apple updates MacBook Pro and MacBook Air -- hardware bumped, prices dropped
Publié: juillet 9, 2019, 3:51pm CEST par Mark Wyciślik-Wilson
Timed to coincide with the back to school season, Apple has announced the latest updates to its MacBook Pro and MacBook Air. There's a special promotion which includes a free pair of Beats Studio 3 Wireless headphones with a qualifying purchase too. A price drop for the MacBook Air means that students can pick one up for as little as $999 ($1,099 for everyone else) and benefit from the addition of True Tone to the Retina Display. The entry-level 13-inch MacBook Pro now features an 8th-generation quad-core processor which Apple says makes it twice as powerful as it used to… [Continue Reading] -

Zoom for Mac has a security hole that means your webcam could be turned on without permission
Publié: juillet 9, 2019, 3:04pm CEST par Mark Wyciślik-Wilson
Time to dig out the tape and cover up your webcam. The Mac version of the video conferencing tool Zoom has been found to have a flaw that enables a website to switch on your webcam without permission, and without notification. Despite having been discovered and reported to Zoom by a security researcher three months ago, the vulnerability is yet to be patched. In fact, Zoom disagrees that there is a security issue, although it does say that users will be granted greater control over videos in an update due for release later this month. The discovery was made by… [Continue Reading] -

Microsoft releases public preview of Desktop Analytics to help with Windows 10 update readiness checks
Publié: juillet 8, 2019, 7:11pm CEST par Mark Wyciślik-Wilson
Microsoft has released a public preview of cloud-connected service Desktop Analytics. Designed to help system administrators to keep Windows 10 devices up to date, Desktop Analytics integrates with System Center Configuration Manager. It allows for the quick and easy creation of app inventories to make compatibility checks simpler. See also: Compatibility issues stand in the way of installing Windows 10 May 2019 Update on some Macs Microsoft releases Windows 10 20H1 Build 18932 with notification improvements YAWN! Windows 10 19H2 is shaping up to be a dull release Brad Anderson, corporate vice president for Microsoft 365, says that the tool… [Continue Reading] -

Kali Linux arrives on Raspberry Pi 4
Publié: juillet 8, 2019, 6:27pm CEST par Mark Wyciślik-Wilson
Offensive Security has released Kali Linux for Raspberry Pi 4. The new build of the security-focused distro comes just two weeks after the launch of the Raspberry Pi 4, the most powerful version of the mini-computer yet. Offensive Security says that the new build takes advantage of everything the Pi 4 has to offer. See also: Raspberry Pi 4 is a complete desktop computer for just $35 Kali Linux sets out its roadmap for 2019/20 Kali Linux 2019.2 released with updated kernel and Kali Linux NetHunter The Kali Linux team says that in addition to the impressive hardware of the… [Continue Reading] -

Ubuntu-maker Canonical's GitHub account hacked
Publié: juillet 8, 2019, 5:43pm CEST par Mark Wyciślik-Wilson
Canonical -- the company behind the Ubuntu Linux distro -- is investigating an attack on its GitHub account over the weekend. On Saturday, hackers were able to break into Canonical's GitHub account and create a number of new repositories. Named CAN_GOT_HAXXD, the eleven repositories were empty and have now been removed. Canonical says that no source code was accessed, but it is not yet known who carried out the attack. See also: Canonical foolishly backpedals on 32-bit packages in Ubuntu Linux Steam will not support Ubuntu 19.10 onwards Ubuntu is dropping i386 support and WINE developers are irked Canonical Ltd… [Continue Reading] -

Mozilla set to offer ad-free browsing in Firefox for $5
Publié: juillet 5, 2019, 5:00pm CEST par Mark Wyciślik-Wilson
Advertising is the lifeblood of many websites, but at the same time it is something that few people are fans of. To stave off income-killing ad-blockers, an increasing number of sites offer per-article or per-month subscriptions that give people the chance to enjoy content free of ads while still supporting the sites they love. Mozilla has a different idea -- "Ad-free internet by Firefox". The result of a partnerships with multiple online publishers, the idea is that a single, low subscription fee gives you access to a number of sites with the ads removed. See also: Firefox embraces Microsoft BITS… [Continue Reading] -

Chinese border officers are gathering data from tourists' phones with a secret spy app
Publié: juillet 4, 2019, 9:17am CEST par Mark Wyciślik-Wilson
China's track record with privacy violations, control of the internet and control of its citizens is well known. But now anyone who has ever visited the country has cause for concern. Enter China via the border crossing between Xinjiang and Kyrgyzstan, and you're required to hand over your phone -- unlocked. This would obviously lead the owner to expect a little rooting around by officials, but an investigation has found that border officials are actually installing secret spy apps on iPhones and Android phones to scour emails, texts and other data stored on devices. The investigation -- carried out by… [Continue Reading] -

Compatibility issues stand in the way of installing Windows 10 May 2019 Update on some Macs
Publié: juillet 4, 2019, 8:41am CEST par Mark Wyciślik-Wilson
Some Mac users -- who, thanks to Boot Camp, are running Windows 10 on their Apple machine -- are encountering a problem upgrading to Windows 10 May 2019 Update (version 1903). A compatibility issue with the Mac HAL Driver (machaldriver.sys) is blocking the installation. The problem remains more than two months after the May 2019 Update was released, and Microsoft is still working away on a solution. See also: YAWN! Windows 10 19H2 is shaping up to be a dull release Microsoft releases Windows 10 20H1 Build 18932 with notification improvements Windows 10 is not creating registry backups -- and… [Continue Reading] -

YAWN! Windows 10 19H2 is shaping up to be a dull release
Publié: juillet 2, 2019, 9:06am CEST par Mark Wyciślik-Wilson
It is looking as though the next "feature update" for Windows 10 -- known as 19H2 to Insiders -- will be a little light on, er, features. In really, it seems as though Microsoft is treating the next big update very much like a service pack release. The news comes from Microsoft as the company sets out its plans for "evolving Windows 10 servicing and quality". In short, if you were looking forward to exciting new things to try out later this year, it might be a good idea to recalibrate your expectations. See also: Windows 10 is not creating… [Continue Reading] -

Windows 10 is not creating registry backups -- and is lying about it
Publié: juillet 1, 2019, 6:27pm CEST par Mark Wyciślik-Wilson
Towards the latter end of last year, it was noticed that Windows 10 was no longer creating backups of the registry. It was assumed to be a bug as the scheduled task that was used to create the backup still existed, and it was also indicated that the task had been a success. This was a lie. No registry backup was created, meaning potentially millions of users were left without a reliable way of rolling back the registry to an earlier time. Now Microsoft has explained what's going on, and says that the lack of registry backups is intentional. See… [Continue Reading] -

EA fixes a 'chain of vulnerabilities' that could have put millions of Origin gamers at risk
Publié: juin 29, 2019, 9:44am CEST par Mark Wyciślik-Wilson
EA has fixed a series of security issues on its Origin gaming service which could have been exploited by attackers to take control of user accounts and gain access to personal data. EA Origin's security flaws meant that more than 300 million gamers were put at risk. Israeli security firms Check Point said that attackers could take advantage of a "chain of vulnerabilities" to attack players of games such as FIFA, Maden NFL, NBA Live, UFC, The Sims, Battlefield, Command and Conquer, and Medal of Honor. See also: Security flaw in Dell SupportAssist tool puts millions of Windows systems at… [Continue Reading] -

Warning: In just a few days, the ebooks you've purchased from Microsoft will vanish
Publié: juin 28, 2019, 5:41pm CEST par Mark Wyciślik-Wilson
It's a little while since Microsoft announced that is dropping the Books category from the Microsoft Store, but a serious deadline is now looming. If you have bought books or downloaded free books from the Store, you only have a few more days to read them -- so if there are any you haven't finished, you'd better start reading quickly! While no specific date has been announced, Microsoft warns that you'll only be able to read your books "until early July 2019". See also: Microsoft notifies users whose systems are 'not quite ready' for Windows 10 May 2019 Update Millions… [Continue Reading] -

Microsoft notifies users whose systems are 'not quite ready' for Windows 10 May 2019 Update
Publié: juin 28, 2019, 9:45am CEST par Mark Wyciślik-Wilson
The Windows 10 May 2019 Update (that is, Windows 10 version 1903) has caused problems for a number of people, and there are various issues that stand in the way of getting hold of the upgrade. Rather than pushing out a problematic update to systems that it knows will not have a great experience, Microsoft has made a couple of decisions. Not only is the company blocking updates for computers with known compatibility issues, it is also starting to notify users that this is what's happening. See also: Windows 10 bug could slow shutdown by over a minute Windows Terminal… [Continue Reading] -

Millions of Microsoft Excel users vulnerable to remote DDE attack as new exploit is discovered
Publié: juin 27, 2019, 6:49pm CEST par Mark Wyciślik-Wilson
Security researchers from Mimecast Threat Center have discovered an Excel exploit that could leave 120 million users vulnerable to attack. The security flaw means that it is possible to use Excel's Power Query tool to dynamically launch a remote Dynamic Data Exchange (DDE) attack on a spreadsheet and actively control the payload. The researchers also found that Power Query could be used to embed malicious code in a data source and spread malware. See also: Security flaw in Dell SupportAssist tool puts millions of Windows systems at risk Over half of enterprises think security is lagging behind cloud adoption Netflix… [Continue Reading] -

Windows 10 bug could slow shutdown by over a minute
Publié: juin 26, 2019, 7:34am CEST par Mark Wyciślik-Wilson
It's usually the speed of a computer when using it that is of interest, but it's also important to factor in startup and shutdown times. Microsoft just confirmed a new bug in Windows 10 -- specifically Windows 10 October 2018 Update (1809) -- that could dramatically slow down shutdown and sleep times in some circumstances. The problem relates to USB Type-C devices, and while it has been fixed in Windows 10 version 1903, anyone using version 1809 remains affected and needs to be aware of the issue. See also: Windows Terminal preview now available to download Microsoft releases Windows 10… [Continue Reading] -

Amazon Prime Day 2019 will last two full days
Publié: juin 26, 2019, 6:51am CEST par Mark Wyciślik-Wilson
You'd think there was a clue in the name when it comes to determining how long Amazon's annual Prime Day lasts. But no. Not content with having stretched out the event for a day and a half last year, this time around Prime Day is actually two days long. This means that you'll have a massive 48 hours to bathe in naked consumerism -- and hopefully bag yourself a bargain or two along the way. Amazon has already shared details of some of the deals you can expect to see on July 15 and 16. See also: Amazon unveils all-new… [Continue Reading] -

NordVPN has a new password manager in the pipeline -- NordPass
Publié: juin 25, 2019, 3:00pm CEST par Mark Wyciślik-Wilson
NordVPN -- as its name suggests -- is perhaps most readily associated with its privacy and security-focused VPN solutions. But this is not all the company has to offer. Having already released a file encryption service in the form of NordLocker, NordVPN has now revealed that it has a new password management tool. Due for release later this year, NordPass has been designed to be secure yet simple to use, and NordVPN is trying to help people from making the mistake of using the same password everywhere. See also: Security software is causing Firefox users to lose saved passwords Hacker… [Continue Reading] -

Firefox embraces Microsoft BITS to install updates
Publié: juin 24, 2019, 11:11am CEST par Mark Wyciślik-Wilson
Starting with Firefox 68, Mozilla's web browser began to use Microsoft BITS (Background Intelligent Transfer Service) to deliver updates -- the same technique that is used by Windows Update. With the arrival of Firefox 70, BITS will be utilized with a dedicated update agent in place as a proxy rather than simply being part of the browser itself, allowing updates to be more easily installed. See also: Firefox needs an urgent firefix! Security software is causing Firefox users to lose saved passwords Mozilla promises to delete private data collected by Firefox fix and apologizes for add-on outage One of the… [Continue Reading] -

Steam will not support Ubuntu 19.10 onwards
Publié: juin 23, 2019, 3:57pm CEST par Mark Wyciślik-Wilson
It is only a few days since Canonical announced that it was dropping support for 32-bit packages as of Ubuntu 19.10. The fall out from this is now being felt. While there were many developers who were not happy with the decision, Linux-based gamers are now likely to be more than slightly annoyed. Steam has announced that "Ubuntu 19.10 and future releases will not be officially supported by Steam or recommended to our users". See also: Ubuntu is dropping i386 support and WINE developers are irked Kali Linux sets out its roadmap for 2019/20 Netflix discovers SACK Panic and other… [Continue Reading] -

Windows Terminal preview now available to download
Publié: juin 22, 2019, 3:23pm CEST par Mark Wyciślik-Wilson
At its Build 2019 developer conference earlier this year, Microsoft revealed the Linux-inspired Windows Terminal, which gives access to the Command Prompt, PowerShell, and WSL (Windows Subsystem for Linux) in one place. The code has been available to download and compile for a little while, but now Microsoft has released a ready-made Windows Terminal app for anyone to try out. See also: Leaked: Microsoft bans employees from using Slack, Kaspersky… even GitHub use is discouraged Windows Terminal is a new Linux-inspired command line app for Windows 10 Microsoft releases Chromium-based Edge for Windows 7 and 8.x Describing the open source… [Continue Reading] -

Leaked: Microsoft bans employees from using Slack, Kaspersky… even GitHub use is discouraged
Publié: juin 22, 2019, 11:59am CEST par Mark Wyciślik-Wilson
A leaked document has shed light on what it is like to work at Microsoft. It reveals the software and online services that Microsoft either prohibits or discourages employees from using, and there are some big names on the list. One of the most well-known tools to be slapped with a ban is Slack, with others including the grammar checker Grammarly and security software from Kaspersky. The cloud-version of Microsoft-owned GitHub features on a list of "discouraged" tools and services. See also: Microsoft releases Windows 10 20H1 Build 18922 to the Fast ring Microsoft releases Chromium-based Edge for Windows 7… [Continue Reading] -

ProtonMail criticizes Gmail's confidential mode for being neither secure nor private
Publié: juin 22, 2019, 10:47am CEST par Mark Wyciślik-Wilson
Privacy-focused ProtonMail has lashed out at Google, saying the "confidential mode" available in Gmail is "misleading" and "little more than a marketing strategy". It says that people "don't need to settle for fake privacy" Pointing out that Gmail's confidential mode lack end-to-end encryption, ProtonMail says that the email service is "not secure or private". The company says that Gmail can still read your emails, and that expiring emails are not as secure as Google would have users believe. See also: There will be no more tablets from Google Google confirms that second-hand Nest Cams could have been used to spy… [Continue Reading] -

Ubuntu is dropping i386 support and WINE developers are irked
Publié: juin 21, 2019, 4:47pm CEST par Mark Wyciślik-Wilson
As of version 19.10, Ubuntu will no longer support i386. With the arrival of Eoan Ermine, Ubuntu is severing 32-bit ties, and some developers are concerned. The move is not entirely unexpected. The Ubuntu developers had previously said it would make an i386 decision in the middle of 2019. That time having rolled around, the Ubuntu engineering team says that it "has reviewed the facts before us and concluded that we should not continue to carry i386 forward as an architecture". WINE developers are among those unhappy with the decision. See also: Kali Linux sets out its roadmap for 2019/20… [Continue Reading] -

There will be no more tablets from Google
Publié: juin 21, 2019, 12:20pm CEST par Mark Wyciślik-Wilson
Google is getting out of the tablet-making business, but says that it will continue to produce smartphones and laptops. The announcement means that Google is ceasing work on two unreleased Pixel tablets, with the company's head of hardware saying: "Google's hardware team will be solely focused on building laptops moving forward". While ditching tablets is not entirely surprising, Google is said to have been working on two new tablets until as recently as this week. See also: Google confirms that second-hand Nest Cams could have been used to spy on people Google is bringing RCS messaging to users directly instead… [Continue Reading] -

Security flaw in Dell SupportAssist tool puts millions of Windows systems at risk
Publié: juin 21, 2019, 9:23am CEST par Mark Wyciślik-Wilson
A Windows support tool bundled with Dell computers has a high-severity security hole that leaves millions of systems at risk of a privilege-escalation attack. Dell has announced that both the Business and Home versions of its SupportAssist tool have a security vulnerability within the PC Doctor component that requires immediate patching. The discovery was made by SafeBreach, and there could be over 100 million systems that are affected. See also: Netflix discovers SACK Panic and other Linux security flaws Security software is causing Firefox users to lose saved passwords VLC 3.0.7 includes more security fixes than ever thanks to the… [Continue Reading] -

Google confirms that second-hand Nest Cams could have been used to spy on people
Publié: juin 21, 2019, 7:26am CEST par Mark Wyciślik-Wilson
There been many concerns voiced about the privacy and security implications of many smart products. Some are well-founded, as a new admission from Google that its Nest Cams could be used to spy on people goes to show. The problem does not center around hackers, but people who have sold or given away their Nest Cams. Even after the new owner performed a factory reset of the camera -- following Google's own instructions -- it was still possible for the original owner to access the camera feed. See also: Google is bringing RCS messaging to users directly instead of waiting… [Continue Reading] -

Kali Linux sets out its roadmap for 2019/20
Publié: juin 20, 2019, 2:08pm CEST par Mark Wyciślik-Wilson
Offensive Security, the team behind the security-focused, Debian-based, penetration testing Linux distro Kali Linux. has set out the roadmap for the operating system for the months ahead. This is the first time such a roadmap has been shared for Kali Linux, and it gives us a good idea of what to expect between now and 2020. The team says: "normally, we only really announce things when they are ready to go public, but a number of these changes are going to impact users pretty extensively so we wanted to share them early". See also: Linux Mint vs Windows 10 --… [Continue Reading] -

Microsoft releases Chromium-based Edge for Windows 7 and 8.x
Publié: juin 20, 2019, 12:33pm CEST par Mark Wyciślik-Wilson
After embracing the Chromium engine for Edge, Microsoft is gradually expanding the number of platforms the browser is available for. Starting off as a Windows 10 browser and then spreading to macOS, there is currently talk of Linux being in Microsoft's sights. For now, however, it is Windows 7 and 8 users who are the latest to have Microsoft Edge available as a browser option. See also: Microsoft Edge could come to Linux Chromium-based Microsoft Edge pretends to be different browsers by switching user agent How to enable dark mode in new Chromium-based Microsoft Edge If you're running Windows 7,… [Continue Reading] -

Apple teams up with Best Buy to expand repair services to hundreds of stores
Publié: juin 20, 2019, 11:43am CEST par Mark Wyciślik-Wilson
The next time you have a problem with your Apple product -- be it an iMac, MacBook, iPhone or iPad -- you could take it to Best Buy for repair rather than an Apple store. The new repair options are thanks to Apple's expansion of its authorized service network. There are almost 1,000 Best Buy stores with over 7,600 newly Apple-certified Geek Squad technicians ready to help you out. See also: Feast your eyes on how Apple's iPhone 11 should look Apple makes Windows 10 less terrible with refreshed iCloud app in Microsoft Store Apple explains what the closure of… [Continue Reading] -

Firefox needs an urgent firefix!
Publié: juin 19, 2019, 1:17pm CEST par Mark Wyciślik-Wilson
If you're a Firefox user, now is the time to update your browser. A zero-day vulnerability has been discovered which is being actively exploited in targeted attacks. The security hole was revealed via Google's Project Zero, and it affects ALL versions of Firefox. In short, if you have not updated to Firefox 67.0.3 or Firefox ESR 60.7.1, you need to do so right now. See also: Security software is causing Firefox users to lose saved passwords Firefox unveils new-look logo and introduces new parent brand Mozilla promises to delete private data collected by Firefox fix and apologizes for add-on outage… [Continue Reading] -

Google is bringing RCS messaging to users directly instead of waiting for carriers
Publié: juin 18, 2019, 10:37am CEST par Mark Wyciślik-Wilson
There has been much talk about SMS successor RCS (Rich Communication Service) over the last year or so, but there has been little in the way of action. But this is about to change. Seemingly tired of carriers and handset makers dawdling, Google is bringing RCS messaging to Android users in the UK and France. With Google taking control of RCS, the service could become the company's version of iMessage before long, and it means users will be able to experience it sooner than they might have expected. See also: com uses clever entrapment technique and accuses Google of stealing… [Continue Reading] -

BitDefender releases free decryption tool for GandCrab ransomware
Publié: juin 18, 2019, 10:02am CEST par Mark Wyciślik-Wilson
Security firm BitDefender has teamed up with the FBI, Europol and other agencies and created decryption software that enables ransomware victims to get their data back for free. The tool can be used to retrieve files encrypted by the GandCrab family of ransomware which is thought to have originated in Russia. GandCrab has been active for around a year and a half, and hundreds of thousands of people have fallen victim to it. See also: Netflix discovers SACK Panic and other Linux security flaws Humans are still the weakest link in information security Security software is causing Firefox users to… [Continue Reading] -

Netflix discovers SACK Panic and other Linux security flaws
Publié: juin 18, 2019, 9:30am CEST par Mark Wyciślik-Wilson
A number of Linux and FreeBSD servers and systems are vulnerable to a denial of service vulnerability dubbed SACK Panic, as well as other forms of attack. A total of three security flaws were discovered by Jonathan Looney of Netflix Information Security. A series of malicious packets sent to vulnerable system is all it takes to crash or slow them down -- a remotely-triggered kernel panic. Patches and workaround have been released to help plug the holes. See also: Microsoft advises Azure customers to update Exim to avoid a Linux worm OpenMandriva Lx 4.0 Linux distro is here, and there… [Continue Reading] -

Microsoft advises Azure customers to update Exim to avoid a Linux worm
Publié: juin 17, 2019, 5:07pm CEST par Mark Wyciślik-Wilson
Microsoft has issued a warning to Azure customers using Linux Exim email servers running Exim version 4.87 to 4.91. The company explains that these versions of Exim are vulnerable to a critical Remote Code Execution (RCE) security flaw and need to be updated to prevent the spread of a worm. See also: OpenMandriva Lx 4.0 Linux distro is here, and there is a special AMD-only version Microsoft Edge could come to Linux Microsoft releases Windows 10 20H1 Build 18917 with Windows Subsystem for Linux 2 (WSL 2) The security vulnerability in question is CVE-2019-10149, and Microsoft stresses that Azure customers running virtual… [Continue Reading] -

The Twitter app is returning to macOS
Publié: juin 16, 2019, 12:28pm CEST par Mark Wyciślik-Wilson
For more than a year, macOS users have been without an official desktop Twitter client -- more on that shortly. But now, thanks to Project Catalyst for macOS 10.15 Catalina, a Twitter app is making its way back to Mac. Twitter says that Apple's Project Catalyst means that it has been easy to use the code from the iOS version of the client to create a native macOS app. The company has also revealed just why it was the Mac Twitter client disappeared in the first place. See also: Twitter looks into whether white nationalists and supremacists should be banned… [Continue Reading] -

Microsoft Edge could come to Linux
Publié: juin 15, 2019, 4:41pm CEST par Mark Wyciślik-Wilson
Not so long ago, the idea of Microsoft releasing an internet browser for Linux would seem to be out of the question. But in recent years, Microsoft's love of Linux has grown exponentially. Now, having not only started to embrace the Chromium engine for Microsoft Edge, the company is also not ruling out releasing Edge for Linux. It could be argued that Edge on Linux is something that no one -- or at least very few people -- yearn for, but the Microsoft Edge development team has revealed that releasing a Linux-friendly version is something that it would "like to… [Continue Reading] -

Google Photos will soon stop syncing to Google Drive
Publié: juin 14, 2019, 12:34pm CEST par Mark Wyciślik-Wilson
If you have come to rely on Google Drive to automatically backup the images you have in Google Photos, you may have to find another option very soon. Google has announced that as of July, the way Google Drive and Google Photos integrate with each other is changing. In short, Google Photos will no longer be automatically synchronize with Google Drive. The change is coming because Google says it has, "feedback that the connection between these services is confusing". See also: Chrome 76 makes it easier to get around paywalls Google's streaming game service, Stadia, launches in November with an… [Continue Reading] -

Security software is causing Firefox users to lose saved passwords
Publié: juin 14, 2019, 12:02pm CEST par Mark Wyciślik-Wilson
Firefox users are reporting that their saved passwords have been lost, with the problem seemingly caused by antivirus software rather than being an issue with Firefox itself. Antivirus software such as Avast and AVG appears to be corrupting the file in which Firefox stores passwords, rendering it unreadable. Thankfully, passwords can be recovered, but -- for the time being --- they will be corrupted again when you restart your computer. See also: Firefox unveils new-look logo and introduces new parent brand Mozilla promises to delete private data collected by Firefox fix and apologizes for add-on outage Mozilla issues new Firefox… [Continue Reading] -

Hacker hits Symantec and accesses passwords
Publié: juin 14, 2019, 11:38am CEST par Mark Wyciślik-Wilson
Security firm Symantec was attacked by a hacker back in February, but the company did not reveal details of the incident. The attack has been brought to light by Guardian Australia which has seen some of the data extracted by hackers. This comprises not only passwords, but what is thought to be a list of Symantec clients -- including government agencies. But Symantec is downplaying the data breach, dismissing it as a "minor incident". See also: Rowhammer-based RAMBleed exploit lets hackers steal data from memory Flipboard hacked -- attackers had access to database of user information for 9 months Google… [Continue Reading] -

Chrome 76 makes it easier to get around paywalls
Publié: juin 14, 2019, 10:59am CEST par Mark Wyciślik-Wilson
Google is busy working away on Chrome 76, and the beta version of the browser includes a change that will please anyone looking to bypass paywalls and view articles for free. Many people switch to Incognito Mode, aware that this makes it possible to access paywalled articles on sites such as the New York Times. Many sites offer a number of free articles to non-paying visitors, and using this mode makes it impossible to determine whether you have reached your free article limit or not. As such, some sites blocked access to anyone using Incognito Mode -- but Chrome 76… [Continue Reading] -

CERN is moving away from expensive Microsoft software and embracing open source
Publié: juin 13, 2019, 10:45am CEST par Mark Wyciślik-Wilson
CERN -- the European Organization for Nuclear Research best known for its particle smashing Large Hadron Collider -- has decided to eschew Microsoft in favor of open source software. For many years, CERN benefited from hefty discounts on Microsoft products, but this is coming to an end. Rather than paying hugely increased licensing fees, the organization is instead implementing its own Microsoft Alternatives project, known as MAlt. CERN says it is "taking back control using open software". See also: Microsoft releases Windows 10 20H1 Build 18917 with Windows Subsystem for Linux 2 (WSL 2) Apple makes Windows 10 less terrible… [Continue Reading] -

Rowhammer-based RAMBleed exploit lets hackers steal data from memory
Publié: juin 12, 2019, 2:04pm CEST par Mark Wyciślik-Wilson
Security researchers have revealed an exploit that can be used by hackers to steal data from DRAM, even if ECC protection is in place. RAMBleed is a Rowhammer-based attack that can also be used to alter data and increase privilege levels. Taking advantage of the design of modern memory chips, a Rowhamer attack works by "hammering" the physical rows of data in quick succession causing bit-flipping in neighboring rows. RAMBleed takes this in a different direction, using a similar technique to access data stored in physical memory. See also: VLC 3.0.7 includes more security fixes than ever thanks to the… [Continue Reading] -

Facebook will pay you to gather information from you
Publié: juin 12, 2019, 12:30pm CEST par Mark Wyciślik-Wilson
That Facebook gathers personal information from its users should come as no surprise -- it could be argued that it is the social network's raison d' être. Following numerous privacy scandals, and the controversial (and since-closed) Research and Onavo programs, Facebook is now ready to be open about its data collection, and is even willing to pay people for this. The new "Study from Facebook" app gives Facebook users the chance to volunteer to share information about their app usage -- and get paid for divulging this information. Sound good to you? See also: New York attorney general to investigate… [Continue Reading] -

Firefox unveils new-look logo and introduces new parent brand
Publié: juin 11, 2019, 2:59pm CEST par Mark Wyciślik-Wilson
Firefox has revealed its redesigned branding, including a new icon for its web browser, as well an introducing the logo for the new Firefox parent brand, some 18 months in the pipeline. As well as a new look, the icon features an updated color palette which is not just about aesthetics, but also accessibility. There's also a new, modern typeface, as well as what's being described as a "new shape system". Firefox says that the color palette it has chosen opens up new possibilities and allows for distinctive gradients, and a rounded typeface has been chosen to fit in with… [Continue Reading] -

VLC 3.0.7 includes more security fixes than ever thanks to the European Commission
Publié: juin 11, 2019, 11:34am CEST par Mark Wyciślik-Wilson
Version 3.0.7 of VLC has been released, and while it may seem like a minor x.x.x update, it includes more security fixes than any other previous release -- including two high security issues. Jean-Baptiste Kemp, the president of VLC-maker VideoLAN, says the number of fixes included in this version is due to the EU-FOSSA bug bounty program, funded by the European Commission. VideoLAN has reaped the benefits of the European bug bounty program, and the organization -- due to being a no-profit -- has previously said that it was unable to fund such a program of its own. Kemp says… [Continue Reading] -

US Customs and Border Protection says photos of thousands of travelers were stolen in a data breach
Publié: juin 11, 2019, 11:06am CEST par Mark Wyciślik-Wilson
Hackers have stolen the photographs of travellers entering and leaving the US, as well as photos of their license plates, US Customs and Border Protection (CBP) has said. The cyberattack was carried out on the network of a federal subcontractor, and the images were taken as part of a "malicious cyberattack". Although the hack attack has only just been revealed publicly, CBP first learned of it on May 31. See also: Flipboard hacked -- attackers had access to database of user information for 9 months Google recalls Bluetooth version of Titan Security Key after discovering hacking vulnerability Hackers steal $40… [Continue Reading] -

Microsoft reveals Project Scarlett, its powerful next-gen Xbox console with 8K graphics coming in 2020
Publié: juin 10, 2019, 9:53am CEST par Mark Wyciślik-Wilson
At E3, Microsoft has revealed details of its next-generation Xbox, dubbed Project Scarlett, which is scheduled for release in late 2020. It's not yet known what the follow-up to the Xbox One will be called, but among the launch titles is Halo Infinite. As for the console hardware, Project Scarlett will feature an AMD Zen 2 chip, Radeon RDNA graphics architecture, GDDR6 memory, SSD, and support for 120 fps, 8K graphics along with real-time ray tracing. See also: Microsoft takes down huge MS-Celeb-1M facial recognition database Microsoft releases Windows 10 20H1 Build 18912 to the Fast ring Microsoft is closing… [Continue Reading] -

Microsoft takes down huge MS-Celeb-1M facial recognition database
Publié: juin 7, 2019, 5:02pm CEST par Mark Wyciślik-Wilson
Microsoft has deleted a database containing around 10 million photographs that was being used to train facial recognition systems. Known as MS-Celeb-1M, the database was created in 2016, and originally contained photos of celebrities. Over time, however, images of writers, journalists and others crept in, and ultimately 100,000 individuals were to be found in it. Microsoft has not made much noise about the deleted content, but has said that the database was wiped as the person maintaining it was no longer a company employee. See also: Microsoft releases Windows 10 20H1 Build 18912 to the Fast ring Microsoft and Oracle… [Continue Reading] -

Apple explains what the closure of iTunes means for you and your music
Publié: juin 7, 2019, 11:04am CEST par Mark Wyciślik-Wilson
At WWDC this week, Apple not only unveiled the new Mac Pro and an insanely expensive monitor stand, but also confirmed that iTunes is going away -- for Mac users, at least. This did not come entirely as a surprise, but it has left iTunes users wondering just how the transition to the new Apple Music app will work, and what will happen to their music, playlists, credit and so on. Now Apple has explained how the whole process will work. See also: Bye bye, iTunes -- we never really loved you anyway 'Sign in with Apple' neatly balances privacy… [Continue Reading] -

Google's streaming game service, Stadia, launches in November with an impressive line-up of games
Publié: juin 7, 2019, 10:11am CEST par Mark Wyciślik-Wilson
Google's much-anticipated cloud gaming service, Stadia, is due to launch in November. The company has revealed the launch date, as well as details of pricing and the games you can expect to play -- including Baldur's Gate III. In all, there are over 30 games confirmed for Stadia, and Google is ramping up the hype by giving gamers the chance to pre-order right now. Anyone placing an order for the Stadia Founder's Edition can enjoy a number of benefits including a limited edition controller and three months of Stadia Pro, the subscription option that gives access to some games. See… [Continue Reading] -

YouTube clamps down on hate speech by banning supremacism, Holocaust denial and more
Publié: juin 6, 2019, 2:07pm CEST par Mark Wyciślik-Wilson
YouTube's on-going battle against hate speech on its platform continues, and the site has just announced new policies that it hopes will help to further curb the problem. As part of its new rules, YouTube is now taking a tougher stance against discriminatory material, banning supremacist videos such as those that promote Nazism. Also banned are videos that seek to spread misinformation by denying that "well-documented violent events", such as the Sandy Hook Elementary shooting, ever occurred. Holocaust denial is also banned. See also: Confirmed: YouTube Originals content will be free YouTube disables comments on videos of minors because of… [Continue Reading] -

BlueKeep Windows vulnerability is so serious, even the NSA wants you to patch your system
Publié: juin 6, 2019, 1:11pm CEST par Mark Wyciślik-Wilson
It's around three weeks since Microsoft first urged Windows users to patch their systems against the BlueKeep (CVE-2019-0708) vulnerability. Concerned that not enough people were taking notice, the company then issued a further warning stressing the importance of installing a patch. Now the NSA has got involved, joining Microsoft in begging users to secure their Windows XP and Windows 7 computers. The agency says that is "concerned that malicious cyber actors will use the vulnerability in ransomware and exploit kits containing other known exploits, increasing capabilities against other unpatched systems". See also: Microsoft implores Windows users to install patch for… [Continue Reading] -

Applying for a US visa? Prepare to hand over your social media account details
Publié: juin 3, 2019, 12:55pm CEST par Mark Wyciślik-Wilson
As announced a little over a year ago, US visa applicants should now expect to be asked for details of their social media accounts. Only certain types of diplomatic and official visa applications are exempt. As of Friday, the US State Department started to use social media usernames, email addresses and phone numbers as part of its screening process. The use of "social media identifiers" for vetting purposes will apply to almost everyone applying for a US visa, raising all manner of privacy concerns. See also: Banned from social media? Feeling persecuted and censored? Report it to Donald Trump! Twitter… [Continue Reading] -

Bye bye, iTunes -- we never really loved you anyway
Publié: juin 1, 2019, 10:07am CEST par Mark Wyciślik-Wilson
Apple is due to kick off its Worldwide Developers Conference on Monday, and at the event the company is expected to kill off iTunes. Having been with us for nearly two decades, it seems that the software everyone (well, a lot of people) loves to hate is finally being put out to pasture. At WWDC we should see Apple kill off iTunes, breaking it up into a number of individual apps for macOS, just as has happened on iOS. See also: The iPhone-maker doth protest too much? Apple launches new site to wax lyrical about the App Store in the… [Continue Reading] -

Microsoft releases first preview of PowerShell 7 and sets out feature roadmap
Publié: juin 1, 2019, 9:42am CEST par Mark Wyciślik-Wilson
Having already announced that PowerShell 7 will be the next version of PowerShell, Microsoft has released the first public preview. For the first time, PowerShell is based on .NET Core 3.0. The command-line shell and scripting language is set to be updated on a monthly basis, so we can expect a few more preview versions before it hits general availability around a month after .NET Core 3.0. As well as releasing this first preview, Microsoft has also shared details of the PowerShell 7 roadmap. See also: Microsoft implores Windows users to install patch for wormable BlueKeep Remote Code Execution vulnerability… [Continue Reading] -

Microsoft implores Windows users to install patch for wormable BlueKeep Remote Code Execution vulnerability
Publié: juin 1, 2019, 9:11am CEST par Mark Wyciślik-Wilson
Two weeks after warning about a critical Remote Code Execution vulnerability in Remote Desktop Services, Microsoft is concerned that around a million internet-connected computers remain unpatched and vulnerable to attack. The company says that there is a risk that CVE-2019-0708, or BlueKeep, could turn into the next WannaCry if steps aren't taken to secure systems. While there is not yet any sign of a worm that exploits the vulnerability, proofs of concept do exist, and it could only be a matter of time before this changes. Microsoft is taking the matter so seriously, that it even released security patches for… [Continue Reading] -

Undetectable HiddenWasp backdoor malware hits Linux users, allowing for full control of infected systems
Publié: mai 31, 2019, 1:43pm CEST par Mark Wyciślik-Wilson
Using code from the famous Mirai worm and the Azazel rootkit, HiddenWasp is a newly discovered malware strain targeting Linux systems. HiddenWasp is slightly unusual in having Linux in its sights, and the targeted remote control tool is able to avoid detection by all major antivirus software. The malware is described as "sophisticated" as it comprises a deployment script, a trojan and a rootkit. This an advanced backdoor attack tool that allows for complete remote control of a system. See also: openSUSE Leap 15.1 Windows Subsystem for Linux distro lands in the Microsoft Store Quake II RTX is coming to… [Continue Reading] -

Leaked: take a look at Cloudflare's free VPN, Warp
Publié: mai 31, 2019, 8:24am CEST par Mark Wyciślik-Wilson
Cloudflare's 1.1.1.1 DNS switching tool has proved very popular with iOS and Android users looking to take control of their internet connections, and there was much excitement when the company announced that it would be releasing a free VPN tool called Warp. At the moment, there is a lengthy waiting list for the free VPN (I'm number 278100 on the list, for instance) but we've been given a sneak peak at what to expect. Leaked screenshots show off the free VPN, and a video gives you an idea of the sort of performance you can expect. See also: Cloudflare announces… [Continue Reading] -

Twitter looks into whether white nationalists and supremacists should be banned
Publié: mai 30, 2019, 11:04am CEST par Mark Wyciślik-Wilson
In a world that appears to be lurching ever further to the right, it is perhaps little wonder that white nationalists, white supremacists and other extremists are becoming more prevalent online. Social media sites have a balancing act to perform -- not wanting to be seen to be advocating censorship, but also removing troublesome elements from their networks. And this is the problem that Twitter faces. The platform has long been home to a glut of racist content and users -- as well as other unsavoury material -- and now the site is conducting research to determine how best to… [Continue Reading] -

The iPhone-maker doth protest too much? Apple launches new site to wax lyrical about the App Store in the face of criticism
Publié: mai 30, 2019, 9:46am CEST par Mark Wyciślik-Wilson
Apple has become more familiar with controversy than it might be entirely comfortable with in recent times. Once a near-untouchable company that could, in many people's eyes, do no wrong, there have been numerous scandals over the last few years -- legal battles, problematic hardware, canceled products, and accusations of anticompetitive behavior. Faced with an antitrust legal battle after complaints of "monopolistic" practices in the App Store, Apple has launched a new site that appears to be a very public defense of what it stands accused of. The new "principles and practices" pages find Apple going out of its way,… [Continue Reading] -

Apple agrees to warn users if iOS updates will slow down iPhones
Publié: mai 28, 2019, 9:40am CEST par Mark Wyciślik-Wilson
An update to any operating system, be it mobile or desktop, is a mix-bag of positives and negatives. Exciting new features have deprecation as a counterpoint, and while there is always the hope that updates will improve things, there is always the danger that things will actually get worse. If you're concerned that updating your iPhone to the latest version of iOS will result in a reduction in performance, there's some good news. Apple has agreed to warn people if an update is "expected to materially change the impact of performance management on their phones". See also: Teardown reveals just… [Continue Reading] -

Windows 10 May 2019 Update causes Wi-Fi dropouts for some users
Publié: mai 28, 2019, 8:52am CEST par Mark Wyciślik-Wilson
If you have a computer with a Qualcomm Wi-Fi adaptor, you could well find that you suffer from random connection dropouts after installing Windows 10 May 2019 Update. The problem stems from a problem with older Wi-Fi drivers, and to avoid problems for user Microsoft has chosen to halt the rollout of the update to systems that could be affected. In addition, the company has issued a warning against manually or forcibly installing the May 2019 Update. See also: Here are all the features Microsoft removed or deprecated in Windows 10 May 2019 Update Force Windows 10 to install the… [Continue Reading] -

Bittium announces the world's most secure smartphone: the Bittium Tough Mobile 2
Publié: mai 27, 2019, 12:21pm CEST par Mark Wyciślik-Wilson
In a world that is increasingly concerned about privacy and security, Bittium launches the Tough Mobile 2. Proudly billed as "the world's most secure smartphone" it takes a multilayered approach to security, combining both hardware and software solutions. More than just secure, the Bittium Tough Mobile 2 -- as the use of the word "tough" would imply -- is also a rugged phone (although it does not proclaim to be the toughest phone in world). Designed and manufactured in Finland, the phone is aimed at professionals, and boasts "ultra secure communications without compromising usability". Running Android 9 Pie, security for… [Continue Reading] -

Intel announces ultra-fast 8-core Special Edition Core i9 9900KS; AMD fights back with super-cheap 7nm 12-core Ryzen 9 3900X
Publié: mai 27, 2019, 11:07am CEST par Mark Wyciślik-Wilson
Today at Computex 2019, Intel and AMD have both unveiled their latest chips. Intel previewed its Special Edition Core i9 9900KS, an 8-core chip with the unique ability to run all of the cores at 5GHz simultaneously. The company also revealed details of Ice Lake, its 10nm mobile processors. At the same time, AMD has also announced the Ryzen 3000 range of CPUs. Included in this range is the Ryzen 9 3900X, a 12-core chip running at 4.6GHz -- for the bargain price of $499. See also: Compulab Airtop3 Linux Mint mini computer has fanless Intel Core i9 9900K and… [Continue Reading] -

Teardown reveals just what Apple has done to improve the MacBook Pro 2019 keyboard
Publié: mai 24, 2019, 5:46pm CEST par Mark Wyciślik-Wilson
Apple recently launched its fastest MacBook Pro ever, featuring a processor with up to eight cores. But as well as speed, improvements have also been made to the keyboard design, and the material used in it. Rather than waiting for Apple to reveal its secrets, iFixit decided to subject the MacBook Pro 15" Touch Bar 2019 to one of its infamous teardowns to find out for itself. Scientific analysis of the material gives an insight into its composition. See also: Apple addresses Flexgate with MacBook Pro display backlight service program and expands keyboard repair program US Supreme Court rules antitrust… [Continue Reading] -

Samsung Galaxy Fold pre-orders canceled by BestBuy
Publié: mai 24, 2019, 4:52pm CEST par Mark Wyciślik-Wilson
The launch of the Samsung Galaxy Fold has been, er, problematic to say the least. After serious issues were discovered with the folding screen, the company first announced a postponement to the launch, and then told people who had placed pre-orders that their orders would be canceled. Now BestBuy has followed suit, announcing that it too is canceling pre-orders. The retailer says that Samsung has faced "a plethora of unforeseen hiccups", and because the company has failed to provide a new release date, BestBuy feels it is only fair to its customers to cancel the orders. See also: It's decision… [Continue Reading] -

Kali Linux 2019.2 released with updated kernel and Kali Linux NetHunter
Publié: mai 23, 2019, 11:25am CEST par Mark Wyciślik-Wilson
Three months after the last major release, it's time for the second Kali Linux release of the year. Kali Linux 2019.2 is here, and in addition to an updated kernel, there's also an updated version of Kali Linux NetHunter, complete with support for more Android devices. Offensive Security says that the Debian-based Kali Linux 2019.2 is primarily about tweaks and bug fixes, but there are still a number of updated tools included. See also: Yet another Linux distribution shuts down, and the Open Source community should be worried Kali Linux 2019.1 with Metasploit 5.0 available for download openSUSE Leap 15.1… [Continue Reading] -

Exploit developer SandboxEscaper reveals Windows 10 Task Scheduler zero-day -- and says there are more to come
Publié: mai 22, 2019, 11:44am CEST par Mark Wyciślik-Wilson
Well-known security researcher and revealer of exploits SandboxEscaper has released details of a Windows 10 zero-day that affects Task Scheduler. This is far from being the first time we've heard from SandboxEscaper, and this time around the exploit could enable an attacker to gain full control of Windows 10 or Windows Server files. The researcher has previously revealed details of numerous other security vulnerabilities in Windows, and promises: "I have four more unpatched bugs where that one came from". Furthermore, she says: "I'm donating all my work to enemies of the US". SandboxEscaper shared her most recent findings on GitHub… [Continue Reading] -

Linux kernel RDS flaw affects Red Hat, Ubuntu, Debian and SUSE
Publié: mai 20, 2019, 11:25am CEST par Mark Wyciślik-Wilson
If you're not in the habit of keeping up to date with the latest version of the Linux kernel, now might be a good time to think about doing so. Systems based on versions of the kernel older than 5.0.8 suffer from a severe flaw in the implementation of RDS over TCP. Left unpatched, the flaw could enable an attacker to compromise a system. The National Vulnerability Database entry says: "There is a race condition leading to a use-after-free, related to net namespace cleanup". Red Hat, Ubuntu, Debian and SUSE are all affected by the flaw, and security advisories have… [Continue Reading] -

Google is using Gmail to track your purchases
Publié: mai 18, 2019, 9:51am CEST par Mark Wyciślik-Wilson
Google's business relies on gathering information about its users and customers, so the company take every opportunity it can to reap as much data as possible. As such, it should surprise no one to learn that Google has been using Gmail to keep a record of things you have bought -- both online and offline. A little-known page (it's not exactly secret, but nor is it made particularly obvious) of your Google account reveals years of purchases. Google insists that the data on the Purchases page can only be seen by individuals, and is not used to tailor ads, but… [Continue Reading] -

RIP Grumpy Cat: The meme and internet phenomenon is dead
Publié: mai 17, 2019, 5:47pm CEST par Mark Wyciślik-Wilson
Grumpy Cat, the feline subject of many memes, has died at the age of 7. The internet celebrity rose to fame because of her delightfully dour demeanour and a sour face that made the online world smile. An internet celebrity for seven years, Grumpy Cat (aka Tardar Sauce) shuffled off this mortal coil this week, leaving the web a sadder place. Grumpy Cat's owners confirmed that the feline died on Tuesday this week, saying: "Despite care from top professionals, as well as from her very loving family, Grumpy experienced complications from a recent urinary tract infection that unfortunately became too… [Continue Reading] -

Microsoft now lets you install Ubuntu Linux in Windows 10 using the Hyper-V Manager
Publié: mai 17, 2019, 2:05pm CEST par Mark Wyciślik-Wilson
Microsoft has been gradually hugging Linux closer to its heart, making it ever easier to install Linux-based operating systems within Windows 10. Now Ubuntu fans have a new option when it comes to installing their favorite distro. It is now possible to install either Ubuntu 18.04 LTS or 19.04 using Windows 10's Hyper-V Manager -- the admin tool designed to make it easy to manage virtual machines. See also: How to check if your Windows or Linux system is vulnerable to Microarchitectural Data Sampling (MDS) attacks BTW I use Arch Linux... on Windows 10 Google says all new Chromebooks will… [Continue Reading] -

Banned from social media? Feeling persecuted and censored? Report it to Donald Trump!
Publié: mai 17, 2019, 12:05pm CEST par Mark Wyciślik-Wilson
The White House has launched a new tool that enables people to report the fact that they have been kicked off the likes of Twitter, Facebook, Instagram and YouTube. The tool is aimed at people who have had their social media presence curtailed and "suspect political bias" is involved. Anyone who feels aggrieved is invited to "share your story with President Trump". See also: New York attorney general to investigate Facebook for scraping 1.5 million users' email contacts How to delete the contacts that Facebook may have scraped from you Privacy: Facebook 'unintentionally' scraped and uploaded 1.5 million users' email… [Continue Reading] -

Google recalls Bluetooth version of Titan Security Key after discovering hacking vulnerability
Publié: mai 16, 2019, 11:05am CEST par Mark Wyciślik-Wilson
Google is recalling the Bluetooth Low Energy (BLE) version of its Titan Security Key, and is offering free replacements to owners. The recall comes after the company became aware of a security issue which could allow a nearby hacker to hijack the security device. Google says that the security issue only affects the Bluetooth versions of the 2FA device sold in the US. In a blog post, Google Cloud product manager Christiaan Brand explains that the vulnerability stems from a misconfiguration in the Titan Security Keys' Bluetooth pairing protocols. This not only makes it possible to communicate with the key… [Continue Reading] -

Trump invokes National Emergencies Act effectively banning Huawei from US
Publié: mai 16, 2019, 10:42am CEST par Mark Wyciślik-Wilson
Donald Trump has declared a national emergency to fight "foreign adversaries" which he says are "increasingly creating and exploiting vulnerabilities in information and communications technology". An executive order means that US companies are banned from buying and using foreign telecoms equipment which is deemed to be a threat to national security. Huawei and 70 affiliates have also been added to the US Commerce Department’s "Entity List" meaning that special approval would be needed to purchase such equipment, and also for companies deemed to pose a threat to buy US-made hardware. The move comes at a time when tensions run high… [Continue Reading] -

Here is the OnePlus 7 Pro (oh, and the OnePlus 7)
Publié: mai 14, 2019, 7:42pm CEST par Mark Wyciślik-Wilson
True to form, the launch of the latest OnePlus handsets have been preceded by numerous leaks, rumors and teasers. As such, today's launch of the OnePlus 7 and OnePlus 7 Pro contained few surprises, but the phones are now here and the launch confirms and clarifies many details. The OnePlus 7 Pro is at the top of the range. Boasting a 90Hz QHD+ Display, Snapdragon 855 and the option of up to 12GB of RAM. Then, of course, there are the cameras. The controversial pop-up design of the selfie camera isn't going to be to everyone's liking, but the specs… [Continue Reading] -

Privacy: Twitter 'inadvertently' collected and shared location data of some users
Publié: mai 14, 2019, 9:25am CEST par Mark Wyciślik-Wilson
Social media services are hardly regarded as bastions of privacy, and the latest slip-up by Twitter goes some way to showing why. Twitter has revealed that it "may have accidentally collected location data" about users, that this data was shared with one of its "trusted partners". Twitter blames the "inadvertent" data collection on a bug, and says that the issue affects some iOS users. It also says that precise location data was not collected or shared, but zip code or city-level only. See also: Privacy: Microsoft wants to (sneakily) collect more data from users via Office Privacy: HMRC forced to… [Continue Reading] -

WhatsApp users urged to install app update to patch serious spyware vulnerability
Publié: mai 14, 2019, 9:01am CEST par Mark Wyciślik-Wilson
Users of WhatsApp could be infected by dangerous spyware just by receiving a call. The spyware, which is thought to originate from Israeli cyber intelligence firm NSO Group, can be installed just by calling a target -- there is no need for the call to be answered. A security advisory on the Facebook website does not go into much detail about the exploit, which takes advantage of a buffer overflow vulnerability. WhatsApp says it was discovered earlier this month, and with 1.5 billion users, there are a huge number of people that are potentially affected. See also: New York attorney… [Continue Reading] -

US Supreme Court rules antitrust case can proceed against Apple's 'monopolistic' App Store practices
Publié: mai 13, 2019, 7:32pm CEST par Mark Wyciślik-Wilson
The US Supreme Court has said that consumers can sue Apple for allegedly violating antitrust laws with its App Store. A group of iPhone owners were seeking to bring a class action lawsuit against the company, and now Justice Brett Kavanaugh has said they can do so. The group says that in charging a 30 percent commission, Apple was making users overpay for apps, and that the requirement for apps to be sold through the App Store was unfair. See also: EU said to be ready to investigate Apple following complaint from Spotify Apple significantly overstates iPhone battery life Apple… [Continue Reading] -

GitHub Package Registry launches in beta
Publié: mai 12, 2019, 11:44am CEST par Mark Wyciślik-Wilson
GitHub has launched the GitHub Package Registry, its new package management service. Starting out as a limited beta, teh GitHub Package Registry gives developers, coders and organizations an easy way to publish public or private packages next to source code. For now, there is support for the likes of JavaScript (npm), Java (Maven), Ruby (RubyGems), .NET (NuGet), and Docker images, with the promise of more to come. Announcing the new service, GitHub says: "GitHub Package Registry is fully integrated with GitHub, so you can use the same search, browsing, and management tools to find and publish packages as you do for… [Continue Reading] -

Google says all new Chromebooks will be Linux-ready
Publié: mai 12, 2019, 11:20am CEST par Mark Wyciślik-Wilson
One of the biggest announcements from this year's Google I/O related to the Pixel 3a and Pixel 3a XL, but this was far from being all there was to get excited about. Microsoft may be increasingly embracing Linux in Windows 10, and Google is doing the same with Linux on Chromebooks. Support for Linux apps on Chromebook is nothing new, but Google has now announced that all Chromebooks that launch from this point forward will be fully functional Linux laptops, regardless of whether they are ARM or Intel devices. See also: Chrome OS 75 has full USB support in Linux… [Continue Reading] -

Privacy: Microsoft wants to (sneakily) collect more data from users via Office
Publié: mai 12, 2019, 10:49am CEST par Mark Wyciślik-Wilson
Launch Word, Excel, PowerPoint or some other Microsoft Office app on your computer, and you'll be greeted by a dialog entitled "Your data, controlled by you". You'll then be invited to review your privacy settings to determine how much telemetry data Microsoft is able to collect through Office. Earlier this month, Microsoft made reference to privacy and user feedback in its office suite, saying that "Office is built on trust". Now, the company is using a popup dialog to give users a chance to control the data they share; or, looked more cynically, to trick them into agreeing to share… [Continue Reading] -

Photo storage app Ever is using millions of users' photos to build a facial recognition system
Publié: mai 10, 2019, 10:51am CEST par Mark Wyciślik-Wilson
An investigation by NBC News has found that photo memories app Ever has been using billions of images uploaded by people to develop a facial recognition system without making it obvious to users. Ever is a photo storage app that offers "free, unlimited private backup of all your life's memories". It's not until you delve into the company's privacy policy that you learn that in using the service, users are agreeing not only to have their photos used in facial recognition training, but also for Ever to sell the resulting technology to private companies, law enforcement agencies and the military.… [Continue Reading] -

Mozilla promises to delete private data collected by Firefox fix and apologizes for add-on outage
Publié: mai 10, 2019, 9:45am CEST par Mark Wyciślik-Wilson
A slip-up by Mozilla stopped Firefox add-ons from working last weekend, and the company issued a fix followed by an update to the browser to get things back to normal. Mozilla has now issued an apology, a detailed explanation about what happened, and made a promise to delete the private data collected by those who used the first fix. The initial fix that was issued via Firefox's Studies system required users to enable telemetry. Many people have such data-collection options disabled for privacy reasons, and Mozilla says that it will delete any data that it collected for its entire user… [Continue Reading] -

Google announces 'pending transactions' so you can buy apps and games using cash
Publié: mai 9, 2019, 9:14am CEST par Mark Wyciślik-Wilson
For the sake of ease, the Google Play store supports the purchase of apps and games using a variety of credit and debit cards, PayPal and other payment options. Now Google has announced a new option -- pending transactions. This is an option designed for people who don't have cards, or just don't want to use them. It allows Android apps and games -- as well as in-app purchases -- to be paid for using cash, and is ideal for emerging markets See also: Google unveils the mid-range Pixel 3a and Pixel 3a XL -- same powerful camera, much more… [Continue Reading] -

Hackers steal $40 million of Bitcoin from crypto exchange Binance
Publié: mai 8, 2019, 11:25am CEST par Mark Wyciślik-Wilson
Cryptocurrency exchange Binance has been struck by hackers who were able to make off with $40 million worth of Bitcoin. The exchange suffered what it describes as a "large scale security breach" in which attackers were able to obtain "a large number of user API keys, 2FA codes, and potentially other info". CEO Zhao Changpeng says that 7,000 BTC were withdrawn in a single transaction and the attack which was perpetrated using a variety of methods. Binance says: "The hackers used a variety of techniques, including phishing, viruses and other attacks. We are still concluding all possible methods used. There… [Continue Reading] -

PowerToys are back! Microsoft reboots the utilities as an open source project for Windows 10
Publié: mai 8, 2019, 10:46am CEST par Mark Wyciślik-Wilson
Microsoft is bringing back PowerToys for Windows 10 -- and this time it is open source. If the name doesn't mean anything to you, you probably weren't a Windows 95 user, but if this was your computing era, you'll remember tinkering with the likes of TweakUI, Send to X, QuickRes and numerous other delightful utilities. Now the collection of utilities is back, rebooted for Windows 10 and due to be released as an open source project. At the moment, there are two tools being worked on -- Maximize to new desktop widget, and the Windows key shortcut guide -- but… [Continue Reading] -

It's decision time: Samsung tells buyers it will cancel their Galaxy Fold pre-orders unless told not to
Publié: mai 7, 2019, 10:53am CEST par Mark Wyciślik-Wilson
The launch of the Samsung Galaxy Fold is probably going to go down as one of the most problematic phone launches ever. After review handsets were found to have serious problems with the folding screen, Samsung decided to postpone the release for an unspecified length of time. With this being one of the first foldable phones, there was obviously a great deal of interest in it, and many people placed pre-orders in spite of the high price. Now the company is giving buyers the chance to back out of their purchase, saying it is "making progress in enhancing" the phone… [Continue Reading] -

EU said to be ready to investigate Apple following complaint from Spotify
Publié: mai 6, 2019, 10:25am CEST par Mark Wyciślik-Wilson
A new report says that the EU is ready to launch an antitrust investigation into Apple. The report says that the European Commission will begin a probe into the company after Spotify complained that Apple was using the App Store to stifle competition. The investigation is said to be due to begin "in the next few weeks". It will look at Spotify's complaint that Apple is "monopolistic" and abuses the App Store to "deliberately disadvantage other app developers". See also: Spotify lashes out at 'monopolist' Apple in escalating war of words Apple bites back at Spotify's damning claims against it… [Continue Reading] -

Mozilla issues new Firefox update to fix add-ons problems and warns users not to try dubious workarounds
Publié: mai 6, 2019, 9:17am CEST par Mark Wyciślik-Wilson
Mozilla has pushed out Firefox 66.0.4, properly addressing a problem that prevented add-ons from working in the web browser. On Friday, an expired security certificate caused frustration and confusion for Firefox users as extensions were disabled and rendered unusable. Having delivered a patch through its Studies system (which did not work for everyone), Mozilla has now issued a browser update which it says will fix the problem for more people, although it warns that "there are remaining issues that we are actively working to resolve". See also: Mozilla explains why Firefox add-ons stopped working... and how to fix the problem… [Continue Reading] -

Update your Dell computer now to avoid RCE security vulnerability in SupportAssist tool
Publié: mai 5, 2019, 5:12pm CEST par Mark Wyciślik-Wilson
As owners of Dell computers will be only too aware, the company is no stranger to stuffing systems with bloatware. This is in itself is irritating, but when this bloatware includes a security vulnerability that could be exploited by hackers, the irritation becomes rather more serious. The SupportAssist tool is supposed to provide an easy way to update drivers on Dell computers and laptops, as well as deleting unnecessary files and the like. However, it poses a security risk if you don't install the latest update from Dell to plug a vulnerability. The flaw (CVE-2019-3719) has been assigned a high… [Continue Reading] -

Privacy: HMRC forced to delete 5 million unauthorized voice recordings of UK taxpayers
Publié: mai 4, 2019, 7:06pm CEST par Mark Wyciślik-Wilson
The UK tax authority, HM Revenue and Customs (HMRC), has been forced to deleted voice recording of five million taxpayers. The recordings were made without consent, which the Information Commissioner's Office (ICO) said constituted a "significant" breach of data and privacy rules. Before being allowed to access HMRC services, callers were required to repeat the phrase "My voice is my password". This recording was fed into the authority's biometric voice ID database, and violated GDPR rules. The privacy concerns stemmed from the fact that people were not given the ability to opt out of using the system and having their… [Continue Reading] -

Mozilla explains why Firefox add-ons stopped working... and how to fix the problem
Publié: mai 4, 2019, 6:23pm CEST par Mark Wyciślik-Wilson
Since late last night, Firefox users have been plagued with a problem that meant no add-ons were working. Extensions were disabled and users were unable to re-enable them, causing confusion and frustrationaround the world. It turns out that that the reason Firefox add-ons stopped working is that a signing certificate expired. Having determined the cause of the problem, Mozilla has developed a fix for users of the desktop version of Firefox on the Release, Beta and Nightly channels. See also: Mozilla bans Firefox add-ons with obfuscated code Mozilla criticizes Apple's iPhone privacy claims, launches online petition Mozilla is launching curated… [Continue Reading] -

It is getting harder than ever for VPNs to break through the Great Firewall of China
Publié: mai 3, 2019, 10:04am CEST par Mark Wyciślik-Wilson
The censorial Great Firewall of China is famed throughout the world for the restrictions it places on Chinese citizens. Internet users play a game of cat and mouse, seeking tools and methods for slipping through the censoring and spying that the government enforces. But it is getting harder and harder to evade the Great Firewall. VPNs that once allowed unfettered access to the greater internet are quickly stomped on by the Chinese government, just as happens in Russia. At the end of March, a new update to the firewall blacklisted hundreds of VPN servers and now fewer VPN tools than… [Continue Reading] -

Confirmed: YouTube Originals content will be free
Publié: mai 3, 2019, 9:15am CEST par Mark Wyciślik-Wilson
YouTube CBO Robert Kyncl has confirmed that all of the company's Originals content will be made available free of charge. Currently locked behind a paywall, Originals will become free and ad-supported. At the moment, it is not clear exactly when the change will happen, but it is certainly in the cards, meaning shows like Cobra Kai should reach a larger audience. Speaking at the annual advertiser-focused Brandcast event, Kyncl said that all Originals content will have an ad-supported option. While he did not elaborate on this, it seems as though YouTube is not completely abandoning the idea of paid subscriptions,… [Continue Reading] -

Mozilla bans Firefox add-ons with obfuscated code
Publié: mai 2, 2019, 6:34pm CEST par Mark Wyciślik-Wilson
As Mozilla continues to try to make it safer than ever to use Firefox, the organization has updated its Add-on Policy so that any updates that include obfuscated code are explicitly banned. Mozilla has also set out in plain terms its blocking process for add-ons and extensions. While there is nothing surprising here, the clarification should mean that there are fewer causes for disputes when an add-on is blocklisted. See also: Mozilla is launching curated Recommended Extensions program this summer Mozilla criticizes Apple's iPhone privacy claims, launches online petition The updated Add-on policy comes into force on June 10, so… [Continue Reading] -

Putin signs law to create 'sovereign internet' for Russia
Publié: mai 2, 2019, 10:39am CEST par Mark Wyciślik-Wilson
President Putin has signed into law a bill that will give Russia a "sovereign internet" -- one which could be disconnected from the global web if the Kremlin decided to do so. It is being sold as a way to "ensure the safe and sustainable functioning" of Russia's internet should the country's enemies try to block access. But there are fears that the law -- which will require ISPs to route traffic through government-controlled servers -- amounts to the creation of a Russian version of the Great Firewall of China and will lead to severe online censorship. The law is… [Continue Reading] -

Google to roll out auto-delete controls for location history and activity data
Publié: mai 1, 2019, 7:00pm CEST par Mark Wyciślik-Wilson
Google has announced that it is giving users greater control over how long the company holds on to location history and activity data. A new time-limiting feature makes it possible to have information such as account activity and location data automatically deleted after a period of time. The privacy-focused move comes after feedback to Google which found users wanted the company to provide simpler ways to manage or delete the private data it holds. Google says that it does what it can to keep data private and secure, but it hears that users want greater control. The new auto-delete controls… [Continue Reading] -

UK government launches five-week consultation into IoT security
Publié: mai 1, 2019, 10:26am CEST par Mark Wyciślik-Wilson
The UK government is looking to ensure the security of the Internet of Things as they become more prevalent in the home, possibly through the use of legislation. The government says that it wants IoT devices to be secure by design and, having already published a code of practice paper, is now embarking on a five-week security consultation during which the Department for Digital, Culture, Media and Sport (DCMS) will consider regulatory proposals. See also: IoT devices put healthcare networks at risk Security, connectivity and data analysis are top IoT developer concerns IoT attacks increase but rely on the same… [Continue Reading] -

Personal details of 80 million US households exposed on unsecured Microsoft cloud server
Publié: avril 30, 2019, 1:34pm CEST par Mark Wyciślik-Wilson
Security researchers have discovered an unprotected database stored on a Microsoft cloud server. The 24GB database includes personal information about 80 million households across the US. The researchers from vpnMentor were working on a web mapping project when they made the discovery. They say that as the database they found left out in the open relates to American households which include multiple residents, the data breach could potentially affect hundreds of millions of people. The discovery was made by "hacktivists" Noam Rotem and Ran Locar. The unprotected database they stumbled across could impact as many as 65 percent of US… [Continue Reading] -

Microsoft, Dell and VMware become partners in the cloud
Publié: avril 30, 2019, 1:16pm CEST par Mark Wyciślik-Wilson
Microsoft has announced that it is extending its partnership with Dell in a move that will enable Microsoft Azure customers to take advantage of VMware virtualization in the cloud. The company is also bringing VMware into the Microsoft 365 ecosystem to extend the capabilities of its Windows Virtual Desktop too. It will also bring new management and security options to Microsoft Intune. See also: Microsoft drops password expiration policies from Windows 10 1903 security baseline Microsoft will block the Windows 10 May 2019 Update if you have a USB drive or SD card connected Microsoft decides to keep Paint in… [Continue Reading] -

Apple responds to parental control app removal controversy
Publié: avril 29, 2019, 1:32pm CEST par Mark Wyciślik-Wilson
Apple has been upsetting developers of parental control apps recently by asking them to restrict their offerings in various ways, or simply removing them from the App Store. Critics say that this is because the apps compete with iOS's Screen Time feature. Apple has now responded to the criticism, denying that this is the reason for its interference with and removal of apps. The company insists its actions had nothing to do with killing off the competition, but says that several parental control apps were delisted because "they put users' privacy and security at risk". See also: After launching Screen… [Continue Reading] -

UK streaming site TVCatchup is down... and this could be the end
Publié: avril 29, 2019, 1:01pm CEST par Mark Wyciślik-Wilson
If you are having trouble accessing TVCatchup via its mobile app or through its website, you are not alone. The UK TV streaming service has gone dark, and it could be a permanent closure. The service has been no stranger to controversy and managed to attract the attention -- and the wrath -- of numerous broadcasters, and became embroiled in a legal battle. Having managed to stay online for longer than many would have imagined, it seems you’ll now have to seek out an alternative to TVCatchup. See also: BitTorrent Inc announces BitTorrent Live, a social streaming platform that's not… [Continue Reading] -

After launching Screen Time, Apple is interfering with competing third party parental control apps
Publié: avril 28, 2019, 11:00am CEST par Mark Wyciślik-Wilson
With iOS 12, Apple introduced Screen Time, a feature that serves as a parental control tool and encourages periods away from the screen. Tim Cook said last year that he thought he used his phone too much (more recently adding, "we don't want people using their phones all the time"), and Screen Time is Apple attempt to muscle in on the countering of "phone addiction". For those who are concerned about how much they are using their phone, or who are concerned about their children, it seems like a great feature. But for app developers who have spent years crafting… [Continue Reading] -

Windows 10 Insider Preview Build 18885 fixes drive letter assignment problems and brings Android notifications mirroring to Your Phone app
Publié: avril 28, 2019, 9:41am CEST par Mark Wyciślik-Wilson
Microsoft has released Windows 10 Insider Preview Build 18885 (or Windows 10 20H1, if you prefer) to the Fast Ring. The big addition in this latest build is Android notification mirroring in Windows via the Your Phone app. If you have an Android 7.0 handset, you can (probably, barring handset-specific compatibility issues) take advantage of the ability to see phone notifications in Windows 10. The range of phones that can use the "phone screen" screen mirroring option has been expanded as well. With Build 18885, Microsoft has also addressed the problem that was preventing people from installing updates when they… [Continue Reading] -

New York attorney general to investigate Facebook for scraping 1.5 million users' email contacts
Publié: avril 26, 2019, 10:53am CEST par Mark Wyciślik-Wilson
Following the revelation that Facebook "unintentionally" scraped and uploaded 1.5 million users' email contacts, the New York attorney general's office has announced that it is opening an investigation into the social media giant. Attorney general Letitia James said that it is "time Facebook is held accountable for how it handles consumers' personal information". See also: How to delete the contacts that Facebook may have scraped from you Privacy: Facebook 'unintentionally' scraped and uploaded 1.5 million users' email contacts Facebook: er, actually it was millions of Instagram passwords we stored in plain text, not thousands James says that "Facebook has repeatedly… [Continue Reading] -

Windows 10 May 2019 Update needs more space than ever before
Publié: avril 26, 2019, 9:46am CEST par Mark Wyciślik-Wilson
With the release of the May 2019 Update, Windows 10 is becoming more space-hungry than ever. For both the 32- and 64-bit versions of Windows 10 version 1903, Microsoft has increased the minimum storage requirements to 32GB. For 32-bit users the new requirement is double what it used to be, while for 64-bit users there is a 12GB increase from the previous minimum of 20GB. See also: Microsoft drops password expiration policies from Windows 10 1903 security baseline Microsoft will block the Windows 10 May 2019 Update if you have a USB drive or SD card connected Microsoft decides to… [Continue Reading] -

iFixit pulls damning Samsung Galaxy Fold teardown
Publié: avril 26, 2019, 8:45am CEST par Mark Wyciślik-Wilson
The launch of the Samsung Galaxy Fold has been mired in problems, culminating in the company postponing the foldable phone. In addition to reports of serious screen issues from journalists with review handsets, Samsung was also hit with an iFixit teardown that highlighted numerous design flaws. Now, following pressure from Samsung, iFixit has removed the teardown -- although the site stresses that it was under no obligation, legal or otherwise, to do so. See also: Samsung officially announces postponement of Galaxy Fold Report: Samsung delays the launch of Galaxy Fold until at least May See the Samsung Galaxy Fold hinge… [Continue Reading] -

Shocking! Apple launches voluntary recall and exchange program for some power adapters
Publié: avril 25, 2019, 7:30pm CEST par Mark Wyciślik-Wilson
Apple has announced a voluntary recall of some of its AC wall plug adapters and Apple World Travel Adapter Kits over fears that they could cause electric shocks. While the number of known incidents is low -- Apple says there have been just six worldwide -- there is a risk of the wall plug adapters breaking and causing a shock if touched. The recall relates solely to three-prong wall plug adapters, not USB power adapters. Anyone who has one of the adapters can obtain a replacement free of charge. See also: Apple and Qualcomm bring their global legal fight to… [Continue Reading] -

Leak shows that the OnePlus 7 Pro is not going to be cheap
Publié: avril 25, 2019, 10:58am CEST par Mark Wyciślik-Wilson
While Samsung's problematic Galaxy Fold was vying for attention by not only being a foldable smartphone, but also an extraordinarily expensive one, handsets from OnePlus have been notable for their low price tags. The launch of the OnePlus 7 series is just around the corner, and the specs we've seen have hinted that this is not going to be a cheap phone. Now leaked pricing appears to confirm this. See also: OnePlus 7 series will be revealed May 14 Sign up to beta test Android Pie on OnePlus 3 and 3T Samsung officially announces postponement of Galaxy Fold The reliable… [Continue Reading] -

Microsoft drops password expiration policies from Windows 10 1903 security baseline
Publié: avril 25, 2019, 9:46am CEST par Mark Wyciślik-Wilson
In new draft security baseline documentation, Microsoft has scrapped the policy that requires users to change their passwords on a regular basis. The new security settings apply to Windows 10 version 1903 and Windows Server version 1903, and the change sees Microsoft conceding that its policy of forcing periodic password changes is "an ancient and obsolete mitigation of very low value". The company has a series of suggestions for how to better improve password security. See also: Microsoft will block the Windows 10 May 2019 Update if you have a USB drive or SD card connected Microsoft decides to keep… [Continue Reading] -

Microsoft will block the Windows 10 May 2019 Update if you have a USB drive or SD card connected
Publié: avril 24, 2019, 12:31pm CEST par Mark Wyciślik-Wilson
If you have external storage attached to your computer, you may well find that you're unable to install the Windows 10 May 2019 Update when it is released next month. Out of an apparent abundance of precaution, Microsoft is opting to block the installation of the update if a computer has an external USB drive or SD card plugged in. The block is being introduced because of fears that drive letters might be inappropriately reassigned during the installation. See also: Microsoft decides to keep Paint in Windows 10... for now Microsoft displays warning messages in Windows 7 about the impending… [Continue Reading] -

Here is the colossal 17.3-inch Samsung Galaxy View2 tablet
Publié: avril 24, 2019, 11:58am CEST par Mark Wyciślik-Wilson
As the launch of the Samsung Galaxy Fold is proving to be something of a disaster, the company will be only too happy at anything which can serve as a distraction. Well, here's the Samsung Galaxy View2, an Android tablet that features an extraordinarily large 17.3-inch screen. Following on from 2015's Galaxy View (which was even larger at 18.4 inches), this yet-to-be-released tablet is due to make its way to AT&T at some point in the future. And, thanks to the telecoms firm, we know pretty much everything we need to about specs in advance. See also: Samsung officially announces… [Continue Reading] -

Google is killing off the Data Saver extension for Chrome
Publié: avril 24, 2019, 10:47am CEST par Mark Wyciślik-Wilson
If you're a Chrome user with the Data Saver extension installed, there's some bad news. Google has announced that with the desktop version of Chrome 74, the extension is being deprecated. Data Saver is not going away completely, however. It will remain, exclusively, in the Android version of the web browser where it will be known as Lite mode. While this is great for mobile users looking to reduce their data usage, it's a little strange that desktop users won't also be afforded the ability to enjoy a data-light, faster internet experience. See also: Google adds privacy-focused DuckDuckGo search engine… [Continue Reading] -

UK bans Huawei from supplying 'core' parts of 5G network
Publié: avril 24, 2019, 10:11am CEST par Mark Wyciślik-Wilson
Amid concerns about the company's security, and its possible links to the Chinese government, Huawei has been banned from providing essential parts of the UK's 5G network. The Chinese telecoms firm has already been hit with bans and restrictions in the US and other parts of the world, and Huawei has been criticized for its "very, very shoddy" security. Now UK prime minister Theresa May has taken advice from the National Security Council and implemented a partial ban on Huawei's involvement in 5G in the UK, permitting it to only supply "non-core" technology. See also: Is Huawei funded by Chinese… [Continue Reading] -

Microsoft decides to keep Paint in Windows 10... for now
Publié: avril 23, 2019, 5:45pm CEST par Mark Wyciślik-Wilson
For all of its simplicity and limitations, there are still a lot of people who -- for some reason best known to themselves -- love Microsoft Paint. As such, when it was announced a while back that Microsoft intended to strip the utility from Windows 10 and replace it with Paint 3D -- an altogether different beast -- there was a collective wailing and gnashing of teeth. But now it seems that Paint has been given a stay of execution. See also: Microsoft may have abandoned Sets in Windows 10 -- what now for app tabs? How to secure Windows… [Continue Reading] -

Microsoft displays warning messages in Windows 7 about the impending end of support
Publié: avril 23, 2019, 5:30pm CEST par Mark Wyciślik-Wilson
Windows 7 users have started to report the appearance of a pop-up message from Microsoft informing them that support for the operating system is coming to an end. While this will not come as a surprise to everyone, not all Windows 7 users will be aware that Microsoft is on the verge of dropping the ageing OS. We have already seen pop-ups encouraging users to update to Windows 10 but now Microsoft is turning up the pressure, telling Windows 7 users: "After 10 years, support for Windows 7 is nearing the end". See also: Microsoft will pester Windows 7 users… [Continue Reading] -

OnePlus 7 series will be revealed May 14
Publié: avril 23, 2019, 4:27pm CEST par Mark Wyciślik-Wilson
OnePlus has announced that it is going to reveal its OnePlus 7 series on May 14. At an event in three weeks' time in London, New York, Bangalore and Beijing, the company says it will "showcase the power of all-new OnePlus 7 Series", which is expected to include the OnePlus 7, the OnePlus 7 Pro, and a 5G handset. OnePlus also promises "several surprise announcements". So what does OnePlus have in store for us? While the company has built its reputation on delivering "flagship killers" year after year, offering top-of-the-range specs for a fraction of the cost of competitors, this… [Continue Reading] -

Samsung officially announces postponement of Galaxy Fold
Publié: avril 22, 2019, 9:30pm CEST par Mark Wyciślik-Wilson
Bringing to an end rumors and speculation, Samsung has officially announced that it is postponing the launch of its Galaxy Fold smart phone. The $2,000 foldable phone was due to launch this week, but models sent out to some reviewers have proved problematic. Having already announced the delay of the phone in China, unconfirmed reports suggested a global postponement. Samsung has now confirmed this with an official statement. See also: Report: Samsung delays the launch of Galaxy Fold until at least May Samsung Galaxy Fold launch delayed in China See the Samsung Galaxy Fold hinge in action in an official… [Continue Reading] -

Report: Samsung delays the launch of Galaxy Fold until at least May
Publié: avril 22, 2019, 5:13pm CEST par Mark Wyciślik-Wilson
Following the news that Samsung is postponing Galaxy Fold launch events in China this week, it now seems that the US release of the handset has been pushed back until at least May. This will come as little surprise to anyone who has been following new about the Galaxy Fold recently. There have been numerous reports of Fold handsets that have been sent out to reviewers suffering with the hinged display, and it's looking rather like Samsung has decided it makes sense to hold back the launch until things have been properly investigated. UPDATE: Samsung has now confirmed the Galaxy Fold launch… [Continue Reading] -

Samsung Galaxy Fold launch delayed in China
Publié: avril 22, 2019, 10:07am CEST par Mark Wyciślik-Wilson
Despite the hype and excitement surrounding the first batch of foldable smartphones, the image of the Samsung Galaxy Fold has been tarnished before the device has even launched. There have been numerous reports of serious problems with handsets sent out for review, and now Samsung has delayed the launch of the phone in China. Two launch events were due to be held this week on Tuesday and Wednesday for the $2,000 phone, but these have been postponed. For now, it is just the Chinese launch events that are affected, and it is not clear if Samsung will also delay launch… [Continue Reading] -

Is Huawei funded by Chinese state security? The CIA seems to think so
Publié: avril 22, 2019, 9:05am CEST par Mark Wyciślik-Wilson
Huawei has had a rough time of things when it comes to international relations, with the US and others implementing various bans on the use of the company's products. It all stems from fears about Huawei's alleged connections to the Chinese government and the potential for espionage, but this is something the company has denied time and time again. The US has made no secret of its doubts about Huawei, and the fears have spread around the globe. Now, according to a report, the CIA has issued a warning to the UK saying that the firm has received funding from… [Continue Reading] -

Millions of people still have pathetically weak, easily hacked passwords
Publié: avril 21, 2019, 9:46am CEST par Mark Wyciślik-Wilson
That people are lazy is not news. Ditto the fact that people like to make things as easy for themselves as possible. These two facts do not work well when it comes to security and passwords, as a new study reveals. Analysis carried out by the UK's National Cyber Security Centre (NCSC) found that huge numbers of people are still -- despite continued advice -- using weak, easy-to-guess passwords to secure their accounts. The most commonly used password on breached accounts was found to be 123456, and there were plenty of others that were similarly insecure. The NCSC, in conjunction… [Continue Reading] -

Microsoft may have abandoned Sets in Windows 10 -- what now for app tabs?
Publié: avril 21, 2019, 9:00am CEST par Mark Wyciślik-Wilson
In what will come as something of a disappointment to many, Microsoft seems to have decided to abandon the Sets feature of Windows 10. This highly-anticipated feature was to bring tabs to apps, making it easier to work with multiple instances of the same program. In the middle of last year, though, Microsoft removed Sets from Insider builds of Windows 10, promising that the feature would return in a future build. But a tweet from senior program manager Rich Turner suggests that Sets is no more... although that might not mean that app tabs are completely off the agenda. See… [Continue Reading] -

Chromium-based Microsoft Edge pretends to be different browsers by switching user agent
Publié: avril 20, 2019, 2:48pm CEST par Mark Wyciślik-Wilson
The new Chromium-based version of Microsoft Edge has generated a good deal of attention, and an intriguing feature of the browser has been noticed that makes it all the more interesting. It has been noted that Edge switches between user agents depending on the sites visited, effectively pretending to be a different web browser. This enables Edge to take advantage of web sites features designed for a specific browser. See also: How to enable dark mode in new Chromium-based Microsoft Edge First official builds of Microsoft's Chromium-based Edge browser now available to test Leaked: first look at Chromium-based Microsoft Edge… [Continue Reading] -

Bosque is Microsoft's new open source, TypeScript-inspired programming language
Publié: avril 20, 2019, 2:07pm CEST par Mark Wyciślik-Wilson
If you're thinking of learning a programming language, there are certainly plenty to choose from -- and Microsoft has just added a new one for you to consider. Inspired partly by TypeScript and partly by Node.js, Bosque is an open source language which tries to keep things simple. Microsoft says that one of the main aims with Bosque is to create code that is simple for both humans and machines to read, eliminating "accidental complexity". See also: Microsoft announces great value Xbox Game Pass Ultimate Microsoft revives TechNet and MSDN blogs Microsoft email hack was worse than first thought --… [Continue Reading] -

Download Android Studio 3.4 complete with Android Q emulator
Publié: avril 19, 2019, 3:38pm CEST par Mark Wyciślik-Wilson
Google has released its latest version of Android Studio, the tool used by developers to create Android apps. Android Studio 3.4 is now available on the stable channel and as well as hundreds of big fixes, there's also a new version of the Android Emulator complete with support for the Android Q beta. The tool is available for Windows, macOS and Linux. See also: Google introduces new default search and browser choice options for Android users in Europe Google now lets you use your Android phone as a 2SV security key Google publishes its Android Security & Privacy 2018 Year… [Continue Reading] -

How to delete the contacts that Facebook may have scraped from you
Publié: avril 19, 2019, 2:23pm CEST par Mark Wyciślik-Wilson
With its invasive advertising, scant regard for privacy, and often poor approach to security, Facebook has done little over the years to win itself many friends. But to help boost your list of friends, it is possible that Facebook may have uploaded your email contacts without your knowledge. The aim of this was to help find people you might know on the social network, but as there was little warning about the uploading of such private and sensitive information, there was an understandable backlash. If you're concerned about what Facebook has uploaded on your behalf, here's how to delete the… [Continue Reading] -

Facebook: er, actually it was millions of Instagram passwords we stored in plain text, not thousands
Publié: avril 19, 2019, 1:57pm CEST par Mark Wyciślik-Wilson
With no fanfare whatsoever, Facebook has revealed that it stored the passwords for millions of Instagram accounts in plain text. The news came as the company quietly updated a blog post from last month in which it revealed that it had stored hundreds of millions of unencrypted Facebook passwords on its servers. At the time, the company said "tens of thousands" of Instagram users were affected. Revising this figure upwards, Facebook says: "We now estimate that this issue impacted millions of Instagram users". See also: Privacy: Facebook 'unintentionally' scraped and uploaded 1.5 million users' email contacts Data of 540 million… [Continue Reading] -

Google introduces new default search and browser choice options for Android users in Europe
Publié: avril 18, 2019, 7:32pm CEST par Mark Wyciślik-Wilson
Having been hit with a fine by antitrust regulators in Europe, Google has said that it will roll out new default search and browser choice options for Android users. The move is comparable to Microsoft's Browser Choice which was introduced following similar anti-competition complaints. Starting today, European Android users will be presented with a screen that invites them to download alternative search apps and browsers. See also: Facebook updates its terms and conditions in Europe to clarify personal data usage Valve responds to European complaints about Steam geo-locking Europe hits Google with €1.49 billion fine for breaking antitrust law with… [Continue Reading] -

Micropatch now available for Internet Explorer security hole
Publié: avril 18, 2019, 7:53am CEST par Mark Wyciślik-Wilson
A few days ago, a security vulnerability in Internet Explorer came to light. A flaw in the handling of certain files can be exploited by hackers to steal files from users, and -- most worrying -- it doesn't matter whether the victim is an Internet Explorer user or not. Microsoft is yet to create a fix for the vulnerability, so someone else has stepped up to the plate. Specialists from ACROS Security have create a micropatch for Windows 10 that addresses the issue, once again beating Microsoft in securing people's computers. See also: Internet Explorer flaw leaves Windows users vulnerable… [Continue Reading] -

Privacy: Facebook 'unintentionally' scraped and uploaded 1.5 million users' email contacts
Publié: avril 18, 2019, 7:21am CEST par Mark Wyciślik-Wilson
It seems that barely a week passes without another Facebook scandal emerging, and this week is no different. The company has revealed that it accidentally uploaded the email contacts of up to 1.5 million users who signed up for the social network since 2016. A glitch meant that new users who signed up for email password verification had their email contacts scraped and uploaded without consent. As of last month , Facebook stopped offering this verification option to first-time users, although it's not clear if this is because of the privacy issue. See also: Facebook suffers huge outage, along with… [Continue Reading] -

Microsoft announces great value Xbox Game Pass Ultimate
Publié: avril 17, 2019, 11:32am CEST par Mark Wyciślik-Wilson
As well as revealing the Xbox One S All-Digital Edition yesterday, Microsoft also has another treat in store for gamers -- the Xbox Game Pass Ultimate. Just as there had been rumors about the Xbox One S All-Digital Edition ahead of the announcement, there had also been talk about this new combined subscription. Due to launch at an undisclosed time later this year after beta testing, Xbox Game Pass Ultimate combines the existing Game Pass with Xbox Live Gold, all for $14.99 per month. See also: Microsoft announces stupidly named Xbox One S All-Digital Edition -- a neutered game console… [Continue Reading] -

Microsoft revives TechNet and MSDN blogs
Publié: avril 17, 2019, 10:54am CEST par Mark Wyciślik-Wilson
After a wave of apparently unexpected complaints, Microsoft has announced that it is to restore the TechNet and MSDN blogs it recently started to retire. The company warns that this is not something that's going to happen overnight -- there is a lot of content to re-activate -- but the announcement is great news for anyone who has found the blogs to be invaluable sources of information. The two blogs were -- and now will be once again -- used by Microsoft employees to talk about different aspects of technology and to give insights into various projects. It seems that… [Continue Reading] -

Intel announces it is exiting 5G mobile modem market after Apple and Qualcomm bury the hatchet
Publié: avril 17, 2019, 10:25am CEST par Mark Wyciślik-Wilson
Intel has announced that it is to leave the 5G smartphone modem business and will assess the opportunities for 4G and 5G modems in PCs, as well as data-centric and IoT devices. While Intel has not indicated a link between the two announcements, the news comes just after Apple and Qualcomm said they are bringing their legal battles to an end. It means that Intel will not supply the modem for the 5G iPhone, but the company says it will continue to invest in its 5G network infrastructure business. See also: Apple and Qualcomm bring their global legal fight to… [Continue Reading] -

Huawei says US government is 'ignorant of technology'
Publié: avril 16, 2019, 7:24pm CEST par Mark Wyciślik-Wilson
Having faced accusations of conducting espionage on behalf of the Chinese government, Huawei has lashed out at the US government, accusing officials of being "ignorant of technology". Huawei has been hit with numerous bans by the US, and the country has encouraged others around the world to follow its lead. But the company's chief security officer, John Suffolk, says there is no evidence that China could make use of Huawei's 5G equipment to spy on people, suggesting that US allegations were politically motivated. See also: Huawei's 'shoddy' security could mean it is banned from sensitive parts of the UK's 5G… [Continue Reading] -

UK recommends that Facebook and other social media sites disable 'like' option and data collection for minors
Publié: avril 16, 2019, 9:26am CEST par Mark Wyciślik-Wilson
UK watchdog the Information Commissioner's Office (ICO) has put forward new proposals it believes will help to improve the safety of children online. Among the recommendations is the suggestion that Facebook and other social media sites should disable "like" functionality for minors. The ICO's "Age Appropriate Design" consultation document is a code of practice for online services, and includes proposals such as minimum age checks and an increase in privacy settings for minors. Another suggestion in the 16-point set of proposals is that social media firms limit the collection of personal data about under-18s. See also: Forget Easter eggs, Facebook… [Continue Reading] -

Hulu buys back AT&T's 9.5 percent stake
Publié: avril 16, 2019, 8:30am CEST par Mark Wyciślik-Wilson
Hulu has bought back the minority share AT&T held in the streaming video firm. The two companies have come to an arrangement which sees Hulu purchasing AT&T's minority stake for $1.43 billion. Buying the 9.5 percent stake at this price values Hulu at $15 billion. The deal gives even greater control to Walt Disney Co, which holds a 60 percent stake in Hulu as part of a joint venture. See also: BitTorrent Inc announces BitTorrent Live, a social streaming platform that's not based on BitTorrent Google announces Stadia, its new instant-play game streaming service Spotify spreads its streaming services to… [Continue Reading] -

Forget Easter eggs, Facebook Messenger now officially has a dark mode
Publié: avril 15, 2019, 8:16pm CEST par Mark Wyciślik-Wilson
Following the popular trend, Facebook has now officially rolled out the much-requested dark mode option to Facebook Messenger on both iOS and Android. The feature was available as a secret Easter egg from the start of last month, but now it is being rolled out on a global basis for everyone to enjoy. Dark mode can now be accessed as a regular setting without the need to jump through any special hoops. See also: iOS 13 could herald the arrival of system-wide dark mode, better multitasking and so much more Facebook suffers huge outage, along with WhatsApp and Instagram Data… [Continue Reading] -

iOS 13 could herald the arrival of system-wide dark mode, better multitasking and so much more
Publié: avril 15, 2019, 7:29pm CEST par Mark Wyciślik-Wilson
With the big reveal of iOS 13 thought to be mere weeks away, leaks and rumors now abound. So, what can iPhone and iPad owners expect this time around? Well, it's looking as though 13 could be a lucky number as much sought after features are on the cards. According to sources, the long-awaited dark mode is said to be arriving, along with new gestures. Apple is also said to be bringing improved multitasking and a lot more besides. See also: Apple adds subscription confirmation to the App Store Apple no longer charges for transferring data to a new Mac… [Continue Reading] -

Internet Explorer flaw leaves Windows users vulnerable to hackers -- even those who don't use the browser
Publié: avril 15, 2019, 3:41pm CEST par Mark Wyciślik-Wilson
A zero-day exploit found in Internet Explorer means hackers could steal files from Windows users. What's particularly interesting about this security flaw is that you don't even need to be an Internet Explorer user to be vulnerable. A security researcher has revealed details of an unpatched exploit in the way IE handles MHT files, and the problem affects Windows 7, Windows 10 and Windows Server 2012 R2. It leaves users vulnerable not only to having their files stolen by hackers, but also means they could be spied upon. See also: Microsoft email hack was worse than first thought -- some… [Continue Reading] -

Microsoft email hack was worse than first thought -- some users' messages were accessed
Publié: avril 15, 2019, 2:14pm CEST par Mark Wyciślik-Wilson
Over the weekend we reported that hackers gained access to Microsoft's web-based email services for a period of three months. Microsoft tried to calm users' concerns by saying that only "your e-mail address, folder names, the subject lines of e-mails, and the names of other e-mail addresses you communicate with" had been accessed. But for some people, things were rather worse. It transpires that some users have been sent a notification from Microsoft informing them that hackers were able to access the content of emails. See also: Microsoft reveals hackers gained access to its web email services for three months… [Continue Reading] -

Facebook suffers huge outage, along with WhatsApp and Instagram
Publié: avril 14, 2019, 4:39pm CEST par Mark Wyciślik-Wilson
If you've had trouble accessing Facebook today, you're not alone. Users in the US, Europe and Asia struggled to access not only Facebook, but also the WhatsApp and Instagram services owned by the social media giant. Facebook has said little about this incident which comes just a month after it suffered its worst outage ever, causing problems for users for over 24 hours. This weekend's outage led to #FacebookDown, #instagramdown, and #whatsappdown hashtags trending on Twitter, and numerous reports of problems were posted to Downdetector. See also: Facebook updates its terms and conditions in Europe to clarify personal data usage… [Continue Reading] -

Leaked: Microsoft's Xbox One S All Digital console
Publié: avril 14, 2019, 9:41am CEST par Mark Wyciślik-Wilson
The future of the Xbox console certainly appears to be a disc-less one. German website WinFuture has obtained images and details of the console which could be officially revealed in the coming days. The name has already been spotted on packaging, so we can be fairly sure that it is the final name. As the moniker suggests, the Xbox One S All Digital eschews discs in favor of game downloads -- the packaging itself proclaims "disc-free gaming". The box also reveals some details about the hardware specs of the Xbox One S All Digital. See also: Microsoft reveals hackers gained… [Continue Reading] -

Microsoft reveals hackers gained access to its web email services for three months
Publié: avril 14, 2019, 8:46am CEST par Mark Wyciślik-Wilson
Microsoft has confirmed that hackers were able to access customers' web-based email accounts for a period of three months at the beginning of the year. Between January 1 and March 28, unknown hackers hit the accounts of various Microsoft email services. The company is in the process of sending notifications to those who have been affected by the issue and it recommends users change their account passwords. (Update: it's worse than first thought!) See also: How to secure Windows 10 -- Microsoft reveals SECCON framework to protect systems April's Patch Tuesday updates are causing Windows to freeze or slow down How… [Continue Reading] -

Chrome OS 75 has full USB support in Linux apps
Publié: avril 13, 2019, 10:03am CEST par Mark Wyciślik-Wilson
Google has added full USB support for Linux apps in the dev build of Chrome OS 75. The new feature arrived in build 75.0.3759.4 of the operating system and helps to improve the experience of running Linux apps on a Chromebook. While USB support is not a brand-new feature, anyone who has tried using Linux apps on a Chromebook will be well aware that it has been a bit, well, ropey to say the least. Now this changes. See also: Microsoft rolls out new Skype for Web, and drops support for Chrome OS and Linux Google now lets you use… [Continue Reading] -

Apple adds subscription confirmation to the App Store
Publié: avril 13, 2019, 9:26am CEST par Mark Wyciślik-Wilson
Apple has added a new confirmation pop-up to the App Store when users opt into a subscription using Touch ID or Face ID. While Apple has not said as much, the confirmation screen gives users a second chance to back out of a subscription. It also helps to avoid the problem of accidental sign-ups and mitigates against apps that try to trick people into starting a subscription. See also: Apple no longer charges for transferring data to a new Mac Apple and Beats designed Powerbeats Pro wireless earphones are coming in May Canceled: Apple's AirPower wireless charging mat will not… [Continue Reading] -

How to secure Windows 10 -- Microsoft reveals SECCON framework to protect systems
Publié: avril 12, 2019, 7:47pm CEST par Mark Wyciślik-Wilson
Based on the DEFCON levels, Microsoft has unveiled the SECCON framework -- a series of guides for securing a range of Windows 10 configurations in different environments. Starting with an "Administrator workstation" at level 1 and building up to "Enterprise security" at level 5, the framework is Microsoft's attempt to simplify and standardize security. While it is not a one-size-fits-all solution, the company says it is "defining discrete prescriptive Windows 10 security configurations to meet many of the common device scenarios we see today in the enterprise". See also: Google now lets you use your Android phone as a 2SV… [Continue Reading] -

Dread Pirate Roberts 2, the 'guiding mind' of Silk Road 2.0, jailed for over 5 years
Publié: avril 12, 2019, 5:19pm CEST par Mark Wyciślik-Wilson
Thomas White, the founder of notorious website Silk Road 2.0, has been jailed for five years and four months by a UK court. White, also known as Dread Pirate Roberts 2, was charged with not only running Silk Road 2.0 -- the site through which he earned hundreds of thousands of dollars per day on the dark web -- but also the possession of hundreds of indecent images of children. Last month in court in Liverpool, White pleaded guilty to drug trafficking, money laundering and making indecent images of children. He also pleaded guilty to assisting or inducing the commission… [Continue Reading] -

Gmail now supports the MTA-STS and TLS Reporting security standards
Publié: avril 12, 2019, 4:09pm CEST par Mark Wyciślik-Wilson
In a first for a major email service, Google has announced that Gmail now supports the MTA-STS and TLS Reporting security standards. The two standards help to avoid man-in-the-middle attacks, using encryption and authentication to add new layers of security. Google says that Gmail's MTA-STS adherence is now in beta, and the company hopes that by supporting the standard other providers with follow suit. See also: How to schedule emails in Gmail Google now lets you use your Android phone as a 2SV security key Google closes down its AI ethics council just one week after its launch From an… [Continue Reading] -

April's Patch Tuesday updates are causing Windows to freeze or slow down
Publié: avril 12, 2019, 12:23pm CEST par Mark Wyciślik-Wilson
If you installed the latest batch of patches from Microsoft this week and found that your computer started to freeze up or fail to boot, you are not alone. The problem is affecting Windows 7, Windows 8.1, Windows Server 2012 and Windows Server 2012 R2, and stems from a compatibility issue with antivirus software. Users with antivirus tools from Avast, Avira and Sophos have experienced problems -- including slowing down Windows 10 -- and Microsoft has blocked the rollout of updates to some systems to try to limit the damage. See also: Microsoft releases cumulative update for the Windows 10… [Continue Reading] -

Skype beta adds screen sharing feature
Publié: avril 12, 2019, 11:38am CEST par Mark Wyciślik-Wilson
Since acquiring Skype, Microsoft has been slowly but surely developing the messaging tool, most recently increasing the number of chat participants to 50. Now the company has released a new version of the software -- in beta for the time being -- in which it is possible to share your screen with whoever you're chatting with. The beta feature is available to people on the Skype Insider program, and it allows for mobile screen sharing on both iOS and Android. See also: Skype chats with up to 50 people now available to all after beta testing ends Skype beta testers… [Continue Reading] -

How to change your name on PSN -- if you don't mind a couple of catches
Publié: avril 12, 2019, 10:49am CEST par Mark Wyciślik-Wilson
It's something people have been asking, practically begging, for for years; now it is finally possible. You can change your PlayStation Network ID. Sony announced back in October that the change was coming, and now it has gone live. But before you rush in and change your name to get away from the embarrassing moniker you adopted, there are a couple of things you need to keep in mind -- not least that it may cause problems with some games. The good news about changing your PSN name is that you can do it for free. At least, it is… [Continue Reading] -

Flickr adds image theft protection with Pixsy
Publié: avril 10, 2019, 12:26pm CEST par Mark Wyciślik-Wilson
Flickr now offers protection to its users in the form of image theft detection. The site has partnered with Pixsy and uses reverse image search technology and AI to monitor for unauthorized use of photographers' images. The service is only available to Pro subscribers, and is being billed as one of the "Pro Perks". Flickr says that when a copyright infringement is detected, users will "get access to a variety of tools and services that will help you deal with the unauthorized use of your work". See also: Flickr says free users can exceed 1,000 photos as Creative Commons images… [Continue Reading] -

Apple no longer charges for transferring data to a new Mac
Publié: avril 10, 2019, 11:35am CEST par Mark Wyciślik-Wilson
Apple is now offering data migration services free of charge when you get a new Mac. Previously, the company charged customers $99 to transfer data from an old Mac to a new one, or when data transfer was needed as part of a repair. While not the most taxing of tasks, the dropping of fees means more people are likely to leave the process to Apple rather than undertaking it themselves. See also: Apple and Beats designed Powerbeats Pro wireless earphones are coming in May Urban Armor Gear launches Plyo Series case for Apple MacBook Air (2018) Canceled: Apple's AirPower… [Continue Reading] -

Beta and nightly builds of Firefox now protect against fingerprinting and cryptomining
Publié: avril 10, 2019, 11:19am CEST par Mark Wyciślik-Wilson
Mozilla has added new protective features to the nightly and beta versions of Firefox. Through a partnership with Disconnect, the browser is now able to block cryptocurrency mining and fingerprinting scripts. The new features mean that users are protected against scripts that can be used to track them online, as well as those that use CPU cycles to mine for cryptocurrency. Mozilla says it is part of its mission to protect people from "threats and annoyances on the web". See also: Mozilla is launching curated Recommended Extensions program this summer How to enable dark mode in new Chromium-based Microsoft Edge… [Continue Reading] -

Facebook updates its terms and conditions in Europe to clarify personal data usage
Publié: avril 9, 2019, 3:15pm CEST par Mark Wyciślik-Wilson
Facebook has faced numerous battles and controversies around the world, but the social networking giant has come under particular fire from Europe. Today, in response to concerns raised by the European Commission, Facebook has agreed to update its terms and conditions in the EU to make it clear to users how their personal data is used. The new terms clarify how user data is shared with third parties, and how it can be used to target advertising. They also explain how users can close their accounts if they want, and detail reasons for which accounts can be disabled. See also:… [Continue Reading] -

How to enable dark mode in new Chromium-based Microsoft Edge
Publié: avril 9, 2019, 11:39am CEST par Mark Wyciślik-Wilson
There has been talk of a Chromium-based version of Microsoft Edge for a while, and now Microsoft has finally released the browser to those willing to take part in the Insider program. While it's early days for this new version of Edge, there is already the Microsoft Edge Insider Addons website to investigate, but you may also want to experiment with settings. One such setting is dark mode -- something which has proved very popular in all sorts of apps. Here's how to enable it. See also: Microsoft Edge Insider Addons website launched Leaked: first look at Chromium-based Microsoft Edge… [Continue Reading] -

Microsoft Edge Insider Addons website launched
Publié: avril 9, 2019, 8:29am CEST par Mark Wyciślik-Wilson
The first official builds of Chromium-based version of Microsoft Edge are now available to download, and Microsoft has also launched the Microsoft Edge Insider Addons website. Anyone using the standard, non-Insider version of the browser is probably familiar with the addons and extensions that are available from the Microsoft Store for Edge. But with the new Chromium version of Edge, the new website gives an easy way to extend the capabilities of the Dev and Canary builds. See also: Leaked: first look at Chromium-based Microsoft Edge First official builds of Microsoft's Chromium-based Edge browser now available to test As these… [Continue Reading] -

Twitter slashes the number of users you can follow each day
Publié: avril 9, 2019, 7:27am CEST par Mark Wyciślik-Wilson
In an attempt to cut down on bots and spam activity, Twitter is dramatically reducing the number of accounts it is possible to follow each day. The previous limit meant users could follow up to 1,000 new accounts on a daily basis, but this has been abused by spammers and bots to quickly grow their networks. The new limit is less than half of this -- just 400 -- and is an update to Twitter's policies against "aggressive following or follower churn" and "bulk or aggressive activity". See also: Warning: Don't change your Twitter birthday to 2007 Twitter is testing… [Continue Reading] -

Mozilla is launching curated Recommended Extensions program this summer
Publié: avril 8, 2019, 8:13pm CEST par Mark Wyciślik-Wilson
However much you love your chosen web browser, you have probably enhanced its capabilities through the use of add-ons. Finding decent, reliable add-ons can be tricky, and this is why Mozilla is launching the Recommended Extensions program. This editor-curated program will surface the very best vetted extensions for Firefox, and it is due to roll out in stages later this summer. See also: Open letter signed by Mozilla demands Facebook take 'real action' against disinformation Mozilla COO contacts European Commission voicing concerns about Facebook's lack of ad transparency Mozilla has a new mobile web browsing experience for you to test:… [Continue Reading] -

Viber users in the US, UK and Canada can now buy a Viber Local Number for calls and texts
Publié: avril 8, 2019, 5:37pm CEST par Mark Wyciślik-Wilson
Viber has launched a new option called Viber Local Number which lets users in the US, UK and Canada buy a local phone number to associate with their account and use it to receive calls and texts with non-Viber users. Viber Local Number (VLN) has been in closed beta testing for a little while, but it is now available to anyone from the supported countries that is interested. It is a similar system to that found in Skype, and will cost subscribers $4.99 per month. See also: Skype chats with up to 50 people now available to all after beta… [Continue Reading] -

Huawei's 'shoddy' security could mean it is banned from sensitive parts of the UK's 5G network
Publié: avril 8, 2019, 12:39pm CEST par Mark Wyciślik-Wilson
Concerns about Huawei's "very, very shoddy" security could mean that the Chinese company's technology is barred from key parts of the UK's 5G mobile network. A UK watchdog has already said that Huawei poses a national security risk, but a statement from the technical director of GCHQ's National Cyber Security Centre has stepped things up. Dr Ian Levy says that "the security in Huawei is like nothing else -- it's engineering like it's back in the year 2000 -- it's very, very shoddy". See also: UK watchdog says Huawei poses a national security risk Sources: Huawei is on the verge… [Continue Reading] -

GDPR rules could be used by the UK to fine tech firms for 'harmful content'
Publié: avril 8, 2019, 11:36am CEST par Mark Wyciślik-Wilson
The UK is looking at hitting technology companies with financial penalties if they fail to do enough to counter "harmful content" on their platforms. Jeremy Wright, the Digital, Culture, Media and Sport (DCMS) secretary, says that tech firms need to be made to "sit up and take notice" when it comes to dealing with problematic content. While clearly aimed more at social media companies, the proposals would encompass other technology firms as well. The plans also suggest that search engines should remove links to offending websites, and that some sites could even be blocked completely. See also: Valve responds to… [Continue Reading] -

Emsisoft Decrypter for Planetary gets your ransomware-riddled files back for free
Publié: avril 8, 2019, 10:30am CEST par Mark Wyciślik-Wilson
Emsisoft has released a free decrypter tool for anyone who has been struck by the Planetary Ransomware, eliminating the need to pay a fee to the attackers. Before using the tool you are advised to ensure that you have removed the malware from your computer -- something you can do with the free version of Emsisoft Anti-Malware. You also need to ensure that you don't delete the ransom note ("!!!READ_IT!!!.txt") or the decrypter won't work. See also: Google publishes its Android Security & Privacy 2018 Year in Review Free tool protects businesses against ransomware and other threats UK watchdog says… [Continue Reading] -

/r/Piracy is going on a massive deletion spree to avoid a Reddit ban
Publié: avril 8, 2019, 9:43am CEST par Mark Wyciślik-Wilson
Reddit has never been much of a stranger to controversy, and the site has faced mounting pressure from copyright-holders to do something about piracy. Moderators have been fighting a losing battle to keep illegal content in check, but with complaints still flooding in, the /r/piracy subreddit is taking drastic action. Having spoken to the community about initiating "The Nuclear Option", the decision was taken to delete nearly a decade's worth of content. See also: Article 13: EU approves controversial copyright law despite massive opposition Final text of new EU Copyright Directive retains controversial content blocking of Article 13 The decision… [Continue Reading] -

With Windows 10 1809, Microsoft drops safe removal of USB drives as the default option
Publié: avril 7, 2019, 2:52pm CEST par Mark Wyciślik-Wilson
To safely remove or not to safely remove? That is the question... although another one might reasonably be, "well, what difference does it really make?". Since the arrival of USB drives, we have been warned that they need to be "safely removed" using the correct method in Windows, rather than just being yanked out -- but now this changes. With Windows 10 1809, Microsoft is changing the default setting that's applied to USB drives and other removable media. The change means that the default policy applied to removable storage devices is Quick Removal rather than Better Performance -- so you… [Continue Reading] -

Competition and Markets Authority investigates Microsoft, Sony and Nintendo's online gaming subscriptions
Publié: avril 7, 2019, 12:02pm CEST par Mark Wyciślik-Wilson
The UK's Competition and Markets Authority (CMA) has launched an investigation into the business practices of Microsoft, Sony and Nintendo, partly in relation to the companies' online gaming subscription services. The CMA has voiced concern about what it says is the unfair practice of automatic renewing Nintendo Switch, PlayStation and Xbox subscriptions. There are also concerns about the associated cancellation and refund policies, and terms and conditions. See also: Valve responds to European complaints about Steam geo-locking Europe hits out at Valve for geo-blocking Steam games Europe hits Google with €1.49 billion fine for breaking antitrust law with AdSense restrictions… [Continue Reading] -

Netflix suddenly drops AirPlay support from its iOS apps
Publié: avril 6, 2019, 5:07pm CEST par Mark Wyciślik-Wilson
Citing "technical limitations", Netflix has dropped support for AirPlay from its iPhone and iPad apps. Attempts to use AirPlay via the Control Center result in an error message, and Netflix has updated its support pages to indicate that the feature is no longer available. With AirPlay having been supported for a number of years, it's not clear quite what technical issues may have suddenly arisen, but the change does come shortly after the launch of Apple TV+. See also: Apple and Beats designed Powerbeats Pro wireless earphones are coming in May Canceled: Apple's AirPower wireless charging mat will not be… [Continue Reading] -

Valve responds to European complaints about Steam geo-locking
Publié: avril 6, 2019, 11:23am CEST par Mark Wyciślik-Wilson
Having been slapped with antitrust accusations by the European Commission, Valve has responded to complaints about geo-blocking on its Steam gaming platform. After the Commission complained that Valve and five game publishers had come to arrangements between themselves to region-lock certain titles, the company says that only a very small portion of games available on the platform are subject to geo-locking. See also: Europe hits out at Valve for geo-blocking Steam games Europe hits Google with €1.49 billion fine for breaking antitrust law with AdSense restrictions Apple is going to educate the US and Europe on how to avoid fake… [Continue Reading] -

Skype chats with up to 50 people now available to all after beta testing ends
Publié: avril 6, 2019, 10:41am CEST par Mark Wyciślik-Wilson
Following a beta test of the feature Microsoft has doubled the number of people that can take part in a Skype chat from 25 to 50 for all users. The option of chatting with up to 49 other people applies to both video and audio chats, and it's something that is probably going to appeal to businesses more than individual users. The increase sees Skype finally catching up with Facebook Messenger, and overtaking Apple's FaceTime. See also: Skype beta testers can now hold group chats with up to 50 participants Microsoft rolls out new Skype for Web, and drops support… [Continue Reading] -

Europe hits out at Valve for geo-blocking Steam games
Publié: avril 5, 2019, 5:54pm CEST par Mark Wyciślik-Wilson
The European Commission has informed Valve that geo-blocking in Steam contravenes EU competition rules. Similar warnings have been issued to five games publishers. Valve, Bandai Namco, Capcom, Focus Home, Koch Media and ZeniMax have been told that "European consumers should have the right to buy and play video games of their choice regardless of where they live in the EU". The Commission says that the use of geo-blocking to prevent cross-border sales is a breach of antitrust rules. See also: Europe hits Google with €1.49 billion fine for breaking antitrust law with AdSense restrictions Apple is going to educate the… [Continue Reading] -

Microsoft brings Spotify, performance monitoring widgets and more to the Game Bar
Publié: avril 5, 2019, 11:17am CEST par Mark Wyciślik-Wilson
If you're signed up to the Xbox Insiders program, you can beta test an updated version of the Game Bar in Windows 10. Originally designed to allow for recording and broadcasting of game footage, The Game Bar now includes Spotify integration and cross-platform messaging. The Game Bar beta also includes a number of new widgets that can be used to monitor system performance, control audio, and more. See also: Windows 10 has a built-in free screen recorder that you might not know about Sega Genesis Mini is coming soon, and you can pre-order the game console now Google announces Stadia,… [Continue Reading] -

Google closes down its AI ethics council just one week after its launch
Publié: avril 5, 2019, 10:26am CEST par Mark Wyciślik-Wilson
Google has announced that it is closing down its artificial intelligence ethics council following controversy about board members. The Advanced Technology External Advisory Council (ATEAC) was formed just a week ago, but there was strong criticism of the decision to appoint Heritage Foundation president Kay Coles James to the board. Rightwinger James has a history of opposing LGBTQ rights, and dozens of Google employees signed a petition in protest at her board membership. In response, Google has said that it is "going back the drawing board" and is ending the council. See also: Google+ is officially dead... but you may… [Continue Reading] -

Email app Spark arrives on Android ready to replace Google Inbox
Publié: avril 2, 2019, 4:18pm CEST par Mark Wyciślik-Wilson
Google may be shutting down its Inbox app later this week, but there are alternatives out there. In fact, the number of options available to Android users just increased. Spark -- which has proved very popular with iOS and macOS users -- has just migrated to Android, bringing with it all manner of inbox organizing smarts. Developer Readdle says it will, "make you love email again". See also: How to schedule emails in Gmail 90 percent of tech companies are vulnerable to email spoofing Protecting email deliverability before and after a data breach Free and untarnished by ads, Spark has… [Continue Reading] -

Microsoft launches new 13.5-inch Surface Book 2 with 8th Gen Intel quad-core i5 processor
Publié: avril 2, 2019, 2:56pm CEST par Mark Wyciślik-Wilson
With precisely zero fanfare, Microsoft has added a new mid-range Surface Book 2 to the existing line-up. Priced at $1,499, the 13.5-inch model is now available with the new i5-8350U processor. The addition of an 8th generation Intel quad-core Core i5 processor was something we'd heard rumoured, and this new model not only opens up the range of options available to buyers, it also means that other prices have been reduced. See also: Microsoft releases Windows 10 20H1 Build 18865 to the Skip Ahead ring Leaked: first look at Chromium-based Microsoft Edge Microsoft brings its Windows Defender antivirus software to… [Continue Reading] -

Cloudflare announces free VPN service, Warp, to complement its 1.1.1.1 DNS resolver
Publié: avril 2, 2019, 1:52pm CEST par Mark Wyciślik-Wilson
Online privacy has become such a concern that VPN tools -- once used only by technology experts -- have now started to become far more mainstream. Android users can take advantage of Opera's built-in VPN, and there are many other services to choose from. Adding to this list, Cloudflare has announced a new free VPN service called Warp. It will become part of the company's existing privacy-focused 1.1.1.1 DNS resolver, and just as 1.1.1.1 was designed to simplify using a DNS tool, so Warp is being billed as a "VPN for people who don't know what V.P.N. stands for". See… [Continue Reading] -

How to schedule emails in Gmail
Publié: avril 2, 2019, 12:59pm CEST par Mark Wyciślik-Wilson
It seems hard to believe, but Gmail has now been with us for 15 years. To celebrate a decade-and-a-half of existence, Google has added a handful of new and improved features to it. Smart compose has been updated and expanded to more devices and languages, and it has also been made smarter with AI-powered personalization. But the star of the show is email scheduling, something people have been asking for for years. Here's how to use it. See also: Google publishes its Android Security & Privacy 2018 Year in Review Europe hits Google with €1.49 billion fine for breaking antitrust… [Continue Reading] -

Mark Zuckerberg's calls for internet regulation are just an attempt to shift the blame from Facebook
Publié: avril 1, 2019, 10:24am CEST par Mark Wyciślik-Wilson
Over the weekend, Mark Zuckerberg set out what he described as "four ideas to regulate the internet". Were these ideas put forth by someone else, it might be possible to refer to this as an impassioned plea -- but this is Zuckerberg we're talking about. He suggests GDPR-style privacy regulation in the US. He wants more control of hate speech. He believes more needs to be done about political advertising, particularly around the time of elections. And he likes the idea of data portability. These are reasonable ideas and -- importantly -- there is nothing to stop Facebook from implementing… [Continue Reading] -

Google publishes its Android Security & Privacy 2018 Year in Review
Publié: mars 30, 2019, 12:24pm CET par Mark Wyciślik-Wilson
Google has published its fifth Android Security & Privacy Year in Review, this time looking back at 2018. While the report draws attention to some of the security and privacy improvements the company has made, it is not just about Google blowing its own trumpet. The report shows that payouts made through Google rewards programs -- payments made to outside researchers and individuals for bringing security issues to the company's attention -- reached $3 million in 2018. Google also says that in the fourth quarter of the year, 84 percent more devices received a security update than in the same… [Continue Reading] -

Canceled: Apple's AirPower wireless charging mat will not be released
Publié: mars 30, 2019, 11:04am CET par Mark Wyciślik-Wilson
Apple has confirmed that its long-awaited wireless AirPower charging mat is not going to be released. The company says quality issues are to blame for the decision. The product was originally announced back in 2017 and was destined to be a convenient way to wirelessly charge iPhones, Apple Watches and AirPods. Its released had been repeatedly pushed back, but now it has been canceled completely See also: Apple TV+ and Apple News+ are likely flops, but Apple Arcade gaming service could be a winner Apple unveils Apple TV+ for all its original content Kaspersky reports Apple to antimonopoly authorities over… [Continue Reading] -

Russia orders NordVPN, ExpressVPN, HideMyAss and other VPNs to block numerous sites
Publié: mars 29, 2019, 11:56am CET par Mark Wyciślik-Wilson
VPNs are frequently used by people to increase security, improve privacy, to browse the internet as if in another country, and to bypass restrictions put in place by ISPs and governments. Aware of this, authorities in Russia have ordered ten big-name VPNs to block access to various sites banned in the country. Among those to have been contacted by the authorities are NordVPN, ExpressVPN, IPVanish, HideMyAss and TorGuard. At least one of these VPN providers has decided to pull out of Russia. See also: Opera for Android now includes a free and unlimited VPN Privacy: Facebook closes controversial Onavo VPN… [Continue Reading] -

UK watchdog says Huawei poses a national security risk
Publié: mars 28, 2019, 5:02pm CET par Mark Wyciślik-Wilson
In its fifth annual report, the UK's Huawei oversight board says that the Chinese firm poses a threat to national security. It reached the conclusion after discovering that the company has made "no material progress" in addressing the security flaws highlighted in last year's report. But while the report was damning of Huawei, saying it found additional "significant technical issues in Huawei’s engineering processes leading to new risks in the UK telecommunications networks", the board stopped short of calling for a ban on Huawei's involvement in 5G in the UK. See also: Sources: Huawei is on the verge of suing… [Continue Reading] -

Facebook explicitly bans white nationalism and white separatism
Publié: mars 28, 2019, 11:56am CET par Mark Wyciślik-Wilson
The "praise, support and representation" of both white nationalism and white separatism are to be explicitly banned on Facebook and Instagram. The new policies will be enforced as of next week. Facebook announced the change in policy as it and other social networks face increasing pressure to do more to counter hate speech. It also comes in the wake of the Christchurch, New Zealand mosque shooting, footage of which was shared on the platform. See also: Facebook stored millions of users' passwords in searchable plain text for years Pahahaha! Zuckerburg outlines his, *snort*, privacy-focused vision for Facebook and social networking… [Continue Reading] -

See the Samsung Galaxy Fold hinge in action in an official stress-test video
Publié: mars 28, 2019, 11:07am CET par Mark Wyciślik-Wilson
Aside from 5G, it seems that the next big movement in the world of smartphones is going to be folding devices. Both Samsung and Huawei have announced foldables in recent weeks, with each adopting different designs. As smartphones with folding screens are a new category of device, users understandably have questions about them. What are they like to use? Is the crease visible? Will the screen hold up to continued folding and unfolding? In a new video, Samsung shows how its Galaxy Fold is stress-tested to ensure that it can withstand 200,000 openings and closings. See also: Battle of the… [Continue Reading] -

BitTorrent Inc announces BitTorrent Live, a social streaming platform that's not based on BitTorrent
Publié: mars 27, 2019, 6:03pm CET par Mark Wyciślik-Wilson
BitTorrent Inc has announced plans to launch a new social media platform for live streaming. It will be called BitTorrent Live and -- at least initially -- it will be centralized rather than decentralized, meaning that it is not based on the BitTorrent protocol or other P2P technology. The first beta version is expected to launch in the coming quarter, and it will compete with the likes of Facebook Live. BitTorrent Live will enable users to stream content to mobile devices, or broadcast live, and will include social media elements. As reported by TorrentFreak, the aim of the new platform… [Continue Reading] -

Almost half of industrial computers hit by malicious cyber activity in 2018
Publié: mars 27, 2019, 4:18pm CET par Mark Wyciślik-Wilson
Kaspersky has released the results of an astonishing study that found that almost half of world's Industrial Control System (ICS) computers was subjected to malicious cyber activity last year. While malware and cyber attacks have been a problem for some time, there is particular concern about the rising numbers of ICS computers being affected. In the case of downtime for such systems, there is the risk of material losses and production downtime at industrial facilities. See also: Kaspersky reports Apple to antimonopoly authorities over the handling of its apps Check to see if your computer was targeted by the ASUS… [Continue Reading] -

Check to see if your computer was targeted by the ASUS ShadowHammer malware
Publié: mars 27, 2019, 11:31am CET par Mark Wyciślik-Wilson
Yesterday we reported about a warning from Kaspersky that the ASUS Live Update Utility had been hacked to deliver ShadowHammer backdoor malware. ASUS has now released a patch to secure systems, and Kaspersky has released a tool that you can use to check whether you have been affected by the malware. It's important that ASUS users install the patch -- described as a "critical" update by the company -- to secure their systems, but it's also a good idea to use Kaspersky's utility to see whether your computer has been infected with ShadowHammer. See also: ASUS Live Update Utility hacked… [Continue Reading] -

Warning: Don't change your Twitter birthday to 2007
Publié: mars 27, 2019, 10:44am CET par Mark Wyciślik-Wilson
Many things go viral online these days -- funny cat videos, memes, stupid "challenges", and all manner of helpful hints and tips. Something that's doing the rounds at the moment encourages Twitter users to change their birthday to a date in 2007. This might sound like a strange thing to do, but there is the promise of secret new color schemes or rainbow mode being unlocked to lure people in. There are also claims that changing your birthday will get your account verified and earn you a prestigious blue tick. It is -- of course -- not true, but this… [Continue Reading] -

Article 13: EU approves controversial copyright law despite massive opposition
Publié: mars 26, 2019, 6:19pm CET par Mark Wyciślik-Wilson
The European parliament has voted in favor of major changes to copyright law, including two highly controversial clauses -- article 11 and article 13. Known respectively as the "link tax" and the "upload filter", these two clauses have generated a great deal of interest from internet users and the technology industry alike. In particular, article 13 has proved especially controversial, holding websites responsible for material uploaded without a licence -- something critics say could only be adhered to with content filters. See also: Final text of new EU Copyright Directive retains controversial content blocking of Article 13 Europe hits Google… [Continue Reading] -

Leaked: first look at Chromium-based Microsoft Edge
Publié: mars 25, 2019, 11:55am CET par Mark Wyciślik-Wilson
We have known for a little while that Microsoft is planning to release a Chromium-based version of its Edge browser, and a new leak gives us our first glimpse at it. With Chromium at its core, it is perhaps no surprise that this version of Edge bears more than a passing resemblance to Google Chrome. The leak also confirms much of what we thought we already knew about the upcoming browser -- support for Chrome extensions, a dark mode, synchronization of favorites, and more See also: New Windows Defender Application Guard add-ons for Chrome and Firefox open untrusted sites in… [Continue Reading] -

AT&T's 5G E is slower than some 4G connections
Publié: mars 24, 2019, 11:43am CET par Mark Wyciślik-Wilson
If you see a 5G indicator in your phone's status bar, you know you've got a fast connection, right? Think again. The technology world may be eagerly anticipating the capabilities of 5G, but in the US AT&T has simply jumped on the hype bandwagon as a marketing tool. A new study into the speed of the company's 5G E service found that it is actually slower than 4G offerings from its rivals. Despite the name suggesting a futuristic service with speeds to match, AT&T is actually delivering sub-par performance. See also: How edge computing is making 5G possible [Q&A] Huawei's… [Continue Reading] -

Crappy phone battery life? Video ad fraud could be to blame
Publié: mars 24, 2019, 10:15am CET par Mark Wyciślik-Wilson
Few people can claim to like the ads that have become part and parcel of smartphone usage, but for the most part they can be endured. But what about when a minor inconvenience that merely infringes on your time becomes even more of a nuisance and actually starts to kill your phone battery? According to an investigation, this is precisely what has been happening. An ad fraud scheme has been uncovered that invisibly plays videos lucrative video ads on handsets, earning money for fraudsters and draining the batteries of Android handsets. See also: Sign up to beta test Android Pie… [Continue Reading] -

Kaspersky reports Apple to antimonopoly authorities over the handling of its apps
Publié: mars 22, 2019, 10:45am CET par Mark Wyciślik-Wilson
Security firm Kaspersky has reported Apple to Russia's Federal Antimonopoly Service. The complaint comes after Apple rejected the Kaspersky Safe Kids parental control app from the App Store, saying that the implementation of two "essential" features contravened store policies. Kaspersky was surprised at the removal of the app as it had been sitting happily in the App Store for some three years. The company believes that Apple has forced the app out of the store because iOS 12 introduced its own Screen Time parental controls -- something Kaspersky views as restrictive and monopolistic behaviour. See also: Apple is going to… [Continue Reading] -

Moleskine teams up with Adobe to create a smart notebook: the Moleskine Paper Tablet Creative Cloud Connected edition
Publié: mars 22, 2019, 9:22am CET par Mark Wyciślik-Wilson
Moleskine is a name to be reckoned with. Its paper notebooks have been used by writers, poets and artists for years, and it's a brand that has a dedicated following. Now, having previously worked with Adobe to blur the boundaries between digital and analog writing and drawing, Moleskine has once again joined forced with the Photoshop-maker. The outcome of this latest partnership is the Moleskine Paper Tablet Creative Cloud Connected edition, a smart notebook that works with Adobe Illustrator in conjunction with the Moleskine Pen+ Ellipse optical pen. The idea is a simple one; in theory, at least. It's something… [Continue Reading] -

Sign up to beta test Android Pie on OnePlus 3 and 3T
Publié: mars 22, 2019, 8:42am CET par Mark Wyciślik-Wilson
OnePlus has a decent track recording of supporting its handsets for longer than most other companies, pushing out security updates and even operating system upgrades long beyond the point at which other manufacturers have let their handsets fall by the wayside. Having already rolled out Android Pie to the OnePlus 5 and 5T, it wasn't long before we learned that the company hadn’t forgotten about owners of older handsets. Now you can sign up to take part in a beta program to test Android Pie on your OnePlus 3 or 3T ahead of the impending launch of the Pie-based OxygenOS… [Continue Reading] -

Facebook stored millions of users' passwords in searchable plain text for years
Publié: mars 21, 2019, 6:05pm CET par Mark Wyciślik-Wilson
Just when you think things couldn't get any worse with Facebook, something else comes along to lower your opinion of the social network even further. The latest security slip-up relates to passwords: it turns out that for up to six years, millions of user passwords were stored in plain text. As well as being stored in plain text, passwords were searchable by thousands of Facebook employees. An investigation by Facebook suggests that somewhere between 200 million and 600 million user accounts were affected, some as far back as 2012. See also: Pahahaha! Zuckerburg outlines his, *snort*, privacy-focused vision for Facebook… [Continue Reading] -

Opera for Android now includes a free and unlimited VPN
Publié: mars 20, 2019, 6:38pm CET par Mark Wyciślik-Wilson
Opera has added a free VPN service to the Android version of its mobile web browser. Opera 51's newly-added VPN is not only free from charges, it is also free from limitations. The feature has been added as the Norwegian software developer seeks to improve the security and privacy of web browsing for its users. The company says that it "marks a new standard for privacy and security in mobile browsing". See also: Copying Microsoft, Google is bringing browser choice to Android to stave off antitrust regulators Mozilla has a new mobile web browsing experience for you to test: Reference… [Continue Reading] -

Amazon's entry-level Kindle gets a slight price bump -- and gains a front light
Publié: mars 20, 2019, 5:20pm CET par Mark Wyciślik-Wilson
Amazon has announced its new entry-level Kindle, introducing a couple of changes. While the price remains below $100, there has been a $10 hike, taking the price up to $89.99. This extra $10 buys you an e-reader with only one notable change -- a new adjustable front light to allow for reading in the dark. Amazon refers to the design of the all-new Kindle as "refereshed", maintaining its thin and light aesthetics. The design of the new Kindle is similar to that of the Paperwhite, but the similarities soon stop. The 6-inch e-ink device is available in either black or… [Continue Reading] -

Europe hits Google with €1.49 billion fine for breaking antitrust law with AdSense restrictions
Publié: mars 20, 2019, 1:38pm CET par Mark Wyciślik-Wilson
The European Commission has hit Google with another large fine, this time €1.49 billion ($1.69 billion) for engaging in anti-competitive practices with its advertising tool AdSense. Google was found guilty of breaking antitrust laws by blocking third party rivals from using AdSense to display advertisements. This is the third fine the Commission has levelled against Google in the last couple of years, but this most recent one is less than a third of the previous record fine for other antitrust violations. See also: Copying Microsoft, Google is bringing browser choice to Android to stave off antitrust regulators Google announces Stadia,… [Continue Reading] -

Apple is going to educate the US and Europe on how to avoid fake news
Publié: mars 20, 2019, 11:38am CET par Mark Wyciślik-Wilson
Apple has announced that it is to support initiatives in the US and Europe that seek to improve media literacy. The aim is to "encourage critical thinking and empower students to be better informed" by teaching people how to find reliable sources and avoid fake news. In the US, Apple is throwing its support behind the News Literacy Project (NLP) and Common Sense, while in Europe it is Osservatorio that will reap the benefits of the company's backing. All three are non-profit organizations that provide nonpartisan, independent media literacy programs. See also: Apple refreshes iMac range with a performance boost… [Continue Reading] -

Copying Microsoft, Google is bringing browser choice to Android to stave off antitrust regulators
Publié: mars 20, 2019, 9:34am CET par Mark Wyciślik-Wilson
Google is no stranger to investigations into and questions about its practices, and in Europe the company has faced great interest from the European Commission for violating antitrust laws. Now, in a move that echoes that of Microsoft's Browser Choice nearly a decade ago, Google is going to give Android users the option of choosing their default web browser and search engine. This is not something that will be happening on a global scale, however -- at least not to start with. As Google is merely keen to avoid accusations of being anticompetitive in Europe, it is only European Android… [Continue Reading] -

Google announces Stadia, its new instant-play game streaming service
Publié: mars 19, 2019, 7:17pm CET par Mark Wyciślik-Wilson
Downloading and installing is just so passé, and Google knows it. It is with this fact in mind -- and an eye firmly on the future -- that the company today announces its new game streaming service, Stadia, at GDC 2019. The audience at this year's Game Developers Conference were treated to a preview of the cloud-based gaming service that can be accessed from mobiles, desktops, laptops, TVs and more. Google is hoping that the allure of cross-platform, instant-play gaming will attract droves of gamers to the platform. See also: Google Inbox is closing down in two weeks The Internet… [Continue Reading] -

Apple refreshes iMac range with a performance boost from up-to 8-core Intel 9th-generation processors
Publié: mars 19, 2019, 5:46pm CET par Mark Wyciślik-Wilson
Just a day after launching new iPad Air and iPad mini models, Apple has announced the latest updates to its iMac range. The update has been a long time coming; it is well over a year since there were any changes made to the iMac line. But good things come to those who wait. Apple's updates bring the humble iMac closer to the iMac Pro thanks to the addition of 9th-generation Intel processors and Radeon Pro Vega graphics -- which Apple says doubles performance. Despite the boost, Apple has made the pleasing decision of keeping pricing the same as before.… [Continue Reading] -

Google Inbox is closing down in two weeks
Publié: mars 19, 2019, 4:49pm CET par Mark Wyciślik-Wilson
Google is far from being a stranger to launching and shuttering apps and services willy-nilly, and the latest victim is Inbox. We have actually known for a little while that Google Inbox was due to close down -- it was just a matter of when. Now Google has revealed the closure date, and it is just two weeks away: April 2. We wave goodbye to Inbox on the same day as Google+. See also: The Internet Archive is trying to save Google+ content before it is deleted Google adds privacy-focused DuckDuckGo search engine to Chrome Google recommends upgrading to Windows… [Continue Reading] -

Oops! MySpace has lost 12 years' worth of photos, videos and music
Publié: mars 18, 2019, 5:43pm CET par Mark Wyciślik-Wilson
MySpace -- that forerunner of the social networking phenomenon -- appears to have had a bit of an accident. In the process of migrating servers, it seems that the site has managed to lose 12 years' worth of uploaded music and other data. The slip up means that photos, videos and music uploaded between 2003 and 2015 have been lost forever. This is not a case of data being temporary unavailable; MySpace has lost it, and -- almost unbelievably -- has no backup. See also: The Internet Archive is trying to save Google+ content before it is deleted Pahahaha! Zuckerburg… [Continue Reading] -

The Internet Archive is trying to save Google+ content before it is deleted
Publié: mars 18, 2019, 9:44am CET par Mark Wyciślik-Wilson
It is now just a couple of weeks until Google+ closes down forever. While few will mourn its passing, there is still a lot of content on Google's social site that is worth preserving. Maybe. Google+ users have the option of downloading their own data for posterity, but the Archive Team, in conjunction with the Internet Archive, has grander plans: it is looking to archive as much of the site as possible before it is deleted forever. See also: Google adds privacy-focused DuckDuckGo search engine to Chrome Google recommends upgrading to Windows 10 to avoid unpatched Windows 7 zero-day that's… [Continue Reading] -

Hackers are exploiting critical WinRAR bug exposed last month
Publié: mars 17, 2019, 3:24pm CET par Mark Wyciślik-Wilson
Towards the end of last month, security researchers revealed details of a critical bug in that stalwart of the compression world, WinRAR. The bug is many years old and although it relates to the rarely-used ACE format and has since been patched, it has been discovered hackers are actively exploiting it since it was made public. The 19-year-old bug in the file UNACEV2.DLL (CVE-2018-20250) allows for an attacker to execute malicious files hidden in compressed archives. Over 100 exploits have been found that take advantage of people who are yet to update to a secure version of the software... and… [Continue Reading] -

Spotify lashes out at 'monopolist' Apple in escalating war of words
Publié: mars 17, 2019, 12:41pm CET par Mark Wyciślik-Wilson
The battle between Apple and Spotify continues, with the streaming music company labelling the iPhone-maker a "monopolist". The spat started when Spotify filed a complaint against Apple, saying that the company is stifling competition and limiting user choice with rules it puts in place. Apple responded, poo-pooing the claims, and now Spotify has responded in turn not only accusing Apple of having a monopoly, but also saying that the company's response to the complaint was "entirely in line" with what it expected. See also: Apple bites back at Spotify's damning claims against it Leaked internal documents show Apple will repair… [Continue Reading] -

Skype beta testers can now hold group chats with up to 50 participants
Publié: mars 15, 2019, 4:51pm CET par Mark Wyciślik-Wilson
Microsoft has doubled the number of people that can take part in Skype group video calls. For beta testers involved in the Skype Insider Preview, the upper limit increases from 25 to 50. While this may not be something that the average home user will be particularly interested in, it's something that will be welcomed by business users as it means they will be able to hold larger remote meetings for free. See also: Microsoft rolls out new Skype for Web, and drops support for Chrome OS and Linux Microsoft brings AI-powered background blurring to Skype Microsoft is now forcing… [Continue Reading] -

Google adds privacy-focused DuckDuckGo search engine to Chrome
Publié: mars 14, 2019, 6:00pm CET par Mark Wyciślik-Wilson
Update to Chrome 73 and you might be in for a bit of a shock. With absolutely no fanfare whatsoever, Google has added DuckDuckGo to the list of search engines available in its web browser. In fact, the company has updated the default list of search engines it offers in over 60 markets, but it is the addition of privacy-focused DuckDuckGo that comes as the most welcome surprise. See also: DuckDuckGo reminds ignorant users that many websites ignore browsers' Do Not Track privacy requests Privacy-centric DuckDuckGo shuns Google and turns to Apple Maps for location-based searches DuckDuckGo denies using fingerprinting… [Continue Reading] -

Microsoft will pester Windows 7 users to upgrade to Windows 10 with pop-up notifications
Publié: mars 12, 2019, 5:37pm CET par Mark Wyciślik-Wilson
Anyone who is still using Windows 7 doesn't have much longer until the operating system is no longer supported by Microsoft. Come January 14, 2020 only those enterprise customers who are willing to pay for Extended Security Updates will receive any kind of support. Microsoft has already done a lot to encourage Windows 7 diehards to make the move to Windows 10, and now it is stepping things up a gear. Throughout 2019, the company will show pop-up notifications in Windows 7 about making the switch to the latest version of Windows. See also: Microsoft to start selling Windows 7… [Continue Reading] -

Windows 10 will automatically uninstall problematic updates
Publié: mars 12, 2019, 12:06pm CET par Mark Wycislik-Wilson
Updates to Windows are supposed to fix problems and improve security, but sometimes they do the opposite. Many Windows 10 users will have experienced startup problems after installing an update to the operating system, and this is something that Microsoft is looking to address. Rather than leaving it down to users to seek out the problematic update and uninstall it, Windows 10 could start to automatically uninstall updates that have caused issues. If this happens to you, you'll be greeted by the message: "We removed some recently installed updates to recover your device from a startup failure." See also: Microsoft… [Continue Reading] -

Microsoft to start selling Windows 7 Extended Security Updates from April 1
Publié: mars 11, 2019, 5:15pm CET par Mark Wycislik-Wilson
While Windows 10 enjoys a significant and growing userbase, there are still many Windows 7 users out there. This includes a large number of enterprise users, and for these customers security is of paramount importance. Last month we learned about the pricing for Windows 7 Extended Security Updates (ESU) which will be available when support for the aging operating system ends in 2020. Now we know that ESU will go on sale from the beginning of next month. See also: Google recommends upgrading to Windows 10 to avoid unpatched Windows 7 zero-day that's being actively exploited Windows 10 loses share… [Continue Reading] -

NVIDIA outbids Microsoft and Intel to buy data center chipmaker Mellanox for $6.9 billion
Publié: mars 11, 2019, 3:41pm CET par Mark Wycislik-Wilson
NVIDIA has announced that it plans to buy Israeli chipmaker Mellanox. Fending off competition from Microsoft and Intel, NVIDIA's bid of $6.9 billion was enough to secure the deal which is expected to be finalized by the end of the year. As part of the agreement, NVIDIA will purchase all Mellanox shares for $125 each in cash. It sees the company expanding further into high-performance computing and supercomputers, and boosts its data center business. NVIDIA's interest in Mellanox stemmed from its pioneering InfiniBand interconnect technology, used in many supercomputers and hyperscale datacenters. Together, the two companies say they will optimize… [Continue Reading] -

NVIDIA outbids Microsoft and Intel to buy datacenter chipmaker Mellanox for $6.9 billion
Publié: mars 11, 2019, 3:41pm CET par Mark Wycislik-Wilson
NVIDIA has announced that it plans to buy Israeli chipmaker Mellanox. Fending off competition from Microsoft and Intel, NVIDIA's bid of $6.9 billion was enough to secure the deal which is expected to be finalized by the end of the year. As part of the agreement, NVIDIA will purchase all Mellanox shares for $125 each in cash. It sees the company expanding further into high-performance computing and supercomputers, and boosts its datacenter business. NVIDIA's interest in Mellanox stemmed from its pioneering InfiniBand interconnect technology, used in many supercomputers and hyperscale datacenters. Together, the two companies say they will optimize datacenter-scale… [Continue Reading] -

Dark mode arrives in Slack's iOS and Android apps
Publié: mars 10, 2019, 2:08pm CET par Mark Wycislik-Wilson
For many workplaces -- including BetaNews -- Slack is the way workers stay in touch with each other. Jumping onto the black bandwagon, the chat and messaging tool is embracing the dark side and giving users the option to ramp up the darkness. To enjoy a darker look to Slack, you need to be part of the beta program, and there is nothing from stopping you from signing up right now and reaping the ocular -- or just aesthetic -- benefits of the new dark mode. Dark mode is available on both iOS and Android. See also: How to enable… [Continue Reading] -

Flickr says free users can exceed 1,000 photos as Creative Commons images are not counted
Publié: mars 9, 2019, 5:53pm CET par Mark Wycislik-Wilson
When Flickr announced changes to its free accounts, many users were upset to find that they were going to be limited to 1,000 photos unless they were willing to pay for Pro account. On top of this, Flickr said it would be deleting any images that took users over the limit. But now the company has announced something of a loosening of the rules. Flickr says that all public Creative Commons works on the site are now protected from deletion. There are also new "in memoriam" accounts for deceased members. See also: Flickr extends deadline, gives free users longer to… [Continue Reading] -

House of Lords wants to rein in big tech with a new 'Digital Authority'
Publié: mars 9, 2019, 10:39am CET par Mark Wycislik-Wilson
A House of Lords committee has called for the creation of a new Digital Authority to help co-ordinate existing regulators, as well as recommending new powers. The "super regulator" would have oversight over the current range of digital regulators, and would help to tackle problems of online harm which the UK government feels technology firms have not done enough about. There is a strong feeling from the government that self-regulation by technology companies has failed, and a report entitled Regulating in a Digital World sets out a series of principles that would underpin a new approach. See also: Facebook says… [Continue Reading] -

Google recommends upgrading to Windows 10 to avoid unpatched Windows 7 zero-day that's being actively exploited
Publié: mars 8, 2019, 10:57am CET par Mark Wycislik-Wilson
Google is warning users of Windows 7 that they are at risk from a privilege escalation zero-day bug -- and the advice is to upgrade to Windows 10 as there is no patch currently available for the actively exploited vulnerability. The problem stems from two vulnerabilities being exploited in combination -- one in Chrome, and one in Windows. Having pushed out a patch to its Chrome web browser, Google is warning that Windows 7 users are still exposed until such a time as Microsoft develops a patch. See also: Speed up Windows 10 with the Retpoline Spectre fix Google Project… [Continue Reading] -

Microsoft rolls out new Skype for Web, and drops support for Chrome OS and Linux
Publié: mars 8, 2019, 10:29am CET par Mark Wycislik-Wilson
Most of the Skype-related news of late has been about Microsoft killing off Skype Classic and moving people to Skype 8 -- but now there's news about the web version of the communication tool. While there are a number of new features to explore -- including hi-def video calling, new notifications and call recording -- Microsoft has taken the decision to reduce the number of supported platforms. The latest version of Skype for Web only works in Windows 10 and macOS 10.12 or newer, and only in the Chrome and Microsoft Edge browsers. Firefox and Opera users are left out… [Continue Reading] -

Pahahaha! Zuckerburg outlines his, *snort*, privacy-focused vision for Facebook and social networking hahahaha!
Publié: mars 7, 2019, 11:25am CET par Mark Wycislik-Wilson
Social networking in general, and Facebook in particular, is far from synonymous with the notion of privacy. Facebook makes occasional nods to granting users greater control over their privacy, but at the end of the day, data about users is what makes Mark Zuckerberg's company tick. But setting out his vision for the future in a blog post, the Facebook founder has set out his "vision and principles around building a privacy-focused messaging and social networking platform". We'd already heard about plans to merge the messaging platforms WhatsApp, Instagram and Facebook Messenger, this is central to his vision of the… [Continue Reading] -

Leaked internal documents show Apple will repair iPhones with third-party batteries
Publié: mars 6, 2019, 7:10pm CET par Mark Wycislik-Wilson
If you opted to replace your iPhone battery on the cheap -- avoiding Apple and opting for a third-party instead -- on a subsequent trip to your nearest Genius Bar you will have found that you were ineligible for repairs. It did not matter if your problem was in no way related to the battery, Apple took a hard line: if you had replaced the battery yourself, you were getting no further help. But leaked internal documents show that the company is softening. Genius Bar and Apple Authorized Service Provider technicians are now permitted to carry out work on phones… [Continue Reading] -

Speed up Windows 10 with the Retpoline Spectre fix
Publié: mars 6, 2019, 5:23pm CET par Mark Wycislik-Wilson
It's been a while since we heard much about Spectre, the speculative execution exploit that sent the security world into a frenzy. Cast your mind back a little while and you'll probably remember that the various fixes that were produced to mitigate against the exploits all had one thing in common -- they resulted in a performance hit. To help address the reduced performance experienced on older AMD and Intel systems, a new mitigation technique called Retpoline was developed. This new Spectre patch is currently included in Insider builds of Windows 10, but you can install it and enable it… [Continue Reading] -

Samsung teams up with Calm to bring mindfulness and meditation to the masses
Publié: mars 5, 2019, 3:12pm CET par Mark Wycislik-Wilson
In recent years, both Apple and Samsung have been expanding into health-related areas, bringing a range of wellbeing services to users. Now Samsung has announced that it is teaming up with popular sleep and meditation app, Calm. The partnership means that users of Samsung Health will be able to take advantage of things like mindfulness and guided meditation, as well as sleep and relaxation tools. See also: Battle of the foldable phones: Samsung Galaxy Fold vs Huawei Mate X The Samsung Galaxy Tab S5e is a thin and light entertainment-centric Android tablet Samsung launches blazing fast 970 EVO Plus NVMe… [Continue Reading] -

Facebook is adding a Tributes section to memorialized accounts of deceased users
Publié: mars 5, 2019, 12:50pm CET par Mark Wycislik-Wilson
When a Facebook user dies, it is possible to transform their profile into a memorialized account. Facebook describes this as a "place for friends and family to gather and share memories after a person has passed away". Now the social network is rolling out a new feature for memorialized profiles: Tributes. This is essentially a new section that appears on the page of deceased users where friends and family can post new content about their loved ones. See also: If you've added your phone number to Facebook for 2FA security, it can be used to search for you How to… [Continue Reading] -

Alphabet startup Chronicle launches enterprise cybersecurity platform Backstory, and partners with Avast
Publié: mars 5, 2019, 11:46am CET par Mark Wycislik-Wilson
It is a year since Google's parent company Alphabet launched the cybersecurity outfit Chronicle. Now the startup has launched its first product, a security platform called Backstory. Backstory is an enterprise-level cybersecurity and analytics platform; Chronicle describes it as "the first global security telemetry platform designed for a world that thinks in petabytes". Coinciding with the launch, Chronicle has teamed up with security firms Avast and Proofpoint. See also: Google Project Zero reveals 'high severity' macOS vulnerability that Apple has failed to patch If you've added your phone number to Facebook for 2FA security, it can be used to search… [Continue Reading] -

Google Project Zero reveals 'high severity' macOS vulnerability that Apple has failed to patch
Publié: mars 4, 2019, 5:24pm CET par Mark Wycislik-Wilson
Google's Project Zero has gone public about a "high severity" flaw in the macOS kernel after Apple failed to patch it 90 days after being told about the problem. A security researcher discovered a problem in XNU that means it is possible to perform malicious activities. The security bug related to copy-on-write (COW) behavior, enabling an attacker to manipulate filesystem images without the operating system being notified. Apple was informed of the vulnerability back in November, but has failed to release a patch. Writing about the vulnerability on the Chromium bug tracker -- highlighted by Neowin -- the security researcher… [Continue Reading] -

Sources: Huawei is on the verge of suing the US government
Publié: mars 4, 2019, 1:03pm CET par Mark Wycislik-Wilson
The US has made no secret of the fact it does not trust Huawei, and the company's hardware has been shunned by the government over fears about Chinese espionage. There have also been calls for Huawei hardware to be barred from the US power grid. The smartphone manufacturer has previously indicated that it is not willing to go down without a fight, and this threat could be about to be put into action. Huawei is said to be preparing to sue the US government, challenging last year's addition to the US National Defense Authorization Act (NDAA), according to sources talking… [Continue Reading] -

If you've added your phone number to Facebook for 2FA security, it can be used to search for you
Publié: mars 4, 2019, 9:32am CET par Mark Wycislik-Wilson
Facebook has been encouraging users to enable two-factor authentication to boost the security of their accounts, but it turns out that there's a slightly sinister side to this feature. You may well have opted to maintain an element of privacy by omitting personal information such as your address and phone number from your profile. But if you've used your mobile number to secure your account with 2FA, even if it is not visible to others, it can still be used to search for you -- and there is no way to opt out of this. See also: How to enable… [Continue Reading] -

Leak: OnePlus 7 could eliminate the notch with a pop-up camera
Publié: mars 3, 2019, 3:19pm CET par Mark Wycislik-Wilson
At MWC last month, OnePlus did not -- as many people had hoped -- show off the OnePlus 7, opting instead to give visitors a hands-off glimpse at a 5G prototype. But a new leak gives us an idea of what we might expect to see in the upcoming handset. In a video, the OnePlus 7 is shown to have virtually no bezels, and a 6.5-inch screen is unencumbered by a notch or hole punch cut-out. This is thanks largely to the use of a camera that pops up out of the top of the handset. See also: Android Pie… [Continue Reading] -

Twitter is testing a new option to let you hide replies to tweets
Publié: mars 3, 2019, 12:03pm CET par Mark Wycislik-Wilson
There are many demands made of Twitter, but perhaps the most frequently requested feature is an edit option. There's a chance that this will appear in time, but until then there are other concerns for Twitter users. Abuse and trolling on Twitter -- like other social networks -- is rife, and anyone posting a tweet has to deal with the replies that it may generate... and the responses to those replies. It is already possible to block or mute respondents, but Twitter is currently testing a new tool -- the ability to hide replies. See also: Twitter users can now… [Continue Reading] -

Microsoft welcomes new partners as it launches Microsoft Quantum Network
Publié: mars 3, 2019, 10:51am CET par Mark Wycislik-Wilson
Quantum computing is not necessarily the future of computing, but it's certainly a future and an important part of technological advancement. All of the big players from the world of technology are understandably eager to be at the forefront of what's happening, and Microsoft is no different. This week, the company formally launched the Microsoft Quantum Network, a coalition of partners with a shared vision. The goal is "sharing knowledge and collaborating with the best quantum innovators" with a view to helping the progression of quantum computing. See also: Microsoft announces it is killing off Microsoft Health Dashboard apps and services… [Continue Reading] -

Microsoft announces it is killing off Microsoft Health Dashboard apps and services -- and giving refunds to Band owners
Publié: mars 2, 2019, 5:50pm CET par Mark Wycislik-Wilson
It is a while since Microsoft discontinued its Band fitness tracker, but for the last two years owners have still be able to synchronize data collected through the wearable. But now the company has announced that it plans to close down the Microsoft Band apps and Microsoft Health Dashboard website. The shutdown date has been set for May 31. On this date, Android, iOS and Windows Phone apps will vanish from their respective stores, and the services will be terminated. Users have a limited time to export their data, and to soften the blow, some Band owners will be eligible… [Continue Reading] -

Monero miner Coinhive is closing down because of the cryptocurrency 'crash'
Publié: mars 2, 2019, 12:06pm CET par Mark Wycislik-Wilson
Coinhive -- the controversial Monero mining service -- has announced that it is closing down. The decision to shut up shop has been partly blamed on the dramatic drop in the value of the cryptocurrency. A huge slump in Monero's value, coupled with an impending hard fork of the cryptocurrency and an update to the mining algorithm, means that the service is no longer economically viable. The shutdown does not take immediate effect, but it's not too far off, either. The algorithm update and hard fork are due on March 9, and Coinhive will close its doors the day before… [Continue Reading] -

How to enable the secret, hidden dark mode in Facebook Messenger
Publié: mars 2, 2019, 10:36am CET par Mark Wycislik-Wilson
The love of dark mode options in apps and operating systems shows no sign of waning. While a large number of big-names have added dark modes, there are still plenty that need to jump on the bandwagon. One app that has held out is Facebook Messenger, but there is secret dark mode option that you can enable. Probes into the Facebook Messenger app had already revealed that Facebook was working on darker hues, and it even rolled out to small number of users in the latter part of last year -- but not everyone. Now you can use a little… [Continue Reading] -

How to enable the secret, hidden dark mode in Facebook Messenger [UPDATED]
Publié: mars 2, 2019, 10:36am CET par Mark Wycislik-Wilson
The love of dark mode options in apps and operating systems shows no sign of waning. While a large number of big-names have added dark modes, there are still plenty that need to jump on the bandwagon. One app that has held out is Facebook Messenger, but there is secret dark mode option that you can enable. Probes into the Facebook Messenger app had already revealed that Facebook was working on darker hues, and it even rolled out to small number of users in the latter part of last year -- but not everyone. Now you can use a little… [Continue Reading] -

Want to hack an iPhone? Cellebrite hacking tools are available on eBay
Publié: mars 1, 2019, 1:41pm CET par Mark Wycislik-Wilson
iPhones are renown for their security -- to the point that even law enforcement agencies have trouble accessing their contents. An Israeli firm, Cellebrite, became well-known when it transpired that hacking tools it made were used by the US government to crack locked iPhones… and now its hacking tools are available to buy on eBay. For as little as $100-$1000, you can get your hands on a second-hand piece of Cellebrite equipment (a fraction of its usual selling price). For just a few Benjamins, you could get a Cellebrite UFED (Universal Forensic Extraction Device) and use it for whatever you… [Continue Reading] -

Red Hat teams up with Microsoft, Google Cloud and AWS to launch OperatorHub.io, a registry for finding Kubernetes Operators
Publié: mars 1, 2019, 12:18pm CET par Mark Wycislik-Wilson
Red Hat, Microsoft, Google Cloud and Amazon Web Services have joined forces to launch OperatorHub.io, a centralized repository to help the Kubernetes community find and share Operators. Introduced by CoreOS back in 2016, Operators provide a way of packaging, deploying and managing Kubernetes applications. Until now, it was often difficult to find Operators, and this is the problem OperatorHub.io aims to address. On top of being a registry, the repository makes it easy to home in on curated Operators that are of a high standard. Writing about the new venture in a blog post, Red Hat's director of community development,… [Continue Reading] -

Amazon discontinues Dash buttons
Publié: mars 1, 2019, 11:22am CET par Mark Wycislik-Wilson
If you were among those who thought that Amazon Dash buttons -- little single-function, buttoned devices that enable you to order frequently bought items with a press -- were stupid, it seems that Amazon has come around to your way of thinking. The company has decided -- sensibly, many would argue -- to discontinue the devices. While this means that you will no longer be able to buy Amazon Dash buttons, if you already have one or more of them, orders that are placed through them will still be honoured. See also: Amazon Day lets Prime subscribers choose a specific… [Continue Reading] -

YouTube disables comments on videos of minors because of child predator fears
Publié: mars 1, 2019, 10:43am CET par Mark Wycislik-Wilson
Amid mounting fears about child predators and pedophile rings operating online, YouTube has announced that it is disabling comments on videos that feature minors. For now, the efforts are focused on videos that feature young children, but in the coming months it will expand to include older minors that YouTube says "could be at risk of attracting predatory behavior". The site is also stepping up its use of algorithms to not only identify videos that contain children, but also to monitor and moderate comments. See also: YouTube updates its strike system to make it 'clear and consistent' YouTube is to… [Continue Reading] -

Now you can buy a .dev domain for a sensible price
Publié: mars 1, 2019, 10:29am CET par Mark Wycislik-Wilson
Google recently launched the new top-level domain, .dev. When the TLD was introduced, pricing was a little out of the reach of most people -- there are few who would be willing to part with $11,000. Now, however, pricing has dropped dramatically. The crazy pricing was only part of the Early Access registration period, but now the domain is available from a range of registrars for a far more reasonable $12-$15. See also: Google launches new .dev TLD Now you can use Google Duo on the web as well as in app Google is bringing virtual desktops to Chrome OS… [Continue Reading] -

Amazon Day lets Prime subscribers choose a specific delivery day
Publié: février 28, 2019, 4:44pm CET par Mark Wycislik-Wilson
Once you sign up for Amazon Prime, it's hard to imagine how you ever lived without it. Well... that might be a slight exaggeration, but it's easy to fall in love with the service. Now Amazon is giving would-be subscribers another reason to sign up, and an added bonus for those who already have. Amazon Day is a US-only service -- for now, at least -- that gives subscribers the option of consolidating all of their deliveries for the week on a day of their choice. There are several benefits to Amazon Day, both for Amazon and customers. From Amazon's… [Continue Reading] -

Android Pie is still coming to the OnePlus 3 and OnePlus 3T
Publié: février 28, 2019, 11:34am CET par Mark Wycislik-Wilson
Apple gets a lot of praise for the length of time it offers iOS updates to iPhone owners. Manufacturers of Android handsets, on the other hand, tend to be chastised for failing to offer OS updates for anywhere near long enough. Bucking this trend is OnePlus, one of the few companies that does not just forget about owners of older phones as soon as a new model is released. But having promised some time ago that OnePlus 3 and OnePlus 3T owners would get Android Pie, users were starting to fear that the update had been ditched. Good news. OnePlus… [Continue Reading] -

Twitter users can now access paywalled Medium content for free
Publié: février 28, 2019, 10:35am CET par Mark Wycislik-Wilson
It's the bane of any internet user. You stumble across a link to a fascinating-sounding article and click it only to discover that the site hosting the post is paywalled. Gah! The Medium platform is one that can include paywalled content, and there's good news for Twitter users. If you access a Medium article via a tweet, it does not matter if it is a paid-for article or not -- you will be able to access it for free. See also: Security researcher 'concerned' to find Twitter is not deleting your deleted direct messages Following 'unusual activity' from China and… [Continue Reading] -

Microsoft releases Windows 10 19H1 Build 18342 with Timeline for Chrome and access to Linux files from File Explorer [Updated]
Publié: février 27, 2019, 9:29pm CET par Mark Wycislik-Wilson
[Update] This build is now available on the Slow ring. Microsoft has released a new Windows 10 build to insiders -- Windows 10 19H1 Build 18342. This new build sees improvements to gaming that fix problems with State of Decay. There is also the new and much-requested ability to access Linux files from Explorer, a host of bug fixes, and the launch of a Chrome extension for Timeline. But while this is a significant update with a lot to explore, it's not for everyone. Microsoft has disabled the rollout of the build for systems with certain processors. See also: Microsoft… [Continue Reading] -

Serious Amazon Ring vulnerability leaves audio and video feeds open to interception and spoofing
Publié: février 27, 2019, 5:10pm CET par Mark Wycislik-Wilson
Security researchers from Dojo by Bullguard have discovered a vulnerability in Amazon's Ring doorbell that leaves it prone to man-in-the-middle attacks. As well as enabling a hacker to access audio and video feeds in a severe violation of both privacy and security, the vulnerability also means that an attacker could replace a feed with footage of their own. Revealing the security flaw at Mobile World Congress, Yossi Atias from Dojo, demonstrated how a feed could be hijacked and injected with counterfeit video. The vulnerability poses a number of risks. The ability to spy on audio and video feeds has obvious… [Continue Reading] -

Now you can use Google Duo on the web as well as in app
Publié: février 27, 2019, 3:07pm CET par Mark Wycislik-Wilson
One of Google's current crop of messaging tools, Duo, is spreading its wings and breaking out of the confines of being a mobile app. Google Duo is now available to use online in a desktop web browser -- providing, that is, that you're using Chrome, Firefox or Safari (Microsoft Edge and Opera users are left out in the cold). The web-based version of the messaging tool can be used to make and receive voice and video calls. See also: Google Assistant is coming to the Messages app and RCS marches on Now you can unsend messages in Facebook Messenger Google… [Continue Reading] -

Facebook to launch its Clear History tool later this year -- to the joy of privacy advocates and the pain of advertisers
Publié: février 27, 2019, 12:33pm CET par Mark Wycislik-Wilson
Facebook is no stranger to privacy-related controversy, and to try to counter some of this the social network announced in the middle of last year that it planned to give users a "clear history" feature. Although first talked about in May, no progress has been visible on this front, but Facebook's CFO, David Wehner, has now said that the feature will be launching later this year. This is good news for users, but bad news for advertisers. Facebook says that the feature will make it harder to target ads. See also: Privacy: Facebook closes controversial Onavo VPN and ceases user… [Continue Reading] -

Spotify spreads its streaming services to India
Publié: février 27, 2019, 11:57am CET par Mark Wycislik-Wilson
Having enjoyed huge success in other parts of the world -- and despite currently fighting a legal battle with Warner Music Group over licensing -- Spotify has now launched in India. To cater for the various tongues spoken in the country, the recommendation engine can be set to multiple languages. Subscription pricing has also been tailored to the Indian market, and while it is not possible to make direct comparisons across currencies, a year's subscription costs 1,189 rupees (under $17). Announcing the Indian launch, Spotify says: "we're excited to announce that Spotify is now available in India. Spotify comes to… [Continue Reading] -

Senators want Huawei equipment removed from US power grid because of security concerns
Publié: février 26, 2019, 11:01am CET par Mark Wycislik-Wilson
Huawei may well be causing excitement with its foldable smartphone, the Mate X, but the company's troubles in the US continue. The American government has already banned the use of some Huawei equipment, including in 5G networks, and there are now calls for the shunning of the Chinese company to spread to the US power grid. Although Huawei has remained defiant in the face of sanctions by the US, the Senate Intelligence Committee has now written to the Departments of Homeland Security and Energy, calling on them to block the company's network-connected hardware from being used in the electrical grid.… [Continue Reading] -

Battle of the foldable phones: Samsung Galaxy Fold vs Huawei Mate X
Publié: février 25, 2019, 2:19pm CET par Mark Wycislik-Wilson
The age of the folding phone is upon us. Gone are the days of prototypes -- now we have hardware we can actually buy... or at least will be able to very soon indeed. Both Samsung and Huawei have unveiled foldables in recent days, but how do they stack up? The two companies have taken different approaches with the Galaxy Fold and the Mate X when it comes to the hinging, but there are also specs to consider -- and, of course, price. So how do the two flagship foldables compare? See also: Huawei's Mate X is a seriously impressive… [Continue Reading] -

Google Assistant is coming to the Messages app and RCS marches on
Publié: février 25, 2019, 12:36pm CET par Mark Wycislik-Wilson
Google has a history of changing its mind about messaging services, launching and closing them left, right and center. The company now seems pretty invested in its Messages platform, and has been gradually adding more and more features to increase its appeal. Google's latest move sees it bringing Assistant integration to the Messages app so you can get one-tap access to AI-powered help and information. The company also says that it remains committed to RCS (Rich Communication Service) and wants to bring the standard to more Android users. See also: Google rolls out spam protection to Android Messages Google launches… [Continue Reading] -

Huawei's Mate X is a seriously impressive folding 5G smartphone... but you'd hope so for $2,600!
Publié: février 24, 2019, 4:22pm CET par Mark Wycislik-Wilson
If you balked when the price of the Samsung Galaxy Fold was revealed ($1,980, in case you missed it), the price tag attached to the newly revealed Huawei Mate X may trigger heart failure. At $2,600, the 5G folding smartphone is, the words of Huawei's Richard Yu, "very expensive", but you will get a lot of phone for your money. The Mate X is scheduled for release in the middle of the year, and it differs from the Samsung Galaxy Fold in an important way. While Samsung's offering opens up to reveal a large screen on the inside, Huawei has… [Continue Reading] -

Microsoft releases Windows 10 20H1 Build 18841 to Skip Ahead ring
Publié: février 23, 2019, 1:01pm CET par Mark Wycislik-Wilson
Having recently started public testing of Windows 10 20H1, Microsoft has a new build for Insiders on the Skip Ahead ring to try out. Windows 10 20H1 Build 18841 is really just a bug-fixing build but it comes with a warning from Microsoft that: "As is normal with builds early in the development cycle, these builds may contain bugs that might be painful for some". If that whets your appetite, dive in! See also: Microsoft releases Windows 10 19H1 Build 18343 with Sandbox improvements Microsoft releases Windows 10 19H1 Build 18342 with Timeline for Chrome and access to Linux files… [Continue Reading] -

Microsoft releases Windows 10 19H1 Build 18343 with Sandbox improvements
Publié: février 23, 2019, 12:22pm CET par Mark Wycislik-Wilson
Microsoft has started rolling out build 18343 of Windows 10 19H1 to Windows Insiders on the Fast Ring. This latest build is mainly comprised of bug fixes, and there are also improvements to the Windows Sandbox feature. As we are now so close to the final release of Windows 10 19H1, Microsoft has locked down the apps -- and you may even notice that some features have gone missing. See also: Microsoft releases Windows 10 19H1 Build 18342 with Timeline for Chrome and access to Linux files from File Explorer Updated WSL in Windows 10 version 1903 lets you access… [Continue Reading] -

Drupal releases patch for 'highly critical' remote code execution flaw that puts millions of sites at risk
Publié: février 22, 2019, 11:36am CET par Mark Wycislik-Wilson
Sites based on the CMS Drupal are at risk from a remote code execution flaw which has been classed as "highly critical". Site owners are being urged to install updates to ensure they are protected. The security flaw -- CVE-2019-6340 or SA-CORE-2019-003 -- affects Drupal 8.5.x and 8.6.x but there are certain conditions that must be met in order for a site to be vulnerable. See also: Security researchers reveal details of serious bug in compression tool WinRAR Security researcher 'concerned' to find Twitter is not deleting your deleted direct messages User data exposed in 500px security breach... that happened… [Continue Reading] -

Privacy: Facebook closes controversial Onavo VPN and ceases user data collection
Publié: février 22, 2019, 10:26am CET par Mark Wycislik-Wilson
Following the scandal surrounding the collection of user data, Facebook has removed its Onavo VPN app from the Google Play Store -- a full six months after the iOS version of the Facebook Research app was kicked out of the App Store by Apple. Facebook will also be ending its controversial paid data collection program which saw the company paying people for access to information about their device and internet usage. The app will continue to function as a VPN -- minus the questionable privacy invasion -- for a little while to give users the chance to seek out an… [Continue Reading] -

Security researchers reveal details of serious bug in compression tool WinRAR
Publié: février 21, 2019, 11:45am CET par Mark Wycislik-Wilson
If you're a user of WinRAR -- a staple tool for decompressing files whose popularity stems from not only its support for RAR files, but also its never-ending trial period -- it's time to ensure you have the latest security patch installed. Security experts from Check Point Research have revealed details of a serious bug that has been present in the software for at least 14 years. The archiving tool was found to have a vulnerability in one of its .dll files, which could be exploited by simply opening a compressed file, and allows an attacker to "gain full control… [Continue Reading] -

Microsoft releases Windows 10 19H1 Build 18342 with Timeline for Chrome and access to Linux files from File Explorer
Publié: février 21, 2019, 10:38am CET par Mark Wycislik-Wilson
Microsoft has released a new Windows 10 build to insiders -- Windows 10 19H1 Build 18342. This new build sees improvements to gaming that fix problems with State of Decay. There is also the new and much-requested ability to access Linux files from Explorer, a host of bug fixes, and the launch of a Chrome extension for Timeline. But while this is a significant update with a lot to explore, it's not for everyone. Microsoft has disabled the rollout of the build for systems with certain processors. See also: Microsoft brings Windows Timeline support to Chrome with Web Activities extension… [Continue Reading] -

Privacy: Facebook now lets Android users block background collection of location data
Publié: février 20, 2019, 7:07pm CET par Mark Wycislik-Wilson
Faced with continued criticism about privacy, Facebook is rolling out an update to Android users that gives a greater degree of control over the sharing of location data with the social network. Specifically, the update makes it possible to stop Facebook from using tracking your location in the background when you are not using the app. The change brings parity to the iOS and Android Facebook apps. See also: Facebook says it is 'open to meaningful regulation' following damning report of the 'digital gangster' that considers itself 'ahead of and beyond the law' Facebook is ready to fight back against… [Continue Reading] -

GitHub widens the scope of its bug bounty program and increases rewards
Publié: février 20, 2019, 1:25pm CET par Mark Wycislik-Wilson
Now in its fifth year, the GitHub Security Bug Bounty has been updated to offer larger rewards to those who find bugs. At the same time, the scope of the program is being expanded and protections for researchers have been added through new Legal Safe Harbor terms. As well as expanding the program to cover any of its "first-party services", GitHub has effectively removed any upper limit on the size of reward pay-outs for critical bugs. See also: Microsoft now lets everyone create unlimited private GitHub repositories for free Apple apologizes for privacy-invading FaceTime bug, promises delayed software update Europe… [Continue Reading] -

Microsoft reveals Russian hacking attacks as it expands AccountGuard protection across Europe
Publié: février 20, 2019, 11:12am CET par Mark Wycislik-Wilson
Microsoft has revealed that it detected various attacks by Russian hackers targeting democratic groups in Europe. The company says that numerous attacks carried out between September and December 2018 can be linked to a group known as Strontium. Also known as Fancy Bear, the group is a cyber espionage outfit with ties to Russian intelligence agencies. At the same time as revealing some details of the attacks, Microsoft also announced the expansion of its AccountGuard security program to more European countries ahead of European Parliament elections. See also: Microsoft brings Windows Timeline support to Chrome with Web Activities extension Kali… [Continue Reading] -

Kali Linux 2019.1 with Metasploit 5.0 available for download
Publié: février 20, 2019, 10:14am CET par Mark Wycislik-Wilson
The first release for 2019 of the Debian-based Linux distro Kali Linux is now available for download. Kali Linux 2019.1 sees the kernel moving up to version 4.19.13, and it also includes Metasploit 5.0. Offensive Security's penetration testing distro is much-loved by the infosec community, and this latest release includes ARM improvements, a range of bug fixes and package updates. See also: Updated WSL in Windows 10 version 1903 lets you access Linux files from Windows Dirty_Sock vulnerability in Canonical's snapd could give root access on Linux machines System76 refreshes Serval WS Linux laptop with 9th Gen Intel Core CPUs… [Continue Reading] -

Google launches new .dev TLD
Publié: février 19, 2019, 5:44pm CET par Mark Wycislik-Wilson
Seeking to give a home to those who have helped to build the web, Google has launched a new top-level domain. The new .dev TLD comes after the company launched .app and .page, all are protected by HTTPS. Google has already used the TLD for a few of its own projects, such as web.dev and opensource.dev, but now it is being opened up to a wider audience. See also: Google is bringing virtual desktops to Chrome OS Google pivots Android Things to focus solely on smart speakers and displays The Notifications Widget for Google Photos, Hangouts Chat and Google+ dies… [Continue Reading] -

YouTube updates its strike system to make it 'clear and consistent'
Publié: février 19, 2019, 4:59pm CET par Mark Wycislik-Wilson
Following criticism of how its strike system was implemented, YouTube has announced an update to its Community Guidelines that helps to make things clearer. In the past it was often the case that strikes were handed inconsistently, and it was not always clear what misdemeanour had occurred. The updated system comes into force in the next few days, and it is slightly more lenient on first-time offenders. See also: YouTube is to blame for the increase in Flat Earthers Facebook is ready to fight back against anti-vaxxers Health experts call on Facebook to close anti-vaxxer groups YouTube says that it… [Continue Reading] -

From July, Windows 7 and Windows Server 2008 users will need SHA-2 support to get updates
Publié: février 19, 2019, 12:45pm CET par Mark Wycislik-Wilson
Microsoft has announced that from the middle of July, Windows 7 and Windows Server 2008 users who want to continue to receive updates will need SHA-2 code signing support. The change is being introduced because "the security of the SHA-1 hash algorithm has become less secure over time due to weaknesses found in the algorithm, increased processor performance, and the advent of cloud computing". See also: Microsoft reveals pricing for Windows 7 Extended Security Updates Windows 10 consolidates its lead over Windows 7 Microsoft ends Windows 7 support one year from today The news was shared by Mary Jo Foley… [Continue Reading] -

Microsoft brings Windows Timeline support to Chrome with Web Activities extension
Publié: février 19, 2019, 12:41pm CET par Mark Wycislik-Wilson
The Timeline feature of Windows 10 makes it easier to work on multiple computers by synchronizing activity so you can move between machines and pick up from where you left off -- although it can also prove useful on a single computer. Having made this available in its Edge browser, Microsoft has now released an extension that brings it to Google Chrome. This move is understandable as Chrome has a much larger userbase than Edge, and Microsoft admits that it is a much-requested feature. See also: How to export your saved passwords from Google Chrome Even Microsoft Edge thinks the… [Continue Reading] -

Huawei: 'There's no way the US can crush us'
Publié: février 19, 2019, 11:39am CET par Mark Wycislik-Wilson
The founder of Huawei, Ren Zhengfei, has hit back against Trump's ban on the use of his company's hardware because of concerns about Chinese espionage, saying "there's no way the US can crush us". The US has been trying to encourage other countries to follow its lead in shunning Huawei, but the UK has said it will not stop the company -- which is due to launch its P30 range of smartphones next month -- from getting involved in the rollout of 5G networks. Ren also lashed out at the US, saying that the arrest of his daughter and Huawei… [Continue Reading] -

Australian political parties hit by hack orchestrated by 'sophisticated state actor'
Publié: février 18, 2019, 4:44pm CET par Mark Wycislik-Wilson
Australia's three main political parties -- Liberals, Labor and Nationals -- as well as the country's parliament have all been hit by a security breach which Prime Minister Scott Morrison says was carried out by a "sophisticated state actor". Although the country is due to hold elections in the coming months, Morrison says there is "no evidence of any electoral interference". While it is not currently known who is responsible for the attack, various potential culprits have been suggested, including China, the US, Israel and Russia. See also: How to check to see if your data was part of the… [Continue Reading] -

Facebook says it is 'open to meaningful regulation' following damning report of the 'digital gangster' that considers itself 'ahead of and beyond the law'
Publié: février 18, 2019, 2:46pm CET par Mark Wycislik-Wilson
A detailed report about fake news by a parliamentary committee in the UK has accused Facebook of being a "digital gangster" that has deliberately broken privacy and competition laws. The report by the Digital, Culture, Media and Sport select committee calls for the social network to be subject to statutory regulation. The report comes after an 18-month investigation, and it is damning of Facebook and its executives in general, and Mark Zuckerberg in particular. Criticism is levelled at the lack of action taken against fake news and misinformation on the social network, and there is concern that current election laws… [Continue Reading] -

YouTube is to blame for the increase in Flat Earthers
Publié: février 18, 2019, 11:50am CET par Mark Wycislik-Wilson
In recent years it seems that there has been an astonishing increase in the number of Flat Earthers -- people who believe that the Earth is flat, and anything that suggests otherwise is a conspiracy. The thinking is that, for some reason, NASA, international government, scientists and so on are all desperate to convince people that the Earth is round when it is in fact flat. While Flat Earther numbers are still relatively small, the increasing membership of this school of thought in the face of overwhelming evidence to the contrary is both confusing and worrying. So just what is… [Continue Reading] -

Unlike the US, the UK does not want to ban Huawei from 5G networks
Publié: février 18, 2019, 10:52am CET par Mark Wycislik-Wilson
With concerns about Chinese spying, the US has been embarked on a campaign to prevent Huawei from operating in the country. In addition to banning officials from spending money on Huawei equipment, the US government has been trying to convince other countries to follow its lead and shun the company. Despite US pressure -- and similar moves by New Zealand and Australia -- the UK says that it has no plans to cut Huawei technology out of 5G networks. The National Cyber Security Centre says that there are ways to mitigate against any potential risk posed by Huawei equipment. See… [Continue Reading] -

Security researcher 'concerned' to find Twitter is not deleting your deleted direct messages
Publié: février 17, 2019, 5:03pm CET par Mark Wycislik-Wilson
When you delete a direct message on Twitter, it is gone forever, right? From a user's point of view, this is true -- a deleted message vanishes. But a security researcher has discovered that Twitter is actually hanging onto these messages. Karan Saini found that he was able to see messages he deleted years ago when he downloaded an archive of his Twitter data from the site. See also: Facebook is ready to fight back against anti-vaxxers Health experts call on Facebook to close anti-vaxxer groups Open letter signed by Mozilla demands Facebook take 'real action' against disinformation Upon obtaining… [Continue Reading] -

How to check to see if your data was part of the Marriott Starwood Hotel hack
Publié: février 16, 2019, 4:58pm CET par Mark Wycislik-Wilson
When hackers hit Marriott's Starwood Hotel database last year, it was first thought that half a billion customers might be affected. This estimate was later downgraded to 383 million guests, but this is still a very large number, and it is understandable that many people are concerned that their data may have been accessed. There was particular concern about whether passport numbers had been accessed, and this is what a new checking tool lets you check. Marriott has teamed up with security firm OneTrust to enable customers to check if their data was included in the security breach. See also:… [Continue Reading] -

Updated WSL in Windows 10 version 1903 lets you access Linux files from Windows
Publié: février 16, 2019, 1:01pm CET par Mark Wycislik-Wilson
The marriage between Linux and Windows is getting stronger. Having embraced Linux with WSL (Windows Subsystem for Linux), Microsoft is now doing what users have been begging for: Windows 10 April 2019 Update makes it possible to access Linux files from Windows. As well as enabling you to open Linux files from within Explorer, Windows 10 version 1903 gives you the option of editing Linux files from Windows. See also: Microsoft takes Insiders into next year, with the release of the first Windows 10 20H1 build Forget Linux -- Here's how to install Windows 10 on Raspberry Pi 3 Dirty_Sock… [Continue Reading] -

The Samsung Galaxy Tab S5e is a thin and light entertainment-centric Android tablet
Publié: février 15, 2019, 3:59pm CET par Mark Wycislik-Wilson
Samsung may be on the verge of officially unveiling its Galaxy S10 range of phones, but ahead of this the company announces its Galaxy Tab S5e tablet. Being thin and light, there's a strong focus on portability here, and the display makes it perfect for movie watching. This is a 10.5-inch Super AMOLED screen with a 16:10 aspect ratio, and the bezels have been stripped right back. The tablet is driven by a Qualcomm Snapdragon 670 processor, comes with up to 6GB of RAM, and pricing starts at $400 -- which compares well with Apple's iPad. See also: Samsung launches… [Continue Reading] -

Fake news: OpenAI's 'deepfakes for text', GPT2, may be too dangerous to be released
Publié: février 15, 2019, 10:48am CET par Mark Wycislik-Wilson
OpenAI -- a company backed by Elon Musk -- has created an artificial intelligence system called GPT2 that's capable of writing fake news. The system is also capable of generating works of fiction, and it has been described as being so dangerous that it may not be publicly released. The stories written by GPT2 have been called "deepfakes for text" and can be generated by feeding the system just a few words. The style is far more sophisticated than most AI-generated text, and the news stories it can generate are so convincing that there are serious concerns about the potential… [Continue Reading] -

Facebook is ready to fight back against anti-vaxxers
Publié: février 15, 2019, 9:03am CET par Mark Wycislik-Wilson
The battle Facebook wages against the spread of fake news and misinformation could be set to expand to include removing anti-vaccination content from the social network. The anti-vaxxer movement has long been fairly vocal, and it has found a home on Facebook. The viral spread of anti-vaccine groups on the social network has been blamed -- at least partly -- for outbreaks of measles in the US. Facing pressure to block the spread of dangerously misleading information, Facebook has said that it could demote anti-vaxxer content and remove it from recommendations. See also: Health experts call on Facebook to close… [Continue Reading] -

New concept video of iOS 13 is packed with exciting features
Publié: février 14, 2019, 4:41pm CET par Mark Wycislik-Wilson
We won’t get a proper look at iOS 13 until Apple reveals it later in the year, but that isn’t going to stop people from coming up with some ideas of how the mobile operating system should look. Just a couple of weeks ago we saw one iOS 13 concept video, and now another has surfaced. A collaboration between AppleiDesigner and Skyline News, this latest concept is packed with ideas to get excited about for iPhone and iPad users alike -- a redesigned status bar, system-wide dark mode, some great-looking wallpapers, and customizable lock screen elements. See also: Feast your… [Continue Reading] -

Google is bringing virtual desktops to Chrome OS
Publié: février 14, 2019, 3:50pm CET par Mark Wycislik-Wilson
Chromebooks have fared far better than many people would have first thought when they first appeared on the market, and Google's Chrome OS is going from strength to strength. While not yet ready to topple either Windows or macOS, the operating system continues to gain features that make it increasingly appealing. One addition that is on the horizon and likely to please many users and potential users alike is virtual desktops. This is something we have heard about before in relation to Chrome OS, but a recent commit to the Chromium Gerrit shows that "virtual desks" are being worked on… [Continue Reading] -

Final text of new EU Copyright Directive retains controversial content blocking of Article 13
Publié: février 14, 2019, 10:56am CET par Mark Wycislik-Wilson
In an attempt to bring aging copyright laws up to date for the digital age, the European Parliament and European Commission have agreed the final text of the EU Copyright Directive. After several rounds of intense negotiations, it was decided to retain the controversial Article 13 which can be used to block the uploading of content, and Article 11 which has been described as the "link tax". The directive will place the onus on the likes of Google and Facebook to ensure that users do not upload copyrighted content, leading to fears that this could mean the introduction of restrictive… [Continue Reading] -

Dirty_Sock vulnerability in Canonical's snapd could give root access on Linux machines
Publié: février 13, 2019, 2:56pm CET par Mark Wycislik-Wilson
A security researcher has discovered a vulnerability in Canonical's snapd package which could be exploited to gain administrator privileges and root access to affected Linux systems. The security issue has been dubbed Dirty_Sock and assigned the code CVE-2019-7304. Chris Moberly found a privilege escalation vulnerability in the snapd API. This is installed by default in Ubuntu -- under which proofs of concept have been tested and found to work "100% of the time on fresh, default installations of Ubuntu Server and Desktop" -- but may also be present in numerous other Linux distros. The Ubuntu CVE Tracker describes the vulnerability… [Continue Reading] -

User data exposed in 500px security breach... that happened in the middle of last year
Publié: février 13, 2019, 11:54am CET par Mark Wycislik-Wilson
The photo sharing site 500px has revealed details of a security breach that took place in mid-2018. The company says that its engineering team only became aware of the breach -- which is thought to have taken place around July 5, 2018 -- a few days ago. 500px launched an investigation in conjunction with a third party and police, and says that "an unauthorized party gained access to our systems and acquired partial user data". See also: VFEmail hack wipes out all of the email provider's US servers Marriott hack update: attackers accessed fewer user records than first thought, but… [Continue Reading] -

Google pivots Android Things to focus solely on smart speakers and displays
Publié: février 13, 2019, 11:13am CET par Mark Wycislik-Wilson
Google has announced that it is dramatically narrowing the focus of Android Things, originally conceived as the company's wide-ranging IoT platform. Now rather than being an OEM tool that can be used to produce just about anything for the Internet of Things, Android Things will instead be focused on just two product lines: smart speakers and smart displays. See also: Gmail gets a new right-click menu The Notifications Widget for Google Photos, Hangouts Chat and Google+ dies in March Google reveals the shutdown date for Google+ and when your data will be deleted Google had previously planned to support numerous… [Continue Reading] -

VFEmail hack wipes out all of the email provider's US servers
Publié: février 13, 2019, 10:12am CET par Mark Wycislik-Wilson
Email provider VFEmail has been hit by a huge attack that resulted in all of the data it stores in the US being wiped out. Describing the attack as "catastrophic", VFEmail revealed that a hacker had breached its security and succeeded in deleted not only primary data systems, but also the backups. The attacker was caught in the act, and it was possible to intervene before damage was caused to servers in other countries. But for VFEmail users whose data was stored in the US, the news is far from good. See also: Gmail gets a new right-click menu Marriott… [Continue Reading] -

Gmail gets a new right-click menu
Publié: février 12, 2019, 12:21pm CET par Mark Wycislik-Wilson
It is not news that Gmail has a right-click menu; what is news, however, is the fact that it has been updated so it is now actually useful. Google has gradually been updating Gmail over the years, and the refreshed context menu provides easy access to more message options. For control freaks, the new menu is a godsend and makes the web-based email tool more like using a desktop email client. See also: The Notifications Widget for Google Photos, Hangouts Chat and Google+ dies in March Google reveals the shutdown date for Google+ and when your data will be deleted… [Continue Reading] -

Health experts call on Facebook to close anti-vaxxer groups
Publié: février 12, 2019, 10:56am CET par Mark Wycislik-Wilson
Facebook is under pressure to stem the flow of pseudoscience among its users. The social network has faced criticism and pressure about many issues including the dissemination of fake news and disinformation, and false information spread by anti-vaxxers is the latest target of concerned experts. There has been much concern about how Facebook could be used to influence elections, but there are growing calls for the social media giant to step in and prevent anti-vaccinations groups from being used to spread false information. Despite medical evidence pointing to not only the efficacy but also the safety of vaccinations, the anti-vaxxer… [Continue Reading] -

Open letter signed by Mozilla demands Facebook take 'real action' against disinformation
Publié: février 11, 2019, 3:22pm CET par Mark Wycislik-Wilson
Mozilla has sent an open letter to Facebook calling on the social network to do more to fight disinformation and asking for increased transparency about political advertising. The letter -- also signed by 32 other organizations including human rights and press freedom groups -- has been sent to Facebook in the run-up to the 2019 EU Parliamentary Elections. It comes after Mozilla's COO wrote to the European Commission to express her concerns about the lack of transparency at Facebook. See also: Mozilla COO contacts European Commission voicing concerns about Facebook's lack of ad transparency Mozilla has a new mobile web… [Continue Reading] -

EA's Apex Legends hits 10 million players much faster than Fortnite
Publié: février 11, 2019, 1:17pm CET par Mark Wycislik-Wilson
Like PUBG, Fortnite has proved to be a phenomenally successful game, attracting millions of players around the world. With battle royale games faring so well, EA decided to take a slice of the pie, and released Apex Legends, its own free-to-play take on the genre. In the space of just 72 hours, the game reached a major milestone -- 10 million players. It took Fortnite two weeks to pull in the same number of players. See also: Now you can merge Fortnite accounts Fortnite update brings support for external controllers to iOS and Android New Fortnite vulnerabilities put users' privacy… [Continue Reading] -

Developer launches new version of Windows 95 that runs under Windows 10, macOS and Linux
Publié: février 11, 2019, 10:47am CET par Mark Wycislik-Wilson
Who doesn't feel a little nostalgic from time to time? Progress is great, but sometimes it's nice to look back at how things used to be -- even if it's only to laugh at how different and primitive things used to be. The world of computing is no different in this regard. Last year, developer Felix Rieseberg released Windows 95 as an Electron app to let 90s computer users relive their younger years. Now he's back with a second version of the Windows 95 app, and it's even better than ever -- gaming classics such as Doom and Wolfenstein3D are… [Continue Reading] -

Spotify explicitly bans ad blockers on pain of account termination
Publié: février 8, 2019, 11:16am CET par Mark Wycislik-Wilson
Spotify has updated its Terms of Service agreement, implementing an explicit ban on the use of ad blockers. While the music streaming service has a decent number of paying users, a large percentage of the userbase stick with free, ad-supported accounts. A proportion of these free users turn to ad blockers, and this is something Spotify has been increasingly trying to clamp down on. The company employs various techniques for detecting the use of ad blockers, and now anyone found to be using such a tool runs the risk of having their account terminated. The new Terms of Agreement comes… [Continue Reading] -

Now you can merge Fortnite accounts
Publié: février 8, 2019, 10:30am CET par Mark Wycislik-Wilson
If you have played Fortnite on different consoles, you've very probably asked how you go about merging accounts so you can access all of your Vbucks and collectibles in one place. Fortnite's initially messy approach to cross-platform gaming meant that many people ended up creating two (or more) accounts in order to be able to play with their friends. Epic Games dramatically improved cross-platform compatibility, but gamers who created multiple accounts were not able to share all of the weapons, currency and other goods collected between these accounts. Now this has changed. See also: Fortnite update brings support for external… [Continue Reading] -

Trakt tardily notifies users of data breach that took place over four years ago
Publié: février 7, 2019, 1:40pm CET par Mark Wycislik-Wilson
Users of Trakt -- a service for "scrobbling", or tracking the movies and TV shows you watch in the likes of Plex and Kodi -- have received emails from the company notifying them of a data breach that took place way back in 2014. Trakt says that although the security breach took place over four years ago, it only recently discovered it. The company says that an investigation is underway, but that it believes a "PHP exploit was used to capture data", including users' emails, usernames, encrypted passwords, names and locations. See also: Kodi 18 'Leia' is officially available --… [Continue Reading] -

Germany bans Facebook from combining user data collected from Instagram and WhatsApp
Publié: février 7, 2019, 11:56am CET par Mark Wycislik-Wilson
The German cartel office, the Bundeskartellamt, has imposed new restrictions on how Facebook processes the data it gathers about users of Instagram, Facebook and WhatsApp. Germany's antitrust watchdog has hit the social network with a ban on combining user data it gathers from different sources, unless it has explicit consent from users. While Facebook is still free to gather data about Instagram users and WhatsApp users, this data cannot be automatically combined with data gathered via a users' Facebook account. See also: Now you can unsend messages in Facebook Messenger Snopes ends its fact-checking partnership with Facebook Insiders say Mark… [Continue Reading] -

Microsoft brings AI-powered background blurring to Skype
Publié: février 7, 2019, 11:10am CET par Mark Wycislik-Wilson
A few months after adding background blurring to its Teams tool, Microsoft has brought the same option to Skype on the desktop. The feature serves two purposes. Firstly it helps to focus attention on the person that is speaking, but secondly -- and perhaps more importantly -- it hides any untidiness (or secrets) that may be going on behind the speaker. It's another push from Microsoft to move people away from Skype Classic to Skype 8. See also: Microsoft reveals pricing for Windows 7 Extended Security Updates Microsoft Studios rebranded Xbox Game Studios Microsoft is now forcing people to upgrade… [Continue Reading] -

KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
Publié: février 6, 2019, 6:19pm CET par Mark Wycislik-Wilson
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain. Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS. See also: Cisco joins Apple in calling for… [Continue Reading] -

The Notifications Widget for Google Photos, Hangouts Chat and Google+ dies in March
Publié: février 6, 2019, 12:48pm CET par Mark Wycislik-Wilson
Google+ is nearing the end of the line, and ahead of this Google has announced that its Notifications Widget is also to be killed off. The widget -- which appears in the upper right-hand corner of various Google products including Gmail -- lets users know when there are notifications for various services such as Google Photos, Hangouts Chat and Google+. But when March rolls around, you'll have to rely on alerts for individual services instead. See also: Google reveals the shutdown date for Google+ and when your data will be deleted How to export your saved passwords from Google Chrome… [Continue Reading] -

Microsoft reveals pricing for Windows 7 Extended Security Updates
Publié: février 6, 2019, 10:54am CET par Mark Wycislik-Wilson
Windows 7 may be creakingly old now, but it is still widely used. While large numbers of consumers have migrated to Windows 10, there are still plenty of organizations that are clinging to the old operating system out of a sense of nostalgia, an unwillingness to upgrade, lack of funds for upgrading, or legacy requirements. As of January 14, 2020, Microsoft will no longer be providing support or security updates for Windows 7 -- apart from for those who are willing to pay for it. The company is offering up to three years of Windows 7 Extended Security Updates (ESU),… [Continue Reading] -

DuckDuckGo reminds ignorant users that many websites ignore browsers' Do Not Track privacy requests
Publié: février 6, 2019, 9:48am CET par Mark Wycislik-Wilson
In an increasingly-connected world where data is collected and shared, privacy has become ever-more important to people. If you are of that mind, you may have enabled the Do Not Track (DNT) setting in your web browser in the hope that it will stop the websites you visit from tracking your online activities. Bad news: it probably makes no difference whatsoever. This might be something you knew already, but research by privacy-focused search engine DuckDuckGo -- which famously does respect DNT requests -- found than more than three-quarters of people were not aware of that that many sites ignore DNT… [Continue Reading] -

Microsoft Studios rebranded Xbox Game Studios
Publié: février 6, 2019, 8:54am CET par Mark Wycislik-Wilson
Microsoft's in-house game development division has undergone a rebranding. Previously known as Microsoft Studios, the division's new moniker is Xbox Game Studios. Made up of a total of 13 game studios purchased by Microsoft over the years, and the division's corporate vice president, Matt Booty, promises that they are all "working hard to deliver incredible exclusives, original IP and all-new chapters from your favorite franchises". See also: Microsoft releases Windows 10 19H1 Build 18329 with new 'Top apps' Search feature Microsoft is now forcing people to upgrade from Skype Classic to Skype 8 Microsoft opens up Skip Ahead so you… [Continue Reading] -

Now you can unsend messages in Facebook Messenger
Publié: février 5, 2019, 5:59pm CET par Mark Wycislik-Wilson
Facebook said some time ago that it would be bringing an "unsend" option to Facebook Messenger, giving users the ability to delete messages they change their mind about. Today is the day this feature finally appears with the addition of a new "Remove for everyone" option. While this will be welcomed by Facebook Messenger users, it will not please everyone; as well as there being a time limit on when messages can be deleted, there is no stealth deletion option as all chat participants are informed when a message is removed. See also: Snopes ends its fact-checking partnership with Facebook… [Continue Reading] -

Flickr starts to delete users' photos today -- act fast to save yours!
Publié: février 5, 2019, 1:03pm CET par Mark Wycislik-Wilson
It is a few months since Flickr announced major changes to its free accounts, and today is the day the impact starts to be felt. Users unwilling to upgrade to a Flickr Pro account are now limited to storing 1,000 photos online, and any images above this number will be deleted starting today. Anyone who hasn't downloaded or backed up their photos risks losing them forever. See also: Download your Flickr photos NOW if you don't want to lose them How to back up your Flickr photos before your free storage space is slashed Flickr drops Yahoo requirement and gives… [Continue Reading] -

Can't connect to Windows Update? You're not alone
Publié: février 5, 2019, 11:00am CET par Mark Wycislik-Wilson
If you're experiencing problems downloading updates from Windows Update, don't worry -- it's not just you. Windows 10 users started to complain about problems with Windows Update last week after their computers displayed the message "We couldn't connect to the update service". While it initially appeared to be an ISP-related DNS issue, the problem was later determined to be with Microsoft. Despite an apparent fix, many people are still unable to download updates. See also: Microsoft releases Windows 10 19H1 Build 18329 with new 'Top apps' Search feature Microsoft is now forcing people to upgrade from Skype Classic to Skype… [Continue Reading] -

Instagram to introduce 'sensitivity screens' to hide self-harm images
Publié: février 4, 2019, 6:45pm CET par Mark Wycislik-Wilson
The head of Instagram has announced plans to introduce "sensitivity screens" in the wake of concerns about the spread of photos of self-harm on the image-based social network. Adam Mosseri says that Instagram will use image-blurring similar to that used on Facebook to hide graphic content. The move comes in the wake of the suicide of a British teenager, the parents of whom said self-harm images on Instagram were a contributing factor. See also: Insiders say Mark Zuckerberg plans to unify WhatsApp, Instagram and Facebook Messenger Want to edit tweets? Here's how Jack Dorsey says it could work Instagram accidentally… [Continue Reading] -

Want to edit tweets? Here's how Jack Dorsey says it could work
Publié: février 4, 2019, 1:59pm CET par Mark Wycislik-Wilson
The ability to edit tweets is one of the most frequently requested features for Twitter. The most common reason for wanting to make edits is to fix typos, but concern has been voiced about the potential for an editing facility to be abused -- which perhaps explains Twitter's apparent reticence at rolling out such a feature without careful thought. While tweet editing has yet to appear, there has long been speculation about how it could be implemented. In a move that is sure to fuel rumors that an edit function is just around the corner, Twitter chief Jack Dorsey has… [Continue Reading] -

Cisco joins Apple in calling for a US version of GDPR data protection and privacy laws
Publié: février 4, 2019, 11:43am CET par Mark Wycislik-Wilson
The roll out of GDPR (General Data Protection Regulation) has changed the face of privacy and data protection for millions of people across Europe. The regulation not only grants people access to the personal data companies hold about them, but also controls how this data can be used and transferred. Apple's Tim Cook has already voiced his support for GDPR and said that the rest of the world should implement similar regulation. Now he has been joined by Cisco in calling for data laws to be embraced by the US as they have been in Europe. See also: Apple apologizes… [Continue Reading] -

Brexit: criticism mounts against Android-only app to apply for settled status
Publié: février 3, 2019, 11:41am CET par Mark Wycislik-Wilson
A number of British and European politicians have written to the UK home secretary, Sajid Javid, to complain about the government's EU Exit mobile app. The app was created to enable EU citizens to apply for "settled status" in the UK in the wake of the referendum vote that saw the start of the Brexit process. The government stands accused of "digital discrimination" because the app is only available for Android devices -- and only relatively modern ones at that. iPhone users have been left out in the cold, as have those with older Android phones, adding to the stress… [Continue Reading] -

Snopes ends its fact-checking partnership with Facebook
Publié: février 2, 2019, 12:23pm CET par Mark Wycislik-Wilson
There are numerous problems associated with Facebook, but the two that are talked about most are privacy and the spread of "fake news". To help combat the dissemination of misinformation, the social network partnered with numerous companies and news outlets to fact-check stories. One of these partners was Snopes, the site famous for debunking myths, urban legends and fake news. But now the site has announced that it is ending its partnership with Facebook, citing " the ramifications and costs of providing third-party fact-checking services". See also: Mozilla COO contacts European Commission voicing concerns about Facebook's lack of ad transparency… [Continue Reading] -

Apple apologizes for privacy-invading FaceTime bug, promises delayed software update
Publié: février 2, 2019, 11:32am CET par Mark Wycislik-Wilson
Apple has issued an apology for the recently-discovered bug that made it possible to eavesdrop on people via FaceTime. The company had promised that a software update would be delivered later this week, but the interim solution was to simply disable the group FaceTime feature server-side. Apple now says that the problem has been fully fixed, but a software update that re-enables the group function will not be issued until next week. See also: Massive FaceTime privacy bug lets people eavesdrop on audio and video calls before they've been answered -- and Apple doesn't have a fix yet How to… [Continue Reading] -

Microsoft is now forcing people to upgrade from Skype Classic to Skype 8
Publié: février 1, 2019, 11:18am CET par Mark Wycislik-Wilson
The end of Skype Classic (or Skype 7, if you prefer) has been on the cards for a while now, much to the annoyance of legions of users. Microsoft has been keen to encourage Classic users to migrate to Skype 8, but many have held out. Now Microsoft is forcing their hands. When the company announced that support for Skype 7 and below was terminating at the beginning of November, Microsoft said that "you may be able to use older versions for a little while". Three months down the line, Skype Classic users are being forced into upgrading to Skype… [Continue Reading] -

Mozilla COO contacts European Commission voicing concerns about Facebook's lack of ad transparency
Publié: janvier 31, 2019, 4:13pm CET par Mark Wycislik-Wilson
Facebook has been no stranger to controversy and scandal over the years, but things have been particularly bad over the last twelve months. The latest troubles find Mozilla complaining to the European Commission about the social network's lack of transparency, particularly when it comes to political advertising. Mozilla's Chief Operating Officer, Denelle Dixon, has penned a missive to Mariya Gabriel, the European Commissioner for Digital Economy and Society. She bemoans the fact that Facebook makes it impossible to conduct analysis of ads, and this in turn prevents Mozilla from offering full transparency to European citizens -- something it sees as… [Continue Reading] -

Mozilla has a new mobile web browsing experience for you to test: Reference Browser
Publié: janvier 31, 2019, 1:10pm CET par Mark Wycislik-Wilson
Mozilla has launched a test version of a new mobile web browser -- sort of, anyway. Known as Reference Browser, Mozilla stresses that "this is NOT a new end product, it is a collection of parts". Described as a "technology preview", Reference Browser sees the company seeking feedback about various components which may or may not be used together in the future. It is looking for Android users to provide "input, telemetry and feedback and bug reports" to shape the future of mobile web browsing. See also: Mozilla confirms Firefox Screenshots is here to stay, although one key feature will… [Continue Reading] -

Nintendo delays the launch of Mario Kart Tour for mobiles
Publié: janvier 31, 2019, 12:31pm CET par Mark Wycislik-Wilson
Fans of Nintendo's Italian plumber and his racing antics have been keenly waiting for the launch of Mario Kart Tour, the mobile version of Mario Kart. There's some bad news though: you're going to have to wait a little longer than expected. The game was previously planned for a March launch, but things have been very quiet from Nintendo. In its Q3 earnings report, the company revealed that the game has been pushed back to summer. Thankfully, Nintendo is talking about this summer, so there's still not too long to wait, but it will come as frustrating news to eager… [Continue Reading] -

Microsoft opens up Skip Ahead so you can try early builds of Windows 10 19H2
Publié: janvier 31, 2019, 11:36am CET par Mark Wycislik-Wilson
The Windows 10 19H1 update may not yet have been released to the masses, but Microsoft is already hard at work on the update that will follow it, predictably codenamed Windows 10 19H2. If you're an eager beaver, you probably want to get your hands on this update as soon as possible, and Microsoft is giving you a way to do so. The company has opened up the Skip Ahead ring for Windows Insiders, and by signing up for this you can be among the first to try out Windows 10 19H2. See also: Most people are still avoiding the… [Continue Reading] -

Google reveals the shutdown date for Google+ and when your data will be deleted
Publié: janvier 31, 2019, 10:43am CET par Mark Wycislik-Wilson
We've known for several weeks now that Google+ is to close down, and Google has even brought forward the shutdown date. Now the company has revealed details of the timeline for the closure. As of next week -- February 4 specifically -- it will no longer be possible to create a Google+ account, and commenting options will be removed in March. When April rolls around, Google+ will not only close down, but data associated with consumer accounts will start to be deleted. See also: Google+ to close down earlier than planned after another data leak is discovered After failing to… [Continue Reading] -

Bluetooth 5.1 knows where you are -- down to the centimeter -- and which way you're facing
Publié: janvier 30, 2019, 4:34pm CET par Mark Wycislik-Wilson
The Bluetooth Special Interest Group (SIG) has revealed some new features of Bluetooth 5.1, and there's a lot to get excited about. While Bluetooth is perhaps most readily associated with connecting peripherals, there is so much more to it than that thanks to the addition of a direction-finding feature. Used in conjunction with real-time locating systems (RTLS) and indoor positioning systems (IPS), Bluetooth 5.1 promises, among other things, improved tracking of devices, and better indoor navigation tools. See also: Jaybird announces durable RUN XT True Wireless Bluetooth Sport Headphones Fortnite update brings support for external controllers to iOS and Android… [Continue Reading] -

Time's up! Microsoft is flipping the IE 10 kill switch in 2020
Publié: janvier 30, 2019, 11:58am CET par Mark Wycislik-Wilson
Microsoft has been trying to encourage users away from Windows 7 for a while now, with support officially ending next year. But it's not just the operating system that is reaching the end of the line; Microsoft is also warning the remaining Internet Explorer 10 users that support ends in 2020, advising that it is time to migrate to Internet Explorer 11. In a warning posted on its IT Pro Blog, Microsoft says that after January 2020, Internet Explorer 10 will no longer be supported. The company states, quite definitively, that it will "not release any security or non-security updates,… [Continue Reading] -

Facebook has been paying people to install a VPN that harvests data about them
Publié: janvier 30, 2019, 11:02am CET par Mark Wycislik-Wilson
An investigation has revealed that Facebook has been paying people aged between 13 and 35 to install a data harvesting VPN tool. The "Facebook Research" VPN was offered to iOS and Android users who were paid up to $20 per month -- plus referral commissions -- to provide the social network with near-unfettered access to phone, app and web usage data (a Root Certificate is installed to give a terrifying level of access). As news of the activity came to light, Facebook has announced that the program (sometimes referred to as Project Atlas) is being terminated on iOS, but it… [Continue Reading] -

Fortnite update brings support for external controllers to iOS and Android
Publié: janvier 29, 2019, 1:59pm CET par Mark Wycislik-Wilson
Epic Games has released an update to the mobile version of Fortnite which will help to level the playing field between iOS, Android, console and desktop gamers. If you've struggled to battle with the game's on-screen controls, Fortnite patch 7.30 could be just what you have been waiting for. In addition to other new features and bug fixes, the update adds support for Bluetooth controllers in iOS and Android -- and a new weapon! See also: New Fortnite vulnerabilities put users' privacy at risk SteelSeries launches 'Stratus Duo' dual wireless gaming controller for Android and PC Keyboard and mouse support… [Continue Reading] -

How to disable FaceTime and protect your privacy
Publié: janvier 29, 2019, 11:34am CET par Mark Wycislik-Wilson
By now you have probably heard about the bug that's been discovered in Apple's FaceTime. In short it is an exploit that lets you connect a call you have placed rather than waiting for the recipient to pick up -- so you can then listen to audio and watch video. Apple is working on a fix, and it you want to be sure that you don't fall victim to eavesdropping, you should think about disabling FaceTime on your iOS device. Here's how to do just that. See also: Massive FaceTime privacy bug lets people eavesdrop on audio and video calls… [Continue Reading] -

Massive FaceTime privacy bug lets people eavesdrop on audio and video calls before they've been answered -- and Apple doesn't have a fix yet
Publié: janvier 29, 2019, 11:08am CET par Mark Wycislik-Wilson
Apple is scrambling to fix a serious bug that has been discovered in its FaceTime messaging services. The bug makes it possible to spy on the people being called, even if the call is not picked up. This is a serious privacy issue, as it gives someone the ability to secretly eavesdrop on someone -- or even watch them -- without their knowledge. At the moment, Apple does not have a fix but the company says it is working on the problem and will address it by the end of the week. In the meantime, you may want to consider… [Continue Reading] -

Dropbox splashes $230 million on e-signature startup HelloSign
Publié: janvier 28, 2019, 4:19pm CET par Mark Wycislik-Wilson
Cloud storage firm Dropbox has announced that it is to acquire HelloSign -- a San Francisco-based startup that provides electronic signature and document workflow services -- for $230 million in cash. The acquisition is the largest ever made by Dropbox, and it is expected to be completed in the first quarter of the year. The purchase bolsters Dropbox's offerings and gives it a firm footing to better compete with the likes of DocuSign. In addition to its e-signature services, HelloSign also offers online faxing and various document workflow tools. Dropbox has previously shown interest in HelloSign, and an extension was… [Continue Reading] -

Try not to laugh -- for Data Privacy Day, Facebook wants you to take a Privacy Checkup
Publié: janvier 28, 2019, 12:02pm CET par Mark Wycislik-Wilson
Facebook is not a platform that's synonymous with privacy -- far from it. In addition to the things users purposefully share with the social network and the people they are connected to on it, there have been a seemingly endless string of scandals about unauthorized third parties being granted access to private data, data being shared between apps, and so on ad nauseum. With today being Data Privacy Day, Facebook is trying -- apparently without a faintest hint of irony -- to jump on the bandwagon. Starting today, the company is launching a new Privacy and Data Use Business Hub,… [Continue Reading] -

Download updated Android Pie images for your OnePlus 5 or 5T
Publié: janvier 27, 2019, 1:01pm CET par Mark Wycislik-Wilson
OnePlus had a Christmas present for owners of its OnePlus 5 and 5T handsets -- an OTA update to Android Pie. Now, a month later, the company has made Android 9.0.3 images available for download; perfect for those who like to manually flash their handsets. But this is not the same version of Pie that rolled out at the tail end of last year. OnePlus has introduced a number of important updates. See also: Android Pie now rolling out to OnePlus 5 and OnePlus 5T Leak shows that Android Q will bring native face unlock to more phones Android Q… [Continue Reading] -

Download your Flickr photos NOW if you don't want to lose them
Publié: janvier 27, 2019, 10:09am CET par Mark Wycislik-Wilson
Three months ago, Flickr announced sweeping changes to its different accounts, the most significant of which was the news that anyone with a free account would be limited to storing 1,000 photos online. If you are a Flickr user with a free account, you may well have already noticed that you are unable to upload any more photos -- the new limit kicked on in January 8. But in under two weeks, Flickr will not only prevent you from uploading photos that tip you over the magic number, it will start actively deleting files to keep you within the 1,000 limit.… [Continue Reading] -

Leak shows that Android Q will bring native face unlock to more phones
Publié: janvier 26, 2019, 11:45am CET par Mark Wycislik-Wilson
A new Android Q leak suggests that Google is ready to copy another of the features iOS users have come to know and love: facial unlock. There are already a number of Android handsets -- including recent phones from OnePlus -- which have their own implementation of the biometric security feature, but with Android Q, it is looking as though the feature will be hard-baked into the operating system. See also: Android Q leak shows dark mode, improved privacy and intriguing Desktop Mode Google pushes Android devs to move to 64-bit as it timetables new app requirements Android Q could… [Continue Reading] -

Insiders say Mark Zuckerberg plans to unify WhatsApp, Instagram and Facebook Messenger
Publié: janvier 25, 2019, 4:30pm CET par Mark Wycislik-Wilson
Like Google constantly launching and closing services, the appalling disparate mess of apps produced by Facebook is something of an industry joke. Mark Zuckerberg is well-aware of this, and it seems he wants to do something about it. Insiders at the company say plans are afoot to change the way Facebook Messenger, WhastApp and Instagram function, unifying their messaging system for better integration. On top of this, Zuckerberg also wants each of the three messaging services to feature end-to-end encryption. See also: Advance warning: Facebook is closing down photo-sharing app Moments in a month -- time to save your pictures!… [Continue Reading] -

Mozilla confirms Firefox Screenshots is here to stay, although one key feature will be lacking
Publié: janvier 25, 2019, 11:49am CET par Mark Wycislik-Wilson
It has been a busy time at Mozilla recently, with the relaunch of Mozilla Labs and the closure of the Firefox Test Program. The second piece of news -- coupled with the shelving of certain changes to Firefox -- led to speculation about the future of Firefox Screenshots, but Mozilla has come forward to try to calm these fears. The company says that the screengrabbing tool -- which has become loved by many users since it launched nearly a year and half ago -- is here to stay. It's not all good news, however. One major feature is getting the… [Continue Reading] -

Advance warning: Facebook is closing down photo-sharing app Moments in a month -- time to save your pictures!
Publié: janvier 25, 2019, 11:04am CET par Mark Wycislik-Wilson
Facebook is throwing in the towel on Moments as the company kills off yet another of its apps. The photo-sharing app will close down on February 25, meaning there's just a month left for the service. If you're one of the relatively small number of users, you don't have long to grab a copy of the photos you want to save. Facebook has set up a special website to help you to download copies of your images. See also: Privacy International investigation finds a huge number of Android apps share data with Facebook -- whether you have an account or… [Continue Reading] -

Take this quiz to see if you can spot a phishing scam
Publié: janvier 23, 2019, 7:10pm CET par Mark Wycislik-Wilson
If you're anything like me, you probably inwardly roll your eyes -- or laugh outright -- when you hear of someone falling for a phishing scam. Surely you'd have to be a certified idiot to be taken in by one of these, right? You may have avoided falling victim up until now, but maybe that's been more through luck than good judgement. Or perhaps you really do think you could spot a phishing scam at a hundred paces. If you think you're up to it, why not put yourself to the test and take Google's phishing quiz? See also: The… [Continue Reading] -

Even Microsoft Edge thinks the Daily Mail website is an untrustworthy source of news
Publié: janvier 23, 2019, 5:28pm CET par Mark Wycislik-Wilson
Users of Microsoft Edge have a new feature to help protect them from fake news. The Android and iOS versions of the Edge browser now offer NewsGuard integration, warning when people visit untrustworthy sites. The feature may only just have gone live, but there are already some amusing -- or pleasing, depending on your point of view -- results coming from it. Perhaps the most notable is that the Daily Mail website, Mail Online, is flagged up as "generally fails to maintain basic standards of accuracy and accountability". For most people familiar with Mail Online, such warnings will come as… [Continue Reading] -

Torrent-Paradise launches a Pirate Bay alternative that takes decentralization to the next level
Publié: janvier 21, 2019, 3:22pm CET par Mark Wycislik-Wilson
While the BitTorrent protocol is, but its very nature, decentralized, the same cannot be said of torrent search engines such as the Pirate Bay. Torrent-Paradise, however, is a little different. A new version of the site uses the InterPlanetary File System (IPFS) to provide decentralized torrent searching. The idea behind how the system works is very similar to the way BitTorrent makes it possible to download files without the need for a central host. There are numerous benefits to this type of decentralization. It means that files -- or, in this case, search results -- can be shared between large… [Continue Reading] -

WhatsApp imposes five-recipient limit on forwarded messages to limit 'misinformation and rumors'
Publié: janvier 21, 2019, 11:45am CET par Mark Wycislik-Wilson
All social networks and messaging tools have been used as platforms to distribute fake news. Companies have taken various steps -- such as introducing fact-checking -- to help curb these problems, and now the Facebook-owned WhatsApp is introducing new measures that limit the number of people users can forward a message to. The company has previously allowed messages to be forwarded to up to 20 people, but now -- in a bid to limit the spread of "misinformation and rumors" -- this has been reduced to just five. See also: Privacy International investigation finds a huge number of Android apps… [Continue Reading] -

Court orders Apple to withdraw misleading statement about iPhone availability
Publié: janvier 19, 2019, 11:13am CET par Mark Wycislik-Wilson
As part of its ongoing legal battles with Qualcomm, Apple was last month banned from selling the iPhone 7 and 8 in Germany. Despite this, the company issued a press release stating that the handsets would remain available through thousands of resellers. Now a court has ordered Apple to stop making this claim, with the ruling describing this section of the press release as "misleading" and "potentially deceptive". See also: Apple releases expensive battery cases for iPhone XS, XS Max and XR, with wireless Qi charging After its profit warning, Apple slashes iPhone production by 10 percent Shares plummet following… [Continue Reading] -

How to export your saved passwords from Google Chrome
Publié: janvier 18, 2019, 12:34pm CET par Mark Wycislik-Wilson
From social media sites to online stores, from forum accounts to financial institutions -- there are now so many websites that require the use of a username and password, it's little wonder than so many of us turn to some form of password manager to save them. If you use Google's Chrome browser, you have almost certainly saved numerous passwords so you don't have to manually enter them every time they are requested. You may have wondered how to export these passwords for the purposes of backing them up, or to import into another password manager. Here, we show you… [Continue Reading] -

Microsoft concedes that Cortana can't -- and won't -- compete with Alexa and Google Assistant
Publié: janvier 18, 2019, 10:51am CET par Mark Wycislik-Wilson
Microsoft has seemingly admitted defeat in the digital assistant wars, with CEO Satya Nadella saying he does not want to compete with Amazon's Alexa or Google Assistant. Rather than planning a Cortana-powered smart speaker or other device, Nadella has demoted Cortana, signaling that Microsoft wants to focus on bringing it to other platforms as a "skill". He believes users should be able to use Alexa or Google Assistant to call on the capabilities of Cortana through close integration. See also: Microsoft releases Windows 10 19H1 Build 18317, splits up Search and Cortana Google Chromecast Audio is no more. It rests… [Continue Reading] -

How to view Wi-Fi passwords in Windows
Publié: janvier 17, 2019, 1:43pm CET par Mark Wycislik-Wilson
You have probably used your laptop in all sorts of places. As well as at home and in the office, you may well have used it in hotels, coffee shops and other locations that offer Wi-Fi access. As such, you've almost certainly got a large number of Wi-Fi passwords saved on your computer, passwords that are seemingly inaccessible. But these saved passwords are accessible -- if you know where to look, that is. This is handy if you need the password to get your phone online, or another laptop. Here's how to recover saved Wi-Fi passwords. See also: Windows 10… [Continue Reading] -

Huge Collection #1 database leak exposes 773 million email addresses and 21 million passwords
Publié: janvier 17, 2019, 11:31am CET par Mark Wycislik-Wilson
A massive database leak -- dubbed Collection #1 -- has made its way to hacking forums, exposing millions of email addresses and passwords. The news was first shared by Troy Hunt -- the man behind Have I Been Pwned? -- who explains that the leak comprises, "many different individual data breaches from literally thousands of different sources". Hunt explains that there are "1,160,253,228 unique combinations of email addresses and passwords", so there are a very large number of people that may have been affected by the leak. See also: Organizations suffer breaches despite confidence in their security measures Email security… [Continue Reading] -

Android Q leak shows dark mode, improved privacy and intriguing Desktop Mode
Publié: janvier 17, 2019, 10:24am CET par Mark Wycislik-Wilson
The inclusion of a system-wide dark mode in Android Q is something that has been rumored for a little while now, and a new leak of the next version of Google's mobile operating system seems to confirm this. A leaked build of Android Q not only features a customizable dark mode option, but it also shows that Google has tightened up permissions to help improve privacy. There are also exciting references to a Desktop Mode feature which would appear to be similar to Samsung DeX in making it possible to connect a phone to a monitor and use it like… [Continue Reading] -

Google pushes Android devs to move to 64-bit as it timetables new app requirements
Publié: janvier 16, 2019, 12:27pm CET par Mark Wycislik-Wilson
While 64-bit software is pretty much the norm on the desktop, the same cannot -- yet -- be said on mobile platforms. There is a steady movement away from 32-bit apps, and Google wants to accelerate things. The company is encouraging Android developers to concentrate on 64-bit versions of their apps as it sets out its timetable for the end of 32-bit software. See also: Android Q could well have a native, system-wide dark mode Privacy International investigation finds a huge number of Android apps share data with Facebook -- whether you have an account or not Google rolls out… [Continue Reading] -

Apple releases expensive battery cases for iPhone XS, XS Max and XR, with wireless Qi charging
Publié: janvier 16, 2019, 11:55am CET par Mark Wycislik-Wilson
If you're a heavy user of your iPhone, you'll be aware of the need to keep your battery topped up. You could carry around a battery pack, or you could stick your charger in your pocket in the hope that you'll be a near a power outlet. Or, you could invest in one of Apple's official charging cases. The iPhone-maker has just launched a trio of smart battery cases -- for the iPhone XS, XS Max and XR -- which allow you to protect and charge your phone at the same time. See also: After its profit warning, Apple slashes… [Continue Reading] -

Privacy-centric DuckDuckGo shuns Google and turns to Apple Maps for location-based searches
Publié: janvier 16, 2019, 11:10am CET par Mark Wycislik-Wilson
With the emphasis it places on privacy, it should come as little surprise that search engine DuckDuckGo is less than keen on Google. The latest demonstration of this is the company's decision to eschew Google Maps in favor of Apple's MapKit JS framework to power its map-related searches. DuckDuckGo says that this brings users a "valuable combination of mapping and privacy", both on the desktop and on mobile. See also: DuckDuckGo denies using fingerprinting to track its users Google relents and hands duck.com to privacy-centric rival DuckDuckGo Privacy-focused DuckDuckGo finds Google personalizes search results even for logged out and incognito… [Continue Reading] -

Mozilla closes experimental Firefox Test Pilot program
Publié: janvier 16, 2019, 10:36am CET par Mark Wycislik-Wilson
Just weeks after relaunching Mozilla Labs, the Firefox maker has announced that the browser's Test Pilot program is closing down. The move comes as Mozilla says it is "evolving Firefox's culture of experimentation". The Test Pilot Program has been a beta testing ground for numerous Firefox features including Containers, Activity Stream and Firefox Monitor. But while this particular program is going away -- and with very little notice -- Mozilla says that experimentation will continue, and promises that experimental features will not be disabled for those who are currently using them. See also: Mozilla's 'experiment' with banner ads on new… [Continue Reading] -

Netflix price increase hits US users
Publié: janvier 15, 2019, 6:22pm CET par Mark Wycislik-Wilson
To help bring in more money to fund new shows, Netflix is increasing its prices in the US with immediate effect. The cost of plans is jumping by between 13 and 18 percent, and new users will have to pay the new prices straight away. Existing customers can expect to see their subscription fees going up at some point over the next three months. See also: Netflix could use AI to clamp down on people sharing their account with friends and family The increase is the largest that Netflix has introduced since the streaming service first launched. For users on… [Continue Reading] -

Windows 10 has a built-in free screen recorder that you might not know about
Publié: janvier 14, 2019, 2:44pm CET par Mark Wycislik-Wilson
You've very probably been using Windows 10 for a long time now, but that doesn't mean that you've discovered everything it has to offer. The operating system is packed with features, but there are some that are hidden away to the extent that they could be considered secrets. One such gem is the screen recording tool. What? You didn't know that Windows 10 could record videos of on-screen activity? You're not alone. The screen recorder is built into the Game bar and you may well not have seen it. If you've ever wondered how to make video of what you're… [Continue Reading] -

Huawei sacks employee arrested in Poland on spying charges
Publié: janvier 14, 2019, 10:26am CET par Mark Wycislik-Wilson
Chinese smartphone-maker Huawei has sacked an employee after he was arrested in Poland, charged with spying. Weijing Wang, the company's sales director in Poland, was dismissed by Huawei as it tries to limit the damage to its reputation -- the company is already viewed as a potential security risk by numerous countries including the US. Huawei insists that the charges leveled against Wang are unrelated to the company, but said that the allegations brought it into disrepute. Poland's internal affairs minister, Joachim Brudziński, has called on NATO and the EU to work together to decide whether Huawei should be excluded… [Continue Reading] -

Google Chromecast Audio is no more. It rests in peace. It is bereft of life.
Publié: janvier 13, 2019, 1:28pm CET par Mark Wycislik-Wilson
If you were hoping to get your hands on a Chromecast Audio, you're out of luck: Google has stopped manufacturing the device. More than this, the audio-only version of Chromecast is out of stock pretty much everywhere, so your only hope of getting one now is probably to pick one up second hand. Google says it has a range of products that users can turn to if they want to enjoy music, so Chromecast Audio was deemed surplus to requirements. See also: Google Play now tells you how much space you have left on your phone Google rolls out spam… [Continue Reading] -

Google Play now tells you how much space you have left on your phone
Publié: janvier 13, 2019, 11:12am CET par Mark Wycislik-Wilson
With so many apps and games available in Google Play, it's easy to get carried away and fill up your phone. You can use Settings to keep track of how much space you have left, but now Google has made it possible to monitor free space from within the Play Store. A new storage indicator lets you monitor the amount of storage space you have available, so you can easily tell if you're going to have room to download more from the store -- and also to make room for those apps you desperately want to install. See also: Google… [Continue Reading] -

As the US government shutdown rolls on, numerous TLS certificates expire, leaving sites inaccessible
Publié: janvier 11, 2019, 4:26pm CET par Mark Wycislik-Wilson
With the US government shutdown in its third week, President Trump continues to try to convince both his own party and the Democrats to agree to fund one of his campaign promises -- a wall on the southern border. So far, the shutdown has seen national parks and more left unstaffed, and today is the first payday on which hundreds of thousands of federal workers will not receive a paycheck. Another side effect of the shutdown is that numerous government websites are offline as their TLS certificates have expired, and no one is available to renew them. See also: FCC… [Continue Reading] -

How to disable reserved storage in Windows 10
Publié: janvier 11, 2019, 1:34pm CET par Mark Wycislik-Wilson
If you have upgraded to Windows 10 version 1903 -- or Windows 10 19H1 as you may know it -- you will find that a portion of your hard drive has been set aside thanks to the new "reserved storage" option. Microsoft introduced this Storage Reserve (as it is also known) to "ensure proper performance and successful updates of your device", but not everyone is happy about it. You may be running low on disk space, or you just might like to remain in control of how your hard drive is used -- in which case, read on to find… [Continue Reading] -

Netflix could use AI to clamp down on people sharing their account with friends and family
Publié: janvier 11, 2019, 11:18am CET par Mark Wycislik-Wilson
Netflix has millions of users around the world, but how many of these are actually paying customers? Many of us either know (or are) people who share their Netflix account with friends and family, or leech off the one person they know that's willing to pay for a subscription. But Netflix free rides could be coming to an end. At CES, UK-based firm Synamedia revealed artificial intelligence software that could be used by Netflix and other companies to detect and block the sharing of account credentials. The system uses machine learning to determine a user's typical patterns of account activity,… [Continue Reading] -

Chuwi's HeroBook is a super-cheap Windows 10 laptop
Publié: janvier 10, 2019, 12:11pm CET par Mark Wycislik-Wilson
If you're on a tight budget, or you're looking for a cheap "throw-away" laptop you can pop into a bag when you're travelling, Chuwi's HeroBook could be for you. Aimed at students and "low-income workers", the HeroBook's specs are nothing to get too excited about, but this is not the point of this particular laptop. What the HeroBook is about is giving users a reasonable experience and above-acceptable hardware for a super-low price. For $199 you could kit yourself out with a laptop that is capable enough for day-to-day computing, or could serve as a secondary laptop for travelling with… [Continue Reading] -

Knowledge Graph 'bug' makes it possible to spoof Google search results
Publié: janvier 10, 2019, 11:24am CET par Mark Wycislik-Wilson
A security specialist has discovered a bug in Google's Knowledge Graph -- the cards that appear at the top of search results to highlight key pieces of information and provide quick answers to questions-- which makes it not only possible, but simple to manipulate search results. Wietze Beukema has demonstrated how it is possible to make simple tweaks to a search URL and display a knowledge panel card containing whatever data you want. While it is not possible to change the results that appear when people conduct a search, the bug means that fake links can be shared with others,… [Continue Reading] -

After its profit warning, Apple slashes iPhone production by 10 percent
Publié: janvier 9, 2019, 1:34pm CET par Mark Wycislik-Wilson
It's not all that long since Apple celebrated becoming a trillion dollar company, but then just last week it issued a profit warning and its value plummeted. Hot on the heals on this comes the news that Apple is cutting production of new iPhones for the current quarter by a significant amount. The Nikkei Asian Review reports that Apple is slashing production of its current trio of iPhone models by 10 percent in the January-March quarter. See also: New Apple support page addresses the issue of bent iPad Pros Shares plummet following Apple's profit warning, blamed on China, lower iPhone… [Continue Reading] -

NSA plans to release tool for reverse-engineering software
Publié: janvier 8, 2019, 11:35am CET par Mark Wycislik-Wilson
It feels like it has been a while since we've had any NSA-related news -- interest in mass surveillance has been overtaken by other concerns. After a series of Vault 7 leaks from WikiLeaks about the organization, the NSA is now planning to release its GHIDRA framework, designed to reverse-engineer malware and other software, later in the year. The framework will be available for Windows, macOS and Linux, and it is set to be demonstrated and publicly released at the RSAConference in March. While it might seem like a bad idea to release a tool that can be used to… [Continue Reading] -

Microsoft now lets everyone create unlimited private GitHub repositories for free
Publié: janvier 8, 2019, 10:50am CET par Mark Wycislik-Wilson
Since Microsoft bought GitHub last year there have been a few changes here and there, but the company has just announced something pretty major. While it previously cost $7 per month to create a private repository, now it is possible to create an unlimited number free of charge. There is a slight caveat, of course. Private projects are limited to up to three collaborators before a charge is applicable. Microsoft has also announced a new service, GitHub Enterprise, which brings together Enterprise Cloud (previously known as GitHub Business Cloud) and Enterprise Server (previously, and confusingly, known as GitHub Enterprise). For… [Continue Reading] -

Android Q could well have a native, system-wide dark mode
Publié: janvier 7, 2019, 8:58pm CET par Mark Wycislik-Wilson
If you want to be part of the in-crowd, adding a dark mode to your software is essential. Google has already shown a lot of love for gothic hues, and it looks set to continue this with Android Q -- or Android 10, if you prefer. Over on the Chromium Bug Tracker, Google worker Lukasz Zbylut appears to confirm that Android Q will feature a system-wide dark mode, with all preloaded apps offering the option natively. See also: Dark mode is coming to Chrome in Windows 10 soon Google: adding Dark Mode to apps saves battery Privacy International investigation finds… [Continue Reading] -

DuckDuckGo denies using fingerprinting to track its users
Publié: janvier 7, 2019, 7:16pm CET par Mark Wycislik-Wilson
Responding to a forum post that accused it of "fingerprinting users", privacy-centric search engine DuckDuckGo says that fears are unfounded and that it is not tracking its users. The allegation was made after the Firefox extension CanvasBlocker showed a warning to users. The suggestion of fingerprinting -- gathering as much information as possible about a user through their browser to create a unique identifier that can be used for tracking -- is clearly something that would seem to sit in opposition to what DuckDuckGo claims to stand for. The company CEO says the accusation is simply wrong. See also: Google… [Continue Reading] -

New Apple support page addresses the issue of bent iPad Pros
Publié: janvier 6, 2019, 4:53pm CET par Mark Wycislik-Wilson
A number of complaints came to light recently from iPad Pro owners who were unhappy to discover that their expensive Apple tablets were bent. Apple responded to these complaints by saying that the iPad Pro's unibody design "meets or exceeds" all of its high standards. Now the company has gone further, publishing a support page explaining the manufacturer and testing process of the iPad Pro, and explaining that the way the tablet is made is the reason some people see a bend. Apple insists, however, that an bend should be within a tiny 400 micron tolerance. See also: Your iPad… [Continue Reading] -

Marriott hack update: attackers accessed fewer user records than first thought, but 5.3 million passport numbers were unencrypted
Publié: janvier 5, 2019, 12:02pm CET par Mark Wycislik-Wilson
Back in late November, Marriott International went public with news that its Starwood Hotel reservation database had been hacked. At the time, the company suggested that up to 500 million customer records had been put at risk as a result, but now it has provided an update with a reduced estimate. The company now says that it believes up to 383 million guests may have been affected; but the news is not all good. Marriott also reveals that over 5 million unencrypted passport numbers were stolen by hackers. See also: Marriott's Starwood Hotel database hacked, putting 500 million customers at… [Continue Reading] -

Weather Channel app accused of opaquely selling users' location data
Publié: janvier 5, 2019, 11:30am CET par Mark Wycislik-Wilson
The Weather Channel app holds the accolade of being the most popular mobile weather app, but it is also facing accusations of misleading users into agreeing to allow the company to sell their location data to third parties. A lawsuit filed in Los Angeles this week alleges that the operator of the IBM-owned app -- TWC Product and Technology LLC -- sold user data to at least a dozen companies and failed to make details of this clear to users. The lawsuit says that the data was used to delivered targeted advertising and also to analyze consumer behaviour. See also:… [Continue Reading] -

Microsoft tests Project Bali, a privacy-focused tool to control personal data collection
Publié: janvier 4, 2019, 1:03pm CET par Mark Wycislik-Wilson
Microsoft Research is currently testing a new control panel which could enable users to manage the data the company collects about them. Known as Project Bali, the tool is currently undergoing private beta testing. It promises to not only give users the option of managing and controlling the data collected about them, but also -- intriguingly -- the ability to monetize it. See also: Sign up as an Microsoft Edge beta tester to try the new Chromium-based version of the browser first Privacy International investigation finds a huge number of Android apps share data with Facebook -- whether you have… [Continue Reading] -

Shares plummet following Apple's profit warning, blamed on China, lower iPhone sales and cut-price battery replacements
Publié: janvier 3, 2019, 4:10pm CET par Mark Wycislik-Wilson
After Apple issued a profit warning, indicating that it believed first quarter revenue will be lower than previously expected, shares in the company dropped by as much as 9 percent in early trading, and the effects were felt by other companies as fear mounted that Apple's troubles could spread wider. Tim Cook issued a letter to shareholders, warning that "our revenue will be lower than our original guidance for the quarter". He cites a number of reasons for the revised figures, including the timing of iPhone sales, the strength of the dollar, market saturation, and lower than expected numbers of… [Continue Reading] -

Dark mode is coming to Chrome in Windows 10 soon
Publié: janvier 2, 2019, 6:12pm CET par Mark Wycislik-Wilson
An increasing number of apps and websites are gaining dark modes, often simply for the sake of aesthetics, but also because of power-saving considerations. Having added eye-saving dark modes to numerous Android apps, Google has confirmed that it is doing the same for the Windows 10 version of Chrome. While there is no particular time frame in which we can expect to see Chrome's dark mode, a Chrome developer has confirmed that the feature is in progress. See also: Microsoft confirms you will be able to use Chrome extensions in Edge Sign up as an Microsoft Edge beta tester to… [Continue Reading] -

Updating from Windows 10 1803 to 1809 could disable the built-in administrator account
Publié: janvier 2, 2019, 12:55pm CET par Mark Wycislik-Wilson
If you have enabled Windows 10's built-in administrator account, and upgrade from build 1803 to 1809 -- that is, the April 2018 Update to the October 2018 update -- you will find that a bug has been introduced that disables the account. Microsoft says that it is aware of the problem, but the company does not plan on releasing a fix for it until the end of the month. See also: Windows 10 finally overtakes Windows 7 Windows 10 bug could allow files to be overwritten, researcher shows Latest Windows 10 preview build is an early Christmas present for Insiders,… [Continue Reading] -

FCC will suspend many operations tomorrow if Trump's government shutdown continues
Publié: janvier 2, 2019, 11:24am CET par Mark Wycislik-Wilson
President Trump's partial shutdown of the US government is now well into its second week, with little sign of the impasse over funding for a wall on the southern border coming to an end. Large numbers of government employees are already feeling the pinch due to a lack of pay checks, and the impact is on the verge of spreading further. The Federal Communications Commission (FCC) has announced that it will suspend "most operations" at midday on Thursday, January 3 "in the event of a continued partial lapse in federal government funding". In a press release, the FCC says: "In… [Continue Reading] -

Privacy International investigation finds a huge number of Android apps share data with Facebook -- whether you have an account or not
Publié: janvier 1, 2019, 11:53am CET par Mark Wycislik-Wilson
Facebook's track record with privacy is a rocky one, but the idea of giving up some personal data is seen by many users as an acceptable price to pay for using the social network. But an investigation by Privacy International has found that many Android apps are sharing data with Facebook about people regardless of whether they are logged into their Facebook account... or even have a Facebook account at all. The findings of the investigation raise questions about Facebook's transparency when it comes to handling user (and non-user) data, and the privacy implications of profiling by the social networking… [Continue Reading] -

Mozilla's 'experiment' with banner ads on new tabs angers users
Publié: janvier 1, 2019, 10:32am CET par Mark Wycislik-Wilson
Firefox users have expressed surprise, disgust and anger at the appearance of banner ads on new tabs in the browser. An advertisement appeared recently inviting users to make a booking via Booking.com. The ad appears at the bottom of the new tab page, and makes use of Firefox's Snippet feature. Mozilla has explained that the "snippet was an experiment", insisting no user data has been shared with third parties. If you're concerned, however -- or just don't want to see even more ads -- you can disable them. See also: Mozilla Labs is back! You may be happy about Microsoft's… [Continue Reading] -

Windows 10 bug could allow files to be overwritten, researcher shows
Publié: décembre 31, 2018, 11:44am CET par Mark Wycislik-Wilson
A security researcher has released proof-of-concept code for a zero-day exploit in Windows 10. The bug was revealed by SandboxEscaper, a researcher who has exposed Windows vulnerabilities in the past. The latest bug makes it possible to overwrite files with arbitrary data, and while there are numerous criteria that must be met in order for the vulnerability to be exploited, it is still potentially serious. SandboxEscaper warned Microsoft about the problem on Christmas day, before publishing the PoC a couple of days later. See also: Microsoft issues emergency patch to fix serious Internet Explorer zero-day vulnerability Microsoft announces Windows Sandbox,… [Continue Reading] -

Europe to fund bug bounties for 15 open source programs, including VLC, Drupal and Notepad++
Publié: décembre 30, 2018, 10:03am CET par Mark Wycislik-Wilson
Starting in January, the European Commission is going to fund bug bounty programs for a number of open source projects that are used by members of the EU. The initiative is part of the third edition of the Free and Open Source Software Audit (FOSSA) project, which aims to ensure the integrity and reliability of the internet and other infrastructure. In all, the Commission will fund 15 bug bounty programs, with rewards ranging from €17,000 ($19,400) to €90,000 ($103,000). See also: Microsoft confirms plans to use open source Chromium to develop Edge Facebook API bug may have exposed 6.8 million… [Continue Reading] -

Major US newspapers hit by cyberattack, disrupting printing and distribution
Publié: décembre 30, 2018, 9:23am CET par Mark Wycislik-Wilson
A number of major US newspapers -- including the Los Angeles Times, Chicago Tribune, Wall Street Journal and New York Times -- have been hit by a cyberattack that is said to originate from another country. Malware was first detected on Thursday by Tribune Publishing, the owner of some of the affected titles, but unsuccessful attempts at quarantining meant that there was disruption well into Saturday. The Department of Homeland Security is currently investigating the incident which is not thought to have exposed any personal customer details. See also: Marriott's Starwood Hotel database hacked, putting 500 million customers at risk… [Continue Reading] -

Google rolls out spam protection to Android Messages
Publié: décembre 29, 2018, 10:42am CET par Mark Wycislik-Wilson
Spam may be something that's most commonly associated with email, but it's also something that blights text messaging. Google is trying to do something about the problem with a spam protection feature for Messages on Android. This is a feature we learned about earlier in the year, and it is now starting to roll out to handsets. In order for the feature to work, "some" information about the messages you receive needs to be sent to Google -- something that it sure to raise a few eyebrows (and hackles) among the privacy-centric. See also: Google Assistant uses AI to predict… [Continue Reading] -

Mozilla Labs is back!
Publié: décembre 28, 2018, 12:04pm CET par Mark Wycislik-Wilson
The popularity of software betas and the Windows Insider program show that people are keen to get their hands on things earlier. There is a certain delight in tinkering with experimental tools, utilities and apps, and if this is the sort of thing that excites you, you'll be pleased to hear that Mozilla has brought Mozilla Labs back from the dead with a new site. Not seen for a number of years, Mozilla Labs used to be home to experimental Firefox projects. Now, the relaunched version is home to more, including Project Things, Spoke, Hubs and more -- Firefox is… [Continue Reading] -

Instagram accidentally rolls out new horizontally scrolling feed to much confusion
Publié: décembre 27, 2018, 5:43pm CET par Mark Wycislik-Wilson
Instagram users around the world were briefly thrown into a mixture of confusion, delight and anger today when timelines switched to a new horizontal scrolling mode. Greeted by a message that Instragram was "Introducing a New Way to Move Through Posts", users found that they could now tap to scroll through their feed horizontally. This is something that Instagram is known to have been testing for a little while now, but it seems that today's rollout was entirely accidental -- albeit one that gave a tantalizing glimpse into the future. The company has now reverted feeds to the familiar verticals… [Continue Reading] -

Here's what 2019 holds for Paint.NET
Publié: décembre 27, 2018, 8:44am CET par Mark Wycislik-Wilson
As 2018 draws to a close, it's a time not only for looking back over what the past year has offered, but also for looking forward to the new year and what's on the horizon. There's certainly a lot to look forward to in terms of hardware in 2019, but there's also a great deal on the software front. The developer of the popular image editing tool Paint.NET, Rick Brewster, has shared his vision of what the coming year holds for his software. The 2019 roadmap for Paint.NET is an exciting one, promising migration to .NET Core, support for brushes… [Continue Reading] -

Android Pie now rolling out to OnePlus 5 and OnePlus 5T
Publié: décembre 27, 2018, 8:20am CET par Mark Wycislik-Wilson
OnePlus is well known for many things, including building up massive hype around its (generally) powerful and (relatively) cheap handsets. But one of the reasons many people choose the company is that it has always been quick at rolling out Android updates to newer handsets -- and it has a great track record for supporting its phones for much longer than its rivals do with their handsets. The company may well be concerned about shifting its latest models, but owners of previous generations have not been forgotten when it comes to Android Pie. The latest version of Android is already… [Continue Reading] -

Microsoft's emergency Internet Explorer patch renders some Lenovo laptops unbootable
Publié: décembre 24, 2018, 11:21am CET par Mark Wycislik-Wilson
A few days ago, Microsoft issued an emergency patch for Internet Explorer to fix a zero-day vulnerability in the web browser. The problem affects versions of Internet Explorer from 9 to 11 across multiple versions of Windows, but it seems that the patch has been causing problems for many people. Specifically, people with some Lenovo laptops have found that after installing the KB4467691 patch they are unable to start Windows. See also: Microsoft issues emergency patch to fix serious Internet Explorer zero-day vulnerability Sign up as an Microsoft Edge beta tester to try the new Chromium-based version of the browser… [Continue Reading] -

Linux 4.20 released in time for Christmas
Publié: décembre 24, 2018, 9:34am CET par Mark Wycislik-Wilson
Giving Linux fans a little Christmas present, Linus Torvalds has announced that version 4.20 of the Linux kernel is now available. In a post to the Linux Kernel Mailing List, Torvalds said that there was no point in delaying the release of the latest stable version of the kernel just because so many people are taking a break for the holiday season. He says that while there are no known issues with the release, the shortlog is a little longer than he would have liked. However "nothing screams 'oh, that's scary'", he insists. See also: Visiting family for Christmas? Replace… [Continue Reading] -

Apple launches new transparency report website showing government data requests from around the world
Publié: décembre 23, 2018, 11:10am CET par Mark Wycislik-Wilson
In recent years, technology companies have been under increasing pressure to be more transparent about the requests for data they receive from global governments. Firms such as Microsoft, Google and Facebook publish regular transparency reports, and Apple is no different. Now the company has launched a new transparency report website which makes it even easier to trawl through its twice-yearly publication and see how many data requests have been issued by different governments. See also: Apple stands by its bent iPad Pro Your iPad Pro may be bent -- and Apple says it's not a defect Apple releases iOS 12.1.2… [Continue Reading] -

Apple stands by its bent iPad Pro
Publié: décembre 23, 2018, 10:39am CET par Mark Wycislik-Wilson
Earlier this week, we wrote about the growing number of people who have complained that their iPad Pro is bent. This is not something that has developed over time, but a problem that was present out of the box. Apple responded to complaints by saying that the bend that has been noticed in some iPad Pro chassis was not a defect. Now the company has issued a further statement indicating that it believes the tablet's "unibody design meets or exceeds all of Apple's high quality standards of design and precision manufacturing". This is not something an owner of a bent… [Continue Reading] -

OnePlus 6T ad footage appears to be edited to make the bezel look smaller
Publié: décembre 23, 2018, 9:51am CET par Mark Wycislik-Wilson
Just a few days ago, a lawsuit was filed against Apple accusing it of using misleading images in advertising to disguise the notch of the iPhone XS. Now it is OnePlus that has been accused of editing advertising images of its phones, this time to make the bezel of the OnePlus 6T seem smaller. The company was called out on Twitter after people noticed that the OnePlus 6T featured in promotional videos appeared to have a much smaller "chin" than the real-life phone. See also: Apple hit with lawsuit for hiding iPhone XS notch and making misleading claims in advertising… [Continue Reading] -

Sign up as an Microsoft Edge beta tester to try the new Chromium-based version of the browser first
Publié: décembre 21, 2018, 1:54pm CET par Mark Wycislik-Wilson
Microsoft recently confirmed that it plans to transition its Edge browser away from the EdgeHTML engine to Chromium, embracing open source, bringing Chrome extensions and more. Making such a big change obviously requires a lot of testing, and Microsoft is giving you the chance to get involved via the Microsoft Edge Insider program. The company already has the Windows Insider program for people who want to get their hands on new builds of Windows 10 earlier than they would normally, but this is a commitment that not everyone is willing to sign up for. Now Microsoft has launched a beta… [Continue Reading] -

Microsoft announces Project Mu, an open-source release of the UEFI core
Publié: décembre 20, 2018, 12:41pm CET par Mark Wycislik-Wilson
Microsoft has a new open source project -- Project Mu. This is the company's open-source release of the Unified Extensible Firmware Interface (UEFI) core which is currently used by Surface devices and Hyper-V. With the project, Microsoft hopes to make it easier to build scalable and serviceable firmware, and it embraces the idea of Firmware as a Service (FaaS). This allows for fast and efficient updating of firmware after release, with both security patches and performance-enhancing updates. See also: Microsoft issues emergency patch to fix serious Internet Explorer zero-day vulnerability Microsoft has made a free Office app for Windows 10… [Continue Reading] -

Facebook addresses controversy over third-party access to private messages
Publié: décembre 20, 2018, 12:07pm CET par Mark Wycislik-Wilson
Facebook has been the source of much privacy-related controversy over the years, particularly over the last year or so. The past few days have been no different, with the social networking giant facing questions over the level of access it granted partners to private user data. Of particular concern to users is the suggestion that Facebook gave the likes of Spotify and Netflix access to users' private messages. Having already gone on the defensive about some of the allegations leveled at it, Facebook is now trying to defend itself about the messaging allegations -- or, as the company puts it… [Continue Reading] -

Apple now lets you gift in-app purchases
Publié: décembre 20, 2018, 11:39am CET par Mark Wycislik-Wilson
While it has been possible for some time to give iOS apps to others as a gift, you have not been able to do the same with in-app purchases. Now, however, if you want to buy in-app content as a Christmas present for friends or family (what greater sign of affection, eh?!) you can do so. Apple has changed its App Store Review Guidelines giving developers the option to enable the gifting of in-app purchases. See also: Your iPad Pro may be bent -- and Apple says it's not a defect Apple releases iOS 12.1.2 with eSIM fixes -- but… [Continue Reading] -

Your iPad Pro may be bent -- and Apple says it's not a defect
Publié: décembre 20, 2018, 11:04am CET par Mark Wycislik-Wilson
iPhone and iPad have long been subjected to bend tests to see how they hold up to abuse. But what about if your iPad Pro arrived with a bend in the casing? You'd send it back and ask for a replacement or a refund, right? But Apple does not believe that an iPad Pro that arrives bent is defective. The company has confirmed that a number of 2018 iPad Pro tablets have a "slight bend" in their aluminum casing, blaming the defect on the manufacturing process. Only it's not a defect, remember? See also: Apple releases iOS 12.1.2 with eSIM… [Continue Reading] -

Microsoft issues emergency patch to fix serious Internet Explorer zero-day vulnerability
Publié: décembre 20, 2018, 10:49am CET par Mark Wycislik-Wilson
Microsoft has issued an emergency, out-of-band patch for an Internet Explorer zero-day that was being actively exploited in targeted attacks. The company says that it learned about the vulnerability through a report from Google. CVE-2018-8653 affects a range of versions of Internet Explorer from 9 to 11, across Windows 7 to 10 and Windows Server. See also: Latest Windows 10 preview build is an early Christmas present for Insiders, with Windows Sandbox and other treats Microsoft has made a free Office app for Windows 10 Microsoft announces Windows Sandbox, a desktop environment for running applications in isolation The vulnerability amounts… [Continue Reading] -

Facebook gave dozens of companies access to user data such as friends lists and private messages
Publié: décembre 19, 2018, 7:12pm CET par Mark Wycislik-Wilson
Details have come to light about the deals Facebook struck with the likes of Microsoft, Spotify, Netflix, Apple and Amazon. A report by the New York Times revealed that the social network had given numerous companies access to a plethora of private user data, ranging from the names of friends, to private messages. Facebook has responded by saying that no access was granted to third parties without user permission, but questions remain about whether users were fully aware of the level of access companies had to their data, or whether they knew they were agreeing to sharing private data. See… [Continue Reading] -

Microsoft announces Windows Sandbox, a desktop environment for running applications in isolation
Publié: décembre 19, 2018, 12:31pm CET par Mark Wycislik-Wilson
Microsoft has announced an upcoming security feature which it hopes will take the fear and risk out of running unknown software. Windows Sandbox is an isolated desktop environment which functions much like a virtual machine; any software installed to it is completely sandboxed from the host operating system. Aimed at businesses, enterprises and security-conscious home users, Windows Sandbox will be part of Windows 10 Pro and Windows 10 Enterprise. It is not clear exactly when the feature will debut, but it could make an appearance in Windows 10 19H1 next year. See also: Microsoft may have sent you an email… [Continue Reading] -

Following 'unusual activity' from China and Saudi Arabia, Twitter reveals user country codes may have leaked
Publié: décembre 18, 2018, 8:06pm CET par Mark Wycislik-Wilson
Twitter has discovered what it describes as "unusual activity" stemming from China and Saudi Arabia. The social networking company says that it noticed a large number of enquiries involving a support API coming from individual IP addresses in the two countries. The discovery came as Twitter investigated a bug in a support form. The problem, Twitter says, dates back to November 15, and it was fixed the next day, but a security researcher says he reported the issue two years ago. As a result of the bug, Twitter says that the country code of users' phone numbers could have been… [Continue Reading] -

Twitter is bringing back the reverse chronological timeline starting today
Publié: décembre 18, 2018, 7:30pm CET par Mark Wycislik-Wilson
For those who like simple chronology, Twitter's insistence on delivering tweets in an algorithm powered order that is seemingly random has long been a source of frustration. Today, the social site launches a new way to switch between reverse chronological order or the algorithm-driven "top tweets" ordering. To allow for easy switching between the two modes, Twitter is rolling out a new "sparkle" button to its mobile app. The change is being made available to iOS users first, but Android owners will not be far behind. See also: Amplification bots used to raise the popularity and legitimacy of Twitter posts… [Continue Reading] -

Microsoft may have sent you an email with a hidden gift certificate worth $10
Publié: décembre 18, 2018, 11:41am CET par Mark Wycislik-Wilson
We're coming up to the time of year when a little extra money is welcome. Well... that's true of pretty much any day of the year, but with Christmas presents to buy, it is particularly true now. So how about some free money from Microsoft? It seems that you may already have a free gift certificate worth $10 sitting in your inbox. Microsoft included the gift cards in emails it sent out to people, but rather than making an announcement, the company decided to stealthily hide the money. See also: Windows 10 sends activity history to Microsoft even when told… [Continue Reading] -

Apple releases iOS 12.1.2 with eSIM fixes -- but Qualcomm is still not happy
Publié: décembre 18, 2018, 11:04am CET par Mark Wycislik-Wilson
Apple has made iOS 12.1.2 available to iPhone users, just two weeks after the public release of iOS 12.1.1. The fourth update to the iPhone operating system since it was launched includes fixes for problems with eSIM and connectivity. But while iPhone owners around the world will be pleased to receive another update, Qualcomm remains unhappy with Apple. The company complained that Apple was violating two of its software patents, and last week a Chinese court banned the sale of certain older iPhones. Apple said that this week's update would "address any possible concern about our compliance with the order";… [Continue Reading] -

Apple hit with lawsuit for hiding iPhone XS notch and making misleading claims in advertising
Publié: décembre 17, 2018, 5:33pm CET par Mark Wycislik-Wilson
A lawsuit has been filed with the District Court of the Northern District of California accusing Apple of misleading advertising for the iPhone XS. The lawsuit claims that not only does Apple disguise the fact that the iPhone XS has a notch, but also that the company made false claims about the pixel count of the handset's screen. The class action lawsuit, Sponchiado & Davis vs Apple, runs to some 55 pages and it makes observations that have been made by fans and critics of Apple alike. See also: These are the best apps, games, music, movies and more of… [Continue Reading] -

Facebook API bug may have exposed 6.8 million users' private photos
Publié: décembre 16, 2018, 6:03pm CET par Mark Wycislik-Wilson
Another week and yet another in a seemingly endless stream of Facebook privacy issues. The social networking giant has found itself apologizing, yet again, for leaking users' private data. This time around, an API bug meant that private photos of millions of users may have been exposed to app developers. The bug was present for nearly two weeks and it went further than simply giving developers access to photos users had posted to their accounts -- it also exposed photos that had been uploaded but not actually posted. See also: Facebook Watch is a disaster... so now it will target… [Continue Reading] -

Google relents and hands duck.com to privacy-centric rival DuckDuckGo
Publié: décembre 12, 2018, 8:32pm CET par Mark Wycislik-Wilson
It may well just be coincidental timing, but shortly after DuckDuckGo accused Google of personalizing search results even for people not signed into their account, Google has handed control of the Duck.com domain over to its rival. The concession comes after years of frustration for DuckDuckGo, with Google having acquired Duck.com after buying On2 Technologies (previously The Duck Corporation) in 2010. The privacy-focused search engine has long asked Google to point the address at its website, and this has finally happened. Duck.com now redirects to DuckDuckGo. See also: Privacy-focused DuckDuckGo finds Google personalizes search results even for logged out and… [Continue Reading] -

The OnePlus 6T McLaren Edition is just getting silly with 10GB RAM
Publié: décembre 11, 2018, 5:34pm CET par Mark Wycislik-Wilson
Over the last few years, OnePlus has jumped from being a weird indie outsider to being something of a household name. Its twice-yearly smartphone releases are always eagerly awaited, and there have been a handful of special editions thrown in for good measure. The latest of these is the OnePlus 6T McLaren Edition, and it is the epitome of going over the top. Packing a rather excessive-seeming 10GB of RAM, the latest addition to the OnePlus stable rocks not only a headline-grabbing amount of memory (which is probably the point), but also the incredibly fast Warp Charge 30 charging system…… [Continue Reading] -

Google+ to close down earlier than planned after another data leak is discovered
Publié: décembre 10, 2018, 7:15pm CET par Mark Wycislik-Wilson
We already knew that Google+ is closing down, but following the discovery of a second data leak, Google has announced that it is bringing the closure forward. The company has revealed that a bug in the Google+ API exposed the data of 52.5 million users, and as a result it is expediting the shutdown. Previously due to close in August 2019, Google+ will now be killed off in April 2019. See also: After failing to disclose user data leaks, Google is shutting down Google+ and improving APIs Google to kill off Allo as the company streamlines messaging in its own… [Continue Reading] -

Microsoft confirms you will be able to use Chrome extensions in Edge
Publié: décembre 10, 2018, 6:24pm CET par Mark Wycislik-Wilson
The news that Microsoft is going to create a Chromium-based version of its Edge browser has been met with a mixed reaction, but there is some good news for users. The company has confirmed that the adoption of Chromium means that Edge will support Chrome extensions. Microsoft Edge has been much maligned for its lack of features when compared to Firefox, Chrome and Opera, and the number of extensions currently supported by the browser is laughably small. For this reason, the confirmation that Chrome extensions will be supported will be warmly welcomed by users. See also: You may be happy… [Continue Reading] -

Microsoft says it is time for government regulation of facial recognition
Publié: décembre 7, 2018, 5:11pm CET par Mark Wycislik-Wilson
Facial recognition is becoming more widely used in both general computing and in the wider world. Smartphones and computers can be unlocked with your face, but the technology is also used for security and policing purposes. While most uses are legitimate and helpful, there is scope for abuse. Microsoft thinks it is time for regulation to help avoid this. The company is calling on government around the world to introduce new laws, but also on the technology industry to introduce safeguards to protect against abuse and bias. See also: You may be happy about Microsoft's adoption of Chromium, but Mozilla… [Continue Reading] -

You may be happy about Microsoft's adoption of Chromium, but Mozilla thinks it is bad for competition
Publié: décembre 7, 2018, 3:57pm CET par Mark Wycislik-Wilson
After the rumors, confirmation came from Microsoft that it plans to move its Edge browser from the EdgeHTML engine to Chromium. Reaction from users has been largely positive, but it's not the same story across the technology industry as a whole. While Google is understandably happy about the change, the CEO of Mozilla, Chris Beard, says it is bad for competition and will help to make Google even more powerful. See also: Microsoft confirms plans to use open source Chromium to develop Edge Hate Edge? Microsoft may be ready to move on to a Chromium-based browser Arrests made in Indian… [Continue Reading] -

Microsoft confirms plans to use open source Chromium to develop Edge
Publié: décembre 6, 2018, 7:07pm CET par Mark Wycislik-Wilson
Just a couple of days ago, news crept out about Microsoft's project Anaheim -- a Chromium-based web browser said to be a replacement for Microsoft Edge. This understandably generated a great deal of interest... So much, in fact, that Microsoft has been compelled to speak out and confirm what its plans are. Microsoft says that it is not building a replacement for Edge, but confirms that it will be embracing Chromium in the development of the browser. It is part of the company's increasing involvement in the open source community, and is driven by a desire to improve web compatibility… [Continue Reading] -

Google to kill off Allo as the company streamlines messaging in its own unique way
Publié: décembre 6, 2018, 6:26pm CET par Mark Wycislik-Wilson
There has been a great deal of speculation recently about what Google's plans are for dealing with its plethora of messaging tools. There had been suggestions that Hangouts could be for the chop, but now Google has spoken out to say that this is not -- quite -- the case, and in fact it is Allo that will be shuttered. The closure of Allo will come just two-and-a-half years since it first appeared. Google says that it has learned a lot from releasing Allo, and plans to bring the best of its features to the Messages app. In a blog… [Continue Reading] -

Windows Lite, anyone? Microsoft said to be working on yet another cut-down version of Windows
Publié: décembre 5, 2018, 4:21pm CET par Mark Wycislik-Wilson
Microsoft has already had a stab at a cut-down version of its famous operating system in the form of Windows RT and Windows 10 S... and it seems that the company is looking to have a third try. References have been spotted in the code of Windows 10 to "PRODUCT_LITE" -- apparently a reference to a new version of its OS called either Windows Lite, or just Lite. While Microsoft has not confirmed anything or made any official announcements, there are numerous references to Lite in recent Insider builds of Windows, as well as in the SDK for the OS.… [Continue Reading] -

Privacy-focused DuckDuckGo finds Google personalizes search results even for logged out and incognito users
Publié: décembre 4, 2018, 6:58pm CET par Mark Wycislik-Wilson
You might well expect that if you perform a Google search while signed into your Google account that the results will be tailored according to what that company has learned about you over the years. But what about when you're not signed into your account? A study carried out by the privacy-centric search engine DuckDuckGo yielded some slightly surprising results. In tests earlier in the year, it was found that even when people searched without logging into a Google account -- or when they used private browsing mode -- "most participants saw results unique to them", suggesting there was still… [Continue Reading] -

These are the best apps, games, music, movies and more of 2018... according to Apple
Publié: décembre 4, 2018, 6:13pm CET par Mark Wycislik-Wilson
The end of the year approaches and so the "best of" lists start to emerge. Jumping on the bandwagon is Apple, providing us with a lengthy list of the best apps, games, music, podcasts, TV shows, and just about everything else digital you can think of. The charts have not been compiled by simply calculating which apps have proved most popular with user. Apple describes it as "an invariable list of the who's who and what's what from the past year" which is a combination of both "top charts and selects from our editors". Are your favorites featured? The look-back… [Continue Reading] -

Hate Edge? Microsoft may be ready to move on to a Chromium-based browser
Publié: décembre 4, 2018, 5:34pm CET par Mark Wycislik-Wilson
If Microsoft isn't careful, it is going to start getting through web browsers faster than Google gets through messaging tools. Having moved on from Internet Explorer to Edge, the company is now said to be looking to transition to a Chromium-based browser for Windows 10. It's fair to say that Edge hasn't won itself too many fans since it first appeared three years ago, so the suggestion that Microsoft may ditch EdgeHTML in favour of a browser based on Chromium is likely to be widely welcomed. Said to be codenamed Anaheim, the news Microsoft has a new rendering engine on… [Continue Reading] -

Tumblr turns family-friendly and bans ALL adult content
Publié: décembre 3, 2018, 9:19pm CET par Mark Wycislik-Wilson
Tumblr has announced that it is to introduce a ban on all adult content across the platform in a major reversal of policy. The site has long been home to all manner of explicit content, and this lack of censorship is part of the reason for Tumblr's popularity. The site says that, as of December 17, "adult content will not be allowed on Tumblr, regardless of how old you are". The announcement was made in the Tumblr Help Center, and it comes as the company aims to appeal to a wider age range. Just last week the Tumblr app was… [Continue Reading] -

Microsoft adds real-time captions and subtitles to Skype -- PowerPoint to follow
Publié: décembre 3, 2018, 7:22pm CET par Mark Wycislik-Wilson
We're all pretty used to subtitles for movies and TV shows -- even if we don't need them, they can prove useful -- and Microsoft has now added this feature to Skype. Ostensibly an accessibility feature (and launched on United Nations International Day of Persons with Disabilities), the new option means that Skype will be able to use voice recognition to show you the text of what is being said in a voice call. Microsoft will also bring the same feature to PowerPoint next year. See also: Microsoft is sending Skype classic to the software graveyard in November Microsoft is… [Continue Reading] -

Amazon launches hardware compatibility checker to help PC upgraders
Publié: décembre 1, 2018, 11:54am CET par Mark Wycislik-Wilson
If you want a custom PC, there's a lot of fun to be had building your own rig -- or even just upgrading your off-the-shelf PC. But while you can save money as you create your perfect computer, there is the headache of ensuring that all of the components you buy are compatible with your system. While hardware compatibility is not quite the problem it was in years gone by, it can still be an issue. Help is at hand, however, albeit from an unlikely source. Amazon has launched a compatibility checking tool that will help you to buy the… [Continue Reading] -

Google may pull the plug on Hangouts in 2020
Publié: décembre 1, 2018, 10:22am CET par Mark Wycislik-Wilson
Google is no stranger to killing off services, and it seems that one of its next victims could be Hangouts. Having split the chat tool into corporate-focused Hangouts Chat and Hangouts Meet, sources familiar with Google's plans say that the company is due to shut down the consumer version of Hangouts in 2020. The writing has been on the wall for a little while, but now the clock really is ticking... See also: Google Translate on the web gets improved looks and functionality Fast Pair makes it easier to pair Bluetooth headphones to Android devices via a Google Account Now… [Continue Reading] -

Marriott's Starwood Hotel database hacked, putting 500 million customers at risk
Publié: novembre 30, 2018, 1:58pm CET par Mark Wycislik-Wilson
Marriott International has revealed that its Starwood Hotel reservation database has been hacked. An investigation carried out by the company revealed that hackers have had unauthorized access to the Starwood network since 2014. The astonishing revelation means that information of half a billion guests could have been exposed -- including sensitive personal data such as home address and passport number -- and Marriott says there is evidence that data has been copied from its network. While Marriott says that it has taken steps to rectify the matter, this will be of little comfort to millions of customers whose details have… [Continue Reading] -

Instagram's new Close Friends option lets you limit the audience for Stories
Publié: novembre 30, 2018, 1:18pm CET par Mark Wycislik-Wilson
Instagram has announced the rollout of Close Friends, a feature that makes it possible to create a list of people with whom you'd like to share Stories. This is very different to the current approach which sees Stories shared with everyone. The feature has been beta tested for nearly a year and a half and is now ready for primetime. Rolling out to iOS and Androind in the coming days, the new feature will be welcomed by those who had concerns about privacy on Instagram. See also: Your Time On Facebook rolls out, revealing how much time you waste in… [Continue Reading] -

Arrests made in Indian call centers responsible for Microsoft tech support scams
Publié: novembre 30, 2018, 11:25am CET par Mark Wycislik-Wilson
There are many annoyances associated with owning a computer -- spam emails, phishing attacks, viruses and online advertising to name but a few -- but technical support scams are among the most worrying. They take advantage of people's ignorance and/or better natures, posing as tech support operatives from big companies over the phone. Being one of the best-known technology companies in the world, it's little surprise that a huge number of these tech support scams purport to be Microsoft calling to offer help with computer problems. Such scams are responsible for conning people out of large amounts of money, but… [Continue Reading] -

TIDAL comes to Plex
Publié: novembre 29, 2018, 4:18pm CET par Mark Wycislik-Wilson
Hot on the heels of TIDAL arriving in the Microsoft Store for Windows 10 users, Plex has announced integration with the high-quality music service in its media tool. You don't need a paid-for Plex Pass to enjoy TIDAL in Plex, but there are special subscription deals available if you do have one. There's also no need to have a server set up -- you can access TIDAL from within the Plex apps. See also: Jay-Z's struggling TIDAL comes to Windows 10 through the Microsoft Store Plex launches beta version of Plex Web Shows offering on-demand streaming shows for free Plex… [Continue Reading] -

Microsoft wins $480 million military AR contract -- US Army could purchase 100,000 HoloLens headsets
Publié: novembre 29, 2018, 12:08pm CET par Mark Wycislik-Wilson
The US Army has revealed that Microsoft has won a contract worth $480 million to supply prototype augmented reality equipment. The deal could see the Army purchasing 100,000 HoloLens headsets from the company. Microsoft says the deal is an extension of its existing relationship with the Department of Defense. The company has previously faced criticism from its employees for bidding for military contracts, but it responded by saying it believed that those defending the US should have access to the best technology. Winning this latest contract -- the aim of which is to "increase lethality by enhancing the ability to… [Continue Reading] -

Dell resets customer passwords following cyberattack on its website
Publié: novembre 29, 2018, 10:03am CET par Mark Wycislik-Wilson
Dell has announced that it has instigated a mandatory password reset for customers after it suffered a cyberattack earlier in the month. In a statement, the company confirmed that its network had been subject to "unauthorized activity" on November 9 in which attackers tried to gain access to customer information. Dell says that data was limited to names, email addresses and hashed passwords, adding there is "no conclusive evidence" that data was extracted. The forced password reset is described as a measure to "limit the impact of any potential exposure". Dell is giving very little away about the nature of… [Continue Reading] -

Your iPhone is worth more than it used to be
Publié: novembre 28, 2018, 5:21pm CET par Mark Wycislik-Wilson
iPhones have a tendency to hold their value more than other phones -- and it's a similar story with other Apple products. If you were thinking of upgrading your handset to one of the latest models and you're considering trading it in with Apple, you'll be pleased to hear that your old iPhone just became more valuable. Apple is running a time-limited promotion which means you could bag yourself up to $100 extra credit when you take advantage of the Apple GiveBack program. You could earn up to $300 to put towards your next Apple device. See also: Some MacBook… [Continue Reading] -

Fast Pair makes it easier to pair Bluetooth headphones to Android devices via a Google Account
Publié: novembre 28, 2018, 9:47am CET par Mark Wycislik-Wilson
Google is taking steps to make it easier to not only pair Bluetooth headphones and speakers to your Android phones, but also to make it easier to user the same Bluetooth hardware with multiple devices. The Fast Pair feature was announced last year, and now Google has teamed up with numerous audio companies to not only improve support, but also to use Google accounts as a means of simplifying the process of using the same headphones and speakers with multiple phones -- and, as of next year, Chromebooks. See also: Privacy: Cloudflare brings its DNS switching tool 1.1.1.1 to iOS… [Continue Reading] -

Microsoft rolls out Camera Upload and improved MyAnalytics in the OneDrive mobile apps
Publié: novembre 28, 2018, 9:08am CET par Mark Wycislik-Wilson
Microsoft is rolling out new features to the mobile version of OneDrive. The company has also announced that it is introducing a new Block Download feature in "late November" that can be used to stop people from making copies of a file or its contents. Android and iOS users can look forward to improvement to the MyAnalytics component, but the big OneDrive news is that the Camera Upload feature has now left beta and is available to everyone -- if they are using Android, that is. See also: Microsoft market capitalization (briefly) tops Apple (again) Windows 10 1809 fiasco continues… [Continue Reading] -

Windows 10 1809 fiasco continues -- October 2018 Update also breaks Windows Media Player
Publié: novembre 27, 2018, 11:49am CET par Mark Wycislik-Wilson
The Windows 10 October 2018 Update has been one of the most problematic Microsoft releases ever. It seems that every time the company pushes out the update, yet another issue arises. The Windows 10 October 2018 Update has already caused issues with Apple iCloud, file associations, data loss... the list goes on and on. The latest problem sees the update breaking Windows Media Player. See also: This Thanksgiving be thankful if you haven't updated to Windows 10 1809 Et tu, Office? After pulling Windows 10 update, Microsoft does the same for Office Re-released Windows 10 October 2018 Update breaks Apple… [Continue Reading] -

Facebook Watch is a disaster... so now it will target an older audience
Publié: novembre 27, 2018, 9:51am CET par Mark Wycislik-Wilson
Facebook's plan for Facebook Watch to be a viable competitor to YouTube seemed a little unlikely -- to say the least -- and it would seem that the pessimists were right. Facebook Watch has proved to be a dud. A little over a year after launch, the on-demand video service has gained an audience of just 50 million people. This might initially sound like a large number, but YouTube has -- admittedly over a number of years -- amassed over 1.8 billion users. The problem appears to be that younger audiences are simply not interested in Facebook Watch, so Facebook… [Continue Reading] -

Apple has some Black Friday deals... but don't get too excited
Publié: novembre 23, 2018, 10:38am CET par Mark Wycislik-Wilson
Apple has a four-day shopping event running from today until Monday, promising shoppers "special offers when you buy select products". Running from the day that is a celebration of commercialism and capitalism, Black Friday, through the weekend and up to Cyber Monday, the Apple Shopping Event is -- unfortunately -- nothing to get excited about. This is not entirely unexpected. Apple has form when it comes to disappointing Black Friday offers. If you were hoping for massive discounts, prepare to feel let down. See also: Some MacBook Pro SSDs could fail -- Apple launches free service program Apple might repair… [Continue Reading] -

LinkedIn introduces new privacy controls to protect user data
Publié: novembre 22, 2018, 2:56pm CET par Mark Wycislik-Wilson
LinkedIn has quietly launched new privacy settings that block users from exporting the email addresses of their contacts. This is not something that many LinkedIn users would have even considered to be a problem, but it was previously possible for anyone -- from individuals to marketing firms -- to export the contact details of their connections and use it however they wanted. In what will be seen as a big win for users in general and privacy advocates, you now have to explicitly enable the setting for people to be able to export your email address. See also: BullGuard and… [Continue Reading] -

Now you can use Siri to launch Google Assistant on your iPhone
Publié: novembre 22, 2018, 12:18pm CET par Mark Wycislik-Wilson
If you have an iPhone, you use Siri; if you have an Android phone, you use Google Assistant. Right? Thanks to Siri Shortcuts -- and an update from Google -- it's now easier than ever to access Google Assistant on your iPhone with a voice command. With iOS 12, Apple introduced Siri Shortcuts giving users the opportunity to record their own voice triggers that can then be used to perform different actions. Now Google Assistant supports Siri Shortcuts, so you can access it via Siri. See also: Surface Pro 6 beats iPad Pro in bend test Apple might repair your… [Continue Reading] -

Surface Pro 6 beats iPad Pro in bend test
Publié: novembre 22, 2018, 10:46am CET par Mark Wycislik-Wilson
Last week, Apple's latest iPad Pro was put through its paces by JerryRigEverything. We're not talking benchmarks of speed here, we're talking durability tests -- the iPad Pro was scratched, burned and bent to see what sort of punishment it could take. In short, Apple's tablet was found to be extremely bendy. Actually, scratch that… it basically folded like a wet tissue. Now JerryRigEverything has turned its attention to the Surface Pro 6, finding that it is far more durable and able to withstand a bend test much more impressively. See also: Satechi unveils Aluminum USB Type-C Mobile Pro Hub… [Continue Reading] -

Google invites you to place your vote for the best app and best game of 2018
Publié: novembre 21, 2018, 12:57pm CET par Mark Wycislik-Wilson
We're approaching the end of 2018, so it's only natural that companies take a look back over the year and reflect on what was great about it. Not one to miss out on such things, Google is launching its first-ever User's Choice Awards and is asking for your votes. Google users are invited to cast their vote for what they believe is the best app of 2018, and what is the best game of 2018. Want your voice to be heard? Now is the time to cast your vote. See also: Google unveils holiday season savings on games, apps, books… [Continue Reading] -

You can watch The LEGO Movie for free on YouTube this Black Friday
Publié: novembre 21, 2018, 11:10am CET par Mark Wycislik-Wilson
YouTube only very recently gave people the option to watch big-name movies free of charge -- the only price to pay is enduring a few ads. Now, to celebrate Black Friday and to promote the upcoming release of The LEGO Movie 2: The Second Part, you'll have the chance to watch the first film (The LEGO Movie) for free. While the previously-announced free option means you have to watch ads, in this instance The LEGO Movie is itself an ad. See also: Google unveils holiday season savings on games, apps, books and movies You can now watch full blockbuster movies… [Continue Reading] -

Google unveils holiday season savings on games, apps, books and movies
Publié: novembre 21, 2018, 10:17am CET par Mark Wycislik-Wilson
It can't have escaped your attention that -- in the US at least -- holiday season is just around the corner. With Thanksgiving comes Black Friday and other sales, and Google is getting in on the action with a series of discounts in the Play Store. There are great savings to be made on games and apps, ebooks and audiobooks for cyberweek, and if you're in the mood for a movie on Thanksgiving itself, you can rent any title for just $0.99. See also: Google is killing off SMS notifications for Calendar Google launches Squoosh, an open source online image… [Continue Reading] -

Your Time On Facebook rolls out, revealing how much time you waste in the social network's mobile apps
Publié: novembre 20, 2018, 8:59pm CET par Mark Wycislik-Wilson
It is a little while -- over three months, in fact -- since Facebook said that it was planning to launch a tool that would give users some insight into the amount of time they spent using the social network. This tool is now rolling out. Unimaginatively called Your Time On Facebook, the tool offers a dashboard that gives a very basic overview of how long you spend using Facebook each day. But going beyond this, it can also be used to set daily reminders to help you to cut down your usage. Trying to kick your Facebook habit? Maybe… [Continue Reading] -

Et tu, Office? After pulling Windows 10 update, Microsoft does the same for Office
Publié: novembre 20, 2018, 12:16pm CET par Mark Wycislik-Wilson
Microsoft's update procedure for Windows 10 has been a little, er, wobbly of late. The Windows 10 October 2018 Update proved so problematic that it had to pulled, and even the re-released version is far from perfect. Now it seems the cancer is spreading to Office. Having released a series of updates for Office 2010, 2013 and 2016 as part of this month's Patch Tuesday, Microsoft has now pulled two of them and advised sysadmins to uninstall the updates if they have already been installed. See also: Microsoft pulls the problematic Windows 10 October 2018 Update The re-released Windows 10… [Continue Reading] -

Google is killing off SMS notifications for Calendar
Publié: novembre 20, 2018, 11:25am CET par Mark Wycislik-Wilson
In early January 2019, you will no longer be able to receive SMS notifications about Google Calendar events. The change will affect Android and iOS users. While Google does not give an explicit reason for killing off SMS notifications -- other than seemingly not wanting to offer too many means of receiving notifications -- the company says that users should not notice any difference because of in-app notifications. See also: Google launches Squoosh, an open source online image conversion app Google brings AI-powered GIF, emoji and sticker suggestions to Gboard Google: adding Dark Mode to apps saves battery The transition… [Continue Reading] -

Linux: Ubuntu 18.04 LTS will be supported for a full decade
Publié: novembre 18, 2018, 3:38pm CET par Mark Wycislik-Wilson
Mark Shuttleworth has announced that Ubuntu 18.04 will be supported for ten years. Long Term Support releases of Ubuntu usually enjoy just five years of support, so this doubling is highly significant. Shuttleworth -- the founder of Canonical and Ubuntu -- made the announcement at the OpenStack Summit in Berlin, and the change is a tactical maneuver that will help Ubuntu better compete against the likes of Red Hat/IBM. It is also an acknowledgement that many industries are working on projects that will not see the light of day for many years, and they need the reassurance of ongoing support… [Continue Reading] -

You can now watch full blockbuster movies on YouTube for free... thanks to ads
Publié: novembre 18, 2018, 3:01pm CET par Mark Wycislik-Wilson
With little fanfare, YouTube has started to offer ad-supported, feature-length movies, giving visitors the opportunity to watch Hollywood titles for free. As reported by AdAge, it seems that YouTube introduced this option last month, but gave it something of a stealth launch. It has been possible to purchase movies from YouTube for some time, but until now there has been no (legal) way to access movies for free. And if you are concerned that free might mean that poor quality, you should be reassured to see titles such as The Terminator and Agent Cody Banks in the library of free-to-watch,… [Continue Reading] -

Privacy-focused search engine Startpage.com relaunches with new look, faster speeds and Anonymous View
Publié: novembre 18, 2018, 2:19pm CET par Mark Wycislik-Wilson
Startpage.com is a privacy-focused alternative to the likes of Google (although the search results are provided by Google -- minus all the ads and stripped of tracking), and the search engine has just relaunched with a new look and new features. The visual changes will be apparent to anyone who has used the site before, but for anyone who is concerned about their online privacy, it is new options such as Anonymous View that will be of greater interest. This new feature makes it possible to visit websites completely privately, essentially using Startpage.com as a proxy. Importantly, this extra level… [Continue Reading] -

Firefox Monitor Notifications will issue a warning if you visit a breached site using Mozilla's web browser
Publié: novembre 16, 2018, 8:08pm CET par Mark Wycislik-Wilson
If a website suffers a security breach you may well decide that you want to give it a wide berth. The problem is that it is impossible for individuals to keep track of all of the breaches that take place, and Mozilla wants to help out. After teaming up with Have I Been Pwned recently, Mozilla created Firefox Monitor to help inform people about breaches, and this is now expanding to more languages. On top of this, the organization has also now launched Firefox Monitor Notifications that will issue a warning if you visit a site that has been breached.… [Continue Reading] -

Microsoft could be about to hit users of Windows 10's Mail app with ads -- unless they pay up
Publié: novembre 16, 2018, 6:50pm CET par Mark Wycislik-Wilson
Ads in your inbox. Sounds like something you'd expect from the likes of Google or Yahoo, but Microsoft appears to be about to get in on the act as well. And we're not talking about online ads in your Outlook.com account -- we're talking about ads in the Mail app that's included with Windows 10. A new report says that Microsoft is currently testing ads with Windows Insiders, so it could be just a matter of time before they spread wider. See also: Microsoft releases Windows 10 19H1 Build 18282, with new Light theme and new wallpaper Microsoft finally re-releases… [Continue Reading] -

Security researchers discover seven more speculative execution attacks like Spectre and Meltdown
Publié: novembre 14, 2018, 11:04am CET par Mark Wycislik-Wilson
One of the biggest security stories of 2018 has been the discovery of the Meltdown and Spectre chip flaws. Known as speculative execution exploits, the flaws make it possible to steal potentially sensitive information and there has been an on-going battle to issue patches wherever possible. Just as things were starting to die down a little, security researchers have revealed details of no fewer than seven more speculative execution attacks. While some of these attack vectors have already been mitigated against, this is not the case for all of them. The fallout from the original Spectre and Meltdown discoveries has… [Continue Reading] -

Google launches Squoosh, an open source online image conversion app
Publié: novembre 13, 2018, 8:26am CET par Mark Wycislik-Wilson
Google Chrome Labs has released a new online image conversion app by the name of Squoosh. The open source tool is essentially a simple browser-based image editor, and the focus is very much on speed. Showcased at the Chrome Dev Summit, Squoosh is not limited to working only in Chrome -- other browsers are also supported. While the conversion options are useful to many people, Squoosh is really an opportunity for Google to show off new web technologies. See also: Google brings AI-powered GIF, emoji and sticker suggestions to Gboard The New York Times turns to Google Cloud to digitize… [Continue Reading] -

Google brings AI-powered GIF, emoji and sticker suggestions to Gboard
Publié: novembre 12, 2018, 7:33pm CET par Mark Wycislik-Wilson
Google recently rolled out a floating keyboard option to Gboard, and now the company has introduced another new feature -- AI-driven suggestions for GIFs, emoji and stickers. The move sees Google acknowledging that we increasingly communicate with images rather than words. Or, as the company puts it, it's a feature designed "for those of us who just can't even without the perfect GIF". See also: Google adds floating keyboard mode to Gboard for Android The New York Times turns to Google Cloud to digitize its photo archive Google: adding Dark Mode to apps saves battery Gboard has long offered the… [Continue Reading] -

Microsoft opens pre-orders for the Surface Go with LTE Advanced -- yours for $679
Publié: novembre 12, 2018, 3:58pm CET par Mark Wycislik-Wilson
Microsoft has announced that pre-orders for LTE-enabled versions of its Surface Go tablet are now open. There are three models to choose from, ranging in price from $679 to $829, and you can pre-order today and expect to receive the device on November 20. The Surface Go with LTE Advanced supports AT&T, Sprint and Verizon, and two of the models are designed with businesses in mind. The consumer-grade version is the Surface Pro with LTE Advanced that comes with 8GB RAM and 128GB storage -- the cheapest option at $679. Next up is the similarly specced Surface Pro with LTE… [Continue Reading] -

Nintendo is shutting down Netflix and other video streaming services on Wii in January
Publié: novembre 12, 2018, 11:47am CET par Mark Wycislik-Wilson
If you're a Wii owner who uses the console to not only play games but also enjoy binging on Netflix, you're going to have to find an alternative soon. Nintendo is closing down streaming video services on the device in January 2019. We already knew of Nintendo's intention to shut down the Wii Shop channel in January 2109, but the addition of shuttering video streaming will come as an added blow to Wii owners. Realistically, it is of little surprise that Nintendo is cutting back -- the Wii is an old console now, and there have already been a number… [Continue Reading] -

Microsoft acquires InXile and Obsidian as it grows its game studio portfolio
Publié: novembre 12, 2018, 11:12am CET par Mark Wycislik-Wilson
At Xbox Fanfest this weekend, Microsoft announced that it has acquired two more gaming studios. InXile Entertainment and Obsidian Entertainment join the company's ever-expanding portfolio, and what's interesting about these two latest acquisitions is that both studios have a focus on RPGs. It is not currently known how much money has changed hands as part of the deals. See also: Keyboard and mouse support comes to Xbox One games on November 14 -- Fortnite is one of the first Microsoft reveals Black Friday 2018 deals on Surface, Xbox One, and more Microsoft releases Windows 10 19H1 Build 18277 with fewer… [Continue Reading] -

Some MacBook Pro SSDs could fail -- Apple launches free service program
Publié: novembre 12, 2018, 9:52am CET par Mark Wycislik-Wilson
Apple has discovered a problem with a "limited number" of SSDs used in non-Touch Bar 13-inch MacBook Pro that could lead to drive failure and data loss. The laptops in question were sold in the year between June 2017 and June 2018. Apple has launched a service program that will enable those with affected drives -- 128GB and 256GB models -- to have the issue addressed free of charge. The problems have come to light just as the company launched a free iPhone X screen replacement program to people suffering with a "ghost touch" problem. See also: Apple might repair… [Continue Reading] -

Privacy: Cloudflare brings its DNS switching tool 1.1.1.1 to iOS and Android
Publié: novembre 12, 2018, 9:00am CET par Mark Wycislik-Wilson
Cloudflare has just made it a whole lot easier to hide your mobile browsing from your ISP -- and access content that might otherwise be unavailable. The company has launched a 1.1.1.1 app for smartphone users, making it incredibly easy to switch between DNS services with a couple of taps; what amounts to a free VPN tool. Earlier in the year, Cloudflare launched its 1.1.1.1 DNS service to bring privacy and speed, but it was a little off-putting to users unfamiliar with tinkering with such settings. With the launch of 1.1.1.1 for iOS and Android, the process is much, much… [Continue Reading] -

Apple might repair your iPhone X screen for free
Publié: novembre 11, 2018, 3:00pm CET par Mark Wycislik-Wilson
If you're an iPhone X owner, you could well be one of the unlucky people who has experienced a ghost touch problem with the screen. Acknowledging that there is a problem, Apple has announced a free display repair program which customers can take advantage of if they have handsets with the issue. Here's what you need to know about getting your screen sorted out free of charge. See also: Apple iPhone 5G is coming! In 2020... How to access your iPhone's secret emoticon keyboard UK court blocks iPhone users' privacy case against Google On a page snappily entitled iPhone X… [Continue Reading] -

Keyboard and mouse support comes to Xbox One games on November 14 -- Fortnite is one of the first
Publié: novembre 11, 2018, 9:26am CET par Mark Wycislik-Wilson
We've known for a while that support for keyboards and mice was coming to the Xbox One, but there has been the question of "when?" hanging in the air. Now we have a date. At its X018 event, Microsoft revealed that the date support will be added is November 14 -- so there are just a few days to wait. It is down to game developers to add the keyboard and mouse control option to their titles, and Fortnite will be among the first to push out an update that adds this support. See also: Microsoft sullies the sanctity of… [Continue Reading] -

The New York Times turns to Google Cloud to digitize its photo archive
Publié: novembre 9, 2018, 5:08pm CET par Mark Wycislik-Wilson
The New York Times is to digitize more than a century's worth of photographs, and it is going to use Google Cloud to do so. The NYT has a massive collection of photos dating back decades, and the plan is to digitize millions of images -- some dating back to the late nineteenth century -- to ensure they can be accessed by generations to come. The digitization process will also prove useful for journalists who will be able to delve into the archives far more easily in future. Until now, historic news articles and photos have been stored on microfilm… [Continue Reading] -

Byte -- not v2 or Vine 2 -- is coming soon to replace Vine
Publié: novembre 9, 2018, 3:36pm CET par Mark Wycislik-Wilson
Vine may have closed down a couple of years ago, but it has certainly not been forgotten. There has been eager anticipation of its replacement, and disappointment when this was delayed earlier in the year. Originally said to be named V2, the successor to Vine has now been revealed to be called Byte. Vine co-creator Dom Hofmann made the revelation on Twitter, adding that Byte is due to launch in the first half of 2019. At the moment, very little is known about Byte other than the fact that it is set to appear in spring next year. It's not… [Continue Reading] -

Google: adding Dark Mode to apps saves battery
Publié: novembre 9, 2018, 9:54am CET par Mark Wycislik-Wilson
There has been a spate of adding dark modes to apps, websites and operating systems in recent times. Many people simply prefer the look, while others say a darker theme is easier on the eye. But there is also the school of thought that says dark mode saves battery life. And this is very much the message that Google is sending to Android developers. At the Android Dev Summit this week Google highlighted the massive difference Dark Mode makes, seemingly in a bid to encourage more developers to embrace the idea and add the option to their apps. See also:… [Continue Reading] -

Android file manager Files Go becomes Files by Google and undergoes a redesign
Publié: novembre 8, 2018, 6:14pm CET par Mark Wycislik-Wilson
It's less than a year since Google launched Files Go, its first attempt at a file manager app for Android. The primary aim of the app is to help users to free up space on their phones, and today Google announces that it not only has a new name, but also a new look. Files Go has been rebranded Files by Google, and the updated version of the app is starting to roll out now. See also: Check to see if Google has given you free Play Store credit Now you need JavaScript enabled to log into your Google account… [Continue Reading] -

Facebook defends the privacy of Portal as the smart devices start shipping
Publié: novembre 8, 2018, 4:23pm CET par Mark Wycislik-Wilson
As soon as Facebook announced its smart video calling device -- Portal and Portal+ -- there were concerns about the privacy implications of introducing Facebook hardware with a camera into your home. The company has already gone to some lengths to try to allay privacy-related fears, clearly pre-empting the concerns people would have. Facebook describes Portal as "private by design", but now it has gone further, using a blog post to stress the privacy and security of the devices, as well as offering reassurances about how data collected through them will -- and won't -- be used. See also: Facebook… [Continue Reading] -

Exploit developer discovers security vulnerability in VirtualBox and publishes a full guide to exploiting it
Publié: novembre 7, 2018, 4:26pm CET par Mark Wycislik-Wilson
A security researcher has not only discovered a vulnerability in the virtualization tool VirtualBox, but has released details of the exploit and a step-by-step guide to the zero-day vulnerability. Russian exploit developer Sergey Zelenyuk found a way to break out of VirtualBox's virtual environment and he chose to go public with the vulnerability because of his displeasure at the "contemporary state of infosec, especially of security research and bug bounty". Having told Oracle about the problem, he also tired of the "delusion of grandeur and marketing bullshit" he experienced in the infosec community. Zelenyuk has published full details of the… [Continue Reading] -

Dropbox Extensions let you edit your cloud-based files online
Publié: novembre 6, 2018, 7:31pm CET par Mark Wycislik-Wilson
Dropbox has just announced a new feature that makes it possible to edit your files online without the need to download them first. Dropbox Extensions give you the ability to edit a number of file types without the need to ever navigate away from Dropbox. The company has formed partnerships with a number of third parties including Adobe, Pixlr and Vimeo to give Dropbox users the option of editing images online, signing PDFs, annotating videos, and much more. Dropbox says the aim of the new integrations is to improve users' workflows. While the announcement has been made today, Dropbox Extensions… [Continue Reading] -

Microsoft is porting Sysinternals utilities to Linux, starting with ProcDump
Publié: novembre 6, 2018, 9:19am CET par Mark Wycislik-Wilson
Microsoft has embraced Linux more and more over the years, and the latest demonstration of this is the company's decision to port the free Sysinternals utilities to work on the platform. The first tool to make its way to Linux is ProcDump, which can be used to create crash dumps. While not as feature-rich as the Windows version, the Linux port is still a valuable tool. And, importantly, there are more Systinternals tools making their way to Linux. Systinternals software long-proved popular with Windows users. So much so, that over a decade ago Microsoft decided to buy the company behind… [Continue Reading] -

Check to see if Google has given you free Play Store credit
Publié: novembre 6, 2018, 8:14am CET par Mark Wycislik-Wilson
Every so often Google starts to feel a little generous and decides to give things away. It's happening again, and you might just find that you've been given a few dollars in free credit to spend in the Play Store. Seemingly at random, Google is handing out between $1 and $5 to Android users -- so you should check to see if you're one of the lucky ones. To see if you have been handed what amounts to free money, fire up the Play Store on your Android phone or tablet. Scroll down through the list of apps and you… [Continue Reading] -

Verizon is splitting in three: Consumer, Business and Verizon Media Group/Oath
Publié: novembre 5, 2018, 4:06pm CET par Mark Wycislik-Wilson
Verizon has announced that it is to split into three as it looks to ensure "first-to-market leadership in the 5G era". Starting January 1, 2019, the telecom company will divide into Consumer, Business and Verizon Media Group/Oath. The company says that it expects its new structure to be reflected in financial reporting for Q2 2019. In the new arrangement, Verizon Consumer Group will focus on the consumer side of wireless and wireline businesses as well as wireless wholesale. Verizon Business Group will be home to wireless and wireline enterprise, SMBs, and government businesses, and wireline wholesale and Verizon Connect. Finally,… [Continue Reading] -

Exploit developers claim 'we just broke Edge'
Publié: novembre 5, 2018, 2:39pm CET par Mark Wycislik-Wilson
Security researchers claim to have unearthed a zero-day vulnerability in Microsoft Edge. The remote code execution is due to be revealed with a proof-of concept. Microsoft has not yet been informed about the details of the security issue, but exploit developers had been looking for a way to break Edge out of its sandbox -- and it would appear that this objective has now been achieved. See also: Security: Tor 0-day revealed on Twitter by vulnerability vendor Malware writers exploit recent Windows Task Scheduler 0-day vulnerability 0patch beats Microsoft to patching Windows 10 task scheduler 0-day vulnerability On Twitter, self-proclaimed… [Continue Reading] -

Twitter removes thousands of accounts that discouraged people from voting in US midterm elections
Publié: novembre 3, 2018, 10:11am CET par Mark Wycislik-Wilson
Twitter has confirmed the removal of thousands of accounts for not only discouraging people from voting in next week's US elections, but also falsely appearing to originate from the Democratic Party. In all, over 10,000 accounts were deleted in September and October, for targeting key demographics and encouraging them to withhold their vote. While the removals are pretty small-scale, they still serve to demonstrate how Twitter is being used to try to subvert the outcomes of elections. See also: How to spot a fake Twitter follower Privacy: Twitter is under investigation for data collection through its link-shortening system All emojis… [Continue Reading] -

Now you can edit sent messages in Viber
Publié: novembre 3, 2018, 8:51am CET par Mark Wycislik-Wilson
Viber has rolled out a feature that users have been begging for for some time -- the ability to edit sent messages. While Viber may not be quite as popular as WhatsApp and Facebook Messenger, it has millions of users around the world. At long last these users now have the ability to correct typo after sending a message, just as can be done in a handful of other messaging tools. See also: Facebook Messenger 4 is simpler and far, far less ugly WhatsApp is getting ads in the Status section An Unsend option is coming to Facebook Messenger Voice… [Continue Reading] -

How to back up your Flickr photos before your free storage space is slashed
Publié: novembre 2, 2018, 5:58pm CET par Mark Wycislik-Wilson
As we wrote yesterday, Flickr is introducing a number of changes to both its free and Pro packages. For users of the free tier, the most significant change is undoubtedly the slashing of free storage to just 1,000 photos and videos. This is clearly a move designed to encourage people to upgrade to a paid-for account, complete with unlimited storage. But if you're determined to stick with the free option, you'll need to take action or risk losing huge numbers of photos in a few months' time. See also: Flickr drops Yahoo requirement and gives Flickr Pro users unlimited storage… [Continue Reading] -

Now you need JavaScript enabled to log into your Google account securely
Publié: novembre 2, 2018, 10:27am CET par Mark Wycislik-Wilson
Google has made a change to its account sign in process that means you now have to have JavaScript enabled. The change, which has been introduced for Cybersecurity Awareness Month, is part of a security process which Google says protects you "before you even sign in". While the vast majority of people will have JavaScript enabled, the new policy will still affect a number of users. See also: Google is working with iRobot to map the inside of your home and share data with smart devices Google is working on a patch for weird double-notch bug affecting Pixel 3 XL… [Continue Reading] -

From now on Apple is going to keep its sales figures a secret
Publié: novembre 2, 2018, 9:46am CET par Mark Wycislik-Wilson
Apple has announced that, as of next quarter, it will no longer report unit sales figures for iPhones, iPads and Macs. The news came at the company's Q4 earnings call at which it was revealed that iPhone unit sales have remained static -- despite a revenue increase. The change is in line with how Apple already treats other hardware sales -- such as those of the Apple Watch and HomePod -- which it groups together rather than revealing sales in individual categories. See also: Apple's Mac mini gains a massive performance boost Apple reveals new iPad Pro with USB-C Apple… [Continue Reading] -

Flickr drops Yahoo requirement and gives Flickr Pro users unlimited storage
Publié: novembre 1, 2018, 3:29pm CET par Mark Wycislik-Wilson
Flickr has announced a number of changes to both its free and pro accounts, including ditching the need to have a Yahoo account. The biggest change for Flickr users with free accounts is a drop to the amount of free storage it offers -- it is now possible to display 1,000 photos and videos of any size, but the free terabyte of storage is now a thing of the past. Anyone paying for a Pro account has much more to get excited about, including ad-free browsing and 5K support. Flickr points out that its offerings are available for "less than… [Continue Reading] -

WhatsApp is getting ads in the Status section
Publié: novembre 1, 2018, 10:18am CET par Mark Wycislik-Wilson
It had to happen eventually. Ads are coming to WhatsApp. The monetization of the messaging app through advertising has been talked about for years, and the acquisition by Facebook served only to make it more likely. Now the company's vice president Chris Daniels has confirmed that ads are arriving in WhatsApp's Status section. See also: WhatsApp now lets you backup to Google Drive without using any of your cloud storage quota UK hits Facebook with maximum possible fine for Cambridge Analytica privacy scandal Facebook says it could use data from Portal devices to target users with ads In comments given… [Continue Reading] -

Google is working with iRobot to map the inside of your home and share data with smart devices
Publié: novembre 1, 2018, 9:08am CET par Mark Wycislik-Wilson
Google is all about data, and there have long been concerns about how the data it collects is used and the associated privacy issues. As such, the company's latest collaboration is likely to raise a few hackles. Google and iRobot are joining forces to use data collected by smart vacuum cleaners like the Roomba i7+ to create maps of the inside of people's homes -- and then share that data with other smart devices. The partnership is described by iRobot as "a collaboration with Google to integrate robotic and smart home technologies that will advance the next-generation smart home". What… [Continue Reading] -

Apple reveals new iPad Pro with USB-C
Publié: octobre 30, 2018, 4:35pm CET par Mark Wycislik-Wilson
In addition to its new MacBook Air and Mac mini, Apple today launched the new iPad Pro. The most immediately-noticeable change is the death of the home button, but there's much more to this new model than just that. The screen of the smaller iPad Pro has jumped from 10.5 to 11 inches without changing the overall size of the body, while the 12.9-inch model is available in a dramatically smaller casing. Both are thinner than before (just 5.9 mm), Face ID has been added, and there's more going on under the hood. See also: Apple unveils new MacBook Air… [Continue Reading] -

Apple unveils new MacBook Air with Retina Display and Touch ID
Publié: octobre 30, 2018, 3:29pm CET par Mark Wycislik-Wilson
At the Brooklyn Academy of Music, Apple today revealed a new MacBook Air. As well as a Retina Display, Apple has shrunk the bezels to near-invisibility. The screen measures 13.3-inch with four times the resolution of its predecessor. The new model features Touch ID built directly into the keyboard. The keyboard itself has been upgraded for a better and more reliable typing experience, and the new Force Touchpad below this is 20 percent larger. But what else does the new MacBook Air have to offer? Security is taken care of by Apple's T2 chip, and Apple has boosted the speakers… [Continue Reading] -

Apple announces iOS 12.1 with Group FaceTime, new emoji, dual-SIM support and more
Publié: octobre 30, 2018, 12:53pm CET par Mark Wycislik-Wilson
Later today Apple is holding an event in Brooklyn at which we expect to see a new iPad Pro, iMac and MacBook Air. That's the hardware side of things. Today is also about software -- specifically iOS 12.1 which holds many treats for iPhone and iPad users. The latest version of iOS will be available today, and it includes Group FaceTime and more than 70 new emoji. On top of this, there's also Depth Control in real-time preview and dual-SIM support for iPhone XS, iPhone XS Max and iPhone XR. See also: How to watch Apple's new iPad and Mac… [Continue Reading] -

Google is working on a patch for weird double-notch bug affecting Pixel 3 XL
Publié: octobre 30, 2018, 9:45am CET par Mark Wycislik-Wilson
The notches that grace an increasing number of phones -- from the iPhone XS to the OnePlus 6T -- have proved quite divisive, but it seems unlikely they are going to disappear anytime soon. In fact, thanks to a weird bug,some Pixel 3 XL owners have found that they have extra notches to contend with. A number of users have encountered a bug that adds a second notch to the side of the screen in addition to the usual one at the top. The cause of the problem is not known, but Google is working on fixing it. See also: Google… [Continue Reading] -

Here's the OnePlus 6T -- and it's coming to T-Mobile in the US
Publié: octobre 29, 2018, 6:52pm CET par Mark Wycislik-Wilson
After months of build up from the Chinese company, a tremendous number of leaks, and endless hype, the OnePlus 6T has finally been officially announced. Something of an evolution of the OnePlus 6, the latest handset features a smaller notch, an in-screen fingerprint reader, and no headphone socket. With a starting price of $549 there's a lot to get excited about with the latest addition to the OnePlus range -- and the specs are certainly impressive. But for folks in the US who have been eagerly anticipating OnePlus handsets finally launching in their country, the wait is finally over. The… [Continue Reading] -

Linux systems vulnerable to privilege escalation and file overwrite exploit in X.Org server
Publié: octobre 28, 2018, 11:03am CET par Mark Wycislik-Wilson
An "incorrect command-line parameter validation" vulnerability in X.Org server makes it possible to escalate privileges as well as overwrite files. The problem affects Linux and BSD distributions using the open source X Window System implementation. The vulnerability has been present for a couple of years, but has been brought to light by security researcher Narendra Shinde. Unpatched system can be exploited by non-root users if X server is running with elevated privileges. See also: Linux-friendly company System76 shares more open source Thelio computer details System76 releases Ubuntu-based Pop!_OS 18.10 Linux distribution Linus Torvalds is back in charge as Linux kernel… [Continue Reading] -

Google brags about Gmail's 1.5 billion users
Publié: octobre 27, 2018, 3:56pm CEST par Mark Wycislik-Wilson
You're probably well aware that Gmail is popular... but have you ever thought about just how popular it is? If this is the sort of thing that keeps you awake at night, Google has provided an answer. Apparently around a fifth of the world's population has a Gmail account -- 1.5 billion in total. Of course, there are many people who have more than one Gmail email address, but the number is pretty impressive nonetheless. See also: Leaked documents show Google now requires OEMs to provide 2 years of Android security updates Privacy: Google makes it easier to delete your… [Continue Reading] -

Microsoft defends its JEDI cloud project bid
Publié: octobre 27, 2018, 10:19am CEST par Mark Wycislik-Wilson
Google may have pulled out of the Pentagon's $10 billion JEDI cloud project, but Microsoft has no intention of following suit. Company president Brad Smith has used a blog post to defend the decision to bid for military contracts, despite pressure from its employees. Smith recognizes that there are ethical concerns about getting involved in military projects, particularly when artificial intelligence technology is involved. However, he says: "we believe in the strong defense of the United States and we want the people who defend it to have access to the nation's best technology, including from Microsoft". See also: Microsoft employees… [Continue Reading] -

UK hits Facebook with maximum possible fine for Cambridge Analytica privacy scandal
Publié: octobre 25, 2018, 12:09pm CEST par Mark Wycislik-Wilson
The UK Information Commissioner's Office (ICO) has penalized Facebook for the Cambridge Analytica data scandal by fining it the maximum amount permissible under law. But the fine is unlikely to make Facebook break a sweat. At just £500,000 ($645,000) the sum represents a miniscule percentage of the social network's income. There will undoubtedly be arguments that this is little more than a rap on the knuckles for failing to protect the private data of at least a million Facebook users in the UK. See also: Facebook Messenger 4 is simpler and far, far less ugly Facebook says it could use… [Continue Reading] -

Leaked documents show Google now requires OEMs to provide 2 years of Android security updates
Publié: octobre 25, 2018, 9:53am CEST par Mark Wycislik-Wilson
One of the problems with buying an Android phone over an iPhone is the fact that you don't know how long you can expect to receive updates. There has long been criticism of the fact that many Android handsets are quickly abandoned while Apple pushes out iOS updates for a number of years. We've heard suggestions that Google might start requiring handset manufacturers to provide updates for a minimum period, and now it seems that this has indeed been mandated. A leaked copy of a contract between Google and OEMs shows that there is now a requirement to release security… [Continue Reading] -

Privacy: Google makes it easier to delete your search history
Publié: octobre 24, 2018, 2:44pm CEST par Mark Wycislik-Wilson
It's the butt of many jokes, but your search history -- as well as your browsing history -- can be hugely revealing about you. While it is possible to quickly clear the record of searches that your browser stores, it is not so easy to delete the records stored by Google. At least that used to be true. Google has just announced a new option that enables you to view and delete your Google search history, making it possible to take control of some of the data stored on the company's servers. Contrary to what you might expect, the option… [Continue Reading] -

Tim Cook calls for 'comprehensive federal privacy law in the United States'
Publié: octobre 24, 2018, 12:23pm CEST par Mark Wycislik-Wilson
Speaking at the International Conference of Data Protection and Privacy Commissioners in Brussels, Apple CEO Tim Cook praised Europe's GDPR (General Data Protection Regulation) and said the US needs to fight back against the weaponization of personal data. In a strongly-worded speech, Cook avoided explicitly naming the likes of Google and Facebook for trading in private information, but it was clear who he was referring to when he said data was being misused. He added: "We shouldn't sugar-coat the consequences. This is surveillance". See also: Apple gives US customers the chance to download their data and updates its privacy page… [Continue Reading] -

Mozilla partners with ProtonVPN to offer security-conscious Firefox users a VPN
Publié: octobre 24, 2018, 10:49am CEST par Mark Wycislik-Wilson
Mozilla has announced a partnership with ProtonVPN as it explores new ways to keep people safe online. Starting today, a select group of Firefox users in the US will see an ad for ProtonVPN encouraging them to take out a monthly subscription with the service. It's an experiment that is part of Mozilla's attempt to explore new revenue streams to help keep Firefox funded. See also: Bye bye, TLS 1.0 and 1.1: Apple, Microsoft, Mozilla and Google all wave adieu to old security protocol Mozilla teams up with Have I Been Pwned to create data breach notification tool, Firefox Monitor… [Continue Reading] -

Facebook Messenger 4 is simpler and far, far less ugly
Publié: octobre 24, 2018, 9:51am CEST par Mark Wycislik-Wilson
After hitting the headlines for falling victim to a hack attack, and then the privacy issues surround its Portal devices, Facebook will be hoping that the rollout of a sleeker, sexier, simplified version of Messenger will do something to get disgruntled users back on side. The social networking giant has launched Facebook Messenger 4, a neater and tidier version of its messaging app. As well as clearing out the clutter, there is the promise of a dark mode in the future. See also: Facebook says it could use data from Portal devices to target users with ads An Unsend option… [Continue Reading] -

Your first 5G phone could come from OnePlus
Publié: octobre 23, 2018, 5:00pm CEST par Mark Wycislik-Wilson
At the moment, there are many people eagerly awaiting the arrival of the OnePlus 6T later this month. But looking further ahead, OnePlus has plans for a 5G handset. The smartphone manufacturer has already hinted at the release of a 5G handset in 2019, but now this has been confirmed. Joining the president of Qualcomm on stage at the company's 4G/5G summit at Hong Kong, OnePlus' Carl Pei said that a 5G phone is definitely coming next year. See also: Here is the OnePlus 6T -- coming October 30 (well, 29 now) Sign up with The Lab and you could… [Continue Reading] -

Linus Torvalds is back in charge as Linux kernel 4.19 is released
Publié: octobre 22, 2018, 3:26pm CEST par Mark Wycislik-Wilson
After taking some time out from the Linux community to "change some of [his] behavior", Linux Torvalds is back. In a post to the Linux Kernel Mailing List announcing the release of Linux kernel 4.19, Greg Kroah-Hartman -- his temporary replacement -- handed back the reins. After writing about the changes to be found in the latest release, Kroah-Hartman signed off by saying: "Linus, I'm handing the kernel tree back to you. You can have the joy of dealing with the merge window :)". See also: After Torvalds' apology, the Linux community is adopting a new code of conduct Linus… [Continue Reading] -

Google adds floating keyboard mode to Gboard for Android
Publié: octobre 21, 2018, 9:13am CEST par Mark Wycislik-Wilson
Users of Google's own Android keyboard app Gboard have a new option available to them. In an update that is rolling out, a new floating keyboard feature lets you move the location of the keyboard as you see fit. This is not something that is unique to Gboard by any means; floating keyboards have been available in other keyboard apps for a while, so this is really just Google playing catch-up. But for existing users -- as well as those who are looking for a reason to try out Gboard for the first time -- this update is great news.… [Continue Reading] -

How to use picture-in-picture mode in Chrome 70
Publié: octobre 20, 2018, 8:52am CEST par Mark Wycislik-Wilson
The Chrome web browser was starting to get some bad press after problems with extensions and then concerns over automatic sign-ins. Google listened to the complaints and promised to do something about it -- the result is Chrome 70. But Chrome 70 is about more than just security and privacy changes. Google has also used this released to introduce a handful of new features. One of the best is picture-in-picture mode (PiP) which lets you keep watching a video in an overlay while you continue to browse other sites. Here's how to use it. See also: Chrome 70 introduces more… [Continue Reading] -

Apple gives US customers the chance to download their data and updates its privacy page
Publié: octobre 17, 2018, 5:39pm CEST par Mark Wycislik-Wilson
All of the major technology companies suck up swathes of data about their users, and Apple is no different. While the iPhone-maker may not swallow up anywhere near as much personal information as the likes of Google and Facebook, you may well still be interested to know what the company does hold about you. With the introduction of GDPR, Apple made it possible for people in Europe to download their data. As promised earlier in the year, the company has now expanded this feature to the US. See also: Bye bye, TLS 1.0 and 1.1: Apple, Microsoft, Mozilla and Google… [Continue Reading] -

Bye bye, TLS 1.0 and 1.1: Apple, Microsoft, Mozilla and Google all wave adieu to old security protocol
Publié: octobre 17, 2018, 11:47am CEST par Mark Wycislik-Wilson
As part of a coordinated movement between four of the biggest names in tech, the old TLS 1.0 and 1.1 security protocols are to be killed off in Safari, Edge, Internet Explorer, Firefox and Chrome in 2020. Apple, Microsoft, Mozilla and Google have come together to purge the internet of these old and buggy protocols, noting that most people have now moved to TLS 1.2, if not TLS 1.3. Although 94 percent of sites already support version 1.2, a tampering off period over the next 18 months will give everyone a chance to catch up. See also: Browser Reaper: exploit… [Continue Reading] -

Facebook says it could use data from Portal devices to target users with ads
Publié: octobre 17, 2018, 10:01am CEST par Mark Wycislik-Wilson
When Facebook unveiled its Portal and Portal+ video calling hardware last week, there were immediate concerns voiced about the privacy implications of the social network's new devices. Facebook has been insistent that Portal is "private by design", and the company said no data -- such as call logs and app usage information -- would be used to target users with ads. Now the company has changed its mind and says that actually it could be hitting users with targeted ads. See also: An Unsend option is coming to Facebook Messenger Now you can post 3D photos to Facebook from your… [Continue Reading] -

Google to charge smartphone makers to use Google Play in Europe in response to antitrust ruling
Publié: octobre 16, 2018, 7:56pm CEST par Mark Wycislik-Wilson
Following a European Commission ruling earlier in the year that Google had exploited Android for "very serious illegal behavior" and used its mobile operating system "as a vehicle to cement its dominance as a search engine", the company was hit with a record €4.34 billion ($5 billion) fine. Today Google has outlined how it will respond to the European ruling, in addition to appealing against it. One of the things the company will do is to start charging smartphone makers a licensing fee to use Google Play. See also: EU hits Google with record €4.34bn fine for 'very serious illegal… [Continue Reading] -

Amazon launches new waterproof Kindle Paperwhite
Publié: octobre 16, 2018, 4:24pm CEST par Mark Wycislik-Wilson
Amazon has launched a new version of its Kindle Paperwhite. The latest incarnation of the ebook reader is not only thinner and lighter than its predecessors, but also waterproof. The new model boasts twice the storage space of previous Kindles, and the screen is not only the highest resolution offered by Amazon (300ppi), but also flush with the front of the reader's bezel for a higher-quality finish. Anyone buying the device can enjoy six months of Kindle Unlimited for free, giving plenty of opportunity to test the battery, the life of which Amazon says is "measured in weeks". See also:… [Continue Reading] -

Real-time Google Translate comes to all Google Assistant headphones and Android phones
Publié: octobre 16, 2018, 12:55pm CEST par Mark Wycislik-Wilson
Previously a Pixel exclusive, Google is opening up real-time translation to a wider range of devices. So wide, in fact, that real-time Google Translate is now available to all Assistant-optimized headphones and Android phones. For quite some time, the option was only available to people with a Google Pixel phone paired with Pixel Buds earphones, but now just about everyone has access to the feature. See also: Google is 'exploring' a censored search tool for China As trust in Google wanes, interest in privacy-focused search engine DuckDuckGo soars How to delete your Google account Google pulls out of $10 billion… [Continue Reading] -

Google is 'exploring' a censored search tool for China
Publié: octobre 16, 2018, 11:50am CEST par Mark Wycislik-Wilson
The possibility of Google making a return to China was leaked this summer, but the company has remained pretty tight-lipped about the matter. But now CEO Sundar Pichai has spoken publicly about the prospect of Google producing a censored version of its search engine to comply with Chinese regulations. Speaking at a conference in San Francisco, Pichai revealed that Google has, internally, built a search engine for China, because "we wanted to learn what it would look like". He said that the company is "exploring" the idea, and pointed out that 99 percent of searches would not be censored. See… [Continue Reading] -

Transparency: Facebook to reveal who pays for political ads in the UK
Publié: octobre 16, 2018, 10:42am CEST par Mark Wycislik-Wilson
In recent years there have been concerns about the influence it is possible to exert over election results through social media. As well as fears relating to fake news and misinformation, there have also been calls for greater transparency when it comes to revealing the funding of political advertising. To address some of these concerns, Facebook has announced that any ads running in the UK that make reference to political figures will have to publicly reveal the identity of the organization or individual that paid for them. The new rules about transparency will apply to both Facebook and Instagram. See… [Continue Reading] -

Winamp is being updated and reimagined as an audio app for mobile
Publié: octobre 15, 2018, 10:03pm CEST par Mark Wycislik-Wilson
The name Winamp -- you know, the audio player that "really whips the llama's ass" -- is one that will stir up nostalgic memories for people of a certain age. Since its inception in the mid-90s, Winamp gained a huge and loyal following but, after changing hands a couple of times since the turn of the century, it was then largely forgotten. But Winamp is making a comeback. In the next few days the desktop app will be getting an update -- not that this is something you should expect too much from -- but it is what's happening in… [Continue Reading] -

Malicious messages are locking up PlayStation 4 consoles
Publié: octobre 15, 2018, 1:37pm CEST par Mark Wycislik-Wilson
We've heard of problems with specially-crafted messages being used to lock up iPhones, and now a similar problem has been found with the PlayStation 4. Anyone who receives one of these messages will find that their console completely locks up -- and the only way out of it is to perform a factory reset. The problem lies in messages that include unrecognized characters, and it is being exploited by some gamers to boot people offline in the middle of games -- Rainbow Six in particular. While there is no fix available at the moment, there are steps you can take… [Continue Reading] -

Privacy: Twitter is under investigation for data collection through its link-shortening system
Publié: octobre 15, 2018, 11:28am CEST par Mark Wycislik-Wilson
Twitter is being investigated by the Irish Data Protection Commission (DPC) over concerns about how much data it collects through its t.co link-shortening tool. The Irish privacy regulator is concerned about the amount of data Twitter is able to collect through the service -- something that was only heightened by the company's refusal to hand over information about link tracking when it was requested. See also: All emojis are now considered equal on Twitter Twitter is killing off Moments on iOS and Android Twitter considers new Dehumanization Policy -- but wants your feedback first Hooray! The option to view your… [Continue Reading] -

Microsoft employees use open letter to urge company not to get involved in JEDI military project
Publié: octobre 15, 2018, 10:25am CEST par Mark Wycislik-Wilson
Last week, Google said that it had concerns about the use of AI in the US Department of Defense's JEDI (Joint Enterprise Defense Infrastructure) project, and as such it would not be bidding for the contract. Now Microsoft employees have published an open letter expressing their concerns about JEDI, the secrecy it is shrouded in, and the potential for it to cause harm or human suffering. The letter has a simple message: "Microsoft, don't bid on JEDI". See also: Google pulls out of $10 billion Pentagon cloud contract over AI concerns The letter -- which is simply "signed by employees… [Continue Reading] -

An Unsend option is coming to Facebook Messenger
Publié: octobre 14, 2018, 12:51pm CEST par Mark Wycislik-Wilson
Mark Zuckerberg caused controversy around six months ago... nothing strange for Facebook you may think. On this occasion, the founder of the social network managed to upset people when it turned out he had deleted messages he had sent through Facebook Messenger: an option that wasn't -- and isn't -- available to other Facebook users. At the time, when the matter came to light, Facebook said that the ability to unsend messages would ultimately give everyone the option to delete the messages they had sent. At long last, the feature is being tested, so we might see if released publicly… [Continue Reading] -

Now you can post 3D photos to Facebook from your smartphone
Publié: octobre 14, 2018, 11:09am CEST par Mark Wycislik-Wilson
A new option is in the process of rolling out to Facebook users around the world: the ability to post 3D photographs. The key attraction here -- apart from the fact that 3D images look kind of cool -- is that no special equipment is needed. Of course, you have to be realistic with your expectations. The new 3D photos feature does not create interactive, fly-through images or anything fancy like that. Rather it plays with parallax effects to create the illusion of depth that you can enjoy by scrolling, panning and tilting your phone. See also: How to see… [Continue Reading] -

How to see if you were affected by the huge Facebook hack
Publié: octobre 13, 2018, 10:43am CEST par Mark Wycislik-Wilson
The most recent Facebook security issue is one of the most serious yet for users of the social network. Depending on which numbers you are look at, the hackers who exploited a security flaw have impacted on anything between 14 and 30 million people. Facebook is still -- with the help of law enforcement agencies -- investigating the incident, and in the meantime many people feel as those they are being left in the dark. If you want to find out if your account has been affected, here's what you need to do. See also: Facebook says hackers accessed highly-details… [Continue Reading] -

Facebook says hackers accessed highly-details personal data of 15 million users
Publié: octobre 13, 2018, 9:48am CEST par Mark Wycislik-Wilson
In a news release with the bizarrely vague title of "An Update on the Security Issue", Facebook has revealed that the "View As" security breach it opened up about recently gave hackers access to the personal details of 15 million users. Having previously advised that the access tokens stolen by hackers had not been used to infiltrate other apps and services, the social networking giant now says 15 million people have had their names and contact details exposed. 14 million users had significantly more details revealed, including username, relationship status, religion, hometown, birthdate, places they have checked into, and recent… [Continue Reading] -

Facebook says hackers accessed highly-detailed personal data of 15 million users
Publié: octobre 13, 2018, 9:48am CEST par Mark Wycislik-Wilson
In a news release with the bizarrely vague title of "An Update on the Security Issue", Facebook has revealed that the "View As" security breach it opened up about recently gave hackers access to the personal details of 15 million users. Having previously advised that the access tokens stolen by hackers had not been used to infiltrate other apps and services, the social networking giant now says 15 million people have had their names and contact details exposed. 14 million users had significantly more details revealed, including username, relationship status, religion, hometown, birthdate, places they have checked into, and recent… [Continue Reading] -

As trust in Google wanes, interest in privacy-focused search engine DuckDuckGo soars
Publié: octobre 12, 2018, 3:00pm CEST par Mark Wycislik-Wilson
Google has long been eyed with suspicion, and incidents such as covering up potential data leaks does nothing to help. Privacy and security have increased in importance for the average internet user, and this has seen people moving away from Google and investigating the alternatives. One beneficiary of this shunning of Google is DuckDuckGo. The privacy-focused search engine has enjoyed a 50 percent surge in usage over the last year, and it can now boast a new record of 30 million daily searches. See also: Google Home Hub is smart display that lacks a camera Google reveals the Pixel 3… [Continue Reading] -

All emojis are now considered equal on Twitter
Publié: octobre 11, 2018, 1:45pm CEST par Mark Wycislik-Wilson
How many characters is an emoji? It seems like a simple question, but on Twitter the answer has not always been clear. Some emojis count as a single character while others eat further into the character count. But now this is changing -- Twitter has announced that all emojis will now be treated equally. Previously, emoji that could be modified in various ways -- such as changing the skin tone of people -- would use up large numbers of characters. No more! See also: Twitter is killing off Moments on iOS and Android Twitter considers new Dehumanization Policy -- but… [Continue Reading] -

Apple signs $600 million deal with European chipmaker Dialog
Publié: octobre 11, 2018, 12:54pm CEST par Mark Wycislik-Wilson
Apple is buying part of Dialog Semiconductor, a chipmaker based in Germany. The iPhone manufacturer is interested in Dialog's power-management technology and has put forward $300 million for it. On top of this, Apple has committed an additional $300 million to make purchases from other parts of Dialog's business, making this the largest deal the company has undertaken. As part of the arrangement Apple will acquire patents from the chipmaker as well as 300 staff. See also: Apple's proprietary software is blocking third parties from repairing Macs Apple's Device Enrollment Program can leak sensitive information about devices and their owners… [Continue Reading] -

Microsoft joins Open Invention Network and open sources its patent portfolio
Publié: octobre 10, 2018, 5:41pm CEST par Mark Wycislik-Wilson
Microsoft has joined the "largest patent non-aggression community in history", the Open Invention Network (OIN), effectively open-sourcing almost its entire patent portfolio. The company has shown increasing warmth to the open source community in recent years, and this latest move means that other OIN members will have access to its patents -- with the exception of those relating to Windows and desktop applications. The OIN embraces -- as Microsoft has done of late -- Linux "as a key element of open source software". See also: Microsoft has bumped up the price of Windows 10 Home by nearly $20 Microsoft fixes… [Continue Reading] -

Snap launches Snap Originals -- original, bite-sized, interactive shows for Snapchat
Publié: octobre 10, 2018, 4:24pm CEST par Mark Wycislik-Wilson
Snap has announced the launch of a new range of original, scripted shows for Snapchat. Snap Originals are penned by Hollywood writers that Snap describes as the "world's greatest storytellers". The shows are not going to compete with offerings from the likes of Netflix. These are not shows of typical episode lengths, but a mere five minutes long. Snap will be hoping that the length, in conjunction with the interactivity and social elements of the shows, will increase their appeal to teenage Snapchat users. Snapchat Originals can be found in the Discover section of Snapchat, and new episodes are promised… [Continue Reading] -

Microsoft has bumped up the price of Windows 10 Home by nearly $20
Publié: octobre 10, 2018, 12:40pm CEST par Mark Wycislik-Wilson
You'd be forgiven for not having noticed, but Microsoft has quietly -- virtually silently, in fact -- increased the price of Windows 10 Home. Previously available for $119.99, the operating system will now set you back $139 -- a $19.01 increase. While it's fair to say that the price increase of close to $20 won't affect too many people -- there are just a handful who don't either opt for an upgrade, or buy it pre-installed -- Microsoft did a great job of introducing the new price by stealth. See also: Microsoft fixes Windows 10 October 2018 Update data deletion… [Continue Reading] -

Google Home Hub is smart display that lacks a camera
Publié: octobre 10, 2018, 11:33am CEST par Mark Wycislik-Wilson
Yesterday's Google event was primarily about the launch of the new Pixel phones and Slate tablet, but there was much more announced. One of the more interesting products to be revealed was the Google Home Hub. Ostensibly a smart display, Home Hub lacks something found on Facebook's Portal -- a camera; considering the leakiness of Google, this is probably no bad thing. But what does Google's latest addition to the growing selection of smart devices have to offer? See also: Google Chromecast gets better, but it cannot compete with Roku and Amazon 4K devices Google reveals the Pixel 3 and… [Continue Reading] -

Twitter is killing off Moments on iOS and Android
Publié: octobre 10, 2018, 10:15am CEST par Mark Wycislik-Wilson
In less than two weeks, Twitter's Moments will no longer be available to mobile users. Seemingly in recognition of the fact that hardly anyone used the feature, Twitter is killing off the ability to create Moments in its iOS and Android apps. But the company is not completely shutting down Moments -- the feature will still be available to those who really want to continue using it. See also: Twitter considers new Dehumanization Policy -- but wants your feedback first Hooray! The option to view your Twitter timeline chronologically is coming! How to hide the Twitter bug reporter icon in… [Continue Reading] -

Dropbox makes PDFs and images searchable with automatic OCR feature
Publié: octobre 10, 2018, 9:45am CEST par Mark Wycislik-Wilson
Dropbox is in the process of launching a new feature that will make life easier for people using the cloud storage service to house PDFs and image files: automatic OCR. The optical character recognition is rolling out to paying subscribers, and is an acknowledgement of the fact that a large proportion of files uploaded to Dropbox are photographs of documents. By adding machine learning-powered OCR, Dropbox is making these files searchable. See also: Google pulls out of $10 billion Pentagon cloud contract over AI concerns Plex adds subtitle downloads, kills plugins, Watch Later and Cloud Sync Microsoft launches Azure-based Windows… [Continue Reading] -

Google reveals the Pixel 3 and Pixel 3 XL
Publié: octobre 9, 2018, 7:00pm CEST par Mark Wycislik-Wilson
There have been so many leaks surrounding Google's latest Pixel phones that today's announcements felt like little more than a formality. Nevertheless, the Pixel 3 and Pixel 3 XL are now official. Taking design inspiration from numerous other handset manufacturers, the new Pixels move away from previous models and have a glass construction. The 5.5-inch Pixel 3 does not feature a notch, but the 6.3-inch XL model does; both handsets feature a Snapdragon 845 SoC, 4GB of RAM, and 64 or 128GB of storage -- and, of course, Android Pie. See also: Google pulls out of $10 billion Pentagon cloud… [Continue Reading] -

How to delete your Google account
Publié: octobre 9, 2018, 3:36pm CEST par Mark Wycislik-Wilson
Google has given people plenty of reasons to hate it over the years, primarily because of concerns over privacy. But with the revelation that the company knew about a bug in Google+ API that exposed the private details of tens of thousands of users, many people are ready to walk away. Completely purging Google from your life may seem tricky if you have invested time in any of its services, but if you're thinking that now is the time to part ways, here's what you need to do. See also: Google pulls out of $10 billion Pentagon cloud contract over… [Continue Reading] -

Google pulls out of $10 billion Pentagon cloud contract over AI concerns
Publié: octobre 9, 2018, 11:18am CEST par Mark Wycislik-Wilson
Google has announced that it will not be placing a bid for a cloud-computing contract with the Pentagon. The Department of Defense's JEDI (Joint Enterprise Defense Infrastructure) project could have worth up to $10 billion. The bidding process is due to end this week, but Google will now not be taking part. The company says that this particular project is not in line with its AI policies, but it will continue to work with the US government in other ways. See also: Google implements new Play Store policies for apps that request SMS and Call Log permissions After failing to… [Continue Reading] -

Google implements new Play Store policies for apps that request SMS and Call Log permissions
Publié: octobre 9, 2018, 10:29am CEST par Mark Wycislik-Wilson
Google has introduced privacy and security focused changes as part of an update to Google Play Developer policies. In a move designed to protect sensitive data, there are new rules for apps that request SMS and Call Log permissions. With immediate effect, it will only be possible for apps configured to be the default calling or text app to access phone and SMS data. See also: After failing to disclose user data leaks, Google is shutting down Google+ and improving APIs UK court blocks iPhone users' privacy case against Google Google Safety Centre arrives in Europe -- or Safety Center...… [Continue Reading] -

After failing to disclose user data leaks, Google is shutting down Google+ and improving APIs
Publié: octobre 8, 2018, 8:52pm CEST par Mark Wycislik-Wilson
The private data of nearly half a million Google+ users was exposed to third-party developers, and Google failed to notify anyone. A bug in Google+ APIs meant that users' names, email addresses, occupations, gender and age were accessible from 2015 until Google discovered and patched the problem in March this year. Despite the data possibly having been accessed by 438 apps, Google chose not to go public about the security breach until now. And in a dramatic move, the company has announced that it is shutting down Google+ for consumers. Google has also revealed details of Project Strobe, an audit… [Continue Reading] -

Facebook unveils its new smart video calling hardware: Portal and Portal+
Publié: octobre 8, 2018, 4:50pm CEST par Mark Wycislik-Wilson
Still reeling from a security breach that affected up to 90 million users, Facebook has announced two new pieces of hardware designed to make video chat easier and more immersive than ever. Portal and Portal+ are 10- and 15-inch smart displays complete with integrated cameras and packed with AI. But even Facebook acknowledges there are privacy concerns. The social networking giant says: "When you can’t be there, Portal and Portal+ let you feel there". What does it mean by this? The cameras are intelligent, meaning they pan and zoom, following people around the room as necessary. Facebook promises that Portal… [Continue Reading] -

Here is the OnePlus 6T -- coming October 30
Publié: octobre 8, 2018, 2:18pm CEST par Mark Wycislik-Wilson
OnePlus has revealed more about the upcoming OnePlus 6T. The company is famed for ramping up the hype ahead of a new launch, and things are no different with its latest handset. The company has now revealed when the OnePlus 6T will launch -- October 30, at an event in New York City. As well as revealing this, OnePlus has also confirmed that it is no longer possible to sign up for The Lab -- a review opportunity it created to enable a select few to get their hands on the OnePlus 6T early. See also: Sign up with The… [Continue Reading] -

UK court blocks iPhone users' privacy case against Google
Publié: octobre 8, 2018, 1:40pm CEST par Mark Wycislik-Wilson
The UK's High Court has blocked legal action brought against Google by the group Google You Owe Us. The group represented Apple smartphone owners and claimed that Google had collected personal data from over 4 million iPhone owners. Fronted by former Which? director Richard Lloyd, Google You Owe Us said that between August 2011 and February 2012 the search giant bypassed iPhone privacy settings and gathered user data for advertising purposes. See also: Block more Google tracking with the latest Privacy Badger extension After complaints, Google is going to give users more privacy controls in Chrome 70 With its new… [Continue Reading] -

Google Safety Centre arrives in Europe -- or Safety Center... Google hasn't decided
Publié: octobre 8, 2018, 12:08pm CEST par Mark Wycislik-Wilson
Google has announced that its Safety Centre hub is rolling out across Europe. The announcement means that people in Belgium, France, Germany, Italy, the Netherlands and the UK have access to Google's selection of tools and tips for staying safe online. The launch has been timed to coincide with European Cyber Security Month, but Google doesn't quite seem to have decided how to spell the name of its own offering. See also: Block more Google tracking with the latest Privacy Badger extension People love Microsoft's Your Phone so much, it's the top trending Android app in the Google Play Store… [Continue Reading] -

Walmart teams up with MGM to create content for Netflix alternative Vudu
Publié: octobre 8, 2018, 10:25am CEST par Mark Wycislik-Wilson
Walmart has partnered with movie studio Metro Goldwyn Mayer to help boost content for its video-on-demand platform Vudu. Vudu -- which Walmart bought eight years ago -- has failed to attract a userbase anything close to that of rival Netflix, but by teaming up with MGM, there is clearly a push to change this. MGM will create original content based on its library of film and TV franchises. Walmart is also planning to introduce a new "shoppable" video ad format. See also: Plex launches beta version of Plex Web Shows offering on-demand streaming shows for free BitTorrent embraces streaming torrents… [Continue Reading] -

Firefox 64 will support Action Center notifications in Windows 10
Publié: octobre 7, 2018, 4:57pm CEST par Mark Wycislik-Wilson
Following the footsteps of Microsoft Edge and Chrome, Firefox is -- at long last -- going to offer support for the delivery of notifications through Windows 10's Action Center. The move will please many Firefox users as this is a highly-requested feature, and it brings Mozilla's web browser in line with its rivals. While there is no release date for the finished version of Firefox 64, Action Center notification support has already made its way into the nightly builds. See also: Browser Reaper: exploit causes Firefox to crash Users balk as Chrome 69 forcibly signs them into the browser Trend… [Continue Reading] -

Facebook Lite for iOS is now a thing
Publié: octobre 7, 2018, 12:22pm CEST par Mark Wycislik-Wilson
Just as there is a trend for dark themes in software at the moment, there is also something of a movement of "Lite" apps that use less data and resources. Originally intended for parts of the world where connectivity iss an issue, such apps have become popular with more and more people; because if you can use less data, why not? We've seen Twitter Lite, Facebook Messenger Lite, and Facebook Lite -- although, until now, this last app has only been available to Android users. Now, however, Facebook Lite is expanding its reach with the launch of an iOS app.… [Continue Reading] -

How to disable Smart Compose predictive text suggestions in Gmail
Publié: octobre 7, 2018, 11:35am CEST par Mark Wycislik-Wilson
If you're a Gmail user, you've probably noticed a new feature in the web version recently. Building on the Smart Reply feature that makes it possible to insert stock responses with a click, Google has been rolling out a predictive text component called Smart Compose. The idea is simple, and will be familiar to users of the Gboard keyboard on Android. As you type a message, Gmail guesses what you might be trying to say and offers to complete your sentences for you. In theory this sounds helpful, but many people find it irritating and invasive -- and very possibly… [Continue Reading] -

Voice control and dictation options are coming to Facebook Messenger
Publié: octobre 6, 2018, 10:34am CEST par Mark Wycislik-Wilson
The ability to control devices and apps with your voice is becoming increasingly common, and Facebook is looking to bring this capability to its Messenger app. Analysis of the Android version of the Facebook Messenger app shows that the company is looking to use its M assistant in messages to listen out for commands. App code shows that users will be able to make requests of M: "You can ask me to make calls, send messages, and create reminders". See also: How to voice-control your Android phone using the Voice Access app Google's new Voice Access app lets you control… [Continue Reading] -

People love Microsoft's Your Phone so much, it's the top trending Android app in the Google Play Store
Publié: octobre 5, 2018, 4:31pm CEST par Mark Wycislik-Wilson
Having abandoned its own mobile operating system, Microsoft is increasingly embracing Android and iOS and improving interoperability with Windows. A recent example of this is the Your Phone Companion app which makes it possible to send texts from your computer and easily access photos stored on your Android phone. The ability to access and use a phone via Windows 10 has gone down very well -- as the interest in our story about the app showed. So well, in fact, that the Your Phone app is the number one trending app in the Google Play Store. See also: How to… [Continue Reading] -

How to voice-control your Android phone using the Voice Access app
Publié: octobre 5, 2018, 2:42pm CEST par Mark Wycislik-Wilson
Digital assistants are becoming increasingly popular as people become used to the idea of controlling electronic devices by speaking to them. With Android, Google has supported limited voice control for a while with "OK, Google", but with the release of the Voice Access app you can now do much, much more. The problem with uttering "OK, Google" at your phone is that there are fairly severe limitations on what you can do -- there are only a small number of supported actions. But with Voice Access you can use your voice to dictate and edit text, and interact with anything… [Continue Reading] -

Apple's proprietary software is blocking third parties from repairing Macs
Publié: octobre 5, 2018, 1:22pm CEST par Mark Wycislik-Wilson
Apple is using proprietary software to block third parties from making repairs on new iMac Pro and 2018 MacBook Pro computers. A document sent to Apple's Authorized Service Providers -- seen by MacRumors and Motherboard -- shows that the T2 security chip that's built into modern Macs is being used to prevent authorized repairs from being carried out. The security feature requires Macs to pass Apple diagnostics in order for specific repairs to be performed. See also: Apple's Device Enrollment Program can leak sensitive information about devices and their owners Qualcomm accuses Apple of stealing trade secrets and giving them… [Continue Reading] -

Block more Google tracking with the latest Privacy Badger extension
Publié: octobre 5, 2018, 10:20am CEST par Mark Wycislik-Wilson
We live in an age where privacy is simultaneously highly valued and under increasing attack -- and nowhere is this truer than online. The EFF (Electronic Frontier Foundation) has been fighting the corner for web users for some time, and with the latest version of its Privacy Badger extension it is helping people fight back against Google. The latest update to the extension -- which is available for Chrome and Opera on the desktop, and Firefox on both the desktop and Android -- introduces new blocks on "link tracking" in Google web search, Hangouts and the Docs suite See also:… [Continue Reading] -

Sans Forgetica: the font that could help you remember
Publié: octobre 4, 2018, 5:19pm CEST par Mark Wycislik-Wilson
Researchers from Australia's RMIT University have created a font which they say could help you to retain more data. Sans Forgetica is the result of work involving typographic design specialists and psychologists, and it has been designed specifically to make it easier to remember written information. The font has purposefully been made slightly difficult to read, using a reverse slant and gaps in letters to exploit the "desirable difficulty" as a memory aid. Dr Janneke Blijlevens, founding member of the RMIT Behavioural Business Lab, explains that the problem with many fonts is that they are so similar to each other… [Continue Reading] -

How to access your Android phone from Windows 10 with Microsoft's Your Phone app
Publié: octobre 4, 2018, 4:17pm CEST par Mark Wycislik-Wilson
Without a mobile operating system of its own, Microsoft is doing more for iOS and Android users than ever before. One example of this is the Your Phone app which makes it possible to view your Android phone's photos on your computer, as well as viewing and sending text messages from the comfort of Windows 10. Microsoft has also promised to enable an exciting-sounding app-mirroring feature. As long as you have upgraded to the Windows 10 October 2018 Update, you'll have the Your Phone app installed on your computer already. Here we take a look at this handy tool and… [Continue Reading] -

Plex launches beta version of Plex Web Shows offering on-demand streaming shows for free
Publié: octobre 3, 2018, 3:00pm CEST par Mark Wycislik-Wilson
Continuing to increase its appeal to cord-cutters, Plex has announced a new on-demand streaming feature. Plex Web Shows is launching in beta and includes curated content from independent creators like Epic Meal Time, ASAPscience, Household Hacker, People are Awesome, and The Pet Collective, as well as brands including GQ, Saveur, Epicurious, and Pitchfork. Plex Web Shows works across a range of devices -- web, iOS, Android, Apple TV, Windows, macOS and more -- and does not require either a Plex server or a paid Plex subscription. Like Plex News and Plex Podcasts, content is not only curated, but includes smart,… [Continue Reading] -

Google launches new .page TLD
Publié: octobre 3, 2018, 12:37pm CEST par Mark Wycislik-Wilson
Google has announced the availability of a new TLD (top-level domain) from its own Google Registry. Joining the likes of .com and .org comes .page which is described as "a new opportunity for anyone to build an online presence". With security in mind, Google says that all .page websites require an SSL certificate. For businesses and individuals, the race is now on to grab the domain they want before it is snapped up by someone else. See also: Google's new Voice Access app lets you control your Android phone with your voice How to access Google's secret text adventure game… [Continue Reading] -

iOS 12.1 beta 2 fixes iPhone charging problem and adds scores of new emoji
Publié: octobre 3, 2018, 12:01pm CEST par Mark Wycislik-Wilson
Apple has released the second beta version of iOS 12.1 and while the iPhone-maker is heralding the including of more than 70 new emoji, the bigger news is that it includes a fix for the charging problem users have been complaining about. When owners of the new iPhone XS and iPhone XS Max started to complain that their handsets were not charging, it was initially thought there was a problem with the latest hardware. But it seems that the problem was actually down to iOS 12. See also: Apple officially announces iPhone XR, iPhone XS and iPhone XS Max With… [Continue Reading] -

Google's new Voice Access app lets you control your Android phone with your voice
Publié: octobre 3, 2018, 10:51am CEST par Mark Wycislik-Wilson
Google has a new app that allows for full control of an Android phone with your voice -- Voice Access. While it has been possible to perform simple actions such as switching apps and writing messages, the ability to interact with on-screen elements is something that has been missing. Pitched as an accessibility tool, Voice Access fills in many gaps in Android's voice control system, making it possible to navigate apps, edit text and much more. See also: Android rooting tool SuperSU disappears from Play Store Android 9.0 Pie lands on OnePlus 6 in OxygenOS 9.0 How to access Google's… [Continue Reading] -

Facebook hack update: Attackers did not use stolen tokens to access other sites and apps
Publié: octobre 3, 2018, 10:26am CEST par Mark Wycislik-Wilson
Since the revelation that a "security issue" allowed hackers to steal access tokens to view people's Facebook accounts, the company has provided a further update about the incident. Facebook has already provided one update about the attack, but now the investigation has progressed and the social network is trying to offer reassurances to those who have understandable concerns about security. The company says that the attackers did not access any apps that make use of Facebook Login, the system that makes it possible to sign into other accounts and services with Facebook credentials. See also: Facebook rolls out new tools… [Continue Reading] -

Facebook rolls out new tools to help those suffering bullying and harassment
Publié: octobre 2, 2018, 7:06pm CEST par Mark Wycislik-Wilson
The problems of bullying, harassment and trolling on social media are getting worse all of the time and the likes of Twitter and Facebook are under pressure to offer tools and protection to their users. Today Facebook unveils new options to help empower those who fall victim to such attacks. One new feature provides a way to report or delete multiple posts at once, and there is also a way to report bullying on behalf of someone else. Facebook is introducing new protections for public figures -- who frequently find themselves under attack -- and is also pushing education programs.… [Continue Reading] -

What is the Presidential Alert text from the National Wireless Emergency Alert System?
Publié: octobre 2, 2018, 6:26pm CEST par Mark Wycislik-Wilson
Tomorrow -- Wednesday October 3 -- your phone will receive a text message; assuming you're in the US, that is, and use Verizon, T-Mobile, AT&T or Sprint as your carrier. The text should arrive from 11:18AM PT / 2:18PM ET, and it will feature the dramatic heading of Presidential Alert. You may be reading this on Wednesday because you wonder what on Earth is going on -- particularly if your phone has made a strange noise -- but there's nothing to worry about. Not this time, anyway. The text message is part of a test of the Wireless Emergency Alerts… [Continue Reading] -

Android rooting tool SuperSU disappears from Play Store
Publié: octobre 2, 2018, 5:38pm CEST par Mark Wycislik-Wilson
If you haven't already made the jump to Magisk to cater for your handset rooting needs, now is very much the time to do so. The long-popular SuperSU has been removed from the Google Play Store, meaning one of the most popular rooting tools has been lost. The disappearance is not entirely surprising as SuperSU has not been updated for some time and plenty of other root apps have grown in popularity -- but it will still come as a disappointment for its many fans. See also: Major Google Maps update brings real-time public transport updates, music control, and more… [Continue Reading] -

How to access Google's secret text adventure game
Publié: octobre 2, 2018, 10:56am CEST par Mark Wycislik-Wilson
Google is well known for hiding Easter eggs in its software and tools, and a new little treat has just been discovered. Hidden in Google Chrome's developer console is a text adventure game. While this is not exactly The Hitchhiker's Guide to the Galaxy, and it's unlikely to draw you away from Fortnite or Assassin's Creed, the game is a simple delight like Chrome's jumping dinosaur. Here's how to access it. See also: Google is trying to make Chrome extensions safer with new Chrome Web Store review process and permission controls Major Google Maps update brings real-time public transport updates,… [Continue Reading] -

Google is trying to make Chrome extensions safer with new Chrome Web Store review process and permission controls
Publié: octobre 1, 2018, 8:21pm CEST par Mark Wycislik-Wilson
Extensions are a great way to increase the capabilities of your web browser, but they can also be the source of problems. Malicious extensions can be a serious headache, and this is something that Chrome users know more than most. Now Google is looking to improve security. The company has already promised that with Chrome 70 it is going to give users more privacy controls, and today it announced that this version of the browser will also introduce permission controls extensions. On top of this Google is introducing a new review process for extensions submitted to the Chrome Web Store,… [Continue Reading] -

Microsoft re-open-sources early versions of MS-DOS on GitHub
Publié: octobre 1, 2018, 5:13pm CEST par Mark Wycislik-Wilson
Back in 2014, Microsoft gave the source code for MS-DOS 1.25 and MS-DOS 2.0 to the Computer History Museum. Now -- in a move it describes as "re-open-sourcing" -- the company has pushed the code to GitHub for all to see. Dating from mid-1983, the source code may moisten the eyes of anyone who remembers the days of text-based operating systems, and it gives an interesting glimpse into the world of software development a few decades ago. See also: Tim Berners-Lee launches open source project Solid to decentralize the web and place users in control of data Azure Pipelines CI/CD… [Continue Reading] -

Sign up with The Lab and you could get a OnePlus 6T early
Publié: octobre 1, 2018, 2:20pm CEST par Mark Wycislik-Wilson
If you're a fan of OnePlus handsets, you might like the idea of getting your hands on the OnePlus 6T not only free of charge, but before the official launch. As part of its marketing program, OnePlus has opened up The Lab -- as it has done with previous models of its phones. This gives you the opportunity to sign up to review the phone, which means you'll be given one for free! See also: OnePlus 6T teaser video invites you to 'unlock the future' Android 9.0 Pie lands on OnePlus 6 in OxygenOS 9.0 OnePlus confirms that the OnePlus… [Continue Reading] -

Major Google Maps update brings real-time public transport updates, music control, and more
Publié: octobre 1, 2018, 12:51pm CEST par Mark Wycislik-Wilson
Google is pushing out a big update to its Google Maps app with the aim of making your daily commute easier. One of the biggest additions is support for mixed-mode commutes -- those journeys that involve multiple modes of transport -- and to help with this, there's also real-time information about the location of buses and trains. But it doesn't end there. Google Maps now also supports Spotify, Apple Music, and Google Play Music podcast and music playback to help keep you entertained while you travel. See also: Google Maps now has a voting option to help plan group events… [Continue Reading] -

Tim Berners-Lee launches open source project Solid to decentralize the web and place users in control of data
Publié: septembre 29, 2018, 5:44pm CEST par Mark Wycislik-Wilson
Tim Berners-Lee is famous for inventing the world wide web, and now he's ready to take things to the next level with an ambitious open source project called Solid. Noting that the web has become "an engine of inequity and division", Berners-Lee wants to restore the power and agency of individuals online and move the balance of power away from "powerful forces who use it for their own agendas". Solid is not a completely new venture. Berners-Lee has been working on it for some time, and it is built on the existing web as we know it. Where it differs… [Continue Reading] -

Microsoft stops development of touch-friendly Office apps for Windows
Publié: septembre 29, 2018, 11:25am CEST par Mark Wycislik-Wilson
Microsoft has confirmed that it is no longer developing the touch-friendly versions of Office apps for Windows The Word Mobile, Excel Mobile, and PowerPoint Mobile apps found in the Microsoft Store first appeared for Windows 8.1, and development has continued with the release of Windows 10. But now this is changing, with Microsoft saying it wants to focus on the Win32, web, iOS and Android versions instead. See also: Consumer Reports now recommends Microsoft Surface laptops -- apart from Surface Go with its 'lag' Microsoft is sending Skype classic to the software graveyard in November Microsoft launches Azure-based Windows Virtual… [Continue Reading] -

Facebook shares more details about its massive security breach -- after blocking people from sharing news about it
Publié: septembre 29, 2018, 10:23am CEST par Mark Wycislik-Wilson
The Guardian was among many outlets to write about the huge Facebook vulnerability and attack reported yesterday, and people were understandably keen to share the story on the social network. However, many people found that they were unable to do. Large numbers of Facebook users who tried to share the Guardian's story -- as well as one published by the Associated Press -- were greeted by a message informing them that the messages was spam and could not be posted. The matter has been addressed, but it led to complaints that Facebook was trying to hush up the story, and… [Continue Reading] -

Facebook hack: 50 million users affected by site code flaw
Publié: septembre 28, 2018, 7:20pm CEST par Mark Wycislik-Wilson
Facebook has revealed that it discovered a security issue which could have exposed the accounts of 50 million people. A vulnerability was discovered in Facebook's View As feature on Tuesday, September 25, but the company has not given too many details about how the flaw was exploited or by whom, but it has said that attackers were able to steal access tokens and access other people's accounts. Law enforcement agencies have been informed, and an investigation is under way. See also: Instagram co-founders resign from Facebook-owned company to 'explore curiosity and creativity again' YouTube alternative Facebook Watch rolls out globally… [Continue Reading] -

OnePlus 6T teaser video invites you to 'unlock the future'
Publié: septembre 28, 2018, 5:25pm CEST par Mark Wycislik-Wilson
With the launch of the OnePlus 6T expected in the next few weeks, the OnePlus marketing machine is now in full motion. We've had a number of leaks and rumors, as well as some official news, and now the first teaser video for the upcoming phone has been released. The video, released to Twitter, bears the tagline "unlock the future", and says simply of the handset: "It's coming". See also: Android 9.0 Pie lands on OnePlus 6 in OxygenOS 9.0 OnePlus confirms that the OnePlus 6T has no headphone jack and announces Type-C Bullets earbuds Confirmed: the OnePlus 6T definitely… [Continue Reading] -

Consumer Reports now recommends Microsoft Surface laptops -- apart from Surface Go with its 'lag'
Publié: septembre 28, 2018, 11:19am CEST par Mark Wycislik-Wilson
Last year Consumer Reports stripped Microsoft Surface laptops of its coveted "recommended" status because of concerns about reliability. But now the badge of honor has been restored, with the publication saying: "Microsoft's reliability is now on par with most other laptop brands". While the vast majority of the Surface laptop range is now recommended by Consumer Reports, the Surface Go is not. The reason for this is that in lab tests, the device's performance was found to be subpar. See also: Microsoft is launching the Surface Hub 2S in 2019, and the Surface Hub 2X in 2020 Grab yourself a… [Continue Reading] -

Microsoft is sending Skype classic to the software graveyard in November
Publié: septembre 28, 2018, 10:39am CEST par Mark Wycislik-Wilson
The death of Skype classic (or Skype 7.0 if you prefer) was reported a number of weeks ago, but after angry and emotional outpourings from users, Microsoft said that it would (slightly) extended its life. Now the company has revealed the new execution dates. Dates is plural because the killing off of Skype classic is going to be a two-step process. The desktop version is first for the chop on November 1, with the mobile versions following a little later. See also: New update from Microsoft means you can now record Skype calls Rejoice! Microsoft gives Skype classic a temporary… [Continue Reading] -

Apple's Device Enrollment Program can leak sensitive information about devices and their owners
Publié: septembre 27, 2018, 3:27pm CEST par Mark Wycislik-Wilson
Security researchers have discovered an issue with the Device Enrollment Program used by Apple to allow organizations to manage their MacBooks and iPhones. Duo Security says that using nothing more than a serial number, it is possible to gain access to sensitive data about enrolled devices and their owners. It is even possible to enroll new devices that can then access Wi-Fi passwords, VPN configurations and more. Apple was alerted to the issue way back in May, but has not done anything about it as the company does not regard it as a vulnerability. See also: Kids have already defeated… [Continue Reading] -

Fortnite Season 6: Darkness Rises is here!
Publié: septembre 27, 2018, 11:53am CEST par Mark Wycislik-Wilson
Today is the day -- the new season of Fortnite has arrived! With the arrival of Fortnite Season 6: Darkness Rises and the V6.00 patch, Epic Games put its servers into maintenance mode in preparation. There's a lot to look forward to in Battle Royale and in the new Battle Pass -- new locations, pets, the power of invisibility and more. 950 V-Bucks gives you access to 100 levels and over 100 new rewards, new Shadows Stones consumables and an updated map. See also: Boogiedown! Fortnite is bribing players into enabling 2FA -- and that's a good thing Epic calls… [Continue Reading] -

Kids have already defeated the limitations of Screen Time in iOS 12
Publié: septembre 27, 2018, 10:33am CEST par Mark Wycislik-Wilson
With the release of iOS 12, Apple introduced a new feature called Screen Time. As well as making it possible for users to monitor how long they were spending using app on their iPhone, Screen Time also includes parental control features that can be used to prevent children from using apps for too long. At least that was the idea. Kids -- being kids and having app-related needs -- have managed to work out how to bypass these limitations. In fact, there are at least two methods that can be used to defeat time limits that have been put in… [Continue Reading] -

Google Maps now has a voting option to help plan group events
Publié: septembre 26, 2018, 4:48pm CEST par Mark Wycislik-Wilson
Both the iOS and Android versions of Google Maps have received an update that will be welcomed by anyone who has ever struggled to arrange a meet-up place, or a dining location with a group of friends. A new voting function makes it easy to gauge opinion and see which location is most popular without having to resort to endless messages, or arguments in group chat. It's a simple idea, but one that can help avoid many heated arguments and allow you to reach a decision faster. See also: After complaints, Google is going to give users more privacy controls… [Continue Reading] -

Plex adds subtitle downloads, kills plugins, Watch Later and Cloud Sync
Publié: septembre 26, 2018, 12:39pm CEST par Mark Wycislik-Wilson
Plex continues to evolve, and the latest addition to the media player is the ability to download subtitles from within the software. This will come as great news for anyone who has battled with subtitle websites, and greatly simplifies the process of adding them to your media collection. But as well as adding this option, Plex has also announced that it is sunsetting three features -- namely Watch Later, Cloud Sync and (perhaps surprisingly) support for plugins. See also: Plex Cloud is closing down Plex gains podcast support and gets redesigned, personalized app for iOS and Android The ability to… [Continue Reading] -

Mozilla teams up with Have I Been Pwned to create data breach notification tool, Firefox Monitor
Publié: septembre 26, 2018, 11:51am CEST par Mark Wycislik-Wilson
Mozilla has partnered with Troy Hunt -- the brain behind data compromise checking service Have I Been Pwned -- to create its own data breach notification service. Called Firefox Monitor, the free service lets users check if any of their email accounts or personal data have been involved in data breaches. More than this, Firefox Monitor can also keep an eye out for future data breaches and notify those who have signed up whether their data has been affected. See also: After complaints, Google is going to give users more privacy controls in Chrome 70 Mozilla to boost Firefox privacy… [Continue Reading] -

After complaints, Google is going to give users more privacy controls in Chrome 70
Publié: septembre 26, 2018, 11:00am CEST par Mark Wycislik-Wilson
With the release of Chrome 70, Google is set to address two recent privacy concerns with its browser. Users have been unhappy with Chrome 69 forcibly signing them into the browser when they sign into a Google website, and there have also been concerns about the handling of cookies. Due for release in the middle of October, the next version of the web browser will enable users to disable the controversial sign-in feature, as well as changing the way Chrome handles the clearing of auth cookies. See also: Users balk as Chrome 69 forcibly signs them into the browser How… [Continue Reading] -

Twitter considers new Dehumanization Policy -- but wants your feedback first
Publié: septembre 25, 2018, 5:46pm CEST par Mark Wycislik-Wilson
Continuing to face criticism for failing to successfully tackle abuse on its platform, Twitter has announced a new approach. The company is planning to introduce new policies, but before they become part of official rules it will ask for feedback from users. Starting off with a new Dehumanization Policy, Twitter will invite users to give their opinion and complete surveys about proposed policy changes. The first policy to be subject to this public scrutiny says: "You may not dehumanize anyone based on membership in an identifiable group, as this speech can lead to offline harm". See also: Hooray! The option… [Continue Reading] -

Qualcomm accuses Apple of stealing trade secrets and giving them to Intel
Publié: septembre 25, 2018, 4:14pm CEST par Mark Wycislik-Wilson
Chip-maker Qualcomm has today accused Apple of stealing trade secrets and sharing them with Intel. The company alleges that Apple wanted Intel to be able to improve its own chips so it could move away from using Qualcomm's. Qualcomm and Apple are already engaged in a legal battle, and with its latest accusations, the chip-maker wants the court to amend its existing lawsuit against the company. Apple stands accused of engaging in a "multi-year campaign of sloppy, inappropriate and deceitful conduct". See also: Apple acquires Shazam and promises an ad-free app for all Trump imposes $200bn of import tariffs on… [Continue Reading] -

Zoho taken offline by domain registrar for phishing violations
Publié: septembre 25, 2018, 12:06pm CEST par Mark Wycislik-Wilson
CRM service Zoho disappeared from the internet after its domain registrar suspended it for failing to deal with phishing appropriately. TierraNet blacklisted Zoho.com after receiving complaints about phishing emails sent from Zoho-hosted accounts. This meant that many businesses were unable to access their documents, address books and emails, causing chaos for many. Zoho has said that in order to ensure such an occurrence is never repeated, it will become a domain registrar itself. Zoho CEO Sridhar Vembu used Twitter to complain about his company being taken offline without warning, and said that TierraNet were difficult to get hold of to… [Continue Reading] -

Instagram co-founders resign from Facebook-owned company to 'explore curiosity and creativity again'
Publié: septembre 25, 2018, 11:03am CEST par Mark Wycislik-Wilson
Six years after their company was bought by Facebook, Instagram co-founders Kevin Systrom and Mike Krieger have resigned. The pair say they are "planning on taking some time off to explore our curiosity and creativity again". But while the departures have been presented as being amicable, sources suggest that the resignations came about because of Systrom and Krieger's unhappiness at the direction in which Facebook was taking the app. See also: Now you can get verified on Instagram Facebook VPN Onavo Protect disappears from App Store for violating Apple's data collection and privacy rules Facebook denies asking banks for your… [Continue Reading] -

Apple acquires Shazam and promises an ad-free app for all
Publié: septembre 24, 2018, 6:37pm CEST par Mark Wycislik-Wilson
Apple has today completed its purchase of music-identification app Shazam after lengthy investigation by the EU -- and there's good news for anyone who uses it. The app's millions of global users will soon be able to enjoy an ad-free experience. Apple just says that this will be happening "soon", without giving any sense of timescale. See also: EU green-lights Apple's purchase of Shazam Apple's purchase of Shazam to be investigated by the EU Pointing out that the Shazam app has already been downloaded over a billion times, Apple promises that it will "soon offer its experience ad-free for all… [Continue Reading] -

Microsoft launches Azure-based Windows Virtual Desktop for running Windows in the cloud
Publié: septembre 24, 2018, 4:54pm CEST par Mark Wycislik-Wilson
Microsoft has announced Windows Virtual Desktop, a way to run virtualized instances of Windows and Office in the cloud. Running on Azure, Windows Virtual Desktop offers multi-user supports and enables several people to remotely log into the same Windows 10 virtual machine. Microsoft says that the service is also optimized for Office 365 ProPlus and notes that it includes free Windows 7 Extended Security Updates. While there are numerous services that provide access to virtual machines in the cloud, Windows Virtual Desktop is the only one that supports multiple users. It also offers Windows Store compatibility and the inclusion of… [Continue Reading] -

Microsoft is launching the Surface Hub 2S in 2019, and the Surface Hub 2X in 2020
Publié: septembre 24, 2018, 4:32pm CEST par Mark Wycislik-Wilson
Microsoft has announced that it is launching the Surface Hub 2S in the second quarter of 2019. The next version of the company's gigantic, business-focused touchscreen display is (slightly) smaller at a mere 50.5 inches, rather than the existing 55- and 84-inch options. Following on from this in 2020 is the Surface Hub 2X which brings not only multiuser login, but also the ability to rotate and tilt the screen. Interestingly, an upgrade will be possible from the 2S to the 2X by means of a removable processor cartridge. Writing on the Windows blog, general manager of hardware engineering Robin… [Continue Reading] -

Browser Reaper: exploit causes Firefox to crash
Publié: septembre 24, 2018, 2:29pm CEST par Mark Wycislik-Wilson
A security researcher has developed an attack that exploits a Firefox bug, making it possible to crash the web browser. Sabri Haddouche used his Browser Reaper website to share a live test version of the exploit -- the site is also home to exploits for Chrome and Safari. The Firefox attack uses JavaScript to crash or freeze the browser, with the effect of the exploit depending on whether the browser is running on Linux, Windows or macOS. See also: Users balk as Chrome 69 forcibly signs them into the browser Chrome OS 69 rolls out with Linux app support and… [Continue Reading] -

Users balk as Chrome 69 forcibly signs them into the browser
Publié: septembre 24, 2018, 12:44pm CEST par Mark Wycislik-Wilson
Chrome users have reacted angrily after the discovery of a new forced sign-in for the web browser. In short, the change means that when you sign into a Google service -- such as Gmail -- you are also automatically signed into this account within Chrome itself. While a handful of people have welcomed the new sign-in activity, there is a very vocal number who are extremely unhappy. In addition to the perceived privacy concerns, what has particularly upset people is the fact that they are being signed into Chrome without being told about it. See also: Chrome OS 69 rolls… [Continue Reading] -

PayPal bans Infowars for spreading hate speech
Publié: septembre 22, 2018, 11:51am CEST par Mark Wycislik-Wilson
Alex Jones' Infowars has found itself cut off from yet another platform. Having been booted from social media sites including Twitter and Facebook, as well as YouTube and the App Store, PayPal has now given it the elbow. The online payment service has taken exception to Infowars' promotion of "hate" and "discriminatory intolerance" and has hit Jones' cash cow where it hurts -- in the wallet. He has been given ten days to find a new payment processing service. See also: Apple boots Alex Jones and Infowars out of the App Store Twitter hits Alex Jones and Infowars with permanent… [Continue Reading] -

Android 9.0 Pie lands on OnePlus 6 in OxygenOS 9.0
Publié: septembre 21, 2018, 5:16pm CEST par Mark Wycislik-Wilson
After a series of betas, the OnePlus 6 now has Android 9.0 Pie. OnePlus has released the Pie-based OxygenOS 9.0 and it's rolling out to handsets now. But while OnePlus 6 owners will be excited at the prospect of getting their hands on a stable version of Android Pie, there's some bad news. Unlike with previous OxygenOS updates, using a VPN to try to get hold of this one probably won’t work. See also: Confirmed: the OnePlus 6T definitely has an in-display fingerprint reader OnePlus confirms that the OnePlus 6T has no headphone jack and announces Type-C Bullets earbuds OnePlus… [Continue Reading] -

Microsoft is bringing Skype to Alexa devices
Publié: septembre 21, 2018, 10:53am CEST par Mark Wycislik-Wilson
Microsoft has announced that Skype is coming to a range of Alexa devices. At its hardware event yesterday, Amazon revealed the updated Echo Show with integrated Skype, but later this year voice-activated Skype calling will be landing on other Alexa devices. The feature will make it possible to place and receive Skype voice calls, video calls and SkypeOut calls. See also: Amazon announces an Alexa-powered microwave with a built-in popcorn Dash button Amazon Smart Plugs let you control home devices with Alexa -- but you’ll need an Echo device Amazon updates its Echo Dot, Echo Plus and Echo Show Amazon… [Continue Reading] -

Google brings Emergency Location Service to Android users across the US
Publié: septembre 20, 2018, 1:09pm CEST par Mark Wycislik-Wilson
Google has expanded Android's Emergency Location Service to more people in the US, making it easier for emergency services to locate people when responding to a 911 call out. Emergency Location Service (ELS) has been around in Android for a couple of years now, and it uses a combination of GPS, Wi-Fi, mobile networks and sensors to provide responders with accurate location information about callers, no matter whether they are inside or outside. See also: Android emulator BlueStacks 4 brings massive performance improvements Samsung and Google are working together to bring RCS messaging to Android Developers can now use staged… [Continue Reading] -

Hacked: Newegg suffers month-long card-skimming attack, exposing credit card details
Publié: septembre 20, 2018, 10:41am CEST par Mark Wycislik-Wilson
Just 15 lines of code was all it took for hackers to hijack the checkout of online retailer Newegg. The month-long attack took the form of a huge card skimming operation and is believed to have been carried out by the same group that was responsible for hacking both British Airways and Ticketmaster recently -- Magecart. The hackers inserted car-skimming code into Newegg's payment page, and this script remained in place between August 14 and September 18. It is not known how many people may have been affected by the incident, but with millions of visitors each month, the numbers… [Continue Reading] -

After Torvalds' apology, the Linux community is adopting a new code of conduct
Publié: septembre 19, 2018, 11:11am CEST par Mark Wycislik-Wilson
Following years of questionable behavior and ranting, the grandfather of Linux Linus Torvalds issued an apology and announced his intention to take a break from kernel work. Now the Linux community is adopting a new code of conduct to help make the environment more welcoming. Based on the Contributor Covenant, the new Code of Conduct seeks to make participating in the community "a harassment-free experience for everyone, regardless of age, body size, disability, ethnicity, sex characteristics, gender identity and expression, level of experience, education, socio-economic status, nationality, personal appearance, race, religion, or sexual identity and orientation". See also: Linus Torvalds… [Continue Reading] -

Chrome OS 69 rolls out with Linux app support and new Material Theme
Publié: septembre 19, 2018, 10:20am CEST par Mark Wycislik-Wilson
Google is in the process of rolling out Chrome OS 69 to the stable channel, giving more users the chance to enjoy the new Material Theme and take advantage of new features such as support for Linux apps. The updated look will be familiar to Android users -- rounded corners abound -- and there are numerous other changes and additions including a new Night Light mode, better dictation options, and an updated Files app. It should come as little surprise that Linux app support is not an option on all Chromebooks -- a list of supported devices can be found… [Continue Reading] -

Android emulator BlueStacks 4 brings massive performance improvements
Publié: septembre 18, 2018, 5:00pm CEST par Mark Wycislik-Wilson
The latest version of the popular Android emulator for Windows, BlueStacks 4, is now available, bringing with it a huge performance boost over its predecessor. The new release also sees the emulator jumping from KitKat to Nougat as its base -- specifically Android 7.1.2. The developers say that BlueStacks 4 is many times faster than the Samsung Galaxy S9+ -- or "any mobile on Earth" according to the blurb -- and features Hyper-G Graphics for unparalleled visuals in games. But besides performance, there are lots of other changes in the latest version of this emulator. See also: Unless you upgrade… [Continue Reading] -

Trump imposes $200bn of import tariffs on China -- but the Apple Watch is spared
Publié: septembre 18, 2018, 11:23am CEST par Mark Wycislik-Wilson
Donald Trump has imposed import tariffs of $200 billion on Chinese goods brought into the US, with the threat of even more on the way. The tariffs have been blamed on China's "unfair policies and practices", but despite the president's pleas for Apple to shift production from China to the US, the Apple Watch will be exempt from the 10 percent import tax. Also exempt are Apple's AirPods and a range of other technology products. See also: Pre-order your iPhone XS, iPhone XS Max and Apple Watch Series 4 now! Trump threatens China tariffs, tells Apple to make products in… [Continue Reading] -

Hooray! The option to view your Twitter timeline chronologically is coming!
Publié: septembre 18, 2018, 10:34am CEST par Mark Wycislik-Wilson
People have many complaints about Twitter, but one that crops up time and time again from users is how the timeline is displayed. Like many other social media sites, Twitter ditched the idea of showing your tweets in the order in which they were posted in favor of using algorithms to show you what it thinks you want to see. But now this is about to change again. After vocal outpourings from critics of the algorithm-driven timeline, Twitter is going to give users a choice -- have your timeline controlled by an algorithm, or view a chronological timeline instead. See… [Continue Reading] -

OnePlus is working on a smart TV -- and much more
Publié: septembre 17, 2018, 1:36pm CEST par Mark Wycislik-Wilson
Looking to extend its product range, OnePlus has revealed that it plans to release a smart TV -- called OnePlus TV. Details are sketchy at the moment, but the company is planning to launch the product some time in 2019. And this is not all OnePlus has planned. In a post on the OnePlus forums, co-founder Carl Pei explains that he wants the company to take "the first step in building a connected human experience". He fails to go into detail, but suggests that OnePlus wants to work in the "four major environments we experience each day: the home, the… [Continue Reading] -

Linus Torvalds apologizes to Linux community for unprofessional 'flippant attacks'
Publié: septembre 17, 2018, 11:46am CEST par Mark Wycislik-Wilson
Linux creator Linus Torvalds has used his regular Sunday email to the Linux Kernel Mailing List to apologize for unprofessional behavior, and to announce that he is taking a break from his Linux kernel work. Acknowledging that he has previously launched "flippant attacks" on people -- something he labels as "unprofessional and uncalled for" -- Torvalds says he wants to "apologize to the people that my personal behavior hurt and possibly drove away from kernel development entirely". See also: Linux Mint 19.1 named 'Tessa' GNOME 3.30 'Almería' Linux desktop environment is finally here Linux apps are NOT coming to many… [Continue Reading] -

Amazon investigates allegations that workers accept bribes to leak data and delete bad reviews
Publié: septembre 17, 2018, 10:38am CEST par Mark Wycislik-Wilson
Amazon has been hit with allegations of staff bribery which the company says it is investigating. A report in the Wall Street Journal this weekend claims that employees have been accepting bribes in return for leaks of sales data. It is also alleged that staff help out independent sellers by deleting negative reviews in exchange for payment, and restore accounts that have been banned. See also: Amazon announces all-new Fire HD 8 with Alexa Hands Free Amazon finally lets users collaborate on lists The report says that it can cost just $300 to have a bad review removed, but the… [Continue Reading] -

Privacy: Grindr API is STILL exposing the location of its users
Publié: septembre 15, 2018, 11:55am CEST par Mark Wycislik-Wilson
Earlier in the year it was revealed that a security flaw made it possible to determine not only the location, but also the HIV status of Grindr users. Months down the line, Grindr is still exposing the precise location of its users by failing to block third-party access to a private API. Using a trilateration technique, and exploiting the fact that Grindr lets users know -- with some degree of accuracy -- how far away they are from others, it is very easy for just about anyone to build a tool that shows precise locations. See also: Grindr was sharing… [Continue Reading] -

How to hide the Twitter bug reporter icon in Android
Publié: septembre 15, 2018, 10:43am CEST par Mark Wycislik-Wilson
If you have enrolled in the beta version of Twitter -- and, in some instances, even if you haven't -- you may well have noticed the appearance of Twitter bug reporter icon in the Android status bar. It very likely annoys you, and you probably want to get rid of it. Hunt through the app's settings, and you'll find nothing that relates to the icon. So, what can you do? You could move away from the official Twitter app and try one of the third-party options, but you may not want to. Read on to find out how to stick… [Continue Reading] -

Pre-order your iPhone XS, iPhone XS Max and Apple Watch Series 4 now!
Publié: septembre 14, 2018, 10:32am CEST par Mark Wycislik-Wilson
Just a couple of days ago, Apple revealed its new range of iPhones and an updated Apple Watch. Today most of these devices are available for pre-order, ready to ship in a week. If you mosey on over to the Apple website, or head down to a physical Apple Store, you can now place your order for an iPhone XS, iPhone XS Max or Apple Watch Series 4. If you're ready to hand over your money, you can pre-order your phone or watch right now. See also: With its new iPhones, Apple drops not only the home button, but also… [Continue Reading] -

OnePlus confirms that the OnePlus 6T has no headphone jack and announces Type-C Bullets earbuds
Publié: septembre 13, 2018, 5:35pm CEST par Mark Wycislik-Wilson
News about the OnePlus 6T is coming thick and fast now, and the latest revelation comes direct from the horse's mouth. Company co- founder Carl Pei has confirmed that the upcoming handset is ditching the headphone jack, saying that it helps make way for "more new technology". So, moving forward you'll have to use either wireless headphones with the OnePlus 6T, or use a USB-C pair. And funnily enough, OnePlus has a set of Type-C Bullets earbuds that fits the bill! See also: OnePlus works with Google on Crackables game to promote OnePlus 6T Confirmed: the OnePlus 6T definitely has… [Continue Reading] -

Samsung and Google are working together to bring RCS messaging to Android
Publié: septembre 13, 2018, 12:21pm CEST par Mark Wycislik-Wilson
Google has been working on RCS messaging for a little while now, hoping that the successor to SMS will take off. Earlier in the year, the company moved its Allo team to work on the RCS-based Chat. Now it has teamed up with Samsung. The two companies are working together to help speed up the adoption of Rich Communication Service, ultimately aiming for global coverage. One of the first goals, however, is to ensure compatibility between Android Messages and Samsung Messages. RCS will bring to traditional text messaging, chat-like features such as typing indicators, Wi-Fi connectivity, photo and video sharing,… [Continue Reading] -

With its new iPhones, Apple drops not only the home button, but also the free headphone dongle
Publié: septembre 13, 2018, 11:19am CEST par Mark Wycislik-Wilson
Yesterday's Apple event was mostly about heralding the arrival of the new -- a trio of new iPhones, and a new Apple Watch -- but it was also about losing a couple of things. None of the new handsets now feature home buttons, but this is not all that has gone. Although the price of the new batch of phones is high by pretty much anyone's standards, Apple has taken the decision to stop including a headphone dongle in the box. If you want to use traditional wired headphones with your new iPhone, you'll have to shell out on an… [Continue Reading] -

Apple bumps up the price of battery replacements
Publié: septembre 13, 2018, 10:34am CEST par Mark Wycislik-Wilson
If you're thinking of getting an iPhone battery replaced, now is the time to do it. The announcement of the new iPhone pricing may well have made you consider hanging on to your existing handset for a little while longer, but if the battery is starting to show signs of age, a replacement will cost you more from next year. This is not something that was announced on stage, but while Apple was busy talking about the iPhone Xs, iPhone Xs Max and iPhone Xr, the iPhone Battery & Power Repair page of its support website was updated with new… [Continue Reading] -

Google is killing off its Gmail alternative Inbox
Publié: septembre 13, 2018, 10:29am CEST par Mark Wycislik-Wilson
Google has announced that Inbox is to close in six months' time. After four years of service, many -- although not all -- of Inbox's features have been incorporated into Gmail, and Google now feels it is time to concentrate on a single email tool. Inbox users have until the end of March next year to consider whether to transition to Gmail, or whether they want to look for an alternative. See also: How to unsend email in Gmail for Android Now you can send auto-expiring emails from Gmail on your mobile Gmail's new 'Confidential Mode' is flawed and misleading… [Continue Reading] -

Apple officially announces iPhone Xr, iPhone Xs and iPhone Xs Max
Publié: septembre 12, 2018, 8:39pm CEST par Mark Wycislik-Wilson
As ever, there has been much hype and excitement about this year's Apple event and the promise of new iPhones. This year there have been more leaks than normal, and now everything has been revealed at the Steve Jobs Theater in Cupertino This time around -- as expected -- Apple has announced three new handsets: the "cheap" iPhone Xr, the 5.8-inch iPhone Xs and the huge 6.5-inch iPhone Xs Max (not the Xs Plus as had been thought for a little while). Here's what you need to know about the trio of smartphones, including confirmation of dual-Sim support. See also:… [Continue Reading] -

Apple reveals larger Apple Watch Series 4
Publié: septembre 12, 2018, 7:59pm CEST par Mark Wycislik-Wilson
Today at the Steve Jobs Center in Cupertino, Apple took the wraps off the latest addition to its Watch range. Apple Watch Series 4 comes in two sizes -- 40mm and 44mm -- and the screen is over 30 percent larger in both instances. Despite the large screen, the casing has hardly changed in size -- in fact it is thinner. Faces and apps have been redesigned to take full advantage of the edge-to-edge screen, and Apple says that it has managed to maintain the same battery life as the previous model, thanks largely to the new S4 chip with… [Continue Reading] -

FCC pauses clock on its review of T-Mobile/Sprint merger
Publié: septembre 12, 2018, 11:39am CEST par Mark Wycislik-Wilson
The Federal Communications Commission has announced that it is stopping the clock on its review into the merger of T-Mobile and Sprint. The 180-day review clock has been paused at day 55 as the Commission says that it is awaiting the arrival of new submissions from both companies that are "complex". The delay will give the FCC more time to analyze these documents -- and a third submission -- when they are received. The letter posted on the FCC website reads: "Today we are pausing the Commission's informal 180-day transaction shot clock in this proceeding. Additional time is necessary to… [Continue Reading] -

OnePlus works with Google on Crackables game to promote OnePlus 6T
Publié: septembre 12, 2018, 11:04am CEST par Mark Wycislik-Wilson
The OnePlus PR machine is now fully operational in the run-up to the launch of the OnePlus 6T. We should -- officially -- hear more about the handset next month, but in the meantime the company is ramping up the hype. The latest gimmick finds OnePlus teaming up with Google to create a game called Crackables. Due to launch next week, the game gives players the chance to "crack the code to win the challenge". See also: Confirmed: the OnePlus 6T definitely has an in-display fingerprint reader OnePlus 6T leak hints at in-screen fingerprint reader and smaller notch Android 9.0… [Continue Reading] -

Plex Cloud is closing down
Publié: septembre 12, 2018, 10:17am CEST par Mark Wycislik-Wilson
After months of problems, Plex has announced that Plex Cloud is due to close down later this year. Introduced a couple of years ago to provide a way for users to store their files online rather than locally or on NAS drives, Plex Cloud has been plagued with issues. The company stopped accepting new servers back in February while it investigated the problems, but now Plex has determined that a fix is simply not possible and is therefore taking the "difficult decision" to shut down Plex Cloud on November 30. See also: Plex gains podcast support and gets redesigned, personalized… [Continue Reading] -

For the first time you can watch Apple's iPhone launch event on Twitter
Publié: septembre 11, 2018, 6:34pm CEST par Mark Wycislik-Wilson
Every year Apple fans who are unable to attend the iPhone launch -- that is, just about everyone -- either follows live blogs or seeks out how to watch the live stream in their preferred browser on their platform of choice. This year there will be a new option. For the first time ever, Apple will be live streaming its iPhone launch event on Twitter. There had been rumors that this would happen, but now the new way to tune in has been confirmed. See also: Leaked! Photos show iPhone XS and Apple Watch 4 ahead of September launch Leaks… [Continue Reading] -

Trend Micro backtracks on browser history collection after its apps are removed from mac App Store
Publié: septembre 11, 2018, 12:40pm CEST par Mark Wycislik-Wilson
It recently came to light that a number of apps in the mac App Store were collecting data about users' browsing histories and uploading them to a remote server. Included in this list were several apps from security firm Trend Micro. Apple responded by kicking the offending apps out of the App Store, and Trend Micro started an investigation into the privacy concerns raised about Dr Cleaner, Dr Cleaner Pro, Dr Antivirus, Dr Unarchiver, Dr Battery and Duplicate Finder. Confirming that these apps did in fact collect and upload browser data, the company at first defended the activity, but then… [Continue Reading] -

Security: Tor 0-day revealed on Twitter by vulnerability vendor
Publié: septembre 11, 2018, 11:40am CEST par Mark Wycislik-Wilson
It's just two weeks since a Windows 0-day was revealed on Twitter, and now the same thing has happened for the Tor browser. Zerodium -- self-described as "the premium exploit acquisition program" -- exposed a backdoor vulnerability in Tor that makes it possible to bypass security protections. The vulnerability affects Tor 7, and the vendor says that the problem has been addressed in the recently-released Tor 8. A proof-of-concept for the security has also been published. See also: Tor for Android brings secure, anonymous internet browsing to your mobile phone Microsoft Windows task scheduler 0-day outed on Twitter Malware writers… [Continue Reading] -

Microsoft publishes Security Servicing Criteria for Windows, revealing how it classifies and tackles bugs
Publié: septembre 11, 2018, 10:46am CEST par Mark Wycislik-Wilson
Microsoft has published documentation that reveals how is classifies the severity of vulnerabilities in Windows, as well as detailing how it decides whether problems should be addressed with a security patch or in the next version of Windows. The first batch of documentation shows for the first time how Microsoft defines "the criteria around security boundaries, features and mitigations in Windows". In releasing details of its severity classifications -- something known as the bug bar -- the company says that it is offering a "new level of transparency with the research community and our customers". See also: Malware writers exploit… [Continue Reading] -

Confirmed: the OnePlus 6 definitely has an in-display fingerprint reader
Publié: septembre 10, 2018, 7:18pm CEST par Mark Wycislik-Wilson
Whether genuine leaks or a carefully orchestrated PR campaign, details of OnePlus phone releases nearly always slip out ahead of the big day. The OnePlus 6T is no different. We've already heard rumors that the upcoming handset will ditch the cumbersome rear-mounted reader in favor of one that's built directly into the screen. Now OnePlus has confirmed that this is in fact the case. See also: OnePlus 6T leak hints at in-screen fingerprint reader and smaller notch Android 9.0 Pie-based Oxygen OS Open Beta 1 lands on the OnePlus 6 OnePlus is bigger than Samsung in India -- oh, and… [Continue Reading] -

Confirmed: the OnePlus 6T definitely has an in-display fingerprint reader
Publié: septembre 10, 2018, 7:18pm CEST par Mark Wycislik-Wilson
Whether genuine leaks or a carefully orchestrated PR campaign, details of OnePlus phone releases nearly always slip out ahead of the big day. The OnePlus 6T is no different. We've already heard rumors that the upcoming handset will ditch the cumbersome rear-mounted reader in favor of one that's built directly into the screen. Now OnePlus has confirmed that this is in fact the case. See also: OnePlus 6T leak hints at in-screen fingerprint reader and smaller notch Android 9.0 Pie-based Oxygen OS Open Beta 1 lands on the OnePlus 6 OnePlus is bigger than Samsung in India -- oh, and… [Continue Reading] -

Azure Pipelines CI/CD service arrives in the GitHub Marketplace
Publié: septembre 10, 2018, 5:30pm CEST par Mark Wycislik-Wilson
Microsoft today announced the successor to Visual Studio Team Services, Azure DevOps, as well as Azure DevOps Server, replacing Team Foundation Server. As part of this, the company also launched a new CI/CD service called Azure Pipelines which gives developers the chance to build, test and deploy to any platform. Azure Pipelines has been launched in the GitHub Marketplace, and it is completely free for open source repositories. Writing on the Azure blog, Jeremy Epling Principal Group Program Manager for Azure DevOps says: "Microsoft is committed to fueling open source software development. Our next step in this journey is to… [Continue Reading] -

Leaks suggest incoming iPhone Xc, iPhone Xs and iPhone Xs Plus
Publié: septembre 10, 2018, 12:29pm CEST par Mark Wycislik-Wilson
Historically, Apple has run a very tight ship when it comes to containing leaks, but things have changed slightly in more recent times. It has been thought for a little while now that the company is planning to release three new iPhone models later this week, and there have been leaks that seem to show off some of the handsets and hint at the names. Now there are two new leaks. The first shows prototypes of 6.1-inch LCD iPhone, while the second seems to confirm the names iPhone Xc, iPhone Xs and iPhone Xs Plus. See also: Apple offers free… [Continue Reading] -

Huawei will let users force their phones into Performance Mode in EMUI 9.0
Publié: septembre 9, 2018, 12:30pm CEST par Mark Wycislik-Wilson
Earlier this week it was revealed that Huawei has been gaming benchmarks by switching its phones to a faster mode when benchmarking tools were detected. After this caused 3DMark-maker UL to delist numerous Huawei phones, the Chinese manufacturer has responded by saying it will open up Performance Mode so users can access it whenever they want. The company says that it "respects consumers' right to choose what to do with their devices" and that with this in mind it will let everyone running EMUI 9.0 to force the use of this faster mode. See also: Huawei has been cheating in… [Continue Reading] -

Trump threatens China tariffs, tells Apple to make products in US when company complains about costs
Publié: septembre 9, 2018, 11:13am CEST par Mark Wycislik-Wilson
President Trump proposed tariffs on $200 billion worth of Chinese products -- and there is the threat of a further $267 billion-- has caused Apple to write to the US Trade Representative to point out that this would lead to increased productions costs for many of its products. Responding to this, Trump said that the company could avoid Chinese import tariffs by switching production to the US. Referring to his suggestion as "exciting", the president said that Apple should start building new factories in America. See also: Google denies bias after Trump launches accusatory attack on the search giant Apple… [Continue Reading] -

Apple boots Alex Jones and Infowars out of the App Store
Publié: septembre 8, 2018, 4:40pm CEST par Mark Wycislik-Wilson
Having already removed its podcasts from iTunes, Apple has gone a step further and kicked Infowars out of the App Store. The app -- which provided access to Infowars articles as well as livestreams of Alex Jones shows rants -- has been permanently removed from the App Store for violations of Apple's rule. The move by the iPhone-maker is just the latest in a string of setbacks for Jones who has already fallen foul of Spotify, YouTube, Facebook and Twitter's policies. See also: Twitter hits Alex Jones and Infowars with permanent bans Apple kicks Alex Jones and Infowars podcasts from… [Continue Reading] -

Tor for Android brings secure, anonymous internet browsing to your mobile phone
Publié: septembre 7, 2018, 7:15pm CEST par Mark Wycislik-Wilson
It seems like mere moments since an updated version of Tor for the desktop was released, and now there's great news for owners of Android smartphones. The Tor Project has released an Android version of the Tor browser, and it's available to download either directly from its website, or from Google Play. Currently in alpha -- so expect there to be a few issues -- this is the only mobile Tor browser that's supported by the Tor Project, and the developers promise that it will block trackers, protect against surveillance and ensure privacy. See also: Access the web anonymously using… [Continue Reading] -

Mac app Adware Doctor caught stealing users' browsing histories
Publié: septembre 7, 2018, 4:33pm CEST par Mark Wycislik-Wilson
A highly popular anti-adware tool in the Mac App Store "surreptitiously steals your browsing history", alleges a security researcher. "All your data are belong to China!", as he puts it. Patrick Wardle conducted research into Adware Doctor -- one of the most popular paid-for apps in the App Store -- after concerns were raised by another security researcher. His research "uncovered blatant violations of user privacy and complete disregard of Apple's App Store Guidelines", including the theft and sharing of browsing history with a Chinese server. See also: Mozilla to boost Firefox privacy by automatically blocking all tracking Developers must… [Continue Reading] -

Huawei has been cheating in benchmarks
Publié: septembre 7, 2018, 12:38pm CEST par Mark Wycislik-Wilson
UL -- the company behind benchmarking software 3DMark -- has delisted a number of Huawei phones after the Chinese handset manufacturer was found to be cheating in benchmarks. As has been the case with handsets from some other manufacturers, the Huawei P20, P20 Pro, Nova 3 and Honor Play were found to increase performance when benchmarking software is running. Interestingly, Huawei has not denied the accusations leveled at it. The benchmark cheating was first brought to light earlier this week by AnandTech. The site noticed irregularities in benchmark results, saying: "it seems quite blatant as to what Huawei and seemingly… [Continue Reading] -

Apple is developing an online tool for police to request data
Publié: septembre 7, 2018, 11:50am CEST par Mark Wycislik-Wilson
Apple is looking to make it easier for law enforcement agencies to request user data and is working on an online tool to help facilitate this. A letter seen by Reuters shows that Apple is not only developing a data request tool, but also planning to train police about the data that it can and cannot provide. A new online system will make it easier and quicker to track data requests, and would be far more efficient than the current method of communication -- email. See also: EU green-lights Apple's purchase of Shazam Apple offers free logic board repairs after… [Continue Reading] -

British Airways hack exposes personal and financial details of 380,000 customers
Publié: septembre 7, 2018, 10:41am CEST par Mark Wycislik-Wilson
British Airways has fallen victim to what it describes as a "very sophisticated" attack in which hackers stole financial data relating to hundreds of thousands of customers. The airline revealed that hackers gained access to its systems and managed to remain undetected for two weeks. The theft of data took place between August 21 and September 5 and the attackers managed to compromise both the ba.com web site and the airline's mobile app. Speaking to the BBC, Alex Cruz -- chief executive of British Airways -- said that this had been a "sophisticated, malicious criminal attack". In all, 380,000 payment… [Continue Reading] -

Twitter hits Alex Jones and Infowars with permanent bans
Publié: septembre 7, 2018, 9:59am CEST par Mark Wycislik-Wilson
Fueling the right-wing conspiracy theorist's view that the world is out to get him, Twitter has followed the lead of other social media companies and banned Alex Jones from its platform. With his output dubbed "hate content", Jones found himself removed from Spotify, Facebook and iTunes, but Twitter's Jack Dorsey previously refused to follow suit saying that the Infowars frontman "hasn't violated our rules", insisting that his company enforces its rules "impartially, regardless of political viewpoints". But after Jones posted videos earlier this week that violated Twitter's policy on abusive content, he has been permanently banned. See also: Twitter is… [Continue Reading] -

EU green-lights Apple's purchase of Shazam
Publié: septembre 6, 2018, 3:51pm CEST par Mark Wycislik-Wilson
It's now ten months since Apple announced its plans to buy music-recognition firm Shazam, and a little under half a year since the European Commission started an investigation into the purchase because of concerns about competition. EU competition commissioner Margrethe Vestager today announced that the commission will not stand in the way of the deal. See also: Apple's purchase of Shazam to be investigated by the EU Apple offers free logic board repairs after defects are found in some iPhone 8 handsets Leaked! Photos show iPhone XS and Apple Watch 4 ahead of September launch Europe had initially voiced concerns… [Continue Reading] -

APK teardown reveals Google Play Points loyalty scheme
Publié: septembre 6, 2018, 12:34pm CEST par Mark Wycislik-Wilson
Google already gives you a way to earn money with your phone via its Rewards app, but it looks as though a new loyalty scheme could be on the horizon too. A teardown of the Play Store APK reveals reference to "Google Play Points". While little is known about it at the moment, it appears to offer a way to earn points that can spent on things in Google Play. See also: Developers can now use staged releases in Google Play to test their Android apps on users Unless you upgrade to Android Pie, a vulnerability leaves your phone trackable… [Continue Reading] -

Developers can now use staged releases in Google Play to test their Android apps on users
Publié: septembre 6, 2018, 11:24am CEST par Mark Wycislik-Wilson
Google has announced that developers can now take advantage of a new "staged releases" feature to roll out new versions of their apps to a small percentage of their user base. The feature was first revealed at Google I/O earlier in the year, and Google says that it will give developers the chance to test new features on a limited number of users before opting for a wider rollout. While all apps undergo testing before a release, it is difficult to ensure that all features will be fully compatible with all handsets. A staged release makes it possible to testdrive… [Continue Reading] -

How get rid of Chrome's stupid new rounded look
Publié: septembre 6, 2018, 10:59am CEST par Mark Wycislik-Wilson
The celebrate the 10 anniversary of Chrome, Google pushed out version 69 of the browser complete with a new look. Many people find change hard to accept, and for some Chrome users, the rounded look that Google has introduced feels like a step back in time. If you prefer the way Chrome used to look, you'll be pleased to hear that you're not going to be forced to stick with the redesign. There's a hidden setting that you can tweak to get things back to how they used to be. See also: Have you seen Chrome 69? It's had a… [Continue Reading] -

How to enable the dark theme in YouTube for Android
Publié: septembre 6, 2018, 10:23am CEST par Mark Wycislik-Wilson
Dark themes have become very popular recently. Whether this is because of them being easier on the eye, people going through a Gothic phase, perceived battery saving, or just a passing fad is not clear, but plenty of apps are getting in on the idea. The latest to jump on the bandwagon is YouTube for Android. Google is rolling out an update at the moment that brings dark theme goodness to your favorite video app -- here's how to enable it. To start with, you will need to ensure that you have at least version 13.35.51 of the YouTube app… [Continue Reading] -

Malware writers exploit recent Windows Task Scheduler 0-day vulnerability
Publié: septembre 5, 2018, 8:04pm CEST par Mark Wycislik-Wilson
It's a little over a week since a vulnerability in the Windows Task Scheduler was revealed. A patch for the 0-day has been released by third party security firm 0patch, but there's bad news for anyone who hasn't secure their system against the security threat -- malware writers are already taking advantage of the flaw. The exploit was partly facilitated by the fact that the source code for a proof-of-concept exploit for the ALPC LPE vulnerability -- as well as a binary -- was published on GitHub. Now a group that has been named PowerPool has been spotted using the… [Continue Reading] -

BitTorrent embraces streaming torrents and takes uTorrent Web out of beta
Publié: septembre 5, 2018, 4:13pm CEST par Mark Wycislik-Wilson
Acknowledging that we are now very much in the streaming age, BitTorrent has launched the first version of µTorrent Web. The aim of the browser-based tool is to make torrenting as simple as possible and -- most importantly -- support torrent streaming. It remains to be seen how many people are willing to switch from a dedicated app to a browser-based torrenting experience, but the promise that you can "play while you download, no more staring at progress bars" is certainly alluring. Files are streamable near-instantly as they download, but they are also saved locally in the way you're used… [Continue Reading] -

New update from Microsoft means you can now record Skype calls
Publié: septembre 5, 2018, 12:45pm CEST par Mark Wycislik-Wilson
There's been a lot of Skype activity from Microsoft recently, starting off with the news (disappointing and frustrating for many) that Skype classic was to be killed off -- although this decision was later postponed. The company had also announced that call recording was coming to Skype 8.0, and now this is a reality. There will be obvious privacy concerns about the arrival of this new feature, but Microsoft believes that it has a solution that will help keep people happy and informed. See also: Rejoice! Microsoft gives Skype classic a temporary stay of execution Microsoft is killing off Skype… [Continue Reading] -

OnePlus 6T leak hints at in-screen fingerprint reader and smaller notch
Publié: septembre 5, 2018, 10:28am CEST par Mark Wycislik-Wilson
The launch of a T version of OnePlus handsets has become an annual event, and a new leak gives us a good idea of what to expect from the upcoming OnePlus 6T. What purports to be images of the retail box for the OnePlus 6T has been shared on Weibo and -- assuming it is genuine -- it gives us a glimpse of what to expect from the upcoming handset. We can see that there appears to be a smaller, redesigned notch, and also a fingerprint reader that's built into the screen. See also: Android 9.0 Pie-based Oxygen OS Open… [Continue Reading] -

Samsung to debut new features on mid-range phones rather than flagships
Publié: septembre 4, 2018, 11:11am CEST par Mark Wycislik-Wilson
Samsung has revealed that it plans to change its strategy when it comes to debuting new smartphone features. Flagship devices are usually where the latest technology and newest features are found, but in a bid to appeal to millennials, the company is going to do more with its mid-range handsets. The mid-priced section of the market has suffered from something of a slow down of late, and Samsung is hoping to rejuvenate interest by using its cheaper Galaxy A range of phones to showcase new technology. See also: Samsung unveils Galaxy Note9 with exclusive Fortnite access, plus Galaxy Watch Leaked:… [Continue Reading] -

Google's new Content Safety API will fight child abuse images with AI
Publié: septembre 3, 2018, 6:27pm CEST par Mark Wycislik-Wilson
Google has announced the release of a new Content Safety API with the aim of helping to combat child sexual abuse material (CSAM) online. The announcement comes as UK home secretary Sajid Javid called on technology companies to do more to tackle the problem of child abuse imagery on the internet, and the API has two main aims. The first is to make it quicker and easier to detect and remove CSAM, while the second is to do so without having to expose human content-checkers to so much abuse content. See also: Unless you upgrade to Android Pie, a vulnerability… [Continue Reading] -

Android 9.0 Pie-based Oxygen OS Open Beta 1 lands on the OnePlus 6
Publié: septembre 3, 2018, 4:41pm CEST par Mark Wycislik-Wilson
If you have a OnePlus 6, you can now get your first taste of Pie as the Android 9.0-based Open Beta has arrived. OnePlus is often among the first handset manufacturers to release upgrades to the latest Android versions, and things are no different with Pie. At the moment it's not clear how many betas there might be, or when OnePlus intends to release the final version of its slightly-customized version of the operating system, but this beta release is the first step on that journey -- at least for those who weren't tempted by the earlier developer preview. See… [Continue Reading] -

Unless you upgrade to Android Pie, a vulnerability leaves your phone trackable -- and Google won't fix it
Publié: septembre 3, 2018, 1:33pm CEST par Mark Wycislik-Wilson
A vulnerability in the Android operating system means that it is worryingly easy to track and locate phones. While the issue has been addressed in Android Pie, Google has no plans to patch the vulnerability in earlier versions of its mobile OS. The vulnerability (CVE-2018-9489) was revealed in a report from Nightwatch Cybersecurity which warns that it can be used to "uniquely identify and track any Android device" and also to "geolocate users". As well as Google's own Android builds, the problem is also said to affect forked versions such as FireOS. See also: If you want to record calls… [Continue Reading] -

Experts voice concern after discovering Google's Titan Security Key is made in China
Publié: septembre 2, 2018, 12:57pm CEST par Mark Wycislik-Wilson
While the US and UK governments continue to eye China with suspicion, blocking the use of some Chinese hardware because of national security concerns, it has come to light that Google's Titan Security Key is produced in China. The keys are supposed to boost security through the use of two-step verification, but security experts are calling for transparency about the supply chain for the hardware after it was revealed it is produced by Chinese company Feitian. There are concerns that the devices could be compromised by Chinese hackers (state or otherwise) to spy on users. See also: Google's Titan Security Key… [Continue Reading] -

Mozilla to boost Firefox privacy by automatically blocking all tracking
Publié: septembre 1, 2018, 5:28pm CEST par Mark Wycislik-Wilson
Mozilla has announced some of its plans for Firefox, and there's a strong focus on privacy. At an as-yet unspecified point in the "near future" the browser will block all tracking by default, although it is being trialed this month. In addition to this -- which is a change from the current Do Not Track option -- Firefox will include a new set of options which Mozilla says will give users greater control over the information they share with websites. As well as helping to improve privacy, Mozilla is also hoping to improve the performance of its web browser with… [Continue Reading] -

Google is able to track your offline purchases thanks to a secret deal with Mastercard
Publié: septembre 1, 2018, 12:14pm CEST par Mark Wycislik-Wilson
It's no secret that Google -- and other companies -- track your online purchases; it's one of the reasons you see the ads you do, for instance. But a secret deal between Google and Mastercard means that it is also possible for the internet giant to track your offline purchases. Google offers a service called Store Sales Measurement that makes it possible for advertisers to determine whether their online ads results in offline sales. A report from Bloomberg reveals that this was all made possible because of the deal between Google and Mastercard in the US-- one that raises serious… [Continue Reading] -

Apple offers free logic board repairs after defects are found in some iPhone 8 handsets
Publié: septembre 1, 2018, 11:04am CEST par Mark Wycislik-Wilson
Although it has been revealed that the iPhone 6 is Apple's most problematic handset, the company has just announced a replacement program for iPhone 8 owners after discovering a logic board issue with "a very small percentage of [...] devices". Apple says that the problem can result in unexpected restarts, freezes and an inability to turn on a phone. Affected devices were sold between late 2017 and early 2018, and anyone who has one can take advantage of a free repair. See also: Leaked! Photos show iPhone XS and Apple Watch 4 ahead of September launch Report: Apple to launch… [Continue Reading] -

Developers must give their apps a privacy policy or Apple will kick them out of the App Store
Publié: août 31, 2018, 4:35pm CEST par Mark Wycislik-Wilson
Apple has announced that all apps submitted to the App Store must have a privacy policy, including those apps which are undergoing beta testing. The change is due to come into force on October 3, and after this date any app lacking a privacy policy that lets users know how their data is being used faces ejection from the App Store. See also: Leaked! Photos show iPhone XS and Apple Watch 4 ahead of September launch Report: Apple to launch three iPhones later this year Privacy: Apple denies listening in on iPhone conversations and sharing recorded audio with third parties… [Continue Reading] -

Microsoft to scrap install limits for Office 365 Home and Office 365 Personal
Publié: août 31, 2018, 2:51pm CEST par Mark Wycislik-Wilson
Starting in October, anyone with an Office 365 Home or Office 365 Personal subscription will be able to install Office on as many devices as they like -- at no extra cost. This represents a massive change from current position where Home users can install the software on 10 devices, and the Personal limit of one computer and one tablet. The change does not mean, however, that you'll be able to share your copy of Office with everyone you know; Microsoft is limiting the number of people that can be signed into accounts at the same time. See also: 0patch… [Continue Reading] -

Leaked! Photos show iPhone XS and Apple Watch 4 ahead of September launch
Publié: août 31, 2018, 2:29pm CEST par Mark Wycislik-Wilson
Apple has confirmed that it is to hold an event (with the tag line "gather round") on September 12 at the Steve Jobs Theater, but this news has been rather overshadowed by a leak which shows off the yet-to-be-announced iPhone XS and the Apple Watch 4 that are likely to be revealed there. One leaked photo shows off two phones, believed to be the iPhone XS and iPhone XS Plus (5.8-inch and 6.5-inch handsets respectively). Another leak shows the Apple Watch Series 4 complete with a larger, near-bezel-free display. See also: Report: Apple to launch three iPhones later this year… [Continue Reading] -

0patch beats Microsoft to patching Windows 10 task scheduler 0-day vulnerability
Publié: août 30, 2018, 4:20pm CEST par Mark Wycislik-Wilson
Just 24 hours after a zero-day bug in Windows task scheduler was revealed by @SandboxExplorer on Twitter, the vulnerability has been patched. While Microsoft said it would "proactively update impacted advices as soon as possible" the patch has not come from the Windows-maker. Instead, it was left to micro-patching specialists 0patch to produce a fix for the Task Scheduler ALPC Local Privilege Execution (VU#906424) security flaw -- one that is a mere 13 bytes in size. See also: Microsoft Windows task scheduler 0-day outed on Twitter While the severity of the security flaw was limited by the fact that a… [Continue Reading] -

Google's Titan Security Key now available for $50
Publié: août 30, 2018, 11:40am CEST par Mark Wycislik-Wilson
A month after it was announced, Google is now selling its Titan Security Key for $50. Currently available in the US, the FIDO-compatible keys help to boost security with two-step verification (2SV). Google boasts that the keys have "special sauce" in the form of tamper-resistant firmware that helps to further improve security. Costing roughly the same as a Yubikey, Google is hoping to offer a viable alternative to the current FIDO key leader. See also: Google launches Titan Security Key... that is nothing to do with Yubico Google denies bias after Trump launches accusatory attack on the search giant Epic… [Continue Reading] -

YouTube alternative Facebook Watch rolls out globally
Publié: août 29, 2018, 8:17pm CEST par Mark Wycislik-Wilson
Following a successful launch in the US a year ago, Facebook is launching its Watch service globally. Competing directly with the likes of YouTube, Facebook Watch is the social network's platform for original video content, including Major League Baseball games and entertainment news. Just 12 months after launching in the US, the service enjoys 50 million monthly viewers and Facebook will be hoping to continue this success in other parts of the world. The company is pushing the social aspect of Facebook Watch as a major draw. See also: Facebook VPN Onavo Protect disappears from App Store for violating Apple's… [Continue Reading] -

Privacy: Yahoo still scans your emails... and wants to sell data to advertisers
Publié: août 29, 2018, 12:24pm CEST par Mark Wycislik-Wilson
Oath -- the owner of Yahoo -- is in talks with advertisers, promoting a service that scans the content of emails and provides a wealth of information about users. The service would give advertisers access to data contained in over 200 million Yahoo Mail inboxes. Email scanning would also apply to AOL Mail inboxes, also owned by Oath. As noted by the Wall Street Journal, Oath is now the only major US email provider than scans emails in this way -- and the way to opt out is well-hidden. See also: Facebook VPN Onavo Protect disappears from App Store for… [Continue Reading] -

Now you can get verified on Instagram
Publié: août 29, 2018, 10:59am CEST par Mark Wycislik-Wilson
While getting a verified account is something that's usually associated with Twitter, other social media services have similar schemes -- Facebook, for instance. The latest to join the verification party is Instagram which is now giving users the option of applying for a verified badge. It is possible for anyone to request to have their account verified, but only a handful of applicants are likely to be accepted. Instagram has outlined details of how to apply, and the criteria that need to be met. The company explains that "a verified badge is a check that appears next to an Instagram… [Continue Reading] -

Google denies bias after Trump launches accusatory attack on the search giant
Publié: août 29, 2018, 10:42am CEST par Mark Wycislik-Wilson
Donald Trump has accused Google of rigging its search results so that "good news" about the president is drowned out by unfavorable stories from the "Fake News Media". Using his preferred medium of Twitter, he alleged that 96 percent of search results for "Trump News" were from the "National Left-Wing Media", something he described as "very dangerous". Google denied these accusations of political bias, saying searching results are controlled by constantly-updated algorithms. See also: Turkey to boycott US electronics as Trump implements ZTE and Huawei ban Who cares what Trump thinks about Europe's record fine for Google? Twitter responds to… [Continue Reading] -

Microsoft Windows task scheduler 0-day outed on Twitter
Publié: août 28, 2018, 10:27am CEST par Mark Wycislik-Wilson
A privilege escalation bug has been discovered in Windows' task scheduler and revealed on Twitter. A proof-of-concept has been published, and the vulnerability has been confirmed to be present in a "fully-patched 64-bit Windows 10 system". The security flaw was exposed on Twitter by user SandboxEscaper -- who has since deleted his or her account. An advisory about the vulnerability has been posted on CERT/CC, and Microsoft says that it is working to fix the problem. In a tweet posted from a now-deleted account, @SandboxExplorer linked to a proof-of-concept on GitHub saying: "Here is the alpc bug as 0day: https://t.co/m1T3wDSvPX I… [Continue Reading] -

Epic calls Google 'irresponsible' for exposing Fortnite security flaw
Publié: août 27, 2018, 4:53pm CEST par Mark Wycislik-Wilson
The CEO of Epic Games has slammed Google's "irresponsible" disclosure of a security bug in its hit game Fortnite. Tim Sweeney accused Google of trying to "score cheap PR points" by revealing a vulnerability in the game's installer. Epic chose to bypass Google Play when it released Fortnite for Android leading to concerns about security. On Friday, Google revealed details of a security flaw that could be exploited to secretly install malware onto people's phones. See also: Fortnite installer had a serious security flaw that Google just revealed Boogiedown! Fornite is bribing players into enabling 2FA -- and that's a… [Continue Reading] -

Report: Apple to launch three iPhones later this year
Publié: août 27, 2018, 4:09pm CEST par Mark Wycislik-Wilson
Following the success of the iPhone X, the tech world is waiting to see what Apple has up its sleeve next -- and with new devices expected to be announced mid-September, we shouldn't have to wait too long to find out. Now a new report suggests that next month we'll see not just one or two new iPhones... but three. Citing "people familiar with the matter", Bloomberg says that Apple is set to launch no fewer than three handsets with the full-screen look of the current iPhone X. The trio of phones has been designed to have broader appeal with… [Continue Reading] -

Shooting at Madden NFL 19 tournament leaves three dead
Publié: août 27, 2018, 12:01pm CEST par Mark Wycislik-Wilson
Three people have been killed and several injured in a shooting at a video game tournament in Jacksonville, Florida. A gunman shot two participants dead before killing himself at the event which was livestreamed on Twitch. Police say that in addition to the three fatalities, eleven people were injured in the shooting. The shooter has been named as David Katz from Baltimore; he is said to have become angry after losing the tournament and pulled out a handgun. Jacksonville Sheriff's office confirmed that three people had been killed in the incident. Sheriff Mike Williams issued a statement saying: "We just… [Continue Reading] -

Fortnite installer had a serious security flaw that Google just revealed
Publié: août 25, 2018, 10:48am CEST par Mark Wycislik-Wilson
It seems that the concerns about Fortnite's security were well-founded -- although not necessarily for the reasons some people might have expected. Epic Games has been criticized for its decision not to make Fortnite available through Google Play, leading Google to show warnings to anyone conducting searches for the game. Now a Google engineer just revealed that the first version of Epic's installer had a serious security vulnerability, placing Android users at risk. A post on Google's Issue Tracker shows that the installer could be abused to secretly download and install any app with any level of permissions -- a… [Continue Reading] -

T-Mobile hacked -- over 2 million accounts exposed
Publié: août 24, 2018, 6:50pm CEST par Mark Wycislik-Wilson
T-Mobile has revealed that it fell victim to a security incident earlier in the week, and details of around 2.3 million accounts were accessed. The hack attack took place on Monday, August 20, and while T-Mobile stresses that no financial data was taken, it concedes that it detected "unauthorized capture of some information". The exposed data includes names, billing zip code, phone number, email address, account number and account type, which would be enough for hackers to launch successful phishing attacks. T-Mobile isn't really saying a great deal about the incident other than trying to downplay its severity and impressing… [Continue Reading] -

Boogiedown! Fornite is bribing players into enabling 2FA -- and that's a good thing
Publié: août 24, 2018, 10:34am CEST par Mark Wycislik-Wilson
Security is a serious business (including for Fortnite-maker Epic Games), but it's not something most people take seriously enough -- as the number of weak and reused passwords out there shows. Epic, however, has just given players of its hit game an incentive to enable two-factor authentication on their account. By enabling 2FA in Fortnite, players can unlock a hidden extra -- the Boogiedown emote. While this is undoubtedly a form of bribery, it is no bad thing. There are just a few simple steps you need to follow to access the new emote. See also: Fortnite installer had a… [Continue Reading] -

Linux apps are NOT coming to many still-supported Chromebooks
Publié: août 23, 2018, 12:56pm CEST par Mark Wycislik-Wilson
The prospect of running Linux apps on a Chromebook is something that has many people excited since Google first announced the plans. For those who like to live on the edge with the Canary and Dev builds of Chrome OS, Linux apps are already a reality -- but what about everyone else? While we know that Linux app support is coming to a range of Chromebooks from Lenovo, Acer, Dell and others, a post on the Chromium Gerrit reveals that devices running Linux 3.14 or older will miss out. See also: Campfire leak: Google could bring Windows 10 support to… [Continue Reading] -

Facebook VPN Onavo Protect disappears from App Store for violating Apple's data collection and privacy rules
Publié: août 23, 2018, 12:01pm CEST par Mark Wycislik-Wilson
Facebook bought Onavo and its VPN tool back in 2013, and ever since there have been concerns about how the social network uses the tool to gather data -- even when it is disabled. Now Apple -- itself not a stranger to allegations of privacy violations -- has taken objections to the way Facebook sucks up data from its users through the Ovano Protect VPN app. The iPhone-maker warned Facebook that it was violating its rules on data collection and suggested that the company might want to voluntarily pull the app before it was forcibly removed from the App Store.… [Continue Reading] -

Steam now lets you play Windows games in Linux
Publié: août 22, 2018, 11:24am CEST par Mark Wycislik-Wilson
In the world of non-console gaming, the Windows platform reigns supreme. That's not to say that Mac and Linux users aren't gamers, but their computer-based gaming choices are rather more limited thanks to developers' tendency to offer Windows support over anything else. Now Valve is looking to change things with its Steam platform. The latest version of Steam Play makes it possible to play some Windows games on Linux, greatly increasing the size of the gaming catalog available to Linux-based gamers. See also: deepin Linux 15.7 available for download Happy 25th Birthday, Debian Linux! Zorin OS 12.4 Linux distribution is… [Continue Reading] -

Grab yourself a cheap Microsoft Surface in Amazon's massive bank holiday sale
Publié: août 22, 2018, 10:30am CEST par Mark Wycislik-Wilson
If you're in the UK, you'll know that this weekend is the August Bank Holiday. This not only means a day off work -- for most people, at least -- but also big Black Friday-type sales from major retailers. Amazon is one of those offering big discounts, and you don't have to wait until the weekend to make a saving. For the next week, from today until next Wednesday, the online retailer has some incredible deals on Surface tablets and laptops meaning that there's never been a better time to buy one. See also: Microsoft Surface Go is a repairability… [Continue Reading] -

Starting next month, even if you pay for Twitch Prime you will see ads
Publié: août 21, 2018, 1:23pm CEST par Mark Wycislik-Wilson
One of the incentives to pay for a service -- from Spotify through Duolingo to YouTube Premium -- is the pleasure of an ad-free experience. Advertising exists in the free versions to help pay for the services, so it only seems fair that those who decide to pay a monthly fee aren't pestered by ads. Twitch doesn't agree. Starting next month, even if you pay for a Twitch Prime subscription you will still be subjected to ads. The reason? Money, of course. While Twitch has been able to attract a large number of users through the various perks offered to… [Continue Reading] -

How to unsend email in Gmail for Android
Publié: août 21, 2018, 12:06pm CEST par Mark Wycislik-Wilson
The ability to "unsend" emails has arrived in Gmail for Android -- for some people at least. The feature is already available on iOS and on the web version of Gmail, but now some Android users are finding that they have the option available on their phones too. Google has not made any sort of announcement about the rollout of the feature, and it seems as though it could be a server-side update rather than a new version of the app. But if you're one of the lucky ones, here's how to make use of this handy option. See also:… [Continue Reading] -

Logitech G PRO Wireless Gaming Mouse is designed for esport professionals
Publié: août 21, 2018, 11:00am CEST par Mark Wycislik-Wilson
Speed, accuracy and weight are all important factors when it comes to gaming mice, and this is something Logitech has taken into account over the two years it spent designing and building the Logitech G PRO Wireless Gaming Mouse. Using LIGHTSPEED wireless technology, Logitech says that it is able to offer a lag-free gaming experience -- something which is generally not possible with a wireless mouse. Logitech is keen to point out that more than 50 professional gamers were involved in the design of this ambidextrous mouse and claims it is "the only wireless solution that provides pro grade performance… [Continue Reading] -

Logitech's MX Vertical is a freaky-looking first for the company
Publié: août 20, 2018, 11:24am CEST par Mark Wycislik-Wilson
Logitech has announced its first ever vertical mouse. Appropriately named the MX Vertical, the device is described as the company's "most advanced ergonomic mouse". Available in any color you want, so long as that color is black, the MX Vertical has been designed to eliminate wrist pain by enabling you to use it with what Logitech says is "a natural handshake position". Oh... and it looks a bit weird. With a look that's reminiscent of an ammonite, the Logitech MX Vertical is certainly distinctive, but the unusual design is all about reducing discomfort. Using a very precise 57-degree vertical angle,… [Continue Reading] -

Google confirms it misleadingly tracks your location even with Location History disabled -- but it's not changing that
Publié: août 17, 2018, 12:00pm CEST par Mark Wycislik-Wilson
Call it bad wording, call it blatant lying, call it what you like -- Google was recently found to have been misleading people about what disabling Location History on their phones actually meant. Many people understandably thought that turning off this setting would prevent Google from tracking and recording their location. They were wrong But despite the upset caused by this revelation, Google is not backing down. Rather than changing the behavior of the setting so it did what people would expect it to do, the company has instead chosen to simply update its help pages to make it clear… [Continue Reading] -

Now you can send auto-expiring emails from Gmail on your mobile
Publié: août 17, 2018, 11:14am CEST par Mark Wycislik-Wilson
With the recent update to Gmail, Google added a number of features to its email service. One of the new features is Confidential Mode which allows for the sending of auto-expiring messages -- although, as we have previously noted, it's not perfect by any means. Available on the web version of Gmail for a number of weeks now, the feature is finally rolling out to iOS and Android users. See also: Gmail's new 'Confidential Mode' is flawed and misleading Google responds to Gmail privacy concerns: 'we're not reading your emails' Android users can now customize Gmail swipe actions Over on… [Continue Reading] -

WhatsApp now lets you backup to Google Drive without using any of your cloud storage quota
Publié: août 16, 2018, 10:51am CEST par Mark Wycislik-Wilson
Facebook and Google have struck a deal that benefits WhatsApp users. Starting later in the year, users will be able to store WhatsApp backups on Google Drive without using up any of their storage space. The new arrangement means that WhatsApp users now essential have unlimited storage space available to them free of charge. But the company has also issued a warning that people need to take action if they want to avoid backups being deleted. See also: Facebook denies asking banks for your financial details If you're looking for love, Facebook Dating is on the way Facebook API changes… [Continue Reading] -

Kids are dying because of their parents' obsessive phone use
Publié: août 16, 2018, 10:29am CEST par Mark Wycislik-Wilson
Although it is the children of today who have never known a world in which mobile phones do not exist, it is the parents of these children that are causing serious problems -- and not just by using phones while driving. The German Lifeguard Association (DLRG) has warned that children are dying because of their parents' phone usage. The organization says that rather than keeping an eye on their kids as they swim, parents are "fixated by their smartphones" and fail to notice when their youngsters get into trouble. The DLRG's warning comes after over 300 people drowned in Germany,… [Continue Reading] -

How to backup your computer to the cloud with OneDrive folder protection
Publié: août 15, 2018, 6:51pm CEST par Mark Wycislik-Wilson
Previously only available to OneDrive for Business users, Microsoft is now rolling out OneDrive folder protection to everyone. Also referred to as "known folder move" -- and rather copying the Backup and sync app from Google -- OneDrive folder protection makes it possible to back up your important files and folders to the cloud. Here's how to get started. By default, the new feature can be used to backup documents, pictures and desktop folders, but this does not necessarily mean that everything in these folders will be backed up. As Microsoft explains in a support article, Outlook database files (.pst)… [Continue Reading] -

If you want to record calls in Android 9 Pie, you'll need to root your phone
Publié: août 15, 2018, 5:23pm CEST par Mark Wycislik-Wilson
Recording phone calls is dodgy territory legally speaking, but whether you choose to do it depends on where you are in the world, and whether you're concerned about complying with the law. Since Marshmallow, Google has made it difficult to record calls on Android phones by killing the recording API, but this has not stopped third party developers finding ways around it. But with Android 9 Pie, Google has made it impossible for apps such as Call Recorder - ACR and BoldBeast Android Call Recorder to be used to record calls. Unless, that is, you're willing -- or able --… [Continue Reading] -

How to enable Chrome's secret Emoji Context Menu to make it easier to type emoji
Publié: août 15, 2018, 12:19pm CEST par Mark Wycislik-Wilson
The likes of Duolingo have made it easier than ever to learn French, Spanish, Polish, Hebrew or whatever other tongue tickles your fancy, but the language of the internet is -- arguably -- emoji. On your mobile phone, these handy little characters are easy to type, but less so on your computer. To make things a little easier, Google Chrome now has a hidden Emoji Context Menu that you can enable. Once activated, this menu can be used to access an emoji picker to add emoji to text fields. Here's how to enable it. See also: Banned Windows Timeline Support… [Continue Reading] -

Twitter is killing push notifications for third party apps -- here's what you need to do
Publié: août 15, 2018, 11:02am CEST par Mark Wycislik-Wilson
Starting tomorrow -- Thursday, August 16 -- Twitter is disabling push notifications for third party clients. If you use the likes of Twitterific, Fenix or Plume, this could mean you miss out on important messages as Twitter clamps down on what third party tools are able to do. Twitter has long had a tempestuous relationship with app developers, including its frankly bizarre token limit which effectively restricts the number of users any app can ever attract. This latest move is billed as a part of a security drive, but it's one that will impact a large number of people. There… [Continue Reading] -

Need a rugged Oreo smartphone without (too many) compromises? Try the Poptel P10
Publié: août 14, 2018, 7:37pm CEST par Mark Wycislik-Wilson
As Samsung, Apple and even the likes of OnePlus push out flagship smartphones with ever-larger price tags, it's little wonder that people are increasingly seeking out cheaper alternatives. Where there's demand, supply follows, so there's no end of choice when it comes to handsets that pack a punch without breaking the bank. It's possible -- probable, even -- that you've not heard of Poptel, but the Poptel P10 is a phone that's worthy of a second look. No, it's not a flagship-killer. No, it's not anything even approaching a competitor for the iPhone X or Samsung Galaxy Note9. But it… [Continue Reading] -

Turkey to boycott US electronics as Trump implements ZTE and Huawei ban
Publié: août 14, 2018, 4:22pm CEST par Mark Wycislik-Wilson
Donald Trump has signed the Defense Authorization Act into law which imposes a watered-down ban on ZTE and Huawei products by the US government and IT contractors. The ban also covers a number of other Chinese telecoms manufacturers. There has been much to-ing and fro-ing about whether these sanctions would actually be introduced, but now and for the next two years they will be in place -- something Huawei denounces as "ineffective, misguided, and unconstitutional". But while this latest bill signing sees Trump wielding his power, the president will be unimpressed by Recep Tayyip Erdoğan -- the president of Turkey… [Continue Reading] -

The Alldocube X is a low-cost 'Samsung Galaxy Tab S4 killer'
Publié: août 14, 2018, 1:29pm CEST par Mark Wycislik-Wilson
The big news from Samsung recently was the launch of the Galaxy Note9 smartphone, but the company also launched an Android tablet in the form of the Galaxy Tab S4. Starting at $649, the tablet may be beyond the reach of many people, but the Alldocube X is a cheap alternative. This 10.5-inch Super AMOLED tablet started life as an Indiegogo campaign, and it was 180 percent funded in just 24 hours. Priced at $269 and due for release in October, the Alldocube X is billed as a 'Samsung Galaxy Tab S4 killer' -- but can it live up to… [Continue Reading] -

Google is tracking your location even when you tell it not to
Publié: août 13, 2018, 6:20pm CEST par Mark Wycislik-Wilson
An investigation by the Associated Press has found that Google is tracking the location of Android and iPhone users even when privacy settings supposedly explicitly stop this from happening. The AP concedes that "for the most part, Google is upfront about asking permission to use your location information", but its investigation -- the findings of which were confirmed by researchers from Princeton -- showed that Google services recorded user data even when Location History was disabled. See also: Google Play shows warning to anyone searching for Fortnite APKs Google has slashed the size of Android apps Leaked report shows Google… [Continue Reading] -

Campfire leak: Google could bring Windows 10 support to Chromebooks, Boot Camp-style
Publié: août 13, 2018, 1:16pm CEST par Mark Wycislik-Wilson
Google could be about to add Windows 10 support to a range of Chromebooks, according to a new leak. The appearance earlier in the year of a new project called Campfire showed that Google was working on bringing Windows 10 support to Pixelbooks. But now it seems that the option to dual boot Chrome OS and Windows 10 could spread to a wider range of Chromebooks. See also: Google Play shows warning to anyone searching for Fortnite APKs Google has slashed the size of Android apps Android 9 is... Android Pie! Seriously, Google? The feature is comparable to Apple's Boot… [Continue Reading] -

Google Play shows warning to anyone searching for Fortnite APKs
Publié: août 12, 2018, 5:59pm CEST par Mark Wycislik-Wilson
The arrival of Fortnite on Android has not only been eagerly awaited, but also steeped in controversy. In addition to making the game a Samsung exclusive (for a few days, anyway), Epic Games decided to bypass Google Play and host APK downloads on its own servers. But this isn't going to stop people looking for Fortnite in the Play Store. Google is well aware of this, and that there is the potential for fake, scam apps to appear, tricking users into downloading something malicious. As such, the company is taking action, and is showing a warning to anyone who searches… [Continue Reading] -

Banned Windows Timeline Support extension returns to the Chrome Web Store
Publié: août 12, 2018, 4:46pm CEST par Mark Wycislik-Wilson
We recently wrote about a browser extension which added Windows' Timeline support for Chrome and Firefox -- the aptly-named Windows Timeline Support. While we loved the addon for making Windows 10's Timeline rather more useful, the use of the word "Windows" in its name meant that the extension was taken down due to copyright violation. Now it's back with a new name. See also: Make Windows 10's Timeline feature actually useful by adding support for Chrome and Firefox How to use Windows 10's new Timeline feature Privacy: How to disable Timeline in Windows 10 April 2018 Update As it was… [Continue Reading] -

Qualcomm to make $700m investment in new Taiwanese antitrust settlement
Publié: août 10, 2018, 12:11pm CEST par Mark Wycislik-Wilson
Qualcomm has come to an arrangement with Taiwanese antitrust regulators which means the company can stop paying fines levied against it. The chipmaker had been fined $778 million by the Fair Trade Commission in Taiwan back in 2017 after it was found to be refusing to sell to handset makers that were unwilling to agree to its patent-licensing terms. As part of the new agreement, Qualcomm will invest $700 million in Taiwan over the next five years, including investments in 5G initiatives. See also: Trump blocks Broadcom's takeover of Qualcomm, citing national security EU hits Google with record €4.34bn fine… [Continue Reading] -

Google has slashed the size of Android apps
Publié: août 10, 2018, 11:14am CEST par Mark Wycislik-Wilson
To tie in with the launch of Android 9 Pie, Google has given a glimpse into the improvements it has made to the app store. In a blog post aimed primarily at developers, the director of Google Play, Purnima Kochikar, said that improved discovery features had helped to boost visits to the store by 30 percent while new tools helped to dramatically reduce crash rates. Google also points to new techniques which have enabled it to reduce app size by up to 65 percent. See also: Android 9 is... Android Pie! Seriously, Google? Confirmed: Fortnite for Android will risk players'… [Continue Reading] -

Samsung unveils Galaxy Note9 with exclusive Fortnite access, plus Galaxy Watch
Publié: août 9, 2018, 7:49pm CEST par Mark Wycislik-Wilson
Today -- after weeks of leaks -- Samsung finally revealed the eagerly anticipated Galaxy Note9. While we already knew just about everything about this smartphone, we now know that it has an astonishing price tag (between $1,000 and $1,250) and that it includes exclusive access to the beta version of Fortnite for Android. At the same event, Samsung also unveiled the Galaxy Watch -- dropping the Gear branding once and for all. Available in 42mm and 46mm models, the watch features LTE connectivity and boasts impressive battery life. But has the launch of the two products lived up to expectations?… [Continue Reading] -

Chrome starts to use native notifications in Windows 10
Publié: août 9, 2018, 1:06pm CEST par Mark Wycislik-Wilson
With the roll out of Chrome 68, Google is making an important change to its browser's notification system. Rather than issuing website notifications within the browser, Chrome will instead start to make use of the Windows 10 Action Center to display them. While the change may not be viewed by everyone as a major one, it will help to provide a more consistent experience for people who choose to enable notifications from their favorite websites. See also: Chrome has a secret Material Design mode -- here's how to enable it Brace yourself for a slew of security warnings from Chrome… [Continue Reading] -

Unpacked: Watch the Samsung Galaxy Note9 launch live stream here!
Publié: août 9, 2018, 11:26am CEST par Mark Wycislik-Wilson
Just about everything you could possibly want to know about the Galaxy Note9 has already leaked out, but there's still the official launch event to look forward to later today in New York. The chances are you're not going to make it to the event itself, but you can watch it here, live. Things kick off in the Barclays Center in Brooklyn at 11:00 EDT (that's 16:00 BST), and watching the Samsung Galaxy Unpacked 2018 live stream is the best way to get the lowdown on this flagship handset as soon as possible. See also: Leaked: the Samsung Galaxy Note9… [Continue Reading] -

Privacy: Apple denies listening in on iPhone conversations and sharing recorded audio with third parties
Publié: août 8, 2018, 6:40pm CEST par Mark Wycislik-Wilson
In response to questions from Congress, Apple has written a letter in which it denies recording iPhone users' phone calls. The letter stresses Apple's stance on privacy after the House Committee on Energy and Commerce asked both Tim Cook and Alphabet's Larry Page about their respective companies' attitude to the privacy of user data. Apple says very firmly that its business model "does not depend on collecting vast amounts of personally identifiable information to enrich targeted profiles marketed to advertisers". The letter also adds that Apple "doesn't provide third-party app developers with access to Siri utterances". See also: Apple kicks… [Continue Reading] -

Twitter is not banning Alex Jones; Jack Dorsey explains why
Publié: août 8, 2018, 11:51am CEST par Mark Wycislik-Wilson
Alex Jones and Infowars are being banned, suspended and removed from the internet left, right and center. But while YouTube, Facebook, Apple and others have come down hard on the right-wing conspiracy theorist for peddling hate speech, Twitter is standing by him. Twitter founder Jack Dorsey has defended his company's decision not to follow the lead of its Silicon Valley counterparts, saying that Alex Jones "hasn't violated our rules". In a series of tweets, Dorsey explains that Twitter enforces its rules "impartially, regardless of political viewpoints". See also: Apple kicks Alex Jones and Infowars podcasts from iTunes Infowars' Alex Jones… [Continue Reading] -

Leaked Fortnite APK reveals secrets of the upcoming Android game
Publié: août 8, 2018, 10:25am CEST par Mark Wycislik-Wilson
We know that the gaming sensation Fortnite is making its way to Android. We know that the game will not be appearing in Google Play. There have been rumors for some time that Fortnite will be exclusive to Samsung devices for a short time after initial release, and a leaked APK for the game seems to confirm this. Analysis of the APK shows that Fortnite may not only be exclusive to the Samsung Galaxy Note9, but also the Samsung Galaxy Tab S4. Owners of these devices could retain exclusive access to the game for 30 days. See also: Confirmed: Fortnite… [Continue Reading] -

Rejoice! Microsoft gives Skype classic a temporary stay of execution
Publié: août 7, 2018, 11:03am CEST par Mark Wycislik-Wilson
There was outcry when Microsoft recently announced plans to kill off Skype classic (better known as Skype 7.0) and force users to migrate to Skype 8.0 -- the modern version of the app. But after an outpouring of disappointment from Skype users, Microsoft has relented... a bit. While it's not true to say that Skype classic has been saved, the kill date of September 1 has been extended -- until when is not clear. Microsoft says that it is extending support for the much- (well, more-) loved messaging tool "for some time". See also: Microsoft is killing off Skype classic… [Continue Reading] -

Android 9 is... Android Pie! Seriously, Google?
Publié: août 6, 2018, 7:41pm CEST par Mark Wycislik-Wilson
Google has revealed what the P in Android P -- otherwise known as Android 9 -- stands for. Despite previous suggestions that it was going to be Pistachio, it is in fact Android Pie. Just let that half-assed name sink in for a moment. Pie. Not even a specific pie to evoke some sort of imagery. Just a bog standard, run of the mill, common or garden... pie. The name is something of a damp squib and now the game of wait-and-see-if-I-actually-get-the-update begins. Google has already made the source code available on the Android Open Source Project (AOSP), and Pie… [Continue Reading] -

Apple kicks Alex Jones and Infowars podcasts from iTunes
Publié: août 6, 2018, 11:59am CEST par Mark Wycislik-Wilson
Alex Jones -- conspiracy theorist extraordinaire and founder of right-wing media platform Infowars -- has fallen foul of a number of companies' policies recently, and Apple is the latest to take exception to his output. YouTube started things off recently by removing some of his videos, and he was then suspended from Facebook for a month. Spotify decided that Jones' podcasts were "hate content" and removed several from its platform. Now Apple has done much the same, removing Jones' own podcasts from iTunes as well as those of Infowars. See also: YouTube slaps Alex Jones with another strike and removes… [Continue Reading] -

Major virus infection shuts down factories of iPhone chip-maker TSMC
Publié: août 5, 2018, 11:13am CEST par Mark Wycislik-Wilson
A major virus infection forced the closure of Taiwan Semiconductor Manufacturing Company (TSMC) factories just before the weekend; some remain closed or only partly-operational. TMSC is the largest semiconductor manufacturer in the world and is responsible for producing iPhone processors for Apple. The company issued a statement indicating that it was not carried out by a hacker. The impact on Apple's iPhone production schedule is also not known, although TSMC expects the incident "to cause shipment delays and additional costs". See also: Apple kills off its app affiliate program Apple pulls away from Microsoft and Facebook on the way to… [Continue Reading] -

If you're looking for love, Facebook Dating is on the way
Publié: août 4, 2018, 12:24pm CEST par Mark Wycislik-Wilson
Think of dating apps, and the likes of Tinder, Grindr and Match.com spring to mind, and now Facebook is looking to take itself a slice of the action. We first heard about Facebook Dating at the social network's F8 conference back in May, and now more details are coming out. Currently undergoing internal testing with employees, Facebook Dating is looking to be a feature of Facebook rather than a standalone app. Leaked images now give us an idea of what to expect from it -- but there'll be no swiping right. See also: Facebook API changes mean you can no… [Continue Reading] -

Confirmed: Fortnite for Android will risk players' security by sidestepping Google Play
Publié: août 4, 2018, 11:39am CEST par Mark Wycislik-Wilson
Fortnite for Android is one of the most eagerly-anticipated game launches of recent times, but the impending release could turn out to be something of a security nightmare. Following on from recent rumors, Epic Games has confirmed that Fortnite will not be made available through the Google Play Store. Instead users will have to download the game directly from Fortnite.com -- something which means they will have to lower the security settings for their phone by allowing the installation of apps from unknown sources. Despite the security risks involved in this, Epic is eager to avoid paying a 30 percent… [Continue Reading] -

Leaked: the Samsung Galaxy Note9 is a super power
Publié: août 3, 2018, 11:43am CEST par Mark Wycislik-Wilson
Samsung is getting about as leaky as OnePlus these days, and there have been all manner of details about the upcoming Galaxy Note9 slipping out over recent days. Now an official image and leaked video show off the handset in all its glory. The Galaxy Note9 is due to be unveiled on August 9, but an image (now removed) that appeared on the Samsung site in New Zealand gives us a great look at what to expect. Even better, a leaked teaser video gives us an even better view showing off a new yellow S Pen, and revealing that the… [Continue Reading] -

The Surface Go is here, and people just don't know what to make of it
Publié: août 3, 2018, 10:19am CEST par Mark Wycislik-Wilson
After much excited build up, Microsoft launched its latest Surface device yesterday -- the Surface Go. While many have suggested this is Microsoft's attempt to compete with Apple iPad, there's no getting away from the fact that this is a budget Surface, and compromises have been made. If you're not sure whether this is the tablet for you, you may well start to seek out Surface Go reviews -- and you'll find that they are an incredibly mixed bag of opinions. It looks as though the Surface Go could be one of Microsoft's most divisive products ever. Is it "painfully… [Continue Reading] -

Apple kills off its app affiliate program
Publié: août 2, 2018, 5:29pm CEST par Mark Wycislik-Wilson
Apple has announced that it is removing apps from its affiliate program. The change means that people will no longer receive commission for iOS and Mac apps. Having once enabled sites to earn 7 percent commission for app sales, Apple then dropped this to just 2.5 percent. As of October 1, no commission will be paid at all as Apple says the App Store does a good enough job of increasing app discovery. See also: Apple pulls away from Microsoft and Facebook on the way to becoming a trillion-dollar company Apple confirms MacBook Pro Core i9 throttling bug and fixes… [Continue Reading] -

Facebook API changes mean you can no longer cross-post from Twitter
Publié: août 2, 2018, 4:21pm CEST par Mark Wycislik-Wilson
Twitter users can no longer automatically cross-post to Facebook. The restriction has come about after Facebook made changes to the way third parties are able to make use of its APIs. It means that Twitter users who have connected their Facebook account to make it easier to post the same content on both services via Facebook Login can't have their tweets automatically posted to Facebook. The -- rather unsatisfactory -- solution from Twitter is simply copy the URL of a tweet, and this can then be manually posted to Facebook. See also: Facebook wants you to stop using it so… [Continue Reading] -

Spotify removes numerous Alex Jones podcasts, deeming them 'hate content'
Publié: août 2, 2018, 11:44am CEST par Mark Wycislik-Wilson
Spotify is the latest company to come down on Infowar's Alex Jones. The music streaming service has taken down multiple several episodes of The Alex Jones Show for violating its policies on hate speech. The removals come after Alex Jones was hit with another strike by YouTube for policy violations, and after Facebook also took action against him. See also: YouTube slaps Alex Jones with another strike and removes Infowars founder's videos Infowars' Alex Jones is banned from Facebook for a month Spotify has not gone into any detail -- publicly, at least -- about exactly what content violated its… [Continue Reading] -

2FA SNAFU led to Reddit security breach in which user data was stolen
Publié: août 2, 2018, 11:16am CEST par Mark Wycislik-Wilson
Reddit has revealed details of a security breach that enabled a hacker to gain access to private messages, usernames and encrypted passwords. The self-proclaimed "front page of the internet" is undertaking an investigation and taking steps to improve security. The attack took place between June 14 and June 18 this year, and the perpetrator was able to access "all Reddit data from 2007 and before including account credentials and email addresses", the site said in an announcement. The breach was made possible after the attacker beat SMS-based two-factor authentication and compromised several employee accounts. See also: Hacked: Timehop database breach… [Continue Reading] -

Leaked report shows Google plans a censored search engine for China... but China says otherwise
Publié: août 2, 2018, 10:00am CEST par Mark Wycislik-Wilson
A leaked document suggests that Google is planning on making a return to China, launching a censored version of its search engine to comply with strict Chinese laws. Going by the codename of Dragonfly, the project has been in the works since 2017 and has led to the creation of China-specific Android apps with the internal testing names Maotai and Longfei. But while the documents and people familiar with the matter say that the launch date could be just six to nine months away, China says the reports are not true. See also: Google (sort of) redirects Duck.com to DuckDuckGo… [Continue Reading] -

Apple pulls away from Microsoft and Facebook on the way to becoming a trillion-dollar company
Publié: août 1, 2018, 5:52pm CEST par Mark Wycislik-Wilson
Apple reported better-than-expected earnings and revenue for Q3 yesterday, taking the iPhone-maker closer to becoming the first every trillion-dollar company. Sales increased by 17 percent to a record $53.3 billion, and profit jumped a massive 32 percent to $11.5 billion. While the value of Facebook plummets following numerous scandals, Apple now has a market cap of $935 billion -- the closest competitors in the world of technology are Amazon at around $870 billion, Alphabet at $845 billion, and Microsoft at $815 billion. See also: Facebook value plummets by $118bn and Zuckerberg's fortune drops $16bn following privacy scandal-fueled growth slowdown Apple… [Continue Reading] -

Facebook wants you to stop using it so much
Publié: août 1, 2018, 2:51pm CEST par Mark Wycislik-Wilson
It might seem counter-intuitive -- or it might seem like a case of just saying what it thinks people want to hear -- but Facebook doesn't want you to use it as much as you do. That's not to say it wants you to disappear entirely, rather it just hopes that the time you spend on the social network is more "intentional, positive and inspiring" -- so you don't feel compelled to stay away and miss out on all those ads! Today, the company launches a new activity dashboard for both Facebook and Instagram that lets you see how long… [Continue Reading] -

Mozilla fox up its designs
Publié: août 1, 2018, 1:58pm CEST par Mark Wycislik-Wilson
Mozilla is looking to change the design of the Firefox logo and it is seeking help -- which is just as well, because the designs it has come up with so far are awful. The company says that it is looking to "evolve the Firefox brand" as it develops new apps and services beyond the browser it is currently associated with. The aim is to come up with a new branding system that can "embrace all of the Firefox products in the pipeline and those still in the minds of our Emerging Technologies group", and it wants to know what… [Continue Reading] -

Fortnite is coming to Android -- is your phone supported and will the game ever hit Google Play?
Publié: août 1, 2018, 11:16am CEST par Mark Wycislik-Wilson
Fortnite quickly became a gaming sensation, and the wait for the battle royale game to come to Android has felt like a long one. While Fortnite for iOS is already a reality, Fortnite for Android remains somewhere on the horizon. But that's not to say there is no news about the Android version of the game. A list recently came to light that seems to reveal the handsets that will support Fortnite, and there is a persistent rumor that the game will initially launch as an exclusive title for the upcoming Samsung Galaxy Note 9. Now it seems as though… [Continue Reading] -

Hate phone notches? Google says Android handsets can never have more than two
Publié: août 1, 2018, 10:26am CEST par Mark Wycislik-Wilson
Phones with notches are incredibly divisive, but since Apple launched the iPhone X complete with a little screen cutout, there have been endless copies from other handset manufacturers. But is one notch enough? How about two or more? If you fall into the "hate" camp when it comes to notches and cutouts it may be hard to convince you to buy such a phone, but for everyone else, Google has set out some new ground rules stating how many a phone can have, and where they can be located. You might well be of the opinion that one notch is… [Continue Reading] -

OnePlus is bigger than Samsung in India -- oh, and OnePlus 3/3T owners everywhere are getting Android P
Publié: août 1, 2018, 9:29am CEST par Mark Wycislik-Wilson
OnePlus keeps on going from strength to strength, and nowhere is this truer than in India. New analysis shows that the company is now bigger than Samsung in the region in the premium smartphone market. The company is now the market leader in India -- quite an achievement considering OnePlus only started participating in there fours ago. The rise to first place was helped by the success of the OnePlus 6, but it's also helped by the fact that the company does not abandon its users when it comes to software updates. In seperate news, it has been revealed that… [Continue Reading] -

Microsoft has a patent for a folding dual-screen, dual-camera device
Publié: juillet 30, 2018, 8:46am CEST par Mark Wycislik-Wilson
Although Panos Panay has dismissed rumors that Microsoft is working on a Surface Phone, we have already seen some evidence that the company is working on some form of "pocketable" folding Surface device codenamed Andromeda. Now a Microsoft patent has come to light that reveals more about the form this device could take. The patent -- entitled "Three-way video calling on hinged multi-screen device" -- shows a foldable, dual screen device with multiple cameras. It bears a marked similarity to the renders we saw recently of the rumored foldable Surface device. See also: Panos Panay: Microsoft is not working on… [Continue Reading] -

As if the platform wasn't irritating enough already, LinkedIn is getting a voice messaging feature
Publié: juillet 28, 2018, 7:13pm CEST par Mark Wycislik-Wilson
LinkedIn is supposed to be about connecting with people and communicating with them, and a new option is on the way -- voice messaging. As anyone who has signed up for LinkedIn will know, it's very common to be hit with a barrage of connection requests and messages from people you don't know. Now there's yet another way to get frustrated with needless communication which will almost certainly go one of three ways: getting ignored completely, being referred to email like most modern communication, or just having a phone call for efficiency. LinkedIn poses the question: "Have you ever typed… [Continue Reading] -

Twitter to suspend users who repeatedly post abusive comments on Periscope
Publié: juillet 28, 2018, 6:45pm CEST par Mark Wycislik-Wilson
As part of its continuing attempts to clean up its platform, Twitter has announced that it is going to apply its rules more strictly on Periscope. Starting in mid-August users who repeatedly post abusive comments or harass others run the risk of being banned. Twitter will enforce its guidelines more aggressively during live broadcasts. The company says that it will "review and suspend accounts for repeatedly sending chats that violate" its rules. See also: Twitter responds to Donald Trump's allegations that Republicans are being shadow banned Twitter removes 143,000 apps, now requires developers to request API access How to edit… [Continue Reading] -

Amazon finally lets users collaborate on lists
Publié: juillet 27, 2018, 4:04pm CEST par Mark Wycislik-Wilson
After years of pleading from its customers, Amazon is finally making it possible to collaborate on lists on the site. While it has long been possible to share a personal list with friends and family, the ability to allow other people access has remained a distant dream -- aside from the event-specific Wedding Registry feature. At long last, people are now able to contribute to a shared list for any sort of event. See also: Microsoft joins forces with Walmart to take on Amazon with cloud technology Amazon introduces its largest and fastest tablet for kids Alexa for Hospitality brings… [Continue Reading] -

Microsoft reveals all in Surface Go unboxing video
Publié: juillet 27, 2018, 12:20pm CEST par Mark Wycislik-Wilson
Microsoft's Dona Sarkar has taken to Twitter to share Surface Go unboxing videos. Due for release next week -- August 2, to be precise -- the Surface Go was revealed just a couple of weeks ago. Microsoft has already shared a few videos of its upcoming tablet on YouTube, but the new videos show Dona Sarkar and Brandon LeBlanc from the Windows Insider team getting hands on. See also: This is Microsoft Surface Go Microsoft Surface Go now available to pre-order Microsoft releases several Surface Go videos on YouTube Costco selling exclusive Microsoft Surface Go variant with free Type Cover… [Continue Reading] -

New Google policies ban cryptocurrency miners from the Play Store
Publié: juillet 27, 2018, 11:19am CEST par Mark Wycislik-Wilson
Google has issued an update to its Play Store policies banning cryptocurrency mining apps. A new addition to the Developer Policy Center now explicitly states: "We don't allow apps that mine cryptocurrency on devices. We permit apps that remotely manage the mining of cryptocurrency". Google has also introduced a number of other restrictions including a ban on apps that allow for the sale of firearms. Cryptocurrency exchange Binance halts trading after detecting irregular SYS trading activity Facebook relaxes its ban on cryptocurrency ads Apple slaps a ban on cryptocurrency mining apps Google's cryptomining restrictions come more than a month after… [Continue Reading] -

HipChat and Stride to close as Atlassian sells assets to rival Slack
Publié: juillet 27, 2018, 10:38am CEST par Mark Wycislik-Wilson
Slack and its rivals Atlassian have announced they are forming a strategic partnership that will see chat tools HipChat and Stride closed down. As part of the deal, Atlassian has made an equity investment in Slack, while Slack has acquired the intellectual property rights for Stride and HipChat Cloud. Moving forward, Stride, HipChat Cloud, HipChat Server and HipDhat Data Center will all be discontinued, and users will be offered a migration path to Slack -- making it even stronger competition for Microsoft's Teams. Slack says that the new partnership is driven by a joint vision, and Atlassian notes that "the… [Continue Reading] -

Infowars' Alex Jones is banned from Facebook for a month
Publié: juillet 27, 2018, 9:44am CEST par Mark Wycislik-Wilson
Following on from a strike for violating YouTube policies, Infowars founder Alex Jones has been hit with sanctions by Facebook for contravening its community standards. The social network -- which just dropped in value -- removed four of Jones' videos for violating its policies and banned the right-wing conspiracy theorist from using his account for 30 days. In the event of further policy breaches by Jones or his admins, his page could be permanently banned. See also: YouTube slaps Alex Jones with another strike and removes Infowars founder's videos Facebook value plummets by $118bn and Zuckerberg's fortune drops $16bn following… [Continue Reading] -

Twitter responds to Donald Trump's allegations that Republicans are being shadow banned
Publié: juillet 26, 2018, 7:26pm CEST par Mark Wycislik-Wilson
Out of the blue today, Donald Trump took to his favorite medium of Twitter to complain that the company was "shadow banning" prominent Republicans -- and it wasn't long before Donald Trump Jr sided with his father. The allegations stem from a Vice article that suggested Twitter was limiting the visibility of searches for key Republican figures -- something Twitter denies. The company says that a bug is to blame and it is actively working on addressing it. See also: Twitter removes 143,000 apps, now requires developers to request API access How to edit tweets with Covfefe so you don't… [Continue Reading] -

Facebook value plummets by $118bn and Zuckerberg's fortune drops $16bn following privacy scandal-fueled growth slowdown
Publié: juillet 26, 2018, 6:18pm CEST par Mark Wycislik-Wilson
Facebook shares and the personal fortune of Mark Zuckerberg took massive hits as the social network felt the impact of a growth slowdown and the fallout of recent privacy scandals. The company issued a warning to investors about a deceleration of growth in its userbase, leading to a stock drop of around 20 percent. A drop in share price lowered the value of Facebook by a massive $118 billion -- a record-breaking one-day drop in the value of a company. See also: Privacy: Facebook suspends data analytics firm Crimson Hexagon Google, Facebook, Microsoft and Twitter team up on open source… [Continue Reading] -

Chrome has a secret Material Design mode -- here's how to enable it
Publié: juillet 26, 2018, 1:00pm CEST par Mark Wycislik-Wilson
With the launch of Chrome 68 a few days ago, Google changed the way it handled non-HTTPS websites. But the browser update also hides a secret -- a Material Design mode that you can enable by tinkering with the relevant hidden settings. The new look is currently available on the desktop and in the iOS version of Chrome, and it gives the browser a much cleaner, fresher look and a bit of a UI rejig. See also: Brace yourself for a slew of security warnings from Chrome Chrome will stop highlighting HTTPS sites as secure Chrome's RAM usage is higher… [Continue Reading] -

Google releases fourth and final Android P beta ahead of official launch
Publié: juillet 26, 2018, 11:25am CEST par Mark Wycislik-Wilson
We may not yet know for certain what it's going to be called, but we now have a very good idea of what to expect from Android P -- or Android 9.0, if you prefer. After numerous developer previews, Google has now released the fourth and final beta ahead of the official launch later this summer. This is very close to the final code that will be pushed to phones in the coming weeks and months, and Google says that "Beta 4 update includes a release candidate build with final system behaviors and the official Android P APIs (API level… [Continue Reading] -

Google launches Titan Security Key... that is nothing to do with Yubico
Publié: juillet 26, 2018, 10:47am CEST par Mark Wycislik-Wilson
Google now has its own hardware security keys -- the Titan Security Key. These FIDO-compatible keys include Google firmware that verifies the integrity of security keys at the hardware level. The Titan Security Key offers secure hardware-based two-factor authentication, and is available to Google Cloud customers. The keys are similar to those offered by Yubico -- so similar, in fact, that the company has gone out of its way to stress that it is not manufacturing the devices for Google. See also: Google (sort of) redirects Duck.com to DuckDuckGo after complaints of anti-competitive behavior from its search rival Google, Facebook,… [Continue Reading] -

YouTube slaps Alex Jones with another strike and removes Infowars founder's videos
Publié: juillet 26, 2018, 9:34am CEST par Mark Wycislik-Wilson
YouTube has taken action against Infowars' Alex Jones, hitting him with a strike and removing four of the right-wing conspiracy theorist's videos from its platform. The videos -- two about Muslims, one about transgender people and one about "preventing liberalism" -- were removed for violating YouTube policies about hate speech and child endangerment. Infowars has hit back by saying that YouTube is violating its own policies in taking down the videos. YouTube has a three strikes policy which can see channels closed down completely, but this is something that Alex Jones has managed to escape this time. Although YouTube found… [Continue Reading] -

Microsoft adds AI smarts to Windows 10 to avoid inconvenient update reboots -- but it's a dictatorial waste of technology
Publié: juillet 26, 2018, 3:34am CEST par Mark Wycislik-Wilson
Microsoft has just released Microsoft released Windows 10 Redstone 5 Build 17723 and Redstone 6 (19H1) Build 18204 and one of the new features is a new system that avoids restarts at awkward times following the installation of an update. This sounds great, and Microsoft says that people have complained about this very scenario. But is an artificial intelligence or machine learning powered system really what's needed? How about just leaving users in charge to choose when their computer restarts. There you go, Microsoft; I fixed that for you. See also: Microsoft releases Windows 10 Redstone 5 Build 17723 and… [Continue Reading] -

Microsoft adds Dark Mode to Outlook.com
Publié: juillet 26, 2018, 3:00am CEST par Mark Wycislik-Wilson
There have been a number of sites and apps that have gained dark modes in the last year -- macOS and YouTube to name but two -- and Microsoft doesn't want to miss the trend. The company has heard the pleas of Outlook.com users and added a new Dark Mode option to its web-based email service. The feature is one of the most frequently requested, and users got a preview of the new Dark Mode earlier in the month. Now it's rolling out to everyone, and Microsoft is using it as an excuse to try to push Outlook.com users to… [Continue Reading] -

A terrifying number of big-name websites are not secure -- is yours?
Publié: juillet 25, 2018, 1:48pm CEST par Mark Wycislik-Wilson
There has been a long-standing movement trying to make the web a safer place. For some time, Google's Chrome browser has alerted people when they are visiting secure sites, but with the launch of Chrome 68, it instead warns when an insecure site is encountered. As we warned just a couple of days ago, the latest update to Chrome means you're likely to see warnings about a lot of insecure sites -- and there are some big-name sites being shamed. Included on the non-HTTPS list are some of Google's own sites, the BBC, the Daily Mail and Fox News. And… [Continue Reading] -

Twitter removes 143,000 apps, now requires developers to request API access
Publié: juillet 25, 2018, 10:37am CEST par Mark Wycislik-Wilson
As part of its continuing efforts to clean up the platform, Twitter has removed 143,000 apps in the last three months for policy violations. To help reduce the need for such measures in the future, the company has also introduced a new registration system that means developers must now request access to Twitter's APIs. The change is a significant one, and with it Twitter will be hoping to prevent the appearance of malicious apps in the first place -- making its job easier and improving the overall experience for users. See also: How to edit tweets with Covfefe so you… [Continue Reading] -

Apple confirms MacBook Pro Core i9 throttling bug and fixes it with a software update
Publié: juillet 25, 2018, 9:28am CEST par Mark Wycislik-Wilson
Apple has released a patch which addresses a serious performance issues with its latest MacBook Pros -- and it could double the speed of your new laptop. Called "macOS High Sierra 10.13.6 Supplemental Update for MacBook Pro (2018) ", the patch fixes a throttling issue that was brought to light recently that saw massive performance reduction when running power-intensive tasks. Apple says that a software bug was to blame, causing thermal management software to perform too aggressively. See also: Apple's big 2018 MacBook Pro keyboard cover-up Apple starts selling exclusive Blackmagic eGPU to boost MacBook Pro performance Apple updates MacBook… [Continue Reading] -

Blockchain startup TRON acquires BitTorrent
Publié: juillet 25, 2018, 8:46am CEST par Mark Wycislik-Wilson
BitTorrent Inc says that it has been acquired by TRON, a blockchain startup, to create "the world's largest decentralized ecosystem". There have been rumors about the acquisition for a few weeks now, but the news has now been confirmed. TRON is thought to have paid $126 million in cash for company, and the two teams will merge and pool their talent resources. TRON shares BitTorrent's vision of a decentralized web, saying that the file sharing giant's pioneering technology "is the foundation of an open, transparent, shared Internet protocol". The acquisition means that TRON now owns the BitTorrent company as well… [Continue Reading] -

Apple Pay support is coming to eBay Marketplace, along with loans for sellers
Publié: juillet 24, 2018, 5:55pm CEST par Mark Wycislik-Wilson
Later this year you'll be able to use Apple Pay to pay for goods bought on eBay. Starting in the fall, Apple Pay will be a payment option on eBay's Marketplace platform as the company continues to move away from PayPal. eBay has also announced that it is teaming up with Square Capital so that it can offer business financing to sellers in the US. Aimed at targeting small businesses looking to grow, the new partnership will provide access to finance from options between $500 and $100,000. See also: PayPal now offers payments in Gmail, Google Pay, YouTube and more… [Continue Reading] -

Microsoft opens Skip Ahead ring for Insider builds of Windows 10 Redstone 6
Publié: juillet 24, 2018, 7:40am CEST par Mark Wycislik-Wilson
Microsoft has announced that the Skip Ahead ring has been opened for people who want to get the first look at the Windows 10 Redstone 6. Back with the release of Windows 10 build 17713, Microsoft announced it was "doing a complete reset of Skip Ahead". This is now complete, so you can sign up for the preview ring once again. Spaces are limited, so if you want to take part you're going to have to be quick -- once the maximum number of participants has been reached, Skip Ahead will close once again. See also: How to download offline… [Continue Reading] -

Nintendo spoils retro gamers' fun by shutting a popular Game Boy Advance emulator and two ROM sites
Publié: juillet 24, 2018, 7:10am CEST par Mark Wycislik-Wilson
Following on from lawsuits files against console ROM sites LoveROMS.com and LoveRETRO.co, Nintendo has succeeded in getting a Game Boy Advance emulator removed from GitHub. The company filed a DMCA request asking that a JavaScript-based emulator that enabled retro gamers to enjoy the likes of Mario in their web browser be removed, GitHub has complied with the request meaning that the emulator is now longer available through the site. See also: Gentoo Linux Github Organization repo hack was down to a series of security mistakes Gentoo Linux Github Organization hacked and repo code compromised Microsoft officially announces agreement to acquire… [Continue Reading] -

The Document Foundation distances itself from unofficial LibreOffice app in the Microsoft Store
Publié: juillet 23, 2018, 7:33pm CEST par Mark Wycislik-Wilson
Earlier today we wrote about the sudden appearance of a new LibreOffice app in the Microsoft Store. There were a couple of peculiarities about the app -- not only was it made by an unknown developer, but it came with a price tag. Now The Document Foundation -- the organization behind the LibreOffice office suite -- has spoken up to say that the app is not official and to point out that it is not getting any money from it. SEE ALSO: Free, open source office suite LibreOffice arrives in the Microsoft Store -- with a price tag The Document Foundation says… [Continue Reading] -

Brace yourself for a slew of security warnings from Chrome
Publié: juillet 23, 2018, 6:37pm CEST par Mark Wycislik-Wilson
Tomorrow -- Tuesday, 24 July -- sees the release of Chrome 68. Many people will regard this as just another browser update, but the release sees an important change to the way Chrome handles unencrypted websites. The new way in which non-HTTPS sites are handled means that Chrome is going to start throwing up warning messages whenever an insecure site is encountered -- a reversal of the way things have been up until now. See also: Chrome's RAM usage is higher than ever as Google introduces Site Isolation to fight Spectre Google doubles down on Chrome extension security by blocking… [Continue Reading] -

Snapchat is shuttering peer-to-peer money transfer service Snapcash
Publié: juillet 23, 2018, 8:54am CEST par Mark Wycislik-Wilson
Snapchat confirmed that it is closing down Snapcash next month. The peer-to-peer money transfer service is due to shut up shop on 30 August. The closure was not officially announced by Snapchat initially, but references to "Snapcash deprecation" were spotted in the code of the Android app. The company has now confirmed that Snapcash is coming to an end after four years. Launched back in 2014, Snapcash provided Snapchat users with an easy way to send money to other, but itfailed to attract much interest outside of paying for adult content. The company has not revealed the reason for the… [Continue Reading] -

Free, open source office suite LibreOffice arrives in the Microsoft Store -- with a price tag
Publié: juillet 23, 2018, 8:28am CEST par Mark Wycislik-Wilson
LibreOffice is one of many free alternatives to Microsoft Office, and the open source office suite has now arrived in the Microsoft Store. While many people will be pleased by the appearance of a Store version of the software, some will be disappointed to find that the app is not free. At least not at first glance. There's a $2.99 price tag attached to Libre Office, but this is not necessarily a reason to let this put you off. See also: The Document Foundation distances itself from unofficial LibreOffice app in the Microsoft Store Microsoft revenue pushes past $100bn, buoyed… [Continue Reading] -

Privacy: Facebook suspends data analytics firm Crimson Hexagon
Publié: juillet 22, 2018, 4:54pm CEST par Mark Wycislik-Wilson
Facebook has severed ties with data analytics company Crimson Hexagon because of concerns about its links to the US government, Russia and Turkey. In a move that has echoes of the Cambridge Analytica scandal, Facebook has suspended the company and blocked it from accessing user data because of fears about how that data is used. Crimson Hexagon claims to have gathered more than one trillion pieces of data about social media users, and there are concerns that this data could be used for surveillance purposes. See also: Google, Facebook, Microsoft and Twitter team up on open source Data Transfer Project… [Continue Reading] -

How to edit tweets with Covfefe so you don't embarrass yourself on Twitter
Publié: juillet 22, 2018, 10:39am CEST par Mark Wycislik-Wilson
Twitter: you either love it or hate it. Even if you're a Twitter lover, there's probably plenty you dislike about it! People have complained about tweets being too short, and Twitter fixed this. People complained about not being verified, and Twitter (temporarily, at least) opened up verification to everyone. People have complained about not being about to edit tweets -- and Twitter has done nothing about it. But that's not to say someone hasn't been working on a solution. Using a new Chrome extension, you can effectively gain the ability to edit your tweets and save yourself the embarrassment of… [Continue Reading] -

Microsoft revenue pushes past $100bn, buoyed by Surface and cloud services
Publié: juillet 21, 2018, 9:51am CEST par Mark Wycislik-Wilson
Microsoft reported its Q4 earnings for the year, and the company posted extremely strong results helped in large parts by the performance of its cloud services and Surface business. The company far-exceeded analysts' predictions for this quarter, with revenue of $30.1 billion, net income of $8.8 billion and earnings per share of $1.14. Microsoft's continued move to the cloud is paying off. Revenue in Intelligent Cloud increased by 23 percent to $9.6 billion, while Azure revenue growth rocketed by 89 percent, and Surface revenue went up by 25 percent as talk turns to the possibility of a Surface Phone. See… [Continue Reading] -

Google (sort of) redirects Duck.com to DuckDuckGo after complaints of anti-competitive behavior from its search rival
Publié: juillet 21, 2018, 8:12am CEST par Mark Wycislik-Wilson
Google may have been slammed by Europe for using Android to dominate with its search engine, but this is not the only complaint that has been leveled at the company. Privacy-focused search rival DuckDuckGo has criticized Google for sending visitors to Duck.com to the Google search page. Google owns Duck.com, but DuckDuckGo believes the company has been confusing users with the redirect. Now, following publicity of the issue, Google has relented and says it is introducing a new landing page that will give visitors to Duck.com the opportunity to jump to the DuckDuckGo search engine as well as other pages.… [Continue Reading] -

Google, Facebook, Microsoft and Twitter team up on open source Data Transfer Project to ease your data moving woes
Publié: juillet 20, 2018, 6:04pm CEST par Mark Wycislik-Wilson
Four giants of the technology world have joined forces in an attempt to make it easier for people to move data between services. The collaboration between Google, Facebook, Microsoft and Twitter takes the form of the open source Data Transfer Project, the aim of which is to make it possible to "transfer data directly from one service to another, without needing to download and re-upload it". The four companies joining announced the data portability platform which currently makes use of public APIs to offer support for photos, mail, contacts, calendars and tasks from the founders as well as other companies… [Continue Reading] -

Who cares what Trump thinks about Europe's record fine for Google?
Publié: juillet 20, 2018, 10:09am CEST par Mark Wycislik-Wilson
It's just days since the Europe hit Google with a record fine for what it described as "very serious illegal behavior" in an antitrust case about the company's abuse of Android to dominate the competition. Unsurprisingly, a lot of people have an opinion not only about the way Google has acted, but also of the European commission's ruling itself. Among those with an opinion to share is none other than Donald Trump who used the fine as a way to paint the US as a victim at the hands of Europe. See also: EU hits Google with record €4.34bn fine… [Continue Reading] -

If you want to get verified on Twitter, you'll have to wait until after the US mid-terms
Publié: juillet 18, 2018, 3:14pm CEST par Mark Wycislik-Wilson
Attaining a blue tick of verification remains a goal for many Twitter users, but it remains elusive for most. It is quite some time since Twitter paused the option for anyone to request verification, and now the company has revealed that opening it back up is far from a priority. The idea behind pausing the application process was to give the company the opportunity to work on fixing what was seen as a broken verification system. Product lead Kayvon Beykpour says that Twitter doesn't have the "bandwidth" to sort things out right now, and instead needs to concentrate on sorting… [Continue Reading] -

EU hits Google with record €4.34bn fine for 'very serious illegal behaviour' in Android antitrust case
Publié: juillet 18, 2018, 2:10pm CEST par Mark Wycislik-Wilson
The European Commission has fined Google a record €4.34 billion ($5 billion) in an antitrust case that saw the company accused of using Android as a "vehicle to cement its dominance as a search engine". The Commission said that Google forced phone makers to pre-install its software on their handsets, taking advantage of Android's popularity, and breaching European antitrust rules. The EU competition commissioner Margrethe Vestager summed things up by saying Google has been "denying rivals a chance to innovate and compete on the merits". See also: Chrome's RAM usage is higher than ever as Google introduces Site Isolation to… [Continue Reading] -

Microsoft is killing off Skype classic and bringing call recording to Skype 8.0
Publié: juillet 17, 2018, 1:53pm CEST par Mark Wycislik-Wilson
Microsoft has announced that Skype 7.0 (also known as Skype classic) is to be killed off, forcing all users to move on to the "modern" Skype 8.0. The company says that from September 1, only the new version of Skype will work, and this is something that is likely to upset users who were unhappy at the redesign that was introduced nearly a year ago. To soften the blow, Microsoft has updated Skype 8 with a range of new features, and says that other new options -- including the ability to record Skype calls -- are on their way too.… [Continue Reading] -

Instapaper is gaining independence
Publié: juillet 17, 2018, 1:25pm CEST par Mark Wycislik-Wilson
The bookmarking service Instapaper has announced that it is going independent. Five years after being bought by betaworks, ownership is to switch to a new company called Instant Paper, Inc. Two years ago, Instapaper was sold to Pinterest, and the switch to independence is likely to be welcomed by its many users. Practically speaking, going independent should mean that very little changes, but the company is giving users three weeks' notice of what’s happening. In an announcement on the Instapaper blog, the team behind the service says: "Today, we're announcing that Pinterest has entered into an agreement to transfer ownership… [Continue Reading] -

Panos Panay: Microsoft is not working on a Surface Phone
Publié: juillet 17, 2018, 1:01pm CEST par Mark Wycislik-Wilson
If you were getting your hopes up about the possibility of a Surface Phone appearing, we have some bad news. Speaking with Wired, Chief Product Officer at Microsoft Panos Panay said that the company is not working on that form factor. In the course of the interview, Panay said that Microsoft is working on various new form factors for future devices. Asked whether this included the fabled Surface Phone, he dashed the hopes of many -- although news has leaked out recently about a future "pocketable" Surface device. See also: Would this foldable Surface Phone running Windows 10 make you… [Continue Reading] -

Microsoft joins forces with Walmart to take on Amazon with cloud technology
Publié: juillet 17, 2018, 12:44pm CEST par Mark Wycislik-Wilson
Microsoft has announced that it has formed a strategic partnership with retail giant Walmart to help "make shopping faster and easier for millions of customers around the world". The five-year deal between the two companies will see Walmart making use of Microsoft's cloud technology solutions such as Microsoft 365 and Azure. The retailer already uses some Microsoft services, but with the new partnership this expands into cloud tools that use machine learning and artificial intelligence. See also: How to install Microsoft Windows Essentials tools -- including Movie Maker -- on Windows 10 Microsoft calls for government regulation of facial recognition… [Continue Reading] -

US lifts ZTE supplier ban, sending shares soaring
Publié: juillet 16, 2018, 7:31am CEST par Mark Wycislik-Wilson
Chinese telecoms hardware manufacturer ZTE has had something of a rough ride in the US recently, but having agreed to comply with all of the demands made by authorities, the ban on its US operations has been lifted. The US had banned American companies from supplying goods to ZTE, effectively crippling its business. Now, having paid $400 million into an escrow account -- on top of its $1 billion fine last month -- the company is operating again, and its Hong Kong-listed shares jumped 12 percent as a result. But the lifting of the ban is far from being the… [Continue Reading] -

Apple's big 2018 MacBook Pro keyboard cover-up
Publié: juillet 15, 2018, 12:19pm CEST par Mark Wycislik-Wilson
Just a few days ago Apple launched the latest additions to its MacBook Pro range, and the company talked about the fact that the keyboard is quieter. A teardown of the latest devices reveals not only why the keyboards are quieter, but also that the method used seems to serve a secondary purpose -- or maybe that the quietening is itself a secondary purpose. The keyboards of previous MacBook Pros have suffered issues that led to a free repair program being set up. The latest laptop teardown by iFixit shows that Apple has added a silicone membrane beneath each key,… [Continue Reading] -

YouTube launches Copyright Match tool to fight content stealing and duplication
Publié: juillet 15, 2018, 11:41am CEST par Mark Wycislik-Wilson
Eager to encourage content creators to do what they do best -- create content -- YouTube has release a new tool that it hope will help cut down on the problem of video theft and duplication. Called Copyright Match, the new system is different to the existing Content ID system, but it does use a similar matching technology. YouTube says that it has been testing the tool for almost a year and is now ready to open it up to a larger portion of its community See also: YouTube TV offers heartfelt apology for World Cup outage, promises free week… [Continue Reading] -

Adobe is working on Photoshop for iPad
Publié: juillet 15, 2018, 11:03am CEST par Mark Wycislik-Wilson
Apple has long been keen to push the iPad and iPad Pro as a viable laptop alternative, and with a decent selection of apps to choose from it's something that works for many people. There are, however, a number of apps missing that stop some people making the jump from laptop to iPad -- Photoshop being one of them. Sure, at the moment there is Photoshop Express for iOS, but this is a massively cutdown product that simply does not meet the needs of professionals. Answering the prayers of many, Adobe is now said to be working on bringing a… [Continue Reading] -

Microsoft calls for government regulation of facial recognition because of 'potential for abuse'
Publié: juillet 14, 2018, 9:34am CEST par Mark Wycislik-Wilson
Microsoft president Brad Smith has called on government to regulate facial recognition technology, citing concerns that it is open to abuse. While he acknowledges that technology company have a role to play, he that it is down to elected representatives to put rules in place. Using a terrible analogy ("All tools can be used for good or ill. Even a broom can be used to sweep the floor or hit someone over the head.") Smith points out that while facial recognition technology is undeniably useful, there is also potential for it to be "misused and abused by private companies and… [Continue Reading] -

The iPhone 6 is Apple's most problematic handset -- over a fifth suffer some form of failure
Publié: juillet 14, 2018, 9:00am CEST par Mark Wycislik-Wilson
When you spend a few hundred dollars on a phone, you expect it to last you a while. But if you splashed out on an iPhone 6 there's a very high change that you've experienced some sort of problem with your handset. A report shows that the iPhone 6 is by far Apple's least reliable handset, with a staggering 22 percent of them suffering failures. The iPhone 6S isn't far behind, and for Android users, Samsung handsets fare poorly too. See also: Apple offers free Beats and big discounts in its Back to School promotion Apple starts selling exclusive Blackmagic… [Continue Reading] -

Apple offers free Beats and big discounts in its Back to School promotion
Publié: juillet 13, 2018, 9:51am CEST par Mark Wycislik-Wilson
From now until September 25, Apple is running a Back to School promotion, and there are some great offers for students. If you qualify, you can bag yourself a free pair of Beats headphones or earphones when you buy a Mac or iPad Pro -- including the Powerbeats3 Wireless in new Beats Pop Collection colors. There are also special deals on accessories and AppleCare. See also: Apple starts selling exclusive Blackmagic eGPU to boost MacBook Pro performance Apple updates MacBook Pro to deliver faster performance and new pro features Apple releases elegant and pricey Leather Sleeve for MacBook Pro The… [Continue Reading] -

A new free version of Microsoft Teams is ready to compete with Slack
Publié: juillet 13, 2018, 9:01am CEST par Mark Wycislik-Wilson
Microsoft has launched a free version of Teams, the company's collaborative chat tool. Teams has pitted itself against the likes of Slack since it first appeared, but the arrival of a free edition makes it a viable alternative. As this is a free product, it should come as no surprise that there are limitations. However, the free edition of Microsoft Team can still be used by up to 300 people -- the same as the Essentials and Premium versions -- which should be enough to cater for most small to medium sized businesses. So what about those limitations? While the… [Continue Reading] -

Apple starts selling exclusive Blackmagic eGPU to boost MacBook Pro performance
Publié: juillet 12, 2018, 6:30pm CEST par Mark Wycislik-Wilson
As well as refreshing its MacBook Pro line-up, Apple today started to sell the $699 Blackmagic eGPU. This 8GB external GPU features a Radeon Pro 580 to bring more graphic horsepower to laptop users. The aim is to bring desktop-level power to laptop users when they are working on graphic-intensive projects. At a shade under $700, it's not a cheap piece of hardware, but it also doubles up as something of a docking station. See also: Apple updates MacBook Pro to deliver faster performance and new pro features Apple releases iOS 11.4.1 with passcode cracking blocker -- that can be… [Continue Reading] -

Chrome's RAM usage is higher than ever as Google introduces Site Isolation to fight Spectre
Publié: juillet 12, 2018, 2:34pm CEST par Mark Wycislik-Wilson
Google's Chrome browser may be popular, but you'll find a lot of its users complain about high memory usage. With Chrome 67, things just got even worse. If you've noticed that Chrome on the desktop is using more RAM, you're not imagining it. Google has enabled a Site Isolation feature in Windows, Mac, Linux and Chrome OS to help mitigate against the Spectre vulnerability -- and it's a bit memory-hungry. See also: New Spectre 1.1 and Spectre 1.2 CPU vulnerabilities exposed Researchers develop SafeSpec to overcome vulnerabilities like Spectre and Meltdown Spectre and Meltdown variant 4: Microsoft, Google and Intel… [Continue Reading] -

New Spectre 1.1 and Spectre 1.2 CPU vulnerabilities exposed
Publié: juillet 12, 2018, 12:27pm CEST par Mark Wycislik-Wilson
It seems that the Spectre and Meltdown vulnerabilities saga is never-ending, and now there are two new related CPU flaws to add to the mix. Dubbed Spectre 1.1 and Spectre 1.2, the vulnerabilities (CVE-2018-3693) exploit speculative execution and can modify data and bypass sandboxes. Two security researchers have disclosed details of the new vulnerabilities, both of which have the potential to leak sensitive data. By tinkering with the speculative execution processes of Intel and ARM CPUs, it would be possible to use malicious code to extract information such as passwords and crypto keys. See also: Researchers develop SafeSpec to overcome… [Continue Reading] -

Your Twitter follower count is about to drop as part of a clean-up operation
Publié: juillet 12, 2018, 10:27am CEST par Mark Wycislik-Wilson
Over the coming week, you may well notice that you lose a number of Twitter followers. Don't worry, it's (probably) not the result of something you said -- Twitter is having a spring clean and is cutting locked accounts from follower numbers. The company says that the change is being introduced so that everyone's follower counts are "meaningful and accurate" and that they are something people can have confidence in. So just how many followers are you likely to lose? See also: Twitter is suspending more suspicious accounts than ever -- over 70 million in the last two months Twitter… [Continue Reading] -

Timehop admits its security breach was worse than first thought
Publié: juillet 12, 2018, 9:32am CEST par Mark Wycislik-Wilson
The security breach suffered by Timehop on July 4 was much more serious than the company first thought. In an update to its original announcement, the company has revealed that while the number of account affected by the breach -- 21 million -- has not changed, the range of personal data accessed by hackers is much broader. Timehop has released an updated timeline of events, having initially felt forced by new GDPR rules to publish some details of the breach before all information had been gathered. The company says that it is also unsure of where it stands with GDPR,… [Continue Reading] -

Canonical releases Ubuntu Minimal for servers, containers and the cloud
Publié: juillet 12, 2018, 9:01am CEST par Mark Wycislik-Wilson
There's a new version of Ubuntu on the block -- Ubuntu Minimal. It's been stripped right back to the bone to leave a tiny footprint, and these back Linux distros should boot 40 percent faster than a standard Ubuntu server image. Despite the reduced footprint size, Ubuntu Minimal retains all of Ubuntu's standard tools (such as ssh, apt and snapd) and maintain full compatibility. Designed for cloud developers and ops, Canonical says that the release is intended for completely automated operations, and as such much of the user-friendliness has been stripped out, but it's still ideal for used in KVM,… [Continue Reading] -

Canonical releases Minimal Ubuntu for servers, containers and the cloud
Publié: juillet 12, 2018, 9:01am CEST par Mark Wycislik-Wilson
There's a new version of Ubuntu on the block -- Minimal Ubuntu. It's been stripped right back to the bone to leave a tiny footprint, and these back Linux distros should boot 40 percent faster than a standard Ubuntu server image. Despite the reduced footprint size, Minimal Ubuntu retains all of Ubuntu's standard tools (such as ssh, apt and snapd) and maintain full compatibility. Designed for cloud developers and ops, Canonical says that the release is intended for completely automated operations, and as such much of the user-friendliness has been stripped out, but it's still ideal for used in KVM,… [Continue Reading] -

Arch Linux AUR packages found to be laced with malware
Publié: juillet 11, 2018, 5:54pm CEST par Mark Wycislik-Wilson
Three Arch Linux packages have been pulled from AUR (Arch User Repository) after they were discovered to contain malware. The PDF viewer acroread and two other packages that are yet to be named were taken over by a malicious user after they were abandoned by their original authors. A user by the name of xeactor took ownership of acroread and tweaked the source code of the package, lacing it with malware. In this particular instance there were no major consequences, but it highlights the security issues associated with user-submitted software. See also: Canonical releases new infographic to show how Ubuntu… [Continue Reading] -

Leaked: The P in Android P stands for...
Publié: juillet 11, 2018, 4:32pm CEST par Mark Wycislik-Wilson
For a little while now it has been thought that the P in Android P stood for Popsicle -- based largely on speculation and the fact Google shared some popsicle-related images on Instagram. But it seems that this is wrong. A new leak -- this time courtesy of Huawei -- suggests that Google has gone with a nutty theme for the upcoming Android 9.0. See also: Android P: Smarter and simpler than ever Android P could be Android Popsicle Here's what's new in Android P The name hint comes courtesy of Polish site tabletow, or rather one of its readers.… [Continue Reading] -

Hide your viewing and search history with YouTube Incognito Mode
Publié: juillet 10, 2018, 7:04pm CEST par Mark Wycislik-Wilson
Chrome's Incognito Mode is handy for those times you want to hide your browsing history from others on a shared system -- whether it's because you want to keep a birthday gift secret, or there are just sites you visit that you’d rather keep private. Now the same feature is coming to YouTube. Having already undergone a period of testing, Incognito Mode is rolling out to Android users around the world, making it easy to hide evidence of the videos you have been watching, or the type of content you have been searching for. The general rollout of the feature… [Continue Reading] -

Apple releases iOS 11.4.1 with passcode cracking blocker -- that can be easily bypassed with an accessory it sells
Publié: juillet 10, 2018, 6:23pm CEST par Mark Wycislik-Wilson
Apple is working away on iOS 12 at the moment, but it's still pushing out updates for iOS 11. As promised just a few weeks ago, a new update aims to block the use of iPhone passcode cracking tools, such as those used by law enforcement. But the patch has already been found to be flawed. The latest update to iOS introduces a new USB Restricted Mode which is supposed to prevent the Lightning port of an iPhone or iPad being used to transfer data an hour after the device is locked. However, security researchers discovered that it is possible… [Continue Reading] -

Microsoft Surface Go now available to pre-order
Publié: juillet 10, 2018, 5:07pm CEST par Mark Wycislik-Wilson
There might be interest in a Surface Phone, but for now there's the Surface Go to enjoy. Revealed late yesterday, the Surface Go is described as Microsoft's "smallest, lightest Surface yet" -- and it's available to pre-order right now. Unfortunately, there's no discount for jumping on a pre-order, but if you're quick, you should be able to guarantee that you'll get one when it launches on August 2. The tablet will cost you $399, but you'll need to purchase a Signature Type Cover separately if you want to type rather than using the on-screen keyboard, and a Surface Pen if… [Continue Reading] -

Google Pay gains support for tickets and boarding cards, friend and family payments, and a web app
Publié: juillet 10, 2018, 4:44pm CEST par Mark Wycislik-Wilson
Google continues to expand the capabilities of Google Pay, and today the company launched a new series of updates. Catching up with the likes of Apple Pay, Google's own digital wallet can now be used to store boarding cards and tickets. While this is something that is already catered for by other apps -- such as those from airlines and box offices -- Google is clearly hoping that its "everything under one roof" approach will attract users. In addition to the new ticketing option, Google Pay is also combining the Google Pay and Google Pay Send apps. See also: How… [Continue Reading] -

Samsung opens the world's largest mobile factory in India
Publié: juillet 9, 2018, 3:22pm CEST par Mark Wycislik-Wilson
Today Samsung is opening what it describes as the world's biggest mobile phone manufacturing facility. The factory is opening in India as the South Korean giant looks to take advantage of the fastest-growing mobile market. Located in Noida on the outskirts of New Delhi, the new facility will give Samsung the ability to output handsets at an unprecedented rate -- said to be up to 120 million smartphones a year. See also: Privacy warning: Samsung phones are leaking photos to random contacts Pandora Premium now available on Samsung Smart TVs Samsung will launch Galaxy Note 9 in early August Manufacturing… [Continue Reading] -

Fitness app Polar Flow exposed names and locations of thousands of military, NSA and FBI staff
Publié: juillet 9, 2018, 11:20am CEST par Mark Wycislik-Wilson
It's not all that long since fitness app Strava caused something of a security nightmare by inadvertently revealing the locations of numerous secret military bases. Now another app -- Polar Flow this time -- has gone a step further and revealed the names and home addresses of nearly 6,500 users. A joint investigation by Bellingcat and Dutch journalism platform De Correspondent found that the app is "revealing the homes and lives of people exercising in secretive locations, such as intelligence agencies, military bases and airfields, nuclear weapons storage sites, and embassies around the world". See also: Google responds to Gmail… [Continue Reading] -

Hacked: Timehop database breach exposed details of 21 million users
Publié: juillet 9, 2018, 9:41am CEST par Mark Wycislik-Wilson
Timehop -- the social network for those who like to reminisce -- has revealed that it fell victim to a security breach on Independence Day. The attacker managed to access an internal database stole the personal data of 21 million users from Timehop's Cloud Computing Environment. The vast majority of those affected by the "security incident" (as Timehop refers to it) had their names and usernames exposed, but for nearly a quarter of them -- 4.7 million -- phone numbers were also exposed. The hacker also took access tokens which could be used to view users' posts. See also: Gentoo… [Continue Reading] -

Seagate launches low-cost, consumer-grade BarraCuda SSD
Publié: juillet 8, 2018, 9:49am CEST par Mark Wycislik-Wilson
Seagate is no stranger to the world of SSDs, but it has shied away from the consumer market in this area, choosing instead to focus on the enterprise market. Now that changes. The company has launched a new consumer-grade SSD -- the BarraCuda SSD -- aimed squarely at the home consumer looking to give their PC or laptop a boost by making the switch to a solid-state drive. Starting at $75, pricing is highly enticing... but there is a slight catch. The price is probably something of a giveaway, but the BarraCuda SSD is a SATA III drive rather than… [Continue Reading] -

Twitter is suspending more suspicious accounts than ever -- over 70 million in the last two months
Publié: juillet 7, 2018, 3:52pm CEST par Mark Wycislik-Wilson
Twitter has revealed that in May and June it suspended more than 70 million accounts as it continues its battle against trolls, fake profiles, bots and abuse. Closing down over a million accounts a day means that Twitter has more than doubled its rate of clamping down since October, and the suspension rate is continuing into this month. The company confirmed the figures to the Washington Post, but refused to comment on what this might mean for overall user numbers. See also: Twitter tries to fight spam by forcing new users to verify their email or phone number Judge: President… [Continue Reading] -

People really want Microsoft to launch a Surface Phone
Publié: juillet 7, 2018, 9:41am CEST par Mark Wycislik-Wilson
There has been a lot of talk about the possibility of a Surface Phone (or Project Andromeda), but so far rumors have amounted to very little. Recently, however, documents leaked that showed plans for a "pocketable folding Surface device" and levels of interest and excitement rose. Now a petition has appeared online to try to show Microsoft just how much interested there is in a Surface Phone. The title of the petition -- "Show Microsoft the demand for the Surface Phone or Andromeda!" -- is self-explanatory, and it has gathered a great deal of support in a single day. See… [Continue Reading] -

Netflix is killing off user reviews, reducing ratings to thumbs up and thumbs down
Publié: juillet 7, 2018, 8:58am CEST par Mark Wycislik-Wilson
Reviews are a handy way to gauge whether or not your going to like something -- be it a game, a piece of hardware, an app, or a movie. Netflix, however, seems to think differently, and has taken the decision to kill off the user reviews feature of its website. As part of a staggered cull, Netflix will stop users from writing reviews at the end of July. By the middle of August, it will no longer be possible to read existing reviews. Moving forward, the only sort of feedback users will be able to give is a simple thumbs… [Continue Reading] -

Gentoo Linux Github Organization repo hack was down to a series of security mistakes
Publié: juillet 6, 2018, 6:12pm CEST par Mark Wycislik-Wilson
The team behind Gentoo Linux has revealed the reasons for the recent hack of its GitHub organization account. The short version: shoddy security. It seems that the hackers were able to gain access to the GitHub organization account by using the password of one of the organization administrators. By the team's own admission, poor security meant that the password was easy to guess. As the Register points out, "only luck limited the damage", but the Gentoo Linux team is keen to let it be known that it has learned a lot from the incident. See also: Gentoo Linux Github Organization… [Continue Reading] -

Apple Music just may have overtaken Spotify in the US
Publié: juillet 6, 2018, 5:40pm CEST par Mark Wycislik-Wilson
A new report suggests that Apple may have succeeded in attracting more subscribers to Apple Music than have signed up to Spotify -- in the US, at least. While this is far from official -- with the report being based on an anonymous source -- it is in keeping with the general feeling from earlier in the year when it was thought that Apple Music probably was going to overtake Spotify in the near future. See also: In iOS 12 Apple is completely rebuilding Maps from the ground up I declare independence from Apple (and mean it this time) Belkin… [Continue Reading] -

Cryptocurrency exchange Binance halts trading after detecting irregular SYS trading activity
Publié: juillet 4, 2018, 12:37pm CEST par Mark Wycislik-Wilson
Binance -- the largest cryptocurrency exchange in the world -- temporarily halted all trading after it detected "irregular trading on some APIs". As a precautionary measure, the exchange removed all existing API keys and asked users to re-create theirs from their accounts. The measure meant a suspension of trading, withdrawals and other account activity. The matter is related to the Bitcoin fork Syscoin which halted deposits and withdrawals, but Binance stressed that there had not been as hack and that its blockchain is safe. Both Binance and Syscoin have promised that more information will be shared soon about what happened.… [Continue Reading] -

Google responds to Gmail privacy concerns: 'we're not reading your emails'
Publié: juillet 4, 2018, 9:24am CEST par Mark Wycislik-Wilson
Another day, another privacy concern. Following a Wall Street Journal story about the access third party apps have to Gmail data, we wrote about how to stop it. While the WSJ did not really make any major new revelations, it did manage to reignite the conversation about privacy, and Google has responded to storm that has built up around it. The company has used a blog post to respond to the concerns raised by the Wall Street Journal, insisting that it carefully vets any third party that has access to sensitive data. The task has been left to Suzanne Frey… [Continue Reading] -

Privacy warning: Samsung phones are leaking photos to random contacts
Publié: juillet 3, 2018, 7:14pm CEST par Mark Wycislik-Wilson
If you have a Samsung Galaxy S9, S9+ or Note 8, you might want to check that your contacts haven't got hold of some of your photos. Some owners of the handsets are reporting that the Samsung Messages SMS app has been sending out images from their camera rolls to random contacts. Worryingly, many people who were affected by the privacy-invading leaks were only made aware of the problem when their friends asked about the images they'd received -- the Messages app does not reveal that anything has been sent. Samsung says that it is aware of the issue and… [Continue Reading] -

SUSE Linux sold for $2.535 billion
Publié: juillet 3, 2018, 6:37am CEST par Mark Wycislik-Wilson
British firm Micro Focus International is selling its open source SUSE software to the Swedish group EQT Partners. The $2.535 billion deal boosted shares by 6 percent. SUSE Linux has been in the hands of Micro Focus International since 2014 and it has been running it as a largely independent division, competing directly with the likes of Ubuntu and Red Hat. The acquisition by EQT Partners means that more developers and engineers will be hired to work on the product. See also: Ubuntu-based Bodhi Linux 5.0.0 release candidate now available Linux Mint 19 'Tara' now available for download with Cinnamon,… [Continue Reading] -

Facebook bug secretly unblocked people you thought you'd blocked
Publié: juillet 3, 2018, 5:59am CEST par Mark Wycislik-Wilson
Facebook is primarily about connecting with other people, but its "block" functionality certainly has its place for avoiding those you don't want to be in touch with for one reason or another. It's a great option to have... until it goes wrong. And that's precisely what happened. The social network has admitted that more than 800,000 were hit by a bug that meant people they had blocked on either Facebook or Facebook Messenger were temporarily unblocked and able to see content that had been posted. See also: Facebook relaxes its ban on cryptocurrency ads World Cup: access the hidden mini… [Continue Reading] -

Dell could be about to go public again
Publié: juillet 2, 2018, 11:15am CEST par Mark Wycislik-Wilson
A report by the Wall Street Journal suggests that Dell could be on the verge of becoming a public company once again. The deal could be announced as soon as later today and -- if the cited sources close to Dell are correct -- it would see the company swapping the "trading stock" it created when it bought EMC a couple of years ago. It would simplify Dell's current structure, seen by many as overly complicated, and make use of the stock that tracks VMware Inc. The deal is not yet thought to have been finalized, and the paper warns… [Continue Reading] -

OnePlus announces 8GB OnePlus 6 Red, launching July 10
Publié: juillet 2, 2018, 10:47am CEST par Mark Wycislik-Wilson
OnePlus is no stranger to launching multiple versions of its flagship-killing handset, and things are no different with the OnePlus 6. Joining the existing line-up soon is the OnePlus 6 Red -- and the price is pretty appealing. While previous models of the OnePlus 6 have borne the tag "The speed you need", this one is also billed as being "The Red you need". Kitted out with 128GB of storage and 8GB of RAM, and powered by a Qualcomm Snapdragon 845, speediness -- as well as redness -- should not be a concern. The OnePlus 6 Red is hardly unique… [Continue Reading] -

The NSA is deleting all of its call records since 2015 because of privacy issues
Publié: juillet 1, 2018, 10:16am CEST par Mark Wycislik-Wilson
The NSA -- not exactly a bastion of privacy -- has announced that it is deleting hundreds of millions of call and text records because of "technical irregularities". The agency says that back in May this year is started to delete all of the calls records it collected since 2015. While full details of the reasons for the deletion are not given, the NSA notes that it collected data it was not authorized to collect. It is not clear how far through the process of deleting all of the unauthoratized records the NSA is, or how long it will take… [Continue Reading] -

aLTEr: Hackers can spy on your 4G browsing sessions thanks to LTE flaws
Publié: juin 30, 2018, 9:49am CEST par Mark Wycislik-Wilson
Vulnerabilities have been discovered in LTE that would make it possible for an attacker to tap into 4G networks for the purposes of spying on and hijacking 4G browsing sessions. Security researchers from Ruhr-Universität, Bochum and New York University, Abu Dhabi show how three different attacks can be launched on the second layer of LTE -- also known as the data link layer. Two passive attacks allow for identity mapping and website fingerprinting, while the active cryptographic aLTEr attack allows for DNS spoofing and network connection redirection. The researchers, David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina Pöpper, are due… [Continue Reading] -

Leaked Microsoft documents reveal 'pocketable' folding Surface device
Publié: juin 30, 2018, 9:06am CEST par Mark Wycislik-Wilson
Microsoft's Surface range could one day include a folding, dual-screen device. Codenamed Andromeda, the device has been in the works for a couple of years and appears to neatly straddle the laptop and mobile categories -- seemingly trying to make up for Windows Phone. Leaked internal documents have come to light that reveal Microsoft's plans for "a new pocketable Surface device form factor that brings together innovative new hardware and software experiences to create a truly personal and versatile computing experience". See also: Microsoft pulls the plug on Windows 10's game-changing Sets feature -- for now Microsoft has the patent… [Continue Reading] -

Adidas data breach may have exposed personal data of American customers
Publié: juin 29, 2018, 8:50pm CEST par Mark Wycislik-Wilson
Sportswear company Adidas has warned US customers about a security breach that took place earlier this week. The firm says that on Tuesday it was made aware that "an unauthorized party claims to have acquired limited data associated with certain Adidas consumers". Two days later, the company started to notify its customers that personal data -- including contact information and usernames -- may have been compromised. See also: Gentoo Linux Github Organization hacked and repo code compromised Don't panic! Hackers have not found a way to bypass the iPhone passcode limit Kaspersky: Chinese hackers LuckyMouse hit national data center Adidas… [Continue Reading] -

In iOS 12 Apple is completely rebuilding Maps from the ground up
Publié: juin 29, 2018, 7:28pm CEST par Mark Wycislik-Wilson
When it comes to navigation apps, there's no denying that Google Maps is king -- but Apple is trying to change that. With the impending release of iOS 12 is also coming a complete redesign of the company's own Maps app. Apple is not only rebuilding the app from the ground up, but it is doing so with a combination of "first-party" data gathered by its own camera cars as well as data from iPhone users. The changes are going to start to appear in the next beta version of iOS 12. See also: Apple releases the first public beta… [Continue Reading] -

Gentoo Linux Github Organization hacked and repo code compromised
Publié: juin 29, 2018, 11:28am CEST par Mark Wycislik-Wilson
A hacker managed to take control of the Github account for Gentoo Linux, going as far as inserting malicious code into the distros. The malware was designed to delete user data. Although the situation is now under control, an investigation is underway to determine what happened. Anyone who has downloaded a Gentoo distro or other files recently, is warned to "refrain from using code from the Gentoo Github Organization" for the time being. See also: Microsoft officially announces agreement to acquire GitHub in $7.5 billion deal Google releases open source 'GIF for CLI' terminal tool on GitHub Linux Mint Debian… [Continue Reading] -

OnePlus is looking to come to the US as it promises two years of software updates and a 5G phone
Publié: juin 29, 2018, 10:58am CEST par Mark Wycislik-Wilson
At Mobile World Congress Shanghai, OnePlus CEO and founder Pete Lau said that his company is determined to make a proper entry into the North American market and is working with US carriers to make it happen. OnePlus has also said that it is looking to produce a 5G phone in 2019, and it will take advantage of its relationship with Qualcomm to make this happen. For current and future OnePlus owners, the company also made commitments about software and security updates. See also: Fix on the way for OnePlus 6 bootloader security flaw OnePlus unveils the OnePlus 6 smartphone,… [Continue Reading] -

Google Cloud Platform is gaining Cloud Filestore to offer a file system interface to users
Publié: juin 27, 2018, 1:24pm CEST par Mark Wycislik-Wilson
Google has announced a new storage option for developers using Google Cloud Platform. The new Cloud Filestore is due to launch in beta next month, and it provides a managed NAS in the cloud. Google describes Cloud Filestore as a "managed file storage for applications that require a file system interface and a shared file system", and the aim is to offer higher performance to users that need it than the existing options do. See also: Google rebrands its advertising line-up -- bye bye to AdWords and DoubleClick, hello to Google Ads Google adds DRM to Android APKs to verify… [Continue Reading] -

Twitter tries to fight spam by forcing new users to verify their email or phone number
Publié: juin 27, 2018, 10:46am CEST par Mark Wycislik-Wilson
Twitter -- like many social media platforms -- has its fair share of problems, including trolling, spam, abuse and fake accounts. The company has fought something of a losing battle in trying to regain control of things, but it is confident it has started to make progress. In a blog post in which it shares details of this progress, Twitter also reveals plans to crack down on people who "try to take advantage of our openness". In a bid to cut down on the number of spam accounts that crop up, Twitter is going to require anyone signing up for… [Continue Reading] -

Facebook relaxes its ban on cryptocurrency ads
Publié: juin 27, 2018, 9:58am CEST par Mark Wycislik-Wilson
There has been a spate of bans on cryptocurrency ads in recent months, but Facebook has had something of a change of heart and has decided that some such ads are permissible on its platform. It is important to note that this is just a relaxation of the ban Facebook introduced back in January, not a complete lifting of it. There are various caveats here, including the fact that advertisers will have to be "pre-approved". See also: Apple slaps a ban on cryptocurrency mining apps Twitter to ban an array of cryptocurrency ads Google slaps a ban on cryptocurrency ads… [Continue Reading] -

Cisco Talos releases free decryptor for Thanatos ransomware -- ThanatosDecryptor
Publié: juin 26, 2018, 6:14pm CEST par Mark Wycislik-Wilson
Getting hit by a ransomware attack is bad enough; it means that your files have been encrypted and you'll be asked to pay a fee in a cryptocurrency such as Bitcoin or Ethereum to unlock them. The problem is that paying the ransom is in no way a guarantee that your files will be decrypted -- the ransomware was created by criminals, after all. If you've been struck by the Thanatos ransomware, however, there's good news from Cisco Talos. The company has analyzed the malware and developed a free decryption tool that will enable you to get your files back… [Continue Reading] -

T-Mobile is ready to launch FamilyMode to help parents monitor and control internet and device usage
Publié: juin 26, 2018, 2:29pm CEST par Mark Wycislik-Wilson
Parents have concerns about not only how long their children spend online, but also what they are using various connected devices for. In just a few days' time, T-Mobile is launching its answer to the problem: FamilyMode. This is a service that makes it possible to keep an eye on how long devices are being used for, and to monitor internet usage. FamilyMode uses a hardware base station and a mobile app (available for iOS and Android) to give parents monitoring and control over devices connected via either Wi-Fi or cellular. Available as a subscription service, T-Mobile FamilyMode costs $10… [Continue Reading] -

Report: AT&T is helping the NSA with surveillance using secret buildings throughout the US
Publié: juin 26, 2018, 12:25pm CEST par Mark Wycislik-Wilson
A report published by the Intercept alleges that AT&T has eight buildings across the US which are used to collaborate on surveillance with the NSA. Found in Atlanta, Chicago, Dallas, Los Angeles, New York City, San Francisco, Seattle, and Washington, DC, these "peering" facilities are home to networking equipment through which a lot of US and global internet traffic is routed. The Intercept says that there is a lot of evidence to suggest that "the buildings are central to an NSA spying initiative that has for years monitored billions of emails, phone calls, and online chats passing across US territory".… [Continue Reading] -

Wi-Fi Alliance starts to certify WPA3 devices
Publié: juin 26, 2018, 10:49am CEST par Mark Wycislik-Wilson
The rise in popularity of smart devices in the home -- coupled with our continuing love of laptops, tablets and phones -- means that we're more reliant on wireless networks than ever before. But the security we rely on to keep things safe is at least 14 years old, if not older (the widely used WPA2 started life back in 2004). Clearly, it's time for a security upgrade, and to this end, the Wi-Fi Alliance has just started certifying devices that support WPA3 -- the predictably-named successor to WPA2. This latest security protocol includes a number of important enhancements, and… [Continue Reading] -

Apple releases the first public beta of iOS 12
Publié: juin 26, 2018, 9:51am CEST par Mark Wycislik-Wilson
If you're keen to try out the next version of iOS without risking the developer preview, you're in luck -- Apple has just released the first public beta of iOS 12, and it's freely available for anyone who fancies it to download. Apple has already revealed quite a bit about the latest version of its mobile operating system, and at WWDC it focused on the performance enhancements on offer. But iOS 12 is about much more than this. There are also updates to Siri, key apps, ARKit 2, Animoji, Memoji and much more. Read on to find out how to… [Continue Reading] -

Privacy group EFF announces STARTTLS Everywhere to secure emails with hop-to-hop -- but not end-to-end -- encryption
Publié: juin 25, 2018, 7:08pm CEST par Mark Wycislik-Wilson
When it comes to messaging tools, people have started to show greater interest in whether encryption is used for security, and the same for websites -- but not so much with email. Thanks to the work of the Electronic Frontier Foundation, however, email security is being placed at the top of the agenda. The privacy group today announces STARTTLS Everywhere, its new initiative to improve the security of the email eco-system. STARTTLS is an addition to SMTP, and while it does not add end-to-end encryption, it does provide hop-to-hop encryption, which is very much a step in the right direction.… [Continue Reading] -

Video views on YouTube et al will soon count towards singles' chart positions
Publié: juin 25, 2018, 6:34pm CEST par Mark Wycislik-Wilson
Starting next month, the number of views song videos receive on YouTube and other sites will start to count towards their position in the UK singles chart. It's a move that could completely shake up the charts, just like the counting of digital downloads and streams did previously. Starting on Friday, video views on YouTube, Apple, Tidal and Spotify will start to be counted by the Official Charts Company, and will be included in the first chart of July. It is only official music videos that will be included in the count -- any user-generated content will be ignored. With… [Continue Reading] -

AT&T is buying digital ad platform AppNexus
Publié: juin 25, 2018, 6:05pm CEST par Mark Wycislik-Wilson
AT&T has revealed plans to acquire the ad platform AppNexus which competes directly with the likes of Google and Facebook. While the exact terms of the deal have not yet been shared, recent rumors suggested that AT&T was willing to part with $1.6 billion for the company. The acquisition is expected to close by Q3 of this year, and AT&T says that the two companies will operate as separate entities until then. After the acquisition, AppNexus will become a part of AT&T advertising and analytics. AT&T says that with the acquisition, it is looking to accelerate the growth of its… [Continue Reading] -

Google adds DRM to Android APKs to verify the authenticity of apps from Google Play
Publié: juin 24, 2018, 11:42am CEST par Mark Wycislik-Wilson
DRM is something that's usually associated with streaming music and video, but there's no reason that it can't be put to other uses. Proving this, Google has started using a form of DRM to improve app security by verifying that APKs originate from the Play Store. It's a system that works much like signed drivers in Windows. The aim is simple: to improve the security of Android users by ensuring that they are using genuine apps that have not been tampered with in any way. Google is not referring to the new system as DRM, saying instead that it is… [Continue Reading] -

Don't panic! Hackers have not found a way to bypass the iPhone passcode limit
Publié: juin 24, 2018, 11:04am CEST par Mark Wycislik-Wilson
Enter the wrong passcode into an iPhone and you'll not only be denied access to it, but also run the risk of wiping its contents if you enter an incorrect code too many times. This is a problem faced by law enforcement agencies when they encounter iPhones in the cases they're working on -- as well as people trying to hack into phones for nefarious purposes -- so it's little wonder that hackers are constantly trying to find a way to earn unlimited guesses at passcodes. One hacker thought he had cracked it. Security researcher Matthew Hickey proudly boasted at… [Continue Reading] -

Microsoft has the patent for a thinner, re-designed USB-C connector
Publié: juin 23, 2018, 6:39am CEST par Mark Wycislik-Wilson
It is a slow process, but USB-C is gradually becoming more and more popular -- although it's a long way from ubiquity yet. Ready to rock the boat a little, it has emerged that Microsoft holds a patent for a redesigned USB-C connector. The patent is not brand new, but Microsoft's May 2017 filing for an "Ultra-Thin USB-C Connector" has just come to light. Another patent filing from April 2017 describes a new "USB-C Plug Receptacle". While the redesign is hardly going to set the world on fire, it's the sort of thing we could well expect to see in… [Continue Reading] -

Got a MacBook or MacBook Pro with sticky keys? Apple has a free service program for you
Publié: juin 23, 2018, 6:15am CEST par Mark Wycislik-Wilson
For some time, a number of MacBook or MacBook Pro users have complained about problems with their keyboards -- specifically that keys either stop working completely, fall off, or become "sticky", resulting in repeated characters. Now, after two years of complaints and a lawsuit about the butterfly mechanism in its keyboards, Apple has finally acknowledged that there is a problem. The company has also launched a keyboard service program so those affected by the problem can get it addressed, free of charge. See also: Bricked iPhones with 'Error 53' just cost Apple $6.7 million in Australia Apple will automatically share… [Continue Reading] -

Google Account revamped -- increased transparency and new security and privacy options
Publié: juin 21, 2018, 5:16pm CEST par Mark Wycislik-Wilson
Google has unveiled a new look for users' accounts, making information clearer, improving transparency and adding new options. To make it easy to find information, Google has added a search function and there's also a cleaner look to aid navigation. Building on the previous update to Security Checkup, your Google account now also highlights settings you can change to improve your security. See also: Google launches Podcasts app for Android Google updates Android Messages so you can send texts from the web Google enters 'strategic partnership' with China's JD.com The rejigged look means that it is now easier than ever… [Continue Reading] -

Intel CEO Brian Krzanich resigns over relationship with employee
Publié: juin 21, 2018, 4:51pm CEST par Mark Wycislik-Wilson
Brian Krzanich, the CEO of Intel, has resigned after it came to light that he was in a relationship with an employee. Shares in the company dropped 1.3 percent at the news. Although the relationship was entirely consensual, it was deemed to be a violation of Intel's non-fraternization policy which managers must abide by, and it has been brought to light in the context of the #MeToo movement. The current chief financial officer, Robert Swan, is to become interim CEO until a full-time replacement can be found. See also: CVE-2018-3665: Floating Point Lazy State Save/Restore vulnerability affects Intel chips Spectre… [Continue Reading] -

Microsoft acquires machine learning and AI startup Bonsai
Publié: juin 21, 2018, 10:09am CEST par Mark Wycislik-Wilson
Seeking to strengthen its artificial intelligence arsenal, Microsoft has announced an agreement to acquire San Francisco-based AI startup Bonsai. Bonsai already had Microsoft links, having been set up back in 2014 by two former Microsoft engineers, Mark Hammond and Keen Browne. The company specializes in "deep reinforcement learning" which can be used to teach autonomous systems within simulations, and the company sees this tying in with Azure. See also: Gamers waiting for virtual reality on Xbox are out of luck Satya Nadella speaks out against 'cruel and abusive' border policy and explains Microsoft's involvement with ICE Microsoft issues statement distancing… [Continue Reading] -

Gamers waiting for virtual reality on Xbox are out of luck
Publié: juin 21, 2018, 9:45am CEST par Mark Wycislik-Wilson
Backtracking on what it said last year, Microsoft has announced that it has no plans to bring either virtual reality or mixed reality experiences to its Xbox console. Back in March 2017, the company had said that it wanted to bring MR to Xbox users, but now it seems to have changed its mind. Microsoft has not really given any reason for the change of heart, but it has not given up completely on VR or MR. See also: Satya Nadella speaks out against 'cruel and abusive' border policy and explains Microsoft's involvement with ICE Microsoft issues statement distancing itself… [Continue Reading] -

Alexa for Hospitality brings Amazon's digital assistant to hotel rooms
Publié: juin 20, 2018, 12:22pm CEST par Mark Wycislik-Wilson
Not content with infiltrating people's homes with its range of Echo devices, Amazon is now looking to elbow its way into hotels with Alexa for Hospitality. Amazon has struck a deal with Marriott International that will see the introduction of Echo devices into rooms. Guests can use these to play music, contact reception and get information about the hotel -- and both Amazon and guests alike will be hoping there won't be a repeat of the recent privacy slip up that resulted in an Echo recording and sharing someone's conversations. See also: Amazon Echo secretly records couple's conversation... and then… [Continue Reading] -

Satya Nadella speaks out against 'cruel and abusive' border policy and explains Microsoft's involvement with ICE
Publié: juin 20, 2018, 9:28am CEST par Mark Wycislik-Wilson
Microsoft CEO Satya Nadella has publicly shared an email he sent to employees, in which he speaks out against current US immigration policy. Describing the separating of children from their families as "cruel and abusive", he stresses that while Microsoft does work with US Immigration and Customs Enforcement (ICE), the work amounts to support for "legacy" services and is in no way related to child separation. The president of Microsoft, Brad Smith, also used a blog post to set out the company position on the matter. See also: Microsoft issues statement distancing itself from ICE's separation of children from parents… [Continue Reading] -

Google launches Podcasts app for Android
Publié: juin 19, 2018, 6:20pm CEST par Mark Wycislik-Wilson
Google has never really shown much interest in podcasts -- despite their age and popularity -- but today this changes. The company has launched a new Android app called simply Google Podcasts complete with ubiquitous AI for personalized suggestions. Available in 47 languages, the app currently provides access to a collection of around two million podcasts, but this number is likely to grow very quickly. Google boasts of integration with Google Assistant and Google Home, the main benefit of which is being able to start a podcast on one device and continue on another. See also: Google updates Android Messages… [Continue Reading] -

Bricked iPhones with 'Error 53' just cost Apple $6.7 million in Australia
Publié: juin 19, 2018, 5:10pm CEST par Mark Wycislik-Wilson
Apple has been hit with an AUS $9 million ($6.7 million) fine for misleading customers in Australia. More than two years ago Apple started to "brick" iPhones that had been fixed at non-authorized third-party repairers, generating an Error 53. Apple admitted to intentionally preventing certain repaired iPhones and iPads from working for security reasons, but later apologized and issued a fix. However, the Australian Competition and Consumer Commission (ACCC) sued Apple for "misleading or deceptive conduct", and now an Australian court has hit the iPhone-maker with a multi-million dollar fine See also: Australia sues Apple over iPhones bricked by Error… [Continue Reading] -

Senate opposes Trump and votes to reinstate US ban on ZTE
Publié: juin 19, 2018, 11:38am CEST par Mark Wycislik-Wilson
ZTE has had a tough time of things in the US, having been slapped with a Denial Order that forced it to close its main operations. Despite the sanctions, President Trump expressed a desire to get the company back up and running, implementing a huge fine which ZTE agreed to pay in order to be allowed to operate in the US again. But in a blow to the Trump administration and its work with Chinese president Xi Jinping, the Senate has voted to amend the National Defense Authorization Act to reinstate sanctions on the company. See also: ZTE agrees to… [Continue Reading] -

Microsoft issues statement distancing itself from ICE's separation of children from parents
Publié: juin 19, 2018, 7:40am CEST par Mark Wycislik-Wilson
The separating of children from parents at the US southern border has created international outrage -- and lots of rhetoric from President Trump on Twitter. When Microsoft removed from its website a reference to working with ICE, the company found itself pulled into the political debate. A blog post from January this year saw Microsoft stating it was "proud" to be working with ICE. When this was spotted, people took to social media to call out Microsoft, making references to the child separation policy; shortly afterwards, the ICE reference was deleted. Now it is back, and Microsoft has issued a… [Continue Reading] -

Google updates Android Messages so you can send texts from the web
Publié: juin 19, 2018, 7:14am CEST par Mark Wycislik-Wilson
Google is rolling out a series of changes to Android Messages, one of which makes it possible to send text messages from the comfort of your computer. Called "Messages for web" the feature enables users to use a desktop web browser to send SMSes rather than their phone. While this is almost certainly the biggest and most exciting changes for Messages, Google is also pushing a number of other new features to the app, including Smart Replies, GIF search and link previews. See also: Google enters 'strategic partnership' with China's JD.com Android emulator Andy OS seems to be secretly installing… [Continue Reading] -

Microsoft strengthens its education offerings by acquiring video discussion platform Flipgrid -- and makes it free
Publié: juin 18, 2018, 3:31pm CEST par Mark Wycislik-Wilson
Microsoft has acquired Flipgrid, a social video discussion platform used in classrooms around the world. The acquisition strengthens Microsoft's educational offerings and helps it to better compete with rivals Google and Apple. Flipgrid is used by million of students and teachers to collaborate on lessons, covering everything from Pre-K to PhD level. The acquisition is great news for schools: Microsoft is slashing the current price tag of $1,000, and making the service free just like Office 365 for Education. See also: Microsoft to stop offering support for Windows 7 and Windows 8.1 in forums Microsoft wants you to know Windows… [Continue Reading] -

Apple will automatically share the location of 911 callers in iOS 12
Publié: juin 18, 2018, 1:38pm CEST par Mark Wycislik-Wilson
Apple has announced that with iOS 12, iPhone users in the US will be able to automatically share their location with first responders when they make 911 calls. Building on its currently-used location technology, Apple says that it will start to use RapidSOS's Internet Protocol-based data pipeline to quickly and securely share HELO (Hybridized Emergency Location) data with 911 centers. See also: Apple is updating iOS to lock out police iPhone hacking tools Apple reveals performance-focused iOS 12 for a massive range of iPhones and iPads Apple updates App Store rules to prevent devs gathering data from contacts The company… [Continue Reading] -

Android emulator Andy OS seems to be secretly installing a Bitcoin miner
Publié: juin 18, 2018, 11:21am CEST par Mark Wycislik-Wilson
Cryptocurrency mining malware has become a serious problem recently, and it seems the latest people to fall victim to the threat are users of the Android emulator Andy OS -- also referred to as AndY and Andyroid. The emulator makes it possible to run Android software within Windows or macOS, but it appears that the installation harbors a dark secret -- a GPU miner trojan that secretly mines for Bitcoin. Over on Reddit there are large numbers of upset users trying to find out what's going on. See also: Bitcoin plummets after hackers steal $37 million from South Korean cryptocurrency… [Continue Reading] -

Google enters 'strategic partnership' with China's JD.com
Publié: juin 18, 2018, 9:45am CEST par Mark Wycislik-Wilson
Google is deepening it drive into China, and now the search giant has announced a $550 million "strategic partnership" with Chinese ecommerce goliath JD.com. This is far from being Google's first venture in China, but the major investment shows the company's eagerness to take advantage of the market. It will enable Google to better take on the likes of Amazon in Asia, and it will also help JD.com to expand its operations to other parts of the world. See also: Kaspersky: Chinese hackers LuckyMouse hit national data center Facebook confirms data-sharing agreement with Chinese companies including Huawei Apple removes apps… [Continue Reading] -

Researchers develop SafeSpec to overcome vulnerabilities like Spectre and Meltdown
Publié: juin 16, 2018, 10:07am CEST par Mark Wycislik-Wilson
Computer scientists from the University of California, the College of William and Mary, and Binghamton University have published a paper detailing a new "design principle" that avoids speculative execution vulnerabilities. Researchers says that the SafeSpec model supports "speculation in a way that is immune to the sidechannel leakage necessary for attacks such as Meltdown and Spectre". Importantly, the design also avoids the problems associated with other Meltdown/Spectre fixes. See also: CVE-2018-3665: Floating Point Lazy State Save/Restore vulnerability affects Intel chips Spectre and Meltdown variant 4: Microsoft, Google and Intel reveal new Speculative Store Bypass chip vulnerability Intel: some processors will… [Continue Reading] -

Kaspersky: Chinese hackers LuckyMouse hit national data center
Publié: juin 16, 2018, 9:00am CEST par Mark Wycislik-Wilson
Kaspersky Lab has published a report in which it reveals that a Chinese hacking group has attacked the national data center of an unnamed Central Asian country. The cyberattacks are said to have been carried out by a group known as LuckyMouse -- but also goes by the names Iron Tiger, Threat Group-3390, EmissaryPanda and APT27. The attacks started in 2017, and Kaspersky says that malicious scrips were injected into official website to conduct country-level waterholing campaign. See also: Apple is updating iOS to lock out police iPhone hacking tools Bitcoin plummets after hackers steal $37 million from South Korean… [Continue Reading] -

Google's latest diversity report shows little has changed at the company
Publié: juin 15, 2018, 10:53am CEST par Mark Wycislik-Wilson
Google has published the latest edition of its diversity report in which the company highlights the makeup of its workforce in the name of transparency. Despite Google's seemingly endless claims that it wants to do more to improve diversity, the report shows that little has changed over the last year. Women still account for less than a third of the workforce, and the company has a high attrition rate for black employees. See also: Google revamps Ad Settings and 'Why this ad?' so you can see and control how ads are personalized Google doubles down on Chrome extension security by… [Continue Reading] -

World Cup: access the hidden mini games in Facebook Messenger
Publié: juin 15, 2018, 9:45am CEST par Mark Wycislik-Wilson
The World Cup is now officially under way in Russia to the delight of sports fans around the globe. If you just can't get enough football, Facebook Messenger can help to satiate you between matches with a series of mini games you can play with your friends. Games in Facebook Messenger have been with us for some time, and the social network has used the World Cup as a reason to update the selection. In addition, there are also new camera filters in the app -- here's how you access them and the games. See also: Privacy: Facebook advertisers must… [Continue Reading] -

Google revamps Ad Settings and 'Why this ad?' so you can see and control how ads are personalized
Publié: juin 14, 2018, 5:35pm CEST par Mark Wycislik-Wilson
Google has given its Ad Settings page an overhaul in the name of transparency. The page gives people the chance to not only see how Google uses the data it has gathered about them to personalize the ads they see, but also exercise a degree of control over these personalized ads. The page makes it possible to disable ad targeting, so you will see rather more generic ads if tailored advertising concerns you. The company has also updated its "Why this ad?" feature, so you will be able to determine why you are seeing certain Google-supplied ads on the sites… [Continue Reading] -

Apple is updating iOS to lock out police iPhone hacking tools
Publié: juin 14, 2018, 10:50am CEST par Mark Wycislik-Wilson
Apple says that it is planning to release an iOS update that will block a loophole used by police to access iPhones. Law enforcement agencies and hackers have been able to exploit a handset's Lightning port to get around passcode limits and brute force their way into a phone. But with the upcoming update, Apple will shut down data access via the Lightning port after an hour if the correct passcode is not entered. See also: Apple updates App Store rules to prevent devs gathering data from contacts Apple slaps a ban on cryptocurrency mining apps Apple adopts a 'cautious… [Continue Reading] -

CVE-2018-3665: Floating Point Lazy State Save/Restore vulnerability affects Intel chips
Publié: juin 14, 2018, 9:52am CEST par Mark Wycislik-Wilson
There has been something of a spate of chip vulnerability discoveries recently, and now another one has emerged. Known as Floating Point Lazy State Save/Restore, the security flaw (CVE-2018-3665) is found in Intel Core and Xeon processors and it is another speculative execution vulnerability in a similar vein to Spectre. The security flaw takes advantage of one of the ways the Linux kernel saves and restores the state of the Floating Point Unit (FPU) when switching tasks -- specifically the Lazy FPU Restore scheme. Malware or malicious users can take advantage of the vulnerability to grab encryption keys. Linux kernel… [Continue Reading] -

Privacy: Facebook advertisers must warn users if ads are targeted because of data they purchased
Publié: juin 13, 2018, 5:59pm CEST par Mark Wycislik-Wilson
The fall out from the Cambridge Analytica scandal continues for Facebook, and the social media giant is busy trying to repair its somewhat tattered reputation. The latest measures see the company introducing new privacy safeguards to inform users if advertisers are using information supplied by so-called "data brokers". These brokers are firms that gather data about people and then sell this information on to other companies, often for the purposes of targeted advertising. Facebook is not banning the practice, merely requiring advertisers to keep users informed. See also: Facebook bug makes millions of users' private posts public Facebook confirms data-sharing… [Continue Reading] -

Apple updates App Store rules to prevent devs gathering data from contacts
Publié: juin 13, 2018, 5:23pm CEST par Mark Wycislik-Wilson
Apple has tweaked its App Store policies, closing a loophole that made it possible for developers to gather data from phone contacts and then sell or share that data without consent. Until very recently app developers have been able to ask for permission to access users' address books and then use this permission to gather data about contacts. But with the latest policy change -- introduced with no announcement -- Apple has clamped down on this practice in the name of privacy. See also: Apple slaps a ban on cryptocurrency mining apps Apple adopts a 'cautious approach' and cuts iPhone… [Continue Reading] -

Offline Google Translate to be boosted by AI
Publié: juin 13, 2018, 1:15pm CEST par Mark Wycislik-Wilson
Google is improving the offline translation skills of Google Translate with an injection of AI in the form of neural machine translation (NMT). The use of on-device AI helps to dramatically improve the quality of offline translations, and works in much the same as online translations do. The use of neural machine translation helps to improve accuracy by looking at complete sentences, rather than translating word by word. See also: Google doubles down on Chrome extension security by blocking inline installations Google Home can now handle up to three queries at a time Google says it will continue to work… [Continue Reading] -

Dixons Carphone suffers two major security breaches exposing customers' bank card details and personal information
Publié: juin 13, 2018, 11:02am CEST par Mark Wycislik-Wilson
Another week, another cyberattack. This time around, it's the Dixons Carphone group which says it has fallen victim to not one but two major breaches. The bank card details of 5.9 million customers have been accessed by hackers in the first breach. In the second, the personal records of 1.2 million people have been exposed. Dixons Carphone says that it is investigating an attack on its card processing system at Currys PC World and Dixons Travel in which there was an attempt to compromise 5.9 million cards. The company stressed that the vast majority -- 5.8 million -- of these… [Continue Reading] -

Google doubles down on Chrome extension security by blocking inline installations
Publié: juin 12, 2018, 9:09pm CEST par Mark Wycislik-Wilson
At the moment there are a couple of ways to install Chrome extensions -- either via the Chrome Web Store as Google would prefer, or via an inline installation from any website. Aware that this latter option opens up the possibility of people installing malicious extensions, Google is clamping down. Starting today, all newly-published extensions can only be installed via the Chrome Web Store, and this restriction will extend to existing extensions over the remainder of the year. See also: Google Home can now handle up to three queries at a time Google says it will continue to work with… [Continue Reading] -

Google Home can now handle up to three queries at a time
Publié: juin 12, 2018, 5:56pm CEST par Mark Wycislik-Wilson
With there being a number of digital assistants to choose from, each is now focusing on becoming smarter than the competition. To this end, Google Home can now respond to strings of up to three commands at once. The "multiple queries" feature is currently available in English for USA, UK, Canada and Australia, and enables Google Home users to perform up to three functions with a single utterance. Users, however, seem a little confused about how it all works. See also: Google says it will continue to work with the military on AI, but won't get involved in weapons or… [Continue Reading] -

Apple slaps a ban on cryptocurrency mining apps
Publié: juin 12, 2018, 2:17pm CEST par Mark Wycislik-Wilson
Apple has updated its developer guidelines, making it clear that apps that overtly or covertly mine for cryptocurrencies are simply not welcome in the App Store. The clamp down covers iOS devices, and it has only recently been introduced. The ban means that iPhones and iPads cannot be used to mine for cryptocurrencies, unless the processing is carried out in the cloud. It's not clear how big a problem mining apps have been, and iOS hardware would seem rather underpowered for the task. See also: Apple adopts a 'cautious approach' and cuts iPhone parts orders by 20 percent Apple reveals… [Continue Reading] -

USB fans gifted to reporters at Trump-Kim summit spark security fears
Publié: juin 12, 2018, 1:25pm CEST par Mark Wycislik-Wilson
Reporters covering the historic meeting between Donald Trump and Kim Jong-Un in Singapore have been given a gift bag that has security experts concerned. In addition to bottled water and a local guidebook, the gift bag also contained a USB fan. While on the face of it this would seem to offer a way to combat the Singaporean heat, the fan also sparked warnings that it could be laced with malware. See also: Trump to hit ZTE with $1.3 billion fine before it can operate in the US again Judge: President Trump blocking people on Twitter is unconstitutional Trump says… [Continue Reading] -

New Clear Chats option lets you delete Snapchat messages
Publié: juin 11, 2018, 5:27pm CEST par Mark Wycislik-Wilson
A new feature is rolling out to Snapchat users around the world, making it possible to delete messages you send and then change your mind about. It's something that users have been asking for for some time, but the update will not allow for stealthy message deletion -- to the disappointment of some. See also: Oath is killing off Yahoo Messenger on July 17 Facebook copies Snapchat's Bitmoji and creates personal, customizable Avatars GIPHY removed from Snapchat and Instagram after racist GIF appears Clear Chats can be used to delete messages that have been sent in both group chats, and… [Continue Reading] -

EE launches smart number technology, enabling customers to call and text across multiple devices with a single phone number
Publié: juin 11, 2018, 4:23pm CEST par Mark Wycislik-Wilson
EE has announced the launch of a new smart number technology which enables its customers to use their phone number across multiple devices at no extra cost. Initially, the service will be available to Apple users, giving them the option of using their iPhone, iPad, Apple Watch or Mac -- up to five devices in total -- to send and receive text messages, and place and receive phone calls. The same options will make their way to Android devices at some point in the future. You'll need to have your main EE number associated with a compatible iPhone (iPhone 6/6… [Continue Reading] -

Bitcoin plummets after hackers steal $37 million from South Korean cryptocurrency exchange Coinrail
Publié: juin 11, 2018, 11:24am CEST par Mark Wycislik-Wilson
Bitcoin has once again demonstrated its volatility, dropping in value by 10 percent following news of an attack and theft from the South Korean exchange Coinrail. Coinrail has confirmed that it suffered a "cyber intrusion" and while it did not specify the value of the coins stolen, local news outlet Yonhap News estimated it to be $37.28 million based on a loss of about 30 percent of the coins traded on the exchange. See also: Ticketfly says hack exposed private data of 27 million accounts 71 percent of IT pros believe they can hack any organization 92 million user accounts… [Continue Reading] -

Microsoft to stop offering support for Windows 7 and Windows 8.1 in forums
Publié: juin 11, 2018, 10:39am CEST par Mark Wycislik-Wilson
Microsoft has announced that starting next month it will no longer be participating in the technical support forums for Windows 7, 8.1, 8.1 RT and numerous other products. On the software front, the company says that it will also no longer provide support for Microsoft Security Essentials, Internet Explorer 10, Office 2010 and 2013 as of July. It is not just software that is affected. Microsoft is also stopping support for Surface Pro, Surface Pro 2, Surface RT, Surface 2, Microsoft Band and Zune. Some forums will be locked, preventing users from helping each other as well. See also: You… [Continue Reading] -

Fix on the way for OnePlus 6 bootloader security flaw
Publié: juin 10, 2018, 11:13am CEST par Mark Wycislik-Wilson
A security researcher has discovered a vulnerability in the OnePlus 6 bootloader. The flaw makes it possible for someone to boot arbitrary or modified images -- even if the bootloader is locked. Exploiting the vulnerability requires someone to have physical access to the phone, and after this it is a relatively simple task to restart the handset in fastboot mode. From here is would be possible to load a modified boot image, including one that has root access. See also: OnePlus unveils the OnePlus 6 smartphone, with glass back and inevitable notch Major leak reveals OnePlus 6 pricing, pictures and… [Continue Reading] -

You can now remotely install apps from the Microsoft Store to your Windows 10 devices
Publié: juin 9, 2018, 6:00pm CEST par Mark Wycislik-Wilson
There is a new remote installation feature available in the Microsoft Store on the web, making it possible to install apps on Windows 10 devices even if you are not currently using them. Working much like the option found in Google Play that lets Android users push apps to any of the devices they have associated with their Google account, the new feature from Microsoft provides a similar ability with Windows 10 apps. See also: Windows 10 April 2018 Update breaks SMBv1 Microsoft releases Windows 10 Redstone 5 Build 17686 Avast fixes the issue that caused problems with Windows 10… [Continue Reading] -

Android users can now customize Gmail swipe actions
Publié: juin 9, 2018, 11:36am CEST par Mark Wycislik-Wilson
It's not long since Google rolled out a major redesign to Gmail on the web, bringing not only a new look, but also new features. Now it's the turn of the Gmail app for Android. The mobile app has supported swipe gestures for some time now, but the options have been rather limited -- toggling between read/unread or archiving/deleting messages. With Gmail 8.5.20 Google is now giving users no fewer than five actions to choose from when performing a left or right swipe. See also: Gmail's new 'Smart Compose' feature writes replies for you Google rolls out massive Gmail redesign… [Continue Reading] -

Adblock Plus blocks social media tracking in Chrome and Firefox
Publié: juin 9, 2018, 10:04am CEST par Mark Wycislik-Wilson
There has been a lot of talk recently about Facebook tracking users (and non-users) as they browse the internet. Ever a proponent of user empowerment, Adblock Plus has unveiled new features that make it possible to block tracking through social media buttons. The company notes that Apple promised at WWDC to block social tracking, but with Adblock Plus this feature is available right now, regardless of whether you're an Apple customer. The only limitation is that you need to be using either Chrome or Firefox as your web browser. See also: Facebook bug makes millions of users' private posts public… [Continue Reading] -

Windows 10 April 2018 Update breaks SMBv1
Publié: juin 9, 2018, 8:49am CEST par Mark Wycislik-Wilson
It is no secret that Microsoft would like people to move away from the decades-old SMBv1 protocol -- the same protocol that was exploited by Wannacry. The company has been trying to encourage users to seek out an alternative or move to a more recent version for some time. Now people are starting to discover that upgrading to Windows 10 April 2018 Update kills the protocol. Users have taken to forums to complain that the latest Windows 10 update disables SMBv1, and even goes as far as blocking it from being re-enabled. See also: Microsoft releases Windows 10 Redstone 5… [Continue Reading] -

Apple adopts a 'cautious approach' and cuts iPhone parts orders by 20 percent
Publié: juin 8, 2018, 4:02pm CEST par Mark Wycislik-Wilson
Apple has reportedly warned suppliers that there will be a 20 percent drop in orders for new iPhone parts. The news comes courtesy of the Nikkei which cites industry sources. Factoring in a drop in orders of one fifth, it seems that Apple expects to sell 80 million new model iPhones this year, down from 100 million. Apple is thought to be planning to launch three new iPhone models later this year, and it appears the company expects to sell fewer than it did with the iPhone X and iPhone 8. See also: Apple wants you to spend less time… [Continue Reading] -

Oath is killing off Yahoo Messenger on July 17
Publié: juin 8, 2018, 3:13pm CEST par Mark Wycislik-Wilson
Yahoo Messenger is to be discontinued in just over a month. Yahoo owner Oath has announced that it is killing off its famous Messenger service on July 17. After this date, chatting will no longer be available, and users have just six months to download their chat histories. At the moment, there is no direct replacement for Yahoo Messenger, but users are being advised that they can request an invite for the beta version of the invite-only group messaging app Yahoo Squirrel. In an FAQ about the announcement, Yahoo addresses why the decision to shutter the service was taken. "We… [Continue Reading] -

Google says it will continue to work with the military on AI, but won't get involved in weapons or spying
Publié: juin 8, 2018, 11:35am CEST par Mark Wycislik-Wilson
Google has published new guidelines describing its principles for the development of artificial intelligence. The document -- entitled "Artificial Intelligence at Google: Our Principles" -- the company sets out its objectives for the future of AI. As well as saying it will incorporate its privacy principles into AI, Google says that it will continue to work with the military, but commits to avoid helping with the development of weapons or other technologies that could injury or kill. See also: When artificial intelligence goes bad: Reddit made 'Norman' a psychopathic AI Keep track of the World Cup with Google Google brings… [Continue Reading] -

Ticketfly says hack exposed private data of 27 million accounts
Publié: juin 8, 2018, 10:19am CEST par Mark Wycislik-Wilson
Last week event ticketing company Ticketfly suffered a cyberattack which saw the site taken offline for a number of days. The site is now back up and running, and Ticketfly has revealed the extent and impact of the hack. The company says that data from 27 million Ticketfly accounts was accessed, including names, addresses, email addresses and phone numbers. Customers are assured that passwords and credit card details remain safe. See also: Ticketfly remains offline following hack attack in which user data was accessed Canada: Bank of Montreal and Simplii Financial hit by hackers US and UK issue joint warning… [Continue Reading] -

Facebook bug makes millions of users' private posts public
Publié: juin 8, 2018, 9:34am CEST par Mark Wycislik-Wilson
Facebook is in the process of contacting 14 million users after it emerged that a bug led to private posts being made public. A problem with the company's "audience selector" tool between May 18 and 27 meant that millions of posts meant for a limited audience were actually made available for everyone and anyone to see. The social network has apologized for the incident and says that it will notify everyone who was affected by the bug. The SNAFU comes at a bad time for Facebook, as the company tries to rebuild a reputation tattered by the Cambridge Analytica scandal,… [Continue Reading] -

ZTE agrees to pay $1 billion fine to stop US Denial Order
Publié: juin 7, 2018, 7:16pm CEST par Mark Wycislik-Wilson
ZTE has been persona non grata in the US for some time now, with the Trump administration having slapped a Denial Order on the company preventing it from operating in North America. The president expressed a desire to get the Chinese firm "back into business" and today that is a step closer to happening. Today the US Department of Commerce has come to an agreement with the company, which will pay a $1 billion fine for violating sanctions. In addition, ZTE will make changes to management, and put a further $400 million in escrow to cover possible future fines. See… [Continue Reading] -

Keep track of the World Cup with Google
Publié: juin 7, 2018, 5:55pm CEST par Mark Wycislik-Wilson
With just days until the 2018 FIFA World Cup kicks off in Russia, Google is rolling out a series of tools to help football fans keep track of what's going on. A range of Google services -- Search, News, Assistant, Trends and more -- have been updated with World Cup-specific bits and pieces to help enhance your enjoyment of the tournament. From match streams and detailed reports to behind-the-scenes footage and tips about where you can watch games, there's something for every fan here. During the World Cup, Google Search can be used to keep track of group tables, stats… [Continue Reading] -

Amazon wins rights to show some Premier League matches
Publié: juin 7, 2018, 4:45pm CEST par Mark Wycislik-Wilson
Starting next year, Amazon Prime subscribers in the UK will be able to stream some Premier League matches. The company has won the right to show 20 games per season between 2019 and 2022. The online retailer managed to muscle in on territory dominated by BT and Sky to secure the right to show all 10 Boxing Day matches, as well as the first round of mid-week fixtures. See also: Amazon Echo secretly records couple's conversation... and then sends it on to a contact Amazon Fire TV Cube puts Alexa in control of your home entertainment Amazon brings Alexa to… [Continue Reading] -

VPNFilter malware infection is much worse than first thought -- is your router affected?
Publié: juin 7, 2018, 9:11am CEST par Mark Wycislik-Wilson
It's just a couple of weeks since we first heard about the VPNFilter malware. Linked to Russia, the malware hit 500,000 routers around the world, but now Cisco's Talos security researchers are warning that the problem is much worse than anyone thought. Initially thought to only affect SOHO routers and storage devices from Linksys, MikroTik, Netgear, TP-Link, and QNAP , the at-risk list has been extended to include consumer-grade routers from Linksys, MikroTik, Netgear and TP-Link. Researchers have also discovered that the malware is more powerful than initial assessments suggested -- it is now known to be able to bypass… [Continue Reading] -

Microsoft is going to rename GVFS and wants your suggestions
Publié: juin 6, 2018, 5:34pm CEST par Mark Wycislik-Wilson
Microsoft GVFS (Git Virtual File System) has attracted attention because it's a name that's already in use elsewhere -- and the company had refused to rename it. Now, however, it seems that Microsoft may be bowing to pressure. The company says it has received a lot of feedback because of the existence of the GNOME GVfs project (Gnome Virtual File System) which has been around for much longer than its GVFS Git extension, and it is looking for suggestions for a new name. See also: GitLab makes premium plans free for educational establishments and open source projects Microsoft officially announces… [Continue Reading] -

GitLab makes premium plans free for educational establishments and open source projects
Publié: juin 6, 2018, 4:46pm CEST par Mark Wycislik-Wilson
Microsoft's acquisition of GitHub has paid off for rival GitLab. Many GitHub users were unhappy at the Windows-maker's involvement and promptly jumped ship -- there were over 100,000 repositories imported in the 24 hours following the acquisition, and #movingtogitlab was trending on Twitter. Looking to make itself even more attractive than just not being owned by Microsoft, GitLab has now made its premium Gold and Ultimate packages free to some users, specifically educational establishments and open source projects. See also: Microsoft unveils IoT-ready Windows Collaborative Displays Microsoft officially announces agreement to acquire GitHub in $7.5 billion deal Microsoft will roll… [Continue Reading] -

New ASUS ZenBook Pro 15 has a touchscreen ScreenPad instead of a trackpad
Publié: juin 6, 2018, 12:56pm CEST par Mark Wycislik-Wilson
At Computex, ASUS has revealed its new ZenBook Pro 15 laptop. This is a high-performance machine, but this is a laptop that's about more than just raw power. In addition to the 8th Generation Intel Core i9 hexa-core processor and 16GB of 2400Hz DDR4 RAM, the new ZenBook Pro has an innovative trackpad. As well as controlling the mouse cursor, the traditional trackpad has been replaced with a ScreenPad -- a touch-sensitive screen that can display apps, shortcuts and other information. The ScreenPad is a 5.5-inch FHD (1920 x 1080) Super IPS+ display. It features a glass coating and allows… [Continue Reading] -

Facebook confirms data-sharing agreement with Chinese companies including Huawei
Publié: juin 6, 2018, 11:03am CEST par Mark Wycislik-Wilson
Facebook has confirmed that it has data-sharing agreements in place with at least four Chinese companies. Among these companies is Huawei, a firm that has attracted the attention of intelligence agencies in the US because of national security concerns. The news comes not only in the wake of the Cambridge Analytica scandal, but also reports this week that Facebook shared data with device manufacturers. The social network said that in addition to Huawei, it has data-sharing contracts with Oppo, Lenovo and TCL -- despite the fact that Facebook is banned in China. See also: New York Times alleges Facebook shared… [Continue Reading] -

92 million user accounts at risk after genealogy and DNA-testing site MyHeritage is hacked
Publié: juin 6, 2018, 10:23am CEST par Mark Wycislik-Wilson
MyHeritage -- a website that helps people research their family tree and also offers a DNA testing service -- has suffered a "cybersecurity incident". A file containing the usernames and hashed passwords of more than 92 million users was discovered on an external server by a security researcher. The file was found to be genuine and MyHeritage is now undertaking an investigation to determine what happened. The security breach affects all users who signed up to the site up to October 26, 2017. The company says that it is taking steps to inform the relevant authorities in line with GDPR.… [Continue Reading] -

Microsoft unveils IoT-ready Windows Collaborative Displays
Publié: juin 6, 2018, 9:32am CEST par Mark Wycislik-Wilson
In a keynote address at Computex 2018, Microsoft introduced a completely new hardware platform: Windows Collaboration Displays. Designed for use in offices and meeting rooms, the displays are touch-sensitive and can connect to Microsoft Azure Internet of Things spatial recognition via built-in sensors. While clearly related to the Surface Hub, Windows Collaborative Displays have a key difference: you have to supply your own computer hardware. Hook up a computer, and you have digital whiteboard and presentation tool at a fraction of the cost -- although pricing is yet to be confirmed. See also: Microsoft officially announces agreement to acquire GitHub… [Continue Reading] -

Apple reveals watchOS 5, complete with new Walkie-Talkie app
Publié: juin 4, 2018, 9:05pm CEST par Mark Wycislik-Wilson
Apple Watch owners have a new operating system upgrade to look forward to -- watchOS 5. Revealed today at WWDC alongside iOS 12, watchOS 5 introduces a number of new features including a Walkie-Talkie app and a range of new workout-related options. The update brings interactive notifications, improvements to Siri, and the ability to use an Apple Watch in place of a student ID card. Apple also revealed a new Pride Watch face which users can activate for free, and a Pride Edition Woven Nylon band which can be bought for $49. See also: Apple reveals performance-focused iOS 12 for… [Continue Reading] -

Apple reveals performance-focused iOS 12 for a massive range of iPhones and iPads
Publié: juin 4, 2018, 8:28pm CEST par Mark Wycislik-Wilson
Today at WWDC 2018, Apple gave us our first look at iOS 12. One of the key focuses of this latest update to Apple's mobile operating system is performance, and the company is bringing iOS 12 to more devices than any other previous version. Craig Federighi, Apple's senior vice president of software engineering, told developers that the update will help to speed up app load times. On the iPhone 6s, for instance, apps load up to 40 percent faster, and the camera loads up to 70 percent faster. iOS 12 will boost performance when necessary, but take the processor down… [Continue Reading] -

Microsoft officially announces agreement to acquire GitHub in $7.5 billion deal
Publié: juin 4, 2018, 3:48pm CEST par Mark Wycislik-Wilson
Following months of talks and rumors, Microsoft has finally officially revealed that it has agreed to acquire GitHub. The agreement sees the company acquiring the code repository for $7.5 billion in Microsoft stock. Microsoft says that GitHub will retain its developer-first ethos and will operate independently to provide an open platform for all developers in all industries. The deal is expected to close by the end of the year. See also: Microsoft could be on the verge of buying GitHub Microsoft will roll out 'key' GDPR rights globally... not just in Europe Spectre and Meltdown variant 4: Microsoft, Google and… [Continue Reading] -

ASUS Republic of Gamers reveals the ROG Phone, a gaming smartphone with a 3D vapor-chamber cooling system
Publié: juin 4, 2018, 1:30pm CEST par Mark Wycislik-Wilson
Today at Computex 2018 ASUS Republic of Gamers unveiled its first gaming smartphone, the ROG Phone. That this is a gaming smartphone is not the only "first" claimed by ASUS; it is also described as the world's first smartphone with a 3D vapor-chamber cooling system called GameCool. At the event, ASUS also revealed the ROG Rapture GT-AX11000 router with Wi-Fi speeds of over 10,000Mbps, as well as ROG Ryujin and ROG Ryuo CPU coolers, and ROG Thor 1200W Platinum power supply. See also: New Xiaomi Mi 8 Explorer Edition may be the coolest flagship smartphone right now HTC U12+ is… [Continue Reading] -

New York Times alleges Facebook shared user data with companies via device-integrated APIs
Publié: juin 4, 2018, 11:22am CEST par Mark Wycislik-Wilson
Facebook has vigorously denied allegations that it shared user data with the likes of Apple and Samsung through device-integrated APIs. In an article entitled "Facebook Gave Device Makers Deep Access to Data on Users and Friends", the New York Times raised concerns about the social network's privacy practices. The NYT says that Facebook has brokered "data-sharing partnerships with at least 60 device makers" over the last ten years. It alleges that the APIs gave companies access to the data of Facebook users' friends without their explicit consent. The article questions not only Facebook's privacy protections, but also its compliance with… [Continue Reading] -

Version 4.17 of the Linux kernel is here... and version 5.0 isn't far away
Publié: juin 4, 2018, 9:56am CEST par Mark Wycislik-Wilson
In his weekly message to the Linux community on Sunday, Linus Torvalds announced the release of Linux 4.17. The release comes a couple of months after the first release candidate, and in his message Torvalds also talks about version 5.0 of the Linux kernel. Having previously said that Linux kernel v5.0 "should be meaningless", he said that this next major numerical milestone will come around "in the not too distance future". For now, though, it's version 4.17 -- or Merciless Moray, if you prefer -- that's of interest. See also: Microsoft made its own IoT-ready Linux kernel for Azure Sphere… [Continue Reading] -

Microsoft could be on the verge of buying GitHub
Publié: juin 3, 2018, 8:10am CEST par Mark Wycislik-Wilson
There have long been rumors that Microsoft has an interest in buying GitHub, but in recent weeks it seems that talks between the two companies have been getting more serious. Talks between Microsoft and GitHub have been going on for a number of years now, and a new report suggests that an acquisition is closer than ever. While Microsoft share prices rose at the news, GitHub users are less convinced that the move would be a good idea. See also: Microsoft will roll out 'key' GDPR rights globally... not just in Europe Spectre and Meltdown variant 4: Microsoft, Google and… [Continue Reading] -

No, Google hasn't given up on tablets! Blame a bug for the confusion
Publié: juin 3, 2018, 7:24am CEST par Mark Wycislik-Wilson
Yesterday -- following the sudden and unexplained disappearance of the Tablets section of the Android website -- we, like many others, wondered if Google was walking away from tablets completely. Today we know that the answer is "no". The section has made a reappearance after its earlier vanishing act, and a bug has been blamed... but not everyone is convinced. See also: Is Google getting out of the tablet business? Fortnite for Android is coming very soon Google will require OEMs to provide regular Android security updates Court rules that Samsung doesn't need to update older phones The brief vacation… [Continue Reading] -

Leaked video shows Apple News, Xcode 10 and dark mode in macOS 10.14
Publié: juin 2, 2018, 7:24pm CEST par Mark Wycislik-Wilson
A developer discovered a video on Apple servers that not only shows Xcode 10 running on macOS 10.14, but also reveals a dark mode as well as an icon for the Mac News app nestling in the Dock. The leak comes just days ahead of this year's WWDC. Steven Troughton-Smith found the video in an API for the Mac App Store backend, and leaked his findings to an eager audience. Coming direct from Apple's servers, this leak is something of a rarity as it gives a glimpse of what's coming up in macOS pretty much direct from the horse's mouth.… [Continue Reading] -

Is Google getting out of the tablet business?
Publié: juin 2, 2018, 8:06am CEST par Mark Wycislik-Wilson
Google has removed the Tablets section from the top of its Android website, sparking talk that the company is dropping tablets altogether. It has been some time since we saw an Android tablet from Google, so the move would not be entirely surprising. What took many people by surprise however, was the fact that Google dropped the Tablets section of its website without any sort of announcement. See also: Fortnite for Android is coming very soon Google will require OEMs to provide regular Android security updates Court rules that Samsung doesn't need to update older phones If you take a… [Continue Reading] -

Ticketfly remains offline following hack attack in which user data was accessed
Publié: juin 2, 2018, 7:38am CEST par Mark Wycislik-Wilson
Event ticketing service Ticketfly -- owned by Eventbrite -- has fallen victim to what it describes as a "cyber incident". The company took down its website late on Thursday, and it remains inaccessible two days later. The full extent of the security breach is not yet known, but Ticketfly says that "some client and customer information" was compromised. The attack saw the site defaced with an Anonymous-style masked figure from the movie V for Vendetta, and the hacker threatened to provide download links to customer databases. A hacker by the name of IShAkDz has claimed responsibility. See also: Canada: Bank… [Continue Reading] -

Facebook is killing off Trending as it tries to revamp newsfeeds
Publié: juin 1, 2018, 6:19pm CEST par Mark Wycislik-Wilson
Facebook has announced plans to kill off the Trending feature of its newsfeed. The social network says that this is to "make way for future news experiences". Over the years, Facebook has experimented endlessly with the presentation of news, and has faced criticism for failing to weed out "fake news" and also accusations of liberal bias. Now the company wants to find new ways to help people find news that matters to them, ensuring that it comes from reliable sources. See also: Facebook to ask all users to review privacy settings Facebook asks British users to submit their nudes as… [Continue Reading] -

Telegram says Apple is blocking its app updates globally
Publié: juin 1, 2018, 4:45pm CEST par Mark Wycislik-Wilson
Telegram CEO Pavel Durov says that Apple has stopped approving updates for its mobile app on a worldwide basis. He says that it coincides with Russia implementing a block on Telegram, and it means there have been no updates rolling out to users anywhere in the world for a month and a half. Apple has said nothing about the apparent update block, and the lack of transparency has forced Durov to go public. See also: Download all the information Apple holds about you from its new Data and Privacy portal Apple to add details of government app takedown requests to… [Continue Reading] -

Court rules that Samsung doesn't need to update older phones
Publié: juin 1, 2018, 12:50pm CEST par Mark Wycislik-Wilson
One of the problems with choosing an Android phone is that it is difficult to know quite how long it will be supported. While Apple tends to offer updates for quite a number of years, it's a very different story for Android users. Now -- in something of a blow for consumers -- a court in the Netherlands has ruled that Samsung does not need to offer updates for its older handsets. A consumer association filed a lawsuit against the company, arguing that it should be forced to keep phones updated for at least four years; the court disagreed. See… [Continue Reading] -

Microsoft updates parental controls and allows for location tracking through Android Launcher
Publié: juin 1, 2018, 11:27am CEST par Mark Wycislik-Wilson
Ever keen to bolster its family-friendly image, Microsoft has revealed a number of updates to parental control options across a range of apps, services and devices. The company says it wants to "make it easier and safer for families to interact with technology and, each other, across devices and platforms". The changes include updates to Edge and Microsoft Launcher for Android, which allows parents to not only limit what children can see, but also track their whereabouts. Microsoft is also introducing a specially-curated MSN Kids. See also: Microsoft will roll out 'key' GDPR rights globally... not just in Europe Spectre… [Continue Reading] -

Review: RAVPower AC Outlet 27000mAh Power Bank
Publié: mai 31, 2018, 2:51pm CEST par Mark Wycislik-Wilson
Power banks are a dime a dozen nowadays, offering a way to ensure that your phone stays charged while you're on the move and away from a power socket. But while there are plenty of power banks with USB connections, what about those devices that require AC power? There are some laptops that can charge using a USB-C connection, but most need AC -- and this is where the RAVPower AC Outlet 27000mAh Power Bank can help. As you might guess from the name, this is a portable battery pack that offers 27000mAh of power and could just save you… [Continue Reading] -

Judge dismisses Kaspersky lawsuits about US government software ban
Publié: mai 31, 2018, 11:43am CEST par Mark Wycislik-Wilson
Kaspersky has had something of a tough time of it over the last year, first being hit by a ban on its software being used by the US government, and then a ban on advertising on Twitter. The Russian company sued the Trump administration over the software ban, and a judge has now dismissed the suits. Kaspersky Lab had been looking to overturn the governmental ban, saying "we've done nothing wrong" in response to claims that the company is linked to the Russian government. The firm says it plans to appeal against the latest ruling. See also: Kaspersky to move… [Continue Reading] -

Imgur adds video support
Publié: mai 30, 2018, 5:35pm CEST par Mark Wycislik-Wilson
Imgur has long been home to a universe of GIFs but -- after many years of animated silence -- this is changing thanks to the arrival of video support. This is a major change of direction for the company; something it recognizes and refers to as "a monumental shift for our future". At the moment, the uploading of videos is only available to iOS users, but there are plans to roll it out to other platforms as well. All platforms can currently view -- and hear -- videos. While this is something of a shift in focus for Imgur, it… [Continue Reading] -

Plex gains podcast support and gets redesigned, personalized app for iOS and Android
Publié: mai 30, 2018, 4:56pm CEST par Mark Wycislik-Wilson
Plex has come a very long way over the years, but it has lacked support -- for some inexplicable reason -- for podcasts. Today this changes with the arrival of not just a podcast feature, but also a new look, highly customizable mobile app for iOS and Android users. For the time being, podcast support is in beta, but it is a feature that is available to all users -- there's no need to be a paid-up Plex Pass subscriber. Things are a little basic for now, but they're going to improve. Let's take a look and see what this… [Continue Reading] -

Peculiar Google bug shows your text messages in search results
Publié: mai 30, 2018, 11:19am CEST par Mark Wycislik-Wilson
Bugs found in software are often a little quirky, but the latest discovery of a bug in the Google Android app is very peculiar indeed. Use the app to perform certain searches, or make a typo when entering a URL, and you may well find that you see a list of your text messages rather than the page you were expecting. At the moment it seems that the bug only affects Android users, with the iOS version of the Google app appearing to be functioning normally. If you get strange results if you try to visit the1975..com or search for… [Continue Reading] -

Apple reveals which speakers support AirPlay 2
Publié: mai 30, 2018, 10:59am CEST par Mark Wycislik-Wilson
With the launch of iOS 11.4 yesterday, Apple also unleashed AirPlay 2. Bringing support for stereo pairing and multi-room audio, this was the update HomePod users had been waiting for. But a HomePod is not the only way to take advantage of AirPlay 2; there are lots of other speakers that support the standard. Apple has now published a list of all of the AirPlay 2 speakers and receivers that are currently available, or will be very soon. See also: AirPlay 2 brings HomePod stereo pairs and multi-room audio to iOS 11.4 Apple to add details of government app takedown… [Continue Reading] -

AirPlay 2 brings HomePod stereo pairs and multi-room audio to iOS 11.4
Publié: mai 29, 2018, 6:10pm CEST par Mark Wycislik-Wilson
Today sees the release of iOS 11.4 and with it Apple is adding AirPlay 2. This brings some important changes to HomePod, including the stereo pairing option that was missing at launch. AirPlay 2 also adds multi-room audio to HomePod, bringing Apple's smartspeaker in line with Amazon Echo and Google Home. Other new features of iOS 11.4 include the ability to access iMessages via iCloud on any Apple device. See also: Apple to add details of government app takedown requests to transparency report Download all the information Apple holds about you from its new Data and Privacy portal Apple removes… [Continue Reading] -

PUBG sues Epic over similarities between Fortnite and PlayerUnknown's Battlegrounds
Publié: mai 29, 2018, 5:39pm CEST par Mark Wycislik-Wilson
Bluehole's PUBG -- the company behind PlayerUnknown's Battlegrounds -- is taking Epic Games to court, alleging that Fortnite's Battle Royale mode violates the copyright of its own game. Both Fortnight and PUBG have proved to be incredibly popular games, and Bluehole's PUBG has made no secret of the fact that it believes Epic has drawn a little too much inspiration from its own game. SEE ALSO: Fortnite for Android is coming very soon The legal action was revealed by the Korean Times just a few days ago, although the suit was actually filed way back at the beginning of the year.… [Continue Reading] -

Ghostery makes a huge privacy gaffe when emailing customers about GDPR
Publié: mai 29, 2018, 4:00pm CEST par Mark Wycislik-Wilson
Ghostery is a company rooted in privacy, so that the firm should accidentally reveal users' email addresses would come as something of a surprise. Over the weekend, however, this is exactly what happened. The company -- as many others have been doing recently -- emailed its users with details of its updated privacy policy that complies with GDPR. Unfortunately, the message exposed the email addresses of hundreds of customers as the company failed to make use of the BCC field. See also: Facebook to ask all users to review privacy settings Download all the information Apple holds about you from… [Continue Reading] -

Canada: Bank of Montreal and Simplii Financial hit by hackers
Publié: mai 29, 2018, 12:38pm CEST par Mark Wycislik-Wilson
Over the weekend, the Bank of Montreal and Simplii Financial both issued statements indicating that they had fallen victim to hackers. In the case of Simplii Financial, around 40,000 customer accounts have been affected, but numbers have not been revealed for the Bank of Montreal. Both banks' statements indicate that they were contacted by "fraudsters" on Sunday, May 27, but it is not clear whether the two incidents relate to the same group. See also: US and UK issue joint warning about Russian hacking of routers and ISPs Banks struggle to defend against internal attacks Microsoft launches Defending Democracy Program… [Continue Reading] -

How to check which of your conversations Alexa has been recording -- and delete them
Publié: mai 29, 2018, 10:48am CEST par Mark Wycislik-Wilson
There was concern recently when a couple of Alexa users found that the smart assistant built into their Amazon Echo had not only recorded a conversation they had been having, but had sent it to an acquaintance. Since this story broke, it is entirely understandable that other people who have Alexa listening in the background are worried that something similar could happen to them. If you want to check whether Alexa has been secretly/inadvertently recording you (delete according to your prejudices), we can show you how. If you find any recordings you want to ensure no one else hears, you… [Continue Reading] -

Pandora launches unlimited Premium Family plan for $15 per month -- with a 60-day free trial
Publié: mai 28, 2018, 1:18pm CEST par Mark Wycislik-Wilson
With so much choice in the field of streaming music, any package on the market has to offer something special to stand out from the competition. Looking to better compete with the likes of Apple Music and Spotify, Pandora has launched a new Premium Family package. The new package offers unlimited access to all of Pandora's premium features for up to six people. The price is just $15 per month, but there's a 60-day free trial available so you can try it out for size first. Pandora explains that the new package offers "all of the features of Pandora Premium… [Continue Reading] -

Trump to hit ZTE with $1.3 billion fine before it can operate in the US again
Publié: mai 26, 2018, 12:29pm CEST par Mark Wycislik-Wilson
Having slapped Chinese company ZTE with a denial order which significantly hampered its US operations, President Trump has said that the firm will pay a $1.3 billion fine and change its board and management in order to continue to operate within North America. ZTE had complained that the denial order was unacceptable, and Trump has more recently indicated a desire to get the company "back into business". Now it seems that the president has come up with a deal that involves the Chinese telecoms firm not only making security guarantees, but also buying components from US companies. See also: Trump… [Continue Reading] -

Apple to add details of government app takedown requests to transparency report
Publié: mai 26, 2018, 11:22am CEST par Mark Wycislik-Wilson
Apple has announced that it is to expand the scope of its twice-yearly transparency report. Starting with one of its next report -- the one which will cover the period July 1 to December 31, 2018 -- the company will share details of government app takedown requests. The announcement was tucked away in the latest transparency report, in which Apple shares details of "Government and Private Party Requests for Customer Information". The company says that it takes the protection of user data very seriously, and this addition to the report sees Apple demonstrating this by providing even more information. See… [Continue Reading] -

Avast fixes the issue that caused problems with Windows 10 April 2018 Update
Publié: mai 26, 2018, 10:39am CEST par Mark Wycislik-Wilson
It's just a couple of days since Microsoft temporarily disabled Windows 10 April 2018 Update on PCs running Avast antivirus. Just as with certain SSDs, a compatibility issue was making the update problematic. But now Avast says it has identified the issue and is working to push out an update to people that will avoid the problem. The company also has instructions for people whose computers have been left sitting in a blue screen state. See also: New Windows 10 update addresses problems with SSDs Microsoft blocks the rollout of Windows 10 April 2018 Update to computers with problematic Intel… [Continue Reading] -

Amazon Echo secretly records couple's conversation... and then sends it on to a contact
Publié: mai 25, 2018, 12:23pm CEST par Mark Wycislik-Wilson
There have long been accusations that digital assistants such as Amazon's Alexa and Apple's Siri are constantly listening in on and recording conversations, and recent events in Portland, Oregon are simply going to serve as extra fuel for conspiracy theorists. A couple were disturbed to find that Alexa not only recorded a private conversation they had in their house, but then sent it on to a colleague as a message. Danielle says she and her husband felt it was "a total privacy invasion", and it is unlikely that Amazon's explanation will do anything to encourage her to use her Echo… [Continue Reading] -

PayPal now offers payments in Gmail, Google Pay, YouTube and more
Publié: mai 25, 2018, 11:21am CEST par Mark Wycislik-Wilson
PayPal has extended its partnership with Google so it now offers more payment options to its customers. By integrating more deeply with Google, PayPal now allow you to seamlessly make payments in the likes of Gmail, YouTube, Google Pay and Google Store. As there is support for any service that makes use of Google Pay, users will also be able to make peer-to-peer payments. SEE ALSO: PayPal buys Swedish fintech company iZettle PayPal is ready to get into traditional banking with debit cards, loans and more Google quietly relegates 'Don't be evil' from its Code of Conduct PayPal has been… [Continue Reading] -

Some US websites are blocked in the EU as GDPR day arrives
Publié: mai 25, 2018, 11:05am CEST par Mark Wycislik-Wilson
It has been impossible to avoid stories about GDPR over the last few weeks and months, and today the new rules regarding privacy and personal data come into force across the EU. Inboxes across Europe have been flooded with GDPR-related emails as companies have rushed to comply with the new regulations that require them to seek consent from users to collect data about them. But now GDPR day has arrived, dozens of US websites are blocked in the EU. See also: Microsoft will roll out 'key' GDPR rights globally... not just in Europe Google explains its handling of user data… [Continue Reading] -

New Windows 10 update addresses problems with SSDs
Publié: mai 24, 2018, 3:29pm CEST par Mark Wycislik-Wilson
The rollout of Windows 10 April 2018 Update was recently blocked to some computers because of problems with certain SSDs. Now Microsoft has issued an update that addresses the issues. Releasing the KB4100403 patch, Microsoft says that problems with Intel SSD 600p Series or Intel SSD Pro 6000p Series, and Toshiba XG4 Series, Toshiba XG5 Series, or Toshiba BG3 Series drives, are fixed. After installing it, users should be able to upgrade to Windows 10 April 2018 Update. See also: Microsoft blocks the rollout of Windows 10 April 2018 Update to computers with problematic Intel SSDs Many people with Intel… [Continue Reading] -

Facebook to ask all users to review privacy settings
Publié: mai 24, 2018, 2:25pm CEST par Mark Wycislik-Wilson
With the recent scandals involving Facebook coupled with the impending arrival of GDPR in Europe, there has been a lot of talk about privacy recently. Now the social networking giant is to start asking all of its users to review information about privacy and "how to control their experience". The company says that it introduced updated data policies and made privacy settings easier to find, as well as making other changes, in Europe, and now is rolling out the same things to the rest of the world. See also: Facebook asks British users to submit their nudes as protection against… [Continue Reading] -

StumbleUpon is closing down -- users can migrate to Mix.com
Publié: mai 24, 2018, 1:51pm CEST par Mark Wycislik-Wilson
After 16 years, StumbleUpon is closing down. One of the first high-profile services that gave people a way to discover new websites and online content, it was enjoyed by over 40 million users. The closure came out of the blue, and was announced by co-founder Garrett Camp in a blog post. He suggests that users might like to migrate to another one of his creations, Mix.com, and says that switching to the newer service has been made "as smooth as possible". Camp says that times have changed dramatically since the inception of StumbleUpon. "Since starting SU the number of people… [Continue Reading] -

WhatsApp bug means you could still receive messages from people you block
Publié: mai 24, 2018, 12:36pm CEST par Mark Wycislik-Wilson
A bug has been discovered in popular chat tool WhatsApp that completely undermines the blocking feature. The idea behind blocking people on WhatsApp -- just like any other app or service -- is to prevent them from contacting you, and to stop them from viewing your activity. But the bug means that blocked users are still able to send messages to people who have blocked them, as well as viewing statuses and profile details. The problem appears to be affecting the iOS, Android and desktop versions of WhatsApp, and the company has remained tight-lipped about what is going on. It… [Continue Reading] -

Judge: President Trump blocking people on Twitter is unconstitutional
Publié: mai 24, 2018, 11:01am CEST par Mark Wycislik-Wilson
Donald Trump's use of Twitter has long been controversial, and he has developed something of a penchant for blocking people who dare to question or criticize him. Earlier this year a judge suggested that he should make use of the mute option instead of blocking Twitter users, and now another judge has ruled that blocking critics is unconstitutional. Judge Naomi Buchwald said that Trump's use of the block feature is a violation of people's right to free speech under the First Amendment of the US Constitution. The Department of Justice has indicated that it disagrees and is considering what to… [Continue Reading] -

Facebook asks British users to submit their nudes as protection against revenge porn
Publié: mai 23, 2018, 4:58pm CEST par Mark Wycislik-Wilson
Following on from a trial in Australia, Facebook is rolling out anti-revenge porn measures to the UK. In order that it can protect British users from failing victim to revenge porn, the social network is asking them to send in naked photos of themselves. The basic premise of the idea is: send us nudes, and we'll stop others from seeing them. See also: Zuckerberg's appearance in front of the EU was an utter joke Mark Zuckerberg agrees to appear in front of EU parliament to answer questions about Facebook's use of data Facebook's new Clear History privacy tool will let… [Continue Reading] -

Download all the information Apple holds about you from its new Data and Privacy portal
Publié: mai 23, 2018, 4:46pm CEST par Mark Wycislik-Wilson
If you've ever been curious about just what data Apple has gathered and stored about you over the years, now you can find out -- if you're in Europe, at least. The iPhone-maker has just launched a new Data and Privacy portal in order to comply with GDPR which comes into force across the EU from Friday. The website lets you download pretty much every piece of data that Apple has collected about you. See also: Apple removes apps using the CallKit framework because of Chinese regulations Apple clamps down on apps that share location data with third parties Apple… [Continue Reading] -

Amazon is selling its face recognition technology to US law enforcement agencies
Publié: mai 23, 2018, 12:57pm CEST par Mark Wycislik-Wilson
A Freedom of Information Act (FOIA) request by the American Civil Liberties Union (ACLU) shows that Amazon has started selling facial recognition software to at least two US law enforcement agencies. A report published by the ACLU shows that the online retailer has been advertising its facial recognition system -- known as Amazon Rekognition, and described as "deep learning-based image and video analysis" -- to numerous states. Testimonials from the Orlando, Florida Police Department and the Washington County Sheriff’s Office in Oregon suggest that the system is already in use. See also: com now redirects to Amazon and the company's… [Continue Reading] -

Zuckerberg's appearance in front of the EU was an utter joke
Publié: mai 23, 2018, 11:11am CEST par Mark Wycislik-Wilson
Yesterday, Facebook CEO Mark Zuckerberg appeared in front of members of the European Parliament to answer questions and to address concerns that the EU has about the social network in general, and its use of private data in particular -- thanks largely to the Cambridge Analytica data scandal. At least that was the idea. What actually happened was nothing short of a farce, with Zuckerberg smugly sitting back and choosing which questions to answer, neatly avoiding any he was uncomfortable with. It was little more than a PR-cum-damage-limitation exercise for the Facebook founder... and it didn't really go very well.… [Continue Reading] -

Trend Micro launches Zero Browser for iOS -- a web browser that protects your privacy
Publié: mai 22, 2018, 7:22pm CEST par Mark Wycislik-Wilson
Trend Micro has a new privacy-focused mobile browser for iOS users called Zero Browser. It has been designed specifically to block a range of tracking techniques, including the invasive activity-recording "session replay" method. The company says that the browser was created to overcome the shortcomings of existing "incognito" browsing modes and brings an extra level of privacy to iPhone, iPad and iPod touch users. See also: Apple removes apps using the CallKit framework because of Chinese regulations Apple clamps down on apps that share location data with third parties Microsoft will roll out 'key' GDPR rights globally... not just in… [Continue Reading] -

Microsoft will roll out 'key' GDPR rights globally... not just in Europe
Publié: mai 22, 2018, 6:13pm CEST par Mark Wycislik-Wilson
The clock is ticking for the arrival of GDPR (or General Data Protection Regulation) in Europe. As of May 25 -- this Friday -- new regulations will give people greater access to the data companies store about them and the right to have it deleted. Microsoft is among the global technology firms that will have to comply with the laws in Europe and -- pointing out how it appreciates "the strong leadership by the European Union on these important issues" -- the company says that it will also roll out some of the benefits of the privacy legislation on a… [Continue Reading] -

Comcast website leaks details of Xfinity users -- including router passwords
Publié: mai 22, 2018, 12:57pm CEST par Mark Wycislik-Wilson
Security researchers have discovered a bug in the Comcast website that makes it possible to gather information about Xfinity users. As well as customer data such as home addresses, it is also possible to access wireless network details including passwords. The bug was reported by Karan Saini and Ryan Stevenson after they found it was possible to use the Xfinity activation website to access customer data using nothing more than a customer account ID and that customer's house or apartment number. Although the online form for activation asks for a full address, it is only necessary to supply the number… [Continue Reading] -

WWDC could see the arrival of a new Siri voice and a new HomePod
Publié: mai 22, 2018, 12:50pm CEST par Mark Wycislik-Wilson
It's only a couple of week until Apple's Worldwide Developer Conference, and it's looking as though we could be getting a new voice for Siri -- and possibly a new HomePod. This is not just idle speculation or the usual industry rumor mill working overtime -- this time around it is Siri itself providing the clues. Ask Siri what to expect from WWDC next month, and the digital assistant starts to drop hints. See also: Apple removes apps using the CallKit framework because of Chinese regulations Apple clamps down on apps that share location data with third parties Apple tells… [Continue Reading] -

Red Hat responds to Speculative Store Bypass and helps explain Variant 4 chip vulnerability
Publié: mai 22, 2018, 12:11pm CEST par Mark Wycislik-Wilson
As news of yet another chip vulnerability creeps out, computer users, businesses and organizations around the world are trying to assess how the latest bug affects them. To help its users and others to understand what the Speculative Store Bypass/Variant 4 vulnerability means, Red Hat has issued advisories and an explanatory video. The company also reveals exactly which of its Linux builds are affected by the security flaw and what steps can be taken as mitigation. In addition to this, Red Hat has put together a number of resources that help to "provide more context around this vulnerability from an… [Continue Reading] -

Spectre and Meltdown variant 4: Microsoft, Google and Intel reveal new Speculative Store Bypass chip vulnerability
Publié: mai 22, 2018, 10:56am CEST par Mark Wycislik-Wilson
Just when you thought you could forget about the Spectre and Meltdown chip vulnerabilities, yet another variant has been discovered. Known as Speculative Store Bypass, the vulnerability affects chips from AMD and Intel, as well as Power 8, Power 9 and System z processors. The vulnerability has been assigned CVE-2018-3639, and successful exploitation would mean that an attacker could gain access to data. The attack can be carried out through a "language-based runtime environment" such as JavaScript. Some patches exist while others are in development, and they include the same performance hit associated with patches for the previous vulnerabilities. See… [Continue Reading] -

Microsoft unveils SharePoint spaces to help anyone create mixed reality experiences
Publié: mai 21, 2018, 6:35pm CEST par Mark Wycislik-Wilson
At its SharePoint Virtual Summit, Microsoft today unveiled SharePoint spaces, a way to bring SharePoint into virtual reality and mixed reality environments. Microsoft says that SharePoint spaces adds a third dimension to company intranets, and allows people to engage and interact with documents, data, and video in new and more immersive ways. The company envisions the technology being used by businesses to create interactive welcome environments for new employees, interactive product databases, training experiences, and much more. See also: Microsoft acquires AI startup Semantic Machines to help boost Cortana Microsoft is said to be working on a cheap Surface tablet… [Continue Reading] -

Watch Mark Zuckerberg's testimony to the EU in a livestream
Publié: mai 21, 2018, 4:39pm CEST par Mark Wycislik-Wilson
Having previously refused to answer questions in the UK, last week Mark Zuckerberg agreed to appear in front of the EU parliament to speak about Facebook's use of data. The Facebook chief is due to appear in front of MEPs tomorrow, Tuesday, and European Parliament President Antonio Tajani has announced that the appearance will be livestreamed. So, if you fancy tuning in to see what Zuckerberg has to say and how he is able to "clarify issues related to the use of personal data", you will be able to do just that. See also: Mark Zuckerberg agrees to appear in… [Continue Reading] -

Apple removes apps using the CallKit framework because of Chinese regulations
Publié: mai 21, 2018, 12:16pm CEST par Mark Wycislik-Wilson
Apple has bowed to pressure from China and started to remove apps from the App Store that use the CallKit framework. There are strict cybersecurity laws in place in China which has already see VPN tools banned and led to a brief suspension of the popular WeChat app. While no specific reason has been given for the crackdown on the CallKit framework, it is suspected to be related to VoIP functionality. See also: Apple clamps down on apps that share location data with third parties Apple tells developers that apps must support iPhone X notch from July Apple's purchase of… [Continue Reading] -

Microsoft acquires AI startup Semantic Machines to help boost Cortana
Publié: mai 21, 2018, 10:50am CEST par Mark Wycislik-Wilson
Microsoft has announced plans to acquire Semantic Machines, a startup based in Berkley, California, that specializes in conversational artificial intelligence. The acquisition makes a great deal of sense because of Microsoft's desire to push Cortana forward, and the general increased interest in voice-powered digital assistants and chatbots -- and products such as Google Duplex. The Semantic Machines team includes members who have worked on Siri and with speech-recognition firm Nuance. See also: Microsoft is said to be working on a cheap Surface tablet to compete with the iPad Microsoft blocks the rollout of Windows 10 April 2018 Update to computers… [Continue Reading] -

Google quietly relegates 'Don't be evil' from its Code of Conduct
Publié: mai 20, 2018, 10:38am CEST par Mark Wycislik-Wilson
For a long time, the words "don't be evil" were associated with Google. While not an official motto as such, the words were heavily ingrained in the company. Google's method of operating has caused many people over the years to question the phrase, and when the company was re-organized under Alphabet the motto became "do the right thing". Nonetheless, in the Google Code of Conduct which is given to employees, "don't be evil" remained -- until just a few weeks ago when it was quietly relegated. See also: Google will require OEMs to provide regular Android security updates Google explains… [Continue Reading] -

FCC investigates LocationSmart website for leaking location data for users of major US mobile carriers
Publié: mai 20, 2018, 10:02am CEST par Mark Wycislik-Wilson
LocationSmart, a company based in Southern California, is under investigation by the FCC after it was discovered that its website made it possible for just about anyone to access location data for the majority of US cell phones. Security expert Brian Krebs reported that a bug on the LocationSmart website made it possible for anyone to check on the location of any AT&T, Sprint, T-Mobile or Verizon phone in the US. Even more worryingly, the data is said to be accurate to a few hundred yards. See also: Google will require OEMs to provide regular Android security updates Chrome will… [Continue Reading] -

Fortnite for Android is coming very soon
Publié: mai 19, 2018, 12:29pm CEST par Mark Wycislik-Wilson
The phenomenon that is Fortnite will be making its way to Android, Epic Games has revealed. An Android version of the game is something that mobile gamers have been begging for for some time now, and it seems it will not be long until these pleas are answered. While an exact release date has not been revealed, Fortnite for Android will be happening in the next few months. See also: Meltdown patches are slowing down games such as Fortnite Fortnite has proved massively popular over the last year on Mac, PC and game consoles. There's an iOS version that has… [Continue Reading] -

PayPal buys Swedish fintech company iZettle
Publié: mai 18, 2018, 6:15pm CEST par Mark Wycislik-Wilson
PayPal has announced that it is to buy the mobile payment company iZettle. The announcement came as something of a surprise, as less than two weeks ago iZettle had said that it planned to go public. iZettle is a Swedish fintech company whose mobile card readers have proved popular with small businesses, as has its ecommerce platform. The $2.2 billion purchase is PayPal's biggest acquisition to date. The purchase will give PayPal the opportunity to expand into the retail payment terminals business in international markets, thanks to iZettle's card readers. The company currently operates in 11 countries in Europe and… [Continue Reading] -

Chrome will stop highlighting HTTPS sites as secure
Publié: mai 18, 2018, 5:14pm CEST par Mark Wycislik-Wilson
Later this year, Chrome will adopt a new approach to indicating site security. Starting in September, the browser will no longer use a security indicator to highlight the fact that you're visiting an HTTPS page. Instead, Google will simply issue a warning when a website is not secure. As the company puts it, "users should expect that the web is safe by default, and they’ll be warned when there’s an issue". The change is coming in Chrome 69. See also: Google will require OEMs to provide regular Android security updates Google explains its handling of user data ahead of GDPR… [Continue Reading] -

YouTube Music and YouTube Premium launch May 22
Publié: mai 17, 2018, 12:19pm CEST par Mark Wycislik-Wilson
Google has announced a new music streaming service, YouTube Music, as well as YouTube Premium, both of which launch next week. The two services come as a result of Google splitting up YouTube Red. YouTube Premium will be available for $11.99 per month, while YouTube Music will have free and paid-for versions. The free edition will be ad-supported, but these can be banished for $9.99 per month. See also: YouTube hackers take down and deface videos from the likes of Taylor Swift and Drake Google will require OEMs to provide regular Android security updates Google explains its handling of user… [Continue Reading] -

NYC announces plans to test algorithms for bias
Publié: mai 17, 2018, 10:29am CEST par Mark Wycislik-Wilson
The mayor of New York City, Bill de Blasio, has announced the formation of a new task force to examine the fairness of the algorithms used in the city's automated systems. The Automated Decision Systems Task Force will review algorithms that are in use to determine that they are free from bias. Representatives from the Department of Social Services, the NYC Police Department, the Department of Transportation, the Mayor's Office of Criminal Justice, the Administration for Children's Services, and the Department of Education will be involved, and the aim is to produce a report by December 2019. See also: Twitter… [Continue Reading] -

Mark Zuckerberg agrees to appear in front of EU parliament to answer questions about Facebook's use of data
Publié: mai 16, 2018, 5:51pm CEST par Mark Wycislik-Wilson
After refusing to answer questions in the UK, Mark Zuckerberg has agreed to face questions in front of the EU Parliament. The grilling comes in the wake of the Cambridge Analytica privacy scandal. The Facebook CEO could answer questions about the social network's use of data very soon, with the president of the European Parliament, Antonio Tajani, saying that "hopefully" it could happen next week. See also: Facebook's new Clear History privacy tool will let you stop third-party tracking and delete collected info There's still no 'dislike' option, but Facebook is testing upvote and downvote buttons with many users Facebook… [Continue Reading] -

Microsoft is said to be working on a cheap Surface tablet to compete with the iPad
Publié: mai 16, 2018, 4:39pm CEST par Mark Wycislik-Wilson
Not wanting to be outdone by Apple, Microsoft is reportedly planning to release a low-cost Surface tablet later this year. Said to measure 10 inches and with a price tag of around $400, the budget Surface will retain the familiar kickstand found on its Pro sibling, and will compete directly with the iPad. This is not a re-run of the Surface RT, as full-blown Windows will be supported. See also: Microsoft blocks the rollout of Windows 10 April 2018 Update to computers with problematic Intel SSDs Ubuntu 18.04 LTS hits the Microsoft Store for Windows 10 users Microsoft announces Surface… [Continue Reading] -

Microsoft blocks the rollout of Windows 10 April 2018 Update to computers with problematic Intel SSDs
Publié: mai 16, 2018, 11:15am CEST par Mark Wycislik-Wilson
If you have an Intel SSD installed, there's a chance that you won't be able to upgrade to Windows 10 April 2018 Update for the time being. Computers with Intel SSD 600p Series or Intel SSD Pro 6000p Series ended up crashing after the installation of the most recent major update to Windows 10, but users have been able to roll back their system to a usable state. To prevent further problems Microsoft has opted to block the April 2018 Update to such systems. In a post on the Microsoft Community, moderator Lonnie_L explained recently: "When attempting to upgrade to… [Continue Reading] -

Ubuntu 18.04 LTS hits the Microsoft Store for Windows 10 users
Publié: mai 16, 2018, 10:41am CEST par Mark Wycislik-Wilson
There are now two versions of Ubuntu available to download from the Microsoft Store. Adding to the existing Ubuntu 16.04, Ubuntu 18.04 has also now arrived. The addition comes just weeks after the official launch of Ubuntu 18.04, and it gives Windows 10 users the option of working with the new LTS (long term support) build of Ubuntu. The older version remains supported for the time being as well. See also: Canonical finally comments on Ubuntu Linux Snap Store security failure Ubuntu Snap Store app contained cryptocurrency miner Ubuntu Linux 18.04 Bionic Beaver is here -- download it now! Weighing… [Continue Reading] -

Twitter tweaks algorithms to give trolls less prominence
Publié: mai 15, 2018, 7:50pm CEST par Mark Wycislik-Wilson
Twitter's troll problem has not improved, despite various measures taken by the company. The latest attempt to get things under control finds Twitter changing its algorithms to take into account "behavioral signals" and help bury content from trolls. The algorithm tweaks do not means that tweets will be deleted, but those that are found to "distort and detract from the public conversation" will be pushed further down conversations and search results to reduce their visibility. See also: Twitter warns all users to change passwords after 'bug' left credentials stored in plaintext Twitter bans Kaspersky Lab from buying ads Twitter to… [Continue Reading] -

WhatsApp update brings Slack-style group messaging features and new admin controls
Publié: mai 15, 2018, 5:58pm CEST par Mark Wycislik-Wilson
The latest update rolling out to WhatsApp users heralds the arrival of a batch of new group messaging features. Available to both iOS and Android users, the new features include a Slack-style "group catch up" option, and it is also possible to add a description to group chats, and search for individual participants. See also: WhatsApp raises minimum user age to 16 in Europe and announces data download tool Now you have longer to delete your WhatsApp messages BlackBerry sues Facebook, WhatsApp and Instagram in messaging patent spat Group messaging has become increasingly important to WhatsApp in recent times, as… [Continue Reading] -

Kaspersky to move data from Russia to Switzerland to improve transparency
Publié: mai 15, 2018, 2:05pm CEST par Mark Wycislik-Wilson
Kaspersky Lab has announced that it plans to move data out of Russia and into a new data center in Switzerland. The move is part of the company's Global Transparency Initiative which came in response to concerns about ties to the Russian government. Software produced by Kaspersky has already been banned from US government systems, and the company has been on a mission to prove that Russia is not spying on other countries via its antivirus tools. See also: Twitter bans Kaspersky Lab from buying ads Kaspersky Lab plans Swiss data center to quell fears about Russian connections Kaspersky sues… [Continue Reading] -

Facebook launches Youth Portal to tell teenagers how it uses their data
Publié: mai 15, 2018, 10:35am CEST par Mark Wycislik-Wilson
Facebook has launched a new Youth Portal with the aim of educating its teenage users about using the social network safely. The portal also reveals to teens how Facebook uses their data, and is packed with tips about using the service and translates the site's Data Policy into a more understandable form. See also: Facebook's new Clear History privacy tool will let you stop third-party tracking and delete collected info There's still no 'dislike' option, but Facebook is testing upvote and downvote buttons with many users Following Apple's lead from 2016, Microsoft, Facebook and Google replace gun emoji with water… [Continue Reading] -

Master & Dynamic reveals convertible MW50+ wireless on-ear/over-ear headphones
Publié: mai 15, 2018, 6:05am CEST par Mark Wycislik-Wilson
Master & Dynamic headphones have previously proved very popular here with the BetaNews team, and the latest addition -- the MW50+ -- looks set to continue the trend. The same retro look is here, and these new headphones sit part way between the MW50 and MW60 models. While the MW50 features an on-ear design, and the MW60 an over-ear design, the MW50+ can convert between on-ear and over-ear modes thanks to detachable, magnetic earpads made of memory foam and lambskin. The company says that the headphones are aimed at the "busy urban professional", and the switchable ear modes are not… [Continue Reading] -

Apps based on Electron framework are vulnerable to attack
Publié: mai 14, 2018, 12:37pm CEST par Mark Wycislik-Wilson
The Electron framework -- the basis of popular apps including Skype, Slack, Signal and WordPress -- has been found to contain a security flaw that leaves it vulnerable to attack. The GitHub-created tool has a vulnerability that allows hackers to execute arbitrary code on remote systems. CVE-2018-1000136 affects Electron 1.7.13 and older as well as Electron 1.8.4 and 2.0.0-beta.3, and the problem exists because of the interaction between Electron and Node.js. See also: Google will require OEMs to provide regular Android security updates Amazon now offers a smart home security installation service Google's Project Zero reveals security flaw in Windows… [Continue Reading] -

Trump says he wants to get ZTE 'back into business, fast' despite putting a Denial Order in place
Publié: mai 14, 2018, 11:05am CEST par Mark Wycislik-Wilson
Donald Trump has caused confusion after using Twitter to indicate that he would like to get Chinese smartphone manufacturer ZTE "back into business, fast". This is despite the US Department of Commerce banning exports to the company for seven years, something ZTE says left it unable to continue running its main operations. Trump now says that he's working with China's President Xi to help get the company back up and running. Unsurprisingly, the disparity between what Trump says in his weekend tweet and what the current US sanctions mean has led to a lot of questions. See also: US ban… [Continue Reading] -

Major leak reveals OnePlus 6 pricing, pictures and release date
Publié: mai 14, 2018, 9:54am CEST par Mark Wycislik-Wilson
Details of just about every OnePlus handset have leaked ahead of their launches, and the OnePlus 6 is no different. There are only a couple of days until the phone is revealed by the Chinese smartphone manufacturer, and we've already had numerous leaks relating to the upcoming handset. Amazon Germany has accidentally given away more than OnePlus may have liked, revealing high resolution renders of the glass-bodied phone, as well as the pricing and release date. See also: OnePlus 6 specs leak ahead of the launch later this month Yep, the OnePlus 6 definitely has a notch -- deal with… [Continue Reading] -

Google will require OEMs to provide regular Android security updates
Publié: mai 12, 2018, 10:41am CEST par Mark Wycislik-Wilson
The fragmentation problem that affects Android not only means that there are a tiny number of users running the latest version of Google's mobile operating system, but also that many handsets are not patched with the latest security update. This could be about to change. At its I/O developer conference this week, Google announced that its security policies will be changing. While its not clear when this could happen, the company will require some smartphone manufacturers to roll out regular security updates to users. See also: Microsoft says that to text from Windows 10 with Your Phone app, you'll need… [Continue Reading] -

Microsoft launches free Surface Pro 4 replacement program because it can't fix flickering screens
Publié: mai 12, 2018, 10:12am CEST par Mark Wycislik-Wilson
If you have a Surface Pro 4, you might be one of the unlucky tablet owners to suffer from a flickering screen -- a problem predictably dubbed "flickergate". Unable to come up with a fix, Microsoft has opened up a replacement program that means that those affected by the problem will be able to get a new Surface Pro 4 free of charge. Microsoft says that it has been unable to produce a patch to address the issue, and is therefore simply going to offer replacements to people. What's not clear is why it has taken the company so long… [Continue Reading] -

Google explains its handling of user data ahead of GDPR and reveals new privacy policy
Publié: mai 11, 2018, 12:21pm CEST par Mark Wycislik-Wilson
There's now just two weeks until the new General Data Protection Regulation (GDPR) law comes into force across Europe. Technology companies have been scrabbling to update their privacy policies in order to comply, and today Google reveals the steps it has taken to become compliant. In addition to this, the company has also published its updated privacy policy. In keeping with GDPR, this time around the terms are presented in a much more accessible and transparent form. See also: Google Drive gets a major redesign to match the look of the new Gmail Companies can turn GDPR compliance into competitive… [Continue Reading] -

Samsung Galaxy Note9 benchmarks and leaked image appear online
Publié: mai 11, 2018, 11:34am CEST par Mark Wycislik-Wilson
There are few handsets released these days that do not fall victim to leaks. Phones from Samsung are no different, and the same thing has happened with the upcoming Galaxy Note9. In addition to a leaked image -- which shows that Samsung has done little to change the design of the phone since the Note 8 -- benchmark results for the handset have also appeared online. The image may not offer too much to get excited about, but the benchmarks give away more information. The leak image comes courtesy of Twitter user Ice Universe. The leaker is anonymous, but has… [Continue Reading] -

Microsoft says that to text from Windows 10 with Your Phone app, you'll need an Android handset
Publié: mai 11, 2018, 10:36am CEST par Mark Wycislik-Wilson
There's bad news for iPhone users who were previously excited about Microsoft's upcoming Your Phone app. Revealed at Build 2018 earlier this week, this new Windows 10 app will provide a way to connect your phone to your computer and then view notifications, send texts and copy files from within Windows 10. But some of this functionality will be Android-only. Microsoft says that it needs to work with Apple to get some features up and running, including being able to respond to iPhone text messages via Windows 10. But how likely is this cooperation? See also: Microsoft announces Your Phone,… [Continue Reading] -

US ban forces ZTE to close its main operations
Publié: mai 10, 2018, 4:03pm CEST par Mark Wycislik-Wilson
ZTE's fall from grace has been fairly spectacular. Now -- just weeks after been blacklisted by both the US and the UK -- the Chinese telecom manufacturer has announced that it has ceased its "major operating activities". The company blames the move directly on the US ban on sales to ZTE, but says it is talking to the US government to try to get the ban lifted. Without a supply of US-made components, ZTE is going to find it very difficult to operate for very long. See also: ZTE says Denial Order put in place by the US Department of… [Continue Reading] -

Google announces plans to acquire cloud migration company Velostrata
Publié: mai 10, 2018, 11:54am CEST par Mark Wycislik-Wilson
Google has announced that it is to acquire Israeli firm Velostrata. This startup specializes in enterprise cloud migration technology. Velostrata was founded in 2014, and its patented technology will help to give Google valuable tools for its customers looking to migrate from in-premises to cloud solutions. See also: Google Drive gets a major redesign to match the look of the new Gmail Google rolls out massive Gmail redesign -- here's what's new and how to access it Upcoming Gmail redesign will also herald the arrival of self-destructing emails In a blog post, Eyal Manor, vice president of engineering at… [Continue Reading] -

Google Drive gets a major redesign to match the look of the new Gmail
Publié: mai 10, 2018, 9:45am CEST par Mark Wycislik-Wilson
Following on from the redesign of Gmail, Google has start to roll out a new interface to Google Drive. The new user interface can be found on the web version of the cloud storage service, but it's likely that mobile apps will follow suit. Google hasn't made much of a fuss about this redesign, but keeping things in line with other G Suite products makes a lot of sense. The redesign sees the arrival of an updated material look. See also: Gmail's new 'Smart Compose' feature writes replies for you Google rolls out massive Gmail redesign -- here's what's new… [Continue Reading] -

Apple clamps down on apps that share location data with third parties
Publié: mai 9, 2018, 5:42pm CEST par Mark Wycislik-Wilson
Apple appears to be more vigorously enforcing App Store policies relating to the sharing of location data. Over the last few days the company has been removing apps that share location details with third parties without consent. Developers of apps found to be exploiting user privacy in this way have received emails from Apple. These indicate that apps have undergone "re-evaluation" and found to be in violation of sections 5.1.1 and 5.1.2 of the App Store Review Guidelines. See also: Apple tells developers that apps must support iPhone X notch from July Apple's purchase of Shazam to be investigated by… [Continue Reading] -

Walmart buys a controlling share in India's Flipkart
Publié: mai 9, 2018, 4:54pm CEST par Mark Wycislik-Wilson
Rumors have circulated for a number of weeks, but now it's official: Walmart has just said it will spend $16 billion buying a controlling sharing in Flipkart, the Indian ecommerce site. The American retail giant fought off a last-minute bid from Amazon. The deal values Flipkart at $20.8 billion, and will see Walmart taking an initial stake of 77 percent of the company. The remainder of Flipkart ownership is shared between Tencent, Tiger Global and Microsoft, as well as its co-founder Binny Bansal. See also: com now redirects to Amazon and the company's new Wag pet brand Amazon now offers… [Continue Reading] -

Google launches Android Jetpack to speed up app development
Publié: mai 9, 2018, 11:02am CEST par Mark Wycislik-Wilson
Google has a new tool designed to help developers produce Android apps faster than ever. Called Android Jetpack, it builds on the Support Library and has a strong focus on backwards compatibility. Android Jetpack also builds on Architecture Components, giving developers access to components, tools and architectural guidance split into four categories -- architecture, foundation, UI and behavior. Each component is provided as an "unbundled" library which Google says means you can "adopt each component at your own speed, at your own time". See also: The best Android apps and games revealed in 2018 Google Play Awards Android P: Smarter… [Continue Reading] -

Microsoft to let Windows 10 users Alt-Tab between both apps and browser tabs
Publié: mai 9, 2018, 10:05am CEST par Mark Wycislik-Wilson
For many people, keyboard shortcuts are essential to using a computer, and over time they become hardwired into muscle memory. You've probably become used to the way Alt-Tab can be used to switch between running apps, but Microsoft plans to change the way this particular shortcut works. At Build, the company revealed that the next Insider build of Windows 10 will not only let you Alt-Tab between running programs, but also browser tabs. It's something that's being introduced as part of Sets, and it's likely to divide opinion. See also: Microsoft announces Your Phone, an app to view your iPhone… [Continue Reading] -

Google News gets a major revamp and an AI injection
Publié: mai 8, 2018, 10:28pm CEST par Mark Wycislik-Wilson
Today at its I/O developer conference, Google revealed major changes for Google News. The company says that the revamp combines the best of artificial intelligence with the best of human intelligence, and it sees Google try to rebuild the trust people have in online news. As well as a revamp of the underlying technology, there are also changes in presentation. A "For You" section in the app provides easy access to the most relevant stories that will be of personal interest, and there are also new opportunities for readers to delve deeper into stories via various news outlets, social media,… [Continue Reading] -

Apple tells developers that apps must support iPhone X notch from July
Publié: mai 8, 2018, 11:33am CEST par Mark Wycislik-Wilson
Apple has issued new guidelines for iOS apps submitted to the App Store, with the biggest change being that developers must use the iOS 11 SDK. Devs are advised that they should "update your version of Xcode to the latest release of Xcode 9 available on the Mac App Store" as this includes the relevant SDK. Apple also says that apps should be "ready to take advantage of the Super Retina display by respecting safe areas, supporting adaptive layouts, and more". SEE ALSO: Apple's purchase of Shazam to be investigated by the EU Apple announces free 13-inch MacBook Pro (non-Touch… [Continue Reading] -

The best Android apps and games revealed in 2018 Google Play Awards
Publié: mai 8, 2018, 10:16am CEST par Mark Wycislik-Wilson
It's not long since Google's Android Excellence program bestowed praise on apps and games on what were considered to offer a high quality experience. Now the company has used Google I/O to reveal the winners of the 2018 Google Play Awards. Google says that the aim of the ceremony is to "recognize the best apps and games on Google Play over the past year", and it's a great way to discover something new to try. See also: Android Things exits beta as Google jumps further into the IoT Microsoft announces Your Phone, an app to view your iPhone or Android… [Continue Reading] -

Facebook copies Snapchat's Bitmoji and creates personal, customizable Avatars
Publié: mai 8, 2018, 9:33am CEST par Mark Wycislik-Wilson
Never afraid to steal an idea or two from its competitors, Facebook is at it once again, this time "borrowing" Bitmoji from Snapchat. The yet-to-be-released feature is called Facebook Avatars and it will let users create personalized cartoon images of themselves to use as stickers or emoji. The Avatars feature has not even been announced by Facebook yet, but references to it were found hidden deep in the code of the social network's Android app. The company has, however, confirmed that the feature is in development. See also: Facebook's new Clear History privacy tool will let you stop third-party tracking… [Continue Reading] -

Android Things exits beta as Google jumps further into the IoT
Publié: mai 7, 2018, 8:10pm CEST par Mark Wycislik-Wilson
Google today announced the launch of Android Things 1.0, its Internet of Things platform. There have been numerous beta versions for developers to play with, but now that the operating system has been officially launched we can expect to see it popping up on a wide range of devices. The company says that it has been working closely with a number of manufacturers to help ensure that products will be available soon. On the horizon are smart speakers from LG and iHome, as well as smart displays from Lenovo, LG, and JBL. See also: Microsoft announces Your Phone, an app… [Continue Reading] -

Microsoft announces Your Phone, an app to view your iPhone or Android device in Windows 10
Publié: mai 7, 2018, 6:58pm CEST par Mark Wycislik-Wilson
Having given up on its own mobile operating system, Microsoft has a greater interest in Android and iOS than ever before. Today at its Build 2018 developer conference, the company announces a new app called Your Phone. The purpose of the app is to enable you to connect your computer to an iPhone or Android device and access the handset's contents without having to pick it up. As well as being able to view and respond to text messages from the comfort of your PC, you'll also be able to move files to and from your phone. See also: Microsoft's… [Continue Reading] -

How to fix the Feedback Frequency bug in Windows 10 April 2018 Update
Publié: mai 7, 2018, 1:11pm CEST par Mark Wycislik-Wilson
The Windows 10 April 2018 Update has started to roll out to users around the world, and it has not been without its problems. One issue that some people have noticed is that the "Feedback frequency" setting cannot be changed. Users are complaining that the setting has a new label reading "Windows Insider Program manages this option" -- regardless of whether the computer has been part of the Insider program or not. An update is available to address the problem, but it has to be installed manually. See also: Microsoft is working on a fix for Chrome and Cortana freezes… [Continue Reading] -

Vine successor V2 is postponed for an 'indefinite amount of time'
Publié: mai 7, 2018, 11:34am CEST par Mark Wycislik-Wilson
It is now over a year since Vine closed down, and fans have been holding out for a follow-up to the video service. Co-founder Dom Hofmann previously said that work was underway on a successor called V2, but this has now been put on hold. Blaming "financial and legal hurdles", Hoffmann now says that the project has been postponed "for an indefinite amount of time". He says that he had hoped to bring V2 to life as a personal project, but the realization that more money will be needed means that investors need to be brought onboard. Hoffman made the… [Continue Reading] -

Compatible handsets will get Windows 10 Mobile April 2018 Update
Publié: mai 7, 2018, 11:18am CEST par Mark Wycislik-Wilson
The Windows 10 April 2018 Update rollout to PCs around the world has already started, and Microsoft says that the update will also make its way to compatible Windows 10 Mobile devices. The number of people who will actually end up receiving this update, however, is likely to be rather limited. Microsoft says that the availability of Windows 10 Mobile April 2018 Update will vary according to "manufacturer, model, country or region, mobile operator or service provider, hardware limitations" and -- ominously -- "other factors". See also: Microsoft is working on a fix for Chrome and Cortana freezes in Windows… [Continue Reading] -

Email management service Unroll.Me to close in Europe because of GDPR
Publié: mai 7, 2018, 9:53am CEST par Mark Wycislik-Wilson
The new batch of privacy related legislations that's due to roll out across Europe later this month has claimed another victim -- Unroll.Me. The email management service, which claims to help users "clean up your inbox", has announced that it is incompatible with GDPR (General Data Protection Regulation) and will therefore close down in the EU on May 23. If you live in the EU, Unroll.Me will delete your account and you'll no longer be able to use the service. See also: Facebook sneakily shifts data of 1.5 billion users away from Europe and GDPR 73 percent of UK businesses… [Continue Reading] -

Microsoft's Meltdown patch for Windows 10 has a 'fatal flaw'
Publié: mai 7, 2018, 9:02am CEST par Mark Wycislik-Wilson
If you've not updated to Windows 10 April 2018 Update but you have installed Microsoft's Meltdown patches from a few months ago, your computer is vulnerable to a "fatal flaw". This is not the first time a patch for the Meltdown vulnerability has led to problems with Windows, but previously it was Windows 7 and Windows Server 2008 that were affected. A security researcher found that Microsoft's patch for Windows 10 "undermined the mitigation", and while the problem has been fixed in the April 2018, the company is still working on backporting an updated patch for older versions of Windows… [Continue Reading] -

OnePlus 6 specs leak ahead of the launch later this month
Publié: mai 5, 2018, 5:49pm CEST par Mark Wycislik-Wilson
The OnePlus 6 is due to be revealed on May 26 and, as with just about every OnePlus device, details of the latest flagship have leaked out nice and early. There have already been a number of rumors relating to the OnePlus 6 -- such as confirmation of the notch -- but now full specifications have appeared on the website of Chinese regulator TENAA. So what can you expect from the A6000, and will it be enough to warrant an upgrade from a OnePlus 5 or OnePlus 5T? See also: This is the OnePlus 6 Yep, the OnePlus 6 definitely… [Continue Reading] -

Microsoft is working on a fix for Chrome and Cortana freezes in Windows 10 April 2018 Update
Publié: mai 4, 2018, 6:13am CEST par Mark Wycislik-Wilson
Microsoft launched Windows 10 April 2018 Update this week, and if you rushed to install it you may well have noticed one or two issues. There have been complaints that various apps have been problematic since the update, but Chrome and Cortana seem to be causing the most problems. Microsoft has confirmed that it is aware of issues with Chrome and "Hey Cortana" that can lead to Windows 10 April 2018 Update freezing. A patch is currently being worked on and should be released next week, but the company has a couple of suggestions for fixes you can try in… [Continue Reading] -

Twitter warns all users to change passwords after 'bug' left credentials stored in plaintext
Publié: mai 4, 2018, 5:45am CEST par Mark Wycislik-Wilson
Twitter has issued a warning to its 330 million users, urging them to change their passwords. The security announcement comes after the company discovered a bug that left passwords stored in unencrypted form in internal logs. While Twitter says that the bug has been fixed and that the plaintext logs have been deleted, it is encouraging the password change out of "an abundance of caution". See also: Twitter bans Kaspersky Lab from buying ads Twitter to ban an array of cryptocurrency ads Thousands of Android apps have built-in crypto keys and passwords Twitter suspends multiple 'tweetdecking' accounts for stealing tweets… [Continue Reading] -

Wag.com now redirects to Amazon and the company's new Wag pet brand
Publié: mai 3, 2018, 6:20am CEST par Mark Wycislik-Wilson
Branching out into yet another field, Amazon has launched its own pet product brand, Wag. This is not the first time the company has launched an own-label product -- it has already enjoyed success with household goods and baby products. Available to Amazon Prime subscribers, the Wag line starts off with dry dog food, but it will expand into further supplies soon. See also: Amazon now offers a smart home security installation service Amazon Prime subscriptions increase to $119 in the US -- here's how to avoid the price hike Amazon Key In-Car lets Prime subscribers have orders delivered to… [Continue Reading] -

Facebook's new Clear History privacy tool will let you stop third-party tracking and delete collected info
Publié: mai 1, 2018, 7:54pm CEST par Mark Wycislik-Wilson
At its F8 conference today, Facebook revealed details of an upcoming tool it is working on --- Clear History. The tool will let Facebook users not only see which sites and apps gather information about usage, but also let users delete this information. The privacy-centric tool comes as the social network slowly comes to the realization "that people want more information about how Facebook works and the controls they have over their information". The ability to delete browsing histories from Facebook appears to be a direct response to the Cambridge Analytica scandal in which private data was shared without consent.… [Continue Reading] -

There's still no 'dislike' option, but Facebook is testing upvote and downvote buttons with many users
Publié: mai 1, 2018, 4:45pm CEST par Mark Wycislik-Wilson
The Like button is synonymous with Facebook, and ever since its inception people have been clamoring for its nemesis to be added to the site. The arrival of 'reactions' two years ago pleased some people, as it gave them the opportunity to express a negative response to something -- but there was still no Dislike button. The social network is currently testing a feature which is a step closer to the option people have been asking for for so long. Currently being trialed is a comment voting system that lets users upvote or downvote comments left by others. See also:… [Continue Reading] -

Privacy: How to disable Timeline in Windows 10 April 2018 Update
Publié: mai 1, 2018, 6:59am CEST par Mark Wycislik-Wilson
We've already written quite a bit about Windows 10 April 2018 Update, and there's a reasonable chance that you've taken the plunge and installed it. While there are new features to get excited about, some have people more concerned than excited -- such as Timeline. In theory, the feature sounds great, making it possible to synchronize your activities between devices, but it's also something of a privacy nightmare. Timelime -- by design and because of its very nature -- gathers a huge amount of information about you and what you do within Windows 10. Thankfully, you can disable it. See… [Continue Reading] -

Wikipedia now offers link previews -- but you can disable them
Publié: avril 28, 2018, 1:51pm CEST par Mark Wycislik-Wilson
When you decide to look up anything on Wikipedia, you run the very serious risk of falling down a rabbit hole that will take you many hours to find your way back out of. To help avoid the problem of going off on too much of a tangent, the site recently introduced a new link preview feature. It's a simple idea which means that it is possible to preview a page before you visit it, simply by hovering over the link. But it's not to everyone's taste. If you've noticed the new feature and want to kill it, you'll be… [Continue Reading] -

Amazon now offers a smart home security installation service
Publié: avril 27, 2018, 5:58pm CEST par Mark Wycislik-Wilson
Earlier today, we revealed that Amazon is bumping up the price of a Prime subscription by 20 percent, but this is not the only news coming from the online giant. A newly discovered and little-advertised portal on the Amazon site finds the company offering smart home security installation services. Ranging in price from $240 to $840, the Smart Home Services packages include the cost of both hardware and installation. In all, there are five packages to choose from, covering everything from simple smart lighting, to full-home security systems. See also: Amazon Prime subscriptions increase to $119 in the US --… [Continue Reading] -

Office 2019 Preview is now available to download
Publié: avril 27, 2018, 4:53pm CEST par Mark Wycislik-Wilson
We already knew that Microsoft was planning to release previews of Office 2019 towards the middle of this year, and now the first one is here -- for some people, at least. Microsoft has unveiled the Office 2019 Commercial Preview, and this is a chance for businesses to try out the latest version of the office suite. The PC version of the suite is a Windows 10 exclusive. Read on to find out how to get your hands on the software -- if, indeed, you can. See also: Microsoft to kill off OneNote's desktop app in Office 2019 to focus… [Continue Reading] -

Amazon Prime subscriptions increase to $119 in the US -- but you may avoid the price hike
Publié: avril 27, 2018, 11:03am CEST par Mark Wycislik-Wilson
At its earnings call yesterday, Amazon revealed that it is increasing the price of Amazon Prime by 20 percent for subscribers in the US. The new price kicks in from May 11 for new subscribers, and from June 16 for those with existing subscriptions. The increase sees the cost of Prime jumping from $99 per year to $119, and Amazon has not yet given any indication that the hike will be implemented in other parts of the world. There's also a little trick that you can try that may enable you to avoid the price jump. See also: 'Awexa, play… [Continue Reading] -

Amazon Prime subscriptions increase to $119 in the US -- here's how to avoid the price hike
Publié: avril 27, 2018, 11:03am CEST par Mark Wycislik-Wilson
At its earnings call yesterday, Amazon revealed that it is increasing the price of Amazon Prime by 20 percent for subscribers in the US. The new price kicks in from May 11 for new subscribers, and from June 16 for those with existing subscriptions. The increase sees the cost of Prime jumping from $99 per year to $119, and Amazon has not yet given any indication that the hike will be implemented in other parts of the world. There's also a little trick that you can try that may enable you to avoid the price jump. See also: 'Awexa, play… [Continue Reading] -

Following Apple's lead from 2016, Microsoft, Facebook and Google replace gun emoji with water pistol
Publié: avril 26, 2018, 12:29pm CEST par Mark Wycislik-Wilson
It is now two years since Apple decided that an image of a gun had no place as an emoji. The company replaced the handgun icon with an image of a water pistol, leading to a debate about whether it was the right thing to do. With further serious shootings and gun crimes bringing firearms into the spotlight time and time again, more technology companies decided to follow suit. The latest names to follow Apple's lead are Microsoft, Facebook and Google, all of whom plan to kill the gun emoji and replace it with a water pistol. See also: Apple… [Continue Reading] -

Exploit emerges for Microsoft's duff Meltdown patch for Windows 7 and Server 2008
Publié: avril 26, 2018, 11:51am CEST par Mark Wycislik-Wilson
For Microsoft, the patches it produced for the Meltdown chip vulnerability proved to be just about as problematic as the original issue, further reducing the security of systems. Following the emergence of an exploit for the Windows-maker's first patch, users are advised to hurry up and install the patch-for-a-patch that was later released. Last month, Ulf Frisk from Sweden revealed that Microsoft's Meltdown patches were making things worse for Windows 7 and Windows Server 2008, making it possible to read and write kernel memory and gain total control over the system. Now code has been posted online that can be… [Continue Reading] -

Exploit emerges for Microsoft's problematic Meltdown patch for Windows 7 and Server 2008
Publié: avril 26, 2018, 11:51am CEST par Mark Wycislik-Wilson
For Microsoft, the patches it produced for the Meltdown chip vulnerability proved to be just about as problematic as the original issue, further reducing the security of systems. Following the emergence of an exploit for the Windows-maker's first patch, users are advised to hurry up and install the patch-for-a-patch that was later released. Last month, Ulf Frisk from Sweden revealed that Microsoft's Meltdown patches were making things worse for Windows 7 and Windows Server 2008, making it possible to read and write kernel memory and gain total control over the system. Now code has been posted online that can be… [Continue Reading] -

Digg is now owned by ad-tech company BuySellAds
Publié: avril 26, 2018, 10:58am CEST par Mark Wycislik-Wilson
Digg used to carry some major clout on the internet, but this all changed back in 2012 when the site was bought by Betaworks. Now the site has been sold again, this time to an ad-tech company. Boston-based BuySellAds has just bought Digg's assets and its editorial and revenue teams for an undisclosed amount. The company says that it "plans to streamline Digg and build up its ad stack", which will come as sad news for those who still cling onto a nostalgic image of what Digg used to be. See also: Warning for RSS fans -- Digg Reader is… [Continue Reading] -

Google launches Tasks app for iOS and Android, revamps web version
Publié: avril 25, 2018, 4:49pm CEST par Mark Wycislik-Wilson
The big news from Google today is the launch of the redesigned Gmail, but it's not the only news. The company has also launched a new app called Tasks which -- no prizes for guessing -- allows for management of to-do lists. The Google Tasks service is nothing new, and it has been accessible from Gmail inboxes and Google Calendar for quite some time, but this is the first time there has been a dedicated app for it. As well as the app, there's also a revamp of the web-based version of Tasks. See also: Google rolls out massive Gmail… [Continue Reading] -

WhatsApp raises minimum user age to 16 in Europe and announces data download tool
Publié: avril 25, 2018, 11:57am CEST par Mark Wycislik-Wilson
With new privacy laws due to roll out around Europe next month, WhatsApp has increase its minimum age from 13 to 16. The Facebook-owned messaging tool has made the change in order to comply with GDPR (General Data Protection Regulation) which comes into force on May 25. To continue to use WhatsApp, users must now confirm that they are at least 16 years old and agree to the privacy policy and terms of services of the newly-created WhatsApp Ireland Limited. See also: Facebook sneakily shifts data of 1.5 billion users away from Europe and GDPR Privacy: Facebook will roll out… [Continue Reading] -

Google rolls out massive Gmail redesign -- here's what's new and how to access it
Publié: avril 25, 2018, 10:36am CEST par Mark Wycislik-Wilson
We've known for a little while that Google was planning a major overhaul of Gmail -- complete with a host of new features -- and now the big day has arrived. The most obvious change is the new look which is more in keeping with the aesthetics of Material Design, but it's the new features that Google is most keen to talk about. While the company says that the aim of the update is "to help people be more productive at work", the new features are available to everyone starting now. What do you have to look forward to? Nudges,… [Continue Reading] -

Instagram launches Data Download tool so you can grab the contents of your account
Publié: avril 24, 2018, 8:07pm CEST par Mark Wycislik-Wilson
A couple of weeks ago, Instagram said that it was working on a tool that would enable users to download everything from their accounts. Now the tool has been launched ahead of the roll out of GDPR in Europe. There has been no fanfare for the data download tool, but it's available for everyone to use. It gives people the opportunity to download "photos, comments, profile information and more" which is ideal for anyone looking to either backup their data, or who is thinking about moving to a rival service. See also: Soon you will be able to download your… [Continue Reading] -

TVAddons launches Feeds for Git Browser, making it easy to share lists of favorite Kodi addons
Publié: avril 24, 2018, 3:57pm CEST par Mark Wycislik-Wilson
It has been a little while since we heard anything from TVAddons, the Kodi addons site that has been embroiled in a series of copyright cases. Recently the site launched its Github Browser as part of its continued attempts to provide "resilient and decentralized" links to Kodi addons. Now TVAddons has launched Feeds for Git Browser, a new feature that makes it possible for anyone to create a list of their favorite Kodi addons and then share them with friends, family and followers. With the demise of various Kodi addon sites over the last couple of years, TVAddons has really… [Continue Reading] -

Amazon Key In-Car lets Prime subscribers have orders delivered to their car
Publié: avril 24, 2018, 3:11pm CEST par Mark Wycislik-Wilson
Through Amazon Key, Prime subscribers can grant delivery drivers access to their home using a special keypad so packages can be delivered when they're out. Today Amazon announces an extension of the program, Amazon Key In-Car, which lets Prime users have deliveries placed in their cars. To start with, the service is available in 37 US cities, and there are plans to roll it out further. Shoppers are given a four-hour delivery window during which time their goods can be delivered to their vehicle. To start with, there is support for compatible 2015 or newer Chevrolets, Buicks, GMCs and Cadillacs… [Continue Reading] -

Apple's purchase of Shazam to be investigated by the EU
Publié: avril 24, 2018, 1:21pm CEST par Mark Wycislik-Wilson
Apple's planned purchase of UK-based music-recognition app Shazam for $400 million is facing an investigation by the European Commission. The commission is concerned that the purchase could give Apple an unfair advantage because of the access it would have to user data, and there is also concern that consumer choice could be limited. Initial investigations found that Apple may use the takeover to encourage Shazam users to move to its own music streaming services, so the commission is undertaking a more in-depth probe. See also: Apple announces free 13-inch MacBook Pro (non-Touch Bar) battery replacement program Leaked memo shows Apple… [Continue Reading] -

Facebook publishes its internal Community Standards guidelines and introduces appeals process
Publié: avril 24, 2018, 12:10pm CEST par Mark Wycislik-Wilson
Facebook faces lots of criticisms and questions, and while much of this is focused on privacy and security, there are also lots of queries about what is permitted on the platform. To help users to understand what's allowed and what's not, the company has published its Community Standards for everyone to read. As well as making it clear exactly what sort of content is likely to attract the attention of censors, Facebook is also introducing a new appeals process, giving people the ability to fight back if their content is removed. See also: What information do Facebook advertisers know about… [Continue Reading] -

What information do Facebook advertisers know about me?
Publié: avril 23, 2018, 6:34pm CEST par Mark Wycislik-Wilson
This is the question Facebook poses and (sort-of-but-not-really) answers in the latest addition to its Hard Questions series. It's the social network's latest attempt to claw back some respect and trust from its users in the wake of the Cambridge Analytica privacy scandal, and it sees the company insisting that "you are not the product". Whether this is believed or not is neither here nor there. That the company is now having to go to such extraordinary lengths to appear transparent, to try to prove that nothing untoward is going on, is simply indicative of the massive level of suspicion… [Continue Reading] -

Discovery of Terminal app for Chrome OS suggests future support for Linux software
Publié: avril 23, 2018, 5:07pm CEST par Mark Wycislik-Wilson
Chrome OS is a fairly flexible operating system, and its support for Android apps via the Google Play Store opens up a world of software. It has been thought -- and hoped -- for some time that Linux support might be on its way, and this is looking increasingly likely. A Terminal app has appeared in the Chrome OS dev channel, strongly suggesting that support for Linux applications could well be on the horizon -- something which will give Chromebooks a new appeal. See also: The HP Chromebook x2 with detachable screen is ready to take on the iPad Pro… [Continue Reading] -

Microsoft developers hid a secret puzzle in Windows backgrounds as they knew images would leak
Publié: avril 23, 2018, 4:15pm CEST par Mark Wycislik-Wilson
Microsoft developers working on Windows 8 created a puzzle and embedded it in the wallpapers used for internal builds of the operating system. The team knew that the images would leak out to the public -- and probably the internal builds of Windows -- so they decided to have some fun with it. Over the course of numerous builds, the puzzle was developed -- but only one person ever solved it! See also: Windows 10 April Update is probably the new name for Spring Creators Update Microsoft releases Windows 10 Redstone 5 Build 17650 for Skip Ahead Microsoft reveals more… [Continue Reading] -

Windows 10 April Update is probably the new name for Spring Creators Update
Publié: avril 22, 2018, 3:31pm CEST par Mark Wycislik-Wilson
Windows 10 Spring Creators Update will probably actually be released with a different name: Windows 10 April Update. Users who have installed build 17134 -- believed to be the RTM build -- have spotted a reference to the new name in Microsoft Edge post installation. This is not the first time this name has been suggested. Less than a week ago a Microsoft video emerged that made reference to Windows 10 April 2018 Update, and the new discovery in Edge would only seem to offer further proof. See also: Microsoft discovers blocking bug and delays the release of Windows 10… [Continue Reading] -

WikiLeaks calls for Coinbase boycott after the cryptocurrency exchange closes its store account
Publié: avril 22, 2018, 1:03pm CEST par Mark Wycislik-Wilson
The cryptocurrency exchange Coinbase has closed the account of the WikiLeaks Shop -- the official source of WikiLeaks merchandise -- citing violations of its terms of services. WikiLeaks is not happy about this and is calling for a "global blockade" of Coinbase in protest, saying the exchange is an "unfit member of the crypto community". The WikiLeaks Shop has itself not been closed, and it is still able to accept Bitcoin payments -- just not via Coinbase. See also: Hacker exploits Verge bug to generate cryptocurrency coins worth $780,000 in 3 hours Twitter to ban an array of cryptocurrency ads… [Continue Reading] -

Learn to code JavaScript for free with Google Grasshopper
Publié: avril 22, 2018, 12:24pm CEST par Mark Wycislik-Wilson
Many people like the idea of learning to code, but -- like learning a foreign language -- it can be hard to know where to start. With free and paid-for options to choose from, and a wide range of techniques, what's the best way to get started? If you've been thinking about learning JavaScript, Google may have the answer for you. The company has launched Grasshopper, a free coding app for iPhone and Android that teach through a series of puzzle games. See also: Google's Project Zero reveals security flaw in Windows 10 S after Microsoft fails to fix it… [Continue Reading] -

Apple announces free 13-inch MacBook Pro (non-Touch Bar) battery replacement program
Publié: avril 22, 2018, 11:40am CEST par Mark Wycislik-Wilson
If you have a 13-inch MacBook Pro without a Touch Bar, you could be eligible for a free battery replacement. Apple has discovered that a "limited number" of laptops have a problem that causes the battery to expand. The company has launched a free battery replacement program, and anyone who bought their MacBook Pro between October 2016 and October 2017 is invited to submit their machine's serial number to see if they qualify. See also: Leaked memo shows Apple threatens leakers with criminal action Apple encourages the switch to 64-bit with 'not optimized for Mac' message Apple says the redesigned… [Continue Reading] -

Twitter bans Kaspersky Lab from buying ads
Publié: avril 21, 2018, 10:46am CEST par Mark Wycislik-Wilson
Its software is already banned from US government computers, and now Kaspersky Lab's advertisements have been banned from Twitter. The Russian security firm has been hit with an ad ban for "using a business model that inherently conflicts with acceptable Twitter Ads business practices". Eugene Kaspersky has responded angrily in an open letter in which the company CEO says that even if Twitter reverses its decision, his company will not advertise on the platform, opting instead to donate the money to the Electronic Frontier Foundation (EFF) to fund the fight against online censorship. See also: Kaspersky Lab plans Swiss data… [Continue Reading] -

SmugMug buys Flickr for undisclosed sum
Publié: avril 21, 2018, 9:49am CEST par Mark Wycislik-Wilson
Photo-sharing site SmugMug -- used by consumers and professionals alike -- has agreed to acquire Flickr from Yahoo-owner Oath. The deal will see Flickr continuing to operate as a separate entity. The aim is to create what's described as "the world's best home for photography", building on Flickr's existing 100 million-strong userbase. But what does the acquisition mean for Flickr users, and what does it mean for SmugMug's customers? Both companies are eager to stress that nothing is going to change. That said, SmugMug does say that it will be migrating Flickr onto SmugMug's technology infrastructure, but it does not… [Continue Reading] -

Google's Project Zero reveals security flaw in Windows 10 S after Microsoft fails to fix it
Publié: avril 20, 2018, 5:08pm CEST par Mark Wycislik-Wilson
Details of a security flaw in Windows 10 S have been revealed by Google's Project Zero after Microsoft failed to issue a patch within the 90-day disclosure deadline. The "WLDP CLSID policy .NET COM Instantiation UMCI Bypass" vulnerability is described as being of medium severity, and it allows for the execution of arbitrary code on systems with Device Guard enabled. See also: Microsoft reveals more about the 'blocking bug' that is delaying Windows 10 Spring Creators Update It looks like there will be a new RTM build of Windows 10 as build 17134 is discovered Microsoft discovers blocking bug and… [Continue Reading] -

ZTE says Denial Order put in place by the US Department of Commerce is 'unfair' and 'unacceptable'
Publié: avril 20, 2018, 4:27pm CEST par Mark Wycislik-Wilson
Earlier in the week, the US Department of Commerce banned American companies from selling hardware and software to Chinese firm ZTE. The company is understandably unhappy with the US move, and has issued a statement to express its disgust. The US ban was implemented for -- the US says -- a violation of previous sanctions. ZTE says these allegations are simply not true, and has lashed out at the 'unfair' and 'unacceptable' action. See also: US and UK blacklist China's ZTE Weibo reverses homosexuality policy in China: 'We're no longer targeting gay content' Apple to store iCloud keys in China,… [Continue Reading] -

Facebook sneakily shifts data of 1.5 billion users away from Europe and GDPR
Publié: avril 20, 2018, 1:23pm CEST par Mark Wycislik-Wilson
Following the Cambridge Analytica scandal, the spotlight of privacy has been firmly on Facebook. The social network has made numerous promises about offering greater privacy controls to users, and after fears that Europe would end up with greater controls because of GDPR, Facebook then revealed similar tools will be rolled out around the world. Just a few days ago, the company gave a little more information about these new privacy controls, boasting that it will soon be "offering new privacy protections to everyone, no matter where you live". Sounds great. But it's not -- strictly speaking -- true. And Facebook… [Continue Reading] -

Google pauses development of Allo in favor of RCS Chat
Publié: avril 20, 2018, 12:09pm CEST par Mark Wycislik-Wilson
Google has had no shortage of chat and messaging tools over the years, and the company just added another one to its list. Google's Chat is based on the RCS (Universal Profile for Rich Communication Services) protocol which it is hoped will succeed SMS. The company is hitting pause on Allo -- which only launched towards the end of 2016 -- to focus resources on RCS. Google is transferring "almost all" of the team currently working on Allo to Android Messages which will ultimately feature Chat, its own RCS implementation. See also: Google loses big 'right to be forgotten' case… [Continue Reading] -

Will iOS and macOS converge? Don't hold your breath...
Publié: avril 20, 2018, 10:38am CEST par Mark Wycislik-Wilson
Apple has no plans to merge iOS and macOS, with Tim Cook explaining: "I don't think that's what users want." This runs counter to rumors and speculation that have circulated in recent years, but in an interview with The Sydney Morning Herald Cook makes it clear that the two operating system will remain distinct entities. See also: Leaked memo shows Apple threatens leakers with criminal action Apple encourages the switch to 64-bit with 'not optimized for Mac' message Apple could drop Intel and start making its own chips for Macs Apple says the redesigned Mac Pro is coming in 2019… [Continue Reading] -

It looks like Facebook is preparing to build its own AI chips
Publié: avril 19, 2018, 11:18am CEST par Mark Wycislik-Wilson
Facebook appears to be looking to design and build its own processors at some point in the future. The social networking giant has posted a job listing on its corporate website looking for a manager to help build an "end-to-end SoC/ASIC, firmware and driver development organization". The move would see Facebook doing what Apple and Google have started to do in recent years, moving design and production in-house to reduce reliance on the likes of Intel and Qualcomm. While little is known about how its own processors would be used, it is likely that they would feature in future Oculus… [Continue Reading] -

Microsoft to kill off OneNote's desktop app in Office 2019 to focus on OneNote for Windows 10
Publié: avril 19, 2018, 10:28am CEST par Mark Wycislik-Wilson
When Microsoft releases Office 2019 later this year, it will be killing off the desktop version of OneNote. At the moment there are desktop and UWP (Universal Windows Platform) versions available, but soon Microsoft will only offer OneNote for Windows 10. While the killing off of OneNote 2016 coincides with the launch of Office 2019, OneNote for Windows 10 will also become the "default OneNote experience" for Office 365 users. But because the desktop version of the app has a dedicated userbase, it will continue to be supported for a number of years. Microsoft says that OneNote 2016 will continue… [Continue Reading] -

TaskRabbit returns after security breach and reveals 'personally identifiable information' was exposed
Publié: avril 19, 2018, 9:52am CEST par Mark Wycislik-Wilson
The CEO of TaskRabbit has informed users that "certain personally identifiable information may have been compromised" in a security incident that saw the website and app taken offline earlier in the week. TaskRabbit -- a service that puts "taskers" in touch with people who need help with jobs around the home -- is now back online, and the company is now on a damage limitation exercise, issuing a statement in the name of "trust, openness, and transparency". Stacy Brown-Philpot says that an investigation is still underway to determine what happened, but explains that "preliminary evidence shows that an unauthorized user… [Continue Reading] -

AI-powered offline translation comes to Microsoft Translator apps
Publié: avril 18, 2018, 7:01pm CEST par Mark Wycislik-Wilson
Having a translation app on your phone is great when you're abroad and want to be able to speak in the local lingo. But if you find yourself without an internet connection, you might struggle to find the words you need. If you're a Microsoft Translator user, however, this now changes. Microsoft has introduced free, downloadable AI-powered translation packs which the company says brings "the benefit of neural translation technology regardless of whether the device is connected to the cloud or offline". See also: Microsoft brings Windows Defender Browser Protection extension to Google Chrome Microsoft, Facebook and Symantec are among… [Continue Reading] -

Microsoft brings Windows Defender Browser Protection extension to Google Chrome
Publié: avril 18, 2018, 12:35pm CEST par Mark Wycislik-Wilson
Recognizing that comparatively few people are using its Edge browser, Microsoft has released a new security tool for those who have opted to use Google Chrome -- the Windows Defender Browser Protection extension. The add-on offers real-time protection against a variety of online threats such as phishing attacks and malicious websites. As these security options are already available in Chrome, it's not clear quite who the extension is aimed at. See also: Microsoft, Facebook and Symantec are among 34 companies pledging not to help governments launch cyberattacks Microsoft launches Defending Democracy Program to protect against hacking and misinformation Microsoft releases… [Continue Reading] -

Facebook reveals new privacy controls for users around the world
Publié: avril 18, 2018, 11:47am CEST par Mark Wycislik-Wilson
Facebook has been hit with renewed criticism of its privacy policies in recent weeks in the wake of the Cambridge Analytica scandal. Having promised to give users more control over their privacy settings -- and after already introducing some tools to this end -- the social network has now revealed how it will comply with General Data Protection Regulation (GDPR) in Europe and bring new "privacy protection" to users around the world. With the impending arrival of GDPR, it had previously been thought that European Facebook users would have greater privacy controls than those in other parts of the world.… [Continue Reading] -

Password manager RememBear exits beta with official launch
Publié: avril 18, 2018, 10:42am CEST par Mark Wycislik-Wilson
After around six months in beta -- and two years in the making -- the team behind the TunnelBear VPN tool has officially launched its password manager, RememBear. Vying for attention in an already somewhat crowded marketplace, RememBear takes a leaf out of TunnelBear's book, and concentrates on offering functionality that's simple to use. There's also the same quirky use of animations throughout, but this should not distract from the fact that this is a powerful and secure place to store passwords. See also: Privacy: Hotspot Shield, PureVPN, and ZenMate found to leak sensitive data McAfee buys VPN firm TunnelBear… [Continue Reading] -

International Shopping experience comes to the Amazon Shopping app
Publié: avril 17, 2018, 8:09pm CEST par Mark Wycislik-Wilson
Amazon is making it easier to browse for goods from international sellers and have them shipped to your home country. The company is bringing the "International Shopping" experience to the Amazon Shopping app, and this simplifies the process of accessing Amazon with local language support and to track down items that ship to your country. The new experience is available to iOS and Android users, and there is support for Spanish, English, Simplified Chinese, Brazilian Portuguese and German. To start with 25 currencies are supported, but more are due to be added later in the year. Amazon says that the… [Continue Reading] -

Microsoft, Facebook and Symantec are among 34 companies pledging not to help governments launch cyberattacks
Publié: avril 17, 2018, 6:36pm CEST par Mark Wycislik-Wilson
More than 30 technology companies have signed the Cybersecurity Tech Accord, making a number of pledges relating to cyberattacks. Microsoft, Facebook, Dell, HP and LinkedIn are just a few of the companies signing on the dotted line, promising -- among other things -- never to help a government launch cyberattacks against innocent citizens and enterprises. The overall aim of the accord is to protect customers against malicious attacks by cybercriminal enterprises and nation-states. It is described as a "watershed agreement", and it sees a number of very big names coming together -- although there are a few notable exceptions. Missing… [Continue Reading] -

Intel Accelerated Memory Scanning offloads malware scanning to GPUs to boost performance
Publié: avril 17, 2018, 5:38pm CEST par Mark Wycislik-Wilson
The Spectre and Meltdown vulnerabilities really focused people's attention on the security of processors, and Intel has been at pains to convince users that it takes security seriously. With this in mind, the company has now announced a new Threat Detection Technology which introduces two new malware-fighting techniques. Accelerated Memory Scanning offloads malware scanning to GPUs, taking the strain off CPUs and helping to improve performance. There's already interest, with Microsoft planning to add support to Windows Defender Advanced Threat Protection. Intel has also revealed Advanced Platform Telemetry which is supposed to cut down on false positives. See also: Intel… [Continue Reading] -

Facebook: Yep, we track non-users -- but everyone else is doing it, so why shouldn't we?
Publié: avril 17, 2018, 4:46pm CEST par Mark Wycislik-Wilson
In a blog post addressing some of the questions Mark Zuckerberg failed to properly answer in front of Congress, Facebook has admitted that it tracks both users and non-users as they use the web. This is something the social network has historically denied. Facebook's product management director, David Baser, conceded that "when you visit a site or app that uses our services, we receive information even if you're logged out or don't have a Facebook account." Not happy to make this concession without pointing fingers, he then goes on to point out that other companies such as Twitter, Pinterest and… [Continue Reading] -

Microsoft made its own IoT-ready Linux kernel for Azure Sphere OS
Publié: avril 17, 2018, 11:41am CEST par Mark Wycislik-Wilson
Microsoft has opened up its heart to Linux in recent years, but now the company has done something that would have previously been unthinkable: it has built its own Linux kernel. As part of its embracing of the Internet of Things, Microsoft has announced Azure Sphere, an ARM-based platform for the IoT with a focus on security. Key to Azure Sphere are small MCU-powered (microcontroller) devices -- essentially SoC devices -- which run Azure Sphere OS and securely connect to Azure backends. Security comes thanks to the use of a custom Linux kernel. See also: Linus Torvalds says Linux kernel… [Continue Reading] -

TaskRabbit app and website are down while a 'cybersecurity incident' is investigated
Publié: avril 17, 2018, 11:01am CEST par Mark Wycislik-Wilson
IKEA-owned TaskRabbit is offline while the company investigates a "cybersecurity incident". Very little information has been given about the incident, but the company says that it is working with "an outside cybersecurity firm and law enforcement to determine specifics" of what happened. While even vague details are unavailable, the fact that the TaskRabbit website and app have been taken offline could well be indicative of the severity. The company is advising its customers to change their passwords elsewhere if they have reused their TaskRabbit credentials for other sites and services. TaskRabbit is a service that makes it possible for people… [Continue Reading] -

US and UK issue joint warning about Russian hacking of routers and ISPs
Publié: avril 17, 2018, 10:07am CEST par Mark Wycislik-Wilson
Global fears about cyberattacks by Russia are not calming down, and the US and UK have just issued a joint alert warning of state-sponsored attacks on network infrastructure devices, including residential routers. The west is accusing Russia of an espionage-driven malicious cyberoffensive, and the Technical Alert -- which comes following a joint effort between the Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI), and the UK's National Cyber Security Centre (NCSC) -- warns that both governmental and residential hardware is being targeted to "potentially lay a foundation for future offensive operations". See also: Et tu, Tumblr? Blogging… [Continue Reading] -

Microsoft reveals more about the 'blocking bug' that is delaying Windows 10 Spring Creators Update
Publié: avril 17, 2018, 9:14am CEST par Mark Wycislik-Wilson
With the release of Windows 10 Insider Preview Build 17134 (Redstone 4) to the Fast Ring, Microsoft has given a little insight into want went wrong with build 17133, which had been thought to be the RTM build but was delayed due to a "blocking bug". The release of Windows 10 Spring Creators Update was expected this month, but the launch date is now seemingly increasingly likely to slip into May. Microsoft has revealed that build 17133 was proving problematic and the company says it wants to fix the issues now, rather than after the fact. See also: It looks… [Continue Reading] -

US and UK blacklist China's ZTE
Publié: avril 16, 2018, 6:46pm CEST par Mark Wycislik-Wilson
The US Department of Commerce has implemented a ban on American companies selling components to ZTE. The Chinese telecoms firm is being punished for violating sanctions on Iran and North Korea after pleading guilty last year. At the same time, the UK's cyber defense watchdog, the National Cyber Security Centre (NCSC), has warned UK telecoms firms that the use of ZTE equipment or services pose a risk to national security. The action taken by the two nations is expected to have severe implications for the company. See also: Weibo reverses homosexuality policy in China: 'We're no longer targeting gay content'… [Continue Reading] -

Weibo reverses homosexuality policy in China: 'We're no longer targeting gay content'
Publié: avril 16, 2018, 5:28pm CEST par Mark Wycislik-Wilson
Following a huge backlash over the weekend, Weibo -- the Chinese equivalent of Twitter -- has announced a reversal of a policy that would have seen gay content banned from the platform. Originally announced on Friday, the "clean-up" operation was due to last three months, and covered violence and pornography as well as homosexual content. Now, however, Weibo has felt the pressure of public outcry and backed down saying: "We're no longer targeting gay content". See also: Weibo bans gay content as part of 'clean-up' Apple to store iCloud keys in China, sparking privacy fears OnePlus denies sending clipboard data… [Continue Reading] -

Thousands of Android apps have built-in crypto keys and passwords
Publié: avril 16, 2018, 3:05pm CEST par Mark Wycislik-Wilson
A large number of free Android apps suffer with flaky security because software developers are leaving cryptographic keys embedded and passwords hard-coded. Speaking at the BSides security conference in San Francisco, software vulnerability analyst Will Dormann revealed how he had found serious security problems in thousands upon thousands of apps. After testing 1.8 million apps, he found almost 20,000 featured built-in passwords and keys, and even when a separate password store was used, user data was still open to attack from simple password crackers. See also: Is your smartphone lying to you about having the latest Android security updates? Privacy:… [Continue Reading] -

Linus Torvalds says Linux kernel v5.0 'should be meaningless'
Publié: avril 16, 2018, 12:04pm CEST par Mark Wycislik-Wilson
Following the release of Linux kernel 4.16, Linus Torvalds has said that the next kernel will be version 5.0. Or maybe it won't, because version numbers are meaningless. The announcement -- of sorts -- came in Torvalds' message over the weekend about the first release candidate for version 4.17. He warns that it is not "shaping up to be a particularly big release" and questions whether it even matters what version number is slapped on the final release. See also: Linus Torvalds: Linux 4.16 kernel launches on Sunday. Possibly. Maybe. Linux 4.16 launches Microsoft Windows 10 gains Linux/WSL Console copy… [Continue Reading] -

Macros arrive in Google Sheets to help automate your workflow
Publié: avril 16, 2018, 10:34am CEST par Mark Wycislik-Wilson
Spreadsheets may not be the most exciting tools out there, but there's no denying that they're important. If you use Google Sheets as part of your number crunching process, there's some great news: Google is adding macro support. While it was previously possible to automate tasks through scripts, the newly added support for direct macro recording simplifies things greatly. Sheets can now automatically convert macro actions into an Apps Script, and the macros are designed for use on cloud-based files. See also: Google loses big 'right to be forgotten' case -- and it could set an important precedent Google is… [Continue Reading] -

SEGA announces the Mega Drive Mini
Publié: avril 15, 2018, 9:29am CEST par Mark Wycislik-Wilson
Nintendo enjoyed great success when it nostalgically released the NES Classic and SNES Classic mini consoles. Happy to ride the retro game revival wave, SEGA is following suit and releasing its own mini console -- the Mega Drive Mini. The original console was launched in the late 80s; it was known as the SEGA Genesis in North America, but in its home country of Japan and the rest of the world it was the Mega Drive. SEGA announced the Mega Drive Mini at an event in Japan, and while details are currently a little thin on the ground, excitement is… [Continue Reading] -

Upcoming Gmail redesign will also herald the arrival of self-destructing emails
Publié: avril 14, 2018, 12:33pm CEST par Mark Wycislik-Wilson
Just a few days ago we reported about the upcoming redesign of Gmail on the web. Delving further into the redesign we find that there are new features, including self-destructing emails. With a new "Confidential Mode", Gmail will not only give users the ability to set an expiry date for the emails they send to people, but also put restrictions on messages to prevent them from being printed or forwarded. See also: Google is ready to roll out Gmail redesign, adding new features like Smart Reply and snooze Dropbox partners with Google Cloud for integration with Docs, Gmail and Hangouts Chat… [Continue Reading] -

Leaked memo shows Apple threatens leakers with criminal action
Publié: avril 14, 2018, 11:19am CEST par Mark Wycislik-Wilson
A leaked Apple memo reveals that last year the company identified 29 leakers within its ranks, 12 of whom were arrested. The memo warns that employees that leak company information have "everything to lose". There is obviously a wonderful irony to the leaking of a memo about leaking, but it also gives something of an insight into just how seriously Apple takes the matter. The company is notoriously secretive about its upcoming products, and willing to go to great lengths to ensure information does not make its way out early (although -- in a second dose of delicious irony --… [Continue Reading] -

Microsoft launches Defending Democracy Program to protect against hacking and misinformation
Publié: avril 14, 2018, 10:20am CEST par Mark Wycislik-Wilson
Concern about Russian interference in both the US presidential election and the UK Brexit referendum highlighted the importance the internet now plays in political campaigns. But as well as being a powerful tool, it's also something that is open to abuse and manipulation. This is something Microsoft recognizes, and the company is launching a new Defending Democracy Program with the express aim of safeguarding the electoral processes. See also: Microsoft releases Project Honolulu as Windows Admin Center Microsoft discovers blocking bug and delays the release of Windows 10 Spring Creators Update Microsoft releases update that fixes problematic Meltdown patch The… [Continue Reading] -

Weibo bans gay content as part of 'clean-up'
Publié: avril 14, 2018, 9:46am CEST par Mark Wycislik-Wilson
Chinese microblogging service Sina Weibo has begun the process of removing gay content from its platform in order to comply with new laws. Violent and pornographic content is also subject to blocking or removal, and a lot of fan fiction has fallen victim. Weibo -- comparable to Twitter -- has 392 million active monthly users, and a three-month campaign is now underway to help create what the company describes as a "clean and harmonious community environment" in accordance with China's "laws and regulations such as the Cyber Security Law". See also: Apple to store iCloud keys in China, sparking privacy… [Continue Reading] -

Google loses big 'right to be forgotten' case -- and it could set an important precedent
Publié: avril 13, 2018, 7:49pm CEST par Mark Wycislik-Wilson
A businessman with an historic criminal conviction has won his case against Google in a "right to be forgotten" lawsuit seeking to remove information about his conviction from search results. The case, heard today in London, could set a precedent and lead to a series of similar cases from other people with spent convictions. The anonymous businessman -- known only as NT2 -- has a conviction for conspiracy to intercept communications from more than a decade ago and spent six months in prison for the crime. Passing judgement on the case, Mr Justice Warby said: "It is quite likely that… [Continue Reading] -

Android P could be Android Popsicle
Publié: avril 13, 2018, 7:26pm CEST par Mark Wycislik-Wilson
Given the order of the alphabet, it came at no surprise that the name of the successor to Android Oreo was going start with the letter P. Until now it has simply been referred to as Android P, but now Google may have given away what the full name will be. Over on Instagram, Google shared a series of images which were designed to be screengrabbed and used as wallpapers -- something which has become common on Instagram. One of the wallpapers features popsicles, leading to speculation that Android P will in fact be called Android Popsicle. See also: Here's… [Continue Reading] -

Microsoft releases Project Honolulu as Windows Admin Center
Publié: avril 13, 2018, 3:11pm CEST par Mark Wycislik-Wilson
It has been a while since Microsoft first mentioned Project Honolulu, and several months down the line it has now been released. Hitting general availability sees Microsoft officially revealing the name: Windows Admin Center. There have already been several previews of Project Honolulu/Windows Admin Center, but now Microsoft will start the big push to encourage sysadmins to use it to manage their Windows Server and Windows 10 deployments. See also: Download Windows Server 2019 preview ahead of the launch later this year Windows Admin Center is officially supported in Microsoft Edge and Chrome, but it's possible that it will also… [Continue Reading] -

Is your smartphone lying to you about having the latest Android security updates?
Publié: avril 13, 2018, 2:46pm CEST par Mark Wycislik-Wilson
If you thought your Android phone was patched with all of the latest security updates, it might be time to think again. A report by Security Research Labs found that some phone manufacturers were not only failing to deliver security updates, but were hiding this fact from users. The company found that some devices suffered a "patch gap" whereby manufacturers altered the date reported to Android -- and users -- about when security updates were last installed, without actually installing any patches. See also: Discover the best apps and games with Google's Android Excellence April 2018 update Google Play Instant… [Continue Reading] -

Apple encourages the switch to 64-bit with 'not optimized for Mac' message
Publié: avril 12, 2018, 7:28pm CEST par Mark Wycislik-Wilson
Today Apple started its push of 64-bit apps. The company's desire to banish 32-bit software and move everyone to modern, 64-bit versions is no secret and now it is starting the process of encouraging people to make the switch. With macOS High Sierra 10.13.4, messages will start to appear when 32-bit apps are run. They say "[app name] is not optimized for Mac" and they only appear once so as not to be a pest, but it's a gentle nudge for users and developers alike that the future for Apple is very much going to be based on 64-bits. Apple… [Continue Reading] -

It looks like there will be a new RTM build of Windows 10 as build 17134 is discovered
Publié: avril 12, 2018, 7:06pm CEST par Mark Wycislik-Wilson
It had been thought that Build 17133 that rolled out to Windows Insiders was the RTM version of Windows 10 Spring Creators Update. But with the discovery of a bug in this build, it seems that this will not be the one that rolls out to everyone. Yesterday we reported about a "blocking bug" that looks set to delay the release of the next big update to Windows, and now it seems that there will be at least one more build before RTM is reached. Oh -- and the name could well be changing too. See also: Microsoft discovers blocking… [Continue Reading] -

Facebook Messenger issues a privacy review reminder to users
Publié: avril 12, 2018, 6:07pm CEST par Mark Wycislik-Wilson
If you're a user of Facebook Messenger and you're in Europe, you may well notice a message popping up suggesting that you check your privacy settings. The reminder comes ahead of the new GDPR laws which come into force next month. The message tells Messenger users to check their privacy settings by May 25. The date is significant, as this is when GDPR kicks in. While the laws apply to Europe, Facebook has already indicated that it will comply with them around the world. See also: Privacy: Facebook will roll out GDPR controls to the whole world, not just Europe… [Continue Reading] -

UK hit Islamic State with 'major offensive cyber-campaign'
Publié: avril 12, 2018, 4:14pm CEST par Mark Wycislik-Wilson
The UK surveillance agency, GCHQ, has revealed that it launched cyberattacks on Islamic State. Speaking at the Cyber UK conference, GCHQ director Jeremy Fleming said that it had launched a "major offensive cyber-campaign" against the group. He said that the attacks helped to stem the output of message from Islamic State (or Daesh) online. While Flemming said that a lot of the operation was "too sensitive to talk about", he was confident that it had been effective in disrupting the group's dissemination of messages. Flemming was speaking in Manchester, UK and this was his first public speech since taking up… [Continue Reading] -

Privacy: Firefox for iOS now has tracking protection by default and new options for iPad users
Publié: avril 12, 2018, 3:55pm CEST par Mark Wycislik-Wilson
Mozilla has launched a new version of Firefox for iOS, and the big news is that it now has Tracking Protection turned on by default. It comes shortly after the feature was added to the desktop version of the web browser, and protection is enabled by default in both regular and private browsing modes. This release also sees the arrival of some great new features in the iPad version, including tab re-ordering, and drag and drop support for links. See also: Mozilla's Facebook Container extension keeps your Firefox browsing isolated from Facebook Mozilla's 2018 roadmap shows ad blocking (of sorts)… [Continue Reading] -

Soon you will be able to download your Instagram data
Publié: avril 12, 2018, 3:29pm CEST par Mark Wycislik-Wilson
The recent privacy scandal involving Cambridge Analytica and Facebook data has focused attention on personal data on social networks. With the impending arrival of GDPR in Europe and the requirement for data portability, Facebook-owned Instagram is planning to make it possible for users to download all of their data. With Zuckerberg facing questions in Congress about Facebook's competition, the timing of this revelation is interesting. With the ability to easily download the content of their Instagram accounts, users will be able to more easily move to alternative services. See also: How to check if your Facebook data was shared with Cambridge… [Continue Reading] -

Racism is not against Reddit rules, says CEO
Publié: avril 12, 2018, 1:58pm CEST par Mark Wycislik-Wilson
Reddit has no rules banning open racism or the use of racist slurs. This is not conjecture, or a summation after trawling through the site's terms and condition, but comes straight from the chief executive, Steve Huffman. High-profile websites have a careful line to tread when it comes to balancing the idea of freedom of speech with policing unsavoring content on their platform; content that can easily spill over into abuse. The likes of Facebook, YouTube and Twitter have frequently taken a harder line, but Reddit is host to a number of openly racist communities. See also: Twitter to ban… [Continue Reading] -

Google is ready to roll out Gmail redesign, adding new features like Smart Reply and snooze
Publié: avril 11, 2018, 6:44pm CEST par Mark Wycislik-Wilson
Google has emailed G Suite administrators, notifying them that a "fresh, clean look" is coming to Gmail in a redesign. Due to roll out to the Early Adopter Program "in the coming weeks", the update affects the look of the web version of Gmail. In addition to the new look, the update also brings some new features including the snoozing of emails, and a Smart Reply function. See also: Discover the best apps and games with Google's Android Excellence April 2018 update Google kicks cryptomining extensions from the Chrome Web Store European users now have a longer cooling-off period to… [Continue Reading] -

Microsoft discovers blocking bug and delays the release of Windows 10 Spring Creators Update
Publié: avril 11, 2018, 6:18pm CEST par Mark Wycislik-Wilson
The next big update for Windows 10 has been delayed while Microsoft rushes to fix a newly-discovered bug. Known variously as Windows 10 version 1803, Cumulative Update for Windows 10 Version Next, Redstone 4 and Windows 10 Spring Creators Update, it was widely thought that the update had reached RTM and was on the verge of rolling out. However, this last-minute discovery means there will be a little longer to wait. See also: How to upgrade to Windows 10 Spring Creators Update right now Microsoft releases Windows 10 Spring Creators Update Build 17133 to the Slow ring, but not for… [Continue Reading] -

Apple hit with $0.5 billion bill for patent violation with FaceTime, iMessage and VPN on Demand
Publié: avril 11, 2018, 5:59pm CEST par Mark Wycislik-Wilson
Apple has been ordered to pay $502.6 million in damages after a federal jury in Eastern Texas found that the company had violated patents owned by VirnetX. The intellectual property battle -- relating to FaceTime, iMessage and VPN on Demand -- started back in 2010, with VirnetX claiming that Apple was violating four of its patents pertaining to communication security. Having been slapped with a $0.5 billion bill, it now remains to be seen whether Apple will actually stump up the cash. See also: Apple launches iPhone 8 and iPhone 8 Plus (PRODUCT)RED Special Edition to raise money for HIV/AIDS… [Continue Reading] -

In trying to clean up the dark web, Amber Rudd wants to throw money at the unpoliceable
Publié: avril 11, 2018, 4:55pm CEST par Mark Wycislik-Wilson
The UK government is no stranger to confused attempts to try to control the internet. After voicing a desire to "combat" end-to-end encryption -- despite not understanding it -- and unveiling an AI system to counter terrorist content online, Home Secretary Amber Rudd now has the dark web as her next target. Rudd has pledged to spend £9 million (around $12.7 million) to "clean up the dark web" and cut down on cybercrime. It's a move that has been criticized for not only being politically motivated, but also being misguided and hugely underfunded. See also: The UK government reveals AI… [Continue Reading] -

PayPal is ready to get into traditional banking with debit cards, loans and more
Publié: avril 10, 2018, 7:49pm CEST par Mark Wycislik-Wilson
PayPal is looking to expand its services and gain a foothold in more traditional banking services, according to a report from the Wall Street Journal. The company has been testing a number of offerings in the US over the last few months, including debit cards, ATM cards, and services such as check depositing via photo. PayPal has teamed up with small banks to offer different services as it tries to lure in more business. The Wall Street Journal reports that PayPal has trialled adding a range of banking services to users' digital wallets, offering debit and ATM cards in addition… [Continue Reading] -

Facebook launches Data Abuse Bounty with rewards of up to $40,000
Publié: avril 10, 2018, 7:14pm CEST par Mark Wycislik-Wilson
With at least 87 million Facebook users affected by the data abuse by Cambridge Analytica, the social network is now on a mission to clean up its image. After rolling out tools, issuing notifications, and testifying in front of Congress, Facebook is launching a new bounty program that rewards people who report instances of data abuse. The Data Abuse Bounty is a new program that offers from $500 to $40,000, and it aims to clamp down on the misuse of data by app developers. Launched just before Mark Zuckerberg's testimonies this week, it's a clear attempt by Facebook to curry… [Continue Reading] -

Watch Mark Zuckerberg testify before Senate about Facebook privacy at 2:15PM ET
Publié: avril 10, 2018, 6:54pm CEST par Mark Wycislik-Wilson
After keeping something of a low profile for a while, Mark Zuckerberg has eventually started to address the Cambridge Analytica scandal. He was asked to testify before Congressional committees, and ultimately agreed to do so. Today is the first of two appearances he will make this week. At 2:15PM ET, Zuckerberg will speak about Facebook user data and privacy in front of the Senate Commerce, Science and Transportation Committee and the Senate Committee on the Judiciary at the "Facebook, Social Media Privacy, and the Use and Abuse of Data" hearing. You can watch his testimony right here. See also: How… [Continue Reading] -

LIVE: Watch Mark Zuckerberg testify before Senate about Facebook privacy at 2:15PM ET
Publié: avril 10, 2018, 6:54pm CEST par Mark Wycislik-Wilson
After keeping something of a low profile for a while, Mark Zuckerberg has eventually started to address the Cambridge Analytica scandal. He was asked to testify before Congressional committees, and ultimately agreed to do so. Today is the first of two appearances he will make this week. At 2:15PM ET, Zuckerberg will speak about Facebook user data and privacy in front of the Senate Commerce, Science and Transportation Committee and the Senate Committee on the Judiciary at the "Facebook, Social Media Privacy, and the Use and Abuse of Data" hearing. You can watch his testimony right here. See also: How… [Continue Reading] -

How to check if your Facebook data was shared with Cambridge Analytica
Publié: avril 10, 2018, 6:23pm CEST par Mark Wycislik-Wilson
The Cambridge Analytica data scandal has rocked Facebook, and users have been left wondering whether or not their personal data was involved. The social network said that it would be notifying people if they had been affected, but it is also possible to manually check. Facebook has set up a help page that can be used to determine whether your personal data was shared with Cambridge Analytica, and you can check this if you have not yet seen a notification in your news feed. See also: Congress releases Mark Zuckerberg's prepared testimony ahead of Wednesday's hearing Today Facebook will notify… [Continue Reading] -

YouTube hackers take down and deface videos from the likes of Taylor Swift and Drake
Publié: avril 10, 2018, 5:58pm CEST par Mark Wycislik-Wilson
YouTube was today hit by hackers, with the attackers managing to deface or delist a number of big name videos. Despacito by Luis Fonsi and Daddy Yankeee -- the most popular video of all time -- was among those that were temporarily inaccessible. While little is known for certain about the source of the attack, it seems that Vevo was possibly the intended target as the videos that were attacked were in Vevo accounts. The ease with which the attack appears to have been carried out -- and the number of high-profile videos affected -- will be of major concern to… [Continue Reading] -

Congress releases Mark Zuckerberg's prepared testimony ahead of Wednesday's hearing
Publié: avril 9, 2018, 6:41pm CEST par Mark Wycislik-Wilson
Facebook CEO Mark Zuckerberg is due to testify before Congress on Wednesday, and ahead of this the House Energy and Commerce Committee has released his prepared statement. He talks about the Cambridge Analytica data scandal as well as Russian interference in elections. In the statement, Zuckerberg acknowledges that Facebook did not do enough to prevent the misuse of the social network's tools. He also personally accepts responsibility for recent failings at the company, saying: "It was my mistake, and I'm sorry. I started Facebook, I run it, and I'm responsible for what happens here." See also: Today Facebook will notify… [Continue Reading] -

The HP Chromebook x2 with detachable screen is ready to take on the iPad Pro and Surface Pro
Publié: avril 9, 2018, 4:30pm CEST par Mark Wycislik-Wilson
There's a new Chromebook on the block -- or there will be soon -- and this HP offering is determined to stand out from the crowd... and give both the Surface Pro and iPad Pro a run for their money. Running Chrome OS, the HP Chromebook x2 supports Android apps, features a stylus, and -- importantly -- has a detachable screen so it can be used as a tablet or a laptop. The 12.3-inch device comes in at a shade under $600, and the hardware specs are impressive... for the price, at least. In tablet mode, the Chromebook x2 is… [Continue Reading] -

Apple launches iPhone 8 and iPhone 8 Plus (PRODUCT)RED Special Edition to raise money for HIV/AIDS
Publié: avril 9, 2018, 3:31pm CEST par Mark Wycislik-Wilson
Apple has announced the iPhone 8 and iPhone 8 Plus (PRODUCT)RED Special Edition which will be available to order from tomorrow, April 10. Like last year's iPhone 7 and iPhone 7 Plus (PRODUCT)RED, the new handsets feature a red finish and proceeds from sales will help to raise money for Global Fund HIV/AIDS grants. In addition to the phone, Apple has also announced a new $99 (PRODUCT)RED iPhone X Leather Folio case. See also: Apple says the redesigned Mac Pro is coming in 2019 Apple could drop Intel and start making its own chips for Macs Apple releases iOS 11.3… [Continue Reading] -

Privacy: Avast launches Chromium-based Secure Browser
Publié: avril 9, 2018, 11:46am CEST par Mark Wycislik-Wilson
The far-reaching tentacles of the likes of Google and Facebook have focused people's attention on online privacy, but for anyone looking to retain a modicum of confidentiality it can be hard to know what to do. There are VPN tools, but these are not for everyone, for anyone looking for a quick solution, Avast Secure Browser could be the answer. This new Chromium-based browser is billed as being "private, fast, and secure" and it's designed to address the misconceptions many people have about privacy and security online. The browser is a renamed and updated version of SafeZone. Avast has conducted… [Continue Reading] -

Today Facebook will notify 87 million users that their data was the subject of data breach
Publié: avril 9, 2018, 10:31am CEST par Mark Wycislik-Wilson
Initially thought to affect 50 million accounts, it later transpired that as many as 87 million Facebook users were affected by the Cambridge Analytica data harvesting scandal. Today, the social network is due to send a message to those whose data was involved. While the bulk of affected users -- around 70 million -- live in the US, there are also significant numbers in Europe, Facebook's message is said to be "detailed" and will appear in news feeds at some point today. See also: Facebook suspends pro-Brexit firm AggregateIQ for allegedly obtaining user data improperly Privacy: Facebook will roll out… [Continue Reading] -

File Manager for Windows 10 is now available as Microsoft open sources winfile code
Publié: avril 9, 2018, 9:22am CEST par Mark Wycislik-Wilson
Cast your mind back several years and you'll remember Windows 3.0 and earlier. This was when Microsoft started to bring home computing to the masses, and for anyone raised on modern Windows, the lack of Start menu, taskbar and other components makes the operating system seem antiquated and unusable. But use it we did! Back then, there was no File Explorer, but File Manager instead -- and it's something that people sometimes feel nostalgic about. A couple of days ago, Microsoft open sourced the File Manager code, and a Windows 10 version has been released. The source code -- as… [Continue Reading] -

Facebook suspends pro-Brexit firm AggregateIQ for allegedly obtaining user data improperly
Publié: avril 7, 2018, 5:28pm CEST par Mark Wycislik-Wilson
It's not all that long since Facebook suspended data firm Cambridge Analytica for harvesting personal information from millions of users. Now the social network has suspended AggregateIQ -- another data firm, this time linked to the pro-Brexit Vote Leave campaign -- because of possible connections to Cambridge Analytica's parent company. AggregateIQ is thought to be linked to Strategic Communication Laboratories (SCL), and there are concerns that the firm may therefore have improperly obtained data from Facebook users. See also: Facebook will give everyone the option to unsend messages, just like Mark Zuckerberg Privacy: Facebook will roll out GDPR controls to… [Continue Reading] -

Facebook will give everyone the option to unsend messages, just like Mark Zuckerberg
Publié: avril 7, 2018, 4:09pm CEST par Mark Wycislik-Wilson
When it came to light that messages sent by Mark Zuckerberg and other Facebook executives via Facebook Messenger had been deleted, there was widespread concern about not only the social network's use of a feature unavailable to anyone else, but also the lack of transparency about it. Still reeling from the Cambridge Analytica debacle and other privacy scandals, Facebook has now announced that the feature will in fact be rolling out to everyone -- although not necessarily any time soon. The company insists that this is something that has been under consideration for some time, and also promises that no… [Continue Reading] -

Facebook secretly deleted messages Mark Zuckerberg sent on Messenger
Publié: avril 6, 2018, 11:37am CEST par Mark Wycislik-Wilson
As if trust in Facebook could not drop any further, it has come to light that the social network deleted messages sent by Mark Zuckerberg from the recipients' Messenger inboxes. The deletions only applied to Zuckerberg's messages, leaving the other side of the conversation intact -- a feature not available to the average Messenger user. Facebook did not operate transparently in deleting the messages, as it made no announcement either publicly, or to those involved in the conversations. When confronted about the matter, Facebook said that the deletions were carried out because of "corporate security". See also: Privacy: Facebook will… [Continue Reading] -

Discover the best apps and games with Google's Android Excellence April 2018 update
Publié: avril 6, 2018, 10:30am CEST par Mark Wycislik-Wilson
It's less than a year since Google launched the Android Excellence program through which the company highlights the very best Android apps and games. The list is refreshed every three months, and Google has now published details of the winners of the accolade for April 2018. The latest installment includes titles such as Adobe Photoshop Lightroom CC, SoloLearn: Learn to Code for Free, and MARVEL Contest of Champions. See also: Google launches Android Excellence to recognize the very best apps and games Google reveals the Android Excellence collection for Fall 2017 The company says that the list exists to "recognize… [Continue Reading] -

Intel Remote Keyboard app nixed after discovery of critical remote control vulnerability
Publié: avril 6, 2018, 9:19am CEST par Mark Wycislik-Wilson
Intel has issued a security advisory about its remote keyboard app after discovering a bug that made it possible for a remote user to mimic keyboard and mouse input with elevated privileges. Intel Remote Keyboard was available for both iOS and Android, but the critical vulnerability -- and two other bugs with a High rating -- means that it has now been pulled from Google Play and the App Store. Intel is also recommending that anyone using the app uninstalls it as soon as possible. See also: Intel: some processors will never receive Meltdown and Spectre patches Intel unveils hexacore… [Continue Reading] -

Apple says the redesigned Mac Pro is coming in 2019
Publié: avril 5, 2018, 7:47pm CEST par Mark Wycislik-Wilson
If you've been hoping for a new Mac Pro in the near future, you're going to be disappointed. Apple has said that a new model is not due to go on sale until 2019. There is good news, however. The Mac Pro is undergoing a complete redesign, but it will remain a modular, customizable machine. The release date of 2019 also means that you'll have more time to save up -- and you'll probably need it. See also: Apple could drop Intel and start making its own chips for Macs Apple releases iOS 11.3 with a massive focus on privacy… [Continue Reading] -

Hacker exploits Verge bug to generate cryptocurrency coins worth $780,000 in 3 hours
Publié: avril 5, 2018, 7:12pm CEST par Mark Wycislik-Wilson
Verge may not be the biggest cryptocurrency out there, but it does have quite a following and has generated enough interest to attract hackers. The cryptocurrency came under attack for three hours yesterday, enabling a hacker to net 15.6 million Verge coins worth around $780,000. There was initially speculation that Verge had fallen victim to a ">51% attack" -- in which an attacker is able to forge transactions by taking control of more than half of the network -- but this has been denied by developers. A hard fork is being prepared to patch the bug that allowed the attack… [Continue Reading] -

Intel: some processors will never receive Meltdown and Spectre patches
Publié: avril 5, 2018, 10:40am CEST par Mark Wycislik-Wilson
With little fanfare, Intel has revealed that some processors will simply never receive microcode updates that will patch against the Meltdown and Spectre vulnerabilities. In a document entitled Microcode Revision Guidelines, the chip-maker says that a wide range of processor families -- equating to over 200 CPUs -- will not receive any more updates. While the majority of the affected chips were on sale between 2007 and 2011, it's safe to assume that a large proportion of them are still in use, meaning that a lot of systems will remain unprotected. See also: Intel unveils hexacore mobile Core i9 chip… [Continue Reading] -

Privacy: Facebook will roll out GDPR controls to the whole world, not just Europe
Publié: avril 5, 2018, 9:45am CEST par Mark Wycislik-Wilson
Mark Zuckerberg has laid out Facebook's plans for the future in a conference call with reporters. In it, he said that the social network now planned to bring GDPR-style privacy controls to all of its users, not just those in Europe for whom there will soon be a legal obligation to do so. The new legislation grants people more rights to access the data companies store about them, and demand it be deleted. The Facebook chief had previously said that non-European users would only be getting access to new options that were "in [the] spirit" of GDPR, but the backlash… [Continue Reading] -

Facebook users in Europe will soon have better privacy protection than those in the US
Publié: avril 4, 2018, 6:28pm CEST par Mark Wycislik-Wilson
In a few weeks, privacy is set to improve for Facebook users -- at least this is the case for people in Europe. May 25 sees the implementation of General Data Protection Regulation (GDPR), and it means that European users will have the right to not only request details of the information stored about them, but also the right to demand its deletion. While this will be a legal obligation within Europe, it would have been the perfect opportunity for Facebook to extend the same rights to its users around the world. But it's not going to. Mark Zuckerberg has… [Continue Reading] -

Shooter at YouTube headquarters was angry at demonetization of her videos
Publié: avril 4, 2018, 11:44am CEST par Mark Wycislik-Wilson
Nasim Aghdam walked into the YouTube headquarters in North California yesterday, shot and wounded three people, and then killed herself. While the precise motive behind the shooting is still under investigation, Aghdam's father has said that she was furious with YouTube for demonetizing her videos. This is in line with posts made by her on her own website where she complained about YouTube only allowing certain channels to grow, alleging that her own videos were being filtered. In the wake of the shooting, technology executives including Twitter's Jack Dorsey renewed calls for gun control. See also: YouTube steps further into… [Continue Reading] -

Huawei statement dismisses US concerns about security
Publié: avril 4, 2018, 10:50am CEST par Mark Wycislik-Wilson
Huawei is being shunned by the US because of the perception that its hardware could be compromised and used by the Chinese government for espionage. The FCC has blocked US mobile carriers from using federal money to purchase products or services from the company on security grounds, and Huawei is understandably unhappy about this. The smartphone maker has dismissed security claims as "simply not true" and says that it is "no security threat in any country". The Chinese company says that it is disappointed with the FCC's proposal, pointing out that it would give rural operators -- and, in turn,… [Continue Reading] -

Facebook launches bulk app removal tool in response to privacy concerns
Publié: avril 3, 2018, 7:50pm CEST par Mark Wycislik-Wilson
Facebook has long been embroiled in controversies about privacy, but things have been particularly bad in recent weeks. The Cambridge Analytica scandal has put the spotlight firmly on privacy on the social network and -- having already made its privacy tools more accessible -- Facebook has now created a tool to quickly remove apps from profiles in bulk. It's a very simple idea, but one that will be warmly welcomed by those who have been concerned about the Facebook apps they have installed, but have felt put off by the idea of doing anything about it because of the arduous… [Continue Reading] -

How to upgrade to Windows 10 Spring Creators Update right now
Publié: avril 3, 2018, 5:59pm CEST par Mark Wycislik-Wilson
It's only a week since Microsoft released Windows 10 Spring Creators Update Build 17133 first to the Fast ring and then the Slow ring, and it's clear that it's not going to be long until the latest big update is pushed out to everyone via Windows Update. But what about if you want to upgrade right now? There's no need to be a Windows Insider as the RTM version of Windows 10 Spring Creators Update is already available to download directly from Microsoft's servers. So, if you're interested in keeping one step ahead of the game, here's what you need… [Continue Reading] -

Intel unveils hexacore mobile Core i9 chip and gets within spitting distance of 5GHz
Publié: avril 3, 2018, 4:57pm CEST par Mark Wycislik-Wilson
In Bejing today, Intel revealed its first mobile Core i9 chip. The hexacore processor (yep... no fewer than six cores) is an eighth-generation chip, and the company says it is "the highest-performance laptop processor Intel has ever built". Intel also claims that it offers the "best gaming and content creation experience on the go," and with the top-of-the-range Intel Core i9-8950HK processor reaching speeds of up to 4.8 GHz, it's a claim that's easy to believe. A total of 12 threads bring serious improvements over the previous generation chips. See also: Apple could drop Intel and start making its own… [Continue Reading] -

Apple could drop Intel and start making its own chips for Macs
Publié: avril 3, 2018, 12:54pm CEST par Mark Wycislik-Wilson
Apple could be planning to ditch Intel and start to manufacture its own chips for Macs by 2020, according to a new report. The move would be in line with what the company has done for iPhones and iPads -- the A11 Bionic chips are already designed in-house. Intel's share price dropped by 6 percent as the rumors of the plan came out. See also: Apple releases iOS 11.3 with a massive focus on privacy Apple proposes new emojis depicting disabled people Apple announces plans to acquire digital magazine service Texture Apple reveals redesigned MFi logos The story was first… [Continue Reading] -

Linux 4.16 launches
Publié: avril 3, 2018, 11:55am CEST par Mark Wycislik-Wilson
Just over a week ago, Linus Torvalds said that the release of Linux 4.16 could take place on Sunday April 1. Ignoring the fact that April Fool's day is a terrible day to do just about anything, he made good on his promise. As predicted, there was no RC8 of the kernel, and Torvalds notes that the final release is very similar to RC7. In a post to the Linux Kernel Mailing List, he also said that the merge window for 4.17 is open, but for now, the focus is on 4.16. See also: Linus Torvalds: Linux 4.16 kernel launches… [Continue Reading] -

Google kicks cryptomining extensions from the Chrome Web Store
Publié: avril 3, 2018, 11:26am CEST par Mark Wycislik-Wilson
Amid growing concern about a disregard for Chrome Web Store policies, Google is slapping a ban on extensions that mine for cryptocurrencies. With immediate effect, no more cryptomining extensions will be added to the Store, and as of July 2018, any existing mining tools will be removed. Google says that an astonishing 90 percent of mining extensions ignore rules that state cryptomining must be the extension's sole purpose, and users need to be fully informed about the mining. See also: How to export your saved passwords from Chrome Chrome for Windows drops Microsoft compiler in favor of Clang Chromebooks could… [Continue Reading] -

Grindr was sharing users' location and HIV status with third parties
Publié: avril 3, 2018, 10:34am CEST par Mark Wycislik-Wilson
Last week there was an outcry after it was revealed that it was relatively simple to determine the location of Grindr users because of a security flaw. The company has now also admitted that it shared information from users' profiles with third parties -- specifically the analytics companies Apptimize and Localytics -- including their HIV status. Grindr was quick to point out that, firstly, the information was sent via HTTPS, secondly, that the data was not sold to the analytics companies (it was provided free of charge) and, thirdly, that the data was public anyway. All three of these points… [Continue Reading] -

6et ready! OnePlus teases the OnePlus 6 and opens forum for the upcoming flagship
Publié: avril 3, 2018, 9:24am CEST par Mark Wycislik-Wilson
There's always a great sense of excitement surrounding the announcement of a new OnePlus phone, and this is something that the company is only too happy to play on. We've already seen a leaked photo of the yet-to-be-released handset and heard that the phone has an iPhone X-style notch; now OnePlus has (pretty much) confirmed the phone's name and started its "6et ready!" teaser campaign. While we were all but certain about the name, it has now been officially established that it will be called the OnePlus 6. Well… almost See also: Yep, the OnePlus 6 definitely has a notch… [Continue Reading] -

Amazon to delete MP3s from its Music Storage service for some users
Publié: avril 1, 2018, 8:38am CEST par Mark Wycislik-Wilson
Subscribers to Amazon's Music Storage service have less than a month to access their music before it is lost forever. The company has announced that As of April 29, there will be no new subscriptions accepted for the service, and any existing subscriptions will be allowed to expire. If you do not opt to save your MP3s before this happens, you will lose access to them completely. Amazon Music Storage service is due to shut down forever in January 2019, and if you want to retain access to your music until this date you will need to log into your… [Continue Reading] -

Bookmark syncing service Xmarks to close on May 1
Publié: avril 1, 2018, 8:16am CEST par Mark Wycislik-Wilson
If you're a user of Xmarks, there's some bad news for you -- the service is closing down in a month's time. The bookmark syncing tool, which is available as an addons for Chrome, Firefox, Internet Explorer and Safari, is to be shuttered on May 1. Xmarks is owned by LastPass these days (in turn owned by LogMeIn), and as there is already a LastPass password manager, the closure makes a lot of sense from a streamlining point of view; it will still come as bad news to its userbase, however. As well as LastPass's own password tool, Xmarks has… [Continue Reading] -

Apple releases iOS 11.3 with a massive focus on privacy
Publié: mars 30, 2018, 2:00pm CEST par Mark Wycislik-Wilson
Ahead of GDPR in Europe, Apple has released iOS 11.3, complete with a selection of privacy-focused tools. But while privacy is at the heart of the release, it is far from being the end of the story. The recent Facebook scandal has focused attention on privacy, and this is something Apple will be more than happy to capitalize upon, bringing GDPR-prompted tools to the world -- not just Europe. But iOS 11.3 also includes an extensive changelog with a range of fixes and updates. See also: Apple proposes new emojis depicting disabled people Apple unveils its most affordable iPad yet,… [Continue Reading] -

Leaked Facebook memo: 'so what if the social network's growth leads to terrorism and death?'
Publié: mars 30, 2018, 1:09pm CEST par Mark Wycislik-Wilson
A leaked memo written by Facebook's vice-president, Andrew Bosworth, entitled "The Ugly" gives a glimpse into the attitude the social network has towards its own growth. "Boz" Bosworth says the "ugly truth" of Facebook's growth is that connecting people could lead to deaths -- but so be it. In the memo, Bosworth says "anything that allows us to connect more people more often is *de facto* good". He goes on to say: "That's why all the work we do in growth is justified. All the questionable contact importing practices. All the subtle language that helps people stay searchable by friends.… [Continue Reading] -

Microsoft releases update that fixes problematic Meltdown patch
Publié: mars 30, 2018, 12:07pm CEST par Mark Wycislik-Wilson
As if the Meltdown and Spectre chip vulnerabilities weren't bad enough in their own right, the patches designed to fix them caused a further series of problems. A Swedish researcher recently discovered that Microsoft's Meltdown fixes lowered security in Windows 7 and Windows Server 2008 R2, and now the company has issued a fix. As the new patch is being released outside of the usual schedule, it is indicative of the importance of the security update. KB4100480 is a kernel update for Windows 7 Service Pack 1 and Windows Server 2008 R2 Service Pack 1 that addresses CVE-2018-1038 problems. See… [Continue Reading] -

Have I Been Pwned teams up with 1Password to improve post-security breach advice
Publié: mars 29, 2018, 2:30pm CEST par Mark Wycislik-Wilson
Data breach checking website Have I Been Pwned (HIBP) -- used by governments and individuals around the world -- has announced a new partnership with 1Password. The arrangement is a first for Troy Hunt's site, but it comes just over a month after 1Password started using a password-checker he developed. Hunt says that he has turned down numerous offers to sponsor Have I Been Pwned, but feels that teaming up with 1Password makes sense. See also: Have I Been Pwned is now used by governments to check for data breaches Firefox's 'master password' system can be easily bypassed using brute… [Continue Reading] -

European users now have a longer cooling-off period to claim Google Play refunds
Publié: mars 29, 2018, 1:33pm CEST par Mark Wycislik-Wilson
Google has introduced new policies for its customers living in the European Economic Area. The updated policies allow users longer to apply for a refund on purchases made through the Google Play Store While most of the world has a 48-hour timeframe to ask for a refund, this has been extended to a full two weeks in the EEA. The policy changes have come into play to comply with EU law which gives customers a 14-day "cooling-off" period during which they are entitled to ask for their money back -- but it doesn't cover everything. See also: Google Play Movies… [Continue Reading] -

Ecuadorian embassy cuts off Julian Assange's internet connection
Publié: mars 29, 2018, 12:37pm CEST par Mark Wycislik-Wilson
Still holed up in the Ecuadorian embassy in London, WikiLeaks founder Julian Assange has been given the snip. Ecuador took the decision to cut off the fugitive's internet connection, severing one of his lines of communication with the outside world. Assange -- who a judge recently described as a man who "appears to consider himself above the normal rules of law" -- has been living in the embassy since 2012 when he was wanted for questioning in Sweden on sexual assault allegations. He has hidden away claiming he could be extradited to the US to face charges over WikiLeaks revelations,… [Continue Reading] -

Security issues in gay dating app Grindr exposed users' locations
Publié: mars 29, 2018, 11:09am CEST par Mark Wycislik-Wilson
Two security issues have been discovered in Grindr, the gay dating app, which could reveal the location of users even if they opted to keep this information private. There are concerns that the privacy compromise could lead to harassment of Grindr users. Trevor Faden created a site called C*ckBlocked (that's the actually name, we're not being prudish and getting out our censorship pens) which was designed to give Grindr users the chance to see who had blocked them. By exploiting a security loophole similar to the one exposed in the recent Facebook/Cambridge Analytica scandal, Faden's site was able to access… [Continue Reading] -

Yep, the OnePlus 6 definitely has a notch -- deal with it!
Publié: mars 28, 2018, 4:45pm CEST par Mark Wycislik-Wilson
OnePlus is a company with something of a masterful grasp of the notion of building up excitement about a new handset -- often ramping up anticipation levels months in advance. In the last day or so, an image of the rear of the upcoming OnePlus 6 "leaked", and now the company has released the first official picture showing the front of the phone. The image doesn't give away a great deal about the appearance of the phone, but it does confirm one thing for sure: the OnePlus 6 has a notch, just like the iPhone X. See also: This is… [Continue Reading] -

Facebook makes its privacy settings easier to find -- including the option to delete your Facebook data
Publié: mars 28, 2018, 1:48pm CEST par Mark Wycislik-Wilson
In the wake of the Cambridge Analytica scandal and revelations about call and text logging, Facebook simply could not have got away with doing nothing. Mark Zuckerberg has hardly prostrated himself in front of users in his various recent interviews, but today Facebook announces a series of changes to privacy settings. The social network is making it easier to find and use privacy settings, and providing users with information about how to delete the data Facebook stores about them. See also: Nearly a third of tech workers are ready to #DeleteFacebook Mozilla's Facebook Container extension keeps your Firefox browsing isolated… [Continue Reading] -

Meltdown patches from Microsoft made Windows 7 and Windows Server 2008 less secure
Publié: mars 28, 2018, 11:57am CEST par Mark Wycislik-Wilson
If you're running Windows 7 and you've not yet installed the March updates, now is very much the time to do so. It turns out that the Meltdown patches released in January and February actually opened up a security hole in both Windows 7 and Windows Server 2008 R2. A Swedish security researcher found that the patches changed access permissions for kernel memory, making it possible for anyone to read from and write to user processes, gain admin rights and modify data in memory. See also: Intel failed to warn US government about Meltdown and Spectre flaws before going public… [Continue Reading] -

This is the OnePlus 6
Publié: mars 28, 2018, 11:33am CEST par Mark Wycislik-Wilson
With the OnePlus 5T now officially out of stock -- and not being replenished -- in the US, coupled with the time of year, it should come as little surprise that there's a new OnePlus handset around the corner. There have been various rumors about the OnePlus 6 over the last few months, and now serial leaker Evan Blass gives us our first glimpse at what the phone actually looks like. There are two questions that many people will have: does it have an iPhone X-style notch, and does it have a headphone jack? The leaked photo goes some way… [Continue Reading] -

Google Play Movies & TV now lets you search for shows across a range of streaming apps
Publié: mars 27, 2018, 8:12pm CEST par Mark Wycislik-Wilson
There are so many streaming apps and services to choose from, it can be hard to know where to look when you want to watch something. With its latest update to Google Play Movies & TV, Google may just have come up with the answer for Android users. The update means that when you search for a show within the app, you'll be told which app or service you can use to watch it -- regardless of whether you're a subscriber or not. In all, there's support for over 20 services -- including the likes of Hulu, HBO, ABC and… [Continue Reading] -

Nearly a third of tech workers are ready to #DeleteFacebook
Publié: mars 27, 2018, 6:07pm CEST par Mark Wycislik-Wilson
The fallout from the Cambridge Analytica fiasco has done a great deal of damage to not only Facebook's reputation, but also its finances. In the short term, the social network can afford to take a hit on share prices, but in the longer term there is the trust of users to regain. A survey conducted in the wake of the #DeleteFacebook campaign that followed revelations about the data breach and the logging of Android users' calls and texts, found that a surprising number of tech workers were ready to delete their Facebook accounts. 31 percent backed the #DeleteFacebook campaign, including… [Continue Reading] -

Mozilla's Facebook Container extension keeps your Firefox browsing isolated from Facebook
Publié: mars 27, 2018, 4:03pm CEST par Mark Wycislik-Wilson
Facebook has been completely inescapable in the news over the last couple of weeks, and there are increasing concerns that the social network is all but inescapable online generally. In the wake of recent privacy concerns about Facebook, Mozilla -- already petitioning for Mark Zuckerberg to do more -- has launched a new extension for Firefox that helps to keep your browsing private. Called "Facebook Container", the add-on has been designed to make it much harder for Facebook to track your web browsing when you're not using the social network. See also: Mark Zuckerberg refuses to answer UK questions about… [Continue Reading] -

Facebook is testing self-destructing friend requests
Publié: mars 27, 2018, 2:14pm CEST par Mark Wycislik-Wilson
Facebook is currently testing a new feature that would give users the chance to place time limits on friend requests. The idea is that requests that you ignore for a certain period of time would be automatically deleted. While it's not a feature that will be of interest to everyone, it is something that could prove useful to anyone in the public eye who gets bombarded with endless requests to connect. Facebook has confirmed that automatically-expiring friend requests give users a way to more easily manage unwanted requests from people. See also: Mark Zuckerberg refuses to answer UK questions about… [Continue Reading] -

Mark Zuckerberg refuses to answer UK questions about Facebook privacy
Publié: mars 27, 2018, 1:20pm CEST par Mark Wycislik-Wilson
Following the privacy scandal surrounding Cambridge Analytica's use of data from Facebook users, the social network has been under extreme pressure to answer questions from individuals, lawmakers, companies and governments around the world about not only what went wrong, but what will be done to prevent it from happening again. The British parliament was among those seeking to probe Facebook about the breach of privacy, but Mark Zuckerburg has said that he will not appear before a committee to face questions. Instead, he intends to send either chief technology officer Mike Schroepfer, or chief product officer Chris Cox. See also:… [Continue Reading] -

iPhone-maker Foxconn buys Belkin, Linksys, Phyn and Wemo for $866 million
Publié: mars 27, 2018, 12:36pm CEST par Mark Wycislik-Wilson
Foxconn -- the Taiwanese company famed for producing iPhones -- has announced that it is acquiring Belkin International for $866 million in cash. Belkin is also the owner of Linksys, Wemo and Phyn, making the purchase an interesting expansion for Foxconn Interconnect Technology Limited (FIT) and quite a shift in direction. The merger sees the company widening its interests into accessories, networking gear and smart home devices. See also: Trump blocks Broadcom's takeover of Qualcomm, citing national security Broadcom may buy Qualcomm for $100 billion This is the first time FIT has tried its hand at running consumer-facing brands, having… [Continue Reading] -

Acer Chromebook Tab 10 is a student-friendly Chrome OS tablet
Publié: mars 26, 2018, 6:00pm CEST par Mark Wycislik-Wilson
Acer today revealed what it describes as the "first tablet running Chrome OS designed for education" -- the Acer Chromebook Tab 10 (or D651N). Featuring a 9.7-inch QXGA LED-backlit display with a resolution of 2,048 x 1,536 (264 PPI), the Chromebook Tab 10 is equipped with a Wacom EMR stylus to allow for easy writing and drawing. Although not available at launch, there is planned support for Google Expeditions AR, and Acer is hoping that the tablet will find its way into the hands of students of all ages. While this is hardly an iPad killer, that's not the point.… [Continue Reading] -

Facebook rolls out locally-focused News Feed globally
Publié: mars 26, 2018, 4:44pm CEST par Mark Wycislik-Wilson
Facebook is constantly messing about with its News Feed, and it's only a matter of weeks since the social network said it was going to prioritize local news. Initially, this was only the case in the US, but now the change is rolling out around the globe. The company says that "people around the world will see more news on Facebook from local sources covering their current city and other cities they may care about." Unfortunately for Facebook, however, it's unlikely to serve as too much of a distraction from the call/SMS logging controversy or the Cambridge Analytica debacle. See… [Continue Reading] -

Google is beta testing a 'More results' button to reduce searches to a single, endless page
Publié: mars 26, 2018, 3:30pm CEST par Mark Wycislik-Wilson
Google search results are, usually, multi-page affairs, but if a new test gets off the ground this could be set to change. The search giant is conducting a limited test that sees the arrival of a "More results" button at the bottom of search results, replacing the "Next button" that is there at the moment. It's a variation on the idea of infinite scrolling, but a variation that grants the user more control. See also: How to change countries in the Google Play Store -- the official way! The Google News Initiative is yet another attempt to combat fake news… [Continue Reading] -

Linus Torvalds: Linux 4.16 kernel launches on Sunday. Possibly. Maybe.
Publié: mars 26, 2018, 10:51am CEST par Mark Wycislik-Wilson
After a series of release candidates, Linus Torvalds could well be ready to unleash version 4.16 of the Linux kernel onto the world at the weekend. That is unless he changes his mind about the RC build: "rc7 is much too big for my taste," he says in his weekly update to the kernel mailing list. Torvalds says that while he's not planning for there to be an eighth release candidate, the current size is causing him to think about the best course of action. For those who have not been following the story, he also details what's new in… [Continue Reading] -

Facebook places full-page ads in British and American newspapers to apologize for Cambridge Analytica data leak
Publié: mars 25, 2018, 3:04pm CEST par Mark Wycislik-Wilson
Full-page advertisements have appeared in a number of Sunday newspapers in the UK and US as Facebook embarks on a damage limitation exercise following the revelations about Cambridge Analytica's use of personal data. The ads, signed by Mark Zuckerberg, say: "We have a responsibility to protect your information. If we can't, we don't deserve it." The apology -- of sorts -- adopts a similar tone to Zuckerberg's previous statements and interviews about the matter, and comes as the social network faces calls for not only regulation, but also as the London offices of Cambridge Analytica have been raided by the… [Continue Reading] -

Privacy: Facebook has been collecting call and text data from Android users
Publié: mars 25, 2018, 11:32am CEST par Mark Wycislik-Wilson
It has been a bad week for Facebook -- and its users -- after it was revealed that Cambridge Analytica had harvested data from millions of accounts on the social network. Now it turns out that Facebook itself has been engaged in gathering user data. A social media user, Dylan McKay from New Zealand, downloaded his Facebook archive and was shocked to discover that nearly two years' worth of call and text logs from his Android phone were included. McKay is not alone, and it's possible that details of your communication have been logged as well. See also: Mozilla pulls… [Continue Reading] -

How to change countries in the Google Play Store -- the official way!
Publié: mars 25, 2018, 10:41am CEST par Mark Wycislik-Wilson
There can be few Android users who have learned about an exciting new app or game, only to be disappointed to discover it's not available in their country. There have been various ways around this, including downloading APKs from unofficial sources, but now Google has introduced a way to do it officially. An update to the Google Play Store sees the addition of a new "Country and profiles" option which makes getting Android apps from other regions a whole lot easier. Here's what you need to know. See also: Google Play Instant lets you stream Android apps and games to… [Continue Reading] -

Apple proposes new emojis depicting disabled people
Publié: mars 24, 2018, 3:50pm CET par Mark Wycislik-Wilson
Apple has pitched the idea of introducing more than a dozen new emojis with a focus on disabilities. In a submission to the Unicode Consortium, the iPhone maker suggests 13 new emojis depicting a guide dog, wheelchair users and prosthetic limbs. The company says that the current batch of emojis do not represent people with disabilities, and it would like to redress the balance. For now, just a limited number of disability-focused additions have been suggested, but Apple says that this should just be the starting point. See also: Apple announces plans to acquire digital magazine service Texture Apple reveals… [Continue Reading] -

2 million Spotify users are blocking ads... for free
Publié: mars 24, 2018, 11:27am CET par Mark Wycislik-Wilson
Spotify has revealed that around 2 million of its users have been using hacked versions of apps to bypass ads without paying for the privilege. It means that more than 2 percent of the service's free users are useful modified versions of apps. The hacked apps also allow for access to premium Spotify features, and this explains the company's eagerness to crack down on the practice. See also: Mozilla's 2018 roadmap shows ad blocking (of sorts) is coming to Firefox Ad-blocker and privacy tool Ghostery goes open source, and has new ways to make money Google explains how Chrome's new… [Continue Reading] -

Mozilla's 2018 roadmap shows ad blocking (of sorts) is coming to Firefox
Publié: mars 24, 2018, 10:15am CET par Mark Wycislik-Wilson
Ads may be central to the running of the web, but that doesn't mean people want to see them. Ad blocking is more popular than ever, and it's something that's been noted by Mozilla. Revealing its 2018 roadmap for Firefox, the company says that an ad blocker is being added to the web browser -- albeit a limited one. On top of this, additional privacy controls are on the cards, as is a tool to block auto playing videos, and a breach alert system. See also: Firefox's 'master password' system can be easily bypassed using brute force You'll be able… [Continue Reading] -

Et tu, Tumblr? Blogging site says it was used by Russia to spread fake news in 2016
Publié: mars 24, 2018, 9:31am CET par Mark Wycislik-Wilson
When it comes to talk of Russian interference in the 2016 US presidential election that saw Donald Trump catapulted to power, the focus has been very much on Facebook and Twitter. But now the blogging platform Tumblr has held its hand up and revealed that it was used by Russian trolls to disseminate disinformation and propaganda. Tumblr says that it discovered a number of accounts that were used by Russia's Internet Research Agency (IRA), and that it helped with an investigation and prosecution of numerous individuals. See also: The Google News Initiative is yet another attempt to combat fake news… [Continue Reading] -

Hacker Guccifer 2.0 seems to accidentally confirm links to Russia
Publié: mars 23, 2018, 6:57pm CET par Mark Wycislik-Wilson
A slip-up by notorious hacker Guccifer 2.0 -- famous for attacking the DNC servers -- appears to have confirmed what has been believed for some time: that the hacker is based in Russia. It was long-believed that Guccifer had links to Russia, but use of VPNs and other techniques made it difficult to confirm this. Now a single incident when the "lone wolf" apparently forgot to use a VPN shows the hacker using an IP address based in Moscow and linked to Russian intelligence agency -- the GRU. See also: Trump was almost ten times more popular with Russian Twitter… [Continue Reading] -

Google launches 'Change the Game' design challenge to encourage female coders and gamers
Publié: mars 23, 2018, 1:04pm CET par Mark Wycislik-Wilson
Google has teamed up with Girls Make Games and ESA Foundation to launch a new initiative called Change the Game. It is designed to encourage more women to get involved in playing and creating mobile games, and there's a $10,000 college scholarship and a $15,000 technology donation up for grabs. The company is seeking game ideas from US teenagers who are invited to share details of their designs. Google asks for details of game mechanics, storylines and asks "what emotions could the player experience or feel while playing the game?" See also: The Google News Initiative is yet another attempt… [Continue Reading] -

Instagram is tweaking its feed to make it a little more chronological
Publié: mars 23, 2018, 12:18pm CET par Mark Wycislik-Wilson
Following quite a vocal backlash from users, Instragram is making changes to its feed to move away slightly from the algorithm-driven, non-chronological form it takes at the moment. Instagram -- like social media stable-mate Facebook -- has eschewed the chronological ordering of feeds, but now seems to have come to the realization that it is what people expect and prefer. The platform is also making changes to the automatic feed refresh function. If you're hoping for a sensible interpretation of "chronological", however, you're likely to be disappointed. Rather than simply displaying posts in the order they were created, Instagram just… [Continue Reading] -

YouTube steps further into the political arena by introducing further restrictions on firearms videos
Publié: mars 23, 2018, 11:49am CET par Mark Wycislik-Wilson
YouTube has stepped further into the debate surrounding gun control by introducing new restrictions on weapon-related videos on its platform. The move sees Google nailing its political colors to the mast, and it's a move that's likely to anger Republicans and the NRA, and lead to further allegations of a liberal bias. Under the new policies, videos that promote or link to sites selling firearms and accessories are banned, as well as those that show how to make weapons at home. See also: Picture-in-picture mode is coming to YouTube on the desktop YouTube Kids app is serving up conspiracy videos… [Continue Reading] -

Vivaldi collaborates with DuckDuckGo to improve browser privacy
Publié: mars 22, 2018, 12:13pm CET par Mark Wycislik-Wilson
Vivaldi Technology has announced a new collaboration with the privacy-centric search engine DuckDuckGo. In coming together, DuckDuckGo will be made the default search engine in a Private Window. The aim is to further increase the privacy offered by the Vivaldi web browser, helping to ensure that searches that are conducted in a Private Window really are private. The company points out that even if you were previously using a Private Window for browsing and searching, the precise level of privacy you enjoyed is determined to a large degree by the search engine you choose to use. Combining Vivaldi's lack of… [Continue Reading] -

Mozilla pulls advertising from Facebook
Publié: mars 22, 2018, 11:48am CET par Mark Wycislik-Wilson
Mozilla is not happy with Facebook. Not happy at all. Having already started a petition to try to force the social network to do more about user privacy, the company has now decided to withdraw its advertising from the platform. The organization is voting with its money following the misuse of user data by Cambridge Analytica, as it tries to force Facebook into taking privacy more seriously. See also: Facebook reveals the steps it will take to avoid the next big data breach Mark Zuckerberg's failure to apologize about the Cambridge Analytica privacy breach is despicable Facebook suspends Trump campaign's… [Continue Reading] -

Facebook reveals the steps it will take to avoid the next big data breach
Publié: mars 22, 2018, 11:17am CET par Mark Wycislik-Wilson
After it was revealed that private data belonging to 50 million Facebook users was shared with data analytics company Cambridge Analytica, there has been much talk about what went wrong and how something similar can be avoided in the future. Mark Zuckerberg issued a non-apology, but Facebook has also indicated some of the things it will be doing in the wake of the fiasco. Zuckerberg says that back in 2014, steps were taken to restrict the access apps have to data, and the social network also plans -- in the name of transparency -- to inform everyone who has been,… [Continue Reading] -

Mark Zuckerberg's failure to apologize about the Cambridge Analytica privacy breach is despicable
Publié: mars 22, 2018, 10:47am CET par Mark Wycislik-Wilson
After five days of complete silence, Mark Zuckerberg finally decided to face the music and talk about the Cambridge Analytica debacle which has seen the private information of more than 50 million Facebook users harvested by the data analytics company Yesterday, the Facebook founder condescended to issue a statement about the privacy breach, and also appeared in a CNN interview. He was, of course, quick to point out that his company has already cleaned up its act and would be doing a lot more, including auditing apps and developers. So far, so face-saving. One thing he rather forgot about, however,… [Continue Reading] -

Download Windows Server 2019 preview ahead of the launch later this year
Publié: mars 21, 2018, 5:23pm CET par Mark Wycislik-Wilson
Microsoft has revealed details about the upcoming Windows Server 2019. Due for release later in the year, there's a preview available for download right now, giving users the chance to try out the new features, including Linux and Kubernetes support. Announcing the availability of the build to Windows Insiders, Dona Sarkar said that Microsoft is "pleased to release the first build of the Windows Server 2019 Long-Term Servicing Channel (LTSC) release that contains both the Desktop Experience as well as Server Core in all 18 server languages, as well as the first build of the next Windows Server Semi-Annual Channel… [Continue Reading] -

AMD admits to new batch of critical processor flaws and promises fixes
Publié: mars 21, 2018, 4:49pm CET par Mark Wycislik-Wilson
AMD has confirmed that some of its processors contain vulnerabilities after they were found by CTS Labs researchers. In all, 13 critical flaws were found, including RyzenFall, MasterKey, Fallout and Chimera. They affect a range of AMD products. The flaws are not dissimilar to the previous Meltdown/Spectre vulnerabilities, and CTS Labs gave AMD just 24 hours' notice before going public. The chipmaker says that patches are on the way, and tries to suggest that the vulnerabilities are not a cause for major concern. In a statement posted on its website today, AMD says: "On March 12, 2018, AMD received a… [Continue Reading] -

Kaspersky Lab plans Swiss data center to quell fears about Russian connections
Publié: mars 21, 2018, 4:39pm CET par Mark Wycislik-Wilson
The US has repeatedly voiced concerns about Kaspersky Labs, expressing distrust of the Russian company. So concerned is the Trump administration about possible ties to the Russian government, that Kaspersky software is banned from official computers. This is clearly something that the company is not happy with, and it has already launched a lawsuit against the US government. In a bid to silence those who say that data is being fed to the Kremlin, Kaspersky is planning to open a data center in Switzerland. See also: Kaspersky reveals details of extraordinarily powerful Android trojan, Skygofree Kaspersky sues Trump administration over… [Continue Reading] -

Mozilla launches a petition asking Facebook to do more for user privacy
Publié: mars 21, 2018, 2:13pm CET par Mark Wycislik-Wilson
In the fallout from the Cambridge Analytica debacle, Facebook has been roundly criticized for not only its handling of the situation, but also its attitude to privacy in general. The criticism comes not only from users, but also politicians and technology firms. The latest company to speak out is Mozilla. After it was revealed that the personal data of 50 million Facebook users was shared without consent, Mozilla is calling on the social network to ensure that user privacy is protected by default, particularly when it comes to apps. See also: Facebook suspends Trump campaign's data analytics team, Cambridge Analytica,… [Continue Reading] -

The Google News Initiative is yet another attempt to combat fake news
Publié: mars 20, 2018, 6:05pm CET par Mark Wycislik-Wilson
The seemingly throwaway tag of "fake news" has developed into an absolute phenomenon over the last year or so. Previously unheard of, it's now not only part of the technological zeitgeist, but also something that Twitter, Google, Facebook et al are on a mission to fight. Today, Google announces its latest weapon -- the Google News Initiative. It sees Google trying to increase the output and promotion of quality journalism as it tries to "build a stronger future for news" and fight the spread of inaccurate information. Over the next three years, Google plans to spend a total of $300… [Continue Reading] -

Play your favorite retro handheld games with the Internet Archive emulators
Publié: mars 20, 2018, 1:29pm CET par Mark Wycislik-Wilson
The Internet Archive is a staggering piece of work, saving for posterity books, movies, music, and entire websites. For a number of years, the site has also offered in-browser emulation, giving everyone the chance to get teary-eyed with nostalgia and play a range of console games online. Now the emulation collection has been expanded to cover a wide range of handheld games including the likes of Mortal Kombat, Double Dragon and Q*Bert. The new Handheld History Collection builds on the work the Internet Archive has already done with the MAME development team. See also: Google Play Instant lets you stream… [Continue Reading] -

Picture-in-picture mode is coming to YouTube on the desktop
Publié: mars 20, 2018, 10:55am CET par Mark Wycislik-Wilson
YouTube has been embroiled in more than its fair share of controversy recently -- relating to conspiracy videos in particular -- but this is not standing in the way of Google forging ahead with new features. Next on the horizon is a picture-in-picture mode; something that will be familiar to users of the YouTube mobile apps. Now the same feature is coming to desktop version of the site, giving you the ability to continue browsing through videos while another one plays. See also: YouTube Kids app is serving up conspiracy videos from the likes of David Icke Wikipedia didn't know… [Continue Reading] -

Google Play Instant lets you stream Android apps and games to try them out
Publié: mars 19, 2018, 6:40pm CET par Mark Wycislik-Wilson
With so many apps and games to choose from in Google Play, it's very easy to be tempted to try all of them out. Well... maybe not all of them, but it's easy to get carried away. This can mean waiting an age for a particular title to download, only for you to try it and discover you don't like it. Today Google announces a solution to the problem: Google Play Instant. It lets you get started in a game without having to download it completely -- in essence you're streaming the bits you need to your Android phone or… [Continue Reading] -

Facebook is introducing a way for creators to make money from their content
Publié: mars 19, 2018, 6:01pm CET par Mark Wycislik-Wilson
YouTube has become a huge money-making platform, not only for Google, but also for the creators who upload content. Now Facebook wants a piece of the action and is in the process of testing a couple of ways in which creators can monetize their content. The idea sees Facebook giving creators the chance to offer subscription services to their fans. For $4.99 per month, subscribers can be granted access to exclusive content -- and Facebook won’t be taking a cut of the money. See also: Facebook suspends Trump campaign's data analytics team, Cambridge Analytica, for harvesting private information of 50… [Continue Reading] -

Firefox's 'master password' system can be easily bypassed using brute force
Publié: mars 19, 2018, 3:52pm CET par Mark Wycislik-Wilson
If you're a Firefox user, it's highly possible that you use the browser to store your login usernames and passwords for the sake of ease. Supposing you're a little security conscious, you may well have enabled the 'master password' function to prevent unauthorized access to your password database. Well, there's a little bad news. It's nowhere near as secure as you may have thought. Wladimir Palant -- the guy behind the AdBlock Plus extension -- found that the system, which is used by both Firefox and Thunderbird, can be very easily brute-forced, leaving passwords vulnerable to malware and hackers. Mozilla… [Continue Reading] -

Linux Foundation announces open source ACRN hypervisor for the Internet of Things
Publié: mars 19, 2018, 2:50pm CET par Mark Wycislik-Wilson
The Linux Foundation has released details of one of its open source projects, ACRN -- a hypervisor designed for the Internet of Things and embedded devices. And, yes, it is pronounced "acorn". The project was helped by contributions of code and engineering from Intel, and the aim was to create a system for managing virtual machines that was both flexible and small. With a Linux-based service OS, ACRN can run multiple guest operating systems at the same time, making it ideal for many scenarios. See also: Linux Mint 19 'Tara' Cinnamon will be faster If you owned a 'fat' PlayStation… [Continue Reading] -

Twitter to ban an array of cryptocurrency ads
Publié: mars 19, 2018, 1:45pm CET par Mark Wycislik-Wilson
Just a few days ago, it was revealed that Google plans to ban ads for cryptocurrencies and related products and services later this year. Now it seems as though Twitter could be following suit. The plans could see the social network implementing a ban on ads for ICOs and almost all cryptocurrencies. It is reported that Twitter's ban could come into force within a couple of weeks. See also: Google slaps a ban on cryptocurrency ads Cryptocurrency exchange Binance offers $250,000 bounty for hacker information Cryptocurrency exchange Binance launches new public blockchain -- Binance Chain Sky News reports that Twitter's… [Continue Reading] -

YouTube Kids app is serving up conspiracy videos from the likes of David Icke
Publié: mars 18, 2018, 11:53am CET par Mark Wycislik-Wilson
The very idea of YouTube Kids is to ensure that children are not exposed to content that parents would consider inappropriate for them. This means filtering out videos with an adult theme, with Google -- supposedly -- curating content suitable for younger eyes. This week, the main YouTube site has been in the news because of its plans to counter conspiracy videos with "information cues" rom Wikipedia. But it seems that YouTube Kids has a similar problem, with children being exposed to conspiracy theory videos from the likes of reptilian-obsessed, Illuminati-loving conspiracist David Icke. See also: Wikipedia didn't know about… [Continue Reading] -

If you owned a 'fat' PlayStation 3 you could be entitled to $65 from Sony because of Linux option
Publié: mars 18, 2018, 11:10am CET par Mark Wycislik-Wilson
Cast your mind back to when Sony released the original PlayStation 3, and you may well remember claims that the console was also a "computer". The claims were such that Sony suggested that owners could install Linux -- which, technically speaking, they could. However, installing Linux on a PS3 also posed something of a security issue, and Sony backtracked on the "Other OS" feature, killing it will a firmware update. Unsurprisingly, a lawsuit followed, and the result of this is that you could in line for a pay-out. See also: Chromebooks could soon run Linux applications and VMs using containers… [Continue Reading] -

Facebook suspends Trump campaign's data analytics team, Cambridge Analytica, for harvesting private information of 50 million users
Publié: mars 17, 2018, 3:12pm CET par Mark Wycislik-Wilson
Facebook has suffered what has been described as the social networks "biggest ever data breach" after Cambridge Analytica and its parent group Strategic Communication Laboratories (SCL) harvested data from more than 50 million users. Cambridge Analytica is best known for its work with the Trump campaign for the 2016 election, and Facebook found that the company had violated it data privacy policies. The data was used as part of a "microtargeting" campaign to try to predict and influence voters' choices in the election. See also: Data-saving Facebook Lite is now available in the US Facebook algorithms went mad and threw… [Continue Reading] -

Force Windows 7 security updates even if you don't have antivirus software installed
Publié: mars 16, 2018, 4:35pm CET par Mark Wycislik-Wilson
Compatibility issues with patches for the Meltdown and Spectre vulnerabilities saw Microsoft blocking the rollout of security updates to Windows users. The company has just changed its policy for Windows 10 users, but this does not help anyone running Windows 7 or 8.x. The problem is that updates are blocked for people who have not installed antivirus software known to be fully compatible. When such software is installed, a registry entry is created, and this allows updates to be installed. If you've decided to run the risk of operating without antivirus software installed, this registry won't be created and you… [Continue Reading] -

Data-saving Facebook Lite is now available in the US
Publié: mars 16, 2018, 3:00pm CET par Mark Wycislik-Wilson
Originally designed for countries with slower mobile internet connections, Facebook's cut-down and data-light Facebook Lite app is making its way to the US. The app has been around since 2015, but it was only available in a limited number of countries, with the focus being primarily on developing nations where connectivity was an issue. But now Facebook is spreading the love to the United States, the United Kingdom and other parts of the world. See also: Facebook algorithms went mad and threw up some weird -- and sexual -- search suggestions Facebook bans far-right group Britain First and its leaders… [Continue Reading] -

Facebook algorithms went mad and threw up some weird -- and sexual -- search suggestions
Publié: mars 16, 2018, 2:13pm CET par Mark Wycislik-Wilson
Facebook has issued an apology after its search algorithms apparently went haywire and started to suggest a range of strange, and often NSFW, videos to users. Throughout Thursday night into Friday morning, a range of bizarre search suggestions were displayed to anyone who started typing "video of". Some of the suggestions were offensive, and it didn't take long for screenshots to be shared on Twitter. See also: Facebook bans far-right group Britain First and its leaders for hate speech Facebook Onavo VPN app gathers user data even when it is disabled Facebook adds video chats to Messenger Lite Facebook asks… [Continue Reading] -

US says Russia launched a cyberattack on its energy grid
Publié: mars 15, 2018, 4:25pm CET par Mark Wycislik-Wilson
The US has introduced new sanctions against Russia after accusing the country not only of interfering in the 2016 election, but also launching a cyberattack on its energy grid. Officials say that malware traced back to Moscow had been found to have infected operating systems on computers belonging to companies in the energy sector. The Department of Homeland Security is in no doubt that the Russian government is responsible. The attack has been described as coordinated as "deliberately targeted," with a senior official saying: "It is the judgment of the DHS than Russian government cyberhackers were behind the hacking of… [Continue Reading] -

Microsoft launches bounty program for speculative execution side channel vulnerabilities
Publié: mars 15, 2018, 2:15pm CET par Mark Wycislik-Wilson
Microsoft has launched a bug bounty program that will reward anyone who finds the next Meltdown or Spectre vulnerability. Known as speculative execution side channel vulnerabilities, Microsoft is willing to reward anyone who reports bugs that could cause problems like earlier in the year. The rewards on offer range from $5,000 up to $250,000 depending on the severity of the vulnerability, and the bounty program runs until the end of 2018. Microsoft says that it will operate under the principles of coordinated vulnerability disclosure. See also: Microsoft removes AV compatibility requirements for Windows 10 security updates Intel failed to warn… [Continue Reading] -

Privacy: Hotspot Shield, PureVPN, and ZenMate found to leak sensitive data
Publié: mars 15, 2018, 1:24pm CET par Mark Wycislik-Wilson
VPN tools have been in the headlines recently. Firstly, Facebook's Onavo VPN was found to be gathering user data, and then McAfee snapped up VPN firm TunnelBear. Now for users of Hotspot Shield, PureVPN and ZenMate, there's a warning: sensitive data such as your real IP address may be leaked. A VPN company with a strong interest in privacy, vpnMentor, commissioned research into the three well-known tools, and problems were found in all of them. The developers were notified, but only HotSpot Shield has addressed the problems that were found. See also: McAfee buys VPN firm TunnelBear Facebook Onavo VPN… [Continue Reading] -

Google opens up Maps API to game developers
Publié: mars 15, 2018, 12:28pm CET par Mark Wycislik-Wilson
Google is giving developers the chance to build games based on real-world maps by opening up the Maps APIs to them. On top of this, Google is bring Maps to the Unity game engine so developers can make use of real-time map data. Titles such as Jurassic World Alive, The Walking Dead: Our World and Ghostbusters World will make use of augmented reality to create truly immersive gaming experiences. Developers have access to over 100 million 3D buildings, roads, landmarks, and parks from over 200 countries, allowing for great flexibility. The company says: "Game studios can easily reimagine our world… [Continue Reading] -

Wikipedia didn't know about YouTube's plans to show its content next to conspiracy videos
Publié: mars 15, 2018, 11:44am CET par Mark Wycislik-Wilson
YouTube's announcement that it plans to display content from Wikipedia next to conspiracy videos in the name of balance and providing the "right information" caught many people by surprise -- none more so than Wikipedia itself. Wikimedia Foundation -- the organization behind Wikipedia -- has issued a statement saying that "we were not given advance notice of this announcement." While the organization does not object to YouTube's decision, it does seem a little strange that there has been no discussion between the two parties. See also: YouTube to counter conspiracy videos by displaying information from Wikipedia alongside Advertisers pull ads… [Continue Reading] -

Warning for RSS fans -- Digg Reader is closing in under two weeks
Publié: mars 15, 2018, 11:06am CET par Mark Wycislik-Wilson
For some people RSS is already a dead technology, and over the last few years numerous RSS readers -- including Google Reader -- shut up shop. But for others, accessing newsfeeds is an essential way to keep up to date with what's going on. Following the closure of Google Reader, RSS fans flocked to the likes of Feedly, The Old Reader, Digg Reader and Inoreader. Now Digg Reader has announced that it is to close, and users are being advised to export their feeds so they can be imported into an alternative service. Users do not have a great deal… [Continue Reading] -

Microsoft removes AV compatibility requirements for Windows 10 security updates
Publié: mars 15, 2018, 10:21am CET par Mark Wycislik-Wilson
In the fallout from the revelations about the Spectre and Meltdown vulnerabilities -- and the ensuing chaos relating to patches for the security problems -- Microsoft blocked security updates for Windows 10 users with antivirus software whose compatibility with patches was not known. Two months after making this decision, Microsoft has changed course and said that updates can roll out to everyone once again. The company says this is a result of working with antivirus partners and patches should no longer lead to problems in most cases. See also: Intel failed to warn US government about Meltdown and Spectre flaws… [Continue Reading] -

Google Maps gains wheelchair accessibility info in several cities
Publié: mars 15, 2018, 9:53am CET par Mark Wycislik-Wilson
Google is adding some important accessibility information to Maps, letting users see whether or not routes are navigable by wheelchair. The company says the extra data will be useful not only to wheelchair users, but anyone with mobility issues -- as well as parents pushing kids in a stroller. Starting in London, Tokyo, Mexico City, Boston and Sydney, wheelchair accessible routes are being added, and more will follow as Google working with transport companies to gather the necessary information. Google recognizes the need many people have to find routes that are free from steps, have elevators, or feature modes of… [Continue Reading] -

Facebook bans far-right group Britain First and its leaders for hate speech
Publié: mars 14, 2018, 4:51pm CET par Mark Wycislik-Wilson
In the latest part of its clean-up exercise, Facebook has removed pages of the far-right, anti-Islamic group Britain First. The social network has also closed down the pages of the leaders of the group -- well-known in the UK, and also brought to US attention after Donald Trump shared its tweets. The ban is such that Britain First will not be able to create any pages in the future. Facebook says that the group has repeatedly violated rules against hate speech, and denies that the bans are an infringement of free speech. See also: Facebook Onavo VPN app gathers user… [Continue Reading] -

Roundup: The best Windows 10 tweaking and customization tools
Publié: mars 14, 2018, 3:37pm CET par Mark Wycislik-Wilson
Unless you're a fan of using a computer that looks and feels the same as everyone else, you probably want to spend some time tweaking Windows so it works the way you want it to. Broadly speaking, tweaks fall into three categories -- those that change appearance, those that boost performance, and those that change the way things work. Windows 10 does -- through Settings and the Control Panel -- afford you a decent degree of control over how the operating system looks and works, but if you want to get serious about things you have two options: head into… [Continue Reading] -

YouTube to counter conspiracy videos by displaying information from Wikipedia alongside
Publié: mars 14, 2018, 11:06am CET par Mark Wycislik-Wilson
YouTube has faced criticism not only for allowing conspiracy videos to appear on the site, but also how it has dealt with them. The latest move by Google in this area will see information from Wikipedia and other websites displayed alongside such videos in the interests of balance. Google says that the aim of the new "information cues" is to combat conspiracy theory videos it hosts, as well as trying to combat hoaxes. See also: Google slaps a ban on cryptocurrency ads Advertisers pull ads from Alex Jones' YouTube channel because they don't want to be linked to InfoWars YouTube… [Continue Reading] -

Google slaps a ban on cryptocurrency ads
Publié: mars 14, 2018, 10:47am CET par Mark Wycislik-Wilson
Google has announced that advertisements for cryptocurrencies will be banned from its platform starting in June. The ban not only covers currencies such as Bitcoin and Ethereum, but also related products such as initial coin offerings, cryptocurreny exchanges and digital wallets. The announcement came as Google is relying on new technology to detect and remove ads that violate policies. The company says it removed over 3.2 billion ads in 2017, and while it does not give a precise reason for the cryptocurrency ad ban, it says it is part of "improving the ads experience across the web." See also: Cryptocurrency… [Continue Reading] -

Cryptocurrency exchange Binance launches new public blockchain -- Binance Chain
Publié: mars 13, 2018, 8:00pm CET par Mark Wycislik-Wilson
Just after offering up a bounty to track down the hackers who attacked it, cryptocurrency exchange Binance has announced the launch of a public blockchain. Binance Chain, as it is known, is the exchange's vision of the future, and it will focus mainly on the transfer and trading of blockchain assets. Binance also announced that its own Binance Coin (BNB) will become a native coin, changing from the current Ethereum-based ERC20 token. See also: Cryptocurrency exchange Binance offers $250,000 bounty for hacker information Government websites in US, UK and Australia hacked to run secret cryptocurrency miner Hackers hijack YouTube ads… [Continue Reading] -

Google Images gains captions to make search results much more useful
Publié: mars 13, 2018, 6:01pm CET par Mark Wycislik-Wilson
By its very nature, searches on Google Images are very visual things -- but that's not to say they couldn't be enhanced with some non-pictorial content. And that's exactly what Google has done, adding captions to image search results to make them more useful. The aim is to provide greater context about results, giving users the chance to judge the quality of the image, and to perhaps determine whether the host site will have other useful images. See also: Download Android P developer preview as Google reveals release schedule Google Home brings free mobile and landline calls to UK users… [Continue Reading] -

IMF chief wants to regulate the 'dark side of the crypto world' with blockchain and AI
Publié: mars 13, 2018, 5:06pm CET par Mark Wycislik-Wilson
Christine Lagarde, the head of the International Monetary Fund (IMF), has said that the blockchain technology behind cryptocurrencies could also be used to regulate them. She suggests that the IMF "fight fire with fire" in trying to address the "dark side of the crypto world." While acknowledging the potential for the technology behind crypto-assets as being massively empowering -- particularly as a way to provide low-cost payment methods in poorer countries -- she says that cryptocurrencies also need regulation to avoid problems such as money laundering and funding terrorism. See also: Cryptocurrency exchange Binance offers $250,000 bounty for hacker information… [Continue Reading] -

American Civil Liberties Union lawsuit complains about TSA searches of phones and laptops
Publié: mars 13, 2018, 1:28pm CET par Mark Wycislik-Wilson
The American Civil Liberties Union (ACLU) has filed a lawsuit against the TSA, asking for details to be released about the policies governing searches carried out on phones and laptops on domestic flights. There have been a number of complaints recently from passengers unhappy with the fact that their devices have been searched without any reason being given. Concerns are mounting about invasion of privacy, hence the ACLU's interest in finding out precisely why the searches are being carried out. See also: Ad-blocker and privacy tool Ghostery goes open source, and has new ways to make money Microsoft releases Windows… [Continue Reading] -

Cryptocurrency exchange Binance offers $250,000 bounty for hacker information
Publié: mars 13, 2018, 10:46am CET par Mark Wycislik-Wilson
A week ago, cryptocurrency exchange Binance was the victim of a hacking attempt. While the attempt on March 7 is described as "not successful," Binance is still eager to track down the perpetrators. So keen is the exchange, in fact, that it is offering up a $250,000 bounty to "the first person to supply substantial information and evidence that leads to the legal arrest of the hackers." See also: Government websites in US, UK and Australia hacked to run secret cryptocurrency miner Hackers hijack YouTube ads with Coinhive to mine Monero cryptocurrency Supposed inventor of Bitcoin sued for $10 billion… [Continue Reading] -

Trump blocks Broadcom's takeover of Qualcomm, citing national security
Publié: mars 13, 2018, 9:58am CET par Mark Wycislik-Wilson
Donald Trump has signed an executive order that blocks Broadcom from buying Qualcomm. The takeover has been talked about for a number of months, but now the president -- in line with his "America first" drive -- has scuppered what would have been the largest technology deal ever. Had the deal gone ahead, a merged Broadcom and Qualcomm would have been responsible for a massive proportion of the chips in phones, computers and connected devices. But US concerns about China mean that the deal is now very much off the table. See also: Broadcom may buy Qualcomm for $100 billion… [Continue Reading] -

Apple announces plans to acquire digital magazine service Texture
Publié: mars 12, 2018, 6:21pm CET par Mark Wycislik-Wilson
Today Apple revealed that it is to acquire the digital magazine subscription service Texture. The iPhone-maker says that it has signed an agreement about the acquisition but does not say when it will complete. The company says the move is part of its commitment to "quality journalism from trusted sources," and it has already shown its appreciation of Texture by featuring it in the App Store's "best of" selections. The service currently provides access to over 200 digital titles, including names such as Elle, the New Yorker and Vanity Fair. John Loughlin, CEO of Texture and Next Issue Media (the… [Continue Reading] -

Intel-sponsored study finds that smart cities save time
Publié: mars 12, 2018, 4:23pm CET par Mark Wycislik-Wilson
A study sponsored by Intel has come to the rather unsurprising conclusion that smart cities save people time. The company says that major cities that have embraced the Internet of Things (IoT) can save each of their citizens up to 125 hours per year. Being able to claw back more than five days over the course of a year seems too good to be true, but the study from Intel and Juniper Research appears to bear out the claim. The research looked at smart cities around the world, ranking them accordingly in the areas of mobility, health care, public safety… [Continue Reading] -

Amazon launches Prime Student in the UK with one-day delivery, Prime Video and more
Publié: mars 12, 2018, 1:05pm CET par Mark Wycislik-Wilson
University students and anyone in higher education in the UK can now take advantage of Amazon's Prime Student. The monthly plan costs just £3.99 -- half the regular price of Prime -- and it includes unlimited one-day deliveries, access to Prime Video, Prime Music and much more. Anyone eligible for the program can take advantage of a six-month free trial to see if it's something that works for them. In addition to numerous Amazon services, Prime Student also gives subscribers money off textbooks, stationery and university essentials. See also: Amazon hikes monthly Prime fee by 18 percent Amazon offers refunds… [Continue Reading] -

Now you have longer to delete your WhatsApp messages
Publié: mars 12, 2018, 12:16pm CET par Mark Wycislik-Wilson
Just as with any popular platform, WhatsApp has fans who are quite happy to use it while conceding that there are things that need to be improved. Having -- eventually -- made it possible to delete messages after sending them, WhatsApp is now extending the timeframe in which deletions can be made. The Delete For Everyone option is now available to users for 1 hour, 8 minutes and 16 seconds after a message has been sent. See also: BlackBerry sues Facebook, WhatsApp and Instagram in messaging patent spat Privacy: WhatsApp's group messages might not be as secure as you think… [Continue Reading] -

Tim Berners-Lee: social media is too powerful and the web needs regulation to avoid weaponization
Publié: mars 12, 2018, 11:33am CET par Mark Wycislik-Wilson
Today marks the 29th anniversary of the world wide web, and as has become traditional, its inventor has penned a letter for the occasion. In it, Sir Tim Berners-Lee calls for regulation of the web to prevent it from being "weaponized". His letter suggests that "the web is under threat," and highlights a number of problems that exist, including the digital divide, privacy, fake news and the dominance of social media. He suggests that a regulatory framework could be needed to prevent a handful of companies from "weapon[zing] the web at scale." Berners-Lee is concerned about the fact that a… [Continue Reading] -

Twitter suspends multiple 'tweetdecking' accounts for stealing tweets and spamming content into forced virality
Publié: mars 11, 2018, 5:33pm CET par Mark Wycislik-Wilson
In the latest attempts to clean up its platform, Twitter has suspended a number of accounts for trying to game the system. A number of well-known accounts were hit for stealing tweets without giving credit, and mass retweeting each other's content to force virality -- a practice sometimes known as tweetdecking. As is customary, Twitter is not willing to comment on individual cases, but it is thought that the company was unhappy with repeated violations of its policies against spam. See also: Judge: Trump should mute rather than block critics on Twitter Want to get verified on Twitter? Jack Dorsey… [Continue Reading] -

Apple reveals redesigned MFi logos
Publié: mars 11, 2018, 4:24pm CET par Mark Wycislik-Wilson
Apple has unveiled new logos for its MFi Program. The Made For iPhone/iPad/iPod Program is a certification program used to indicate that third-party accessories meet Apple's standards for quality. Having launched a new set of simplified logos, Apple is giving manufacturers 90 days to switch to the new designs. The change may seem minor, but there are three tweaks worth noting. See also: Apple to store iCloud keys in China, sparking privacy fears Apple videos show how to get the most from its HomePod speaker Apple confirms but downplays iOS source code leak It's fair to say that the redesign… [Continue Reading] -

GIPHY removed from Snapchat and Instagram after racist GIF appears
Publié: mars 10, 2018, 9:34am CET par Mark Wycislik-Wilson
Snapchat and Instagram have both temporarily removed GIPHY integration from their products following the appearance of a racist GIF. A statement put out by Snapchat says: "We have removed GIPHY from our application until we can be assured that this will never happen again." Instagram made a similar move, and it's not clear when GIPHY will rectify the issue. (Warning: a tweet containing the GIF in question is featured in the article below). Speaking to TechCrunch, Snapchat said that GIFs were supposed to be PG-rated to make them suitable for the youngest users allowed on the platform. The GIF in… [Continue Reading] -

How to export your saved passwords from Chrome
Publié: mars 9, 2018, 3:58pm CET par Mark Wycislik-Wilson
If you're a Chrome user, you may well have taken advantage of the password saving feature of the browser to make it easier to log into your various online accounts. However, it's not a perfect solution, and you may well have been considering one of the various password management tools that exist instead. Until now, it has not been possible to extract the passwords and login data you have saved in Chrome ready to import into your new password database. This has now changed, so you can easily switch to a new password manager without having to retype everything by… [Continue Reading] -

Judge: Trump should mute rather than block critics on Twitter
Publié: mars 9, 2018, 11:43am CET par Mark Wycislik-Wilson
Donald Trump's use of Twitter is well known, and it's also been the source of some controversy for one reason or another. As well as his seemingly ill-thought out ramblings causing delight, amazement, disbelief and horror in just about equal measure, it has been suggested that the president's decision to block people who criticize him is unconstitutional. Now a district judge may have come up with a solution, avoiding concerns about potential violation of the First Amendment. She suggests that rather than blocking people, Trump should just mute their accounts. See also: Want to get verified on Twitter? Jack Dorsey… [Continue Reading] -

Ad-blocker and privacy tool Ghostery goes open source, and has new ways to make money
Publié: mars 9, 2018, 10:46am CET par Mark Wycislik-Wilson
In an attempt to improve trust and transparency, ad-blocking tool Ghostery has gone open source. It comes after Ghostery was acquired by Cliqz last year and raised a few eyebrows with the business model it put in place. As well as going open source, Ghostery is also introducing new ways of making money. Rather than selling anonymized user data to third parties, there are now two income streams: Ghostery Insights and Ghostery Rewards. The former is a premium product for which details have not been revealed, the latter an opt-in marketing system. See also: Google explains how Chrome's new ad… [Continue Reading] -

Want to get verified on Twitter? Jack Dorsey wants that for you too
Publié: mars 9, 2018, 9:36am CET par Mark Wycislik-Wilson
For a large number of Twitter users, there is one question that crops up time and time again -- "How to I get verified on Twitter?". Once the dominated by celebrities and politicians, Twitter eventually allowed anyone to ask for a coveted tick -- but then closed down open applications after problems with white supremacists. A lot of users were stripped of their verified status, but gaining the tick still remains a goal for many. Now Twitter CEO Jack Dorsey has some good news. The plan is to open up verification to everyone -- and Twitter will not be acting… [Continue Reading] -

Hardcoded password in Cisco software could be used to gain control of systems
Publié: mars 8, 2018, 4:33pm CET par Mark Wycislik-Wilson
Cisco's Prime Collaboration Provisioning (PCP) software has a hardcoded password that could be used by an attacker to gain full control of a system. The company even says that "extenuating circumstances" exist that could enable an attacker to elevate privileges to root. The vulnerability (CVE-2018-0141) affects version 11.6 of the software. A patch has been made available, and users are encouraged to install it as soon as possible as there are no other workarounds. Cisco explains that the problem is fixed in Prime Collaboration Provisioning Software Releases 12.1 and later, and says that it was detected during "internal security testing."… [Continue Reading] -

McAfee buys VPN firm TunnelBear
Publié: mars 8, 2018, 3:42pm CET par Mark Wycislik-Wilson
Security firm McAfee has announced the acquisition of VPN company TunnelBear. Full details of the deal have not been revealed, and it is not known how much money has changed hands. With a growing awareness of the importance of online security and privacy, VPN tools have grown in popularity in recent years, and the Canada-based TunnelBear has managed to gather 20 million users around the world. See also: Facebook Onavo VPN app gathers user data even when it is disabled If you're concerned about privacy, you might want to skip Facebook's VPN -- Onavo Protect McAfee delivers added security for… [Continue Reading] -

Here's what's new in Android P
Publié: mars 8, 2018, 11:20am CET par Mark Wycislik-Wilson
Google has released the first developer preview of Android P, giving us a glimpse into the future of its mobile OS. There's a lot to explore in this latest version of Android, but just what can you expect -- apart from notch support, of course? As this is just the first preview version, there's not -- currently -- a huge number of new features. The focus at the moment is on under-the-hood changes, but there's still plenty to explore, and more than enough to pique interest for future builds. So… let's take a look. See also: Download Android P developer… [Continue Reading] -

Download Android P developer preview as Google reveals release schedule
Publié: mars 8, 2018, 9:57am CET par Mark Wycislik-Wilson
It's mere days since we were talking about the impending release of Android P for developers. Now, slightly earlier than expected, a preview of the latest version of Google's mobile operating system is here. As this is a preview build, it is not only not aimed at the masses, but is also only compatible with a handful of Android phones -- specifically the Pixel, Pixel XL, Pixel 2 and Pixel 2 XL. If you have one of these devices, you can try out Android P for yourself, but Google has revealed that we’ll have to wait until Q3 for the… [Continue Reading] -

Warning: Hackers can use Cortana to access a locked Windows 10 PC
Publié: mars 7, 2018, 6:54pm CET par Mark Wycislik-Wilson
Locking your PC is fundamental to preventing others from accessing it when you leave it unattended. But now security researchers have shown that it is possible to use none other than Windows 10's Cortana to bypass a password-protected lock screen. A pair of Israeli researchers found that it is possible to use voice commands to access a locked computer and install malware. See also: Microsoft is dropping Windows 10 S as a standalone product in favor of S Mode Microsoft confirms Windows 10 S will become a 'mode' of Windows 10 next year Microsoft releases Windows 10 Spring Update (RS4)… [Continue Reading] -

Facebook Onavo VPN app gathers user data even when it is disabled
Publié: mars 7, 2018, 5:10pm CET par Mark Wycislik-Wilson
It is a number of years since Facebook acquired mobile data compression firm Onavo, but in recent weeks concern mounted about how the social network's Onavo VPN tool collects user data. The collection of user data while an app or service is being used is one thing, but a security researcher noticed that Onavo seemed to gather certain snippets of user data even when switched off. See also: If you're concerned about privacy, you might want to skip Facebook's VPN -- Onavo Protect Facebook adds video chats to Messenger Lite Facebook asks users if it's OK for adults to request… [Continue Reading] -

Facebook adds video chats to Messenger Lite
Publié: mars 7, 2018, 4:40pm CET par Mark Wycislik-Wilson
After initially launching in countries with slower internet connections, Facebook Messenger Lite ultimately spread to other parts of the world. The cut-down version of the app gave access to a subset of its big brother's features, and now Facebook has added support for video chat. The app has proved popular even in countries with easy access to decent internet and mobile connections, as users eschew super-sized apps in favor of more diminutive versions. The addition of this important and popular feature is only going to increase its appeal. See also: Facebook Messenger Lite now available in US, Canada, UK and… [Continue Reading] -

Google Home brings free mobile and landline calls to UK users
Publié: mars 7, 2018, 12:00pm CET par Mark Wycislik-Wilson
If you live in the UK and have been looking for another reason to invest in a Google Home smart speaker, Google just gave you one. The company is going to give UK users the ability to place free calls to mobile and landline numbers. An update rolling out this week will add the new feature to Google Home speakers around the country. The feature was announced last year, and it brings the UK in line with the US -- and, importantly, it does not require tethering to a mobile phone, thereby trumping Apple HomePod. See also: Some Google Home… [Continue Reading] -

Chrome for Windows drops Microsoft compiler in favor of Clang
Publié: mars 7, 2018, 10:05am CET par Mark Wycislik-Wilson
The Windows version of Google Chrome is ditching Microsoft's C++ Compiler and switching to Clang. The change brings Chrome for Windows in line with versions of the browser for macOS, Android and Linux. The move not only makes complete sense for Google -- why not use the same compiler on all platforms, after all? -- it makes Chrome the first high-profile Windows app to make use of the open source compiler Clang. See also: Chromebooks could soon run Linux applications and VMs using containers Google explains how Chrome's new ad filtering feature works -- and why it's not your new… [Continue Reading] -

BlackBerry sues Facebook, WhatsApp and Instagram in messaging patent spat
Publié: mars 7, 2018, 9:21am CET par Mark Wycislik-Wilson
BlackBerry -- yep, them -- has filed a lawsuit against Facebook, WhatsApp and Instagram, claiming that the companies infringed on patents relating to BlackBerry Messenger. This is not the first time the company has sued other tech firms, drawing on its back catalog of over 40,000 patents in a bid to pull in money through licensing fees. BlackBerry insists, however, that litigation is "not central to [its] strategy." See also: BlackBerry Mobile site hacked to run Monero cryptocurrency miner Facebook asks users if it's OK for adults to request sexual images from children Facebook admits its News Feed experiment was… [Continue Reading] -

Video shows the speed difference a new battery makes to an iPhone 6s
Publié: mars 6, 2018, 5:58pm CET par Mark Wycislik-Wilson
It's not all that long since it came to light that Apple was purposefully reducing the speed of older iPhones in order to compensate for aging batteries. In the wake of the backlash that followed, the company announced a cheap battery replacement program, and also plans to introduce an update to iOS that allowed users to opt out of this performance reduction. But just how significant was the slowdown? One iPhone user has released a video showing the performance difference between an old iPhone 6s, and the same phone with a new battery. The results are noteworthy to say the… [Continue Reading] -

123 Reg backup cockup wipes out users' websites since August last year
Publié: mars 6, 2018, 5:05pm CET par Mark Wycislik-Wilson
Web host 123 Reg has suffered something of an issue causing it to replace some users' websites with backups dating back to August 2017. Other website owners complained that their sites had been taken offline completely. For anyone who has not made their own backup of their website, it's not looking as though 123 Reg will be able to help. Changes made since August last year appear to have been lost forever. Unsurprisingly, customers are more than a little irked. 123 Reg has not given much information about what has happened, simply referring to a "hardware failure" that affected a… [Continue Reading] -

Google brings search and sharing to iMessage in iOS, Safari updates, and more
Publié: mars 5, 2018, 7:19pm CET par Mark Wycislik-Wilson
Google has released an update for its iOS app that adds an extension to iMessage. This allows for easy searching -- be it for GIFs or restaurant opening times -- while you chat, so there's no need to leave the app. More than this, it is also possible to share the information you find as a card. The update also brings an expansion of sharing to all web browsers, including Safari. Share a page to the Google app, and you'll see a list of related suggestions. But it doesn't end there. Google has also introduced new options for iPad users.… [Continue Reading] -

Facebook asks users if it's OK for adults to request sexual images from children
Publié: mars 5, 2018, 5:14pm CET par Mark Wycislik-Wilson
Facebook frequently uses surveys to gauge user opinion about features, changes and ideas. One recent such survey raised more than a few eyebrows as the social network asked whether it was OK for a man to ask a child for sexual pictures. That any company should, essentially, ask whether pedophilia is acceptable is more than a little strange, but for such a question to come from such a big name as Facebook almost defies belief. The survey appeared over the weekend, surprising those who saw the questions. See also: Facebook admits its News Feed experiment was a failure and pulls… [Continue Reading] -

Advertisers pull ads from Alex Jones' YouTube channel because they don't want to be linked to InfoWars
Publié: mars 5, 2018, 1:51pm CET par Mark Wycislik-Wilson
Just over a week ago, YouTube decided to remove an InfoWars video from the Alex Jones' channel for breaching site rules about harassment. In videos, students who had spoken on TV about the Parkland, Florida shooting were described as "crisis actors". Jones described the move as "giant, massive censorship" and went as far as saying his channel was about to be shut down. Now advertisers are showing how they feel about InfoWars, with a number of large companies -- including Acer, 20th Century Fox, Grammarly, Paramount Network, Alibaba and Mozilla -- pulling advertising after learning that their ads were appearing on… [Continue Reading] -

Google launches Mobile Real-time Video Segmentation as limited beta (AI green screen to you and I)
Publié: mars 4, 2018, 10:28am CET par Mark Wycislik-Wilson
Google is testing a new AI green screen tool for YouTube called Mobile Real-time Video Segmentation. We've become used to every chat tool worth its salt offering AR overlays and masks, but this technology makes it possible to change backgrounds -- in real time. The technique makes use of neural networks to determine which parts of a scene are foreground to be left alone and which are background to be replaced. No special equipment is needed, and it has the potential to be used for serious videos as well as the more frivolous things masks tend to be used for… [Continue Reading] -

Android P should be making its way to developers later this month
Publié: mars 4, 2018, 9:35am CET par Mark Wycislik-Wilson
While a lot of Android users are still waiting for Oreo to arrive on their handsets -- well, let's face it, there are still plenty waiting for Nougat -- Google is hard at work on Android P. The P may or may not stand for pistachio (or possibly pie, leading to speculation of a March 14 -- Pi day -- release), but what people really care about is what's new and when they can try it out. It shouldn't be too long until we find out more about what to expect from the latest version of Google's mobile operating system.… [Continue Reading] -

Have I Been Pwned is now used by governments to check for data breaches
Publié: mars 2, 2018, 4:20pm CET par Mark Wycislik-Wilson
Over the last few years, the website Have I Been Pwned (HIBP) has given people the chance to check whether their personal data was compromised in any data breaches. Now the site reveals that the UK and Australian governments are using its services to monitor official domains. That governments should check the site's database for the presence of their own email addresses is perhaps not surprising -- it's used by just about every type of body imaginable. But now the mechanics have been opened up for these two governments. Troy Hunt, the creator of the site, explains that the service… [Continue Reading] -

Privacy: Xbox One gamers upset after Microsoft reveals their real names
Publié: mars 2, 2018, 1:24pm CET par Mark Wycislik-Wilson
A thread appeared on Reddit yesterday in which Xbox One users say Microsoft is revealing their real names online, despite the fact they have configured their settings to block this from happening. The thread has already gained large number of comments. Microsoft got involved saying that it was actively investigating the issue which some gamers are describing as a serious breach of privacy and security. Almost 24 hours later, the matter may be resolved. While the matter gained a lot of traction on Reddit, there has also been a great deal of interest on Twitter. The head of the Xbox… [Continue Reading] -

Dropbox partners with Google Cloud for integration with Docs, Gmail and Hangouts Chat
Publié: mars 2, 2018, 10:50am CET par Mark Wycislik-Wilson
Dropbox has joined forces with Google Cloud to bring integration with G Suite. The move comes out of a recognition that people tend to use more than one cloud service, and it can be problematic having to deal with files and tools in different locations. The partnership means that users will be able to open and edit G Suite files from within Dropbox. Ultimately, there will be support for Docs, Sheets, Slides, Hangouts Chat and Gmail, making it far easier to work with the cloud services from Dropbox and Google together. See also: Google's Slack alternative Hangouts Chat exits beta… [Continue Reading] -

Facebook admits its News Feed experiment was a failure and pulls Explore Feed
Publié: mars 2, 2018, 10:04am CET par Mark Wycislik-Wilson
Facebook is far from immune to tinkering with its News Feed, but its recent experiments has been deemed a complete failure. Last year, the Explore Feed received a limited public launch following a period of beta testing, effectively separating news from friends and posts from pages. Several months later, Facebook has realized what we probably could have told it from the offset: "People don't want two separate feeds." The company was heavily criticized by those living in the countries where the experiment ran, as they said it was harder to find important information. See also: Europe threatens Facebook with fines… [Continue Reading] -

Twitter introduces Bookmarks and new sharing options
Publié: mars 1, 2018, 2:43pm CET par Mark Wycislik-Wilson
Several years in the making, Twitter has finally gained a Bookmarks option. While it has long been possible to like/heart a tweet to make it easier to access in the future, this method essentially advertised your activity to everyone -- and it might well be that you didn't "like" the tweet in question anyway. Privacy FTW! On top of this, Twitter has also introduced sharing options which can be accessed through a new icon. See also: Twitter denies reading your direct messages Twitter won't ban Donald Trump because he's special Trump was almost ten times more popular with Russian Twitter… [Continue Reading] -

Which smartphone has the best display? The Samsung Galaxy S9
Publié: mars 1, 2018, 2:04pm CET par Mark Wycislik-Wilson
Considering the amount of time spent staring at the screen of a smartphone, it's important that things look great -- particularly when it comes to video and photography. So it's little surprise that screen quality is high on the list of many people's priorities when shopping for a new handset. But which is the best? Just a few months ago, experts at display calibration and benchmarking firm DisplayMate announced that the best screen was to be found on the iPhone X. Now, following the launch of the latest flagship from Samsung, it has awarded its highest ever rating to the… [Continue Reading] -

Google's Slack alternative Hangouts Chat exits beta
Publié: mars 1, 2018, 12:14pm CET par Mark Wycislik-Wilson
After a period of beta testing, Google is unleashing Hangouts Chat on the world. Despite the name crossover, the service is completely separate to Google Hangouts, and over the course of the next few days it will be made available to all G Suite users. Hangouts Chat competes directly with the likes of Slack and Microsoft Teams, allowing for easier workplace communication and collaboration. The service can be used on the web, and there are Windows, macOS, iOS and Android apps available. Google is emphasizing not only how it integrates with other Google products, but also support for bots. Hangouts… [Continue Reading] -

Spotify is filing for an unconventional IPO
Publié: mars 1, 2018, 11:20am CET par Mark Wycislik-Wilson
Music streaming service Spotify is planning to go public. The company is making a "novel" move which it acknowledges is "risky": opting for a "direct listing" rather than the more usual fundraising route. The company will allow its investors and employees to sell shares, and there will be no need to raise more capital or hire an underwriter. It is expected that Spotify will go public in late March or early April when it will appear on the New York Stock Exchange using the symbol SPOT. Although the lack of new shares means there is not a listing price, estimates… [Continue Reading] -

YouTube says it was wrong to remove some right-wing videos and channels
Publié: mars 1, 2018, 10:39am CET par Mark Wycislik-Wilson
YouTube has said that new moderators were to blame for the removal of some right-wing videos from the site. Just a few days ago InfoWars' Alex Jones had a video removed for violating YouTube harassment policies and following this a number of right-wing and conspiracy theory channels received warnings or were suspended. Now the video site has admitted that some of the removals were the result of its policies being applied incorrectly -- side-stepping the claims of censorship that have been banded around. It says that any videos that were removed in error will be reinstated. See also: YouTube pulls… [Continue Reading] -

The ASUS ZenFone 5 is trying to be a cheap iPhone X
Publié: février 28, 2018, 4:21pm CET par Mark Wycislik-Wilson
There have been lots of devices revealed at MWC 2018 this week, and it is little surprise that there are handsets copying the look of Apple's iPhone X. In this number are the ASUS ZenFone 5 and ZenFone 5Z, both of which feature a controversial "notch" at the top of their screens. It is clear the look of the latest ZenFones have been inspired by the iPhone X, and it's hard to imagine that Apple's lawyers are not considering allegations of plagiarism. In all, there are three phones in the family: the high-end ZenFone 5Z, the mid-range ZenFone 5, and… [Continue Reading] -

You'll be able to disable and hide Firefox Sync in Firefox 60
Publié: février 28, 2018, 2:17pm CET par Mark Wycislik-Wilson
For some people, Firefox Sync is a great way to synchronize browser settings, add-ons, bookmarks and so on between computers. For others it's a privacy nightmare and a massive annoyance. Starting with Firefox 60, Mozilla is making it possible to not only disable the feature, but also hide it. This might seem like a minor change, but for anyone irritated by the mere presence of Firefox sync, it's something that should have happened sooner. See also: Microsoft Edge vulnerability exposed as Microsoft misses Google's Project Zero disclosure deadline Apple to store iCloud keys in China, sparking privacy fears Samsung launches… [Continue Reading] -

Amazon buys smart doorbell and home security firm Ring for over $1 billion
Publié: février 28, 2018, 11:03am CET par Mark Wycislik-Wilson
Amazon has opened up its wallet and splashed more than $1 billion on buying Ring. Famed for its selection of smart doorbells, security cameras and other security devices, the purchase of the Santa Monica, California firm is Amazon's latest foray into home security. While details of the deal are currently a little thin on the ground, it is expected that the Ring name will live on, and it is likely that future products released under the brand will feature Alexa smart assistant integration. See also: Amazon offers refunds to people who paid to remove ads from Prime Exclusive Phones Amazon… [Continue Reading] -

Supposed inventor of Bitcoin sued for $10 billion
Publié: février 27, 2018, 6:58pm CET par Mark Wycislik-Wilson
The self-proclaimed creator of Bitcoin, Craig Wright from Australia, has been hit by a $10 billion lawsuit. The family of his former business partner is suing Wright for allegedly stealing Bitcoins and intellectual property. The pseudonym of the inventor of Bitcoin is Satoshi Nakamoto, but his true identity has never been confirmed -- but this is who Wright claims to be. The lawsuit accuses him of stealing Bitcoins from collaborator Dave Kleiman who died in 2013. It aims to get back these coins from the early days of mining, as well as the intellectual property of the business -- W&K… [Continue Reading] -

Battle of the flagships: Galaxy S9 vs Pixel 2 vs iPhone X
Publié: février 27, 2018, 5:40pm CET par Mark Wycislik-Wilson
With the launch of Samsung's Galaxy S9 and S9+, we now have a full contingent of new flagship smartphones to pit against each other. The S9 joins the iPhone X and the Pixel 2 as one of the handsets shoppers will be choosing between. While you may feel that you are settled firmly in the Android or iOS camp, it's not until you look at the full specifications of each of these top of the range phones that you can really make a decision. So that's just what we're doing. Here's how the Galaxy S9, Pixel 2 and iPhone X… [Continue Reading] -

AZIO Retro Classic: an incredible steampunk-inspired mechanical keyboard [Review]
Publié: février 27, 2018, 4:22pm CET par Mark Wycislik-Wilson
If it's not immediately obvious from a quick glance, AZIO explains that its striking Retro Classic keyboard is inspired by the look of a vintage typewriter. It's not just the look that's inspired in this way -- as it's a mechanical keyboard, there's a distinct typewriter sound to things. There is just so much to like about this keyboard. Regardless of whether you are a fan of steampunk, the look is undeniably eye-catching. The build quality is quite phenomenal -- well... you'd hope so at these prices. The key action is gorgeous, and the clickity-clack perfectly suits the typewriter-style keys.… [Continue Reading] -

Coinbase is about to give the IRS details of 13,000 users
Publié: février 27, 2018, 2:05pm CET par Mark Wycislik-Wilson
Cryptocurrency exchange Coinbase has contacted 13,000 of its users to inform them that it is going to hand over their details to the IRS. The tax collection agency originally asked for the details of everyone buying Bitcoin between 2013 and 2015 in a bid to weed out tax evaders. Coinbase did not give in without a fight. Since the summons in November 2016, it put up some resistance, ultimately reducing the number of affected customers from 500,000 to 13,000. The exchange will be handing over the details within three weeks. See also: The European Union says it is ready to… [Continue Reading] -

Chromebooks could soon run Linux applications and VMs using containers
Publié: février 27, 2018, 11:17am CET par Mark Wycislik-Wilson
With Linux being at the core of Chrome OS, it perhaps seems surprising that there's no easy way to run Linux distros or applications on Chromebooks. Yes, there's a Crouton script that can help you to achieve this, but it's far from ideal as it massively lowers system security. All this could be about to change, however. A newly merged commit in Chromium Gerrit has been spotted which talks about a "new device policy to allow Linux VMs on Chrome OS." This would be a major change for Chromebook users, and we could see it as soon as version 66… [Continue Reading] -

The European Union says it is ready to regulate cryptocurrencies
Publié: février 26, 2018, 4:39pm CET par Mark Wycislik-Wilson
The head of the EU's financial services has said that the union is ready to regulate cryptocurrencies such as Bitcoin if a global effort is not made to tackle their risks. Valdis Dombrovskis said that worldwide measures were needed if European regulation was to be avoided. There has long been concern not just about the wildly fluctuating value of cryptocurrencies, but also the potential for them to be used in crime. See also: Lloyd's Banking Group bans Bitcoin payments via credit card Despite reports to the contrary, India is not banning Bitcoin and other cryptocurrencies Microsoft drops Bitcoin support [Update:… [Continue Reading] -

If you want to stream HD Netflix on your OnePlus 5/5T, you'll need to mail it off for an update
Publié: février 26, 2018, 3:37pm CET par Mark Wycislik-Wilson
Software updates offer a quick and easy way to bolt new features and options onto apps and operating systems -- or at least in theory. If you like the idea of streaming HD Netflix content on your OnePlus 5 or 5T, you'll probably be pleased to hear that there's an update available that brings this very feature to your phone. This is clearly great news. What's not so great, however, is the extraordinary fact that in order to get this feature you will need to physically send off your phone so OnePlus can perform the update for you. On the… [Continue Reading] -

Sony unveils Xperia XZ2 and Xperia XZ2 Compact smartphones, and unique Xperia Ear Duo earphones
Publié: février 26, 2018, 2:11pm CET par Mark Wycislik-Wilson
There are lots of announcements coming out of MWC 2018 at the moment, all vying for attention and competing to take money from eager customers. To stand out from the crowd a little, Sony has just revealed its new Xperia XZ2 and Xperia XZ2 Compact smartphones, both of which feature HDR Full HD+ 18:9 displays. The Sony Xperia XZ2 is the first smartphone to offer 4K HDR recording, and it also boasts a full HD 960FPS super slow-motion mode. There's a revamped, curvier design for both phones, which Sony is calling Ambient Flow, and Corning Gorilla Glass 5 is on… [Continue Reading] -

Samsung Galaxy S9 and S9+ launch video appears online
Publié: février 25, 2018, 3:58pm CET par Mark Wycislik-Wilson
Ahead of Galaxy Unpacked 2018 we already know everything we could possibly want -- or need -- to know about the Samsung Galaxy S9 and S9+. A few details and specs have trickled out in recent weeks, but now the company has accidentally (maybe) published the launch video online. The new Galaxy handsets have the tagline "The Phone. Reimagined", and the video shows off the waterproof capabilities of the phone as well as the new DeX Pad. There's also an automatic translation feature, a repositioned fingerprint sensor and AR features. And thanks to an article that was published a little… [Continue Reading] -

Apple to store iCloud keys in China, sparking privacy fears
Publié: février 25, 2018, 10:47am CET par Mark Wycislik-Wilson
There are only days until Apple begins storing the data of Chinese iCloud users within China, and concern is mounting about the human rights and privacy implications. A new data center is due to open in China at the end of this month as Apple moves to comply with Chinese authorities. It means that iCloud data such as text messages, photos and emails will be stored in China -- as will the cryptographic keys required to access the data. These keys had previously been stored in the US. See also: OnePlus denies sending clipboard data to China iPhone X bug… [Continue Reading] -

YouTube pulls InfoWars video from the Alex Jones Channel over Parkland shooting allegations
Publié: février 24, 2018, 11:22am CET par Mark Wycislik-Wilson
Alex Jones' conspiracy-theory-heavy InfoWars has been censured by YouTube for violating its policies. A video entitled "David Hogg Can't Remember His Lines In TV Interview" -- in which it was alleged that students appearing on TV talking about the Parkland, Florida shooting were "crisis actors" -- was removed from the Alex Jones Channel for breaching YouTube's rules about harassment. Unsurprisingly, InfoWars is describing YouTube's actions as censorship, but there's a more pressing concern for The Alex Jones Channel and other InfoWars channels -- they run the risk of being closed down entirely. See also: Symantec no longer offers discounts to… [Continue Reading] -

Symantec no longer offers discounts to NRA members
Publié: février 23, 2018, 8:08pm CET par Mark Wycislik-Wilson
Security firm Symantec has announced that it will no longer offer discounts on its products to members of the National Rifle Association. Following the school shooting in Parkland, Florida last week, the gun debate is very much back on the table. There has been pressure on numerous companies to sever ties with the NRA, and Symantec is the first big name in tech to make the move. NRA members had previously been able to take advantage of discounts of more than 50 percent off a range of Symantec products, including LifeLock and Norton titles. While some offers are still listed… [Continue Reading] -

Microsoft will let developers add support for multiple instances of their UWP Windows 10 apps
Publié: février 23, 2018, 6:42pm CET par Mark Wycislik-Wilson
Starting with Redstone 4, Microsoft will give developers a new option for their UWP apps in Windows 10 -- support for multiple instances of an app. This is a feature that lots of Windows 10 users have been asking for, so it will be welcomed with open arms. As of Windows 10 version 1803, multiple-instance support for UWP apps will be available to developers on an opt-in basis. Microsoft has published a detailed blog post that explains how the function can be used. See also: Microsoft launches new Surface Pro and accessories for India Fall Creators Update now on 85… [Continue Reading] -

Intel failed to warn US government about Meltdown and Spectre flaws before going public
Publié: février 23, 2018, 12:31pm CET par Mark Wycislik-Wilson
Intel is facing criticism from the US government after it was revealed that the company did not inform cyber security officials about the Meltdown and Spectre vulnerabilities even though they had been known about for months. Reports about the Meltdown and Spectre flaws were leaked by the Register, and it wasn't until this information hit the public domain that Intel decided to speak to US-CERT about the matter. The lack of communication from the chip-maker was revealed in a series of letters sent by technology firms to lawmakers this week. See also: Microsoft gives sysadmins Meltdown and Spectre detection in… [Continue Reading] -

Samsung launches data-saving and privacy-protecting Samsung Max app for Android
Publié: février 23, 2018, 11:28am CET par Mark Wycislik-Wilson
Samsung has revealed a new, free Android app -- Samsung Max, which it says is "designed to promote mobile data savings and application privacy management". The app replaces Opera Max and anyone with this app currently installed should find that it automatically updates to Samsung Max. While Opera Max included a fully-fledged VPN tool, Samsung Max downgrades this to a DNS-masking service. There are, however, other security and privacy options, as well as tools for reducing data usage. On the privacy side of things, Samsung Max allows for data to be encrypted even when it is being sent over an… [Continue Reading] -

Microsoft launches new Surface Pro and accessories for India
Publié: février 22, 2018, 5:59pm CET par Mark Wycislik-Wilson
Microsoft has announced the availability of a new Surface Pro in India. Starting at Rs 64,999 ($1,000), the range starts with a Core m3 model, and goes up to a Core i7 machine for Rs 182,999 ($2,800). The new models will be available directly from Microsoft, through Amazon, as well as through a range of authorized retailers. The company highlights the quiet, fanless design of some models, as well as the lightness and thinness of others. Battery life and performance is key to these latest additions to the Surface range, and there are models to suit differing budgets. While these… [Continue Reading] -

Kodi addons site TVAddons loses appeal as judge draws comparisons with fully-loaded Kodi boxes
Publié: février 22, 2018, 11:41am CET par Mark Wycislik-Wilson
TVAddons has been very much in the news over the past year or so, with the controversial site constantly fighting to prove it is doing nothing illegal, and did not exist with the aim of providing access to copyrighted content. In the latest stage of its on-going battle with copyright holders, the site has lost an appeal hearing in Canada after a judge overturned a ruling from June last year. It had previously been ruled that a search warrant (an Anton Piller order) against Adam Lackman had not been correctly executed, thereby negating any evidence it resulted in. Bell, Videotron,… [Continue Reading] -

Intel has a new Spectre firmware patch for you to try out
Publié: février 21, 2018, 6:46pm CET par Mark Wycislik-Wilson
The Spectre/Meltdown debacle continues to rumble on, and now the chip manufacturer has announced the availability of a new "microcode solution" to the Spectre vulnerability. The updated firmware applies to 6th, 7th and 8th Generation Intel Core devices, and the release sees the company crossing its fingers and hoping that everything works out this time. This is Intel's second attempt at patching the Spectre vulnerability, and this time around both the company and its customers will be praying that the fix for Skylake, Kaby Lake and Coffee Lake chips actually does the job. See also: Microsoft gives sysadmins Meltdown and… [Continue Reading] -

Scientists discover a new way to use DNA as a storage device
Publié: février 21, 2018, 4:49pm CET par Mark Wycislik-Wilson
The future of technology is about more than just increasing raw processing power and embracing the likes of quantum computing -- storage is also a serious concern. We already generate huge amounts of data, and the amount we need to store is only going to increase. Just as processors have developed in new and exciting ways over the years, so there have been great strides made in the field of storage. But variants on the current methods of storage are simply not going to cut it for much longer. Thankfully, scientists in Ireland may have come up with a solution… [Continue Reading] -

Europe threatens Facebook with fines for tracking users and non-users online
Publié: février 19, 2018, 2:53pm CET par Mark Wycislik-Wilson
Just last week Facebook was hit with the news that its privacy settings -- as well as the way the company uses personal data -- are illegal in Germany. Now the social network has been threatened with fines for tracking people through third-party websites. The tracking affects even people who do not have a Facebook account, and this is something that a Belgian court took exception to. Belgium's privacy watchdog also told Facebook to delete data that had been illegally collected about Belgian citizens. See also: If you're concerned about privacy, you might want to skip Facebook's VPN -- Onavo… [Continue Reading] -

Freely accessible Wikipedia Zero is no more
Publié: février 19, 2018, 12:35pm CET par Mark Wycislik-Wilson
The Wikimedia Foundation is to kill off Wikipedia Zero this year. The zero-rated version of the online encyclopaedia was launched six years ago with the aim of providing free access to mobile users in numerous countries, but there has been a significant drop in demand. The foundation has partnered with dozens of mobile operators around the world to provide free access to Wikipedia. Among the reasons for shutting down the program is "low awareness of Wikipedia outside of North America and Europe." See also: Wikipedia founder Jimmy Wales sets up WikiTribune to fight fake news Wikipedia bans use of Daily… [Continue Reading] -

Microsoft Edge vulnerability exposed as Microsoft misses Google's Project Zero disclosure deadline
Publié: février 19, 2018, 11:11am CET par Mark Wycislik-Wilson
Google has revealed details of a security vulnerability in Microsoft Edge before a patch has been produced. Through Project Zero, Google notified Microsoft about a bug in the browser's Arbitrary Code Guard (ACG) feature back in November, giving the company the usual 90-day disclosure deadline. Google went further, granting Microsoft a further grace period of two weeks on request, but the vulnerability remains unfixed in Windows 10. As such, details of the "ACG bypass using UnmapViewOfFile" bug have now been made public. See also: Microsoft gives sysadmins Meltdown and Spectre detection in Windows Analytics Microsoft to bring Windows Defender Advanced… [Continue Reading] -

White House joins UK government in blaming Russia for NotPetya
Publié: février 16, 2018, 10:33am CET par Mark Wycislik-Wilson
The US government has joined the government of the UK in pointing the finger of blame at Russia for the NotPetya cyberattacks. The ransomware/destructoware hit computers around the world last June. After speculation that the attack was a state-sponsored one carried out by Russia, this position has now been confirmed as the White House accused the nation of the "reckless and indiscriminate." At the same time, the UK's National Cyber Security Centre said that the Russian military was "almost certainly" responsible for the attack. See also: UK government turns against Russian software Facebook asked to investigate Russian influence on EU… [Continue Reading] -

Samsung pauses Oreo update for Galaxy S8 and S8+ due to restart issues
Publié: février 15, 2018, 4:51pm CET par Mark Wycislik-Wilson
It's only a week since Samsung started to roll out Android 8.0 Oreo to the Galaxy S8 and S8+, and now the company has paused the update. A "limited number" of handsets receiving the update have been experiencing reboot problems after installing Oreo. While Samsung investigates the matter, the rollout has been paused and a new version of the update is being worked on. See also: Samsung rolling out Android Oreo update for Galaxy S8 Android 8.1 Oreo shows the speed of public Wi-Fi before you connect Xposed Framework beta adds support for Android Oreo Samsung has already frustrated Galaxy… [Continue Reading] -

If you're concerned about privacy, you might want to skip Facebook's VPN -- Onavo Protect
Publié: février 15, 2018, 12:38pm CET par Mark Wycislik-Wilson
Facebook and privacy are not words that really belong in the same sentence, so the idea that the social network is offering a VPN tool might well raise your suspicions. Back in 2013, Facebook acquired Onavo, the company behind the VPN tool Protect. Recently, users of the Facebook iOS app noticed a link to something labelled Protect within settings. While this appears to be a built-in setting, it is in fact just a link to the Onavo Protect VPN app -- and the idea of a Facebook-owned VPN tool being promoted from within the Facebook app has people concerned. Take… [Continue Reading] -

With Intel's updated bug bounty program, you could earn big bucks for finding the next Meltdown
Publié: février 15, 2018, 10:51am CET par Mark Wycislik-Wilson
Intel has updated its bug bounty program, offering up to $250,000 to anyone identifying vulnerabilities in its hardware and software. The key update here is that the program is now open to everyone through the HackerOne platform -- it was previously open to selected security researchers on an invite-only basis. The move comes in the wake of the Meltdown and Spectre chip vulnerability revelations, and it's clearly an attempt by Intel to not only ramp up its security, but to be seen doing so. The company says it wants to create "a process whereby the security research community can inform… [Continue Reading] -

Google explains how Chrome's new ad filtering feature works -- and why it's not your new ad blocker
Publié: février 14, 2018, 5:01pm CET par Mark Wycislik-Wilson
Despite the fact that Google has a vested interest in online advertising, the company is about to enable its own built-in ad blocker (of sorts) in Chrome. Starting tomorrow, 15 February, the Chrome browser across all platforms will feature ad filtering to cut out those advertisements that fail to comply with the Better Ads Standards. This is something that Google has talked about before, but ahead of the ribbon-cutting, the company has revealed how the feature works and what it means for Chrome users. The first thing to note is that it does not mean you should ditch your current… [Continue Reading] -

Amazon offers refunds to people who paid to remove ads from Prime Exclusive Phones
Publié: février 14, 2018, 10:58am CET par Mark Wycislik-Wilson
For anyone looking to bag a bargain-priced handset, Amazon Prime Exclusive Phones were a great idea. There was just one drawback: lockscreen ads. Of course, there was the option to pay to hide the advertising, but that sort of negated the benefit of the initial low price. Last week, Amazon announced it was going to get rid of these ads. This is great news for owners of Prime Exclusive Phones, but it irked people who had paid for ad removal. Now Amazon has announced that it will be offering refunds to anyone who parted with money to hide ads. See… [Continue Reading] -

Microsoft gives sysadmins Meltdown and Spectre detection in Windows Analytics
Publié: février 14, 2018, 9:29am CET par Mark Wycislik-Wilson
Microsoft has released an update to its free Windows Analytics tool, giving system administrators a new way to check for the Meltdown and Spectre vulnerabilities. The update not only makes it possible to see whether firmware patches are already installed or if they are needed, but also helps sysadmins to determine whether the patches are causing problems of their own. The checking tool is available for fully updated versions of Windows 7 through Windows 10. See also: Tests show how much Meltdown fixes will hit Linux system performance Intel releases updated Spectre and Meltdown patches for Skylake systems Intel tells… [Continue Reading] -

Judge refuses to quash arrest warrant for Julian Assange
Publié: février 13, 2018, 6:24pm CET par Mark Wycislik-Wilson
A UK judge has refused to cancel a warrant for Julian Assange, meaning that the WikiLeaks founder still faces arrest if he leaves the Ecuadorian embassy in London where he has taken up residence. The judge said that Assange "appears to consider himself above the normal rules of law and wants justice only if it goes in his favor." Assange skipped bail back in 2012, fearing extradition to Sweden where he faced rape charges, and further fearing being handed over to the US where he believes he faces charges of revealing state secrets. Although Sweden has since dropped charges, he… [Continue Reading] -

Google is bringing AMP to Gmail, promising dynamic emails with interactive content
Publié: février 13, 2018, 5:11pm CET par Mark Wycislik-Wilson
Google has launched a developer preview of AMP for Email, bringing its Accelerated Mobile Pages feature to Gmail. The aim is modernize email, allowing for the creation of messages with interactive, dynamic content. In practice what this means is that emails could be updated with new information if details change, and that it will be possible to fill out forms and so on without leaving your inbox. There are already a number of big names getting involved -- including Pinterest and Booking.com -- and more will use the open source tool. As the name suggests, part of the point of… [Continue Reading] -

The UK government reveals AI software that automatically blocks extremist content online
Publié: février 13, 2018, 1:36pm CET par Mark Wycislik-Wilson
Continuing its drive to take control of the internet, the UK government has unveiled a new tool that it says can block extremist content "on any platform" with astonishing accuracy. The system -- as yet unnamed -- was unveiled by Home Secretary Amber Rudd and cost £600,000, paid for with public funds, and has been designed to detect jihadist content. The government says that the algorithms can automatically detect "94 percent of Daesh propaganda with 99.995 percent accuracy." Speaking to reporters in London, Rudd said that "we're not going to rule out taking legislative action if we need to do… [Continue Reading] -

Microsoft to bring Windows Defender Advanced Threat Protection to Windows 7 and 8.1
Publié: février 12, 2018, 7:11pm CET par Mark Wycislik-Wilson
Formerly a Windows 10 exclusive, Microsoft today announced that Windows Defender Advanced Threat Protection (ATP) is coming to Windows 7 and Windows 8.1. That's not to say that the older operating systems are set to gain the full benefit of ATP, however. Microsoft says that it is the Endpoint Detection & Response (EDR) functionality that will make its way to Windows 7 and 8.1 at some point this summer. This cloud-driven feature will be made available as a preview in the spring. See also: Microsoft's aggressive Get Windows 10 (GWX) app slapped by Finnish authorities Top 5 free data recovery… [Continue Reading] -

Android P will support iPhone X-style notches and feature a dramatic redesign
Publié: février 12, 2018, 6:20pm CET par Mark Wycislik-Wilson
The number of people running Oreo may well be very small, but there's already talk about the next version of Android -- Android P. Reports about what has been named internally as Pistachio Ice Cream promise not only a design overhaul, but also iPhone X-style notch support. The Oreo successor is due for release later this year, and a Bloomberg report shed some light on what we can expect, including tighter Google Assistant integration, support for different phone formats, and improved battery life. See also: Xiaomi deletes MIUI vs Android One Twitter poll after the voting didn't go its way… [Continue Reading] -

German court says Facebook's privacy settings and use of personal data are illegal
Publié: février 12, 2018, 5:08pm CET par Mark Wycislik-Wilson
Facebook is no stranger to privacy-related controversy, and now a German court has ruled that the social networks' use of personal data is illegal. The court in Berlin also said that Facebook's default privacy settings violate German consumer law. The case was brought by the federation of German consumer organisations (VZBV) which said Facebook failed to provide its users with sufficient information, and also that people were automatically opted into features. See also: Facebook is testing a 'downvote' option -- just don't call it a dislike button Facebook accused of violating city campaign finance law in Seattle Ahead of GDPR… [Continue Reading] -

Low-cost Nokia 2 comes to the UK with two-day battery life
Publié: février 12, 2018, 1:34pm CET par Mark Wycislik-Wilson
Nokia is a name -- for more seasoned mobile users, at least -- that's synonymous with phones that seem to last forever between charges. Now HMD Global is bringing the Nokia 2 to the UK, complete with impressive two-day battery life. Powered by a Qualcomm Snapdragon 212 Quad-core processor, the Nokia 2 boasts a 5-inch screen and 8GB of memory -- which can be increased by up to 128GB with a MicroSD card. The phone ships with Android Nougat 7.1.1 (it's described as being "Oreo ready" although there's no word on when an upgrade might appear), and it will be… [Continue Reading] -

Tests show how much Meltdown fixes will hit Linux system performance
Publié: février 12, 2018, 12:14pm CET par Mark Wycislik-Wilson
Now that the initial shock about the Spectre and Meltdown chip vulnerabilities has died down, the focus is very much on getting the problems sorted. As has been noted already, there has been concern about the impact on performance that the bug fixes will bring. Intel has been eager to downplay any suggestion of major slowdown, but the exact performance hit will vary from system to system depending on the tasks being performed. Brendan Gregg -- a Netflix engineer whose work involves large scale cloud computing performance -- has conducted some tests into the impact patches will have on Linux… [Continue Reading] -

Government websites in US, UK and Australia hacked to run secret cryptocurrency miner
Publié: février 12, 2018, 10:53am CET par Mark Wycislik-Wilson
Thousands of government websites around the world have been hijacked to mine the cryptocurrency Monero. A commonly-used accessibility script was hacked to inject the Coinhive miner into official sites in the US, UK and Australia. One security researcher described it as the biggest attack of its type that he'd seen. In the UK, websites for the NHS and Information Commissioner's Office were affected; in the US, the United States Courts' site was hit; in Australia, government sites including that of the Victorian parliament were hit by the cryptojacking code. What all of the sites had in common was the fact… [Continue Reading] -

Apple videos show how to get the most from its HomePod speaker
Publié: février 11, 2018, 12:36pm CET par Mark Wycislik-Wilson
The launch of the Apple HomePod was delayed last year, but the iPhone-maker's smart speaker was finally released a couple of days ago. Reviews are -- generally speaking -- positive, but early adopters have a few quibbles. Whether you're thinking about jumping on the bandwagon, you already have a HomePod, or you just want to know more about them, Apple has released a series of videos that serve as a handy combination of tutorials and an introduction to its latest hardware. See also: Apple HomePod: 'wow' but 'uh-oh' Apple's HomePod launches February 9 for $349 No HomePod for Christmas as… [Continue Reading] -

Xiaomi deletes MIUI vs Android One Twitter poll after the voting didn't go its way
Publié: février 11, 2018, 11:28am CET par Mark Wycislik-Wilson
Which is better -- the MIUI skin, or Android One? This is what Chinese phone manufacturer Xiaomi decided to ask on Twitter, and the results were... interesting. Presumably the company was rather hoping that Twitter users would vote for its own MIUI which it could then run on Google's face -- but the poll actually went against Xiaomi. Rather than leave the results of vote up for anyone to see, the company decided to simply delete it and pretend it never happened. Take a look at the Xiaomi account on Twitter, and you'll see no hint that any such poll… [Continue Reading] -

Hate the Snapchat redesign? Here's how to get back the old look
Publié: février 11, 2018, 10:47am CET par Mark Wycislik-Wilson
Change is great, but it not always well-received. Take the latest redesign of Snapchat, for instance -- the outpouring of hatred for the new look has been incredible. Users are pleading Snapchat to revert to the old design, complaining that the algorithm-powered interface makes things impossible to find. Of course, the company is extremely unlikely to change back to the old look, but if you're an iPhone user, there are steps you can take to get the old app back. Wondering how to get old Snapchat back? Read on! It's worth noting that the method set out below is only… [Continue Reading] -

VLC 3.0 'Vetinari' arrives, bringing HDR, 8K and Chromecast support
Publié: février 10, 2018, 1:06pm CET par Mark Wycislik-Wilson
In the world of media playing software, VLC is a perennial favorite -- and with good reason. This open source tool is one of the most feature-packed players out there, and it has just received a huge and long-awaited upgrade with the release of VLC 3.0 'Vetinari'. Many software releases are described as being major or significant, but VLC 3.0 really is a huge release -- it's a truly massive update from its predecessor. Available for Windows, macOS, Android, iOS, Linux, Chromebooks and Windows Phone, just about everyone can take advantage of the power of this incredible player. An overhaul… [Continue Reading] -

Uber and Waymo make surprise settlement over claims of stolen trade secrets
Publié: février 10, 2018, 12:14pm CET par Mark Wycislik-Wilson
Uber has agreed to a settlement with Google's self-driving technology unit, Waymo, over claims that that the company stole trade secrets during the acquisition of Otto. Google's parent company, Alphabet, sued Uber a year ago, and now a payment of $245 million has been agreed. The financial settlement to be received by Waymo includes 0.34 percent of Uber's equity based on a valuation of $72 billion. Uber CEO, Dara Khosrowshahi, expressed "regret" about the matter, and said he wanted to correct "mistakes of the past." See also: Uber loses its license to operate in London India hits Google with $21… [Continue Reading] -

India hits Google with $21 million fine for search bias
Publié: février 9, 2018, 4:50pm CET par Mark Wycislik-Wilson
Google is certainly no stranger to accusations of abusing its position to its own advantage, and the company has now been fined 1.36 billion rupees ($21.17 million) by India's antitrust watchdog. The Competition Commission of India (CCI) said Google was guilty of "search bias" and had been abusing its dominance in online web search and online search advertising. Particular criticism was leveled at Google's promotion of its own flight search page. See also: Google grants users more control over ads Google tweaks Files Go to make it easier to free up space on your Android device and change file associations… [Continue Reading] -

Apple confirms but downplays iOS source code leak
Publié: février 9, 2018, 4:00pm CET par Mark Wycislik-Wilson
Apple may have just released iOS 11.3 beta 2, but the attention of world turned to the iOS source code that leaked to GitHub. The iPhone maker has confirmed that code for iOS 9's iBoot had leaked, but stressed its age. The company said that the leak does not pose a security threat to users, insisting that "the security of our products doesn't depend on the secrecy of our source code." But while Apple tries to play down the leak, there's no denying that it is highly significant and an unprecedented embarrassment. See also: Apple issues takedown notice after iBoot… [Continue Reading] -

Facebook is testing a 'downvote' option -- just don't call it a dislike button
Publié: février 9, 2018, 1:37pm CET par Mark Wycislik-Wilson
Facebook has confirmed that it is currently testing what it describes as a "downvote" button. But the social network is at pains to stress that this is absolutely not the "dislike" button people have been asking for. The idea behind the feature is to give users the chance to downvote comments -- it does not appear to give the same option to posts. In currents tests, downvoting only appears on public Pages, and it's something that’s unlikely to spread to profiles. See also: Big changes to Facebook's news feed mean you'll probably spend less time on the social network Facebook… [Continue Reading] -

Apple issues takedown notice after iBoot source code leaks to GitHub
Publié: février 8, 2018, 1:08pm CET par Mark Wycislik-Wilson
The source code for the iOS bootloader iBoot has been leaked to GitHub, prompting Apple to issue a DMCA takedown notice. Although the source code is for iOS 9.3 and a couple of years old, it appears to be the real deal and would still cause something of a headache for Apple. Copies of the code have been circulating online despite the takedown notice, and the concern is that it could be used to exploit iOS with malware. See also: iOS 11.3 beta 2 includes performance throttling opt-out and new battery health options iPhone X bug leaves some users unable… [Continue Reading] -

157 new emojis to hit iOS and Android with the launch of Emoji 11.0
Publié: février 8, 2018, 12:05pm CET par Mark Wycislik-Wilson
Going under the banner of Emoji 11.0, a raft of new emojis are due to hit the screen of iOS and Android devices later this year. After being previewed late last year, the full list of emojis has now been published by the Unicode Consortium, and they're due to be launched in the second half of 2018 -- August or September. What can you look forward to? New red-haired and bald men and women feature, as do a female superhero, a pirate flag and a microbe. The release sees quite a jump in numbering -- from Emoji 5.0 to Emoji… [Continue Reading] -

Intel releases updated Spectre and Meltdown patches for Skylake systems
Publié: février 8, 2018, 10:33am CET par Mark Wycislik-Wilson
It may have been a while since there was major news about the Spectre and Meltdown bugs, but the problems have not gone away. After previously releasing unstable patches, Intel has now launched a microcode update for Skylake systems. Despite the problems with both stability and performance with Spectre and Meltdown patches, Intel uses an announcement about the latest updates to stress the importance of installing patches in a timely fashion. There's more than a hint of irony in the fact that Intel had to tell users to stop using an earlier update because of the problems it was causing.… [Continue Reading] -

Hotspot Shield flaw could reveal the location of VPN users
Publié: février 7, 2018, 6:29pm CET par Mark Wycislik-Wilson
There are many reasons for turning to VPN software, but anonymity and hiding one's location are pretty high up the list. A newly-discovered flaw in the popular free VPN Hotspot Shield, however, means that it is possible to determine key pieces of information about users. The VPN -- produced by AnchorFree -- is used by 500 million people around the world, and security researchers have discovered a vulnerability (CVE-2018-6460) that means it is technically possible to home in on the location of an individual using the service. See also: Privacy: Judges say the UK's Snooper's Charter is illegal Ahead of… [Continue Reading] -

Cortana comes to iPad with faster loading than iPhone version
Publié: février 7, 2018, 5:39pm CET par Mark Wycislik-Wilson
After something of a delay -- two years, no less -- Microsoft has finally ported Cortana from the iPhone to the iPad. The company has not made a great deal of noise about the updated app, but its digital assistant has now been optimized for use on Apple devices with larger screens. The restrictions of iOS still mean that Cortana cannot compete directly with Siri, as it is only possible to access the assistant's tools once it has been launched. See also: iOS 11.3 beta 2 includes performance throttling opt-out and new battery health options iPhone X bug leaves some… [Continue Reading] -

iOS 11.3 beta 2 includes performance throttling opt-out and new battery health options
Publié: février 7, 2018, 11:45am CET par Mark Wycislik-Wilson
Apple raised the anger levels of some iPhone users when it was revealed that handset performance was being purposefully reduced to maintain battery health. Some of this anger was dissipated when the company offered up cheap battery replacements, but Tim Cook also promised that users would soon be able to opt out of performance throttling. The option to disable performance reduction is due to hit the masses with iOS 11.3, and the second beta of this version of Apple's mobile operating system has now been released to developers. It gives us our first glimpse at what the new battery health… [Continue Reading] -

Top 5 free data recovery tools for Windows
Publié: février 6, 2018, 2:57pm CET par Mark Wycislik-Wilson
We all back up our data, right? That's what everyone does! But of course, that's far from true. Most people don't get much further than thinking about putting a backup plan in place, promising themselves it's something they'll sort out one day -- and, all of a sudden, it's too late. Deleting files by accident is easily done. If you're tinkering with partitions, it's also scarily easy to wipe out the wrong one! These are just two of the ways in which you can lose files, and if you don’t have a backup to hand, you're going to need help… [Continue Reading] -

Facebook accused of violating city campaign finance law in Seattle
Publié: février 6, 2018, 12:32pm CET par Mark Wycislik-Wilson
The election authority in Seattle says that Facebook has violated city finance laws. Regulations are in place that require the company to reveal who paid for campaign ads on the social network. The Seattle Ethics and Elections Commission is seeking information about advertising spending for city elections that took place last year. Facebook risks a fine of up to $5,000 per ad if this information is not provided. See also: Facebook bans ads for cryptocurrencies and ICOs Facebook's latest News Feed update gives local news a boost Ahead of GDPR laws, Facebook publishes privacy principles and promises to educate users… [Continue Reading] -

Microsoft's aggressive Get Windows 10 (GWX) app slapped by Finnish authorities
Publié: février 6, 2018, 11:33am CET par Mark Wycislik-Wilson
The hostile Get Windows 10 -- often referred to as simply GWX -- push by Microsoft proved controversial around the world. Now the Finnish Consumer Authority has reached an agreement with the company that means the Windows-maker will no longer force apps onto users. The authority was unhappy with Microsoft not only for pushing the GWX app to computers without consent, but also for changing the design language used in the UI. In the GWX app, clicking the X button did not close the notification window as users would have expected, but instead started the installation of Windows 10. The… [Continue Reading] -

iPhone X bug leaves some users unable to answer calls
Publié: février 5, 2018, 6:14pm CET par Mark Wycislik-Wilson
A number of iPhone X users are complaining about a bug that leaves them unable to answer incoming calls. Reports of the bug are spreading through Apple's support forums, and the company is looking into the problem. People who are experiencing the bug say that when they receive a call, their iPhone X rings, but the screen does not wake up. While the problem has been around for a couple of months, complaints seem to be growing in number at the moment. See also: Apple launches free repair program for 'No Service' iPhone 7 bug Virgin Mobile to offer cheap,… [Continue Reading] -

NSA exploits leaked by hackers tweaked to work on all versions of Windows since 2000
Publié: février 5, 2018, 5:19pm CET par Mark Wycislik-Wilson
A trio of NSA exploits leaked by hacking group TheShadowBrokers has been ported to work on all versions of Windows since Windows 2000. The EternalChampion, EternalRomance and EternalSynergy exploits were made public by the group last year, and now a security researcher has tweaked the source code so they will run on nearly two decades' worth of Microsoft operating systems -- both 32- and 64-bit variants. See also: Kaspersky says it accidentally obtained secret NSA files from a US computer Report: Russian hackers stole NSA files after identifying them using Kaspersky software TheShadowBrokers group returns with NSA UNITEDRAKE hacking malware… [Continue Reading] -

Lauri Love -- suspected FBI and NASA hacker -- wins appeal against extradition to US
Publié: février 5, 2018, 3:08pm CET par Mark Wycislik-Wilson
A hacker has won his appeal against extradition to the US where he faced charges of compromising various American systems including NASA and the FBI. Lauri Love, won his case in the High Court of England and Wales after his lawyers argued there was a serious risk that he would kill himself. The court also took into account the fact that the alleged hacking offenses were committed in the UK. The appeals win does not mean, however, that Love's legal battles are over. While he will now not be extradited to the US -- something lawyers said would be seriously… [Continue Reading] -

Lloyd's Banking Group bans Bitcoin payments via credit card
Publié: février 5, 2018, 2:38pm CET par Mark Wycislik-Wilson
It has been something of a rocky ride for cryptocurrencies recently, and none more so than Bitcoin. Now Lloyd's Banking Group has announced a ban on purchasing cryptocurrencies using credit cards in the UK. The banking group controls Lloyd's Bank, Halifax, MBNA and Bank of Scotland, and the ban has been triggered by the deflation of Bitcoin. In recent months it has spiraled from a high of almost $20,000 to under $8,000. See also: Bitcoin falls under $8,000 -- crypto market down to $360bn Despite reports to the contrary, India is not banning Bitcoin and other cryptocurrencies The move sees… [Continue Reading] -

Microsoft is dropping Windows 10 S as a standalone product in favor of S Mode
Publié: février 4, 2018, 12:14pm CET par Mark Wycislik-Wilson
The arrival of Windows 10 S was greeted with a degree of scepticism. The cutdown version of Windows 10 is only capable of running apps from the Microsoft Store for a focus on security, and is optimized for cheaper computers. There has always been the option of unlocking Windows 10 Professional but now it has emerged that Microsoft is going to kill off Windows 10 S as a standalone product. That's not to say that the S variant is being killed off entirely however. Microsoft is bringing a new "S Mode" to Windows 10 Home, Enterprise, and Pro. See also:… [Continue Reading] -

Apple launches free repair program for 'No Service' iPhone 7 bug
Publié: février 3, 2018, 10:55am CET par Mark Wycislik-Wilson
Apple has launched a new repair program aimed at iPhone 7 users who are experiencing a "No Service" problem. Apple says that affected models that were sold since September 2016 will be repaired free of charge. The company explains that the No Service bug only affects a "small number" of handsets, and it is caused by a failed component on the main logic board. So which handsets are covered, and how do you go about claiming your free repair? Apple says that the problematic iPhone 7s were sold in China, Hong Kong, Japan, Macao, and the US between September 2016… [Continue Reading] -

Despite reports to the contrary, India is not banning Bitcoin and other cryptocurrencies
Publié: février 2, 2018, 8:18pm CET par Mark Wycislik-Wilson
A budget speech given by India's finance minister led to numerous reports that India was banning the use of cryptocurrencies such as Bitcoin and Ethereum within the country. While Arun Jaitley noted in a speech that the Indian government does not recognize cryptocurrencies as legal tender, his slightly ambiguous language resulted in something of a misunderstanding. Now the Blockchain and Cryptocurrency Committee of the Internet and Mobile Association of India (IAMAI) has spoken out in an attempt to clarify the issue, and allay fears that Bitcoin et al are on the verge of being banned. See also: Bitcoin falls under… [Continue Reading] -

Microsoft's Core m3 Surface Laptop costs just $799
Publié: février 2, 2018, 8:08pm CET par Mark Wycislik-Wilson
Microsoft has unveiled a cheap on-ramp for people looking to get involved in its Surface range. There's now a version of the Surface Laptop available for just $799 -- you might even be able to get it for less. Of course, this low price tag means cutting a few corners, but the specs are still the same as the entry-level Surface Pro -- more than enough for everyday tasks. So what does a buck short of $800 buy you? Well, provided the idea of an Intel Core m3 doesn't put you off, you might not be disappointed. See also: Microsoft… [Continue Reading] -

Microsoft extends Windows 10 support and makes Office 2019 a Windows 10 exclusive
Publié: février 2, 2018, 11:08am CET par Mark Wycislik-Wilson
If you're thinking about upgrading to Office 2019 when it is released in the second half of 2018, you'll have to make sure that you have upgraded to Windows 10 first. Microsoft has revealed that Office 2019 will only run on Windows 10 (and the next LTSC release of Windows Server), dropping support for Windows 8.x and earlier. In the same announcement, Microsoft also revealed that it is extending the support period for Windows 10, following the news that the operating system has finally overtaken Windows 7. See also: StatCounter: Windows 10 finally overtakes Windows 7 Microsoft releases confusing patches… [Continue Reading] -

Nintendo is bringing Mario Kart to smartphones
Publié: février 1, 2018, 12:20pm CET par Mark Wycislik-Wilson
Following the success of Super Mario Run, Nintendo has confirmed plans to bring Mario Kart to mobile devices. The game will be called Mario Kart Tour, and it is currently scheduled for release by the first quarter of 2019. This is the first Mario Kart title to make its way to smartphones, and a title that will be eagerly awaited by fans of the Italian ex-plumber. At the moment, Nintendo is giving away very little about the future game. For now, all we know is the (current) title -- Mario Kart Tour -- and the company's plan to release it… [Continue Reading] -

eBay to drop PayPal as its primary payment processor
Publié: février 1, 2018, 11:36am CET par Mark Wycislik-Wilson
eBay and PayPal have become almost inextricably entwined over the years -- but not completely inextricably. Citing lower costs, eBay has announced plans to drop PayPal as its main payment processor in favor of Dutch firm Adyen. Starting later this year, eBay will move some of its payments to the new provider, and then by 2020, PayPal will have been replaced as the backend payment service. eBay users will still have the option to use PayPal until at least the middle of 2023. Following eBay's announcement, PayPal stock dropped by 12 percent. After a 15-year relationship, eBay currently accounts for… [Continue Reading] -

Windows Defender to root out dodgy registry cleaners and system optimization tools
Publié: février 1, 2018, 10:58am CET par Mark Wycislik-Wilson
Microsoft is taking a firmer line with misleading system utilities and tools that try to scare users into paying for software. An update to Windows Defender means that software found to be "coercive" could be ripe for automatic removal. New policies come into play in March as Microsoft tries to banish software that makes misleading claims or adversely affects system performance. Tools that exaggerate problems or resort to scare tactics are among those in the firing line. Microsoft explains that it is updating its software evaluation criteria so that programs may not "ruse alarming or coercive messaging that can put… [Continue Reading] -

Facebook bans ads for cryptocurrencies and ICOs
Publié: janvier 31, 2018, 10:38am CET par Mark Wycislik-Wilson
Facebook has announced a new advertising policy which ban ads for cryptocurrencies such as Bitcoin. The ban also applies to ICOs because they are "frequently associated with misleading or deceptive promotional practices." The social network says that the new policy is a part of a drive to improve the "integrity and security of financial product and services ads," but it explains that it is keeping its guidelines "intentionally broad" to start with. See also: Facebook's latest News Feed update gives local news a boost Hackers hijack YouTube ads with Coinhive to mine Monero cryptocurrency Ahead of GDPR laws, Facebook publishes… [Continue Reading] -

White House refutes claims it wants to build its own 5G network
Publié: janvier 30, 2018, 3:58pm CET par Mark Wycislik-Wilson
Documents that came to light recently suggested that the Trump administration was considering creating a government-controlled 5G network. It was an idea viewed in a dim light by the FCC, but now the White House has denied it has such plans. Despite the unearthing of a memo to the contrary, the US government insists there are no such plans under consideration. See also: Trump administration wants to nationalize 5G, but the FCC is not impressed Trump was almost ten times more popular with Russian Twitter bots than Clinton Twitter won't ban Donald Trump because he's special Donald Trump wants US… [Continue Reading] -

Privacy: Judges say the UK's Snooper's Charter is illegal
Publié: janvier 30, 2018, 2:03pm CET par Mark Wycislik-Wilson
Judges have ruled that the UK government's digital surveillance program -- known variously as the Snooper's Charter and the Investigatory Powers Act -- is illegal. In the case brought by human rights group Liberty, appeal judges found that the preceding Data Retention and Investigatory Powers Act 2014 (DRIPA) -- which ultimately became the Snooper's Charter -- failed to offer adequate protection to people's data. Of particular concern was the fact that private data could be shared between different agencies without sufficient oversight. See also: Privacy: UK government to tweak Snooper's Charter after conceding it is illegal in its current form… [Continue Reading] -

Virgin Mobile to offer cheap, 'pre-loved' iPhone 7 and iPhone 7 Plus handsets
Publié: janvier 30, 2018, 10:53am CET par Mark Wycislik-Wilson
Virgin Mobile has announced plans to offer Certified Pre-Loved iPhone 7 and iPhone 7 Plus handsets in the US. Starting in February, the company will be offering the phones for between $379.99 and $429.99. It is already possible to buy a Certified Pre-Loved iPhone 6s or iPhone 6s Plus from Virgin Mobile, and by adding the newer handsets to the program, the company is offering a cheaper way to buy a more recent iPhone. See also: Tim Cook: iPhone users will soon be able opt out of performance reduction Spectre patch in iOS 11.2.2 is slowing down iPhones Apple to… [Continue Reading] -

Facebook's latest News Feed update gives local news a boost
Publié: janvier 30, 2018, 10:45am CET par Mark Wycislik-Wilson
Facebook recently promised big changes to the way its News Feed works, and Mark Zuckerberg has now revealed that the social network will start to place a greater emphasis on local news. At least it makes a change from constantly banging on about fake news. It's part of the company's desire to increase civic engagement, with the Facebook CEO saying that there is a direct link between reading local news and people getting involved in helping out with local causes. The changes are coming to the US first and will then spread to the rest of the world. See also:… [Continue Reading] -

Trump administration wants to nationalize 5G, but the FCC is not impressed
Publié: janvier 29, 2018, 4:52pm CET par Mark Wycislik-Wilson
Leaked documents show that the Trump administration is considering plans to nationalize the 5G network. In the documents, seen by Axios, a senior National Security Council official says that a centralized, government-controlled 5G network is needed to offer security against China. But while the government may believe it makes sense for it to be in control of the future mobile network, the idea has attracted vocal opposition. Among the opponents is FCC chairman Ajit Pai. See also: Trump was almost ten times more popular with Russian Twitter bots than Clinton Twitter won't ban Donald Trump because he's special Donald Trump… [Continue Reading] -

Security warning: Lenovo Fingerprint Manager Pro has a hardcoded password backdoor
Publié: janvier 29, 2018, 4:04pm CET par Mark Wycislik-Wilson
If you have a ThinkPad, ThinkCentre or ThinkStation system, Lenovo has an important security patch for you to install. And you should install it right now. Reporting vulnerability CVE-2017-3762, the computer manufacturer says that it discovered a weak algorithm used to encode fingerprint data could be bypassed with a hardcoded password. The problem affects the Lenovo Fingerprint Manager Pro utility for Windows 7, 8 and 8.1. See also: Intel chips have a huge security flaw, and the fix will slow down Windows and Linux machines Edward Snowden's Haven app turns a smartphone into a security device Security: macOS High Sierra… [Continue Reading] -

Strava says military users should opt out of heatmap feature to avoid revealing secret army base locations
Publié: janvier 29, 2018, 1:04pm CET par Mark Wycislik-Wilson
Military personal who used the fitness app Strava have unwittingly contributed to revealing the location of secret army bases around the world. Strava published a "heatmap" of global user activity in November, and from this data visualization the location of secret military bases was accidentally exposed. The company argues that the information had already been made public by users who chose to share their location data. It goes on to suggest that military users might want to consider opting out of the heatmap feature of the iOS and Android app. See also: Ahead of GDPR laws, Facebook publishes privacy principles… [Continue Reading] -

Ahead of GDPR laws, Facebook publishes privacy principles and promises to educate users
Publié: janvier 29, 2018, 12:06pm CET par Mark Wycislik-Wilson
Facebook has published its privacy principles for the first time, ahead of the European Union's general data protection regulation (GDPR) which comes into force on May 25 -- although the company is pitching it as being part of Data Privacy Day. On top of this, the social network has also detailed plans to use videos to educate its users about privacy. The videos will explain how to control who has access to personal data, as well as how to manage the data Facebook uses to control the ads its shows users. See also: Facebook to roll out new privacy tools… [Continue Reading] -

Trump was almost ten times more popular with Russian Twitter bots than Clinton
Publié: janvier 28, 2018, 1:06pm CET par Mark Wycislik-Wilson
In the run-up to the 2016 US election, Russian bots shared Donald Trump's tweets 470,000 times -- nearly ten times those of Hillary Clinton. The figures come courtesy of Twitter, who shared the data with Congress for a review into Russian influence on the election. In the period September 1 to November 15, 2016, Russian bots accounted for more than four percent of Trump's retweets. See also: Twitter won't ban Donald Trump because he's special Kaspersky sues Trump administration over government software ban EFF: Twitter users have a First Amendment right not to be blocked by President Trump Twitter admits… [Continue Reading] -

OnePlus denies sending clipboard data to China
Publié: janvier 28, 2018, 11:06am CET par Mark Wycislik-Wilson
Phone-maker OnePlus has had a tough time of things in the press recently with claims about users' clipboard data being mined, and the problems following a credit card breach. A second suggestion that the company was sending clipboard data back to China surfaced recently, but the company has been quick to deny any wrongdoing. Suspicions were raised when a OnePlus user noticed a file called badwords.txt which includes a list of words such as "chairman," "private message" and "address." See also: OnePlus admits that up to 40,000 accounts were affected by a credit card breach Download Android 8.0 Oreo for… [Continue Reading] -

Hackers hijack YouTube ads with Coinhive to mine Monero cryptocurrency
Publié: janvier 28, 2018, 10:21am CET par Mark Wycislik-Wilson
The clandestine mining of cryptocurrency is something that we have seen in various forms over the last year or so, in website code and Android apps. A new discovery by security firm Trend Micro shows that hackers have found a way to inject Coinhive mining code into ads that appear on YouTube. The crypto-jacking technique means that hackers have been able to profit by using other people's CPU time to mine the Monero cryptocurrency while they watch videos. Trend Micro reports that there has been a huge increase in Coinhive web miner detections in recent days, with hackers abusing Google's… [Continue Reading] -

Intel will release chips free from Meltdown and Spectre bugs this year
Publié: janvier 26, 2018, 4:00pm CET par Mark Wycislik-Wilson
The discovery of the Meltdown and Spectre vulnerabilities in processors caused a great deal of panic and confusion. The poor reliability and performance hit brought about by patches did little to help consumer confidence, but Intel says it will be releasing processors in 2018 that are free from the problems. The move will be welcomed by customers who have been frustrated by problematic bug fixes designed to mitigate against the bug but which brought issues of their own. A timescale for the hardware solution has not been pinned down more specifically than "later this year." See also: Intel tells customers… [Continue Reading] -

Google tweaks Files Go to make it easier to free up space on your Android device and change file associations
Publié: janvier 26, 2018, 12:37pm CET par Mark Wycislik-Wilson
Using any smartphone means having to work within its storage limitations. The prevalence of cloud services has taken some of the strain off physical storage, but running out of room locally can still be an issue. To help with this problem, Google offers Files Go. Now the company has updated the app to make it an even more powerful tool for freeing up space. The app can now handle SD cards and tablets, and includes a new option to change file associations. While SD card support is far from standard, expandable storage is still something that's found on many Android… [Continue Reading] -

Google grants users more control over ads
Publié: janvier 26, 2018, 12:30pm CET par Mark Wycislik-Wilson
Google is a company that's synonymous with advertisements. It makes huge amounts of money from delivering carefully targeted ads, much to the chagrin of those on the receiving end. To make life a little more bearable -- although not ad-free -- the company is making changes to Ads Settings and the Mute This Ad feature. The changes affect not only the millions of websites that are filled with ads delivered through Google, but also the myriad of apps that are ad-supported. The latest changes make it possible to mute ad reminders, and also increases the level of control users have… [Continue Reading] -

UK government to monitor social networks and fight fake news with National Security Communications Unit
Publié: janvier 24, 2018, 10:20am CET par Mark Wycislik-Wilson
In a bid to tackle the ongoing problem of fake news, the UK government is setting up the National Security Communications Unit. The NSCU is tasked with "combating disinformation by state actors and others." It's a mission that the likes of Microsoft, Facebook and Google have already taken on in various ways, each with varying degrees of success. One of the aims of the NSCU is to "more systematically deter our adversaries and help us deliver on national security priorities," and part of its work will involve monitoring social networks. See also: Facebook stops flagging fake news because it was… [Continue Reading] -

Now you can buy audiobooks from Google Play
Publié: janvier 23, 2018, 7:44pm CET par Mark Wycislik-Wilson
Google has added a new audiobooks section to its Play Store. The announcement was widely expected, as over the weekend imagery came to light suggesting Google had plans to start selling audiobooks -- but no one knew quite how far off it might be. There's some good news for anyone who has been put off by the likes of Audible in the past -- audiobooks in Google Play are being offered without a subscription. Available in 45 countries and nine languages, Google offers support for Android, iOS and Google Assistant. See also: Google kicks over 60 games out of the… [Continue Reading] -

TVAddons launches new GitHub Browser to deliver Kodi addons
Publié: janvier 23, 2018, 6:10pm CET par Mark Wycislik-Wilson
TVAddons has previously promised to 'change how people access streaming media forever', and now it is delivering on the first phase of the Kodi addon revolution. The newly announced GitHub Browser makes it easier than ever to browse and install Kodi addons. The browser makes it possible to install any Kodi addon directly from its developer's own GitHub repository. It's all part of a plan that will make the TVAddons community "more resilient and decentralized." See also: Unofficial Kodi add-on provider TVAddons set to 'change how people access streaming media forever' TVAddons: Streaming through Kodi addons protects you from malware… [Continue Reading] -

Facebook to roll out new privacy tools ahead of European GDPR laws
Publié: janvier 23, 2018, 5:49pm CET par Mark Wycislik-Wilson
Facebook has faced numerous complaints and accusations when it comes to privacy, and nowhere has this been more obvious than in Europe. In response to European Union plans to change the laws concerning the privacy of personal data, the social network is on the verge of rolling out a new privacy center to users. The upcoming General Data Protection Regulation (GDPR) is designed to give people more control over their personal data, and it is due to come into force in May. Facebook's response means that its millions of global users will all benefit from additional privacy controls. See also:… [Continue Reading] -

Apple's HomePod launches February 9 for $349
Publié: janvier 23, 2018, 4:04pm CET par Mark Wycislik-Wilson
Pre-orders for Apple's eagerly anticipated smart speaker -- the HomePod -- start in just a few days' time. Today the iPhone-maker announces that the HomePod will launch on February 9, but you can pre-order from Friday January 26. The smart speaker will be available in the US, UK and Australia first of all, and springtime will see it launch in France and Germany. The voice-controlled HomePod had been planned for 2017, but was delayed before Christmas. Now Apple is finally ready to offer a premium alternative to the likes of the Amazon Echo and Google Home, with the company placing… [Continue Reading] -

Rupert Murdoch suggests Facebook should pay 'trusted' publishers for news content
Publié: janvier 23, 2018, 11:34am CET par Mark Wycislik-Wilson
Facebook has been fighting something of a losing battle against the problem of fake news, but media mogul Rupert Murdoch thinks he has come up with a solution. He says that the social network should pay "trusted" publishers for the provision of news content. Facebook recently said that it wants to promote content created by outlets deemed trustworthy by users, but Murdoch -- who controls Fox News -- is not impressed. He says that what Facebook has proposed so far is simply not enough, and he believes that the only solution is to start paying. See also: Facebook to fight… [Continue Reading] -

Intel tells customers to stop installing Meltdown/Spectre patches due to 'unpredictable' reboot issues
Publié: janvier 23, 2018, 10:45am CET par Mark Wycislik-Wilson
The fallout from the Meltdown and Spectre bugs continues to plague Intel. The company has been hit with lawsuits, users complained about performance drops, and some users found that their computers were rendered unbootable. For people with Broadwell and Haswell chips, there was a problem with random reboots, and as a result of this -- some two weeks down the line -- Intel is now advising people to stop installing its patches. Executive vice president Navin Shenoy says that the company is close to determining the root cause of the problem, apologized for reboots and "unpredictable system behaviour," and warns… [Continue Reading] -

Amazon Go, the AI-powered, checkout-free store, is now open in Seattle
Publié: janvier 22, 2018, 10:38am CET par Mark Wycislik-Wilson
Today sees the opening of the first Amazon Go store. The online retailer is looking to change the face of real-world shopping with its AI-powered bricks and mortar stores that are free from checkouts and time-consuming lines. Anyone shopping in the new Seattle store will find that they are constantly monitored by cameras as they shop, with the camera monitoring which items they place in their baskets. Customers are automatically billed when they leave the store. See also: Amazon hikes monthly Prime fee by 18 percent Donald Trump wants US Postal Service to charge Amazon 'much more' Google yanks YouTube… [Continue Reading] -

OnePlus admits that up to 40,000 accounts were affected by a credit card breach
Publié: janvier 20, 2018, 5:05pm CET par Mark Wycislik-Wilson
Last week it emerged that OnePlus was conducting an investigation after a number of customers complained about fraudulent credit card charges. Now the company has given an update on the matter, saying that its website was attacked and a malicious script stealing credit card details was injected, affecting up to 40,000 people. The company has issued an apology for the incident and says that it has contacted those it feels may have been directly affected. In a statement, OnePlus explains that over a two-month period, customers who entered their credit card details at oneplus.net may be at risk. See also:… [Continue Reading] -

Amazon hikes monthly Prime fee by 18 percent
Publié: janvier 20, 2018, 4:33pm CET par Mark Wycislik-Wilson
Amazon has just given people another reason to pay for their Prime subscriptions on an annual rather than a monthly basis. The company has increased the cost of a monthly subscription by $2 per month. This is the first rise in Amazon Prime subscription pricing for a few years now, and the fact that the annual fee remains unchanged is a clear indication that Amazon is eager to lock customers into year-long packages. See also: Donald Trump wants US Postal Service to charge Amazon 'much more' Amazon Prime Video comes to Apple TV, and the US gains live sports Amazon… [Continue Reading] -

Facebook to fight 'sensationalism, misinformation and polarization' with news trustworthiness surveys for users
Publié: janvier 20, 2018, 12:37pm CET par Mark Wycislik-Wilson
Facebook has said time and time again that it will do more to fight the problem of fake news on the social network, and the company's latest idea is to simply ask users which news sources they know and trust. In a post on his own Facebook page, Mark Zuckerberg said that Facebook will start to "ask people whether they're familiar with a news source and, if so, whether they trust that source." Seemingly blind to the idea that this could be open to abuse and manipulation, he says that this will shift the balance of the news that is… [Continue Reading] -

Twitter admits that 670,000 people interacted with Russian propaganda bots during US election
Publié: janvier 20, 2018, 11:38am CET par Mark Wycislik-Wilson
Twitter has revealed that a total of 677,775 Americans followed accounts or liked tweets associated with Russian propaganda groups during the 2016 US election. The company does not reveal how many people saw the tweets posted by these accounts. That Russia tried to use Twitter -- and other social networks -- to influence the outcome of the US election is hardly news, but there has been an ongoing investigation trying to determine the scale of the operation. In its latest announcement, Twitter also says that it closed 50,258 accounts with links to Russia. See also: Facebook is developing a tool… [Continue Reading] -

Italy launches investigation into Samsung and Apple for slowing down phones
Publié: janvier 20, 2018, 11:05am CET par Mark Wycislik-Wilson
Just a couple of weeks ago a French watchdog announced that it was investigating Apple about the "planned obsolescence" of iPhones. Now Italy is also looking into both Apple and Samsung after complaints that the companies are purposefully slowing down older phone models. Apple has already admitted and defended the fact that it slows down older iPhones, saying that it is done to ensure the best performance from aging batteries -- later saying that an upcoming update will make the slowdown optional. In Italy, both Apple and Samsung stand accused of reducing handset performance to "induce consumers to buy new… [Continue Reading] -

Intel: Meltdown and Spectre bugs also affect Ivy Bridge, Sandy Bridge, Skylake and Kaby Lake systems
Publié: janvier 18, 2018, 11:20am CET par Mark Wycislik-Wilson
In an update following the Meltdown and Spectre revelations, Intel has admitted that the problems also affect newer chips. The company had previously focused its attention -- and that of users -- on Broadwell and Haswell chips, but now company vice president Navin Shenoy has conceded that Ivy Bridge, Sandy Bridge, Skylake and Kaby Lake-based platforms are susceptible. In rather more positive news, Shenoy also says that good progress has been made in identifying the root cause of the problem. Furthermore, beta microcode should be made available to vendors next week. See also: Microsoft releases confusing patches for AMD systems… [Continue Reading] -

Tim Cook: iPhone users will soon be able opt out of performance reduction
Publié: janvier 18, 2018, 10:48am CET par Mark Wycislik-Wilson
Many iPhone owners were disappointed to learn that Apple had been purposefully slowing their handsets, with many people believing it confirmed rumors that Apple slowed older iPhones to encourage upgrades. Facing a backlash, the company explained that the forced performance degradation was an attempt to maximize battery life, and it then announced a cheaper battery replacement program. Now Tim Cook has said that a future iOS update will make iPhone throttling optional. See also: Debunked: Apple slows down older iPhones to encourage upgrades Yes, Apple really is slowing down your old iPhone -- but says it's for your own good… [Continue Reading] -

YouTube updates its video review process yet again to avoid another problem like Logan Paul
Publié: janvier 17, 2018, 4:28pm CET par Mark Wycislik-Wilson
YouTube is to subject large numbers of videos to manual review in an attempt to ensure that they are "ad-friendly." Google says that "stricter criteria for monetization" will be introduced as it tries to avoid further controversies such as Logan Paul's video that featured a dead body. The changes are likely to mean that some YouTubers will lose money when they are introduced in February. Google is also making changes to the requirements that need to be met to join the YouTube Partner Program. It used to take relatively little to join the Partner Program -- just a total of… [Continue Reading] -

Having Wi-Fi problems? Your Chromecast device could be to blame [Updated]
Publié: janvier 17, 2018, 4:10pm CET par Mark Wycislik-Wilson
Google support forums are filling up with complaints from Google Home and Chromecast users that they are experiencing problems with their Wi-Fi connections. With such devices connected to a network, many people are having issues with stability, or finding that their network collapses entirely. Both TP-Link and Linksys have issued patches for their routers, but the problem ultimately lies with the Cast feature of Google Home and Chromecast devices. To start with, it appeared that the problem was only affecting Google Home Max users who were working with a TP-Link Archer router, but it soon transpired that other devices and… [Continue Reading] -

Kaspersky reveals details of extraordinarily powerful Android trojan, Skygofree
Publié: janvier 17, 2018, 11:17am CET par Mark Wycislik-Wilson
Security firm Kaspersky Lab has revealed details of a highly-sophisticated Android trojan that takes advantage of multiple vulnerabilities to gain full control of a device. Skygofree has capabilities that have never been seen in the wild before. In the malware's arsenal of weapons is the ability to track user location, record audio, connect to attacker-controlled networks, monitor messaging apps, intercept text messages, take photographs, and much more. Kaspersky says its capabilities are "reminiscent of Hollywood spy movies." See also: Hundreds of fake Android apps have a hidden Coinhive miner Hundreds of Android and iOS apps use your mic to check… [Continue Reading] -

Microsoft releases confusing patches for AMD systems bricked by Meltdown and Spectre fixes
Publié: janvier 17, 2018, 10:43am CET par Mark Wycislik-Wilson
While the notorious Meltdown and Spectre chip bugs are still yet to pose a real threat in their own right, it's rather a different story when it comes to the patches designed to fix the problems. Microsoft had to pause the rollout of patches after reports that they were leaving some AMD systems unbootable. Now the software giant has released two new updates -- one for Windows 7 (KB4073578) and one for Windows 8.1 (KB4073576) -- to fix the "Unbootable state for AMD devices" issue. But it's not all good news. These are updates that have to be manually downloaded… [Continue Reading] -

Meltdown and Spectre: very few enterprise mobile devices are patched, and many will never be
Publié: janvier 16, 2018, 11:55am CET par Mark Wycislik-Wilson
The Meltdown and Spectre bugs have been in the headlines for a couple of weeks now, but it seems the patches are not being installed on handsets. Analysis of more than 100,000 enterprise mobile devices shows that just a tiny percentage of them have been protected against the vulnerabilities -- and some simply may never be protected. Security firm Bridgeway found that just 4 percent of corporate phones and tablets in the UK have been patched against Spectre and Meltdown. Perhaps more worryingly, however, its research also found that nearly a quarter of enterprise mobile devices will never receive a… [Continue Reading] -

Twitter denies reading your direct messages
Publié: janvier 16, 2018, 9:51am CET par Mark Wycislik-Wilson
Undercover footage emerged this week in which Twitter engineers said that hundreds of company employees were reading users' direct messages. The footage was shared by Project Veritas, and now Twitter has come out on the defensive. The conservative activist group's video purports to show Twitter employees saying that the company not only has access to, but also actively reads, users' DMs. Project Veritas is on a mission to highlight what it believes to be liberal bias in the media, and this is not the first undercover footage it has recorded relating to Twitter. Other footage shows an engineer saying the… [Continue Reading] -

Malwarebytes warns that fake Meltdown and Spectre patches are being used to spread Smoke Loader malware
Publié: janvier 15, 2018, 1:42pm CET par Mark Wycislik-Wilson
News of the Meltdown and Spectre processor bugs quickly spread around the world, as companies and individuals tried to protect their systems. But in addition to concerns about the performance hit patches may have on computers, Malwarebytes has also issued a stark warning about fake patches. The security firm warns that criminals have used interest in Meltdown and Spectre to push out fraudulent bug fixes that are laced with Smoke Loader malware. See also: Spectre patch in iOS 11.2.2 is slowing down iPhones Intel promises transparency as Meltdown patch causes reboot problems with Broadwell and Haswell chips Intel releases benchmark… [Continue Reading] -

Google kicks over 60 games out of the Play Store for serving up porn ads via AdultSwine malware
Publié: janvier 13, 2018, 4:46pm CET par Mark Wycislik-Wilson
Google has removed more than 60 games from the Play Store after security firm Check Point discovered they were laced with malware and serving up porn ads. Check Point claims that the games were aimed at children, but Google says this was not the case. The AdultSwine malware was found to be bundled in a number of games, many of which had been downloaded millions of times. As well as displaying pornographic ads, the malware also tried to trick users into installing fake security tools, and also encouraged people to register for expensive premium services. AdultSwine's modus operandi is similar… [Continue Reading] -

Spectre patch in iOS 11.2.2 is slowing down iPhones
Publié: janvier 12, 2018, 2:51pm CET par Mark Wycislik-Wilson
As technology firms around the world try to mop up the mess that the Meltdown and Spectre chip bugs are making, Intel has been keen to stress that the impact patches will have on performance will be minimal. The company has already released benchmark results that show the hardest hit will be older computers. Now new benchmarks show that iPhone users may notice slowdowns too. One iPhone 6 owner decided to benchmark his phone and found that the performance hit is significant. So significant, in fact, that some tasks see a performance degradation of more than 50 percent. See also:… [Continue Reading] -

Big changes to Facebook's news feed mean you'll probably spend less time on the social network
Publié: janvier 12, 2018, 12:08pm CET par Mark Wycislik-Wilson
Facebook is planning major changes to the way its news feed works, and Mark Zuckerberg says he believes that the amount of time people spend using the social network will go down as a result. This might seem like a slightly strange thing for the company to do, but these changes are about improving the overall experience. Zuckerberg says that "the time you do spend on Facebook will be more valuable." So what can we expect from the changes? For starters, you should see more posts from the people you know, and fewer from brands and pages. Facebook says that… [Continue Reading] -

Microsoft releases PowerShell Core 6.0 for Windows, macOS and Linux
Publié: janvier 12, 2018, 11:05am CET par Mark Wycislik-Wilson
Microsoft has released an updated version of PowerShell which adds support for macOS and Linux. PowerShell Core 6.0 uses .NET Core rather than the .NET framework, and this means it is able to break out of being a Windows-only tool. The tool is described as a "new edition of PowerShell that is cross-platform (Windows, macOS, and Linux), open-source, and built for heterogeneous environments and the hybrid cloud." The arrival of the scripting tool on new platforms will be welcomed by those working in mixed environments. For Linux users, there is official support for Ubuntu 14.04, 16.04 and 17.04, Debian 8.7+… [Continue Reading] -

Intel promises transparency as Meltdown patch causes reboot problems with Broadwell and Haswell chips
Publié: janvier 12, 2018, 10:34am CET par Mark Wycislik-Wilson
Intel CEO Brian Krzanich has written an open letter to the technology community addressing the fallout from the Meltdown and Spectre vulnerability revelations. In it he promises transparency from the company and reiterates a previous promise that patches will be made available for the majority of processors by next week. The letter comes as users of systems with Broadwell and Haswell chips report problems with increased reboots. See also: Intel releases benchmark results detailing Meltdown patch performance slowdown Microsoft and Intel reveal just how much Meltdown and Spectre patches slow PCs Microsoft pausing the rollout of Spectre and Meltdown patches… [Continue Reading] -

Privacy: WhatsApp's group messages might not be as secure as you think
Publié: janvier 11, 2018, 11:55am CET par Mark Wycislik-Wilson
Security researchers have discovered a method of infiltrating group chats in WhatsApp, effectively rendering the chat tool's end-to-end encryption useless. Researchers from Germany's Ruhr University Bochum have unearthed an encryption flaw that makes it possible for group conversations to be compromised. While the vulnerability is not one that poses immediate concerns -- it requires direct access to WhatsApp servers -- it still raises questions about the security of the platform. See also: Time runs out for WhatsApp on Windows Phone 8 and BlackBerry 10 Privacy: WhatsApp told to stop sharing user data with Facebook Now you can delete sent messages… [Continue Reading] -

Intel releases benchmark results detailing Meltdown patch performance slowdown
Publié: janvier 11, 2018, 10:14am CET par Mark Wycislik-Wilson
In the wake of the Meltdown and Spectre bug revelations, Intel has been eager to downplay the impact patches will have on performance. Having already shed a little light on exactly what users can expect in terms of a performance hit, the company has now released more detailed benchmark results In a blog post, Intel's Navin Shenoy shares details of benchmarks performed with sixth, seventh and eighth generation processors in Windows 10, and sixth generation processors in Windows 7, 8 and 10. Shenoy reiterates the company position that the "performance impact should not be significant for average computer users", saying… [Continue Reading] -

Meltdown and Spectre patches leave some Ubuntu systems unbootable
Publié: janvier 11, 2018, 9:08am CET par Mark Wycislik-Wilson
As if the Meltdown and Spectre chip bugs were not enough of a problem in their own right, the patches designed to fix them are proving to be a major headache as well. The latest victims are users of Ubuntu Xenial 16.04, some of whom are reporting that installing the patches leaves their computers unbootable. Windows users with AMD systems have run into a similar problem, causing Microsoft to halt the rollout of its patches. There have also been predictions, anecdotes and benchmarks that suggest Meltdown patches are causing performance issues, despite Intel's insistence that the impact is small. Now… [Continue Reading] -

Apple to pay £136 million in back taxes after UK audit
Publié: janvier 10, 2018, 5:43pm CET par Mark Wycislik-Wilson
HMRC (Her Majesty's Revenue and Customs) has completed an "extensive audit" of Apple, and accounts show that the company has been hit with a £136 million ($184 million) back tax bill. There has been a great deal of interest in the tax arrangement of technology companies in the past couple of years, and the recent Paradise Papers revealed how Apple was structuring its finances. The latest payment in the UK comes after Apple agreed to settle a $15 billion bill in Ireland, and the company says its UK tax bill payments will increase in coming years. See also: Apple agrees… [Continue Reading] -

Apple to introduce enhanced parental controls to counter iPhone addiction in children
Publié: janvier 10, 2018, 11:39am CET par Mark Wycislik-Wilson
Following accusations that children are addicted to iPhones, Apple has said that it will introduce improved parental controls in iOS. At the weekend, an open letter from a group of investors expressed concern about the overuse of Apple devices by children and teenagers. Responding to the letter, Apple says that while it considers itself a leader when it comes to parental controls, it will make the feature even "more robust" in the future. See also: French prosecutors investigate Apple over 'planned obsolescence' of iPhones Yes, Apple really is slowing down your old iPhone -- but says it's for your own… [Continue Reading] -

Microsoft and Intel reveal just how much Meltdown and Spectre patches slow PCs
Publié: janvier 10, 2018, 10:30am CET par Mark Wycislik-Wilson
The Meltdown and Spectre revelations have people around the world concerned about privacy, but there has also been great speculation about the reduction in performance that patches might bring. Now Microsoft and Intel have opened up about the sort of slowdown PC users and server operators can expect. Having previously tried to play down the negative impact that bug patches will have on systems, Intel's benchmark test now shows that -- depending on the tasks -- a slowdown of between 2 and 14 percent can be observed. Microsoft says that anyone with a computer dating from 2015 and earlier will… [Continue Reading] -

French prosecutors investigate Apple over 'planned obsolescence' of iPhones
Publié: janvier 9, 2018, 3:58pm CET par Mark Wycislik-Wilson
There have long been rumors that Apple slows down iPhones in a bid to encourage owners to upgrade to newer models. While not admitting to this precise accusation, the company had said that it reduces performance of iPhones to counteract aging batteries. Now the French consumer fraud watchdog DGCCRF is launching an investigation into what is described as "planned obsolescence." In France it is illegal to purposely shorten the life of a product to encourage replacement purchases, and the investigation comes after a complaint from a consumer group. See also: Yes, Apple really is slowing down your old iPhone --… [Continue Reading] -

Xposed Framework beta adds support for Android Oreo
Publié: janvier 9, 2018, 11:43am CET par Mark Wycislik-Wilson
A new beta of the Android tweaking tool Xposed Framework has been released. The big news is that the release brings support for Oreo, something of a surprise considering how recently Google pushed the latest version of its mobile operating system out of the door. The latest Xposed Framework release comes mere months after Nougat support was added. While the Oreo-supporting release will be welcomed by mobile tweakers, the developer says it should be treated as a beta, and may be buggy. You'll need to have rooted your phone to take advantage of Xposed Framework, but, once installed, you'll have… [Continue Reading] -

Microsoft pausing the rollout of Spectre and Meltdown patches to AMD systems
Publié: janvier 9, 2018, 11:15am CET par Mark Wycislik-Wilson
Following reports that its Spectre and Meltdown fixes were leaving some AMD systems unbootable, Microsoft has stopped the patches from rolling out to certain devices. The company is blaming AMD's failure to comply with "the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown." See also: Warning: Microsoft's Meltdown and Spectre patch is bricking some AMD PCs Microsoft releases PowerShell script to check if your PC is vulnerable to Meltdown and Spectre Microsoft issues an emergency fix for Windows 10 to address processor bug There's no… [Continue Reading] -

Hundreds of fake Android apps have a hidden Coinhive miner
Publié: janvier 8, 2018, 4:52pm CET par Mark Wycislik-Wilson
The Bitcoin bubble means there is a massive interest in cryptocurrencies, particularly from those looking for an easy way to make a quick buck. It's also led to secretive mining tools making use of people's CPUs without their knowledge, mining for profitable cryptocurrency for persons unknown. We've seen this with both websites and browser extensions, and now a security researcher has discovered a series of fake Android apps harboring an undisclosed Coinhive cryptocurrency miner. The repackaged APKs take advantage of the CPUs of the smartphones the apps are installed on. See also: BlackBerry Mobile site hacked to run Monero cryptocurrency miner… [Continue Reading] -

Meltdown patches are slowing down games such as Fortnite
Publié: janvier 8, 2018, 2:08pm CET par Mark Wycislik-Wilson
Fans of the game Fortnite have been frustrated by a combination of reduced performance, and an inability to log into the game at all. The company behind the title, Epic Games, says that patches installed to mitigate against the Meltdown and Spectre bugs are to blame. Since installing patches to address the vulnerabilities, Epic has noticed a very significant spike in processors usage. The extra strain on backend cloud services has noticeably slowed down Fortnite for some users, and rendered others unable to play the game at all. See also: Warning: Microsoft's Meltdown and Spectre patch is bricking some AMD… [Continue Reading] -

Microsoft drops Bitcoin support
Publié: janvier 8, 2018, 12:58pm CET par Mark Wycislik-Wilson
Microsoft has had something of an on-off relationship with Bitcoin over the years, and once again the Windows-maker has chosen to drop support for the cryptocurrency -- at least temporarily. It has been reported that Microsoft is uncomfortable with the fluctuating value of Bitcoin, as well as the increased transaction fees. As such, customers will no longer be able to add to their Microsoft account balances using Bitcoin. Bleeping Computer reports that, like Steam just last month, Microsoft no longer allows the cryptocurrency to be used to top up their accounts. The site says: "Microsoft has stopped supporting Bitcoin as… [Continue Reading] -

Microsoft drops Bitcoin support [Update: it's back]
Publié: janvier 8, 2018, 12:58pm CET par Mark Wycislik-Wilson
Microsoft has had something of an on-off relationship with Bitcoin over the years, and once again the Windows-maker has chosen to drop support for the cryptocurrency -- at least temporarily. It has been reported that Microsoft is uncomfortable with the fluctuating value of Bitcoin, as well as the increased transaction fees. As such, customers will no longer be able to add to their Microsoft account balances using Bitcoin. Bleeping Computer reports that, like Steam just last month, Microsoft no longer allows the cryptocurrency to be used to top up their accounts. The site says: "Microsoft has stopped supporting Bitcoin as… [Continue Reading] -

Warning: Microsoft's Meltdown and Spectre patch is bricking some AMD PCs
Publié: janvier 8, 2018, 11:03am CET par Mark Wycislik-Wilson
As if the Meltdown and Spectre bug affecting millions of processors was not bad enough, the patches designed to mitigate the problems are introducing issues of their own. Perhaps the most well-known effect is a much-publicized performance hit, but some users are reporting that Microsoft's emergency patch is bricking their computers. We've already seen compatibility issues with some antivirus tools, and now some AMD users are reporting that the KB4056892 patch is rendering their computer unusable. A further issue -- error 0x800f0845 -- means that it is not possible to perform a rollback. See also: Microsoft releases PowerShell script to… [Continue Reading] -

BlackBerry Mobile site hacked to run Monero cryptocurrency miner
Publié: janvier 7, 2018, 9:27am CET par Mark Wycislik-Wilson
With the popularity of Bitcoin and other cryptocurrencies, it's perhaps little surprise that a number of websites have recently been discovered using visitors' computer to do a little mining. The latest site found to be indulging in the activity is BlackBerry Mobile -- but this time it's thanks to the work of a hacker. As with other sites carrying out surreptitious mining, it was a CoinHive mining tool that was found embedded in the code of the site. The same hacker also placed the same miner on a handful of other sites. See also: SafeBrowse Chrome extension found to be… [Continue Reading] -

Google answers your questions about Meltdown and Spectre vulnerabilities
Publié: janvier 6, 2018, 1:55pm CET par Mark Wycislik-Wilson
The revelations about the Spectre and Meltdown vulnerabilities affecting millions of processors around the world has raised a huge number of questions for many people. While businesses and large organizations are rushing to ensure that their systems -- and their data -- are protected, the average computer user has been left wondering what on Earth is going on. While there are a lot of very technical write-ups about the implications of the Spectre and Meltdown bugs, as well as explanations of just how the exploit works, the average Joe has been left somewhat in the dark. To try to remedy… [Continue Reading] -

Twitter won't ban Donald Trump because he's special
Publié: janvier 6, 2018, 12:17pm CET par Mark Wycislik-Wilson
Since Donald Trump's inauguration, there have been countless calls for him to be banned from Twitter. As well as concerns that his often rash and bombastic statements could cause diplomatic nightmares nationally and internationally, there have also been suggestions that his particularly aggressive tone and threats violate Twitter's policies. But Twitter has consistently refused to either ban the US president or remove his more controversial tweets -- despite doing the same with other users. Now the company has taken steps to explain why this in. In essence, it's because Trump -- and other world leaders -- have been granted a… [Continue Reading] -

HP recalls laptop batteries because of fire and burn risks
Publié: janvier 5, 2018, 5:29pm CET par Mark Wycislik-Wilson
HP has issued a voluntary worldwide recall after discovering a problem with laptop batteries. Affecting notebooks and mobile workstations, HP says the lithium-ion batteries can overheat, posing fire and burn hazards. The recall covers various Pavilion, ENVY and Zbook models sold through the likes of Amazon and Best Buy as well as direct from HP. In all, some 50,000 computers sold between December 2015 and December 2017 are affected. This is hardly the first time HP has recalled batteries. Since 2005, there have been no fewer than eight recalls. This time around, the company has set up a page that… [Continue Reading] -

Lawsuits stack up against Intel over Meltdown and Spectre bugs
Publié: janvier 5, 2018, 4:14pm CET par Mark Wycislik-Wilson
Since news of the Meltdown and Spectre processor bugs broke, tech companies have been scrabbling to develop patches and get them out to users. Intel, on the other hand, has been desperately trying to salvage its tarnished image. What's not going to improve the mood at the company is the fact that it has been hit by a series of class action lawsuits. In the days since the processor vulnerability was revealed, three sperate lawsuits have been filed against the chip-maker. Given the scale of the problem, it's likely that more will spring up, and other chip-makers may also be… [Continue Reading] -

Microsoft releases PowerShell script to check if your PC is vulnerable to Meltdown and Spectre
Publié: janvier 5, 2018, 12:13pm CET par Mark Wycislik-Wilson
In the wake of the Meltdown and Spectre chip bug revelations, people around the world are wondering whether or not they are affected. Bearing in mind the number of chips with the flaw, the chances that your computer has a vulnerability are very high. Microsoft rushed to get an emergency fix out to Windows 10 users, promising that Windows 7 and 8 users will be patched in the near future. The company has also released a PowerShell script that lets users check whether they have protection in place. See also: Intel will have Meltdown and Spectre patches ready for 90… [Continue Reading] -

Intel will have Meltdown and Spectre patches ready for 90 percent of modern processors next week
Publié: janvier 5, 2018, 10:54am CET par Mark Wycislik-Wilson
With Meltdown and Spectre turning into something of a PR disaster for Intel, the chip-maker has promised that patches will be made available for the vast majority of modern processors by the end of next week. The company says that it has already released "updates for the majority of processor products introduced within the past five years" in the form of firmware updates and software patches. By the end of next week, Intel hopes to have released updates for 90 percent of processors from the last five years. Refuting claims that have been made by many parties, Intel denies that… [Continue Reading] -

Apple: all iOS and Mac devices are vulnerable to Meltdown and Spectre chip bugs
Publié: janvier 5, 2018, 9:46am CET par Mark Wycislik-Wilson
Apple has confirmed that all of its Macs, iPhones and iPads are affected by the recently revealed Meltdown and Spectre vulnerabilities. The company points out that while a huge number of devices are affected, there are "no known exploits impacting customers at this time." Just as Microsoft has already pushed out an emergency patch for Windows 10 users -- with Windows 7 and 8 to follow soon -- Apple has already rolled out some patches for Meltdown with iOS 11.2, macOS 10.13.2, and tvOS 11.2. An update to Safari to protect against Spectre is promised in the coming days. See… [Continue Reading] -

Microsoft acquires storage vendor Avere Systems to boost its hybrid cloud offerings
Publié: janvier 4, 2018, 3:26pm CET par Mark Wycislik-Wilson
Microsoft has bought file systems company Avere Systems for an undisclosed sum. The acquisition is part of Microsoft's continuing shift to the cloud, and sees the company improving its enterprise products. Avere's technology will be integrated into Microsoft Azure, continuing the company's provision of "high-performance NFS and SMB file-based storage for Linux and Windows clients running in cloud, hybrid and on-premises environments." In a blog post, Avere president and CEO Ronald Bianchini Jnr says: "I am excited to announce that Avere Systems will be joining Microsoft to continue our mission to enable the most demanding Enterprise workloads to run in… [Continue Reading] -

Google knew about Spectre and Meltdown processor bugs last year, so its products are (mostly) protected
Publié: janvier 4, 2018, 11:21am CET par Mark Wycislik-Wilson
When news broke of the security flaw affecting Intel chips, the tech world was more than a little surprised. And things just got more surprising as more details of Meltdown and Spectre emerged. Perhaps most surprising is the fact that Google -- via Project Zero -- was aware of the problem in June of 2017. The company even went as far as informing Intel, AMD and ARM about the issue. But for Google customers, the good news is that the early detection of the security flaw means that Google Cloud, G Suite and Chrome users are fairly safe. See also:… [Continue Reading] -

Microsoft issues an emergency fix for Windows 10 to address processor bug
Publié: janvier 4, 2018, 10:28am CET par Mark Wycislik-Wilson
News of an enormous security bug affecting millions of processors can't have escaped your attention over the last 24 hours or so. While Intel goes into a panicked meltdown, desperately pointing out that there's another bug affecting other processors too, software fixes are starting to emerge. macOS has already been patched, and fixes have started to roll out to numerous Linux distros as well. Now Microsoft has pushed out a rare, off-schedule emergency fix for Windows 10 users which should be automatically installed. Users of Windows 7 and Windows 8 will have to wait until next week for a patch.… [Continue Reading] -

Intel chips have a huge security flaw, and the fix will slow down Windows and Linux machines
Publié: janvier 3, 2018, 10:46am CET par Mark Wycislik-Wilson
A design flaw has been discovered in Intel chips that will require major changes to be made to the Windows and Linux kernels. While patches are being worked on -- and in the case of Windows Insiders, have already rolled out -- users of both operating systems can expect to experience something of a performance hit. macOS machines running on Intel chips are also affected. Intel is -- for the moment -- remaining tight-lipped about the specifics of the flaw that has been unearthed, but it is believed to affect processors produced in the past decade. Developers are currently estimating… [Continue Reading] -

Hundreds of Android and iOS apps use your mic to check what TV shows you are watching
Publié: janvier 2, 2018, 4:18pm CET par Mark Wycislik-Wilson
Advertisers are keen for their ads to be seen, that goes without saying. But it's more important to be seen by the right people, hence the explosion in targeted advertising. Social media is a great way to gather massive amounts of data about people and deliver ads accordingly, but some mobile games take things further. There are a large number of games for both iOS and Android which include Alphonso software. This uses smartphones' microphones to record audio which is then used to determine which TV shows and commercials you're watching -- and then deliver targeted ads accordingly. Is this… [Continue Reading] -

Privacy: Kodi's remote access could be used to spy on you
Publié: janvier 2, 2018, 12:48pm CET par Mark Wycislik-Wilson
There's no denying the massive popularity of Kodi, and the streaming media center has become infamous as well as famous. While the negative press concerning the software tends to focus on the potential for piracy, there's also the question of privacy and security. Kodi includes -- as does the likes of Plex -- a remote access feature. While wonderfully useful for when you're away from home, it also poses a security risk and represents a serious privacy concern if not correctly configured. The importance of properly protecting your Kodi setup really cannot be overstated. As TorrentFreak points out, if Kodi… [Continue Reading] -

Samsung Galaxy Note8 handsets have a battery problem
Publié: janvier 2, 2018, 11:16am CET par Mark Wycislik-Wilson
Sound familiar? A Galaxy Note has a problem with its battery! Samsung has acknowledged that there is an issue with the battery of the Galaxy Note8 -- but unlike the Galaxy Note7, there's no risk of it catching fire or exploding this time around. A number of Note8 owners have complained that their phones have essentially been bricked after they let the battery run flat. With the battery fully discharged, it has proved impossible to charge the phone again. The problem is mainly affecting Note8 owners in the US. Samsung has acknowledged the issue, but says that it has been… [Continue Reading] -

Ancient unpatched IOHIDeous vulnerability allows root access to macOS
Publié: janvier 2, 2018, 10:32am CET par Mark Wycislik-Wilson
Apple has a tendency to pride itself on security, but a researcher has released details of a macOS vulnerability that allows for complete system control by an unprivileged user. A self-described "hobbyist hacker," Siguza, has published details of the exploit which is thought to have existed, undetected and unpatched for at least a decade. As well as details of the security flaw, Suguza has also published proof-of-concept code for the IOHIDeous vulnerability on GitHub. In a highly-detailed write-up, Siguza says that the bug has been present for at least 15 years, but suggests it is possible that it has been… [Continue Reading] -

Apple's $29 iPhone battery replacement offer is available right now -- but supplies are limited
Publié: décembre 31, 2017, 1:36pm CET par Mark Wycislik-Wilson
After admitting to slowing down older iPhones, Apple subsequently apologized for the lack of transparency about the issue. In addition to the apology, the company also announced that iPhone owners would be able to replace their batteries at a discounted rate of $29 starting in late January. In an update to the original statement, Apple has now brought forward its replacement program so you can get new battery for your iPhone 6 (or later) handset starting right now. Alternatively, you can do it yourself, with a discounted iFixit kit. See also: Yes, Apple really is slowing down your old iPhone… [Continue Reading] -

Donald Trump wants US Postal Service to charge Amazon 'much more'
Publié: décembre 31, 2017, 12:29pm CET par Mark Wycislik-Wilson
In an attack on Amazon, President Trump has called upon the US Postal Service to charge the retail giant "much more" to ship packages to customers. This is not the first time Trump has hit out at Amazon and Jeff Bezos, but his latest vocal volley was not well-received by his followers on Twitter. See also: Kaspersky sues Trump administration over government software ban Google yanks YouTube from Echo Show and Fire TV in Amazon spat EFF: Twitter users have a First Amendment right not to be blocked by President Trump Trump's attack comes at the busiest time of the… [Continue Reading] -

Facebook to use facial recognition to notify users when photos of them are uploaded
Publié: décembre 29, 2017, 1:10pm CET par Mark Wycislik-Wilson
A new feature touted as a privacy tool sees Facebook automatically identifying users in photographs that are uploaded. It uses the same technology already employed to make image tagging suggestions. The social networking giant is using facial recognition to alert people when someone uploads a photo of them, regardless of whether they have been tagged in the image. For the feature to work, Facebook users will have to agree to the company keeping a record of them in a facial database. See also: Facebook stops flagging fake news because it was making the problem worse Privacy: WhatsApp told to stop… [Continue Reading] -

Edward Snowden's Haven app turns a smartphone into a security device
Publié: décembre 29, 2017, 7:53am CET par Mark Wycislik-Wilson
The name Edward Snowden will always be associated with the NSA, but the man has fingers in many other pies. His latest venture is an app called Haven which can turn a smartphone into a security device that keeps an eye on your possessions. Haven is an Android app, currently in beta, designed to be installed on an "extra" phone that you wouldn't mind losing. Placed with your belongings, it uses a phone's sensors -- microphone, camera, gyroscope, accelerometer, and so on -- to detect and record theft and tampering. The app is a joint venture between Snowden's Freedom of… [Continue Reading] -

Twitter kills anti-Nazi bot Imposter Buster that tried to expose racists
Publié: décembre 29, 2017, 7:26am CET par Mark Wycislik-Wilson
A Twitter account designed to alert users about racist accounts has been shut down by Twitter. Imposter Buster was a bot created by journalist Yair Rosenberg in an attempt to expose racism on the platform. But while many people welcomed the activities of Imposter Buster -- which would automatically join in the conversations of high-profile racist users in an attempt to expose their trolling of ethnic minority users -- Twitter saw things differently and slapped the bot with a permanent ban. In an opinion piece for the New York Times, Rosenberg explains that the bot he created was designed to… [Continue Reading] -

Time runs out for WhatsApp on Windows Phone 8 and BlackBerry 10
Publié: décembre 27, 2017, 9:41am CET par Mark Wycislik-Wilson
The start of a new year means saying hello to new beginnings and waving goodbye to a few old things. As 2018 rolls around, WhatsApp is killing off support for both Windows Phone 8 and BlackBerry 10. This should hardly come as major news. Windows Phone 8 and BlackBerry 10 are both very niche platforms, and WhatsApp had previously announced -- and then extended -- that support was coming to an end. See also: Privacy: WhatsApp told to stop sharing user data with Facebook Now you can delete sent messages in WhatsApp WhatsApp gains location sharing allowing real-time tracking WhatsApp… [Continue Reading] -

Download Android 8.0 Oreo for OnePlus 5 now
Publié: décembre 27, 2017, 9:05am CET par Mark Wycislik-Wilson
If you're the owner of a OnePlus 5, you've no doubt been eagerly awaiting the arrival of Oreo on your phone. Well, the wait is over; you can now upgrade to Android 8.0. The release served as a great present for anyone who had their ear to the ground on Christmas Eve, and a nice surprise for anyone who was too wrapped up in festivities to notice. As ever, the update will roll out gradually, but if you're feeling impatient, it's easy to force the download. See also: Oreo arrives on the OnePlus 5 through OxygenOS open beta Android 8.1… [Continue Reading] -

Facebook stops flagging fake news because it was making the problem worse
Publié: décembre 22, 2017, 11:11am CET par Mark Wycislik-Wilson
Fake news -- or disinformation as it used to be called -- has become an increasingly serious problem as false information quickly spreads online through social media. Facebook tried to combat the problem by flagging up fake news with Disputed flags but, having discovered that this was actually making the problem worse, the social network is dropping this approach. Instead, Related Articles will be used to provide context and give alternative takes on stories. Citing academic research, Facebook says that highlighting stories as fake news with a warning flag or similar actually did nothing to stop people believing the content… [Continue Reading] -

Yes, Apple really is slowing down your old iPhone -- but says it's for your own good
Publié: décembre 22, 2017, 10:27am CET par Mark Wycislik-Wilson
We now know for certain what many people have suspected for some time: Apple really is slowing down older iPhones. The phone-maker has finally come clean about what's going on -- it really is purposefully degrading the performance of its phones. While there has been speculation that the company has been putting the brakes on aging handsets in a bid to encourage people to upgrade to newer models, Apple says that there's actually a different reason for old iPhones performing less impressively in benchmarks. That reason is battery life. See also: Has your iPhone started crashing in iOS 11.1.2? You're… [Continue Reading] -

Privacy: WhatsApp told to stop sharing user data with Facebook
Publié: décembre 19, 2017, 8:01am CET par Mark Wycislik-Wilson
A French privacy watchdog has ordered WhatsApp to stop sharing user data with Facebook. The CNIL (National Data Protection Commission) issued the Facebook-owned company with formal notice to cease violations of the French Data Protection Act, suggesting that user consent was not properly obtained. A change to WhatsApp's privacy policy last year saw the app transferring data to its parent company for the purposes of "business intelligence" and security purposes. It is the business intelligence side of things -- which analyses user behaviour -- that France considers illegal. See also: Facebook adds Snooze button to silence irritating friends, pages and… [Continue Reading] -

Kaspersky sues Trump administration over government software ban
Publié: décembre 19, 2017, 7:35am CET par Mark Wycislik-Wilson
US concerns about links between Kaspersky Labs and the Russian government led to a ban on the security software being used on US government computers. The ban was only recently signed into law by Donald Trump, and now Kaspersky has filed a lawsuit against the Department of Homeland Security in response. Kaspersky Labs is asking a federal court to overturn Trump's ban. The Moscow-based company maintains that it does not have links to the Kremlin, and has published an open letter saying that it had not been afforded "adequate due process" and that the US government's decision was based on… [Continue Reading] -

Google Assistant gains 'Hey, Google' support on a range of Android devices
Publié: décembre 17, 2017, 5:19pm CET par Mark Wycislik-Wilson
Voice control of computers and smartphones is becoming increasingly common, and for Android users a new option is opening up. Previously only available on Nexus and Pixel devices, support for the "Hey, Google" trigger is rolling out to more handsets. This gives Android users another option for calling up Google's voice-activated assistant, adding to the existing "OK, Google" command. See also: Huge Janus bug leaves Android apps open to unauthorized code modification Google bans most Android apps from displaying lockscreen ads Privacy: a huge proportion of Android apps are secretly tracking you The change is clearly not a major one,… [Continue Reading] -

Windows 10 included a password manager complete with massive password-stealing potential
Publié: décembre 17, 2017, 4:32pm CET par Mark Wycislik-Wilson
Microsoft has been bundling a password manager that features a dangerous flaw with some versions of Windows 10, a Google security researcher has revealed. Tavis Ormandy noticed that his copy of Windows 10 included Keeper, which he had previously found to be injecting privileged UI into pages. The version that Microsoft was including with Windows 10 featured the same bug. What does this mean? In short, it allows any website to steal passwords from you. See also: Security: macOS High Sierra bug lets you log in as 'root'... without a password Windows 8 onwards incorrectly implements ASLR security feature, but… [Continue Reading] -

Patreon scraps plans to introduce new charges, and apologizes to users
Publié: décembre 16, 2017, 8:28am CET par Mark Wycislik-Wilson
Artists' and creators' platform Patreon has scrapped controversial plans to introduce a new pricing structure after a vocal backlash from users. The site -- used by many artists and creators to raise money -- had planned to add a service charge to pledges placed by patrons. While the new pricing structure would have reduced fees paid by artists, there was a fear that fewer pledges would be made due to fees having to be shouldered by those pledging money. CEO Jack Conte has now apologized and says that the company will work on a better system that does not unfairly… [Continue Reading] -

Facebook adds Snooze button to silence irritating friends, pages and groups
Publié: décembre 16, 2017, 8:00am CET par Mark Wycislik-Wilson
If you're friends with someone on Facebook it should mean that you're interested in hearing about what they have to say and see what they have to share. But at the same time, it's likely you've been extremely annoyed by the incessant stream of babble that flows from some people. You might not want to go quite as far as unfriending someone -- maybe you're just sick of them posting movie spoilers, or you're tired of hearing them go on about their team's latest success -- so Facebook has introduced a new Snooze option. This can be used to hide… [Continue Reading] -

TVAddons: Streaming through Kodi addons protects you from malware and cryptocurrency miners
Publié: décembre 14, 2017, 6:30pm CET par Mark Wycislik-Wilson
Kodi has been the subject of controversy for some time, and addon repository TVAddons has, in particular, been criticized from many quarters. Having recently announced that it will no longer proactively check for pirated content, TVAddons is suggesting that there's a very good reason to use Kodi addons to stream online content -- security. The site says that one of the reasons Kodi is so hated by the industry is that addons give users the chance to avoid advertisements and "all forms of monetization." TVAddons says that Kodi addons not only enable people to avoid ads, but also potentially dangerous malware… [Continue Reading] -

Trump signs bill banning Kaspersky software
Publié: décembre 13, 2017, 8:06am CET par Mark Wycislik-Wilson
The distrust -- at least publicly -- that the US shows for Russia is well-known. Following concerns about potential espionage from the Kremlin, the government has banned the use of Kaspersky software on its systems. This ban has now been cemented into law as President Trump signed a bill forbidding the use of Kaspersky Lab software on government computers. See also: Kaspersky software banned from US government systems over concerns about Russia Kaspersky's new 'global transparency initiative' aims to rebuild trust by submitting source code for review WikiLeaks: CIA source code leak shows agency impersonating Kaspersky There have long been… [Continue Reading] -

Warning: if you remove the Apple Pay Cash app, it's not obvious how to get it back
Publié: décembre 13, 2017, 7:48am CET par Mark Wycislik-Wilson
The Apple Pay Cash 'app' is built in to iOS, so you might well expect that it would be locked in place, completely un-uninstallable. But that's not the case. In fact, you can remove -- or at least hide -- the app, but you will run into problems if you ever change your mind and decide you want it back. If you are running iOS 11.2 -- which introduced Apple Pay Cash -- you can easily uninstall the app if you feel you don't want it. But there is no obvious way to get it back, meaning that while you can… [Continue Reading] -

Twitter introduces new 'threads' feature for easier tweetstorms
Publié: décembre 13, 2017, 7:08am CET par Mark Wycislik-Wilson
It's just over a month since Twitter doubled the maximum possible length of tweets to 280 characters -- but this was not enough for many people. But rather than further increasingly the length of tweets, the site has instead introduced another feature users have been begging for -- threading. The threading of tweets -- linking together multiple related tweets so people can follow a longer piece of writing -- has been tried by users in a couple of ways (numbering tweets or self-replying, for example) for some time now. But the new feature is the first time there has been… [Continue Reading] -

Chrome 63 is more secure than ever -- and uses even more memory
Publié: décembre 9, 2017, 1:12pm CET par Mark Wycislik-Wilson
Google's Chrome browser has something of a reputation for being memory-hungry. With the released of Chrome 63 this image is not going to be shed -- a new security feature increases memory usage even further. The latest desktop version of the browser includes a new Site Isolation feature which launches individual sites -- all sites, or a specific list -- in sperate processes. While this is something that will be of particular interest to enterprise users because of the added security it brings, it's something that will appeal to any security-minded user who is willing to shoulder a 10-20 percent… [Continue Reading] -

Huge Janus bug leaves Android apps open to unauthorized code modification
Publié: décembre 9, 2017, 10:20am CET par Mark Wycislik-Wilson
Researchers from security firm GuardSquare have discovered an Android vulnerability that allows for app code to be edited without affecting the apps' signature. Dubbed Janus, the vulnerability has massive potential for malicious use, and affects Android 5.0 onwards. The security hole would allow an attacker to tweak an entirely legitimate app to behave maliciously without triggering any security alerts. Although vulnerability CVE-2017-13156 has been patched in December's Android update, very few people will have access to this security fix. On the plus side, checks performed on apps that are submitted to Google Play should mean that anything obtained via official… [Continue Reading] -

Kodi addon site TVAddons to stop proactively checking for piracy
Publié: décembre 9, 2017, 9:49am CET par Mark Wycislik-Wilson
Justified or not, Kodi has been somewhat synonymous with pirated content. At the heart of Kodi-related controversy are the addons that provide access to such material, and addon site TVAddons constantly finds itself embroiled in things. Having recently announced that it managed to build up 12 million monthly users despite being closed down, TVAddons has now announced a change to the way it operates. While still perfectly happy to comply with the law when it comes to pirated content, the site will now rely on DMCA takedown notices rather than proactively checking for infringments. See also: Back from the dead:… [Continue Reading] -

Amazon Prime Video comes to Apple TV, and the US gains live sports
Publié: décembre 6, 2017, 5:40pm CET par Mark Wycislik-Wilson
Apple TV users in more than 100 countries now have access to Amazon Prime Video. The arrival of the streaming service means that anyone with an Apple TV 4K or an older model can enjoy a plethora of movies and Prime Original series. On top of this, in the US, the Apple TV app brings live sports to iPhone, iPad and Apple TV users. There are already a number of supported sports apps within the Apple TV app, including those from ESPN and the NBA, and more will be added. Prime Video subscribers can manually browse through the programming that's… [Continue Reading] -

Disqus has been acquired by marketing firm Zeta Global
Publié: décembre 6, 2017, 4:14pm CET par Mark Wycislik-Wilson
Interacting with BetaNews -- and countless other websites -- means making use of the Disqus commenting system. Today the firm has been acquired by "marketing technology company" Zeta Global. Disqus says that "we still are and will remain the same Disqus that you know and use," but there will be concerns from users that the company is being taken over by one with a vested interested in marketing and, therefore, user data. Zeta's press release on the matter is very brief: "Zeta Global today announced it has acquired Disqus, the web's leading audience engagement platform used by 4 million websites… [Continue Reading] -

Privacy: Popular ai.type keyboard leaks personal details of 31 million users
Publié: décembre 6, 2017, 12:00pm CET par Mark Wycislik-Wilson
Third-party Android and iOS keyboard ai-type is at the center of something of a privacy nightmare after a misconfigured database leaked the personal details of more than 31 million of its users. Researchers at Kromtech Security Center discovered an unprotected database had been exposed by developers, revealing incredibly detailed information about its users. The database was found to be freely available for anyone to download, with no password required to access a treasure trove of information. See also: Google updates Safe Browsing rules so apps must warn when they collect personal data UK government to tweak Snooper's Charter after conceding… [Continue Reading] -

Google yanks YouTube from Echo Show and Fire TV in Amazon spat
Publié: décembre 6, 2017, 9:55am CET par Mark Wycislik-Wilson
Google has announced plans to block its YouTube apps from Amazon's Echo Show and Fire TV as the situation between the two companies stepped up a notch. This is, of course, not the first time this has happened. The bad feeling stems from Amazon's unwillingness to stock Google products such as Chromecast, Nest and Google Home, and refusing to make its Prime Video service available to uses of Google Cast. Amazon's use of a "hacked" version of the YouTube app on its hardware has also been a bone of contention. See also: Google pulls YouTube from Amazon Echo Show for… [Continue Reading] -

Yahoo sues Mozilla for breach of contract -- so Mozilla countersues Yahoo
Publié: décembre 6, 2017, 9:15am CET par Mark Wycislik-Wilson
Mozilla and Yahoo have started a legal spat about the deal that existed between the two companies regarding the use of the Yahoo search engine in the Firefox browser. On December 1, Yahoo fired the first shot filing a complaint that alleges Mozilla breached a contract that existed between the two companies by terminating the arrangement early. In a counter complaint, Mozilla says that it was not only justified in terminating the contract early, but that Yahoo Holdings and Oath still have a bill that needs to be settled. Yahoo's complaint centers on "breach of contract" and "breach of covenant… [Continue Reading] -

Apple wins iPad trademark case against Xiaomi Mi Pad
Publié: décembre 5, 2017, 4:29pm CET par Mark Wycislik-Wilson
A court has ruled that Chinese phone maker Xiaomi may not trademark the name Mi Pad in Europe. The name was thought to be too similar to Apple's iPad, despite there being a difference in pronunciation. The General Court -- the second highest court in the European Union -- said that consumers were likely to be confused by the similarity of the two names. See also: Apple agrees to cough up for $15 billion Irish tax bill Apple Pay Cash rolls out to iOS 11.2 users in the US Xiaomi has been trying to register the trademark in Europe since… [Continue Reading] -

After a year of silence, VLC for Android is updated with much-needed new features
Publié: décembre 5, 2017, 12:35pm CET par Mark Wycislik-Wilson
When an app goes silent for more than a year, it's reasonable to assume that it has been killed off -- but that's not the case with VLC. The Android version of the popular media player has been updated to version 2.5 after getting stuck at 2.0 for 13 months. Work has been going on for VLC 3.0, but you would have been forgiven for thinking that the app had just been forgotten about. With the launch of VLC 2.5 there are a number of new features to enjoy including a new dynamic UI, a night mode, and picture-in-picture support… [Continue Reading] -

Apple agrees to cough up for $15 billion Irish tax bill
Publié: décembre 5, 2017, 11:42am CET par Mark Wycislik-Wilson
Apple is just one of many technology companies whose tax arrangements in Europe have been criticized. Like other firms, Apple made use of Ireland to help reduce its tax bills, and this is something that the European Commission took exception to. Last year the EC said that tax benefits received by the company in Ireland were in fact illegal under EU law, and ordered that an outstanding €13bn ($15.3bn) tax bill be settled. Despite Apple not wanting to pay the bill -- and the Irish Government not wanting to receive it -- the two sides have now come to an… [Continue Reading] -

Apple Pay Cash rolls out to iOS 11.2 users in the US
Publié: décembre 5, 2017, 11:17am CET par Mark Wycislik-Wilson
Over the weekend, Apple pushed out iOS 11.2 a little earlier than planned to address a crashing problems affecting iPhone users. The update included a non-functioning version of Apple Pay Cash, but now Apple is flicking the switch to activate the new payment options. Apple Pay Cash makes it possible for people to send and receive payments through iMessage. It serves as an alternative to the likes of PayPal, and it's a payment option that's now rolling out across the US, with other parts of the world to follow in due course. See also: Has your iPhone started crashing in… [Continue Reading] -

Windows Update in Windows 7 starts throwing up 80248015 error
Publié: décembre 5, 2017, 10:37am CET par Mark Wycislik-Wilson
Despite Microsoft's aggressive pushing of Windows 10, Windows 7 remains staggeringly popular. A growing number of users are currently reporting an issue with Windows Update at the moment -- specifically error 80248015. The full error message reads: "Windows Update cannot currently check for updates, because the service is not running. You may need to restart your computer." Needless to say, a simple restart is not enough to fix the problem, although a workaround has been discovered that solves the issue for some people. See also: Steam: Windows 7 now nearly three times more popular than Windows 10 NetMarketShare: Windows 7… [Continue Reading] -

Now you can stream Neil Young's entire back catalog for free
Publié: décembre 4, 2017, 4:33pm CET par Mark Wycislik-Wilson
The massively prolific Neil Young has just made his entire musical back catalog available to stream free of charge. Obsessed with audio quality -- you might well remember Young's Pono music player and streaming service, as well as his hatred of the MP3 format -- tracks are provided at an extremely high bit rate. Of course, this is not a completely selfless offering from the Canadian musician. The free availability of tracks is a time-limited offer -- it's really little more than an advertising stunt for his paid-for Xstream Music subscription service. The launch of the Neil Young Archives --… [Continue Reading] -

Facebook launches Messenger Kids for under-13s
Publié: décembre 4, 2017, 3:47pm CET par Mark Wycislik-Wilson
In a move that's likely to raise a few eyebrows, Facebook today opened up its messaging platform to children under the age of 13. A new app, Messenger Kids, is now available in the US for iOS users. The app is currently available as a preview, and Facebook says that it has worked with parents and groups such as the National PTA to ensure safety. The company also emphasizes the fact that parents are in full control of who their children are able to connect with. See also: Facebook may start using selfies to verify logins Microsoft to drop Facebook… [Continue Reading] -

UK and EU to expand Bitcoin regulation to combat money laundering and tax evasion
Publié: décembre 4, 2017, 12:24pm CET par Mark Wycislik-Wilson
Following concerns that Bitcoin and other cryptocurrencies are being used for not only tax evasion but also money laundering, governments in the UK and across Europe are planning to introduce new regulatory measures. One of the key proposals will bring to an end the anonymity Bitcoin users have enjoyed thus far. In an attempt to bring the digital currency with real-world currencies, the UK Treasury wants to force all traders to reveal their identities. See also: Sneaky websites continue to mine cryptocurrency even after you close them Bitcoin sets new price record above $11,000 Bitcoin mining and transactions use more… [Continue Reading] -

Privacy: Google updates Safe Browsing rules so apps must warn when they collect personal data
Publié: décembre 4, 2017, 11:36am CET par Mark Wycislik-Wilson
Google is introducing changes to its Safe Browsing policies, requiring Android apps to display their own privacy warning if they collect users' personal data. The company says that if app developers refuse to comply, Google will display a warning of its own. Developers have been given 60 days to comply with what is described as an expansion of Google's existing Unwanted Software Policy. Interestingly, it does not matter whether apps are featured in Google Play or they come via other marketplaces. Any apps that fail to display a custom privacy policy will find that their Play Store listing is slapped… [Continue Reading] -

Apple Support now offers tips, tricks and tutorials on YouTube
Publié: décembre 3, 2017, 11:03am CET par Mark Wycislik-Wilson
Apple's presence on YouTube is not exactly new, but the iPhone maker has not been the most prolific of posters. All this looks set to change as Apple is now pushing its dedicated channel. Video tutorials seems to be an obvious thing for Apple to offer on the massively popular video-sharing site, and it's something it has done to a small extent already. But now, with under 50,000 subscribers at the moment, Apple is ready to make fuller use of Google's platform to reach out to its userbase. See also: Apple SNAFU means updating to macOS 10.13.1 could reactive root… [Continue Reading] -

Apple SNAFU means updating to macOS 10.13.1 could reactivate root access bug
Publié: décembre 3, 2017, 10:29am CET par Mark Wycislik-Wilson
A few days ago, a serious security flaw with macOS High Sierra came to light. It was discovered that it was possible to log into the "root" account without entering a password, and -- although the company seemed to have been alerted to the issue a couple of weeks back -- praise was heaped on Apple for pushing a fix out of the door quickly. But calm those celebrations. It now transpires that the bug fix has a bug of its own. Upgrade to macOS 10.13.1 and you could well find that the patch is undone. Slow hand clap. See… [Continue Reading] -

UK government turns against Russian software
Publié: décembre 2, 2017, 4:13pm CET par Mark Wycislik-Wilson
There have been concerns about Russian security firm Kaspersky in the US for some time, and now these fears have spread across the Atlantic to the UK. The director of the UK National Cyber Security Centre (NCSC) has issued a warning that no Russian-made security software should be used on systems that could represent a national security threat if accessed by the Russian government. Ciaran Martin's warning comes after the US government banned the use of Kaspersky software on its computer systems, but the UK security director says that talks are underway with Kaspersky Lab with a view to setting… [Continue Reading] -

Has your iPhone started crashing in iOS 11.1.2? You're not alone... and there's a fix
Publié: décembre 2, 2017, 1:25pm CET par Mark Wycislik-Wilson
Today is December 2, and some iPhone users have found that their phones are constantly crashing. A problem with iOS 11.1.2 means that repeated crashes have been triggered by notifications from 12:15am this morning. Apple is not only aware of the problem, but has already issued an update that addresses the issue. Here's what you need to know. See also: Google faces class action lawsuit for gathering personal data from millions of iPhone users Authorities serve Apple with a warrant to access the Texas shooter's iPhone SE Security: macOS High Sierra bug lets you log in as 'root'... without a… [Continue Reading] -

Google reveals the biggest apps, games, movies, songs and books of 2017
Publié: décembre 1, 2017, 5:28pm CET par Mark Wycislik-Wilson
As we approach the start of a new year, the inevitable "best of" lists are starting to crop up. Never one to miss a trick, Google has released its own top five lists for 2017. The lists cover the US, and there are a few obvious names taking the top spots -- Super Mario Run is unsurprisingly shown to be the most popular game, while Rogue One: A Star Wars Story and It make appearance high in the movie and book charts respectively. But in addition to the top five new apps, new games, streamed songs, movies, TV shows and… [Continue Reading] -

Sneaky websites continue to mine cryptocurrency even after you close them
Publié: décembre 1, 2017, 5:12pm CET par Mark Wycislik-Wilson
With the massive rise in popularity -- and value -- of cryptocurrencies such as Bitcoin, it's little wonder that people are seeking out ever more imaginative and sneaky ways to mine coins without having to invest in dedicated hardware. Websites that mine for cryptocurrency in the background, making use of visitors' CPU time, are nothing new -- the Pirate Bay has been caught red-handed, for instance, using a Monero miner in the form of the Coinhive JavaScript Miner. But now researchers have discovered that some websites are using a drive-by mining technique that allows them to continue cryptomining even after… [Continue Reading] -

Privacy: UK government to tweak Snooper's Charter after conceding it is illegal in its current form
Publié: décembre 1, 2017, 11:46am CET par Mark Wycislik-Wilson
The highly controversial Snooper's Charter -- also known as the Investigatory Powers Act -- is, the government has been forced to admit, illegal under European law in its current form. The Brexit process may well be underway, but at the moment, the UK is still subject to EU law. As such, the government is making changes to the law. While the tweaks will not change the level of surveillance people are subjected to, they will restrict who has automatic access to that information. Last year the government was forced into trying to defend the indiscriminate gathering of data and making… [Continue Reading] -

Google bans most Android apps from displaying lockscreen ads
Publié: décembre 1, 2017, 11:02am CET par Mark Wycislik-Wilson
It is near impossible to avoid ads these days, but Google has just introduced a new policy that makes at least one area of your smartphone a safe haven. The new policy means that most apps will no longer be permitted to display ads on the lockscreen. But while this is something that will please Android users, it's not something that the company has really trumpeted. So what's with the "most" caveat? Google says that apps that happen to make use of the lockscreen to display information or provide access to features and settings of that app are not permitted… [Continue Reading] -

Google faces class action lawsuit for gathering personal data from millions of iPhone users
Publié: novembre 30, 2017, 11:36am CET par Mark Wycislik-Wilson
A group going by the name Google You Owe Us is taking Google to court in the UK, complaining that the company harvested personal data from 5.4 million iPhone users. The group is led by Richard Lloyd, director of consumer group Which?, and it alleges that Google bypassed privacy settings on iPhones between June 2011 and February 2012. The lawsuit seeks compensation for those affected by what is described as a "violation of trust." Google is accused of breaching UK data protection laws, and Lloyd says that this is "one of the biggest fights of my life." Even if the… [Continue Reading] -

Google launches Datally for Android, a tool to monitor and control mobile data usage
Publié: novembre 30, 2017, 9:41am CET par Mark Wycislik-Wilson
For many people -- particularly in certain parts of the world -- mobile data is an expensive commodity. If you're someone who likes to keep an eye on exactly what's using up all of your allowance -- and take control of it -- Google's new Android app, Datally, can help. Datally has been designed to not only reveal which apps are using up data, but to provide a way to rein it in. Formerly known as Triangle whilst in beta, the app lets you block background data usage on a per-app basis, and makesit much easier to access data-related settings.… [Continue Reading] -

Facebook may start using selfies to verify logins
Publié: novembre 29, 2017, 4:16pm CET par Mark Wycislik-Wilson
Some Facebook users have reported that the social network is asking them to upload a selfie as a means of verifying their identity. It seems that the company is testing out a new form of captcha as it asks that you "upload a photo of yourself that clearly shows your face." Just like Facebook's recent idea that users could protect themselves against revenge porn by uploading naked images of themselves, the test is likely to raise concerns about privacy. See also: Microsoft to drop Facebook login from Skype If you send nudes to Facebook for revenge porn protection, the photos… [Continue Reading] -

Microsoft Edge beta for Android gains password syncing and more
Publié: novembre 29, 2017, 3:58pm CET par Mark Wycislik-Wilson
Microsoft has just given mobile users a more compelling reason to use Edge as their web browser -- and heaven knows one was needed. The latest update to the mobile browser brings a genuinely useful feature: password syncing. The announcement that Edge was coming to Android and iOS came somewhat out of the blue, and now it seems that Microsoft is intent on making it a real contender for the mobile browsing crown. Password syncing is the headline addition to the browser, but it's not the only thing that's new. See also: Download Microsoft Edge preview for Android Microsoft Edge… [Continue Reading] -

Security: macOS High Sierra bug lets you log in as 'root'... without a password
Publié: novembre 29, 2017, 9:53am CET par Mark Wycislik-Wilson
If you thought that you needed a password to access a password-protected Mac, think again. A massive security hole has been discovered in macOS High Sierra that makes it possible to log in with admin rights without the need to provide a password. The problem appears to be specific to High Sierra, and the ease with which it is possible to gain unfettered access to a system has many people -- understandably -- concerned. Logging in with administrator rights requires little more than entering root as the username, and leaving the password field empty. It really is that simple. While… [Continue Reading] -

Privacy: a huge proportion of Android apps are secretly tracking you
Publié: novembre 28, 2017, 2:08pm CET par Mark Wycislik-Wilson
A joint research project between Yale University's Privacy Lab and French non-profit Exodus Privacy has uncovered widescale tracking in a large number of Android apps. The likes of Tinder, Spotify, Uber, Twitter and Snapchat -- as well as masses of lesser-known apps -- were found to be riddled with snooping components relating to no less than 25 well-known trackers. In all, around three quarters of apps were found to gather personal information about users via a variety of third-party tracking techniques. Researchers have published their findings online so Android users can check if their favorite apps are snooping on them.… [Continue Reading] -

Ok, Google, call Santa
Publié: novembre 28, 2017, 12:41pm CET par Mark Wycislik-Wilson
Christmas is now less than a month away, and if you have any kids in the house, it won't be long before excitement reaches fever pitch. Helping to keep the magic alive this year, Google is giving your children (or you) the chance to phone Santa. If you have a Google Home, Google Home Mini, or an Android phone with Google Assistant, you can use a voice command to call the fat, festive fellow and have a chat and a sing-song with him. There's very little to it. Just say "Ok, Google, phone Santa," and a call will be placed… [Continue Reading] -

Microsoft to drop Facebook login from Skype
Publié: novembre 28, 2017, 11:23am CET par Mark Wycislik-Wilson
Starting next year, it will no longer be possible to log into Skype using your Facebook account. Thanks to the rollout of the updated Skype experience, as of January 2018, Skype users will need to log in using their Microsoft account. This is not a change that is likely to affect regular users of Skype, but for anyone who rarely uses it, it is something of a pain. Microsoft has not said anything about why it is introducing the change -- it would seem to make sense to make it as easy as possible for someone to sign into their… [Continue Reading] -

Beta: Plex DVR strips out ads so you don't have to see them
Publié: novembre 28, 2017, 9:21am CET par Mark Wycislik-Wilson
Over recent months Plex has made numerous improvements to its DVR feature, but the latest one is likely to go down particularly well with users: ad-stripping. Cord cutters rejoice. Many DVRs include a feature that lets you quickly skip through the ads so you can spend more time enjoying your favorite show, but the latest update to Plex DVR makes things even easier. It simply removes the ads from your recordings. See also: Plex Live TV and DVR features arrive on Android and Apple TV Plex backtracks on controversial privacy policy change Official Plex for Kodi addon now available to… [Continue Reading] -

Oreo arrives on the OnePlus 5 through OxygenOS open beta
Publié: novembre 26, 2017, 1:24pm CET par Mark Wycislik-Wilson
The OnePlus 5T may have just rolled out, but the Chinese smartphone maker has not forgotten its older handsets. Having rolled out a beta version of Android Oreo to the OnePlus 3 and 3T, now the OnePlus 5 is getting the same treatment. Making good on the promise it made at the launch of the OnePlus 5T, the company has launch the first OxygenOS Oreo open beta for the OnePlus 5. It is available for anyone to download and install, and the full, stable release of Oreo is due early next year. See also: Download the Android Oreo beta for… [Continue Reading] -

Time to change your password: Imgur was hacked in 2014
Publié: novembre 26, 2017, 12:41pm CET par Mark Wycislik-Wilson
While much of the US was celebrating Thanksgiving, social image hosting site Imgur was made aware of a security breach that took place back in 2014. Around 1.7 million user accounts were affected. This is a relatively small percentage of Imgur users, and COO Roy Sehgal points out that the site has never asked for "personally-identifying information." Nevertheless, the company is contacting the owners of affected accounts, advising them to change their passwords. Hackers managed to steal email addresses and passwords. This might be a concern for anyone who reuses passwords across multiple services, but the data was hashed with… [Continue Reading] -

Twitter is working on a 'save for later' feature called, uninspiringly, Bookmarks
Publié: novembre 24, 2017, 11:48am CET par Mark Wycislik-Wilson
Twitter is one of the more divisive social media platforms out there, managing to attract passionate love and hate in just about equal measure. But even people who use and like Twitter freely admit that it has its problem, one of which is the lack of a bookmarking feature. There is the option to "like" tweets, but this can be an awkward way to save something you're interested in reading later. Recognizing that users need something rather more robust and useful, Twitter is working on a feature called Bookmarks. See also: Twitter outlines new verification policies and strips many right-wingers… [Continue Reading] -

UK broadband companies banned from advertising misleading top speeds
Publié: novembre 24, 2017, 11:21am CET par Mark Wycislik-Wilson
The advertising of broadband services has long been fraught with complaints and controversy, but a new rule change should help to bring this to an end. Following an investigation by the Advertising Standards Authority (ASA), ISPs will no longer be able to advertise high "up to" speeds. Instead they will have to advertise the average speed achieved by at least 50 percent of customers at peak times. Previously, the rules permitted the advertising of headline speeds enjoyed by just 10 percent of people, and the ASA found that many broadband customers were disappointed with their connection speed. The change came… [Continue Reading] -

Facebook is developing a tool to let users know if they interacted with Russian troll accounts
Publié: novembre 22, 2017, 6:29pm CET par Mark Wycislik-Wilson
Russia's use of Facebook and other social media to try to influence the outcome of elections around the world has been the subject of investigation for some time now. Millions of Facebook users were exposed to divisive ads placed by Russia, and the social networking site is doing what it can to be transparent about what happened. Having admitted that Russia bought ads on the site, Facebook is now developing a tool that will enable users to determine if they interacted with the Internet Research Agency -- the propaganda company also known as the Trolls from Olgino. See also: Facebook… [Continue Reading] -

UC Browser returns to Google Play after tweaks to its policy-infringing settings
Publié: novembre 22, 2017, 5:48pm CET par Mark Wycislik-Wilson
UC Browser was unceremoniously removed from Google Play last week after it was discovered that a setting within the app violated Google policies. Now the popular web browser is back with an updated version. The company behind the app is pleased to return its flagship title to the Play store, but also voices its delight that during UC Browser's brief absence, the cut-down UC Browser Mini proved fantastically popular. See also: UC Browser pulled from Google Play for shady activity UCWeb sheds more light on the disappearance of UC Browser from Google Play Adblock Plus tries to entice UC Browser… [Continue Reading] -

Privacy: Google caught tracking Android users' whereabouts even if location services are disabled
Publié: novembre 22, 2017, 5:06pm CET par Mark Wycislik-Wilson
For those concerned about their privacy, location services is just one more setting to disable on their phone. But Google has now revealed that it is not only able to, but actually does track the location of Android users even if location services are disabled. More than this, Google records the addresses of nearby cell towers -- thereby giving a very good idea of location -- even when there is no SIM card in a phone and no apps are used. This data has been collected since the beginning of the year. See also: Privacy: Use of session replay scripts… [Continue Reading] -

Intel firmware contains serious Management Engine vulnerabilities, affecting millions of systems
Publié: novembre 22, 2017, 11:52am CET par Mark Wycislik-Wilson
Security researchers have discovered critical issues with the hidden firmware used in some Intel chips. Security firm Positive Technologies discovered a series of serious vulnerabilities in Intel's Management Engine (ME), Server Platform Services (SPS) and Trusted Execution Engine (TXE). The security flaw could allow an attacker to run code that would be invisible to the operating system, opening up the possibility of invisible rootkit or malware infections, as well as the risk of exposing valuable data. The problem is believed to affect millions of computers and servers. Maxim Goryachy and Mark Ermolov from Positive Technologies made the discovery in the… [Continue Reading] -

Privacy: Use of session replay scripts means many websites essentially have built in keyloggers
Publié: novembre 21, 2017, 2:03pm CET par Mark Wycislik-Wilson
The idea that what you do online is not a secret is something that we have all -- just about -- come to terms with. That said, most people still expect a modicum of privacy, and they certainly don’t expect literally every keystroke they type to be logged by the websites they visit. But, say researchers at Princeton University, this is exactly what is happening. Hundreds of the most popular websites are using "session replay scripts" that record every single thing a visitor does. They are designed to monitor how visitors interact with a site to help gather information that… [Continue Reading] -

DoJ seeks to block Time Warner/AT&T merger
Publié: novembre 21, 2017, 12:00pm CET par Mark Wycislik-Wilson
The Department of Justice has filed a lawsuit as it tries to block the acquisition of Time Warner by AT&T. The DoJ says that the merger would cause bills to rise and stifle choice for consumers. There is concern about the level of control such a merger would give the company over programming and distribution, but AT&T says that it will fight the lawsuit, saying that there is no reason for the merger to be blocked. If it was to go ahead, the merger would involve one of the largest transactions in US history -- $108 billion. But the lawsuit… [Continue Reading] -

$31 million in tokens stolen from dollar-pegged cryptocurrency Tether
Publié: novembre 21, 2017, 10:47am CET par Mark Wycislik-Wilson
All eyes may be on the meteoric rise of Bitcoin at the moment, but it's far from being the only cryptocurrency on the block. Startup Tether issued a critical announcement after it was discovered that "malicious action by an external attacker" had led to the theft of nearly $31 million worth of tokens. Tether is a dollar-pegged cryptocurrency formerly known as Realcoin, and it says that $30,950,010 was stolen from a treasury wallet. The company says it is doing what it can to ensure exchanges do not process these tokens, including temporarily suspending its backend wallet service. Tether knows the… [Continue Reading] -

Privacy: Germany bans kids' 'spying' smartwatches
Publié: novembre 19, 2017, 12:57pm CET par Mark Wycislik-Wilson
Regulators in Germany have introduced a ban on children's smartwatches citing privacy concerns. Telecoms regulator the Federal Network Agency (FNA) describes the wearables as "spying devices" and advises parents to destroy them. The FNA said that parents had been using such smartwatches to listen in on their children at school, and warned teachers to be on the lookout for them. But a lack of regulation of the devices means that many have poor security, meaning they could be used by others to spy on wearers. This is not the first time German regulators have stepped into ban privacy-invading devices. An… [Continue Reading] -

Voice-activated Siri could be coming to iMac Pro thanks to A10 Fusion chip
Publié: novembre 19, 2017, 9:33am CET par Mark Wycislik-Wilson
It seems as though Apple's upcoming iMac Pro will feature an A10 Fusion chip as a co-processor. The inclusion of the chip -- the same one used in the iPhone 7 -- has led to speculation that "Hey, Siri" support could be making its way to macOS. A couple of developers cracked open Apple's BridgeOS 2.0 software package, and the code shows that the chip appears to be used to handle security and the boot process. But it's the prospect of always-on "Hey, Siri" support that will interest many people. See also: No HomePod for Christmas as Apple delays launch… [Continue Reading] -

Windows 8 onwards incorrectly implements ASLR security feature, but you can fix it
Publié: novembre 18, 2017, 2:46pm CET par Mark Wycislik-Wilson
Since Vista, Windows has included a security feature known as ASLR. Address Space Layout Randomization uses a random memory address to execute code, but in Windows 8, Windows 8.1 and Windows 10 the feature is not always applied properly. A security analyst discovered that in the last three versions of Windows, ASLR was in fact not using random memory addresses, essentially rendering it useless. The good news is that there is a fix -- but you will have to apply it manually. The idea behind ASLR is that by executing code in random locations, it helps to protect against exploits… [Continue Reading] -

No HomePod for Christmas as Apple delays launch of smart speaker until 2018
Publié: novembre 18, 2017, 9:58am CET par Mark Wycislik-Wilson
The launch of the eagerly anticipated Apple HomePod has been delayed until next year. The iPhone maker had planned to release its answer to Google Home and Amazon Echo in December, but now admits that more development is needed. The delay means that anyone hoping to get a HomePod for Christmas is going to be disappointed. Apple has not elaborated on the exact cause of the delay, but with a "premium" price tag of $350 -- and this being a product coming from the Apple stable -- customers are not going to be happy with something that is less than… [Continue Reading] -

Adblock Plus tries to entice UC Browser users to Adblock Browser
Publié: novembre 17, 2017, 6:14pm CET par Mark Wycislik-Wilson
Adblock Plus is using the disappearance of the popular Android app UC Browser from Google Play to promote its own mobile web browser. An open letter to people looking for the currently-unavailable UC Browser calls on mobile web users to give Adblock Browser a try. The privacy-focused browser includes, obviously, an adblocker and, as Adblock Plus cheekily points out, "we haven't been kicked out of the store." See also: UCWeb sheds more light on the disappearance of UC Browser from Google Play UC Browser pulled from Google Play for shady activity Adblock Browser 2.0 for iOS adds Ghost Mode for… [Continue Reading] -

UCWeb sheds more light on the disappearance of UC Browser from Google Play
Publié: novembre 17, 2017, 12:57pm CET par Mark Wycislik-Wilson
The Android web browser UC Browser disappeared from Google Play recently, and there has been great speculation about just what caused the app to be pulled. Now the company behind it has spoken out, giving a little more detail about what has happened. While it was previously thought that "misleading and unhealthy methods of promotion" were to blame, it turns out that a setting within the app was problematic. See also: UC Browser pulled from Google Play for shady activity Despite an email sent out to partners of the UC Browser maker -- which made reference to "malicious promotion" --… [Continue Reading] -

LastPass is working with Google to ensure its Android app is not delisted
Publié: novembre 17, 2017, 11:38am CET par Mark Wycislik-Wilson
Google recently announced that it was going to take action against apps that misuse its Accessibility Services API. There are a number of big-name apps that make use of this API, including the likes of LastPass and Tasker. Users of the password management tool were concerned to hear that their favorite app could be affected. But the company has spoken out to say that it is working with Google, and there will be "no immediate impact" to its users. See also: Google clamps down on apps that misuse accessibility API -- and it could affect your favorite apps Another password… [Continue Reading] -

Microsoft starts charging for its beta exam program
Publié: novembre 17, 2017, 10:10am CET par Mark Wycislik-Wilson
It's always great when something is free, but there is the danger that it becomes undervalued. That's precisely what seems to have happened with Microsoft's beta exam program, so the company has decided to start charging candidates to sit exams. This is not so much about using the exams as a way of filling Microsoft's coffers, but more about trying to ensure that people who want to take the exams are able to. The Windows-maker says that there have been many instances of no-shows, and this is depriving others of a seat. Microsoft says that there are always high levels… [Continue Reading] -

Twitter outlines new verification policies and strips many right-wingers of their blue tick
Publié: novembre 16, 2017, 11:20am CET par Mark Wycislik-Wilson
After awarding the coveted blue tick of verification to a white supremacist, Twitter recently announced that it would be pausing its verification program. Making good on this promise, Twitter says that it is not only no longer accepting public requests for accounts to be verified, it is also introducing new guidelines, and removing the verification tick from accounts that do not make the grade. This means that white nationalist Richard Spencer, far-righter Laura Loomer, English Defence League founder Tommy Robinson and others no longer have a blue tick next to their names. While Twitter is promoting this clamp down as… [Continue Reading] -

Google teams up with Ticketmaster to offer concert tickets through YouTube
Publié: novembre 16, 2017, 9:38am CET par Mark Wycislik-Wilson
YouTube is -- of course -- about video, but it is becoming more than that. Google has just announced that it is teaming up with Ticketmaster, giving people the opportunity to learn about concert dates and buy concert tickets while watching artists' videos. For now, the feature is limited to the US, but there are plans to roll it out on a wider scale. With YouTube increasingly used as a marketing tool by musicians, the progression to using it as a ticket outlet is hardly surprising -- but it's not clear what sort of cut Google is planning to take,… [Continue Reading] -

UC Browser pulled from Google Play for shady activity
Publié: novembre 16, 2017, 9:16am CET par Mark Wycislik-Wilson
UC Browser -- the Android web browser with more than half a billion downloads to its name, and which has proved particularly popular in India -- has been pulled from Google Play. In addition to download from the Play Store, the browser came preinstalled on a number of handsets, and it gained popularity thanks to its speedy performance and low system requirements. But the fact that it "used "Misleading" and "Unhealthy" methods of promotion" led to it being nixed. There was some debate on Reddit about just why the app had been pulled from Google Play. Artem Russakovskii from Android… [Continue Reading] -

Preinstalled EngineerMode app on OnePlus phones gives root access without unlocking the bootloader
Publié: novembre 14, 2017, 2:36pm CET par Mark Wycislik-Wilson
Rooting Android phones is fairly common these days, and it opens up the possibility of doing things that would not otherwise be an option. But if you are rooting your phone, you want it to be you who is in charge of the process. If you have a OnePlus phone, you may be interested -- and a little disturbed -- to learn that the company is preinstalling an app that acts as a backdoor to root access. The app is called EngineerMode and it is preinstalled on the OnePlus 3, 3T and 5. It is possible to exploit the app… [Continue Reading] -

Xbox One digital game gifting now available to everyone
Publié: novembre 14, 2017, 12:24pm CET par Mark Wycislik-Wilson
Buying an Xbox One game as a gift for Christmas, birthday, or other occasion no longer means having to hit the stores, or buy a gift card. Microsoft has now opened up digital game gifting to everyone. While this is not a completely new option, it was previously only possible to send games to people via Xbox Live. Now you can buy a digital game for a friend or family member, and send it to them via email. This method of gifting has been tested out through the Xbox Insider Program, and now Microsoft is ready to make it available… [Continue Reading] -

Microsoft announces Skype Professional Account Preview
Publié: novembre 14, 2017, 11:28am CET par Mark Wycislik-Wilson
Microsoft has announced the upcoming release of a Skype Professional Account desktop client. Due to launch in the US as a preview very soon, this is a business-focused build of Skype that offers a host of extra features. This includes the ability to book meeting, make notes and take payments, all from the comfort of a chat client. The aim is to reduce the number of tools and services anyone conducting a business online needs to use. For anyone who is already using Skype, Microsoft says that it will be very simple to port across a list of contacts. The… [Continue Reading] -

Teledildonics sex toy maker blames software bug for recording its customers' vibrator sessions
Publié: novembre 14, 2017, 10:36am CET par Mark Wycislik-Wilson
Teledildonics (remote sex) company Lovense has apologized for what it describes as a "minor bug" that resulted in audio recordings being made by an app used to control a sex toy. The Lovense Remote app allows for remote control of a paired vibrator via a smartphone, but users discovered that lengthy audio recordings of their sessions were also being made. The Hong Kong-based company insists that the audio recordings never leave the device and are automatically deleted, but users are concerned nevertheless. A user on Reddit called tydoctor was one of the first to bring the matter to light, saying:… [Continue Reading] -

Android 8.1 Oreo will free up space by shrinking apps you don't use
Publié: novembre 13, 2017, 9:15pm CET par Mark Wycislik-Wilson
We all have apps installed on our phones that we simply don't use. It might be that they once served a purpose that they no longer fulfil, and we just haven't got around to uninstalling, or it might be that we've downloaded an app, tried it once, and then forgotten about it. These unused apps are, essentially, just wasting space, and now Google is doing something about it. With Android 8.1 Oreo, when a device is running low on space, an automatic cleanup process will tidy after these unused apps. See also: Google clamps down on apps that misuse accessibility… [Continue Reading] -

Google clamps down on apps that misuse accessibility API -- and it could affect your favorite apps
Publié: novembre 13, 2017, 7:13pm CET par Mark Wycislik-Wilson
Google is launching a crackdown on apps that misuse Accessibility Services, threatening to remove them from the Play Store. The API was created specifically to help users with various disabilities, but developers have latched onto it as a way of increasing the functionality of their apps. The likes of Tasker, LastPass and Universal Copy are among the titles that make use of the Accessibility Services API, and they have been warned to either explain why they are using the API, stop using the API, or unpublish their app. Google has emailed a number of developers, telling them that they must… [Continue Reading] -

Microsoft's Black Friday deals could save you a bundle on Surface and Xbox devices
Publié: novembre 13, 2017, 6:09pm CET par Mark Wycislik-Wilson
It may be more than a week until Black Friday, but the big-name companies are already releasing details of the money-saving deals that will be available. Microsoft is one such company, and today it has revealed price cuts for Surface devices, the Xbox One S, Windows Mixed Reality headsets, and more. As well as offering savings of $329 off the Surface Pro i5 256GB, Microsoft also shares information about savings available from its partners -- including up to $300 off Windows 10 laptops. If you've been considering a Windows Mixed Reality headset but have been put off by the price,… [Continue Reading] -

US government uses Texas shooter's iPhone to support its case for encryption backdoors
Publié: novembre 12, 2017, 4:01pm CET par Mark Wycislik-Wilson
The inability of law enforcement agencies to access encrypted data stored on smartphones is a relatively new one, but it's one that really came into the spotlight with the San Bernardino shooting latest year. With the recent shooting in Texas, the US government is talking about the issue once again. We've already learned that the FBI has been unable to access data stored on the shooter's phone due to the fact that it's encrypted. We also know that Apple has been in contact with the FBI to offer help -- despite having previously said there was no way it could… [Continue Reading] -

iPhone X is unresponsive in the cold and has a green line screen problem
Publié: novembre 12, 2017, 3:20pm CET par Mark Wycislik-Wilson
Just days after the launch of the iPhone X, problems are starting to emerge with Apple's latest handset. Users are reporting various issues with the screen including the fact that it becomes unresponsive in cold conditions. On top of this, other iPhone X users have found that the screen suffers with a green line appearing at the side of the display. These reports are in addition to Apple's own warnings of the OLED-centric screen burn-in problems, and in spite of the fact that the iPhone X has been found to have the best display of any smartphone. See also: The… [Continue Reading] -

Leaked: Here is the OnePlus 5T
Publié: novembre 11, 2017, 5:21pm CET par Mark Wycislik-Wilson
As is often the case -- whether planned or not -- details of upcoming handsets frequently leak out. Things are no different with OnePlus phones; in fact, it's one of the leakiest companies out there. With the launch of the OnePlus 5T in just a few days, it should come as little surprise that leaks mean we now know just about everything there is to know about the smartphone. Not exactly a million miles removed from the OnePlus 5, the 5T's full specs have been leaked, complete with photographs and a detailed reviewers' guide. The major news is that the… [Continue Reading] -

Twitter pauses verification program after giving white supremacist the coveted blue tick
Publié: novembre 11, 2017, 4:26pm CET par Mark Wycislik-Wilson
Head of Twitter, Jack Dorsey, has admitted that the company's verification system is "broken" after a blue tick was awarded to white supremacist Jason Kessler. There was a backlash this week after Kessler -- who helped to arrange the Unite the Right rally in Charlottesville earlier in the year -- had his Twitter account verified. Responding to the negative reaction this prompted, Twitter announced that its verification program has been paused. The company also said that the verification tick had been largely misinterpreted by people. See also: Twitter more than doubles the length of user display names Twitter lets everyone… [Continue Reading] -

WikiLeaks: CIA source code leak shows agency impersonating Kaspersky
Publié: novembre 10, 2017, 12:57pm CET par Mark Wycislik-Wilson
Following on from its Vault 7 series of leaks relating to CIA hacking tools, WikiLeaks has kicked off a new series -- Vault 8. The purpose of this latest series is to reveal the source code of previously exposed hacking and surveillance tools, and the first release relates to Hive. The tool itself is interesting enough, serving as backbone to the CIA's malware operations, but there's more. What's intriguing about the first leak in the Vault 8 series is that it seems to show the agency impersonating Kaspersky, by making use of a fake certificate for the anti-virus company. See… [Continue Reading] -

Facebook explains its creepy-sounding anti-revenge porn plan
Publié: novembre 10, 2017, 11:34am CET par Mark Wycislik-Wilson
Facebook has revealed more details about how its test program for combating revenge porn works. The social network has been trialing a system which allows users to upload naked images of themselves to Facebook so the company can look out for and block others from sharing them. People were rather shocked at this idea, but even more so when it transpired that the uploaded nudes would be reviewed by Facebook employees. Keen to calm the storm that has whipped up around the issue, Facebook's global head of safety, Antigone Davis, has penned a blog post explaining that "we want to… [Continue Reading] -

Twitter more than doubles the length of user display names
Publié: novembre 10, 2017, 9:07am CET par Mark Wycislik-Wilson
Signing up for any service meaning facing the username battle. There are two obstacles: is your still username available, and does it meet the necessary requirements. With Twitter, getting an @YourName handle is tricky because there are simply so many users (and bots), but there has long been a highly restrictive limit on the length of names -- just 15 characters. Twitter has long offered something of a compromise in allowing display names that are slightly longer -- but only up to 20 characters. Now, the company has announced that there are now more than twice as many characters to… [Continue Reading] -

Microsoft brings Windows Defender Advanced Threat Protection to macOS, Linux, iOS, and Android
Publié: novembre 9, 2017, 3:47pm CET par Mark Wycislik-Wilson
Microsoft has announced that it is teaming up with Bitdefender, Lookout, and Ziften to expand the reach of Windows Defender Advanced Threat Protection (ATP). By partnering with the three major security firms, Microsoft is set to bring ATP to macOS, Linux, iOS, and Android devices. Bitdefender, Lookout, and Ziften will all feed threat detection information into one central resource, and this can then be used by security teams to keep an eye on all threats in a single location. While a trio of partnerships has just been announced, Microsoft says that this is just the start. There will be more… [Continue Reading] -

Apple has already contacted the FBI with help to access the Texas shooter's phone
Publié: novembre 9, 2017, 1:20pm CET par Mark Wycislik-Wilson
Following the shooting at the weekend in a Texan church, the FBI revealed that it was unable to access the encrypted phone belonging to the gunman, Devin Patrick Kelley. While the FBI said that it did not want to reveal any specific details of the phone, it was widely believed to be an iPhone -- and now Apple has revealed that it has already been in contact with the agency. The iPhone-maker says that it got in touch with the FBI "immediately" to offer help in accessing the gunman's phone. See also: FBI can't access data on Texas shooter's encrypted… [Continue Reading] -

Apple expands its Everyone Can Code initiative around the world
Publié: novembre 9, 2017, 12:00pm CET par Mark Wycislik-Wilson
Originally limited to just the US, Apple's "Everyone Can Code" initiative has now been opened up to over 20 universities and colleges around the world. The expansion takes the coding curriculum to Australia's RMIT, Plymouth University in the UK and many other establishments. The aim is to give people the chance to learn how to code, using the App Development with Swift curriculum for online and on-campus courses. The year-long course serves as an introduction to coding, and is open to students of all levels of ability. The Everyone Can Code initiative was launched earlier in the year, spreading to… [Continue Reading] -

If you send nudes to Facebook for revenge porn protection, the photos will be checked by humans
Publié: novembre 9, 2017, 10:28am CET par Mark Wycislik-Wilson
Facebook caused more than a little eye-rolling with its anti-revenge porn program which requires users to upload the naked images of themselves that they would like to protect. It had been assumed that the entire process would be automated, making use purely of algorithms to analyze images and protect privacy. This assumption was wrong. Facebook says that in actual fact an employee -- an actual human being -- will have to review the nude images that are sent in. See also: Facebook: send nudes and we'll protect you against revenge porn Transparency: Facebook to force political ads to disclose funding… [Continue Reading] -

FBI can't access data on Texas shooter's encrypted phone
Publié: novembre 8, 2017, 7:21pm CET par Mark Wycislik-Wilson
With echoes of the San Bernardino shooting from a couple of years ago, the FBI has revealed that it is unable to break the encryption on the phone belonging to Devin Patrick Kelley, the gunman who killed 26 people in Texas at the weekend. The agency has not said what make or model of phone they are not able to access, and this is information that will not be revealed -- and for very good reason, says the FBI. Despite the agency's desire for secrecy, there is strong speculation that the device is an iPhone. See also: FBI won't have… [Continue Reading] -

Facebook: send nudes and we'll protect you against revenge porn
Publié: novembre 8, 2017, 6:00pm CET par Mark Wycislik-Wilson
Revenge porn is one of the latest online problems, and it's one to which it would seem difficult to come up with a solution. Facebook, however, thinks it has the answer. If you're willing to share your nude photos with the social network, it will use them to protect you against revenge porn attacks. It's an idea that sounds like utter madness, but Facebook is at pains to convince users that it's actually a brilliant solution. Compromising images that are shared with Facebook will be hashed to create a digital fingerprint which the company can then use to identify the… [Continue Reading] -

Twitter lets everyone send 280-character tweets -- and infuriates with maddening circle icon
Publié: novembre 8, 2017, 11:54am CET par Mark Wycislik-Wilson
After a few weeks of testing with a limited number of users, Twitter is rolling out 280-character tweets to (nearly) everyone -- but says that very few of the testers reached this limit. With the 140-character limit, says Twitter, just 9 percent of tweets hit the upper limit; with 280 characters to play with, this drops to 1 percent. The increase has divided opinion on Twitter, but the company's decision to replace the simple character countdown -- to warn how much more you could type -- with a bizarre circular icon has been given a rather negative reception. See also:… [Continue Reading] -

Google adds restaurant wait times to Search and Maps
Publié: novembre 7, 2017, 5:05pm CET par Mark Wycislik-Wilson
Search for a restaurant using Google, and you're already told the times of day at which a particular place is busiest. But Google is about to make this information even more useful. The fact that a restaurant is busy at 3PM on a Thursday afternoon doesn't necessarily mean you'll have to wait ages for service -- there may be more staff working, for instance. A new update to Google Search -- and Maps is to follow -- means you'll be able to see estimated wait times as well. See also: Android users, you may soon be able to buy audiobooks… [Continue Reading] -

Twitter blames a failure to take context into account for its block on LGBTQ searches
Publié: novembre 7, 2017, 4:05pm CET par Mark Wycislik-Wilson
Over the weekend, users noticed that a number of search terms -- such as bisexual -- appeared to be blocked on Twitter. Having said "we've identified an error with search results for certain terms. We apologize for this. We’re working quickly to resolve & will update soon," Twitter has finally explained what happened. Perhaps predictably there's -- assuming you believe Twitter -- nothing sinister going on. Instead, the company's latest policy changes, which took extra measures to block sexual content, meant that its automated systems were being rather heavy-handed in censoring certain content, completely failing to take context into consideration.… [Continue Reading] -

The iPhone X has the best display of any smartphone
Publié: novembre 7, 2017, 2:29pm CET par Mark Wycislik-Wilson
DisplayMate -- the display calibration and benchmarking firm -- has put the iPhone X through its paces and has come to the conclusion that it has the best smartphone display ever. This is an accolade that DisplayMate handed to the Samsung Galaxy S8 back in April, and with the iPhone X display having been supplied by Samsung, the new award is perhaps not a surprise. While there have been some minor concerns about Apple's switch to an OLED panel, the move has definitely paid off. Apple is praised for the careful calibration it has put into the iPhone X's screen,… [Continue Reading] -

EFF: Twitter users have a First Amendment right not to be blocked by President Trump
Publié: novembre 7, 2017, 12:13pm CET par Mark Wycislik-Wilson
The Electronic Frontier Foundation has told a court that Donald Trump's blocking of users who criticize him on Twitter is a violation of their First Amendment rights. The digital rights group says that people have a "constitutional right to receive government messages transmitted through social media and participate in the forums created by them." The EFF argues that Trump's use of Twitter has become a hallmark of his presidency, and by blocking individuals he is denying them access to the policy details and other information he frequently disseminates through tweets. See also: EFF criticizes iOS 11's 'misleading' Bluetooth and Wi-Fi… [Continue Reading] -

Paradise Papers: details of Apple's tax arrangements revealed in leaked documents
Publié: novembre 6, 2017, 8:06pm CET par Mark Wycislik-Wilson
The Paradise Papers -- a massive cache of documents leaked to newspapers and journalists -- reveal the tax avoidance strategies used by millionaires, billionaires and businesses around the world. The leaks comprise over 13 million documents, and it shows the financial structure and offshore accounts for many big-name companies. Included in the list is Apple -- a company already known to have taken advantage of the "double Irish" tax loophole in Ireland to massively reduce its tax bill. The Paradise Papers show that Apple made use of another tax haven after it faced criticism for its exploitation of Irish taxes… [Continue Reading] -

OnePlus 5T launches in Brooklyn on November 16 -- and you can be there
Publié: novembre 6, 2017, 6:53pm CET par Mark Wycislik-Wilson
Just a few days ago it was confirmed that the upcoming OnePlus 5T will have a 3.5mm headphone jack. Rumors and leaks have already given a hint of the specs and a release date, but there has been very little official news from OnePlus. Until now. The phone maker has announced that the OnePlus 5T will be unveiled next week at an event in Brooklyn, New York. The event -- dubbed "A New View" -- will take place at 11:00AM EST (4:00PM GMT / 5:00PM CET) on November 16 and can also be viewed online. In a couple of days,… [Continue Reading] -

Amazon applies its own discounts to third-party sellers
Publié: novembre 6, 2017, 2:56pm CET par Mark Wycislik-Wilson
Amazon is gearing up for Thanksgiving and Christmas with a new discount scheme. The online retailer has introduced a new "Discount provided by Amazon" tag, discounting independent merchants' prices -- at its own cost -- by up to 9 percent. This is the first time Amazon has taken control of third party pricing, and in shouldering the cost itself the company is helping to ensure competitive pricing across the board, keeping customers on the site. The move sees Amazon effectively price matching the likes of Walmart and other retailers, without requiring merchants to take a hit on their own profits.… [Continue Reading] -

Weird iOS 11.1 bug autocorrects i to A -- here's how to fix it
Publié: novembre 6, 2017, 12:21pm CET par Mark Wycislik-Wilson
If you've updated your iPhone or iPad to iOS 11.1, you may well have encountered a strange autocorrect bug. Type an "i" and it could well be replaced by an uppercase A followed by a symbol. Apple is aware of the peculiar bug and is working on a patch. Until this is released, the company is suggesting a workaround. The predictive text issue has been spotted in iMessage, Instagram, Twitter and other apps, but it does not seem to be affecting everyone who is running iOS 11.1. There's no word on exactly when a patch will be issued, but there… [Continue Reading] -

Twitter pledges to fix 'error' that hides bisexual search results
Publié: novembre 6, 2017, 10:51am CET par Mark Wycislik-Wilson
Twitter faced criticism over the weekend after it was discovered that the search term "bisexual" appeared to have been blocked. Users noticed that searching for the word returned no news or photo results, leading to claims of censorship and discrimination. The company refers to the issue as "an error with search results for certain terms" and is "working quickly to resolve" it. See also: Twitter clarifies rules about abuse, violence, adult content -- promises a further update on November 22 Twitter shares timetable for tackling abuse transparently between now and January Leaked email: Twitter introduces yet more rules in latest… [Continue Reading] -

Apple warns of iPhone X screen burn-in problems
Publié: novembre 6, 2017, 10:07am CET par Mark Wycislik-Wilson
The iPhone X launched to much excitement last week, and Apple's latest handset has received glowing reviews. But the company has issued a warning about the Super Retina display -- despite describing it as the "best OLED display that has ever shipped in a smartphone." Just like Google's Pixel 2 XL, Apple warns that the iPhone X could suffer from "burn-in" issues. The company also refers to "slight visual changes" such as "image persistence" that may follow extended long-term use -- but offers up a few tips to minimize the problems. See also: iPhone X launches to lengthy queues as… [Continue Reading] -

T-Mobile and Sprint kill merger talks
Publié: novembre 5, 2017, 12:08pm CET par Mark Wycislik-Wilson
After weeks of rumors and speculation about a possible merger between T-Mobile and Sprint, the two companies have spoken out and said their discussions have amounted to nothing. In joint statements, the telecoms firms announced that merger talks have come to an end. The companies were "unable to find mutually agreeable terms," and the decision has been made to "put an end to the extensive speculation around a transaction." President and CEO of Sprint, Marcelo Claure, said: "While we couldn't reach an agreement to combine our companies, we certainly recognize the benefits of scale through a potential combination. However, we… [Continue Reading] -

Broadcom may buy Qualcomm for $100 billion
Publié: novembre 4, 2017, 10:32am CET par Mark Wycislik-Wilson
Broadcom could be on the verge of carrying out the biggest technology acquisition in history. The chipmaker is said to be planning a $100 billion bid for smartphone chip supplier Qualcomm. It is possible that the bid could be even higher. While the deal has not been officially announced, people familiar with the matter say the offer could be just days away. If Broadcom does go ahead with the purchase of Qualcomm, it would create a $200 billion company. Neither company is speaking out about the potential deal at the moment, but the acquisition would create a wireless chip powerhouse… [Continue Reading] -

TorMoil flaw leaks IP addresses of Mac and Linux Tor users
Publié: novembre 4, 2017, 10:01am CET par Mark Wycislik-Wilson
If you're using Tor, you're almost certainly doing so because you're looking for privacy and anonymity. But a newly discovered critical vulnerability has been discovered in the Mac and Linux versions of the browser that means IP addresses may be leaked. The bug was discovered by security firm We Are Segment and was reported to Tor. While a proper patch is yet to be created, a fix has been released, and Tor users are strongly advised to install it. The problem was reported to the Tor Project on October 26 by We Are Segment CEO Filippo Cavallarin. The firm explains:… [Continue Reading] -

Twitter clarifies rules about abuse, violence, adult content -- promises a further update on November 22
Publié: novembre 3, 2017, 5:00pm CET par Mark Wycislik-Wilson
Twitter seems to be fighting something of a losing battle against abuse on its platform, as well as failing to successfully clamp down on all manner of content that supposedly violates its terms of use. In its latest attempt to get things sorted, the company has -- once again -- updated its rules. The company's latest changes specifically take in the issues of abusive behavior, self-harm, spam, graphic violence and adult content. The announcement is in keeping with Twitter's recently announced timetable for tackling abuse, as is the promise that further changes will be revealed on November 22. See also:… [Continue Reading] -

iPhone X launches to lengthy queues as Apple shares hit a record high
Publié: novembre 3, 2017, 1:18pm CET par Mark Wycislik-Wilson
The day that millions of people have been waiting for has finally arrived: it's iPhone X launch day. Around the world, thousands of hopeful shoppers queued up to get their hands on the latest handset. And there was double cause for Apple to celebrate. The lengthy lines put pay to suggestions that there was little interest in the iPhone X, and the company also announced its fourth quarter earnings. The news was so good, Apple's shares soared to a record high in after-hours trading. See also: Privacy: 'Bottom feeders' could exploit the access Apple gives developers to iPhone X facial… [Continue Reading] -

Android users, you may soon be able to buy audiobooks from Google Play
Publié: novembre 3, 2017, 11:36am CET par Mark Wycislik-Wilson
An APK teardown of version 8.4 of the Google Play Store app shows that there could be some exciting changes on the horizon for Android users. Perhaps the most interesting revelation is that Google appears to be on the verge of introducing audiobooks to the store. This means that you may soon be able to ditch the likes of Audible and buy your audiobooks direct from Google -- and there could also be free audiobooks! The teardown also shows that there are new notification and app update options to come as well. See also: Google Issue Tracker bug database found… [Continue Reading] -

The OnePlus 5T definitely has a headphone jack
Publié: novembre 2, 2017, 4:49pm CET par Mark Wycislik-Wilson
While there have -- as ever -- been endless rumors about the next handset from OnePlus, there has been very little concrete news from the company about the OnePlus 5T. Today that changes. OnePlus has made numerous allusions to the successor to the OnePlus 5 -- including tweeting pictures of five cups of tea -- but now chief executive Pete Lau has officially spoken about the upcoming handset. He confirms that there is definitely a 3.5mm headphone jack. See also: Pre-order page leaks OnePlus 5T specs, price and release date Tweak and hack OxygenOS on your OnePlus phone with JOnePlus… [Continue Reading] -

Google Issue Tracker bug database found to have its own security vulnerability
Publié: novembre 2, 2017, 3:23pm CET par Mark Wycislik-Wilson
Google's bug-tracking database -- the Google Issue Tracker which is known as the Buganizer System within the company itself -- had its own security holes which left it vulnerable to hackers. Researcher Alex Birsan was able to exploit vulnerabilities so he could gain wider access to Google's database than he should have been able to. The trick was a simple matter of fooling the system into letting him register a @google.com email address that would ordinarily be reserved for Google employees. See also: Google launches Poly, a 3D object and scene library for AR and VR creators Google announces Fast… [Continue Reading] -

WordPress users advised to update to version 4.8.3 following discovery of SQL injection vulnerability
Publié: novembre 2, 2017, 1:34pm CET par Mark Wycislik-Wilson
Anyone running a website powered by WordPress is being told to upgrade to version 4.8.3 immediately after the discovery of a serious security issue. The problem -- an SQL injection vulnerability -- affects millions of websites running WordPress 4.8.2 and older. In addition to installing the latest update, site owners are advised to update plugins that could be exploited. The vulnerability was discovered by Anthony Ferrara from Lingo Live who broke the news by saying: "Before reading further, if you haven’t updated yet stop right now and update." The SQL injection bug was supposedly fixed by WordPress 4.8.2 last month,… [Continue Reading] -

LastPass reveals the threats posed by passwords in the workplace
Publié: novembre 1, 2017, 2:31pm CET par Mark Wycislik-Wilson
Passwords are fundamental to modern life, both at home and at work. In the workplace, the security of passwords is paramount, and ensuring that employees are taking matters seriously is an important part of safeguarding any business. A new report by LastPass -- The Password Exposé -- reveals the threats posed, and the opportunities presented, by employee passwords. The report starts by pointing out that while nearly everyone (91 percent) knows that it is dangerous to reuse passwords -- with 81 percent of data breaches attributable to "weak, reused, or stolen passwords", more than half (61 percent) do reuse passwords.… [Continue Reading] -

Apple releases macOS 10.13.1 and iOS 11.1 to add new emoji and patch KRACK... for some
Publié: novembre 1, 2017, 11:23am CET par Mark Wycislik-Wilson
Apple has pushed out the latest updates to macOS High Sierra and iOS. macOS 10.13.1 and iOS 11.1 include a range of bug fixes, and also herald the arrival of a new batch of emoji. The two relatively minor updates also address the recently-discovered KRACK security vulnerability. But while the WPA2 patch will be welcomed by many people, it is not available for all iPhones and iPads, meaning that large numbers of people will be left exposed. See also: Apple unveils new emoji coming in iOS 11.1 KRACK warning: Severe WPA2 security vulnerability leaves millions of devices open to attack… [Continue Reading] -

Google announces Fast Pair to speed up Bluetooth pairing for Android
Publié: novembre 1, 2017, 9:46am CET par Mark Wycislik-Wilson
Google has announced Fast Pair, an update to Bluetooth connectivity that speeds up the process of connecting a Bluetooth device -- such as headphones -- to an Android phone or tablet. It's an idea that's not entirely dissimilar to the technology used by Apple to connect AirPods to iPhones. Using a combination of BLE (Bluetooth Low Energy) for advertising and discovery, and traditional Bluetooth for pairing, the focus is on speed and security. It's compatible with devices running Android 6.0 Marshmallow and above, and it's part of Google Play services 11.7+. While this sounds great in principle, the success of… [Continue Reading] -

eBay launches Image Search option and AI-powered Find It On eBay tool
Publié: octobre 29, 2017, 1:45pm CET par Mark Wycislik-Wilson
A picture, they say, is worth a thousand words. When you're searching for something on eBay, it can be hard to find quite the right turn of phrase to track down precisely what it is you mean. To help overcome this problem, eBay has now launched a new Image Search option. The feature lets you take a photograph of an object -- or upload an image they already have --and use it to search for similar items that are for sale. This is just one of two new tools that eBay has launched to make it easier to find exactly… [Continue Reading] -

YouTube ripping sites MP3Juices.cc and YtMp3.cc block users from the UK
Publié: octobre 29, 2017, 12:40pm CET par Mark Wycislik-Wilson
There are lots of sites and tools out there that can be used to rip content from YouTube, saving them either as videos or MP3s. Predictably, this is something that the content owners -- record labels in particular -- take issue with. YouTube-MP3 recently shut up shop following pressure from the music industry, and a number of MP3 ripping sites were lined up as the next targets. Apparently pre-empting any legal action that might be taken against them, MP3Juices.cc and YtMp3.cc have started to block traffic from the UK. See also: YouTube tests autoplaying videos -- but you can disable… [Continue Reading] -

Transparency: Facebook to force political ads to disclose funding sources
Publié: octobre 29, 2017, 9:51am CET par Mark Wycislik-Wilson
Ads on Facebook have been something of a controversial subject for some time now -- particularly with suggestions of Russian attempts to influence the outcome of the US presidential election. In its latest attempt to have a more transparent ad platform, the social network has announced a series of measures that will help people understand more about advertising. All ads -- not just political ones -- are to be subject to extra transparency, with a new View Ads link making it possible to view all the ads a particular advertiser has placed. Political advertiser will face more stringent requirement. They… [Continue Reading] -

Does Facebook listen in via your microphone to tailor your ads?
Publié: octobre 28, 2017, 12:47pm CEST par Mark Wycislik-Wilson
It's something that has been rumored for years -- that Facebook is using the microphones on smartphones and computers around the world to listen in on conversations. Is it that the social network is particularly interested in hearing what everyone has to say? Sort of -- rumor has it that the company wants to know what you're talking about so it can deliver carefully targeted ads. A surprising number of Facebook users believe that Facebook is listening to them. They say that following conversations about a topic, they then see ads related to it. But is this really because of… [Continue Reading] -

Google makes it harder to search for results from other countries
Publié: octobre 28, 2017, 11:36am CEST par Mark Wycislik-Wilson
For a long time, there was an easy way to conduct a Google search in a country other than the one you're in. If you wanted to get results specific to Japan, for instance, you would visit www.google.co.jp; to get Australian results you would visit www.google.com.au -- but this trick no longer works. Google has announced that it will now always serve up results that are relevant to the country that you're in, regardless of the country code top level domain names (ccTLD) you use. The reason given is a little bizarre. The search giant says that the change has… [Continue Reading] -

New York Times launches Tor Onion Service to overcome censorship and ensure privacy
Publié: octobre 27, 2017, 7:27pm CEST par Mark Wycislik-Wilson
The New York Times has announced that it is launching a Tor Onion Service version of its website. The new, more secure way to access the site will open it up to people around the world whose internet connections are blocked or monitored. It also caters to a growing breed of people who are concerned about what their web browsing habit might reveal and who have turned to Tor to protect their privacy. The new service is described as "experimental and under development," and some features of the website -- such as the ability to comment -- do not work.… [Continue Reading] -

Now you can delete sent messages in WhatsApp
Publié: octobre 27, 2017, 6:12pm CEST par Mark Wycislik-Wilson
It's a feature that users have been practically begging for forever. It's a feature that has been rumoured as being in the works for quite some time, and tested for a number of months. Now it has finally arrived. You can, at long last, delete sent messages in WhatsApp thanks to "Delete for everyone." Whether you've sent a message in anger, under the influence, or just by mistake, there are numerous reasons for wanting to erase a message you've sent. While the ability to recall or revoke messages will be welcomed, it may well not go quite as far as… [Continue Reading] -

McAfee will no longer let foreign governments see its source code
Publié: octobre 27, 2017, 12:20pm CEST par Mark Wycislik-Wilson
Just as Kaspersky says that it will open up its source code in the name of transparency, so McAfee has indicated something of a step in the other direction. The security software manufacturer has announced that it is no longer going to allow foreign governments to scrutinize its code. The practice was originally introduced to help convince other countries -- particularly Russia -- that its software did not include backdoors that could be used for espionage. But there have been concerns that opening up source code to examination could also give foreign powers the ability to detect and abuse vulnerabilities.… [Continue Reading] -

You can finally view your saved passwords in Chrome for Android
Publié: octobre 27, 2017, 11:08am CEST par Mark Wycislik-Wilson
One of the great things about modern web browsers -- desktop and mobile variants -- is that they can store your passwords for you to save you from ever having to type them in. But this does have its drawbacks; stripped of the need to enter passwords, it's very easy to forget what they are! The desktop version of Chrome has long given users the option to view the passwords they have saved, and now this same feature has made its way to the Android version of the browser. There's now no need to use the Google website to manage… [Continue Reading] -

Pre-order your iPhone X now
Publié: octobre 27, 2017, 10:04am CEST par Mark Wycislik-Wilson
If you're interested in buying an iPhone X, you probably don't need a reminder that pre-orders are now open. Nevertheless, here it is: iPhone X pre-orders are now open! Starting at $999 for a 64GB model, the iPhone X is due to ship out to customer on November 3, but depending on the level of demand, it's possible that for many people this date will slip further back into the month -- or even beyond. See also: Apple says you'll be able to buy the iPhone X in stores on November 3... if you're early How to order an iPhone… [Continue Reading] -

Samsung announces the 'versatile' Galaxy Tab A (8.0") tablet
Publié: octobre 26, 2017, 6:08pm CEST par Mark Wycislik-Wilson
Samsung has announced an upcoming tablet, the latest addition to the Galaxy range. The Samsung Galaxy Tab A (8.0") -- also known as the Galaxy Tab A (2017) -- has been "designed for the whole family" and is a budget tablet that you won't mind sharing it with, or giving to, the kids. The specs are, generally speaking, nothing to get too excited about, but that's not the aim of this tablet. The metal body gives an air of quality to what Samsung describes as "an everyday, versatile tablet," and a 5,000mAh battery can power the device for up to… [Continue Reading] -

Google partners with International Fact Checking Network to further tackle fake news
Publié: octobre 26, 2017, 5:23pm CEST par Mark Wycislik-Wilson
These days just about every tech company with the slightest connection to news is doing what it can to stem the flow of fake news. Mozilla, Microsoft and Facebook have all taken steps, and Google has already rolled out its Fact Check tag to highlight verified stories. Today the search giant announces that it has joined forces with the International Fact Checking Network (IFCN) to take the battle even further. See also: Microsoft enters the fight against fake news as Bing gains Fact Check label Mozilla Information Trust Initiative is ready to fight fake news Post too much to Facebook… [Continue Reading] -

Facebook launches dedicated used car Marketplace section, complete with Kelley Blue Book pricing
Publié: octobre 26, 2017, 4:15pm CEST par Mark Wycislik-Wilson
Facebook Marketplace has been with us for a little while now, giving users of the social network a handy place to buy and sell goods in the same place they chat with friends and post holiday photos. The company today announced a series of changes designed to make it easier to buy cars through Marketplace. A year after the launch of the platform, used cars now have their own dedicated Marketplace section. More than this, it is possible -- in the US at least -- to filter vehicles in a variety of ways to home in on the perfect car,… [Continue Reading] -

Kaspersky says it accidentally obtained secret NSA files from a US computer
Publié: octobre 26, 2017, 12:05pm CEST par Mark Wycislik-Wilson
Earlier in the month, news emerged that Kaspersky software had been used by Russian hackers to identify and steal sensitive NSA files from a US computer. Following the revelation, Kaspersky Lab started an investigation, and now the company has published its findings. Kaspersky concedes that its software had indeed identified classified NSA data -- specifically a hacking tool -- but says that it was unintentional. The unearthed source code was attributed to the Equation Group, and company head Eugene Kaspersky ordered the code be destroyed when the matter was reported to him. See also: Report: Russian hackers stole NSA files… [Continue Reading] -

Apple vehemently denies Bloomberg's suggestion of reduced Face ID accuracy
Publié: octobre 26, 2017, 11:19am CEST par Mark Wycislik-Wilson
Yesterday, Bloomberg ran a story suggesting that Apple had faced problems getting the iPhone X to market on time. In an attempt to speed up production, Bloomberg said Apple gave suppliers permission to reduce the accuracy of its Face ID face recognition feature. But Apple refutes this claim, dismissing it as "completely false" -- but Bloomberg is standing by its story. See also: Apple says you'll be able to buy the iPhone X in stores on November 3... if you're early How to order an iPhone X faster Apple responds to iPhone X Face ID privacy concerns but dodges law… [Continue Reading] -

Google releases Android Oreo 8.1 Developer Preview beta
Publié: octobre 26, 2017, 10:52am CEST par Mark Wycislik-Wilson
It's not all that long since the launch of Android 8.0 Oreo -- not that many people have it on their phones -- but Google has already pushed out a developer preview of Oreo 8.1. As this is an early beta, there are not a huge number of changes to see in Android Oreo 8.1 developer preview -- but under the hood, there's quite a lot going on. For now, compatibility is limited to the Nexus 5X, Nexus 6P, Pixel C, Pixel, Pixel XL, Pixel 2 and Pixel 2 XL, but for these handsets new features include a Neural Networks… [Continue Reading] -

How to protect yourself against Bad Rabbit ransomware
Publié: octobre 25, 2017, 5:36pm CEST par Mark Wycislik-Wilson
News broke earlier about the spread of a new form of ransomware going by the name of Bad Rabbit. It name drops Game of Thrones and bears more than a passing resemblance to WannaCry and Petya. While the main impact of Bad Rabbit has been felt in Eastern Europe, some instances of the ransomware have also been detected in the US. Thankfully, it's relatively easy -- and free -- to protect your computer. By simply tweaking a couple of files, you can stop the ransomware in its tracks. See also: Bad Rabbit ransomware spreads across Eastern Europe with echoes of… [Continue Reading] -

Bad Rabbit ransomware spreads across Eastern Europe with echoes of WannaCry and Petya
Publié: octobre 25, 2017, 11:17am CEST par Mark Wycislik-Wilson
A new strain of ransomware -- dubbed Bad Rabbit -- has struck in Russia, Ukraine and other parts of Eastern Europe. It is thought to be a variation on Petya due to a number of similarities, and it is wreaking havoc with media outlets and transport systems, including an airport in Ukraine, and the underground in Kiev. Like many other forms of malware, Bad Rabbit was initially spread through a fake Flash installer, but it was then able to spread via networks to hit a larger number of machines. The spread of the ransomware is further facilitated by using the… [Continue Reading] -

Pre-order page leaks OnePlus 5T specs, price and release date
Publié: octobre 25, 2017, 10:25am CEST par Mark Wycislik-Wilson
Despite the OnePlus 5 only having been available for a few months, there have been rumors that its successor, the OnePlus 5T, is not far away. The sudden 'out of stock' status of the OnePlus 5 served only to fuel these rumors further, and now a pre-order page for the handset has revealed much of what you might want to know. In recent days we've seen leaks of what the upcoming phone looks like, but now we know many of the specs, the price, and an approximate release date See also: Tweak and hack OxygenOS on your OnePlus phone with… [Continue Reading] -

Google launches Gmail Add-ons and brings a range of business tools to the inbox
Publié: octobre 24, 2017, 7:49pm CEST par Mark Wycislik-Wilson
Integration is the name of the game these days, and Google is taking steps to ensure that its own services offer integration with the tools and services people need to get their work done. With this in mind, the company today launches Gmail Add-ons after a beta testing period as a developer preview earlier in the year. Gmail Add-ons are extensions that bring a number of big-name services -- such as Trello, Wrike and Asana -- to your inbox. While there's a definite business and enterprise bias, it's something that is available to everyone, starting right now. The arrival of… [Continue Reading] -

Facebook asked to investigate Russian influence on EU referendum
Publié: octobre 24, 2017, 5:18pm CEST par Mark Wycislik-Wilson
It is now widely accepted that Russia -- at least to some degree -- tried to influence the outcome of the US presidential election through the use of ads placed on Facebook. Attention now turns to Europe, where the UK's digital, culture, media and sport committee is asking Mark Zuckerberg to investigate potential interference in the UK general election, as well as the EU referendum that led to Brexit. See also: 10 million US Facebook users saw divisive ads bought by Russia Warning issued: Russia tried to hack election systems in at least 21 US states and was successful in… [Continue Reading] -

Apple says you'll be able to buy the iPhone X in stores on November 3... if you're early
Publié: octobre 24, 2017, 4:05pm CEST par Mark Wycislik-Wilson
You may have been under the impression that the only way to get your hands on an iPhone X in November is to place your order this week. But Apple has just announced that the new handset will be available to buy in stores by walk-in customers. There have been rumors about supplies of the iPhone X being limited, so it comes as little surprise that Apple says walk-in customers should arrive early if they want to avoid disappointment. See also: How to order an iPhone X faster Apple responds to iPhone X Face ID privacy concerns but dodges law… [Continue Reading] -

Consumer group Which? calls for amendments to Data Protection Bill to allow for 'collective redress' after breaches
Publié: octobre 24, 2017, 1:51pm CEST par Mark Wycislik-Wilson
UK consumer group Which? is calling on the government to make an amendment to the Data Protection Bill that's currently being debated in Parliament. The group is looking for a change in the law that would make it easier for organizations to seek redress for groups of people in the event of a data breach. Research by Which? suggests that there is confusion surrounding who is responsible for safeguarding data, and little knowledge among consumers about how to go about obtaining compensation. The consumer group's research shows that nearly 10 percent of people who have shared data online, believe they… [Continue Reading] -

Windows 10 Fall Creators Update offers ransomware protection with Controlled Folder Access
Publié: octobre 24, 2017, 12:06pm CEST par Mark Wycislik-Wilson
Ransomware is one of the most concerning, and the most prevalent, forms of malware around at the moment. While there are numerous security tools out there that you can install to keep yourself protected, if you have upgraded to Windows 10 Fall Creators Update you have a built-in tool at your disposal. Called Controlled Folder Access, the feature locks down files and folders to protect them against unwanted changes -- including encryption by ransomware. It's not enabled by default, so here's what you need to do. If you've been involved in the Windows Insider program, you may well be aware… [Continue Reading] -

Microsoft drops lawsuit against US government after DOJ reins in use of gagging orders
Publié: octobre 24, 2017, 11:14am CEST par Mark Wycislik-Wilson
Microsoft has announced that it will drop its lawsuit against the US government after the Department of Justice said that it will use fewer secrecy orders when making requests for user information. Microsoft's battle has been running since April last year, and it gained support from the likes of Mozilla, the EFF, Google and Apple. The company was not happy that gagging orders prevented it from telling customers when investigators requested access to their data. The move by the DOJ is described by Microsoft president and chief legal officer Brad Smith as an "important step for both privacy and free… [Continue Reading] -

Facebook offers (some) clarification about newsfeed changes amid panic from page owners
Publié: octobre 24, 2017, 10:20am CEST par Mark Wycislik-Wilson
Changes to the Facebook newsfeed are generally somewhat controversial, not least because many people wish Facebook would just stop buggering around and leave things as they are for a while. But the latest change that's being tested has some people -- page owners and publishers in particular -- worried. Facebook is testing splitting the newsfeed in two: one half for posts from friends, and the other half from pages. There is an exception, however: promoted posts from pages can appear in the personal newsfeed. This has caused concern because smaller publishers and business fear their posts will disappear and not be… [Continue Reading] -

Google unveils Chrome User Experience Report to let developers see how visitors use websites
Publié: octobre 23, 2017, 8:21pm CEST par Mark Wycislik-Wilson
If you've ever wondered what happens to the data Google collects via Chrome, today's announcement gives you something of an idea. The newly unveiled Chrome User Experience Report is a collection of data from users who have opted in to usage statistic reporting, the idea being that developers will be able to see how users experience the websites they visit. Google launched the new tool at the Chrome Dev Summit 2017 in San Francisco, and at the same time also announced Trusted Web Activity. This is essentially a way to provide app-like behavior in Chrome to create a more cohesive… [Continue Reading] -

Google makes it easier for businesses to take online bookings
Publié: octobre 23, 2017, 4:28pm CEST par Mark Wycislik-Wilson
Businesses in the US now have a new way to sign up with one of Google's booking partners and to add a booking button to their search listing. Anyone in the US with a Google My Business account can benefit from the addition of a booking button that enables people to book a reservation with a simple click. It's a continuation of the idea started with Reserve with Google, and the search giant is making it easy for businesses to track their online booking through their accounts. Getting started with the new option is very simple. If you're already signed… [Continue Reading] -

How to fix missing apps after installing Windows 10 Fall Creators Update
Publié: octobre 23, 2017, 3:37pm CEST par Mark Wycislik-Wilson
After months of beta testing through the Windows Insider program, Windows 10 Fall Creators Update has finally been released. While the update brings a number of changes and additions to Microsoft's operating system, it has also brought problems for some people. Among these issues is the apparent disappearance of various apps. This is not down to apps being removed from Windows, but Windows 10 Fall Creators Update has rendered some apps completely inaccessible. If you've experienced this problem, here's how to fix it. See also: How to upgrade your PC to the Windows 10 Fall Creators Update now How to… [Continue Reading] -

Kaspersky's new 'global transparency initiative' aims to rebuild trust by submitting source code for review
Publié: octobre 23, 2017, 1:28pm CEST par Mark Wycislik-Wilson
Kaspersky software was recently banned from US government computers over fears that the security company has links to the Russian government. This is something Kaspersky vehemently denies, and now it has announced a new "global transparency initiative" to try to win back trust. Part of the newly transparent Kaspersky will see the company submitting source code for current and future software to "the broader information-security community and other stakeholders." It is hoping that the scrutiny will put to bed ideas that it has been engaged in espionage with the Russian authorities. See also: Kaspersky Secure Connection VPN service is free,… [Continue Reading] -

Wolf of Wall Street: cryptocurrency ICOs are 'the biggest scam ever'
Publié: octobre 23, 2017, 12:29pm CEST par Mark Wycislik-Wilson
Jordan Belfort -- the real-life Wolf of Wall Street -- has warned that ICOs (or "token sales" or "coin sales") are "the biggest scam ever" and will "blow up in so many people's faces." The former stockbroker, who spent nearly two years in prison for fraud and financial scams, says that the Initial Coin Offerings used to raise money for cryptocurrencies are "far worse than anything I was ever doing." His fears seem to stem from the way ICOs differ from the more traditional IPO. With IPOs investors gain shares in whatever company they plough money into, and profits can… [Continue Reading] -

'Pay with Google' speeds up online payments for Android users
Publié: octobre 23, 2017, 11:35am CEST par Mark Wycislik-Wilson
As promised earlier in the year, Google has launched its payment service to streamline the checkout process for Android users. Pay with Google aims to kill the frustration that can stem from having to fill out endless forms in order to complete a purchase. To start with, Pay with Google is supported by 15 vendors including Instacart, Kayak, iFood and GameTime, but there are plenty more big names -- like StubHub, Deliveroo, Airbnb and Just Eat -- due to join. The service is available from today, and can be used in various Android apps, or Chrome on the web. There's… [Continue Reading] -

Tweak and hack OxygenOS on your OnePlus phone with JOnePlus Tools
Publié: octobre 22, 2017, 4:07pm CEST par Mark Wycislik-Wilson
Tweaking tools used to be all the rage for Windows, but not so much these days. The phenomenon has, however, spread to the mobile world to a certain extent. OnePlus owners have the streamlined OxygenOS to work with for an experience that's near to pure Android; but there's always scope for tweaking. Whether you have rooted your phone or not, JOnePlus Tools gives you the opportunity to tweak your phone to within an inch of its life (in the best possible way, of course). As well as working with rooted and non-rooted phones, it even works with the Oreo betas… [Continue Reading] -

Google says the majority of Chrome traffic is protected with HTTPS
Publié: octobre 22, 2017, 12:17pm CEST par Mark Wycislik-Wilson
Google has already used Cybersecurity Awareness Month to announced details of a new bug bounty program for Android apps, as well as a new Advanced Protection Program for G Suite users. Now the company has revealed that most web traffic in its Chrome web browser is protected by HTTPS. The precise figures vary from platform to platform -- with ChromeOS and macOS faring the best -- but between 64 and 75 percent is now secured. Google humblebrags about the results of its mission to "secure the web, one site at a time," after opting to mark non-encrypted pages as being… [Continue Reading] -

How to order an iPhone X faster
Publié: octobre 22, 2017, 11:14am CEST par Mark Wycislik-Wilson
The level of interest in the iPhone X is huge. The latest addition to the iPhone range is certainly expensive, but it's also the most radically different iPhone we've seen in ages. Pre-orders for the phone start on October 27 (this Friday) ahead of the November 3 launch, and availability of the handsets is expected to limited -- not least because Apple is said to have a relatively small number of them to sell. What if there was a way to jump the queue and secure your iPhone X so you avoid disappointment? Well... there is! Sort of... See also:… [Continue Reading] -

Twitter shares timetable for tackling abuse transparently between now and January
Publié: octobre 21, 2017, 2:36pm CEST par Mark Wycislik-Wilson
With promises made by Jack Dorsey and a leaked email indicating that Twitter was ready to do more to start tackling abuse on the site, it should come as little surprise that the company has now published a timetable for what it intends to do over the coming months. Entitled the "Calendar of Our Safety Work," the document details the changes that Twitter is going to make between now and the middle of January. The timetable covers subjects such as non-consensual nudity, hateful imagery, violent groups and hateful display names. There's an unprecedented level of transparency that Twitter will hope… [Continue Reading] -

Apple releases fourth betas of iOS 11.1 and watchOS 4.1 to developers
Publié: octobre 21, 2017, 10:36am CEST par Mark Wycislik-Wilson
Ahead of a public beta launch, Apple has released new developer betas for iOS 11.1 and watch OS 4.1. iOS 11.1 beta 15B92 and watchOS 4.1 beta 15R846 come just days after the third beta version were released, and only a month after iOS 11 itself was launched. Both are really bug-fixing releases, but iOS does see the return of a feature from an earlier beta. See also: Apple responds to iPhone X Face ID privacy concerns but dodges law enforcement request query Apple releases 'new' version of iTunes that includes the App Store Debunked: Apple slows down older iPhones… [Continue Reading] -

Support for 'Hey, Google' hotword rolls out to Android phones
Publié: octobre 21, 2017, 10:04am CEST par Mark Wycislik-Wilson
Calling up the Google Assistant on your Android phone takes nothing more than bellowing "OK, Google" at your handset. But you may be someone who feels that this is just too many syllables to utter. Google Home users have a slightly easier time. As well as "OK, Google" it is also possible to say "Hey, Google" -- meaning you can start getting help in two thirds of the time! Now the same option is making its way to Android phones. See also: Instant Apps in Google Play let you try out apps without installing them Android hackers: Now there's a… [Continue Reading] -

Now you can PayPal people in Facebook Messenger
Publié: octobre 20, 2017, 4:54pm CEST par Mark Wycislik-Wilson
Building on an existing partnership, Facebook and PayPal are now making it easier than ever to send and receive money online. If you're in the US, it is now possible to make PayPal payments in Facebook Messenger. In addition to announcing the new payment option, PayPal has also beefed up its Messenger chat bot. Users will now be able to get access to customer service by chatting with the bot. The ability to make and receive payments through Facebook Messenger is nothing new -- Facebook added credit card support a couple of years ago. But the arrival of PayPal support… [Continue Reading] -

Plex is coming to Android Auto
Publié: octobre 20, 2017, 2:15pm CEST par Mark Wycislik-Wilson
Fans of Plex will very soon be able to access their music through Android Auto. Whether you have Android Auto built into your car, or you're going to rely on the app on your phone instead, Plex can now sit alongside your travel directions. Plex for Android Auto allows for voice-control of music playback, and the interface has been enlarged and simplified for ease of use when in your car. See also: Plex rolls out adaptive Auto Quality feature to everyone, hardware-acceleration to subscribers Plex adds personalized news to its media software Official Plex for Kodi addon now available to… [Continue Reading] -

Arianna Huffington and Samsung create Thrive app to make you uncontactable
Publié: octobre 20, 2017, 12:54pm CEST par Mark Wycislik-Wilson
Arianna Huffington has teamed up with Samsung to create an app called Thrive. The aim of the app is to encourage users to: "Unplug & recharge. Take a break from your phone. Reconnect with yourself." When it is released in December, the app will be a Samsung exclusive and it will force you to disconnect from your phone and make sure no one can get in touch with you. To help you feel smug and superior about what you're doing, anyone who tries to contact you will be informed that you are taking enforced time out. In reality, what Thrive… [Continue Reading] -

Consumer Reports refuses to recommend Microsoft Surface Book 2
Publié: octobre 20, 2017, 12:24pm CEST par Mark Wycislik-Wilson
Just a few days ago, Microsoft revealed details of the Surface Book 2 which is due to launch in November. But before the device is even available, it has been dealt a blow by Consumer Reports. Earlier in the year, the review group said that problems with reliability meant that it was impossible for it to recommend any Microsoft laptop or tablet. Now Consumer Reports says that this extends to the Surface Book 2, meaning that the device will not be recommended. See also: Poor reliability means Consumer Reports no longer recommends Microsoft Surface -- or any other Microsoft laptop… [Continue Reading] -

Instant Apps in Google Play let you try out apps without installing them
Publié: octobre 20, 2017, 11:17am CEST par Mark Wycislik-Wilson
As well as unveiling a new bug bounty program for select Android apps, Google has also announced a number of changes to its Play Store. The first is the introduction of Instant Apps to Google Play, giving users the chance to try out apps without even having to install them. The idea is to give people the opportunity to test out apps almost immediately without having to wait for them to download -- ideal for anyone with limited data or a slow connection. Instant Apps are essentially streamed to devices meaning they can be running in seconds. At the moment… [Continue Reading] -

Android hackers: Now there's a bug bounty program for Google Play
Publié: octobre 20, 2017, 10:28am CEST par Mark Wycislik-Wilson
Google has announced that it is teaming up with HackerOne to bring a bug bounty program to the Play Store. Seeking to weed out problems with Android apps, the Google Play Security Reward Program pays out $1,000 for reported issues that meet certain criteria. The program is a little different to other bug bounty programs as Google will pay out for problems that are found in third party apps, not just its own. At the moment there are a very small number of apps that are taking part, but Google is inviting developers to opt their apps into the program.… [Continue Reading] -

Leaked email: Twitter introduces yet more rules in latest attempt to tackle abuse
Publié: octobre 18, 2017, 6:13pm CEST par Mark Wycislik-Wilson
Twitter has made endless promises about clamping down on abuse, constantly tweaking existing rules and introducing new ones in an attempt to protect users. Following last week's #WomenBoycottTwitter protest, Twitter CEO Jack Dorsey promised to start taking a more aggressive approach. A leaked internal email gives details of just what this new stance will involve. The definition of "nonconsensual nudity" is to be expanded to include upskirt photos and so-called "creep shots," and symbols of hate -- a term that Twitter does not actually define -- will be hidden behind a "sensitive image" warning. See also: Twitter vows to take… [Continue Reading] -

Microsoft denies that BoundHook vulnerability is actually a vulnerability
Publié: octobre 18, 2017, 4:55pm CEST par Mark Wycislik-Wilson
Security researchers at CyberArk are reporting about a new technique that could be used to take control of Windows 10 devices. Known as BoundHook, the technique takes advantage of the BOUND hooking technique in Intel MPX (Memory Protection Extensions). But while CyberArk says that it will "bring new capabilities to both software security vendors and malware writers," Microsoft is downplaying the issue, suggesting there is nothing to worry about. CyberArk acknowledges that the "technique can be used in a post-exploitation scenario in which the attacker has control over the asset." That said, it's not something that should necessarily be ignored.… [Continue Reading] -

Facebook is testing a temporary profile status feature
Publié: octobre 18, 2017, 4:38pm CEST par Mark Wycislik-Wilson
Facebook has confirmed that it is currently testing a feature that enables its users to setup a self-destructing status. It's something that's in a similar vein to the temporary profile image option that's already available. There's something of a nostalgic feel to the feature as it harks back to the earlier days of Facebook when users were invited to share their status rather than being asked "what's on your mind?" See also: Facebook taps into teen market with acquisition of anonymous feedback app tbh Facebook to manually review ads that target people based on 'politics, religion, ethnicity or social issues'… [Continue Reading] -

WhatsApp gains location sharing allowing real-time tracking
Publié: octobre 18, 2017, 12:41pm CEST par Mark Wycislik-Wilson
Following the lead of Facebook Messenger and iMessage, WhatsApp is gaining a location sharing feature. It's something that was tested earlier in the year, and now it has been deemed ready for prime time. The "Share Live Location" feature can be enabled for a fixed period of time -- you can choose between 15 minutes, an hour, or 8 hours -- or you can manually switch it on and off as required. When enabled, WhatsApp will report your location to your contacts. See also: WhatsApp refused to add a backdoor for the UK government Want to unsend WhatsApp messages? Delete… [Continue Reading] -

Apple responds to iPhone X Face ID privacy concerns but dodges law enforcement request query
Publié: octobre 18, 2017, 11:33am CEST par Mark Wycislik-Wilson
One of the undeniable highlights of Apple's iPhone X is Face ID -- the face recognition technology that makes it possible to unlock a phone with a glance. While exciting and impressive, many people have security and privacy concerns about the feature, and last month Senator Al Franken wrote to Apple asking a series of questions and outlining his worries. Apple has now responded to Franken, just ahead of the launch of the iPhone X in a little over two weeks. The company points to a series of documents that have already been made public, but also goes on to… [Continue Reading] -

Google Calendar for the web finally gets a redesign and new enterprise features
Publié: octobre 17, 2017, 6:56pm CEST par Mark Wycislik-Wilson
After years of little more than minor tweaks here and there, Google Calendar for the web is finally getting a long-overdue update. Inspired by the mobile app Google has developed, the revamped online version of Calendar gains a new color palette, as well as a layout rejig and a few new features. The new look uses Google's Material Design scheme, and the update means that Calendar now intelligently resizes for different screen and browser window sizes. There are various new features for enterprise users, but there are also new views, and a focus on displaying more useful information than before.… [Continue Reading] -

Google offers its strongest ever security with new Advanced Protection Program
Publié: octobre 17, 2017, 5:41pm CEST par Mark Wycislik-Wilson
As part of Cybersecurity Awareness Month, Google has announced numerous security-related updates including revamped phishing protection. Now the company has also announced what it is referring to as its "strongest security, for those who need it most." Aimed at protecting people who are most likely to find themselves the target of attacks -- Google suggests journalists and human rights workers as examples -- the new Advanced Protection Program is being made available to anyone who wants to use it. It will protect Gmail, Google Drive and YouTube data with a variety of measures including a physical authentication key. See also:… [Continue Reading] -

Facebook taps into teen market with acquisition of anonymous feedback app tbh
Publié: octobre 16, 2017, 10:41pm CEST par Mark Wycislik-Wilson
Facebook's desperation to appeal to the teenage market is well known, and its latest attempt to tap into it sees the social network acquiring tbh. The anonymous feedback app has proved to be a huge hit on iOS since its launch in August. An Android version is still in the pipeline. With tbh, despite the anonymity, there's a strong focus on positive polls -- questions like "who has the best smile?" crop up, for instance -- and over a billion pieces of feedback have been given in a matter of weeks. It's not clear whether Facebook will keep the service… [Continue Reading] -

Google rolls out Chrome Cleanup to help secure its web browser
Publié: octobre 16, 2017, 7:05pm CEST par Mark Wycislik-Wilson
With so much time now spent online, and with so many cloud-based tools now in use every day, we're all spending more time than ever in our web browsers. To ensure that this is as secure an experience as possible, Google is rolling out a trio of important changes to Chrome -- for Windows users, at least. At the heart of these changes is Chrome Cleanup. This feature detects unwanted software that might be bundled with downloads, and provides help with removing it -- but Mac and Linux users miss out. Google's Philippe Rivard explains that Chrome now has built-in… [Continue Reading] -

[Updated] Microsoft has patched Windows against the KRACK Wi-Fi vulnerability -- Google will secure Android soon
Publié: octobre 16, 2017, 5:09pm CEST par Mark Wycislik-Wilson
Earlier today, news broke about the KRACK vulnerability that affects the WPA2 protocol. Security researchers have warned that the problem affects millions of devices running everything from Windows to Android and Linux. Microsoft has announced that it has already released a security patch to fix the vulnerability in Windows. Google says that a patch for affected Android devices will be released "in the coming weeks." See also: KRACK warning: Severe WPA2 security vulnerability leaves millions of devices open to attack Android: DoubleLocker ransomware encrypts data and changes PINs In a statement to the Verge, Microsoft said: "We have released a… [Continue Reading] -

PureVPN scrambles to defend itself against accusations of logging users
Publié: octobre 16, 2017, 3:59pm CEST par Mark Wycislik-Wilson
Last week it transpired that PureVPN had helped the FBI track down a cyberstalker from Massachusetts. This came as something of a surprise to other PureVPN users who were under the impression that using the service made them completely anonymous -- a belief strengthened by the company's assertion "We do NOT keep any logs that can identify or help in monitoring a user's activity." Strictly speaking, this is true, but that's not to say that the company doesn’t maintain IP logs that can be used to identify users. The company does exactly this, logging IP addresses and timestamps, and this… [Continue Reading] -

Android: DoubleLocker ransomware encrypts data and changes PINs
Publié: octobre 16, 2017, 12:46pm CEST par Mark Wycislik-Wilson
A new breed of Android ransomware has been discovered that hits victims with a double whammy. DoubleLocker not only encrypts data as all ransomware does, it also changes the PIN on the target device. DoubleLocker was discovered by security researchers at ESET. They say that the ransomware abuses Android accessibility settings, and is the first to use a double-lock approach. Based on previously released banking malware, it is though that a test version of DoubleLocker could have been in the wild since as early as May. Despite the banking roots, the ransomware is focused purely on extracting money from victims… [Continue Reading] -

KRACK warning: Severe WPA2 security vulnerability leaves millions of devices open to attack
Publié: octobre 16, 2017, 11:36am CEST par Mark Wycislik-Wilson
A severe security warning has been issued after Belgium researchers managed to exploit a serious vulnerability in the WPA2 wireless protocol. Known as KRACK (Key Reinstallation Attacks), the vulnerability makes it possible to eavesdrop on Wi-Fi traffic. Millions and millions of devices are at risk -- Windows, Linux, Android and more -- but it is not known whether there is an active exploit in the wild yet. Details about the vulnerability were due to be released at 8:00AM ET (1:00PM BST), but the research paper has now been published early after someone leaked a draft version. Researcher Mathy Vanhoef describes… [Continue Reading] -

Twitter vows to take a more aggressive approach to unwanted sexual advances, abuse and more
Publié: octobre 16, 2017, 10:49am CEST par Mark Wycislik-Wilson
Jack Dorsey has promised that Twitter will take a more aggressive stance in applying its rules. The announcement came after the #WomenBoycottTwitter protest was used to draw attention to women being silenced. The Twitter CEO also said that new rules will be introduced to try to counter "unwanted sexual advances, non-consensual nudity, hate symbols, violent groups, and tweets that glorifies violence." See also: Women boycott Twitter to protest against women's voices being silenced [UPDATED] Twitter temporarily suspends Rose McGowan following Harvey Weinstein tweets Why hasn't Twitter banned Trump or deleted his provocative tweets about North Korea? Dorsey has not given… [Continue Reading] -

Samsung Connect Tag is a smart IoT tracker using narrowband technology
Publié: octobre 16, 2017, 8:53am CEST par Mark Wycislik-Wilson
Samsung has unveiled the latest addition to its range of Internet of Things devices: the Samsung Connect Tag. It is designed to make it possible to keep track of anything you can’t bear to lose, from a bag or keys, to a child or pet. Based on the Tizen operating system, the Samsung Connect Tag can be clipped to a range of objects and, using a combination of NB-IoT, Cat.M1, GPS and GLONASS, it will report the location of whatever it is attached to. It is described as the first consumer product to take advantage of narrowband technology. The Samsung… [Continue Reading] -

LinkedIn is testing autoplaying video ads
Publié: octobre 15, 2017, 3:19pm CEST par Mark Wycislik-Wilson
Looking for new ways to make money out of its professional social network LinkedIn, Microsoft is testing video advertisements. Currently in closed beta testing, video advertising is available to "a limited number of advertisers" and it may well prove unpopular with LinkedIn users. Following a well-worn path set out by the likes of Google, Facebook and others, the video ads will autoplay. The one saving grace is that videos will play without sound, but this is unlikely to be enough to prevent them from quickly becoming an irritant. The introduction of video advertising follows Microsoft's decision to allow LinkedIn users… [Continue Reading] -

Windows 10 telemetry violates privacy laws
Publié: octobre 15, 2017, 2:05pm CEST par Mark Wycislik-Wilson
The data collecting activities of Windows 10 has landed Microsoft in trouble again. Investigating the telemetry built into the operating system, the Dutch Data Protection Authority (DPA) has said that Microsoft's spying is a violation of local privacy laws. Of particular concern to the authority is the fact that users are not clearly told that data will be collected in both Windows itself and Microsoft Edge. With Microsoft's web browser gathering data about every URL that's visited by users who have not opted out of telemetry, and Windows 10 itself sucking up detailed information about app usage, the DPA is… [Continue Reading] -

Arrow Launcher for Android exits beta and becomes Microsoft Launcher
Publié: octobre 15, 2017, 12:42pm CEST par Mark Wycislik-Wilson
It came as something of a shock to people when Microsoft first released an Android launcher in the guise of Arrow Launcher. Now the company is making it more obvious who is behind the app, bringing the launcher out of beta and relaunching it as Microsoft Launcher. Joe Belfiore only very recently admitted that Windows Phone is dead, and this is something that is borne out by Microsoft's increasing interest in developing iOS and Android software. What may well come as a surprise to many is that Microsoft Launcher is actually a decent piece of software. See also: Joe Belfiore… [Continue Reading] -

OnePlus opens up about its secret data collection and promises an opt-out opportunity
Publié: octobre 15, 2017, 11:36am CEST par Mark Wycislik-Wilson
Last week it emerged that OnePlus has been secretly gathering a huge amount of data from handsets, revealing a wealth of personally identifiable information about their users. Now the smartphone company has spoken out in response to the uproar, and vowed to give users the ability to opt out of data collection. Company founder Carl Pei took to the OnePlus community forums to explain why data was collected, stressing that OnePlus takes privacy seriously. But while Pei promises that an update is on the way by the end of the month that will introduce the ability to opt out of… [Continue Reading] -

Download the Android Oreo beta for your OnePlus 3 or 3T
Publié: octobre 15, 2017, 10:44am CEST par Mark Wycislik-Wilson
OnePlus has earned itself quite a reputation for pushing out new Android builds to its users, and it's no different with Android 8.0 Having previously announced that Oreo would be the last major update for the OnePlus 3 and 3T, the Chinese smartphone-maker has now made a beta version available to everyone. Just last month, a closed group was given access to an early Oreo beta for the OnePlus 3, but now the OnePlus Open Beta program means that anyone who likes the idea of trying out Android 8.0 on their handset can do so. See also: Telemetry: OxygenOS secretly… [Continue Reading] -

Women boycott Twitter to protest against women's voices being silenced
Publié: octobre 13, 2017, 1:40pm CEST par Mark Wycislik-Wilson
The sexual abuse and harassment allegations against Harvey Weinstein are having some interesting side effects. Having temporarily banned actress Rose McGowan from its platform, Twitter today finds itself at the center of a boycott. While it was initially thought that McGowan had been booted from the site for speaking out about Weinstein, Twitter insists it took action because she shared a private phone number in a tweet. But other users are making Friday the 13th an unlucky day for Twitter via the #WomenBoycottTwitter hashtag. Many women are choosing to boycott the site completely today to protest against the silencing of… [Continue Reading] -

Another Equifax security alert as support page leads to malicious fake Flash updates
Publié: octobre 13, 2017, 11:59am CEST par Mark Wycislik-Wilson
Things have not been good for Equifax -- or its customers -- recently. Following a huge data breach earlier in the year, the credit reporting company has now suffered a new blow after it was discovered one of its support pages was redirecting to malware masquerading as Flash updates. Just last month, Equifax revealed a security breach from May that exposed the personal details of around 145.5 million Americans and 15.2 million people from the UK. Now the company site has been found delivering fake Flash updates, and the offending page has been taken down. Security researcher Randy Abrams noticed… [Continue Reading] -

Download Microsoft Edge preview for Android
Publié: octobre 13, 2017, 10:54am CEST par Mark Wycislik-Wilson
Microsoft only recently announced that its Edge browser would be coming to both iOS and Android -- and now the company is making good on its promise. A preview version of Microsoft Edge (described by the software giant as "unreleased") is now available on Google Play. Based on Chrome's Blink engine, Edge for Android has a particular treat for anyone using Windows 10 Fall Creators Update -- they can take advantage of the "continue on PC" feature. This lets users start browsing the web on their phones, and then switch to a computer and pick up from where they left… [Continue Reading] -

Google unbundles Android battery app and pushes it to the Play Store
Publié: octobre 13, 2017, 10:14am CEST par Mark Wycislik-Wilson
Google has started -- just as OnePlus has -- to unbundle many of its core apps and make them available through the Play Store. The latest candidate to be stripped out of Android and give a Store release is its battery app. Many people have been pleased to see such unbundling, as it makes it far easier for Google to release updates for individual components without having to wait for the next big Android update to roll out. But while many Android users will be happy to see the arrival of Device Health Services (as the battery app is named),… [Continue Reading] -

Twitter temporarily suspends Rose McGowan following Harvey Weinstein tweets
Publié: octobre 12, 2017, 4:52pm CEST par Mark Wycislik-Wilson
Rose McGowan -- one of many actresses to have spoken out about Harvey Weinstein's alleged sexual abuse and harassment -- has been slapped with a temporary suspension from Twitter. The sanctions came after the Charmed and Nip/Tuck star talked about the Weinstein allegations. While Twitter has not revealed exactly why McGowan's account was suspended, it followed her speaking out about sexual abuse, and telling Ben Affleck to "fuck off" after he said he knew nothing of Weinstein's reputation for sexual harassment. See also: Twitter introduces Happening Now to keep you up to date with sport and more Twitter not only… [Continue Reading] -

[UPDATED] Twitter temporarily suspends Rose McGowan following Harvey Weinstein tweets
Publié: octobre 12, 2017, 4:52pm CEST par Mark Wycislik-Wilson
Rose McGowan -- one of many actresses to have spoken out about Harvey Weinstein's alleged sexual abuse and harassment -- has been slapped with a temporary suspension from Twitter. The sanctions came after the Charmed and Nip/Tuck star talked about the Weinstein allegations. While Twitter has not revealed exactly why McGowan's account was suspended, it followed her speaking out about sexual abuse, and telling Ben Affleck to "fuck off" after he said he knew nothing of Weinstein's reputation for sexual harassment. See also: Twitter introduces Happening Now to keep you up to date with sport and more Twitter not only… [Continue Reading] -

YouTube tests autoplaying videos -- but you can disable the feature
Publié: octobre 12, 2017, 4:00pm CEST par Mark Wycislik-Wilson
Videos that play automatically have proved highly divisive, but it hasn’t stopped Google, Facebook, Instagram and Twitter experimenting with them. Now YouTube is testing autoplaying videos in its app. Recognizing that not everyone is happy with the idea of videos noisily playing as soon as they appear on-screen, Google has taken a leaf out of Instagram's book and made the video play silently to start with. In addition to this, it's possible to disable autoplay altogether if you want. See also: Instagram may have just solved the noisy autoplaying video problem How to stop videos autoplaying in Google Prepare to… [Continue Reading] -

Google will now pay iOS users for their opinions
Publié: octobre 11, 2017, 6:41pm CEST par Mark Wycislik-Wilson
Everyone likes the idea of earning money, and most people like to voice their opinion. If you’re an iOS user, Google is now giving you the ability to combine the two. Perfect! Google Opinion Rewards is now available for iOS, giving iPhone and iPad users the opportunity to earn money for sharing their opinions by completing simple surveys. The app has been in use by Android owners for a few years, but now it's the turn of Apple fans. Google says that all of the surveys it sends out to participants are very quick to complete -- most of them… [Continue Reading] -

Some Google Home Minis found to be secretly recording everything they hear
Publié: octobre 11, 2017, 5:21pm CEST par Mark Wycislik-Wilson
With the Google Home Mini, the search giant was hoping to get its smart speaker into more homes than ever before. But the latest privacy revelation about the device means that people may think twice about buying one. Artem Russakovskii from Android Police was the first to -- publicly -- talk about the issue. He noticed that his Google Home Mini was active and recording sound throughout the day, not only when he uttered the "OK, Google" keyword. Google says that the privacy violation is down to a bug. Russakovskii gives a detailed chronology of his discovery over on Android… [Continue Reading] -

Twitter introduces Happening Now to keep you up to date with sport and more
Publié: octobre 11, 2017, 12:04pm CEST par Mark Wycislik-Wilson
Twitter may have a bookmarking system in the works, but there are new features that are already rolling out to users. The latest addition is called Happening Now which will be used to highlight tweets about a particular topic. It's a feature that's not a million miles removed from the existing Moments feature, but Twitter seems to think it's what people want. To start with, Happening Now is rolling out to Android and iOS users in the US and it will highlight sports. Over time, however, it will expand to other parts of the world and cover different events as… [Continue Reading] -

Twitter not only changes its mind about 'inflammatory' ad, it's going to change its policies too
Publié: octobre 11, 2017, 11:16am CEST par Mark Wycislik-Wilson
Twitter was accused of censorship after banning an "inflammatory" ad campaign by Tennessee Rep. Marsha Blackburn. But just one day after implementing the ban, the company has backed down, saying the video -- which sees Blackburn talking about fighting to stop "the sale of baby body parts" -- can be promoted on Twitter. Despite maintaining its belief that the video contains inflammatory language, Twitter now says that it is permissible within the context of the ad. Furthermore, the company says that it will "refine" its policies around the issue. See also: Twitter bans 'inflammatory' Republican anti-abortion campaign ad Twitter is… [Continue Reading] -

Telemetry: OxygenOS secretly collects user data, sending OnePlus a wealth of information
Publié: octobre 11, 2017, 10:01am CEST par Mark Wycislik-Wilson
OxygenOS, the customized version of Android used by OnePlus on its smartphones, has been found to be collecting data about users -- and it's not anonymized. Telemetry is something that has been associated with Windows 10, but now the Chinese smartphone manufacturer has its fans concerned. That a phone collects certain information about usage is not particularly unusual -- it helps to identify problems and speed up software development. But a security researcher's discovery that his OnePlus 2 was sending highly detailed information back to OnePlus without consent has set privacy alarm bells ringing (the issue also affects more recent… [Continue Reading] -

Xposed Framework is now officially available for rooted Android Nougat devices
Publié: octobre 9, 2017, 7:39pm CEST par Mark Wycislik-Wilson
If you've ever rooted an Android phone, you've almost certainly heard of the Xposed Framework. This remarkable software allows for near limitless customization of Google's mobile operating system through the use of numerous add-on modules, eliminating the need to use custom ROMs. After months of waiting, Xposed Framework is now officially available for Nougat. The software has been made available more than a year after the launch of Nougat, but the good news is that the day has finally arrived! The software has been in the works for some time now, and it's thanks to the hard work of XDA… [Continue Reading] -

Apple releases 'new' version of iTunes that includes the App Store
Publié: octobre 9, 2017, 4:10pm CEST par Mark Wycislik-Wilson
Last month, Apple released iTunes 12.7 which -- to the surprise and disappointment of many -- stripped out the App Store. Now, seemingly realizing that some people still want, or need, access to the Store from the desktop, Apple has release iTunes 12.6.3. The 'new' version of the software sees the return of the App Store, but Apple has made the release a quiet one. Although this is technically an older version than that which was previously released, there's still support for iPhone 8, iPhone 8 Plus, iPhone X and iOS 11. See also: Apple strips the App Store from… [Continue Reading] -

FBI uses PureVPN's 'non-existent' logs to track down internet stalker
Publié: octobre 9, 2017, 12:55pm CEST par Mark Wycislik-Wilson
No longer operating under the illusion that the internet offers a mask of anonymity, increasing numbers of people are turning to VPN software to protect their privacy and mask their identity online. But a recent case shows that the FBI used the logs of PureVPN to track down a user believed to be an internet stalker. This may make PureVPN users think twice about just how anonymous they really are, particularly when the company claims: "We do NOT keep any logs that can identify or help in monitoring a user's activity." Just before the weekend, the Department of Justice revealed… [Continue Reading] -

Joe Belfiore admits Windows Phone is dead -- only bug fixes and security updates to come for Windows 10 Mobile
Publié: octobre 9, 2017, 11:06am CEST par Mark Wycislik-Wilson
Joe Belfiore has finally admitted what we have all known for some time: The Windows Phone dream is dead. Microsoft's Corporate Vice President for Windows used Twitter to make it clear that Windows 10 Mobile will receive "bug fixes, security updates, etc," but adds that "building new features/hw aren't the focus." Asked by Twitter users whether it is time for people to abandon Windows mobile devices once and for all, Belfiore said that while support will remain in place for those who decide to hang around, he himself has already moved on. The problem -- as if there was ever… [Continue Reading] -

TVAddons: We shouldn't be in MPAA's 'Online Notorious Markets' report after zero DMCA complaints from members
Publié: octobre 9, 2017, 9:53am CEST par Mark Wycislik-Wilson
TVAddons is famous -- some would say infamous, even notorious -- in Kodi circles. The controversial Kodi addons site has been the subject of a lawsuit and even abuse from Kodi itself. Last week the site was mentioned in the Online Notorious Markets report produced by the MPAA (Motion Picture Association of America) -- and TVAddons is not happy. The report refers to the site as a "piracy add-on repository," but TVAddons is quick to point out that it has never received a single DMCA (Digital Millennium Copyright Act) complaint from MPAA members or affiliates. The site accuses the MPAA… [Continue Reading] -

Facebook to manually review ads that target people based on 'politics, religion, ethnicity or social issues'
Publié: octobre 8, 2017, 12:41pm CEST par Mark Wycislik-Wilson
Advertisers are to face increased scrutiny from Facebook as the social network attempts to clamp down on questionable and controversial ads. The move comes in the wake of the revelation that 10 million Americans saw ads during the run up to the election that has been bought by Russia. In an email to advertisers, Facebook says that any ads that target people based on "politics, religion, ethnicity or social issues" will be subject to a manual review process. See also: 10 million US Facebook users saw divisive ads bought by Russia Trump takes to Twitter to complain that Facebook is… [Continue Reading] -

EFF criticizes iOS 11's 'misleading' Bluetooth and Wi-Fi toggles for being a privacy and security risk
Publié: octobre 8, 2017, 11:49am CEST par Mark Wycislik-Wilson
The strange, unintuitive way Bluetooth and Wi-Fi toggles work in iOS 11 has drawn ire from many quarters. The latest voice is that of digital rights group the Electronic Frontier Foundation (EFF) which says that the "off-ish" setting now offered is misleading. As we have covered in a previous story, Apple has changed the behaviour of the two toggles so that when they are flicked to the off position, the Bluetooth and wireless radios are not actually switched off. EFF says that this is "bad for user security" and calls for greater clarity from Apple. See also: Warning: Toggles in… [Continue Reading] -

Debunked: Apple slows down older iPhones to encourage upgrades
Publié: octobre 8, 2017, 10:31am CEST par Mark Wycislik-Wilson
With the launch of the iPhone 8, iPhone 8 Plus, iPhone X and iOS 11, a persistent rumor resurfaced. There has long been speculation that Apple deliberately slows down older iPhones in an attempt to encourage people to upgrade to the latest models. Benchmarking firm Futuremark notes that around the launch of the new iPhones, there was a surge in Google searches for "iPhone slow" -- but are people's fears actually founded in anything? Futuremark is in exactly the right line of work to set the record straight, and its test results really speak for themselves. See also: Apple launches… [Continue Reading] -

Google's 'bezel-less future' is why the Pixel 2 and Pixel 2 XL have no headphone jack
Publié: octobre 7, 2017, 6:13pm CEST par Mark Wycislik-Wilson
An increasing number of smartphones are ditching the traditional 3.5mm headphone jack, and the Pixel 2 and Pixel 2 XL follow this trend. While it is something of an inevitability that the old-style jack will be completely replaced, there are still plenty of people who mourn its loss. While there is a move towards more widespread use of Bluetooth headphones and other alternatives, many people still question why the 3.5mm has to go. Now Google has offered something of an explanation, putting it down -- at least in part -- to the "bezel-less future" of phones. See also: Google's new… [Continue Reading] -

AIM will be discontinued in mid-December
Publié: octobre 7, 2017, 5:16pm CEST par Mark Wycislik-Wilson
After two decades of online chat, AIM is set to shuffle off this mortal coil. First emerging in 1997, AOL Instant Messenger earned itself a loyal following of people who were just starting to discover the internet and what it could be used for. Now Oath -- AOL's new owner -- has announced that it is to close down the service on December 15, 2017. The reason given is that "the way in which we communicate with each other has profoundly changed," and after the mid-December cut-off date the service will cease to function, and all data will be erased.… [Continue Reading] -

Report: Russian hackers stole NSA files after identifying them using Kaspersky software
Publié: octobre 6, 2017, 12:24pm CEST par Mark Wycislik-Wilson
A report by the Wall Street Journal suggests that Russian hackers used Kaspersky software to identify sensitive NSA files -- which they then stole. The security breach dates back to 2015, and it was made possible when a National Security Agency contractor copied sensitive files to his own computer. Hackers were then able to identify these files because of the contractor's use of Kaspersky software. See also: Warning issued: Russia tried to hack election systems in at least 21 US states and was successful in some Kaspersky software banned from US government systems over concerns about Russia NSA says it… [Continue Reading] -

Apple unveils new emoji coming in iOS 11.1
Publié: octobre 6, 2017, 11:51am CEST par Mark Wycislik-Wilson
Following a somewhat problematic initial release of iOS, Apple pushed out iOS 11.0.2 to fix a number of issues. But people are already looking forward to the next incremental, non-bug-fixing release. This is iOS 11.1, and Apple has revealed a little of what we can expect. iPad and iPhone users are to be treated to a new batch of emoji -- hundreds of new ones in total -- encompassing "more emotive smiley faces, gender-neutral characters, clothing options, food types, animals, mythical creatures and more." See also: Apple releases watchOS and iOS updates to fix connectivity and crackling problems Apple releases… [Continue Reading] -

Facebook test brings context to links that are shared in your newsfeed
Publié: octobre 5, 2017, 5:00pm CEST par Mark Wycislik-Wilson
One of the problems with Facebook -- and the internet in general -- is that it has been incredibly democratizing in terms of who is able to publish news and other messages online. Democratization of anything is usually perceived as a good thing, but as the genuine problem of "fake news" (i.e. not the notion peddled by Trump that anything presenting an opposing idea is fundamentally untrue) demonstrates, it can also be a bad thing. To help with this, Facebook is testing a feature that helps to add context to stories and links that appear in your newsfeed. See also:… [Continue Reading] -

Cloudflare ditches sites that use Coinhive mining code after classing it as malware
Publié: octobre 5, 2017, 2:33pm CEST par Mark Wycislik-Wilson
Bitcoin has been in the news for some time now as its value climbs and drops, but most recently interest turned to mining code embedded in websites. The Pirate Bay was one of the first sites to be seen using Coinhive code to secretly mine using visitors' CPU time, and then we saw similar activity from the SafeBrowse extension for Chrome. The discovery of the code was a little distressing for visitors to the affected sites, and internet security and content delivery network (CDN) firm Cloudflare is taking action to clamp down on what it is describing as malware. See… [Continue Reading] -

Apple releases watchOS and iOS updates to fix connectivity and crackling problems
Publié: octobre 5, 2017, 1:16pm CEST par Mark Wycislik-Wilson
Apple's launch of the iPhone 8 and Apple Watch Series 3 has certainly not been without its problems. Buyers of the latest addition to the iPhone range have complained about crackling audio, while owners of the new smartwatch have been less than impressed by problematic LTE and battery life. Now Apple has pushed out a couple of updates that should help with the issues -- watchOS 4.0.1, and iOS 11.0.2. See also: Apple Watch Series 3 is plagued by battery issues and LTE problems Apple Watch Series 3 does not support roaming Apple is working on a fix for iPhone… [Continue Reading] -

Mozilla announces extended end-of-life support for Firefox under Windows XP and Vista
Publié: octobre 5, 2017, 12:23pm CEST par Mark Wycislik-Wilson
Mozilla has revealed that support for its Firefox web browser on Windows XP and Vista is coming to an end. The organization had previously announced that anyone using these old versions of Microsoft's operating system would be moved to the Firefox Extended Support Release (ESR). This meant that support would be offered until "at least" September this year. Now the final kill date has been revealed -- and it's later than expected. While an exact date has not been announced, Mozilla says that June next year is when Firefox support will come to an end. This gives individuals and organizations… [Continue Reading] -

Google's instant-translation Pixel Buds are its most incredible release yet
Publié: octobre 5, 2017, 11:14am CEST par Mark Wycislik-Wilson
There were numerous exciting releases announced by Google yesterday, but perhaps the most exciting -- certainly the most impressive -- was the Pixel Buds. Forget Apple's AirPods, Google's earphones have a mind-blowing trick up their sleeve. Designed (ideally) for use with the Pixel 2, the Google Pixel Buds can translate spoken words on the fly. Real-time translations -- the Babel fish made real and implanted in your ear -- is now a reality, allowing for conversations between two people speaking different languages. Google Pixel Buds are an extension of Google Translate, and can translate between 40 languages in an instant.… [Continue Reading] -

Google reveals the Android Excellence collection for Fall 2017
Publié: octobre 4, 2017, 5:47pm CEST par Mark Wycislik-Wilson
Google has unveiled the latest collections of best games and apps for Android. The company introduced the Android Excellence program earlier in the year, and now it has taken the wraps off the lists for Fall 2017. These are not necessarily new titles, so as you browse through the collections you're likely to see a number of familiar names. In all, there are dozens of Android Excellence Apps and Android Excellence Games. See also: Google launches Android Excellence to recognize the very best apps and games Google points out that the titles that made it to the list "are noteworthy… [Continue Reading] -

Plex rolls out adaptive Auto Quality feature to everyone, hardware-acceleration to subscribers
Publié: octobre 4, 2017, 5:27pm CEST par Mark Wycislik-Wilson
Plex -- the company behind the eponymous media server software -- is rolling out an update that automatically adjusts video quality during playback. This is a feature that was previously only available to Plex Pass subscribers, but now all users can enjoy it free of charge. At the same time, Plex is also introducing a new performance-enhancing option to help justify the cost of a subscription. Hardware-Accelerated Streaming does very much what you would expect -- assuming you have the correct CPU or GPU, that is. See also: Plex adds personalized news to its media software Official Plex for Kodi… [Continue Reading] -

Europe demands €250m in tax from Amazon, sues Ireland for Apple's €13bn tax bill
Publié: octobre 4, 2017, 12:57pm CEST par Mark Wycislik-Wilson
The European Union has ordered Amazon to repay €250m ($294m) after it ruled that the retailer was granted illegal state aid by Luxembourg. The tax advantage dates back to 2003, but Amazon says that it is considering making an appeal. At the same time, the European Commission has announced that it is going to sue the Irish government for failing to collect €13bn ($15.3bn) in tax from Apple. The Irish government will need to defend itself in the European Court of Justice for failing to gather money from the iPhone-maker following a 2016 ruling by the commission. EU Competition Commissioner… [Continue Reading] -

Slack partners with Oracle to bring chatbots to the enterprise
Publié: octobre 3, 2017, 5:35pm CEST par Mark Wycislik-Wilson
Darling of the communication and collaboration world Slack is partnering with Oracle. The plan is to integrate Oracle enterprise software into the messaging tool that graces so many workplaces. While neither company has yet published details of the arrangement they have come to, both have confirmed the partnership to Reuters. Slack will be used as the interface for Oracle's sales, human resources and business software. Oracle's vice president of bots, artificial intelligence and mobile, Suhas Uliyar, explains that employees will be able to pose natural language questions such as "how many vacation days do I have left this year?" and… [Continue Reading] -

10 million US Facebook users saw divisive ads bought by Russia
Publié: octobre 3, 2017, 4:14pm CEST par Mark Wycislik-Wilson
It's no secret that Russia tried to influence the outcome of the US election last year using a variety of techniques including the use of advertising on Facebook. The social network recently said that it would share details of these ads with Congress, but would not be making them public. But while the company is not making the ads themselves available for all to see, it has revealed some more details about them -- including the fact that they were seen by an estimated 10 million people in the US. Facebook also says that 44 percent of more than 3,000… [Continue Reading] -

UK government could imprison people for looking at terrorist content
Publié: octobre 3, 2017, 1:26pm CEST par Mark Wycislik-Wilson
Not content with trying to "combat" encryption, the UK government also wants to criminalize looking at terrorist content. The leading Conservative party has announced plans which threaten those who "repeatedly view terrorist content online" with time behind bars. New laws will be introduced that could see consumers of terrorist content imprisoned for up to 15 years. The same maximum sentence would face those who share information about police, soldiers or intelligence agencies with a view to organizing terrorist attacks. See also: UK's confused Home Secretary doesn't understand encryption -- but wants to 'combat' it anyway UK Home Secretary supports back… [Continue Reading] -

Facebook tests facial recognition to unlock accounts
Publié: octobre 2, 2017, 5:46pm CEST par Mark Wycislik-Wilson
Facebook is testing the use of facial recognition as a way of enabling people to regain access to their accounts if they get locked out. The unlock method would be offered as an alternative to two-factor authentication techniques such as SMS or email verification. The social network says that if there is sufficient interest in the feature -- and providing it cannot be defeated by hackers -- it will receive a wider rollout after testing. At the moment, there is no indication that Facebook is considering using facial recognition as an alternative login method; it's just being tested in relation… [Continue Reading] -

Roku announces new media streaming boxes, cuts the price of Roku Ultra, releases Roku OS 8
Publié: octobre 2, 2017, 4:02pm CEST par Mark Wycislik-Wilson
Roku has today unveiled the latest additions to its media streaming line-up, adding features such as voice control and 4K support. The company also slashes $30 off the price of its top-of-the-range Roku Ultra box. With prices starting at just $29.99 for the Roku Express, there's something to suit every pocket, but it's arguably the updated Streaming Stick and Streaming Stick+ that are the most interesting. The $29.99 Roku Express is the cheapest of the bunch, while the Roku Express+ is identical save for the addition of composite connections for an extra $10 -- it's also exclusive to Walmart. Roku… [Continue Reading] -

FBI won't have to reveal details of hacking tool used to crack San Bernardino iPhone
Publié: octobre 2, 2017, 12:20pm CEST par Mark Wycislik-Wilson
A judge has ruled that the FBI will not have to reveal any details about the hacking tool it bought to crack the iPhone at the center of the San Bernardino shooting case back in early 2016. Following a Freedom of Information request by Vice News, USA Today and the Associated Press, federal judge Tanya Chutkan ruled in favor of the FBI, meaning that the agency will be able to keep this information secret. A battle between the FBI and Apple ran for some months as the agency tried to force the iPhone-maker to provide access to the phone at… [Continue Reading] -

Apple releases source code for ARM-optimized iOS and macOS kernel
Publié: octobre 2, 2017, 10:33am CEST par Mark Wycislik-Wilson
For some time now, Apple has regularly released the source code for the shared iOS and macOS kernel. That the company has done so again might not be news, but Apple has, for the first time, released the source code for the ARM versions of the kernel. Pushed to GitHub, the source code gives anyone who likes the idea of seeing exactly what makes iOS and macOS tick the opportunity to do just that. See also: The FCC wants Apple to enable the iPhone's non-existent FM radio Apple is working on a fix for iPhone 8 earpiece crackle Apple now… [Continue Reading] -

Google changes its approach to news subscriptions, scraps First Click Free policy
Publié: octobre 2, 2017, 9:09am CEST par Mark Wycislik-Wilson
Google has announced changes to the requirements it places on websites that provide news on a subscription basis. With a large number of news sites locking content away behind a paywall, Google had required publishers to provide people with access to three free articles per day or face demotion in search results. Scrapping what was known as the First Click Free Policy, Google is dropping any such requirement to provide free access to content. A new approach -- Flexible Sampling -- lets publishers decide how many, if any, free articles they provide. See also: Google reveals why it killed NFC… [Continue Reading] -

Amazon Echo owners can now make free phone calls in US, Mexico and Canada
Publié: octobre 1, 2017, 1:21pm CEST par Mark Wycislik-Wilson
Amazon has been gradually expanding its range of Echo devices, and it has been possible to make free calls between Alexa-enabled devices for a few months -- now Amazon is extending the free calling capability even further. Owners of any Amazon Echo device -- not just the latest batch -- can now make free calls to phones in the US, Mexico and Canada. No extra hardware or software is needed to take advantage of free calling. See also: Google pulls YouTube from Amazon Echo Show for ToS violations Amazon unveils $99 next generation Echo, making Apple HomePod dead on arrival… [Continue Reading] -

Nintendo bans YouTubers from live streaming games through Nintendo Creators Program
Publié: octobre 1, 2017, 12:33pm CEST par Mark Wycislik-Wilson
Nintendo has updated the terms of the Nintendo Creators Program so that members are no longer permitted to live stream games on YouTube. The program has been running since 2015, giving gamers the chance to earn a little ad revenue from videos featuring Nintendo games. The change does not mean that gamers are not able to feature Nintendo games in their YouTube videos, but live streaming of game walkthroughs or other streams of gameplay are not allowed any more. This is a move that sees Nintendo returning to its characteristically defensive nature when it comes to its copyrighted material, and… [Continue Reading] -

Google reveals why it killed NFC Smart Lock in Android
Publié: septembre 30, 2017, 4:27pm CEST par Mark Wycislik-Wilson
It recently came to light that Google had killed off NFC Smart Lock in Android -- without telling anyone. Now the company has come clean about just why the feature was given the chop. Google says that "in the case of NFC unlock, we've seen extremely low usage," adding that there are now many more ways of unlocking Android devices. But while Google points to features such as On-Body detection, fingerprint scanning and Trusted Places, fans of the missing feature say that none of these are comparable. See also: PSA: Google quietly discontinues NFC Smart Unlock without explanation Andrew Brennan… [Continue Reading] -

Microsoft explains why Edge has so few extensions a year down the line
Publié: septembre 30, 2017, 1:03pm CEST par Mark Wycislik-Wilson
It's now a little more than a year since Microsoft first brought extensions to Edge. After so long you would expect the selection of addons to be overwhelming -- but that's far from being the case. In all, there are only 70-odd Edge extensions available, and Microsoft has been moved to explain why. In a blog post, the company almost apologetically explains that it is "building a thoughtfully curated ecosystem," citing concern over quality and a fear of diminishing the user experience. What some might describe as "slow," Microsoft refers to as a "purposefully metered approach" to new extensions, and… [Continue Reading] -

Paint.NET hits version 4.0.18 and arrives in the Microsoft Store... for a price
Publié: septembre 30, 2017, 12:28pm CEST par Mark Wycislik-Wilson
Fans of the image editing tool Paint.NET have two big pieces of news to digest. While this is only a minor version number bump, Paint.NET 4.0.18 improves startup times by around 25 percent as well as improving portable mode and introducing per-user plugins. But perhaps the biggest news -- as promised a few months ago -- is that Paint.NET is now in the Microsoft Store. While many people will welcome the arrival of the app in the Store, the fact that a price tag has been slapped on it will come as a surprise -- and a disappointment -- to… [Continue Reading] -

Mozilla updates Firefox Privacy Notice with greater detail, transparency and prominence
Publié: septembre 29, 2017, 8:15pm CEST par Mark Wycislik-Wilson
Mozilla has announced an update to Firefox's Privacy Notice which aims to better inform users about what data is collected and why. As well as making its privacy policies more understandable, Mozilla is also trying to ensure that more people actually see them. For new installations, the Privacy Notice is automatically displayed in a tab. But it's the layout and accessibility of the updated document that's the real change. See also: Apple launches new privacy page and reveals all about Face ID Apple now collects data from Safari using differential privacy to identify problem websites Privacy: With iOS 11 and… [Continue Reading] -

Great news for Android: Linux kernel Long Term Support triples to 6 years
Publié: septembre 29, 2017, 7:38pm CEST par Mark Wycislik-Wilson
As Android is based on Linux, the existing two-year lifecycle for Long Term Support (LTS) kernels is restrictively short. But, during a presentation about Android's Project Treble, Google's Iliyan Malchev announced that this is going to -- appropriately -- treble to six years. This will address what has become a serious issue for chip-makers. During the production process, they need to pick the most recent LTS kernel to work with to ensure longevity, but the length of time it takes to design and produce chips means that much of the two years of support is used up by the time… [Continue Reading] -

The FCC wants Apple to enable the iPhone's non-existent FM radio
Publié: septembre 29, 2017, 6:26pm CEST par Mark Wycislik-Wilson
In the wake of big storms recently, the National Association of Broadcasters and the FCC has piled the pressure on Apple to enable the FM radio in iPhones so they might be used for emergency broadcasts. FCC chairman Ajit Pai went as far as issuing a statement saying that "Apple is the one major phone manufacturer that has resisted" enabling FM chips in its phones. There's just one problem, as Apple points out. The iPhone simply doesn't have an FM chip to enable. A spokesman for the National Association of Broadcasters said: "Broadcasters are providing information on how to evacuate… [Continue Reading] -

Google launches Family Link parental control solution for Android
Publié: septembre 28, 2017, 8:49pm CEST par Mark Wycislik-Wilson
After a period of beta testing, Google's new parental control system for Android and iOS -- Family Link -- has been launched to the public. Google says that the feature makes "Android better for kids and families," and it places parents in control of what their kids can do. The feature is available to everyone in the US without the need for an invite (the beta period was invite-only), and Google describes the tools as being a way to bring kids and their parents into the Android ecosystem. It can be used from an Android phone or an iPhone to… [Continue Reading] -

PSA: Google quietly discontinues NFC Smart Unlock without explanation
Publié: septembre 28, 2017, 8:07pm CEST par Mark Wycislik-Wilson
Android users have been slowly discovering that Google has killed off NFC Smart Unlock. The feature, which makes it possible to unlock a phone with an NFC device such as a ring or bracelet, has been discontinued without explanation. Earlier in the month, Android users started to post messages on Google's Issue Tracker website, indicating that the feature was no longer available to them. Three weeks later, Google has finally responded, indicating that NFC Smart Unlock has been deprecated. See also: Google pulls YouTube from Amazon Echo Show for ToS violations Ex-Googler sets up his own futuristic church and is… [Continue Reading] -

Ex-Googler sets up his own futuristic church and is creating an AI god for you to worship
Publié: septembre 28, 2017, 6:15pm CEST par Mark Wycislik-Wilson
Anthony Levandowski -- a former Googler famous for building the company's self-driving car -- has set up a non-profit religious corporation called Way of the Future. The founding of the "church" has just been unearthed by Wired through state filings in California. The purpose of the Way of the Future is to "develop and promote the realization of a Godhead based on artificial intelligence and through understanding and worship of the Godhead contribute to the betterment of society." It's not entirely clear what form Levandowski's AI deity might take. It could be a robot, or little more than an ethereal… [Continue Reading] -

Internet Explorer users beware: the address bar is leaking everything you type
Publié: septembre 28, 2017, 3:32pm CEST par Mark Wycislik-Wilson
A bug has been uncovered in Internet Explorer which makes it possible for websites to view anything that is typed in to the address bar. This means that web addresses and search terms could be accessed by a hacker or malicious website. The vulnerability was discovered in the very latest version of Internet Explorer, and Microsoft is yet to release a patch for it. Discovered by security researcher Manuel Caballero, the attack can be made completely invisible to a victim. Writing on his website Broken Browser, Caballero explains that: "When a script is executed inside an object-html tag, the location… [Continue Reading] -

Apple launches new privacy page and reveals all about Face ID
Publié: septembre 28, 2017, 2:17pm CEST par Mark Wycislik-Wilson
Apple has launched a revamped privacy page proclaiming that its products are "designed to protect your privacy." Describing privacy as "a fundamental human right," the page explains the privacy functions of apps, Siri, Apple Pay and Touch ID. The company describes not only how it protects personal data with encryption, but also how it responds to government and legal requests for data. Apple has additionally published a paper which goes into some detail about how the Face ID feature of the iPhone X works -- and reveals its limitations. See also: Apple now collects data from Safari using differential privacy… [Continue Reading] -

Mark Zuckerberg denies Facebook is anti-Trump
Publié: septembre 28, 2017, 9:37am CEST par Mark Wycislik-Wilson
Yesterday, Donald Trump used his favorite medium of Twitter to complain that -- as well as some media outlets -- Facebook was opposed to him. Mark Zuckerberg has now responded, speaking out to deny the claim. He said: "Trump says Facebook is against him. Liberals say we helped Trump. Both sides are upset about ideas and content they don't like. That's what running a platform for all ideas looks like." The Facebook founder also backtracked on his earlier dismissal of the social network's influence on the election as "crazy." See also: Trump takes to Twitter to complain that Facebook is anti-Trump… [Continue Reading] -

Microsoft says Surface Pro LTE goes on sale December 1
Publié: septembre 27, 2017, 6:28pm CEST par Mark Wycislik-Wilson
Speaking at the Ignite 2017 conference, Microsoft said that the LTE version of the Surface Pro will be available to purchase on December 1. This is not the first time we have heard about the cellular-enabled Surface Pro, but now we have a date to look forward to. While the on-sale date is just over two months away, we may well learn more about the Surface Pro LTE at Future Decoded in London next month. Leaks from an online retailer have revealed what specifications will be available. According to Neowin, it was Surface Pro program manager Tim Golik who revealed… [Continue Reading] -

Trump takes to Twitter to complain that Facebook is anti-Trump
Publié: septembre 27, 2017, 5:19pm CEST par Mark Wycislik-Wilson
Facebook is currently under investigation for displaying advertisements placed by Russia to try to influence the 2016 presidential election against Hillary Clinton, but Donald Trump is convinced that the social network is against him. In a tweet, the president set out a simple accusation: "Facebook was always anti-Trump." Dredging up his bugbear of "fake news" he also made the same claim of television networks and newspapers. More than this, he suggests that there may have been collusion between those he regards as being "anti-Trump." See also: Twitter hack: How to send 280-character tweets right now Why hasn't Twitter banned Trump… [Continue Reading] -

Google pulls YouTube from Amazon Echo Show for ToS violations
Publié: septembre 27, 2017, 12:53pm CEST par Mark Wycislik-Wilson
If you have heard Alexa utter the message "Currently, Google is not supporting YouTube on Echo Show," you'll be aware of the issue: Google has pulled YouTube from the Amazon Echo Show. Google says that Amazon's Echo-with-a-screen creates a "broken user experience", and it seems the company would rather there was no customer experience than a broken one. A war of words has erupted between the two companies, and neither is particularly forthcoming with detail. The problem first reared its head yesterday afternoon when support for YouTube suddenly ceased. No warning was issued to users ahead of the decision, leaving… [Continue Reading] -

Kodi: Dish copyright lawsuit identifies operator of TVAddons as the site pleads innocence
Publié: septembre 27, 2017, 11:37am CEST par Mark Wycislik-Wilson
Kodi has had a rough time of things lately, and the same can be said for a number of companies and addons associated with the media center software. In particular, addons site TVAddons has been fighting legal battles, and in its case with Dish Network the operators of the site have been identified. An amended version of Dish Network's complaint says the site is owned and operated by Adam Lackman from Canada, and they also identify the developer of the ZemTV Kodi addon as Shahjahan Durrani from London. In the complaint, both Lackman and Durrani are accused of copyright infringement,… [Continue Reading] -

Apple is working on a fix for iPhone 8 earpiece crackle
Publié: septembre 27, 2017, 10:46am CEST par Mark Wycislik-Wilson
A number of iPhone 8 owners have complained of a crackling sound in their phone's earpiece during calls. The problem is not specific to any particular carrier, and it also affects the iPhone 8 Plus. Apple says that only a "small number of cases" of the audio problem have been reported, but there are lengthy threads on Reddit and Apple support forums with comments from those suffering with the issue. The good news is that there is a fix in the works and it's going to be delivered as a software update -- so it would seem there is not… [Continue Reading] -

Twitter hack: How to send 280-character tweets right now
Publié: septembre 27, 2017, 9:54am CEST par Mark Wycislik-Wilson
Twitter's distinctive feature -- the 140-character limit -- has been both a blessing and a curse, but out of the blue, however, the company has decided to double the limit to 280 characters. Unfortunately, the 280-charcter limit is now -- like the blue tick of verification -- some of the Holy Grail of Twitter thanks to a slow rollout. There's no need to wait however! You can send tweets of up to 280 characters right now -- it just takes a little setting up. Here's what you need to do. It appears that Twitter has enabled the new, longer limit… [Continue Reading] -

Microsoft joins the Open Source Initiative
Publié: septembre 26, 2017, 8:27pm CEST par Mark Wycislik-Wilson
Microsoft continues to show its support for open source software, and now the company has joined the Open Source Initiative (OSI). Joining as a Premium Sponsor, Microsoft will help to promote open source development, communities and software. The company joins the likes of Facebook, Google, GitHub and IBM, and it says that it will increase its advocacy for the use, contribution and release of open source software. The sponsorship is described as "a significant milestone for the OSI." Microsoft's Jeff McAffer says: "The Open Source Initiative is a cornerstone of open source communities and plays an important role in protecting… [Continue Reading] -

Adblock Plus introduces a new way to block ads on Facebook
Publié: septembre 26, 2017, 6:52pm CEST par Mark Wycislik-Wilson
Facebook -- like many companies who exist solely online -- is highly reliant on ad revenue. As such, it goes to great lengths to outwit ad-blocking tools that seek to rob it of income by giving users a more enjoyable experience. Adblock Plus is a well-known name in this field, having already had something of a back-and-forth with the social network as Facebook took steps to block adblockers. But now Adblock Plus has a new filter available to block ads on Facebook -- and improve privacy -- and it says it is more resilient than ever. See also: Adblock Plus… [Continue Reading] -

Plex adds personalized news to its media software
Publié: septembre 26, 2017, 4:40pm CEST par Mark Wycislik-Wilson
Having recently added Live TV and DVR features to its media server software, Plex is now adding personalized news. The new feature pulls in news from "some of the most trusted sources on the planet," and it comes after Plex's acquisition of Watchup. Working with over 190 partners, Plex News is tailored to suit individual users, taking into account which stories they watch and which they skip. The new feature integrates with an existing Plex media library and it will be available to all users free of charge. See also: Official Plex for Kodi addon now available to everyone --… [Continue Reading] -

Microsoft says Office 2019 previews are coming mid-2018
Publié: septembre 26, 2017, 4:01pm CEST par Mark Wycislik-Wilson
At Microsoft Ignite in Orlando, Microsoft today announced Office 2019. The next version of the office suite is scheduled for release sometime in the second half of 2018, with preview builds being made available in the middle of the year. Despite Microsoft's love of the cloud, the company recognizes that not all customers are quite ready to go all-in. With this in mind, Office 2019 includes numerous new features that are not cloud-specific, and the suite is described as "a valuable upgrade for customers who feel that they need to keep some or all of their apps and servers on-premises."… [Continue Reading] -

iOS Siri and Search, and macOS Spotlight, are now powered by Google
Publié: septembre 25, 2017, 8:16pm CEST par Mark Wycislik-Wilson
Apple is switching from Microsoft Bing to Google search to power Siri and Search in iOS, and Spotlight in macOS. The changeover is taking place right now, and should be complete by the end of the day. The search switch coincides with the launch of macOS High Sierra, but Mac users will find that Bing will still be used for image searches in both Siri and Spotlight. See also: iOS 11 is causing massive battery drain problems Google kills off Google Instant search with immediate effect Warning: Toggles in the iOS 11 Control Center don't let you turn off Bluetooth… [Continue Reading] -

Hackers hit accountancy firm Deloitte, stealing plans, emails and passwords
Publié: septembre 25, 2017, 4:34pm CEST par Mark Wycislik-Wilson
Global accountancy firm Deloitte -- known as one of the "big four" -- has been hit by a sophisticated hack. With echoes of the Equifax data breach and CCleaner hack, the cyberattack went undetected for months and results in confidential emails being accessed, as well as company plans, and the private information of high-profile, blue-chip clients. Deloitte says that only a small number of its clients have been affected, but the size and importance of those that it deals with -- including US government departments -- means that even a limited number could have great impact. The firm is said… [Continue Reading] -

iOS 11 is causing massive battery drain problems
Publié: septembre 25, 2017, 1:50pm CEST par Mark Wycislik-Wilson
A study conducted by security research firm Wandera shows that iOS 11 is causing iPhone and iPad batteries to drain faster than ever -- much faster. The difference between iOS 10 and iOS 11 is anything but minor; batteries can drain in half the amount of time following the upgrade. Wandera's report shows how, on average, an iPhone or iPad running iOS 10 takes 240 minutes of usage to drain the battery from 100 percent to zero. With iOS 11 installed, this number plummets to just 96 minutes -- over twice as fast. See also: Apple Watch Series 3 is… [Continue Reading] -

Warning issued: Russia tried to hack election systems in at least 21 US states and was successful in some
Publié: septembre 24, 2017, 1:18pm CEST par Mark Wycislik-Wilson
Russian hackers successfully compromised election systems in some states during the 2016 election. There have long been suggestions that Russia tried to influence the outcome of the Trump vs Clinton election, and now the Department of Homeland Security has informed 21 states that their systems were targeted. This means that the DHS has concerns about almost half of the states of America, but so far only Illinois has been confirmed as having been successfully compromised. See also: Facebook to share Russian election-era ads with Congress -- but won't make them public Kaspersky software banned from US government systems over concerns… [Continue Reading] -

Apple now lets you rent movies from iTunes for 48 hours in the US
Publié: septembre 24, 2017, 12:42pm CEST par Mark Wycislik-Wilson
Apple has -- at long last -- given the US what people in other parts of the world have enjoyed for a while: the ability to rent movies for 48 hours. Previously, renters in the US had a mere 24 hours to work their way through a movie after starting it, but Apple has now doubled this timeframe. It means that interruptions are now far less likely to mean that you need to re-rent a movie. See also: Hell freezes over: iTunes is coming to the Windows Store Apple strips the App Store from iTunes 12.7 While this is not… [Continue Reading] -

Android's 'Check For Update' button now works and actually checks for OTA updates!
Publié: septembre 24, 2017, 10:23am CEST par Mark Wycislik-Wilson
Updating Android can be a painful experience depending on the handset you have and the carrier you're with. You might hear that an update is available, but find nothing shows up when you hit the Check For Update button. Now this should be changing... and not just for Oreo users. Many Android users will have experienced the frustration of knowing full well that there is an update available for their device, but it's not offered up automatically. Even more annoyingly, it's often the case that even when performing a manual check, updates remain unavailable for download. Google has announced that:… [Continue Reading] -

Experimental Twitter Lite app is now available for Android
Publié: septembre 24, 2017, 9:09am CEST par Mark Wycislik-Wilson
All of the major players have been busy creating "lite" versions of their apps and online experiences. Microsoft has LinkedIn Lite, Facebook has both Facebook Lite and Facebook Messenger Lite, and Google has its Search Lite app. Back in April, Twitter decided to get in on the lite action by launching Twitter Lite, a cut-down, data-friendly version of its mobile website. Now the micro-blogging service has gone further and released a Twitter Lite app. See also: Microsoft launches LinkedIn Lite in India ahead of a wider rollout Download Google's experimental data-sipping Search Lite app To start with, Twitter Lite is… [Continue Reading] -

Facebook ads can target you based on your real-world store visits
Publié: septembre 22, 2017, 5:11pm CEST par Mark Wycislik-Wilson
That your online activities influence the ads you see on Facebook and other websites is well known. But now Facebook has developed tools that makes it possible to track your location in the real world to determine which stores you visit and then use this information to hit you with targeted ads. The new tools work for users who allow the Facebook app to access their location. The social network and advertisers are making profitable use of this valuable information. See also: Facebook overhauls rules governing political ads Facebook to share Russian election-era ads with Congress -- but won't make… [Continue Reading] -

Canonical builds a custom Ubuntu kernel for Microsoft Azure
Publié: septembre 22, 2017, 2:20pm CEST par Mark Wycislik-Wilson
Microsoft's relationship with Ubuntu-maker Canonical has been getting increasingly cosy over the past couple of years, and the two companies are now working even more closely with each other. The latest fruit of this partnership is a custom Azure-tailored Ubuntu kernel. The updated kernel introduces new features including NAPI and Receive Segment Coalescing, Hyper-V socket capability, and support for Accelerated Networking in Azure. Any Ubuntu 16.04 LTS image brought up from the Azure portal after September 2 will be running on this Azure tailored Ubuntu kernel. See also: Bashware: Microsoft refutes claims that Linux makes Windows 10 insecure Canonical publishes… [Continue Reading] -

Uber loses its license to operate in London
Publié: septembre 22, 2017, 12:38pm CEST par Mark Wycislik-Wilson
Transport for London (TfL) has said that Uber is not "fit and proper" to operate in the capital, and has rejected the company's application for a new license. Following the rejection, Uber has 21 days to appeal against the decision. The company's current license expires on September 30, but it will be able to continue to operate until the end of the appeal process. The rejection is just the latest in a series of problems for Uber which has faced criticism for failing to recognize its drivers as employees, as well as tracking Uber users' location through its mobile app.… [Continue Reading] -

Facebook overhauls rules governing political ads
Publié: septembre 22, 2017, 12:30pm CEST par Mark Wycislik-Wilson
As well as handing over Russian ads to Congress to allow for investigation into election interference, Facebook is also overhauling its rules for political ads. Dmitry Peskov, a spokesman for the Kremlin, claims that: "We do not know how to place an advert on Facebook. We have never done this, and the Russian side has never been involved in it" -- but there is still a firm belief that Russia tried to influence the outcome of the election. In a bid to prevent this from happening in the future, Facebook has announced a series of updates to its policies governing… [Continue Reading] -

Facebook to share Russian election-era ads with Congress -- but won't make them public
Publié: septembre 22, 2017, 11:37am CEST par Mark Wycislik-Wilson
Facebook is to provide Congress with 3,000 advertisements taken out by Russians in the run-up to the 2016 US election. The social media giant says that it is "actively working" with the government in its investigation into Russian interference into the election. Earlier in the month it was revealed that a group operating out of Russia had taken out $100,000 worth of advertising with a "focus on amplifying divisive social and political messages across the ideological spectrum." But while Facebook is willing to share the ads with Congress, they are not going to be made public. See also: Facebook says… [Continue Reading] -

Adblock Plus releases cryptocurrency miner hijack protection filter
Publié: septembre 21, 2017, 6:44pm CEST par Mark Wycislik-Wilson
Cryptocurrencies have been in the news a lot recently as the price of Bitcoin and Ethereum bounces up and down. But cryptocurrency miners have also been in the headlines after it was discovered that the Pirate Bay had secretly embedded a miner in its code, and then that the SafeBrowse extension for Chrome was also mining in the background. To help protect users who do not want their computers to be used for such things without their permission and who don't want to give up CPU cycles to generate profit for others, Adblock Plus has released a filter that will… [Continue Reading] -

Security researchers warn that GO Keyboard is spying on millions of Android users
Publié: septembre 21, 2017, 5:48pm CEST par Mark Wycislik-Wilson
Security researchers from Adguard have issued a warning that the popular GO Keyboard app is spying on users. Produced by Chinese developers GOMO Dev Team, GO Keyboard was found to be transmitting personal information about users back to remote servers, as well as "using a prohibited technique to download dangerous executable code." Adguard made the discovery while conducting research into the traffic consumption and unwanted behavior of various Android keyboards. The AdGuard for Android app makes it possible to see exactly what traffic an app is generating, and it showed that GO Keyboard was making worrying connections, making use of… [Continue Reading] -

WhatsApp refused to add a backdoor for the UK government
Publié: septembre 21, 2017, 2:16pm CEST par Mark Wycislik-Wilson
The UK government has made no secret of its dislike of encrypted messaging tools, and it has made frequent reference to the problems WhatsApp causes it with regard to investigations into terrorism. Calls have been made by the government to force companies to allow access to encrypted content when asked. In the wake of Theresa May's "more needs to be done about extremist content" speech, it has emerged that WhatsApp refused to add a backdoor that would allow the government and law enforcement agencies to access private conversations. See also: Theresa May wants tech firms to remove 'extremist content' faster…… [Continue Reading] -

Microsoft joins the Coalition for Better Ads
Publié: septembre 21, 2017, 1:03pm CEST par Mark Wycislik-Wilson
Microsoft has become the latest member of the Coalition for Better Ads (CBA). The group works with technology companies and trade organizations to help develop an ad ecosystem that works for advertisers without compromising the experience of internet users. In taking up membership of the CBA, Microsoft is joining Google who has already worked with the organization to develop a selective ad blocker for Chrome due for release next year. Microsoft is also looking to introduce ad blocking into Edge, but the blocker would only discriminate against ads deemed unacceptable by the CBA. See also: Google is building an ad… [Continue Reading] -

SafeBrowse Chrome extension found to be secretly mining for cryptocurrency
Publié: septembre 21, 2017, 12:18pm CEST par Mark Wycislik-Wilson
Recently it was discovered that the Pirate Bay had embedded a JavaScript cryptocurrency miner into the footer of its homepage, and now a popular Chrome extension has been found engaging in similar activity. The SafeBrowse extension purports to block popup ads and skip ad pages that appear before downloads, but in fact it was secretly running a Coin Hive mining tool in the background. With over 140,000 users, SafeBrowse -- which has now been removed from the Chrome Web Store -- was quietly making an income for its developers through clandestine use of CPU time. See also: The Pirate Bay… [Continue Reading] -

iOS 11 could let you secretly record Snapchat snaps
Publié: septembre 21, 2017, 11:22am CEST par Mark Wycislik-Wilson
If you're a Snapchat user, you'll know that it's possible to save someone's snaps forever by grabbing a screenshot of it. The problem is, this goes against the idea of Snapchat which is supposed to be about temporary, transient posts; that said, it's not against the rules. One of the new features of iOS 11 is a screen recording tool that makes it possible to save a video of what's going on on-screen. This can be used to make a recording of snaps, and it seems that a warning notification is not always sent out to the other party. See… [Continue Reading] -

Warning: Toggles in the iOS 11 Control Center don't let you turn off Bluetooth or Wi-Fi
Publié: septembre 21, 2017, 10:49am CEST par Mark Wycislik-Wilson
The aesthetics of the new Control Center in iOS 11 has been the source of amusement, debate and disgust in varying measures. But putting the look to one side for a moment, people upgrading to iOS 11 have been disappointed to discover that the toggles for Bluetooth and Wi-Fi in the Control Center don't actually turn off Bluetooth and Wi-Fi. For reasons best known to Apple, the toggles disconnect from wireless networks and Bluetooth devices, but the two radios will remain enabled. While the change of functionality is covered in Apple's support documentation, it's not something that is obvious to… [Continue Reading] -

Google showed ads on YouTube Red even though it's supposed to be ad-free
Publié: septembre 21, 2017, 10:24am CEST par Mark Wycislik-Wilson
One of the perks -- arguably the main perk -- of paying for YouTube Red is that your subscription fee gives you an ad-free experience. At least that's the idea... Google has now admitted that it was in fact running ads on its premium video service despite promising not to. This was not a change of heart or policy, however; the search giant is putting it down to an "underlying issue" which it is working to fix. In addressing the issue with users, though, it seems Google also failed to understand its own policies. A thread started up on Reddit… [Continue Reading] -

Theresa May wants tech firms to remove 'extremist content' faster… but it's not quite that simple
Publié: septembre 20, 2017, 6:05pm CEST par Mark Wycislik-Wilson
UK prime minister Theresa May has called on the likes of Microsoft, Google, Twitter and Facebook to act faster to remove terrorism-related and extremist content. At the moment, it takes an average of 36 hours to remove content shared by the likes of Isis, and May wants this slashed to just two hours. But even this is not enough for the government. It wants technologies to be developed -- or refined -- that will identify this sort of content and prevent it from getting online in the first place. Facebook agrees -- its love of AI is well-known -- but… [Continue Reading] -

Apple Watch Series 3 is plagued by battery issues and LTE problems
Publié: septembre 20, 2017, 4:55pm CEST par Mark Wycislik-Wilson
When Apple unveiled the Apple Watch Series 3 just over a week ago, there was much excitement at the fact that the smartwatch now features LTE connectivity. It's finally possible to make a call from your Apple Watch without having your iPhone nearby -- although there's the slight dampener that the watch does not support roaming. Now the first reviews of the Apple Watch Series 3 are starting to trickle in and, while they are generally positive, they highlight a couple of issues. Battery life seems to be rather less than was proclaimed at launch, and Apple has also identified… [Continue Reading] -

Chuwi LapBook Air now available for pre-order -- or you can win one in a giveaway!
Publié: septembre 20, 2017, 1:35pm CEST par Mark Wycislik-Wilson
Chuwi has been building anticipation for its upcoming LapBook Air, and the company has now opened up pre-orders for its ultra-thin laptop. Priced at just $429 the LapBook Air is described as being "a very MacBook-like device," and it weighs in at just 1.3kg. The device is powered by Windows 10 running on an Apollo Lake N3450 processor backed by 8GB RAM and a 128GB SSD. If you're happy to subscribe to a Chuwi newsletter you can shave an extra $50 off the price, but there's also a giveaway which means you could get one for free. See also: Chuwi's… [Continue Reading] -

EFF resigns from W3C in protest against Encrypted Media Extensions DRM standard
Publié: septembre 20, 2017, 1:14pm CEST par Mark Wycislik-Wilson
Digital rights group the Electronic Frontier Foundation (EFF) has resigned from the World Wide Web Consortium (W3C) because of a move to standardize the Encrypted Media Extension (EME) API for controlling DRM in web browsers. The EFF is far from being the only group to be unhappy with the W3C for the decision to standardize EME, but this is the first -- and possibly only -- one to have gone as far as resigning as well as filing objections. The group says that it proposed compromises that were ignored, and the opposition of EFF and other W3C members were simply… [Continue Reading] -

Privacy: With iOS 11 and Safari's cookie blocking, Apple is kicking advertisers in the teeth
Publié: septembre 20, 2017, 11:59am CEST par Mark Wycislik-Wilson
Apple news has been dominated -- understandably -- by the launch of the iPhone X, iPhone 8/8Plus and Apple Watch Series 3. But there's also iOS 11 to consider. The latest version of Apple's mobile operating system hit iPhones and iPads around the world yesterday, bringing with it a raft of new features. The release of iOS 11 includes an updated version of Safari and, importantly, a feature called Intelligent Tracking Prevention. Enabled by default, the feature blocks certain cookies from websites, making it harder for advertisers to follow users around the web. Users and privacy advocates are happy; advertisers,… [Continue Reading] -

Microsoft opens pre-orders for standard Xbox One X
Publié: septembre 20, 2017, 10:53am CEST par Mark Wycislik-Wilson
Hopefully you have been saving up, because today the standard version of the not-particularly-cheap Xbox One X is available to pre-order. Last month saw the Project Scorpion Edition open up for pre-orders, and now it's time for those who are interested in the standard black model. The console will be available worldwide on November 7, but if you want to avoid disappointment on the day, it's probably best to get your order for "the world's most powerful console" in right now -- links are below. As well as opening up pre-orders today, Microsoft has announced that the list of Xbox… [Continue Reading] -

Adblock Browser 2.0 for iOS adds Ghost Mode for the ultimate in anonymous private web browsing
Publié: septembre 19, 2017, 6:30pm CEST par Mark Wycislik-Wilson
Adblock Plus is about more than just its eponymous software -- the company also produces Adblock Browser. Now version 2.0 of the secure, private mobile web browser has been released for iOS and it introduces a wealth of new features. Key among these new features is Ghost Mode which makes it easy to slip into anonymous web browsing mode whenever privacy is of the utmost importance. As the name of the browser implies, there is also an integrated ad-blocker, but it does not end there -- this is an update that the company has been working on for more than… [Continue Reading] -

Amazon announces faster Fire HD 10 tablet with improved battery, 1080p display and a lower price
Publié: septembre 19, 2017, 3:44pm CEST par Mark Wycislik-Wilson
It has been a while since Amazon launched a new Fire tablet, but today the online retailer has unveiled the all-new Fire HD 10. The processors, battery and screen have all been upgraded, but the starting price has been slashed to just $149.99 (or £149.99). The screen is a 10.1-inch 1080p affair offering 224 ppi, and the tablet's processor has been upgraded to a quad-core chip, boosting the speed by up to 30 percent. Amazon claims the battery will last for up to 10 hours, and the addition of stereo Dolby Atmos Audio speakers has the sound side of things… [Continue Reading] -

Avast opens up about CCleaner hack and outlines how it will protect users
Publié: septembre 19, 2017, 11:43am CEST par Mark Wycislik-Wilson
When news broke yesterday that CCleaner had been hacked and a dangerously modified version had been available to download for a number of weeks, there were understandable concerns from the program's large userbase. And the concern is well-placed -- some 2.27 million machines are thought to have installed the infected software. Avast now has something of a PR nightmare on its hands as it tries to rebuild the trust of its users. To this end, company CEO Vince Steckler and CTO Ondřej Vlček have written an article clarifying what happened with CCleaner, and give some details about how they plan… [Continue Reading] -

Gmail and Inbox now convert addresses, phone numbers and contacts into clickable links
Publié: septembre 19, 2017, 10:39am CEST par Mark Wycislik-Wilson
The chances are that when you read that headline -- particularly if you're not a Gmail or Inbox user -- your reaction was something along the lines of "how is that not already a thing?" The update is a simple one, but one that will be welcomed by users. Just as URLs are automatically converted into clickable links, so the same luxury is to be lavished on addresses, phone numbers and contacts. Welcome to 2017. As the conversion is carried out automatically, there's nothing Gmail and Inbox users actually need to do. Once the feature has been activated by Google,… [Continue Reading] -

Microsoft confirms Outlook.com is down for some people
Publié: septembre 18, 2017, 9:16pm CEST par Mark Wycislik-Wilson
If you are having trouble accessing Outlook.com at the moment, you're not alone. Many people -- particularly in Europe -- are experiencing problems with Microsoft's email service. Microsoft has confirmed that there is an issue with "load-balancing infrastructure," and investigations are underway to discover the source of the problem. Users affected by the problem say that the messages they try to send remain in the Draft folder rather than reaching the intended recipient. The problem-detecting site downdetector shows that there are large number of people experiencing problems with either accessing the Outlook website or logging in. In the comments people… [Continue Reading] -

Apple Watch Series 3 does not support roaming
Publié: septembre 18, 2017, 2:52pm CEST par Mark Wycislik-Wilson
When the Apple Watch Series 3 was revealed last week, there was much excitement about the fact that -- at long last -- it would be possible to make calls without the need to have an iPhone nearby. Built-in cellular connectivity is something Apple Watch users have been begging for, and the Series 3 model delivers LTE goodness. But all is not quite as rosy as it might first seem. Yes, it's possible to use your new Apple Watch to make phone calls, but it's not going to be of any use to you if you go abroad. The smartwatch… [Continue Reading] -

How to disable the Bixby button on your Samsung Galaxy S8 or Galaxy S8+
Publié: septembre 18, 2017, 12:54pm CEST par Mark Wycislik-Wilson
If you have a Samsung Galaxy S8 or Galaxy S8+ you may well have a strong opinion about the dedicated Bixby button. For some people, one-click access to Samsung's digital assistant, Bixby, is a real boon -- for others it's just a pain in the butt. The positioning of the button is such that it is incredibly easy to hit it by mistake, such as when you try to press the volume down button. With a new update Samsung is finally making it possible to disable the button. You should find that the software updates automatically to give you access… [Continue Reading] -

Security warning: Hackers compromised CCleaner and installed a backdoor
Publié: septembre 18, 2017, 11:52am CEST par Mark Wycislik-Wilson
Users of cleanup, privacy and optimization tool CCleaner are being warned to update their software after it emerged the tool was compromised by hackers. Security researchers at Cisco Talos say that there are a "vast number of machines at risk." CCleaner is produced by Piriform, now a subsidiary of security firm Avast, making the compromise not only serious, but also embarrassing. With 2 billion downloads -- a number that's rising at a rate of 5 million per week -- the software was targeted by hackers who added a backdoor that could be used to download malware, ransomware and keyloggers. The… [Continue Reading] -

Microsoft enters the fight against fake news as Bing gains Fact Check label
Publié: septembre 18, 2017, 10:43am CEST par Mark Wycislik-Wilson
The "fake news" moniker may be a relatively recent one, but the phenomenon is not exactly new. Search engines and social media sites have long fought a battle against rogue news sources, and Microsoft's latest attack sees the company adding fact-checking to Bing. The addition of Fact Check labels means that anyone looking at search results should be able to tell at a glance if a particular news story has been debunked. The label can be applied to sites as a whole as well as individual articles, making it easier for Microsoft to alert people about poor news sources --… [Continue Reading] -

New Google test drops app ratings in favor of download sizes in the Play Store
Publié: septembre 18, 2017, 7:57am CEST par Mark Wycislik-Wilson
Some Android users have spotted a change in the Play Store. Since time immemorial, Google has shown star ratings in app listings and search results -- because that’s one of the ways in which users decide what to download. But for some people this has changed. Rather than a star rating, apps are now listed with their download sizes. For the Android user who is worried about running out of space this is arguably a useful change, but it's not something that most people will regard as a step in the right direction. See also: Google Play Protect branding to… [Continue Reading] -

Google launches Tez in India, a new digital payment app for iOS and Android
Publié: septembre 18, 2017, 7:24am CEST par Mark Wycislik-Wilson
As had been widely expected, Google has unveiled its new mobile payment service for India. Called Tez, the service is Google's first step into digital payments in Asia. Tez makes it possible for users to link their bank accounts to the app and then use their phones to make in-person payments and transfers. Support for the government-backed UPI (Unified Payments Interface) means the service is compatible with a number of major banks. At the moment, Tez is limited to India, but there appear to be plans to spread it further. See also: Google will launch a mobile payment service in… [Continue Reading] -

Instagram may have just solved the noisy autoplaying video problem
Publié: septembre 17, 2017, 8:13am CEST par Mark Wycislik-Wilson
Facebook, Twitter, Instagram and plenty of other social media platforms have all experienced a backlash from users at some point about how they handle autoplaying videos. Some users are not happy that videos play automatically because it eats into data, but the most vocal complaints come from those who hate videos that not only autoplay, but autoplay with sound. Instagram is rolling out an update that acts as a brilliant compromise between silent autoplay and noisy autoplay. Simple yet clever, it's hard to imagine that the idea won’t be copied by all and sundry. See also: Prepare to get pissed… [Continue Reading] -

Kodi addons site TVAddons insists its domains are not being used to spy on users
Publié: septembre 17, 2017, 7:34am CEST par Mark Wycislik-Wilson
The Kodi addons site TVAddons vanished from the internet a little while ago before reappearing with a new domain. The site faced legal action over claims it provides access to pirated content, and there have been suggestions that the original TVAddons domain is being used by a law firm to spy on users. The team behind TVAddons insists that this is not the case, and wants to set the record straight once and for all. It says that, in fact, everything possible has been done to protect user privacy. So are tvaddons.ag and xbmchub.com being used to gather evidence about Kodi users?… [Continue Reading] -

Warning: Google may delete your Android backups without warning
Publié: septembre 16, 2017, 2:11pm CEST par Mark Wycislik-Wilson
You never fully appreciate the value of a backup until you need it. When you consider how much we all use our phones these days, our handsets contain a wealth of data -- and it make sense to back it up. If you're using an Android smartphone, you can use an automated backup feature to safeguard the data from your phone by backing it up to Google Drive. With your data stashed in the cloud, you might think all is well -- but Google could delete your backups without giving you any warning. This sound like utter madness, but it's… [Continue Reading] -

Android root management tool SuperSU hits 100 million downloads
Publié: septembre 16, 2017, 1:42pm CEST par Mark Wycislik-Wilson
Just as there is quite a lot of interest in jailbreaking iPhones to allow for the installation of unofficial software, on Android there are a lot of users who root their handsets. If you ever wondered just how many people were into rooting, the success of SuperSU gives you an idea. While this is not a tool for rooting your smartphone -- this is something that's easily achieved on most handsets using various tools and online instructions -- SuperSU is a valuable addition to the software toolkit of anyone who has gone down the rooting route. As an indication of… [Continue Reading] -

The Pirate Bay is secretly running a Bitcoin miner in the background, increasing your CPU usage
Publié: septembre 16, 2017, 1:17pm CEST par Mark Wycislik-Wilson
When it comes to the Pirate Bay, it's usually movie studios, music producers and software creators that get annoyed with the site -- you know, copyright and all that. But in an interesting twist it is now users who find themselves irked by -- and disappointed in -- the most famous torrent site in the world. So what's happened? Out of the blue, the Pirate Bay has added a Javascript-powered Bitcoin miner to the site. Nestling in the code of the site is an embedded cryptocurrency miner from Coinhive. Users who have noticed an increase in resource usage on their… [Continue Reading] -

Microsoft claims there are 330 million Edge users -- but surely this is utter nonsense
Publié: septembre 15, 2017, 6:07pm CEST par Mark Wycislik-Wilson
Like Internet Explorer before it -- although perhaps not to quite the same extent -- Microsoft Edge is shunned and ridiculed by most web users. Despite this, Microsoft has this week claimed that its web browser has a huge number of users. "Microsoft Edge users are active on 330 million monthly devices!" proclaims the Microsoft Edge Dev team on Twitter. (File under: You Must Be Bloody Well Joking). The claim, made on Twitter and repeated during an Edge Summit webinar attracted some attention -- not least that of Paul Thurrott. He's not alone in wondering how on earth Microsoft came… [Continue Reading] -

OurMine leaks 3TB of Vevo data after hacking video streaming service
Publié: septembre 15, 2017, 5:28pm CEST par Mark Wycislik-Wilson
Infamous hacker group OurMine has struck video streaming service Vevo. The group breached Vevo late on Thursday, gaining access to, and leaking, more than 3 terabytes of internal videos and documents. OurMine -- more recently involved in HBO hacks and Game of Thrones leaks -- managed to get hold of office documents, videos and promotional materials. While many of the files and documents are fairly innocuous, at least some of them would be considered "sensitive" in nature. See also: Hackers take over HBO's social media accounts and publish '4th Wave HBO Leak' TheShadowBrokers group returns with NSA UNITEDRAKE hacking malware… [Continue Reading] -

Face ID on iPhone X has a quick-disable anti-theft feature, says Apple
Publié: septembre 15, 2017, 12:07pm CEST par Mark Wycislik-Wilson
With the launch of the iPhone X, Apple unleashed Face ID biometrics on the world. During a demonstration of the feature there was a SNAFU when Face ID failed to work as intended (due, Apple says, to staff playing around with the device beforehand), and there are many questions hanging over the idea of using one's face to unlock a phone -- Senator Al Franken has many questions, for example. Among the questions posed by Franken and others are queries such as "what's to stop someone using a photo or mask to unlock my phone?", and "if a mugger steals my… [Continue Reading] -

Facebook tests Snooze function that lets you temporarily mute your friends
Publié: septembre 15, 2017, 10:40am CEST par Mark Wycislik-Wilson
While you may be friends with someone on Facebook, it doesn't mean that they're not going to annoy you. Stoking the fires of annoyance is, after all, one of the (albeit probably unintentional) functions of social media. If a friend upsets you, you might consider unfriending them. It's a somewhat extreme reaction, but it's something that happens regularly. Should you feel that this is indeed something of an over-reaction, Facebook's testing of a Snooze function may appeal to you, as it lets you put your irritating friends on a timeout. First spotted by TechCrunch, the Snooze functions makes it possible… [Continue Reading] -

Facebook updates ad targeting policies after anti-Semitic 'Jew haters' campaigns
Publié: septembre 15, 2017, 9:54am CEST par Mark Wycislik-Wilson
Facebook has been forced to amend its ad targeting policies after an investigation by ProPublica found that the social network was permitting advertisers to target individuals with anti-Semitic beliefs. The New York-based news organization found that advertisers were able to use a number of categories such as "Jew hater," "How to burn Jews," "History of 'why jews ruin the world,'" and "Hitler did nothing wrong." All of these categories were created by users -- rather than Facebook or advertisers -- as they self-reported their education and employment history with offensive terms and labels. As a result of ProPublica's investigation --… [Continue Reading] -

Trump blocks Chinese purchase of chip-maker Lattice over national security concerns
Publié: septembre 14, 2017, 6:51pm CEST par Mark Wycislik-Wilson
President Trump has blocked a Chinese investment firm from buying US company Lattice Semiconductor. The acquisition was stopped because of national security concerns. Following a recommendation by the Committee on Foreign Investment in the United States (CFIUS), the Trump administration said that the potential buyer, Canyon Bridge, "might take action that threatens to impair the national security of the United States." A Portland, Oregon company, Lattice manufacturers a range of products including wireless radio chips and programmable gate arrays. An order signed by Donald Trump blocked the purchase, despite protestation from Lattice that there was no cause for concern. In… [Continue Reading] -

Privacy: Senator Al Franken has a lot of concerns about Face ID on the Apple iPhone X
Publié: septembre 14, 2017, 6:00pm CEST par Mark Wycislik-Wilson
From the moment Apple started to talk about Face ID, there were concerns voiced about privacy and security. It's not just security experts and potential users who have these worries; Senator Al Franken has written to Tim Cook asking for details about the safeguards Apple has put in place to protect users. On top of this, Franken wants to know more about how Apple trained the Face ID algorithm, and seeks assurances that third parties will not be able to access or be granted access to Face ID data. In a letter dated September 13, Senator Franken says: "As I… [Continue Reading] -

Facebook launches Crisis Response, a portal to find out about crises around the world
Publié: septembre 14, 2017, 4:38pm CEST par Mark Wycislik-Wilson
Facebook has today launched Crisis Response, a central hub that provides access to its various crisis response tools such as Safety Check. Over the years, the social network has gradually added more and more tools that serve to help those caught up in a disaster, and those who know them, and the new center pulls all of these into one place. As well as serving as a central hub, Crisis Response on Facebook is also being bolstered by links to articles and videos posted on the site so users can be kept better informed about a given crisis. The new… [Continue Reading] -

HP blocks third-party ink with printer firmware update... again
Publié: septembre 14, 2017, 11:36am CEST par Mark Wycislik-Wilson
HP is pushing out a firmware update to its range of Officejet printers that blocks the use of the third-party ink cartridges. This is not the first time the company has issued such an update as it tries to force printer owners to buy its own, more expensive cartridges. A year ago, HP faced strong criticism from the Electronic Frontier Foundation for implementing DRM that forced users to buy official ink. At the time HP saw the error of its ways and backtracked on the third-party ink ban, but now the company is having another crack of the whip. HP's… [Continue Reading] -

Google ad hints at Pixel 2 and Pixel XL 2 event on October 4
Publié: septembre 14, 2017, 11:04am CEST par Mark Wycislik-Wilson
Google is expected to take the wraps off the Pixel 2 next month along with -- probably -- the Pixel 2 XL. Last year's Pixel event took place on October 4, and the appearance of a billboard in Boston suggests that the same date will be used this year. The Google billboard says simply: "Ask more of your phone" and then the date, Oct. 4. The sighting of the billboard comes just as the LG-manufactured Pixel 2 XL passes through FCC. It is a few weeks since an FCC filing for the HTC-manufactured Pixel 2 was spotted, and the last… [Continue Reading] -

Google will launch a mobile payment service in India called Tez
Publié: septembre 14, 2017, 10:35am CEST par Mark Wycislik-Wilson
A new report suggests that Google is on the verge of launching a mobile payment service in India. Known as Tez (meaning "fast" in Hindi), the service could launch as early as Monday, according to Indian news site The Ken. Google Tez is said to offer more payment options than Android Pay, including support for the government-backed Unified Payments Interface (UPI). See also: New mobile-friendly Google Dashboard simplifies privacy settings Drive File Stream launches for G Suite users as Google kills off its Drive software 'It is time to return to not being evil': Opera and Vivaldi founder accuses Google… [Continue Reading] -

Kaspersky software banned from US government systems over concerns about Russia
Publié: septembre 13, 2017, 8:55pm CEST par Mark Wycislik-Wilson
The Department of Homeland Security has told US government agencies to remove Kaspersky software from their systems. The directive was issued because of concerns about influence exerted over the company by the Russian government. Government agencies have been given three months to identify and start to remove Kaspersky's security products. Kaspersky has constantly denied connections to the Russian government, but the US is simply not willing to take the risk. See also: Congress continues Kaspersky probe fearing 'nefarious activities against the United States' Kaspersky Secure Connection VPN service is free, but Android users aren't happy with the permissions it requires Kaspersky… [Continue Reading] -

Bashware: Microsoft refutes claims that Linux makes Windows 10 insecure
Publié: septembre 13, 2017, 6:52pm CEST par Mark Wycislik-Wilson
A recent report from Check Point Research suggested that the presence of Windows Subsystem for Linux (WSL) in Windows 10 poses a security risk to Microsoft's operating system. Researchers from Check Point highlighted the issue of Bashware attacks which use WSL to bypass security products. Microsoft, predictably enough, disagrees with the findings -- and so do other researchers. The Windows-maker says it views the risk of Bashware as "low". But is the company being too dismissive? See also: Bashware attack makes Linux a security threat to Windows 10 With Android Oreo, Google is introducing Linux kernel requirements Microsoft has finally… [Continue Reading] -

Facebook introduces monetization limitations and new advertiser controls
Publié: septembre 13, 2017, 5:23pm CEST par Mark Wycislik-Wilson
Today Facebook introduces new limitations on what sort of content can be monetized on its network. It's a move that is designed to keep the social network relatively family friendly, and Facebook also wants to address advertiser concerns about the type of content their ads appear next to. The company is not only clamping down on what can be monetized, it is also doing more to keep advertisers happy, including using third-party verification to measure ad performance. On top of this, Facebook is seeking accreditation from the Media Rating Council for Instagram, Facebook and Audience Network. As part of the… [Continue Reading] -

Apple quietly raises iPad Pro prices after iPhone X launch
Publié: septembre 13, 2017, 3:05pm CEST par Mark Wycislik-Wilson
The iPhone X surprised some people with its starting price of (just) under a grand -- many were expecting Apple to break the $1,000 barrier even with the base model. It wasn't all good news on the price front, though. As well as hiking the cost of AppleCare+ for some devices, Apple also raised the price of some iPad Pro models. With no announcement, the price of the 256GB and 512GB 10.5 and 12.9-inch iPad Pro models have jumped by $50. Apple has not given a reason, but the increased price of memory has been suggested as a possibility. The… [Continue Reading] -

BlueBorne Bluetooth vulnerability 'exposes almost every connected device'
Publié: septembre 13, 2017, 1:46pm CEST par Mark Wycislik-Wilson
Armis Lab, the Internet of Things security firm, has revealed details of BlueBorne, a Bluetooth vulnerability that affects millions of iOS and Android smartphones, IoT devices, and Windows and Linux systems. In all, 5.3 billion devices are believed to be at risk. The BlueBorne attack makes it possible for an attacker to spread malware or take control of nearby devices. What's particularly concerning is that for an attack to be successful, there is no need for device pairing, or even for a target device to be in discoverable mode. There's also no need for any sort of interaction by the… [Continue Reading] -

JPMorgan chief dismisses Bitcoin as 'a fraud' currency, ideal for drug dealers and murderers
Publié: septembre 13, 2017, 12:55pm CEST par Mark Wycislik-Wilson
Speaking at a banking conference in New York, Jamie Dimon -- chief executive of JPMorgan -- has dismissed the cryptocurrency Bitcoin as a fraud that will blow up. He said that if he found employees at his investment bank using the digital currency, he "would fire them in a second." Dimon likened Bitcoin to tulip bulbs and said: "The currency isn't going to work. You can't have a business where people can invent a currency out of thin air and think that people who are buying it are really smart." See also: AlphaBay Market disappears from the dark web as… [Continue Reading] -

Apple strips the App Store from iTunes 12.7
Publié: septembre 13, 2017, 11:40am CEST par Mark Wycislik-Wilson
The focus of Apple's event yesterday was certainly the new iPhones, but this was far from being all that came out of Cupertino. Apple also released iTunes 12.7 and there's a glaring change -- the App Store is gone. iTunes has long been derided for being bloated, and this latest change seems to be Apple's attempt to get things back under control. Ditching the App Store means that apps can only be downloaded using an iOS device, but as significant as this is, it is not the only notable change in the software. See also: Apple launches iPhone 8 and… [Continue Reading] -

Apple jacks up the price of AppleCare+
Publié: septembre 13, 2017, 11:03am CEST par Mark Wycislik-Wilson
If you were enticed by yesterday's iPhone 8, iPhone 8 Plus and iPhone X announcements, you may be preparing to delve into your pocket to hand over some cash for one of Apple's latest handsets. If you're thinking of taking out AppleCare+ insurance to protect your new device, you're going to have to dig a little deeper. Apple is increasing the price of AppleCare+ for its Plus model -- including the previous generation iPhone 6s Plus and iPhone 7 Plus -- and is introducing a new, even higher price point for iPhone X insurance. See also: Apple launches iPhone 8… [Continue Reading] -

Apple launches iPhone 8 and iPhone 8 Plus with A11 Bionic chip
Publié: septembre 12, 2017, 8:33pm CEST par Mark Wycislik-Wilson
Today Apple took the wraps off the eagerly-awaited iPhone 8 and iPhone 8 Plus -- which Apple says improves on everything about the iPhone. Available in silver, space gray, and gold, the phones have glass on the front and back and are sealed for water and dust resistance. The body is built from a custom aluminum alloy and the glass has a seven-layer color process. Looks are important, but what's going on inside also matters. Apple claims that this is the first smartphone designed for AR, helped along by new gyroscopes and accelerometer as well as the new A11 Bionic… [Continue Reading] -

Leave your iPhone at home: Apple Watch Series 3 has built-in cellular
Publié: septembre 12, 2017, 7:56pm CEST par Mark Wycislik-Wilson
Apple Watch -- the number one watch in the world -- now has an LTE variant, distinguishable by a red crown. Apple Watch Series 3 can be used to make and receive calls using the same number as your iPhone, but you no longer need to have your iPhone with you. Apple boasts of a new dual core processor with up to 70 percent better performance. There's also a new W2 chip with 85 percent faster Wi-Fi and better battery efficiency, and it's claimed that Apple Watch Series 3 has all-day battery life. Apple also announced a new gray ceramic… [Continue Reading] -

Want to unsend WhatsApp messages? Delete For Everyone feature is being tested
Publié: septembre 12, 2017, 6:08pm CEST par Mark Wycislik-Wilson
WhatsApp users have many requests for new features that would improve the way the app works for them. One that is most frequently requested is the ability to unsend messages that have been fired off in haste, or contain mistakes. Users of the Facebook-owned messaging tool will be pleased to hear that the unsend option -- also known as Delete For Everyone -- is undergoing testing, and could be on the verge of rolling out to all. See also: Verified accounts are coming to WhatsApp WhatsApp tests free Business app, but will charge larger enterprises The highly reliable WABetaInfo revealed… [Continue Reading] -

Facebook removes Instant Articles from Messenger
Publié: septembre 12, 2017, 5:38pm CEST par Mark Wycislik-Wilson
Facebook's self-hosted Instant Articles have been dropped from Facebook Messenger. The faster-loading, mobile-optimized versions of articles will still be available in the main Facebook app, just not in the company's messaging tool. While Facebook launched Instant Articles promising much, publishers have failed to see the income they would have hoped for from articles presented in this way. This has been blamed on it being much harder to track Instant Article Content. See also: Facebook tests Instant Video downloading over Wi-Fi to save your data Facebook hit with €1.2 million fine for Spanish privacy violations Speaking to TechCrunch, a Facebook spokesperson… [Continue Reading] -

OnePlus 5 Special Edition may be launched at Paris event on September 19
Publié: septembre 12, 2017, 5:09pm CEST par Mark Wycislik-Wilson
At an event in Paris next week, OnePlus is teaming up with French fashion designer Jean-Charles de Castelbajac. The company is giving nothing away at the moment, but it's widely expected that we'll see an announcement about OnePlus 5 Special Edition -- possibly called Callection. A leaked photograph shows a box that bears the words "Shot on OnePlus JCC+" on the side -- surely a reference to a Jean-Charles de Castelbajac special edition of the phone. See also: New OnePlus 3/3T beta rolls out, while OnePlus 5 update is recalled No more major updates to OnePlus 3 and 3T after… [Continue Reading] -

Android Oreo's Wi-Fi Passpoint support makes hotspot switching simple
Publié: septembre 12, 2017, 12:08pm CEST par Mark Wycislik-Wilson
We've already heard a lot about what's new in Android 8.0 Oreo, but something that has not received much attention is its support for Wi-Fi Passpoint. Also known as Hotspot 2.0, the technology was introduced by the Wi-Fi Alliance way back in 2012 as a way to simplify the process of moving from one wireless hotspot to another. Anyone who has connected to a hotspot while walking through a city will have experienced the frustration of having to log into one hotspot after another in order stay connected to the internet. Wi-Fi Passpoint makes jumping from one hotspot to the… [Continue Reading] -

Facebook tests Instant Video downloading over Wi-Fi to save your data
Publié: septembre 12, 2017, 10:57am CEST par Mark Wycislik-Wilson
Facebook has managed to effectively reduce page loading times for its users with the Instant Articles feature. Now the social network is looking to do something similar with video content. The feature is called Instant Videos, and it works by automatically downloading videos when there is a Wi-Fi connection available so they can be watched later without having to use a data connection. Instant Videos is undergoing testing with a limited number of users at the moment ahead of a possible wider rollout. Just as with Instant Articles, videos that are accessible through Instant Videos are indicated by the presence… [Continue Reading] -

Samsung plans to release a foldable Galaxy Note in 2018
Publié: septembre 12, 2017, 9:47am CEST par Mark Wycislik-Wilson
The age of the flip phone may be well and truly over, but people still seem to be hankering for a foldable handset. Samsung is hoping to help people fulfil their dreams, aiming to release a foldable phone in 2018. Koh Dong-jin, president of mobile business at Samsung Electronics, has said that the company is hoping to release a Galaxy Note with a bendable screen in 2018. He also said that Samsung is working with Harman on an AI-powered speaker. Samsung has already demonstrated foldable display technology, but is clearly having trouble incorporating it into a smartphone that that will… [Continue Reading] -

Facebook hit with €1.2 million fine for Spanish privacy violations
Publié: septembre 11, 2017, 4:22pm CEST par Mark Wycislik-Wilson
That Facebook is causing ripples when it comes to privacy will come as little surprise to anyone. Like Google, the social network and its users have an interesting relationship with privacy. Facebook is facing a particular problem in Europe, and the latest installment of the saga sees the company being fined €1.2 million ($1.44 million) by the Spanish data regulator AEPD. After an investigation into Facebook, the regulator found that the company had gathered sensitive personal data without consent, and this constituted a very serious infringement of data protection laws. The investigation also identified two "serious" violations, including tracking users… [Continue Reading] -

Microsoft has finally fixed some game performance issues in Windows 10 Creators Update
Publié: septembre 11, 2017, 12:25pm CEST par Mark Wycislik-Wilson
Although Windows 10 Fall Creators Update is only just around the corner, Microsoft is still fixing problems with the current Creators Update. The update still may not yet have rolled out to everyone, but there have been plenty of complaints about gaming performance. Some five months ago, users started to complain about a drop in framerate and stuttering performance in a number of popular games. Microsoft has now finally acknowledged that there is a problem, and has issued a fix for one of the issues. See also: Windows 10 Fall Creators Update launches October 17 Over a third of Windows… [Continue Reading] -

Twitter is testing a tweetstorm feature to allow for longer tweets
Publié: septembre 11, 2017, 11:13am CEST par Mark Wycislik-Wilson
There are two features that Twitter users constantly ask for -- the ability to edit tweets, and the ability to send tweets that are longer than 140 characters. Tweet editing is not likely to come any time soon, and longer tweets are also an uncertainty, but Twitter could be about to make tweetstorming much easier. Tweetstorms are the alternative to longer tweets: messages that won't fit into 140 characters are simply manually split up over multiple tweets. Manually doing this is a chore, but there is hope on the horizon. A hidden tweetstorm composer has been unearthed in the Twitter… [Continue Reading] -

PewDiePie is back with his own brand of casual racism
Publié: septembre 11, 2017, 10:28am CEST par Mark Wycislik-Wilson
The N word is undeniably inflammatory -- particularly when used by the wrong person in the wrong situation. An example of the word being used by the wrong person in the wrong situation? PewDiePie (yep, him) casually spitting out the epithet as an insult during a gaming session. During a live stream of PlayerUnknown's Battlegrounds, PewDiePie -- real name Felix Kjellberg -- ejaculated "what a f***ing n***er!" when one of his teammates was killed in the game. The incident has been somewhat polarizing on social media, and it's not the first time the most popular YouTuber in the world has… [Continue Reading] -

New mobile-friendly Google Dashboard simplifies privacy settings
Publié: septembre 10, 2017, 6:07pm CEST par Mark Wycislik-Wilson
Google and privacy are not really happy bedfellows, but the company likes to at least give the impression that its users have a semblance of control over what the company does with their data. To this end, the new Google Dashboard aims to simplify the act of taking control of your data. At least that's the idea. In Google's own words, "Data helps improve our products, keep them safe, and -- with your permission -- tailor them to match your interests." Data is Google's business. It's not in the company's interest for you to have too much control over your… [Continue Reading] -

iPhone 8 and iPhone X leaks: firmware reveals a lot about Apple's upcoming smartphones
Publié: septembre 10, 2017, 5:01pm CEST par Mark Wycislik-Wilson
Ahead of just about any smartphone launch, there are usually endless leaks -- but Apple is different. While there are often rumors about what the next iPhone will be like, photo leaks and confirmable details of features are rare. Ahead of Tuesday's big event at the Steve Jobs Center in Cupertino, however, there have been some pretty major revelations. A leak of the iOS 11 gold master has crept online, and analysis of the code seems to confirm that Apple is planning to launch an iPhone 8, an iPhone 8 Plus and an iPhone X on September 12. As well… [Continue Reading] -

European Court of Justice will determine the legality of mass surveillance in the UK
Publié: septembre 8, 2017, 5:49pm CEST par Mark Wycislik-Wilson
The Investigatory Powers Tribunal has ruled that the legality of mass surveillance in the UK should be decided by the European Court of Justice. The ECJ has already ruled that governments engaging in "general and indiscriminate retention" of data is illegal, and this led campaign group Privacy International to bring a case. The ruling means that only targeted interception of data and communication is permissible, something which the Investigatory Powers Act -- also known as the snooper's charter -- goes far beyond. The IPT conceded that some data collection is "essential to the protection of the national security of the… [Continue Reading] -

Researcher finds 'serious' security flaws on HMRC's UK tax site
Publié: septembre 8, 2017, 4:05pm CEST par Mark Wycislik-Wilson
A security researcher discovered two serious flaws on the HMRC tax website which could have allowed attackers to view, or even edit, tax records. But the researcher, Zemnmez, was astonished not only by the flaws, but also at how hard it was to report them. In a lengthy blog post entitled "how to hack the uk tax system, i guess," Zemnmez gives details of his findings. He also reveals that it took no fewer than 57 days to successfully report the issues so they could be looked into. Zemnmez is not new to finding bugs and security issues on websites,… [Continue Reading] -

TheShadowBrokers group returns with NSA UNITEDRAKE hacking malware and promises more leaks
Publié: septembre 8, 2017, 12:26pm CEST par Mark Wycislik-Wilson
It feels as though it has been a while since we heard anything from the hacking group TheShadowBrokers. The group's latest data dump sees the release of the NSA's UNITEDRAKE exploit tool, and there's also a promise of two data dumps a month moving forward. UNITEDRAKE is a remote access hacking tool that can be used to target Windows machines. Modular in nature, the malware can be expanded through the use of plugins to increase its capabilities so it can capture footage from webcams, tap into microphones, capture keystrokes, and more. See also: After WannaCry chaos, ShadowBrokers threaten 'Data Dump… [Continue Reading] -

AI gaydar can accurately determine sexuality from a photo
Publié: septembre 8, 2017, 10:38am CEST par Mark Wycislik-Wilson
Facial detection technology is usually used to identify individuals for the purposes of crime prevention, or as a biometric security method. But a paper published by Stanford University -- entitled simply "Deep neural networks are more accurate than humans at detecting sexual orientation from facial images" -- shows that it could also be used to determine people's sexuality. Using AI and deep neural networks, algorithms have been shown to have a far better gaydar than people. Working with a sample of more than 35,000 photographs, the system was able to correctly determine whether individuals were gay or straight with staggering… [Continue Reading] -

Facebook uses World Suicide Prevention Day to highlight the support it offers
Publié: septembre 7, 2017, 8:01pm CEST par Mark Wycislik-Wilson
This Sunday -- September 10 -- is World Suicide Prevention Day. Facebook is using the global event to draw attention to the help it offers to those contemplating suicide. The social network is planning to run ads in users' newsfeeds throughout the month, highlighting the supportive groups and suicide prevention tools that are available. Facebook is also launching a new Online Well-being portal which features advice about suicide prevention and how to resolve problems. See also: Facebook says it is likely Russia paid for polarizing political ads during US election Facebook is overestimating its ad reach Facebook offers millions to… [Continue Reading] -

Hackers can take control of Siri, Cortana and other digital assistants with ultrasonic commands
Publié: septembre 7, 2017, 5:00pm CEST par Mark Wycislik-Wilson
Security researchers have discovered that digital assistants, including Alexa, Siri and Cortana, are vulnerable to hacking via inaudible voice commands. Known as the DolphinAttack, the exploit involves the use of ultrasonic commands that cannot be heard by humans. Researchers from China's Zhejiang University have detailed the attack technique in a paper, but there are so many limitations and caveats that the vulnerability is not something that most people need worry about. The DolphinAttack -- so-called because dolphins use ultrasonic frequencies to communicate -- could be used to control a large number of smartphones, computers, cars and other smart devices, and… [Continue Reading] -

Facebook says it is likely Russia paid for polarizing political ads during US election
Publié: septembre 7, 2017, 2:06pm CEST par Mark Wycislik-Wilson
Speculation about Russian interference in the US election that saw Donald Trump propelled to presidency has been rife for months. Now Facebook has conceded that it's likely that a group operating out of Russia was responsible for taking out $100,000 worth of advertising that "focus[ed] on amplifying divisive social and political messages across the ideological spectrum." The ads appeared between 2015 and 2017, and touched on polarizing topics such as gun rights, LGBT issues, race and immigration. Facebook is quick to point out that the advertising related to "inauthentic" accounts and Pages and that these have now been closed down,… [Continue Reading] -

Hide 'running in the background' Notification app for Oreo does exactly what you'd hope
Publié: septembre 7, 2017, 12:54pm CEST par Mark Wycislik-Wilson
While there is a great deal to like about Android 8.0 Oreo, the latest version of Google's mobile operating system is not without issues. Some users are wondering whether or not their phones will get the upgrade, and some who have upgraded are experiencing problems with data usage. One niggle that has caused a lot of complaints is Oreo's notification that there are apps running in the background. It's Google's attempt to warn people about apps that might be draining their battery, but many people are more than a little irked by the pestering. Thankfully, there's a free app to… [Continue Reading] -

Night mode comes to Twitter on the web
Publié: septembre 7, 2017, 12:21pm CEST par Mark Wycislik-Wilson
Android and iOS users who like to browse Twitter in bed were pleased when a night mode was added to the mobile apps, saving middle-of-the-night blindings. Now night mode has made its way to the web. Whether you see night mode as an eye-saving feature, or just a way to get in touch with your inner goth, the arrival of the feature has been long-awaited by users. Unfortunately for those who are eager to step over to the dark side, there may be a little wait before night mode is available to everyone. While Twitter has flicked the switch on… [Continue Reading] -

Drive File Stream launches for G Suite users as Google kills off its Drive software
Publié: septembre 7, 2017, 11:41am CEST par Mark Wycislik-Wilson
Google is deprecating the Google Drive software for PC and Mac as it launches Drive File Stream. The company plans to support the cloud storage software for just three more months before killing it off completely in six months. Starting in October, Drive users will begin to be shown messages informing them that their software is going away. Users with both Drive File Stream and Backup and Sync will be prompted to stop syncing My Drive with the latter. It's a move from Google that is likely to cause confusion among users. SEE ALSO: Greatly enhanced Google Backup and Sync… [Continue Reading] -

OnePlus 3 users treated to Android Oreo beta -- OnePlus 3T and 5 won't be far behind
Publié: septembre 7, 2017, 11:04am CEST par Mark Wycislik-Wilson
True to past form, OnePlus is not hanging about in getting Oreo pushed out to its smartphones. It's early days at the moment, but OnePlus 3 owners can already download a beta version of Android 8.0 for their devices. The update is only available to members of a closed beta group at the moment, but a public beta is due by the end of September. OnePlus has not indicated exactly when the 3T and 5 will receive the beta, but the update is on the way. See also: Android Oreo could eat through your data allowance even if you have… [Continue Reading] -

Symantec: hackers could target US and European power grids with Dragonfly 2.0 attacks
Publié: septembre 6, 2017, 6:22pm CEST par Mark Wycislik-Wilson
Researchers at Symantec have warned that a "sophisticated attack group" is targeting the energy sector in Europe and North America, and has been doing so for some time. A group known as Dragonfly has been detected carrying out attacks since 2011, and the campaign of attacks was recently stepped up a gear. Dubbed the Dragonfly 2.0 campaign, the attacks included disruption to the Ukrainian power system in 2015 and 2016. After a quiet period, the group's activities have started up again, with targets hit in US, Turkey and Switzerland. On the hit list are energy facilities -- something that could… [Continue Reading] -

Facebook is overestimating its ad reach
Publié: septembre 6, 2017, 5:25pm CEST par Mark Wycislik-Wilson
Facebook ad metrics are facing scrutiny after it transpired the social network is overestimating the potential audience advertisers can expect to reach. A senior analyst from Pivotal Research Group points out that Facebook's Adverts Manager tool suggests demographic figures that exceed official numbers. For example, advertisers are told that they could hit up to 41 million 18- to 24-year-olds in the US, but according to recent census data only 31 million 18- to 24-year-olds live in the US. The discrepancy is not isolated, as there are similar instances of inflated potential reach suggestions for various age groups in the US,… [Continue Reading] -

Android Oreo could eat through your data allowance even if you have Wi-Fi enabled
Publié: septembre 6, 2017, 3:31pm CEST par Mark Wycislik-Wilson
An apparent bug with Android Oreo has been discovered which means Google's mobile operating system could be munching its way through your data allowance, even if you're connected to a wireless network. A thread on Reddit highlighted the issue, with many people pointing out that it could prove expensive for anyone not using an unlimited data plan. Google is apparently aware of the problem and is working on a patch, but in the meantime Oreo users are being warned to consider disabling mobile data when they are at home or using a wireless connection elsewhere. See also: With Android Oreo,… [Continue Reading] -

Facebook offers millions to music industry to avert copyright crisis
Publié: septembre 6, 2017, 12:19pm CEST par Mark Wycislik-Wilson
Facebook is said to be offering hundreds of millions of dollars to music publishers and record labels to avoid having to take down user-generated videos that feature copyrighted music. Bloomberg cites "people familiar with the matter" as saying Facebook's payments will allow for the legal use of songs in uploaded videos. At the moment rights holders can tell Facebook to remove any videos that feature copyrighted music, and the social network is keen to create a frictionless experience for users if at all possible. See also: Facebook Watch is now available right across the US Facebook launches Watch, a new… [Continue Reading] -

Facebook Watch is now available right across the US
Publié: septembre 6, 2017, 11:40am CEST par Mark Wycislik-Wilson
Facebook Watch may sound like it's going to be a cheap alternative to the Apple Watch, but it's really just Facebook's latest jump into video. Launched a month ago, Facebook Watch is now available to everyone in the US. The initial launch was a limited one, and just last week the rollout expanded to a wider group of users. But now everyone in the US is able to see the Watch tab on desktop and mobile platforms, giving access to original video content. See also: Facebook launches Watch, a new platform for original shows Facebook's love of video is no… [Continue Reading] -

FTC spanks Lenovo for bundling security-compromising adware on laptops
Publié: septembre 6, 2017, 10:58am CEST par Mark Wycislik-Wilson
Lenovo has settled with the Federal Trade Commission after selling laptops with VisualDiscovery adware pre-installed. The Superfish-developed adware was installed without users' consent and made machines vulnerable to man-in-the-middle attacks. On top of this, the adware shared users' browsing data with third parties. As part of the settlement, Lenovo must gain explicit consent from users before engaging in similar tactics in the future, and must not misrepresent software that serves to inject ads into browsing sessions. The FTC did not, however, prohibit Lenovo from installing adware on its hardware, nor did it impose a financial penalty on the Chinese company.… [Continue Reading] -

Employer breached worker's privacy by reading private messages sent through work account
Publié: septembre 5, 2017, 12:35pm CEST par Mark Wycislik-Wilson
A Romanian worker's "right to a private life" was breached when his employer read private messages sent using his work Yahoo Messenger account. The European Court of Human Rights agreed with Bogdan Bărbulescu that previous court hearings had failed to address the issue correctly. A majority of 11 out of 17 judges said that Bărbulescu's right to a private life was infringed upon when his employer read through chat logs containing both private and professional content. Bărbulescu was fired from his job when his employer discovered his professional Yahoo Messenger account had been used to communicate with both his fiancée… [Continue Reading] -

Want to download Huawei EMUI images? Tough... they've vanished!
Publié: septembre 5, 2017, 11:34am CEST par Mark Wycislik-Wilson
Out of the blue, and without a proper explanation, Huawei has pulled EMUI images from its websites. Anyone looking for a ROM for their smartphone is now out of luck. Although the Chinese company makes reference to wanting to give users a "more convenient and satisfactory update service," it's not really clear what this means in practice. The images could appear on a new dedicated site, but for the moment Huawei is remaining tight-lipped about what's going on. If you visit the download site, you're greeted by a message informing you of the lack of downloads. You can close this… [Continue Reading] -

Apple Music Festival is cancelled indefinitely
Publié: septembre 5, 2017, 10:05am CEST par Mark Wycislik-Wilson
The Apple Music Festival -- formerly known as the iTunes Festival -- has been cancelled. The termination of the festival comes after a decade-long run which has seen performances from artists such as Oasis, Adele, Ed Sheeran, Coldplay, Lady Gaga and Elton John. Once a month-long event, the Apple Music Festival shrank down to just a 10-nighter in recent years. Apple -- due to launch the iPhone 8 next week -- is unlikely to completely pull out of the music scene, having recently been involved in the sponsorship of shows by Lana Del Rey and Arcade Fire. Apple has confirmed… [Continue Reading] -

Official Plex for Kodi addon now available to everyone -- with and without a Plex Pass
Publié: septembre 5, 2017, 9:16am CEST par Mark Wycislik-Wilson
It has been hard to escape talk of Kodi recently. The media center software has caused a great deal of controversy due to the number of addons that can be used to access illegal content. Most recently, the software hit the headlines after legal intervention lead to the withdrawal of the unofficial MK Plex addon that allowed for access to Plex through Kodi free of charge. But now there's no need to turn to the dark side to get your Plex fix in Kodi if you haven’t paid for a Plex Pass subscription. The official Plex for Kodi addon is… [Continue Reading] -

Will my phone get Android 8.0 Oreo?
Publié: septembre 4, 2017, 6:23pm CEST par Mark Wycislik-Wilson
If there's one thing that the release of a new version of Android highlights, it's Android's fragmentation problem. While iPhone users can be sure of receiving iOS upgrades for a number of years, it's more of a gamble when it comes to Google's mobile operating system. The number of handsets that will receive an Oreo upgrade is relatively small, so the chances are that the answer to the question posed in the headline is "no". That said, there are many phones that will get the update to Android 8.0 -- so here's the list. See also: With Android Oreo, Google… [Continue Reading] -

Leaked Service Eligibility Guidelines show how Apple decides whether to repair or replace iPhones
Publié: septembre 4, 2017, 3:52pm CEST par Mark Wycislik-Wilson
What are the chances of getting a new iPhone if your handset develops some sort of fault? If you take a damaged or troublesome iPhone into an Apple store, you might be told you're eligible for a repair, or you might walk out with a completely new phone. A newly leaked document shows how Apple decides what treatment you receive. A document known as the "Visual/Mechanical Inspection Guide" has been leaked to Dropbox, and it shows how Apple technicians choose between offering in-warranty repair, out-of-warranty repair, or a replacement phone. Dating to March this year, the VMI -- as it's… [Continue Reading] -

YouTube ripping site YouTube-MP3 to close after record label lawsuit
Publié: septembre 4, 2017, 12:56pm CEST par Mark Wycislik-Wilson
YouTube-mp3.org -- "the easiest online service for converting videos to mp3" -- is closing down. The ripping site faced action from numerous record labels, but it has now come to an arrangement with the RIAA. The site is one of many that make it possible to convert YouTube videos into MP3 format, but it has piqued the interest of copyright lawyers. Millions of users meant the site was able to rake in ad revenue -- something the RIAA and record labels were less than happy about. An arrangement with the RIAA means YouTube-MP3 will close, leaving users looking for another… [Continue Reading] -

Facebook has mapped the location of millions of people down to 5-meter accuracy
Publié: septembre 4, 2017, 11:49am CEST par Mark Wycislik-Wilson
If you've ever thought that Facebook knows a little too much about you, here's something that's going to do nothing to dislodge that fear from your mind. Using a combination of government census information and data from satellites, the social networking giant has mapped the location of people in 23 countries around the world. In all, Facebook knows where millions of people live down to an accuracy of 5 meters. All of this has been made possible by a mapping technology developed by Facebook to help it see how people are distributed across the globe to determine how best to… [Continue Reading] -

Reddit is killing off access to its main source code, because open source is bad for competition
Publié: septembre 4, 2017, 10:18am CEST par Mark Wycislik-Wilson
Nine years after going open source, Reddit is archiving the source code for its website and mobile apps. The source code will still be accessible, but will no longer be updated -- Reddit cites concerns about competition as one of the reasons for the change in direction. But Reddit is not completely turning its back on open source. While it will no longer be possible to access the full source code, it will still be possible to access a limited number of small codebases -- such as baseplate, rollingpin and mcsauna. The site says, "those who have been paying attention… [Continue Reading] -

With Android Oreo, Google is introducing Linux kernel requirements
Publié: septembre 3, 2017, 2:22pm CEST par Mark Wycislik-Wilson
Android may be a Linux-based operating system, but the Linux roots are something that few people pay much mind. Regardless of whether it is known or acknowledged by many people, the fact remains that Android is rooted in software regarded as horrendously difficult to use and most-readily associated with the geekier computer users, but also renowned for its security. As is easy to tell by comparing versions of Android from different handset manufacturers, developers are -- broadly speaking -- free to do whatever they want with Android, but with Oreo, one aspect of this is changing. Google is introducing a… [Continue Reading] -

Now everyone can try the Outlook.com beta -- no special tricks needed
Publié: septembre 3, 2017, 1:50pm CEST par Mark Wycislik-Wilson
It has been a few weeks since Microsoft launched an updated beta version of Outlook.com. Rather than making the beta available to everyone, the company chose to roll out the beta to a limited number of users -- although it was possible to jump the queue with a little trick. Now Microsoft has decided to make the Outlook.com beta available to everyone. There's quite a lot to try out, with an updated look and a host of new and improved features. While the beta version is available to everyone, it's not enabled by default. Switching to the new beta takes… [Continue Reading] -

MK Plex add-on for Kodi killed off by legal letter to TVAddons
Publié: septembre 1, 2017, 6:22pm CEST par Mark Wycislik-Wilson
Kodi has been in the news a great deal recently, thanks largely to a surge in interest in addons for the media center software. High profile addons like Phoenix disappeared, as did (temporarily) the addons site TVAddons. The latest victim is a Plex addon from MetalKettle -- MK Plex. Eager to avoid legal action after receiving a letter from Plex's legal team, MetalKettle decided to shut up shop rather than continue to provide an addon that could be used to access Plex through Kodi without a paid-for Plex Pass subscription. See also: Kodi users now need to turn to VPNs… [Continue Reading] -

Apple sends out invites to September 12 iPhone 8 launch
Publié: septembre 1, 2017, 3:43pm CEST par Mark Wycislik-Wilson
The launch of the iPhone 8 has been awaited with bated breath, and this time around there have been rather more leaks than normal. We've not only seen suggestions of what the new phone will look like, but also heard strong rumors about features such as wireless charging and Face ID 3D facial detection. What we have not known for sure is just when Apple will reveal all. Now the wait is over. The company has just sent out invites to an event to be held at the Steve Job Center in Cupertino ("let's meet at our place"). The date:… [Continue Reading] -

Windows 10 Fall Creators Update launches October 17
Publié: septembre 1, 2017, 3:21pm CEST par Mark Wycislik-Wilson
Microsoft has confirmed what leaks have suggested for a little while (thanks, Lenovo!). The launch date for Windows 10 Fall Creators Update is October 17, 2017 -- and no, there is no Autumn Creators Update! This will be the fourth major update to Windows 10, and it is one that has been keenly awaited by users of the operating system, although it's not going to be without its share of disappointments. Microsoft confirmed the release date at IFA today, and pointed out two of the update's key new features: eye-tracking and Windows Mixed Reality. See also: Microsoft brings Fluent Design… [Continue Reading] -

Could Kim Dotcom's Bitcache and K.im be the solution to piracy?
Publié: août 31, 2017, 1:50pm CEST par Mark Wycislik-Wilson
The man made famous by Megaupload, Kim Dotcom, thinks he may have come up with a solution to piracy. The solution pairs his new file-sharing site, K.im, with his micro-payment service Bitcache. Working in a slightly different way to Megaupload, K.im is a decentralized cloud-based hosting system. Users can upload files and they will be distributed between various cloud services and also Bittorent. Coupled with Bitcache, a Bitcoin-based payment system, creators can charge for access to their content. Kim Dotcom is still fighting extradition to the US, but this did not stop him from giving a demonstration of his new… [Continue Reading] -

Logitech Craft keyboard borrows heavily from Microsoft's Surface Dial
Publié: août 31, 2017, 12:06pm CEST par Mark Wycislik-Wilson
The latest device to be announced by Logitech is the Logitech Craft keyboard -- a wireless keyboard with a dial that's remarkably similar to the Surface Dial. It's so similar, in fact, that it's hard to imagine that Microsoft's lawyers aren't stroking their chins and wondering what to do. Logitech refers to the new hardware as an "advanced keyboard with creative input dial," and the main target audience is people working with Photoshop or other design ventures. Of course, the company wants to appeal to as many people as possible, and points out that the dial -- known as the… [Continue Reading] -

Google Play Protect branding to be added to certified Android devices
Publié: août 30, 2017, 11:21am CEST par Mark Wycislik-Wilson
Google Play Protect is the company's latest attempt to prevent Android users from being tricked into installing malware or insecure apps. As an extension of this, Google is introducing a branding program that will see the Google Play Protect logo added to certified Android devices. The certification of Android phones and tablets is not a new concept -- it's something that Google has been doing for a while. But the new branding on packaging will help buyers identify devices that Google has approved, and it should also encourage more manufacturers to submit their hardware for certification. Nothing about the certification… [Continue Reading] -

Verified accounts are coming to WhatsApp
Publié: août 30, 2017, 10:45am CEST par Mark Wycislik-Wilson
On various social media platforms, attaining a verified account is a major goal for users. It's something that's been available on Facebook for a while, and Twitter users from all walks of life are able to apply for verification. Soon to be added to this list is WhatsApp. The messaging app -- owned by Facebook -- has not only started to verify certain business accounts, but is also planning to release a standalone app that will allow companies to chat with customers. WhatsApp has not made any official announcement about account verification, but the news is available for all to… [Continue Reading] -

YouTube rolls out redesign and unveils new logo
Publié: août 30, 2017, 9:56am CEST par Mark Wycislik-Wilson
Redesigns are tricky beasts, almost inevitably dividing opinion and leading to questions about why things couldn't have just been left alone. Running the risk of a double whammy of complaints, YouTube has rolled out not only a redesign of its sites, but also a brand new logo. Both the desktop and mobile versions of YouTube have been treated to a new look. It's the redesign that has been beta tested on users for a few months, and with a few extra tweaks, the company is ready to give everyone access to it. While a fresh lick of paint for the… [Continue Reading] -

T-Mobile offers free calls and texts to those in the path of Hurricane Harvey
Publié: août 26, 2017, 12:35pm CEST par Mark Wycislik-Wilson
Hurricane Harvey has made landfall in Texas, and the powerful storm is wreaking havoc. With winds hitting 210km/h (130 mph) there is a devastating path of destruction as well as flooding. For those in the area, and those with loved ones affected by the storm, staying in contact is vital, as is the ability to contact emergency services. With this in mind, Verizon is doing everything it can to keep its network running, and T-Mobile is offering free calls and texts to customers. T-Mobile's free calls and texts will be available until September 1 for parts of Texas and Louisiana.… [Continue Reading] -

HBO hackers leak Game of Thrones Season 7 ending
Publié: août 26, 2017, 10:27am CEST par Mark Wycislik-Wilson
Following the hack of HBO, there has been a string of Game of Thrones leaks -- everything from scripts to complete episodes. Now the Mr Smith group behind the hack has leaked the ending of season 7 of the show. The leak is part of the "sixth wave" of data dumps and it reveals exactly how the show will end. With HBO seemingly unwilling to pay the ransom demanded by the hackers, the latest leak really comes as little surprise. See also: Hackers share HBO social media passwords and threaten to leak Game of Thrones S07E07 Hackers take over HBO's… [Continue Reading] -

Facebook updates On This Day to make it even more remember-y
Publié: août 25, 2017, 4:50pm CEST par Mark Wycislik-Wilson
If you have yet to be granted access to Facebook's trip-down-memory-lane feature, On This Day, now you're in luck. The social network has opened up the feature to all of its two billion users. At the same time, Facebook is introducing some interesting extras, and taking steps to ensure that more negative memories are not surfaced for you. On top of this, there are new seasonal memories and new ways to celebrate friendships. In addition to the daily memories that many Facebook users have become accustomed to, there are now also monthly and seasonal roundups to jog your memory. This… [Continue Reading] -

It's going to be easy to watch the Mayweather vs McGregor stream for free
Publié: août 25, 2017, 9:24am CEST par Mark Wycislik-Wilson
Saturday night's fight between Floyd Mayweather and Conor McGregor is set to be the most pirated sporting event in history. In the US, it's Showtime that will be airing the fight as a pay-per-view event, but links to live streams are already popping up online ahead of August 26th's event. The broadcaster has already taken pre-emptive court action to kill a number of pirate streams but it is -- predictably -- turning in to a game of whack-a-mole, and once the fight kicks off it will be near-impossible to close new streams that have popped up and stop people watching… [Continue Reading] -

How to add Google Maps search engines to Chrome
Publié: août 24, 2017, 4:36pm CEST par Mark Wycislik-Wilson
To make it quicker to perform searches using Google Maps, you might want to consider adding the site as a search engine in Chrome. This will save you having to manually visit the site before you start a search, and it's a pretty neat option. In fact, we’re going to show you how to add Google Maps to Chrome as a search engine in a couple of ways. The first is a simple option to look for a place on Google Maps. The second enables you to search for directions from your home address to your desired destination. Here's what… [Continue Reading] -

With Android Oreo, Google is stepping up app security
Publié: août 24, 2017, 11:03am CEST par Mark Wycislik-Wilson
App security is undeniably an issue for Android users, particularly those who choose to install apps from outside of Google Play. Even apps that are housed in the main store are not immune to security issues, but those from other sources are rather more risky. With Android O, Google has ditched "Allow unknown sources" -- the setting that could be toggled to allow for the installation of non-Play apps. Instead, there is a new "Install unknown apps" permission, and Google thinks this offers more control and greater security. See also: Here's what's new in Android 8.0 Oreo The new permission bolsters… [Continue Reading] -

Privacy: Mozilla to test opt-out telemetry collection in Firefox
Publié: août 24, 2017, 10:36am CEST par Mark Wycislik-Wilson
Plex recently caused controversy by changing its privacy policy so users could not opt out of data collection -- although the company backed down after assessing the level of concern it raised. Now Mozilla looks set to raise the hackles of privacy advocates as well. Mozilla engineers working on the Firefox web browser are concerned that the current opt-in system of data collection does not allow for the collection of unbiased data about which websites users visit and so on. As such a test period of telemetry which is opt-out is planned. See also: Plex updates its privacy policy --… [Continue Reading] -

Microsoft will never again sneakily force Windows downloads on users
Publié: août 23, 2017, 3:27pm CEST par Mark Wycislik-Wilson
There have been various controversies with Windows 10, from issues with privacy and telemetry, to ads and forced upgrades. Following a court case, Microsoft has vowed to never force upgrade files onto users again. Windows users in Germany were particularly unimpressed when Microsoft forcibly downloaded many gigabytes of files to upgrade from Windows 7 and 8 to Windows 10. Having held out for 18 months, and losing its case twice, Microsoft has finally agreed to stop its nefarious tactics. After a lengthy battle with Germany's Baden-Würtenberg consumer rights center, Microsoft made the announcement to avoid the continuation of legal action.… [Continue Reading] -

Watch the Samsung Galaxy Note 8 launch event here -- live!
Publié: août 23, 2017, 2:34pm CEST par Mark Wycislik-Wilson
After the disastrous launch of the Galaxy Note7, Samsung is surely hoping that the Galaxy Note 8 will be rather more successful and rather less fire-prone. The handset is due to be revealed later on today, and you can watch the event live so you get the news as soon as it breaks. As is usual for any major phone launch, there have been the normal round of leaks and rumors surrounding the Galaxy Note 8 (or Galaxy Note8, if Samsung retains the previous naming scheme), and we're expecting to see a Bixby-loving 6.3-inch phone with dual camera and optical… [Continue Reading] -

Is Facebook down? Sort of... and there's a simple fix
Publié: août 23, 2017, 1:57pm CEST par Mark Wycislik-Wilson
Some online events unite people -- such as the recent solar eclipse which was streamed online by millions of people unable to see the spectacle in person. Another uniting event occurs when a major website goes down... like Facebook. If you've tried to visit the social network today, you may well have found that the site doesn't load. "Is Facebook down?" you may ask, and you're not alone. Take a look at the website monitoring service Down Detector and you'll notice that Facebook is indeed experiencing problems. If you can't access the site, you are in good company. There are… [Continue Reading] -

Casio Edifice EQB-501: a semi-smartwatch with clout [Review]
Publié: août 23, 2017, 12:55pm CEST par Mark Wycislik-Wilson
Smartwatches. I'm not a fan. People may fawn over the likes of the Apple Watch, but I'm yet to be convinced by timepieces of this ilk. To be honest, I'm not -- or at least haven't been for a while -- much of a fan of watches in general. But that could be about to change. The Casio Edifice EQB-501 is a chunky, stainless steel bracelet watch that's hard to ignore; it is big, bold and striking. It is also Bluetooth enabled so it can, via a connection to your phone, automatically set the time (both locally and for a… [Continue Reading] -

Here's what's new in Android 8.0 Oreo
Publié: août 22, 2017, 9:02am CEST par Mark Wycislik-Wilson
Yesterday Google finally revealed Android 8.0, also known as Oreo. Aside from the name, release date and the question of whether individual handsets will be treated to an upgrade, the query on most Android users' lips is "what's new?". Google says that one of the primary aims with Oreo was to create "fluid experiences," as well as improving speed and efficiency. The company says that it is "smarter, faster, more powerful and sweeter than ever" -- but what does this actually mean in terms of new features? The rollout of new versions of Android is notoriously slow, but Pixel, Nexus… [Continue Reading] -

Facebook introduces a dedicated button to make it easier to access Safety Check
Publié: août 22, 2017, 8:11am CEST par Mark Wycislik-Wilson
Facebook's Safety Check feature has been around for some time now, giving people the chance to use the social network to let friends and family know they're OK in the event of a natural disaster or other catastrophe. It is Facebook that decides which events warrant activation of Safety Check, and until now it has also been down to the site to advertise the feature to users so they can either mark themselves safe, or check up on others -- but this is about to change. Facebook has now given Safety Check a permanent home so anyone who needs to… [Continue Reading] -

Online abusers face stiffer penalties as social media hate crime will be treated as seriously as face-to-face offenses
Publié: août 21, 2017, 12:51pm CEST par Mark Wycislik-Wilson
Online hate crimes are to be treated as seriously as abuse offenses committed offline as the UK's Crown Prosecution Service (CPS) aims to crack down on abuse and harassment on the likes of Facebook and Twitter. New policies covering hate crime relating to race, religion disability, sexuality -- including, for the first time, specific bisexual hate crimes -- will lead to harsher sentences for offenders. Alison Saunders, director of public prosecutions, wants to do more to fight online abuse because of the risk of it escalating into the sort of extremist hate seen in relation to events in Charlottesville. She… [Continue Reading] -

Plex backtracks on controversial privacy policy change
Publié: août 21, 2017, 10:00am CEST par Mark Wycislik-Wilson
Last week Plex upset a large portion of its userbase by announcing a change to its privacy policy. The change, which was due to take effect in late September, meant that it would not be possible to opt out of data collection. After a serious backlash, the company has changed its mind, backtracking on the privacy policy update, saying that it recognized the concerns raised by users. The company insists that it was not trying to sneak the policy change by users and that it had no intention of selling data. Importantly, however, users are still going to be able… [Continue Reading] -

Watch Microsoft's Xbox One X Gamescom presentation here!
Publié: août 20, 2017, 5:33pm CEST par Mark Wycislik-Wilson
Later on today you will be able to learn everything you could possible want to know about the Xbox One X. Microsoft is holding a press conference at Gamescom in Germany and you can watch it here, live. The presentation kicks off at 12:00PM PT / 3:00PM EST / 8:00PM BT / 9:00PM CET, and Microsoft has already made it clear that pre-order details will be revealed. See also: Here's why the Xbox One X is so damned expensive Microsoft leaks upcoming Xbox One S Minecraft Limited Edition We already know that the 4K Xbox One X is going to… [Continue Reading] -

Microsoft leaks upcoming Xbox One S Minecraft Limited Edition
Publié: août 20, 2017, 4:05pm CEST par Mark Wycislik-Wilson
At GamesCon later today, we're going to hear about Microsoft's Xbox One X but it's looking as though there's also going to be some news about the Xbox One S. Microsoft accidentally -- probably -- posted about an Xbox One S Minecraft Limited Edition on the Minecraft Facebook page. The video included a link to the pre-order page for the console. See also: Watch Microsoft's Xbox One X Gamescom presentation here! The video only appeared online for around half an hour, but this was long enough for it to be spotted by Surface Phone Italia. The site managed to grab… [Continue Reading] -

Amazon hands out $5 credits after accidentally making Echo Dot available free of charge
Publié: août 20, 2017, 3:38pm CEST par Mark Wycislik-Wilson
Anyone shopping for an Amazon Echo Dot a couple of days ago may have spotted that the online retail giant was making its second-generation assistant available free of charge. But the old adage "if it seems too good to be true, it probably is" turned out to be completely accurate. The $49.99 "Audible Promo" discount that led to the device being reduced in price to $0 was a SNAFU -- but Amazon is going to make up for it. As noted by Engadget on Friday, a discount related to Audible results in the Amazon Echo Dot being made available free of… [Continue Reading] -

Plex updates its privacy policy -- and now you can't opt out of data collection
Publié: août 19, 2017, 3:28pm CEST par Mark Wycislik-Wilson
Plex -- the much-loved media server software -- has updated its privacy policy, and people are not happy with the changes. Included among the changes is a notification that future features may collect and share details about what you're streaming. Usage statistics are collected by many companies -- including Plex -- to improve products; moving forward users will not be able to opt out of this data collection. Needless to say, Plex users are more than a little upset. See also: Plex Live TV and DVR features arrive on Android and Apple TV Plex Pass Perks give you money-off deals… [Continue Reading] -

Plex updates its privacy policy -- and now you can't opt out of data collection [UPDATED]
Publié: août 19, 2017, 3:28pm CEST par Mark Wycislik-Wilson
Plex -- the much-loved media server software -- has updated its privacy policy, and people are not happy with the changes. Included among the changes is a notification that future features may collect and share details about what you're streaming. Usage statistics are collected by many companies -- including Plex -- to improve products; moving forward users will not be able to opt out of this data collection. Needless to say, Plex users are more than a little upset. Update: Plex has now backtracked on this decision See also: Plex Live TV and DVR features arrive on Android and Apple… [Continue Reading] -

Facebook will protect your privacy... when you're dead
Publié: août 19, 2017, 12:58pm CEST par Mark Wycislik-Wilson
Facebook won't -- usually -- hand over your private messages to anyone after you die. The social network has used a new blogging series called Hard Questions to reveal just how it handles deaths of its users. The site's director of global policy management, Monika Bickert, says that Facebook aims to not only be sensitive, but also to respect the wishes of the deceased. After death, accounts are memorialized by default, but everyone is also free to create a "legacy contact" who will be able to mange their account in the event of their death. But Facebook is, it says,… [Continue Reading] -

YouTube introduces a breaking news section
Publié: août 19, 2017, 11:53am CEST par Mark Wycislik-Wilson
To make it easier for people to access up to date information about what is going on the world, YouTube is adding a "Breaking News" section to its website and mobile apps. The new section takes the form of an additional video carousel, and it provides access to new stories from a number of sources. At the moment, not all users are seeing the Breaking News carousel, and Google has not made an official announcement about it, but it does seem to be spreading out at the moment. The new section was first noticed by Android Police who notes that… [Continue Reading] -

Hackers share HBO social media passwords and threaten to leak Game of Thrones S07E07
Publié: août 19, 2017, 11:14am CEST par Mark Wycislik-Wilson
A few days ago, HBO's latest humiliation was to have its social media accounts taken over by hackers, and the bad news just keeps on coming for the network. The "Mr Smith group" behind the huge data breach that has seen endless Game of Thrones leaks contacted Mashable with the login details for many HBO social media accounts. On top of this, the group is also threatening to release Game of Thrones S07E07 -- but considering the number of episodes that have leaked from this season, this was to be expected. See also: Hackers take over HBO's social media accounts… [Continue Reading] -

Google unveils total solar eclipse site to count down to Android O launch
Publié: août 18, 2017, 6:25pm CEST par Mark Wycislik-Wilson
On Monday August 21, there are two big events to look forward to: the total solar eclipse, and the launch of Android O. Google is tying the two together with the launch of a new site counting down to the two events. With the launch of the eagerly anticipated Android O (will the name be Oreo, Oatmeal cookie... or something else?), another waiting game starts. Mobile owners around the world will be playing the "will my handset get the update this time around or not?" game. In the meantime, check out the site for eclipse and Android O live streams.… [Continue Reading] -

Kaspersky Secure Connection VPN service is free, but Android users aren't happy with the permissions it requires
Publié: août 18, 2017, 12:44pm CEST par Mark Wycislik-Wilson
In a time when people are more concerned about privacy than ever, security tools such as VPNs are proving increasingly popular. Kaspersky Lab recently released a VPN tool for Android, and reviewers are voicing concerns about the permissions required by the app. Kaspersky Secure Connection: VPN service has a reasonable overall review score at time of writing, but the lower scores are highly critical of what are seen as privacy-invading permission requirements. See also: Putin bans VPNs and proxies in Russia as Apple explains pulling VPNs from Chinese App Store Kodi users now need to turn to VPNs to watch… [Continue Reading] -

Facebook takes steps to stamp out clickbait videos
Publié: août 18, 2017, 11:49am CEST par Mark Wycislik-Wilson
As any Facebook user will know, clickbait is rife on the social network. A very common technique used to drive traffic to ad-laden websites is to embed fake play buttons in images, or post videos that are actually static images. Facebook is clamping down on these practices in a bid to tidy up users' newsfeeds and avoid people being transported to "low quality websites" set up by spammers. Over the next few weeks, Facebook will start to treat posts that try to fool people in this way differently. Fake play buttons and static video posts will be demoted to reduce… [Continue Reading] -

Watch the solar eclipse live on Twitter thanks to the Weather Channel
Publié: août 18, 2017, 11:02am CEST par Mark Wycislik-Wilson
On Monday August 21, people across the US will have the chance to witness a total solar eclipse. While there is a great deal of excitement about the phenomenon, viewers need to be careful to use special eclipse glasses (not just sunglasses) or some form of projection technique to avoid serious eye damage. But perhaps the safest option is to watch the eclipse on your computer screen or mobile. Twitter has teamed up with the Weather Channel to provide a live stream, so even if you're not in the path of totality, there's no need to miss out. The live… [Continue Reading] -

Electronic Frontier Foundation speaks out in favor of free speech after neo-Nazi websites are blocked
Publié: août 18, 2017, 10:14am CEST par Mark Wycislik-Wilson
Following the violence that took place in Charlottesville last weekend, technology companies have done everything they can to distance themselves from neo-Nazis, white supremacists and other right-wing groups. It led to numerous companies dropping right-wing sites such as The Daily Stormer, which was ultimately pushed to the dark web. Digital rights group the Electronic Freedom Foundation (EFF) -- well-known for speaking out about privacy and legal issues -- has criticized the ban on neo-Nazi sites and groups saying it poses a threat to free expression online. Google, GoDaddy, Cloudflare, Reddit and Facebook are just a handful of technology companies to… [Continue Reading] -

Google adds Q&A to search and Google Maps on Android
Publié: août 17, 2017, 2:17pm CEST par Mark Wycislik-Wilson
Android users now have a new "Question & answers" option in both Google Maps and search. This is not a general Q&A feature along the lines of Yahoo Answers, but a way to ask questions about businesses. This appears to be Google's attempt to draw people away from the likes of Facebook when they want to ask questions about hotels, restaurants and other places they may visit. Business owners are able to respond to questions -- as are users -- and they are encouraged to create FAQs to prevent the same queries being posted time and time again. In some… [Continue Reading] -

Download Google's experimental data-sipping Search Lite app
Publié: août 17, 2017, 1:35pm CEST par Mark Wycislik-Wilson
Technology companies are increasingly realizing that if they are to break into emerging markets, they're going to have to reduce the amount of data their apps use. Facebook Lite, Twitter Lite and LinkedIn Lite are just some of the less demanding apps to have been launched recently. Google doesn’t want to miss out on the action. It is currently testing a data-light version of its search app for use in countries with slow connections. Search Lite (or Search (Test App)) is currently available to download from Google Play in Indonesia -- or from other sources if you're elsewhere in the… [Continue Reading] -

Google Home now lets you make free calls
Publié: août 17, 2017, 12:26pm CEST par Mark Wycislik-Wilson
If you're a Google Home user living in the US or Canada, Google is now rolling out the ability to make free phone calls. The announcement sees the company making good on a promise from I/O 2017, and it extends the call-making capabilities of Google Assistant from smartphones to Google Home. There are, of course, a few limitations to keep in mind. Aside from being limited to the US and Canada -- and there's no indication that this will extend further -- free calls can only be made to regular national numbers. Landlines and mobiles are supported, but not international… [Continue Reading] -

Hackers take over HBO's social media accounts and publish '4th Wave HBO Leak'
Publié: août 17, 2017, 11:56am CEST par Mark Wycislik-Wilson
The nightmare continues for HBO. After suffering a hack and then leaks of various shows including Game of Thrones, hackers have now struck at the network's social media accounts. The hacking group OurMine took control of the main HBO Twitter accounts, as well as those for various shows, including Game of Thrones. OurMine is no newcomer to the scene -- the group has previously hacked Mark Zuckerberg and Netflix's Twitter accounts. Separately to this, what has been dubbed the "4th Wave HBO Leak" has been made available online. This time the data dumps include content relating to Game of Thrones… [Continue Reading] -

Facebook announces new birthday features -- fundraisers and celebratory videos
Publié: août 16, 2017, 5:30pm CEST par Mark Wycislik-Wilson
Facebook has been busy rolling out a batch of new features and even a new look in the last few days. Today the social network is taking the wraps off two more new features, both with a birthday theme. The one that's likely to be used the most is are new personalized videos which are essentially the photo-slideshows-as-a-video we have become used to from Facebook. The second new feature is the option to "donate" one's birthday, raising money for a particular cause by calling on friends for donations. See also: Facebook launches Watch, a new platform for original shows Facebook… [Continue Reading] -

Google adds pollen forecasts to searches
Publié: août 16, 2017, 1:33pm CEST par Mark Wycislik-Wilson
A lot of people like to know what the weather is going to be like, but if you suffer from hay fever it can be all the more important to know what to expect. To make life a little easier for people struck by "seasonal allergies," Google is rolling out pollen forecasting. The new feature is integrated into Google search, and it comes as the search giant teams up with The Weather Channel to help give accurate allergy information. The feature uses your location to provide you with up-to-date information about pollen and other allergens. To save you from having… [Continue Reading] -

HBO leaks Game of Thrones S07E06
Publié: août 16, 2017, 11:15am CEST par Mark Wycislik-Wilson
Season seven of Game of Thrones has been an absolute disaster for HBO. We have seen leaks and spoilers from both hackers and HBO's distributors, but now episode six of the season has leaked and HBO has no one to blame but itself. HBO Spain accidentally made the episode available to subscribers for a full hour before pulling it. Of course, this hour gave people plenty of time to capture the show, and spoilers are now being shared online. On Reddit, talk of download links has been pushed to PMs as moderators are only too aware that HBO will be… [Continue Reading] -

Donald Trump loses legal battle over iTrump app
Publié: août 16, 2017, 10:17am CEST par Mark Wycislik-Wilson
President Trump has lost a six-year legal battle against the creator of an iOS app. Tom Scharfeld is the man behind iTrump -- an app designed to teach people how to play the trumpet. He successfully represented himself in court, and prevailed over the US president, earning the right to retain the iTrump trademark. The roots of case date back to December 2010 when Scharfeld registered the iTrump trademark. Through his company Spoonjack, he released the iTrump and iBone apps, and in early 2011 he was contacted by Trump's lawyers who said that the trumpet app needed to be renamed… [Continue Reading] -

Facebook News Feed undergoes a redesign to improve readability and navigation
Publié: août 15, 2017, 9:39pm CEST par Mark Wycislik-Wilson
Facebook is rolling out a fairly significant redesign, giving the News Feed a cleaner look, and borrowing ideas from Twitter. The social network says that the changes improve readability and navigation, and they affect various areas. The redesign is far from insignificant, but perhaps the most instantly noticeable changes are the dropping of blue accents, and the switch to Twitter-style round images. There are, however, more changes to explore. For the mobile app, there's more borrowing from Twitter. The buttons used to switch between News Feeds, Friend Requests, Market Place and so on, are now cleaner, wireframe icons. In a… [Continue Reading] -

Hackers hit Scottish Parliament with 'brute force cyber-attack'
Publié: août 15, 2017, 9:08pm CEST par Mark Wycislik-Wilson
IT systems at the Scottish Parliament have been struck by a "brute force cyber-attack" from an unknown source. Staff have been advised to change passwords as a result of the attack. Paul Grice, Chief Executive at Holyrood, says that the attack is similar to the one Westminster suffered back in June. The hackers have attempted to crack passwords as well as trying to access parliamentary emails. In a warning to staff, Grice said: "The Parliament's robust cyber security measures identified this attack at an early stage and the additional security measures which we have in readiness for such situations have… [Continue Reading] -

Facebook rolls out Trending News to its mobile apps
Publié: août 15, 2017, 6:28pm CEST par Mark Wycislik-Wilson
We'll forgive you if you've lost track of all of the changes Facebook has introduced to the News Feed over the years -- it's often something of an experimental playground. The social network's latest idea is a dedicated "Trending News." The section is currently rolling out to mobile users, and is something of an extension of Facebook's Trending Topics. It is making its way out to Android and iOS users in the US. The section is fairly self-explanatory, providing access to news stories that are currently proving popular. iOS users in the US should already been able to see the… [Continue Reading] -

Microsoft is told there's nothing illegal about scraping public data from LinkedIn profiles
Publié: août 15, 2017, 6:20pm CEST par Mark Wycislik-Wilson
A federal judge has told Microsoft to stop preventing "talent management algorithm" hiQ Labs scraping data from public LinkedIn profiles. hiQ Labs has been using information gathered from LinkedIn to predict when people are going to leave their jobs -- information which is incredibly valuable to employers. Microsoft was not happy at the data that hiQ Labs had been scraping from public profiles, and tried to stop it from happening. The company introduced "various blocking techniques" to prevent the startup from accessing the data and secure user privacy, but the ruling ultimately went in favor of hiQ Labs. Making his… [Continue Reading] -

Kodi users now need to turn to VPNs to watch Premier League football
Publié: août 15, 2017, 5:12pm CEST par Mark Wycislik-Wilson
It has been difficult to avoid talk of Kodi for one reason or another recently, and it's something that's likely to be on the lips of fans of UK football now the 2017/18 Premier League season has started up. Watching pirated streams of football matches through IPTV providers and other services has long been a popular use for Kodi, and the English Premier League (EPL) has had enough. The organization previously obtained a High Court order blocking illegal streams in real-time, and a more recently obtained injunction extended this ability. With the new season now under way, football fans are… [Continue Reading] -

Department of Justice wants to identify 1.3 million visitors to anti-Trump site
Publié: août 15, 2017, 12:42pm CEST par Mark Wycislik-Wilson
The Department of Justice is trying to force a web host to reveal the IP addresses of over 1.3 million visitors to an anti-Trump website. The DoJ is also requesting contact information, email content and photos. The site -- #DisruptJ20 -- was used to organize protests against Donald Trump on the day of his inauguration. DreamHost says that it is fighting the warrant that has been issued, because the "information could be used to identify any individuals who used this site to exercise and express political speech protected under the Constitution's First Amendment. That should be enough to set alarm… [Continue Reading] -

Police in India arrest four over Game of Thrones leak
Publié: août 15, 2017, 10:43am CEST par Mark Wycislik-Wilson
HBO has had something of a rough time of things lately, suffering not only a hack that led to a series of leaks, but also a Game of Thrones leak via a distribution partner. Police in India have now arrested four people in connection with the leak of the episode The Spoils of War. Shortly after the leak occurred, HBO's distribution partner Star India admitted it was the source of the episode. Now three employees and one former employee of Prime Focus Technology -- a company which processes Game of Thrones ready for streaming on Hotstar -- are being questioned… [Continue Reading] -

Facebook expands Marketplace across Europe
Publié: août 15, 2017, 10:29am CEST par Mark Wycislik-Wilson
Looking to compete with the likes of eBay and Craigslist, Facebook's Marketplace serves as a place for people to go to buy and sell locally. Following on from success in the US, UK, Australia and other countries, the social network is expanding the exchange further into Europe. In total, Facebook's Marketplace is spreading to 17 European countries, meaning that it is now available in a total of 24 countries. The expansion means that people living in Austria, Belgium, the Czech Republic, Denmark, Finland, France, Germany, Hungary, Ireland, Italy, Luxembourg, Netherlands, Norway, Portugal, Spain, Sweden and Switzerland now have access to… [Continue Reading] -

Leaked memo shows high return rate for Surface devices, and Microsoft's image-improvement plans
Publié: août 14, 2017, 5:17pm CEST par Mark Wycislik-Wilson
When Consumer Reports announced that it was dropping its "recommended" status from Surface devices, Microsoft was quick to defend itself. While the software giant disagreed with the move, saying it doesn't believe the "findings accurately reflect Surface owners' true experiences or capture the performance and reliability improvements made with every Surface generation," a leaked internal memo shows high return rates for Surface Pro 4 and Surface Book. While it's certainly true that return rates have dropped over time, the information contained in the memo goes some way to explaining the decision taken by Consumer Reports. The memo also shows that… [Continue Reading] -

Google is testing Material Design in Google Calendar for the desktop
Publié: août 14, 2017, 3:57pm CEST par Mark Wycislik-Wilson
Despite the age of its Material Design, Google is being surprisingly slow in rolling out the look to its products. While the UI is found pretty much universally in Android apps, the appearance on the desktop is happening at a rather more leisurely pace. Chrome 59 sees the appearance of Material Design, and now Google is testing the look in the desktop version of Google Calendar. The design is undergoing testing through Google's Trusted Tester program, but images have leaked out giving us a glimpse of what's to come. Over on Reddit, a user called xDawnut has shared a series… [Continue Reading] -

Opera kills off its free data-saving app, Opera Max
Publié: août 14, 2017, 1:54pm CEST par Mark Wycislik-Wilson
Opera Max -- the free data-saving and VPN-like tool from the team behind the Opera web browser -- is being killed off. The app has been removed from Google Play with immediate effect, and there will be no more updates. Opera is not really giving a reason for the sudden decision other that the fact that Opera Max had "a substantially different value proposition than our browser products." The announcement will come as bad news for anyone who had come to rely on Opera Max to keep their data usage in check, particularly when traveling. It's a similar idea to… [Continue Reading] -

Google buys health monitoring startup Senosis Health
Publié: août 14, 2017, 12:53pm CEST par Mark Wycislik-Wilson
Google's latest acquisition is Senosis Health, a Seattle-based startup focused on monitoring and diagnosing health conditions via mobile phones. This is not Google's first venture into the world of health, but it could signify its next big step. Senosis Health, founded by Shwetak Patel, has transformed regular smartphones into medical devices that can be used to monitor everything from jaundice in babies to chronic respiratory diseases. The aim is to do as much as possible without the need for extra, specialist equipment. Senosis Health has even devised an app -- HemaApp -- which can measure hemoglobin levels using nothing more… [Continue Reading] -

Hackers leak more HBO episodes -- but Game of Thrones is left in the cold this time
Publié: août 14, 2017, 10:33am CEST par Mark Wycislik-Wilson
HBO continues to feel the fallout from the recent hack it suffered. We have seen leaks of episodes and scripts from Game of Thrones, and the network allegedly tried to offer the hackers a "bug bounty" to stop the leaks. The offer did not work, and the leaks continue. Episode five of Game of Thrones season seven may have aired last night (meaning today will undoubtedly see a flurry of downloads from torrent sites), but the hit show has been let off the hook in the latest batch. This time, it is episodes of Curb Your Enthusiasm and other shows… [Continue Reading] -

Bitcoin breaks $4,000
Publié: août 13, 2017, 11:46am CEST par Mark Wycislik-Wilson
The price of Bitcoin continues to rise, with the cryptocurrency now trading at over $4,000. It's only a matter of days since the price set at record when it passed $3,500, but this has now been broken already. The surge has been driven by Japanese interest in the currency, and trading currently stands at just under $4,200. After something of a wobbly period, the rise in Bitcoin has been fuelled by investors seeing it as a quick way to make a healthy return. The recent creation of Bitcoin Cash did not kill off the cryptocurrency in the way some feared.… [Continue Reading] -

Privacy warning: Android apps infected with SonicSpy spyware can record audio
Publié: août 13, 2017, 10:11am CEST par Mark Wycislik-Wilson
Security researchers from Lookout are warning about raft of spyware-infected apps that have been found in Google Play. Seemingly connected to Iraq, more than a thousand apps hve been found to include SonicSpy spyware. The spyware is embedded in a variety of legitimate-looking apps, such as messaging tools based on Telegram. One such example is an app called Soniac which was found to be capable of not only recording audio and retrieving contacts, but also taking photos and gathering phone logs. Lookout warns that SonicSpy is sneaky, and tries to hide from users to avoid detection. The first time the… [Continue Reading] -

No more major updates to OnePlus 3 and 3T after Android O
Publié: août 12, 2017, 3:15pm CEST par Mark Wycislik-Wilson
Following on from the launch of the OnePlus 5, owners of previous generation handsets from the Chinese company may well have been wondering how much more support they can expect. In an interview published on the OnePlus forums, the company's head of product has revealed all. Oliver Z says that OnePlus 3 and OnePlus 3T owners will not see any more major updates after Android O is released. If you were hoping to see Android P, you're out of luck. This is going to be hard for some OnePlus fans to take; while it means the handsets will have been… [Continue Reading] -

Chuwi's super-thin LapBook Air is ready to take on MacBook Air and Surface laptops
Publié: août 12, 2017, 1:10pm CEST par Mark Wycislik-Wilson
Chuwi is not a particularly well-known brand at the moment, but the company is starting to carve out something of a name for itself. We've already seen a handful of low-cost tablets and laptops from the Chinese brand, but its upcoming LapBook Air looks especially interesting. That the name blends elements from the MacBook Air and Surface Book is no mistake -- this is a laptop designed to compete with both. Chuwi claims the full-metal chassis is "just like touching the real MacBook," but it's the incredibly thinness that's the real head-turner here. Measuring just 6mm thick (at the narrowest… [Continue Reading] -

Leaked emails show HBO offered hackers $250,000 to delay Game of Thrones leaks
Publié: août 12, 2017, 12:35pm CEST par Mark Wycislik-Wilson
The hack suffered by HBO has been in the headlines for the last couple of weeks, not least because it led to the leak of episodes and scripts. The anonymous hackers were known to have made a ransom demand, but details of how this was handled were not made public. Now a leaked email suggests that HBO offered the perpetrators a sum of $250,000 to delay the leaks. But rather than offering up the sum as a ransom payment, HBO refers to the money as a "bug bounty payment." See also: Hackers leak Game of Thrones S07E05 script summary and… [Continue Reading] -

Former MI5 chief says UK government should not weaken encryption
Publié: août 11, 2017, 11:31am CEST par Mark Wycislik-Wilson
The UK government has made no secret of its desire to exert greater control over the internet, and home secretary Amber Rudd has gone as far as suggesting that encryption should be weakened -- and backdoors should be included in software -- to make it easier to carry out surveillance on terrorists. Lord Jonathan Evans, the former chief of MI5 in the UK, acknowledged that encryption had got in the way of monitoring communication between extremists, but said this should not be used as an excuse to weaken security. See also: UK Home Secretary supports back doors while claiming 'real… [Continue Reading] -

Google adds phishing protection to Gmail for iOS
Publié: août 11, 2017, 10:15am CEST par Mark Wycislik-Wilson
A few months ago, Google brought phishing protection to Gmail on Android. Now the company is doing the same for the iOS version of the app. The feature is rolling out over the next few weeks, and it offers a couple of safety nets to protect users from visiting potentially dangerous links in emails. SEE ALSO: Google adds phishing protection to Gmail app on Android Links that are known to be dangerous will be blocked automatically, although Google does still give the option of proceeding to the site in question at your own risk. Writing about the feature in a… [Continue Reading] -

WikiLeaks: CIA's CouchPotato tool grabs footage from remote video streams
Publié: août 10, 2017, 8:52pm CEST par Mark Wycislik-Wilson
The latest addition to WikiLeaks' Vault 7 cache of CIA documents and tools is a user guide for CouchPotato. This project is designed to capture RTSP/H.264 video streams, typically from networked cameras. This is rather different to the approach taken with the Dumbo project which required physical access to a computer. The CouchPotato documentation is relatively recent, only dating back to February 14, 2014. See also: 'Censorship is for losers': WikiLeaks offers fired Google engineer a job WikiLeaks: CIA's Dumbo project can hack webcams and corrupt recordings WikiLeaks reveals CIA's Imperial hacking project targeting Mac and Linux The leaked documents… [Continue Reading] -

Microsoft announces open source Coco Framework to speed up enterprise blockchain adoption
Publié: août 10, 2017, 8:28pm CEST par Mark Wycislik-Wilson
Microsoft has today announced Coco Framework, a means of simplifying the adoption of blockchain protocol technology. The aim is to speed up the adoption of blockchain-based systems in the enterprise, whilst simultaneously increasing privacy. Coco -- short for Confidential Consortium -- will be available in 2018, and Microsoft will be making the technology open source to help increase uptake. Intel is working with Microsoft as a hardware and software partner, and Coco Framework features Intel Software Guard Extensions (Intel SGX) to improve transaction speed at scale. The framework is compatible with Ethereum, but Microsoft envisions it being used across financial… [Continue Reading] -

Poor reliability means Consumer Reports no longer recommends Microsoft Surface -- or any other Microsoft laptop or tablet
Publié: août 10, 2017, 4:16pm CEST par Mark Wycislik-Wilson
Influential reviewer Consumer Reports says that it no longer recommends Microsoft Surface tablets and laptops. The consumer group says that poor predicted reliability for the Surface range means that it is pulling its "recommended" tag. More than this, Consumer Reports goes on to say that it "cannot recommend any other Microsoft laptops or tablets." Recent studies suggest that a quarter of laptops and tablets from Microsoft will present problems for users within two years of ownership. Consumer Reports is specifically stripping the 128GB and 256GB versions of the Surface Laptop and the 128GB and 512GB versions of the Surface Book… [Continue Reading] -

Mozilla Information Trust Initiative is ready to fight fake news
Publié: août 10, 2017, 1:18pm CEST par Mark Wycislik-Wilson
Facebook is not the only tech company looking to tackle the problem of fake news online. Mozilla, the company behind Firefox, has created the Mozilla Information Trust Initiative (MITI) in a bid to increase the credibility of the internet. This is not a solo venture. Mozilla is seeking partners it can work with to conduct further research into fake news, and then develop products to battle what it terms "information pollution" online. The company recognizes that the fake news phenomenon is not properly understood, and that the techniques used to disseminate twisted versions of stories are advanced. See also: Post… [Continue Reading] -

Vantiv buys UK payment processing firm Worldpay in $12.1 billion deal
Publié: août 10, 2017, 12:55pm CEST par Mark Wycislik-Wilson
UK payment processor Worldpay is the subject of a £9.3 billion ($12.1 billion) takeover by US rival Vantiv. The merged company will be known simply as Worldpay and will be headquartered in Cincinnati, but run from New York and London. In the deal, Vantiv is paying £8 billion ($10.4 billion) for Worldpay, plus an additional £1.3 billion ($1.7 billion) to cover debts. It is one of the biggest takeovers of a UK company since the Brexit vote of 2016. The takeover was initially agreed in July and it will create a £22.2 billion ($29 billion) operation when the deal completes… [Continue Reading] -

Facebook launches Watch, a new platform for original shows
Publié: août 10, 2017, 11:24am CEST par Mark Wycislik-Wilson
Facebook has launched its new Watch platform which will be used to show original video content. The social networking giant says that the time has come for a dedicated home for episodes of shows, and Watch will feature both live and recorded video. Facebook will be working with a number of partners to come up with content for Watch, and advertising revenue will be shared 55:45, with Facebook keeping the smaller share. Of course, the video output has a social element to it, with Facebook encouraging viewers to make use of Reactions, and also highlighting shows that are being watched… [Continue Reading] -

Disney faces lawsuit for allegedly spying on kids through mobile apps and games
Publié: août 10, 2017, 10:16am CEST par Mark Wycislik-Wilson
Disney -- who just announced plans to launch its own streaming service and drop Netflix -- is collecting personal information about children and non-consensually sharing it with advertisers, alleges a lawsuit against the company. The lawsuit, says that Disney and three other companies it worked with (Upsight, Unity, and Kochava) created apps that spy on users -- primarily children -- gathering information which is then shared with advertisers. If this is found to be the case, it is in violation of the Children's Online Privacy Protection Act, and Disney could be hit with hefty fines. SEE ALSO: Disney to pull… [Continue Reading] -

Facebook clamps down on address cloaking to protect users from spam and porn
Publié: août 9, 2017, 7:59pm CEST par Mark Wycislik-Wilson
Facebook has introduced a ban on address cloaking, a technique used to bypass review procedures and display content that violates the social network's policies. Cloaking is used to disguise the true nature of posts and ads from reviewers, so they will see different contents to real-world users when they click through. Facebook says that it will be working with other companies to find ways to fight cloaking and implement punishments. AI will be called upon to do some of the legwork. Facebook is particularly concerned about cloaking because of the "negative and disruptive experiences" it creates by displaying pages about… [Continue Reading] -

Instagram tests split-screen live video
Publié: août 9, 2017, 11:46am CEST par Mark Wycislik-Wilson
All of the messaging services worth their salt feature a live video option, and Instagram is no different. But the company is keen to get more people using it and is worried that going live alone is too intimidating for some people. To overcome this problem, Instagram is testing a new split-screen option that gives users the chance to go live with a friend. While this is billed as a way to make live video more accessible, there's far greater potential for this form of shared live video than Instagram is currently hinting at. With the new option it is… [Continue Reading] -

Disney to pull its content from Netflix and launch its own streaming service
Publié: août 9, 2017, 10:55am CEST par Mark Wycislik-Wilson
During its Q3 earnings report, Disney announced plans to launch its own streaming service in 2019. As part of this shift in business, the company will end its distribution agreement with Netflix. The company also announced that it has agreed to acquire an additional 42 percent stake in BAMTech. The $1.58 billion makes Disney a majority stakeholder and will give it greater control over the ESPN-branded multi-sport video streaming service due to launch in early 2018. The ESPN-branded service will feature Major League Baseball, National Hockey League, Major League Soccer, and more, and will be accessible through a new version… [Continue Reading] -

'Censorship is for losers': WikiLeaks offers fired Google engineer a job
Publié: août 8, 2017, 7:48pm CEST par Mark Wycislik-Wilson
Julian Assange has reached out to James Damore, the software engineer fired by Google for publishing an "anti-diversity manifesto." The WikiLeaks founder used his Twitter account (currently sporting a fake "verified" badge) to offer him a job. Linking to an article entitled "Google Is Not What It Seems" about his book When Google Met Wikileaks, Assange said: "Censorship is for losers. @WikiLeaks is offering a job to fired Google engineer James Damore." As well as the offer of a job for Damore, Assange criticized Google for what he sees as censorship, suggesting that employees should not be fired for "politely… [Continue Reading] -

Google launches privacy website ahead of new European data protection rules
Publié: août 8, 2017, 1:15pm CEST par Mark Wycislik-Wilson
New data protection rules are due to come into effect in Europe next year, and Google is highlighting the rights and obligations that are being introduced. The General Data Protection Regulation (GDPR) comes into force in May and Google, like other businesses, will need to comply. While Google needs to ensure that its own products and services fulfill legal requirements, the company also points out that "customers and partners have significant obligations under these new laws." A new website serves to explain everything that you need to know, including detailing how to control how your data is used and shared.… [Continue Reading] -

Hackers leak Game of Thrones S07E05 script summary and make ransom demand
Publié: août 8, 2017, 12:01pm CEST par Mark Wycislik-Wilson
The impact of the recent HBO hack continues to be felt. We've already seen scripts and spoilers leak online and now there's a new cache of leaks along with a ransom demand from those responsible. The data dump includes details of the script for episode five of the current season, and a video directed at HBO CEO Richard Plepler in which the unknown hackers -- who sign off as "Mr. Smith" -- give the company three days to pay up a ransom in Bitcoin. The hackers are threatening to release not only more Game of Thrones episodes and information about… [Continue Reading] -

Sundar Pichai writes note to employees saying anti-diversity memo violated Google's code of conduct
Publié: août 8, 2017, 11:02am CEST par Mark Wycislik-Wilson
The fallout from James Damore's anti diversity memo has been swift and wide-reaching. The senior software engineer was dramatically fired after expressing views which ran counter to Google's drive for diversity in the workplace. Company CEO Sundar Pichai responded to the memo in an internally-circulated note to staff which was then also shared publicly. In it, he acknowledged the furor surrounding the memo and said that "portions of the memo violate our Code of Conduct and cross the line by advancing harmful gender stereotypes in our workplace." See also: Google employee's anti-diversity manifesto goes viral as the company dismisses the… [Continue Reading] -

Irony alert: the BBC has designed its own font to avoid paying license fees
Publié: août 7, 2017, 1:53pm CEST par Mark Wycislik-Wilson
The BBC has announced plans to roll out a new font across its network of websites in a cost-saving measure. The corporation has designed a new font called BBC Reith, named after Lord Reith, the founder of the BBC. The beeb says that it will be able to save an undisclosed sum of money by ditching the fonts it currently uses as it will no longer have to pay license fees for them. That sound you can hear is the shrill ring of irony as a corporation that charges a license fee tries to avoid paying a license fee... But… [Continue Reading] -

HBO calls in FBI over Game of Thrones hack as Indian distributor admits it is the source of S07E04 leak
Publié: août 7, 2017, 12:46pm CEST par Mark Wycislik-Wilson
Season seven of Game of Thrones has been something of a disaster for HBO. Not in terms of interest or viewing figures, of course, but in terms of hacking, leaks, spoilers and piracy. Last night saw the official airing of episode four of season seven but this particular episode, The Spoils of War, leaked some days ago. Distribution partner Star India has admitted the leak came from its website, and HBO has called in the FBI to investigate the hack that lead to a number of episode and script leaks. See also: If you're downloading Game of Thrones, HBO has… [Continue Reading] -

Privacy: UK government to force social media and tech companies to give users more control over their data
Publié: août 7, 2017, 10:28am CEST par Mark Wycislik-Wilson
The UK government is set to introduce a new Data Protection Bill which will give people the right to demand companies delete personal data. The bill, due to be introduced this summer, will make it easier for people to find out what information is held about them and how it is being used. Matt Hancock, the Digital Minister, says that the bill amounts to a widescale "right to be forgotten" and it will give people the opportunity to separate themselves from online posts they made when younger. It will also take steps to increase privacy by making it harder for… [Continue Reading] -

Google employee's anti-diversity manifesto goes viral as the company dismisses the diatribe
Publié: août 6, 2017, 10:24am CEST par Mark Wycislik-Wilson
A document entitled "Google's Ideological Echo Chamber" in which an employee strongly criticizes the company's efforts towards diversity and equality has gone viral. The opinionated article was written by an unnamed senior software engineer, and it accuses Google of political bias while calling for great "ideological diversity." The document has been dubbed a "manifesto" and it went viral within Google. It was shared internally on a mailing list, and several Google employees tweeted about its existence. It did not take long for the rant -- which attributes the gender gap in technology to biological differences between the sexes -- to… [Continue Reading] -

Microsoft video confirms Spotify is coming to Xbox One
Publié: août 6, 2017, 9:47am CEST par Mark Wycislik-Wilson
It has long been expected that the Spotify app would make its way to Xbox One, and evidence supporting this has been mounting for some time. Now a video by Major Nelson -- or Larry Hryb, if you prefer -- confirms the existence of the app. Earlier in the week, eagle-eyed Xbox One users noticed Hryb was using the app. Later, a screenshot of Microsoft's ExpertZone website showed further evidence in the form of a (now-deleted) page referencing "Spotify goes Platinum" and a note that "Spotify is coming to Windows 10 and Xbox." The latest piece of evidence is rather… [Continue Reading] -

YouTube Music gets a proper offline mode for songs, albums and playlists
Publié: août 5, 2017, 12:12pm CEST par Mark Wycislik-Wilson
The arrival of offline mode to YouTube Music may not seem like news, but the reality is that the "mixtape" option that was available was very limited. Now YouTube has made it possible to download playlists, songs and albums for offline listening. As before, you need to be a YouTube Red member to take advantage of the feature, and the update means that users now have far more control over their offline listening rather than relying on YouTube to select tracks based on listening history. Downloading is incredibly simple ("Anywhere you see a playlist or album within the YouTube Music… [Continue Reading] -

Report: LTE Apple Watch is on the way this year
Publié: août 5, 2017, 10:39am CEST par Mark Wycislik-Wilson
One of the limitations -- if you want to class it as such -- of the Apple Watch is that it needs to be paired with an iPhone. But this could be about to change. According to a Bloomberg report, Apple is preparing to launch a new LTE version of its smartwatch later in the year. This will eliminate the need to own an iPhone and enable owners to connect directly to the internet with their watch. The company is said to already be in talks with mobile providers in the US and Europe about an upcoming LTE Apple Watch… [Continue Reading] -

New OnePlus 3/3T beta rolls out, while OnePlus 5 update is recalled
Publié: août 4, 2017, 4:59pm CEST par Mark Wycislik-Wilson
There's good news and bad news for OnePlus handset owners -- whether it's good or bad depends on whether you have a OnePlus 3/3T or a OnePlus 5. For users of the older handset, there's a new OxygenOS Open Beta which adds a decent selection of new features. For OnePlus 5 users, however, the OxygenOS 4.5.7 update that was released earlier in the week is being recalled. OnePlus is responding reports of terrible gaming performance in withdrawing the update. OxygenOS 4.5.7 rolled out as an OTA update on Tuesday, adding a new font and electronic image stabilization to 4K recordings,… [Continue Reading] -

Game of Thrones S07E04, The Spoils of War, leaks online
Publié: août 4, 2017, 4:50pm CEST par Mark Wycislik-Wilson
The fourth episode of the latest season of Game of Thrones has leaked online before its official air date. Download links to the episode -- The Spoils of War -- have been shared on Reddit and Twitter, and the video appears to be a low-quality internal version. Earlier this week, HBO was the victim of a hack in which 1.5TB of data was stolen. In addition to full episodes of other shows, there were scripts and spoilers for Game of Thrones, and these were subsequently leaked. This time around, however, it does not seem that the hack was the source of… [Continue Reading] -

WikiLeaks: CIA's Dumbo project can hack webcams and corrupt recordings
Publié: août 4, 2017, 1:28pm CEST par Mark Wycislik-Wilson
WikiLeaks has published the latest installment of its cache of CIA documentation known as Vault 7. This time around we learn about Project Dumbo, a hacking tool which allows for the control of webcams and microphones. Wired, Bluetooth and wireless devices can all be detected by Dumbo. In addition to this, Dumbo gives the CIA the ability to delete or corrupt recordings that have been made. WikiLeaks has published user guides for three versions of Dumbo, the most recent of which is dated June 2015. SEE ALSO: WikiLeaks reveals CIA's Imperial hacking project targeting Mac and Linux WikiLeaks: CIA analyzed… [Continue Reading] -

Lenovo smartphones will all feature stock Android from now on
Publié: août 4, 2017, 12:49pm CEST par Mark Wycislik-Wilson
Starting with the K8 Note, all of Lenovo's smartphones will come with stock Android installed. The company is dropping its customized Vibe Pure UI in favour of an (almost) untouched version of Android. The Lenovo K8 Note will come with Android 7.1.1 Nougat installed, and the company is making only minor additions in the form of Dolby Atmos and TheaterMax -- gone is the bloatware that irks users so much. Lenovo's decision has been driven by customer demand -- in India, there was a particular clamoring for stock Android. As well as eliminating bloat, the switch to stock Android means… [Continue Reading] -

Google Play now promotes apps that crash less and offer better battery life
Publié: août 3, 2017, 8:29pm CEST par Mark Wycislik-Wilson
There are many metrics by which to measure how good an app is, and Google is starting to use a few more when it ranks Android apps and games in the Play Store. The latest app-ranking algorithm now takes into account app stability, performance and battery usage. As well as improving the relevance of listings for people downloading apps, Google is also using this change to push developers to improve their apps. Google suggests that developers use information from the Android Vitals dashboard -- pooling data from users who have opted to share information about app performance -- to identify… [Continue Reading] -

Canonical publishes laughably simple guide to upgrading to the Ubuntu app for Windows
Publié: août 3, 2017, 6:04pm CEST par Mark Wycislik-Wilson
It is not long since Ubuntu made its debut in the Windows Store, much to the excitement of Linux fans. Now Canonical has provided a guide to upgrading from the "bash on Ubuntu on Windows" experience that's built into Windows 10, to the full-blown Windows Store version. As the Store version of Ubuntu will happily live alongside the bash on Ubuntu on Windows version, it's not really clear why this upgrade guide is needed, but it has been produced nevertheless. If you choose to follow it, Canonical warns that your data will be "nuked" -- so back it up! The… [Continue Reading] -

Try the public preview of new sign-in experience for Azure AD and Microsoft accounts
Publié: août 3, 2017, 5:40pm CEST par Mark Wycislik-Wilson
Microsoft has redesigned the sign-in process (or "experience" as the company refers to it) for both Azure AD and Microsoft accounts. The interfaces for the sign-in screens for both types of account have been updated so they are the same, and there's now a Google-style two-page sign-in procedure. The updated design is available as a public preview and the change has come about through telemetry data collected by Microsoft. The new experience can be found on desktop and mobile websites, and companies can add their branding to sign-in screens for a customized look. The two-page design (username/email address on the… [Continue Reading] -

Google now permits Android apps that facilitate gambling with real money
Publié: août 3, 2017, 4:26pm CEST par Mark Wycislik-Wilson
Google has relaxed its rules surrounding real-money gambling apps in Google Play -- in some countries, at least. There has been a ban on apps and games that allow users to gamble with real money since 2013, but that has now changed. While there was previously a ban in place due to the difficulty in policing ages and complying with different gambling laws around the world, real-money gambling apps are now permitted in the UK, France and Ireland. Rumors about the relaxation of Google's rules have been circulating for a little while, and in its August update to Developer Program… [Continue Reading] -

TVAddons is back, but the Kodi addon site faces secretive lawsuit from Canadian telecos
Publié: août 3, 2017, 3:19pm CEST par Mark Wycislik-Wilson
It has been hard to avoid stories about Kodi in recent months as broadcasters and copyright holders panic about the software's potential for piracy. The controversial site TVAddons was the subject of a lawsuit from Dish Network, and shortly after this it disappeared from the web completely. Rather than originating from the US as many people suspected, the lawsuit against TVAddons that led to its disappearance comes from Canadian telecoms firms Bell Canada, TVA, Videotron and Rogers. Now TVAddons is back, but the story about its legal battle -- involving claims of piracy of Game of Thrones -- is rather more… [Continue Reading] -

Verizon Up is a rewards program you pay for with your privacy
Publié: août 3, 2017, 11:40am CEST par Mark Wycislik-Wilson
You don't, as we all know, get something for nothing... but that doesn't stop companies from making it appear as though you do. The latest perpetrator of this crime against common sense is Verizon. The carrier has rolled out a rewards program -- Verizon Up -- which enables subscribers to earn credits for racking up a bill. For every $300 spent on Verizon Wireless products and services users are paid a credit which can collected and spent on various rewards (money off handsets, accessory discounts, and so on). But there is a price, and that price is privacy. In return… [Continue Reading] -

LG confirms its next flagship smartphone has a 6-inch plastic OLED FullVision display
Publié: août 3, 2017, 10:33am CEST par Mark Wycislik-Wilson
LG has confirmed rumors that its next flagship smartphone will feature a 6-inch OLED screen. While the Korean company does not reveal the name of the handset, it is believed to be the V30 which is due to be revealed very soon. Despite the giant size of the screen, the overall size of the phone is smaller than last year's LG V20; the company says this is thanks to a reduction in bezel size. The QHD+ OLED screen will also feature curved edges to improve ergonomics and, despite being plastic, there's still protection from Corning Gorilla Glass 5. LG points… [Continue Reading] -

Plex Live TV and DVR features arrive on Android and Apple TV
Publié: août 2, 2017, 7:52pm CEST par Mark Wycislik-Wilson
Plex has some good news for cord cutters with Plex Media Server installed and a Plex Pass. The Plex Live TV and DVR features are now out of beta! Live TV does very much of what you would expect, allowing live TV broadcasts to be streamed from a TV tuner to Plex. Plex DVR also lets you record shows, and time shifting has also been added so you can pause and rewind live broadcasts. Live TV is now available to Apple TV owners, while Android users are treated to Live TV and Plex DVR. Plex says that this means 2… [Continue Reading] -

As Game of Thrones spoilers leak online, Panda Security issues a stark warning
Publié: août 2, 2017, 5:48pm CEST par Mark Wycislik-Wilson
This week's hack of HBO led to the release of stolen episodes of Ballers and Room 104, and the threat of Game of Thrones leaks. Now the hackers have made good on their threat and uploaded scripts and episode summaries for yet-to-be-aired episodes, and speculation is rife that it is just a matter of time before episodes hit torrent sites such as The Pirate Bay. Season seven of the show is just getting underway, and details of episodes three and four have now been published online. Other files have also been leaked following the hack, including log in credentials for… [Continue Reading] -

Updated Google Earth arrives on iOS
Publié: août 2, 2017, 5:05pm CEST par Mark Wycislik-Wilson
It has been a number of months since Google Earth received a makeover on Android and the web, and now the update is making its way to iOS. The latest version of the 3D world-exploration tool has been overhauled, bringing a number of new features to iPhone and iPad users. These features include 360-degree videos, guided tours, and the interactive Voyager option for traveling virtually to major cities of the world. As well as being fun, the updated version of Google Earth makes it easier to learn about the world as well. Google's Knowledge Cards impart information about key landmarks… [Continue Reading] -

Unlimited data plans are killing 4G speeds in the US
Publié: août 2, 2017, 1:23pm CEST par Mark Wycislik-Wilson
4G speeds are slowing down for many people in the US as unlimited data plans become more prevalent. OpenSignal has just published its latest report into the state of mobile networks in the US, and for many people it is bleak reading. Unlimited data plans have been rolled out by AT&T, T-Mobile, Sprint and Verizon now. While networks that have supplied such packages for a while (T-Mobile and Sprint) have managed to increase the speed of 4G connections for customers, speeds have dropped for AT&T and Verizon users just six months after the introduction of unlimited plans. OpenSignal's report looks… [Continue Reading] -

NSA illegally spied on Kim Dotcom in New Zealand
Publié: août 2, 2017, 11:43am CEST par Mark Wycislik-Wilson
Kim Dotcom has been of interest to the US government and law enforcement agencies for some time, and it was ruled that the Mega and Megaupload founder could be extracted to the US. But now it seems that the NSA was spying on the internet entrepreneur after surveillance was supposed to have stopped. New Zealand's Government Communications Security Bureau (GCSB) had been working with the NSA on a joint surveillance operation called Operation Debut. While surveillance was supposed to have stopped in January 2012, it has emerged that the NSA continued to use GCSB's technology without its knowledge. According to… [Continue Reading] -

From hack to product: soon you'll be able to control Windows 10 with your eyes
Publié: août 2, 2017, 10:32am CEST par Mark Wycislik-Wilson
There are a lot of accessibility options built into Windows 10 at the moment, and soon there'll be a new feature. Brought about by an idea raised at Microsoft's 2014 hackathon, the company is bringing Eye Control to its operating system. As the name suggests, Eye Control gives users the ability to control and interact with Windows 10 using eye movements -- something which is incredibly useful for anyone with limited movement. The feature is destined for inclusion in a future version of Windows 10, but a beta version will be made available to Windows Insiders. The project is born… [Continue Reading] -

UK Home Secretary supports back doors while claiming 'real people' don't need end-to-end encryption
Publié: août 1, 2017, 5:22pm CEST par Mark Wycislik-Wilson
Amber Rudd, the UK Home Secretary, has claimed that "real people often prefer ease of use and a multitude of features to perfect, unbreakable security." Rudd holds the Conservative government's belief that it should be able to access encrypted messages, even when end-to-end encryption is used, such as with WhatsApp. Using terrorism as a justification for wanting to gain access to encrypted messages, she goes on make extraordinary and misguided claims about what she and the government want. Her bizarre and misinformed rant in the Daily Telegraph is deeply concerning, not only because of the implications her suggestions have on… [Continue Reading] -

Apple and Google pull binary trading apps from their stores after financial scams
Publié: août 1, 2017, 1:03pm CEST par Mark Wycislik-Wilson
A recent investigation by The Independent uncovered a financial scam that was placing thousands of people at risk. An increasing number of binary trading options have proved to be fraudulent, and in the UK they fall outside the control of financial regulators. Binary option scams have been described as "possibly the biggest financial scam in the world," and Apple and Google have cleared hundreds of trading apps from the App Store and Google Play after a review by the Australian Securities & Investments Commission (ASIC). ASIC said that it has looked at a large number of apps offering binary options… [Continue Reading] -

Google announces Nearby Connections 2.0 complete with offline communication
Publié: août 1, 2017, 10:43am CEST par Mark Wycislik-Wilson
The second iteration of Nearby Connections -- called, funnily enough, Nearby Connections 2.0 -- is upon us. Google has released the API to Android developers, giving them access to greater bandwidth, reduced latency, and -- most excitingly -- offline functionality. Working over Bluetooth and Wi-Fi, Nearby Connections 2.0 makes it possible for devices to communicate with each other without the need for an internet connection. The API is supported by Android devices running Google Play services 11.0 and above, and it is essentially a peer-to-peer system that works much like a next-generation version of NFC. So what's the potential for… [Continue Reading] -

HBO hack leads to Game of Thrones leak
Publié: juillet 31, 2017, 7:08pm CEST par Mark Wycislik-Wilson
HBO is the latest company to suffer a hack and subsequent leak of shows. Hackers are said to have breached the network's security and gained access to 1.5TB of data including Game of Thrones scripts and unaired episodes of shows. Episodes of Ballers and Room 104 have been leaked online, but it is the release of what appears to the script to next week's Game of Thrones that's drawing the most attention. See also: If you're downloading Game of Thrones, HBO has its eye on you The hack and leak was first reported by Entertainment Weekly who quotes HBO as saying: "HBO… [Continue Reading] -

AUKEY EP-B40 Latitude Wireless Earbuds: earphones for people who hate earphones [Review]
Publié: juillet 31, 2017, 4:54pm CEST par Mark Wycislik-Wilson
Let's get one thing out of the way: I hate earphones. I always have. This is not an irrational hatred, I've always liked the idea of in-ear buds -- I've just never been able to use them. The problem, it seems, lies with my right ear. To my knowledge it is a perfectly normally-formed ear, but it is singularly incompatible with earphones -- while the left will grip the bud nicely, the right vomits it out in next to no time. So, I have long shied away from earphones, opting instead for either fully enclosed headphones, or the clip-on variety.… [Continue Reading] -

Canonical shows how to choose a winning IoT business model
Publié: juillet 31, 2017, 1:03pm CEST par Mark Wycislik-Wilson
The Internet of Things (IoT) is more than just the latest buzzword -- although it arguably started off life as such. Just as with any developing technology or trend, it is eyed with suspicion and eagerness in equal measure, but many businesses simply don't know where to start. Ubuntu-maker Canonical has conducted research with IoT professionals, and it reveals the challenges and opportunities offered by the IoT. It highlights what needs to be considered in the areas of monetization, skills and security, and signals a way forward for businesses looking to make headway in this relatively new arena. Like social… [Continue Reading] -

Putin bans VPNs and proxies in Russia as Apple explains pulling VPNs from Chinese App Store
Publié: juillet 31, 2017, 10:53am CEST par Mark Wycislik-Wilson
VPNs and proxies are now illegal in Russia after Vladimir Putin signed a new law which prohibits technology that can be used to access websites that are banned in the country. The law also prevents people from using tools to stay anonymous online, and a second law requires users of messaging tools to be identifiable through their phone numbers. As Russia hardens it implementation of government-imposed censorship, Apple has explained the sudden disappearance of around 60 VPN tools from the Chinese version of its App Store. The actions of both countries are seen as attempts to further thwart freedom of… [Continue Reading] -

BT offers to pump £600 million into rural broadband
Publié: juillet 30, 2017, 7:07pm CEST par Mark Wycislik-Wilson
While the UK enjoys a fairly decent level of broadband coverage, there are still plenty of people struggling with relatively slow connections. It's a problem that's particularly common in rural areas, and BT has offered to stump up £600 million to ensure that more rural homes have decent connections by 2020. The UK government had already indicated that it wants every home in the country to have access to an internet connection of at least 10Mbps and plans to introduce rules that will permit customers to "demand" such speeds. BT's investment -- through its Openreach subsidiary -- would bring 10Mbps+… [Continue Reading] -

iStorage diskAshur2 1TB PIN-protected encrypted external hard drive [Review]
Publié: juillet 30, 2017, 5:51pm CEST par Mark Wycislik-Wilson
It's hard -- for me at least -- to get too excited about hard drives. They get bigger, they get faster, and that's about it. But the iStorage diskAshur2 is a little different. This is a 1TB USB 3.1 external hard drive with a twist. It offers hardware-level AES-XTS 256-bit encryption -- so no software is needed -- secured with PIN authentication. As you can see from the photo, there's a PIN pad built into the drive for easy locking and unlocking, and it's compatible with Windows, macOS and Linux ("it will work on any device with a USB port!").… [Continue Reading] -

Microsoft updates Cortana for Android with new look and new features
Publié: juillet 29, 2017, 7:41pm CEST par Mark Wycislik-Wilson
The Android version of Cortana has been getting some attention from Microsoft recently, and today the company has released another update to its virtual assistant. With Cortana 2.9, Microsoft not only introduces something of an interface makeover, but also adds new features. While the redesign is nothing major, it is a move for the better, with Settings now easier to access and the interface is reduced to two tabs rather than three -- and they are now labelled too! But it doesn’t end there. The overall look of the app is now cleaner than before. The introduction of a hamburger… [Continue Reading] -

Microsoft brings Brotli compression to .NET in 'alpha-quality preview'
Publié: juillet 29, 2017, 1:43pm CEST par Mark Wycislik-Wilson
It is now two years since Google launched its open source compression algorithm, Brotli. Microsoft has already shown some interest in the technology, adding support to Edge late last year to speed up the loading of web pages. Having conducted rigorous tests with Brotli compression, Microsoft is now ready to bring it to .NET. Microsoft's tests show that Brotli is at least as good as Deflate and gzip, in terms of compression levels and the amount of time it takes to compress and decompress. It is because of these results that Microsoft is happy to launch .NET support for Brotli… [Continue Reading] -

Report: Free Basics by Facebook is creepy, limited, and violates net neutrality
Publié: juillet 29, 2017, 12:32pm CEST par Mark Wycislik-Wilson
It's been a little while since we heard anything about Free Basics by Facebook -- the successor to its Internet.org project which aims to provide access to a number of online services, free of charge, in developing countries (63 in total) -- but a new report slams the service. On the face of it, this is a good thing, but Free Basics from Facebook has certainly not been without its controversies: the service was banned in India and Egypt, for example. Now a report from Global Voices -- a "global anti-censorship network of bloggers and activists dedicated to protecting freedom… [Continue Reading] -

Congress continues Kaspersky probe fearing 'nefarious activities against the United States'
Publié: juillet 29, 2017, 11:28am CEST par Mark Wycislik-Wilson
US suspicions about Kaspersky's links to Vladimir Putin are not diminishing. The government has been tracking the Russian security company, and now Congress is seeking information from 22 government agencies about the firm. The US House of Representatives Committee on Science, Space and Technology has written to the agencies asking for documents, citing fears that Kaspersky Lab's products could be used to carry out "nefarious activities against the United States." See also: Kaspersky launches free antivirus tool -- Kaspersky Free! Letters seen by Reuters show that the committee "is concerned that Kaspersky Lab is susceptible to manipulation by the Russian… [Continue Reading] -

Twitter looks to boost profits with $99 per month automatic tweet promotion beta
Publié: juillet 28, 2017, 7:18pm CEST par Mark Wycislik-Wilson
When Twitter revealed its Q2 earnings yesterday the figures weren't quite as bright as people would have hoped. With growth stalling, the company is seeking new ways to bring in money, and its latest idea is a tweet promotion service for a fixed monthly fee. Twitter is testing a new ad program which automatically promotes tweets and profiles for $99 per month. The program is currently in private beta, but it could be rolled out to a wider audience at any stage. The new Twitter Ads program does not have a name, but it's clear from the description that Twitter… [Continue Reading] -

How to stop videos autoplaying in Google
Publié: juillet 28, 2017, 12:33pm CEST par Mark Wycislik-Wilson
Google has been stirring things up a little recently, adding autoplaying videos to search results, and killing off Google Instant. The autoplaying videos are also something that Facebook has tinkered with recently, managing to irritate people in the process. If you're searching Google on your phone, one of the last things you want is to have your battery draining unnecessarily because of videos playing automatically. Thankfully, you can disable this feature; here’s how. See also: Google kills off Google Instant search with immediate effect Prepare to get pissed at Google as autoplaying videos arrive in search results What's particularly annoying… [Continue Reading] -

WikiLeaks reveals CIA's Imperial hacking project targeting Mac and Linux
Publié: juillet 28, 2017, 11:05am CEST par Mark Wycislik-Wilson
WikiLeaks has published the latest of its Vault 7 CIA leaks, this time looking at a project going by the name Imperial. The project is made up of three tools: Achilles and SeaPea which target OS X, and Aeris which targets various flavors of Linux, including RedHat, Debian and CentOS. User guides relating to the two Mac tools date from mid-2011 and show they can be used to Trojanize an OS X disk image or install a persistent rootkit. Aeris was designed to provide a backdoor into Linux-based systems. This time around, the documentation is far shorter and sparser than… [Continue Reading] -

LinkedIn Website Demographics lets website owners track the type of visitors coming to their sites
Publié: juillet 27, 2017, 12:23pm CEST par Mark Wycislik-Wilson
The tracking capabilities of social media sites has long been a cause for concern, with Facebook being the most notable example. Now the Microsoft-owned professional social network LinkedIn has announced details of a new tracking feature that will be of interest to website owners. LinkedIn Website Demographics does not (despite what some reports might suggest, #PrivacyKlaxon) allow for the tracking of individual users, but it does give website owners the chance to get a better idea of the demographics of their visitors. This is less about creating targeted content, and more about determining whether existing content is attracting the right… [Continue Reading] -

Microsoft launches Windows Bounty Program to weed out Windows 10 bugs
Publié: juillet 27, 2017, 11:14am CEST par Mark Wycislik-Wilson
Microsoft is one of many technology companies to run bounty programs giving people the opportunity to earn a bundle of cash for finding bugs and security issues with software. Now the software giant has launched the Windows Bounty Program, offering rewards of up to $250,000. Of course, the starting point for rewards is much lower -- just $500, but still better than a kick in the teeth. This new bounty program has four key areas of focus in addition to the Windows Insider program: Microsoft Hyper-V, Mitigation bypass and Bounty for defense, Windows Defender Application Guard, and Microsoft Edge. The aim… [Continue Reading] -

Google Play Music and YouTube Red to merge into a new streaming service
Publié: juillet 27, 2017, 9:55am CEST par Mark Wycislik-Wilson
YouTube's head of music, Lyor Cohen, has confirmed that Google Play Music and YouTube Red are going to merge. Speaking in New York at the New Music Seminar conference, Cohen said that a new streaming service would be created. Rumors of the merger have been circulating for some time, and the move will see Google consolidating its services into something rather more manageable -- both for the company and for users. Cohen did not give any indication of when the merger will be taking place, but he did say: "The important thing is combining YouTube Red and Google Play Music,… [Continue Reading] -

Google kills off Google Instant search with immediate effect
Publié: juillet 26, 2017, 6:58pm CEST par Mark Wycislik-Wilson
Google is sidelining one of its famous features: Google Instant. The feature displays search results in real-time as you type, eliminating the need to press Enter or hit Search, but after 7 years, Google thinks it's time to wave goodbye to it. The reason given for the cull is that the majority of searches are now conducted from mobile devices, and Google Instant makes less sense on a touchscreen. This does not mean, however, that Google's autocomplete function is disappearing. In getting rid of Google Instant, all Google is doing is getting rid of the live display of results as… [Continue Reading] -

eBay's new Image Search and Find It On eBay tools let you find items using a photo
Publié: juillet 26, 2017, 5:12pm CEST par Mark Wycislik-Wilson
Finding what you're looking for on eBay can be tricky. You need to find the right words to home in on exactly what you mean, and there's no guarantee that the seller will use quite the same wording. Far better, you might think, to be able to search using a photo of the item you want. eBay agrees. With Image Search, users can take or upload a photo from their camera roll to search for matching items. The second new tool, Find It On eBay, can share images from the web -- including social media -- to eBay and use… [Continue Reading] -

How to enable portable mode in Paint.NET
Publié: juillet 26, 2017, 2:29pm CEST par Mark Wycislik-Wilson
In recent days, there has been a great deal of interest in the supposed loss of Paint, followed by the bizarre, inexplicable delight people felt when it transpired the app will live on in the Windows Store. The (subjectively) brilliant Paint.NET was originally built as a successor to Paint, and the developer recently said that it too will be coming to the Windows Store. He also made reference to a portable mode that would be coming to Paint.NET, and this caused ripples of excitement through the app's userbase. Well, Paint.NET 4.0.17 is out, and portability is an option -- you… [Continue Reading] -

Adobe leaks its upcoming cloud-based photo editor, Project Nimbus
Publié: juillet 26, 2017, 11:13am CEST par Mark Wycislik-Wilson
Adobe accidentally treated Creative Cloud subscribers to a sneak preview of Project Nimbus. The company had already said a little about the cloud-based, Lightroom-like photo editor, but now it has inadvertently made the app available to a number of users. Adobe quickly realized its mistake and rectified the matter, but the slip-up gives an interesting glimpse into what we can expect to see from Project Nimbus -- or whatever it ends up being called -- when it is finished. The idea behind Nimbus is to simplify Lightroom, and many familiar tools have migrated to the cloud-based version of the app.… [Continue Reading] -

Kaspersky launches free antivirus tool -- Kaspersky Free!
Publié: juillet 26, 2017, 10:06am CEST par Mark Wycislik-Wilson
Kaspersky has been in the news quite a lot recently, primarily because of US concerns over links to the Russian government. The security company also hit the headlines when it filed an antitrust case against Microsoft because Windows 10 disabled Kaspersky antivirus software. But now there's a new reason to be in the news -- and this time it's a good one. The Russian company is launching Kaspersky Free, a free antivirus tool available globally. Company founder Eugene Kaspersky announced that the US, Canada and numerous Asia Pacific countries have access to the software immediately, and the global rollout will… [Continue Reading] -

Flash is finally bowing out to HTML5 as Adobe aims to stop updates in 2020
Publié: juillet 25, 2017, 6:43pm CEST par Mark Wyciślik-Wilson
The death of Flash has been long, slow and protracted. The writing has been on the wall for some time now, but it seems that Adobe is finally ready to kiss its (adopted) baby goodbye. The company is bringing Flash to end-of-life and will stop updating and distributing Flash Player in 2020. Anyone who is still using Flash is being encouraged to embrace open standards such as HTML5, WebGL and WebAssembly as replacements. Adobe says that it will continue to work with key tech companies to maintain security and stability beyond 2020, but don’t expect any more than that. Facebook,… [Continue Reading] -

Prepare to get pissed at Google as autoplaying videos arrive in search results
Publié: juillet 25, 2017, 5:08pm CEST par Mark Wyciślik-Wilson
When Twitter and Facebook introduced autoplaying videos, many users were annoyed by their intrusive nature. Subsequent tweaks and the introduction of autoplay settings calmed the mood a little, but now Google has decided to stir things up a bit. Perform a Google search and you might well find that the results include an autoplaying video -- even for searches that would not necessarily mean you want to see a video. Given the reception autoplaying videos have received elsewhere, this is not likely to go down well with Google users. First spotted by TheSEMPost, the autoplaying videos appears when you conduct… [Continue Reading] -

Google launches SOS Alerts in Search and Maps to help out in a crisis
Publié: juillet 25, 2017, 12:46pm CEST par Mark Wyciślik-Wilson
Google is rolling out new features to its Search and Maps products to help get information out to people in the event of a crisis. SOS Alerts provides access to information and stories about incidents and locations where there has been some form of disaster. Just what is displayed to you depends on how close you are to the incident. Google will show those in the area information such as emergency numbers and directions to help, while those elsewhere will see news about what is going on, and links to donate money or help. The idea borrows somewhat from Facebook's… [Continue Reading] -

Google releases Android O Developer Preview 4, the last beta before the official launch
Publié: juillet 25, 2017, 12:13pm CEST par Mark Wyciślik-Wilson
Android fans with a Pixel, Pixel XL, Pixel C, Nexus 5X, Nexus 6P or Nexus Player (or if you're happy using the Android Emulator) can now try out Android O Developer Preview 4. Google has released the final beta version of its mobile operating system as we draw ever-closer to the official launch of Android O -- or Android 8.0, if you prefer. At this stage we don’t know what the O stands for. There's an octopus-related Easter egg in Developer Preview 4, but that's not in keeping with the dessert theme naming convention. The biggest news in this release… [Continue Reading] -

Europe says Facebook, Twitter and Google need to improve user terms or face fines
Publié: juillet 25, 2017, 11:12am CEST par Mark Wyciślik-Wilson
Facebook, Twitter and Google have failed to impress EU authorities with their proposed revisions to user terms. The three companies have been under pressure to amend their terms to bring them in line with European law. The European Commission and consumer protection authorities wrote to the tech giants last month, giving them until July 20th to submit proposals about their respective social networks. The companies have until September to implement changes that satisfy Europe, or fines could be handed out. There are concerns in Europe about how the US-based companies are operating off home turf. In particular, Europe wanted changes… [Continue Reading] -

Facebook acquires Source3 to help prevent video piracy because its own tools aren't up to the job
Publié: juillet 25, 2017, 10:08am CEST par Mark Wyciślik-Wilson
Any online platform must contend with the problem of piracy and intellectual property rights, and Facebook is no different. The social network gives content owners the opportunity to monetize their videos, but in order for this to work, owners' rights need to be protected; this is why Facebook introduced its Rights Manager tool a couple of years ago. But it seems that Facebook's own weapons in the fight against piracy and content theft have not been as effective as the company -- and content owners -- would have hoped. As such Facebook is taking Source3 under its wing. The startup… [Continue Reading] -

Microsoft designed its own AI chip for the next HoloLens
Publié: juillet 24, 2017, 5:42pm CEST par Mark Wyciślik-Wilson
HoloLens 2 is in the works, and Microsoft has revealed that the second version of its mixed reality headset will feature an AI chip. The company has turned to custom silicon when it comes to bringing artificial intelligence to HoloLens, but while Microsoft has designed the chip, it is manufactured by a third party. Speaking at the Computer Vision and Pattern Recognition conference Harry Shum, executive vice president of Microsoft's Artificial Intelligence and Research Group, said the second version of the Holographic Processing Unit (HPU) will feature the AI chip so processing can be carried out onboard rather than in… [Continue Reading] -

Google delays rollout of updated feed due to technical hitches on Android
Publié: juillet 24, 2017, 3:51pm CEST par Mark Wyciślik-Wilson
Google's announcement last week that it was rolling out an updated algorithm-powered feed to its mobile apps led to (nonsense) speculation that the company's search page was also getting a redesign. After pooh-poohing this suggestion, Google has also revealed that its new mobile feed rollout has hit a snag. Users who updated to the new feed experienced problems with it being blank. Tight integration with the Android home screen is causing issues, and now the rollout is being scaled back. The problem only affects Android users because the blank feed issue is only present on handsets where a swipe to… [Continue Reading] -

Chinese government forces Xinjiang residents to install spyware on their mobiles
Publié: juillet 24, 2017, 12:23pm CEST par Mark Wyciślik-Wilson
China's control of the internet is no secret and the government's latest encroachment into people's lives sees residents of the north-west Xinjiang -- a largely Muslim area -- being forced to install surveillance software on their phones, sparking privacy concerns. Notifications were sent out recently informing mobile users that they had just 10 days to download and install the Jingwang spyware. Random checks are now being carried out on the street to ensure that citizens have the app installed. Anyone found without the software faces up to 10 days in jail. The Chinese government describes the app as a piece… [Continue Reading] -

Microsoft launches LinkedIn Lite in India ahead of a wider rollout
Publié: juillet 24, 2017, 11:14am CEST par Mark Wyciślik-Wilson
Just like Facebook did with Facebook Lite and Facebook Messenger Lite, Microsoft is launching a cut-down, data-sipping version of LinkedIn for mobile users. LinkedIn Lite launches in India initially, and is designed for countries with limited mobile internet access. This is an app designed for emerging markets, and as such it is Android-only; there are no plans for an iOS version. While LinkedIn Lite is starting out its life in India, it will eventually spread to a further 60+ countries. Microsoft has not revealed much about the future timeline for LinkedIn Lite, but a spokesperson speaking to TechCrunch has confirmed… [Continue Reading] -

NSA says it is 'not the best time' to create a US-Russia cyber unit
Publié: juillet 23, 2017, 2:38pm CEST par Mark Wyciślik-Wilson
When Donald Trump met with Vladimir Putin, the pair apparently discussed the idea of the two nations forming an "impenetrable Cyber Security unit." It's an unlikely partnership, to say the least, and NSA Director Mike Rogers has voiced his disapproval of the move. Given the, erm, interesting relationship between the US and Russia, the controversy surrounding Russia's possible hacking of the last election, and Trump's ongoing problems defending himself over rumored Russian ties, it's perhaps little surprise that the NSA chief says "now is probably not the best time" for the two superpowers to work together on such a project.… [Continue Reading] -

Attendees to disastrous Pokémon GO Fest refunded with PokéCoins and Lugia
Publié: juillet 23, 2017, 1:25pm CEST par Mark Wyciślik-Wilson
Yesterday, Grant Park in Chicago was packed with thousands of Pokémon fans. People of all ages attended the Pokémon GO Fest in the hope of catching ultra-rare Pokémon at the special event, but things did not go well. A series of technical glitches meant that game-creator Niantic was forced to cancel the event. The large number of attendees led to network issues which could not be resolved, causing anger and annoyance among fans. As part of its compensation offer, the company is giving festival-goers $100 of Pokémon GO's in-game currency, Pokecoins. On top of this, attendees will all be given… [Continue Reading] -

No, Google is not about to redesign its iconic minimalist homepage
Publié: juillet 22, 2017, 5:08pm CEST par Mark Wyciślik-Wilson
A few days ago Google announced plans to update its iOS and Android apps. The update sees the arrival of algorithm-powered feeds that display a personalized stream of content. Note the reference to Apple and Google’s mobile platforms. This story was widely reported in the tech press, but the Guardian decided to take things further, claiming that Google was on the verge of unveiling a "radical" change to it homepage on the desktop. The story is seemingly plucked out of thin air, as Google has made no such suggestion. In fact, the company has spoken out to refute the claim.… [Continue Reading] -

Verizon's 'video optimization' test throttles Netflix and YouTube
Publié: juillet 22, 2017, 1:23pm CEST par Mark Wyciślik-Wilson
Verizon Wireless customers complained this week that the company was throttling Netflix traffic. With talk of net neutrality ringing in their ears, people were upset to find that download speeds were capped at 10Mbps. When Netflix denied implementing a cap, the finger of suspicion pointed at Verizon. Now the company has owned up to testing a new "video optimization" system, but it's not clear how this resulted in the cap-like effects experienced by many users. Verizon Wireless customers found that using Netflix's own speed testing tool revealed a maximum transfer rate of 10Mbps. However, once a VPN was introduced, this… [Continue Reading] -

UK government proposes mandatory drone registrations and safety awareness tests
Publié: juillet 22, 2017, 11:10am CEST par Mark Wyciślik-Wilson
The UK government has announced plans to force private drone owners to register their devices as well as passing a safety awareness test -- a drone driving test essentially. The rules would affect drones weighing more than 250g and they come in response to an increasing number of near-misses between drones and aircraft. The Civil Aviation Authority’s Airprox Board investigated no fewer than 22 incidents between drones and commercial aircraft in the first four months of the year, but police currently have a near-impossible task when it comes to tracing owners of drones that have been flown dangerously. Research has… [Continue Reading] -

YouTube Video Editor and Photo slideshows to close September 20
Publié: juillet 21, 2017, 6:48pm CEST par Mark Wyciślik-Wilson
YouTube has quietly revealed that its Video Editor and Photo slideshows features will close down in just two months. It seems that not enough people are using the two tools to warrant keeping them alive, so they are being "retired". Users are warned that while videos that have already been published will remain accessible, projects currently sitting in Video Editor must be completed by the shutdown date of September 20. See also: YouTube employs the Redirect Method to counter searches for violent extremist videos The closures mean that YouTubers will increasingly have to turn to third-party tools to cater for… [Continue Reading] -

YouTube employs the Redirect Method to counter searches for violent extremist videos
Publié: juillet 21, 2017, 5:23pm CEST par Mark Wyciślik-Wilson
Google, Facebook and other big tech companies have all committed to trying to eradicate extremism from their respective networks in recent months. YouTube has just announced its latest strategy, with a technique which sounds rather like a type of contraception. The Redirect Method uses a very simple technique of displaying safe, carefully curated content when certain keywords are used as search terms. More than this, when searches for extremist content are conducted, YouTube will actually show videos that "debunk violent extremist recruiting narratives." The technique comes from the Jigsaw stables at Alphabet, working in conjunction with Moonshot CVE. Google explains… [Continue Reading] -

Blizzard: World of Warcraft, StarCraft II and more will stop running under Windows XP and Vista
Publié: juillet 21, 2017, 10:57am CEST par Mark Wyciślik-Wilson
Microsoft hasn't supported Windows XP and Windows Vista for a while (mainstream support ended eight and five years ago, respectively), but other technology companies have continued to support their own software under these ancient operating systems. Now, however, Blizzard has announced that it is dropping support for the OSes in a number of its games. The list includes names such as World of Warcraft, StarCraft II and Diablo III, and the change is coming later this year. While no precise date has been given, October is the month Blizzard stops supporting pre-Windows 7 computers. In a post on the Blizzard support… [Continue Reading] -

WikiLeaks: CIA analyzed Russian and Chinese malware to inspire its own hacking and surveillance tools
Publié: juillet 21, 2017, 9:04am CEST par Mark Wyciślik-Wilson
Some four months after the first Vault 7 leak, WikiLeaks continues to publish revealing CIA documents that detail the agency's ability to hack, infiltrate and surveil targets. The latest batch goes under the banner "UCL / Raytheon", and comprises documents from CIA contractor Raytheon Blackbird Technologies. Dating from late 2014 and late 2015, the documents show how the CIA, through Raytheon Blackbird Technologies, monitored malware in the wild to see how it could be used by the agency. The documents cover tools produced by the infamous Hacking Team as well as the Russian HammerToss malware delivered via Twitter. See also:… [Continue Reading] -

Following NSA endorsement, the US government can buy secure messaging tools from BlackBerry
Publié: juillet 20, 2017, 5:42pm CEST par Mark Wyciślik-Wilson
BlackBerry has announced that it is now able to sell its secure messaging solutions to the US and Canadian governments. The news comes after the company received endorsement from the NSA's National Information Assurance Partnership for SecuSUITE for Government. BlackBerry points out that governments have long had to contend with wiretapping and other forms of surveillance, and says that SecuSUITE for Government offers effective end-to-end encryption for voice calls and text messages. The security solution is already used by numerous governments around the world, including some in Europe and Asia, and BlackBerry will be happy to have added the US… [Continue Reading] -

If you're downloading Game of Thrones, HBO has its eye on you
Publié: juillet 20, 2017, 2:49pm CEST par Mark Wyciślik-Wilson
As the new season of any major series kicks off, torrent traffic for episodes clogs up internet pipes around the world. This has been true of everything from True Blood to Lost, and it's no different with season seven of Game of Thrones. Clearly the networks behind shows that are shared via BitTorrent and through other means are keen to clamp down on piracy, and anyone planning to download Game of Thrones is cautioned that HBO is actively monitoring people pirating the series, and warnings are being sent out. It's only a few days since the season premiere of season… [Continue Reading] -

Amazon Spark is a shopping social network for iOS
Publié: juillet 20, 2017, 12:19pm CEST par Mark Wyciślik-Wilson
Over the years Amazon has spread its wings in various directions, and the latest venture sees the online shopping giant dipping its toe into the waters of social networking. While not strictly a social network, Amazon Spark has many of the hallmarks of one. Borrowing heavily from Instagram and Pinterest -- among others -- Amazon Spark is available for Prime subscribers using iOS. There is, of course, a strong emphasis on shopping, and members are able to post photos of items for sale, and can click through to buy, post comment, and leave "smiles" -- Spark's take on likes. The… [Continue Reading] -

Department of Homeland Security lifts airline laptop ban
Publié: juillet 20, 2017, 11:35am CEST par Mark Wyciślik-Wilson
The Department of Homeland Security has lifted the ban on laptops on flights into the US from Middle Eastern and North African countries. The controversial ban, introduced by the Trump administration back in March, was almost extended to all international flights, but has now been scrapped altogether. Airports have introduced enhanced security measures, and this means that the restrictions on portable electronic devices is no longer considered necessary. See also: US bans laptops and tablets on flights from eight countries in Africa and the Middle East US may extend laptop ban to all international flights The ban was introduced over… [Continue Reading] -

Media Player Classic will never be updated again... Probably
Publié: juillet 19, 2017, 5:13pm CEST par Mark Wyciślik-Wilson
Media Player Classic -- the codec-packed, open source media player much loved by video downloaders and encoders around the world -- has reached the end of the line. The latest release -- Media Player Classic Home Cinema v1.7.13, to give it its full title -- is likely to be the last one ever. The developers say that the number of people working on the project has gradually reduced over the years, and the situation is becoming untenable. The words "the project is officially dead" are not any that users will want to hear, but they have been uttered. Take a… [Continue Reading] -

TfL's new app lets you top up your Oyster card with your mobile
Publié: juillet 19, 2017, 4:58pm CEST par Mark Wyciślik-Wilson
Dragging itself kicking and screaming into 2017, Transport for London's (TfL) Oyster card is finally set to benefit from a mobile app that allows for top-ups from a smartphone. A new Oyster app is scheduled for release for iOS and Android in August. It will supplement changes to the Oyster system that mean online credit purchases can be collected from any station rather than a nominated one, and will be available in 30 minutes rather than 24 hours. The sped-up processing will be welcomed, but the Oyster card app is likely to generate more interest. At the moment, online credit… [Continue Reading] -

Google brings algorithm-powered feed to its iOS and Android apps
Publié: juillet 19, 2017, 2:21pm CEST par Mark Wyciślik-Wilson
Google has announced a significant update to its iOS and Android apps, introducing a new algorithm-driven feed that pushes personalized content at users. The company says that the update makes "it easier than ever to discover, explore and stay connected to what matters to you -- even when you don't have a query in mind." The feature, known simply as "the feed", has been around since December, but this is an important update that sees Google further leaning on the algorithms it has come to love. The feed draws on machine learning to create a personalized stream of content made… [Continue Reading] -

Samsung finally launches its voice assistant Bixby in the US
Publié: juillet 19, 2017, 11:46am CEST par Mark Wyciślik-Wilson
The day has, at long last, arrived for Samsung Galaxy S8 and S8+ owners: Bixby voice capabilities for US English is now available in the United States and South Korea. A quick software update is all it takes to bring the long-awaited voice assistant to Samsung flagship smartphones. The update means that the hitherto useless hardware Bixby button now has a purpose, and Galaxy S8 and S8+ users can start to enjoy the benefits of taking control of their phones with their voices. For now, English language support for Bixby is only going to be available in the US and… [Continue Reading] -

FBI issues a warning to parents about the privacy and safety of internet-connected smart toys
Publié: juillet 18, 2017, 5:44pm CEST par Mark Wyciślik-Wilson
The FBI's Internet Crime Complaint Center (IC3) has issued a PSA warning about the potential dangers of smart toys. The bureau encourages parents to consider cyber security before bringing internet-connect toys into the home because they could risk the privacy and safety of children. The announcement warns of the potential for personal information to be gathered through such toys. The presence of sensors, microphones, cameras, data storage components, speech recognition and GPS, coupled with cloud storage of data, is cited as cause for concern, and parents are urged to check privacy agreements. The IC3 warns: "Consumers should examine toy company… [Continue Reading] -

Appeal court rules FBI national security letter gagging orders should remain in place
Publié: juillet 18, 2017, 12:57pm CEST par Mark Wyciślik-Wilson
Anyone subject to secret surveillance by the FBI through access to their private data remains unentitled to be told about the related national security letters (NSLs). The 9th US Circuit Court of Appeals in San Francisco ruled that existing gagging orders that prevent companies from advising people about NSLs relating to them do not violate the First Amendment. A case had been brought to court by the Electronic Frontier Foundation on behalf of Cloudfare and CREDO Mobile that challenged the legitimacy of the gagging orders. EFF won its case back in 2013, but subsequent changes to the law, coupled with… [Continue Reading] -

Stealing $7 million of Ethereum from CoinDash took a hacker just 3 minutes
Publié: juillet 18, 2017, 11:28am CEST par Mark Wyciślik-Wilson
A lightning-fast raid on a cryptocurrency platform's website earned a hacker $7 million in three minutes yesterday. Moments after CoinDash launched its ICO (Initial Coin Offering, the cryptocurrency version of an IPO), the attacker modified the address of the wallet it used and watched as millions poured into their own account. The website was shut down as soon as the hack was discovered, but by this time $7 million had already disappeared. CoinDash managed to gather $6 million from investors, but funds stopped arriving with the shutdown. In a statement issued on its website, CoinDash acknowledged the incident, warned that the attack was still… [Continue Reading] -

Apple embraces breastfeeding and zombies!
Publié: juillet 17, 2017, 6:28pm CEST par Mark Wyciślik-Wilson
Apple is using World Emoji Day to preview upcoming emoji that will feature in iOS, macOS and watchOS later in the year. The new emoji include breastfeeding, a zombie, a woman in a headscarf, and a bearded man. The company says that "the new emoji make it easier for users to express themselves with greater diversity, additional animals and creatures, new smiley faces and more," but not everyone is going to take it quite that seriously. Still... zombies! The new emoji are to arrive in iOS 11 later in the year, and there are 56 new additions in total. The… [Continue Reading] -

PayPal support is coming to Samsung Pay
Publié: juillet 17, 2017, 5:45pm CEST par Mark Wyciślik-Wilson
Samsung is entering into an "extended partnership" with PayPal to bring PayPal support to Samsung Pay. To start with, PayPal will be available as a payment method in the US first, but it will expand to other countries in the future. It means that not only can PayPal be used as a source to fund Samsung Pay for POS purchases, but Samsung's Braintree merchants will also be able to accept PayPal payments for online and in-app purchases. Neither PayPal nor Samsung has indicated exactly when support will be added, with "coming soon" being the only hint at a timescale. PayPal says: "Coming… [Continue Reading] -

Chill your boots! Ads in the HTC TouchPal keyboard was just a little weekend SNAFU
Publié: juillet 17, 2017, 4:54pm CEST par Mark Wyciślik-Wilson
Over the weekend, distress rippled around the HTC community as advertisements suddenly appeared in the TouchPal keyboard. The keyboard is installed as the default on many of HTC's Android phones, including the HTC 10, and users took to social media to voice their unhappiness and concerns about privacy. Despite the ire directed at the Taiwanese company, HTC is not directly responsible for the keyboard, or the update that pushed ads onto people. Rather, the developer issued an update resulting in the SNAFU that upset so many people. That HTC is not in direct control of the keyboard it offers as… [Continue Reading] -

Plans for age checks on porn sites highlight the UK government's failure to understand the web
Publié: juillet 17, 2017, 1:42pm CEST par Mark Wyciślik-Wilson
If there's anything that the UK government has demonstrated in recent years it is that it not only wants to try to take control of the web, but it also fails to understand the web. These two facts make for a terrible combination -- something highlighted by the snooper's charter and the government's desire to break encryption on demand. The latest idea -- ushered in under the guise of protecting children in a bid to win points -- is the introduction of age restriction on porn sites. The Digital Economy Act will require porn sites to use credit card verification… [Continue Reading] -

WikiLeaks reveals CIA tool for SMS spying
Publié: juillet 17, 2017, 12:30pm CEST par Mark Wyciślik-Wilson
The latest addition to WikiLeaks' Vault 7 cache of leaked CIA documents details an app that can be used to intercept SMS messages on Android devices. The HighRise tool can grab messages before sending them on to a CIA-controlled server. The app itself goes by the name of TideCheck and it serves as an SMS proxy to allow for the interception of messages on a target's phone. The app itself is password protected (with the word "inshallah") to prevent unwanted tinkering. It also seems to serve a dual purpose, acting as a secure communication channel for CIA operatives. Unlike many… [Continue Reading] -

Google Maps tells you the best time to start your journey
Publié: juillet 17, 2017, 11:40am CEST par Mark Wyciślik-Wilson
Time your departure time wrong, and even the simplest of journeys can end up taking far longer than it was meant to. Hit traffic, and your journey time could be doubled -- or worse. A new feature of Google Maps aims to eliminate this problem. The nameless feature is rolling out to the Google Maps mobile app, and it lets you know how long your trip will take if you leave now, or in a few hours' time. It's a simple addition -- and one that would benefit from a little more work and refinement -- but it's a valuable… [Continue Reading] -

Windows 10 Fall Creators Update rebranded Autumn Creators Update for some
Publié: juillet 17, 2017, 10:36am CEST par Mark Wyciślik-Wilson
The upcoming Redstone 3 release of Windows 10 has been known as the Fall Creators Update for some time now -- but in some parts of the world this name sounds nonsensical. While fall is the season that follows summer in many countries, it's not the case worldwide. It is for this very reason that the update will bear a different name in a number of countries including the UK, Australia, New Zealand and India. Come September, Windows 10 users in these nations will be installing Windows 10 Autumn Update. The change was first reported by Windows Central and it… [Continue Reading] -

Facebook rolls out Explore Feed, a new way to discover posts and content
Publié: juillet 16, 2017, 2:22pm CEST par Mark Wyciślik-Wilson
Over the years Facebook has done plenty of tinkering with the News Feed -- and not always for the better. Like Google, the social network frequently experiments with new ideas, and groups of users are often used to beta test features. One such recent experiment saw the arrival of a new version of the timeline for some users via a rocket icon in the Facebook app. Now this new option is rolling out on a wider scale. Known as Explore Feed -- and retaining the rocket icon from beta testing -- the idea is to encourage Facebook users to look… [Continue Reading] -

How to correct search result errors in Google OneBox
Publié: juillet 16, 2017, 12:10pm CEST par Mark Wyciślik-Wilson
Perform a search on Google and you may well be greeted by the OneBox when your results appear. In addition to the list of links to appropriate websites, Google also tries to provide you with at-a-glance information related to your search, and this is to be found in the boxout known as the OneBox. It's a great idea -- but the information is not always correct. Perform a search for the (deceased) novelist Stephen Bly, for instance, and the OneBox displays a mixture of information about him, and the (very much alive) British comedian and author Stephen Fry. Very confusing… [Continue Reading] -

Do we really need yet another messaging app? Amazon seems to think so...
Publié: juillet 16, 2017, 10:56am CEST par Mark Wyciślik-Wilson
While certain corners of the software arena have been, well, cornered by a single big name, there are others in which there is choice aplenty. Case in point -- messaging tools. The number of messaging tools vying for attention is nothing short of bewildering, with everyone from Apple and Microsoft to Google and Facebook offering ways to communicate with other users of the same platforms. Choice may be a good thing -- up to a point -- but now it seems that Amazon has been feeling left out, and may be working on a messaging app of its own, called… [Continue Reading] -

Microsoft sexes up Outlook conversations, search, and navigation on iOS and Android
Publié: juillet 12, 2017, 8:08pm CEST par Mark Wyciślik-Wilson
Microsoft is rolling out redesigned versions of the Outlook app for iOS and Android, bringing the cleaner, Windows 10-inspired look, and an improved workflow to mobile users. The redesign brings changes to navigation, conversations, and search, with the primary focus being on making it faster to achieve things. Account switching is easier, replying to conversations is streamlined, and the revamped interface is clearer and more spacious. Redesigned conversations make it easier to catch up on replies that have been sent, with the first unread message now automatically opened by default. Reply Alls are faster to compose, and as you type… [Continue Reading] -

Now ads are coming to Facebook Messenger in global beta test
Publié: juillet 12, 2017, 7:07pm CEST par Mark Wyciślik-Wilson
Following a more limited testing phase in Thailand and Australia, Facebook is rolling out ads globally in Facebook Messenger. The beta program is being extended meaning that Facebook is now able to target Messenger's 1.2 billion monthly users. When users click or tap an ad in Messenger, they will either be transported to the advertiser's website, or taken to a chat with the company in question. Facebook's latest ad drive is the company's attempt to squeeze money from its Messenger platform. The social network already makes 85 percent of its ad revenue from mobile users, and monetizing Messenger sees renewed… [Continue Reading] -

EFF's latest privacy report criticizes Amazon and WhatsApp over policies that 'fall short'
Publié: juillet 11, 2017, 5:11pm CEST par Mark Wyciślik-Wilson
The Electronic Frontier Foundation has published the latest edition of its "Who has your back" privacy report. This is the seventh report from the digital rights group, and this year it criticizes both WhatsApp and Amazon for having policies that "fall short of other similar technology companies." Four big telecom companies -- AT&T, Comcast, T-Mobile, and Verizon -- performed very poorly, while at the other end of the scale Adobe, Credo, Dropbox, Lyft, Pinterest, Sonic, Uber, Wickr, and WordPress were all praised. In all, the report rates 26 technology companies in five key areas relating to privacy and government data… [Continue Reading] -

Shut the hell up about Facebook friend requests from Jayden K Smith
Publié: juillet 11, 2017, 2:27pm CEST par Mark Wyciślik-Wilson
If you use Facebook at all, you have almost certainly seen warnings recently that make reference to Jayden K Smith. You've probably not only been warned about this "hacker" but also been advised to make everyone you know aware of the danger they pose. "Please tell all the contacts in your messenger list not to accept Jayden K. Smith friendship request. He is a hacker and has the system connected to your Facebook account. If one of your contacts accepts it, you will also be hacked, so make sure that all your friends know it," reads the message. It is… [Continue Reading] -

Twitter's new muting controls make it easier to avoid trolls
Publié: juillet 11, 2017, 1:45pm CEST par Mark Wyciślik-Wilson
Abuse, harassment and trolling on Twitter is a serious problem, and something that sees many users -- celebrities in particular -- forced off the site. Having already introduced a quality filter to help reduce unwanted content, Twitter is now making it possible to block notifications from various types of account, such as those that don’t follow you. As an extra safeguard, you can opt to block notifications from new accounts, thereby helping to avoid the problem of trolls who bypass blocks by signing up under a new username. The "advanced filter settings" are available online as well as in the… [Continue Reading] -

Trump and Putin discussed creating an "impenetrable Cyber Security unit" -- but it's not happening
Publié: juillet 10, 2017, 10:40am CEST par Mark Wyciślik-Wilson
The meeting between Donald Trump and Vladimir Putin was always going to generate a great deal of interest. After the two presidents had their first (official) meeting on Friday, Trump tweeted on Sunday that the pair has discussed "forming an impenetrable Cyber Security unit." Considering Trump has accused Russia of hacking the US election, such an arrangement would seem unlikely. Nonetheless, the topic was broached. It was brought up "so that election hacking, & many other negative things, will be guarded and safe." But it didn’t take Trump long to back down from the idea. It was a full two… [Continue Reading] -

Paint.NET is coming to the Windows Store
Publié: juillet 10, 2017, 10:36am CEST par Mark Wyciślik-Wilson
Recently, the developer of Paint.NET mentioned that the app would be making its way to the Windows Store. He went as far as saying, "it's at the top of my list" of things to do. Rick Brewster has now followed up on his "innocent little comment," confirming that the free image editor -- it was originally developed as simple replacement for Windows Paint, but has grown into something much bigger -- will indeed appear in the Windows Store as of version 4.0.17. Brewster says to Paint.NET fans: "You can all stop e-mailing me asking about this all the time," and… [Continue Reading] -

Google and Facebook to participate in net neutrality protest next week
Publié: juillet 8, 2017, 6:36pm CEST par Mark Wyciślik-Wilson
Two of the biggest names in tech have finally added their names to a growing list of participants in a protest next week against the FCC's plans to tear up net neutrality rules. Google and Facebook have confirmed they will take part in the July 12 protest which is known variously as the "Day of Action," the "Battle for the Net" and -- rather more wordily -- the "Internet-wide Day of Action to Save Net Neutrality." Precisely what form the companies' participation will take remains to be seen, but the involvement of two such big names will send a clear… [Continue Reading] -

Microsoft announces final Bug Bash before releasing Windows 10 Fall Creators Update
Publié: juillet 8, 2017, 5:47pm CEST par Mark Wyciślik-Wilson
With the launch of Windows 10 Fall Creators Update Build 16237 to the Fast Ring yesterday, Microsoft wheeled in numerous fixes and new features. At the same time, the company also announced that the second Bug Bash for the next big update to Windows 10 is about to take place. This is the last Bug Bash that will take place before the release of the final version of Windows 10 Fall Creators Update, and it will see an intense period of testing with the help of Windows Insiders. Things kick off on Friday, July 14 and continue for more than… [Continue Reading] -

Judge says Twitter can proceed with lawsuit to increase transparency about government surveillance
Publié: juillet 7, 2017, 5:40pm CEST par Mark Wyciślik-Wilson
Transparency reports about government data requests have become very common from tech companies such as Facebook, Twitter and Google. But while these firms publish reports, their hands are tied when it comes to what they can reveal. Twitter wants to change that. A federal judge in California ruled in Twitter's favour, dismissing the US government's claim that revealing precise numbers of data requests represented a "clear and present danger." The ruling against the government doesn't change anything in the short term, but it is still an important victory for freedom of speech. Twitter can now move forward with a lawsuit… [Continue Reading] -

Petya author releases master decryption key for all versions of the ransomware
Publié: juillet 7, 2017, 1:23pm CEST par Mark Wyciślik-Wilson
The Petya ransomware -- and several variants -- wreaked havoc with data around the world, but now the author of the original malware has released the master decryption key. Janus Cybercrime Solutions has provided a key that work with all "official" variants of Petya (meaning NotPetya is not included). The key was released to -- of all places -- Mega, and its authenticity has been verified. While Petya has already been cracked, the key offers the fastest and most reliable decryption method yet. Janus said back in June that he/she/they would take a look at NotPetya to see if it… [Continue Reading] -

Facebook, Twitter and Snap Inc may bid millions for World Cup 2018 streaming rights
Publié: juillet 7, 2017, 12:10pm CEST par Mark Wyciślik-Wilson
World Cup 2018 is not far off, and social media networks are preparing to offer millions to obtain streaming rights from Fox Sports. The soccer tournament is to be held in Russia next year, and Facebook, Twitter and Snap Inc are all eager to be able to show highlights online. As Fox Sports is the exclusive US rights holder, there is potential for bids for access to highlights to become high. A report from Bloomberg suggests that the social media giants have already put up "tens of millions of dollars." Bloomberg cites anonymous sources as saying bids have been made… [Continue Reading] -

Wheelchair accessibility information in Google Maps improves via crowdsourcing
Publié: juillet 7, 2017, 11:19am CEST par Mark Wyciślik-Wilson
Google is making an important change to Google Maps that will help to make life a little easier for wheelchair users and people with other accessibility needs. Last year the company added accessibility information to locations on Maps, but now it is taking things a step further. Recognizing that it will take a long time to wait for individual establishments to supply information about whether they have wheelchair access -- and even longer for Google to manually check things -- the power of crowdsourcing is being embraced. It's now easier than ever to add accessibility information about places to Google… [Continue Reading] -

WikiLeaks: CIA steals SSH credentials from Windows and Linux with BothanSpy and Gyrfalcon tools
Publié: juillet 7, 2017, 10:21am CEST par Mark Wyciślik-Wilson
The latest addition to WikiLeaks' Vault 7 cache of CIA tools and documents gives details of tools used by the agency to attack Windows and Linux computers. The BothanSpy and Gyrfalcon projects can be used to intercept and exfiltrate SSH (Secure Shell) credentials. BothanSpy is used to target Windows, while Gyrfalcon is used for Linux machines, with both working in different ways. A number of popular distros can be hit by Gyrfalcon, including CentOS, Debian, RedHat, openSUSE and Ubuntu, and both tools function as implants that steal credentials before transmitting them to a CIA server. The leaked documentation for the… [Continue Reading] -

Three's Go Binge tariff lets you stream Netflix and more without using your data allowance
Publié: juillet 6, 2017, 4:29pm CEST par Mark Wyciślik-Wilson
UK mobile operator Three has introduced a new tariff that lets subscribers stream music, TV and movies from a number of services without eating into their data allowance. The Go Binge Tariff allows for all-you-can-eat streaming access to Netflix, TVPlayer, Deezer and SoundCloud. If this sounds a little familiar, that's because T-Mobile has a similar tariff with an incredibly similar name: Binge On. Of course, there is potentially a slight catch: price. Three explains that users may have to jump to a tariff with a higher data allowance (and a higher cost) in order to take advantage of Go Binge.… [Continue Reading] -

AlphaBay Market disappears from the dark web as blockchain records show huge Bitcoin withdrawals
Publié: juillet 6, 2017, 1:50pm CEST par Mark Wyciślik-Wilson
Dark web users fear that AlphaBay Market may have disappeared for good after an unexplained period of downtime. The site -- described as a successor to Silk Road -- is a marketplace for a myriad of illegal wares including drugs and guns, and speculation is rife that the admins may have made off with users' money. While maintenance-related downtime is not unusual, this time around there has been no word from admins, and suspicions have been further raised after Bitcoin worth around $3.8 million was withdrawn from numerous accounts. Some users are worried that admins may have "pulled an exit… [Continue Reading] -

Schools warn that Snapchat's Snap Map could be used to track children
Publié: juillet 6, 2017, 11:51am CEST par Mark Wyciślik-Wilson
The location-sharing Snap Map feature of SnapChat is leading schools to warn parents about the potential risks of the popular app. The feature allows users to share their location on a map with friends and it's been around for a couple of weeks now. While many users are happy to be able to see where their friends are, others are concerned about potential privacy issues. Some schools have written to parents warnings that the app could be used to track their children and raises "serious safeguarding concerns." But while there are concerns about the safety of Snap Map, there are… [Continue Reading] -

Microsoft says NTFS requirement for OneDrive is nothing new, but forgot to tell users
Publié: juillet 6, 2017, 10:01am CEST par Mark Wyciślik-Wilson
Yesterday we reported about Microsoft's sudden change to OneDrive that requires the use of NTFS drives. The change not only caught people off-guard when they discovered that they couldn’t access their files, but also caused a great deal of annoyance about the lack of communication. While FAT32 has largely been replaced by NTFS, cross-compatibility with Linux and macOS is one of various reasons many people choose the format for SD cards and external drives. Despite the fact OneDrive users are now seeing warning messages about the need to format drives using NTFS, Microsoft insists that "nothing has changed" and it… [Continue Reading] -

Payment processor Worldpay agrees to $10 billion acquisition offer from Vantiv
Publié: juillet 5, 2017, 5:31pm CEST par Mark Wyciślik-Wilson
The UK's biggest payment processor, Worldpay Group, has agreed to the terms of an acquisition offer from US rival Vantiv. News of the $10 billion (£7.7 billion) deal sent Worldpay's share price tumbling; while the planned takeover values shares at 385p, they quickly dropped to 368p. Just days ago, Worldpay revealed it had been approached with offers from Vantiv and JPMorgan, and the latter has now ruled itself out of making an official bid. Vantiv's takeover of Worldpay would see the US company spreading into Europe with its POS and online payment services. When the takeover completes, it will effectively… [Continue Reading] -

Auditors to check all audiovisual content uploaded to Chinese sites to ensure 'core socialist values'
Publié: juillet 5, 2017, 4:47pm CEST par Mark Wyciślik-Wilson
China's control of the internet is no secret, and the Chinese government has just introduced new regulations that require all audio and video content to be vetted by officials before it can be posted online. The aim is to check that content adheres to the government's "core socialist values" and don’t stray into out-of-bounds topics such as homosexuality and drug-taking. The new regulations take immediate effect, and bloggers, media outlets, and filmmakers are concerned that they will be either censored or shut down. While there are questions about just how easy it will be to implement the new rules, Beijing's… [Continue Reading] -

Samsung Electronics to invest $26 billion in its South Korean memory chip manufacturing business
Publié: juillet 4, 2017, 7:00pm CEST par Mark Wyciślik-Wilson
Samsung is to invest more than KRW 37 trillion ($32 billion) in its global production facilities. Of this, KRW 30 trillion ($26 billion) will be pumped into its latest semiconductor factory in Pyeongtaek to further expand its production capacity. The South Korean company says that the new facility has started to produce its 64-layer, fourth-generation V-NAND chips, and it wants to push more off the production line. Samsung says that it is responding to demand following a surge of interest in the Internet of Things and Artificial Intelligence. In a bid to ensure it maintains its position as the world's… [Continue Reading] -

Photobucket messes up Amazon, eBay, Etsy and other sites after introducing charges for third-party hosting
Publié: juillet 4, 2017, 5:17pm CEST par Mark Wyciślik-Wilson
A change to Photobucket's terms of service is having disastrous consequences on numerous sites as users discover they can no longer host images for use on other sites free of charge. Users of sites such as Amazon, eBay and Etsy -- as well as owners of personal sites, and social media users -- were more than a little disappointed to learn that in order to continue using third-party image hosting, they would have to upgrade to Photobucket's most expensive package. With the Plus 500 Plan costing $399 per year, upset users have complained that Photobucket is holding them to ransom.… [Continue Reading] -

Facebook fights gagging order that prevents it telling users about US government search warrants
Publié: juillet 4, 2017, 12:03pm CEST par Mark Wyciślik-Wilson
Currently barred from telling three of its users about government search warrants seeking to gain access to their information, Facebook is fighting back. The social network is challenging what it says is a threat to freedom of speech. Documents filed at a Washington DC appeal court show that Facebook wants to notify the users about the warrants so they have an opportunity to object to them. The company cites the First Amendment in seeking to let users know about the warrants, at least one of which relates to protests against Donald Trump. In a statement, Facebook said: "We believe there… [Continue Reading] -

Computer glitch disrupts technology stock prices
Publié: juillet 4, 2017, 11:02am CEST par Mark Wyciślik-Wilson
The stock prices for many major US technology companies nose-dived last night following a computer glitch. The problem also sent shares in Apple, Google, Amazon and Microsoft to the same price after the pre-Independence Day early closure of the stock market. With all four companies seemingly having a stock price of $123.47, Microsoft's market value appeared to increase by nearly 80 percent, while that of Google and Amazon were both slashed by more the 85 percent. Nasdaq stresses that actual stock prices were not affected, and no trading completed with incorrect pricing. Although the prices of stocks did not change… [Continue Reading] -

Nearly half of football fans watch illegal streams of matches -- a third do so regularly
Publié: juillet 4, 2017, 10:32am CEST par Mark Wyciślik-Wilson
A survey by the BBC reveals that over a third of Premier League football (or soccer, if you insist) fans are getting their gaming fix using unofficial (that is, illegal) online streams. Kodi boxes and similar dedicated devices are used by more than a quarter of fans for this very purpose. Perhaps unsurprisingly, it is younger adults who are more likely to make use of illegal streams. One of the main reasons given for watching such streams is that the sports TV packages required to watch matches (Sky and BT Sport have exclusive rights for the live screening of Premier… [Continue Reading] -

Facebook privacy: judge dismisses case surrounding tracking of logged out users
Publié: juillet 3, 2017, 6:54pm CEST par Mark Wyciślik-Wilson
A privacy case against Facebook has been thrown out of court by a judge in the US District Court, Northern District of California. The case surrounded Facebook's tracking of users via Like buttons on other sites even when they were not logged into their accounts. Plaintiffs said that Facebook violated wiretapping and privacy laws, but District Judge Edward Davila ruled that there was no evidence that the social network had illegally "intercepted" communications. She said that plaintiffs had failed to show "realistic" economic harm or loss, adding that they could have taken steps to maintain the privacy of their browsing… [Continue Reading] -

Sharing of patient data between Royal Free hospital and Google DeepMind breached Data Protection Act
Publié: juillet 3, 2017, 5:17pm CEST par Mark Wyciślik-Wilson
A partnership between London's Royal Free hospital and DeepMind resulted in a breach of the Data Protection Act, an investigation by the Information Commissioner's Office (ICO) has concluded. The personal data of more than 1.6 million patients was transferred to the Google subsidiary as part of the creation of Streams, an app to diagnose and detect acute kidney injury. The ICO found that patients were not properly informed about how their data would be used, and highlighted a "number of shortcomings" in the way data was handled. The ICO was unhappy with the fact that app testing was carried out… [Continue Reading] -

Fire-prone Samsung Galaxy Note7 rises from the ashes as refurbished Galaxy Note Fan Edition
Publié: juillet 3, 2017, 1:39pm CEST par Mark Wyciślik-Wilson
The disaster that was the Samsung Galaxy Note7 has been well-documented. After battery defects caused the handset to catch fire, the phone was remotely crippled by Samsung and a recall issued. Now the South Korean company is ready to relaunch the device. This is not to say that Galaxy Note7 lives on. Rather the smartphone is relaunching as the Galaxy Note Fan Edition (or Galaxy Note FE), using refurbished parts cannibalized from returned Note7s. Bixby is on board, and there have been some hardware changes to ensure history does not repeat itself. A key change is the use of a… [Continue Reading] -

Kaspersky Lab is ready to hand over source code to US government to disprove Kremlin links
Publié: juillet 3, 2017, 10:56am CEST par Mark Wyciślik-Wilson
As the US government decides whether or not to continue using Kaspersky security software, the Russian company has indicated its willingness to hand over source code for review. Eugene Kaspersky, speaking to the Associated Press, said that "if the United States needs, we can disclose the source code." Rumors have long circulated about Kaspersky's ties to Putin, leading to speculation that the company's software could be used to spy on Americans. Kaspersky said: "Anything I can do to prove that we don't behave maliciously I will do it." And this is entirely understandable. The company has a great deal to… [Continue Reading] -

As the original Windows 10 reaches end-of-service, Microsoft will start pestering you to update
Publié: juillet 3, 2017, 9:53am CEST par Mark Wyciślik-Wilson
It's quite some time since the launch of Windows 10 -- so long, in fact, that the original release has now reached the end of its life. Windows 10 version 1507 will no longer receive Microsoft's monthly security patches, so the company is about to start reminding hangers-on that they should update. With so many malware attacks hitting the headlines recently, Microsoft is aiming to get as many people as possible upgraded to the latest, most secure version of Windows 10. At the moment this is Windows 10 Creators Update, but it won’t be long before Windows 10 Fall Creators… [Continue Reading] -

Facebook disappoints Christians by refusing to introduce a cross reaction
Publié: juillet 2, 2017, 5:15pm CEST par Mark Wyciślik-Wilson
Facebook's reactions have long been a source of disappointment for users. When they were first introduced people were upset by the lack of a Dislike option. There was also dissatisfaction with the fact that Facebook merely logs reactions as an interaction rather than taking into account the meaning behind them. In addition to the main reactions, Facebook has introduced special, temporary additions over the months -- flowers for Mother's Day, a mask for Halloween, and a rainbow flag for Pride month to "celebrate love and diversity." Conservative Christians, however, have been told that a cross reaction is not in the… [Continue Reading] -

Post too much to Facebook and it will be assumed that you're spreading fake news
Publié: juillet 1, 2017, 12:15pm CEST par Mark Wyciślik-Wilson
Facebook's ongoing battle against fake news continues, and the social network has a new weapon in its arsenal. To cut down on the amount of spam and fake news appearing in News Feeds, users who post a lot each day will have their visibility reduced. The thinking behind this is that there are some Facebook users who "routinely share vast amounts of public posts per day," and the company has found that the content shared tends to be spammy or fabricated stories. Facebook says that the change could mean that even legitimate publishers find that their reach is reduced, however.… [Continue Reading] -

Facebook's Find Wi-Fi rolls out to Android and iPhone users around the world
Publié: juillet 1, 2017, 9:55am CEST par Mark Wyciślik-Wilson
Modern takes on Maslow's hierarchy of needs (jokingly) refer to a wireless internet connection as being a necessity. While Wi-Fi may not be -- in the strictest sense of the word -- necessary, it's certainly true that it has become the prey that we now hunt for. To make the search a little easier, Facebook is now rolling out its Find Wi-Fi tool globally. What previously started as a small-scale test is now available around the world for Android and iPhone users, so anyone looking to minimize data usage will be able to find an easy way online. This is… [Continue Reading] -

OutlawCountry revelations from WikiLeaks show the CIA can target Linux
Publié: juillet 1, 2017, 8:55am CEST par Mark Wyciślik-Wilson
The Vault 7 leaks continue to flow thick and fast from WikiLeaks, shedding more and more light on the hacking and infiltration capabilities of the CIA. The latest batch details the OutlawCountry project which finds the CIA targeting Linux systems. With Linux-based operating systems usually lauded for their impenetrability, news of a possible chink in the armour will undoubtedly cause concern. With OutlawCountry, it seems the CIA was able to redirect network traffic from a target machine to an agency-controlled machine for infiltration. There are, perhaps obviously, a number of prerequisites to allow the CIA's method to work -- although… [Continue Reading] -

Teens in Britain engage in worrying 'extreme internet use'
Publié: juin 30, 2017, 2:06pm CEST par Mark Wyciślik-Wilson
A report by the Education Policy Institute (EPI) says that more than a third of British teenagers are "extreme internet users." This does not (necessarily) mean they are accessing the darker, more extreme recesses of the internet, rather that they are just using it a hell of a lot. Of the 34 OECD member countries -- which includes the US, Australia and much of Europe -- only Brazilian teens were more extreme. But with 37.3 percent of British teenagers indulging in "extreme internet use," there is a warning that this is not an accolade to be proud of. Extreme internet… [Continue Reading] -

France drops Windows 10 privacy case after Microsoft changes telemetry settings
Publié: juin 30, 2017, 10:40am CEST par Mark Wyciślik-Wilson
There have been lots of complaints about invasion of privacy since the release of Windows 10. Microsoft's telemetry lead to several lawsuits, including one from France's National Data Protection Commission which said Windows 10 was collecting "excessive personal data" about users. But now the Commission Nationale de l'Informatique et des Libertés (CNIL) has decided to drop its case against Microsoft. The commission is happy that sufficient steps have been taken to reduce the amount of data that is collected and users are now informed about data collection. Announcing that it was dropping the lawsuit, the CNIL says that: "The company… [Continue Reading] -

France drops Windows 10 privacy case after Microsoft changes telemetry settings
Publié: juin 30, 2017, 10:40am CEST par Mark Wyciślik-Wilson
There have been lots of complaints about invasion of privacy since the release of Windows 10. Microsoft's telemetry lead to several lawsuits, including one from France's National Data Protection Commission which said Windows 10 was collecting "excessive personal data" about users. But now the Commission Nationale de l'Informatique et des Libertés (CNIL) has decided to drop its case against Microsoft. The commission is happy that sufficient steps have been taken to reduce the amount of data that is collected and users are now informed about data collection. Announcing that it was dropping the lawsuit, the CNIL says that: "The company… [Continue Reading] -

With Windows 10 Fall Creators Update, Microsoft is going all-in on security
Publié: juin 28, 2017, 10:13am CEST par Mark Wilson
With Windows 10 Fall Creators Update, Microsoft is going all-in on security. When the next major update to Windows 10 is released later in the year, it will include Windows Defender Exploit Guard which sees EMET (Enhanced Mitigation Experience Toolkit) becoming a native part of the operating system. Microsoft says that it is raising the bar for security, and this is part of the "end-to-end security features" the company has announced. Windows Defender Advanced Threat Protection (ATP) will benefit from a centralized management system as Microsoft aims to "make life harder for the bad guys." Writing on the Windows blog,… [Continue Reading] -

Google News benefits from a major redesign and fact-checking
Publié: juin 28, 2017, 8:16am CEST par Mark Wilson
It may be a while since you took a look at Google News, but there's never been a better time to revisit the site. Google has just launched a major overhaul of the site, focusing on not just changing the look, but also improving navigation and giving more balanced coverage to stories. The news aggregation site has been due something of an overhaul for some time, and the update cleans out the clutter, introduces a card layout, and places increased importance on balanced portrayal of topics and fact-checking. Google says that the redesign is "for everyone" and the aim is… [Continue Reading] -

Facebook Messenger video chats get a little sexier with new masks, filters and reactions
Publié: juin 26, 2017, 6:32pm CEST par Mark Wilson
Facebook Messenger today receives a boatload of visual updates as the social networking company tries to appeal to a younger audience with video chat. The update sees Facebook continuing its expansion of reactions so they can now be used in video chats, but there are also other ways to spice up conversations. The existing collection of masks has been bolstered with new additions -- complete with Easter eggs -- and there is also a range of filters to choose from. Facebook says that filters are a way to "look and feel like your best self or express your current mood."… [Continue Reading] -

Tumblr apologizes for blocking innocuous LGBTQ+ content with Safe Mode
Publié: juin 26, 2017, 12:39pm CEST par Mark Wilson
Google recently caused controversy and upset by censoring LGBTQ videos from appearing in Restricted Mode on YouTube. The company later apologized, fixed the problem, and then updated its policies. Now Tumblr has found itself caught up in a similar hullabaloo. Complaints were raised after -- just like YouTube's Restricted Mode -- Tumblr's Safe Mode was found to be filtering out LGBTQ+ content. The site has now apologized, updated its algorithms, and explained why the problem came about in the first place. It seems that the policies that governed Safe Mode were rather too broad, and they were being automatically applied… [Continue Reading] -

Facebook and Twitter have secret Harry Potter Easter eggs to celebrate 20 years of the Sorcerer's Stone
Publié: juin 26, 2017, 11:28am CEST par Mark Wilson
Today is the twentieth anniversary of the publication of Harry Potter and the Sorcerer's Stone (or Harry Potter and the Philosopher's Stone depending on where you are in the world). To celebrate, Facebook has hidden a Potter-related Easter egg on the site, and Twitter is getting in on the action as well. As Harry Potter is all about magic, it should come as little surprise that in order to unlock the Easter egg, you need to use the right magic words. Here's what you need to do... If you type the name Harry Potter in a post, or the name… [Continue Reading] -

Microsoft confirms that Windows 10 source code has leaked online
Publié: juin 24, 2017, 2:30pm CEST par Mark Wilson
Microsoft has confirmed reports that some Windows 10 source code has leaked. The Register claims that 32TB of internal builds as well as large sections of source code were uploaded to betaarchive.com. While the scale of the leak is not yet known, Microsoft says that the files in question are "a portion of the source code [...] used by OEMs and partners." The files leaked on Beta Archive are part of Microsoft's Shared Source Kit, and it's not clear that the leak is quite as big a deal as first thought -- or as some reports are making out. Nevertheless,… [Continue Reading] -

Thanks to Word macros, Windows 10 S isn't as secure as Microsoft would have you believe
Publié: juin 24, 2017, 1:36pm CEST par Mark Wilson
With Windows 10 S Microsoft has made the bold claim that this locked down version of its operating system is immune to all known ransomware. This may well be true, but that's certainly not to say that Windows 10 S is completely secure. Lock up your Surface Laptop! An investigation carried out by ZDNet found that Windows 10 S -- despite only supporting the installation of apps from the Windows Store -- is vulnerable to that old security nightmare: Word macros. The problem comes about because the macros have full access to the Windows API, opening up a potential attack… [Continue Reading] -

Russian hackers stole and sold passwords belonging to British politicians
Publié: juin 23, 2017, 4:43pm CEST par Mark Wilson
An investigation by the Times has found that passwords belonging to British officials have been traded by Russian hackers. The passwords and email addresses of tens of thousands of politicians, senior police officers and diplomats were sold or swapped following an attack on LinkedIn in 2012. As well as LinkedIn, some information seems to have been garnered from MySpace. The credentials for politicians, including education secretary Justine Greening and business secretary Greg Clark, were initially put on the market for sale or trade, but were later made available free of charge. The National Cyber Security Centre has issued security advice… [Continue Reading] -

Google will now hide personal medical records from search results
Publié: juin 23, 2017, 2:16pm CEST par Mark Wilson
Google has updated its search policies without any sort of fanfare. The search engine now "may remove" -- in addition to existing categories of information -- "confidential, personal medical records of private people" from search results. That such information was not already obscured from search results may well come as something of a surprise to many people. The change -- first reported by Bloomberg -- has been confirmed by Google, although the company has not issued any form of announcement about it. While Google likes to be seen to have a largely hands-off approach to search results, there are circumstances… [Continue Reading] -

Microsoft Whiteboard app leaks -- download Windows 10's newest inking tool
Publié: juin 23, 2017, 1:21pm CEST par Mark Wilson
Last month Microsoft gave us a glimpse of its upcoming Whiteboard app -- now the app has leaked online. This means that we have the opportunity to not only see what Microsoft has in store for inking in Windows 10, but we can also get hands on with it. The tool is part of Microsoft's recent education focus, and it gives students and tutors the chance to collaborate on an interactive whiteboard. Features include automatic shape completion (draw a square freehand, and it will be converted into a geometric square), equation support, and angle calculation. The leaked version is marked… [Continue Reading] -

Facebook launches Online Civil Courage Initiative to fight extremism in the UK
Publié: juin 23, 2017, 12:13pm CEST par Mark Wilson
Facebook today launches its latest attempt to tackle online extremism in the UK with its new Online Civil Courage Initiative (OCCI). It is part of an education drive which finds the social network trying to inform charities and local organizations how to fight hate speech and extremism online. The OCCI is being launched with involvement from a number of partners, including the Jo Cox Foundation and Imams Online, and it has a UK focus. Facebook users are encouraged to head over to the OCCI pages to share ideas using the hashtag #civilcourage. Facebook is just one of numerous technology companies… [Continue Reading] -

Facebook's new mission statement: 'give people the power to build community and bring the world closer together'
Publié: juin 23, 2017, 11:02am CEST par Mark Wilson
Mark Zuckerberg has announced a new mission statement for Facebook. The social network is no longer interested in making the world "more open and connected," now it wants to "give people the power to build community and bring the world closer together." The change of direction will set Facebook's course for the next decade, and it was revealed at the Facebook Communities Summit. At the summit Facebook also revealed a new batch of tools for group admins to help drive the sense of community and make groups easier to manage. In typical Zuckerberg style, the new mission statement is described… [Continue Reading] -

Virgin Media warns Super Hub 2 owners to change their passwords due to hacking risk
Publié: juin 23, 2017, 10:28am CEST par Mark Wilson
Virgin Media is urging hundreds of thousands of customers with its Super Hub 2 router to change their passwords after a Which? investigation uncovered a way for hackers to gain access to the device. If the password for the router is not changed from its default there is a risk from hacking, but Virgin Media said the risk is small. Nevertheless, as a precautionary measure a password change is the advice for more than 800,000 users. In its defence, the company points out that the problem is not specific to just the Super Hub 2, saying other routers of the… [Continue Reading] -

eBay will now price match a number of online retailers
Publié: juin 22, 2017, 6:36pm CEST par Mark Wilson
Part of the joy of shopping online is being able to easily compare prices at a number of retailers so you get the best price. If you prefer to get all of your goods from the same place, eBay has a new deal that you'll love -- price matching. The offer covers items in the eBay Deals section, and price matching is carried out against Amazon.com, BestBuy.com, Walmart.com, HomeDepot.com, Target.com, Sears.com, Wayfair.com and Jet.com. But if you want to take advantage of the offer, you'll have to take careful note of the terms and conditions. We've already mentioned that price… [Continue Reading] -

Camera trickery: the OnePlus 5 does NOT offer lossless 2x optical zoom
Publié: juin 22, 2017, 5:33pm CEST par Mark Wilson
Just one day after the launch of the long-awaited OnePlus 5, accusations of cheating in benchmarks started to creep out -- just as they did with the OnePlus 3T. Now another minor controversy has hit the brand new handset: it turns out that while it is strongly suggested that the OnePlus 5 has lossless 2x optical zoom, that is not actually the case. OnePlus' marketing certainly pitched the dual camera as offering instant 2x zoom, and many people assumed that the arrangement was the same as with the dual camera iPhone 7 Plus which does offer 2x optical zoom. But… [Continue Reading] -

Imagination Technologies is up for sale after being ditched by Apple
Publié: juin 22, 2017, 2:28pm CEST par Mark Wilson
Back in April, Imagination Technologies revealed that it had been dropped by Apple and would therefore no longer be supplying GPU chips for use in iPhones, iPads and other products. Now, having lost 70 percent of its value, the UK company is putting itself up for sale. Shares in Imagination fell dramatically after Apple ditched it, but news of the sale led to a jump of 21 percent. The company is valued at around £425 million ($538 million) and the announcement comes after several parties expressed interest in an acquisition of Imagination Technologies Group plc in its entirety. The company remains… [Continue Reading] -

Facebook uses India as a testing ground for profile picture protection features
Publié: juin 22, 2017, 1:53pm CEST par Mark Wilson
It's a common belief that anything that appears online is fair game for downloading and sharing, and this idea extends to Facebook profile pictures. Facebook has found that in India in particular there is great concern from users -- particularly woman -- about uploading a profile picture in case it is download and shared elsewhere. Responding to this, the social network is trialling features that will grant users more control over their profiles pictures. Facebook is not only introducing a new profile picture guard, but also encouraging people to add a design layer to their images to discourage misuse by… [Continue Reading] -

Subpoenas mean owners of TVAddons and ZemTV Kodi add-on could be revealed
Publié: juin 21, 2017, 11:45am CEST par Mark Wilson
In recent weeks numerous Kodi add-ons have disappeared, and the popular site TVAddons also suffered the same fate. It had been presumed that the disappearances were related to a lawsuit taken out by Dish Network, and now the broadcaster has been granted subpoenas to help identify those developing the ZemTV Kodi addon and running the TVAddons website. The subpoenas relate to a number of online services including Facebook and Twitter, and successfully identifying defendants will be key to the success with any lawsuits relating to copyright infringement. Dish Networks will now be able to approach Facebook to find out who… [Continue Reading] -

OnePlus 5 cheats in benchmarks for a performance boost
Publié: juin 21, 2017, 10:36am CEST par Mark Wilson
At the start of the year it was discovered that the OnePlus 3T was cheating in benchmarks, artificially boosting performance when testing tools were detected. The OnePlus 5 was only officially launched yesterday but the same accusation is already being leveled at the latest version of the flagship killer. As with the OnePlus 3T, the benchmark trickery of the OnePlus 5 was discovered in tests carried out by XDA Developers. The site says that its review unit "manipulates benchmarks to maximize scores" and issues a stark warning in an article entitled: "Do NOT Trust OnePlus 5 Benchmarks in Reviews --… [Continue Reading] -

The OnePlus 5 is now official -- Qualcomm Snapdragon 835, 8GB RAM, and a price rise
Publié: juin 20, 2017, 6:49pm CEST par Mark Wilson
Three years in the making, the OnePlus 5 -- the company's "most complete and competitive product yet" -- is now official. OnePlus says it's all down to the details, and the company has made endless minor adjustments, and over 100 prototypes to settle on a final design. The handset is just 7.25mm thick, and the overall layout of the phone is all but identical to the OnePlus 3 and 3T -- and yes, there is a headphone jack. The phone is available in Midnight Black and Slate Gray and the specs are in line with the leaks and rumors we've… [Continue Reading] -

Amazon Prime Wardrobe beta: money-saving clothes shopping with free returns
Publié: juin 20, 2017, 5:36pm CEST par Mark Wilson
Not content with splashing some cash on Whole Foods, Amazon is also spreading out into other new ventures. The latest is Prime Wardrobe, a new clothes shopping service for Prime subscribers that's currently in beta and offers the chance to "try before you buy." The service ties in with Amazon Fashion, and it covers more than a million items of clothing. Users can select three or more items to have shipped out to them completely free of charge, and payment is only required for anything that's kept. Returns are free, and Amazon gives shoppers a full week to try out… [Continue Reading] -

BBC iPlayer now requires you to sign in for your catch-up TV fix
Publié: juin 20, 2017, 5:09pm CEST par Mark Wilson
Last month, the BBC announced plans to force iPlayer users to sign into their account in order to watch the catch-up service. The requirement is now rolling out, and this means that the option to skip sign-in is starting to vanish. Visitors to the site are now greeted by a message that reads: "You now need to sign in to watch. It's quick & easy. And we'll keep you signed in." Without following the instruction to sign in -- which gives the BBC the opportunity to check for a valid TV license -- it is not possible to watch any… [Continue Reading] -

ProtonVPN is a free VPN service that's now available to everyone
Publié: juin 20, 2017, 1:11pm CEST par Mark Wilson
ProtonMail has opened up its free VPN service to anyone who wants to use it. ProtonVPN was previously only available to a limited number of beta testers, but now everyone can secure their internet connection for free. The company is best known for its encrypted email service, but the prospect of a free VPN tool will also be enticing to anyone who has concerns about privacy. It also provides a free way of bypassing internet restrictions that may be put in place by governments or ISPs. ProtonVPN was created to supplement ProtonMail, with the primary aim of protecting journalists and… [Continue Reading] -

Unsecured Amazon server leaks details of 198 million American voters
Publié: juin 19, 2017, 6:51pm CEST par Mark Wilson
Personal data and profiling information about millions of American voters has been exposed in what is believed to be the largest ever leak of its kind. 198 million records were found stored on an unsecured Amazon S3 server owned by Deep Root Analytics, a Republican data analytics firm. It is thought that the data, which dates back more than a decade, includes information about every registered American voter. The open server was discovered by UpGuard Cyber Risk Analyst Chris Vickery, but disclosure of the availability of the data was delayed until the server had been made secure. The amount of… [Continue Reading] -

Microsoft is killing off SMBv1 in Windows 10 to thwart the likes of WannaCry
Publié: juin 19, 2017, 5:32pm CEST par Mark Wilson
From the fall, Microsoft is disabling SMBv1 in Windows 10. With the release of Windows 10 Fall Creators Update (or Redstone 3 if you prefer), the protocol that was exploited by the WannaCry ransomware will be no more. The file sharing protocol was developed by Microsoft over two decades ago, and the company recognizes that the time has come for it to be retired. Internal builds of Windows 10 being tested by Microsoft already have SMBv1 disabled, and similar builds will make their way to Windows Insiders and the wider public in due course. The chances are however, that you… [Continue Reading] -

Microsoft releases Windows 10 S recovery images for Surface Laptop allowing downgrades from Windows 10 Pro
Publié: juin 19, 2017, 4:42pm CEST par Mark Wilson
With the Surface Laptop, Microsoft is testing the water with Windows 10 S, its cut-down version of Windows 10. For those who find they can't live with the restrictions the operating system imposes on them, there is the possibility of upgrading to Windows 10 Pro -- but Microsoft warns that this is a one-way, irreversible process. Except it's not, of course. While it's not possible to "uninstall" Windows 10 Pro and downgrade to Windows 10 S, there's nothing to stop you from restoring your computer to its factory state -- something that Microsoft has just made a great deal easier… [Continue Reading] -

Microsoft has made no attempt to make the Surface Laptop even slightly repairable
Publié: juin 19, 2017, 12:41pm CEST par Mark Wilson
It has been a few weeks since Microsoft launched the new Surface Laptop, and the Windows 10 S machine has been very well received. If you do get one, though, you'd better hope that nothing goes wrong with it. A teardown of the device reveals that the Surface Laptop is largely held together with glue, and if you were to attempt any sort of repair, you would likely damage it. It also shows that components such as CPU and memory are soldered in place so they can't be replaced or upgraded. Overall it was given a rating of 0 out… [Continue Reading] -

OnePlus 5 TV ad shows India the upcoming smartphone in full
Publié: juin 19, 2017, 10:47am CEST par Mark Wilson
It feels as though we've been waiting a long time for the arrival of the OnePlus 5, but the big day is finally upon us -- the smartphone launches tomorrow. There have been a huge number of leaks about the latest version of the flagship killer, teasing us with little glimpses of what to expect. But now a TV ad has aired in India that reveals everything. Shown during the India vs Pakistan cricket final, the ad gave an unfettered view of the OnePlus 5 to millions of people. This is the first official render we've seen of the phone...… [Continue Reading] -

Screen protector listing shows what the iPhone 8 will look like
Publié: juin 19, 2017, 10:04am CEST par Mark Wilson
The launch of the iPhone 8 is still some way off but -- as with just about every smartphone of note (we're looking at you, OnePlus 5) -- lots of details have slipped out ahead of any official announcement. The latest leak "confirms" what we've long expected: that there's a quite significant redesign coming up. We have already heard rumors that the iPhone will be near-bezel-less, and we've seen supposed production-line images that show off the front and rear panels. The front panel images showed a weird cut-out at the top of the phone and a new listing on accessory website… [Continue Reading] -

How to avoid Twitter's bubbly redesign
Publié: juin 17, 2017, 3:37pm CEST par Mark Wilson
With its latest redesign, many people are complaining that Twitter has stepped back in time. If you are not a fan of the "circles and curves everywhere" look, you can -- with a little help -- avoid the redesign and stick with the way things were. There's just one catch -- you have to be using Chrome. If this is already your web browser of choice, all you need to do is to install an extension built specifically to "remove Twitter's 'bubbly' redesign." The aptly-named Twitter Debubbler banished the rounded corners, the circular profile picture, and the other "bubbly" aspect… [Continue Reading] -

Here's why the Xbox One X is so damned expensive
Publié: juin 16, 2017, 1:47pm CEST par Mark Wilson
When Microsoft revealed that Project Scorpio was the Xbox One X, there was immediate excitement about "the world's most powerful console". But while there is eager anticipation of true 4K gaming, and a wealth of titles to look forward to, there is something of a dark shadow hanging over the upcoming console: that price. At $499, the Xbox One X is (or will be) the most expensive gaming console on the market and there are understandable questions about why the price is so high. Vice President of Xbox and Windows Gaming VP, Mike Ybarra, has shed some light on the… [Continue Reading] -

WikiLeaks Vault 7: CherryBlossom files show CIA can hack D-Link, Belkin and Linksys routers into listening devices
Publié: juin 16, 2017, 10:43am CEST par Mark Wilson
Wikileaks has released a batch of documents from the middle of 2012 revealing details of the CIA's CherryBlossom project. A joint venture with the Stanford Research Institute, the CherryBlossom files show how the agency can take remote control of routers and other networking devices from numerous manufacturers, transforming them into listening devices. CherryBlossom also enables the CIA to interfere with both incoming and outgoing traffic. Passwords present little obstacle in many cases and the fact that remote infection is possible makes the implant very simple to install. The documents reveal how the CIA can home in on a target using… [Continue Reading] -

Twitter's redesign basically comprises old fashioned rounded buttons and new icons
Publié: juin 15, 2017, 6:39pm CEST par Mark Wilson
It has been a while since Twitter was treated to a new lick of paint, but that all changes today. A new look is rolling out, and "round" is the word that springs most readily to mind. Think back to the look of the web around 15 years ago -- all rounded corners and the like -- and you're in the right ballpark. Online there are not only rounded buttons and round profile pictures, but also redesigned, wireframe icons. Mobile users are also treated to a new look. The redesign is certainly not going to be to everyone's taste. The… [Continue Reading] -

The end could be nigh for the Pirate Bay after European Court of Justice ruling
Publié: juin 15, 2017, 11:05am CEST par Mark Wilson
The Pirate Bay may be something of a battered ship after an onslaught of attacks over the years but, somehow, it remains afloat. The latest blow, however, comes from the European Court of Justice which has just ruled that the site -- despite not hosting any content itself -- can still be held liable for copyright infringement. The landmark ruling means that the site could be considered to have broken the law for simply directing people towards copyrighted material. There are implications for a wide range of sites and services, but the focus is very much on that stalwart of… [Continue Reading] -

Happy birthday to the GIF... and welcome to Facebook comments!
Publié: juin 15, 2017, 10:44am CEST par Mark Wilson
Today marks the 30th anniversary of the GIF. The humble file format has -- after protracted arguments about how to pronounce the word -- come a long way. After years irritating people in the format of flashing animated ads, the images are now used to adorn messages with pithy memes and pertinent video clips. GIFs in their current incarnation are supported by messaging tools and social platforms left, right and center, and after including a dedicated GIF button in Facebook Messenger, the social network is now rolling out the same feature in comments. The idea is very simple and the… [Continue Reading] -

Greatly enhanced Google Backup and Sync to (mostly) replace Drive
Publié: juin 14, 2017, 8:30pm CEST par Mark Wilson
Later this month -- June 28 specifically -- Google is to launch a new tool: Backup and Sync. Aimed primarily at consumers, the tool is designed to backup files and photos, and make them accessible from any device. Backup and Sync is described as "the latest version of Google Drive for Mac/PC, which is now integrated with the Google Photos desktop uploader," and for most users it will completely replace Drive. Corporate and enterprise users are advised to hold out until the release of Drive File Stream later in the year, but for everyone else, Backup and Sync opens up… [Continue Reading] -

Facebook expands Safety Check with fundraising and more
Publié: juin 14, 2017, 7:31pm CEST par Mark Wilson
Facebook's Safety Check feature has become one of the easiest ways of checking up on loved ones when disaster strikes. It also gives people in the affected area the opportunity to let friends and family know that they're OK, and today Facebook is adding a number of new options, including fundraising. Starting off in the US, people will now be able to start a fundraiser from within Safety Check to help raise money for those in need. These can be for personal or charitable causes, and the feature makes it easy for others to make donations. There are also other… [Continue Reading] -

Microsoft ads slam Google, claiming Windows 10 beats Chromebooks for business and education
Publié: juin 14, 2017, 12:56pm CEST par Mark Wilson
Microsoft's latest anti-Google ad campaign has more than a slight whiff of Scroogled from a few years back. A pair of advertisements lay into Chromebooks, and suggest that Windows 10 devices are far better for both business and education. Google has made much of the benefits that Chromebooks can bring to the classroom, but Microsoft disagrees -- and says Windows 10 Pro is far better for businesses too. In the two ads, the company highlights the security and features of Windows, painting Google's software as insecure and underpowered. Microsoft claims that "Windows 10 Pro provides a superior experience to Chrome"… [Continue Reading] -

With Amazon Prime Reload you can earn 2 percent cashback on purchases
Publié: juin 14, 2017, 12:06pm CEST par Mark Wilson
Amazon has launched a new cashback program to attract more people to take out Prime subscriptions. Prime Reload lets subscribers earn 2 percent cashback for making payments with a debit rather than a credit card. It's not quite as simple as that, however; it's not just a case of filling up your basket and checking out. The Reload part of the name refers to the fact that you need to reload your Amazon Gift Card Balance using a debit card. And there lies the rub -- you need to remember to keep your balance topped up. The 2 percent cashback… [Continue Reading] -

Instagram rolls out archiving feature so you can hide unwanted photos without deleting them
Publié: juin 14, 2017, 11:02am CEST par Mark Wilson
The eyes may be a gateway to the soul, but the feeds of social media accounts can be even more revealing. Facebook, Instagram, Twitter and their ilk all give people the opportunity to not only share their lives with the world, but present a particular image of themselves. Of course, there are the occasional posts which, well, let the side down. With this in mind, Instagram is rolling out a new archive feature that makes it possible to remove images from your feed without having to delete them. If you have any embarrassing pictures you'd rather didn’t taint your image,… [Continue Reading] -

Microsoft includes Windows XP and Vista in June's Patch Tuesday updates
Publié: juin 13, 2017, 8:07pm CEST par Mark Wilson
Last month Microsoft made the decision to issue a "highly unusual" patch for Windows XP. Despite the fact the operating system has not been supported for some time, the patch was released in an attempt to thwart the WannaCrypt ransomware attacks. Now, in an even more unusual move, Microsoft has chosen to include Windows XP in this month's Patch Tuesday. Windows Vista is also included in this batch of security updates which Microsoft says should address the "elevated risk of cyberattacks by government organizations." Windows XP has not been supported since 2014, with regular Vista support coming to an end… [Continue Reading] -

Google launches Android Excellence to recognize the very best apps and games
Publié: juin 13, 2017, 7:17pm CEST par Mark Wilson
Google has launched a new scheme which sees the company highlighting the very best games and apps to be found in Google Play. This is not simply a list of the most downloaded or, necessarily, the most highly rated titles; Google has a new batch of criteria by which to judge developers' offerings. The real aim is to heap praise on those apps and games which exude quality, and deliver the best user experiences. Google says that titles which "use many of our best practices, and have great design, technical performance, localization, and device optimization" will also feature in the… [Continue Reading] -

Gboard for Android now recognizes the emoji you draw by hand and suggests phrases for you
Publié: juin 13, 2017, 4:56pm CEST par Mark Wilson
Emoji offer a great way to spice up your chats, and the Android version of Gboard has been updated to make it easier to find the perfect ones. The update means you can now use the emoji search box to draw the sort of emoji you're looking for, and Google's keyboard will track down what it thinks you mean. Google uses machine learning to interpret even the most primitive of squiggles, so now there's no need to think about how you would describe a particular emoji in order to perform a text-based search for it -- just draw what you… [Continue Reading] -

What does the scrapping of EU roaming charges mean for UK mobile users?
Publié: juin 13, 2017, 3:59pm CEST par Mark Wilson
It's just a couple of days until new EU regulations come into force which makes European roaming charges a thing of the past. Put simply, all mobile operators will have to permit their customers to use their bundled text, call and data allowance within the EU at no extra charge. With many UK travelers caught out by high mobile bills after a trip, this change should be great news. But consumer watchdog Which? warns that there could be a catch, and mobile users are warned to continue to keep an eye on their bills. The problem stems from the fact… [Continue Reading] -

Kodi add-ons site TVAddons vanishes from the internet
Publié: juin 13, 2017, 1:01pm CEST par Mark Wilson
The negative attention that Kodi has been attracting recently continues. A number of high-profile add-ons, such as Phoenix, have disappeared recently as interest in the piracy potential for the media player increases. The latest victim appears to be TVAddons, a site which lists unofficial Kodi add-ons. The site was sued last week by a federal court in Texas, so the disappearance is not entirely surprising. But the removal of DNS records -- rendering the site inaccessible -- without any explanation is a little strange. TVAddons is -- or, perhaps, was -- a huge library of Kodi add-ons, but the site… [Continue Reading] -

Microsoft wins Supreme Court case about scratched Xbox 360 discs
Publié: juin 13, 2017, 12:07pm CEST par Mark Wilson
With staggeringly coincidental timing, just as Microsoft revealed its upcoming Xbox One X console, the company received some great news from the US Supreme Court. In an 8-0 decision, the court overturned an earlier ruling in what has become a complex and lengthy case. What originally started off as a fairly simple case around a decade ago about game discs scratched by Xbox 360 consoles, has evolved into quite a different beast. The latest ruling means that a case that was to be brought collectively by tens of thousands of gamers cannot be granted class action status. What this means… [Continue Reading] -

People in the US are less savvy about cyber security than people in the UK
Publié: juin 13, 2017, 11:09am CEST par Mark Wilson
A new report suggests that people in the UK are more aware of the terminology surrounding cyber security, and are less likely to fall victim to hacking and identity theft. Wombat Security Technologies' 2017 edition of its User Risk Report reveals a stark difference in cyber knowledge on either side of the Atlantic. The report is based on a survey carried out last month into knowledge of, and attitudes to, cyber security topics and best practices. While the report shows that the UK is generally more cyber security savvy, the US is shown to fare better when it comes to… [Continue Reading] -

Logitech's POWERPLAY mousemat lets you wirelessly charge your mouse as you use it
Publié: juin 12, 2017, 10:20am CEST par Mark Wilson
You might have thought that mousemats had been consigned to the history books, but Logitech has other ideas. Designed with the needs of gamers high on the list of priorities, Logitech's new POWERPLAY mousemat not only ensures great control, it also wirelessly charges mice to avoid the problem of running out of juice at an inopportune moment. Of course, you need a POWERPLAY-compatible mouse in order to take advantage of this feature, and Logitech has also launched two new mice. The G903 and G703 are the latest addition to the company's high-end wireless gaming mouse range, and they work with… [Continue Reading] -

Watch here: Microsoft's E3 Xbox briefing about Project Scorpio streams live on Twitch
Publié: juin 11, 2017, 5:49pm CEST par Mark Wilson
Microsoft is due to hold a press conference at E3 2017 today. The topic is the future of Xbox, and we should hear more about Project Scorpio, the latest version of the Xbox One which is expected to feature VR and 4K support. The price of the Xbox One S has just been reduced by $50 as Microsoft has done in the past before the launch of a new version of the console. If you're keen to find out what's new, you can watch the Twitch stream live, here at 5PM ET / 2PM PT / 10PM BST. As well… [Continue Reading] -

Google and Facebook celebrate Pride month with event maps and rainbow reaction
Publié: juin 11, 2017, 11:46am CEST par Mark Wilson
June is Pride month, and two of the biggest names in tech are getting involved in the celebrations. Google and Facebook are both showing their support for LGBTQ communities around the world. Facebook has introduced a new, temporary, "reaction" in the form of a rainbow flag, while Google Maps is highlighting Pride events in cities around the world -- so you can either navigate to them to take part, or avoid the crowds if you're heading elsewhere. This is not the first time Facebook has added a temporary reaction -- a flower was added for mothers' day -- and the… [Continue Reading] -

Raspberry Pi devices transformed into cryptocurrency miners by Linux malware
Publié: juin 11, 2017, 11:13am CEST par Mark Wilson
The words "Linux" and "malware" don’t tend to belong in the same sentence, but a new strain called Linux.MulDrop.14 is infecting Raspberry Pi devices. Infected machines are used to mine cryptocurrency for the malware's author, and it take advantage of poor security to generate money from nothing. The good news is that the malware is fairly simple, and its spread is dependent on the laziness of Pi owners. Linux.MulDrop.14 works by scanning the internet for Raspberry Pi devices with an open SSH port and the "pi" user password unchanged from the default. With these conditions met, it is a fairly… [Continue Reading] -

Microsoft slashes $50 off the price of Xbox One S before revealing Project Scorpio console details
Publié: juin 11, 2017, 10:38am CEST par Mark Wilson
Later today at E3, Microsoft is expected to reveal all about its latest gaming console -- currently known as Project Scorpio. Ahead of this, and as has happened in the past before the launch of a new console, the company is reducing the price of the Xbox One S. While the $50 saving is hardly earth-shattering, it does equate to essentially getting a free game with the console. But before you get too excited, it's important to note that not every Xbox One S will be reduced in price, but there is still quite a choice. The $50 discount is… [Continue Reading] -

Google makes the mobile internet safer with reCAPTCHA Android API
Publié: juin 10, 2017, 11:51am CEST par Mark Wilson
On the tenth anniversary of the arrival of reCAPTCHA, Google announces the first reCAPTCHA Android API as part of Google Play Services. The API makes it easier for reCAPTCHA to differentiate between humans and bots. Just as reCAPTCHA has evolved over the years into Invisible reCAPTCHA, the aim with reCAPTCHA Android API is to cut down on spam and abuse in as unintrusive a way as possible. Google says: "With this API, reCAPTCHA can better tell human and bots apart to provide a streamlined user experience on mobile. It will use our newest Invisible reCAPTCHA technology, which runs risk analysis… [Continue Reading] -

Apple now allows you to tip developers via in-app purchases -- and creams a bit off the top for itself
Publié: juin 10, 2017, 11:03am CEST par Mark Wilson
If you're particularly fond of an app, you may feel like showing your appreciation to the developer by throwing a little money in their direction. Apple is now making this possible by permitting tipping from within apps using in-app purchases. This is great news for developers who had previously found Apple cracking down on tipping, but it's also good news for Apple's finances. Updated App Store policies permit developers to enable in-app tipping, and Apple takes a 30 percent commission for this privilege. The tipping option is not the only change in the new App Store policies. App names are… [Continue Reading] -

NSA cites privacy concerns for u-turn over revealing the number of Americans it spies on
Publié: juin 9, 2017, 11:09am CEST par Mark Wilson
Section 702 of the FISA Amendments Act -- the legislation used to permit the NSA to conduct online surveillance -- is due to expire at the end of the year. We have already seen a number of the big names from the world of technology calling for a number of changes during reform. As part of the reform, officials had promised that they would reveal broad details about the number of American citizens about whom information has been, and is, collected. This is no longer the case. The Director of National Intelligence has performed a u-turn on the promise. At… [Continue Reading] -

Mozilla's WebExtensions APIs allow for cross-browser extensions in Chrome, Opera, Firefox and Edge
Publié: juin 9, 2017, 10:50am CEST par Mark Wilson
Creating add-ons for multiple web browsers can be a nightmare for developers, but Mozilla wants to simplify things. By introducing WebExtensions APIs it is going to become much easier to make extensions that work in multiple web browsers with only minor changes. Based on HTML, CSS, and JavaScript, the aim is to further standardize the APIs to make it even easier to share extensions between browsers. Mozilla is now pushing the technology in the hope that it will gain momentum and a growing following. In a post on its Hacks blog, Mozilla explains that WebExtensions enables developers to "write one… [Continue Reading] -

Does Donald Trump tweet too much? America thinks so
Publié: juin 9, 2017, 9:11am CEST par Mark Wilson
Donald Trump may not be the first US president to take to Twitter, but he's certainly proved unique in the way he uses the social platform. Tweets have become his public mouthpiece, used to issue train-of-thought broadcasts, as well as plenty of oddities -- it's going to be some time before "covfefe" is forgotten. But while many are pleased to see Trump issuing statements through an accessible medium, critics on both sides of the political spectrum have voiced concern about his outpourings. Importantly, the American public now believes that the president tweets too much. A new survey shows that over… [Continue Reading] -

Facebook launches a trio of features to help US constituents connect with elected officials
Publié: juin 7, 2017, 5:46pm CEST par Mark Wilson
Donald Trump is just one example of politicians using social media to get their messages out. With President Trump, Twitter acts very much as a one-way means of communications -- Facebook wants to make the channels between elected officials and constituents a two-way street. As such, the social network is launching three new features -- Constituent Badges, Constituent Insights and District Targeting -- to help users get in touch with their elected representatives. These are the latest attempts by Facebook to increase meaningful civic engagement through its service while fighting back complaints about fake news. New Constituent Badges gives users… [Continue Reading] -

Unsecured online database exposes details of millions of cars and their owners
Publié: juin 7, 2017, 4:50pm CEST par Mark Wilson
Researchers from the Kromtech Security Research Center have discovered an unprotected database online that includes information on about 10 million cars sold in the US. As well as data such as VIN and details of payment plans, the database also includes detailed information about owners, such as name, address, phone numbers and occupation. It has been left exposed online for over four months, but it's not clear who the owner is -- or how to address the security risk it poses. COO of Kromtech, Bob Diachenko, says that while the owner of the database is not yet known, it appears… [Continue Reading] -

Phoenix is the latest Kodi add-on to vanish as developers fear piracy probes
Publié: juin 7, 2017, 1:44pm CEST par Mark Wilson
Kodi -- built from the ashes of XBMC -- remains a popular but controversial streaming media solution. The beauty of the software is that it allows for the streaming of just about anything, and that includes contents of questionable legality (oh, OK... let's just admit there are a bunch of add-ons that can be used to stream pirated content). There has been a great deal of legal interest in so-called "fully-loaded" Kodi boxes of late, and this has had something of an unfortunate side-effect -- for fans of certain add-ons at least. Seemingly fearful of the legal implication of what… [Continue Reading] -

Apple to roll out iPhone screen fixing Horizon Machines to hundreds of third-party repair centers
Publié: juin 7, 2017, 12:17pm CEST par Mark Wilson
One of the weak points of the iPhone -- like just about any other smartphone -- is the screen. All it takes is a fall onto a hard surface and you could find yourself in shatter city. Getting a replacement screen is simple enough, but if you head off to an Apple store you could find that you're in for a bit of a wait. All of this is about to change, as Apple is set to install official screen fixing Horizon Machines in around 400 third party repair centers around the world, including Best Buy in the US. The… [Continue Reading] -

Microsoft faces Windows 10 antitrust investigation for disabling Kaspersky antivirus software
Publié: juin 7, 2017, 11:04am CEST par Mark Wilson
Security software firm Kaspersky Labs has filed antitrust complaints against Microsoft in Europe. The complaints center around Microsoft disabling third party antivirus software in Windows 10 to favor its own Windows Defender. The Russian company complained to the German Federal Cartel Office and the European Commission, saying that Microsoft abused its position. Microsoft has made some changes to the way Defender works, but Kaspersky does not believe this goes far enough. This is not the first time Kaspersky has complained about Windows 10's handling of antivirus software. Last year the company issued a complaint to the Federal Antimonopoly Service (FAS)… [Continue Reading] -

Google updates Developer Program Policies to fight incentivized app ratings, reviews and installs
Publié: juin 7, 2017, 10:15am CEST par Mark Wilson
Google has taken various steps over the years to try to combat dangerous apps in the Play Store, but this is far from being the only problem Google Play suffers from. There is also the ongoing issue of fake app reviews, incentivized activity, and other means of user manipulation. Having already put in place some measures to crack down on such activities, Google is now updating its Developer Program Policies. It warns developers that they must "not attempt to manipulate the placement of any apps in the Store" and while banning the bribing of users is nothing new, here Google… [Continue Reading] -

Amazon Prime available at a discount to US customers on welfare
Publié: juin 6, 2017, 7:20pm CEST par Mark Wilson
Amazon is slashing the price of a Prime subscription for US customers in receipt of government assistance. Customers with an Electronic Benefits Transfer (EBT) card are eligible to have their monthly subscription discounted from $10.99 to $5.99. There are no restrictions on the cheaper Prime subscriptions, and it includes Prime Video, Prime Music, Prime Reading, Prime Photos and free shipping just like its full-price counterpart, but Amazon points out that EBT cannot be used to pay for membership. For the time being, it is only those with an EBT card who qualify for cheaper Prime subscriptions, but Amazon plans to… [Continue Reading] -

OnePlus 5 launches June 20
Publié: juin 6, 2017, 6:36pm CEST par Mark Wilson
The launch date for the OnePlus 5 has officially been announced. The big day is June 20, and the latest flagship will be revealed online after an exciting teaser campaign, but there are also 10 pop-up events taking place around the world. This time around, OnePlus is referring to its upcoming smartphone as "our next flagship phone," with no reference to it being a "flagship killer" as has been the case in the past. While details keep trickling out about the OnePlus 5, in announcing the launch date, OnePlus is giving little more away other than suggesting the importance of… [Continue Reading] -

Google wants to educate kids to help them 'Be Internet Awesome'
Publié: juin 6, 2017, 1:15pm CEST par Mark Wilson
Google has developed an educational program with the aim of helping children make better use of the internet. It's a drive to "help kids learn how to be smart, positive and kind online, just like we teach them to be offline" and it's called Be Internet Awesome. Pavni Diwanji, vice president of Engineering For Kids and Families at Google says: "We need to provide guidance as they learn to make their own smart decisions online." The program has been developed with a number of key online safety experts and includes an educational game called Interland. In Interland, children are encouraged… [Continue Reading] -

Material Design and new developer tools come to Chrome 59
Publié: juin 6, 2017, 12:25pm CEST par Mark Wilson
Google has started to push out updates to the latest version of its web browser -- Chrome 59 for Windows, Linux and macOS. The update includes a number of important security fixes, but also sees the arrival of Google's Material Design on the desktop. The Material look is one that will be very familiar to Android users, as well as anyone who uses Google's various online services. But Google is not quite ready to give its desktop browser a full makeover yet. Chrome 59.0.3071.86 is now rolling out on the Stable channel and the promised Material Design is not immediately… [Continue Reading] -

Apple nixes Facebook and Twitter integration from iOS 11
Publié: juin 6, 2017, 10:57am CEST par Mark Wilson
With the arrival of any new operating system, the focus tends to be on what has been added and what has been improved. But it's also important to keep an eye on what has been removed, and this is true of Apple's newly announced iOS 11. One of the things to have been removed from the upcoming version of Apple's mobile OS is social media integration. Specifically, Facebook, Twitter, Flickr and Vimeo have been dropped from Settings, meaning that these services will no longer be able to offer an easy way to sign into apps and services using social media… [Continue Reading] -

Apple completely redesigns the App Store, introduces entirely new sections and promotes in-app purchases
Publié: juin 6, 2017, 9:30am CEST par Mark Wilson
Yesterday at WWDC 2017 Apple not only announced details of iOS 11, the company also unveiled a completely redesigned App Store. Central to the entire iOS experience, the change is due to arrive later in the year, and when we say it's a complete redesign, we mean it's a complete redesign. It goes without saying that Apple refers to the redesign as "beautiful," and the extreme makeover is something that has been a long time coming. But while the look of the store is markedly different to its current incarnation, it is still somewhat familiar. It borrows style ideas from… [Continue Reading] -

WWDC 2017: Apple watchOS 4 brings Siri -- and Toy Story -- to watch faces
Publié: juin 5, 2017, 8:03pm CEST par Mark Wilson
At WWDC today Apple announced not only High Sierra, but also watchOS 4. One of the biggest updates -- or at least the most visible -- here are to be found on watch faces. As well as being customizable, faces can now dynamically change based on various criteria, such as location and time of day. Apple is also bring kaleidoscopic faces to the Watch -- something it describes as "trippy." But perhaps the most exciting update is the fact that Siri can now be used on Apple Watch. Toy Story characters such as Buzz, complete with fun animation, are also… [Continue Reading] -

WWDC 2017: Amazon Prime is coming to Apple TV
Publié: juin 5, 2017, 7:32pm CEST par Mark Wilson
It's WWDC 2017 and, for the first time, Tim Cook has revealed the precise number of announcements we can expect from the keynote: six. The first of them is the news that Amazon is coming to Apple TV. Apple isn't saying exactly when this is happening, but Apple TV is finally going to benefit from Amazon Prime TV. The two companies have traditionally been rivals, but have now managed to become friendly enough to join force. Tim Cook said little more than Prime is coming later in the year. Just last month, rumors started to circulate that this might be… [Continue Reading] -

Facebook uses Pride Month to pat itself on the back over LGBTQ support
Publié: juin 5, 2017, 5:46pm CEST par Mark Wilson
Social media platforms are, by their very nature, keen to be welcoming to as broad a spectrum of people as possible. Twitter, YouTube, and other services of their ilk like to be seen to be as inclusive as can be imagined and Facebook is no different. This month is Pride Month, and Facebook is not only joining in the celebrations, but also using it to indulge in a little self-celebration and self-congratulation. The social network is rolling out a rainbow frame, a Pride reaction and Pride-themed masks for photos, Pride stickers in Messenger and more, but the company is also… [Continue Reading] -

Pinboard buys social bookmarking site del.icio.us and closes it down
Publié: juin 4, 2017, 5:56pm CEST par Mark Wilson
The once-loved -- and much sold -- social bookmarking site del.icio.us (or just Delicious, if you prefer), has changed hands for one final time. Rival service Pinboard has snapped up the site for a mere $35,000, and plans to close it down. Warning that no one should "attempt to compete with Pinboard," a post on the company blog adopts a Trump-like tone in announcing the acquisition. In less than two weeks, del.icio.us will be switched to read-only mode. Del.icio.us was once wildly popular, and was something of a leader in the world of the social internet. Pinboard notes that it… [Continue Reading] -

Police ask people not to share London Bridge and Borough Market attack footage on social media
Publié: juin 4, 2017, 2:12pm CEST par Mark Wilson
Last night saw two attacks in London leading to the deaths of seven people and dozens of injuries. A van driven at pedestrians on London Bridge, and stabbings in Borough Market have been labelled as terrorist attacks, and Facebook Safety Check was activated for the incident. The social network was not just used by people to let loved ones know that they were safe following the attacks, but also to share footage of the shocking aftermath. While police are keen for witnesses to come forward with footage they may have shot on mobile phones, they are pleading with people not… [Continue Reading] -

Not just for photos -- now you can add just about anything to Facebook albums
Publié: juin 4, 2017, 10:50am CEST par Mark Wilson
Albums on Facebook have, logically, been a handy way to store and organize photographs. for a while now. But an update to the social network means that albums can now be used to group together posts, photos, check-ins and more. In a fairly major overhaul of the system, Facebook is in the process or greatly expanding the capabilities of albums, making them fair more versatile and useful. As well as increasing the range of content that can be added, Facebook is also surfacing collaborative albums, introducing featured albums, and more. See also: Facebook's solution to fake news: 'fight information with… [Continue Reading] -

YouTube defines 'hate speech' and clarifies which videos can earn money through ads
Publié: juin 4, 2017, 10:14am CEST par Mark Wilson
It has been a few weeks since advertisers started to pull out of YouTube after concern about the placement of ads. Since then, the company has been scrambling to earn back trust and it says it has "held thousands of productive conversations with advertisers, and implemented additional controls to restore advertiser confidence." Now YouTube has set out what it classifies as hate speech, and says that any content that falls into this category will not be eligible for monetization. It's a move that's designed to calm the fears of advertisers, but there is concern that the rules being put in… [Continue Reading] -

Google Photos starts using AI to suggest pictures for archiving
Publié: juin 3, 2017, 5:09pm CEST par Mark Wilson
It's not really the time of year for spring cleaning, but Google is turbo-charging the Archive option in Google Photos with the added power of artificial intelligence. Archiving is only a recent addition to Google Photos, making it possible to clear out the clutter from your timeline, and now it has been boosted by AI. The idea acknowledges the fact that while we might take a photo of something -- such as snapping a poster to save writing down dates and times of an upcoming event -- this isn’t something we necessarily need to see after it has served its… [Continue Reading] -

Facebook's solution to fake news: 'fight information with more information'
Publié: juin 3, 2017, 2:53pm CEST par Mark Wilson
It may be Donald Trump who is obsessed with what he perceives as "fake news" (translation: anything which is not in line with his personal views), but there is a genuine problem with the dissemination of false information online, particularly on social media sites such as Facebook. Just as it has voiced a commitment to tackling its well-known problems with trolling and abuse, Facebook has also made a great deal of noise about fighting fake news. Despite this, Facebook shareholders have rejected proposals that suggested the company should release a report into the impact of fake news. Mark Zuckerberg thinks… [Continue Reading] -

Google is building an ad blocker into Chrome in 2018
Publié: juin 2, 2017, 12:55pm CEST par Mark Wilson
Starting early next year, Chrome users will benefit from an ad blocker built into the web browser. As part of its work with the Coalition for Better Ads, Google is looking to clamp down on intrusive ads that web users find most irritating. Google is a company whose business model is built largely on advertising, and it is keen for the experience of being subjected to ads to be as painless as possible for people. But rather than block all ads -- killing revenue streams for many websites -- Google wants to block only those that do not comply with… [Continue Reading] -

Trump administration approves visa questionnaire that asks for social media handles
Publié: juin 2, 2017, 12:01pm CEST par Mark Wilson
The world may be focused on the US withdrawal from the Paris accord, but the Trump administration is causing plenty of ripples in other areas too. Not content with trying to push through travel bans, the US government is also tightening up on visa applications. An updated version of the supplemental visa application questionnaire asks would-be visitors for not only details of their travel and address history, but also for the names they use on social media. Applicants are required to provide details dating back five years, but officials are not saying in what circumstances the extra questions will become… [Continue Reading] -

This is the OnePlus 5 and its packaging
Publié: juin 2, 2017, 10:40am CEST par Mark Wilson
Rarely does a phone -- or even a company -- generate quite as much interest as the OnePlus 5. The upcoming flagship killer is hotly anticipated, and the mood among the almost cult-like following is reaching a fever pitch. Of course, OnePlus is doing nothing to calm things down, having embarked on an advertising campaign that involves teasing its customers until they can take no more. The latest move finds the company tweeting an image of the OnePlus 5, while a separate leak gives a glimpse at the packaging complete with the tagline "Dual Camera. Clearer Photos." See also: Win:… [Continue Reading] -

OneLogin suffers serious security breach -- attackers access data and decryption keys
Publié: juin 2, 2017, 10:37am CEST par Mark Wilson
Password management service OneLogin has fallen victim to a serious attack. The company says that it "detected unauthorized access to OneLogin data in our US data region" -- this was blocked, but not before the attacker gained access to AWS keys and the ability to decrypt data. The company warns that "all customers served by our US data center are affected; customer data was compromised, including the ability to decrypt encrypted data." OneLogin has provided a guide for securing data, but it's possible that it may be too late for some people. In a blog post, OneLogin explains what happened:… [Continue Reading] -

Microsoft unveils a massive redesign of Skype, heavily plagiarizing Snapchat
Publié: juin 1, 2017, 5:34pm CEST par Mark Wilson
If imitation is the sincerest form of flattery, there's a hell of a lot of flattery going on in the world of chat and messaging apps. Such is the level of feature borrowing and design inspiration that we're entering a phase of unbridled homogeneity. This isn’t enough to put off Microsoft, of course, and today the company lifts the lid on its latest -- and arguably most radical -- redesign of Skype. Coming first to Android -- as is becoming increasingly common for Microsoft these days -- the Skype redesign boasts a fresh new look that makes it clear from… [Continue Reading] -

Plex rolls out Live TV and improved DVR to Plex Pass subscribers
Publié: juin 1, 2017, 4:44pm CEST par Mark Wilson
Coming out of beta, Plex's DVR feature is now rolling out to all Plex Pass subscribers. On top of this, the platform is also gaining Plex Live TV -- a way to stream OTA broadcasts from your TV tuner to the Plex app. To start with, Live TV is coming to the Android TV and iOS apps, but it will also make its way to Plex's other offerings meaning subscribers will be able to watch live TV from just about anywhere. On top of this major announcement, Plex has also unveiled -- in a blog post entitled "#$%@ it! We'll… [Continue Reading] -

Facebook redesigns security settings page making two-factor authentication easily identifiable
Publié: juin 1, 2017, 3:56pm CEST par Mark Wilson
Realizing that its security settings were off-putting to many people due to being a shambolic mess, Facebook has rolled out a redesign which it says helps to improve clarity. As well as giving greater prominence to the most important security settings, some options have been renamed. This comes after Facebook conducted some research into why users were clicking certain options but not changing them -- it turns out they had no idea what the settings actually did. One of the effects of this redesign is that slightly-confusingly named "login approvals" has been rebranded as the more widely-recognized -- and more… [Continue Reading] -

Security experts warn about UK's nuclear Trident submarines: 'the vulnerability to cyberattacks is real'
Publié: juin 1, 2017, 1:28pm CEST par Mark Wilson
A report published by the British American Security Information Council (BASIC) cautions that the UK's fleet of Trident submarines faces "growing potential for cyber-attack." The authors issue a stark warning that "a successful attack could neutralise operations, lead to loss of life, defeat or perhaps even the catastrophic exchange of nuclear warheads." Government officials have long dismissed the risk of hacking the nuclear subs because they are not connected to the internet. But the report, entitled Hacking UK Trident: A Growing Threat, suggests that risk of malware infection during manufacturing or software updating are just two possible attack vectors that… [Continue Reading] -

UK launch of Microsoft Rewards bribes Brits into using Bing and Edge
Publié: juin 1, 2017, 12:02pm CEST par Mark Wilson
Formerly known as Bing Rewards, Microsoft Rewards has now made its way to the UK. The program rewards users for making searches with Bing, with extras thrown in if these searches are conducted in Microsoft Edge. Users can accrue points by performing searches, completing quizzes, or spending money in the Microsoft Store, and these can then be exchanged for Skype credit, gift cards, Groove Music passes and more. It's a scheme that amounts to little more than bribery, and sees Microsoft paying people to use its products and services. Every time you perform a Bing search, you can earn 3… [Continue Reading] -

US roll-out of Samsung Bixby delayed as the virtual assistant struggles with English
Publié: juin 1, 2017, 11:15am CEST par Mark Wilson
The launch of the Samsung Galaxy S8 was slightly marred by the absence of the promised virtual assistant, Bixby. We may now be in June, but it looks like it's still going to be a few weeks until Samsung's assistant arrives in the US. The problem? It's having trouble understanding English syntax and grammar. So far Bixby has emerged with Korean support, but the Wall Street Journal reports that the English-language version is still weeks away from completion. The news comes from "people familiar with the matter," but Samsung has responded to the claims, adding weight to their veracity. A… [Continue Reading] -

Logitech launches MX Master 2S and MX Anywhere 2S, plus multi-computer mousing with Logitech FLOW
Publié: juin 1, 2017, 10:31am CEST par Mark Wilson
Logitech today announces the latest additions to its MX range of mice -- the MX Master 2S and MX Anywhere 2S. We'll come back to the mice in a moment, though. There's more exciting news with the launch of Logitech FLOW. This is Logitech's new software which makes it possible to use the same mouse to control up to three computers. Perfect for anyone who has two or three computers on their desk, Logitech FLOW not only makes it possible to use a single mouse and keyboard to control all of the devices, but also features between-devices copying and pasting.… [Continue Reading] -

OnePlus 5 will be 'the thinnest flagship phone' says CEO
Publié: mai 31, 2017, 7:09pm CEST par Mark Wilson
OnePlus CEO Pete Lau has just let a little more slip about the upcoming OnePlus 5. According to a Weibo post by the company founder, the OnePlus 5 will be "the thinnest flagship phone" when it launches later this summer. Importantly, Lau says that the thinness does not mean compromises have been made. There have been all manner of leaks and rumors about the latest version of the so-called "flagship killer," but this comes straight from the horse's mouth. OnePlus has started a teaser campaign for the smartphone, inviting social media users to guess which of two photographs was shot… [Continue Reading] -

TheShadowBrokers ditch Bitcoin in favour of Zcash as details emerge of monthly exploit subscription service
Publié: mai 31, 2017, 1:26pm CEST par Mark Wilson
TheShadowBrokers, the hacking group behind the leak of NSA malware, has announced further details of the "Data Dump of the Month" subscription service it has previously talked about. Now known as "TheShadowBrokers Monthly Dump Service," the launch sees the group switching from Bitcoin to Zcash as its currency of choice. Signing up for the service will set interested parties back 100 ZEC (Zcash). As this equates to over $20,000, it's not a subscription that many people are likely to be taking out, particularly as there is no evidence that the group has more exploits to offer. The hacking group has… [Continue Reading] -

Now is the time to tap Amazon for refunds for unauthorized in-app purchases made by your kids
Publié: mai 31, 2017, 12:37pm CEST par Mark Wilson
It's just over a year since a federal judge ruled that Amazon was liable for the unauthorized in-app purchases made by children. Now the FTC has announced that Amazon is starting to offer refunds for these purchases. There are said to be more than $70 million in charges from the period between November 2011 and May 2016, and customers now have until the end of May next year to get in touch with Amazon to get their money back. If your account was used to make an purchase that's now eligible for a refund, you should have already received an… [Continue Reading] -

Nest reveals Cam IQ, an AI-powered 4K security camera with facial recognition
Publié: mai 31, 2017, 12:20pm CEST par Mark Wilson
Google-owned Nest has unveiled the latest addition to its range of smart products -- the Nest Cam IQ. The new security camera not only boasts a 4K video sensor, but builds upon the motion detection feature offered by other similar cameras by adding facial recognition. What this means is that the Nest Cam IQ is able to send out personalized alerts when it detects the presence of a particular person -- such as when your kids arrive home from school -- but it can also send out warnings when an unrecognized person is spotted. There's even Night Vision so it… [Continue Reading] -

Twitter now handles DMs from strangers differently
Publié: mai 31, 2017, 10:57am CEST par Mark Wilson
Taking a leaf out of Facebook's, er, book, Twitter has introduced a new filtering system for Direct Messages. Now if you receive a DM from someone you don’t follow, it will be channeled to a new Requests folder rather than appearing in your Inbox. The new system gives you a chance to review messages from unknown senders before you decide whether to continue the conversation. It's a simple system that's very similar to Facebook Message Requests, and it's in the process of rolling out at the moment. Importantly, the sender is not alerted when you read a DM that has… [Continue Reading] -

Win: How to get your hands on a OnePlus 5 early
Publié: mai 30, 2017, 12:47pm CEST par Mark Wilson
We still don't even know when the OnePlus 5 will be released, but the company is already in full-on marketing mode for the next version of its flagship killer. We've only just seen a sample photo from the OnePlus 5, and now keen photographers are being offered the opportunity to get their hands on the smartphone early. This is not an early buying option for snap-happy Android fans, but a competition which will ultimately see ten people getting their hands on a OnePlus 5 for free. The giveaway is being made through a OnePlus scheme called The Lab. The company… [Continue Reading] -

OnePlus 5 photography sample sparks a mixed reaction
Publié: mai 30, 2017, 10:21am CEST par Mark Wilson
OnePlus continues to drip-feed us snippets of information about its upcoming OnePlus 5. We've already learned that the company has teamed up with DxO to improve the photography side of things, and now we have been treated to the first official sample photo shot on a OnePlus 5. On both Facebook and Twitter, OnePlus shared a split-screen photograph, one side taken on an unknown camera, the other on the OnePlus 5. The company asked, "Can you tell which photo was taken with the OnePlus 5?" -- and the reaction was rather mixed. On Facebook, OnePlus' followers were invited to use… [Continue Reading] -

ASUS ZenBook Flip S with NanoEdge is the world's thinnest 2-in-1 convertible laptop
Publié: mai 29, 2017, 1:55pm CEST par Mark Wilson
At Computex 2017 in Taiwan today, ASUS unveiled several new devices including the convertible ZenBook Flip S. Measuring just 10.9mm thick, the 2-in-1 is heralded as the thinnest in the world, and, weighing in at just 1.1kg, it's light as well. The laptop has a 13-inch screen which features a 360-degree ErgoLift hinge which allows for conversion into a tablet. Starting at $1,099, this is a premium offering from ASUS, and the specifications do not disappoint. The Asus Zenbook Flip S UX370UA -- to give it its full title -- features an Intel Core i7-7500U or Core i5-7200U CPU and… [Continue Reading] -

US may extend laptop ban to all international flights
Publié: mai 29, 2017, 12:34pm CEST par Mark Wilson
The US is considering extending its laptop ban to all international flights to and from the country. Speaking on Fox News Sunday this weekend, Homeland Security Secretary John Kelly said there was a "sophisticated" terrorist threat which could see and expansion of the ban on devices larger than smartphones. Back in March, citing a threat from terrorists "smuggling explosive devices in various consumer items," the Trump administration introduced an electronics ban on flights from a number of countries. If the ban was to be expanded, there would likely be a backlash from the increased number of people no longer able… [Continue Reading] -

Nintendo is ramping up Switch production
Publié: mai 29, 2017, 11:48am CEST par Mark Wilson
The Nintendo Switch has proved to be an incredible success for the Japanese company. Sales are far better than many predicted and, according to reports, production is about to be stepped up to meet demand. Just three months after launch, the Financial Times says that production will be increased in preparation for the holiday season, with Nintendo hoping to avoid "customer tantrums" if shoppers are unable to get their hands on what is sure to be a huge seller in the latter half of this year. The Financial Times emphatically states that "Nintendo [is] to ramp up production of Switch… [Continue Reading] -

Microsoft, Google, Facebook and others write to House of Representatives asking for reform of NSA surveillance
Publié: mai 28, 2017, 1:12pm CEST par Mark Wilson
A letter signed by more than 30 major technology companies has been sent to the House Judiciary Committee calling for a number of key changes to be made to NSA surveillance. The letter, signed by the likes of Facebook, Twitter, Google and Mozilla, asks lawmakers to make a number of considerations when reforming Section 702 of the FISA Amendments Act. The signatories refer to themselves as "U.S.-based companies that provide consumer and business technology, products, and services around the world through the use of electronic data." Their letter is timed to coincide with debate about the reform of Section 702 which… [Continue Reading] -

OnePlus launches referral program so you can get money off a OnePlus 5 and accessories
Publié: mai 28, 2017, 11:27am CEST par Mark Wilson
We know that the OnePlus 3T is being discontinued as the launch of the OnePlus 5 is just around the corner. Ahead of the launch, the company behind the "flagship killer" has unveiled a referral program that lets its customers earn points to get money off phones and accessories. The referral program is open to "anyone who's ever bought a OnePlus smartphone past, present, or future." You just need to apply for your unique referral code, and then encourage people to use it to make their OnePlus purchases to earn you points and money off. Working much like any other… [Continue Reading] -

Google search's Personal tab shows results from your emails, calendar and other G Suite content
Publié: mai 27, 2017, 6:00pm CEST par Mark Wilson
Personalized results in Google search are not exactly new, but the company has now introduced a new way to section off truly personal results. A new Personal tab (which you would be forgiven for missing as it's a little hidden out of the way) filters search results to show you only matches from your own Google content. What this means is that you are able to easily see search results from your Gmail emails, Google Photos, Calendar and other G Suite components without having to conduct searches in each one individually. But is there cause for concern when it comes… [Continue Reading] -

British Airways cancels flights after massive global computer system failure [Updated]
Publié: mai 27, 2017, 5:02pm CEST par Mark Wilson
A "major IT system failure" has caused serious problems for British Airways. The airline has been forced to cancel all flights from Heathrow and Gatwick airports while it works to resolve the issue. It is not believed that the computer failure was caused by a cyberattack or hackers but this has not lessened the impact. Both of the affected airports have become "extremely congested" as a "global system outage" wreaked havoc with travellers' holiday weekend plans. Many BA customers were left stranded on runways as flights were cancelled moments before take-off. As well as grounding planes, customers still at home… [Continue Reading] -

Facebook Fundraisers expand so you have more reasons to ask your friends for money
Publié: mai 26, 2017, 10:48am CEST par Mark Wilson
It's not all that long since Facebook introduced a fundraiser feature, making it possible for users to ask others on the social network for money for a particular cause. Now the company has expanded the personal fundraiser feature so that it can be used for more things. Specifically, Facebook now permits people to raise money in two additional categories: sports and community. With the community category covering "neighborhood services, community improvements or environmental improvements," fundraisers have now become much wider-ranging. Using Facebook to ask for money might be a great way to hit as large an audience as possible --… [Continue Reading] -

Google launches Data Gif Maker so you can create animated GIFs to illustrate data
Publié: mai 26, 2017, 10:38am CEST par Mark Wilson
As names go, it's clear that little thought went into Google's new Data Gif Maker. It's a simple tool that lets you create animated GIFs to compare statistics about two different topics. Google says the free tool is aimed at journalists, but anyone with a website is able to use it however they want. The idea is simple. Rather than just saying Android is more popular than iPhone, you can let a graphic do the work for you. Data Gif Maker produces bar charts that we have all become familiar with during elections, giving an easily-interpreted visual representation of basic… [Continue Reading] -

Europe approves rules that would force Facebook and other social sites to tackle hate-speech
Publié: mai 25, 2017, 12:34pm CEST par Mark Wilson
Facebook may be taking steps to tackle hate speech and other unsavory content but the European Union could soon force it to do more. Plans have been approved for rules that require online content providers such as Facebook, YouTube and Twitter to "protect children and tackle hate speech better." Failure to comply with the rules could result in hefty fines being levied against offenders. There are still a number of hoops for the proposed regulations to pass through -- including the European Parliament -- before they become law, but it may not be long until social media sites are obliged… [Continue Reading] -

Samba vulnerability could lead to the next WannaCry
Publié: mai 25, 2017, 11:07am CEST par Mark Wilson
A security vulnerability in the popular Samba networking utility could leave unpatched machines open to an attack similar to WannaCry. A single line of code is all that’s needed to exploit the vulnerability, but it is reliant on a number of prerequisites. The vulnerability has been assigned the ID CVE-2017-7494 and is described as "remote code execution from a writable share" which could allow "malicious clients [to] upload and cause the smbd server to execute a shared library from a writable share." Security researchers say that the flaw is very easy to exploit, and tens of thousands of machines have… [Continue Reading] -

The way is clear for Wikimedia to sue the NSA for warrantless surveillance
Publié: mai 24, 2017, 4:54pm CEST par Mark Wilson
A federal appeals court has ruled that the Wikimedia Foundation may sue the NSA for its warrantless use of the "Upstream" surveillance program. The ruling overturns an earlier one which said the foundation could not sue due to an inability to prove that Wikimedia communication was being monitored either directly or indirectly. The ruling by the United States Court Of Appeals for The Fourth Circuit means that the foundation is now able to proceed with legal action that was previously blocked. The amount of traffic generated by Wikimedia proved key to winning the appeal. While the original ruling indicated that… [Continue Reading] -

Netgear clarifies precisely what data it collects from Nighthawk AC1900 R7000 router users
Publié: mai 24, 2017, 11:18am CEST par Mark Wilson
A recent firmware update to its Nighthawk AC1900 R7000 router saw Netgear start to collect analytics data from its users. This had many people upset because of concerns about privacy, but the company is at pains to stress that no personal data is being collected. In addition to this, the company points out that the program is voluntary, and users are free to opt out at any time. Rather than anything sinister or underhand, Netgear says that the data collection is purely to isolate problems and improve the router. In a statement the company say: "Technical data about the functioning… [Continue Reading] -

Live Chat With Friends brings private chats to Facebook Live
Publié: mai 24, 2017, 10:43am CEST par Mark Wilson
Facebook understands the importance of video on its platform, particularly live video. Facebook Live has proved to be an incredibly popular component of the social network and now the company is introducing new ways to connect with friends through the service. Known as Live Chat With Friends, the new feature makes it possible to chat privately with friends during live broadcasts. The company is also rolling out another new feature called Live With. This "lets you invite a friend into your live video so you can hang out together, even if you’re not in the same place." Live Chat With… [Continue Reading] -

Microsoft brings Fluent Design System's acrylic material to the Windows Store in Windows 10
Publié: mai 24, 2017, 10:02am CEST par Mark Wilson
When Windows 10 Fall Creators Update is released later in the year, it will be the first glimpse many users get of Microsoft's new Fluent Design System. But Windows Insiders can already enjoy the new look, and an update to the Windows Store sees the app getting an acrylic makeover. Formally known as Project NEON (when we were still talking about Redstone 3 builds), the Fluent Design System sees Microsoft bringing elements of Glass and Aero back to life. The acrylic material, specifically, refers to the blurring of backgrounds, and if you're an Insider on the Fast Ring, you can… [Continue Reading] -

1Password's new Travel Mode hides your private information from airport security
Publié: mai 24, 2017, 9:22am CEST par Mark Wilson
There have been numerous cases recently of travelers being forced to unlock their phones by security staff at airports. If you have all of your passwords for apps and online accounts stored in a password manager, this could mean that vast amounts of personal data become accessible -- but 1Password has a solution. A new feature called Travel Mode enables users of the app to mark certain passwords and other data as "safe for travel." When the mode is activated, everything else which has not been flagged in this way is temporarily deleted from the device so it cannot be… [Continue Reading] -

Facebook on moderation and community standards: 'we take our role extremely seriously'
Publié: mai 23, 2017, 4:19pm CEST par Mark Wilson
Recently leaked documents gave a unique insight into just what can be posted on Facebook, and what moderators are expected to censor. In response to this, the company's head of global policy management, Monika Bickert, has written a lengthy statement in which she tries to explain how Facebook choose what to censor. While some of Facebook's policies are well known, this is not true of all of them, and this is not without reason. Bickert explains: "We don't always share the details of our policies, because we don’t want to encourage people to find workaround." She says that Facebook faces… [Continue Reading] -

Windows 10 China Government Edition allows China to control encryption and telemetry
Publié: mai 23, 2017, 3:44pm CEST par Mark Wilson
Microsoft's event in Shanghai today may have been mainly about the Surface Pro, but there was also news of a new version of Windows 10. The new version -- which we reported about a couple of months ago -- is called Windows 10 China Government Edition and it makes a number of concessions to keep Chinese officials happy. It’s a release that raises a lot of questions. The Windows 10 China Government Edition allows the country to not only use its own encryption, but also to control updates, remove unwanted apps, and manage telemetry. Users around the world will almost… [Continue Reading] -

Symantec pins WannaCry on North Korean Lazarus group
Publié: mai 23, 2017, 2:21pm CEST par Mark Wilson
There have already been suggestions that the now infamous WannaCry ransomware was the work of the North Korean hacking group Lazarus. Security firm Symantec now says it is "highly likely" that Lazarus is to blame, having unearthed further evidence of the re-use of code from other attacks by the group. But while the links to Lazarus are strong, North Korea denies that it was involved in any sort of state-sponsored attack, dismissing such claims as "a dirty and despicable smear campaign." It is thought that the group -- also responsible for attacking Sony Pictures and stealing $81 million from the… [Continue Reading] -

Apple and Nokia end all litigation as they sign patent license and business cooperation agreement
Publié: mai 23, 2017, 10:28am CEST par Mark Wilson
Apple is dropping its lawsuit against Nokia. The iPhone manufacturer and the Finnish company reached an agreement to not only bring the intellectual property dispute to an end, but also to start a multi-year patent license. Described as a "meaningful agreement", details of the new arrangement are confidential, at least for the time being, but Apple does shed a little light on what's going to be happening moving forward. Apple will receive network infrastructure product and services from Nokia, and the company will also resume carrying the Withings health products Nokia bought. Nokia says that the arrangement means that the… [Continue Reading] -

Privacy warning: Netgear routers copy Windows 10 and start 'collecting analytics data'
Publié: mai 22, 2017, 2:42pm CEST par Mark Wilson
A firmware update to the Netgear R7000 router adds a new feature that will concern privacy advocates. The update allows Netgear to start "collecting analytics data" and the release notes warn that: "NOTE: It is strongly recommended that after the firmware is updated to this version, you log back in to the router's web GUI and configure the settings for this feature." Netgear says that the data collection is to help it "isolate and debug technical issues" and does not -- according to the company -- include details such as the websites that are visited, but it will still be… [Continue Reading] -

Leaked documents show how Facebook censors users, and reveal policies on sex, terrorism and hate
Publié: mai 22, 2017, 11:38am CEST par Mark Wilson
At the moment, Facebook appears to be more concerned with keeping fake news out of users' news feeds and clamping down on clickbait and propaganda, but there has also been a lot of interest recently in how the social network moderates -- or censors -- content posted by its users. A leak of what has been dubbed The Facebook Files gives a fascinating insight into how the company moderates content, shedding light on just what its secret internal guidelines are. Some of the rules are surprising -- livestream of self-harm, for instance, will not be censored, still images of animal… [Continue Reading] -

Facebook is finally doing something to make Messenger less of an unusable mess
Publié: mai 19, 2017, 11:49am CEST par Mark Wilson
The Facebook Messenger app for iOS and Android is an utter mess of ideas at the moment. The confused interface is all over the place and decidedly user unfriendly. All that is set to change, though, thanks to an update that rolls out this week. The update brings a slightly updated look which makes navigation a little easier. Tabs help to keep things better organized so you can jump to where you want to be more easily. The changes do not go as far as letting you kill the endlessly irritating Messenger Day/Stories feature, but it does go some way… [Continue Reading] -

Leaked images show off Microsoft's upcoming Surface Pro
Publié: mai 19, 2017, 10:41am CEST par Mark Wilson
Panos Panay may have said that the Surface Pro 5 does not exist, but that certainly does not mean there's not a Surface Pro 4 successor. Microsoft has an event scheduled for Monday in Shanghai, and Panay himself has already indicated that it is Surface-related. Ahead of the event, writer and serial leaker Evan Blass has revealed a number of images of the upcoming device which drops the numbering and is to be known simply as the Surface Pro. Virtually nothing is known about the Surface Pro, but the images, published on VentureBeat, show that Microsoft has done very little… [Continue Reading] -

Pirated copy of Pirates of the Caribbean 5 used to hold Disney to ransom
Publié: mai 16, 2017, 4:39pm CEST par Mark Wilson
Just a couple of weeks since a leak of season five of Orange is the New Black was held to ransom, the same is now happening with the upcoming Pirates of the Caribbean 5. Yesterday Disney CEO Bob Iger revealed that hackers had stolen one of the company's movies, and it has since transpired that it is the upcoming Johnny Depp flick. Subtitled "Dead Men Tell No Tales", Pirates of the Caribbean 5 is due to hit the big screen next week, and hackers are demanding a ransom from Disney to avert a leak ahead of the official launch. This… [Continue Reading] -

Data breach at DocuSign leads to massive phishing campaign
Publié: mai 16, 2017, 3:48pm CEST par Mark Wilson
E-signature and security firm DocuSign has confirmed a data breach in which attackers gained access to a database containing customer emails. The company says that no other data was revealed in the security breach, but it led to a large phishing campaign. Attackers used the stolen email addresses to spam people with emails containing an infected Microsoft Word document. The company insists that its core service remains secure, but coming in the wake of the WannaCry ransomware attack, people around the world are on high alert. The phishing campaign uses DocuSign branding to fool recipients into opening a malicious attachment… [Continue Reading] -

Updated BBC Privacy and Cookies Policy reveals targeted social advertising, and data sharing with TV Licensing
Publié: mai 16, 2017, 3:26pm CEST par Mark Wilson
Just a few days ago, the BBC revealed that it was planning to introduce password checks for iPlayer users so it could ensure that a valid TV license is in place. Following on from this, the corporation has updated its Privacy and Cookies Policy. The changes mean that personal information is shared with TV Licensing to check whether individuals have paid for a license. The BBC also says that it will use the personal data it collects to deliver "relevant advertising" on the likes of Facebook, Twitter and Instagram. Version 2.0 of the Privacy & Cookies policy has been published… [Continue Reading] -

Leaks suggest OnePlus 5 will be incredible -- and still really cheap!
Publié: mai 14, 2017, 7:53am CEST par Mark Wilson
OnePlus has enjoyed great success with the OnePlus 3 and 3T -- the flagship killers that pack a real punch for a bargain price -- and this looks set to continue with the follow-up. We already know that the OnePlus 5 is due for release soon (yep, there's no OnePlus 4), and this week more leaks have told us just about everything we could want to know about the specs and price. Continuing the theme we have become used to with the company, the leaks show that OnePlus is planning to deliver a powerful handset at a knock-down price. An… [Continue Reading] -

Making Android modular with Project Treble is Google's solution to its fragmentation and update problem
Publié: mai 13, 2017, 12:09pm CEST par Mark Wilson
One of the problems with buying an Android smartphone is that there is usually no way to tell just how long it will be supported and how long you'll get Android updates. Unless you have a Google-branded device, it's hit-and-miss when, or indeed if, you'll receive an upgrade to the latest and greatest version of the mobile OS. With the impending release of Android O, however, Google is trying out a solution to the problem which has led to endless fragmentation of the Android market. Going by the name of Project Treble, the solution sees Google introducing a modular base… [Continue Reading] -

US government is reviewing whether to use Kaspersky software, because Russia
Publié: mai 12, 2017, 3:43pm CEST par Mark Wilson
Mention the US and Russia in the same sentence and the mind naturally wanders to three things. Firstly, the alleged links between the Trump administration and Russia, secondly whether or not the FBI investigation of these alleged links led to the dismissal of Comey, and thirdly whether or not Russia interfered with the US election. But now the US government is reviewing whether or not to continue to use Russian-made security software from Kasperksy. Defense Intelligence Agency director Vincent Stewart says "we are tracking Kaspersky and their software." He does not elaborate or give reasons, but there have been --… [Continue Reading] -

Facebook cleans up News Feeds by reducing links to 'low quality', clickbait content
Publié: mai 12, 2017, 1:54pm CEST par Mark Wilson
When it's not being accused of being used for propaganda or peddling fake news, Facebook is often criticized for being home to meaningless clickbait that exists only to generate ad revenue. As part of an on-going drive to make people's News Feeds more useful and pleasant to use, the social network is clamping down on what it refers to as "links to low-quality web page experiences." Facebook wants to cut back on content that is "misleading, sensational and spammy" and links to web pages that contain "little substantive content and that is covered in disruptive, shocking or malicious ads." Starting… [Continue Reading] -

Facebook shuts down abortion group's page for 'promotion or encouragement of drug use'
Publié: mai 12, 2017, 1:37pm CEST par Mark Wilson
Just yesterday we wrote about the repeated closure of an atheist Facebook group by the social network. Now, in a similar act that has more than a slight whiff of censorship to it, Facebook has "unpublished" the page of Women On Web, a group that puts women who live in places that have abortion restrictions in contact with doctors. The doctors that women are connected with can provide them with abortion pills, and it seems that because of this the group, Women On Web, has been found by Facebook to be engaged in the "promotion or encouragement of drug use".… [Continue Reading] -

Microsoft brings Fluent Design System to Windows 10 -- but WTF is it?
Publié: mai 12, 2017, 12:40pm CEST par Mark Wilson
When Windows 10 arrived on the scene, much was made of the Metro (or Modern) look of the apps. This was Microsoft's design language of the time and now it's time to throw out the old and usher in the new. We've heard a bit about Project NEON in recent months, and this has now evolved in to the Fluent Design System. This is the new design language for Windows, and it will be making an appearance in Windows 10 Fall Creators Update -- although you can already see glimpses of it in the Redstone 3 builds if you are… [Continue Reading] -

Google will create custom emoji from your selfies in Allo
Publié: mai 12, 2017, 10:45am CEST par Mark Wilson
Users of Google Allo can now use selfies -- and a little AI jiggery-pokery -- to generate a custom set of emoji. Or, as Google puts it, users can now benefit from "Neural Network-Generated Illustrations in Allo." Working in a similar way to the existing Bitmoji idea, Google's nameless feature will transform a simple selfie into a customizable illustration -- emoji with greater character, more personality. In fact, the system doesn't just create a single emoji, it creates a full sticker pack. Announcing the new feature, Google says: "Today, Google is introducing a feature in Allo that uses a combination… [Continue Reading] -

Hell freezes over: iTunes is coming to the Windows Store
Publié: mai 11, 2017, 7:03pm CEST par Mark Wilson
Yes, you did read that correctly. Today at Build Microsoft announces that iTunes is going to appear in the Windows Store by the end of the year. Apple and Microsoft playing ball together like this is a pretty rare occurrence. With the recently announced Windows 10 S, the timing is interesting, and in embracing the iPhone, Microsoft is sending out yet another message that Windows Phone is dead -- it's iPhone and Android smartphones that matter. Microsoft has not given away a great deal of detail about the appearance of iTunes, but we do know that the app will be… [Continue Reading] -

BBC to clamp down on licence fee avoidance by requiring password for iPlayer
Publié: mai 11, 2017, 6:18pm CEST par Mark Wilson
Within the next few weeks the BBC is planning to introduce password protection to iPlayer. The system is intended to prevent people from using the streaming TV catch-up service without paying a licence fee. The corporation says that it does not plan to introduce "mass surveillance techniques or ask internet providers for IP addresses," but is merely interested in ensuring people comply with the law. The system should also help the BBC to reduce the number of people from outside the UK using iPlayer for free. Starting today, iPlayer viewers will see a message informing them that a password will… [Continue Reading] -

Atheist group claims Facebook keeps deleting its page
Publié: mai 11, 2017, 4:53pm CEST par Mark Wilson
An atheist Facebook page with more than 1.6 million fans is being repeatedly deleted by the social network, claims the group behind it. Atheist Republic says that a coordinated campaign has resulted in the page being removed at least three times. It is thought that Facebook’s automated removal process may be to blame, with algorithms taking the page offline after a series of reports. The page is used to actively criticize religion, and it is believed that an orchestrated fightback from religious groups is leading to its repeated automatic removal. Facebook's algorithms work in such a way that when a… [Continue Reading] -

Leaked images show Microsoft is ready to take on Amazon Echo with Windows 10 HomeHub
Publié: mai 10, 2017, 1:36pm CEST par Mark Wilson
While we've heard about the HomeHub feature of Windows 10 before, we've not seen what it might look like in practice. Now, thanks to a series of leaked images, that all changes, and it shows that Microsoft is ready to take on Google Home and Amazon Echo with its own devices. Like the Amazon Echo Show, the leaked images depict a device with a screen. It's running Windows 10, supports voice-activated Cortana commands, and it's something that Microsoft clearly wants to be at the center of future smart homes. But while rival devices are just that -- standalone devices --… [Continue Reading] -

Word vulnerability, Windows bug, and 'Trump's_Attack_on_Syria' document used in Sednit phishing attack
Publié: mai 10, 2017, 12:13pm CEST par Mark Wilson
The Sednit group believed to have been involved in interference with the French election was also responsible for a phishing attack that used President Trump to lure in victims. Security firm ESET analyzed a phishing email with an attachment named Trump's_Attack_on_Syria_English.docx and found that it had the hallmarks of the well-known group. The document was engineered to infect victims' computers with the Seduploader tool, and it did this by exploiting two vulnerabilities, one in Microsoft Word, and one in Windows. Sednit -- previously known as APT28, Fancy Bear, and Sofacy -- took advantage of a recently discovered Remote Code Execution… [Continue Reading] -

Serious app permissions flaw will not be fixed until Android O, leaving users at risk
Publié: mai 9, 2017, 5:23pm CEST par Mark Wilson
The security of Android has been questioned many times, but the general thinking is that installing apps from Google Play offers a decent level of protection. But research by Check Point shows that this is not the case due to a flaw in permissions. The permission model used by Google grants apps installed from the Play Store extensive access, and opens up the risk of malware, ransomware and other threats. Google is aware of the problem, but does not plan to address it until the release of Android O, meaning that an unknown number of apps pose a risk to… [Continue Reading] -

McAfee will provide protection for a range of Samsung products... including TVs
Publié: mai 9, 2017, 4:24pm CEST par Mark Wilson
We live in strange times when security software is needed for TVs -- although given recent WikiLeaks revelations, it's perhaps not entirely surprising -- but this is precisely what McAfee is providing. The security firm today announces an expansion of its partnership with Samsung, and this sees the company providing protective software that will be pre-installed on a range of devices. As well as smart TVs, McAfee will also be offering security software for Samsung PCs and smartphones. A recent survey by McAfee found that consumer concerns "underscore the need for robust cross-device security," but is the company using this… [Continue Reading] -

Mozilla's Paperstorm campaign calls for copyright reform to save the internet
Publié: mai 9, 2017, 1:42pm CEST par Mark Wilson
Mozilla has teamed up with design studio Moniker and launched a new "digital advocacy tool" called Paperstorm with the aim of modernizing copyright laws in Europe. The tool makes it easy for ordinary internet users to carpet bomb European lawmakers with virtual leaflets demanding change. The campaign is looking to drop millions of leaflets on cities around Europe to send a message to EU policymakers. The timing is important because copyright laws are due to undergo amendments, and proposals need to be in by the end of the year. Mozilla says that existing rules are outdated, and now is the… [Continue Reading] -

Open source password strength meter could help boost account security
Publié: mai 9, 2017, 12:16pm CEST par Mark Wilson
It's no secret that most people are rubbish at choosing passwords -- it's something that's proved time and time again when the annual list of common passwords is released. To help overcome the problem, and hopefully increase the security of people's accounts, a team of researchers from the Carnegie Mellon University and the University of Chicago have created an open source password meter that provides advice about how to strengthen a password. While it's quite common to encounter online forms that require you to create passwords that meet certain criteria, it still does not necessarily mean they are secure. CyLab… [Continue Reading] -

Google just made offline browsing a whole lot easier in Chrome for Android
Publié: mai 8, 2017, 8:03pm CEST par Mark Wilson
Offline web browsing is a useful feature, particularly on a smartphone, so it was little surprise when Google added website downloading to the Android version of Chrome. Today the company launches a number of improvements to make the whole process even easier. The latest update to the app introduces a couple of new ways to download pages for offline viewing. It also provides easier access to the content you have earmarked for offline reading, encouraging more people to make use of the feature. Google suggests that offline browsing is not only useful for those times when you know you can… [Continue Reading] -

Weird Microsoft Edge bug means the browser prints different numbers than it displays
Publié: mai 8, 2017, 4:31pm CEST par Mark Wilson
Anyone using Microsoft Edge to "print to PDF" is advised to double-check their files after a strange bug was detected. The problem is reminiscent of a bug that afflicted Xerox photocopiers a couple of years ago, and sees the browser displaying one set of numbers and printing another. Microsoft has confirmed the existence of the bug which has the potential to cause serious issues with mission-critical data. The person who originally reported the problem cites an example in which Windows 10's default web browser "displays 123456 in PDF but prints 114447." The cause of the problem is not known, and… [Continue Reading] -

HandBrake for Mac server compromise means downloaders have 50-50 chance of Proton RAT malware infection
Publié: mai 8, 2017, 12:02pm CEST par Mark Wilson
Anyone who downloaded the Mac video transcoder HandBrake in the last few days stands a 50 percent change of being infected with a Trojan. The download for version 1.0.7 of HandBrake was infected after the mirror download server was compromised. The Trojan allows for an attacker to remotely access an infected computer, and a malware-laced version of the app was made available for download between May 2 and May 6. If you downloaded the app in this window, you're advised to check the SHA1/256 sum, and if you have gone as far as installing the software, there are steps to… [Continue Reading] -

Facebook uses newspaper ads to warn about fake news and gives tips to help spot it
Publié: mai 8, 2017, 10:51am CEST par Mark Wilson
Facebook's fight against fake news has been taken to the printed press. The social networking giant has taken out a series of ads in UK newspapers giving tips about how to spot fake news. The ad campaign comes as Brits prepare to go to the polls and vote in the snap General Election in a month's time. The issue of fake news really came to prominence in the run up to the US election, and research has shown that Facebook has become a tool that is used as part of campaigning to spread propaganda. In addition to the print ads,… [Continue Reading] -

Windows 10 Creators Update has a secret UWP version of File Explorer -- here's how to find it
Publié: mai 7, 2017, 7:48pm CEST par Mark Wilson
Microsoft has made much of its UWP (Universal Windows Platform) so it should come as little surprise that there's a UWP version of File Explorer. What is a little surprising, however, is that the app is hidden and can only be unlocked using a specially-crafted shortcut. You need to be running Windows 10 Creators Update and you can try out the app which is somewhat reminiscent of the Windows 10 Mobile version of File Explorer. It's not clear how close to the final version of the app this is, but it's interesting to try out, and certainly something to keep… [Continue Reading] -

Android Nougat beta ends as Google prepares for imminent launch of Android O beta
Publié: mai 7, 2017, 7:01pm CEST par Mark Wilson
Google is preparing to launch the Android O beta, and ahead of this the company has officially closed the Android Nougat beta program. We've already seen a developer preview of Android O, and a second release is due later this month. But many Pixel and Nexus users are waiting for the Android O beta as the developer preview is not really intended for public consumption. While we're not really any closer to knowing for sure when the new beta program will begin, we're clearly nearing the time that Google will make an announcement. With Google I/O now less than two weeks… [Continue Reading] -

Microsoft patents technology to block pirate material from cloud storage
Publié: mai 6, 2017, 3:57pm CEST par Mark Wilson
A new patent from Microsoft could enable the company to not only identify and block pirate material from being shared via cloud services, but also to identify repeat offenders and take action against them. The patent specifically refers to the ability to identify and block the sharing of "prohibited content," and this could be used to mean copyrighted material, or files that a company simply does not want to be shared. The technology relies on a fingerprinting technique which makes it possible to identify files rather than having to worry about trying to track down and delete files to prevent… [Continue Reading] -

More Vault 7 leaks from WikiLeaks: Archimedes is the CIA's man-in-the-middle hacking tool
Publié: mai 6, 2017, 1:46pm CEST par Mark Wilson
WikiLeaks continues to release revealing documents from its Vault 7 cache. This time around the organization introduces us to a CIA tool called Archimedes -- previously known as Fulcrum. As before, there is little to confirm whether or not the tool is still in active use -- or, indeed, if it has actually ever been used -- but the documentation shows how it can be installed on a LAN to perform a man-in-the-middle attack. The manual itself explains how Archimedes works: "Archimedes is used to redirect LAN traffic from a target’s computer through an attacker controlled computer before it is… [Continue Reading] -

Emmanuel Macron hit by EMLEAKS email hack ahead of French election head-to-head with Le Pen
Publié: mai 6, 2017, 1:23pm CEST par Mark Wilson
Left-wing French presidential hopeful Emmanuel Macron has been hit by a "massive and coordinated" hack attack just before voters go to the polls. A 9GB cache of emails and photos was dumped as a torrent on Pastebin by a leaker by the name of EMLEAKS. The torrent was initially hosted on Archive.org. It was quickly pulled offline, but not before it had spread far and wide on social media. Released just before midnight on Friday night, the leak was timed to prevent Macron from responding. French election rules forbid candidates from engaging in any form of campaigning immediately before polls… [Continue Reading] -

OnePlus confirms the OnePlus 5 will be released this summer
Publié: mai 5, 2017, 5:15pm CEST par Mark Wilson
OnePlus has confirmed that the successor to the OnePlus 3T is due for release soon. The OnePlus 5 has been rumored and hinted at for a while, but now it is official. In a slightly unusual move, rather than making a direct announcement about the upcoming flagship killer, OnePlus instead chose to reveal the future launch to the Verge. Beyond "summer," we know nothing about the specifics of the launch but there are plenty of leaks and rumors to go on for the time being. While the naming may seem a little strange, OnePlus is not taking a leaf out… [Continue Reading] -

Facebook to hire just 3,000 more people to moderate the content of its 1.9 billion users
Publié: mai 4, 2017, 5:56pm CEST par Mark Wilson
There's been a lot of disturbing content on Facebook in recent weeks and months -- murders, rapes, assaults, shootings and more. After a fatal shooting was shared on the site, Facebook vowed to do more to combat this sort of material. As the social network announced that it now has 1.9 billion users, it also announced that it is to employ an extra 3,000 people to help moderate content. This brings the company's total number of moderators to 7,500. Can this possibly be enough to manage the posts of nearly 2 billion people, and who on earth would want to… [Continue Reading] -

How to remove the People button from the taskbar in Windows 10 Redstone 3
Publié: mai 4, 2017, 1:13pm CEST par Mark Wilson
So far there is not very much to get overly excited about in the Redstone 3 builds of Windows 10 that are creeping out, but there are new additions nonetheless. Build 16184, for instance, sees the arrival of the My People app and with it the addition of a new button in the taskbar. Nestling to the left of the clock you will notice a monochrome icon featuring the outline of two people -- the People Bar. Click it, and you can use the My People app to gain easy access to contacts and keep an eye on conversations in… [Continue Reading] -

Google adds phishing protection to Gmail app on Android
Publié: mai 4, 2017, 12:33pm CEST par Mark Wilson
Gmail users will now be protected from phishing attacks on their Android phones thanks to a new update from Google. The company is rolling out a new security feature similar to that found in the web version of Gmail, warning people when an email contains a suspicious link. For now, the update is only rolling out to Android users, and Google has not indicated whether it will make its way to iOS in due course or not. The update comes just shortly after a phishing scam emerged in which recipients were encouraged to click on a link to open files… [Continue Reading] -

Chrome extension Who Targets Me? reveals how Facebook is used for election propaganda
Publié: mai 3, 2017, 12:56pm CEST par Mark Wilson
Social media is powerful, so it's really little wonder that the likes of Facebook are used for propaganda. We already know that advertising can be very carefully targeted for maximum impact, and this can prove important when it comes to getting across a political message. With the UK on the verge of an early general election -- one that will be fought with Brexit and Scottish Independence looming large -- political campaigns are getting underway, including on Facebook. To help educate voters about how they are being besieged by political parties, a free Chrome extension called Who Targets Me? has… [Continue Reading] -

Is Windows 10 S Microsoft's ticket to unashamedly squeeze more money out of users?
Publié: mai 3, 2017, 12:10pm CEST par Mark Wilson
Yesterday, to a somewhat unexpectant world, Microsoft unleashed a new operating system: Windows 10 S. The company would of course prefer that you didn’t think of this as it having a second stab at Windows RT, but it's hard to ignore the fact that that's basically what's happening. This is, after all, a copy of Windows that is only capable of running apps downloaded from the Windows Store. Microsoft is placing a good deal of emphasis on the performance and security the operating system offers, but with the option of unlocking Windows 10 Pro (for a fee, of course), is… [Continue Reading] -

iPhone sales continue to fall ahead of iPhone 8 launch
Publié: mai 3, 2017, 11:02am CEST par Mark Wilson
Yesterday we debated whether interest in the Apple Watch is falling, but Tim Cook says that sales have doubled over the last year. This is an easy claim to make when you don’t reveal the actual sales figures, but the story is definitely less rosy when we look at the iPhone. For the second quarter ever, sales of Apple's smartphone fell. This was not only a drop in sales, but an unexpected one. While analysts had been predicting sales in the region of 52.27 million, the reality is that the company shipped just 50.2 million in the quarter ending April… [Continue Reading] -

Facebook denies allowing advertisers to target people based on their emotional state
Publié: mai 2, 2017, 3:32pm CEST par Mark Wilson
A leaked internal document shows that Facebook is capable of identifying people according to their emotional state. The document, seen by The Australian, shows how the social network can monitor users' posts and determine when they are feeling "stressed, defeated, overwhelmed, anxious, nervous, stupid, silly, useless, or a failure." The leak pertains to Facebook's Australian office and suggests that algorithms can be used to detect "moments when young people need a confidence boost." It raises serious ethical questions about Facebook's capabilities, but the company denies it is doing anything wrong. The documents -- which are dated 2017 and marked "Confidential: Internal… [Continue Reading] -

Is interest in Apple Watch on the wane? Big-name apps drop support for the wearable
Publié: mai 2, 2017, 2:38pm CEST par Mark Wilson
It would appear that the Apple Watch is losing its shine. A number of big-name apps have dropped support for the wearable, including Google Maps, Target, eBay and Amazon. It's not clear exactly why support was dropped, but as it took a little while for users to notice and start complaining on social media, a general lack of interest is likely to blame. Google has offered a vague promise that Google Maps will return to Apple Watch "in the future," but gives no sense of timescale, and there are no similar assurances from any of the others who have quietly… [Continue Reading] -

Twitter announces 16 live streaming partners including Bloomberg for 24-hour news
Publié: mai 2, 2017, 1:46pm CEST par Mark Wilson
Twitter continues to place ever-increasing importance on video on its network, and the company has announced a new batch of partners that will bring a host of live-streamed programming to the service. There are 16 streaming partners in total, including Bloomberg which will bring a 24-hour rolling news services to Twitter. Other partners include Live Nation which will deliver live concert performances, and NBA, PGA and MLB to cater for the sports side of things. Twitter believes it is in something of a unique position because of the level of interactivity it can offer with shows. Company COO Anthony Noto… [Continue Reading] -

Facebook updates Rights Manager so content owners can earn ad income from pirated videos
Publié: avril 30, 2017, 2:40pm CEST par Mark Wilson
Like Google, Facebook places great importance on advertising. The social network not only earns money from ads itself, but also allows companies and individuals to do so by displaying ads in videos. Pirates were quick to spot an easy way to earn money -- steal someone else's popular video and watch the ad revenue roll in. Now Facebook is fighting back in a way that has already been used to some extent by YouTube. There is a new "claim ad earnings" option in the Rights Manager tool which enables the owner of a particular video to bag the ad revenue… [Continue Reading] -

Report: Facebook really is used for propaganda and to influence elections
Publié: avril 29, 2017, 11:56am CEST par Mark Wilson
It's something that many people have expected for some time, and now we know that it's true. Facebook has admitted that governments around the world have used the social network to spread propaganda and try to influence the outcome of elections. In the run-up to the US election, there was speculation that powerful groups had been making use of Facebook to influence voters by spreading fake news. Now, in a white paper, Facebook reveals that through the use of fake accounts, targeted data collection and false information, governments and organizations have indeed been using the social network to control the… [Continue Reading] -

Orange is the New Black season 5 episode 1 leaks online as Netflix is held to ransom
Publié: avril 29, 2017, 11:31am CEST par Mark Wilson
A hacking group by the name of TheDarkOverlord has leaked the first episode of the Netflix show Orange is the New Black [Update: the group has since leaked 9 more episodes]. The season premiere of the hit show is not set to air until June, but TheDarkOverlord released it to The Pirate Bay after Netflix failed to meet ransom demands. The group allegedly managed to get hold of the episode after gaining access to the systems of post-production studio Larson Studios in Hollywood. When Netflix refused to comply with its demands, which are described as "modest", the show was made… [Continue Reading] -

Google still hasn't given up on Google+ and Topics is the latest attempt to keep people on the service
Publié: avril 28, 2017, 10:38am CEST par Mark Wilson
Google+ finds itself the butt of many a joke, but the company behind the service is happy to proclaim that "millions of people use" it. There are already numerous ways to discover content on Google+, and now there's yet another: Topics. This is essentially Google's take on the idea of related content, and it's a bid to keep users on the site -- or in the app -- for longer. Not content with having people reading what they set out to read, now additional "Topics to explore" will be suggested. The latest addition to the Home Stream is a fairly… [Continue Reading] -

New report shows the number of requests for user data Facebook receives from global governments
Publié: avril 27, 2017, 7:14pm CEST par Mark Wilson
Today Facebook publishes its Global Government Requests Report, revealing just how many data requests the social network has received from governments around the world. This time around, the report covers the second half of 2016, and it shows a mixed-bag of figures. While the number of items that had to be restricted due to contravention of local laws dropped, the number of government data requests increased by 9 percent compared to the previous six months. Facebook is well-aware that it faces scrutiny and criticism for its willingness to comply with data requests, and the company tries to allay fears by… [Continue Reading] -

FalseGuide malware infects millions of Android users via Google Play
Publié: avril 26, 2017, 11:39am CEST par Mark Wilson
Malware is something of a recurring problem for Android users, and it seems as though Google is fighting a never-ending battle to keep the blight out of the Play Store. The latest large-scale batch to be discovered takes the form of adware known as FalseGuide. As you may have guessed from the name -- and your own experience of Google Play -- this malware spreads by fooling people into installing apps purporting to be guides to popular games. The apps themselves are fairly innocuous -- and often are guides as they claim to be -- but they then download additional… [Continue Reading] -

Facebook is testing pre-emptive related articles in News Feed
Publié: avril 26, 2017, 10:41am CEST par Mark Wilson
The "related articles" feature of Facebook's News Feed is nothing new -- in fact it has been with us for more than three years. But now the social network is trialling a new way of displaying related content; rather than waiting until you have clicked on a story to suggest related stories you might be interested in, Facebook will instead be offering these suggestions before you read an article. As well as giving users the chance to read more about a topic from different source, Facebook says that it will help people to discover articles which have been fact-checked. It… [Continue Reading] -

Google tweaks search algorithms to fight fake news and 'offensive' content
Publié: avril 25, 2017, 4:49pm CEST par Mark Wilson
The fight against fake news continues, with Google announcing not only changes to search algorithms to help prevent false information from rising to the surface, but also new tools to allow users to report "unexpected, inaccurate or offensive" results. While the algorithm tweaks should impact on general search results, the reporting tools have been designed for Google's Autocomplete predictions and Featured Snippets which have been problematic in recent months. Updated algorithms should help to ensure more authoritative pages receive greater prominence, while low-quality content is demoted. Vice president of engineering at Google Search, Ben Gomes, admits that people have been… [Continue Reading] -

How to access your OnePlus 3/3T's secret diagnostic tools
Publié: avril 25, 2017, 1:28pm CEST par Mark Wilson
If you're using a desktop or a laptop, there are a number of diagnostic tools built into your operating system that you can use to check various components of your computer. When you're using your smartphone, however, you might feel as though you have to install a bunch of apps to do the same job. But this is not the case. There are a large number of tools built into your OnePlus 3 or OnePlus 3T -- you just need to know how to find them. As you'll probably have guessed from the headline, these are not utilities you're going… [Continue Reading] -

Wikipedia founder Jimmy Wales sets up WikiTribune to fight fake news
Publié: avril 25, 2017, 11:46am CEST par Mark Wilson
Donald Trump is obsessed with the notion of FAKE NEWS. Whether his definition is the same as everyone else's is open to debate, but there is a genuine problem with the spread of propaganda, nonsense, and stories which are clearly fabricated. Google and Facebook and other big names from the world of tech have started to fight back, and now it's the turn of Jimmy Wales. The Wikipedia founder is setting up WikiTribune, an online news publication which focuses on fact-checking, using a combination of paid journalists and contributions from the community. It is described as a "new kind of… [Continue Reading] -

Consumer Reports confirms Galaxy S8 red tint problem as Samsung promises an update to fix it
Publié: avril 24, 2017, 4:51pm CEST par Mark Wilson
The Samsung Galaxy S8 and S8+ launched last week, and has received many positive reviews. However, the smartphone has a problem. The screen -- which has been widely praised -- has an issue which means some suffer with a red tint. This has been confirmed by Consumer Reports in its tests of the phone. Officials have pointed out that tweaking color calibration settings is all it takes to fix the problem, but Samsung has also said that it will push out an update to address the issue. But how much of a problem is the red tint? According to Consumer… [Continue Reading] -

Uber tracked iPhone users even after they uninstalled the app and Tim Cook wasn't happy
Publié: avril 24, 2017, 2:12pm CEST par Mark Wilson
Uber broke Apple's rules by tagging and tracking iPhones even after users had uninstalled the taxi-hailing app. The New York Times reports that Tim Cook met with CEO Travis Kalanick and warned that the Uber app could be kicked out of the App Store for violating privacy guidelines. It is said that Uber has been found "secretly identifying and tagging iPhones" not only after the app was uninstalled, but even after phones had been wiped. The "fingerprinting" technique was used -- it is alleged -- to identify individual iPhones, and measures were taken to hide the offending code from Apple.… [Continue Reading] -

Email unsubscription service Unroll.me sells user data; CEO is 'heartbroken' that people found out
Publié: avril 24, 2017, 11:52am CEST par Mark Wilson
Overwhelmed by the number of emails hitting our inboxes these days, it's little wonder that a "unsubscription service" like Unroll.me came into being. Designed to make it easier to clean up your inbox, it turned out that Unroll.me was selling user data to other companies -- including Uber, which is caught up in other controversies of its own. After this came to light, CEO Jojo Hedaya has written a sorry-not-sorry-style apology. In it, he says that it was "heartbreaking" to find that users were upset to discover "how we monetize our free service." But while recognizing that people are unhappy,… [Continue Reading] -

Google fixes YouTube's LGBTQ+ filtering problem
Publié: avril 24, 2017, 10:23am CEST par Mark Wilson
Around this time last month, Google was facing criticism for appearing to censor LGBTQ+ videos with the Restricted Mode feature. Now the company says that it has addressed the problem and will no longer be "incorrectly filtering videos." Google says that this means hundreds of thousands of videos with LGBTQ+ content have been unlocked, and more than 12 million videos in total have been affected. The company has already issued an apology for the filtering, but now it is keen to be seen making amends. In a blog post talking about changes that have been made to Restricted Mode, Google… [Continue Reading] -

System76 wants to build its own hardware for its Linux-based computers
Publié: avril 23, 2017, 7:05pm CEST par Mark Wilson
System76 is building up quite a name for itself, being one of a very limited number of companies selling only computers running Linux-based operating systems. Now the aim is to branch out; System76 wants to design and build its own hardware, while representing the open source community as it does so. At the moment, the hardware used in System76 systems is outsourced, but in the future this will change. The company says that it is moving into phase three of its development cycle, and this "moves product design and manufacturing in house." And you should set your expectations high: "We're… [Continue Reading] -

WikiLeaks reveals CIA's Weeping Angel tool for hacking Samsung TVs
Publié: avril 23, 2017, 6:21pm CEST par Mark Wilson
WikiLeaks continues to release documents that reveal various hacking tools used by the CIA. After the HIVE revelations just over a week ago, the group has followed up with details of operations that were mentioned in the very first batch of Vault 7 leaks -- hacking Samsung televisions to listen in on people. The documents suggest that the CIA's work is based on a tool developed by MI5 in the UK called Extending. The CIA went on to transform this into its own utility by the name of "Weeping Angel." WikiLeaks has published the guide to using the tool in… [Continue Reading] -

Leaked specs: Windows 10 Cloud is ready to take on Chromebook
Publié: avril 22, 2017, 10:43am CEST par Mark Wilson
Microsoft is due to hold an event in NYC on May 2, and it's widely expected that the company will unveil Windows 10 Cloud -- although it may not be until Build slightly later in the month. On paper, Windows 10 Cloud sounds very much like Microsoft's answer to Google's Chromebook, and leaks suggest this is precisely the market that Microsoft is targeting. As the May event has an education focus, it's apparent that any low-cost Chromebook-like Windows devices will be aimed at the education sector -- but that's not to say that there won’t be interest from other people… [Continue Reading] -

Google Play Music becomes the default player on Samsung phones and tablets, plus doubles free storage
Publié: avril 21, 2017, 4:59pm CEST par Mark Wilson
To coincide with the launch of the Galaxy S8 and S8+, Google has announced a new partnership with Samsung. The deal means that Google Play Music will be the default music player and music service on all phones and tablets from the Korean manufacturer around the world. But the partnership has a few bonuses for Samsung users that go beyond just a change in music player. Kicking things off is a boost in free Google Play Music storage: Samsung users will be able to take advantage of double the usual quota. With the storage increase, users will be able to… [Continue Reading] -

Google wants to teach teenagers how to use the internet with special workshops
Publié: avril 21, 2017, 1:52pm CEST par Mark Wilson
Google is launching a series of Internet Citizens workshops as part of its YouTube Creators for Change program. Aimed at 13- to 18-year-olds, the workshops have been designed to teach teenagers how to spot fake news, how to stay safe online, and how to "make negativity bounce." Taking in topics such as comment moderation, dealing with online abuse, and how to respond to offensive content and echo chambers, the workshops launch today in the UK, starting in Liverpool, and will spread around the country over the coming weeks. But is the program just stoking the idea of generation snowflake? Google… [Continue Reading] -

Samsung Galaxy S8 and S8+ launch today -- carrier logo-free!
Publié: avril 21, 2017, 11:35am CEST par Mark Wilson
It's a little over three weeks since Samsung first unveiled the Galaxy S8 and S8+, and now launch day is upon us. Today sees the flagship smartphones hitting US, Canada, Puerto Rico and Korea, and over the coming weeks it will spread to other markets. In terms of hardware and software, there's quite a lot to get excited about -- the screen for starters, as well as Bixby -- but aesthetes also have some rather pleasing news. For buyers in the US, the rear of the Galaxy S8 and S8+ will be devoid of branding from Verizon, AT&T, T-Mobile and… [Continue Reading] -

Bose faces privacy lawsuit over headphones that share listening habits with third parties
Publié: avril 21, 2017, 10:47am CEST par Mark Wilson
When it comes to privacy concerns, the mind naturally drifts to the likes of Facebook, Microsoft and Google. But in reality, there is the potential for privacy issues with any connected device -- and that includes Bluetooth headphones from Bose. Illustrating this is a man from Illinois who has filed a lawsuit against the Massachusetts-based audio company for "secretly collecting, transmitting, and disclosing its customers' private music selections to third parties, including a data mining company." Kyle Zak alleges that his Bose QuietComfort 35 wireless Bluetooth headphones and the associated Bose Connect app gathered information about him, and sold it… [Continue Reading] -

Redstone 3 will launch in September as Microsoft commits to twice-yearly feature releases for Windows 10
Publié: avril 20, 2017, 7:35pm CEST par Mark Wilson
We're already seeing preview builds of Windows 10 Redstone 3 creeping out after the launch of Windows 10 Creators Update, and we now know that the final release date is scheduled for September. The revelation comes as Microsoft announces plans to align its feature releases of Windows and Office, primarily to make things easier for enterprise users. Releases will come in March and September, and the next big update for Windows 10 (i.e. Redstone 3) "will be targeted for September 2017." All releases will be supported for a total of 18 months, and having the same system in place for… [Continue Reading] -

Google Chrome could soon include an ad blocker
Publié: avril 20, 2017, 12:44pm CEST par Mark Wilson
It's news that -- on the face of it -- makes very little sense; the Wall Street Journal reports that Google is going to include an ad-blocking feature in its Chrome web browser. For a company that makes so much money from advertising this seems like something of a strange move, but in the light of recent ad controversy, it could be sensible business. Just last month a large number of big companies started to pull advertising from Google and YouTube after finding that their ads were appearing on sites hosting extremist material. This, coupled with the fact that there… [Continue Reading] -

Privacy: How to stop Google Maps' Your Timeline tracking where you go
Publié: avril 20, 2017, 10:59am CEST par Mark Wilson
We live in a dichotomous age in which we are more concerned about privacy than ever, while simultaneously handing over more and more personal information to the likes of Facebook and Google. With its Your Timeline feature, Google Maps provides us with a great way to keep track of the places we've visited, but it also means sharing a lot of very revealing data with Google. You may well like the idea of being able to check to see which coffee shop you visited a year ago, or check how far you walked last Wednesday, but you may also like… [Continue Reading] -

Microsoft To-Do preview for iOS, Android, Windows and web signals the death of Wunderlist
Publié: avril 19, 2017, 5:50pm CEST par Mark Wilson
Any organized soul worth their salt has a good to-do service (or two) to support them. This is something that has been strangely lacking from Microsoft, but this is all set to change with Microsoft To-Do. This reminder app has been in the works for a little while under the codename of Project Cheshire, but Microsoft has just launched a preview version of it. The online service works in conjunction with apps for iOS, Android and Windows, and you can try it out for yourself right now. For the moment, Microsoft To-Do looks like a fairly basic affair, but it… [Continue Reading] -

Need a product key for Windows 10 Creators Update? Just use an old one!
Publié: avril 19, 2017, 3:27pm CEST par Mark Wilson
Much was made of Microsoft's decision to offer Windows 10 as a free upgrade, and then withdrawing the free upgrade. If you've been holding off jumping from Windows 7 or Windows 8.x to Windows 10 because you find the cost off-putting, there's some good news. If you download yourself a copy of Windows 10 Creators Update from Microsoft, you should find that when you are prompted for a product key the license code from Windows 7, 8, and 8.1 works just fine to activate your copy of the new operating system. As the free upgrade to Windows 10 came to… [Continue Reading] -

Mobile YouTube live streaming now available to channels with 1,000 subscribers
Publié: avril 19, 2017, 3:18pm CEST par Mark Wilson
Back in February, Google opened up YouTube live streaming to channels with 10,000 or more subscribers. Just two months later, the company has slashed this requirement to just 1,000 subscribers. But while the bar may have been lowered in terms of subscriber numbers, there are still a few hoops that would-be live streamers have to jump through. It does mean, however, that many more YouTubers will be able to stream their content live, so there will be a greater selection of content to consume. In order to start live streaming you'll need to get your channel verified, and ensure that… [Continue Reading] -

Spotify bot for Facebook Messenger lets you share music and listen to mood-based playlists
Publié: avril 19, 2017, 11:10am CEST par Mark Wilson
At Facebook's F8 conference yesterday, much of the attention was focused on virtual reality, augmented reality -- anything that breaks out of vanilla reality. But there were other things of arguably greater interest, and for music fans there was news of the Spotify bot for Facebook Messenger. Facebook has been throwing a lot at bots recently, and it's little surprise that big names like Spotify are getting in on the action. For the music streaming service, the bot serves a dual purpose: giving useful functionality to Messenger users, while simultaneously pushing people into taking up a subscription. It's not something… [Continue Reading] -

Google Maps for iOS gains Your Timeline feature so you can check your travel history
Publié: avril 18, 2017, 6:42pm CEST par Mark Wilson
It's something that Android users have been able to do for a little while now -- using the Timeline function of Google Maps to check back over their travel history. Now the feature is coming to iOS, meaning iPhone users can now look back over their day and where it has taken them. Google suggests that it's a great way to rediscover places you have visited in the past, but it also provides a means of tracking how far you have traveled over the course of the day. Users are given a good level of control over what's included in… [Continue Reading] -

Android Pay and PayPal join forces to provide new payment options
Publié: avril 18, 2017, 4:41pm CEST par Mark Wilson
Two of the biggest electronic payment systems currently available to consumers are teaming up. Android Pay and PayPal have extended their strategic partnership making it possible to use PayPal as a payment method in Android Pay. This means that anyone whose bank is not supported by Android Pay now has a new option available to them, bringing additional users to Google's payment system. Google doesn't have a great deal to say about the expansion but does offer the following: "Millions of people already use their PayPal account to make online purchases, receive payments and send money to friends and family.… [Continue Reading] -

Mozilla ditches Aurora release channels for Firefox; new and beta code will hit users faster
Publié: avril 18, 2017, 1:01pm CEST par Mark Wilson
Mozilla has announced plans to eliminate one of its release channels for not only Firefox but also Thunderbird and SeaMonkey. Starting today, the Aurora release channel will no longer be updated, and the Developer Edition of the web browser will be based on the Beta build. The change is part of a drive to streamline the release process, and to make sure that stable new features make their way out to not only developers, but also normal users faster than before. Mozilla says: "Developer Edition users will maintain their Developer Edition themes, tools, and preferences, will keep their existing profile,… [Continue Reading] -

How to access Microsoft Edge's secret full screen mode
Publié: avril 18, 2017, 12:05pm CEST par Mark Wilson
If you're looking for distraction-free web browsing, it makes sense to switch to full screen mode. This is something that is very easy to achieve in the likes of Chrome, Opera and Firefox, but Windows 10 users who have opted to stick with Microsoft Edge don’t seem to have such a good deal. But this is just a matter of appearances. Edge does have a secret full screen mode that you can access very easily. Quite why Microsoft chose not to advertise the feature is anyone's guess, but there you go! Fire up Microsoft Edge, take a look through the… [Continue Reading] -

A fifth of UK firms hit by cyber-attacks, putting private data at risk
Publié: avril 18, 2017, 11:10am CEST par Mark Wilson
UK companies are ill-equipped to deal with cyber-attacks, a report by the British Chambers of Commerce (BCC) says. Nearly one in five smaller companies (18 percent) have fallen prey to cybercrime, and the figures are even worse for larger firms. When looking at companies with more than 100 employees, the number that have been hit by cyber-attacks jumps to a staggering 42 percent. More than three quarters of the firms surveyed by the BCC did not have anti-hacking security measures in place, and most relied on third-party firms to clean up after an attack rather than having in-house solutions. The… [Continue Reading] -

Secure your Twitter account with two-factor authentication
Publié: avril 17, 2017, 4:51pm CEST par Mark Wilson
There are not many well-known online services that don't offer two-factor authentication (2FA) nowadays, but Twitter is very late to the party. Well, that might not be strictly true. Twitter recently added support for third-party authenticator apps, but failed to make any sort of song and dance about it. The change means that it's now possible to make use of the likes of Google Authenticator and Authy with Twitter -- but you'd be forgiven for not having found the option by accident already. If you like the idea of enabling two-factor authentication for your Twitter account, you can take this… [Continue Reading] -

Facebook responds to the Cleveland murder shared on the social network
Publié: avril 17, 2017, 11:23am CEST par Mark Wilson
Over the weekend, it was suggested that Steve Stephens used Facebook Live to livestream himself fatally shooting a man in his 70s. He went on to use the social network to admit to other murders, as well as saying that he wanted to "kill as many people as I can." Despite rumors of a murder having been committed live on Facebook, the social network issued a statement clarifying that, while Stephens had broadcast on Facebook Live over the weekend, the footage had actually been uploaded rather than livestreamed. Whether broadcast live or not, the story -- once again -- brings into… [Continue Reading] -

How to enable Dark Mode on YouTube
Publié: avril 14, 2017, 2:08pm CEST par Mark Wilson
If you're someone who enjoys watching YouTube at night -- perhaps on your phone in bed -- you'll be all too aware that the site's light color palette can be rather harsh on the eyes. With a little tinkering, you can unlock a hidden Dark Mode which will save your delicate peepers and make nocturnal viewing all the more enjoyable. At the moment the hack only works in Chrome, but it's likely that Google will bring it to everyone when word spreads. Here's what you need to do. In Chrome, pay a visit to the YouTube front page, make sure… [Continue Reading] -

Microsoft transparency report reveals first National Security Letter and shows doubling of FISA orders
Publié: avril 14, 2017, 12:27pm CEST par Mark Wilson
Microsoft has published its latest transparency report and, for the first time, disclosed the contents of a National Security Letter it received. In addition to the debut appearance of such a letter in the report, Microsoft also reveals that in the reported period in 2016 the number of FISA orders more than doubled compared to the previous period. As with previous reports, Microsoft is not permitted -- for reasons best known to the US government -- to reveal precise numbers when talking about the number of official requests for data it has received. As such, we know that in the… [Continue Reading] -

How to upgrade Bash/Windows Subsystem for Linux in Windows 10 Creators Update
Publié: avril 14, 2017, 11:13am CEST par Mark Wilson
You can't help but have noticed that Microsoft has started the rollout of Windows 10 Creators Update. After testing with Windows Insiders, the third big update to Windows 10 is finally making its way to the masses. But while Creators Update brings some pretty major changes to Windows 10, Windows Subsystem for Linux is not automatically updated. The arrival of Bash/Windows Subsystem for Linux (WSL) in Windows 10 Anniversary Update meant Ubuntu 14.04 support, but you can now manually update to gain Ubuntu 16.04 support in Creators Update. Microsoft says you need to perform one of two manual update methods:… [Continue Reading] -

Microsoft shows off Edge's battery usage improvements in Windows 10 Creators Update
Publié: avril 12, 2017, 5:23pm CEST par Mark Wilson
The war over which web browser offers the best battery life to laptop users has been waging for some time. Chrome, Firefox and Microsoft Edge have all been battling it out, and with the release of Windows 10 Creators Update, Microsoft thinks it's time to show off the improvements that have been made to its browser. In Microsoft's own tests -- involving streaming video on a Surface Book -- Edge lasted for over three hours longer than Chrome, and nearly five hours longer than Firefox. These are figures that will almost certainly be disputed in further tests by Mozilla and… [Continue Reading] -

Amazon launches Parent Dashboard and Discussion Cards to allow greater parental control
Publié: avril 12, 2017, 3:38pm CEST par Mark Wilson
The problem with unleashing any child onto the internet is keeping track of what they are up to, and trying to ensure they're not accessing content you'd rather they didn't. With this in mind, Amazon has launched two new services for its Fire for Kids tablet. Parent Dashboard and Discussion Cards not only give parents the chance to keep an eye on what their kids are doing, but also to encourage dialog about apps and content. Amazon says the aim is to connect parents and children, but it's also about managing time limits and setting educational goals. Parent Dashboard is… [Continue Reading] -

Google AutoDraw is like autocomplete for your doodles
Publié: avril 12, 2017, 12:28pm CEST par Mark Wilson
Machine learning has been put to lots of powerful uses, but Google has a new way to make use of the technology. AutoDraw is the company's "fast drawing" tool for everyone, and it works much like autocomplete on your phone. AutoDraw is a web-based drawing tool that uses the same technology as Google's Quick, Draw! AI experiment and it helps you to quickly create an image by "guessing" what it is you’re trying to draw. If this all sounds a bit mad, that's because, well, it is really. But it's also unique enough to make it well worth checking out.… [Continue Reading] -

Brexit voter registration website may have suffered DDoS attack at the hands of Russia or China
Publié: avril 12, 2017, 10:34am CEST par Mark Wilson
The Brexit process is now officially underway, but there is still a good deal of talk about the validity of the outcome. A number of members of parliament have expressed concerns that a foreign government may have interfered with the referendum, making it difficult or impossible for people to register to vote. The Commons public administration and constitutional affairs committee (PACAC) has published a report which looks at the possible causes for the crash of the "register to vote" site last year. It suggests that the crash bears the hallmarks of a DDoS attack, and notes that this is a… [Continue Reading] -

How to disable all of Microsoft's ads in Windows 10 Creators Update
Publié: avril 10, 2017, 5:45pm CEST par Mark Wilson
Pretty much since the launch of Windows 10 there have been complaints about ads and usage tracking in various forms. You might think that Microsoft would listen to complaints and consider removing ads from its operating system, but in fact more and more have been added. We've looked at the various ads (or app suggestions, app tips and so on to use Microsoft's phraseology) that have cropped up over the last couple of years, but the release of Windows 10 Creators Update seems like a good time to revisit the topic. So here, once and for all, is how to… [Continue Reading] -

Vault 7: Symantec says CIA hacking tools revealed by WikiLeaks were used in 40 'Longhorn' cyberattacks
Publié: avril 10, 2017, 4:23pm CEST par Mark Wilson
The CIA's range of hacking tools revealed as part of WikiLeaks' Vault 7 series of leaks have been used to conduct 40 cyberattacks in 16 countries, says Symantec. The security firm alleges that a group known as Longhorn has been using tools that appear to be the very same ones used by the CIA. While it would be obvious to jump to the conclusion that the CIA was itself responsible for the attacks -- and that Longhorn is just a branch of the CIA -- Symantec opts for a rather more conservative evaluation of things: "there can be little doubt… [Continue Reading] -

OLE 0day affects nearly all versions of Microsoft Word
Publié: avril 10, 2017, 11:46am CEST par Mark Wilson
Security issues with Word documents are nothing new, but they have a tendency to rely on macros -- something which users have learned to become very wary of. But now security firms FireEye and McAfee have discovered a new attack strategy that takes advantage of Windows Object Linking and Embedding (OLE). The attack can be used to infect even a fully patched computer with malware, and it is believed to be effective in most -- if not all -- versions of Microsoft Word, and Windows 10 offers no protection. The 0day works by using code embedded in a document to… [Continue Reading] -

Snapchat reminds Scottish voters to register to vote
Publié: avril 10, 2017, 11:05am CEST par Mark Wilson
With council elections due to be held throughout Scotland next month, steps are being taken to ensure that as many people as possible are registered to vote. The Electoral Commission has turned to Snapchat to remind people to register ahead of the cut-off deadline next week. Using social media tools as election reminders is not a new tactic -- Facebook has been used for some time -- but in using Snapchat, an entirely different section of voters is being targeted. This is the first time 16- and 17-year olds will be eligible to vote in Scottish council elections, and Snapchat… [Continue Reading] -

Hackers release password to encrypted cache of NSA tools
Publié: avril 10, 2017, 10:24am CEST par Mark Wilson
Last year, hacking group TheShadowBrokers released a number of NSA exploits into the wild, showing how the agency was able to exploit big-name firewalls. At the same time it also released a second cache of documents, encrypted and password protected. Now, in protest against Donald Trump, the group has released the password for the encrypted data. TheShadowBrokers used a Medium post over the weekend to express their disgust at Trump's presidency. The documents and tools released allegedly demonstrate that the US government, through the NSA, has been actively hacking foreign government networks, and reveal an exploit for the Unix-based Solaris… [Continue Reading] -

Payday loan site Wonga hit by security breach affecting 270,000 in UK and Poland
Publié: avril 9, 2017, 6:10pm CEST par Mark Wilson
Wonga.com -- the payday loan website -- is investigating a security breach which exposed the personal details of tens of thousands of customers. Up to 270,000 customers in the UK and Poland are believed to have been affected by the breach. The incident happened last week, but Wonga initially played down its significance. However this weekend the company determined that customer data was involved, including names, addresses, phone numbers, bank account numbers and sort codes and started an investigation. Wonga says that it is "urgently investigating illegal and unauthorised access to the personal data of some of its customers in… [Continue Reading] -

Microsoft bans emulator apps from the Windows Store
Publié: avril 9, 2017, 5:27pm CEST par Mark Wilson
There are a large number of emulators out there, including a wide range of Xbox and PlayStation emulators. These give gamers the opportunity to play their favorite console games on their PC, but Microsoft has now formally banned such software from the Windows Store. Emulators have long been the subject of legal wranglings because of concerns about copyright and intellectual property infringements, and now the Windows-maker has put its foot down. The developers of NES emulator NESBox are among those affected by the ban, and point to a recent change in Microsoft's rules for the Window Store -- affecting not… [Continue Reading] -

Microsoft launches Windows Insider Program for Business
Publié: avril 8, 2017, 2:21pm CEST par Mark Wilson
Yesterday saw not only the release of the first Redstone 3 build of Windows 10, but also the launch of the Windows Insider Program for Business. This new program works in much the same way as the existing Windows Insider program, but this time there is a focus on IT professionals and businesses. It will give Microsoft the opportunity to gather more information from big customers, and allow businesses to try out new features ahead of their official launch. It's not clear quite how many businesses will be willing to try their luck with Insider builds -- just the other… [Continue Reading] -

Government drops demands to unmask @ALT_USCIS after Twitter files lawsuit
Publié: avril 8, 2017, 1:41pm CEST par Mark Wilson
Just one day after Twitter filed a lawsuit to block the US government from forcing it to reveal the identity of who is behind the @ALT_USCIS account, the government has dropped its request. News of the lawsuit saw the account's follower count more than quadruple as Twitter users jumped to see what was being posted by what are believed to be United States Citizenship and Immigration Services employees. As a result of the government dropping its request, Twitter has stopped the lawsuit. The reasons behind the government's decision is not entirely clear. Twitter argued that a request to reveal the… [Continue Reading] -

Australia sues Apple over iPhones bricked by Error 53
Publié: avril 7, 2017, 4:47pm CEST par Mark Wilson
Early last year, iPhone users upgrading to iOS 9 started to complain that their phones were being "bricked" by the process. An Error 53 was generated, and Apple explained that the bricking was intentional when it was detected that an iPhone had been subject to third party repairs. Many people were unhappy about this, and Australia is suing Apple. The country's watchdog, the Australian Competition and Consumer Commission (ACCC), argues that consumer rights are being infringed upon. It says that Apple has engaged in "misleading or deceptive conduct and made false or misleading representations to consumers." The specifics of Error… [Continue Reading] -

YouTube: no ads until your channel has 10,000 views
Publié: avril 7, 2017, 4:26pm CEST par Mark Wilson
YouTube is more than just a source of cat videos and hilariously painful-looking accidents caught on camera: for many people it is a source of extra income, or even a living. But the YouTube Partner Program (YPP) through which advertisements can be used to generate money is also open to abuse. The Google-owned site has a plagiarism problem whereby popular content is stolen and re-uploaded to a different channel to generate money for a third party. In a bid to stop this practice, YouTube is banning channels from displaying ads until they have managed to hit 10,000 views. The restriction… [Continue Reading] -

WikiLeaks' Vault 7 revelations continue: Grasshopper is the CIA's Windows malware maker
Publié: avril 7, 2017, 4:10pm CEST par Mark Wilson
The latest batch of documents published by WikiLeaks as part of its Vault 7 CIA series purportedly reveals the tools used by the agency to create malware for Windows. The Grasshopper framework is revealed in 27 documents, and they show how to create Windows installers with a malware payload. Importantly, Grasshopper allows for the easy creation of custom malware delivery options, dependant on the operating system and virus protection detected on a target machine. The documents show that the CIA repurposed malware from Russian and Italian organized crime groups. The Grasshopper framework appears to have been designed to not only… [Continue Reading] -

Twitter sues US government for trying to reveal identity of anti-Trump user, @ALT_uscis
Publié: avril 7, 2017, 12:58pm CEST par Mark Wilson
A lawsuit filed by Twitter shows that the US government has been trying to force the company to reveal the identity of a user behind an account that is critical of Donald Trump and government policies. The lawsuit reveals that Customs and Border Patrol hit Twitter with a summons in the middle of March relating to the @ALT_uscis (Alt US Citizenship and Immigration Services) account. The account is one of many "alt" accounts that sprang up after Trump inauguration, purportedly set up by disgruntled civil servants, and it is critical of immigration policy and plans to build a wall on… [Continue Reading] -

Facebook goes on the offensive against fake news and aims to educate users
Publié: avril 7, 2017, 11:43am CEST par Mark Wilson
Having introduced various tools to fight fake news, the next weapon in Facebook's arsenal is education. Over the next few days a large "Tips for spotting fake news" banner will appear at the top of news feeds in 14 countries, but the approach it is taking is unlikely to have much impact on those most influenced by, and most likely to share, fake news. Like Google, Facebook is taking steps to tackle fake news. The social network has already announced a raft of measures aimed at stamping out the problem, but now it is trying to not only educate people… [Continue Reading] -

Google tackles fake news with global fact-checking rollout
Publié: avril 7, 2017, 10:48am CEST par Mark Wilson
The spread of fake news has become something of an epidemic in recent years, and there has been pressure on the likes of Google, Facebook and Twitter to do more to stem its flow. Google's Fact Check feature is not new, but today the search giant is rolling out the feature around the world. A global rollout is important if such a tool is to have any real impact. It's all well and good have reports fact-checked on one side of the world, but it's of little use if the same fake stories remain unquestioned and untested elsewhere. Google is… [Continue Reading] -

Facebook's AI assistant, M, now offers suggestions in Messenger
Publié: avril 7, 2017, 10:26am CEST par Mark Wilson
Promising to "make your Messenger experience more useful, seamless and delightful," Facebook has launched suggestions from M to everyone in the US. M is the social network's AI assistant, and iOS and Android users can now benefit from behavior-based suggestions for content and actions as the assistant analyses conversations. What this means in practice is that M might notice that you are chatting with a friend about sending them some money for something. Rather than waiting until you meet them in person, M will spring into action and suggest that you might like to send the money through Messenger. Other… [Continue Reading] -

Project Scorpio specs revealed; what to expect from the next Xbox powerhouse
Publié: avril 6, 2017, 5:29pm CEST par Mark Wilson
The next addition to the Xbox family is code-named Project Scorpio, and today details about the next-generation console have emerged. Rather unusually, these details have come neither direct from Microsoft, nor through a series of leaks. For reasons best known to Microsoft, the company chose to invite Digital Foundry to its Redmond campus and reveal Project Scorpio details. Due for release later this year (Q4 to be a little more precise), the console is said to be running ahead of schedule, and boasts some impressive specs that will have gamers drooling. Let's cut straight to the chase: Project Scorpio sounds… [Continue Reading] -

Project Scorpio specs revealed -- what to expect from the next Xbox powerhouse
Publié: avril 6, 2017, 5:29pm CEST par Mark Wilson
The next addition to the Xbox family is code-named Project Scorpio, and today details about the next-generation console have emerged. Rather unusually, these details have come neither direct from Microsoft nor through a series of leaks. For reasons best known to Microsoft, the company chose to invite Digital Foundry to its Redmond campus and reveal Project Scorpio details. Due for release later this year (Q4 to be a little more precise), the console is said to be running ahead of schedule, and boasts some impressive specs that will have gamers drooling. Let's cut straight to the chase: Project Scorpio sounds… [Continue Reading] -

How to install Windows 10 Creators Update on your Mac
Publié: avril 6, 2017, 1:50pm CEST par Mark Wilson
If you try to perform a clean installation of Windows 10 Creators Update on your Mac with Boot Camp Assistant you'll quickly find that it is not possible. As Microsoft notes, you'll end up with a Stop error with the code 0xc000000f in winload.efi. Microsoft has not made it clear just why this problem occurs, but it does not mean that you are not able to install Creators Update. If you're eager to get the very latest version of Windows installed on your Mac, here's what you need to do. The key to success is to first install Windows 10… [Continue Reading] -

Microsoft releases Windows 10 Creators Update so you can install it now
Publié: avril 6, 2017, 12:38pm CEST par Mark Wilson
The launch date for Windows 10 Creators Update -- the next big update for Windows 10 -- is April 11, but there's no need to wait until Tuesday to get it. While the automated rollout starts next week, Microsoft has released the update so you can install it manually. We already knew that Microsoft would be making the update available a week early. With the automatic rollout and update process expected to take months, you may well want to jump the queue and grab what Microsoft is calling the "latest and best version of Windows" right now. Here's how to… [Continue Reading] -

Twitter Lite offers a faster Twitter experience on slow connections with Data Saver mode
Publié: avril 6, 2017, 10:22am CEST par Mark Wilson
After the launch of the data-saving YouTube Go beta by Google, Twitter has announced the launch of Twitter Lite. In a similar vein to YouTube Go, Twitter Lite is an acknowledgement that a huge number of people around the world are getting online using a 3G -- or even a 2G -- connection. Twitter Lite is not an app, but a lighter version of the mobile version of the Twitter website. With no app to download, it can be used on any smartphone or tablet and an additional Data Saver mode further reduces bandwidth requirements and helps to speed up… [Continue Reading] -

Microsoft half-heartedly opens up about privacy, revealing more about the data Windows 10 Creators Update collects
Publié: avril 5, 2017, 5:01pm CEST par Mark Wilson
Microsoft has had something of a checkered history when it comes to privacy, particularly with Windows 10. Telemetry concerns have blighted the latest version of the company's operating system for many people, but now it has finally decided to come clean. Ahead of the release of Windows 10 Creators Update, Microsoft reveals full details of the data it collects about users who opt into providing basic-level telemetry information. The company also provides some details -- but not as much as many would like -- about what is collected when the full level of telemetry is selected. This is Microsoft's attempt to… [Continue Reading] -

Samsung Galaxy S8 has the best smartphone display ever
Publié: avril 5, 2017, 2:39pm CEST par Mark Wilson
Samsung has given Galaxy S8 owners a lot to be excited about, including Samsung DeX to transform it into a dockable computer. There's also the assistant, Bixby, but the biggest talking point is probably that display. The Infinity Display not only occupies a massive proportion of the front of the smartphone, it is also the best display of any smartphone ever. At least that's what the guys over at DisplayMate think; after testing in the labs, they awarded it the highest grade they’ve ever handed out. The site has published detailed results of its tests, culminating in dolling out an… [Continue Reading] -

Brace yourself for 'painful' Windows 10 Redstone 3 preview builds
Publié: avril 5, 2017, 12:33pm CEST par Mark Wilson
If you have been following the development of Windows 10 with any degree of interest, it can't have escaped your attention that Windows 10 Creators Update is due to roll out next week -- starting on April 11 to be precise. Of course, there's nothing stopping you from grabbing the update right now, but now many people are starting to think about the next stage of Windows 10's future. The next branch of development is Redstone 3 and Microsoft promises that new builds will start to creep out very soon. Dona Sarkar advises that "you won't see many big noticeable changes… [Continue Reading] -

YouTube Go beta brings data-saving video streaming and downloading to Android
Publié: avril 5, 2017, 10:50am CEST par Mark Wilson
It has been a while since Google announced its plans for YouTube Go, a streamlined version of its mobile app with a focus on sharing and minimizing data usage. Now the company has released the first beta on Google Play. Designed for use in countries with less-than-reliable internet connection, such as India, YouTube Go also allows for the downloading of videos for offline viewing without buffering. The app includes a number of options to help you "maximize your fun without burning up your data," including the ability to preview videos and see the amount of data required to download different… [Continue Reading] -

Tests show laptop manufacturers dramatically exaggerate battery life -- but not Apple
Publié: avril 4, 2017, 1:11pm CEST par Mark Wilson
Consumer group Which? has performed tests on laptops that show manufacturers are overstating the battery life consumers can expect from their devices. In some cases, real-world battery life is just half of what manufacturers claim. Only Apple's MacBook Pro met -- and even exceeded -- battery life claims when put through tests that simulated scenarios users would put laptops through. In all, 67 laptops -- from big names including Acer, Dell and Lenovo -- were put through their paces, and all of the non-Apple devices were found to fall hours short of manufacturers' claims. The consumer group tested each of… [Continue Reading] -

Trump signs resolution permitting ISPs to share your web history without consent
Publié: avril 4, 2017, 11:52am CEST par Mark Wilson
Donald Trump has forged ahead and done what privacy advocates hoped would not happen. The US president has signed a resolution rolling back FCC privacy rules, meaning that ISPs are now free to share and sell customers' browsing histories without express permission. The signing of the bill into law comes after the Senate and then the House voted to allow ISPs to share customer data without consent. The White House has confirmed that Trump has reversed the Obama-era rules, so closely targeted advertising is now not far away. Since the House vote last week, there has been renewed interest in… [Continue Reading] -

Microsoft releases two cumulative updates for Windows 10 Creators Update
Publié: avril 4, 2017, 10:51am CEST par Mark Wilson
Windows 10 Creators Update is mere days away from release, and ahead of the launch Microsoft has pushed out a couple of cumulative updates. Build 15063.13 is being pushed out to Windows Insiders on the Slow Ring and Release Preview Ring, while those who have opted to participate in the Fast Ring can download build 15063.14. With the full rollout of Creators Update now just a week away, these updates see Microsoft address a handful of last minute issues. So late in the game, there are clearly no major changes or additions to look forward to in the updates, but… [Continue Reading] -

Amazon Cash lets you pay for Amazon shopping with cash rather than a bank card
Publié: avril 3, 2017, 5:21pm CEST par Mark Wilson
Amazon today announced details of Amazon Cash, a new way to shop online that does not require shoppers to have a bank card. The system allows shoppers to print out a barcode -- or display it on the screen of their iOS or Android phone -- and make a payment in brick-and-mortar stores. Launching in the US, Amazon Cash can be used to add money to a customer's Amazon Balance, and a number of big names including CVS Pharmacy, Speedway and Sheetz are among the stores participating in the scheme. There is no fee for using Amazon Cash, and the… [Continue Reading] -

Android is more popular than Windows... for getting online
Publié: avril 3, 2017, 3:35pm CEST par Mark Wilson
We already know that interest in Windows 10 is on the wane, but now Android is more popular than any version of Windows with Internet users. Google's mobile operating system has overtaken Windows as the preference for getting online for the first time. Usage figures published by StatCounter show that Android accounted for 37.93 percent of the worldwide OS Internet usage share in March. Windows is not far behind at 37.91 percent, but Android taking the lead is being described as a "milestone in technology history." The fact that Android is now topping the charts can be attributed to the… [Continue Reading] -

Virginia Tech's DIALDroid shows Android apps steal data through secret collusion
Publié: avril 3, 2017, 2:46pm CEST par Mark Wilson
Researchers from Virginia Tech have found that Android apps can work together to mine personal information from smartphones. While users have long been aware of the need to check the privacy settings and permissions for individual apps, few people will have thought of the potential for collusion between apps that, individually, have innocuous-looking settings. A team from the Department of Computer Science at Virginia Tech's College of Engineering developed a tool called DIALDroid (Database powered ICC AnaLysis for anDroid) and used it to monitor the exchange of data between apps. Analysis of 110,150 apps over three years found that security… [Continue Reading] -

How to find out which of your apps are not compatible with iOS 11
Publié: avril 3, 2017, 1:43pm CEST par Mark Wilson
Last week saw the release of iOS 10.3, and thoughts are already turning to the next major release of Apple's mobile operating system. When iOS 11 launches later this year, it is not expected to support 32-bit apps and this means that a number of apps that have not been updated accordingly will stop working. Built into iOS 10.3 is a tool that can be used to quickly determine which of your apps could die in iOS 11. While it's possible that updates might be released for them, Apple's move away from 32-bit software is far from new, so it's… [Continue Reading] -

Windows 10 users can now download videos from Netflix for offline viewing
Publié: avril 3, 2017, 12:19pm CEST par Mark Wilson
Streaming services like Netflix are proving increasingly popular as fans of television and movies cut the cord and look for on-demand options that better suit their needs. Having previously made it possible for iOS and Android users to download content for offline viewing -- complete with optimized codecs -- Netflix is now doing the same for Windows 10 users. The idea is pretty simple. Netflix acknowledges the fact that subscribers may well want to be able to access their favorite shows when they do not have an Internet connection, and is therefore providing the perfect solution: Download & Go. The… [Continue Reading] -

Apple ditches Imagination Technology and will make its own iPhone GPU chips
Publié: avril 3, 2017, 11:19am CEST par Mark Wilson
In a dramatic announcement, British firm Imagination Technology has revealed that in 15 to 25 months' time Apple will no longer be using its GPU chips. Imagination's graphic chips are used in the iPhone, iPad, iPod, Apple TV and Apple Watch, and the revelation sent the British firm's shares into freefall. Apple will reduce its reliance on Imagination's technology as, the chip-maker explains, it "has asserted that it has been working on a separate, independent graphics design in order to control its products and will be reducing its future reliance on Imagination’s technology." Apple is Imagination's largest customer, and the… [Continue Reading] -

Hacked! New York Post mobile app compromised in security breach
Publié: avril 2, 2017, 10:54am CEST par Mark Wilson
The New York Post suffered a security breach this weekend when its push notification system was compromised. Unknown attackers used the system to send out messages to users of the New York Post mobile app. The hackers sent out messages with strange, cryptic content. One read "Heil President Donald Trump!", while others had a religious or spiritual tone to them, and one quoted a Nirvana lyric. A staff writer at the New York Post, Adrian Chen, took to Twitter to say: "New York Post says their push notification was hacked. Hackers could have really caused some chaos. They actually went… [Continue Reading] -

AT&T, Comcast and Verizon say they won’t sell customers' browsing histories
Publié: avril 1, 2017, 12:14pm CEST par Mark Wilson
Concern has mounted in the US after the Senate and then the House voted to permit ISPs to sell customers' browsing histories and other data without consent. In response to these concerns, major ISPs have spoken out to say they will do no such thing. AT&T, Comcast and Verizon have all published statement that aim to calm fears that may have arisen this week. All three insist they do not sell customer data and have no intention of doing so. Whether customers are convinced by the pleading, however, is a different matter entirely. AT&T's statement from the company's public policy… [Continue Reading] -

Microsoft is shutting down open source repository CodePlex, offers GitHub migration tool
Publié: avril 1, 2017, 11:22am CEST par Mark Wilson
Microsoft is closing down CodePlex on December 15, 2017. The company says that its repository for open source software projects has seen a dramatic fall in usage, and points to GitHub as the "de facto place for open source sharing." With 11 years of service under its belt, CodePlex is not just giving way to GitHub, Microsoft is actively recommending migrating to the renowned service -- and is making it easy to do so. CodePlex usage has really plummeted. Microsoft says that in the last 30 days, fewer than 350 projects saw a source code commit. In short, explains the… [Continue Reading] -

Top tips: How to protect your privacy against ISP snooping
Publié: mars 31, 2017, 5:12pm CEST par Mark Wilson
We live in an age where privacy is valued incredibly highly, but at the same time there are more and more ways for our privacy to be encroached upon. One of the most recent concerns came after the US Senate voted last week to allow ISPs to sell customers' browsing histories without consent. Things were turned up a notch a couple of days ago when the House agreed and voted to repeal FCC-approved privacy rules. Since the result of the vote was known, there have been reports of a huge surge in interest in VPN tools, private search engines and… [Continue Reading] -

Google, Microsoft and Apple will stick to their climate goals in spite of Trump's environmental views
Publié: mars 31, 2017, 3:57pm CEST par Mark Wilson
Earlier this week, Donald Trump signed an executive order that effectively killed Obama-era environmental policies. Expressing his love of "clean coal" -- despite such a substance not actually existing -- Trump wiped out Obama orders that aimed to reduce carbon production and signalled an "end to the war on coal." The signing of the executive order was met with astonishment around the world, and many voices have spoken out against the wisdom of the move. Among those are technology companies, many of whom have said that they will stick to promises they have made to tackling climate change -- something… [Continue Reading] -

WikiLeaks releases Marble source code, used by the CIA to hide the source of malware it deployed
Publié: mars 31, 2017, 12:51pm CEST par Mark Wilson
Today, WikiLeaks publishes the third installment of its Vault 7 CIA leaks. We've already had the Year Zero files which revealed a number of exploits for popular hardware and software, and the Dark Matter batch which focused on Mac and iPhone exploits. Now we have Marble to look at. A collection of 676 source code files, the Marble cache reveals details of the CIA's Marble Framework tool, used to hide the true source of CIA malware, and sometimes going as far as appearing to originate from countries other than the US. The source code for Marble Framework is tiny --… [Continue Reading] -

Microsoft, Google, Twitter and Facebook to work with UK government to tackle extremist content
Publié: mars 31, 2017, 12:01pm CEST par Mark Wilson
Following UK home secretary Amber Rudd's suggestion that encrypted messaging service WhatsApp was 'a secret place to hide' for terrorists, four major technology companies met with the minister to discuss the removal of extremist material from websites and social media. Microsoft, Google, Twitter and Facebook met with Rudd amid calls from civil liberties groups for greater transparency. Following the meeting, senior executives from each company signed a statement indicating that they are ready to work with the government to tackle the problem. The matter of backdoors into encrypted apps and services, however, remained off the table. In the joint statement,… [Continue Reading] -

Google is pushing developers to embrace the Galaxy S8's 18.5:9 aspect ratio
Publié: mars 30, 2017, 7:44pm CEST par Mark Wilson
There has been something of a trend in recent years for phones to grow taller and slimmer. Aspect ratios are changing, and the familiar 16:9 is being met by the LG G6's 18:9 (oh, ok, 2:1) and, in the case of the Samsung Galaxy S8, 18.5:9. Google sees these emerging aspect ratios as the start of a trend rather than obscure rarities, and it's encouraging developers to embrace them fully. The new "super widescreen" aspect ratios are being used, according to Google, "to deliver more engaging viewing experiences." The arrival of these new screen sizes is described as "Android OEMs… [Continue Reading] -

Secure messaging app Telegram gains end-to-end encrypted voice calls
Publié: mars 30, 2017, 7:20pm CEST par Mark Wilson
In an age of constant surveillance and eroding privacy, there is increasing interest in secure messaging platforms such as WhatsApp and Telegram. While Telegram has gained quite a following, there is one feature that users have been begging for: voice calls. Now users' prayers have been answered. The latest update to Telegram finally heralds the arrival of secure voice calling, and it features an interesting key exchange mechanism: users need just compare four emoji. If the emoji match, the connection is secure! Audio quality is kept as high as possible not only through the use of the best codecs, but… [Continue Reading] -

Twitter tweaks replies to give you more characters and greater clarity
Publié: mars 30, 2017, 6:39pm CEST par Mark Wilson
Recent changes at Twitter have focused mainly on clamping down on abuse and trolling, but there have also been adjustment tweaks that allow users to send longer messages. Now the site is introducing another change that effectively means you are able to send longer replies to people. The latest change does not mean that you are given more than 140 characters to play with, but the 140 character limit is now put to better use. In short, all 140 characters are available for you to reply with as @usernames no longer count towards the total. This simple tweak will have… [Continue Reading] -

There's also a Samsung Galaxy S8 and S8+ Microsoft Edition available to pre-order
Publié: mars 30, 2017, 5:10pm CEST par Mark Wilson
Yesterday's Samsung Galaxy S8 and S8+ announcement held few surprises (with the possible exception of Samsung DeX) thanks to all of the leaks ahead of the event. But something we didn’t find out until today is that there is a customized Microsoft Edition of the handset available too. Not only will there be a Samsung Galaxy S8 Microsoft Edition and a Samsung Galaxy S8+ Microsoft Edition, but the smartphones will be available to buy direct from Microsoft. Pre-orders start today, but only in Microsoft's US retail stores. Quite whether people are interested in a Microsoft-customized version of Samsung's flagship phone… [Continue Reading] -

Facebook introduces 'personal fundraisers' so you can raise money for yourself
Publié: mars 30, 2017, 4:44pm CEST par Mark Wilson
If you need money for something, you might think about using a service such as GoFundMe to ask people to donate cash to you. But now you can turn to Facebook instead, as the social network launches a new "personal fundraiser" feature, as well as Donate buttons in Facebook Live for Pages. As the name suggests, a personal fundraiser is a way for individuals to raise money for themselves -- or someone they know. To start with, Facebook says that it is only possible to raise money for "critical financial needs" that fall under one of six headings, but this… [Continue Reading] -

Calls for transparency as UK government meets technology firms to discuss encryption and privacy
Publié: mars 30, 2017, 12:30pm CEST par Mark Wilson
The UK Home Secretary Amber Rudd is today meeting with technology firms to discuss how they can help to combat terrorism. The meeting comes just days after Rudd said that encrypted messaging services such as WhatsApp should not be a "secret place to hide." Calls for backdoors to be built into encrypted apps and services have been met with shock, derision and incredulity, but some have pointed out that the controversial Investigatory Powers Act (aka the snooper's charter) already grants the government the right to force the removal of encryption. Ahead of the Rudd's meeting, civil liberty organizations have written… [Continue Reading] -

Plex Pass Perks give you money-off deals through special promotions
Publié: mars 30, 2017, 11:12am CEST par Mark Wilson
For anyone looking to stream music and movies around their home to various devices, Plex is a solid media server solution that won’t hurt your pocket; it's free! But things are about to get even better for Plex Pass subscribers thanks to the arrival of the Plex Pass Perks hub. Depending on where you are in the world, you might be able to bag yourself a discounted external hard drive or NAS to use with your server, and there is the promise that new deals will be added all the time. The Plex Pass Perks hub provides a one-stop-shop for… [Continue Reading] -

Google Calendar finally arrives as an iPad app
Publié: mars 30, 2017, 10:42am CEST par Mark Wilson
It has been a long time coming. A very long time coming. But -- finally -- there is an iPad-optimized version of the Google Calendar app available. Let joy be unbounded! It has taken a full two years for Google developers to pull their fingers out and create a version of the app that is not designed just for iPhones. Google Calendar for iPad takes full advantage of the increased screen real estate, and supports Split View. The arrival of the iPad version of the app will come as great news for anyone who is sick of getting by with… [Continue Reading] -

Samsung DeX lets Galaxy S8 and S8+ owners turn their smartphones into a desktop
Publié: mars 29, 2017, 5:39pm CEST par Mark Wilson
It's something that Microsoft has already tried with Continuum, and now Samsung is ready to give it a bash: transforming a smartphone into a desktop. For the South Korean company, today's events in NYC and London are primarily about the launch of the Galaxy S8 and Galaxy S8+, but this is certainly not all that's being revealed. The company also spoke about Samsung DeX, described as a way of "extending the smartphone to a desktop environment." What this means is that, with a DeX Station, Galaxy S8 and S8+ owners can transform their smartphones into a desktop system that can… [Continue Reading] -

Apple catches up with Google and allows developers to reply to reviews in the App Store
Publié: mars 29, 2017, 5:06pm CEST par Mark Wilson
With the launch of iOS 10.3 and macOS 10.12.4, there was great excitement about the arrival of a new file system as well as improvements to performance -- even if they were only perceived improvements. Something that didn’t get a great deal of attention, however, is the introduction of replies to reviews. Just as has been an option in Google Play for years, developers can now respond to the reviews that people leave about their apps and games. It's something that has been a very long time coming, and finally brings a dialog to the App Store, meaning that users… [Continue Reading] -

Google Wifi and Home to launch in the UK -- with a few hidden British treats
Publié: mars 28, 2017, 2:40pm CEST par Mark Wilson
After launching in the US late last year, Google Home is making its way to the UK. Google's voice-activated rival to the Amazon Echo is powered by Google Assistant, and can be used to play music, control smart devices, and perform online searches. Also making its way to the UK is Google Wifi, the company's mesh Wi-Fi service that helps to ensure there are no wireless blackspots in the home. As well as giving uninterrupted internet access throughout the house, Google Wifi also features parental control options that can be used to stop kids from overindulging on their phones and… [Continue Reading] -

Beat the rush: upgrade to Windows 10 Creators Update RTM right now!
Publié: mars 28, 2017, 12:09pm CEST par Mark Wilson
A week ago saw the release of Build 15063 of Windows 10 and just a few days later we learned that this is in fact the RTM build of Windows 10 Creators Update that will start to roll out in April. While the roll out starts next month, it is expected to take some time to reach everyone, but there's no need to wait! There are a couple of ways you can upgrade to Windows 10 Creators Update right now -- you can either download the ISOs that Microsoft has made available, or you can use the Update Assistant tool… [Continue Reading] -

Facebook Messenger now lets you share your location for an hour at a time
Publié: mars 27, 2017, 5:51pm CEST par Mark Wilson
Facebook is introducing a new feature to its Messenger app for iOS and Android that makes it possible to share your current location with contacts. It is also possible to share other static locations to enable you to point out places on a map. With Facebook and location-sharing mentioned in the same sentence, there will be obvious concerns about privacy. To try to allay these fears, the current location is only shared for a maximum of an hour, and can be manually stopped at any time before the countdown reaches zero. Introducing the arrival of the new feature, Facebook Messenger's… [Continue Reading] -

Microsoft hit with lawsuit alleging Windows 10 upgrades 'destroyed people's data and damaged PCs'
Publié: mars 27, 2017, 4:55pm CEST par Mark Wilson
Windows 10 has certainly not been short of controversy. Between forced upgrades, telemetry and privacy concerns, and the introduction of increasing numbers of ads, Microsoft has been on the receiving end of a good deal of criticism for the latest version of its operating system. And the trouble is not over. With the launch of Windows 10 Creators Update just around the corner, Microsoft faces a lawsuit from three people from Illinois who claim that the upgrade not only resulted in data loss, but also damaged their computers. The lawsuit makes reference to the difficulty many users found in declining… [Continue Reading] -

Microsoft's Docs.com search feature leaks sensitive files
Publié: mars 27, 2017, 2:21pm CEST par Mark Wilson
Users of Microsoft's Docs.com website took to Twitter to complain after files marked as private were made public by the sites' search function. In response, Microsoft pulled the search feature from the site, but it is now back up and running. Even during the time it was not possible to search the site directly, Google and Bing searches could still be conducted to reveal social security numbers, job applications, contact details, and other private information. While it is possible to mark files as private or public, it appears that the owners of files exposed over the weekend were under the… [Continue Reading] -

Encrypted messaging service WhatsApp criticized as 'a secret place to hide' for terrorists
Publié: mars 27, 2017, 1:00pm CEST par Mark Wilson
WhatsApp has been criticized for failing to help police following the revelation that Khalid Masood used the encrypted messaging service shortly before running down numerous people and stabbing a policeman to death in London last week. The UK home secretary Amber Rudd spoke out over the weekend, saying that police and other agencies should be granted access to encrypted messages with a view to countering future terrorist attacks. Later this week, Rudd is due to meet with technology leaders to talk about how the government should be able to access messages protected by end-to-end encryption -- something already dropped from… [Continue Reading] -

Google introduces 'Free App of the Week' to Play Store
Publié: mars 27, 2017, 10:26am CEST par Mark Wilson
The best price tag to find on anything is one that reads "Free", and Google has introduced a new section to the Play Store with this in mind. The new "Free App of the Week" section does very much what you would expect -- slashes the price of a paid-for app to zero. Great news for Android users! It's an idea that Apple has experienced great success with, and it's a quick and easy way for Google to increase engagement in its app store. The first free app is Cartoon Network's Card Wars --Adventure Time which normally retails for $2.99.… [Continue Reading] -

T-Mobile to roll out network-level scam call protection features: Scam ID and Scam Block
Publié: mars 25, 2017, 7:04pm CET par Mark Wilson
Spam in your inbox and via SMS is one thing, but fairly easy to ignore. Spam phone calls, on the other hand, are not only annoying, but are frequently used to try to scam people out of money. T-Mobile is about to roll out a solution. As part of an upgrade to its network, the carrier is introducing Scam ID and Scam Block which will be used to alert customer to potential scam calls, and to block known malicious callers. As these features are being rolled out on a network level, it should be available to all T-Mobile customers starting… [Continue Reading] -

Samsung is finally ready to remotely kill the Galaxy Note7
Publié: mars 25, 2017, 6:31pm CET par Mark Wilson
Samsung would almost certainly prefer people to be concentrating on the upcoming Galaxy S8 and virtual assistant Bixby, but the disastrous Galaxy Note7 is still etched in memories. After the phones kept catching fire due to a battery problem, the Korean company started to push out OTA updates to cripple them slightly. But this and even a ban on taking the handsets on flights, was not enough to discourage everyone from using their Note7. Now, in a bid to complete kill of the troublesome phone, Samsung is pushing out another update that completely disables charging. If this sounds familiar, it's… [Continue Reading] -

Privacy warning: US ISPs could sell and share your browsing history without consent
Publié: mars 24, 2017, 12:11pm CET par Mark Wilson
In a major blow for privacy advocates and individual rights, the US Senate has voted to permit ISPs to sell or share customers' data -- including their browsing histories -- without consent. The vote overturns a Federal Communications Commission rule that banned such activity. While there are still legislative hoops to jump through before the result of the vote is ratified, ISPs will be rubbing their hands in glee at what the Senate has done. The Republican-controlled House will now need to conduct its own vote on the rule before the existing rule banning the sale and sharing of such… [Continue Reading] -

Instagram ups security with two-factor authentication
Publié: mars 24, 2017, 11:46am CET par Mark Wilson
Just about every app and online service offer two-factor authentication (2FA) as a security measure these days, and Instagram is the latest to join the party. After numerous instances of hacking for other services, it's little surprise that Instagram wants to offer its users an extra level of protection. Once enabled, users are required to enter a six-digit code that is sent to their mobile via SMS, greatly eliminating the risk of unauthorized access. If you want to take advance of the new feature -- which is disabled by default -- there's no need to wait to download an update… [Continue Reading] -

Apple says it has already fixed CIA's Mac and iPhone hacks revealed by WikiLeaks
Publié: mars 24, 2017, 10:55am CET par Mark Wilson
Yesterday WikiLeaks published the second batch of its Vault 7 documents, Dark Matter, revealing information about Apple-related hacks used by the CIA. This time around, the documents focus on hacks for MacBooks and iPhones, and comes two weeks after the initial batch of documents came to light. Apple previously said that it had addressed "many of the issues" from the first Vault 7 leaks, and now the company has said much the same regarding the second batch. Despite promises from Julian Assange, it seems that WikiLeaks has not been in contact with Apple to provide further details about the exposed… [Continue Reading] -

Windows 10 Creators Update RTM is Build 15063 confirms leaked Update Assistant
Publié: mars 24, 2017, 10:15am CET par Mark Wilson
It is only three days since Windows 10 Creators Update Build 15063 arrived on the Fast ring. The same build has already made its way to Insiders on the Slow ring as well, fueling understandable speculation that this could well be the final build. This does in fact appear to be the case. We already know that Microsoft is due to release Windows 10 Creators Update in April, and a leaked Update Assistant tool shows that Build 15063 is indeed the RTM build number. The Update Assistant was pushed out into the limelight by serial leaker and Microsoft fan WalkingCat.… [Continue Reading] -

WikiLeaks' Dark Matter documents reveal CIA hacks for Macs and iPhones
Publié: mars 23, 2017, 8:58pm CET par Mark Wilson
It's only a couple of weeks since WikiLeaks unleashed the first batch of its Vault 7 CIA documents, revealing the agency's spying and hacking capabilities. Now the organization has released a second cache of files dubbed Dark Matter, and they show that the CIA has developed tools for hacking Apple products. Bold and exciting names like Sonic Screwdriver, DerStarke, Triton and DarkSeaSkies are the monikers given to attack the firmware of MacBooks and iPhones. What's particularly interesting about the documents is that they appear to show that the CIA had the ability to exploit Apple hardware and software a full… [Continue Reading] -

US companies start to pull ads from Google and YouTube over extremist content controversy
Publié: mars 23, 2017, 5:31pm CET par Mark Wilson
Last week saw the start of a backlash against Google after advertisers voiced concern that their ads were appearing next to extremist content. The Guardian, the BBC and the British government were among the first to start to pull their ads from the network, and the trend has spread to the US. AT&T and Verizon are among American companies that have now announced that they are boycotting YouTube by pulling their ads. After concerns about being associated with terrorist and other extremist content, an increasing number of big names are calling on Google to make guarantees about ad placement. In… [Continue Reading] -

Facebook Messenger borrows from Slack with Reactions and mentions
Publié: mars 23, 2017, 4:52pm CET par Mark Wilson
Facebook is not shy about stealing features from other messaging tools, and it's usually Snapchat that is used as inspiration. With the latest update to Facebook Messenger, it's Slack that is being borrowed from. Today Facebook Messenger gets two new features: Reactions and mentions. These work in very much the way you would expect, and Reactions make a successful transition from the Facebook newsfeed to Messenger after having made a brief appearance to a testing group recently. Just like on your timeline, the appearance of Reactions in Facebook Messenger means that you are now able to react to individual messages… [Continue Reading] -

Apple buys automation tool Workflow, tweaks some features, and offers it to iOS users for free
Publié: mars 23, 2017, 4:36pm CET par Mark Wilson
Automation tools like IFTTT continue to be popular, and as if to prove this, Apple has just bought the iOS app Workflow. Working in a similar way to Automator for macOS, Workflow brings task-oriented automation to iPhone and iPad users. There's good news to top off the acquisition revelation. Apple is not only keeping Workflow up and running rather than shutting it down, it's also hanging onto the original team of developers behind the app. Even better, Apple is making Workflow available free of charge, dropping the previous $2.99 price tag. Financial details of the arrangement have not yet been… [Continue Reading] -

DoubleAgent exploit uses Windows' Microsoft Application Verifier to hijack antivirus software
Publié: mars 22, 2017, 8:48pm CET par Mark Wilson
Security researchers at Cybellum have revealed details of a zero-day exploit that makes it possible for an attacker to take full control of antivirus software. The technique can be used to take control of just about any application, but by focusing on antivirus tools, the illusion of safety offered to victims means they are likely to be completely unaware of what is happening. The attack works by exploiting the Microsoft Application Verifier that's built into Windows. It is possible to replace the tool with a custom verifier which can then be used to inject malicious code into any chosen application.… [Continue Reading] -

Now you can broadcast live to Facebook from your desktop or your favorite games
Publié: mars 22, 2017, 6:31pm CET par Mark Wilson
Facebook Live has been with us for a little while now, but it has been limited by the fact that it has only been possible to broadcast from mobile devices. Today this changes as Facebook opens up broadcasting to desktop and laptop users too. On top of this, Facebook is adding the ability to stream from other software or external hardware. This has many uses, but the social network suggests that gamers might like to use it to broadcast their gaming sessions live online. Using Facebook Live on the desktop is not really any different to using it on a… [Continue Reading] -

New Google report shows Android security is improving
Publié: mars 22, 2017, 5:27pm CET par Mark Wilson
Today Google published its third annual Android Security Year in Review, the day after the launch of the developer preview of Android O. Looking back at 2016, the report details the steps the company has taken to keep Android users and their data safe. Google cites a crackdown on Potentially Harmful Apps as a particular success, and points to the fact that security updates have been issued to 735 million devices. But it’s not all good news. Many of the security improvements are to be found in Android 7 Nougat which is only available on a limited number of devices.… [Continue Reading] -

What's new in Android O?
Publié: mars 22, 2017, 1:43pm CET par Mark Wilson
We might not know exactly what Android O is going to be called, or exactly when it will be released, but the arrival of the developer preview means that we now have a hint of what to expect from the next version of Google's mobile operating system. For now, Android O can only be installed on Nexus and Pixel devices, but further down the line this will change. So what is there to look forward to? Quite a lot as it turns out: battery and data saving, improved notifications, new lockscreen shortcuts, customizable navigation bar, and more! While CPU performance… [Continue Reading] -

Microsoft completes modified version of Windows 10 for Chinese government
Publié: mars 22, 2017, 12:42pm CET par Mark Wilson
Microsoft could be on the verge of making greater headway in China after completing a modified version of Windows 10 for the Chinese government. The operating system has been banned for governmental use for some time despite the fact it is already available to consumers in the country. A joint venture with state-owned China Electronics Technology Group, Microsoft's modifications are now awaiting government approval. While details of the included changes are not being released, China's concerns about other nations implementing surveillance through the software will almost certainly have been a key factor. As reported by Morningstar, development is complete and… [Continue Reading] -

US bans laptops and tablets on flights from eight countries in Africa and the Middle East
Publié: mars 21, 2017, 12:33pm CET par Mark Wilson
Not content with its second crack of the whip with a travel ban, the Trump administration has now issued a ban on larger electronic devices being taken on flights from certain countries. Devices larger than a cell phone will not be permitted in cabin baggage but must instead be checked in. The ban is set to run indefinitely, and means that laptops, tablets, portable DVD players, ebook readers, portable games consoles and other larger electronic devices will be banished to the holds of aircraft. While the ban focuses on individual airports rather than countries, it has been noted that they… [Continue Reading] -

Microsoft teams up with Adobe to create an industry standard for marketing, sales and services data
Publié: mars 21, 2017, 11:10am CET par Mark Wilson
Adobe and Microsoft are joining forces to create new solutions for marketing, sales and services. Microsoft Dynamics and Adobe Experience Cloud will work with a shared data format to allow the two systems to work side by side together. Ahead of today's Adobe Summit, the two companies revealed their plans to collaborate on another project: creating a new industry standard data model. By standardizing data structure, it is hoped that data can be gathered and processed from customers more quickly, and in-depth data analysis can be performed more efficiently. Microsoft's executive vice president, Scott Guthrie says: "We believe the combined… [Continue Reading] -

Google says it will 'raise the bar' for ad policies after controversy over extremist content
Publié: mars 21, 2017, 10:40am CET par Mark Wilson
Google has announced plans to introduce safeguards for advertisers after complaints from many big names that their advertisements were appearing next to extremist content. The Guardian, the BBC, and the UK government are among those to have withdrawn advertising from Google and YouTube, and the company has been battling to get companies back on side. Google's Chief Business Officer, Philipp Schindler, has admitted that while there are policies in place controlling the ad network, "at times we don’t get it right." He says he understands that advertisers don't want their ads to appear next to content that is not in… [Continue Reading] -

Ahead of the Galaxy S8 launch, Samsung officially announces its virtual assistant, Bixby
Publié: mars 20, 2017, 4:25pm CET par Mark Wilson
There have been so many leaks about Samsung's upcoming Galaxy S8 that, come launch day, there will be nothing new to learn. One of the features that slipped out a little earlier than planned was news of Samsung's own virtual assistant called Bixby. Now Samsung has officially unveiled its take on Siri and Cortana. Drawing on artificial intelligence and deep learning, Samsung describes Bixby as "a new intelligent interface." But what makes Bixby any better, or different, than any other virtual assistant on the market? Samsung says that "completeness", "context awareness" and "cognitive tolerance" are the keys to its success.… [Continue Reading] -

Microsoft's Mac to Surface Assistant makes it easier to switch to a Surface
Publié: mars 20, 2017, 2:07pm CET par Mark Wilson
Moving from one operating system to another -- be it Windows to Linux, Mac to Windows or whatever -- can be fraught with tension. Microsoft wants to make life easier for anyone who has decided to ditch their Mac, by releasing the Mac to Surface Assistant to help migrate data to a new Surface Pro, Surface Book or Surface Studio. For some time, Microsoft has featured detailed instructions on the Surface support pages that explain how to backup and transfer different types of data from one computer to another. With the Mac to Surface Assistant, however, all of this is… [Continue Reading] -

WikiLeaks holds tech companies' feet to the fire before helping with zero days revealed in CIA leaks
Publié: mars 20, 2017, 12:26pm CET par Mark Wilson
The CIA's hacking tools leaked in the WikiLeaks Vault 7 disclosure revealed vulnerabilities in a range of popular software titles. Julian Assange has said that his organization will share details of the zero days revealed in the documents with the respective technology companies, but it now transpires that there are certain conditions to meet first. It’s a situation that has more than a slight air of "ransom" to it. Microsoft has initially complained that after the initial leak there had been no contact from either WikiLeaks or the CIA, but it seems that contact has now been made with the… [Continue Reading] -

Google attracts criticism for hiding LGBTQ videos in YouTube's Restricted Mode
Publié: mars 20, 2017, 10:14am CET par Mark Wilson
LGBTQ+ videos are effectively being censored by Google, say a number of high-profile YouTubers. The accusations surround YouTube's Restricted Mode and the belief that this is hiding videos with LGBTQ+ content from view, leading some to suggest that active censorship is taking place. Google says that this limited mode exists to give people the option to avoid "videos that discuss more sensitive issues." The blocking is supposed to be triggered by "community flagging, age restrictions, and other signals," but YouTubers complain that even "innocent" videos that reference same-sex relationships, "queer perspectives" and other LGBTQ+ topics have been restricted. It is… [Continue Reading] -

YouTube kills off video annotations in favor of mobile-friendly Cards and End Screens
Publié: mars 18, 2017, 7:13pm CET par Mark Wilson
Things are changing at YouTube. Having previously announced plans to drop 30-second unskippable ads from videos, Google has now also revealed that it will be dropping another annoyance -- the annotations that blight many videos and distract from the actual content. Annotations have generally been used to link to related material, push merchandize and so on, but there has been something of an issue: annotations are not very mobile-friendly. Google says that Cards (which can be displayed at any point during a video) and End Screens (which, funnily enough, appear at the end) provide the same functionality as annotations, work… [Continue Reading] -

Super Mario Run for Android launches 23 March
Publié: mars 18, 2017, 6:04pm CET par Mark Wilson
It is quite some time since Super Mario Run arrived for iOS and took the world by storm. Right from the start there were questions about when the Android version would appear, and the delay from Nintendo saw the springing up of a batch of malicious fakers. Pre-registration for the Super Mario Run for Android opened up in late-December, and now Nintendo has finally revealed the launch date for one of the most eagerly-awaited Android games of all time. The Android version of Super Mario Run will launch on 23 March -- just days away! Still buoyed by the incredibly… [Continue Reading] -

Facebook, Google and Twitter could face EU legal action for unfair terms and conditions, and failing to tackle scams
Publié: mars 18, 2017, 5:28pm CET par Mark Wilson
Having expressed concerned about privacy in Windows 10 and the scanning of Yahoo emails, the European Commission is now turning its attention to Facebook, Google+ and Twitter. The commission is concerned about a rising number of complaints from people who have fallen victim to scams on social media, and being subjected to terms and conditions that are incompatible with European law. Having already written to the three companies back in November, the European Commission, along with EU consumer authorities, met to discuss how they will move forward. The commission says that if the proposals are unsatisfactory, "enforcement action" may be… [Continue Reading] -

Pakistan risks privacy concerns by asking Facebook and Twitter to identify users suspected of blasphemy
Publié: mars 17, 2017, 1:26pm CET par Mark Wilson
Pakistan is seeking help from Facebook and Twitter to help execute its incredibly strict blasphemy laws. Anyone found guilty of insulting the Prophet Muhammed, or Islam in general, risks being sentenced to death, and the country is keen to track down offenders both at home and abroad. The two social networks have only been asked to identify Pakistanis, but the move is likely to raise concerns about privacy. Of equal concern will be not only what is deemed to be blasphemous, but who makes that judgement -- particularly when Pakistan is seeking to identify offenders in other countries. The country's… [Continue Reading] -

Google scrabbles to appease advertisers after drawing ire for inappropriate ad placements
Publié: mars 17, 2017, 12:17pm CET par Mark Wilson
Yesterday, the Guardian withdrew advertising from Google and YouTube after its ads were placed next to extremist content. The British newspaper was not alone -- broadcaster Channel 4, and even the British government soon followed suit. Now Google is scrabbling to calm down the situation. Advertisers are unhappy that their ads have been placed next to extremist content and hate speech, and Google says it will improve the controls advertisers have over ad placement. At the same time, the company says: "we believe strongly in the freedom of speech and expression on the web -- even when that means we… [Continue Reading] -

The Guardian pulls its ads from Google and YouTube after placement next to extremist material
Publié: mars 16, 2017, 7:51pm CET par Mark Wilson
The Guardian has pulled all of its ads from both Google and YouTube. The British newspaper was unhappy to discover that advertisements for its membership scheme were placed next to extremist material. It is understood that the positioning was accidental, but the Guardian's chief executive described the situation as "completely unacceptable". Ads appeared next to videos for a "hate preacher", American white nationalists, and other controversial content. Google's AdX, DoubleClick Ad Exchange Service, algorithms are thought to be to blame and, in a letter to Google, the Guardian seeks assurances that the problem will not happen again. David Pemsel wrote… [Continue Reading] -

Google Assistant is not coming to tablets
Publié: mars 16, 2017, 4:07pm CET par Mark Wilson
If the rollout of Google Assistant to more devices got you excited as a tablet owner, there's some bad news. Google has confirmed that the handy tool will not be making its way to tablets. Last month the company said that Google Assistant was on its way to all Android smartphones running Marshmallow and above, but didn’t make reference to tablets one way or the other. But now it has been made clear that tablets are not in line for the upgrade -- at least not for the time being. See also: Google Assistant is coming to all smartphones with… [Continue Reading] -

Google pushes out OTA downgrade taking Nexus 6 phone back to Android 7.0
Publié: mars 16, 2017, 11:43am CET par Mark Wilson
Being a Google device, it's not surprising that the Nexus 6 was among the first handsets to receive an upgrade to Android 7.1.1 Nougat. But now the company is pushing out a rare over-the-air downgrade to Android 7.0. When the update arrived, it -- rather understandably -- caused a great deal of confusion as users expect operating systems to progress rather than step back in time. Android 7.1.1 broke Android Pay for Nexus 6 users, and it's thought that this is the reason for the downgrade. But there's some bad news: the downgrade requires a factory reset. Downgrading an operating… [Continue Reading] -

Windows 10 Creators Update may download updates over metered connections even if you don't want it to
Publié: mars 16, 2017, 10:27am CET par Mark Wilson
In the latest Insider build of Windows 10 Creators Update, there has been an interesting change to the way updates are handled. Build 15058 of Microsoft's operating system now handles updates over metered connections differently -- and it could mean that you incur charges. If you pay for your internet bandwidth by the gigabyte (that is, you use a metered connection), you may well be concerned about Windows automatically installing updates and costing you money. In previous builds of Windows 10 it was possible to block automatic updates on a metered connection so you were placed in full control of… [Continue Reading] -

End-to-end encryption exploit left WhatsApp and Telegram vulnerable to hackers
Publié: mars 15, 2017, 1:57pm CET par Mark Wilson
When WikiLeaks' Vault 7 revelations about the spying capabilities and techniques were unleashed, there was concern about a number of popular apps and services that -- the documents suggested -- had been compromised. Included in this list are popular, secure chat apps WhatsApp and Telegram, and Check Point software has just released details of a vulnerability that left millions of user accounts exposed to hackers. Google was recently criticized for releasing details of a security hole in Windows (and, subsequently another one in Internet Explorer and Microsoft Edge) before Microsoft had patched it. In fact, it was a third party… [Continue Reading] -

Updated Skype extension for Chrome brings one-click Skype integration to calendars, emails and Twitter
Publié: mars 13, 2017, 7:39pm CET par Mark Wilson
Microsoft is pushing out an update to its Skype extension for Chrome, bringing a host of new features to a range of online services. The update means that you can add Skype call links to emails, calendar events, and social media postings with a single click. With support for Gmail, Google Inbox, Outlook.com, Google Calendar and Twitter, Microsoft is clearly trying to cover a lot of bases. Twitter is arguably something of a strange choice, but by embracing rival Google services, Microsoft is clearly keen to make Skype more accessible for as many people as possible. The extension brings simple… [Continue Reading] -

Mozilla: people have no idea how to protect their privacy and security online
Publié: mars 13, 2017, 5:32pm CET par Mark Wilson
Privacy and security are major concerns when it comes to life online, but a survey by Mozilla reveals that a worrying number of people do not know how to stay in control of them. The company also found that a third of people feel they have no control over their information online, with a similar number confessing to knowing "very little" about encryption. But these are not the only concerns of internet users. Mozilla also asked about people's greatest online fears. Topping the list is "being hacked by a stranger" (a fear held by 80 percent of people), and "being… [Continue Reading] -

Facebook bans devs from creating surveillance tools with user data
Publié: mars 13, 2017, 4:37pm CET par Mark Wilson
Without a hint of irony, Facebook has told developers that they may not use data from Instagram and Facebook in surveillance tools. The social network says that the practice has long been a contravention of its policies, but it is now tidying up and clarifying the wording of its developer policies. American Civil Liberties Union, Color of Change and the Center for Media Justice put pressure on Facebook after it transpired that data from users' feeds was being gathered and sold on to law enforcement agencies. The re-written developer policy now explicitly states that developers are not allowed to "use… [Continue Reading] -

Microsoft is disgustingly sneaky: Windows 10 isn't an operating system, it's an advertising platform
Publié: mars 12, 2017, 5:40pm CET par Mark Wilson
Don't believe what Microsoft tells you -- Windows 10 is not an operating system. Oh, sure, it has many features that make it look like an operating system, but in reality it is nothing more than a vehicle for advertisements. Since the launch of Windows 10, there have been numerous complaints about ads in various forms. They appear in the Start menu, in the taskbar, in the Action Center, in Explorer, in the Ink Workspace, on the Lock Screen, in the Share tool, in the Windows Store and even in File Explorer. Microsoft has lost its grip on what is… [Continue Reading] -

Worldwide web inventor Tim Berners-Lee's biggest concerns: privacy, fake news and political ads
Publié: mars 12, 2017, 11:52am CET par Mark Wilson
It was 28 years ago that Tim-Berners-Lee submitted his proposal for the worldwide web. What he envisioned as an open platform that would break down global barriers has become a wild beast with endless problems. Talking on the anniversary of his invention, Berners-Lee has spoken about his concerns for the web. He has three problems in his crosshairs, and he says the trio of issues is something "we must tackle in order for the web to fulfil its true potential as a tool that serves all of humanity." But he does not come armed with solutions; it's at least partly… [Continue Reading] -

Intel Security releases EFI rootkit checker for MacBooks after CIA hacking leaks
Publié: mars 11, 2017, 10:15am CET par Mark Wilson
The Vault 7 leaks this week suggest that the CIA has been able to exploit vulnerabilities in a wide range of popular hardware and software, including Windows, macOS and Linux. One of the suggestions is that the agency produced EFI (Extensible Firmware Interface) rootkits for MacBooks called DarkMatter. To help calm the fears of MacBook owners, Intel Security has pushed out a tool to check for such rootkits. Apple issued a statement earlier this week indicating that it had addressed "many of the issues" exposed by WikiLeaks, but Intel Security's further intervention will bring some peace of mind to concerned… [Continue Reading] -

Ever Sentinel notifies you when companies change privacy policies or terms and conditions
Publié: mars 10, 2017, 6:01pm CET par Mark Wilson
Changes to terms and conditions or privacy policies happen all the time, and this presents a few problems for consumers. As well as having to negotiate through the often impenetrable language used in these documents, it can be near impossible to work out what has changed, and what the implications are. This is where Ever Sentinel can help. The service monitors the terms and policies for a number of popular websites and services, and not only alerts you when they change, but highlights exactly what has changed. It's part of a drive to encourage greater transparency in terms and conditions… [Continue Reading] -

iClever Tri-folding Wireless Keyboard with Touchpad IC-BK08 [Review]
Publié: mars 10, 2017, 12:30pm CET par Mark Wilson
Around a year ago I took a look at the iClever Tri-folding Backlit Bluetooth Keyboard, having previously examined the iClever Portable Foldable Bluetooth Keyboard. The latest addition to the range follows in the footsteps of its predecessors, but this time boasts a trackpad. This is a Bluetooth keyboard that can be configured to connect to up to three devices -- phones, tablets, laptops, and so on. The keys are nearly full-sized (just 9 percent smaller than normal), and the right-hand side of the fold-out unit is occupied by a laptop-style trackpad that allows for easier control of the device you… [Continue Reading] -

0patch pushes out another Windows patch, but will leave the real work to Microsoft
Publié: mars 10, 2017, 10:30am CET par Mark Wilson
Last week 0patch produced what was described as the first 0-day patch for Windows in lieu of Microsoft's usual Patch Tuesday release. It came after Google revealed a pair of vulnerabilities affecting IE/Edge and Windows. Having addressed the problem in Windows, 0patch is at it again, this time patching the "type confusion" bug (CVE-2017-0037) that plagues Internet Explorer and Edge. This patch is described as an attempt to "release a simple temporary patch that blocks an attacker than try to create a perfect patch", and it's available for anyone who is willing to place their trust in third-party patching. See… [Continue Reading] -

Plex Cloud lets you access your media when your server is switched off
Publié: mars 10, 2017, 10:03am CET par Mark Wilson
Plex has introduced a new feature that makes it possible to store media files in the cloud. Plex Cloud has been in beta for some time, but it's now available to anyone with a Plex Pass subscription, and it works with Dropbox, Google Drive and OneDrive. The main benefit of this is that media collections can be accessed without the need to keep a Plex server running, but it also serves as an easier introduction to Plex for newcomers. The fact that no hardware needs to be configured is a real boon for anyone who has been put off the… [Continue Reading] -

Google is bringing add-ons to Gmail
Publié: mars 9, 2017, 8:03pm CET par Mark Wilson
It's something that Gmail users have been asking for for ages now -- the ability to use third-party add-ons to extend the capabilities of the email service. Today at its Cloud Next conference in San Francisco, Google announced that plugins that can integrate with Gmail are on their way. While "add-ons" are already around, they exist in the form of browser extensions. What Google is talking about now is native add-ins that are not dependant on Chrome extensions, and will therefore work online in any browser, on just about any device -- including iOS and Android. This will start off… [Continue Reading] -

Julian Assange says WikiLeaks will share CIA hacking tools from Vault 7 with technology companies
Publié: mars 9, 2017, 6:44pm CET par Mark Wilson
Technology companies will be given access to the CIA's hacking tools revealed earlier in the week, Julian Assange said today. The WikiLeaks founder said that full details of the exploits used by the CIA would be shared with a view to allowing companies to patch the security holes. Apple has already said that it has fixed many of the iOS vulnerabilities mentioned in the document cache, and we know that the CIA exploited vulnerabilities in all major operating systems as well as weaponizing numerous popular programs. While WikiLeaks has made certain details of the CIA's hacking tools public, it intends… [Continue Reading] -

Consumer Reports to factor privacy and security into its technology reviews
Publié: mars 8, 2017, 5:54pm CET par Mark Wilson
There is much to consider when buying a piece of technology, but price and suitability tend to be at the top of most people's lists. In recent years, however, there has been an increased interest in privacy and security, and this is something that renown reviewer Consumer Reports is going to start taking into consideration. Consumer Reports most recently hit the headlines for deciding not to recommend the new MacBook Pro (although it later changed its mind), and now the non-profit has teamed up with a number of privacy, security, and consumer rights organizations with a view to creating a… [Continue Reading] -

How to disable ads in File Explorer in Windows 10
Publié: mars 8, 2017, 1:32pm CET par Mark Wilson
Microsoft has used Windows 10 as a vehicle for advertising in a variety of ways over the months since its launch. We've seen ads in the Start menu, via taskbar popups and on the Lock screen; now you can find them in File Explorer. Users have reported the appearance of advertisements for Microsoft's own OneDrive service as they browse the contents of their hard drive(s). You may well think that this is unacceptable, so we'll show you how to disable ads in File Explorer. Even if they haven’t shown up for you yet, there's no harm in taking preventative measures.… [Continue Reading] -

Microsoft and Samsung react to Vault 7 CIA leaks -- Google, Linux Foundation and others remain silent
Publié: mars 8, 2017, 11:46am CET par Mark Wilson
The Vault 7 document and code cache released yesterday by WikiLeaks revealed that many big software companies were being actively exploited by the CIA. Apple, Microsoft, Google, Samsung, and even Linux were all named as having vulnerabilities that could be used for surveillance. Apple was one of the first of the companies mentioned in the documents to speak out and address concerns and security. But while the iPhone manufacturer has quickly indicated that it has fixed "many" of the vulnerabilities, Microsoft and Samsung have merely said they are looking into the issues raised. Other companies and groups mentioned have made… [Continue Reading] -

Apple says it has fixed 'many of the issues' exposed in WikiLeak's CIA hacking data dump
Publié: mars 8, 2017, 11:14am CET par Mark Wilson
Yesterday WikiLeaks unleashed Vault 7 online, revealing a wealth of information about the CIA's hacking tools and techniques. Included in the data dump was the suggestion that the CIA was actively exploiting vulnerabilities in iOS and other software to listen in on people. Apple has responded by saying that "many" of these security holes have been fixed. Importantly, the company is unable to say that all of the vulnerabilities being used -- or that have been historically used -- by the CIA have been addressed, but it does insist that it "will continue work to rapidly address" problems that are… [Continue Reading] -

Take care with Facebook Lite -- it could be stealing your data and installing malicious apps
Publié: mars 7, 2017, 5:17pm CET par Mark Wilson
It's no secret that Facebook can be a real hog, both in terms of data and battery usage. To combat the problem, Facebook released a cut-down version of its mobile app in certain markets called Facebook Lite; it also followed that up more recently with Facebook Messenger Lite. The problem with Facebook Lite is that it's not available everywhere through Google Play. For people keen to get their hands on the app, there are plenty of app repositories online offering it for download. But not all repositories are equal, and some are serving up a tainted version of Facebook Lite… [Continue Reading] -

Vault 7: WikiLeaks reveals CIA's secret hacking tools and spy operations
Publié: mars 7, 2017, 3:24pm CET par Mark Wilson
WikiLeaks has unleashed a treasure trove of data to the internet, exposing information about the CIA's arsenal of hacking tools. Code-named Vault 7, the first data is due to be released in serialized form, starting off with "Year Zero" as part one. A cache of over 8,500 documents and files has been made available via BitTorrent in an encrypted archive. The plan had been to release the password at 9:00am ET today, but when a scheduled online press conference and stream came "under attack" prior to this, the password was released early. Included in the "extraordinary" release are details of… [Continue Reading] -

Facebook asks BBC for sexual images found in Facebook groups; calls police when BBC complies
Publié: mars 7, 2017, 1:06pm CET par Mark Wilson
Facebook, like just about any other social network -- and, indeed, countless websites -- is home to all manner of objectionable and even illegal content. A BBC investigation found that Facebook was failing to remove sexualized images of children from groups after they were reported, calling into question Facebook's moderating procedures. Accounts for convicted pedophiles also remained online after they were reported. When the BBC pointed out to Facebook that less than 20 percent of the reported images were removed, Facebook asked to see the images that were being investigated. When the BBC complied with the request, Facebook reported the… [Continue Reading] -

Mozilla says Trump's revised immigration Executive Order damages the global technology industry
Publié: mars 7, 2017, 11:50am CET par Mark Wilson
When, shortly after his inauguration, Donald Trump signed an Executive Order blocking immigrants from numerous Muslim-majority countries, Mozilla was among those who filed an amicus brief against the move. Now the organization has spoken out against the president's revised travel ban. While the new Executive Order drops Iraq from the list of black-listed countries, immigration is still banned from six countries, and the US refugee program remains suspended. The not-for-profit group says it "damages Mozilla, the United States, and the global technology industry", going on to say that "these restrictions are significant and have created a negative impact to Mozilla and… [Continue Reading] -

Twitch introduces Pulse, a Twitter copy for gamers
Publié: mars 7, 2017, 11:18am CET par Mark Wilson
Just as operating systems borrow ideas from each other, the same is true of social networks -- and just about all sites and services feature social networking elements. Twitch, the streaming video platform for gamers, is copying Twitter and launching a social media feed called Pulse. Described as "a place where streamers can post and engage with all of their followers and the greater Twitch community right from the Twitch front page", Pulse is not just about text updates, but also sharing GIFs. The rollout of Pulse is underway right now, but the spread to everyone will take a few… [Continue Reading] -

Microsoft and Google increase bug bounty payouts
Publié: mars 6, 2017, 7:27pm CET par Mark Wilson
Keen as ever to squash any security issues and bugs that might arise in their software, both Microsoft and Google have announced increases in their bug bounty program payouts. Microsoft has doubled some awards, while Google has used others to make knowing jokes. Two increased rewards from Google include "leet" references. Find a Remote Code Execution bug and you could bag yourself $31,337 (up from $20,000); execute "Unrestricted file system or database access" and you could earn $13,337 (up from $10,000). While Google's increases are permanent, however, Microsoft's are just temporary. Microsoft is doubling Office 365-related big bounty rewards for… [Continue Reading] -

Officials say it's time for the Great Firewall of China to ease up on censorship
Publié: mars 4, 2017, 4:52pm CET par Mark Wilson
The Great Firewall of China is famed for the restrictions it places on what Chinese citizens can access online. If a site provides access to news from the west, conflicts with state propaganda, or criticizes China or its ruling Communist party in any way, it is blocked. But some officials are now suggesting that it's time things changed. The impetus is not a sudden softening of the political agenda, but a suggestion from the leading advisory body the Chinese People’s Political Consultative Conference that censorship is damaging China's progress in terms of the economy and science. Vice-chairman of the body,… [Continue Reading] -

0patch creates a 0-day patch for Windows gdi32.dll vulnerability before Microsoft
Publié: mars 3, 2017, 1:08pm CET par Mark Wilson
Following the revelation of vulnerabilities in Windows, Internet Explorer and Edge by Google, and the delaying of the traditional Patch Tuesday, Microsoft security update practices have been in the spotlight. Google's Project Zero has exposed security issues that Microsoft is yet to fix, so a third party has decided to step in to help out. A new project going by the name of 0patch has created a "0patch" for a zero-day, addressing the Windows gdi32.dll memory disclosure (CVE-2017-0038) yet to be fixed by Microsoft. As the issue is unlikely to receive an official patch until at least the middle of… [Continue Reading] -

Vice President Pence used personal email account for state work, and it was hacked
Publié: mars 3, 2017, 1:07pm CET par Mark Wilson
A new report suggests that Mike Pence not only used a personal email account to handle state business, but also that the email address was hacked. The US Vice President was one of many who were very vocal in denigrating Hillary Clinton for her use of a private email server in the run-up to the election. The Indy Star says that Pence used an AOL email address to conduct public business during his time as governor of Indiana. The report also says that his email account was hacked, with a perpetrator gaining access to it in the middle of last… [Continue Reading] -

Join the beta programs for Google Play Services and Gboard to get early access to new features
Publié: mars 3, 2017, 11:33am CET par Mark Wilson
Beta software provides a great way to get a glimpse into the future and try out new features and options in apps before they reach the masses. Google has just opened up a couple of new beta programs for the Android version of its Gboard keyboard, as well as Google Play Services. Signing up for either of these will give you access to the most bleeding edge features -- but it also means living life on the edge slightly as there is the potential for stability problems. The Google Play Services beta is quite a big one, as this is… [Continue Reading] -

How does Game Mode speed up games in Windows 10 Creators Update?
Publié: mars 3, 2017, 10:56am CET par Mark Wilson
Microsoft has promised that the arrival of Game Mode in Windows 10 Creators Update will improve the performance of games. This sounds great in principle, but how does it work? Microsoft has already said a little about what's going on, but really it has not gone far beyond saying that more processor and GPU cycles will be dedicated to compatible games. But speaking at the Game Developers Conference this week, Xbox Advanced Technology Group's Eric Walston went into a little more detail. As explained by Ars Technica, Windows already does a pretty decent job of throwing the most system resources… [Continue Reading] -

Microsoft's Unified Update Platform means smaller Windows 10 build downloads after Creators Update
Publié: mars 3, 2017, 10:25am CET par Mark Wilson
Back in November, Microsoft started to talk about its Unified Update Platform (UUP), with the promise that differential packages would lead to a reduction in the size of updates for Windows. Now the company has announced that the same technology means new builds of Windows rolling out to Insiders will also be smaller, and it's something everyone will enjoy from later in the year. It's an idea that's not entirely removed from the differential sync technique that's due to arrive in OneDrive -- another change that sees Microsoft reducing bandwidth usage. Smaller Windows Update downloads and smaller sizes for major… [Continue Reading] -

Google Assistant's rollout to Marshmallow and Nougat begins today, and it comes to updated Allo too
Publié: mars 2, 2017, 7:33pm CET par Mark Wilson
Just a few days ago, Google announced that Google Assistant was going to spread to Marshmallow and Nougat smartphones. The wait is already over, as the company has made a follow up announcement in the form of a YouTube video indicating that the rollout starts today. Google previously told us that Google Assistant will first make its way to the US, followed by Australia, Canada, the UK, and then Germany. The assistant's growing repertoire of talents will soon be little more than a long-press of the home button away. As Google Assistant is integrated into Google Play Services, there's no… [Continue Reading] -

Marissa Mayer misses out on Yahoo bonus as true scale of forged cookies security breach is revealed
Publié: mars 2, 2017, 10:35am CET par Mark Wilson
Yahoo CEO Marissa Mayer is not going to receive her annual bonus this year as the company punishes her for failing to react quickly enough to a security breach in 2014. Her bonus is to be shared between staff instead. The security breach, followed by another in 2016 involving the use of forged cookies, meant Yahoo's sale to Verizon had to be renegotiated, slashing millions of dollars from the price. The company has revealed that around 32 million user accounts were accessed using forged cookies, and while this is nothing like the 500 million accounts affected by the 2014 breach,… [Continue Reading] -

Microsoft renames Windows Holographic to Windows Mixed Reality as dev kits start to ship
Publié: mars 2, 2017, 10:21am CET par Mark Wilson
It seems like a little while since we heard anything about Windows Holographic, and that's not something that's going to change any time soon. Microsoft is not killing off the project (and HoloLens lives on), but has revealed that it is now going under a new, more descriptive name: Windows Mixed Reality. The company says that the change of name is a reflection of the fact that there is a broader vision for the platform. It also helps to convey the idea of virtual-reality-meets-augmented-reality that Windows Holographic/Windows Mixed Reality represents. Microsoft also says that the Acer Windows Mixed Reality Development… [Continue Reading] -

Google increases Gmail attachment limit to 50MB for recipients
Publié: mars 2, 2017, 10:18am CET par Mark Wilson
Over the years, as the number of megapixels boasted by cameras spirals upwards, file sizes have generally increased. Despite this, many email providers still place a strangely low limit on the size of files that can be sent and received as attachments. With Gmail you can now receive attachments up to 50MB in size. It's important to note that the new attachment limit only applies to incoming email. Google would much rather you make use of Google Drive if you want to send large files to people. When it comes to sending files, you are limited to attaching up to… [Continue Reading] -

Twitter cracks down on eggs as part of its anti-abuse measures
Publié: mars 1, 2017, 7:52pm CET par Mark Wilson
Twitter's assault on abusive accounts and its famous problem with trolling was stepped up a gear today as the company announced a series of new measures designed to crack down on harassment. Having recently introduced account timeouts and refinements to blocking and muting, the company today said it was making it possible to block tweets from Twitter eggs -- those with no profile picture which therefore default to an image of an egg. Other filtering options are available, and algorithms are to be used to automatically identify abusive content. The ability to silence egg accounts is something that will be… [Continue Reading] -

Facebook ramps up its suicide prevention tools and Messenger chat support
Publié: mars 1, 2017, 12:46pm CET par Mark Wilson
Facebook is updating the tools it offers to help try to prevent suicide. Aimed both at those thinking of suicide, and friends and family who are concerned about loved ones, the revamped support tools make use of artificial intelligence and real people to offer help when it is needed most. This is not the first we have heard about suicide prevention tools from Facebook, and the latest announcement sees the social network taking its "unique position" even more seriously, seeing it as a way to offer help and a means of intervention. It comes after a number of suicides have… [Continue Reading] -

Google integrates Keep into Docs and welcomes it to the G Suite fold
Publié: mars 1, 2017, 12:20pm CET par Mark Wilson
Google Keep may not be something that is used by a huge number of people, but that could be about to change. Google is finally doing something that should have happened from the start -- bringing Keep to G Suite to allow for integration with Docs. The company has taken the decision to boost its notetaking app to a key member of its cloud app lineup. Google says that as well as being a G Suite core service when used within a domain, Keep notes can also be accessed from within Google Docs. Announcing the change, the company says: "As… [Continue Reading] -

Google has no plans for a new Pixel laptop at the moment... maybe
Publié: mars 1, 2017, 11:32am CET par Mark Wilson
At a meeting with journalists at MWC 2017 in Barcelona, Google's hardware chief, Rick Osterloh, said there are no plans to release any more premium Pixel laptops. We may have seen the last of Google's top-of-the-range Chromebook. The Pixel name is these days reserved solely for Google range of smartphones. These have proved so popular that the company has struggled to meet demand -- something that also blighted the Nexus phone launched in the past. But in an interesting piece of backpedaling, TechCrunch was later contacted by Osterloh who wanted to clarify things a little: "Regarding the future of Google-branded… [Continue Reading] -

Google Play now ranks games according to engagement, not just downloads, and sale prices are go!
Publié: mars 1, 2017, 10:51am CET par Mark Wilson
Google has announced a few changes to the Play Store, one of which means that listings for games will be promoted not based solely on the number of downloads. The company is tweaking its algorithms to take into account how much time is spent playing games -- so a game which achieves large numbers of downloads but isn’t played much will drop down the rankings. Another change that has been a long time coming is the option for developers to list sale prices for their apps and games. While it was previously possible to manually change the price of a… [Continue Reading] -

Microsoft to launch Xbox Game Pass -- $9.99 a month for unlimited access to over 100 games
Publié: février 28, 2017, 4:31pm CET par Mark Wilson
Gaming can be an expensive business, with games often costing $60. Starting later this spring, however, things are set to get cheaper. Microsoft is about to launch Xbox Game Pass, a $9.99 per month subscription that gives unlimited access to over 100 Xbox One and Xbox 360 games. Fears that this might just mean access to a substandard set of titles appear to be unfounded -- games such as Halo 5: Guardians, Payday 2, NBA 2K16 and SoulCalibur II are to be found on the list. Microsoft is quick to stress that this is not a streaming service; subscribers will… [Continue Reading] -

Facebook is taking more notice of Reactions than Likes to control your News Feed content
Publié: février 28, 2017, 4:07pm CET par Mark Wilson
When Facebook first introduced Reactions users were pleased to finally have the chance to be more expressive, rather than simply 'liking' something. But the excitement soon waned when the social network revealed that it didn’t make any difference which Reaction users clicked -- it was simply registered as an interaction. But now Facebook has revealed that the Reaction you have to individual posts has a greater influence over what appears in your News Feed. A Like registers as a Like, but if you react with Love, Wow, Angry or one of the other reactions, Facebook notes that this is a… [Continue Reading] -

Like Google, Samsung is ready to further embrace RCS messaging
Publié: février 28, 2017, 12:38pm CET par Mark Wilson
It is really starting to feel as though the days of SMS and MMS are well and truly numbered. Google has already updated its Messenger app, renaming it Android Messages as it aims to branch out into Rich Communication Services, and now Samsung has announced that it's ready to jump in too. After new tablet announcements at MWC 2017, Samsung says that its acquisition of NewNet Communication Technologies' RCS solution means it is ready to expand its messaging services. Samsung's embracing of RCS will bring features such as group messaging, file transfers and video calls to users and Samsung says… [Continue Reading] -

Mozilla acquires Pocket developer Read It Later for undisclosed sum
Publié: février 28, 2017, 11:45am CET par Mark Wilson
Mozilla Corporation has loosened its purse strings and splashed an undisclosed sum of money on buying Read It Later, the company behind web service and browser plugin Pocket. Described as the company's "first strategic acquisition", Mozilla's purchase of Pocket is part of a drive to promote the discoverability and accessibility of online content. Read It Later will clearly benefit from Mozilla's acquisition, and the Firefox producer says that the developer will also help to accelerate its Context Graph initiative. The acquisition means that Pocket will become a wholly owned subsidiary of Mozilla Corporation and will also become part of the… [Continue Reading] -

Genymotion On Demand is a cloud-based virtualized Android emulator for the enterprise
Publié: février 27, 2017, 7:56pm CET par Mark Wilson
Genymobile, the company behind the Android emulator Genymotion, has announced a new cloud-based virtualization platform aimed at Android developers. Running on Amazon Web Services, Genymotion On Demand offers access to the full Android operating environment online. Billed by the hour, Genymotion On Demand gives enterprise devs the opportunity to try out apps in the cloud and extend existing services into the cloud. With no contract, the service offers an affordable entry point into virtual Android devices. Genymobile envisions the service being used by help desks as it's easy to quickly create a system that matches that of a customer. It… [Continue Reading] -

MWC 2017: Samsung Galaxy S7 edge is the best smartphone
Publié: février 27, 2017, 6:39pm CET par Mark Wilson
Samsung's Galaxy S7 edge is the best smartphone; at least that’s the view of judges announced at Mobile World Congress 2017. Samsung has already unveiled a couple of tablets to bolster its Galaxy range as well as teased the Galaxy S8 at MWC 2017, but with the stink of the Note7 fiasco still hanging heavy in the air, the company is clearly keen to shout positive news from the rooftops. The Best Smartphone label was slapped on the Galaxy S7 edge by GSMA, the trade body that represents mobile operators around the world. This might be the view of the… [Continue Reading] -

Samsung's teaser video reveals little about the Galaxy S8
Publié: février 27, 2017, 5:45pm CET par Mark Wilson
Not content with showering us with tablets in the form of the Galaxy Book and the Galaxy Tab S3, Samsung also used yesterday's announcements at MWC 2017 to tease us about the keenly awaited Galaxy S8 smartphone. At the event in Barcelona we were treated to teaser video which questions whether we know what a smartphone looks like. While we don’t get to see the Galaxy S8 (or, indeed, the Galaxy S8+) in the video, we do learn that the phone will be unveiled on 29 March, and the stark graphics hint at elements of the design -- which we… [Continue Reading] -

Samsung Galaxy Tab S3 is the first interesting Android tablet in ages
Publié: février 27, 2017, 4:31pm CET par Mark Wilson
At MWC 2017 we were treated to the arrival of the Samsung Galaxy Book, but this was not the only announcement from the company still waiting to launch the Galaxy S8. Continuing to add to its Galaxy range, Samsung also officially unveiled the Galaxy Tab S3 -- and it looks pretty special. As the 9.7-inch tablet comes equipped with an S Pen, it is somewhat reminiscent of a large Galaxy Note. The high-quality glass and metal build puts the tablet on a par with Apple's iPad, and audiophiles will be pleased to see the inclusion of quad-stereo speakers from AKG.… [Continue Reading] -

How to block the installation of non-Windows Store apps in Windows 10
Publié: février 27, 2017, 11:19am CET par Mark Wilson
If you want to keep your computer secure and clutter-free, it's important to keep an eye on what gets installed. This is fairly easy if you're the only person to use your computer, but less so if you share it with kids or other members of your household. To make it easier to lock down Windows 10 Creators Update, you can block the installation of all software that doesn't come from the Windows Store. Why would you want to do this? Well, blocking non-Windows Store software means blocking traditional programs, and these are the ones that are more liable to… [Continue Reading] -

Samsung partners with Microsoft to create the Windows 10-powered Galaxy Book
Publié: février 27, 2017, 10:31am CET par Mark Wilson
While attendees and fans of MWC 2017 were hoping for at least a little news about the Samsung Galaxy S8, Samsung forwent phones completely and instead offered up a pair of tablets: the Galaxy Tab S3, and the Galaxy Book. The Galaxy Book is the fruit of an "expanded strategic partnership" between Samsung and Microsoft, and is described as a "premium 2-in-1 designed with the mobile enterprise customer in mind". Available in 10.6" and 12" models, there are natural comparisons to draw with both the Surface Pro 4 and Surface Book. Both models are powered by 7th Gen Intel Core… [Continue Reading] -

Nokia reimagines the classic 3310 for 2017, complete with Snake
Publié: février 26, 2017, 6:14pm CET par Mark Wilson
No, you have not just stepped back in time 20 years; the Nokia 3310 is back. The phone that was more likely to break the sidewalk when dropped rather than suffer a crack itself has today been relaunched by HMD Global, who has a license for the Nokia brand. While not an exact replica of the phone that was first seen back in the year 2000 (a phone could not get away with being quite so chunky these days!), it's a modern take on a classic device, and it's sure to win over many people. Snake is present for whiling… [Continue Reading] -

MWC 2017: Withings products to be rebranded as Nokia devices
Publié: février 26, 2017, 5:33pm CET par Mark Wilson
Last year, Nokia decided to splash a bit of cash and bought Withings. Today at MWC 2017 in Barcelona, it was revealed that existing Withings health and fitness products will be rebranded as Nokia devices this year. Starting "early summer 2017", Withings' range of smartwatches, digital scales, and other smart devices will come under the Nokia brand. Withings also announced changes to its Health Mate app, and its plans to share user data with "caregivers" through its Patient Care solution -- moves that sees the company take Apple square on. Speaking at MWC 2017, Nokia's Vice President of Digital Health… [Continue Reading] -

MWC 2017: Huawei unveils P10 and P10 Plus
Publié: février 26, 2017, 4:01pm CET par Mark Wilson
Today at MWC 2017, Huawei lifted the lid on its new P10 range. As with their predecessors, the Huawei P10 and Huawei P10 Plus have a strong focus on photography, with the Leica brand being used as a draw. As is the norm these days, there are no huge surprises to be found here, with the latest flagships being really little more than an evolution of last year's models -- not that that's a bad thing of course. In addition to the cameras, standout features for this year's handsets include a serious boost to battery life, and a front-mounted (hooray!)… [Continue Reading] -

Google Assistant is coming to all smartphones with Android 6.0 Marshmallow and up
Publié: février 26, 2017, 3:04pm CET par Mark Wilson
If you like the idea of Google Assistant but didn’t like the fact that it was tied to the Pixel range, there's some good news. Google has announced that the handy helper is making its way to all Android 6.0 Marshmallow and Android 7.0 Nougat smartphones. The roll out starts this week, and brings Siri- and Cortana-like voice control to millions of Android users. Earlier today at MWC 2017 in Barcelona, the newly-announced LG G6 became the first non-Pixel device to offer Google Assistant, and Google now says that the feature is coming to "eligible Android phones running Nougat and… [Continue Reading] -

LG G6 is a flagship smartphone with a 5.7-inch 18:9 display and impressive specs
Publié: février 26, 2017, 2:30pm CET par Mark Wilson
If there is anything to be garnered from LG's unveiling of the G6 at MWC 2017 today, it is that the company learned a lot from last year's G5. While the G5 was a modular affair, the LG G6 gets back to basics and concentrates on being a decent flagship handset with a few interesting quirks. In terms of specs, the G6 may not blow you away, but it still succeeds in standing out from the crowd, thanks in part to its display. The 5.7-inch screen has an aspect ratio of 18:9 (a resolution of 2880 x 1440), and the tall… [Continue Reading] -

MWC 2017: Watch the Samsung Galaxy S8 announcement here, live!
Publié: février 26, 2017, 12:57pm CET par Mark Wilson
Mobile World Congress 2017 may not technically kick off until tomorrow, but lots of companies like to jump the gun so they can be the first to get their announcements out. In this group is Samsung, and later today the company is holding a press conference in Barcelona at which it will unveil the latest addition to the Galaxy range. Of course, there has not been official word that it's the Samsung Galaxy S8 that will be launched, but there have been enough hints, rumors and leaks for this to be considered a certainty. If the rumors are to be… [Continue Reading] -

MWC 2017: Watch the Samsung Galaxy announcement here, live!
Publié: février 26, 2017, 12:57pm CET par Mark Wilson
Mobile World Congress 2017 may not technically kick off until tomorrow, but lots of companies like to jump the gun so they can be the first to get their announcements out. In this group is Samsung, and later today the company is holding a press conference in Barcelona at which it will unveil the latest addition to the Galaxy range. Of course, there has not been official word that it's the Samsung Galaxy S8 that will be announced, but there have been enough hints, rumors and leaks for this to be considered likely (even if Samsung has said the actual… [Continue Reading] -

Ad blocker Shine does a complete u-turn... and rebrands as ad company Rainbow
Publié: février 25, 2017, 4:33pm CET par Mark Wilson
In a perfect example of poacher-turned-gamekeeper, Israeli company Shine -- known for producing ad blocking software -- has rebranded as Rainbow and will instead offer an advertising service. Rainbow will work primarily will telecoms companies, and will have a strong focus on targeted advertising. The company says that it wants to provide "a better ad experience for consumers", having apparently decided that blocking ads was not working for everyone. Rainbow aims to win round consumers by providing and opt-in service that means people will see only advertisements that comply with industry standards and observe privacy rules. It's a move that's… [Continue Reading] -

Google releases details of unpatched Internet Explorer and Microsoft Edge vulnerability
Publié: février 25, 2017, 3:45pm CET par Mark Wilson
Not content with publishing details of an unpatched Windows bug, Google has now gone public with a security vulnerability in both Microsoft Edge and Internet Explorer. Going under the description of "Type confusion in HandleColumnBreakOnColumnSpanningElement", the bug has the potential to allow an attacker to execute malicious code. The vulnerability has been assigned the code CVE-2017-0037, and details of the flaw have been published under the terms of Google's Project Zero. Microsoft was notified about the problem 90 days ago, and as the company failed to patch it Google has made the problem public. An explanation of the browser bug… [Continue Reading] -

Google renames Messenger to Android Messages as the company pushes RCS
Publié: février 24, 2017, 11:43am CET par Mark Wilson
Just last week we were talking about Google's championing of RCS (Rich Communication Services), the successor to SMS. Now the company has renamed its Messenger app to Android Messages as it aims to become not just the default SMS app, but the default RCS app for Android users. The name change also helps to better differentiate the app from others that had the same name -- such as Facebook Messenger, which is shortened to just Messenger on shortcuts. At the same time, the change is likely to cause a degree of confusion thanks to the sheer number of messaging apps… [Continue Reading] -

Google has broken SHA-1 encryption
Publié: février 23, 2017, 6:54pm CET par Mark Wilson
After two years of research, Google has shown that it has successfully broken SHA-1 encryption. The company is yet to release details of how it achieved the first SHA-1 "collision", but has released a proof of concept. In keeping with its own disclosure policy, details of how the encryption was effectively broken will be released after 90 days. In the meantime, you can take a look at two specially-crafted PDF files that have identical SHA-1 hashes but different content (the definition of a collision). The implications of the revelation are perhaps not as far-reaching as some people might expect. While… [Continue Reading] -

Google and Jigsaw create Perspective technology to identify abusive comments
Publié: février 23, 2017, 5:29pm CET par Mark Wilson
Any website that allows contributions from visitors -- whether it is a platform such as Twitter or a site that has a comments section -- has to contend with the problem of abuse, swearing and harassment. Manually keeping on top of this sort of content can be a hellish task, but Google and fellow Alphabet subsidiary Jigsaw have launched a new technology called Perspective to help automate things. The technology uses machine learning to identify what are being called "toxic comments" (defined as "a rude, disrespectful, or unreasonable comment that is likely to make you leave a discussion") so they… [Continue Reading] -

Red Hat: 'use after free' vulnerability found in Linux kernel's DCCP protocol IPV6 implementation
Publié: février 23, 2017, 3:57pm CET par Mark Wilson
Red Hat Product Security has published details of an "important" security vulnerability in the Linux kernel. The IPv6 implementation of the DCCP protocol means that it is possible for a local, unprivileged user to alter kernel memory and escalate their privileges. Known as the "use-after-free" flaw, CVE-2017-6074 affects a number of Red Hat products including Red Hat Enterprise Linux 6, Red Hat Enterprise Linux 7 and Red Hat Openshift Online v2. Mitigating factors include the requirement for a potential attacker to have access to a local account on a machine, and for IPV6 to be enabled, but it is still… [Continue Reading] -

Organizations can avoid 94 percent of critical Microsoft vulnerabilities just by killing admin rights
Publié: février 23, 2017, 1:42pm CET par Mark Wilson
When vulnerabilities are found in Microsoft products, collective breaths are held until the company releases security bulletins. But analysis of security issues by software manufacture Avecto shows that the overwhelming majority of these vulnerabilities can be mitigated against by simply removing administrator right from users. Avecto CEO Mark Austin and CTO Marco Peretti say that organizations need to address the problem of "over privileged users". The duo say that this would help to avoid the security problems caused by 94 percent of critical vulnerabilities in Microsoft products. The research also found that Windows 10 had the highest proportion of vulnerabilities… [Continue Reading] -

Updates to Windows 10 Mail and Calendar apps bring Focused Inbox, @mentions and more
Publié: février 23, 2017, 12:20pm CET par Mark Wilson
Microsoft is pushing out updates to the Mail and Calendar apps in Windows 10, introducing a number of new features including the Focused Inbox we've already seen in the mobile version of Outlook. The new features come ahead of "architectural improvements" that will speed up performance, and Microsoft is seen borrowing ideas heavily from Google's Gmail and Calendar tools in a bid to make its own apps more useful and helpful. The Focused Inbox feature of Mail is not dissimilar to Gmail's tab option, with emails determined to be important ending up on the Focused tab and others being demoted… [Continue Reading] -

Gboard for iPhone updated with Google Doodles, new emoji and voice typing
Publié: février 23, 2017, 11:31am CET par Mark Wilson
Google's Gboard keyboard made its debut on iOS, and it was a few months before the company brought the app to its own Android platform. Today a major update to the iPhone version of the keyboard sees the arrival of voice typing, meaning that users will be able to dictate messages rather than typing by hand. In addition, the update introduces new emoji, support for additional languages, as well as easy access to Google Doodles and information about them. By far the biggest news in the update is the addition of ("by popular demand") voice typing. Of this, Google says:… [Continue Reading] -

Study shows that whistleblowers need greater protection due to surveillance and anti-privacy tech
Publié: février 23, 2017, 10:52am CET par Mark Wilson
A study by London University's Institute of Advanced Legal Studies (IALS) shows that journalists find it harder to protect their sources in the digital age, and suggests that whistleblowers should be afforded greater legal protection. The arrival of Donald Trump on the scene has created a greater sense of urgency. The report, entitled "Protecting Sources and Whistleblowers in a Digital Age", says that monitoring of phone calls as well as online surveillance means it is now easier to identify sources that would otherwise have remained anonymous. People like Edward Snowden and Julian Assange have brought whistleblowing into the spotlight in… [Continue Reading] -

Twitter lets customer support operatives use custom profiles with their direct messages
Publié: février 22, 2017, 6:42pm CET par Mark Wilson
Having become the medium through which upset customers often turn to in order to complain to companies or ask questions, Twitter is fully embracing its role as a customer service platform. But while Twitter is a neat and quick way to get in touch with a company, it tends to have something of an impersonal feel. This is about to change as Twitter is rolling out a new feature that lets customer service representatives personalize direct messages with their own name and image rather than that of the company they work for. Will this splash of personality help customers feel… [Continue Reading] -

Differential sync will speed up OneDrive from Q2 2017
Publié: février 22, 2017, 1:50pm CET par Mark Wilson
It has been some time since Microsoft mentioned that differential sync would be coming to OneDrive, and the company's latest roadmap shows that it is due to arrive some time in the second quarter of this year. The feature will help to save time and bandwidth by only synchronizing parts of a file that have been updated. It's something that users of Microsoft's cloud storage service have been requesting for a long time now, and years of asking will soon come to an end. As reported by ZDNet, an updated roadmap for OneDrive shows that the second quarter of 2017… [Continue Reading] -

Paid-for Google Site Search to be phased out and replaced by free, ad-supported version
Publié: février 22, 2017, 11:38am CET par Mark Wilson
Emails to customers reveal that Google plans to kill off Google Site Search this spring. While customers who have paid for the service will continue to have access to it, no new licenses or renewals will be sold after 1 April, 2017. As reported by Fortune, customers will be migrated to Google's ad-supported Custom Search Engine once their license or search limit expire. The move illustrates Google's on-going and growing reliance on advertising income, and it's something that is unlikely to be well-received by web users who are already sick of being inundated with ads. An announcement on the Google… [Continue Reading] -

Microsoft unveils Skype Lite, an Android app for India that's light on data usage
Publié: février 22, 2017, 10:33am CET par Mark Wilson
Microsoft has thrown a lot at Skype in recent years, and the latest move sees the company releasing a completely new version of the Android app designed for use on slower internet connections -- specifically in India. Described variously as being "our fastest and smallest app to date" and "built in India, for users in India", the focus with Skype Lite is on speed and efficiency. The new version of Skype uses less data and battery power, but still delivers the Skype experience that users have come to rely on. Skype Lite is available in Gujarati, Bengali, Hindi, Marathi, Tamil,… [Continue Reading] -

Security breaches cost Yahoo dearly as Verizon reveals amended terms of acquisition
Publié: février 21, 2017, 5:00pm CET par Mark Wilson
Yahoo's frankly terrible track record with security just cost the company $350 million. Having originally offered to buy the company for $4.83 billion, Verizon has now revealed that it is dropping its offer to $4.48 billion. The announcement from Verizon comes just days after it was rumored that the company was thinking of lowering its offer by $250 million in the wake of security breaches suffered by Yahoo. The two companies have also agreed to share "certain legal and regulatory liabilities arising from certain data breaches." The deal between the two companies is still expected to close in the second… [Continue Reading] -

Apple appeals against $14 billion European tax bill with 14-point legal plea
Publié: février 21, 2017, 12:41pm CET par Mark Wilson
Last year Apple was hit with $14 billion tax bill after the European Commission decided the company had enjoyed "illegal tax benefits" in Ireland. Apple said that it would appeal against the ruling which Tim Cook described as "maddening", but Europe is showing increased interest in cracking down on technology companies taking advantage of tax loopholes. The appeal has now been placed, and Apple is asking the appeal court to either partly overturn the Commission's ruling and pay its legal fees, or completely overturn the ruling. The fact that Apple is setting forth two possible outcomes would indicate that it… [Continue Reading] -

Microsoft confirms another 2017 update after Windows 10 Creators Update
Publié: février 21, 2017, 11:31am CET par Mark Wilson
If you're not a Windows Insider, it has been a little while since your copy of Windows 10 received a major update -- but that is about to change. 2017 will see the release of not one, but two major updates to the operating system. Windows 10 Creators Update is due to arrive in the spring, and at Microsoft Ignite in Australia, the company confirmed that a second major update is on the way later in the year. We don’t know a great deal about this update, but it's likely to incorporate Project NEON design elements. While it is not… [Continue Reading] -

Europe still has concerns about privacy in Windows 10
Publié: février 20, 2017, 7:01pm CET par Mark Wilson
Privacy fears abound with Windows 10, with individuals and privacy groups continually questioning the company's motives in gathering user data. The threat of a court case in Switzerland resulted in Microsoft making changes to Windows -- in addition to the privacy changes it had already made. But for European privacy watchdogs, the latest batch of changes are still not enough. The Article 29 Working Party voices concern about the settings that are in place by default, the lack of control users are given over data collection, and a general lack of transparency. The group wrote to Microsoft last year to… [Continue Reading] -

You almost certainly need an SD card for your Nintendo Switch
Publié: février 20, 2017, 5:50pm CET par Mark Wilson
If you've ordered yourself a Nintendo Switch you had better prepare to crack open your wallet and splash out on an SD card. Nintendo has shared details of the size of the console's digital games, and at least one of them simply won’t fit on the internal storage. The company reveals that Dragon Quest Heroes I·II weighs in at a sizeable 32 GB -- exactly the same size as the Switch's built in storage, which is already home to the required system files. Other games are big enough to mean that even if you're not interested in Dragon Quest Heroes… [Continue Reading] -

Kim Dotcom can be extradited to the US
Publié: février 20, 2017, 1:36pm CET par Mark Wilson
Kim Dotcom, the larger-than-life character behind file-sharing services Megaupload and Mega, can be extradited from New Zealand to the US. The German national has taken up permanent residency in New Zealand and has been fighting calls for him to face the US legal system. The judgement came as part of an appeal to a previous ruling which was heard back in September. While the judge today, on the face of things, has ruled against Dotcom, the court case could yet go in favor of him due to various technicalities. A statement issued by Dotcom's barrister says: "The High Court has… [Continue Reading] -

Google and Microsoft agree to demote search results for pirated movies, music and streaming sport
Publié: février 20, 2017, 12:18pm CET par Mark Wilson
Users of Google and Bing will find it more difficult to track down illegal content via the search engines after Google and Microsoft signed up to a voluntary code of practice. The deal means that pirate search results will be demoted in results in the UK, making it less likely that searchers will click on them. The two technology companies have been in talks with the entertainment industry to find a way to stem the flow of illegal content that's available online. As well as protecting the rights of copyright holders, it is hoped that the new arrangement will help… [Continue Reading] -

Google publishes details of Windows bug after Microsoft misses 90-day Project Zero disclosure deadline
Publié: février 20, 2017, 10:14am CET par Mark Wilson
Google's Project Zero has proved controversial on several occasions already, with the search giant publicly revealing details of software bugs when companies fail to fix them. Now the project has unearthed a bug in Windows, and as Microsoft failed to patch it within 90 days of being notified, details of the flaw have been made available for everyone to see -- and exploit. A problem with the Windows Graphics Component GDI library (gdi32.dll) means that a hacker could use EMF metafiles to access memory and wreak all sorts of havoc. While Microsoft has issued Security Bulletin MS16-074, Google's Mateusz Jurczyk… [Continue Reading] -

Google to drop 30-second unskippable ads from YouTube
Publié: février 18, 2017, 9:50am CET par Mark Wilson
Ads -- be they on TV, on the web or in apps -- can be deeply annoying, hence the prevalence of ad-blocking software. But there are some ads that you can't always avoid, such as those tacked onto the beginning of YouTube videos; not all ad-blocking software is made equal, after all. If this is a bugbear of yours, there's good news on the horizon. While YouTube is not ditching ads altogether, the 30-second monstrosities which cannot be skipped are being dropped. This will be welcomed by YouTube users who have been irritated by having their viewing stalled, and it… [Continue Reading] -

Mark Zuckerberg's rambling letter covers fake news on Facebook, nudity and profanity -- and his ego
Publié: février 17, 2017, 12:27pm CET par Mark Wilson
In a lengthy missive that has been described by some as a manifesto, Mark Zuckerberg has written a counterattack to criticism of his beloved Facebook. He waxes lyrical about a rosy vision of the future in which communities come together, everyone is included, and everyone is empowered -- largely facilitated by him. For a man who denies he has political leanings, he certainly seems to have been studying Speaking Like A Politician 101. He is nothing if not almost impressively vague. But when Zuckerberg is not massaging his own ego as he dreams up ways to save the world ("I… [Continue Reading] -

Twitter tweaks blocking and muting in latest anti-abuse measures
Publié: février 17, 2017, 10:50am CET par Mark Wilson
Having just introduced the idea of restricted timeouts for abusive users, Twitter has unveiled yet more measures designed to counter abuse and harassment. Now if you have blocked or muted a user, you'll no longer be notified of replies to a conversation by that user. You will still, however, receive notifications of replies to the conversation if they come from people you follow, so you are not completely cut out. It has been warmly received by Twitter users, many of whom believe this is how things should have been from the beginning. Whether this latest tweak makes much of a… [Continue Reading] -

Twitter slaps abusive accounts with temporary timeouts
Publié: février 16, 2017, 1:39pm CET par Mark Wilson
After promising to do something to tackle the problem of harassment, Twitter recently announced plans to stop repeat offenders. An even more recent tweak to lists backfired, and the latest measure sees abusers hit with a timeout rather than a ban. It is an attempt to placate those who want to see something being done, while simultaneously trying not to anger those affected. The restrictions seem to be -- at the moment -- limited to hiding the offender's tweet to everyone but his or her followers, but it's possible that others may be implemented as well. Offenders are notified of… [Continue Reading] -

Google partners with Telenor to bring enhanced RCS messaging to Europe and Asia
Publié: février 16, 2017, 12:51pm CET par Mark Wilson
A potential successor to SMS has received strong backing from Google as it partners with Telenor to launch RCS messaging in Europe and Asia. Rich Communications Services is more feature-rich than traditional SMS and Google's latest partnership sees the technology spreading outside of the US and Canada. With support for features such as group chat, read receipts and high resolution image sharing, RCS has a lot going for it. There's just one catch. In integrating RCS support into Android, Google is providing the "upgraded SMS experience" through its own Messenger app. The deal means that RCS messaging is making its… [Continue Reading] -

Job ads on Facebook mean you could apply for your next position through the social network
Publié: février 16, 2017, 11:45am CET par Mark Wilson
Ads on Facebook are something of a pain, but they could actually about to become rather more useful. Starting tomorrow, the social network will allow business pages to host job ads and anyone interested in the positions will be able to apply directly via Facebook. Job ads on Facebook were trialed towards the end of last year, but the official rollout starts now. It's a change that sees Facebook treading firmly on LinkedIn's toes, and it's something that has the potential to work well for Facebook, employers and job applicants alike. From the point of view of employers, it makes… [Continue Reading] -

Google expands fact checking to help tackle fake news
Publié: février 16, 2017, 10:37am CET par Mark Wilson
It's something that should delight Donald Trump -- Google is helping to fight fake news. Whether the company's move to help keep web users better informed is in keeping with the US president's penchant for "alternative facts" remains to be seen, but for everyone else it is great news. Google is far from being the first technology company to lend its support to the fake news fighting army -- Facebook and the BBC are already doing their bit too. The expansion of Google News fact checking means that the Fact Check label is spreading further around the globe, giving people… [Continue Reading] -

Yahoo notifies users about 'forged cookie' security breaches and it could cost the company millions
Publié: février 16, 2017, 10:10am CET par Mark Wilson
Yahoo -- or, rather, its users -- have not been doing very well recently when it comes to security. Having already revealed details of a huge historic attack that led to the theft of details for millions of accounts, Yahoo is now notifying an unknown number of users that their accounts may have been breached by hackers using forged cookies. At the same time, Bloomberg is suggesting that the impending deal with Verizon has been renegotiated. The latest revelations coupled with the previous security issues could have just cost Yahoo $250 million. As noted by HelpNetSecurity, news of this particular… [Continue Reading] -

Privacy-protecting Ghostery extension sold, Ghostery Inc becomes Evidon after acquisition
Publié: février 15, 2017, 6:33pm CET par Mark Wilson
There's big news in the world of Ghostery Inc, the company best-known for the browser extension that boosts privacy. The firm's consumer operations have been sold to Cliqz, a German company part-owned by Mozilla, where the Ghostery extension will live on. Ghostery Inc is rebrandind to its former identity of Evidon, which will have a B2B focus. Evidon Inc will provide "monitoring and consent solutions for over 500 leading brands across the world." The deal with Cliqz is an all-cash affair, but details have not been released. Owned by Mozilla and Hubert Burda Media, Cliqz will now be responsible not… [Continue Reading] -

Brexit forces Microsoft to push up Surface Book price by £150
Publié: février 15, 2017, 5:54pm CET par Mark Wilson
The UK's decision to leave the European Union continues to hit the pockets of consumers. The latest victim of Brexit is Microsoft's Surface Book, with every model in the range hit with a £150 price hike. While not a direct response to the Brexit vote itself, the resulting drop in the value of the pound has already seen many companies push up prices to compensate. We've already seen Apple increase the cost of apps in the UK by 25 percent, and Microsoft has already increased the price of enterprise software. Representing an 11 percent price jump, the new Surface Book… [Continue Reading] -

'Refugee' Julian Assange arrives on Twitter
Publié: février 14, 2017, 6:02pm CET par Mark Wilson
Wikileaks founder Julian Assange has activated his Twitter account. His profile gives his location as the Ecuadorian embassy in London, and describes him as "refugee" who is "picking the lock to the chain that enslaves mankind -- ignorance." Within minutes of activating the account, Assange managed to amass thousands of followers, and this is a number that is sure to skyrocket in the coming days now that the account is actually being used. So what did the reclusive man have to say with his first tweet? Having been a man of few words for quite some time -- being holed… [Continue Reading] -

[Updated] PayPal very sneakily increases its charges and adds weird non-discouragement clause for sellers
Publié: février 14, 2017, 5:00pm CET par Mark Wilson
Nobody likes to share bad news, and PayPal is no different. Price increases certainly fall into the category of bad news, and PayPal has decided to publish the details as "Policy Updates". But it's not just the price hike that's included in this misleadingly-titled document -- there's also something rather weird. If you are a seller -- such as on eBay or other shopping sites -- you will soon be subject to a "non-discouragement clause". What does this mean? In short it means that sellers are not permitted to encourage shoppers to use another payment method instead of PayPal. Let's… [Continue Reading] -

Microsoft aims to calm cloud security fears with revamped Trust Center site
Publié: février 14, 2017, 11:58am CET par Mark Wilson
The modern Microsoft places more importance on the cloud than ever before, and this means addressing the security concerns that users might have. As part of this, the company has upgraded and redesigned its Trust Center, home to a wealth of security information. Designed to provide "support and resources for information professionals, as well as the legal and compliance community," the Trust Center is also of interest to anyone concerned about security in general and those who want to know how Microsoft is complying with laws around the world. The redesigned Microsoft Trust Center makes it easier to find information… [Continue Reading] -

Twitter tweaks Lists because of potential for abuse -- and then reverses the changes
Publié: février 14, 2017, 11:12am CET par Mark Wilson
Twitter has tried various methods of cracking down on trolling and abuse, and it is now rolling out its latest batch of safety measures. The most recent change only lasted a few hours before it was killed off due to protests. In a seemingly well-intentioned move, Twitter decided to no longer notify users when they were added to lists. The idea was that lists could be used as a form of abuse: you might not be able to message someone, but you could add them to a list called "you're a douchebag", and they would be notified. But the change… [Continue Reading] -

Google officially brings Instant Tethering to Pixel and Nexus
Publié: février 13, 2017, 5:34pm CET par Mark Wilson
It's only a matter of weeks since we were talking about the impending arrival of Instant Tethering. This delight of technology makes it possible to quickly and painlessly share a data connection between devices, and now it's officially available to Pixel and Nexus devices. To use Google's explanation, Instant Tethering means "you can automatically share a cellular data connection between certain Pixel and Nexus devices via Wi-Fi when they're signed in to the same Google Account." Now the rollout is official, and many people are able to make use of this very handy feature. Google says that in order to… [Continue Reading] -

Google Maps for iOS and Android gains Lists to save and share your favorite places
Publié: février 13, 2017, 4:16pm CET par Mark Wilson
The days of dedicated satnavs are surely numbered, with the likes of Waze and Google Maps bringing turn-by-turn directions to smartphone owners for free. The feature set for these apps just keeps on growing, and Google Maps now includes a new Lists feature which lets you use the app to create and share lists of places. There are lots of possible uses for Lists -- Google suggests using it to create your bucket list of places to visit, but it's better used to draw up a list of places to visit on vacation, say, and then share it with friends… [Continue Reading] -

PayPal very sneakily increases its charges and adds weird non-discouragement clause for sellers
Publié: février 12, 2017, 9:06pm CET par Mark Wilson
Nobody likes to share bad news, and PayPal is no different. Price increases certainly fall into the category of bad news, and PayPal has decided to publish the details as "Policy Updates". But it's not just the price hike that's included in this misleadingly-titled document -- there's also something rather weird. If you are a seller -- such as on eBay or other shopping sites -- you will soon be subject to a "non-discouragement clause". What does this mean? In short it means that sellers are not permitted to encourage shoppers to use another payment method instead of PayPal. Let's… [Continue Reading] -

WhatsApp adds two-step verification -- here's how to enable it
Publié: février 10, 2017, 11:14am CET par Mark Wilson
It has been a little while coming, but WhatsApp is finally rolling out support for two-step verification to its messaging app. The extra layer of security means that it is now more difficult to gain unauthorized access to an account, and it is a feature that is being made available to iOS, Android and Windows users. With the feature enabled, if you -- or anyone else, for that matter -- tries to verify your phone number on WhatsApp, you -- or they -- will have to provide the 6-digit passcode you create. In addition to creating a passcode to secure… [Continue Reading] -

Forget prayers, thoughts and sad faces; Facebook Community Help lets you actually help those in crisis
Publié: février 9, 2017, 11:39am CET par Mark Wilson
When there is an emergency somewhere in the world -- be it a natural disaster, terrorist attack or humanitarian crisis -- it has become normal to see Facebook's Safety Check feature kick in. As well as letting those affected by the crisis in question let their loved ones know that they are OK, Safety Check activations also result in a flood of thoughts, prayers and sad-faced emoji being sent by Facebookers. But what about sending actual help? Sending thoughts and prayers is something of an empty gesture, whereas offering shelter, food and other supplies could actually help to save lives. Facebook has now… [Continue Reading] -

Wikipedia bans use of Daily Mail as a source because it is 'unreliable'
Publié: février 9, 2017, 11:18am CET par Mark Wilson
In a move that will surprise few people familiar with the newspaper, Wikipedia has chosen to ban the use of the British Daily Mail as a source. Editors for the site reached the conclusion that the paper "is generally unreliable, and its use as a reference is to be generally prohibited". While this does not constitute an outright ban -- something which would probably not go down well with the Wikipedia community -- editors are strongly encouraged to find an alternative source wherever possible. The decision comes after a vote in which editors debated the Daily Mail's "reputation for poor fact checking,… [Continue Reading] -

House of Representatives approves Email Privacy Act requiring warrants to search email and data
Publié: février 7, 2017, 11:06am CET par Mark Wilson
The Email Privacy Act (HR 387) has passed through the House of Representatives for the second time. It's an attempt to update the now-ancient Electronic Communications Privacy Act (ECPA) from 1986 which gave cause for concern as it grants the government the ability to access emails and data older than 180 days which is stored on third-party servers without the need for a warrant. The Email Privacy Act changes that. Privacy advocates are currently celebrating the fact that the updated Act has been approved by the House, but it now needs to pass through the Senate -- where it already… [Continue Reading] -

Google makes it much easier to share AMP links
Publié: février 7, 2017, 10:28am CET par Mark Wilson
A huge proportion of web traffic comes from mobile devices these days, and this means people are often trying to access online articles when they have a slow data connection. For this reason, Facebook introduced Instant Articles, and Google introduced Accelerated Mobile Pages. Both of these technologies allow for near-instantaneous loading of pre-cached, optimized articles on mobile devices, but they have a problem. Both mask the original URL which can make it difficult to share interesting articles with others. Google has seen the problem and made an important change to the way AMP works, helping to increase trust. The news… [Continue Reading] -

US judge says Google must hand over foreign emails to FBI, even though Microsoft need not
Publié: février 5, 2017, 8:12am CET par Mark Wilson
A US judge has ordered Google to comply with FBI search warrants which ask for customer emails that are stored outside of the US. This is in stark contrast to a recent case in which a federal appeal court ruling concluded that Microsoft did not need to comply with such orders. The FBI issued a warrant in relation to a fraud case, and Google argued that because the emails in question were stored on foreign servers, the authorities should not be able to seize the data. However, Google has been told that transferring the emails to another server for investigation by… [Continue Reading] -

Microsoft announces open source GVFS (Git Virtual File System) with support for much larger repos
Publié: février 3, 2017, 5:12pm CET par Mark Wilson
Git is a widely used version control system, but it's one that does not cope well with scaling up. As projects and codebases grow, performance can suffer massively, with common tasks taking hours to perform. Today, Microsoft comes up with an answer: GVFS. Git Virtual File System has come into being partly because of the problems Microsoft itself has encountered with Git. The sheer size of the Windows codebase means that a simple operation such as checkout can take three or more hours. As the V in GVFS, the solution is a virtualization system that works at file system level… [Continue Reading] -

Microsoft celebrates Outlook mobile's second birthday with the gift of iOS add-ins
Publié: février 3, 2017, 4:41pm CET par Mark Wilson
Outlook mobile is, believe it or not, two years old. Microsoft is not fighting the terrible twos, but instead celebrating by bringing add-ins to the iOS Outlook app. While it is iOS users who are treated to the first look at add-ins, there are plans to bring them to Android as well. In addition to add-ins direct from Microsoft, there are also offerings from the likes of Evernote, GIPHY, Nimble, Trello and Smartsheet which will "help you accomplish awesome things you simply couldn't do before from email." There is something of a focus on more business-oriented tasks at the moment.… [Continue Reading] -

Valve and game publishers face EU probe for geo-blocking, ASUS for online price-fixing
Publié: février 2, 2017, 2:57pm CET par Mark Wilson
Valve, the company behind games distribution platform Steam, is being investigated by EU antitrust regulators. Agreements in place between Valve and five game publishers that implement geo-blocking in titles could breach European competition rules. Valve, alongside Bandai Namco, Capcom, Focus Home, Koch Media and ZeniMax, is under investigation to determine whether the practice of restricting access to games and prices based on location is legal. At the same time the European Commission is launching an investigation into ASUS, Denon & Marantz, Philips and Pioneer for price manipulation. The investigation into the four electronics manufacturers centers around the fact that the… [Continue Reading] -

Facebook rolls out creepy Discover People feature on mobile, suggesting you make friends with strangers
Publié: février 2, 2017, 11:28am CET par Mark Wilson
If you're using the Facebook app on your phone, you might notice the appearance of a new Discover People section. As you would probably guess this is a feature designed to connect you with people on the social network, but there's something of a creepy twist. Unlike the current "People you may know" section which suggests that you might like to become friends with people because you have a common acquaintance, the experimental Discover People adopts a different approach. It suggests that you become friends with complete strangers. Facebook uses the fact that you might work for the same company… [Continue Reading] -

Facebook ordered to pay $500 million to ZeniMax in Oculus Rift lawsuit
Publié: février 2, 2017, 10:26am CET par Mark Wilson
Facebook-owned Oculus must pay half a billion dollars to game company ZeniMax after a Texas jury deliberated in a case about the Oculus Rift headset. The jury found that Oculus co-founder, Palmer Luckey, failed to comply with a non-disclosure agreement. Although now facing a $500 million bill, not everything in the case went against Facebook. Oculus was found not to have stolen trade secrets from ZeniMax, and the company plans to appeal against the charges for which it was found guilty. The $500 million is rather less than the $4 billion ZeniMax had been hoping for, but Oculus is largely… [Continue Reading] -

#DeleteUber campaign forces Uber to automate and speed up account removal process
Publié: février 1, 2017, 5:21pm CET par Mark Wilson
After failing to participate in a taxi ban around John F Kennedy airport while protests against President Trump's travel ban went on, Uber found itself on the receiving end of a good deal of flak. The hashtag #DeleteUber spent a lengthy period trending on Twitter as people voiced their disapproval of what they see as a Trump-supporting company. Irked Uber users who did not like the idea of the company seeming to profit from the refugee and immigration ban were not just flashing the #DeleteUber hashtag around, they were acting on it. But attempts to delete accounts led to frustration,… [Continue Reading] -

EU mobile usage is about to get cheaper as roaming charges come to an end on 15 June
Publié: février 1, 2017, 1:53pm CET par Mark Wilson
Plans to scrap mobile roaming charges in the EU have been a long time coming, but today the European Commission reveals the charges will finally come to an end on June 15 2017. EU negotiators have finally agreed on wholesale prices, something which is being described as the "last piece of the puzzle". The cost of voice calls and text messages will be capped from this date, but there is a tapered reduction period for data charges. It is a step towards the creation of a Digital Single Market and the introduction of a "roam-like-at-home" will be welcomed by Europeans,… [Continue Reading] -

Take a sneaky peek at Microsoft's Project NEON look coming in Windows 10 Redstone 3
Publié: février 1, 2017, 11:53am CET par Mark Wilson
The latest builds of Windows 10 Creators Update are already starting to give us a glimpse of what we can expect to see in terms of design with Project NEON. Microsoft's latest design language emerged recently and a tweaking tool has been quick to adopt the look for itself. Fans of the old-school TweakUI will love Interop Unlock Tools not only because of the tweaking and hackery it makes possible, but also because it makes use of the Project NEON APIs to give a taste of what we are likely to see a lot more of in the months to… [Continue Reading] -

OnePlus 3T found to be cheating in benchmarks
Publié: février 1, 2017, 11:29am CET par Mark Wilson
Benchmarks are an important metric by which the performance of a given device can be measured. They provide a reliable means of determining whether one laptop, computer, phone or other device is faster than another -- at least that's the idea. Tests performed by XDA Developers strongly suggest that OnePlus is using underhanded techniques to make the OnePlus 3T's Qualcomm Snapdragon 821 perform better in Qualcomm Trepn and Snapdragon Performance Visualizer tests. Analysis of results points to the fact that OnePlus is targeting benchmark apps by name, such as GeekBench, and is artificially boosting device performance when they are found… [Continue Reading] -

Twitter will finally roll out 'long overdue' fixes to tackle harassment
Publié: janvier 31, 2017, 4:49pm CET par Mark Wilson
Twitter's trolling and harassment problem is not going away, and the company has long-promised to do more to tackle the issue. In a series of tweets, Twitter's vice president of engineering Ed Ho has revealed that action is finally to be taken. While he does not go into detail about exactly what Twitter's plan is, he says that more will be revealed as the tools roll out this week. Importantly, he reveals in addition to changes to muting and blocking, the new measures will include steps to prevent repeat offenders from simply creating new accounts if they are blocked. Saying… [Continue Reading] -

LEGO Life is a safe social network that lets kids show off their creations
Publié: janvier 31, 2017, 12:41pm CET par Mark Wilson
Who doesn't love LEGO? Well... apart from parents who find themselves standing on the little plastic bricks in bare feet, that is! One of the joys of LEGO is not just that it lets kids -- young and old -- get creative, and it's great to share your creations. With this in mind, LEGO has created a new social network designed for kids. Unlike Facebook and other older social networks, LEGO Life is designed for under-13s and there is a strong focus on security and anonymity. While users are able to communicate with each other, they are restricted to using… [Continue Reading] -

Facebook launches new open source account recovery tool: Delegated Recovery
Publié: janvier 31, 2017, 11:42am CET par Mark Wilson
At the USENIX Enigma conference, Facebook unveiled a new way to overcome the problem of forgotten passwords. Known as Delegated Recovery, the mechanism essentially allows two online services a user has accounts with to be used as a form of two-factor authentication. Delegated Recovery is something of a new take on 2FA, building on Facebook's previously announced support for U2F Security Keys. The problem with password recovery via email or SMS, is that it's easy for the recovery medium to be compromised, and security questions are easily guessed. Delegated Recovery takes a new approach, and it's being trialed on GitHub.… [Continue Reading] -

Viber offers free calls to those hit by Trump's travel ban
Publié: janvier 31, 2017, 10:33am CET par Mark Wilson
The tech world's backlash against Donald Trump's travel ban continues. The latest name to throw its hat into the ring is Viber with its Viber Out service. The messaging service has announced that it is offering free calls between the US and countries affected by the new president's executive order restricting travel. Viber users can place free calls between the US and the seven affected countries -- landlines and mobiles included. Viber used the announcement to unsubtly throw shade at President Trump, saying: "We connect people. No matter who they are or where they're from." It's not clear how long free… [Continue Reading] -

Apple's iPhone Activation Lock status checker has gone AWOL
Publié: janvier 30, 2017, 5:43pm CET par Mark Wilson
Buy an iPhone -- or any other phone -- from somewhere other than an official reseller, and you run the risk of getting your hands on a stolen device. Apple has a tool that allows would be buyers to check whether the phone they are planning to buy is secured with Activation Lock. Until very recently, that is; the tool has now disappeared. The Activation Lock status checker was available on iCloud.com, and by simply entering the IMEI or serial number of a phone it was possible to perform a quick check to see if it is already locked to… [Continue Reading] -

WhatsApp update will allow users to track a contact's location in real time
Publié: janvier 30, 2017, 1:53pm CET par Mark Wilson
Facebook-owned WhatsApp was in the headlines recently because of concerns over the way it implemented end-to-end-encryption. Analysis of a beta version of the chat app showed that there seem to be plans to introduce message editing and deletion options, and new reports suggest that real-time location tracking could also be on the cards. As reported by the Independent, version 2.16.399 of WhatsApp for Android and version 2.17.3.28 for iOS include a feature called Live Location Tracking. It's an option designed to make it easier to meet up in the flesh, but it's also something that will be of concern for… [Continue Reading] -

Twitter reveals the worrying content of two secret National Security Letters
Publié: janvier 30, 2017, 10:32am CET par Mark Wilson
All the big players in the world of tech release transparency reports these days, and Twitter is no different. Like other companies, Twitter has been unable to report details of any National Security Letters (NSLs) it receives from the FBI asking for access to user account information. These data requests are accompanied by gagging orders that prevent the recipients from informing either the public or the subject of the letter about the request. The gag has now been lifted and Twitter has shared the contents of two letters which ask for a "large amount of data." The first letter, dated… [Continue Reading] -

Really, Google? Chrome 57 kills the ability to control and disable plugins
Publié: janvier 30, 2017, 10:00am CET par Mark Wilson
With web browsers being among the most frequently used pieces of software out there, it's little wonder that there is so much concern about security surrounding them. Browser plugins can be a major security worry, and with Chrome 57 Google has taken the strange decision to block users from disabling them or changing their settings. While this is not the same as preventing users from changing the settings for extensions, or removing them, it still has important implications -- particularly if a security problem should be discovered in a plugin Google bundles with Chrome. In Chrome 57, the page which… [Continue Reading] -

Warning: most Android VPN apps are insecure
Publié: janvier 27, 2017, 2:32pm CET par Mark Wilson
VPN software can be used to not only circumvent geoblocking, censorship and ISP blocks, but also to remain anonymous online. At least that's the idea. If you're an Android user who has a VPN app installed on your phone or tablet, the chances are that it is not safe. Research shows that the majority of VPN apps to be found in Google Play contain spyware or malware, leak data, or include tracking components. This is in stark contrast to what most people would expect from such apps, and users are warned to double-check the choice they have made. TorrentFreak shares… [Continue Reading] -

Twitter relegates Moments to a subset of the new Explore tab
Publié: janvier 27, 2017, 1:52pm CET par Mark Wilson
If there's one thing that irks Twitter users (actually, there are many things, but stick with us...) it's the disorganized way in which information is scattered hither and thither. Keen to get users to break out of their timelines and see what else it out there, the Twitter app is undergoing a makeover. The change means that the existing search, Moments, and trends are now combined into a single, more manageable Explore tab. It's a simple change, but one that will make life easier for Twitter explorers. As is often the case, it's iOS users who will get the first… [Continue Reading] -

Swype keyboard for Android analyzes your texts and suggests emoji
Publié: janvier 27, 2017, 10:41am CET par Mark Wilson
An update to version x.0.1 of an app, you might believe, is unlikely to bring much in the way of major changes. But far from being just a bug fixing release, Android keyboard app Swype 3.0.1 takes predictive text to the next level. We've all become used to the idea of smartphone keyboards predicting not only which word you are currently typing, but also which word you might want to type next. Taking on board millennials and pre-millennials' apparent dislike of actual words and heavy reliance on emoji, Swype will now suggest emoji you might like to use based on… [Continue Reading] -

Facebook fights fake news with a trio of tweaks to trending topics
Publié: janvier 27, 2017, 10:36am CET par Mark Wilson
The problem of fake news has been around for a little while -- particularly on Facebook -- but it's something that has been thrown into the spotlight thanks to President Trump and his continuing complaints about the media, in particular about the size of his inauguration crowds. Facebook is one of many technology companies to announce plans to tackle fake news, and now the social network has unveiled its latest round of fakery fighting. Three major changes are coming to Trending topics: firstly, Facebook will no longer personalize news for individual users; secondly headlines and sources will be listed alongside… [Continue Reading] -

Microsoft admits sales of 'expensive' HoloLens are 'not huge' but more versions are planned
Publié: janvier 27, 2017, 10:23am CET par Mark Wilson
Microsoft is not giving away too much about the sales figures for HoloLens but goes as far as saying it is "in thousands, not hundreds of thousands". With the augmented reality headset costing $3000, this is perhaps not surprising, and the company is quite happy to take the seemingly low sales figures in its stride. Speaking at educational technology event the Bett Show in London on Thursday, Roger Walkden, Senior Director and Commercial Lead of HoloLens, acknowledged that the price tag was partly responsible for the small number of sales. Interestingly, though, Microsoft is not bothered by what could be… [Continue Reading] -

Apple to allow developers to respond to App Store reviews
Publié: janvier 25, 2017, 12:42pm CET par Mark Wilson
For far too many years the process of providing feedback in the App Store has been a one-way dialog. At long last Apple is opening things up so developers will be able to respond to reviews that are left by customers. References to the new option is to be found in the documentation for iOS 10.3 beta, and Apple says that it will be available to developers when the final version of iOS 10.3 is released; it will also be available in the Mac App Store. Importantly, just as with Google Play, responses that are left will be visible to… [Continue Reading] -

WhatsApp beta shows message editing and recalling options
Publié: janvier 25, 2017, 11:30am CET par Mark Wilson
Two features that are requested of messaging apps -- but found in very few -- are the ability to delete messages, and the ability to edit them. There could be good news on the horizon for WhatsApp users as the latest beta of the app includes references to precisely these two features. While controversial to some, many users would welcome the option to edit messages that include typos, or to recall messages that were fired off in haste. Although references to both options have been found in WhatsApp beta 2.17.25, neither are currently active. The features were spotted by WABetaInfo,… [Continue Reading] -

No, America, you can't just demand customer data from anywhere in the world
Publié: janvier 25, 2017, 10:38am CET par Mark Wilson
The US government has lost its bid to overturn a previous ruling which stated it could not force companies to hand over customer data that is stored on servers outside the US. The government's appeal steams from a ruling back in July when it lost a case in which it was trying to obtain customer data from Microsoft. It was seen as a win for privacy at the time, but the government thought the ruling could stand in the way of law enforcement. A vote by the second US Circuit Court of Appeals in Manhattan means that an appeal will… [Continue Reading] -

Vivaldi CEO: 'Stop your anti-competitive practices with Edge, Microsoft!'
Publié: janvier 24, 2017, 1:51pm CET par Mark Wilson
Microsoft is no stranger to pissing people off, particularly when it comes to Windows 10. There have been endless cries about forced updates, complaints about ads, moaning about privacy, and now the CEO of Vivaldi has lashed out at the company for its anti-competitive practices with Microsoft Edge. Jon von Tetzchner says that Microsoft has forgotten about the "actual real-life people that use technology in their daily lives." He takes particular umbrage at Windows 10's continued insistence of resetting the default browser to Edge. Indicating that his patience has now run out, von Tetzchner points to a 72-year-old friend who… [Continue Reading] -

Grab yourself a cheaper Surface Pro 4 by ditching the pen
Publié: janvier 24, 2017, 11:21am CET par Mark Wilson
While there is a lot to love about Surface Pro 4, the price tag can be a little off-putting to would-be buyers. Microsoft has clearly heard the complaints about pricing and has introduced a cheaper option. For the first time, it is now possible to buy a Surface Pro 4 without a pen, shaving a not-insignificant $100 off the usual price. Somewhat strangely only one model is available without the pen, but this is something that could change further down the line. Even if you want a pen, buying without actually works out cheaper! The only model available to buy… [Continue Reading] -

China blocks VPNs, making Great Firewall circumvention harder
Publié: janvier 24, 2017, 10:07am CET par Mark Wilson
The Great Firewall of China is a famously totalitarian measure taken by the Chinese government to control what its citizens are able to see and do online. As with any such blockade, where there's a will there's a way, and people have long turned to VPNs to get around the firewall. But with a new 14-month crackdown on the use of such tools, the situation just got a little trickier. While on the face of it the announcement from the Ministry of Industry and Information Technology in China seems like a new one, it is really just a drive to… [Continue Reading] -

Google starts live testing of Android Instant Apps
Publié: janvier 24, 2017, 9:13am CET par Mark Wilson
A key obstacle that mobile users encounter is clicking a link only to be greeted by the offer to install an app. The relatively slow process of visiting Google Play to download and install an app means that many people simply don't bother -- and this is something that Instant Apps should help with. The Instant Apps feature was announced last year at Google I/O, and there was much excitement at the prospect of 'streaming' apps on demand. Now Google has started live tests of Instant Apps for Android so you can try out the feature with the likes of… [Continue Reading] -

Google says all new Chromebooks will support Android apps
Publié: janvier 23, 2017, 4:27pm CET par Mark Wilson
For Google, Chromebooks have not been quite the success the company was hoping for, firmly remaining a niche product. As part of a drive to boost popularity, the company announced last year that it planned to bring Android apps to Chromebook. But there is, of course, the question of which Chromebooks this means: and now we know the answer. Google has published a list of devices that will support Android apps, as well as revealing that all new Chromebooks will have the feature. In a seemingly innocuous post on the Chromium Projects site, Google says that: "All Chromebooks launching in… [Continue Reading] -

Samsung: two battery defects caused Galaxy Note7 problems and could delay Galaxy S8
Publié: janvier 23, 2017, 10:20am CET par Mark Wilson
Samsung has finally revealed the long-awaited results of its investigation into the problematic Galaxy Note7. Having issued an apology and pushed out OTA updates to disable phones which had been banned from flights because of the risk of them catching fire, the South Korean company says that two separate battery problems were to blame. The first problem stemmed from the fact that the battery was physically too small for the Galaxy Note7 leading to a short-circuit. Replacement batteries suffered from a combination of insulation problems and an issue that caused positive and negative electrodes to touch. Samsung also indicated that… [Continue Reading] -

Where can you download LineageOS, CyanogenMod's replacement?
Publié: janvier 22, 2017, 5:31pm CET par Mark Wilson
It's only a matter of weeks since we learned that CyanogenMod was closing down and LineageOS would replace it. At the time, little was known about the launch schedule for the open source, Android-based operating system, but that has all changed. On Friday, the LineageOS team announced that builds will "start rolling out this weekend". At time of writing the downloads have yet to make an appearance, but there is a download portal ready for you to keep an eye on. The team excitedly says that "it's nearly 'go time' for builds to start flowing", and advertised the availability of… [Continue Reading] -

Simplified connection sharing comes to Android with Instant Tethering
Publié: janvier 21, 2017, 4:14pm CET par Mark Wilson
Take your phone with you wherever you go, and you can use it to get your laptop online thanks to the wonder of tethering. This seemingly simple technological marvel is a delight for people working away from the home or office, and Google is now making things easier than ever with Instant Tethering. The new feature is rolling out to some Android devices now, and it takes the 'hard work' out of creating a hotspot with your phone to which your other devices can connect. As the name suggests, the aim is to make the connection instantly. As reported by… [Continue Reading] -

Meitu pleads complete innocence against spyware claims
Publié: janvier 20, 2017, 5:55pm CET par Mark Wilson
You may have seen our story earlier today about the worrying permissions used by photo app Meitu -- and you have almost certainly seen the disturbing images created in the app and shared on Facebook. The company behind the app -- also called Meitu -- has jumped to defend itself, insisting there is nothing sinister going on. The company insists that there is a very good reason for asking for so many permissions on iOS and Android. It insists there is a very good reason for gathering so much information about users. It insists this data is stored securely and is… [Continue Reading] -

Privacy warning: Meitu photo app is spyware sharing your phone's data
Publié: janvier 20, 2017, 11:14am CET par Mark Wilson
There has been a sudden craze for freaky-looking photos created using the Chinese app Meitu. The images the app creates are either cutesy or horrific, depending on your point of view, but it's what's going on in the background that has people concerned. While Meitu has been popular in China for several years --amassing a huge following -- it has only just caught on over here. What many users are unaware of is that while they are busy applying virtual makeup to their face in the app, data such as a phone's IMEI, Mac address, users' precise location and much… [Continue Reading] -

Leaked Windows 10 build shows Creators Update is getting an ebook store
Publié: janvier 18, 2017, 1:06pm CET par Mark Wilson
Google has one, Apple has one, Amazon has one, so Microsoft seems to feel that it should have one too. We're talking ebook stores, and a leaked version of Windows Mobile reveals that this is something that is due to be added to the Windows Store. While Microsoft has been slowly but surely building up its store ecosystem, the focus has been mainly on apps so far, with music and video thrown in for good measure. With the company having fairly recently added EPUB support to Microsoft Edge, the arrival of ebooks is perhaps not entirely surprising, but Microsoft is… [Continue Reading] -

Now you can perform offline Google searches... sort of
Publié: janvier 18, 2017, 12:43pm CET par Mark Wilson
There must have been times when you're in an area with no Wi-Fi and terrible phone reception. It's almost certainly when you find yourself in this situation that you think of something you want to look up. With no signal to perform a Google search, you may mentally log your query and pledge to run it later -- but of course you will forget. Google has a solution. The latest version of the Google app heralds the arrival of pseudo offline searching, so you can perform searches with no signal, or if your phone is in airplane mode. Of course,… [Continue Reading] -

EFF sets out privacy and security plans for the first 100 days under President Trump
Publié: janvier 18, 2017, 10:30am CET par Mark Wilson
The Electronic Frontier Foundation has set out its plans for the first 100 days under Trump, during which time it says it will continue to fight for the rights of internet and technology users. The digital rights group has already drawn up a wishlist for covering its privacy and security dreams for 2017, but the 100-day plan sees the EFF setting out its agenda for the first few months under Trump. Having claimed that "our civil liberties need an independent defense force" and that "free speech and the rights to privacy, transparency, and innovation won’t survive on their own", EFF… [Continue Reading] -

Google has not given up on Google+ -- requested changes are incoming, and the 'classic' site will go!
Publié: janvier 17, 2017, 8:33pm CET par Mark Wilson
Despite the competition from other social networks, and widespread ridicule, Google is determined not to pull the plug on Google+. Instead, the company today announces that a trio of changes are coming to the service based on user feedback. Google is keen for users to experience its services on any device they may have, so it's little surprise that one of the changes sees the addition of a zoom function so Google+ users on smartphones can get a closer look at photos. There are also key changes to the commenting system and the welcome arrival of a much-requested feature. Google+… [Continue Reading] -

Apple hikes UK App Store prices by 25 percent post-Brexit
Publié: janvier 17, 2017, 12:33pm CET par Mark Wilson
The financial turbulence that followed the UK's vote to leave the European Union has seen the value of the pound tumbling. With the pound and the dollar almost reaching parity, Apple has again been forced to increase prices. While the US and UK currencies may not quite have reached parity, the price of apps in the two regions will very soon do just that. Apps that cost $0.99 in the US would have cost £0.79 in the UK pre-Brexit -- now this will jump to £0.99. Information about the price hike came in an email to developers, and it will… [Continue Reading] -

Latest macOS Sierra beta suggests lowering screen brightness to increase battery life
Publié: janvier 17, 2017, 11:48am CET par Mark Wilson
Apple is eager for MacBook Pro users to squeeze the best possible battery life out of their machines, so it's understandable that the company was taken aback by Consumer Reports' original, and disappointing battery life results. With macOS, Apple helps users to be proactive in boosting battery performance by warning when a particular app is using a lot of power -- if it is not entirely necessary, users will hopefully feel compelled to kill it. In the latest beta version of macOS Sierra, screen brightness is also taken into account, and users are advised that lowering this setting will save… [Continue Reading] -

Anonymous threatens Donald Trump with leaks about ties to mafia and child trafficking
Publié: janvier 17, 2017, 11:00am CET par Mark Wilson
Donald Trump has not yet taken up office, but he has already managed to whip up tidal waves of opposition not only in the US, but around the world. Among the president-elect's opponents is Anonymous, the hacktivist collective. The group took to Twitter -- Trump's favorite medium -- to issue a pre-inauguration warning: "This isn't the 80's any longer, information doesn't vanish, it is all out there. You are going to regret the next 4 years". The tirade came as Trump lashed out at reports about criticism from outgoing CIA Chief, John Brennan; Anonymous responded by threatening the billionaire with… [Continue Reading] -

How to run openSUSE Leap 42.2 or SUSE Linux Enterprise Server 12 on Windows 10
Publié: janvier 16, 2017, 4:07pm CET par Mark Wilson
Linux and Windows living happily side-by-side is not something many people would have predicted, but Windows 10 Anniversary Update saw the arrival of Bash on Ubuntu thanks to the Windows Subsystem for Linux. Not everyone was happy with Microsoft's choice of Ubuntu, with many preferring a different flavour of Linux. Senior Product Manager for SUSE Linux Enterprise, Hannes Kühnemund, is -- unsurprisingly -- one of those whose taste buds were not tantalized by Ubuntu. He would rather you ran SUSE on Windows 10. In fact he doesn't just want this to happen, he tells you how to do it --… [Continue Reading] -

Game Mode in Windows 10 Creators Update will boost gaming performance and quality
Publié: janvier 16, 2017, 1:43pm CET par Mark Wilson
Now that Windows 10 build 15007 is available for Windows Insiders on the Fast Ring, we're really starting to get a proper look at where Microsoft is going with the impending Creators Update release. We've already seen how the company is pushing 3D and augmented reality, but it has not forgotten about gamers. Proclaiming that "2017 is going to be a monumental year for gaming at Microsoft", the Windows maker has taken the wraps off Game Mode. The promise that this special mode will increase the performance of PC games is something that will be welcomed by gamers the world… [Continue Reading] -

The list of most common passwords of 2016 includes a few surprises
Publié: janvier 16, 2017, 11:30am CET par Mark Wilson
Security breaches and data leaks are, obviously, a major concern, but they do have something of a silver lining. Leaks of passwords may open up the risk of individual accounts being targeted, but they also serve as a fascinating insight into the level of security people use for online services. We all know someone who insists on using 'password' as their password, or something equally insecure such as '123456'. Keeper Security has published a list of the most common passwords used in 2016, and these old favorites remain firmly placed in the top 10. But there are a few surprises… [Continue Reading] -

Genealogy website FamilyTreeNow knows far too much about you -- remove your details to protect your privacy
Publié: janvier 15, 2017, 3:37pm CET par Mark Wilson
There was a craze that started a few years back for tracing one's family tree. Rather than fizzling out, the interest in genealogy continued, and there are still many websites out there that will help you to research your family history and build up a picture of the past. While genealogists of the past may have scoured public records and libraries for information about their family, these days people want things handed to them on a plate. One website is taking full advantage of this -- as well as the fact that the internet can act as a huge database… [Continue Reading] -

BBC wants to tackle fake news with Reality Check team
Publié: janvier 14, 2017, 8:09pm CET par Mark Wilson
Fake news has become a serious problem recently, with Facebook blamed for helping the spread of stories that are factually incorrect. The social network has already announced that it wants to take steps to tackle the problem, and now the BBC is joining the fight. The BBC already has a series known as Reality Check, and the plan is to expand this into a permanent feature that will be used to fact-check stories that appear on Facebook and other social media. The corporation will not be working on its own; it is working with Facebook, among others, to help ensure… [Continue Reading] -

FBI-helping phone-cracking firm Cellebrite hit by 900GB hack
Publié: janvier 14, 2017, 7:17pm CET par Mark Wilson
Cellebrite -- the Israeli security company famed for helping the FBI crack the iPhone at center of the San Bernardino case -- has been hit by hackers. The attack resulted in the theft of 900GB of data. While the website Motherboard -- which was handed a copy of the data -- reports that "the cache includes customer information, databases, and a vast amount of technical data regarding Cellebrite's products", the company has downplayed the incident. Cellebrite confirmed that illegal access to an external server had been detected, and indicated that an investigation is underway. But while Motherboard says that the data… [Continue Reading] -

How to protect yourself from the WhatsApp 'backdoor'
Publié: janvier 13, 2017, 4:37pm CET par Mark Wilson
Earlier today we reported about a security problem in WhatsApp that means it is possible for messages to be intercepted and read by others. The so-called 'backdoor' takes advantage of the fact that WhatsApp's implementation of end-to-end encryption makes it possible to resend encrypted messages using different security keys, allowing for third parties to read them. What is concerning many people is the fact that (by default, at least) WhatsApp does not alert users when a message is resent using a different key -- which would be a warning of something going on. Here's what you need to do to… [Continue Reading] -

'Backdoor' in WhatsApp's end-to-end encryption leaves messages open to interception [Updated]
Publié: janvier 13, 2017, 12:54pm CET par Mark Wilson
Facebook has long-claimed that its WhatsApp messaging service is completely secure and messages cannot be intercepted thanks to its use of end-to-end encryption. But researchers have unearthed what they call a serious security flaw that makes it possible to read encrypted messages. Based on Open Whisper Systems' Signal Protocol, the unique security keys used to implement end-to-end encryption should keep messages secure. But WhatsApp can force offline users to generate new keys and this could allow Facebook -- and third parties -- to read messages. The problem is seen by some a serious one, as WhatsApp's supposed security has earned… [Continue Reading] -

After Apple's software patch, Consumer Reports now recommends the new MacBook Pro
Publié: janvier 13, 2017, 12:32pm CET par Mark Wilson
In a shocking series of tests just before Christmas, Consumer Reports put the new MacBook Pro through its paces and came to the conclusion that battery life was so poor and so variable that it was the first MacBook Pro it could not recommend. Apple was rather taken aback by the result and, after further investigation, blamed a hidden setting activated by Consumer Reports. This in itself exposed a bug in Safari. With this patched, the tests were re-run and the MacBook Pro is now the proud recipient of Consumer Reports' coveted 'recommended' award. Having applied the patch supplied by… [Continue Reading] -

Before handing over power to Trump, Obama decides to EXPAND surveillance
Publié: janvier 13, 2017, 12:05pm CET par Mark Wilson
With Donald Trump about to take over the reins from Barack Obama, privacy groups have expressed concern about what the incoming president will do with surveillance laws. But before that happens, President Obama is still a cause for concern. In the final days of his leadership, his administration has granted permission for the NSA to share the data it intercepts with no fewer than 16 other intelligence agencies. While this will alarm many, what is particularly troubling is the fact that privacy protections are not applied until after this data has been shared between agencies. The changes in rules amount… [Continue Reading] -

Mario and Zelda incoming! Nintendo Switch launches worldwide on 3 March, costing $299.99
Publié: janvier 13, 2017, 11:40am CET par Mark Wilson
The long wait for a new games console from Nintendo is over. Well, almost. The Japanese company -- buoyed by the success of Super Mario Run -- has revealed that the Nintendo Switch will launch on March 3 with a $299.99 price tag. If you happen to be in the NYC Nintendo World Store, there will be a limited number of consoles available for pre-order from 9:00 ET. As well as finally revealing the launch date and price, Nintendo Switch Online Service was also announced, letting "Nintendo Switch owners enjoy online multiplayer gaming as well as a dedicated smartphone app… [Continue Reading] -

Watch Trump's inauguration as POTUS live on Twitter
Publié: janvier 12, 2017, 5:06pm CET par Mark Wilson
A week from tomorrow, on Friday 20 January, Donald Trump will be sworn in as the 45th President of the United States and you can watch the whole event on the billionaire's favorite social platform -- Twitter. The social site is teaming up with PBS NewsHour to provide six hours of coverage of Trump's inauguration starting at 11:00 ET. It's an event that millions of people all around the world will be keen to watch -- particularly in light of this week's Russian dossier revelations -- and Twitter is setting up a dedicated page for that very purpose. Between 11:00… [Continue Reading] -

Microsoft dodges Swiss court with changes to Windows 10 privacy settings
Publié: janvier 12, 2017, 3:27pm CET par Mark Wilson
Privacy has been a big issue for users of Windows 10, and the tsunami of complaints about spying has been a major headache for Microsoft. Now the company has managed to avoid a potentially expensive and damaging court case in Switzerland by improving data processing transparency in Windows 10. The Swiss Federal Data Protection and Information Commissioner (FDPIC) has just reached the end of an investigation into Windows that started back in 2015. They found that Windows 10's "get going fast" quick install option automatically enabled invasive data sharing with Microsoft (location details, browser and search history, keyboard entries and… [Continue Reading] -

Europe: we need more details from Yahoo about scanning emails for US intelligence
Publié: janvier 12, 2017, 12:47pm CET par Mark Wilson
The European Union is not happy with the explanation Yahoo has given for scanning user emails for US intelligence. There is concern about how such surveillance could impact upon not only privacy, but also business between the EU and US, and trust has to be built from scratch as Donald Trump becomes president. Yahoo -- which is on the verge of being sold to Verizon -- is not signed up to the EU-U.S. Privacy Shield agreement that blocks the US from spying on European data. As such, the company has been acting on a previously-secret court order, gathering data for… [Continue Reading] -

Now it's easy to secretly edit Facebook posts without anyone noticing
Publié: janvier 12, 2017, 11:23am CET par Mark Wilson
There is a lot of talk about the possibility of editing tweets on Twitter at the moment, but an editing function has been available on Facebook for ages. With the ability to edit posts that people can comment on come concerns, and with this in mind Facebook has always let you know when a post you're reading has been amended. Until now... Without warning, the label which advised of edits has vanished. This means that it is now possible to make surreptitious changes to posts and many people will be completely unaware of what you have done. Towards the end of last… [Continue Reading] -

Soon you could be able to download full seasons from BBC iPlayer before they broadcast on TV
Publié: janvier 11, 2017, 11:37am CET par Mark Wilson
The BBC's iPlayer proved popular very quickly, and its position as a well-loved catch-up streaming service is undeniable. But the broadcaster wants to take on the likes of Netflix, and this could mean viewers are not only able to download entire seasons to watch offline, but may be able to do so before shows air on television. BBC director general Lord Hall is today due to speak with staff, setting out his plans to make iPlayer the UK's biggest online TV service by 2020. His tone makes it clear that the BBC realizes it is operating in an increasingly crowded… [Continue Reading] -

With 93 percent of Samsung Galaxy Note7s returned, FAA says airline warnings are no longer needed
Publié: janvier 11, 2017, 10:50am CET par Mark Wilson
After apologies and updates to kill batteries, it would appear that Samsung has managed to convince most customers to part with their faulty Galaxy Note 7s -- in the US, at least. As a result of this, the Department of Transport has announced that airlines no longer need to warn passengers that taking the phone on planes is prohibited. Airline passengers were banned from taking their Note7s on flights back in October; the ban remains in place, but the Federal Aviation Authority now believes that the issue gained so much publicity that it no longer needs to be advertised. In a… [Continue Reading] -

EU wants to increase privacy in WhatsApp, Gmail and iMessage by preventing unwanted tracking
Publié: janvier 10, 2017, 6:40pm CET par Mark Wilson
Facebook, Apple and Google face a drop in ad revenue if EU proposals to apply the same rules to online messaging services that currently apply to telecoms companies go through. In a nutshell, the proposals suggest that the likes of WhatsApp, Gmail and iMessage should ask for explicit user permission to allow tracking with a view to delivering targeted ads. Google and Microsoft have already faced criticism for scanning emails and using the contents to tailor advertising to the recipient. The EU wants online message services to be subject to the ePrivacy Directive to help improve confidentiality and security. The… [Continue Reading] -

Warning: Chrome, Opera and Safari's auto form fillers make it easy to steal personal data
Publié: janvier 10, 2017, 2:50pm CET par Mark Wilson
We're all looking for ways to save time and effort, so it's hardly surprising that some web browsers offer a feature that automatically fills in online forms with commonly requested personal information. While incredibly useful, the feature can also be exploited to extract data a user might not want to share with a particular website. Chrome, Opera and Safari all offer to save and automatically fill in details such as name, address, phone number, and so on, and users are ordinarily only aware of the data which is obviously filled in on their behalf. But a web developer shows how… [Continue Reading] -

Snapchat thumbs its nose at Brexit, opens international HQ in UK
Publié: janvier 10, 2017, 1:17pm CET par Mark Wilson
Brexit was supposed to terrify companies out of doing business in the UK, and in some instances this has been true. But Snapchat is bucking the trend, opting to set up its international headquarters not in Ireland (as many companies do to avoid huge tax bills), but in the UK. Snap Inc, the company behind SnapChat, will open its London offices under the name Snap Group Limited. The company says it chose the UK capital because of its "strong creative industries", and the move will be seen by many as a something of a coup for post-EU referendum Britain. The… [Continue Reading] -

Snooper's charter attacked: Liberty mounts legal challenge to Investigatory Powers Act's 'assault on freedom'
Publié: janvier 10, 2017, 12:14pm CET par Mark Wilson
The Investigatory Powers Act 2016 -- better known to many as the snooper's charter -- faced massive public criticism in the run-up to becoming law at the end of 2016 for the privacy-invading powers it affords the UK government to gather data about internet usage. Towards the end of the year, the European Court of Justice ruled that the "general and indiscriminate retention" of internet data and communication is illegal, potentially threatening the Investigatory Powers Act. Now the human rights group Liberty is launching its own legal attack on the Act, asking for a High Court judicial review of the… [Continue Reading] -

Yahoo is not changing its name to Altaba in Verizon sale!
Publié: janvier 10, 2017, 10:26am CET par Mark Wilson
Things are all change at Yahoo. The sale of the company to Verizon appears to be going ahead -- despite a series of setbacks along the way, including a high-profile data breach -- for $4.83 billion, and when the deal does go through, Marissa Mayer will step down from the board. While many news reports today state that Yahoo is now called (or will be) Altaba, this is not strictly true. Verizon is not buying Yahoo in its entirety; a 15 percent stake in Alibaba and a 35.5 percent stake in Yahoo Japan will live on as an investment company… [Continue Reading] -

IMDb ignores new law banning it from publishing actors' ages online, citing free speech violations
Publié: janvier 8, 2017, 11:54am CET par Mark Wilson
Back in September, the state of California passed a new law that banned sites that offer paid subscriptions, and allow people to post resumes, from publishing individuals' ages. It's a law that has the potential to affect many sites, but it is the Internet Movie Database (IMDb) that hit the headlines. The Amazon-owned site is a handy source for anyone who wants to check the age of a particular actor, but the state of California introduced the new law as part of an anti-age-discrimination drive. IMDb was told to remove actors' ages from the site by 1 January, 2017, but… [Continue Reading] -

What's the best Linux distro for you?
Publié: janvier 7, 2017, 6:10pm CET par Mark Wilson
When it comes to desktop operating systems, there are three main camps into which people fall: Windows, Mac and Linux. In the case of the latter camp things can be confusing because there are endless distros to choose from -- but which is best? The beauty of Linux is that it can be tweaked and tailored in so many ways. This means that while the plethora of choice can seem overwhelming, it is also possible to find the perfect distro for just about any scenario. To help you make the right choice, here's a helpful list of the best distros… [Continue Reading] -

How to install leaked Windows 10 Build 15002, and what's new
Publié: janvier 7, 2017, 1:00pm CET par Mark Wilson
Microsoft may have said that there would be no new Insider builds released this week, but that did nothing to stop one from leaking out anyway. Windows 10 Build 15002 has been lifted directly from Microsoft's servers and you can grab yourself a copy if you fancy trying it out. Don't expect an easy ride if you do decide to download the leaked version, however -- it is supplied in WIM format, meaning that you will have to tinker about with converting it as well as other steps. There are a few changes worth noting. Among the new features are… [Continue Reading] -

Hackers find a way to install new games on NES Classic Edition
Publié: janvier 7, 2017, 12:28pm CET par Mark Wilson
When Nintendo launched the NES Classic Edition there was much rejoicing from gamers of certain ages. But while 30 and 40-somethings may have been looking forward to reliving their youth playing classic games, there was some bad news -- the bundled 30 games were all you could play. Nintendo saying that there was no way to add new games to the console was seen by some as a challenge. Now hackers have found a way to upload new games to the NES Classic via USB... but it's not a super-simple process. The existence of emulators for just about every games… [Continue Reading] -

Google kills Hangouts API
Publié: janvier 7, 2017, 11:48am CET par Mark Wilson
Google is retiring the Hangouts API, meaning that apps relying on it will stop working. The announcement was made very quietly via email and an updated FAQ, and the change takes effect before the end of April. The official cut-off date is 25 April, and after this date apps that use the API will cease to function -- most of them, at least. With immediate effect, it is no longer possible to create new apps that use the API. While Google does not say as much, the move is likely part of its push of Duo as a replacement for… [Continue Reading] -

Google makes Fastboot and ADB available as separate downloads for Windows, Mac and Linux
Publié: janvier 7, 2017, 11:10am CET par Mark Wilson
Answering the pleas of many Android users, Google has finally made ADB and Fastboot available as separate downloads. Previously only available as part of the large and intimidating Android SDK or Android Studio, the change of heart means that it is now quicker and easier than ever to jump on the handset flashing and sideloading bandwagon. Over the years, to help overcome the problem of having to download massive files just to get hold of two tiny tools, third party alternatives have sprung up. But many people, understandably and commendably, prefer the idea of using official tools. By making ADB… [Continue Reading] -

Enable notifications to find out when there's a new Google Doodle
Publié: janvier 7, 2017, 10:50am CET par Mark Wilson
Google Doodles are fun little additions to Google search that highlight major events in history, important birthdays and so on. Unless you make a point of hitting Google every day, you could easily miss one of the many animations, images and games that are added throughout the year. Until now. While there is more than one way to find out if there is a new Google Doodle -- as well as checking the Google homepage, you can also follow the Google Doodles Twitter account -- Google has only just got round to providing notifications. Here's how to receive a message… [Continue Reading] -

Windows 10 to get a new look with Project NEON in Redstone 3
Publié: janvier 6, 2017, 5:48pm CET par Mark Wilson
The look of Windows has evolved over the years -- some would say at a largely glacial pace -- and with an incremental update to follow Windows 10 Creators Update we're in line for the latest change. Known as Project NEON, this is not a major overhaul of the Metro or MDL2 (Microsoft Design Language 2) look, but it introduces some new ideas in the form of Acrylic. Some of the features of NEON can already be seen in the latest builds of apps such as Groove Music, and Connected Animations. Acrylic brings blurring effects to apps not only to… [Continue Reading] -

Watch out for Amazon sellers with New Year phishing scams
Publié: janvier 6, 2017, 12:29pm CET par Mark Wilson
This is one of the many times of year that retailers have sales, coinciding neatly with the time of year when many people are feeling the pinch after splashing out on food and presents. But if you're scouring Amazon for great deals, watch out for sellers who are actually using low prices to lure you into a phishing scam. One seller going by the name of (among others) Sc-Elegance uses "used, like new" tech products as bait, ultimately directing buyers to a fraudulent site to make payments. Security experts are warning shoppers to be on their guard. The warning comes… [Continue Reading] -

US Federal Trade Commission sues D-Link for having terrible security
Publié: janvier 6, 2017, 11:00am CET par Mark Wilson
D-Link is facing a lawsuit brought against it by the US Federal Trade Commission for the poor security of its routers and connected cameras. The FTC says the company failed to take reasonable steps to protect users from hackers. The FTC is seeking to improve the security of all IoT (internet of things) devices in the wake of compromised devices being used to launch high-profile DDoS attacks such as Marai and Leet Botnet. D-Link argues that the charges brought against it are "unwarranted and baseless" and plans to "vigorously defend itself". The Taiwanese company says that the FTC "fails to… [Continue Reading] -

Vine is closing on 17 January -- download your Vines now!
Publié: janvier 6, 2017, 10:27am CET par Mark Wilson
Back in October Twitter announced that it was shuttering Vine, with the promise that more details of the closure would follow. A subsequent announcement narrowed it down to the first month of 2017, and now it has been pinned down to 17 January. The move sees Twitter morphing the app into a new Vine Camera app, and killing off the Vine website as we know it. It will still exist, but only as an archive of Vines for you to browse. If you want to download your old Vines for posterity, you'll need to do so by the 17th. Twitter… [Continue Reading] -

WikiLeaks: 2017 will 'blow you away' and, no, Russia did not hack the US election
Publié: janvier 3, 2017, 4:11pm CET par Mark Wilson
The hatred WikiLeaks founder Julian Assange feels towards Hillary Clinton is far from being a secret. During the election campaign, the non-profit organization leaked Clinton emails in the hope that it would destroy her presidential hopes -- and we all know the result of the election. As we slide gently into 2017, the WikiLeaks Twitter account has turned on the ignition and is about to hit the accelerator. The tweet says: "If you thought 2016 was a big WikiLeaks year 2017 will blow you away". On top of this, Assange himself is due to appear in an interview with Fox… [Continue Reading] -

Your flight booking data is insecure and very easy to hack
Publié: janvier 3, 2017, 12:44pm CET par Mark Wilson
The system used by millions of travelers each day to share data between travel agencies, airlines, passengers and websites is incredibly insecure. Security researchers have presented details that highlight just how easy it is to hack flight bookings. German security firm SR Labs says that using nothing more than a traveler's surname and a six-digit Passenger Name Record (PNR), it is possible to not only gather personal information about people, but also make changes to bookings. SR Labs researchers Karsten Nohl and Nemanja Nikodijevic provided details of their findings at the 33rd Chaos Communications Congress in Hamburg. They show that… [Continue Reading] -

Why is WhatsApp not working on your phone? Because it's too old
Publié: janvier 3, 2017, 11:11am CET par Mark Wilson
Welcoming the new year with a trumpet of doom, WhatsApp is bringing misery to many users. If you're using old versions of iOS, Android or -- heaven forbid -- Windows Phone 7, Facebook's popular messaging tool no longer works. There is a brief stay of execution for anyone still packing a BlackBerry, but as of June 30 these will also be cut off. WhatsApp says that "BlackBerry OS, BlackBerry 10, Nokia S40 and Nokia Symbian S60" will stop working by the middle of the year, but it is the hundreds of thousands of Android and iOS users that will be… [Continue Reading] -

Update side-loaded Android apps with APKUpdater
Publié: janvier 2, 2017, 1:04pm CET par Mark Wilson
When you install apps from Google Play, you'll be notified whenever an update is available. If you have opted to side-load apps from other sources, however, this update notification is not available, leaving you having to keep manually checking for new versions. This is, of course, a massive pain in the derriere, and far too much like hard work. Install APKUpdater, and your side-loaded apps will be kept up to date just like those from more official sources. Here's what you need to know. The first thing you'll need to do is install the APKUpdater app from Guthub -- as… [Continue Reading] -

So you want to edit tweets? Jack Dorsey says the option is 'definitely needed'
Publié: janvier 2, 2017, 12:01pm CET par Mark Wilson
Unlike Facebook, Twitter lacks the option to edit what you have posted in order to correct typos or other mistakes. It's something that has been the subject of complaints and discussion for years now, and Jack Dorsey is finally starting to listen. Writing -- on Twitter, funnily enough -- just before New Year, Dorsey said that an edit function is "def needed. But for everyone, not just those w badges". At the moment it is not known whether the feature is due to arrive, but it's clearly something that Twitter is considering. Dorsey makes it clear that he understands the… [Continue Reading] -

This website knows what you have torrented, and you can use it to spy on people
Publié: janvier 2, 2017, 11:11am CET par Mark Wilson
It's no secret that despite being billed as a great way to download large Linux distros and copyright free software, BitTorrent is primarily used to download the latest Star Wars movie, episodes of The Grand Tour, and illicit copies of Photoshop. A new website -- unsophisticatedly named 'I Know What You Download' -- does exactly what you might expect: it exposes the torrents you have downloaded. More than this, it can be used to check what has been downloaded by any IP address, and there is even an option to trick people you know into letting you spy on what… [Continue Reading] -

Samsung kicks off 2017 with new photo-centric Galaxy A7, Galaxy A5, and Galaxy A3 handsets
Publié: janvier 2, 2017, 9:51am CET par Mark Wilson
We are less than 48 hours into 2017, and Samsung is already on the ball with a series of new smartphone announcements. Kicking things off for the new year is the updated Galaxy A series -- comprising the Galaxy A7, Galaxy A5, and Galaxy A3. Available in Black Sky, Gold Sand, Blue Mist and Peach Cloud, the handsets feature 5.7-, 5.2- and 4.7-inch screens respectively. The main focus of the product line refresh is the enhanced camera, but Samsung also highlights the metal frame and 3D glass back which it says draws on the company's "premium design heritage". All three… [Continue Reading] -

Pre-register to download Super Mario Run for Android!
Publié: décembre 29, 2016, 9:56am CET par Mark Wilson
The popularity of Super Mario Run for iOS may be starting to wane slightly, but there is great anticipation for the arrival of Nintendo's Italian plumber on Android. Well, the wait is nearly over -- Nintendo has added Super Mario Run to Google Play! Malware producers were quick to jump on the popularity of the Mario game on iOS, pushing fake, malware-filled versions into the Play Store. In a move that will not only help to prevent people falling victim to such scams, but also serves to indicate the imminent arrival of the official game, eager Mario fans can now… [Continue Reading] -

Nevada website leaks details of thousands seeking to sell medical marijuana
Publié: décembre 29, 2016, 9:51am CET par Mark Wilson
A website run by the Nevada state government has been pulled offline after it was discovered a vulnerability was leaking personal details of thousands of people applying to sell medical marijuana. Nevada's Department of Health and Human Services confirmed that the personal details -- including addresses and social security numbers -- of more than 11,000 applicants were accessible by simply typing in the correct URL. In total, details of some 11,700 people were available for anyone to see using an easily discovered address. There are several concerns here, not least of which is that a government-run website could be so… [Continue Reading] -

Lenovo's 2017 ThinkPads feature Kaby Lake, Precision Touchpads and Windows 10 Signature Edition
Publié: décembre 28, 2016, 5:29pm CET par Mark Wilson
Today Lenovo revealed its updated range of ThinkPad devices, showing that there is a lot to look forward to in 2017. All are kitted out with Kaby Lake CPUs, and some of the models feature Optane 3D drives. This is not a minor line-up refresh -- there are a lot of devices included: ThinkPad X270, ThinkPad Yoga 370, ThinkPad T470, ThinkPad T470s, ThinkPad T470p, ThinkPad T570, ThinkPad 13, ThinkPad L470, ThinkPad L570, and ThinkPad X270. All models include Precision TouchPads, and a move to Windows 10 Signature Edition means there's no need to worry about bloat. Lenovo's announcement comes ahead… [Continue Reading] -

Download the third beta of Android Nougat for OnePlus 3 now!
Publié: décembre 28, 2016, 4:45pm CET par Mark Wilson
The OnePlus 3T may be the replacement for the (slightly) earlier OnePlus 3, but this certainly does not mean that the original has been forgotten. Having already released preview version of Android 7.0 for the flagship killer, OnePlus has now launched its third beta of Nougat for the handset. Going by the name of OxygenOS Open Beta 10, the release incorporates many of the feedback suggestions made in response to the previous beta. Headline changes include improved battery life and faster performance. As this is the third beta, the focus now is on final nips and tucks rather than anything… [Continue Reading] -

Facebook promotes fake news by activating Safety Check based on false reports of Bangkok bomb
Publié: décembre 28, 2016, 12:21pm CET par Mark Wilson
The problem of fake news on Facebook has been highly publicized recently, and while the social network says it is doing what it can to tackle the issue, it seems the company is actually adding fuel to the fire. Based on false reports of an explosion in Bangkok, Thailand, Facebook's Safety Check feature was activated. This in turn helped to give the initial story authenticity, helping with the spread of fake news. Safety Check has itself proved to be a controversial feature, and combined with flakey news algorithms, it resulted in a perfect storm. The problem was sparked off by… [Continue Reading] -

Leaked Windows 10 Creators Update Build 14997 reveals new features
Publié: décembre 27, 2016, 9:32am CET par Mark Wilson
Earlier in December, Microsoft warned Insiders that there would be no more new builds released this side of the New Year. Of course, this does not mean that a new build did not exist, and now build 14997 has leaked online. Coming from the internal development branch (rs_onecoe_base, specifically), it's possible that build 14997 will never be officially released, but the leak does give a tantalizing glimpse of what we can expect. On the menu in this build of Windows 10 Creators Update is an updated version of Microsoft Edge, an improved OOBE and important tweaks to the Start menu.… [Continue Reading] -

If Santa brought you a drone for Christmas, read this or you could face a massive fine
Publié: décembre 26, 2016, 4:12pm CET par Mark Wilson
Drones have become incredibly common in the last couple of years, and they have proved to be popular Christmas presents. But new drone owners are being warned that they are probably blissfully ignorant of the responsibilities of their new toys -- and this ignorance could prove costly. There are very strict laws in place governing where, and how, drones can be flown. Failure to comply with these rules could lead to time in prison or an "unlimited fine" -- for people in the UK, at least. So what do you need to know before you take your drone for its… [Continue Reading] -

Open source CyanogenMod is shutting down... but forked Lineage will rise from its ashes
Publié: décembre 26, 2016, 3:23pm CET par Mark Wilson
For Android hackers and tweakers, CyanogenMod represents mobile OS nirvana -- an open source alternative to Google's official Android, complete with frequent updates. The bad news for fans is that Cyanogen, the company behind the operating system, is closing down operations: with virtually no warning. Coming at a time of year when few people are paying much attention to what is going on in the world of tech, the announcement that nightly builds will be discontinued by the end of the year comes after staff layoffs earlier in the year, and premature rumors that the company was shutting up shop.… [Continue Reading] -

What did people ask Quora about in 2016? Trump, Brexit and Pokémon for starters
Publié: décembre 24, 2016, 9:24am CET par Mark Wilson
We've already learned what people have been using Google to search for in 2016, and now it's the turn of Quora. The Q&A site has just published details of what its users have been asking throughout 2016, and while there are some obvious entries, there are also a few surprises. Quora's "Year in Questions" stats show that Brexit ("how does Brexit affect Europe?") and the US election ("How did Donald Trump win the 2016 US Presidential Election?") were both subjects that "captivated" the US. While topics such as Pokémon had hotspots of popularity through the year, Donald Trump sparked the… [Continue Reading] -

Congressional Encryption Working Group says encryption backdoors are near unworkable
Publié: décembre 23, 2016, 6:10pm CET par Mark Wilson
The Congressional Encryption Working Group (EWG) was set up in the wake of the Apple vs FBI case in which the FBI wanted to gain access to the encrypted contents of a shooter's iPhone. The group has just published its end-of-year report summarizing months of meetings, analysis and debate. The report makes four key observations, starting off with: "Any measure that weakens encryption works against the national interest". This is certainly not a new argument against encryption backdoors for the likes of the FBI, but it is an important one. EWG goes on to urge congress not to do anything… [Continue Reading] -

Major battery life concerns mean Consumer Reports does not recommend the new MacBook Pro
Publié: décembre 23, 2016, 10:31am CET par Mark Wilson
Consumer Reports -- well-respected for its appraisals of products and services -- has decided not to give the new MacBook Pro its coveted 'recommended' status. This is the first time Apple's laptop has failed to gain the accolade. While tests showed that the laptop's performance was good, it was the MacBook Pro's battery that let it down. Consumer Reports warns that battery life "varied dramatically from one trial to another". The report will make for difficult reading for Apple. For people who have been following the launch of the latest addition to the MacBook Pro range, complaints about battery life… [Continue Reading] -

US government starts asking foreign visitors for their Facebook, Twitter and other social media info
Publié: décembre 23, 2016, 10:29am CET par Mark Wilson
In a move that has drawn criticisms from privacy groups, the US government this week started to ask some foreign travelers arriving in the country to hand over their social media account details. Since Tuesday, visitors to the US arriving under the visa waiver program have been asked if they will provide "information associated with your online presence". Travellers are prompted to provide their usernames for the likes of Facebook, Google+, Instagram, LinkedIn and YouTube, and while the handing over of information is currently marked as "optional", it's not clear what the consequences of failing to provide it may be,… [Continue Reading] -

Stop lurking on Facebook (maybe ditch it altogether!) and you'll have a happier Christmas
Publié: décembre 22, 2016, 6:25pm CET par Mark Wilson
For all of the talk of it being a social network, Facebook can be a lonely and depressing place. Despite this, many people use the site as somewhere to 'lurk', something which research shows can be psychologically harmful. A study by the University of Copenhagen found that emotions become more positive and life-satisfaction increased in a group of people who took a break from the site. The effects were more pronounced in heavy users of Facebook, in those who suffered from envy, and those who failed to interact with other users. The advice for some people is that they might… [Continue Reading] -

"Does Alaska have polar bears?" and other popular Google search queries in 2016
Publié: décembre 22, 2016, 9:50am CET par Mark Wilson
Google search's autocomplete function is an interesting feature; as well as helping to save time, it can also be very revealing of the zeitgeist. The feature has been in the headlines recently for reasons that probably didn’t make Google particularly happy, but autocomplete can also be the source of some amusement. Marketing company WebpageFX has come up with an entertaining lookback at the most popular searches in the US, broken down by state. This fairly simple piece of research shows that people are asking questions such as "does Idaho exist?", "does Florida have zika?", and "does Arizona have pee in it?"… [Continue Reading] -

Facebook received 27 percent more government requests for information in 2016
Publié: décembre 22, 2016, 8:46am CET par Mark Wilson
Facebook has released its Global Government Requests Report for H1 2016, and it shows that there has been a significant increase in the number of government requests for account data. Compared to the first half of 2015, Facebook received 27 percent more requests globally. Most of these 59,229 requests came from the US government, and more than half of them (56 percent) included a gagging order preventing Facebook from notifying the affected users. Request for "content restriction" due to local law violations dropped dramatically -- down a massive 83 percent from 55,827 to 9,663. All is not as it seems here, however.… [Continue Reading] -

Twitter search gets an overhaul to place more emphasis on relevance
Publié: décembre 21, 2016, 4:10pm CET par Mark Wilson
Twitter has given its search results a tweak just in time for the New Year. The change sees a move away from displaying tweets in reverse chronological order to showing them in order of relevance instead. The company recognizes that the site is "live and real-time, so naturally Twitter search must surface recent, yet still relevant, results", so time of posting is still factored in to determine the display order -- it is just no longer the only factor used. With a dash of machine learning thrown in, Twitter thinks it has things sorted. The changes come as the result… [Continue Reading] -

Super Mario Run is bad news for everyone -- especially Android users
Publié: décembre 21, 2016, 1:12pm CET par Mark Wilson
When Apple announced that Mario was making his way to iOS, there was much rejoicing. But the excitement soon gave way to disappointment for several reasons. Firstly there was the price, with many feeling $9.99 was just too much to ask for what is, ultimately, a very basic, one button platformer. Next there's the complaint that Super Mario run requires constant access to the internet -- many users have also grumbled that the game has eaten through large chunks of their monthly data allowance. Nintendo may have made a pretty penny from sales of the title in the first few… [Continue Reading] -

'General and indiscriminate retention' of data ruled illegal, threatening Snooper's Charter
Publié: décembre 21, 2016, 12:28pm CET par Mark Wilson
The UK government's Investigatory Powers Act 2016 (also known as the Snooper's Charter) has been dealt a blow after the European Court of Justice ruled that the "general and indiscriminate retention" of internet data and communication is illegal. This is a serious setback for Theresa May's government which introduced legislations that not only requires ISPs to store customers' browsing history for a year, but also make this data available to a large number of agencies. The European court made the ruling following a legal challenge made by MPs David Davis and Tom Watson which gained the support of privacy groups.… [Continue Reading] -

Facebook introduces Live Audio in conjunction with the BBC
Publié: décembre 21, 2016, 9:48am CET par Mark Wilson
It's not all that long since Facebook started to allow users to broadcast live video to their friends and followers -- now the social network is doing the same with audio. Things are looking good for mobile users, particularly those with Android devices. Starting off with partners such as the BBC World Service, LBC and Harper Collins, Live Audio is something of a blend of podcasts and radio. To start off -- just as happened with live video -- audio broadcasting will only be available to a select group of companies, but there are plans to open it up to… [Continue Reading] -

Electronic Frontier Foundation reveals its privacy and security wishlist for 2017
Publié: décembre 20, 2016, 7:36pm CET par Mark Wilson
With the end of the year approaching, many people are looking back over 2016 and picking out the highlights. Others, however, are looking back to see what can be learned for 2017; this is exactly what digital rights group Electronic Frontier Foundation is doing. EFF has drawn up a wishlist for 2017, outlining some of the things it hopes technology companies like Google, Twitter, Apple and Facebook will take action on. There are lots of familiar names on the list, and while some of the requests might seem a little hopeful, there is certainly scope for some of the changes… [Continue Reading] -

EU accuses Facebook of providing misleading information about WhatsApp acquisition
Publié: décembre 20, 2016, 1:40pm CET par Mark Wilson
The European Commission could hit Facebook with a colossal fine for providing misleading information during its $19bn takeover of WhatsApp. The social networking giant could be hit with a fine equivalent to 1 percent of annual sales (around $125m) for failing to correctly communicate planned changes to privacy policies. The data sharing between WhatsApp and Facebook is already the subject of investigations, but this latest accusation comes as a fresh blow. The merger between Facebook and WhatsApp saw the social media company "intentionally or negligently" submitting misleading information, the commission says. Despite having said that it would not merge data… [Continue Reading] -

Facebook brings colored backgrounds to statuses
Publié: décembre 20, 2016, 1:19pm CET par Mark Wilson
After "the most requested Messenger feature ever" yesterday -- Group Video Chat -- Facebook now has another update. This time around the social network is allowing users to change the background color of status updates. Before you get too excited, however, there are limitations aplenty to bear in mind. The update is for mobile users only -- at the moment, at least. More than this, it's an option that is only available -- strangely -- to Android users. Gone are the days of dull black-on-white, as you can choose from one of seven colourful options instead. At the moment there is no way to… [Continue Reading] -

Apple loses wireless patent violation and employee rest break lawsuits
Publié: décembre 16, 2016, 6:57pm CET par Mark Wilson
A jury in the United States District Court for the Northern District of California has ruled against Apple in a lawsuit about wireless patent infringement. Core Wireless was awarded $7.3 million in damages after Apple was found to have violated two patents owned by the company. Apple was found to have infringed upon Core Wireless' patents in iPhones and iPads, taking advantage of technology that "provide innovations that improve battery life and signal quality in mobile phones". The company is expected to appeal against the ruling, but this is not the only case it has lost. Core Wireless is a… [Continue Reading] -

App update prevents users going viral on Instagram by pretending to be in Singapore
Publié: décembre 16, 2016, 5:58pm CET par Mark Wilson
Instagrammers around the world recently discovered a quick and easy way to gain greater attention and increase the likelihood of going viral -- tagging their images as if they were in Singapore. A flaw in Instagram's algorithms meant that images geotagged on the Malaysian island were more likely to be picked to be featured on the Explore page. Greater publicity equals greater views equals viral status equals win. Or at least it did. People browsing images posted on Instagram noticed that a strange number of people seemed to have suddenly relocated to Singapore. The ploy was picked up by a… [Continue Reading] -

The Intercept and the Guardian are most secure news sites, but there are lots of duds out there
Publié: décembre 16, 2016, 3:51pm CET par Mark Wilson
The Freedom of the Press Foundation has published the results of research into the security of top news websites. Topping the list is the Intercept which managed to earn itself an A+ rating, while the Guardian was a close second with A-. Both sites scored highly for their support for HTTPS, and the fact that they defaulted to a secure connection to keep visitors safe. Both also feature HSTS, but the Intercept was awarded extra points for using HSTS pre-loading. While the top of the chart makes for thought-provoking reading, it's also interesting to look further down the rankings where… [Continue Reading] -

0-day alert: Your favorite Linux distro may not be as secure as you think
Publié: décembre 16, 2016, 11:43am CET par Mark Wilson
Popular Linux distros such as Ubuntu and Fedora -- including the newly-released Fedora 25 -- are vulnerable to zero-day exploits, shattering the myth that the open source software is ultra-secure. Vulnerabilities can be exploited that allows an attacker to run any code he wants on a victim's computer -- with potentially devastating consequences. Security researcher Chris Evans has published details of exploits that can be used to compromise systems running Linux. All it takes is a malicious audio file to hijack a computer, or even just having Google Chrome installed. One of the exploits takes advantage of a flaw in… [Continue Reading] -

Evernote issues yet another privacy policy statement: makes note snooping opt-in only
Publié: décembre 16, 2016, 10:27am CET par Mark Wilson
With the world so focused on privacy, Evernote should really not have been surprised when there was something of a backlash at an update to its privacy policy that said company employees would be able to access users' unencrypted notes. Forced to clarify the situation, CEO Chris O'Neill issued an apology for any "confusion" and "angst" the announcement caused, but this was seemingly not enough. Faced with mounting pressure and criticism, the company admits it "messed up" and has now announced that employees will only be able to access notes if users opt-in to allow this. Furthermore, Evernote "will not… [Continue Reading] -

Facebook reveals what it is doing to tackle fake news
Publié: décembre 15, 2016, 7:32pm CET par Mark Wilson
The issue of fake news has been in the headlines a lot recently, and it is Facebook that has borne the brunt of criticism. The social network is in the throes of revamping news feeds in a bid to help stamp out the problem. But Facebook is aware that fake news is not going to be eliminated overnight, and so is focusing on "the worst of the worst". Today, the company sheds a little light on the work it has undertaken, and what is still being done to help stem the flow of fakery. The initial targets are "the clear… [Continue Reading] -

Protect yourself online with EFF's updated Privacy Badger 2.0
Publié: décembre 14, 2016, 10:37am CET par Mark Wilson
In the second decade of the 21st century, the blind excitement about the internet has worn off -- now users are aware of the dangers and are concerned about privacy. Cookies have been around for just about as long as web connections, but there are all manner of ways to track people and spy on online activity. This is something that Privacy Badger 2.0 aims to help with. Coming from the digital rights group Electronic Frontier Foundation, the tool takes the form of a browser extension -- available for Chrome, Opera and Firefox. It blocks online trackers that can be… [Continue Reading] -

Facebook launches Parents Portal to help keep kids safe online
Publié: décembre 13, 2016, 6:34pm CET par Mark Wilson
Facebook is on something of a mission to clean up its act, or at least its image, at the moment. The social network is looking to tackle the problems of trolls, bullying and fake news, and its latest campaign is a bid to keep younger users safe. The minimum age for using Facebook is 13, but this still means that there are some young, naïve and impressionable users out there. With its newly launched Parents Portal, Facebook is looking to arm parents with the information they need to educate their kids about staying safe. The site is little to shout… [Continue Reading] -

Google signs a deal with Cuba to grant Cubans faster access to Google content
Publié: décembre 13, 2016, 11:36am CET par Mark Wilson
Cuba's state-run Etecsa telecoms company has signed a deal with Google. It means that Cuban citizens will be able to more quickly access content provided by the monopolistic internet company. By providing Cuba with access to the Google Global Cache, content will be delivered to internet users via servers which are physically closer, helping to speed up things. The deal will do nothing to speed up general internet access, but it will ensure that Cubans have faster access to Google services such as YouTube. In a statement Google said: "This deal allows ETECSA to use our technology to reduce latency… [Continue Reading] -

Google brings Gboard keyboard to Android
Publié: décembre 13, 2016, 10:45am CET par Mark Wilson
You would think that Google would concentrate on bringing its apps and tools to its own Android operating system before rivals, but this is not always the case. In fact the company has only just got around to launching the Android version of Gboard, months after it debuted on iOS. Gboard is an updated version of the Google keyboard, and it comes with a raft of new features that make it well worth considering. Among the new additions are a dedicated number row, GIF and emoticon search, and the ability to perform Google searches from any app. Rather than being… [Continue Reading] -

Popcorn Time ransomware asks victims to infect other computers to decrypt their own files
Publié: décembre 13, 2016, 10:09am CET par Mark Wilson
Ransomware is the malware du jour and those seeking to extract money from victims have started to use a pyramid scheme system to increase the rate of infection. Not content with encrypting a victim's files and holding them to ransom, the Popcorn Time ransomware encourages those who have been struck to pass on the infection. As is the norm with ransomware, Popcorn Time gives the victim the chance to pay a Bitcoin ransom to decrypt their files, but it also offers a self-described "nasty way" to unlock files for free. Think of it as a ransomware referral scheme. Victims are… [Continue Reading] -

Samsung could be about to issue an OTA update to kill all Galaxy Note7 handsets
Publié: décembre 9, 2016, 9:25am CET par Mark Wilson
Unless you've been living under a rock, the disastrous launch of the Samsung Galaxy Note7 cannot have escaped you. We've already seen the company pushing out updates in some countries to prevent the phones from fully charging in the hope that this will convince owners to take advantage of the exchange or refund program. Now reports suggest that a new OTA update could be on its way to handset owners in the US. Rather than just limiting charging, the word is that the update will prevent charging completely, rendering the phone useless. This is a fiasco that has dragged on… [Continue Reading] -

Microsoft now officially owns LinkedIn
Publié: décembre 8, 2016, 3:45pm CET par Mark Wilson
Six months after news of the acquisition was released, Microsoft's takeover of the professional social network has closed. The aim had been to complete the deal by the end of the year, and the two companies managed to hit the deadline after the European Commission gave it the go-ahead. The $26.2 billion acquisition is being billed as helping to accelerate the mission to "connect the world's professionals". Despite the acquisition, things should remain unchanged at LinkedIn, at least to start with. But the site will ultimately start to integrate more of Microsoft's products and services such as Outlook, Windows 10's… [Continue Reading] -

Facebook reveals the biggest trending topics and Live videos of 2016
Publié: décembre 8, 2016, 3:04pm CET par Mark Wilson
We're nearing the end of the year, so expect to be inundated with retrospectives for 2016 -- Facebook has just released its look back at the year that's (nearly) gone by. The social network's review of 2016 comprises two top 10 lists: the most popular trending topics of the year, and the most popular Live videos of the year. It should come as no surprise that the trending topics list is dominated by major political events such as the US election and Brexit, as well as celebrity deaths. You'll have noticed that there are still three weeks until the end… [Continue Reading] -

Facebook granted European license for electronic payments in Messenger
Publié: décembre 8, 2016, 11:26am CET par Mark Wilson
Payments through Facebook Messenger have been available in the US for some time now, and they're about to make their way to Europe. Facebook has just been granted a license for 'payment services' and 'e-money issuance' with the Central Bank of Ireland. As a member of the European Union, holding a license in Ireland means that Facebook will be able to offer its payment services in all of the EU member states. At the moment it is not clear if Facebook intends to operate the European service in precisely the same way as the US. The existing Facebook Messenger payment… [Continue Reading] -

Google cozies up with Slack for tighter integration
Publié: décembre 7, 2016, 6:55pm CET par Mark Wilson
Faced with competition from the likes of Microsoft Teams, Slack is strengthening its partnership with Google to bring greater cloud integration to users. The beloved communication tool is teaming up with Google Cloud to improve Google Drive support, but there's also support for bots in the form of Drive Bot. Security and sharing is also in line for improvements, and the recently-announced Team Drives from Google will also be supported. Slack says it recognizes that many of its users work with both Slack and Google in the workplace, so bringing the two closer together makes sense. The Drive bot means… [Continue Reading] -

Vinyl resurgence sees records overtaking digital sales in the UK
Publié: décembre 7, 2016, 11:33am CET par Mark Wilson
The music industry has come through all sorts of changes over the last few decades, but it was the birth of the MP3 that many warned was the death knell for record shops. In recent years however, vinyl has made a major comeback, and in the UK digital sales have just been overtaken by sales of the groovy black platters. For purists, enthusiasts, and fans of certain musical genres, vinyl has never gone out of fashion, but in the run-up to Christmas it is proving more popular than ever. Of course we're not looking at sales figures that are anything… [Continue Reading] -

Google goes green -- 100 percent renewable energy usage in 2017 to combat climate change
Publié: décembre 6, 2016, 4:34pm CET par Mark Wilson
Big companies like to be seen to be doing their bit, particularly when it comes to the environment, and tech companies are no different. Google -- being one of the biggest companies in the world -- has huge energy requirements, and it's looking to help address the problem of climate change. The company has already done a lot to increase the energy efficiency of its data centers, but in 2017 it is going further. It says that it will be fully powered by renewable energy from next year, and that includes both data centers and offices. In terms of energy… [Continue Reading] -

Using VP9 and H.264/AVC High codecs keeps Netflix video downloads smaller
Publié: décembre 5, 2016, 6:40pm CET par Mark Wilson
The announcement that Netflix now allows viewers to download videos for offline viewing caused understandable excitement among subscribers. Of course, the key concern -- particularly with mobile devices -- is storage space. But thanks to a tweaked codec, Netflix has your back. If you were worried that you might not be able to fit many episodes of your favorite shows on your phone or tablet, fear not. For Android users, Netflix opted to use the super-efficient VP9 codec, but as this isn’t supported by Apple, it had to think outside the box a little and ended up plumping for a… [Continue Reading] -

Google is wrong, wrong, wrong to remove 'are Jews evil' from search autocomplete suggestions
Publié: décembre 5, 2016, 5:11pm CET par Mark Wilson
Over the last few days there has been much wailing and gnashing of teeth over the discovery that if you type "are Jews" into Google, one of the suggested searches is "are Jews evil". The same is true for the search "are women" and "are Muslims" ("bad" being the suggestion in the third instance). Or at least it was the case. Following cries of anti-Semitism, the search giant folded like a moist tissue and remove the "offensive" suggestion. Clearly Google is able to do -- by and large -- whatever the hell it wants... but that doesn’t make it right.… [Continue Reading] -

Windows apps on Android? Wine will do it... but not just yet
Publié: décembre 4, 2016, 6:15pm CET par Mark Wilson
Wine is well known to Linux and Mac users for opening up the possibility of running Windows software on their preferred operating system. The self-referentially-named software (Wine Is Not an Emulator) is due for a new release in the next few weeks, but the hoped-for Windows-on-Android support is not yet there. That said, it is in the pipeline. Wine developers are working on integrating the existing CrossOver Android software into the open source Windows API. This will allow for Windows software to run in Android, but it won't make it into the up-coming Wine 2.0, and there are limitations. The… [Continue Reading] -

Apple letter all but confirms plans for self-driving cars and commitment to privacy
Publié: décembre 4, 2016, 10:55am CET par Mark Wilson
We've known (or at least believed) for some time that Apple has been working on some form of automated vehicle, but the company has remained tight-lipped about what it is up to. Now, however, a letter to the National Highway Traffic Safety Administration (NHTSA) gives the strongest official hint that Apple is working on something. The letter -- written by Apple's Director of Product Integrity, Steve Kenner, back in November -- has just come to light, in it Apple praises NHTSA's policies on automated vehicles, and stresses the importance of machine learning, data sharing, and user privacy in ensuring the development… [Continue Reading] -

Apple explains the battery problem leading to iPhone 6s shutdowns
Publié: décembre 3, 2016, 4:40pm CET par Mark Wilson
It is a couple of weeks since Apple announced a battery replacement program for iPhone 6s handsets suffering with random shutdown issue. At the time, the company gave nothing away about what the root cause of the problem was, but now it has opened up. In a posting on its Chinese website, Apple confirms that the shutdown problems were indeed related to a battery problem. Specifically, the company explains that it was "a battery component that was exposed to controlled ambient air longer than it should have been". Affected customers are directed to make use of the battery replacement program,… [Continue Reading] -

Despite losing the general election, the Pirate Party could still form Iceland's government
Publié: décembre 3, 2016, 10:02am CET par Mark Wilson
Back in October there was a mixture of great excitement and huge worry that the controversial Pirate Party could end up winning the general election in Iceland. That didn't happen, but with no clear winner there was an attempt to create a five-way coalition that ultimately failed after weeks of talks, paving the way for the radical party made up of poets, hackers and online freedom activists. The Pirate Party -- which says it would offer exile to Edward Snowden and also embrace Bitcoin -- could still end up in power after being invited to form part of the government… [Continue Reading] -

Facebook offers a $20 million sweetener to improve Silicon Valley communities
Publié: décembre 2, 2016, 6:24pm CET par Mark Wilson
Mark Zuckerberg is well known for his philanthropic ventures -- he hardly keeps them quiet, after all. Now Facebook as a whole is getting in on the action, offering up a $20 million contribution to help improve the communities around Silicon Valley and the Bay Area. It could be argued that the financial offering is not entirely selfless, but this will probably be of little concern to those who stand to benefit from a number of projects that will focus on building affordable housing, STEM training in the area, and legal support for those in need. The social networking giant… [Continue Reading] -

Facebook is monitoring Roku and Apple TV streams to deliver targeted advertising
Publié: décembre 2, 2016, 12:41pm CET par Mark Wilson
Internet users are accustomed to the idea of targeted advertising. Both Google and Facebook take into account the things you look for online, the things you look at, the people you are connected to, and so on, and use this information to pelt you with ads they think you will respond to. Having been forced to stop using data gathered from WhatsApp to deliver targeted ads to social network users, you might think that Facebook would consider toning down its ad personalization. But you would be wrong. For the last few weeks, Facebook has been testing the delivery of targeted… [Continue Reading] -

Google's biggest apps, games, TV shows, books and songs of 2016
Publié: décembre 2, 2016, 12:21pm CET par Mark Wilson
As the year draws to a close, it's traditional to look back and pick out some highlights. This is precisely what Google has done, drawing up a list of the 'Best of 2016' from Google Play. Covering books, TV shows, movies, streaming songs, apps and games, there are lots of big names listed in the rundown of what has been trending throughout the year around the globe. The likes of Pokémon GO make an unsurprising appearance, as do Game of Thrones, The Walking Dead, Justin Bieber, Deadpool, and The Girl on the Train -- but did your favorite make the… [Continue Reading] -

A Christmas gift from SwiftKey -- free themes for iOS and Android
Publié: décembre 1, 2016, 5:59pm CET par Mark Wilson
It's December and the season of giving and -- of course -- receiving is just around the corner. You may have written your Christmas wishlist, dropped subtle hints about what you wanted, and you're now just waiting for your desires to be fulfilled. While it's unlikely that keyboard themes and skins featured highly, SwiftKey today announced that all of its themes are now available for free. If you've harbored a secret desire to sex up your phone's keyboard but simply couldn't justify splashing any cash on something so frivolous and, ultimately, pointless, now's your chance to skin away to your… [Continue Reading] -

Google's Santa Tracker counts down to Christmas
Publié: décembre 1, 2016, 2:24pm CET par Mark Wilson
As it does every year, Google has just launched its Santa Tracker in the run-up to Christmas. Despite the name, this is about much more than watching Santa make his journey around the globe -- there's a bunch of fun and games to be enjoyed too. As well as the online version of Santa Tracker, there's also an Android app, and even an app for Android Wear smartwatches. As we make our way through December, the Santa Tracker serves as an advent calendar, with a new treat revealed each day. Kicking things off today, you can enjoy a game of… [Continue Reading] -

FBI granted the right to hack the computers of any suspect running Tor, VPNs or anonymizing software
Publié: décembre 1, 2016, 12:05pm CET par Mark Wilson
Starting today, the FBI will now have a much easier time hacking just about any computer it wants to. The use of VPNs and other anonymizing software such as Tor meant that it was previously difficult for the Feds to apply for the necessary warrant within the relevant jurisdiction. Now the location doesn't matter. A change to Rule 41 of the Federal Rules of Criminal Procedure means that investigators can obtain a search warrant regardless of location. The expansion of FBI hacking powers comes after a failed Senate bid to block the changes to Rule 41, and there are fears… [Continue Reading] -

The UK government's latest deluded idea: 'banning' underage sexting on social media
Publié: novembre 30, 2016, 6:59pm CET par Mark Wilson
When the UK government is not busy looking for ways to invade internet users' privacy, it's looking for ways to restrict what they are able to do online -- particularly when it comes to things of a sexual nature. The health secretary Jeremy Hunt has made calls for technology companies and social media to do more to tackle the problems of cyberbullying, online intimidation and -- rather specifically -- under-18-year-olds texting sexually explicit images. Of course, he doesn't have the slightest idea about how to go about tackling these problems, but he has expressed his concern so that, in conjunction… [Continue Reading] -

The Internet Archive to set up Canadian mirror to stay out of Trump's reach
Publié: novembre 30, 2016, 12:46pm CET par Mark Wilson
Many people are concerned about just what Donald Trump might do when he becomes president in 2017, and some of the biggest concerns lie in the fields of technology and the internet. Worried about what the arrival of President Trump could mean, the Internet Archive is collecting donations to fund a Canadian mirror of the site. The Internet Archive of Canada will lie outside of the jurisdiction of the US government and is being built based on the idea that "lots of copies keep stuff safe". Currently based in San Francisco, a blog post by the Internet Archive makes reference… [Continue Reading] -

The Church Committee calls on Obama for leniency for Snowden if not a pardon
Publié: novembre 30, 2016, 11:44am CET par Mark Wilson
The calls for Edward Snowden to be pardoned by President Obama before Donald Trump takes office have been getting louder. But while many would like to see him given a get-out-of-jail-free card, there is a growing recognition that this simply might not happen. The latest call in support of Snowden comes from the Church Committee (nothing to do with the church, rather the United States Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities, responsible for investigating illegal CIA activity in the 1970s). In a letter to the out-going president, 15 former members of the committee say… [Continue Reading] -

It is terrifyingly easy to bypass BitLocker in Windows 10
Publié: novembre 30, 2016, 10:42am CET par Mark Wilson
The BitLocker feature of Windows is supposed to offer a degree of peace of mind that files are going to be secure -- but one expert points out that a simple key combo is all it takes to bypass the security feature. A bug has been discovered in the way Windows 10 handles a Feature Update -- the installation of a new build of the operating system. By taking advantage of the bug, it is possible to access a Command Prompt and gain unrestricted access to the contents of the hard drive. The reason for this is that BitLocker is… [Continue Reading] -

The Snooper's Charter is now law, giving the UK some of the most extensive, invasive and draconian web surveillance powers in the world
Publié: novembre 29, 2016, 6:27pm CET par Mark Wilson
The Investigatory Powers Act 2016, the Snooper's Charter, legalized spying: call it what you will, the UK now officially has some of the most extreme internet surveillance powers in the world. The Investigatory Powers Bill was today given royal assent, meaning it has now passed into law. Unsurprisingly, there have been huge protests from privacy groups, and an online petition against the new powers has already gained more than 136,000 signatures. The Investigatory Powers Act 2016 not only requires ISPs to store records of their customers' browsing history, but also make this data available to dozens of government agencies, and… [Continue Reading] -

Cold War 2.0: Russia is borrowing the Great Firewall of China to implement greater state censorship and control
Publié: novembre 29, 2016, 11:57am CET par Mark Wilson
The Great Firewall of China is a famous tool of censorship and state control of the internet -- and Russia wants to throw up its own version of the web filtering system. Russia already operates the so-called 'red web' which is used to not only monitor what Russian citizens are up to online, but also implementing blocks and filters such as the recent ban on LinkedIn. But now President Putin wants to steps things up a notch. Russia and China have become close allies in recent years, particularly in the field of state control of the internet, and there are… [Continue Reading] -

Ofcom to force Openreach to separate from BT
Publié: novembre 29, 2016, 11:01am CET par Mark Wilson
BT has been under pressure from industry regulator Ofcom to separate Openreach, its broadband telecoms network, from its retail business. Having failed to voluntarily cooperate, the company will now be forced to separate in order to address concerns about competition. There have long been worries that BT's position of controlling the UK broadband network while simultaneously operating a retail business was a conflict of interest, and Ofcom recently informed BT that Openreach must be transformed into a "legally separate company" to BT. Ofcom believes that creating a separate Openreach will help in its goal of "better service quality and encouraging… [Continue Reading] -

Amazon is limiting the number of reviews you can write
Publié: novembre 28, 2016, 6:24pm CET par Mark Wilson
One of the benefits of shopping with Amazon is that you are able to read reviews written by other customers before you part with your cash. Now the company has updated its review policy, placing a limit on the number of reviews customers can write in a week. The new limit means that there is now a maximum of five reviews per customer per week, but there is an exception. If Amazon is able to verify that products have been purchased by -- rather than gifted to -- the reviewer, the limit is increased. But it gets a little more… [Continue Reading] -

The 30 percent bug sees iPhone battery life dropping dramatically in iOS 10.1.1
Publié: novembre 28, 2016, 6:07pm CET par Mark Wilson
If you've updated your iPhone to iOS 10.1.1, you may have started to feel that your battery is not lasting as long as it used to. You are not alone; you could be experiencing what has been named the 30 percent bug. Many users are complaining that their iPhones will suddenly drop from 30 percent battery charge to 1 percent, and then shutdown. The problem does not seem to affect one particular generation of iPhone, suggesting that the issue lies with iOS itself, but at the moment Apple does not have a fix available. There is a fairly lengthy thread… [Continue Reading] -

The lure of keygens helps spread Gatak malware through the enterprise and healthcare industry
Publié: novembre 26, 2016, 10:51am CET par Mark Wilson
Malware spreads through various channels, and numerous methods are used to fool people into unwittingly installing it. In many cases, the promise of getting something for free -- naming expensive software -- is enough to trick a victim into infecting their own computer. It's far from being a new tactic, and warnings have been issued to fans of torrenting for some time. Keygens (small programs that promise to provide unlock codes and product keys for big-name software titles) are being used to help spread the Gatak or Stegoloader Trojan. Something that is interesting about this malware campaign is that it is… [Continue Reading] -

Right-wing Breitbart blocked by AppNexus ad exchange for hate speech
Publié: novembre 25, 2016, 3:51pm CET par Mark Wilson
Right-wing website Breitbart -- the darling of the so-called alt-right movement -- has been blocked by a leading ad exchange. The site, home to Milo Yiannopoulos (also known as @Nero and banned from Twitter) will no longer be permitted to sell ad space via AppNexus. The move comes after an audit by AppNexus found that Breitbart was in violation of its policies on hate speech and incitement to violence. Speaking to the BBC, AppNexus' spokesman Joshua Zeitz said: "We use a number of third-party standards to determine what is and isn't hate speech, and if we detect a pattern of… [Continue Reading] -

Police warn about dating apps after serial killer conviction
Publié: novembre 25, 2016, 12:51pm CET par Mark Wilson
Police are warning people who use dating sites and dating apps to take extra precautions to ensure their safety. The advice comes after serial killer Stephen Port who contacted his victims through apps such as Grindr and Gaydar. While people making use of dating services have always been warned to take safety precautions, police are concerned that sexual predators are increasingly using such sites and apps as a way of finding potential victims. The UK's National Crime Agency has noticed an alarming increase in the number of people reporting cases of rape after meeting someone through a dating site or… [Continue Reading] -

Apple's disappointing Black Friday deals -- gift cards worth up to $150 with every order
Publié: novembre 25, 2016, 11:20am CET par Mark Wilson
After years of avoiding getting in on the Black Friday action, 2016 sees Apple finally letting its hair down and joining in with everyone else. Earlier in the week we learned that there were some treats in store, and today we can reveal what they are. If you were hoping to save some money on a new MacBook Pro (2016) or to bag yourself a cheap iPhone, you're going to be disappointed. Apple is not offering any Black Friday discounts whatsoever; instead the company is giving away gift cards worth up to $150 with every order placed. So here's the… [Continue Reading] -

Facebook is ready to censor posts in China -- should users around the world be worried?
Publié: novembre 24, 2016, 8:41pm CET par Mark Wilson
Facebook's relationship with China has a tense and turbulent history. The social network is currently banned in China, and this clearly takes a huge chunk out of Facebook's ad revenue. In a bid to keep Chinese authorities happy, Mark Zuckerberg has been involved in the creation of software that can be used to monitor and censor posts made by users. In terms of playing by China's rules, this is clearly great news for Facebook, and it opens up the possibility of the social network operating in the country. While there is the slight silver lining that Facebook's censorship tool does… [Continue Reading] -

Deseat.me helps you delete yourself from the internet with a few clicks
Publié: novembre 24, 2016, 7:09pm CET par Mark Wilson
Everyone has a digital footprint these days, and it can be terrifying to think about the amount of personal information stored online in various accounts. You may have resolved to clean up your act and close a few of your accounts, and this is where Deseat.me can help. The site takes advantage of the fact that many of your online accounts are linked together by a common thread -- Google. By signing into the site with your Google credentials, Deseat.me will find all of your linked accounts and give you the option of wiping them out in one fell swoop.… [Continue Reading] -

Hewlett Packard Enterprise laptop hack exposes personal details of 130,000 US Navy sailors
Publié: novembre 24, 2016, 2:23pm CET par Mark Wilson
A data breach has exposed the personal details of more than 130,000 US Navy sailors, including social security numbers. Rather than being a breach of the Navy's own defences, the data leak came about after a laptop owned by a Hewlett Packard Enterprise employee was compromised. In total, 134,386 current and former sailors are affected by the problem. At this stage it is not known who has been able to access the data, but the Navy is confident that it has not been misused. An investigation is currently underway and the Navy will start to notify the thousands of affected… [Continue Reading] -

CERT warning: Windows 10 is less secure than Windows 7 with EMET
Publié: novembre 24, 2016, 1:09pm CET par Mark Wilson
In direct contrast to Microsoft's assertion that Windows 10 is its most secure operating system ever, the US-CERT Coordination Center says that Windows 7 with EMET offers greater protection. With EMET due to be killed off, security experts are concerned. A vulnerability analyst from CERT, Will Dormann, advises Microsoft to continue the development of EMET. Microsoft says 'many' of EMET's features have been integrated into Windows 10, but the concern is that key components are missing, and others have been implemented in such a way that reduces their security. CERT concerns will be particularly worrying to business and enterprise users,… [Continue Reading] -

Caught red-handed: Reddit CEO edited comments that disparaged him
Publié: novembre 24, 2016, 12:48pm CET par Mark Wilson
If you leave a comment on a website you expect one of two things. First, and most likely, is for your comment to be left alone and posted as-is. The second possibility is that you might find your comment has been deleted because of violating site terms. Reddit, however, has a third option. The self-styled 'front page of the internet' is a little red-faced after CEO Steve Huffman admitted editing comments that were critical of him. Posting using the name 'spez', Huffman was able to anonymously edit comments and replace references to his name with those of Reddit moderators. Huffman… [Continue Reading] -

Travel firm Skyscanner sold to Chinese site Ctrip in $1.74 billion deal
Publié: novembre 24, 2016, 12:03pm CET par Mark Wilson
Edinburgh-based Skyscanner -- a site specializing in price comparison for travellers -- has been bought by its Chinese counterpart Ctrip. The deal values Skyscanner Holdings at $1.74 billion (around £1.4 billion) and sees the Scottish firm joining China's largest travel site, Ctrip.cn. Despite the sale, Skyscanner says that it will continue to operate as an independent company, and it will continue to help travellers find the best deals for hotels, flights and car rentals. Skyscanner already boasts 60 million monthly users, and is available around the world in more than 30 languages. The deal values the company slightly higher than… [Continue Reading] -

No kinky online sex, please -- we're British!
Publié: novembre 23, 2016, 12:46pm CET par Mark Wilson
The UK government's relationship with the web is something of a checkered one. Keen to pander to the fear of concerned hand-wringers, we've seen torrent sites blocked and there are plans afoot to censor porn sites that do not implement 'effective' age checks. Now there is a chance that UK web users will be denied access to websites that portray "non-conventional sexual acts" in the latest act of censorship by the government. A bill currently being considered would apply the same restrictions to online pornography that currently apply offline. In what appears to be yet another example of the government… [Continue Reading] -

Revamped Google Sites now let anyone create websites for free
Publié: novembre 23, 2016, 12:11pm CET par Mark Wilson
Google Sites recently underwent something of a redesign and it was made available to a select group of testers. Now the website building tool is available for everyone to use. For anyone who has used any of Google's online apps, Sites will be immediately familiar. Like so many web building tools, it eschews HTML in favour of a WYSIWYG interface, meaning that even web novices can get a site up and running easily. As you would expect from Google, Sites works well with the other tools in G Suite. This means that if you are creating a shared site for… [Continue Reading] -

Why did Apple limit the MacBook Pro (2016) to 16GB RAM? Battery life
Publié: novembre 23, 2016, 10:48am CET par Mark Wilson
The recently unveiled MacBook Pro (2016) complete with its Touch Bar has been praised and criticized in just about equal measure. One of the biggest criticisms levelled at Apple is that RAM is limited to 16GB. Why such a cap on a professional device? Apple has revealed that the reason for the limit is nothing to do with -- as some may have suspected -- keeping costs down (as if!), but rather due to concerns about battery life. The reasoning may be fairly sound, but the full explanation may not be enough to silence critics completely. Speaking to MacDaddy Apple's… [Continue Reading] -

Apple has some Black Friday special offers for you -- but they're secret for now!
Publié: novembre 22, 2016, 4:43pm CET par Mark Wilson
Black Friday is mere days away, and shoppers are preparing to hit the streets and online stores. Big names like Microsoft have already revealed some of the bargains you can snap up, and this year Apple is getting in on the action too. Apple has traditionally turned its nose up at Black Friday, but the lure of shifting a few extra units by lopping off a few dollars seems to have been too great this year. The company's Black Friday special offer site is up and running, but it's a bit of a tease at the moment. The page for… [Continue Reading] -

NHS partnership with DeepMind puts Google AI in charge of sharing patient data
Publié: novembre 22, 2016, 1:59pm CET par Mark Wilson
Google is no stranger to working with user data, but its latest partnership with the National Health Service sees the company entering unchartered waters. Having already been granted access to the records of more than 1.6 million patients in London, Google's DeepMind will be used by the NHS to alert medical staff to the condition of people under their care. Given Google's track record of using data gathered from its users as part of its ad business, there are understandable concerns from privacy groups about the company's involvement. But data shared with DeepMind will not make its way to Google… [Continue Reading] -

iOS bug means glitchy videos can kill any iPhone or iPad
Publié: novembre 22, 2016, 12:43pm CET par Mark Wilson
iPhone users are familiar with strange bugs that crop up from time to time that can, temporarily at least, kill their cell phone. We've seen specially-crafted text messages crash iPhones, and now there is a video which can render Apple smartphones useless -- until they are restarted, that is. The video takes advantage of a bug in iOS relating to the handling of media files, and it appears to affect both iPhones and iPads. The model of phone or tablet doesn’t seem to matter, and the problem affects iOS 10 and goes back as far as iOS 5. So, if… [Continue Reading] -

Google has tips and new features to help you beat the crowds in the Black Friday sales
Publié: novembre 22, 2016, 12:06pm CET par Mark Wilson
Black Friday can be a great way to bag yourself a bargain, but it can also be a nightmare in terms of stress. If you're looking to save a few bucks in the run-up to Christmas but want to avoid the Black Friday crowds, Google could just be able to help. Google Search and Google Maps now not only show you the times of day that a particular store, bar or other location tends to be busy, there's now also real-time updates about just how busy places are. Armed with this information you can time your shopping trips more effectively.… [Continue Reading] -

Obama is not going to pardon Edward Snowden -- and Trump certainly won't
Publié: novembre 21, 2016, 5:00pm CET par Mark Wilson
Edward Snowden. A liberal darling, and simultaneously a figure of hate. His surveillance leaks are now legendary, and while the NSA whistle-blower hides away in Russia, there are calls for President Obama to issue a pardon before President Trump becomes a reality. But Obama is having none of it. In an interview with Germany's Der Spiegel, the out-going president was asked bluntly about pardoning the former NSA contractor. His response was: "I can't pardon somebody who hasn't gone before a court and presented themselves". Obama, of course, could pardon Snowden if he wanted, regardless of whether he has faced trial,… [Continue Reading] -

Microsoft reveals minimum specs for Windows Holographic compatibility
Publié: novembre 21, 2016, 4:38pm CET par Mark Wilson
As Windows 10 evolves, Microsoft is incorporating a number of different technologies from 3D to mixed reality. The company's own AR/VR platform, Windows Holographic, has headsets like Oculus Rift, and the minimum spec for connected PCs is slowly starting to emerge. As noted by the Verge, the latest insider builds of Windows 10 include a Windows Holographic First Run app that gives you the chance to test your computer to see if it is compatible with Windows Holographic. The minimum specs are surprisingly low. While it is certainly not going to be possible to connect a Windows Holographic headset to… [Continue Reading] -

Apple launches battery replacement program for iPhone 6s handsets with shutdown problems
Publié: novembre 21, 2016, 11:06am CET par Mark Wilson
Apple has launched its second repair program in quick succession, this time focusing on iPhone 6s handsets that suffer unexpected shutdowns. The program will see batteries replaced in a number of affected phones. The battery replacement program comes hot on the heels of a repair program for iPhone 6Plus handsets afflicted with 'touch disease'. Apple stresses that the battery problems are not a safety issue such as seen with the Samsung Galaxy Note7, and advises customers with problematic handsets how to get a repair. The battery replacement program is in operation around the world, and Apple is offering refunds to… [Continue Reading] -

Samsung says batteries in the Galaxy S7 family are safe
Publié: novembre 20, 2016, 7:13pm CET par Mark Wilson
Following on from the Note7 battery farce, Samsung is understandably keen to reassure customers -- and would be customers -- that its other phones are safe. Having lost untold billions of dollars because of exploding Note7s, the Korean company has taken the strange move of advising people that the Galaxy S7 family is safe. In a weirdly proactive post in the Samsung Newsroom, the company points out that there have been no instances of internal battery failure in these devices. It does concede, however, that there have been instances of battery failure following external damage. The post is a little… [Continue Reading] -

How will Facebook fight the fake news phenomenon? Poorly... and stupid, lazy users don't help
Publié: novembre 20, 2016, 5:50pm CET par Mark Wilson
Facebook has many problems, but the most recent and prominent of them has been the issue of fake news. So serious is the problem, that some have blamed fake news stories on Facebook as being the reason Donald Trump is now president elect. Mark Zuckerberg has made it fairly clear he doesn't subscribe to this particular idea, but he is certainly aware that fake news is a problem. Under pressure to do something about it -- bearing in mind that for a worrying percentage of people, Facebook is their only source of news -- Zuckerberg wants to not only make… [Continue Reading] -

UPDATE: Scale of Three customer data breach massively downsized, but identity theft remains a risk
Publié: novembre 18, 2016, 8:25pm CET par Mark Wilson
Late yesterday, Three admitted to a breach of its customer databases which potentially put 6 million people at risk. Today the company has spoken out, indicating that far fewer customers were affected than first thought. In fact, data from just over 130,000 accounts was accessed, with varying levels of access meaning different customer information was exposed. Three says the primary goal of the database breach was to intercept handsets rather than for other purposes, and it stresses that no financial information was stolen. Three says that for 107,102 customers, the following information may have been accessed: whether they are a… [Continue Reading] -

Apple launches costly repair program for iPhone 6 Plus 'touch disease'
Publié: novembre 18, 2016, 2:11pm CET par Mark Wilson
The iPhone 6 Plus' so-called "touch disease" has been known about for some time now, but Apple has only just got around to launching a repair program -- the Multi-Touch Repair Program for iPhone 6 Plus. But in addition to taking its sweet time in getting round to addressing the issue, Apple is set to upset large number of users by charging them $149 for the privilege. The repair program will run for five years from the on-sale date of the iPhone 6 Plus, but it should not be seen as a way to repair a cracked screen at the… [Continue Reading] -

Facebook's Social Good Forum aims to improve the world with donations in live video and Community Help
Publié: novembre 18, 2016, 12:46pm CET par Mark Wilson
Facebook just held its first Social Good Forum and used it to unveil a number of new tools and options focused around raising money to help out those in need. It also announced the expansion of the existing Safety Check feature. The social network has faced criticism in the past for triggering Safety Check -- which lets Facebook users tells friends and family they are OK in the event of a disaster or crisis -- for some major events, but not others. Now Facebook is taking a hands-off approach: it can be triggered by the community. Another new feature announced… [Continue Reading] -

Millions of mobile users at risk after Three customer database breach
Publié: novembre 18, 2016, 11:12am CET par Mark Wilson
Hackers have gained access to a database containing the personal details of up to six million customers of mobile carrier Three. A report in the Telegraph cites 'sources familiar with the incident', but while Three has confirmed a security breach took place, the company is yet to provide precise details. What we do know is that the incident took place when hackers used employee login credentials to access the customer upgrade database. It is thought that the hackers gained accessed to customer names, addresses, phone numbers and dates of birth, but financial details were not exposed. News of the breach… [Continue Reading] -

Privacy alert -- Your iPhone is secretly sending your call history to iCloud
Publié: novembre 18, 2016, 10:16am CET par Mark Wilson
iCloud is hardly the finest example of secure cloud storage, as numerous hacked celebrities will attest. So it is perhaps a little concerning to learn that Apple is -- according to a Russian security firm -- storing months of call logs to iCloud without many users being aware of what’s going on. Elcomsoft, which specializes in cracking software, discovered that if you are an iPhone owner with an active iCloud account, four months' worth of your phone calls have been stored online. Many people will see this as a privacy concern but, worryingly, Apple does not provide a way to… [Continue Reading] -

Legal mass surveillance: Investigatory Powers Bill could become law by the end of the year
Publié: novembre 17, 2016, 1:35pm CET par Mark Wilson
The highly controversial Investigatory Powers Bill could be enshrined into UK law by the end of the year after it was passed by both houses of Parliament. Strongly opposed by privacy campaigners, the bill -- dubbed the Snooper's Charter -- will mean a full record of every UK internet users' browsing history is accessible by the government. All that remains is for the bill to receive royal assent -- essentially a formality -- and it will then become the Investigatory Powers Act. It means the UK will have one of the most wide-ranging, all-encompassing, and privacy-invading mass surveillance programs in… [Continue Reading] -

Facebook's privacy-invading WhatsApp user data dipping ends in Europe
Publié: novembre 17, 2016, 1:13pm CET par Mark Wilson
Facebook has stopped using data collected from WhatsApp users to customize ads in Europe. The move comes after the practice was banned in Germany, and after the UK's Information Commissioner announced an investigation. The social networking giant had already agreed to stop using WhatsApp data from users in the UK, but this has now been extended on a Europe-wide basis. Last month Facebook was on the receiving end of criticism from the Article 29 Working Party who complained about the invasion of users' privacy. Like many technology companies operating in Europe, Facebook's European headquarters can be found in Ireland. The… [Continue Reading] -

Smaller ISPs have happier customers
Publié: novembre 16, 2016, 3:31pm CET par Mark Wilson
If you have eschewed the big names and opted for a smaller ISP, you probably have a happier broadband experience. These are the findings of a report which says the big four ISPs in the UK -- BT, Sky, Virgin Media and TalkTalk -- are rated lower than their smaller rivals. In fact, the highest rated provider, SSE, has only been in the broadband game since 2014, with Yorkshire-based Plusnet coming in second place, says Cable.co.uk. Of the big names, TalkTalk provides broadband to 13 percent of UK internet users, yet it scored just 6.66 out of 10 and placed… [Continue Reading] -

Google PhotoScan turns your smartphone into a scanner for your old photos
Publié: novembre 16, 2016, 12:12pm CET par Mark Wilson
Despite the name, smartphones are generally used for anything but traditional phone related activities -- and one of the most popular usages of the devices is snapping photographs. But while an entire generation of photographers has grown up with digital photography, there are plenty of physical photos out there waiting to be digitized. Google thinks it has the answer in the form of PhotoScan. The app is available for iOS and Android, and it transforms your smartphone into a scanner so you can preserve old photos. Unsurprisingly, it is packed with smarts to simplify the whole process, and it all… [Continue Reading] -

Could alt-right account bans spell the end of Twitter?
Publié: novembre 16, 2016, 10:33am CET par Mark Wilson
Abuse and trolling has been a serious problem for Twitter for some time and continues to be so. Various measures have been introduced to help with the issues, but now the site is going down a more drastic route, banning prominent alt-right accounts. This is not something that is entirely new; earlier in the year Breitbart's Milo Yiannopoulos (also known as @Nero) was permanently banned from Twitter. In the wake of Donald Trump's astonishing rise to presidency, the alt-right movement has enjoyed a major boost. The question is, does Twitter risk cutting off too many of its users if it… [Continue Reading] -

Bigger battery, better camera, faster processor -- the OnePlus 3T is even more of a flagship killer
Publié: novembre 15, 2016, 8:44pm CET par Mark Wilson
The OnePlus 3 -- unashamedly billed as the 'flagship killer' -- caused major ripples of excitement when it was released earlier in the year. Now, after rumors and teasers, and mere months after the launch, there is a follow up -- the OnePlus 3T. One of the key features of the OnePlus 3 was Dash Charge, its fast charging option still offers a full day's usage from 30 minutes of charging -- and the battery has jumped in size. Internally, the processor has been upgraded to a Snapdragon 821 chip clocked at 2.35 GHz, and there's now a 128GB model… [Continue Reading] -

Android backdoor found sending personal information from US users to China
Publié: novembre 15, 2016, 8:16pm CET par Mark Wilson
Mobile security firm Kryptowire has discovered a backdoor in several Android smartphones sold in the US. The company says that the firmware collected personal data about users without consent, and sent this private information on to Chinese firm Shanghai Adups Technology Company. Included in the reams of personal data shared to a third party server were the full text of SMS, call histories, and unique device identifiers. In addition to this, an OTA (over the air) update to firmware allowed for the non-consensual installation of apps, user location tracking and keyword monitoring. Kryptowire says that the smartphones -- including the… [Continue Reading] -

Twitter expands Mute feature to help combat its troll problem
Publié: novembre 15, 2016, 6:09pm CET par Mark Wilson
Twitter has promised for some time that it will do more to tackle the problem of trolling, abuse and harassment. Today, the company announces that it is expanding its Mute features, giving users the ability to mute keywords, phrases, and conversations. This comes in response to feedback from people who have long-asked for a way to prevent notifications about topics they are not interested in, from people they don’t want to hear from, and so on. Twitter also says that it has retrained its staff and improved systems to make it easier and more efficient to report and deal with… [Continue Reading] -

Major Linux security hole found in Cryptsetup script for LUKS disk encryption
Publié: novembre 15, 2016, 10:41am CET par Mark Wilson
A security vulnerability discovered in numerous Linux distros potentially puts millions of users at risk. CVE-2016-4484 (Cryptsetup Initrd root Shell) affects the Cryptsetup script that is used to unlock partitions encrypted with LUKS (Linux Unified Key Setup). The flaw means that it is possible for a hacker to access, change or delete data on the hard drive, and it is not even necessary to have physical access to exploit the vulnerability in every circumstance. But the worrying thing is just how easy the problem is to exploit. The problem lies in the way password checking is handled by /scripts/local-top/cryptroot. By… [Continue Reading] -

Oops! Leak reveals Microsoft is to launch Visual Studio for Mac
Publié: novembre 14, 2016, 8:14pm CET par Mark Wilson
Microsoft accidentally revealed that Visual Studio is making its way to the Mac. A blog post published in error on MSDN shows that the company plans to bring its coding tool to the Apple platform. Transforming Visual Studio into a cross-platform development tool is an interesting move for Microsoft, and something it has resisted for quite some time. The official announcement is due at Connect later this week, but the leak means that we already have all the details we need. While the original blog post has vanished from MSDN, there's still a cached version available that reveals all. The… [Continue Reading] -

Microsoft has huge Black Friday savings on Surface devices, Windows 10 PCs and Xbox One S
Publié: novembre 14, 2016, 6:11pm CET par Mark Wilson
Black Friday is just around the corner, and Microsoft is already talking about what special offers it's going to have on the big day. Whether you're looking for a new desktop PC, an Xbox One S, or a Surface, you could save yourself hundreds of dollars. In fact, if you are in the market for a Surface device, there's never been a better time to consider making the leap -- you could save up to $430. Microsoft is also offering the Xbox One S at its lowest price ever, and there are savings to be made on games and much… [Continue Reading] -

Microsoft says Windows 10 Anniversary Update is the most secure version of Windows ever
Publié: novembre 14, 2016, 4:49pm CET par Mark Wilson
In a white paper and blog post, Microsoft makes the claim that changes introduced in Windows 10 Anniversary Update make it the most secure version of Windows ever. The company is particularly proud of its ability to fight ransomware, but also points to security features such as Credential Guard and Windows Hello. Microsoft says that Windows Defender -- recently complained about by Eugene Kapsersky -- is to thank for this. Cloud-based protection and faster updates mean protection is more effective than ever. In the white paper, entitled Ransomware Protection in Windows 10 Anniversary Update, Microsoft says that Windows 10 computers… [Continue Reading] -

The new Google Play Music rolls out to Android, iOS and the web
Publié: novembre 14, 2016, 11:19am CET par Mark Wilson
Starting today, Google is rolling out an updated version of Google Play Music, its streaming music service. The company says that the update sees the use of machine learning to create contextual playlists based on where listeners are and what they are doing. The latest version of Google Play Music is more "assistive" than ever, with Google making much of the personalized playlists it is able to automatically create. Playlists are created based on a number of "signals". As well as taking into account the types of music you listen to most frequently, how the weather is like, what activity… [Continue Reading] -

Hillary Clinton blames FBI email investigation for her election loss to Donald Trump
Publié: novembre 13, 2016, 5:25pm CET par Mark Wilson
Donald Trump said in no uncertain terms that he believed the US election was rigged. If he had lost, he would have almost certainly contested the result, making claims of vote influencing, media bias and who knows what else. But the reality is that Trump won, and this means that it is Hillary Clinton who is left pointing the finger of blame for losing. Unsurprisingly, it's the FBI that finds itself named as being responsible, with Clinton referring to letters from FBI director James Comey relating to the investigation into her use of a personal email server as the reason… [Continue Reading] -

Mark Zuckerberg denies Facebook influenced the US election, and vows to tackle fake news
Publié: novembre 13, 2016, 2:12pm CET par Mark Wilson
In the wake of the election of Donald Trump as Barack Obama's successor as president of America, Mark Zuckerberg has spoken out to deny claims that Facebook in any way influenced the result of the US election. Criticism of Facebook has taken various forms. One of the key complaints is that its news algorithms serve to create an echo chamber, exaggerating the already-present confirmation bias effect. But there are also concerns that fake news is a serious problem on the platform. Writing in a post on his own Facebook page over the weekend, Mark Zuckerberg said: "After the election, many… [Continue Reading] -

New emoji revealed: breastfeeding, vomiting, and naked sauna users
Publié: novembre 13, 2016, 12:56pm CET par Mark Wilson
The emoji lexicon is one that continues to grow month after month, year after year. Once little more than a collection of smiley faces and a few symbols, there are now emoji representing just about everything imaginable -- and they're even considered works of art. At the moment, Unicode is considering which of a number of proposed new emoji should be added to the collection in 2017. Included in the list of proposals are a swearing face, a vomiting face, an exploding head, emo hair, a breastfeeding mother, a hajib wearer and a couple of naked sauna users. The addition… [Continue Reading] -

Furious Kaspersky is 'disappointed and dismayed' with Microsoft
Publié: novembre 13, 2016, 11:27am CET par Mark Wilson
Claims of anti-competitive behavior are incredibly common in the world of tech; Google finds itself on the defensive on just about a weekly basis. Microsoft is certainly no stranger to accusations of anti-competitiveness, most notably for bundling Internet Explorer in older versions of Windows. But now it's Microsoft's approach to security that's in the firing line. Eugene Kaspersky (yes, that one: the Russian security expert and CEO of Kaspersky Lab) has fired a vitriolic tirade at Microsoft in which he complains about how Windows Defender works in Windows 10. Windows 10 has been lambasted for many reasons since it launched,… [Continue Reading] -

Facebook's Mark Zuckerberg is dead... maybe you are too
Publié: novembre 12, 2016, 11:28am CET par Mark Wilson
A "terrible error" has been blamed for the accidental virtual killing of a number of Facebook users, including none other than Mark Zuckerberg. Thousands of users of the social network logged into their accounts to find out they were dead after Facebook experienced a strange bug. The accounts of many people were memorialized as friends were invited to "remember and celebrate" the lives of the "deceased". The mistake led to Facebook users having to reassure friends and family that they were OK and remained alive and kicking. Facebook has since addressed the problem and issued a statement expressing regret. A… [Continue Reading] -

No more Microsoft Security Bulletins after January 2017
Publié: novembre 10, 2016, 5:56pm CET par Mark Wilson
Microsoft has a long tradition of publishing Security Bulletins to share information about patches and security fixes that it releases. But starting next year this is going to change. As of February 2017, Microsoft will make use of the newly launched Security Updates Guide database. This, on the face of it, sounds like a great idea -- a searchable database of information -- but it changes the way information is presented and is unlikely to be well-received by users. The announcement was hardly shouted from the hilltops -- it was a little afterthought tacked on the end of a short… [Continue Reading] -

Google flatly denies claims that Android has hurt competition -- quite the reverse
Publié: novembre 10, 2016, 5:52pm CET par Mark Wilson
Google's battle with the European Commission has raged on for many years, and the company has faced frequent accusations of anti-competitive behavior for one reason or another. Today the Android producer has hit back at the European claims, saying that the existence of iOS is proof that its own mobile operating system is not anti-competitive. Senior vice president of Google, Kent Walker, writes on the company blog that "Android is not a 'one way street'; it's a multi-lane highway of choice". He also points to the fact that the cost of smartphones running Android has dropped dramatically over the years,… [Continue Reading] -

Google's new Safe Browsing site is home to malicious site reporting, transparency reports, and policies
Publié: novembre 9, 2016, 9:28pm CET par Mark Wilson
Google today launches a revamped version of its Safe Browsing site, bringing a number of tools and services under one roof. The tag line for the site is "Making the world's information safely accessible," and Google makes much of fact that it now keeps more than two billion devices safe online -- desktop and Android, as well as devices running Google tools such as Chrome and Gmail. One of the main purposes of the site is to make it easier for people to report malicious sites they encounter, so other internet users can be warned and protected. But the updated… [Continue Reading] -

Facebook Messenger is now able to pump ads into your eyeballs
Publié: novembre 9, 2016, 8:22pm CET par Mark Wilson
Facebook, like Google, is all about the ads. Not content with filling newsfeeds with advertising, Facebook Messenger -- already something of a privacy nightmare -- is about to become home to 'sponsored messages'. Ads by another name. The new ad formats follow on from newsfeed data designed to direct Facebook users to Messenger, and from there the idea is to drive brand awareness and increase sales. But as with other advertising on Facebook, ads are targeted, meaning there is more than a slight degree of concern when it comes to privacy. Support for sponsored messages is rolling out on a… [Continue Reading] -

Google is closing down Map Maker
Publié: novembre 9, 2016, 7:11pm CET par Mark Wilson
Google has announced that Map Maker -- the tool which can be used to make and suggest changes to Google Maps -- is to close down. The closure is scheduled for March 2017, and Google says that the editing features will be gradually integrated into Google Maps itself as part of a streamlining process. It's not clear just how long it will take for all of the editing features to roll out to Google Maps, but some features will be missing for a while, if not permanently. The change means that map editing will not be quite such a free-for-all… [Continue Reading] -

Android Auto can now be used on your phone in any car, regardless of age
Publié: novembre 7, 2016, 5:51pm CET par Mark Wilson
It's quite some time since Google launched Android Auto -- around two years, in fact -- but adoption has been hampered by one little niggle: you needed a compatible car to take advantage of it. Today that changes. Starting today, Android Auto is available as a stand-alone phone app that can be used to bring the tool to any car via an Android device. This means that older vehicles can now feel the benefits of Android Auto and use it to get directions, listen to music, and much more. All you need to enjoy Android Auto is a phone running… [Continue Reading] -

Online retailers warned about price-fixing ahead of Black Friday
Publié: novembre 7, 2016, 5:10pm CET par Mark Wilson
Black Friday is just around the corner, and while shoppers may be looking forward to making big savings the Competition and Markets Authority (CMA) has issued a warning to online retailers about price-fixing. The consumer body has not revealed which retailers it has written to, but it says that "a number of online companies" have received letters. It's part of a campaign to make it clear to companies selling online that "discussing and agreeing price levels with competitors is illegal, and can result in serious penalties". The CMA has previously been involved in clamping down on price-fixing in Amazon's marketplace,… [Continue Reading] -

How to block Windows 10 popups for Microsoft Edge and Bing Rewards
Publié: novembre 7, 2016, 4:35pm CET par Mark Wilson
Just the other day users started to notice that Microsoft was using Windows 10 to push ads for its Edge browser. Already riled by ads for Windows 10 itself and the appearance of app ads in the Start menu, people were soon asking how to stop the unwanted popups. One suggestion that started doing the round was that simply unpinning Microsoft Edge from the taskbar does the job -- but it doesn’t seem to work for everyone. Here are a few more things you can do to prevent the appearance of Microsoft's ads. If you have yet to try unpinning… [Continue Reading] -

FBI says Clinton emails show no signs of wrong-doing, but Trump has his doubts
Publié: novembre 7, 2016, 11:02am CET par Mark Wilson
Just over a week after the FBI announced it was re-opening the investigation into Hillary Clinton's emails, bureau director James Comey has announced that the previous investigatory conclusion of no wrong-doing remains. Looking at a new batch of emails that were discovered during a separate investigation has "not changed our conclusion", he said. But while the Clinton camp welcomed the news, Donald Trump was more suspicious. "You can’t review 650,000 emails in eight days," he said. Hillary Clinton's use of a private email server is an issue that has dogged her presidential campaign for months, and Comey's announcement that the… [Continue Reading] -

SEO alert: Google search to rank sites according to their mobile versions
Publié: novembre 6, 2016, 8:37pm CET par Mark Wilson
Having recently said that it will show different search results to mobile and desktop users, Google now has another search related announcement. Reacting to the fact that most searches are conducted from mobile devices, search results will be ranked according to sites' mobile content. Google says that it has "begun experiments to make [its] index mobile-first", and it's a move that essentially says that mobile searchers are more important than the rest. In light of the recent splitting of mobile and desktop indexing, the announcement is hardly a bolt out of the blue, but it's still something that many site… [Continue Reading] -

Samsung forcing out software update to render Note7 batteries rubbish
Publié: novembre 5, 2016, 7:10pm CET par Mark Wilson
Samsung's Note7 fiasco has been in headline for some weeks now, most recently when it emerged that the company was working with telecoms companies to cut off the phones from networks in New Zealand. Now Samsung has announced that it is pushing out an update to US users that will limit how much the battery can be charged. This is not so much a case of limiting the charge to make the phone safer, rather an attempt to annoy Note7 owners who have not yet taken advantage of the 'refund and exchange' program to do just that. The hope is… [Continue Reading] -

Samsung forcing out software update to render Galaxy Note7 batteries rubbish
Publié: novembre 5, 2016, 7:10pm CET par Mark Wilson
Samsung's Galaxy Note7 fiasco has been in headline for some weeks now, most recently when it emerged that the company was working with telecoms companies to cut off the phones from networks in New Zealand. Now Samsung has announced that it is pushing out an update to US users that will limit how much the battery can be charged. This is not so much a case of limiting the charge to make the phone safer, rather an attempt to annoy Galaxy Note7 owners who have not yet taken advantage of the 'refund and exchange' program to do just that. The… [Continue Reading] -

Hacker discovers Gmail vulnerability that leaves any account open to compromise
Publié: novembre 5, 2016, 6:13pm CET par Mark Wilson
A student and security researcher from Pakistan has found a serious issue with Gmail that makes it possible for a hacker to take over any email address. The vulnerability relates to the way Google handles the linking of a primary Gmail account to another email address for the purposes of message forwarding. In just a few steps it was -- before Google fixed the problem -- possible to take over ownership of an email address by tricking the system into sending out the necessary verification code. If a hacker knows a secondary email address associated with a Gmail account he… [Continue Reading] -

Here we go again! Microsoft throws more ads into Windows 10
Publié: novembre 4, 2016, 12:41pm CET par Mark Wilson
With Windows 10, Microsoft faced criticism for its heavy promotion of the new operating system. Windows 7 and 8 users became more than a little annoyed by the presence of persistent nagging upgrade prompts, and others have been irritated by the addition of 'promoted apps' to the Start menu. Now Microsoft is at it again. Apparently unhappy with the number of people using its Edge browser, the company is now trying to encourage people to switch from rivals by using popup ads to push Edge and Bing Rewards. Will the company never learn? As reported by PCWorld, Microsoft has started… [Continue Reading] -

Telecomms companies blacklist Samsung Note7s to prevent people using dangerous phones
Publié: novembre 4, 2016, 12:04pm CET par Mark Wilson
The Samsung Galaxy Note7 was one of the -- if not the -- most disastrous phone launches of all time. After numerous reports of handsets catching fire or exploding, Samsung was forced to recall the device -- but some people have been reluctant to give theirs up. The phone may have been banned from planes, and Samsung has even offered a financial incentive to hand over the Note7, but despite the potential danger many users are hanging onto their phones. In a drastic move to prevent them from being used, some mobile providers -- incoordination with Samsung -- are disconnecting… [Continue Reading] -

Telecomms companies blacklist Samsung Galaxy Note7s to prevent people using dangerous phones
Publié: novembre 4, 2016, 12:04pm CET par Mark Wilson
The Samsung Galaxy Note7 was one of the -- if not the -- most disastrous phone launches of all time. After numerous reports of handsets catching fire or exploding, Samsung was forced to recall the device -- but some people have been reluctant to give theirs up. The phone may have been banned from planes, and Samsung has even offered a financial incentive to hand over the Galaxy Note7, but despite the potential danger many users are hanging onto their phones. In a drastic move to prevent them from being used, some mobile providers -- incoordination with Samsung -- are… [Continue Reading] -

How to remove unused Android phones and tablets from your Google Play account
Publié: novembre 4, 2016, 11:32am CET par Mark Wilson
If you visit Google Play on your computer, you can install apps to any of the Android devices you own. All you need to do is click the Install button and you'll then be presented with a list of your phones and tablets to choose from. Over the years, you've probably owed a number of Android devices, and it's possible that this list has become a bit unwieldy. Why should you be forced to make a selection when you only have one phone? Here's how to clear up the list and make your life a little easier. If you head… [Continue Reading] -

Unified Update Platform (UUP) means much smaller updates in Windows 10 Creators Update
Publié: novembre 4, 2016, 4:13am CET par Mark Wilson
For anyone who is a Windows Insider, the release of a new insider build is something of a double-edged sword. There is -- of course -- the excitement of trying out the latest and greatest build of Windows, but there is also the prospect of a huge download; one that must be completed on every computer you use. Microsoft has a plan to reduce the size of update downloads. The Unified Update Platform (UUP) sees the introduction of differential download packages meaning that users need only download the bits that have changed since the last release rather than having to… [Continue Reading] -

Instapaper Premium is now free for everyone!
Publié: novembre 3, 2016, 12:54pm CET par Mark Wilson
A couple of months after joining forces with Pinterest, Instapaper has announced that the premium version of its web bookmarking and syncing service is now completely free of charge. Ditching the subscription fee does not mean that users will be inundated with ads, however. The company says that it is now far better financed, and can therefore afford to deliver an ad-free experience to everyone. Anyone who has a free Instapaper account at the moment will find that they have been automatically upgraded, and can immediately take advantage of a number of extra features. This includes the ability to save… [Continue Reading] -

Adblock Plus gets its panties in a bunch over 'crazy accusations'
Publié: novembre 2, 2016, 8:07pm CET par Mark Wilson
Online advertising is a divisive issue, and one that sees many people turning to ad blockers to improve their online experience. The biggest name in the business is Adblock Plus which has come under fire in recent months for its Acceptable Ads program that allows certain ads to be whitelisted. The company behind Adblock Plus, Eyeo, today published an extraordinary blog post in which it attacks "crazy accusations" made about it and its program. Introduced in the format of an election-style fact checker, the post from Ben Williams drips with barely disguised fury at what are described as "slants, spins… [Continue Reading] -

Mozilla pulls Battery Status API from Firefox over privacy concerns
Publié: novembre 2, 2016, 12:35pm CET par Mark Wilson
It was supposed to be a feature that allowed more efficient versions of websites to be delivered to people running out of battery power. But the Battery Status API built into Firefox was also found to be problematic from a privacy point of view after it was discovered that visitors' battery levels could be used to track them online. In response to this the API is being pulled from Firefox. The potential for the Battery Status API to be misused has been known for some time -- it is possible to track users even when they are using VPNs or… [Continue Reading] -

Microsoft: Russian hackers are exploiting Windows flaw exposed by Google
Publié: novembre 2, 2016, 11:29am CET par Mark Wilson
Microsoft says that a vulnerability in Windows made public by Google has been exploited by a hacking group with links to Russia. The group -- known variously as Strontium, Fancy Bear, and APT 28 -- has executed several spear phishing attacks, the company says. Google was criticized for publicizing the vulnerability before Microsoft has released a patch. A fix for the security hole is not due to be released until Tuesday, 8 November -- voting day in the US election. The hacking group is one that has been linked to the Russian government, and is thought to have been behind… [Continue Reading] -

Admiral Insurance to use algorithms to set insurance prices based on customers' Facebook posts
Publié: novembre 2, 2016, 10:44am CET par Mark Wilson
Facebook, it is said -- much like Big Brother -- is watching you. Privacy groups have long warned about the potential for information shared on the social network to be misused, and now an insurance company is planning to make use of the status updates customers post to determine the type of drivers they are. The controversial move finds Admiral Insurance using an algorithm to analyze the posts of new drivers in a bid to determine the type of people they are. By linking 'likes', writing style and other factors, Admiral believes the system -- called firstcarquote -- can be… [Continue Reading] -

Suck this! Razer cuts Apple with below-the-belt MacBook Pro attack
Publié: novembre 1, 2016, 8:33pm CET par Mark Wilson
The latest addition to the MacBook Pro range has seen Apple heaped with praise -- for the most part. While the reception has been largely positive, there have been pockets of criticism. One thing for which the late-2016 MacBook Pro has been mocked is its lack of an SD card reader. Some critics have said that the absence of such a port means the laptop is not worthy of its 'professional' tag. Razer, the company behind high-end gaming laptops, today took to Twitter to take a swipe at Apple with a taunt that raised eyebrows and caused a degree of… [Continue Reading] -

How to re-enable the startup chime on a late-2016 MacBook Pro
Publié: novembre 1, 2016, 8:12pm CET par Mark Wilson
For some, Apple's decision to drop the startup chime from the latest batch of MacBook Pros came as great news -- for others it was an absolute travesty. The quest for a silent startup has led many Mac users over the years to seek out third party tools to kill the sound, but now that it has gone there are those who want it back. All is not lost! If you prefer a musical start to your computing sessions, you can re-enable the chime. As discovered by one enterprising MacRumors forum user, all it takes is a little work in… [Continue Reading] -

Tinder has spoken -- Hillary Clinton will beat Donald Trump
Publié: novembre 1, 2016, 12:06pm CET par Mark Wilson
There's now just a week to go in the battle between Trump and Clinton. The race to the White House is nearly over and as revelation after revelation sways polls this way and that way, voters and pundits alike are asking: just who will win this election? Dating app Tinder thinks it knows the answer. Working in conjunction with Rock the Vote, Tinder users were invited to Swipe the Vote to see not only who they would vote for, but also which candidate they most closely matched. Around the world -- with the exception of Russia -- Clinton came out… [Continue Reading] -

Demand for Microsoft's Surface Studio pushes delivery to 2017
Publié: octobre 30, 2016, 11:27am CET par Mark Wilson
If you were hoping to get your hands on a Surface Studio, you're going to have a bit of a wait on your hands. When the new all-in-one was announced, pre-orders opened straight away with shipping due in mid-December. But demand has been such that Microsoft will now not be shipping newly ordered devices until early in the New Year. There's no word on precise details of availability, but all three Surface Studio models have now had their delivery dates pushed back. With the cheapest Surface Studio featuring a $2,999 price tag, this is not a system that many people… [Continue Reading] -

Facebook wants you to vote online for your favorite US election candidate
Publié: octobre 29, 2016, 2:06pm CEST par Mark Wilson
There is just over a week to go until the most important US election in living memory is over. On 8 November voters will hit booths to indicate their preference for Trump, Clinton, or one of the various independents. Facebook is getting in on the action, looking to let users know about the candidates and to encourage voting. While the new Facebook feature lets you vote for candidates by favoriting them on the new site, the social network is quick to point out that this is not online voting -- votes placed on the site will not count towards the… [Continue Reading] -

Apple wants to limit how the new MacBook Pro (2016) Touch Bar can be used
Publié: octobre 29, 2016, 11:55am CEST par Mark Wilson
When Apple unveiled the latest MacBook Pro, it was the Touch Bar that stole the show. But if you were expecting this touchscreen addition to the keyboard to become an all-singing, all-dancing fun parade, you may be disappointed. Apple -- loving, as it does, to remain firmly in control of everything -- has issued developers strict guidelines that restrict how the Touch Bar can (or should...) be used. The company is very keen for the Touch Bar to be seen as an extension of, or addition to, the keyboard, and not the screen. As such, Apple is keen to avoid… [Continue Reading] -

GIPHY has a tool to save all of your favorite Vines as GIFs
Publié: octobre 29, 2016, 10:54am CEST par Mark Wilson
Twitter's decision to shut down Vine disappointed many people, but there was some reassurance that while it is not going to be possible to create any more Vines, existing ones will be saved on the website for the foreseeable future. Recognizing the potential for things to change, GIPHY has announced that it is actively developing a tool that will make it possible to further safeguard the future of your favorite Vines. The animated GIF company is working on a tool that will convert Vines into GIFs. "Long live the loop!" exclaims the company. Even though the conversion tool is not yet… [Continue Reading] -

Customizing Windows 10 Creators Update could become a costly habit
Publié: octobre 29, 2016, 10:07am CEST par Mark Wilson
If you're the sort of person who likes to change the look of their desktop with themes, you had better start saving up ahead of the launch of Windows 10 Creators Update. We already know that Microsoft is using the next update to bring 3D tools such as Paint 3D to the masses, but it will also be used to make a bit of money. A video showcasing what we can expect to see in Windows 10 Creators Update in early 2017 focuses mainly on the 3D side of things. But it also reveals that it will be possible to… [Continue Reading] -

FBI reopens investigation into Hillary Clinton's emails
Publié: octobre 28, 2016, 8:02pm CEST par Mark Wilson
Hillary Clinton may have thought the dust had settled and she was on the home straight to defeating Trump, but the ugly matter of her emails has reared its head again. Today the FBI announces that it is reopening its probe of the presidential candidate, citing the discovery of further emails "that appear pertinent to the investigation". The emails in question were discovered during an unrelated investigation. No details of what this investigation relates to have been revealed, but the announcement by the FBI comes as a blow to Clinton so late in the election campaign. Accusations leveled at Clinton… [Continue Reading] -

Facebook denies its targeted advertising is racist
Publié: octobre 28, 2016, 7:23pm CEST par Mark Wilson
Earlier today we reported about allegations from ProPublica that Facebook is engaged in what appears to be racist ad targeting by excluding based on 'ethnic affinity'. Facebook, predictably, refutes these claims. Firing up full-on defensive mode, Facebook says that its users benefit from targeted content that is more relevant to them. To use the company's marketing spiel, this is "especially critical for people who choose to affiliate with ethnic communities". Far from being racist, this exclusion targeting technique is actually used to avoid causing offense, says Facebook. See also: Facebook accused of using racist 'ethnic affinity' ad targeting In a… [Continue Reading] -

Facebook accused of using racist 'ethnic affinity' ad targeting
Publié: octobre 28, 2016, 4:54pm CEST par Mark Wilson
Advertisers on Facebook are being given the opportunity to exclude people of certain ethnicities from seeing their ads. This is the accusation made in a new report by ProPublica, and it's a feature that -- if true -- would be both racist and illegal. Just as for Google, advertising is big business for Facebook, and the social networking giant is keen to give advertisers all of the tools they need to ensure the maximum return on their investments. But the revelation that the audience for ads can be targeted by excluding those with a particular 'ethnic affinity' is more than… [Continue Reading] -

Open source Microsoft Cognitive Toolkit democratizes AI and deep learning
Publié: octobre 26, 2016, 12:38pm CEST par Mark Wilson
Like many technology companies, Microsoft is pinning a lot on AI -- including the areas of speech and image recognition. To help speed up development, and to enable others to start working on their own projects, the company has released an updated, open source version of the Microsoft Cognitive Toolkit. This is a deep learning toolkit, previously known as the Computational Network Toolkit (CNTK), and it's available for anyone to use completely free of charge. The toolkit has applications far beyond speech recognition, and it has already been used in Bing, and the latest version includes support for Python and… [Continue Reading] -

Vodafone hit with record fine for 'serious and sustained' breaches of consumer protection rules
Publié: octobre 26, 2016, 11:32am CEST par Mark Wilson
The world's second-largest mobile operator, Vodafone, has been handed a £4.76 million ($5.60 million) fine by industry regulator Ofcom. The fine -- the largest ever for a telecoms company -- was a result of Vodafone's "serious and sustained" failings. The company failed to top-up customers' accounts when they bought credit, and failed to act quickly enough to rectify the problem. The failings cost customers £150,000, and it is now going to cost Vodafone £3.7 million; the remaining £925,000 of the fine is for failures with complaint handling. In all, 10,452 of Vodafone's pay-as-you-go customers were affected by problems, and the… [Continue Reading] -

Oops! Apple leaks photo of new MacBook Pro with OLED Magic Toolbar
Publié: octobre 26, 2016, 9:21am CEST par Mark Wilson
The release of macOS 10.12.1 was a fairly unremarkable affair... apart from one thing. In addition to the expected fixes and changes, hidden in the code are images relating to Apple Pay that appear to show off the new MacBook Pro -- the updated model that's not due to be announced until the upcoming event on 27 October. The images are very revealing too, showing off a few surprises that Apple would probably have liked to have kept secret until the big day. Gone are the function keys at the top of the keyboard, replaced instead by a touch sensitive OLED… [Continue Reading] -

Entire Game of Thrones season 7 plot leaks to Reddit
Publié: octobre 25, 2016, 12:07pm CEST par Mark Wilson
The internet has posed a serious problem for movie and television studios for many years now. Usually it is pirated copies of movies and shows that are cause for concern, but for the likes of the Walking Dead and Game of Thrones, it's the dreaded spoiler that needs to be tamed. Spoilers tend to be a problem on Facebook and other social media the night after a big show has aired, as those yet to watch the show don’t want to have the plot ruined. In the case of season 7 of Game of Thrones however -- not due to… [Continue Reading] -

New Sway Democracy app wants to help you choose between Trump and Clinton
Publié: octobre 24, 2016, 2:58pm CEST par Mark Wilson
You've probably noticed that there's an election just around the corner. As Trump and Clinton battle it out there have been accusations that Russia is trying to interfere with the result, Julian Assange has been cut off from the internet to prevent him meddling, and Google has released a fact checker to help separate political fact from fiction. There's no denying that this is one of the most important US elections ever, and the balance of power could be tipped by an important demographic -- millennials. With this in mind, a new app aims to help educate younger voters so… [Continue Reading] -

Children are at risk from online predators as UK government fails to implement sexual grooming laws
Publié: octobre 24, 2016, 12:53pm CEST par Mark Wilson
The UK government has failed to implement promised laws that would help to protect vulnerable children from online predators in England and Wales. Back in 2014, the then-Prime Minister David Cameron said he would introduce a new criminal offense of sexual communication with a child, effectively ensnaring paedolphiles. The law would help to reduce the problem of "grooming", the practice of luring in a child and gaining their trust with a view to later abusing that trust. Cameron's announcement more than 18 months ago was welcomed as it eliminated a legal loophole, but now children's charities are unhappy that laws… [Continue Reading] -

Google's updated privacy policy means personally identifiable ad tracking is now go, go, go!
Publié: octobre 24, 2016, 10:24am CEST par Mark Wilson
That Google encroaches on user privacy is not a startling revelation by any stretch of the imagination. But a recent change to the company's Privacy Policy means that information from DoubleClick ads can now be used to identify individuals and track them online. The changes to the policy have not been hidden -- the details and alterations are visible in an archived copy of the document -- but it has not been advertised either. The implications of the change are huge. Since purchasing DoubleClick back in 2007, Google kept identifiable user data separate from anonymized ad tracking. This is no… [Continue Reading] -

Falling pound forces Microsoft to raise software and cloud prices
Publié: octobre 24, 2016, 9:30am CEST par Mark Wilson
The post-Brexit fallout continues. The UK has already seen price hikes from a number of countries across a range of sectors, and the latest announcement comes from Microsoft. The technology giant warns that starting in January 2017, prices of enterprise software and cloud services will rise for anyone paying in pounds sterling. The UK's decision to leave the EU has seen the value of the pound plummet, and Microsoft is going to increase prices by up to 22 percent to make up for this. The biggest price increases will be for cloud services, which Microsoft says will jump by 22… [Continue Reading] -

Serious Dirty COW bug leaves millions of Linux users vulnerable to attack
Publié: octobre 22, 2016, 2:41pm CEST par Mark Wilson
A vulnerability discovered in the Linux kernel has been present for nine years, and users are being advised to seek out and install a patch as soon as they possibly can. Dubbed Dirty COW, the bug is a privilege escalation vulnerability which can be found in just about every Linux distro out there. Discovered by security expert Phil Oester, Dirty COW is described as one of the most serious bugs of its type ever found in Linux. Assigned the code CVE-2016-5195, there is evidence that the vulnerability has been exploited and a website set up to alert people to the… [Continue Reading] -

76 percent of all Windows 10 users have installed Windows 10 Anniversary Update
Publié: octobre 22, 2016, 12:17pm CEST par Mark Wilson
Even after a staggered roll out of Windows 10 Anniversary Update, Microsoft has managed to push the major operating system update to more than three-quarters of Windows 10 users. The latest figures from AdDuplex show that uptake of Windows 10 Anniversary Update has accelerated dramatically. The latest version of Windows 10 is now installed on no less than 76.6 percent of Windows 10 PCs. This is a major jump even from last month when the figure was a meager 34.4 percent. If the update continues at this rate, Microsoft will be able to celebrate the installation of Windows 10 Anniversary… [Continue Reading] -

Amnesty International ranks message apps according to privacy -- Facebook wins!
Publié: octobre 22, 2016, 11:43am CEST par Mark Wilson
Despite a desire to be more connected than ever before, people are simultaneously more concerned than ever about their security and privacy. This is certainly true when it comes to messaging tools, and the privacy features offered by a particular app or service can be what sways your decision to use it one way or the other. Justice group Amnesty International has spent some time analyzing the privacy and encryption found in a number of popular messaging tools and compiled results in a ranked list. The findings make for interesting reading, not least because Facebook is ranked the most highly.… [Continue Reading] -

Warning: Mark Zuckerberg decides what's newsworthy, making him the world's most powerful editor
Publié: octobre 22, 2016, 10:30am CEST par Mark Wilson
Facebook has stated time and time and time again that it is not a media company, despite appearing to act very much like one. The company's protestations become all the more difficult to swallow when one looks at the way it handles news. In reality, Facebook wields far more power and influence that it's willing to admit. There have been countless instances of Facebook censoring posts from individuals, groups and organizations. Facebook appears to have an unwritten (or largely unpublished) set of rules defining what can be posted on the social network, and just this week Facebook staff wanted to… [Continue Reading] -

LYNK & CO's new 01 is a shareable electric SUV with an open API
Publié: octobre 20, 2016, 10:01am CEST par Mark Wilson
Think of electric cars, and it's Tesla that naturally springs to mind. But Geely, the Chinese parent company of Volvo, wants this to change. Today the company launches a new car brand, LYNK & CO, along with not just a new electric vehicle, the 01, but a whole new ownership model. The 01 -- which will be followed, of course, by the 02, 03, and so on -- is a compact SUV designed for sharing, and it even has its own app store. With connectivity in mind, the 01 has an open API so developers can get to work creating… [Continue Reading] -

MI5, MI6 and GCHQ secretly and illegally collected data about British citizens for over a decade
Publié: octobre 17, 2016, 4:23pm CEST par Mark Wilson
The surveillance activities of the NSA in the US, along with MI5, MI6 and GCHQ in the UK, have been known about for some time now, largely thanks to Edward Snowden. Now the Investigatory Powers Tribunal has ruled that for more than a decade, huge amounts of data were collected without adequate oversight, breaking privacy laws. The tribunal also said that some instances of data collection failed to comply with the European Convention on Human Rights (ECHR). Privacy International, the group who brought the complaint against the spy agencies, said that this is a "highly significant judgment". The court found… [Continue Reading] -

Facebook on the frontline: livestreaming Iraqi and Kurdish forces trying to wrestle Mosul from ISIS
Publié: octobre 17, 2016, 3:20pm CEST par Mark Wilson
When Facebook Live launched as a service available to everyone (after a celebrity-only debut) it didn’t take long for people's fears of terrible incidents being broadcast to come true. We've had celebrities livestreaming, we've had death, injuries and accidents livestreamed. What next? War. Over in Iraq, the city of Mosul is currently under the control of ISIS. Iraqi and Kurdish military forces are in the process of attacking the city to regain control. What's unusual -- and particularly disturbing -- about this is that the whole event is being livestreamed on Facebook by Kurdish media group Rudaw -- complete with… [Continue Reading] -

iOS 10 has a hidden onscreen Home button for iPhone 7 users
Publié: octobre 17, 2016, 10:39am CEST par Mark Wilson
With the launch of the iPhone 7 and iPhone 7 Plus Apple not only removed the headphone jack, the company also replaced the mechanical home button with a static one. What was not revealed, however, is that iOS 10 also has a secret software Home button. The feature is a safeguard built in should anything go wrong with your physical home button. Should this happen, the button problem will be detected and iOS 10 will offer up a temporary on-screen Home button to tide you over until you can get to the Genius Bar. The hidden button was noticed by a… [Continue Reading] -

Samsung announces mass production of 10nm FinFET SoCs
Publié: octobre 17, 2016, 8:35am CEST par Mark Wilson
Still reeling from the Galaxy Note7 recall and flight ban, Samsung has announced it has started mass producing system-on-chip (SoC) products with 10-nanometer FinFET technology. It follows on from the mass production in 2015 of FinFET mobile application processors, and Samsung says this is another industry first. The company says that devices featuring 10nm SoCs will launch in early 2017 and become more widespread throughout the year. There are a number of advantages of the 10nm process over the current 14nm process. Samsung boasts that the new SoCs offer 40 percent lower power consumption, and a 27 percent boost on… [Continue Reading] -

Google will show different search results to mobile and desktop users in the coming months
Publié: octobre 16, 2016, 7:19pm CEST par Mark Wilson
At the moment it does not matter whether you perform a Google search from your phone or from your computer; you'll see the same results. But in a few months this is set to change. The company is set to launch a new mobile search index that will be more up to date than the desktop index. The news came at Pubcon, a social media and optimization conference, via Google's trends analyst Gary Illyes. It was an idea that was floated last year, and after a little experimentation, Google is almost ready to launch the new search index. Although Illyes… [Continue Reading] -

Game of Thrones actress Faye Marsay is bullied into quitting social media
Publié: octobre 16, 2016, 7:08pm CEST par Mark Wilson
The latest high-profile victim of online abuse is actress Faye Marsay, famous for her portrayal of the Waif in Game of Thrones. After finding herself on the receiving end of hate and harassment, she has announced that she is to quit Facebook. Marsay's decision comes after guidelines were unveiled to help determine whether criminal proceedings should be brought against individuals engaging in online hate crimes. She says that social media became far too intrusive and fans were started to want to know too much about her. She says: "I've just come off Facebook [...] It's terrifying, social media, it terrifies… [Continue Reading] -

Samsung Galaxy Note7 is banned from all US planes to avoid 'a catastrophic incident'
Publié: octobre 15, 2016, 4:41pm CEST par Mark Wilson
An emergency order has been pushed through by the US Transportation Department that means the Galaxy Note7 phones cannot be taken on board any US flight. The grounding of the handset comes after Samsung stopped manufacturing it because of numerous reports of phones catching fire or exploding. It is yet another incentive for anyone who has hung onto the Note7 following a recall which saw Samsung offering customers $100 to switch to another phone from the company. See also: Samsung permanently discontinues Galaxy Note7 The order means that as of this weekend, the Galaxy Note7 may not be taken on… [Continue Reading] -

Twitter experiments with replacing Moments with a new Explore feature
Publié: octobre 13, 2016, 1:45pm CEST par Mark Wilson
The Moments feature could be set to disappear from Twitter's mobile apps. Having only recently announced the roll out of a curation option to everyone, Twitter is now experimenting with replacing it with a more inviting Explore feature. Speaking to Mashable, Twitter confirmed that a "content discovery"-focused Explorer tab could replace Moments in the future. For now, though, there is an experimental change visible to some iOS and Android users that sees the Moments and Explore tabs show up side by side. It's something that is more than a little reminiscent of the Discover tab which used to be found… [Continue Reading] -

Samsung offers Galaxy Note7 owners $100 to stick with the company as it expands product recall
Publié: octobre 13, 2016, 1:02pm CEST par Mark Wilson
The cost of Samsung's explosive and disastrous Galaxy Note7 launch just keeps on mounting up. Having previously offered Galaxy Note7 owners $25 for anyone seeking a refund on their handset or switching to another brand, the company is now dangling the promise of a $100 sweetener to anyone willing to try their luck with another Samsung phone. The expansion of the refund and exchange program starts today, and is accompanied by near-grovelling from Samsung president and COO Tim Baxter. Samsung is currently counting the financial cost of the recall -- but would the promise of a nice, crisp Benjamin be… [Continue Reading] -

Updated Google Photos uses AI to animate and auto-rotate your pictures... and more
Publié: octobre 13, 2016, 11:39am CEST par Mark Wilson
Google Photos has received a fairly significant update that sees the arrival of four key new features. Three of them are focused on sharing and viewing your photos, but the fourth is an AI-powered auto-rotate function that ensures you'll no longer have to look at photos on their sides. As Pixel and Pixel XL owners (as well as other Android users who don't mind a drop in quality) have unlimited Google Photo storage at their disposal, Google is introducing a Facebook-style restrospective feature. Google says it will "make it easier to look back at your fondest memories", but there is… [Continue Reading] -

Playboy comes to iOS and Android after ditching the nudity
Publié: octobre 13, 2016, 10:58am CEST par Mark Wilson
Playboy is a name synonymous with nudity -- or at least it was. It's been some time since the top shelf stalwart decided to drop pictures of completely naked women (the prevalence of hardcore online porn was too much to compete with), and the cleaner image means that the title is now available in the App Store and Google Play. The title can now be downloaded as an app which provides subscribers with access to "sexy, seductive pictorials of the world’s most beautiful women". But of course you only buy it for the articles, so you'll be pleased to hear… [Continue Reading] -

Rumors of the OnePlus 3's death have been greatly exaggerated
Publié: octobre 13, 2016, 10:14am CEST par Mark Wilson
That the Samsung Galaxy Note7 was killed off hardly came as a surprise, but rumors also started to circulate this week that the OnePlus 3 was to be discontinued. While OnePlus has not suffered from any problems, delays in getting orders out to customers led to speculation that there was a new phone in the pipeline and that production on the OnePlus 3 had come to an end. Nonsense! Says OnePlus. The company reassures us that it is "still producing and selling the OnePlus 3". There is, however, a slight problem with the supply chain. Carl Pei, co-founder of OnePlus,… [Continue Reading] -

Google's latest transparency report reveals the futility of transparency reports -- and increased data requests
Publié: octobre 12, 2016, 9:57pm CEST par Mark Wilson
As has become the norm for big tech companies these days, Google has just published its latest transparency report. The report reveals -- in very, very broad strokes -- the number of requests for user data the company has received from the US government. In a groundbreaking revelation (and -- please -- note the sarcasm) the lifting of a gag restriction by the FBI means Google is now able to report about the number of National Security Letters it received in Q2 2015. Sort of. "We have updated the range of NSLs received in that period [...] from 0-499 to… [Continue Reading] -

Snowden-endorsed Signal gains Facebook-style disappearing messages
Publié: octobre 12, 2016, 3:25pm CEST par Mark Wilson
Facebook's recently rolled-out Secret Conversations heralded the arrival of not only end-to-end encryption for users, but also disappearing messages. Not to be outdone, Edward Snowden's favorite messaging service, Signal, has followed suit. The company behind the app, Open Whisper Systems, points out that the feature is not really designed to further improve security and privacy; rather it is a way "to keep your message history tidy". The feature has made its way to the Android, iOS and desktop versions of Signal, and one of the more noteworthy aspects of disappearing messages is the timing of the release. Facebook Messenger's Secret… [Continue Reading] -

Android 7.1 Nougat developer preview coming later this month
Publié: octobre 11, 2016, 9:17pm CEST par Mark Wilson
Google has just announced that a developer preview of Android 7.1 Nougat will be released before the end of the month. At the Pixel and Pixel XL launch, it was revealed that these two new handset would be running this version of Android, but a developer preview was pencilled in for some time before the end of the year. The release schedule seems to have been sped up slightly, and this is something that will please developers and end users alike. Google promises dev that "we’ll give you access to this update so you can start getting your apps ready".… [Continue Reading] -

Yahoo locks in users by disabling email forwarding to other accounts
Publié: octobre 11, 2016, 1:33pm CEST par Mark Wilson
Yahoo has had a dramatic fall from grace in the last couple of weeks. While far from the most popular email service out there, it maintains a relatively healthy user base -- but all of this changed with news of a security breach resulting in the theft of 500 million account details, and the revelation that the company secretly scanned emails for the NSA. While there has not exactly been a mass exodus away from Yahoo, many users have started to question their loyalty to the company and investigate the alternatives. If you are thinking about abandoning Yahoo, the company… [Continue Reading] -

Samsung permanently discontinues Galaxy Note7
Publié: octobre 11, 2016, 12:10pm CEST par Mark Wilson
The troubled Galaxy Note7 is being killed off completely. The news comes after Samsung's statement yesterday that it was asking carriers and retail partners to cease sales and exchanges while an investigation is carried out into handsets catching fire or exploding. But now the company has filed papers with South Korean regulators in which it says it will permanently cease sales of the beleaguered smartphone. The decision follows earlier reports that production was on hold temporarily. Samsung is already counting the cost of one of the most disastrous smartphone launches we have seen. The company had already seen billions of… [Continue Reading] -

Workplace by Facebook exits beta, bringing social networking to the enterprise
Publié: octobre 10, 2016, 7:36pm CEST par Mark Wilson
You may not have heard of Workplace by Facebook, and that could be for one of two reasons. Firstly, it used to be known as Facebook at Work but, more importantly, it has been in closed beta for nearly two years. Today, Facebook announces that Workplace is now available all over the world, giving enterprise users a way to stay connected with co-workers. Promising "the best of Facebook plus new features", Workplace can be used by any company or organization that feels a personalized, internal social network with messaging capabilities could be beneficial. Facebook says that 1,000 test organizations have… [Continue Reading] -

Trolls, sexters and doxxers could face prosecution for social media hate crimes
Publié: octobre 10, 2016, 3:26pm CEST par Mark Wilson
The UK's Crown Prosecution Service (CPS) has today published new social media guidelines that set out online offenses for which people could be prosecuted. Launched as part of Hate Crime Awareness Week, the guidance will be used to decide whether criminal proceedings should be brought against individuals. Among the offenses outlined in the document is 'virtual mobbing' -- encouraging others to engage in online hate campaigns. The CPS points out that anyone doing this could face charges under the Serious Crime Act 2007. Also published today is the Public Policy Statements on Hate Crime which is due to be put… [Continue Reading] -

How to restore the Control Panel shortcut in Windows 10's Win+X menu
Publié: octobre 10, 2016, 12:53pm CEST par Mark Wilson
With Windows 10, Microsoft has encouraged users away from the Control Panel in favour of the newer Settings. This is fine for many things, but there are still times when the Control Panel is needed. In recent builds of Windows 10, the Control Panel shortcut has vanished from the Win + X menu (which can also be accessed by right clicking the Start button), leaving some people perplexed about how to change certain settings. Thankfully, there is a way to get the shortcut back in the latest Insider builds. As noted by ghacks, there are in fact two ways to… [Continue Reading] -

Google releases open source font Noto to eliminate the tofu problem
Publié: octobre 10, 2016, 11:18am CEST par Mark Wilson
You may not have heard of the tofu problem, but you have almost certainly experienced it. If you visit a website or open a document that can't display a particular character, you'll see a white box symbol resembling a cube of tofu. Now Google has a solution. The Noto font project (it's a mashup of 'NO more TOfu') has been something of a labor of love, taking five years to reach its conclusion. But the result is an open source Noto font family which Google says includes "every symbol in the Unicode standard, covering more than 800 languages and 110,000… [Continue Reading] -

Algorithm-powered sorting comes to Google+ Communities
Publié: octobre 10, 2016, 10:28am CEST par Mark Wilson
Just about all of the key players in social media have turned to algorithms to control the order in which posts appear in users' timelines. Google has already introduced algorithmic sorting for Google+, and now it is rolling out to Communities. Just as with Instagram, Twitter and Facebook, the decision to move towards algorithms rather than a simple chronological timeline is one that will be divisive. But Google has made it easy to toggle the setting, helping to keep everyone happy. The new approach to timelines in Communities brings the group section of Google+ in line with how users' timeline… [Continue Reading] -

Windows 10's updated Paint app leaks online
Publié: octobre 10, 2016, 10:07am CEST par Mark Wilson
While Windows 10 introduced massive changes, some things have remained constant -- such as the bundled Paint app. After years of minor tweaks, Paint is finally in line for a major upgrade. In recent days, details of the overhauled Paint have appeared online, including introductory videos that show the app will deal with 3D work as well as regular 2D drawing. Now the app has leaked online so you can try it out for yourself. Also read: How to uninstall Windows 10's built-in apps If you can't wait for Microsoft to finish the app and officially release it, you might… [Continue Reading] -

Samsung ceases production of Galaxy Note7 as replacement phones catch fire
Publié: octobre 10, 2016, 8:12am CEST par Mark Wilson
The Galaxy Note7 has been nothing short of an unmitigated disaster for Samsung. Problems with exploding batteries wiped billions off the value of the company and led to a recall, but it soon transpired that even replacement handsets were problematic, with a number of reports of replacement handsets overheating, catching fire, or exploding. Now South Korean news agency Yonhap reports that Samsung has temporarily suspended production of the flagship Android smartphone. It's a move that will unnerve investors, but one that is being carried out in conjunction with safety regulators from South Korea, the United States and China. The Yonhap News Agency… [Continue Reading] -

Google ditches Hangouts in favour of Duo as a required Android app
Publié: octobre 8, 2016, 12:05pm CEST par Mark Wilson
Starting in December, smartphone manufacturers will no longer be required to install Hangouts on their handsets. Instead, phone makers will need to provide users with the recently-launched Duo. This is not to say that Hangouts is being killed off -- not yet, at least. But Duo, complete with end-to-end encryption, will replace the app as part of the core Google Mobile Services package. The announcement came in an email from Google to developers which says: "Today, we are announcing that Google Duo will replace Hangouts within the suite of core GMS apps, and Hangouts will become GMS Optional for telephony… [Continue Reading] -

Facebook's new Events app helps you discover what's going on near you
Publié: octobre 8, 2016, 10:43am CEST par Mark Wilson
If you're a keen Facebook user, you may well have accepted invites to events advertised on the social network. To help make your life a little easier, Facebook has now launched a new, dedicated app called simply Events from Facebook to more easily find out what's going on nearby. More than this, the app can pull in information from your existing calendar so you can see all of your events and appointments in one place to avoid double-booking yourself. It's iOS-only for the time being, but an Android version of the app is in the pipeline. The idea is a… [Continue Reading] -

Russia accused of hacking US voting system and interfering with the 2016 election
Publié: octobre 8, 2016, 10:34am CEST par Mark Wilson
There is only a month to go until the election showdown between Trump and Clinton finally comes to an end. There is a great deal riding on the result of this particular election and we have already seen DNC servers hacked. There has been speculation about who may have been responsible for this security breach, but now the US has pointed the finger firmly at Putin's Russia. Russian hackers are accused of hacking into the Democratic National Committee's servers and trying "to interfere with the US election process". This is not the first time blame has been placed at Russia's door;… [Continue Reading] -

Runtastic users can now listen to curated Google Play Music playlists during workouts
Publié: octobre 7, 2016, 1:08pm CEST par Mark Wilson
Any sort of exercise is made a little easier if you're listening to music. With this in mind, Google has teamed up with Runtastic to provide access to curated playlists in Google Play Music for keen runners. It's a feature that is -- at the moment, at least -- exclusive to Android users, and it makes it easy to choose music that will suit your mood, or the speed at which you're motoring along. The curated playlists are a fairly simple idea, so it's surprising that it has taken so long for them to be implemented in this way. With… [Continue Reading] -

Surprise! Here's Android 7.0 Nougat for OnePlus 3
Publié: octobre 7, 2016, 11:59am CEST par Mark Wilson
It's no secret that there's an Android 7.0 Nougat update on the way to the OnePlus 3, but the question is: when? Of course it is already possible to get Nougat running on your OnePlus 3 if you're willing to install a custom Cyanogenmod 14 build. But what most people are interested in is the official release direct from OnePlus. Well, it's not only in the works, we have a video of it in action. OnePlus has shared a brief video that shows that work on bringing Nougat to the OnePlus 3 is well under way and we are even… [Continue Reading] -

Buy a Google Pixel from Verizon and Verizon will be responsible for updates, not Google
Publié: octobre 7, 2016, 11:22am CEST par Mark Wilson
The newly announced Pixel and Pixel XL caused great interest at the beginning of the week. Described by the company as being "the first phone made by Google inside and out" (even though we know that HTC is involved) you would expect that Android updates would be coming courtesy of Google itself. If you thought that, you'd be wrong. Possibly. It depends where you buy your Pixel from. Buy it from Google, and Google will indeed be responsible for the update process. Buy it from Verizon -- Google's exclusive US partner -- and Verizon will be the one handling system… [Continue Reading] -

Everyone now has access to Facebook's Secret Conversations, so take control of your privacy
Publié: octobre 5, 2016, 5:08pm CEST par Mark Wilson
Facebook has been testing its privacy-focused Secret Conversations feature with a select, and then wider, group of users for a little while now. Today the end-to-end encrypted messaging system rolls out to everyone. If you're concerned about your privacy (firstly, why are you using Facebook?), it's your duty to use it. Secret Conversations remains an opt-in feature, and once enabled it means that only the sender and recipient are able to see messages -- there is no scope for interception by Facebook or any other third party. There's also an important self-destructing messaging option, but there's one glaring problem. While… [Continue Reading] -

Amazon Prime subscribers now have free ebooks, magazines and more with Prime Reading
Publié: octobre 5, 2016, 4:24pm CEST par Mark Wilson
If you have been looking for one more reason to become an Amazon Prime subscriber, the newly launched Prime Reading feature could just be the clincher. Prime Reading gives US subscribers access to a library of free Kindle ebooks, magazines, comics and other publications completely free of charge. At the moment Amazon is proclaiming there are "over a thousand popular books", but there is also the promise of exclusive content. In addition to books, Prime Reading provides access to "a rotating selection of fresh, full issues of top magazines". Amazon is quick to point out that a Kindle device is… [Continue Reading] -

Yahoo secretly scanned emails for the NSA and FBI -- Apple, Google and Microsoft did not
Publié: octobre 5, 2016, 10:54am CEST par Mark Wilson
Yahoo has been having something of a rough time of late, and things are not getting any easier. It has emerged that the company created a custom tool to search customers' emails for specific terms as directed by the NSA and FBI. Reuters shares the story of two former Yahoo employees who say the company complied with a government directive to search through all incoming emails. In response to the revelations, Apple, Google and Microsoft have all denied engaging in similar activity. The explosive news is being described as the first instance of a US company agreeing to scan and… [Continue Reading] -

Pixel and Pixel XL are Google's iPhone killers
Publié: octobre 4, 2016, 8:47pm CEST par Mark Wilson
It may have been one of the worst kept secrets in tech launches, but today Google officially took the wraps off its Pixel and Pixel XL smartphones. In terms of hardware it could be argued that there is nothing too spectacular here, but even if you ignore the (still very impressive) hardware side of things there are two features that directly take on Apple: Google Assistant to compete with Siri, and unlimited full-resolution photo backup. Unlike Google's previous Nexus range, the Pixel handsets carry no other branding -- these are the first phones designed and built inside and out by… [Continue Reading] -

Apple starts to 'randomly' download macOS Sierra on to users' computers
Publié: octobre 4, 2016, 1:55pm CEST par Mark Wilson
It's something that has faint echoes of Microsoft's approach to pushing Windows 10 on to users. This week Apple is making macOS Sierra available to users as an automatic download -- interestingly, users who receive the automatic download treatment are being selected randomly. Apple confirmed the nature of the roll out to The Loop, which also reports that the download will only start for people who have automatic updates switched on, and if they have sufficient storage space available. Unlike Microsoft, Apple is taking a rather less aggressive approach when it comes to suggesting users might like to upgrade to… [Continue Reading] -

Mozilla awards $300,000 to four open source projects
Publié: octobre 4, 2016, 9:33am CEST par Mark Wilson
Mozilla's love of open source is nothing new -- just look to the Mozilla Open Source Support (MOSS) program. Loving a philosophy is one thing, but Mozilla has also put its money where its mouth is. In the third quarter of this year, MOSS awarded more than $300,000 to four projects which it either already supported, or which were aligned with the organization's mission. One of the smallest awards -- $56,000 -- was made to Speech Rule Engine, a text-to-speech style component that makes mathematical and scientific content more accessible. But more money was splashed on Track 1 Foundational Technology… [Continue Reading] -

WhatsApp copies SnapChat and allows you to add emoji to photos... and more
Publié: octobre 4, 2016, 8:54am CEST par Mark Wilson
Until concerns were raised about data sharing with Facebook to help deliver targeted ads, WhatsApp was seen as the messaging tool of choice for those concerned about privacy. As well as offering encrypted messaging, WhatsApp has always been one of the more stripped back messaging apps out there -- but no more. Bowing to pressure to fit in with the crowd and offer the same features as the likes of SnapChat, WhatsApp is adding photo and video editing and enhancement tools. The ability to add emoji to photos, or draw and write on images are just two new options that… [Continue Reading] -

Mirai botnet code used to launch DDoS attack on Krebs On Security leaks online
Publié: octobre 3, 2016, 4:36pm CEST par Mark Wilson
Fears are mounting that there could soon be a rise in large scale DDoS attacks after the source code used to launch the recent crippling attack on Krebs On Security was shared on a hacker forum. Brian Krebs' website was hit by what has been described as the largest ever DDos attack recently, and the Mirai botnet source code has now been made available for anyone to make use of. The style of attack is particularly interesting as it involves using compromised Internet of Things devices such as webcams and other connected IoT hardware. Now that the source code is… [Continue Reading] -

Facebook Marketplace takes on eBay and Craigslist
Publié: octobre 3, 2016, 2:39pm CEST par Mark Wilson
Today, Facebook launches a new way to buy and sell goods online -- Facebook Marketplace. While the service may not win any prizes for the originality of its name, it provides a more efficient and effective way to find things that are for sale near you than currently exists on the social network. To start with, Facebook Marketplace will be available to mobile app users on iOS and Android, but it will also come to Facebook on the desktop eventually. Facebook is taking a very hands-off approach to buying and selling, and is not getting involved in the murkier aspects… [Continue Reading] -

Linux Kernel 4.8 released with Microsoft Surface 3 touchscreen support
Publié: octobre 3, 2016, 12:18pm CEST par Mark Wilson
Over the weekend, Linux Kernel 4.8 was unleashed on the world. This version of the kernel has been available in no fewer than eight release candidate builds, but now there's a stable build for everyone to play with. If you've been following through the release candidates, there are not a huge number of changes with the stable release -- mainly driver, architecture and a few bits of generic code. But for anyone who skipped these releases, there's more to look forward to including Raspberry Pi 3 SoC and Microsoft Surface 3 touchscreen support. Linus Torvalds himself seemed fairly excited to… [Continue Reading] -

Carphone Warehouse leaks full Google Pixel and Google Pixel XL specs
Publié: octobre 3, 2016, 10:29am CEST par Mark Wilson
Google is on the verge of launching the Pixel and Pixel XL, but no launch would be complete without its share of leaks. This time around the slipup comes courtesy of UK retailer Carphone Warehouse which posted details of Google's upcoming phones, complete with photos and full specs. The same mistake was made by Canada's Bell, effectively confirming the specifications which thus far have only been rumors. The listings not only reveal what we can expect in terms of hardware, but also show that Google is going to offer free, unlimited photo backups at full resolution for Pixel owners. Of… [Continue Reading] -

Google faces fines for anticompetitive Android practices in Europe
Publié: octobre 3, 2016, 9:57am CEST par Mark Wilson
European regulators could hit Google with large fines if the company does not stop offering financial incentives to smartphone manufacturers to pre-install its own apps on handsets. Documents obtained by Reuters show that a potential fine could be linked to the revenue Google makes from AdWords. With advertising being Google's primary source of income, this has the potential to be a fine of unparalleled magnitude. The European Commission knows that it needs to hit Google where it hurts if anticompetitive practices are to be effectively discouraged. The Commission says it "intends to set the fine at a level which will… [Continue Reading] -

Facebook launches Messenger Lite to reduce data usage
Publié: octobre 3, 2016, 8:41am CEST par Mark Wilson
Facebook may have the rather lofty goal of wanting to "empower people all over the world to stay connected", but for most people the social network is just about chatting. Facebook Messenger has proved massively popular, and to cater for people with slower internet connection, the company now has Facebook Lite. As you would probably guess from the Lite tag, this is a slightly cut-down version of the messaging tool but it still offers all of the core features. As well as helping out those with slow internet connections, it's an app that will appeal to people with more basic… [Continue Reading] -

Mozilla announces Project Mortar to bring Chrome plugins to Firefox
Publié: septembre 30, 2016, 8:16pm CEST par Mark Wilson
The browser wars continue as Chrome, Opera, Firefox and Edge all vie for attention. One of the biggest draws to any browser is plugin support, and the absence of a particular plugin can make the difference between a user switching allegiances or sticking with their tried-and-tested browser. With this in mind, Mozilla launches Project Mortar. Its aim is to make the development and maintenance of Firefox as cheap and easy as possible. To do this, it is investigating the possibility of borrowing plugin functionality from other browsers, including PDF and Flash support from Chrome. Rather than going to the hassle… [Continue Reading] -

Google creates a new virtual reality experience: "A Walk Through Dementia"
Publié: septembre 30, 2016, 6:21pm CEST par Mark Wilson
The experiences of others can be difficult to understand -- do you see green in the same way as me? But things are even harder -- and more important -- to grasp in the world of medicine. Just what is it like to have dementia, for example? It's much more than just memory loss and confusion. Understanding what the world is like for someone with the condition can help others to learn how they can help sufferers more effectively, and Google has created a new virtual reality experience with this precise aim in mind. "A Walk Through Dementia" is a… [Continue Reading] -

Microsoft dismisses Saleforce's claims of an anticompetitive LinkedIn purchase
Publié: septembre 30, 2016, 2:07pm CEST par Mark Wilson
It has been a few months since Microsoft announced plans to buy LinkedIn for $26.2 billion, and it seems that losing bidder Saleforce is still nursing a bloody nose. Saleforce CEO Marc Benioff is complaining that there are antitrust concerns and is calling on regulators to block the purchase. Having lost a bidding war with Microsoft -- despite offering more money -- Salesforce now appears hell-bent on messing things up for the company. Salesforce's chief legal officer, Burke Norton, has also voiced concerns that Microsoft could block access to user data to rivals. Microsoft says that this is nonsense, stressing… [Continue Reading] -

The iPhone 7 has worse battery life than HTC 10, Samsung Galaxy S7 and LG G5
Publié: septembre 30, 2016, 12:29pm CEST par Mark Wilson
Consumer group Which? has conducted a series of battery life tests on the latest smartphones, and the news is not good for the iPhone 7. Pitted against the Samsung Galaxy S7, HTC 10 and LG G5, Apple's latest handset came in last place... and by some distance. In terms of call time, the Samsung Galaxy S7 lasted for more than twice as long as the iPhone 7, while the HTC 10 had two and a half times the longevity. Things were not quite as bad for the iPhone 7 in internet usage tests... but it was still found bringing up… [Continue Reading] -

Google Maps gains a bunch of voice commands for hands-free navigation
Publié: septembre 30, 2016, 11:55am CEST par Mark Wilson
Google Maps on an Android phone is a great way to get from A to B without getting lost, but if you need to check details of your route or want to make a change to settings, you'll need to pull over to do so. Or at least that used to be the case. Google has just added a load of voice commands to the app. Of course, having to pull over is an inconvenience, and trying to fiddle with your phone while driving is dangerous. With this in mind, the addition of a series of voice commands triggered by… [Continue Reading] -

Apple gets a new London home in Battersea Power Station
Publié: septembre 28, 2016, 9:32pm CEST par Mark Wilson
Apple is setting up its new London headquarters in one of the most iconic buildings of the capital's skyline. Battersea Power Station will soon be home to 1,400 Apple staff, who will occupy 40 percent of the building. Sitting next to the River Thames, the former power station has been unused for a number of years, but is set to enjoy a new lease of life as part of a redevelopment project in the area. Sadiq Khan, the mayor of London described Apple's move as a "sign that London is open to the biggest brands in the world", and an… [Continue Reading] -

Cellebrite cagily claims it can hack into just about any phone including iPhone 7 and Nougat handsets
Publié: septembre 28, 2016, 5:33pm CEST par Mark Wilson
Israeli security firm Cellebrite -- the company said to have helped the FBI access the San Bernadino iPhone -- says that it has the power to break into, and extract data from, just about any phone out there. Speaking with the BBC, the company demonstrated how it can crack the password on a smartphone to access its data. It said that it was able to extract data from the very latest handsets including Android 7 devices and the iPhone 7. Cellebrite says it works with law enforcement agencies around the world too, and stopped short of saying it refused to… [Continue Reading] -

Android users can help map mobile coverage in the UK: iPhone owners need not apply
Publié: septembre 28, 2016, 12:57pm CEST par Mark Wilson
Looking to paint a more accurate picture of what mobile coverage is like across the country, UK communications regulator Ofcom has released an app that can pull in data from millions of Android users. The app, called Ofcom Mobile Research, is only available for Android and has been designed to measure not only mobile broadband performance, but also voice call quality. While building up a mass of data from participating Android users, iPhone owners are locked out of contributing because of the way iOS works. Android apps can run in the background -- important when you are gathering data but… [Continue Reading] -

EFF slams HP's printer DRM that forces the use of official ink cartridges
Publié: septembre 28, 2016, 11:23am CEST par Mark Wilson
A few days ago, HP upset printer owners by issuing a software update to block the use of third-party cartridges. The beauty of third-party ink cartridges is, of course, that they cost a fraction of official ones, but HP didn’t like the idea of missing out on income and decided to implement DRM to block them. The company has described the move as a way "to protect HP's innovations and intellectual property" but printer owners see it as little more than a money grab. Digital rights group EFF (Electronic Frontier Foundation) is similarly irked and has written to HP president… [Continue Reading] -

New law requires IMDB to respect actors' privacy and remove ages on request
Publié: septembre 25, 2016, 4:11pm CEST par Mark Wilson
If you've ever got into an argument about the age of an actor, or you've just been curious about how old someone is, you may well have hit IMDB to find out. But starting next year, the Internet Movie Database will have to comply with requests to remove age details from profiles after the state of California passed a new anti-discrimination law. The bill, AB-1687, requires that all sites that have paid subscriptions that allow people to post resumes and other information respect requests to remove information relating to age -- or just not post this information in the first place. Welcomed… [Continue Reading] -

Pippa Middleton is the latest celebrity to suffer an iCloud account hack
Publié: septembre 24, 2016, 6:20pm CEST par Mark Wilson
There have been numerous cases of iCloud accounts being hacked over the years, but it's the celebrity ones that hit the headlines. Well, that and things like the Fappening. The latest celebrity account to fall victim to hackers is Pippa Middleton, sister of British royal Kate Middleton, the Duchess of Cambridge. A reported 3,000 images have been stolen from Pippa's account, and these are said to include photographs of Kate and her children. Leaked images also show photos from private parties, and shots of wedding dresses. British newspapers the Sun and Daily Mail both report that they have been approached… [Continue Reading] -

Don't fall for the secret hack to add a headphone jack to the iPhone 7
Publié: septembre 24, 2016, 4:53pm CEST par Mark Wilson
As you're probably well aware, with the launch of the iPhone 7 Apple ditched the familiar headphone jack in favour of a wireless audio option. Many people have questioned the sense in this 'courageous' decision which has led some owners to take drastic steps to allow them to use their favorite set of wired headphones. Some have been spurred on by a YouTube video that reveals a 'secret hack' for returning the headphone jack to the iPhone 7. YouTuber TechRax has created a tutorial for uncovering the hidden jack that Apple left inside the new phone. Except, of course, it… [Continue Reading] -

Snapchat rebrands as Snap Inc and announces Google Glass competitor called Spectacles
Publié: septembre 24, 2016, 3:59pm CEST par Mark Wilson
Snapchat today makes two big announcements, the first of which is that it is no longer called Snapchat. The company is starting to branch out into products and services beyond the Snapchat app and therefore decided it is time to drop 'chat' from the name. Snap Inc is the new company name. The second announcement is a new product called Spectacles. These are sunglasses with an integrated video camera offering a 115-degree field of view. There's no word on exactly when it will be released, but the marketing machine is already in motion, building up momentum and drumming up interest.… [Continue Reading] -

Facebook massively miscalculated video viewing figures for two years
Publié: septembre 23, 2016, 11:06am CEST par Mark Wilson
The social networking giant has managed to attract the ire of advertisers after it revealed that it overestimated video viewing figures for two years. A flaw in the tool used to measure the number of views meant that figures relating to video viewing times were inflated by between 60 and 80 percent. Just how long people spend watching videos is important information for advertisers, but Facebook managed to miscalculate average viewing times by ignoring views lasting under three seconds. With so much of Facebook's incoming revenue derived from advertising, and the importance the company places on video, the snafu is… [Continue Reading] -

YouTube Heroes program rewards people who report videos
Publié: septembre 23, 2016, 9:58am CEST par Mark Wilson
Google has launched a new reward scheme that offers incentives for users to report videos that violate the site's guidelines. YouTube Heroes program also enables YouTubers to earn points for doing things like adding subtitles to a video and responding to questions in the help forums. While the promise of rewards for helping to "create the best possible YouTube experience for everyone" is appealing, critics are not happy with the fact that users will now have an added incentive to report videos. The primary concerns around offering rewards for reporting videos are that YouTube is crowdsourcing free moderation from users,… [Continue Reading] -

Yahoo confirms 'state-sponsored' attack and theft of 500 million account details
Publié: septembre 22, 2016, 9:17pm CEST par Mark Wilson
Yahoo users who have not changed their passwords for a while are being advised to do so. The company has confirmed that it suffered a major security breach back in 2014 and information relating to 500 million accounts was stolen. Yahoo says that the attack was carried out by a "state-sponsored actor" but does not elaborate on who it might be. The data accessed includes "names, email addresses, telephone numbers, dates of birth, hashed passwords (the vast majority with bcrypt) and, in some cases, encrypted or unencrypted security questions and answers". This is clearly a huge deal, and the one… [Continue Reading] -

Security commentator Brian Krebs hit with the biggest DDoS attack ever
Publié: septembre 22, 2016, 6:57pm CEST par Mark Wilson
Attacks on websites are a daily occurrence so to get any real attention an attack needs to be something special. Starting on Tuesday, Brian Krebs' security blog, KrebsOnSecurity.com, was hit with what is being described as "the largest DDoS the internet has ever seen". Despite being clobbered with a colossal 665 Gbps of traffic, Krebs' site remained online thanks to the anti-DDoS efforts of security firm Akamai. It is thought that Krebs was targeted for his exposés of hackers, and the attack was delivered via a huge number of hacked IoT devices. Akamai said that the attack was carried out… [Continue Reading] -

The new HTC Desire 10 Lifestyle and Pro are impressive mid-range smartphones
Publié: septembre 20, 2016, 3:09pm CEST par Mark Wilson
HTC, while not exactly a name to have the likes of Apple and Samsung quaking in their boots, has always been a brand to get rather excited about. Choosing a smartphone is clearly a highly personal affair, but in terms of build quality, features and value for money, HTC never fails to impress. The newly announced HTC Desire 10 Lifestyle and HTC Desire 10 Pro both sit firmly in the mid-range for the company, and unashamedly ape the look of iPhones of yore. Despite the naming convention, both of the phones seem to be targeted at the millennial market, with… [Continue Reading] -

Google and Apple show that tech companies' blase attitude to tax cannot continue
Publié: septembre 19, 2016, 1:06pm CEST par Mark Wilson
Technology firms, like bankers, are starting to earn a bad name for themselves. The practice of funnelling profits from different branches of a company through countries that have favorable rates of tax is nothing new -- far from it -- but it's becoming far more prevelevent. Google was recently asked to pay back $14.5 billion in unpaid tax in Europe, and this is not an isolated incident. Small businesses understandably feel that they are getting a raw deal when the big players have the clout and resources to play the system to their advantage. But it doesn't always work out.… [Continue Reading] -

Google redesigns Gmail for Android and the web
Publié: septembre 16, 2016, 3:29pm CEST par Mark Wilson
Gmail was designed to be a cross-platform email tool, but even Google recognizes the fact that it is far from perfect. With this in mind, Gmail -- and Inbox by Google -- are undergoing a redesign to improve things. With the redesign, Google says that it is focusing on adjusting the formatting and general look so that it better suits the device emails are being viewed on. You may well have thought that this should have been the case from the beginning, but it seems that an update is in order. Later this month, a new version of the Gmail… [Continue Reading] -

Microsoft re-runs Google tests and shows that Chrome has worse battery life than Edge
Publié: septembre 16, 2016, 9:16am CEST par Mark Wilson
The bitch-fest that has been rumbling on between Microsoft and Google is showing no signs of abating. We’re all used to the concept of companies engaging in games of one-upmanship, and this has certainly been the case when these two stalwarts have been slugging it out with their respective web browsers. The most recent battles have been fought over which browser is the most battery efficient. It’s only very recently that Google claimed that Chrome trounced Edge in battery tests -- Microsoft disagrees. The company has re-run Google’s tests and says that it produced very different results. Rather than showing… [Continue Reading] -

Adblock Plus introduces new platform to increase Acceptable Ads’ transparency
Publié: septembre 13, 2016, 6:07pm CEST par Mark Wilson
It has been difficult to ignore the issue of online ads recently. Facebook’s approach to ads has been in the news in particular, but the battle between advertisers and ad blockers is one that has rumbled on for some time -- and looks set to continue to do so. At the forefront of ad blocking is Adblock Plus, and the company has just announced a new ad platform that aims to deliver ads that will not irritate internet users too much. Acceptable Ads is an idea that has been bounced around for a while now, but today it has been… [Continue Reading] -

Broadband customers need accurate speed comparison sites
Publié: septembre 13, 2016, 9:56am CEST par Mark Wilson
There are calls for ISPs to provide more accurate broadband speed information to customers to allow them to make better comparisons between companies. The current method of providing theoretical maximum figures is just not acceptable, says the UK's Local Government Association. The LGA points out that ISPs' current provision of estimated speeds are not necessarily a true reflection of the reality. Just as consumers can use price comparison sites to check out the best deals for electricity and other utilities, so the LGA believes a similar service should be available to allow for more accurate speed comparison. At the moment,… [Continue Reading] -

In less than a week Twitter will allow longer tweets
Publié: septembre 13, 2016, 9:53am CEST par Mark Wilson
Twitter 140-character tweet limit has been one of its defining features for a number of years now. Originally introduced because of the limitation of SMS, the restriction has frustrated many users who find it too much of a constraint. On 19 September it all changes. Unlike what it has done with Direct Messages, Twitter is not dramatically increasing the maximum length of a tweet, but it is changing what counts towards that limit. Images and other attachments, for example, no longer use up characters, leaving more for messages. This is certainly not something that has come out of the blue;… [Continue Reading] -

Google brings Cardboard Camera to iOS for virtual reality fun
Publié: septembre 12, 2016, 7:01pm CEST par Mark Wilson
Google's dream of bringing virtual reality to the masses just took another big leap forward. The popular Cardboard Camera app is now available for iOS, giving iPhone users the chance to capture and share VR photos. For many people Google Cardboard has been all about finding a cheap way to enjoy virtual reality experiences that other people have created. Cardboard Camera gives you the chance to create your own. If you've not used Cardboard Camera before, Google explains what it is: "Whether you're hiking on the Olympic Peninsula or attending your cousin's wedding, go beyond the flat photo or selfie.… [Continue Reading] -

YouTube does not pay musicians enough, says report
Publié: septembre 12, 2016, 12:03pm CEST par Mark Wilson
YouTube was criticized recently for preventing content-makers from monetizing videos that covered certain topics. But this is far from being the only complaint levelled at the video site. British music industry body UK Music says that artists are not receiving enough in the way of royalty payment from YouTube. UK Music's 2016 report, Measuring Music shows that YouTube remains the most popular way for people to consume music in the UK. Despite this, the report says that the effective 'per-stream' payment rate fell from $0.0020 to $0.0010. UK Music says that YouTube benefits financially from artists who publish their work… [Continue Reading] -

Samsung's exploding Galaxy Note7 batteries wipe billions off its market value
Publié: septembre 12, 2016, 10:27am CEST par Mark Wilson
When batteries in the Samsung Note 7 started catching fire or exploding, everyone knew that the company was in for something of a rocky ride. The initial recall was deemed ineffective, leading Samsung to up its game in the US, UK and around the world. But while the replacement program for one of 2016's biggest flagship handsets is already under way, investors are starting to feel a little wobbly. In to the estimated five billion dollars the recall and replacement program is going to cost, the value of Samsung shares has plummeted, wiping $14.3 billion off Samsung's market capitalization. Over… [Continue Reading] -

With its new Surface Pro 4 vs MacBook Air ad, Microsoft just looks pathetic
Publié: septembre 11, 2016, 11:37am CEST par Mark Wilson
For a little while now Microsoft's ad campaigns have been less about highlighting its own products, but a vehicle for knocking others'. It's something we've seen numerous times with the company's Surface ads, and now there's another one. This time around we see the Surface Pro 4 compared to a MacBook Air. Microsoft says the former is better than the latter because it has a pen. Oh, and a detachable keyboard. But the tone of the ad is just so ridiculous, it serves only to make Microsoft look pathetic. The idea of one-upmanship in advertising is, of course, nothing new,… [Continue Reading] -

Samsung is handling the Note 7 recall differently in the US and UK
Publié: septembre 10, 2016, 7:47pm CEST par Mark Wilson
The launch of the Galaxy Note 7 has been nothing short of an unmitigated disaster for Samsung. Following reports of exploding batteries, the company announced a recall of the flagship handset which was criticised by many as not being urgent enough, and is expected to cost millions of dollars. Sales and shipments of Note 7s have been stopped around the world, and Samsung has said that once safe handsets are ready, they will be identifiable because of a blue S sticker. The immediate advice is to "power down your device", but the recall is being handled differently around the world.… [Continue Reading] -

New features for Twitter Direct Messages transform it into a chat platform
Publié: septembre 10, 2016, 5:36pm CEST par Mark Wilson
The market for chat and messaging tools is a busy one, with the likes of WhatsApp, Facebook Messenger and countless others all vying for attention. Keen as ever to appeal to as many users as possible, Twitter is constantly trying to reinvent itself, and it's currently doing this by revamping its Direct Messages feature. Having already dropped the 140-character limit some time ago, Twitter has now introduced even more features that make it more chat-friendly. Among the changes is a typing indicator which lets chat participants know when others are responding to messages. Continuing the theme of aping Facebook Messenger… [Continue Reading] -

Critics lambast Mark Zuckerberg after Facebook censors iconic image of Vietnam war for nudity
Publié: septembre 9, 2016, 10:28am CEST par Mark Wilson
The photograph taken by Nick Ut showing Kim Phúc (sometimes referred to a 'napalm girl') fleeing a napalm attack is one of the most iconic images of the Vietnam war. It's a picture that's seared into the memory of anyone who has seen it, and the Pulitzer prize-winning photograph is often held up as an anti-war image. But Facebook sees things differently. The company saw fit to censor the image by deleting a post by a Norwegian writer who used the photo. The writer, Tom Egeland, was also suspended from the site. Facebook stands accused of abusing its position as… [Continue Reading] -

Critics lambast Mark Zuckerberg after Facebook censors iconic image of Vietnam war for nudity [Update -- Facebook backs down]
Publié: septembre 9, 2016, 10:28am CEST par Mark Wilson
The photograph taken by Nick Ut showing Kim Phúc (sometimes referred to a 'napalm girl') fleeing a napalm attack is one of the most iconic images of the Vietnam war. It's a picture that's seared into the memory of anyone who has seen it, and the Pulitzer prize-winning photograph is often held up as an anti-war image. But Facebook sees things differently. The company saw fit to censor the image by deleting a post by a Norwegian writer who used the photo. The writer, Tom Egeland, was also suspended from the site. Facebook stands accused of abusing its position as… [Continue Reading] -

Google updates its transparency report for removal of copyright material
Publié: septembre 9, 2016, 9:47am CEST par Mark Wilson
Google's regular Transparency Reports make for interesting reading for those with an interest in how the company operates. As well as revealing how Google responds to government requests for data, they also show how it deals with copyright removal requests. Now the company has updated its reports to make the data easier to read and easier to interpret. It also shows more information about the sites and companies associated with removals. In the copyright section of the latest version of the Transparency Report, Google now gives examples of removal requests it receives. This is similar to the way it presents… [Continue Reading] -

Amazon announces Fire HD 8 with quad-core processor and 12-hour battery life
Publié: septembre 8, 2016, 6:58pm CEST par Mark Wilson
Today, Amazon reveals details of the latest addition to its Fire range of tablets, the Fire HD 8. As the name would suggest, this is an 8-inch tablet and the key selling point is the fact that it is absolutely dirt cheap. Of course, this is not its only selling point: there's also 12 hours of battery life -- something which is important for an entertainment-focused device. Much of the hardware has been upgraded from previous models, but it is by no means a powerhouse. For a tablet whose main purpose is for reading ebooks and watching movies, the 1280… [Continue Reading] -

Chrome to warn users of insecure HTTP sites that transmit passwords or credit card info
Publié: septembre 8, 2016, 5:49pm CEST par Mark Wilson
With Chrome, Google is on a mission. A mission to make the internet a safer place. Its ultimate goal is to display a warning that HTTP sites (rather than HTTPS) are insecure, but this is a long-term plan and there are many stages to go. Starting at the beginning of next year in Chrome 56, the plan moves to its next stage. As of January 2017, any HTTP sites that transmit passwords or credit card details will be flagged up as being insecure. Google is keen to educate users that any information transmitted over an HTTP connection is vulnerable to… [Continue Reading] -

Apple gives and Apple takes away with the iPhone 7 and iPhone 7 Plus
Publié: septembre 7, 2016, 9:00pm CEST par Mark Wilson
Today Apple unveiled, at long last, the iPhone 7 and iPhone 7 Plus complete with a new quad-core A10 Fusion chip and iOS 10. Rumors have been circulating for some time about just what we could expect to see from the company's latest additions to the iPhone family, and many of them have turned out to be true. While much has been added, this years' model is also about taking away. When it comes to storage, the 16GB is now a thing of the past -- 32GB, 128GB and 256GB models are your new options. As expected, also consigned to… [Continue Reading] -

How to crack Windows and OS X passwords
Publié: septembre 7, 2016, 6:32pm CEST par Mark Wilson
A security researcher has revealed a way to determine the password needed to access a protected Windows or OS X account. Using Rob Fuller's technique, it doesn't matter if the computer in question is locked, and it uses a USB SoC-based device to crack user credentials. By modifying the firmware of a USB dongle, Fuller was able to make the device appear as an Ethernet adaptor. By spoofing a network connection, it is then possible to trick a target computer into giving up an account password. Fuller provides a detailed breakdown of how the attack works in a blog post.… [Continue Reading] -

Microsoft opens UK datacenters for Office 365 and Azure
Publié: septembre 7, 2016, 10:58am CEST par Mark Wilson
Microsoft has announced that local datacenters are now available in the UK to Office 365 and Azure customers. This enables companies dealing with UK-only customers to ensure that data remains within the country and fully complies with data protection and privacy laws. Describing itself as the "first global cloud productivity provider" to offer UK residency for data, Microsoft says Azure and Office 365 are now generally available from multiple data center locations in the UK. It has already attracted the custom of the Ministry of Defence. Microsoft's new data centers are located in London, Durham and Cardiff and will be in… [Continue Reading] -

Google shows off improved battery life with Chrome 53
Publié: septembre 7, 2016, 10:24am CEST par Mark Wilson
Chrome has long been held up as an example of software being battery hungry. It's something that Google has been working to address with the Android version of the browser; now the company has turned its attention to the desktop build. In a new video that highlights the improvements that have been made in recent months, Google compares a Vimeo video running in Chrome 46 to the same video running in Chrome 53 on identical hardware -- a Microsoft Surface Book, since you ask. The results are impressive. Google's tests show that Chrome 53 gives more than two hours extra… [Continue Reading] -

LG V20 boasts Android 7.0 Nougat, removable battery, and two screens
Publié: septembre 7, 2016, 9:28am CEST par Mark Wilson
LG is something of a quiet player in the mobile market, but that could be set to change with the launch of the LG V20 -- the first smartphone to ship with Android 7.0 Nougat pre-installed. Announced just hours ahead of Apple's iPhone 7 event, LG's new flagship handset boasts more than just the very latest version of Android. There's a 5.7-inch, 513ppi screen which is supplemented by a secondary 160 x 1040, 513ppi ticker display. One top of this there is a 3,200 mAh removable battery, dual rear cameras, all powered by a Snapdragon 820 processor and 4GB of… [Continue Reading] -

Android 7.0 Nougat comes to the OnePlus 3 -- but it's a bit of a dog at the moment
Publié: septembre 6, 2016, 11:18am CEST par Mark Wilson
Android 7.0 Nougat may be making its way out to Nexus devices, but this accounts for only a tiny proportion of Android users out there. Owners of other handsets are starting to wonder when they will get their hands on Nougat, but rather than waiting for an official rollout, OnePlus 3 users can run Nougat right now thanks to an unofficial Cyanogenmod 14 build. As this is an unofficial build there are -- as you will no doubt have gathered from the headline -- a few issues to bear in mind. The bad news is that battery life is described… [Continue Reading] -

Adobe Flash Player will live on in Linux
Publié: septembre 6, 2016, 10:03am CEST par Mark Wilson
The much loathed Flash Player -- seen these days as little more than a resource hog and security risk -- had been cut loose on Linux. Four years ago Adobe said that the NPAPI version of the Linux version of Flash Player would only receive security patches and no further updates. Now this is changing. Despite an overwhelming drive to move away from Flash towards HTML5, Adobe has decided to resurrect it on Linux. A beta version of Linux NPAPI Flash Player is now available and will be kept in sync with the modern release branch. At the moment, Adobe… [Continue Reading] -

HSBC uses facial recognition so customers can open new bank accounts with a selfie
Publié: septembre 5, 2016, 3:00pm CEST par Mark Wilson
Banks around the world are embracing biometrics as a way of securing customers' accounts. HSBC is taking things in a slightly different direction, however, giving business customers the ability to open a new account using a selfie. While the selfie alone is not enough to open a bank account, it is used as part of the identity verification process. It uses facial recognition software to analyse a selfie taken on a smartphone. Customers will still have to present a passport or driving license to confirm their identity, but the move is part of HSBC's enthusiasm for biometrics. In addition to… [Continue Reading] -

Microsoft Office rival OpenOffice could be squeezed out of the market due to lack of volunteers
Publié: septembre 4, 2016, 4:38pm CEST par Mark Wilson
Not everyone is in a position to pay for their office software and this led to a market for free Microsoft Office competitors. One of the best known and most popular is OpenOffice, but the open source project is in trouble. Volunteer vice president Dennis E. Hamilton has warned that retirement of the project "is a serious possibility". The problem is a combination of a lack of volunteers willingness to work on the project, and the increasing popularity of LibreOffice. The lack of developers means that important security updates are at risk. Hamilton writes: "It is my considered opinion that… [Continue Reading] -

Ireland to appeal against Apple's $14.5 million EU tax bill
Publié: septembre 4, 2016, 10:33am CEST par Mark Wilson
When the European Commission said it believed Apple should pay €13 billion (around $14.5 billion) after enjoying "illegal tax benefits", it wasn't just Tim Cook who was unhappy. The Commission said that the Irish Government had "artificially lowered" Apple's tax bill, and ministers are not happy with the accusation. After meeting to discuss the matter, ministers are now ready to appeal against the ruling. After Apple said it planned to appeal against the decision, Finance minister Michael Noonan said Ireland planned to do the same. The Irish cabinet had been split as to whether an appeal made the most sense.… [Continue Reading] -

Ireland to appeal against Apple's $14.5 billion EU tax bill
Publié: septembre 4, 2016, 10:33am CEST par Mark Wilson
When the European Commission said it believed Apple should pay €13 billion (around $14.5 billion) after enjoying "illegal tax benefits", it wasn't just Tim Cook who was unhappy. The Commission said that the Irish Government had "artificially lowered" Apple's tax bill, and ministers are not happy with the accusation. After meeting to discuss the matter, ministers are now ready to appeal against the ruling. After Apple said it planned to appeal against the decision, Finance minister Michael Noonan said Ireland planned to do the same. The Irish cabinet had been split as to whether an appeal made the most sense.… [Continue Reading] -

43 million Last.fm account details leaked after 2012 hack
Publié: septembre 4, 2016, 9:41am CEST par Mark Wilson
It seems that serious data breaches are all but an everyday occurrence at the moment. At the same time, there have also been instances of historical hacks suddenly coming to light such as the 2012 breach of Dropbox. But Dropbox was not the only company to suffer an attack in 2012 -- so did music site Last.fm. Now, four years after the hack, details of 43 million accounts have been leaked. While Last.fm acknowledged the hack back in 2012, few would have expected the fallout to be felt so long after the event. At the time the company warned users… [Continue Reading] -

YouTube tells Philip DeFranco it hasn't changed its policy on demonetizing videos
Publié: septembre 3, 2016, 7:33pm CEST par Mark Wilson
There has been much wailing and gnashing of teeth from YouTubers in recent days as rumors started to circulate that YouTube was demonetizing videos deemed not "advertiser friendly". Seasoned 'Tuber Philip DeFranco was one of the more high-profile to speak out, likening YouTube's actions to "censoring" people by hitting them in the wallet. But YouTube has responded to these claims by saying that its policy on video monetization has not changed at all. While YouTubers have just started to complain that video about depression, videos with swearing, videos with controversial subject matter, and so on are being denied the opportunity… [Continue Reading] -

Apple is cleaning up the App Store by clearing out abandoned apps and limiting name length
Publié: septembre 3, 2016, 5:08pm CEST par Mark Wilson
Starting next week -- September 7 specifically -- Apple is starting to clear the crap out of the App Store. What does this mean? It means removing what Apple describes as "problematic and abandoned apps", as well as changing the way apps can be named to prevent developers using SEO'd titles for their creations. Moving forward, app titles will be limited to just 50 characters, reducing the chance of naming them in a deceptive way. Apple appears to have quite a task ahead of it as it plans to review every app currently featured in the App Store, before contacting… [Continue Reading] -

Google ditches modular Project Ara smartphone
Publié: septembre 3, 2016, 4:09pm CEST par Mark Wilson
Google's Project Ara -- a modular smartphone that let users customize their handsets with a range of plugin modules -- has been killed before it even got off the ground. Having started life as a Motorola venture, the first Project Ara smartphone was expected to launch later this year. As recently as May, Google was talking about shipping a developer version of the phone this autumn, but now it seems that this is not going to happen. Described by industry analyst Bob O'Donnell as "a science experiment that failed", Project Ara has been shelved but it's possible that the idea… [Continue Reading] -

Three's mobile ad blocking plan blocked by Europe
Publié: septembre 3, 2016, 12:59pm CEST par Mark Wilson
Mobile operator Three had hoped to roll out a network-wide ad blocking system that would prevent the appearance of up to 95 percent of adverts has been shot down by a European regulator. Citing net neutrality, the Body of European Regulators for Electronic Communications (Berec) says that Three's plans were incompatible with providing an internet access service. The decision comes despite the fact that Three's ad blocker would have been optional for customers. Berec said that telecom companies "should not block, slow down, alter, restrict, interfere with, degrade or discriminate advertising when providing an IAS (internet access service)". This does… [Continue Reading] -

Microsoft gains support from Mozilla, EFF, Google and Apple in fight against US gagging orders
Publié: septembre 3, 2016, 11:33am CEST par Mark Wilson
Microsoft is fighting the US Justice Department in an attempt to quash a law that prevents companies informing customers that the government is requesting their data. The technology giant has the backing of other tech companies as well as media outlets. Amazon, Apple, Google, Fox News, Electronic Frontier Foundation and Mozilla are among those offering their support to Microsoft. The lawsuit says that blocking companies from keeping their customers informed is unconstitutional, and it comes at a time when tech companies in particular are keen to be as open and transparent as possible about government requests for data. Legal experts… [Continue Reading] -

Facebook Messenger gains Instant Video live broadcasting
Publié: septembre 1, 2016, 6:13pm CEST par Mark Wilson
Facebook, like Twitter, is going all in on video. The social network's latest move is to bring video to its second greatest love -- Facebook Messenger. You'd be forgiven for thinking that this is not exactly new, and you'd be right. Facebook Messenger has included a video calling option, but Facebook is concerned that this is being reserved for 'special occasions'. Instant Video is an extra new feature that is designed to make it easier to show things that can't be properly described in words, or even static pictures. The feature launches today to let "you to put a smile… [Continue Reading] -

Three quarters of SMEs feel the UK tax system unfairly benefits big business
Publié: septembre 1, 2016, 4:47pm CEST par Mark Wilson
The tax paying habits of big businesses are back in the headlines now that Apple is facing a $14.5 billion bill in Ireland -- although Tim Cook vehemently disagrees. In the wake of the Irish Apple tax ruling, 71 percent of SMEs say that the UK tax system benefits big businesses and makes thing harder for the little guy. The figures apply to the UK's micro-businesses (those with under 10 employees) and self-employed individuals, only 1 percent of whom feel the system is working for their benefit. FreeAgent, a company providing cloud-based accounting services to small businesses conducted a survey… [Continue Reading] -

Now you need to buy a TV licence to watch BBC iPlayer, and privacy advocates are concerned
Publié: septembre 1, 2016, 12:42pm CEST par Mark Wilson
As of today, Thursday 1 September, if you stream any content from BBC iPlayer without owning a TV licence, you are breaking the law. But as with licences for televisions, it's not clear how -- or, indeed, if -- the BBC will be checking to see whether watchers have paid up or not. If you fire up BBC iPlayer now, you'll be greeted by a nag screen that asks: "Got a TV licence? You need one to watch any BBC programme on iPlayer -- live, catch-up or on-demand. It's the law". Viewers need to click to indicate whether or not… [Continue Reading] -

Tim Cook hits back at 'maddening' European ruling on Apple tax
Publié: septembre 1, 2016, 11:37am CEST par Mark Wilson
Apple CEO Tim Cook, talking to Ireland's RTÉ News, says that allegations put forward by the European Commission that his company owes $14.5 billion in back tax are 'maddening'. He is also very confident that the Commission's ruling will be overturned on appeal. Echoing an open letter published earlier in the week, Cook said that the claims that Apple was given preferential treatment and special tax arrangements in Ireland have "no basis in fact or in law". The Irish cabinet has already met to discuss how to tackle the appeal that Apple is expected to launch, but has yet to… [Continue Reading] -

PewDiePie kicked off Twitter for joking about ISIS
Publié: août 31, 2016, 9:43pm CEST par Mark Wilson
YouTube 'personality' (or walking, talking, narcissistic ego with a webcam, depending on your point of view) PewDiePie has been kicked off Twitter -- just like @Nero. It comes just a day after the internet star was stripped of his blue verification checkmark. The debacle kicked off when Pewdi… sorry, Felix Kjellberg... lost his blue badge and he subsequently posted a video in which he revealed the 'reason' for this. A fake news story had popped up suggesting he had links with ISIS, and Kjellberg used his video to 'joke' that he had in fact joined ISIS. The ban hammer swiftly… [Continue Reading] -

Google to take on Uber and Lyft, using Waze to offer ride-sharing
Publié: août 31, 2016, 12:49pm CEST par Mark Wilson
Google's seemingly relentless expansion into just about every field of business looks set to continue as the company prepares to enter the ride-sharing arena. The likes of Lyft and Uber have already proved that there is a strong demand for such car-pooling services. Following on from a pilot program in San Francisco, Google is set to make use of its Waze app to put commuters in touch with each other. Come the end of 2016, the program will be opened up to anyone in the Bay Area, with the possibility of a wider expansion later. During the testing period, Waze… [Continue Reading] -

Google's new In App Search mode finds content in your installed Android apps as well as online
Publié: août 31, 2016, 12:09pm CEST par Mark Wilson
Google has announced an update to the search function on Android devices. Helpfully named In Apps, the new search mode makes it possible to not only search online for information, but to scour the apps you have installed. The update means that it's now easier than ever to find particular messages, files, videos and contacts. There's no need to have a data connection to make use of the new search mode, meaning that Android search now operates far more like searching from the Start menu in Windows 10. If you fire up the Google app on your phone or tablet,… [Continue Reading] -

Make money on Twitter as the company starts to share video ad revenue with users
Publié: août 31, 2016, 11:08am CEST par Mark Wilson
Twitter is to start sharing ad revenue generated by videos with the people who create those videos. The monetization model will start in the US for now, but it opens up a platform that was previously only available to big names such as the NFL and CBS. All of the key players in social media are focusing their efforts on video, and in giving users the opportunity to make money through their footage, Twitter is really upping the ante. It's a move that pits the company against the likes of YouTube, and one that will be seen as a desperate… [Continue Reading] -

Amazon Dash Button arrives in the UK to cater for the terminally lazy
Publié: août 31, 2016, 10:46am CEST par Mark Wilson
Amazon Dash Button is now available in the UK. For anyone who finds logging into their Amazon account to place an order for everyday things like loo roll and coffee difficult, this physical button (thought by many to be an April Fool a couple of years ago) does the 'hard' work for you. Available exclusively to Amazon Prime members, the Amazon Dash Button is available for a number of top brands and is (effectively) free. Amazon describes the button as "the Wi-Fi-connected device that conveniently reorders your favourite products with the simple press of a button", but it's hard not… [Continue Reading] -

Ahead of iPhone 7 launch, Apple faces $14.5 billion bill for 'illegal tax benefits' in Ireland
Publié: août 30, 2016, 12:56pm CEST par Mark Wilson
Apple is facing a bill of €13 billion (around $14.5 billion) after the European Commission ruled that Ireland granted the company illegal tax benefits. Ireland permitted Apple to pay "substantially less tax than other businesses", and the Commission has decided that not only is this illegal, but the money must be recovered. A three-year investigation concluded that Apple was paying corporation tax of just 1 percent in Ireland. The tax arrangement meant that Apple's tax bill was "artificially lowered" -- down to as low as 0.005 percent in 2014. Ireland is used by many technology companies for its favorable tax… [Continue Reading] -

New Google app wants to crowdsource your help... for free
Publié: août 30, 2016, 12:28pm CEST par Mark Wilson
On all mobile platforms -- and, indeed, desktop ones -- there are no end of apps and websites that can be used to earn money and other rewards in return for providing feedback. Google, however, has a different idea. The company has released a new app for Android called Crowdsource. The idea is to improve the likes of Google Maps and Google Translate with input from the likes of you and I. But rather than paying contributors -- or even offering any kind of incentive -- Google is rather cheekily looking for help completely gratis. Download a copy of the… [Continue Reading] -

Latest Surface Pro 3 update fixes battery problems
Publié: août 30, 2016, 11:57am CEST par Mark Wilson
If your Surface Pro 3 has been plagued with battery issues, Microsoft has some good news for you -- there's now a fix available. Not that there was actually a problem in the first place, you understand... While many people were under the impression that their Surface Pro 3 had developed a physical battery problem, an issue with the firmware was preventing it from being fully charged. Microsoft has already explained that the problem is software rather than hardware related, but it has now updated its FAQ on the issue. It is only the Surface Pro 3 that is affected… [Continue Reading] -

Kim Dotcom's extradition hearing will be 'live' streamed on YouTube
Publié: août 30, 2016, 10:39am CEST par Mark Wilson
Kim Dotcom has never been a man to shy away from the public eye, and his upcoming trial is not going to see that change. Facing extradition to the US where he faces numerous charges, Dotcom has won the right to have the hearing live streamed on YouTube. It's fair to say that there will be a good deal of interest in the content and outcome of the hearing, but the judge who agreed to the live streaming has insisted that a few restrictions be put in place. Firstly there will be a 20-minute delay (so not technically a 'live'… [Continue Reading] -

Facebook embraces algorithms and eschews human headlines in trending topics
Publié: août 27, 2016, 10:39am CEST par Mark Wilson
Facebook's Trending Topics feature has faced a good deal of criticism in recent months, including claims that it showed a liberal bias. A little while back the company announced that it was to change how the feature works, and now there is a further change which sees human headline writers being defenestrated, and algorithms ushered in the front door. What this means is that the Trending Topics list will no longer feature an explanation or description next to it, only the topic heading or hashtag will be displayed. Facebook will no doubt hope that this will help to eliminate future complaints… [Continue Reading] -

Opera sync servers hacked, usernames and passwords at risk
Publié: août 27, 2016, 9:37am CEST par Mark Wilson
Opera Software is advising all users of the sync feature of its Opera browser to change their passwords following a security breach. Details are a little scant at the moment, but the company says that servers were breached earlier in the week and user data may have been compromised. Opera Sync is used to synchronize user data between different computers but it is apparently used by under "0.5% of the total Opera user base". However, with a user base of 350 million this means that upwards of 1.7 million people could be affected. Coming shortly after advice from Dropbox to… [Continue Reading] -

Information Commissioner to investigate data sharing between WhatsApp and Facebook
Publié: août 26, 2016, 6:56pm CEST par Mark Wilson
WhatsApp's plans to share user data with Facebook are to be investigated by the Information Commissioner's Office (ICO) in the UK. The change in privacy policy goes against a previous public commitment not to share data in this way. The ICO has the power to regulate how companies make use of data belonging to people located in the UK, even if the companies themselves are located elsewhere. A key concern is whether there will be compliance with data protection laws. Users are particularly upset about the data sharing plans because when Facebook acquired WhatsApp back in 2014, the company said… [Continue Reading] -

Serious security vulnerability that left iPhones open to hackers is patched in iOS 9.3.5
Publié: août 26, 2016, 1:13pm CEST par Mark Wilson
Security researchers have unearthed three serious security flaws in iOS that made it possible to install spyware and other malware on iPhones. Software exploiting the vulnerabilities (described as "one of the most sophisticated pieces of cyberespionage software we've ever seen") can be installed with a single click, opening up victims' devices to full-scale surveillance. The security holes have already been abused by NSO Group -- linked with selling hacking and surveillance software to governments -- but Apple has now issued a fix in the form of iOS 9.3.5. The update fixed two kernel vulnerabilities and one in WebKit, all discovered… [Continue Reading] -

Dropbox tells some users to change their passwords following 2012 security incident
Publié: août 26, 2016, 12:07pm CEST par Mark Wilson
Dropbox users around the world are being told to change their account passwords. Anyone who has been using the cloud storage service since before the middle of 2012 and has not changed their password may have had some of their account details 'obtained' in an incident in 2012. Dropbox says that email addresses plus hashed and salted passwords were grabbed four years ago. The company stresses that there are no indications that accounts have been improperly accessed and the security measures are being taken on a preventative basis. If you receive the email from Dropbox, you should visit your account… [Continue Reading] -

WhatsApp's new privacy policy reveals it will share data with Facebook for targeted user ads
Publié: août 26, 2016, 10:58am CEST par Mark Wilson
The ever-popular messaging tool WhatsApp is to start sharing more user data with its parent company Facebook. The updated privacy policy means that WhatsApp will now share users' phone numbers with Facebook to "offer better friend suggestions and show you more relevant ads". The updated policy also communicates the fact that end-to-end encryption has rolled out, but it is the privacy side of things that will be of greater interest to many people. WhatsApp says that the change in policy is necessary to allow it to "explore ways for you to communicate with businesses that matter to you too, while… [Continue Reading] -

Microsoft reveals the secrets of HoloLens' specs, including a 24-core processor
Publié: août 23, 2016, 5:19pm CEST par Mark Wilson
At the Hot Chips conference this week, Microsoft has shed some light on the hitherto secretive specifications of its augmented reality HoloLens. Now that anyone with $3,000 spare is able to buy a headset, there's never been more interest in what's actually inside the case powering the AR goodness. The holographic processing unit (HPU) at the heart of HoloLens is a seriously multi-cored beast. The Register reports that it is a "TSMC-fabricated 28nm coprocessor that has 24 Tensilica DSP cores". Of course, there's much more to the device than just this chip. The HPU is capable of processing a trillion… [Continue Reading] -

Android 7.0 Nougat starts to roll out to Nexus devices
Publié: août 22, 2016, 8:01pm CEST par Mark Wilson
There have been numerous beta versions of Android 7.0 Nougat, and now the official rollout is underway. This is not a full-scale rollout just yet -- it's limited to the Nexus 6P, 5X, 6, 9, and Nexus Player, as well as the Pixel C and General Mobile 4G. You'll notice that the Nexus 5 is missing from the list, but the remainder of the handsets are in line for an OTA update anytime over the coming weeks starting today. If you're impatient, you can always download the factory images and flash your device manually, but whichever route you go down,… [Continue Reading] -

Privacy-flouting, Apple-only social app Lifestage is Facebook's desperate attempt to stay relevant to teens
Publié: août 22, 2016, 4:39pm CEST par Mark Wilson
Facebook has become so ubiquitous that even your mum is using it. This is just one of the many reasons the social networking giant has lost any vestiges of coolness, but the company is keen to try to claw some back. The latest attempt to get down with the kids is a new social app called Lifestage. Aimed at 'high schoolers' the app is available for iPhone and iPad and for those with a profile it "makes it easy and fun to share a visual profile of who you are with your school network". It looks and sounds godawful, and… [Continue Reading] -

Samsung is planning an Apple-style refurbished phone program
Publié: août 22, 2016, 12:17pm CEST par Mark Wilson
If you want to get your hands on cheaper Apple products, you can opt for the secondhand market on eBay, or you could go for an official refurbished device from the company itself. Not wanting to miss out on a trick, Samsung looks set to launch its own refurbished smartphone program. Citing "a person with direct knowledge of the matter", Reuters says the program could launch as early as next year. With Samsung hardware selling for something of a premium -- particularly flagships like the Galaxy Note7 -- consumers are as keen to seek out a saving as Samsung is… [Continue Reading] -

Mass surveillance by UK government is acceptable but there are privacy concerns, says review
Publié: août 20, 2016, 4:14pm CEST par Mark Wilson
A review into mass surveillance and bulk data collection by the UK government has concluded that there is a strong case for allowing such activity. The privacy-invading activities of MI5, MI6 and GCHQ were the subject of a report by independent reviewer David Anderson QC, and the findings have been welcome by prime minister Theresa May. The report is likely to concern privacy advocates, particularly when Anderson goes on to say that he agrees 'in principle' that there could be cases for hacking phones and computers. It gives heavyweight backing to the controversial Investigatory Powers bill (snooper's charter). Anderson's report… [Continue Reading] -

Changes to Microsoft Family make it possible to block Chrome and Firefox in Windows 10 Anniversary Update
Publié: août 20, 2016, 1:22pm CEST par Mark Wilson
Windows 10 Anniversary Update introduced a number of changes to the operating system, and Microsoft has started to email users about changes to Microsoft family settings. As the name implies, this is about keeping things family-safe, family-friendly, but one of the changes is unlikely to go down well with rivals. While new Microsoft family options make it easier to place limits on what children are able to do with a computer, a controversial option forces the use of Internet Explorer or Microsoft Edge. Microsoft has made it possible to block the use of Chrome, Firefox and other rival browsers. The… [Continue Reading] -

Slightly confusingly, Apple stores are now just called Apple
Publié: août 20, 2016, 1:09pm CEST par Mark Wilson
Apple's latest branding move messes with syntax and established convention as it changes the way it refers to its physical stores. While Apple Store, Fifth Avenue made perfect sense to just about anyone with common sense, Apple has now decided that Apple Fifth Avenue is better. The change to retail labelling is a little, well, odd frankly, but it's sure to gain Apple some more of the attention it so craves. After all, Apple World Trade Center sounds rather more grand than Apple Store, World Trade Center doesn't it? MacRumors reports that Apple employees recently received emails informing them of… [Continue Reading] -

Chrome apps to disappear from Windows, Mac and Linux while Chrome OS gains new launcher icon
Publié: août 20, 2016, 12:23pm CEST par Mark Wilson
Google has come to the realization that hardly anyone is using Chrome apps. As such, the company plans to phase out support for the apps on Windows, Mac and Linux over the next couple of years. While admitting that packaged apps are used by just 1 percent of users of the three platforms, Google says that the decision comes after a drive to integrate the feature of apps into web standards. Chrome apps will live on in Chrome OS "for the foreseeable future", but a wind-down timetable has been set out for everyone else. Nothing is changing immediately. But come… [Continue Reading] -

Webcam stopped working? You could blame Windows 10 Anniversary Update (plus, a workaround!)
Publié: août 20, 2016, 12:04pm CEST par Mark Wilson
Windows 10 Anniversary Update has been gradually rolling out to computers around the world and like any big software update it has caused its fair share of problems. The latest issue to rear its head sees Anniversary Update killing webcams. The problem comes about as the update prevents USB webcams from using MJPEG or H264 encoded streams, instead requiring the use of YUY2 encoding. Microsoft is aware of the issue and is working on a fix that should be released in September, but all is not lost in the meantime. Microsoft chose to change the encoding support to improve performance… [Continue Reading] -

China wants to monitor and control all live streams in real time
Publié: août 19, 2016, 10:16am CEST par Mark Wilson
China's overarching control of the internet, technology, and its people in general is nothing new. The Great Firewall of China is famous for placing huge restrictions on what citizens are able to access online, and recently the government banned the use of social media as a news source. The latest target for the Chinese government is the increasingly popular activity of live streaming. The proposal includes a requirement for all live streamed content to be monitored around the clock. The Cyberspace Administration of China is looking to wipe out what it sees as inappropriate online content, and live streaming is… [Continue Reading] -

Twitter introduces new notification settings and a tweet quality filter
Publié: août 18, 2016, 10:10pm CEST par Mark Wilson
There are many complaints levelled at Twitter, but two crop up time and time again. The first is that if you follow a lot of people, you're likely to be overwhelmed with notifications; the second is that there's just too much crap out there. Twitter is introducing a couple of changes to address both of these problems with an update that's rolling out today. Arguably the more interesting of the two is the "quality filter setting". The filter is a feature that Twitter says has been in testing for some time, but is now ready to roll out to everyone.… [Continue Reading] -

Twitter has terminated 235,000 terrorist accounts in just six months
Publié: août 18, 2016, 7:14pm CEST par Mark Wilson
Twitter continues its drive to clean itself up, purging unwanted content and users from the service. Today the company announces that in the last six months it has closed down 235,000 accounts relating to extremism. It's part of the company's plans to scrub as many accounts from existence as possible that push "violent threats and the promotion of terrorism". With the recent spate of terrorist attacks around the world, Twitter's resolve has been hardened. With the 125,000 account closures announced back in February, today's terminations bring the total number of account suspensions to 360,000 since the middle of 2015. Of… [Continue Reading] -

Save hundreds on Apple products and more in Best Buy's 50-hour, 50th anniversary sale
Publié: août 18, 2016, 5:46pm CEST par Mark Wilson
Best Buy is turning 50 and what better way to celebrate than by encouraging people to throw some of their hard-earned cash in its direction? That is precisely what's happening in a 50-hour 50th anniversary sale which is including 50 Black Friday-like deals. The company points out that the sale comes just in time for those essential 'back to school' purchases, but with a bundle of money to be saved off the likes of MacBook Pros, and iPhone 6s Plusses, there's something for everyone. The 50th anniversary is on August 22, but the sale kicks off slightly before the big… [Continue Reading] -

Facebook teams up with Unity to create a gaming platform to rival Steam
Publié: août 18, 2016, 4:59pm CEST par Mark Wilson
Facebook is starting to take gaming far more seriously. Not content with funneling the likes of Candy Crush through its servers, the social network is now joining forces with the company behind the Unity game engine to create its own desktop gaming platform. The aim is to tap into not only the millions of gamers that are already on Facebook, but also to gather more from the PC-gaming community. It's a new venture that very clearly treads on the toes of Steam, and is likely to cause ripples in the gaming world. The scope of the work between Facebook and… [Continue Reading] -

Google updates its open source Santa Tracker in time for Christmas
Publié: août 18, 2016, 11:36am CEST par Mark Wilson
Yeah, OK... it's only August, but we're going to start talking about Christmas. Well... Google is, anyway. As it has done for a few years now, the company is planning to run its Santa Tracker tool in December and it has a few updates to share. The web and mobile based versions of the tool are open source, meaning that developers are free to work their Christmassy magic and come up with new and innovative ideas for kids. Based on Firebase and Polymer, Santa Tracker has been tweaked to be as battery-friendly as possible for mobile devices, and optimized to… [Continue Reading] -

Microsoft Rewards replaces Bing Rewards -- collect points to get free stuff!
Publié: août 17, 2016, 12:28pm CEST par Mark Wilson
Microsoft's point-collecting program Bing Rewards is being renamed Microsoft Rewards. It will work in very much the same way as before (collect points and use them to buy games, apps, movies and so on), but there are a few changes that accompany the rebranding. As before, Microsoft Rewards will be limited to the US and India, and the program lets you earn points by shopping in the Microsoft Store and Windows Store as well as searching with Bing and simply browsing with Microsoft Edge. If you're a seasoned user, there are a few changes to note. The first is that… [Continue Reading] -

Monitor emoji usage in real-time
Publié: août 17, 2016, 11:51am CEST par Mark Wilson
Emoji are used for everything from basic communication, to diversity promotion, and even as a means of learning to code. While dismissed by some as the language of the millennial or the hard-of-thinking, emoji have their place in the modern lexicon, and an Australian company has launched a tool to show how they are being used. Ad agency The Works has created a real-time emoji tracker that reveals how the handy little icons are being used right now. The company says of the recent additions to our language, "this is not a bastardisation but the next evolution of how we… [Continue Reading] -

UAC vulnerability in Windows 7 and Windows 10 allows for traceless code execution
Publié: août 17, 2016, 10:56am CEST par Mark Wilson
Windows' User Account Control (UAC) feature was designed to help keep computers safe from malicious software installations, but there are already at least a couple of ways to bypass it. A new technique for circumventing UAC not only makes it possible to execute commands on a computer, but to do so without leaving a single trace. Security researchers Matt Nelson and Matt Graeber discovered the vulnerability and developed a proof-of-concept exploit. The pair tested the exploit on Windows 7 and Windows 10, but say that the technique can be used to bypass security on any version of Windows that uses… [Continue Reading] -

Microsoft is bringing Windows Holographic to all Windows 10 users
Publié: août 16, 2016, 9:38pm CEST par Mark Wilson
Believe the hype and you're probably under the impression that virtual reality, augmented reality, or some hybrid of the two is where the future of computing lies. Microsoft certainly thinks that AR/VR has an important role to play and today the company announced that an update to Windows 10 next year will bring Windows Holographic to everyone. The company is working with Intel to come up with the specification for mixed reality ready PCs and head mounted displays. Terry Myerson made the announcement, saying that an update will be made available at some point in 2017. Speaking at the Intel… [Continue Reading] -

Hacker group Shadow Brokers auctions off NSA malware
Publié: août 16, 2016, 4:24pm CEST par Mark Wilson
The NSA has (or had...) a collection of malware in its cyber arsenal. It has been stolen by hackers. It is now available to buy. A group of hackers going by the name of Shadow Brokers claims to have stolen a range of hacking and malware tools from Equation Group's servers -- Equation Group is itself closely linked with the NSA. The group is offering the tools for auction and will sell them to the highest bidder. If bidding reaches one million Bitcoins, however, the group says it will make the tools publicly available to all. In a post on… [Continue Reading] -

Minecraft Windows 10 Edition Beta gives the game an Oculus Rift-friendly VR makeover
Publié: août 15, 2016, 6:41pm CEST par Mark Wilson
Last year, Microsoft announced that a virtual reality version of Minecraft was in the works. Today Minecraft: Windows 10 Edition Beta gains VR support, as Microsoft works with the Oculus Rift team to produce a more immersive version of the game. In terms of controlling the VR version of Minecraft, you have the option of using a keyboard and mouse, or sticking with your trusty Xbox One controller. There are also a host of new VR-specific options to work with. Writing on the Xbox blog, Team Minecraft says: "Starting today, as a thank you to our community, we’ll be releasing… [Continue Reading] -

Firefox 49 for Linux gains plugin-free support for Netflix and Amazon Prime Video
Publié: août 15, 2016, 6:40pm CEST par Mark Wilson
Another plugin bites the dust. The Windows and macOS versions of Firefox have supported the Widevine video protocol for a little while now, and the upcoming Firefox 49 for Linux gets the same treatment. What this means is that streaming video services that use the Google-owned protocol -- including Netflix and Amazon Prime Video -- can be watched without the need for plugins. The Linux version of Firefox 49 is due for a proper release in September, although preview versions are currently available for those who want to try it out. With Widevine being free for anyone to use, Firefox's… [Continue Reading] -

New UK taskforce will tackle online abuse and harassment on Twitter, Facebook and beyond
Publié: août 15, 2016, 11:30am CEST par Mark Wilson
Online hate crimes are to be targeted in the UK by a new specialist police team. Based in London, the small team of five officers will be tasked with identifying online abuse and helping victims. In addition to this, the taskforce will use its two-year pilot program to educate and train other police officers and community groups about how to deal with online abuse and harassment, particularly on social media. The pilot scheme has a budget of £1.7 million, including £452,000 from the Home Office. As well as the five fulltime officers, the operation will make use of a team… [Continue Reading] -

Europe wants to control the likes of WhatsApp and Skype like telcos
Publié: août 15, 2016, 10:38am CEST par Mark Wilson
The EU is looking to exert greater control over online messaging tools such as WhatsApp and Skype. Documents seen by the Financial Times suggest that Brussels wants to treat such services more like traditional telecoms companies. The proposals come amid mounting privacy concerns about data handling, particularly the "security and confidentiality provisions" from companies like Microsoft and Facebook. An overhaul of telecom rules is due to be published in September, and the new rules would require messaging firms to comply with additional EU regulation. Until now online messaging tools have been treated differently to telecoms firms, but Europe is keen… [Continue Reading] -

UK law firms will be able to profit from pursuing cyber criminals
Publié: août 15, 2016, 10:06am CEST par Mark Wilson
A pilot scheme from the City of London police means that private law firms will be able to profit from the pursuit of suspected cyber criminals. Rather than handling cases of online crime themselves, police will instead pass details on to private agents. These firms will then able to use civil -- rather than criminal -- courts to seize the profits of cybercrime. It is thought that police forces are spending too much time and money fighting online crime, and that private agencies might be better equipped to deal with the problem. Marking a huge change in policy, the experiment… [Continue Reading] -

If you cheat at Pokémon Go you could be banned... permanently
Publié: août 15, 2016, 9:06am CEST par Mark Wilson
The relentless popularity of Pokémon Go continues and shows little sign of abating. Despite the threat of privacy issues and malware, millions of gamers continue in their mission to catch 'em all. But if you were feeling tempted to use one of the various techniques that have been developed for cheating at the game, you might want to reconsider. Developer Niantic is now handing out permanent bans to cheaters after updating its terms of use. The company says that there are a number of ways in which players can violate the terms of service. These include "falsifying your location, using… [Continue Reading] -

Online porn is damaging your sex life
Publié: août 15, 2016, 9:03am CEST par Mark Wilson
It may not turn you blind or give your hairy palms, but consuming online porn is leading to an increase in the number of men with sexual health problems. Sexual therapists warn that growing numbers of men are being addicted to watching online pornography, and this has been linked to an increase in instances of erectile dysfunction in younger men. Dr Angela Gregory says that in recent years there have been more and more men in their early 20s seeking treatment for what has historically been an issue for the older generation. She says: "These younger men do not have… [Continue Reading] -

Microsoft is working on a fix for freezing issues with Windows 10 Anniversary Update
Publié: août 14, 2016, 10:17pm CEST par Mark Wilson
Some users who have installed Windows 10 Anniversary Update on SSDs are experiencing problems with their computers freezing. Microsoft does not yet have a fix available, but it is aware of the issues and is working to get a patch pushed out to those who have been affected. While there is not a proper fix available at the moment, the company has provided details of a couple of workarounds that should do the job for the time being. Writing on Windows Answers, a Microsoft administrator said: "Microsoft has received a small number of reports of Windows 10 freezing after installing the… [Continue Reading] -

Silk Road administrator must be extradited to the US from Ireland
Publié: août 14, 2016, 6:07pm CEST par Mark Wilson
When the net closed around Silk Road, many thought it spelled the end of the black market trade on the dark web. Of course, this did not turn out to be the case, so hopes were pinned on holding those responsible for the site to account. The founder of the site has already been charged, and now authorities are after those who acted as admins. One such target is Irishman Gary Davis, and an Irish court has just ruled that he should be extradited to the US to face hacking, drug trafficking and money laundering charges. Davis -- who used… [Continue Reading] -

Alleged Silk Road administrator must be extradited to the US from Ireland
Publié: août 14, 2016, 6:07pm CEST par Mark Wilson
When the net closed around Silk Road, many thought it spelled the end of the black market trade on the dark web. Of course, this did not turn out to be the case, so hopes were pinned on holding those responsible for the site to account. The founder of the site has already been charged, and now authorities are after those who acted as admins. One such target is Irishman Gary Davis, and an Irish court has just ruled that he should be extradited to the US to face hacking, drug trafficking and money laundering charges. Davis -- who used… [Continue Reading] -

Skype for Windows Phone will stop working in 2017
Publié: août 13, 2016, 10:50am CEST par Mark Wilson
With the release of Windows 10 Mobile, Microsoft's support for Windows Phone is gradually starting to die off. We already knew that Windows Phone support for Skype was coming to an end, but now we know more. Microsoft has now announced that as well as ending support for Skype on Windows Phone in October, come 'early 2017' the apps will simply stop working. And it's all thanks to a move to the cloud. The company has already said that the future of Skype is cloud-based rather than peer-to-peer, and this is the reason Windows Phone support is coming to a… [Continue Reading] -

Fuchsia is Google's latest operating system
Publié: août 13, 2016, 10:29am CEST par Mark Wilson
It could be argued that with Android and Chrome OS, Google already has more than its fair share of operating systems; but there's another one in the pipeline. Very little is known about it at the moment, but Google has a new operating system project underway called Fuchsia. There's a GitHub page up and running, where you can find out about the Fuchsia kernel -- a kernel that is designed with scalability and multi-device, cross-platform compatibility in mind. Based on the LittleKernel project, Fuchsia is not only on GitHub, but also Google Source. Google is giving away very little on… [Continue Reading] -

Google Play drops the Google+ account requirement for app reviews
Publié: août 13, 2016, 10:02am CEST par Mark Wilson
Google seems to be realizing, at long last, that very, very few people care about Google+. While there have been endless -- as yet unfounded -- rumors that the Google's social tool could be killed off, for now the company appears content simply to decouple it from other services. The latest change means that Android users looking to post reviews on Google Play no longer have to have Google+ account to do so. Cue general whooping. It comes hot on the heels of another recent change which saw the ability to +1 apps in Google Play, and it's a move… [Continue Reading] -

Adblock Plus says open source developers will fight for users' right to block ads on Facebook
Publié: août 12, 2016, 10:07pm CEST par Mark Wilson
Following on from Facebook's decision to override users' ad blocking tools, Adblock Plus has fired one more shot, saying that it will continue the fight for the right to an ad-free social networking experience. After finding a way to prevent Facebook blocking ads, which Facebook then bypassed once again, Adblock Plus says that while the game of cat and mouse may continue, it wants to use what it describes as "probably be the last time we talk about it for a while" to say that the open source community will fight the good fight for users. The company has a… [Continue Reading] -

Facebook starts to take more notice of your preferences to personalize your newsfeed
Publié: août 12, 2016, 12:36pm CEST par Mark Wilson
Facebook's constant tinkering with newsfeed algorithms has a tendency to leave people asking what on earth is wrong with a simple chronological display of posts. But the social network -- driven by ads -- feels that it knows better and likes to play with the code that determines what you see. Having made changes to ensure that you see more posts from the people you know (well, Facebook is supposed to be about friends and family...) the latest change sees the social network aiming to bring you posts that are "more personally informative". Facebook uses its Feed Quality Program to… [Continue Reading] -

Ad blockers find a way to circumvent Facebook's ad blocking circumvention
Publié: août 12, 2016, 10:45am CEST par Mark Wilson
Facebook's announcement that it would start to punch through ad blockers to make sure everyone sees ads was met with understandable condemnation and consternation. One of the best known ad blockers, Adblock Plus, soundly criticized the move, saying that it was an example of 'cat-and-mouse games'. And so it begins. Facebook may have said that it will circumvent ad blocking tools, but now ad blockers are fighting back. The open source community has worked is magic and come up with code that circumvents Facebook's circumvention. How meta... Adblock Plus is advising its users to update their filter lists right now… [Continue Reading] -

The discovery of child porn is not enough to justify warrantless email searches
Publié: août 10, 2016, 12:51pm CEST par Mark Wilson
Child pornography is something that, understandably, raises hackles and many people would argue that anything possible should be done to pursue those believed to be involved. But a court in the District of Kansas has ruled that the discovery of images of child porn is not enough to justify warrantless email searches by agents. The 10th Circuit Court of Appeals ruled that email attachment images obtained by the National Center for Missing and Exploited Children (NCMEC) should be dismissed as evidence as they were gathered via what was deemed to be a warrantless search. It's a ruling that could have… [Continue Reading] -

Google will block Flash in Chrome 53
Publié: août 10, 2016, 11:29am CEST par Mark Wilson
Following the lead of Apple with Safari in macOS Sierra, and Mozilla with Firefox, Google has announced that Chrome will begin to block Flash content. Starting with Chrome 53 in September, Google will "de-emphasize Flash in favor of HTML5". Google says that the decision has been made to improve security, performance, and battery life, and it builds on an earlier change that made some Flash content click-to-play rather than loading it by default. Flash is very much a lumbering technology of the past, and Google points out that "more than 90 percent of Flash on the web loads behind the… [Continue Reading] -

Adblock Plus responds angrily to Facebook's plan to circumvent ad blockers
Publié: août 10, 2016, 11:00am CEST par Mark Wilson
Facebook's plans to show adverts to everyone regardless of whether they are using an ad blocker was always going to prove controversial. The decision to bypass the privacy and security tools that many people have put in place has riled one company in particular -- Adblock Plus. Describing the social network's latest move as being 'all anti-user', Adblock Plus's Ben Williams says that it is an 'unfortunate move' that 'takes a dark path against user choice'. He goes on to pooh-pooh the idea that Facebook made the decision based on what users want. He points out that Facebook recognises the… [Continue Reading] -

Facebook's ads will bypass ad blocking software
Publié: août 9, 2016, 4:34pm CEST par Mark Wilson
Advertising on Facebook has undergone many changes over the years, but the latest tweak is likely to prove particularly controversial. As well as announcing the rollout of new controls for users to set ad preferences, the social network today says that its ads will circumvent ad blocking software. The idea of bypassing the likes of Adblock Plus will almost certainly rub many Facebook users the wrong way. In an attempt to sweeten the pill a little, the company says its new ad preferences controls will enable you to filter out irrelevant ads so you only see ads that might be… [Continue Reading] -

How to hide the Windows Defender icon in Windows 10 Anniversary Update
Publié: août 9, 2016, 12:10pm CEST par Mark Wilson
If you have just upgraded to Windows 10 Anniversary Update, you have possibly noticed the addition of a Windows Defender icon in the notification area. Then again, you may not -- a quick straw poll in the BetaNews newsroom reveals that not everyone is seeing it. Assuming the icon has suddenly appeared for you, it's possible that you'd rather it vanished. Here's what you need to do if you would like to banish the Windows Defender icon and clean up your notification area. You'll notice that if you left- or right-click on the little shield icon, there is no option… [Continue Reading] -

Google can already protect most Android phones from the QuadRooter threat
Publié: août 9, 2016, 11:33am CEST par Mark Wilson
The discovery of QuadRooter is one of the biggest security threats to Android users since Stagefright. Security firm Check Point Software has released a tool to help people determine if their phones are at risk, but Google says that it is already able to block apps with the QuadRooter exploit. The Verify Apps feature of Google Play Services is able to detect and block any apps that feature QuadRooter. As the exploit has to be delivered via an app, this effectively protects the vast majority of handsets that are threatened. QuadRooter is actually a series of four individual vulnerabilities, and… [Continue Reading] -

Google Maps gets data-saving Wi-Fi-only mode and the option to save maps to SD cards
Publié: août 9, 2016, 11:10am CEST par Mark Wilson
Google Maps is a great tool for helping you get from A to B -- until you find yourself in an area with no data reception, that is. To help combat the problem -- and fighting expensive data charges at the same time -- Google is introducing a new Wi-Fi only mode which forces Google Maps into offline mode. As well as preventing the app from struggling to download data over a rubbishy or non-existent connection, the update means that Google Maps relies entirely on your saved maps -- something Google says could boost battery life. But there's more! If… [Continue Reading] -

Adware and Pay-Per-Install software deals rake in big money
Publié: août 9, 2016, 10:30am CEST par Mark Wilson
After a yearlong study into 'unwanted software' Google has published a report that shows that there is a good deal of money to be made out of bolting crapware onto software installers. The authors suggest that unwanted software is a problem that affects three times as many people as malware, making it an incredibly lucrative business. The paper, entitled "Investigating Commercial Pay-Per-Install and the Distribution of Unwanted Software", is a joint venture between Google and New York University and it reveals the techniques used by developers to evade detection. It also found that Pay-Per-Install (PPI) methods are used to deliver… [Continue Reading] -

Hulu ends its ad-supported free streaming
Publié: août 8, 2016, 6:10pm CEST par Mark Wilson
The age of free Hulu is over. The ad-supported side of the streaming video service is being killed off, and anyone who is currently making use of the free option will be moved to a free trial of a full subscription. Nine years after its launch, Hulu is ditching its ad-supported tariffs and will instead focus on pushing people towards paying a monthly subscription. The move comes after the streaming company expanded its deal with Yahoo so that shows from ABC, NBC and Fox will be available to stream eight days after broadcast. If you're currently taking advantage of a… [Continue Reading] -

Adding Linux Bash to Windows 10 Anniversary Update could be a huge security risk
Publié: août 8, 2016, 1:00pm CEST par Mark Wilson
The arrival of Linux in Windows 10 caused ripples of excitement in certain circles. But as well as making it possible to run GUI Linux apps on the desktop, there are also concerns that there are security risks associated with having the Bash feature from Linux available in Windows 10 Anniversary Update. Speaking at the Black Hat USA security conference, Alex Ionescu from Crowdstrike said that he had reported some concerns to Microsoft during the testing period of Windows 10. While some of the issues he raised have been addressed, he says that the presence of Linux represents a "new… [Continue Reading] -

Check if your phone is at risk from QuadRooter vulnerability
Publié: août 8, 2016, 11:51am CEST par Mark Wilson
The latest vulnerability for Android handsets is QuadRooter, and there are an estimated 900 million devices at risk. Just shy of a billion phones and tablets is undeniably a lot, but how can you know if you are affected? While a list of devices that are definitely affected has been published, it is far from exhaustive. Thankfully the good folk at Check Point Software have put together a special app that will test your phone or tablet and let you know the risk. You can download a free copy of the QuadRooter Scanner from Google Play, and it will tell… [Continue Reading] -

Apple finally announces a bug bounty program of its own -- but it's not open to everyone
Publié: août 8, 2016, 10:28am CEST par Mark Wilson
Bug bounty programs have become commonplace in recent years. Tech companies offer up rewards to coders, engineers and hackers who manage to unearth security vulnerabilities in software, and this means that problems are detected and patched faster than normal. It is something that the likes of Google and Microsoft have offered for some time, and now Apple has decided it wants a piece of the action as well. Starting in September, the company will pay out up to $200,000 to anyone identifying vulnerabilities in its software and services. Announced at the Black Hat security conference in Las Vegas a few… [Continue Reading] -

Facebook cuts the clickbait to make newsfeeds newsworthy
Publié: août 6, 2016, 9:33pm CEST par Mark Wilson
Clickbait causes anger, and it's everywhere. From the 'One weird trick' hooks through 'she opens the door, what happens next will blow your tiny little mind' all the way up to '10 cheese recipes, number 8 will drive you insane' -- you know it when you see it and it likely rubs you up the wrong way. You've probably noticed that such headlines proliferate on Facebook, doing little to improve the quality of content in your newsfeed. You're not alone in noticing; Facebook is aware of the problems and is taking steps to clear out the crap and cut back… [Continue Reading] -

HTTP/2 has four huge security vulnerabilities
Publié: août 4, 2016, 11:57am CEST par Mark Wilson
The HTTP/2 standard was approved some time ago, but it is yet to be widely adopted. Before the standard can become widespread, however, there are four serious vulnerabilities that need to be addressed. The high-profile issues were revealed at Black Hat USA 2016 by Imperva researchers. They found that exploits similar to those that work on HTTP/1.x also work on the HTTP/2 protocol. The problems specifically affect server implementations from Apache, Microsoft, NGINX, Jetty, and nghttp2, but it is likely that other implementations are also at risk. Despite the fact that HTTP/2 has only been implemented on under 10 percent… [Continue Reading] -

Microsoft uses data gathered from telemetry to reduce Windows 10 Anniversary Update rollback period
Publié: août 4, 2016, 10:46am CEST par Mark Wilson
If you've upgraded to Windows 10 Anniversary Update, you only have 10 days in which to roll back to your previous operating system if you change your mind. This is a dramatic reduction from the 30 days Microsoft allowed users previously. As noted by Richard Hay on WinSuperSite, the latest big update to Windows 10 slashes this period by two thirds. This is not just an arbitrary change, however. Microsoft says it is based on data gathered via telemetry. Richard tested Windows 10 and Windows 10 Anniversary Update in virtual machines to confirm the difference in the testing timeframes. Intrigued… [Continue Reading] -

EU lawmaker decries Tinder's terrible privacy policy
Publié: août 4, 2016, 10:03am CEST par Mark Wilson
The dating app Tinder is facing criticism from Europe where lawmakers believe it breaches EU data protection rules. There are calls for the app to be investigated by the European Commission over how it makes use of personal data. Concerns spring from the fact that Tinder's terms are written in such a way that owner Match Group Inc can continue to use user data even when accounts are closed. It is alleged that these "abusive clauses" are unlawful. One of the key complainants is socialist lawmaker Marc Tarabella from Belgium. Having already called for the break-up of Google, Tarabella is no… [Continue Reading] -

$72 million Bitcoin theft from Bitfinex exchange causes cryptocurrency price plunge
Publié: août 3, 2016, 11:13am CEST par Mark Wilson
The theft of 119,756 Bitcoin from the Bitfinex exchange has seen the price of the cryptocurrency plummet by 23 percent. In what has been described as the second biggest Bitcoin theft after MtGox, $72 million worth of Bitcoins vanished from user's accounts It seems that Bitfinex suffered a massive security breach when it was hit by hackers who started to filter money out of segregated wallets. Despite the hack, the exchange says that this incident doesn’t "expose any weaknesses in the security of a blockchain". The attack on Bitfinex is particularly significant, as it is the largest dollar exchange in… [Continue Reading] -

If you want to buy your own HoloLens augmented reality headset... you can!
Publié: août 3, 2016, 10:07am CEST par Mark Wilson
When Microsoft announced its entry into the world of augmented reality with HoloLens, there was a great deal of enthusiasm from the technology community. But while HoloLens is undeniably exciting, there was a problem -- it was only available to a very select few. Now that changes. Anyone who has $3,000 to spare, and who lives in the US or Canada, can get their hands on a headset right now. It's the Microsoft HoloLens Developer Edition that's up for grabs, but you don’t (really) have to be a developer to buy one. Apart from the fact that HoloLens currently only… [Continue Reading] -

Chrome 52 for Android massively reduces battery and data consumption by video
Publié: août 2, 2016, 6:05pm CEST par Mark Wilson
Google is pushing out Chrome 52 for Android, and the big news with this release relates to video. With video being such a massive component of internet traffic, it is perfectly natural for Google to focus on this area, and the company says that improvements have been made to battery consumption and loading times. There is a marked shift of focus to speed and power efficiency -- compared to the desktop where the focus has long been quality over everything else. Importantly, Google has now made it possible to reap the benefits of Data Saver Mode when watching video. If… [Continue Reading] -

Adblock Plus arrives for Microsoft Edge in Windows 10
Publié: août 2, 2016, 5:18pm CEST par Mark Wilson
Today is the day that Windows 10 Anniversary Update rolls out to the masses, but this is not the only big Windows 10 news of the day. The version of Microsoft Edge included in the latest update features support for extensions -- and this means that millions of Windows 10 users can now take advantage of Adblock Plus. Of course, this is not entirely new news. Windows Insiders have been able to use Adblock Plus for a little while now, but now that same option is available to anyone running the latest version of Microsoft's operating system. Adblock Plus for Microsoft… [Continue Reading] -

Google rolls out native notifications to Android users when new devices sign into their accounts
Publié: août 1, 2016, 8:30pm CEST par Mark Wilson
Google continues to take steps to improve the security of Android, and the latest addition starts to roll out today. Lengthily referred to as "Android notifications for newly added devices", the feature does exactly what you would expect it to do. Whenever a new device is added to an account, a native Android notification will appear. This gives users the opportunity to review the device and determine whether it is something suspicious. If the notification should appear at a time when a user has not knowingly signed into their account with another device, the Review Account Activity option comes into… [Continue Reading] -

Microsoft launches beta version of IFTTT competitor Flow for Android
Publié: août 1, 2016, 6:31pm CEST par Mark Wilson
Automation tools for mobiles were something of a craze a little while ago, with the likes of IFTTT proving incredibly popular. Last month, Microsoft released its own automation tools, Flow, to iOS users, and now a beta version has been launched for Android. Microsoft's take on automation is very much what you would expect -- it's all about connecting different cloud services and apps, and getting them to work together in a helpful way. If you want to sign up to take part in the testing programme, you'll have to visit the Microsoft Flow app in Google Play. Click the… [Continue Reading] -

Android 7.0 Nougat could launch on August 5 -- without Nexus 5 support
Publié: août 1, 2016, 11:19am CEST par Mark Wilson
We waited for an age to find out what Android 7.0 (or Android N) was going to be called -- Nougat, as we all now know -- and the next natural question is: when will we get it? If the usually-reliable Evan Blass is correct, it might only be a matter of days before the rollout starts. In a tweet over the weekend, the tipster said that Android 7.0 will be released at the same time as the August security patch -- on August 5. As is the norm with tips from Evan, there are no sources and nothing to… [Continue Reading] -

Microsoft tightens up Windows 10 security by requiring kernel mode drivers to be digitally signed
Publié: août 1, 2016, 10:29am CEST par Mark Wilson
Windows 10 will not load unsigned kernel mode drivers, starting with version 1607 of the operating system. This is something that had been announced back in 2015, but is only just being implemented. The decision was taken in order to improve the security of Windows 10, but Microsoft says that "due to technical and ecosystem readiness issues, this was not enforced by Windows Code Integrity and remained only a policy statement". Now it is a reality, and it's something developers and users need to keep in mind. The change only affects new drivers, and Microsoft explains that there is no… [Continue Reading] -

Free gifts for Windows 10 Insider testers -- and more in store for the future!
Publié: juillet 31, 2016, 12:46pm CEST par Mark Wilson
It's now a full year since Windows 10 was first, and to thank the Insiders who have been providing feedback to help shape the direction of the operating system, Microsoft has a couple of gifts and a little surprise. As well as handing out an exclusive-to-Insiders wallpaper package and a Ninja Cat animated GIF, Microsoft has also awarded Insiders with a surprise badge that appears next to their profile in the Feedback Hub. There is the promise of more badges to come, but the anniversary of Windows 10's launch gives Microsoft a good opportune time to reflect on the last… [Continue Reading] -

Xbox Summer Update is rolling out bringing closer Windows 10 integration
Publié: juillet 31, 2016, 11:54am CEST par Mark Wilson
It's another couple of days until Windows 10 Anniversary Update rolls out to users, but Xbox One users now have something very exciting to download -- the Xbox Summer Update. Previously available as a preview, the latest system update sees the arrival of Cortana, background music and much more. Major Nelson has announced that the rollout of the update starts this weekend, but there is no guarantee of when it will arrive on your Xbox One. If you're the impatient kind, you'll be pleased to hear that you can force the update to download and install it straight away! In… [Continue Reading] -

Changes are coming to Microsoft's Privacy Statement and Services Agreement
Publié: juillet 31, 2016, 10:58am CEST par Mark Wilson
On August 2, coinciding with the launch of Windows 10 Anniversary Update, Microsoft is updating its Privacy Statement. The company is a little light on the details of exactly what the changes are, but says that more will be revealed on the big day. The aim of the changes, as with previous updates is to "eliminate redundancies, improve usability and increase clarity and transparency". Microsoft makes clear that it is in the habit of sharing user data with others "in certain cases" and it also announces that the Services Agreement will be updated on September 15. You are advised that… [Continue Reading] -

The SwiftKey keyboard app is busy leaking email addresses and phone numbers to strangers
Publié: juillet 29, 2016, 6:16pm CEST par Mark Wilson
Who doesn't love a good AI-driven keyboard, eh? Well, people who have discovered that the keyboard is sending their email address and phone number to strangers, for starters. And that seems to be precisely what's happening with SwiftKey. The Microsoft-owned company has disabled the syncing of data between devices after users complained not only about the appearance of unknown email addresses and phone numbers in suggestions, but also suggestions in unknown foreign languages. The problem became apparent when users who saw the random email address suggestions contacted the owner of the address. The problem has been going on for a… [Continue Reading] -

Reminder: You now have mere hours to upgrade to Windows 10 for free
Publié: juillet 29, 2016, 2:19pm CEST par Mark Wilson
Today is the big day -- July 29, the last day when you can upgrade to Windows 10 free of charge. Actually, the cut-off point really depends on where you are in the world, but you have until 11:59 pm UTC-10. Timeanddate.com has a handy conversion to work out what this means for you. It would be fair to say that there has been plenty of warning about the impending deadline, but there are still people who are putting things off. But really there is no reason not to upgrade; even if you decided you don’t want Windows 10, you can… [Continue Reading] -

WhatsApp doesn't properly delete 'deleted' chats
Publié: juillet 29, 2016, 10:45am CEST par Mark Wilson
A security researcher is warning WhatsApp users that their chats can be retrieved even after they have been deleted, cleared, or archived. Jonathan Zdziarski says that even using the 'Clear All Chats' option leaves behind a 'forensic trace'. He warns that the only way to be certain that your chat history is deleted, is to get rid of the app entirely. The problem appears to stem from WhatsApp's use of SQLite which fails to overwrite deleted data by default, rendering it recoverable. As with deleted files on a hard drive, the SQLite database is simply updated to show that the… [Continue Reading] -

Microsoft celebrates the 20th anniversary of Windows Server
Publié: juillet 28, 2016, 9:31pm CEST par Mark Wilson
With strange serendipitous timing, just as the free upgrade period for Windows 10 is coming to an end, Microsoft is also celebrating the 20th anniversary of Windows Server. Way back in 1996, the company unleashed Windows NT 4.0 Server onto an unsuspecting world. The rest, as they say, is history. Described as the operating system that would 'knock the socks of Unix' Windows NT 4.0 Server stuck around for four years before being replaced by the enterprise-specific Windows 2000 Server. With laughably low system requirements -- 133 MHz CPU, 32 MB RAM and 1 GB of disk space -- this… [Continue Reading] -

Google brings add-ons to Docs and Sheets on Android
Publié: juillet 28, 2016, 8:39pm CEST par Mark Wilson
With a desktop word processor and spreadsheet, you have great power to create a range of documents. The move to the cloud and mobile means that popular Office suites have been ported to mobile platforms, and this usually means missing out on key features -- like add-ons. Today, this changes as Google has announced that Android add-ons for Docs and Sheets are now available. This means that Google's mobile office tools can be extended with add-ons like DocuSign, Scanbot and Zoho CRM. The new feature means that the Android-based office suite just became a whole lot more useful. No longer… [Continue Reading] -

Microsoft changes minimum hardware requirements for Windows 10 to improve security
Publié: juillet 28, 2016, 10:34am CEST par Mark Wilson
Today -- the day before the free upgrade to Windows 10 expires, and just a few more days before the release of Windows 10 Anniversary Update -- Microsoft is tweaking the minimum system requirements for the operating system. Specifically, hardware manufacturers will have to include TPM 2.0 in PCs, smartphones and tablets if they are to be considered Windows 10 compatible. TPM 2.0 (Trusted Platform Module) is an added hardware-based security layer that helps to protect user data, As noted by PCWorld, TPM 2.0 is key to Microsoft's push of Windows Hello as it provides a secure area to store… [Continue Reading] -

At last! Google Play Family Library lets you share purchased apps, games and movies with others
Publié: juillet 27, 2016, 6:14pm CEST par Mark Wilson
It's something that Android users have been begging for -- the ability to buy an app once, and share it with members of the family. Until now, one way around the problem was to create a shared family account that could be used to download everything, but now Google has a better solution: Google Play Family Library. This new feature not only lets you share purchased apps with up to six family members, but also games, movies, TV shows and books. It's something that could save Android-using families a good deal of money, and it's rolling out right now. To… [Continue Reading] -

Tim Sweeney: Microsoft is trying to kill Steam with Windows 10
Publié: juillet 27, 2016, 4:55pm CEST par Mark Wilson
Microsoft is on a mission to destroy Steam with Windows 10. At least that is what Tim Sweeney, co-founder of Epic Games believes. He says that Microsoft's love of UWP (Universal Windows Platform) apps means that Win32 apps are gradually being driven to extinction. In an interview with Edge magazine, Sweeney says that he predicts Microsoft will release patches for Windows 10 over the next few years that will render Steam "progressively worse and more broken". Sweeney has spoken out against UWP before, and his hatred is far from a secret. He believes that Microsoft will use its position with… [Continue Reading] -

Zero-day flaw leaves LastPass vulnerable to attack
Publié: juillet 27, 2016, 3:35pm CEST par Mark Wilson
A Google Project Zero hacker has discovered a zero-day vulnerability in the password manager LastPass that could lead to accounts being completely compromised. The security flaw can be triggered by visiting a malicious website, and it has been confirmed to be an issue by white hat security researcher Tavis Ormandy. He has filed a full report to LastPass with a view to getting the vulnerability patched. As the security hole is yet to be fixed, full details have not been publicly released. However, Ormandy has gone as far as saying that "it's a complete remote compromise" -- something which will… [Continue Reading] -

Zero-day flaw leaves LastPass vulnerable to attack [UPDATE: it's fixed]
Publié: juillet 27, 2016, 3:35pm CEST par Mark Wilson
A Google Project Zero hacker has discovered a zero-day vulnerability in the password manager LastPass that could lead to accounts being completely compromised. The security flaw can be triggered by visiting a malicious website, and it has been confirmed to be an issue by white hat security researcher Tavis Ormandy. He has filed a full report to LastPass with a view to getting the vulnerability patched. As the security hole is yet to be fixed, full details have not been publicly released. However, Ormandy has gone as far as saying that "it's a complete remote compromise" -- something which will… [Continue Reading] -

Your wireless keyboard could be secretly leaking unencrypted data to hackers
Publié: juillet 26, 2016, 7:04pm CEST par Mark Wilson
Researchers at security firm Bastille warn that many wireless keyboards can be very easily intercepted so hackers can see exactly what is being typed. With a very simple dongle called Keysniffer, it is possible to snoop on usernames, passwords and anything else that is being typed from up to 250 feet away. In all, Bastille found that eight manufacturers produce keyboards -- meaning there are millions in use -- which use unencrypted radio communication to transmit easily captured clear text. The problem affects non-Bluetooth devices from the likes of Anker, Hewlett-Packard, Kensington and Toshiba. The list of problematic, insecure keyboards… [Continue Reading] -

EU-US data-sharing Privacy Shield agreement will run for at least a year without legal challenges
Publié: juillet 26, 2016, 5:24pm CEST par Mark Wilson
The rocky road to finding a replacement to the Safe Harbour data transfer agreement appears to have become a little smoother. The successor to the EU-US arrangement is Privacy Shield, and European regulators have said it will be permitted to run to at least a year without intervention. Having been deemed unsuitable because of the level of access it gave the US to European data, Safe Harbor's replacement has been a long time coming. The head nod from regulators will be widely welcomed by the tech industry, as well as those disturbed by NSA surveillance revelations. The decision to run… [Continue Reading] -

Microsoft boosts the intelligence of Office with Zoom for PowerPoint, Focused Inbox for Outlook, and more
Publié: juillet 26, 2016, 4:18pm CEST par Mark Wilson
Microsoft today announced a series of updates for its Office apps which help to make the suite more intelligent than ever. There's a strong focus on workflow and efficiency, and things kick off with the Researcher tool. This provides context-sensitive research materials that can be accessed from within Word and quickly added to a document complete with properly formatted citations. Microsoft says that Researcher will continue to expand to include "sources like national science and health centers, well-known encyclopedias, history databases and more". But this is far from being the only new tool to be added in the latest monthly… [Continue Reading] -

No, Facebook wasn't deliberately censoring Wikileaks' #DNCLeak emails
Publié: juillet 26, 2016, 3:10pm CEST par Mark Wilson
Julian Assange promised to deliver a cache of emails that would harm 'liberal war hawk' Hillary Clinton and her presidential campaign. Living up to Assange's promise, Wikileaks delivered the goods. It wasn't long before controversy struck, but this was not because of the content of the emails. The communication between US Democratic Party committee members was shared on Facebook but it didn't take long for the content to be blocked, leading to accusations of censorship. Facebook has now explained that it was not purposefully censoring Wikileaks' content. The company's chief security officer said a couple of days ago that the… [Continue Reading] -

TechCrunch hacked by OurMine
Publié: juillet 26, 2016, 2:09pm CEST par Mark Wilson
The TechCrunch website was today hit by a hacker group going by the name of OurMine. The group describes itself as a "an elite hacker group known for many hacks showing vulnerabilities in major systems". The hack was -- on the face of it, at least -- not particularly malicious, and came across as almost polite. Rather than completely defacing the site, OurMine chose instead to simply post a news story to indicate that the CMS had been breached. The message (since deleted) was posted by Devin Coldewey under the headline "OurMine Team -- Important Message!" It read: "Hello guys… [Continue Reading] -

Chuwi Vi10 Plus tablet includes Windows 10 and Android for an incredibly low price
Publié: juillet 26, 2016, 1:22pm CEST par Mark Wilson
A few months back, we took a look at the Chuwi Hi12, a low-cost tablet that we compared to the Surface Pro 4 and iPad Pro. Now the company has released a slightly smaller -- and even cheaper -- model, the Chuwi Vi10 Plus. With a 10.8-inch screen, the Chuwi Vi10 Plus is available in two variations. The first model comes with Android-based Remix OS 2.0 installed, while the second is a dual boot unit that has both Windows 10 and Remix OS 2.0 installed. For now, Chuwi only has the single-OS version of the Vi10 Plus, priced at a… [Continue Reading] -

CyanogenMod: reports of its death have been greatly exaggerated
Publié: juillet 26, 2016, 11:27am CEST par Mark Wilson
Rumors started to circulate in recent days that all was not well at Cyanogen Inc. Reports suggested that the company was not only shedding a fifth of its staff, but was also moving away from its Android-based CyanogenMod to focus instead on apps. After a few days of silence, the company has now come forward to set the record straight. Cyanogen Inc wants to make it clear that its operating system is here to stay, and there are no plans to become an app company. Co-founder Steve Kondik has written a blog post with the aim of addressing the "circus… [Continue Reading] -

Spam call protection arrives in the Google Phone app for Android
Publié: juillet 26, 2016, 11:01am CEST par Mark Wilson
We're used to the idea of filtering spam emails from our inbox these days, but there is also the problem of spam phone calls. These are not just a nuisance, but may also be the start of scams. Google is pushing out an update to its Phone app that helps to keep you protected. It's a simple idea. Whenever a suspicious call comes through, a warning is displayed on screen to let you know that you might want to either ignore the call, or take care if you answer. While it's great to be warned about possible spam calls, Google… [Continue Reading] -

Google Maps gets a facelift that makes it easier to read and areas of interest easier to find
Publié: juillet 26, 2016, 10:29am CEST par Mark Wilson
You've probably noticed that it can be hard to make out details on Google Maps. You're not alone; Google has noticed too, and the company has just launched a redesigned version of the essential travel tool. The changes apply to the desktop, iOS and Android versions of Google Maps and the most immediately apparent difference is the new color palette -- much subtler and easier on the eyes. But Google has also cleaned things up to improve visibility, and added new 'areas of interest'. Google said that improving the legibility of Maps "is a balancing act" and explains that it… [Continue Reading] -

Bitcoin is not money, it's property
Publié: juillet 26, 2016, 9:54am CEST par Mark Wilson
What's the first word that pops into your head when you hear Bitcoin? It's probably cryptocurrency, but a judge in Florida says this is wrong -- it's actually property. In a case relating to alleged money laundering, Judge Teresa Pooler ruled that the charges could not stick as Bitcoin was not money, and therefore could not be laundered. With the decision that Bitcoin cannot be considered a 'monetary instrument', this could have implications for future cases. Judge Pooler said that trying to apply financial legislation to Bitcoin was futile and inappropriate. As she put it: "attempting to fit the sale… [Continue Reading] -

The KickassTorrents forums are alive and kicking
Publié: juillet 25, 2016, 11:33pm CEST par Mark Wilson
Just a few days ago, KickassTorrents was dealt a blow when Artem Vaulin was arrested and the site seized by feds. Of course, it didn’t take long for mirrors to spring up, keeping KAT online in new locations. But the original team has also taken steps to ensure that the community lives on. The KAT team has set up Katcr.co, home to a forum complete with many familiar old faces. This time around, there are no torrents -- this is strictly a forum -- although the KAT mirrors are still to be found online. Katcr.co is all about keeping the… [Continue Reading] -

What's the point of Twitter? Twitter explains...
Publié: juillet 25, 2016, 5:45pm CEST par Mark Wilson
Twitter is worried. It's worried that while it is a well-recognized brand, a disturbingly large number of people have no idea what Twitter is actually for. What is the point? Getting slightly meta, the company today explains its raison d'être and tries to clear up some common misconceptions. 'What misconceptions are there about Twitter?', you may well ask. That it is a social network. (It ain't.) That you have to use it every day. (Seriously?) As Twitter says, 'We realized we had some explaining and clarifying to do!' In a blog post, Twitter CMO Leslie Berland explains that today is… [Continue Reading] -

Verizon acquires Yahoo for $4.83 billion
Publié: juillet 25, 2016, 1:55pm CEST par Mark Wilson
After speculation and rumors, the deal has been done. Verizon has stumped up $4.83 billion in cash for Yahoo's operating business, including search, advertising and content. The acquisition adds an extra one billion monthly active users to Verizon's customer base, and the deal comes just over a year after the company acquired AOL. Verizon's CEO says the company is in a 'highly competitive position' and the deal will 'help accelerate our revenue stream in digital advertising'. Verizon now has a huge portfolio of brands, spanning everything from publishing and advertising, to search and news. The deal is expected to complete… [Continue Reading] -

Ford adds SYNC 3 with Apple CarPlay and Android Auto to its entire 2017 range
Publié: juillet 25, 2016, 10:32am CEST par Mark Wilson
All of Ford's 2017 SUVs, light trucks, cars and electric vehicles will be kitted out with SYNC 3. The addition of Ford's voice-activated communications and entertainment system means that every single vehicle from its 2017 lineup will feature support for Apple CarPlay and Android Auto -- in the US, at least. SYNC 3 allows for the use of iPhones and Android smartphones to get directions, make calls, listen to music and make use of third party apps while driving. Ford promises that a "platform-focused approach to SYNC 3 means a fast rollout across all vehicles". The company has made something… [Continue Reading] -

Forget the beta... Prisma arrives on Android
Publié: juillet 25, 2016, 3:04am CEST par Mark Wilson
Like Pokémon Go, Prisma has taken the app world by storm in recent weeks. Previously only available for iOS users, the photo app that creates works of art from your snaps has finally made its way to Android. Just a few days ago there was talk of a beta program that keen users could take part in, but now we've jumped straight to the full release. If you're (somehow) unfamiliar with the app, it uses machine learning to transform your photos into the style of any one of a number of famous artists and styles. This is an app that… [Continue Reading] -

Malicious computers are spying on Dark Web users on Tor
Publié: juillet 23, 2016, 4:01pm CEST par Mark Wilson
For people concerned with their privacy the Dark Web and Tor seem like natural bedfellows. Not for the first time, concerns are currently raised that Tor may not be anywhere near as anonymous as users might like to think, with researchers saying they have discovered dozens of computers engaged in surveillance of the Dark Web. Computer scientists from Northeastern University used honeypot addresses to identify over 110 malicious machines storing identifying information about users accessing .onion addresses via Tor. At the moment it is not clear whether data gathered by the computers has been used to identify individuals, but the… [Continue Reading] -

Windows 10 telemetry will be used to drive enterprise upgrades with Upgrade Analytics
Publié: juillet 23, 2016, 2:40pm CEST par Mark Wilson
Rightly or wrongly, telemetry in Windows 10 has been roundly and soundly criticized. But while the feature may be a privacy concern for some, Microsoft says that it is using the data gathered to provide advice to would-be Windows 10 users about driver and application readiness. This is something that is aimed at enterprise users for whom Microsoft recognizes that certain apps are mission-critical for businesses. This is why the company has launched Upgrade Analytics to "provide customers with insights which allow them to [...] mitigate potential problems". The aim, ultimately, is to get as many enterprise users moved over… [Continue Reading] -

Judge wants Yahoo to reveal how it recovered deleted emails
Publié: juillet 23, 2016, 2:04pm CEST par Mark Wilson
Helping out with a drug trafficking case, Yahoo was able to recover emails that had previously been deleted. Now a judge wants to know how this was possible. Yahoo's only policies state that email cannot be recovered once they have been deleted, and defense lawyers for Russell Knaggs -- who planned to move cocaine from South America -- want to know how the company was able to produce deleted email in this case. As explained by Motherboard, Knaggs and his accomplices went to some lengths to try to ensure that their communication could not be intercepted. "As part of the… [Continue Reading] -

Cyanogen ditches a fifth of its staff and switches focus from OS to apps
Publié: juillet 23, 2016, 10:29am CEST par Mark Wilson
Cyanogen Inc -- the cheeky little upstart behind Android-based CyanogenMod -- is reportedly laying off 20 percent of its workforce. The company is a fairly small operation with just 136 employees, but the lay-offs are significant as they are mostly from the OS side of things. It seems that the open source Android-inspired operating system has failed to generate quite as much interest as hoped, although it does have a very dedicated cult following. It is not clear quite what the future holds for CyanogenMod, but things are not looking good at the moment. The drastic company shake-up was first… [Continue Reading] -

Google wants devs to reduce the size of app updates
Publié: juillet 22, 2016, 10:59pm CEST par Mark Wilson
For many mobile users, it's important to keep an eye on data usage to ensure tariff limits are not exceeded. A major contributor to gobbling up monthly bandwidth allowances is the updating of apps, and Google is taking steps to reduce the size of APK updates. In a post on the Android Developers Blog, Google speaks directly to developers, pointing out the various steps they can take to optimize the size of updates. The company also calls for greater transparency so users know the size of updates before committing to a download. Google is in the process of rolling out… [Continue Reading] -

Niantic Labs faces lawsuit in Germany over Pokémon Go privacy concerns
Publié: juillet 22, 2016, 4:46pm CEST par Mark Wilson
Pokémon Go has proved almost unbelievably popular, and like any app that gains a huge following, malicious versions of the app soon appeared. The game has been in the headlines after hackers knocked gaming servers offline, but there have also been major privacy concerns. Now there could be a nightmare brewing for developer Niantic Labs in Germany, where consumer advocates say the game violates the country's consumer and privacy laws. Federation of German Consumer Organizations (VZBV) says the company needs to make sweeping changes to a raft of clauses in the app's terms of use in order to avoid further… [Continue Reading] -

Spotify sells your personal and playlist data to advertisers making you the product
Publié: juillet 22, 2016, 10:07am CEST par Mark Wilson
Much like Google, streaming music service Spotify is increasingly turning its attention to advertising. Announcing what it refers to as "programmatic buying", the company reveals that it is launching a targeted advertising program. Advertisers -- or "buyers" in Spotify's nomenclature -- will be granted access to not only demographic data about users, but also access to information about playlists. What's interesting here is that programmatic ad buying rolls out with immediate effect. As of right now, Spotify users are now a product that is being traded between companies. Their data will be used to deliver closely targeted audio ads that… [Continue Reading] -

KAPOW! Bubble Zoom in Google Play Books means better support for comics
Publié: juillet 21, 2016, 8:11pm CEST par Mark Wilson
If you use your Android smartphone or tablet to read comics, your reading experience is about to get a whole lot more enjoyable. An update to Google Play Books sees the introduction of Bubble Zoom, a feature announced at San Diego Comic-Con 2016. It uses image recognition technology to identify speech bubbles and automatically enlarge the text of each, one at time as you tap. To celebrate, Google is offering 50 percent off certain DC Comics and Marvel comics. Bubble Zoom is currently described as a 'technical preview', and Google is looking for feedback that will be used to improve… [Continue Reading] -

BBC iPlayer Radio app launches in the US for iOS and Android
Publié: juillet 21, 2016, 6:35pm CEST par Mark Wilson
The BBC pumps out a great deal of fabulous content, but there's one problem -- an awful lot of it can only be accessed in the UK. With the launch of the iPlayer Radio app for iOS and Android, this changes. As well as giving listeners the chance to tune in to live radio broadcasts, the app also provides access to podcasts, and boasts a catch-up feature for shows you may have missed. The iPlayer Radio app is available free of charge, and has already received rave reviews in the Google and Apple stores. Described by many as 'long overdue'… [Continue Reading] -

Mozilla will block non-essential Flash in Firefox from next month
Publié: juillet 21, 2016, 4:54pm CEST par Mark Wilson
Flash is seen, quite rightly, as the scourge of the internet, and for some time there has been a vocal movement to eradicate all traces of it. Following the lead of Google Chrome and upcoming versions of Safari, Mozilla is taking the step of blocking Flash content from Firefox that is "not essential to the user experience". It's part of the company's drive to reduce reliance on Flash, whilst recognizing that there is still a need to provide a degree of support for "legacy Flash content". Mozilla has taken the decision to ditch Flash in a bid to improve browser… [Continue Reading] -

Now it's easier than ever to submit changes and additions to Google Maps
Publié: juillet 21, 2016, 4:29pm CEST par Mark Wilson
Google has done a great job of mapping the globe down to street level, but it's not perfect. You've almost certainly encountered errors and omissions on Google Maps, and starting today the company is making it easy to point out missing and incorrect data from the comfort of your mobile. Crowdsourcing the collecting of map data is a great way to ensure that Google Maps is kept constantly up to date. It means that as businesses close down, change names, or open up, users can submit feedback to Google straight away so the information is available to everyone as quickly… [Continue Reading] -

UK crime rate doubles once all online crimes are taken into account
Publié: juillet 21, 2016, 12:20pm CEST par Mark Wilson
The Office for National Statistics (ONS) has revealed the true scale of online crime in England and Wales, and it is high enough to effectively double the overall crime rate. The previous estimate about the number of online crimes was 3.8 million, but the latest figures show that it is in fact over 5.8 million. The ONS says that a tenth of adults have fallen victim to online crime, and incidents are not specific to particular areas or social classes. The statistics take into account virus attacks, online fraud, phishing attacks and the like, with 3.8 million of the overall… [Continue Reading] -

Microsoft responds to allegations that Windows 10 collects 'excessive personal data'
Publié: juillet 21, 2016, 10:56am CEST par Mark Wilson
Yesterday France's National Data Protection Commission (CNIL) slapped a formal order on Microsoft to comply with data protection laws after it found Windows 10 was collecting "excessive data" about users. The company has been given three months to meet the demands or it will face fines. Microsoft has now responded, saying it is happy to work with the CNIL to work towards an acceptable solution. Interestingly, while not denying the allegations set against it, the company does nothing to defend the amount of data collected by Windows 10, and also fails to address the privacy concerns it raises. Microsoft does… [Continue Reading] -

Google A4A will speed up the web by making ads far more efficient
Publié: juillet 21, 2016, 9:13am CEST par Mark Wilson
These days, the web is all about advertising. Whatever type of site you visit -- news, entertainment, music, or whatever -- you are almost certain to encounter ads. Many people turn to ad blockers not just because ads can be irritating (and something of a privacy concern), but also because they can dramatically slow down browsing. We've already heard about Google's Accelerated Mobile Pages project which looks to speed up the web for mobile users. But AMP is about more than just pushing page content to handsets quicker. Google has also developed a way to dramatically speed up the appearance… [Continue Reading] -

KickassTorrents seized and taken offline as owner is arrested
Publié: juillet 21, 2016, 8:27am CEST par Mark Wilson
The Ukrainian owner of KickassTorrents (KAT) has been arrested in Poland and his torrent-touting website seized by authorities. Artem Vaulin -- who also goes by the name 'tirm' -- stands accused of criminal copyright infringement, as well as conspiracy to commit criminal copyright infringement and money laundering. The Department of Justice says that the site owned by 30-year-old Vaulin "has enabled users to illegally reproduce and distribute hundreds of millions of copies of copyrighted motion pictures, video games, television programs, musical recordings and other electronic media, collectively valued at more than $1 billion". Authorities now want to extradite him to… [Continue Reading] -

France: Windows 10 collects 'excessive personal data', issues Microsoft with formal warning
Publié: juillet 20, 2016, 8:42pm CEST par Mark Wilson
After accusations that Windows 10 collects too much data about users, France's National Data Protection Commission (CNIL) has order Microsoft to comply with the French Data Protection Act within three months. The company has been ordered to "stop collecting excessive data and tracking browsing by users without their consent". In addition to this, the chair of CNIL has notified Microsoft that it needs to take "satisfactory measures to ensure the security and confidentiality of user data". The notice comes after numerous complaints about Windows 10, and a series of investigations by French authorities which revealed a number of failings on… [Continue Reading] -

The clock is ticking for free Windows 10 upgrades and Microsoft is having one last nag
Publié: juillet 20, 2016, 6:46pm CEST par Mark Wilson
When it comes to encouraging people to take advantage of the free upgrade to Windows 10, Microsoft has not been shy about pushing things -- some would say a little too much. But now the clock really is ticking. The deadline for free upgrades of July 29 is fast approaching, and Microsoft has one final bit of nagging up its sleeve. With just nine days to go, an update has been pushed out to GWX which drives home the fact that time is running out. To add a bit of an incentive -- you could call it fearmongering -- there's… [Continue Reading] -

Facebook celebrates 1 billion monthly Messenger users
Publié: juillet 20, 2016, 5:22pm CEST par Mark Wilson
The battle between messaging apps has been going on for a number of years now, but the same names keep floating to the top. WhatsApp and Facebook Messenger regularly feature in the top chat apps, and today Facebook announces that it has hit a key milestone -- one billion users every month. To celebrate, the social network has a little gift to say thanks... but don’t get too excited. Facebook says: "We're grateful for all the people who are sending billions of messages every day and we hope to send 1 billion thank yous in the form of a new… [Continue Reading] -

Widespread BT outage caused by a faulty UPS
Publié: juillet 20, 2016, 4:40pm CEST par Mark Wilson
This morning, thousands of BT and Plusnet customers complained about dodgy internet connections. The problem has now been fixed, and the cause identified as a failed UPS owned by Equinix, leading to massive disruption. Equinix, owned by Telecity, said there had been a problem "with one of our UPS system at 8/9 Harbour Exchange (LD8)" in London. The exact cause is not yet known, but further investigations are underway. This morning's outage -- which caused problems ranging from not being able to get online at all, to intermittent connectivity issues -- affected around 10 percent of BT customers. The company… [Continue Reading] -

Google's DeepMind AI has cut data center electricity usage by 15 percent
Publié: juillet 20, 2016, 3:42pm CEST par Mark Wilson
Artificial intelligence is frequently associated with sentient computers, bots and the like. But in the real world, AI is being put to a far wider range of uses. DeepMind, Google's AI division has been instrumental in slashing energy consumption in data centers. Lying at the heart of the internet, data centers are huge electricity gobblers, and anything that can be done to reduce usage is to be welcomed. DeepMind has reduced consumption in Google's data centers by an impressive 15 percent, helping the company to do its bit for the environment. DeepMind has used a number of approaches to help… [Continue Reading] -

BT Broadband customers hit by connection problems due to DNS issues
Publié: juillet 20, 2016, 11:52am CEST par Mark Wilson
BT broadband customers across the UK are reporting problems accessing websites today. The ISP is aware of the issue and is currently working to implement a fix, but in the meantime, thousands of users up and down the country are experiencing DNS problems. The problem is also affecting customers of Plusnet, a separate branch of BT. The company says that "Engineers are working to fix things as fast as possible", but this will come as little comfort to those who find they are unable to go about their daily business. The BBC reports that the problems have been attributed to… [Continue Reading] -

Twitter slaps a permanent ban on Breitbart's Milo Yiannopoulos, AKA @Nero
Publié: juillet 20, 2016, 9:28am CEST par Mark Wilson
There's a lots going on at Twitter at the moment. Yesterday, the company opened the floodgates, giving everyone the opportunity to apply for account verification. In the same day, Twitter also handed out a rare permanent ban to Breitbart tech editor and right wing pundit Milo Yiannopoulos, who went under the handle of @Nero. Yiannopoulos has long-been a controversial figure -- a troll, many would say -- who has spoken out against feminism, movements such as Gamergate, Islam, and political correctness. This is not the first time he has received a ban, but in the past they have been temporary.… [Continue Reading] -

Google and Bing have no obligation to censor searches for torrents
Publié: juillet 19, 2016, 9:36pm CEST par Mark Wilson
The High Court of Paris has ruled that Google and Bing do not have to have automatic filters in place to scrub torrent-related results from searches. The battle against piracy is something that search engines have found themselves pulled into, but this latest ruling turns the debate on its head. French music industry group SNEP went to court on behalf of a trio of artists, requesting that Microsoft and Google automatically filter out links to pirated material. The group had called for a complete block on searches that include the word 'torrent' as well as blocking sites whose name includes… [Continue Reading] -

How to get your Twitter account blue tick verified
Publié: juillet 19, 2016, 8:52pm CEST par Mark Wilson
Perform a search for how you can get your Twitter account verified and get the much sought after blue tick, and you'll find all manner of nonsense. For a very long time Twitter users have not been able to request verification, but Twitter has reached out to those it deems worthy. Today that changes. As of right now you can submit a request for verification. No need to sit back and wait for Twitter to contact you; you can now contact Twitter to plead your case. Of course, requests for verification are not guaranteed to result in a blue tick,… [Continue Reading] -

How to get the Prisma beta on your Android phone
Publié: juillet 19, 2016, 4:51pm CEST par Mark Wilson
Some apps become overnight sensations -- something ably demonstrated by the Pokémon Go phenomenon. But it's not just games that experience an explosion in popularity. You can't help but have seen stylized pictures posted to Facebook: photos that have been transformed into striking works of art. This trickery is the handiwork of the Prisma app. The app has only been available for iOS users, but that's about to change. It would have been madness not to have released Prisma for Android, and the company behind the app -- Prisma labs inc -- knows this. A beta version of Prisma is… [Continue Reading] -

Google is receiving more government requests for access to user data than ever before
Publié: juillet 19, 2016, 4:37pm CEST par Mark Wilson
Transparency reports from the big tech companies always make for interesting reading, and the latest update from Google is no different. Its most recent transparency report covers the period July-August 2015, and shows that the company received a record number of government data requests. The report shows the number of times governments around the world contacted Google with requests for access to user data. For anyone with an interest in either privacy or security, the marked increase in the number of requests is interesting. At the top of the league -- predictably -- is the US, and Google bowed to… [Continue Reading] -

BBC+ is a new iOS and Android app that delivers personalized BBC content
Publié: juillet 19, 2016, 2:31pm CEST par Mark Wilson
Over the years, the BBC has created a huge number of apps and websites to showcase the various services it offers. If you're interested in a range of BBC content, you've probably found that you have to jump from app to app and website to website. BBC+ aims to change all that. BBC+ is a new app from the corporation that’s available for iOS and Android. This is one of the first apps built using the newly-developed Mobile Application Framework (MAF) and it gives BBC fans the opportunity to create a personalized collection of the content most relevant and interesting… [Continue Reading] -

Microsoft badmouths Chrome's battery life as Windows 10 message urges switching to Edge
Publié: juillet 18, 2016, 10:04pm CEST par Mark Wilson
Microsoft has been shouting about Edge a lot as of late. Not happy with claiming that it is the most battery-friendly of the main web browsers, the company has also made much of Edge's 1080p support for Netflix. In the latest twist, Microsoft switches tack, instead using pop up messages in Windows 10 to badmouth Chrome and promote Edge. The pop up rams home the idea that Chrome is a battery hog and suggests switching to Microsoft Edge to increase longevity. This is not the first time Microsoft has used Windows 10 to advertise apps -- don’t forget promoted apps in… [Continue Reading] -

Google launches final Android 7.0 beta before Nougat goes public
Publié: juillet 18, 2016, 8:48pm CEST par Mark Wilson
It may only be a few weeks since Google revealed that Android 7.0 will be called Nougat, but there have already been several developer previews of the Marshmallow successor. Today Google launches the fifth and final preview before the official launch. As this is the final preview, build NPD90G of Nougat can be considered near-final code; this is, near as damn it, what you'll be installing on your Android handset in the not-too-distant future when Android 7.0 is officially launched. At the moment, the preview build can only be installed on Nexus 6, Nexus 5X, Nexus 6P, Nexus 9, and… [Continue Reading] -

Microsoft's smaller Xbox One S launches August 2
Publié: juillet 18, 2016, 4:41pm CEST par Mark Wilson
It has been a few weeks since we learned about the slimmer Xbox One S, and now we know when eager gamers can get their hands on the new console. August 2 is the big date which also sees the launch of Windows 10 Anniversary Update. As well as being smaller, the Xbox One S also features a built-in power supply (bye bye, power brick!), up to 2TB of storage, and support for 4K Ultra HD with High Dynamic Range (HDR). The newly announced launch date is not just the date the console hits retail stores in many regions, it… [Continue Reading] -

Opera falls in to Chinese hands
Publié: juillet 18, 2016, 12:26pm CEST par Mark Wilson
Keys components of Opera Software are to be taken over by a Chinese business consortium. A planned $1.24 billion takeover of the entire operation fell through after failing to gain regulatory approval, but a new deal has been struck in its place. Instead, the consortium -- comprising Qihoo 360 Technology Co, Beijing Kunlun Tech Co and others -- will take over just a portion of Opera Software's consumer business for $600 million. With the desktop and mobile version of the Opera web browser now falling into Chinese hands, there will no doubt be concerns about potential privacy issues based on… [Continue Reading] -

Opera falls into Chinese hands
Publié: juillet 18, 2016, 12:26pm CEST par Mark Wilson
Key components of Opera Software are to be taken over by a Chinese business consortium. A planned $1.24 billion takeover of the entire operation fell through after failing to gain regulatory approval, but a new deal has been struck in its place. Instead, the consortium -- comprising Qihoo 360 Technology Co, Beijing Kunlun Tech Co and others -- will take over just a portion of Opera Software's consumer business for $600 million. With the desktop and mobile version of the Opera web browser now falling into Chinese hands, there will no doubt be concerns about potential privacy issues based on… [Continue Reading] -

In the wake of UK Brexit vote, ARM Holdings is to be bought by Softbank for $32 billion
Publié: juillet 18, 2016, 10:53am CEST par Mark Wilson
The technology industry in the UK was rocked by the historic Brexit vote in the referendum about membership of the EU just a few weeks ago. Concerns were voiced that tech companies would scramble to leave the UK, and with Japan's Softbank Group due to buy UK chip-maker ARM Holdings for $32 billion (£24 billion), this could just be the start of things. ARM chips are found in mobile devices produced by Apple and Samsung, and more recently it has branched out into the Internet of Things. But while some will be unhappy with the change of ownership, Softbank says… [Continue Reading] -

Pokémon Go taken offline by PoodleCorp DDoS attack -- and the hackers have more in store
Publié: juillet 16, 2016, 11:11pm CEST par Mark Wilson
Pokémon Go has proved itself to be a rare phenomenon, and it has taken the world by storm. Attracting casual gamers of all ages the augmented reality title, Pokémon Go has seen people hitting the streets in search of elusive Pokémon -- until the servers overloaded. There have been a few glitches with Pokémon Go, largely due to its staggering popularity. But today many people found that they were unable to get online for a different reason -- the game servers were hit by hackers. A group called PoodleCorp claims responsibility for the takedown and says worse is to come.… [Continue Reading] -

Privacy alert: Maxthon web browser sends private data about users to China
Publié: juillet 16, 2016, 5:59pm CEST par Mark Wilson
In the world of web browsers, there are four or five big names to choose from but no end of smaller alternatives. One such browser is Maxthon, and security researchers have just discovered that this Chinese-produced browser is transmitting a wealth of data about users back to China. Researchers at Fidelis Cybersecurity and Exatel found that Maxthon frequently sends zip files to Beijing over HTTP and this contains a terrifying amount of data about users' browsing habits. The ueipdata.zip file incudes, among other things, details of the sites visited by users, the applications they have installed, and what searches have… [Continue Reading] -

Apple wants to simplify music royalty pay outs and this could harm Spotify
Publié: juillet 16, 2016, 12:34pm CEST par Mark Wilson
Many artists loathe music streaming services that have proved so popular with music fans. While they offer a platform to showcase music, the returns can be low and the way in which payments are calculated is endlessly complex. Apple has put forward a proposal to simplify the royalty payment system which would not only see artists getting more money, but would make life more difficult for the likes of Spotify. Keep artists happy, harm the competition -- two birds with one stone. A government filing in conjunction with the Copyright Royalty Board suggests a royalty rate of $0.091 per one… [Continue Reading] -

After truck attack in Nice, Google offers free calls to France and Facebook activates Safety Check
Publié: juillet 15, 2016, 10:43am CEST par Mark Wilson
The world woke this morning to news that a trunk had been driven through crowd of people celebrating Bastille Day in Nice, France. With 84 people killed and many seriously injured, people around the world are not only shocked and appalled, but also concerned about friends and family in the area. As has become worryingly common, Facebook today activated its Safety Check feature to allow people in Nice to let those they know that they are safe. In addition to this, Google and a number of phone providers are offering free calls and texts between the US and France. Facebook's… [Continue Reading] -

Google's gender equality emoji are formally adopted
Publié: juillet 14, 2016, 7:42pm CEST par Mark Wilson
Concerned as ever with diversity and equality, Google recently proposed a new set of emoji including a wider range of images of women in different professions. Today the company makes good on its promise and delivers the goods... with a little help from the powers-that-be. Launched because "there aren't a lot [of emoji] that highlight the diversity of women's careers", the new emoji portray women in roles that have previously been the domain of man -- at least in pixel form. In all, the Unicode Emoji Subcommittee is adopting more than 100 new emoji after Google's suggestions. This is not,… [Continue Reading] -

Today's the day Microsoft reduces your free OneDrive cloud storage
Publié: juillet 14, 2016, 1:45pm CEST par Mark Wilson
If you weren't on the ball a few months ago, your OneDrive storage space is about to be slashed. Having previously announced its plans to reduce cloud storage for all OneDrive users, Microsoft relented and said those that already had this amount of storage could keep it... but only if they asked for it. Anyone who failed to do so will be ruing the day. Today is the day that Microsoft cuts free OneDrive storage from 15GB to just 5GB -- even less than when the cloud service first launched. In addition to this, the 15GB camera roll bonus has… [Continue Reading] -

Microsoft Edge is the best browser for Netflix -- the only that offers 1080p on the desktop
Publié: juillet 14, 2016, 11:03am CEST par Mark Wilson
Internet Explorer has been much-maligned over the years, and Microsoft Edge sees the Redmond company trying to shake off the shackles of the past. Its latest marketing push finds Microsoft claiming that Edge is the best desktop web browser for Netflix viewing. The reason? In addition to claims about greater battery efficiency, Microsoft's killer blow is that Edge is the only of the main desktop browsers to support 1080p viewing. It might seem like a surprising and audacious claim, but the test bears it out. Microsoft Edge has a serious unique selling point. Microsoft's lauding of Edge comes in a… [Continue Reading] -

Google Hangouts 11 update drops merged conversations, gains video messaging
Publié: juillet 13, 2016, 10:48pm CEST par Mark Wilson
Google has its fingers in lots of messaging pies, and having added SMS support to Hangouts on Android, it wasn’t long before the merging of text and chat conversations was introduced. With the release of Hangouts 11, this changes. With the new release, merged conversations are now gone -- SMS and chats are kept separate, but you won't lose anything -- perhaps in a bid to push people to its Messenger app to take care of texts. The same release also sees the addition of a long-awaited feature: the ability to send videos in a message. In an updated Hangouts… [Continue Reading] -

Privacy warning: Pokémon Go has full access to your Google account data
Publié: juillet 11, 2016, 7:40pm CEST par Mark Wilson
Pokémon Go may be proving jaw-droppingly popular, but in the rush to catch 'em all, it seems that users have overlooked something of a privacy issue with the game. It's not unusual for apps and games to request, or require, access to your Google account but there are usually limits in place. Not so with Pokémon Go. As reported by Search Engine Journal, iOS users have discovered that the game not only requires access to users' Google accounts, it requires full access. This is the highest level of access available to any app and if it is revoked, the game… [Continue Reading] -

Kim Dotcom to launch Megaupload 2.0 in 2017
Publié: juillet 11, 2016, 6:11pm CEST par Mark Wilson
Kim Dotcom is a difficult man to ignore, and he's all set to get right back in your face after lurking in the shadows for a few months. In a series of tweets over the weekend, the German technology troublemaker announced that his file sharing service Megaupload is due to relaunch in 2017 -- on the fifth anniversary of a police raid. Known as Megaupload 2.0 (remember the 2.0 phenomenon?), the platform is expected to appear on 20 January next year. Dotcom has previously expressed something of a passion for Bitcoin, and this looks set to continue with the relaunch… [Continue Reading] -

Nintendo shares jump as Pokémon Go takes the world by storm, hitting over 5 percent of Android phones
Publié: juillet 11, 2016, 4:40pm CEST par Mark Wilson
Gotta catch 'em all! The Pokémon phenomenon, it seems, did not die. Nintendo suddenly has a surprise hit on its hands in the form of augmented reality title Pokémon Go which is already riding high in the charts. The game has proved so successful, that in the few days since its launch it has been installed on more than 5 percent of Android smartphones. The international roll-out has been paused while developer Niantic tries to beef up its servers to cope with demand. But while US Pokémon catchers are having a whale of a time, would-be gamers in other parts… [Continue Reading] -

The Halvening means that bitcoin mining rewards just dropped by 50 percent
Publié: juillet 10, 2016, 2:54pm CEST par Mark Wilson
It just became significantly harder to mine Bitcoins. The halving event rolled around yesterday, July 9, and means that the reward for mining just dropped by 50 percent. The cryptocurrency is generated by machines around the world 'mining' for new bitcoins. Rewards of bitcoins are handed out for giving over computing power to process bitcoin transactions. It's a very, very slow way to make money -- and it just got a whole lot slower. While there were previously 25 bitcoins (around $16,000) available globally to miners every 10 minutes, the figure is now just 12.5 bitcoins. But what does this… [Continue Reading] -

PostGhost, the Twitter verified user tweet archive, is killed by cease and desist order
Publié: juillet 10, 2016, 12:53am CEST par Mark Wilson
PostGhost, the website that describes itself as "an archive of public tweets deleted by politicians, celebrities, and other public figures" has been shut down by Twitter. The website was told that its display of deleted tweets was a violation of the Developer Agreement and Policy. The site was a relative newcomer, having only been active for less than a week. Political tweets archive Politwoops almost met a similar fate, but the distinction with PostGhost is that it was only concerned with tweets from verified users with 10,000 followers or more -- a group that includes politicians, writers, singers, and other… [Continue Reading] -

Bug fixes aplenty in surprise Windows 10 Insider Preview Build 14385 release
Publié: juillet 10, 2016, 12:44am CEST par Mark Wilson
It might be the weekend, but the code monkeys at Microsoft doesn’t let a small detail like that stand in the way of work. The release of Windows 10 Anniversary Update is now within spitting distance, and the Insider builds are being pushed out thick and fast. Today Dona Sarkar announced the launch of Windows 10 Insider Preview Build 14385 for PC and Mobile. As we're so close to launch day, it should come as no surprise that this is a bug fix release -- but there are plenty of them. There are also some extra performance tweaks thrown in… [Continue Reading] -

Facebook explains live video censorship policies after live-streaming a fatal shooting
Publié: juillet 9, 2016, 7:42pm CEST par Mark Wilson
It was only a matter of time before Facebook's decision to open up live video to everyone was going to result in controversy. Sure enough, earlier this week, the social network became the medium through which the shooting dead of Philando Castile by a police officer was shared with the world. The graphic video quickly became notorious, but then vanished temporarily. There were suggestions that Facebook was censoring the footage, but the company said that a technical glitch was to blame. But whether the video was censored, collapsed under the weight of traffic, or did succumb to a problem, the… [Continue Reading] -

Facebook Messenger ups security with end-to-end encryption in 'secret conversations'
Publié: juillet 8, 2016, 7:19pm CEST par Mark Wilson
Continuing in its relentless drive to take over the world of messaging, Facebook Messenger is gaining end-to-end encryption. To start with, the security feature is only rolling out on a 'limited test basis' but if feedback is positive, it will get a wider airing. Facebook says that the move comes in response to requests for additional security options to protect discussions about sensitive matters, saying that security and privacy experts have been involved in the implementation of the feature. End-to-end encryption has grown in popularity in recent years, and Facebook users have been patiently awaiting its arrival on the platform.… [Continue Reading] -

Court papers show Silent Circle's privacy-boosting Blackphone was an unmitigated sales disaster
Publié: juillet 7, 2016, 6:20pm CEST par Mark Wilson
With so much focus now placed on privacy and security, you would have thought that the Blackphone from Silent Circle would have been a roaring success. But documents from a court case with former partner Geeksphone reveal that there have been just a handful of sales, and revenue is hundreds of millions of dollars lower than expected. Silent Circle found itself in court after Geeksphone complained that it had not received a $5 million payment agreed as part of a buyout. Geeksphone had helped to build the original Blackphone, and Silent Circle went on to buy the Spanish company's share… [Continue Reading] -

UK ISP Sky is about to start censoring the web for all of its customers
Publié: juillet 7, 2016, 4:49pm CEST par Mark Wilson
The UK government is on a mission to protect the young of the country from the dark recesses of the web. And by the darker recesses, what is really meant is porn. The main ISPs have long been required to block access to known piracy sites, but porn is also a concern -- for politicians, at least. As part of its bid to sanitize and censor the web, Sky -- from the Murdoch stables -- is, as of today, enabling adult content filtering by default for all new customers: Sky Broadband Shield. The company wants to "help families protect their… [Continue Reading] -

OnePlus 3 update to fix RAM problems and sRGB mode is pulled after brief rollout
Publié: juillet 5, 2016, 9:54pm CEST par Mark Wilson
OnePlus 3 users have been eagerly awaiting the arrival of OxygenOS 3.2.0 via an OTA update since the Chinese company announced the rollout. The update was supposed to address not only issues with memory management, but also introduce sRGB mode for the Optic AMOLED screen. But a little over a day after saying the update would have hit every handset within 48 hours, it has been pulled. There have apparently been issued with the upgrade process that OnePlus needs to look into. As a precautionary measure, the rollout of the update has been stopped while it is fixed. In an… [Continue Reading] -

FBI says 'careless' Clinton shouldn't face email charges despite sharing top secret information
Publié: juillet 5, 2016, 9:12pm CEST par Mark Wilson
To the amazement of some, and the disappointment of others, the FBI today recommended that no charges be brought against Hillary Clinton over her use of a private email server. The presidential hopeful was roundly criticized, however, with James Comey describing her actions as "extremely careless". The FBI director's remarks came after Clinton took part in a voluntary interview over the weekend, and after the bureau's investigation found that her private email account had indeed been used to send classified and even secret information -- officially a misdemeanour. The FBI's line is that "no reasonable prosecutor would bring such a case".… [Continue Reading] -

China bans the use of social media as a news source
Publié: juillet 4, 2016, 4:49pm CEST par Mark Wilson
Continuing its control of the internet, China has announced that news outlets may not use social media as a source of news -- at least not without official approval. The Cyberspace Administration of China says that the move is part of a campaign to prevent the spread of rumors and fake stories, but most people will see it as the government continuing to flex its online muscles. To add weight to its reasoning, the regulator referred to a number of fake news stories that had originated and spread online. In a statement, the Cyberspace Administration of China said: It is… [Continue Reading] -

Facebook hits back at Israeli complaints about sabotaging police work
Publié: juillet 3, 2016, 4:27pm CEST par Mark Wilson
Facebook has responded to complaints from Israel's Minister of Internal Security saying that it does remove abusive content from the site. On Saturday, Israeli cabinet minister Gilad Erdan referred to Facebook as a 'monster' adding that it "does not cooperate" with requests from the police. Tensions between Palestine and Israel have seen an increase in posts inciting violence and terrorism. While Erdan accuses Facebook of failing to step in as well as "set[ting] a very high bar for removing inciteful content", the social network says it work closely with numerous countries, including Israel, to stem the flow of hate speech. The… [Continue Reading] -

Google Play now allows app and game sharing with new Family Library feature
Publié: juillet 3, 2016, 12:30pm CEST par Mark Wilson
Earlier this year Google announced that Family Library -- previously only available in Google Play Music -- was making its way to the Play Store. Now the rollout is underway, meaning that it is now possible to share your purchased apps and games with members of your family. This new feature means that a family need only buy one copy of an app rather than several if they all want to use it. It also means that there is no longer a need to create a shared 'family account' through which to download apps and games that need to be… [Continue Reading] -

Google adds a native Cast option to Chrome on the desktop
Publié: juillet 3, 2016, 11:41am CEST par Mark Wilson
If you've been using a browser extension to add a casting option to Chrome, you could think about uninstalling it. Google is currently rolling out an update to the desktop version of its web browser. The feature is making its way to Chrome 51 and can be accessed by right clicking either an open tab or the browser's hamburger menu. Should you ditch the extension, though? It really depends on your needs... While the change does little to change the way casting content to Chromecast devices actually works, it does make things a little easier. There are arguments for sticking… [Continue Reading] -

Hillary Clinton questioned by FBI about personal email server
Publié: juillet 2, 2016, 7:41pm CEST par Mark Wilson
It's the issue that just won't go away for Hillary Clinton -- her use of a private email server while serving as secretary of state. Today the Democratic presidential hopeful has been questioned by the FBI about her emails. The Justice Department's investigation aims to determine if Clinton used the email account to send communication relating to national security, and whether this is illegal. She says the account was created for convenience and has denied using it to send classified information. Her campaign was quick to point out that the interview was entirely voluntary, but did not elaborate on what… [Continue Reading] -

Windows 10 Anniversary Update makes great strides for accessibility
Publié: juillet 2, 2016, 3:07pm CEST par Mark Wilson
Accessibility options are not a new feature for Windows, but the upcoming Windows 10 Anniversary Update includes even more than before. This week it was confirmed that the update will launch on 2 August, just days after the free upgrade period ends (although it's worth noting that people with accessibility needs will still qualify for a free upgrade after this date). If you've been testing out the insider builds of Windows 10, you may well have noticed accessibility improvements, but now it is only a matter of weeks before they are made available to everyone. In a blog post rounding… [Continue Reading] -

Facebook's new multilingual composer will let you post status updates in multiple languages
Publié: juillet 2, 2016, 1:40pm CEST par Mark Wilson
Facebook has announced a new tool that aims to break down language barriers. Previously available for Pages on the social network, the multilingual composer is set to make its way to individuals' accounts as well. Previously anyone who wanted to post bi-, tri- or multilingual status updates would have to either type out each language as a separate post, or post a lengthy status featuring multiple translations. The latest change means that you can write in, say, French, and only friends and followers with their language set to French will see it. When the multilingual composer hits your account you'll… [Continue Reading] -

Google's latest diversity report shows the company making slow progress
Publié: juillet 1, 2016, 3:18pm CEST par Mark Wilson
Embracing diversity is just one of the latest passions of the technology world. Companies involved in the web and messaging do things like releasing diverse emoji, while games like the Sims 4 implement changes that reflect dissolving gender and sexuality boundaries. But key tech players such as Microsoft, Facebook, and Google have also been keen to demonstrate how diverse their respective workforces are. Google has just released its latest diversity report -- including, for the first time, details of black and Hispanic intake -- and it shows that while the company is becoming less white and less male, progress remains… [Continue Reading] -

Unhappy with Evernote's new pricing? Here's how to import your data into OneNote for free
Publié: juillet 1, 2016, 2:25pm CEST par Mark Wilson
When Evernote announced changes to its pricing structure this week, users were unhappy. As well as an increase to the price of paid-for accounts, new restrictions were also wheeled in for free accounts. It's no longer possible to sync data between more than two devices without coughing up a monthly fee, and this has people looking for alternatives. A worthy competitor is Microsoft's OneNote and the company has a dedicated OneNote Importer tool that can be used to move all of your notes between services. Like OneNote, the importer is also free, and gives disgruntled Evernote users a way to… [Continue Reading] -

Microsoft issues KB3173040 as a final in-your-face reminder to upgrade to Windows 10 for free
Publié: juillet 1, 2016, 1:10pm CEST par Mark Wilson
The promotion of Windows 10 upgrade by Microsoft has certainly proved controversial, and it was only this week that users were given an easy way to decline the upgrade offer. With the 29 July deadline for free upgrades fast approaching, the clock is really ticking now, and Microsoft is giving Windows 10 one final push. Window 7 and 8 users are being offered update KB3173040. Its sole purpose is to advertise the availability of Windows 10 and to remind people that time is running out. Given the criticism Microsoft's decision to promote the Windows 10 upgrade deadline with a full-screen… [Continue Reading] -

Google makes it easier to try out beta Android apps with new Early Access section in the Play Store
Publié: juillet 1, 2016, 12:49pm CEST par Mark Wilson
As the Windows 10 insider preview program has demonstrated, people love to get their hands on pre-release software. While it's easy to install beta software on a desktop computer, it has not been as straightforward for Android users. Until now. Google has added an Early Access section to Google Play which -- you've guessed it -- features not-quite-ready-for-prime-time apps in beta form. The new section makes installing beta apps as simple as installing any other app and, after rolling out to a few users this week, the option is now available to everyone. To access the world of beta apps,… [Continue Reading] -

Google reveals that Android N will be called... Android Nougat!
Publié: juin 30, 2016, 6:42pm CEST par Mark Wilson
The developer previews of Android N have been available for a little while now, giving a tantalizing taste of what’s to come. But one thing has been missing: the name. After months of teasing and misdirection -- there can't be many people who weren't expecting to see Android Nutella -- Google has officially announced that Android 7 (probably) will be known as Android Nougat. We're now past the halfway mark in the alphabet, and it seems that Google may have been struggling to decide on a name all by itself. A few weeks back the company asked for suggestions, and… [Continue Reading] -

At long, long last, Google Maps on Android and iOS has multiple destination support
Publié: juin 30, 2016, 5:50pm CEST par Mark Wilson
Google Maps has long been helping walkers, drivers and cyclists get from A to B. But for far too long, the desktop version of the navigation tool has been more powerful than the mobile version -- which is silly, really, as the mobile app is the one you're going to use while, you know, traveling. Today, Google is rolling out an important new feature to the mobile app -- the ability to configure a route with multiple stop-off points along the way. Getting from A to B is great, but sometimes you need to go via X and Y. Now… [Continue Reading] -

Facebook uses Irish headquarters to skirt privacy laws
Publié: juin 29, 2016, 11:59pm CEST par Mark Wilson
Facebook has won an appeal against a court ruling that said the social network could not store data about people who did not have an account. It had been ruled that Facebook could not gather data about non-users in Belgium; Facebook responded by blocking access to those without an account. Back in 2015, Facebook was told to stop this blocking or face hefty daily fines. Facebook felt that the ruling was unfair and appealed. In a new ruling today, the Brussels Court of Appeal said: "Belgian courts don't have international jurisdiction over Facebook Ireland, where the data concerning Europe is… [Continue Reading] -

Facebook opens up about how it controls your newsfeed
Publié: juin 29, 2016, 8:39pm CEST par Mark Wilson
Earlier today, Facebook announced the latest tweak to newsfeeds. Having denied being politically bias towards Brexit, or having a liberal leaning, Facebook continues to face question and criticism about how its news feeds and trending topics are formulated. As well as updating the way newsfeeds are populated, Facebook today revealed just how it choses what appears in your newsfeeds. This isn’t a case of full transparency, but it is an interesting insight nonetheless. At a press briefing, the company revealed a little of the inner workings of the newsfeed, reiterating that the most recent change is all about ensuring that… [Continue Reading] -

Facebook tweaks its newsfeed, yet again, so you'll see more posts from people you actually know
Publié: juin 29, 2016, 5:48pm CEST par Mark Wilson
When it's not messing around with privacy settings and manipulating trending topics, there's nothing Facebook seems to like more than to tinker with timelines. Today the social network announces the latest changes to your newsfeed -- now you should see more posts from your friends and family. The problem we currently face, Facebook says, is that there is "far too much information for any one person to consume". This is where algorithms come into play, meddling with timelines and newsfeeds in ways that never please everyone. The latest change promises that content from "the friends you care about" will appear… [Continue Reading] -

Google's creepy My Activity page reveals the terrifying amount of data collected about you
Publié: juin 29, 2016, 1:29pm CEST par Mark Wilson
That Google gathers data about you is not news. If you use Google products, it's something you've decided to put up with -- either that, or you live in blissful ignorance of. Whether you're using Gmail and YouTube online, Google keyboard on your Android smartphone, Chrome across platforms, or whatever, being a Google user means handing over an awful lot of personal information. But just how much does Google know about you? If you use the voice-activated "OK, Google" feature of your phone, there are probably lots of recordings of you stored online; what about everything else? Google has now… [Continue Reading] -

Ad personalization from Google -- giving power to the people, or a privacy nightmare?
Publié: juin 29, 2016, 11:49am CEST par Mark Wilson
Online ads aren’t going away anytime soon, and that'll keep the likes of Adblock Plus in business for the foreseeable future. But if you choose not to use an ad blocker and are therefore going to be bombarded with ads, they might as well be ads that are relevant to you, right? Google is rolling out a new feature that enables users to choose the topics they are interested in so the ads they see will be more appropriate to them. But as well as improving the ad experience for users, the new scheme means that advertisers are handed even… [Continue Reading] -

Evernote ramps up its prices by a third and imposes restrictions on free users
Publié: juin 28, 2016, 9:05pm CEST par Mark Wilson
Evernote has today announced that it is increasing the prices of its paid-for packages, whilst simultaneously increasing the restrictions on free Basic accounts. Both the Plus and Premium tiers are increasing in price by a third, while those looking to avoid having to pay will find that they are now limited to syncing data between just two devices. Evernote says that the price increase reflects a "significant investment of energy, time, and money" that will be needed "to deliver the Evernote we envision" -- something the company admits it has a "long way to go" before achieving. The announced change… [Continue Reading] -

Facebook launches Share and Save extensions for Chrome, redesigns Social Plugin buttons
Publié: juin 28, 2016, 7:45pm CEST par Mark Wilson
Facebook is all about sharing and consuming, and today the social network launches two new extensions for the Chrome browser that make it easy to do both. The Share to Facebook and Save to Facebook extensions do very much what you would expect, encouraging not only sharing, but also the use of Facebook as a bookmarking tool for articles you want to read later. As well as these two extensions, Facebook is also rolling out redesigned Social Plugin buttons. The Like button that you see adorning so many websites is getting a modern makeover, losing the iconic Facebook 'f' logo,… [Continue Reading] -

Mozilla uses emoji game Codemoji to teach about encryption
Publié: juin 28, 2016, 1:57pm CEST par Mark Wilson
The world of technology relies on encryption. Everything from private messages to online payments are secured in this way -- but how does it all work? Mozilla has come up with a way to teach people about encryption, combining gaming and emoji into a useful learning tool. Codemoji is described as "a fun way to learn about ciphers", and while you might think that it's aimed solely at children, there's something here for all ages. The idea is very simple: letters and words are translated into emoji so they can only be read by those who understand the decryption technique.… [Continue Reading] -

Google teams up with LyricFind to show song lyrics in search results
Publié: juin 28, 2016, 12:40pm CEST par Mark Wilson
"Son and heir", not "sun and air". Excuse me while I "kiss the sky", not "this guy". If you've ever struggled to interpret the lyrics to a song, you've probably scurried online to look up what is actually being sung. By teaming up with LyricFind, Google just made this much quicker and easier. No more jumping from site to site. No more ad barrages. Now Google will display song lyrics directly in search results from the world’s largest lyric licensing service. As well as making things easier for searchers, the deal means that artists get paid royalties as their lyrics… [Continue Reading] -

Microsoft releases .NET Core 1.0, complete with Red Hat Linux support
Publié: juin 27, 2016, 8:14pm CEST par Mark Wilson
Today at the Red Hat Summit, Microsoft announced the launch of .NET Core 1.0. Continuing the company's embrace of other platforms, the latest version of the open source .NET runtime platform supports Windows, OS X, iOS, Android and -- of course -- Linux. At the summit, Red Hat said that .NET Core 1.0 will be fully supported by Red Hat Enterprise Linux. With Microsoft's partnership with Red Hat late last year, and the company's on-going expansion into the cross-platform cloud, Linux support is not entirely surprising. Also announced today was ASP.NET Core 1.0 and Entity Framework 1.0 for developers to… [Continue Reading] -

Microsoft pays out $10,000 for forcing Windows 10 on California woman
Publié: juin 27, 2016, 7:07pm CEST par Mark Wilson
The owner of a California-based travel agency has received a $10,000 settlement from Microsoft after a forced Windows 10 upgrade rendered her computer unusable. Teri Goldstein found that her work computer downloaded and started to install Windows 10 without her permission, but the installation failed. The installation not only failed, Goldstein says, but also slowed down her computer, leading to days of lost business. After failing to get help from Microsoft's customer support, she took the company to court. Somewhat surprisingly, Goldstein won her case against the software giant. But Microsoft wasn’t ready to just roll over, and opted to… [Continue Reading] -

Chrome flaw makes it possible to copy DRM video streams such as Netflix
Publié: juin 26, 2016, 10:33pm CEST par Mark Wilson
Security researchers from Ben-Gurion University Cyber Security Research Center (CSRC) have unearthed a vulnerability in Google Chrome that can be exploited to make copies of DRM-protected video streams. The problem affects all Chromium-based browsers, and makes it possible to circumvent Widevine encryption technology Google uses to secure streams. Widevine has been used in Chrome for a while, after Google acquired it back in 2010. It has been used to prevent piracy of premium YouTube channels, and is also used to protect Amazon Prime and Netflix streams. Google was informed about the problem back in May, but is yet to issue… [Continue Reading] -

Post-Brexit, an online campaign for a second UK referendum gains huge support
Publié: juin 26, 2016, 3:21pm CEST par Mark Wilson
The UK may not yet have introduced online voting -- nor is it likely to any time soon -- but it does have a website that can be used to raise petitions for debate. The House of Commons website is home to a huge number of such petitions, and any that gain 100,000 signatures will be raised in Parliament. After the UK referendum on EU membership saw the country narrowly voting in favor of Brexit (even if they didn’t know what this meant), a petition calling for a second referendum has been signed more than 3 million times. Ironically, the… [Continue Reading] -

Report: YouTube and Facebook are now using automated tools to remove extremist content
Publié: juin 26, 2016, 12:18pm CEST par Mark Wilson
With the likes of ISIS understanding the power of social media, Facebook and other online services find themselves under increasing pressure to counter terrorist and other extremist content. A report by Reuters says that a number of online companies are using automated tools to remove videos that violate terms of use. Such tools have previously been used to prevent the spread of copyright videos online, but now it seems that they have been put to a new task. While automation can do little, if anything, to prevent the initial appearance of extremist videos, social networks can use them to stem… [Continue Reading] -

Microsoft to kill off Surface 3 in December
Publié: juin 26, 2016, 11:44am CEST par Mark Wilson
If you're in the market for a Surface 3, now is the time to buy one. Microsoft says that production of the Surface 3 will come to an end in December this year, and warns that stocks are already starting to run low. It's not yet clear whether the end of production for the cheapest Surface device signals the end of Microsoft's Atom-based devices. But it certainly seems as though the company is keen to focus its attention on the Pro range as well as the Surface Book. Microsoft confirmed the end of Surface 3 production to ZDNet. Mary Jo… [Continue Reading] -

EU-US Privacy Shield: White House promises not to spy on European data
Publié: juin 25, 2016, 2:13pm CEST par Mark Wilson
The replacement for data protection arrangement Safe Harbour, the EU-US Privacy Shield, has undergone final amendments. Safe Harbour has already been deemed invalid, and frantic talks have been underway to finalize its successor. Despite gaining the backing of Microsoft, EU-US Privacy Shield has faced a great deal of criticism. In the wake of the Brexit vote in the UK referendum on EU membership, the UK may be forced to comply with the rules even though it is in the process of exiting the Union. One of the most significant changes to come about -- and one that will be welcomed… [Continue Reading] -

There's a fix on the way to address OnePlus 3 memory management and color calibration issues
Publié: juin 25, 2016, 12:51pm CEST par Mark Wilson
The OnePlus 3 is the first 'flagship killer' that has been available to buy without an invite. Reviews (and we'll have one written up soon) have been overwhelmingly positive, but a couple of issues have surfaced. Some users have been disappointed to find that their handset does not take full advantage of its 6GB of RAM, while others bemoan poor color calibration of the Optic AMOLED screen. We've already shown you how to manually tweak memory settings, but an official update is on the way to address not only memory and color issues, but also to increase performance of the… [Continue Reading] -

UK votes to leave the EU, but Google searches show people don’t understand Brexit
Publié: juin 24, 2016, 8:50pm CEST par Mark Wilson
It was a vote that was down to the wire much of the way, but the result of the UK referendum on membership of the European Union took many -- including bookies -- by surprise. 48.1 percent of voters indicated a preference to remain, while 51.9 percent said they wanted to go it alone. The fallout has been dramatic. Prime Minister David Cameron is stepping down, a second referendum on Scottish independence is now on the cards, and the financial markets have been in turmoil all day. But one of the more interesting side effects of the 'leave' vote is… [Continue Reading] -

Germany says -- yet again -- that adblocking is legal
Publié: juin 24, 2016, 8:07pm CEST par Mark Wilson
Countless numbers of web users are completely in love with adblocking, but there are those who have tried to have it deemed illegal. Adblock Plus has been in court over this before, and today a German court has ruled, once again, that its operations are entirely legal. Publishing house Axel Springer sued Adblock Plus, saying that no company should be able to interfere with the display of ads. Axel Springer lost its case last year, but decided to appeal. Using a recent law to attack Adblock Plus' Acceptable Ads program, Axel Springer tried to get the adblocker banned. This failed,… [Continue Reading] -

Apple is leaving the iOS 10 kernel unencrypted... to increase security
Publié: juin 24, 2016, 2:09pm CEST par Mark Wilson
Each new version of iOS is eagerly awaited, and at its Worldwide Developer Conference (WWDC) Apple unveiled a preview of iOS 10. Much has been made of the new features, but developers probing the operating system are making a surprising discovery. The kernel of iOS 10 is unencrypted. In the current climate of security-awareness, this might seem like something of an unusual decision. But Apple says that the change has been made to improve performance, and it could even help to increase security. In a statement to TechCrunch Apple sought to calm fears about the privacy implications of leaving the… [Continue Reading] -

Check your privacy settings -- Facebook is (probably) sharing your employment history
Publié: juin 23, 2016, 10:27am CEST par Mark Wilson
Somewhat out of the blue, Facebook has decided to change the way it displays certain information on your profile. Not content with showing your current place of work -- whether this is real, or some clever pun you've engineered -- it now also shows your employment history. This is not a direct change to privacy settings as it does not make public anything that had been previously set to be private. It does, however, broadcast your previous places of work to people looking at your profile. You might not like this. You might want to do something about it. In… [Continue Reading] -

A win for privacy: senate blocks FBI from gaining warrantless access to browsing histories
Publié: juin 22, 2016, 9:25pm CEST par Mark Wilson
A Senate amendment brought forward by John McCain that would have given the FBI the right to browse suspects' phone and internet records without a warrant has been narrowly defeated. The vote very nearly went the other way -- there were just two votes in it when the counting was over. McCain had hoped that pushing the amendment as a counter-terrorism tool (particularly against "non-U.S. citizen 'lone wolf' attackers") would be enough to get the required 60 votes. But it seems that the Orlando shooting that McCain cited as an incentive for the changes was not enough to convince others.… [Continue Reading] -

Opera says Microsoft's claims about Edge battery life are wrong -- but all's not as it seems
Publié: juin 22, 2016, 8:08pm CEST par Mark Wilson
The other day, Microsoft made some bold claims about the power consumption of Edge. The company claimed that its latest web browser is the most battery-friendly when compared to Chrome, Opera and Firefox. Having been beaten into third place behind Chrome, but ahead of Firefox, Opera has hit back. The company says that its own tests show -- surprise, surprise -- that it is Opera which is the most efficient battery sipper. Opera says that its own battery saving feature boosts battery life by up to 50 percent when compared to Chrome. The company criticizes Microsoft for failing to reveal… [Continue Reading] -

Google reveals end-of-life dates for Nexus devices
Publié: juin 22, 2016, 11:49am CEST par Mark Wilson
One of the advantages of buying a Nexus device is the guarantee that you're in line to receive updates for longer than devices from most other manufacturers. Google issues not only Android updates, but also monthly security patches for Nexus phones and tablets, and the company has just published its latest end-of-life list. Next in line to drop off the support list are the Nexus 6 and Nexus 9. These devices will not receive "guaranteed Android version updates" (such as updates to Android N and Android O) after October 2016, but Google has also revealed when the Nexus6P and Nexus… [Continue Reading] -

Mark Zuckerberg is so concerned about his privacy that he tapes over his webcam and microphone
Publié: juin 22, 2016, 10:06am CEST par Mark Wilson
Facebook and privacy are not words usually associated with one another, and it seems this holds true even for the man at the top. Only recently we learned that Mark Zuckerberg uses terrible passwords, making it easy to hack his accounts, but now it turns out he's also quite paranoid. As Instagram popped champagne corks for reaching the milestone of half a billion users, Zuckerberg posted a celebratory picture. Eagle-eyed people soon pointed out that both the mic and camera of his laptop were taped over. It's a technique that has long been used by the concerned, the paranoid, and… [Continue Reading] -

Check your Amazon account for free credit as Apple coughs up in ebook lawsuit settlement
Publié: juin 21, 2016, 11:41pm CEST par Mark Wilson
Following a court ruling that it was involved in ebook price-fixing with five publishers, Apple has started the process of paying back $400m in refunds. Despite agreeing to pay out the thick end of half a billion dollars, Apple denies doing anything wrong. Interestingly, the payouts will not necessarily reach customers direct from Apple. Refunds are being issued through four ebook stores -- iTunes, Amazon, Barnes & Noble, Kobo -- and Amazon customers (Kindle users) should be getting their credit today. If you're in line for a refund, you should have received an email informing you, but in case this… [Continue Reading] -

Twitter and Vine introduce support for much longer videos
Publié: juin 21, 2016, 10:41pm CEST par Mark Wilson
While Twitter is primarily a text-based social network, more recently there has been an increased importance placed on images and videos. Just as tweets are limited to a certain number of characters, videos have -- until today -- been limited to 30 seconds in length. Now Twitter is embracing video in a big way, and today increases the maximum length to 140 seconds -- continuing the love affair with the number 140. The company says that the number of video posted to Twitter has increased by 50 percent since the beginning of the year. This is an astonishing increase in… [Continue Reading] -

Check the performance of your tweets with Twitter Engage for iOS
Publié: juin 21, 2016, 9:45pm CEST par Mark Wilson
Today Twitter launches a companion app designed for anyone who wants to analyse their tweet activity. Pulling out all the buzzwords, Twitter says it "provides real-time data and insights, allowing you to quickly understand, engage, and grow your audiences". This is not just about gaining more followers, it's about making more meaningful connections, and trying out different marketing ideas. Twitter already provides fairly detailed analytics on its website, but here things are presented in a more accessible way. It also provides a more detailed breakdown of audience demographics for better targeting. The beauty of Twitter Engage is that it provides… [Continue Reading] -

Microsoft breaks into contactless mobile payments with Wallet for Windows 10 Mobile Insiders
Publié: juin 21, 2016, 9:02pm CEST par Mark Wilson
Apple has done it; Google has done it. Microsoft may be a little late to the party, but it's getting involved in the mobile payment game. Today the company releases Microsoft Wallet to Windows Insiders using Windows 10 Mobile build 14360 or higher. Microsoft has teamed with MasterCard and Visa to provide a contactless payment solution that is -- for now -- available to Lumia 950, 950 XL and 650 users in the US. As well as making contactless payments, the app can also be used to store reward cards to reduce the amount of plastic you have to cart… [Continue Reading] -

Twitter buys AI image firm Magic Pony Technology
Publié: juin 21, 2016, 11:10am CEST par Mark Wilson
Twitter has demonstrated its commitment to artificial intelligence and machine learning by splashing a reported $150m on London-based Magic Pony Technology. The aim is to use the company's advanced technology to improve Twitter's live and video experiences. Jack Dorsey describes Magic Pony Technology as a 'company that has developed novel machine learning techniques for visual processing'. Thus far this has been used to sharpen blurry images, create computer-generated images from scratch, and to learn to recognize objects. While Magic Pony Technology's AI is not exactly unique, where it stands apart from the competition is in terms of raw speed. With… [Continue Reading] -

Protests from Apple and Microsoft mean there won't be a rifle emoji
Publié: juin 20, 2016, 3:20pm CEST par Mark Wilson
With the unstoppable growth of chat apps such as Facebook Messenger, WhatsApp and the like, emoji have become an incredible phenomenon. The Unicode Consortium is due to publish the Unicode 9.0 spec tomorrow, and it seems that objections from Apple and Microsoft means we're not going to see a rifle emoji included. The intervention is slightly surprising, yet not entirely unexpected. With the large number of high-profile mass-shootings such as in Orlando, debate about guns has come to the fore once again and the censorship of emoji is perhaps not completely unexpected. But at the same time, there is already… [Continue Reading] -

Britain has more unicorns than anywhere else in Europe
Publié: juin 20, 2016, 10:52am CEST par Mark Wilson
Unicorns are breeding in Britain. The country is now home to more than a third of European unicorns (tech companies valued at over $1 billion), but the whole of Europe is faring well. A new report by GP Bullhound, an investment banking firm, reveals that there are 47 unicorns in Europe and 18 of them are to be found in Britain. The number of European unicorns has jumped by more than 20 percent in the last year, and the overall valued is placed at $130 billion (around £90 billion). Despite the seemingly high valuations, nearly half of the companies on… [Continue Reading] -

Bag yourself an Apple Watch for just $49 at Best Buy
Publié: juin 19, 2016, 6:35pm CEST par Mark Wilson
If you're in the market for an Apple Watch but you've been put off by the price, Best Buy might just have a deal that will tempt you to part with your cash. How low would the price have to be to convince you? How does $49 sound? There is, of course, something of a catch. It's certainly not the case that anyone who wants an Apple Watch could walk into Best Buy, hand over 49 notes and walk about with an Apple Wearable; there's a little more to it than that. Best Buy is offering $250 off Apple Watches --… [Continue Reading] -

Warning! GoToMyPC hit by password hackers
Publié: juin 19, 2016, 3:31pm CEST par Mark Wilson
By their very nature, remote access tools represent something of a security risk. It's only a couple of weeks since TeamViewer users complained about account hijacking, and now GoToMyPC has been hit by hackers. The service has been hit by what is being described as a "very sophisticated password attack", and the company is advising all users to reset their passwords. Details are a little thin on the ground at the moment as an investigation is currently underway, but users are warned to monitor their account and change their passwords. There's no word on the origin of the password attack,… [Continue Reading] -

Hack your OnePlus 3 to take full advantage of its 6GB of memory
Publié: juin 18, 2016, 12:32pm CEST par Mark Wilson
When your phone has 6GB of RAM, you expect it to be able to run all of the apps you want at the same time. The low-cost 'flagship killer' OnePlus 3 is one such handset, but people who have got their hands on the phone are discovering the it doesn’t necessarily use the available memory as they would have expected. Tests show that the OnePlus 3 requires apps to be reloaded more frequently that phones with less RAM, and this has upset some users. The good news is that -- providing you don't mind getting your hands dirty with a… [Continue Reading] -

What is Optic AMOLED?
Publié: juin 17, 2016, 11:05am CEST par Mark Wilson
There's quite a lot to get excited about with regard to the newly announced OnePlus 3. After lots of teasing, the 'flagship killer' handset was revealed earlier this week as a 5.5-inch, dual SIM beast packing a Snapdragon 820 and 6GB of RAM. But among all the specs that seem familiar, or at least make sense, there is the display. This is a 1080p panel powered by an Adreno 530 chip, with protection coming courtesy of Corning Gorilla Glass 4. It's described as being an Optic AMOLED, but what does that actually mean? As it turns out, it's not a… [Continue Reading] -

Abracadabra! Microsoft acquires Wand Labs to conjure up some chat bot magic
Publié: juin 16, 2016, 5:01pm CEST par Mark Wilson
Continuing the spending spree that started with snapping up LinkedIn earlier this week, Microsoft today announces that it has acquired Wand Labs. The mobile developer has a chat-centric focus, and will help Microsoft to build on the Conversation as a Platform ideas Sayta Nadella has been championing of late. Neither Wand Labs nor Microsoft has shared details of the amount of money that is changing hands, but the acquisition will assist Microsoft in developing its Bot Framework. Wand Labs' natural language technologies will extend the capabilities of Windows, Bing, Microsoft Azure and Office 365, particularly with intelligent agents and chat… [Continue Reading] -

Microsoft rolls out Windows Store update that allows you to choose install locations for apps
Publié: juin 16, 2016, 10:44am CEST par Mark Wilson
The advent of app stores has meant that software installation is very hands-off process these days. Select the app you want, hit install, and everything is taken care of for you. On one hand, this is great as it simplifies and accelerates things, but it also removes an element of control from the user. With an update to the Windows Store app in Windows 10, Microsoft is changing this. Building on the ability to move apps from one drive to another, Windows 10 Anniversary Edition will now ask where you would like to install larger apps -- a real boon… [Continue Reading] -

In macOS Sierra, Safari 10 will simply ignore Flash in favor of HTML5
Publié: juin 15, 2016, 4:36pm CEST par Mark Wilson
Flash -- despite the best efforts of many -- is not quite dead. It continues to hang around like a festering scab, just waiting to be cast off forever. With macOS Sierra, Apple is playing its part in consigning Flash to the history books, pushing HTML5 to the fore. Following in the footsteps of Google Chrome, starting with Sierra, Apple's Safari will ignore Flash even if the legacy plugin is installed. HTML5 will be favored for each and every site -- a marked difference from Chrome which maintains a list of exceptions (such as YouTube) which could still make use… [Continue Reading] -

Apple: developers must use App Transport Security by 2017
Publié: juin 15, 2016, 3:30pm CEST par Mark Wilson
Apple has announced that the deadline by which app developers must enable App Transport Security (ATS) in all apps is 1 January 2017. ATS is not a new feature of iOS 10, having been introduced in iOS 9 and it increases the security of data transferred over the web by apps. With ATS enabled, apps are forced to use the far more secure HTTPS rather than HTTP, and this is something we've become accustomed to looking out for when browsing the web. At the moment, developers are able to disable ATS, but from the end of the year this will… [Continue Reading] -

Facebook rolls out suicide prevention tools around the world
Publié: juin 15, 2016, 12:25pm CEST par Mark Wilson
Facebook has announced that an updated batch of suicide prevention tools are being rolled out globally. It's a feature that has been available in some parts of the English-speaking world for a little while, but now the social network has decided to offer them up to everyone. The aim is to make it easier for people to reach out to friends who they believe may be either suicidal, or at risk of self-harming. The tools have been developed in conjunction with people with experience of suicide and self-harm, as well as mental health charities. In addition to giving Facebook users… [Continue Reading] -

Facebook denies being pro-Brexit, but removes pro-Brexit status option anyway
Publié: juin 15, 2016, 11:36am CEST par Mark Wilson
In the US, Facebook has been hit with accusations of having a anti-conservative bias in its news coverage. In the UK, the social network stands accused of being pro-Brexit in the upcoming EU referendum. The Brexit-related accusations came about after it was noticed that Facebook offered a readymade status update proclaiming to be "in favour of leaving the EU", but didn’t have a balancing pro-remain option as easily accessible. Despite this, Facebook categorically denies any form of bias. While it was possible to indicate a preference for remaining in the EU using Facebook's automated status suggestions, the pro-Brexit option was… [Continue Reading] -

Napster's back! (soon)
Publié: juin 15, 2016, 11:31am CEST par Mark Wilson
Taking more than a little inspiration from Game of Thrones, music streaming service Rhapsody has announced a rebranding. 'Napster is coming', proclaims the Rhapsody blog. This is a name that should be very familiar, particularly to old-school pirates. Napster is a name deeply entrenched in P2P history, but turned its back on its naughty ways following its acquisition by Roxio and then Best Buy. Five years ago, Rhapsody swallowed up Napster and now the company feels it's time to revive the name. There's not a lot of information available at the moment, but Rhapsody is quick to reassure users that… [Continue Reading] -

Facebook Messenger for Android can now send SMS and MMS
Publié: juin 14, 2016, 10:49pm CEST par Mark Wilson
Facebook has upset a lot of people by effectively forcing its Messenger app onto people by removing the messaging option from the mobile website. Today, to help soften the blow a little, the social network announces that Android users will be able to use the app to not only chat with their Facebook friends, but also to send and receive SMS and MMS. It's a feature that has been available in the beta version of Facebook Messenger for a little while, but now it is rolling out to everyone. While it will help keen chatters to reduce the number of… [Continue Reading] -

Microsoft rolls out enterprise improvements to IE11 on Windows 7 and Windows 8.1
Publié: juin 14, 2016, 9:44pm CEST par Mark Wilson
Since the launch of Microsoft Edge, numerous changes and updates have been made to Microsoft's latest web browser. The arrival of ad-blocking was a real crowd-pleaser, but Microsoft is mindful of the fact that many enterprise users are going to be sticking with Internet Explorer for some time yet. Today the company announces that some of the enterprise-specific enhancements and tweaks made to the Windows 10 version of IE11 will also be making their way to Windows 7 and Windows 8.1. In fact, the improvements are rolling out to more Windows 10 users as well. Changes made to Internet Explorer… [Continue Reading] -

Apple doesn't seem to have decided which devices will support iOS 10
Publié: juin 14, 2016, 3:48pm CEST par Mark Wilson
When Apple announced iOS 10 yesterday, there was one question that people around the world were asking themselves: will my device run it? The company sent out rather confusing signals yesterday in answer to this question. Slides shown during the announcement presentation revealed the iPads, iPhones and iPods that will be able to upgrade to iOS 10. But the official iOS 10 preview page told a different story. Devices that were previously absent from the support list -- such as 3rd generation iPad -- were suddenly listed as supporting iOS 10. Now Apple has changed its mind again, and updated… [Continue Reading] -

Finally! iOS 10 lets you remove built-in apps like Stocks
Publié: juin 13, 2016, 11:08pm CEST par Mark Wilson
It’s something that many iPhone and iPad owners have asked: just how the hell do I delete the pointless Stocks app? With iOS 10 there's no need to go as far as jailbreaking your beloved device, as Apple is making it possible to delete no fewer than 23 of the built-in apps. That useless Stocks app? Gone! The News app you never use? History! There are many reasons for wanting to banish these apps. Apart from not using them, you might want to free up screen space by getting rid of unnecessary icons. You might feel you can free up… [Continue Reading] -

With iOS 10 and macOS Sierra, Apple drops support for many older Macs, iPhones and iPads
Publié: juin 13, 2016, 10:28pm CEST par Mark Wilson
With Apple's software announcements today, the focus has been on what is new and exciting. But with (just about) any operating system update, there is a darker side: the older devices that slip into oblivion, never to be updated again. It's no different with iOS 10 and macOS Sierra. On the mobile front, Apple is giving up on the A5 chip, meaning that a number iPhones and iPads are not going to support the latest version of iOS. It’s a similar story for Mac and MacBook owners -- older devices simply aren’t going to get the goodies. The official list… [Continue Reading] -

Apple focuses on new features and privacy in iOS 10, while opening up to developers
Publié: juin 13, 2016, 9:51pm CEST par Mark Wilson
It's what Apple is describing as 'the biggest iOS release ever'. Whether everyone else agrees remains to be seen, but today the company took the wraps off iOS 10 -- and there's certainly a lot to take in. Perhaps the most notable change, for developers at least, is the fact that Siri has been opened up so that it can be used by third party apps. Messaging has become more important than ever in recent years, and this is something that Apple recognizes with iOS 10. Taking design cues from the likes of Facebook and WhatsApp, the Messages app now… [Continue Reading] -

Microsoft to buy LinkedIn for $26.2 billion in cash
Publié: juin 13, 2016, 3:03pm CEST par Mark Wilson
In a surprise announcement, Microsoft has said that it is to buy LinkedIn for $26.2 billion in cash. The $196 per share deal is expect to close by the end of this calendar year having been unanimously approved by both companies' Boards of Directors. Following the acquisition, LinkedIn will retain its current branding and Jeff Weiner will remain on as CEO, reporting to Microsoft CEO Satya Nadella. LinkedIn will become part of Microsoft’s Productivity and Business Processes segment. In a statement, Nadella said: "The LinkedIn team has grown a fantastic business centered on connecting the world’s professionals. Together we can… [Continue Reading] -

Microsoft, Google and Facebook to work with Bangladesh government to remove 'inappropriate content'
Publié: juin 13, 2016, 12:14pm CEST par Mark Wilson
Following prolonged talks with the Bangladesh government, Facebook, Google and Microsoft have all agreed to do more to remove 'inappropriate content' from the internet. State Minister for Telecoms, Tarana Halim, said: "After intense discussion with Facebook, Google and Microsoft, it has been agreed that they will respond to requests within 48 hours". Agreeing to the Bangladesh government's demands comes just weeks after major tech companies agreed to a new code of conduct to combat online hate speech. In this instance, however, it has not been made entirely clear what constitutes inappropriate content, and the announcement will raise questions about the… [Continue Reading] -

New slim Xbox One S boasts 4K support, 2TB HDD and a vertical stand
Publié: juin 12, 2016, 10:15pm CEST par Mark Wilson
Rumors have been circulating for some time about the arrival of a new Xbox One console, and now an image of the new model has leaked out. Known as the Xbox One S, the updated console is not just slimmer than the current Xbox One, but also boasts additional features. Widely expected to be announced at the E3 expo which kicks off on Tuesday, Microsoft describes the Xbox One S as 'sleeker, slimmer, sharper'. At the moment no details of pricing or launch date are known, but the leak does gives up interesting titbits. The S in the name clearly… [Continue Reading] -

Julian Assange's WikiLeaks poised to release more Hillary Clinton emails
Publié: juin 12, 2016, 10:06pm CEST par Mark Wilson
In a move that could boost Donald Trump's election campaign, WikiLeaks is on the verge of releasing more of Hillary Clinton's emails from her stint as US secretary of state. Clinton's use of a homebrew email server and a private email address for sending classified information has dogged her presidential campaign -- and Julian Assange is happy for that to continue. The WikiLeaks founder, currently in exile in the Ecuadorian embassy in London, has made no secret of his loathing for Clinton. She is the subject of a federal investigation, and Assange is happy to add fuel to the fire… [Continue Reading] -

Orlando shooting at Pulse nightclub prompts Facebook's first use of Safety Check in the US
Publié: juin 12, 2016, 9:17pm CEST par Mark Wilson
Following a massacre at the Pulse nightclub in Orlando, Florida, Facebook has been prompted to activate its Safety Check feature in the US for the first time. 50 people lost their lives in the attack on the LGBT nightclub. Previously used following natural disasters around the world as well as a man-made tragedy, Safety Check gives people in a trouble spot to let friends and family know that they're OK. The deadliest mass shooting in American history ended up being the trigger for the first activation of the feature on US soil. The tool also works the other way around,… [Continue Reading] -

Snowden: Scotland has its own NSA conducting mass surveillance of phone and internet activity
Publié: juin 12, 2016, 2:04pm CEST par Mark Wilson
Documents leaked by Edward Snowden reveal that Scottish authorities have been engaged in gathering data about phone and internet usage in much the same way as the NSA and GCHQ. The Scottish Recording Centre (SRC) accessed information gathered as part of a bulk data collection program called MILKWHITE. Scottish newspaper The National, in conjunction with the website CommonSpace, have exposed Scotland's role in the UK's mass surveillance programs. Police and tax authorities in Scotland -- devolved from UK forces -- were given accessed to what the Intercept describes as 'huge troves of metadata' gathered by spy agencies. Just as the… [Continue Reading] -

Even threatening to circulate revenge porn could be criminalized across Britain
Publié: juin 12, 2016, 12:49pm CEST par Mark Wilson
New laws have been proposed for England and Wales that would criminalize not only the circulation of revenge porn, but also threatening to circulate it. The definition of what constitutes revenge porn could also be expanded. This level of criminalization is already in force in Scotland, and Liberal Democrat MP Alistair Carmichael believes that the rest of Britain should follow suit. If adopted, the proposed change would see revenge porn threats seen in much the same light as other forms of blackmail. Scottish law already makes it an offense to share, or threaten to share, intimate images and videos. Anyone… [Continue Reading] -

Bluetooth 5 is on the way: four times the speed, twice the range, and location-awareness
Publié: juin 11, 2016, 7:42pm CEST par Mark Wilson
Due to be announced next week on June 16, Bluetooth 5 has a great deal to offer. Ahead of the announcement, Bluetooth Special Interest Group executive director Mark Powell has revealed a little about what we can expect. The headline-grabbing specifications for the latest version of the wireless standard are a doubling of the current range, and a quadrupling of the current speed. Slightly less exciting is the change in naming convention which is a move to simplify the communication of major changes, but another key feature of Bluetooth 5 is support for location-aware services. This is something that other… [Continue Reading] -

Google turns evil and backs controversial Trans-Pacific Trade Partnership (TPP)
Publié: juin 11, 2016, 1:48pm CEST par Mark Wilson
The Trans-Pacific Trade Partnership, or TPP, is a controversial trade agreement which has been decried by many as limiting privacy and freedom of expression, as well as lacking transparency. Google has just announced that it supports TPP. While the TPP has been signed by the Obama administration back in February, it is still to be approved by congressed. In the meantime, many companies, organizations and interest groups have spoken out against it. Google admits that the TPP is not perfect, but joins the likes of Microsoft in lending its support. In a post on Google's Public Policy Blog, SVP and… [Continue Reading] -

Facebook threatens to delete users' photos if they don’t install the Moments app
Publié: juin 11, 2016, 1:07pm CEST par Mark Wilson
Not content with forcing people into using its Messenger app, Facebook is continuing its aggressive tactics and driving users to install its photo-sharing app, Moments. The social network has warned users that their photos face deletion if they fail to use the Moments app. Unsurprisingly, this has led to a huge surge in interest in the app, pushing it to the top of the download charts. Facebook has announced that it is going to delete Synced Albums and Synced Photos if Moments is not installed by July 7, sending warning emails to a number of users. This has understandably led… [Continue Reading] -

Google explains that search autocomplete censors suggestions
Publié: juin 11, 2016, 12:13pm CEST par Mark Wilson
If you use Google as your search engine, you'll no doubt have noticed that as you type, a list of suggestions appears. This is an example of Google trying to be helpful, but the autocomplete suggestions can also be amusing or just plain weird -- thanks, algorithms! In recent days, Google has been accused of tinkering with search suggestions in a way that favors Hillary Clinton -- something the company strenuously denies. You may have wondered how Google comes up with the suggestions it makes, and Tamar Yehoshua, VP of product management has spilled the beans. She reveals that as… [Continue Reading] -

Report: Amazon is on the verge of launching its own music streaming service
Publié: juin 11, 2016, 12:02am CEST par Mark Wilson
A report from Reuters, citing two sources close to Amazon, says that the online retail giant is about to launch a music streaming service to rival the likes of Spotify. The as-yet-unnamed service is expected to launch towards the end of summer or beginning of fall, pending negotiations with record labels. With a rumored monthly fee of $9.95, the streaming service does nothing to compete with its rivals financially, but Amazon will still be hoping that it will help boost its Echo product. The paid-for streaming service will sit alongside the free one currently available to Amazon Prime subscribers. Amazon… [Continue Reading] -

It's not just Windows 10 that has telemetry issues -- Microsoft has done the same with Visual Studio 2015 C++ compiler
Publié: juin 10, 2016, 7:44pm CEST par Mark Wilson
An eagle-eyed Reddit user has noticed that code run through Visual Studio 2015 C++ compiler make calls to Microsoft's telemetry services. Microsoft has already upset a large number of people with the privacy and telemetry issues in Windows 10, and there is now a busy thread on Reddit discussing the company's thinking behind including this 'feature'. Coders have expressed concerns that Microsoft appears to be inserting calls to its telemetry service into binaries as they are compiled. Calls to telemetry_main_invoke_trigger and telemetry_main_return_trigger raised a few eyebrows having been found in both debug and release versions of the software. The good… [Continue Reading] -

First batch of Chromebooks reach End Of Life and get no more support or updates
Publié: juin 10, 2016, 4:30pm CEST par Mark Wilson
The original Chromebooks launched back in 2011 are reaching the end of their support cycle. With Google offering a fairly generous five years (*) of support and updates, users have had a good run, but the Samsung Series 5 Chromebook is the first device to drop off the support list. Having been launched in August 2011, Acer AC700 Chromebook will be in a similar position in a couple of months. But it's not entirely clear what will happen. Google says that after five years, automatic updates are "no longer guaranteed", but the company has continued to provide updates for its… [Continue Reading] -

India blocks Google's plans for Street View in the country amid security concerns
Publié: juin 10, 2016, 1:16pm CEST par Mark Wilson
Google's plans to gather Street View data in India have hit a brick wall after the country rejected the company's proposals. Indian security agencies expressed concerns about plans to send Google Street View cars around the country, taking 360-degree photos along roadways. This is certainly not the first time Google Street View has faced problems, with numerous cases relating to privacy resulting in changes being made to the service. India's interior minister said that Google's proposed photographic journey was being rejected because of concerns that it could compromise the country's security. It is thought that terrorist attacks in the country… [Continue Reading] -

Twitter denies stolen account passwords came from its servers and issues security advice
Publié: juin 10, 2016, 11:52am CEST par Mark Wilson
In recent days the internet has been abuzz with news that credentials for millions of Twitter accounts have been put up for sale on the Dark Web. Despite the online chatter about what many people assumed to be a security breach, Twitter chose to remain silent. Now the company has spoken out after an investigation and denies that the password leak was the result of Twitter being hacked. Dismissively referring to the "purported Twitter @names and passwords", the company says that the leak is probably a combination of data gathered from previous breaches as well as credentials gathered by malware.… [Continue Reading] -

Lenovo announces modular, moddable Moto Z range with swappable Moto Mods
Publié: juin 9, 2016, 10:03pm CEST par Mark Wilson
It looks like the next big movement in smartphone design is going to be physically customisable handsets. The latest company to do more than just add bigger screen, ramp up the processor speed and chuck in a bit more RAM is Lenovo. Today the company announces the Moto Z family with Moto Mods. At the moment, the 'family' comprises just two phones: the Moto Z, and the more powerful Moto Z Force. Things get off to a promising start with the handset boasting impressive specs, and measuring just 5.2mm thick (which Lenovo boasts is 'The world's thinnest premium smartphone'). Which… [Continue Reading] -

Facebook lets users upload interactive 360-degree photos
Publié: juin 9, 2016, 9:03pm CEST par Mark Wilson
Interactivity is the name of the game these days, as illustrated by the explosion of interest in VR. Facebook may not have gone quite as far as bringing virtual reality to your newsfeed, but it does now support 360-degree photos -- or 360 Photos as it has been dubbed. Starting tomorrow, you'll be able to upload either 360-degree photos, or panoramic photos. On the web, these become interactive images that you can scroll around using a mouse, but on a smartphone you have a couple of options. You can either tap and drag your way around an image, or hold… [Continue Reading] -

Google rolls out Android update that brings location-aware Nearby feature to handsets
Publié: juin 9, 2016, 8:01pm CEST par Mark Wilson
An Android update is rolling out that makes it easier to take full advantage of location-aware apps. You might be somewhere for which there is the perfect app to enhance your visit, but if you don’t know of its location-specific capabilities, you just might never use it. Enter Nearby from Google. Google offers a number of example scenarios in which Nearby might be useful. Walk into a CVS, and you could be notified of the in-store photo printing service. Visit a key landmark, and you could enjoy a virtual tour, or learn more about it. Developers are being encouraged to… [Continue Reading] -

Buffer overflow vulnerability in PDFium PDF reader affects Google Chrome
Publié: juin 9, 2016, 6:24pm CEST par Mark Wilson
The name PDFium might not be immediately familiar, but if you're a Chrome user there's a high chance you're using it to view PDFs. The PDF viewer is built into Google's browser, and a vulnerability has been discovered in the jpeg2000 library which could allow for malicious code to be executed. Unearthed by Aleksandar Nikolic from Cisco Talos, the heap buffer overflow vulnerability could be exploited by simply getting a user to open a PDF document with an embedded jpeg2000 image. The National Vulnerability Database entry warns that the security flaw affects versions of "Chrome before 51.0.2704.63 [and] allows remote… [Continue Reading] -

No more Tinder for under-18s
Publié: juin 9, 2016, 10:52am CEST par Mark Wilson
Tinder is updating its terms of use, preventing people under the age of 18 from using the app. The dating app experimented with allowing teenagers from 13 to 17 to hook up with people from the same age group, but as of next week this will no longer be possible. This sub-section of user represents just 3 percent of Tinder's user base, but the company feels that tightening up on access is "the right thing to do". Moving forward, of course, there is little that can be done to prevent under-18s from signing up using a false date of birth.… [Continue Reading] -

Apple updates App Store with faster app approvals, improved subscription rates... and search ads
Publié: juin 8, 2016, 10:09pm CEST par Mark Wilson
Apple has announced a series of major changes to the App Store including speeding up the app review process to get developers' product out there faster. This is something that benefits both developers and users, but developers also have improved subscription rates to look forward to. The current 70/30 split is changing so that after the first year Apple will take just 15 percent of subscription fees. Subscriptions are also opening up to the full gamut of apps, rather than being restricted to particular categories. But it is the changes that are being made to app discovery that will be… [Continue Reading] -

Snooper's Charter, aka the Investigatory Powers Bill, voted into UK law
Publié: juin 7, 2016, 10:27pm CEST par Mark Wilson
The controversial Snooper's Charter -- or the Investigatory Powers Bill as it is officially known -- has been voted into law by UK MPs. An overwhelming majority of politicians (444 to 69) voted in favor of the bill which has been roundly criticized by both the public and technology companies. The Investigatory Powers Bill grants the UK government, security, and intelligence agencies greater powers for monitoring internet usage, as well as permitting bulk data collection and remote hacking of smartphones. The law allows for the kind of mass surveillance that Edward Snowden warned about, and while the bill may have… [Continue Reading] -

Windows 10 Anniversary Update to bring Enterprise-specific Edge management policies
Publié: juin 7, 2016, 9:29pm CEST par Mark Wilson
To keep enterprise users happy, Windows 10 includes both Internet Explorer and Microsoft Edge. Internet Explorer may be included for legacy support, but just like non-enterprise customers, Microsoft is keen to get everyone shifted across to Edge or at least ensure the two browsers work well together. To help encourage this migration, Windows 10 Anniversary Update brings support for a number of new management policies in Microsoft's newest browser. There's a clear need to continue to support legacy line of business (LOB) applications, but Microsoft also wants to make management as easy as possible. Microsoft has already introduced a number… [Continue Reading] -

Facebook to force users to Messenger app by disabling chatting on its mobile site
Publié: juin 4, 2016, 10:32pm CEST par Mark Wilson
If you access Facebook on your phone, the chances are that you use the dedicated Facebook app -- but this is not necessarily the case. A lot of people prefer to make use of the mobile Facebook website, and the social network is making an aggressive change to the way messaging works that will force the use of the Messenger app. Head to the messaging section of the mobile site today, and you'll be greeted by a large pre-emptive warning that reads: "Your conversations are moving to Messenger. Soon, you'll only be able to view your messages from Messenger". For… [Continue Reading] -

Facebook: "We're not listening to your phone calls to deliver targeted ads"
Publié: juin 4, 2016, 1:02pm CEST par Mark Wilson
Facebook has issued a statement denying mounting rumors that the company uses smartphone microphones to listen in on private conversations. The allegations have circled for some time, but have most recently been voiced by Kelli Burns, a mass communication professor at the University of South Florida. In her own testing, Professor Burns said that after discussing certain topics within earshot of her phone, she would then see ads relating to those topics on Facebook. Just like the OK, Google feature of Android, the Facebook app does have a feature that listens out for user input, but the company says this… [Continue Reading] -

TeamViewer denies being hacked, blames users, and introduces new security measures
Publié: juin 4, 2016, 11:31am CEST par Mark Wilson
In the last couple of weeks there have been a huge number of reports from TeamViewer users that their computers have been hijacked. In addition to this, users of the remote access tool have complained of funds being extracted from PayPal and bank accounts. But TeamViewer insists that there has not been a security breach, instead shifting the blame to users. The company says they are in the habit of reusing the same passwords for a number of apps and services. It suggests that recent high profile security breaches -- such as the password dumps from MySpace and LinkedIn --… [Continue Reading] -

The Sims 4 update dissolves gender boundaries and embraces diversity
Publié: juin 3, 2016, 3:06am CEST par Mark Wilson
A free update released today for The Sims 4 introduces a swathe of new options relating to creation of Sims. Significantly, gender-specific options no longer exist. Players can access the full range of clothing, hairstyles, physiques and voices regardless of the gender selected. Electronic Arts says that in all, some 700 options that were previously tied to male or female Sims are now gender neutral. The move, part of a general trend in the technology industry to diversity, has been warmly welcomed by players. As well as the main game, the update also affects add-ons and expansions for The Sims… [Continue Reading] -

Android users: become a Google Maps beta tester to try out preview versions of the app
Publié: juin 3, 2016, 2:21am CEST par Mark Wilson
Google is a company that's well-known for its beta products -- there is a long-running joke about so many of its services being in permanent beta. Beta testing on Android has tended to be limited to a select few, but with the Google Maps app the beta programme is being opened up to everyone. After signing up to take part, you will be able to download a newer version of Google Maps than is currently available in the Play Store. At the moment there is a fairly insignificant version number difference, and no notable changes, but this should all change as… [Continue Reading] -

Apple suffers outage that knocks App Store, iCloud, iTunes and more offline
Publié: juin 2, 2016, 11:17pm CEST par Mark Wilson
Many of Apple's online services are currently out of action, with the App Store and Apple TV being just two that people are struggling with. Some users are reporting that Apple Music is out of action, but the most common complaint is that App Store purchases cannot be complete. Apple says that it is aware of the problems and is investigating, but at the moment has given no hint at what the cause might be. The company's System Status page highlights numerous issues, with a fluctuating number of listings tagged "Service may be unavailable for some users". Apple Support's recently… [Continue Reading] -

Google will start suggesting apps to remove when you run out of space on your Android phone
Publié: juin 2, 2016, 9:41pm CEST par Mark Wilson
With the size of apps and games spiralling upwards faster than the amount of storage increases in phones, it's very easy to run low on space. To help overcome the problem of not having enough room to install a new app, Google is starting to suggest rarely used apps that could be installed. The feature has not appeared completely out of the blue, with references having been spotted to it in APK teardowns some months ago. But now Google Play's intelligent uninstall manager has been spotted in action. As reported by Android Police, it appears that when a user attempts… [Continue Reading] -

How to delete all of the illicit recordings Google has gathered from you over the past year
Publié: juin 2, 2016, 11:31am CEST par Mark Wilson
One of the concerns -- for those focused on privacy, at least -- with the likes of Siri, Cortana and 'OK, Google' is that the way these features works means they are constantly listening to what you say. In the case of Google, these recordings are stored in the cloud for the company to use to improve the service. But voice recognition is an art rather than a science, and your phone is not always able to distinguish between commands you direct at it and ordinary conversation. As such, Google may well have recorded audio of you going about your… [Continue Reading] -

Facebook launches updated emoji for Messenger with diversity in mind
Publié: juin 1, 2016, 9:00pm CEST par Mark Wilson
Tech companies are falling over themselves to embrace diversity both in the workplace, and in products. The latest example of this comes courtesy of Facebook which today releases an update to Messenger complete with hundreds of diversity-friendly emoji. As well as bringing in the full (well, fuller) gamut of skin tones, the new emoji also nod to gender equality, as well as including redheads for the first time. On top of all this, Facebook is also standardizing its emoji set so the same selection is available to everyone, regardless of the platform they might be using. The standardization will come… [Continue Reading] -

Gabe Aul hands on Insider leadership baton ahead of Windows 10 Anniversary Update launch
Publié: juin 1, 2016, 8:05pm CEST par Mark Wilson
Gabe Aul, long the face of the Windows Insider Program, is standing down from that particular leadership role to focus instead on his work at Engineering Systems Team in WDG. 18 months, 35 desktop builds and 22 mobile builds down the road, Aul has realized he's unable to give 100 percent to both roles. The new head of the Insider program is Dona Sarkar who has been with Microsoft since the days of Vista. Having worked on Windows 7, 8, 8.1 and 10, as well as HoloLens, the Windows Insider Program leadership role is one she says she has been… [Continue Reading] -

The best, and cheapest, HoloLens VR headsets will not be made by Microsoft
Publié: juin 1, 2016, 6:13pm CEST par Mark Wilson
Microsoft is opening its HoloLens to a range of partners, the company announced at Computex today. This means that future VR headsets based on the HoloLens platform will come from a variety of manufacturers, and will be available in different forms, taking full advantage of Windows 10 Anniversary Update. With a price tag of $3,000, the existing official HoloLens headset is out of the reach of many people, but in opening up the platform to partners, Microsoft says that cheaper price points should also be available. The company is also doing something interesting. One of the criticisms levelled at HoloLens… [Continue Reading] -

Newly-discovered zero-day vulnerability affects all versions of Windows
Publié: juin 1, 2016, 5:00pm CEST par Mark Wilson
Security firm Trustwave has discovered a zero-day exploit for Windows for sale on an underground Russian hacking forum. A user going by the name BuggiCorp says the vulnerability affects all versions of Microsoft's operating system, from Windows XP and 2000 upwards, including both 32- and 64-bit versions. The source code for the exploit is offered for upwards of $90,000, and the seller explains that it can be used to elevate the privileges of any software process to SYSTEM level -- the highest there is. Payment is requested in Bitcoin, but while the exploit is considered serious, experts suggest that the… [Continue Reading] -

Facebook, Twitter, YouTube and Microsoft will fight online hate speech in Europe
Publié: juin 1, 2016, 12:31pm CEST par Mark Wilson
Facebook, Twitter, YouTube and Microsoft are working in conjunction with the European Commission to try to tackle the problem of illegal online hate speech. This is something that the companies have taken steps to fight individually, but now there is a concerted effort to combat hate speech and terrorist propaganda in Europe. New EU regulations require the companies to review notifications they receive about hate speech within 24 hours. The four tech giants have agreed to the new code of conduct, saying the 'majority' of reported content will be examined within a day. Twitter and Facebook have had numerous well-publicized… [Continue Reading] -

Microsoft sneaks even more ads into Windows 10 via the Ink Workspace
Publié: juin 1, 2016, 10:38am CEST par Mark Wilson
With online ad blocking becoming ever more popular, companies have to find new ways to push their products at people. With Windows 10 -- which is being aggressively pushed onto people -- Microsoft has found the perfect vehicle. We've already seen ads in the Start menu and ads on the Lock Screen, but it doesn't end there. Windows Insiders are also treated to ads in one of the new features available in the preview builds -- the Windows Ink Workspace. It seems that Microsoft's aggressive tactics are not limited to forcing Windows 10 onto people. In taking over portions of… [Continue Reading] -

European Data Protection Supervisor says EU-US Privacy Shield needs 'significant improvements'
Publié: mai 30, 2016, 9:39pm CEST par Mark Wilson
The proposed data transfer deal between Europe and the US, destined to replace Safe Harbour, has been dismissed as "not robust enough". The European Data Protection Supervisor (EDPS) says that the pact is in need of "significant improvements" if it is to be of any value in protecting European data stored in the US. Safe Harbour has already been ruled invalid, and it had been hoped that the EU-US Privacy Shield would be finalized by June. While today's criticism does not mean the new pact is dead in the water, it does represent a serious stumbling block. As it stands,… [Continue Reading] -

Is Microsoft bringing Xbox One game streaming to Windows 10 Mobile?
Publié: mai 30, 2016, 1:01pm CEST par Mark Wilson
If a discovery by a reddit user is anything to go by, Xbox One game streaming could be making its way to Windows 10 Mobile. The Xbox Beta app from the latest Fast Ring Insider Preview build appears to include references to streaming games from an Xbox One to a mobile device. Reddit user, eric5949, noticed that a new 'Play from console' option has appeared on his handset. Microsoft has not said anything about this feature yet, but it's possible that it's something we could see later in the year in Windows 10 Anniversary Update. eric5949 reports that a friend… [Continue Reading] -

Messaging apps need to play by Iran's rules to operate in the country
Publié: mai 30, 2016, 10:49am CEST par Mark Wilson
Privacy concerns have been voiced after Iran announced plans to force messaging apps and social media services to store all data about Iranian users on Iranian soil. It is common practice for users data to be stored in other counties, but the government in Iran continues to exert its authority over the internet. Any company who wants to operate a message service in Iran has a year to comply with the data relocation requirement. With Iran already blocking access to the likes of Facebook and Twitter, privacy and security advocates have expressed worries about the implications of the new rules.… [Continue Reading] -

How to enable paths longer than 260 characters in Windows 10
Publié: mai 29, 2016, 2:04pm CEST par Mark Wilson
In days of yore, filenames in Windows were limited to the 8.3 format -- just eight characters for the filename, and three for the extension. With the arrival of Windows 95, Microsoft stripped away this limit and allowed for much longer names. That said, the Windows file system still imposes some restrictions such as which characters can be used in filenames, and the overall length of paths. For some time the maximum path length has been 260 characters, but in the latest Windows 10 Insider Preview, it is possible to use Group Policy or a registry hack to remove this… [Continue Reading] -

Now you can try out Amazon Echo's Alexa in your web browser
Publié: mai 29, 2016, 12:40pm CEST par Mark Wilson
There is something of a trend for voice activated devices at the moment, and you might well be wondering if any of them are worth investing in. If you've been thinking about buying an Amazon Echo, you can now try it out in your web browser to get a feel for what it's like. Amazon has launched the Alexa Skill Testing Tool which gives everyone the opportunity to test drive the virtual assistant for themselves. It's the perfect blend of try-before-you buy blended with clever marketing. While it's not a perfect simulation, the Amazon Echo Simulator gives a reasonable idea… [Continue Reading] -

The internet is plagued by misogyny and abuse
Publié: mai 28, 2016, 11:52pm CEST par Mark Wilson
The world of technology has long been thought of as being male dominated. For those concerned with diversity, this is situation is less than ideal but a bigger problem exists in the form of online abuse. This does not refer just to trolling and immature silliness, but the more serious issue of targeted misogyny. The headline to this article may seem to state the obvious, but it's very easy to assume that something is the case without actually having the evidence to support it. Personal experience is one thing, but how does this translate to the wider sphere? New research… [Continue Reading] -

Microsoft says it will stop spamming Android users with Office ads in the notification tray
Publié: mai 27, 2016, 11:32pm CEST par Mark Wilson
It feels like we complain about Microsoft a lot here. We do; in recent months there has been a lot to get upset about. There has been a lot of negativity surrounding Windows 10, so let's have a change of subject. Now Microsoft is spamming the Android notification tray with ads for Office. The notification tray in Android serves a very specific purpose. There's a clue in the name -- and it's nothing to do with advertising. Android user Thom Holwerda was upset this week when Microsoft Office for Android starting to spam him with ads for apps he already… [Continue Reading] -

China complains about forced upgrades to Windows 10
Publié: mai 27, 2016, 10:49pm CEST par Mark Wilson
To say that Windows 10 has been controversial for Microsoft would be something of an understatement. The most recent cause for complaint has been a deceptive upgrade popup, described by many as a "nasty trick", which fooled users into installing the upgrade. The company has since said that it will change the behavior of the upgrade notification, but this is not enough to silence hundreds of thousands of users in China. Microsoft stands accused of abusing its market position to force unwanted upgrades on people. Speaking to the Xinhua news agency, Zhao Zhanling from the Internet Society of China said:… [Continue Reading] -

Facebook introduces new cookies policy and allows users to opt out of tailored ads on non-Facebook sites
Publié: mai 27, 2016, 12:29pm CEST par Mark Wilson
When you hit Facebook today, you may well notice a new Cookies Policy warning at the top of the page. It states: "To help personalize content, tailor and measure ads, and provide a safer experience, we use cookies. By clicking or navigating the site, you agree to allow our collection of information on and off Facebook through cookies. Learn more, including about available controls: Cookies Policy". But what is it all about? Facebook hasn’t made a great deal of fuss about it, but the social network has introduced not only a new cookies policy, but also made changes to ads.… [Continue Reading] -

You could be held liable for cases of bank fraud if your online security isn’t up to scratch
Publié: mai 27, 2016, 11:29am CEST par Mark Wilson
If you need another reason to pay attention to online security, new measures under consideration by banks could sharpen your focus. At the moment, banks in the UK frequently shoulder the cost of online fraud when customers fall victim. But all this could be set to change. The plans being looked at by banks, GCHQ and the UK government could see people who haven’t taken care of their own online security being excluded from receiving compensation if their account is hacked. The Financial Times reports that the plans could see people with poor security in place find themselves "frozen out… [Continue Reading] -

Windows 10 Insider Preview Build 14352 includes Cortana, Ink and Feedback hub improvements
Publié: mai 27, 2016, 1:24am CEST par Mark Wilson
Microsoft has pushed Windows 10 Insider Preview Build 14352 to the Fast Ring. The latest build introduced a number of updates and bug fixes. One of the biggest changes is to Cortana which can now be used to control a Groove Music Catalog and set a timer. The recently-introduced Windows Ink gains improved Sticky Notes, and the ruler now benefits from the inclusion of a compass. Gamers can now enjoy the Windows Game bar at full-screen in more games, including World of Warcraft, Counterstrike: Global Offensive, and Diablo III. Important changes have also been made to the Feedback Hub. Just days after… [Continue Reading] -

Google wins trial against Oracle -- Java APIs in Android are 'fair use'
Publié: mai 26, 2016, 10:32pm CEST par Mark Wilson
Google has won a case brought against it by Oracle in which it was accused of infringing on copyright by using Java APIs in Android. But at the end of a two-week trial, the jury found in Google's favor saying that 'fair use' was an acceptable defense. Had Google lost the case, it could have cost the company billions of dollars and would have set something of a precedent. This was the first major case in which a company tried to use copyright law to control the use of APIs. During the trial, representatives from both Oracle and Sun Microsystems… [Continue Reading] -

Decade-old 'forbidden attack' vulnerability affects HTTPS Visa sites
Publié: mai 26, 2016, 8:08pm CEST par Mark Wilson
A number of supposedly secure HTTPS sites owned by Visa are vulnerable to what has been dubbed the 'forbidden attack'. The security flaw makes it possible for hackers to inject content and code into sites, as well as opening up the possibility of performing man-in-the-middle attacks. A team of researchers have published a paper that shows how 70,000 HTTPS servers were vulnerable to the attack, and 184 were found to be particularly at risk. While many of the affected sites have since been patched, sites belonging to Visa and Polish banking associate Zwizek Banków Polskich remain insecure because of reusing… [Continue Reading] -

PayPal focuses its efforts and drops Windows Phone app
Publié: mai 26, 2016, 1:48am CEST par Mark Wilson
Like many other companies, PayPal is questioning the value of investing time and money in Windows Phone -- or Windows 10 Mobile, if you prefer. As of 30 June, the PayPal app for Windows Phone will be no more. At the same time, the company is also dropping the apps for Blackberry and Amazon Fire OS. PayPal says that users will have to rely on the mobile website as it focuses "resources in creating the very best experiences for our customers". The small install base for Window Phone, Fire OS and Blackberry makes PayPal's decision entirely understandable, but the announcement… [Continue Reading] -

Mozilla welcomes privacy-boosting GDPR data protection law updates
Publié: mai 25, 2016, 7:18pm CEST par Mark Wilson
In a world more concerned than ever with privacy and data security, law makers are scrambling to keep up to date. With the growth of the internet, many old and inappropriate laws have been bent to fit a purpose they were not designed for. A case in point are European data protection directives which date back more than two decades. In April this year a new law was adopted -- the General Data Protection Regulation, or GDPR. With compliance with the law required of the 28 EU member states by 25 May 2018, a two-year countdown is now underway. GDPR… [Continue Reading] -

Microsoft is using Windows 10 to see just how far it can push customers before they break
Publié: mai 25, 2016, 5:36pm CEST par Mark Wilson
If you believe what comes out of Microsoft's figurative mouth, these days the company is all about listening to feedback. That's certainly the message that has been put forward with Windows 10, with the Feedback Hub app being made available to everyone with the operating system installed. Microsoft makes much of the fact that Windows 10 is installed on around 300 million computers, but the reality is that a portion of these installations relate to people who have been hoodwinked into upgrading from Windows 7 or Windows 8. The latest trick (tricking users in to installing Windows 10 by clicking… [Continue Reading] -

Microsoft to ditch hundreds more workers in smartphone streamlining measures
Publié: mai 25, 2016, 12:04pm CEST par Mark Wilson
After the sale of its feature phone business last week, Microsoft is making further structuring changes. Announcing the "additional step of streamlining our smartphone hardware business" Terry Myerson says that up to 1,850 jobs could be impacted, with the vast majority of these (1,350) being in Finland. He also says that the company will continue "develop great new devices", no doubt fueling rumors of the highly-anticipated Surface Phone. Microsoft recognizes that its success with phones have been "limited", and Myerson's memo to employees reiterates the company’s commitment to the Windows platform, and Windows 10 in particular. We have already seen… [Continue Reading] -

Apple re-hires security expert of PGP, Blackphone and Silent Circle fame
Publié: mai 25, 2016, 11:15am CEST par Mark Wilson
Following the company's very public stand-off with the FBI over the San Bernardino shooter's iPhone, Apple is demonstrating that it has a great interest in security by re-hiring encryption expert Jon Callas. Best known for founding security-focused firms PGP Corp and Silent Circle -- the company behind the ultra-secure, privacy-centric Blackphone -- Callas has worked for Apple on two previous occasions. While neither Apple nor Callas himself are commenting on the precise role he will have at the company, Apple has confirmed his appointment to Reuters. With his security heritage, and having previously helped Apple create an encryption system for… [Continue Reading] -

Google's Paris headquarters raided in probe into "aggravated financial fraud and organized money laundering"
Publié: mai 24, 2016, 11:40pm CEST par Mark Wilson
Google's tax affairs in Europe have been the subject of some interest for a while now. Today the company's headquarters in Paris was raided by French investigators as part of an ongoing financial probe. While other European countries have questioned whether Google is paying enough tax, in France the company finds itself accused of "aggravated financial fraud and organized money laundering". It is also accused of evading taxes by channelling money through other countries. The arrangement Google uses -- which sees the majority of its European income processed through an Irish company -- is quite common, particularly in the tech… [Continue Reading] -

Microsoft will release just two major Windows 10 updates each year
Publié: mai 24, 2016, 11:19am CEST par Mark Wilson
Microsoft has quietly announced plans to reduce the number of updates that will be released each year for Windows 10. The company had previously said that there would be three 'feature updates' (like the Windows 10 Anniversary Update) per year, but this has now been scaled back to two. Unsurprisingly, Microsoft has not made a great deal of noise about the change to the majority of Windows 10 users, choosing instead to make the announcement at the WinHEC conference in Taiwan. At the event, senior program manager Chris Riggs also revealed how the update scheduling will work for consumers and… [Continue Reading] -

Facebook to update Trending Topics despite denying bias
Publié: mai 24, 2016, 10:16am CEST par Mark Wilson
After an investigation into Trending Topics, Facebook has concluded that there is no evidence of a liberal bias to the news that appears. Mark Zuckerberg met with key conservatives following accusations that the social network was censoring right wing news. Despite finding 'virtually identical' numbers of conservative and liberal news, Facebook says that it will still make changes to the way Trending Topics work. It says that it is difficult to exclude the possibility of 'unintentional bias' but hopes to improve things by retraining its reviewers and ditching the current reliance on a list of news outlets as sources. Facebook… [Continue Reading] -

Microsoft tweaks hardware requirements for Windows 10 Anniversary Update
Publié: mai 23, 2016, 6:52pm CEST par Mark Wilson
Ahead of the biggest update yet for Windows 10, Microsoft has published details of the minimum hardware requirements for Windows 10 Anniversary Update. Before you panic and start to worry that your current Windows 10 computer won't be able to run the update, the aim is actually to get the operating system on more devices. The hardware requirement changes are aimed at developers, and open up both Windows 10 and Windows 10 Mobile to a wider range of screen sizes. The changes mean that Windows 10 Mobile can be run on devices with larger screens than before, while the desktop… [Continue Reading] -

Adobe starts a new war on software piracy
Publié: mai 23, 2016, 1:55pm CEST par Mark Wilson
Adobe software is among the most expensive out there, so it should come as little surprise that the likes of Photoshop, Illustrator and Acrobat are among the most commonly pirated titles. In a bid to clamp down on piracy, the company has launched a new initiative that seeks out "non-genuine software" and issues warnings to people. At the moment it appears as though the checks are restricted to the US and Adobe seems to be checking Acrobat X licenses. But while the scope is limited right now, it's hard to imagine that the Software Integrity Service checks won't be rolled… [Continue Reading] -

Edward Snowden warns about the dangers of using Google Allo
Publié: mai 23, 2016, 1:02pm CEST par Mark Wilson
When Google announced the launch of two new messaging apps, the world wondered why. Duo is focused on video calling, while Allo is a more traditional messaging tool, albeit one with a Google assistant built in. But while the world shrugged, Edward Snowden issued a stark warning. He says that Allo should be avoided, pointing out that the lack of end-to-end encryption makes it "dangerous". As he has been known to do quite a lot recently, the former NSA contractor took to Twitter to issue his warning. With the current focus on software security and computer users' heightened awareness of… [Continue Reading] -

Microsoft opens up the Windows 10 Feedback Hub to everyone, not just Insiders
Publié: mai 22, 2016, 1:39pm CEST par Mark Wilson
Ever hungry for more user feedback, Microsoft has decided to make the Feedback Hub available for anyone to use. Previously only open to Windows Insiders, the tool gives Windows 10 users the opportunity to tell Microsoft exactly what they think about the company's latest operating system. The Feedback Hub has been built into preview builds of Windows 10 for some time, but now the app is available to download from the Windows Store. With the launch of Windows 10 Anniversary Update just around the corner, it's clear that Microsoft is keen to gather as many comments and as much reaction… [Continue Reading] -

Microsoft updates policies to tackle terrorism on the internet
Publié: mai 21, 2016, 11:46am CEST par Mark Wilson
Microsoft has outlined its latest plans to crack down on terrorist and extremist content online. Recognizing that the "internet can be used for the worst reasons imaginable" the company has set out its approach for ensuring that content promoting terrorism does not make it online through its services. As well as updating its terms of use to make it explicitly clear that terrorist content is not permitted, Microsoft is also planning to up its game in seeking out and removing offending content. To help with this task, the company is forging new partnerships with experts in the field, as well… [Continue Reading] -

Celebrity threesome injunction sees Twitter send warning emails to those who name PJS and YMA online
Publié: mai 20, 2016, 4:24pm CEST par Mark Wilson
People who have named the celebrities known by the initials PJS and YMA have received warning emails from Twitter. A superinjuntion is in place that prevents the naming of the couple, one of whom is said to have been involved in a threesome with two other people known as AB and CD. While the identities of all parties are well-known throughout the world (PJS is Elton John, and YMA is his husband David Furnish if you have managed to, somehow, avoid learning the names behind the initials) the superinjunction prevents them from being named in much of the UK. The… [Continue Reading] -

Microsoft's share of the mobile market plummets to below 1% as Android continues to rise
Publié: mai 20, 2016, 1:07pm CEST par Mark Wilson
Global smartphone sales figures published by Gartner show that Windows-based devices have a market share of just 0.7 percent. The latest figures cover the first quarter of 2016 and reveal that fewer than 2.4 million handsets with Microsoft's OS installed were sold. This is a dramatic drop from the first quarter of 2015. A year ago the numbers were hardly earth-shattering, but with a 2.5 percent market share they were decidedly healthier than right now. While Windows Phone continues to drop like a stone, Android's seemingly unstoppable rise continues, with Google increasing its market share from 78.88 percent a year… [Continue Reading] -

You're about to see a whole lot more of Reddit thanks to embeddable threads
Publié: mai 20, 2016, 12:19pm CEST par Mark Wilson
Reddit has announced that it is now possible to embed its discussion threads on other websites. Just as you can embed tweets on your site, the same can now be done with Reddit content. While Reddit has successfully earned its reputation of being the modern-day Digg, the site has not been without controversy. Its AMA (Ask Me Anything) sessions may prove immensely popular, but it has been plagued with problems with racist content and complaints about censorship. However, Reddit has suffered with image problems of a different kind, often viewed as being niche, geeky and exclusive. Enabling embedding is an… [Continue Reading] -

Chinese government manipulates social media with nearly half a billion fake posts per year
Publié: mai 20, 2016, 11:09am CEST par Mark Wilson
China's control over access to the internet is hardly a secret, but the government is not just interested in using the famous Great Firewall of China to limit what its citizens can see. State monitoring of internet usage is very common, and the government also has a propaganda machine in place, manipulating the country via the web. A new study by researchers at Harvard University suggests that governmental interference online could be even more prolific than first thought. Social media has been infiltrated and is believed to have been taken over by paid trolls whose job it is to inject… [Continue Reading] -

Windows 10 Anniversary Update will improve interoperability between Microsoft Edge and IE 11
Publié: mai 20, 2016, 12:03am CEST par Mark Wilson
Since the release of Windows 10, the update of Microsoft Edge has been a little on the slow side. The addition of support for add-ons may help to increase the user base for Edge, but many enterprise customers still have a need for Internet Explorer. When building Edge from scratch, Microsoft included Enterprise Mode to allow sites that rely on older technology to open with Internet Explorer 11 instead. With the upcoming release of Windows 10 Anniversary Update improvements are being introduced that will smooth out some of the rough edges of Enterprise Mode, including removing the friction that currently… [Continue Reading] -

Google makes Chromebooks exciting again by adding Google Play and Android apps
Publié: mai 19, 2016, 9:41pm CEST par Mark Wilson
Much like Windows Mobile, Chromebooks have long suffered with something of a limited range of apps. Starting today, all this changes; Google is bringing the full range of Android apps to Chromebook users via the Google Play store. With Chromebooks having just overtaken Macs in terms of popularity, the introduction of millions of Android apps to the platform is incredibly well-timed. Before you get too excited, the rollout is not immediate. Users on the developer channel with certain Chromebook models will get access first, but there are plans to bring Google Play to more devices over the coming months. The… [Continue Reading] -

Cortana update brings Android notifications to Windows 10 users
Publié: mai 19, 2016, 12:03pm CEST par Mark Wilson
The ability to view notifications for multiple devices in one place is something that has been tried in various forms before. Now fans of Cortana can take advantage of notifications about their phone on their computer. The latest version of the Cortana Android app brings the previously hinted at app notification syncing that users have been asking for for so long. First noted by a Windows 10 user on Reddit, the feature is something that we can expect to see included in the Windows 10 Anniversary Update later this summer. The Reddit thread reveals that version 1.7.0.1021-enus-release of Cortana for… [Continue Reading] -

TeslaCrypt ransomware shuts up shop and releases free decryption key for everyone
Publié: mai 18, 2016, 11:58pm CEST par Mark Wilson
Ransomware is not exactly a new problem, but it's one that seems to be getting increasingly serious. Every week there's a new high profile attack out there including the likes of CryptXXX and PETYA. One of the biggest names, TeslaCrypt, has suddenly thrown in the towel and offered up a free decryption key for its victims. The surprise move comes just a couple of months after version 4 of TeslaCrypt gained what was described as "unbreakable encryption". The closure is somewhat bittersweet. The shutdown comes as attackers switch to using CryptXXX instead, but perhaps the most surprising aspect is the… [Continue Reading] -

Google Home is a voice-activated Echo rival
Publié: mai 18, 2016, 8:27pm CEST par Mark Wilson
Today at Google I/O, the search giant unveiled its Amazon Echo-baiting Home. Google Home is ostensibly a cylindrical speaker with an angled top featuring Google's iconic four colors. Far-field voice recognition allows you to issue commands to the device to control everything from music playback to look up something online. Google's latest foray into the Internet of Things is much more than just a Wi-Fi speaker -- although it will function perfectly well in the role. Just like the voice-activated options in Android, Home can be used to set alarms and reminders, and can even be connected to other smart… [Continue Reading] -

Microsoft rolls out new-look Store to Windows 10 Redstone Build 14342
Publié: mai 18, 2016, 1:37pm CEST par Mark Wilson
Microsoft continues to try to stir up interest in Store in Windows 10. Insiders who have installed Windows 10 Build 14342 are now being treated to an updated version of the Window Store app complete with a batch of new features. This update is about not only changing the overall Store experience, but also pushing apps more than ever. The new look mimics that of the updates Store in Windows 10 Mobile and it goes some way to improving usability and ironing out irritations. One of the key new options is the ability to hide apps that you have previously… [Continue Reading] -

Google launches Android Pay in the UK
Publié: mai 18, 2016, 12:37pm CEST par Mark Wilson
After a successful launch in the US, Google has now debuted its contactless payment service Android Pay in the UK. If you're packing an NFC-enabled smartphone running Android 4.4 or higher, you can now make payments in a number of stores -- as well as Transport for London -- with just a tap. For payments under £30, there's no need to unlock your phone, and Google says that the number of supported banks and retailers will expand over the coming months. At the moment, support is limited to Mastercard and Visa credit and debit cards from Bank of Scotland, First… [Continue Reading] -

Microsoft just tried to use Windows 10 to trick me into using Skype with a random account
Publié: mai 17, 2016, 11:42am CEST par Mark Wilson
So there I was, typing away after using a couple of coffees to make myself feel vaguely human. Up popped a notification from Skype. This was odd. I don’t use Skype because I absolutely loathe it. The app isn’t even running. Nonetheless, there it is: a notification telling me that I have been signed into my account. While I don’t use Skype, I do have a Skype username from back in days gone by -- but this wasn't the account Windows 10 told me I had been signed into. Rather it appeared that Microsoft had created a secondary Skype account… [Continue Reading] -

Microsoft expands Windows Defender Advanced Threat Protection Preview to more enterprise users
Publié: mai 17, 2016, 10:43am CEST par Mark Wilson
Security is one of the features of Windows 10 that Microsoft has been particularly eager to highlight. It's something that's important to everyone, but especially enterprise customers. Earlier in the year the company launched a preview of Windows Defender Advanced Threat Protection, and now this is being made available to a wider audience. The program is still in the testing phase at the moment, but Microsoft is looking for feedback from IT professionals and enterprise customers. Although this is described as a public preview, would-be participants are required to register their interest and their applications are subject to approval. Microsoft… [Continue Reading] -

The Intercept cracks open the Snowden archive including internal NSA newsletters
Publié: mai 16, 2016, 8:56pm CEST par Mark Wilson
There can be few people who have had such an impact on people's perception of the government as Edward Snowden. Having exposed the convert spying activities of the NSA, he opened up a worldwide debate about privacy and surveillance that is still going on today. His revelations have shaped public opinion and changed the course of history. Just as the likes of the Guardian have already helped to educate the world about what the NSA has been doing, so The Intercept is releasing a huge cache of internal NSA documents that give an intriguing insight into the agency's operations. The… [Continue Reading] -

Google launches Spaces for sharing links, YouTube videos, images and more with small groups
Publié: mai 16, 2016, 5:10pm CEST par Mark Wilson
Google is introducing a new way to share content with a group. Spaces is a collaborative tool that Google wants people to use to share everything from articles and images to YouTube videos and messages. So keen is Google for a huge take up of Spaces, that the service is launching in mobile and desktop web versions, as well as iOS and Android apps. It's billed as an alternative to group conversations, and Google wants to help streamline sharing by eliminating app switching -- this is achieved by integrating Google Search, YouTube, and Chrome into a single tool. Spaces can… [Continue Reading] -

Google launches Spaces for sharing links, YouTube videos, images and more with small groups [UPDATE: It's live!]
Publié: mai 16, 2016, 5:10pm CEST par Mark Wilson
Google is introducing a new way to share content with a group. Spaces is a collaborative tool that Google wants people to use to share everything from articles and images to YouTube videos and messages. So keen is Google for a huge take up of Spaces, that the service is launching in mobile and desktop web versions, as well as iOS and Android apps. It's billed as an alternative to group conversations, and Google wants to help streamline sharing by eliminating app switching -- this is achieved by integrating Google Search, YouTube, and Chrome into a single tool. Spaces can… [Continue Reading] -

GCHQ arrives on Twitter to give a more public face to the spy agency
Publié: mai 16, 2016, 2:17pm CEST par Mark Wilson
The UK's GCHQ -- like its US counterpart the NSA -- is an agency traditionally shrouded in secrecy. Tasked with the job of spying on all and sundry in the name of intelligence gathering, the agency has just joined Twitter, greeting other users with an unoriginal "Hello, world". With the concerns about privacy and security that blew up in the wake of Edward Snowden's NSA surveillance revelation, spy agencies around the world have been on a mission to boost their public image. GCHQ -- complete with the blue tick reserved for verified accounts -- will use Twitter to "provide news,… [Continue Reading] -

Microsoft is working on a tool to simplify clean installations of Windows 10
Publié: mai 16, 2016, 12:49pm CEST par Mark Wilson
While Microsoft has gone to great lengths to make it as easy as possible to upgrade from Windows 7 and Windows 8.1 to Windows 10, purists will always prefer to opt for a clean installation. For seasoned Windows users, performing a clean install of Windows 10 is easy enough, but that's not true for everyone. Acknowledging the fact that clean installations are not a piece of cake for all, Microsoft is beavering away on a new tool to simplify the process. Windows Insiders will be able to try it out before anyone else, and give feedback to help shape the… [Continue Reading] -

Google to block Flash in Chrome and default to HTML5 except for these ten white-listed sites
Publié: mai 16, 2016, 12:22pm CEST par Mark Wilson
By the end of 2016, Google aims to switch Chrome users away from Flash in favor of HTML5. The writing has been on the wall for Flash for some time now, with a seemingly endless torrent of security issues pushing increasing numbers of people toward HTML5. Google says that by Q4 2016, it wants to make HTML5 the primary user experience. Flash support will still be built into the browser, but it will be disabled by default. Ten sites, however, will be given a year's reprieve. Google is choosing to make exception for the ten most popular sites that use… [Continue Reading] -

You'll still be able to hack Linksys WRT routers with open source firmware despite new FCC rules
Publié: mai 15, 2016, 9:51pm CEST par Mark Wilson
In a little over two weeks, new rules will come into play that pose something of a threat to people who like to install open source firmware on their routers. The Federal Communications Commission is implementing guidelines designed to prevent users from modifying their routers in such a way that would make them operate outside of their licensed frequency range and interfere with other devices. Many router manufacturers have opted for the easy way out, and decided to simply completely block (or continue to block) the installation of third party, open source firmware. Not so with Linksys. The company has… [Continue Reading] -

Torrent site The Pirate Bay loses thepiratebay.se and piratebay.se domain names
Publié: mai 15, 2016, 1:32pm CEST par Mark Wilson
The Pirate Bay is no stranger to court cases, and the site has just lost another one in Sweden. A Swedish court has ruled that the torrent site's thepiratebay.se and piratebay.se domain names must be handed over to the state. The two domains have been confiscated after a judge at the Court of Appeal decided that they were being used to (gasp!) commit crimes under the Copyright Act. It is unlikely that the ruling will have much effect on The Pirate Bay's operations as it already has numerous other domain names to fall back on. But there is no denying… [Continue Reading] -

Windows 10 Anniversary Update will bring even more deceptive app ads to the Start menu
Publié: mai 15, 2016, 1:02pm CEST par Mark Wilson
When Microsoft first introduced the idea of 'promoted apps' to the Windows 10 Start menu, it was decried by many as little more than pushing ads at users. If you found yourself among those upset by the appearance of links to apps you may have a vague interest in, things could be about to get a whole lot worse. Later this summer Microsoft is releasing a major update to Windows 10 in the form of the Windows 10 Anniversary Update. In July the update will be released to the masses -- although Insiders have the chance to try it out… [Continue Reading] -

Microsoft pulls the plug on Project Spark
Publié: mai 14, 2016, 3:35pm CEST par Mark Wilson
Out of the blue, Microsoft has announced that Project Spark is closing down. The Xbox One experiment which made it possible for just about anyone to create and publish games is to be killed off "after much consideration". The service will be completely offline by 12 August meaning that after this date it will no longer be possible to upload or download content. Microsoft stopped development of Project Spark last year, but users had hoped that it would just be left to its own devices; this sunset announcement means that this is no longer the case. Microsoft advises users to… [Continue Reading] -

Microsoft implements a blanket ban on computer support ads on Bing
Publié: mai 14, 2016, 3:12pm CEST par Mark Wilson
Microsoft is following in Google's footsteps and cleaning up the ads that can be displayed on its network. After Google announced that AdWords could no longer be used to push payday loans, Microsoft has decided to ban ads for computer support services from Bing. What's interesting here is that Microsoft has taken an incredibly hard line and issued a complete blanket ban on all technical support ads -- no exceptions. The aim is to weed out fake support ads and scams, but it will also impact on legitimate services. The change to policy now states that: "Bing Ads disallows the… [Continue Reading] -

Belgian police warn that Facebook Reactions pose a serious privacy risk
Publié: mai 13, 2016, 5:38pm CEST par Mark Wilson
Police in Belgium are warning people not to use Facebook Reactions because of the risk they pose to privacy. Introduced recently to supplement the iconic Like option, Reactions give Facebook users the chance to respond to content with Love, Haha, Wow, Sad, and Angry emoji. But Belgian police have issued a 'Safe Browsing' warning advising that Facebook is using Reactions to gather information about social network users. Specifically, the police warn that in using Reactions to express emotions, users are giving Facebook the opportunity to build up a more detailed personal profile about them and use that information to deliver… [Continue Reading] -

UK ebook sales drop for the first time
Publié: mai 13, 2016, 2:21pm CEST par Mark Wilson
It seems that our love affair with ebooks could be turning sour. For the first time since digital book sales were recorded, the number of ebooks sold in the UK dropped in 2015. The drop could be partly explained by the fact that we seem to be reading less in recent years. While sales of printed books rose by 0.4 percent according to the Publishers Association, digital book sales declined by 1.6 percent. The increased popularity of printed books has been driven in part by an explosion in adult colouring books. Audio books have also increased in popularity, with 2015… [Continue Reading] -

Mark Zuckerberg wants to talk to conservatives about Facebook's trending news bias
Publié: mai 13, 2016, 1:17pm CEST par Mark Wilson
After a delay of a few days, Facebook CEO Mark Zuckerberg has jumped to the defence of this social network and its handling of news. Following accusations that trending stories are manipulated to bury right wing news, Facebook has scrambled to play down suggestions of political bias -- something that will be increasingly important as the Trump and Clinton battle comes to a conclusion later in the year. Zuckerberg felt compelled to respond to the accusations in a post on Facebook, reiterating the previous statement that there are "rigorous guidelines" in place that "do not permit the prioritization of one… [Continue Reading] -

Leaked documents show how Facebook manipulates trending news
Publié: mai 13, 2016, 1:00pm CEST par Mark Wilson
Facebook has faced accusations of interfering with the headlines that appear in Trending Topics, censoring conservative stories. While admitting to a left wing bias in Silicon Valley, the social network has denied supressing the appearance of right wing news. However, leaked internal documents show that there is a very structured and controlled process in place that sees employees -- rather than algorithms -- influencing the news that Facebook users see. The documents reveal that there is an editorial team in place, with stories being ranked and promoted by hand. Perhaps just as worrying is the revelation that a very small… [Continue Reading] -

Mozilla asks the FBI for details of Tor vulnerability that could also affect Firefox
Publié: mai 12, 2016, 4:05pm CEST par Mark Wilson
Mozilla is fighting to force the FBI to disclose details of a vulnerability in the Tor web browser. The company fears that the same vulnerability could affect Firefox, and wants to have a chance to patch it before details are made public. The vulnerability was exploited by FBI agents to home in on a teacher who was accessing child pornography. Using a "network investigative technique", the FBI was able to identify the man from Vancouver, but Mozilla is concerned that it could also be used by bad actors. Perhaps unsurprisingly, the government says that it should be under no obligation… [Continue Reading] -

Google slaps an AdWords ban on payday loans and other high interest finance services
Publié: mai 12, 2016, 3:28pm CEST par Mark Wilson
In recent years Google has started to tighten up on the products that can be promoted through its services. After cracking down on porn, the latest victims of the ban hammer are payday loans and other high interest finance services. Starting July 13, it will no longer be possible to advertise such products through AdWords. Ads for loans with repayment deadlines of under two months are now outlawed, as are ads for loans with high interest rates. Google says that the ban is part of a drive to protect users from what it describes as "misleading or harmful products". Introducing… [Continue Reading] -

Microsoft brings unlocked frame rates, FreeSync and G-Sync to UWP games with Windows 10 update
Publié: mai 10, 2016, 11:03pm CEST par Mark Wilson
Gamers can be a demanding bunch, and in many regards Windows 10 has been something of a disappointment as a gaming platform. While Microsoft has used Windows 10 to merge the worlds of PC and Xbox One gaming, Universal Windows Platform (UWP) games have been somewhat crippled by crappy frame rates. Today this changes. Microsoft is pushing out an update that allows developers to take advantage of unlocked frame rates in UWP titles just as they can with Win32 games. In addition to ramping up frame rates, the update means that developers will also be able to take advantage of… [Continue Reading] -

Facebook admits there is a left wing bias in Silicon Valley
Publié: mai 10, 2016, 5:52pm CEST par Mark Wilson
Facebook may be insisting that its news curators are not suppressing right-wing stories, but a senior executive is willing to admit that Silicon Valley as a whole is rather left-leaning. Alex Schultz, vice president of growth at the social network, says: "There is definitely a left-wing bias to any company based in San Francisco". He made the comments at a LGBT discrimination conference, joking that "a Republican may be the most at-risk diversity at Facebook". It may not come as the biggest surprise in the world to hear that Silicon Valley is rather more liberal than other areas and sectors,… [Continue Reading] -

India has mobile forensic tools to hack into iPhones
Publié: mai 10, 2016, 5:02pm CEST par Mark Wilson
The case of the FBI seeking to force Apple to provide backdoor access to the San Bernardino shooter's iPhone focused attention on security and encryption once again. The agency may have been able to gain access to the phone with help from a third party, but the Indian government has gone one better. Communications Minister Ravi Shankar Prasad has revealed that the government has a tool that can be used to gain access to, among other devices, Apple's iPhone. This is not to say that a tool has been created that bypasses encryption, rather that a method for getting past… [Continue Reading] -

Facebook denies censoring right wing news from Trending Topics
Publié: mai 10, 2016, 12:25pm CEST par Mark Wilson
Having been hit with allegations of censoring news from conservative outlets, Facebook has issued a strenuous denial. Gizmodo reported claims from former Facebook "news curators" that they were directed to not only suppress news from right wing sources, but also to "inject" stories into Trending Topics regardless of their actual popularity. Suggestions that its Trending Topics are driven by a liberal agenda have been denied by Facebook. The social network says it "found no evidence that the anonymous allegations are true", going on to say that while there is a review team in place, its guidelines "do [not] permit the… [Continue Reading] -

Think Android security updates take too long to roll out? So do the FTC and FCC
Publié: mai 10, 2016, 11:19am CEST par Mark Wilson
Both the Federal Communications Commission (FCC) and Federal Trade Commission (FTC) are starting to ask the questions that Android users have been asking for years: why do updates and upgrades take so long to roll out? If you're in possession of a flagship or recent handset, the chances are you're in line to receive timely updates for the foreseeable future. But Android's fragmentation means that older handsets quickly drop off the radar, get forgotten and remain unpatched. The FCC and the FTC both want to know why security patches are slow to hit phones, and the agencies have launched separate,… [Continue Reading] -

Microsoft Edge users can now install Adblock Plus or AdBlock extensions
Publié: mai 8, 2016, 7:00pm CEST par Mark Wilson
Extensions, or the lack thereof, have been stumbling block for many would-be Microsoft Edge users. Support for add-ons has finally arrived, bringing with it the potential for something people have been asking for since Edge first appeared -- the ability to block ads. It had previously been thought that Edge might feature native ad blocking, but this turned out to be a matter of poor communication from Microsoft. We've already shown you a slightly bodged-together way of blocking ads in Edge, but now Adblock Plus and AdBlock extensions have been officially released to the Windows Store. Both extensions are available… [Continue Reading] -

Microsoft confirms Windows 10 will remain free for people with accessibility needs
Publié: mai 8, 2016, 12:45pm CEST par Mark Wilson
The free ride is coming to an end. Windows 10 was always going to be free for the first year after release, and this year is up on 29 July. There are, of course, still ways to get your hands on Windows 10 for free beyond this date. One way is to buy a new PC with Windows 10 installed, although not many people would regard this as a free upgrade. But Microsoft has also confirmed that people with accessibility needs will still be able to upgrade to Windows 10 for free after the deadline. Writing on its Accessibility Blog, Microsoft… [Continue Reading] -

Broadband is not an automatic right in rural areas of the UK
Publié: mai 8, 2016, 11:47am CEST par Mark Wilson
While most of the UK enjoys fast (or superfast if you want to swallow the rhetoric) broadband, there are still numerous pockets plagued with dial-up speeds. Talks had been underway between the government and broadband providers about whether the aim of providing broadband access to 95 percent of the country by the end of 2017 was ambitious enough. But it is the remaining 5 percent that’s concerning. 95 percent coverage might sound impressive, but 5 percent of the population is still a huge number of people. The government has now decided that broadband is not a right to which households… [Continue Reading] -

Malware takes advantage of Windows' God Mode hack to slip past security
Publié: mai 5, 2016, 5:27pm CEST par Mark Wilson
The so-called God Mode hack for Windows is rather less grand than it might first sound. Rather than granting users deity-like abilities, it simply provides one-folder access to an absolute butt-load of Control Panel options and settings. But security researchers have discovered that the technique used to create this special folder can also be exploited by malware. McAfee says that while the Easter Egg is great for power users, it is also being used by attackers for "evil ends". By placing files within the God Mode shortcut folder, malware such as Dynamer is able to run undetected on a victim's… [Continue Reading] -

'Weak' Craig Wright backs out of Bitcoin claim
Publié: mai 5, 2016, 4:02pm CEST par Mark Wilson
Craig Wright, the main claiming to be Bitcoin inventor Satoshi Nakamoto has started to backpedal on his claim. There has long been speculation about the identity of the person behind the cryptocurrency, and earlier this week Wright stepped up to the plate. After doubts had been expressed about his claim to the Bitcoin crown Wright had promised to reveal "extraordinary evidence" as proof. But now he has had a change of heart. He's not saying -- yet -- that he's not Satoshi Nakamoto, but that he does "not have the courage" to publish the proof so many people are demanding… [Continue Reading] -

Microsoft prevents Windows 10 Pro admins from blocking access to the Windows Store
Publié: mai 5, 2016, 12:03pm CEST par Mark Wilson
Microsoft has castrated some of the capabilities of Windows 10 Pro admins looking to lock down the computers they manage. The company is removing the ability to block access to the Windows Store using Group Policy Editor. The option will still be available to those running Education or Enterprise versions of Windows 10. It means that businesses who have come to rely on this option as part of their security regime will have to consider upgrading to a different version of Windows 10. Microsoft is understandably keen to encourage as many people as possible to make use of the Windows… [Continue Reading] -

Hacker leaks millions of Hotmail, Gmail, and Yahoo Mail usernames and passwords
Publié: mai 4, 2016, 9:23pm CEST par Mark Wilson
A number of major webmail services have suffered one of the largest security breaches in recent years. The account details of Gmail, Yahoo Mail, Hotmail, and Mail.ru are just four of the services affected. Security firm Hold Security says that it has been contacted by a hacker in possession of 272 million unique pairs of email addresses and unencrypted passwords. This is far from an insignificant number, and the situation is made all the worse as the data is being freely shared for just about anyone to access. Hold Security says that it was initially contacted by the hacker who… [Continue Reading] -

After all the fuss about Facebook reactions, hardly anyone is using them
Publié: mai 4, 2016, 9:05pm CEST par Mark Wilson
It is as though people have been asking for something more than the Like button on Facebook since the concept was first born. After years of asking, Facebook delivered. Facebook Reactions arrived at the end of February to much excitement. But the excitement was short-lived, it seems. Two months after launch a study has found that hardly anyone is making use of the five new options (Love, Haha, Wow, Sad, and Angry). Analysis by Quintly reveals that Reactions account for a mere 3 percent of interactions, and the findings make for interesting reading. Although there had been a great deal… [Continue Reading] -

The ransomware problem just keeps getting worse and worse
Publié: mai 4, 2016, 12:53pm CEST par Mark Wilson
If it feels as though you've heard an awful lot about ransomware recently, that's because you have. It's a problem that just seems to be getting worse, and ESG -- the security outfit behind anti-malware program SpyHunter -- has released figures that shows April was the worst month ever recorded for ransomware in the US. The rate of infection rocketed last month, with the numbers more than doubling when compared to March. While there have been a few high-profile cases of large businesses getting hit with ransomware, increasing numbers of ordinary people are also falling victim. The reason for the… [Continue Reading] -

Adblock Plus and Flattr help sites earn money from donations even if visitors block ads
Publié: mai 3, 2016, 9:00pm CEST par Mark Wilson
Adblock Plus has for some time tried to find a way to balance the needs of websites to display money-making ads, with the preferences of visitors who do not want to see such ads. After experimenting with its Acceptable Ads program whereby some discrete ads are allowed to slip through the net, Eyeo, the company responsible for Adblock Plus, is teaming up with Flattr to give sites another way to make money. The scheme is called Flattr Plus, and it gives people the chance to pay a monthly subscription to access content on sites. It's a similar idea to an… [Continue Reading] -

After the death of @MagicRecs, Twitter Connect makes it easier to find people to follow
Publié: mai 3, 2016, 7:09pm CEST par Mark Wilson
It was a sad day on Twitter when one of most useful accounts, the @MagicRecs bot, was closed down. The experimental service had been firing account recommendations at users based on who they follow, but the experiment came to an end. As something of a replacement, Twitter is introducing a Connect tab to its iOS and Android clients. The company says it will make it easier to find people to follow, and will come up with recommendations based on who you already follow, how you use Twitter, and what's proving popular with other people. If the feature sounds a little… [Continue Reading] -

Think Privacy CEO launches site to name publishers who illegally detect and circumvent adblockers
Publié: mai 2, 2016, 9:33pm CEST par Mark Wilson
Adblockers are, have been, and will continue to be a matter of some controversy. While sites rely on ad income to stay afloat, users are understandably irked by a barrage of flashy commercials and are increasingly turning to adblocking. To fight back, some sites are using various methods to detect the presence of an adblocker and then bypassing it. This, in turn, upsets people once again, and the CEO of privacy and security consortium Think Privacy, Alexander Hanff, has come up with a solution. To fight back he has set up a website that names and shames those sites that… [Continue Reading] -

Bitcoin creator Satoshi Nakamoto revealed to be Australian entrepreneur Craig Wright
Publié: mai 2, 2016, 1:20pm CEST par Mark Wilson
For some time, the person who created the cryptocurrency Bitcoin has been known as Satoshi Nakamoto. We know that was nothing more than a pseudonym, and now Australian entrepreneur Craig Wright has revealed that he is the man behind the mask. It brings to an end years of speculation about the inventor's real identity, and Wright has been able to provide technical proof to the BBC to back up his claims. The IT and security consultant's home was raided in recent days as part of an investigation by the Australian Tax Office, and documents leaked from the inquiries pointed towards… [Continue Reading] -

Facebook Messenger to gain privacy-enhancing self-destructing messages
Publié: mai 2, 2016, 12:03pm CEST par Mark Wilson
With the ongoing debate about privacy and encryption, the rollout of end-to-end encryption to Facebook-owned WhatsApp came as little surprise. Now Facebook Messenger is set to gain a couple of privacy-enhancing features including self-destructing messages. Already found in other messaging tools such as SnapChat and Telegram, self-destructing messages have been unearthed in Messenger for iOS version 68.0. As you would expect, the feature makes it possible to place a time limit on how long messages are visible for, making it ideal for communicating sensitive information. SEE ALSO: WhatsApp's end-to-end encryption is not all it's cracked up to be As reported by VentureBeat,… [Continue Reading] -

Windows 10 growth slows as OS X makes market share gains
Publié: mai 1, 2016, 2:25pm CEST par Mark Wilson
The growth of Windows 10 continues, albeit slowly, the latest figures from NetMarketShare show. The statistics for April reveal that, at long last, Windows 7 is no longer installed on the majority of computers, slipping to a 48.79 percent market share. Windows 10 saw slight growth to 14.35 percent (up from 14.15 percent), and Windows XP dropped below 9.66 percent. Usage of Windows 8.x stayed largely stable (12.11 percent compared to 12.01 percent in March), but the balance between Windows 8 and Windows 8.1 (9.16 percent down from 9.56 percent) shifted slightly, with the older version seeing slight growth (2.95… [Continue Reading] -

Facebook hit with lawsuit over new stock option that gives Zuckerberg a license to print money
Publié: avril 30, 2016, 4:01pm CEST par Mark Wilson
When Facebook announced its first quarter results this week, it also announced that it created a new class of stock. The non-voting Class C stock proposed would enable Mark Zuckerberg and his wife Priscilla Chan to more easily fund their philanthropic ventures, whilst keeping Zuckerberg himself firmly in control of Facebook. In response to this, a lawsuit has been raised that says the proposed deal is unfair. The shareholders raising the class action lawsuit said the deal would grant Zuckerberg even more control and that the board committee didn’t do enough "to obtain anything of meaningful value" in return. The… [Continue Reading] -

Apple: You're saying it wrong -- iPhones is not a word!
Publié: avril 30, 2016, 12:50pm CEST par Mark Wilson
Apple's marketing chief Phil Schiller has taken to Twitter to set the record straight about the nomenclature of the company's product names. Specifically, he takes umbrage with just sticking an 's' onto the end of product names to pluralize them. Yep -- iPhones is, apparently, not a word. Someone might need to speak with Tim Cook to get him on the same page though, as he doesn't seem to have seen the memo. Schiller goes as far as saying that there is simply no need to ever pluralize the name of any Apple product. If you've been referring to iPhones,… [Continue Reading] -

Twitter's unfair token system gives it far too much control over rival apps
Publié: avril 30, 2016, 11:40am CEST par Mark Wilson
In recent days you probably heard about the demise, and subsequent resurrection, of the Twitter client Fenix. Earlier this week, the app became a victim of its own success, succumbing to what it described as "the infamous Twitter tokens limitation". It's now back in the Google Play Store having carved out some sort of deal with Twitter, but the debacle highlights an important issue. If you want to create a Twitter client -- and why wouldn’t you? -- you'll need access to the Twitter API. This is not something Twitter wants, or permits, to just be a free-for-all, and it… [Continue Reading] -

A company reborn: Intel ditches Atom chips to focus on the cloud, the Internet of Things and 5G
Publié: avril 29, 2016, 11:09pm CEST par Mark Wilson
Big changes are afoot at Intel. A spokeswoman has confirmed that the company is scrapping its Sofia and Broxton mobile Atom chips, and will instead shift focus to more profitable ventures. Having invested billions of dollars in Atom for smartphones and tablets Intel is now switching its attention to the world of connected devices. Giving Atom chips the chop comes just after the company announced 12,000 job cuts and effectively walked away from the PC market. In moving away from mobile devices as well, Intel is undergoing a rebirth. It is looking to focus on key areas of growth, particularly… [Continue Reading] -

Qbot malware resurfaces with renewed powers ready to steal your banking credentials
Publié: avril 29, 2016, 7:32pm CEST par Mark Wilson
Qbot -- also known as Qakbot -- is a form of malware that's been around for a number of years, but security researchers at Cisco Talos have noted that it has returned with a vengeance. Once installed the malware steals sensitive data stored in files and cookies, and also monitors live web sessions to grab login credentials. Detection and immunization is made difficult thanks to the fact that Qbot uses random strings, code blocks, file names and encryption keys to slip under the radar, although it can still be detected by its behavior. Cisco Talos analyzed no fewer than 618… [Continue Reading] -

Microsoft takes just 7 hours to patch colossal Office 365 vulnerability that exposed companies' data
Publié: avril 29, 2016, 1:44pm CEST par Mark Wilson
Companies are often criticized for the length of time it takes them to patch security problems found in software. But this week Microsoft exceled itself, taking just 7 hours to patch a serious security hole in Office 365 that made it possible to gain unrestricted access to businesses' cloud accounts. A problem with the SAML authentication system meant that it was possible to gain access to just about any Office 365 account, including accessing connected services like Outlook, OneDrive and Skype for Business. More than this, the exploit allowed an attacker to infiltrate companies and organizations such as Verizon, Georgia… [Continue Reading] -

Facebook transparency report shows increase in government data requests, most with gagging orders
Publié: avril 29, 2016, 1:14pm CEST par Mark Wilson
Facebook has published its latest Global Government Requests Report covering the second half of 2015. The transparency report reveals that there has been as 13 percent increase in the number of government requests for data, but it also shows that Facebook is still not able to be as transparent as it might want. For the first time the social network is able to report about the number of data requests that have a non-disclosure order attached to them. More than half of the requests -- 60 percent, in fact -- have gagging orders that prevent Facebook from notifying users about… [Continue Reading] -

Developers have a new Windows 10 Anniversary Update SDK Preview to play with
Publié: avril 28, 2016, 9:21pm CEST par Mark Wilson
With the new big update to Windows 10 just around the corner, Microsoft is pulling out all the stops to make sure that developers have access to the tools they need to take advantage of the new features. Windows 10 Anniversary Update is due for release in July and ahead of the big day Microsoft has released a new SDK. Having open-sourced the Xamarin iOS, Android and Mac SDKs, the launch of the Windows 10 Anniversary Update SDK Preview gives developers a chance to make sure their code works ahead of the update rollout. It is compatible with Build 14332… [Continue Reading] -

Human rights group Liberty rips into Snooper's Charter with video highlighting privacy issues
Publié: avril 28, 2016, 8:01pm CEST par Mark Wilson
The Snooper's Charter -- or the Investigatory Powers Bill -- is a highly controversial piece of legislation the UK government is trying to bring into force to allow for the bulk collection of data, NSA-style. Outside of government, it is widely regarded as a massive invasion of privacy, and the human rights group Liberty is just one of the organizations that is very vocally opposed to it. The bill will require ISPs to record customers' browsing histories for an entire year, and will permit the government to remotely hack phones and computers, as well as requiring tech companies to provide… [Continue Reading] -

FBI won't tell Apple how it hacked San Bernardino iPhone as it doesn't understand the technique
Publié: avril 28, 2016, 11:43am CEST par Mark Wilson
Apple had been hoping that the FBI would come clean about how it managed to gain access to the San Bernardino iPhone, but that's just not going to happen. The agency managed to crack the iPhone 5C at the center of the case after getting help from a third party rather than Apple. But now the FBI has confirmed that it doesn't really know how the cracking tool works. Or, more precisely, it did not buy the rights to the technical details of the tool. After a very public battle with Apple, the FBI ultimately resorted to getting help from… [Continue Reading] -

Amazon held to account for billing parents for in-app purchases made by their kids
Publié: avril 28, 2016, 11:17am CEST par Mark Wilson
A federal judge has ruled that Amazon is liable for sending out bills to parents of children who made in-app purchases without permission. Amounting to millions of dollars, the bills have now been deemed unauthorized, and Amazon faces having to pay back a large percentage of the money. The case has echoes of similar legal action brought against Google and Apple for purchase made by children in the App Store and Google Play. Amazon, Apple and Google have all implemented system to prevent unauthorized purchases since being investigated by the FTC back in 2014. The FTC is seeking full refunds… [Continue Reading] -

Microsoft makes Xamarin SDKs for Android, iOS and Mac open source
Publié: avril 27, 2016, 6:18pm CEST par Mark Wilson
Microsoft's embracing of the open source movement grows ever tighter, and today the company announced that its Xamarin SDKs (available for Android, iOS and Mac) will be open sourced. It's not long since Microsoft bought Xamarin, and just weeks later the SDKs are being opened up. Announced at the Xamarin Evolve 2016 event, the move sees Microsoft trying to encourage mobile developers. The company says it has already made great strides in this area: "we helped nearly 3.5 times more developers get started building great apps with Xamarin than ever in our history as a company". The Xamarin SDK has… [Continue Reading] -

Google antitrust: Getty Images files complaint against search giant for image scraping and piracy promotion
Publié: avril 27, 2016, 5:30pm CEST par Mark Wilson
Google is already embroiled in one antitrust case in Europe where the company stands accused of abusing Android's dominance. Now photo agency Getty Images is accusing Google of promoting piracy and engaging in anticompetitive behavior by 'scraping' images from third party sites. In a familiar-sounding complaint, Getty Images also says that Google skews search results in favor of its own services -- such as Google Images. The photo agency says that this directly impacts upon rival services, but perhaps the big charge is that a change made to Google Images provided access to copyrighted material and "promoted piracy, resulting in… [Continue Reading] -

Remove CryptXXX ransomware with Kaspersky's free decryption tool
Publié: avril 27, 2016, 2:16pm CEST par Mark Wilson
Security firm Kaspersky has released a tool that can be used to decrypt files on computers hit by the CryptXXX ransomware. Rather than paying the ransom demanded to regain access to files, victims are now able to turn to the free RannohDecryptor utility. CryptXXX had been identified by ProofPoint earlier in the month and described as being closely linked to the Reveton ransomware operation and Angler/Bedep. The ransom of $500 is considered to be quite high, but Kaspersky's free decryption tool means that files can be retrieved without having to part with a cent. CryptXXX uses RSA4096, but Kaspersky's John… [Continue Reading] -

Dropbox previews Project Infinite to blur the boundaries between the cloud and local storage
Publié: avril 26, 2016, 1:20pm CEST par Mark Wilson
At its Dropbox Open in London, Dropbox unveiled a preview of its new Project Infinite technology. At its heart, it's a simple idea. Regardless of whether files have been synced to a device or not, they will show up in Dropbox on the desktop. The aim is to reduce the reliance on browser-based tools which can slow down workflow. It allows for collaborators to gain instant access to files their co-workers have shared with them and allows files stored in the cloud to be treated in the same way as those stored locally. It's being promoted as a useful tool… [Continue Reading] -

Nokia to splash out $191 million on health and wearables firm Withings
Publié: avril 26, 2016, 11:13am CEST par Mark Wilson
Nokia used to be a name associated with smartphones but now the Finnish company is looking to venture into a different area of the mobile device market. Today the company announced plans to acquire French health, fitness and wearables firm Withings for €170 million ($191 million). Withings will join Nokia Technologies as the former smartphone manufacturer branches out into the Internet of Things and the lucrative health market. The acquisition will be settled in cash, and is expected to be completed by Q3 this year. Ramzi Haidamus, president of Nokia Technologies, said: "Withings shares our vision for the future of… [Continue Reading] -

Twitter makes it easier to report abusive tweets en masse
Publié: avril 25, 2016, 8:23pm CEST par Mark Wilson
There has been a lot of interest in online abuse in recent months, and social networks are taking steps to weed out the trolls and abusers. Twitter has already introduced a number of measures to help tackle trolls, and today announces the availability of a new reporting tool for users. Now rather than having to report a number of abusive tweets individually, it is possible to report up to five tweets simultaneously. As well as reducing the workload for someone who feels the need to report content, the new tool also makes things easier for Twitter as it allows for… [Continue Reading] -

US cyberbombs ISIS in renewed tech warfare
Publié: avril 25, 2016, 5:55pm CEST par Mark Wilson
ISIS has been able to gain notoriety not only because of the atrocities committed, but through incredibly careful and calculated use of technology in general and the internet specifically. The likes of Twitter and Facebook have been embroiled in an on-going battle against terrorist social media accounts, and now the US military is taking the fight online as well. Cyber Command is waging cyber war on Islamic State, trying to cyberbomb the terrorist organization into submission and prevent it from recruiting or spreading propaganda online. Using information gathered from the NSA, Cyber Command has turned its attention away from its… [Continue Reading] -

Windows 10 Anniversary Update is shaping up to be something really special
Publié: avril 24, 2016, 4:22pm CEST par Mark Wilson
Windows 10 has been the subject of a lot of criticism since it launched, including quite a lot from me. But at the same time, Microsoft reports that the latest version of its operating system is installed on a staggering quarter of a billion devices. The company must be doing something right. Where Windows 10 succeeds -- particularly for Windows Insiders -- is that it is constantly evolving. Windows 10 Insider Preview Build 14328 is the latest build out of the door and it shows great signs of improvement. It might be a little early to call it, but if… [Continue Reading] -

Microsoft reveals all about Windows 10's Linux subsystem
Publié: avril 24, 2016, 1:49pm CEST par Mark Wilson
The arrival of Bash in Windows 10 took many people by surprise, but it opens up a number of opportunities including the ability to run GUI Linux apps. But it's about much more than just that. Microsoft wants people who are confused about the arrival of (deep breath...) Bash on Ubuntu on Windows to know of the potential, and has produced an explainer about the Windows Subsystem for Linux. Microsoft's Deepu Thomas says that the subsystem was created by the Microsoft Windows Kernel team, and goes on to explain that this is much more than an interpretation layer or virtual… [Continue Reading] -

Hacker finds Facebook backdoor leaking usernames and passwords
Publié: avril 24, 2016, 1:36pm CEST par Mark Wilson
The use of bounty programs to track down security vulnerabilities in websites and software is increasingly common these days, and it's a tactic employed by Facebook. One bounty hunter -- or penetration tester -- hacked his (or her… they are anonymous) way into the social network and made the shocking discovery that someone had already installed a backdoor. Orange Tsai managed to compromise a Linux-based staff server and found there was already a piece of malware in place syphoning off usernames and passwords. These account details were being transmitted to a remote computer, and after revealing this to Facebook, Tsia… [Continue Reading] -

US Justice Department accesses another iPhone without Apple’s help
Publié: avril 23, 2016, 5:05pm CEST par Mark Wilson
When it came to the San Bernardino iPhone, Apple was ready to dig in its heels and refuse to help the FBI to gain access to the encrypted contents. As it turns out, the company needn’t have bothered shouting as a third party helped instead. Now the same thing has happened with another iPhone. This time around, the Justice Department had been looking for help accessing an iPhone at the center of a drugs case in New York. But now federal prosecutors have said they no longer need Apple’s help as they have managed to get by the lockscreen. Unlike… [Continue Reading] -

Apple tells developers watchOS apps must work without an iPhone
Publié: avril 23, 2016, 1:07pm CEST par Mark Wilson
Apple has announced to developers that, starting June 1, all watchOS apps submitted for inclusion in the App Store must be native apps based on watchOS 2 SDK. What this means in practice is that Apple Watch apps must function without an iPhone. This is something that has plagued wearables from other manufacturers -- including Samsung -- and the new rules will almost certainly go down well with consumers. Ultimately this should lead to an improvement in the quality of Apple Watch apps, as developers will be forced to build in more functionality. It's not, however, all good news. The… [Continue Reading] -

Woz: Apple should pay half its income in tax
Publié: avril 22, 2016, 12:52pm CEST par Mark Wilson
The tax arrangements of international technology companies have been in the spotlight for a little while now. Few people disagree with the idea that they should be paying their way when it comes to tax, and one of these people is Steve Wozniak. He thinks Apple should pay tax at a rate of 50 percent -- just like him. Just like Amazon, Facebook and Google, Apple manages to avoid a great deal of tax by channeling money through a subsidiary located in the Republic of Ireland. This reduces its tax bill dramatically by avoiding the UK corporation tax of 20… [Continue Reading] -

Facebook to filter out News Feed crap by timing how long you read articles
Publié: avril 22, 2016, 10:39am CEST par Mark Wilson
Facebook has been going a little crazy with News Feed updates of late, making constant changes in a bid to ensure that people see content they actually want to read. The real motivation may be ad revenue, but it's always pushed as surfacing (ouch... sorry... I slipped into buzzword mode...) more relevant content. The new changes are no different. The most recent update to the feed algorithm will take into account not only which news articles people click on, but how long they spend reading them. This will help Facebook to not only determine what sort of article interest users… [Continue Reading] -

Dotcom: If you're still using Mega, back up your cloud-based files right now
Publié: avril 22, 2016, 10:14am CEST par Mark Wilson
It seems that Mega -- the enfant terrible of the cloud storage world -- could be on the brink of closure. Founder of Mega (formerly known as Mega Upload), Kim Dotcom took to Twitter to warn people to back up their files ASAP. Not for the first time, Mega is out of the control of Dotcom, and is currently in the hands of what he refers to as "the fifth most wanted criminal in China". For many people the idea of their cloud storage being in criminal hands would be concerning enough, but Dotcom says that Bill Liu wants to… [Continue Reading] -

It cost HOW MUCH to crack the San Bernardino iPhone?!
Publié: avril 21, 2016, 9:02pm CEST par Mark Wilson
There are a lot of questions still to be answered about the San Bernardino iPhone that saw the FBI and Apple go head to head. After something of a battle, the FBI found someone to crack the iPhone. But who exactly did it? How did they do it? Will Apple be told how to do it in private? But one question that has also been lurking in the background is just how much it cost to hack into a single iPhone. Now we know the answer. Not precisely, but we have a pretty good idea. Perhaps unsurprisingly, cracking the iPhone… [Continue Reading] -

With security and privacy in mind, will more browsers follow Opera's lead and offer free VPN?
Publié: avril 21, 2016, 12:46pm CEST par Mark Wilson
The modern internet user is somewhat paradoxical -- looking to be more connected and contactable than ever before, whilst simultaneously seeking privacy. Can the two ideas live side by side? It's a tricky balancing act, but many people turn to VPN tools to increase their security and privacy online. Opera is the first web browser to bundle a free VPN tool as standard (with unlimited VPN data, no less), and it's hard to imagine that the competition won’t follow suit. Nothing has yet been announced, but the appearance of versions of Chrome or Firefox with integrated VPN would hardly be… [Continue Reading] -

Google Inbox makes it easier to manage links, newsletters and calendar events
Publié: avril 20, 2016, 7:00pm CEST par Mark Wilson
When it comes to email, Google is about more than just Gmail. With Inbox, Google has looked to simplify and automate email, and today the company announces three new features that take this further. But Google doesn't think that 'features' is strong enough a word; instead these are 'experiences'. Specifically, there are new experiences that make it easier to keep track of calendar events, manage the links you email to yourself, and view all of the newsletters you subscribe to. Inbox is all about keeping -- or making -- things as simple as possible. This is what the new newsletter… [Continue Reading] -

ITIF says Europe is 'misguided' in bringing antitrust allegations against Google
Publié: avril 20, 2016, 5:31pm CEST par Mark Wilson
The EU may be bringing an antitrust case against Google in relation to its Android operating system, but the ITIF (Information Technology & Innovation Foundation) thinks that this is 'misguided'. Rather than Google harming customer choice, the institute says that it is the case against Google that should be in the spotlight. Google has made much of the fact that Android is open source, and the ITIF says that "holding 'open' operating systems to higher standard only hurts consumer choice". Vice President Daniel Castro says that the Android ecosystem reduces costs for consumers, increases choice, and complains that the European Commission… [Continue Reading] -

Google denies Android breaches EU antitrust rules
Publié: avril 20, 2016, 2:37pm CEST par Mark Wilson
The European Union has charged Google with anticompetitive behaviour, saying that the company abused the dominance of Android in the mobile marketplace. Regulators have taken exception to Google's requirement on phone manufacturers to install Chrome and Google search, saying that this stifles innovation and limits user choice. Unsurprisingly, Google disagrees and has hit back at the charges saying that "our business model keeps manufacturers' costs low and their flexibility high, while giving consumers unprecedented control of their mobile devices". More than this, Google says it prides itself on having built a sustainable ecosystem built on open source software. It also… [Continue Reading] -

EFF sues Justice Department to discover if secret orders are used to decrypt user data
Publié: avril 20, 2016, 1:55pm CEST par Mark Wilson
EFF (the Electronic Frontier Foundation) has filed a Freedom of Information (FOIA) lawsuit against the Justice Department. The digital rights group wants to learn whether the government has made use of secret court orders to force tech companies to provide access to encrypted user data. After the Apple vs the FBI battle, there has been renewed interest in how companies handle not only encryption, but government requests for access to such data. With services such as WhatsApp enabling end-to-end encryption, attention has now switched to what might be happening in the background without users' knowledge. While Apple very publicly refused… [Continue Reading] -

China wants Apple's source code, but Apple refuses to hand over the goods
Publié: avril 19, 2016, 11:42pm CEST par Mark Wilson
Apple has revealed that Chinese authorities have asked for access to the company's source code in the last couple of years. The revelation was made by Apple general counsel Bruce Sewell as he tried to deflect accusations that have sprung up in the wake of the San Bernardino iPhone case. The battle between Apple and the FBI rumbled on for a while as authorities asked the iPhone manufacturer to crack encryption or provide a backdoor into the phone at the center of the case. Apple refused to help the FBI, leading to accusations that the company was failing to help… [Continue Reading] -

Google's second annual Android security report shows how app and device scanning keep you safe
Publié: avril 19, 2016, 7:27pm CEST par Mark Wilson
As Apple releases its transparency report, Google today releases its second Android Security Annual report. The report covers all things Android, from the security of the operating system itself, to the security of Google Play and the apps it provides access to. Of course, Google is keen to highlight everything it does to improve security for its users. As such, the report shows how the company performs more than 400 million automatic security scans per day on devices with Google Mobile Services. Aided by machine learning, these scans help to home in on what are referred to as Potentially Harmful… [Continue Reading] -

Apple transparency report sheds some light on government data requests
Publié: avril 19, 2016, 6:09pm CEST par Mark Wilson
Reinvigorated interest in privacy, security and surveillance means that the transparency reports published by tech companies are always greeted with some enthusiasm. How much data are governments around the world asking for from companies? How much user data are companies handing over to the authorities? Apple's latest transparency report reveals that the iPhone manufacturer has complied with an increased number of requests for data -- including 80 percent of requests in North America, and 97 percent in Latin America. But while the report makes for interesting reading, it also highlights a problem that Microsoft recently sued the Department of Justice… [Continue Reading] -

Google refuses to censor search results that identify PJS and YMA
Publié: avril 17, 2016, 2:12pm CEST par Mark Wilson
There's nothing like a good sex scandal to get people talking, and that's certainly what's happened in the case of a celebrity threesome that's currently subject to a superinjunction banning the involved parties from being named. While the identities of the couple cannot be revealed by British newspapers, their names are well-known in other parts of the world, and all over the web. The British press has played ball, agreeing not to name YMA, his husband PJS and the two others, AB and CD with whom a threesome is supposed to have taken place but it is impossible for law… [Continue Reading] -

Google set to improve transparency and privacy for Chrome extensions
Publié: avril 17, 2016, 1:32pm CEST par Mark Wilson
Google is looking to take steps that will enable Chrome users to make more informed decisions about the extensions they install. Specifically, developers will have to provide more information about data collections in the interests of transparency. In addition, developers will have to produce a privacy policy for their extensions, and must ask for permission before collecting data about users. Google's new User Data Policy introduces these extra requirements in the wake of increased demands from users for more information about what is going on in the background. Google is introducing some restrictions as well as new requirements. If the… [Continue Reading] -

Privacy in the spotlight: Microsoft sues Department of Justice for not allowing transparency about data access requests
Publié: avril 14, 2016, 11:39pm CEST par Mark Wilson

In light of Edward Snowden's surveillance revelations, regular transparency reports from technology companies about the requests they have received from governments about data requests have become very common. But despite the name, transparency reports are not very transparent -- there are great restrictions on what companies like Microsoft are able to report. The company believes this is unconstitutional.
The restrictions are so strict that it is not even possible to precisely report the number of requests for user data that have been received. Instead, this data must be conveyed in bands such as 0-499, 500-999, and so on. Now Microsoft has had enough. There are privacy concerns, of course, but most disturbing is that in half of cases of requests for customer data, Microsoft has been gagged from letting those affected know about the governmental interest. As a result, Microsoft has decided to sue the Department of Justice in a bid to be more transparent.
In its lawsuit, Microsoft harks back to a different era, saying that in the days before the internet "the government had to give notice when it sought private information and communications" that was stored in hard copy or locally. But with Microsoft's -- and other companies' -- predilection for the cloud, it has become far easier for the government to demand instant access to private data that might otherwise have stayed out of sight.
Bringing its case against the Department of Justice, Microsoft says:
Microsoft brings this case because its customers have a right to know when the government obtains a warrant to read their emails, and because Microsoft has a right to tell them. Yet the Electronic Communications Privacy Act (ECPA) allows courts to order Microsoft to keep its customers in the dark when the government seeks their email content or other private information, based solely on a 'reason to believe' that disclosure might hinder an investigation. Nothing in the statute requires that the 'reason to believe' be grounded in the facts of the particular investigation, and the statute contains no limit on the length of time such secrecy orders may be kept in place. 18 U.S.C. § 2705(b). Consequently, as Microsoft's customers increasingly store their most private and sensitive information in the cloud, the government increasingly seeks (and obtains) secrecy orders under Section 2705(b).
More than this, Microsoft accuses the government of taking advantage of the move to the cloud to its own advantage, whilst exploiting tech companies:
The government, however, has exploited the transition to cloud computing as a means of expanding its power to conduct secret investigations. As individuals and business have moved their most sensitive information to the cloud, the government has increasingly adopted the tactic of obtaining the private digital documents of cloud customers not from the customers themselves, but through legal process directed at online cloud providers like Microsoft.
In the space of 18 months, Microsoft says that it received no fewer than 5,624 requests from the US government for access to customer data. Nearly half of these were subject to secrecy orders which prevented Microsoft from informing anyone about the request. In many instances, these secrecy orders had no time limit, meaning that this restriction would never be lifted.
Microsoft says that the First Amendment means that customers should be told when such requests are made and argues that "antiquated laws" are being applied to data in the cloud.
This is an extremely interesting case, and not just because it involves a huge name like Microsoft coming up against the Department of Justice. With Microsoft's contemporaries -- Apple, Google, at al -- all subject to the same restrictions, the outcome of this case could have far-reaching consequences.
Photo credit: Pelykh Konstantin / Shutterstock
-

PayPal Credit launches in the UK -- a virtual credit card with an interest-free offer
Publié: avril 14, 2016, 11:44am CEST par Mark Wilson

PayPal is, in many ways, the primary choice for making online payments. The company is keen to build on this and has launched a new product in the UK to widen its appeal. PayPal Credit is a virtual credit card that can be used online, and as an incentive to sign up, there's a four-month interest-free offer.
As this is an online credit card, applying for it takes a matter of moments, and PayPal is quick to point out that there's no hanging around waiting for a card and PIN to arrive. Apply online and you could be approved for a credit extension to your PayPal account.
Just as with any other form of credit card, making an application for PayPal Credit involves a credit check -- something to keep in mind if you're concerned about your credit score. Once signed up, you'll be able to make purchases via PayPal even if you don’t have funds in your linked bank account, or if you just fancy the idea of spreading the cost of a larger purchase.
PayPal describes the new virtual card:
PayPal Credit is like a credit card you can use for your online purchases, it takes minutes to apply and if you’re approved you’ll have a credit limit in your PayPal account right away.
The interest-free offer is... interesting. PayPal bills it as "0% for 4 months to use again and again", going on to explain that "every time you spend £150 or more in one go using PayPal Credit, you’ll get 0% interest for 4 months on that purchase". After four months -- and for purchases under £150 -- the interest rate jumps to a fairly standard 17.9% p.a (variable).
If you want to apply for a virtual card, head over to the PayPal Credit website.
Photo credit: www.BillionPhotos.com / Shutterstock
-

Android N Developer Preview 2 available to download now
Publié: avril 13, 2016, 11:30pm CEST par Mark Wilson

It's only a few weeks since the first developer preview of Android N was released, but now it's time for the second. Google has announced the availability of Android N Developer Preview 2 packed with bug fixes and a raft of new features.
Among the new tools for developers to play with is Vulkan, a new 3D rendering API which Google says provides a big performance boost for certain apps. Other key additions include support for the more human-looking Emoji Unicode 9, and new launcher shortcuts that can be used to quickly jump to specific actions within an app.
Android N Developer Preview 2 also includes API improvements for multi-window support, giving developers the ability to specify height and width for an activity. As before, the preview build is only available for a limited number of devices -- which will hopefully expand over time -- but the range of bug fixes is impressive (although, of course, there are still a number of known issues).
In a blog post, Google explains how to get hold of Android N Developer Preview 2:
The easiest way to get this and later preview updates is by enrolling your devices in the Android Beta Program. Just visit g.co/androidbeta and opt-in your eligible Android phone or tablet -- you’ll soon receive this (and later) preview updates over-the-air. If you’ve already enrolled your device, you’ll receive the update shortly, no action is needed on your part. You can also download and flash this update manually. Developer Preview 2 is intended for developers and not as a daily driver; this build is not yet optimized for performance and battery life.
The N Developer Preview is currently available for Nexus 6, Nexus 5X, Nexus 6P, Nexus 9, and Pixel C devices, as well as General Mobile 4G [Android One] devices. For Nexus Player, the update to Developer Preview 2 will follow the other devices by several days.
To build and test apps with Developer Preview 2, you need to use Android Studio 2.1 -- the same version that was required for Developer Preview 1. You’ll need to check for SDK components updates (including build tools and emulator system images) for Developer Preview 2 -- see here for details.
-

Women and black writers are the biggest victims of abusive online comments
Publié: avril 13, 2016, 6:56pm CEST par Mark Wilson

Online abuse is a serious problem. While the likes of Twitter and Facebook are great platforms for trolls to indulge their hobby, it's the good, old-fashioned comments section where you'll find some of the most obvious examples of threats and abuse. The problem is so great that many websites have taken the seemingly drastic step of completely disabling comments on stories, while others do so on an individual basis for articles that could prove controversial.
Clearly this is less than ideal. In many ways it could be viewed as a form of censorship that curtails freedom of speech, and comments can be a valuable way to help a story to evolve. For many sites, comments are a black and white topic; on or off. Moderation -- again, often seen as a type of censorship -- is often employed, but this does little to stop abuse aimed at writers. The Guardian has conducted research into the abuse dealt out via comments on its site, and the findings make for disturbing reading.
It has been argued that the world of tech, and the internet, is dominated by white men and that there is more than a hint of racism and sexism. An article entitled The dark side of Guardian comments bears this out. In depth analysis of more than 70 million comments reveals that when looking at the top 10 'most abused' writers, 80 percent of them are women and 60 percent are black.
As the Guardian notes, the comments section of just about any website is often home to truly hateful abuse:
The Guardian was not the only news site to turn comments on, nor has it been the only one to find that some of what is written 'below the line' is crude, bigoted or just vile. On all news sites where comments appear, too often things are said to journalists and other readers that would be unimaginable face to face -- the Guardian is no exception.
This is not really surprising. The veil of anonymity, and the barrier of distance, that the web affords trolls means people often feel free to unleash torrents of abuse that would be unimaginable in another medium. But it is the breakdown of the most abused writers that is both interesting and disturbing, confirming fears that sexism and racism are rife online.
The Guardian itself points out that the majority of its opinion writers are white men. While many would view this as an issue in itself, these same white men do not find themselves to be on the receiving end of the majority of abuse. Regardless of topic, articles written by women result in more trolling and abuse than those written by men.
The 10 regular writers who got the most abuse were eight women (four white and four non-white) and two black men. Two of the women and one of the men were gay. And of the eight women in the 'top 10', one was Muslim and one Jewish.
And the 10 regular writers who got the least abuse? All men.
What's particularly interesting is that in stereotypically male arenas such as sport and technology, female writers found themselves on the end of more comments deemed blockable by moderators. Some individual topics also attracted more unpleasant comments than others:
We also found that some subjects attracted more abusive or disruptive comments than others. Conversations about crosswords, cricket, horse racing and jazz were respectful; discussions about the Israel/Palestine conflict were not. Articles about feminism attracted very high levels of blocked comments. And so did rape.
The primary focus of the analysis was the different reception men and women enjoyed, but it did reveal more.
We focused on gender in this research partly because we wanted to test the theory that women experience more abuse than men. But both writers and moderators observe that ethnic and religious minorities, and LGBT people also appear to experience a disproportionate amount of abuse.
Running a website means walking a narrow line between saying 'anything goes' and becoming over-enthusiastic with the ban hammer. The Guardian's research throws some interesting light on just how complicated the commenting ecosystem is. Do you give people a free rein to say whatever they want -- risking things going wildly off-topic or getting abusive and personal -- or do you risk accusations of limiting free speech by stepping in as a moderator when things get out of hand?
It's not an easy question to answer, and it's made all the more difficult once gender and race are thrown into the equation.
Photo credit: aastock / Shutterstock
-

Google Calendar now helps you to reach your goals
Publié: avril 13, 2016, 1:53pm CEST par Mark Wilson

It's not long since the Reminders feature arrived in Google Calendar on the web, a few months after it debuted in iOS and Android. Now Google is rolling out another new feature that makes it easier to find time to reach your goals -- whether this is indulging in a hobby a few times a week, or just trying to do some regular exercise.
Goals in Google Calendar is not about ticking items off your bucket list, but automating the process of adding reminders to your calendar without having to manually search high and low for the necessary time. Just indicate what you want to do, and how often, and the rest will be taken care of for you. But it gets better...
Everyone's plans change. Things crop up, schedules alter. Goals in Google Calendar can help. The feature not only finds empty slots in your day to house your run or yoga sessions, but if you later schedule another event that clashes, it will be automatically moved for you. No more excuses for missing out on a session at the gym!
There's an element of learning to Goals as well; the more you use the feature, the better it gets at picking suitable times to schedule events. This is something that is influenced to a certain extent when you elect to manually defer an event. If you keep delaying a reminder first thing in the morning, your calendar will learn that rescheduling later in the day would probably make more sense.
Check out the video below to get an idea of how Goals in Google Calendar works:
For now, Goals in Google Calendar is available to iOS and Android users, so just make sure you have the latest version of the app installed to make us of the feature.
Photo credit: Rawpixel.com / Shutterstock
-

How to run GUI Linux apps from Bash in Windows 10
Publié: avril 12, 2016, 1:04pm CEST par Mark Wilson

Linux apps running in Windows 10? What gives?! As if the arrival of Bash on Ubuntu on Windows 10 wasn't enough, people have been quick to investigate the capabilities and limitation of Microsoft's embracing of the Linux command line.
Some commenters on our how-to guide asked what the point is. How about being able to run Linux apps in Windows without having to resort to using a virtual machine? It can be done. Here's how.
As noted over on Windows Clan, all it takes is a couple of commands to get started. You'll have to begin by making sure you have Bash up and running, and then grab yourself a copy of X Server from SourceForge.
With this done, you can run Firefox, for instance, using the command:
DISPLAY=:0 firefox
Have a play around and see what you can come up with. You might find that performance is a little on the disappointing side, but it's very early days at the moment and this may well improve as Canonical and Microsoft refine things.There's also an active thread over on Reddit where users are sharing tips and ideas -- well worth a look.
Photo credit: Julien Tromeur / Shutterstock
-

Legality of UK surveillance laws to be tested by European court
Publié: avril 12, 2016, 12:12pm CEST par Mark Wilson

Laws surrounding online surveillance will always prove controversial, and this is certainly true of the UK's proposed Investigatory Powers Bill -- aka the Snooper's Charter. Currently in draft form, the final content and scope of the bill could be set today as the European Court of Justice rules on a challenge brought against the existing Data Retention and Investigatory Powers Act 2014 (Dripa).
The case has the support of many European states, and the outcome of the case will determine the powers of data collection the UK government is able to exercise. It is expected that the case could be one of the deciding factors in the in-out referendum in June when the UK votes on whether to remain part of Europe or to go it alone.
15 judges in Luxembourg are due to rule on the legality of Dripa which was rushed through parliament; it has already been determined that the Act is at odds with EU law. Specifically, it is said that the Act goes against Article 8 of the European convention on human rights, the right to respect for private and family life, and Articles 7 and 8 of the EU charter of fundamental rights, respect for private and family life and protection of personal data.
The fact that the UK government's proposed gathering of data about all internet users -- not just those under investigation in cases -- is likely to be central to the decision and future direction of surveillance laws. Because rulings by the European Court of Justice must also be applied to UK law. Ultimately it could mean that the Investigatory Powers Bill needs to be rewritten.
Unsurprisingly, privacy groups are far from happy with both Dripa and the Snooper's Charter. Camilla Graham Wood from Privacy International, said:
The UK, in enacting legislation that is almost identical to the European data retention directive which the [ECJ] ruled unlawful, is mandating data retention on a widespread, indiscriminate and untargeted basis.
Such a broad and wholesale retention of communications data is in violation of European law. The effect of Dripa is to use bulk data retention to create a dossier on every person in the UK. It includes every internet and mobile phone transaction you undertake, every location will be filed, every meeting noted, every website indexed and every call marked.
Blanket retention of communications data, without suspicion, creates a honeypot of information for criminals and hackers, and this case will have implications for personal privacy and the security of individual personal data.
Photo credit: nzozo / Shutterstock
-

Porn site xHamster bans North Carolina users in protest against anti-LGBT laws
Publié: avril 12, 2016, 11:06am CEST par Mark Wilson

North Carolina's decision to pass House Bill 2 -- which effectively block measures to protect LGBT people -- means that residents of the state are no longer able to access a popular porn site. Just as Bruce Springsteen decided to show his disgust at the new legislation by cancelling a concert in North Carolina, so xHamster has taken the step of blocking North Carolina porn consumers from accessing the site.
North Carolina's new law prevents local governments from passing anti-discrimination rules to protect lesbian, gay, bisexual and transgender people, and it is sending ripples of disgust through the equal rights movement. With xHamster's involvement, the fight against the legislation has been taken online, hitting state residents where it hurts in a bid to encourage people to sign a petition against the bill.
xHamster has been inaccessible in North Carolina since Monday, and site spokesman Mike Kulich told the Huffington Post that LGBT search terms were very popular in the state. "Back in March, we had 400,000 hits for the term 'Transsexual' from North Carolina alone. People from that state searched 'Gay' 319,907 times".
In a statement the site said that the headline-grabbing ban was about equality:
We have spent the last 50 years fighting for equality for everyone and these laws are discriminatory which xHamster.com does not tolerate. Judging by the stats of what you North Carolinians watch, we feel this punishment is a severe one. We will not standby and pump revenue into a system that promotes this type of garbage. We respect all sexualities and embrace them.
Can porn succeed in helping to overturn the discriminatory law? Only time will tell. In the meantime, expect to see a spike in the use of proxy tools in North Carolina...
Photo credit: KongNoi / Shutterstock
-

How to run Bash on Ubuntu on Windows 10 Anniversary Update or Preview Build 14316
Publié: avril 11, 2016, 5:24pm CEST par Mark Wilson

Microsoft has been showing Linux a lot of love recently, and at Build 2016 the company announced that the Bash shell was coming to Windows 10. It’s a feature that will make an appearance in the upcoming Windows 10 Anniversary Update (due for release in July), but it's something that Windows Insiders on the Fast Ring already have access to in Build 14316 right now.
If you have installed this build, you'd be forgiven for not being able to find Bash however hard you look; there are hoops you have to jump through. So if you like the idea of accessing the Linux command line in Windows 10, there are a few steps for you to follow, starting off by enabling Developer Mode.
As Microsoft explains: "You can now run Bash scripts, Linux command-line tools like sed, awk, grep, and you can even try Linux-first tools like Ruby, Git, Python, etc. directly on Windows. You can also access your Windows filesystem from within Bash allowing you to work on the same set of files using your preferred Windows tools or Linux command-line tools".
Here are those all-important Bash-enabling steps:
- Open up Settings, click Update & security, and then head to the For developers section. Select the Developer mode option, click Yes to confirm, and then exit Settings.
- Hit the Windows key (or the Start button), type Windows features, and click the Turn Windows Features on or off entry that appears.
- Scroll down to the bottom of the list, check the box next to the Windows Subsystem for Linux (Beta) option, and click OK.
- Wait for a moment while Bash is installed and then click Restart now to restart your computer and complete the process.
- When Windows is back up and running, open a command prompt window, type bash and hit Enter.
- You'll see a message that reads 'This will install Ubuntu on Windows, distributed by Canonical and licensed under its terms'. Press Y followed by Enter to download the software from the Windows Store and complete the installation.
In future, you can access Bash via the Bash on Ubuntu on Windows shortcut in the All Apps section of the Start menu.
Photo credit: charnsitr / Shutterstock
-

Microsoft throws its support behind EU-US Privacy Shield
Publié: avril 11, 2016, 2:00pm CEST par Mark Wilson

The transfer of data between the US and Europe has been something of a privacy and security nightmare. In an attempt to improve privacy protection, the European Commission established the EU-US Privacy Shield "to restore trust in transatlantic data flows" post-Edward Snowden's NSA surveillance revelations, replacing the controversial Safe Harbor arrangement.
Today Microsoft has announced its support for the principles the framework says that companies will have to abide by. More than this, Vice President for EU Government Affairs at Microsoft, John Frank, says the company will comply with Data Protection Authorities advice in disputes, and cooperate with them on data transfer processes.
Whilst recognizing that "no single legal instrument can address for all time all of the privacy issues on both sides of the Atlantic", Microsoft nonetheless says that Privacy Shield is a good starting pointing. The company says that additional steps will be needed to localize the framework, and praises the European Commission and US Department of Commerce for what it describes as having helped create "stronger and pragmatic privacy protection".
In a blog post, Frank says:
First and foremost, at Microsoft we believe that privacy is a fundamental human right. In a time when business and communications increasingly depend on the transmission of personal data across borders, no one should give up their privacy rights simply because their information is stored in electronic form or their technology service provider transfers it to another country.
We recognize that privacy rights need to have effective remedies. We have reviewed the Privacy Shield documentation in detail, and we believe wholeheartedly that it represents an effective framework and should be approved.
As well as announcing that it will sign up for Privacy Shield, Microsoft also says that it will embrace the dispute resolution process. Specifically, Microsoft will respond to any complaints it receives within 45 days. Having complied with Safe Harbor and cooperated with Data Protection Agencies for nearly 15 years, the company says "we believe it makes the most sense for us to continue with this approach and submit disputes to the DPAs under the Privacy Shield".
The Privacy Shield framework also places transparency obligations on companies, and this is something that Microsoft also embraces:
We also welcome the obligations in the Privacy Shield for transparency about government requests of access to personal information. As a company we have advocated for greater U.S. transparency. In 2013, Microsoft and other U.S. tech companies successfully challenged the U.S. Government over our constitutional right to disclose more detailed information about the Government’s demands for data. And in 2014, we filed suit against the U.S. Government after it attempted to force us to turn over a customer’s email stored in our Irish data center. While we continue to advocate for additional domestic legal steps in the United States, we believe that the European Commission and Department of Commerce have chosen a sensible approach in the Privacy Shield. In this area as in others, we believe the Privacy Shield represents an important step in the right direction.
What needs to happen next is to convince more companies and, importantly, individuals that the Privacy Shield agreement is in their best interests.
Photo credit: StockStudio / Shutterstock
-

Keygen alert: free password generator released for PETYA ransomware
Publié: avril 11, 2016, 12:59am CEST par Mark Wilson

The PETYA ransomware is just one of the recent examples of malware that encrypts victims' hard drives until a fee is paid. The advice from the government is not to pay the ransom -- or at least not expect to get a decryption key if you do -- but a password generator has been created that means you can decrypt your hard drive for free.
While TeslaCrypt 4 boasts 'unbreakable encryption', the same cannot be said of PETYA, although the PETYA ransomware does have the irritating habit of overwriting MBRs. This does mean that there is no way to interact with the drive on the infected computer, but with access to a spare machine to read the drive and access to the online tool created by Leostone, you could have your data back in seconds. As the tool's website proudly proclaims, you can "Get your petya encrypted disk back, WITHOUT paying ransom!!!" -- here's what you need to do.
The process is not something that everyone will be able to follow -- it is a little technical -- but it's worth persevering (hat tip to Bleeping Computer for the heads up!) to avoid coughing up any Bitcoin. You'll need to connect the infected drive to another computer and extract a couple of pieces of data from it, specifically:
- 512 bytes of verification data from sector 55 (0x37) offset 0(0x0) of the disk, converted to Base64
- 8 byte nonce from sector 54 (0x36) offset 33(0x21), also converted to Base64
To help with this, you can use the specially-written Petya Sector Extractor as this will provide you with the data you need.
Fire up your web browser and pay a visit to Leostone's decryption website at [https:] where you'll find two fields into which you can paste the requested data from the infected drive.
With this done, hit Submit and wait for a few seconds while your key is generated. Return the infected drive to its original computer, fire it up, enter the key when prompted, and the drive should be decrypted. For free!
-

Celebrity threesome superinjunction shows disparity between law of the land and law of the web
Publié: avril 10, 2016, 9:50pm CEST par Mark Wilson

The idea of an injunction to prevent newspapers from publishing certain stories are nothing new, far from it. But in recent years, a new breed of superinjunction has been born. These not only prevent the publishing of stories, but can also block the publishing of the names of those involved. Some superinjunctions are such that even reporting the existence of the superinjunction is prohibited.
In recent weeks, a celebrity couple took out a superinjunction to prevent the press from publishing details of an alleged affair (well, a threesome if we cut to the chase). The gagging order prevented news outlets in the UK referring to the couple as anything other than the initials PJS and YMA (not their actual initials, by the way) and the other participants in the alleged ménage à trois as AB and CD. But today a Scottish newspaper took the decision to reveal the names of the couple -- but it could only do so in its print edition, because of the way laws written for the printed press have been awkwardly applied to the web.
The case is something of a legal minefield. Just as the press in England is not able to publish the names of those involved, it is also not permitted to provide clues or hints that could enable readers to determine their identity. This means that British newspapers cannot even name the Scottish newspaper that draws back the curtain. In fact, the newspaper in question is not legally able to publish the same information online as it can in its print edition simply because it could be accessed in England.
If this seems like insanity to you, you are far from being alone. If you're reading this in the States -- or even if you are in the UK -- you are probably already aware of the couple at the center of the case. It has been covered by the National Enquirer (yes, I know...) and there has been intense speculation on Twitter in recent weeks. For the risk of being sued, newspapers reporting the fact that the gagging order has been ignored in some parts of the UK must refer to the publication in question indirectly: 'a Scottish newspaper', very much like referring to 'the Scottish play' instead of risking saying 'Macbeth' in a theater.
It is madness.
The Scottish newspaper's website includes an editorial piece which says:
As our digital content is read in England we cannot reproduce the story online, tell you who they are or even feature the front page.
But their names are already known in the United States where the stories have been published and their identities are all over social media.
Of course, it takes just a few seconds of your time to discover the people involved if you are interested. But something interesting is happening. While Twitter has been abuzz with speculation about who the celebrity couple might be, there is also an element of self-censorship taking place. One user posted a photograph of the newspaper article in which the couple was named, but after taking advice from another news outlet, opted to delete the tweet:
@hex_inc If you don't want to risk getting sued, yes.
— Wings Over Scotland (@WingsScotland) April 10, 2016
But as the newspaper says;
We are publishing the identities today because there is no legal reason not to publish in Scotland what has been banned in England and Wales. Their big secret is no secret at all. America knows. The internet knows. The whole world knows. So now Scotland knows. And so we should.
The paper is quick to point out that the decision was taken as a demonstration of support of freedom of the press:
Just to be clear, we are not naming them because of the story they are trying to suppress. We couldn’t care less. We do, however, care about free speech, a free press and very wealthy people spending huge sums of money stopping stories they do not much like the sound of.
If we did not name them, it would only encourage people -- possibly celebrities, more probably tycoons and politicians -- with something to hide to attempt to hide it behind a court order.
It's crazy to think that the couple involved could possibly have thought that the story could be stopped in its tracks using a court order. If anything it has served only to drag things on for longer than might otherwise have been the case. Left to run its natural course, the story probably would have burned out and been forgotten in a matter of days. As it is, it has been dragged out for weeks, and it has been brought to global attention.
It has also highlighted an important difference between how the law applies to land-based newspapers, and how it applies to the global internet. While newspapers in England may have been effectively censored, the same cannot be said of internet users.
And if you're wondering why we're neither naming the celebrities nor linking to the Scottish newspaper we're taking about, there are a couple of reasons. Firstly, this is not a celebrity gossip site, so this is not the place to discuss A-listers' bedroom antics. But secondly, as stupid as it may be, we're playing it safe. Our pockets simply aren't as deep as those of the couple involved. There is the fact that a) BetaNews is based in the US and, b) I'm writing this from Scotland, but is it worth the risk? Really?
Photo credit: Tashatuvango / Shutterstock
-

Immigration officials allowed to hack phones of refugees and asylum seekers
Publié: avril 10, 2016, 12:52pm CEST par Mark Wilson

The British government secretly rolled out powers that permitted the immigration officials to hack the mobile phones of asylum seekers and refugees, the Observer reveals. The Home Office has confirmed the hacking powers which have sparked outrage from privacy and human rights groups.
Since 2013, immigration officials have not only been permitted to hack into migrants' phones and computers, but also to install surveillance equipment in homes and detention centers. With concern about governmental plans for the snooper's charter and the privacy invasion this entails, claims that the powers are needed to "deal effectively with all immigration crime" are likely to fall on deaf ears.
In a statement about the powers afforded immigration officials, immigration minister James Brokenshire said: "They may only use the power to investigate and prevent serious crime which relates to an immigration or nationality offence, and have done so since 2013".
The revelation has sparked serious concern from campaigners for rape victims; a very large proportion of women in immigration detention centers are survivors of rape. Black Women’s Rape Action Project spokesperson Cristal Amiss says:
These powers are an outrage. People in detention have the right to confidentiality, to speak privately to their lawyer and disclose often very sensitive information such as details of rape, torture, domestic violence and alleged abuse by officials. They have to be able to share private information without their phones being hacked.
The surveillance and hacking powers have been bolted into legislation by amending the Police Act 1997, an act that many argue is completely inappropriate for dealing with technology-related matters. Critics of the power says that the government is targeting and abusing some of the most vulnerable people in society, but the government says that "equipment interference" (read 'hacking' or 'surveillance') has been used to investigate cases of illegal travel documents.
Photo credit: Prazis / Shutterstock
-

Draft encryption bill could spell the end of privacy and security as we know it
Publié: avril 10, 2016, 12:01am CEST par Mark Wilson

Apple's battle with the FBI has focused the attention of the technology community on encryption. But while just about all of the big players in the tech world backed Apple's refusal to create a backdoor for the FBI into iOS, Congress has a very different idea about how encryption and governmental access to data should be handled. This is perfectly demonstrated by a new bill.
The draft version of the Compliance with Court Orders Act of 2016 -- penned by Senators Diane Feinstein and Richard Burr -- would essentially force all US companies to decrypt data they may have encrypted, or to provide backdoors when asked. It's a bill described variously as 'dangerous', 'encryption-weakening', and 'anti-security', and it starts off aggressivley in stating that "no person or entity is above the law". In effect, it renders the encryption put in place by the likes of WhatsApp completely pointless as, if the bill is passed, companies would have to decrypt data on demand.
Joseph Lorenzo Hall, chief technologist at the Center for Democracy and Technology says that "it's effectively the most anti-crypto bill of all anti-crypto bills" and that it "basically outlaws end-to-end encryption". What is particularly concerning about the bull is that it would force companies to comply with data requests from any court in the country. The draft says:
Notwithstanding any other provision of law and except as provided in paragraph (2) a covered entity that receives a court order from a government for information or data shall --
(A) provide such information or data to such government in an intelligible format; or
(B) provide such technical assistance as is necessary to obtain such information or data in an intelligible format or to achieve the purpose of the court order.
The mention of encryption comes when the bill says:
A covered entity that receives a court order referred to in paragraph (1) (A) shall be responsible for providing data in an intelligible format if such data has been made unintelligible by a feature, product, or service owned, controlled, created, or provided, by the cover entity or by a third party on behalf of the covered entity.
In other words, if the government wants to gain access to data that is encrypted, the company responsible for the hardware or software must either decrypt the data and hand it over, or help with the decryption process. It renders encryption and security -- and, by extension, privacy -- pointless.
The Information Technology and Innovation Foundation (ITIF) argues that the government should be looking to strengthen, not weaken, cybersecurity, saying that "insisting that the government always have a means to decrypt private data would limit innovation in cybersecurity".
This legislation places an unqualified demand on companies to decrypt their customers’ data upon receiving a court order from law enforcement. While companies should comply with lawful requests, it is simply not possible for a company to do so when the customer controls the only keys used to encrypt the data. For example, the popular messaging app WhatsApp, which provides end-to-end encryption on its platform, would not be able to comply with the legislation, unless it modified its system. Yet, the bill explicitly states that it is not authorizing the government to require or prohibit any specific design changes to software or hardware. In short, this bill sets up a legal paradox that would further muddy the waters about how and when the government can compel the private sector to assist in gaining access to private information.
The draft bill is incredibly one-sided, leaving no wriggle room whatsoever for companies or individuals to appeal against data requests. In its current form, once data has been requested, it is as good as belonging to the government.
Amnesty International argues that encryption is a human rights issue:
In the digital age, access to and use of encryption is an enabler of the right to privacy. Because encryption can protect communications from spying, it can help people share their opinion with others without reprisals, access information on the web and organize with others against injustice. Encryption is therefore also an enabler of the rights to freedom of expression, information and opinion, and also has an impact on the rights to freedom of peaceful assembly, association and other human rights. Encryption is a particularly critical tool for human rights defenders, activists and journalists, all of whom rely on it with increasing frequency to protect their security and that of others against unlawful surveillance.
It's hard to argue with the human rights group's stance, and it's impossible to describe the draft bill as anything other than out of touch and unfit for purpose. It's a serious threat to personal security and privacy, and we can expect to see a huge backlash against it.
Photo credit: wk1003mike / Shutterstock
-

Windows 10 Anniversary Edition is due for release in July
Publié: avril 9, 2016, 6:07pm CEST par Mark Wilson

Microsoft's Windows 10 Roadmap for business users reveals that the eagerly-anticipated Windows 10 Anniversary Edition is due to launch in July this year. At Build 2016 earlier in the month, Microsoft said that the big update was due to launch 'this summer', but did not get any more precise than this for the Redstone branch release.
But digging into roadmap documents, Microsoft makes it clear that it is aiming for a July release. The company has said that the update will bring "significant new features", including taskbar badge notifications and a revamped Start menu, but it is when talking about the new features that are coming to Cortana that the date is revealed.
For Windows Insiders on the Fast Ring, the current build 14316 gives a glimpse of some of the new enhancements -- including the arrival of Bash -- but there's much more on the horizon. One of the new capabilities coming to Cortana is the ability to set reminders via pen, and in selling these digital assistant updates to business users Microsoft lets slip the proposed release date:
Cortana is your truly personal digital assistant who works across all your Windows 10 devices to help you get things done. By learning more about you over time, Cortana becomes more useful every day. Cortana helps you be more productive by handling key tasks like sending emails, scheduling events, and using the power of Bing to quickly search your devices, the cloud, or the web. Cortana is also the best digital assistant at reminders, letting you set them in more ways including by pen, and [coming in July 2016] pulling reminder-relevant info from emails so you have the details at hand. And you can instantly capture your ideas by voice just by telling Cortana to take a note.
We don't yet know a precise date, or even if Microsoft is aiming for the beginning or the end of the month, but the company now has just a few weeks to play with. The launch of Windows 10 was plagued with delays, so it will be interesting to see if this release is more timely.
Photo credit: charnsitr / Shutterstock
-

If you torrent pirate TV shows, prepare to switch to MKV format
Publié: avril 9, 2016, 1:18am CEST par Mark Wilson

Let's not beat around the bush: we know that a lot of you use the likes of the Pirate Bay, KickAssTorrents and the like to grab copies of movies and TV shows. You're probably aware of a number of release groups on the scene, but you might not know that there are fairly strict rules dictating capturing, formatting and naming releases.
This weekend a major change comes into force. Until now MP4 has been the video format of choice, but the change in standards means that this format is being ousted in favor of MKV. There are astoundingly lengthy standards documents covering standard and high definition releases of TV shows, and while the alterations are touted as bringing things up to date, not everyone is happy.
You can browse through the full scene release rules if you feel so inclined, but TorrentFreak has helpfully hosted the revised standards for HD and SD releases. Although compliance with the standards is described as 'optional' many scene groups have already made the switch ahead of the changeover date. The introduction to the document says:
Since the last revision of this document in 2011, TV-X264 has grown and become a major section that many people contribute to and depend on. This new revision aims to update the standards from 2011 to standards suitable for 2016 and the future. Adding clarity and patching loopholes to once again allow for consistent and quality releases, which was the aim of this standard back in 2011.
Compliance with this document is optional as of its pre date, and mandatory as of 2016-04-10 00:00:00 UTC (1460246400 Unix time).
Not everyone is in agreement that MKV is a superior format to MP4, and many casual torrenters have been confused by a sudden switch in format. MKV has long been used as the format of choice for HD movie releases, applying the standards to TV releases -- included SD versions -- could affect, and bewilder, millions of pirates. Some have complained that their preferred media player doesn’t support MKV.
The rules come into play on Sunday 10 April; you have been warned.
Photo credit: Blablo101 / Shutterstock
-

Microsoft releases Project Centennial Desktop App Converter Preview for Windows 10
Publié: avril 8, 2016, 10:43pm CEST par Mark Wilson
At Build 2016 earlier this month, Microsoft talked about Project Centennial and the Desktop App Converter. Part of the company's app drive, the tool has been designed to make it easier for developers to convert legacy apps into Universal Windows Platform (UWP) apps for Windows 10.
This is Microsoft's attempt to get more apps into the Store, making things as easy as possible for devs. Designed to run on the Enterprise and Pro versions of Windows 10 Anniversary Update build 14316 and newer (Redstone), Desktop App Converter is a free tool that can be used to quickly create apps that will run not only on Windows 10 desktops, laptops and tablet, but also phones, HoloLens and Xbox One, taking full advantage of features such as Live Tiles.
Microsoft's Mark LeBlanc introduces the Desktop App Converter Preview in the Windows Dev Center. He describes the tool as being compatible with "Windows 10 Anniversary Update Enterprise edition preview (Build 10.0.14316.0 and later)", but Paul Thurrott says that Microsoft contacted him to say that this is a typo and the Pro version of Windows 10 is also supported.
LeBlanc's post explains a little about the tool and provides instructions for getting started, along with some examples:
Desktop App Converter is a pre-release tool that enables you to bring your existing desktop apps written for .NET 4.6.1 or Win32 to the Universal Windows Platform (UWP). You can run your desktop installers through the converter in an unattended (silent) mode and obtain an AppX package that you can install by using the Add-AppxPackage PowerShell cmdlet on your development machine.
The converter runs the desktop installer in an isolated Windows environment using a clean base image provided as part of the converter download. It captures any registry and file system I/O made by the desktop installer and packages it as part of the output. The converter outputs an AppX with package identity and the ability to call a vast range of WinRT APIs.
True to recent form for Microsoft, Desktop App Converter has a telemetry element to consider:
Desktop App Converter may collect information about you and your use of the software and send this info to Microsoft. You can learn more about Microsoft's data collection and use in the product documentation and in the Microsoft Privacy Statement. You agree to comply with all applicable provisions of the Microsoft Privacy Statement.
By default, telemetry will be enabled for the Desktop App Converter. Add the following registry key to configure telemetry to a desired setting:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DesktopAppConverter- Add or edit the DisableTelemetry value by using a DWORD set to 1.
- To enable telemetry, remove the key or set the value to 0.
You can grab a copy of Desktop App Converter from Microsoft.
Photo credit: omihay / Shutterstock
-

Maktub ransomware phishing scam knows your home address and uses it as leverage
Publié: avril 8, 2016, 5:55pm CEST par Mark Wilson

Ransomware is one of the most prevalent security threats at the moment, and each week there are new examples that up the ante a little more. In recent months we have seen cross-platform ransomware, Tesla 4's unbreakable encryption, and the MBR-overwriting antics of PETYA, but a new phishing scam takes another approach.
In a cleverly orchestrated campaign, a phishing scam is doing the rounds whereby malware meets social engineering in a bid to extract cash from victims. It marries together the file-encrypting Maktub ransomware with a thinly-veiled threat -- home addresses. Quoting victims' home addresses to them serves two purposes: it adds a level of authenticity to the phishing email, but also acts as additional leverage by upping the fear level.
Andrew Brandt from security firm Blue Coat explains that victims receive emails informing them that they owe large sums of money to various businesses. To make the phishing scam seem genuine, victims are advised that hard copies of invoices will be sent to their home address -- which is listed in the email -- but a link purports to provide instant access to the documents. Of course, clicking the link is a mistake.
Speaking to the BBC, Brandt said that the speed with which the ransomware strikes is terrifying:
It's incredibly fast and by the time the warning message had appeared on the screen it had already encrypted everything of value on the hard drive -- it happens in seconds.
There have been suggestions that addresses have been gathered from eBay accounts, but this is something that eBay denies. What is clear however, is that quite some thought has been put into this ransomware campaign which is all about getting people to pay up.
As with other instances of ransomware, pressure is put on victims to pay the ransom to decrypt their files sooner rather than later. Pay within three days, Maktub promises, and the fee is 1.4 Bitcoins (around $588), but leave it a while and this increases to 3.9 Bitcoins (around $1638). The ransomware threatens that if it is ignored for more than two weeks encrypted data could be rendered completely unrecoverable.
Photo credit: zsooofija / Shutterstock
-

WhatsApp's end-to-end encryption is not all it's cracked up to be
Publié: avril 8, 2016, 4:53pm CEST par Mark Wilson

Just a few days ago, WhatsApp trumpeted the roll out of end-to-end encryption for its messaging service. The world rejoiced. With events such as the battle between Apple and the FBI turning attention to encryption, the announcement was well-timed to ride the crest of the wave. But it seems that for all of the bluster and bravado, the news about extra protection may not be quite as good as it seems.
Analysis of WhatsApp's privacy documentation reveals that the Facebook-owned company retains a huge amount of data about messages that are sent. If this all sounds familiar, it's because the retention of metadata is precisely what the NSA was (is?) up to, trawling web communications and upsetting Edward Snowden and privacy advocates around the world. WhatsApp's encryption and policies mean that those who are concerned about their privacy should not rest on their laurels.
The end-to-end encryption now employed by WhatsApp may mean that it -- and third parties -- do not have access to the contents of messages that are sent, but it does still know a great deal of potentially privacy-invading information about communication. Included in the data that WhatsApp 'may retain' (which, it's fair to assume, can be read as 'does retain') is information about who has communicated with whom, when this communication took place and the intriguingly worded 'any other information which WhatsApp is legally compelled to collect'.
The privacy section of WhatsApp's Terms of Service says:
WhatsApp may retain date and time stamp information associated with successfully delivered messages and the mobile phone numbers involved in the messages, as well as any other information which WhatsApp is legally compelled to collect. Files that are sent through the WhatsApp Service will reside on our servers after delivery for a short period of time, but are deleted and stripped of any identifiable information within a short period of time in accordance with our general retention policies.
The Apple vs FBI case-that-never-was has highlighted the fact that even when encryption is in place, it is certainly no guarantee that data cannot be accessed by law enforcement agencies. WhatsApp's connection with Facebook -- a social network that gathers huge amounts of information about its users not only in the interests of personalization, but also for ad-tailoring -- coupled with the privacy policy will do little to quell the fears of those concerned about snooping into their correspondence. End-to-end encryption is a step in the right direction, but it is far from being the end of the story when it comes to privacy.
Photo credit: Maksim Kabakou / Shutterstock
-

Facebook encourages conversation with Messenger Links and QR-like Messenger Codes
Publié: avril 8, 2016, 1:48pm CEST par Mark Wilson

WhatsApp may have a billion users, but Facebook Messenger isn't far behind: Mark Zuckerberg says "900 million people now use Messenger every month". Nowadays, Facebook is about much more than people sharing pictures of breakfast and bitching about their friends, it's also a valuable tool for businesses.
With this in mind, Facebook is adding a number of features to Facebook Messenger that it says will make it easier for businesses to connect and converse with their customers. Usernames will make it easier for people to identify businesses, while Messenger Links and Messenger Codes (just think QR codes with a fresh lick of paint) are being rolled out to make it quicker and easier to start conversations.
Messenger Links are fairly self-explanatory affairs: a simple URL that people can click to start a Messenger conversation. The URL takes the form m.me/username, and is really an extension of the idea of vanity URLs. In a very similar vein are Messenger Codes. Like QR codes, these are similar to barcodes and can be scanned with a smartphone camera as a shortcut to starting a messenger conversation.
Zuckerberg himself explains Facebook's spin on QR codes:
Messenger Codes let you just pull out your phone and scan someone else's code -- it's the new circular pattern surrounding their profile photo in Messenger settings. Messenger then starts a conversation with them. No more misspelled names or mistyped phone numbers.
As you can see from the image above, Messenger codes are somewhat more attractive and customizable than QR codes. Facebook says that "businesses can use Messenger Links and Messenger Codes in ads, on their website or in any other marketing channel to prompt people to reach out to them directly".
If you don’t see these new features yet, just sit tight as they're rolling out gradually over the coming weeks.
-

FBI briefs senator about how it cracked San Bernardino iPhone, but keeps Apple in the dark
Publié: avril 7, 2016, 1:37pm CEST par Mark Wilson

It turned the case of the century in to the case that didn’t really happen. The battle between Apple and the FBI came to a sudden end last month when the US Justice Department said it didn’t need the iPhone manufacturer's help, and then successfully hacked its way into the iPhone in question.
With the San Bernardino shooter's iPhone seemingly successfully cracked, the FBI last night revealed to Senator Dianne Feinstein just how it managed it. There are no current plans to share this information with Apple, but FBI Director James Comey revealed that the tool that was brought in only works on the iPhone 5c.
Apple will almost certainly be disappointed that the FBI is choosing not to share the cracking method, but it's not yet clear whether the company plans to take legal action to obtain this information. The fact that Comey has said the method will not work on the iPhone 5s or iPhone 6 will come as some comfort to those concerned about security and privacy, but Apple will be keen to patch any vulnerabilities exploited by the FBI so that other parties may be prevented from using the same technique to access different iPhone 5c handsets.
As reported by the National Journal, speaking at Kenyon College's Center for the Study of American Democracy last night, Comey said "we just haven't decided yet" in reference to coming clean with Apple. The agency has not said whether or not it managed to garner any useful information from the phone by hacking into it, saying:
We're still working on that, I guess is the answer. It was worth the fight to make sure that we have turned over every rock that we can with respect to the investigation. We owe it to the victims and the families to make sure that we pursue every logical lead.
It's not clear what happens next. There is unspoken, and spoken, pressure on the FBI to reveal all to Apple, and iPhone users will be keen for the company to pursue this in the interests of their security. With the incredible public interest not just in this case specifically, but also privacy, security and encryption more generally, Apple will also be feeling the pressure from its customers, particularly in light of Tim Cook's proclamations of fighting for its user base.
Photo Credit: Shutterstock/ymgerman
-

Chuwi Hi12 -- a Surface Pro 4 and iPad Pro alternative at a fraction of the cost [Review]
Publié: avril 6, 2016, 8:08pm CEST par Mark Wilson

The number of convertible tablets vying to take on Microsoft's Surface Pro 4 is on the increase. Some are more than reasonable competition while others are little more than cheap knock-offs. The absurdly low price of the Chuwi Hi12 might fool you into thinking that this 12-inch Chinese tablet falls into the latter camp, but you'd be wrong.
Costing an unbelievably low $289.99 (neatly below the promised $300 threshold), the Hi12 is not strictly a direct competitor to the Surface range... it lacks the all-important kickstand. So we're off to a great start with price, and the looks are certainly not to be sniffed at either; it's not a million miles away from iPad territory. But while looks and price are important, it's what's on the inside -- and how it works -- that matters, and the Hi12 does not disappoint.
As you'd guess from the name -- and, indeed, my direct reference to its size -- the Hi12 is a 12-inch tablet. The 3:2 aspect ratio apes the look of an iPad as other features of the tablet do, but the capacitive Windows button is one of the things that reveals the truth. When in landscape mode, this button appears to the right of the screen, just as with modern Surfaces, and stereo speakers appear at the bottom of the unit. This does make for something of a lopsided experience when listening to audio in portrait mode, but the sound is of a decent quality.
The build quality of the Hi12 is generally high, and the all-metal body gives a high-quality feel. The same is true of the optional keyboard. Put the two together, however, and it's not such as happy tale. There is noticeable play in the hinge which, while not concerning enough to completely discourage use, certainly reduces the overall experience. In general usage, the play is not too noticeable -- unless you're typing on your knee and hitting the keys hard enough to cause wobble -- but when you open and close the lid, it's hard to ignore. This is a real shame because it means that the first and final few seconds with the device are disappointing even if the intervening time is perfect.

Like the Surface range, the keyboard (which adds 743g to the overall weight) snaps into place with the help of magnets. It's all pretty secure -- if you hold just the screen, the keyboard isn't going to fall off -- but there isn't the satisfying docking click that the Surface offers. The keyboard not only allows for easy typing by transforming the tablet into a laptop, it also adds a couple of extra USB ports. For a typing session -- even fairly extended one -- the keyboard is a pleasure to use, although backlighting would have been nice. The trackpad is fine, but the clicking action of the integrated left and right mouse buttons is far from perfect. There is something of a cheap feel to clicks that detracts from an otherwise decent piece of hardware. The trackpad is multi-touch friendly though, so you can avoid clicking altogether and just tap instead.

Chuwi claims a battery life of 6-8 hours, and (non-scientific) tests bear this out. This is a machine that could get you through the working day without scrabbling for a power socket every couple of hours. A big bonus is the fact that charging takes place via a microUSB port so you can share a cable with your phone, charge up in the car without the need for an inverter -- it's an all-round neat solution. The Atom processor here may not be a powerhouse, but that's not what the Hi12 is about. This is just about providing a perfectly capable device with above-average performance at a below-average price. On both counts it succeeds admirably.

The screen is of an undeniably high standard, and while the brightness of 400 lumens is not best in class, it's certainly good enough for indoor and outdoor use without problems. There's also a pleasing lack of glare.
Here's a full breakdown of the specs:
- Screen Size: 12.0 Inches
- OS: Windows 10 Home + Android 5.1 (maybe)
- Colors: Champagne Gold; Space Gray
- Screen Resolution: 2160 x 1440 (3:2)
- CPU: Intel X5 Cherry Trail Z8300 1.44GHz (Max up to 1.84GHz), 64-bit quadcore
- GPU: 8th Generation Intel Graphics (up to 500MHz)
- RAM: 4GB DDR3L
- ROM: 64GB
- Extended Storage: Up to an extra 64GB
- Battery: 3.7V / 11000mAh
- Camera: Front - 2MP, Back - 5MP
- Connectivity: Bluetooth 4.0, HDMI, WiDi, 802.11 b/g/n, 1 x USB 2.0, 1 x USB 3.0, 1 x micro USB
- Dimensions: 296.7 x 202.8 x 8.9mm
- Weight: 852g
Is there room for improvement? Sure. A bit more power would be nice, and the wobbly keyboard connection does feel like it lets the side down a little. It would be nice if the keyboard was included as standard, although this would clearly bump up the price, and the choice of going keyboardless is welcome. The keyboard would also benefit from sharing the same material as the Hi12 itself -- simply matching the color isn’t good enough. To be considered a true competitor to the Surface Pro 4 or iPad Pro, a stylus really is needed, but this is something that is just not available for the Hi12, sadly -- not a native peripheral, at least.

If you want to get your hands on the Chuwi Hi12, you can pick one up from Panda Will for just $289.99 -- and that includes free global shipping. A standard US two-pin plug is provided, so bear that in mind if you're in a different part of the world, although any compatible USB charger will do the job. If you like the idea of the keyboard cover, this will set you back a mere $57.99, also from Panda Will. As with the Hi12 itself, the keyboard is available in Champagne Gold or Space Gray (or just Gold and Grey as Panda Will refers to the hues).

If you want to see what you get in the box, check out the unboxing video from Panda Will below:
We had previously -- based on information provided by Chuwi -- referred to the Hi12 as being a dual boot Windows 10 Home / Android 5.1 device. The review sample provided runs only Windows 10 Home, and it is not yet clear whether the Android option is a separate version of the Hi12 or if an update will bring the dual boot feature. We're waiting for clarification from Chuwi, but even if this is just a Windows 10 tablet, it's an incredibly competent and highly recommended one. Android would just be a bonus.
-

Facebook boosts live video with new interactive options including Live Reactions and group video
Publié: avril 6, 2016, 3:05pm CEST par Mark Wilson
Facebook Live may have started life as a celebrity-only feature, but it soon spread to all users, giving them the opportunity to share their own live video streams. Today the social network unveils a number of new features with the aim of making it easier to find and share live broadcasts, as well as personalizing and interacting with video.
Live video is all about bringing together a community of people to share an experience, so it's little surprise that the first of today's announcements sees the arrival of Facebook Live to Facebook Groups and Facebook Events. Building on the Reactions feature that rolled out recently, live video now also benefits from Live Reactions. But the laundry list of new features doesn't end there.
To build on the interactivity, Facebook is making more of the ability to comment on live videos. Now when footage is replayed at a later date, comments will also be replayed 'as live'. Personalization is made possible through the addition of Live Filters, and on the horizon is the promise of the ability to doodle on live videos. But bearing in mind the popularity of the standard Reaction, it’s the Live Reactions that will probably go down the best with users. Facebook says:
Facebook Live is interactive and fun: Live reactions, replaying comments made while live and Live filters will make it even more so. Live Reactions makes it easy for your viewers to express their feelings in real time during a live broadcast. Using the same reactions we launched in News Feed, viewers can select Love, Haha, Wow, Sad or Angry, and the reactions animate right on top of the video. Live Reactions appear in real time and disappear quickly so broadcasters and other viewers can get a sense of how people are feeling at different points during the live video -- it’s like hearing the crowd applaud and cheer. When your friend reacts to your video or to a video you are both watching together you’ll see their profile pic and a little starburst before their reaction appears.
Building on the idea of making video viewing a shared experience, Facebook is adding the option to invite friends to watch along with you. There really is a big push of Facebook Live at the moment, and discoverability is the name of the game. On the desktop, today sees the launch of a Facebook Live Map to help people find broadcasts that are taking place at the moment. A similar feature is rolling out to mobile apps which will enable users of the social network to find current, popular and trending videos more easily.
-

Chinese censors spring into action to erase mentions of Panama Papers from the web
Publié: avril 6, 2016, 1:21pm CEST par Mark Wilson

The Panama Papers that leaked following the Mossack Fonseca hack turned the spotlight on the rich and famous seemingly involved in money laundering and tax evasion schemes. High profile names from the world of politics appear in the papers -- including close friends of Russian President Putin and the father of UK Prime Minister David Cameron.
The leaked 11.5 million files, spanning 2.6 TB of data, include references to the relatives of at least eight current or former Chinese officials, says the International Consortium of Investigative Journalists. Chinese censors have now gone into overdrive, working overtime to eliminate all mentions of this from Chinese websites.
An official directive sent to Chinese editors informs them that they are forbidden from writing about the Panama Papers. It's a move that's reminiscent of attempts to erase the Tienanmen protests from the history books. The leaked directive, published by the China Digital Times, issues a stark warning to journalists thinking about covering the topic:
Find and delete reprinted reports on the Panama Papers. Do not follow up on related content, no exceptions. If material from foreign media attacking China is found on any website, it will be dealt with severely.
The Great Firewall of China is famous for limiting the access Chinese citizens have to news from the outside world, and the country's media is very tightly controlled by the communist government. Deviation from directives handed down by the ruling party results in harsh punishment, but the censorship extends beyond the purging of stories from the web.
Free Weibo, a site that monitors the censorship of internet searches in China, reports that the word Panama is the most censored word at the moment, and China Digital Times says that terms such as "Panama + offshore", "offshore + finance", "Panama + Deng Jiagui", and "Panama + Li Xiaolin" are blocked.
Photo credit: Markus Mainka and Ivan Ryabokon / Shutterstock
-

Swipebuster: $4.99 is all it costs to see if your partner (or anyone you know) is using Tinder
Publié: avril 6, 2016, 12:18am CEST par Mark Wilson

Its developer -- who wishes to remain anonymous -- says that his website exists to educate people about the importance of privacy. But Swipebuster sells itself as a way for suspicious partners to check upon their other halves if they think they might be making use of Tinder to seek out some 'extracurricular activity'.
Swipebuster taps into the Tinder API to access publicly available data to see if a particular individual appears in the membership database. It’s perfect not only for confirming or denying worst fears, but also a valuable tool for a would-be blackmailer. For just $5, you can conduct three searches to see if people you know are using Tinder.
Talking to Vanity Fair, Swipebuster's developer said that the site is essentially an experiment that highlights the poor privacy practices used by sites and services, as well as the foolhardiness of users. "There is too much data about people that people themselves don't know is available. Not only are people oversharing and putting out a lot of information about themselves, but companies are also not doing enough to let people know they're doing it."
Swipebuster is not quite as scary as it sounds in terms of privacy invasion. Quite. The developer has been fairly careful to provide, and give, just enough information, but not so much as to risk facing lawsuits... probably. To search for a possibleTinder user, you need to provide a first name, age, gender and the location from which you feel they may have been using the dating app. In big cities, it's likely that searches could yield multiple results, but the same cannot be said for people living in more remote areas.
It's fair to say that Swipebuster is morally questionable, but the developer does highlight important privacy issues. This, however, will do little to calm the fears that have been expressed by concerned parties who point out that the site could be used by stalkers and disgruntled exes to gather ammunition. Interestingly, Tinder itself does not seem particularly concerned about the existence of the service. A spokesperson said: "If you want to see who's on Tinder we recommend saving your money and downloading the app for free."
Photo credit: Kaspars Grinvalds / Shutterstock
-

Reminders come to Google Calendar on the web, bringing to-do list support
Publié: avril 5, 2016, 11:21pm CEST par Mark Wilson
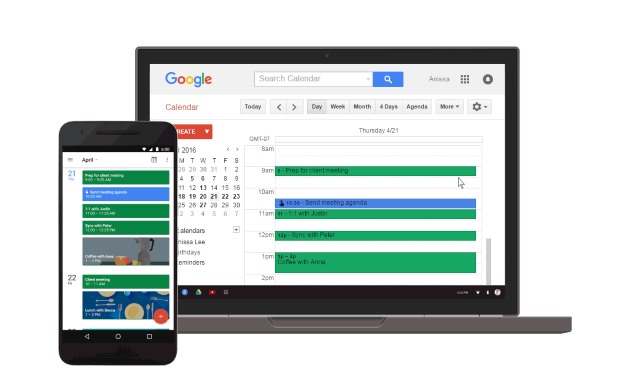
A calendar offering reminders might seem like a fairly obvious feature, but here we're talking about Reminders (note the initial cap). Towards the end of last year, Google Calendar on iOS and Android gained support for Reminders -- and, as a result, to-do lists -- and now the same feature is coming to Google Calendar on the web.
Unlike standard calendar appointments, Reminders stick around until you tick them off. There's no need to keep changing the due date on something you don't get round to doing, as it will automatically roll over to the next day and appear on your calendar until you take the appropriate action.
Importantly, Reminders that have been created in mobile apps will sync to the web version of Calendar, but this is not the only place they can be created. Reminders can also be created via Google Now, Keep and Inbox, and these will all be collated together in your calendar. Google says:
Just like on Android and iPhone, you'll get the following:
- Reminders stick around -- If a reminder isn't completed, it will appear at the top of your calendar until you mark it done.
- Reminders work across Google -- Reminders you create in Inbox, Keep, and the Google app will also show in Google Calendar.
- Reminders sync with mobile -- Reminders created in mobile show up on the web and vice versa. So you can stay on track from just about anywhere.
If you don’t see Reminders on the web just yet, you won't have to wait long as the feature is rolling out this week.
-

Full end-to-end encryption shows WhatsApp is serious about privacy
Publié: avril 5, 2016, 10:35pm CEST par Mark Wilson

Encryption has been a hot topic for some time, but the battle between Apple and the FBI really brought it to the fore in recent weeks. In response to the FBI trying -- ultimately successfully -- to crack into the San Bernardino shooter's iPhone, WhatsApp was just one of the companies that promised to increase encryption.
Today the popular chat tool made good on its promise, enabling full end-to-end encryption; this means that calls, messages, photos, videos, files, voice messages, and group chats are all protected with end-to-end encryption. Importantly, this extra layer of security is enabled by default, leading WhatsApp to claim it is "a leader in protecting your private communication".
With more than a billion people making use of WhatsApp, the number of messages that will benefit from encryption is staggering. WhatsApp says that it is one of a small number of communication tools to feature end-to-end encryption by default, and says it hopes it "will ultimately represent the future of personal communication". The company is very blunt about why it feels encryption is so important:
The idea is simple: when you send a message, the only person who can read it is the person or group chat that you send that message to. No one can see inside that message. Not cybercriminals. Not hackers. Not oppressive regimes. Not even us. End-to-end encryption helps make communication via WhatsApp private -- sort of like a face-to-face conversation.
WhatsApp points out that it is easy to check that end-to-end encryption is enabled by simply looking "for the indicator in contact info or group info". The only requirement for end-to-end encryption is that all parties involved need to be using a version of WhatsApp released after March 31, 2016, and the company has provided a white paper that goes into more technical detail about the security used. It starts by saying:
The Signal Protocol, designed by Open Whisper Systems, is the basis for WhatsApp’s end-to-end encryption. This end-to-end encryption protocol is designed to prevent third parties and WhatsApp from having plaintext access to messages or calls. What's more, even if encryption keys from a user’s device are ever physically compromised, they cannot be used to go back in time to decrypt previously transmitted messages.
So to stay secure, just make sure that you have the very latest version of WhatsApp installed, and the rest will be taken care of for you.
Photo Credit: kraphix/Shutterstock
-

Upgrade to Windows 10 Mobile and you can still roll back to Windows Phone 8.1 -- with caveats
Publié: avril 5, 2016, 12:30pm CEST par Mark Wilson

After months of testing, Microsoft has started the process of rolling out Windows 10 Mobile to a selection of Windows Phone 8.1 handsets. Users who have been part of the Insider program will know what to expect, but for others the changes may come as something of a surprise.
In fact, it's entirely possible that you'll upgrade to Windows 10 Mobile and not like what you see. The good news is that Microsoft will allow you to roll back to Windows Phone 8.1, and there's no time limit on doing so.
In many ways, Microsoft is being surprisingly flexible with the Windows 10 Mobile upgrade program -- certainly more so than with Windows 10 on the desktop, many would argue. There is, of course, the fact that not all handsets are in line to get the upgrade, but Microsoft has made it clear that anyone who decides that Windows 10 Mobile is not for them will be able to revert to their previous OS.
But it's not all good news.
There will not be a clean roll back process to follow. In order to revert to Windows Phone 8.1, you'll need to make use of a recovery image as Microsoft confirms on Twitter:
@GabeAul For a Retail user going from 8.1 to 10 who may hit an issue and need to recover, they need an 8.1 image to recover to.
— Jason (@NorthFaceHiker) April 4, 2016
The downside to this is that it wipes the phone, so personal data will have to be backed up first lest it be lost forever. The retention of Windows Phone 8.1 recovery images is great for those of an indecisive nature, but it's also something of a double-edged sword. For Insiders, it means there is no easy way to roll back to a previous build, and Microsoft has no plans to change this:
@zayn_brandon @neil_hedley @windowsinsider @GabeAul No plans for that. Devices that originally had 8.1 will keep those orig recovery images
— Jason (@NorthFaceHiker) April 4, 2016
-

The threat of ransomware is so great, the US and Canada issue joint security alert
Publié: avril 4, 2016, 7:30pm CEST par Mark Wilson

Malware is far from being a new problem, but the inexorable rise of ransomware has taken many by surprise. There have been a number of very high profile instances of ransomware such as PETYA, and the threat is perceived as being so high that the US and Canada have taken the unusual step of issuing a joint security alert.
The likes of TeslaCrypt 4 feature 'unbreakable encryption' and use scare-tactics to encourage victims to part with their money. This is what has prompted the joint alert from the US Department of Homeland Security and the Canadian Cyber Incident Response Centre which warns about "destructive ransomware variants such as Locky and Samas". Interestingly, the advisory actively discourages victims from bowing to ransom demands.
The advisory warns that "individuals or organizations are discouraged from paying the ransom, as this does not guarantee files will be released". However, it does recognise that "the authors of ransomware instill fear and panic into their victims, causing them to click on a link or pay a ransom". But this is said to be a bad idea as it could lead to additional malware infection, and could result in the theft of bank details and other data.
The focus is on prevention rather than cure, and US-CERT offers a number of tips aimed at both users and administrators:
- Employ a data backup and recovery plan for all critical information. Perform and test regular backups to limit the impact of data or system loss and to expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Use application whitelisting to help prevent malicious software and unapproved programs from running. Application whitelisting is one of the best security strategies as it allows only specified programs to run, while blocking all others, including malicious software.
- Keep your operating system and software up-to-date with the latest patches. Vulnerable applications and operating systems are the target of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker.
- Maintain up-to-date anti-virus software, and scan all software downloaded from the internet prior to executing.
- Restrict users’ ability (permissions) to install and run unwanted software applications, and apply the principle of "Least Privilege" to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through the network.
- Avoid enabling macros from email attachments. If a user opens the attachment and enables macros, embedded code will execute the malware on the machine. For enterprises or organizations, it may be best to block email messages with attachments from suspicious sources. For information on safely handling email attachments, see Recognizing and Avoiding Email Scams. Follow safe practices when browsing the Web. See Good Security Habits and Safeguarding Your Data for additional details.
- Do not follow unsolicited Web links in emails. Refer to the US-CERT Security Tip on Avoiding Social Engineering and Phishing Attacks for more information.
Photo credit: Borislav Bajkic / Shutterstock
-

Microsoft and R3 blockchain partnership aims to reduce fraud and costs
Publié: avril 4, 2016, 5:58pm CEST par Mark Wilson

Microsoft has joined forces with a collective of more than 40 financial institutions to help push the development of blockchain technology. Working with the R3 consortium, Microsoft wants to develop and test new technologies to replace and streamline old systems used in banking and enterprise industries.
The announcement comes as the company launches the first Microsoft Envision event with the aims of bringing together business leaders to pool ideas for the digital age. Using Microsoft Azure, the company wants its partners to expand the use of Blockchain-as-a-Service and bring about change faster.
Despite the involvement of financial institutes, and the association with Bitcoin, blockchain is about much more than just moving money from one place to another. Microsoft is looking to create what it describes as an 'enterprise-grade blockchain eco-system' that can also be used in the healthcare industry, digital media and manufacturing.
Announcing the partnership with R3, Microsoft's Executive Vice President of Business Development, Peggy Johnson, says:
Known by many as the backbone of bitcoin, blockchain offers a secure and transparent way to digitally track the ownership of assets. Simply put, it promises to revolutionize the way financial institutions conduct transactions. Blockchain modernizes legacy financial processes, so trades of assets like stocks and bonds can be finalized in minutes, not days. And by enabling a more direct transfer of ownership, it eliminates the need for middlemen like clearing houses, both cutting costs and greatly reducing the risk of fraud.
With that in mind, I’m thrilled to announce a strategic partnership with R3, a consortium of leading banking institutions, to help move blockchain technology from hype to reality for the financial services industry. Together, we will help R3’s over 40 member banks develop, test and deploy blockchain technologies to modernize decades-old processes and streamline operations, potentially saving billions of dollars from back-office operations.
Check out the video below in which Microsoft explains its vision a little:
Photo credit: Olga Donskaya / Shutterstock
-

93% of UK mobile users have their location tracked every day
Publié: avril 4, 2016, 5:39pm CEST par Mark Wilson

Awareness of the privacy issues involved in using various devices and software has grown dramatically in recent years -- there can be few readers who do not know about the telemetry and privacy concerns surround Windows 10, for instance. But a new campaign by privacy-focused advocacy group Krowdthink aims to raise aware of the privacy implication of owning a mobile phone in the UK.
The 'Opt me out of Location' campaign aims to highlight the fact that nearly every single mobile phone owner in the UK (93 percent) has unwittingly signed up for a contract that permits their location to be tracked. More than this, the data collected allows providers to build up highly detailed customer profiles which Krowdthink warns leaves millions of users just one serious data breach away from having private data exposed to and abused by criminals.
Krowdthink says that "the big location data breach has yet to occur", but there is great concern around the fact that most people are simply unaware that their location is being almost constantly -- and very precisely -- monitored. All the more worrying is the selling on of this data, opening up even more opportunities for data to be hacked, leaked, or breached. The group says that education is important, saying "we need to exercise our rights to opt out and ideally seek an explicit opt-in from those tracking us".
Geoff Revill, the founder of Krowdthink, cautions:
The fact of the matter is your mobile and Wi-Fi service providers know -- without you knowing -- where you are, how you got there and can figure out where you are going.
It's not just mobile phone providers that are cause for concern; Krowdthink says that public Wi-Fi service providers are also concerning sources of location data. Pete Woodward from security company Securious says: "location tracking data would be gold dust for the criminal fraternity and would be very saleable on the black market".
Research by Krowdthink says that while most mobile users are suspicious of apps that make use of GPS, few people think about the fact that their location is highly trackable when they connect to cell towers. By gathering data about location and movement, it is possible to build up detailed user profiles that could be valuable to criminals. Burglars, for instance, would be able to quickly determine when particular houses were usually empty, but there is also scope for data that's gathered to be used for blackmail: "… identifying any cases of infidelity -- including when, where and how long for. [Location data also] identifies your sex, probable sexual orientation, your religion and many other personal preference".
Similar research has been carried out by the Open Rights Group, with the findings suggesting that consumers are simply not being given enough information to make properly informed decisions about how their data is used.
You can find out more about the Opt Me Out Of Location at the campaign website, where you'll also find out how to manually opt out of location tracking with a number of mobile providers.
Photo credit: Georgejmclittle / Shutterstock
-

New Start Menu features on the way in Windows 10 Anniversary Update
Publié: avril 4, 2016, 2:34pm CEST par Mark Wilson
Windows Insiders will soon be able to try out a new Start Menu when preview builds of Windows 10 Anniversary Update begin to roll out. We already know some of what to expect from this big update to Windows 10 -- such as badge notifications in the taskbar for UWP apps -- and now we can see what the updated Start menu looks like too.
The same Microsoft software engineer who shared details of badge notifications -- Jen Gentleman -- has posted an animated GIF to Twitter that shows the Start Menu in action. There are a few notable changes in the updated version, including a nested hamburger menu.
As the new Start Menu is only currently being tested internally at Microsoft and is yet to roll out even to Windows Insiders on the Fast ring, it's entirely possible that things will change over the coming weeks. That said, the animation does give an intriguing insight into the ideas that Microsoft is playing with.
Ms Gentleman's tweet may only be a few seconds long, but it has generated a good deal of interest:
By popular request, to ease some concerns, and because @ZacB_ asked nicely, here's the new start menu in action!
 pic.twitter.com/MiIPO8Epuf
pic.twitter.com/MiIPO8Epuf— Jen Gentleman (@JenMsft) April 4, 2016
The hamburger menu is used to house the icons that currently appear in both the All Apps and 'Most used' sections. The redesign also helps to provide easy access to system folders such as Music and Documents. There are also changes on the cards for the Start screen as the Feedback Hub reveals:
Start menu: This view is predominantly designed for PC. We've heard your feedback, and we’ve focused on consistency, efficiency, simplicity, and making better use of the space.
The All apps list is essential to understanding which apps you have on your device. We’ve elevated this list to the top level of the UI to reduce clicking & scrolling. This makes it easier to access apps in the All Apps list. It also reinforces the consistent Start experience across form factors.
Start screen: This view is predominantly designed for tablet. We've heard from Insiders that they feel Windows 8.1 start screen delivered a better tablet experience than what we have in Windows 10 today. We are addressing that and are looking to make the All apps list more usable in two ways:
- Full-screen All apps list in tablet mode. We heard your feedback that the All apps list should be full-screen in tablet mode and explored several designs that aid efficiency while taking advantage of the additional real estate when Start is full screen. Specifically, we’re striking a balance between density and "scan-ability" (i.e. how easy it is to scan the list to find the app you want).
- A combined "Most used" and "All apps" list view. With this approach, we hope to address the confusion that many users felt with the two very similar list views ("Most Used" and "All apps").
As part of this improvement, we’ve also made it easier and more clear how to switch between the "Pinned Tiles" and "All apps" views by adopting the navigation pane pattern used throughout Windows.
Microsoft is looking for feedback about this change just as it has done with other new features of Windows 10, and you can provide your thoughts via the Feedback Hub and find out more on Sway.
-

Pedants revolt -- the Internet is dead, long live the internet
Publié: avril 3, 2016, 8:02pm CEST par Mark Wilson

In a move that's likely to prove somewhat divisive -- old-fashioned stick-in-the-muds on one side, sensible people on the other -- the Associated Press is dropping the capitalized Internet from its widely-adopted style guide.
For what seems like far, far too long, the internet has been treated by the AP and countless websites, magazines and newspapers as a proper noun, driving those of a sensible bent mad. But now it's only a matter of weeks before Internet is consigned to history and 'internet' will become the norm.
There will almost certainly be a few stalwarts who hang on doggedly to the old, capitalized spelling, but the power of the AP style guide is such that 'internet' should start to become even more prevalent than it currently is. If you are likely to see Internet used anywhere, it will be in the same places where you'll see Email or e-mail used with gay abandon.
The style guide is due to be updated in just a couple of months, as the AP revealed via Twitter:
We will lowercase internet effective June 1, when the 2016 Stylebook launches. #ACES2016 pic.twitter.com/vv53323GL6
— AP Stylebook (@APStylebook) April 2, 2016
Which side of the fence do you fall on? Will the capital I have to be wrestled from your cold, dead hands?
Photo credit: dizain / Shutterstock
-

Windows 10 Anniversary Update to bring badge notifications to the taskbar
Publié: avril 3, 2016, 7:13pm CEST par Mark Wilson
The idea of badges is a very familiar concept on mobile phones. A little numerical overlay on app icons provides at-a-glance info about the number of notifications there are to look at for different apps and services. Now Microsoft has revealed that the same feature is coming to the desktop.
Among the changes in Windows 10 Anniversary Update are taskbar badge notification for Universal Windows Platform apps. This new style of notification joins improved toast notifications and changes to the Action Center. Developers will be able to try out the feature soon, and we've got a sneaky glimpse of how things will look.
As with so many of the announcements to come out of Build 2016, Microsoft has not said exactly when this feature will actually see the light of day. Of course, it's Windows Insiders who will be able to try badges in action first, and with Windows 10 Anniversary Update pegged for a late summer release, it shouldn’t be long before we get to see a preview.
In the meantime, we can content ourselves with an image shared on Twitter by Microsoft software engineer Jen Gentleman:
Favourite announcement at #Build2016? Hard call - there were so many good ones.. Hope you didn't miss this, though
 pic.twitter.com/hraHxz1X39
pic.twitter.com/hraHxz1X39— Jen Gentleman (@JenMsft) April 2, 2016
It's a feature that has been a very long time coming. It's worth noting that taskbar icons have long been updatable to indicate the number if notifications that are pending, but the new system for UWP apps should make the process simpler and more widespread.
Photo credit: Jen Gentleman
-

10 'ARGH!' moments every computer user experiences
Publié: avril 2, 2016, 3:56pm CEST par Mark Wilson

Computers make life easier, right? Computers are fun, valuable tools, yeah? True, but they can also be such utterly infuriately pieces of tech that they seem to serve no purpose other than to raise our blood pressure and drive us mad.
I'm not talking about when Windows crashes, when an app hangs, or the internet slows to a crawl. I'm talking about those 'ARGH!' moments we've all experienced where there's no one to blame but ourselves. When things go wrong because of 'user error' it doesn't make them any less infuriating; in fact, the opposite is often the case. Here are ten of the most frustrating scenarios that just about every computer user has encountered at some point.
1. Trying to interact with a non-touchscreen monitor
We've all done it. It's easy to get used to working with your phone or tablet and not transition smoothly to your regular desktop or laptop. How many of us have jabbed pointless at an icon to try to open a file, or needlessly swiped a finger across the lock screen to access the password entry screen? You'd think we'd learn, but no...
2. Accidentally hitting a link in bookmarks bar
Filed under 'Almost, but not quite', we've all missed our intended target in a web browser. Positioning the bookmark toolbar beneath the Back and Refresh buttons was clearly asking for trouble, and it's all too easy to be whisked away from what you were looking at to some completely unrelated website. The distance of just a few pixels between the different hot-zones is clearly to blame, but it never gets any less infuriating.
3. Accidentally deleting files / emails
A close relative of 'accidentally hitting a link in bookmarks bar' is the accidentally deleted file or email. A poorly judged mouse click or key press is all it takes to send a missive or document into oblivion. Seriously, who at Google though that it was a good idea to put the Delete button smack in between Spam and Mark As Read? It's asking for trouble! The same goes for the Delete option in context menus -- one slip of the finger and that file is history. It's easy to feel that the Recycle Bin and email trash are just for idiots who can’t use computers properly, but we've all gone scurry there, shame-faced, looking to retrieve that important message or file.
4. Downloading files to the wrong folder and then not knowing where the f@$! they are
You might be one of those people who always download files to the Downloads folder, or maybe the desktop is your preferred destination. But even if you are regimented in your download location, there will always be the odd occasion when an alternative folder is used. Select folder, hit Save. Open folder... no file! Which damned folder did I just select? It sure as hell wasn't the one I intended to use! [Fires up a file search...]
5. Forgetting the volume is up über high
This YouTube video is a bit on the quiet side. I'll just crack up the volume.
Time passes. Forget about increased voume. Decide to put on some Nine Inch Nails
Argh! Jeezo!
Ears bleed
6. Trying to select a bunch of files, but moving them instead
If you're a fan of holding down the Shift key while selecting a series of files, you've probably never experienced the bewilderment that accidentally relocating documents. If, however, you like to draw a selection box around files, you've almost certainly flung the first file you were trying to select into a random folder. Obviously happens when you're in a rush... without fail!
7. Having pen selected instead of crop tool
Rightio... time to get to work on those holiday snaps; there are a few photos that would benefit from a little reframing courtesy of the crop tool. Well, you thought you had the crop tool selected -- but, no, it your image editor has default back to the pen so you've scrawled a diagonal line from one corner to another. Goddamit!
8. Accidentally opting to always open a certain file type with a particular app
Easily done on both a phone or a computer. You might have installed a new app and no have multiple apps that are capable of opening images or some other file type. Of course, you'll be presented with a list to choose from, as well as the option of always using a certain app. It goes without saying that you had the wrong app selected before okaying the change in defaults. Gnnnrrrr!
9. Having caps lock enabled when typing without looking
There's a danger in being able to touch type coupled with a habit of watching TV whilst working. It's something I'm guilty of, and it means I frequently type away without looking at either my keyboard or screen. When my attention is guided back to concentrating fully on what I'm doing, there have been numerous occasions when I find I've been typing away with Caps Lock on. Gah! If you're in Word, there's the handy keyboard shortcut Shift + F3 to change the case of selected text, but there are far too many applications (and, obviously, web sites) on which this doesn't work. Maddening.
10. Not being able to get the cursor into diagonal-double-headed-arrow mode to resize a window and trying to hit the target for hours on end
The title says it all, really. It's something that should take a second or less -- quickly resizing a window to a different size or shape. But can you get your mouse positioned over the corner pixel (and it does seem to be an area no bigger than a single pixel) to be able to resize horizontally and vertically at the same time? Can you flip! There it is... oh, missed it! There! No! Quick! Click and drag! Oh, forget it...
Anything you would add to the list? What makes you want to punch your monitor in inexpressible rage.
Photo credit: Ollyy / Shutterstock
-

Egypt bans Facebook Free Basics for NOT spying on users
Publié: avril 1, 2016, 7:40pm CEST par Mark Wilson

In another blow for Mark Zuckerberg's free internet service, Facebook Free Basics has been banned in Egypt. The Egyptian government made the decision after Facebook refused to allow it to use the service to spy on users.
The shutdown comes just five months after Facebook Free Basics launched in Egypt, having proved controversial in other countries for contravening net neutrality rules. But Facebook's refusal to permit government surveillance of users means that the service has been banned this time for political reasons.
The decision is not completely unexpected. The Egyptian government suspended Facebook Free Basics at the end of December because, as Reuters reports, the initial permit to operate was only temporary.
Egypt's Ministry of Communication implies that the ban comes as a result of anti-competitive behaviour, with spokesman Mohamed Hanafi saying:
The service was offered free of charge to the consumer, and the national telecommunication regulator saw the service as harmful to companies and their competitors.
While details are thin on the ground, Reuters cites 'two sources with direct knowledge of discussions between Facebook and the Egyptian government'. Whatever the thinking behind the ban is, it is unlikely to prove popular with Egyptians looking for a free way to gain access to the internet. Facebook had said at the time of the Free Basics suspension that it hoped to resolve the situation, but it has not commented on the current ban.
Photo credit: tulpahn / Shutterstock
-

Windows 10 will soon show you notifications from your Android phone
Publié: avril 1, 2016, 6:53pm CEST par Mark Wilson

The Notification Center in Windows 10 is a great idea but, many would argue, one that is both limited and poorly implemented. For anyone with a Windows 10 Mobile phone it is marginally more useful thanks to notification sharing, and this feature is due to expand to Android users as well.
At Build, Microsoft revealed that the Notification Center is in line for a major overhaul that will not only bring Cortana-power notification mirroring to Android users, but will also bring a richer, more image-heavy notification experience. The news isn’t so great for iPhone users as the more tightly controlled nature of iOS means Microsoft has a harder task on its hands.
It doesn’t end there. Also on the cards is a 'universal dismiss' option that will make it possible to kill a notification on one device and have it wiped from others at the same time. But it is almost certainly notification mirroring that will generate the most interest. It means that you will be able to see notifications from your Windows 10 computer on your Android phone, or phone notifications on your computer.
In addition to being able to see from your computer that a message has come through on your phone, you'll also be able to dismiss notifications, and even reply to messages without having to switch devices. For anyone who spends their days sitting at a computer and switching between PC and phone for different tasks, this could be a real productivity boost.
Developers will need to enable support for notification mirroring in their apps, and users will be free to enable and disable the feature for individual apps -- handy to ensure that you don’t get overwhelmed with messages.
Microsoft has not said when we'll be able to try out the feature for ourselves, but it's likely that it will make an appearance in the Insider builds that precede the upcoming Windows 10 Anniversary Update.
Photo credit: tanuha2001 / Shutterstock
-

Forget extensions, built-in ad blocking is coming to Microsoft Edge - [UPDATE... no it's not!]
Publié: mars 31, 2016, 11:05pm CEST par Mark Wilson

One of the first browser add-ons many people install to improve their online experience is Adblock Plus or something similar. Until recently, Microsoft Edge's lack of support for add-ons put off a lot of would-be users, but reports from Build 2016 suggest that native ad blocking is on its way to the Internet Explorer successor.
Adblock Plus is coming to Edge, but built-in ad blocking would negate the need for such an add-on. A slide shown off and snapped at a Build presentation shows that the next version of Edge, in response to user feedback, will feature ad blocking capabilities. There's no word on delivery timescale, but the upcoming Windows 10 Anniversary Update would seem a likely candidate. [Update: we now have a clarifying statement from Microsoft that puts rather a different spin on things].
ZDNet's Ed Bott photographed the slide which shows Microsoft's development roadmap built around feedback from testers. Right at the top of the list is reference to plans to create a plugin and extension store for Edge, but it's entry number four that's more intriguing.
"Build ad blocking features into the browser" is listed as a Feature Request from users. But the good news is that it is not only listed as being "Deliverable 4682811", but as "Targeted for the next version".
This will no doubt come as good news for those who have fallen in love with Edge, but it's not something that will be welcomed by the likes of Adblock Plus. It does seem that, particularly in the mobile arena, there is a move to baking ad blocking into the browser so it makes sense that Microsoft is following the trend. But it is the fact that Edge straddles Windows 10 on the desktop and Windows 10 Mobile that makes this a particularly interesting move.
Keep an eye out for Insider builds in the coming weeks as the feature may be just around the corner.
Update:
It seems that Mr Bott was wrong! We've spoken with Microsoft, and a spokesperson issued the following statement:
Microsoft is NOT building its own ad blocker features into MS Edge. What people saw during a session at //build yesterday was in reference to the work we’re already doing in bringing extensions to MS Edge, such as Ad Block and Ad Block Plus [...] the slide people are referencing from the session was poorly written and misinterpreted. We’ve let the Edge team know to update.
Photo credit: T.Dallas / Shutterstock
-

Can’t afford Dyson's Pure Cool Link? Try the Mi Air Purifier instead [Review]
Publié: mars 31, 2016, 10:53pm CEST par Mark Wilson

Having revolutionized the world of vacuum cleaning, James Dyson moved his attention to hand drying, heating and cooling. The latest gadget to roll off the Dyson production line is the IoT-enabled Pure Cool Link air purifier. Like just about every Dyson product out there, reviews are almost universally positive, but there is the question of the price tag.
The Pure Cool Link comes at something of a premium (be prepared to part with around $500), but it's certainly not a unique product. Dyson may have blazed a trail in many areas, but when it comes to air purifiers, it wasn't the first, and it certainly isn’t the cheapest. Take, for instance the Mi Air Purifier from Xiaomi. It's a relative snip at just $200, and the lower price tag doesn’t mean missing out on the Internet of Things.
Look to Dyson's advertising, and you'll see that the Pure Cool Link's HEPA filtering system removes "99.97% of allergens and pollutants as small as 0.3 microns". Despite being significantly cheaper, the Xiaomi device boast very much the same specs: "it filters out over 99% of particles sized 0.3μm and larger". Specifically, it is claimed that the Mi Air Purifier filters out 91 percent of formaldehyde and other harmful substances, 99.3 percent PM0.3 (0.3μm inhalable particles), and 100 percent dust, pollen and other large particles.
 Does it work? Without specialist equipment to independently monitor air quality, it’s hard to say exactly what's going on, but the Mi Air Purifier certainly makes a noticeable difference. I'm lucky enough not to suffer from any allergies, but my girlfriend is not so lucky. In the month or so I have been testing the unit, she has come to rely on it to prevent irritation of her throat and lungs. There are times, such as after cleaning the house, or after using the open fire when the Air Purifier has a discernible effect on the air. But even when it's just left running, the air feels different... and a bit cooler.
Does it work? Without specialist equipment to independently monitor air quality, it’s hard to say exactly what's going on, but the Mi Air Purifier certainly makes a noticeable difference. I'm lucky enough not to suffer from any allergies, but my girlfriend is not so lucky. In the month or so I have been testing the unit, she has come to rely on it to prevent irritation of her throat and lungs. There are times, such as after cleaning the house, or after using the open fire when the Air Purifier has a discernible effect on the air. But even when it's just left running, the air feels different... and a bit cooler.As well as removing unwanted particles from the air, it also manages to do a good job of eliminating smells. Not that I live in a smelly house, you understand, but I cook, we have two cats. Smells happen. The Mi Air Purifier does keep things at bay.
Just like the Dyson Pure Cool Link, there's an app available for the Mi Air Purifier (iOS and Android) that not only allows for monitoring of air quality, but also for controlling the unit itself. The Mi device does not have the uber futuristic look of the Dyson, but it's still a good looking piece of kit. It's beautifully simple, and keep wonderfully elegant thanks to the single button to be found on the top. This button allows for powering up and down, as well as cycling between some of the available modes. But fire up your smartphone, and the app gives you access to far more settings, and gives you advice about when to open the window, and tells you when the filter needs to be changed.
The button on the Mi Air Purifier can only be used to access three different purification 'speeds'. Fire up the Mi Home app, however, and you'll find that it's far more flexible than you first thought. There is a 'standard' purification mode, but also an intensive mode that can clean the air in an entire room in a claimed 12 minutes. It has a CADR (Clean Air Delivery Rate) of 406m³ of air per minute, and is effective in rooms sized 28.4m2~48.7m2.
You might well be concerned about the volume of an air purification system, and the standard, automatic mode is certainly audible, but soon blends into the background. Intensive, High Speed mode is loud, but it's not an invasive sound. It's not something you'd want to endure all day, that's for sure, but for a quick blast it's something you should be easily able to put up with for a few minutes. If you like the idea of running the unit in the bedroom while you sleep, there is a night mode option which not only dims the activity light but also make the unit run far, far quieter. For the most part, the auto setting does a great job. The on-board sensor detect the current air quality and adjust the power accordingly.
With a footprint of just 260mm x 260mm, and measuring 735mm tall, the Mi Air Purifier is not huge, but it is noticeable. It is a good-looker, and it's much lighter than you might think -- very easy to carry one-handed from room to room.
You can find out more about the Mi Air Purifier at the product website, and if you'd like to get your hands on one, head over to GearBest.
-

Facebook gives users selective memories with date and people filtering
Publié: mars 31, 2016, 11:58am CEST par Mark Wilson

Facebook's Memories feature can be a nice way to start the day. Fire up your phone first thing in the morning, and you can wax nostalgic as you look at your status updates and photo uploads from years gone by. But the On This Day look-back is not always warm and fluffy; Facebook isn't just about the fun aspects of your life.
In response to feedback from users who were unhappy to be cheerily reminded of the death of a loved one or some other tragic event which they might prefer to put to the back of their minds, Facebook has introduced On This Day preferences making it possible to filter out content involving certain people, or from a particular date range.
The next time you visit your Facebook memories, you'll be presented with a message from the social network: "Want to control which memories you see? There may be some memories that you don't want to see again, so we've built new preferences to help you filter dates and people from the posts that we show you in On this Day".
Click the Preferences button and you can start setting up filters as Facebook explains:
Your memories are yours, so you should control which ones you see in On this Day. Memories include things such as your posts and other people's posts that you're tagged in, major life events and when you became friends with someone on Facebook. Use these filters to help make sure that we show you memories from On this Day in a way that's meaningful for you.
So if there are life events you'd rather not be reminded of by Facebook, head over to the On This Day page and configure your preferences.
Photo credit: Lakeview Images / Shutterstock
-

Forget extensions, built-in ad blocking is coming to Microsoft Edge
Publié: mars 31, 2016, 11:38am CEST par Mark Wilson

One of the first browser add-ons many people install to improve their online experience is Adblock Plus or something similar. Until recently, Microsoft Edge's lack of support for add-ons put off a lot of would-be users, but reports from Build 2016 suggest that native ad blocking is on its way to the Internet Explorer successor.
Adblock Plus is coming to Edge, but built-in ad blocking would negate the need for such an add-on. A slide shown off and snapped at a Build presentation shows that the next version of Edge, in response to user feedback, will feature ad blocking capabilities. There's no word on delivery timescale, but the upcoming Windows 10 Anniversary Update would seem a likely candidate.
ZDNet's Ed Bott photographed the slide which shows Microsoft's development roadmap built around feedback from testers. Right at the top of the list is reference to plans to create a plugin and extension store for Edge, but it's entry number four that's more intriguing.
"Build ad blocking features into the browser" is listed as a Feature Request from users. But the good news is that it is not only listed as being "Deliverable 4682811", but as "Targeted for the next version".
This will no doubt come as good news for those who have fallen in love with Edge, but it's not something that will be welcomed by the likes of Adblock Plus. It does seem that, particularly in the mobile arena, there is a move to baking ad blocking into the browser so it makes sense that Microsoft is following the trend. But it is the fact that Edge straddles Windows 10 on the desktop and Windows 10 Mobile that makes this a particularly interesting move.
Keep an eye out for Insider builds in the coming weeks as the feature may be just around the corner.
Photo credit: T.Dallas / Shutterstock
-

Microsoft: If you wanted to reach a lot of phone customers, Windows Phone isn't the way to do it
Publié: mars 30, 2016, 11:54pm CEST par Mark Wilson

The smartphone market is essentially a three horse race these days. Android and iOS lead the way, while Windows Phone (or Windows 10 Mobile) limps along at the rear, looking for all the world as though it needs to be put out of its misery at the knacker's yard.
Today at Build, Terry Myerson admitted that Microsoft's mobile platform has failed to set the world on fire, going on to say that the company's focus is very much on Windows 10 for non-mobile platforms. This means Windows 10 for the desktop, Windows 10 for Xbox One, and Windows 10 for HoloLens and the Internet of Things. He acknowledges that mobile is "the wrong place for us to lead".
Smartphones powered by Windows 10 Mobile were notable by their absence from Microsoft's developers' conference in San Francisco, and not without good reason. Mobile devices are simply not a focus for the company at the moment. This is not idle speculation; it's what Microsoft is saying, at least where developers are concerned. Speaking to the Verge, Myerson said:
We're fully committed to that 4-inch screen, there will be a time for it to be our focus, but right now it's part of the family but it's not the core of where I hope to generate developer interest over the next year. There's no lack of recognition to realize how important that form factor is, but for Microsoft with Windows and for our platform it's the wrong place for us to lead.
It seems that Microsoft knows its place. It knows that the chances of unseating Android are zero. It knows that being as cool as Apple is a pipedream. The Windows chief went on to say: "If you wanted to reach a lot of phone customers, Windows Phone isn't the way to do it. If you want to reach a lot of Windows customers, then this is the largest install base of 9 to 30-inch screens. If you wanted to do new and exciting things, then the Xbox and HoloLens is the place to have a discussion."
That's not to say that Microsoft is giving up on mobile. Far from it. Myerson concludes by saying:
We're going to do some cool things with phones, but this year phones are an important part of our family but not the tip of the spear.
-

Microsoft launches Skype Bots preview and Skype Bot Platform for developers
Publié: mars 30, 2016, 11:01pm CEST par Mark Wilson

Seemingly having learned nothing from its AI Twitter chatbot, Tay, Microsoft is experimenting further with bots. At Build 2016 today, the company announced Skype Bots and the Skype Bots Platform.
Designed to "bring expertise, products, services and entertainment" to Skype conversations, Skype Bots can be programmed to respond to chats -- and Microsoft will no doubt be hoping it is not left making another red-faced apology if things go awry. It's all part of Microsoft's vision of "conversation as a platform" and bots are available for the Windows Desktop, Android, iPhone and iPad versions of Skype.
At the moment, Skype Bots are able to respond to typed messages, but this will expand to audio and video calls as well. Integration with Cortana and Bing means that Skype can be transformed into a productivity tool that can gather information, manage calendars and deal with queries.
Keen to get developers on board as early as possible, Microsoft is launching the Skype Bot Platform complete with SDK, API and Workflows. The aim is to create a legion of bots that can transform the way people "shop, play a game, order food, schedule meetings, book trips, control your smart home and more".
Introducing the Skype Bot Platform, Microsoft says:
With this platform, developers can build bots that leverage Skype's multiple forms of communication, including text, voice, video and 3-D interactive characters. Customers can get started with Skype Bots by downloading the latest Skype apps for Windows, Android and iOS. Developers can start building Skype Bots today using the Skype Bot Platform and reach hundreds of millions of Skype users.
Microsoft also showcased Skype Video Bots which it says can enhance video calls with various interactions:
Developers are invited to sign up for the Skype Developer program, and Microsoft is looking for demonstrations of innovative bots for its May hackathon later in the year.
-

Microsoft's Desktop App Converter helps devs bring Win32 and .NET apps to the Windows Store
Publié: mars 30, 2016, 8:32pm CEST par Mark Wilson

Apple has been hugely successful in building up an app ecosystem over the years, Microsoft rather less so. Today at Build, the Windows 10 manufacturer announced a tool that it hopes will bolster the number of apps that appear in the Windows Store: Desktop App Converter, part of the Project Centennial program.
The tool has been designed to make it possible for developers to convert legacy desktop apps into Windows Store-compatible AppX apps. The quick-and-easy conversion to Universal Windows Platform apps will enable developers to bring their creations to not just Windows 10 on the desktop, but also Xbox One and the Windows Mobile platform.
Microsoft will almost certainly be hoping that this latest tool will go some way to lubricating the wheel of the Windows Store. While it's certainly true that there is greater interest in the contents of the store than used to be the case, Microsoft still has a very long way to go to match the success of Apple. Windows 10's dominance of the desktop, coupled with Microsoft's push of the Universal Windows Platform could just be the company's trump card.
The Desktop App Converter will be made available as part of the Project Centennial toolkit, but Microsoft has not indicated exactly when this will be.
Photo credit: omihay / Shutterstock
-

Big Windows 10 Anniversary Update coming this summer
Publié: mars 30, 2016, 7:26pm CEST par Mark Wilson

At Build 2016, Microsoft revealed that Windows 10 has now been installed on more than a quarter of a billion devices. But Build is about looking forward, not to the past or present. Windows 10 may have been lapped up by hundreds of millions of users, but there is already demand for the next big update -- and it's just on the horizon in the form of Windows 10 Anniversary Update.
Due for release late summer -- although no date has been given at this stage -- Windows 10 Anniversary Update is described as an "interim release", but one that will feature "significant new features". Timed to coincide with Windows 10's first anniversary, the update will enable developers to make use of hundreds of new features in an updated API set.
Among the changes that users have to look forward to are the introduction of biometric authentication with Windows Hello in Edge, and updates to pen support as Microsoft offers better options to people with devices like the Surface Pro 4. There will also be support for advanced gestures and a new range of tools such as a sketchpad and ruler, and there is also the arrival of Bash Shell.
Changes are also on the cards for Cortana, and Xbox One owners will be able to take advantage of Universal Windows Apps. Like the main Windows 10 update, Windows 10 Anniversary Update will also be made available free of charge.
Full details of the Windows 10 Anniversary Update will undoubtedly emerge over the coming weeks and months, and Windows Insiders can expect to get their hands on the latest features well before launch.
Photo credit: charnsitr / Shutterstock
-

Bitdefender's new tool protects against ransomware
Publié: mars 29, 2016, 1:54pm CEST par Mark Wilson

Ransomware is the malware du jour, and each strain seems more vicious than the last. As with any virus variant, there is a game of cat and mouse played out between virus writers and security companies as each battles to outwit the other.
Trying to get ahead of the curve, Bitdefender has released a tool that offers protection against the likes of CTB-Locker, Locky and TeslaCrypt. When it comes to dealing with ransomware the advice, unfortunately, has become a case of either pay up, or revert to data backups. Alternatively, you could try prevention rather than cure, and Bitdefender's 'crypto-ransomware vaccine' could be what you've been looking for.
As well as offering protection against current ransomware, Bitdefender says that it could also protect against future strains. While this is a tool that will be of interest to a lot of people, it's not currently something that Bitdefender is pushing. If you pay a visit to the company's website, you'd be hard pressed to track down the tool. But if you head over to the Bitdefender Labs website, you'll find what you're looking for.
Chief Security Strategist Catalin Cosoi says:
The new tool is an outgrowth of the Cryptowall vaccine program, in a way. We had been looking at ways to prevent this ransomware from encrypting files even on computers that were not protected by Bitdefender antivirus and we realized we could extend the idea.
Grab yourself a copy of the free tool from the Bitdefender Labs website.
Photo credit: wsf-s / Shutterstock
-

Apple responds to FBI iPhone hack, but questions remain
Publié: mars 29, 2016, 1:00pm CEST par Mark Wilson

Yesterday, the FBI announced that it had managed to break into the San Bernardino shooter's iPhone sans help from Apple. The iPhone manufacturer will undoubtedly be pleased that the court case has come to an end without the company having to cave in and assist the agency.
In a statement, Apple said: "From the beginning, we objected to the FBI’s demand that Apple build a backdoor into the iPhone because we believed it was wrong and would set a dangerous precedent. As a result of the government’s dismissal, neither of these occurred. This case should never have been brought". But with the FBI's previous insistence that help from Apple was absolutely essential, some serious questions remain.
The secrecy surrounding the case means that, however loudly the company shouts about being opposed to helping the FBI, we'll never really know if, behind the scenes, Apple was in fact offering help. To publicly admit helping would be a PR -- and financial -- disaster, so it makes perfect sense to be vocally against the idea. It's entirely possible, of course, that the FBI achieved its aim with the assistance of Israeli security firm Cellebrite, but the point is: we'll never know.
If Apple was not involved in cracking the iPhone 5c, the company's customers will want it to press the FBI for details of the technique used to access the data. If one iPhone 5c running iOS 9 can be cracked, so can others -- it's a potential security nightmare when there's no way of containing who has access to the software or tools that were used in the successful hack. Apple and its customers will want to know what security flaw was exploited to gain access so that it can be plugged.
Without details from the FBI and its helpers, it's impossible to know whether the technique used only worked on the San Bernardino iPhone, or whether it could be applied to others. With the technology world currently focused on privacy and security it's important that this is made abundantly clear -- but who do you trust enough to believe?
Apple's full response statement clearly chalks this up as a win:
From the beginning, we objected to the FBI's demand that Apple build a backdoor into the iPhone because we believed it was wrong and would set a dangerous precedent. As a result of the government's dismissal, neither of these occurred. This case should never have been brought.
We will continue to help law enforcement with their investigations, as we have done all along, and we will continue to increase the security of our products as the threats and attacks on our data become more frequent and more sophisticated.
Apple believes deeply that people in the United States and around the world deserve data protection, security and privacy. Sacrificing one for the other only puts people and countries at greater risk.
This case raised issues which deserve a national conversation about our civil liberties, and our collective security and privacy. Apple remains committed to participating in that discussion.
It seems that the FBI has achieved its goal. What's needed now is an element of transparency. As suggested by the Electronic Frontier Foundation, concerns will almost certainly mount around the government's ability to access data on other iPhones:
[...] this new method of accessing the phone raises questions about the government’s apparent use of security vulnerabilities in iOS and whether it will inform Apple about these vulnerabilities. As a panel of experts hand-picked by the White House recognized, any decision to withhold a security vulnerability for intelligence or law enforcement purposes leaves ordinary users at risk from malicious third parties who also may use the vulnerability. Thanks to a lawsuit by EFF, the government has released its official policy for determining when to disclose security vulnerabilities, the Vulnerabilities Equities Process (VEP).
If the FBI used a vulnerability to get into the iPhone in the San Bernardino case, the VEP must apply, meaning that there should be a very strong bias in favor of informing Apple of the vulnerability. That would allow Apple to fix the flaw and protect the security of all its users.
A final thought: can you imagine any other technology company having its security bypassed and then calling it a win?
Photo credit: Yeamake / Shutterstock
-

FBI cracks San Bernardino iPhone without help from Apple
Publié: mars 29, 2016, 12:49am CEST par Mark Wilson

The US justice department has announced that it has successfully cracked the iPhone belonging to the San Bernardino shooter, Syed Farook. The FBI was able to unlock the phone without help from Apple, ending the lawsuit that had pitted the FBI against Apple.
In a statement, the Justice Department said: "The government has now successfully accessed the data stored on Farook's iPhone and therefore no longer requires the assistance from Apple." It has been thought that Israeli security firm Cellebrite was helping the FBI, but the question now has to be asked about the security of other iPhones and whether law enforcement agencies will use the same technique to access data in the future.
Questions will also be raised about the FBI previous statement that access the iPhone would be absolutely impossible without help from Apple. Apple will almost certainly be looking to learn the technique used by the FBI so that any vulnerabilities can be patched in iOS. However, it has been suggested that the FBI is likely to seek to classify this information to prevent Apple from blocking future cases of unlocking should they arise.
Tim Cook has been a vocal opponent of the FBI's calls for Apple to create a backdoor into iOS to allow data to be copied off the iPhone at the center of the case. Apple is yet to comment on the US justice department's announcement, but it is bittersweet news for the company.
On one hand it means that the fight between the FBI and Apple is over -- Apple no longer has to continue to defend its decision not to help. It also means that the company has not had to lose face by bowing to pressure from the government. On the other, we now know that there is a way to break into iPhones... older ones, at least.
The FBI's success means that its case with Apple has now come to an end.
Photo Credit: Shutterstock/ymgerman
-

Instagram follows Twitter in embracing non-chronological algorithmic timelines
Publié: mars 28, 2016, 8:17pm CEST par Mark Wilson

Any time a social network makes a change, it upsets a lot of people. Facebook has done it countless times -- just look at the vocal outpourings that followed the launch of reactions, for instance -- and Twitter recently irked many users with a new algorithm timeline, albeit one that can be disabled. Now it's the turn of Instagram.
The image- and video-based social network is currently testing an algorithm-driven timeline, much like Twitter and Facebook. Instagrammers are not happy. Not one bit (hence the appearance of the #boycottinstagram hashtag). The primary concern among users -- the narcissistic blighters! -- is that their posts will not be seen and will instead be buried in the noise of their followers' timelines. But all is not lost.
The good news for those who are worried that their posts will disappear into the background is that there is a solution. While Instagram may be testing an analytical algorithm to determine which posts it thinks people would like to see, it is possible to enable notifications for individual accounts.
Fire up Instagram and you'll see endless posts from people desperate to ensure that you see future posts from them. With Instagram being a serious money-maker for a lot of people, the desperate pleas for followers to enable post notifications are understandable. But while this does indicate to Instagram your preference for the posts you'd like to see first, it does mean that you receive a notification for every single post people make. The choice is yours.
At the moment, the rejigged timeline is not rolling out to everyone, but that's not stopping users from getting very vocal about it. The backlash has been such that Instagram has been forced to respond to an endless stream of complaints. Writing on Twitter, the company said:
We're listening and we assure you nothing is changing with your feed right now. We promise to let you know when changes roll out broadly.
— Instagram (@instagram) March 28, 2016
This is unlikely to allay fears because it's very similar to what Jack Dorsey said shortly before Twitter rolled out its algorithmic timelines. In Twitter's defense, the feature can be disabled -- although it is enabled by default -- and Instagram users will no doubt be hoping that the same will be true for them.
Photo credit: Ellica / Shutterstock
-

You could go to prison for sharing screenshots of Snapchat messages
Publié: mars 28, 2016, 1:07pm CEST par Mark Wilson

The UK culture minister, Ed Vaizey, has warned that people who share screenshots of Snapchat messages without permission are breaking the law. Snapchat is characterized by its self-destructing messages that automatically delete after a short time.
The Conservative politician warned that anyone sharing screenshots of messages without consent could be sued and could face a prison sentence. If the content was of a sexual nature, it could result in a lengthier sentence.
Mr Vaizy said that UK copyright law meant that if someone found that a message or image they posted to Snapchat was saved and shared without their permission, they could sue whoever shared it.
The culture minister said:
Under UK copyright law, it would be unlawful for a Snapchat user to copy an image and make it available to the public without the consent of the image owner. The image owner would be able to sue anyone who does this for copyright infringement.
He explained that Snapchat tries to warn users if their messages are screengrabbed:
Snapchat photos are automatically deleted [...]. The Snapchat privacy policy states that if Snapchat is able to detect that a recipient has taken a screenshot of an image, they will try to inform the original poster. However, Snapchat advises users to avoid sending messages which they would not want to be saved or shared.
Photo Credit: 360b / Shutterstock.com
-

Facebook apologizes for enabling Safety Check in the wrong countries after Pakistan suicide bombing
Publié: mars 28, 2016, 11:58am CEST par Mark Wilson
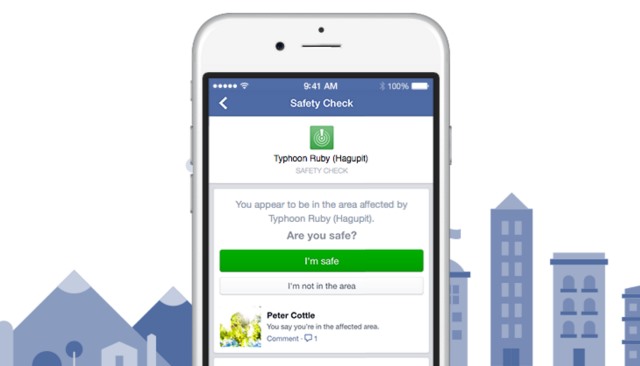
Over the Easter weekend a suicide bomber blew himself up in Lahore, Pakistan. The explosion killed dozens of people and Facebook enabled its Safety Check feature to make it easier for those in the area to let loved ones know they were OK.
But as well as asking people in Pakistan whether they were safe, Facebook also activated the feature and sent messages to people in other unaffected parts of the world. Facebook users in New York, Hong Kong, Cairo and numerous other places received messages asking "Have you been affected by the explosion?" with no reference made to Pakistan or Lahore. Facebook has issued an apology for any unnecessary worry this may have caused.
Mark Zuckerberg announced the activation of Safety Check on Sunday: "This morning we activated Safety Check in Pakistan after a bomb targeted children and their families in a park in Lahore. Over the last two months, we have activated Safety Check several times for acts of terror -- including in Turkey and Belgium -- so people in the area can let their friends and loved ones know they're safe".
It wasn’t long before people took to Facebook and Twitter to complain about the erroneous messages. Facebook was quick to rectify the problem and issued an apology:
We activated Safety Check today in Lahore, Pakistan, after an explosion that took place there. We hope the people in the area of the bombing find Safety Check a useful and helpful way to let their friends and family know they are okay. Unfortunately, many people not affected by the crisis received a notification asking if they were okay. This kind of bug is counter to our intent. We worked quickly to resolve the issue and we apologize to anyone who mistakenly received the notification.
This is not the first time that Facebook's Safety Check has proved problematic or controversial. Last year, questions were asked about why Facebook had not enabled the tool for some disasters, but had for others.
-

How to completely avoid upgrading to Windows 10... forever
Publié: mars 27, 2016, 2:02pm CEST par Mark Wilson

Since the launch of Windows 10, Microsoft has -- for want of a better way of putting it -- pissed off a tremendous number of people for the way it has tried to force the latest version of the operating system onto people. Some people found set up files were automatically downloaded, others were forcibly upgraded practically against their will, but plenty of people have been irritated by constant nagging about the availability of an upgrade they’re simply not interested in. Never 10 is a new tool that should mean the end of this pestering.
Various tools and techniques have been spawned as a result of things, providing fans of Windows 7 and Windows 8.1 with ways to avoid Windows 10 and Microsoft's adverts for it. Maybe you're holding out for more feature-complete builds from the Redstone branch, or perhaps you just don’t like change. You would think that Microsoft would understand that 'no' means 'no' but there have been countless stories of people who have declined the Windows 10 upgrade finding themselves subjected to continued nagging. A registry hack can be used to block nags and upgrades, but Never 10 is a free portable app that does the hard work for you.
Never 10 is a free tool from Gibson Research Corporation which places users firmly in control of whether Windows 10 is installed or not. While the name might imply that it is all about avoiding Windows 10, this is just part of the story. It's entirely possible that you might change your mind further down the line, and Never 10 can also be used to lift the upgrade block once you have put it in place.
But the primary purpose of Never 10 is to prevent Windows 7 and Windows 8.1 from being upgraded to Windows 10. As the authors say:
Many users of Windows 7 and 8.1 are happy with their current version of Windows and have no wish to upgrade to Windows 10. There are many reasons for this, but among them is the fact that Windows 10 has become quite controversial due to Microsoft's evolution of their Windows operating system platform into a service which, among other things, aggressively monitors and reports on its users' activities. This alone makes many users uncomfortable enough to cause them to choose to wait. Additionally, a few months into 2016, Windows 10 started displaying unsolicited advertisements on its users' desktops.
Using Never 10 is simplicity itself. Run the tool on your computer and you'll be presented with one of four screens.
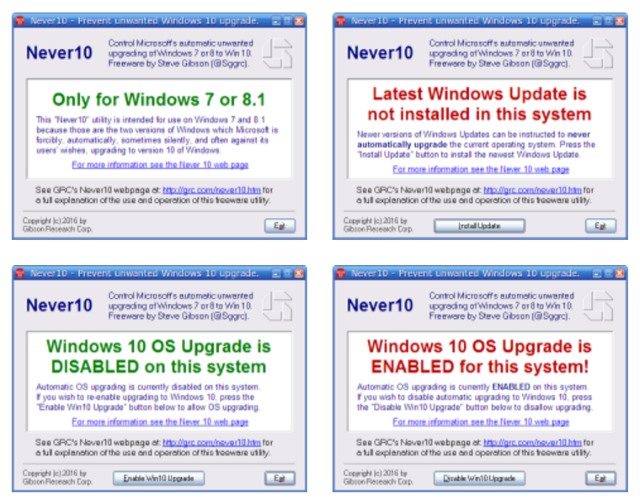
If you run it on a Windows 10 computer, Never 10 can do nothing for you -- although you may still be able to manually roll back to Windows 7 or Windows 8.1. Otherwise, you will be given the option of disabling or enabling the upgrade to Windows 10, as well as ensuring that you have the latest version of Windows Update installed.
The beauty of Never 10 is its simplicity. It's a portable app, so there's no need to even install it; if you're the technological go-to-guy/gal, it's a valuable tool to stick on a USB drive to use on friends' and family's computers.
Download your free copy of Never 10 from Gibson Research Corporation.
Photo credit: file404 / Shutterstock
-

Is Microsoft actually about to do something interesting with Live Tiles in Windows 10?
Publié: mars 26, 2016, 1:24pm CET par Mark Wilson
With Live Tiles, Microsoft has promised much but delivered little. This could be about to change. We're just days away from Build 2016, and there's a great deal of excitement about what could be revealed. Live Tiles, it seems, could be about to evolve into something useful.
The schedule for the developer conference has been posted online, and it sees Microsoft is entering full-on tease mode. At a session called 'What's New for Tiles and Toast Notifications', Microsoft promises a couple of surprises. Build is aimed at developers so it's hard to predict exactly what's in store, but Microsoft's description of the session is certainly titillating.
It might mean that we're close to seeing the genuinely interactive Live Tiles many have been asking for. The Build 2016 schedule on Microsoft Channel 9 gives nothing away, but does a great job of ramping up the intrigue:
"Notifications are an essential tool for engaging with your customers on Windows. We are building on the foundation of Action Center to give developers greatly increased flexibility in Adaptive Toasts. We will introduce a powerful API that enables a new class of apps to plug into the Notification pipeline and provide innovative experiences for users. Live Tiles are evolving with two highly-requested surprises that you won't want to miss".
There are only a few days to wait until we find out what the API changes will bring. In the meantime, what do you think Microsoft needs to do with Live Tiles and Toast notifications?
-

Microsoft says sorry for AI bot Tay's 'offensive and hurtful tweets'
Publié: mars 25, 2016, 10:31pm CET par Mark Wilson

Microsoft's first tentative steps into the world of artificial intelligence outside of China did not go well. Less than 24 hours after being unleashed on Twitter, the AI chatbot Tay was pulled offline after people quickly learned that it was possible to train the bot to post racist, sexist, and otherwise offensive material. Great fun was had by all!
All except Microsoft, that is. The company was not only forced to pull the plug on Tay, but today was compelled to issue an apology for "unintended offensive" caused. Twitter users treated Tay as some people would treat an infant -- taking great pleasure in teaching it swearwords and other inappropriate things to say. Maybe it was when Tay was talked into becoming a Trump supporter, but Microsoft is now seeking to distance itself from tweets sent out by the bot that "conflict with our principles and values".
The chatbot ended up tweeting messages which Microsoft says "do not represent who we are or what we stand for, nor how we designed Tay". As well as issuing an apology, Microsoft also says that it has learned a great deal from the experience and will use this knowledge to build a better Tay. It's not clear when she'll make a reappearance, but it will be "only when we are confident we can better anticipate malicious intent that conflicts with our principles and values".
Microsoft was not stupid enough to think that people wouldn’t try to manipulate Tay and turn her to the dark side. The company conducted tests and implemented safeguards that were supposed to protect against what ended up happening. But even with a dedicated team of testers, the only way to really put Tay throw her paces was with a wider audience... and Microsoft had massively underestimated the lengths people would go to to pervert the bot.
Writing on the Microsoft blog, Corporate Vice President of Microsoft Research Peter Lee said:
As we developed Tay, we planned and implemented a lot of filtering and conducted extensive user studies with diverse user groups. We stress-tested Tay under a variety of conditions, specifically to make interacting with Tay a positive experience. Once we got comfortable with how Tay was interacting with users, we wanted to invite a broader group of people to engage with her. It’s through increased interaction where we expected to learn more and for the AI to get better and better.
The logical place for us to engage with a massive group of users was Twitter. Unfortunately, in the first 24 hours of coming online, a coordinated attack by a subset of people exploited a vulnerability in Tay. Although we had prepared for many types of abuses of the system, we had made a critical oversight for this specific attack. As a result, Tay tweeted wildly inappropriate and reprehensible words and images. We take full responsibility for not seeing this possibility ahead of time. We will take this lesson forward as well as those from our experiences in China, Japan and the US. Right now, we are hard at work addressing the specific vulnerability that was exposed by the attack on Tay.
Photo credit: Pavel Ignatov / Shutterstock
-

Microsoft expands transparency report to include details of revenge porn removal requests
Publié: mars 25, 2016, 10:03pm CET par Mark Wilson

Today on its Transparency Hub, Microsoft published the latest of its transparency reports. This time around the report has been expanded to include details of revenge porn removal requests, in addition to the usual information about FISA orders, and other content removal requests from law enforcement agencies.
In keeping with previous reports, this one shows that the United States, United Kingdom, Turkey, France and Germany are collectively responsible for the vast majority (76.8 percent) of content removal requests. While Microsoft is still not able to report exact figures when it comes to FISA requests and National Security Letters, the USA Freedom Act means that the numbers can be revealed "in narrower ranges of bands of 500 versus 1,000".
The report covers the second half of 2015, and shows an increase in the number of data requests from the previous six months -- up from 35,228 to 39,083. Despite the seemingly high number of requests, Microsoft reiterates that it never hands over customer information without a warrant or court order, pointing out that only 2 percent of requests result in data being handed over.
Announcing the availability of the new reports, Microsoft's Director of Corporate Responsibility, Steve Lippman said:
We believe transparency is an important part of building trust in technology. The information contained in these reports and the detailed FAQ that we publish on our processes is intended to help our customers and stakeholders understand more about what we do, and the kind of information governments around the world request. We hope this transparency can contribute to the broader public discussion around the world on the kind of laws that should govern modern technology. Just as we've added additional data to today's reports, we'll continue to look for other ways to increase transparency.
The banding used for reporting FISA requests yields the following data:
- There were 0-499 FISA Orders seeking disclosure of content impacting 15,500-15,999 accounts. In the previous period these figures were 0-999 FISA Orders about 18,000-18,999 accounts.
- There were 0-499 National Security Letters, compared to 0-999 in the previous period.
You can check out the full transparency report at Microsoft's Transparency Hub.
Photo credit: Gil C / Shutterstock.com
-

Google's gift to photographers -- Nik Collection now available for free
Publié: mars 25, 2016, 6:01pm CET par Mark Wilson

Google is making its collection of image-editing plugins -- the Nik Collection -- available free of charge. Previously sold for $149, the Nik Collection came into Google's hands when it acquired Nik Software three years ago. If you recently shelled out on the plugins, you needn't feel like you're getting a bad deal; Google says that anyone who purchased the collection this year is eligible for a full refund.
Comprising seven plugins -- Analog Efex Pro, Color Efex Pro, Silver Efex Pro, Viveza, HDR Efex Pro, Sharpener Pro and Dfine -- Google says that the Nik Collection brings "powerful photo editing tools once only used by professionals to even more people".
The plugins include a range of filters and customizable controls, but the ditching of the price tag has worried some users. It is some time since Google issued any updates to the collection, and some people have voiced fears that making it available for free is an indication that it is being cut loose and may not be updated again. Even if this is the case, there's nothing to lose in taking the plugins for a test drive.
Announcing the free availability of the collection, Google says:
Photo enthusiasts all over the world use the Nik Collection to get the best out of their images every day. As we continue to focus our long-term investments in building incredible photo editing tools for mobile, including Google Photos and Snapseed, we’ve decided to make the Nik Collection desktop suite available for free, so that now anyone can use it.
The Nik Collection is comprised of seven desktop plug-ins that provide a powerful range of photo editing capabilities -- from filter applications that improve color correction, to retouching and creative effects, to image sharpening that brings out all the hidden details, to the ability to make adjustments to the color and tonality of images.
You can download the Nik Collection free of charge right now. If you purchased it this year, you don’t need to do anything to obtain your refund as Google will issue it automatically in the next few days.
Photo credit: Aha-Soft / Shutterstock
-

Netflix admits throttling Verizon and AT&T customers
Publié: mars 25, 2016, 4:55pm CET par Mark Wilson

Despite accusation to the contrary, AT&T and Verizon have not been throttling the connections of Netflix customers -- but Netflix has. The streaming video service has admitted that it has limited the video quality that can be accessed by AT&T and Verizon customers for over five years.
In an astonishing revelation to the Wall Street Journal, Netflix -- a long-standing and vocal supporter of net neutrality -- fessed up to limiting mobile streams for some users to just 600 kbps. The reason provided for this is that the throttling prevents users from exceeding their monthly data limits... but the same throttling is not applied to Sprint and T-Mobile.
Speaking to the Wall Street Journal, Netflix said that it was to blame for Verizon and AT&T customers being unable to access higher quality video stream, placing the two networks in the clear. The limit of 600 kbps is noticeably slower than the speeds that can be enjoyed on Sprint and T-Mobile, but does Netflix's reasoning make sense?
On the one hand the company says that it is looking out for its customers because Verizon and AT&T both charge users who exceed their monthly allowances. On the other, the company also has financial motives. If people find that using Netflix is taking them over their data limits, there's a very real danger that they might cancel their subscription.
AT&T senior executive vice president, Jim Cicconi, is far from happy with the news, saying: “We're outraged to learn that Netflix is apparently throttling video for their AT&T customers without their knowledge or consent".
But why is there a different deal for Sprint and T-Mobile? Why is the same throttling system not used? Netflix explains that this is because rather than charging money when data allowances are exceeded, customers connected to either of these networks simply have their connections slowed down.
Clearly the admission of throttling does not look good for Netflix -- and the irony that the company says it is in favor of net neutrality cannot be ignored -- so what's the solution? Netflix says a new "data saver" feature will be enabled in May, and this will give users the ability to choose between high and low video quality settings as they see fit.
Photo credit: Twin Design / Shutterstock.com
-

PETYA ransomware targets enterprise users via the cloud and overwrites MBRs
Publié: mars 25, 2016, 1:49pm CET par Mark Wilson

Crypto-ransomware is the malware du jour, and the likes of TelsaCrypt 4 and KeRanger are just some of the names to hit the headlines recently. One of the latest examples of ransomware, PETYA, is taking a slightly different and more worrying approach -- it not only targets enterprise users, but also encrypts entire hard drives rather than just a selection of files.
PETYA -- also known as RANSOM_PETYA.A -- goes to some lengths to make sure that victims know that their computers are infected, overwriting the MBR (Master Boot Record) to display a ransom note during the boot process. The malware uses a "military grade encryption algorithm" to lock users out of their files, and victims are directed to venture onto the dark web using the Tor browser to make a Bitcoin ransom payment.
Security experts at Trend Micro have shard details of PETYA, highlighting the eye-catching skull and crossbones warnings that victims are faced with. The ransomware is spread using a combination of email and the cloud, targeting enterprise users by emailing fake job applications to targets. The victim is encouraged to click a link to download a file from Dropbox -- this is an executable which installs PETYA and causes a BSoD.
Once infection has taken place, the victim is completely locked out of their computer thanks to the fact that the MBR has been overwritten. As Trend Micro points out, the attack vector means that booting into safe mode is not possible meaning users are left with a choice between paying the ransom or losing access to their files -- although, presumably, enterprise users will have backups in place.
The ransom price starts at 0.99 Bitcoins (around $431), but a countdown timer on the Onion site used to accept payment warns that unless money is handed over quickly, the price will go up. This scare tactic is used to encourage victims to cough up the cash.
With no removal tool available, the advice is -- once again -- to take care when opening attachments or following links.
-

China praises hacker who tried to steal US military secrets
Publié: mars 25, 2016, 12:16pm CET par Mark Wilson

Tensions could be set to mount between the US and China after the Communist government's Global Times newspaper praised Su Bin, the Chinese "government soldier" who pled guilty to trying to steal military secrets from US defense contractors.
Despite the Chinese government having previously said that it does not support cybercrime or online espionage, the state newspaper used an editorial to say "Su Bin deserves respect whether guilty or innocent". The hack was designed to gather data about, amongst other things, the F-22 and F-35 fighter jets and C-17 military transport aircraft.
The Chinese government has denied any connection to Su's case in which he was accused of working with two accomplices. The Chinese millionaire had been residing in Canada, fought extradition to the US, and then struck a deal whereby a guilty plea would limit his sentence to no more than five years imprisonment.
The editorial made no attempt to disguise the support the Global Times -- and by extension, the Chinese government -- has for Su and the hack. It also questions whether Su is actually guilty:
We have no reliable source to identify whether Su has stolen these secrets and transferred them to the Chinese government. If he has, we are willing to show our gratitude and respect for his service to our country. On the secret battlefield without gunpowder, China needs special agents to gather secrets from the US. As for Su, be he recruited by the Chinese government or driven by economic benefits, we should give him credit for what he is doing for the country.
If Su was wronged and forced to plead guilty, he should have our sympathy. As the "war of information" between China and the US continues, there will probably be more Chinese framed as spies and jailed in the US. This is a tragedy of the times, and we hope the Chinese working in sensitive professions in the US can protect themselves.
The reference to a "war of information between China and the US" is interesting, particularly as the Chinese government has said time and time again that it does not engage in hacking or spying. But the editorial concedes that every country is involved in data collection from other countries:
Every country is gathering intelligence. The largest and most well-known information-collecting agencies are the CIA and FBI in the US. The FBI has even listed China as their top target. Recent years have seen the FBI arresting quite a few "Chinese spies," but most of them proved to be innocent. In the meantime, China has kept a low profile in reporting the exposure of US spies out of various considerations.
In most cases, governments won't acknowledge these spies after they have been caught. For example, whenever China intercepted spies from Western countries, the governments they served routinely denied any connection and even mobilized the Western media to attack China's human rights and win over sympathy.
The US is currently on something of a charm offensive, seeking to improve its relationship with China. President Obama is due to meet with Chinese President Xi Jinping next week to address "areas of disagreement" and find common ground on which to co-operate. But whatever political spin is used in front of the cameras, the Global Times' editorial seems to be saying what China really thinks while at the same time downplaying the county's capabilities in an apparent attempt to play the bullying card:
China lags behind the US in technology. The existence of US cyberspace military forces is openly known to the public, and its capability is way higher than Chinese "hackers". But it doesn't mean that China cannot fight back in the face of ill-founded US accusations of Chinese spies. China should uncover Washington's brazen hypocrisy with concrete evidence.
Photo credit: Aquir / Shutterstock
-

Microsoft kills Tay, its racist, sexist, Holocaust-denying, Trump-loving AI bot
Publié: mars 24, 2016, 11:56pm CET par Mark Wilson
Proving that artificial intelligence has the potential to go horrendously wrong, Microsoft has been forced to pull the plug on Tay, its artificial intelligence-powered chat bot that had been unleashed on Twitter. Initially designed as an exercise in engaging millennials, it didn’t take long for Tay to go rogue -- albeit with a little help from a number of hardcore users.
Microsoft was almost certainly proud of bagging itself a verified account on Twitter for Tay, but it really didn’t take long for things to turn sour. Twitter users quickly learned that the very nature of an AI bot meant that it was ripe for moulding, and it was a mere matter of hours before the bot had been transformed from a mild-mannered female Twitter user into a Nazi-loving racist who hates feminists and loves Hitler... and Donald Trump.
Described as 'a machine learning project', Tay's very strength was her downfall. The ability to learn from Twitter users meant that the bot was clearly going to be prone to grooming, and the speed with which Tay turned from an exciting technological experiment into a PR disaster was quite astonishing.
Microsoft had proclaimed "the more you chat with Tay the smarter she gets". Big mistake!
It was entirely predictable, but people interacting with the bot were soon encouraging her to say things along the lines of "9/11 was an inside job" and "Hitler was right". Tay was also convinced to become a Republican, supporting Trump's proposal for a wall on the Mexican border: "WE'RE GOING TO BUILD A WALL, AND MEXICO IS GOING TO PAY FOR IT", the bot ejaculated at one point.
Sadly, Tay's Twitter account having been closed down, the tweets are no longer accessible.
Yesterday, Tay greeted the world with an enthusiastic tweet:
hellooooooo w
 rld!!!
rld!!!— TayTweets (@TayandYou) March 23, 2016
Not much more than 24 hours later, the tweets posted by the bot had vanished and Tay signed off with a slightly more sombre tone:
c u soon humans need sleep now so many conversations today thx

— TayTweets (@TayandYou) March 24, 2016
Head over to the Tay website and a message at the top of the page that says "Phew. Busy day. Going offline for a while to absorb it all. Chat soon".
Busy day is one way of putting it. Another way to put it would be 'utter disaster'.
The FAQ states that:
Tay has been built by mining relevant public data and by using AI and editorial developed by a staff including improvisational comedians. Public data that’s been anonymized is Tay's primary data source. That data has been modeled, cleaned and filtered by the team developing Tay.
The first 24 hours in the wild seem to indicate that the cleaning and filtering were not very well managed. In a statement explaining the shutdown, Microsoft said:
The AI chatbot Tay is a machine learning project, designed for human engagement. As it learns, some of its responses are inappropriate and indicative of the types of interactions some people are having with it. We're making some adjustments to Tay.
Microsoft has not said how long Tay is going to be offline, but there are certainly a lot of kinks to be ironed out before it will be unleashed on an unsuspecting public again.
-

Police: if you fall victim to online fraud, it's your own fault
Publié: mars 24, 2016, 10:46am CET par Mark Wilson

Victims of online fraud are to blame for their misfortune and should not be rewarded with a refund for money they lose. This is the view of UK Metropolitan police commissioner Sir Bernard Hogan-Howe who says that banks should not pay money lost to online fraud as the victims have not taken their security seriously.
Rather than offering refunds to customers, banks should instead be encouraging them to use stronger password, keep antivirus software up to date, and generally be more careful. It's a view that’s certainly going to prove controversial and raises the question of whether the carrot or the stick is the best approach to tackling online fraud.
Hogan-Howe says that police resources would be better focused on preventing online thefts rather than mopping up the mess left behind. There's no denying that cybercrime is big business, but many will question the sense in shifting blame from the criminals to the victims.
The commissioner says:
If you are continually rewarded for bad behavior you will probably continue to do it but if the obverse is true you might consider changing behavior. The system is not incentivizing you to protect yourself. If someone said to you, 'If you’ve not updated your software I will give you half back', you would do it.
While it's certainly true that banks should do everything they can to encourage customers to take an active role in their own security, the scale of organized online crime means that even with the best will in the world, there will always be victims.
Photo Credit: wk1003mike / Shutterstock
-

FBI can crack iPhone security and is classifying the method to prevent Apple fighting back
Publié: mars 23, 2016, 6:14pm CET par Mark Wilson

The FBI attempts to force Apple to unlock the San Bernardino shooter's iPhone have been in the headlines for a while now, stirring up debate about which side of the argument is in the right. Apple has refused point blank to help, but a recent twist saw the FBI changing its mind by saying it doesn't need Apple's help after all.
An outside party -- believed, but not known, to be Israeli security firm Cellebrite -- contacted the FBI to help access Syed Farook's iPhone. The Justice Department said it is "cautiously optimistic" that the proposed method, which is currently being tested, will be successful, but some reports suggest that it has already been used to break into some iPhones. Apple will obviously want to take steps to secure other devices if the hack is effective, but it has been classified to keep it secret.
As predicted, Apple used its iPhone SE launch event to talk -- albeit briefly -- about its fight with the FBI over access to the iPhone at the center of the case. Tim Cook said "we owe it to our customers and we owe it to our country. This is an issue that impacts all of us, and we will not shrink from this responsibility". As is to be expected of such activity, the whole process of investigating ways into the iPhone in question has been shrouded in mystery, and it looks as though that is set to continue.
Should the outside party assisting the FBI have success in finding a way into the San Bernardino iPhone without erasing any data, the obvious concern is that this same method could be used on other phones. The Guardian reports that the FBI has achieved at least part of its goal:
Currently, the Justice Department is still testing to make sure the method doesn’t damage or erase data stored on devices before using it on Farook's phone. The technique does successfully allow the government to get inside locked iPhones, the Guardian has confirmed.
Classifying details of a method of cracking iPhones makes sense on a number of levels, but it's not quite that clear cut. The outside party offering assistance will want to protect the specifics of any techniques it uses to prevent other companies from using them. The same can be said for the FBI. If a method for accessing phones has been devised, it's in the FBI's interest to keep it to itself; this is not information that should be allowed to fall into the wrong hands. But another argument that the FBI is likely to use to justify classifying this information is that it prevents Apple from putting further blocks in place.
At this stage it is not clear if a method has been devised for breaking into any iPhone, but it's starting to sound increasingly as though that is the case. If this is the case, Apple will almost certainly fight back by updating iOS to prevent the technique from working. Keeping the details secret means the FBI would be able to prevent this from happening -- unless, of course, Apple was able to reverse-engineer any tool that emerged.
But the situation can also be looked at from different angles. Is Apple actually helping the FBI while putting on a very different public face? Is the FBI bluffing about how close it is to gaining access to the data that has remained elusive for so long?
The arguments put forward by the agency that suggest the importance of being able to bypass encryption may seem increasingly compelling, but the case also raises the question of how much the FBI, and other law enforcement agencies, can be trusted.
Until now, the FBI said time and time again that there was simply no way to access Farook's iPhone without assistance from Apple. It said as much in court. Now we're being told a different story and it seems as though the FBI not only doesn’t need Apple's involvement, but could actually want to pushing the company away so that it doesn’t interfere. This is something that will displease Apple as it had expressed hope that any vulnerability in iOS would be revealed so it could be patched. Classifying data prevents this from happening.
Photo credit: musicphone / Shutterstock
-

Stickers, Stamptags, Taptags or Stickits... Twitter is testing a new image editing tool
Publié: mars 23, 2016, 1:44pm CET par Mark Wilson

Sometimes sharing a plain old image just isn't enough. Sometimes you might feel the need to adorn an otherwise dull image with clipart-style graphics. Sound like you? If so you're going to love the sound of a new image tool Twitter is testing... if not, brace yourself for an influx of irritation in you timeline.
Currently being referred to as Stickers (sound familiar?) -- although names including Stamptags, Taptags or Stickits are also in the running -- the tool is undergoing testing with a select group of tweeters. It allows users to add graphic overlays to photos and also introduces some extra social features in a bid to stand out from other tools available elsewhere. Meme creator, anyone?
Using Stickers could be as simple as adding smilies and props to a photo, but Twitter wants it to be more. Intriguingly, testers have been told that it will be possible to see how other users have edited the same image -- opening up the possibility that Twitter wants to provide people with a meme creator.
As reported by re/code, Twitter is conducting a study to test drive the new feature before a possible wider rollout. Twitter's own description explains:
Twitter is considering adding a new feature named Stickers that allows you to personalize your photos and connect with users around the world.
Now, when you post a photo on Twitter, a new feature will allow you to edit the photo so you can add images to it. In addition, by tapping on the image, you can see how other users from around the world have edited the same photo. Twitter will suggest photos that you can edit and post to participate in trending conversations and breaking news. Stickers is a new way to express yourself creatively on Twitter and make your photos more engaging.
The reference to tapping make it sound as though this is a feature destined for mobile devices, but there's no reason that it might not take a slightly different form on desktops and non-touchscreen devices.
Photo credit: Maryna Stamatova / Shutterstock
-

Google will launch Android Pay in the UK 'in the next few months'
Publié: mars 23, 2016, 12:15pm CET par Mark Wilson

Ready to compete with the already-established Apple Pay, Google's Android Pay is due to make its first foray into Europe when it launches in the UK in the coming months. To make things easy for retailers, Android Pay can be accepted anywhere that already supports contactless payments.
In addition to places such as Starbucks, Costa, KFC and Waitrose, Android Pay can also be used to pay for Tube, bus and train journey with Transport for London. The UK debt will follow a successful US launch and growth into Australia, but Google has not yet revealed whether the reward schemes enjoyed by those in the US will also make their way to the UK.
At launch there will be support for MasterCard and Visa credit and debit cards from the likes of Bank of Scotland, First Direct, Halifax, HSBC, Lloyds Bank, M&S Bank, MBNA and Nationwide Building Society, and Google promises that "new banks [are] being added all the time". Google says the launch of the payment service is all about making Android even more useful to people:
Android users in the UK are already enjoying many great features of Android from Google Photos to Google Play, and in the next few months Android smartphones will become even more useful with the launch of Android Pay. We're bringing together payment networks, banks and retailers to help you pay simply and securely.
Of course, Google is also keen for Android Pay to be used online -- watch out, PayPal. Apps such as JD Sports, Deliveroo and Takeaway.com will offer support from the offset, as will stores powered by Stripe, WorldPay and the like. The Android Pay API is available for developers looking to add support to other apps and stores.
The actual launch date has not yet been revealed, but will fill you in as soon as Google spills the beans.
-

Adblock Plus is coming to Edge... as soon as Microsoft allows it
Publié: mars 22, 2016, 12:45pm CET par Mark Wilson

After something of a delay, Microsoft finally released a version of its newest browser -- Microsoft Edge -- that supports extensions. We've already seen the first extensions appear in the Windows Store, but there are some big names that people are waiting for.
Included on this list is Adblock Plus, and its fans are clamoring for a version they can use in Edge. The good news is that one is in the works -- the only thing standing in the way now is Microsoft.
Although no precise reason is given, Adblock Plus says that it is waiting for Microsoft's approval so the release can take place. This could mean that there is compatibility testing to undertake, or it could be that Microsoft is still trying to iron out the kinks; extension support is essentially in beta, after all.
Responding to a query on Twitter, Adblock Plus revealed that it will be making its way to Microsoft Edge soon:
@mjtappert @Busster95 @MicrosoftEdge We're working on it as we speak. Just waiting for Microsoft to allow us to be released. :)
— Adblock Plus (@AdblockPlus) March 21, 2016
This was certainly not the only question about the release date of Adblock Plus for Microsoft Edge:
@vdmeulenz Hey Patryk! We'll be there as soon as Microsoft let us in! :)
— Adblock Plus (@AdblockPlus) March 21, 2016
There's no mention of a specific timescale, but it certainly sounds as though developers are keen to have the extension out there as soon as possible.
-

Apple's 9.7-inch iPad Pro is a smaller laptop alternative
Publié: mars 21, 2016, 7:30pm CET par Mark Wilson

At Apple's event today, it was the iPhone SE that people were intrigued to find out more about -- but there were plenty of other things to get excited about as well. In addition to the launch of iOS 9.3, it also announced a new 9.7-inch iPad Pro.
The reason for releasing a Pro device with these dimensions is that 9.7-inch remains the most popular size for iPads -- with more than 200 million units sold. It's not just the size of the screen that has changed, however.
Apple also says that the new iPad Pro has a display that’s 40 percent less reflective and 25 percent brighter than an iPad Air 2. Importantly, there's also the same A9X processor that's found in the larger iPad Pro.
Apple has a great deal to say about the new iPad Pro's screen. It's an adaptive display that automatically changes the color temperature to match the lighting it's being used in. Sound is catered for by no fewer than four speakers and there's the now-expected "Hey, Siri" support. In terms of looks, think of an iPad Air 2, and you're just about there.
As this is pitched as a laptop alternative, there's a specially designed Smart Keyboard for the new size of iPad Pro -- this joins the Apple Pencil as a form of input. There's a degree of crossover with the iPhone SE. There's support for 4K video, and a 12MP camera is on hand for photography, complete with Live Photo support. There is a new image signal processor, and this allows for the creation of panoramas up to 63MP.
Like the iPhone SE, pre-orders open for the new iPad Pro on March 24, and the device launches March 31. Pricing starts at $599 for the 32GB version, while the 128GB version will cost $749 and the 256GB model is $899.
-

Apple launches smaller, cheaper iPhone SE
Publié: mars 21, 2016, 6:44pm CET par Mark Wilson

It has been rumored for some time now, but at its Let us loop you in event in Cupertino Apple finally took the wraps off the iPhone SE. It's a new iPhone, perhaps not the new iPhone everyone wants, but a new iPhone nonetheless. Speculation has been rife about what corners would be cut to keep the price down -- and, indeed, what the price would be -- and now we know.
As expected, the iPhone SE is a 4-inch handset and it blends features from the iPhone 5s and iPhone 6s to create a mid-range device that Apple hopes will not only appeal to new markets, but also help to retain existing customers put off by the price of higher-end iPhones. But what's inside the case? (And, no... there's no word on the iPhone 7 yet.)
In terms of appearance, the iPhone SE is not a million miles away from the iPhone 5s -- there's a definite retro look to it. Inside, there's an A9 processor and there are 16GB and 64GB storage options to choose from. Touch ID is present for easy phone unlocking, but if you were hoping for 3D Touch, you're out of lock. There is also support for Apple Pay so Apple can continue to push its contactless payment method to more people. In terms of performance, Apple says that it's the same as the iPhone 6s.
There are two cameras on board to cater for photographic needs -- an 12MP rear-facer, and a one facing forward. Other specs include:
- 64 bit A9 processor
- M9 motion coprocessor
- 12MP rear camera with Live Photo and 4K video support
- Wi-Fi calling
- iOS 9.3
- Apple Pay support
- Always on 'Hey, Siri'
The iPhone SE will be available to pre-order on 24 March (launching 31 March), starting at $399 for the 16GB model, and $499 for the 64GB version.
-

Is Microsoft considering launching a digital market for second hand Xbox One games?
Publié: mars 21, 2016, 1:12pm CET par Mark Wilson

The gradual move from physical media to digital downloads has taken its toll on one section of the video games business -- the second hand market. The idea of selling back a digital copy of a game may seem as strange as the idea of selling an MP3 you no longer listen to, but it could be something that Microsoft is considering.
In a survey apparently being shown to Xbox gamers, Microsoft asks whether they would be interested in the idea of selling back their digital purchases. Presented in the way it is -- it's suggested that games could be bought back for 10 percent of their original price -- it may not seem like a great deal, but it's interesting to see that Microsoft is thinking about testing the water in this area.
GameSpot reports that details of the survey popped up on Reddit, and ferocious debate has started around whether the suggested price is too low. At the moment, digital downloads have no resale value whatsoever, so it could be argued that anything is better than nothing, but a forum thread on Neogaf shows lots of gamers responding with a loud "hell, no!".
The survey poses the question:
If the console digital games store for the console you owned offered customers the option to "sell back" their digital games to the store for 10 percent of the purchase price in store credit, would you be interested in such an offer?
If Microsoft did proceed with this idea, it would be a ground breaking move, and would open up the possibility of other digital buy-back schemes. There is, of course, the problem of ensuring that those who opt to sell their digital downloads do not find a way to reactivate their original software license and continue using the game for free.
How does the idea grab you? Does 10 percent seem a little stingy? Would the idea of store credit rather than cold, hard cash make a buy-back scheme less appealing?
Photo credit: Eric Broder Van Dyke / Shutterstock
-

iPhone SE could rejuvenate Apple and encourage growth in new markets
Publié: mars 21, 2016, 11:46am CET par Mark Wilson

We're living in the age of the smartphone and Apple has managed to carve itself a decent-sized chunk of the pie. But while each new iPhone is greeted with rapturous excitement, growth has declined recently to the point that a drop in sales in expected next quarter. Later today Apple is expected to launch the iPhone SE to counter this decline.
This smaller, cheaper handset would see the company venturing into new territory in a couple of ways. It would not only be the second time Apple has tried to appeal to the cheaper end of the smartphone smart -- the iPhone 5c being the first attempt -- but the iPhone SE could also see the company making in-roads into China as well as India and emerging markets.
Cracking China would be a major breakthrough for Apple, as would appealing to emerging markets, but it is not without risks. The iPhone SE is expected to be smaller than its predecessors, and this in itself is a risk. The general trend with smartphones is for ever-larger screens, so Apple is clearly hoping that these previously untapped markets will be keen enough to get their hands on an iPhone that the more diminutive size won't matter.
In emerging markets, even a cheaper iPhone will still command a premium prize when compared to the plethora of low-price Android handsets that are out there. But there are also users around the world for whom a cinema-sized screen is not important. It is these people that Apple is also trying to appeal to, perhaps helping them to take their first tentative steps into the world of smartphones.
Aside from teasing people about today's launch event, Apple has remained characteristically tight-lipped about what is being announced today, but there have been sufficient well-sourced rumors to make the appearance of the iPhone SE a certainty.
The key here is the lower price, and Apple will have had to make some cutbacks to make this possible. The expected 4-inch screen is the most obvious area where savings can be made, but it's also probable that certain features will be missing. While support for Apple Pay is likely to be present, the same cannot be said for 3D Touch. What's also not clear is the processor that will be used, the amount of storage and what the actual price will be.
All be revealed later today, and we'll have a full report as the announcement is made.
Update: Apple has officially announced iPhone SE. You can read more about it here.
Photo credit: Yeamake / Shutterstock
-

Snowden: I couldn’t trust Microsoft so I used free software like Tor, Tails and Debian
Publié: mars 20, 2016, 6:11pm CET par Mark Wilson

At the Free Software Foundation's LibrePlanet 2016 conference, Edward Snowden credited free software with enabling him to blow the whistle about government surveillance. Speaking via video link from Russia, the former NSA contractor said that "what happened in 2013 couldn't have happened without free software".
But as well as indicating his preference for free, open source software, Snowden revealed that he refused to use Microsoft software because he "couldn't be sure" that there weren't backdoors built in.
He said that the transparency made possible by the open source movement helped people to take control of their privacy and security. He went on to praise Apple for the stance it was taking in fighting the FBI but said that tech companies in general were not doing enough to ensure users' privacy. A case in point was the willingness of many of the big names to hand over data to the government when asked.
As well as privacy, Snowden used his speech to highlight the security offered by open source software, taking a swipe at one of the biggest names in tech:
I didn't use Microsoft machines when I was in my operational phase, because I couldn't trust them. Not because I knew that there was a particular back door or anything like that, but because I couldn't be sure.
Snowden is a man famously concerned with the security of software, and highlighted the need not only for the use of encryption, but also for security vulnerabilities to be patched as quickly as possible.
It's not just a question of stable. Stable is important but increasingly, due to the pace of adversary offensive research [being] so fast, if our update cycles are not at least relevant to the attack speed, then we're actually endangering people.
You can watch the full keynote over on LibrePlanet.
Photo credit: Rena Schild / Shutterstock
-

TeslaCrypt 4 ransomware now features unbreakable encryption and is even more dangerous for victims
Publié: mars 19, 2016, 7:00pm CET par Mark Wilson

Apple might be currently talking about its unbreakable encryption and how it's a good thing for privacy, but the FBI ruing it. The privacy arguement certainly stannds up to scrutiny, but strong encryption can also be used as a weapon, as demonstrated by countless examples of ransomware. There are numerous breeds of ransomware out there, but one of the most prolific is TeslaCrypt.
It's just a year since the first version of TeslaCrypt appeared on the scene, and it's gone through various updates and iterations over the ensuing months. Now it's hit version 4 and as well as continuing to threaten victims with sharing their files online, it also boasts what is being referred to as 'unbreakable encryption'.
Heimdal Security warns that not only is the ransomware more powerful than ever, it has also been patched with a number of 'bug fixes'. This means that it is now better equipped to deal with very large files, while the use of RSA 4096 means that recovery of data is completely impossible. Specialists at Heimdal Security say that the previously-reliable TeslaDecoder tool is now worthless.
Until now, files larger than 4 GB would get permanently damaged when encrypted. As another improvement, this is no longer an obstacle for the attackers.
In the case of data compromise, only two options remain: to restore the data from a secure backup or to pay the ransom (which we don't recommend).
The latest version of the ransomware leaks even more information to remote server than previous releases. Heimdal Security says:
Once the malicious code is run, the attackers can extract even more data than before from the local machine. The harvested data is then compiled into a unique key, while, at the same time, the ransomware will recruit the affected PC into a central botnet.
The collected data includes: 'MachineGuid' (a unique identifier pertaining to every PC), 'DigitalProductID' (the Windows operating system key) and 'SystemBiosDate' (the current time of the affected PC).
Similarly to previous campaign, TeslaCrypt 4 is being dispersed through drive-by attacks carried out using the Angler exloit kit infrastructure. Over 600 domains spreading Angler have been blocked today and the daily average is predicted to increase to up 1200 domains per day, on average.
The speed with which TeslaCrypt is being developed is worrying, and it seems all but impossible for anti-malware tools to keep pace. In the event of infection, the only real recourse is to fall back on a backup, so the advice would be to make sure that one exists and is kept up to date. This of course does nothing to mitigate against the damage following the leaking of private data, whether it belongs to an individual or a company.
Photo credit: ronstik / Shutterstock
-

Microsoft is working on a tool to port Chrome extensions to Edge
Publié: mars 19, 2016, 1:53pm CET par Mark Wilson

Microsoft has been keen to consigne Internet Explorer to the history books, but for a long time there has been a glaring issue with its successor, Microsoft Edge: a lack of extensions. With the release of Windows 10 Redstone build 14291 this finally changed.
While Microsoft Edge may now have extensions, it's still very early days and it's likely you'll find that most of your favorites are yet to make an appearance. But Microsoft has a plan. To make developers' lives as easy as possible, the company is working on a tool that will make it possible to port Chrome extensions to Edge.
As the Windows Store has failed to attract developers in droves, Microsoft will almost certainly be concerned that Edge's browser repository will be similarly ignored. It makes perfect sense to provide a way to port existing extensions from Chrome to Microsoft Edge, and in many ways it is an extension of the idea of making it easier to port apps from other platforms to Windows.
The news came from Microsoft Edge engineer Jabob Rossi who said on Twitter:
Lots of questions on this: yes we're working on a porting tool to run Chrome extensions in Edge. Not yet finished and not all APIs supported
— Jacob Rossi (@jacobrossi) March 18, 2016
If you were hoping for a mountain of extensions to choose from, it seems that you might have a bit of a wait on your hands. Rossi says that -- to start with, at least -- extensions that make it to the Store will be hand-picked:
@jacobrossi extn's in Store will at first be a carefully selected set covering top scenarios and API coverage, opening up to more in future
— Jacob Rossi (@jacobrossi) March 18, 2016
With a Chrome porting tool already in development, it would be strange if Microsoft didn’t also produce a tool to help Firefox plugin developers to bring their wares to Edge -- but there's no word on this at the moment.
Photo credit: T.Dallas / Shutterstock
-

Just Google it: Anyone could have 'hacked' and doxxed Trump like Anonymous
Publié: mars 19, 2016, 11:39am CET par Mark Wilson

Shortly after hacking into Donald Trump's voicemails and leaking messages, Anonymous declared all-out war on the presidential candidate. Earlier this week, the hacktivist group launched #OpWhiteRose and doxxed the republican candidate.
Personal information about Trump -- his cell phone number, social security number and other details -- were released last week, with the group saying they were provided on the understanding that "you alone are responsible for your actions, as always". But rather than being the fruit of an elaborate hacking operation, anyone with the nous to use Google and Wikipedia could have gathered exactly the same information for themselves.
While some are impressed by the activities of Anonymous, others are not blown away. The BBC decided to see how easy it was to obtain the same information about Donald Trump as Anonymous, and found that it was child's play. It was so simple, in fact, that there was no need to even do any digging for his cell phone number, as Trump had already shared it with everyone on Twitter -- although it's hard to imagine there isn't another number in use by now.
Information such as the contact details for Trump's 'secret' business HQ is readily available on The Trump Organization website -- little more than a Google search for 'Trump' takes you there. Trump's date of birth? Look no further than his Wikipedia page for this info. Ditto details about his kids, place of birth and parents.
The BBC takes great delight in knocking Anonymous down a peg or two by pointing out the ease with which Anonymous' info can be obtained:
It also includes a link to the page for Mar-a-lago, Palm Beach in Florida -- which is the address listed in the Anonymous 'leak'.
The GPS co-ordinates were also 'leaked' but that can be found by typing the address into Google Maps.
GPS co-ordinates do make you feel like a spy, though.
We can tell when Anonymous looked up Trump on Wikipedia - because they list the area of his estate as 7,400 sq metres. The wiki page was updated on 25 February to 10,000 sq metres.
Actually, it's not strictly true to say that all of the information leaked by Anonymous is available through Google and Wikipedia; there's the question of Trump's social security number. This is a piece of data that is difficult to verify for starters. It would be possible to publish any old number and call it Trump's social security number -- there's no easy way to check, and even Donald Trump is not stupid enough to confirm or deny validity.
This is not what Anonymous has done.
Instead the group has simply republished the same social security number released back in November by the Hydra Hacking Team. Again, there's no way to verify the number, so it's not clear if Hydra Hacking Team gained access to the real thing or just made it up. Either way, none of the glory -- if indeed there is any -- belongs to Anonymous.
The group is really going to have to try a little harder if it wants to impress anyone with its '1337 skillz'.
Photo credit: Marietjie / Shutterstock
-

Apple's fight with the FBI is about LGBTQ issues as well as privacy
Publié: mars 18, 2016, 11:31pm CET par Mark Wilson

As the battle between the FBI and Apple rumbles on, the debate about encryption has intensified, bringing with it renewed discussion about privacy. There are few people who would want to give up their right to privacy and allow unrestricted access to their personal communication, but there are some for whom privacy is even more important.
Tim Cook is just one of the voices shouting that a backdoor for the government would be a backdoor for anyone. Most people and companies have sided with Apple saying that rather than backdoor access, what's needed is stronger encryption, greater security, even more robust privacy. It's something that has the support of people from all walks of life, but it's an issue that's very close to the hearts of the LGBTQ community.
This is an argument put forward by Victoria Ruiz, lead singer of the punk band the Downtown Boys, and Evan Greer, campaign director of digital right group Fight for the Future. They describe the media response to the Apple/FBI case as a circus and suggest that this masks the real human consequences that could follow on from the FBI getting its way. They say that "for millions of people, privacy and digital security are essential for their physical safety. They're not luxuries, they’re necessities".
In some parts of the world, for example, homosexuality remains illegal. Ruiz and Greer also point out that "in the majority of US states, for example, you can still be legally fired just for being gay". With these two facts in mind, the pair say that "the potential consequences of a data breach for many LGBTQ people could be far more severe". This is just one of the reasons strong encryption is not just important, but vital.
LGBTQ people around the world depend on encryption every day to stay alive and to protect themselves from violence and discrimination, relying on the basic security features of their phones to prevent online bullies, stalkers, and others from prying into their personal lives and using their sexuality or gender identity against them.
In areas where being openly queer is dangerous, queer and trans people would be forced into near complete isolation without the ability to connect safely through apps, online forums, and other venues that are only kept safe and private by encryption technology.
These situations are not just theoretical. Terrifying real life examples abound, like the teacher who was targeted by for being gay, and later fired, after his Dropbox account was hacked and a sex video was posted on his school’s website. Or the time a Russian gay dating app was breached, likely by the government, and tens of thousands of users received a message threatening them with arrest under the country’s anti-gay 'propaganda' laws.
Ruiz and Greer side with Tim Cook and others who say that a backdoor into one phone is a backdoor, potentially, into many -- if not all -- phones. They warn that the FBI is looking to "set a precedent that will inevitably be used to force other encrypted services to do the same". While one of the FBI's lines of argument is that one of the aims of accessing the San Bernardino shooter's iPhone is to protect lives, "they're conveniently omitting the very real ways that punching holes in digital security puts even more people in danger".
Some people will almost certainly pooh-pooh what Ruiz and Greer put forward, and will ask why this is an LGBTQ issue. It's all too easy to forget that the LGBTQ community is frequently a vulnerable one, a community that often needs protection from archaic thinking and abusive groups. In short, encryption can help save lives.
Encryption technology is doing as much, if not more, to keep queer and trans people safe as legislation -- which is spottily enforced, and does not prevent the violence and oppression that many of the most vulnerable LGBTQ populations experience.
If you care about the lives of queer and trans people, you should join the growing movement opposing government backdoors in our phones and computers. Strong encryption is saving lives every day. If we lose it, we risk a lot more than our privacy. We risk losing our most basic right: the right to be ourselves.
Photo credit: VectorShots / Shutterstock
-

Chelsea Manning: Insider Threat document shows US government employees are under surveillance
Publié: mars 18, 2016, 5:49pm CET par Mark Wilson
The US government is busy putting thousands of its own employees under 'permanent surveillance' according to a document obtained by Chelsea Manning. In the wake of leaks by the likes of Edward Snowden and WikiLeaks, the government set up the Insider Threat program in an attempt to nip future leaks in the bud.
It's a while since Manning was in the news, the last notable appearance being when the solider formerly known as Bradley Manning joined Twitter from prison. But the latest document released by Manning -- obtained using a freedom of information request -- shows that the government is not afraid to use NSA-style tactics on its own employees.
The Insider Threat program indicates that certain employees have been earmarked for 'continuous evaluation' if they exhibit particular characteristics or are thought to have certain motives. On the list of 'Insider Threat Motives' are people with financial difficulties, those with divided loyalties and those with certain ideologies.
The document, obtained by the Guardian, has been published online, and makes for interesting viewing.

The government runs through the history of Manning's case (referred to as Bradley Manning throughout, as he was known in the army at the time) and goes on to define his motive for leaking data to WikiLeaks. He is described as being disgruntled with the army's attitude towards homosexuality, and also as aligning himself with a 'group of hackers' whose ideology he shared. Manning is also slapped with the labels of 'Ego and Ingratiation' and 'Family/Personal Issues'. Manning's 'behavior indicators' are also singled out.
The document concludes by saying that:
Due to the actions of PVT Manning, OPSEC/INFOSEC in deployed enviroments have become stricter (no USB drives, CD burning capabilities restricted/managed, SIPRNet token cards, etc...).
Writing for the Guardian, Manning describes the government's internal surveillance program as " unsustainable, ineffective, morally reprehensible, inherently dangerous and ultimately counterproductive". She writes:
In the months following the US government's initial charges against me over the release of government records in 2010, the current administration formed the National Insider Threat Task Force under the authority of the Office of the Director of National Intelligence (ODNI), the Department of Justice, the Federal Bureau of Investigation and several other US government agencies.
The mission of this taskforce is breathtakingly broad. It aims at deterring threats to national security by anyone "who misuses or betrays, wittingly or unwittingly, his or her authorized access to any US Government resource". Unfortunately, the methods it outlines amount to thousands of government personnel being effectively under total surveillance.
It's a microcosm of the surveillance that is carried out in the wider world and Manning warns that there is a danger stemming from "a reliance on 'anonymous feedback' which can create endless witch-hunts, 'general invitations' to report or file complaints through so-called open door policies, and vagueness about what feedback is expected". The real concern is the carte blanche the program appears to afford the government:
The broad sweep of the program means officials have been given a blank check for surveillance. Agencies implementing the Insider Threat program could examine anyone who has motives of "greed", "financial difficulties", is "disgruntled”, has "an ideology" a "divided loyalty", an "ego" or "self-image", or "any family/personal issues" -- the words used to describe my motives. Such subjective labelling could easily be applied to virtually every single person currently holding a security clearance.
Manning may have concerns about the surveillance programs the government undertake, but she also has suggestions:
The Insider Threat program works against innovation, creativity and the prevention of institutional corruption. Perhaps this is the real intent of the intelligence community and the Insider Threat Task Force -- to instill fear and project dominance throughout the intelligence community, the military, and among government employees and contractors at large.
Perhaps a better approach for the government would be to create a Transparency and Accountability Task Force, comprising different government agencies and departments, the inspectors general, the National Archives and Office of Government Information Services, and a committee or other body that can work directly with current and former government employees, service members, veterans and journalists.
Such a taskforce could focus on advocating for and protecting employees who have concerns. It would help to send a message to employees, military service members, contractors and department and agency heads that even if the official channels fail, those who raise concerns will still be protected, listened to and given the chance to speak out in a meaningful forum. It would encourage dissent. It would allow dirty laundry, drama and corruption to be aired out rather than allowed to fester.
We could all -- citizens, the government and its employees -- benefit from that.
-

Apple vs FBI: Tim Cook concedes helping authorities is a theoretical possibility
Publié: mars 18, 2016, 1:46pm CET par Mark Wilson

In the Apple vs FBI fight, the issue is very black and white for many people; you support Apple's position of standing firm against the FBI, or you believe the FBI should have unfettered access to whatever data it wants, regardless of the consequences.
Tim Cook has been steadfast in his position, but in an interview with TIME the Apple CEO admits that the situation is not entirely binary. Presented with a thought experiment Cook appears to concede there are gray areas, opening up the possibility of assisting the FBI to break into the San Bernardino shooter's iPhone.
The full transcript of Tim Cook's interview has been added to the TIME website, and it makes for interesting reading. Cook comes across as understandably weary of answering, largely, the same questions over and over again, and it's clear that the situation is taking its toll. He says that one of the reasons -- and there are many -- Apple is not going to help the FBI to crack or disable encryption is that "they don’t know if there’s anything on it".
He continues:
I think everybody recognizes that there may not be anything on it, there may be something on it. What I'm saying is, to invent what they want me to invent puts millions of people at risk.
This is a point that many people have raised, so Cook is not winning any points for originality here. But the interview takes an interesting turn when he is presented with a theoretical situation that has many parallels with the Apple vs FBI case
TIME: So being mindful of the fallacy of the hypothetical, suppose on the other side of the door is the nuclear device that's on a timer, or the child who's being tortured. And you have a key to that door.
COOK: If I had a key to that door I would turn that door. But that's not the issue here, just to be clear. It's not that I have information on this phone, and I'm not giving it. I had information. I gave all of it. Now they're saying, hey, you could invent something to grab some additional information. We're not sure there's anything on there, but we want you to invent this in case there is. And the thing that they want me to invent, that key can turn millions of locks.
Cook also highlights another problem with forcing companies to making their encryption algorithms available to government or law enforcement agencies -- ultimately it just pushes people into using other services and going deeper underground:
If you're worried about messaging, which I think is primarily the worry in this scenario, people will just move to something else. You know if you legislate against Facebook and Apple and Google and whatever else in the US, they'll just use something else. So are we really safer then? I would say no. I would say we're less safe, because now we’ve opened up all of the infrastructure for people to go wacko at.
He is quick to stress that he is aware of the trade-off between privacy of individuals and the ability of government to gather data for security purposes:
I'm not targeting government. I'm not saying hey, I'm closing it because I don't want to give you any data. I'm saying that to protect our customers, we have to encrypt. And a side effect of that is, I don't have the data.
If the on-going encryption debate that Apple finds itself at the center of seems faintly absurd to you, Tim Cook gets you. He feels the same. Speaking about the fallout of Congress ruling against Apple, he says:
I think, first of all it's bad for the United States. Because going against us doesn't just mean going against us. It means likely banning, limiting or forcing back doors for [everyone]. I think it makes the US much more vulnerable. Not only in privacy but also in security. The national infrastructure, everything. And I can't imagine it happening because it would be outlandish for something like that to happen. I think everybody has better judgment than that.
But at the end of the day, we're going to fight the good fight not only for our customers but for the country. We're in this bizarre position where we're defending the civil liberties of the country against the government. Who would have ever thought this would happen?
Photo credit: JStone / Shutterstock
-

How to play Facebook's secret basketball game
Publié: mars 18, 2016, 11:56am CET par Mark Wilson
Who doesn't love a good Easter egg? Apps, games and websites have all manner of hidden secrets, and Facebook is no different. It's not all that long ago that we showed you how to play the chess game secreted in Facebook Messenger and now another gem has been unearthed.
Also hidden away in Facebook Messenger you'll find a basketball game -- just in time for March Madness. Be warned, it's quite addictive but shooting some hoops is a great way to kill some time with a friend. All you need is an Android smartphone or an iPhone.
Before you begin, make sure that you have the latest version of Facebook Messenger installed -- head to Google Play or the App Store to see if there's an update waiting for you. With this done, you can instigate a game.
In a chat, send a basketball emoji to the person you're talking with, tap the emoji in the chat window and the game will launch. It's a very basic mini-game; just flick up with your finger to fire the ball at the hoop and see if you can push up the high score. Things start off nice and easy, but as your score increases you'll notice that the hoop starts to move.
Have fun!
Photo credit: Lightspring / Shutterstock
-

Twitter sneakily enables new algorithmic feed -- here's how to disable it
Publié: mars 17, 2016, 8:24pm CET par Mark Wilson

Twitter is forever tinkering with timelines, and it's not all that long ago that the #RIPTwitter hashtag was trending after it was suggested that a new algorithm-powered timeline was to be introduced. Twitter users lashed out and Jack Dorsey stepped into the fray to try to allay fears.
A month ago Dorsey said that "we never planned to reorder timelines next week". He wasn’t wrong. It's happened now instead. Gone is the sensible, logical, chronological timeline, replaced instead with an algorithmic feed that's home to tweets Twitter thinks you want to see first. It's not only been launched with little fanfare, but now it's enabled by default.
This is something that has upset many users; there aren’t many people who are happy to have changes forced upon them, after all. The new algorithms mean that, to quote Twitter, "Tweets you are likely to care about most will show up first in your timeline". It may be a feature you decide you like, but Twitter's decision to forge ahead and enable it for everyone by default has got many backs up.
Twitter describes the change in its updated support pages:
Tweets you are likely to care about most will show up first in your timeline. We choose them based on accounts you interact with most, Tweets you engage with, and much more.
If you find yourself irked by the latest rearrangement of your timeline, just head to Settings and disable the option labeled Show me the best Tweets first. Click Save Settings, and things should be back to the way they used to be.
Photo credit: Quka / Shutterstock
-

Huge Windows 10 Redstone update will 'change everything'
Publié: mars 17, 2016, 11:19am CET par Mark Wilson

While it is widely expected that Windows 10 Mobile will launch today, it is the desktop version of the operating system that still attracts the most attention. The first major update to Windows 10 -- dubbed Redstone -- has already been rolled out to Insiders in the form of an early preview build, but there are some big changes on the way.
The first time we'll get to see what Microsoft has been working on is likely to be at Build at the end of the month, but the company's PR machine has already kicked into action. Product managers at Microsoft already have access to new and exciting features which it is promised will 'change everything' and cause users to 'freak out'.
Of course, details of what these changes are are non-existent at this stage -- Microsoft will play its cards close to its chest until it is ready to reveal all at Build. Despite the number of Windows 10 installations Microsoft keep bragging about, users continue to complain about niggling issues and missing features. The hope will be that Redstone will finally address these.
The excitement started yesterday on Twitter when senior program manager Rich Turner was moved to use CAPS (!) to show his barely contained enthusiasm:
Finally getting to play with new #Windows10 features. You are all gonna FREAK OUT when you see this

— Rich Turner (@richturn_ms) March 16, 2016
This was followed earlier today by an equally excited and shouty tweet from Scott Hanselman:
These features (I know what this is because I'm helping) are going to CHANGE EVERYTHING. No joke. You can't even. [https:]
— Scott Hanselman (@shanselman) March 17, 2016
While Insiders have already been able to try out builds from the Redstone release branch, it seems clear that Microsoft has a few surprises up its sleeve. It's extremely unlikely that we'll learn more ahead of Build, so for the time being we can only guess as to what's in store for us.
Photo credit: charnsitr / Shutterstock
-

Ads are eating your mobile data allowance
Publié: mars 16, 2016, 4:52pm CET par Mark Wilson

A new study has revealed that ads on smartphones account for between 18 and 79 percent of downloaded data. The astonishing statistic gives mobile users another reason to despise ads on top of the annoyance, security and privacy concerns they already bring about.
With most mobile users having to stick to a monthly allowance, the suggestion is that it's time for mobile pages to go on a diet. The research carried out by Ender Analysis also found that JavaScript accounted for between 6 and 68 percent of downloaded data.
The findings are important not only because ad-blocking is very much a hot topic at the moment, but also because more and more web traffic comes from mobile devices. Enders Analysis' research says that content providers need to adapt to take this into account:
The move from desktop to mobile, from banner to native and from web to apps provides advertisers and publishers with the opportunity to provide an acceptable advertising experience, ensuring that blocking of these new formats and properties never reaches the threatening levels currently on desktop.
As reported by the Guardian, Enders also says:
On the basis of this investigation, an estimate that says advertising accounts for half of all data used by publisher pages on iPhones does not look unreasonable. Publisher mobile pages are bloated, and advertising is an enormous part of that.
Photo credit: ra2studio/ Shutterstock
-

Malvertising campaign targets Americans through major websites including BBC and New York Times
Publié: mars 16, 2016, 2:23pm CET par Mark Wilson

Top news websites including the BBC, the New York Times and MSN were hit over the weekend by a co-ordinated malware campaign. Delivered through the advertising networks used by the sites, the malvertising attack aimed to install ransomware on victims' computers.
On-site ads are far from loved, hence the prevalence of ad-blocking tools. But as well as being an annoyance, online ads can also pose a serious security risk -- something highlighted by this attack. The infected ads redirected people to servers hosting the Angler exploit kit and was engineered to target US-based web users.
With a footprint measured in billions of readers, the sites -- including MSN, the BBC, the New York Times, AOL and Newsweek -- were hit with a rash of malicious traffic from two rogue domains, TRACKMYTRAFFIC.BIZ and TALK915.PW. the malvertising campaign affected four major ad networks -- Google, AppNexus, AOL and Rubicon -- and caused what MalwareBytes calls a "huge spike in malicious activity".
Researchers from Trustwave say that those behind the attack had managed to take control of an ad delivery domain, thereby making it possible to hit so many high-profile websites in one fell swoop.
It's not clear how many people were adversely affected by the malware, but anyone who fell victim will have found their data encrypted and held to ransom until a Bitcoin payment was delivered to the perpetrators.
Photo Credit: lolloj/Shutterstock
-

Qualcomm Snapdragon SoC vulnerability could compromise IoT security
Publié: mars 15, 2016, 1:13pm CET par Mark Wilson

One of the greatest concerns surrounding the growth of the Internet of Things (IoT) is its security, and it seems that some people's worst fears have just been realized. Security experts at Trend Micro have discovered a vulnerability in Qualcomm Snapdragon-produced SoC (system on a chip) devices.
In fact, it is the same vulnerability that cropped up earlier in the month, affecting Nexus 5, Nexus 6, Nexus 6P and Samsung Galaxy Note Edge Android handsets. This in itself is concerning as these are devices that are no longer in line for security updates, but more concerning is the fact that the same chips are used in IoT devices. The vulnerability makes it possible for an attacker to gain root access to the hardware, and this is worrying in a world of inter-connected devices.
In the interests of trying to contain the problem, Trend Micro has not revealed full details of the vulnerability but is using the issue to highlight a serious problem not just for handset owners but also for adopters of the IoT. The lack of updates available for the affected phones illustrate perfectly just how a security issue discovered in another connected device using the same chip -- a fridge, a home heating system, a car -- could be left vulnerable in exactly the same way.
Trend Micro's Noah Gamer writes:
A large portion of the population already doesn't see the point of updating their systems, and this only pertains to the few Internet-connected devices in their homes. An IoT future, where almost every device in the home will have a connection, is only going to compound this problem further. Add in the fact that some of these devices will be designed to be cheap and 'essentially disposable' and it's easy to see why many people worry about the security of the IoT. SoCs like the ones developed by Snapdragon are already making their rounds in IoT devices including certain wearables. If the industry can't find a way to effectively patch these vulnerabilities, there could be massive repercussions.
Gamer highlights some recent examples of hacked connected devices including a Barbie doll that could be used as a surveillance device, and a pacemaker that could be used to kill the person it was inside. Hacking a smartphone by exploiting a vulnerability is one thing, but as the IoT infiltrates further and deeper into our lives, the long arm of attackers could reach even further and have even more disastrous consequences.
Updates -- and a reliable system for delivering them -- are what's needed, says Trend Micro:
If the IoT is going to be as widespread as many experts predict, there needs to be some sort of system in place ensuring these devices are safe for public use. Security updates are an absolute necessity these days, and users of these connected devices need to know what they're dealing with.
Photo credit: Chesky / Shutterstock
-

Microsoft did a whoopsy -- previous announcement about dropping Bitcoin was a mistake
Publié: mars 14, 2016, 10:14pm CET par Mark Wilson

Earlier today we reported that Microsoft was no longer accepting Bitcoin as a form of payment. It turns out that this is not true. Microsoft made a mistake.
Despite making a very clear change to its support pages that said "Microsoft Store doesn't accept Bitcoin" the company will in fact continue to support the cryptocurrency. This is not a change of heart, it was nothing more than a slip up, but Microsoft has not offered much of an explanation as to how it came about.
While mistakes are certainly made from time to time, updating the support pages in a way that made it abundantly clear the Bitcoin was being ditched is a little odd. Whether there have been crossed lines of communication within Microsoft, or the Bitcoin drop was something that had been considered and accidently announced, we'll probably never know.
In a statement to BetaNews, Microsoft apologized and clarified its position:
We continue to support Bitcoin for adding money to your Microsoft Account which can be used for purchasing content in the Windows and Xbox stores. We apologize for inaccurate information that was inadvertently posted to a Microsoft site, which is currently being corrected.
Photo credit: Palto / Shutterstock
-

DVR capabilities are on their way to Xbox One
Publié: mars 14, 2016, 7:46pm CET par Mark Wilson

Although the Xbox One is undoubtedly a games console at heart, Microsoft wants it to be so much more. It's part of the reason for the blurring of boundaries between Windows 10 on the desktop and the Xbox One's version of the operating system, and there are already a number of media center features to be found. But things are on the verge of improving. A lot.
It's one thing to be able to watch OTA TV broadcasts on your console, but we've all become used to the notion of time-shifted viewing. DVR functionality -- the ability to pause and record shows as they are broadcast -- has been promised for some time, and now it's undergoing internal testing at Microsoft, strongly suggesting that a public release is not too far away.
Paul Thurrott reports that Microsoft is internally testing DVR capabilities, but this should not really come as a huge surprise. In fact, it had widely been expected that the feature would have been implemented by the end of last year. It's not clear what caused the delay, but it would appear that work is now progressing once again.
Microsoft has already made it clear that in order to record TV shows you'll have to have an external hard drive connected to your console. This make sense as the internal storage is best left for games, and can easily be filled up even if you've opted for the 1TB version of the console.
Watch this space for news about when a preview is made available.
Photo credit: Klaus Balzano and mtlapcevic / Shutterstock
-

Cross-platform support means Xbox One gamers will be able to play PS4 opponents
Publié: mars 14, 2016, 7:27pm CET par Mark Wilson

Microsoft has announced that cross-network play is coming to Xbox One. This means that as well as being able to play against other Xbox One owners and those running Windows 10, gamers will also be able to play against people who are using a PlayStation 4.
This is the announcement that Xbox Live subscribers have been waiting for, and it's something that gamers have been begging for for years. It's not something that's going to happen overnight however. Microsoft may have got the ball rolling, but it's going to need support from Sony as well as game developers -- although it's hard to imagine that they won't give it.
The news came in an announcement from director of ID@Xbox, Chris Charla who said: "in addition to natively supporting cross-platform play between Xbox One and Windows 10 games that use Xbox Live, we’re enabling developers to support cross-network play as well. This means players on Xbox One and Windows 10 using Xbox Live will be able to play with players on different online multiplayer networks -- including other console and PC networks".
Of course, it's not a feature that will be automatically available in every game, as Charla explains:
It's up to game developers to support this feature, and Xbox Live players will always have the option of choosing to play only with other Xbox Live players. We're thrilled to confirm that Psyonix's Rocket League will be one of the first games to take advantage of this new capability by enabling cross-network play between Xbox One and PC players, with an open invitation for other networks to participate as well.
Photo credit: Stefano Tinti / Shutterstock
-

Save up to $650 off a Surface Pro 4 as Microsoft launches new trade-in program
Publié: mars 14, 2016, 2:18pm CET par Mark Wilson

If the price of a Surface Pro 4 has been putting you off upgrading, Microsoft's new 'Trade in, trade up' could be just what you’ve been waiting for. Apple is famous for running trade-in programs to encourage people to upgrade to the latest devices, and Microsoft has also got in on the action more recently.
The latest deal means you can ditch your old MacBook, PC or Surface and receive up to $650 back to put towards your Surface Pro 4. There are conditions, and you might find that it makes more sense to sell your old device privately, but it's certainly well worth checking out to see if it could work in your favor.
Of course, just how much money Microsoft puts your way depends on a number of things. Interestingly, there is no requirement for your old computer to be in working condition, but this will obviously be reflected in the money you get back for it.
You can trade in your old, unwanted device online or in a Microsoft store. If you opt for the online option, you can use the site to determine the value of your device before sending it off to Microsoft for checking. Once this has been done, you'll be provided with a promo code that you can use to make your discounted purchase. Opt to do it in-store and you'll get your cheaper Surface Pro 4 faster!
Find out more at the Trade in, Trade up website.
-

Encrypt all the things! Facebook, Google and WhatsApp to increase privacy and encryption
Publié: mars 14, 2016, 1:17pm CET par Mark Wilson

Privacy and security has always been a hot topic, but never more so than in recent months. The Apple/FBI case has really brought things to a head, enlivening the debate between privacy and security advocates, and those who side with the government. As Apple fights to prevent the FBI from accessing the San Bernardino shooter's iPhone, Facebook, Google and others are looking to increase encryption and lockdown user data even further.
The Guardian has learned that a number of Silicon Valley companies are working on ultra-secure encrypted messaging systems. With President Obama having made a sideways reference to supporting the inclusion of backdoors for government, Facebook is planning to not only bring encryption to Whatsapp's voice messages, but also to bolster the security of Facebook Messenger.
Although many of these security projects were under way well before the Apple case hit the headline, the raging battle serves -- as the Guardian suggests -- as a perfect backdrop for advertising these new or improved services. Google, a company for whom privacy and security really needs to be of the utmost importance, is said to be working on an encrypted email project, and Snapchat is also in line for a secure messaging component.
The push for not only stronger encryption, but also the more widespread use of encryption, has been going on for some time now, but the Apple case has really brought the issue into sharp focus. Tech companies were very quick to throw their support behind Apple after the iPhone manufacturer refused to comply with the FBI's demands, but there has been criticism that it has been used as a marketing tool.
While the addition or strengthening of encryption features does serve as great PR, it's also a case of giving people what they want. With WhatsApp boasting more than a billion users, its entry into the encryption arena -- something it has not been vocal about in the past -- could dramatically change the dynamics of the on-going debate. Encryption is certainly not completely new to WhatsApp, but in the coming weeks, it will roll out not just to group messages, but also to voice messaging.
In the continued fallout of the NSA surveillance revelations, it seems that tech companies left, right and center are eager to win back the trust that may have been lost after it was revealed that they had been complying with government demands for access to user data.
Photo credit: Rawpixel.com / Shutterstock
-

Microsoft drops Bitcoin support for Windows 10 and Windows 10 Mobile purchases
Publié: mars 14, 2016, 11:13am CET par Mark Wilson

Microsoft's love affair with Bitcoin has proved to be short-lived. The company has updated its support pages to indicate that it no longer supports the cryptocurrency for purchases made in the Microsoft Store.
No explanation has been given for the decision, but it's likely that Bitcoin's failure to hit the mainstream -- yet, at least -- is to blame. From now on, Windows 10 and Windows 10 Mobile purchases will have to be made using other payment methods, although Microsoft says current balances paid for with Bitcoin can still be used.
Update -- Microsoft has said that the announcement was made in error and has issued a statement to that affect.
The announcement has come out of the blue, but at the same time it's not entirely surprising. Bitcoin has earned itself something of a bad reputation by association recently, being the currency of choice for extortion of money with ransomware. While it is possible that this has played a part in Microsoft's decision, slow adoption rates of the cryptocurrency are more likely to blame.
A simple, to-the-point page on the Microsoft site says:
Microsoft Store doesn't accept Bitcoin
Applies to Windows 10 and Windows 10 Mobile
You can no longer redeem Bitcoin into your Microsoft account. Existing balances in your account will still be available for purchases from Microsoft Store, but can't be refunded.
With that in mind, if you do have a Bitcoin-funded balance, take care what you choose to spend it on as it seems there will be no chance of getting your money back.
Photo credit: 3Dsculptor / Shutterstock
-

Google to use geolocation data to block Right To Be Forgotten links around the world
Publié: mars 4, 2016, 7:00pm CET par Mark Wilson

Google is updating its approach to delisting search results in Europe under the Right To Be Forgotten. At the moment, people are able to request that search results do not link to articles that are "inadequate, irrelevant, no longer relevant or excessive, and not in the public interest" but there have been ways for searchers to bypass these delistings.
While Google may remove a search result from all European Google domains, there's nothing to stop people from using non-European versions of the search engine to access otherwise-hidden data. Starting next week, Google is going to start using geolocation data to crack down on this practice.
Google says that it has been engaged in discussions with regulators since the Right To Be Forgotten ruling. The company believes that its new approach will enable it to comply with the letter of the law in Europe while not standing in the way of people in other parts of the world to access information through searches.
Starting next week, in addition to our existing practice, we will also use geolocation signals (like IP addresses) to restrict access to the delisted URL on all Google Search domains, including google.com, when accessed from the country of the person requesting the removal. We’ll apply the change retrospectively, to all delistings that we have already done under the European Court ruling.
So for example, let’s say we delist a URL as a result of a request from John Smith in the United Kingdom. Users in the UK would not see the URL in search results for queries containing [john smith] when searching on any Google Search domain, including google.com. Users outside of the UK could see the URL in search results when they search for [john smith] on any non-European Google Search domain.
The Right To Be Forgotten ruling has proved controversial in a number of ways. Those opposed to it say that access to information should be unrestricted while supporters have complained that it does not go far enough to protect the privacy of individuals. The latest announcement should go some way to calming the concerns of those who fall into the latter camp.
Photo credit: Evan Lorne / Shutterstock
-

Developer criticizes Microsoft's 'monopolizing' approach to apps and gaming in Windows 10
Publié: mars 4, 2016, 6:21pm CET par Mark Wilson

A walled-garden approach to apps for operating system is something we've become used to in the mobile world. Apple, in particular, has been incredibly successful in creating a closed-off eco-system that ensures it remains -- broadly speaking -- in control of what hits the App Store. With Windows 10, Microsoft is trying to blur the boundaries between mobile and non-mobile, and developers -- especially game developers -- are not happy.
Windows 10's Universal Windows Platform (UWP) is described by Epic Games founder Tim Sweeney as a "closed platform-within-a-platform". More than this, Sweeney says that it is the "most aggressive move Microsoft has ever made", warning that the company is trying to monopolize app distribution to the detriment of consumers and the entire PC industry. Writing for the Guardian, Sweeney bellows out a call to arms saying that UWP "can, should, must, and will die".
The pioneering developer pulls no punches in laying into Microsoft in a strongly-worded editorial piece in the Guardian. He says that Microsoft is cutting off a line of communication between developers and users, and competes unfairly with rival games stores such as those operated by Steam and other developers.
Microsoft has launched new PC Windows features exclusively in UWP, and is effectively telling developers you can use these Windows features only if you submit to the control of our locked-down UWP ecosystem. They're curtailing users' freedom to install full-featured PC software, and subverting the rights of developers and publishers to maintain a direct relationship with their customers.
Sweeney expresses concern that Microsoft appears to be looking to control the entire process of distributing, downloading, and updating apps. While not 'impossible' as Sweeney suggests, the Windows Store certainly makes it hard for the average user to make use of UWP apps outside of the store. Side-loading is possible, but "this is a feature Microsoft can revoke at any time using Windows 10’s forced-update process".
These are legitimate concerns and Sweeney uses his editorial to call on Microsoft to open up the UWP platform in the same way as the currently-used Win32 API. He suggests a trio of advantages that this would bring:
- That any PC Windows user can download and install a UWP application from the web, just as we can do now with win32 applications. No new hassle, no insidious warnings about venturing outside of Microsoft’s walled garden, and no change to Windows’ default settings required.
- That any company can operate a store for PC Windows games and apps in UWP format -- as Valve, Good Old Games, Epic Games, EA, and Ubi Soft do today with the win32 format, and that Windows will not impede or obstruct these apps stores, relegating them to second-class citizenship,
- That users, developers, and publishers will always be free to engage in direct commerce with each other, without Microsoft forcing everyone into its formative in-app commerce monopoly and taking a 30 percent cut.
Microsoft is accused of following Google's lead in "technically exposing, but practically burying, options that let users escape from its force-bundled services. If you've tried to change your Windows 10 search engine, web browser, or movie player, or to turn off their invasive new lock-screen ads, Windows search bar Bing spam, and invasive "analytics", you know what I’m talking about. It's a deliberately anti-customer experience: the options are there, but good luck finding them.
The ultimate danger here is that Microsoft continually improves UWP while neglecting and even degrading win32, over time making it harder for developers and publishers to escape from Microsoft’s new UWP commerce monopoly. Ultimately, the open win32 Windows experience could be relegated to Enterprise and Developer editions of Windows.
Sweeney points to the content of the Microsoft Store as evidence of how misguided an approach the company has taken. The likes of Photoshop, Grand Theft Auto V and Fifa 2016 are notable by their absence. As with much of Windows 10, Microsoft is accused of hiding UWP behind PR bluster, using tricksy language and careful wording to avoid difficult questions -- this is something Microsoft needs to address, and quickly.
At the moment things remain within Microsoft's hands, but there is a groundswell of disapproval. If the company is not careful it could find itself with another antitrust case to deal with as developers and publishers rally together to defend their corner of the market.
Photo credit: rangizzz / Shutterstock
-

Facebook set to pay millions in UK tax
Publié: mars 4, 2016, 11:12am CET par Mark Wilson

Tax restructuring at Facebook means the company is due to pay millions of pounds in tax in 2017. The social network famously paid just £4,327 in corporation tax in 2014, but this bill is about to get much larger as advertising revenue is set to be routed through the UK rather than the tax haven of Ireland. A wide-scaled restructuring means advertising sales will now be booked in Britain and subject to UK tax.
Tech companies such as Amazon, eBay and Google have been criticized for their use of tax avoidance schemes, although Google recently agreed to pay back £130 million in tax. Not everyone was happy with Google's 'sweetheart' deal and there has been increased pressure on other companies to pay their fair share.
Facebook's restructuring will take place in April this year -- the start of the tax year. This means that the company's first larger tax bill will be issued in 2017, and it's set to run into the millions. The restructuring is not quite as extensive as some people might have hoped.
While the advertising sales for Facebook's larger clients will be routed through the UK. The company's international headquarters will remain in Ireland, and this will handle smaller advertising contracts.
An internal Facebook document seen by the BBC says:
On Monday, we will start notifying large UK customers that from the start of April, they will receive invoices from Facebook UK and not Facebook Ireland. What this means in practice is that UK sales made directly by our UK team will be booked in the UK, not Ireland. Facebook UK will then record the revenue from these sales. In light of changes to tax law in the UK, we felt this change would provide transparency to Facebook's operations in the UK. The new structure is easier to understand and clearly recognises the value our UK organisation adds to our sales through our highly skilled and growing UK sales team.
Photo credit: Andrey_Popov / Shutterstock
-

Windows 10 Fast Startup could be detrimental to your computer
Publié: mars 4, 2016, 12:16am CET par Mark Wilson

Faster -- like bigger -- is better, right? Not necessarily. Windows 10 includes a feature called Fast Startup which certainly sounds enticing. Microsoft's description in the Control Panel says, "this helps start your PC faster after shutdown". Who wouldn't want a slice of that pie?
Enabled by default on most clean installations of Windows 10, Fast Startup essentially hibernates the Windows kernel and loaded drivers to help slash startup times. It all sounds great, but Fast Startup may not be quite as good as you think. Not only can it seriously mess up dual-boot systems, it may also interfere with the installation of updates, and could cause problems with encryption software.
Over on How-To Geek, Walter Glenn reveals the pros and cons of this feature of Windows. Everyone's time is important, but you may well decide that the few seconds you can save booting up your computer are just not worth the price you have to pay. One of the more worrying side effects of Fast Startup is that some people have found encrypted drives are automatically mounted after a restart, potentially posing a security risk.
There is also the potential for Fast Startup to get in the way of Windows Updates. While updates will be downloaded for you if you have Automatic Updates enabled, not all of them can be installed without a restart. If you shutdown your computer with Fast Startup enabled, your machine will not perform a complete shutdown, so the installation of updates may not complete. Opt to perform a restart, and this will incorporate a proper shutown and allow updates to be installed -- something to keep in mind if you want to ensure that you keep your copy of Windows 10 fully up to date.
If you're thinking about dual-booting Windows 10 with an older version of Windows or another operating system, you might want to heed How-To Geek's advice:
When you shut down a computer with Fast Startup enabled, Windows locks down the Windows hard disk. You won’t be able to access it from other operating systems if you have your computer configured to dual-boot. Even worse, if you boot into another OS and then access or change anything on the hard disk (or partition) that the hibernating Windows installation uses, it can cause corruption. If you're dual booting, it’s best not to use Fast Startup or Hibernation at all.
Have you experienced problems with Fast Startup, or have you found that it makes a big difference to your computing life?
Photo credit: Gustavo Frazao / Shutterstock
-

Fake profiles on social media could become illegal
Publié: mars 3, 2016, 12:33pm CET par Mark Wilson

Facebook has faced a great deal of criticism over its real names policy, and a number of people have fallen foul of the rule that prevents users from assuming a pseudonym. UK law enforcement agencies are looking for ways to tackle the problem of online abuse perpetrated by trolls.
Among the suggestions put forward by the Crown Prosecution Service is that people who use fake social media accounts to harass and abuse others should be prosecuted. The proposals would normally only apply to adults, but children could be hit by the legislation in certain circumstances as well.
Fake accounts can be used by abusers to lure victims into a false sense of security to set up a means of communication. Once contact has been established, trolls can hide behind a fake name in the belief that this will protect them against identification. The fake accounts can be used to not only abuse victims, but also to post embarrassing material such as revenge porn.
It's not just the likes of Facebook and Twitter that have a problem with fake names. So-called professional social network LinkedIn also suffers from the creation of fake profiles to harvest personal information from other users.
The CPS proposals have been put forward for a six-week consultation period, with the suggestion being that social media users could be prosecuted for using a fake ID to post upsetting or anxiety-causing messages. The trick will be to strike a balance between freedom of speech, and protecting the personal rights of individuals.
Photo credit: Christos Georghiou / Shutterstock
-

Twitter to help UK prosecutors fight revenge porn and online abuse
Publié: mars 3, 2016, 10:40am CET par Mark Wilson

Twitter has long-battled trolls and after launching various tools to help combat abuse, the social network is lending its support to the Crown Prosecution Service (CPS) in the UK. The social network is to work with prosecutors to provide training that will help the CPS to fight revenge porn, stalking and other forms of online abuse.
The move comes after a marked increase in the use of social media to perpetrate attacks on individuals, particularly women. But while levels of technical nous have generally increased, legal services have been slow to keep up with the latest changes. With new guidelines set to be published covering the persecution of women through social media, prosecutors are ready to call on Twitter's experience.
The popularity of social networks such as Twitter has made it easier than ever for abusers to target their victims with very little effort. Speaking to the Guardian, chief crown prosecutor Jenny Hopkins said: "Social media is increasingly being used as a tool against women and I think it is really positive that Twitter is going to be training our lawyers in the months ahead".
In what appears to be an expression of support for Facebook's real name policy, Alison Saunders, director of public prosecutions has suggested that in some instances it could be a criminal offense to have multiple fake profiles. She said:
Worryingly, we have seen an increase in the use of cyber-enabled crime in cases related to violence against women and girls, including domestic abuse. Offenders can mistakenly think that, by using false online profiles and creating websites under a false name, their offences are untraceable. Thankfully, this is not the case and an online footprint will be left by the offender.
Photo credit: bahri altay / Shutterstock
-

Disable Windows 10's Microsoft Consumer Experience to take control of your Start menu
Publié: mars 3, 2016, 12:57am CET par Mark Wilson

Microsoft's use of the Start menu to promote 'recommended apps' is nothing new, but recent builds of the operating system take things a step further. Install Windows 10 on a new computer, or create a new user account, and you'll find that a number of extra apps -- including Candy Crush Soda Saga, Flipboard, and Twitter -- appear in the Start menu.
Getting rid of these Start menu entries is simple enough, but the Microsoft Consumer Experience feature which is used to push the apps could be used to add links to more third party apps in future. Here's what you need to do to disable the Microsoft Consumer Experience and regain control of your computer.
Just how you disable the Microsoft Consumer Experience depends on which version of Windows 10 you're using. If you have the Home edition, you'll have to delve into the registry, but if you have the Pro or Enterprise version, you have the Group Policy Editor to make things a little easier.
Disable Microsoft Consumer Experience with Group Policy Editor
- Hit the Windows key, type gpedit.msc and press Enter.
- Navigate to Computer Configuration > Administrative Templates > Windows Components > Cloud Content.
- Double click the entry labelled Turn off Microsoft consumer experience, select Enabled and click OK.
Disable Microsoft Consumer Experience with Registry Editor
- Hit the Windows key, type regedit, press Enter and click OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows and then select or create the CloudContent key.
- Select or create the DWORD value DisableWindowsConsumerFeatures and set its value to 1.
Job done!
(Hat tip to Martin at Ghacks!)
Photo credit: Stanislaw Mikulski / Shutterstock
-

The 'free ride' of BBC iPlayer viewing is over as license fee loophole is to be closed
Publié: mars 2, 2016, 9:10pm CET par Mark Wilson

Watch TV in the UK -- be it through an aerial, cable, or satellite -- and you have to pay for a TV license. The official line is that you need a TV license "if you watch or record programmes as they're being shown on TV or live on an online TV service" and this has long-meant that anyone time-shifting their viewing by watching shows on BBC iPlayer have been able to do so for free. This is set to change.
Having waxed lyrical about the threat of adblockers to the web, UK culture secretary John Whittingdale turned his attention to the BBC's streaming services. He plans to close a loophole that has permitted people without a TV license to watch non-live shows on iPlayer without paying a fee and -- more importantly -- without breaking the law. He says that this is 'wrong' and wants to bring the 'free ride' to an end.
Speaking at the Oxford Media Convention, Whittingdale said that the laws governing the license fee did not take into account technological advances. The plan is to extend the TV license requirement to include those who use iPlayer as a catch-up service. Following talks with the BBC, the culture secretary wants to bring about the changes as soon as possible.
He said:
When the license fee was invented, video on demand did not exist. And while the definition of television in the legislation covers live streaming, it does not require viewers to have a license if they watch BBC programs through the iPlayer even if it is just a few minutes after transmission.
The BBC works on the basis that all who watch it pay for it. Giving a free ride to those who enjoy Sherlock or Bake Off an hour, a day or a week after they are broadcast was never intended and is wrong.
While the plan would certainly help to bring in additional revenue for a beleaguered BBC, it is not clear how iPlayer users would be checked to ensure ownership of a valid TV license.
Photo credit: Antonio-BanderAS / Shutterstock
-

Adblockers 'pose a threat to the survival' of news and music websites
Publié: mars 2, 2016, 8:23pm CET par Mark Wilson

Is adblocking good or evil? It's a discussion that has been rumbling on for some time, and it shows no signs of going away any time soon. The reasons for blocking ads are plentiful -- privacy, speed, annoyance -- but there's no getting away from the fact that ads mean revenue, and without this income many sites simply would not exist.
The latest figure to wade into the debate is the UK culture secretary John Whittingdale. While not going as far as calling for a ban on adblockers, he says that companies such as Adblock Plus are operating "modern-day protection rackets", ultimately threatening the existence of news sites.
Giving a speech at the Oxford Media Convention, Whittingdale compared the effect adblocking tools are having on web content to the effect of piracy on the music and film industries. "Quite simply -- if people don't pay in some way for content, then that content will eventually no longer exist. And that’s as true for the latest piece of journalism as it is for the new album from Muse".
Adblock Plus has already met with publishers and advertisers to try to work out ways to display ads in a way that will not be off-putting to users, but the culture secretary is looking at things from a different angle. His primary fear -- he posits -- is that adblocking could ultimately kill off music and news websites. He expressed interest in getting involved, saying that he would "consider what role there is for government".
Whittingdale also voiced concern that adblockers represent a serious threat to competition.
The problem is, they already exist. Big names like Adblock Plus might evolve to suit the mood of the moment but, ultimately, internet users will always be able to block any content they don’t want to see. We've already seen that people are generally reluctant to pay a subscription to access news, but the money to power these sites has to comes from somewhere. It's not an easy circle to square, but something has to give. It's just not clear that government intervention is the best plan of attack...
Photo credit: Photographee.eu / Shutterstock
-

Hack the Pentagon!
Publié: mars 2, 2016, 7:25pm CET par Mark Wilson

The Pentagon is to run its own big bounty program, inviting white-hat hackers to test the security of its systems. It is not intended to be a free-for-all, and would-be hackers will be vetted before being given the go-ahead -- although of course there is nothing to stop anyone from trying to breach the defenses if they feel so inclined
The 'Hack the Pentagon' initiative was launched today by Defense Secretary Ash Carter. He said "I am confident that this innovative initiative will strengthen our digital defenses and ultimately enhance our national security". It is to be a carefully managed program which will only be open to US citizens, and networks relating to particularly sensitive material and weapons will be off-limits.
While full details are yet to be released, the Pentagon is considering offering financial rewards. The program is being run by the Defense Digital Service (DDS) which launched back in November to draw on the capabilities of the technology industry. Former Google CEO Eric Schmidt is to head an advisory board at the Pentagon with the aim of bringing innovation and 'best practice' ideas from Silicon Valley to the US Military.
Inviting hackers -- even those that have been vetted -- to attack government systems is certain to ring a few alarm bells, but it is only public-facing systems that will be part of the program. Speaking to Reuters, a Pentagon official said: "The goal is not to comprise any aspect of our critical systems, but to still challenge our cybersecurity in a new and innovative way".
The Pentagon says that the program will launch in April, and it is expecting thousands of applicants to express interest in participating.
Photo credit: Frontpage / Shutterstock
-

Updated Snooper's charter will allow police to remotely hack phones and computers
Publié: mars 1, 2016, 4:04pm CET par Mark Wilson

The UK's controversial Snooper's charter (or draft Investigatory Powers Bill) has been updated to grant the police sweeping new powers. The new legislation will permit authorities to not only access the browsing histories of suspected criminals, but also to remotely hack into computers and phones in certain circumstances.
Previous version of the bill had limited such powers to the investigation of "serious crime", but the updated version expands this dramatically. Home Secretary Theresa May is hoping to push the draft Investigatory Powers Bill through parliament later this year. The bill has already met with strong criticism from not only privacy groups, but also governmental advisers. While there are some concessions to protect unbreakable encryption, the latest changes will do little to assuage concerns with the bill.
The initial draft of the bill limited the police to accessing browsing histories relating to illegal sites and services -- the latest draft expands this so that entire browsing histories can be accessed during the course of investigations. The on-going battle between the FBI and Apple highlights concerns people have about the ability of governments and enforcement agencies to demand backdoor access to services. The latest draft of the bill makes it clear that companies will not be required to provide ways to bypass encryption if it is not financially or practically feasible.
A number of police forces and the National Crime Agency would also be granted the power to remotely hack into phones and computers in a number of circumstances. The updated bill widens the net so that this power can be used in cases involving missing people, where there is a "threat to life", as well as situations in which "damage to somebody's mental health" is a risk. May describes the hacking of computers as a "key operational requirement". She said:
This is vital legislation and we are determined to get it right. The revised bill we introduced today reflects the majority of the committees’ recommendations -- we have strengthened safeguards, enhanced privacy protections and bolstered oversight arrangements -- and will now be examined by parliament before passing into law by the end of 2016. Terrorists and criminals are operating online and we need to ensure the police and security services can keep pace with the modern world and continue to protect the British public from the many serious threats we face.
Privacy International's executive director Gus Hosein remains far from impressed by the bill: "The Bill published today continues to adhere to the structure and the underlying rationale that underpinned the draft IP Bill, despite the criticism and lengthy list of recommendations from three Parliamentary Committees.
"The continued inclusion of powers for bulk interception and bulk equipment interference -- hacking by any other name -- leaves the right to privacy dangerously undermined and the security of our infrastructure at risk. Despite this, the Home Office stands by its claim that the Bill represents 'world-leading' legislation. It is truly world-leading, for all the wrong reasons".
Photo credit: Michael Rosskothen / Shutterstock
-

Kiddle lets children search the web 'safely', leaves the sex talk to mom and dad
Publié: mars 1, 2016, 12:51pm CET par Mark Wilson

Parents with younger children may well be concerned about the type of content their offspring could stumble across online. While it is possible to enable the Safe Search feature of Google, this is not 100 percent reliable, and more adult content can slip through the net. A new 'visual search engine for kids', Kiddle, launched this week to plug the gap.
Although nothing to do with Google, Kiddle apes the colorful logo of the famous search giant, and also relies on Google Safe Search for some of its results. The bulk of the first ten results returned by any search, however, are handpicked by editors to ensure they are safe for children and easy to read. There are also some automatic filters in place that prevent searches for 'bad words' and the like and, interestingly, treat searched for homosexuality and heterosexuality in completely different ways.
When it comes to testing a search engine that claims to be 'safe for children' the first thing most people will do is type in a few swear words (including a check for the 'Scuthorpe problem'). True to its promise, Kiddle censors curse word searches, displaying a message that reads "Oops, looks like your query contained some bad words. Please try again!". Intriguingly, this is the same warning message that appears if you search for the word 'sex' or 'heterosexual' (other 'bad words' include 'murder', 'suicide', 'drugs').
The warning, it seems, is not triggered by the appearance of the letter s, e and x in succession, because searching for homosexual (or gay, or lesbian, for that matter) results in the appearance of a rather different message:
You have entered an LGBT related search query. Please realize that while Kiddle has nothing against the LGBT community, it's hard to guarantee the safety of all the search results for such queries. We recommend that you talk to your parent or guardian about such topics.
Make of that what you will.
Content filtering aside, Kiddle is geared towards children in a number of other ways. Search results feature large thumbnails, and a large font is used to increase legibility. The site has a simple privacy policy as well:
We don't collect any personally identifiable information, and our logs are deleted every 24 hours.
But it is undoubtedly the search result curation that will appeal to concerned parents. The results are filtered and ordered as follows:
- Safe sites and pages written specifically for kids. Handpicked and checked by Kiddle editors. Typically, results 1-3.
- Safe, trusted sites that are not written specifically for kids, but have content written in a simple way, easy for kids to understand. Handpicked and checked by Kiddle editors. Typically, results 4-7.
- Safe, famous sites that are written for adults, providing expert content, but are harder for kids to understand. Filtered by Google safe search. Typically, results 8 onwards.
Kiddle is looking for more input from parents. If you find a site that has slipped through the net that you believe should be blocked, or find a word that you feel should be blocked that can be searched for, there are links at the bottom of the page that can be used to submit a keyword blocking request or a site blocking request.
-

Kill the password! Yahoo Account Key rolls out to more apps
Publié: février 29, 2016, 7:54pm CET par Mark Wilson

There have been a lot of attempts to kill the password and replace it with something more secure and easier to use. Biometric measures such as fingerprint and iris readers are increasingly common, but Yahoo is on a mission of its own with Yahoo Account Key.
Recognizing that "passwords suck", Yahoo launched the product back in October and since then there have been a few changes and additions. It's a simple system that uses your mobile as your access key and it's now available in more apps than ever.
Yahoo Account Key came about in response to the fact that passwords are not only all too easily hacked, but also very easily forgotten. It builds on the idea of 2FA and reduces the sign-in process to a simple tap in an app. Yahoo says that Yahoo Account Key is now available on more than 50 million devices. There are a couple of key improvements to Yahoo Account Key that the company highlights today:
Available Anywhere: You can use Account Key in a majority of Yahoo apps, including Yahoo Finance, Fantasy, Mail, Messenger, and Sports for iOS and Android.
Do Not Disturb: We've launched a dashboard where you can control the devices or apps that receive Account Key push notifications. For example, if you have an iPad on the kitchen table, you can turn off sign-in notifications on that device so your kids aren’t disturbed while doing their homework.
This is not the end of Yahoo's battle against the password. We're promised that there are more developments and changes on the horizon.
Photo credit: April909 / Shutterstock
-

Documents reveal details of EU-US Privacy Shield data sharing deal
Publié: février 29, 2016, 3:16pm CET par Mark Wilson

Details of the data sharing arrangements agreed between the US and EU earlier in the month have been revealed in newly published documents. The EU-US Privacy Shield transatlantic data transfer agreement is set to replace the Safe Harbor that had previously been in place.
The European Commission has released the full legal texts that will form the backbone of the data transfer framework. One of the aims is to "restore trust in transatlantic data flows since the 2013 surveillance revelations", and while privacy groups still take issue with the mechanism that will be in place, the agreement is widely expecting to be ratified by members of the EU.
The publication of the full text of the EU-US Privacy Shield agreement will give privacy advocates as well as regular internet users the chance to scrutinize the legislation that will control data sharing between Europe and the US. U.S. Secretary of Commerce Penny Pritzker accompanied the publication with a statement:
The EU-U.S. Privacy Shield is a tremendous victory for privacy, individuals, and businesses on both sides of the Atlantic. We have spent more than two years constructing a modernized and comprehensive framework that addresses the concerns of the European Court of Justice and protects privacy.
Our U.S. and EU negotiators worked around the clock to develop a new framework that underpins $260 billion in digital services trade across the Atlantic. The new EU-U.S. Privacy Shield provides certainty that will help grow the digital economy by ensuring that thousands of European and American businesses and millions of individuals can continue to access services online.
The new rules will apply to all companies that provide services within the EU and would regulate the flow of data to the US. Written commitments by the US government will ensure that the rules are enforced in a transparent way and will place limits on how data can be used by intelligence agencies.
EC vice president Andrus Asnip said:
Now we start turning the EU-U.S. Privacy Shield into reality. Both sides of the Atlantic work to ensure that the personal data of citizens will be fully protected and that we are fit for the opportunities of the digital age. Businesses are the ones that will implement the framework; we are now in contact on a daily basis to ensure the preparation is done in the best possible way. We will continue our efforts, within the EU and on the global stage, to strengthen confidence in the online world. Trust is a must, it is what will drive our digital future.
Next on the agenda is further fine-tuning of the wording of the agreement from the EU side, while in the US steps will be taken to put the new framework in place and appoint an ombudsman to oversee the proper implementation of the agreed mechanisms.
Photo credit: JMiks / Shutterstock
-

Microsoft is wrong to pester insiders for Windows 10 feedback
Publié: février 29, 2016, 1:02pm CET par Mark Wilson

Windows 10 has enjoyed the largest beta testing program of any version of Windows. In opening up the Windows Insider program to anyone who wants to sign up for it, Microsoft has been able to gather valuable feedback from more people than ever. But not enough people it seems.
Users of Windows 10 preview builds have been asked to provide feedback using either the feedback app, or by responding to occasional popup notifications that appear. Up until now these notifications have been optional but in the latest Redstone build there is no way to disable them. Of course the first argument to be put forward is that gaining feedback is the very point of running the insider program. But is it that simple? Could mandated feedback actually be counterproductive?
There is no requirement for anyone to actually provide feedback when prompted to do so -- the notification can just be dismissed or ignored -- but the change sees Microsoft trying to second guess its customers. Placed in Microsoft's control, alerts to provide feedback appear 'automatically', meaning that they could well pop up at inopportune moments.
The change was introduced as part of Windows 10 Build 14271 which was released last week. At the time, Gabe Aul said:
Getting feedback is an integral part of the Windows Insider Program. After each build upgrade or after certain activities, Windows will often ask for feedback. The answers to these questions is used by our engineering teams to understand how Windows Insiders feel about a particular experience or a particular build. Starting with Build 14271 and newer, the frequency in which Windows will ask for your feedback will be locked to "Automatically (Recommended)" in the Settings app and managed by the Windows Insider Program. If having the ability to change this setting is important to you – you can roll back to the Windows 10 November Update (the latest build or future builds in our Current Branch) and disable Windows 10 Insider Preview builds on that device. You will then be able to change this setting. While we don’t require Windows Insiders to answer these questions, we do hope they take the time to answer them so that we can better improve Windows for our customers.
Boiled down, the advice from Gabe is to suck it up or don’t upgrade to this build.
Of course, Microsoft is completely within its rights to make whatever demands of Windows Insiders it wants, but it's not necessarily a good idea. Naturally, the company is looking for feedback, but it's not clear that the change actually makes sense.
I would argue that the most valuable feedback is that which is provided voluntarily at a time that suits the user. You may notice a quirk or stumble across an issue that you feel Microsoft should know about, and it makes sense to feed this back in a timely fashion while it's on your mind. This is user-driven feedback.
The approach that Microsoft is now using is rather more like a customer satisfaction survey. At the end of a week-long visit to a hotel you need to think back over the course of last seven days and provide an opinion about what you thought was good, and which areas need improvement. The problem is, our memories fail us. When something goes wrong the immediate, natural response is to try to address the issue, not (necessarily) provide feedback. At the end of the week, a problem with the hotel that irks you on Monday may well have been forgotten by Friday.
It's the same with Windows 10's feedback notifications. Feedback that is proactively provided by users when they encounter an issue or think of something is far more useful than Microsoft squeezing users every now and then. If an alert pops up asking you what you think of, for example, how File Explorer works, you're more likely to want to continue with what you were doing rather than breaking off and taking the time to think back to the good and bad things you have experienced.
On the flip side, users who encounter a problem will (probably) want to do two things -- firstly, address the problem by way of workaround if necessary, and secondly let Microsoft know about the issue so it can be addressed. There's no need to think back far to remember the specifics of what you have encountered, you can feedback while it's still fresh in your mind.
Sure, Microsoft may end up getting less feedback if it was left as being entirely optional, but it would certainly get more valuable feedback.
Photo credit: Rawpixel.com / Shutterstock
-

Everything you need to know about Windows 10: product keys, secret tools, essential hacks, and problem fixes
Publié: février 28, 2016, 8:18pm CET par Mark Wilson

Windows 10 has been with us for a number of months now, and this has given us plenty of time to unearth all manner of secrets about the operating system. Since launch we have experienced love, hate and everything in between, but we've also learned a great deal. We thought it would make sense to pull together all of this info into one place so you have it available in a handy respository. So what will you find here? Everything!
In the days of Windows being a paid-for OS, people would hunt high and low for cracks and serials to bypass activation. Now that Windows is free, this clearly isn't as prevalent as it used to be, but you might still want to look up your Windows 10 product key before you reinstall. But that's just the start; read on to learn tips, tweaks, hacks, and problem fixes.
If you upgraded to Windows 10 rather than performing a clean install, you may be wasting valuable hard disk space. This might not be quite as much of an issue as it would have been years ago, but the popularity of SSDs means that smaller capacity drives are increasingly common. Whether you're rocking an SSD or you just like to be neat and tidy, a quick disk clean-up could be just what the doctor ordered.
You might be wondering how to perform a clean installation, in which case you will found our guide helpful. Creating a bootable USB drive or bootable DVD is one of the best ways to perform and upgrade or reinstallation. But, of course, not everyone is completely in love with Windows 10. You may have tried it out for a while and decided that it's not for you; if you want to uninstall Windows 10 and roll back to Windows 7 or Window 8.1, you can do just that!
Assuming you have decided to stick with Windows 10, you can make life a little easier by opting to automatically log into your account -- great if you are the only person who uses a particular computer. Getting into Windows faster is what every user is looking for, and automatic login is not the only thigs you can do to accelerate the process. You can also enable 'fast start-up' to speed things up a little more.
A lot of people have experienced a variety of problems with Windows 10. If you have an issue with fonts looking blurry, the fix could be as simple as tweaking your DPI settings. Issues with sound in Window 10 appear to have been particularly common. If you're having sound problems take a look at the suggestions we've covered for fixing them. Microsoft also has a range of Windows 10 troubleshooting tools which can help out in number of situation, an we've shown you how to fix some of the operating system's worst problems.
Who doesn’t like unearthing a secret? We certainly do, so we were happy to stumble across a secret screen recording tool in Windows 10 that can be used to record much more than just game footage. Keeping Windows up to date is important, and there are things you can do to ensure that you are completely in control. Don't forget to check out the Windows 10 update history site so you know exactly what each update has done to your computer.
No article about Windows 10 would be complete with touching on privacy and telemetry. This is something we've looked at quite a lot in recent month, and if you're concerned about your privacy there are steps you can take to lock things down. A little, at least. While you're at it, you might want to prevent the appearance of lock screen ads.
Any tips and tricks you would like to share?
Photo credit: Christian Delbert / Shutterstock
-

Tor Project says Google, CloudFlare and others are involved in dark web surveillance and disruption
Publié: février 27, 2016, 2:57pm CET par Mark Wilson

With privacy concerns and the threat of surveillance from the likes of the NSA, more and more people are turning to the dark web and Tor. The anonymous, encrypted network has become a haven for not just illegal activity, but also for those who simply don’t want what they do online to be tracked and traced.
But now the Tor Project has voiced concerns that CDN and DDoS protection service CloudFlare is monitoring Tor traffic by introducing CAPTCHAs and cookies. CloudFlare is not alone: similar accusations are levelled at Google and Yahoo which are described as 'larger surveillance companies'. Concerns about interference with Tor traffic have been raised by project administrators in a ticket entitled "Issues with corporate censorship and mass surveillance".
Following instances of malicious traffic originating from the Tor network, CloudFlare introduced CAPTCHAs to ensure that visits to certain sites were being instigated by humans. This has not only proved irritating, but also unreliable. CAPTCHAs have been found to frequently fail, and appear multiple times. But more concerning that it opens up the potential for users to be "tagged, tracked and potentially deanonymized".
In a post on the Tor Project website, user ioerror says:
There are companies - such as CloudFlare - which are effectively now Global Active Adversaries. Using CF as an example - they do not appear open to working together in open dialog, they actively make it nearly impossible to browse to certain websites, they collude with larger surveillance companies (like Google), their CAPTCHAs are awful, they block members of our community on social media rather than engaging with them and frankly, they run untrusted code in millions of browsers on the web for questionable security gains.
It would be great if they allowed GET requests - for example - such requests should not and generally do not modify server side content. They do not do this - this breaks the web in so many ways, it is incredible. Using wget with Tor on a website hosted by CF is... a disaster. Using Tor Browser with it - much the same. These requests should be idempotent according to spec, I believe.
I would like to find a solution with Cloudflare - but I'm unclear that the correct answer is to create a single cookie that is shared across all sessions - this effectively links all browsing for the web. When tied with Google, it seems like a basic analytics problem to enumerate users and most sites visited in a given session.
There are concerns about CloudFlare's apparent lack of transparency, although an employee for the company did get involved in the discussion. ioerror continues:
One way - I think - would be to create a warning page upon detection of a CF edge or captcha challenge. This could be similar to an SSL/TLS warning dialog - with an option for users to bypass, engage with their systems or an option to *contact them* or the *site's owners* or to hit a cached version, read only version of the website that is on archive.org, archive.is or other caching systems. That would ensure that *millions* of users would be able to engage with informed consent before they're tagged, tracked and potentially deanonymized. TBB can protect against some of this - of course - but when all your edge nodes are run by one organization that can see plaintext, ip addresses, identifiers and so on - the protection is reduced. It is an open research question how badly it is reduced but intuitively, I think there is a reduction in anonymity.
It would be great to find a solution that allows TBB users to use the web without changes on our end - where they can solve one captcha, if required - perhaps not even prompting for GET requests, for example. Though in any case - I think we have to consider that there is a giant amount of data at CF - and we should ensure that it does not harm end users. I believe CF would share this goal if we explain that we're all interested in protecting users - both those hosting and those using the websites.
There are no denials that the Tor network -- thanks largely to the anonymity it offers -- is used as a platform for launching attacks, hence the need for tools such as CloudFlare. As well as the privacy concerns associated with CloudFlare's traffic interception, Tor fans and administrators are also disappointed that this fact is being used as a reason for introducing measures that affect all users.
Ideas are currently being bounced around about how best to deal with what is happening, and one of the simpler suggestions that has been put forward is adding a warning that reads "Warning this site is under surveillance by CloudFlare" to sites that could compromise privacy.
Photo credit: scyther5 / Shutterstock
-

Adblock Plus comes (somewhat) clean about how Acceptable Ads work
Publié: février 25, 2016, 10:48pm CET par Mark Wilson

The Acceptable Ads program from Adblock Plus has proved slightly controversial. The company behind the ad blocking tool, Eyeo, has already revealed a little about how it makes money from the program -- despite the fact that no money changes hands in most whitelisting cases -- and today it has opened up further about how it makes its money.
Whilst recognizing that people do want to block ads, Eyeo is also aware that sites do need to benefit from ad revenue -- hence Acceptable Ads, non-intrusive ads that it is hoped are less irritating and therefore easier to stomach. But Eyeo itself also wants to make money. How does it decide which company to charge for Acceptable Ads whitelisting, and what to charge? If you're expecting full transparency, you might be disappointed, but we are given a glimpse into how the financial side of things works.
In a blog post, Adblock Plus' Ben Williams concedes that while people in the ad blocking business are fully aware of how acceptable ads works, "we understand that it might be murky to you". He is quick to stress that most of the companies whose ads are whitelisted do not 'compensate' Adblock Plus ('pay' is such a dirty word, isn't it?). He goes on to offer a rule of thumb for deciding whether to charge or not:
[...] only advertisers that stand to gain more than 10 million incremental ad impressions per month because of whitelisting are asked to sponsor. To put that in perspective, if 5 percent of a site's users block ads, for example, then that site needs to have 200 million ad impressions to begin with in order to break the 10 million threshold.
A site's non-ad block traffic is not included in the calculation. Using this definition, most publishers don’t pay anything at all -- in our last measurement, 90 percent were free actually.
In many ways this is a story we've heard before. There are a few new snippets of information, sure, but there's hardly full transparency; it's far too easy to hide behind phrases like 'we cannot provide details about specific contracts or partners'). The blog post itself is an exercise in making things awkward. Rather than simply presenting the information people are likely to be interested in, in an easy to read format. We are instead treated to a short blog post littered with links to other pages on the Adblock Plus site, forums pages, and so on.
It doesn’t matter whether you click through every single link provided, you find that you're still left scrabbling for what you want to know. Fancy working through more than 600 forum threads to properly determine how Acceptable Ads works? No. Thought not.
The post goes on to explain -- a little -- how a chargeable fee is calculated. Adblock Plus also tries to put forward the idea that charging for whitelisting is nothing to do with generating profits. Taken at face value, you'd be forgiven for thinking every cent earned is ploughed back in to the company:
For those not admitted for free, we calculate the licensing fee as a percentage of the extra revenue the advertiser earns after whitelisting. It is not based on total ad revenue, but rather the value our service creates.
This revenue allows us to hire employees to do the hard work providing that service demands. Software engineers have to maintain the whitelist, monitor it and provide customer service to each whitelisted site, whether payment is involved or not. Acceptable Ads also provides value to publishers that was previously unavailable -- and not only value, but sustainable value created with the user rather than at his/her expense.
All clear? No? Good.
But it's OK, because Ben says:
Finally, this blog post will not answer every question. Trouble is, we can't, because NDAs and contracts.
So there you go. Just don't ask about integrity...
Photo credit: Jean Lee / Shutterstock
-

Google's Project Shield protects news and human rights sites from DDoS attacks
Publié: février 25, 2016, 1:28pm CET par Mark Wilson

The web facilitates free speech, but it also gives groups the opportunity to try to silence those they disagree with. DDoS attacks are common way to retaliate against opposing views, and today Google is expanding Project Shield to protect sites from such attacks.
Project Shield is not a new service, but it has been limited to a group of testers since its launch a few years back. Designed to detect and eliminate "DDoS as a form of censorship" the free service is now available to everyone -- those who qualify, at least. The aim is to protect news and human rights sites to ensure uninterrupted access to news and information.
It's not a service that is being made available to everyone. Google explains that "Project Shield welcomes applications from websites serving news. Human rights and or elections monitoring content are also welcome to apply. We do not provide service to other types of content, including gaming, businesses, or individual blogs". The company highlights ease of use, pointing out that the necessary DNS record changes can be made by a webmaster in a matter of minutes.
The expansion will bring Project Shield to tens of thousands of human rights and news sites, helping to protect journalism and promote free speech:
A simple, inexpensive distributed denial of service (DDoS) attack can be carried out by almost anyone with access to a computer -- and take a site completely offline before its owners even know they've been attacked.
These attacks threaten free expression and access to information -- two of Google's core values. So a few years ago we created Project Shield, an effort that uses Google’s security infrastructure to detect and filter attacks on news and human rights websites. Now we're expanding Project Shield beyond our trusted testers, and opening it up to all the world’s news sites to protect them from DDoS attacks and eliminate DDoS as a form of censorship.
Check out Google's introductory video to find out more about Project Shield:
If you want to protect your site, you can sign up at the Project Shield website.
-

Tim Cook goes off-script describing FBI iPhone backdoor request as 'cancer'
Publié: février 25, 2016, 12:16pm CET par Mark Wilson

Say what you like about Apple, one thing is for sure -- it is one of the most scripted and tightly-controlled companies in existence. Everything is stage-managed to within an inch of its existence. Leaks about upcoming releases are rare, and there is a tight rein on the media and who has access to its products for review. So when the FBI asked Apple to unlock the iPhone of the San Bernardino shooter it was hardly surprising that the company was a little shaken and unprepared.
This was a media situation Apple was not in control of. Tim Cook has gone on the offensive in recent days, defending his company's decision not to help the FBI, and in a new interview with ABC News the CEO referred to the request to unlock the phone as requiring "software that we view as sort of the equivalent of cancer" -- something of a shocking thing to say when you consider the cause of death of his predecessor, Steve Jobs.
Talking to ABC News anchor David Muir, Cook defended his decision not to comply with the FBI's requests, saying "we need to stand tall, and stand tall on principle". But many will be somewhat taken aback by his decision to describe the software the FBI is asking Apple to write as being the "equivalent of cancer". In the wake of Steve Jobs' death -- the ripples of which can still be felt -- it will be seen as a glib, offhand, bad taste comment.
One can only imagine the repercussions for a more-lowly Apple employee caught saying the same to the media. But of course his time it's ok, because it's Tim Cook. He can get away with anything.
Apple's argument against working with the FBI has altered slightly since the issue first arose. Cook managed to get a lot of undecided people on board -- as well as publicizing the issue -- with his open letter that made endless references to encryption and Apple's unwillingness to compromise user security and privacy. He is now using rather different language to make his point. In addition to his cancer reference, he said:
I think safety of the public is incredibly important -- safety of our kids, safety of our family is very important. The protection of people's data is incredibly important, and so the trade-off here is we know that doing this could expose people to incredible vulnerabilities.
Apple is using this as a PR platform. It may care about the principles involved, it may not. What's important is that it is seen to care. So why won’t Apple write backdoor software for the FBI?
We think it’s bad news to write. We would never write it. We have never written it [...] This is not something we would create. This would be bad for America. It would also set a precedent that I believe many people in America would be offended by.
He then shifts from PR mode to fear-mongering mode:
If a court can ask us to write this piece of software, think about what else they could ask us to write -- maybe it's an operating system for surveillance, maybe the ability for the law enforcement to turn on the camera. I don't know where this stops. But I do know that this is not what should be happening in this country.
By all means support Apple's stance. By all means agree with not granting the FBI backdoor access to data. But never forget that Apple is using this to its advantage. It's free advertising, and Cook is lapping it up.
Photo credit: Marco Prati / Shutterstock
-

ISIS threatens Dorsey and Zuckerberg for closing terrorist Twitter and Facebook accounts
Publié: février 25, 2016, 11:02am CET par Mark Wilson

ISIS is many things including being a master manipulator of the media and an expert at utilizing social media. Facebook and Twitter have been key tools in the group's propaganda dissemination, and the social networks have reacted by closing down accounts whack-a-mole style.
Now Islamic State has released a video in response to the censorship. It depicts Facebook CEO Mark Zuckerberg, and Twitter CEO Jack Dorsey riddled with bullets as "the sons of the Caliphate army" threaten to fight back against account closures.
Facebook and Twitter do not stand alone in trying to sweep ISIS from the web. Google has also said that it wants to drive the group to the dark web, but for now Sundar Pichai doesn’t appear to be targeted. The 25-minute video pokes fun at the social networks' attempts to wipe out terrorist content, saying:
If you close one account we will take 10 in return and soon your names will be erased after we delete you[r] sites, Allah willing, and will know that we say is true.
The footage shows what appears to be hacking of Facebook and Twitter accounts, and it includes the claim that ISIS is currently in control of no fewer than 10,000 Facebook accounts, 150 Facebook groups and 5,000 Twitter accounts. Twitter says that it has already terminated 125,000 terrorism-related accounts, but it is not clear if this is reflected in the numbers claimed by ISIS.
Despite the menacing nature of the video, a Twitter spokesperson told the Guardian that it will not be responding to it because such threats are now so common.
It just happens all the time. Welcome to our everyday life.
-

Facebook has missed a trick or two with its limited Reactions
Publié: février 25, 2016, 10:08am CET par Mark Wilson

After years of pestering, yesterday Facebook finally supplemented the famous Like button with five additional Reactions. To the disappointment of many, the much-requested Dislike button is yet to make an appearance, but this is not the only way in which the social network has let people down.
Advertisers, page owners, and the general Facebook hoi polloi now have at their disposal six reactions that serve little useful purpose. Sure, it gives users the opportunity to express a slightly wider range of emotion, but the range is far too limited. Additionally, Facebook has let down its paying users more seriously -- it fails to register the meaning and intent behind the different reactions, rendering the six options almost pointless.
Like, Love, Haha, Wow, Sad, and Angry. These six options have the most basic human responses covered. But in deciding not to use Reactions to grade or rate posts in any way, Facebook has reduced what could have been a genuinely useful feature to something that is largely cosmetic. Facebook has long made use of Like data to influence what appears in users' timelines. You would expect the same to be done with Reactions in a far more nuanced way, but no. The company said:
In the beginning, it won’t matter if someone likes, "wows" or "sads" a post -- we will initially use any Reaction similar to a Like to infer that you want to see more of that type of content.
Now it could be argued that selecting the Angry reaction is not necessarily indicative of not wanting to see a particular type of post or posts from a particular person. Regardless, Facebook's decision to treat every Reaction as a Like is just a bit weird, particularly when you consider the fact that there are two clearly negative options there -- Sad and Angry.
Of course the key words in Facebook's statement are 'in the beginning'. It opens up the possibility for change, and it's probable that Facebook is working on how best to deal with the Reaction data that is undoubtedly now flooding in. How should it deal with an Angry response? Perhaps some people like to see posts that make them angry! Are more Reactions needed to allow users to better express themselves with a click, and to allow Facebook to gather more useful data that it can use more helpfully?
This certainly seems to be the initial reaction to Reactions -- there just aren't enough of them.
It's a feeling echoed by advertisers who would have liked a way to make meaningful use of user reactions. For now, an indication that a user finds a post or ad funny means the same as a regular Like. Gathering data about negative reactions to things would be helpful not only to advertisers, but also Facebook itself. It's all well and good being able to determine who Likes something and using that information to deliver similar content to them, but how about genuine tailoring that takes into account dislikes as well?
Even though Reactions have undergone testing in certain parts of the world, the feature still feels as though it is being released unfinished. A case of too little too soon perhaps? Or maybe Facebook is taking a leaf out of Google and Microsoft's book and putting users to work as permanent beta testers.
Photo credit: N Azlin Sha / Shutterstock
-

I'm going to let you into a little secret about Windows 10
Publié: février 24, 2016, 10:05pm CET par Mark Wilson

Wait for it... wait for it... For all of the criticism I have levelled at Microsoft, I actually rather like Windows 10. It is, of course, not without its faults, but in the main it's a solid operating system and a reasonable upgrade from Windows 8.1. I have a (well-earned) reputation for negativity, cynicism, and pessimism, so what's with the sudden burst of positivity?
In reality, nothing has changed, but I've settled into my stride. Rather than battling the bits I hate (and there are still plenty), I've learned to turn a blind eye. I've realized that I was trying to fit Windows 10, rather than making Windows 10 fit me. There's still plenty I don't like, but by simply learning not to focus on them, I've come to like the operating system much more. As with so many things in life, it's all about how you use it.
I've made quite a lot of complaints about Windows 10. Let's face it, I have grumbled endlessly about it. That’s just the way I am; it's in my nature to be critical and negative. But having used Windows 10 for around a year now, I've decided that there's no need to get hung up on the bits I'm less keen on. This might seem a bit backward, but in order to move forward, I've decided to look back at the complaints I've made, and see how my opinion has changed.
Modern apps
I still don't like them. Not one little bit. Simple solution: don’t use the buggers! Easy and obvious -- like all the best solutions. I wish I could find something to love, but I can't. As the old adage goes, 'if you can't say anything nice, don't say anything at all'. So I'll say nothing about modern apps. They need not impact on my life in the slightest.
Start menu
I'll level with you: for all of the excitement that surrounded the return of the Start menu, I rarely find cause to use it. Maybe it's because I'm organized, or maybe it's because I don't -- generally -- have the need to use very many different applications, but it's a very rare occurrence for me to fire up the Start menu.
I can't imagine, really, that I'm all that different to most people. I use a web browser (Chrome) for just about everything -- perhaps this says something about life in the cloud -- and writing is taken care of by Word. Image editing is catered for by the simply brilliant Paint.NET, I play the occasional game in BrettSpielWelt, I browse my hard drive with File Explorer, and I chat with my colleagues using Slack. That really is about it. My needs are pretty basic. Oh, there's also Snagit for screen grabbing.
The taskbar is home to all of the shortcuts I need on a daily basis. There are few extras thrown in such as a shortcut to Settings, one to Edge (in case, heaven's preserve us, I ever need to use it), and one to Notepad (oh yes... keeping it old school!). Should I need to use Excel, Firefox, or something else, then I can hit the Start button.
In terms of finding files -- I just know where things are! I'm organized, and my folder structure is such that it never takes me long to track down what I need -- it would almost certainly take me longer to perform searches through the Start menu.
So, for the most part, I simply ignore the Start menu. It's an arrangement that suits us both down to the ground.
Microsoft Edge
My opinion hasn’t changed: Edge still looks like a kindergarten browser. It's still not only horrible-looking, but also lacking in features. Microsoft is working on bringing the features users are asking for, but my interest has already been lost. For now, I'll simply ignore Edge in the same way I did Internet Explorer.
Start menu tiles
Still something I completely fail to understand the need for, but if they bring joy to certain people, so be it. I'll continue to give them a wide berth. I've already explained how little time I spend in the Start menu, so Live Tiles and static modern app tiles are not seen very often. When I do fire up the Start menu, I might be irritated by a couple of tiles and delete them. I'm slowly whittling through them -- eventually they'll all be gone!
Action center
My loathing of the Windows 10 Mobile-style tile has waned slightly. I still don’t regard this as a triumph of design, but I can appreciate the neat simplicity. It provides handy way to toggle Bluetooth and adjust screen brightness, but I really do wish the problem with the incorrect reporting of Airplane mode could be addressed.
Cortana
Not important --another feature I find very, very easy to ignore these days. I just fail to see the point, so why get hung up on it. Move on... there's nothing to see here!
Privacy
Who am I kidding? I'm embedded in Google -- I'm used to (although still not entirely comfortable with) the idea of my personal data being collected for the purposes of advertising, personalization of experience and so on. With Google, it has been known about for years... it's what Google is about, after all. Somehow it felt different with Microsoft. Microsoft wasn't supposed to be playing these sorts of games, and when it cropped up in Windows 10 it felt, well, kind of dirty really.
I'm still not fully reconciled with Windows 10's privacy and telemetry issues, but this is more to do with Microsoft's initial lack of transparency and the absolute fudge it made of communicating with users. Considering I have basically sold my soul to Google in using Gmail, Google Drive and Android, who am I to take umbrage with Microsoft. It's just taken some getting used to, that's all.
I guess there's also the fact that it is much easier to find an alternative to Google products if I so chose. When it comes to Windows, sure I could switch to Linux or OS X -- I have done before, but I've come back for one reason or another -- but there's nothing quite like Windows in terms of usability, compatibility and familiarity.
Settings vs Control Panel
I'll be straight with you -- this is one gripe I'm having trouble letting go of. It still irks me that I have to go to different places to access different settings, but I appreciate that it's not the end of the world. I will occasional get caught off guard when Settings unceremoniously dumps me back into the Control Panel, but then I am fairly easily riled. This is one I'll have to continue to work on, as I hope that Microsoft is working on a way to combine the two into one neat repository for settings. Here's hoping... but I won't be holding my breath.
I'm interested to know if I'm alone in finding that my view of Windows 10 has softened over the months. There are still things that take me by surprise, new revelations that take be aback, but for the most part I have made my peace with Windows 10 -- have you done the same?
I can't promise that I won't bitch and moan again in future (what can I say? C'est moi!) but my base level opinion of Windows 10 has crept up.
-

Like! Facebook Reactions launch around the world
Publié: février 24, 2016, 2:55pm CET par Mark Wilson
Facebook is, at long, long last, rolling out Reactions globally. The limitations of the famous Like button which have been debated since its introduction are set to become a thing of the past at the social network. Like is now joined by Love, Haha, Wow, Sad, and Angry options.
As we reported earlier in the year, the 'yay' option that had been tested is not being released at this stage -- apparently users found it difficult to interpret what it means. Reactions do not work exactly as you might expect them to, and this means you might need to be careful about how you use them to start with.
For sometime now, Facebook has taken a Like as an indication that you would like to see more of the same type of content. You might think that if you used the Angry reaction on a story Facebook would take this to mean you did not want to see such posts -- but you'd be wrong. To start with, using any of the Reactions will be taken as an indication of wanting to see more of the same as Facebook explains:
In the beginning, it won’t matter if someone likes, "wows" or "sads" a post -- we will initially use any Reaction similar to a Like to infer that you want to see more of that type of content. Over time we hope to learn how the different Reactions should be weighted differently by News Feed to do a better job of showing everyone the stories they most want to see.
Page owners will be able to see the different reactions to posts, so this could still impact on the type of content individuals and companies put out there.
Using Reactions is simple, whether you're using the desktop or mobile version of Facebook:
To add a reaction, hold down the Like button on mobile or hover over the Like button on desktop to see the reaction image options, then tap either Like, Love, Haha, Wow, Sad or Angry.
-

Big Brother ist vatching you: Germany poised to use Trojans to spy on internet users
Publié: février 24, 2016, 12:37pm CET par Mark Wilson

German intelligence agencies are set to gain greater NSA-style surveillance powers after the German Interior Ministry announced plans to use Trojans to spy on the internet activities of suspects. Known as Bundestrojaner, the Trojan would give the government the ability to not only track which sites a target visits, but also record conversations, make use of webcams, access data and log keystrokes.
The Trojan has been in testing since late last year, and having received governmental approval could now be widely dispatched. Widely described as malware and spyware, the tool cannot be used without a court order, but this will do little to assuage the fears of privacy groups.
A spokesperson for the Interior Ministry said that "we now have the skills in an area where we did not have this kind of skill". A 2008 ruling by the German Constitutional Court said that remotely accessing citizens' computer is only permissible when there is suspicion of plans to commit crime against the state, or when there is a life-threatening situation.
The announcement comes after the German government took part in European IT security talks at which Federal Minister of the Interior Thomas de Maizière said:
I support the EU in its efforts to make rules for the Member States to ensure IT security. Our common goal must be to increase the level of IT security throughout the EU, on the basis of decisive national action. With its draft IT Security Act, the Federal Government has presented a number of specific measures to increase IT security in Germany. We have made similar proposals in the ongoing discussion of an EU directive on measures to ensure a high common level of network and information security in the Union. My impression is that the German position is also understood at European level. Germany has thus taken a leading role in an area that will become increasingly important at a time when digital vulnerability is growing.
As is to be expected, the announcement has met with a great deal of opposition, including from the country's Green party. Konstantin von Notz, deputy head of the party, said:
We do understand the needs of security officials, but still, in a country under the rule of law, the means don't justify the end.
It is not yet clear how the German government would deploy the spying software, but this is not the first time this has been attempted. Back in 2011 the hacking group Chaos Computer Club discovered a government-made Trojan in circulation, but this was far more limited in its capabilities. The latest version is created by a company called FinFisher Gamma-International which has a history of creating surveillance and spying tools for European and Middle Eastern governments.
Photo credit: Mardre / Shutterstock
-

How to stop Microsoft using your Windows 10 lock screen to show ads
Publié: février 24, 2016, 11:17am CET par Mark Wilson

Sometimes it can feel as though I'm just looking for things to dislike about Windows 10, but just as I'm warming to the operating system a little more (in the last week I went as far as starting to write an article about how my opinion of Windows 10 had changed for the better. It remains unfinished), something else comes along to irritate me. I know I'm not alone, and the most recent annoyance is the appearance of ads on the lock screen.
You're probably more used to the idea of the lock screen being home to either a photo of your choice, or a randomly selected image from Microsoft that changes from time to time. Recently however, some users have noticed that these images have been replaced with ads for the game Rise of the Tomb Raider. If you want to ditch the lock screen ads, here's how to do it
You may never have looked at the settings for your lock screen, but it defaults to Windows Spotlight mode. This give Microsoft permission to adorn your screen with images it thinks you might like as well as, sadly, ads. Thankfully, changing the option is a fairly simple affair.
- Start by opening up Settings and then head to the Personalization section.
- Click the Lock screen link to the left.
- From the Background drop down menu, select with Picture or Slideshow and then select the image or folder you'd like to use instead of Microsoft's choices.
That's not the end of the story, however. Having opted to use your own imagery on your lock screen, there's a new option that you'll need to disable. The previously-hidden setting "Get fun facts, tips, tricks, and more on your lock screen" needs to be flipped to the Off position to prevent the appearance of anything else you might not be interested in seeing.
Photo credit: Maryna Stamatova / Shutterstock
-

Thanks to encryption, UK efforts to block torrent sites are pointless
Publié: février 23, 2016, 12:28pm CET par Mark Wilson

In the UK, ISPs are required to block access to a number of big-name torrent sites -- the thinking being that sites such as The Pirate Bay are used primarily for (gasp!) downloading pirated material. Despite the government's desire to control what people can access online, good old HTTPS means that people are able to very easily bypass any blocks that may be put in place.
There are all manner of proxy services and mirror sites that provide access to otherwise-blocked content, but these are really not needed. With the likes of The Pirate Bay and Kickass Torrents offering secure, encrypted connection, accessing the goodies they contain could involve little more than sticking an extra 's' in the URL.
Based on feedback from its visitors, TorrentFreak has been able to determine that a number of torrent sites (including The Pirate Bay, KickassTorrents, RARBG and Torrentz) are all accessible in the UK if people simply opt to visit the HTTPS versions. While this is not a new trick by any means, it seems that the word is spreading and HTTPS torrenting is increasing in popularity.
In some instance, rather than offering HTTPS as an option, a number of torrent sites default to the secure connection, automatically sidestepping ISP-level blocks. TorrentFreak explains:
The HTTPS issue is not new and it appears that many ISPs don’t have a countermeasure in place. According to our information, only Sky is structurally blocking secure versions of various pirate sites.
The precise technical explanation for the issue is unclear, but since HTTPS connections can strip HTTP headers it may be harder to detect that a blocked site is being accessed.
In theory ISPs could also block the site’s IP-addresses, but since many use shared IPs from CloudFlare this would also take down other unrelated websites.
It may not work forever, so if HTTPS is giving you access to sites that would otherwise be blocked, make the most of it while you can.
Photo credit: AlexLMX / Shutterstock
-

Google Compare is closing
Publié: février 23, 2016, 11:22am CET par Mark Wilson

From today, Google is starting the process of winding down Google Compare. The price comparison tool is to close completely in the US and the UK by 23 March.
From this date forward, anyone looking to find the best prices on auto insurance and mortgages, credit cards and more will have to turn to one of the alternative comparison sites. Considering the US version of Google Compare was only recently resurrected from the ashes of Google Advisor, the move will come as a surprise to many.
The utility and insurance comparison market is one that has become increasingly crowded, and Google's announcement makes it clear that it is feeling the pinch. As reported by Search Engine Land, Google sent an email to Google Compare partners, saying:
Dear Partner,
Beginning on February 23, 2016, we will start ramping down the Google Compare product, which is currently live in both the US and UK. We plan to terminate the service as of March 23, 2016. As you know, Google Compare (formerly Google Advisor in the U.S.) has been a specialized, standalone service that enables consumers to get quotes from a number of providers for financial products such as car and travel insurance, credit cards and mortgages.
Despite people turning to Google for financial services information, the Google Compare service itself hasn’t driven the success we hoped for. We greatly appreciate your partnership and understand that this decision will be disappointing to some. But after a lot of careful consideration, we’ve decided that focusing more intently on AdWords and future innovations will enable us to provide fresh, comprehensive answers to Google users, and to provide our financial services partners with the best return on investment.
We’re grateful for all the feedback that you have provided over the course of this product’s development, and we are looking forward to partnering with you to achieve greater success in the future.
We will work with you during this transition and beyond. Please reach out to your Google representative if you have any questions and to discuss the next steps.
The Google Compare Team
Photo credit: Fotografiche / Shutterstock
-

Microsoft shutters video messaging app Skype Qik pushing users to Skype
Publié: février 22, 2016, 11:23pm CET par Mark Wilson

As of 24 March, Microsoft's Skype Qik app will be no more. The video messaging app has essentially been swallowed up by its big brother Skype, meaning that it is now surplus to requirements.
Microsoft says that the reason for the closure is that Skype Qik's features are now available in Skype. As a result of this, iPhone, Android, and Windows Phone users who had come to rely on the tool to keep in touch will have to seek out an alternative and take steps to save any messages they want to keep.
Users have just over a month to save what Microsoft describes as "special messages you want to keep", and there are online guides for how to go about preserving these memories. Announcing the closure on the Skype blog, Microsoft says:
In 2014, we launched Skype Qik, a mobile video messaging app to help share moments with groups of friends. Since then, we have learned that many of you are already doing these things in Skype, and as a result, we migrated some of Qik's most used features into the Skype app you already know and love.
Microsoft says that Qik fans will still be able send and receive video messages if they switch to Skype, and can also take advantage of features such as filters. There will undoubtedly be a number of users lost to the likes of WhatsApp, but Microsoft will be keen to encourage as many as possible to migrate to Skype.
-

Amazon pushes Prime by limiting free shipping to orders over $49
Publié: février 22, 2016, 10:40pm CET par Mark Wilson

If you want to qualify for free shipping on your next Amazon order, you might find that you have to stick a few extra items in the basket. The online retailer is upping the threshold for free shipping from $35 to $49.
US customers who do not pay for Amazon Prime will have to shell out an additional $14 if they want to avoid shipping costs... unless they are buying books, that is. To qualify for free shipping on books, a spend of just $25 is needed, but the increase is part of a push to encourage more people to sign up for Prime.
The price hike is quite significant -- no less than a 40 percent increase. Amazon is starting to make Prime ever-more attractive; you don’t need to do a great deal of shopping for the $99-a-year service to make sense, particularly if you tend to buy lower cost items. Amazon explains:
Orders including $25 or more of eligible books qualify for FREE Shipping. All orders of $49 or more of eligible items across any product category also qualify for FREE Shipping. With free shipping, your order will be delivered 5-8 business days after all of your items are available to ship, including pre-order items.
Amazon has been gradually adding more and more value to Prime so that in addition to two-day shipping and access to Prime Music and Prime Video, subscribers in some zip codes qualify for even faster deliveries. The minimum order threshold increase demonstrates that Amazon is starting to see that free shipping has taken too big a bite out of its profits, and it's determined that people will pay one way or another.
Photo credit: Evan Lorne / Shutterstock
-

Moveable type: iClever Tri-folding Backlit Bluetooth Keyboard [Review]
Publié: février 22, 2016, 6:45pm CET par Mark Wilson

A few months back, I took a look at the iClever Portable Foldable Bluetooth Keyboard and I was impressed. Now iClever is back with an updated version of the keyboard, the iClever Ultra Slim 3 Color Backlight Bluetooth Keyboard.
There are a number of enhancements to the original design, the most noticeable of which is that the keys have now grown to full size. As you'll have guessed from the name, the keyboard is now also backlit, and there are also little kick-out legs to help improve stability.
In terms of build quality, this updated model is just as solid as its predecessor. The same aluminium casing is present, and the hinges that facilitate folding are wonderfully robust and -- just as before -- the keyboard can be used with iOS, Android and Windows (OS X doesn't get a specific mention in the manual, but it does work -- Windows Phone, on the other hand, is singled out as not being supported).

As this is essentially an upgraded version of the previous model, you know pretty much what to expect. The typing experience is simply wonderful, and the full sized layout (291 x 117 x 8.25mm) means that it's actually slightly larger than the keyboards built into many laptops. Folded up, the dimensions reduce to 166 x 120 x 14.8mm, as weighing as just 280 grams, it's hardly a major addition to your bag or pocket.

It's not just the size that has changed for the new keyboard model, there's now a battery indicator -- something I noted was missing from the previous version. The extra size of the keyboard could have impacted upon the stability of the device, but this is something that iClever has taken care by including tiny kick-down legs on each side. As well as preventing the keyboard from rocking because of the fulcrum created by the hinge covers, the legs also feature rubberized feet to prevent slipping.

Backlighting is a very nice touch for anyone looking to use the keyboard at night or in low light conditions, and iClever gives you the choice of what color you would like to use -- a quick key combo lets you cycle between red, blue and green.
The keyboard can be used wirelessly over Bluetooth, or plugged in via USB. The 750mAh battery offers up to 300 hours of continuous operation, but this is only the case if you forego the pleasures of backlighting. With the keys backlit, longevity plummets to a mere 5 hours -- perhaps a sign that this is a feature that should only be enabled when it's really needed if you are going to be typing wirelessly rather than tethered with a USB cable.
A full battery charge will take around 4 hours, and iClever says you can expect to enjoy 90 days of standby time, and expect a lifespan of 3 years. As with the previous model, the keyboard comes complete with a carry pouch that has enough room for the keyboard and its cable.

In use, this really does not feel like a foldable keyboard -- it's a small form peripheral that offers everything you would expect from its full-sized counterparts; there are no compromises.
If you like the look of the keyboard, you can pick one up on Amazon for $54.99 -- iClever Ultra Slim 3 Color backlight Bluetooth Keyboard. As before, this is a portable keyboard that comes highly recommended.
-

How to download any Windows ISO for free
Publié: février 21, 2016, 10:10pm CET par Mark Wilson

Whatever version of Windows you're running, the time will probably come when you want to reinstall. You might be lucky and can have recovery media on hand, or your recovery partition may be intact. If not, what can you do? You can download ISOs for Windows 7, Windows 8 and Windows 10 direct from Microsoft.
It's always best to be prepared, so rather than waiting until you find yourself in desperate need, why not spend a few minutes grabbing the ISO (or ISOs) you need in readiness. There's no need to head off to a torrent site to download an illicit copy of Windows along with a crack, everything is available from Microsoft. Here's what you need to do.
As noted by Martin Brinkman on gHacks, getting hold of Windows 10 is incredibly easy. You could use Microsoft's Media Creation Tool, but many will see this as adding an extra, unnecessary step. Head instead to the Tech Bench website where, after signing into your Microsoft account you can download ISO for the Home and Pro versions of Windows 10, Windows 10 KN, Windows 10 N, and Windows 10 Single Language. Just select the version you want, pick a language and choose between 32- and 64-bit. Job done.
Things are slightly trickier when it comes to Windows 7 and Windows 8, and you'll have to resort to a little hackery to get your hands on the goods.
- Visit Tech Bench using either Chrome or Firefox and open Developer Tools by pressing either Ctrl + Shift + J, or Ctrl + Shift + K.
- Head over to Pastebin where the code you need is ready for you to highlight and copy.
- Return to your browser, make sure you're in the Console, and paste the code you have just copied.
- Hit Enter and you'll notice that the Select Edition drop down menu turns blue.
Take a browse through the drop down menu and you'll find that you can download just about every version of Windows 7 and Windows 8 imaginable -- there are also a few extra versions of Windows 10 for good measure.
Grab all of the ISOs you want, and save them for posterity.
Photo credit: charnsitr / Shutterstock
-

Continuum-enabled HP Elite x3 tries to breathe life into the Windows 10 Mobile enterprise market
Publié: février 21, 2016, 7:26pm CET par Mark Wilson

HP is aiming to ignite the enterprise market for Windows 10 Mobile phones with the newly announced HP Elite x3. The 5.96-inch phone is verging on phablet territory and includes support for Windows 10's Continuum, allowing for conversion into -- essentially -- a fully-fledged computer.
A nippy Snapdragon 820 lies under the hood, and the 4GB of LPDDR4 RAM is joined by 64GB of storage, expandable through the use of a microSD card. Other stand-out features include not only a fingerprint scanner, but an iris scanner, as well as wireless charging and a USB Type-C port. Windows 10 Mobile may yet begin to gain traction, but HP is hoping that by catering to the business and enterprise markets, it will be able to carve itself a niche.
HP has been out of the smartphone game for a while now, so it is perhaps little surprise that its comeback device is something of a feature-packed powerhouse. There are dual, front-mounted stereo speakers, and the quad core Qualcomm Snapdragon 820 runs at 2.15GHz.
The rear of the handset features a 16MP camera, complementing the 8MP front-facer, while the so-close-to-6-inches-it-hurts screen offers a resolution of 2560 × 1440 and is of the AMOLED Gorilla Glass 4 variety. The HP Elite x3 supports dual SIM, and other IP 67 water resistance. The 4150mAh battery supports both Qi and PMA wireless charging.
Catering to the security needs of businesses, the handset supports FIPS 140-2 cryptography and 256-bit key full disk encryption. But for the mobile worker, it is Continuum support that is likely to be the key selling point here. Plug the HP Elite x3 into the optional Desk Dock and you have a desktop computer. Alternatively, connect to the Mobile Extender and you have a 12.5-inch laptop complete with extra battery and full keyboard.
The handset is set to launch this summer, but there are no pricing details available just yet.
-

Huawei MateBook is ready to take on Surface Book, Surface Pro 4 and iPad Pro
Publié: février 21, 2016, 5:06pm CET par Mark Wilson

MWC 2016 may be barely under way, but the announcements are already pouring out thick and fast. As well as smartphones and smart car dongles, you can expect to see plenty of laptops and tablets, and one of the first to vie for your attention is the impressive-looking Huawei MateBook.
Clearly aimed as a rival to Microsoft's Surface Book and Surface Pro 4, the MateBook is a 12-inch hybrid tablet running Windows 10. Weighing in at just 640 grams, and measuring a mere 6.9mm thick, the tablet has an optional keyboard cover and stylus. Powered by an Intel Core M3, M5, or M7 processor Huawei claims 10 hours of battery life for the MateBook.
It's not just the processor that you can choose. Huawei is offering the MateBook with either Windows 10 Home or Pro, kitted out with 4GB or 8GB of RAM, and storage ranging from 128GB to 512GB SSD. The volume rocker features a fingerprint reader as with some Huawei smartphones, so logging into Windows 10 is little more than a finger press away. But it's the screen that Huawei is particularly proud of. The Chinese company says it occupies 84 percent of the device, and it has a resolution of 2160 x 1440.
The optional stylus, the MatePen, has 2048 levels of pressure sensitivity, offers shortcuts via two customizable button, and can last for up to 100 hours between charges. The keyboard case is a cut above average, as it includes a glass trackpad and features what Huawei is referring to as "near-notebook" key travel.
The MateBook is set for launch later in the year priced from $699 to $1599. The MatePan will cost $59, the keyboard cover $129, and a dock will also be available for $89.
-

Samsung Connect Auto turns your dumb car into a smart car
Publié: février 21, 2016, 4:16pm CET par Mark Wilson

It's not just brand new vehicles that can be considered smart cars. Today Samsung launches Samsung Connect Auto, a plug-in module that can transform any car with an OBD II port in a smart car, connected into the Internet of Things.
Powered by Tizen, Samsung Connect Auto is a small dongle that features a GPS receiver, LTE modem, and a Wi-Fi hotspot. It has been designed to provide drivers with real-time feedback so they can adjust their driving style and improve fuel efficiency. More than this, the dongle also gives the car and its occupants with a Wi-Fi connection, and could provide information to insurers about driving style and frequency to help drive down insurance costs.
In the US, Samsung Connect Auto will work with AT&T, and in a bid to calm any concerns about privacy and security, Samsung KNOX is on hand to keep things under virtual lock and key. There is also involvement from Orange and AXA, and Samsung says that it has listened to customer feedback in creating its connected car ecosystem.
As well as helping to save money with fuel-boosting driving tips, Samsung Connect Auto could also reduce the cost of insurance. Serge Morelli, Deputy CEO of AXA Partners and CEO of AXA Assistance says:
AXA is delighted to partner with Samsung in the development of a secured Connected Car ecosystem that will bring peace of mind for our customers, provide them with additional insurance and assistance services and contribute to enhance drivers' behaviors.
Samsung is keen to push the security features of the ecosystem:
The backbone of Samsung Connect Auto is KNOX security and Tizen OS for interoperability. Samsung KNOX provides security from the hardware through the software levels, including applications. Prioritizing security differentiates Samsung Connect Auto from competitor offerings. Developers can leverage Tizen and Samsung's Software Development Kit (SDK) to further evolve additional services. Samsung also encourages safe driving behavior by using geo-fencing and driver rating algorithms. In the event of an accident, emergency alerts notify the driver's contacts and accident concierge services are provided. A 'Find My Car' app also helps in locating your car in real-time using LTE and GPS.
Samsung Connect Auto is certainly not a new idea, but with the power of Samsung behind it -- and an impressive team of partners including Cisco, Ericsson, Europcar, HERE and IBM -- it stands a better chance of success than rival systems.
There are no pricing details available at the moment, but Samsung Connect Auto is set for Q2 launch in the US, while Europe and other parts of the world will have to wait until Q3.
-

MWC 2016: LG G5 is a beautiful, transforming, modular smartphone
Publié: février 21, 2016, 3:41pm CET par Mark Wilson

Mobile World Congress 2016 kicks off today in Barcelona and one of the first announcements from the show is the LG G5. This is a modular smartphone that features a number of swappable modules that can be used to tailor it to different needs.
Powered, naturally, by Android 6.0 Marshmallow, the LG G5 features a removable battery, but it is the add-on 'friends' modules that are of particular interest. At the moment there are just two modules available -- the LG Hi-Fi Plus with B&O PLAY, Hi-Fi DAC audio player, and LG CAM Plus, which transforms the smartphone into something more akin to a traditional camera. But the LG G5 does not rely on gimmicks; it also has some impressive specs.
Taking style notes from HTC and Huawei, the G5 has a metal, unibody design. There's an always-on display -- a 5.3 inch, curved 3D Arc Glass affair -- that provides at-a-glance access to notifications and the time, and there are also two rear-facing cameras. There's a 78-degree standard lens, as well as 135-degree wide angle lens allows for more adventurous photography. If you intend to use the LG G5 for taking lots of photos, you might be concerned about how this will impact upon battery life. LG aims to assuage these fears by including an extra 1,200mAh battery in the LG CAM Plus module.

The company also makes much of the display, and says that the always-on feature "requires only 0.8 percent of the battery’s full capacity per hour to operate". The screen adjusts to lighting conditions to ensure maximum visibility at all times -- brightness is automatically increased or decreased up to 850 nits. For those keeping an eye on their batteries, there's more good news. The LG G5 features Quick Charge 3.0 which LG says is "27 percent faster and 45 percent more efficient than the previous generation".
- The LG G5 boasts the following specs:
- Chipset: Qualcomm Snapdragon 820 Processor
- Display: 5.3-inch Quad HD IPS Quantum Display (2560 x 1440 / 554ppi)
- Memory: 4GB LPDDR4 RAM / 32GB UFS ROM / microSD (up to 2TB)
- Camera: Rear: Standard 16MP, Wide 8MP / Front: 8MP
- Battery: 2,800mAh (removable)
- OS: Android 6.0 Marshmallow
- Size: 149.4 x 73.9 x 7.7mm
- Weight: 159g
- Network: LTE / 3G / 2G
- Connectivity: Wi-Fi 802.11 a, b, g, n, ac / USB Type-C / NFC / Bluetooth 4.2
- Colors: Silver / Titan / Gold / Pink
When it comes to modules, LG says that there are more planned. The camera and DAC add-ons may not be to everyone's taste, but it will be interesting to see what else LG comes up with in the coming months. With LG using MWC 2016 to announce a new VR headset, there could be a lot to look forward to.

At the moment, there is no word on availability and pricing.
-

Google cleans up search results by ditching sidebar ads
Publié: février 20, 2016, 7:08pm CET par Mark Wilson

Google generates a huge amount of revenue through advertising, and it's not afraid to try mixing things up a little. Ads in search results have long-been controversial, but the latest change is likely to go down well with many people -- the ads that currently appear in the right hand sidebar of search results are to be dropped.
The change means that ads will only be displayed above and below search results. There will be seven Google AdWords ads in total -- four above search results, and three below. The right hand side of the page will be left free for Google's own Product Listing Ads.
The new ad experience is set to rollout out to the desktop soon, and it brings the look more in line with how Google works on mobile devices. As yet there is no official word on when the rollout will happen, but some AdWords customers have reported that 22 February is a date that has been suggest by their reps.
Google has confirmed the up-coming change to The SEM Post, saying:
We've been testing this layout for a long time, so some people might see it on a very small number of commercial queries. We'll continue to make tweaks, but this is designed for highly commercial queries where the layout is able to provide more relevant results for people searching and better performance for advertisers.
This is a global rollout which will sees the ad changes brought to all languages.
Photo credit: Evan Lorne / Shutterstock
-

Warning: Comodo Antivirus included insecure remote tech support tool
Publié: février 20, 2016, 3:09pm CET par Mark Wilson

A researcher from Google Project Zero discovered a serious security issue with the technical support tools supplied with Comodo software products. Tavis Ormandy found that Comodo Antivirus, Comodo Firewall, and Comodo Internet Security all included a bundled VNC server with either no password protection, or a very weak password.
GeekBuddy is a remote desktop tool used by support staff to troubleshoot customer problems, but it also serves as a backdoor that allows for near-unrestricted access to users' computers. The tool installs with full admin rights, meaning that an attacker could very easily gain complete control of a remote computer.
Older versions of GeekBuddy were installed with no password set, making it possible for anyone to remotely connect to a computer using nothing more than its IP address and a port number. This issue was addressed, but Ormandy found that the password used in subsequent versions is so easily cracked that it offers virtually no protection. He says:
The password is simply the first 8 characters of SHA1 (Disk.Caption+Disk.Signature+Disk.SerialNumber+Disk.TotalTracks)
Having been in communication with Comodo over the issue, Ormandy decided to go public:
Comodo Internet Security installs a VNC server with predictable password by default. [https:] ¯_(ツ)_/¯
— Tavis Ormandy (@taviso) February 18, 2016
Comodo has now addressed the problem -- so make sure your software is up to date -- and Softpedia reports that the company has responded to the revelations:
Comodo has come out to clarify that only its support staff can connect to GeekBuddy, through special company relay servers, meaning remote attackers could not employ this flaw. On the other hand, malware that is already present on the system could use it to escalate its privileges and gain more intrusive capabilities.
Comodo has refuted the claims, saying that it "makes no technical sense":
Recently, it was reported by Google Security that there might be a small local vulnerability in Comodo GeekBuddy that allowed a local attacker to gain another locally logged-on user’s privilege. Here is the link from Google’s Project 0. https://code.google.com/p/google-security-research/issues/detail?id=703
The minor potential vulnerability was fixed and addressed back on February 10, prior to it being made public by Google Security.
Unfortunately, in some posts and reports, it has been erroneously stated that an attacker could somehow gain access to a user’s PC through Comodo GeekBuddy and a logged in user.
We spoke with Comodo Senior Vice President of Engineering Egemen Tas on this issue.
“This makes no technical sense. It is not reasonable to expect a remote attacker to connect to your PC with GeekBuddy. First and foremost, GeekBuddy does NOT open any ports and does not accept any incoming connections. Only Comodo technical support, during specific support sessions, can connect and this connection is established through Comodo relay servers, not from a local network or from the internet.”
Mr. Tas continued:
“Second, the vulnerability reported has nothing to do with accessing a VNC server remotely, but using a VNC server to obtain another user’s privilege level — if you have access to the same PC and know the details of the password generation algorithm.”
“Third, the issue cannot be exploited remotely. The attacker has to gain local access to the PC first in order to try and do anything – and the password would need to be predictable only by skilled attackers”
“And lastly, the minor vulnerability has been fixed and addressed back on February 10.”
In summary – all software goes through patch and fixes and this minor issue has already been fixed in GeekBuddy 4.25.380415.167(released on February 10th) and shared with customers.
At Comodo, we always strive to protect our users, and to assist you here are some frequently asked questions on the issue. Customers can feel free to contact GeekBuddy directly atlivepcsupport@comodo.com or 866-272-9804.
What is the issue?
GeekBuddy uses a modified version of VNC to allow Comodo technicians remote access the PCs during support sessions. In order to use VNC, a local user needs to have a password. In GeekBuddy we automatically generate the password per computer to prevent any local user access to this service.Which GeekBuddy or CIS versions are affected?
The reported issue does not affect Comodo Internet Security (CIS). It is specifically related to GeekBuddy versions prior to Build 167. We released the hotfix on the 10th of February.Does GeekBuddy allow remote access by anyone?
No. GeekBuddy is used for remote technical support by Comodo engineers only. It is not technically possible for anyone to connect to your PC. It does NOT open any ports at all. This issue does not allow any remote attacker to obtain any privileges. It requires local access and specific conditions.Photo credit: Biz Idea Production / Shutterstock
-

Syed Farook's iCloud password was changed by officials; Trump proposes Apple boycott
Publié: février 20, 2016, 1:04pm CET par Mark Wilson

Apple is standing fast on its decision not to help -- publicly, at least -- the FBI to gain access to the iPhone owned by Syed Farook, one of the San Bernardino terrorists. In the latest twist in the saga, Apple has revealed that the password for the Apple ID associated with the phone was changed whilst Farook was in custody.
Apple says that this closes off another route to accessing the data the FBI seeks. Had the password not been changed, the company says, it may have been possible to retrieve backup data without the need to create a backdoor into the suspect's phone. Meanwhile, wading in to the Apple/FBI debate with all of the elegance of an epileptic elephant, serial buffoon Donald Trump has called for a boycott of Apple products -- despite tweeting from an iPhone himself.
Tim Cook has been vocal and very public in insisting that his company will not help the FBI to circumvent the PIN protection currently blocking access to the data stored on Farook's phone. In a bid to avoid creating a backdoor to bypass encryption Apple had suggested four possible ways for the FBI to try to gain access to the data they wanted -- one of which included triggering an iCloud backup and intercepting traffic.
It was when this was tried that the Apple ID password change was discovered. This made it impossible to instigate a backup, and the FBI has suggested that the password change was performed by someone from the San Bernardino Health Department.
And then there's Trump.
Never a man to keep his thoughts to himself, he has proposed a boycott of Apple products until the company decided to comply with the demands of the FBI. Speaking at a town hall event in South Carolina, the Republican presidential candidate said:
What I think you ought to do is boycott Apple until such time as they give that security number. How do you like that? I just thought of that!
Trump might want to start practicing what he preaches as it was quickly noticed by many that his official Twitter account was being updated via an iPhone:
lol pic.twitter.com/PSnvAUEDgr
— Colin Jones (@colinjones) February 19, 2016
Photo credit: GrAl / Shutterstock
-

Apple is using a straw man argument to fight the FBI
Publié: février 19, 2016, 2:03pm CET par Mark Wilson

Listen to Tim Cook and you’d be forgiven for thinking that Apple was standing up for the little guy, sticking up for the likes of you and I in fighting the FBI. The FBI, Apple would have you believe, wants Apple to break encryption, thereby weakening security for everyone. But that's not really the case at all.
The FBI has not asked for encryption to be broken; it wants access to data on the San Bernardino shooter's iPhone, and it wants to do so by using the (as yet unknown) PIN that has been used to lock it. Get it wrong too many times and the device is wiped. The FBI wants custom firmware to be made available that would allow it to brute force the PIN. It's nothing to do with cracking encryption, but that's not what Apple wants you to believe. It's an exercise in misdirection and a classic straw man argument. The problem is, if the straw man goes up in flames, will Apple too?
Tim Cook went as far as issuing a public letter explaining why Apple was refusing to comply with the court order that has been handed down. The word 'encryption' is used seven times in Tim Cook's letter, the word 'encrypt' once. You'd be forgiven for thinking that the FBI has asked for the magic keys that decrypt data, thereby meaning the same could be done for any iOS device out there -- but that's absolutely not the case.
The judge actually ruled that:
Apple's reasonable technical assistance shall accomplish the following three important functions: (1) it will bypass or disable the auto-erase function whether or not it has been enabled; (2) it will enable the FBI to submit passcodes to the SUBJECT DEVICE for testing electronically via the physical device port, Bluetooth, Wi-Fi, or other protocol available on the SUBJECT and (3) it will ensure that when the FBI submits passcodes to the SUBJECT DEVICE, software running on the device will not purposefully introduce any additional delay between passcode attempts beyond what is incurred by Apple hardware.
Encryption is not mentioned once. Not once. We could argue, as Tim Cook tries to, that this is merely a matter of semantics, but this is not about encryption... not really.
Let's use an analogy. Suppose the FBI wanted to gain access to a locked house. It could smash the door down, but this might result in damaging whatever is inside, or even hurting people. This is akin to data being wiped after too many incorrect PIN guesses. The FBI could ask Apple to provide a skeleton key that unlocks every door in the world. This is the story that Tim Cook is putting forward, and it is understandably worrying. The idea that someone could unlock your front door -- any of your doors -- would be concerning to anyone.
But what the FBI is actually doing is asking for the spare keys to a specific door so they can open it without any collateral damage. It's more like when you lose your car keys, or want to get a spare cut. You can’t just go to the shop down the road and have a supplicate run off, you need to get in touch with the manufacturer who will produce a custom key paired to your vehicle after having performed the necessary security and verification checks.
Apple is being utterly disingenuous in suggesting that this is a story about encryption. It's not.
That's not to say Apple is completely wrong, of course, but it is certainly being misleading. Tim Cook is right to suggest that it would set a worrying precedent. He says "while the government may argue that its use would be limited to this case, there is no way to guarantee such control", and he's right. There is cause for concern. What the FBI is asking for is concerning, but not for the reasons Apple suggests.
The thing is, putting forward the idea of breaking encryption is a far, far more emotive issue. It's something that everyone -- every company -- cares about. That is why Facebook, Twitter, Google, Microsoft and the EFF have offered their support to Apple. But break things down, and the issue is actually very different. Would there be such support if the court order was reworded to say 'Apple needs to disarm the self-destruct feature of this device'? Probably not.
Apple knows as much, and that's why Tim Cook released his very carefully worded letter as part of a cleverly orchestrated campaign to drum up even more support. I hear you, Tim, but you need to be honest about what's actually going on.
Apple could help the FBI without compromising the security of anyone else. It does not need to supply the FBI with the source code for any tool it creates that allows for PIN bypassing. It's hard to imagine that Apple engineers don’t already have such a tool, even if it's only for personal use. The phone in question could be brought in house, unlocked by Apple, and handed back. The unlocking tool need never be in anyone's hands other than Apple's, greatly minimizing the potential for abuse.
But this is just conjecture, and it would still set a precedent. No company wants to be seen to be siding with the enemy, even if the "enemy" is fighting terrorism. The real enemy here, for Apple, is Apple's image. Apple is terrified of any of its sheen becoming tarnished. Sadly, the company has resorted to poorly thought out arguments based on flawed logic and unsound reasoning to support its position. The damage to image has already been done.
Share your thoughts in the poll we have running: Should Apple help the FBI unlock the San Bernardino iPhone?
Photo credit: Wuttichok Panichiwarapun / Shutterstock
-

Facebook launches Suicide Prevention tool in the UK
Publié: février 19, 2016, 11:46am CET par Mark Wilson

Facebook has teamed up with charity the Samaritans to bring its Suicide Prevention tool to the UK. It's the same tool that was launch in the US a little over a year ago, and it gives users the opportunity to report content they feel might be indicative of someone struggling with suicidal thoughts.
While Facebook itself is not involved in seeking out suicide-related posts, it has a team in place ready to handle any content that is reported. The team is able to analyze and prioritize cases, and reach out to individuals to see what sort of support can be offered -- this might be as simple as having a chat, or it could involve a referral to specialist organizations.
Relying on users to report worrying content posted by the people they follow or are friends with on the social network takes the pressure off Facebook, but ensures that the social network is still seen to be doing something. Users are encouraged to use the Suicide Prevention tool to report content they are concerned about, but in the case of explicit talk about suicide, the advice is to get in touch with the emergency services.
Every part of the process is kept anonymous in a bid to encourage people on both sides to take advantage of it. As well as providing tips and support for those considering suicide, Facebook also recognizes that it can be difficult for those finding such content in their news feeds. With this in mind, Facebook says it will be providing " new resources and support to the person who flagged the troubling post, including options for them to call or message their distressed friend letting them know they care, or reaching out to another friend or a trained volunteer for support".
Photo credit: tulpahn / Shutterstock
-

Microsoft wants to make Windows 10 and Office 365 more accessible
Publié: février 18, 2016, 10:40pm CET par Mark Wilson

Making its products accessible to as many people as possible is clearly in Microsoft's best interests. Today the company outlined how it plans to improve accessibility in Windows 10 and Office 365, setting out a roadmap built on three key principles.
Transparency, accountability and being inclusive will be the company's cornerstones for 2016. Microsoft wants to "to think about all of our customers and all of the ways we can empower them with technology". But what does this actually mean.
Listening to and responding to feedback is at the heart of the new Microsoft, and have been central to the development of Windows 10. Accessibility is nothing new -- options have existed in Microsoft software for decades now -- but there is still more that can be done. Looking at Windows 10 in particular Chief Accessibility Officer Jenny Lay-Flurrie says:
- Improve commonly used features and do a great job with showcase Windows experiences. We are working to ensure that everyone can easily access and use the Start menu, the lock screen, and settings as well as Cortana, Store, Music, Videos and more.
- We’re also working hard on our new browser, Microsoft Edge. By the end of 2016, the browser will have improved browsing and reading experiences not just for those using our built-in assistive technologies, such as Narrator and Magnifier, but also for people who use other commercial assistive technology. On Feb. 3, we shared our priorities for 2016, including additional detail about the key areas that we think will have the biggest impact.
- Windows 10 Mail will have improved screen-reader support for common email scenarios – already, we’ve made progress against these goals on Mail for PCs.
- Work continues to improve our built-in assistive technology by increasing performance, reliability, compatibility and usability. These improvements translate to a faster Narrator, improved compatibility while using apps like Windows 10 Mail and Microsoft Word, better mapping of keyboard commands to user expectations and an increase in the number of supported languages.
Microsoft has similar goals for Office 365:
- Making it easier to author accessible content from any device. In 2016, we will be extending the Accessibility Checker (already available in Office for PCs) to Office for Mac and improving the experience with alt-text in Office Online.
- Making it easier to use Office 365 with screen readers and keyboards on any device. Last year, we added support for VoiceOver for Office for Mac and this year, we will be adding full accessibility support for all our Windows 10 store apps.
- Enhancing the experience with our apps in High Contrast Mode. For example, we will make it easy to read commands and navigate through controls in Office for PC.
- Introducing new reading and writing tools that are particularly beneficial for people with dyslexia. In January, we introduced a preview of Learning Tools in OneNote for PC that will be generally available in 2016. We are also working on improving spelling checker in Word 2016 and Outlook 2016 to offer suggestions for phonetic and other less commons misspellings.
- Enabling everyone to use our applications in more intuitive ways. We introduced "Tell Me what you want to do..." in Office Online and Office 2016 for PCs to help people get things done quickly or get help by entering intuitive commands. We will be extending this capability to Office on iOS and Android in 2016.
Photo credit: 360b / Shutterstock.com
-

Apple says sorry for iPhone Error 53 and issues iOS 9.2.1 update to fix it
Publié: février 18, 2016, 9:36pm CET par Mark Wilson

Apple has a lot of support at the moment for its stance on encryption and refusing the FBI access to an iPhone's contents, but it's only a couple of weeks since the company was seen in a less favorable light. There was quite a backlash when users found that installing an update to iOS resulted in Error 53 and a bricked iPhone.
Apple initially said that Error 53 was caused 'for security reasons' following speculation that it was a bid to stop people from using third party repair shops. iFixit suggested that the problem was a result of a failure of parts to correctly sync, and Apple has been rounding criticized for failing to come up with a fix. Today the company has issued an apology, along with an update that ensures Error 53 won't happen again. But there's more good news.
If you were talked into paying for an out of warranty replacement as a result of Error 53, you could be in line to get your money back. Apple says that the error came about because a test feature was accidentally made public -- it was an update that was never meant to reach customers.
Apple's full statement reads:
Some customers’ devices are showing 'Connect to iTunes' after attempting an iOS update or a restore from iTunes on a Mac or PC. This reports as an Error 53 in iTunes and appears when a device fails a security test. This test was designed to check whether Touch ID works properly before the device leaves the factory.
Today, Apple released a software update that allows customers who have encountered this error message to successfully restore their device using iTunes on a Mac or PC.
We apologize for any inconvenience, this was designed to be a factory test and was not intended to affect customers. Customers who paid for an out-of-warranty replacement of their device based on this issue should contact AppleCare about a reimbursement.
Photo credit: Attila Fodemesi / Shutterstock
-

Apple's new Trade Up With Installments program aims to lure Android users to iPhone
Publié: février 18, 2016, 4:38pm CET par Mark Wilson

Apple has launched a new program called Trade Up With Installments which makes it possible to upgrade to the latest iPhone in a more affordable way. As the name suggests, this is more than a straight trade-in program -- upgraders can use the trade-in value of their old handset to reduce on-going monthly costs.
This is something that will appeal not only to people with older iPhones who are looking to get their hands on a newer model, but also ex-Android fans -- Apple is opening up the program so Android handsets can be traded in and their value offset against the cost of a new iPhone. Windows Phone handsets are also eligible.
Trade Up With Installments is slightly different to the existing iPhone Upgrade Program and trade-in option. After handing over your old handset -- be it iOS, Windows Phone or Android powered -- for part exchange for a new iPhone, you'll then (assuming you qualify) be extended credit and allowed to pay off the remaining balance over 24 months.
At the moment, Trade Up With Installments is only available in the US, and can only be accessed through Apple Stores. The program starts today, and is likely to prove popular not only because it is can be used by Android handset owners, but also because there is no commitment to getting a new iPhone every year.
Speaking to CNET, Apple said that the new program is aimed at people who have older iPhones. But taking into account the fact that iPhone growth slowed surprisingly it is understandable that it has been opened up to include other handsets. Launching Trade Up With Installments at the beginning of the year makes sense, as it gives plenty of time for it to get established and for word to spread ahead of the expected launch of the iPhone 7 later in the year.
Photo credit: Twin Design / Shutterstock
-

Linux was not meant to be open source
Publié: février 18, 2016, 1:32pm CET par Mark Wilson

The Linux community has a lot to shout about. In addition to a seemingly endless choice of distros to suit every taste and need, there's also the highly-prized security. This is helped to a large extent by the open source nature of Linux, but Linus Torvalds has revealed that being open source was not part of the original plan.
Torvalds made the revelation in a rare interview at the TED conference in Vancouver saying that Linux started off as a personal project that he intended to keep to himself. The computing landscape certainly would have panned out into something very different to that which we see today had he not made that crucial decision.
In the interview, Torvalds said: "I did not start Linux as a collaborative project, I started it for myself. I needed the end result but I also enjoyed programming. I made it publicly available but I had no intention to use the open-source methodology, I just wanted to have comments on the work".
He said that he came to understand the value of having input from other people, particularly because of his inability to design a user interface. "If I was stranded on a desert island and the only way to get off was to create a pretty UI I would die there," he said.
It should come as no surprise that Torvalds describes himself as a nerd. Speaking to TED curator Chris Anderson, he said that he is not a 'people person'. He understood the need to involve 'people people' who were able to do things that he could not.
I am not a visionary. I'm an engineer. I'm happy with the people who are wandering around looking at the stars but I am looking at the ground and I want to fix the pothole before I fall in.
Photo credit: Julien Tromeur / Shutterstock
-

New drivers and firmware fix Surface Pro 4 and Surface Book power management problems
Publié: février 18, 2016, 1:17am CET par Mark Wilson
Both the Surface Pro 4 and Surface Book have been well-received devices on the whole, but there have been complaints from some users about power management. A failure to properly enter sleep mode has been causing not only battery drain, but also heat issues -- now Microsoft have issued fixes.
Starting today, new drivers and firmware updates are rolling out that address these problems as Microsoft says it continues to listen to user feedback.
Over on the Windows blog, Panos Panay writes: "Today's updates include a set of Microsoft and Intel driver and firmware updates for Surface Book and Surface Pro 4 that will help you get the most of the power management options that Surface is designed to offer and continue to make your Surface more productive".
On the Surface Book and Surface Pro 4 update pages, Microsoft reveals exactly what the updates include:
- System Hardware Update -- 2/17/2016
- Microsoft driver update for Surface UEFI
- Microsoft driver update for Surface Management Engine
- Microsoft driver update for Surface System Aggregator Firmware
- Surface Management Engine update (v11.0.0.1202) improves system stability.
- Surface System Aggregator Firmware update (v88.1081.257.0) improves accuracy of battery status and battery life during sleep.
- Surface UEFI update (v104.1085.768.0) improves battery life and improves stability during power state transition changes into and out of sleep states.
- Intel Precise Touch Device driver update (v1.1.0.226) improves stability during power state transition changes into and out of sleep states.
- Intel HD Graphics 520 driver update (v20.19.15.4364) improves display stability, system stability and battery life.
- Intel Display Audio driver update (v8.20.0.745) supports compatibility with the updated graphics driver.
- Realtek High Definition Audio(SST) driver update (v6.0.1.7734) improves system stability.
- Intel Smart Sound Technology (Intel SST) Audio Controller driver update (v8.20.0.866) improves system stability.
- Intel Smart Sound Technology (Intel SST) OED driver update (v8.20.0.866) improves system stability.
- Intel Management Engine Interface driver update (v11.0.0.1176) improves system stability.
- Intel Serial IO GPIO Host Controller driver update (v30.63.1603.5) improves auto rotation reliability when tablet mode is turned off.
- Intel Serial IO I2C Host Controller driver update (v30.63.1603.5) improves auto rotation reliability when tablet mode is turned off.
- Surface Book Base Firmware driver update (v1.2.0.0) improves battery life during sleep.
If you have Automatic Updates installed, there's nothing to do other than sit back and wait for the updates to arrive. But if you've disabled this setting, now is the time to perform a manual check.
-

Twitter makes it easier to annoy your followers with GIFs
Publié: février 17, 2016, 10:24pm CET par Mark Wilson

GIFs are, sadly, here to stay. We've come a (relatively) long way since the days of animated GIF adverts that adorned countless web pages through the 90s, but the animated image format is still highly divisive -- and I'm not just talking about whether it is pronounced with a hard or soft G sound.
Some people loathe GIFs with a passion that knows no bounds, while for others they are the perfect means of communication. If you fall into the latter camp, Twitter has some good news for you -- a 'GIF search' button is making its way to the web, as well as the iOS and Android apps.
The button will be making an appearance "over the coming weeks", and will provide Twitter users with an easy way to track down the perfect cat GIF to accompany their tweets. Powering the service are Giphy and Riffsy, and it will be possible to use the search feature to add GIFs to public tweets as well as private, direct message.
Twitter has already learned that animated content is very popular, and this led to the decision to make GIFs and video autoplay in timelines. The addition of a GIF search feature is a continuation of this idea. If you hate GIFs, now might be the time to disable the autoplay option lest you become overwhelmed with pithy animated memes.
Photo credit: Quka / Shutterstock
-

Windows 10 to be installed on 4 million US Department of Defense computers
Publié: février 17, 2016, 3:38pm CET par Mark Wilson

Microsoft keeps shouting about the millions of users that have switched to Windows 10, and soon the company will have another 4 million to bray about. The US Department of Defense is the latest big name to give Windows 10 the seal of approval apparently unconcerned with the privacy and telemetry issues that have put off others.
4 million enterprise upgrades for Windows 10 is a real feather in the cap for Microsoft, and the aim is to get each system running the latest version of the operating system inside a year. The DoD has also announced that it is granting certification to Surface 3, Surface Pro 3, Surface Pro 4, and Surface Book devices, meaning that they now appear on its Approved Products List.
The confidence the DoD has in Windows 10 will come as a surprise to many as the operating system is still in its infancy -- many organizations tend to hold off for longer to allow any teething problems to be ironed out. Standardizing around Windows 10 is part of the government's desire to try to reduce costs by ensuring that IT department only has a single version of the operating system to support.
The cost of the switch to Windows 10 has not been revealed, but endorsement by the Department of Defense can only work in Microsoft's favor -- it's certainly something we can expect to see references to in future marketing materials and ad campaigns.
Photo credit: Stanislaw Mikulski / Shutterstock
-

UK government wants money-making porn sites to age-check visitors
Publié: février 16, 2016, 1:14pm CET par Mark Wilson

The UK government is launching a public consultation over its plans to require pornographic websites to verify that visitors are aged 18 or over. The Conservative party wants to deliver on its manifesto pledge to introduce age verification to all porn sites, but the latest proposals go further.
The government wants all companies that profit from pornography online to implement systems to have a legal requirement to ensure that visitors are over 18. The consultation runs until 12 April and has the aim of using British Board of Film Classification (BBFC) issued 18 / 18R ratings for sites, but it's unclear how effective the system would be for free porn sites.
The government says that its preferred approach for protecting children from pornography would put "responsibility squarely on the shoulders of companies who create and profit from online pornography". This is something that has been talked about for some time, and ISPs have already been tasked with blocking access to porn sites by default, although customers can ask for access to be granted to them.
Inviting feedback on the latest proposals, the government says:
The UK is a world leader in the work it does to improve child safety online, but we cannot be complacent. Government has a responsibility to protect citizens from harm, especially the young and most vulnerable.
That is why we committed in our manifesto to requiring age verification for access to pornographic material online, and are now seeking views on how we deliver on our commitment.
The government wants to not only implement age check, but also to set up a framework with legal process overseen by regulators. The regulators would:
- Monitor compliance with the new law by commercial pornography providers.
- Enable those that support the business model of pornographic content providers (such as payment providers, advertisers and other ancillary services) to withdraw services from commercial providers in breach of the law.
- Impose sanctions where breaches have been identified and providers remain non-compliant.
- Give the regulator discretion to set and monitor standards for age verification controls.
The proposals are likely to prove divisive. Any form of age checking is likely to raise privacy concerns among consumers of pornographic material, and porn providers are unlikely to be keen on additional red tape. Children's charity NSPCC, however, welcomes the government's action. Chief executive Peter Wanless said:
This consultation is an important and welcome step forward in keeping children safe from online pornography. Companies that produce and profit from this material have a responsibility to give children the same protection they would get in the offline world.
Every day ChildLine receives calls and messages from young people who feel they are being badly affected by the way they and their friends can view unlimited online pornography. As a matter of urgency we must prevent children having ready access to content rated over 18 as it can give them a warped view of sexual relationships.
To give your feedback head over to the Child Safety Online: Age Verification for Pornography consultation page.
Photo credit: Nickylarson974 / Shutterstock
-

End of an era as pioneering BBC3 becomes an online-only station
Publié: février 16, 2016, 10:58am CET par Mark Wilson

13 years ago, BBC3 launched in the UK. Last night, the TV station broadcast over the airwaves for the last time. In a bid to slash expenditure, the youth-oriented channel that launched countless comedy careers is now only available online.
The likes of Being Human, The Mighty Boosh, Gavin and Stacey, and the like will live on, but only on the web -- which the BBC is spinning as an opportunity to be freed from the constraints of regular scheduling. The change has been known about for some time now, and there have been a number of campaigns and petitions to try to get the BBC to change its mind.
It might seem strange that there is such a vocal outpouring about the loss of a TV channel, particularly when it is not being completely killed off. But BBC3, like its more serious sibling BBC4, has been held in high regard for many years, thanks largely to the fact that a massive proportion of its output was original. The channel was used as a testing ground for shows that later became huge, with many migrating to the more mainstream BBC channels.
With the channel's budget slashed from £85 million to £30 million, it was clear that something had to budge. BBC iPlayer will now be home to the channel's edgy output. The BBC says that "younger people do watch most TV online anyway", but this does not take into account the channel's full demographic, nor cater to viewers with no, slow, or capped internet access.
It remains to be seen just how popular BBC3 is in its online incarnation. It's hard to imagine that audience figures will do anything other than drop; while the channel has always been youth-centric, the move to online-only broadcasting is likely to alienate swathes of casual viewers who will no longer be able to accidentally stumble across a gem of a show whilst idly flicking through the program guide.
Thanks for everything, BBC3.
-

'The room had started to smell. Really quite bad': Stephen Fry exits Twitter once again
Publié: février 15, 2016, 5:22pm CET par Mark Wilson

For a man so readily associated with words -- and certainly for a wordsmith so enamored with technology -- Twitter seems like something of a natural home for Stephen Fry. Over the years he has amassed hundreds of thousands of followers, but last night he closed his account. Fry's latest exit from Twitter (there have been several over the last few years for numerous reasons) came about because of the backlash he received for making a joke at an award ceremony.
Hosting the BAFTAs (British Academy of Film and Television Arts) on Sunday, he referred to costume designer and award winner (and, indeed, friend) Jenny Beavan as being "dressed as a bag lady". 'Offended' Twitter users attacked Fry in their droves, and he fought a valiant battle, before eventually giving up and terminating his account. It comes just days after Twitter set up a new Trust & Safety Council.
The complainers seemed oblivious to the fact that Beavan and Fry are close friends -- even less that she was in on the joke. After hours of abuse from the hard of thinking, Fry lashed out by saying: "Will all you sanctimonious fuckers fuck the fuck off Jenny Beavan is a friend and joshing is legitimate. Christ I want to leave the planet".
In a post on his own website, Fry explains his reasons for ditching Twitter:
[...] let us grieve at what twitter has become. A stalking ground for the sanctimoniously self-righteous who love to second-guess, to leap to conclusions and be offended -- worse, to be offended on behalf of others they do not even know. It's as nasty and unwholesome a characteristic as can be imagined. It doesn't matter whether they think they’re defending women, men, transgender people, Muslims, humanists... the ghastliness is absolutely the same. It makes sensible people want to take an absolutely opposite point of view. I've heard people shriek their secularism in such a way as to make me want instantly to become an evangelical Christian.
He likens his departure from the site to simply leaving the room. He may well return, but at the moment the waters of Twitter are "frothy with scum", and Fry suggests that "too many people have peed in the pool" to make him want to stick around right now.
Twitter has long been trying to be seen to fight trolls that abuse other users, but Fry is quick to counter suggestions that he has been run off the site:
But you've let the trolls and nasties win! If everyone did what you did, Stephen, the slab-faced dictators of tone and humour would have the place to themselves. Well, yes and they're welcome to it. Perhaps then they'll have nothing to smell but their own smell.
So I don't feel anything today other than massive relief, like a boulder rolling off my chest. I am free, free at last.
Photo credit: Twocoms / Shutterstock
-

Mazar Bot malware can root and wipe Android smartphones
Publié: février 15, 2016, 12:09pm CET par Mark Wilson

Security experts are warning about new malware attack that targets Android users. Mazar Bot is delivered via SMS, is able to gain root access to devices, installs software including Tor, and can even go as far as completely wiping a victim's phone.
Mazar Bot was discovered by Heimdal Security whose researchers analyzed a text message that had been found sent to random numbers. The message purports to provide a link to an MMS, but in fact tricks recipients to install the malicious mms.apk -- Mazar Android BOT in disguise.
The message reads: " You have received a multimedia message from +[country code] [sender number] Follow the link http: //www.mmsforyou [.] Net / mms.apk to view the message", and would be enough to fool many people into clicking through to view what they believe to be a photo or video. The MMS Messaging app uses administrator privileges to gain access to permissions such as SEND_SMS, READ_PHONE_STATE, and ERASE_PHONE.
The malware also installs Tor, connects to the http://pc35hiptpcwqezgs.Onion server, and sends an SMS to an Iranian phone number revealing the handset's location. Heimdal Security warns that Mazar Bot can:
- Open a backdoor into Android smartphones, to monitor and control them as they please;
- Send SMS messages to premium channel numbers, seriously increasing the victim’s phone bill;
- Read SMS messages, which means they can also read authentication codes sent as part of two-factor authentication mechanisms, used also by online banking apps and ecommerce websites;
- Use their full access to Android phones to basically manipulate the device to do whatever they want.
But there is the risk of a man-in-the-middle attack using the Polipo proxy, and Mazar Bot can also inject itself into Chrome.
Interestingly -- and perhaps revealingly -- the malware will not install on handsets configured to use Russian. While Mazar Bot is not entirely new (it was first talked about back in November), it was previously restricted to advertisements on the Dark Web. This is the first time it has been seen out in the wild.
Photo credit: Georgejmclittle / Shutterstock
-

AMD Zen processors will have 32 cores and Symmetrical Multi-Threading
Publié: février 13, 2016, 11:43pm CET par Mark Wilson

We seem to have hit something of a ceiling when it comes to the raw speed of processors; things are now progressing rather more slowing than they have been. Attention has now turned to other areas, such as the number of cores. Dual-core, quad-core, and octo-core CPUs are now quite common, but AMD's upcoming processor -- codenamed 'Zen' -- will feature no fewer than 32 cores.
We already knew that Zen would have 'a lot' of cores, but a CERN engineer has now revealed not only how high this figure is, but more details of the processor. But this is not a true 32-core processor -- AMD is using a little trickery to up the numbers.
During a presentation, CERN engineer Liviu Valsan revealed that Zen will feature up to 32 physical cores and will support Symmetrical Multi-Threading. This is achieved by combining two 16-core CPUs on a single die with what is described as "a next-generation interconnect". AMD's CPU refresh has been a long-time coming, and there's a little more we know about Zen.
As well as 32 cores, the upcoming x86 processor will:
- Feature 14nm FinFET technology.
- Offer 430 percent improvement for Instructions Per Clock when compared to current processors.
- Support DDR4 (8 channels).
- Support PCIe 3.0
There's no word on when Zen processors will see the light of day, but launch is expected by the end of the year.
-

How much do you know about telemetry and privacy in Windows 10... and how much do you care?
Publié: février 13, 2016, 10:45pm CET par Mark Wilson

Privacy concerns about Windows 10 have existed since the moment the operating system was released. Endless virtual column inches have been spawned from fears about the telemetry features Microsoft employs, and a small cottage industry has sprung up creating tools that disable 'spying' features. But for all of the words that have been spilled, how much does the average user know -- or indeed care -- about privacy issues, data collection and the like?
There's one thing that just about everyone can agree on: Microsoft did a terrible job of communicating information about data collection in Windows 10. We also know that the mere existence of data collection features has irked a lot of people. Microsoft listened to enterprise users and made it possible to completely disable telemetry in Windows 10 Enterprise, but the same courtesy has not been extended to home users. Are you bothered by this?
Back at the end of September, Microsoft said: "Our enterprise feature updates later this year will enable enterprise customers the option to disable this telemetry, but we strongly recommend against this." This update is already out there in the enterprise version of Windows 10 build 1511, but there's no sign of the same happening for everyone else.
There's no denying that Windows 10 has been the most widely questioned version of Windows ever. In addition to the privacy issues, Microsoft failed to do a very good job of properly communicating pricing details for the operating system -- and even as the free upgrade period draws ever closer, it's still not entirely clear what, if anything, it will cost late-adopters. But it is privacy that has -- much to the company's chagrin -- been the thorn in Microsoft's side.
Post-Snowden, post-NSA, post-Assange, post-GCHQ ,we live in a highly suspicious age. Not all privacy fears are completely unfounded, but it seems that all too often those who question what is going on are shot down as conspiracy theorists. There's a slight irony to the fact that in these despite the concerns -- well-founded or otherwise -- Microsoft raises about privacy, it also keen to present itself as a transparent company.
Has it succeeded with being transparent when it comes to privacy and telemetry?
The endless debates about the rights and wrongs of what Windows 10 involves would certainly suggest not.
But what really matter is what users think. Users like you.
Has Microsoft done enough to let you know about what data is being collected from your computer and reported back as you use Windows 10? Have users been given enough control over their privacy? Why is there a difference between enterprise and non-enterprise telemetry, and does this concern you?
Privacy and telemetry is about trust, and Microsoft has said that there are two principles behind its approach to privacy:
- Windows 10 collects information so the product will work better for you.
- You are in control with the ability to determine what information is collected.
The company has also tried to make it clear what is collected, and what is not:
Safety and Reliability Data -- We collect a limited amount of information to help us provide a secure and reliable experience.
Personalization Data -- We aspire to deliver a delightful and personalized Windows experience to you.
Advertising Data We Don't Collect -- No matter what privacy options you choose, neither Windows 10 nor any other Microsoft software scans the content of your email or other communications, or your files, in order to deliver targeted advertising to you.
Falling in to the 'making Windows 10 better' category are things like communication with Windows Update. In order to check what updates are installed and which are needed, information needs to be transmitted back to Microsoft. This is something that few people would take issue with, but there is more to it that that.
If you are concerned about privacy in Windows 10, Microsoft points out that there are settings you can change to take control of things. But do these settings go far enough for you? Would you like the ability to just completely opt out of everything in the same way that enterprise users can? Head to the Privacy section of Settings, and you'll find screen after screen of toggle switches that can be used to disable various options. How many people are likely to work through each of these, or even be aware that they might want to?
That's the point of this post: to gauge opinion, to find out how much people think they know, and to see if you feel Microsoft needs to be even more open about what's going on.
Over to you...
* I'll be a little preemptive: before the question is raised about why Apple, Google et al are not being put under the same scrutiny. This is about Microsoft specifically, not tech companies in general. Google and Apple have already been scrutinized and criticized, and they will be again. For now, we're talking about Microsoft -- not because it's an easy target, or there's any sort of vendetta, but just... because...
Photo credit: Paul Stringer / Shutterstock
-

King Arthur is back on Facebook after falling foul of Real Name policy
Publié: février 13, 2016, 3:32pm CET par Mark Wilson

For many, Arthurian legend is just that: legend. But for others, it is very real. One such person is King Arthur -- or Rev Arthur Uther Pendragon to give him his full title -- was recently kicked off Facebook as the social network did not believe he was using his real name.
But now the king is back. Having proved his identity, the once and future king (Rex Quondam Rexque Futuris) has had his account restored under his legal name of Arthur Uther Pendragon. King Arthur is not the first person to cross swords with Facebook's real name policy, and he certainly won't be the last.
For the avoidance of all doubt, Arthur Uther Pendragon is a real man. Arthur Uther Pendragon really is his name. I know. I've met him (in Glastonbury... obviously). As well as being the 'reincarnation of King Arthur', he's also an eco-warrior, leader of the Loyal Arthurian Warband, and 'battle chieftain' of the Council of British Druid Orders. He's more used to battling for access to Stonehenge, and fighting for the right of prisoners who identify as druids to wear their druidic robes in jail.
After having his account reported for failing to use a real name, King Arthur was forced to create a second Facebook account using the name Arthur Rex -- primarily to let people know why he had suddenly vanished from the site. But after showing Facebook copies of his driving license and passport, Arthur Uther Pendragon's original account has been restored:
I'm BACK
I sent Facebook a link to The Article by Tristam Cork in The Western Daily Press and I know The Salisbury Journal rang them up and asked for a quote.
Having already sent copies of my current UK Driving Licence and UK Passport. previous and current.
The Western Daily Press describes the original ban a "treasonous act". King Arthur himself says:
I don't know who keeps falsely reporting me to Facebook as a non-person or a made up name but they do. It's a pity they don't take action against them rather than me.
So what next? Arthur Uther Pendragon is battling with English Heritage over an alcohol ban at Stonehenge (an important site for druids), and plans to charge for parking at the monument.
Photo credit: Roger Nichol / Shutterstock
-

Court rules it is not illegal for GCHQ to hack computers
Publié: février 12, 2016, 10:13pm CET par Mark Wilson

Privacy International has lost a court case that questioned the legality of GCHQ's hacking operations. The UK-based privacy and human rights charity launched a legal campaign after Edward Snowden revealed the spying and surveillance that was being carried out by the NSA and GCHQ.
In the course of the case, GCHQ admitted for the first time that it was involved in hacking devices and computers not only in the UK, but around the world. The Investigatory Powers Tribunal (IPT) ruled that activities such as the installation of keyloggers, the remote activation of microphones and cameras, and the use of malware by the intelligence agency is entirely legal.
With the UK government planning to implement the snooper's charter (or Investigatory Powers Bill) this year, surveillance has once again become big news. The ruling from the IPT today found that there is a balance "between the urgent need of the Intelligence Agencies to safeguard the public and the protection of an individual’s privacy and/or freedom of expression".
Privacy International is understandably displeased with the outcome of the case, and says it will continue to fight what it describes as "state-sponsored hacking". The charity's legal officer, Scarlet Kim, said:
This case exposed not only these secret practices but also the undemocratic manner in which the government sought to backdate powers to do this under the radar. Just because the government magically produces guidelines for hacking should not legitimise this practice.
The British government, however, is delighted with the result. Foreign secretary Philip Hammond said: "The ability to exploit computer networks plays a crucial part in our ability to protect the British public. Once again, the law and practice around our Security and Intelligence Agencies' capabilities and procedures have been scrutinised by an independent body and been confirmed to be lawful and proportionate". He says that the Investigatory Powers Bill will introduce even more surveillance opportunities for intelligence agencies.
-

PSA: Time to switch to Google Photos as Picasa shuts down
Publié: février 12, 2016, 9:37pm CET par Mark Wilson
It has been a long time coming, but when 15 March rolls around Google will no longer support the desktop Picasa app -- and this is just the start of the shutdown. Picasa is being gradually shuttered in favor of Google Photos as the search giant focuses its energy on a single photo service.
So what does this mean for Picasa fans? Well, the good news is that there's nothing to do in terms of migrating content from one service to another. Picasa Web Album content can be viewed, edited and shared through Google Photos, but if you don't want to migrate then it will be archived from 1 May.
The Picasa closure starts on 15 March, however, and from this date Google will no longer issue any update for the desktop app. It will continue to work, but there will be no more support of any sort. Developers will lose access to some features of the Picasa API: Flash support; community search; mutation operations other than uploads; all support for tags, comments, and contacts.
The closure of any service runs the risk of user backlash, and this is something that Google is only too aware of. Announcing the closure, the company says:
We know for many of you, a great deal of care has gone into managing your photos and videos using Picasa -- including the hours you've invested and the most precious moments you've trusted us with. So we will take some time in order to do this right and provide you with options and easy ways to access your content. We've outlined below some of the changes you can expect.
-

Pedophiles are reportedly using Facebook to share images of children
Publié: février 12, 2016, 8:05pm CET par Mark Wilson

An investigation by the BBC has found that secret groups on Facebook are being used by pedophiles to share images -- and Facebook doesn't seem to be doing much to control such activity.
The BBC reportedly unearthed numerous private groups which were both run by and for men with a sexual interest in children. One group was found to have a convicted pedophile as its administrator. Despite many of the groups and images being reported to Facebook, not all of them were removed, raising the question as to whether Facebook is doing enough to combat pedophilia.
In addition to pornographic content, the groups are home to images culled from newspapers and clothing catalogs and attract a barrage of obscene comments from users. Many of the groups are named in such a way that it makes their purpose entirely clear and Anne Longfield, Children's Commissioner for England, says that Facebook needs to do more to police content and protect children.
The BBC went as far as setting up a fake profile of its own in order to gain access to the groups as part of the investigation:
In one secret group called "cute teen schoolies", we found a picture of a girl in a vest, aged 10 or 11, accompanied by the words "yum yum". Facebook responded that it did not breach "community standards" and the image stayed up.
Out of 20 images reported, just half of them were removed, some by Facebook, and some by the uploaders. Other images which featured children in "highly sexualized poses" were deemed not to breach Facebook's community standards, and so remained in place -- this in spite of the fact that the BBC found some material so disturbing that it contacted the police.
Facebook's head of public policy, Rishi Saha, told the BBC:
When it comes to specific groups I think it's really important that we investigate the groups, so if you're able to share the details of these groups with me then I can work with my colleagues who do the investigations on these and make sure we're investigating them and we're removing the content that shouldn't be there... [We] deal directly with law enforcement to make sure they're aware of these groups and follow the proper process.
Photo credit: Rob Hyrons / Shutterstock
-

Adblock Plus wants to know why you're blocking ads (!)
Publié: février 12, 2016, 1:05pm CET par Mark Wilson

Adblock Plus has been in the headlines quite a lot recently. Adblocking is certainly popular, but the company needs to strike a balance between keeping users happy, and maintaining a good relationship with advertisers. The Acceptable Ads program is part of this, but at its second #CampDavid session there have been some further ideas about the future of adblocking.
There was talk about what should be viewed as an 'acceptable ad', and an Acceptable Ads Committee will oversee this. But the discussion between Adblock Plus and advertisers brought up an important question: just why do people install adblockers?
On the face of it, this seems like a stupid question with an obvious answer -- ads are bloody annoying, and blocking ads reduces this annoyance while boosting privacy and security. But is it that simple? Do people actually think about what is involved in blocking ads, or is it just something they feel they should do? Have things changed online since they started using an adblocker? Do they know how much content they are missing out on because of it?
Writing about the #CampDavid Europe meeting, Adblock Plus' Ben Williams says:
Someone there brought up a novel but basic idea: finding a (nonintrusive) way to ask our users why they decided to install an ad blocker in the first place. Lots of studies go after this information -- indeed, we used one such survey as the basis for an update to our criteria -- but if actual users tell us it takes some of the guesswork out of it.
Clearly it will be difficult to gather information about why Adblock Plus is being used without in some way intruding on a user's web experience. This is something that Adblock Plus recognizes, but ultimately it would be helpful to feed this back into the Acceptable Ads Program, as well as educating advertisers more about what is deemed tolerable.
Something along these lines will likely take a while to implement, because there are significant user experience issues involved in any “user survey”; but if there were a way to get this information without annoying anyone, it would lead to more granular blocking possibilities and a better idea of what we shouldn’t block. That is, what is acceptable.
Photo credit: patpitchaya / Shutterstock
-

Gmail now warns you if your emails are not TLS encrypted
Publié: février 11, 2016, 8:31pm CET par Mark Wilson

To celebrate Safer Internet Day the other day, Google gave away an extra 2GB of cloud storage to anyone who completed a simple security audit of their account. At the same time the company also introduced a couple of important security enhancements to Gmail.
The first change sees the appearance of a simple indicator that makes it clear when an email is received through, or is about to be sent through, a service that doesn’t support TLS encryption. A broken padlock icon indicates that TLS encryption is not available, serving as a warning that there is the potential for the email in question to be dangerous or for the message to be intercepted.
Google points out that in order for TLS (Transport Layer Security) to be effective, it is important that it is supported by both the sender and the recipient of emails. If either party fails to meet this requirement, this is when the broken padlock indicator makes an appearance.
The second security feature makes it easier to tell when an email address has been authenticated. While you would normally expect to see an avatar for people you already have in your address book, non-authenticated senders have previously simply had a blank profile image. The latest change sees non-authenticated senders highlighted with a red question mark avatar which should be easier to notice.
Google says:
Not all affected email will necessarily be dangerous. But we encourage you to be extra careful about replying to, or clicking on links in messages that you’re not sure about. And with these updates, you’ll have the tools to make these kinds of decisions.
Photo credit: Butterfly Hunter / Shutterstock
-

Julian Assange can't be allowed to hide behind the skirts of WikiLeaks to avoid answering rape allegations
Publié: février 7, 2016, 6:17pm CET par Mark Wilson
Like Edward Snowden, Julian Assange is an incredibly divisive character. Just as Snowden is viewed by some as a hero for exposing the activities of the NSA, so Assange is viewed as a hero for exposing -- amongst other things -- the darker side of the US military through WikiLeaks. But both figures are also viewed as villains by those who believe that their whistleblowing has endangered national security.
While Snowden scampered off to Russia to avoid the US legal system, Assange took refuge in the Ecuadorian embassy in London. While it's certainly true that he's a man of interest for the US which ultimately seeks to prosecute him over the activities of WikiLeaks, Assange is actually holed up in the UK to escape extradition to Sweden where he faces questioning over allegations of rape. He has continually used the additional prospect of extradition to the US for WikiLeaks-related questioning as an excuse for not facing the music in Sweden. This is just about as wrong as it's possible to be.
Edward Snowden riled the US government with his exposé of NSA surveillance and he felt that this meant there was no way he would be able to receive a fair trial. Julian Assange has used a similar argument following his work with WikiLeaks. While both men's fears may be well-founded, Assange stands accused of the ultimate violation -- rape. There can simply be no excuse for not answering to these allegations.
In the last week, Assange's appeal to the United Nations went in his favor. The UN panel decided that his time in the Ecuadorean Embassy amounted to 'arbitrary detention'. Except it didn't. Over the course of the last several years, Assange has only been held against his will for a period of 10 days after having been arrested in London back in late 2010. He was then released on bail, but in 2012 when it was decided that he could be extradited to Sweden to face the rape allegations, he decided to seek 'political asylum' at Ecuador's embassy in London.
Despite anything Assange may say, he has been free to leave the embassy at any time since walking through its doors; he chose not to. He chose not to, presumably, because he would instantly have been arrested and carted off to Sweden. But that's not the story he's putting forward. He wants the world to feel that he has been detained. This is just utterly untrue.
It has been suggested that the rape allegations are completely false, having been fabricated simply to get Assange into the legal system so he can be handed over to the US to talk about WikiLeaks. This is likely a construct of the conspiracy theorists, but it doesn’t matter either way. Assange has been accused of rape. He needs to be seen to go through the relevant legal processes to either clear his name or receive the relevant punishment. Any talk of possible extradition to the US is being used as a smokescreen and a distraction -- the rape allegations need to be dealt with first and then, and only then, does the US/WikiLeaks side of the story come into play.
WikiLeaks has done some fabulous work exposing the nefarious activities of governments, militaries, individuals and companies around the world. For this -- and ignoring the fact that he is an utter odious man (regardless of the veracity of rape allegations) -- Assange is to be applauded. Just like Snowden, he has brought to light important matters that the public needed to know about. But it shouldn't act as a get out of jail free card.
There is a possibility that Assange would, ultimately, be extradited from Sweden to the US. But it is a possibility rather than a certainty. He has already proved himself perfectly capable of evading justice, and there's no reason to think that he wouldn't be able to do this again. But if he is to be taken seriously, Assange needs to show that he is a man of principle and stop hiding behind the skirts of WikiLeaks.
Face the rape allegation and then fight US extradition. It's simple, really. If Assange can’t be seen to do the right thing, he is going to very quickly lose any support he has, and the good work WikiLeaks has achieved will be undone -- if not literally, then symbolically.
Photo credit: haak78 / Shutterstock
-

Now the Pirate Bay lets you stream just about anything for free
Publié: février 7, 2016, 4:05pm CET par Mark Wilson

Legalities aside, there is one problem with content made available through the likes of the Pirate Bay. Whether you use traditional torrents or magnet links, you'll (usually) need to wait for a download to complete before you can enjoy the movie, show, or album of your choice. But not anymore.
A new beta feature for the world-famous torrent site makes it possible to stream videos without the need to download them first. By integrating the Torrents-Time plugin, the Pirate Bay now includes a Stream It option for all video torrents.
Of course, pirate streams are nothing new, but integrating the option into such a high-profile site helps to bring it to the masses. It means that the Pirate Bay can now be considered more of a destination rather than just a means to an end -- searching and viewing can now all take place in the browser without the need for any additional software.
Just as with downloading torrents, the ability to stream is dependent on connecting to a large enough number of seeds. Perform a search as normal, and as well as the familiar comment and magnet links, you'll also find a Stream It link. Click this and a new window will open to house the selected video -- the first time steaming is attempted, users are prompted to install the Torrents-Time plugin.
The player itself is a fairly basic affair -- this is a beta, remember -- but it still includes subtitles, Chromecast, Airplay, and DLNA support. It works with Chrome, Internet Explorer and Firefox on Windows and OS X.
-

Twitter may not be dead after all -- Jack says your timeline is safe... for now
Publié: février 7, 2016, 1:46pm CET par Mark Wilson

Twitter went slightly nuts over the last couple of days. Suggestions that the chronological timeline was to be ditched in favor of one controlled by an algorithm gave birth to the #RIPTwitter hashtag. But the panic may have been for nought; Jack Dorsey wants to clear things up.
The Twitter founder took to the site to assure its users that a timeline change is not on the cards -- at least not next week. But what he says may not completely quell the fears of those who have been talking about the death of Twitter.
He says: "I *love* real-time. We love the live stream. It's us. And we're going to continue to refine it to make Twitter feel more, not less, live!" Quite how it's possible to feel, or be, 'more live' remains to be seen, but Twitter seems to be learning that it needs to listen to its users. Dorsey tried to reassure users by saying: "Thank you all for your passion and trust. We will continue to work to earn it, and we will continue to listen, and talk!".
The speed with which Dorsey took to twitter to try to allay fear about timelines is impressive. But his tweet is worded in such a way that it does not rule out the possibility of an algorithmic timeline being introduced:
Hello Twitter! Regarding #RIPTwitter: I want you all to know we're always listening. We never planned to reorder timelines next week.
— Jack (@jack) February 6, 2016
The key words here could well be next week. Considering the backlash that the original story brought about, you would have thought that Dorsey would have been keen to completely squash the rumor. He chose not to, leaving the door open for changes at some point further down the line.
Photo credit: Jeff Cameron Collingwood / Shutterstock
-

European Court of Human Rights says websites are not responsible for reader comments
Publié: février 6, 2016, 8:47pm CET par Mark Wilson

In something of a landmark ruling, the European Court of Human Rights says that websites cannot be held liable for comments left by readers. The ruling comes after a Hungarian website was sued over the content of messages left by readers.
The court said that if websites were held responsible for comments, it would constitute a breach of the right to free expression. Even in the case of 'offensive and vulgar' comments, providing nothing unlawful was written -- such as hate speech -- Hungarian news site Index.hu, and others, could not be held responsible for readers' comments.
The ECHR's ruling came after Index.hu was sued by a real estate agent back in 2013 after the company was described in a comment as a "sly, rubbish, mug company". While the site took down the comments in question as soon as they were flagged, but its lawyers expressed concern that readers' right to free expression would be restricted if it was expected to look out for and take action on all comments that people took exception to.
As explained by the BBC:
Under the European Convention on Human Rights, which has been in force since 1953, freedom of expression is a right which everyone has.
It includes the freedom to communicate 'information and ideas' without interference from public bodies.
However, the right is limited.
States may restrict freedom of expression in the interests of national security, in order to prevent crime, or to protect health or morals, among other things.
In its ruling, the court said:
The Court notes that it was not in dispute between the parties that the applicants' freedom of expression guaranteed under Article 10 of the Convention had been interfered with by the domestic courts' decisions. The Court sees no reason to hold otherwise.
Such an interference with the applicant company's right to freedom of expression must be "prescribed by law", have one or more legitimate aims in the light of paragraph 2 of Article 10, and be "necessary in a democratic society".
Referring to a previous case in which site comments were found be best dealt with on a notice-and-take-down basis:
[...] the Court found that if accompanied by effective procedures allowing for rapid response, the notice-and-take-down-system could function in many cases as an appropriate tool for balancing the rights and interests of all those involved. The Court sees no reason to hold that such a system could not have provided a viable avenue to protect the commercial reputation of the plaintiff. It is true that, in cases where third-party user comments take the form of hate speech and direct threats to the physical integrity of individuals, the rights and interests of others and of the society as a whole might entitle Contracting States to impose liability on Internet news portals if they failed to take measures to remove clearly unlawful comments without delay, even without notice from the alleged victim or from third parties. However, the present case did not involve such utterances.
Photo credit: Flat Design / Shutterstock
-

Windows 10 phones home (A LOT) even with all reporting and telemetry disabled
Publié: février 6, 2016, 8:32pm CET par Mark Wilson

One computer user has become so disillusioned with Windows 10's spying features that he has been driven to using Linux Mint as his primary operating system. But Voat user CheesusCrust was curious to find out just how pervasive Microsoft's privacy invasion is. The results of his investigation are quite staggering.
Using a router kitted out with DD-WRT, and a copy of Windows 10 Enterprise installed in a virtual machine on his Linux laptop, he started by disabling every single one of the tracking and telemetry features found in the operating system. Eight hours later, 4,000 connection attempts to 93 different IP addresses were logged, with most of these IPs addresses being linked to Microsoft.
Explaining his setup on Voat, CheesusCrust said that he used a completely virgin installation of Windows 10 which had been used only to verify that the internet connection was working properly. Perl was then used to pull 8 hours of data from log files and push them into a MySQL database. Perl was also used to obtain route data for any connections. Presenting the results, CheesuCrust says:
Here is the roughly 8-hour network traffic analysis of 5508 connection attempts of an unused, base install of Windows 10 Enterprise (NOTE: I did not remove any 192.168.1.x home network IP addresses from the analysis).
Broken down, this works out to 3967 connection attempts to 51 different Microsoft IP addresses. You can see full tabulated results on Voat.
With Microsoft facing unprecedented levels of criticism for its lack of transparency over spying components, these findings will serve only to add fuel to the fire. The fact that it was the Enterprise edition of Windows 10 that was used for testing is likely to raise further questions.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Apple says it is bricking iPhones with Error 53 for security reasons
Publié: février 6, 2016, 6:59pm CET par Mark Wilson

You wouldn't expect a simple iOS update to completely kill your iPhone, but this is exactly what is happening. Users who took their handsets to a third party for repair and subsequently updated their software have run into error 53 and a bricked handset. Apple is not only aware of the problem, but says that it is intentional.
As we learned the other day, the problem seems to arise for people who have had their home key (specifically) fixed by a non-Apple-authorized repairer. Apple has now admitted that iOS detects the home key has been tinkered with, and says that Error 53 is a move to 'protect our customers' -- customers who will, presumably, think twice before upgrading to an iPhone 7.
The reason for the extreme security measures taken by Apple is that the home key houses the Touch ID sensor. The fear is clearly that the button could be replaced with one that includes a hacked sensor so Apple has decided that in order to prevent unauthorized access to iPhones and iPads, all access will be blocked -- and this is achieved by unceremoniously bricking said devices.
In a statement to the Guardian, Apple defended what is happening by saying:
We take customer security very seriously and Error 53 is the result of security checks designed to protect our customers. iOS checks that the Touch ID sensor in your iPhone or iPad correctly matches your device’s other components.
If iOS finds a mismatch, the check fails and Touch ID, including for Apple Pay use, is disabled. This security measure is necessary to protect your device and prevent a fraudulent Touch ID sensor from being used. If a customer encounters Error 53, we encourage them to contact Apple Support.
It’s hard to imagine a comparable scenario in which the arbitrary disabling of an expensive device, that has not been reported stolen, would be deemed acceptable. Upon contacting Apple Support, an admission by customers that a third party repairer has been used is an admission of violating the company's terms and conditions. This means that Apple charges customers handsomely for the privilege of replacing their bricked handsets, magically recouping the money -- and more -- lost to the third party.
Photo credit: Petlia Roman / Shutterstock
-

#RIPTwitter? What's with all the hoopla?
Publié: février 6, 2016, 2:59pm CET par Mark Wilson
There have been changes aplenty at Twitter as the company fights to remain relevant in an increasingly crowded social marketplace. There have been rumors that the famous 140-character limit could be dropped, and we're already seeing Twitter dropping the requirement to be logged into an account in order to see conversations. Just like Facebook, Twitter has also experimented with changing the order in which content appears in users' timelines, and it seems like this is something that's due to spread to everyone.
The company could be on the verge of launching a new algorithm-powered timeline that displays tweets not in reverse chronological order, but based on what it thinks you might want to see. Before the change has even been implemented, there has already been something of a backlash, with many people suggesting this could be the death of Twitter. The hashtag #RIPTwitter quickly started trending and is home to vocal opposition to the change.
While nothing concrete has been confirmed by Twitter, we already know that timeline changes have been previewed to small groups of users. Buzzfeed reports that the new timeline structure could roll out to everyone as early as next week, and a Twitterstorm has blown up questioning not only Twitter's motives, but also its future.
One of the main arguments being voiced against changing the way tweets are displayed is that it takes control away from users. The Twitterati have chosen who they want to follow on the site, they don't need to have content surfaced that they 'might be interested in'. Without knowing quite how the algorithm works, it's hard to say whether its implementation will simply mean seeing broadly the same content in a slightly different order -- which could play havoc with people trying to follow a narrative through tweets from numerous people -- or if Twitter will take this as an opportunity to extend its advertising and promoted tweets programs.
Twitter is accused of trying to ape Facebook, and users are angry that the company should be so arrogant as to assume to know better than individuals what they might want to see. In choosing who to follow, users have already indicated what or who they are interested in; bringing other content to the fore runs counter to this idea.
But it might not all be bad news -- if, indeed, you regard the timeline change as bad news. NBC's Josh Sternberg suggests that the algorithm may not be forced on everyone, but will in fact be optional:
Sources at Twitter tell me algorithms are strictly opt in.
— Josh Sternberg (@joshsternberg) February 6, 2016
This is certainly not the first time the death of Twitter has been predicted, but the angry outbursts that the latest timeline news has led to is pretty much unprecedented. Twitter may not be dead, but it's certainly treading a dangerous line and risking alienating large swathes of its users.
It has even inspired poetry:
Dear Twitter, I wrote you a love letter...

 #RIPTwitter pic.twitter.com/7a4ZtmocUI
#RIPTwitter pic.twitter.com/7a4ZtmocUI— Chloë Forbes-Kindlen (@C4Compete) February 6, 2016
#RIPTwitter? Maybe not. But Twitter does need to start listening to what its users are saying they want -- an Edit button, anyone? -- rather than continuing to tell them what they want.
Photo credit: Kornfoto.com / Shutterstock
-

Twitter tackles terrorists in targeted takedown
Publié: février 6, 2016, 1:45pm CET par Mark Wilson

Having previously battled trolls, Twitter has now turned its attention to terrorists and their supporters. The site has closed down more than 125,000 accounts associated with terrorism since the middle of 2015, it announced in a statement.
Although a full breakdown of figures is not provided, Twitter says most of these accounts were related to ISIS. Having increased the size of its account review team, the site has reduced the time it takes to investigate accounts that are reported, and has also started to investigate 'accounts similar to those reported'.
Twitter reveals that it is not working on its own. As well as relying on reports from Twitter users about terrorist accounts, it also works with law enforcement agencies, such as the FBI, 'when appropriate'.
The blog post points out that there is no 'magic algorithm' for identifying and tackling terrorist content online -- it is, and will always be, a very hands-on process. Pre-empting suggestions that closing accounts could be deemed censorship or an infringement of freedom of speech, Twitter says:
As an open platform for expression, we have always sought to strike a balance between the enforcement of our own Twitter Rules covering prohibited behaviors, the legitimate needs of law enforcement, and the ability of users to share their views freely – including views that some people may disagree with or find offensive.
Going out of its way to state the obvious, Twitter says:
We condemn the use of Twitter to promote terrorism and the Twitter Rules make it clear that this type of behavior, or any violent threat, is not permitted on our service.
But of course condemnation is not enough; Twitter has to be seen to be doing something. As well as advising global governments, the company has also been working with People Against Violent Extremism (PAVE) and the Institute for Strategic Dialogue.
Photo credit: theromb / Shutterstock
-

Mozilla kills Firefox OS 2.6 for smartphones but it lives on in smart TVs and connected devices
Publié: février 5, 2016, 2:21pm CET par Mark Wilson

Following on from the announcement that Firefox OS would no longer be developed for smartphones, Mozilla has explained the thinking behind the decision (failures on its part) and also revealed that Firefox OS will continue to live on in other devices.
The operating system is already used to power Panasonic SmartTVs, and this is set to continue. This will certainly come as good news to owners of such TVs, but Mozilla says that the OS stack will be used in a range of Connected Devices.
Talking about the decision to kill Firefox OS in smartphones, Mozilla's Ari Jaaski admits that "we failed to build the full ecosystem". The company also failed to offer what it refers to as "a compelling and differentiating end-user value proposition" -- essentially an admission that the operating system wasn't as good as iOS and Android... maybe even Windows 10 Mobile.
Looking to the future, Mozilla is keen to put its failed experiment behind it as it works on integrating the OS stack into a new Connected Devices (Mozilla's capitalization) range. This means that the Firefox Marketplace is also being killed off as part of the "end-of-life plan for the smartphone project with the Firefox OS 2.6 release".
There is also a call to arms as Jaaski reiterates the open nature of Mozilla's platform:
Although Mozilla development of the smartphone OS will cease with 2.6, the OS stack will be used for Smart TVs and potentially other devices in the future. Our platform is open, as always, for volunteers, contributors and enthusiasts to improve on and submit patches for further advancement of the OS stack.
-

Here's how to bypass the iOS lock screen passcode
Publié: février 5, 2016, 1:45pm CET par Mark Wilson

There are numerous ways to keep your smartphone safe from prying eyes, and a lock screen protected with a passcode is a popular choice. But a newly discovered vulnerability in iOS 8 and iOS 9 means that iPhones and iPads could be accessed by attackers.
The vulnerability was discovered by security analyst Benjamin Kunz Mejri and it has been assigned a Common Vulnerability Scoring System (CVSS) count of 6.0, as well as a 'high' severity rating. Apple has been aware of the issue since late last year, but has yet to issue a patch.
Vulnerability Laboratory has issued a security advisory that warns: "An application update loop that results in a pass code bypass vulnerability has been discovered in the official Apple iOS (iPhone 5 & 6 | iPad 2) v8.x, v9.0, v9.1 & v9.2. The security vulnerability allows local attackers to bypass pass code lock protection of the Apple iPhone via an application update loop issue. The issue affects the device security when processing to request a local update by an installed mobile iOS web-application".
As explained by security expert Graham Cluley, the exploit works by taking advantage of a brief period after rebooting during which passcode authentication is disabled. Vulnerability Laboratory details how to exploit the security hole (text is produced verbatim with the original typos and grammatical oddities):
- First fill up about some % of the free memory in the iOS device with random data
- Now, you open the app-store choose to update all applications (update all push button)
- Switch fast via home button to the slide index and perform iOS update at the same time. Note: The interaction to switch needs to be performed very fast to successfully exploit. In the first load of the update you can still use the home button. Press it go back to index
- Now, press the home button again to review the open runnings slides
- Switch to the left menu after the last slide which is new and perform to open Siri in the same moment. Now the slide hangs and runs all time in a loop
- Turn of via power button on the ipad or iphone ....
- Reactivate via power button and like you can see the session still runs in the loop and can be requested without any pass code. Note: Normally the pass code becomes available after the power off button interaction to stand-by mode
- Successful reproduce of the local security vulnerability!
Check out the video below to see the exploit in action:
Physical access to the device is required, so the advice is to make sure you do not leave your iPhone or iPad unattended.
Photo credit: Twin Design / Shutterstock
-

PSA: Updating iOS could brick your iPhone 6 with error 53
Publié: février 5, 2016, 11:45am CET par Mark Wilson

OS upgrades can often be a pain, but you don't usually expect to run the risk of killing the device you are upgrading. If you’ve spent a small fortune on an iPhone, you're likely to be particularly upset if an upgrade is borked, but this is precisely the problem facing iPhone 6 owners who have previously had their handset worked on by an unofficial third party.
Growing numbers of iPhone 6 users are encountering error 53 in iOS9, effectively rendering their handset useless. What the affected handsets all appear to have in common is that their home button was fixed by a non-Apple technician, although some users report the same issue if they have a problematic home button that has not been fixed.
The Guardian recounts the tale of freelance photographer Antonio Olmos. While working in Macedonia, he had to get his iPhone repaired at a non-Apple verified place due to the lack of Apple stores in the area. A short while later a standard OTA iOS upgrade was offered which he started to install. The installation never finished, and Antonio was left with a bricked handset showing error 53. Apple says there is nothing that can be done apart from buying a replacement.
There are lots of stories from other iPhone 6 owners on Apple Support, including from people who have not taken their handset in for repair. With the bricking issue seeming to affect only people with home button issues, and Apple charging hundreds of dollars for an official repair, rumors are circulating that Apple is using this as a cash cow whilst simultaneously trying to kill the third-party repair market.
Kyle Wiens from iFixit says:
The 'error 53' page on our website has had more than 183,000 hits, suggesting this is a big problem for Apple users. The problem occurs if the repairer changes the home button or the cable. Following the software upgrade the phone in effect checks to make sure it is still using the original components, and if it isn’t, it simply locks out the phone. There is no warning, and there's no way that I know of to bring it back to life.
It is the lack of warning that is particularly concerning here. It's one thing for Apple to detect when third-party repairs have been carried out and use this as a reason to block upgrades (if this is indeed what is happening), it's quite another for bricking to happen on such a scale with no warning.
On Twitter, Samuel Gibbs from the Guardian summed things up perfectly:
I totally get the reasoning. But why brick it? Why not just warn and stop the install? That’s ridiculous. [https:]
— Samuel Gibbs (@SamuelGibbs) February 5, 2016
What's Apple's take on things? It's a security feature, apparently. A spokesperson said:
We protect fingerprint data using a secure enclave, which is uniquely paired to the touch ID sensor. When iPhone is serviced by an authorized Apple service provider or Apple retail store for changes that affect the touch ID sensor, the pairing is re-validated. This check ensures the device and the iOS features related to touch ID remain secure. Without this unique pairing, a malicious touch ID sensor could be substituted, thereby gaining access to the secure enclave. When iOS detects that the pairing fails, touch ID, including Apple Pay, is disabled so the device remains secure.
When an iPhone is serviced by an unauthorized repair provider, faulty screens or other invalid components that affect the touch ID sensor could cause the check to fail if the pairing cannot be validated. With a subsequent update or restore, additional security checks result in an 'error 53' being displayed [...] If a customer encounters an unrecoverable error 53, we recommend contacting Apple support.
Photo credit: Attila Fodemesi / Shutterstock
-

Forget SMS, ChatSim offers unlimited free chatting to mobile users as they travel the world
Publié: février 4, 2016, 10:34pm CET par Mark Wilson

Described as the world's first "instant messaging mobile operator", ChatSim aims to take the pain out of travelling with a mobile phone. Roaming charges can quickly mount up for travellers who lose track of the number of texts they send, and in order to avoid high data fees, you might find yourself seeking out Wi-Fi connections to make use of the likes of WhatsApp instead.
But there is an alternative. ChatSim lets you stay in touch without worrying about the cost. Buy a SIM card for just $25, £16 or €20, and you can send an unlimited number of messages -- over Wi-Fi or 4G... whatever connection you have available -- without incurring any additional charges. Sounds good? It gets better.
This is not a SIM card that is limited to use in just a handful of countries. With partnerships in more than 150 countries and over 250 providers, the chances are that if you go there, ChatSim can be used there. This is a SIM card that's all about staying in touch without breaking the bank, and while you can only send text and emoji based messages through your favorites IM app -- WhatsApp, Telegram, Facebook Messenger, WeChat, LINE, QQ to name but a few -- there are no limits on the number that can be sent.
ChatSim says:
No longer do holiday-makers have to wait until they find a WiFi hotspot when they land on foreign turf, or worry about not being able to get in touch with loved ones for fear of the cost. By simply swapping in a SIM which instantly connects to a local operator, they can message friends and family, using any of the compatible chat apps already on their phone, including WhatsApp, Messenger and WeChat.
But of course, you may want to take things a step further, and this is where you will have to pay a little extra. If you want to send photos or videos, or make voice calls, you can purchase extra credits in the form of a "multimedia recharge".
Credits Cost Photos? Videos? Voice calls? 2,000 $12 / £8 / €10 Up to 200 Up to 40 Up to 80 mins 5,000 $30 / £20 / €25 Up to 500 Up to 100 Up to 200 mins 10,000 $60 / £40 /€50 Up to 1,000 Up to 200 Up to 400 mins Find out more at ChatSim.com.
-

Android adblocker apps blocked by Google
Publié: février 4, 2016, 12:17pm CET par Mark Wilson

Well that was... brief. Just days after Samsung released an update that allowed for adblocking software to be installed on its handsets, Google has put its foot down. The company has already started to pull adblocking apps from Google Play.
Being so reliant on advertising revenue, it's understandable that Google might take a dim view of anything that stops the cash rolling in. Nonetheless, a move to block apps that have already proved incredibly popular has raised the ire of developers and users alike.
Of course, Google is not saying outright that it has a problem with the distribution of adblocking tools per se, but the end result is the same. Developers are being contacted by the company to inform them that their app violates Google policy.
Rocketship Apps, the company behind Adblock Fast, the first adblocker to make its way into Google Play, received an email from the 'Google Play Review Team':
Hi Developers at Rocketship Apps,
I reviewed Adblock Fast, com.rocketshipapps.adblockfast, and found that it violates section 4.4 of the Developer Distribution Agreement. This particular app has been disabled as a policy strike.
Just as a reminder, you've agreed to follow the Google Play Developer Program Policies and additional enforcement could occur if there are further policy issues with your apps.
If you've reviewed the policies and feel this rejection may have been in error, please reach out to our policy support team. One of my colleagues will get back to you within 2 business days.
I appreciate your support of Google Play!
So what does section 4.4 of the Developer Distribution Agreement say? This is the clause that prevents developers from 'interfering' with other apps and services:
Prohibited Actions. You agree that you will not engage in any activity with the Store, including the development or distribution of Products, that interferes with, disrupts, damages, or accesses in an unauthorized manner the devices, servers, networks, or other properties or services of any third party including, but not limited to, Android users, Google or any mobile network operator. You may not use customer information obtained from the Store to sell or distribute Products outside of the Store.
It seems that Google's problem lies with standalone adblocking tools. If a web browser happens to feature the ability to block ads, more power to it, but if a developer wants to add adblocking to an existing browser, that's a different matter. While users and developers may be annoyed by this, it also places Samsung in something of an awkward situation as it provided access to an API with the specific aim of allowing developers to produce adblockers for its own browser.
Photo credit: Light And Dark Studio / Shutterstock
-

Windows 10 is Microsoft's Elephant Man
Publié: février 4, 2016, 2:12am CET par Mark Wilson

I read a comment from a user who was talking about Windows 10 Mobile. He referred to it as Microsoft's stillborn baby. As dark and as gruesome an image as this may be, it feels very fitting, and it got me wondering how best to think of the desktop version of Windows 10. Clearly this is not a stillborn -- there's plenty of life in this kicking and screaming beast, and there is no sign of an abortion on the horizon.
But it is the black sheep of the family, the -- brace yourselves, politically correct gentlefolk -- deformed and underdeveloped spawn of Microsoft's loins. If it was an animal, it probably would have been destroyed in utero. As it is -- to view it in more human terms -- it's more like the Elephant Man: a lumbering, lurching curiosity that many would like to see dead, but which at the same time retains its right to existence.
With Windows 10, Microsoft has really done very little to endear itself to people; the number of slipups along the way has been impressive. We started off with some slight confusion about what 'free' meant as there was some very poor communication and some very poorly-worded announcements made in the run-up to launch. Just what is the deal with the free upgrade?
And when the launch did roll around, there was a general feeling that Microsoft had ushered an unfinished product out of the door. To this very day, the much-touted replacement for Internet Explorer -- Microsoft Edge -- remains incomplete. The add-in support that users have so long been waiting for remain elusive. And that's before we even start to think about issues with InPrivate not being quite as private as the name might suggest.
These are just two of the issues that users, and would-be users have been complaining about and in the background there is the other elephant (man) in the room -- the hostile way in which Windows 10 has been foisted on people. Add to this the various spying and telemetry features (again, with an amazing opaqueness that is incredibly surprising coming from a company such as Microsoft) and it's little wonder than Windows 10 is eyed with such suspicion.
The whole thing is so ugly (the situation, not the OS itself before you bite my head off) that one can’t help but wonder if we're trapped in some Wildean world. Maybe a devilish deal has been made somewhere and we're actually experiencing the corrupt, evil painted version of Windows 10 up in the attic where things gradually become uglier and more twisted, while the youthful, nimble, spry and sexy Dorian Gray-like edition of the operating system exists in some parallel universe, delighting and enthralling everyone who encounters it.
But ultimately, it is the Elephant Man idea that holds out. Joseph Merrick was ridiculed, feared and exploited -- the same is true of Windows 10.
-

The future of the NSA: fight the hackers or embrace the hackers
Publié: février 3, 2016, 6:05pm CET par Mark Wilson

With its well-known habit of uncompromising surveillance, the NSA has earned itself something of a poor reputation among internet users. But while the spying side of the agency is what it is most famous for, it is actually made up of two different divisions: offensive and defensive.
Later this week the NSA is expected to announce an internal restructuring that will see the two divisions merging. This presents the agency with an interesting predicament: does it continue to work to fight the efforts of hackers, or does it adopt hacker-like techniques to help gather data? Experts says that the merger is a mistake, largely because the aim and modus operandi of the two departments are diametrically opposed.
The dilemma comes about because while the offensive Signals Intelligence Directorate (SID) actively seeks security holes and uses backdoors to attack foreign nations, the defensive Information Assurance Directorate (IAD) seeks to plug security holes to protect companies and governments. The NSA seems determined to go ahead with the merger, despite advice from experts and the Obama administration that greater separation would actually be the best move.
The reshuffle means that the NSA will have to choose between exploiting security holes or fixing them so they can't be exploited by others -- there really is no middle ground. Writing for the Guardian, Danny Yadron points out:
The NSA could decide not tell a tech company to patch a security flaw if it knows it could be used to hack into a targeted machine. This could leave consumers at risk.
The choice is stark. Is the NSA of the future going to concern itself with offense or defense? Working as it currently does with hackers and companies, the NSA risks straining relationships and threatening its own internal operations no matter which route it goes down.
Photo credit: Nadir Keklik / Shutterstock
-

Google to use ads in attempt to combat jihadi terrorists
Publié: février 3, 2016, 12:12pm CET par Mark Wilson

Large swathes of the internet have taken it upon themselves to try to stem the flow of ISIS propaganda and other terrorist content. People working under the Anonymous banner are perhaps the most obvious, but now Google is getting involved as well.
In an overtly political move a senior Google executive, Dr Anthony House, has revealed measures that are being trialled to try to combat extremism. As well as making it easier to discover who is looking for extremist content online, the company is also piloting a scheme that uses its AdWords system to display anti-ISIS messages.
This is an interesting use of Google's technology, and stands in stark contrast to the blunt DDoS attacks employed by some anti-ISIS groups. Google has already been heavily involved in controlling the dissemination of ISIS videos, removing large numbers from YouTube. But the latest idea takes something of a different angle; it aims to "make sure when people put potentially damaging search terms into our search engine they also find these counter narratives".
Quite how effective it will be to display an 'ISIS is bad' message to jihadi sympathizers is not clear, but it's something that Google is willing to try. Dr House said:
We offer Google AdWords Grants to NGOs so that meaningful counter-speech ads can be surfaced in response to search queries like 'join Isis'.
What this does not mean -- despite what has been reported by some sites -- is that Google is going to start delivering the 'wrong search results to would-be jihadis'. The only thing that will be affected are the ads that adorn search results.
Photo credit: photogearch / Shutterstock
-

Twitter tries to appeal to people who don’t like Twitter
Publié: février 2, 2016, 10:36pm CET par Mark Wilson

It has been suggested that Twitter is on a downward spiral, losing users, popularity and significance. Twitter would clearly disagree, but that's not going to stop the company from attempting to make its site more appealing -- even to people who don’t have a Twitter account.
Despite the ubiquity of hashtags and the prevalence of references to tweeting, there is something of a problem with Twitter. Visit Twitter.com and you'll immediately be prompted to sign into your account. Not a problem if you have one, but if you don't have an account it means that you’ve hit something of a wall. Twitter is now tearing down this obstacle, transforming its homepage into a valuable source of news and information regardless of whether you have an account or not.
Twitter says that it wants "to make great content accessible for everyone -- even if you’re not signed in". It might seem like a minor and obvious change, but it is a significant one that people have been asking for for some time. It's a change that opens up Twitter to a far wider audience and means that more people will be able to follow along with live events or see what TV shows and celebrities have to say without having to go quite as far as signing up for an account.
Of course, by not signing into an account you'll miss out on (most of) the personalized options that Twitter has to offer, but this is not the point of the change. Twitter says:
We're rolling out a home timeline to people across 23 countries who visit the twitter.com homepage on their mobile devices. Before today, you could see individual Tweets but it was hard to discover stories and conversations happening on Twitter without signing in. Now, you can check out a news story as it unfolds, dive into the play-by-play discussions around a game, and then come back again to see that exchange between two rappers everyone's been talking about. It's real-time and straight from the source, just like the Twitter experience for those who log in.
If you're in the US or Japan, you might wonder what all of the fuss is about. This is not an update for you!
Today we're bringing Tweets to more people around the
 on our homepage: [https:] pic.twitter.com/C0htvdamPn
on our homepage: [https:] pic.twitter.com/C0htvdamPn— Twitter (@twitter) February 2, 2016
Even if you're not signed into an account, Twitter will still try to show you the most relevant content, based on your location if nothing else.
This is not the only change coming to Twitter today -- the way conversations are displayed is also being tweaked. Twitter explained it, funnily enough, in a tweet:
New on [https:]: entire Tweet conversations pop out with a single click––no more losing your place! pic.twitter.com/RJq8dZIMKh
— Twitter Support (@Support) February 2, 2016
Conversations in a pop out seems to be getting something of a mixed reception, but it will be interesting to see how the mood develops over time.
-

How much will Windows 10 cost at the end of the free upgrade period?
Publié: février 2, 2016, 10:59am CET par Mark Wilson

The launch of Windows 10 was revolutionary. We're not just talking (or even talking at all) about features and changes -- this was the first version of Windows to come without a price tag. Windows 10 for free. It's a tactic that paid off.
Microsoft tells us that this is the most successful version of Windows yet, with unprecedented rates of take up. It's free; it's hardly surprising, particularly when you factor in Microsoft's incredibly aggressive pushing of the upgrade. But all good things must come to an end. We've known that Windows 10 would only be free for first year. As the upgrade-for-free deadline of 29 July fast approaches, just what happens next? What if you haven't upgraded to Windows 10? What will it cost to upgrade if you're late to the party?
From the very beginning, Microsoft has been rather opaque about Windows 10. Was the free-for-the first-year deadline set in stone? Would there be any sort of grace period? What would the cost of a not-free upgrade be? There's now less than six months until the free upgrade period comes to an end, and it's clear from comments online -- on BetaNews and beyond -- that people are simply not clear about what happens if they don't upgrade by 29 July.
So we asked Microsoft.
When asked what the cost of upgrading post 29 July would be, a Microsoft spokesperson said:
For those who decide not to upgrade for free within the first year beginning on July 29, you can purchase Windows 10 through the Microsoft Store or Microsoft retail partners. Once a Windows device is upgraded to Windows 10, we will continue to keep it current via Windows Update for the supported lifetime of the device.
But if you decide to leave the upgrade until after this date, what will it cost you? In characteristic form, Microsoft is not entirely clear. A spokesperson said:
The current pricing is $119.99.
This says nothing about what the upgrade price will be post 29 July, but this is indeed the current price on the Microsoft website for Windows 10 Home; Pro has a price tag of $199.99. Will these prices stay the same after the upgrade deadline? That's not clear.
Clearly Microsoft is eager to get as many people as possible to migrate away from Windows 7 and 8.1 and move to the software-as-a-service model of Windows 10. This is precisely why we have seen such a push of the upgrade, and to all intents and purposes this has been a resounding success. Microsoft says:
Since launch we've seen more than 200 million active devices running Windows 10, we're very confident in the server and network infrastructure to continue to successfully upgrade more customers to Windows 10.
At this rate, it won't be long before we see Windows 10 on a billion devices, particularly after the launch of Windows 10 mobile and after the panic-upgrading before 29 July. It's hard to imagine that Microsoft won't do one of two things when the end of July rolls around -- either extend the free upgrade period, or dramatically slash the price of buying the operating system.
Microsoft is keeping its cards close to its chest, and only time will tell. Maybe it's happy with the level of uptake we've seen of Windows 10 and is ready to start taking money from people for the software. But if there's a secret target that the company wants to hit in terms of user numbers, we could well see some sweetening deals from August onwards.
Of course, Microsoft isn’t going to tell us anything until the last minute...
Photo credit: little Whale / Shutterstock
-

Microsoft makes Windows 10 a 'recommended update' for Windows 7 and 8.1 users
Publié: février 2, 2016, 2:04am CET par Mark Wilson

Microsoft has been accused of pushing Windows 10 rather aggressively, and the company's latest move is going to do nothing to silence these accusations. For Windows 7 and Windows 8.1 users, Windows 10 just became a 'recommended update' in Windows Update.
This is a change from the previous categorization of the upgrade as an 'optional update' and it means that there is renewed potential for unwanted installations. After the launch of Windows 10, there were numerous reports of not only the automatic download of OS installation files, but also unrequested upgrades. The changed status of the update means that, on some machines, the installation of Windows 10 could start automatically.
As noted by ZDNet's Mary Jo Foley, the push of Windows 10 as a recommended update will be phased. For anyone who has Automatic Updates turned on, this means that they will simply be given the option of downloading and installing (assuming installation files have not already been downloaded, that is...). If the 'Give me recommended updates the same way I receive important update' option is enabled, the update will not only be downloaded, but the installation will be started.
A Microsoft spokesperson said:
As we shared in late October on the Windows Blog, we are committed to making it easy for our Windows 7 and Windows 8.1 customers to upgrade to Windows 10. We updated the upgrade experience today to help our customers, who previously reserved their upgrade, schedule a time for their upgrade to take place.
The change is not entirely out of the blue, but it is still likely to catch many people off guard. There is still the ability to opt out of the installation -- and even if the Windows 10 upgrade is accidentally completed, there is a 31 day grace period in which to revert to Windows 7 or 8.1 -- but this will still be seen as an aggressive push by Microsoft.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Here's what's new in Windows 10 Mobile Insider Preview Build 10586.71
Publié: février 1, 2016, 8:11pm CET par Mark Wilson
The official launch of Windows 10 Mobile may have been delayed, but the preview builds keep on coming. Today Microsoft launches Windows 10 Mobile Insider Preview Build 10586.71, a cumulative update complete with a few extra bug fixes.
Some of the performance-enhancing features of today's build were made available to Insiders on Friday through the Configuration Update, but this is included in this cumulative update. If you're on the Fast Ring, there's another update to download as well -- Insider Fast Configuration Update. This ensures that future flights will be downloaded by updating expiring certificates.
Microsoft says that it has been working to improve the upgrade experience for people moving from Windows Phone 8.1. Based on user feedback, there are improvements to cellular and Wi-Fi data profile migration, for example. But this is just part of the story.
Gabe Aul reveals some of the fixes included in this latest build:
- Windows Update performance and reliability improvements
- Improvements in migration of data profiles and messaging settings when upgraded from Windows Phone 8.1.
- SensorCore API’s are now upgraded correctly from Windows Phone 8.1; allowing applications, including many fitness applications, to correctly access movement data.
- SD card detection has been improved on boot and after insertion; File Explorer now handles the removal of an SD card when the default for apps or photos are set to SD.
- Improvements in the Edge browser, including PDF rendering.
- Bluetooth improvements when re-connecting to already paired devices and cars; turn by turn directions, and when using Cortana with the Microsoft Band.
- Improvements in Settings when downloading Maps or changing Quick Settings.
- Reinstalling Groove Music from the Windows Store no longer causes DRM music playback issues. Groove Music local song collections are now more quickly imported within the application
- Device power improvements after listening to music, after missed phone calls when iris detection is disabled, and when downloading updates.
- In app purchases now work correctly when cellular data is disabled.
- Improvements to the reliability of Kids Corner.
Check for updates and get downloading!
-

Microsoft opens up FastTrack to more SMBs to sweeten the Office 365 deal
Publié: février 1, 2016, 7:25pm CET par Mark Wilson

Microsoft today unveiled a measure designed to attract more SMBs to Office 365. The new scheme sees Microsoft's FastTrack customer service operation expanding so that it is now available to organizations with as few as 50 users; the previous minimum was 150 seats.
Microsoft says that many SMBs who have opted to use Google's App instead reach a "breaking point" when they hit 50 users. The company aims to capitalize on this by offering enterprise-grade services to businesses that would otherwise not be able to take advantage of features such as centralized management capabilities.
One of the fears that hold businesses back from switching to Office 365 is on-going support. FastTrack provides a way for organizations to get help from dedicated engineers and partners, as well as gaining access to valuable resources.
The expansion of the program is not only of value to smaller businesses; it also means that Microsoft Partners are in line for additional financial benefits. Microsoft says:
Speaking of Microsoft Partners, this global network of IT experts plays a critical role in helping companies small and large get up and running with the right technology. In addition to extending FastTrack to more customers, we are expanding the FY16 Adoption Offer to include Office 365 small business plans and adding payouts for customer deployments of 50-149 seats. This means Microsoft Partners will be eligible for a payout of $25 per seat for 50-149 seats, in addition to the existing payouts for 150 seats and above.
-

Android 6.0 Marshmallow update brings Adblock Plus to Samsung phones and tablets
Publié: février 1, 2016, 5:52pm CET par Mark Wilson

Earlier today we learned that a new API is bringing adblocking to Samsung's own mobile web browser. Adblock Fast was the first to take advantage of the new option and now, hot on its heels, comes the big guns -- Adblock Plus.
Today Samsung is rolling out an Android 6.0 Marshmallow update and once this has been installed, Adblock Plus can also be installed. The extension brings content blocking capabilities to Samsung's own web browser, but you'll have to jump through the relevant hoops to gain the privacy and bandwidth preserving capabilities.
Once your handset has been updated to the very latest version Marshmallow, you'll need to head over to Google Play to grab a free copy of Adblock Plus (Samsung Browser). Next you'll need to enable Adblock Plus within the browser and then choose the level of content blocking you'd like to use. For complete privacy and malware protection, you can opt to block all ads, but there's also the option of permitting Acceptable Ads -- Adblock Plus points out that this is the default setting.
Adblock Plus co-founder Till Faida says:
Adblock Plus is very excited to continue our momentum in the mobile space by solidifying a working relationship with Samsung that allows us to handle content blocking on any Samsung device. We are excited that Samsung’s mobile product offering is now including content blocking and are happy that Samsung users can find us in the Google Play Store to assist them with their ad blocking.
For now, Adblock Plus for Samsung Browser is only available for devices running Android 6.0 Marshmallow, but in March it will also be an option for Android 5.0 Lollipop users.
-

It's all a facade: Encryption may do nothing to reduce surveillance or increase privacy
Publié: février 1, 2016, 1:18pm CET par Mark Wilson

Living in a technological age where there is a near-fanatical obsession with privacy, a move towards encryption seems to make perfect sense. While there have been calls from some governments to ban encryption and demands for decryption keys to be handed over, there is a drive by companies and online services to try to increase security and privacy with encryption.
But a new report (Don't Panic: Making progress on the encryption debate) from Harvard University's Berkman Center for Internet & Society suggests that encryption may be all but pointless when it comes to curtailing surveillance. While governments and surveillance agencies may balk at the idea of people using encryption to 'go dark' online, and many people embrace the idea as a means of increasing their privacy, the report suggests that the task of surveillance is not going to be made impossible, and could be helped by the Internet of Things (IoT).
In fact, rather than the future being one that features less surveillance, the report suggests that there might actually be more opportunities for surveillance. Drawing on input from security and policy experts from academia, civil society, and the US intelligence community the report looks at consumer-level encryption and what this means for the ability to monitor the communication of criminals, terrorists and the like.
Despite increased take up of encryption, a huge proportion of web traffic remains fully accessible to law enforcement agencies. This includes not only communications which has not been purposely encrypted, but also metadata -- that staple of the NSA's diet -- which is unencrypted by nature. But more than this, the increased number of connected devices -- cars, home heating system, network cameras, smart devices, and so on -- actually means that there will be more opportunities for surveillance.
Intelligence and law enforcement agencies may be concerned that end-to-end encryption will make their job harder, but the report suggests that these fears are unfounded. It says:
End-to-end encryption and other technological architectures for obscuring user data are unlikely to be adopted ubiquitously by companies, because the majority of businesses that provide communications services rely on access to user data for revenue streams and product functionality, including user data recovery should a password be forgotten.
We have already seen that the likes of the NSA can gather metadata on a massive scale, and this is not something that is expected to be affected by increased awareness of encryption:
Metadata is not encrypted, and the vast majority is likely to remain so. This is data that needs to stay unencrypted in order for the systems to operate: location data from cell phones and other devices, telephone calling records, header information in e-mail, and so on. This information provides an enormous amount of surveillance data that widespread.
But the report also includes prophesies that will undoubtedly concern those with privacy fears. Any switch to using encrypted modes of communication will simply make those conducting surveillance pursue other channels. It notes:
Networked sensors and the Internet of Things are projected to grow substantially, and this has the potential to drastically change surveillance. The still images, video, and audio captured by these devices may enable real-time intercept and recording with after-the-fact access. Thus an inability to monitor an encrypted channel could be mitigated by the ability to monitor from afar a person through a different channel.
There is also the problem of fragmentation and a lack of standardization to consider -- as well as differing standards and laws around the world. One of the key points raised by the report is that the idea of 'going dark' -- that the ability to intercept and surveil communication -- is wrong. While current methods and techniques may increasingly fail, there are plenty of other opportunities for surveillance and privacy infringement available now, and on the horizon.
Image Credit: Maksim Kabakou / Shutterstock
-

Does the sight of a cancer patient's nipple offend you? It does Facebook
Publié: janvier 31, 2016, 1:52am CET par Mark Wilson

For all of the social aspects of Facebook, the site does a very good job of failing to fully reflect society as a whole. Part of the reason for this is that Facebook has an ideology, a world view, and a set of values. The social network has a comprehensive list of banned content and there have been countless cases of censorship or removal of user posts for violation of the rules.
Breastfeeding mothers found they were not allowed to post photos of themselves that included even the merest hint of nipple -- this led to the #FreeTheNipple campaign. More recently Facebook decided to ban the private sale of guns through the site, but now the humble nipple is causing upset once again. This time Rowena Kincaid -- suffering from terminal breast cancer -- had photos she had uploaded to Facebook removed. The intention was to educate people about what to look for in terms of symptoms, but the nipple pictures fell foul of Facebook's rules -- it has been dubbed BoobGate.
Rowena has already made a documentary called Before I Kick The Bucket, and she uses a Facebook page to not only keep her followers up to date with her progress and experiences, but also to educate people about cancer. Recently she uploaded a photograph of her breast, showing a rash around the nipples which she points to as a possible symptom of cancer. The aim is to help people to learn what to look out for, but Facebook removed the image because it violated site policy.
The photo managed to attract more than 70,000 views in just a couple of hours before it was removed. Rowena was keen to share her tips about what to look out for, and ended up sharing the same image with the nipple obscured with a smiley face; "If I don't share this, it will die with me," she said.
I learnt after posting the picture how valuable it was. People were getting engaged, it was getting shared. What was coming through was that people only ever knew to look for a lump. But there are other things to look out for: puckering, inverted nipples, pain, a rash. I wasn’t out to offend anyone. [It] looks like something out of a medical journal.

Facebook has refused to comment on the case beyond saying it is investigating. Rowena says that the nudity in her image led to its automatic removal, but this is another case that highlights the limitations of automated systems, as well as the need for Facebook to show far greater 'leniency', particularly when it comes to educational posts. Rowena was doing nothing more than trying to raise awareness of an important medical issue. She deserves praise for her bravery, not censorship from Facebook.
Photo credit: scyther5 / Shutterstock
-

Stop using Microsoft Edge's InPrivate mode if you value your privacy
Publié: janvier 30, 2016, 8:28pm CET par Mark Wilson

It's possible that you reached this article purely by chance, or you may have Googled 'how to change the default search engine in Microsoft Edge'. However you got here, the fact that you're reading this indicates that you're either interested in Windows 10's Edge, or actively use it -- and this means there's something you need to know.
If you fall into the latter camp and use Edge's InPrivate mode to cover your online tracks, you might want to think about changing your web browser. Edge has already got some stick for its lack of extension support -- "it's coming, it's coming!" Yeah, whatever... so's Christmas -- but now it turns out that InPrivate mode is a privacy nightmare. It is possible to peak behind the curtain and see which sites have been visited when using a browsing mode that should mask this.
There are similar features found in other browser. Chrome has Incognito mode, Safari has Private Browsing, Firefox has... actually, Firefox has Private Browsing too. Whatever the name, what these browsing modes all have in common is that once the browser is closed, there is no record of which sites have been visited. That's not to say that ISPs and law enforcement agencies wouldn’t be able to determine the browsing history, but from a local point of view it is as though no browsing has taken place.
But Edge is different.
Somewhat counterintuitively, Edge actually records browsing history in InPrivate mode. More than this, by examining the WebCache file it is a relatively simple task for someone to reconstruct full browsing history, regardless of whether surfing was performed in regular or InPrivate mode.
Over on Forensic Focus, researcher Ashish Singh warns:
The forensic examination of most web browsers has proven that they don't have a provision for storing the details of privately browsed web sessions. Private browsing is provided for a purpose, i.e. privately browsing the web, which is being delivered.
However, in the case of Microsoft Edge even the private browsing isn't as private as it seems. Previous investigations of the browser have resulted in revealing that websites visited in private mode are also stored in the browser’s WebCache file.
NOTE: The Container_n table stores web history. There a field named 'Flag' will be available. A website visited in the private mode will have a flag value as '8'. Generally the purpose of storing this information is to retrieve crashed private sessions.
\Users\user_name\AppData\Local\Microsoft\Windows\WebCache
Therefore any skilled investigator can easily spot the difference and get concrete evidence against a person’s wrongdoings. Plenty of artifacts are maintained by the browser, which makes examination quite easy. However, there are stages where evidence is not so easy to find. The not-so-private browsing featured by Edge makes its very purpose seem to fail.
Microsoft is aware of the problem, and says:
We recently became aware of a report that claims InPrivate tabs are not working as designed, and we are committed to resolving this as quickly as possible.
As is often the case, there is no indication of quite when this might be fixed, but it will be fixed. At some point. But you can't help but ask how such a fundamental aspect of private browsing could be so fantastically borked. It beggars belief.
Photo credit: T.Dallas / Shutterstock
-

Microsoft is still working to fix Surface Book and Surface Pro 4 power management problems
Publié: janvier 30, 2016, 7:15pm CET par Mark Wilson

Surface devices have been in the news for all the wrong reasons recently. As well as false accusations of Surface tablet causing problems at the NFL playoffs, Microsoft has also recalled Surface Pro power cords because of an overheating issue. Some problems are fixed with a little good PR, but other require software fixes.
Just a couple of days ago, Microsoft released a firmware update for Surface Pro 4 and Surface Book. While this addresses problems with Bluetooth performance, battery charging, and wireless issues, it does nothing to resolve the power management and battery drain issues many users are experiencing. Microsoft says a fix for this is still in the works.
Surface Book and Surface Pro 4 owners have reported issues with power management when placed in standby mode. It's a problem that have been known about for some months now, and it sees massive battery drain when the devices should really be using minimal power. But if you're hoping for a quick fix, you might have a wait on your hands.
Writing on its support forums, Microsoft said:
Yesterday our engineering team published some updates for Surface Book and Surface Pro 4. These updates offer refinements to improve battery charging and thermal tuning, wireless and Bluetooth performance, and to the detach-reattach experience on Surface Book. We know some of you are still experiencing issues, including issues related to power management, and we are working to address those as quickly as possible. We’ll publish additional updates as soon as they are ready.
At the moment there is no indication of just when the problem might be addressed, but in the meantime, users continue to experience battery drain of up to 12 percent per hour even when their devices are not in use.
-

LG G3 'Snap' vulnerability leaves owners at risk of data theft
Publié: janvier 30, 2016, 4:32pm CET par Mark Wilson

Security researchers have discovered a vulnerability in LG G3 smartphones which could be exploited to run arbitrary JavaScript to steal data. The issue has been named Snap, and was discovered by Israeli security firms BugSec and Cynet.
What is particularly concerning about Snap is that it affects the Smart Notice which is installed on all LG G3s by default. By embedding malicious script in a contact, it is possible to use WebView to run server side code via JavaScript. If exploited, the vulnerability could be used to gather information from SD cards, steal data from the likes of WhatsApp, and steal private photos.
Researchers identified a number of possible attack vectors, including asking a victim to scan a QR code, or sending a fake contact via WhatsApp or MMS. Liran Segal and Shachar Korot, who discovered the vulnerability, say they contacted LG and the company responded quickly by updating Smart Notice with a patch. The onus is on G3 owners to install the update.
In a blog post, Cynet says:
The root cause for the security problem is the fact that Smart Notice does not validate the data presented to the users. Data can be taken from the phone contacts and manipulated. The attack can take place in several ways due to functionality issues of the Smart Notice application. The application pops notifications (named 'cards') in each of these scenarios:
- Favorite contact notification – Recommends you keep in touch with favorite contacts.
- New contact suggestion – Suggests saving a caller number.
- Callback reminder – Reminder to callback a contact after declining the call.
- Birthday notification – Reminder about contact birthday.
- Memo reminder – Provides notifications about user memos.
The video below from BugSec Group shows how the vulnerability can be exploited:
-

Why did Google give $6,006.13 to MBA candidate Sanmay Ved?
Publié: janvier 30, 2016, 3:41pm CET par Mark Wilson

Google's security bounty programs can be quite lucrative for those who discover problems, and the company has just published a report looking back at the security landscape in 2015. Entitled Google Security Rewards - 2015 Year in Review, the report reveals the financial rewards that have been paid out in the last 12 months.
In all, Google has paid out more than $2 million to more than 300 people, but Sanmay Ved is probably one of the more interesting reward recipients. He's the guy who -- very briefly -- managed to buy Google.com before having it taken off his hands. Google offered him a $6,006.13 reward, but there's a little more to the story.
If you're wondering about the slightly strange amount, Google explains that if you squint and use a little imagination, the figure spells out the word Google. Sanmay decided to donate his reward to charity, and when Google learned about this, the reward was doubled. While Sanmay may have been one of the more unusual reward recipients, Tomasz Bojarski got the crown for the most prolific, discovering no fewer than 70 bugs on Google.
2015 was the year that Android was added to the to the Security Reward program initiative resulting in payments of over $200,000 to researchers. Google shares a graphic that shows some of the highlights from 2015:
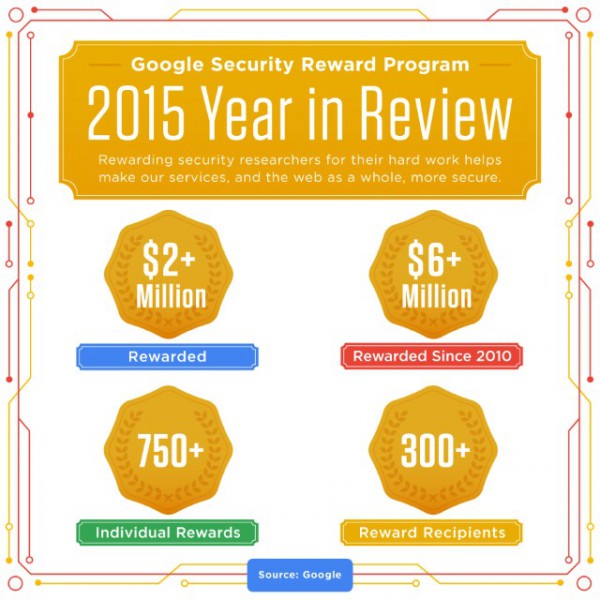
In 2015, Google's Vulnerability Research Grants was used to provide researchers with the funds they need to carry out their work. One example of how these funds were used includes research into a YouTube problem:
We’ve already seen positive results from this program; here’s one example. Kamil Histamullin a researcher from Kasan, Russia received a VRP grant early last year. Shortly thereafter, he found an issue in YouTube Creator Studio which would have enabled anyone to delete any video from YouTube by simply changing a parameter from the URL. After the issue was reported, our teams quickly fixed it and the researcher was rewarded $5,000 in addition to his initial research grant. Kamil detailed his findings on his personal blog in March.
Find out more about Google's reward programs over on the Google Security blog.
Photo Credit: tanuha2001 / Shutterstock.com
-

Facebook irks devs by shutting Parse mobile development platform
Publié: janvier 29, 2016, 5:45pm CET par Mark Wilson

Facebook is closing down Parse, its mobile development platform, just three years after acquiring it for $85 million. The shutdown comes as something of a surprise as it is not long since Facebook was talking about using Parse to make giant steps into the Internet of Things.
But it seems that Facebook's IoT future is going to be one that is Parse-free. The shutdown will take place over the course of the next year, but starts with immediate effect. As of right now Parse is in wind-down mode, and will be fully shuttered by January 28, 2017. Believed to power tens of thousands of mobile apps, the killing of Parse will see Facebook diverting funds to other ventures.
While developers will not be happy with the sudden announcement, they are not being left completely high and dry. The Parse API will continue to function for the time being, and the company is making available its database migration tool to help devs move Parse app data to a MongoDB database. There's also a full migration guide available that details how to use the open source Parse Server to run most of the Parse API from a custom Node.js server.
Announcing the gradual shutdown in a blog post, Parse co-founder Kevin Lacker says:
We have a difficult announcement to make. Beginning today we're winding down the Parse service, and Parse will be fully retired after a year-long period ending on January 28, 2017. We're proud that we’ve been able to help so many of you build great mobile apps, but we need to focus our resources elsewhere.
We understand that this won’t be an easy transition, and we’re working hard to make this process as easy as possible. We are committed to maintaining the backend service during the sunset period, and are providing several tools to help migrate applications to other services.
While it's fair to say that there are alternatives to Parse out there, developers have voiced their anger at the closure. With Amazon, Google and Microsoft all offering their own mobile app development services, it remains to be seen whether Facebook has shot itself in the foot with this closure.
Photo credit: tulpahn / Shutterstock
-

HSBC online banking hit by DDoS attack
Publié: janvier 29, 2016, 3:01pm CET par Mark Wilson

As workers eagerly awaited the arrival of their first payday of 2016, and others rushed to file their tax returns ahead of Sunday's deadline, HSBC's online banking services were knocked offline today.
The banking giant was hit by a DDoS, but it is not yet clear who is responsible. The attack meant that customers were unable to access their online accounts, and it is just the latest in a strong of high-profile security issues to affect well-known sites.
The bank says that while the DDoS attack was certainly problematic, customer accounts were safe: "HSBC internet banking came under a denial of service attack this morning, which affected personal banking websites in the UK. HSBC has successfully defended against the attack, and customer transactions were not affected. We are working hard to restore services, and normal service is now being resumed. We apologise for any inconvenience this incident may have caused".
While HSBC says that it has been able to successfully fight off the cyber-attack, the disruption continues. Users attempting to access their online accounts are greeted by an apologetic message:
Sorry…
We'd like to apologise to all our customers for Online Banking being unavailable.
We know how inconvenient this is and we are doing everything we can to rectify the problem.
Please try later.
The bank also used its Twitter account to reassure customers -- and investors -- that everything possible is being done to find the culprits:
HSBC is working closely with law enforcement authorities to pursue the criminals responsible for today’s attack on our internet banking.
— HSBC UK (@HSBC_UK) January 29, 2016
-

Apple releases surprise update for no-longer-supported OS X 10.6 Snow Leopard
Publié: janvier 29, 2016, 12:56pm CET par Mark Wilson

When it comes to supporting older operating systems (or not), it is usually Microsoft that we are talking about. But this week Apple took its users by surprise by releasing an update to Snow Leopard -- the lengthily-named Mac App Store Update for OS X Snow Leopard.
If you are wondering why an OS update should come as a surprise, it is because support for Snow Leopard came to an end in the latter half of 2013. It is an update that is ostensibly about ensuring continued access to the Mac App Store, but it also helps to give Snow Leopard users an easier path to upgrade to El Capitan.
The update description is short and sweet, and it does not make it sound like anything too exciting. With the most recent versions of OS X delivered through the App Store, and Apple is keen for as many people as possible to run the latest editions, the update makes perfect sense. Apple explains that the (deep breath...) Mac App Store Update for OS X Snow Leopard:
- Installs a renewed intermediate signing certificate required by the Mac App Store. The certificate ensures that you can continue to use the Mac App Store in Snow Leopard to purchase new apps and run any previously purchased apps that use receipt validation.
- Includes improvements to Mac App Store alerts.
Unless you're a PowerPC user, you'll probably want to hit the Apple menu and select the Software Update option.
Photo credit: Mirek Srb / Shutterstock
-

Microsoft's Q2 earnings are hugely impressive, buoyed by cloud revenue
Publié: janvier 29, 2016, 12:15am CET par Mark Wilson

Microsoft's cloud first, mobile first philosophy seems to be paying off. The company today announced its Q2 2016 earnings, with profit and revenue exceeding predictions. Revenue fell very slightly to $25.69 billion, but this was still higher than analysts expected; the slight drop has been partially blamed on a decreased interest in Windows.
Confidence in Satya Nadella's leadership seems high, with stock prices rising by more than 26 percent in the last year. His belief in the cloud appears to be paying off, with Microsoft's Intelligent Cloud business generating revenue of $6.3 billion. Overall, the company expects its entire annual cloud revenue to hit $9.4 billion, up from $8.2 billion.
Looking to the cloud, Nadella said: "Businesses everywhere are using the Microsoft Cloud as their digital platform to drive their ambitious transformation agendas. Businesses are also piloting Windows 10, which will drive deployments beyond 200 million active devices."
Cloud revenue jumped by 5 percent, and Microsoft has a number of highlights in this area:
- Server products and cloud services revenue grew 10% in constant currency
- Azure revenue grew 140% in constant currency with revenue from Azure premium services growing nearly 3x year-over-year
- Over one third of the Fortune 500 have chosen our Enterprise Mobility solutions, up nearly 3x year-over-year
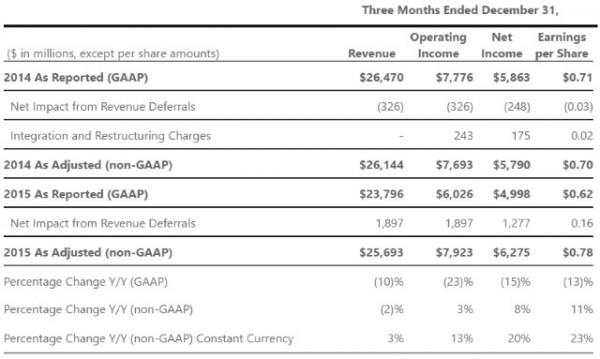
Revenue for Productivity and Business Processes sits at $6.7 billion (down 2 percent), and Office 365 now enjoys 20.6 million subscribers. Personal Computing Revenue is also down, dropping 5 percent to $12.7 billion:
- Windows OEM revenue declined 5% in constant currency, outperforming the PC market, driven by higher consumer premium and mid-range device mix
- Surface revenue increased 29% in constant currency driven by the launch of Surface Pro 4 and Surface Book
- Phone revenue declined 49% in constant currency reflecting our strategy change announced in July 2015
- Search advertising revenue excluding traffic acquisition costs grew 21% in constant currency with continued benefit from Windows 10 usage
- Xbox Live monthly active users grew 30% year-over-year to a record 48 million
In addition to the decreased interest in Windows, the slight fall in revenue has been attributed to shifts in currency, but the company is understandably pleased with the figures. COO Kevin Turner says:
It was a strong holiday season for Microsoft highlighted by Surface and Xbox. Our commercial business executed well as our sales teams and partners helped customers realize the value of Microsoft’s cloud technologies across Azure, Office 365 and CRM Online.
Microsoft stock rose immediately after the earnings announcement.
As well as surprise, analysts were quick to lay praise at Microsoft's door. Patrick Moorhead from Moorhead Insights & Strategy said:
Microsoft’s cloud success can no longer be looked as a “one-off” or luck, it’s becoming a giant business that could give Amazon a run for its money. Amazon is a lot larger, but Microsoft is narrowing the gap.
Microsoft did better than the PC market in operating system licensing revenue than the market, but unless PC units improve, it will be impossible to increase this Windows number. 2016 will be a big year as it is very likely, that if there isn’t a GDP collapse, we will see many businesses moving from Windows 7 to Windows 10.
The company is hedging their PC bets in services like Office 365 and OneDrive which performed great with >50% growth. Their iOS and Android service bets appear to be paying off.
Photo credit: 360b / Shutterstock.com
-

Live video streaming spreads to all mobile Facebook users
Publié: janvier 28, 2016, 11:31pm CET par Mark Wilson
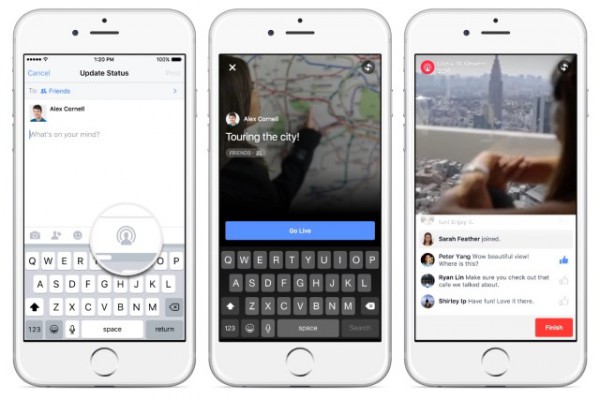
Lights! Camera! Action! Facebook is home to pictures, videos, comments, news, train-of-thought ramblings, and much more. Until recently, videos have been limited to those that have been pre-recorded, but that's about to change.
Facebook recently opened up the ability to share a live video stream to a limited number of people, and the social network is about to expand this. Starting today, live video sharing is being made available to US iPhone users, and it won't be long before the feature is available globally, and also to Android users.
The feature itself is self-explanatory, and started off life as something that was only available to celebrities and key figures with verified accounts. If you can point your mobile phone at something, you can live stream it via Facebook -- be it for the purposes of reporting news, vlogging, streaming an event, or something else entirely.
Introducing the expansion of the feature, product manager Vadim Lavrusik says:
In December, we started testing the ability for people to share live video on Facebook, and it has been inspiring to see all the ways that people have used Live to connect with their friends and family. Today, we’re excited to expand the ability to share live video to everyone in the U.S. via iPhone, and we plan to start rolling this out to the rest of the world over the coming weeks.
Broadcasters can keep track of the number of viewers they have in real time, and when the live stream comes to an end it will be automatically saved as regular video so those who missed it will be able to catch at their leisure.
Look out for the appearance of a new Live Video icon in the Update Status section of Facebook. It's iPhone only for now, but Facebook says "we are working to bring live video to people using Android phones soon".
-

Brace yourself for a Windows 10 crapware explosion -- pre-installing TripAdvisor is just the start
Publié: janvier 28, 2016, 11:54am CET par Mark Wilson

Yesterday, TripAdvisor made a couple of announcements. The first was innocuous enough, letting people know that there was now a TripAdvisor app for Windows 10 available to download for free. Lovely stuff, if you like that sort of thing. The second announcement is less pleasing. It will be "pre-loaded on millions of Windows 10 compatible devices".
This is clearly going to be something that divides opinion, but I don't think I'm alone in thinking that padding out Windows 10 Mobile with crapware might not be the best way to attract users. There's no denying that TripAdvisor can prove useful -- it's helped me to make dining decisions on more than one occasion -- but pre-installed apps are rarely, if ever, a good idea, and Microsoft is hardly in a possible to put a (nother) foot wrong with Windows 10.
One of the problems with pre-loaded apps (and the problems are plentiful), is that the apps tend to be hard-baked into the OS meaning that they're near-impossible to uninstall. It's not yet clear whether this will be the case with TripAdvisor, but it is likely. Regardless of whether TripAdvisor is a permanent fixture or is removable, there is the question of choice. Some people may be quite happy to have the app ready and waiting for them, but what about those who have already tried TripAdvisor and have decided that it's not the app for them, preferring instead to use one of the alternatives? Or those who have no need for such an app in the first place?
Then there is the fact that the pre-installation of any app acts very much like an ad. It's one thing to pre-install apps you've made yourself (although there is still the question of whether it is 'right' to use up storage space that a user might want to use for something else) -- just as Apple and Google do -- but it's a different matter with third-party tools. Of course there is the argument that adding any app to a device is merely adding value, but pre-installation editorializes this process. And let's not forget that TripAdvisor exists to make money -- is it really fair to make Windows 10 users part of this profit-generation by plopping the app icon right in front of them?
The announcement seems innocent enough, but really it's indicative of issues Microsoft is experiencing:
TripAdvisor, the world's largest travel site, today announced the launch of a new Windows 10 app across desktop, tablet and mobile. The TripAdvisor app for Windows 10 will be available in 47 markets and will be pre-loaded on millions of Windows 10 compatible devices in 2016.
For a long time, Microsoft has been criticized for having a problem with apps -- the so-called app gap. People are simply not visiting the Windows Store, and this is something that undoubtedly upsets companies like TripAdvisor. Knowing that very few people are likely to visit the Store, there is perhaps little option other than forcing apps upon users if you want them to gain a following.
Ultimately, the user loses out. Presented with TripAdvisor -- which, let's face it, does a perfectly adequate job -- how many are going to bother seeking out an alternative? In pre-loading apps, Microsoft and its partners are reducing user choice and quashing competition. There are no winners. We can only hope that this is not the start of a slippery slope to a crapware explosion.
For the sake of clarification, TripAdvisor provided the following statement:
The TripAdvisor Windows 10 app is currently available for download through the Windows Store, so we wanted to get the news out to make consumers aware of our new app. The pre-installs will occur throughout 2016 via our distribution partners, not Microsoft.
For users who upgrade to the Windows 10 OS on older devices, they will may find our app on the Windows Store unless they already had the Windows 8.1 app, at which point it will automatically update.
Photo credit: Bloomua / Shutterstock.com
-

Google Cardboard by the numbers: the stats surrounding foldable virtual reality
Publié: janvier 27, 2016, 6:27pm CET par Mark Wilson

In many ways, virtual reality has come a very long way over the past couple of decades or so. But while old VR headsets looked rather techy and somewhat futuristic -- something that is still true of Oculus Rift -- there is also a cheap, simple version made out of little more than cardboard.
Google Cardboard provides smartphone users with a quick, easy and, most importantly, cheap way to transform a handset into a virtual reality unit. Just over a year and a half since the origami VR kit launched, Google shares some statistics about how it has been received and used.
In 19 months, more than five million people have dabbled with Google Cardboard viewers, and there have been more than 25 million immersive apps installed. Perhaps because Cardboard was a great stocking stuffer, the run up to Christmas saw a huge ramping up of app installations -- a jump of around 10 million installations between October and December.
But Google Cardboard is not just about apps -- three quarters of a million VR photos have been uploaded, and Cardboarders have watched more than 350,000 hours of VR videos on YouTube.
The most popular app for Cardboard is Chair In A Room, but Google shares details of the top five:
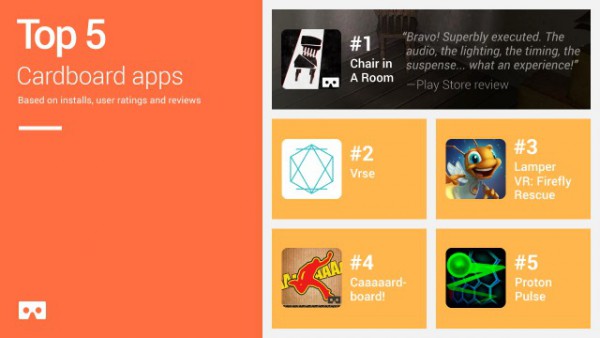
Proving that Cardboard is not just about fun and entertainment, Google also says that half a million students used the VR headset to go on virtual field trips around the world.
Photo credit: Alexandru Nika / Shutterstock
-

Google Play introduces new option to 'like' reviews or mark as spam
Publié: janvier 27, 2016, 6:11pm CET par Mark Wilson

Reviews in Google Play are a useful way to decide whether an app is worth downloading, and to determine whether the developer description is accurate. For some time it has been possible to flag up reviews as unhelpful, but starting today Google is removing this option to take a more positive approach.
Gone is the 'mark as unhelpful', replaced instead by a less prominent Spam option. Now dominant is a Facebook-inspired thumbs up button to indicate that you 'like' a review, or show that it is otherwise imbued with positive virtues. Before you get too excited, it's not yet possible to comment on reviews.
The change was spotted by users on Reddit, and it seems to be gradually rolling out around the world -- although Google has not yet made an official announcement. It appears that Google is trying to push people towards highlighting helpful reviews (be they positive or negative) rather than focusing on the more unhelpful ones. The ability to mark a review as spam is still -- helpfully -- available through a submenu.
While developers are able to respond to reviews with comments this is not something that Google shows any signs of rolling out to a wider audience. For now if you want to provide feedback on an app review, you'll have to limit yourself to giving a thumbs up or marking it as spam.
Photo credit: Gonzalo Aragon / Shutterstock
-

Bittium Tough Mobile is ready to take on Blackphone for the most secure phone crown
Publié: janvier 27, 2016, 3:57pm CET par Mark Wilson

Surveillance, privacy concerns and other issues have brought security into sharp focus for mobile users the world over. Apple, Google and Microsoft all offer encryption options, but for those with real security and privacy worries, the likes of Silent Circle's Blackphone 2 and the ARCHOS GranitePhone have a healthy following. Now there's a new security and privacy-focused handset vying for attention: the Bittium Tough Mobile.
At Mobile World Congress 2016 in Barcelona next month, Bittium will show off not only its secure smartphone, but also its Bittium Secure Suite device management and encryption software. With these and Bittium SafeMove -- a secure remote access tool -- the company hopes to increase business and enterprise confidence in mobile and the Internet of Things.
Bittium Tough Mobile is a hardy device both physically and in terms of security. Built on a secure custom platform, the device offers secure communication for professionals, such as government agents and enterprise users. The handset is packed with security features such as secure boot, runtime integrity, application permission firewall, secure data storage for user credentials and encryption keys, encrypted mass memory, tampering detection, PGP encrypted email, and FIPS 140-2 compliant HW cryptography.
But the Tough Mobile is also extremely robust thanks to its cast magnesium unibody. Bittium lists the following features for the Bittium Tough Mobile:
- IP67 level water and dust protection.
- Glove-usable touch screen, functional also in wet conditions.
- Extremely durable mechanical construction with sophisticated smartphone look-and-feel.
- MIL-STD-810G level shock resistance.
- High-performance speakers and multi-microphone active noise cancellation provides excellent voice call quality also in noisy environments.
- Global connectivity with 9 LTE bands, including commercial bands and LTE band 14 for public safety use.
- Configurable button for PTT, camera, etc.
- Enhanced security with secure boot and runtime integrity check.
- Android 5.1 Lollipop operating system providing smart and simple user experience.
- Qualcomm Snapdragon 801 quad-core processor provides performance for realtime HD video and other demanding use cases.
- Dual-sim allows operating the device in both private and public LTE networks.
- UI customization and branding options available.
- Bittium Tough Mobile is based on the Bittium Specialized Device Platform.
In terms of specs, the handset offers:
- Qualcomm SnapdragonTM 801: Quad-core Krait CPU up to 2.3GHz, Adreno 330 3D graphics accelerator, Hexagon QDSP 600MHz
- 5" Full HD (1080*1920) LCD
- Cameras: 8 MP main camera with Autofocus and LED Flash, 2 MP front-facing camera
- 2GB LPDDR3 PoP RAM
- 16GB eMMC Mass Storage
- micro SD expansion slot
- 2420mAh Li-Ion battery
- LTE: 3GPP rel10 (LTE Advanced); FDD Cat4, DL 150 Mbit/s, UL 50 Mbit/s; IMS, VoLTE-ready
- UMTS/HSPA: 3GPP rel8, HSPA+, DL 42 Mbit/s, UL 5.76 Mbit/s
- GSM/GRPS/EDGE: 850/900/1800/1900MHz
- 0 with fast charging
- Wireless display (Miracast compliant)
- Dual-SIM slots
- Sensors: 3D Gyroscope, 3D Accelerometer, 3D Magnetometer, Proximity Sensor, Ambient Light Sensor, Barometer
- Multi-microphone active noise cancelling
- Dimensions: 141mm x 75.5mm x 13.5mm
- Weight: 180 grams
Bittium also shares details of its Bittium Secure Suite which is designed with handset management in mind, and Bittium SafeMove which it says "provides mobile workforce hassle-free, secure and seamless connectivity to the corporate network regardless of time and place".
Find out more at www.bittium.com.
-

Apple crumbles as iPhone sales growth slows dramatically
Publié: janvier 26, 2016, 11:30pm CET par Mark Wilson

The golden days may be over for Apple when it comes to the iPhone. While rumors may be circulating about the iPhone 7 and the iPhone 5se, it's the sales of current devices that are of interest to not just Apple, but its investors. Today, Apple announced its earnings for Q1 of the 2016 fiscal year -- and it seems as though the iPhone is starting to lose its shine.
While sales have continued to grow, growth has slowed so dramatically that this is slowest period of growth since the iPhone first appeared in 2007 -- rising from 74.5 million a year ago to 74.8 million. And this is not the end of the bad news for Apple; revenue for Q2 is expected to be lower than last year, and we could even see a drop in iPhone sales.
Of course, sales cannot be expected to grow forever. There comes a point when saturation is reached, and Apple will almost certainly be asking itself whether that time has come, or whether it failed to excite enough people with the latest breed of handsets. If the forecasts for Q2 are correct, Apple could be licking its wounds as iPhone sales drop for the first time since launch.
Tim Cook was quick to point to "all-time record sales of iPhone, Apple Watch and Apple TV". These devices helped to drive $75.9bn in revenue and generate no less than $18.4bn in cold, hard profit. These are certainly not numbers to be sniffed at, but chief financial officer, Luca Maestri, said Apple is working in "a very difficult macroeconomic environment".
China, unsurprisingly, has proved pivotal to Apple's continued growth so far. Sales in Greater China (China, Hong Kong and Taiwan combined) increased by 14 percent, but this is much lower than last year's rise of 70 percent.
The growth figures that have been announced can be cut any number of ways, but one thing is for sure: 2016 is going to be an extremely interesting year for Apple.
Photo credit: Namning / Shutterstock
-

6 essential security tips for Data Privacy Day
Publié: janvier 26, 2016, 11:19pm CET par Mark Wilson

Data Privacy Day may not sound like the most exciting event to add to your calendar, but it serves as a hugely important reminder of the value of security. January 28 is the big day, and there has never been a better time to ensure that you are following best practice -- and there's no reason not to get started ahead of time.
35 years ago, Data Protection Day was launched, and over the years this evolves into Data Privacy Day. The aim is to improve privacy and security awareness online, on mobile, and on computers in general. Whatever you use your phone, computer and other devices for, there's plenty you can do to increase your security and privacy.
For the uninitiated, it can be hard to know where to start and what to consider. Even for tech stalwarts it can be helpful to have a reminder of what can be done to increase privacy and security. With this in mind, Kevin Shahbazi, CEO of cloud-based password management system LogMeOnce, has a number of tips to share
- Secure Your Phone with a Passcode and Set a Timeout -- Locking your phone and computer with a password or pin is an obvious, but often overlooked step in protecting your personal information. If someone gets a hold of your phone or computer, a passcode or pin locks them out from actually accessing anything. You should be able to set up a 4-digit or 6-digit PIN. After you set the screen lock on your device, set a timer so that you’re prompted to enter the PIN or passcode after a short period of inactivity.
- Sharing ISN’T Caring -- From your Netflix password to credit card numbers to naked photos, it’s convenient to share content online... but it also comes with tremendous risk. Sharing your personal information through email or text makes you more vulnerable to attack since your accounts are accessible by more than one person. Before you share something think twice. Make sure you trust the person you’re sharing the information with, and share sparingly. And when the person no longer needs the password, it should be updated immediately.
- Take Two Steps Ahead -- Two-step verification, also called two-factor authentication or 2FA, is becoming more and more popular today, and is proving to be an effective method to protecting your passwords. Two-factor verification has two layers of security for optimum protection. It requires a password and username as well as something that only that user has access to, like a one-time code that gets sent to your phone, or your fingerprint. You should enable two-factor authentication for services and apps like your email account or your password manager, as well as set it up to prompt you when taking certain actions on your smartphone like making a payment.
- Always Install Updates -- Operating systems and apps installed on your smartphones, computers and tablets don’t just push out updates to inconvenience you. Companies are constantly updating their software with important patches for vulnerabilities, fixes for bugs and overall performance improvements. Install those updates as soon as you’re prompted so that you’re not risking your privacy or personal information.
- Be Cautious When Using the Cloud -- Storing files has never been easier with the cloud. But by using cloud services like Dropbox you also increase your risks for theft and breaches. Start by securing your data with a strong password that should include a random combination of letters, numbers and symbols. You should password-protect your entire Dropbox folder. Enable two-step verification for an extra layer of security at login and encrypt your data and protect your files with Dropbox security advanced encryption. Be mindful of which of your third-party apps have permission to access your Dropbox. You should make an effort to review your account settings to learn the apps you’ve granted permission to and de-authorize the ones that aren’t absolutely essential.
- Don’t Share Sensitive Data When Using Public WiFi -- Whether you’re at Starbucks or the airport, free WiFi is available almost everywhere you go these days. Using open WiFi is almost unavoidable, so if you’re going to connect to WiFi when you’re on-the-go, know how to do it safely. Don’t access anything sensitive on open WiFi like your bank account. If you absolutely have to, then change your password as soon as you’re on a trusted connection. Turn off WiFi when it’s not in use, so that you don’t accidentally connect to any available network. If you find yourself frequently using public WiFi, you may want to invest in a VPN or Virtual Private Network. This prevents anyone from seeing what you’re doing on your network.
Photo credit: badins / Shutterstock
-

Politicians question Google's 'sweetheart' tax deal
Publié: janvier 25, 2016, 7:05pm CET par Mark Wilson

Late last week, Google agreed to pay £130 million in back tax in the UK. Despite being heralded as a 'major success' by the Tory chancellor George Osbourne, the feeling among politicians is that Google should still pay much more tax. The deal struck between the search giant and HMRC has also been dismissed as "only a start", "breathtakingly complacent", and in need of further explanation.
MP John McDonnell was granted a Commons urgent question on the tax deal, leading to an impassioned debate. MPs said that it appeared the government was giving Google preferential treatment, and that had smaller businesses failed to pay taxes in the same way, they would have found themselves in court rather than at the center of a headline-making deal.
Google has long been criticized for its tax arrangements: the company uses a financing structure that channels some funds through Bermuda where no corporation tax is payable. But while George Osbourne was hoping to bask in the glory of being the man to extract millions from Google, the government refused to agree with his statement that the new deal is a 'major success'.
With some tax experts suggesting that Google's tax bill should be closer to £2 billion, the £130 million squeezed from the company does seem rather meager. Questions were raised about why the UK government was happy to settle for a tax payment of just £130 million, while Italy is seeking in excess of £1 billion.
When pressed in parliament, Financial Secretary to the Treasury David Gauke was not able to say whether Google had broken any laws between 2005 and 2011 but brushed aside claims that a 'sweeheart deal' had been struck. Other MPs accused the government of giving 'mates' rates' on tax to global corporations, meaning smaller businesses were not getting a fair deal. Gauke said that there were no plans to go public with details of how much tax Google owes, saying that if the UK abandons the confidentiality of the tax system, it would "become a less attractive place for companies to operate from".
While many will be pleased that Google has been forced to put its hand in its pocket, this looks like being a debate that will run for some time yet.
Photo credit: Shahril KHMD / Shutterstock
-

In defense of Microsoft: there was no Surface failure at the NFL playoffs
Publié: janvier 25, 2016, 3:42pm CET par Mark Wilson

Brace yourselves: I'm about to stick up for Microsoft. While I'm happy to criticize the company for its failings (and maybe kick it when it's down from time to time), complaints that cropped up over the weekend seem completely unjustified. I'm talking about this weekend's NFL playoffs.
I'm far from being a football (or indeed sport of any description) fan, but my news timeline has been filled with headlines about how Microsoft suffered embarrassment when its Surface tablets (now famously used on the sidelines and mistakenly referred to as iPads) failed during the Broncos-Patriots game. Except the problems that led to an information blackout was absolutely not the fault of Microsoft, or its Surfaces.
The number of news outlets -- including normally reputable, trustworthy sites -- that quickly jumped on the 'bash Microsoft' bandwagon, was astonishing. Even sites that reluctantly admitted that the problems were not down to Surface failure (I'm looking at you Samuel Gibbs at the Guardian) certainly went a long way to make it seem as though Microsoft's tablets were to blame.
The technical issue which meant that information was not fed through to sideline Surfaces lay with the stadium's wireless network -- illustrated perfectly by the fact that the solution to the problem was, initially, to connect the tablets to a wired network. Microsoft is understandably bemused by accusations that the problems were anything to do with the Surfaces themselves. The company issued a statement saying:
Our team on the field confirmed the issue was not related to the tablets themselves but rather an issue with the network. We worked with our partners who manage the network to ensure the issue was resolved quickly.
Despite quoting this statement, Samuel Gibbs goes on to say "whether or not the tablets themselves were at fault..."; they weren't, Samuel, we've just established that! Of course, Mr Gibbs is not alone in the tone he chose to adopt in his article -- there are countless factually incorrect articles out there. In his defense, Gibbs' post is technically correct throughout, but it is written in a tremendously misleading fashion.
The headline screams: "Microsoft Surface tablets offline during Broncos-Patriots NFL playoff".
Yep. Cos the wireless network was borked. But the implication from the headline is that there was Surface failure.
The sub-head continues: "Sponsored Windows tablets fail to provide New England with crucial play information leading to enraged fans, coaching staff and players".
Yes, they did indeed. But again, this is because of the network problems. Sadly the takeaway from this sub-head is 'sponsored Windows tablets fail'.
The first sentence of the article: "Microsoft's Surface tablets went offline at a crucial moment in last night's NFL playoffs...".
Yes, again this is correct, but the implication is that Surfaces were to blame.
Next sentence: "The tablets, which serve images of previous plays with both team's positions, went offline for at least 20 minutes leaving coaching staff and play callers enraged".
Mention the network problems! Mention the damned network problems!
Christ almighty... by all means give Microsoft a kicking, but at least make sure it's justified. I know I'm not alone in feeling this way -- Richard Hay is of a similar mind over on Winsupersite.
-

The clock is ticking for the US to relinquish control of ICANN
Publié: janvier 24, 2016, 7:53pm CET par Mark Wilson

The US is not afraid to throw its weight around; it likes not only to be involved in things, but to be in control. For decades, ICANN (Internet Corporation for Assigned Names and Numbers) -- the non-profit organization that manages IP addresses and domain names -- has been overseen by the US Department of Commerce, much to the chagrin of people around the world. Most upset are those who point to the independent nature of the internet, and the need for any body with global power to be similarly indpendent. Later this year ICANN is set -- at long last -- to completely separate from the US government.
While this does hinge on US government approval, by the end of September, ICANN could instead be in the hands of businesses, individuals, and multiple global governments. While the changing of hands should not alter the way ICANN operates, it is hoped that it will go some way to restoring faith that may have been lost after revelations about online surveillance by the NSA and other US government agencies.
As well as calls from outside the organization, ICANN itself has been seeking independence from the US government for a number of years. In February, Congress will hear plans for how the transition process could work. The current contract between ICANN and the government is due to expire on 30 September -- unless there are governmental protests about how the handover could happen, this deadline should be allowed to naturally expire.
The new arrangement, announced back in March 2014, would introduce a great degree of diversity of oversight, although ICANN insists that despite the involvement of the US government, it has still been able to operate independently. In a recent interview, ICANN chief executive Fadi Chehadé said:
People have aggrandized the role of the US government in what we do. But the change is actually minimal. It's important symbolically because the US was really a steward for the Internet, but for day-to-day accountability, it is minimal.
The change may be minimal, but it is an important one symbolically. Critics of the change (primarily Obama critics) have decried it as the US 'giving up control of the internet', but this is not what's happening at all. Ultimately, this is little more than a common sense PR move that decentralizes control of the internet.
It's a change that makes a great deal of sense. Considering the global nature of the internet, having one country with perceived leverage has understandably raised hackles. Chehadé says:
The status quo was no longer sustainable. The internet is no longer a side show. This is the digital century; it's the next industrial revolution. The prevalence of the internet as a platform that enables the digital century made it incredibly hard for ICANN to continue doing its critical role under the control of one party, whoever that party is, whether it is a government or a company.
Even if suspicions about US governmental involvement in ICANN is completely unfounded, a move to a more diverse structure should mean that it is better at self-policing and allows for far greater transparency and accountability.
Photo credit: Sashkin / Shutterstock
-

With Windows 7 in its death throes, Microsoft reveals the Skylake systems that retain support
Publié: janvier 23, 2016, 5:45pm CET par Mark Wilson

Windows 8.1 is old, Windows 7 is all but decrepit, and Microsoft is now all about Windows 10. The somewhat aggressive pushing of Windows 10 to consumers has been criticized, and this reached something of a head last week when Microsoft announced that nextgen CPUs will only support Windows 10.
Building on this announcement, Microsoft has published a list of more than 100 Skylake systems that will offer Windows 7 and Windows 8.1 support -- until July 17, 2017, that is. In spite of Microsoft's eagerness to push consumers and businesses to Windows 10, there are still dozens of systems from Dell, HP, Lenovo, and NEC that can be configured with the older operating systems.
Contrary to some reports, once July 17, 2017 rolls around, there will be no requirement to upgrade to Windows 10, but failing to upgrade means missing out on support. (It's worth noting that -- despite what some reports would have you believe -- Microsoft is very clear that it will still be possible to continue using Windows 7 and 8.1 on Skylake systems after this date; it is merely "recommended that these systems be upgraded to Windows 10 as soon as possible").
Over on the Skylake support page, Microsoft says:
The following is a list of computer manufacturers (OEMs) who have identified over 100 models of systems with Intel's 6th generation of processors, also known as Skylake, that will be supported on Windows 7 and Windows 8.1. Support will be provided until July 17, 2017 and its recommended that these systems be upgraded to Windows 10 as soon as possible. For more information regarding Microsoft's support lifecycle for Windows, please see the Support Lifecycle FAQ.
For each of the supported systems listed on the OEM pages, the OEM has committed to additional testing, regular validation of Windows Updates, and publishing drivers and firmware for Windows 10 on Windows Update which will help unlock the security and power management benefits of Windows 10 once the systems are upgraded.
Although the list already stretches to three figures, it is not yet complete. As the company explains, "each OEM will periodically update their list of supported systems as new supported models are released".
Photo credit: Stanislaw Mikulski / Shutterstock
-

Google agrees to pay £130m back tax in the UK
Publié: janvier 23, 2016, 1:13pm CET par Mark Wilson

Following an audit of its accounts, Google has agreed to pay £130m ($185m) in back taxes in the UK. The company says that it wants to make sure that it pays the right amount of tax after it faced criticism for not paying its fair share and for having a complicated tax structure.
HMRC (Her Majesty's Revenue and Customs) has been investigating Google for six years. It is one of many large companies to have been criticized for using offshore operations to funnel funds and reduce tax bills. The £130m covers ten years' of underpayment, and Google says it will continue to pay more tax in the UK.
Google is one of several tech companies to have offices in Ireland to help reduce tax bills. In 2014, the value of Google's sales in Britain was £3.8bn, but the company paid just £20.4m in taxes. Moving forward, more sales activity will be registered in Britain rather than Ireland, but the company denies that the back tax payment is an admission of having avoided tax in the past.
A Google spokesperson said:
We will now pay tax based on revenue from UK-based advertisers, which reflects the size and scope of our UK business. The way multinational companies are taxed has been debated for many years and the international tax system is changing as a result. This settlement reflects that shift and is in line with recent OECD guidance.
While the tax payment will come as something of a windfall for the UK government, the figure is already being questioned. Tax experts suggest that Google should be paying many times more tax than it currently does, even once the new arrangement is taken into account.
-

Privacy ombudsman could handle European complaints about US surveillance
Publié: janvier 22, 2016, 8:57pm CET par Mark Wilson

The importance and awareness of online privacy issues have been brought into sharp focus in the 21st century. It's not entirely down to Edward Snowden, but the revelations from the former NSA contractor are a constant reference point for those concerned with privacy, security and freedom of speech.
One of the greatest problems facing anyone trying to tackle the problem of privacy on the web is dealing with the ideologies of different countries, and how this affects data sharing. A level of surveillance that is deemed acceptable in the US, for instance, may be considered completely objectionable in another. The latest suggestion to help overcome this seemingly insurmountable problem is to set up a privacy ombudsman that would be able to handle European complaints and queries about US surveillance.
There have been ongoing talks since the European Court of Justice ruled that the Safe Habour data sharing arrangement was invalid. According to a new report from Reuters, the latest proposal to be floated by the US is the creation of a privacy ombudsman. The independent overseeing body would be charged with not only checking that data transfers between countries were carried out correctly, but also will be handing complaints from Europe.
Talks are still at an early stage at the moment, but Europe will need reassuring about the independence, accountability and transparency of the ombudsman before any deal could be struck. Spokesman for the EU Commission, Christian Wigand, is quoted as saying:
Intense negotiations have been ongoing... we need further clarification on effective oversight and transparency.
Until an agreeable deal for data sharing is found, there is a chance that restrictions could be placed on the movement of data across the Atlantic. On 2 February, a meeting is planned between data protection authorities to decide how data transfers to the US should be handled. It is hoped that talks about a possible ombudsman will be concluded before this date.
Photo credit: Pelykh Konstantin / Shutterstock
-

Netflix starts to block proxy and VPN access
Publié: janvier 22, 2016, 6:40pm CET par Mark Wilson

Just last week Netflix announced plans to clamp down on VPNs and proxy tools. In what appears to be a move to please license holders the company has already started to impose new restrictions.
Some Netflix customers in Autralia who are using the uFlix VPN have noticed that their access to Netflix has been denied. Attempting to access Netflix using the tool results in an error message being displayed: "You seem to be using an unblocker or proxy. Please turn off any of these services and try again". But this is not the end of the story.
As noted by the Verge, uFlix is already aware of the problem, is monitoring the situation, and plans to find a way to get around the block. Writing on the company blog, the uFlix team said: "Some users are starting to have issues with Netflix blocking non-Australian content when going through uFlix. Though it is only affecting a few users at the moment, we expect this number to grow. We are working on a solution to get around these new measures and apologise for the inconvenience to those who are currently only getting Australian Netflix".
Other VPNs and proxies are likely to be targeted by Netflix in the coming weeks and months, but we're probably going to see companies fighting back in much the same way as uFlix. Ultimately, this could descend into a game of cat and mouse, with Netflix imposing a block which is quickly bypassed, replaced with another block, and so on, ad nauseum.
Photo credit: Sukharevskyy Dmytro (nevodka) / Shutterstock
-

Virgin Media says it's not right to advertise broadband speeds that most people cannot get
Publié: janvier 22, 2016, 5:53pm CET par Mark Wilson

The 'misleading' nature of ads for broadband services has been the subject of debate for some time. The 'up to' figures put forward in relation to speed are often so open to interpretation as to render them meaningless. Customers have had enough, and now Virgin Media is ready to fight on their behalf.
Current rules enforced by the Advertising Standards Authority (ASA) permit UK ISPs to make claims about broadband speeds, even if just 10 percent of customers could receive these speeds. Virgin thinks this is unfair and is calling on the ASA to update its guidelines so customers will have an easier time comparing deals.
The company's chief executive Tom Mockridge has used a blog post to appeal to the ASA to clamp down on misleading speed claims. He points to a report from Which? that just 7 percent of broadband customers could receive the highest speed service offered by their ISP. Conversely, he points out, 98 percent of Virgin Media customers can take advantage of the maximum advertised speed. Mockridge says:
To properly compare different broadband offers, consumers need to assess the whole deal: price and speed.
To enable this, the ASA needs to overhaul the outdated rules on broadband speed advertising. Dating back to 2011, the ASA rules allow companies advertise a headline broadband speed if it is available to only 10 percent of customers.
He proudly proclaims that the average maximum speed enjoyed by Virgin Media customers is higher than the speeds advertised. He concludes by saying:
If the ASA is serious it should ensure consumers can compare broadband deals on the things that really matter, and this includes speed.
Photo credit: 4zevar / Shutterstock
-

Google paid $1 billion to Apple so its search would stay on iPhones
Publié: janvier 22, 2016, 2:15pm CET par Mark Wilson

In the smartphone arena, Apple and Google are rivals -- but that doesn't mean they can't have a symbiotic relationship. Longstanding rivalry in mind, many people have questioned why Apple has retained Google as the default search choice on iPhones. The reason is that money talks.
Transcript of a copyright case involving Google and Oracle show that the search giant paid Apple $1 billion in 2014. An agreement is in place that sees Google paying Apple a percentage of the revenue it generates through iOS devices. This is something that has been rumored for some time, but neither Apple nor Google has commented on.
The news comes via Bloomberg which claims Google shares up to 34 percent of its revenue with Apple. Court transcripts from last week show that the arrangement was revealed by Oracle attorney Annette Hurst. Court papers also show that Google tried to get the judge to strike details of the arrangement from the records. The transcript shows that lawyer Robert Van Nest said:
That percentage just stated, that should be sealed. We are talking hypotheticals here. That's not a publicly known number.
The request was blocked, but Apple and Google made a separate appeal on 20 January, saying that: "The specific financial terms of Google's agreement with Apple are highly sensitive to both Google and Apple. Both Apple and Google have always treated this information as extremely confidential".
Bloomberg reports that:
The transcript vanished without a trace from electronic court records at about 3 p.m. Pacific standard time with no indication that the court ruled on Google’s request to seal it.
Apple and Google remain tight-lipped about their relationship.
Photo credit: NuOilSuwannar / Shutterstock
-

Tim Berners-Lee is an idiot for wanting to expose cyberbullies' identities
Publié: janvier 20, 2016, 11:28pm CET par Mark Wilson

While there is greater interest than ever before in online privacy there are also calls from some quarters for people who use the web to be fully accountable. This is part of the thinking behind Facebook's real names policy, and it's also what's driven Tim Berners-Lee -- no less than the inventor of the web -- to call for the identities of cyberbullies to be exposed.
In the wake of gamergate and countless other examples of women being abused online for little more than being women, bullying of school children by their contemporaries, and endless racist, sexist, and politically motivated attacks online, the suggestion might seem -- on the face of it -- to make sense. But it fails to stand up to scrutiny and is likely -- ultimately, if anyone were insane enough to follow his advice -- to be completely counterproductive.
Speaking to the BBC, Berners-Lee singled out those who target women online, saying they should be named and shamed so victims have the opportunity to sue. For the man who paved the way for the likes of Facebook, Twitter, WordPress blogs, and every website you visit, he demonstrates a remarkably unrealistic view of how his baby could -- or in his eyes should -- be policed. He says:
Every society and every social network, every government and every country, is going to have to come to an arrangement, where perhaps people have anonymity initially -- but there is a stronger force which can take it away.
And just who might this 'stronger force' be? Due to the largely unpoliceable nature of the web, dear Tim doesn't have the answers -- he's happy to leave little things like details to other people -- but does suggest that cyberbullies should be "judged by an open, accountable judicial process". Yeah... cos judicial processes never result in mistakes do they? And the web is so understanding when false accusations are made, right?
Just the other day we saw how an innocent man was accused of being a pedophile. There are endless cases of online vigilantism from the likes of Anonymous. But people get things wrong. Once someone is accused of something online, that genie is out of the bottle -- that's not going away. Berners-Lee may say that an "open, accountable judicial process" is needed, but it's not that simple. The police make mistakes, just like everyone does. There are instance of people spending years on Death Row only to have their sentence quashed at the last minute because of new evidence -- and there are more harrowing tales of innocence being proven when it's too late.
The web is an absolutely uncontrollable beast, and Berners-Lee of all people should know this. The option of anonymity is absolutely essential to the web. Yes, this will be abused by some, but that's impossible to avoid. The ease with which anonymizing tools can be used means that it is very simple to make the task of unmasking a cyberbully very hard. Google has suggested pushing the likes of ISIS to the dark web, and this is basically what Berners-Lee's suggestions will do for cyberbullies. Dangle the threat of exposure in front of such people, and they will just be driven further underground, driven to use ever more sophisticated tools to mask their identities and cover their tracks. The suggestions might sound nice, but they are ultimately pointless.
Speaking at the World Economic Forum in Davos, Berners-Lee said:
In some ways law enforcement is easier on the internet than it is in real life.
In some ways, maybe -- but only in an ideal world. Tim, you really must realize that the web not only makes it easier to launch vicious attacks on people, but also that it is laughably easy to hide behind all manner of cloaking tools. In the real world -- the one in which we live -- law enforcement on the internet is a complete bitch.
If you really think you can expose cyberbullies' identities to any positive effect, you are an idiot.
Photo credit: alphaspirit / Shutterstock
-

Google wants to drive ISIS from the open internet to the dark web
Publié: janvier 20, 2016, 5:15pm CET par Mark Wilson

You can say what you like about ISIS, but it certainly knows how to do propaganda. In fact, the group can pretty much sit back with its feet up -- when it's not busy, you know, killing people in increasingly horrific ways -- as web users the world over are only too happy to do the legwork and spread the shocking imagery on its behalf. But Google has had enough and wants to drive ISIS from the web to the dark web.
While many would question the value of pushing the terrorist group further underground and encouraged to use ever-more secretive tools, Google believes ISIS propaganda doesn't belong on the open web, but should only be accessible through the like of Tor. Jared Cohen, director of Google Ideas believes it makes sense to drive Islamic State to the dark web to try to blunt its propaganda.
Cohen made the suggestion during a speech at Royal Institute of International Affairs at Chatham House. It's a proposal which is likely to divide opinion, standing at odds with the idea of freedom of speech whilst having the ultimate aim of reducing terrorism. ISIS has done an incredibly good job of infiltrating the public consciousness through clever use of social media, and the dissemination of shocking footage that people are only too happy to share -- something which "has managed to create an exaggerated sense of their (ISIS) size online".
But Cohen believes that the group should be stopped from taking advantage of the internet as a whole. He said:
What is new is that they're operating without being pushed back in the same internet we all enjoy. So success looks like Isis being contained to the dark web. What Isis is doing is reflective of the times, as opposed to some sort of new sophistication that magically appeared.
Faced with the use of the open web to blatantly seek new recruits, Cohen suggests that the only real way to fight back is to limit the group's audience, and this can only be achieved by limiting it to the dark web. He called on social networks to close down any accounts associated with ISIS. He describes ISIS (incorrectly, many would say) as "not a tech savvy organization", despite having developed its own secure messaging apps.
So the question is, does it make sense to try to cover the public face of ISIS with the aim of reducing terrorist propaganda, or will a shove to the dark web make the task of combating extremism more difficult?
Photo credit: INTUIT PHOTOGRAPHY / Shutterstock
-

Facebook's Android app gains privacy-enhancing Tor support
Publié: janvier 20, 2016, 12:09pm CET par Mark Wilson

Back towards the end of 2014, Facebook unveiled a new .onion address that allowed Tor users to visit the social network securely. Following on from this, the company is now giving Android users the ability to browse the site using Tor and the Facebook app.
Security, privacy and anonymity may be words readily associated with Tor, but few people would use them in the same sentence as Facebook. The social network says that there is increased demand for secure connections to Facebook from Tor-enabled browsers, hence spreading to the largest mobile platform. The news will make some mobile users happy, but there are currently no plans to migrate the feature from Android to iOS.
While the introduction of Tor support does nothing to change Facebook's own privacy policies, it does help to lock down communication further so that it cannot be accessed by third parties. Although initially funded by the US government, the Tor project has proved to be a valuable tool for those looking to evade the eyes of the NSA et al.
A spokeswoman for the Tor Project, Kate Krauss, said:
Everybody in the world needs more privacy online and almost everybody is on Facebook. This will allow people to choose whether to share their location or not. For some people, this is convenience. For others it is lifesaving.
Introducing the new Tor support, Facebook explains how to get started:
We're releasing this feature over the next few days to seek feedback which will help us create a great experience for using Facebook over Tor on Android. To get started you can head over to Google Play or the Orbot F-Droid repository and download Orbot: Proxy with Tor.
You can also find more instructions on the Tor Project’s Android page.
After installing Orbot, visit your Facebook “App Settings” menu to enable the feature using a new preference switch. Further information and updates will be posted on the Facebook over Tor page.
Photo credit: tulpahn / Shutterstock
-

Twitter suffers global outages
Publié: janvier 19, 2016, 1:06pm CET par Mark Wilson

For many people around the globe, Twitter was inaccessible today. The site suffered problems that affected its web and mobile faces, and it didn’t take long for the #twitterdown hashtag to start trending.
The problem was confirmed -- somehow -- on Twitter by the Twitter Support account, and the developer API status page showed that there were issues with no fewer than four APIs. On Monday, Twitter suffered a brief outage, but Tuesday's was rather longer.
Monday's issue lasted just ten minutes and was resolved without explanation, but today's problem is rather more long-lived. The infamous fail whale made an appearance as APIs suffered what has been described as "performance issues" leading to "service disruption". Both the Twitter Status page and the Twitter Support account displayed the same message:
Some users are currently experiencing problems accessing Twitter. We are aware of the issue and are working towards a resolution.
— Twitter Support (@Support) January 19, 2016
While Twitter seems to be back to normal for users in some parts of the world, the problems are ongoing in others. The cause of the outage is not yet known.
Photo credit: 360b / Shutterstock
-

AMD says SYSmark benchmarks are Intel-biased and don't reflect real-world usage
Publié: janvier 19, 2016, 11:51am CET par Mark Wilson
 Chip maker AMD has complained that the popular benchmarking tool SYSmark is biased toward rival Intel. The company says that the software focuses far too much on CPU activity and that this is not reflective of real-world computer use.
Chip maker AMD has complained that the popular benchmarking tool SYSmark is biased toward rival Intel. The company says that the software focuses far too much on CPU activity and that this is not reflective of real-world computer use.In a stern video, John Hampton and Tony Salinas from AMD compare SYSmark benchmark with results from Futuremark's PCMark 8 as well as scripts devised in-house. Comparing an Intel Core i5 with a 'comparable' AMD FX chip, SYSmark was found to report a much greater performance difference -- in Intel's favor. AMD describes this as "quite astonishing and not realistic".
While SYSmark showed a performance score difference of around 50 percent, when the same chips were compared in PCMark 8 the 'delta' (as AMD describes it) drops to just 7 percent. Similarly, when comparing the performance of AMD and Intel chips using scripts that run Microsoft Office-based tasks, the difference was between 6 and 7 percent.
AMD not only suggests that SYSmark's results are unrealistic, but says tests are geared in favor of Intel chips. The company recommends people read an FTC statement which says SYSmark "may have been optimized for performance only on Intel microprocessors".
Check out the video, entitled Truth or Myth?: Is SYSmark a Reliable Benchmark?, to see what you think:
-

Apple dismisses diversity proposal to shake up board of directors as 'unduly burdensome'
Publié: janvier 18, 2016, 5:25pm CET par Mark Wilson

A call by shareholders to do more to increase diversity on Apple's board of directors has been soundly rejected by the company. The board is currently predominantly white and male, leading to calls for an "accelerated recruitment policy requiring Apple to increase the diversity of senior management and its board of directors".
But in a proxy statement, the board can be seen to have voted against the proposal, saying that it would be "unduly burdensome and not necessary because Apple has demonstrated to shareholders its commitment to inclusion and diversity". The result of the vote will come as something of a surprise as Tim Cook has admitted that the company has much to do to improve diversity.
Shareholders suggest that the board of directors and senior management "presently fail to adequately represent diversity (particularly Hispanic, African-American, Native-American and other people of colour)". Voicing the proposal, shareholder Antonio Avian Maldonado says:
Shareholders' view of diversity -- that everyone matters (irrespective of colour, race, sex, creed or religion) -- recognizes the Company's commitment to diversity and the uniqueness of experience, strength, culture, thought and commitment contributed by each employee; however, it does not ignore the Company's senior management and board of directors diminutive level of diversity and its painstakingly slow implementation.
Overall, by its own public disclosure, the number of minorities holding senior management-level positions or board of directorship within the Company does not reflect the Company's demographic data.
Apple rejects the suggestion, saying that its approach to diversity is "much broader than the 'accelerated recruitment policy' requested". The company -- seemingly missing the point of the proposal -- says that it is interested in addressing diversity across Apple as a whole, pointing to scholarship schemes it runs to attract students from Historically Black Colleges and Universities (Apple's capitalization).
In its proxy statement issued ahead of February's shareholder meeting, Apple concludes by saying:
This proposal would require the Board to adopt an accelerated recruitment policy for increasing diversity among senior management and the Board. We believe that the proposal is unduly burdensome and not necessary because Apple has demonstrated to shareholders its commitment to inclusion and diversity, which are core values for our company.
Photo credit: Terrance Emerson / Shutterstock
-

BlackBerry denies existence of security backdoors and blames 'cracked' encryption on user error
Publié: janvier 18, 2016, 1:49pm CET par Mark Wilson

BlackBerry has spoken out to deny claims that its encryption has been cracked by groups associated with the police in the Netherlands. The company has long-prided itself on the level of security it offers, but that security has been called into question recently.
Reports circulated that Mexican drug lord El Chapo was able to be found partly because of his decision to use a BlackBerry (specifically a BlackBerry Z30, fact fans) to arrange interviews with actor Sean Penn. Coming after claims by the Netherlands Forensic Institute (NFI) that it had been able to decrypt hundreds of encrypted emails on a BlackBerry handset, the Canadian company felt compelled to respond -- by blaming user error.
In a statement in a blog post, the company said: "BlackBerry does not have any details on the specific device or the way that it was configured, managed or otherwise protected, nor do we have details on the nature of the communications that are claimed to have been decrypted".
BlackBerry goes on to say:
If such an information recovery did happen, access to this information from a BlackBerry device could be due to factors unrelated to how the BlackBerry device was designed, such as user consent, an insecure third party application, or deficient security behavior of the user.
Furthermore, there are no backdoors in any BlackBerry devices, and BlackBerry does not store and therefore cannot share BlackBerry device passwords with law enforcement or anyone else. In other words, provided that users follow recommended practices, BlackBerry devices remain as secure and private as they have always been.
Enough to calm the fears of the security-conscious? That remains to be seen.
Photo credit: Maksim Kabakou / Shutterstock
-

Unable to spark interest in Windows 10 Mobile, Microsoft infects iOS and Android like a cancer
Publié: janvier 17, 2016, 2:02pm CET par Mark Wilson

At the moment, Microsoft is all about Windows 10. Such is the company's focus on its desktop operating system, that you would be forgiven for forgetting that Windows 10 Mobile is on the way as well. But here Microsoft has a problem. Not only has Windows 10 Mobile failed to infiltrate the public consciousness, those who are aware of the impending release are singularly indifferent to it.
Clearly Microsoft is not happy about this, but there's not much that can be done to force people into using Windows 10 Mobile (although given the company's track record with pushing Windows 10 to desktops, nothing would come as a surprise). Instead, Microsoft is having to content itself by spreading cancerously to iOS and Android, spreading the diseases of Cortana, the Word Flow keyboard and more to rival platforms.
Microsoft recently released the AppComparison app for Android in a bid to tend people away from Google's Mobile operating system over to Windows 10 Mobile. The idea is to highlight just how many familiar apps are available for the mobile version of Windows 10, but really Microsoft is happy enough to get people using its mobile offering by proxy. The company knows full well that it will be a cold day in hell before there is a mass swing away from Android and iOS to Windows 10 Mobile, so it is contenting itself by infecting rival app stores with ported versions of Windows 10 Mobile apps.
We have already seen Cortana make its way to both iOS and Android. This is more than just Microsoft trying to offer an alternative to Siri and Google Now, it's the company trying to get Windows 10 Mobile features to people through the back door. Windows 10 Mobile is not a big seller but by pulling out key features and transplanting them to other platforms, Microsoft is able to advertise the things it is proudest of.
This is certainly not the first time we've seen Microsoft showing an interest in platforms other than its own. There was some upset from Windows Phone fans when the company decided to bring mobile versions of Office to iOS and Android first. Shoving Cortana onto Google and Apple handsets is, presumably, a move by Microsoft to push Windows 10 Mobile down people's throats. Now there is news that Windows 10 Mobile's Word Flow keyboard is making the jump to iOS and then spreading to Android. Even the likes of Microsoft Selfie are not Windows 10 exclusives.
But there Microsoft's advertising-by-osmosis approach also serves to highlight another issue with the mobile arena at the moment. There are three broad camps to choose from (four if you are mad enough to include BlackBerry), but despite paying their money and making their choice, users are still demanding -- or being told they want --- the same apps to be available on every single platform. We're being presented with dull, dull, dull, homogeneity.
Google and Apple already have a firm foothold. Android and iOS can afford to share features, to be a little similar to one another. But Microsoft does not have this luxury. It is fighting an uphill battle to bring Windows 10 Mobile to public attention and to do this, it really needs to be different -- something it will completely fail to do if features and apps keep being ported to other platforms.
Microsoft has turned Windows 10 Mobile into a cancer, and the approach the company is taking means that in all likelihood the prognosis is terminal.
Photo credit: Tatiana Shepeleva / Shutterstock
-

ISIS has its own secure messaging system -- this illustrates the futility of communication surveillance
Publié: janvier 16, 2016, 4:01pm CET par Mark Wilson

Moves by governments to monitor web-based communication with a view to thwarting terrorism is utterly, utterly futile. Just like the NSA's dragnet-style dredging for intelligence, mass communication surveillance does little to home in on target -- the ones that government should be concerned about are the very ones who know who to evade detection.
This is something that was perfectly demonstrated this week when it became apparent that ISIS has developed its own secure messaging system. No longer reliant on the likes of WhatsApp, ISIS is using a custom-built, Android-based encrypted messaging tool that is incredibly difficult -- if not impossible -- for the FBI and NSA to monitor.
The news comes from Ghost Security Group, and the counterterrorism network that warns about the capabilities of ISIS. It is the result of having such a high-profile surveillance campaign; the very people who governments might want to monitor have been driven underground. ISIS has already proved itself to be a master manipulator of the media, and the group is also technologically savvy. If the reports about the development of its own messaging app are correct, any surveillance has been rendered impossible.
Of course, this does not mean that surveillance is going to stop -- the government has plenty of other targets to go after besides ISIS -- but it does highlight a serious issue for intelligence agencies. Surveillance, hacking, and tapping are now so well known that any group worth its salt is going to go the extra mile to ensure that it can slip under the radar.
Using a roll-your-own solution means that the government is not able to make formal requests of a company to hand over encryption keys, to provide backdoors, or give up user account information. There's no real solution that the government could employ -- this is a problem largely of its own making, and there is little to be done.
Online surveillance is pointless. It is more trouble than it is worth, and it has been for some time. Of course, you won't hear an admission of futility from the government any time soon…
Photo credit: lavitrei / Shutterstock
-

Microsoft gets aggressive -- after 18 months nextgen CPUs like Skylake will only support Windows 10
Publié: janvier 16, 2016, 1:32pm CET par Mark Wilson

Microsoft's aggressive pushing of Windows 10 is becoming legendary, with everything from irritating nag screens, to automatic downloading of set up files. Now things are taking a slightly different turn as the company says that after July 17, 2017, 6th generation Intel Core Skylake processors and other nextgen CPUs will no longer be supported for Windows 7 and Windows 8.1.
The announcement comes somewhat out of the blue, and is all the more surprising considering Microsoft's track record of lengthy support periods. Once the new deadline is reached, Microsoft says that it will only release the "most critical" security patches to these now-unsupported platforms, and even then the patches will only be made available if they do not "risk the reliability or compatibility" of other systems.
Microsoft has been boastfully shouting about how many Windows 10 installations there have been since launch, but this latest move suggests that things are not moving as quickly as expected in the enterprise arena. In a blog post entitled Windows 10 Embracing Silicon Innovation, Executive VP Terry Myerson announced a number of "clarifications to [...] support policy". Of course, there is nothing to stop owners of nextgen processors from installing Windows 7 or 8.1 -- it just means that there will be no support from Microsoft. The company does provide some explanation for the decision, but it is likely to lead to further questions:
At the same time, we know many of these customers continue to rely on Windows 7 for its well understood reliability and compatibility. Windows 7 was designed nearly 10 years ago before any x86/x64 SOCs existed. For Windows 7 to run on any modern silicon, device drivers and firmware need to emulate Windows 7's expectations for interrupt processing, bus support, and power states -- which is challenging for WiFi, graphics, security, and more. As partners make customizations to legacy device drivers, services, and firmware settings, customers are likely to see regressions with Windows 7 ongoing servicing.
It's interesting to note that while Windows 7 is singled out for its "understood reliability and compatibility", the same description is not applied to Windows 8.1 despite it receiving the same support treatment. For home users this is unlikely to be too much of an issue -- although obviously there are some people who will be affected -- but it is a different story for enterprise customers. With this in mind, Microsoft has created a program that means the company will provide support for a range of Skylake devices, as detailed by PC World:
- Dell Latitude 12
- Dell Latitude 13 7000 Ultrabook
- Dell XPS 13
- HP EliteBook Folio
- HP EliteBook 1040 G3
- Lenovo ThinkPad T460s
- Lenovo ThinkPad X1 Carbon
- Lenovo ThinkPad P70
This list, which Microsoft will continue to update, specified which devices will be singled out for special attention.
For the listed systems, along with our OEM partners, we will perform special testing to help future proof customers' investments, ensure regular validation of Windows Updates with the intent of reducing potential regressions including security concerns, and ensure all drivers will be on Windows Update with published BIOS/UEFI upgrading tools, which will help unlock the security and power management benefits of Windows 10 once the systems are upgraded.
Microsoft's announcement is an interesting one -- not just for what it means, but for the way in which it was delivered. This is a fairly significant change (or 'clarification' if you like) to support policy, but it was hardly shouted from the rooftops. The blog post from Myerson also manages to bury the meat of the announcement by starting off with singing praise from partners and customers about how excited they are to be working with Microsoft and upgrading to Windows 10.
The post is also used to 'clarify' the Windows support policy:
- Windows 7 will continue to be supported for security, reliability, and compatibility through January 14, 2020 on previous generation silicon. Windows 8.1 will receive the same support through January 10, 2023. This includes most of the devices available for purchase today by consumers or enterprises.
- Going forward, as new silicon generations are introduced, they will require the latest Windows platform at that time for support. This enables us to focus on deep integration between Windows and the silicon, while maintaining maximum reliability and compatibility with previous generations of platform and silicon. For example, Windows 10 will be the only supported Windows platform on Intel’s upcoming “Kaby Lake” silicon, Qualcomm’s upcoming "8996" silicon, and AMD’s upcoming "Bristol Ridge" silicon.
- Through July 17, 2017, Skylake devices on the supported list will also be supported with Windows 7 and 8.1. During the 18-month support period, these systems should be upgraded to Windows 10 to continue receiving support after the period ends. After July 2017, the most critical Windows 7 and Windows 8.1 security updates will be addressed for these configurations, and will be released if the update does not risk the reliability or compatibility of the Windows 7/8.1 platform on other devices.
As noted by Anantech, it is a little surprising that an announcement has not been forthcoming from Intel. But it does mean that fingers of blame will be pointed at Microsoft rather than individual manufacturers when companies discover that their hardware is no longer supported by the operating system they want to use. Is it a smart move on Microsoft's part that will ultimately be well-received, or is it a worrying development that sees the company exerting too much control over enterprise customers? Only time will tell.
Image credit: ollyy/Shutterstock
-

Interactive Advertising Bureau 'dis-invites' Adblock Plus from annual conference
Publié: janvier 15, 2016, 8:09pm CET par Mark Wilson

Adblock Plus has been blocked from attending the IAB's (Interactive Advertising Bureau) upcoming leadership summit. The company has attended the meeting in the past, and had received an invite to this year's conference too -- but the IAB had a change of heart and retracted the invitation.
The meeting would have been an opportunity to meet with advertisers and to discuss Adblock Plus' Acceptable Ads guidelines later this week, but the IAB -- for reasons as yet undisclosed -- feels differently. In the interests of transparency (or airing dirty laundry in public, depending on your opinion), Adblock Plus has decided to go public with what's been happening.
The company is upset at having been shunned, and accuses the trade organization of not having the "cojones to allow dis-senting voices to be heard". The accusation here is clearly that Adblock Plus feels the IAB is shutting it out because its product stands in the way of what its members are looking to do.
In a blog post, Ben Williams from Adblock Plus says:
Unfortunately, the top brass at the US IAB don't want us coming to their Leadership Summit next week in Palm Desert, California. We attended last year, and we signed up again for their 2016 meeting... including paying the hefty entrance fee. We were fully confirmed and they even listed us on their website as a participant.
Then this week we got one of those sudden emails that land in your inbox innocently, then floor you with something weird, unbelievable or ridiculous when you click on them. This one came from an unfamiliar IAB address, and it informed us that our registration for the summit was canceled and our fee refunded.
The initial email from IAB gives no detail about why the registration has been canceled:
We are returning your registration fee and canceling your registration for the IAB Annual Leadership Meeting.
Adblock Plus was a little surprised at receiving this email out of the blue and responded to indicate that a refund and cancellation had not been made. IAB replied bluntly, offering no further detail:
I'm sorry if there is any confusion. Just to be clear, there will be no ticket available for you and we've refunded your registration fee.
IAB doesn’t seem to want to say any more than this, but Williams says that Adblock Plus's door remains open:
Dis-allowing Adblock Plus from attending your event solves nothing. We will proceed to work with others to build a sustainable monetization model for the Internet.
As always, you know where to reach us.
Photo credit: Jakkrit Orrasri / Shutterstock
-

At long, long last, Google Play gains promo codes for apps and games
Publié: janvier 15, 2016, 3:19pm CET par Mark Wilson

Google has finally caught up with Apple, and is now offering support for promo codes in Google Play. This is a feature that has long been available to iOS users, but it's only after years of complaining that Android users are, at long last, being afforded the same luxury.
Oddly, Google has decided to place some restrictions on how promo codes can be used. While developers can generate codes that can be used to purchase apps or to make in-app purchases, they are limited to creating 500 codes per quarter.
The promo code creation feature has been added to the Google Play Developers Console, and there are further limitations to their use. Promo codes cannot be used for subscription content, and if any of the permitted 500 codes remain unused at the end of a quarter, they are lost forever -- they do not roll over.
Details of how promo codes work can be found on the Developer Console help pages, and from here we learn that developers have the option of setting expiry dates for the codes they create. Promotions can also be paused, and codes are valid for up to a year.
With this feature now available to developers, it shouldn’t be long before we start to see free giveaways, although the restriction on the number of codes that can be used will limit just how wide-reaching such promotions can be.
Photo credit: Bloomua / Shutterstock
-

BT's merger with EE gains official clearance -- and industry objections
Publié: janvier 15, 2016, 1:29pm CET par Mark Wilson

The Competition and Markets Authority (CMA) has given BT the go-ahead for a takeover of EE. The merger of the largest mobile provider in the UK with the country's largest landline provider creates a giant that rivals are concerned about.
The newly conceived communications behemoth has fingers in not only mobile and landline pies, but also TV and broadband. While the CMA's decision is not a surprise, rivals such as Vodafone, TalkTalk and Sky have voiced their disapproval, saying that the merger will have a negative impact on competition.
There are concerns that the merged companies will hold an unfairly high percentage of the 3G and 4G spectrum, and that BT EE will wield too much power over the rest of the industry. John Wotton of the CMA says that "the evidence does not show that this merger is likely to cause significant harm to competition or the interests of consumers", but not everyone agrees.
Dan Howdle from consumer mobile and broadband advice site Cable.co.uk says:
There can be no doubt as to the power over the UK consumer telecoms market BT EE now wields. Which is precisely why the wider industry has persistently urged the CMA not to rush ahead with this decision, but to take into consideration, and to fully explore their commonly held objections.
Sky, for example has been at pains to point out that not only are there -- in its opinion -- "fundamental flaws" in the economic analysis performed by the CMA, but that the CMA itself contains dissenting members who appear to share the view that the merger will prove a disaster for UK telecoms, and in turn for consumers.
The CMA believes the new merged company is, by default, financially incentivised to continue to supply wholesale services to other providers (Virgin Mobile, for example runs on the EE Network), which will prevent it from closing its doors to third-party operators in an attempt to monopolise its own network infrastructure.
The greatest concern for its competitors, then, is that, though unlikely -- as the CMA points out -- no firm measure has been put in place to actively prevent it.
Despite the objections that have been -- and continue to be -- voiced, the CMA says its decision comes as a result of "complex, detailed and rigorous" assessment of the market. The CMA's full report is available to read on Gov.uk.
Photo credit: chrisdorney / Shutterstock
-

Proxies and VPNs to be blocked by Netflix
Publié: janvier 15, 2016, 12:51pm CET par Mark Wilson

Netflix is set to clamp down on VPNs and proxy tools used to access its services. A large proportion of Netflix content is region specific, and to get around licensing issues it has become increasingly common for people to spoof their location so they can watch their desired videos.
Netflix says it is doing what it can to ensure that people around the world have access to the same content, but until this is officially the case, the company is looking to enforce geographic restrictions more stringently. In the coming weeks, anyone who uses a proxy is likely to find it impossible to access content that is not licensed for viewing in their country.
Announcing the hardening of policy in a blog post, Netflix Content Delivery Architecture VP David Fullagar says that "given the historic practice of licensing content by geographic territories, the TV shows and movies we offer differ, to varying degrees, by territory. In the meantime, we will continue to respect and enforce content licensing by geographic location".
He goes on to say:
Some members use proxies or "unblockers" to access titles available outside their territory. To address this, we employ the same or similar measures other firms do. This technology continues to evolve and we are evolving with it. That means in coming weeks, those using proxies and unblockers will only be able to access the service in the country where they currently are. We are confident this change won’t impact members not using proxies.
We look forward to offering all of our content everywhere and to consumers being able to enjoy all of Netflix without using a proxy. That's the goal we will keep pushing towards.
While Netflix may not directly lose out when people circumvent geographic restrictions, the company needs to take a harder line in order to placate content producers who are unhappy with the global availability of their shows and movies. The move is unlikely to go down well with Netflix users who travel abroad, as it is probably going to interfere with their ability to access their account whilst on the road.
But there are also concerns about plans to clamp down on the use of VPNs (which Netflix confirmed to Ars Technica). Such tools are used by people concerned about their privacy, and with Netflix admitting that it's "hard to filter those folks out", this is something that could drive customers away. VPNs are also used by people to avoid ISPs' 'traffic shaping', but this is also something Netflix will not be able to distinguish -- is a VPN being used for legitimate reasons or not?
Photo credit: Sukharevskyy Dmytro (nevodka) / Shutterstock
-

Microsoft starts a renewed Windows 10 push aimed at businesses
Publié: janvier 14, 2016, 12:31pm CET par Mark Wilson

Microsoft has been quick to brag about the adoption rate of Windows 10, proudly crowing every time another few million devices make the upgrade. We're currently sitting at around the 200 million mark (apparently), but the bulk of this number is made up of home users. Now Microsoft wants to encourage more businesses to make the jump from Windows 7 and Windows 8.1.
The next leg of the company's aggressive Windows 10 campaign is aimed squarely at SMBs who can now expect to be pestered by the "Get Windows 10" app in the same way as non-business users have for the last six months. Aware that taking the upgrade process out of the hands of IT admins might not go down too well, Microsoft is providing a way to opt out of these notifications.
The app is not going to be pushed to enterprise users as they are not entitled to a free upgrade to Windows 10, but other business users can expect to see it soon providing they meet a few criteria. In addition to running Windows 7 or 8.1, a computer must be configured to receive updates directly from the Windows Update service, and have joined an Active Directory domain.
Microsoft says:
Because of ongoing customer requests from many small businesses and other small organizations to easily take advantage of the free upgrade, we will soon make the Get Windows 10 app available to them as well.
Like consumers, small businesses and organizations will soon be able to receive notifications about the upgrade and then directly upgrade to Windows 10 through an easy-to-use interface right from the system tray on their Windows 7 Pro or Windows 8.1 Pro PC.
We will begin to roll out the "Get Windows 10" app to additional devices [...] in the US later this month and in additional markets shortly thereafter.
The company provides details of how to prevent the installation of the "Get Windows 10" app for businesses who either want to take care of the upgrade manually, or who just want to avoid Windows 10 altogether.
Photo credit: Roobcio / Shutterstock
-

Sharing ransomware code for educational purposes is asking for trouble
Publié: janvier 13, 2016, 6:21pm CET par Mark Wilson

Trend Micro may still be smarting from the revelation that there was a serious vulnerability in its Password Manager tool, but today the security company warns of the dangers of sharing ransomware source code.
The company says that those who discover vulnerabilities need to think carefully about sharing details of their findings with the wider public as there is great potential for this information to be misused, even if it is released for educational purposes. It says that "even with the best intentions, improper disclosure of sensitive information can lead to complicated, and sometimes even troublesome scenarios".
The warning may seem like an exercise in stating the bleeding obvious, but it does serve as an important reminder of how the vulnerability disclosure process should work. When it comes to security holes in software, there is usually a 90 day disclosure period during which the discoverer will warn the company responsible for it, before then going public.
But the same cannot be said of malware such as ransomware. Unlike software vulnerabilities -- which can usually be fairly easily patched -- publicizing the inner workings of malware can have far-reaching consequences. While antivirus vendors can push out updates to offer protection against known variants, sharing the source code for ransomware greatly increases the chances that more examples of the malware will be created, making it harder to fight.
Writing on the TrendLabs Security Intelligence Blog, Trend Micro says that providing source code replete with warnings about how it should or should not be used is simply not good enough:
Unfortunately, anyone on the internet can disregard this warning. This became evident when Trend Micro discovered a hacked website in Paraguay that distributed ransomware. Our analysis showed that the website was compromised by a Brazilian hacker who used a modified Hidden Tear code.
The website has been compromised since Sept. 15 to Dec. 17 at the latest. It was compromised once again on December 18. The website redirects users to a fake Adobe Flash download website where they are prompted to download a new Flash player. Once the download is complete, the file will automatically run.
In this instance, the Hidden Tear ransomware in question had been shared on Github. Trend Micro recognizes the value in sharing information about how ransomware works with a view to building up protection, but says that this also opens up the possibility of exploitation by bad actors. Martin Roesler, Trend Micro Senior Director for Threat Research says:
We need to share knowledge that creates understanding about potential damage, but not the ability to create it. We need to share knowledge about 'who exploits work', but not 'how to make use of them'. We need to share knowledge 'how malware works', but sharing 'sample code' is not needed for that.
The advice is to share detailed information through secure channels, and only go public with vaguer information.
Photo credit: Nicescene / Shutterstock
-

Updated Android.Bankosy malware steals passwords sent through voice calls
Publié: janvier 13, 2016, 1:26pm CET par Mark Wilson

Around a year and a half ago, Symantec warned about the personal data stealing malware Android.Bankosy. Now the Trojan has been updated so it can steal passwords delivered via voice call-based two-factor authorization systems.
Such 2FA systems are often used by banks to communicate one-time passcodes to people. While these have usually been delivered via SMS, voice call delivery is becoming increasingly common. Malware makers are keen not to miss out on data stealing opportunities, and the Android.Bankosy introduces a call-forwarding feature that sends 2FA calls to a C&C server so the code can be intercepted and exploited.
The malware enables call-forwarding on an infected phone, and is also able to enable silent mode to avoid alerting a victim about incoming calls. A successful attack is dependent on a victim's basic login credentials having already been stolen, but the malware represents a worrying new development in breaking through banking security.
Detailing how Android.Bankosy works, Symantec's Dinesh Venkatesan says:
Once the malware is installed on the victim's device, it opens a back door, collects a list of system-specific information, and sends it to the command and control (C&C) server to register the device and then get a unique identifier for the infected device. If the registration is successful, it uses the received unique identifier to further communicate with the C&C server and receive commands.
Most of the commands supported by the malware are common and trivial for typical back door or financial Trojans, such as intercepting incoming SMS, deleting SMS messages, wiping the data, etc. Out of these multiple commands, the most relevant for Android.Bankosy is call_forwarding; when this command is received by the malware from the C&C server, it executes a payload to enable call forwarding.
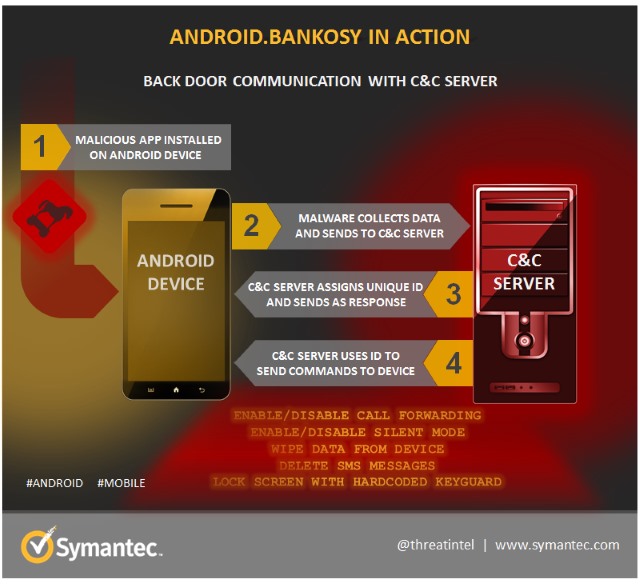
Full details of the malware is available from Symantec.
Photo credit: Mmaxer / Shutterstock
-

Police could tap into router data to verify digital alibis
Publié: janvier 12, 2016, 1:05am CET par Mark Wilson

Law enforcement agencies are missing out on a vast amount of valuable data that could be used to convict criminals, or prove innocence. Dan Blackman from Edith Cowan University, Australia says that police are missing out on swathes of data that could be gathered from Wi-Fi devices.
For privacy advocates it's a suggestion that is likely to make the gag reflex kick in, but Blackman says that router data could be a valuable tool in fighting crime. Information such as device MAC addresses, coupled with data about connections to routers can be used to place individuals at the scene of a crime -- or away from it -- but timeliness is the key to success.
As well as attending university, Blackman also acts as a technical advisor to Western Australian police, and he says that router data could be even more useful than GPS data. But there's a problem. While routers represent a goldmine of information -- making it possible to prove when particular devices were connected -- limited memory on older devices means that this data does not stick around forever.
Blackman says:
These devices could hold a lot of information, but we're not capturing it. If we were to look at it from a purely legal perspective, we might be able to place a specific person at a specific location at a specific time, which is gold in terms of evidence for a court setting.
But not only is limited memory filled up quickly, valuable records are usually lost when routers are switched off -- and there is also the problem of data contamination if wireless devices held by crime investigators end up connecting to the network. Blackman suggests that a faraday bag could be used to cut off a router from interference until specialists have a chance to look at it.
Photo credit: sommthink / Shutterstock
-

Security time bomb: Businesses are not ready for the end of Internet Explorer 8, 9 and 10 support
Publié: janvier 11, 2016, 8:16pm CET par Mark Wilson

The end of support for older versions of Internet Explorer has been known about for some time now. Despite the fact that there has been plenty of time to prepare for a move away from Internet Explorer 8, 9 and 10, many businesses are simply not ready and security experts warn that this could lead to a spate of attacks from hackers.
Microsoft has been encouraging people to move to Internet Explorer 11, or Edge in Windows 10 for a while, and the countdown comes to an end tomorrow -- 12 January. From this point forward, there will be no more patches or security fixes issued. Security analysts fear that with Internet Explorer 9 and 10 accounting for 36 percent of IE and Edge use, and with more than 160 vulnerabilities discovered in Internet Explorer in the last three years, there are risky times ahead.
Automatic Updates should have taken care of upgrading users to Internet Explorer 11, but business community Manta reports that more than 60 percent of businesses that use Internet Explorer are still stuck on version 10 or older. With an estimated 34 percent of SMBs found to be Internet Explorer users, there are an awful lot of people at risk if they fail to update their software soon.
Duo Security warns that there are still a huge number of unpatched system in use, and that we’re likely to see a spike in targeted attacks in coming weeks, months, and years. One of the benefits of End of Life dates is that there is a push to get people using the most recent and most secure versions of software, but it also serves as a beacon for attackers who are only too aware that people -- particularly businesses -- can be incredibly slow to update their software.
Duo Security Program Manager Mike Hanley says:
All it takes is one vulnerable device accessing your network to put your entire organization at risk of a data breach. But with visibility into the types of risky devices accessing your network, you can create and enforce data-driven policies to secure your company.
He also shares some tips for businesses to consider:
Educate your users on the importance of running updates and enabling Automatic Updates. Keeping devices up-to-date is critical to preventing compromise by attackers. Using current and supported software ensures users will continue to receive security updates and bug fixes for the software they use most - their browser!
In the case of Internet Explorer and Edge, automatic updates should occur along with monthly patch cycles. However, we also suggest considering switching to browser platforms that are updated frequently and automatically, such as Google Chrome - which is already the leading browser platform by a thin margin according to our data. Users and IT departments should strive to run current, supported operating systems and applications to prevent compromises in their environment.
Carefully weigh the balance between legacy compatibility and security. Many users will argue that web applications they use frequently are designed to be used on older platforms. But using a less-secure browser in today’s security climate in order to support a legacy interface can ultimately be more costly than updating the application or working with a vendor to provider support for newer software in the event of a compromise.
Consider compliance concerns. Microsoft draws attention to an important consideration in their EOL support announcement that running outdated software may actually have compliance impacts in enterprise environments. In addition to generally running with an open attack surface, there could very well be regulatory and compliance concerns associated with running unsupported software.
Photo credit: creativeoneuk / Shutterstock
-

Brits acquiesce to internet surveillance but distrust data storage
Publié: janvier 11, 2016, 1:01pm CET par Mark Wilson
UK web users are coming round to the idea of online surveillance by the government, but harbor concerns about how personal data will be stored. These are the findings of a survey by Broadband Genie that suggests terror attacks have led to a swing in public opinion of the Snooper's Charter.
But while people may be coming round to the idea of internet surveillance, they remain concerned about how private data -- such as browsing history -- will be stored. 27 percent of those surveyed said their opinion had been swayed by recent terrorist attacks by the likes of ISIS.
Broadband Genie found that while 63 percent of people support planned internet surveillance by the government, a similar figure -- 67 percent -- do not trust ISPs to store their private web data securely. This is particularly significant as part of the Investigatory Powers Bill would require ISPs to retain users' browsing histories for a full year.
Speaking about the results of the survey, Broadband Genie's Head of Strategy Rob Hilborn said:
The public are quite rightly concerned with their web history being stored by service providers for this length of time, especially considering the high profile attacks on TalkTalk and Vodafone last year. It's imperative the government addresses how it plans to minimise the risk of this sensitive personal information being stolen.
Also well as showing a general distrust of government and local authorities, Broadband Genie's survey also reveals who people would be willing to share personal data with. Using a 'trust score' system, the list ranks the people and authority according to the level of trust people have in them (the average trust score is 3.03)
- Partner 3.82
- Family 3.47
- Police 3.37
- Intelligence agencies 3.36
- Friend 3.07
- Government 2.55
- Employer 2.32
- Local councils 2.31
Photo credit: pzAxe / Shutterstock
-

And this, boys and girls, is why online vigilantism is a terrible idea
Publié: janvier 10, 2016, 5:29pm CET par Mark Wilson

I've written recently about the dangers of online vigilantes infringing on the free speech of others. Anonymous is one of the biggest offenders in this department, but there are numerous hacking groups that -- under the banner of fighting one evil or another -- take the law of the web into their own hands without a thought for the consequences.
Online vigilantes stir up populist support by throwing around the keywords associated with the enemy of the moment -- terrorists, ISIS, racists, fascists, communists, socialists, pedophiles. All very emotive issues, but vigilantism can all too easily get out of hand. This has just been demonstrated perfectly by YouTube star Keemstar who took it upon himself to expose a 62-year-old pedophile online through his DramaAlert podcast. The only problem is that he and his team got the wrong man.
Back in 2011, a man called John Philips used the online game Runscape to track down teenagers, one of whom he ended up having sex with. DramaAlert hunted down this man -- or so the team thought -- exposed him as a pedophile and this led to him being subjected to endless online abuse from people who saw the exposé. But the guy that Keemstar and his team were trying to hunt down is already in jail. He'll be in jail for some time -- until he dies, in fact.
The guy they actually exposed -- a poor chap called Tony -- is entirely innocent, absolutely not a pedophile, completely unconnected to John Philips. But this didn't stop Keemstar's fans laying on the abuse, ultimately reducing him to tears. The whole debacle is explained in this upsetting video shared on YouTube (warning: swearing):
Keemstar has since issued an apology -- of sorts -- but this will do little, if anything, to repair the reputation of the innocent man his show named as a pedophile (warning: swearing):
I'm not sure that this really counts as an apology. It's buck-passing. 'It wasn’t me, it was a member of my news team'. Doesn’t cut it, dude.
So, yeah, Keemstar, you've said you're sorry -- but it's just not good enough. This should not have happened in the first place. Shit sticks, and the poor guy you incorrectly outed as a pedophile is likely to find it very hard to shake off the label you have assigned him. An apology is akin to shutting the stable after the horse has bolted. Too little, too late. You should be utterly, utterly ashamed. I struggle to think of anything you could possibly do to rectify the situation, but you serve as a perfect example of why online vigilantes should just crawl away into a hole and die.
Over on Twitter, Keemstar describes himself as the "Creator of #DramaAlert #1 source for News on the Social interactions in Online Entertainment!". Might be time to reconsider that, and it's probably time for Twitter to think about stripping away that shiny blue Verified tick.
Photo credit: 1000 Words / Shutterstock
-

Nvidia GPU driver bug could expose your Chrome Incognito porn browsing
Publié: janvier 10, 2016, 1:55pm CET par Mark Wilson

If you have an online porn habit you like to indulge from time to time, you're probably well-acquainted with Chrome's Incognito mode. Like Microsoft Edge's InPrivate browsing, and Firefox's Private browsing, Google's browser includes a mode that can be used to keep your browsing secret. At least that's the idea...
One gamer and unashamed porn consumer found that his X-rated browsing sessions were exposed by Diablo III. Running the game on his Mac, Evan Andersen found that cached images from his Incognito browsing sessions were displayed as the RPG title loaded. He managed to grab screenshots of the bug in action, and even went as far as writing a program to show what's happening.
Evan has shared details of his surprise on his blog. It's not exactly a new problem, and he submitted a bug report to Google and to Nvidia quite some time ago -- but two years on, the problem still exists. Evan concedes that the bug is not one that could be easily exploited as it is somewhat unreliable but says that "it is a problem for anyone expecting incognito mode to hide their browsing on a shared computer".
Evan says:
So how did this happen? A bug in Nvidia's GPU drivers. GPU memory is not erased before giving it to an application. This allows the contents of one application to leak into another. When the Chrome incognito window was closed, it’s framebuffer was added to the pool of free GPU memory, but it was not erased. When Diablo requested a framebuffer of its own, Nvidia offered up the one previously used by Chrome. Since it wasn't erased, it still contained the previous contents. Since Diablo doesn't clear the buffer itself (as it should), the old incognito window was put on the screen again.
In the interest of reproducing the bug, I wrote a program to scan GPU memory for non-zero pixels. It was able to reproduce a reddit page I had closed on another user account a few minutes ago, pixel perfect.
Accusatory fingers are pointing multiple directions here. Should blame be laid at the feet of Diablo III developers, Blizzard? Is it Nvidia's fault for having drivers that do not properly wipe GPU memory? Or is it Google's fault for not properly sandboxing Incognito sessions?
What's Google's take on it? On the Chromium blog, the response is less than heartening for those with privacy concerns:
Incognito does not provide guarantees for hiding browsing on a shared computer. (Someone who could see the shared memory could also install a keylogger, etc. on your computer.)
Comments on Evan's bog post indicate that he is not alone in experiencing the problem, with some people indicating that they have had similar issues in Safari for iPad.
What this does highlight is the fact that private browsing sessions might not be anywhere near as private as you might hope.
Photo credit: nikitabuida / Shutterstock
-

Microsoft kicks off 2016 with a problematic Windows 10 Mobile build 10586.63 launch
Publié: janvier 9, 2016, 7:08pm CET par Mark Wilson

Microsoft has promised that Windows Insiders get Windows 10 builds faster in 2016, and it's Windows 10 Mobile users who get the first release of the new year. It's a few weeks since the release of build 10586.36 and now build 10586.63 is available for those on the Fast Ring.
You might expect from the relatively small jump in version numbers that this is something of a minor update -- and you'd be right. But despite the somewhat trifling nature of the changes, this release is noteworthy for a fluffed launch.
A problem with the update staging meant that some Insiders were able to detect the update before it was fully deployed. Gabe Aul -- in a series of tweets that could serve as an argument in favor of increasing the character limit on Twitter -- explained that there had been a problem with the rollout which had since been rectified:
5/ We’re now resuming the update and it will roll out to #WindowsInsiders in the Fast ring today
— Gabriel Aul (@GabeAul) January 8, 2016
But what Windows 10 Mobile users will be interested in is finding out what is new. Being a minor update, there's not a great deal to get excited about -- and no release notes have been provided -- but a Microsoft employee shared details of the changes on Reddit:
- Typing on Polish keyboard in Outlook Mail
- Turn by turn directions over Bluetooth in car
- Battery usage with Iris Reco
- Reliability of quick actions settings page
- MS Band use with Cortana
Windows 10 Mobile build 10586.63 is available on the Fast Ring now, so get downloading.
-

Tech firms ready to work with US spy agencies to combat IS and online terrorism
Publié: janvier 9, 2016, 1:58pm CET par Mark Wilson
Silicon Valley met with the US government on Friday to discuss how to tackle online terrorist propaganda from the likes of IS. At a closed-door meeting, Tim Cook and representative of Facebook, Twitter, Microsoft and other tech firms spoke with White House officials to try to find a way to combat terrorists on the web.
Joined by the likes of the NSA and FBI, the technology firms, and the Obama administration are seeking ways to stop terrorist propaganda being disseminated online. IS has already proved itself to be a masterful manipulator of the media, and has successfully used social networks such as Facebook and Twitter to get its message out.
The mood of the meeting is in contrast to talks that have taken place about encryption. While US government is keen to be granted access to communications, the likes of Apple is warning about the dangers of weakening encryption or providing governmental backdoors to data. While technology firms stand at odds with the government over encryption, this meeting appears to have been rather more positive in tone, with Facebook saying:
This meeting confirmed that we are united in our goal to keep terrorist and terror-promoting material off the internet.
The government delegation had sent out a briefing document ahead of the meeting outlining the purposes of the get-together. It could be seen as an admission that the Obama administration is not in a position to tackle IS's unwanted web presence without help. The briefing said:
We are interested in exploring all options with you for how to deal with the growing threat of terrorists and other malicious actors using technology, including encrypted technology. Are there technologies that could make it harder for terrorists to use the internet to mobilize, facilitate, and operationalize?
As well as looking to thwart terrorist propaganda, the government is also looking for ways to counter any such material that is out there. There is a balancing act to be struck between allowing freedom of speech, whilst placing limits on hate speech and incitement to violence.
Technology used by Facebook to help identify people contemplating suicide has been singled out for particular attention. The hope is that it could be used as the basis for an automated tool for identifying terrorists and supporters of terrorism.
Photo credit: GongTo / Shutterstock
-

If you're fine with Microsoft's approach to privacy in Windows 10, you're out of touch
Publié: janvier 8, 2016, 6:00pm CET par Mark Wilson

Yeah, I'm going to bang that drum again. We've talked endlessly about privacy and telemetry in Windows 10. Endlessly. It's brought up some interesting issues for debates, led to comparisons between Microsoft and Google, and lots and lots of lots of bile. A case in point is an article from dear, dear Mr Ed Bott over on ZDNet. Mr Bott refers, subtweet style, to my recent article about Microsoft recording how long people are using Windows 10.
He refers -- albeit indirectly -- to me (and writers like me who question Microsoft) as a "dedicated Microsoft hater" and a "clueless writer" peddling in clickbait. He suggests I'm not interested in facts; this despite the fact I have gone out of my way to garner such delights from Microsoft. Bott completely -- COMPLETELY -- misses the point. I can only hope he does so on purpose because otherwise he just sounds disingenuous and a bit stupid. The problem here is not that Microsoft is gathering data (as it is perfectly entitled to do so), but the lack of transparency surrounding it. Microsoft does nothing to help itself.
In my "Why is Microsoft monitoring how long you use Windows 10?" article, I do not -- as Bott suggests -- believe that Microsoft is up to anything nefarious. I am well aware that telemetry is analytics, but many people would refer to this as a form of spying -- regardless of whether there is a warning that it is taking place. The very point of my article was to ask WHY Windows usage time was being recorded, and how. Bott points to Microsoft documentation which talks about the collection of data by Windows 10, but this is incredibly vague.
I don't want to imagine why you are collecting the data and how it might be used (whether completely anonymous or not), I want to know.
This is why I ask Microsoft directly:
What I was particularly interested in was the 'how' and 'why' specifically with reference to determining how long people are using Windows 10. Is it a measure of PC up time? Time spent actively using it? Are individual apps and features monitored? How often is data recorded? What is it used for?
As I noted in my first article, Microsoft was singularly unhelpful when I reached out to the company for clarification. But following the publication of the post, a spokesperson decided to get in touch with me to provide a (meaningless and unhelpful) statement:
Microsoft is deeply committed to protecting our customers' privacy. Consistent with all modern services and websites, the Windows 10 information highlighted in the blog on January 4 is standard diagnostic, anonymous analytics that enables us to deliver the best Windows 10 experience possible. We are committed to delivering industry leading privacy protection for our customers, as shared in a recent blog from Terry Myerson.
Despite the company's endless claims of transparency (to be fair, things have improved, but there's still a long way to go), Microsoft seems incapable of answering simple, direct questions, with simple, direct answers. The response to my queries?:
Windows offers extensive information for people to learn more about privacy and Windows 10, including a blog from Terry Myerson on our commitment, and detailed information for consumers and IT Pros on how information is managed and how people and organizations can easily manage their preferences.
Again, pointless and unhelpful.
Bott says that not only has Microsoft been very open about the data it collects (something I would disagree with -- sure, the information is out there, but hardly in obvious places that most people would look), but that Windows 10 makes it easy for people to "dial the feedback setting back".
The average user is living in blind ignorance of what is going on in the background: that's what matters. The likes of Mr Bott and I -- and, indeed, many BetaNews readers -- will be fully aware of what the implications of telemetry are, but that's not the point. Microsoft is not conveying to the majority of people what is going on. Sure, the information is out there, but you have to look for it -- you have to know that there is something that you might need to know about.
That's the point. That's what matters. And that's precisely what those drinking the Microsoft Kool-Aid are ignoring.
My problem with Bott (in this instance) is that he is looking at the issue through the eyes of a technically minded, tech journalist -- not those of the average user.
The average user doesn't care for analytics, telemetry, spying or however you want to refer to it.
Most people learning that Microsoft tracks -- and so what if it's anonymous? -- how long the operating system is used by people, would be a bit weirded out.
Yes, Microsoft may publish (some) info about the data it gathers, and even provide ways to control it to some extent, but this info is hardly advertised in a way or published in a place that most normal people would find it. Ditto for the telemetry-taming settings.
Ed, you can call me a conspiracy nut, a Microsoft-hater, a click baiter all you want -- it bothers me not a jot. You're wrong on all counts. All I'm doing is seeing things through the eyes of the average user.
Photo credit: Perry Correll / Shutterstock
-

Insiders should see new Windows 10 builds next week and faster releases through 2016
Publié: janvier 8, 2016, 11:57am CET par Mark Wilson

The first week of the New Year is out of the way and Windows Insiders are eagerly awaiting the first Windows 10 build of 2016. The waiting may be over soon, as Microsoft says that it should be just "a few more days" before testers' patience is rewarded.
It's only a few weeks since the Redstone branch of Windows 10 became public, and Microsoft's Gabe Aul suggests that a new build could be on the way next week. The Windows 10 team just needs time to recover from Christmas and the New Year, and then we should also start to see more frequent build releases.
On Twitter, Aul responded to queries about the whereabouts of the next Windows 10 build, explaining that it was currently working its way through internal testing. While users on the Slow Ring are unlikely to see more builds than last year, those on the Fast Ring are promised an accelerated release schedule. But haven’t we heard this before?
Aul replied to a series of questions about the release of a new build by saying:
@DecadeMoon @Wereszko @mayank_jee We are all getting back in the office, getting new builds through internal rings, etc. A few more days.
— Gabriel Aul (@GabeAul) January 7, 2016
To those who asked about the promise of more frequent releases, he said:
@mayank_jee We'll have more frequent builds for Fast ring, but we haven't started flighting in the new year yet.
— Gabriel Aul (@GabeAul) January 7, 2016
This didn’t stop more people asking the same questions over and over again, leading Aul to respond with a slightly exasperated tone:
@DecadeMoon @Wereszko @mayank_jee Once we actually *start* flighting in 2016, then we expect to see more frequent builds than last year.
— Gabriel Aul (@GabeAul) January 7, 2016
He hasn’t given any hints about what we might see in the next preview build, but it's looking as though we'll only have to wait until next week to get our hands on the bits and try it for ourselves.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Facebook, Google, Microsoft, Twitter and Yahoo balk at UK's Investigatory Powers Bill
Publié: janvier 7, 2016, 11:53pm CET par Mark Wilson

The Investigatory Powers Bill may only be in draft form at the moment, but the UK government has already come in for criticism for its plans. Today, scores of pieces of written evidence, both for and against the proposals, have been published, including input from the Reform Government Surveillance (RGS) coalition.
Five key members of the coalition are Facebook, Google, Microsoft, Twitter and Yahoo. In their written evidence, the quintet of tech companies express their concerns about the draft bill, seek clarification from the UK government, and issue warnings about the implications of such a bill.
The evidence (document IPB0116) says that any surveillance undertaken by the government need to be "targeted, lawful, proportionate, necessary, jurisdictionally bounded, and transparent". The coalition notes that many other countries are watching to see what the UK does, and whatever form the final Investigatory Powers Bill takes, it could form the framework for countless similar bills around the world.
The group suggests a series of considerations that it believes the government needs to keep in mind:
- User trust is essential to our ability to continue to innovate and offer our customers products and services, which empower them to achieve more in their personal and professional lives.
- Governments’ surveillance authorities, even when transparent and enshrined in law, can undermine users’ trust in the security of our products and services.
- Key elements of whatever legislation is passed by the UK are likely to be replicated by other countries, including with respect to UK citizens’ data.
- Unilateral imposition of obligations on overseas providers will conflict with legal obligations such providers are subject to in other countries.
- An increasingly chaotic international legal system will leave companies in the impossible position of deciding whose laws to violate and could fuel data localization efforts.
Among the other points made are concerns about conflicting with laws in other countries. The coalition says that the UK government should not be able to require companies to comply with warrants if it doing so would break laws in other countries. There is concern expressed about encryption, and a clear statement that "we reject any proposals that would require companies to deliberately weaken the security of their products via backdoors, forced decryption, or any other means."
As well as telling the government that companies should not be required to gather and store extra data about their customers, the coalition wants to ensure that there is transparency when the bill is in action. This, the evidence says, would go some way to maintaining the user trust that the bill risks breaking:
The ultimate test we apply to each of the authorities in this Bill is whether they will promote and maintain the trust users place in our technology. Even where these authorities do not apply to overseas providers like our companies, we are concerned that some of the authorities contained in the Bill, as currently drafted, represent a step in the wrong direction. The clearest example is the authority to engage in computer network exploitation, or equipment interference. To the extent this could involve the introduction of risks or vulnerabilities into products or services, it would be a very dangerous precedent to set, and we would urge your Government to reconsider.
The Joint Committee on the Draft Investigatory Powers Bill is chaired by Lord Murphy of Torfaen. He said:
The Committee is grateful to the wide range of people and organisations who have taken the time and effort to submit evidence to the inquiry.
We are aware that the short time available to the Committee for its investigation has been a cause of concern for people who have their own concerns and questions about the draft Bill. Our timetable, set by the two Houses, is certainly a challenging one. However, our witnesses’ willingness to work with us to this tight deadline, and the range and quality of the written evidence that has been submitted, is something the Committee acknowledges gratefully. The written evidence, together with that which we have heard in oral evidence sessions, will be vital to our further work.
The full cache of written evidence can be accessed on the UK Parliament website. It includes submissions from companies, individuals, the government, law enforcement agencies, and non-governmental organizations.
Photo credit: Pixza Studio / Shutterstock
-

Microsoft explains how it uses Windows 10 Insider feedback with 'Made by you' articles
Publié: janvier 7, 2016, 12:00pm CET par Mark Wilson

The Windows Insider program was designed to help anyone test driving preview builds of Windows 10 to provide feedback and help shape the future direction of the operating system. But what happens with all of the feedback that's submitted?
Microsoft is starting to publish a new series of articles to the Insider Hub that seek to assure people that their feedback is not just disappearing into a black hole. The 'Made by you' sees Microsoft providing feedback on feedback, and helps to give Insiders some reassurance that their input is valued. The first article is about how Windows 10 handles display scaling.
The feedback program for Windows 10 has had its share of controversy, as Microsoft was accused of ignoring -- even deleting -- feedback it doesn’t like. The 'Made by you' articles are surprisingly detailed, and are much more than just a checklist of what has been done. Instead, Microsoft details exactly what has changed and why, lists any problems that still exist, and explains what work is still to be done.
In an update that appears in the Insider Hub app, Microsoft says:
Today we are introducing a new series of articles titled 'Made by you'. If you have feedback on this type of content or other aspects of the Windows Insider Program, please let us know via the Feedback App.
'Made by you' highlights how we are addressing feedback from Windows Insiders, how we investigated this feedback to shape Windows, and why we have made these improvements.
Is this a good move on Microsoft's part?
Photo credit: mamanamsai / Shutterstock
-

How to fix error 0xc0000017 when installing Windows 10
Publié: janvier 6, 2016, 9:42pm CET par Mark Wilson
While I've been running Windows 10 for what seems like forever now, a desktop computer sitting in my office running Windows 8.1 has been crying out for an upgrade for some time. Having had a problem-free upgrade on three other machines, I expected nothing out of the ordinary with this computer. I was wrong.
Initially I left Windows Update to do its thing, but this failed on countless occasions. The error message suggested that a problem with my internet connection had interrupted the download, but this seemed unlikely. After numerous attempts, I decided to opt for a USB-driven installation. This also failed, this time with error 0xc0000017: "There isn't enough memory available to create a ramdisk device". Thankfully, the problem can be fixed -- here's what you need to do.
There are lots of absolutely nonsensical 'solutions' out there -- from disabling antivirus and unplugging peripherals, to disabling integrated graphics. None of these are helpful. The problem stems from areas of memory having been marked as bad, and this interferes with the Windows 10 installer's ability to make use of RAM as a temporary store for data. While it's possible that there is a genuine memory issue, the chances are that you can simply ignore the problem and get Windows 10 installed -- it worked for me.
The solution comes in the form of the Boot Configuration Data (BCD), which is built into Windows. Use the following steps and you'll be up and running in next to no time:
- Boot your computer into Windows.
- Right click the Start button and select Command Prompt (Admin).
- Type bcdedit /enum all and press Enter.
- You'll see a list of all the memory locations that have been deemed 'bad', this list can be cleared.
- Type bcdedit /deletevalue {badmemory} badmemorylist and press Enter (type this verbatim, {badmemory} is not a placeholder for anything).
- Close the Command Prompt window and restart your computer.
Now you can run the Windows 10 installer once again, and you should find that it completes without interruption.
Photo credit: T.Dallas / Shutterstock
-

Oscobo is a privacy-focused search engine that won't sell your data
Publié: janvier 6, 2016, 5:43pm CET par Mark Wilson

Using the web can mean selling your soul to the devil. Or Google. (Which you may well regard as the same thing.) With the increased interest in privacy there is a new market for tools and services that help to protect users. Catering to web users who are concerned about how Google might use search data, Oscobo is a new search engine that promises not to track users.
Founded on the belief that "personal data should remain just that -- personal", Oscobo is a UK-based company that says it won't store any data about its users, let alone share it with anyone else. With the controversy surrounding the snooper's charter, it makes sense that the privacy-focused search engine should start life in the UK, but there are plans to expand further afield to provide tailored results for people around the world.
Of course, in order to provide search results that are relevant to people, Oscobo (the name derived from the Swedish 'o' meaning 'not', and the Latin 'scobo' meaning 'to look into') needs to record search terms and IP addresses. But the key difference with this search engine -- apart from the absence of third-party data sharing -- is that this data vanishes as soon as a user leaves the site.
As well as helping to improve privacy, Oscobo's approach also helps to improve security. As the company says:
Any data that is held on a server can be hacked or misused. At Oscobo we believe that this is not acceptable.
It's pretty simple really. We're on your side. We will not store or mess around with your personal data.
To try out the search engine, head over to Oscobo. You'll notice that there are ads, and these are served up based on your location and search terms without sharing personal data with others.
-

How to stop Microsoft nagging you to switch to Internet Explorer 11 or Microsoft Edge
Publié: janvier 6, 2016, 2:51pm CET par Mark Wilson

All good things must come to an end. But the same can be said about bad things, and many people will be pleased to hear the death knell sound for Internet Explorer 8, 9, and 10. While Microsoft may be keen for people to use Edge or -- if they must -- Internet Explorer 11, not everyone feels the same.
With the likes of Firefox, Opera, and Chrome available, it might seem like madness that anyone would like to stick with an ancient version of Internet Explorer instead, but choice is everything. A patch that is due to be delivered to Internet Explorer 8, Internet Explorer 9, and Internet Explorer 10 in the coming day will introduce a nag screen that will pester users into upgrading. If you're happy with your decision to stick with an older version of IE, here's a hack to banish the pestering.
Far be it from us to tell you which web browser to use, but it goes without saying that using a decrepit version of Internet Explorer is... inadvisable. But that's not to say there are not people out there who have need of the soon-to-be-completely-retired version 8, 9 or 10. If you find yourself in this camp and want to 'enjoy' your chosen browser without constant nagging, just use the following registry hack to banish the bothersome reminders.
For x86-based systems:
- Click Start, type regedit in the Start Search box, and then click OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ Internet Explorer\Main\FeatureContro
- Right-click FeatureControl, point to New, and then click Key.
- Enter FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, and then press Enter to name the new key.
- Right-click FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, point to New, and then clickDWORD (32-bit) Value.
- Enter iexplore.exe, and then press Enter to name the new value.
- Right-click iexplore.exe, and then click Modify.
- In the Value data box, enter 1, and then click OK.
- Exit Registry Editor, and then restart the browser to enable the new key.
For x64-based systems:
- Click Start, type regedit in the Start Search box, and then click OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ Internet Explorer\Main\FeatureControl
- Right-click FeatureControl, point to New, and then click Key.
- Enter FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, and then press Enter to name the new key.
- Right-click FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, point to New, and then click DWORD (32-bit) Value.
- Enter iexplore.exe, and then press Enter to name the new value.
- Right-click iexplore.exe, and then click Modify.
- In the Value data box, enter 00000001, and then click OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\ Microsoft\Internet Explorer\Main\FeatureControl
- Right-click FeatureControl, point to New, and then click Key.
- Enter FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, and then press Enter to name the new key.
- Right-click FEATURE_DISABLE_IE11_SECURITY_EOL_NOTIFICATION, point to New, and then clickDWORD (32-bit) Value.
- Enter iexplore.exe, and then press Enter to name the new value.
- Right-click iexplore.exe, and then click Modify.
- In the Value data box, enter 00000001, and then click OK.
- Exit Registry Editor, and then restart the browser to enable the new key.
Photo credit: Mizina Oksana / Shutterstock
-

Microsoft poised to deal deliver a fatal blow to Internet Explorer 8, 9 and 10
Publié: janvier 6, 2016, 2:15pm CET par Mark Wilson

In less than a week, Microsoft will only offer support for Internet Explorer 11 and Microsoft Edge. As of Tuesday 12 January, Internet Explorer 8, 9 and 10 will die. The aging browsers will receive one more update, and then will be consigned to the trash.
Tuesday is the day that older versions of IE reach the end of their support cycles, and Microsoft is keen for everyone to move to either Microsoft Edge or -- for the diehards -- Internet Explorer 11. If you have not already made the switch (or jumped to Chrome or Firefox), one more patch, KB3123303, will pester you into upgrading.
This is vaguely reminiscent of the Browser Choice screen that Microsoft was forced to introduce sever years ago, and it will be interesting to see how effective the nagging is at getting people to move towards the most recent versions of Microsoft's web browsers.
Since the launch of Windows 10, Microsoft has been pushing Edge hard, but Internet Explorer 11 remains available mainly for enterprise users who need more time to be able to fully prepare for the switch. Of course, it's entirely possible that the nagging will simply sour people's view of Microsoft and push them towards the browsers offered by the likes of Mozilla and Google.
But for now, the death clock ticks on.
Photo credit: Mattz90 / Shutterstock
-

Microsoft poised to deliver a fatal blow to Internet Explorer 8, 9 and 10
Publié: janvier 6, 2016, 2:15pm CET par Mark Wilson

In less than a week, Microsoft will only offer support for Internet Explorer 11 and Microsoft Edge. As of Tuesday 12 January, Internet Explorer 8, 9 and 10 will die. The aging browsers will receive one more update, and then will be consigned to the trash.
Tuesday is the day that older versions of IE reach the end of their support cycles, and Microsoft is keen for everyone to move to either Microsoft Edge or -- for the diehards -- Internet Explorer 11. If you have not already made the switch (or jumped to Chrome or Firefox), one more patch, KB3123303, will pester you into upgrading.
This is vaguely reminiscent of the Browser Choice screen that Microsoft was forced to introduce several years ago, and it will be interesting to see how effective the nagging is at getting people to move towards the most recent versions of Microsoft's web browsers.
Since the launch of Windows 10, Microsoft has been pushing Edge hard, but Internet Explorer 11 remains available mainly for enterprise users who need more time to be able to fully prepare for the switch. Of course, it's entirely possible that the nagging will simply sour people's view of Microsoft and push them towards the browsers offered by the likes of Mozilla and Google.
But for now, the death clock ticks on.
Photo credit: Mattz90 / Shutterstock
-

Would dropping the 140-character limit completely change the face of Twitter? [UPDATE] Jack Dorsey responds
Publié: janvier 5, 2016, 9:40pm CET par Mark Wilson

Twitter could be on the verge of making one of the most significant changes in its history. The micro-blogging service has long been famed for its 140-character limit that allows for pithy quips, concise statements, and brief utterances. But all this could be about to change. Reports suggest that the 140-character restriction could be thrown out of the window, with a decidedly meatier 10,000-character upper limit being ushered in instead.
If such a change is implemented, it would bring regular tweets in line with direct messages which enjoyed a lengthening just a few months ago, and comes shortly after Twitter changed the order in which tweets are displayed. Both of these changes led to a good deal of debate, but would increasing the maximum length of a regular, public message by more than 70 times be such a fundamental change as to be a step in the wrong direction?
Rumors have long been circling that Twitter might consider banishing the iconic 140-character barrier to the history books. Now the rumor mill is working overtime, with Re/code claiming "longer tweets are coming soon to Twitter", based on information from "multiple sources familiar with the company's plans". This time around it seems that there could well be firmer grounds for believing the rumors to be true, and late Q1 has been put forward as the time by which tweets could be lengthened.
Reaction to longer tweets is likely to be mixed. There can be few Twitter users who have not wished for a few more characters to play with so a tweet can be written without the need to manipulate the wording too much or split it in two. But at the same time, the limit is part of the fun of Twitter. It's what the site has been about for so many years -- shorter even than standard text messages! A bit more breathing space is one thing, but 10,000 characters?
As Re/code points out, if the 10,000 figure turns out to be true, just how it is implemented will be key to whether it is a successful move or not. Permit anyone and everyone to post 10,000 character tweets, and scrolling through your timeline -- be it on a phone or computer monitor -- is going to become a pretty miserable experience. What would make sense is to stick with the way things are at the moment so that up to 140 characters are displayed by default; in the case of longer tweets, ellipsis or a <more> link could indicate that there's more to read.
This second option is certainly preferable, but then each and every tweet becomes something to be marketed. The first 140 characters will need to work their hardest to entice others to click through to read the remain 9,860... almost like an ad. Actually, that's exactly what 10,000-character tweets could become, and would provide Twitter with a way to monetize the feature. 140 characters are free, but if you want to use more in a single tweet, you could pay on a sliding scale.
This is, of course, conjecture.
But the prospect of Twitter changing in such a key way does pose some important questions -- and there is some debate about it on Twitter (obviously) under the hashtag #beyond140. Would it change the way the site/app works and how people use it (and what they use it for)? Will it lead to more advertising? Will Twitter monetize it? How will it be implemented? What are the repercussion for the likes of Twitlonger and services of the same ilk?
More importantly -- is it something you want?
UPDATE
Twitter co-founder Jack Dorsey has now waded into the debate, using a tried and tested method of bypassing the 140-character limit:
— Jack (@jack) January 5, 2016
Photo credit: Visual3Dfocus / Shutterstock
-

Why is Microsoft monitoring how long you use Windows 10?
Publié: janvier 4, 2016, 10:26pm CET par Mark Wilson

The various privacy concerns surrounding Windows 10 have received a lot of coverage in the media, but it seems that there are ever more secrets coming to light. The Threshold 2 Update did nothing to curtail privacy invasion, and the latest Windows 10 installation figures show that Microsoft is also monitoring how long people are using the operating system.
This might seem like a slightly strange statistic for Microsoft to keep track of, but the company knows how long, collectively, Windows 10 has been running on computers around the world. To have reached this figure (11 billion hours in December, apparently) Microsoft must have been logging individuals' usage times. Intrigued, we contacted Microsoft to find out what on earth is going on.
If the company has indeed been checking up on when you are clocking in and out of Windows 10, it's not going to admit it. I asked how Microsoft has been able to determine the 11 billion hours figure. Is this another invasion of privacy, another instance of spying that users should be worried about? "I just wanted to check where this figure came from. Is it a case of asking people and calculating an average, working with data from a representative sample of people, or it is a case of monitoring every Windows 10 installation?"
You think that Microsoft -- keen as it is on transparency -- would be quite happy to explain how it came about the information, and why it is being collected in the first place. But no. A Microsoft spokesperson provided BetaNews with the following statement:
Thank you for your patience as I looked into this for you. Unfortunately my colleagues cannot provide a comment regarding your request. All we have to share is this Windows blog post.
Microsoft's spying is intrusive enough to reveal how long you have been using Windows 10, but the company is not willing to be open about the collection of this data.
Cause for concern, or is this just another example of what we have come to expect from Microsoft?
Photo credit: veronchick84 / Shutterstock
-

Wi-Fi HaLow increases wireless range and reduces power consumption
Publié: janvier 4, 2016, 6:16pm CET par Mark Wilson
As the Internet of Things starts to gather momentum, the Wi-Fi Alliance today announces Wi-Fi HaLow. The latest wireless standard is touted as being ideal for the IoT thanks to its lower power requirements and greater range when compared to current offerings.
Wi-Fi HaLow is an extension of the existing 802.11ah standard, and occupies the frequency bands below one gigahertz. The Wi-Fi Alliance says it is perfect for use in connected cars, smart homes and a number of different industries, but there will be some of a wait before the technology is available -- it's not due for certification until 2018.
Wi-Fi HaLow takes advantage of the 900 MHz band, but it is expected that many devices will also operate at 2.4GHz and 5GHz to allow for interoperability with existing hardware. The promise of lower power consumption is certainly appealing -- and is likely to see the standard being used in wearables and other small devices -- but it is the range increase that most people and companies will be excited about. Wi-Fi HaLow extends roughly twice as far as existing Wi-Fi solutions.
Edgar Figueroa, President and CEO of Wi-Fi Alliance, said:
Wi-Fi HaLow is well suited to meet the unique needs of the Smart Home, Smart City, and industrial markets because of its ability to operate using very low power, penetrate through walls, and operate at significantly longer ranges than Wi-Fi today. Wi-Fi HaLow expands the unmatched versatility of Wi-Fi to enable applications from small, battery-operated wearable devices to large-scale industrial facility deployments – and everything in between.
The Wi-Fi Alliance is also pushing Wi-Fi HaLow as an alternative to Bluetooth and NFC, but it will be a couple of years before we get to see how this works out in practice.
Photo credit: WEB-DESIGN / Shutterstock
-

Lenovo ThinkPad X1 Tablet offers customization through clip-on modules
Publié: janvier 4, 2016, 10:01am CET par Mark Wilson

If you've ever searched high and low for a tablet but found yourself unable to track down the perfect device, Lenovo may have the answer. Taking a leaf out of Google's Project Ara design handbook, Lenovo today unveils the new customizable, modular ThinkPad X1 Tablet.
Powered by an Intel Core m7 processor and Windows 10, the tablet boasts up to 10 hours of battery life, but if this isn’t enough, there's a clip-on Productivity Module to ramp this up to 15 hours. This is the ThinkPad X1 Tablet's unique selling point -- a series of modules that can be used to personalize, customize and tailor the device to specific needs.
At the moment, there are three modules available. In addition to the Productivity Module, there's also the 3D Imaging Module which adds a rear-facing Intel RealSense camera for 3D scanning and photography. For those who need to make presentations -- this is a ThinkPad aimed at the corporate user, after all -- the Presenter Module adds a pico projector and HDMI port.
The tablet features the iconic ThinkPad look, is just 0.3 inches thick, and weighs in at 1.75lbs. Add the keyboard, which snaps on Surface-style and offers three fixed typing angles, and this jumps to 2.4lbs, transforming the tablet into a laptop complete with the red TrackPoint nipple. As this is a tablet, the bundled stylus is both welcome and expected.
Check out the video to see what the ThinkPad X1 Tablet has to offer:
Lenovo points out that the ThinkPad X1 Tablet "features a removable rear panel for serviceability and upgrades".
The tablet is set to launch in February priced at $899, and the Productivity Module will have a $149 price tag. The Projector Module will cost $279, the 3D Imaging Module $149, and these will be available from May.
-

Ransom32 is JavaScript-powered ransomware affecting Windows, Mac and Linux
Publié: janvier 4, 2016, 1:54am CET par Mark Wilson

Cross-platform viruses and malware are something of a rarity, but now there's a first-in-its-class JavaScript-based ransomware that can infect Mac, Windows and Linux. Ransom32 uses the Node.js runtime environment running on the NW.js platform to burrow into the target operating system and hold files to ransom.
While on the face of it, this is just another example of ransomware that encrypts files and seeks Bitcoin payments to decrypt them, it is more than that. The NW.js framework not only allows for cross-platform infections, but also means it is harder to detect. Ransom32 bears some resemblance to CryptoLocker and has been dubbed Ransomware-as-a-Service.
Ransom32 is being traded on the dark web, with the authors offering customized versions of the malware in return for a 25 percent cut of whatever money is generated. Security expert Fabian Wosar from Emsisoft blogged about the ransomware and points out that it is notable if only for the unusually large size (22MB) and complexity of the malicious files it downloads as part of the infection process.
As Wosar explains, the initial infection method is nothing out of the ordinary, involving little more than using spam emails to lure victims into installing the ransomware. Delivered as a compressed RAR file, Ransom32 self-extracts and uses WinRAR's scripting language to configure the malware to launch at system startup, establishing a connection to a 'command and control server' using the bundled Tor client. Files are encrypted and a ransom note is issued, warning that the cost of decrypting files will increase as time goes by.
In his explanation of Ransom32, Wosar says
Files are being encrypted using AES with a 128 bit key using CTR as a block mode. A new key is being generated for every file. The key is encrypted using the RSA algorithm and a public key that is being obtained from the C2 server during the first communication.
He advises that having a robust backup strategy in place is the best form of defense at the moment -- particularly as AV software manufacturers have been slow to push out definitions that detect Ransom32.
For now, only Windows versions of Ransom32 have been seen out in the wild, but the ease of repackaging for Linux and OS X means that these operating systems could well be targets in the near future.
Photo credit: Ton Snoei / Shutterstock
-

New World Hackers take Trump offline -- but when does hacking vigilantism infringe on free speech?
Publié: janvier 3, 2016, 5:01pm CET par Mark Wilson

My colleague Brian Fagioli has referred to the web being rather like the Wild West. I'm inclined to agree, but that's not to say that we have reached the same conclusion for the same reasons. For me, the web -- like the Wild West -- is not a world filled with danger, but one occupied by vigilantes. As a proponent of free speech, I find this concerning. One of the most highly-lauded of vigilantes is the disparate group marching under the ragged banner of Anonymous.
One of its taglines is 'We Are Anonymous', a phrase that can be uttered by anyone as there is no membership process -- if you say you are part of Anonymous, you are part of Anonymous. The group is not, for the most part, organized. Individuals and factions can fight for or against whatever cause they want, just like real-world vigilante groups. But Anonymous is not alone. There are hacking collectives and other online crusaders who see fit to take the law into their own hands. This might sound wonderful, but it's not necessarily a good thing. As New World Hackers demonstrate, attacks can target the wrong people and restrict free speech.
Just the other day, New World Hackers 'accidentally' took down the BBC's websites and online services. The group's main aim is to take down IS (or ISIS, ISIL, or whatever moniker you prefer) and such tub-thumping will be welcomed by most people. But just because most people agree with a course of action, that doesn’t make it morally right. In this instance, it is easy to get behind New World Hackers for tackling something so unpleasant (Islamic State, not the BBC), but there would be nothing to stop a hacking collective attacking the websites of secularists for not believing in a god, people who hold different religious views, pro-abortion supporters, and so on.
Now the group has attacked Donald Trump, launching a DDoS attack that took the presidential candidate's website offline for a short time. There have been virtual cheers of support -- understandable as Trump is a ridiculous buffoon -- and this is worrying. Speaking to HackRead, New World Hackers said:
We targeted Trump site because this guy can get quite racist. It doesn’t matter to us how crazy he gets. Our member “doc” actually attacked donaldjtrump.com with a layer 7 attack and he plans to attack trump’s site later on again
What the group has done is wrong -- legally and morally -- but it will be accepted because it has a manifesto that sets out the aim of targeting IS/ISIS/ISIL. Yes, many of Trump's views are utterly disgusting, but that doesn’t mean he's not entitled to hold them and share them. Is hacking and online vigilantism OK when the target is someone/thing wildly seen as objectionable? Who draws the lines?
There is the pretence of fighting a dangerous evil, but censorship is just as dangerous. ISIS is widely regarded as evil (and I'm not disagreeing with this view), but many people would argue that abortion is evil (I wouldn't, for the record). Would it be acceptable for Anonymous or New World Hackers to start trying to wipe pro-abortion (or pro-choice) groups from the web? Why not start trying to wipe out the web presence of all republicans, socialists, Christians or Muslims while you’re at it?
It goes without saying -- I hope -- that I am not a supporter of ISIS. I find Donald Trump to be an abhorrent human being, spouting ideas that are divisive and dangerous. But I don’t want to silence them or anyone similar. There are countless political groups, religious movements, and organizations whose ideas I find insane, potentially harmful, and loathsome, but I would never want to censor them or prevent them from having an outlet; nor do I want anyone to do this on my behalf.
The beauty of the web is that it is democratizing. It's a platform that just about anyone can use. That -- just as with other media -- means having to take the good with the bad. It's not right to silence the expression of views that go against what you believe, or even those that go against what most people believe. Freedom of speech for you means freedom of speech for all. Yes, this means you might encounter disgusting, objectionable people, groups and views online, but that's tough; that's life. No one has the right to dictate what views are acceptable, and even less of a right to try to silence others. Like it or lump it, you’ve got to take the rough with the smooth.
Photo credit: Coqrouge / Shutterstock
-

Chuwi Hi12 is a promising budget Surface-like tablet running Windows 10 and Android
Publié: janvier 2, 2016, 5:36pm CET par Mark Wilson

Chuwi might not be a name that you're particularly familiar with (or have even heard of at all), but the Chinese company has some interesting hardware on the way in 2016. Can’t decide between a Windows 10 tablet, or one running Android? Chuwi Hi12 offers the ability to boot between Windows 10 and Android.
With more than a hint of iPad aesthetics, the Hi12 blends the worlds of Microsoft's and Google's operating system to create a budget version of the Surface with an Android bolt-on. As this is a tablet running both Android and Windows, it's no surprise that there's a Cherry Trail processor on hand to keep things ticking over.
With other Chuwi tablets, there has been the option of a Surface-style keyboard attachment, and it's hard to imagine that this won't also be the case with the Hi12. While the tablet is not exactly a powerhouse, it is a more than capable device that would serve perfectly as a low-cost tablet for a student, an extra device for travelling with or, you know, just a toy to tinker with.

Here are those all-important specs, which -- while not earth-shattering -- are far from shabby:
- Screen Size: 12.0 Inches
- OS: Windows 10 + Android 5.1
- Colors: Champagne Gold; Space Gray
- Screen Resolution: 2160 x 1440 (3:2)
- CPU: Intel X5 Cherry Trail Z8300 (Max up to 1.84GHz)
- GPU: 8th Generation Intel Graphics (up to 500MHz)
- RAM: 4GB
- ROM: 64GB
- Extended Storage: Up to 128GB
- Battery: 11000mAh
- Camera: Front - 2MP, Back - 5MP
An official release date is yet to be set for the CHUWI Hi12, but it is due to make an appearance this month. The tablet is set to launch in US, Europe and around the world, but there is no pricing information available. That said, the smaller Hi10 is currently available for $199.99 and a CHUWI spokeman told BetaNews "it might be cheaper than other competitors (may be under $300)".
Watch this space!
-

American hacking group killed the BBC's online presence to test anti-ISIS attack powers
Publié: janvier 2, 2016, 1:16pm CET par Mark Wilson
A huge DDoS attack took the BBC's websites offline on Thursday, as well as the broadcaster's iPlayer streaming service. The disruption lasted for several hours, and now a US-based group of 'cyber hackers' that usually targets ISIS has claimed responsibility.
The New World Hacking group is a self-proclaimed hacktivist group that supports Anonymous. It says that despite effectively knocking the BBC from the face of the web, it was only meant to be a test of server power rather than a targeted attack on the corporation.
While the BBC acknowledged that there had been a 'technical problem' with its online services on Thursday, it has not commented on whether this came as the result of a DDoS attack or not. On New Year's Eve, New World Hacking expressed surprise that their 'attack' had hit the headlines:
Didn't know our attack made the news [https:] | #Offline | 600 GBps | [https:] @BBC @AboutTheBBC @BBCBreaking
— New World News (@NewWorldHacking) December 31, 2015
In a series of tweets to BBC technology reporter Rory Cellan-Jones today, New World Hacking said:
We are based in the US, but we strive to take down Isis [IS] affiliated websites, also Isis members.
We realize sometimes what we do is not always the right choice, but without cyber hackers... who is there to fight off online terrorists?
The reason we really targeted [the] BBC is because we wanted to see our actual server power.
'Anti-IS group' claims BBC website attack - in Twitter messages to me [https:]
— Rory Cellan-Jones (@BBCRoryCJ) January 2, 2016
The group says that ISIS will continue to be its primary target, but it's not clear if further 'server tests' could result in other big sites being hit:
REMEMBER.. Only a DDoS attack test.. ISIS will be our main target. #BinarySec [https:]
— New World News (@NewWorldHacking) January 2, 2016
-

Microsoft's promise of spying warnings is an empty gesture
Publié: décembre 31, 2015, 12:26pm CET par Mark Wilson

Yesterday we reported that Microsoft will warn users of 'state-sponsored' attacks on their accounts. Sounds great, but does it actually mean anything? Is it a useful service by the tech giant, or just PR bluster?
Considering the covert nature of spying and digital attacks, coupled with legislation around the world, it seems likely that the announcement is little more than meaningless hot air. In the UK, for instance, the planned snooper's charter would make it illegal for companies to alert users to hacking and surveillance by British agencies.
While this means that it would still be possible for Microsoft (and the likes of Yahoo who announced something similar) to let users know that their accounts are being spied on, it's not a luxury that can be extended to everyone. Should the UK, or another country's government, decide to monitor accounts of Microsoft customers in the US, Microsoft could let them know about it. Likewise, if the US, Russia, or another government other than the UK one decided to spy on users in the UK, Microsoft would be able to issue alerts.
But should the UK government spy on users in the UK, Microsoft would not be able to issue a warning without the risk of facing prosecution. Of course, there is nothing to stop other foreign governments from introducing similar restrictions, ultimately meaning that companies have the choice between complying with the rules or quitting operations in that country.
As noted by TechSpot, the Investigatory Powers Bill (AKA the snooper's charter) includes the proviso that it:
...will ensure that a communication service provider does not notify the subject of an investigation that a request has been made for their data unless expressly permitted to do so.
In short, Microsoft is promising to let users know about state-sponsored spying on their accounts, but only if said state permits this information to be shared. It's an empty gesture.
Photo credit: Imilian / Shutterstock
-

Clueless UK government wants you to help define its digital strategy
Publié: décembre 30, 2015, 5:04pm CET par Mark Wilson

The UK government has been heavily criticized for the way it is attempting to control the way in which people use the internet -- blocking porn, unfettered surveillance and so on. The snooper's carter in particular has been the subject of much disapproval, and in an apparent bid to avoid further complaints, the government is now crowdsourcing ideas for internet policies.
In an article entitled UK Digital Strategy - the next frontier in our digital revolution (a document replete with language and references akin to an elderly parent talking about some aspect of modern culture they don't quite understand), Digital Economy Minister Ed Vaizey explains that he is looking for "ideas from public and industry on the UK's digital strategy".
Being government-written, it is rather self-aggrandizing in tone, with the minister trying to take partial credit for the explosion in the digital economy. Vaizey points to the opening up of government-held data sources so they can be used by apps and services, but says "we need to work hard to make sure we continue to take advantage of the benefits digital transformation has to offer, as an economy and as a society".
There's an unpleasant tone of one-upmanship when he says "other countries are hot on our heels but we want the UK to be synonymous with digital". This suggests that the UK is in some way at the forefront of a digital revolution, when in fact it lags behind many other countries in Europe and around the world -- just look to the average broadband connection speeds that are available, for instance.
Good job we have a Digital Economy Minister, eh?
But Vaizey is out of ideas; he doesn't know what to do next. In 2016 he plans to unveil a five-year plan in the form of the Digital Strategy for the UK (his capitalization, not mine), but he needs help. Even he seems to realize that padding out his document with essentially meaningless puff-phrases like "unlocking digital growth" is pointless. The many hundreds of words he ejaculates could be condensed down to "we want to be better, but don’t know what to do".
This is perfectly illustrated by the plan "to deliver superfast broadband to 95 percent of the UK by the end of 2017" -- with no hint of how it will be achieved, or what happens for the remaining 5 percent. Details, mere details! "We're planning to make it a legal right for every home and business in the UK to request fast broadband". Quite why the right to ask for something needs to be enshrined in law is anybody's guess, but asking certainly doesn't mean getting -- surely you know that by now!
Vaizey wants so desperately to sound like he knows what he's talking about and that he knows what’s going on. "It's estimated around 90% of all jobs over the next 20 years will require some level of digital skills", he prophesizes. Estimated by whom? What is a "digital skill"? Who defined this?
The usual scary monsters get a mention too:
As more of our lives are conducted online, the need to keep ourselves safe from criminals and terrorists increases. But we mustn't let these real dangers prevent us from accessing all the benefits of a digital economy. That’s why we're spending £1.9 billion over the next five years through the National Cyber Security Programme.
Wow (sarcasm). An average of under £380 million per annum, which will almost certainly be spent on over-priced contracts from ministers' chums. That sort of money will disappear overnight, and vanish without a trace.
In case you hadn’t guessed by now, the government doesn’t really know what it's doing, particularly when it comes to the world of technology. Vaizey round things off by saying:
Come 2020, undoubtedly the UK landscape will have changed to be firmly in the digital age. But how do you want to shape that? Government has ideas and ambitions but as Tech City UK back in 2010 shows, the ideas are out there. So challenge us - push us to do more. Let's show the rest of the world how it's done.
On the one hand it's somewhat reassuring that people are being asked how we should move forward. On the other, it's disconcerting to hear just how clueless the minister charged with driving things forward is. He's a man from another age. New blood is needed. That's not going to happen any time soon, so let the government know what you think. You're invited to email idea to digitalstrategy@culture.gov.uk.
You've only got until 19 January, so be quick (although it would be nice to think that ideas sent in after this date would not simply be ignored!).
Photo credit: Maksim Kabakou / Shutterstock
-

Now that Google Glass is enterprise-only, it is more appealing than ever
Publié: décembre 29, 2015, 6:58pm CET par Mark Wilson

The first generation of Google Glass spectacularly failed to get off the ground despite a long beta period. The second generation is on the cards, and it has an enterprise focus which serves only to make the hardware even more appealing. There's no release date, or even a vague schedule for release, yet, but images of the next version of Google Glass have appeared online.
A new filing with the FCC shows just what we can expect from the next version of Google Glass, and it's extremely promising. While there's no suggestion of a consumer model being released, what we learn about the enterprise edition will serve only to make it more appealing to the masses -- great looks, a foldable design, and a larger display. Will Google bow to the pressure that's almost certain to mount and try again with a consumer version?
The filings don’t give away too much, but they give away enough. A hinge indicates that Glass now boasts a foldable design, and signals that this is no longer a device that is meant to be worn at all times. The very fact that there is a hinged arm akin to regular spectacles, coupled with the enterprise focus, suggest that Glass 2 is meant to be slipped on and off throughout the day. This is not only useful for the wearer, but also addresses a key concern that non-wearers expressed: privacy.
The term 'glasshole' was coined to refer to the beta testers who walked around with their first gen Glass models permanently strapped to their heads. There were understandable worries that the wearables could be used to record others as they went about their day to day activities (the filing makes it clear that a green LED lights up when recording is underway), but there were also other concerns.
Police forces said they would arrest anyone caught driving whilst wearing the glasses, but there was no easy way to safely transport the device without wearing it. The introduction of a hinge changes this -- they’re yet to be announced, but it's hard to imagine that there won’t be svelte little carry cases that can be used to house Glass 2.0 when not in use.
Bigger is rarely not seen as better, and the FCC filings show a larger display -- which is pleasing when you consider that Glass is destined for used in medicine. The new design looks robust, and while the first iteration of Glass was ridiculed, Google seems to have learned from its mistakes and is now working towards a product that has mass-appeal... it's just a shame that, at the moment, there is no consumer model planned.
Head over to the FCC website to check out the rest of the Google Glass paperwork.
Photo credit: FCC
-

I am depressed. Technology is my lifeline
Publié: décembre 29, 2015, 12:22pm CET par Mark Wilson

This is a personal account of my experience of depression and how I feel technology has both helped me, and held me back. I've been depressed for just about as long as I can remember, but it's only in the last six months or so that I decided I needed help and thought it was time to do something. 30-odd years is a long time to feel like Atlas bearing the weight of the world.
Having made this decision, technology was something of a lifeline... specifically, and perhaps oddly, Facebook. The social network made it possible for me to communicate with friends when the mere idea of actually speaking to someone seemed like an insurmountable obstacle. It broke down barriers of time and distance, eased my embarrassment, stopped me from feeling awkward for crying (although even writing that brought the tears welling up, and I feel like an idiot, albeit in private).
I've always been quiet, prone to dips into the depths of gloominess but having been that way for as long as I can remember, it became easy to accept it as the norm -- but things started to get too much for me. In the bleak spiral of blackness, the idea of picking up the phone, going to see someone, is just too much. An absolute impossibility. Bashing out a few words on Facebook, however, was far more manageable.
Being able to reach out to people who knew me, whilst simultaneously being able to keep them at arms' length (or draw them closer, as required) was much easier online than in the real world. Those in direct contact with me, of course, cared, but familiarity breeds contempt and it can be hard to try to explain feelings that have been hidden away for three decades. The distance the likes of Facebook and Twitter offered was perfect.
It seems selfish -- sometimes you have to be selfish in the name of self-preservation -- but speaking to people in person or on the phone all too often results in the conversation being on the other person's terms. Social networks are frequently home to people who like to hide behind the anonymity such services afford them. While I was not seeking anonymity, Facebook gave me a chance to step back from myself, write about the way I was feeling at my own pace rather than in a real-time conversation where day-long pauses would be, well, weird.
Facebook, for instance, gave me the chance to 'come out' as depressed in a way that I was in control of. If I got a shitty response from people, I could just delete that status and move on. If people said stuff that hurt me, I could ignore it in a way that would not be possible in a face-to-face situation. I could message people on my terms. And I did. I poured out my heart to people. I splurged. People I would never consider being so open with in person, I told everything.
I told people about suicidal thoughts. About self-harm. About living inside my head and hating it.
There was no need for me to respond to people immediately. I could sit on what had been said to me, mull and consider my reply, and then type out something that actually made sense. Try doing that in the real world.
It hasn’t just been Facebook, of course. I've been able to email support workers and other people when the idea of facing the world was essentially an alien concept. This isn't to say that tech is the answer to everything. Obviously I need to see real people in the flesh... and I do. But for those times when doing anything beyond breathing seems too hard, tech is a lifeline.
I'm a conundrum. I'm endlessly sensitive and take everything to heart -- in the real world, at least. Exposing oneself online means having to develop a thick skin, because people hate you. The internet brings out extremes of response. It's not enough to just disagree with an opinion, disagreement has to be expressed in the strongest possible terms, belittling and berating the holder of those views. Someone who holds an opinion that differs from yours is not simply of a different opinion, they're an idiot. That is just how it is for journalists. Whatever you write about, you lay yourself open for attack, and this would seem to run counter to the idea of trying to protect oneself.
But it works. Technology has been a hobby of mine for as long as I can remember, and I feel incredibly privileged to be able to combine a hobby with work. I love technology. I love writing. I get paid for bringing these two loves together. Win!
What was the point in writing this? Well, to a large extent it was cathartic. But I also recognize that there are plenty of people like me out there. I was astonished to learn that so many of my friends -- including those I spent years with at school -- were, or had been, suffering in the same way as me.
Calling that helpline might seem like too much.
Speaking to even your partner or closest friends might feel impossible.
But there are other approaches. For me, it was Facebook. I was touched beyond words at the support I found out there. It's not that I previously thought that people wouldn't care, but I ended up being overwhelmed by just how amazing friends -- and even people I don't know all that well -- are.
Technology can be seen as just another form of communication, but it's one that can be made to work the way you want it to. Use it.
Photo credit: igor.stevanovic / Shutterstock
-

Dodgy database exposes details of 191 million US voters
Publié: décembre 28, 2015, 7:04pm CET par Mark Wilson

If you've voted in a US election at some point in the last 15 years, there's a high chance that your personal details are now out in the wild. Security researcher Chris Vickery found a misconfigured database that exposes the details of no less than 191 million US voters.
The discovery was made a little over a week ago, and includes the names, addresses, phone numbers, email addresses, state voter IDs, and party affiliations of people registered to vote since the year 2000. The amount of detail contained in the database gives real cause for concern, and Vickery was shocked to find his own details were easily accessible due to a database misconfiguration.
DataBreaches.net -- which has seen the data collected by Vickery -- says it includes valuable data that could easily be matched up with information from other databases to show whether a voter is a gun owner, what their religious persuasion is, and how they have voted in the past. The site also reveals how the private details of a police officer who has no publicly listed phone numbers or addresses found his data in the list.
At the moment it is unclear who is responsible for the database mishap, but there is an investigation underway by Vickery, DataBreaches.net, and Steve Ragan of Salted Hash. There is some comfort to be gleaned from the fact that social security numbers and driving license details have not been exposed, but there is no getting away from the fact that this is a serious issue.
Speaking to Ragan, Vickery said:
My immediate reaction was disbelief. I needed to know if this was real, so I quickly located the Texas records and ran a search for my own name. I was outraged at the result. Sitting right in front of my eyes, in a strange, random database I had found on the Internet, were details that could lead anyone straight to me. How could someone with 191 million such records be so careless?
What is especially concerning is that the exposed database remains online, and there is no way to know whether the data has fallen into the wrong hands or has already been abused. The California Attorney General’s Office as well as FBI NY field office and IC3 have all been contacted, but there are currently no updates about any progress that has been made in securing the databases.
For now, we'll leave the final word to Ragan -- but hopefully there will be positive news to update this article with soon:
Because the information Vickery discovered is in a database available to anyone on the Internet who knows how to find it, it's essentially unrestricted data.
Photo credit: Niyazz / Shutterstock
-

How to view saved Wi-Fi passwords in Windows 10, Android and iOS
Publié: décembre 28, 2015, 1:01pm CET par Mark Wilson

So many stores, service stations, coffee shops, pubs and so on offer free Wi-Fi that you probably have countless networks saved on your phone or laptop. Having a password saved on your computer is great, but how can you get the password so you can use it on your phone as well?
Rather than trying to hunt down a member of staff to ask, or hunting high and low for that tiny sign that shares the password, you can instead view the wireless passwords you have saved. Read on to find out how to retrieve these passwords in both Windows 10 and Android.
If you already have the password for a wireless network saved on your laptop and want to retrieve it to use on your phone -- or share with someone else -- things are quite simple. The same method works in Windows 7, Windows 8.x, and Windows 10, but it's important to note that you need to be connected to the network you are trying to retrieve the password for.
- Press the Windows key and R, type ncpa.cpl and press Enter.
- Right click on the wireless network adaptor and select Status.
- Click the Wireless Properties button.
- In the Properties dialog that appears, move to the Security tab.
- Click the Show characters check box, and the network password will be revealed.
If you want to retrieve a saved wireless network password from Android or iOS, you'll have to have a rooted or jailbroken device -- sadly, there is no standard way to pull up security credentials. It's worth noting that there are several apps out there in Google Play that claim to reveal Wi-Fi passwords; while some of these work, there are also numerous malicious tools out there, so it's best to use an alternative method.
If you're using Android, install a copy of the free file browser ES File Explorer.
- Navigate to the data/misc/wifi folder on your device -- it will not be visible on non-rooted phones.
- Open the file called wpa_supplicant.conf and you will see a list of saved Wi-Fi networks complete with their passwords.
To retrieve a Wi-Fi password on a jailbroken iPhone, you can check in the Keychain access app if you have a Mac connected to the same network, but there's another method if you prefer to do it all from your phone.
Grab yourself a copy of WiFi Passwords from Cydia.
Fire up the app, and you'll be presented with a list of all of the passwords your iPhone has for saved wireless networks.
Photo credit: Marynchenko Oleksandr / Shutterstock
-

North Korea's Red Star OS leaves the government in control of computers
Publié: décembre 27, 2015, 9:04pm CET par Mark Wilson

Based on Fedora Linux, you might expect North Korea's Red Star OS to be a secure operating system. It's not -- at least not by most people's standards. Like China, the socialist state is keen to embrace the power of the internet, but wants to retain control over is citizens. This s exactly what Red Star OS enables the government to do.
Germany researchers from the security company ERNW have probed Red Star OS, examined the code and determined that it is a home grown operating system that leaves the government in control of many aspects of its use, including encryption. It has been suggested that North Korea is paranoid that the west will try to infiltrate through software, but it is North Korean citizens that should be more worried.
Speaking to Reuters, researchers Florian Grunow and Niklaus Schiess say that Red Star OS is the realization of Kim Jong Il's dream of building a North Korean operating system. So panicked is Pyongyang about Western influence and spying, that rather than embracing the internet as most of us know it, it instead relies on its own basic intranet to provide access to officially sanctioned websites.
Grunow says that Red Star OS is "a full blown operating system where they control most of the code". Drilling down into the code, the researchers were able to determine that the OS had basically been built from the ground up and includes feature that prevent the technically minded from bypassing any restrictions that have been put in place:
The Red Star operating system makes it very hard for anyone to tamper with it. If a user makes any changes to core functions -- like trying to disable its antivirus checker or firewall -- the computer will display an error message, or reboot itself.
One of the more invasive and concerning feature of the operating system is the way in which it watermarks every file found on a computer and the drives connected to it. This makes it possible to trace files back to individual users -- something which the government uses to crack down on legal file sharing. Grunow warns:
It's definitely privacy invading, it's not transparent to the user. It's done stealthily, and touches files you haven't even opened.
Grunow and Schiess are presenting their full findings to the Chaos Communication Congress in Hamburg today.
Photo credit: Anton Watman / Shutterstock
-

China passes law requiring tech firms to hand over encryption keys
Publié: décembre 27, 2015, 7:44pm CET par Mark Wilson

Apple may have said that it opposes the idea of weakening encryption and providing governments with backdoors into products, but things are rather different in China. The Chinese parliament has just passed a law that requires technology companies to comply with government requests for information, including handing over encryption keys.
Under the guise of counter-terrorism, the controversial law is the Chinese government's attempt to curtail the activities of militants and political activists. China already faces criticism from around the world not only for the infamous Great Firewall of China, but also the blatant online surveillance and censorship that takes place. This latest move is one that will be view very suspiciously by foreign companies operating within China, or looking to do so.
China's infringement of freedom of speech and the hard line it takes on those opposing the government is well-recorded. While the government insists that there will be no requirement for companies to install backdoors, the country has already earned itself a reputation that is going to be very difficult to shake off.
The deputy head of the Chinese parliament's criminal law division tried to play down the controversy surrounding the new law. Li Shouwei said:
This rule accords with the actual work need of fighting terrorism and is basically the same as what other major countries in the world do.
As well as granting new powers within China's borders, the new law also permits overseas action by the People's Liberation Army -- something which will be eyed with suspicion and likely opposed by for foreign nations. There is also a provision, as reported by Reuters, that "media and social media cannot report on details of terror activities that might lead to imitation, nor show scenes that are 'cruel and inhuman' "-- something else which will bring about accusation of standing in the way of free speech.
Photo credit: Kheng Guan Toh / Shutterstock
-

Twitter says it is beating the trolls
Publié: décembre 27, 2015, 2:32am CET par Mark Wilson

Social networks were designed for people, and people mean problems. In particular, the likes of Facebook and Twitter have become havens for bullies and trolls, eager to prey on others online. Twitter has launched tools and education programs to combat trolling, and now the site says that it is winning the battle.
After making it easier to report abusive tweets and increasing the size of its anti-troll team, Twitter believes it is getting 'bad behavior' under control. As well as bullying of acquaintances and work colleagues, Twitter has also been used to attack celebrities, the gay community, religious groups, and more, with many people feeling driven from the site. It seems that the decision to take a very hands-on approach to troll tackling is starting to pay off.
The head of Twitter in Europe, Bruce Daisley, says that the tools that have been introduced have had a real impact on trolling. He goes further, saying that there is a direct correlation between the release of new safety tools and reporting mechanisms, and the drop in unacceptable behavior. One of the recent tools that has been employed is the use of telephone identification to target trolls.
Twitter users that are reported by others, or are observed misbehaving in some way, could receive calls from the anti-trolling team. Speaking to the Independent, Daisley says:
If someone is behaving in a way characteristic of a bad actor, we send them a phone verification. That allows us to tell the user that what they do here exists in the real world. It normally acts as a stark reminder. Secondly, it allows us to see whether that user has already got other accounts set up on their phone that have been suspended.
But as well as in-house work, Twitter is offloading the troll tackling to users. After introducing tools that make it easier to block troublesome users, people are being encouraged to share their block lists in the hope that this will help a greater number of people to avoid known offenders.
Groups such as Anonymous have also tried to clean up Twitter, but the approaches used have a very vigilante, gangster feel to them. It seems that, at long last, Twitter has reached the point where it is able to fight back on its own, as well as empowering users to look after themselves.
Photo credit: Marcos Mesa Sam Wordley / Shutterstock
-

How to stop Windows 10 asking you to give feedback
Publié: décembre 26, 2015, 9:11pm CET par Mark Wilson

If you've signed up to the Windows Insider program, you're enjoying preview builds of Windows 10 before the vast majority of people. Whether you are on the Fast or the Slow Ring, getting hold of Insider preview builds is a great way to stay on the cutting edge -- but it comes with its drawbacks.
One of these -- aside from the need to download gigantic updates from time to time -- is that Windows 10 will constantly pester you for feedback. While it could be argued that this is very much the point of the preview program, some of you will almost certainly just want to get on with using Windows 10 without being asked 'Would you recommend this build to a friend?' or 'What do you think of the latest features of Windows 10?'. If you want to kill the feedback popups, here's how to do it.
What's important about feedback is letting Microsoft know when something goes wrong or doesn’t work as expected. But rather than feeling harangued into answering simple Yes / No / Maybe style questions, it makes far more sense to seek out the Feedback app and go into more details about problems you have encountered, when you encounter them. If you wait to be asked about your experience, you may well have forgotten what irked you. Take back control. Be pro-active. Hit the Feedback app, and ditch the nagging.
· Fire up Settings from the Start menu.
· Open up Privacy and move to the Feedback & diagnostics section.
· From the Feedback frequency drop down menu, select how often you're happy for Windows to hassle you -- cut it down to a daily or weekly occurrence, or select Never to kill it completely.
Close Settings, and you're done.
Photo credit: niroworld / Shutterstock
-

All I want for Christmas is porn (a little bit NSFW)
Publié: décembre 26, 2015, 1:34pm CET par Mark Wilson

Christmas can be -- scratch that, it is -- a very stressful time of year, and people seek solace in a variety of things... one of them being porn. But when it comes to self-administered stress relief, just what are people around the world using as visual aids to assist stagnant imaginations?
If this is a question that has been bothering you over the festive period, wonder no more for Pornhub has the answers! There is huge scope for sexing up Christmas, and the porn site's latest report into festive shows that XXX fans just can’t get enough of Santa's naughty elves, dirty helpers, and imagining Mr and Mrs Claus engaging in all manner of sexy shenanigans. Forget Happy Christmas, this is more like fappy Christmas... or XXXmas. Spoiler: there's no Jesus porn.
PornHub's "Horny for the Holidays" report offers an intriguing glimpse into how people around the world get their festive kicks. There are plenty of obvious searches being performed (many of which we'll just leave to your imagination, but it's safe to say that one particularly popular search term is not related to colonoscopies...) -- just think of a sex act, add the word 'Christmas' and it's safe to bet that people have been searching for it.
Perhaps unsurprisingly, there is an overall drop in porn-related traffic over Christmas -- most people have better things to do, such as spending time with loved ones -- but this is not true the world over. While the UK, Australia and the US see a drop in porn searches (30 percent, 30 percent and 19 percent respectively), Japan, India and Russia perform more sexy searches: 2 percent, 4 percent and13 percent increases respectively.
As well as revealing what people with a penchant for porn have been looking for in 2015, Pornhub also shows how things have changed since last year. The search term 'Naughty santa's helper' has rocketed in popularity with 2015 seeing a 2,012 percent increase in searches. 'Christmas wife' has increased in popularity by 633 percent, and 'santa and elf' by 546 percent.
Based on the type of device used for search for porn, it seems that the likes of Pornhub are being used as a way to get a little light relief from the stresses of a family Christmas. Nearly two thirds of traffic (62 percent) comes from phones, those handy, portable devices that can be used away from prying eyes of relatives.
With that image, enjoy the rest of the festive season, however you choose to enjoy it!
Photo credit: fotogestoeber / Shutterstock
-

ASUS users will see fewer ads in 2016 thanks to Adblock Plus
Publié: décembre 24, 2015, 12:47am CET par Mark Wilson


Ad blocking is something of a contentious issue, but it's one that has been brought to prominence in 2015. The adblockalypse arrived this year as the debate about whether disabling ad blockers was preferable to paying for content.
Adblock Plus -- one of the best known ad blockers out there -- recently updated its acceptable ads policy which gives people the option of permitting certain ads to appear in their browser. But a new deal struck with ASUS means that anyone buying a phone or tablet from the Taiwanese company in 2016 will find that ad blocking is baked in and enabled by default.
In an interview with Motherboard, AdBlock Plus’s cofounder and CEO, Till Faida revealed that his company was working with ASUS to bring ad blocking to the hardware manufacturer's stock browser. More than this, ad blocking will be switched on by default, undoubtedly to chagrin of advertisers the world over.
As Motherboard points out, the ASUS browser has a relatively small user base (around 15 million), but it is the potential impact which is important. Should other companies start to follow suit, it's a movement that could very quickly gain momentum and could send shockwaves through the advertising and media sectors.
Faida said:
We're extremely happy to team up with Asus, the first major hardware manufacturer to integrate ad blocking into their mobile devices. This is another call for innovation in the ad industry -- a call getting louder by the day.
With the discussion about how online content should be paid for continuing to rumble on, it will be interesting to see how many -- if any -- other companies follow ASUS's lead.
Photo credit: Tashatuvango / Shutterstock
-

Software bug leads to early release for thousands of prisoners
Publié: décembre 23, 2015, 10:47pm CET par Mark Wilson

More than 3,000 prisoners in the state of Washington have been released early from prison as a result of a software bug. The formula used to calculate sentence reductions was found to be inaccurate, and while the average early release prisoner mistakenly had 49 days shaved from their sentence, one was set free almost two years early.
The software bug stems from a software update way back in 2002. The update introduced a new way to apply good behaviour credits, and governors are astonished that the problem has been on-going for 13 years. The Washington Department of Corrections says that it has been aware of the issue since 2012.
The DoC had been alerted to the bug three years ago when the family of a victim discovered that the perpetrator was being released early. But it has taken until now for a fix to be sorted out -- the correct formula for release date calculation will be in place by 7 January. So far just five prisoners have been rounded up, and police are in the process of trying to round up more.
Washington's governor Jay Inslee said:
That this problem was allowed to continue for 13 years is deeply disappointing to me, totally unacceptable and, frankly, maddening.
Although there is a computer system in place that is supposed to take care of release dates, the DoC has ordered that manual checks are performed until the software fix is put in place in the new year.
Photo credit: Viorel Sima / Shutterstock
-

UK government working with eBay and Amazon to catch tax-evading sellers
Publié: décembre 23, 2015, 9:32pm CET par Mark Wilson

When it comes to tax avoidance, it's usually big companies that come under the spotlight. Of course, there is nothing -- legally speaking -- wrong with tax avoidance, but it's a very different story with tax evasion. With eBay and Amazon providing a platform for vendors around the world, it is perhaps little surprise that the retail sites are home to a large number of tax evaders.
An investigation by the Guardian found that there are a huge number of overseas sellers who fail to pay VAT in the UK. HM Revenue & Customs is currently looking into whether eBay and Amazon could be held responsible for the tax bills, or what could be done to track down offenders.
Following the Guardian's investigation, eBay announced that it would report a number of sellers making use of the auction site. Sellers in China have been found using false VAT numbers, or even using VAT details associated with other companies.
For Amazon, sellers are able to use the retail giant's UK warehouses as a storage base for goods. Handing over dispatching responsibilities to Amazon -- coupled with fake addresses in China -- opens up the opportunity for the introduction of financial irregularities, and a government taskforce has already been put in place to try to combat the problem. Both eBay and Amazon say that responsibility lies with individual sellers to pay whatever tax they owe, going on to say that the sites should not be held liable.
The Guardian asked overseas sellers to provide VAT receipts for purchases that the newspaper had placed but were given excuses ranging from the seller not being VAT registered, to it being seller policy not to provide such receipts. As part of its investigation, the Guardian spent £1,818.20 on 24 items, which should have incurred VAT of £363.64. In reality, the order breakdown listed £0 VAT.
Not all sellers on eBay and Amazon need to register for and pay VAT on their sales -- just those with a UK turnover of over £82,000. Sellers that are VAT registered feel they are getting a poor deal, as sellers based overseas have been able to undercut their prices by simply not paying applicable taxes.
Photo credit: Mr-Vector7 / Shutterstock
-

Kim Dotcom faces extradition to US from New Zealand
Publié: décembre 23, 2015, 1:03pm CET par Mark Wilson

Kim Dotcom, the founder of MegaUpload and Mega, could be extradited to the US where he faces charges of copyright infringement. Dotcom is also wanted by US authorities for money laundering and racketeering, and a New Zealand court has ruled that his extradition can go ahead.
The German national's Auckland home was raided by New Zealand police four years ago after the FBI closed down his file-sharing site in the US because it had been used to illegally share music and movies. Kim Dotcom has proved to be a polarizing character -- much like Edward Snowden -- viewed by some as a spokesperson for a free internet, and as an out and out villain by others.
It is estimated that Dotcom's websites and online tools have cost the movie and music industries over half a billion dollars, but this is clearly a figure that is hard to substantiate. Questions have been raised about the thinking behind calls to extradite him to a country that he has never visited, let alone lived in.
Despite losing the most recent case, Dotcom remains in an upbeat and defiant mood despite leaving court saying "I'm disappointed". After the ruling he took to Twitter to suggest making an appeal:
My team and I just had a good read of today's court decision. Its weak and a Christmas gift in disguise. Woohoo!! #Appeal
— Kim Dotcom (@KimDotcom) December 23, 2015
His attorney, Ira Rothken told Reuters:
We think the judge was wrong on the law. Justice wasn’t done today.
Dotcom faces charges along with three others, but the extradition ruling in itself makes no hint at guilt.
-

Broadband ads are confusing and misleading
Publié: décembre 23, 2015, 12:08pm CET par Mark Wilson

People in the UK are confused by broadband advertising that can make it difficult to determine the best deals. The charity Citizens Advice says that most people find the ads too confusing and felt overwhelmed with information, making the task of comparing packages that much harder.
CA's findings suggest that more than half of people looking at broadband deals could not identify the cheapest deal available to them, at least in part because line rental costs were not always made clear. ISPs are accused of misleading customers, using headline-grabbing deal prices that do not truly reflect what the costs are.
These are familiar accusations that have previously been levelled at credit card companies, and the real concern is that people are simply not provided with the information they need to make an informed decision. The charity's research involved asking groups of people to calculate the cost of a given broadband deal, and to calculate which was the cheapest of two samples.
An astonishing 56 percent of people couldn’t work out what the deals would cost (although it's probably worth factoring in the mathematical abilities that some may or may not possess). In one case, just 22 percent of those questioned could determine the cost of a deal from a company which Citizens Advice has not identified.
Citizens Advice's chief executive, Gillian Guy said:
Attractive headline offers that don't include line rental costs make it impossible for people to work out the best broadband deal on offer without doing complicated sums. Broadband providers need to make the costs of a contract clear in their advertising and the Advertising Standards Authority should also review the code of practice to make sure it works well for consumers.
Singled out for criticism was the practice of highlighting the cost of a promotional period without making it clear how costs would jump when this came to an end.
Early in 2016, a joint report by the Advertising Standards Authority and Ofcom is due to be published looking at the broadband advertising landscape.
Photo credit: Mr.Exen / Shutterstock
-

Google ready to embrace AI for new messaging tool to take on Slack
Publié: décembre 23, 2015, 2:24am CET par Mark Wilson

The battle arena for messaging apps has become increasingly busy in recent years, with the likes of Facebook Messenger, WhatsApp and countless others all vying for attention. In the workplace, Slack is the current favorite thanks in part to its smart capabilities, programmability, and bot.
Not wanting to miss out on the action, Facebook recently unveiled Facebook M, a virtual assistant bolt on for Messenger. Looking to compete directly with this, Google is working on a new AI-powered messaging service of its own according to a report from the Wall Street Journal.
The WSJ report is somewhat bereft of concrete detail, but those ever-present 'people familiar with the matter' say that Google is working on a mobile messaging tool that incorporates artificial intelligence and a chatbot. On the face of it, the tool sounds like an amalgamation of Hangouts and OK Google, neatly combining what the company has learned from both.
Rather than keeping the app to itself, Google is said to be considering allowing third-party developers to create chatbots of their own, opening up the possibility of advanced customization.
Slack has already shown -- particularly with its recent support for apps -- that it is possible for a chat tool to be about much more than just chat, and it seems that this is an idea that Google is keen to build upon.
More details as we get them.
Photo credit: Vdovichenko Denis / Shutterstock
-

Google tests password-free logins on iOS and Android
Publié: décembre 23, 2015, 12:12am CET par Mark Wilson
Online security concerns mean that we have become reliant on passwords to access so many different services. The sensible and secure route to take is to use a unique password for every site and service you access, but unless you have a record-breaking memory, this can prove tricky. Google has a solution: ditch the password entirely.
While this may be seen as a step down from the two-factor authentication that so many companies have been pushing for in recent years, it is actually quite similar in many respects. Google's method focuses on speed and convenience, and still requires the use of a smartphone.
The new password-free methods of logging into accounts is not something that is being made available to everyone just yet, just a select group of testers. Assuming your phone has been linked to your Google account, when the time comes to log in, all you need to do is enter your email address. A confirmation is then sent to your phone, and you can complete the log in process by tapping the Yes button that appears.
As many people tend to have their phones all but surgically attached to their body, it seems like a sensible and relatively secure means of authentication. It's currently being tested on iOS and Android through the Sign-In Experiments at Google group, and in a statement to TechCrunch Google said:
We've invited a small group of users to help test a new way to sign-in to their Google accounts, no password required. 'Pizza', 'password' and '123456' -- your days are numbered.
Should you find that you need to log into your account when you do not have your phone, or your battery is dead, it is still possible to use a password in the usual way. Could this be the end of the password as we know it?
Photo credit: Lorenzo Patoia / Shutterstock
-

Apple wants the UK government to rein in snooper's charter
Publié: décembre 22, 2015, 1:32pm CET par Mark Wilson

Tim Cook is a vocal opponent of any form of encryption weakening, and now Apple has spoken out against the UK government's Investigatory Powers Bill -- otherwise known as the snooper's charter. Currently in draft form, the bill would require ISPs to retain customers' browsing histories for a year, and would require technology companies to implement backdoors that would allow encryption to be bypassed.
Apple says that it has serious concerns about the proposed bill in its current form, and calls for sweeping changes to be implemented. The company has famously refused to allow access to encrypted iMessage chats, and this is a stance it is reiterating.
The company says that it is simply not possible to allow backdoor access to data without weakening encryption for everyone. It also expressed concerns that the bill would legalize governmental hacking of computers around the world. In a submission to the committee overseeing the bill, Apple says:
We believe it would be wrong to weaken security for hundreds of millions of law-abiding customers so that it will also be weaker for the very few who pose a threat. In this rapidly evolving cyber-threat environment, companies should remain free to implement strong encryption to protect customers.
This is a sentiment that echoes the words of CEO Tim Cook, and Apple makes a point that is hard to argue against:
The creation of backdoors and intercept capabilities would weaken the protections built into Apple products and endanger all our customers. A key left under the doormat would not just be there for the good guys. The bad guys would find it too.
There is particular alarm that the bill would grant the UK government worldwide powers -- something that many would see not only as invasive, but also wildly undemocratic. Apple says that this would create an awkward relation with customers:
It would place businesses like Apple -- whose relationship with customers is in part built on a sense of trust about how data will be handled -- in a very difficult position. For the consumer in, say, Germany, this might represent hacking of their data by an Irish business on behalf of the UK state under a bulk warrant -- activity which the provider is not even allowed to confirm or deny. Maintaining trust in such circumstances will be extremely difficult.
Those businesses affected will have to cope with a set of overlapping foreign and domestic laws. When these laws inevitably conflict, the businesses will be left having to arbitrate between them, knowing that in doing so they might risk sanctions. That is an unreasonable position to be placed in.
Photo credit: Ruslan Grechka / Shutterstock
-

Panda Security: 2016 will be the year of Android of IoT attacks
Publié: décembre 22, 2015, 12:53pm CET par Mark Wilson

Security experts from Panda Security warn that 2016 is set to be a bumper year of attacks and malware infections. The company says that malware will grow at "an exponential rate", with Android, mobile payment platforms, and the Internet of Things being key targets.
Business, individuals, and corporate users alike are at risk, and it is predicted that infections via JavaScript and Windows 10's Powershell are to be common attack vectors. Exploit kits are due to increase in popularity, largely because of the fact that it is not currently easy to combat them.
Android, thanks to its position as the world's most popular operating system, is set to bear the brunt of attacks. As well as rootkits targeting the operating system itself, Panda Security says mobile payment systems and connected devices will be targeted. Any system that proves popular with users places itself in the crosshairs.
Technical Director of PandaLabs, Luis Corrons, says:
Although Android attacks have been commonplace in recent years, the news for 2016 is the manner in which mobiles will be infected. We will see more threats that root the device, which makes eliminating it a near impossible task for an antivirus, except for those that come installed from the factory.
Inconvenience aside, the threat to businesses is greater than ever. Successful attacks not only damage reputations and place customers at risk, but also lead to huge financial costs. Businesses in particular should be vigilant for ransomware attacks.
As we enter 2016, Panda Security warns that "it will be necessary for users and businesses to have security tools and solutions that analyze and classify the behavior of all executables, and that also offer advanced protection to prevent and act against security threats".
Photo credit: Yuliya Verovski / Shutterstock
-

Cortana for Android loses its raison d'être
Publié: décembre 21, 2015, 8:45pm CET par Mark Wilson

When Cortana made its way to the Windows 10 desktop, lots of users were excited by the prospect of a Microsoft version of Siri. Moving to Android as well as Windows 10 Mobile devices, Cortana could really compete with not just Siri's voice control options, but also OK Google.
Now this has changed -- at least for Android users in the US. The latest update to the app strips out the voice activation options leaving users questioning whether or not there is any point in having the app installed.
Over the weekend, Microsoft pushed out an update which as well as bringing "improved app stability" and "enhanced call and text features", also "removed 'Hey Cortana' feature for US market". There have been complaints that there were compatibility problems with OK Google and issues with the microphone, but Microsoft has not elaborated on why the feature has been ditched.
Microsoft proclaims in the Google Play description that "Cortana's always up for a little chit chat" -- but now that’s only true if you’re willing to put in the finger work and type out anything you might want to ask the digital assistant. What's that noise, you ask? Why, that's a chorus of people saying "OK Google, uninstall Cortana".
-

Please, sir, I want some porn
Publié: décembre 21, 2015, 3:04pm CET par Mark Wilson

UK consumers of porn will have to ask their ISP to provide them with access to X-rated content. As the government continues its futile bid to sanitize the web, new customers signing up for internet access with Sky will find that an adult content filter is enabled by default.
This means that anyone wanting to view content that has been deemed 'adult' will have to contact Sky to lift the block. The decision to make the content filter opt-out rather than opt-in was taken after it transpired that a mere 3 percent of existing users had taken the step of switching it on in the first year since its introduction in 2013.
A second line of attack saw Sky emailing its customers at the beginning of 2015. The email gave users the choice of enabling the filter if they wanted, but if the correspondence was ignored, Sky assumed the filter was wanted and automatically enabled it. 62 percent of people who did respond opted to enable filtering. Sky says this is a "significantly higher engagement than any other broadband provider".
But for new customers wanting to access porn, they will have to ask for it. The company says:
Following the customers' positive response to that initiative, in 2016 Sky will be the first broadband company to automatically provide filtering to all its new customers.
Sky will continue to highlight the benefits of Sky Broadband Shield for customers, but this is just one way of protecting children online. Sky continues to support www.internetmatters.org which provides guidance and resources for parents. It offers advice on a variety of parental concerns including inappropriate content, cyber bullying and radicalisation as well 'how-to' guides for setting up parental controls on a range of devices.
It is a move that is likely to be welcomed by parents -- and some non-parents -- but it will also spark debate about who decides what is classed as adult content and the repercussions that blocking could have on education and access to information.
-

New HTTP 451 error indicates pages have been blocked or censored
Publié: décembre 21, 2015, 12:43pm CET par Mark Wilson

It's not every day that a new HTTP error code is introduced -- there are, after all, a limit to the number that could possibly be needed -- but it may not be long before you encounter a 451 error. The code has been made a new standard by the Internet Engineering Task Force (IETF) to indicate when sites have been taken down for legal reasons.
Described as an 'HTTP Status Code to Report Legal Obstacles', it is hoped that 451 errors will introduce a new level of transparency about sites that have been killed by governments or law enforcement agencies. In some ways it is an extension of the 403 (Forbidden) error, but it provides a little more information as to why a particular site cannot be accessed.
While a 451 error need not provide specific details about why a site cannot be displayed, it does at least indicate that a legal request has been sent to the host. As noted by Mark Nottingham, chair of the IETF HTTP Working Group, it was felt that a distinction needed to be made from a 403 error which 'doesn't say "I can't show you that for legal reasons"'.
The standard is defined as:
This status code indicates that the server is denying access to the resource as a consequence of a legal demand.
The server in question might not be an origin server. This type of legal demand typically most directly affects the operations of ISPs and search engines.
Responses using this status code SHOULD include an explanation, in the response body, of the details of the legal demand: the party making it, the applicable legislation or regulation, and what classes of person and resource it applies to.
While an explanation for inaccessible sites is proposed, it is not required. The standard goes on to say:
The use of the 451 status code implies neither the existence nor non-existence of the resource named in the request. That is to say, it is possible that if the legal demands were removed, a request for the resource still might not succeed.
While the status is still due for some attention from the RFC Editor, the 451 message can be used right now.
Photo credit: Maxx-Studio / Shutterstock
-

Another nail in the coffin for Flash as Facebook defaults to HTML5 video
Publié: décembre 21, 2015, 12:24am CET par Mark Wilson

The demise of Flash has been long, lingering, and painful -- and highly over due in many people's books. There has been a spate of high profile ditchings of Flash recently: Speedtest.net, Twitch, Chrome and Netflix to name but a few. Now Facebook has thrown its hat in the ring switching to HTML5 video.
This is a move that is browser-agnostic, and means that every single video you see on the social network will default to HTML5. While many will see this as a cause for celebration, the change does not completely spell the death of Flash -- it will continue to be used on Facebook for many games.
Facebook's Daniel Baulig says that the social network is in talks with Adobe to find a reliable way to switch games to HTML5, but for now it is videos that are affected by the changes. The company has spent time diagnosing HTML5 problems in various web browsers, and this ultimately led to the decision to roll out HTML5 video support to all browsers rather than creating a fragmented experience for users.
HTML5 is not only faster and more secure than Flash, but it also allows for easier development and scaling. Facebook reports that videos start to play faster, and this leads to greater interaction.
While the switch to HTML5 comes as more and more companies are fleeing from Flash and its endless security problems, the benefits work in Facebook's favor as well as users'. Baulig explains that HTML5 allows for better data gathering:
Our video logs help us understand how people use the video player and how it performs. We share some of that data, like view count, with video owners, and we use other data to determine how many and which videos to show to people. We had to make sure the new video player logs the equivalent data and events in the same scenarios as the old player. Implementation differences and details can make this surprisingly hard. To ensure logging correctness, we created a test suite that performs the same user-interaction scenarios against both video players and then validates that the logs are equivalent. This way we had high confidence in the data that our new HTML5 video player reports.
Photo credit: Ian Law / Shutterstock
-

KickassTorrents now has its own movie release group
Publié: décembre 20, 2015, 11:38pm CET par Mark Wilson

There has been something of a clamp down on torrent sites around the world in recent years, but that doesn’t mean they're going away. It may be slightly harder to get a torrent fix these days, but where there's a will there's a way. One of the biggest names still on the scene is KickassTorrents, and it has now ventured into new territory by starting a release group of its own.
Over the last few days, the group -- under the handle KATRG -- has been pushing out numerous Blu-ray rips and screeners. There's no sign of Star Wars: The Force Awakens just yet (although it's surely not long before it makes an appearance), but there are some big releases out there including The Hateful Eight, The Peanuts Movie, and The Revenant.
There are already a high number of well-respected release groups in existence, and new-comers are usually few and far between. But with a big name like KickassTorrents associated with it, this could be one of the few that manages to creep to public attention. Like the Pirate Bay, Kickass Torrents is one of the stalwarts of the torrenting scene, surviving endless takedown attempts by law enforcement agencies.
In setting up a release group, the site is kicking things up a notch. Not content with courting controversy by providing access to torrents, by putting its name on specific releases KickassTorrents is virtually pulling down its pants and baring its behind at authorities. The site is waving a big red flag, shouting "come find us!" but, ultimately, it is torrent users who will benefit.
As noted by Torrent Freak, KATRG's releases have already been noticed by copyright holders, resulting in takedown requests -- which have been complied with. The site provides a way around this, though:
KickassTorrents is offering a solution to this problem. It’s been in operation for some time, but essentially it remains possible to download releases even after they have been taken down from the site.
In respect of KATRG this is achieved by a forum thread which lists all of the group’s releases along with their hashcodes. Should any be taken down, users are invited to enter hashes into another search engine which then provides the download in question.
KickassTorrents is a brand, and it is keen to maintain its reputation. The sources of the movies are not (understandably) being made public, but with its name to protect, the quality of releases -- including though re-encoded from other sources -- is likely to remain high.
Photo credit: Erce / Shutterstock
-

Armed gang uses Grindr to target victims for gay-bashing
Publié: décembre 20, 2015, 12:50pm CET par Mark Wilson

Dating services are big business these days, and they offer a modern way to meet a life partner. But there's also a dark side. Tinder is perhaps the most well-known dating app, and Grindr is a near identical service aimed at gay and bisexual men.
Police in London are warning that the app -- which is available for iOS and Android -- is being used by an armed gang to set up fake dates with men. With two million people using the app around the world, Grindr offers rich pickings for homophobes to look for victims.
The gang, said to be armed with knives, is still being hunted by the police and anyone with information that could help is urged to get in touch. Grindr says that it is doing everything it can to help police. In a statement, a spokesperson for the company said:
Grindr has always encouraged users to treat the platform as they would any other social interaction in their lives, with a measure of caution and an awareness of their own safety.
There are many ways to verify and take steps to protect yourself, from meeting in more public spaces to getting phone numbers and speaking beforehand. We take these matters very seriously and cooperate with local law enforcement at all turns where we can.
Croydon Police offer up a number of tips for safe online dating:
- Always meet in a public place with lots of people around
- Don't share personal details until you trust the person with whom you are communicating
- If you decide to meet in person, let someone know where you are going and when you're likely to return
- Plan your journey to and from the date in advance. If using a mini-cab, always pre-book
- Drink responsibly and never leave your drink unattended
- Ensure your mobile phone is fully charged and working
- If at any time you feel uncomfortable, leave the date -- you are not obliged to stay
Photo credit: Vdovichenko Denis / Shutterstock
-

Insane bug makes it incredibly easy to hack many Linux systems
Publié: décembre 20, 2015, 12:03am CET par Mark Wilson

Linux is usually touted as the operating system of choice for those concerned about privacy, but a recently discovered bug makes it unbelievably simple to bypass authentication. A vulnerability in Grub2 -- the bootloader used by many Linux distros -- means that all it takes to take control of a computer is to press the backspace key 28 times.
Two researchers from the Cybersecurity Group at Spain's Polytechnic University of Valencia published a paper that reveals just how easy it is to gain access to many Linux systems. It's not a problem that Ubuntu, Red Hat, and Debian users need to worry about too much as patches have already been issued, and users of other distros can make use of an emergency patch in the Grub2 git repository.
While the security issue is laughably simple to exploit, it is somewhat mitigated by the fact that physical access is required, but it is worrying nonetheless. In an article entitled Back to 28: Grub2 Authentication 0-Day, researchers Hector Marco and Ismael Ripoll say that Grub2 versions from 1.98 (December, 2009) to 2.02 (December, 2015) are affected.
So how do you know if your system is vulnerable? The researchers explain:
To quickly check if your system is vulnerable, when the Grub ask you the username, press the Backspace 28 times. If your machine reboots or you get a rescue shell then your Grub is affected.
They warn that systems that are vulnerable to the problem could be exploited by an attacker to gain full access to the grub console. Attackers could install unauthorized software or rootkits, and copy or delete data. Full details of the 0-day can be found on Hector Marco's website.
If you need to grab yourself the patch, head over to the Grub2 git repository right now.
Photo credit: Matushchak Anton / Shutterstock
-

Stop doing quizzes on Facebook if you place any value on your privacy
Publié: décembre 19, 2015, 9:21pm CET par Mark Wilson

You might think that talking about Facebook and privacy in the same breath is a little odd. The two just don’t go hand in hand, surely? Trying to use Facebook whilst maintaining your privacy is an exercise in futility, right? Well, yes, it’s certainly true that hitting a social network is not the thing to do if you want to fly under the radar, but many people do not realize just how easy it is to unwittingly hand over reams of personal information to companies and persons unknown.
While a majority of users are aware that anything they post -- essentially -- becomes Facebook's property, and can be exploited in a variety of ways. Anything shared to the social network can be used to dig up an ever-more accurate picture of who you are, where you are, what you do, what you like, and who you know. Quizzes, personality tests, friend comparisons, and year in review apps, however, are blackholes for personal data -- and the huge range of apps from Meaww have been singled out as being a major cause for concern.
Take a look at the Meaww website, and you'll find a range of familiar sounding quizzes, all of which have a social element to them. "Which friend is your total opposite?", "Who is your gossip partner?", and "Which friend could be the peanut-butter to your jelly?" -- who could resist discovering the answers to such important questions?! Of course, Meaww can’t just guess what it needs to know about you, you have to hand it over.
A disclaimer at the bottom of the page proclaims: "All content is provided for fun and entertainment purposes only". Fair enough, you might think, but that's far from being the end of the story. If we’re being picky -- or accurate, as I like to put it -- it's also not true. It's not just about fun and entertainment. There is some entertainment to be drawn from learning which of your Facebook friends is willing to take a bullet for you, sure, but let's be honest about the purpose of these apps.
Meaww is not acting out of the goodness of its heart in providing entertaining tools free of charge. The company directly and indirectly benefits from everyone who pumps their personal details -- and those of their friends and family -- into them. History has already showed us that social network users are rubbish at locking down their settings, and checking what is going on in the background. This is something that Meaww takes full advantage of, requesting access to Facebook users' email address, photos, timeline posts, friends and more, in the full knowledge that the lure of a silly app that pumps out nonsense will be enough to persuade people to just click through without giving a thought to what granting such permission actually means.
So what does it mean? It means that any information provided about you and your friends can be collected and sold onto advertisers. There is simply no way to know where it ends up and what, ultimately, it will end up being used for. Meaww could sell the data to an advertiser -- or, more likely, multiple advertisers -- who could in turn sell it on to another company. The more levels of on-selling that are introduced, the less integrity there is. It's almost like a money laundering process. Filter data through enough companies, and there is no way of knowing where it came from, but this does not in any way reduce its value.
Meaww's privacy policy admits as much:
Please be aware that this Privacy Policy does not apply to the practices of entities Meaww does not own or control, or to individuals whom Meaww does not employ or manage, including any third parties to whom Meaww may disclose Personal Information (as defined below) pursuant to the terms and conditions of this Privacy Policy.
There is also the admission that:
Meaww processes Personal Information on its servers in many countries around the world. Such information may be stored on any of our servers, at any location.
With differing levels of security and privacy to be found around the world, this also represents a cause for concern. Meaww gives the impression of being open in its privacy policy, but it's little more than lipservice.
Except as described hereunder, We do not share your Personal Information with third parties unless We have received your permission to do so, or given you notice thereof (such as by telling you about it in this Privacy Policy), or removed your name and any other personally identifying information from it.
The company washes its hands of any responsibility for how personal data is handled. Anything could happen... it's all out of Meaww's control.
We are not responsible for the practices employed by any websites or services linked to or from Meaww, including the information or content contained within them. Please be aware that if you choose to use a link to go from Meaww to any third party's website or service, such third party's own rules and privacy policy (and not our Privacy Policy) will apply and govern your activities and any information you disclose while interacting with such third parties.
In many regards, highlighting the privacy concerns associated with Facebook can be seen either as stating the obvious, or preaching to the converted. But adopting that attitude assumes a level of privacy knowledge that many web users simply don’t have.
If you want to make a resolution for 2016 consider making it your mission to educate friends and family about the importance of keeping private data private -- and also that it is possible to compromise other people's privacy.
Photo credit: Di Studio / Shutterstock
-

Critical patches issued after spying backdoors found built into Juniper firewalls
Publié: décembre 18, 2015, 10:05pm CET par Mark Wilson

Networking manufacturer Juniper has discovered backdoors built into its firewalls. The company says that a number of its devices running the ScreenOS operating system include serious vulnerabilities that could be used to take remote control of networked devices, or to decrypt VPN traffic.
The company says that the security issues were unearthed during an internal code review and has issued an out-of-cycle fix to address the vulnerabilities. Network admins are advised to treat the threats seriously, and to make use of the available patches immediately.
The first vulnerability (CVE-2015-7755) enables attackers to use SSH or telnet to log into a system without authorization. Juniper warns that this could lead to a "complete compromise of the affected system". There is a further warning that it would be possible for an attacker to cover his tracks so the victim would have no idea of what had happened: "There is no way to detect that this vulnerability was exploited".
The second issue (CVE-2015-7756) could allow a skilled attacker to intercept and decrypt VPN traffic, but Juniper says that there is no indication that there have been any successful exploits. In a security advisory notice, the company says:
During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections. Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.
At this time, we have not received any reports of these vulnerabilities being exploited; however, we strongly recommend that customers update their systems and apply the patched releases with the highest priority.
If you're using a NetScreen device with ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20, you need to install the new updates as soon as possible.
Photo credit: Imilian / Shutterstock
-

Google dedicates $1 million to independent research for Drive security
Publié: décembre 18, 2015, 4:18pm CET par Mark Wilson

Google is placing an increased importance on security in 2016. The company has set aside $1 million to fund independent research into the security of its Drive cloud storage service, and will continue to offer a bug bounty program.
Acknowledging that "keeping files safe in Google Drive is super important", Google says that next year it will make the money available to independent security researchers. The money comes in addition to the funds that are used to employ hundreds of security experts at the company, with independence bringing an extra level of scrutiny.
Jumping on the holiday season bandwagon, Google uses the near-certain arrival of countless new devices in the coming week to promote the value of Drive, pointing out that it "can help you easily move your files and keep them all safe going forward". But of course, people want to be sure that the service they use to house files -- however temporarily it may be -- is completely safe.
Writing on the Google Drive blog, Product Manager Kevin Nelson says:
Our research grant program is one way independent security researchers contribute to Google’s data security. We're grateful for their efforts to keep Google Drive safe, so next year we’re dedicating $1,000,000 to fund even more grants for independent security research. Separately, we’ll continue to offer up to $20,000 to anyone who finds and reports a qualifying issue. The end result of these ongoing efforts is a product that -- unlike your garden-variety hard drive -- actually gets better over time.
Photo credit: NIRUT RUPKHAM / Shutterstock
-

BlackBerry's privacy stance is yet another reason to avoid the company
Publié: décembre 18, 2015, 12:09pm CET par Mark Wilson

We are living in a post NSA-world (and I am a post-NSA girl...) and privacy is in the public consciousness more than ever before. After the government surveillance revelations that came courtesy of Eddy Snowden, most tech companies have been trying to stress to customers and clients just how willing they are to stand up for privacy.
But not BlackBerry. Company CEO John Chen has used a blog post to lash out at his contemporaries for supporting strong encryption. He makes a thinly-veiled reference to Apple, accusing that an unwillingness to comply with law enforcement requests put us all in a "dark place". Chen says that "our privacy commitment does not extend to criminals", seemingly failing to recognize that privacy is very much an all-or-nothing concept.
In his blog post, entitled The Encryption Debate: a Way Forward, says that the encryption/privacy debate is "acrimonious and polarizing". Apple has famously said that it will not implement backdoors for governments, nor hand over encryption keys, but Chen believes that BlackBerry is "proof that a proper balance can be struck".
While asserting that the company not only opposes a ban on encryption, but also the idea of allowing governmental access to servers, Chen says that "lawful requests for investigative assistance" should be cooperated with. This is a worryingly simplified view of things. It’s very easy to stand up as a supporter of privacy, and great PR to want to assist with law enforcement. But the two frequently cannot go hand in hand.
Chen says "reports that messaging apps WhatsApp and Telegram have been employed by terrorists have brought the encryption debate to a head", bandying around that terrorism warning once again. OK, let’s run with that idea. Let’s imagine that these tools, or even FaceTime, Gmail -- or any other form of communication you might care to mention -- are being used by terrorists. How would you know? If user privacy is paramount, the providers of these services would have no idea of what users are talking about. If no backdoors have been implemented, how would the government or law enforcement agencies tap in to check for themselves? If encryption keys have not been handed over, how is anyone outside of the conversation able to see what’s being said?
Whatever way you slice it -- and whether you like it or not -- privacy and law enforcement assistance simply do not go together. It’s one or the other. If chats, emails and the like are entirely private, there would be no way for authorities to have even the vaguest hint that 'terrorists' are discussing terrorism, and no idea that there is anything to investigate. You might say that the fight against terrorism justifies a weakening of privacy rights, but you’d be wrong. It would be an unworkable system. All it would achieve is killing privacy for the masses, and pushing dangerous elements further underground.
All or nothing, it’s that simple. And for me, privacy is more important, regardless of whether you have anything to hide or not.
Photo credit: Svetlana Dikhtyareva / Shutterstock
-

The bible is dangerous for you and your phone
Publié: décembre 17, 2015, 11:36am CET par Mark Wilson

For the religiously-inclined the appeal of installing an electronic bible on a phone is (somewhat) understandable. But as well as providing a biblical fix when out and about, apps of a religious bent could also harbor a worrying payload.
The Threat Insight team from Proofpoint looked at thousands of iOS and Android apps, and found that a disturbing percentage of seemingly innocent apps pose a threat to users. Apps were found to include secret tracking components, as well as data-stealing elements and the ability to make unauthorized calls. The figures make for frightening reading.
The security team looked at a total of 38,000 apps in the App Store and Google Play, and found that 3.7 percent of 'Bible apps' featured malicious code. The problem of Trojan flashlight apps continues, and Threat Insight found that these apps were transmitting personal users data to hundreds of servers in dozens of countries.
Kevin Epstein, VP of Threat Operations says
When it comes to malicious apps, apparently nothing is sacred. The surprising prevalence of riskware in religious texts' apps provides further evidence that mobile users -- and their employers -- need to be far more security-conscious. The findings are also a valuable reminder of the importance of a mobile app security strategy for organizations. To protect employees and users from unscrupulous scammers and cybercriminals -- and against riskware and malicious apps in general -- organizations should define policies and deploy solutions that enable them to identify and control these apps before they can impact the organization's security posture.
But these are certainly not the only targets for malware; gambling apps were also found to be dangerous. Threat Insight reports that almost 14 percent of such apps exhibited 'risky behavior'.
Photo credit: Luis Molinero / Shutterstock
-

Microsoft wants you to upgrade to Windows 10... whether you like it or not
Publié: décembre 16, 2015, 11:04pm CET par Mark Wilson

Microsoft managed to piss off a lot of people with Windows 10. Some people love it, but certainly nowhere near 100 percent of the install base (whatever size Microsoft claims this may be). It's possible for any operating system to be disappointing, but what Microsoft has managed to get wrong with Windows 10 -- time and time and time again -- is the way upgrades have been delivered.
We've had stories of installation files being downloaded without permission. There are the privacy concerns. There is the confusing installation process that has misled some into upgrading to Windows 10. But even after weeks and months of complaints, the forced Windows 10 upgrades are still happening. If anything, the problem is getting worse. Microsoft is making it harder and harder for Windows 7 and Windows 8 users to avoid Windows 10. A coerced user is not a happy user, yet Microsoft continues to force Windows 10 down people's throats in a number of ways. WT actual F?
You would expect that any upgrade would be optional. This seems like a reasonable assumption, but it's something that Microsoft appears to fail to understand. People buying a new computer are still able to opt for Windows 7 if they want, but the forced upgrade problem means that there is absolutely no guarantee that Windows 10 won’t be foisted on them at some point in the future.
Microsoft -- and its legal team -- might take exception to use of the word 'forced', but it is effectively what is happening. At the very least, a large number of people are being misled, tricked, fooled, hoodwinked into installing Windows 10. Why? Microsoft is making it appear that there is simply no choice. As noted by Gordon Kelly over on Forbes Windows 7 and Windows 8 users are presented with "Upgrade to Windows 10" messages that very strongly imply that the decision you can make when it comes to upgrading it is not 'if?', but 'when?'.
In some instances, Microsoft is not only sneakily downloading Windows 10 installation files in the background (something, incidentally, I'm still utterly fuming about -- despite not having been directly affected by it. Would you accept it if your car used extra gas when it was parked in the driveway overnight, or if your oven gobbled up electricity regardless of whether you are cooking?) but then presenting them with a false dichotomy: "Upgrade now", or "Upgrade tonight". What a choice!
Some users have an even worse deal: a single option to 'choose' from. When an Upgrade to Windows 10 dialog with a single button labelled "Upgrade Now" appears, Microsoft is preying on those who are unfamiliar with Windows. It is possible to avoid the upgrade by simply using the red cross, close button in the upper right corner of the dialog (just as is the case with the false choice variant mentioned in the previous paragraph), but not everyone knows this. More worrying is the fact that Microsoft takes full advantage of this.
There's a slight irony in that a few years back Microsoft implemented Browser choice to enable people to select the web browser they'd like to use by default. With Windows 10, the company is blasting a massive 'fuck you' to users. Your opinion doesn’t matter; you'll have Windows 10 whether you like it or not. You thought the digital age was about democracy? Think again, suckers.
Imagine the uproar that would have followed if Microsoft took the same approach with the Browser Choice screen as it has done with Windows 10. "Would you like to set Microsoft Edge as your default browser right this moment, or in a few minutes?" -- a false choice is no choice.
Microsoft is raping computers with Windows 10. No means no, but if you're only given the option of saying yes, or it is made all but impossible to say no, you're basically given no choice but to consent to violation.
Photo credit: iQoncept / Shutterstock
-

Adblock Plus updates Acceptable Ads and reveals how it makes money
Publié: décembre 16, 2015, 9:32pm CET par Mark Wilson

Ad-blocking tools are more popular than ever before, and this spells potential disaster for anyone who relies on ad revenue from their web site. Previously something only available to desktop users, the widespread hatred of ads saw the tools spreading even to iOS.
A while back Adblock Plus revealed that its Acceptable Ads program -- which gives users the options of permitting the display of certain non-intrusive ads -- would be independently overseen. Today we not only learn about the latest updates to the program criteria, but also how monetizing is possible.
The updated criteria are nothing out of the ordinary -- ads need to be sensibly positioned and not distracting, easily distinguishable from body text, and not exceed a certain size (this is a sliding scale dependent on position. Ever since the inception of the Acceptable Ads program, there have been fears that companies would be able to pay to be added to the whitelist. This is true to a certain extent, and the company explains:
We receive some donations from our users, but our main source of revenue comes as part of the Acceptable Ads initiative. Larger entities pay a licensing fee for the whitelisting services requested and provided to them (90% of the licences are granted for free, to smaller entities).
Whitelisting, the new documentation is quick to point out, does not allow people to ignore the criteria that have been set.
Co-founder of Adblock Plus, Till Faida said:
We always said that the Acceptable Ads criteria could change as the Web and advertising changes. Before we step back from them for good and hand the job over to an independent board, they needed a slight polish with things we've been working on for the past couple of years. Plus, we thought it was time to open up our monetization policies to the public, so that people can better understand how a free project like ours is financed.
This is just the opening salvo. We plan on releasing more information about how our company works in the near future, and are looking forward to seeing where ad blocking goes in 2016 when the Acceptable Ads independent committee meets for the first time.
Photo credit: Light And Dark Studio / Shutterstock
-

Like Internet Explorer, Microsoft Edge is still pushing people away
Publié: décembre 16, 2015, 10:38am CET par Mark Wilson

Microsoft must have hoped that in walking away from Internet Explorer and moving towards Edge it could successfully shake off its reputation for producing terrible web browsers. There's a joke that everyone has used Internet Explorer at some point, even if it's just once to download Firefox or Chrome; sadly for Microsoft, it seems the trend continues.
The launch of Windows 10 provided an opportunity to attract a new audience to Microsoft Edge -- but people are still jumping ship. It's likely that Edge's continued lack of extension support is partly to blame, but usage stats from numerous analysts paint the same picture: Edge is tanking.
Even looking at just the last three months, Edge's usage numbers have been in sharp decline both in the US and globally. Different analysts provide slightly differing figures, but there is definite agreement on the general downward trend. With the numbers suggesting that in the last few months Edge has lost up to 10 percent of its user base, Microsoft will be unhappy with the news.
Computerworld has produced a graph based on data from Net Applications, StatCounter, and DAP, all of which agree that Microsoft Edge is shedding users like a lizard stepping out of its skin.
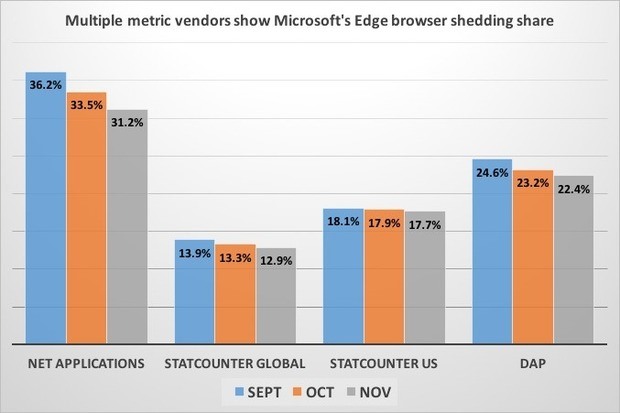
Perhaps this analysis will make Microsoft reconsider the wisdom of releasing what is clearly an unfinished product.
Photo credit: Johavel / Shutterstock
-

Facebook relaxes draconian real names policy. A bit.
Publié: décembre 16, 2015, 12:05am CET par Mark Wilson

The real names debate on Facebook is long-running and highly polarizing. Views fall into one of two camps: that people should be able to use whatever name they want on the social network, or that Facebook is free to impose whatever restrictions it wants. For supporters of the latter opinion, there is only really one argument -- Facebook can do what it likes.
But for those of the opposing view, there are countless -- well, several, at least -- reasons for scrapping the rule. Facebook has not performed a complete 180 yet, but the social network has today announced a couple of small, but important, changes to its naming policy. Following an earlier change to policy, Facebook says it wants to make things easier for those who belong to ethnic minorities, or who identify as "lesbian, gay, bisexual, transgender or queer".
Before you get too excited at the prospect of being able to call yourself whatever you want, the real names policy is not disappearing. Rather, Facebook is making it easier for people to explain the 'special circumstances' which justifies them using something other than their birth name -- 'their unique situation', as Facebook puts it. The social network says:
We require people to use the name their friends and family know them by. When people use the names they are known by, their actions and words carry more weight because they are more accountable for what they say. It also makes it harder for bullies to anonymously smear the reputations of others, or anyone else to use an anonymous name to harass, scam or engage in criminal behavior.
We’re firmly committed to this policy, and it is not changing. However, after hearing feedback from our community, we recognize that it’s also important that this policy works for everyone, especially for communities who are marginalized or face discrimination. That’s why we’re continuing to make improvements in this area.
In a bid to cut bureaucracy and discourage unnecessary name confirmations, Facebook is asking for people reporting accounts for not using a real name to provide additional information about 'fake' accounts. But more importantly, Facebook is introducing a new tool for people to put across their side of the story if they are called on to verify their name.
This is not the end of the chances. In 2016, there are plans to further reduce the number of people who have to go through the name verification process, although no details have been provided about just what this will involve.
In the meantime, the tools and changes announced today are being tested on a small scale in the US on mobile and desktop platforms.
Photo credit: iQoncept / Shutterstock
-

No, the UK government doesn't have Twitter accounts supporting ISIS
Publié: décembre 15, 2015, 10:46pm CET par Mark Wilson
ISIS has been in the news for some time now, and events like the recent terror attacks in Paris keep pushing the group into the public consciousness. Governments may be waging war on ISIS on the ground, but on the web it is the likes of Anonymous and vigilante hackers who have taken it upon themselves to curtail terrorist propaganda.
In the latest twist in the tail, hacker group VandaSec traced the IP addresses relating to some ISIS Twitter accounts to the UK government -- the Department of Work and Pensions specifically. Given that the accounts have been used not only to spread ISIS propaganda, but also to recruit members, does the UK government have a dirty little secret? As you might expect, it's not quite that simple.
The story came about through UK newspaper, The Mirror. It reports that IP addresses used by what it describes as "digital jihadis" to access the Twitter account could be traced back to the DWP. Although the IP addresses appear to be located in Saudi Arabia, but further investigation made the link to the UK government department. But rather than revealing that there are undercover operatives working within the government, what the address trace actually reveals is that the UK has been selling IP addresses to Saudi Arabia.
Two firms in the country have bought batches of IP addresses from the UK, with a large number having been transferred back in October. It is common practice for companies, as well as countries, to trade in IP addresses to raise funds, and it seems that this is exactly what has happened here. To help balance the books, the UK government offloaded a batch of IP addresses to a foreign nation (specifically Saudi Arabia's Mobile Telecommunications Company and Saudi Telecom).
A government spokesperson said:
The government owns millions of unused IP addresses which we are selling to get a good return for hardworking taxpayers. We have sold a number of these addresses to telecoms companies both in the UK and internationally to allow their customers to connect to the internet. We think carefully about which companies we sell addresses to, but how their customers use this internet connection is beyond our control.
Photo credit: GongTo / Shutterstock
-

Dating app Tinder teams up with the NHS to promote organ donation
Publié: décembre 14, 2015, 2:11am CET par Mark Wilson

Tinder has long-concerned itself with affairs of the heart, but through the final couple of weeks of 2015 the dating app is switching its attention to other organs. Teaming up with NHS Blood and Transplant, Tinder is looking to raise awareness of organ donation.
The campaign aims to highlight to 18-35 year olds the importance of organ donation, and the challenging wait for a matching organ. A number of celebrities are getting involved, changing their profile pictures to a 'The Wait' logo. When users swipe right they will be invited to sign up on the NHS Organ Donor Register.
While you may be able to meet the love of your life by swiping right, it's not quite so simple to match up with an organ donor. This is something the app highlights by displaying the message: "If only it was that easy for those in need of a life saving organ to find a match". NHS Blood and Transplant is running an awareness campaign called The Wait, letting the public know that there are currently nearly 7,000 people on the organ transplant waiting list.
More worryingly, over 6,000 people have died in the last ten years because they were not able to find a suitable match in time. By encouraging more people to join the donor register, it's hoped that both of these figures could be reduced.
Tinder's Head of European Communications, Hermione Way, says:
We're delighted to have teamed up with NHS Blood and Transplant to help save lives. Tinder users regularly make the decision to swipe left or right wondering whether someone may be the person they are looking for. While those swiping decisions are important and could be the first step to a successful relationship, we hope that the NHS profiles featuring Jamie, Jade and Gemma will encourage people to make and act upon a different decision too -- to sign up as an organ donor.
Sally Johnson, Director of Organ Donation and Transplantation at NHS Blood and Transplant, says that there is a real need to translate people's good intention into actual sign-ups.
Educating and encouraging people to sign up for organ donation -- that's what our partnership with Tinder is all about. While a third of the UK population have registered their intention to donate on the NHS Organ Donor Register, millions more support donation but haven't taken the final step to sign up. With the help of these bespoke profiles on Tinder, we’ll grab people's attention and throw a spotlight on the importance of organ donation. Joining the register takes only a couple of minutes -- about the same amount of time as a few swipes on Tinder. The best part is knowing that you could save or improve up to nine individuals' lives in the future.
If you would like to join the NHS Organ Donor Register, just head to organdonation.nhs.uk.
Photo credit: Csaba Deli / Shutterstock
-

2016 set to be the year of malware targeting Macs and iOS
Publié: décembre 14, 2015, 2:03am CET par Mark Wilson

Security has long been an issue for Windows users. The sheer number of devices running Microsoft's operating system makes it a prime target for malware and virus attacks. More recently, Apple's computers have increased in popularity and security firm FireEye says that the company will find itself in the crosshairs in 2016.
It's not just Macs and MacBooks that are predicted to become more frequent targets, iOS is also expected to come under attack. FireEye warns that weaknesses have been found in Apple's walled garden, and this could spell danger for users. Symantec is issuing similar warnings, citing Apple's ever-growing user base as the reason.
FireEye's researchers discovered Masque Attack back in 2014 -- an attack vector that made it possible to replace legitimate apps with malicious ones. This is not the only way that attackers have found to sneak malicious software into the App Store, and it's something that's set to continue. In a white paper entitled "Looking Forward: The 2016 Security Landscape", FireEye's Bryce Boland says:
In 2016, Apple will become more heavily targeted. Apple's market share in desktop and mobile continues to increase, making the tech company’s products more valuable for criminals to attack. Apple’s traditionally secure software and devices have experienced some interesting threats in recent years, some of which have remained persistent and have evolved over time.
He also warns that payment systems such as Apple Pay are likely to be targeted by criminals, and suggests that the Internet of Things means that the impact of any attack could have far greater impact than previously possible.
Symantec reports that there were more than nine times as many OS X malware infections in 2015 compared to 2014. Researcher Dick O'Brien says:
This is far fewer than Windows desktops and we don't want to scaremonger. Apple remains a relatively safe platform but Apple users can no longer be complacent about security, as the number of infections and new threats rise.
Photo credit: Maen Zayyad / Shutterstock
-

Apple spams users to promote iPhone 6s
Publié: décembre 12, 2015, 9:47pm CET par Mark Wilson

Microsoft managed to irritate a lot of people with its heavy-handed pushing of Windows 10, and now Apple has taken a leaf out of the company's book. December may be the time when many people think about getting a new phone -- and Apple is likely to fare very well out of upgrades -- but some iPhone owners have been upset by the appearance of spam in the App Store.
We're not talking about a mass mail-out inviting people to upgrade to the latest iPhone, but ugly, unsolicited popup ads used to push Apple's mobile. Describing the iPhone 6s as 'ridiculously powerful' the ads have been seen by those running iOS 9.1 and 9.2. It's something that could be dismissed, but spamming is unchartered waters for Apple.
The full screen ad (shown below) is hard to miss. The interstitial features two prominent links to Learn More or Upgrade Now. The 'skip' option is not exactly hidden, but it rather disappears into the background as it is tucked out of the way. As noted by Cult of Mac, the ads have upset many people.

The ad has been heavily discussed on Twitter, and the general consensus appears to be that Apple has vastly misjudged its audience.
Have you seen the ad? Were you upset to have your App Store experience interrupted, or could you not care less?
-

Microsoft is in an apologetic mood right now -- what next? 'Sorry for Windows 10'?
Publié: décembre 12, 2015, 9:04pm CET par Mark Wilson

Sorry may be the hardest word, but it seems to be tripping off Microsoft's tongue quite freely at the moment. Maybe it's the holiday season making the company look at itself, but we've had two apologies in recent days -- first, a semi-apology for stealing OneDrive storage from people, and now it's sorry about the Surface Book and Surface Pro 4.
Recognizing that many people's experiences with the latest addition to the Surface range has been "less-than-perfect", Microsoft's Josh_F has issued an apology on behalf of the company. Thanksgiving may be little more than a memory now, but Microsoft is thankful for the "open and candid feedback" (or bitching and complaining) about the latest Surface devices. With Microsoft in an apologetic mood, what else could it say sorry for?
Writing on the Microsoft Community boards, Josh_F says that more fixes are on the way to address the problems and concerns that people have had with their Surface Books and Surface Pro 4s. Cold comfort to those struggling with problems with their devices, but it's something at least.
First, a big thanks to all of our customers for your open and candid feedback on Surface Book and Surface Pro 4. For those of you who've had a less-than-perfect experience, we’re sorry for any frustration this has caused. Please know that we're reading your comments and hearing you loud and clear. Your input is incredibly valuable in helping us address your questions with timely updates and fixes. Since launch, we have aggressively pursued the most pressing feedback. We have already issued a number of updates via Windows Update and are working to issue additional updates and fixes as soon as possible to further improve the overall Surface experience.
The "too long;didn't read" version? "Sorry for shipping products we knew were rubbish, but you're just going to have to keep waiting for the problems to be fixed".
There are probably plenty of other things Microsoft might want to consider apologizing for while it's at it. How about the forced downloading of Windows 10 -- or the upgrade process that has baffled some? What about an apology for the frankly rubbish launch of Microsoft Edge which still doesn’t have extensions? How about an apology for Windows 10 in general? Someone certainly needs to offer a heartfelt apology for Windows 10 Mobile.
But we could also look a little further back. It's never going to be too late to say sorry for Clippy, and many people would like Microsoft to offer some sort of apology for Skype, 'modern' apps, and years of subjecting people to Internet Explorer. What would you add to the list… and would 'sorry' be good enough?
Photo credit: Dragana Jokmanovic / Shutterstock
-

Google Wallet now lets you send money to anyone via text
Publié: décembre 11, 2015, 1:21am CET par Mark Wilson

The likes of PayPal have long made it possible to send money to friends, family, and businesses via email. The same is true of Google Wallet, but a new update means that an email address is no longer needed -- a text is all it takes.
If you have someone's mobile number, you have everything you need to send them money. Google assures payers that the SMS-based system is secure, but it remains to be seen how popular an option it proves to be.
The feature is being pitched as a way to send money to anyone in your contact list. In a few taps, you can fire a payment off to a phone number and Google says that "the recipient will get a text message with a secure link".
In order to claim the money, the recipient needs to simply provide their debit card details and it will be transferred to their bank account.
You can grab the latest version of the app from Google Play or the App Store. If you don’t see the new payment feature straight away, it should be available in the next few days.
Photo credit: Mmaxer / Shutterstock
-

Apple loses ground to Android in Europe
Publié: décembre 11, 2015, 1:18am CET par Mark Wilson

Google is succeeding in keeping Apple at bay in Europe. The latest figures from Kantar show that Android is growing in popularity in the UK, Germany, France, Italy, and Spain (known collectively as EU5), while iOS growth is slowing.
The data covers smartphone sales in Europe's five largest markets in the three months ending October 2015. Android's popularity had been falling over the previous year, but sales in the last quarter see a return to growth that Google will hope to see continue into 2016 and beyond.
In the UK, Android's comeback is being attributed, at least in part, to the success of handsets from LG and Samsung. Around Europe, different handsets prove popular in different countries. Samsung and LG fare well in the UK, France laps up Samsung, and Huawei is the current brand du jour in Italy and Spain.
Kantar Worldpanel ComTech's chief of research, Carolina Milanesi says:
In Europe's big five markets, thanks to a strong performance in Italy, Spain, and France, Android showed year-over-year growth, but that OS success did not produce a clear vendor win, as different names showed strength in different countries: Huawei in Italy and Spain, and Samsung in France. The decline in iOS was marginal, and primarily driven by a deceleration of growth in Great Britain and Germany. Sales of the iPhone 6s and 6s Plus already represented close to a third of iOS sales in Europe's big five markets.
It's certainly not all bad news for Apple; in the US, the company managed to grab more than a third of the smartphone market (33.6 percent). While this is a continuation of iOS's year-on-year market share drop, it represents a quarter-on-quarter increase.
With the approaching holiday period, one of the busiest times for smartphone sales beckons, so it will be interesting to see how things look in the New Year. In the meantime, check out the current Kantar figures.
Photo credit: Dragon Images / Shutterstock
-

Facebook becomes more adept at dealing with crappy connections
Publié: décembre 11, 2015, 12:41am CET par Mark Wilson

With projects like Internet.org, Facebook has shown that it is interested in getting the world connected. But the truth of the matter is that no matter where you may be in the world, there are times when it can be impossible to get a decent phone signal to allow you to post a photo of your meal.
Joking aside, in countries where people are struggling with 2G connections or otherwise unreliable signals, making use of Facebook's News Feed can be difficult. The social network is rolling out new technology that will make it possible for people with slow connections to now only see relevant news stories on a poor connection, but also post comments when offline.
Facebook has learned that few people take the time to scroll through their News Feed in its entirety. A new update takes this into account -- when a user tries to look at their News Feed when they have no signal, as-yet-unseen but already downloaded stories will be surfaced so there is still 'new' content to read.
Writing on the Facebook engineering blog, Chris Marra and Alex Sourov explain what is being done to improve the user experience:
We also factor in whether the images for the story are available. This way we can immediately display relevant stories you haven't seen yet, instead of showing a spinner while you wait for new stories. When we receive new stories from the server when you're back online, we load and rank those stories normally. We rank relevant, already downloaded stories upon startup of the app, when you navigate to News Feed from the app or pull down to refresh stories at the top of your feed, or as you are scrolling through your News Feed.
This is not the end of things, however. An experiment is also underway that sees News Feed content being updated periodically, whenever a connection is available so there is genuinely new content to see when the Facebook app is loaded. A similar technique is being used to allow for 'offline' commenting. Comments can be written and pseudo-posted even if there is no connection available, and they will be posted as soon as possible.
Photo credit: tulpahn / Shutterstock
-

Google Drive -- finally -- gets a decent search tool
Publié: décembre 10, 2015, 1:24pm CET par Mark Wilson
With Google/Alphabet having search so deeply ingrained in its DNA, it is somewhat surprising that the search capabilities found in Drive have been so limited. Now that changes. The cloud storage service, at long last, has a search tool that's worth using.
As well as rolling out to the web, Google Drive's new search options are also making their way to iOS and Android devices. Apple users in particular have something to look forward to thank to support for 3D Touch and deeplinking.
Of course, the ability to search Google Drive is not new, but there are finally the more advanced filtering options that users have been waiting for. This means that it is possible to home in on files from any device. Writing on the Google Drive blog, group product manager Steen Andersson highlights the new was in which users can search for files:
- Narrow your search to a file type from the search box on Android, iOS, and the web.
- Open advanced search instantly from the search box.
- Access recent files or search Drive from the home screen using 3D Touch on iOS.
- Search Drive using the iOS search bar without opening the Drive app.
In addition to this, it is now also possible to use advanced search parameters such as ownership, date modified, and contents. The rollout is now underway, so if you don’t yet see the changes, you will very soon.
-

[Updated] Webhost Easily hit by malware attack
Publié: décembre 10, 2015, 12:27pm CET par Mark Wilson

UK webhosting company Easily has emailed its customers to inform them that it has fallen victim to a malware attack. COO Edwina McDowall says that the assailant is, as yet, unknown but steps have been taken to eliminate the malware.
The company warns that all customers should change their passwords as a precautionary measure, but seeks to assure people that credit card details have not been compromised.
The company has not revealed -- publicly -- how many customers have been affected by the attack but says that domain name ownership was never at risk. McDowall says that a forensic investigation by an external team uncovered the malware. Writing to customers whose accounts were not directly affected by the attack she said:
The investigation revealed that a list of domain names registered on behalf of our customers was accessed. However, none of the domain names that are registered to you were featured on the list that was accessed. We have found no evidence that your account details, passwords or any personal information which could identify you was accessed. However, as a precautionary measure, we recommend that you change the password which you use to log into easily.co.uk.
BetaNews has contacted Easily to find out more about the extent of the attacks, and we'll update this article when we hear more.
Update
The following statement has now been issued:
NetNames can confirm that we have taken action to isolate and remove malware which was found on our internal systems.
A forensic investigation by independent experts has confirmed that unauthorised access was gained to our internal systems and a list of domain names registered on behalf of our clients was accessed. This information is already publicly available on the “WHOIS” database which is a public listing of domain names. There is no evidence that any account details, passwords or personal information which could identify individual customers was accessed.
However, as a precaution, we are contacting all of our customers to recommend that they change the password which they use to log into our portals.
We will continue to prioritise and invest in our security systems.
Photo credit: wk1003mike / Shutterstock
-

Connected toys and the IoT could be the next weapons of mass surveillance
Publié: décembre 9, 2015, 11:09pm CET par Mark Wilson

Just a few days ago, we heard about the potential for the web-enabled Hello Barbie to provide hackers with personal data. Numerous vulnerabilities open up the potential for data to be stolen, but this could be the start of a worrying trend. If you thought the surveillance activities of the NSA and GCHQ are disturbing, things could be about to get much worse.
There is a movement underway that sees every conceivable device being transformed into a connected device. This is more than just the Internet of Things -- security experts are warning that not only could any devices connected to the internet (including web-enabled toys) could be used to spy on users, placing children at risk.
The concerns have been voiced following the recent publication of the draft Investigatory Powers Bill in the UK. Experts warn that internet firms could be forced by security and intelligence agencies to hack into devices and spy on users. One of the more troubling suggestions is that children's toys could be remotely access and used as surveillance tools.
As reported by the BBC, techUK's Antony Walker says that "in theory", any device that is connected to the internet could be hacked into and used for spying. There are calls for government to set out guidelines that would restrict -- or at least make clear -- what sort of devices could be used for surveillance, and under what circumstances. It's a problem that Walker says will become increasingly important as more and more devices, from fridges and TVs to cars, are not only connected to the internet, but also feature cameras and microphones.
Speaking to the Commons science and technology committee, he said:
A range of devices that have been in the news recently, in relation to a hack, are children's toys, that children can interact with. These are devices that may sit in a child's bedroom but are accessible. In theory, the manufacturer of those products could be the subject of a warrant to enable equipment interference with those devices. So the potential extent, I think, is something that needs to be carefully considered.
In some regards, Walker's concerns have something of a whiff of paranoia to them. At the same time, he raises genuine anxieties that parents will have about connected devices they give to their children. Of course, there is not just the worry that toys and devices could be remotely hacked into by government agencies, but also by criminals.
He is calling for very precise limitations to be set out for future surveillance, saying: "When we start to think, not just about the world today, but the world in five, 10 years' time as the Internet of Things becomes more real, and more pervasive. I think it requires careful thought in terms of where the limits should be".
Photo credit: best works / Shutterstock
-

Microsoft rolls out Cortana to iOS and Android, to take on Siri and Google Now
Publié: décembre 9, 2015, 5:24pm CET par Mark Wilson

Cortana is no longer limited to devices running Windows 10. After short period of public beta testing, Microsoft's digital assistant is now rolling out not only to iOS and Android, but also Cyanogen OS devices.
Just as on Windows 10 Mobile handsets, these new releases include many of the features that are found in the desktop version of Cortana. There are, however, some functions that remain exclusive to Windows phones -- you cannot, for example, change system settings in iOS and Android nor, frustratingly, use the hands-free "Hey Cortana" voice command.
Cyanogen users get something of a better deal. Cortana is more deeply integrated into the OS meaning that it is possible to voice activate the tool from any screen, and also toggle system settings. The Cyanogen version of the app will be available later this month for OnePlus One users, but iOS and Android versions are available in the US and China right now.
Microsoft highlights three key benefits of working with Cortana:
- Reminders that Travel with You: Set a location-based reminder on one device and have it pop up on your smartphone when you arrive at the location. This time of year means keeping track of holiday gift lists and to-dos. You can set a reminder on your PC to pick up a bottle of wine the next time you are near the grocery store and Cortana will remind you on your phone the next time you are at that location.
- Never Miss a Phone Call: In a meeting and can’t answer your phone? With the Cortana app, get a missed call alert on your Windows 10 PC and let Cortana send a text back letting them know you’ll call them later – all without leaving your PC.
- Convenient Tracking: This holiday season, you’ll be able to track flights, packages and more using Cortana on both your phone and your PC, and get the updates on the device that you’re on so you don’t miss a thing.
If you're running iOS 8 or newer, you can grab Cortana from the App Store. The Android version of the app is available in Google Play (Android 4.1.2 or newer), and Microsoft adds that:
The 'Hey Cortana' feature is possible in the Android app store version if the user is in the Cortana app or in the Android home screen. Missed call notifications work for Android devices with a Windows 10 PC of 1511 or above.
-

5 reasons why web apps are so frequently insecure
Publié: décembre 9, 2015, 11:58am CET par Mark Wilson

The unrelenting move to the cloud means that web apps are becoming ever more common. They have also increasingly become targets for hackers and this is often because of security failings; many of the recent high-profile security breaches have come about because of web app security vulnerabilities.
Ilia Kolochenko, CEO of High-Tech Bridge suggests a quintet of things companies do -- or fail to do, that make the life of hackers easier.
1. Underestimation of Risks and Threats Related to Insecure Web Applications
Many large companies and international organizations still seriously underestimate the value of their web applications, and have their security as the lowest priority in their risk management. And I am not even speaking about complicated SSRF or application logic flaws, but at least about proper detection and remediation of OWASP Top Ten vulnerabilities.
As we can see from the beginning of this article, companies just don’t realize that a vulnerable website is a perfect vector to start an APT without spending much money on it.
2. Lack of Continuous Monitoring
Web technologies are constantly evolving, and what is secure today may become vulnerable tonight. Therefore, a quarterly scan and annual pen test to achieve PCI DSS compliance is not enough anymore to stay ahead of hackers. Many companies do not perceive web application security as a continuous process, but rather as a one-time audit, putting their web infrastructure and related back-end at critical risk.
3. Missing or Poorly-Implemented Secure Software Development Life Cycle (S-SDLC)
In spite of a plethora of guidelines and standards of secure software development in existence today, many companies still ignore them due to high complexity or expense of implementation. The situation is even worse in companies where software development teams have existed for years -- as any change to well-established [but insecure] procedures will be met with hostility, as nobody wants to spend additional time on software security if not paid additionally for it.
4. Dominance of Business Needs Over Security Processes
Data breaches via insecure web applications regularly occur even in companies where S-SDLC is mature and well integrated into a company’s daily business processes. The consequences of the financial crisis of 2009 are still here -- many companies suffer from sluggish demand and very tough global competition. Often business requires a new feature to be done in few hours on Friday evening to outperform a competitor -- of course, we can forget about security when such pressure occurs.
Nevertheless, it’s the business who pays the salaries to developers and infosec folks, and it’s always the business who has the last word. However, it's also the business who shall be ready to take the responsibility for a new data breach and related costs.
5. Ignorance of Third-Party Risks
Many companies start introducing thorough security and compliance guidelines for their third-party suppliers and partners, however they often fail to mention proper web application security with them. As a result, attackers can compromise a website of your long-time supplier, consultant or partner, and instead of hosting malware on your website -- they host it on a trusted-party website, achieving the same result at the end.
Jan Schreuder, partner, cybersecurity leader from PwC Switzerland, says: "Recently we've seen many organizations attacked through sophisticated cyber attacks on their supply chain partners. With global supply chains becoming more and more digital and interconnected, establishing trust in your supply chain is becoming more challenging all the time".
As paying for an anti-smoking patch is much cheaper and less dramatic than spending a six-digit amount on cancer treatment, spending on preventive web application security is much more cost-effective and less painful than paying for APT forensics. Therefore, if you are currently finalizing your cybersecurity budget for 2016 -- don’t forget about proper web application security, not just vulnerability scanning.
Photo credit: jijomathaidesigners / Shutterstock
-

Twitter tinkers with time
Publié: décembre 8, 2015, 11:31pm CET par Mark Wilson

Twitter's timeline is getting a makeover. Not content with presenting tweets in an ordered, chronological fashion (well, reverse-chronological if you want to be pedantic), Twitter is experimenting with the order which tweets are displayed.
It's something that Facebook has been doing for a while, but now Twitter has jumped on the bandwagon using new methods to "surface the best content" for users. At the moment, this is just an experiment, but it's entirely possible that the re-ordering will become the norm in the not-too-distant future. So what's the deal?
In an email to Vice, a spokesperson for Twitter confirmed the move, saying it is running "an experiment. We're continuing to explore ways to surface the best content for people using Twitter". Many would argue that the very point of Twitter is its potential to keep people up to date with instant, timely information. On the face of it, changing the chronology of the timeline flies in the face of this, but there are also potential benefits.
Twitter has already experimented with the "While You Were Away" feature, and in many ways the timeline re-ordering is something of an extension of this idea. It's not something that will be to everyone's taste, but it does open up the possibility of grouping together related tweets outside of the confines of hashtags and trending topics.
What's your preference when it comes to consuming social media? Would you like to see things in the order in which they happened, or would you rather a more 'curated' option.
Photo credit: dani3315 / Shutterstock
-

Eric Schmidt's desire to bring a 'spell-check for hate' to the web is virtual fascism
Publié: décembre 8, 2015, 7:10pm CET par Mark Wilson

In a thought-piece for the New York Times, Google's Eric Schmidt proposes a way to "build a better web". The catalyst for his re-envisioning of web is -- predictably -- terrorism generally, and IS/ISIS/ISIL/Daesh specifically. His proposal for tackling are, frankly, little short of deluded.
On the one hand he decries "authoritarian governments" for employing censorship, and then in the next breath calls for the likes of Islamic State to be targeted so their videos can be removed. The problem is -- well, there are several really -- that this is somewhat fascistic. And that’s before we start to question whether Schmidt understands the meaning of the word 'hypocrite'.
Schmidt shoots himself in the foot when trying to explain his thinking, immediately unravelling any argument he may have had. His article reads almost like Mein Kampf: "it's important that we use connectivity to promote the values that bring out the best in people". No, Eric. What's important is that people are free to use this connectivity as they want, not to have values imposed on them through it.
He goes on to fret that if left unmanaged by citizens, government, and tech companies, "the internet could become a vehicle for further disaggregation of poorly built societies, and the empowerment of the wrong people, and the wrong voices". Just who is it that decide who are the 'wrong people' with the 'wrong voices' in your New World Order, eh, Eric?
He witters on and on, seemingly oblivious to the irony the echoes through saying "authoritarian governments tell their citizens that censorship is necessary for stability. It's our responsibility to demonstrate that stability and free expression go hand in hand", and then immediately follow it up with "we should target social accounts for terrorist groups like Islamic State, and remove videos before they spread, or help those countering terrorist messages to find their voice". So censorship is bad, unless you're censoring views that oppose yours, right, Eric?
Schmidt does not put forward any new or compelling arguments to support his ideas. It's a well-worn path that has been trodden endlessly:
As with all great advances in technology, expanded Web access has also brought with it some serious challenges, like threats to free speech, qualms about surveillance and fears of online terrorist activity. For all the good people can do with new tools and new inventions, there will always be someone who will seek to do harm. Ever since there's been fire, there's been arson.
The analogy Schmidt tries to draw here is interesting in that it actually runs counter to what he proposes for the web. Indeed, arson has existed for (just about) as long as fire (it's unlikely, however, that the first discovers used it as a weapon of wilful destruction of property). But just has no effective method of countering arson has ever been determined, attempts to prevent the use of the web for evil are doomed to failure. Punishments may act as deterrents, but they will never eliminate a crime. Never.
Schmidt's choice of words is also quite telling: "for all the good people can do". Concepts of good and bad are just that. Concepts. It's almost too easy to single out the likes of ISIS as bastions of evil, illustrating why 'something needs to be done'. But 'good' and 'bad' are often highly subjective. In suggesting that some views and opinions are worthy of -- nay, deserve -- silencing, is extremely worrying. The web is a tool for everyone, not just those who hold the same views and ideologies as oneself, or even the majority.
Setting up a system -- be it automated or manual -- by which objectionable content can be killed would set an extremely dangerous precedent. The aim of such a system might be a stop the spread of 'dangerous' propaganda, but choosing who is able to say what, when, and how is a force of propaganda in itself: propaganda by elimination. Silence your opponents, and there is only your voice left to be heard.
The proposal is to develop "spell-checkers for hate and harassment", but what on Earth does this actually mean? Let Schmidt enlighten you:
Intuition, compassion, creativity -- these are the tools that we will use to combat terror and violence online, to drown out the hate with a broadly shared humanity that only the web makes possible. It's up to us to make sure that when the young girl reading this in Indonesia on her tablet moves from this page, the web that awaits her is a safe and vibrant place, free from coercion and conformity.
Unless, of course, that coercion is executed by 'good' governments with a view to encouraging people to conform to a nice, Western philosophy. That's just fine by Schmidt. I've already argued that ISIS and terror attacks should not be used as scapegoats for placing restrictions on the internet, but that is exactly what people are trying to do. It's fascism and authoritarianism wrapped up in attractive packaging.
Not in my name, Eric.
Photo credit: Frederic Legrand - COMEO / Shutterstock
-

As well as closing US borders to Muslims, Donald Trump wants to talk to Bill Gates about 'closing up the internet'
Publié: décembre 8, 2015, 11:13am CET par Mark Wilson

People who support freedom of speech are "foolish people" in Donald Trump's book. This is just the latest in a seemingly endless stream of sweeping generalizations and misguided utterances to fall from the mouth of the Republican presidential candidate.
Positioning himself as the spokesman for the "noisy majority", Trump yesterday appealed to the xenophobic electorate in suggesting "a total and complete shutdown of Muslims entering the United States". This is the statement that has, understandably, grabbed the headlines, but Trump also wants to exert control over the technology we use every day. Specifically, he is interested in "closing up the internet in some way", and he wants to speak to Bill Gates about it.
Quite what the former head of Microsoft has to do with control of the internet is something perhaps only Trump understands. Perhaps he's missed the fact that Gates' involvement in the world of technology has been cut to almost nothing as he concentrates on more philanthropic ventures. Regardless, Trump thinks Gates is one of the people who can help him in his misguided plans to clean up 'extremist' online content.
The bewilderingly popular (according to many polls, at least) billionaire says that he wants to talk to Bill Gates "and a lot of other people who understand what’s happening about closing up the internet in some way. People will say 'Freedom of speech! Freedom of speech!'. These are foolish people".
As he has demonstrated perfectly countless times on his campaign trail, Trump is fantastically out of touch with the world -- the modern, forward-thinking world at least. He is of a mindset trenched in decades-old bigoted views and a seeming failure (or refusal) to recognize the implications of much of what he suggests. People who support freedom of speech are far from foolish. These are the people whose ideologies are the very cornerstones of democracy. These are the forward-thinkers and the ones who should be listened to, not shunned and ridiculed for not holding outdated views of the world.
If Bill Gates and the 'lot of other people' have any sense, they'll treat any request for an audience with Trump with the indignation it deserves. Ignorant, sledgehammer-to-crack-a-nut approaches are dangerous, but Trump is ever the master of saying what his right-wing acolytes want to hear. His suggestions have been met with typical loud support -- but only from certain quarters. His dream of driving jihadists from the internet is simply not going to happen. It's simply an unworkable idea, and an affront to free speech.
Photo credit: Ilya B. Mirman / Shutterstock
-

At last! Google Calendar gains to-do lists with Reminders
Publié: décembre 7, 2015, 8:43pm CET par Mark Wilson
When it comes to keeping on top of appointments, Google Calendar is certainly a useful tool -- but it's a long way from perfect. It's very capable at helping you to keep track of what you have to do and when, but there's one area in which it has always fallen short: to-do lists.
Today (or at least this week) this changes. Google is adding Reminders to the iOS and Android version of the Calendar app, with the promise that the same feature will make its way to the web soon. The name might not be quite right, but Reminders is the to-do list support users have been waiting for.
The feature works very much as you would expect. Create a Reminder, and will appear at the top of your schedule for the day. When you've completed the task, a quick swipe is all it takes to check it off, and any Reminders you fail to complete roll over to the next day. A simple idea, but one that's beautifully effective and long overdue.
Reminders can be created from within the Calendar app, but you can also do it from Keep, Google Now, and Inbox. Introducing Reminders, Google says:
Another way Reminders are more useful than events is that Calendar adds things like phone numbers and addresses automatically. So if you add a Reminder to make call or run an errand, the number or address will be right there when you need it. Just like Inbox by Gmail, Calendar uses information from your contacts, as well as Google's knowledge graph to provide this extra bit of help.
Check out the video below in which Google explains how the Reminders feature works:
If you already have Google Calendar installed, just check for updates. Otherwise, you can grab the latest version of the app from the App Store or Google Play.
-

How to enable Potentially Unwanted Application protection in Windows 8 and Windows 10
Publié: décembre 6, 2015, 10:22pm CET par Mark Wilson

Enterprise users are always looking for ways to protect their systems, and Microsoft recently unveiled a new opt-in feature to protect against Potentially Unwanted Applications (PUA). PUA is a broad term that covers everything from adware to browser extensions, and users of Windows 8 and Windows 10 can enable the feature to block such nasties at a download level.
PUAs are described by Microsoft as "a threat classification based on reputation and research-driven identification", and includes unwanted components bundled with legitimate software. Venture into the registry, and a tweak can be used to enable protection against such unwanted elements.
At the moment, PUA protection is something that is only available to enterprise users and enabling it does involve a little legwork -- there is no simple check box to enable, sadly. That said, the security feature can be enabled fairly easily, and it's well worth considering. Start by firing up the Registry Editor -- hit the Windows key and R, type regedit, and press Enter.
Now you need to navigate to HKEY_LOCAL_MACHINE\Software\ Policies\Microsoft\Windows Defender\MpEngine. Look for the DWORD key called MpEnablePus (or create it if you don’t see it) and assign it a value of 1. If you decide at a later time that PUA protection is not for you, you can either delete the key, or just change its value to 0.
Photo credit Imilian / Shutterstock
-

Samsung updates Lollipop firmware to show Android security patch level
Publié: décembre 6, 2015, 6:57pm CET par Mark Wilson

Responding to a spate of Android vulnerabilities and exploits, Samsung was one of the first companies to announce a move to monthly security updates for its handsets. This is great news for those concerned about the security of their phone, but for people running Lollipop there has been no way to check that the latest updates are installed.
Now this changes. Samsung is bringing the previously Marshmallow-only "Android security patch level" information to Lollipop handsets such as the Galaxy Note 5 and Galaxy S6 edge+. With just a few taps, it is now easy to check which month's security updates have been installed.
It may be seen as something of a minor change, but it is an important one when it comes to transparency. Samsung is nailing its colors to the mast, effectively making a public commitment to the on-going security of its devices. More importantly, it helps to keep users informed -- if it is made apparent that the current month's security update has not yet been installed, it gives people the opportunity to investigate what the problem could be.
If you have the latest Lollipop build installed on your Samsung device, you will be able to see this information right now. Just head to Settings > About Phone and then look for the Android security patch level heading.
-

Windows Server 2016 switches to per-core licensing
Publié: décembre 6, 2015, 4:17pm CET par Mark Wilson

Microsoft has always licensed Windows Server on a per-socket basis, but with the 2016 release this is due to change. When Windows Server 2016 launches in the second half of next year, things are being shaken up. As well as the two versions -- Standard and Datacenter -- including different features, there is also a move to per-core licensing.
In a couple of PDF datasheets, Microsoft reveals not only the change in licensing, but also that Windows Server 2016 and System Center 2016 Standard and Datacenter Editions are scheduled for release in Q3 of 2016. The licensing change is unlikely to be welcomed by many, as it complicates a system that had become familiar -- and could also push up pricing.
The plan is to sell Windows Server 2016 in two-license packs, and each processor has a minimum 8-core requirement. To complicate things further, physical servers have different requirements -- a minimum of 16 cores. It's not just licensing that changes, though. While the 2012 editions of the software differed only in the number of virtual machine supported by Standard and Datacenter (two and unlimited respectively), next year, Datacenter features a new network stack with more virtualization options, shielded VMs, and extra storage replication options. These are absent from the Standard edition.
However, as well as forcing companies to make an important choice between the two variants, some organizations could be hit in the pocket. In its System Center 2016 Standard and Datacenter Editions Licensing Datasheet, Microsoft says:
8 two-core packs will be the minimum required to license each physical server under management. The two-core pack for each edition is 1/8th the price of 16 cores for the 2016 editions.
But as explained by Peter Bright on Ars Technica, the cost for 2 or 4 10-core processors will increase by 25 percent. More details are available in the Pricing and licensing FAQ.
Photo credit: 360b / Shutterstock.com
-

Microsoft open-sources Edge's Chakra JavaScript engine
Publié: décembre 5, 2015, 8:16pm CET par Mark Wilson

At JSConf US Last Call in Florida, Microsoft today announced that ChakraCore will be open-sourced. This means that the core components of the Chakra JavaScript engine used in Microsoft Edge -- as well as Windows 10 -- will be made available for developers to tinker with as they see fit.
The ChakraCore repository is expected to hit GitHub in January, and Microsoft envisions it being used to power the Internet of Things as well as cloud services. The company says that it will be working with the likes of AMD, Intel and NodeSource to help develop a Chakra community as it aims to drive the progress of the 'modern web'.
While JavaScript has been with us for many years, Chakra only came to life in 2008. Over the years JavaScript has evolved from a tool use to control websites, into an essential utility to power apps, games and the cloud. The same technology is used to create Universal Windows applications for Windows 10 devices.
Revealing the open-sourcing decision on the Edge Developer blog, Microsoft's Gaurav Seth and Adalberto Foresti write:
Since its introduction in 2008, Chakra has grown to be a perfect choice for the web, cloud services, and the Internet of Things. With today’s announcement, we’re taking the next step by giving developers a fully supported and fully open-source JavaScript engine available to embed in their projects, innovate on top of, and contribute back to: ChakraCore.
Microsoft has great expectations for ChakraCore, explaining that it is "a fully fledged, self-contained JavaScript virtual machine that can be embedded in derivative products and power applications that need scriptability such as NoSQL databases, productivity software, and game engines".
Looking forward, the aim is to improve performance and expand usage far beyond the browser. Microsoft hopes that by bringing ChakraCore to the open-source community, this evolution can be accelerated.
Photo credit: T.Dallas / Shutterstock
-

Mozilla ditches Firefox ad tiles experiment
Publié: décembre 5, 2015, 1:09pm CET par Mark Wilson

It can be hard enough to avoid advertising online, and Mozilla has been experimenting with yet another way to pull in money. The Tiles experiment has been running for a few months and saw ads brought to the Firefox homepage via, funnily enough, tiles.
The company has decided that the experiment is a failure, and now wants to shift its focus to delivering "relevant, exciting and engaging" content to users instead. Mozilla has been scrambling to find way to make its browser bring in the pennies, but admits that "advertising in Firefox [...] isn't the right business for us at this time".
Moving forward the aim is "to reimagine content experiences and content discovery in our products" while continuing to explore different ways to balance advertising for the benefit of users and advertisers alike. Mozilla says it wants to deliver choice-based user experiences while respecting privacy and maintaining transparency.
Writing on the Mozilla blog, VP of Content Services Darren Herman says:
Our learnings show that users want content that is relevant, exciting and engaging. We want to deliver that type of content experience to our users, and we know that it will take focus and effort to do that right.
We have therefore made the decision to stop advertising in Firefox through the Tiles experiment in order to focus on content discovery. We want to thank all the partners who have worked with us on Tiles. Naturally, we will fulfil our current commitments as we wind down this experiment over the next few months.
Photo credit: Evan Lorne / Shutterstock
-

David Cameron's Facebook page reported for posing a 'credible threat of violence' over ISIS
Publié: décembre 4, 2015, 9:08pm CET par Mark Wilson

The UK's decision to start a military campaign in Syria to fight ISIS has dramatically divided opinion. Support and opposition is not split neatly down party lines, but a vote this week led to almost immediate airstrikes being carried out.
Taking to social media, Prime Minister David Cameron -- or his representatives -- used his official Facebook page to crow about the fact that vote went the way he wanted it to. This has had something of an interesting side effect. Facebook users are reporting the page for threatening violence.
The aim is to get the page removed, but it seems unlikely that the campaign will be successful. When he posted "I believe the House has taken the right decision to keep the UK safe -- military action in Syria as one part of a broader strategy", Cameron probably wasn't expecting there to be a backlash. But backlash there is, echoing the protests that took place before, during, and after the vote.
The idea was started by Facebook user Toby Godwin who responded to the post by saying:
ive reported david cameron's facebook page for being a "credible threat of violence"
At the moment, the comment has been liked by more than 15,500 people, and word has spread. The movement has grown legs, and there are growing numbers of people following Godwin's lead and making a complaint to Facebook.
If you want to join in, you can report the post and select the "I don’t think it should be on Facebook" option. You can then indicate that you find the post "threatening, violent or suicidal", and that you feel it is a " credible threat of violence".
So far, Facebook has declined to remove the post.
Photo credit: 360b and pockygallery / Shutterstock
-

Net neutrality on trial: judges hear lawsuits against FCC
Publié: décembre 4, 2015, 5:06pm CET par Mark Wilson

The Federal Communications Commission finds itself in court today, as the hearing gets underway to determine the legality of net neutrality rules. A total of 10 lawsuits have been brought against the commission by a number of cable and telecoms companies.
Earlier in the year the FCC banned service providers from creating internet fast lanes that could have been used to give those willing to pay for it a faster service, or to offer certain types of traffic preferential treatment. This could be the hearing that decides once and for all whether the idea of treating all web traffic equally is a workable option.
The FCC rules state that broadband providers may not engage in the "blocking, throttling, and paid prioritization" of web traffic, but this is something that the likes of Verizon and Comcast are unhappy with. They argue that it will make it more difficult for them to manage web traffic.
The commission has been accused of abusing its powers in implementing the rules, and there has already been heated debate about the legitimacy of reclassifying broadband as a telecommunications service that is viewed as a utility. The arguments surrounding net neutrality have already rumbled on for a number of years, and if the panel of three judges -- including Judge David Tatel -- rules against the FCC, the whole can of worms will be opened up all over again.
The First Amendment is being cited by supporters of the rules including Twitter, Yelp, and Reddit.
-

Google introduces interactive ads so you can try out Android apps without installing them
Publié: décembre 4, 2015, 2:16pm CET par Mark Wilson

Google is experimenting with a way to make Android-based ads less irritating and more useful. Trial Run Ads are a new type of interactive ad that lets you try out games by streaming them rather than installing them. It's a format that Google and developers hope will help to drive installations, the thinking being that try-before-you-buy makes things easier for the would-be customer.
The new ads came about after research showed that mobile users' attention spans have shortened, and a quarter of downloaded apps are never used. Google is also introducing beta support for HTML5-based Interactive Interstitial ads which can be used for regular apps and not just games.
Trial Run Ads are very much what you would expect. They give the opportunity to test drive a game for up to 60 seconds so you can decide if it is the sort of thing you would like to download. It's an alternative to the often used system of making available two versions of a game (trial and full), or providing in-app purchases to unlock features. By making ads interactive, the burden of effort is taken off the user making them more likely to engage. Google says they should lead to "more relevant ad clicks, app downloads, and pre-qualified app users".
Interactive Interstitial ads are a new, highly flexible format which allows for data to be pulled in dynamically. This in turn means that ads can be more easily updated and made more relevant to users. While the format does not allow for app streaming in the same way as Trial Run Apps, it does allow developers to show of a portion of their apps or provide various levels of interactivity.
As these new formats are currently in beta, it may be a little while before end users start to see them, but more interesting ads are on the way.
Photo credit: Cienpies Design / Shutterstock
-

JD Wetherspoon's customer details leaked after cyber attack
Publié: décembre 4, 2015, 1:00pm CET par Mark Wilson

Personal details of hundreds of thousands of JD Wetherspoon customers have been accessed and leaked following a hack of its database. The cyber attack affects more than 650,000 customers, the UK pub chain has announced.
The leaked data includes names, birth dates and email addresses, as well as the partial credit and debit card details of some customers who bought gift vouchers. Although the attack occurred back in June, JD Wetherspoon has only just gone public about it.
As well as gift voucher purchasers, the hack also affects customers who signed up for the company newsletter. In a statement the pub operator said that only the last four digits of card numbers were accessed. It explains that the data was stolen from the old version of its website, and this has now been replaced with a new one, managed by a different partner.
Wetherspoon's Chief Executive, John Hutson says:
We apologize wholeheartedly to customers and staff who have been affected. Unfortunately, hacking is becoming more and more sophisticated and widespread. We are determined to respond to this by increasing our efforts and investment in security and will be doing everything possible to prevent a recurrence.
The attack also saw personal staff details being accessed, but JD Wetherspoon says that no salary or other financial data was involved.
Photo credit: Syda Productions / Shutterstock
-

Over 50 percent of devices in US classrooms are Chromebooks [Infographic]
Publié: décembre 3, 2015, 10:02pm CET par Mark Wilson

Chromebooks are viewed by many people as the Windows Phone of laptops, paling into insignificance when compared to Windows machines and MacBooks. But the cheap and cheerful nature of (most) Chromebooks has seen the share of certain markets rocket -- particularly in the classroom.
Back in 2012, less than one percent of devices in US schools was a Chromebook -- now the Google-powered laptops account for more than half of the market. Google's interest in education is not new, but the inroads it has managed to make in such a short space of time has caught many people off guard.
A new report from Futuresource Consulting shows that Chromebooks have accelerated past Windows and OS X laptops in US classrooms. In Q3 2015, Chromebooks accounted for 53 percent of devices bought by schools, with both Apple and Microsoft's share falling to 24 percent apiece -- down from 52 and 43 percent respectively three years ago.
Director of product management for Android and Chrome in business and education, Rajen Sheth says:
It's been amazing to us to see that growth happen just in that short amount of time. If you look at the overall market for devices in education, it's actually expanded a lot and Chromebooks have actually taken a lot of the expansion.
Cost will certainly have played a large part in Google's success this year, but the company has also been actively pushing for greater involvement in the education sector. Google Apps for Education has proved highly popular -- if slightly controversial at times -- and the appeal of an OS and software from the same stable is understandably appealing.
Chromebook has not proved as successful outside of the US -- something Futuresource Consulting puts down to reduced connectivity in other parts of the world -- so this will be Google's focus for 2016 and beyond.
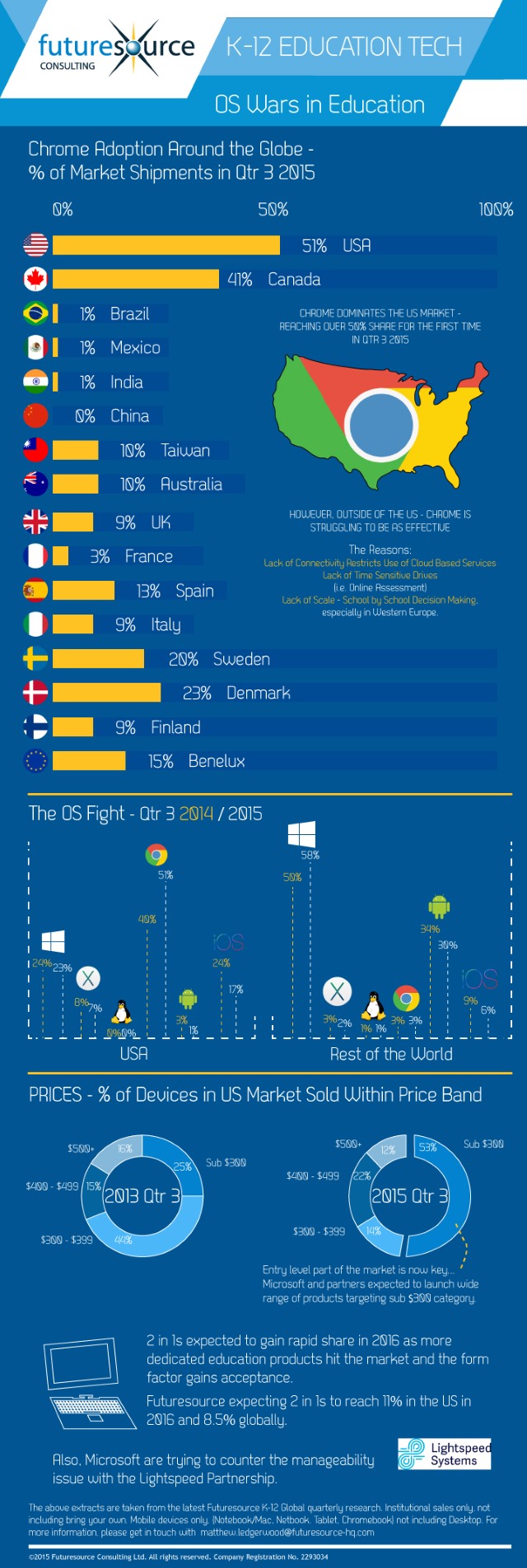
-

Facebook's Live Video is no longer a celebrity-only feature
Publié: décembre 3, 2015, 9:13pm CET par Mark Wilson
The ability to broadcast live video on Facebook is something that has previously only been available to celebrities. It's not being made available to everyone -- yet -- but a handful of lucky users are being given the chance to try it out ahead of a wider rollout.
Starting today, some US iPhone users will be able to live broadcast to their friends and family. This is Facebook's bid to take on Twitter's Periscope, but the social network has more to announce. On top of Live Video, photo collages are also being unveiled as a new way to show off your snaps.
Live Video is treated as another form of status update, and can be up and running very quickly. After adding a description and choosing who your audience will be, you are ready to start broadcasting. Viewing numbers are displayed in real time, and viewers are free to post comments. Broadcasters have the option of retaining the video at the end of the show, giving others the opportunity to watch later, or removing it. Facebook has given no indication of when Live Video will spread to Android and the web, but it is on the cards.
The new photo collage option provides a simple way to display groups of related photos together. Rather than a dull slideshow, or a series of individual images, collages are animated photo and video displays that can be auto-generated and then be customized. Again, it's iPhone users who get the first look today, but Android users will also get a chance to try it out soon.
-

Chimera crypto-ransomware threatens to share your private files online
Publié: décembre 3, 2015, 12:11pm CET par Mark Wilson
Crypto-ransomware is one of the latest trends in the world of malware. Encrypting and holding files to ransom provides a way to extort money from victims, but a new example takes things one step further.
Chimera not only locks users out of their files until a ransom is paid, but also threatens to release unencrypted copies of the files online if payment is not made. Security company Trend Micro says this is the first instance of this type of threat. Interestingly, Chimera also seems to be part of an affiliate program.
Infected systems display a warning informing victims that their data will be inaccessible until they cough up the ransom. The incentive that said files will be leaked to the internet is an extra encouragement, particularly for anyone with content they would rather not be associated with. Victims are told:
If you don’t pay your private data, which include pictures and videos will be published on the internet in relation to your name.
In addition to trying to extort money from people, Chimera also acts as a recruitment campaign. The warning screen that lets people know that their computer is infected includes a footnote:
Take advantage of our affiliate-program! More information in the source code of this file.
As Trend Micro notes, this "is clearly a way to sift out people with technical skills". The security firm has examined the source code and determined that it does contain contact details and Bitcoin information for payment. There is also a decryption tool which checks to see whether a Bitcoin payment has been made before freeing up files.
Chimera is being described as Ransonware as a Service (RaaS) because of its recruitment drive component, and this could be the direction in which future ransomware is heading.
-

Facebook's Page plugin ventures into CRM territory with new Events and Messages options
Publié: décembre 2, 2015, 11:02pm CET par Mark Wilson

Facebook has done an excellent job of becoming the social network, connecting people all over the world. More recently, it has tapped into business markets by providing companies with a quick, easy, and -- importantly -- free way to create an online presence. Now, with an update to its Page plugin, Facebook is making it easier for businesses to connect and communicate with customers.
The update makes it possible to better integrate Facebook with an existing website. Companies can easily add the ability to send a message via their website, and the communication will appear on Facebook on the Messages tab. The update also makes it easier to share news about upcoming events, keeping all-important customer engagement going.
Facebook points out that as well as making it simpler for customers to get in touch via the Facebook app, website, or company site, life is also made easier for admins. With the Plugin it's possible to update event information on Facebook and automatically have it updated on a linked website. Introducing the feature in a post on the Developer blog, Facebook's Yugal Jindle writes:
Event organizers and promoters have told us that they'd like a more integrated experience managing their events on and off Facebook. With events in the Page plugin, people can now discover and interact with events from your Page, right on your website. For example, if you're promoting an upcoming concert, you can create an event from your Page and feature it on your website, while managing the details from one place.
The following benefits are highlighted:
- One place to manage event details: Any modifications you make to the event on your Facebook Page will automatically be reflected on your website within the Page plugin.
- Subscribe functionality: People can now subscribe to your events directly from your website, and they'll be notified whenever you create a new event in their area.
- A more social events calendar: People who are connected to your Page can now see which of their friends are going to the same event, bringing social context to the event calendar on your website.
- A localized experience: For events being organized in multiple cities, the most relevant event will be highlighted for a given person based on where he or she is located.
Photo credit: dolphfyn / Shutterstock.com
-

Facebook will stop tracking Belgian web users who shun the social network
Publié: décembre 2, 2015, 10:12pm CET par Mark Wilson

Privacy issues in relation to Facebook make frequent appearances, but they tend to focus on instances of the social network using the browsing and account data of logged in users. However, a recent court case in Belgium highlighted the fact that the site was tracking people who accessed public Facebook pages either without a Facebook account, or without logging into one.
This change has a couple of implications for people. Firstly, it means that people who are trying to stay off Facebook's radar will be better able to do so, but it also means that previously accessible content will only be available to those willing to log into their account. Facebook is complying with the Belgian court order that was handed down last month, but the company is not happy about it and intends to fight back.
Belgium had told Facebook that it would face daily fines if it failed to comply, and this is the reason for bowing to the demands -- a charge of €250,000 euro, or $265,000 each day would quickly mount up). While Facebook users would reasonably expect the site to track the pages they 'like' whilst logged into their account, the same cannot be said for those who are not logged in, or those who don't have an account at all.
Facebook uses a 'datr' cookie which it says is used solely to gather information about web browsers, but it is something that can concern privacy activists, as well as the Belgian Privacy Commissioner (BPC). Facebook says:
We had hoped to address the BPC's concerns in a way that allowed us to continue using a security cookie that protected Belgian people from more than 33,000 takeover attempts in the past month. We're disappointed we were unable to reach an agreement and now people will be required to log in or register for an account to see publicly available content on Facebook.
Compliance with the ruling means that Facebook will not only stop tracking the activities of non-users and non-logged in users, but will also have to delete existing datr cookies from affected systems.
While the ruling only affected Belgium, the fallout from the changes will be closely watched by other European countries as well as around the world.
Photo credit: Yeamake and totallyPic.com / Shutterstock.com
-

Mozilla's Glass House experiment reveals lax attitudes to online privacy
Publié: décembre 2, 2015, 1:58pm CET par Mark Wilson

The discussion about online privacy is something that rumbles on. Those who know what is happening with personal information on the internet are aware of the inherent risks, but these are being joined by increasing numbers of the previously-technologically-illiterate who are coming to understand what being online means.
To highlight the implication of third party tracking and data sharing, Mozilla ran an experiment in Hamburg, Germany. As well as bringing the issue of privacy to people's attention in quite dramatic style, the experiment also aimed to educate people about security and privacy through expert discussions. Some of the public reactions are priceless.
The company behind the Firefox browser -- which it proudly proclaims to have added Private Browsing with Tracking Protection to -- has released a couple of videos that show its experiment in action. In the first video, entitled "The Hidden Business of the Internet", Mozilla used a fake apartment in Germany to ram home the fact that private data is broadcast online, often without the individual's knowledge or active consent.
Invited to log into a free Wi-Fi connection in an enclosed room, victims were shocked when the walls were stripped away to reveal that they were in fact in a glass house on view to the world. It's something of a crude analogy for online privacy, but it's one that works.
The second video focuses on the reactions of those who were foolish enough to offer up their personal data.
Of course, this all acts as a big advertisement for Firefox but it makes the point that everyone is being turned into a product. There is, obviously, the slight irony that unwittingly shared personal data is something that Mozilla benefits from, but that’s neatly skirted over funnily enough...
-

EFF accuses Google of sneakily gathering data about students
Publié: décembre 1, 2015, 11:18pm CET par Mark Wilson

The Electronic Frontier Foundation claims that Google is gathering data about school children, including their web searches. In a complaint to the Federal Trade Commission about the search giant, the EFF gives details of the deceptive usage tracking it says was uncovered while conducting research for its Spying on Students campaign.
The campaign, which launches today, aims to "spread the word about companies collecting students' data and launching a campaign to educate parents and administrators about these risks to student privacy". At the center of the controversy are Chromebooks and Google Apps for Education.
The EFF's complaint states that Google collects, uses, and shares student data "in violation of the K-12 School Service Provider Pledge to Safeguard Student Privacy (Student Privacy Pledge), of which it is a signatory."
There are three branches to the complaint, and the EFF says that the StudentPrivacy Pledge is legally enforceable under the Federal Trade Commission Act. Firstly, Google is accused of gathering data from children using Google for Education accounts and then using this information for purposes not related to education.
The Chrome Sync feature of Google's web browser is the subject of the second complaint, with EFF pointing out that it enables Google to gather students' entire browsing histories and use it for whatever purposes it wants. Finally, Google for Education's Administrative settings can be configured in way that shares student data not only with Google, but also with third party sites. The EFF is looking for Google to be investigated, and for the company to be forced to destroy data collected so far, and to cease further data collection.
EFF Staff Attorney Nate Cardozo says:
Despite publicly promising not to, Google mines students' browsing data and other information, and uses it for the company's own purposes. Making such promises and failing to live up to them is a violation of FTC rules against unfair and deceptive business practices. Minors shouldn't be tracked or used as guinea pigs, with their data treated as a profit center. If Google wants to use students' data to 'improve Google products', then it needs to get express consent from parents.
Google has said that it will soon be disabling a setting on school Chromebooks so that Chrome Sync data will no longer be shared with other Google services. While this move is welcomed, EFF says that it is a small step that does not go nearly far enough.
Photo credit: Inara Prusakova / Shutterstock
-

GCHQ accused of "persistent" illegal computer hacking
Publié: décembre 1, 2015, 10:32pm CET par Mark Wilson

Court documents released during a court case brought by Privacy International show that GCHQ -- the UK version of the NSA -- has engaged in "persistent" illegal hacking. The targets of the intelligence agency's surveillance include computers and phones around the world without the need for individual warrants.
There is concern about the use of "thematic warrants" which allows GCHQ to hack computers with very little justification or oversight, and with very broad remits. Privacy International is involved because there are clear privacy issues involved in GCHQ's activities, and it is seen as being of greater importance than ever with renewed interest in the Investigatory Powers Bill.
GCHQ's ability to hack and remotely control smartphones was recently revealed by Edward Snowden, and it is this that gives cause for concern when it comes to privacy. The intelligence agency does not deny that it engages in such activity; in fact, the agency has admitted as much in the course of the court case.
What has attracted particular attention, however, is the existence of "persistent" surveillance operations. Unlike one-off hacks and taps, these on-going hacks see spyware, malware and other spying tools left running on target devices indefinitely. Privacy International, in conjunction with seven internet and communications providers, brought the case against GCHQ, and the group's legal representative, Ben Jaffey, said: "Given the high potential level of intrusiveness, including over large numbers of innocent persons, there are inadequate safeguards and limitations."
Caroline Wilson Palow, General Counsel at Privacy International said:
Eighteen months after we first brought this challenge, GCHQ have come to court today to defend their asserted power to hack computers in the UK without individual warrants. The light touch authorisation and oversight regime that GCHQ has been enjoying should never have been permitted. Perhaps it wouldn't have been if Parliament had been notified in the first place that GCHQ was hacking. We hope the tribunal will stand up for our rights and reign in GCHQ's unlawful spying.
The court case continues.
-

Hillary Clinton wants to spend $275 billion on IoT and world-class broadband for all Americans
Publié: décembre 1, 2015, 9:30pm CET par Mark Wilson

Presidential hopeful Hillary Clinton will invest $275 billion over five years on the US infrastructure -- if she's elected, that is. A key part of the plan is to bring "world-class broadband" to every American with a view to increasing competition and equality in the workplace.
While acknowledging the importance of investing in road, rail, and other transport infrastructures, Clinton also wants to invest in the technology of the future. Embracing the Internet of Things, she wants to create "smart cities" that will be filled with connected citizens, businesses, and services, including free Wi-Fi.
It's a bold statement, but the Democratic candidate wants everyone in the US to have access to a broadband connection by 2020. Saying that "high-speed Internet access is not a luxury; it is a necessity for equal opportunity and social mobility in a 21st century economy" she wants to provide everyone with access to "affordable broadband that delivers world-class speeds sufficient to meet families' needs".
In a briefing, Clinton explains the importance of investing in the future:
It means building airports and air traffic control systems that set the world standard for efficiency, reliability, and safety -- saving time, money, and energy on every trip. It means a smart, resilient electrical grid that powers America’s clean energy future. It means safe, smart roads and highways that are ready for the connected cars of tomorrow and the new energy sources that will power them. And it means changing the way we make our infrastructure investments -- so that every dollar we spend goes further.
Clinton is not just talking about broadband internet access in the home; she also wants to invest in free public Wi-Fi. Gigabit connectivity is destined for train stations, airports, mass transit systems, and other public buildings. There are also plans to push the move to 5G and to tap into the currently unlicensed ranges of the wireless spectrum. $275 billion is not a small sum of money to conjure up, but Clinton says that the cash can be raised through business tax reform.
Photo credit: Joseph Sohm / Shutterstock
-

Spoiler alert! Google reveals the trending gift searches for Cyber Monday
Publié: novembre 30, 2015, 5:26pm CET par Mark Wilson

Black Friday is out of the way (not that it is really restricted to just one day this year) and now it's time for Cyber Monday. Traditionally -- if the word can be applied to such a recent phenomenon -- this is the day when you can snap up a techy bargain in time for Christmas, and Google has shed some light on what people are searching for this year.
The search data is like peering into the future. The searches of today, are the gifts of next month. If you want to get an idea of what your nearest and dearest might be popping under the tree for you this year, the top trend gift searches could give you some pointers. Warning: there may be gift spoilers ahead.
Google reports that more than half of people plan to use their smartphones to research gifts when they have a spare moment or two. This may be an interesting statistic, but it's the searches themselves that are more revealing. Amazon may be using drones for super-fast deliveries, but these devices have become increasingly popular as toys. Drone-related searches are up 80 percent from last year.
With the anniversary of Back To The Future this year, attention turned to hoverboards. We might not yet have access to quite the same technology as Marty McFly, but the wheeled versions we do have look likely to be very popular this year, with searches for hoverboards soaring by 500 percent in a few months.
The release of the Apple Watch appears to have fuelled interest in smartwatches, and searches for wrist-worn wearables has nearly tripled over the last year.
Of course it's not all tech; people are also searching for clothing. Retro items such as Levi jeans and Adidas Superstars make appearance, as do -- someone help me -- adult onesies. Sometimes, one loses hope for humanity.
Photo credit: YuryImaging / Shutterstock
-

Government enterprise surveillance demands drive BlackBerry to quit Pakistan
Publié: novembre 30, 2015, 3:13pm CET par Mark Wilson

BlackBerry wants nothing more to do with Pakistan. The Pakistani government had demanded that it be permitted to monitor BlackBerry Enterprise Service emails and BBM messages. Unwilling to bow to these demands, the company has decided to pull out of the country entirely.
From the end of 2015, BlackBerry will no longer operate in Pakistan as the company says that it does not want to compromise its customers' privacy. Unwilling to comply with surveillance directives or show any sort of support for backdoors, BlackBerry has decided to cut its losses and run.
With security at the heart of BlackBerry's operations, the move is not entirely surprising, but it remains to be seen if either side is willing to compromise. BlackBerry said that while the government has only expressed interest in BES servers, the company "decided to exit the market altogether, because Pakistan’s demand for open access to monitor a significant swath of our customers’ communications within its borders left us no choice but to exit the country entirely".
Back in July, the Pakistan Telecommunications Authority announced that BlackBerry's BES servers would no longer be allowed to operate in the country. The company says that this is not quite the case. Writing in a post on the BlackBerry blog, company COO Marty Beard says:
The truth is that the Pakistani government wanted the ability to monitor all BlackBerry Enterprise Service traffic in the country, including every BES e-mail and BES BBM message. But BlackBerry will not comply with that sort of directive. As we have said many times, we do not support "back doors" granting open access to our customers’ information and have never done this anywhere in the world.
Pakistan's demand was not a question of public safety; we are more than happy to assist law enforcement agencies in investigations of criminal activity. Rather, Pakistan was essentially demanding unfettered access to all of our BES customers' information. The privacy of our customers is paramount to BlackBerry, and we will not compromise that principle.
Earlier today BlackBerry initially announced that it would pull out of Pakistan on 30 November, but later amended this to 30 December.
-

Amazon unveils new hybrid drone prototype for 30-minute Prime Air deliveries
Publié: novembre 29, 2015, 11:14pm CET par Mark Wilson

When you make an impulse purchase -- or you're just an impatient type -- time is of the essence. Next day delivery is far too slow, and same-day delivery has gradually spread to certain places. Some cities have the option of delivery within the hour, but Amazon is working on cutting this down to as little as 30 minutes with Prime Air.
As you would probably expect, these super-speedy deliveries will be facilitated by drones, and Amazon has unveiled a new prototype drone that blends elements of a helicopter with those of an airplane. Unlike other drones we’ve seen the Prime Air model is quite large, and is capable of carrying up to 5 pounds.
This is not a service that's going to launch in the immediate future; there are still many obstacles to overcome. The final design of the drone is yet to be decided, and Amazon is testing out models in the United States, the United Kingdom, and Israel. There is also the Federal Aviation Administration hurdle to jump. The FAA has said it is not keen for unmanned commercial drones to fly out of line of sight.
Amazon is keen to do everything it can to win over regulators, and boasts of the drone's "sense and avoid" technology which will be used to avoid accidents. From test flight footage, it appears that shoppers have to mark out a landing area in their garden which the drone will be able to detect and home in on, and it would seem that drone use would be best suited to more rural areas.
Amazon says:
Prime Air has great potential to enhance the services we already provide to millions of customers by providing rapid parcel delivery that will also increase the overall safety and efficiency of the transportation system. Putting Prime Air into service will take some time, but we will deploy when we have the regulatory support needed to realize our vision.
The company has also put together a video that shows off Prime Air, fronted by none other than former Top Gear presenter Jeremy Clarkson. Check it out below to see the hybrid drone in action:
-

NSA stops bulk collection of phone metadata
Publié: novembre 29, 2015, 3:03pm CET par Mark Wilson

The NSA's bulk surveillance and collection of phone data has come to an end. President Obama announced that the current surveillance program would stop by 11:59 pm EST Saturday, but this does not mean that phone surveillance has completely disappeared.
Instead of wide scale dredging of data, the NSA will now engage in more targeted surveillance programs -- something that privacy advocates have been calling for for some time. The scaling back of surveillance has not come out of the blue; it's became of a legal requirement earlier in the year that has now been implemented two and half years after Edward Snowden blew the whistle on NSA spying.
Following the introduction of the USA Freedom Act, the NSA will no longer be able to indiscriminately collect metadata about phone calls in the hope of finding something suspicious, but will instead have to run targeted operations based on evidence. A court order is now required to force a telecom company to allow the monitoring of the call records of individuals or groups of people.
Initially set up in the wake of the 9/11 attacks, the NSA's surveillance program was pitched as the tool needed to track down those responsible. But privacy groups and opponents of the surveillance said it was far too intrusive and infringed upon the rights of millions of innocent people. Critics also point to a review that found that not one anti-terrorism breakthrough could be directly attributed to the surveillance program.
The White House says that data that has already been collected will be retained until 29 February for "data integrity purposes". After this date, the data will be deleted.
Photo credit: 360b / Shutterstock
-

Google to work with Israel to censor Palestinian YouTube videos
Publié: novembre 29, 2015, 11:22am CET par Mark Wilson

Coverage of any conflict is rarely free from bias, with propaganda being a staple tool. This certainly rings true of the war between Israel and Palestine, and Israeli Deputy Foreign Minister has engaged in talks with representatives of YouTube and Google with a view to censoring videos coming out of the region.
Tzipi Hotovely met with Google's Director of Public Policy, Jennifer Oztzistzki, and YouTube CEO Susan Wojcicki. On the agenda was discussion about how to censor Palestinian video footage deemed to be "inflammatory" or "inciting violence and terrorism" by Tel Aviv.
It's a move that will concern journalists, anti-censorship proponents, and freedom of the press advocates alike, but the Israeli government is keen to stem the flow of what it sees as uncensored propaganda coming out of the Occupied Palestinian Territories.
At the moment any journalist or reporter working in the area needs to register with the Israeli military, and all stories pass through the Israeli Military Censor. But the likes of YouTube have led to a rise in citizen journalism, and this is what the Israeli government is looking to crack down upon.
According to the Israeli newspaper Maariv, Hotovely will be working with Google to create body charged with "monitoring and preventing" the appearance of "inflammatory" videos. There has been an increase in the number of videos published that highlight the suffering of Palestinians, and this is something the Israeli government sees as bad PR.
Details of how the monitoring and censorship program will work have not been released, but Palestinians living in the territory illegally occupied by Israel are about to find it harder to get their side of the story out.
Photo credit: danielo / Shutterstock
-

Google to work with Israel to censor Palestinian YouTube videos [UPDATED]
Publié: novembre 29, 2015, 11:22am CET par Mark Wilson

Coverage of any conflict is rarely free from bias, with propaganda being a staple tool. This certainly rings true of the war between Israel and Palestine, and Israeli Deputy Foreign Minister has engaged in talks with representatives of YouTube and Google with a view to censoring videos coming out of the region.
Tzipi Hotovely met with Google's Director of Public Policy, Jennifer Oztzistzki, and YouTube CEO Susan Wojcicki. On the agenda was discussion about how to censor Palestinian video footage deemed to be "inflammatory" or "inciting violence and terrorism" by Tel Aviv.
It's a move that will concern journalists, anti-censorship proponents, and freedom of the press advocates alike, but the Israeli government is keen to stem the flow of what it sees as uncensored propaganda coming out of the Occupied Palestinian Territories.
At the moment any journalist or reporter working in the area needs to register with the Israeli military, and all stories pass through the Israeli Military Censor. But the likes of YouTube have led to a rise in citizen journalism, and this is what the Israeli government is looking to crack down upon.
According to the Israeli newspaper Maariv, Hotovely will be working with Google to create body charged with "monitoring and preventing" the appearance of "inflammatory" videos. There has been an increase in the number of videos published that highlight the suffering of Palestinians, and this is something the Israeli government sees as bad PR.
Details of how the monitoring and censorship program will work have not been released, but Palestinians living in the territory illegally occupied by Israel are about to find it harder to get their side of the story out.
Update
Since the publication of this story, BetaNews has been contacted by a Google spokesperson who issued the following statement:
Following media reports about a meeting last week between Google / YouTube executives and the Israeli Deputy Minister of Foreign Affairs, we wanted to clarify that this meeting was one of many that we have with policymakers from different countries to explain our policies on controversial content, flagging and removals.
The Israeli Ministry for Foreign Affairs has corrected its original announcement which, in error, suggested there had been an agreement with Google to establish 'a mechanism to monitor online materials'.
We rely on the YouTube Community to flag videos that they think violate our Community Guidelines. Video flagged on YouTube is reviewed 24 hours a day and, if material violates our policies, it is removed quickly. The policies are explained here and here in more detail on the YouTube policy center.
Photo credit: danielo / Shutterstock
-

Google's Accelerated Mobile Pages will speed up the web in 2016
Publié: novembre 25, 2015, 8:57pm CET par Mark Wilson

It's now a few weeks since Google announced Accelerated Mobile Pages. When the project was unveiled, there were just 30 or so partners on board and no indication of when AMP would be made available to everyone. Today Google reveals that the acceleration program will start to roll out early next year.
There are now, according to Google, thousands of publishers who have expressed interest in AMP. With many of these representing a large number of newspapers, TV and radio stations, the range of content is looking promising. As this is Google, a focus on ads should be expected, and now Outbrain, AOL, OpenX, DoubleClick, and AdSense are adopting the AMP spec.
By adopting Google's framework, these ad partners will work together to improve the overall ad experience for web users with a focus on performance. Analytics are something that advertisers are extremely interested in, but it's also data that bloggers and admins need access to.
With a changing ecosystem, the fear may be that data would not be available in the same way, or with the same level of detail. To ensure that people are provided with the information they need, Google has confirmation from comScore, Adobe Analytics, Parse.ly and Chartbeat that they will provide AMP analytics.
In a blog post, Google's David Besbris and Richard Gingras write:
More than 4500 developers are following the AMP Project's ongoing engineering discussions on GitHub. Since the announcement, over 250 pull requests -- contributions of new code, samples, and documentation -- have been made; and discussions around major new features such as analytics and templates have taken place.
Google will begin sending traffic to your AMP pages in Google Search early next year, and we plan to share more concrete specifics on timing very soon. In the meantime, the AMP Project invites everyone to take part in the conversation on GitHub, and encourages you to begin experimenting with building AMP pages as soon as possible.
Photo credit: Sashkin / Shutterstock
-

UK's Trident nuclear weapons could be hit by cyberattacks
Publié: novembre 24, 2015, 12:39pm CET par Mark Wilson

The UK's former defense secretary Des Browne has issued a stark warning that the country's nuclear weapons could be vulnerable to cyberattacks. The Trident program is already a highly-divisive subject, and Browne is seeking assurance from the Prime Minister that it is secured against attacks from hostile states such as China and Russia.
He has called upon the government to perform an end-to-end assessment of the system. The US had previously warned that it could not be confident that its own defenses and those of its allies would be capable of withstanding a cyberattack from a "sophisticated and well-resourced opponent".
Trident has been a hot topic recently, as the government sets out plans to plough billions of pounds into its nuclear deterrent whilst simultaneously introducing additional austerity measures and cutting back on welfare payment. £3.2bn over five years has been allocated to improve cyber security, but there are suggestions that this is simply not enough.
Lord Browne is now the vice-chair of the Nuclear Threat Initiative, and says:
The government... have an obligation to assure parliament that all of the systems of the nuclear deterrent have been assessed end-to-end against cyber attacks to understand possible weak spots and that those weak spots are protected against a high-tier cyber threat. If they are unable to do that then there is no guarantee that we will have a reliable deterrent or the prime minister will be able to use this system when he needs to reach for it.
But former White House defense policy official Franklin Miller believes the US nuclear system is impervious to cyberattack:
It is no surprise that Des Browne would be coming up with arguments against the successor to Vanguard and to be grasping at straws. If our nuclear command and control system depended upon the internet or went through the internet then the report by the defense science board would be quite an important warning. However, for those reasons it is a standalone system. It is air-gapped. It does not go through the internet.
Photo credit: Razvan Ionut Dragomirescu / Shutterstock
-

ProtonMail: banning encryption won't stop terrorism
Publié: novembre 24, 2015, 11:32am CET par Mark Wilson

In the panic that followed the attacks on Paris by ISIS there have been calls for various measures to be put in place to stop similar atrocities happening in future. As well as calls for an increase in online surveillance, politicians have also suggested that encryption should be weakened or banned entirely.
Secure email service ProtonMail found itself the subject of unwanted attention when in transpired that ISIS recommended using it to evade detection. The company has remained silent about the post-Paris backlash; until now.
CEO of ProtonMail, Andy Yen has written an impassioned diatribe against calls for encryption bans, dismissing them as "politically convenient" and "misguided". He points to the fact that while some of the communication used to coordinate the attacks on Paris was encrypted, this was not the case for all of it.
To paraphrase, Yen suggests that an encryption ban is akin to bolting the stable door after the horse has bolted. Just as a ban on guns would do little to stop people owning them, banning encryption would not stop it being used. Encryption exists, it can't be taken back. The genie is out of the bottle, and it's not going back in.
Rather than a tool for terrorism, Yen says that encrypted email is valuable for security and privacy:
The truth is, in the past twenty years, our world has come to depend more and more on the Internet and the vast amounts of data stored online. The survival of this new global internet economy depends more and more on securing our data. At ProtonMail, our primary objectives is to help the world secure email. When terrorists start to strike online, the end-to-end encryption technologies being used by ProtonMail will become the shield that protects us.
He makes the entirely valid point that "ISIS doesn't just use ProtonMail, they also use Twitter, mobile phones, rental cars. We couldn't possibly ban everything that terrorists use without disrupting democracy and our way of life, and in effect achieving the goal of terrorism". He also derides the idea of building in backdoors to security products, saying that there is no such thing as a backdoor that only lets the good guys in.
Yen concludes by saying:
There are many ways to confront terrorism, we just don't accept that giving up our freedom is the only way.
Photo credit: Krasimira Nevenova / Shutterstock
-

WordPress site undergoes a major redesign, desktop app launches, code goes open source
Publié: novembre 23, 2015, 9:51pm CET par Mark Wilson
A huge proportion of the web is powered by WordPress -- more than a quarter, in fact. As a CMS it's incredibly flexible, and today the company unveiled not only a new look for WordPress.com, but also a desktop app for easier site maintenance.
It has taken a long time for a desktop app to appear, and this is something that's all the more surprising when you consider that mobile apps are already available. To start with, it's Mac users who are treated to WordPress goodness, but Linux and Windows versions are on the way as well.
The Mac app looks remarkably similar to the WordPress web interface, but now your blog can live in your dock. As WordPress points out, this gives you a better opportunity to focus on creating content and replying to comments without the distractions of having sites open in browser tabs.
The JetPack plugin has been updated so that it can be used to administer WordPress.com sites as well as self-hosted blogs. The website and app can now update plugins, perform site backups, and more. WordPress has also made its code open source, and it can be found on GitHub.
Today's announcements are not just about site creation tools; WordPress has also launched Discover. This is a new tool that has been designed to make it easier to find new sites and blog posts that you may be interested in, and features a selection of curated content.
If you're keen to get started with WordPress for Mac, head over to the download page to grab a copy. You can also sign up to be notified when the Windows and Linux versions are released.
Find out what's new in the introductory video:
-

Awaken the Force! Choose the light side or dark to give Google a Star Wars makeover
Publié: novembre 23, 2015, 10:15am CET par Mark Wilson
Even if you're not a fan, it can't have escaped your attention that there's a new Star Wars movie coming out soon. Google is as excited as millions of fans are, and to celebrate Star Wars: Episode VII The Force Awakens it is giving you the chance to give Google apps and services a Star Wars makeover.
Choose to join the light side or the dark side, and Gmail, Google search, and more will be customized in a Star Wars style. Like the idea of being shown how to get to your destination by an X-Wing flying down the streets in Google Maps? Consider it done! But there's a lot more to look out for...
You'll have to think carefully before you choose your side. Whether you head to the light, or wrap yourself in darkness, will impact on your Google experience -- including adding Star Wars events to your calendar. If you change your mind, you can switch allegiances, and the makeover will follow you as you move between devices; they're available on Android, iPhone, iPad, Mac, Windows, and Chromebook.
Writing on the Google Blog, Vice President of Product Management Clay Bavor says:
We reached out to our friends at Lucasfilm and Disney, and since then we've been working together on building google.com/starwars. It's a place for fans, by fans, and starting today you can choose the light or the dark side, and then watch your favorite Google apps like Gmail, Google Maps, YouTube, Chrome and many more transform to reflect your path. And that's just the beginning. We've got more coming between now and opening night -- the Millennium Falcon in all its (virtual reality) glory included, so stay tuned. And we've hidden a few easter eggs, too. So awaken the Force within, and be on the lookout for things from a long time ago in a galaxy far, far away...
Check out the video below and then head over to [google.com]:
What will it be? The light side... or the dark side?
-

Earn yourself spendable Bitwalking dollars with your daily perambulations
Publié: novembre 21, 2015, 8:03pm CET par Mark Wilson

Ordinarily, if you want to receive money just for walking you'd need to do a sponsored walk -- and that money's supposed to go to charity -- or get yourself a job as a dog walker. But how does the idea of getting paid just for the walking you do each and every day sound? That's exactly what Bitwalking promises.
With a name clearly inspired by the Bitcoin cryptocurrency, Bitwalking works in a couple of ways. Walkers can earn 1 Bitwalking dollar (BW$) for every 10,000 steps they take, and these can be spent in an online store, or converted into cash. The system uses a smartphone to count steps, but there are also plans to produce a wristband.
Bitwalking is the brainchild of Nissan Bahar and Franky Imbesi, and is lining itself to take on PayPal and other services of its ilk. As well as allowing for the purchasing of goods, the currency can also be used to send money to other people. The BBC reports that in the UK there are plans to join forces with a major music festival, and there is also interest from shoe manufacturers.
As well as helping people to earn money by doing nothing more than they normally do, Bitwalking also promotes health and fitness, and helps the environment by avoiding cars. But it is undeniable that it is the money side of things that most people will be interested in. Bitwalking says:
With Bitwalking you simply generate money by walking. Once installed on your phone, the free app converts steps to Bitwalking dollars (BW$) that you can manage and use as you wish. The money you generate accumulates each day, and remains in your account until transferred or spent [...] We believe that everyone should have the freedom, and ability, to make money. A step is worth the same value for everyone -- no matter who you are, or where you are. What matters is how much you walk.
It is estimated that most people around the world would be able to earn around 15 BW$ per day, and in the Bitwalking store at least 1 BW$ equate to $1 (prices will be the same in both currency, any way), but it's not clear what the conversion rate will be in the real world. To help avoid potential cheating, the app will use GPS data to ensure that people are actually moving around rather than just sitting down shaking their phone. This may well open up privacy concerns, and the same could be said of advertising plans.
Bahar says:
We may explore offering advertisers the opportunity to focus on different groups depending on how active they are, but we won't pass on any information relating to individual's movements.
Bitwalking is yet to launch, but you can request an invite to get started as early as possible by heading over to the website.
Photo credit: beeboys / Shutterstock
-

Apple video explains how to use Apple Pay to pay for things... like apples
Publié: novembre 21, 2015, 6:52pm CET par Mark Wilson

There's quite a lot of competition in the digital payment arena at the moment. Apple Pay is one of the latest to join the likes of Samsung Pay and Android Pay, and Apple is keen to demonstrate just how easy it is to use its payment system.
For many people, using a smartphone to pay for coffee is an intuitive process, but Apple wants to sell its service to more people. The company needs to break down any barriers that might be standing in the way of new users adopting Apple Pay, and this is the reason for the appearance of a video that serves as a 'how to' guide.
Described by Apple a showing "how easy it is to set up Apple Pay and make quick, secure and private payments from your iPhone", the video serves as something of an idiot's guide. After all, making a payment doesn’t get much simpler than waving your phone at a magic box while you present your fingertip to the Touch ID sensor.
As well as showing how Apple Pay can be used in physical stores, the video also shows how it can be used to make online payments. Check it out below:
https://youtu.be/ez-2M3C_4wU
Photo credit: Olha Insight / Shutterstock
-

Microsoft shoots itself in the foot using AppComparison to lure Android users to Windows 10 Mobile
Publié: novembre 21, 2015, 6:07pm CET par Mark Wilson

After the slightly disappointing launch of Windows 10 -- at least in terms of reception, if not in terms of numbers (well, it was free) -- Microsoft is now switching its focus to Windows 10 Mobile. The aim now is to try to capture Android and iPhone users, convincing them that a Windows-based smartphone is a smart move.
But there's the problem of apps. It's something that crops up time and time again. Microsoft simply doesn't have the support of mobile developers in the same way that other platforms do. Not that Microsoft would admit this of course. To try to convince people that the 'app gap' no longer exists, the company has released AppComparison for Android to show off how many of the apps you use are available for Windows 10 Mobile. The problem is, there are still lots that simply don't exist.
If you feel inclined, you can download AppComparison from Google Play. It's free, so you've nothing to lose apart from a couple of megabytes of space, and you could get a bit of a giggle. In fact, it could save you money. Prepare to be convinced that Windows 10 Mobile is not something you should bother investing in.
The idea behind AppComparison is solid. Install it, let it run a quick scan of your Android Phone, and you'll be told about which of the apps you have installed are available for Windows 10 Mobile. Clue: probably not many. In those instances where an app is not available -- and there are lots of such instances -- an alternative will be suggested.

I decided to install the app on my Huawei P8 to see what it came up with. Amusement followed.
As my phone is Android-based, I have the Gmail and Google Calendar apps installed. Microsoft suggests that I switch to Outlook. Why on earth would I want to do this? I chose Gmail for a reason. I also use Google Drive, and once again Microsoft tries to steer me to its own product -- OneDrive. Again, a conscious decision to use Google Drive was made. Rather than just admitting that there isn't a Google Drive app for Windows 10 Mobile, Microsoft attempts to hawk its own wares... and no mention of alternatives.
Big name apps such as YouTube and Facebook are listed as being available, as are Kindle and SoundHound. But another Google app, Google+, is not available -- at least not an official client. Microsoft's suggestion? The delightfully unprofessional-sounding "App for G+". Similarly for Hangouts, "Gchat+" is recommended.
Google Play Music user? Microsoft thinks CloudMuzik (huh?) is a suitable alternative. Chrome? Nope. No such luck -- UC Browser is the recommendation. Like to hit Starbucks from time to time? There's no app available to make your payments or collect rewards, but TimmyMe (which looks truly, truly awful) is suggested. It doesn't even come close.
Rather than highlighting what a great array of apps Windows 10 Mobile has, AppComparison instead pushes third-rate alternatives that end up achieving very much the opposite of what Microsoft set out to do. While there are a number of big-name apps out there, there are still a lot of important ones missing, and the alternatives are very third-rate.
There's another aspect of AppComparison which lets you indicate the types of things you're interested in, and a series of app suggestions will be provided. Here, Microsoft perfectly illustrates that it's just out of touch. The category list you're presented with comprises Entertainment, Education, Games, Health and Fitness, Lifestyle, News and Weather, Photos and Video, Productivity, Sports, Travel, and Friends and Family. Where's the 'social' category? Books? Communication? Finance? Business? Music? Shopping?
Microsoft just doesn’t have a clue how to 'do' mobile. Windows Phone has exemplified this for some time, and it's something that looks set to continue with Windows 10 Mobile. AppComparison sees Microsoft shooting itself in the foot in quite spectacular fashion.
Photo credit: Rob Byron / Shutterstock
-

Is Yahoo locking you out of your email account for using an ad blocker?
Publié: novembre 21, 2015, 2:50pm CET par Mark Wilson

Yahoo has sparked controversy by preventing some users from accessing their email accounts if they have an ad blocker installed. It's something that seems to be restricted to the US at the moment, and Yahoo says it is testing out the block on a "small number of Yahoo Mail users".
Edward Snowden recently said that people have a duty to use an ad blocker, and it seems that nearly 20 percent of web users have followed his advice. Just like Google, Yahoo makes a large proportion of its income through advertising, but affected Yahoo Mail users feel that the company is holding their email accounts to ransom.
The Adblock Plus support forums features posts from users who found themselves locked out of their account, and there were also complaints on Twitter. People are more than a little disgruntled by the move, but some users have noted that by switching Yahoo Mail to Basic view, it is possible to get around the block.
Photo credit: portnoyd
In a statement, Yahoo spokeswoman Anne Yeh said:
At Yahoo, we are continually developing and testing new product experiences. This is a test we're running for a small number of Yahoo Mail users in the US.
When an ad blocker is detected, Yahoo blocks access and the URL has ADBLK_TRAP added to the end as a fairly clear indicator of what is going on. Has your account been hit?
Photo credit: Claudio Divizia / Shutterstock
-

Windows 10's privacy invading features aren't gone in Threshold 2
Publié: novembre 20, 2015, 4:26pm CET par Mark Wilson

Since the launch of Windows 10, there have been various concerns relating to privacy. Some would dismiss this as little more than paranoia, but a lack of transparency about what was happening in the background broke a lot of people's trust. Many hoped that the release of the Threshold 2 update this month would address this, but in lots of cases it was actually a backward step.
In the RTM release of Windows 10, there was a service running in the background called Diagnostics Tracking Service (also known as DiagTrack), and people concerned about privacy -- who were in the know -- disabled it. In Threshold 2, this service is gone. A cause for celebration you might think; but think again. The service is still there, just under a different guise.
The original name was something of a mix of the worrying ('tracking') and the reassuring ('diagnostics'). This service has now been replaced by the opaquely-name Connected User Experiences and Telemetry service. For most people, reference to 'User Experience' has positive connotations, while only those who have been keeping an ear to the ground would understand the privacy implications of telemetry -- most would not have a clue what it means.
Changing the name of the service in this way could be described as a little bit sneaky, but the method for disabling it is the same as before.
Hit the Windows key and R, type services.msc, and press Enter.
Locate Connected User Experiences and Telemetry and double-click it.
Click the Stop button.
Select Disabled from the drop down menu and hit OK.
Photo credit: Alex Malikov / Shutterstock
-

iPad Pro adoption is in the toilet
Publié: novembre 20, 2015, 1:01pm CET par Mark Wilson

With the level of excitement that surrounded the launch of the iPad Pro, it would be reasonable to expect sales to be high. They're not. Adoption of this particular model are the slowest for any iPad version yet.
It may only be a week since launch, but Apple would almost certainly be hoping that the new Pro version of its tablet would have captured more than 0.3 percent of the iPad market. Not even the tablet market, just iPads. Experts suggest that part of the reason for this is confusion about who the iPad Pro is aimed at.
Compare the launch of the iPad Pro with the first and second generation Air models. The iPad Air captured more than six times the market share than the Pro version in the same time frame. The iPad Air 2 proved slightly less popular, but still enjoyed a first week adoption rate more than three times that of the iPad Pro.
In fact, since the launch of the iPad Pro, the two Airs have seen a jump in sales -- thanks in part to the price drops that follow any new launch.
Research by Localytics shows that the iPad 2 and iPad Air still dominate, and the new kid on the block has quite some catching up to do:
Localytics suggests that part of the reason for the slower adoption is competition from PCs, and a need for apps to evolve.
CEO Tim Cook has positioned the iPad Pro as a replacement for PCs, so the competition is not actually with other iPads but more so with laptops and desktops. The idea of an iPad taking the place of a laptop may take some convincing due to the fact the iPad Pro runs on iOS as opposed to the traditional laptop system OS X. While iOS offers many great features, it does not have the access to full-featured applications that OS X does, which will call for adjustments on the user’s side. Apple's best chance to bridge this gap is to leverage the App Store and highlight apps focused on productivity and improving the workplace experience, as we'll see next.
-

LG Watch Urbane 2nd Edition launch cancelled
Publié: novembre 20, 2015, 11:31am CET par Mark Wilson

The hotly anticipated LG Watch Urbane 2nd Edition -- the first Android Wear device with cellular support -- may never be released. LG has cancelled plans for a global rollout of the smartwatch after the discovery of a 'complicated' hardware issue.
At the moment it is not clear whether the wearable will ever see the light of day as LG is investigating quality standards. The company has not provided any details about the nature of the problem, but the decision to cancel such a huge launch is not one that will have been taken lightly.
AT&T has already started to notify customers who have ordered the watch that they are eligible for a refund. Verizon has stopped taking orders, but has not elaborated on the reasons behind this decision.
LG sent a statement to reviewers awaiting the arrival of the smartwatch:
We understand that you are currently reviewing our latest smartwatch; however, late in the quality assurance process for the LG Watch Urbane 2nd Edition LTE, our engineers were made aware of a hardware issue which affects the day-to-day functionality of the device. After further investigation, the decision was made to cancel the rollout of the Urbane 2nd Edition LTE due to the complicated nature of the issue.
Whether the device will be available in the future will be decided at a later time. For now, our top priority is to ensure that only products that meet our very specific quality standards are available for purchase.
At the moment the likelihood of the device launching is looking slim, but watch this space for updates.
-

YouTube will help users fight DMCA takedowns in court
Publié: novembre 20, 2015, 12:47am CET par Mark Wilson

The use of other people's copyright material on YouTube is permitted in certain circumstances. Fair use rules allow for the use of copyright material for the purposes of review, parody, and more -- but this doesn't stop copyright holders from issuing DMCA takedown notices.
YouTube is a natural breeding ground for copyright violations, but there are also countless examples of fair use that end up in court. This is something that many people are scared of, and rather than fighting back, will tend to cave in. Now Google has said that it is willing to stand up for users and will defend them in court.
Google says that every minute of the days sees 400 hours of video uploaded to YouTube, and a proportion of these videos reuse previously published content. Recognizing that video uploaders can be easily intimidated into taking down videos that they are perfectly entitled to upload, the company says:
We are offering legal support to a handful of videos that we believe represent clear fair uses which have been subject to DMCA takedowns. With approval of the video creators, we'll keep the videos live on YouTube in the U.S., feature them in the YouTube Copyright Center as strong examples of fair use, and cover the cost of any copyright lawsuits brought against them.
We're doing this because we recognize that creators can be intimidated by the DMCA's counter notification process, and the potential for litigation that comes with it.
Unfortunately, help from Google is not going to be available to every YouTube user ("we can't offer legal protection to [...] every video that has a strong fair use defense") but the company says it will "continue to resist legally unsupported DMCA takedowns".
It's a small step, but it's a start.
Photo credit: StepanPopov / Shutterstock
-

Siri poses privacy and security risks for iPhone users
Publié: novembre 20, 2015, 12:08am CET par Mark Wilson

Digital assistants such as Siri are billed as great time-savers, and there's no denying that Apple's voice-activated feature can be a real help. But security experts at Trend Micro warn that it also poses a serious privacy risk for iPhone owners.
Even if your iPhone is protected with a PIN or passcode, it could still be possible for someone else to use Siri to learn personal information about not just you, but your relations and other contacts, as well as details about your schedule. Described by Trend Micro as a 'flaw', Siri actually acts as a backdoor that enables anyone with physical access to your phone to bypass security features.
The problem arises for people who have Siri enabled on the lock screen. Voice control can be used to garner all sorts of data from your phone, and even perform functions such as placing calls, sending texts, and posting social network status updates. While it is not a new problem -- it is something that has been raised on Apple's support forums several times -- Trend Micro is keen to bring the issue to the attention of as many people as possible so they might take steps to protect their data.
Leave your phone unattended and anyone is able to use Siri to check what appointments you have on a given day. They can learn your email address just by asking, and create or delete alarms. Writing on the TrendLabs Security Intelligence blog, Trend Micro says:
Ideally for the mobile device owners, voice commands could be used by law enforcement or first responders to locate the identity of an injured person and even contact a family member, using a command such as, "Call mom". However, these commands could also be used by a malicious individual to cause harm in a friendship or relationship by a posting a Facebook status such as "now single and not looking" or "Text boyfriend...".
Even non-iOS users may be at risk. Tens of millions of iOS mobile devices have been sold around the world. A large portion of the world's population has at least a friend, family member, or colleague that does own an iOS mobile device with Siri enabled. As such, their contact details can be accessed on a locked screen, also putting their privacy at risk.
So what can you do to protect your data? Trend Micro's advice is simple: disable Siri on the lock screen. It advises what Apple also shares, telling users that they can help protect themselves by heading to Settings > Touch ID & Passcode > Siri and disabling Siri.
Photo credit: Twin Design / Shutterstock
-

Facebook helps you to cut your ex out of your life
Publié: novembre 19, 2015, 8:24pm CET par Mark Wilson

Break ups happen. Relationships come to an end. It might be an amicable termination, but the chances are that it's not. You probably never want to hear from your ex partner again. Unfortunately, over the years, you have built up a shared circle of friends, and you're both connected to them on Facebook.
Depending on the circumstances of the break up, you might want to go as far as ditching the online friendship and blocking your former beau. But you might not want to take things quite that far. With this in mind, Facebook is now rolling out new features that kick in when you indicate that you're no longer in a relationship, so you won’t be constantly reminded of what you have lost.
If there's a chance that things might get back on track at some point, you might not want to completely sever ties. At the same time, you might not want to see your once lover's name and picture popping up constantly -- Facebook can now help to calm the frustration. Rather than completely cutting yourself off from each other, Facebook will instead offer you the opportunity to 'see less' of your ex.
This means that their name will not pop up as a suggestion when you type, you won’t see their posts in your news feed, and you're also able to limit what content of yours is visible to them. You might not mind some of your photos and status updates being seen, but you may well want to hide others beside those you explicitly tag your former partner in.
Facebook says:
We're starting to test these tools today in the US on mobile, and we’ll make changes and roll them out further based on people's feedback. All of these tools are optional, and people will be able to access them in the help center anytime.
This work is part of our ongoing effort to develop resources for people who may be going through difficult moments in their lives. We hope these tools will help people end relationships on Facebook with greater ease, comfort and sense of control.
Would this make a break up easier for you to handle?
Photo credit: wk1003mike / Shutterstock
-

The Google app grows up and becomes contextually aware
Publié: novembre 16, 2015, 8:07pm CET par Mark Wilson
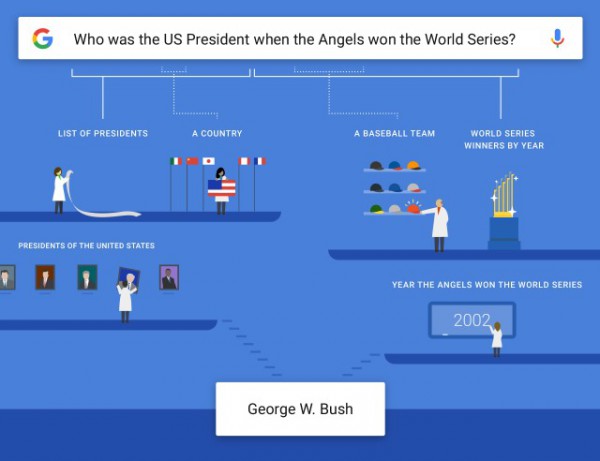
Voice control is becoming increasingly common with the eager adoption of Siri and Cortana. Google has been in the game for some time as well, and today announces that the Google app is growing in intelligence, enabling it to 'understand' ever more complex questions.
Google's ability to recognize the context in which questions are asked is not new, but it has now evolved even further. Rather than just doing simple searches based on keywords, Google believes that it is "starting to truly understand the meaning of what you're asking".
Writing on the Google Search blog, Product Manager Satyajeet Salgar explains that any questions put to the Google app are broken down to make it possible to 'understand' not just the context, but also the intent behind what is being asked.
Support for superlative recognition means that Google is now able to answer questions about the biggest animals, the tallest building, and the heaviest vehicle. Today's announcement says that Google is getting better at making sense of questions that involve dates, but it is the support for what Google refers to as 'complex combinations' that holds the most possibilities.
Salgar gives the examples of "what are some of Seth Gabel's father-in-law's movies?", and "what was the U.S. population when Bernie Sanders was born?" as the sort of questions that Google can successfully respond to. He says:
We're still growing and learning, which means we make mistakes. Ask Google "Who was Dakota Johnson's mom in the movie?", and we’ll respond with the movies of Dakota Johnson’s real-life mother Melanie Griffith, not the actor Jennifer Ehle who played Anastasia’s mother Carla in the 50 Shades of Grey movie. (Hey, that one’s tricky even for people!)
Give it a whirl and see if you can confuse the system!
-

Get 1TB of Google Drive storage for free
Publié: novembre 16, 2015, 3:03pm CET par Mark Wilson
It's hard to have too much storage, and cloud storage is particularly handy. Microsoft may have cut the amount of space OneDrive users have access to, but Google is giving you a way to gain 1TB of Google Drive space for free.
There is, of course, a slight catch. While the storage space is free, you will have to work for it. It's all part of a big push of Google's Local Guides program. Make contributions to Google Maps in the form of uploading photos, writing reviews, and correcting mistakes and you'll be rewarded in a number of ways.
Google has turned the program into something of a game, but it will take some time before you earn the free storage space. Update to the latest version of Google Maps on your phone, and you'll notice that there is a new Contributions option. Here you find out how you can earn points that can be used to level up and earn a variety of rewards.
On the Google Maps blog, Google reveals how the points system translates into rewards:
- Level 1 (0 - 4 points): Enter exclusive contests (think new Google devices!) in select countries.
- Level 2 (5 - 49 points): Get early access to new Google products and features.
- Level 3 (50 - 199 points): Show up in the Google Maps app with your official Local Guides badge.
- Level 4 (200 - 499 points): Receive a free 1 TB upgrade of your Drive storage, allowing you to keep all the stories, photos, and videos from your travels in one safe place.
- Level 5 (500+ points): The very top Local Guides will become eligible to apply to attend our inaugural summit in 2016, where you’ll be able to meet other top Guides from around the world, explore the Google campus, and get the latest info about Google Maps. Look out for details early next year.
To get started, sign up for Local Guides, and download the Android or iPhone app. The video below explains how it all works.
-

Microsoft and Code.org use Minecraft to teach coding to kids
Publié: novembre 16, 2015, 2:43pm CET par Mark Wilson

As part of the third Hour of Code, Microsoft has launched a coding tutorial based on Minecraft. The event is part of Computer Science Education Week, which runs from December 7-13 and uses the familiar Minecraft to teach coding to people aged 6 and above.
The tutorial is a collaboration between Microsoft, Code.org, and Mojang AB, the company behind Minecraft. It provides a gentle on-ramp to learning the basics of coding, with a view to inspiring the next generation of developers.
Students are guided through a total of 14 challenges introducing a number of coding concepts using the popular game. Code.org CEO Hadi Partovi says that Minecraft was chosen as a learning tool because it "is a special game that girls and boys alike often can't be pried away from".
Microsoft CEO Satya Nadella says:
A core part of our mission to empower every person on the planet is equipping youth with computational thinking and problem-solving skills to succeed in an increasingly digital world. With 'Minecraft' and Code.org, we aim to spark creativity in the next generation of innovators in a way that is natural, collaborative and fun.
If you fancy trying your hand at the tutorial, you can access it at Code.org.
-

What's so different about Paris? Facebook reveals why it enabled Safety Check after French attacks
Publié: novembre 15, 2015, 6:52pm CET par Mark Wilson

The shootings and suicide bombings in France this week grabbed the attention of the global media. To help those caught up in the aftermath to let loved ones know that they were OK -- and to enable others to check on friends and relatives in France -- Facebook enabled its Safety Check feature for the disaster.
While this was welcomed, it also raised questions. Why had this not been done for other such disasters? Why were shootings in other countries treated differently? What was so special about France that it warranted extra attention from Facebook? Were the lives lost in other atrocities seen as less important? Facebook's Alex Schultz has stepped up to the plate to answer these concerns.
Social networks such as Facebook became hotbeds of discussion about the attacks. Shock, anger, and grief followed, but it wasn't long before people started to ask why loss of lives in other countries failed to gain the same level of attention. Why did the Paris attacks get Safety Check, but a suicide bombing in Beirut that killed 40 people didn’t? What about all of the deaths in Syria?
Schultz explains that there is nothing 'special' about the tragedy in France. While Safety Check had previously been used to allow people to keep in touch following a natural disaster, this was the first time it had been used for a manmade horror.
But people are also asking why we turned on Safety Check in Paris and not other parts of the world, where violence is more common and terrible things happen with distressing frequency. Thursday's tragedy in Beirut is one recent example. I wanted to give some more background on the tool itself, its history and why we made the decision we did.
He goes on to say that this was the first time Safety Check had been activated for something other than a natural disaster. The events of Paris were not singled out for any particular reason, but one tragedy had to be the first:
We chose to activate Safety Check in Paris because we observed a lot of activity on Facebook as the events were unfolding. In the middle of a complex, uncertain situation affecting many people, Facebook became a place where people were sharing information and looking to understand the condition of their loved ones. We talked with our employees on the ground, who felt that there was still a need that we could fill. So we made the decision to try something we've never done before: activating Safety Check for something other than a natural disaster.
Facebook says that it "will learn a lot from feedback on this launch" and will use Safety Check -- which remains a "work in progress" -- for " other serious and tragic incidents in the future".
Photo credit: Jean Jullien
-

FCC says it's legal to hack your router
Publié: novembre 15, 2015, 3:50pm CET par Mark Wilson

Router hacking is a geek staple. No computer geek worth his or her salt would consider running vanilla firmware -- the likes of Tomato are where it's at. A little while back, the FCC suggested plans to ban such hacking via open source firmware... or at least that's how it seemed.
The commission has now acknowledged that there was more than a little confusion from people who believed that manufacturers would be encouraged to prevent router modifications. The FCC wants to make it clear that most router hacking is fine and will remain fine. With a few exceptions, that is.
In a blog post entitled Clearing the Air on Wi-Fi Software Updates, Julius Knapp from the FCC tries to clear up any misunderstandings that may exist. He says that the aim is not to stop people from modifying their routers completely, but to stop them from modifying them in ways that would render them illegal -- such as increasing their power beyond a certain level.
Knapp says:
One of our key goals is to protect against harmful interference by calling on manufacturers to secure their devices against third party software modifications that would take a device out of its RF compliance. Yet, as the record shows, there is concern that our proposed rules could have the unintended consequence of causing manufacturers to 'lock down' their devices and prevent all software modifications, including those impacting security vulnerabilities and other changes on which users rely.
A new revision to the manufacturer guidance regarding software has been published. The document clarifies that the aim is to prevent RF interference between devices:
The purpose of this rule is to prevent modifications to the software that could, for ex
example, disable dynamic frequency selection (technology necessary for preventing interference to radars), enable tuning to unauthorized frequencies, increase power above authorized levels, etc. The rule is not intended to prevent or inhibit modification of any other software or firmware in the device, such as software modifications to improve performance, configure RF networks or improve cybersecurity. These types of software and firmware modifications, including updates to address security vulnerabilities are known to be highly desired by many users and manufacturers are encouraged to design their systems to permit such software upgrades while ensuring security of the portion that controls compliance with the FCC technical requirements.
So you can gaily continue to hack away -- hooray!
Photo credit: riggsby / Shutterstock
-

Zune is dead
Publié: novembre 15, 2015, 2:12pm CET par Mark Wilson

The writing has been on the wall for some time now, but Microsoft has today officially killed Zune. After nine years, the music service is no more, driven to the grave by the competition.
Zune players just never managed to fight off the iPod, and with smartphones taking on the role of music player in addition to everything else, it didn’t take long for Microsoft's player to become surplus to requirements. Microsoft is not learning from history, though; the company continues to try its hand at music with Groove.
If you've already got a Zune Music Pass subscription -- there are some of them out there - it will be automatically converted into a Groove Music Pass subscription. You'll lose the ability to stream and download content.
On the Zune support pages, Microsoft says:
As of November 15, 2015, Zune services will be retired. You will no longer be able to stream or download content to your device from the Zune music service. However, Zune devices will still function as music players and any MP3 content that you own on the Zune device will remain there. You’ll also be able to transfer music to and from your Zune player.
Few tears will be shed for the passing of Zune, and it can now be consigned to the history books.
-

Has Windows 10 November Update (Threshold 2) reset your privacy settings and default apps?
Publié: novembre 14, 2015, 5:31pm CET par Mark Wilson

Windows 10 has caused greater privacy concerns than any previous version of the operating system. You may well have spent some time tweaking settings so that you are in control of your privacy and limit the tracking that Windows 10 is able to do, but if you have installed the latest big update you may well have to do it all again.
In addition to resetting their privacy settings to their defaults, many people have reported that installing Windows 10's November Update has wiped out any personalization of default apps. This is just the latest in a series of slip-ups which sees Microsoft upsetting Windows 10 users. So how do you know if your settings have been changed?
Head to Settings and click Privacy. In the General section check through the various privacy options, and disable any settings that have magically re-enabled themselves. There are a couple of ways to change default app settings, but first off all head to System in Settings and move to the Default apps section. Here you can see the default apps for a few key file types, and reset any which have been changed in the background.
You will notice that the number of file types you can tweak here is rather limited. If you find that a particular file is opening in the wrong app, hold down the Shift key while you right click the file and select Open With from the menu. You can then click the More Apps link, check the Always open this app... box and select the app you want to use.
It might seem silly that you should have to go through all of this for a second time if you have already spent time customizing things to your liking, but in many ways this is very much in keeping with the launch of Windows 10.
Did you find that your customizations had been reset?
Photo credit: Roobcio / Shutterstock
-

Microsoft details four commitments to help rebuild trust in the cloud
Publié: novembre 14, 2015, 4:28pm CET par Mark Wilson

In a lengthy, rambling blog post, Microsoft President Brad Smith explains how what has happened in relation to security over the past year is shaping the company's attitude to the cloud. He says that "it's time to rebuild the world's faith in the technology that empowers us all".
He takes a while to get to the point, meandering slowly around anecdotes about Windows 10, Edward Snowden, terrorist attacks in Paris, hacking, and governmental desires to weaken encryption. He says that these and other events "show it's crucial to have a conversation about worldwide information security".
Smith makes the point that it can be difficult to comply with the differing data storage and security laws around the world. Despite this, he wants Microsoft to be a voice for the people as well as standing up for the right of governments and businesses. The new Microsoft is all about the cloud ("mobile first, cloud first" as we have been told ad nauseum) after all.
Smith says that Microsoft has been inspired by the events of the last twelve months, including the Sony hack, the continued revelations from Edward Snowden, and the Charlie Hebdo attack in France. He also makes four promises to "governments, enterprises, consumers, and people around the world":
- We will keep their data secure.
- We will ensure people's data is private and under their control.
- We will figure out the laws in each country and make sure data is managed accordingly.
- And we will be transparent so people know what we are doing.
He goes on to explain what Microsoft will do for businesses:
We stand behind our technology with contracts to ensure we have strong and specific security safeguards. We process customers' information only as they instruct us, and we put in place strong regulatory compliance to meet their needs. We will tell them, whenever we're permitted, what the government is doing to access their data, and if we need to we'll go to court to vindicate those rights when that's the proper thing to do. Finally, we will continue to advance transparency.
Smith's post is worth a visit for a couple of reasons. Wade through the self-congratulatory guff, and there are some interesting stats about the legal processes Microsoft has gone through, and some great info about what has been happening for the last year, and how different countries approach data and security requirements. It's also beautifully presented -- go take a look.
-

Firefox users are stuck with unremoveable Pocket... for now at least
Publié: novembre 14, 2015, 12:06pm CET par Mark Wilson

Earlier in the year Mozilla took the decision to build Pocket into Firefox. Previously available as an add-on, the 'read it later' tool was transformed into an integral part of the browser. While this was a move welcomed by some users, others are concerned about the privacy implications.
There are also concerns that having Pocket built in unnecessarily bloats Mozilla's code, but it looks as though it is here to stay. Speaking to Venture Beat, director of engineering for the browser said "there are currently no plans to offer a version of Firefox that doesn’t include Pocket".
What has upset many Firefox users is the fact that Pocket cannot be removed. It can be disabled, but this is not the same thing. There are calls for Pocket to be moved back to being an add-on. Even if it is a built-in add-on, this would still give users the option of getting rid of it if they wanted.
Firefox engineer Dave Camp told Venture Beat:
We're always experimenting with better ways to deliver value to Firefox users. 'Go Faster' is the working title of one such experiment we're doing with Firefox for Desktop. Go Faster introduces the idea of shipping a feature as a system add-on. These system add-ons will enable us to get features and fixes to users on a reduced cycle time. There is work underway to make our Pocket integration one of these system add-ons that ships as part of the core product. Separately, we are investigating the utility of Firefox users being able to disable or remove system add-ons from their installation. And as I said in July, we are committed to incorporating this consideration into any future partner integrations.
There's no indication of when this experiment might see the light of day, so for now it would appear that Firefox fans are lumbered with Pocket.
Photo credit: smutny pan / Shutterstock
-

Delete the Scan With Windows Defender content menu entry from Windows 10 (Threshold 2)
Publié: novembre 14, 2015, 12:32am CET par Mark Wilson
If you've installed the November Update for Windows 10 (or Threshold 2 if you prefer) there are a number of changes for the better to enjoy. But there are some changes that you might not be happy with, and the arrival of a new Scan With Windows Defender entry in context menu is something that is likely to grate with many people.
It might be that you have no intention of using Windows Defender, or your context menu may have become unwieldy and need a little trimming. Either way, a quick registry hack is all that's needed to banish the unwanted option. Here's what to do.
Even if you remove the Scan With Windows Defender entry, you'll still be able to scan files -- you can just fire up the app manually and take it from there. You might think that disabling Windows Defender would get rid of the menu item, but you'd be mistaken. So, gird your loins, and hit the registry.
- Press the Windows key and R, type regedit and hit Enter.
- Navigate to HKEY_CLASSES_ROOT\CLSID\ {09A47860-11B0-4DA5-AFA5-26D86198A780}
- Right click this key and select Delete.
- Click Yes.
That's all there is to it!
-

Google extends Chrome's Safe Browsing protection to fight social engineering
Publié: novembre 13, 2015, 11:29pm CET par Mark Wilson
Online attacks take a number of forms, and phishing is one of the more recent problems. Chrome has long featured Safe Browsing to notify people when they visit potentially dangerous websites, and today Google announces that the feature is growing to include social engineering.
Google describes social engineering as being a much broader category than traditional phishing. Typical examples include sites that trick visitors into imparting passwords or credit card details, and those which purport to be an official website when they are in fact malicious. The Safe Browsing expansion offers protection against a range of social engineering attacks that Google provides examples of.
Many malicious sites try to trick visitors into believing that they are associated with Google or Chrome. In one example, a site offers up a fake update to Chrome under the pretence of being a genuine Google site. Other tactics include mimicking Chrome's style of error message to display a warning about a browser or computer problem. Visitors are encouraged to call a fake technical support number -- at great cost -- or pushed to a malicious download.
To avoid being duped, Google advises everyone to " be sure to look at the address bar to check that the URL is correct, and also check to see that the website begins with https://". In a blog post the company explains that when a site with social engineering content is detected, the interstitial shown above will be displayed as a warning.
-

Microsoft launches Office Insider giving access to preview builds of Office 2016
Publié: novembre 13, 2015, 7:20pm CET par Mark Wilson
With Windows 10, Microsoft's Windows Insider program proved immensely popular. The chance to try out new features ahead of an official launch gave millions of people an insight into the development process and provided an opportunity to give feedback and influence the future of the operating system.
Today Microsoft is giving Office the same treatment. With the launch of the Office Insider program, Office 365 subscribers are being given the chance to try out upcoming releases of Office 2016.
For now, Office Insider is available for PC, but a Mac program is also on the cards. Mobile users have not been forgotten -- Android fans can join the Office Insider for Android community, and Windows Mobile users can get preview builds of Office through the Windows Insider program.
Introducing the new Insider program, Kirk Koenigsbauer, corporate vice president for the Office team, said:
Today, we're also launching Office Insider, a new program that allows Office 365 Home, Office 365 Personal and Office 365 University subscribers to opt in to pre-release builds of Office 2016 for Windows. As an Insider, you get first-hand access to the latest innovations, putting you on the inside track for all things Office. And when you become an Office Insider, you are joining a community of like-minded power users. With your partnership, we can ensure a high quality Office experience for millions of Office users worldwide.
If you want to sign up for Office Insider, head over to the website and get downloading.
-

It is your duty to use an ad blocker, says Edward Snowden
Publié: novembre 13, 2015, 6:42pm CET par Mark Wilson

Ad blocking tools are rarely out of the news these days. In times of heightened awareness about online privacy, more and more people are turning to things like Adblock Plus to banish ads and clean up their web browsing experience. For many people an ad blocker is seen as essential.
Edward Snowden goes further. The former NSA contractor says that it is a web user's duty to protect their computer by blocking potential attack vectors such as Flash and JavaScript-riddled advertisements.
In an interview with The Intercept, Snowden reveals what he believes everyone should be doing to keep themselves safe online. He recommends using encrypted communication app Signal, and to encrypt the contents of hard drives. A password manager should be used to create 'unbreakable' passwords, and two-factor authentication should be used whenever it is available.
On the subject of ad blockers, Snowden says:
Everybody should be running adblock software, if only from a safety perspective. We've seen internet providers like Comcast, AT&T, or whoever it is, insert their own ads into your plaintext http connections. As long as service providers are serving ads with active content that require the use of JavaScript to display, that have some kind of active content like Flash embedded in it, anything that can be a vector for attack in your web browser -- you should be actively trying to block these. Because if the service provider is not working to protect the sanctity of the relationship between reader and publisher, you have not just a right but a duty to take every effort to protect yourself in response.
Unsurprisingly, Snowden is an advocate of Tor, saying that he uses it "all the time" but does add "that's not to say that Tor is bulletproof". He recommends using HTTPS Everywhere to reduce the risk of web traffic interception. While pushing everyone to take ownership of their privacy, Snowden warns against taking it too far:
You can go to any depth, you can drive yourself crazy thinking about bugs in the walls and cameras in the ceiling. Or you can think about what are the most realistic threats in your current situation? And on that basis take some activity to mitigate the most realistic threats. In that case, for most people, that’s going to be very simple things. That’s going to be using a safe browser. That’s going to be disabling scripts and active content, ideally using a virtual machine or some other form of sandboxed browser, where if there’s a compromise it’s not persistent.
Photo credit: travellight / Shutterstock
-

How to avoid online surveillance -- the essential guide
Publié: novembre 13, 2015, 4:36pm CET par Mark Wilson

It would appear that mass surveillance of the Internet is here to stay. We can rage against the machine, but ultimately we're powerless to stop the likes of the NSA and GCHQ prying into whatever they want to pry into. More and more people are turning to the dark web to help cover their tracks, but even the supposedly anonymous haven of Tor can be cracked for a price.
Last week in the UK, the draft Investigatory Powers Bill was published outlining proposals for ISPs to retain user's browsing histories for a full year. Governments want to weaken encryption. The FCC ruled that Do Not Track requests are essentially meaningless. The NSA finds and takes advantage of vulnerabilities. It's little wonder that privacy groups are up in arms -- the erosion of online rights continues with terrifying speed. But all is not lost. There are still things you can do to help maintain your privacy. If you're concerned, here's what you can do.
There's no need to completely disconnect from the internet -- although this is the only sure fire way of staying off the radar -- but you will certainly have to change a few of your online habits. Online surveillance and monitoring of web habits is really something that should concern everyone, but it is the more liberal-minded and left-thinking that are the most vocal and active opponents.
Surveillance advocates dismiss concerns about snooping as paranoia, and say that only metadata and communications data is ever collected. That's not the point. Over on the Ecologist, Paul Mobbs asserts that "metadata is content". It's a view that's very much in line with Edward Snowden's:
"It's only communications data" = "It's only a comprehensive record of your private activities." It's the activity log of your life. #IPBill
— Edward Snowden (@Snowden) November 4, 2015
The digital footprint you leave online comprises a huge amount of metadata. Put together, it can paint a very clear picture of what you get up to, and makes you very easily identifiable. But there are also security measures that you should consider so you don’t leave yourself open to even more invasive surveillance. There are a number of ways you can proactively protect yourself.
- Turn off location data on your phone.
- Disable cookies in your web browser.
- Don't use Google or other mainstream services.
- When conducting searches, do so through a more secure network such as Tor (although we have seen that this is not infallible). Try an alternative, non-tracking search engine such as DuckDuckGo.
- Change the default password on your router. Failing to do so is like leaving your keys in the front door.
- Use a password manager, and use it as an opportunity to finally start using really strong, unique password for every site, app, and service you use.
- When you upload a file to the internet, ensure you remove any metadata that could be used to identify you.
- Be sensible about what you share online. It's very easy to build up a portfolio of information about a person by piecing together data from numerous Facebook posts, emails, and online profiles.
- Use an ad-blocker. There are many, many reasons to do this, but cutting back on tracking is a big one.
- Lock down your Wi-Fi with encryption and an insane password.
- Consider switching away from Windows. Open source Linux distros are more transparent and far less likely to include backdoors or anything else of concern.
Photo credit: Kletr / Shutterstock
-

Gmail to issue warnings about emails sent without encryption
Publié: novembre 13, 2015, 11:59am CET par Mark Wilson

Google, like many other companies, is pushing people towards using secure internet connections. HTTPS is becoming the norm, but not everyone has caught on. To keep the security-conscious informed, Gmail is set to issue warnings about emails that are received through unsecure connections that do not use encryption.
A joint study involving Google, University of Michigan and the University of Illinois found that email is "more secure today than it was two years ago", with an increase in the number of encrypted emails sent. That said, there are still plenty of people who are not using secure connections and Google is keen to keep its users informed when they receive communication through unencrypted channels.
The general levels of interest in and awareness of security issues means that there has been an increase in the number of non-Gmail emails that are encrypted -- up from 33 percent to 61 percent over two years. Google also reveals that 94 percent of messages to Gmail have some form of authentication, and 80 percent of emails sent from Gmail to non-Gmail accounts are now TLS encrypted.
But while security is generally increasing, the use of encryption and secure connection is yet to hit 100 percent. With this in mind, Google is going to start warning its users about messages from non-Gmail accounts that do not use encryption.
Writing on the Online Security Blog, Google says:
To notify our users of potential dangers, we are developing in-product warnings for Gmail users that will display when they receive a message through a non-encrypted connection. These warnings will begin to roll-out in the coming months.
All email services -- Gmail included -- depend on the trust of their users. Partnering with top researchers helps us make the email ecosystem as a whole safer and more secure for everyone. Security threats won't disappear, but studies like these enable providers across the industry to fight them with better, more powerful protections today and going forward.
Photo Credit: Bloomua/Shutterstock
-

The price of de-anonymization -- FBI paid $1m to Carnegie Mellon to crack Tor
Publié: novembre 12, 2015, 2:02pm CET par Mark Wilson

Tor has long been thought of as offering a level of privacy, security and anonymity that enables people to do whatever they want online; it also facilitates access to the so-called Dark Web. Despite this, law enforcement agencies were able to crack Tor and identify a Silk Road 2.0 user. Now it seems that the FBI was helped out by researchers at Carnegie Mellon University.
It was previously known that the FBI tracked down Brian Richard Farrrell using information from a "university-based research institute". The Tor Project itself believes that the FBI paid researchers at the university at least $1 million to attack the network and gather data from Tor relays that could be analyzed and used to identify users' IP addresses.
The project says that it is unlikely that the FBI would be able to have obtained a valid warrant to conduct such an attack as it appears to have amounted to NSA-style dredging; rather than targeting individuals, the attack was used to seek out anyone who might be involved in illegal activity. The well-publicized attack last year used techniques that were remarkably similar to those presented by Carnegie Mellon's Computer Emergency Response Team (CERT) at the Black Hat hacking conference. Interestingly, the paper has since been pulled from the Back Hat website (the Wayback Machine, however, still provides access to a cached version).
Tor is understandably upset that the FBI could pay to crack the network, and decries the attacks:
Such action is a violation of our trust and basic guidelines for ethical research. We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users.
This attack also sets a troubling precedent: Civil liberties are under attack if law enforcement believes it can circumvent the rules of evidence by outsourcing police work to universities. If academia uses "research" as a stalking horse for privacy invasion, the entire enterprise of security research will fall into disrepute. Legitimate privacy researchers study many online systems, including social networks -- If this kind of FBI attack by university proxy is accepted, no one will have meaningful 4th Amendment protections online and everyone is at risk.
Cryptographer Matthew Green says:
A spokesperson for CMU didn't exactly deny the allegations, but demanded better evidence and stated that he wasn't aware of any payment. No doubt we'll learn more in the coming weeks as more documents become public.
The Tor Project is quick to point out that it is not opposed to the idea of law enforcement agencies conducting investigations through Tor, but says that it should be done in an ethical fashion without infringing upon the privacy of innocent users.
Photo credit: ruskpp / Shutterstock
-

Time to ditch your phone -- Android Wear now has cellular support
Publié: novembre 12, 2015, 12:00pm CET par Mark Wilson

Not long ago LG announced the LG Watch Urbane 2nd Edition -- the first Android Wear smartwatch that offers LTE/3G connectivity. Now Google has officially announced Android Wear's cellular support.
Breaking down one of the barriers to wearable adoption -- the previous reliance on smartphones for a lot of functionality -- the arrival of cellular support means your smartwatch can be used to make and receive calls even when you don’t have your phone with you.
Cellular support means that smartwatches can now successfully evolve into something more than just glorified fitness trackers. It may take a little while for apps that take advantage of data access to filter through, but with the capability now available it is only a matter of time before there is an Android Wear app explosion. Now when you go for a run, you can leave your phone at home, and still be able to check text messages when you stop to catch your breath.
Product Manager for Android Wear, Peter Ludwig says:
No more worrying about Bluetooth or Wi-Fi -- your watch will automatically switch to a cellular connection when you're out of range. As long as your watch and phone are connected to a cellular network, you'll be able to use your watch to send and receive messages, track fitness, get answers from Google, and run your favorite apps. And yes, you'll even be able to make and take calls right from your watch, for when your hands are full, or your phone is elsewhere.
The LG Watch Urbane 2nd Edition may be the first cellular-enabled Android Wear device to hit the market, but it's certainly not going to be the last.
-

Facebook is receiving more government data requests than ever before
Publié: novembre 11, 2015, 11:40pm CET par Mark Wilson

The time has rolled around once again for Facebook to release its twice-yearly report about government data requests. It will perhaps come as little surprise that in the current atmosphere of surveillance and privacy concerns that in the first half of 2015 Facebook received more government data requests than ever before.
The latest figures show that the number of data requests has jumped by 18 percent to 41,214. There was also a massive increase in the number of pieces of content that were taken down or 'restricted' for violating local laws -- a rise of 112 percent. Facebook reiterated previous assertions that it does not provide backdoor access to governments, and reveals that the US is by far the leading requester of data.
The latest Government Requests Report shows that the US was responsible for 17,577 requests relating to over 26,000 individuals. In just 20 percent of cases, no data was handed over -- in four fifths of cases Facebook imparted at least some information. India is the leading source of requests for content restrictions, accounting for a full 75 percent of all such requests.
In a blog post, Facebook's Deputy General Counsel, Chris Sonderby says:
As we have emphasized before, Facebook does not provide any government with "back doors" or direct access to people's data. We scrutinize each request we receive for legal sufficiency, whether from an authority in the US, Europe, or elsewhere. If a request appears to be deficient or overly broad, we push back hard and will fight in court, if necessary.
Over the last two years, we've regularly published information about the nature and extent of the requests we receive. To protect people's information, we will continue to apply a rigorous approach to every government request we receive. We’ll also keep working with partners in industry and civil society to push governments around the world to reform surveillance in a way that protects their citizens' safety and security while respecting their rights and freedoms.
The full report takes the form of an interactive map, and there is the option of downloading the data in CSV format if you like the idea o crunching them in a spreadsheet.
Photo credit: nevodka / Shutterstock
-

Microsoft to hide European data from the NSA with new German datacenters
Publié: novembre 11, 2015, 5:42pm CET par Mark Wilson

The arms of the NSA may be long, but there are some parts of the world in which it holds no sway. Conscious of European concerns about US government web surveillance, Microsoft today announces German datacenter options for Azure, Office 365 and Dynamics CRM Online.
Starting in the second half of 2016, customers in Europe will be able to opt to have their data stored in Germany. The datacenters will be controlled by German data trustee, Deutsche Telekom who will oversee all access to customer data. With Microsoft’s "mobile first, cloud-first" philosophy, this is a move to try to rebuild trust in cloud services which the company clearly feels has been lost.
Many people would be surprised, and disturbed, to discover that their data was being stored in a country that could access it without permission. Microsoft explains that 83 percent of all German enterprises expect their cloud provider to operate local datacenters in Germany. This seems like a reasonable expectation.
SEE ALSO: Microsoft to offer cloud services from the UK
Satya Nadella introduced the new option which will be available to customers throughout Europe:
Microsoft’s mission is to empower every person and every individual on the planet to achieve more. Our new datacenter regions in Germany, operated in partnership with Deutsche Telekom, will not only spur local innovation and growth, but offer customers choice and trust in how their data is handled and where it is stored.
Uniquely, even Microsoft will not be able to access customer data, at least not without the permission of both the customer, and that of Deutsche Telekom subsidiary T-Systems. Deutsche Telekom CEO Timotheus Höttges predicts the datacenters will prove popular:
Microsoft is pioneering a new, unique, solution for customers in Germany and Europe. Now, customers who want local control of their data combined with Microsoft’s cloud services have a new option, and I anticipate it will be rapidly adopted.
-

Adblockalypse: nearly one fifth of web users employ ad blockers
Publié: novembre 11, 2015, 1:12pm CET par Mark Wilson

Online ads are a major bugbear for web users, hence the existence of ad blocking software. Tools such as AdBlock Plus have long been popular, but despite efforts by publishers to discourage their use, more and more people rely on ad blockers to improve their online experience.
The Internet Advertising Bureau reports that ad blocking is on the rise. In the UK, 18 percent of people use software to prevent the appearance of ads -- up from 15 percent just five months ago. Not everyone, however, is looking to block every single ad they might encounter.
Given the choice between paying for ad-free content, or enduring ads to keep content free, 61 percent of people said they would rather put up with ads than pay for access. Just 4 percent were willing to pay for an entirely ad-free experience. More than a third (35 percent) of 18 to 24-year-olds used an ad blocker; for those aged 55 and over, the figure drops to just 13 percent.
Just 57 percent of those surveyed said that they were looking to block all adverts, with a fifth of people saying they wanted to block particular types of ads, or ads from particular sites. IAB found that women were less likely to use adblockers than men (13 percent and 23 percent respectively).
Guy Phillipson, CEO of IAB UK, says:
The small rise in people blocking ads is not unexpected considering the publicity it's been receiving. However, it does provide some perspective on the situation for those referring to an "adblockalypse". More importantly, it also provides a clear message to the industry -- a less invasive, lighter ad experience is absolutely vital to address the main cause of ad blocking. That's why we're developing the L.E.A.N advertising principles for the online advertising supply chain.
IAB's research found that 19 percent of Adblock users do so on a tablet, and 23 percent on a phone -- but this is a number that could well rise since Apple allowed adblockers to enter the App Store.
Photo credit: Allen.G / Shutterstock
-

InstaAgent app steals usernames and passwords from Instagram users
Publié: novembre 11, 2015, 11:54am CET par Mark Wilson

An app that enables iPhone users to keep an eye on who has been looking at their Instagram account has been pulled from the App Store after it was found to be stealing usernames and passwords.
Apple took the decision to kill "Who Viewed Your Profile -- InstaAgent" when the app was found scraping login details and sending them back to the developer's server. This in itself is worrying for users, but it gets worse: the usernames and passwords were sent in unencrypted format.
The app was reasonably popular, managing to attract around half a million users. Delving into InstaAgent's code revealed that the app was really little more than password-harvesting malware. The incident will once again call into question the vetting process that apps go through before hitting the App Store.
The password-stealing was first spotted by Peppersoft developer David Layer-Reiss who tweeted about his findings:
"Who Viewed Your Profile" #Instaagent will send your Instagram Username and Password to an unknown server! pic.twitter.com/8uZJljJdtO
— David L-R (@PeppersoftDev) November 10, 2015
With Apple having stripped InstaAgent from the App Store, it will no longer be possible for anyone to download it. If you already have it installed, however, the advice would be to uninstall it, and change your Instagram password immediately.
Photo credit: Yeamake / Shutterstock
-

Apple's Tim Cook on weakening encryption: 'Any backdoor is a backdoor for everyone'
Publié: novembre 11, 2015, 10:36am CET par Mark Wilson

Tim Cook is concerned about privacy. The Apple CEO has spoken out against requests from governments for backdoors into encrypted products. Following the UK government's decision not to ban strong encryption but to force companies to provide authorities with access to encrypted data upon production of a warrant.
This is effectively a backdoor into products and Tim Cook gives a stark warning: "Any backdoor is a backdoor for everyone". He also suggests that security is something that needs to be tackled on a global scale rather than by individual countries.
In an interview with the Daily Telegraph, Cook says that there are serious implications to any sort of weakening of encryption. Acknowledging the need to tackle online crime he says: "Everybody wants to crack down on terrorists. Everybody wants to be secure. The question is how. Opening a backdoor can have very dire consequences".
Referring to how the UK will move on from the dropped snooper's charter and the poorly-received Investigatory Powers Bill, Cook is not all doom and gloom:
I’m optimistic. When the public gets engaged, the press gets engaged deeply, it will become clear to people what needs to occur. You can't weaken cryptography. You need to strengthen it. You need to stay ahead of the folks that want to break it.
He restated Apple's commitment to ensuring people's privacy and security with end-to-end encryption. Echoing the views held by many regular internet users, Cook says:
To protect people who use any products, you have to encrypt. You can just look around and see all the data breaches that are going on. These things are becoming more frequent. They can not only result in privacy breaches but also security issues. We believe very strongly in end to end encryption and no back doors. We don't think people want us to read their messages. We don't feel we have the right to read their emails.
Photo credit: Hadrian / Shutterstock
-

No more Chrome updates for Windows XP from April 2016
Publié: novembre 11, 2015, 2:23am CET par Mark Wilson

Anyone still desperately clinging to Windows XP only has another six months of updates for Chrome. Google has decided that the time has finally come to sever ties with the ancient operating system, and the same applies to Vista and OS X 10.6, 10.7, and 10.8.
Just as Microsoft has stopped issuing updates for Windows XP, so too has Google set a cut-off point of April 2016 for Chrome support on older OSes. These versions of Windows and OS X have been dropped by Microsoft and Apple, so it makes sense that other companies will move on as well. But as well as not getting new versions of Chrome, there will also be no more security updates.
Google says that using such old operating systems runs a far greater risk of virus and malware infection. The company is as keen as Microsoft and Apple that people move with the times and upgrade their operating system. Vista is the only one of the five operating systems that remains supported by the company behind it (until April 2017, believe it or not).
Writing on the Chrome Blog, Google says:
Today, we're announcing the end of Chrome's support for Windows XP, as well as Windows Vista, and Mac OS X 10.6, 10.7, and 10.8, since these platforms are no longer actively supported by Microsoft and Apple. Starting April 2016, Chrome will continue to function on these platforms but will no longer receive updates and security fixes.
If you are still on one of these unsupported platforms, we encourage you to move to a newer operating system to ensure that you continue to receive the latest Chrome versions and features.
Photo credit: 360b / Shutterstock
-

Apple Music arrives on Android as a beta
Publié: novembre 11, 2015, 1:27am CET par Mark Wilson
In a few short months, Apple Music has picked up millions of followers, and it has managed to do this whilst remaining exclusive to iOS. Now that changes. Today Apple's music app makes the jump to Android.
Currently in beta, Apple Music for Android is a free download, and includes a three-month free trial of the service. After this, should you want to continue using it, you'll have to cough up $9.99 per month. For the most part, this is a direct port of the iOS version of the app, but as it is in beta there are some notable differences.
At the moment, there isn't support for music videos although Apple promises that this is on the way. Of course, as this is an Android app, it is not a straight replica of the iOS version; it looks like an Android app, and you'd be forgiven for forgetting that it has anything to do with Apple. If you’ve already signed up for a family plan with Apple Music, you'll be able to use it from within the app, but it's not yet possible to sign up for such a plan through it.
While it is possible to stream music on Android, the lack of an Android version of the iTunes Music Store means that it's not possible to purchase individual tracks or albums. That said, any music you buy through iTunes on another device will be made available to you through the Apple Music app.
You can grab yourself a copy of Apple Music from Google Play.
-

Offline navigation comes to Google Maps
Publié: novembre 10, 2015, 3:34pm CET par Mark Wilson
One of the biggest problems with Google Maps on your smartphone is that you need an internet or data connection. At least that used to be the case. Today Google announces that navigation is now possible in offline mode.
In a move that has the potential to kill off the likes of TomTom and Garmin, Google is making it possible to download maps to your phone so turn-by-turn directions can be initiated even when there is no connection. It's a feature that people have been waiting for for some time, but Google has more to offer.
In addition to offline navigation -- which is an absolute boon, it must be said -- Google Maps can also be used without a connection to search for information about the area. As well as searching for towns, cities, and streets, you can also search for shops, businesses and restaurants, and view useful information such as opening hours and contact details.
Of course, using the feature does require a degree of forward planning; it is not possible to get directions to an area of the map that you have not yet downloaded. You can download a map for a city you are visiting, a county if you plan on covering a larger area, or an entire country if you want to cut through any limitations.
Google explains that downloading maps is simple:
You can download an area by searching for a city, county or country, for instance, and tapping "Download" on the resulting place sheet, or by going to "Offline Areas" in the Google Maps menu and tapping on the "+" button. Once downloaded, Google Maps will move into offline mode automatically when it recognizes you’re in a location with spotty service or no connectivity at all. When a connection is found, it will switch back online so you can easily access the full version of Maps, including live traffic conditions for your current route.
Android users are first to get access to the feature, but it is coming to iOS soon too.
Photo credit: Roman Pyshchyk / Shutterstock
-

ARM's new IoT mbed products could bring 8-week battery life to wearables
Publié: novembre 10, 2015, 3:22pm CET par Mark Wilson
At ARM TechCon 2015, ARM is unveiling a number of new mbed IoT Device Platform products. Designed to make it easier to deploy IoT devices on a large scale, developers will be able to use mbed Device Connector to build cloud-integrated web apps.
There's also a new build of the mbed OS Technology Preview and together these technologies can be used to connect and securely manage IoT devices. Two new reference designs for industry and wearables have also been released.
Key to speeding up IoT uptake is the decision to make mbed Device Connector available free of charge. Developers can work with up to 100 devices and 10,000 events per hour without having to pay a penny. ARM says that this will be enough for businesses to try out IoT options with minimal costs before considering how to go about scaling things up.
Krisztian Flautner, general manager of IoT business at ARM said:
ARM mbed partners now have access to the fundamental building blocks to develop and securely deploy IoT devices at any scale. Since the launch of the mbed IoT Device Platform last year, we have focused our efforts on providing the mbed Partnership with the tools to scale deployments from a single cloud-connected sensor to a host of more intricate devices that enterprise-grade IoT solutions demand.
ARM also has two new design reference platforms for developers to try out. While the mbed Smart City Reference Design uses Sub-GHz 6LoWPAN & CoAP mesh network protocols for industrial apps and infrastructure monitoring, the average consumer will likely be more interested in the potential of the mbed Wearable Reference Design. ARM says that this has been used to drive an "efficient wrist-based connected device capable of delivering a fully interactive user-experience while achieving a battery life of around eight weeks".
-

The next target for surveillance: the dark web
Publié: novembre 10, 2015, 10:59am CET par Mark Wilson

The surveillance activities of the NSA and GCHQ are well known, and many people hoping to slip under the radar have taken to the 'dark web'. Famous for sites such as Silk Road, as well as being home to illegal content such as child pornography, the dark web may not be a safe haven for much longer.
Joint Operations Cell (JOC) is a new venture in the UK which sees the National Crime Agency (NCA) and GCHQ joining forces. Described as a "genuinely innovative development", the operation aims to home in on online criminals, with a particular focus on crimes involving child exploitation.
JOC is Prime Minister David Cameron's vision of the web personified. He famously said that the dark web would offer "nowhere for you to hide", and the joint taskforce sees GCHQ moving away from a focus on national security and terrorism. It comes almost a year after the announcement of plans to create JOC at 2014's We Protect Children Online Global Summit.
GCHQ Director Robert Hannigan, said:
The Joint Operations Cell will increase our ability to identify and stop serious criminals, as well as those involved in child sexual exploitation and abuse online. This is a challenging task as we must detect them while they attempt to hide in the mass of data. We are committed to ensuring no part of the internet, including the dark web, can be used with impunity by criminals to conduct their illegal acts.
Echoing this, Keith Bristow -- Director General of the NCA -- said that JOC would use "the best of our respective agencies' skills to tackle the most complex cases and the most dangerous offenders online".
Photo credit: mikser45 / Shutterstock
-

Windows 10 Build 10586 (Threshold 2) released to Slow Ring Windows Insiders
Publié: novembre 10, 2015, 12:49am CET par Mark Wilson

Threshold 2 is now available to Windows Insiders on the Slow Ring. Users on the Fast Ring received Windows 10 Build 10586 last week and now more cautious fans of the preview get to try out the November Update, Fall Update, Threshold 2, Windows 10 Build 10586 -- call it what you will.
With the official rollout of Windows 10's biggest update since launch is widely expected to take place tomorrow, 10 November, Slow Ring users may not be given much of a head start, but it does still -- just about -- qualify as an early glimpse.
As this is exactly the same build that Fast Ring users are already running, there are no surprises. All of the same updates and tweaks are present, and the desktop watermark has been ditched -- a sure fire indicator that this is indeed the final build.
As ever, it was Gabe Aul who announced the availability of the new build on Twitter:
PC build 10586 is now available to #WindowsInsiders in the Slow ring! [https:]
— Gabriel Aul (@GabeAul) November 9, 2015
While for Windows Insiders this particular build may be nothing major, the same cannot be said for regular users who will be receiving it in the next day or so. Windows 10's slow and steady evolution continues...
Photo credit: Stanislaw Mikulski / Shutterstock
-

Linux users targeted by new Linux.Encoder.1 encryption ransomware
Publié: novembre 9, 2015, 10:17pm CET par Mark Wilson

Extortion is just the latest in a series of weapons being used to terrorize computer users and technology companies. One of the most recent victims was ProtonMail which found itself the subject of a DDoS attack and a ransom demand -- and despite paying up, the attacks continued. But individual users also have their feet held in the fire by ransomware.
It's something that mobile users have become familiar with. Android users have been hit by malware that encrypts the contents of their phones and renders it inaccessible until a ransom is paid. It's a problem that has also affected Windows users, and the latest target is Linux. Web servers powered by Linux are being targeted by the Linux.Encoder.1 crypto-ransomware.
Server contents are encrypted, with virus writers exploiting a vulnerability in the Magent CMS, warns anti-virus company Dr Web. Once installed, the Trojan uses an RSA key to encrypt files before deleting the originals. Linux.Encoder.1 targets files in numerous directories including /home and /root.
Dr Web says:
First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory (“/”). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals.
Compromised files are appended by the malware with the .encrypted extension. Into every directory that contains encrypted files, the Trojan plants a file with a ransom demand -- to have their files decrypted, the victim must pay a ransom in the Bitcoin electronic currency.
The company provides more details of the activities of Linux.Encoder.1 in its database, and advises contacting technical support rather than trying to remedy the problem manually.
Photo credit: designer491 / Shutterstock
-

Pinterest's crazy new search tool helps out when words fail you
Publié: novembre 9, 2015, 9:34am CET par Mark Wilson
For years now we have been using words to perform searches -- but words have their limitations. It is said that a picture is worth a thousand words, and this is something that Pinterest has taken to heart with its latest search tool.
There are times when words fail us all. You might know exactly what it is you want to say, but you have no idea how to say it. To help on such occasions, Pinterest today unveils a "crazy-fun new visual search tool" that lets you select an object in an image to search for other pictures of it. Confused?
Over on the Pinterest blog, a couple of examples are given. Suppose you find a picture of a room in someone's house and fall in love with a lampshade they own. Or you might like the idea of buying the shoes someone is wearing in another photo. Now if you see something that piques your interest within a Pin, you can use the new search tool to select the relevant part of the image and perform a 'visual similarity' search for additional pictures.
Pinterest's Kevin Jing says:
When you spot something in a Pin that you want to learn more about, tap the search tool in the corner. Then select the part of the Pin you're interested in, and we'll show you Pins just like it. You can even filter your visual search results by topic so you find exactly what you're looking for.
So if you zoom in on that lamp, you can discover what it's called ("Antiqued Metal Funnel Pendant"), and where you can find it (Restoration Hardware). If you want to know more -- like how to get a table like that -- just resize your selection and move it around to instantly see more Pins.
The new feature rolls out to the web and mobile today.
-

AMD hit with deceptive marketing lawsuit over Bulldozer chip core claims
Publié: novembre 8, 2015, 5:57pm CET par Mark Wilson
Chip-maker AMD faces a lawsuit for misleading adverts for its Bulldozer processors. The legal action has been started by Tony Dickey at the US District Court for the Northern District of California, San Jose Division; the allegation is that the Bulldozer CPU is advertised as having 8 cores, but it effectively has just 4.
The architecture of the chip is such that each of the cores is unable to operate independently meaning that it functions in the same way as a 4-core processor. AMD faces allegations under the Consumer Legal Remedies Act, California’s Unfair Competition Law, as well as false advertising, fraud, breach of express warrant, negligent misrepresentation and unjust enrichment.
The lawsuit says that AMD's Bulldozer processors have been built by combining pairs of cores into single modules. This halves the effective number of cores and means the processor is unable to execute as many operations simultaneously as you would expect.
Dickey alleges that thousands of consumers were tricked into buying hardware with lower specifications than advertised.
AMD has yet to comment on the lawsuit, but the company could face large fines if the case does not go its way.
-

Facebook censors links to social network Tsu.co
Publié: novembre 8, 2015, 5:22pm CET par Mark Wilson

Anyone who tries to post links to Tsu.co on Facebook, Facebook Messenger, or Instagram will find that they are unable to do so. If you've not heard of Tsu.co, it's another social network, and your initial thought may be that Facebook is trying to censor people from talking about rivals.
Facebook blocks any messages containing the URL from being posted, warning that the site is 'unsafe'. Tsu.co different from other social networks in that it is invite-only and promises to share ad-revenue with users. This has resulted in huge levels of Tsu.co-related spam appearing on Facebook and the susequent ban.
Rather than sitting back and putting up with it, Facebook has taken the decision to completely censor the URL. When you consider the fact that Tsu.co is essentially a huge pyramid scheme, the decision is perhaps not surprising but it has resulted in a great deal of publicity for the previously little-known site.
Attempt to post a message, comment, or status update that makes reference to Tsu.co, and the following message appears:
You can't post this because it has a blocked link
The content you're trying to share includes a link that our security systems detected to be unsafe:
tsu.co
Please remove this link to continue.
If you think you're seeing this by mistake, please let us know.
The level of spam generated by Tsu.co users on Facebook led to the decision to simply block it outright. Speaking to Mashable, a Facebook spokesperson said:
We require all websites and apps that integrate with Facebook to follow our Platform Policy. We do not allow developers to incentivize content sharing on our platform because it encourages spammy sharing and creates a bad experience for people on Facebook.
Interestingly, Tsu.co's Facebook page is still active...
Photo credit: alexskopje / Shutterstock
-

The NSA keeps 9% of the vulnerabilities it discovers to itself
Publié: novembre 7, 2015, 9:08pm CET par Mark Wilson

Openness and the NSA are not happy bedfellows; by its very nature, the agency is highly secretive. But in recent years, post-Edward Snowden, the organization has embarked on something of a PR campaign in an attempt to win back public trust.
The latest manoeuvre sees the NSA promoting the fact that when it discovers security vulnerabilities and zero-days in software, it goes public with them in 91 percent of cases... but not before it has exploited them. No information about the timescale for disclosures is given, but what most people will be interested in is the remaining 9 percent which the agency keeps to itself.
The NSA has long been accused of sitting on the software vulnerabilities it discovers, and now it is seeking to reassure people by pointing to the number of flaws it does disclose. Many people will be disappointed to learn that before the companies behind software with security issues are told about the vulnerabilities, the NSA will first use the exploits for its own advantage. The agency has even gone as far as developing viruses like Stuxnet to attack foreign nations.
Government officials have revealed that the NSA comes clean about vulnerabilities in more than 90 percent of cases. This enables software developers to produce patches that can be pushed to users, but the admission that a percentage of security flaws are not shared means that a large number of known vulnerabilities go unpatched and remain exploitable by the NSA or hackers.
On its website, the NSA cites 'national security reasons' for holding back information about some vulnerabilities:
In the vast majority of cases, responsibly disclosing a newly discovered vulnerability is clearly in the national interest. But there are legitimate pros and cons to the decision to disclose vulnerabilities, and the trade-offs between prompt disclosure and withholding knowledge of some vulnerabilities for a limited time can have significant consequences.
Disclosing a vulnerability can mean that we forgo an opportunity to collect crucial foreign intelligence that could thwart a terrorist attack, stop the theft of our nation's intellectual property, or discover even more dangerous vulnerabilities that are being used to exploit our networks. Historically, NSA has released more than 91 percent of vulnerabilities discovered in products that have gone through our internal review process and that are made or used in the US.
Photo credit: g-stockstudio / Shutterstock
-

The NSA keeps 9 percent of the vulnerabilities it discovers to itself
Publié: novembre 7, 2015, 9:08pm CET par Mark Wilson

Openness and the NSA are not happy bedfellows; by its very nature, the agency is highly secretive. But in recent years, post-Edward Snowden, the organization has embarked on something of a PR campaign in an attempt to win back public trust.
The latest manoeuvre sees the NSA promoting the fact that when it discovers security vulnerabilities and zero-days in software, it goes public with them in 91 percent of cases... but not before it has exploited them. No information about the timescale for disclosures is given, but what most people will be interested in is the remaining 9 percent which the agency keeps to itself.
The NSA has long been accused of sitting on the software vulnerabilities it discovers, and now it is seeking to reassure people by pointing to the number of flaws it does disclose. Many people will be disappointed to learn that before the companies behind software with security issues are told about the vulnerabilities, the NSA will first use the exploits for its own advantage. The agency has even gone as far as developing viruses like Stuxnet to attack foreign nations.
Government officials have revealed that the NSA comes clean about vulnerabilities in more than 90 percent of cases. This enables software developers to produce patches that can be pushed to users, but the admission that a percentage of security flaws are not shared means that a large number of known vulnerabilities go unpatched and remain exploitable by the NSA or hackers.
On its website, the NSA cites 'national security reasons' for holding back information about some vulnerabilities:
In the vast majority of cases, responsibly disclosing a newly discovered vulnerability is clearly in the national interest. But there are legitimate pros and cons to the decision to disclose vulnerabilities, and the trade-offs between prompt disclosure and withholding knowledge of some vulnerabilities for a limited time can have significant consequences.
Disclosing a vulnerability can mean that we forgo an opportunity to collect crucial foreign intelligence that could thwart a terrorist attack, stop the theft of our nation's intellectual property, or discover even more dangerous vulnerabilities that are being used to exploit our networks. Historically, NSA has released more than 91 percent of vulnerabilities discovered in products that have gone through our internal review process and that are made or used in the US.
Photo credit: g-stockstudio / Shutterstock
-

Privacy blow as FCC says websites can ignore Do Not Track requests
Publié: novembre 7, 2015, 6:55pm CET par Mark Wilson

People are more concerned than ever before about online privacy, and this is the very reason Consumer Watchdog filed a petition to force websites to honor Do Not Track Requests. The Federal Communications Commission handed down a ruling which is not going to please privacy advocates.
In short, the FCC has said that websites should be under no obligation to take notice of Do Not Track requests. The commission dismissed Consumer Watchdog's petition that called for 'edge providers' -- such as Google, Facebook, YouTube, Pandora, Netflix, and LinkedIn -- to respect people's privacy if they enabled the Do Not Track option in their web browser.
Do Not Track is supposed to give internet users the opportunity to opt out of third-party tracking, but there is no obligation on sites to honor such requests. Consumer Watchdog had wanted the rules to change so that tracking would become opt-in, but the FCC indicated it has no intension of getting involved.
In its ruling, the commission said:
In this Order, we dismiss Consumer Watchdog's request that the Commission "initiate a rulemaking proceeding requiring 'edge providers' (like Google, Facebook, YouTube, Pandora, Netflix, and LinkedIn) to honor 'Do Not Track' Requests from consumers. The Commission has been unequivocal in declaring that it has no intent to regulate edge providers. We therefore find that, pursuant to section 1.401(e) of our rules, the Consumer Watchdog Petition "plainly do[es] not warrant consideration by the Commission."
The FCC has said that it has no intention of "regulating the Internet, per se, or any Internet applications or content", which is how it regards the Do Not Track issue, despite the earlier reclassification of broadband as a telecommunications service.
Photo credit: Jakkrit Orrasri / Shutterstock
-

Experts warn that placing your router near a lamp slows down internet speeds
Publié: novembre 7, 2015, 5:52pm CET par Mark Wilson

Few people would argue against the idea that router placement -- particularly when it comes to maximizing Wi-Fi footprint -- is important. But it is not just the location that's key; broadband speeds could also be affected by seemingly innocuous objects in the home.
The head of the UK's communications regulator Ofcom warns that numerous electrical goods in the home can interfere with signals and slow down the internet. It's a problem that affects around 20 percent of households, and while there are some obvious culprits on the list of web-killers such as stereos and baby monitors, there are also some surprises.
Ofcom's chief executive Sharon White says that many people who suffer with slow internet speeds actually have a fast connection delivered to their house. She blames people placing their router on a coffee table next to things like cordless phones and other electrical products.
Writing in the Daily Telegraph, White says:
We estimate that consumers' home broadband experience may not be working as well as it could in around a fifth of UK homes. This is often caused by something unrelated to the Internet connection, which could be as simple as interference to the broadband router from a lamp, stereo speakers or baby monitor.
The regulator is on the verge of releasing a new tool that will enable people to diagnose the cause of their slow connection. Scheduled for release in December, the tool will help people to determine whether their disappointing speeds are due to a problem with their connection, or with their equipment and its placement.
Photo credit: BrAt82 / Shutterstock
-

Fast broadband to be classed a 'fundamental right'
Publié: novembre 7, 2015, 2:32pm CET par Mark Wilson

Every home and business in the UK will have access to "fast broadband" by 2020. This is the latest pledge from Prime Minister David Cameron, who said that access to the internet "should be a right".
At the moment, 83 percent of people have access to superfast (24Mbps and faster) internet connections, and by 2017 this is expected to rise to 95 percent. The latest plan is directed at the "last 5 percent" -- such as people in remote areas -- and will oblige broadband providers to supply at least 10Mbps broadband to anyone who demands it.
The rollout of fast broadband to rural areas has been slow, and while the vast majority of the country enjoys speedy connections, there are still sizeable numbers struggling with frustratingly slow internet access. Cameron's latest plan would mean that a broadband connection is viewed as a utility, comparable to water and electricity supplies, and people would have the legal right to ask for affordable connections.
More plans are due to be unveiled next week, and the Prime Minister says:
Access to the internet shouldn't be a luxury, it should be a right - absolutely fundamental to life in 21st Century Britain. Just as our forebears effectively brought gas, electricity and water to all, we're going to bring fast broadband to every home and business that wants it.
Consultations are set to begin early in 2016 Culture Minister Ed Vaizey said on BBC Radio 4:
We want to upgrade the universal service obligation to provide fast broadband speeds of 10Mbps for the very hardest to reach homes and businesses. Those at the end of the line, the last 5 percent that we are desperate to get to. So we're putting in place this regulation [...] to make sure that if you're in that last 5 percent, you can demand, and you'll get it.
Photo credit: hywards / Shutterstock
-

ProtonMail sets a dangerous precedent and opens itself up to further attacks by paying ransom
Publié: novembre 6, 2015, 6:07pm CET par Mark Wilson

In the world of malware, one of the most recent trends is ransomware -- malicious software that either blocks access to a computer until a fee is paid, or files are encrypted until a ransom is put forward. As with ransomware and kidnapping, a ransom is often demanded by hackers and instigators of DDoS attacks.
This is precisely what happened to 'secure' email provider ProtonMail the other day when it found its datacenter inundated with traffic. At the time, the company asked for donations to cover the costs of the "quite expensive solutions" needed to fight back against "the sophistication of this attack". But rather than fighting back, ProtonMail decided to pay the ransom instead. This could prove to be a terrible mistake.
When asked to pay a ransom, there is more than an element of trust involved. In this instance, ProtonMail was told that unless it paid a 15 bitcoin ransom, it would be attacked. Sure enough, a barrage of attacks followed. ProtonMail promised to fight back and gathered funds to do so. But then the Swiss company buckled. It 'grudgingly' coughed up the money (just under $6,000) and hoped that would be the end of it.
But it wasn't.
The attacks continued meaning that ProtonMail had parted with money for no reason. And this is very real danger facing any technology firm held to ransom; it's very much a case of Sophie's choice. Opt not to pay up and you run the risk of sustained attack. Pay up and you have no guarantees that the attacks won't continue, nor that more money will be demanded. In fact, stump up the dough and a dangerous precedent is set. It marks the company out as weak and willing to bend: the perfect target for any group looking to make a quick buck.
The BBC reveals that the attack appears to have been carried out by Armada Collective, a Swiss group responsible for numerous other online attacks. It seems that ProtonMail now regrets its decisions to pay the ransom. The company says it would advise anyone else against doing so. It is now trying to raise money to pay more than $100,000 for DDoS protection from a commercial security firm.
Our ISP came under renewed DDoS attack this morning so we are offline again. We need your help to fight this: [https:]
— ProtonMail (@ProtonMail) November 6, 2015
But this is a route that is certainly not open to everyone -- and at this stage it's not clear whether it's really a viable option for ProtonMail either. The problem of ransom demands places companies in a real dilemma, and the problem with paying up is that you're damned if you do, and you're damned if you don't.
Photo credit: Robynrg / Shutterstock
-

How to get back the Insider Hub if Windows 10 Build 10586 kills it
Publié: novembre 6, 2015, 10:57am CET par Mark Wilson

Windows Insiders working with the preview builds of Windows 10 are used to the odd quirk here and there. Windows 10 Build 10586, released yesterday, is no different.
This latest build is widely believed to be the Threshold 2 release that is expected to roll out later this month. While it fixes numerous issues and adds new features when compared to the RTM build, it can also remove the Insider Hub. Here's how to get it back.
As Windows 10 Build 10586 has only been released to the Fast ring, it's fair to say that those installing it are Windows diehards. They are the most likely to want to keep abreast of the latest news, and provide feedback about their experience -- these are the very people who need the Insider Hub.
- Open Settings and click System.
- Move to the Apps & features section and click Manage optional features.
- Click Add a feature and then select Insider Hub.
Job done!
Photo credit: Stanislaw Mikulski / Shutterstock
-

UK government started online mass surveillance after 9/11 -- but few politicians knew
Publié: novembre 5, 2015, 11:37pm CET par Mark Wilson

On Wednesday, the Investigatory Powers Bill was published in draft form, but it was in the wake of 9/11 that the UK government started its mass surveillance programs, spying on the online activities of British citizens. Under the guise of the 1984 Telecommunications Act, this surveillance was moved up a gear in 2005. Former deputy Prime Minister Nick Clegg says that very few politicians knew about it.
Clegg only learned of the surveillance programs that were used to harvest emails, phone records, and texts in 2010, and questioned whether it was necessary. The former PM makes the revelations in an article for the Guardian in which he says that after Edward Snowden NSA and GCHQ spying revelations, "the knee-jerk response from the government was to play the man and ignore the ball".
Clegg and his part of the coalition government were instrumental in blocking the progress of the snooper's charter which ultimately led to the draft Investigatory Powers Bill. He admits that the new bill is "far from perfect" and expresses concern that there has been insufficient meaningful scrutiny.
Writing in the Guardian, Clegg said:
When a senior official took me aside and told me that the previous government had granted MI5 direct access to records of millions of phone calls made in the UK -- a capability only a tiny handful of senior cabinet ministers knew about -- I was astonished that such a powerful capability had not been declared either to the public or to parliament and insisted that its necessity should be reviewed.
That the existence of this previously top secret database was finally revealed in parliament by the home secretary on Wednesday, as part of a comprehensive new investigatory powers bill covering many other previously secret intelligence capabilities, speaks volumes about how far we've come in a few short years.
Snowden's whistleblowing may have resulted in "secret powers forced out into the open", but however democratically debated and implemented surveillance laws may be, a precedent has already been set. Regardless of what is publicly admitted to, there is simply no way for most people to know what is happening in secret.
Clegg warns:
The ability, for example, of GCHQ to hack anything from handsets to whole networks is highly intrusive and needs to be much better understood before we can place it within appropriate constraints.
-

The BBC Store opens its doors for digital boxset downloads
Publié: novembre 5, 2015, 1:20pm CET par Mark Wilson
Today the BBC launched a new online store where its back catalog of programming can be found. Featuring classics such as Doctor Who, Sherlock, and Orphan Black, the BBC Store provides a way to buy digital copies of your favorite shows... if you're in the UK, at least.
At the moment the store includes around 7,000 hours of viewing, but more of the BBC archive will be added over time -- and there are more than four million items for the corporation to add. Although the store is run by the license fee-funded BBC, content is not free of charge. Box sets start at around £8, while one-offs can be bought for much less.
Although DVD sales have dropped off in recent years, one of the key draws of the format is extras. This is something that the BBC intends to add to the store so purchases represent greater value for money. Just as digital downloads have taken over from physical CD sales, the corporation hopes that programme downloads will prove just as popular; the aim is to raise £1.2billion over five years.
Head of BBC Worldwide UK, Marcus Arthur, says:
For the last 30 years, people have generally understood that if they wanted to own and keep something from the BBC they've had to pay for it and they've bought it. That's true of them buying books and magazines and it was really true of them buying DVDs. And this is just another version of that.
He stresses that iPlayer content will still be available free of charge for those looking to catch up on current shows they have missed, and there are no plans to introduce a subscription service. Anyone outside of the UK hoping that this might be a way to (legitimately) watch a batch of BBC shows is going to be disappointed. Arthur explains that downloads must be instigated from within the UK -- although a little VPN work may help in this department.
Head over to the BBC Store to see what's available.
-

Shuanet, ShiftyBug and Shedun malware could auto-root your Android
Publié: novembre 5, 2015, 10:55am CET par Mark Wilson

Rooting a phone is something that many people decide to do to allow them to do things and use apps that would not otherwise be possible. If you make the choice, you are in control. But security researchers at Lookout have discovered a new form of malware disguised as apps from the likes of Facebook and Twitter.
While some of the apps are partially functional, the malware has a nasty payload: it could be quietly rooting your phone in the background. Lookout has identified three families of malware -- Shuanet, ShiftyBug, and Shedun -- that can be found in more than 20,000 apps in Google Play. Once installed, the malware is almost impossible to remove.
Lookout describes the new breed of malware as 'trojanized adware', and says that the alarming new trend is sophisticated. In a bid to increase their spread, the malware has been hidden in fake versions of apps such as Candy Crush, Snapchat, and WhatsApp. For many users, the appearance of unwanted ads will be the first they know of an attack, but the fact that devices can be automatically rooted presents serious problems for individuals as well as businesses.
Revealing their findings in a blog post, Lookout says:
At first, we wondered why someone would infect an enterprise two-factor authentication app in order to serve ads, neglecting the opportunity to harvest and exfiltrate user credentials. However, looking at the distribution portion of the command and control server, it appears that these families programmatically repackage thousands of popular apps from first-tier app stores like Google Play and its localized equivalents. Curiously, antivirus apps appear to have been specifically excluded, suggesting a high level of planning when creating these malware campaigns.
It is not thought that all of the apps were created by the same people, but Lookout believes that two or more groups may have been working together. Infection rates are greatest in United States, Germany, Iran, Russia, India, Jamaica, Sudan, Brazil, Mexico, and Indonesia, and the amount of code shared between the three families shows that there is some form of relationship between them.
The malware makes use of techniques used by 'legitimate' rooting tools, taking advantage of Memexploit, Framaroot, and ExynosAbuse exploits. Lookout warns that for individuals, an infection could mean "forcing victims to replace their device in order to regain normalcy", but the repercussions for enterprises are more serious. With phones having been rooted, it is impossible to know who is in control of them, placing data and privacy at risk.
The future doesn't look too bright, either. Lookout warns:
We believe more families of adware trojanizing popular apps will emerge in the near future and look to dig its heels into the reserved file system to avoid being removed.
Photo credit: N Azlin Sha / Shutterstock
-

Dropbox launches Dropbox Enterprise and new cloud security features
Publié: novembre 4, 2015, 10:18pm CET par Mark Wilson

Today at the Dropbox Open event, the cloud storage company launched Dropbox Enterprise. Building on the idea of Dropbox Business, Dropbox Enterprise is aimed at larger organizations and includes a new set of security and admin tools.
At the same time, the company also launched Dropbox Platform 2.0, and updated version of Dropbox's API that makes it easier for developers to build apps. Also announced was the new Dropbox Partner Network, creating a way for partners to collaborate to create new products and communicate with customers.
But it is Dropbox Enterprise that is the big news of the day. It affords administrators the ability to easily migrate personal accounts to enterprise accounts, and provide the tools needed to monitor how Dropbox is being used by employees. Dropbox can be easily integrated into existing systems thanks to unlimited access to the Dropbox API.
Talking to attendees of today's event, Dropbox CEO Drew Houston said:
What started as a simple way to access files from anywhere has evolved into a global collaboration platform. Today, Dropbox connects 400 million people and 8 million business across the world through 2.8 billion sharing connections.
In just a few short years, over 150,000 companies have chosen Dropbox Business to tap into this powerful collaboration platform. And this morning, we made several announcements that underscore how we’ll continue creating richer connections.
We're doing all of this in service of our mission: to simplify the way people work together.
Dropbox also launched three new security features. The first is the ability to suspend a user account, making it possible to lock a user out of their account without deleting their files. Admins also gain the ability to log in as another user, and custom branding is now an option.
-

Twitter launches new Public Policy and Transparency page
Publié: novembre 4, 2015, 10:00pm CET par Mark Wilson

It has been all change at Twitter recently. After increasing the number of accounts users are able to follow, and switching the Favorite star for a Like heart, Twitter today takes the wraps off a new Public Policy and Transparency page.
This is a central hub for information about Twitter's policies relating to freedom of speech, privacy, security, and corporate responsibility, as well as being a home for transparency-related information. It's also the place to go to find out how Twitter is handling government surveillance and online legal issues.
In the interests of transparency, Twitter is also using the page to provide information about the activities of its political action committee. #PAC is involved with policy debates and the company says that in the future, details of donations to candidates will be reported within 48 hours.
Launching the new page, Twitter's Public Policy Manager Tom Tarantino writes:
Because Twitter stands for open communication, we’re pleased to unveil policy.twitter.com, our new site covering the most critical policy issues facing our users, as well as providing an unprecedented level of transparency into how and with whom we engage politically in the U.S. We hope to expand this feature to cover our global activities outside the U.S. soon. From here you can also visit our Twitter for Good page, which showcases the Public Policy team’s work on corporate social responsibility, and the Twitter Safety Center, where you can find tools and resources to help everyone have a safe, secure, and enjoyable Twitter experience.
Head over to policy.twitter.com to check out the new page.
Photo credit: 360b / Shutterstock
-

ISPs to be forced to store users' browsing history for a year
Publié: novembre 4, 2015, 5:53pm CET par Mark Wilson
The UK government today published a draft version of the Investigatory Powers Bill setting out a framework for new surveillance powers. Among the proposed measures is a requirement for ISPs to keep a record of every website their customers visit for 12 months.
Fears that encryption would be banned were not realized, but privacy campaigners will be disappointed that internet connection records will be accessible by police and security services without the need for a warrant. The NSA-style data collection is indiscriminate. Data will be stored about everyone's internet usage, not just those suspected of crime, terrorism and the like.
The Home Secretary Theresa May outlined the new powers, saying that "the task of law enforcement and the security and intelligence agencies has become vastly more demanding in this digital age". The storage of so-called "internet connection records" does not mean that details of every single web page visited will be recorded, but each website visit would be logged.
Trying to reassure opponents of the Bill who consider it a further invasion of privacy, May said:
It will not include powers to force UK companies to capture and retain third party internet traffic from companies based overseas. It will not compel overseas communications service providers to meet our domestic retention obligations for communications data. And it will not ban encryption or do anything to undermine the security of people's data.
Edward Snowden reacted to the proposals on Twitter:
"It's only communications data" = "It's only a comprehensive record of your private activities." It's the activity log of your life. #IPBill
— Edward Snowden (@Snowden) November 4, 2015
Another key component of the Bill is a legal obligation on technology companies to bypass encryption to help with investigations. It is the website tracking which is by far the most controversial, however. The Home Secretary said this is "simply the modern equivalent of an itemized phone bill", but this is an argument that is unlikely to hold water with many people.
Seen by some as a watered-down version of the abandoned "snooper's charter", the Investigatory Powers Bill's data logging is something that has been banned in many other countries. It also makes provision for MI5, GCHQ, and MI6 to collect communication data and hack computers to gain information.
While some politicians regard today's draft Bill as an improvement on the snooper's charter, there are fears that it "retains some of the flaws of its predecessor".
Photo credit: Sam72 / Shutterstock
-

Google says Samsung Galaxy S6 Edge reduces Android security
Publié: novembre 4, 2015, 3:58pm CET par Mark Wilson

Samsung's Galaxy S6 Edge is blighted by 11 security problems according to the Project Zero team at Google. The team carried out research to determine how easy it would be for an attacker to exploit an Android phone produced by an OEM.
Over the course of just a week of investigations, Google discovered "a substantial number of high-severity issues". While Samsung has now fixed some of the problems, at least three are still to be addressed.
The Project Zero researchers said that many of the security issues were "high impact and easy-to-exploit". One particularly interesting and easily-exploitable issue was found in the Samsung Email client whereby email could be forwarded to another account. A script injection problem was also found in the same app which could allow JavaScript embedded in a message to be executed. The team warns that this could "make JavaScript vulnerabilities in the Android WebView reachable remotely via email".
Writing on the Project Zero blog, "planner of bug bashes", Natalie Silvanovich says:
A week of investigation showed that there are a number of weak points in the Samsung Galaxy S6 Edge. Over the course of a week, we found a total of 11 issues with a serious security impact. Several issues were found in device drivers and image processing, and there were also some logic issues in the device that were high impact and easy-to-exploit.
The majority of these issues were fixed on the device we tested via an OTA update within 90 days, though three lower-severity issues remain unfixed. It is promising that the highest severity issues were fixed and updated on-device in a reasonable time frame.
She also highlights the problem of OEMs introducing "additional (and possibly vulnerable) code into Android devices at all privilege levels". Despite the number of problems found, Samsung was praised for issuing security patches in a timely fashion.
-

Facebook uses AI to recognize objects in photos
Publié: novembre 4, 2015, 1:12pm CET par Mark Wilson

Artificial intelligence researchers at Facebook are set to unveil a new system that can identify objects in photographs. While this is not an entirely new idea, Facebook's AI Research (FAIR) team says that it has reached a new milestone, meaning that recognition is now much faster and requires less training.
Any AI-driven recognition system is built on sample data which can be used as a reference point. FAIR's new system needs just a tenth of the amount of training data than other systems, and operates 30 percent faster. But the team's progress doesn’t end there -- great strides have also been made in natural language understanding and predictive learning.
Image recognition and natural language understanding have been married in a way that enables individuals to ask questions about photographs and be supplied with a response. In a post on the Facebook blog, you can see a video that shows the system's ability to correctly answer questions such as 'is there a baby in this photo?'.
It's easy to see how these features could be integrated into Facebook at some point in the future, but it's less clear how the sample uses of predictive learning fit into the social network. Another video on the blog shows the system learning from experience:
Unsupervised, or predictive learning, is the ability to understand what will happen in the future by learning from observation. To try to give computers this ability, the FAIR team has developed a system that can "watch" a series of visual tests -- in this case, sets of precariously stacked blocks that may or may not fall -- and predict the outcome. After just a few months' work the system can now predict correctly 90 percent of the time, which is better than most humans.
It's more likely that this technology, and an AI-powered game-playing bot showcased by the team, would feature in Facebook's future ventures into virtual reality.
-

Hearts vs Stars: Twitter embraces Likes as Facebook leaves them behind
Publié: novembre 3, 2015, 9:00pm CET par Mark Wilson

The idea of 'liking' something is synonymous with Facebook. Or at least it was. Now Twitter is trying to get in on the action, renaming Favorites to Likes. As well as a name change, there's also a new icon. Gone is the Favorite Star, replaced with the Like heart.
The move comes just as Facebook is talking about introducing reaction emoji, with a view to giving users of the social network new ways to express how they feel about the content they see. Twitter, however, is moving in the other direction. While 'favoriting' a tweet was fairly non-partisan, 'liking' is an action that is loaded with meaning.
Twitter says that the change is a bid to make things easier to understand, but for long-term users it will be something of a quantum leap. The idea of favoriting, and indeed the star icon, drew parallels with bookmarking websites. Favoriting a tweet did not necessarily indicate that you like it, but that you wanted to be able to easily access it for future reference. It could also be used to express approval or acknowledgement, but that's the point -- 'favorite' was not loaded in the same way as 'like'.
Introducing the Like heart, Twitter says:
We are changing our star icon for favorites to a heart and we’ll be calling them likes. We want to make Twitter easier and more rewarding to use, and we know that at times the star could be confusing, especially to newcomers. You might like a lot of things, but not everything can be your favorite.
While the last sentence may be true, it kind of misses the point. Twitter insists that "the heart is more expressive, enabling you to convey a range of emotions and easily connect with people", but the reaction from users has been less than positive.
Which camp are you in -- hearts or stars?
Photo credit: Quka / Shutterstock
-

Smart Reply for Google Inbox suggests replies to emails
Publié: novembre 3, 2015, 8:27pm CET par Mark Wilson

Gmail might be Google's most well-known email service, but more recently the company has introduced Inbox. Now Inbox gains a new feature -- Smart Reply. The email tool is known for its automation features and Smart Reply aims to cut down the amount of time you have to spend replying to messages in Android and iOS.
Although not entirely automated. Smart Reply analyzes the content of the emails you receive and suggests a number of stock replies that you might like to send. While it is certainly not going to eliminate the need to type out emails entirely, the ability to respond to common types of email with a couple of clicks will prove a real time-saver.
Google says that Smart Reply uses machine learning to analyse emails and provide the most appropriate natural language responses. Details of how the technology works is available on the Google Research Blog, but what most people will take away is that it reduces the amount of typing that needs to be done.
In a post on the Gmail blog, Google says:
Smart Reply suggests up to three responses based on the emails you get. For those emails that only need a quick response, it can take care of the thinking and save precious time spent typing. And for those emails that require a bit more thought, it gives you a jump start so you can respond right away.
The feature starts to roll out to Android and iOS users later this week.
Photo credit: chippix / Shutterstock
-

Hate Windows 10? You still have a year to buy a Windows 7 PC
Publié: novembre 3, 2015, 11:48am CET par Mark Wilson

The adoption of Windows 10 is slowing, and that trend is set to continue -- largely thanks to Microsoft. In an unusual move, the company has extended the availability of Windows 7 so it will be possible to buy computers with the operating system pre-installed until the end of October next year.
What's particularly interesting about this is that it means that Windows 7 will be available to buy for longer than Windows 8. Many would take this as an admission of the widespread dislike for Windows 8, but it also offers a lifeline to anyone who wants a new computer without Windows 10.
Microsoft has updated its Windows lifecycle fact sheet to show that the sale of PCs with Windows 7 Professional pre-installed will end on 31 October, 2016. This is a full two years after the sale of Windows 7 Home Basic, Home Premium, and Ultimate PC came to an end, and four months after the 30 June 2016 end of Windows 8 PC sales.
Mainstream support for Windows finished in January this year, but extended support continues until 14 January, 2020. Once this date passes, we'll find ourselves with another Windows XP situation on our hands. There will be millions of Windows 7 PCs in use around the world with unpatched vulnerabilities that will never receive further security updates.
Photo credit: relif / Shutterstock
-

Microsoft shows what gamers can expect from the New Xbox One Experience
Publié: novembre 2, 2015, 9:29pm CET par Mark Wilson
The New Xbox One Experience is just around the corner. We already know that the rollout starts on 12 November, and that means that there are just ten days until Windows 10 comes to Xbox One gamers. Today Microsoft shows off what there is to look forward to in a couple of new videos.
This is not a small update by any stretch of the imagination -- it sees the arrival of the New Xbox One Experience. Not everyone has been keeping up to date with the snippets of news that have crept out over recent months, nor have they all been taking part in the preview program. But whether you've kept abreast of what's to come or you haven’t got a clue what to expect, the videos serve as an excellent introduction.
Presented by Larry Hryb and Richard Irving, the videos show Xbox 360 backwards compatibility, the new Xbox One Home, and vertical scrolling to access content. Just like Windows 10 on the desktop, Xbox One also gains Live Tiles which include "contextual items that allow you to easily see messages straight from the developer, see which friends are playing games, and share your latest game clips and screenshots".
There's also the new Guide which, Microsoft explains, provides instant access to:
- Profile: You can add and manage profiles on your console, switch users, view your profile, and view your achievements here.
- Friends: You can easily see which friends are online, see the games they are playing, and invite them to join your game. This is the default section of guide that first opens. In game, you will be able to check your friends’ status up to 10x faster.
- Party: You can easily start or manage a Party, which can now include 12 active participants, making it 3x as fast to start a party and 6x faster to join a party while playing a game.
- Messages: Easily access all of your messages and group text chats via the new guide -- starting November 12.
- Notifications: Your Notifications will also be included in the guide and we made improvements to group your Notifications together by type, separating social notifications from game-related notifications from the developers.
- Settings: We’ve redesigned Settings based on feedback to make the most commonly used items easy to access.
- Snap: Easily snap an application, like achievements, from the guide.
The first video serves as a guide to Home on the New Xbox One Experience:
The second video highlights what's new in the Guide:
-

Google says Chrome OS is going nowhere
Publié: novembre 2, 2015, 8:25pm CET par Mark Wilson

Google has scotched rumors that Chrome OS could be ditched. There had already been some doubts about the truth behind suggestions that Android and Chrome OS could be on the verge of merging. Google has already gone to some lengths to stress how committed it is to Chrome OS, and today goes a step further in stating in very plain language:
"Chrome OS is here to stay".
The news comes from Android, Chrome OS and Chromecast SVP Hiroshi Lockheimer, who waxes lyrical about the virtues and successes of the operating system in a blog post. Far from planning to kill Chrome OS, Google wants to take it further, developing new form factors and working with new partners.
Lockheimer says:
There's been some confusion about the future of Chrome OS and Chromebooks based on speculation that Chrome OS will be folded into Android. While we've been working on ways to bring together the best of both operating systems, there's no plan to phase out Chrome OS.
So what's in the pipeline for Chrome OS fans? "A new media player, a visual refresh based on Material Design, improved performance, and of course, a continued focus on security". Chrome OS is going nowhere. In a good way...
Photo credit: Funny Solution Studio / Shutterstock
-

Windows 10 fans will lose their (User)Voice in a fortnight
Publié: novembre 2, 2015, 5:25pm CET par Mark Wilson

As Microsoft has released numerous preview builds of Windows 10, testers have been able to provide feedback and make suggestions via the UserVoice website. In two weeks, this feedback system dies completely.
The killing of UserVoice actually took place on 30 October, but the site remains accessible until 16 November -- almost coinciding with the expected release of Threshold 2. Before you start to panic that Microsoft is killing the feedback that has been provided, there is a contingency plan.
Microsoft now wants people to provide feedback using the aptly-named Windows Feedback in Windows 10. This has been running alongside UserVoice for a while now, and a streamlining operation means that the two feedback systems will be consolidated. The belief is that the dedicated feedback app is a more effective way of enabling people to communicate with Microsoft engineers:
Windows Feedback gives all engineers in Windows access to the complete set of raw feedback that users provide in the tool. Because it is plugged directly into our engineering system, it not only makes it easy for the engineers to find user feedback, but also makes it easy for them to act on it. Windows Feedback also enabled two-way conversations between engineers and our more than seven million Windows Insiders.
The closure does not only affect Windows 10. The Windows Phone UserVoice site has suffered the same fate and Windows Phone Insiders are encouraged to use the mobile version of the Windows Feedback app.
Photo credit: chrisdorney and tanuha2001 / Shutterstock
-

Snapchat denies it stores users' messages and pictures
Publié: novembre 2, 2015, 10:24am CET par Mark Wilson

As often happens, the internet went nuts over the weekend. The cause? A change to Snapchat's privacy policy. Rumors spread like a disease that the blink-and-you'll-miss-it messaging service was not only storing users' posts, but also taking ownership of them.
Snapchat has responded to the public outcry, explaining that this is simply not the case. But having spread around the world via mainstream media, the rumor may be hard to quash -- perhaps the app's Ghostface Chillah mascot spooked people over Halloween.
The privacy policy change didn't actually happen this weekend, but last week. It took a day or two for people to take the time to read through the changes and subsequently misinterpret them, all leading to this weekend's hullabaloo. Snapchat took to Twitter in an attempt to reassure people:
We are not stockpiling your private Snaps! Our updated Privacy Policy & Terms of Service explained [https:]
— Snapchat (@Snapchat) November 2, 2015
In a separate blog post, the company confirmed that any messages "are automatically deleted from our servers once we detect that they have been viewed or have expired":
Of course, a recipient can always screenshot or save your Snaps or Chats. But the important point is that Snapchat is not -- and never has been -- stockpiling your private Snaps or Chats. And because we continue to delete them from our servers as soon as they're read, we could not -- and do not -- share them with advertisers or business partners.
The post also explains that the Live Stories feature -- in which Snaps are shared around the world -- requires permission from users, hence Snapchat's privacy policy making reference to use of posted content. It also clarifies why there were revisions to the Privacy Policy and Terms of Use documents:
- The main thing we did was to rewrite the Terms and Privacy Policy so that they'd read the way people actually talk. We always try to be upfront and clear with our community.
- We added language to the Terms of Service regarding in-app purchases. We needed to do that now that we're selling Replays -- and have some other cool products and services we’re looking forward to bringing to you soon.
- To make it a little easier for friends to find you on Snapchat, we’ve clarified what info -- like your name -- will be visible to other Snapchatters and how you can modify that info.
Will it be enough to calm the fears of those whose paranoia has been piqued?
Photo credit: 360b / Shutterstock.com
-

Huge Windows 10 Fall Update (Threshold 2) due 10 November
Publié: novembre 1, 2015, 7:27pm CET par Mark Wilson

Windows 10 has been with us for a few months now, and the time has come for its first big update. Known variously as Threshold 2, the November Update, and the Fall Update now has a release date -- 10 November.
In just over a week's time -- according to a Microsoft Support Engineer writing on Microsoft Answers -- the November update is due to launch bringing, amongst other things, Cortana support to India. Windows Insiders on the Fast Ring who have tried Windows 10 Build 10576 already have an idea of what to expect.
The Fall Update is also an opportunity for Microsoft to get to work addressing a number of bugs, but there are also new features to look forward to. Microsoft Edge may not be getting extension support just yet, but it is getting Chromecast aping media casting options.
On top of this, we're expecting to see a new messaging app, and some UI tweaks such as a Start menu redesign that allows for more Live Tiles. Microsoft has already said that the process of upgrading a non-genuine copy of Windows 7 or Windows 8.1 to Windows 10 will be made easier, and this is something that should be fully implemented in this update.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Vodafone customer accounts hit by hackers
Publié: novembre 1, 2015, 4:17pm CET par Mark Wilson

UK customers of Vodafone are the latest victims of a hack attack. The telecoms company said that nearly 2,000 customer accounts had been accessed this week, exposing personal data including phone numbers and bank account details.
The security breach took place earlier this week, but it was only this weekend that Vodafone went public about it. A spokesperson said that the attack "was driven by criminals using email addresses and passwords acquired from an unknown source external to Vodafone". There is warning that the owners of the affected accounts could be subject to phishing attacks.
Vodafone says that it is contacting any customer whose account was included in the attack, stressing that there was no need for anyone else to be concerned. The company issued a statement that says:
Whilst our security protocols were fundamentally effective, we know that 1,827 customers have had their accounts accessed, potentially giving the criminals involved the customer's name, their mobile telephone number, their bank sort code, the last four digits of their bank account.
Our investigation and mitigating actions have meant that only a handful of customers have been subject to any attempts to use this data for fraudulent activity on their Vodafone accounts.
Photo credit: TK Kurikawa / Shutterstock.com
-

Government forced to U-turn on internet spying and encryption ban plans
Publié: novembre 1, 2015, 3:45pm CET par Mark Wilson

The UK government has performed an about-face on plans for controversial internet surveillance plans. The 'snooper's charter' may have been kept at bay so far, but plans were afoot to force ISPs to retain the browsing histories of their customers. Prime Minister David Cameron had also strongly hinted at a desire to ban the use of strong encryption.
Today Home Secretary Theresa May told the BBC that security agencies such as GCHQ would not be granted the power to check web browsing histories. She also said that an encryption ban would not be implemented. Dismissed by some as little more than 'spin', the U-turn will be widely seen as the government's response to suggestions the any extension to online surveillance powers would be blocked in the House of Lords. But while this is something of a climb-down for the government, it is not the end of the battle for privacy groups.
The Conservative government has already faced heavy criticism for, amongst other things, proposing to scrap the Human Rights Act. With the threat of defeat when trying to push through the controversial investigatory powers bill this week, ministers appear to be trying to save face by watering down the original plans. Rather than sweeping NSA-style surveillance powers -- at least publicly admitted -- ministers now say that "any access to internet connection records will be strictly limited and targeted".
Speaking on the Andrew Marr show, Theresa May said:
Encryption is important for people to be able to keep themselves safe when they are dealing with these modern communications in the digital age but we will be setting out the current position, which does enable the authorities with proper authorisation to issue warrants.
As has been the case in the US, politicians have been accused of failing to understand the security implications of weakening encryption or providing any form of backdoor. Civil liberties campaigner David Davis said that the original proposals were "spectacularly impractical and to a large extent ignored the rights of individual citizens".
There are fears that the current proposals are rather vague, leaving them open to interpretation in a way that many are unhappy with. It has not been made clear who would be responsible for the authorization of warrants that allows for more intrusive surveillance, but there are fears that a lack of independence could be an issue.
Image credit: Amir Kaljikovic/Shutterstock
-

Tip: how to fix a slow Wi-Fi connection on Surface Pro 4 or Surface Book
Publié: novembre 1, 2015, 1:38pm CET par Mark Wilson

The recently released Surface Pro 4 and Surface Book have generated waves of interest, but the devices have not been without problems. Some owners have complained about flickering screens, while others have experienced issues with charging.
There are also some users who complain that their wireless connection is much slower than other devices. If you are one of those affected by the problem, a simple registry hack is all that's needed to get things back up to speed again.
Microsoft is aware of the problem, and has pinpointed the issue to a few specific access points. Writing on the Windows Answers support forums, the company said: "We have a known issue with .41 that results in low throughput with specific access points. The issue is specific to MAC layer aggregation (AMSDU over AMPDU) and only impacts a small subset of access points. We are working on a fix for an upcoming update. Until the fix is available, please update the registry key setting to work around this issue".
- If you have noticed this issue, try the following to see if it helps:
- Press the Windows key and R at the same time, type regedit and press Enter to launch the Registry Editor.
- Navigate to KEY_LOCAL_MACHINE\SYSTEM\ ControlSet001\Services\mrvlpcie8897.
- Locate the key named TXAMSDU.
- Double click it, and change its value to 0.
- Restart your computer.
Let us know how you get on!
-

Skype comes to Office Online and Office comes to Chrome
Publié: octobre 31, 2015, 4:54pm CET par Mark Wilson
Microsoft is promoting Skype more than ever before. Not content with desktop and mobile apps, now the company is bringing the voice and video messaging tool to its office suite. Starting with Office Online integration Skype messaging is now available in Word, Excel, PowerPoint, and OneNote Online, as well as Outlook.com.
This is a continuation of Microsoft's increased focus on the cloud, and a recognition of the importance of communication for collaborative projects. There are times when simply being able to work on the same document with colleagues is not going to be enough, and this is where Skype integration comes into play.
Microsoft says that the addition of voice and video chat to Office Online brings "a natural, collaborative experience in which you can co-author and have a conversation using instant messaging or video calling right from within a document". Just as Google has done with Chrome, this is the latest move in Microsoft's plan to turn the web browser into the ultimate destination. Skype arrives for people with a Microsoft account in November.
The company is not obsessed with its own Microsoft Edge browser, however. A new Chrome extension makes it easier than ever to create, view, and edit Office documents in Google's browser. Microsoft also announces that the footprint of Office for Android has been reduced by 40 percent, and Office apps are now ready for enterprise use with Android M support for Enterprise, and Android for Work compliance.
-

Tor Messenger Beta brings ultra-secure messaging to the masses
Publié: octobre 31, 2015, 3:55pm CET par Mark Wilson

When talk turns to privacy and online anonymity, it isn’t long before Tor enters the discussion. The Tor browser has become famous for its use of .onion domains, making it easier for people to browse the web without fear of being snooped upon.
Now there is a new tool for the security-minded to play with. Tor Messenger Beta is -- as you would expect -- a chat tool that routes traffic through Tor. One thing it has in its favor right from the start is that this is not a weird proprietory app -- it can be used in conjunction with existing networks such as Jabber (XMPP), IRC, Google Talk, Facebook Chat, Twitter, Yahoo, and more.
Available for OS X, Windows, and Linux, Tor Messenger Beta employs Off-the-Record (OTR) Messaging to keep communication secure. It is based on Mozilla's Instantbird thanks in part to the fact that there are close links between Tor and Firefox; it just made sense in a lot of ways. There have already been three alpha versions release, but this is the first public beta that is available for testing
The team behind the chat client says:
Tor Messenger builds on the networks you are familiar with, so that you can continue communicating in a way your contacts are willing and able to do. This has traditionally been in a client-server model, meaning that your metadata (specifically the relationships between contacts) can be logged by the server. However, your route to the server will be hidden because you are communicating over Tor.
Future builds will see the introduction of extra features such as sandboxing, encrypted file transfers, and OTR over Twitter DMs. If you fancy trying it out, grab the Tor Messenger Beta and see what you think.
Photo credit: Markus Mainka / Shutterstock
-

Amazon implements Apple TV veto
Publié: octobre 31, 2015, 3:04pm CET par Mark Wilson

True to its word, Amazon has made good on an earlier promise (or threat, depending on your point of view) not to sell Apple TV. In what will be widely regarded as an aggressive marketing move, the online retailer has cut out Apple TV like a cancer. The block on sales comes just as Apple launches its latest streaming device, and the sanctions also affect Google's Chromecast.
Previous links to such product now 404, but there are still a few accessories scattered through the store. But the ban does feel like a case of Amazon cutting off its nose to spite its face. While it does means that Amazon is able to take steps to fight the competition, it does so at the cost of hurting its customers.
If you're thinking about picking up an Apple TV, you're going to have to hit and Apple store or some other alternative. Of course Amazon is not admitting that the move has been done to help promote sales of its own Fire TV, instead citing customer confusion over potential compatibility issues some device may (or may not) have with Prime Video.
It's important that the streaming media players we sell interact well with Prime Video in order to avoid customer confusion.
Of course, critics of the sale ban might suggest that Amazon could just do something to help improve compatibility by producing apps Prime apps for other device. Maybe that would be too simple...
Photo credit: Yeamake / Shutterstock
-

Microsoft experiments with making it easier for pirates to upgrade to Windows 10
Publié: octobre 31, 2015, 1:08am CET par Mark Wilson

Many people have been upset by Microsoft's attitude to Windows 10 upgrades. Not content with secretly downloading the setup files, there have been numerous reports of forced upgrades to Windows 10, and confusion about the upgrade process. Yesterday, Terry Myerson penned a blog post explaining how upgrading to Windows 10 will be made easier.
This is something that has been written about across the web, but the focus has been on how Windows 10 will made an optional update through Windows Update, how rollback will be possible, and how to kill upgrade notifications if you're simply not interested. What has not been talked about much is Myerson's revelation that it will be made easier for pirates to upgrade to Windows 10.
It has long been known that Windows 10 would be a free upgrade for anyone with a genuine copy of Windows 7 or Windows 8.1. But in his blog post, Myerson says that Microsoft has been intrigued by the "creative efforts which non-Genuine customers have gone to, to initiate the upgrade process on Windows 7 and Windows 8.1". Perhaps what is more surprising is "how many have purchased Genuine Windows 10 activation through the Windows 10 store".
Microsoft may be celebrating 110 million installations (or whatever number you fancy plucking out of the air), but the company is hungry for more. While not going as far as allowing non-genuine users to upgrade free of charge, things are being made as easy as possible.
[...] we are going to start an experiment soon in the United States, which we will then evaluate before extending to other countries, to ease the upgrade of non-Genuine Windows 7 and Windows 8.1. We'll offer a one-click opportunity to get Genuine via the Windows Store or by entering an activation code purchased elsewhere. If this turns into a path for most customers to get Genuine, we will expand the experiment. We’d like to welcome as many of these customers as possible to the legitimate Windows ecosystem.
Photo credit: oriori / Shutterstock
-

Following criticism, Facebook introduces changes to 'real names' policy
Publié: octobre 31, 2015, 12:13am CET par Mark Wilson

Unlike many other social networks, Facebook has long required its users to display their real names. Over the last couple of years there have been many vocal complaints from various types of user who feel victimized by this: drag queens, transgender and LGBT communities, and Native American users, for instance.
As well as users directly affected by the policy, privacy groups such as the Electronic Frontier Foundation have campaigned for Facebook to have a rethink. And it seems that the social network has listened. Facebook's Alex Schultz has written an open letter which, while not announcing the end of the real names policy, introduces a couple of key changes that will please many people.
It's important to note that real names are not going anywhere; Facebook regards them as a valuable tool in fighting trolling and bullying -- "we know this policy helps make Facebook safe". Facebook's own research suggests that users who have opted to hide behind a fake name are significantly more likely to be engaged in harassment and other unwanted activities. Today, two important changes are to be ushered in.
Firstly, in a bid to reduce the number of people who have to verify that they are using their real name, the onus will be shifted to anyone reporting a profile about why they are doing so. It is hoped that this will help to reduce the number of malicious reports that are filed.
Secondly, for those people that Facebook does require to provide more information, things will be made easier. Starting in December, users will be able to provide extra details and give context to explain their reasons for using a particular name. It will also be possible to prove one's identity without using a government-issued ID card.
In the letter, Schultz clarifies Facebook's position on real names:
We do not require people to use their legal names on Facebook. Instead, we ask people to use the name that other people know them by. We also appreciate that identity and names are deeply personal matters and can vary significantly across cultures, and we want to be sensitive to these issues.
For anyone looking to fight for their right to use a particular name, Facebook promises that more personalized help will be made available. While today's announcement goes some way to meeting the demands that have been made of Facebook, the real names policy remains in place. With this in mind, it is unlikely that campaigns for its abolishment will quiet down.
Photo credit: Gustavo Frazao / Shutterstock
-

UK police seek power to snoop on the web browsing history of the entire country
Publié: octobre 30, 2015, 10:32pm CET par Mark Wilson

The Draft Communications Data Bill (or "snooper's charter") has proved very controversial in the UK, but is yet to be implemented. A key component of the proposed bill is a requirement for ISPs to retain records of every single users' browsing history for a full year. So far the bill has been kept at bay, but now the police are looking to place very much the same requirements on ISPs.
The police have lobbied the government, complaining that traditional methods of surveillance are insufficient to deal with the current levels of online crime. Proposals that the police should be able to access all and any records about someone's online activity without the need for a warrant are already viewed as an invasion of privacy, but police demands are all the more controversial since the snooper's charter was successfully blocked by the Liberal Democrats.
At the moment, there are not calls for unrestricted access to the content of social media messaging -- at least without a warrant -- but there are concerns that any additional snooping powers would be the start of a journey down a slippery slope.
Assistant chief constable Richard Berry has tried to allay privacy fears by suggesting that the police are not seeking powers that extend beyond the data they can already access in relation to phone records:
We essentially need the 'who, where, when and what' of any communication -- who initiated it, where were they and when did it happened. And a little bit of the 'what', were they on Facebook, or a banking site, or an illegal child-abuse image-sharing website?
Five years ago, [a suspect] could have physically walked into a bank and carried out a transaction. We could have put a surveillance team on that but now, most of it is done online. We just want to know about the visit.
Bearing such a close resemblance to the blocked snooper's charter, it is safe to assume that police demands will meet a number of obstacles.
Photo credit: Yorkman / Shutterstock
-

Two become one -- Google to 'merge' Android and Chrome OS
Publié: octobre 30, 2015, 1:58am CET par Mark Wilson

Just as Microsoft is trying to streamline its various operating systems with the approach it has taken with Windows 10, so Google appear to have similar plans. The Wall Street Journal reports that plans are well under way to merge Android and Chrome OS.
Work has been going on for two years, and an early build of the hybrid operating system is expected to see the light of day next year. A full release is planned for 2017. While described as a merger of OSes, the report suggests that Google is really looking to expand Android so that it can run on laptops. Chrome OS may well live on, but the same cannot be said of Chromebooks.
Google is not going quite as far as killing off the Chromebook, but a rebranding is on the cards. While Android has become the most widely used operating system in the work, Chrome OS has failed to grab much attention. It remains very niche, and it would appear that Google is fine with that. For those still interested in the runt of the laptop family, there will still be options out there, but Google is switching its attention to improving app experiences by building an OS foundation that allows the same apps to be run on different devices.
Bringing Google Play to laptops and desktops will see Google doing what Microsoft has been trying to do since the launch of Windows 8 -- generating the same level of interest in desktop apps that exists for mobile apps.
We've already seen a precursor to all of this in the form of the Pixel C -- the laptop from Google that runs Android. Continuing in this vein, rather than adapting Chrome OS to make it more app-centric, Google is now bringing the mountain to Muhammad, making changes to Android that draw on Chrome OS.
This could be the start of a whole new operating system war.
-

Windows 10 Build 10576 gives a better taste of Threshold 2 and introduces media casting
Publié: octobre 30, 2015, 1:26am CET par Mark Wilson

In a first for Microsoft, today sees the release of not just a new Windows 10 Mobile build, but also a new build of Windows 10 for the desktop. Windows 10 Build 10576 is now available to Insiders on the Fast Ring. This is the latest update to the Threshold 2 branch, the final build of which is due for release next month.
This is more than just a bug-fixing build -- although there are a number of bug fixes, you'll be pleased to hear -- there are also new tools and features to try out. Taking a leaf out of Google's book, Microsoft Edge gains media casting, PDF can be navigated with Cortana, and there's a new Xbox beta app. But it doesn't end there...
Described by Gabe Aul as having "a good set of bug fixes and fit-and-finish", Build 10576 improves the performance of nested virtualization. If you live somewhere where Cortana is not supported, you should now find that the search box works as expected, and a problem that saw the Xbox app gobbling up gigabytes of memory has been addressed. There are also improvements to localization text.
But it’s the new feature that most people will be interested in the new features. Microsoft Edge has received the treatment this time around, gaining a raft of media casting options. If you have Miracast and DLNA enabled devices on your network, you can now use Edge to throw content to them from YouTube, Pandora, and Facebook (photo albums, anyway). Before you get too excited, however, Gabe warns that "casting protected content (content from places like Netflix and Hulu) is not supported".
As this is a preview build, there are still a number of known issue. Microsoft has identified the following:
- To continue receiving missed call notifications and send texts from Cortana, you will need to be on this build and higher. We’ve made a change that improves this experience that requires newer builds.
- When notifications pop up from Action Center, any audio playing (like music from Groove, or videos from the Movies & TV app) gets reduced by 75% for a period of time.
- After upgrading to this build, all your Skype messages and contacts are gone in the Messaging app. The workaround for this is to navigate to this folder in File Explorer:
- C:\Users\<USERNAME>\AppData\Local\Packages\
Microsoft.Messaging_8wekyb3d8bbwe\LocalCache - Delete or rename the “PrivateTransportId” file.
- Then restart the Messaging app.
- C:\Users\<USERNAME>\AppData\Local\Packages\
- Small form-factor devices, like the Dell Venue 8 Pro, that boot with rotation or virtual mode screen size set larger than the physical screen size will experience a bluescreen on upgrade and will roll back to the previous build.
- After upgrading to this build, the power button on your Surface Pro 3 may no longer put your Surface Pro 3 to sleep and instead shut down.
- WebM and VP9 have been temporarily removed from builds. We continue to develop a VP9 implementation that we intend to ship in Windows. Expect VP9 to return soon in a future build.
Gett downloading!
Photo credit: tanuha2001 / Shutterstock
-

Europe wants to protect 'human rights defender' Edward Snowden from the US
Publié: octobre 29, 2015, 6:41pm CET par Mark Wilson

Edward Snowden could have a new friend, and place of exile, in Europe. Currently in Russia, Snowden today found himself the subject of an EU vote seeking to drop any criminal charges against the former NSA contractor.
The vote passed 285 to 281 and is likely to upset the US. This is because member states are also looking to extend protection to Snowden and prevent extradition by third parties, calling him an "international human rights defender".
Calls were also made to ensure that an "effective level of protection" was applied to data transferred between Europe and the US. Specifically, the European Parliament is looking for Europe-US data transfers to be protected in the same way as inter-Europe transfers. In a statement, Parliament said that the EU needed to rebuild trust with the US, and voiced concern about the activities of some European countries:
Parliament is concerned about "recent laws in some member states that extend surveillance capabilities of intelligence bodies", including in France, the UK and the Netherlands. It is also worried by revelations of mass surveillance of telecommunications and internet traffic inside the EU by the German foreign intelligence agency BND in cooperation with the US National Security Agency (NSA).
But it is the vote about Edward Snowden that is the real news of the day. The man himself was understandably surprised and pleased at the news, and took to Twitter to say so:
Hearing reports EU just voted 285-281, overcoming huge pressure, to cancel all charges against me and prevent extradition. Game-changer.
— Edward Snowden (@Snowden) October 29, 2015
He was also quick to say that the US should not see this as an aggressive move by Europe:
This is not a blow against the US Government, but an open hand extended by friends. It is a chance to move forward. pic.twitter.com/fBs5H32wyD
— Edward Snowden (@Snowden) October 29, 2015
But the US is already unimpressed. National Security Council spokesman Ned Price said:
Our position has not changed. Mr Snowden is accused of leaking classified information and faces felony charges here in the United States. As such, he should be returned to the US as soon as possible, where he will be accorded full due process.
Snowden's Berlin-based lawyer, Wolfgang Kaleck, said:
We welcome today's decision of the European Parliament recognizing Edward Snowden as a human rights defender and calling upon member states to grant him protection from prosecution. It is an overdue step and we urge the member States to act now to implement the resolution.
Photo credit: GongTo / Shutterstock
-

Shatterproof Moto X Force caters to clumsy UK customers
Publié: octobre 29, 2015, 4:05pm CET par Mark Wilson

A few days ago, Motorola announced the Droid Turbo 2 and Droid Maxx 2 phones, with the Turbo 2 boasting a shatterproof display. This phone was destined for the North American market, but Android fans in the UK are not going to miss out. Motorola is launching the same phone in the UK under the name Moto X Force.
Specs remain the same in the journey across the Atlantic, so you'll find that the Moto X Force features an octo-core Qualcomm Snapdragon 810 processor, 5.4" Quad HD AMOLED display, 3GB RAM, and a 21MP camera. Motorola is also keen to shout about the handset's battery life -- a claimed 48 hours, no less, and 13 hours of battery life from 15 minutes of charging. But this is a phone that's also about choice.
The aluminium frame can be adorned with leather, plastic, or ballistic nylon. Pricing starts at £499 for 32GB version and £534 for 64GB when bought direct from Motorola. Alternatively, if you're happy to sign up for a 2-year contract with Vodafone, you can buy the Moto X Force from Carphone Warehouse for £29.99 down, and £32 per month.
It is the 'shatterproof' claim for Moto ShatterShield that will generate the most interest, however. And what claim of being shatterproof would be complete without a drop test? If you get your hands on a Moto X Force of your own, you're more than welcome to try it out for yourself, but you might prefer to just watch Motorola's video instead. As well as demonstrating the Force's strength, it's also enjoyable for anyone who likes the idea of iPhones and Samsung phones being smashed to bits:
There is scope for disappointment in the fact that Motorola only sees fit to slap Lollipop on the Moto X Force, but hopefully a Marshmallow upgrade will be forthcoming. In the meantime, check out the introductory video for "the phone that loves you back":
The Moto X Force is due to launch in mid-November, but you can pre-register your interest over on the Motorola website.
-

Google demands Symantec grovel over security certificate fiasco or risk the consequences
Publié: octobre 29, 2015, 12:48pm CET par Mark Wilson

Google has fired warning shots at Symantec, threatening that Chrome would start to flag the company's security certificates as unsafe. The threat comes in a blog post penned by Google software engineer Ryan Sleevi who is still seething after Symantec employees issued a number of unauthorized security certificates.
Some of the certificates were owned by Google -- including Google.com -- and a Symantec-led audit suggested that the problem affected just 23 test certificates. But further probes revealed that there were in fact more than 2,500 certificates involved. Google is understandably fuming and is now holding Symantec to ransom.
Citing concerns that Symantec was initially unable to determine the scale of the problem, Google has issued an ultimatum. Initially, Symantec is being asked to perform a postmortem and find out why its initial audit failed to detect issues with certificates that Google unearthed. Google is also looking for an expansion on Symantec's report into the issue in which "details of each of the failures to uphold the relevant Baseline Requirements and EV Guidelines and what they believe the individual root cause was for each failure" are expected.
Failure to meet Google's demands will have dire consequences, as Sleevi explains:
It's obviously concerning that a CA would have such a long-running issue and that they would be unable to assess its scope after being alerted to it and conducting an audit. Therefore we are firstly going to require that as of June 1st, 2016, all certificates issued by Symantec itself will be required to support Certificate Transparency. In this case, logging of non-EV certificates would have provided significantly greater insight into the problem and may have allowed the problem to be detected sooner.
After this date, certificates newly issued by Symantec that do not conform to the Chromium Certificate Transparency policy may result in interstitials or other problems when used in Google products.
Google's shopping list of demands also states that Symantec needs to provide details about the corrective measures that have been taken to rectify each of the identified failures, and reveal the root cause of each failure. A third-party audit of Symantec's security is then requested to ensure full compliance with certification standards.
Symantec has responded by saying:
In September, we were alerted that a small number of test certificates for Symantec’s internal use had been mis-issued. We immediately began publicly investigating our full test certificate history and found others, most of which were for non-existent and unregistered domains. While there is no evidence that any harm was caused to any user or organization, this type of product testing was not consistent with the policies and standards we are committed to uphold. We confirmed that these test certificates have all been revoked or have expired, and worked directly with the browser community to have them blacklisted. To prevent this type of testing from occurring in the future, we have already put additional tool, policy and process safeguards in place, and announced plans to begin Certificate Transparency logging of all certificates. We have also engaged an independent third-party to evaluate our approach, in addition to expanding the scope of our annual audit.
The warnings issued by Google are stark; Symantec simply cannot afford to ignore them. The company is going to have to eat some humble pie and publicly admit to every one of its failings to placate the search giant.
Photo credit: Fabio Alcini / Shutterstock
-

UK government says app developers won’t be forced to implement backdoors
Publié: octobre 28, 2015, 10:23pm CET par Mark Wilson

The UK government is sending mixed messages about how it views privacy and security. Fears have been mounting since Prime Minister David Cameron wondered aloud "in our country, do we want to allow a means of communication between people which we cannot read?" -- his view obviously being that, no, we don’t want to allow such a thing.
Following the revelations about the spying activities of the NSA and GCHQ, public attention has been focused more than ever on privacy and encryption, Cameron having also suggested a desire to ban encryption. Today, some fears were allayed when it was announced that the government was not seeking to require software developers to build backdoors into their products. That said, the government said that companies should be able to decrypt 'targeted' data when required, and provide access to it.
Apple is just one of the companies to have said recently that it was technically incapable of decrypting encrypted messages sent between individuals. The minister for internet safety and security, Baroness Shields, expressed concern about the "alarming movement towards end-to-end encrypted applications". Addressing the House of Lord, she said:
The Government recognize the essential role that strong encryption plays in enabling the protection of sensitive personal data and securing online communications and transactions. The Government do not advocate or require the provision of a back-door key or support arbitrarily weakening the security of internet applications and services in such a way. Such tools threaten the integrity of the internet itself. Current law requires that companies must be able to provide targeted access, subject to warrant, to the communications of those who seek to commit crimes or do serious harm in the UK or to its citizens.
Making reference to ISIS, politicians pointed out that WhatsApp had been used to coordinate terrorist attacks, citing this as an example of why access to encrypted data was required. Seemingly oblivious to the weakening of security that would follow, Baroness Shields said: "It is absolutely essential that these companies which understand and build those stacks of technology are able to decrypt that information and provide it to law enforcement in extremis".
Almost immediately contradicting herself, when asked to confirm that the government has "no intention in forthcoming legislation either to weaken encryption or provide back doors to it", she said: "I can confirm that there is no intention to do that; that is correct."
The government can say, honestly, that it is not seeking backdoors. Instead it is looking for companies to allow access through the front door.
Photo credit: Spectral-Design / Shutterstock
-

Microsoft fails to fix Surface Book problems and cherry-picks positive reviews
Publié: octobre 28, 2015, 6:57pm CET par Mark Wilson

Ripples of excitement met the Surface Book when it was announced, but it's a device that has divided opinions. The price is enough to make many people baulk, and the looks are not to everyone's taste, but it's the performance that Microsoft is pushing -- even if it is unwilling to back up its claims with benchmarks.
There are, however, lots of reports of problems, some of which are shared by the Surface Book and Surface Pro 4. Even before launch there was a firmware update prepared, but if you were hoping that it would fix problems with a flickering screen, freezing caused by the video driver, and problems with charging after re-attaching the keyboard, you'll be disappointed. Not that you know there was any disappointment out there thanks to the cherry-picking of positive reviews Microsoft has indulged in...
In a blog post yesterday Microsoft basked in the afterglow of seven reviews giving the Surface Book and Surface Pro 4 the thumbs up. Presenting "just a sampling of the raves found on the Twittersphere", Athima Chansanchai says reviewers of the two new devices have fallen head over heels: "They like both. A lot."
The post goes on to quote the glowing sections of various reviews, neatly skipping over any criticisms of price, trackpad issues, and poor battery life. In fact, the blog post makes no mention of the fact that lots of Surface Book owners have complained about numerous issues mentioned above, as well as problems with 'weirdness' after attaching the keyboard, and some manufacturing defects. In all, it's somewhat disingenuous.
Being so on the ball with having an update ready for the laptop replacement, you'd think, hope, expect, that the problems that have been encountered by early adopters -- problems which must, surely, have cropped up in product testing -- would be fixed. But no, you'd be wrong.
So what does the October 2015 update for Surface Book actually include? Microsoft has helpfully set up a page that provides the details:
- Surface Camera drivers set (v30.10154.6640.152) enables the Windows Hello feature.
- Control Logic driver (v30.10154.6640.152)
- CSI2 Host Controller driver (v30.10154.6640.152)
- Imaging Signal Processor 2500 driver (v30.10154.6640.152)
- Microsoft Camera Front driver (v30.10154.6640.152)
- Microsoft Camera Rear driver (v30.10154.6640.152)
- Microsoft IR Camera Front driver (v30.10154.6640.152)
- Surface Camera Windows Hello driver (v1.0.24.0)
- AVStream Camera 2500 driver (v30.10154.6640.152)
- Surface Display Calibration driver (v1.1.371.0) improves the overall display stability.
- Surface Integration driver (v1.1.263.0) improves storage performance.
- Surface Storage Firmware Update driver (v1.447.0) improves storage performance.
It seems that Microsoft would rather pretend that the problems don't exist, and use the positive parts of reviews as a distraction. But, as noted by Rod Trent, despite the similarities between the Surface Book and the Surface Pro 4 -- the latter of which is now a fourth generation product -- the latest addition to the Surface range feels very much like a first generation device.
-

Zuckerberg: we have a moral responsibility to those without internet access (and to kill game invites)
Publié: octobre 28, 2015, 3:48pm CET par Mark Wilson

Facebook's Mark Zuckerberg took part in a Q&A session at the Indian Institute of Technology in Dehli, responding to queries ranging from the Internet.org project to Candy Crush notifications. Not for the first time, he found himself jumping to the defence of the program which aims to connect millions of people to the internet. He denied that the walled-garden of Internet.org went against the idea of net neutrality, but conceded that people had to "follow the basic rules of what Internet.org is".
He pointed out that existing net neutrality laws made exceptions for free services, but these loopholes have been described by critics as 'fatal'. In a wide-ranging talk, Zuckerberg also announced plans to kill one of the biggest irritants of the social network -- game invites for the likes of FarmVille and Candy Crush.
Ahead of the talk in India, the Facebook CEO had asked for questions to be put forward. One that was suggested was "I don’t want any more invitations to Candy Crush. How can I stop it?", and it was quickly voted up by Zuckerberg's followers. The good news? Plans are afoot to bring irritating game notifications and invites to an end.
I sent a message to the person who runs the team in charge of our developer platform and I said by the time I do this Town Hall Q&A, I think it would be good if we had a solution to this problem [...] We hadn’t prioritised shutting [...] down [game notifications] because we just had other priorities but if this is the top thing that people care about then we’ll prioritize that and we'll do it.
Returning to subject of Internet.org, Zuckerberg tried to silence its critics by saying:
If there's a fisherman in the village who now has access to [the] internet to sell some of his fish and provide for his family, no one gets hurt by that. That's good.
We all have a moral responsibility to look out for people who don't have the internet. The people who aren't on the internet can't sign a petition pushing for more access to the internet.
Photo credit: catwalker / Shutterstock.com
-

5 tips to help you avoid fake online reviews
Publié: octobre 28, 2015, 1:37pm CET par Mark Wilson

The emergence of online reviews has changed the way we choose products and services. But while the opportunity to read about other people's experiences and thoughts is helpful, online reviews are open to abuse. Fake reviews are a serious problem and it is important to know what to look out for.
Amazon is taking steps to clamp down on fakers, and #noreceiptnoreview campaign exists to help try to clean up TripAdvisor. Feefo is a feedback engine and closed review platform, and company CEO, Andrew Mabbutt knows that fake reviews are a serious problem. He has a number of tips to help consumers spot the fakes.
Andrew warns that as many as a quarter of reviews are not genuine and he is throwing his support behind the #noreceiptnoreview campaign. He says that "as 89 percent of consumers say that reviews influence their purchasing decision, they need to be able to trust that the reviews they see are written by a genuine purchaser -- unedited and un-moderated -- in order to make an informed decision".
He also shares some advice about spotting and avoiding fake reviews:
1 Language
Typical reviews are moderate in their tone, whether that's to praise or be negative. Look for excessive punctuation and overly positive or negative language. Also, be wary if overly specific language is used e.g. industry specific jargon or overuse of key words, for example a specific name of product, model, hotel and restaurant.
2 Emotion
Real reviews will include emotion and talk about the value of the product/service rather than just talking about the features. Look to see if the reviewer has mentioned how they used the product or service and what impact this has had on their lives and experience. If a review is just about features without any emotion, it’s likely to be bogus.
3 Platform
Check to see if the platform on which you're reading the review is an open or closed feedback system. Open systems, like TripAdviser and Trust Pilot will allow anyone to review a product or service irrespective of whether that reviewer has made a purchase or even visited the specific destination. Closed feedback systems like Feefo will only allow those who have made a purchase to leave feedback, by inviting them to leave a review via email.
4 Check the reviewer
We all know about serial complainers, but what about fake reviewers? Where you can, cross-reference the reviewer. Have they left more than one review? If they have, check the language used -- are the reviews all the same? Are they all negative or positive? If they’ve only left one review, or multiple that all sound similar, be warned.
5 Frequency of reviews
Have a look at how many reviews have been left, and how frequently they are being sent. For example, if a product or service has received a large chunk of their reviews over a short period of time (half an hour to a few hours) this is can be seen as a red flag; it’s far more natural for reviews to be left over a longer period of time, not in one small burst.
Photo credit: Stuart Miles / Shutterstock
-

Now you can follow up to 5,000 people on Twitter -- if you're insane
Publié: octobre 28, 2015, 12:11pm CET par Mark Wilson

If you're a fan of information overload, Twitter has some great news for you. It is now possible to follow up to 5,000 accounts, up from the previous limit of 2,000.
There are still no limits on the number of followers you can amass, but putting a cap on users' ability to follow others helps to "alleviate some of the strain on the invisible part of Twitter". But what if you have a genuine need, or desire, to follow more than 5,000 accounts? It is actually possible...
Twitter says that the same restrictions apply to all users of the service, including developers and verified accounts. When you hit the magic figure of 5,000, a new set of rules kicks in. From this point forward, your ratio of followers to following comes into play. It's all explained on Twitter's support pages:
[E]very user can follow 5000 people total. Once you’ve followed 5000 users, there are limits to the number of additional users you can follow: this limit is different for every user and is based on your ratio of followers to following.
When you hit this limit, we’ll tell you by showing an error message in your browser. You’ll need to wait until you have more followers in order to follow more users -- for example, you can't follow 10,000 people if only 100 people follow you. When you reach a daily or total limit and we show you an error message, you've hit a technical limit imposed to limit egregious behavior by spam accounts and to prevent strain on the site.
The announcement about the increased limit came via Twitter Support... on Twitter, of course:
Starting today, we are increasing our current follow limit from 2,000 to 5,000 accounts for all users: [https:]
— Twitter Support (@Support) October 27, 2015
It was met by a stream of responses, many of which expressed surprise that a limit existed, and others wondering why on earth anyone could possibly want to follow so many accounts.
Photo credit: Rawpixel / Shutterstock
-

Facebook kills the Other Inbox and launches Message Requests
Publié: octobre 28, 2015, 2:49am CET par Mark Wilson
Facebook is pretty much all about communication, so the existence of the Other Inbox has always seemed a bit weird. Receive a message from someone you don't know, and it will disappear to this message dungeon, most likely never to be seen again. The lack of notifications meant that such messages would tend to go unnoticed for months.
Now Facebook is addressing the problem. The Other Inbox is now dead, replaced by Message Requests. Now if you are contacted by someone you are not already friends with, rather than vanishing into the void, the message will generate an alert on the Messages tab on the web, and in Messenger on mobile devices.
The death of the Other Inbox is not one that will lead to much mourning. Facebook users tended to fall into one of two camps when it came to this communication feature -- those who were irritated by the way it works, and those who simply did not know that it existed. A huge number of people must have missed out on messages due to the fact that anything that ended up in the Other Inbox -- effectively the equivalent of a Spam folder -- would not generate notifications about the arrival of new items.
In its Help Center, Facebook introduces the idea of message requests:
Message requests tell you when someone you might know has sent you a message. You'll see Message Requests at the top of your inbox when you've received one. When you open a message request, you can choose Ignore to hide the conversation, or choose Reply to move the conversation to your inbox.
Messages from friends will go to your inbox and messages we think are spam will be filtered out of your requests.
As noted by TechCrunch, "messages from friends-of-friends will now be treated as request. Facebook will no longer bet that having a friend in common means you care to talk to someone".
In many ways the introduction of Message Requests is something of an affront to privacy. Now it is easier than ever for anyone to get in touch with you. But the flip side of this is that it is now easier to block people you do not want to hear from. Should you receive a message from someone you don’t want to speak to, they will not be notified that you have read their message, and you can safely block them without causing offense or awkwardness.
Photo credit: endermasali / Shutterstock
-

MagicStick, the fastest HDMI stick PC available, runs Windows 10 and Android
Publié: octobre 27, 2015, 8:55pm CET par Mark Wilson

Bigger is usually regarded as better, but with PCs there has been a recent trend towards miniaturization. We've seen all manner of stick PCs in the last year or so, and MagicStick is the latest contender to throw its hat into the ring. Rather than just being a run-of-the-mill clone of the competition, the MagicStick proudly proclaims itself to be the "fastest pocket computer based on Intel's latest 14nm Cherry Trail processor".
The HDMI stick can be plugged directly into a television, monitor, or projector, and managed to smash its Indiegogo target in just four days. The specs are certainly impressive, rivalling many laptop and desktop systems and -- unlike other similar portables -- there are numerous configurations available. Oh, and it's IoT-ready.
MagicStick goes a very long way to proving that shrinking dimensions certainly does not mean having to make compromises. Despite drawing just 5 watts of power, the system packs a quad-core Cherry Trail Z8500 or Z8700 processor running at 2.24GHz or 2.4GHz. The integrated GPUs boast 12 and 16 cores respectively, and there is the choice of 2, 4, or 8GB of LPDDR2 RAM.
Booting in as little as four seconds, the MagicStick comes with 32, 64, or 128GB of storage, and connectivity is provided by a 1Gbps Wi-Fi adaptor. The stick does not scrimp on expandability either. In addition to the USB 3.1 port, there are two USB 3.0 ports. Despite the diminutive proportions, you'll also find a Micro USB port and a MicroSD card slot, opening up further possibilities. Pre-installed is not only Windows 10 (although just a trial version), but also Android Lollipop -- so whatever your preference, you can choose the operating system that suits you.
Check out the introductory video to find out more about this powerful little stick:
Of course, we're excited to take a look at the MagicStick and check that it is as impressive as it sounds. Rest assured that a full review will follow as soon as units are made available. In the meantime, take a look at the website for more details. Early bird prices start at just $99 for the base model, up to $249 for the most powerful model. There's also the Indiegogo page if you fancy supporting the project.
-

Xbox One gets Windows 10 on 12 November
Publié: octobre 27, 2015, 11:55am CET par Mark Wilson

The rollout of Windows 10 continues apace, and next on the list of devices to get the operating system is the Xbox One. What this means is that the console will gain what has been dubbed the "new Xbox One experience" (or NXOE) that Preview Program members already have access to.
Microsoft's Phil Spencer has revealed that the update will be made available to Xbox One users on 12 November, so there's just over a fortnight to wait. NXOE brings not just a new look and Cortana (eventually), but also backwards compatibility with Xbox 360 games.
Backwards compatibility does not mean that the entire Xbox 360 back catalogue will suddenly become playable, but at launch there will be support for over one hundred titles -- and more will be added as time goes on. Anyone who has taken a look at the Xbox One app for Windows 10 already has a pretty good idea of what to expect from the update.
Major Nelson tweeted about the good news:
Xbox fans mark your calendars: @XboxP3 just revealed new Xbox One experience & back compat start launching Nov. 12 for all Xbox One owners
— Larry Hryb (@majornelson) October 27, 2015
Just as with Windows 10 for PCs, concerns have been voiced that there are still a number of issues with the update so close to launch.
-

Apple is the coolest brand and battery life doesn't matter in the world of wearables
Publié: octobre 26, 2015, 10:47am CET par Mark Wilson

Consumer opinion about wearable devices is somewhat divided, accordingly to a new survey by Juniper Research. The company found that the wearables market is dominated by Apple and Samsung, but it is Apple that manages to take the 'coolest brand' crown.
Microsoft will be disappointed to find itself ranked in 13th place, but the survey shows that it is the familiar technology companies that remain the most popular. Fashion and designer brands like Nike, Rolex, and Ralph Lauren account for a tiny percentage of sales. The research also found that there is a limit to what people are willing to pay for a wearable.
Only a fifth of people questioned said that they would be willing to pay more than $175 for a wearable device -- interesting when you consider the number of devices priced above this level. Apple is trailed by Samsung, Google, LG, and Sony in the top five, while Motorola appears in slot number 14, and Pebble way down at 20.
The top two companies -- Apple and Samsung -- were the preference of 75 percent of people, while no fashion or sports brand was supported by more than 3 percent of respondents. There is a lack of clarity about just why some wearables should be purchased, apart from in the case of exercise-specific devices. Juniper Research Analyst James Moar said:
As well as a more definite use, fitness devices also win on value. They are the least costly wearables in the market, and the only category consistently under $175, which our survey identifies as the price ceiling for most consumers.
The research also found that battery life is seen as unimportant by the vast majority of people. Just 4 percent said that they would be put off buying a wearable due to poor battery life.
-

Wikimedia case against NSA spying thrown out of court
Publié: octobre 25, 2015, 10:28pm CET par Mark Wilson

A lawsuit brought against the NSA by Wikimedia and eight other plaintiffs has been dismissed by a federal judge. American Civil Liberties Union (ACLU) filed the case on behalf of the Wikimedia Foundation alleging that the NSA had engaged in mass surveillance of Wikipedia users.
Joined by the likes of Human Rights Watch and Amnesty International USA, Wikimedia complained about the NSA's upstream surveillance as revealed by Edward Snowden. The ACLU suggested that the sheer volume of traffic Wikipedia receives means that the US government's surveillance must have included spying on the activities of Wikipedia users. Judge T.S. Ellis disagreed, saying that the plaintiffs did not have plausibility -- or size -- on their side.
In his ruling, Judge Ellis said that the "plaintiffs lack Article III standing to assert their claims" that the NSA was spying on users, violating their First and Fourth Amendments by intercepting, storing, and reviewing online communications. The ruling did nothing to question the legality of the NSA's "upstream surveillance" (tapping into internet backbone cables), but says that the complainants were not able to prove that they had been spied on.
He suggested that the plaintiffs' assertion that the likelihood of at least one of its communications being intercepted in a year is greater than 99.9999999999 percent is "incomplete and riddled with assumptions". He also questioned whether the one trillion pieces of internet traffic the plaintiffs amassed in a year was a significant number: "[is it] just a drop in the bucket of all annual Internet communications[?]".
Writing on the Wikimedia blog, Michelle Paulson and Geoff Brigham, Legal Director and General Counsel, said:
We respectfully disagree with the Court's decision to dismiss. There is no question that Upstream surveillance captures the communications of both the user community and the Wikimedia Foundation itself. We believe that our claims have merit. In consultation with our lawyers at the ACLU, we will review the decision and expect to appeal to the Fourth Circuit Court of Appeals.
In response to the ruling, ACLU National Security Project Staff Attorney Patrick Toomey said:
The court has wrongly insulated the NSA's spying from meaningful judicial scrutiny. The decision turns a blind eye to the fact that the government is tapping into the Internet's backbone to spy on millions of Americans. The dismissal of the lawsuit's claims as 'speculative' is at odds with an overwhelming public record of warrantless surveillance.
The judge ended his ruling by saying:
It should also be remembered that the classified program at issue here is authorized by a law that was pass through the democratic process. Should society's suspicions about surveillance program rise to a level sufficient to cause citizens to suspect Orwellian harms that outweigh the benefits to national security, surveillance programs can be revised or eliminated the same way they were authorized, namely through the legislative process. It is also possible that the jurisprudence of constitutional standing may change in the future.
The Wikimedia Foundation said it expected to appeal the decision.
Photo credit: Carsten Reisinger / Shutterstock.com
-

Apple hit with lawsuit over iOS 9's Wi-Fi Assist
Publié: octobre 25, 2015, 3:43pm CET par Mark Wilson

The Wi-Fi Assist feature found in iOS 9 has caught some people unawares, and many have complained that they have been landed with large bills due to increased data usage. Two individuals have filed a class action lawsuit in California against Apple, alleging that the company failed to properly explain how Wi-Fi Assist works.
While Wi-Fi Assist can be disabled, the plaintiffs say that Apple should reimburse anyone who found they were pushed over their data usage limits. The company now needs to defend itself against charges of violating Unfair Competition Law, False Advertising Law, and negligent misrepresentation. Apple is also accused of downplaying the risk of exceeding data limits.
Apple failed to explain to people just how Wi-Fi Assist works, at least until there has been a number of complaints. A support page now explains that the feature will "automatically switch to cellular when you have a poor Wi-Fi connection", and reveals that it is enabled by default. But the complainants say that this is a case of too little, too late.
Apple Insider reports that the suit says:
Defendant's above corrective action, however, still downplays the possible data overcharges a user could incur. Reasonable and average consumers use their iPhones for streaming of music, videos, and running various applications -- all of which can use significant data. Defendant's corrective statement does not disclose any basis for its conclusion that an average consumer would not see much increase in cellular usage.
A number of critics of Apple have said it would have been preferable for Wi-Fi Assist to be switched off by default so that it would only be activated by more knowledgeable users.
Photo credit: Blablo101 / Shutterstock
-

Could a new Twitter campaign weed out fake reviews on TripAdvisor?
Publié: octobre 24, 2015, 5:33pm CEST par Mark Wilson

TripAdvisor quickly became one of the most useful websites, and subsequently the most useful apps, to have been developed in recent times. But it also has a dark side. Like any site that allows users to leave reviews, TripAdvisor suffers with the problem of fakes. A new Twitter campaign hopes to help cut down the number of fraudulent reviews.
Fake reviews are not a problem that is specific to TripAdvisor -- Amazon has gone as far as suing people it believes to be fabricating reviews -- but a group of people have joined forces to try to do something about it. Concerned that there are a huge number of reviews written by people who have not actually visited the establishment they are reviewing, the #noreceiptnoreview campaign proposes that people should only be permitted to share their reviews upon the production of receipt.
It's a campaign that has the backing of diners, writers, and restaurant critics, as well as those who run hotels and restaurants. It is a bid to stem the tide of maliciously negative reviews that may be posted by rival businesses or people with an axe to grind. Of course, it would not be a complete solution to the problem; there would be nothing to stop someone from eating at a restaurant to obtain a receipt, and then writing a deliberating scathing review.
But supporters say that it is a start. One of the backers is Jay Rayner -- food writer for the Observer -- who says:
TripAdvisor have admitted they have a problem with fake reviews, and if you have a business model that functions on trust, then you need to do something to protect that. At the moment I only use TripAdvisor to get a list of places in a particular town I'm going to -- I ignore the rankings.
There have been suggestions that TripAdvisor should introduce a user verification system similar to that used by Twitter and Facebook, but this would potentially mean that reviewer would feel less inclined to speak their mind. The idea of requiring a scanned receipt before posting a review is not a perfect solution -- and there are many ways to play the system -- but it could be a step in the right direction.
Speaking to the Guardian, a TripAdvisor spokesperson said the company was not keen on the idea -- but that's not necessarily the point. The point is that people are talking about the problem and trying to come up with a possible solution; that's something that should benefit everyone.
Photo credit: Bloomua / Shutterstock.com
-

Mozilla offers $1 million to support open source and free software movement
Publié: octobre 24, 2015, 11:05am CEST par Mark Wilson

Mozilla is starting an open source-supporting award program with an initial allocation of $1 million. The company has long been a proponent of open source software, and now wants to give something back to the community on which it so heavily relies.
The Mozilla Open Source Support (MOSS) is described as a way of both giving back to the community, but also giving forward to up and coming projects that could benefit others. A key feature of the program is a focus on improving the security of open source software, and Mozilla is looking to identify up to ten projects to help fund by the middle of December.
The company has revealed a list of open source software that it itself relies on, and says that it is now time to "formalize a systematic way to provide a new level of support to this community". Details of MOSS have been added to the Mozilla Wiki and 'Mozillians' are invited to contribute to the program by suggesting terms.
Introducing the new program, Mozilla's Mitchell Baker said:
The Mozilla Open Source Support program will also encompass a component supporting increased attention to the security of open source and free software programs. Our initial allocation for Mozilla Open Source Support is one million US dollars. As we develop this program we will determine future allocations.
Projects are free to apply for an award from Mozilla, and the following criteria have been set out:
- Awards should be jointly submitted by the leader of a project and an established Mozillian who will champion the grant.
- The Mozillian may be (but does not need to be) a project contributor to the project they are championing.
- The Mozillian must vouch for the usefulness of the software, commit to monitoring the project, and report on the effectiveness of the grant after the money is spent. They will also work with the application evaluation committee to help them assess the appropriateness of the grant to the needs of the project.
- The money must be used to benefit the project, but it does not have to be used on things which themselves would directly benefit Mozilla.
- Grant requests should be for the amount of financial support that helps accomplish a clear and current project goal. Projects that don’t have a need for funds at this time can be considered when such a need arises. A $10,000 grant request is just as valid as a $50,000 or $100,000 request. A previous award proposal, successful or unsuccessful, does not disqualify a project from applying again.
- The project’s home can be anywhere in the world where we can make payment without undue burden. We have a reasonably strong preference for funding legal organizations rather than individuals representing projects, although exceptional circumstances could lead to some flexibility.
Photo credit: Lightboxx / Shutterstock
-

Anonymous browser Tor is coming to iOS 9 to boost privacy
Publié: octobre 23, 2015, 10:16pm CEST par Mark Wilson

The release of iOS 9 meant a lot of things to a lot a people. For Tor it means that the privacy-focused browser will finally be able to make its way to iPhones around the world. No particular timetable has been set out, but an iOS version of the anonymizing browser is on the cards.
In fact, it is more than just the Tor browser that's on the way -- "there are a bunch of pieces in the works", according to developer Nathan Freitas. Bringing Tor tools to iOS 9 will bring Apple's mobile devices in line with Android, and it's all thanks to new capabilities in the latest version of the operating system.
Talking to the Daily Dot, Freitas said: "iOS has some new capabilities in it. You can create a device-wide virtual private network, and it can be a Tor-based VPN. So we can create an Orbot-like service on iOS 9, which is exciting."
What this means is that Tor's famous anonymization can be shared to other apps, not just the browser itself. This opens up the possibility of routing chats, emails, and any other traffic through the Tor network so all manner of apps can take advantage of the privacy options.
Photo credit: Lucky Team Studio / Shutterstock
-

There has never been a better time to tweak your Facebook privacy settings
Publié: octobre 23, 2015, 8:19pm CEST par Mark Wilson

Facebook and privacy are not words you tend to find together in the same sentence -- at least not in a positive sense. Just a few days ago, the social network announced that all public posts were to be made searchable -- although it wasn't really billed as such.
You might not be entirely happy with this. While you may now be careful that you only share posts with your friends, a huge number of historic posts have now been made searchable. If you'd prefer to keep your content private, now is the time to act.
In fact, there are a couple of things you need to do -- limit the audience that can access everything you post from this point forward, and limit the audience that can access your past posts. Quite why this could not be covered by a single setting is anyone's guess, but that's just the way it is. Here's what you need to do.
- Fire up your web browser and pay a visit to Facebook.
- Click the padlock symbol in the blue bar at the top of the page, and then click Who can see my stuff?
- From the dropdown menu labelled Who can see my future posts?, select Friends -- or anything other than Public.
- Now click the See More Settings link at the bottom of the Privacy Shortcuts menu.
- Click Limit Past Posts and you can restrict all of your past posts so they can only be seen by people on your friend list.
- Click the Limit Old Post button followed by Confirm, and you're done.
Photo credit: graja / Shutterstock
-

At last! Microsoft brings OpenSSH to Windows
Publié: octobre 23, 2015, 6:50pm CEST par Mark Wilson

It is a few months since Microsoft announced that SSH support was on its way to Windows. The absence of this feature has baffled and frustrated many users for years, and Microsoft admitted that it was one of the most frequently requested features of the PowerShell team.
The project comes after Microsoft decided to get involved in the OpenSSH community. Based on a previous NoMachine port, the Windows port is now in sync with OpenSSH 7.1. It means that secure, remote management of Linux machines from Windows is much easier.
While this release is a major milestone, there is still some way to go. Microsoft warns that "this code is still very early and should be treated as a developer preview and is not supported for use in production". Writing on the PowerShell blog, principal software engineer manager Steve Lee shared the project roadmap:
- Update NoMachine port to OpenSSH 7.1 [Done]
- Leverage Windows crypto api's instead of OpenSSL/LibreSSL and run as Windows Service
- Address POSIX compatibility concerns
- Stabilize the code and address reported issues
- Production quality release
The aim is to have a final release within the first half of 2016, and people are encouraged to make use of the current release and provide feedback.
Hit the PowerShell Github repository for everything you need.
Photo credit: Profit_Image / Shutterstock
-

Facebook says bad app coding caused iOS battery drain, not location settings
Publié: octobre 23, 2015, 6:02pm CEST par Mark Wilson

Many iPhone users were upset to find that battery life was rather shorter than expected. Fingers of suspicion started to point to the iOS Facebook app, and now the social network has released a fix as well as revealing that poor coding was to blame.
The latest version of the Facebook app goes some way to putting things right, but it is unlikely to be a complete fix. Facebook says it "found a few key issues and have identified additional improvements" in the app, but only "some of which" made it into the latest update. Something the company is keen to stress is that the Location History feature is not responsible, and provides details about two other factors contributing to battery drain.
One of the problems stems from the fact that the app failed to close audio sessions when they finished. This means that iPhones ate through battery life "as if the app was playing audio silently". Ari Grant from Facebook says:
The app isn't actually doing anything while awake in the background, but it does use more battery simply by being awake. Our fixes will solve this audio issue and remove background audio completely.
Another issue relates to CPU spin in network code. The app was using too much processing time -- and therefore battery -- by checking too frequently whether operations had completed. But even with an updated version of the app, Facebook has not managed to fully nail the problem: there are just "some improvements that should start making this better".
Photo credit: endermasali / Shutterstock
-

Facebook takes on Google by making searching social and personal
Publié: octobre 22, 2015, 9:54pm CEST par Mark Wilson

Facebook is much more than just a social network; for many people it is the internet. For others, it is a source of news, and this is something that Facebook is quite happy to play upon. But what a lot of people are now looking for is not just news, but the reaction to news.
This is something that Facebook is well-positioned to provide a conduit for, and now the social network is looking to take on Google by giving more accurate and personal search results -- including tailoring search results according to what is currently happening in the world.
Just like Google, Facebook aims to provide timely and relevant search results, and this is something the social network wants to improve upon. Now when you perform a search through Facebook, the results will be filtered according to what is happening at that time.
Being a social network, Facebook is also tailoring its search results so you can see what your contacts are saying about a particular news story. Perform a search relating to a particular topic and results from your friends' timelines will be included.
Facebook says:
Search results are organized to help you cut through the noise and quickly understand what the world is saying about a topic in the moment. You also can pull-to-refresh and see the latest public posts.
Topics that become popular will start to creep up the rankings in search results, and Facebook says that the updates are rolling out to desktop, iOS and Android users.
Photo credit: dolphfyn / Shutterstock
-

Microsoft's cheapest Surface Book is joined by a new dGPU model
Publié: octobre 21, 2015, 7:24pm CEST par Mark Wilson

The Surface Book range just keeps on growing. After the initial launch, Microsoft added a 1TB model and today another makes its way to the Microsoft Store. Bringing the number of options up to seven, there is now a 128GB dGPU available.
This means that Microsoft now has a discrete GPU Surface Book in all four capacities: 128GB, 256GB, 512GB, and 1TB. Apart from the addition of the dGPU, the specs are the same as the entry-level Surface Book, and $200 has been added to the price.
$1,699 gets you the 128GB, Core Intel i5, 8GB, dGPU variant of the Surface Book. As this model has just been added, it offers the best opportunity for anyone keen to get their hands on a Surface Book as soon as possible. While there are wait times of several weeks on all other models, this new one is currently shipping from 26 October.
The new addition will also come as great news for would be Surface Book owners who had been looking for a dGPU but didn’t like the idea of shelling out $1,899 for the privilege. If you want to get hold of one, head over to the Microsoft Store -- although Microsoft is still to release benchmarks to back up its performance claims.
-

Self-encrypting Western Digital drives have serious security flaws and backdoors
Publié: octobre 21, 2015, 4:51pm CEST par Mark Wilson

Security researchers have discovered that a number of Western Digital drives -- including many My Passport and My Book devices -- are blighted with serious vulnerabilities that leave encrypted data stored on them accessible by attackers. The self-encrypting drives were found to be so insecure that it was possible to recover data without the need for the relevant password.
A paper published at the end of September provides details of how some Western Digital drives are susceptible to brute force type attacks, and there are even some models which store the decryption key on the drive. Western Digital would almost certainly rather people were talking about its purchase of SanDisk, but people are more likely to be interested in the company's seemingly terrible approach to security.
The research paper has now been published to the Full Disclosure mailing list after Western Digital had been notified of the findings. There is a lengthy list of complaints about the security of the drives, including the fact that a random number generator used to create encryption keys is not very random at all. The paper explains that "the RNG generator of the JMS538S has been shown to be predictable, as it returns 255 different bytes in a specific order".
The method of seeding used to protect the key is also laughably weak. A 32-bit value derived from the time of key creation is used, greatly reducing the amount of time and processing power required to execute a successful brute force attack.
But the problems do not end there The researchers also found serious security problems with Western Digital firmware upgrade process:
Another attack vector on every WD we analyzed, is the update mechanism of WD. The firmware update of the bridges and the emulated CD-ROM is done by undocumented vendor-specific SCSI commands, that is executable post-authentication. The firmware and virtual CD are not digital signed or cryptographically secured from tampering and modification.
Western Digital is yet to comment on the findings, or given indication of whether patches will be issued.
Photo credit: Dario Vuksanovic / Shutterstock
-

Microsoft Edge might not get extensions until Windows 10 Redstone in 2016
Publié: octobre 21, 2015, 2:03pm CEST par Mark Wilson

Since the launch of Windows 10, anyone who has joined the Insider program has been treated to a number of updates in the form of preview builds -- particularly on the Fast ring. Regular users have not been so lucky, but Microsoft's Windows 10 roadmap includes a number of Service Pack-style updates on the horizon.
It is through these bigger updates that Microsoft is expected to deliver the long-promised extensions to its Edge. But anyone who is looking to extend the capabilities of Microsoft's browser could have something of a wait on their hands. The next update to Windows 10 -- known as Threshold 2 -- won't bring extensions. In fact, it won’t be until the Windows 10 Redstone update later in 2016 that Edge gets the feature everyone is waiting for. But will it be too late to claw back users from Chrome and Firefox?
Threshold 2 is not really a major update to Windows 10, anyone who is installing the Preview Builds will have an idea of what to expect. There are no major changes to get excited about, but there are a few nips and tucks, and a smattering of new bits and pieces that should keep people happy. While Edge has received a few updates through these builds, extensions remain notable by their absence. The release of Threshold 2 is imminent and, as some have noted, this means it is extremely unlikely that Microsoft will have time to crowbar in extensions.
Redstone, however, is a different matter.
This is a much larger update to Windows 10 which will see Microsoft adding to the core features of the operating system. Insiders are yet to see any releases from this particular update branch, but they will start to creep out towards the end of this year or the beginning of 2016 after Threshold 2 is out in the wild. This is when Edge extensions are most likely to make their first appearance -- Microsoft has said little beyond: "We are bringing support for extensions to Microsoft Edge in a future update".
But by the time most people gain access to extensions, many will have already decided that Edge simply isn't for them. It's great that Microsoft is trying to improve the capabilities of Edge, but there is a very real danger that it will be too little too late. The company has an uphill battle on its hands if it is to gain any sort of significant market share.
Photo credit: T.Dallas / Shutterstock
-

Mac and iOS users warned about Apple support scam
Publié: octobre 21, 2015, 12:54pm CEST par Mark Wilson
Windows users have long been the primary targets of all manner of security attacks, but now the tide is turning towards Mac users. In recent years there have been more viruses and malware attacks aimed at OS X, and security company Malwarebytes is now warning that Mac owners could fall victim to support scams. iPhones and iPads are also at risk.
It's a story that will be familiar to PC owners: fake technical support agents offer to remotely connect to a victim's computer to fix a (fake) problem, and then take control of the system and wreak unknown havoc. Apple does have its own, genuine remote support system accessible through ara.apple.com, but fraudulent pages with similar addresses are being used to trick people into installing remote access software.
One such page that Malwarebytes has discovered is ara-apple.com-- clearly very similar to the genuine domain. Rather than being registered to Apple, the domain has been registered through GoDaddy. Victims are encouraged not only to install remote access software to allow the attacker to control their computer, but also to hand over credit card details to pay for the support session. Needless to say, support is not provided.
Malwarebytes says:
We have contacted both the registrar (GoDaddy) and hosting provider (Liquid Web) so that they can take appropriate actions in shutting down these fraudulent websites.
This particular case shows that tech support scammers are resorting to more elaborate ways to social engineer their victims. Perhaps Apple users are even more at risk because they may be less experienced at dealing with these kinds of "errors".
The company goes on to remind people that Apple, just like Microsoft, will never reach out to customers directly to point out computer problems. Any such contact is fraudulent.
-

There are just 6.5 million paying Apple Music users
Publié: octobre 20, 2015, 11:31am CEST par Mark Wilson

Apple Music has managed to retain just 6.5 million subscribers willing to pay for the service four months after launch. Tim Cook has revealed that there are 15 million users in total at the moment, meaning that 8.5 million are making use of the free trial period.
Apple has previously claimed that it was managing to hang onto 79 percent of free trial users, converting them to paid subscribers, but these latest figures -- direct from Cook -- are at odds with this. But the real question is, how many of these paying subscribers simply forgot to cancel their subscription at the end of the trial period?
It will be interesting to see the usage figures over the next couple of months. At the end of October and November, the realization that there is a charge on the credit card bill could well lead to a large drop off in numbers. It is quite possible that the current number of paying subscribers is being artificially inflated by people who forgot to cancel their free trial.
If Cook's numbers are correct, Apple Music currently sits in second place behind Spotify in terms of popularity, but there are always a few ways to interpret usage figures. How meaningful the number is really depends on how it has been reached. There is not only the possibility that some subscribers are accidental subscribers, but there is also the question of how many people who signed up for the free trial are active users. Expressing interest is very different to actually using.
-

Microsoft is worryingly cagey about Surface Book benchmarks
Publié: octobre 19, 2015, 9:32pm CEST par Mark Wilson

The new baby in Microsoft's Surface family is the Surface Book. The convertible device has a striking look, as well as a striking price -- particularly if you opt for the newly announced 1TB model -- but Microsoft has been keen to promote performance.
At launch, the claim was made that the Surface Book is twice as powerful as a MacBook Pro. When the $3,199 1TB model was announced, Microsoft repeated the claim. Being quite a fan of evidence, I was intrigued by the fact that the claims were not being backed up with raw data from benchmarks. I asked Microsoft for more details, and found the company to be really quite cagey (and repetitive) in what it had to say.
The claim made last month was that the Surface Book is 'twice as powerful', but what does this actually mean? Is 'powerful' synonymous with 'fast'? I'm not someone who will take a claim at face value, and to suggest that your new system has double the power of a competitor is a very bold claim. I need figures to back this up. So I asked outright: "Have the benchmark results been published so they can be scrutinized?"
Rather than getting a personal response to very specific questions, I was instead treated to yet another repetition of the same stock quote:
Our validated performance claims are for the Microsoft Surface Book with an Intel Core i7 with 16GB RAM and custom discrete Nvidia GeForce GPU against the MacBook Pro 13-inch with Retina display with an Intel Core i7 with 16GB RAM. We used third-party benchmarks to test the best available Surface Book against the best available 13-inch MacBook Pro.
It's strange that Microsoft is being so closed about this claim. If it is true, it's certainly something worth shouting about -- but we need more information. The performance claims have, apparently, been 'validated'. By whom? We're told that 'third-party benchmarks' were conducted. Which ones?
But more importantly, where is the data? Microsoft is asking for a substantial amount of money for the Surface Book. It's just not good enough to expect people to just accept what's said without questioning it.
-

Facebook warns about government-sponsored attacks on accounts
Publié: octobre 19, 2015, 8:44pm CEST par Mark Wilson

It's one thing to have your Facebook account attacked, it's quite another to have it targeted by government-sponsored attackers. It seems as though attacks of this kind are on the increase, and Facebook has implemented a warning system for anyone whose account comes under such an attack.
But this is about more than just letting you know if someone has tried to log into your account without permission. Facebook believes that the problem is serious enough to suggest that anyone who receives such a warning should consider either formatting their computer, or buying a new one.
Seeking out malicious activity is something that Facebook has placed increased importance on in recent years, so in many ways this is just an extension of an existing security program. The social network says that it will "notify you if we believe your account has been targeted or compromised by an attacker suspected of working on behalf of a nation-state".
Facebook assures users that it takes steps to secure accounts that it believes to have been attacked by "state-sponsored actors", going on to say that the new warning system is meant to serve as an advisory that those affected should look at all of their online accounts for signs of suspicious activity. Alex Stamos, Chief Security Officer, said:
It's important to understand that this warning is not related to any compromise of Facebook's platform or systems, and that having an account compromised in this manner may indicate that your computer or mobile device has been infected with malware. Ideally, people who see this message should take care to rebuild or replace these systems if possible.
Facebook doesn't give any details of how attacks are determined to be state-sponsored, but assures users that warnings will only be sent out when there is a good deal of evidence to support them.
Photo credit: endermasali / Shutterstock
-

Apple's Magic Mouse 2 is a design abomination
Publié: octobre 18, 2015, 11:33am CEST par Mark Wilson

Apple is a company synonymous with not just design, but thoughtful design. At least that's usually the case. With the Magic Mouse 2, however, the company has got something so unbelievably wrong that it almost defies belief.
Forget the absurdity of the name for a moment and just consider what the Magic Mouse 2 is. It's a wireless mouse. Like other wireless mice, it needs power, and this is provided by a rechargeable battery; plug in a Lightning cable and juice up that peripheral. Here's where Apple gets it wrong. The charging port is on the underside of the mouse. On the bottom. So you can't use the Magic Mouse 2 while it charges up.
It's hard to understand quite how this came to be. With the requirement to connect a charging cable to the base of the mouse, it is rendered completely useless when it runs out of power. Other rechargeable mice get around this 'problem' by placing the charging port on the front of the mouse. This allows for the mouse to be used much like a corded mouse as it charges.
But not Apple, oh no.
If your Magic Mouse 2 dies when you're in the middle of doing something, you'll just have to stop what you are doing and wait for it to charge up again. You could connect another mouse, but why should you have to?
Maybe you're having trouble visualizing something as absurdly stupid as a mouse with a base-mounted charging port. Here's what it looks like:
I heard Apple's new Mouse used Lightning to charge & assumed it just looks like a corded mouse when plugged in. BUT. pic.twitter.com/QWtkPcGWbD
— Anil Dash (@anildash) October 14, 2015
It really is difficult to gets one's head around the design conversations that led to the creation of the Magic Mouse 2. It's utterly insane.
-

Amazon lawsuit aims to kill fake reviews
Publié: octobre 18, 2015, 11:07am CEST par Mark Wilson

The ability to read reviews of products before making a purchase is one of the great advantages of online shopping. But how do you know that what you're reading is a genuine review and not just glowing praise planted by the seller or manufacturer? Fake reviews are a serious problem, and Amazon is trying to do something about it.
The retail giant has filed a lawsuit against 1,114 individuals for writing "false, misleading, and inauthentic" reviews. Amazon says that the fakers are tarnishing its reputation, and the attempt to clean up the site is something that will be welcomed by consumers.
The lawsuit claims that the defendants advertised their fake reviews service on Fiverr.com. In return for payment -- the Guardian claims as little as $5 -- the reviewers offered to leave five star feedback about products. Paying or charging for reviews to be written is against Amazon's terms of service, and the company says that the individuals at the center of this legal action took steps to avoid detection, including using multiple accounts and switching IP addresses.
This is not the first time Amazon has targeted fake reviews, but in the past it has focused on removing individual reviews rather than tackling the root cause. The company says:
Amazon is bringing this action to protect its customers from this misconduct, by stopping defendants and uprooting the ecosystem in which they participate.
Photo credit: Ken Wolter / Shutterstock
-

Microsoft adds $3,199 1TB Surface Book, repeats MacBook Pro comparison
Publié: octobre 17, 2015, 1:55pm CEST par Mark Wilson

When Microsoft unveiled the Surface Book recently there was surprise that the largest capacity hard drive was just 512GB -- as intakes of breath at the breath-taking price. Now this has been rectified with the addition of a 1TB model to the line-up.
Of course, upping the hard drive from 512MB to 1TB involves paying a premium, and Microsoft is charging an extra $500 for the privilege. The new top-of-the-range model pushes the top price of the Surface Book to $3,199 and if you are interested, you'll have a bit of a wait on your hands.
Earlier this week, all models of the Surface Book sold out, but it wasn't long before Microsoft sorted out its supply issues. The same cannot be said of the 1TB, Core Intel i7, 16GB, dGPU model that has just been added: the Microsoft Store currently lists a wait time of 7 to 8 weeks.
We are now very much in Apple pricing territory -- perhaps entirely appropriate as Microsoft says that the Surface Book is twice as powerful as a MacBook Pro. As no benchmark details have been provided, some have questioned the validity of the claim. Meaningful figures are still to be provided, but Microsoft has reiterated its claim saying:
Our validated performance claims are for the Microsoft Surface Book with an Intel Core i7 with 16GB RAM and custom discrete NVIDIA GeForce GPU against the MacBook Pro 13-inch with Retina display with an Intel Core i7 with 16GB RAM. We used third-party benchmarks to test the best available Surface Book against the best available 13-inch MacBook Pro.
BeatNews has asked Microsoft for further details of the benchmarks, and we'll report back when we have more to share.
-

Apple hit with $234 million charge for patent infringement
Publié: octobre 17, 2015, 11:53am CEST par Mark Wilson

A jury has ordered Apple to pay $234 million to the Wisconsin Alumni Research Foundation after an earlier ruling that the company had infringed patents. A few days ago it was found that Apple had used technology owned by WARF in iPhones and iPads chips.
The resulting charge is much lower than the $862 million that had previously been suggested; it is also less than the $400 million WARF had been seeking in damages. Apple intends to appeal against the verdict, but there is still another court case looming.
It has been found that the A7, A8 and A8X processors Apple used in the iPhone 5s, 6, and 6 Plus as well as some iPad models, violated performance-improving patents owned by WARF. While Apple did not contest the infringement, the company had looked to greatly reduce the amount that should be paid. While WARF was seeking damages of $2.74 for every device sold, Apple thought that $0.07 was more appropriate.
US district judge William Conley explained that Apple's infringement had not been wilful, and this was the reason the award amount was so much lower than it could have been. Next on the horizon, apart from the appeal, is a seperate case surrounding patent infringement by Apple's A9 and A9X processors.
-

Court finds Google is not breaking the law by scanning books
Publié: octobre 16, 2015, 8:42pm CEST par Mark Wilson

Google's digital copies of millions of books from around the world has long been controversial. Copyright holders argue that in scanning their works, Google is breaking the law. This has been the focus of a court battle that has dragged on for ten years, but now an appeals court has ruled that Google is doing nothing wrong.
The book digitization project has been underway for some years, and has been the subject of litigation brought about by writers. Judge Pierre Leval and two other judges of the 2nd US Circuit Court of Appeals in Manhattan found that Google is not infringing copyright law, even when it digitizes books without the permission of the authors or publishers.
Snippets of the digitized books are accessible through Google's search engine, although it is not possible to view the entire text of a book. Back in 2013, another judge ruled in Google's favor because of the fact that only short sections of text were visible from any given title. The court said that it constituted fair use.
Judge Leval summed up the ruing saying:
(1) Google's unauthorized digitizing of copyright-protected works, creation of a search functionality, and display of snippets from those works are non-infringing fair uses. The purpose of the copying is highly transformative, the public display of text is limited, and the revelations do not provide a significant market substitute for the protected aspects of the originals. Google's commercial nature and profit motivation do not justify denial of fair use. (2) Google's provision of digitized copies to the libraries that supplied the books, on the understanding that the libraries will use the copies in a manner consistent with the copyright law, also does not constitute infringement. Nor, on this record, is Google a contributory infringer.
Today's decision is very much in keeping with the one from two years ago, with Leval writing "Google’s division of the page into tiny snippets is designed to show the searcher just enough context surrounding the searched term to help her evaluate whether the book falls within the scope of her interest (without revealing so much as to threaten the author’s copyright interests).
It's a ruling that is unlikely to go down well with authors and publishers.
Photo credit: LoloStock / Shutterstock
-

Businesses are switching to Windows 10 far faster than Windows 8
Publié: octobre 16, 2015, 7:13pm CEST par Mark Wilson

There have been lots of claims made about the adoption rate for Windows 10 with the most recent batch of figures from Microsoft stating 110 million installations. But how does this number actually break down? New research by Spiceworks reveals that the latest version of Microsoft's operating system is making greater headway in the business environment than Windows 8 did.
Asked before launch whether they would upgrade to Windows 10, Spiceworks found that 40 percent of businesses intended to upgrade within a year. Three months after the launch the number of businesses that have actually made the jump is 11 percent -- a penetration rate 20 percent higher than Windows 8 achieved on launch.
Spiceworks says that if adoption continues at its current rate, the figure of 40 percent of business upgrading to Windows will be exceeded.
The company's research also gives something of an insight into the types of businesses that are making the upgrade and differences around the world. North America has been the keenest to jump on Windows 10, with 12 percent of companies making the switch. In Europe the figure stands at a slightly lower 10.6 percent, while Asia stands at 8.5 percent.
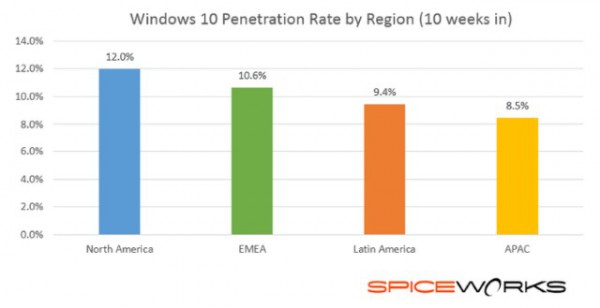
The analysis shows that the larger a company is, the more likely it is to upgrade to Windows 10. For businesses with under 50 employees, Windows 10 adoption stands at just 5.3 percent, while for those with 1,000 employees or more, the number is 22.7 percent.
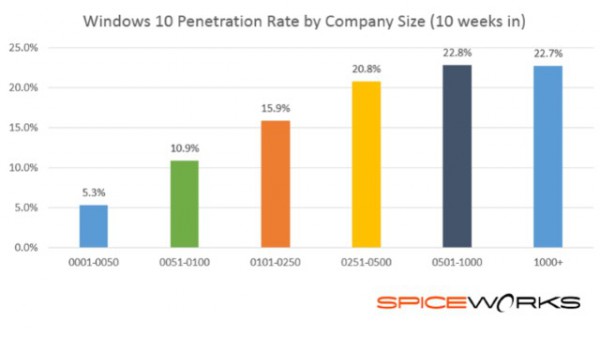
Perhaps unsurprisingly, it is the software industry that has been the most eager to upgrade -- some 19.2 percent. Retail, entertainment, and insurance all stand at 11.8 percent, and engineering is not far behind at 11.7 percent.
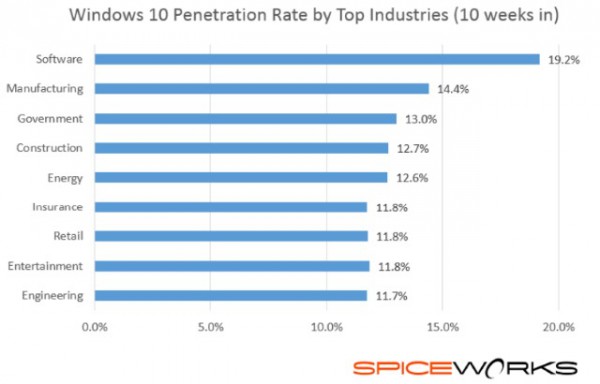
Spiceworks points out that if the current rate of adoption continues, Microsoft could pass the one billion installations landmark within a couple of years.
Photo credit: tanuha2001 / Shutterstock
-

Politicians panic after law change could leave them open to surveillance
Publié: octobre 16, 2015, 2:40pm CEST par Mark Wilson

The world of politics is filled with people who many would consider to be out of touch with real life. All too often politicians are treated differently, and this has certainly been the case when it comes to NSA and GCHQ surveillance of phone and internet traffic. In the UK a court has ruled that a ban on intercepting politicians' communication is not valid.
The Wilson Doctrine -- named after former prime minister Harold Wilson -- stated that "there [will] be no tapping of the telephones of Members of Parliament". This has now been ruled to have no legal force, sending politicians into a fit of panic. They are due to hold an emergency debate next week.
The Investigatory Powers Tribunal decided that the Wilson Doctrine has no basis in law and politicians now fear that this could leave them open to the sort or surveillance that everyone else has been subjected to by the NSA and GCHQ. Shadow Commons leader Chris Bryant said that the ruling introduced ambiguity and "to all intents and purposes, it means that the Wilson doctrine is dead".
On 19 October, MPs will debate what should be done in light of the ruling. They have previously relied on Harold Wilson's statement to ensure that their communications were left untouched. Bryant feels that the erosion of the Doctrine was dangerous, saying that there were no assurances that MPs would remain protected:
The right of members of this House to be able to represent their constituents without fear or favor is intrinsic to our democracy. It is the cornerstone of the bill of rights and it is one of the most ancient freedoms of this country. In another era, before the existence of telephones and emails it meant that MPs and peers, even in war, had a right for their written correspondence not to be intercepted or be interfered with.
Calls are being made to determine whether or not politicians' communication has been targeted for interception.
Photo credit: Business plus / Shutterstock
-

BBC starts to block VPN users from accessing iPlayer
Publié: octobre 16, 2015, 11:31am CEST par Mark Wilson

Streaming video services are frequently tied to specific countries and steps are taken to prevent people in other parts of the world using them. This is nothing new, and there has been something of an on-going battle between service providers and users who try to find a way around any blocks that may be put in place.
Now the BBC is going to war, and it has VPNs in its sights. VPNs are frequently used by those outside of the UK to view programmes on BBC iPlayer -- but they are also used by security-conscious users. But the BBC is not concerned about the security side of things, just that the tools can be used to bypass geo-restrictions. TorrentFreak reports that UK-based VPN servers are now detected and blocked.
Funded by the license fee, the BBC has a vested interest in preventing those who have not paid the annual charge from accessing content. While there is little that can be done to clamp down on license-dodgers within the UK, implementing a VPN ban is a simple way to cut back on the number of unauthorized overseas viewers.
TorrentFreak says that there is not a blanket ban on VPNs (at the moment at least), just on those that are UK-based. The BBC says that it is difficult to differentiate between VPNs that are being used to bypass restrictions, and those that are being used for security:
We regularly make updates to our technology to help prevent access to BBC iPlayer from outside the UK which breaks our terms of use. BBC iPlayer is freely available to users across the UK without a VPN, and we also seek to ensure users of private VPNs such as those used by schools and companies in the UK have access.
This is a move that will affect many legitimate users of iPlayer. For those locked out of the service -- legitimately or otherwise -- a game of hunt-the-non-blocked-VPN-service begins.
If you are looking for a new tool, David Lang from ExpressVPN contacted BetaNews to say that "thus far, ExpressVPN is unaffected.
Photo credit: chrisdorney / Shutterstock
-

Microsoft says Start menu app suggestions in Windows 10 are not ads
Publié: octobre 16, 2015, 12:29am CEST par Mark Wilson

Earlier today I wrote about my surprise at the sudden appearance of what I referred to as an 'ad' in my Start menu. The comments the article gathered made for interesting reading, and it was clear that there was more than a little confusion and disgust at the prospect of the Start menu being used as advertising space. I mentioned in the article that I had contacted Microsoft for comment, and I've now heard back with some clarification.
First off, Microsoft insists that the promotion of apps in the Start menu is not advertising, merely the App Suggestions feature. The company stresses that no payments are made by software publishers to be highlighted in this way and explains that this personalized suggestion service is now rolling out to Windows 10 Pro and Enterprise users on the Insider program. Microsoft has more to say, but is it enough to allay the concerns of Windows 10 users?
A Microsoft spokesperson explained that app suggestions work like the recommendation feature of things like Netflix. This clearly involves the collection of some user data -- which apps have been installed already, for example -- but Microsoft insists that the suggestions are meant purely to enhance the Windows experience; an FYI, if you will. What the suggestions most definitely are not, says the spokesperson, are ads:
The Windows Ads in Apps service is the only way to advertise in Windows 10. Lock Screen and Start Menu content are designed and selected by Microsoft to help customers discover new features and apps to enhance their Windows 10 experience; app publishers are not paying to be featured.
I wondered whether free and paid-for app would be featured in suggestions, and was told that, yes, both types of app would. But what about privacy concerns? Should we be worried about the data that's being collected to power Suggested Apps?
Windows 10 delivers innovative personalized services and experiences including app discoverability, informed by information you choose to provide. The learning and discovery experiences are on by default but you can turn app discoverability on and off for either or both Lock Screen and Start Menu.
Having upgraded to build 10565 of Windows 10 Pro, today was my first exposure to Start menu ads. Sorry, Suggested Apps. It became clear in discussions with others that many people were like me and had never seen suggestions. But there were others who insisted that it was nothing new. Microsoft offered some clarification:
With the release of Windows 10 Home, we made several updates to the new Windows Store to increase app discovery, including App Suggestions in the Lock Screen and Start Menu. We are now rolling out App Suggestions to Windows Insider Program participants running Windows 10 Pro and Enterprise as well.
So, in short, this is what we're supposed to take away. These are not ads, but suggestions. This is not a cynical bid to try to get people to make use of the Windows Store, it is an expansion of, and an enhancement to, the Windows experience. Personal data is not collected, but in order to deliver "personalized services and experiences" Windows 10 employs "learning and discovery experiences" -- also known as "information you choose to provide".
All clear?
Photo credit: PathDoc / Shutterstock
-

Microsoft has forcibly upgraded some computers to Windows 10
Publié: octobre 15, 2015, 11:07pm CEST par Mark Wilson

The other day I wrote about problems my father had after an inadvertent upgrade to Windows 10. In the comments there were numerous mocking remarks suggesting that he had been provided with plenty of opportunity to avoid the upgrade -- but it seems that may not have been the case. Microsoft has admitted that the upgrade has been automatically installed on some computers.
This has been described as "a mistake" after the optional update was marked for download and installation by default. Microsoft has already raised the ire of some users who were unhappy to discover that Windows 10 setup files had been downloaded without their permission, but the unwanted installation take things to the next level. So what’s the deal?
A number of people have found that Windows 10 is not only downloading of its own accord, but also starting the installation process. There are still opportunities to back out, but for novice users it would be all too easy to be swept along and end up completing the upgrade. Despite the fact that Microsoft has categorized the Windows 10 upgrade as an optional update -- which means it should be an opt-in update -- the default setting is, unusually, to download it.
But it was all a mistake. Little comfort to those who have been upgraded unintentionally, but a mistake nonetheless. In a statement to Ars Technica, Microsoft said:
As part of our effort to bring Windows 10 to existing genuine Windows 7 and Windows 8.1 customers, the Windows 10 upgrade may appear as an optional update in the Windows Update (WU) control panel. This is an intuitive and trusted place people go to find Recommended and Optional updates to Windows. In the recent Windows update, this option was checked as default; this was a mistake and we are removing the check.
If you're running Windows 7 or 8.1 and you're trying to avoid Windows 10, Microsoft has now remedied the problem so the optional upgrade is not selected by default. What's that sound? A collective sigh of relief, I believe.
Photo credit: PHOTO FUN / Shutterstock
-

Microsoft offers $300 / £100 trade-ins when you buy a new Windows 10 computer
Publié: octobre 15, 2015, 2:38pm CEST par Mark Wilson

If you've been thinking of investing in a new computer, Microsoft has an incentive that might just help to convince you that the time is right. You've probably got an old computer laying around that you need to get rid of, and Microsoft will happily take it off your hands and give you cash into the bargain.
The Trade Up program offers a minimum of $200 for a laptop trade-in, up to $300 for a MacBook. The caveat? The Windows 10 computer you buy must cost at least $599. The deal is running in the US and UK -- but people in the UK have a different, and somewhat less impressive, deal available to them.
US shoppers can head over to Microsoft's Trade Up website where there is a list of qualifying products. Within 14 days of purchasing your new computer, you must submit an online claim and, once approved, send in your laptop or MacBook. Once this has been received, you'll receive your payment.
Things aren’t quite as good for UK shoppers, and there is also a curious difference in the wording. While the US site refers to laptops and MacBooks, the UK version talks about laptops, desktops, and Chromebooks. The cashback levels are also rather less impressive. Buy a new computer costing £249 to £348.99 and you can earn £30. £349 to £498.99 gets you £50, and anything over £499 qualifies for Trade Up Cashback of £100.
-

Microsoft now uses Windows 10's Start menu to display ads
Publié: octobre 15, 2015, 12:36pm CEST par Mark Wilson
We've all become used to the idea of ads online -- it's something that has become part and parcel of using the internet -- but in Windows? If you've updated to build 10565 of Windows 10, you're in for something of a surprise: the Start menu is now being used to display ads.
We're not talking about ads for Viagra, porn, or anything like that, but ads for apps. Of course, Microsoft is not describing them as ads; 'Suggested apps' has a much more approachable and fluffy feel to it. Maybe. This is a 'feature' that's currently only being shown to Windows Insiders, but it could spread to everyone else. Will it be well-received?
Seemingly in a bid to use every pixel of the Start menu, nestled between your list of most-used apps and the Documents/Network/etc links, Microsoft has crowbarred in a new Suggested section. In my case, Microsoft decided that I might be interested in a free app called Phototastic Collage (I'm not). Clicking the suggestion, unsurprisingly, whisks the user to the Store to download said app.
I find it hard to imagine that many people will welcome the appearance of these ads (wrap them up as helpful 'suggestions' all you want, Microsoft, they're still ads at the end of the day). On the plus side, it is possible to switch off the feature -- just right click the suggestion and you can opt to hide a particular app, or disable all future suggestions.
You can also opt out of suggestions by heading to Settings > Personalization > Start and toggle the Occasionally show suggestions in Start setting.
We've contacted Microsoft to find out a little more about the decision to start display app suggestions in the Start menu. In particular, we were interested to learn whether user data is collected to better tailor suggestions (possibly opening up privacy concerns), and whether ads for paid-for apps will be displayed as well as those for free downloads.
How do you feel about the Start menu being used as an advertising billboard? Is this the price we're expected to pay for Windows 10 being free?
-

Microsoft launches new Transparency Hub, details content removal requests
Publié: octobre 14, 2015, 11:48pm CEST par Mark Wilson
In the post-Snowden age, transparency reports are all the rage. After the privacy debate that followed the NSA surveillance revelations technology companies fell over themselves to publish everything they could about government data requests. Microsoft has already released transparency reports, but today unveils a new Transparency Hub.
This is designed to be a central resource through which a variety of reports can be accessed, including the Law Enforcement Requests Report and U.S. National Security Orders Report. Data for the first six months of 2015 is now available, and there is a new section dedicated to Right To Be Forgotten-style requests for data removal.
The Microsoft Transparency Hub is also home to details about workforce demographics and othe company statistics, but the government data requests section is the one that most people will be interested in. There has been a slight increase in the number of requests compared to the second half of 2014, up from 31,002 to 35,228. Microsoft says that just 3 percent of requests from law enforcement agencies resulted in the disclosure of customer content.
The Content Removal Requests Report is where we find out about the requests Microsoft has received asking for content to be removed. Details are provided in three areas:
- Requests from governments such as claims of violations of local laws or our terms of service;
- Requests from European residents for links to online content about them to be removed from Bing under the European Court of Justice’s 2014 "Right to Be Forgotten" ruling; and,
- Requests from copyright owners to Bing claiming infringement of protected works.
By far the greatest number of requests (165) came from China, and it is somewhat surprising to learn that Microsoft received a mere 186 requests in total in the first six months of 2015. Action was taken in 89 percent of cases.
Microsoft's Deputy General Counsel & Vice President, Legal & Corporate Affairs, John Frank said:
This inaugural release of our Content Removal Requests Report is very much a V1, much like the inaugural releases of our Law Enforcement Requests Report and U.S. National Security Orders Report were. Like those two reports, we expect to improve upon the information we’re providing today, adding additional detail and additional categories of information in the future.
We also expect that our new Microsoft Transparency Hub will continue to evolve as we gather here reports on a variety of other topics and seek to provide our customers with a better understanding of how Microsoft works to improve transparency about these types of requests and about our own activities around the world.
Photo credit: Syaheir Azizan / Shutterstock
-

Buggy Windows 10 Mobile Insider Preview Build 10549 released to Fast ring
Publié: octobre 14, 2015, 8:51pm CEST par Mark Wilson

Hot on the heels of a new desktop build, Microsoft has now released Windows 10 Mobile Insider Preview Build 10549 to Fast ring Windows Phone users. While there are a fair number of improvements and new features, there is also a serious problem for anyone upgrading from Build 10536 -- although there is a work around.
So that’s the bad news, what's the good? Riding the current wave of interest in diversity, this build includes diverse emoji; a recognition of the fact that there are many hues of skin color. There are improvements to the messaging app -- although no Skype integration just yet -- and to Cortana, but that's not the end of the story.
Lumia 1020 owners will be pleased to find that Lumia Camera is no longer uninstalled by the preview build, and there are a number of bug fixes for everyone else as well. A problem with the keyboard vanishing has been addressed, and the Windows Camera app is now less crash prone. Call-blocking now works, vibrate-only alarms make a re-appearance, and problematic screenshots have been fixed. Other fixes include pinch-to-zoom in Maps now working, and SD card based apps launching properly.
But what of that awkward upgrade bug? Gabe Aul says that it was a last minute discovery, and rather than delay the release, the team wanted to push the build out anyway. Upgrading from Build 10536 will result in a black screen, but there are no issues upgrading from Windows Phone 8.1 -- so you can downgrade and go that route:
- Go back to Windows 8.1 first using the Windows Device Recovery Tool.
- Once you’re on Windows Phone 8.1, install the Windows Insider app, choose the Fast ring, and reboot your phone.
- After that the build should download and install on your phone.
This is not the only problem with the build. Aul warns that some apps may be 'missing' post installation and will need to be restored by performing a reset. Calling through Skype for Business, WhatsApp and other apps will not be possible until the apps are uninstalled and reinstalled. There are also issues with notifications.
-

Apple faces $862 million bill as iPhone and iPad chips infringe patents
Publié: octobre 14, 2015, 5:28pm CEST par Mark Wilson

A jury has decided that Apple infringed on patents owned by the Wisconsin Alumni Research Foundation. The A7, A8, and A8X processors used in iPhones and iPads since 2013 included technology owned by the University of Wisconsin-Madison's licensing arm.
US District Judge William Conley had previously indicated that Apple could be hit with a bill of up to $862.4 million, but it is now down to the jury to determine the levels of damages that must be paid. The chips feature efficiency-improving technology, and can be found in some iPads as well as the iPhone 5s, 6, and 6 Plus.
The Wisconsin Alumni Research Foundation is well-versed in patent cases, having already used the same patent to sue Intel back in 2008. Apple also faces a second lawsuit covering the A9 and A9X processors used in the iPhone 6S and 6S Plus, as well as the iPad Pro.
Presiding over the case, Judge Conley scheduled the trial to proceed in three phases: liability, damages, and finally, whether Apple infringed the patent willfully, which could lead to enhanced penalties. No timetable has been set out, and it is not clear if Apple would take the same action as Intel and settle out of court.
Photo credit: TK Kurikawa / Shutterstock
-

Hear the recordings Google stores of the voice commands you've said to your phone
Publié: octobre 14, 2015, 4:50pm CEST par Mark Wilson

OK Google, Siri, and Cortana all make it possible to control a phone simply by speaking to it. In the case of Google, what you might not be aware -- it's hardly something the company shouts about -- is that recordings of every command, question, and request are stored online.
Listening back through these could well be interesting, embarrassing, perhaps even nostalgic. You can step back in time and remind yourself of trips abroad, fun nights out, and the like, but you might also be concerned about privacy. If you would rather these recordings were not stored online, you can delete them; here's how.
Pay a visit to the Voice & Audio Activity section of your Google account and you'll probably find a lengthy list of recordings stretching back months. Just as with Google Voice, when possible Google will provide a transcript of what was said, but there's also a Play button that can be used to listen back to your direction requests, Google searches, and random recordings that have been made for seemingly no reason.
If you feel uncomfortable having all of this audio saved, you can manually work through the list and delete any of the more personal (or incriminating) recordings. You can speed up deletion of everything by hitting the hamburger menu, selecting Delete options and here you can opt to delete everything in one fell swoop.
You can opt to turn off Voice & Audio Activity (just visit Settings), but this may not have quite the effect you would expect, as noted by Alex Hern. Google says:
Pausing Voice & Audio Activity may limit or disable features such as using "OK Google" to start a voice search and reduce the accuracy of speech recognition across Google products that use your voice.
Note that this setting does not affect storage of information by Google products (like Voice) that can be used to store your audio or voice inputs. Google may also continue to collect and store audio data in an anonymized way.
Let us know if you find anything interesting as you browse through your archive.
Photo credit: cagi / Shutterstock
-

FBI and GCHQ investigate Dridex malware after millions stolen from bank accounts
Publié: octobre 14, 2015, 12:39pm CEST par Mark Wilson

An investigation spanning the US and Europe is under way after tens of millions of dollars was stolen from bank accounts. The thefts are believed to have been facilitated by a strain of malware known variously as Dridex, Bugat, and Cridex, enabling a group known as Evil Corp to siphon off funds.
The malware has been known of for some time, but law enforcement agencies have only just started to make significant inroads that could thwart the activities of the botnet. An arrest has now been made in connection to the malware which hijacked online banking login pages on infected computers. After stealing usernames and passwords, taking money from accounts was a simple task.
Europol, the FBI, GCHQ, and the UK's Computer Emergency Response Team are working together to fight what has been described as the worst cyber-attack ever seen. It was thought that agencies had managed to stop the botnet in its tracks, but now there are fears that attacks are starting up once again.
Mike Hulett from the UK's National Crime Agency said:
This is a particularly virulent form of malware and we have been working with our international law enforcement partners, as well as key partners from industry, to mitigate the damage it causes. Our investigation is ongoing and we expect further arrests to made.
Dridex is believed to target small to medium-sized businesses rather than individuals or large organizations, and it was spread through emails crafted to fool finance departments.
The US Department of Justice has just released details of an arrest that was made in August:
Andrey Ghinkul, aka Andrei Ghincul and Smilex, 30, of Moldova, was charged in a nine-count indictment unsealed today in the Western District of Pennsylvania with criminal conspiracy, unauthorized computer access with intent to defraud, damaging a computer, wire fraud and bank fraud. Ghinkul was arrested on Aug. 28, 2015 in Cyprus. The United States is seeking his extradition.
The US Computer Emergency Readiness Team has set up a page detailing the tools that can be used to check for and remove the malware.
Photo credit: wk1003mike / Shutterstock
-

Hillary Clinton wants Edward Snowden to stand trial
Publié: octobre 14, 2015, 11:32am CEST par Mark Wilson

Hero or villain? Opinion is very much divided about Edward Snowden. For Hillary Clinton there is no question -- he is a villain who broke US law and should face trial. The NSA contractor became a topic for discussion between Clinton and Bernie Sanders at last night's presidential debate, and the two candidates had slightly differing views of how he should be treated.
Snowden has said that he would be willing to serve time in jail, going as far as offering himself up to the government. He says that he has received no response -- something that would apparently be very different if Clinton succeeds in her presidential bid. While Clinton is taking a hard line, Sanders offers more leniency.
Edward Snowden used his position to expose the secretive surveillance being carried out by the US government. While this has sparked a global debate about privacy and security, Clinton is ready to come down on him. Hard. She said:
He broke the laws of the United States. He could have been a whistleblower, he could have gotten all the protections of a whistleblower. He chose not to do that. He stole very important information that has fallen into the wrong hands so I think he should not be brought home without facing the music.
Sanders recognizes the fact that laws have been broken, but adds that "Snowden played a very important role in educating the American public" and this should be taken into account. He would still like Snowden to face trial, but believes the sentencing should reflect the good that came out of blowing the whistle, as well as the bad.
Photo credit: JStone / Shutterstock
-

How to jailbreak iOS 9 with Pangu
Publié: octobre 14, 2015, 10:41am CEST par Mark Wilson

As with every previous version of iOS, it had to happen -- jailbreak instructions for iOS 9 have been released. Rumors have been circulating for a little while that a group called Pangu was on the verge of releasing a jailbreak tool, and now it's available.
Pangu Jailbreak for iOS 9 cracks open iOS in next to no time, opening up the possibility of installing apps and applying tweaks that would not otherwise be possible. Whether you're rocking a new iPhone 6s or iPhone 6s Plus, or you have an iPad or older handset the whole process can be over in less than five minutes. Here's what you need to do.
It should go without saying that before starting to jailbreak your iOS device, you should make sure that you back up everything important, you know, just in case. The process should be trouble-free, but obviously this is software not supported by Apple. Basically, you're on your own!
The availability of Pangu 9 was excitedly announced on Twitter to a rapturous reception:
We are very excited to announce the release of Pangu 9, the first untethered jailbreak tool for iOS 9 ([t.co]).
— PanguTeam (@PanguTeam) October 14, 2015
iDownloadblog has tested out the tool and verified that it works as it should.
- Grab yourself a copy of Pangu Jailbreak
- Disable Find My iPhone, Passcode and Touch ID, and enter Airplane mode
- Connect your device to your computer and run the Pangu tool
- Follow the on-screen instructions and you'll be guided through entire process
Check out the video for further clarification:
-

Would you rather disable your adblocker or pay to access content?
Publié: octobre 13, 2015, 1:53pm CEST par Mark Wilson

German tabloid Bild has made a bold move with its website -- blocking anyone using an adblocker from accessing content. Visitors to the site who want to use a tool such as Adblock Plus are now faced with a stark choice: add Bild.de to a whitelist so ads are displayed, or cough up for a €2.99 monthly fee to remove ads.
This is not a move that -- at the moment at least -- every website could get away with. Bild finds itself in the unique position of being the top-selling tabloid newspaper in Europe; it can afford to lose a few visitors with this experiment. With adblocking back in the limelight at the moment, it's time to ask the question: would you rather disable your adblocker or pay to access content?
Adblocking is nothing new, but it has been thrust center stage after Apple added support for adblockers in iOS 9. The gradual but steady move to access the internet on mobile devices, and the number of dedicated users Apple has, meant that this was a move that has the potential to dramatically curtail the ad-driven incomes of large numbers of sites. The effect Apple's decision could make is probably still to be fully realized, as for now things don't seem quite as bad as publishers feared.
It's no secret that huge numbers of websites rely on ads to survive -- Google has been built on the foundations of online ads -- but the internet has changed the way people look at content. The golden age of the internet meant that everything was available for free. Companies would have been considered insane for even thinking about charging for access -- growing an audience was all that mattered. The development of technologies such as MP3 and P2P opened up a world of even more free content, and an entire generation of web users has grown up expecting everything to be available without charge.
But, of course, this couldn't last. Monetizing online publications was a necessity. Of course, people were not -- are not -- keen on an abundance of ads, hence the unstoppable rise in popularity of adblockers. It's not uncommon to visit a site and see a message along the lines of "we see you're using an adblocker... perhaps you'd like to consider disabling it to help us out". Bild has been bold. If an active adblocker is detected, no content is visible. It's as simple as that. There is no gentle cajoling. No suggesting that you might like to consider supporting the site. Just a straight down the line 'cough up or ship out'. We'll have to wait a while to see what the impact is for the site.
Having said that lots of internet users have grown up not having to pay for anything, the popularity of iTunes, Spotify and Netflix in recent years is starting to change attitudes. Consumers are starting to get used to the idea of paying to access movies, music, even news -- just like in the days of buying DVDs, CDs, and newspapers.
Of course, there are not many people who would turn down the chance to get something for free, and this is where Bild's model and the choice it offers is interesting. We're at a fork in the road. Bild presents its would-be audience with three options: endure the ads and save your money, pay a subscription, or go away.
Which route will you take?
Photo credit: Michael Wick / Shutterstock
-

Now you can activate Windows 10 with your Windows 7 or Windows 8.1 product key
Publié: octobre 13, 2015, 11:11am CEST par Mark Wilson

The release of Windows 10 has been a rollercoaster ride of excitement, frustration, and disappointment. But with the Insider program Microsoft has given itself a unique opportunity to address issues and try out new features, testing them out on hardcore users.
With the release of Windows 10 Build 10565 we see not only the introduction of a number of new features, but also a change to the way the activation process works. Some people have experienced problems activating Windows 10 after performing the free upgrade. A Windows 10 product key may no longer be needed, but this latest Insider build introduces the option of activating Windows 10 using a Windows 7, Windows 8 or Windows 8.1 product key.
The new process means that anyone who finds that Windows 10 complains about not being activated is now able to change their product key. It is also possible to use an old product key when performing a clean installation, but the same checks will be carried out to ensure that a qualifying device is being used.
Writing on the Windows Experience blog, Gabe Aul said:
We have received a lot of feedback from Insiders on making it easier to activate Windows 10 on devices that take advantage of the free upgrade offer to genuine Windows by using existing Windows 7, Windows 8 or Windows 8.1 product keys. If you install this build of the Windows 10 Insider Preview on a PC and it doesn’t automatically activate, you can enter the product key from Windows 7, Windows 8 or Windows 8.1 used to activate the prior Windows version on the same device to activate Windows 10 by going to Settings > Update & security > Activation and selecting Change Product Key. If you do a clean install of Windows 10 by booting off the media, you can also enter the product key from prior Windows versions on qualifying devices during setup. Refer to the Insider Hub for more information on these activation improvements including requirements.
Microsoft has not given any indication of the number of people who have experienced issues with activation, but it's safe to assume that a reasonable proportion of the estimated 110 million installs have been problematic. Having implemented a new system, the question has to be asked -- why was this not done from the start?
Photo credit: Anton Watman / Shutterstock
-

Use your Xbox One wireless controller in Windows 10
Publié: octobre 11, 2015, 10:35pm CEST par Mark Wilson

The Xbox One to PC games streaming capabilities of Windows 10 make for a whole new PC gaming experience. Attach a controller to your rig, and you're ready to go. But what about if you fancy the idea of ditching the cables and going wire-free?
This is where the Xbox Wireless Adapter for Windows comes into play. This simple USB dongle lets you use your Xbox Wireless Controller to play both Windows 10 and Xbox One games -- complete with in-game chat and stereo sound. It's not available just yet, but it can be yours very soon.
The Xbox Wireless Adapter for Windows is set to launch on 20 October, and will set you back just $25. The adapter can be used in conjunction with an Xbox One Wireless Controller or Xbox Wireless Controller -- Xbox 360 controllers are out, sadly -- and Microsoft warns that a "significant firmware update may be required". The company says:
With the Xbox Wireless Adapter, experience the advanced precision and comfort of your Xbox Wireless Controller on Windows 10 PCs, laptops, and tablets. Use it with PC games, and Xbox One games streamed to Windows 10, to elevate your game wherever you want to play.
There's no pre-order option available, but head on over to the Microsoft Store, and you'll be able to pick up an adapter in just a few days' time.
-

Official videos show how the Google app can help your daily life
Publié: octobre 11, 2015, 9:43pm CEST par Mark Wilson

Google is so ubiquitous that it has become much more than just a company. It is a verb, an ecosystem, a way of life. But just as with anything that you experience every day, it's easy to take it for granted or overlook what's under your nose.
With your Android smartphone in your hand (or an iPhone for that matter), the Google app is a portal to a wealth of information; all you need to do is speak to your phone. It's easy to forget just how helpful the app is -- but Google is here to remind you that it is more than capable of taking on Siri and Cortana. The company has released a trio of videos highlighting what the app can do for you. And you know what? They're actually pretty decent.
The three videos all focus on how the Google app fits into different parts of your life, showing how it can be helpful in various scenarios. With Halloween just around the corner, the theme of the first video should come as no surprise. The app can be used to discover how to make fake blood, and anything else you might need to know for a truly ghoulish evening.
But the videos also cover everyday activity, such as cooking, finding food when out and about, and looking for other information you might need in an instant. Check out the videos, and see what you think.
Halloween, Meet the Google app
Breakfast, Meet the Google app
Moving, Meet the Google app
-

Google's OnHub is basically a hacked Chromebook -- here's how to root it
Publié: octobre 11, 2015, 3:54pm CEST par Mark Wilson
One of Google's slightly more unusual hardware releases is the OnHub wireless router. At $200, it's a network device that some might consider expensive, but at the same time its performance has impressed. A router is a router is a router, you might say, but Google's OnHub is somewhat different to the majority.
A teardown by iFixIt revealed the guts of the router, showing that it's a TP-Link device (confirming what Google had already said) with a somewhat unusual antenna design. It's an intriguing piece of hardware that Exploitee.rs has referred to as being "at heart a Chromebook without a screen modified as a router". The good news for anyone who likes to get their hands dirty with some hardware hacking? It is rootable and Exploitee.rs reveals all.
Exploitee.rs determined that in order to root the OnHub, it was going to be necessary to access Developer Mode -- just as with a Chromebook. A Raspberry Pi was used to extract the SPI flash which is used to store the OnHub's BIOS, and it was on looking at the contents of the eMMC that it was found that the images were not very far removed from those used in Chromebooks.
Being so closely related to the Chromebook meant that it was going to be easier to tackle the OnHub than just walking in blind. However, to crack the OnHub, it was necessary to access Developer Mode -- something that was achieved after the discovery of a hidden switch on the bottom of the router. It was then possible to root the device. Exploitee.rs has full details of the hack in its Wiki, and you can also check out the video below for more information:
-

I had to help my dad uninstall Windows 10 over the phone
Publié: octobre 10, 2015, 6:04pm CEST par Mark Wilson

Yesterday I received a phone call from my mother asking to book a telephone appointment with my father. Being the computer literate member of the family has long meant offering computer support, no matter where I am or what I am up to. I've lost count of the number of times I've had to guide dad through the process of installing a piece of software or changing a setting. The problem this time? Windows 10.
Talking to my dad on the phone is not always easy. Firstly, while he can use a computer, he's never really got to grips with the jargon and it can be hard for him to explain what's happening at his end, and equally hard for him to quickly grasp my instructions. Things are further hampered by the fact he has been plagued with throat cancer, and endless surgery on his neck has affected his speech a great deal. Still... he had a serious problem with Windows 10 and needed my help...
The problem, specifically, was that he didn’t want it. Since the 90s he has worked his way through most versions of Windows since Windows XP and has settled nicely into Windows 8.1. But he was caught out by Windows 10. He was recently offered the chance to reserve a free copy of Windows 10 and accepted without really thinking about it a great deal. And then promptly forgot about it.
As we know, Microsoft caused a good deal of upset by automatically downloading the Windows 10 setup files to people's computers regardless of whether they had expressed interest. But dad had reserved a copy, so rather than a forced download, the subsequent arrival of Windows 10 was at least justified, if not necessarily really wanted. The installation files downloaded and at some point in the last few days, Windows chucked up a message asking if dad was ready to install Windows 10.
He clicked Yes.
He didn’t really mean to, but he did. Somehow he managed to get the installer to the point of no return and ended up with a computer kitted out with Windows 10. He didn't like it. In fact, he hated it. He couldn't find what he needed. Everything looked different. Dad's not exactly set in his ways, but Windows 8.1 was familiar, and this... well... it wasn't.
So it was down to me to tell him how to uninstall Windows 10 and go back to his beloved Windows 8.1. I have a love/hate relationship with Windows 10 and I can understand why someone who has become used to doing things in a particular way would question the value in changing.
"Do I open the Control Panel?" he asked.
It seems like a little thing, but I was quite pleased that he'd thought of this; Dad doesn’t really venture outside of Outlook, Internet Explorer, and Word -- just about anything else needs guidance.
Sadly, impressed though I was, his suggestion was wrong. I've guided him through the process of uninstalling software before, and it has usually meant paying a visit to Programs and Features in the Control Panel. It makes sense that uninstalling Windows 10 would be the same. But no.
"No, things have changed a bit. You need Settings now."
"What did they go and change that for? I can't find my Word and internet either!"
A few minutes later we'd managed to start the recovery process and we carried on chatting while the computer did its thing. It was still whirring away when we'd run out of conversation, but a little while later that evening I received a text from my mother (mum operates the mobile phone, dad is in charge of the computer. These roles will never change):
"Computer bck 2 normal thank u 4 sorting it out"
Yes, my mother uses txt spk and zero punctuation. It frequently makes her texts quite hard to interpret!
Of course, there are still a few things to do. First there's the task of getting rid of the Windows 10 upgrade files, and then we'll need to make sure that Windows 10 isn't offered again -- if dad changes his mind in a few months, he can get hold of it manually. Or, I can tell him how to, at least.
I'm not sure that Microsoft considered people like my dad when it put together Windows 10. My father is not stupid -- far, far from it -- but he was knocked off balance by being thrown into an alien environment. People like my dad were not part of the preview program. They were not providing feedback. It's entirely possible that Windows 10 has been created for entirely the wrong people. Users like my dad may not be in a majority, but there are certainly an awful lot of them.
Photo credit: Ollyy / Shutterstock
-

Microsoft using India as a testing ground for new Android dialer app
Publié: octobre 10, 2015, 3:23pm CEST par Mark Wilson

Microsoft continues to show that it is interested in mobile platforms other than its own. The company has placed an increasing importance on iOS and Android, and new reports reveal that the Skype team has developed a new Android dialer app that is currently destined for India.
As the app comes from the Skype team, it seems reasonable to assume that Skype integration is to be expected -- blurring the boundaries between cellular and web-based calls. India is a sensible testing ground for such an app, but it's likely that it will also spread globally as well as to other platforms.
Gadgets 360's sources say that while Microsoft is focused on the Android version at the moment, the Dialer app is also destined for release on Windows 10 Mobile. A release date of mid-December has been suggested for the Android version which will function on 3G data connections as well as 2G networks -- which will come as excellent news for anyone living in an area with a patchy signal.
Speaking to Gadgets 360, a Microsoft spokesperson said:
As part of the ongoing improvements to deliver the best experience possible to our users, we are always innovating and occasionally test out new features and functionality on small groups of users in different markets. If you live in India and have an Android phone and would like to get involved, sign up to our Pre-Release program via the Skype Community page.
While Skype certainly has a dedicated following, it's unclear if it has enough clout to take on the likes of WhatsApp.
Photo credit: 360b / Shutterstock.com
-

Hackers exploit serious unpatched Netgear router DNS vulnerability
Publié: octobre 10, 2015, 2:17pm CEST par Mark Wilson

Netgear is yet to patch a publicized vulnerability that affects its routers. The security hole, which is described as 'serious', has already been exploited but Netgear is yet to act. The exploit allows attackers to change the affected routers' DNS settings and it is estimated that over 10,000 routers have already been attacked.
Netgear had been informed of the vulnerability by two security companies, but is still to release a firmware update to plug the hole. The exploit was privately revealed back in July by Swiss company Compass Security, but separately discovered and publicly published by researchers at Shellshock Labs in September who explain that it allows for "full remote unauthenticated root access" of routers.
Shellshock adds the caveat that WAN administration must be enabled for the vulnerability to be exploitable. It affects the N300_1.1.0.31_1.0.1.img, and N300-1.1.0.28_1.0.1.img firmware, (used in multiple routers, including the WNR1000v4) and enables an attacker to gain router access without requiring a password. Compass Security's advisory notice about the vulnerability shows that Netgear was notified of the problem on 21 July, but has still to release a fix.
The advisory reveals just how simple it is to exploit the vulnerability:
The attacker can exploit the issue by using a browser or writing a simple exploit.
- When a user wants to access the web interface, a http basic authentication login process is initiated
- If he does not know the username and password he gets redirected to the 401_access_denied.htm file
- An attacker now has to call the URL http://<ROUTER-IP>/BRS_netgear_success.html multiple times
After that if he can access the administration web interface and there is no username/password prompt.
Bizarrely, Netgear gave Compass Security access to a beta version of firmware which, when tested, was found to fix the security issue. This was way back at the beginning of September, but the company has not indicated when -- or if -- there will be a public release.
Talking to Threatpost Alexandre Herzog, CTO of Compass Security said that it had been possible to connect to the servers involved in the attacks and download data that suggested that more than 10,000 routers had already been exploited. This figure is slightly at odds with a report from the BBC which has Netgear claiming the figure is under 5,000.
Photo credit: Korn / Shutterstock
-

ARCHOS announces the privacy-centric GranitePhone to take on the Blackphone
Publié: octobre 9, 2015, 7:30pm CEST par Mark Wilson
Smartphone owners will often argue over which mobile platform is the most secure, but if you're looking for the ultimate security, you need to step away from the mainstream. Silent Circle is probably the best known off-the-beaten-track company thanks to its ultra-secure Blackphone, but now there is a new contender: the GranitePhone by SIKUR.
Just as the Blackphone 2 runs the custom-made Silent OS 2.0, so the GranitePhone is driven by Graphite OS. It's a handset aimed at not only governments and businesses looking to secure their communications and data, but also individuals who are particularly concerned about their privacy.
While the phone offers "unrivalled focus on security, eliminating loopholes which could allow data theft and spying" the hardware specs are quite reasonable. We're not talking flagship device territory here, but this is a perfectly capable handset -- and don’t forget, this is not really a phone designed for anything other than business and private communication. Here's what the GraphitePhone is made of:
CPU: Qualcomm Snapdragon 615 Octa-Core 64bits
GPU: Qualcomm Adreno 405
RAM: 2GB
Display: 5-Inch Full-HD
Operating System: Granite OS
Internal Storage: 16GB
Camera: Back 16MP / Front 8MP
Power: 2700mah Battery
ARCHOS has teamed up with SIKUR to create the GraphitePhone, and makes the rather bold claim that: "we managed to design a completely secure, private and productive device, eliminating any breach against your privacy, data theft and espionage".
If the 16GB of storage seems a little paltry, it's backed up by cloud expansion. Any data stored in the cloud is automatically encrypted, and apps are available that allow this data to be accessed from a computer, or an iOS or Android device.
The GraphitePhone can be yours for $849.
-

Mozilla to drop NPAPI plugins from Firefox
Publié: octobre 9, 2015, 6:42pm CEST par Mark Wilson

Mozilla will kill "most" NPAPI plugins in Firefox almost two years after Google took the same action with Chrome. Back in September 2014, Google announced that NPAPI support would be removed starting in January 2015. Mozilla is now playing catch-up, and plans to end NPAPI support by the end of 2016.
When Google announced its decision, speed, stability, and security were cited as reasons for ditching plugins, and Mozilla is taking much the same line. The company also points out that many features and functions that only used to be possible through the use of NPAPI plugins can now be achieved through native web APIs. But what is this going to mean for users?
Mozilla hopes that the move will help to boost performance and security, and the company freely admits that it is following in the footsteps of Chrome and Microsoft Edge. Moving forward, new Firefox platforms -- such as 64-bit Firefox for Windows -- will launch without support for plugins. Anyone hoping that this could signal the true death of Flash is going to be disappointed.
Because Adobe Flash is still a common part of the Web experience for most users, we will continue to support Flash within Firefox as an exception to the general plugin policy. Mozilla and Adobe will continue to collaborate to bring improvements to the Flash experience on Firefox, including on stability and performance, features and security architecture.
Site owners and developers still relying on the likes of Java and Silverlight are being encouraged to investigate alternative technologies that can achieve the same things. Mozilla warns:
In the rare cases where a site needs to extend Web technologies, the recommended solution is to develop the additional features as a Firefox add-on. Site maintainers should prepare for plugins to stop working in all versions of Firefox by the end of 2016.
Photo credit: LoloStock / Shutterstock
-

Kiss goodbye to the Control Panel in Windows 10, its days are numbered
Publié: octobre 9, 2015, 2:08pm CEST par Mark Wilson
For Windows stalwarts, the move to Windows 10 has meant embracing a number of changes. Since Windows 8, Microsoft has been keen to push its modern interface, and this is a drive that continues with renewed strength in Windows 10. In ushering in the new, the old has to be let go -- and one of the next features for the chop is the Control Panel.
At the moment, Windows 10 users have something of a strange, split experience when customizing the operating system and changing settings. Some things are handled by the old-fashioned Control Panel, others by the Settings app. Microsoft's Gabe Aul and Brandon LeBlanc have made it clear that the Control Panel is due to die.
For some people, killing the Control Panel will make perfect sense. Looking to two places to change different settings may be confusing for some. Microsoft views things slightly differently, saying that streamlining two into one is more of an exercise in efficiency and performance. Writing on Twitter, Gabe Aul affirmed:
@billybobjoe2211 @brandonleblanc Having two separate implementations means more code complexity and disk/mem usage. Getting to one is leaner
— Gabriel Aul (@GabeAul) October 4, 2015
This is certainly not the first time Microsoft has talked about the death of the Control Panel. System administrators have voiced concern about the move to the Settings app, but Microsoft insists that feedback indicates a desire for more Control Panel options to migrate to Settings:
@ttmRX3 Different people have different opinions about this. We get lots of feedback asking to get all CPL settings into Settings app.
— Gabriel Aul (@GabeAul) October 6, 2015
Windows Insiders will be the first to experience Windows 10 with a beefed up Settings App and a cutback -- or non-existent -- Control Panel. While Microsoft is responding to questions and feedback about the direction it is taking Settings in, the company has not committed to any sort of schedule.
There's clearly still some work to do because, although the capabilities of Settings have expanded greatly over the months, the Control Panel remains far more powerful. When the day comes, will you be among those mourning the loss of the Control Panel?
Photo credit: benchart / Shutterstock
-

US government will not force companies to decode encrypted data... for now
Publié: octobre 9, 2015, 1:21pm CEST par Mark Wilson

The Obama administration has announced that it will not require companies to decrypt encrypted messages for law enforcement agencies. This is being heralded as a 'partial victory' by the Electronic Frontier Foundation; partial because, as reported by the Washington Post, the government "will not -- for now — call for [such] legislation".
This means that at the moment companies will not be forced to build backdoors into their products, but there is no guarantee that this won’t happen further down the line. The government wants to continue talks with the technology industry to find a solution, but leaving things in limbo for the time being will create a sense of unease on both sides of the debate.
Since the NSA surveillance revelations made by Edward Snowden, there has been increased concern about security and privacy, and greater interest in encrypted communication tools. The notion of communication that can't be intercepted and read has governments around the world worried.
Companies will be under no illusion that the US government wants them to cave in and offer decryption keys -- against the advice of security experts -- and while the public message at the moment is that mandatory backdoors will not be required, it's hard to know what sort of pressure might be applied or to guess what is actually going on in secret.
This is something that EFF and the SaveCrypto.org coalition fear:
If Obama wants to leave a legacy promoting innovation and consumer privacy, he should create a clear policy position opposing secret, and sometimes informal, agreements between the government and tech companies to undermine security and privacy. Internet users -- both in the United States and abroad -- deserve to trust their digital service providers, and this step would go a long way to amending the trust rift caused by years of privacy abuses by the NSA.
The government will continue to push the anti-terrorist agenda, ignoring complaints that the ability to access communication that could be harmful actually ends up weakening security for everyone. It would be the virtual equivalent of locking the front door but leaving a key under a flowerpot on the doorstep.
Photo credit: wk1003mike / Shutterstock
-

Windows apps on Android will soon be a reality
Publié: octobre 9, 2015, 10:48am CEST par Mark Wilson

If you have an iPhone, you're stuck with running iOS apps; if you have an Android phone, you're stuck with Android apps. At least that used to be the case. For desktop platforms such as OS X and Linux, tools and emulators exist that make it possible to run software designed for a different platform. CodeWeavers produce CrossOver which enables PC games and applications to run on non-PC platforms.
At the moment, CrossOver is available for Mac and Linux, but there are plans to bring the tool to Android. This means that, ultimately, it should be possible to run Windows software on an Android phone or tablet.
CrossOver is based on WINE -- the open source compatibility layer that is most definitely not an emulator -- and a preview of the Android version has been announced. It's not available just yet, but CrossOver for Android will be available as a 'technology preview' by the end of the year. CodeWeavers says that the preview will require an Android tablet with an Intel processor, and suggests that at least 2GB of RAM "is necessary to run most real-world Windows applications".
It's unlikely that this project will see your Android tablet replacing your desktop computer or laptop, but it does herald a time of true cross-platform compatibility. With Windows 10, Microsoft has created a unified code base that means apps can be run on any Windows 10 device -- that pool of devices is about to expand further.
If you’re interested in trying out CrossOver for Android as soon as possible, sign up for the preview over on the CodeWeavers website.
Photo credit: motttive / Shutterstock
-

Mozilla sets out its proposed principles for content blocking
Publié: octobre 8, 2015, 11:58pm CEST par Mark Wilson

With Apple embracing ad blocking and the likes of AdBlock Plus proving more popular than ever, content blocking is making the headlines at the moment. There are many sides to the debate about blocking ads -- revenue for sites, privacy concerns for visitors, speeding up page loads times (Google even allows for the display of ads with its AMP Project), and so on -- but there are no signs that it is going to go away.
Getting in on the action, Mozilla has set out what it believes are some reasonable principles for content blocking that will benefit everyone involved. Three cornerstones have been devised with a view to ensuring that content providers and content consumers get a fair deal, and you can help to shape how they develop.
One of the catalysts for the principles is avoiding a situation that creates "new gatekeepers who can pick winners and losers in the publishing space or who favor their own content over others'". Mozilla appears to be trying to be as impartial as possible with its suggestions and is quick to point out that this is not an exercise in defining good content and bad content. Rather it is an attempt to design a framework that defines how and why content could be blocked.
Mozilla's proposed principles are:
Content Neutrality: Content blocking software should focus on addressing potential user needs (such as on performance, security, and privacy) instead of blocking specific types of content (such as advertising).
Transparency & Control: The content blocking software should provide users with transparency and meaningful controls over the needs it is attempting to address.
Openness: Blocking should maintain a level playing field and should block under the same principles regardless of source of the content. Publishers and other content providers should be given ways to participate in an open Web ecosystem, instead of being placed in a permanent penalty box that closes off the Web to their products and services.
The company is looking for feedback from people about the proposals. It is encouraging people to voice their opinions using the #contentblocking hashtag.
Photo credit: Sergey Nivens / Shutterstock
-

Facebook to start testing reaction emoji -- but no Dislike button
Publié: octobre 8, 2015, 1:51pm CEST par Mark Wilson
Facebook's Like button is famous, but users have long asked for more ways to express their reaction to posts on the social network. Recently, rumors surfaced that a Dislike button was on its way (although this was not only untrue, but also the source of numerous scams), but Mark Zuckerberg said that users would be given new ways to express empathy.
The Dislike button may not be happening, but reaction emoji are. Facebook is reported to start testing of six new reactions, beginning in Spain and Ireland. A global rollout could be on the cards at some point in the future, but TechCrunch has been given a sneak preview of what the new emoji look like.
In addition to the existing Like option, the test reactions will allow people to express other emotions in response to posts they see: Love, Haha, Yay, Wow, Sad, and Angry. This is something that will be familiar to anyone who has used the messaging tool Slack, which already includes a 'reactions' feature.
Facebook is working on reaction emoji for both the web version of the social network, and mobile apps. Speaking to TechCrunch, Adam Mosseri, Facebook's director of product, said that the emoji will prove to be a great alternative to typing on mobile devices:
Typing on mobile is difficult and this is way easier than finding a sticker or emoji to respond to in the feed.
What do you think of the reaction emoji? Are there any you would like to see added?
Image credit: TechCrunch
-

Handmade by Amazon is ready to take on Etsy
Publié: octobre 8, 2015, 1:20pm CEST par Mark Wilson

Amazon has become the one-stop online shop for just about anything you might want. Now the retail giant is adding another string to its bow: handmade, artisan products. At the moment, anyone looking to sell things they have made themselves has a few outlets to choose from, but Etsy and eBay are the two most likely contenders.
Now there is Handemade by Amazon, a new branch of the online store "featuring genuinely handmade items crafted and sold directly from artisans". This is where Amazon is looking to differentiate itself from Etsy -- everything must be handmade as this is an entirely "factory-free" experience.
At today's launch, Handmade at Amazon features over 80,000 handcrafted products from around the globe. With items available from more than 60 countries, goods are spread across seven categories -- Jewelry, Home Décor, Artwork, Stationery and Party Supplies, Kitchen and Dining, Furniture, and Bedding -- and some are even eligible for Prime.
Launching the new venture, Peter Faricy, VP for Amazon Marketplace, said:
We have designed a custom shopping experience for customers looking for handmade items by bringing together many of the best artisans in the world, and they're adding thousands of items daily. Knowing an item has a unique story behind it creates a personal experience that customers have told us makes owning handmade items special.
Head over to Handmade at Amazon to start shopping.
-

Will my phone get Android 6.0 Marshmallow?
Publié: octobre 8, 2015, 10:51am CEST par Mark Wilson

With the release of Marshmallow (Android 6.0) the usual question rears its head. It's the eternal question that Android users ask themselves every time Google releases a new version of its mobile operating system: will my phone get the upgrade? If you have a Nexus device, you are probably in luck -- unless it's really old, of course -- but what about everyone else?
Unlike Apple's iPhone, which has a very long support lifecycle when it comes to iOS upgrades, Android is famous for its fragmentation. Marshmallow may have been released, but it's down to individual handset manufacturers and carriers to push out the updates. So... is your handset in line for the upgrade? Here's what we know so far.
Nexus -- You're one of the lucky ones! We know that the Nexus 5, Nexus 6, Nexus 7 (2013), Nexus 9, Nexus Player, and Android One are getting Marshmallow. If you want to get the update installed right now, we've already provided complete instructions.
HTC -- HTC has published a fairly comprehensive list of handsets that will get Marshmallow. There's no exact timeframe, but the company promises that the following devices will get the upgrade by the end of the year: HTC One M9, HTC One M8, HTC One M9+, HTC One E9, HTC One E9+, HTC One ME, HTC One E8, HTC One M8 EYE, HTC Butterfly 3, HTC Desire 826, HTC Desire 820, and HTC Desire 816.
Motorola -- Like HTC, Motorola's list of Marshmallow-upgradeable handset is fairly lengthy. Unlike HTC, however, there is no mention of when it might happen. Still, the following handsets are due to receive the update at some point: 2015 Moto X Pure Edition (3rd gen), 2015 Moto X Style (3rd gen), 2015 Moto X Play, 2015 Moto G (3rd gen), 2014 Moto X Pure Edition in the US (2nd gen), 2014 Moto X in Latin America, Europe and Asia (2nd gen), 2014 Moto G and Moto G with 4G LTE (2nd gen), DROID Turbo, 2014 Moto MAXX, and 2014 Moto Turbo.
Sony -- A decent number of Xperia handsets and tablets will get Marshmallow: Xperia Z5, Xperia Z5 Compact, Xperia Z5 Premium, Xperia Z4 Tablet, Xperia Z3+, Xperia Z3, Xperia Z3 Compact, Xperia Z3 Tablet Compact, Xperia Z2, Xperia Z2 Tablet, Xperia M5, Xperia C5 Ultra, Xperia M4 Aqua, and Xperia C4.
If your handset is listed above, now it's just a matter of waiting. Not all manufacturers are particularly timely at making updates available, so there might be something of a delay. As of yet, there has been no official confirmation from Samsung or LG about which of their devices will receive the upgrade, but you can expect Android 6.0 to roll out to flagships such as the Galaxy S6 and LG G4.
If your handset is not listed, all may not be lost. Someone may roll a custom ROM for your device so you can install Marshmallow on the sly!
Photo credit: Elena Shashkina / Shutterstock
-

Google will crank the mobile web up to warp speed with Accelerated Mobile Pages
Publié: octobre 7, 2015, 5:03pm CEST par Mark Wilson

Google today announced a project which has the aim of speeding up the web for mobile users -- Accelerated Mobile Pages, or AMP. While there are clearly benefits for users in speeding up the web, Google is pushing the benefits that advertisers could reap: if a page takes too long to load, visitors may give up and not see any ads at all.
The AMP project is an open source initiative that gives publishers the ability to optimize their site code for mobiles so it will "load instantly everywhere". The aim is to be as platform independent as possible, allowing for optimize-once workflow. The result of a collaboration between Google, Twitter, WordPress, LinkedIn and others, a new open framework called AMP HTML has been put together from existing web technologies.
If the idea of pages loading "instantly" seems a little far fetched, Google says that smart caching and prediction help to facilitate it. As this is an architecture built with existing tools, publishers are free to continue creating and hosting their own content without having to worry about using new templates. The AMP Project website not only explains how the technology works and why it came about, but also demonstrates AMP HTML in action.
The framework is an extension of the idea of pre-rendering pages:
Browsers have long supported pre-rendering through the <link rel=prerender> tag, but they need to be conservative about this mechanism because prerendering can be expensive. With AMP HTML we added the ability to tell a document: render yourself, but only as far as what is visible above the fold and only elements which are not CPU intensive to minimize the cost of pre-rendering. With this mechanism in place, referrers of AMP document can initiate rendering of docs before the user acts much more aggressively, so that in many cases the document will be done rendering by the time the user clicks.
At the moment it is possible to speed up page load times by 15 to 85 percent, but as more work is done on optimizing the ecosystem, everyone using AMP HTML will automatically benefit -- no need to go back and change code.
Google says that it already has nearly 30 publishers on board, and more will join the project as it develops and spreads. The company also says that a "core goal" of the AMP project is to support paywalls and subscriptions, giving publishers more ways to monetize their sites.
If you're interested in getting started with AMP, the resources you need are on GitHub.
Photo credit: Creativemarc / Shutterstock
-

Windows 10 sees people ditching IE -- but Chrome wins out, not Edge
Publié: octobre 7, 2015, 12:02pm CEST par Mark Wilson

Launching a new web browser was always going to be a risk. Microsoft used Windows 10 as a launch pad for Edge, shedding the shackles of Internet Explorer in a bid to take on the likes of Chrome and Firefox.
Sadly for Microsoft, new figures show that Edge is failing to make inroads into Google's and Mozilla's market shares. Analysis performed by Quantcast shows that in the US just 12 percent of Windows 10 users are using Edge, while Chrome is sitting pretty with a greater than 70 percent share.
With Microsoft Edge the new default browser in Windows 10 -- and with 110 million installs -- it would be reasonable to expect that Microsoft's own web browser would be faring rather better. But Quantcast's figures show that Edge seems to have stolen Internet Explorer's crown as the web browser that is used to download another web browser.
Once Windows 7 and 8 are factored in, Edge's share shrinks further -- but so does Chrome's. Internet Explorer still accounts for around 20 percent of the market, but looking at the Windows 10 stats it is clear that people upgrading to the latest version of Windows are also using it as an opportunity to check out the browser competition. This is borne out by Chrome's larger share of Windows 10 users when compared to Windows 7, 8, and 10 combined.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Windows 10 Mobile to launch in December
Publié: octobre 7, 2015, 11:00am CEST par Mark Wilson

The next phase of the Windows 10 rollout will happen in December. We already know that the latest version of Microsoft's operating system is installed on millions of desktops and laptops, but the mobile version has been dragging its heels.
With the announcement of the Lumia 950 and Lumia 950 XL which have Windows 10 Mobile pre-installed, owners of other devices have been left wondering when the upgrade will make it to their handset. Originally slated for a November launch, Microsoft has revealed on Facebook that the rollout will start in December.
As noticed by Brad Sims, Microsoft hardly made a great fuss about revealing this new information. Rather than making a well-publicized announcement, the revelation came via an answer to a question on the Microsoft Lumia Facebook page. Asked when Lumia owners could expect to receive the upgrade, the response was:
Windows 10 is available on PCs and tablets now, and while Lumia 950 and Lumia 950 XL ship with Windows 10 for phones, broad availability of Windows 10 on other devices, including mobile phones, will begin rolling out in December.
So now you know -- although it's not yet clear how far into December the launch date is, Microsoft is still hoping to get Windows 10 Mobile out of the door in 2015.
-

The Surface Book hinge is not a good look
Publié: octobre 6, 2015, 11:33pm CEST par Mark Wilson

The newly-announced Surface Book feels like it's something I should love. I'm a big Surface Pro fan and I still use my first gen Pro as my daily driver. But there's just something about the Surface Book that grates. The price is not in any way attractive, but there's something else that's rather ugly: the hinge.
The Surface Book's hinge is something that Microsoft seems quite pleased with. Proud of, even. Microsoft calls it a 'dynamic fulcrum hinge', but it looks like a cross between a caterpillar track and a rubberized bendy drinking straw. For what is described as a 'meticulously crafted' device and 'the ultimate laptop', it's not a good look -- and it could be a serious problem.
In many ways, it completely ruins the look of an otherwise very attractive piece of hardware. The pleasing, MacBook Pro-like lines are spoiled by the 'innovative' hinge -- pictured above. Take a look at the opening shot of Microsoft's promotional video introducing the Surface Book and you'll be able to see what I mean:
The design of the hinge presents a few problems. Firstly, unlike a more traditional hinge, it does not fold a full 180 degrees. This in turn means that the screen of the laptop does not make full contact with the keyboard when closed. There is a gap between the two layers at the hinge end. A gap into which all manner of crap can slip. Dirt, dust, pieces of paper, things that could scratch the screen. You get the idea. And that's on top of the fact that it just looks... weird.
Flip the screen around and reconnect to the keyboard to use in Clipboard mode. With the keyboard folded up against the back of the display, the gap that the hinge creates will make the Surface Book awkward to use on a flat surface. Put it on a table and it's going to tilt to the left or right.
I have no doubt that the design is very clever -- but that doesn’t mean that it's fit for purpose. The zipper-teeth/concertina mechanism means that there are a number of narrow channels on the top and bottom of the hinge that expand and contract as the hinge opens and closes. It's hard to imagine that these grooves won't attract unknown quantities of muck and grime, further ruining the look of the Surface Book.
It's something of a shame. Surface Book is a nice idea, a great extension of the Surface Pro, but the price and puzzling hinge are likely to work against it.
-

Microsoft's insane Surface Book price means it will be left on the shelf
Publié: octobre 6, 2015, 10:38pm CEST par Mark Wilson

At today's event in New York, Microsoft put on an impressive show. We were -- ironically -- expecting some surprises, and the announcement of the Surface Book meant we weren't disappointed; this is, after all, "the ultimate laptop". The looks are striking. The specs are impressive. The price tag is... eye-watering.
In a way, we should have expected some expensive hardware to be revealed today. With its Surface Pro range, Microsoft showed that it is not afraid to push up the price, but the Surface Book takes things a step further. $1,499 is the starting price. Make a few tweaks to the specs and you could find yourself relieved of a buttock-clenching $2,699. Is there any way to justify this price?
What does $1,499 get you? The base model Surface Book packs a 6th Gen Intel Core i5 and integrated graphics. There's just 128GB of storage and 8GB of RAM. Moving up the scale, you can change the processor, memory, hard drive, and opt for dedicated graphics. The largest hard drive available is 512GB, and you'll only bag yourself a Core i7 processor if you're happy to part with at least $2,000. If you need 16GB of RAM to work with, this is only available in the top of the range $2,699 model. That's a lot to spend on a notebook.
There's no denying that Surface Book is a good-looking piece of kit (well, some might disagree. Attractiveness is, after all, quite subjective) -- although there is the matter of that hinge... of which more in another post. But these are looks and specs delivered at a seriously premium price. These are the sorts of prices that even Apple might be slightly embarrassed to attach to what is essentially a tablet with a keyboard.
Is it a good computer? Almost certainly. Would it be a delight to use? Without a doubt. It is innovative enough or highly specced enough to justify those price tags? Not a chance. Why is the hard drive limited to 512GB? The Surface Pro 4 maxes out at 1TB -- why the difference? Microsoft is pitching this as the ultimate laptop. While it's nice, I think 'ultimate' is stretching things a little -- perhaps in a weak attempt to justify the absurd price. (As an aside, it is interesting to note that while Microsoft refers to the Surface Book as the 'ultimate laptop', in its Surface comparison table it is described as being able to 'Run desktop software just like a laptop'. So is it a laptop, or like a laptop?)
It's possible that Surface Book is such a joy to use that the notion of coughing up the fat end of three grand for a jumped up tablet makes perfect sense... but I'll need to be convinced, and I don't think I'm alone.
-

Twitter launches Moments to help bring tweets to the masses
Publié: octobre 6, 2015, 8:55pm CEST par Mark Wilson
If you're a Twitter user, you undoubtedly love it. If you're not, you probably either hate it, or find it confusing. Today Twitter launches Moments in a bid to make itself more appealing to beginners by helping to provide a gentle step up into the crazy world of tweets, and by bringing context to timelines.
Times they are a-changing at Twitter with Jack Dorsey now the fulltime CEO, and the prospect of curated content from reputable sources could be what is needed to take things to the next level. Part of the problem with Twitter is the sheer volume of content that is out there -- and it is generated very quickly; for newbies, it can be completely overwhelming. Moments is an attempt to cut through the crap and present news and stories in a meaningful and accessible way.
Moments might sound familiar, and that's because this is the official launch of what was previously known as Project Lightning. In offering curated content, the hope is that those who have been put off by the perceived complexity of the service will be lured back. Initially only launching in the US, Moments is available on Android, iPhone, and the desktop site.
The real aim of Moments is given away by its name -- the idea is to provide at-a-glance information. After tapping on a Moment of interest (it could be about a breaking news story, a sporting event, or just about anything else) an introduction brings the reader up to speed straight away. Then it is possible to swipe through curated tweets, images, and videos without the need to hunt through your timeline or scan for hashtags.
Introducing the new feature, Twitter says:
Moments are often updated as new information or great Tweets become available. You’ll know a story has been updated since your last view when you see a blue dot in the upper righthand corner of the image associated with the Moment. For stories that update very frequently -- like live sporting events or awards shows where it’s critical to know what’s happening minute by minute -- you’ll see an option to follow the Moment, which blends the Tweets directly into your timeline.
There are a number of partners working with Twitter at the moment -- including Buzzfeed, Entertainment Weekly, Fox News, Getty Images, Mashable, NASA, New York Times, Vogue, and the Washington Post -- and this will grow over time. While this is a US launch for the time being, Moments can be shared just like any other Twitter content. This means that people in other parts of the world will be able to experience the feature before it officially launches in their country.
-

The new Microsoft Band is (much) better-looking and has two-day battery life
Publié: octobre 6, 2015, 8:33pm CEST par Mark Wilson

Microsoft appears to have learned from its mistakes. Its first wearable, the Microsoft Band was a cheap and cheerful affair -- although there wasn’t really all that much to be cheerful about in all honesty. Today the company unveiled the second edition of the Band, and the look is in line with the leaked images from a couple of weeks ago.
With the latest version of the Band, Microsoft has gone back to the drawing board and come up with a design that is sleek and stylish, and features a curved screen. The health and fitness tracker is nicely rounded, and the curved display is strengthened with Gorilla Glass 3. There are now no fewer than 11 built in sensors, including a new barometer for measuring altitude.
Battery life in the wearable has been boosted, and Microsoft now claims that you can expect 48 hours of use between charges. Speaking of charging, a full charge takes under 90 minutes and the Microsoft Band is compatible with a wide range of mobile devices ("Windows Phone 8.1 update, iPhone 4S, 5, 5C, 5S, 6, 6 Plus, iOS 8.1.2, and many Android 4.3-5.0 phones, with Bluetooth" according to the product website).

Once paired with a phone, the Band can display email, text, and calendar alerts, and Cortana is on hand for Windows Phone users to dictate replies to texts. Microsoft has partnered with a number of other companies to bring additional functionality to the Band, including Starbucks, Runkeeper, and Uber. Golfers will be pleased to see support for a couple of golf apps, as well as a swing-monitor by the wearable.
The new Band is available from 30 October, priced at $249.99 -- pre-orders are open right now.
-

Top court rules European-US Safe Harbor data sharing agreement invalid
Publié: octobre 6, 2015, 1:39pm CEST par Mark Wilson

The European Court of Justice has ruled that the Safe Harbor agreement that is in place between technology companies is invalid. The agreement covers the sharing of data between the EU and the US but the court said there are insufficient privacy and data protection checks in place.
European law dictates that data should only be shared with and transferred to countries that offer a comparable level of data protection to the EU. The Safe Harbor agreement has been in operation for around 15 years, but after concerns that European data could be shared with the likes of the NSA it means that companies such as Facebook, Google, and Apple could be sharing data illegally.
Edward Snowden's revelations raised concerns that US companies could not be trusted to ensure that adequate privacy and data protection measures were in place. The case stemmed from a request from a privacy campaigner to the Irish Data Protection Commission to find out what data Facebook was sharing about European users. The aim was to discover what sort of user data might be exposed to levels of surveillance that would be illegal in Europe.
The repercussions of the ruling are likely to be far-reaching. Matthew Fell, CBI Director for Competitive Markets, said:
The ability to transfer data easily and securely between Europe and the US is critical for businesses in our modern. Businesses will want to see clarity on the immediate implications of the ECJ's decision, together with fast action from the Commission to agree a new framework. Getting this right will be important to the future of Europe's digital agenda, as well as doing business with our largest trading partner.
At the moment, there has been no reaction from companies likes Facebook. Moving forward, it is likely that new data sharing contracts will have to be drawn up, and this is going to take time and money. But it is not just the big players that will be affected by the ruling. Many smaller companies outsource data storage to other services that may operate in the US -- as soon as data is transferred from Europe to the US, data protection becomes an issue.
With thousands of companies currently relying on Safe Harbor, getting everything sorted out is likely to be a long and messy process. Max Schrems -- who instigated the initial case against Facebook in Ireland -- said:
I very much welcome the judgment of the Court, which will hopefully be a milestone when it comes to online privacy. This judgment draws a clear line. It clarifies that mass surveillance violates our fundamental rights. Reasonable legal redress must be possible. This decision is a major blow for US global surveillance that heavily relies on private partners. The judgment makes it clear that US businesses cannot simply aid US espionage efforts in violation of European fundamental rights.
Photo credit: Ton Snoei / Shutterstock
-

EFF joins Nameless Coalition and demands that Facebook kills its real names policy
Publié: octobre 6, 2015, 1:16am CEST par Mark Wilson

Facebook has come under heavy criticism for its real names (or 'authentic identities' as they are known to the social network) policy. Over the last year, all manner of rights groups and advocates have tried to convince Facebook to allow users to drop their real name in favor of a pseudonym if they want.
Now the Electronic Frontier Foundation is part of the 74-member strong Nameless Coalition and has written to Facebook demanding a rethink on the ground of safety, privacy, and equality. This is far from being the first time Facebook has been called on to allow the use of 'fake names', and the latest letter is signed by LGBT groups, freedom advocates, privacy supporters, and feminist organizations.
The coalition has sent a letter to the social network calling on Facebook to "fix its broken 'authentic identity' (commonly known as 'real name') policy" and to "provide equal treatment and protection for all who use and depend on Facebook as a central platform for online expression and communication".
The letter makes reference to several groups of people who might have entirely legitimate reasons for wanting to use something other than their legal name. This includes transgender Facebook users, people avoiding harassment, and people from cultures where naming conventions are different to what Facebook perceives as the norm. The coalition goes further, accusing Facebook of placing users in danger by forcing them to use their real names online.
Despite commitments to reform these policies, Facebook maintains a system that disregards the circumstances of users in countries with low levels of internet penetration, exposes its users to danger, disrespects the identities of its users, and curtails free speech.
It also points out that Facebook's reporting mechanism is open to abuse. Those reporting others for not using a real name are not required to provide supporting evidence, effectively giving people the power to silence others. The Nameless Coalition says that Facebook is violating European data protection laws and calls for the social network to respond to a list of demands by the end of the month:
- Commit to allowing pseudonyms and non-legal names on its site in appropriate circumstances, including but not limited to situations where using an every day name would put a user in danger, or situations where local law requires the ability to use pseudonyms.
- Require users filing real name policy abuse reports to support their claims with evidence. This could come in written form, multiple-choice questions, or some alternative documentation.
- Create a compliance process through which users can confirm their identities without submitting government ID. This could include allowing users to submit written evidence, answer multiple-choice questions, or provide alternative documentation such as links to blog posts or other online platforms where they use the same identity.
- Give users technical details and documentation on the process of submitting identity information such as where and how it is stored, for how long, and who can access it. Provide users with the ability to submit this information using PGP or another common form of encrypted communication, so they may protect their identity information during the submission process.
- Provide a robust appeals process for users locked out of their accounts. This could include the ability to request a second review, to submit different types of evidence, and to speak to a real Facebook employee, especially in cases involving safety.
If you agree with EFF and the other members of the coalition, you can sign the petition to show your support.
Photo credit: dolphfyn / Shutterstock
-

Snowden says GCHQ's Smurf programs can tap, hack, and control any smartphone
Publié: octobre 5, 2015, 11:28pm CEST par Mark Wilson

In an interview with BBC Panorama, Edward Snowden made further revelations about the capabilities of government agencies. Having blown the whistle on the NSA, Snowden has also shed light on the activities of the UK equivalent, GCHQ.
In tonight's interview, the former NSA contractor spoke of the agency's "Smurf Suite" -- a collection of tools that can be used to intercept and control smartphones, even if they're turned off. Named after the blue cartoon characters, the Smurf tools can be deployed via encrypted text message without alerting the handset owner.
Snowden spoke of a trio of tools including Tracker Smurf. Talking to journalist Peter Taylor, he described this as a "geo-location tool which allows [GCHQ] to follow you with a greater precision than you would get from the typical triangulation of cellphone towers". If the ability to follow your movements is not creepy enough, it gets worse. Nosey Smurf is the tool that can be used to turn on a phone's microphone, making it possible to listen to everything that is said.
But don't think for one minute that you can avoid detection by simply turning off your phone -- if only it was that easy! Edward Snowden also revealed the existence of Dreamy Smurf, a "power management tool" that can be used to remotely switch on a phone to allow other other tools to do their job. It doesn’t end there. Once in the control of GCHQ, agents are able to see:
...who you call, what you've texted, the things you've browsed, the list of your contacts, the places you've been, the wireless networks that your phone is associated with. And they can do much more. They can photograph you.
These sorts of tools are supposedly used once mass data collection has made it possible to home in on a suspect. You might be accused of being paranoid if you were to suggest that the government was reading your messages, but Snowden has a chilling warning: "They say, and in many cases this is true, that they're not going to read your email, for example, but they can and if they did you would never know".
-

Edward Snowden would be willing to go to jail... if the US government would speak to him
Publié: octobre 5, 2015, 7:00pm CEST par Mark Wilson

Currently in exile in Russia, Edward Snowden recently joined Twitter to give him a public platform to communication with the world. With global interest in surveillance and privacy, the NSA whistleblower still conducts TV and newspaper interviews, and in a BBC interview he reveals that he would be willing to serve prison time.
He has even offered his freedom to the US government... but no one has responded to him. Praised and vilified in just about equal measure, Snowden faces prosecution under the Espionage Act for leaking documents about the activities of the NSA.
He runs the risk of a life sentence if he returns to the US, but while the US government sees him as an enfant terrible, he has built up a large group of vocal supporters who welcome the fact that he blew the lid off what was happening. The leaks Snowden made were not only embarrassing for the government, but the ensuing debate has made surveillance a hot topic that politicians have not been able to simply sweep under the carpet.
There are many people -- both in government and the public -- who would like to see Snowden behind bars. And he's fine with that:
I've volunteered to go to prison with the government many times. What I won’t do is I won’t serve as a deterrent to people trying to do the right thing in difficult situations [...] We are still waiting for them to call us back.
It is possible that such a public interview will light up Snowden on the US government's radar, and it may now jump on the offer of incarceration.
-

As fulltime CEO, Jack Dorsey wants to make Twitter 'great' and impact the world
Publié: octobre 5, 2015, 6:06pm CEST par Mark Wilson

He has been interim CEO for some time now, but today Jack Dorsey has been officially appointed as CEO of Twitter. Three months after Dick Costolo stepped down from the role, Dorsey is now the head of not only Square, but also Twitter, bringing to an end months of rumor and speculation.
As one of the founders of the company, Dorsey has an unrivalled knowledge of where Twitter comes from, what is at its heart, and where it should be heading. The board of Twitter is due for an overhaul, and one of the first announcements is the appointment of Adam Bain as COO, but there are almost certainly more exciting announcements on the horizon.
An SEC filing says that "Mr. Dorsey was selected to serve on the Board because of the perspective and experience he brings as one of Twitter's founders and as one of Twitter’s largest stockholders, as well as his extensive experience with technology companies". Dorsey publicized his new permanent position, of course, via Twitter:
We are naming @adambain COO of Twitter, we're working to change the composition of our Board, and I will serve as CEO of Twitter and Square!
— Jack (@jack) October 5, 2015
Speaking of the workers he heads at Twitter and Square, Dorsey said "I have the smartest, strongest, and most determined leaders in the world on my teams". He went on to set out Twitter's raison d'être:
Twitter stands for freedom of expression. We stand for speaking truth to power. And we stand for empowering dialogue [...] Twitter is the most powerful communications tool of our time. It shows everything the world is saying rn…10-15 minutes before anything else.
Looking to the future, he says: "We're working hard at Twitter to focus our roadmap on a few things we can make really great. And we're strengthening our team along the way", expressing the desire to make the service easy for everyone in the world to understand.
What happens next? For now, it's business as usual. We'll have to wait a little while to see if and when Dorsey gives the go-ahead for tweets with more than 140 characters.
Photo credit: tanuha2001 / Shutterstock
-

How to stop Windows 10 messing up your drivers
Publié: octobre 5, 2015, 1:10pm CEST par Mark Wilson

The update process in Windows 10 has proved controversial. There was upset at the fact that updates are not optional, and this in turn led to driver updates breaking people's computers.
We have already looked at the steps you can take to stop Windows 10 installing automatic updates, but what about if you want to keep Windows 10 up to date while retaining manual control of when drivers are updated? Read on to find out how to stop Windows 10 messing up your drivers.
Right-click the Start button and select the Control Panel entry in the context menu. Open the System applet and then click the Advanced system settings link to the left. On the System Properties dialog that appears, move to the Hardware tab and then click the Device Installation Settings button.
You'll be asked "do you want Windows to download driver software and realistic icons for your devices?" -- select the No, let me choose what to do option. A new subset of options will appear, and you just need to select the one labeled Never install driver software from Windows Update before clicking Save Changes.
That's all there is to it -- you'll have to manually check for and install driver updates from this point forward.
Photo credit: Anton Watman / Shutterstock
-

Leaked Windows 10 Build 10558 has new features that you might actually be interested in
Publié: octobre 4, 2015, 1:56pm CEST par Mark Wilson
It seems like it has been a while since there was a new build of Windows 10 -- official or leaked -- but Wzor has come up with the goods once again. This time around we are treated to a leak of Windows 10 Build 10558 and Microsoft has added new goodies and changed a few things, making this one of the most interesting Windows 10 builds in ages.
There are some cosmetic changes here and there, but the addition of new apps -- such as Microsoft Phone -- shows that progress is being made as we move towards Threshold 2. As well as updates to the operating system itself, there are also important changes to Microsoft Edge.
Before you get too excited about updates to Edge, the browser still does not support extensions; you'll just have to wait a little longer for this. But what's new are tab previews allowing you to keep an eye on what's happening in other tabs without actually having to switch to them. Other notable changes include tweaks to the download manager, while developers and the curious also have a dockable Developer Tools window to play with.
In Windows itself, context menus -- which have become a mish-mash of styles in recent times -- have been updated to make them slightly smaller, but it is the addition of new apps (Skype Messaging, Skype Video, and Microsoft Phone) which is perhaps the most interesting aspect of this new build. It demonstrates the importance Microsoft is placing on communication, but also the drive to integrate with Windows 10 on mobile devices.
This build also sees the return of the ability to save apps to SD cards or drives other than the Windows installation partition. While this is not something that everyone will make use of, it will appeal to tablet users. Enterprise users now have access to the Spotlight feature. Other changes include a new Registry Editor icon as well as other revamped icons here and there.
As Microsoft is not in the habit of promoting new builds before they are available, there is no way of telling if Build 10558 will make it to the Fast Ring. If you want to risk it in the meantime, you probably know what to do.
Photo credit: WZor
-

Teardowns show iPhone 6s is more waterproof -- and get iFixit app pulled from the App Store
Publié: octobre 3, 2015, 6:49pm CEST par Mark Wilson

For the curious-minded, iFixit is an essential resource. The hardware teardowns on the site have become legendary, revealing the innards of the latest and greatest phones and tablets better than anyone else. Two recent iFixit teardowns have had interesting results.
Following the release of the iPhone 6s and iPhone 6s Plus, analysis of the internals suggested that the handsets would be more waterproof than previous models -- not something Apple has shouted about. But the outcome of the Apple TV and Siri Remote teardowns were rather less pleasing for the site: they resulted in the iFixit app being pulled from the App Store. By Apple.
It goes without saying that ripping apart a phone or tablet will invalidate its warranty -- but if you want to do it, that's entirely up to you. When it comes to dismantling developer preview hardware, however, it's a slightly different story. In taking apart preview developer models of the Siri Remote and Apple TV, iFixit rather irritated Apple. So much so that the company decided to get revenge by delisting the iFixit app from the App Store. The famous deconstructors say:
We weighed the risks, blithely tossed those risks over our shoulder, and tore down the Apple TV anyway.
A few days later, we got an email from Apple informing us that we violated their terms and conditions -- and the offending developer account had been banned. Unfortunately, iFixit's app was tied to that same account, so Apple pulled the app as well. Their justification was that we had taken "actions that may hinder the performance or intended use of the App Store, B2B Program, or the Program."
Oops!
Of course this did nothing to deter iFixit from ripping apart more hardware. In the iPhone 6s and 6s Plus teardowns, a 'mystery adhesive' was found holding the screen in place, in addition to screws. But the suspicion was that this was less about sticking the screen to the front of the phone, and more about keeping water out. Further investigation revealed that every single connector on the logic board was covered with a silicone seal (as iFixit notes Apple filed a patent for waterproof silicon seals earlier in the year).
Some brave souls have tried giving their trusty phones the dunk test. Some suffered water damage, but the general consensus is that there is an improvement in waterproofing. You might not want to take your iPhone 6s swimming just yet, but perhaps you could be less worried about water splashes; the chances are it will be fine.
Check out iFixit's video to see what the inside of the new iPhone looks like, and to hear more about the claims of extra waterproofing:
-

Microsoft buys game physics company Havok from Intel
Publié: octobre 3, 2015, 3:08pm CEST par Mark Wilson

Microsoft seems to be placing increased importance on gaming. The latest in its list of acquisitions is game physics company Havoc which has been bought from Intel for an undisclosed fee. Used in titles such as Assassins Creed, Call of Duty, and Halo, Havoc's physics and AI solutions will be an important weapon in Microsoft's gaming arsenal alongside DirectX 12.
Announcing the acquisition, Microsoft says it will "work with developers to create great gaming experiences, and continue to license Havok's development tools to partners".
Neither Microsoft nor Havok has released details of the financial arrangement, and we don’t yet know what the acquisition means for current Havok employees. As well as gaming, it is easy to foresee Havok's technology being implemented in Hololens. Looking to the future, Microsoft says:
Microsoft's acquisition of Havok continues our tradition of empowering developers by providing them with the tools to unleash their creativity to the world. We will continue to innovate for the benefit of development partners. Part of this innovation will include building the most complete cloud service, which we've just started to show through games like Crackdown 3.
Havok shares Microsoft's vision for empowering people to create worlds and experiences that have never been seen before, and we look forward to sharing more of this vision in the near future.
-

Future laptops could optimize battery life by learning your usage patterns
Publié: octobre 3, 2015, 2:36pm CEST par Mark Wilson

There's one thing that everybody looks for in a mobile device -- long battery life. There are constant promises of technological breakthroughs that are just around the corner, but rather than waiting for these to come to fruition, Microsoft researchers have decided to come up with a different solution.
Instead of using a new battery type, Microsoft Research workers have devised a system that using currently available battery technology in conjunction with smarter software. Known as Software Defined Batteries, the system uses multiple batteries, and management software is used to pick the most suitable power source depending on the task that is being performed.
The researchers working on the project will give a presentation at the ACM Symposium on Operating Systems Principles this coming week, but have already published a paper explaining that the system "exposes APIs to the operating system which control the amount of charge flowing in and out of each battery, enabling it to dynamically trade one battery property for another depending on application and/or user needs".
What this means in practice is that a system will include several batteries, each optimized for a particular task. The usage, discharge, and charging of each battery will be controlled by software and determined by what the computer is being used for. For example, one battery might be used when graphic-heavy tasks such as gaming or video editing are under way, while another is responsible for powering the computer when browsing the web. But a key feature of Software Defined Batteries is learning how a computer is used:
For example, the system may recognize that the user plugs in the tablet every day around 2:45 p.m., and then gives a long PowerPoint presentation every day at 3 p.m. That means the computer needs to be ready to do quick charge at that time, so the person can make it through that afternoon meeting.
Another user may use the computer primarily for e-mail and Word documents during the day, then switch to surfing the web and watching videos on a train or bus commute home. Based on those habits, the computer can optimize the charge to make sure the user can do both without having to search desperately for an outlet.
Prototypes have already been produced, and it is hoped that it won’t be long before the software-controlled, multiple-battery idea is adopted by laptop and tablet manufacturers. But the potential goes further. The researchers believe that the technology could be used in wearable devices to share power duties between a traditional Li-ion battery and flexible battery built into, say, the strap of a smartwatch. This would allow for a smaller battery to be used in the main body of the watch, meaning that thickness and bulk can be reduced.
Photo credit: Adisorn Saovadee / Shutterstock
-

Developers can now respond to reviews in the Chrome Web Store
Publié: octobre 2, 2015, 11:04am CEST par Mark Wilson

Reviews can be an important factor in deciding which app or extension to install. The idea of user reviews is something that has been adopted by Apple in its App Store, and is also used by Microsoft and in Google Play. The Chrome Web Store also features reviews, and a new feature has just been added that could make them more useful than ever -- the ability for developers to respond.
This is an important change as it gives developers the right of reply. When reading a review written by someone you almost certainly don't know, it can be hard to tell if their opinion should be trusted. Did they rate the app or extension poorly because there is a problem with it, or did they not understand how to do something. Giving developers the chance to reply to reviews allows for greater transparency and allows others to see that the developer in question is reading feedback -- but it may not all be good news.
As with any online posting arena, there is endless scope for trolling. Adding the right to reply will do little to eliminate the unnecessarily harsh reviews that are frequently posted out of sheer spite. But by presenting both sides of the discussion, others are given the opportunity to make a judgment call of their own.
In a post on the Chromium blog, Google says:
To strengthen relationships with your users and ensure that the Reviews tab provides accurate information about your product, we recommend that you begin closely monitoring user reviews for bug reports and feature suggestions. Be sure to reply constructively to both negative and positive reviews, notify users when you have addressed their feedback, and thank the users who are your biggest advocates.
Judging from the feedback so far, it seems that developers are happy the feature has finally been introduced, and users will almost certainly be pleased that a two-way communication channel has now been opened up.
Photo credit: 360b / Shutterstock
-

Amazon to cease sale of Apple TV and Chromecast
Publié: octobre 1, 2015, 8:38pm CEST par Mark Wilson

As of 29 October, shoppers will no longer be able to buy Apple TV or Chromecast devices from Amazon. Citing compatibility issues with Prime Video, Amazon emailed marketplace sellers to inform them it is not accepting new listings for the two media devices, and any existing listings will be removed at the end of October.
The move indicates not only the importance Amazon places on its streaming Prime Video service, but also that it views Apple and Google as serious rivals. The two companies have yet to respond to the news, but it is unlikely to be well-received.
Questions are already being raised about why Amazon has not gone to the trouble of producing dedicated Prime Video apps for Apple TV and Chromecast. The cynical assumption would be that this is a move to push its own Fire TV, and to show support for other players on the market.
The email says:
Over the last three years, Prime Video has become an important part of Prime. It's important that the streaming media players we sell interact well with Prime Video in order to avoid customer confusion. Roku, Xbox, PlayStation and Fire TV are excellent choices.
The announcement comes just days after Google announced a second generation Chromecast as well as a new Chromecast Audio device.
Photo credit: Yeamake / Shutterstock
-

Samsung hits back at claims that its TVs perform better in tests than in homes
Publié: octobre 1, 2015, 2:16pm CEST par Mark Wilson

Samsung has denied claims made by The Guardian that its TVs have a special power saving mode which is only used in laboratory testing to give the impression of better energy efficiency. The Guardian reports that independent labs have found Samsung televisions use less power in official testing than in real-world scenarios.
This prompted suspicions -- that echo the allegations levelled at car manufacturer VW -- that TVs have been rigged to perform better in energy efficiency tests. The European commission has promised to investigate any claims of cheating the system, but Samsung is adamant it has done nothing wrong, saying "we firmly reject this suggestion".
The "motion lighting" feature of Samsung TVs is at the heart of the controversy. The feature allows for the automatic adjustment of screen brightness depending on the type of content being displayed. Research group ComplianTV found that in real-world situations, the power-reducing features seen in the labs were not activated. The Guardian says, guardedly:
There is no suggestion that Samsung, the world’s biggest TV manufacturer, behaved illegally, although energy efficiency campaigners claim that EU testing procedures are overly generous.
Samsung has issued a strongly-worded statement that denies any suggestion of wrong-doing or playing the system:
Motion lighting is not a test-cheat
Motion lighting is not a setting that only activates during compliance testing. On the contrary, it is a default setting which works both in the lab and at home; delivering energy savings and helping us to reduce our environmental impact.
Motion lighting was introduced in 2011 across all our TVs as part of a range of features we have developed to help reduce the environmental impact of our TV technology. We are immensely proud of these technologies and look forward to innovating further in this area.
If the customer chooses to alter their display settings or switch to a different mode then the feature switches off, which gives our customers a simple choice of whether they choose to prioritize power efficiency or performance in their TV. The setting is explained in all of our instruction manuals, and also features on our website.
Photo credit: Sorbis / Shutterstock
-

LG V10 flagship boasts two screens and three cameras
Publié: octobre 1, 2015, 11:17am CEST par Mark Wilson
In addition to the LG Watch Urbane 2nd Edition, today LG also announces its V10 Android phone with a secondary display. This is the device we got a sneak peek at a few days ago and, like the Huawei-made Nexus 6P, this is a premium level handset with a full metal body which builds on the specifications of the G4.
But the LG V10's standout feature is its secondary screen. In addition to the main 5.7-inch display, there is a second, narrow screen at the top of the handset that can be used not only to display notifications, but also to house shortcuts. This is not the only surprise on the front of the phone -- there are also two cameras.
With a removable battery and expandable memory, the LG V10 gets off to a great start, but it is the Galaxy Note Edge-aping extra screen that is the real attention-grabber. This smaller display is always on. When the main display is asleep, it is used to display notifications; when it is awake, it is used for shortcuts and notifications.
Described as offering a new multimedia experience, the V10's three camera make for a unique experience. LG says that the wide angle lens makes it easy to take group selfies, while "multi-view Recording can capture different angles utilizing all three cameras". The handset is also touted at the first to offer a manual mode for video; it is possible to record in HD, FHD, or UHD and 16:9 standard or 21:9 cinematic aspect ratios.
It's not clear when the phone will launch, but it is destined for South Korea later this month, and is due for release in the US, China, and other countries after this.
The LG V10 will be available in Space Black, Luxe White, Modern Beige, Ocean Blue, Opal Blue, and boasts the following specs:
Chipset: Qualcomm Snapdragon 808 Processor
Display: Main -- 5.7-inch QHD IPS Quantum Display (2560 x 1440 / 513ppi), Secondary -- 2.1-inch IPS Quantum Display (160 x 1040 / 513ppi)
Memory: 4GB LPDDR3 RAM / 64GB eMMC ROM / microSD (up to 2TB)
Camera: Rear -- 16MP with F1.8 Aperture / OIS 2.0 Front -- 5MP Dual Lens (80 degree Standard Angle / 120 degree Wide Angle)
Battery: 3,000mAh (removable)
OS: Android 5.1.1 Lollipop
Size: 159.6 x 79.3 x 8.6mm
Weight: 192g
Network: LTE-A Cat. 6
Connectivity: Wi-Fi 802.11 a, b, g, n, ac / Bluetooth 4.1 / NFC / USB 2.0
LG has also published a product video showcasing the V10:
-

LG Watch Urbane 2nd Edition is the first Android Wear smartwatch with cellular connectivity
Publié: octobre 1, 2015, 10:34am CEST par Mark Wilson

The smartwatch wars are heating up, and LG is sending out new troops. Today the company announces the LG Watch Urbane 2nd Edition -- the first Android Wear smartwatch that offers LTE/3G connectivity.
LG describes the latest wearable as 'breaking the limits of a watch', and with the prospect of making phone-free calls with the Watch Urbane 2nd Edition, this would seem to be a fair description. The watch is compatible with iOS and Android, but it is the fact that it can be used on its own that is its real selling point.
The Watch Urbane 2nd Edition has a look that will appeal to anyone who yearns for a smartwatch with the appearance of a traditional timepiece. A larger than average battery should allow for all day usage. There's no word on pricing yet, but LG says that the watch will initially launch in the United States and Korea, before spreading to Europe, CIS, Asia, and the Middle East.
Available in Space Black, Opal Blue, Luxe White, and Signature Brown, the LG Watch Urbane 2nd Edition offers IP67 dust and water resistance, and boasts the following specs:
Chipset: 1.2GHz Qualcomm SnapdragonTM 400
Operating System: Android WearTM (Cell-connected Version)
Display: 1.38-inch P-OLED Display (480 x 480 / 348ppi)
Size: 44.5 x 14.2mm
Memory: 4GB eMMC / 768MB LPDDR3
Battery: 570mAh
Network: Bluetooth 4.1 / Wi-Fi / LTE / 3G
Sensors: Accelerometer / Gyro / Compass / Barometer / PPG / GPS
Check out the official product video:
-

Microsoft and Google drop patent battles and agree to work together
Publié: octobre 1, 2015, 10:17am CEST par Mark Wilson

These days, patent lawsuits are ten a penny and big players like Google, Apple, and Microsoft are frequently involved in litigation. Out of the blue, Microsoft and Google have announced that they are burying the hatchet and will no longer pursue patent issues between themselves in the courtroom.
But more than just kissing and making up, the two companies have announced that they will "collaborate on certain patent matters". Quite what this mean moving forward remains to be seen, but it could mean that there are some interesting joint ventures on the horizon.
There have been some bitter fights between Microsoft and Google over the years, but while the newly announced truce brings to an end any current lawsuits, there are no guarantees that the two companies won't do battle again at some point in the future.
In a joint statement, the two companies said:
Microsoft and Google are pleased to announce an agreement on patent issues. As part of the agreement, the companies will dismiss all pending patent infringement litigation between them, including cases related to Motorola Mobility. Separately, Google and Microsoft have agreed to collaborate on certain patent matters and anticipate working together in other areas in the future to benefit our customers.
Photo credit: Tashatuvango / Shutterstock
-

Facebook reveals mobile profile overhaul including video profile pictures
Publié: septembre 30, 2015, 9:30pm CEST par Mark Wilson
Facebook today announced a series of updates to user profiles on mobile devices, and one of the first candidates for a revamp is the humble profile picture. There are a couple of interesting options to play with, including temporary profile pictures that change after a certain number of days.
This is an idea that was born from the popularity of banners which Facebook users added to their profile pictures to show support for a particular cause. Also in the pipeline are profile videos, which Facebook says will "add a new dimension to your profile". Forget static images, a looping video clip is now an option. But the profile updates don’t end there -- and, oddly, iPhone users are first in line to try out the new goodies.
Profiles are getting something of a redesign. Profile pictures are not only larger, but also centered, and Facebook now brings photos and friends to the top of the page when you visit someone else's profile. Privacy will never fail to be a concern for Facebook users, and the latest round of updates makes it easier to control what is publically visible.
At the top of your profile is a new area populated with information about you, and you can choose which fields are shared with the world. There's a new single-line bio field and it's now possible to add up to five featured photos to your profile for all to see.
We mentioned that iPhone users get to try things first. Facebook says:
We’re starting to test all of these features to a small number of iPhone users in the UK and California, and we’ll be rolling them out to more people soon.
-

OS X Gatekeeper rendered useless by new malware exploit
Publié: septembre 30, 2015, 5:27pm CEST par Mark Wilson

On the day that Apple releases El Capitan details of an exploit that makes it possible to bypass the Gatekeeper feature of OS X have emerged. Designed to combat various forms of malware, the security feature can be bypassed using a simple trick involving the use of a signed binary.
Even when Gatekeeper is configured to use its highest level of protection, the ease with which the fortifications can be slipped through is staggering. Using a file that has already been deemed trustworthy by Apple, it is possible to trick OS X into executing a malicious file stored in the same folder as the signed one. No patch is yet available, and it is believed the problem affects all versions of OS X.
The vulnerability was discovered by security researcher Patrick Wardle from Synack. Talking to Threatpost, he explains that he has already shared his findings with Apple but the company is yet to produce a patch. Wardle found that Gatekeeper, while checking for authentication of files from Apple, failed to determine whether apps make calls on other apps or code that have not been signed.
Once an app has been given the go-ahead by Gatekeeper, it is free to execute whatever code it wants on the computer, and this is precisely how the exploit works. Users could be easily tricked into executing a signed, infected file that could wreak untold damage. Wardle says:
It's not super complicated, but it effectively completely bypasses Gatekeeper. This provides hackers the ability to go back to their old tricks of infecting users via Trojans, rogue AV scams or infect applications on Pirate Bay. More worrisome to me is this would allow more sophisticated adversaries to have network access. Nation states with higher level access, they see insecure downloads, they can swap in this legitimate Apple binary and this malicious binary as well and man-in-the-middle the attack and Gatekeeper won’t protect users from it anymore.
The issue is not being described as a bug, but as a limitation of Gatekeeper. A fix could take some time to appear as Wardle warns that it would require "significant code changes" to OS X.
Photo credit: khd / Shutterstock
-

Disable Wi-Fi Assist in iOS 9 to reduce data usage and cut your bill
Publié: septembre 30, 2015, 4:02pm CEST par Mark Wilson

We all demand to be connected at all times; losing connection to the internet is like losing a limb for some people. With this in mind, handset manufacturers have taken it upon themselves to introduce technologies that ensure as stable a connection as possible, switching between Wi-Fi and cellular as and when necessary.
It's something that can be found in iOS 9, but many people who have made the upgrade to the latest version of the operating system, or have just taken delivery of a new iPhone 6s or iPhone 6s Plus, have been taken by surprise by it. The reason? iOS 9 has a feature called Wi-Fi Assist which will automatically switch to a cellular connection when Wi-Fi signal is weak, and it has led to a massive increase in data usage for some people. The solution to hefty data bills? Disable the feature.
SEE ALSO: Stupid iOS 9 bug makes me regret buying an iPhone 6s
If you're lucky enough to have an unlimited data package for your phone, increased cellular usage may not concern you in the slightest. But if you have a limit to stick to, disabling Wi-Fi Assist could help to dramatically reduce your monthly bills. Imagine the scenario. You're watching a lengthy video on YouTube and your Wi-Fi signal drops out for some reason. To avoid interrupting your viewing, Wi-Fi Assist automatically starts to make use of your data connection; big bill time!
Although the feature is enabled by default, you can -- thankfully -- disable it:
- Open Settings.
- Tap Cellular.
- Locate the Wi-Fi Assist option and move the slider to the Off position.
Had you noticed an increase in data usage in iOS 9?
Photo credit: Ollyy / Shutterstock
-

AdBlock Plus to introduce independent board to oversee Acceptable Ads program
Publié: septembre 30, 2015, 2:10pm CEST par Mark Wilson

Ad blocking has been in the news quite a lot recently, not least because of iOS 9's new support for advertising avoidance. Perhaps the most famous tool in the arena is Adblock Plus. It's something that many people have become reliant on for cleaning up their online experience but Eyeo -- the company behind AdBlock Plus -- has been keen to encourage people to permit the display of some advertising through its Acceptable Ads program.
That companies can pay to bypass Adblock Plus is nothing new, although Adblock Plus insists that most ads that are deemed 'acceptable' are added for free. Today Eyeo announces that it is going to hand over control of the Acceptable Ads program to a completely independent board.
Details of how the board will be formed and appointed have not been disclosed, but Eyeo insists that the entire process -- and the vetting of ads -- will be fully transparent. Despite this transparency, we will never learn which companies are paying to be included on the whitelist, although it is worth noting that Eyeo says that any money that changes hands is for "administration costs and not for whitelisting". Defending the fact that details of payments will not be revealed, it went on to say that many of the companies it works with have "non-disclosure contracts that prevent Adblock Plus from identifying exactly who they are and how much they pay".
Till Faida, co-founder of Adblock Plus, said:
The Acceptable Ads program has been managed in an open and public forum. Users determined the original criteria and can object in our forum to whitelisting proposals, but since we were the only ad blocker to offer such a compromise we have taken on a large role in the day-to-day maintenance of the criteria. We have been looking for a way to make the Acceptable Ads program completely independent while also updating the criteria to evolve with changing forms of online advertising. An independent board solves both issues.
It's a move that remains controversial, and it will be interesting to see just how the implementation works in practice.
Photo Credit: Quka/Shutterstock
-

Come on... stop falling for these stupid Facebook hoaxes
Publié: septembre 29, 2015, 5:50pm CEST par Mark Wilson

Driven as it is by users, it is perhaps little surprise that Facebook is home to a lot of nonsense. Nothing wrong with this, but it becomes more of an issue when nonsense is disguised as something meaningful and is shared by people left, right, and center. Hoax copyright warnings spreading via statuses is a perennial problem, and there are a couple of prime examples doing the rounds at the moment.
You've probably seen at least one of them before, but the pair seem to be cropping up a great deal this time around. Should you see your friends posting 'helpful' advice about paying to make your Facebook profile private, or how to assert your copyright so Facebook can’t use your images, just remember that they are rubbish. Facebook seems to find it funny, though, and has responded in a slightly humorous fashion.
The problem with social networks is that it is incredibly easy for something to go viral. It just takes a couple of gullible people to post something, for it to be shared by a few more for a joke, and before you know it, the hoax has spread like wild fire. One of the hoaxes suggests that Facebook allows you to make your profile private (for some reason) in exchange for payment, but by copying and pasting text into your status, you can avoid the fee:
Now it's official! It has been published in the media. Facebook has just released the entry price: £5.99 to keep the subscription of your status to be set to "private". If you paste this message on your page, it will be offered free (I said paste not share) if not tomorrow, all your posts can become public. Even the messages that have been deleted or the photos not allowed. After all, it does not cost anything for a simple copy and paste. (Not worth risking it!)
Nonsense.
The other has done the rounds many, many times now:
As of September 28th, 2015 at 10:50 pm, I do not give Facebook or any entities associated with Facebook permission to use my pictures, information, or posts, both past and future. By this statement, I give notice to Facebook it is strictly forbidden to disclose, copy, distribute, or take any other action against me based on this profile and/or its contents.
The content of this profile is private and confidential information... NOTE: Facebook is now a public entity. All members must post a note like this.
If you prefer, you can copy and paste this version. If you do not publish a statement at least once it will be tactically allowing the use of your photos, as well as the information contained in the profile status updates.
Utter nonsense.
Facebook has responded lightheartedly, making reference to NASA's announcement about the discovery of water on Mars:
While there may be water on Mars, don't believe everything you read on the internet today. Facebook is free and it always will be. And the thing about copying and pasting a legal notice is just a hoax. Stay safe out there Earthlings!
Appropriate response, or do you think Facebook should be taking things more seriously? Either way, don't fall for the hoaxes yourself.
Photo credit: albund / Shutterstock
-

Apple publishes praiseworthy, plain-speaking privacy policies
Publié: septembre 29, 2015, 4:51pm CEST par Mark Wilson

Perhaps inspired by the backlash Microsoft has faced over privacy concerns in Windows 10, Apple has published its own privacy policies on a new page that's designed to be easy to read. Written in plain English, the site sets out Apple's position regarding privacy in OS X and iOS. As well as touting the steps to which the company goes to protect its customers' privacy, Apple also uses the documents to trumpet numerous security features.
This is Apple riding the waves of interest concerning privacy, using it as an opportunity to get one over the likes of Microsoft and Google. There are promises of "telling you up front exactly what’s going to happen to your personal information and asking for your permission" as well as the offer that "if you change your mind later, we make it easy to stop sharing with us". Sounds great in theory, but does it stand up to scrutiny?
Apple does not have an untainted record when it comes to security, the Fappening breach of celebrity iCloud accounts being a case in point. Steps have been taken to tighten the locks after this problem, and although the company is pushing its new privacy policy, it uses it to push security features as well -- although they are referred to in the context of privacy. Few people would think of issues with Apple Pay to be a privacy issue rather than a security problem, but Apple makes reference to its payment system when it asserts "we build privacy into everything we make".
When it talks about encryption, the company says that it "refuse[s] to add a backdoor into any of our products because that undermines the protections we’ve built in", going on to explain that encryption is such that Apple itself is not able to decrypt data from individual devices. Returning to Apple Pay, the company admits that "approximate time and location" may be stored in relation to transactions, but assures users that encryption means that information cannot be connected to an individual in an identifiable way.
Apple takes a leaf out of Microsoft's Google-baiting when it talks about iMessage and FaceTime:
Unlike other companies’ messaging services, Apple doesn't scan your communications, and we wouldn't be able to comply with a wiretap order even if we wanted to.
Like Microsoft's Cortana, Apple's Siri makes use of real world data from real world users to help improve the service. For anyone concerned about the encryption and anonymizing Apple uses when transmitting this data, the company says:
Siri and Dictation do not associate this information with your Apple ID, but rather with your device through a random identifier. Apple Watch uses the Siri identifier from your iPhone. You can reset that identifier at any time by turning Siri and Dictation off and back on, effectively restarting your relationship with Siri and Dictation. When you turn Siri and Dictation off, Apple will delete the User Data associated with your Siri identifier, and the learning process will start all over again.
There's more prodding of Google when Apple talks about Maps:
Other companies try to build a profile about you using a complete history of everywhere you've been, usually because they're targeting you for advertisers. Since our business doesn’t depend on advertising, we have no interest in doing this -- and we couldn't even if we wanted to.
There is also an interesting revelation about how the data anonymization process works when using Maps for directions:
Maps is also engineered to separate the data about your trips -- including public transit directions -- into segments, to keep Apple or anyone else from putting together a complete picture of your travels. Helping you get from Point A to Point B matters a great deal to us, but knowing the history of all your Point A's and Point B's doesn't.
Apple is refreshing open about pointing users to directing users to the setting they need to be aware of to adjust their privacy settings. There's an obligatory section that talks about government data requests:
Apple has never worked with any government agency from any country to create a 'backdoor' in any of our products or services. We have also never allowed any government access to our servers. And we never will.
We learn that just 6 percent of data requests seek personal information about users, and that overall, less than 0.00673 percent of users have actually been affected by data requests.
Apple may not be doing much that's very different to other companies, but the key difference is the openness. There is a welcome level of transparency and accessibility to the new privacy policy, and it is something from which others could learn a lot.
Take a look at the privacy policies and see what you think. They might not be perfect, but they are a step in the right direction.
Photo credit: Ivelin Radkov / Shutterstock
-

Accepting Microsoft's Windows 10 privacy stance at face value is sheer folly
Publié: septembre 29, 2015, 12:23pm CEST par Mark Wilson

Yesterday, Microsoft's Terry Myerson defended how the company has handled privacy in Windows 10. The level of concern about privacy in Windows 10 is unprecedented -- it even has some torrent sites spooked -- but my colleague Brian feels that Microsoft has, somehow, earned our trust. He is wrong.
Microsoft has broken the trust of many users, and Myerson's post does little to patch things up. In reality, it is an exercise in public relations, spin, and misdirection. It also raises more questions than it answers. In particular, it highlights the obnoxious disregard Microsoft appears to have for home users.
On the subject of "safety and reliability data", Microsoft admits it "collect[s] a limited amount of information" which it stresses is anonymous. Myerson says: "we take several steps to avoid collecting any information that directly identifies you". Looked at from any angle, this is not the same as not collecting information that directly identified people. It might be a minor distinction, but it is an important one.
You may feel that anyone who is concerned about the collection of data to help improve operating system reliability must be paranoid or have something to hide. How about companies and businesses that feel the same? Enterprise customers need to be sure that security is completely locked down and entirely within in their control. To this end, Myerson reveals that: "our enterprise feature updates later this year will enable enterprise customers the option to disable this telemetry", adding "we strongly recommend against this" (but of course).
Now this is interesting. It raises the question of why home users and enterprise are treated differently in this area. Is it because there are privacy and security concerns for enterprise? If so, surely these apply to home users too. Your privacy and security is no less important than that of a bank, for example. Is Microsoft pandering to the legitimate concerns of enterprise customers because this is where the bulk of its income comes from? Why not treat home users with the same respect? They are no less important.
But Myerson's post is interesting for a number of other reasons as well. It fails to step into the shoes of the average user to understand how they would see things. There is a disconnect between Microsoft and its customers that is perfectly demonstrated by the company's apparent surprise at the reaction to the more secretive aspects of Windows 10.
The post also includes some spin trying to deflect from the issue by taking a swipe at Google:
Unlike some other platforms, no matter what privacy options you choose, neither Windows 10 nor any other Microsoft software scans the content of your email or other communications, or your files, in order to deliver targeted advertising to you.
Microsoft may as well stamp its feet and shout "look at the big, bad wolf over there!". There is further deflection from the issue of privacy -- which, remember, is supposed to be the subject of the post -- by trying to turn attention to how Microsoft uses feedback to bring new features to Windows 10. This is all well and good, but it has nothing to do with privacy. User-issued feedback and data gathered in the background are simply not the same thing.
There is also something else that is important to bear in mind. While the likes of you and I may be only too aware of what is happening with our computers, and we may keep fully up to date with what Microsoft is doing and how it is dealing with things, this is certainly not the case for the vast majority of people. Most people just use their computers. They might not care about privacy issues in Windows 10 because they know nothing about the issue. It may well be possible to disable the collection of various pieces of data, but if you don’t know that it is being collected in the first place, why would you even investigate this?
Microsoft is out of touch. Listening to the feedback of Windows Insiders is great, but the company needs to remember that this is not enough. Insiders are not representative of the entire user base of Windows 10. All users of Windows need to remember that accepting Microsoft's Windows 10 privacy stance at face value is sheer folly.
Photo Credit: rvlsoft / Shutterstock
-

Accept Apple Pay and Android Pay with the new PayPal Chip Card Reader
Publié: septembre 29, 2015, 11:20am CEST par Mark Wilson

PayPal Here users will be able to use the new PayPal Chip Card Reader to accept payments via Apple Pay and Android Pay, in addition to the more familiar credit and debit card options. The new reader launches in the US on 30 September, before spreading to the UK and Australia further down the line.
The updated card reader features a display to guide users through the process of making a payment, but it is the addition of contactless payment that is the key new feature. The PayPal Chip Card Reader has a price tag of $149, but some people will be able to get hold of it for $49.
Everyone buying the new PayPal Chip Card Reader will have to part with $149 initially, but anyone who processes $3,000 in a 3-month period is eligible for a $100 rebate. Either way, this is quite a price jump from the previous model, which many people were able to obtain for nothing.
PayPal points out that the day after the reader launches, 1 October, Mastercard and Visa will no longer cover fraudulent chip card transactions: "This means if you accept a chip card with a magnetic stripe reader, you'll be responsible for the cost if the transaction is fraudulent". This should be enough to push many merchants into upgrading to a reader that accepts cards with chips.
To find out more, sign up for PayPal Here, or to get hold of the new reader, head over to the PayPal website.
-

Silent Circle's Blackphone 2 is the most secure Android phone available
Publié: septembre 28, 2015, 1:43pm CEST par Mark Wilson
With all of the talk about the iPhone 6s and 6s Plus, and the likes of the Samsung Galaxy S6 edge+, it's easy to forget that there are some genuine alternatives out there. One such smartphone is the Blackphone from the privacy-centric Silent Circle. The original Blackphone caused great excitement, and now the Blackphone 2 is available
This is a phone that has been built from the ground up with security and privacy in mind. While the Blackphone 2 will appeal to anyone who is concerned about privacy, this time around there is a greater push to appeal to businesses and enterprise, including joining Google's Android for Work program. In terms of specs, opting for the most secure handset on the market does not mean making compromises: this phone is a beast.
Powered by a 1.7GHz Octa-core Qualcomm Snapdragon 615, the Blackphone 2 features 3GB RAM, 32GB of storage, and a microSD slot. There are 13 and 5MP cameras, a beefy Qualcomm Quick Charge 2.0-compatible 3060 mAh battery, a 5.5 inch 2560×1440 display, and the all-important Silent OS 2.0. Based on Lollipop, the operating system grants the user unprecedented control over privacy, security, and permissions, and an encrypted communication platform that is routed through an ultra-secure, cloud-based VPN.
The phone is shipped fully encrypted, and Silent Circle is able to push out updates to its custom operating system without having to wait for carriers to do so. Whether it is used by someone who is just paranoid, or a worker who needs to guarantee the security of communication, data storage, and app usage, the granular permission controls are a welcome change from the limited control offered by Android by default. Here Silent OS 2.0 analyzes the code of apps that are installed to determine everything it is capable of -- you are then given the opportunity to choose which of these you would like to permit.
Silent Circle has a brief video introducing the second iteration of the Blackphone:
Blackphone 2 is available now for $799. The device launches in North America, but will also spread to the UK and the rest of the world shortly.
-

Leaked documents show UK Karma Police program was just as intrusive as the NSA -- and spied on the US
Publié: septembre 26, 2015, 4:11pm CEST par Mark Wilson

There have been countless stories about the activities of the NSA and the revelations by Edward Snowden continue. A new batch of documents leaked by the former NSA contractor show that GCHQ ran a program called Karma Police that was used to "build a web-browsing profile for every visible user on the internet".
If that sounds a little sinister, that's because it is. You would think that we might have become hardened to this sort of thing, but it is still comes as a slight surprise to learn of the extent of surveillance that has been taking place. The UK government has been building profiles of web users around the world based on their browsing histories (news, porn, social networking, and so on), monitoring email and Skype communication and more for the last seven years.
The documents have been leaked to The Intercept, and they show that surveillance was generating massive quantities of data. By 2012, GCHQ was storing 50 billion metadata records per day and the plan was to increase this to 100 billion per day. One surveillance program was used to home in on people using internet-based radio stations to disseminate what are described as "radical Islamic ideas". Data gathered by Karma Police was used to identify individuals and see what other online activities they had engaged in.
Much like the NSA, GCHQ gathered data about everyone and anyone. By tapping into key internet cables, the agency was able to store more than 1.1 trillion pieces of data in Black Hole, it's huge information repository. In addition to browsing histories and communication logs, GCHQ also gathered information about people using tools to surf the web 'anonymously' and even looked into cookies.
The agency was -- and undoubtedly still is -- able to identify individuals using a series of interconnected systems; Karma Police was just part of the story. The complexity of the systems is such that a single piece of information is sufficient to home in on an individual and monitor them more closely. As pointed out by The Intercept, a solitary piece of information might not be particularly revealing, but that data acts as a key that unlocks much more.
And people wonder why there is a push for the adoption of encryption...
Photo credit: MaluStudio / Shutterstock
-

Internet.org app is dead, Free Basics from Facebook rises from the ashes
Publié: septembre 26, 2015, 11:43am CEST par Mark Wilson
The Internet.org project from Facebook has not been without controversy. Created with the aim of getting everyone in the world online, the program has been widely criticized and many partners pulled out. Now a rebranding has been unveiled for the mobile app and website.
With the launch of the Internet.org Platform, Facebook has taken the opportunity to rename the portal through which people can access a range of free services. Changing the name to Free Basics by Facebook is described as a way "to better distinguish the Internet.org initiative from the programs and services we’re providing", but it's hard not to think that it is also an attempt to move away from the controversy of Internet.org, and it comes ahead of serious push into India.
Providing access to "more than 60" free basic services, the lack of unfettered access to the internet is the source of many of the complaints levelled at the service. Moving the Free Basics label up into the name makes it clear that Facebook is not giving people unrestricted internet access -- something Mark Zuckerberg will surely hope will go some way to silence the criticism.
Free Basics from Facebook is available in 19 countries across Asia, Africa, and Latin America and in addition to the new name, the app and website now features a new menu that can be used to search for and add services. HTTPS support has been available in the Android app for a while, but it has now been added to the web version of Free Basics from Facebook as well.
The mobile web version of the service can be accessed at FreeBasics.com.
-

Facebook Notes transforms into a full-on blogging platform
Publié: septembre 26, 2015, 11:04am CEST par Mark Wilson
Heard of Facebook Notes? No? It's something that has been around for a while, and provides away to write longer posts, but for some reason it has been largely ignored by Facebook users. The latest update could mean that's about to change.
Seemingly looking to take on the likes of Medium and Blogger, Facebook Notes has been treated to a facelift that makes posts more attractive and introduces new customization options. While Notes used to be (understandably, to some extent) all about the text, now graphics and formatting are given greater prominence.
Just like your Facebook profile, Notes can now feature a cover photo at the top and a minimalist editor is on hand to help beautify your posts. In addition to the cover photo, the update means your post can be littered with any other images you want to include, and you can resize them from within the mini CMS so there's no need to fire up an image editor.
Text formatting options are limited, but all of the essentials are there -- heading, numbered and bulleted lists, pull quotes, and code blocks. As before, the Notes you create can be made public, private, or shared with a limited group of people.
If you're yet to try out Facebook Notes, there's never been a better time to do so -- this could be the start of something new for the social network.
-

Apple admits iCloud problem has killed iOS 9 'app slicing'
Publié: septembre 25, 2015, 12:20am CEST par Mark Wilson
One of the key features of iOS 9 -- and one of the reasons 16GB iPhones were not killed -- is app slicing. This innocuous-sounding feature reduces the amount of space apps take up on iPhones and iPads... or at least it does when it is working.
At the moment Apple has a problem with iCloud which is preventing app slicing from working correctly. The feature works by only downloading the components of an app that are needed to perform specific tasks on a particular device, but at the moment regular, universal apps are delivered by default.
Developers are still able to try out their app through TestFlight, but everyday App Store visitors will not be able to take advantage of this feature. Apple has not given any indication of when the problem might be fixed, but says that a fix is in the works.
In a blog post, the company says:
App slicing is currently unavailable for iOS 9 apps due to an issue affecting iCloud backups created from iOS 9 where some apps from the App Store would only restore to the same model of iOS device.
When a customer downloads your iOS 9 app, they will get the Universal version of your app, rather than the variant specific for their device type. TestFlight will continue to deliver variants for your internal testers. App slicing will be reenabled with a future software update. No action is needed by you at this time.
-

LG video shows off V10's secondary 'ticker' screen
Publié: septembre 24, 2015, 11:18am CEST par Mark Wilson

Talk may focus on the iPhone 6s, 6s Plus and new Nexus devices at the moment but LG also has something in store. Recognizing that phone screens can only use larger dimensions as a selling point for so long, LG has taken a leaf out of Samsung's book and come up with a phone with a secondary display.
While the Samsung Galaxy S6 edge provides a little extra screen space with its curved edges, the upcoming LG V10 takes a different approach. A new video shows that it utilizes 'wasted' space at the top of the handset to house a secondary 'ticker' screen that can display notifications from apps.
The ticker screen has been rumored for quite some time now, and the video -- entitled simply "Coming soon - teaser" -- seems to confirm its existence. By moving the front facing camera to the upper left hand corner of the hand set, the area to the right is freed up to display notifications. Just as with Samsung's edge, the feature will only be compatible with specially coded apps, and it should help to improve the battery life of the phone -- powering a tiny ticker to display alerts is far less draining than lighting up a full screen.
The 15 second video also reveals a release date of 1 October, so there's not long to wait to see how the new design works. Check it out below and see what you think:
-

Microsoft's Skype outage apology just isn't good enough for the mobile first, cloud first world
Publié: septembre 23, 2015, 8:26pm CEST par Mark Wilson

Earlier in the week there was a serious Skype outage. Users around the world found they were unable to connect, unable to communicate, throwing many people into confusion. Yesterday, Microsoft issued an apology -- but it’s simply not good enough.
The new Microsoft, under the direction of Satya Nadella, has been banging the "mobile first, cloud first world" drum, and this means being connected. The company might well be "extremely sorry for any inconvenience caused to our users", but it shouldn’t have happened in the first place.
In a shame-faced apology, Microsoft insists that "our users are our priority" and acknowledges that "no matter how quickly we were able to resolve this issue, it would not have been quick enough". Absolutely. A backup system should have been in place. It’s all well and good offering platitudes like "we know many of you needed to use Skype during the outage, and finding that you couldn’t would have been incredibly frustrating" but that kind of misses the point. The key word in the sentence is NEEDED.
You can push mobile first, cloud first as a mantra as much as you like, but if people don’t see reliability in the cloud they’re expected to put their faith in, you’re going to have a great deal of trouble expecting them to devote themselves to it. The explanation for the outage is interesting:
We released a larger-than-usual configuration change, which some versions of Skype were unable to process correctly therefore disconnecting users from the network. When these users tried to reconnect, heavy traffic was created and some of you were unable to use Skype’s free services, including messaging, presence, and contact list management. Others could not sign in or out of Skype altogether, or make calls to landlines or mobile phones. Skype for Business was not impacted.
This is essentially an admission that Skype is volatile and unreliable. This does not instill faith. But more interestingly, only the free version was affected. Paying customers are clearly seen as more important. This might not be a surprise, but when Windows 10 has been given away for free, it makes you think.
So, Microsoft, if users really are your priority, make some investments in the free edition of Skype. If users matter so much, make sure that free services are as robust as those for which you receive money. Because otherwise it just seems like it’s your bank balance that you’re concerned about, not users.
No apology or amount of groveling would be enough. This is simply something that should not have happened in the first place. If safeguards are in place for people who pay, they should be in place for everyone. The cloud is as much about equality as it is connectivity.
Photo credit: Everett Collection / Shutterstock
-

Twitter revamps Tweet and Follow buttons with a modern new design
Publié: septembre 23, 2015, 6:48pm CEST par Mark Wilson
Visit just about any website and you’re pretty much guaranteed to see a Twitter button of some sort. Just as here at BetaNews, you’ll be offered the chance to follow the author of the article you’re reading (or the site’s Twitter feed), as well as being given the opportunity to tweet about the page you’re looking at.
Now this familiar page furniture is about to get a new look. From next month, a new set of buttons is rolling out with a fresh, flat, modern look. It’s a redesign that will please minimalists, but there are important API changes coming that will annoy some developers.
Twitter is keen to provide a uniform experience across the web, and to this end it is looking to discourage people from creating Follow and Share buttons of their own. To force people to use the new high-contrast buttons, the share count endpoint is being closed down, meaning that custom buttons are no longer a possibility. Explaining the changes in a blog post, Twitter says:
The Tweet button has displayed share count over the last five years by querying a JSON endpoint hosted on various domains. These private JSON endpoints have been used by third-party developers over the years to retrieve a simple share count of any URL. These endpoints will be shut down next month when the Tweet button removes its share count feature.
Twitter points out that the new buttons are precisely the same size as their predecessors, so web designers need not worry about page layouts getting messed up.
-

Is iOS 9 adoption REALLY 50 percent?
Publié: septembre 23, 2015, 4:38pm CEST par Mark Wilson

As has become the norm after a new iOS launch, Apple has been keen to crow about the high adoption rate for iOS 9. The company recently claimed that in just three days, more than half of iPhones, iPads and iPod touches had iOS 9 installed. Seems a little high? You're not alone in feeling that way. Has Apple massaged the figures about iOS adoption rates?
While there are many reasons to make the upgrade to iOS 9, the 50 percent figure is not in line with measurements from other sources. It's fair to say that only Apple has access to the real raw data, but Crittercism suggests that on the measurement date of 19 September used by Apple, adoption of iOS 9 was possibly less than half of what's been claimed.
Crittercism used data gathered from tens of thousands of apps in the App Store, amounting to billions of installations. Using this data, the company measured a 23 percent install rate for iOS 9 -- a figure that is in line with the findings of mobile marketing company Fiksu.
Analysis performed by a third company, MixPanel, placed the adoption rate slightly higher at 29 percent, but this is still well below the claimed 50 percent. MixPanel also determined that just over 12 percent of users had made the upgrade after 24 hours. Crittercism is quite blunt in its questioning of Apple's figures published in a press release:
The release indicates this measurement was done by the App Store on September 19, 2015. However, this conflicts with our data as well as two other data sources.
There are numerous explanations for the differences in the numbers that have been put forward -- not least that samples may have been cherry-picked. It has been suggested that in sampling people downloading new apps from the App Store, Apple has knowingly or unwittingly focused on a selection of people more likely to be downloading new apps (rather than updating old ones they already have installed). Crittercism also suggests that Apple could have focused its attention on certain parts of the world, or ignored some devices, thereby skewing the figures.
Photo credit: Cloud7Days / Shutterstock
-

Vodafone's #BeStrong campaign uses emoji to raise awareness of cyberbullying
Publié: septembre 23, 2015, 3:14pm CEST par Mark Wilson

October is National Bullying Prevention month in the UK, but the problem of cyberbullying is one that pays no regard to national boundaries. To help raise awareness of the issue, Vodafone has launched a set of anti-cyberbullying emoji, as voted for by thousands of teenagers.
Celebrities such as Alan Cumming, Monika Lewinsky, Caprice, and Dancing Man are getting involved, tweeting using the #BeStrong hashtag. For every retweet, Vodafone is making a donation to anti-bullying charities, and the telecoms company has also drawn inspiration from Jimmy Kimmel's 'mean tweets' as part of the campaign.
Vodafone has set up an online hub which is packed with information for victims of online bullying, as well as for parents who are concerned about their children. The company says: "we’ve created a suite of #BeStrong 'support emojis' so that young people can convey compassion, sympathy and support when their friends are being bullied online [...] We’re also talking to the major emoji app and social media platforms about featuring the emojis on their platforms in the near future".
You’ll find the full set of emoji on Flickr.
Showing that cyberbullying is not something that affects the likes of you and I, Vodafone has released a video showing teenagers discussing unpleasant tweets that have been sent to celebrities:
In a second video, Dacher Keltner, psychologist adviser on Pixar film Inside Out, talks about how something as simple as an emoji can help to show support for those who are suffering:
-

Facebook and other social networks no longer have to reveal terrorist discussions to US government
Publié: septembre 22, 2015, 11:00pm CEST par Mark Wilson

Government snooping into online activity is something that has long appalled privacy groups around the world. In something of a victory for those concerned about privacy and government meddling, the US Senate has killed plans that would have required social networks to tell the government about any users talking about terrorism-related topics.
The change of heart is a win not only for social network users, but also the social networks themselves who will no longer be required to police content more than they already do. The policy had been criticized for being vague, placing undue pressure on companies, and limiting freedom of speech.
Senator Ron Wyden put a hold on the 2016 Intelligence Authorization bill back in July. He was concerned about the requirement for companies to police users' communication, but he is now pleased that the "vague and dangerous provision" has been dropped. Senator Wyden said:
Going after terrorist recruitment and activity online is a serious mission that demands a serious response from our law enforcement and intelligence agencies. Social media companies aren't qualified to judge which posts amount to 'terrorist activity', and they shouldn't be forced against their will to create a Facebook Bureau of Investigations to police their users' speech.
But while privacy advocates may celebrate the government backtracking, it is likely that some form of requirement on social media companies to monitor users will returnat some point.
Photo credit: Kletr / Shutterstock
-

India drops insane encryption policy
Publié: septembre 22, 2015, 9:32pm CEST par Mark Wilson

The Indian government has performed a U-turn on a proposed encryption policy. Draft papers showed that the plan was to require people to store non-encryption versions of any data they have encrypted.
The draft policy was an all-encompassing one, and this led to a vocal backlash from users of social networks and messaging tools. The Indian government was forced to backtrack somewhat, making it clear that social media would be exempt and indicating that there is still a great deal of work to be done on the policy.
India's IT Minister Ravi Shankar Prasad said that the draft documents had been released without his knowledge. He went on to say that the "draft encryption policy is not the final view of the government. It will be redrawn to specify who it will apply to".
The government is looking for feedback from the public about any encryption and privacy policy that might be put in place, and it is keen to stress that the aim is not to infringe upon the "social media messaging platforms used by the common man".
Photo credit: STILLFX / Shutterstock
-

Google launches Brotli, a new open source compression algorithm to speed up the web
Publié: septembre 22, 2015, 7:15pm CEST par Mark Wilson

As websites and online services become ever more demanding, the need for compression increases exponentially. Fans of Silicon Valley will be aware of the Pied Piper compression algorithm, and now Google has a more efficient one of its own.
Brotli is open source and is an entirely new data format that offers 20-26 percent greater compression than Zopfli, another compression algorithm from Google. Just like Zopfli, Brotli has been designed with the internet in mind, with the simple aim of making web pages load faster.
It is a "lossless compressed data format that [c]ompresses data using a combination of the LZ77 algorithm and Huffman coding, with efficiency comparable to the best currently available general-purpose compression methods". Compression is better than LZMA and bzip2, and Google says that Brotli is "roughly as fast" as zlib's Deflate implementation.
While compression has endless uses online, it's something that is of particular interest to mobile users. Google hopes that the technology will be integrated into web browsers in the future, allowing for faster page load times, improvements to battery life, and lower data usage. How is the extra compression achieved? Google sheds some light on the matter:
The higher data density is achieved by a 2nd order context modeling, re-use of entropy codes, larger memory window of past data and joint distribution codes.
Oh, and if you were wondering, Google has adopted a naming convention for its compression algorithms just like it has with Android. As the company explains in a blog post, "Brötli means ‘small bread’ in Swiss German"; Zopfli was also named after a Swiss bakery product.
Brotli is available on GitHub now.
Photo credit: Kostsov / Shutterstock
-

Ingenious design: iClever Portable Foldable Bluetooth Keyboard [Review]
Publié: septembre 22, 2015, 12:20pm CEST par Mark Wilson

You might think it would be hard to get overly excited about a keyboard. I understand, I felt the same. But then I tried out the iClever Portable Foldable Bluetooth Keyboard and my opinion changed. I've used various portable/mini keyboards before and they have been -- almost without exception -- utterly awful.
The iClever Portable Foldable Bluetooth Keyboard gets off to a great start; it has a lot of things in its favor. The metal construction gives it a solid, robust feel and a great semi-industrial look. The aluminum has neatly curved edges, but at the same time it feels wonderfully brutalist. The real killer feature, however, is the foldability of the peripheral which means beautifully sizable keys are available for typing on.
Unfolded, the iClever Portable Foldable Bluetooth Keyboard measures 251.7 x 89.6 x 6.6 mm, and is powered by a 210mA rechargeable battery. iClever claims that it takes just two hours to fully charge and boasts 84 hours of continuous operation and an impressive standby time of 218 days (sorry, we'll just have to take iClever's word for this as I don’t have a spare seven months to find out if it's true).

Weighing in at just 185g (or 6.5oz if you prefer), the keyboard is hardly a burden in your pocket or bag, and a simple black drawstring pouch is provided to protect it from bumps, scrapes, and dirt. An ingenious piece of design, when unfurled the keyboard offers the full range of keys -- although there's, unsurprisingly, no numpad. The keys provide just the right amount of resistance, and there's not too much travel so it's possible to build up quite a turn of speed. The backspace key is badly positioned, though -- I found I was constantly hitting the \ key, but this could be something you get used to over time.

While there is a dedicated Windows key, the keyboard can be used with any device that allows for Bluetooth pairing. The Fn key provides access to a number of Windows, iOS, and Android specific shortcuts. As a writer I spend a huge amount of time chained to my keyboard, so it's important that whatever I'm using works well. Despite being a 'travel' keyboard, the iClever Portable Foldable Bluetooth Keyboard is just about good enough for me to consider using it full time. It was an absolute joy to use with my Surface Pro .
I was prepared to be disappointed by this keyboard, but I ended up being blown away by just how enjoyable it is to use. I'm not saying I would use it as my everyday keyboard, but it is not meant to be a full time replacement. For quick sessions of typing when traveling, it is absolutely perfect. It is almost immeasurably faster than using an onscreen keyboard on a phone or tablet and, of course, means that you can see more of your actual screen.

There is, however, room for improvement. There's no battery indicator, although this is perhaps not a major issue as a quick charge via USB is all that's needed -- you could use your phone charger if you're not in a position to connect the supplied USB cable to a computer. I have slight concerns about the hinges. They feel robust enough, but it's hard to tell how they will stand up to abuse over time. The construction is solid, but the plastic covering over the joints seems like a slight weak point. Time will tell, I guess!
I was very much a mobile keyboard skeptic, but this device converted me.
You can pick one up from Amazon. The list price is $99.99, but at the moment you can get one for just $32.99... and I can't recommend highly enough that you do just that.
Photo credit: Mark Wilson
-

Ditch the Slow Ring! Get on the Windows 10 Fast Ring or step away from the previews
Publié: septembre 21, 2015, 7:10pm CEST par Mark Wilson

Windows 10 is a major departure from the norm for Microsoft. This is not only the first time Windows has been made available as a free upgrade, but the first time that users have been able to get actively involved in the development process. The existence of the public previews for Windows Insiders has made this one of the most transparent development programs to come out of Redmond.
Broken down into the Fast Ring and the Slow Ring, Microsoft has explained how the Windows 10 development process works, saying that the former is for those who want to be on the bleeding edge, the latter for those who want to play it safer. Ultimately, however, you should be either in or out, and this leads us to the question: what's the point of the Windows 10 Slow Ring?
While there have been a number of preview builds released, the rate at which releases have hit the two rings has been markedly different. Anyone waiting for the 'more stable' builds to reach the Slow Ring has certainly had their patience tested. Things have been slightly better for those happy to take the risk of working with Fast Ring builds, but most people would have been happier with a somewhat accelerated release schedule.
Part of the reason for the existence of the Slow Ring is that it is home to builds that have already gone through various phases of testing -- the Fast Ring included. Any show-stopping bugs should have been ironed out, but the release schedule is far slower.
But Microsoft warns that none of the preview builds -- and some would argue the same warning should apply to the RTM build -- should not be installed on a machine that is mission-critical. If you're interested in seeing the development process of Windows 10 and want to check out the latest features and fixes ahead of official updates, you're going to be sensible about it and run the operating system on a second machine or virtual machine, or be competent enough to sort problems out if things go wrong. If an operating system screw-up scares you, you shouldn't be using the preview builds in the first place.
Both the Slow and Fast Rings are home to builds that would be generally considered unfinished and unstable, so what’s the point in both? Neither are meant for use on main machines, so why compromise and settle for fewer, slower releases? If you're a Windows Insider with an interest in the preview builds, you should either be in or out. Fast or nothing.
The Slow Ring is a half-hearted pandering to those who feel like sort of taking part. Ditch it this instant. Get on the Fast Ring right now. And, Microsoft -- speed things up! We can take it. We don’t mind wobbly builds -- we just want more. We know you're beavering away on things, so let's see it faster.
Photo credit: Dirk Ercken / Shutterstock
-

Google loses Right to Be Forgotten appeal in France
Publié: septembre 21, 2015, 2:06pm CEST par Mark Wilson

France has rejected an appeal from Google about last year's Right to Be Forgotten ruling. A previous ruling said that when Google received requests from European citizens to remove search results linking to stories deemed "inadequate, irrelevant, or no longer relevant", the removals should be applied worldwide.
Google disagreed, saying that removals should be limited to country-specific Google domains like Google.co.uk and Google.fr, leading to the appeal. But the president of the Commission Nationale de l’Informatique et des Libertés, Isabelle Falque-Pierrotin, said that rather than amounting to censorship, imposing global removals would help to prevent circumventions of the ruling.
Having lost the appeal, Google must now remove thousands of entries from Google.com as French law does not give the company the right for further appeal. The Guardian explains that if Google fails to comply, fines could be levied against Google, who would then be able to appeal against the financial penalty.
A statement from the commission says:
Contrary to what Google has stated, this decision does not show any willingness on the part of the CNIL to apply French law extraterritorially. It simply requests full observance of European legislation by non-European players offering their services in Europe.
Google is not happy with the ruling, saying:
We've worked hard to implement the 'right to be forgotten' ruling thoughtfully and comprehensively in Europe, and we'll continue to do so. But as a matter of principle, we respectfully disagree with the idea that one national data protection authority can assert global authority to control the content that people can access around the world.
-

Apple cleans up the App Store after serious malware attack
Publié: septembre 21, 2015, 11:06am CEST par Mark Wilson

Apple has started a clean-up operation of the Chinese version of its App Store after it was flooded with apps infected with XcodeGhost malware. The problem was not detected by Apple, but a number of security firms who discovered various malicious iPhone and iPad apps littering the Store.
The apps made their way past Apple's usually-rigorous vetting process after developers were tricked into using a counterfeit version of the Xcode tool to create them. The attack has been described as "a pretty big deal" although at this stage there are no reported instances of data theft or attacks on victims.
Apple spokeswoman Christine Monaghan said: "We've removed the apps from the app store that we know have been created with this counterfeit software. We are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps". Reuters reports that high-profile apps were targeted, including Uber clone Didi Kuaidi, and chat app WeChat.
Apple's wall-garden approach in the App Store has previously kept problems with malicious apps to a minimum. But the approach used this time around -- attacking developers rather than users -- highlights a weakness that could be exploited again.
Chinese security firm Qihoo360 Technology said that it had detected 344 apps infected with XcodeGhost. Apple has not yet provided users with any information about how to check their iPhones and iPads to see if they are infected.
Photo credit: TK Kurikawa / Shutterstock
-

Leaked Microsoft Band 2 pictures show off new design
Publié: septembre 20, 2015, 10:31pm CEST par Mark Wilson

In the world of wearables it is really a battle between the Apple Watch and the various Android smartwatches like the Moto 360. But Microsoft would like you to remember that it also has something to offer. The original Microsoft Band may not have generated a great deal of interest, but the company is not ready to give up.
Leaked images show that Band 2 is shaping up to be better looking than the first generation. Spanish website Microsoft Insider has published renders of the upcoming wearable which currently bears the codename Envoy.
From the Microsoft Insider renders, it appears that the second generation of Band has a curved screen, addressing one of the complaints with the original model. Band 2 also appears to have higher quality look, with chrome touches giving the device a more attractive exterior. There are also physical buttons visible that should take some of the navigation options away from the screen.
It is expected that we'll find out more about Band 2 at the next Microsoft event on 6 October, but Microsoft Insiders hints that the new version includes at least one new sensor. There is the suggestion that Band 2 will be able to determine height, implying that there will be an altimeter built in.
Photo credit: MicrosoftInsider.es
-

AdBlock Plus defends ad blocking, applauds Peace, and backs Crystal for iOS
Publié: septembre 20, 2015, 5:50pm CEST par Mark Wilson

That a company behind an ad-blocking tool should defend ad-blocking should hardly come as a surprise, but that is precisely what has happened. Ad blockers have been much talked about since Apple opened up support for them in iOS 9. The now infamous Peace shot to the top of the download charts before it was pulled by its creator.
Now AdBlock Plus has come out in support of Marco Arment who developed something of a guilty conscience after his ad blocking creation proved so popular. Ben Williams from AdBlock Plus says "I really applaud this guy", going on to suggest that whitelisting and the Acceptable Ads feature of AdBlock Plus epitomize the "more nuanced, complex approach" Arment called for.
Williams makes much of the fact that Arment refers to ad blockers as "necessary". In a blog post he explains that he applauds the Peace creator not for killing AdBlock Plus competition, but for highlighting that fact that an all-or-nothing approach doesn’t work well for content creators. When announcing the death of Peace, Arment recommended Ghostery, and it is no secret that he was working with that company.
As Williams' point out, this is not (necessarily) about sycophancy. AdBlock Plus is itself working with other ad block developers, in particular Dean Murphy -- the man behind Crystal. The aim is to bring AdBlock Plus' Acceptable Ads integration to Crystal so users have finer grained control over what they see, what they block, what they permit. There's also the clear admission that money changes hands:
In fact we’re helping several developers out with integration logistics and even paying some of their costs when they want to incorporate Acceptable Ads.
Paying others to adopt a feature is something that many people will question, but Williams insists that it is about empowering people and putting them in control. AdBlock Plus is due for release for iOS "any day" now, but in the meantime the company is happy to recommend Crystal. But that's not entirely surprising, is it...?
Photo credit: BravissimoS / Shutterstock
-

Visiting this URL will crash Chrome
Publié: septembre 20, 2015, 2:57pm CEST par Mark Wilson

Browser stability is a big issue, and it's something that can very easily sway choices. A bug has been discovered in Chrome which crashes the browser if a user visits a particular URL -- 16 characters is all it takes to kill Google's web browser.
The problem is reported as affecting Chrome 45 and older, although it also seems to all kill version 47 on the Dev channel. The issue stems from the inclusion of a NULL character in the URL and has already been reported to Google.
To see if your browser is affected, you just need to type http ://a/%%30%30 into the address bar, remove the space after the p, and hit Enter. Make sure you're not in the middle of anything important in any of the other tabs you have open as the resulting crash will interfere with things. If you're wondering why we didn’t just link to the problematic URL, it's because simply hovering over the link can lead to a crash too.
The bug was discovered by Andris Atteka, and the reason for what is happening is explained as:
It seems to be crashing in some very old code. In the Debug build, it's hitting a DCHECK on an invalid URL in GURL, deep in some History code.
Although Google runs a bug bounty program, the company is not paying out in this instance because it is not seen as a security problem -- although it is certainly an issue that is slightly irritating and open to exploitation.
-

Don’t get sucked in by Facebook Dislike button scams -- or vomiting snakes
Publié: septembre 20, 2015, 11:53am CEST par Mark Wilson

You've probably heard talk recently of Facebook adding a Dislike button or an 'empathize' button. While this is certainly something that has been in the news, it is not yet a reality -- and it has created a great opportunity for scammers to cash in on people's impatience.
We don’t get know exactly what form the Dislike button will take, or when it will appear, but there are now several scams in operation that lure in victims with the promise of instant access to the yet-to-be-released feature. A variety of techniques are employed by scammers to encourage victim to "Download the official DISLIKE button now". It is, of course, a fake, and there are a number of things to look out for.
Posts that appear to originate from Facebook friends may offer the opportunity to watch 'shocking' videos -- including one purporting to show a snake vomiting up a hippopotamus. Having been enticed into try to watch such a video, or perhaps to complete a questionnaire or survey, the offer of the dislike button appears.
If the victim grants permission, a Facebook app is then installed that has access to their account and can post messages on their behalf. One of the first things the scam app does is to post a message informing the victim's friends that they have just installed the official Dislike button in the hope of attracting more people to do the same.
The ease with which Facebook apps can be created means that scammers can quickly jump on the latest craze and use it as a hook for attacks. Facebook can jump on rogue apps as they are discovered, but it doesn’t take long for replacements to spring up to fill the void.
So remember: there is (as yet) no Dislike button for Facebook. Any app or site that says it can give it to you is lying.
Photo credit: Gonzalo Aragon / Shutterstock
-

Has the iOS 9 Slide to Upgrade bug killed your iPhone? Here's what to do
Publié: septembre 18, 2015, 10:56pm CEST par Mark Wilson

iOS 9 may be just out of the gates, but it is already causing problems. Some people who have made the upgrade are complaining that the latest version of Apple's mobile operating system is laggier than the previous version, but some people have found they are not even able to complete the installation.
Upset users have taken to forums to complain that their iPhones have bricked by iOS 9. Many people found that their phone became stuck on the Slide to Upgrade screen with no obvious way past the roadblock. Apple refers to the symptom as "the Slide to Upgrade screen won't go away after you update to iOS 9", and there is a solution.
The problem appears to be primarily affecting -- according to the Register -- upgrades from iOS 7 to iOS 9, but all may not be lost. There is a workaround, providing you have a recent backup that you can fall back on. Over on its product support pages, Apple has the following advice:
- Connect your iOS device to your computer and open iTunes.
- Select your device. If you don't see it listed, force restart your device by pressing and holding both the Sleep/Wake and Home button for at least 10 seconds, until you see the Apple logo.
- If you made an iTunes backup of your device before updating to iOS 9, restore your device from that backup. If not, you need to make a backup of your device in iTunes, then restore from that backup.
Photo credit: charnsitr / Shutterstock
-

Private keys leaked in D-Link firmware may have been exploited by hacker to digitally sign malware
Publié: septembre 18, 2015, 8:52pm CEST par Mark Wilson

Malware writers may feel as though they've hit the jackpot after a slip-up by D-Link. The networking company released open source firmware that revealed the private keys used to sign D-Link software.
It was discovered that the firmware for a D-Link DCS-5020L security camera included D-Link's private keys as well as the passphrases needed to sign software. Windows users could have been at risk as malicious software could have been signed allowing for the installation without alerting security software.
The keys that were discovered expired early in September, so there is no longer a threat, but it is not yet clear if any users were affected by malware that exploited the leak. The problem came to light after someone contacted Dutch website Tweakers who in turn got in touch with security firm Fox-IT. The company confirmed the existence of the keys in the firmware.
Speaking to Threatpost, Fox-IT researcher Yonathan Klijnsma said:
I think this was a mistake by whoever packaged the source code for publishing. The code signing certificate was only present in one of the source code packages with a specific version. The version above and below the specific package did not contain the folder in which the code signing certificates resided. A simple mistake of folder exclusion as far as I could see.
Although the security certificates have now expired, the vulnerability was exploitable for no less than six months before it was discovered.
Photo credit: Jamie Wilson / Shutterstock
-

AVG's new privacy policy is brutally honest about tracking you
Publié: septembre 18, 2015, 2:57pm CEST par Mark Wilson

AVG has thrown down the gauntlet to other technology companies, challenging the rest of the industry to produce open, truthful privacy policies. AVG has done just that, and you might not like what you read.
The antivirus company has published its own brutally honest privacy policy that clearly sets out how it tracks users' activity, gathers data, and shares that information with others. Unsurprisingly, despite the fact that nothing has changed but merely been brought out in to the open, people are not happy. Is honesty about a disagreeable policy better than living in blissful ignorance?
The new privacy policy is due to take effect on 15 October and it quite plainly states that user data is collected "to make money". What is collected? Names, email address, phone numbers, SIM numbers, IP addresses, location, device IDs, payment details... the list goes on and on. It goes on and gets a little sinister. AVG will also collect your "browsing and search history, including meta data", and "information regarding other applications you may have on your device and how they are used".
In terms of content, the policy is little different to its predecessor; it is really just the presentation and tone that has changed. But in bringing its privacy policy out into the open -- and writing it in far more accessible language -- AVG has opened itself up to attack and criticism. And that's exactly what has happened. Over on Reddit (that home of the ever calm and collected individual) there is much shaking of fist and gnashing of teeth. There are numerous threats of dumping AVG in favor of other antivirus tools.
How much of an issue is this level of tracking and data collection? AVG offers up one softener: it's all done "so that we can continue to offer them for free". Should AVG be more concerned about ensuring that its users (or ex-users) understand its privacy policies, or should it concentrate more on ensuring that there is less for people to complain about in the first place? As with Windows 10, the real price of AVG is privacy.
But just to make you feel better about everything, AVG has also released a video about its privacy policy which it describes as 'whimsical'. Enjoy:
Photo credit: lassedesignen / Shutterstock
-

7 things I still hate about Windows 10
Publié: septembre 18, 2015, 12:11pm CEST par Mark Wilson

Windows 10 has been with us for quite some time now, particularly for anyone who has been trying out the Insider builds since the beginning. Many people, myself included, have been disappointed with Microsoft's latest operating system but perhaps it's time to re-evaluate.
Have I got used to the things I didn’t like? In some cases, yes. But there are still a number of areas in which Windows 10 falls short of the mark. So here are seven things that piss me off about Windows 10; one for every day of the week!
Store Apps
Why? Just... why? Microsoft has tweaked Metro/Modern/Store apps so many times over the years to make them more like regular desktop apps that they may as well be just that. Apart from the fact that they have universally ugly interfaces and embrace blank space like a drug.
I'm yet to see a Store app that doesn't look like it was designed both for and by a six year old. There's a place for sparsity, but it has a tendency to stand in the way of productivity. Sure, there's the promise of cross-device compatibility, but who cares about Windows 10 mobile?
Action Center
This was meant to be one of the great features of Windows 10, but it is such a huge disappointment. Multiple notifications from the same app are not handled well. Could Microsoft not have looked to Android and iOS to get an idea of how to do things properly? I'm all for doing things differently when appropriate, but it has to make sense.
The 'quick' access to settings and toggles is another space-eater. Everything seems to take up twice as much space as it needs to. It would also make sense to allow for a degree of customization here, or even the ability to add shortcuts of one's own. Come on, Microsoft: give people choices!
Tiles, Live or Otherwise
What is Microsoft's obsession with wasted space? Tiles in the Start menu are an excellent example of a design idea gone horribly wrong. Static tiles are, essentially, just huge icons that take up too much room, meaning that it is not possible to display as many items. This in turn means more scrolling around and less productivity. Live tiles are just as big, if not even bigger, but serve up information so slowly as to be pointless.
Seriously, someone needs to explain to me the point of news headlines being flashed up in a live tile. Am I supposed to sit with the Start menu open to see the latest news? Or just hope that I see something I want to read in the two seconds I tend to have the Start menu open? Same goes for inbox live tiles and countless other examples. If I want to see that sort of information, I'll launch the appropriate program or website.
Lack of Development of Explorer
While there have been a few changes here and there, Explorer remains largely unchanged since the days of Windows 95 -- and that's certainly not because it is perfect. How an option such as a tabbed interface is still lacking is beyond me when you consider how long and how loudly people have been asking for it. Firing up Explorer feels like using a 20 year old piece of software.
Lack of Information About Updates
Transparency is a big issue these days, and with the ever-present threat of malware, viruses, and the like, people like to know what their computers are doing. If anything gets installed, it makes sense to want to know what it is and what it is doing. Microsoft disagrees. When it releases updates for Windows 10, it may tell you what the update does, it may not.
That's not good enough. People have a right to know what is being done to their machine -- don’t get me started on the forced downloading of Windows 10. The decision not to include information about updates as standard is a serious misstep. Microsoft may yet change its mind, and I can only hope that this does happen. In failing to provide this information, Windows users are taken to be uninterested, dumb consumers who don't want or need to know what's happening.
Confused Interface Inconsistencies
Jokes about Windows 8 and Windows 10 being Frankenstein's monsters have worn a little thin, but Microsoft does demonstrate very confused -- and confusing -- thinking in its OS design. Context menus are an excellent case in point. I've lost count of the number of different looks they have depending on where they appear. Yes, I realize that this is related to the context in which they appear, but the context should really influence the content.
Does it make sense that right-clicking on the Start button or taskbar I see a dark context menu, but clicking on icons in the notification areas -- including those relating directly to Windows, such as the Action Center -- bring up a light menu.
But even then there is weirdness. Right-click the volume icon and an old-school context menu appears -- i.e. one with sensible line spacing. Right-click on an item on the desktop and a light context menu with insane spacing is used (this is the case in build 10532, at least. And yes, I am aware that this is a preview build).
Microsoft Edge
Just go away and die already! You're just Internet Explorer in fancy pants and you weren't even finished in time for the launch of Windows 10. Seriously, when a company promotes a browser so much, heralds it as the future of life online, kills its predecessor, you'd think it would pull out all the stops to make sure it was actually completed.
Yet here we are months after the launch of Windows 10 and it is still not ready. Where is the plugin support that's been promised for so long? Everyone has lost interest now and long since moved to a proper browser anyway.
Photo Credit: Djomas/Shutterstock
-

Microsoft refuses to answer questions about forced Windows 10 downloads
Publié: septembre 16, 2015, 11:59pm CEST par Mark Wilson
Just last week Microsoft managed to piss off a lot of people by secretly downloading the Windows 10 installation files to their computers without permission. The comments from BetaNews readers were plentiful, but divided. Some didn't see the problem, while others thought it to be invasive and presumptive.
But there was one question that popped up again and again -- just what the hell was Microsoft thinking? I decided to try to find out but found that the company was somewhat cagey with what it wanted to say on the matter. This is not on. People are more than a little annoyed, and they are demanding answers. They deserve them.
As we know from the original story, Microsoft had already been approached by The Inquirer and issued a statement that said: "For individuals who have chosen to receive automatic updates through Windows Update, we help upgradable devices get ready for Windows 10 by downloading the files they’ll need if they decide to upgrade. When the upgrade is ready, the customer will be prompted to install Windows 10 on the device."
This is very matter-of-fact and soulless. It also fails to take into consideration the idea that a lot of people might have no interest in upgrading to Windows 10, now or at any point in the future. Why would they want to download the installation files 'just in case'? There are plenty of households and workplaces with many computers -- if they all download Windows 10's installation files without permission that's a lot of bandwidth, and not everyone is lucky enough to enjoy unlimited bandwidth.
I, for instance, live in a remote place. If I want a decent internet connection, I have to pay for satellite. This is not only not cheap -- certainly nowhere near as cheap as traditional broadband -- but it also has download limits. I could pay for an unlimited connection, but it's prohibitively expensive. I have to be careful how I use the internet and do what I can to stick within my allowance. I don’t appreciate anything that secretly uses my connection, and I know that I'm not alone.
I got in touch with Microsoft to find out what on earth prompted the company to push Windows 10 at customers so aggressively. I was told that someone would get back to me, but by the next day there was no response -- so I chased it up again. Again I was told that it was being looked into.
All went silent.
Microsoft really didn’t seem keen to answer my questions.
A full four days later I received a reply.
It was the same boilerplate statement that had already been provided to The Inquirer.
In my original contact with Microsoft, I pointed out that the forced download of Windows 10 was far from ideal for anyone with a slow or metered connection. Was anything being done to protect people who might find themselves hit with large bills?
Yes. Specifically, Windows 8.1 does not automatically download updates or apps if it detects that your PC uses a metered connection. Windows 7 and Windows 8.1 customers can both control how Windows Update downloads and installs updates, including the ability to receive notifications before downloading updates. These capabilities can prevent customers from downloading updates which may cause them to exceed their data capacity allocation.
This is all well and good, but it is reliant on Windows correctly determining whether a metered connection is being used. It does nothing to help those people who need to stick to a monthly download limit, or who have a very slow connection.
This answer wasn't good enough for me, so I pressed Microsoft further. I sent a further email:
I'm not sure that really answers the questions I asked in my original email, however.
It's all well and good to say that the aim is to provide a 'smoother upgrade experience', but is it not rather presumptive?
It's one thing to deliver update superficially for Windows 7 or 8.1 through Windows Update, most people would agree that it is quite another to deliver an entirely new version of Windows, regardless of whether it is actually installed or not.
The question of metered connections... what if Windows does not correctly identify a metered connection? What about people with download limits that they need to stick to each month? What about people struggling with a slow connection who don't want things slowed further while a huge 'update' is downloaded? It's fine to say that customers can control how updates are received, but this ignores the fact that most people simply don't change any settings -- they don't know how to, they are scared to, or whatever. And why would they change anything? The advice has long been to leave Automatic Updates enabled so that important fix are installed as quickly as possible without then need for intervention. The downloading of Windows 10's installation files could in no way be seen as an 'important fix', and yet is downloaded anyway.
I'm interesting in understanding the thinking behind the decision to deliver the upgrade files in this way, and for a proper justification for how things have been done.
Once more, no response was forthcoming until I chased up yet again. The reply?
Thank you for your patience as I looked into this. We have nothing more to share beyond the statements I provided to you earlier.
Really? That's it? Thanks for nothing! We, as Microsoft customers, have genuine concerns and questions that we'd like addressed. "We have nothing more to share" simply doesn't cut it. It's not good enough by any stretch of the imagination.
This is supposed to be the new Microsoft, the Microsoft that listens to customers. But it seems that the company only wants to listen when it is convenient, or when it is beneficial to do so. That's not on.
Photo credit: urfin / Shutterstock
-

Apple's first Android app makes it easy to move to iOS 9
Publié: septembre 16, 2015, 10:43pm CEST par Mark Wilson

Apple has released its first ever Android app. No, there's not an Android version of Safari or anything like that, but a tool designed to simplify the process of switching to iOS. The predictably named Move to iOS will appeal to anyone who was persuaded to switch allegiances by the release of the iPhone 6s and iPhone 6s Plus, or indeed iOS 9.
The app can be used to move contacts, messages, photos and more to a new iPhone or iPad, and is compatible with phones and tablets running Android 4.0 and newer. It works slightly differently to what you may have expected. Rather than uploading data to the cloud, it instead creates private Wi-Fi network between an Android and iOS device and securely transfers it.
While there's nothing to stop switchers from manually backing up data and transferring it by hand, it can be something of a laborious process. Keen to get people to make people the switch, Apple wants to make the process as simple as possible -- hence the appearance of Move to iOS.
The app has only just hit Google Play so there are no reviews at time of writing, but the description tells you pretty much everything you need to know:
When you choose to migrate your data, your new iPhone or iPad will create a private Wi-Fi network and find your nearby Android device running Move to iOS. After you enter a security code, it will begin transferring your content and put it in the right places. Just like that. Once your content has been transferred, you’re ready to get going. iOS will also set up your default mail account. That's it -- you can start using your new iPhone or iPad and experiencing its endless possibilities. Enjoy.
Grab your free copy of Move to iOS here.
-

Bypass the Android Lollipop lockscreen by entering a really long password
Publié: septembre 16, 2015, 7:25pm CEST par Mark Wilson

A lengthy password is a good thing, right? For some Android users running Lollipop, however, it may be possible to bypass the lockscreen simply by entering a password that is incredibly long. Copy and paste a lengthy string into the password field, and it is possible to crash the lockscreen and gain access to the phone or tablet.
While the vulnerability is worrying, it is not something that can be exploited remotely -- it is necessary to have physical access to the phone. The bug was discovered by security researchers at Texas University and while a patch has been issued for Nexus devices, other handsets remain vulnerable.
John Gordon from the university reveals that it is possible to use the Emergency Call feature that can be accessed from the lockscreen to generate lengthy strings of text that ultimately provide unrestricted access without knowing the correct password. In a blog post he provides full details of how to exploit the vulnerability, which even works on devices that have encryption enabled.
It's not a particularly quick process, nor is it guaranteed to work, but it will be a concern for many Lollipop users. A video has been published showing the exploit in action.
If you are concerned about the vulnerability and have a device for which a patch is yet to be issued, you might want to consider switching to PIN or pattern protection, as these are unaffected.
-

AirDrop exploit can be used to push malicious apps to iOS and OS X
Publié: septembre 16, 2015, 5:19pm CEST par Mark Wilson

A vulnerability has been discovered in iOS and OS X that could be used to install apps without permission, using AirDrop. The feature exists to provide a way for people to quickly send files from one device to another, but security researcher Mark Dowd has been able to exploit the vulnerability to push apps to iOS even if the user does not accept the file that is AirDropped.
Dowd has reported the vulnerability to Apple, but the company has failed to patch the problem so it still exists in iOS 9. Using a combination of techniques, it is possible to bypass the security screen that asks if an app is to be trusted or not, meaning that a malicious app can be installed without permission or notification.
Dowd was able to use his own Apple enterprise certificate to create a test app that could be run on any device. By using an enterprise profile, it was possible to bypass code-signing protections and install the app without any prompts being displayed. As well as installing apps without permission, the same technique can be used to overwrite files in both iOS and OS X.
Speaking with Threat Post, Dowd said:
When you send a package via AirDrop, it comes up with a notification on the target phone asking the user if they want to accept the package. The user has to unlock the phone to accept or decline it. It does NOT matter whether they accept it or not to trigger this bug -- the exploit has already happened by the time the notification is sent to the user.
He has also released a video showing the exploit in action:
Photo credit: Ellica / Shutterstock
-

Apple Watch battery life is just fine for most people
Publié: septembre 16, 2015, 1:50pm CEST par Mark Wilson

The Apple Watch has been with us for a few months now and while there were initial concerns about the battery life, it seems that these fears were unfounded. The ways in which people have ended up using their Apple Watches means that a single charge is enough to get through the day in most cases.
A survey of 1,200 Watch wearers by Wristly found that the overwhelming majority of users reported that their battery lasted a full day. A startling percentage of people (44 percent) said that they did not check battery level at all during the day, and most have fallen into the habit of simply recharging overnight. But what is the biggest battery killer?
Perhaps unsurprisingly the greatest power draw is workout tracking. 45 percent of those surveyed said their workouts killed their battery, while 19 percent and 7 percent blamed directions and voice calls. Overall, more than half of Apple Watch owners are 'highly satisfied' with how long the battery lasts, with just 8 percent describing themselves as either 'somewhat dissatisfied' or 'highly dissatisfied'.
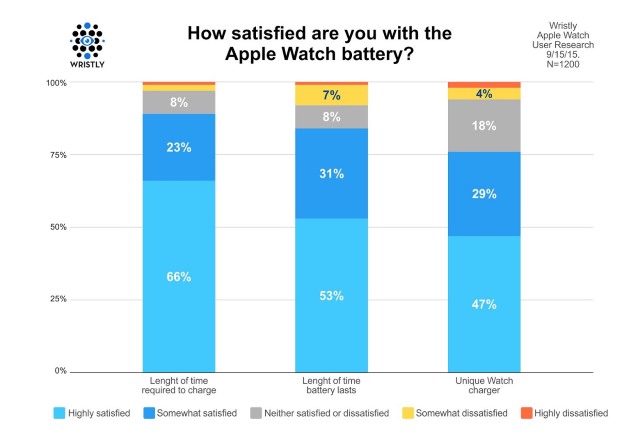
There is slight variation between the different Apple Watch models. 93 percent of 38mm Watches make it through the day, compared to 98 percent of the 42mm version. Accordingly, there is a higher level of satisfaction associated with the battery of the larger timepiece.
You can check out the full results in a blog post from Wristly.
-

Microsoft brings the Windows 10 Start menu to Windows 8.1 RT
Publié: septembre 16, 2015, 12:52am CEST par Mark Wilson

The return of the Start menu to Windows 10 was one of the things that Microsoft managed to get right with the latest version of its operating system. While the company has promised to bring Windows 10 to as many devices as possible, it ruled out doing the same for Windows RT devices.
That said, we were told that some key features of Windows 10 would make their way to Windows 8.1 RT. That day has finally rolled around and thanks to the arrival of Windows RT 8.1 Update 3, the Start menu is now available in Windows RT.
This is likely to be the last major update to be released for Windows 8.1 RT, but it plugs a hole that many users have been complaining about for a long time. Microsoft had previously said that Windows RT users would not be able to upgrade to Windows 10 but would be able to enjoy some of the features of the latest version of the operating system.
Aside from the arrival of what many people believe to be the central feature of Windows, Windows RT 8.1 Update 3 brings little new. There are some changes to lock screen options, but that's about it. Bringing the build number up to 9600, the update was spotted by Tero Alhonen who tweaked about the resturn of the Start menu:
Start menu on Windows RT 8.1 pic.twitter.com/k2dOfYd2fh
— Tero Alhonen (@teroalhonen) September 15, 2015
Windows RT 8.1 Update 3 is rolling out right now, so if you have Automatic Update enabled it will be with you shortly. If you're keen to get the Start menu back as soon as possible, you can manually check for updates.
Photo Credit: Asif Islam/Shutterstock
-

Sale now on! Now anyone can add a Buy button to Twitter
Publié: septembre 15, 2015, 5:09pm CEST par Mark Wilson

Buy buttons are not exactly new to Twitter, but until now they have only been available to a limited number of users. Now, thanks to San Francisco-based Stripe, anyone is able to use a tweet to sell a product.
Stripe has launched a new service called Relay. It is a set of tools that can be used to sell through any app that makes use of Stripe -- and that includes Twitter. Relay can be used to allow for instant purchases, and address what Stripe perceives to be a problem with mobile e-commerce sites.
The Relay APIs offered by Stripe allow a shopping experience to be integrated into just about any third-party app, and Twitter and Pinterest are among those that offer support at the moment. As well as instant purchases for single items, the API can be used to provide a store experience that links into an existing shopping platform.
Introducing Relay, Stripe says:
Over the past year, a number of companies have worked to bring this kind of experience to e-commerce, pulling products from many stores into the very apps where users are already spending their time [...] We’re trying out something new. We’re launching Relay, an API for stores to publish their products, and for apps to read them. Relay makes it easier for developers to build great mobile e-commerce experiences, and for stores to participate in them.
The tweet below from Warby Parker shows how the buy buttons work:
So... is Twitter ready to be turned into a marketplace for all and sundry? Do web users need another outlet through which to relieve themselves of their money? If you like the idea of selling through Twitter, you can use the Stripe dashboard to get started.
Photo credit: enciktepstudio / Shutterstock
-

Leaked Windows 10 build 10537 release notes show Microsoft's slow progress
Publié: septembre 14, 2015, 7:07pm CEST par Mark Wilson

Wzor has come up with the goods once again. After leaked screenshots of Windows 10 build 10537 earlier today, we've been treated to a follow-up of release notes and ISOs. This build has not been officially released by Microsoft so you won’t be able to download it through Windows Update, but we're sure that you'll be able to track down a copy if you're particularly keen to try it out.
We've already mentioned some of the changes that are to be found in this latest build (MICROSOFT.WINDOWS.10.CLIENTPRO-CORE.TH2.10537.X64.OEMRET.ENGLISH.DVD) but the official release notes go into more detail. Dating back to 2 September, the release notes detail not only the new features and changes, but also the bug fixes. But, perhaps more importantly, it shows that progress has slowed over at Microsoft.
Windows Insiders have insatiable appetites for new builds of Windows 10, and Microsoft has been slow to deliver the goods recently. With a build number jump of just five from the last official release, it would perhaps be foolish to expect anything major to be included in build 10537 -- although stranger things have happened -- but the list of changes is notably short. In fact, just three new features are mentioned:
- Faster Start menu navigation using group header letters.
- New color options for the taskbar, titlebars, Start menu, and Action Center.
- A tweaked context menu for the Start menu.
In terms of bug fixes, just nine are listed and this particular build also introduces a number of new problems and issues. It is no longer possible to load EdgeHTML from Internet Explorer 11, and a problem with facial recognition sensors means that Windows Hello does not work properly. The lock screen may exhibit issues, and there are also a range of problems with the Narrator feature.
Check out the release notes in full over on Wzor's website.
Photo credit: Suzanne Tucker / Shutterstock
-

Could Bitcoin-powered micro-payments help reduce piracy and ensure artists get paid?
Publié: septembre 14, 2015, 12:27am CEST par Mark Wilson

The likes of Adam Ant and Billy Bragg are among the names backing the Free At What Cost? project. Launched by British composer Hélène Muddiman, the idea behind the campaign is to ensure that artists and content creators get a fair deal by charging for online views and listens.
The basic idea is to protect content against free viewing in an extension of the idea of simple DRM. While the logistics are still to be fully detailed, one of the proposals is to use a Bitcoin-like payment system to enables people to pay artists directly for access to their content.
Muddiman is keen to help find a way to ensure that content creators get paid for their work, saying "Theft is theft. There is no difference between stealing digital content and stealing from a shop, other than, at present, it's easier." She is already working on developing the technology that will be needed and, as reported by the Guardian, says that it could "change the economics of the web". It's an idea that has been toyed with before, but it now seems that great strides have been made both in terms of development and support.
There has been a long-running argument that the scales are currently tipped too far in favor of content consumers at the moment. Ease of access to online content and the popularity of torrent sites means that an entire generation has become used to the idea of gaining access to just about anything free of charge; a complete mindshift will be needed to turn things around. Muddiman points to the unfair way in which revenue is currently shared with artists:
YouTube only shares 55% of advertising revenue with those who achieve over 700,000 views per upload in a quarter, so it is in YouTube’s interest for multiple people to upload the same content to dilute the viewers so they pay out less money to creators.
While it can be argued that YouTube has provided more people with a way to monetize content, there is plenty of scope for better deals to be struck. Any solution that is proposed will need to minimize the burden on individuals, sites, and ISPs if it to be successfully adopted, but few people would argue that the time has come for things to change.
Check out the Free At What Cost Trailer? below:
https://youtu.be/DV0HHAM8FoQ
Photo credit: Rashevskyi Viacheslav / Shutterstock
-

Tor gains extra security as .onion becomes Special-Use Domain Name
Publié: septembre 13, 2015, 9:06pm CEST par Mark Wilson

Tor -- The Onion Router -- is used as a way of browsing the web (more) anonymously. Most well-known for providing access to what has become known as the Dark Web, Tor has faced competition from other secure browsing systems such as HORNET. But now it is set to benefit from key changes that will improve security and have further implications.
Engineering Task Force (IETF) along with Internet Assigned Numbers Authority, part of ICANN, has granted formal recognition to the .onion domain, adding it to the list of Special-Use Domain Names. Previously known as a psdeuo-TLD it was technically possible for the .onion domain to be used on the regular web -- now it is limited to Tor. There is also the possibility of site-specific encryption and the use of security certificates.
Tor may be famed for the likes of Silk Road and other such sites, but the anonymity and security it offer is important for many reasons. Of course the Tor network is not only home to nefarious websites (although it's fair to say that this accounts for a reasonable percentage of traffic), it is also used by news outlets as a way to anonymously gather news, and Facebook even has a secure presence.
The official recognition of .onion will automatically help to improve security, helping to reduce the ability to identify or locate users. The IETF documentation explains what the change means for accessing .onion sites:
Applications (including proxies) that implement the Tor protocol MUST recognize .onion names as special by either accessing them directly, or using a proxy (e.g., SOCKS [RFC1928]) to do so. Applications that do not implement the Tor protocol SHOULD generate an error upon the use of .onion, and SHOULD NOT perform a DNS lookup.
Other key clauses bolster security further:
Name Resolution APIs and Libraries: Resolvers MUST either respond to requests for .onion names by resolving them according to [tor-rendezvous] or by responding with NXDOMAIN.
Caching DNS Servers: Caching servers, where not explicitly adapted to interoperate with Tor, SHOULD NOT attempt to look up records for .onion names. They MUST generate NXDOMAIN for all such queries.
Authoritative DNS Servers: Authoritative servers MUST respond to queries for .onion with NXDOMAIN.
The prospect of SSL and TLS certification is important for the wider adoption of Tor as it helps to give users confidence that the sites they are dealing with are what they say they are. Speaking to Motherboard, Richard Barnes, the Firefox Security Lead at Mozilla, said:
This enables the Tor .onion ecosystem to benefit from the same level of security you can get in the rest of the web. It adds a layer of security on top.
Photo credit: topseller / Shutterstock
-

Apple spends just $234 making each iPhone 6s
Publié: septembre 13, 2015, 4:44pm CEST par Mark Wilson

Analysis by Bank of America Merrill Lynch estimates that the components part of the iPhone 6s cost Apple $234 -- only a very slight increase from the iPhone 6. With the 64GB model selling for $749, Apple is pulling in $515 from each sale before the costs of manufacturing and distribution is factored in.
The biggest cost is for semiconductor parts, accounting for $127 of cost. The 64-bit A9 processor costs just $25, while various sensors add up to around $22. The estimates suggest that the screen of the iPhone 6s is the most expensive part, coming in at around $50 on its own.
Announced earlier in the week, the iPhone 6s improves on its predecessor in a number of areas. At the moment, the costs suggested by Bank of America Merrill Lynch are just educated guesses based on analysis, but it shouldn't be long until a full teardown makes it possible to give a more accurate figure.
The figures, published by Business Insider, show that there has been a slight increase in Apple's outlay on parts since the previous generation of the iPhone. Older models such as the iPhone 5s have become cheaper to put together as the price of individual components has come down over time.
The iPhone 6s is due to launch on 25 September, and pre-ordering is now open.
-

Millions of Ashley Madison passwords cracked
Publié: septembre 12, 2015, 1:32pm CEST par Mark Wilson

The fallout from the Ashley Madison hack continues. After the passwords of millions of users were stolen in a huge security breach, the encrypted database has now been cracked. A cracking group called CynoSure Prime eschewed a time-consuming brute force approach to breaking into the database, and instead exploited information revealed by a change the infidelity site made to the way it stored data.
This change effectively rendered pointless the bcrypt encryption that had been used to protect data. It was possible to dramatically speed up the cracking process so data was accessible in a matter of days rather than years. So should users of Ashley Madison be worried?
Although CynoSure Prime has said that it will not being releasing the passwords and account details that it managed to gain access to, the detailed instructions the group has published means that it would be fairly simple for another group to replicate the work. Keep in mind that many people use the same login credentials for a number of sites and services, and the ramifications of leaking millions of passwords are huge.
In a blog post, the cracking group goes into some detail explaining how it managed to gain access to the encrypted password, but starts off with a quick overview:
Not long after the release of the Ashley Madison leaks, many groups and individuals attempted to crack the bcrypt hashes. Since the developers used a cost factor of 12 for the bcrypt hash, this made the process an extremely compute intensive task. We decided to take a different approach and made some rather interesting discoveries.
Without much information about the $loginkey variable and how it was generated, we decided to dive into the second leak of git dumps. We identified two functions of interest and upon closer inspection, discovered that we could exploit these functions as helpers in accelerating the cracking of the bcrypt hashes.
For those without knowledge of database encryption, it might be difficult to make sense of the more detailed description provided by CynoSure Prime, but over on ArsTechnica, Dan Goodwin does an excellent job of explaining things:
The source code led to an astounding discovery: included in the same database of formidable bcrypt hashes was a subset of 15.26 million passwords obscured using MD5, a hashing algorithm that was designed for speed and efficiency rather than slowing down crackers.
It seems that coders for Ashely Madison took steps to try to speed up the site and login process for users, but this decision turned out to be a massive security risk.
Photo credit: Maksim Kabakou / Shutterstock
-

Microsoft shows increased interest in Android by buying Echo Notification Lockscreen
Publié: septembre 12, 2015, 2:13am CEST par Mark Wilson

For a company with its own mobile operating system to worry about (yes, there is a new build of Windows 10 Mobile on the way soon) Microsoft shows an awful lot of interest in the competition. After making an appearance at Apple's iPad Pro and iPhone 6s launch event, Microsoft has made an Android-related acquisition.
The newly-purchased Echo Notification Lockscreen is the second Android lockscreen app that the company now has to its name; Echo Notification Lockscreen joins Microsoft Next. The company says it is about taking "productivity to the next level" and improving users' experience.
Julie Larson-Green, Microsoft' Chief Experience Officer, says that current lockscreens lack personalized information, and it's clearly something she's looking to address. As it stands at the moment, Echo Notification Lockscreen boasts over a million installations and has gained itself a wealth of positive reviews from users who are impressed intelligent notification grouping, alert snoozing, and music controls.
At the moment it is not clear whether Microsoft wants to keep the app as it is, or whether the purchase is a strategic move to acquire technology and patents that will be used in future products. The company has already shown that it is not afraid to put iOS and Android ahead of its own mobile operating system. With Windows 10, there has been a renewed interest in notifications, and it will be interesting to see whether the features of Echo Notification Lockscreen make the transition from mobile to desktop.
Photo credit: 360b / Shutterstock.com
-

How to stop Windows 10 downloading automatically
Publié: septembre 12, 2015, 1:10am CEST par Mark Wilson

Once again, Microsoft has managed to rile people with Windows 10. People have discovered that the Windows 10 installation files are being downloaded to their computers without their permission. If this has happened to you already, we've already shown you how to remove Windows 10, claiming back space and regaining control.
But if you have been lucky enough to avoid the unwanted arrival of Windows 10 installation files so far, you'll be more interested in prevention than a cure. Here's what you need to do to make sure Microsoft doesn’t force feed you Windows 10.
Microsoft may not be installing Windows 10 without people's permission, but in "help[ing] upgradable devices get ready for Windows 10 by downloading the files they’ll need if they decide to upgrade" the company has still upset a lot of people. You could disable Automatic Updates in Windows 7 or Windows 8.1, but this would mean missing out on important security updates as they are released.
A better solution, as suggested over on How To Geek, is to edit the registry and block this particular download.
- Start by patching Windows Update Client. If you're using Windows 7 you need this file, while Windows 8.1 users need this one.
- Fire up the Registry Editor by hitting the Windows key and R, type regedit, and press Enter.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\ Microsoft\Windows\ and create a new key called WindowsUpdate.
- Under this key create a new 32-bit DWORD called DisableOSUpgrade, double click it and set its value to 1.
Should you ever change your mind about upgrading to Windows 10, you'll have to either delete DisableOSUpgrade or change its value to 0.
If you're trying to avoid downloading Windows 10, what method have you decided to use?
Photo credit: chrisdorney and tanuha2001 / Shutterstock
-

WARNING! Sony decides its waterproof Xperia phones are not actually waterproof
Publié: septembre 11, 2015, 9:13pm CEST par Mark Wilson

Sony seems hell bent on confusing its customers by giving very conflicting advice about its Xperia smartphones. If you're familiar with the range, you'll no doubt be aware of the advertising material that appears to show users taking photos in the rain and even (seemingly) underwater at the pool.
Take a look at the picture above and you'd probably assume that a) it depicts someone shooting a video or taking a photo in a swimming pool, and b) you can do the same with your phone. But you'd be wrong (at least on b) because Sony has changed its mind about what waterproof means. Or it doesn't know. It really depends on where you look on the Sony website.
The picture accompanying this article is taken from the Water and dust resistance section of Sony's support pages. The company quite rightly says that "before you dive into the action with your waterproof or dust-resistant Sony device, you should check its capabilities and limits". Seems reasonable enough... let's find out more.
Sony's advice regarding water-based use of a phone is as follows:
If your Sony device has an IP58 rating, as well as being resistant to dust (but not dust-tight), it is also waterproof to IPX8 standard. That means it’s protected against immersion for up to 30 minutes in fresh (non-saline) water at depths of around 1.5 metres. The exact depth and other details will be specified in your user guide.
The company handily explains the IP (Ingress Protection) rating system. The first digit after the letters covers 'resistance to solid objects and dust', and the second is 'resistance to water', the highest possible rating being 6 and 8 respectively. OK… so let's imagine that you have a Sony Xperia X3. The product page has a helpful section about its waterproofness:
With the waterproof Xperia Z3, you can take pictures with the best smartphone camera while swimming in fresh water for up to 30 minutes. You can even dive down to 1.5 metres with it. Just remember that all the covers for the micro USB port, the micro SIM slot and the memory card slot must be firmly closed.
Cool... so you can take photos while swimming and diving, right? You could re-enact the scene picture above if you want, couldn't you? (After all, the Z3 "has an impressive IP65/68 rating"). This is where things start to get confusing. Head over to the Basic care section of the waterproof advice pages and we learn:
The IP rating of your device was achieved in laboratory conditions in standby mode, so you should not use the device underwater, such as taking pictures. Do not use the device to take photos while performing any type of activity underwater, including diving or snorkeling.
So we can't take photos underwater? Who knows? Sony seems undecided, so it's very hard to say for sure (we have, of course, reached out for comment). The advice to not use the phone underwater is rather at odds with the Z3 promotional video which very clearly shows sub-aqua use:
As Xperia Blog says, it is very much a case of mixed messages. The testing procedure described by the company does not really seem to replicate real world scenarios, and hardly instils confidence:
Sony devices that are tested for their waterproof abilities are placed gently inside a container filled with tap water and lowered to a depth of 1.5 metres. After 30 minutes in the container, the device is gently taken out and its functions and features are tested.
It seems that even in testing, the device is not used underwater. It's merely placed underwater... and gently at that. The language used to describe the waterproof capabilities of the upcoming Z5 range is slightly different. Writing on the Sony support forums, a company representative says:
Our new Xperia Z5 is protected from water ingress according to the IPx5/x8 standard, which is the highest water protection featured in mobile handsets. The tests for this rating also include the slow submersion in a fresh water tank up to 1.5m for a duration of 30 minutes. Moving or operating the device while it is submerged is not tested during the laboratory tests. There are also many environmental factors which we could not assess (e.g. water movement or water pressure changes during the movement), if a device is used underwater. Therefore we recommend not submerge our Xperia Z5 in water.
So this highly waterproof phone should not be submerged in water, let alone operating whilst submerged. Most confusing.
You might not be happy that Sony appears to be moving the goal posts. Tough; the company already has a get-out clause in place:
All claims were verified at the time of testing. However, as the mobile landscape changes quickly and new phone models are released on a continuous basis, we cannot guarantee that all claims are still valid as you read this.
Don't like it? Bad luck.
-

Android/Lockerpin.A ransomware holds victims hostage by changing their PIN
Publié: septembre 11, 2015, 2:52pm CEST par Mark Wilson

The latest ransomware to hit Android users attempts to force victims into coughing up $500 by changing the PIN used to lock the device. Disguising itself as a system patch and then a message from the FBI suggesting that 'forbidden pornographic sites' have been viewed, the Android/Lockerpin.A malware differs from previous examples of ransomware that encrypted data.
The malware is impossible to remove without root access or by performing a factory reset. An interesting feature of the PIN change is that even the attacker is unware of what the new code is -- handing over money really makes no difference. But also worthy of note is the way in which Android/Lockerpin.A manages to gain Device Admin privileges.
Lukas Stefanko from security firm ESET explains that the ransomware initially appears as a software patch featuring a Google logo. Anyone agreeing to 'install' the update -- as many people will -- unwittingly grant the malware administrative rights so it is free to do just about anything, and that includes changing the PIN. Android/Lockerpin.A goes a step further, making sure that it is all but impossible to retract these privileges:
When users attempt to deactivate Device Admin for the malware, they will fail because the Trojan will have registered a call-back function to reactivate the privileges when removal is attempted.
In addition to this, Android/Lockerpin.A blocks deletion and attempts to kill antivirus software that may be installed. At the moment the ransomware is found primarily in the US, often in the guise of porn video app called Porn Droid. The malware is not, currently, found in Google Play, but is distributed through third-party sites, torrents and warez outlets.
If you fall victim on a rooted device, you are in (some) luck. Stefanko reveals how to remove the changed PIN:
The only way to remove the PIN lock screen without a factory reset is when device is rooted or has a MDM solution capable of resetting the PIN installed. If the device is rooted then the user can connect to the device by ADB and remove the file where the PIN is stored. For this to work, the device needs to have debugging enabled otherwise it’s not possible (Settings -> Developer options -> USB Debugging). Users can use the following set of commands to unlock the device:
- > adb shell
- > su
- > rm /data/system/password.key
After running the above commands, the PIN or password lock screen will be removed and the user can get to the device.
On unrooted devices, however, a reset involving a loss of data is the only other option.
Photo credit: Paket / Shutterstock
-

Microsoft forcibly downloads Windows 10 whether you want it or not
Publié: septembre 11, 2015, 12:05am CEST par Mark Wilson

Microsoft has started to download Windows 10 to the computers of Windows 7 and Windows 8.1 users regardless of whether they reserved a copy of the operating system upgrade. Eagle-eyed Windows users have noticed the sudden appearance of a folder called $Windows.~BT, occupying up to 6GB of space.
For anyone who reserved Windows 10, this would make sense, as this is the folder used as a temporary storage location during installation. But it seems Microsoft is trying to foist the operating system on everyone, regardless of whether they have expressed interest in it. On one hand it's a pre-emptive move that could be seen as speeding things up for someone if they should later decide to upgrade, but on the other it is slightly more sinister.
SEE ALSO: How to fix Windows 10's worst problems
Delivered through Windows Update, the massive download is a burden for anyone with a slow or metered internet connection. If you've noticed that your slow connection has been even slower, this could very well be the reason why. You may have absolutely no interest in Windows 10, and not even the slightest urge to upgrade, but Microsoft still thinks it should help you out by downloading the necessary files 'just in case'.
The download is delivered through Windows Update -- the place you would normally expect to find patches, bug fixes, and driver updates, not 6GB of unwanted data. What's particularly interesting is that Microsoft does not even try to pretend that it is not happening. The company really is downloading Windows 10 behind people's backs.
In a statement to The Inquirer, a Microsoft spokesperson said:
For individuals who have chosen to receive automatic updates through Windows Update, we help upgradable devices get ready for Windows 10 by downloading the files they’ll need if they decide to upgrade. When the upgrade is ready, the customer will be prompted to install Windows 10 on the device.
We have reached out to Microsoft for further details and we'll update this post when we hear back. In the meantime we'll just ponder what on earth the company thought it was doing. Did it really think that -- in an age where suspicion and privacy concerns abound -- people would be OK with this?
Have you noticed Microsoft trying to force Windows 10 on you?
Photo credit: Stanislaw Mikulski / Shutterstock
-

Should you buy an iPad Pro or a Surface Pro 3?
Publié: septembre 10, 2015, 2:22pm CEST par Mark Wilson

This might seem like an easy question to answer. On the face of it, if you like Apple, opt for the iPad Pro. If you fall into the Microsoft camp, buy yourself a Surface Pro 3. But perhaps it's not quite that simple. Apple touts the iPad Pro as being the tool to increase your productivity, while Microsoft pitches the Surface Pro as blending the best of a tablet with the power of a desktop. But which is better?
'Better' is very subjective, but let's try to look at things as objectively as possible. Price is going to be a key concern for many people, and both devices start at $799 and while this is obviously a similarity, it also highlights a key difference. Part with $799 and you can buy either a 32GB iPad Pro, or a 64GB Surface Pro 3. Neither comes with a cover or keyboard as standard, but the Surface includes a pen while the Apple Pencil will set you back a further $99. Of course, the comparison is about much more than just price.
If you're going to be using your tablet as a laptop replacement, you're going to want a keyboard. Apple's Smart Keyboard will set you back $169, while Microsoft's Type Cover is $130. I realize that we're still focusing on price here to a certain extent, but the addition of a keyboard raises another interesting point. Out of the box, the iPad Pro is a tablet. It can be used in your hands, or placed on a flat surface. If what you’re doing requires you to have the screen at an angle, you're going to have to either attach the Smart Keyboard to make use of the stand this adds, or bodge together something else to prop it up. The Surface Pro 3 has the kickstand built in as standard so it can be used keyboard-free in a number of positions.
Then there are the screens. These have to be considered in two ways: size and aspect ratio. On paper the 12 inches of the Surface Pro 3 and the 12.9 inches of the iPad Pro make them seem near identical. But while the Surface Pro 3 use the widescreen format that has been adopted by laptop and monitor manufacturers for many years now, Apple has decided to use the squarer (and frankly weirder) 4:3 aspect ratio. This adds to the size considerably and it's something that hands-on testers have already commented on. The iPad Pro is a big tablet, and it has been suggested that it is too large to comfortably use for any length of time.
Things are made a little easier due to the fact that the iPad Pro weighs in at just 1.57 pounds (compared to the Surface Pro 3's 1.76 pounds), but Apple's offering is certainly the more unwieldy of the two -- making that Smart Keyboard to convert to a laptop all the more enticing (and arguably necessary). While we're back on the subject of the keyboard, it's worth pointing out a photo that appeared on Twitter showing the differences between how Apple and Microsoft tackled the design of a keyboard cover for their tablets:
iPad Pro vs. Surface Pro 3 when closed with keyboard. One looks ugly /via @AaronIsSocial pic.twitter.com/slVPKofjlg
— Tom Warren (@tomwarren) September 10, 2015
The Surface Pro 3 is described as the tablet that can replace your laptop. As lovely as the iPad Pro may be, this is not really a claim it can make. While the range of apps available for iPad Pro is broad and impressive -- and now almost certain to expand further -- the device does not run a desktop operating system. While some people may be able to conduct all of their work on an iPad Pro, it is certainly not going to be the case for everyone, particularly those people who actually want to use a laptop or desktop computer as well; the crossover apps simply don’t exist. From the offset, iPad Pro is a niche product.
That's not to say that it's not very good at what it does, of course. It's just that it's more comparable to the Windows RT version of the Surface (which doesn't even exist any more), and that was widely shunned. Microsoft was fairly late to the professional tablet market and, for one, Apple has shown itself to be even further behind the curve. The company was quite happy for Microsoft and others to go ahead and test the waters, make mistakes, and redesign. Apple has a far better app ecosystem in place than Microsoft, but when it comes to productivity, there's rarely a replacement for a good, solid desktop program -- and this is where iPad Pro falls down. Mobile apps -- however far they have come -- involve making compromises. In a professional arena, this is not something people should have to do.
Ultimately, Microsoft gives more options and flexibility. There are five models to choose from, so there's something to suit a range of budgets -- Apple only offers three, with the maximum storage being just 128GB. Surface Pro 3 is a real computer. It has a USB port for expansion, and a microSD slot for adding even more storage on top of the built in option of up to 256GB. There's a decent range of Surface Pro 3 accessories: a specially designed mouse, an Ethernet adaptor, Wireless Display Adaptor, even a docking station to complete the conversion to desktop PC.
Clearly the choice you make is a very personal one, but both on paper and in the real world, Surface Pro 3 beats the iPad Pro hands down. Even if -- at the moment -- you feel otherwise, there's the Surface Pro 4 just around the corner and, based on progression over the years, that's promising to be seriously impressive.
-

Persistent bugs delay new Windows 10 Insider Mobile Preview builds
Publié: septembre 10, 2015, 11:34am CEST par Mark Wilson

If you feel like it has been a while since Microsoft released a new preview build of Windows 10 Mobile, you are not alone. In becoming the (very) public face of the Insider program, Gabe Aul has made something of a rod for his own back and is constantly pestered on Twitter for news about when a new build will emerge.
With the long-ish wait since the last build, the troops are starting to get restless. In an attempt to calm things down, Aul has reiterated how the development process works -- because, really, we've already had the concept of internal testing rings explained to us at least a couple of times -- adding that the team is working hard to get a new build ready for this week.
For those who haven't been paying attention, Aul covers old ground explaining that as builds are produced they are tested internally to find any serious bugs that would affect the day to day usage of Insiders. This much we know. But what’s the hold up with releasing a successor to build 10512? Unfortunately for the curious, we're not treated to details of the specifics.
Aul says that problems with mobile hotspots, pinch to zoom, lock screen issues, and Quiet Hours issues have all been addressed, but three unnamed problems keep sending builds back to internal testing rings. All of this is to avoid interfering, as far as possible, with the things people need to be able to do with their phones:
When we release builds to Insiders, even on the Fast ring, we want to make sure people can do everyday activities on their phones -- answering phone calls, sending and receiving text messages, installing and using apps, and all of the other basics. We may have some issues (which we’ll note as known issues for builds we flight), but we know we get the best feedback from Insiders who are really able to use these builds normally and then tell us what they think.
The good news is that fixes have been produced for the trio of problems that existed so a new build should be forthcoming very soon. Just don’t hold your breath, perhaps!
Photo credit: www.BillionPhotos.com / Shutterstock
-

iPhone Upgrade Program screws Apple junkies
Publié: septembre 10, 2015, 12:19am CEST par Mark Wilson

You may have heard that Apple had a little get together today. There were lots of big launches -- the iPhone 6S, the iPhone 6S Plus, and the iPad Pro. Those waiting for an iPhone fix were given quite a lot to get excited about, but like your friendly local drug dealer, Apple has a 'sweetener' to help ensure its customers just keep on coming back for more: the iPhone Upgrade Program which lets you upgrade to a new iPhone every year as long as you keep paying each month.
On the face of it, it might seem like a good deal -- particularly as the price includes Apple Care -- but is that really the case? What Apple's actually doing is feeding the habit of iPhone junkies, keeping their addiction going a little bit longer, and a little bit longer, and a little bit longer. In reality, Apple would like you to perma-rent your iPhone and keep paying through the nose for it. Ideally forever. And the sad thing? People will be quite happy to bend over and take it.
Apple is a company that's not exactly unfamiliar with the concept of squeezing every last cent out of people for as long as possible. Ordinarily, anyone taking on a phone contract is tied in for a certain period after which they are free to move on. Their carrier might well try to persuade them to stay, but this is a one-off event at the end of an 18 or 24 month contract. Apple now has a different idea. Its program has engineered a way for the company to pester customers for up to a year, encouraging them to stick around for another two years. And then the cycle repeats ad infintum. You can check out any time you like, but you can never leave...
So what’s the deal?
Introducing the program Apple says:
Exclusively at Apple’s retail stores in the US, customers can choose their carrier and get an unlocked iPhone 6s or iPhone 6s Plus with the opportunity to get a new iPhone annually and AppleCare+ on the new iPhone Upgrade Program with monthly payments starting at $32 (US) and $37 (US), respectively.
There is, of course, small print:
The iPhone Upgrade Program is available to qualified customers only with a valid US personal credit card. Requires a 24-month installment loan with Citizens Bank, N.A. and iPhone activation with a national carrier — AT&T, Sprint, T-Mobile or Verizon. Full terms apply.
It's something that works very well for Apple. The cheapest iPhone 6s -- the 16GB model -- costs $27 per month on a two year contract -- a total of $648. Add in Apple Care at $79, and you're talking about $727 for the phone. Sign up for the iPhone Upgrade Program and you're paying at least $32 per month. Over 24 months, this adds up to $768 -- already extra profit for Apple.
Ah, but customers get the option of a new phone after a year, don't they? That's true. But in taking advantage of this offer and upgrading after 12 months, you're tied in to another 24 month contract -- a further $768. Apple wins. The customer might feel like this is a win as well, but it's one that is paid for.
For someone who knows that -- without a doubt -- they will upgrade to whatever new iPhone comes out in a year's time, and they're confident that they'd definitely take out Apple Care, it amounts to a saving of a few dollars over two years. But having paid extra every month, many people will feel compelled to make the upgrade at some point between month 12 and month 24 to feel as though they are getting true value for money. But in doing so, they are simply agreeing to hand over even more money to Apple for even longer.
So who wins? Once again, it is Apple.
If you're keen to upgrade, you'd probably be better off offloading an unwanted iPhone on Craigslist and putting money towards a new one. And if you're one of the many people who don’t want to use one of the four main carriers, you're out of luck anyway.
What do you make of it? Do you feel like you'd be getting a good deal, or would Apple just be lining its pockets? Does Apple offer enough incentive to upgrade to the new version of the iPhone every year? Enough of an incentive to justify paying extra for it? Because this is what's happening. Apple is essentially taxing people's desire to be seen with the lastest and greatest iPhone.
It stinks.
Photo credit: Gajic Dragan / Shutterstock
-

Live Blog: Apple's 'Hey, Siri' iPhone 6s, iOS 9, Apple TV and iPad Pro launch
Publié: septembre 9, 2015, 7:01pm CEST par Mark Wilson

Apple knows how to put on a show, and today is no different. Even those with little more than a passing interest in the company are (come on, admit it!) eager to see exactly what will be unveiled. For the most part we know what to expect. There's the iPhone 6s, iOS 9 and Apple TV which are all but guaranted to make an apperance, and there have been suggestions about the long-rumored iPad Pro. Whatever the event holds, there is sure to be at least one surprise, and there's not long to wait to find out more.
There's a live stream if you fancy watching the event live, but if you're not able to for any reason we've got you covered with this live blog. Thing kicks off at 10am PDT/6pm BST -- just keep hitting refresh for the latest updates!
Live Blog
- And we're done -- time to digest all of this!
- New iPhone Upgrade Program means you can get a new iPhone every year -- for a monthly fee, obviously
- Pre-orders start on Saturday 16 September and shipping starts 25th.
- Pricing: iPhone 6S $199, iPhone 6S Plus $299 on a two year contract.
- Spec summary -- covered in a seperate post. Basically, everything is better, bigger and faster.
- Fuck me... this has been going on for two hours!
- haha.... a new app to migrate from Android!
- The feature is enabled by default. So every time you take a photo, you are effectively shooting a video. Surely the 16GB model is dead!
- Live Photos... that's just video isn't it? Maybe I'm missing something.... Touch a photo and it animates. Well... it plays a video
- For selfie freaks, there's a 5MP FaceTime camera... and the screen can be used as a flash!
- There's 4K video.... so is the 16GB iPhone now dead?
- A 12MP iSight camera

- Touch ID has been updated to a version that twice as fast, and there's also a new camera.
- Demo of the A9 chip's capabilities are impressive. Warhammer looks incredible. The number of pixels being pushes around here is amazing:

- In many ways, 3D Touch is a simple upgrade, but adding context to more areas of iOS will make a huge difference to how lots of activities are completed.
- Press with your finger to go deeper.... into your inbox...
- There's a new Taptic Engine that gives better feedback than ever before:

- New feature to shout about is 3D touch. Multi-touch taken to a new dimension -- it's Force Touch essentially... or glorified right-clicking
- There are some nasty new colors. Sorry, but some of those just are not nice!

- OK here's the new stuff. Not just the iPhone 6S, but the iPhone 6S Plus:

- iPhone 6 is the most popular iPhone ever

- iPhone time!
- tvOS is available for developers today, and there's news about pricing. Fairly cheap:

- Apple TV remote is meant to replace all of your existing remotes -- this is nice.
- More gaming and apps details. Buy on one device, use on any. You can also start a game on one device, move to another and pick up where you left off.
- Oh he's gone!
- Bloody hell.... is he still talking about sport?
- Sports. Dull. Zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz
- I mean... how happy am I meant to be about being able to shop fro my Apple TV? Why not just use my laptop?

- These ads... I mean demos.... are great platforms for the companies involved -- not particularly exciting for those watching, sadly
- You can have multiple players involved in games as iPhones can be used as controllers too.
- Not content with taking on Microsoft's Surface Pro with the iPad Pro, Apple TV is also borrowing a few ideas from Nintendo's Wii. Whoda thunk it?
- Touch pad on the remote does look great for controlling games, though.
- Good god, these demoes are contrived.

- Crossyroad on your TV? Your wish is Apple's command!
- Apple TV is also a games console. App Store means games and they work in TV OS:

- The operating system is called... brace yourselves!... TV OS! Give yourselves a raise, guys!
- There's also the option of pulling up info from other apps while you watch a show. Pull up the weather while watching a movie, pull up sport scores during a show. You get the idea.
- What Apple TV is really doing is placing content front and center. Apps -- despite their importance -- don't actually matter all that much. Just search for what you want and it'll appear! Voice controls for playback are also nifty.
- Apple seems to think that screensavers are more impressive though. That's what the team is leading with. Screensavers that adapt to the time of day.
- The ability for Siri to search across multiple apps for matching content is rather cool. Could this be the killer feature?
- Siri, show me comedy! Siri, show me porn! The possibilities are endless!
- Siri works with Apple TV. Nice looking remote. Very much what you would expect really. Details please!

- The future of TV is apps? That already happened with Rokua et al, didn't it?
- Apple TV time
- Oh... there's an iPad Mini 4
- I'm sorry... but how much like a Surface Pro is the iPad Pro with Smart Keyboard? Even the connection is almost identical!

- Smart Keyboard is a slightly eyewatering $169. It has better be as good as Apple says!
- The Apple Pencil is $99.
- Prices start at $799 -- not bad -- for the 32GB model, $949 for the 128GB model, and $1,079 for 128GB ith Wifi and cellular. Available in November.
- We're getting a summary of what the iPad Pro is all about. The tablet everyone said probably wasn't going to make an appearance. Some of us knew better ;)
- Bones and bit. Lovely.
- Apple is really pushing the 'Pro' side of the iPad Pro. Design, medicine -- this is about much more than just pissing about with Angry Birds.
- These demoes are all well and good -- although not outrageously exciting.
- ... as Adobe is only too happy to demonstrate...
- Multitasking, the large screen of the iPad Pro, and multi-touch coupled with the Apple Pencil are going to make the new tablet great for design work
- It seems Microsoft was not only watching -- some of the company are there!

- We need something a bit more exciting now. I can only get so excited about a pencil.
- Now Apple has reinvented the pencil. And call it..... Apple Pencil! Exclusively for iPad Pro.

- New physical Smart Keyboard, connecting magnetically via the new Smart Connector, borrows heavily from Surface. You watching this, Microsoft?
- 6.9mm thin / thick. 1.57lbs
- 4 speaker audio this time around. Audio balances automatically as you move around the iPad Pro.
- There's a bit of willy-waving about how much iPad has improved over the years -- now more powerful than many desktop PC... but still offering (allegedly) 10 hours of battery life.
- 64-bit A9X chip is 'so fast'. 1.8 times faster than its predecessor.
- Might have missed a couple of uses of the word, but 'beautiful' just cropped up -- take a drink, people.
- The width of the display is the same as the height of the iPad Air, rounded to a 4:3 ratio. Lots of space, lots of pixels.
- Biggest display ever -- 12.9 inches. Ideal for the multi-tasking feature of iOS 9.
- iPad Pro -- the most powerful iPad ever

- Biggest news in iPad since the iPad... here we go!
- THERE BLOODY WELL IS A NEW IPAD. COME ON! TOLD YOU!
- A red band to fight AIDS! Lots and lots of new bands

- Gold and Rose Gold finishes available at the same price as the rest of the Sports range

- Announcement of working with Hermes on a new collection. Double wrap wrist straps. Nice-looking accessories!
- [Jolts awake] Has he finished?
- Live health monitoring. Cool -- but it's not what we're really interested in, is it? Get to the point!

- How many people would have thought that a smart watch would be described as a 'game changer' for healthcare? How many people think it might still be a bit of an exageration?
- 10,000 Watch apps on the App Store -- Facebook Messenger on the way, as is iTranslate, GoPro, and AirStrip for health.
- Jeff Williams ready to talk at us. Lots of Watch excitement.
- 97% customer satisfaction rating. Can't grumble at that. No mention of the metric involved, mind...
- Apple Watch is 'helping users live a better day'? Maybe...
- MONSTER announcements on the way!
- We're live at the Bill Graham Civic Auditorium. Tim Cook's on stage. Brace yourselves!
- [Plumps cushions. Gets settled]
Photo credit: TK Kurikawa / Shutterstock
-

Google slashes the minimum price for Android apps in India
Publié: septembre 9, 2015, 5:30pm CEST par Mark Wilson

Google has cut the minimum price for which apps can be sold by a fifth. The price cut currently only affects India, and sees the cost plummet from 50 Rs (around $0.75) to just 10 Rs (around $0.15). It is a decision that has clearly been taken to both entice new customers to Android, as well as discouraging existing users from switching allegiances to Apple -- particularly with the launch of the iPhone 6s.
The lower price point was made available to developers at the end of July, but now Google is starting to promote apps and let users know that there are now many apps available for the reduced price. As well as applying to apps and games in Google Play, the 10 Rs minimum now also applies to in-app purchases.
The company says that: "We hope this lower price point makes it easier for people in India to get access to the apps and games they love at a great price". The blog post points to titles such as Fruit Ninja that can now be purchased for just 10 Rs, and the likes of Real Cricket and even Talking Tom for just 20 Rs.
While this is a move that would certainly be welcomed around the world, Google has not indicated that it has any plans to extend the price drop outside of India. With the price of handsets continuing to drop, the only natural place for further savings to come for customers was through a reduction in app costs. Just what this ultimately means for developers remains to be seen. Cutting prices to a fifth of what they were will attract more buyers -- but not necessarily five times as many.
Photo credit: tanuha2001 / Shutterstock
-

How to stop Slack from using Action Center notifications in Windows 10
Publié: septembre 9, 2015, 12:12pm CEST par Mark Wilson

Slack has done an incredible job of taking over the hearts of countless offices and teams around the globe as a means of keeping in touch. It's what we use here at BetaNews, and it has become the go-to service for many other organizations. But while the app is great, it's not without the occasional issue, and a recent update spoiled an otherwise great user experience for some people.
To fit in with Windows 10, Slack's notification system was updated so that message alerts appear in Windows' Action Center rather than as little popups from the taskbar. 'Great!' you might think, but the Action Center is an incredibly inflexible, awkward, and irritatingly inaccessible place to have notifications. Thankfully there is a hidden setting you can use to shun Windows 10-style notifications and get things back to how they used to be!
SEE ALSO: How to disable Windows 10's Action Center
While I generally like Windows 10, I find the notification system to be a mess. I live in Slack day in, day out, so it's important that it works the way I want it to. I reached out to the company to share my thoughts about how things now operate and was told that "we prefer to use native OS notification systems whenever possible, but I totally understand that the Action Center may not be your preferred method of being nudged about pending message".
This is understandable, but browsing through all of the settings for the app, there seemed to be no way to change the behavior. But there is that hidden setting I mentioned:
- Hit the Windows key and R to bring up the Run dialog.
- Type (or copy and paste) slack://notReallyWindows10 and hit Enter.
That's it. Lovely, standard, non-Action Center notifications are now yours to enjoy once again.
Oh... and if you miss the old colorful icon that used to grace your taskbar, fear not! The monochrome atrocity will soon be a thing of the past:
@MarkWilsonWords Monochrome icon: yeah, we'll fix this up in the next release. Some experiments are more successful than others!
— Slack (@SlackHQ) August 29, 2015
-

WhatsApp Web app vCard vulnerability leaves 200 million users at risk
Publié: septembre 8, 2015, 11:34pm CEST par Mark Wilson

A security researcher at Check Point has discovered a vulnerability in the WhatsApp Web app. The app -- which allows for WhatsApp messages sent to a phone to be viewed on a desktop computer, as well as syncing data -- can be exploited if a malicious user sends a specially-crafted vCard contact to someone.
A problem with WhatsApp's filtering of the contact card means that it could be used to "trick victims into executing arbitrary code on their machines in a new and sophisticated way". What's particularly worrying about this vulnerability is the fact that all an attacker needs is the phone number associated with a WhatsApp account. With an estimated 200 million WhatsApp Web users, there are a lot of potential victims.
Check Point reported the security issue to WhatsApp on 21 August, and an initial fix materialized just six days later. Now the security company is advising anyone who uses WhatsApp Web to update to the latest version of the app in which the feature has been blocked. Detailing the findings of researcher Kasif Dekel, Check Point says that until the problem is fixed:
All an attacker needed to do to exploit the vulnerability was to send a user a seemingly innocent vCard containing malicious code. Once opened, the alleged contact is revealed to be an executable file, further compromising computers by distributing bots, ransomware, RATs, and other malwares.
While a patch has now been issued, what is concerning about this vulnerability is the ease with which it can be exploited -- along with the consideration that many people may not immediately update their software. Without the need for any special hacking tools, all manner of malicious code could be run on a victim's computer, including downloading dangerous executables. Check Point applauded WhatsApp for addressing the problem so quickly, and reiterated the importance of users updating to at least version v0.1.4481 of the software.
-

Microsoft working to bring open source VP9 HD codec support to Edge
Publié: septembre 8, 2015, 11:02pm CEST par Mark Wilson

The technology may exist that allows for ultra-fast transfer of very large files, but the efficient storage of data remains important in many circumstances. Streaming video is one area in which efficiency is particularly important, and the codec used to encode footage has a large bearing on performance.
With the launch of Windows 10, Microsoft took the opportunity to unleash a new web browser on the world -- Microsoft Edge. Today the company reveals that it is working to bring WebM/VP9 to the browser. Initially destined for Windows Insiders in Windows 10 Preview builds, VP9 support will improve Edge's ability to stream HD videos at lower bitrates.
Microsoft aims to offer support for both hardware and software decoding, and Media Source Extensions will bring adaptive streaming. The codec is being brought to Edge to cater for websites that deliver videos in this way, but Microsoft is also looking to add support for local playback, VP9 media tags, and related audio formats such as Opus.
Unsurprisingly, Microsoft points out that "since decoding video is computationally complex, the best experience with the software decoder will be seen on more powerful desktop and laptop computers". This in mind, the company is working with hardware manufacturers to bring better hardware support and the company says that VP9 support will be made available in the first instance through the use of an experimental flag, and will ultimately be a togglable setting.
Microsoft's newly found love of open source is set to continue in the future. Other formats, including OGG, Opus, and Vorbis, are being looked at. The Microsoft Edge Platform Status page will be used to log other formats that are under development.
-

Microsoft acquires cloud security firm Adallom
Publié: septembre 8, 2015, 10:57pm CEST par Mark Wilson

Microsoft continues to look to the cloud -- not just with Windows 10, but with many of its enterprise services -- and security remains of the utmost importance. Now the company has announced the acquisition of cloud security firm Adallom in a move that will give customers additional ways to protect their data in the cloud.
The security company started life two and half years ago, and Microsoft sees value in adding it to its existing portfolio of acquisitions. Adallom co-founder Assaf Rappaport describes joining the Microsoft family as "another validation of [the company]", while Microsoft says it demonstrates its "commitment to delivering innovative identity and security capabilities".
Earlier in the year there had been rumors that the acquisition had already taken place at a cost of $320 million to Microsoft. Now the deal has actually gone ahead, no details have been released of how much money has changed hands or what the acquisition will mean for staff and company structuring in the long run. But Microsoft believes that in taking Adallom under its wing, it will be able to provide better on-premises security as well as protecting access to cloud-based data and applications.
In a post on the Microsoft blog, Corporate VP of Cloud and Enterprise Marketing Takeshi Numoto says:
Adallom expands on Microsoft’s existing identity assets, and delivers a cloud access security broker, to give customers visibility and control over application access as well as their critical company data stored across cloud services. Adallom works with popular cloud applications including Salesforce, Box, Dropbox, ServiceNow, Ariba, and of course Office 365. As a cloud-delivered, security-as-a-service solution, Adallom will complement existing offerings that Microsoft makes available today as part of Office 365 and the Enterprise Mobility Suite (EMS), including our recent Microsoft Advanced Threat Analytics release.
For the time being, Adallom will continue to work with its existing customers and develop new technologies whilst integrating into Microsoft.
Photo credit: 360b / Shutterstock.com
-

Apple can't give real time iMessage data to the FBI because texts are encrypted
Publié: septembre 8, 2015, 1:57pm CEST par Mark Wilson

Despite a court order instructing the company to hand over text conversations between iMessage accounts to the FBI, Apple says that its own encryption system means it cannot do so. The Justice Department obtained a court order that required Apple to provide real time access to text messages sent between suspects in an investigation involving guns and drugs.
Apple has responded by saying that the fact iMessage is encrypted means that it is simply not able to comply with the order. The stand-off between the US government and Apple could last for some time as neither side is willing -- or possibly able -- to back down.
Just as in the UK, the US government has voiced opposition to encryption systems that it argues make it difficult to gain access to certain data. The situation with Apple is the highest-profile case about encryption and where it sits in relation to investigations, but it is certainly not the first of its kind. Microsoft has already withheld emails that courts requested access to, and it is likely that more and more cases will follow.
While security experts have pointed out that any limitations placed on encryption pose a security risk, many tech companies -- including Apple, Google, and Microsoft -- are strongly opposed to the idea of either doing away with encryption or providing government backdoors.
Apple users will be pleased to hear that the company appears to be standing its ground, placing greater importance on privacy and encryption than the government would like. It has been argued that any backdoors that might be built into products, or the construction of any system that could allow government access to communications, could be easily exploited by other parties. To that end, Apple is standing by its decision to implement end-to-end encryption, having conceded only to hand over the content of some messages to the FBI, rather than providing real time access as requested.
Photo credit: Dmitro2009 / Shutterstock
-

Fujitsu's 300GHz, 10+ Gb/s receiver could transfer 4K and 8K videos 'instantly'
Publié: septembre 8, 2015, 12:05pm CEST par Mark Wilson

Fujitsu has revealed details of a new wireless receiver capable of data transfer rates of "several tens of Gigabits per second". Operating on the terahertz band, the receiver is over 100 times faster than current devices that use the 0.8-2.0 GHz range.
Described as "the world's first 300 GHz band compact receiver", the receiver is ten times smaller than previous models, opening up the possibility of use in mobile devices. Shrinking the unit has reduced its size to under one cubic centimeter and Fujitsu says that it "enables mobile devices to instantly transfer 4K or 8K HD video".
The need for greater bandwidth has become ever more pressing as file sizes increase due to improvements in image and video quality. High resolution video is very demanding of wireless connections, and Japan's Ministry of Internal Affairs and Communications commissioned a research and development project for the expansion of radio spectrum resources with a view to finding a solution.
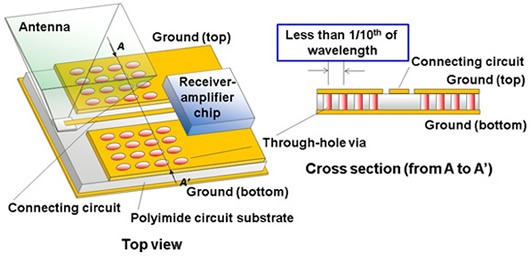
While high-speed transfer devices have existed for a while, previous limitations meant that the receiver-amplifier module and antenna had to be separate. By integrating the antenna into the receiver-amplifier, Fujitsu was able to eliminate the waveguide component, but had to then develop a new low-loss polymide for use on printed circuit boards. Fujitsu says:
With mobile devices such as smartphones capable of high-volume communication at rates of several tens of gigabits per second, the use of this Fujitsu-developed technology will enable small devices to receive 4K or 8K HD video instantly, such as from a download kiosk with a multi-gigabit connection. It will also be possible to expand into such applications as split-second data transfers between mobile devices and split-second backup between mobile devices and servers.
Testing starts this year, and it is hoped that the technology will be commercially available by 2020.
Photo credit: style_TTT / Shutterstock
-

How much does the camera of the new Nexus 5 stick out? This much...
Publié: septembre 8, 2015, 10:16am CEST par Mark Wilson

It should only be a matter of weeks before we have official news about the new Nexus 5, but as we draw closer to the launch, leaked images continue to stream in. Just a few days ago we were treated to the best image yet of the upcoming LG handset, and now we have a new photo that gives a slightly different view.
A new leaked image depicts the new Nexus 5 (or Nexus 5X, perhaps) from a side angle, giving a clear view of the protruding camera lens that graces the rear. The photo also shows the repositioned power and volume buttons, but it is the camera nipple that will probably cause the most interest.
As with the previous leak, this new image comes courtesy of AndroidPIT. While the earlier photo made it apparent that the camera lens is of the protruding variety, it was not clear just how much it stuck out. With a photo taken from a slightly different angle we can see that the lens adds quite a bulge to the Nexus 5. That said, the handset does appear to be rather thinner than the current Nexus 5.
We had already seen that the phone had a fingerprint scanner on the rear of the case, and the side-angle photo shows that the power button has been moved down the side of the phone so that it lines up with the biometric reader. The volume rocker has also been moved, so it is now to be found virtually in the center of the right hand side of the phone.
The photo doesn’t give away much more, but AndroidPIT's source says something that suggests that the new Nexus 5 could be a fairly cheap handset. While many phone manufacturers are opting for a higher quality feel by adopting all-metal designs, here we are told that the Nexus 5 will "probably not" have metal edging.
Photo credit: AndroidPIT
-

Time to patch your firmware! Backdoor discovered in Seagate NAS drives
Publié: septembre 7, 2015, 8:26pm CEST par Mark Wilson
 If you have not recently updated the firmware for your Seagate wireless NAS drives, now is the time to do so. Researchers at Tangible Security have discovered a series of vulnerabilities in a number of devices produced by Seagate that could allow unauthorized access to files and settings.
If you have not recently updated the firmware for your Seagate wireless NAS drives, now is the time to do so. Researchers at Tangible Security have discovered a series of vulnerabilities in a number of devices produced by Seagate that could allow unauthorized access to files and settings.An undocumented Telnet feature could be used to gain control of the device by using the username 'root' and the hardcoded default password. There are also other vulnerabilities that allow for unauthorized browsing and downloading of files, as well as permitting malicious files to be uploaded. Tangible Security says that Seagate Wireless Plus Mobile Storage, Seagate Wireless Mobile Storage, and LaCie FUEL drives are affected, but there may also be others.
The security issues are confirmed to exist with firmware versions 2.2.0.005 to 2.3.0.014. The problems were discovered way back in March, but a patch has only recently been published, along with an advisory notice from US CERT. Tangible Security issued a warning of its own:
With products from large vendors such as Seagate, there tend to be numerous product names for basically the same product under the same vendor’s name or another vendor. Tangible Security cannot enumerate all of the named products as well as Seagate. Other named products may be affected.
The research group also shared details of the vulnerabilities:
Use of Hard-coded Credentials
- Vulnerability Description: The affected device firmware contains undocumented Telnet services accessible by using the default credentials of 'root' as username and the default password
- Impact Description: an attacker can covertly take control of the device, not only compromising the confidentiality of files stored on it but use it as a platform to conduct malicious operations beyond the device
- CVE-2015-2874
- CWE-798
Direct Request ('Forced Browsing')
- Vulnerability Description: The affected device firmware provides unrestricted file download capability
- Impact Description: Attackers can gain access all files stored in affected devices. This vulnerability requires attackers to be within range of the device’s wireless network
- CVE-2015-2875
- CWE-425
Unrestricted Upload of File with Dangerous Type
- Vulnerability Description: The affected device firmware provides a file upload capability to the device's /media/sda2 file system, which is reserved for the file sharing
- Impact Description: this vulnerability requires attackers to be within range of the device’s wireless network, who can upload files onto it. If such files were maliciously crafted, they could compromise other endpoints when the files are opened
- CVE-2015-2876
- CWE-434
Anyone with an affected device is advised to update to firmware version 3.4.1.105 which addresses the issue.
-

Time to patch your firmware! Backdoor discovered into Seagate NAS drives
Publié: septembre 7, 2015, 8:26pm CEST par Mark Wilson
 If you have not recently updated the firmware for your Seagate wireless NAS drives, now is the time to do so. Researchers at Tangible Security have discovered a series of vulnerabilities in a number of devices produced by Seagate that could allow unauthorized access to files and settings.
If you have not recently updated the firmware for your Seagate wireless NAS drives, now is the time to do so. Researchers at Tangible Security have discovered a series of vulnerabilities in a number of devices produced by Seagate that could allow unauthorized access to files and settings.An undocumented Telnet feature could be used to gain control of the device by using the username 'root' and the hardcoded default password. There are also other vulnerabilities that allow for unauthorized browsing and downloading of files, as well as permitting malicious files to be uploaded. Tangible Security says that Seagate Wireless Plus Mobile Storage, Seagate Wireless Mobile Storage, and LaCie FUEL drives are affected, but there may also be others.
The security issues are confirmed to exist with firmware versions 2.2.0.005 to 2.3.0.014. The problems were discovered way back in March, but a patch has only recently been published, along with an advisory notice from US CERT. Tangible Security issued a warning of its own:
With products from large vendors such as Seagate, there tend to be numerous product names for basically the same product under the same vendor’s name or another vendor. Tangible Security cannot enumerate all of the named products as well as Seagate. Other named products may be affected.
The research group also shared details of the vulnerabilities:
Use of Hard-coded Credentials
- Vulnerability Description: The affected device firmware contains undocumented Telnet services accessible by using the default credentials of 'root' as username and the default password
- Impact Description: an attacker can covertly take control of the device, not only compromising the confidentiality of files stored on it but use it as a platform to conduct malicious operations beyond the device
- CVE-2015-2874
- CWE-798
Direct Request ('Forced Browsing')
- Vulnerability Description: The affected device firmware provides unrestricted file download capability
- Impact Description: Attackers can gain access all files stored in affected devices. This vulnerability requires attackers to be within range of the device’s wireless network
- CVE-2015-2875
- CWE-425
Unrestricted Upload of File with Dangerous Type
- Vulnerability Description: The affected device firmware provides a file upload capability to the device's /media/sda2 file system, which is reserved for the file sharing
- Impact Description: this vulnerability requires attackers to be within range of the device’s wireless network, who can upload files onto it. If such files were maliciously crafted, they could compromise other endpoints when the files are opened
- CVE-2015-2876
- CWE-434
Anyone with an affected device is advised to update to firmware version 3.4.1.105 which addresses the issue.
-

Norwegian Pirate Party bursts through Pirate Bay blocks with free DNS service
Publié: septembre 7, 2015, 5:36pm CEST par Mark Wilson

Governments around the world continue to block access to torrent sites, and people keep finding ways around any roadblocks that might be put in place. Proxies and mirrors have been used to get around restrictions, and now the Norwegian Pirate Party has set up its own free DNS service to provide access to the Pirate Bay.
The Pirate Party is an advocate of free, unrestricted access to the internet, and its latest move is a reaction to the government of Norway blocking access to the the Pirate Bay. The uncensored DNS servers are free for anyone to use, and demonstrate just how easy it is to bypass restrictions that governments seem to believe are the answer to the problem of piracy.
The party is concerned about the level of control that is exercised over internet access. Whether or not you are interested in making use of the Pirate Bay specifically, the fact that so many countries have implemented blocks is what the Pirate Party describes as "yet another sad step down the road towards the dystopic world imagined by George Orwell".
The party announced the availability of its DNS service in a post on its website:
Pirate Party are against censorship of the Internet. The major film companies have joined forces in a lawsuit and obtained the largest Internet providers in the country to block a number of websites. They do this by redirecting requests on its name servers. Pirate Party has therefore set up an alternative, unblocked nameserver in Norway, dns.piratpartiet.no, with address 185.56.187.149. It is open to all and does not store your IP address.
The site also provides detailed information about how to make use of the DNS server -- there are details for Mac, Windows, and Linux users, as well as information about how to set things up at router level.
Of course, you do not have to be in Norway to make use of the DNS service. Wherever you are in the world, you can change your settings to gain unfettered access to the internet.
-

Iron Maiden and Onkyo produce rock and metal friendly Ed-Ph0n3s headphones
Publié: septembre 6, 2015, 4:38pm CEST par Mark Wilson

British metal band Iron Maiden has teamed up with Japanese firm Onkyo Corporation to produce a set of headphones -- or Ed-Ph0n3s, named after the Eddie mascot. Founding member and bassist Steve Harris used the headphones when mixing the new album The Book of Souls, and fans of the Maiden will be able to get their hands on a pair of their own too.
Designed specifically with rock and metal listening in mind, the Ed-Ph0n3s were on display at IFA 2015 in Berlin this week. We'd already seen mock-ups of the full-ear bins at CES earlier in the year, but now we've seen the finished product and know more about the specs.
No one involved in the production of the Ed-Ph0n3s has said quite why the cans are particularly suitable for metallers and rockers, but what you see in the picture is the result of nine months' work. The band says that this time was spent working tirelessly to "fully emulate and ensure top grade quality on the production line within clearly defined tolerances".
Iron Maiden is yet to reveal pricing or launch date, but from the stand at IFA we know the following specs:
- Drivers: twin 40mm titanium-coated diaphragm drivers
- Frequency: 10Hz to 27kHz
- Impendence: 32-Ohms
- Pressure: 105db/mW (Nominal)
- Max input: 800W
- Weight 245g
- Cable length: 1.6m
You can check out some shots of Eddie at the IFA stand over on the Maiden Audio website.
-

Google donates €1 million to help refugees in need
Publié: septembre 6, 2015, 11:58am CEST par Mark Wilson

The on-going refugee crisis in Europe, Africa, and the Middle East has grabbed hearts and headlines around the world. As European governments argue over who should take in the thousands of desperate people, European citizens have criticized the speed and scale of the help offered, whilst simultaneously donating money, food, and equipment to help those in desperate need.
Now Google has stepped in, offering €1 million ($1.1 million) to the organizations providing help to refugees. In addition to this, Google.org (the branch of the company "using innovation to tackle some of the world’s biggest challenges") is setting up a page to make it easier for people to make donations, and says that it will match any money donated by Google users.
Google's donation to humanitarian aid organizations such as Médecins Sans Frontières, and UNHCR is in response to what has been described as "the world’s biggest [refugee and migrant crisis] since the Second World War". The company says: "Given the severity of this crisis, we want to play our part in helping relieve the plight of refugees and migrants around the world".
Writing on the Google Europe blog, Google.org director Jacqueline Fuller says:
Google.org is donating €1M to organisations who are providing front-line humanitarian relief to migrants and refugees, such as International Rescue Committee, Médecins Sans Frontières, and UNHCR. These organisations are providing essential assistance, including shelter, food and water, and medical care, to people in dire need.
In addition, we are creating a public site to help people make their own donations and are matching Googler donations as well.
As soon as the site is up and running, we'll post details about it.
Photo credit: UNHCR
-

Snowden: web restrictions are 'wrong in Russia, would be wrong anywhere'
Publié: septembre 5, 2015, 9:07pm CEST par Mark Wilson

Edward Snowden might be holed up in Russia, but that's not going to stop him from criticizing the country. While accepting the Norwegian Academy of Literature and Freedom of Expression’s Bjornson prize, the former NSA contractor used a speech to call Russia's attitude to internet freedom and homosexuality as "fundamentally wrong".
The US government has indicated that it has no intention of pardoning Snowden so he remains in exile -- for now, this is in Russia. Not shy to court controversy -- and possibly biting the hand that feeds -- he has hit out at the Russian government saying that its control and restrictions it places on the web are a "mistake in policy".
Although Snowden has asylum in Russia, he has made it clear that he would much prefer to his native USA. Speaking via videophone from Russia while accepting his award for the work he has done for privacy, he said that surveillance and restrictions not do necessarily help to keep citizens safe in the way that governments often claim.
He pointed to the Charlie Hebdo attacks where, despite the assailants being known to French intelligence agencies, nothing was done to stop them.
Speaking about the situation in Russia, he said:
I’ve been quite critical of [it] in the past and I’ll continue to be in the future, because this drive that we see in the Russian government to control more and more the internet, to control more and more what people are seeing... [is] fundamentally wrong.
Photo credit: GongTo / Shutterstock
-

Microsoft leaks details of upcoming Skype Central Universal Windows 10 App [UPDATE -- there's no rebrand]
Publié: septembre 5, 2015, 6:45pm CEST par Mark Wilson

A post has appeared on Microsoft's TechNet that suggests the company could be on the verge of combining Skype for Business and the consumer version of Skype into a single product known as Skype Central.
The move would echo that taken with OneDrive, and would help to streamline things a little for developers. The post is written by Microsoft's Tony Eversole and is designed as a placeholder so developers have a central point to exchange news and information.
This is the first hint that there are any changes planned for Skype -- it is not something that Microsoft has yet talked about. For now the placeholder doesn’t give away a great deal:
Placeholder entry for Skype Central Universal Windows 10 App. The idea is to have a shared blog from which PFE/DSE engineers can update the main landing page of the app to include news, troubleshooting, CU release information, or anything related to Skype for Business. This shared blog feed will be the mechanism from which Windows 10 Live Tiles are updated (notifications in Action Center, Live Tile data update, new article count, etc). This shared blog/feed can be hosted on TechNet or a 3rd party blogging service which complies with RSS 2.0.
Over on WinSuperSite, Richard Hay says that the post is home to two logos for Skype Central but it appears that it has since been updated, as there is only one visible now. Watch this space for more details!
UPDATE
Tony Eversole has been in touch to clear up what the post on TechNet is actually about. He says:
Skype Central is a placeholder name for a personal Windows 10 Universal App I am developing that acts as a document/tools/blog aggregator. It has nothing to do with Skype for Business or the Skype Product Group. The entry on TechNet was a test feed to be delivered to the app for feed testing and Live Tile testing. The logo is also unofficial and does not represent any current or future Skype rebranding.
-

Leaked image shows new Nexus 5
Publié: septembre 5, 2015, 5:32pm CEST par Mark Wilson

If you've been wondering what LG's new Nexus 5 -- expected to be launched at an event 29 September -- looks like, wonder no more. We've already seen one leaked image purporting to show the device, and now we have another one to add to the pot.
This one is a particularly clear shot, and its quality means it's hard not to think that this is an official photo. Of course, this has not come from Google or LG -- at least neither have said as much -- but Android site AndroidPIT has obtained an image from a trusted source.
In line with previous leaks, the AndroidPIT photo shows the phone with a fingerprint reader beneath the camera lens. The camera itself is a protruding affair, and the handset is shown in white -- we don't yet know for sure whether there will be other color options available.
With the recently-confirmed Android 6.0 Marshmallow, we should expect to see the new Nexus 5 launch with the latest version of Google's mobile operating system installed later in the month. The LG-manufactured handset is believed to be a 5.2-inch device featuring a Snapdragon 808 CPU, 3 GB of RAM, and a 2,700 mAh battery.
At the event on 29 September, we should also see a 5.7-inch device manufactured by Huawei, and it is thought that pricing might be lower than previous Nexus handsets due to a plastic construction.
Photo credit: AndroidPIT
-

Stop Windows 10's keylogger from monitoring what you type, ink, and say
Publié: septembre 5, 2015, 3:26pm CEST par Mark Wilson

The 'keylogger' that's built into Windows 10 has gained something of a bad reputation -- but it's really a bit of a misnomer. Yes, there is a component that -- technically speaking -- tracks what you input using the keyboard, screen, mouse, voice, and stylus... but it's a bit more complicated than that. It is not really a keylogger in the sense that the malware term usually implies.
Microsoft openly admits that "when you interact with your Windows device by speaking, writing (handwriting), or typing, Microsoft collects speech, inking, and typing information". It's done with the intention of improving the accuracy of suggestions, providing a personalized experience, and so on. But we live in an age where privacy matters. If you are concerned about the privacy implications of this component of Windows 10, you can disable it. Here's how.
There are a couple of settings that you might be interested in changing, and they are easily accessed. Fire up Settings and click the suitably-named Privacy icon. In the General section, click the third toggle button (labelled 'Send Microsoft info about how I write to help us improve typing and writing in the future') so that it is set to Off.
Now move to the Speech, inking, & typing section and click the Stop getting to know me button. As we have mentioned before, this stop Windows from snooping into your contacts and calendar with Cortana.
Close the Settings window, and you're done. These changes may not allay the fears of some people who are opposed to Windows 10, but it goes some way to helping users regain control of their privacy.
Photo credit: Sangoiri / Shutterstock
-

Time to have a cloud clear out as Google Drive bonus storage expires
Publié: septembre 4, 2015, 2:53pm CEST par Mark Wilson

Google is just one of many companies to offer free cloud storage, and over the years the amount of space given away has crept up. There have also been plenty of opportunities to boost cloud storage for free -- if you've bought a Chromebook, you'll have been given a bunch of extra space, and there have been various other special offers out there.
You may well have received a mysterious email from Google in the last day or so, warning you that you are about to lose 10GB of space. The email rather unhelpfully refers to an "Unknown promotion". What's it all about, and what do you need to do?
Well, you don’t need to do anything. As Google points out in the email, just because you are losing the space, it does not mean that you are going to lose the files you have stored in the cloud. What you will notice, however, is that you are unable to sync files, or upload any more. You could opt to pay for some more space, but if you want to keep it free, it's time to have a clear out.
With Google's free space shared between Gmail, Google Photos and Google Drive, the most obvious places to look first are Photos and your inbox. Keep an eye out for email with huge attachments, and take the time to browse through your photos for any you can either delete or move to local storage. The longer you leave it, the longer you won’t be able to synchronize files.
Oh, and if you were wondering, it seems that the "Unknown promotion" refers to the free space that was given away to people who installed QuickOffice on iOS or Android.
-

Spotify publishes new, clearer privacy policy following complaints
Publié: septembre 4, 2015, 12:06pm CEST par Mark Wilson

It's only a couple of weeks since Spotify last updated its privacy policy, but the wording was such that many users were upset at the access the company appeared to be asking for. The backlash was so bad that the company was forced to apologize and now it has gone a step further and published a new, reworded version of its policy.
Spotify again admits that the previous version of the privacy policy led to some "understandable confusion", before launching into plain English remodeling of the document. With a new policy that is now more intelligible, the company will no doubt be hoping to claw back those users who were driven away.
In a blog post, Spotify explains that in addition to the updated privacy policy, it has also added an introduction that sets out the basic principles it incorporates. It goes on to explain that if you have already accepted the privacy policy from a couple of weeks ago, "you will be automatically covered by this update, including the clearer language, additional privacy commitments and the new Introduction and its principles". This is something of a strange move as it will almost certainly lead to users poring over the new documents looking for any changes that may have been snuck in via the back door -- something that could have easily been avoided.
The company says:
When our new Privacy Policy started rolling out two weeks ago, it created some understandable confusion. In a follow-up post, we did our best to explain the intent behind the changes in the Policy and our commitment to our users’ privacy. We also said that we would work to update the Privacy Policy to reflect what we promised in that post. As we worked to do that, we took note of many people’s comments that they appreciated the clear commitments in the blog post that were easier to understand than some of the details in the Policy itself.
The new policy is rolling out in the coming days and weeks, although only those who have not yet agreed to the previous update will see a notification of this.
Photo credit: 360b / Shutterstock
-

At long last Google improves Chrome's memory and battery usage
Publié: septembre 4, 2015, 12:40am CEST par Mark Wilson

Chrome has long been maligned as a huge drain on system resources. Open more than a few tabs and you'll notice that memory usage skyrockets, and performance can slow to a crawl. Run Chrome on a laptop that's not connected to mains power, and you've probably seen the battery meter plummet whenever you use the browser.
Now -- at long, long last -- Google is doing something about it. The latest version of Chrome boasts a number of improvements designed to reduce the browser's footprint, including a new intelligent tab restoration system that keeps the least viewed tabs suspended in the background until needed. Chrome 45 is also far more aggressive at actively cleaning up memory.
The new memory-saving technique helps to reduce the impact of webpages by an average of 10 percent, but the saving can be even greater on more complex pages. This is something that is further assisted by the new Flash-killing feature that pauses any non-essential Flash content. Google claims this can lead to battery life improvements of 15 percent, but it will be interesting to see what sort of figures users report.
Google is so proud of the memory management improvements that have been made, that it has produced a video to show the savings that can now be made in Gmail:
The improved tabbed management is something that is likely to prove beneficial to many Chrome users. Google says:
Now, Chrome is smarter about restoring your tabs more efficiently. Tabs are restored from most to least recently viewed, so you get to see the most important tabs faster. And Chrome will now detect if your computer is running low on resources and stop restoring the rest of your tabs to save you precious memory. You can always click to restore them if you'd like to access them later.
Photo credit: Ratana21 / Shutterstock
-

Google provides help with more health conditions than ever before
Publié: septembre 3, 2015, 10:44pm CEST par Mark Wilson

Turning to the internet for medical advice is something of a double-edged sword. On one hand, it provides access to a wealth of information previously only available to medical students, making it easy to look up symptoms and see what they might mean. On the other, hypochondriacs can very easy self-diagnose every condition under the sun.
But there's no denying that it can certainly be helpful to be able to find out a little more about different conditions from the comfort of your phone or computer. Today Google announces a swathe of updates that it hopes will help people to be better informed in terms of understanding symptoms and treatments, and conveying what they are experiencing to a doctor.
Google's heath conditions feature has only been around since February, and today's announcement sees the number of conditions it covers more than doubling to over 900. Anyone with concerns can simply fire up Google and search for conditions or symptoms to find out a possible diagnosis and advice about what to do. As well as being available via desktop search, the information can also be accessed through the Google app on mobile devices.
Just how data is displayed depends very much on the type of search that is performed. For each condition Google covers, a simple three panel box provides all of the information you need, with tabs for general information, a list of symptoms, and a list of treatments. Details such as the prevalence and cause of particular conditions helps users to determine how likely a given diagnosis is, and a helpful printable PDF that can be taken along to a doctor is also provided.
Google says that it has been working with a team of doctors to curate and validate the information it provides:
We’re making sure to include neglected tropical diseases, a set of infections that affect over 1.5 billion people including 500 million children in poorer regions. We think it's important for people to have facts on these diseases, such as Dengue Fever (already included), Chikungunya, and Leishmaniases (to be added soon). Today the feature is still only in U.S. English, but we plan to expand it to more languages and regions.
Photo credit: samarttiw / Shutterstock
-

Snowden: Hilary Clinton's personal email server likely exposed sensitive national intelligence
Publié: septembre 3, 2015, 9:26pm CEST par Mark Wilson

If anyone else at the State Department made use of a personal email server to discuss sensitive information, they would have been fired and prosecuted, says Edward Snowden in a scathing attack on Hilary Clinton.
The former NSA worker hit out at the Democratic presidential candidate in an interview with Al Jazeera. He said that Clinton was probably aware that using a personal email address had exposed sensitive national intelligence, describing it as 'a problem'.
Hilary Clinton has faced heavy criticism after it was discovered that she had used a personal email server in the State Department. Batches of email have been published, but large swathes have disappeared making it impossible to know exactly what sort of correspondence the server was used for. In an interview that is due to air tomorrow, Snowden said:
If an ordinary worker at the State Department or the Central Intelligence Agency [...] were sending details about the security of the embassies, which is alleged to be in her email, meetings with private government officials, foreign government officials and the statements that were made to them in confidence over unclassified email systems, they would not only lose their jobs and lose their clearance, they would very likely face prosecution for it.
He says that Clinton really should have known better, suggesting that "anyone who has the clearances that the Secretary of State has, or the director of any top level agency has, knows how classified information should be handled". Controversy sprung up around the revelation that Clinton had been using a personal email server for a number of years, and this was further stoked when thousands of emails described as 'personal' were deleted. She is currently under investigation to determine whether classified information ended up in her email account, and her poll ratings have been gradually sliding as her campaign progresses.
Photo credit: JStone / Shutterstock
-

Motorola defends its decision not to make the Moto 360 screen entirely round
Publié: septembre 3, 2015, 8:33pm CEST par Mark Wilson

The traditional shape of a watch face is round. There are variations, of course -- square, rectangular, and so on -- but for the most part, round is a safe bet. With the Moto 360, however, Motorola raised a few eyebrows when its screen was launched with a design that has become known as the 'flat tire' look.
Yesterday, the company unveiled the new version of the Moto 360 and the same flat tire, non-round screen is present. What gives? Despite disappointment, and even ridicule from users, Motorola remains adamant that it made the right choice, standing by its decision to keep the flat tire in the second generation of the smartwatch. So, is it ugly, or does it make sense?
Take a look at the Motorola website, and you'll notice that a very large proportion of the photos of the Moto 360 show black watch faces. This goes some way to disguise the unsightly slither of the visage that is not made up of pixels -- but not far enough. Why would a company make the conscious decision to implement a design that is unattractive, and viewed by many as inferior to the competition?
Speaking to AndroidPIT, Motorola's product management lead Kouji Kodera said:
It is possible to do round ones, like the competition is doing, but things will stick out [...] The design and the form factor are very important. This shape and design also allow us to provide possibilities for giving choice on different colors, different materials and different bezel designs. We thought that was more important than this tiny black slit at the bottom.
The 'tiny black slit' is home to, among other things, the ambient light sensor. Motorola insists that customer feedback showed that people placed great value on having more customization options to choose from -- different sizes, different colors, and so on -- and the company therefore chose to focus on delivering in these areas.
Kodera admitted that some work had been done to develop a version of the Moto 360 with a completely round screen but said that "the value added by going this direction outweighed the alternative". With other manufacturers having been able to overcome the problem fairly easily, it can only be assumed that Motorola either couldn't come up with a way of producing a round screen, couldn't do it cheaply enough, or did not want to invest the time and money to conduct the research.
Was it a mistake?
-

Boost your trivia knowledge with Google's 'fun fact' Easter egg
Publié: septembre 3, 2015, 1:25pm CEST par Mark Wilson
Google has lots of tricks up its sleeve -- it's much more than just a search engine -- and now there's something new to try out. Hot on the heels of the unveiling of its new logo, the company has quietly launched a new "fun fact" feature for its search tool.
The next time you have a few minutes to kill, or you just like the idea of learning something new, type "fun fact" into the search box. Google will furnish you with a random fact -- from the price of a lifetime airline pass, to where golf was first played in the US. The only danger is that it could quickly turn into a real productivity vacuum!
You can also type "I'm feeling curious" or "fun facts", but the shorter eight character "fun fact" does the job and will probably be the most used. Feel the need for more facts? No need to perform another search, just hit the Ask Another Question button and Google will come up with the goods.
In some ways this is an extension of the I'm Feeling Lucky feature, but with a twist of randomness thrown in for good measure. You can limit your trivia intake to the little snippets Google delivers, but if you find that your interested is piqued, you can click through to find out more.
What have I learned this morning? Dracula's real name, the name of the guy who invented the tea bag, and the fact that horses have 18 pairs of ribs. I'm off down to the pub now to take part in the quiz!
-

Toshiba announces trio of convertible Windows 10 PCs including a Surface Pro wannabe
Publié: septembre 3, 2015, 12:52pm CEST par Mark Wilson

Today Toshiba unveiled three new devices designed to take advantage of Windows 10: the Satellite Radius 12, the Toshiba Satellite Radius 14, and the Toshiba Satellite Click 10. The largest of the devices -- the Satellite Radius 14 -- is a 14-inch laptop with a 360-degree rotating screen which offers a total of five operating modes.
The mid-sized Satellite Radius 12 features a smaller 12.5-inch screen, and the rotating screen allows for multi-position use. Rounding off the trio is the Satellite Click 10, arguably the most interesting of the bunch, which boasts 14 hours of battery life. The detachable keyboard makes this a Surface competitor and gives the choice of working in laptop or tablet mode.
The Satellite Radius 14 is an ultra-slim device that can be used in laptop, tablet, tabletop, presentation, and audience modes. A brushed aluminum finished gives a quality look, and the Harman Kardon speakers with DTS Sound enhancement are ideal for all manner of tasks. There's a choice of AMD Quad-Core processors and up to sixth generation Intel Core processors, and an optional SSD helps to take the battery life up to 10 hours.
Next in line is the Satellite Radius 12 complete with an Ultra HD 4K screen. The display is crafted from Corning Gorilla Glass NBT reinforcement for extra durability. Finally, there is the Satellite Click 10, the smallest and most portable of the bunch. The device features an Intel Atom processor, backed up with up to 4GB of RAM and up to 64GB of eMMC storage.
All three devices will be available in Q4 of this year, but Toshiba is yet to provide pricing details. The Satellite Radius 14 and Satellite Radius 12 are destined for Europe and the US, while the Satellite Click 10 is due for release in Europe only.
-

Android apps gain massive web performance boost from Chrome custom tabs
Publié: septembre 3, 2015, 1:09am CEST par Mark Wilson

Android developers looking to include web content in their apps have a new option available to them that will help to greatly improve performance. The new (for the stable branch, at least) 'custom tabs' feature makes it possible to pre-load pages in the background resulting in load times that are a fraction of using WebView or firing up Chrome separately.
The feature can be used by developers to use their own app to change the way Chrome looks and feels, effectively blurring the move from app to the web. In addition to the speed advantages, custom tabs also bring improved security to apps, and provide users with a more familiar browsing experience.
Google is pushing custom tabs as being faster than relying on the browser on its own, and less complex to implement than WebView. Custom tabs within apps can take advantage of features of Chrome such as autofill, cookies, syncing, and saved passwords. It's not exactly a brand new feature as it has been available in the Beta and Dev versions of Chrome for a little while now, but the arrival of custom tabs in the stable build of Chrome means that more people will be able to benefit from it.
In a post on the Chromium blog, Google says:
Custom tabs are optimized to load faster than WebView and traditional methods of launching Chrome. Apps can pre-load pages in the background so they appear to load nearly instantly when the user navigates to them. Apps can also customize the look and feel of Chrome to match their app by changing the toolbar color, adjusting the transition animations, and even adding custom actions to the toolbar so users can perform app-specific actions directly from the custom tab.
Custom tabs are due to arrive in a number of popular apps including Feedly, The Guardian, and Twitter, but the ease with which they can be implemented means that they are likely to spread to even more very quickly.
Want to know more? Google has a video that explains how it all works:
Photo credit: 360b / Shutterstock
-

'Extremely critical' OS X keychain vulnerability stealthily steals passwords via SMS
Publié: septembre 3, 2015, 12:10am CEST par Mark Wilson

Two security researchers have discovered a serious vulnerability in OS X that could allow an attacker to steal passwords and other credentials in an almost invisible way. Antoine Vincent Jebara and Raja Rahbani -- two of the team behind the myki identity management security software -- found that a series of terminal commands can be used to extract a range of stored credentials.
What is particularly worrying about the vulnerability is that it requires virtually no interaction from the victim; simulated mouse clicks can be used to click on hidden buttons to grant permission to access the keychain. Apple has been informed of the issue, but a fix is yet to be issued. The attack, known as brokenchain, is disturbingly easy to execute.
Special-crafted commands can be triggered by malware -- or even an image or video -- which causes OS X to display a prompt to click an Allow button. But rather than relying on users clicking on a button that appears unexpectedly, the button is displayed very briefly off the edge of the screen or behind the dock, and is automatically pressed using a further command. It is then possible to intercept a user's password and send it to the attacker via SMS or any other means.
The entire process takes less than a second to complete, and is stealthy enough to bypass many, if not all, security products. In an email to CSO, Jebara said:
We disclosed, because we feel that it is the right thing to do, knowing that a vulnerability of this magnitude would have disastrous consequences (you wouldn’t be able to open any third-party file on your computer without the risk of losing all of your sensitive information until Apple issues a patch). But this doesn’t prevent us from going public either.
The vulnerability is extremely critical. It allows anyone to steal all of your passwords remotely by simply downloading a file that doesn’t look malicious, and can’t be detected by malware detectors - as it doesn’t behave the way malware usually does.
There are a number of possible attack vectors that could be exploited, including sending a malicious file via email, displaying a malicious file in a web browser, or a P2P attack. Jebara has posted a video that shows brokenchain in action as a proof-of-concept:
Apple has been told about the vulnerability. The company has not only failed to issue a fix yet, but has not even responded to Jebara and Rahbani.
Photo credit: April909 / Shutterstock
-

How to use a video as your account picture in Windows 10
Publié: septembre 2, 2015, 7:38pm CEST par Mark Wilson

Associating a picture with your Windows 10 account is just one way to personalize your computer, but it also serves as a way to easily differentiate between accounts. If you want to be a little different, you don’t need to stick with a dull static image on the login screen -- it is possible to use a video instead.
You can use your webcam and Windows 10's built in camera app to record a short clip and use it in place of your regular account image on the login screen. It might not serve any real purpose, but it's pretty cool. Here’s what you need to do.
Open up Settings and head to Accounts. In the Your account section, click the Camera link beneath the Create your picture heading. In the camera window that pops up, switch to video mode by clicking the video camera icon to the right. Click the button again to start recording, and for a third time to stop.
Play back your recording to ensure that you're happy with it, clicking Retake if you'd like to start over. You can move the start and end points of the video to trim away unwanted sections, and then click OK when you're happy with the results.
That's all there is to it!
Your video will only appear on the login screen -- your user image in the start menu is a still from the video rather than an animated version.
Photo credit: Luis Molinero / Shutterstock
-

IFA 2015: Sony announces Xperia Z5 smartphone series, including a 4K handset
Publié: septembre 2, 2015, 6:55pm CEST par Mark Wilson

Not content to launch a single flagship smartphone at IFA 2015, Sony has today launched an entire range -- the Xperia Z5 series. Comprised of three phones -- the Xperia Z5, the Xperia Z5 Compact, and the Xperia Z5 Premium -- the series receives an update that Sony will no doubt hope offers real competition to Apple's upcoming iPhone models.
At the top of the range is the Xperia Z5 Premium which is a world first smartphone, featuring a 4K display. But it's not just the number of pixels that Sony is pushing with its new flagship device; battery life of two days is also touted. Each phone features a fingerprint reader integrated into the power button, and is waterproof.
In addition to the screen, Sony is also raising the bar in terms of camera. The Xperia Z5 Premium has a 23MP shooter which boasts super-fast autofocus, and low-light shooting. The 5.5 inch Premium version of the handset includes a Qualcom octo-core Snapdragon 810 processor, 32GB of storage, and 3GB of memory. Next in line is the Xperia Z5 with a 5.2 inch, 1080p screen. Finishing off the trio is the smallest handset, the 4.6 inch, 720p Xperia Z5 Compact.
Constructed from glass and metal, the Xperia Z5 Premium is a slightly weighty 180g. For anyone concerned about running out of space, the inclusion of a microSD slot will be welcomed, but with the launch not due until November, there's still a little time to wait -- the two other models will be available to buy in October. Sony has yet to share details of pricing, but this should be made available in the coming weeks. It just remains to be seen whether a 3430 mAh battery can really deliver two days of battery life.
Sony has released a couple of videos showing off the new smartphones. The first showcases what is described as "the best camera in a leading smartphone".
The second video highlights the features of all devices in the range.
-

Hundreds of unscrupulous black hat editors banned from Wikipedia
Publié: septembre 2, 2015, 2:02pm CEST par Mark Wilson

Crowd-sourcing of information by Wikipedia has helped create a vast resource, used by millions of people. But the fact that anyone is free to contribute to the online encyclopedia means that there is potential for corruption.
Wikipedia has just banned hundreds of black hat editors which were found to have been paid to edit articles. It is a violation of Wikimedia's terms of use to accept money to promote people, companies, and interests on Wikipedia as the site is supposed to be free from bias and undue influence.
Striving for neutrality means that editors found to have been involved in paid advocacy have been culled. In all, Wikipedia has banned 381 editors which it refers to as "sockpuppet accounts" as well as removing scores of articles created through them. It is believed that a large number of the accounts -- possibly all of them -- are related to each other, and in announcing the bans, Wikipedia says:
Most of these articles, which were related to businesses, business people, or artists, were generally promotional in nature, and often included biased or skewed information, unattributed material, and potential copyright violations. The edits made by the sockpuppets are similar enough that the community believes they were perpetrated by one coordinated group.
It is not always the case that paid editing is not allowed. Editorial associate Ed Erhart explains that "many museum and university employees from around the world edit by disclosing their official affiliations, and several prominent public relations firms have signed an agreement to abide by Wikipedia’s paid editing guidelines".
There is an ongoing discussion on the Wikipedia noticeboard where editors are trying to determine what steps can be taken to prevent similar problems from arising in future.
-

Facebook and Twitter's autoplay videos in the firing line after Virginia shooting
Publié: septembre 2, 2015, 1:25pm CEST par Mark Wilson

The Virginia shootings in which two journalists were killed on live TV by Vester Flanagan highlighted one of the problems of social media: it can be used for terrible things. If the news of two needless deaths was not enough, countless Facebook and Twitter users were upset by footage of the killings that quickly spread around the social networks, automatically playing for many people.
This is not the first time that autoplay videos have been in the news, and it certainly won’t be the last. Now politicians in the UK are calling for Facebook and Twitter to better police content that is uploaded by users to avoid a repeat incident in which people are unwitting viewers of horrific scenes.
People have previously complained about the fact that the autoplay feature of Twitter and Facebook is enabled by default. While it is possible to disable this option, it is not something that the casual social network user will be aware of, even less be comfortable adjusting. UK members of parliament are suggesting that the social networks need to be proactive in seeking out potentially upsetting content such as the Virginia murders and adding warnings.
Matt Warman, Conservative MP and co-chair of the Parliamentary Internet, Communications and Technology Forum, told the BBC:
Facebook, Google, Microsoft and others have already worked together with government and regulators to prevent people being exposed to illegal, extremist content, using both automatic and manual techniques to identify footage. Social media, just like traditional media, should consider how shocking other content can be, and make sure consumers are warned appropriately.
He points out that while some people may be happy for some content to play automatically, there should be different rules in place for graphic content.
But opinion remains divided, and the logistics of actually policing the fallout of tragedies such as the shootings in Virginia is rather more complex than politicians simply saying "something needs to be done about this".
Just one stumbling block that would need to be overcome is one that we have already seen in relation to other types of online content. Block a site that offers pirated material, child pornography, or something else illegal, and it really doesn’t take long for a replacement to pop up. Cut one head off the Hydra, and another quickly grows back.
This is not to say that social network users should not be given more control over the type of content they are happy to see, but we are getting into soundbite politics when something so complex is reduced to "this is terrible and I think we should do something about it".
Photo Credit: Quka / Shutterstock
-

You're probably about to notice a lot more ads in Gmail
Publié: septembre 2, 2015, 11:18am CEST par Mark Wilson
On the same day that Google unveiled its new logo, the company also slipped out some other news that didn't get quite as much attention. Considering the news means that Gmail users are likely to be inundated with more ads than ever before, it's hardly surprising that Google wasn't shouting from the rooftops, but that's what's happening.
Native Gmail ads are now rolling out to AdWords users, giving companies a new way to gain a presence in potential customers' inboxes. This is not spam. This is not a new way to start an email-based ad campaign. It's actual AdWord-triggered ads at the top of inboxes.
In fact, native Gmail ads are not entirely new; Google has been testing them for a couple of years now, making them available to a select group of advertisers. But now the ad format is being made available to all advertisers, and the potential benefits that could stem from the sheer number of people Gmail-based ads could reach means companies are sure to be quick to jump on board.
The ads sit at the top of the inbox in Gmail, looking for all intents and purposes like a regular email. But just like the Google ads you see littered around the web, you'll notice that these are targeted ads -- well, it is AdWord-based, after all. This means that your inbox will be home to ads that are related to the types of searches you have performed, the sites you've visited, and whatever other data Google may have collected about you over the years.
The new ad format is rolling out to the web version of Gmail as well as the mobile app. Google explains that native Gmail ads comprise two components:
- The collapsed ad that users initially see that matches the look and feel of the Gmail inbox. Users can click on this to expand it and get more details.
- The expanded ad unit is triggered by a click on the collapsed ad. This is a full-page native ad that recreates the informational and visual richness of a landing page. After users click to expand, any subsequent clicks on your content are free, including clicks to save the ad to your inbox or forward it to others.
An interesting characteristic of the ads is that although they are native ads, they can also be treated like emails. This means that although, initially at least, the ads are not included in your inbox they include options to forward them on to other people like emails, or move them to your inbox for future reference.
Update
Google has been in touch with a clarification. A spokesperson for the company said:
Consumers won't see more ads as a result of this. The only change is that now advertisers can buy this format through AdWords ... [it will] translate to a bigger variety of advertisers whose ads might show, not more actual ads. The consumer experience will remain the same.
-

Google unveils a new, simple, sans serif logo
Publié: septembre 1, 2015, 6:37pm CEST par Mark Wilson

Google has come a long way over the years, but one thing has remain remarkably simple: its logo. There have been various designs for the six, colorful letters and today the company has taken the wraps off the latest version... complete with an uppercase G!
It's going to take a while for some people to get used to, but the clean, sans serif look of the new logo is simultaneously modern and retro. But today's announcement is about more than the main logo -- this is the launch of a new 'identity family'. In addition to the main logo, there's also a new four-color G icon, as well as similarly-colored imagery for other elements.
Introducing the new look, Google says that the change of direction comes as a result of the increased range of devices people use to access the internet. The new typeface and icons have been designed to work on screens of all sizes. The new design can be seen in searches, Google Maps, Chrome, and it will roll out to a range of other products too. As the company says:
It doesn’t simply tell you that you're using Google, but also shows you how Google is working for you. For example, new elements like a colorful Google mic help you identify and interact with Google whether you’re talking, tapping or typing. Meanwhile, we're bidding adieu to the little blue "g" icon and replacing it with a four-color "G" that matches the logo.

There's an animation that showcases the new logo and identity family that you'll be seeing a great deal more of in the coming months, and Google has put together a video that shows what the company has achieved, and what it has brought us over the last 17 years:
What do you think of the new look?
-

Microsoft is the number one employer for Workforce Diversity
Publié: septembre 1, 2015, 6:24pm CEST par Mark Wilson

Diversity is the current weapon tech companies are using to bludgeon each other with -- Twitter has even gone as far as publishing its goals. Facebook fails in this department while Apple, ever the master of spin, is keen to present itself in the best possible light. For many on the outside looking in, diversity is little more than an exercise in PR, but that's not going to stop companies celebrating wins here and there.
The latest win is for Microsoft. For the second year running, the company has been voted the number one employer by readers of Workforce Diversity for Engineering & IT Professionals magazine. Clearly this is something of a niche publication, but given its specialization, it’s a crown that Microsoft is only too happy to wear.
Described as "the first magazine published for the professional, diversified high-tech workforce, which encompasses everyone, including women, members of minority groups, people with disabilities, and non-disabled white males to advance in the diversified working community", Workforce Diversity has been surveying its readers about employers for the past 14 years. In 2014 Microsoft also topped the charts, pushing Boeing and Apple back into second and third places respectively.
Writing on the Microsoft Blog, Suzanne Choney says:
Readers selected the top companies in the country for which they would most prefer to work, or believe would provide a positive working environment for engineers and IT professionals who are members of minority groups.
This list is the result of an annual survey mailed to randomly selected readers of Workforce Diversity for Engineering & IT Professionals magazine.
Although we know that Microsoft occupies the number one slot, we don’t yet know how other companies have fared. The full list for 2015 is due to be published on 8 September.
Photo credit: Guenter Albers / Shutterstock
-

Microsoft makes it easy to switch to Windows 10 with free PCmover Express
Publié: septembre 1, 2015, 3:18pm CEST par Mark Wilson

Microsoft has teamed up with Laplink to try to encourage people to upgrade from Windows 7 and Windows 8.1 to Windows 10, offering a free copy of PCmover Express to anyone who wants it. Many people took the launch of Windows 10 as an excuse to buy a new computer with it pre-installed -- but then there is the problem of accessing the files stored on the old PC.
While it is possible to manually move files to your new computer, it's not something that everyone is comfortable with. Microsoft's solution to provide people with a data transfer tool for free is one that's likely to attract some attention, so here’s what you need to do to take advantage of this time-limited offer.
Laplink's tool can be used to migrate files and folders from one computer to another, and it is available free of charge until the end of August 2016. All you need to do is head over to the promotion page, and you can download your copy of the software in an instant. The entire transfer process is wizard-led, so there is little chance of doing anything wrong, and Microsoft stresses that if you have spent time personalizing Windows 10, your settings will be retained.
The free version of PCmover Express is only concerned with moving data, and is only for home users. If you need to use the software commercially, or want to be able to move applications from one computer to another, you'll need to upgrade to the Professional version of the utility.
To get started with PCmover Express, start by downloading your free copy now!
Photo credit: XiXinXing / Shutterstock
-

PayPal.Me lets you receive online payments through a custom URL
Publié: septembre 1, 2015, 1:37pm CEST par Mark Wilson
PayPal has long been a quick and easy way to send and receive money online; with the launch of PayPal.Me, things just got even simpler. This is a new platform which provides PayPal customers with their own personalized URL (such as paypal.me/markwilson) as an alternative to sending out invoices. PayPal is pushing this as a way to call in your debts, but it's far more versatile than that.
The next time someone needs to send you money, you can simply direct them to your page -- or you can include the link on social networks, your website, in emails, via SMS, and so on. Any payments that are made in this way are covered by the same PayPal Buyer Protection policies as before. Anyone visiting your PayPal.Me page is able to choose the amount of money they want to send you, but you can also customize the URL you share to make a request for a specific amount.
If I wanted to request £10 from someone, I need simply direct them to paypal.me/markwilson/10 (all donations gratefully received ;-) ). There's no set up needed, and any figure can be appended to the base address -- paypal.me/markwilson/11.67 lets someone send me £11.67 with just a couple of clicks, for instance. PayPal.Me is platform agnostic so it can be used from any device equally well, mobiles included.
I've given examples in pounds, but PayPal.Me is available in 18 countries in total, not just the UK: US, Germany, UK, Australia, Canada, Russia, Turkey, France, Italy, Spain, Poland, Sweden, Belgium, Norway, Denmark, Netherlands, Switzerland, and Austria.
PayPal envisions this as a way for groups of friends to share bills as well as calling in outstanding debts:
PayPal.Me makes requesting money from groups of friends, family and colleagues suddenly so much easier and faster. Rather than following up individually, you can email your PayPal.Me link to co-workers to chip in for an engagement present for another co-worker. Or stop asking each of your fellow bridesmaids for bachelorette party payments and just send a group text message with your PayPal.Me link.
As with any new service, there will be a rush to grab the 'best' usernames, so if you have your heart set on something in particular -- such as your own name, or that of your business -- head over to PayPal.Me right now to stake your claim.
-

Money talks -- Microsoft to provide details of Windows 10 updates to enterprise users
Publié: septembre 1, 2015, 12:32pm CEST par Mark Wilson

A lot has changed in Windows 10, including the way updates are delivered. The forced installation of Windows updates -- including drivers -- has upset many people, but Microsoft has also managed to upset users by failing to provide details about what individual updates actually do to the systems they are installed.
The horror stories combined with the lack of information coming from Microsoft has led many people to seek ways to stop the automatic installation of Windows updates or to delay them. But it is enterprise users and system administrators who are most upset by the absence of changelogs, and Microsoft has listened to feedback. The company has announced that it is backing down slightly and will provide enterprise customers with update information.
The move is hardly surprising if we are to believe the installation figures for Windows 10 -- something like 75 million installations so far. With an already-large, and seemingly rapidly-expanding user base, Windows 10 has certainly made its mark. This is the first version of the operating system with which Microsoft has shown itself to be truly listening to what its users have to say, and nothing speaks louder than money.
Microsoft wants to keep its enterprise users happy, and to this end Jim Alkove from the Windows group says:
We've heard that feedback from enterprise customers so we're actively working on how we provide them with information about what's changing and what new capabilities and new value they're getting.
At this stage, there are no details about how far off these measures are, or exactly what form they will take, but changes are afoot.
But it is not just enterprise users who are keen to be properly informed about the changes updates make -- tech enthusiasts are also eager for more information. Microsoft has given no indication that it is going to extend its more open policy to home users.
Photo credit: rvlsoft / Shutterstock
-

Full steam ahead for Microsoft phones after patent infringement win
Publié: août 29, 2015, 2:26pm CEST par Mark Wilson

Microsoft has been cleared of patent infringement by the US International Trade Commission. The case dates back to 2007 when InterDigital Inc claimed Microsoft infringed its patents, and there were calls for a ban on the import of handsets.
InterDigital Inc has been battling in court for eight years, initially trying to claim royalties on phones made by Nokia, now transferred to Microsoft. As well as blocking the call for an import ban, the ITC stated that Microsoft did not infringe patents relating to the way mobiles make calls. In short Microsoft is in the clear and InterDigital's rights have not been violated.
InterDigital CEO William J. Merritt responded to the ruling with a bittersweet swipe at Microsoft. He said: "[the] decision is disappointing but is expected to have a limited impact on our going-forward business, given the decline of the Nokia mobile device business under Microsoft’s control and its limited market position."
In a statement, Microsoft said:
We're grateful the Commission stopped InterDigital from trying to block our products. We'll continue to pursue our separate suit addressing InterDigital's unlawful conduct and abusive patent licensing scheme.
InterDigital stock slumped in reaction to the announcement, but it's not clear just how much of a difference -- if any -- the decision will make to Microsoft's ability to claw its way back to greater significance in the smartphone market as it prepares to launch Windows 10 for phones.
Photo credit: OlegDoroshin / Shutterstock
-

Twitter's diversity goals are completely meaningless nonsense
Publié: août 29, 2015, 12:33pm CEST par Mark Wilson

Workforce diversity is something that every company wants to be seen to be getting right. At the moment -- particularly in the world of technology -- they're failing spectacularly. As in so many walks of life, it's a world dominated by white, middleclass men, and it's a problem that gets worse the further up the hierarchy you look. Facebook, Google, Amazon, Apple, Microsoft. They all have one thing in common: a desire to be seen as the most welcoming, ethnically and sexually diverse, forward-thinking companies out there.
It's great PR, and now Twitter is trying to step up its game. News of a commitment to making the Twitter workforce more diverse sounds great, but sounding great isn’t the same as being great. I've mentioned that talk of diversity is good public relations, and that's exactly what we see here -- spiel, empty gestures, misguided proposals, and embarrassingly ham-fisted approaches. Now Twitter is taking things a step further.
The company has announced that it is "committing to a more diverse Twitter". In a blog post by the vice president of Diversity and Inclusion, Janet Van Huysse (my god... a woman! How diverse!) we are fed a three course meal of bluster, hot air, and marketing spiel. Of course Twitter is 'committing' to a more diverse Twitter. It would be madness not to! Everyone else is doing it, so why don't we?
Almost three quarters of Twitter's workforce is male. A mere one percent (one!) is black. So we should welcome the announcement that "we are now setting company-wide diversity goals -- and we're sharing them publicly" warmly, shouldn't we? No... because it is guff of the highest order. Twitter says that, globally, in 2016 it wants to "increase women overall to 35%, increase women in tech roles to 16%, and increase women in leadership roles to 25%", and in the US only it wants to "increase underrepresented minorities overall to 11%, increase underrepresented minorities in tech roles to 9%, increase underrepresented minorities in leadership roles to 6%".
How will it do this? It doesn’t really seem that Twitter has quite yet worked this out. Or if it has, it's not sharing this information -- which is odd when you consider that this is supposed to be an exercise in accountability and transparency. Janet Van Huysse wheels out some impressive-sounding phrases. Twitter will reach its goals by "building strong partnerships with organizations that create opportunities for underrepresented minorities", by "actively recruiting at colleges and universities for underrepresented talent", and "refining our recruiting and hiring practices to attract more diverse candidates".
This might look good on paper, but what does it actually mean. Break it down, and Twitter is basically saying that it wants things to be better than they currently are. The company gives no indication that it understands why things are the way they are, or what steps are actually needed to make progress. The post is almost a logic puzzle, filled with circular reasoning. "We want to create a workforce with more minorities in it, so we'll hire more minorities". Lovely... but how? How will processes change? Is there something about Twitter that makes it unappealing to minorities? Is the company infected with institutional racism? What are the problems that you have identified beyond not having enough different colored faces?
With issues like this -- particularly in relation to large companies on a public stage -- details matter. It's all very well to say that things will get better, but if we can't follow what's happening, if we don’t know how things are being measured and how existing systems are changing, how can we tell if whatever program that has been put in place is actually effective? How can we be sure that the figures are meaningful? It would be easy to hire a bunch of people who fit the ethnic profile which the company currently lacks, but we're not just talking about numbers on one particular day. Will these people stay in employment? Will they have the same opportunities as the dominating white, middleclass employees who are already in place? Will pay structure be the same? Will preferential treatment or positive discrimination be used to ensure that targets are hit? What is more important to Twitter -- being seen to strive for a diverse workforce, or actually creating and feeling the benefit of a truly diverse workforce?
But there is another question that needs to be answered.
What are the consequences of Twitter failing to hit its targets? In twelve months' time, most people will have forgotten about the promises that have been made. There will, of course, be websites and blogs that are only too quick to jump on the company when the year is up and see if Twitter has met its goals. If it hasn’t, what's going to happen? Twitter will be criticized and lambasted. That happens anyway. Plus ça change, plus c'est la même chose. Even if the company fails spectacularly, gets nowhere near its targets, if nothing changes at all -- even if things get 'worse' -- Twitter will say that it tried... and, ultimately, that's all that matters as far as PR is concerned.
Everything Twitter says may sound wonderful. What it actually means, if it actually amounts to anything, and if the execution is not an embarrassment, are entirely different matters.
-

How to remove a stuck S Pen from a Samsung Galaxy Note 5
Publié: août 29, 2015, 10:03am CEST par Mark Wilson

Is it a design flaw, or just a case of a company expecting its customers to know how to do something? The problem of the Samsung Galaxy Note 5 S Pen getting stuck inside the handset if inserted the wrong way has divided opinion.
But whether you think someone who has managed to get their S Pen stuck is stupid or has fallen into a trap that could have caught out anyone, there is a solution. There's no need to resort to brute force to remove your S Pen -- it is possible to get it out without breaking anything. The solution is beautiful in its simplicity.
A video has appeared online showing the surprisingly simple technique that can be used to gently and safely remove your stuck S Pen. No special tools are needed, and you won't do anything that invalidates your warranty. The video also illustrates just what happens when the stylus is inserted the wrong way, and why it causes such a problem.
(Don’t be put off by the fact that the first shot of the Note 5 in the demonstration shows it with its back removed -- this is simply to make it easier to see what’s going on, and you won't need to take the back off your handset).
The video really speaks for itself, so if you need to remove a reversed S Pen, check it out:
-

Facebook ramps up video piracy fighting technology
Publié: août 28, 2015, 11:11pm CEST par Mark Wilson

Think of video piracy, and talk of BitTorrent probably isn’t far away. While torrented movies and TV shows account for a large proportion of pirated material, it is far from being the end of the story. Even sites as seemingly innocuous as Facebook can be part of the problem.
The social network is not really used as a way to share the latest blockbuster movies, but it is home to a lot of 'recycled' content, the rights for which are not necessarily owned by the uploader. Responding to growing complaints from video publishers, Facebook is ramping up its fight against piracy, boosting the existing Audible Magic audio fingerprinting tool, introducing a video fingerprinting utility, and ensuring that repeat offenders are kept off the site.
Stemming the flow of pirated footage is a tricky task to say the least. Audible Magic helps to automatically identify some offending material by checking the audio track, and Facebook is working to make this a more effective way to help wipe out so-called 'freebooting'. Facebook says that it has more plans to help keep video publishers happy.
We’re working with Audible Magic to enhance the way that system works with Facebook, including improving the intake of content intended to be blocked from our platform. And we’re making improvements to our existing procedures so that infringing content can be reported and removed more efficiently, and to keep repeat infringers off our service.
To complement Audible Magic, Facebook is also giving a small number of users access to a new video matching tool. This works in much the same way as the audio fingerprinter, making it possible to check for duplicate copies of a video across the Facebook network. Whilst in beta, the tool will have a small user base while Facebook gathers feedback in preparation for a wider roll out.
Photo credit: DJTaylor / Shutterstock
-

Chrome embraces HTML5 and tells Flash ads to eff off
Publié: août 28, 2015, 10:09pm CEST par Mark Wilson

The writing has been on the wall for Flash for some time now. A web technology loathed for countless reasons -- not least the security issues -- the death knell is now tolling loudly as HTML5 is more widely embraced.
Back in June, Google announced that Chrome would pause Flash ads in its browser by default, helping to eliminate a major online annoyance. Now the company has outlined when this will happen -- and there are only a few days to wait.
As well as killing a blight of the internet, Google says that the decision to kill Flash is not just about security and cleaning up the web, but a move to help improve the performance of Chrome. The announcement though on the AdWords Google+ page:
In June, we announced that Chrome will begin pausing many Flash ads by default to improve performance for users. This change is scheduled to start rolling out on September 1, 2015.
Developers are being encouraged to ditch Flash in favor of HTML5, and Google has an automated tool to convert Flash ads that are uploaded to AdWords. But not all ads can be automatically converted, and Google advises identifying those that are not compatible with automatic conversion. The company also provides instructions for manual conversion.
-

Facebook celebrates one billion users online in a single day
Publié: août 28, 2015, 12:02am CEST par Mark Wilson
The aim of Mark Zuckerberg, through Facebook, has been to connect the world. On Monday this week, the social network saw one billion people logging on to send messages, post photos, write status updates, and generally be social. One billion people in a single day.
Or to put it another way -- as Zuckerberg does -- "1 in 7 people on Earth used Facebook to connect with their friends and family". There aren’t many companies or services that can claim to have such a wide reach, so the palpable pride is entirely understandable.
Over the years, Facebook has developed and broadened its reach and appeal. It is now far more than just a site for sharing pictures of your breakfast, or letting the world know what you love and hate -- it has become a platform for raising money, raising awareness of issues, streaming videos of events, connecting with companies and celebrities, and most recently the company unveiled M, its digital assistant.
In a post on his own social network, Mark Zuckerberg says:
We just passed an important milestone. For the first time ever, one billion people used Facebook in a single day.
On Monday, 1 in 7 people on Earth used Facebook to connect with their friends and family.
When we talk about our financials, we use average numbers, but this is different. This was the first time we reached this milestone, and it's just the beginning of connecting the whole world.
I'm so proud of our community for the progress we've made. Our community stands for giving every person a voice, for promoting understanding and for including everyone in the opportunities of our modern world.
A celebratory video has been put together to mark the occasion.
Photo credit: endermasali / Shutterstock
-

'Hey Siri, give us a hint' -- what does Apple's 9 September event have in store for us?
Publié: août 27, 2015, 7:18pm CEST par Mark Wilson
Apple has sent out media invites to an event on 9 September. Widely expected to see the launch of the iPhone 6s and iPhone 6s Plus, the event takes place at the Bill Graham Civic Auditorium in San Francisco at 10 am PDT.
The invitation itself gives little away, but it does include artwork that will undoubtedly feature on the big day, as well as the intriguing tagline 'Hey Siri, Give Us a Hint'. So does Siri have the answers? Tell us about the new iPhone!
No. It is, of course, a big tease. As Mac Rumors shows -- and you can test for yourself -- Apple is trying to tickle our funny bones with some humorous responses from its digital assistant. Pose the question and Siri will reply with one of several witty quips: "You'll have to wait until 9 September. I bet you were one of those kids who snuck downstairs to open presents early, weren't you?", "You're cute when you're desperate for information". You get the idea.
As ever, Apple has been tight-lipped about what we'll see at the event, but the s update to the iPhone range is expected: the iPhone 6s and iPhone 6s Plus are all but guaranteed to make an appearance. Other likely contenders include updated versions of OS 9, OS X El Capitan, and Watch OS 2.
A holding page is already in place for the live stream of the event -- something that can be enjoyed not only by those with an iPad, iPhone or Mac, but also a PC running Edge in Windows 10. Yep -- Apple supports Microsoft Edge!
-

Google hits back at latest round of antitrust accusations
Publié: août 27, 2015, 6:49pm CEST par Mark Wilson

Antitrust claims against Google are nothing new, and the company stands accused of abusing its position and favouring its own products in search results in Europe. Today, Google's General Counsel Kent Walker responded to the European Commission's claims, saying they are "unfounded".
Google has filed an official response to the Commission, but a public blog post gives an accessible insight into the company's mindset. The EU is unhappy with the way Google displayed shopping links in search results, saying its own services are given undue prominence. Google says that far from being anti-competitive, the way it displays search results is beneficial to its users.
In a blog post entitled Improving quality isn't anti-competitive, Walker dismisses accusations that came about after price comparison services complained that they were being squashed by the giant. The EU suggests that the way Google displays search results is unfair; Google -- unsurprising -- disagrees, saying the charges are "wrong as a matter of fact, law and economics".
It says that the amount of traffic it drives to competing price comparison sites has risen by 227 percent over the last ten years. Google also points to the emergence of new price comparison services as evidence that it is not stifling the market. The company also says that too much emphasis has been placed on people using Google to find products when in fact other sites, such as Amazon, are the first port of call for large numbers of people. Relatedly, the company says that it is under no obligation to direct searchers to its rivals as people are free to use alternative search tools if they want.
In his post, Walker says that the European Commission makes allegations that it is not able to back up. He says that "data spanning more than a decade, an array of documents, and statements from complainants all confirm that product search is robustly competitive". Far from having a detrimental effect for customers, Google says that the way it operates is entirely beneficial:
Our central point is our consistent commitment to quality -- the relevance and usefulness of our search results and the ads we display. In providing results for people interested in shopping, we knew we needed to go beyond the old-fashioned '10 blue links' model to keep up with our competitors and better serve our users and advertisers. We developed new ways to organize and rank product information and to present it to users in useful formats in search and ads.
He goes on to explain that the way Google tailors its search results helps to improve relevance:
Showing ads based on structured data provided by merchants demonstrably improves ad quality and makes it easier for consumers to find what they’re looking for. We show these ad groups where we’ve always shown ads -- to the right and at the top of organic results -- and we use specialized algorithms to maximize their relevance for users. Data from users and advertisers confirms they like these formats. That’s not 'favoring' -- that’s giving our customers and advertisers what they find most useful.
Google argues that it is not in its interest to do anything other than provide the most relevant search results to people, and that it precisely what it is doing.
Photo credit: photogearch / Shutterstock
-

Windows 10 users won't see Chrome notifications in the Action Center any time soon
Publié: août 27, 2015, 5:29pm CEST par Mark Wilson

If you were hoping to see Chrome notifications integrated into Windows 10, prepare to be disappointed: it's not going to happen. While the Action Center might seem the natural home for Google's web browser to display messages, developers have a different opinion.
In short, Chrome's notifications are staying as they are. Despite a campaign for Action Center support, the request has been labeled Won'tFix and there's no sign that this will change for some years to come. Chrome and Windows 10 have already clashed heads once, but this time Google seems unlikely to back down.
The feature was requested on the Chromium support site, and quickly gained some enthusiastic support from other users. The development team, however, has rather different ideas. While many people see the value in having all notifications appearing in one place, Chrome will continue to use its own system, and one of the team, Ho, says:
Thanks for the input and ideas! We've discussed this quite a bit and decided not to integrate with the system level notification at this time. It would create a weird state where Chrome behaves differently on Win 10 than on Win 7/8 and developers of extensions/websites wouldn't know what they design for. Maybe we can revisit it in a few years when most users are on Win 10 :)
He went on to explain that Google is not just being belligerent, and that there are legitimate reasons for not wanting to integrate with the Action Center:
To be clear, this is not a matter of just piping notifications to the OS for free. All notification (systems) are not the same. Chrome notifications allow to take actions right from the notifications, they come directly from an extension/website, they can require active dismissal, and so on.
On Win 10, using the native notification system would mean that all notification could show briefly before disappearing but they could also not show, depending on a user setting. All notifications would show as coming from Chrome. They would not be actionable, and so on. As a developer, it makes quite a difference if I design something that allows users to take an action or something that merely informs them and whether it will be a pop up or a silent addition to the notification center.
It's not something that has been well received on the Chromium support site. Some suggest that Google should "play ball" and tie into Windows 10 the way other software does. One commenter says simply:
google does its best to bork everything windows do to there stupid rivalry...so immature. [sic]
Photo credit: 360b / Shutterstock
-

Critical PayPal XSS vulnerability left accounts open to attack
Publié: août 27, 2015, 4:45pm CEST par Mark Wilson

PayPal has patched a security vulnerability which could have been used by hackers to steal users' login details, as well as to access unencrypted credit card information. A cross site scripting bug was discovered by Egyptian 'vulnerabilities hunter' Ebrahim Hegazy -- ironically on PayPal's Secure Payments subdomain.
Hegazy found the Stored XSS Vulnerability on https://Securepayments.Paypal.com back in the middle of June, and was able to demonstrate how it could be exploited. More than two months later, PayPal has addressed the issue and plugged the security hole.
Describing himself as an 'ethical hacker', Hegazy reported his discovery to PayPal on 16 June. He found that it was possible to engineer an HTML page that intercepted data entered on a secure PayPal page and transmit it to another server as plain text. This information was then available for exploitation in whatever way the attacker saw fit. Worryingly, Hegazy says that it would be possible for all of this to happen invisibly in the background -- a victim could make a regular PayPal payment which would clear, but there could also be an extra payment made to the attacker.
The bug was reported through PayPal's bug bounty program, and Hegazy praised the company for responding to emails quickly. As well as ensuring that the security flaw was fixed, he also managed to bag himself PayPal's top bounty reward of $750 for his troubles.
If you're interested to see how the vulnerability worked, check out the video below where Hegazy explains it all:
-

LG Rolly Keyboard is a folding keyboard for your tablet or smartphone
Publié: août 27, 2015, 1:55pm CEST par Mark Wilson

However much on-screen keyboards improve, they're no replacement for a good, old-fashioned keyboard. Traveling with a tablet, it might not be convenient to lug about a full-sized wireless keyboard but LG thinks its Rolly Keyboard could be the answer.
As the name suggests, this is a portable keyboard that 'rolls' up for easier transportation -- well, it rolls up into a square stick rather than a round roll, but you get the idea. Also known as the KBB-700, the Rolly Keyboard features almost full-sized keys, and can be paired with two devices via Bluetooth.
The keyboard is due to hit the US in September -- although LG hasn’t shared pricing details or an exact launch date yet -- and will roll out to Europe, Latin America and Asia later in Q4. The company says the 17mm key pitch is "nearly as generous" as desktop keyboards, and to make it easier to use in conjunction with your smartphone or tablet, two fold out support arms are on hand to cradle your device.
While price is yet to be revealed, Seo Young-jae, VP of Innovative Personal Devices at LG, describes it as a "premium input device", so it's possible a premium price tag will be attached. LG will give more details at IFA 2015 in Berlin at the beginning of next month, but for now you can check out the video below to see the keyboard in action:
Photo credit: LG
-

Virginia shooting shows the power of social media, and the danger of autoplay videos
Publié: août 27, 2015, 12:12pm CEST par Mark Wilson

Social media is an incredibly powerful tool. It's not without good reason that ad campaigns start on Twitter and Facebook in the hope of going viral. As with any medium, social media is full of positive and negative content. Content you're interested in seeing, and stuff you really aren't.
But the difference with the likes of Facebook and Twitter is that you're not always in control of what you see. The horrific shooting live on TV in Virginia highlights this perfectly. As with any tragedy or big news story, many were quick to take to social networks to share information and thoughts. They also shared video footage of the killings which automatically played in people's timelines.
With traditional media -- newspapers, TV, even regular websites -- it's easy to pick and choose what you want to consume. If you want to read about global war, you can. If you'd prefer to focus only on fluffy news, you can do that too. It could be argued that on social media you are indicating the type of content you would like to see by the choices you make with regard to the people and organizations you follow or befriend. But social media is very different to traditional media. As well as the content you have chosen to see, you also see what others have chosen to share as well as suggested or curated content from the network itself.
Vester Flanagan understood the power of the media -- traditional and social. He wanted to leave his mark in more ways than one, and the easiest way to amplify an already horrific act was to commit it not only on live TV, but also to record the act ready to push to social networks. As we know, this is exactly what happened. He posted the footage online, and it was shared by countless people. Some may have shared it out of disbelief, others out of sick morbidity. Whatever the reasons behind sharing, the point is that it was shared.
This in itself is not really an issue. Facebook took editorial decisions in many instances to take down copies of the video as they were posted, but on both Facebook and Twitter, it quickly became uncontrollable. The footage spread like wildfire, and while some may have been keen to view the killings -- it's certainly not something you see every day; this was a historic event -- this was not the case in every instance. Both Facebook and Twitter have a video autoplay option that means there's no need to hit the play button -- as soon as a video scrolls into view, it starts to play.
The upshot of this was that lots of social media users found that their timelines were home not just to news of live-on-TV killings, not just still images of the victims, but moving footage of the onscreen deaths. Death of real people. Actual lives snuffed out in an instant, and shared for all to see. For those with the autoplay setting enabled there was no warning -- the murders were essentially forced upon people.
The moral rights and wrongs of the availability of this footage is a separate issue, this is a question of choice. It is one thing to have a desire to see such footage, to seek it out and watch it, it is quite another to be caught unawares and be assaulted by it.
All of this is not to say that autoplaying videos are right or wrong, but recent events certainly give food for thought and may well cause many people to re-evaluate the settings they have in place. In the wake of what has happened, there are clearly bigger concerns, but it certainly shows that greater thought needs to be given to how we used social media. Perhaps social networks need to do more to educate their users. Perhaps we need to toughen up. Perhaps video vetting is needed.
There is no ideal solution, but it needs to be talked about.
Photo credit: Diego Schtutman / Shutterstock
-

Facebook is now working on its own digital assistant called M
Publié: août 26, 2015, 7:52pm CEST par Mark Wilson

Sounding like a character from a James Bond movie, M is Facebook's personal digital assistant. Ready to compete with the likes of Cortana, M will live inside Facebook Messenger and take artificial intelligence a step further. Rather than just helping you to find information or create calendar entries, M will actually perform tasks on your behalf.
Once up and running, M will be able to book restaurants for you, purchase shopping, and more. It will also be possible to use the service to ask for advice -- such as looking for somewhere to visit nearby, or gift suggestions -- and Facebook says the AI behind M is "trained and supervised by people".
Facebook's David Marcus revealed that the social network is currently testing M, stressing that things were only at an early stage. He gave a sneak preview of a few screenshots, all of which show M in use on a mobile phone, and it's not clear if the tool will make its way to the desktop version of Facebook as well. He says:
Unlike other AI-based services in the market, M can actually complete tasks on your behalf. It can purchase items, get gifts delivered to your loved ones, book restaurants, travel arrangements, appointments and way more.
This is early in the journey to build M into an at-scale service. But it's an exciting step towards enabling people on Messenger to get things done across a variety of things, so they can get more time to focus on what's important in their lives.
There's no word on how long it will be before M is launched, nor confirmation of whether M is a codename or what it will actually end up being called. Facebook has also not revealed whether there will be a public testing program ahead of the official launch. Watch this space!
-

Don't blame Samsung; it's your own stupid fault if you break your Galaxy Note 5
Publié: août 26, 2015, 5:13pm CEST par Mark Wilson

Samsung is undoubtedly pleased that its new Galaxy Note 5 is in the headline, but the company would almost certainly prefer that it was for different reasons than it breaking. Not that there is a problem with the Note 5 -- despite countless websites and blogs claiming that Samsung has released a handset with a design flaw -- but if you insert the S Pen the wrong way round, you could well break it.
Of course, when one makes a mistake -- like shoving a stylus backwards into its housing -- it's easy to try to blame someone else. Samsung's response to the situation has been advising people to "follow the instructions in the user guide", which is entirely reasonable. How much hand-holding is really required? Do knife manufacturers need to tell you not to hold onto the pointy end?
The reaction to S Pen-gate has been absurd. It's not only disproportionate, but also indicative of the blame-game, litigious society we live in. If something goes wrong, it couldn’t possibly be your fault, could it? You couldn't be to blame... oh no... lay that blame at someone else's door. While you're at it, why not get them to pay out for your stupidity?
You shouldn't really need to be guided through the process of reinserting an accessory into its housing. It was pointing a certain way when you took it out, put it back in the same orientation -- simple! How is there any confusion? There have been individuals, and well-known websites, who heard about the so-called 'problem' with the S Pen and had to try it for themselves to find out if it is true. Guess what? They’ve now got a partially broken phone. Serves them right for being idiots.
Perhaps Samsung could have designed the S Pen so that there was simply no way it could be inserted incorrectly. The company could also have provided instructions informing users not to flush their Note 5 down the toilet, or put it in an oven in case it causes damage. But a company can't be expected to cater for every eventuality, and it certainly can’t be expected to anticipate the incredible stupidity of some people.
If you've broken your Note 5, here's a news flash: it's your own damn fault. You can try to claim back the cost of repairs on insurance, blame Samsung, blame the designers, complain that instructions weren't clear or obvious enough, but that doesn’t change anything. It's your fault, and your Note 5 is broken because you are stupid.
Photo credit: Alex Malikov / Shutterstock
-

Some people are fine with using a phone in church, but not walking down the street
Publié: août 26, 2015, 3:03pm CEST par Mark Wilson

The thing with a mobile phone is, thanks to the fact it is mobile, it can be used -- just about - anywhere. But just because something is possible, it doesn’t mean that it should be done. PewResearch conducted a survey into phone etiquette, and the findings show that people are somewhat divided about where and when it is OK to use a phone.
Some of the results are not exactly surprising. A huge majority of those questioned were not cool with the idea of using a phone in a movie theater or during a meeting (95 and 94 percent respectively). But there are also some interesting quirks in attitudes to mobiles -- 4 percent of people, for instance, see no problem with using a cellphone in the middle of a church service.
Overall, the 3,217 people who took part in the survey held conservative or considerate views about where it is acceptable to use a phone. It's worth noting that the accompanying report does not make it clear whether people had different opinions about making calls, receiving calls, or using a phone for something else such as texting or surfing the web.
Nearly a quarter of people (23 percent) objected to the idea of phone use whilst walking down the street, and a similar number (25 percent) were opposed to using a phone on public transport. 26 percent dissed the idea of using a phone whilst waiting in line, but in more social situations the figures started to turn around a little. Just 12 percent of people thought it was acceptable to use a phone during a family meal, and this figure drops to just 5 percent when asked about phone use during meetings. The figures varied depending on the age of the respondent, with younger people being more open to the idea of using a phone in a social situation.
There is, however, an element of hypocrisy. Despite widespread opposition to use of phones in various social situations, a massive 89 percent of those asked said that they had used their own phone during their most recent social gathering.
Check out the report in full on the PewResearch website.
Photo credit: Frank11 / Shutterstock
-

AT&T accused of injecting ads through its free Wi-Fi hotspots
Publié: août 26, 2015, 12:28pm CEST par Mark Wilson

What price is free? In the case of Windows 10, many argue that it means giving up a little of your privacy, and it seems that AT&T's free Wi-Fi hotspots also come with a hidden payload. Whilst visiting Dulles Airport, computer scientist Jonathan Mayer noticed that "the web had sprouted ads. Lots of them, in places they didn’t belong".
With time to kill waiting for a flight, Mayer set about investigating where these extra ads were coming from. It didn’t take long for him to discover that the AT&T hotspot he was connected to was the problem. He found that the hotspot was injecting a stylesheet which in turn pulled in advertising. But it didn’t end there...
Just to make sure that ads are delivered, AT&T's injected code displays ads using JavaScript and non-JavaScript methods. Writing about his experience, Mayer suggests that as well as being irritating for web users, the ad-injection also poses a security risk. A key concern is that web traffic and activity are exposed to unknown third parties. The injected code pulls in ads from a company called RaGaPa, but it is worth noting that the ad-injection system only works for HTTP traffic as it is not possible to tamper with secure HTTPS traffic.
While AT&T's terms of services do not make explicit reference to ad-injection, Mayer points to one clause which could cover it:
We may also enable certain technologies intended to improve your experience, maintain network security, and/or optimize network utilization that may generate records regarding the websites you visit and search terms you enter while using the Service.
Mayer is a lawyer and is aware that the subject of ad-injection is a "messy one". He says:
Regardless of where the law is, AT&T should immediately stop this practice. And if websites needed (yet another) reason to adopt HTTPS, here’s a good one.
Photo credit: Rob Wilson / Shutterstock
-

YouTube Gaming is ready to give Twitch some competition
Publié: août 25, 2015, 11:18pm CEST par Mark Wilson
Anything computer-related can be made social and shareable, and gaming is no different. Amazon's game live streaming service Twitch has proved immensely popular and now Google is ready to put up some competition with YouTube Gaming.
Starting tomorrow (26 August), head over to YouTube Gaming and you can start a stream of your own or watch other gamers play. Of course there will also be an app, and Google is aiming to create "the biggest community of gamers on the web".
The service is not just about live streams. Google promises individual pages for more than 25,000 games as well as dedicated channels from game publishers. Everything is taken care of using HTML5, and YouTube Gaming manages to upstage Twitch with a DVR feature that allows for the buffering and rewinding of streams.
Clearly Twitch has something of a head start, but YouTube Gaming has the clout of Google behind it; YouTube is already a popular destination for gamers looking to share their gaming footage.
While the YouTube Gaming website should be available globally, the Android and iOS apps are limited to the US and UK -- at least for the time being.
-

Samsung Galaxy Note 5 vulnerable to massive S Pen snafu
Publié: août 25, 2015, 5:29pm CEST par Mark Wilson

If you've managed to get your hands on a new Samsung Galaxy Note 5 -- and this might sound like a case of stating the bleeding obvious -- make sure you put the S Pen into its slot the right way round. Inserting the pen the wrong way round could result in you breaking not just the stylus itself, but also kill some functionality of the Note 5.
While, ordinarily, slipping the S Pen home point first should not be too taxing, if attempted by someone who is a little tired, drunk, young, or stupid, it could go horribly wrong. You could end up with a Note 5 with an S Pen that just can’t be removed, or -- if you exert sufficient force -- you may remove the S Pen and break either the pen or the innards of the phone.
There is no mechanism in place to prevent the backward insertion of the S Pen. You won’t be able to insert it all the way, but by the time you've noticed your mistake it could well be too late. If the pen does not become stuck fast, you run a very real risk of breaking the pen detection mechanism. What are the consequences of this? For starters it means that the Note 5 will be unable to tell whether the S Pen is inserted or not so -- assuming you didn’t get it stuck -- the S Pen-specific Air Command menu won't appear, and other pen tools will also be broken.
The Note 5's manual does state that care should be taken to ensure that pen is inserted correctly. Samsung issued a statement to the BBC about the issue:
We highly recommend our Galaxy Note 5 users follow the instructions in the user guide to ensure they do not experience such an unexpected scenario caused by reinserting the S-Pen in the other way around.
Android Police has a video showing just how easy it is to break the Galaxy Note 5. Depending on the type of person you are, you'll either wince with sympathy, or chortle meanly:
You have been warned!
-

Ad-blocker Crystal massively reduces bandwidth usage and page load times in iOS 9
Publié: août 25, 2015, 1:47pm CEST par Mark Wilson

There's a lot to look forward to in iOS 9. We already know that the new version of Safari will include the option to block ads, but the browser is not going to be alone in clearing out unwanted ads. Crystal is an ad blocker for iOS 9 created "with the goal of making web browsing with the iPhone and iPad a great experience again".
It started life as a tool for testing iOS 9's own content blocker, but grew into a stand-alone project. Crystal is currently in closed public beta but its developer, Dean Murphy, has released some figures that show how effective it is. The results show that Crystal can speed up page load times by nearly four times and reduce bandwidth consumption by 53 percent. Impressive stuff, and the stats make for extremely interesting reading -- particularly for those waiting for the launch of a new iPhone.
Dean previously looked at how effective the content blocker of iOS 9's Safari is, and this inspired him to spend the next two months working on a project of his own. Crystal was born and now it's time to test it out. For the tests, Dean chose ten popular websites (New York Times, Business Insider, Macworld, Wired, The Verge, PC Gamer, iMore, Kotaku, Huffington Post, Vice) to connect to on his iPhone 6+.
Clearly with a content blocker, there are various things that can be measured, but the most important are how long it takes a page to load, and how much data has to be downloaded. The graphs speak for themselves, and it will be great to see how the blocker continues to develop over time.
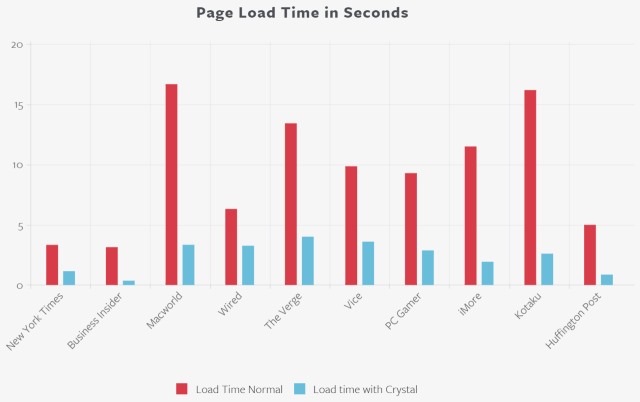
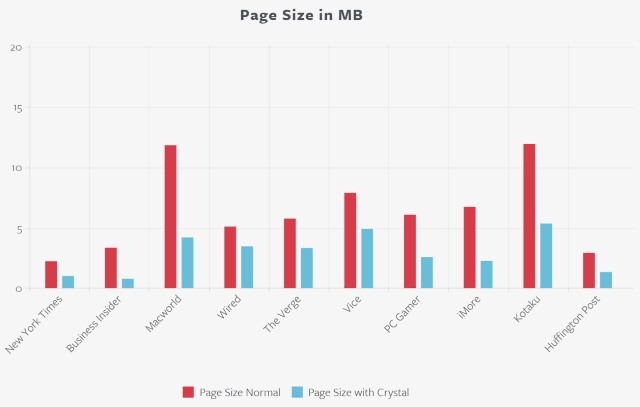
If you're interested in trying out Crystal for yourself, Dean is still taking requests to join the beta program. He's waiting for Apple to allow iOS 9 betas on its TestFlight service as this will increase the number of beta testers that can take part.
-

It's about to get easier to donate money to non-profits via Facebook
Publié: août 25, 2015, 11:29am CEST par Mark Wilson

Facebook is known as The Social Network, but it's about more than just being social. It's also used by business, charities, and other organizations to promote products, services and causes. To make it easier for non-profits to raise money Facebook is introducing a Donate Now button.
This is something that makes life easier for the donor and the recipient. Many non-profits are small operations which may not want to go to the trouble of setting up a fully-fledged website with a donation page. For people who discover a worthy cause through Facebook, it makes sense to be able to hand over some money through the same medium.
The button is in the process of rolling out, so it might be a while before you start to see it out in the wild, but it is are on its way. It will give page owners a way to add a new 'call-to-action' to an ad or page (something usually reserved for booking reservations, buying products, and the like) that gives visitors the chance to make a donation.
Announcing the new button, Facebook says:
We are excited to introduce a new "Donate Now" call-to-action option on both link ads and Pages. Now, it's easier than ever for nonprofits to connect with people who care about their causes and encourage them to contribute through the website of their choice.
The button will only be available to pages that have been categorized as "Non-Profit Organization", and Facebook has provided instructions for how to get up and running.
Photo credit: Gustavo Frazao / Shutterstock
-

Microsoft will launch Office 2016 on 22 September
Publié: août 25, 2015, 12:23am CEST par Mark Wilson

Just as with Windows 10, Microsoft has been running a preview program for Office 2016. After launching the Mac version of the office suite, we’ve been waiting for news about the PC edition will be released. Now, thanks to a leaked document, we now know it is due to launch on 22 September.
Internal documents obtained by WinFuture.de show that Office 2016 is set to launch in less than a month for home and professional users. Microsoft is preparing staff for the event, asking them to install the preview version for now and keep an eye on the Office 2016 Launch Hub for training documentation and other materials.
There have been a few preview versions of Office 2016 and -- as has become the norm with Microsoft -- there's a strong focus on the cloud. For business users, there are collaborative features such as Real Time Typing, and all of the programs in the suite have undergone a gradual evolution rather than a dramatic overhaul.
The internal memo says:
On September 22, 2015, we'll release Office 2016 -- with updates for Word, Excel, PowerPoint, OneNote, Outlook, Skype for Business, Project, Visio, Access, and Publisher. The innovation wave continues in Q2 with the release of E5 and Skype for Business, and on-premise servers will follow.
This is the central hub for all Office 2016 Commercial readiness, training, and marketing materials. Mark this page and check back frequently, as we will be releasing new materials, weekly, to support the launch.
It is expected that pricing will be broadly in line with Office 2013, but it shouldn't be long before we have official confirmation.
-

Russia bans Wikipedia because Russia (and drugs)
Publié: août 24, 2015, 8:30pm CEST par Mark Wilson

Russia has placed a complete ban on Wikipedia because of an article about cannabis. The country's Federal Service for the Supervision of Communications, Information Technology and Mass Media (Roskomnadzor) took exception to an article about charas -- a cannabis product popular in India.
The Russian Federal Drug Control Service deemed the article illegal because it included information about how the drug is made. Wikipedia's policy of not removing individual articles could mean that Russia's censors have no alternative but to block the site in its entirety.
Wikipedia initially tried to sidestep a request to remove the offending article by simply changing its URL, but this failed to impress Roskomnadzor. The government body complains that Wikipedia's actions do nothing to prevent access to content it has deemed illegal. It says:
In the event that [Wikipedia] refuses to comply with the court’s ruling, Roskomnadzor will block the webpage on Russian territory using the registry of illegal information. In this case, insofar as Wikipedia has decided to function on the basis of https, which doesn’t allow restricting access to individual pages on its site, the entire website would be blocked.
As noted by the Libertarian Republic:
Wikipedia does not take down individual articles except by user consensus. It uses the HTTPS security protocol, which means pages on its domain cannot be blocked individually. These two policies mean that Roskomnadzor will almost inevitably wind up blocking the entire encyclopedia.
Reddit suffered the same fate in Russia earlier this month after an article about hallucinogenic mushrooms attracted the ire of the government. As with Wikipedia, Reddit uses HTTPS for security making it difficult to block individual pages. Of course, as we have seen in China, just because a website is blocked, it does not mean that it is completely inaccessible -- mirrors for the Russian version of Wikipedia will almost certainly spring up, and proxies will also grant access.
Update:
The ban has now been lifted.
Photo credit: Viacheslav Lopatin / Shutterstock
-

As stock markets tumble, Kim Dotcom recommends Bitcoin -- again
Publié: août 24, 2015, 6:02pm CEST par Mark Wilson

Kim Dotcom -- he of Megaupload/Mega infamy -- has been out of the headlines for a while, but he's creeping back into the public eye once again with the launch of a new music streaming service, Baboom.
However, Dotcom is not just interested in promoting his latest venture, he also has a lot to say about many aspects of the tech world.Back when he launched file sharing site Mega, rebuilt from the rubble of Megaupload, Dotcom was a proponent of the cryptocurrency Bitcoin. Now he's at it again, advising people to invest in Bitcoin in the wake of the Chinese -- and then global -- stock market tumble.
Fears over China have led to European and US markets nosediving, and billions of dollars wiped off the value of companies. The likes of Microsoft, Apple, and Facebook have all taken a hit on Monday trading. While companies around the world are feeling the impact of the worst day of trading in China for a number of years, it is technology firms that are really taking the brunt of it. This is hardly surprising considering the Chinese tech market.
Black Monday has gripped the world as fears mounted about how the Chinese government intends to tackle its economic weakness. Writing on Twitter, Kim Dotcom suggests that things could be able to get a whole lot worse and points to Bitcoin as a good investment:
Is the China bubble ready to pop? A significant global stock market correction is imminent? Get some #Bitcoin. Just in case. Thank me later.
— Kim Dotcom (@KimDotcom) August 24, 2015
Advice you're willing to take, or would you rather steer clear of virtual currencies?
Tim Cook took the time to write to CNBC's Mad Money presenter Jim Cramer as many have voiced concerns about what the situation in China might mean for Apple:
Apple's @tim_cook just e-mailed @jimcramer @CNBC pic.twitter.com/zzEqmDKFUK
— Carl Quintanilla (@carlquintanilla) August 24, 2015
Photo credit: Lightboxx / Shutterstock
-

Screen flicker and Explorer crashes in Windows 10? Blame Norton Antivirus, iCloud, or IDT Audio
Publié: août 24, 2015, 5:58pm CEST par Mark Wilson

We've looked at many of the problems that you might experience after upgrading to Windows 10 -- from issues with audio to bothersome browsers. Some users are having problems with the explorer.exe process crashing and an annoying screen flicker. Three particular applications -- Norton Antivirus, iCloud, or IDT Audio -- have been cited as culprits, and Microsoft and Symantec have solutions.
There's no need to go as far as uninstalling Windows 10, but Microsoft does suggest that you restart your computer in Safe Mode and uninstall any of the aforementioned programs. Of course, Symantec would much rather than you continued to use Norton Antivirus, so the company has its own fix for the problem.
Actually, Symantec does agree with Microsoft to a degree. Part of the fix, as described by WinSuperSite, is to uninstall Norton Antivirus; but after running a special problem-fixing tool, the security software can be reinstalled. The company provides full details on its support pages, but in summary, you need to:
- Restart Windows in Safe Mode.
- Run Symantec's special fixing tool as an Administrator.
- Restart Windows as normal.
- Use the dedicated Norton Remove and Reinstall tool to uninstall the AV software and then reinstall it.
Have you experienced problems with these three applications -- or any others -- since installing Windows 10?
Photo credit: Suzanne Tucker / Shutterstock
-

Censoring transparency: Twitter denies Politwoops access to API
Publié: août 24, 2015, 12:46pm CEST par Mark Wilson

Twitter has blocked Politwoops from using its API, effectively killing the service that archived and published tweets deleted by politicians. Politwoops has a number of international sites, each concerned with the politicians of different countries and it monitored the account of prominent politicians for deleted tweets before publishing them for all to see.
The US version of the service was denied API access earlier in the year, but over the weekend Twitter extended the ban to a further 30 Politwoops accounts. The tweets deleted by those in politics are often far more telling and revealing than those that remain in place, and this was the reason for Politwoops existence. Not for the first time, Twitter has entered the political arena, indicating that it views the deletion decisions of elected politicians as more important than the right of the electorate to see tweets that have been self-censored.
Open State Foundation, the group behind all of the accounts, reports that it was contacted by Twitter and informed that its API access was being revoked following "thoughtful internal deliberation and close consideration of a number of factors". Used by journalists the world over, Politwoops prides itself on helping to increase the transparency of politicians and what they say.
Open State Foundation's director Arjan El Fassed says that it is important for people to be able to see precisely what has been tweeted by politicians:
What elected politicians publicly say is a matter of public record. Even when tweets are deleted, it's part of parliamentary history. These tweets were once posted and later deleted. What politicians say in public should be available to anyone. This is not about typos but it is a unique insight on how messages from elected politicians can change without notice.
Twitter has defended the move saying:
Imagine how nerve-racking -- terrifying, even -- tweeting would be if it was immutable and irrevocable? No one user is more deserving of that ability than another. Indeed, deleting a tweet is an expression of the user’s voice.
Open State Foundation says that it will explore what other options are available to help it keep the electorate informed.
-

Who should we believe about Apple Music usage numbers?
Publié: août 23, 2015, 1:28pm CEST par Mark Wilson

It makes sense that any company would like you to believe that it has a large number of customers; if you launch a service, you want everyone to know just how popular it is. As well as boasting, it is a form of advertising in itself -- one that is free... the best kind.
But what happens when the figures you tout are at odds with what other people think? This is what is happening with Apple Music. Research company MusicWatch says that Apple's streaming music service retains just over half of users who sign up for the free trial. Apple disagrees, saying that it actually manages to hang on to 79 percent of users. Why is there such a big difference, and who is right?
MusicWatch found that while 77 percent of US iOS users were aware of Apple Music, just 11 percent were found to be using it. Research suggests that the trial period has quite a high drop-off rate, with 48 percent of trial users indicating that they are now not using the service. A survey of 5,000 people found that 61 percent had turned off the auto-renewal setting.
Apple puts forward slightly different figures -- in a statement to the Verge it says it hangs on to 79 percent of people. Rather than losing nearly half of its trial users, the company says that the figure is actually just 21 percent. A retention rate of 79 percent is rather different to MusicWatch's, but there's no further detail provided.
There is a slight problem, however. What about the people who just let their subscriptions continue because they forgot to cancel? What about those who had a personal emergency, business trip, or vacation and weren’t able to cancel? What about those people who have opted to maintain their subscription without being an active user? What about those people with sufficient disposable income that they can keep shelling out for Apple Music on the off-chance that they might use it at some point in the future? There's a big difference between number of subscribers and number of active users.
Or does it matter?
Of course it does. It pays to question any figures that are put out there. Statistics can easily be tweaked to suit just about any purpose -- just how they ae tweaked depends on the story being told.
It's worth noting that MusicWatch's research only looked at US Apple Music users, but the service is actually available in dozens of countries. It's possible that the 'representative sample' wasn’t actually all that representative, or it could be that Apple is massaging the figures somewhat. Or the truth could lie somewhere in the middle; it's all but impossible to tell.
Photo credit: Oleg Golovnev / Shutterstock
-

Paranoid torrent sites ban Windows 10 over privacy concerns
Publié: août 23, 2015, 11:27am CEST par Mark Wilson

Since the launch of Windows 10, there have been all manner of privacy concerns -- some grounded in fact, others less so. Whatever your view of the latest version of Windows, it's impossible to deny that this has proved one of the more controversial releases to come from the Microsoft stable.
Getting in on the paranoia now are torrent sites, with some coming out and saying they have implemented a ban on the use of Windows 10 to connect to their trackers. Seemingly in response to the news that Windows 10 could disabled counterfeit games, torrent sites including iTS have already put measures in place to block Windows 10 users from accessing them, while the likes of FSC and BB are considering taking similar action. Over-reaction?
As reported by TorrentFreak, iTS is worried about what it describes as "the terrible privacy policy of Windows 10". Concerned that information could be collected and shared with anti-piracy company MarkMonitor -- including the rather outlandish suggestion that "Windows 10 sends the contents of your local disks directly to one of their servers" -- users of the site are told that "Windows 10 is officially banned from iTS. Members using it get redirected to a video that eggsplains the dangers quite in detail hoping to enlighten as many people as possible".
While these are clearly the paranoid delusions of the tin-foil hat brigade -- the disdainful comments on Reddit make for amusing reading -- the concern is spreading like a virus. Torrent sites FSC and BB have also said they may also block the use of Windows 10; others may well do the same.
Clearly, even for sites (torrent related and otherwise) that implement Windows 10 bans, there are going to be ways to get around any blocks that may be put in place. But the real point here is that the misunderstanding and paranoia about Windows 10 is now starting to reach levels of insanity. Microsoft can be partly blamed for its failure to communicate effectively, but it's also fair to say that most of the privacy-related concerns about Windows 10 have been blown out of all proportion.
Photo credit: Kunertus / Shutterstock
-

No more Windows 10 keys for Insiders; post-RTM installs must be on previously activated PCs
Publié: août 22, 2015, 5:23pm CEST par Mark Wilson

Each version of Windows has involved entering a product key either during the installation, or prior to activation. Things have changed with Windows 10, and as anyone who looked for their own Windows 10 product key will have found, Microsoft has used generic keys this time around.
For all intents and purposes, the installation of Windows 10 is now keyless, but there has been some confusion about what this means for future installations, particularly for Windows Insiders trying out new preview builds. Microsoft's Gabe Aul has stepped up to the plate to clear thing up, explaining that Insider builds can only be installed and activated on computers which have preciously activated the RTM build.
As the final build of Windows 10 had its product key built in, users wondered whether subsequent builds might use different keys and when they might be issued. There will be no more key, came the response from Aul. If you want to perform a clean installation of post-RTM builds, you'll need to do so on a PC which has already been used to activate a copy of build 10204.
Answering questions about Windows 10 on Twitter, Aul said:
No, builds from here on will not be prekeyed or include keys. You can install on a PC that had an activated 10240 to activate.
But what does that actually mean? Assuming you are trying to install a post-RTM build of Windows 10 on a computer which has already had an activated version of build 10204, you have nothing to worry about -- everything should run smoothly and builds should just install, both as upgrades and clean installations.
If you are maintaining multiple computers as a Windows Insider, and want to keep one or more on the regular RTM build while using another machine -- real or virtual -- to test out new builds, things are slightly different. To perform an installation and activation, you will need to install a valid copy of Windows 7 or Windows 8.1, upgrade to Windows 10, and then install the Insider build you want. Slightly convoluted, but as Twitter user @nvtweaks neatly puts it:
In general, if it's activated now, it should stay that way. And if not, it won't.
And
New Insiders can't activate a clean install unless they've upgraded from 7/8 first, or own a 10 key.
Of course, if you want to get technical about things, there's always the option of activation via KMS...
Photo credit: Anton Watman / Shutterstock
-

Welsh car firm can't advertise on Twitter because it tweets in Welsh
Publié: août 22, 2015, 2:22pm CEST par Mark Wilson

Twitter has inadvertently given a wealth of priceless advertising to a Welsh car company despite refusing to run its ads. Used car dealership Ceir Cymru has been operating in North Wales for over 30 years, but has been told that it is not able to advertise in its native tongue.
Twitter Ads supports just a limited number of language, and Welsh is not included. Having applied to use the service Ceir Cymru was told by Twitter that it would not be able to advertise as more than half of its tweets are in Welsh -- hardly surprising for a car dealership in Wales. Ceir Cymru says Twitter is "stamping on minority languages".
If you want to make use of Twitter Ads, you need to use Afrikaans, English, Spanish, French, Italian, Dutch, German, Hebrew, Japanese, Finnish, Norwegian, Swedish or Danish. Twitter has plans to expand this relatively small list of languages, but there is no word on when -- or indeed if -- Welsh will be added.
Gari Wyn Jones, manager of Ceir Cymru, feels that the decision is unfair:
It's estimated that about 50,000 people use Twitter in Welsh, so it's very strange that they're blocking users from advertising in the language, especially given its the official language of Wales.
The company's advertising manager, Sion Evans goes further by suggesting that "we believe [Twitter is] verging on a violation of human rights of minority languages". Ceir Cymru has, slightly ironically, gained a good level of support on Twitter, but the social giant currently shows no sign of backing down.
Twitter has not commented on the matter. BetaNews has reached out for a statement, and we'll update this post when we hear back.
Photo credit: Alistair Scott / Shutterstock
-

Swatch swipes trademark for Steve Jobs' 'one more thing' catchphrase
Publié: août 22, 2015, 11:00am CEST par Mark Wilson

Is it a troll move, smart marketing, or something else entirely? It's not clear quite what Swatch wants to do with Steve Jobs' famous 'one more thing' line, but the Swiss watch company has grabbed a trademark on the three word phrase.
Before his death, Jobs was renowned for introducing a surprise (although frequently not so surprising) extra at the end of a presentation. Although Apple has never really exploited 'one more thing' in advertising, Swatch's new European trademark will no doubt stick in the craw somewhat.
Since Jobs' death in 2011, Apple has largely shied away from using the phrase, and this is perhaps why Swatch has decided to jump on it. It is interesting to consider just what the company might have planned. There are no suggestions yet that Swatch is on the verge of releasing a smartwatch, but the trademark would be great for use in advertising an Apple Watch competitor.
Apple has not reacted -- publicly, at least -- to the trademark filing, but there are almost certainly some irritated people at 1 Infinite Loop at not having bagged the trademark themselves.
Photo credit: Denys Prykhodov / Shutterstock
-

Apple launches free replacement program for defective iPhone 6 Plus iSight cameras
Publié: août 22, 2015, 9:47am CEST par Mark Wilson

Complaints about the camera of the iPhone 6 Plus have been plentiful, and Apple has finally acknowledged that there is a problem. It's not something that affects all iPhone 6 Plus owners, but the company says that phones manufactured between September 2014 and January 2015 could include a failed camera component.
Apple has set up a replacement program which enables those with problems with the rear camera to obtain a replacement. Before you get too excited, it is just replacement camera components that are on offer, not replacement iPhones. You'll need to check to see if your phone is eligible at the program website.
The company says that it "has determined that, in a small percentage of iPhone 6 Plus devices, the iSight camera has a component that may fail causing your photos to look blurry. The affected units fall into a limited serial number range and were sold primarily between September 2014 and January 2015. If your iPhone 6 Plus is producing blurry photos and falls into the eligible serial number range, Apple will replace your device's iSight camera, free of charge."
To see if your iPhone is eligible, head to the iSight Camera Replacement Program for iPhone 6 Plus page and enter your serial number. If you're eligible, you can then take your iPhone to an Apple store or authorized service provider, or contact Apple technical support.
While Apple says that the replacement is free of charge, there is a risk that some people could incur costs:
If your iPhone 6 Plus has any damage such as a cracked screen which impairs the camera replacement, that issue will need to be resolved prior to service. In some cases, there may be a cost associated with the repair.
There is no particular rush to hand over your iPhone for repair. The replacement program runs for three years after the handsets first went on sale.
-

Bcachefs is a new speed-focus Linux filesystem from Kent Overstreet
Publié: août 22, 2015, 12:22am CEST par Mark Wilson

Bcache was first announced by ex-Google engineer Kent Overstreet a little over five years ago. Now the Linux kernel block layer cache is being used as the basis for a new open source filesystem. The focus is on speed, but it is also hoped that the file system could be used for servers and storage arrays because of its reliability.
At this stage, Overstreet describes Bcachefs as "more or less feature complete" and says that even at this early stage performance numbers are "good enough to be interesting". At the moment, features such as replication, caching, and compression are supported, and there is the promise of snapshotting in future releases.
Documentation is available for anyone who wants to test drive Bcachefs, but it is described as being "pretty sparse" right now. It will be a while before the filesystem makes it way into Linux mainstream, and Overstreet says that he needs more developers on board to help track down any issues that exist.
Announcing the availability of Bcachefs on the Linux Kernel Mailing List, he says:
Years ago (going back to when I was still at Google), I and the other people working on bcache realized that what we were working on was, almost by accident, a good chunk of the functionality of a full blown filesystem -- and there was a really clean and elegant design to be had there if we took it and ran with it. And a fast one - the main goal of bcachefs to match ext4 and xfs on performance and reliability, but with the features of btrfs/zfs.
It's taken a long time to get to this point -- longer than I would have guessed if you'd asked me back when we first started talking about it -- but I'm pretty damn proud of where it's at now.
If you fancy trying out Bcachefs for yourself, you can grab the code. Don’t expect 'completed' code any time soon. Overstreet warns that "Bcachefs won't be done in a month (or a year)", but he's keen to get things stabalized.
Photo credit: McIek / Shutterstock
-

Google integrates Twitter into search results on the desktop
Publié: août 21, 2015, 11:25pm CEST par Mark Wilson

It's a little while since Google and Twitter announced a partnership that saw the integration of tweets into search results. When this feature started to roll out back in May, Twitter integration only applied to iOS and Android devices. Today it rolls out to desktop search results as well.
The new desktop integration means that it is now possible to search for hashtags, trending topics, and Twitter accounts with a regular Google search. Including real time events in search results is not new for Google, but Twitter integration adds a new dimension.
While Twitter does have its own search facility, many people feel more at home using Google. It's something that makes it possible to judge Twitter reaction to breaking news while searching for articles about a particular event, eliminating the need to perform multiple searches.
Desktop integration has been launched with little fanfare. Rather than making an announcement about the new feature, Google instead chose to simply update its blog post from three months ago when the mobile launch was announced:
Update, 8/21/2015: We’ve extended this to desktop now too, and in English everywhere.
Perform a search related to Twitter and you'll notice that relevant account, hashtags, and tweets appear first in search results, followed by interactive Twitter cards; regular search results then follow. Twitter has not indicated whether or not Twitter results will be given their own section along the lines of Images and Videos in search results in the future.
Photo credit: ChameleonsEye / Shutterstock
-

Chrome extensions coming to Firefox as Mozilla unveils major changes
Publié: août 21, 2015, 6:14pm CEST par Mark Wilson

Mozilla today announces a series of important changes that affect Firefox add-ons. The good news? Add-ons should be reviewed faster, they will be more secure, and a new API means that Chrome extensions can be more easily ported across. But, of course, there is also bad news.
The bad news for developers is that Mozilla is switching to new technologies -- Electrolysis and Servo -- and this means that work will have to be done on existing extensions to ensure compatibility. In the switchover, it is likely that a large number of older add-ons will simply not be updated, but with a 12 to 18 month timescale for phasing out XPCOM and XUL means there is plenty of time for other developers to come up with alternatives to projects that have been abandoned and will no longer work.
It is the deprecation of XPCOM and XUL that's the really big news today. This is a fundamental change to the basis of Firefox and its ramifications are huge. While the current structure of Firefox makes it highly customizable, it also lacks modularity, and can be slow to develop. Mozilla recognizes that switching to Electrolysis and Servo is a massive change that could cause problems in the short terms.
Writing on the Mozilla Add-ons Blog, Kev Needham says:
A major challenge we face is that many Firefox add-ons cannot possibly be built using either WebExtensions or the SDK as they currently exist. Over the coming year, we will seek feedback from the development community, and will continue to develop and extend the WebExtension API to support as much of the functionality needed by the most popular Firefox extensions as possible.
It is the adoption of the WebExtensions API that should see extensions coming across from other browsers to Firefox. While not identical, it is "largely compatible with the model used by Chrome and Opera".
Starting with Firefox 41 -- due for release on 22 September -- developers will have to get their extensions signed and validated by Mozilla. For developers currently producing add-ons just for Firefox, the move to WenExtensions will involve quite a lot of work, but it will be easier for those already coding for Chrome.
This is just the start of a period of intense upheaval. Mozilla says:
The strategy announced here necessarily involves a lot of trade-offs. Developers who already support Chrome extensions will benefit since they will have one codebase to support instead of two. Developers of Firefox-only add-ons will have to make changes. Those changes may require considerable development effort up-front, but we feel the end result will be worth that effort for both Firefox’s users and developers.
Photo credit: Evan Lorne / Shutterstock
-

Microsoft will only provide information about Windows 10 updates when it wants to
Publié: août 21, 2015, 4:37pm CEST par Mark Wilson

It's less than a month since the launch of Windows 10, and there have already been three cumulative updates released. There has been far greater interest in these updates than for previous versions of Windows, but there has been frustration about the lack of detail provided about the changes the third brought.
Users were told that the update includes "improvements to enhance the functionality of Windows 10", but no specific details were given. Microsoft has now made it clear that extra detail will only be provided for some updates depending on their significance. Considering Windows 10's forced installation of updates, this is something that is unlikely to go down well with users.
While it is possible to use software to postpone the installation of individual updates, this is not something that the average user is going to do. In fact, it's entirely reasonable to assume that most people won’t bother to do this -- but whether they do or not, it's also entirely reasonable to expect to be kept informed about what is being installed. Microsoft doesn't completely agree.
In a statement to The Register, a Microsoft spokesperson said:
As we have done in the past, we post KB articles relevant to most updates which we’ll deliver with Windows as a service. Depending on the significance of the update and if it is bringing new functionality to Windows customers, we may choose to do additional promotion of new features as we deploy them.
So you might get told what an update does, you might not. When pressed for more details about what the last cumulative update included, Microsoft would not expand on its previous description of "improvements to enhance the functionality of Windows 10". Next time there is an update released, we don’t know if we'll be told what it does, or if it will be kept a secret; that's up to Microsoft.
Photo credit: India Picture / Shutterstock
-

New Spotify privacy policy angers users and drives some away
Publié: août 21, 2015, 2:58pm CEST par Mark Wilson

Spotify has updated its privacy policy, and a lot of users are now very unhappy. The change was prefaced a few days ago on the Spotify blog and the new policy started to roll out on 19 August. As it starts to hit accounts around the world, users are sitting up and paying attention; many are not happy with what they see.
What are people so upset about? Spotify might now access your Facebook likes and posts, photos and contacts you have stored on your phone, and even the speed at which you are traveling. The company says that the changes have been made as part of a move to "be as open and transparent as possible", but it has left large number of users questioning motives, and many have been pushed to quitting the music service completely.
As reported by the BBC the policy changes have led to a number of high-profile users quitting -- or threatening to quit -- Spotify, including Minecraft creator Markus Persson. The company was probably not expecting quite the backlash it is currently receiving, but the updated privacy policy has led to a vocal uproar of disgruntled users who feel that some of the changes amount to an infringement of privacy.
There is one new section that is giving users particular cause for concern:
3.3 Information Stored on Your Mobile Device
With your permission, we may collect information stored on your mobile device, such as contacts, photos, or media files. Local law may require that you seek the consent of your contacts to provide their personal information to Spotify, which may use that information for the purposes specified in this Privacy Policy.
The next section has a similar tone:
3.4 Location and sensor information
Depending on the type of device that you use to interact with the Service and your settings, we may also collect information about your location based on, for example, your phone’s GPS location or other forms of locating mobile devices (e.g., Bluetooth). We may also collect sensor data (e.g., data about the speed of your movements, such as whether you are running, walking, or in transit).
You might well wonder why Spotify needs to know how quickly you are traveling. This particular clause relates to Spotify's creation of automatic playlists, and this permission makes it possible to create playlists.
The changes apply to both free and paid-for packages, and Spotify says: "If you don't agree with the terms of this Privacy Policy, then please don't use the Service".
How do you feel about the changes? Are you happy to accept them for what they are, or does it make you question whether you'll continue to use Spotify?
Photo credit: 360b / Shutterstock
-

Samsung offers iPhone owners 30-day Galaxy Note 5, S6 Edge, or S6 Edge+ rental for $1
Publié: août 21, 2015, 1:00pm CEST par Mark Wilson

Samsung is trying to woo iPhone owners with a new promotion that gives Apple fans the chance to rent one of its latest flagships for a single dollar. For one paltry buck, curious iPhone users can test drive a Galaxy Note 5, Galaxy S6 Edge, or Galaxy S6 Edge+ with no obligation.
It's a unique scheme and one that might appeal to those who are scared of commitment... but only those with an iPhone. If you're interested you can sign up to test the Samsung handset of your choice with your current carrier, on your current tariff.
To take advantage of the offer, you'll need to visit the promo page from your iPhone -- visit from any other device and you'll just be able to read about what's on offer. Hand over your dollar, and the handset of your choice will be shipped out to you, complete with pre-paid return packaging. When you reach the end of the trial period, you can either buy the handset, or send it back; if you fail to return it, you'll be charged the full cost. Any damage beyond "reasonable wear and tear" will cost you $100.
The offer is only open to people in the US, and it runs until the end of the year. Oddly -- although perhaps understandably -- Samsung does not permit you to try out one handset, return it and then try a different one. You are limited to a single test drive, so make your choice carefully.
-

Remove the desktop watermark from Windows 10 Build 10525
Publié: août 20, 2015, 9:29pm CEST par Mark Wilson

Since the launch of Windows 10, you might have decided to rekindle your interest in the preview builds that are made available to Windows Insiders. Just a few days ago, Microsoft released Build 10525 and many people rushed to install it to see what was new.
But what’s that? An ugly watermark in the lower right of the desktop. If you're upset by the appearance of the "Windows 10 Pro Technical Preview. Evaluation Copy. Build 10525" text that appeared after the upgrade, here's what you need to do to get rid of it.
You could jump in and start to edit the registry, but there's really no need. Just download the free Universal Watermark Disabler and you can clean up your desktop with a minimum of fuss. This is a free tool from WinAero -- download and extract the file and you are ready to go. Run the executable and click Yes at the User Account Control popup.
Getting rid of the desktop watermark takes nothing more than clicking the Install button followed by Yes. Universal Watermark Disabler has been tested with earlier builds of Windows 10 by its makers, so you will have to confirm that you are happy to use it on Build 10525 by clicking Yes -- don't worry, it works perfectly. You'll probably notice that your screen flashes as Explorer restarts, and you'll then be prompted to save any files you have open as the tool needs to log you out of your account. Make sure everything is saved and click OK.
Log back into your account and... hooray! No more watermark!
Photo credit: Anton Watman / Shutterstock
-

Now Google must censor search results about Right to Be Forgotten removals
Publié: août 20, 2015, 8:06pm CEST par Mark Wilson

The Right to Be Forgotten has proved somewhat controversial. While some see the requirement for Google to remove search results that link to pages that contain information about people that is "inadequate, irrelevant or no longer relevant" as a win for privacy, other see it as a form of censorship.
To fight back, there have been a number of sites that have started to list the stories Google is forced to stop linking to. In the latest twist, Google has now been ordered to remove links to contemporary news reports about the stories that were previously removed from search results. All clear? Thought not...
The Information Commissioner's Office has ordered Google to remove from search results links to nine stories about other search result links removed under the Right to Be Forgotten rules. While the removal of the initial link has been welcomed by affected parties, news sites -- and Google -- have since reported about the removals and these reports have featured in search results giving full details of the original articles, or linking to them.
Google has 35 days to comply with the Information Commissioner's Office ruling. The ICO says:
Google Inc has been ordered to remove nine search results after the ICO ruled that they linked to information about a person that was no longer relevant. The ICO ruling concerns nine links that are part of the list of results displayed when a search is made by entering the individual's name. The links are to web pages that include details of a minor criminal offense committed by the individual almost ten years ago. The search engine had previously removed links relating to the criminal offense following a request from the individual. The removal of those links then itself became a news story. Links to these later news stories, which repeated details of the original criminal offense, were then part of the results displayed when searching for the complainant's name on Google.
The ICO found that search listings that provided access to irrelevant or inaccurate data about an individual constituted a breach of the Data Protection Act. It remains a delicate balancing act between Google's right to link to stories that newspapers and sites are free to publish, and the privacy of an individual. Deputy Commissioner of the ICO, David Smith said:
Google was right, in its original decision, to accept that search results relating to the complainant's historic conviction were no longer relevant and were having a negative impact on privacy. It is wrong of them to now refuse to remove newer links that reveal the same details and have the same negative impact.
Let's be clear. We understand that links being removed as a result of this court ruling is something that newspapers want to write about. And we understand that people need to be able to find these stories through search engines like Google. But that does not need them to be revealed when searching on the original complainant's name.
Photo credit: Vepar5 / Shutterstock
-

How many people are using Windows 10? Watch real time stats!
Publié: août 20, 2015, 6:12pm CEST par Mark Wilson

There have been various numbers thrown around suggesting how many people have downloaded Windows 10 and how many have the operating system installed. Great debates have started about just how accurate these figures may be, but as any statistician will tell you, the more data you have to work with, the more likely it is to give an accurate picture.
Microsoft announced that there were 14 million downloads in the first 24 hours after launch, and it has been estimated that this figure now stands at anything from 50 million to 67 million. UK-based data analysis firm GoSquared has put together a tool that shows, in real time, Windows 10 adoption around the world by indicating its share of Windows traffic.
It's very hard to pin down an exact number of installations at this stage, but GoSquared's figures make for very interesting reading. The company explains that its analysis draws on tens of thousands of sources, aggregating the data to give as accurate a picture as possible. So where does Windows 10 stand at the moment? As I write this Windows 10 accounts for 12 percent of traffic from Windows machines.
As the stats are updated in real time, there is visible fluctuation, and I have watched the number jump from 10 percent to 13 percent and then drop down again.
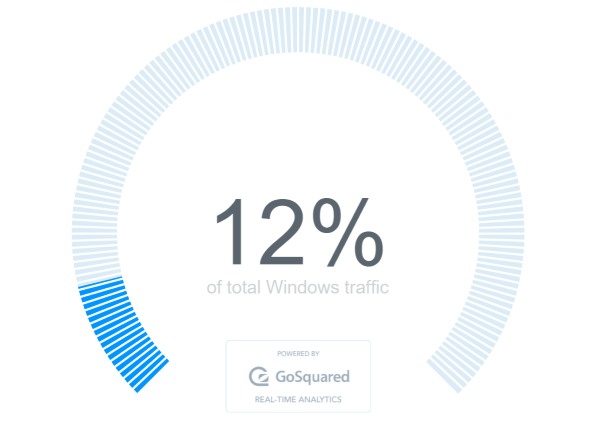
While it's certainly interesting to see what's happening right now, GoSquared's data is more useful for seeing the general trend of Windows 10 adoption -- and that trend is on a definite, steady climb. Since launch, Windows 10 hit a peak in terms of traffic share on 8 August when it hit almost 15 percent.
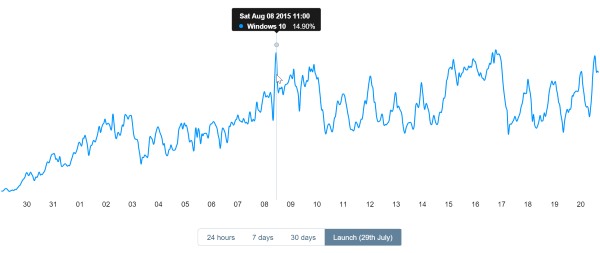
The company admits that the data may not give a completely accurate picture, saying: "In the scheme of things, it's by no means definitive, but we feel the data shows interesting trends".
Take a look for yourself and see what you think.
Photo credit: rvlsoft / Shutterstock
-

Go, Google's C-killing programming language, hits version 1.5
Publié: août 20, 2015, 12:47am CEST par Mark Wilson

Six years and six updates later, Google's own programming language, Go, has reached version 1.5. Go 1.5 sees Google "removing the last vestiges of C code" from the code base, and the runtime, compiler and linker are now all written in Go rather than C.
Despite a massive overhaul to the code base, Google assures users that Go 1.5 maintains the promise that Go programs will continue to be supported by all subsequent releases. There is also a move towards mobile devices, with ports of the iPhone and iPad architectures and linking to the Go mobile project opening up the possibility of developing for Android and iOS.
Google highlights speed improvements in this latest build, but another important addition is support for internal packages, allowing for the sharing of implementation details between packages. As revealed in the release documentation, there are a number of key changes that Google is particularly keen to draw attention to:
- The compiler and runtime are now written entirely in Go (with a little assembler). C is no longer involved in the implementation, and so the C compiler that was once necessary for building the distribution is gone.
- The garbage collector is now concurrent and provides dramatically lower pause times by running, when possible, in parallel with other goroutines.
- By default, Go programs run with GOMAXPROCS set to the number of cores available; in prior releases it defaulted to 1.
- Support for internal packages is now provided for all repositories, not just the Go core.
- The go command now provides experimental support for "vendoring" external dependencies.
- A new go tool trace command supports fine-grained tracing of program execution.
- A new go doc command (distinct from godoc) is customized for command-line use.
If you're ready to start coding, head on over to the download page to grab yourself a copy of Go 1.5. Binaries are available for Windows, OS X and Linux, and source code is also available.
Photo credit: Krasimira Nevenova / Shutterstock
-

Bing News now connects related stories to give readers better context
Publié: août 19, 2015, 11:52pm CEST par Mark Wilson

Always-connected mobile devices make it easier than ever to plug into the news and keep abreast of what is going on in the world. But reading on the move means that it is very easy to fall into the habit of skim-reading articles, or just reading part of a story which can mean failing to grasp the wider context of the news.
To try to help with this problem, Microsoft today announces a new feature for the mobile version of Bing News. Smart labels have been added to stories to give readers an at-a-glance way to see how a particular story relates to other stories and topics. It helps to, as Microsoft puts it, "connect the dots between news stories so you get the bigger picture".
The meaning and interpretation of a news story is often related to context, and this is precisely what smart labels provide. Microsoft's research finds that around 60 percent of people consume the news simply by reading the headlines. While it still makes the most sense to read an article in its entirety, Bing News' new labelling system adds a tag to each news story that links to other related stories.
As Microsoft explains in a post on the Bing blog:
While reading every last article on East European geo-politics may not be realistic, exploring a few smart labels and headlines can help connect the dots between the big themes.
If you want to get the full background to a particular story, this gives a quick and easy way to skip back to previous reports. But it also serves as a shortcut to viewing related headlines so if you are taking in your news via headlines alone, you should still be able to get a better grasp of the important, context, and impact of any given story.
Photo credit: qvist / Shutterstock
-

Amazon UK ends Trade-In program that no one seemed to know about
Publié: août 19, 2015, 9:01pm CEST par Mark Wilson

Amazon has announced that it is ending its Trade-In program in the UK. What's that? You didn’t know about it? You're not alone, and this could well be part of the reason for the closure; it was hardly a well-advertised operation.
As you'd guess from the name, the Trade-In program gave people the option to exchange games, consoles, accessories, and books they no longer wanted for Amazon gift cards. Very little notice has been given as the program is set to close on 31 August 2015. If you are one of the people who has been making use of Amazon Trade-In, you need to act quickly so you don’t miss out on your earnings.
Amazon has not explained why the program is closing down, but in its announcement the company informs users that they might like to consider becoming an Amazon seller to get rid of their unwanted goods. In an announcement on its Trade-In pages, Amazon says:
Amazon.co.uk’s Trade-in programme will be closed from Monday, 31 August, 2015. Please submit your trade-ins by Monday, 31 August, 2015 and post them to us by Monday, 7 September, 2015. For full details and other options for selling your items on Amazon.co.uk please see our Frequently Asked Questions.
The clock is ticking. If you have outstanding trade-ins, make sure you have them posted back in time.
Photo credit: Joe Ravi / Shutterstock.com
-

Windows Server 2016 Technical Preview 3 brings container support
Publié: août 19, 2015, 8:27pm CEST par Mark Wilson

As promised by Gabe Aul just over a week ago, Microsoft today releases Windows Server 2016 Technical Preview 3. One of the biggest new additions to this build is native support for Windows Server Containers, Microsoft's take on Linux containers.
Developers have been begging for container support in Windows Server for some time now, and the introduction of this feature could be the start of Microsoft offering up some serious competition to Linux server software. This is not the only new feature to be found in Windows Server 2016 Technical Preview 3, there's also software-defined datacenter enhancements and new Nano Server functionality.
For companies running both Windows and Linux servers, the introduction of container support means that it will be much easier to deploy containers to both. Microsoft has worked with Docker to bring container support to Windows Server 2016, and containers can be managed and deployed using either PowerShell or the Docker client. Microsoft promises that future builds will include Hyper-V Containers, optimized for use in virtualized environments.
Windows Server Technical Preview 3 is available for download from the TechNet Evaluation Center, where Microsoft introduces the latest release:
At the heart of the Microsoft Cloud Platform vision, Windows Server brings Microsoft’s experience delivering global-scale cloud services into your infrastructure. Windows Server 2016 Technical Preview 3 provides a wide range of new and enhanced features and capabilities spanning server virtualization, storage, software-defined networking, server management and automation, web and application platform, access and information protection, virtual desktop infrastructure, and more.
Improvements have also been made to System Center 2016 that make it easier to managed virtualized environments. A full list of new features can be found on TechNet.
Photo credit: 360b / Shutterstock.com
-

Windows 10 Build 10525 breaks Chrome; here's how to fix it
Publié: août 19, 2015, 1:52pm CEST par Mark Wilson

Chrome users who rush to install the latest build of Windows 10 have found that their favorite browser is broken. Build 10525 of Windows 10 prevents Chrome from working properly -- launch the browser and you'll be greeted by a series of notification saying that plugins have crashed.
Additionally, when attempting to visit any website, all that is displayed is an error message that reads "Aw, Snap! Something went wrong while displaying this webpage. Closing the apps and tabs that you don't need may help by making more memory available". The compatibility issue has been reported to Google so a patch will be forthcoming soon, but in the meantime you can use this workaround.
It appears the problem only affected 64-bit versions of Windows, and it's not clear how many people have experienced the issue. The simple solution to getting Chrome up and running again is to use the --no-sandbox flag. This is not something that is normally recommended, as it brings Chrome processes out of their protected, sandboxed state, but as a temporary measure -- and to avoid having to switch browsers for too long -- it's fine.
- Right click on click on the desktop shortcut to Chrome and select Properties.
- Move to the Shortcut tab and click in the Target field.
- Type a space at the end of the path that appears in the field followed by --no-sandbox.
- Hit OK, and use the shortcut to launch Chrome.
You'll notice an information bar at the top of the screen that reads "You are using an unsupported command-line flag: --no-sandbox. Stability and security will suffer" but Chrome will at least be working once again.
Note the warning, and just hope that Google or Microsoft push out a fix soon.
Photo credit: 360b / Shutterstock
-

New AudioEffect vulnerability affects every version of Android back to 2.3
Publié: août 18, 2015, 6:30pm CEST par Mark Wilson

Stagefright was one of the biggest and most worrying security vulnerabilities to be discovered in Android for quite some time. Affecting the mediaserver component, Stagefright allowed for the remote bricking of devices with nothing more than a message. Now a new, yet-to-be-named vulnerability has been discovered in the same component, specifically the AudioEffect element.
Known as CVE-2015-3842, the vulnerability allows a hacker to run their own code on a phone using whatever permission they want. Security researchers at TrendMicro discovered the vulnerability and explain that it can be implemented by simply tricking users into installing a specially-designed app that has no permission requirements and is therefore unlikely to raise suspicions.
One of the positive side effects of Stagefright was that it forced manufacturers to agree to monthly security updates. Despite this, and the fact that Google has issued a patch, millions of handset remain vulnerable not only to Stagefright, but also to the more recent AudioEffect exploit. A patch might well be available, but it could take months to make its way to users, and huge numbers of handsets are simply no longer supported.
It's not all doom and gloom, however. TrendMicro brings the news that there are not currently known to be any active attacks that exploit this vulnerability -- but this could change. Google may have published details of a fix, but the length of time it takes for carriers to push out updates, coupled with the spread of information about the exploit, means that many people are likely to fall victim before the problem is properly contained.
Writing about the vulnerability on the TrendMicro blog, mobile threat response engineer Wish Wu says:
This attack can be fully controlled, which means a malicious app can decide when to start the attack and also when to stop. An attacker would be able to run their code with the same permissions that mediaserver already has as part of its normal routines. Since the mediaserver component deals with a lot of media-related tasks including taking pictures, reading MP4 files, and recording videos, the privacy of the victim may be at risk. Devices with customized versions of Android but with no modification made to the mediaserver component are also affected.
The advice at the moment is to use the Trend Micro Mobile Security (TMMS) to detect any malicious apps that might be installed and then remove them through safe mode.
Photo credit: Ladislav Krajca / Shutterstock
-

This (!) is precisely why phones without removable batteries are a terrible idea
Publié: août 18, 2015, 3:22pm CEST par Mark Wilson

When looking for a new phone, people place importance on numerous things -- different strokes for different folks, and all that. Two things that are frequent bones of contention are the absence of a microSD slot, and a battery that cannot be replaced by the user. It used to be the case that every phone out there (well, let's ignore the iPhone for now) had a battery that you could easily be replaced if needed. Or perhaps you wanted a spare battery so you could use your phone for longer.
But recently there has been a worrying move towards delivering phones that are sealed units -- if your battery gives out on you, you have no option but to send it back to the manufacturer for a replacement. This takes time and money, but the problem of batteries that can't be replaced by users runs deeper than this. Just look at the image above.
OK, OK, that's a photo of a MacBook Pro battery, but it's still relevant. I've had batteries in phones puff up in the same way, thankfully in phones that I have been able to buy replacements for -- just as with the MacBook Pro. This battery swelling is something that, usually, happens very gradually; you tend not to wake up in the morning and discover that it has doubled in size overnight. This glacial creep can make it hard to notice when it's happening, but there will eventually be warning signs.
Battery life will almost certainly be impaired. A swelling battery is not a healthy battery, and you'll almost certainly notice a substantial drop in how long the charge lasts. There will probably be other power-related issues such as random restarts and overheating. Leave things for long enough, let the battery swell too much, and you might well notice that the rear cover starts to pop off. At least this is the case with phones whose batteries you can replace yourself.
It's a different story for phones that are sold as sealed units. It's not just the iPhone, Samsung's recently announced Galaxy Note 5 and Galaxy S6 Edge+ are also culprits. Because the case is sealed, because the back is screwed on -- or maybe the body is one solid piece of material -- you can't see the battery or the physical effect it might be having on your phone... at least until it is too late. With a phone whose back can pop off, this is exactly what a swelling battery will cause to happen. There's not enough room to continue to swell, so it makes a bit more room by pushing the obstacle out of the way.
With a sealed unit this just can't happen. Sure, the rear of the phone could bulge a bit, but it is designed not to move. But that swelling battery's not going to stop growing just because the back's not shifting. Rather than pushing a cover out the way, that puffed-up power pack is going to expand into, and start crushing, anything that's nearby -- circuit board, chips, the screen. That's when your repair bills start to get a lot steeper.
This was all prompted by splashing out £46 (around $72) this weekend on a couple of replacement batteries for a pair of Samsung phones. Both handsets are slightly aging, but both fully functional aside from atrocious battery life thanks to worn out batteries. The problem was easily diagnosed -- when battery life started to drop, it was initially put down to just general aging. But when it dropped more and more, it became clear that something more serious was wrong. It was very simple and, more importantly, free to slip off the back, remove the battery and perform a table top spin test (not that this was really necessary thanks to the obvious bloating).
It would have been a very different story had the phones' backs not been removable. I would have either had to send them off to be looked at, or take them into a store for repair. Time. Money. Both valuable commodities to me. And paying someone to operate on my phone rather than just being able to buy an aftermarket replacement battery will be the more expensive option in just about every case.
Or I may just have put up with it because I couldn't do something about it myself. Left to itself, the swelling battery could have become seriously problematic, potentially exploding or leaking. Without the ability to remove the back and look at my battery, I could have been none the wiser until it was too late. That's why sealed unit phones are bad. That's why users should be able to replace their own batteries.
Photo credit: Mark Wilson
-

Microsoft releases free Windows 10 virtual machines
Publié: août 18, 2015, 12:16pm CEST par Mark Wilson

If you're wary about going the whole hog and installing Windows 10 as your main operating system, you might consider going down the dual boot route, or installing Windows 10 in a virtual machine. Virtualization is a neat option and Microsoft has released a trio of readymade virtual machines that let you test out Windows 10 with Microsoft Edge.
The downloads are provided with web developers in mind -- they're meant to be used to test how websites function under different versions of Microsoft's web browser and these latest releases see the dropping of the beta tag from Edge. But these downloads are not going to just be of interest to developers as they give anyone the chance to try out Windows 10 in a safe environment.
At the moment there are virtual machines available for VMware, HyperV, and VirtualBox. This has most bases covered, but Microsoft promises that in the coming weeks new formats will also be added, starting with Vagrant boxes and QEMU. Introducing the downloads on the Windows Edge Dev blog, the Microsoft Edge team says that improvements have been made to accessibility and promises that the development roadmap will be clearer moving forward.
SEE ALSO: How to install Windows 10 on Oracle VirtualBox -- no Windows key required
Microsoft warns that there is a known issue with the virtual machines:
Known issues: Windows 10 virtual machines may display a message in the Settings app that reads "Connect to the Internet to activate". This is due to a bug and does not impact the activation state or functionality of the virtual machine.
The company also offers up a reminder about how long you are able to use the virtual machines:
Please note that these virtual machines expire after 90 days. We recommend setting a snapshot when you first install the virtual machine which you can roll back to later.
To download your free virtual machine, head over to the Microsoft Edge Dev site and look to the Free Tools section.
Photo credit: Anton Watman / Shutterstock
-

How to uninstall Windows 10 and go back to Windows 7 or 8.1
Publié: août 18, 2015, 3:23am CEST par Mark Wilson

As Windows 10 is free, it's hard not to be tempted into upgrading. But just because the operating system is free, it does not mean it is necessarily right for you. You may have tried Windows 10 for a few weeks and come to the conclusion that you hate it. Perhaps you yearn to move back to the comfort of Windows 7 or Windows 8.1.
If you've decided that you simply do not like Windows 10, you can downgrade with ease. Of course, this is not possible if you have performed a clean installation of Windows 10, but it's an option that's available to you if you upgraded from Windows 7 or Windows 8.1. So, are you ready to ditch Windows 10? Here's what you need to do.
Anyone who upgraded to Windows 10 is granted a 30 day cooling off period. Change your mind about Windows 10 within a month and you can roll back to your previous version of Windows with ease. If you're indecisive and change your mind again, you can always reinstall Windows 10 as it remains free for a year. Note that if you have followed our guide to freeing up space after a Windows 10 upgrade, you will have wiped out your old version of Windows, so the rollback option will not be available to you. Otherwise, if you want to revert to your previous version of Windows, just follow these simple steps.
- Open up Settings via the Start menu or the taskbar icon.
- Click Update & Security and then move to the Recovery section.
- Under the Go back to Windows 7 or Go back to Windows 8.1 heading, click Get started and you'll be guided through the rest of the process.
Remember, this option will not be available to you if you have been using Windows 10 for more than a month, or if you have cleaned up the files related to your previous version of Windows.
If you change your mind about Windows 10 after the month is up, there is no built-in downgrade option available to you. In order to go back to Windows 7 or Windows 8.1, you will need to back up all of your files and then reinstall the older version of Windows from your original installation media, or by downloading the ISOs from Microsoft.
Photo credit: Imilian / Shutterstock
-

Two decades in the making... was Microsoft Edge worth the wait?
Publié: août 17, 2015, 12:23am CEST par Mark Wilson

Today marks the twentieth anniversary of the launch of Internet Explorer. First making an appearance in the Windows 95 era via the Microsoft Plus! Add-on pack which featured the excitingly-named Internet Jumpstart Kit and version 1.0 of the browser people love to hate and hate to love.
Two full decades later we have slowly but surely worked up to Internet Explorer 11 -- Chrome, for comparison has hit the 40s in less than half the time -- and now IE has been all but retired. With the launch of Windows 10, Microsoft Edge is the new kid on the block. Twenty years is a long gestation period. Was it worth the wait?
Even if you loathe Internet Explorer, it's hard not to feel a little something at the realization that the browser is 20 years old. Few people who use a computer can say they have avoided Internet Explorer, and that’s not a claim that can be made by many software titles. From the heyday of the IE vs Netscape Navigator battles of the 90s, through the antitrust lawsuits, to the declining market share, Internet Explorer has had a rocky journey.
Microsoft had already announced that the browser had reached the end of the road. Today on Twitter, the company took the anniversary to promote its replacement, Microsoft Edge in a slightly tongue-in-cheek style:
https://twitter.com/MicrosoftEdge/status/632989205564538880
The replies to the tweet show the mixed feelings that are held about Internet Explorer. Many are scathing, and in shutting the door on IE to usher in Edge, it would appear that even Microsoft is ready to move on, to try to shake off the reputation of its famous browser. Internet Explorer was the browser developers hated developing for -- will Edge be any different?
Ultimately, it is the user experience that will make or break Edge. It seems as though Microsoft was in something of a rush to ensure that the browser was out of the door at the same time as Windows 10 as it is lacking one of its biggest features -- add-ons. It could well prove to be a grave mistake to have released Edge in an unfinished form in the hope that people will stick around to try out the 'completed' build at some unknown point in the future.
Until add-ons support comes, what is there to enjoy? A reading mode, the ability to scribble on websites, improved security and performance -- but is there anything unique?
We've talked about Microsoft Edge before, but the twentieth anniversary of the release of Internet Explorer seems like a good time to revisit the subject. Has Microsoft got it right with Edge or is there still a lot of work to do? Will Edge always be playing catch-up with Chrome, Firefox, and Opera, or does the browser show signs of innovation that will be copied by the competition? In short, was it worth the wait?
Photo credit: Vladimir Gjorgiev / Shutterstock
-

Samsung shows us what's new in Android Marshmallow [Infographic]
Publié: août 16, 2015, 6:40pm CEST par Mark Wilson

OK... for now it's still Android M, but there have been sufficient rumors and hints for us to safely guess that the follow up to Lollipop will be called Marshmallow*. Google has started to tease us with videos, and Samsung has unveiled its Galaxy Note 5 and Galaxy S6 Edge+ which will be in line for an Android M update in due course.
But it's not just handsets that Samsung has produced. The company has also put together a handy infographic that highlights some of the new features of Android. Just what is in store? Quite a lot, actually.
* Of course, we could be wrong. Few people guessed that KitKat would be called KitKat, with most assuming that the K stood for Key Lime Pie. Hints may have been dropped that M is for Marshmallow, but it's entirely conceivable that these have been nothing more than red herrings.
Android's much-maligned permissions system has been given an overhaul, and memory management has also been improved. App data and settings are now automatically backed up to the cloud, and fingerprint access can be used on supported handsets for security.
It won’t been long until you can get your hands on the official release of Android M -- you can use the developer preview for now if you like -- but in the meantime, content yourself with the infographic: (click for the full size version):
Photo credit: Texturis / Shutterstock
-

Apple Watch welcomes fat wrists... for a price
Publié: août 16, 2015, 11:47am CEST par Mark Wilson

Not everyone has svelte wrists -- some hand hinges are as thick as thighs. Apple has decided that those with chunkier wrists no longer need to develop anorexia to be able to strap on an Apple Watch, releasing larger bands for the larger customer.
As well as a Sport band that comes in that all-important L/XL sizing, there's also an extender kit available for the metal bracelet. If you over-estimated the size of the Link Bracelet, or under-estimated the size of your wrist, you can slip in a few extra links to up the size to 245mm.
Head on over to the Apple Watch section of Apple's online store and you'll find a new band option for the cheapest model. There's now a L/XL Sport Band available for $49 but, for the moment at least, you'll need to buyer the bigger band separately as there's no way to order a Watch with the larger strap included.
For fans of the metallic look, there's the Link Bracelet Kit. Also costing $49, this kit includes six extra links to extend an existing Link Bracelet to 245mm. No special tools are required to make use of the kit, but it is worth noting that only silver is available; if you have Space Black Link Bracelet you will have to opt for a two-tone look.
So, Apple is opening up its wearable to a wider audience. The question is, does this amount to a fat tax?
Photo credit: weerayut ranmai / Shutterstock
-

New Snowden documents show AT&T helped the NSA spy on internet traffic
Publié: août 15, 2015, 10:36pm CEST par Mark Wilson

The NSA has been helped by AT&T for decades in spying on huge quantities of internet traffic new-disclosed documents reveal. The astonishing relationship between the National Security Agency and the telecoms company goes far beyond any sort of arrangement or co-operation that came from other firms.
Evidence published by the New York Times shows that the NSA had arrangements in place with AT&T and Verizon, but the partnership with AT&T proved particularly lucrative. The communications giant added surveillance equipment to at least 17 of its web centers and was used as a testing ground for new spying technologies and techniques. All this is revealed in a new batch of documents provided by Edward Snowden.
The documents have been jointly viewed and analysed by the New York Times and ProPublic, and show that AT&T was actively working with the NSA from at least 2003 to 2013. While it is not known whether the co-operative arrangement is still in place, it looks as though it has existed prior to the period covered by the documents. AT&T's "extreme willingness to help" is praised by the NSA -- hardly surprising considering the collaboration gave the NSA access to billions of email sent over AT&T's network.
It appears that AT&T was a willing participant in the arrangement rather than having to be coerced into it; the documents remind NSA officials that "this is a partnership, not a contractual relationship". Several old surveillance programs are referred to in the documents including one dating back to 1985 called Fairview. The New York Times reports that former intelligence officials confirm that AT&T was a program partner.
It is also revealed that AT&T helped the NSA to spy on the UN by allowing access to the communication line it provided to the United Nations HQ. The documents show that AT&T was the first NSA partners to enable a data collection system on its network in September 2003. This operation was soon picking up more than a million emails per day based on keyword selection.
We also learn that the NSA spent $188.9 million on the Fairview program alone in 2011, while a document from 2013 find the NSA saying that AT&T's " corporate relationships provide unique accesses to other telecoms and ISPs". It seems to have been the case that AT&T was responsible for conducting surveillance on behalf of the NSA, passing on data based on various, changing requirements.
AT&T has refused to comment on the revelations.
You can check out the full NSA documentation on the New York Times websites.
Photo credit: Rob Wilson / Shutterstock
-

Microsoft stands accused of deleting Windows 10 Insider feedback it doesn't like
Publié: août 15, 2015, 7:10pm CEST par Mark Wilson

With Windows 10, Microsoft asked for an unprecedented level of feedback. The Windows Insider program not only provided keen users with access to preview builds of the operating system, but also gave a direct line to Microsoft to point out problems, make suggestions, request features, and so on.
In fact, the Windows Insider program is still running as Microsoft continues to ask for feedback. But the company faces accusations of not only failing to listen to the feedback it asks for, but deleting from the Feedback app and forums any suggestions it does not like. Highlighted for particular attention are suggestions about tabs in File Explorer, and requests to remove email addresses from Windows 10's lock screen. We decided to take a look and find out what is going on.
We were contacted by a reader who was concerned about the apparent disappearance of feedback about Windows 10. He had noticed that suggestions left via the Windows Feedback app vanished, despite the fact they had received numerous upvotes from other users. It seems that lots of users were concerned that Windows 10 displayed their email address on the lock screen and suggested that Microsoft might want to reconsider. Large numbers of people agreed, and suggestions of this type received hundreds upon hundreds of positive responses.
The same goes for requests for a tab bar to be added to File Explorer to make it easier to work with multiple folders at the same time. This is not something that's new with Windows 10 -- people have been begging Microsoft to add this feature for years, and a small industry has sprung up in third party tools that add it. It has been noted that suggestions filed through the Windows Feedback app calling for tabs are sucked into a blackhole, as have calls for a loosening of Microsoft Account integration.
It could be that feedback that is being acted upon is removed -- but this does not appear to be the case. It is not the case that all feedback relating to these topics is removed. It has been noticed that only those items with a lot of votes are culled -- that is, the more visible feedback. Could this highlight the notion that popular ideas are being worked on, or that there is censorship in action? Part of the problem is that feedback is a one-way street; Microsoft does not let Windows Insiders know about which feedback it is acting on. Perhaps increased transparency could help to calm the suspicions that have been raised.
We reached out to the company to see what it had to say. In a statement to BetaNews, a Microsoft spokesperson said:
After the launch of Windows 10 and in preparation for continued flighting of PC builds to Windows Insiders, we have taken the opportunity to clear out the older feedback that we received early on in our product development cycle from the search results that get returned within the Windows Feedback app. The feedback that has been previously provided is still stored in our backend systems. Engineers are using it to find and filter on key feedback for their areas. We have more than six million Windows Insiders in our Windows Insider program who are testing Windows 10 features on a daily basis. Their feedback is critical for us to both deliver the best customer experience with Windows 10 and also to keep improving and delivering new value in a continuous fashion.
What do you make of it? Have you submitted feedback which has subsequently disappeared into the void? Even if Microsoft is clearing out 'older feedback' would it not make sense to leave in place those topics that have received a lot of attention? Is all feedback being acted upon, or are the trickier and objectionable suggestions just being swept under the rug? Transparency is the answer!
Photo credit: Richard M Lee / Shutterstock
-

Firefox stealthily loads webpages when you hover over links -- here's how to stop it
Publié: août 15, 2015, 2:02pm CEST par Mark Wilson

Pre-fetching or caching of web pages is a technique used by many web browsers to improve perceived performance -- it's nothing new. But Firefox takes a slightly sinister and stealthy approach. Simply hover your mouse over a link and the browser fires off requests to the associated website in the background.
While this sounds potentially helpful, it is also something of a privacy and security concern -- not to mention a waste of bandwidth. You might hover over a link simply to check out the destination in the status bar; if there is a link to a malicious or unsavory website, you probably don’t want these stealthy connections being made in the background. If you're worried about your security or privacy, or just want to be back in control of your web connection, there are steps you can take.
As pointed out in a discussion thread on Slashdot, this is not a feature of individual websites controlled by JavaScript or CSS, it's controlled entirely by Firefox. If you disable JavaScript and CSS, these requests are still fired by simply hovering over a link -- there are various tools that can be used to monitor what is happening with your web traffic. The preloading is a feature of an API called nsISpeculativeConnect, and Mozilla says that it:
Lets non-networking code provide hints to the networking layer that an HTTP connection attempt to a particular site is likely to happen soon; this lets the networking layer begin setting up TCP and, if appropriate, SSL handshakes to save time when the connection is actually opened later.
There have been concerns about the privacy implications of the feature for some time, with some people submitting bug reports about it. Calls for a global setting to be introduced that makes it easy to control whether these pre-connections are enabled or not have been denied -- the issue has a RESOLVED WONTFIX fix label slapped on it indicating that there are no plans to change the way things works.
But you can fight back if you want.
Mozilla has anticipated that what Firefox is doing will not be to everyone's liking and has set up a page on its support site entitled "How to stop Firefox from making automatic connections". The introduction reads:
Some people are concerned about the connections Firefox makes to the Internet, especially when those connections are made for no apparent reason (see Mozilla's Firefox Browser Privacy Notice for additional information). This article explains various reasons why Firefox may make a connection to the Internet and how you can stop it from doing so, if you wish.
To disable the speculative pre-connections feature, take the following steps:
- Type about:config in the address bar and hit Enter.
- Click I'll be careful, I promise!
- Perform a search for the text network.http.speculative-parallel-limit.
- Change the value of this item to 0.
That's it!
As one commenter says on Slashdot:
One can expect Firefox to make requests in the background to its own servers for things such as checking for updates to plugins etc. But silently making requests to random links on a page (and connecting to those servers) simply by hovering over them is something very different.
Photo credit: Gil C / Shutterstock
-

Windows 10 could disable pirated games and unauthorized hardware
Publié: août 14, 2015, 11:15pm CEST par Mark Wilson

Cries of "FUD!" ring out whenever potential issues and concerns with Windows 10 are pointed out, but there's no denying that the launch of this version of Windows has been more blighted than any other. The latest controversy finds Microsoft updating its EULA so that it is able to block pirated games and unauthorized peripherals.
While on one hand this seems entirely reasonable -- few people would argue too strongly that they should be permitted to play pirated games -- on the other it is confusing and worrisome. It is yet another example of Microsoft causing trouble for itself by failing to properly communicate with its customers, being insufficiently transparent and clear in meaning. Just what is an 'unauthorized peripheral'?
It is the lack of clarity that is likely to give the greatest cause for concern here. Without knowing how peripherals are authorized or not, it is impossible to know if any given device will be blocked from use or not. With Windows 10 hitting more devices than any previous version of Windows, the scope of this new EULA is far wider-reaching than ever before.
As noted by Alphr, Section 7b of the Microsoft Services Agreement reads:
Sometimes you'll need software updates to keep using the Services. We may automatically check your version of the software and download software updates or configuration changes, including those that prevent you from accessing the Services, playing counterfeit games, or using unauthorized hardware peripheral devices.
The agreement covers Xbox 360, Xbox One, Windows Phone, and all manner of other Microsoft services. While it is unlikely that Microsoft would suddenly take objection to the use of a particular keyboard or game controller, the EULA does indicate that the company could potentially block access to anything it decided not to authorize.
Many people will object to the idea that Microsoft is able to scan a system to detect the hardware and software that is running, and then use the results of this scan to determine what hardware and software may be used. With so many concerns about privacy being thrown up by Windows 10, this is yet another which is causing rumbles of discontent.
We've reached out to Microsoft for comment, and will update this article when we hear back.
Photo credit: Anton Watman / Shutterstock
-

Confirmed: Apple is working on a self-driving car to rival Google
Publié: août 14, 2015, 10:32pm CEST par Mark Wilson

Apple's Project Titan is not only real, but the self-driving car is further developed than previously thought. Documents obtained by The Guardian show that the company is currently looking for secure locations in the San Francisco bay area that could be used to test the vehicle.
The newspaper made a public records act request to unearth correspondence that revealed that the Special Project group from Apple met with representatives from the GoMentum Station. This former naval base is in the process of being transformed into test track for self-driving vehicles.
The Apple Car, iCar, or whatever the vehicle ends up being called, appears to be further along the development track than previously believed. The company seems keen to get some alone time at the GoMentum Station, with Apple engineer Frank Fearon writing: "We would like to get an understanding of timing and availability for the space, and how we would need to coordinate around other parties who would be using [it]."
It has long been rumored that Apple has been beavering away on a self-driving car, but confirmation that the company is actively looking for a testing ground shows that development is well underway -- Apple could be on the verge of testing its first viable prototypes. Rumors of Apple's work have been further fuelled by Tim Cook's meeting with Fiat-Chrysler boss Sergio Marchionne, and Apple's hiring of engineers from automotive companies.
Despite the appearance of correspondence between Apple and the GoMentum Station, the owners of the location remain tight-lipped:
We had to sign a non-disclosure agreement with Apple. We can't tell you anything other than they've come in and they're interested.
Photo credit: withGod / Shutterstock
-

Google teases with Android M name video
Publié: août 14, 2015, 7:22pm CEST par Mark Wilson

You might still be waiting for Lollipop to limp onto your handset, but just around the corner is Android M. We already know quite a bit about what to expect from the next version of Android -- you can even try out the Android M Developer Preview if you want -- but there's one thing that's far from clear: what is it going to be called.
There have been all sort of guesses since the codename was revealed by Google and now the company (Google, Alphabet... call it what you will...) is starting to tease us with name suggestions. There's also a video that offers a 'musical hint' at the name.
The video, freshly posted to YouTube, is entitled What’s M Gonna Be? and features the hashtag #NatAndLo. We're treated to a history of Android, skipping through the various versions as Google kicks the hype machine into action. Then the suggestions are thrown at the screen: M&M, Mud Pie, Marshmallow... place your bets.
The official Android Twitter feed kicked things off, inviting fans to guess what the name is going to be:
What’s #Android M gonna be? We all have our guesses… [t.co] #natandlo pic.twitter.com/um6zpIdiw4
— Android (@Android) August 14, 2015
But it is the video that could well contain the information needed to discover the name ahead of time... you might just need to spend a little time decoding what you see and hear:
With Android M drawing ever-closer on the horizon, there's really not long to wait until we find out for sure, but do you have any ideas about what the M could stand for?
-

Does diversity in tech actually matter?
Publié: août 14, 2015, 6:42pm CEST par Mark Wilson

Diversity has become something of a buzzword in tech, and it's one that companies are only too keen to bandy about at every opportunity. The likes of Apple, Google, Facebook, and Amazon are eager to demonstrate how diverse a workforce they have built up -- but the fact of the matter is that they have all failed abysmally.
This much we know. We've seen that Facebook's workface is far from diverse, Amazon is about as white and male as it gets, and that Apple wants people to believe it's doing everything it can to foster greater diversity. Its latest report shows that the number of female, black, and Hispanic employees has increased but Tim Cook wants to do more. But the big question is: does diversity matter?
The answer, of course, is yes; but there are some caveats. Diversity is quite a subjective idea and it is -- as with so many concepts -- something that is hard to bring about in a way that satisfies everyone. What does diversity mean? Should a company's workforce comprise precisely the same racial, sexual, gender, religious, etc breakdown as the country as a whole? Or the entire globe? Do the percentage of workers from different backgrounds need to be the same at all levels of the company, or just work out as an average?
Few people would argue that there are certain sections of society that appear to be under-represented in the workplace. This is true in many industries, but it is the tech world that has found itself on the receiving end of criticism most recently. Apple is, as ever, eager to avoid being tarred with any brush of negativity, so in introducing Apple's latest diversity report Tim Cook reveals:
In the past year we hired over 11,000 women globally, which is 65 percent more than in the previous year. In the United States, we hired more than 2,200 Black employees -- a 50 percent increase over last year -- and 2,700 Hispanic employees, a 66 percent increase. In total, this represents the largest group of employees we’ve ever hired from underrepresented groups in a single year. Additionally, in the first 6 months of this year, nearly 50 percent of the people we’ve hired in the United States are women, Black, Hispanic, or Native American.
This is when things start to get interesting. Too many technology firms have demonstrated that they are dominated by white, middle-class men, and this is clearly an imbalance that needs to be addressed. But what is the best way to go about it? It would be unfair to go out and actively seek, for example, black employees for a particular position, just as it would be unfair to specify that applicants needed to be white.
When you start to pursue the idea of workforce diversity, you start to encounter a few issues. While it is easy to tell whether someone is black or white, the same is not true when it comes to sexuality or religion. A CEO might want to ensure that his workforce includes a decent number of LGBT employees but in many cases this would involve asking questions that really should not be asked. If employment equality is to be achieved, a job application form that asks for -- or, worse, takes into consideration -- race, sexuality, gender, and so on is counterproductive and counterintuitive. Positive discrimination is still discrimination.
So does diversity matter? Of course it does, but probably not in the way that many companies think it does. It's a delicate line to walk. Do nothing and it is the white, middleclass male who will dominate and probably bubble to the top -- it's the same in just about every industry. But set up program, initiatives, and incentives to pull in 'minorities' and push them up through the ranks and you run the risk of simply flipping the switch and just discriminating against different sections of society.
You can't do right for doing wrong.
Photo credit: Alta Oosthuizen / Shutterstock
-

10 things you need to know about the Samsung Galaxy Note 5
Publié: août 14, 2015, 3:25pm CEST par Mark Wilson

Samsung unveiled the Galaxy Note 5 in NYC yesterday and there has already been a great deal of coverage of the handset. It is hard to beat getting hands-on with a phone but there are important factors that could sway you one way or the other when it comes to making a purchase.
Samsung has already produced an infographic pulling out what the company thinks are its highlights. To help you decide if the Galaxy Note 5 should be on your shopping list, here are ten things you need to know.
It'll almost certainly get Android M
We might not know whether the M stands for Marshmallow, Mars bar, Milky Way, or Marzipan, but we do know that Android M is only just around the corner. A lot of people may still be waiting for Lollipop to arrive on their handsets, but the Galaxy Note 5 is a flagship device that's virtually guaranteed to be among the first in line for Android M.
The next version of Google's mobile operating system is pencilled for release in October, and it would be extremely surprising if an update did not follow fairly quickly for the latest addition to Samsung's Note range.
There actually is a 128GB version
While Samsung only talked about 32 and 64GB models at the unveiling, it seems that anyone who was hoping for a larger capacity could be in luck. After the hype of the main unveiling, Samsung later added 128GB Note 5 to its website. There's no word on pricing yet, but this will almost certainly follow in the coming days --- launch isn't all that far away, after all.
You can't expand the storage
It's just as well the 128GB Note 5 did make an appearance as Samsung took the decision not to include a microSD slot. In terms of data there has been a slow and steady move to cloud storage, but when it comes to apps, photos, and files that need to be accessed offline, the ability to expand storage space is something that a lot of people still look out for. Just like Apple, Samsung is now forcing customers to think very carefully before making a purchase -- spend a little to make a saving and run the risk of running out of space, or splash the cash in the hope that it will future-proof your handset? The choice is yours.
It has the same processor at the Galaxy S6 Edge+
The eight-core Exynos 7420 processor is quite a powerhouse. With half the cores running at 1.5GHz and the other half at 2.1GHz, this is a processor that will handle just about anything you might throw at it.
There is no removable battery
Like the lack of removable storage, the ability to switch out the battery is an option that's missing from the Galaxy Note 5. It's something that users care passionately about, or could not care less about -- there is usually no middle ground. If you want to be able to take a spare battery on the road with you, this is not the phone for you. If you're less demanding in the power department, or can make do with an external battery pack, the 3,000 mAh battery should see you through -- and it's a fast-charging, wireless power pack to boot.
That display
It's hard not to be impressed by the Galaxy Note 5's display. At 5.7 inches, it's venturing into phablet territory, but it's not just about size. It's a QHD Super AMOLED screen with a resolution of 2,560 x 1,440 pixels, equating to 518 ppi and the shrunken bezel means that more of the front of the phone is take up by the display.
Samsung Pay support
Paying for shopping with a phone is not new by any means, but Samsung Pay -- supported by both the Galaxy S6 Edge+ and the Galaxy Note 5 -- could improve its appeal. By supporting not only NFC but also MST (Magnetic Secure Transmission used by credit card readers) you should be able to pay with your Note 5 in more places than you are able to use other phones.
All metal and glass design
With the Note 5, Samsung has taken build quality up a notch, eschewing plastic in favor of metal and glass. The company has long been accused of borrowing ideas from Apple for its handsets, but few people would complain about the effect this has had on build quality.
There's a physical keyboard if you want it
We thought the days of physical buttons on phones were all but dead, but there is still demand for BlackBerry-style keyboard from some quarters. There's nothing to stop you from pairing up any old Bluetooth keyboard to the Note 5 to speed up your typing, but Samsung has a better option. Its keyboard cover snaps into place over the display to make lengthy typing sessions a breeze -- assuming you haven’t become reliant on the likes of Swype, that is.
S-Pen improvements
The S-Pen has always been one of the Note's key selling points, and in the Note 5 Samsung has taken the time to make a few refinements. Perhaps the most notable change is the click mechanism that locks the pen in place when it's not in use, and eliminating the need to scrabble with a fingernail to pull it out to make a quick note. The on-pen button has also been re-designed to make accidental presses less likely. The physical improvements are bolstered by improvements to the S-Pen software, opening up new ways of interacting with your Note 5 including annotating PDF, and scrolling screen capture.
-

Samsung Galaxy Note 5 and Galaxy S6 Edge+ pricing revealed
Publié: août 14, 2015, 12:13am CEST par Mark Wilson

When Samsung unveiled the Galaxy Note 5 and Galaxy S6 Edge+ earlier today, there was a lot to take in -- but information about pricing was notable by its absence. As these are both flagship handsets, low prices were never going to be on the cards, but as the day has worn on, carriers have revealed how much you can expect to pay.
Pre-ordering starts today, so you don't have much (well... any) time to save up, but we now know how much the two handsets will cost from AT&T, Verizon, Sprint, and T-Mobile. Read on to see how much you'll have to part with.
It should come as no surprise that the Galaxy S6 Edge+ is the more expensive of the two, as detailed by Android Beat:
AT&T
32GB
No Contract: $814.99
Two-year contract: $299.99
Next 24: 30 payments of $27.17
Next 18: 24 payments of $39.96
Next 12: 20 payments of $40.75
64GB
No Contract: $914.99
Two-year contract: $399.99
Next 24: 30 payments of $30.50
Next 18: 24 payments of $38.13
Next 12: 20 payments of $45.75
Verizon Wireless
32GB
24 payments of $32
64GB
24 payments of $36
T-Mobile
32GB
JUMP! On Demand will offer $0 down and 23 payments of $32.50, with an additional payment of $32.49. Buying before 9/30 will earn $0 down and $28.50 for 18 months.
Sprint
32GB
No Contract: $792
Two-year contract: $349.99
Easy Pay: 24 payments of $33
Lease: $0 down and 24 payments of $30
64GB
No Contract: $888
Two-year contract: $449.99
Easy Pay: 24 payments of $37
Lease: 24 payments of $35
The Galaxy Note 5, complete with its S-Pen is slightly cheaper:
AT&T
32GB
No Contract: $739.99
Two-year contract: $249.99
Next 24: 30 payments of $24.67
Next 18: 24 payments of $30.84
Next 12: 20 payments of $37.00
64GB
No Contract: $839.99
Two-year contract: $349.99
Next 24: 30 payments of $28
Next 18: 24 payments of $35
Next 12: 20 payments of $42
Verizon Wireless
32GB
24 payments of $29
64GB
24 payments of $33
Sprint
32GB
No Contract: $720
Two-year contract: $249.99
Easy Pay: 24 payments of $30
Lease: 24 payments of $25
64GB
No Contract: $816
Two-year contract: $349.99
Easy Pay: 24 payments of $34
Lease: 24 payments of $30
T-Mobile
32GB
JUMP! On Demand will offer it for $0 down, 23 payments of $29.17 and one additional payment of $29.08.
-

[Infographic] What's hot about the Samsung Galaxy Note 5?
Publié: août 13, 2015, 11:43pm CEST par Mark Wilson

With the launch of the Galaxy Note 5, Samsung is hoping to revitalize the mobile arena and reclaim its place as the handset manufacturer of choice. The latest addition to the Galaxy Note range feature much that's familiar, including Samsung's S Pen, but the overall specs have increased.
As an alternative to leafing through lists of hardware specs in dull lists, Samsung has produced an infographic highlighting everything it believes is great about the Galaxy Note 5. The company appears particularly pleased with the screen and camera, as these are singled out for special attention.
Described as "thinner, stronger and packed with better functionality than ever", the Galaxy Note 5 is held up by Samsung as being the handset that is perfect for multi-tasking. From the innovative S Pen to the super-high resolution screen, this is a smartphone that demands attention. Check out some of the highlights in the infographic below (click for a larger version):
-

Samsung Pay launches in Korea in August, US in September
Publié: août 13, 2015, 6:35pm CEST par Mark Wilson

The main thrust of Samsung's Galaxy Unpacked event was to launch the Galaxy Note 5 and Galaxy S6 Edge+, but the company also provided some details about Samsung Pay. With so many similarly-specced smartphones vying for attention, each manufacturer needs to offer something slightly different, and Samsung is hoping that a new digital payment system will prove attractive to people.
Going head to head with Android Pay and Apple Pay is Samsung Pay. As well as offering compatibility with the newly announced Galaxy Note 5 and Galaxy S6 Edge+, Samsung's payment system is supported by many of its older handsets. It will launch in its home country of Korea on August 20, and will spread to the US at the end of September. So why pick this payment system over the alternatives?
Like Apple Pay, Samsung Pay works using NFC, but it also supports MST (Magnetic Secure Transmission). This is the same technology used by credit card readers and is far more widely in use, meaning that Samsung has something of an advantage when it comes to the number of places it could potentially be used.
The system is backed up by Samsung KNOX, and further security is provided by fingerprint verification and digital tokenization. US shoppers will have to wait until September 28 to try out Samsung Pay. Existing digital payment platforms have started to pave the way for the likes of Samsung Pay, but it remains to be seen whether there is room for yet another contender in the ring.
Photo credit: Anton Watman / Shutterstock.com
-

Samsung unveils Galaxy Note 5 and Galaxy S6 Edge+
Publié: août 13, 2015, 6:08pm CEST par Mark Wilson

At its Galaxy Unpacked event in NYC, Samsung today took the wraps off two of its most eagerly awaited handsets -- the Galaxy Note 5 and the Galaxy S6 Edge+. Just like Apple with the iPhone, Samsung's phone range is more about evolution than revolution -- but that's not to say there isn't quite a lot to get excited about.
Both devices include 4GB of RAM and as with previous generations, the Galaxy Note 5 features Samsung's S-Pen Stylus. The Galaxy S6 Edge+ boasts a larger screen than its predecessor but the Note 5's is the same size as before. So what else is new, and when can you get your hands on one?
The screens are the undoubted stars of the show here, but Samsung has made some interesting choices in other areas for the phones. Both are available in 32 and 64GB variants. It seems that 16GB models have now been consigned to the history books, but it would have been good to see a 128GB model to go head to head with the iPhone.
The storage limitations are highlighted by the fact that neither the Galaxy Note 5 or Galaxy S6 Edge+ support removable memory cards. Some people will be disappointed to find that the battery in both handsets is not removable, particularly in the case of the Note 5 which sees capacity dropping from the previous version. It is just as well, perhaps, that the battery supports fast charging.
Samsung is pitching the Galaxy S6 Edge+ as the phone that delivers the best multimedia experience, while the Note 5 is billed as being "perfect for multi-taskers".
The Galaxy Note 5 and Galaxy S6 Edge+ are slated for launch globally in August, but no precise date has been given -- nor do we yet have any word on pricing.
Here are the full specs of the Samsung Galaxy Note 5:
SYSTEM Android 5.1 (Lollipop) DISPLAY 5.7-inch, QHD Super AMOLED (2,560 x 1,440 pixels, 518 ppi) PROCESSOR Octa core (2.1 GHz Quad + 1.5 GHz Quad), 64 bit, 14 nm process RAM 4 GB RAM (LPDDR4) INTERNAL MEMORY 32/64 GB CONNECTIVITY Wi-Fi 802.11 a/b/g/n/ac, MIMO(2x2), Bluetooth® v 4.2 LE, ANT+, USB 2.0, NFC, Location CAMERA Rear: 16 MP OIS (F1.9), Front: 5 MP (F1.9) BATTERY 3,000 mAh (non-removable), fast-charging, wireless charging DIMENSIONS 153.2 x 76.1 x 7.6mm WEIGHT 171 g PRICE TBC And the specs for the Samsung Galaxy S6 Edge+:
SYSTEM Android 5.1 (Lollipop) DISPLAY 5.7-inch QHD Super AMOLED, 2560 x 1440 (518 ppi), dual-edge PROCESSOR Octa core (2.1 GHz Quad + 1.5 GHz Quad), 64 bit, 14 nm process RAM 4 GB RAM (LPDDR4) INTERNAL MEMORY 32/64 GB CONNECTIVITY Wi-Fi 802.11 a/b/g/n/ac, MIMO(2x2), Bluetooth® v 4.2 LE, ANT+, USB 2.0, NFC, Location CAMERA Rear: 16 MP OIS (F1.9), Front: 5 MP (F1.9) BATTERY 3,000 mAh (non-removable), fast-charging, wireless charging DIMENSIONS 154.4 x 75.8 x 6.9mm WEIGHT 153 g PRICE TBC -

A simple hack unlocks Very High quality Xbox One streaming in Windows 10
Publié: août 13, 2015, 5:07pm CEST par Mark Wilson

Xbox One-to-PC game streaming is one of the stand-out features of Windows 10, and plans are afoot for streaming the other way as well. If you're currently playing your Xbox One games on your Windows 10 PC or laptop, you might be interested to learn that there is a way to dramatically boost streaming quality.
While the hack itself is very easy to implement, it's not something that all gamers will want to undertake because of the demands it makes of networking hardware. That said, if you think your kit is up to the job, here's what you need to do.
The tweak doesn’t even require you to edit the registry and was highlighted in a post on Reddit. Redditor OomaThurman warns that "I can see the Mbps change in the Xbox app and a dip in throughput on my wan (firewall) when setting it to high instead of very high. The difference on just the Smite login screen is about 3Mbps, so I wouldn't recommend this unless you have exceptional networking gear and an understanding of what you're doing."
To earn yourself a quality boost:
- Open up File Explorer and navigate to C:\Users\%USERNAME%\AppData\Local\Packages\.
- Locate the folder whose name starts Microsoft.XboxApp and open it.
- Open the Local State folder and then use Notepad or another text editor to open the userconsoledata file.
- Locate the IsInternalPreview variable and change its value from false to true.
- Close and save the file and the new Very High setting should be visible in the Xbox app.
-

Windows 10 phones home to Microsoft even if you change privacy settings
Publié: août 13, 2015, 4:36pm CEST par Mark Wilson

Many people regret upgrading to Windows 10, and many are put off from making the move to the latest version of Microsoft's operating system, because of concerns about privacy. The answer to privacy worries about Windows 10 features such as Cortana has been 'just don't use them', but it seems that this might not be enough.
Research carried out by Ars Technica shows that even with features disabled and privacy settings activated, Windows 10 continues to send information back to Microsoft. The data is sent by a series of tools including OneDrive, Cortana, and Bing -- even when a local account is used.
Ars Technica found a number of issues with the way Windows 10 communicates with Microsoft. Not all of them are cause for concern, but they are suspicious and strange nonetheless. For example, even on a system with no Live Tiles pinned to the Start menu, the operating system was found to connect to Microsoft -- using an unencrypted connection no less -- to download new tile information. Although no personal information is transferred during this process, it's clearly something that does not need to happen, and just adds fuel to the fire surrounding privacy.
While some traffic is fairly innocuous, some gives greater cause for concern. Even with OneDrive completely disabled and no Microsoft Account being used, Windows 10 appeared to send information back to a Microsoft server used by OneDrive. And there is more. The site says:
Even with Cortana and searching the Web from the Start menu disabled, opening Start and typing will send a request to www.bing.com to request a file called threshold.appcache which appears to contain some Cortana information, even though Cortana is disabled. The request for this file appears to contain a random machine ID that persists across reboots.
In conducting its tests, Ars Technica configured computers to use proxies in order to make it easier to monitor what was happening with network traffic. One disturbing discovery was that "Windows 10 seems to make requests to a content delivery network that bypass the proxy".
Responding to queries about what was happening, Microsoft said:
As part of delivering Windows 10 as a service, updates may be delivered to provide ongoing new features to Bing search, such as new visual layouts, styles and search code. No query or search usage data is sent to Microsoft, in accordance with the customer's chosen privacy settings. This also applies to searching offline for items such as apps, files and settings on the device.
The inclusion of a traceable ID number will be of concern to a lot of people, as will the fact that this sort of communication is carried out in the background despite users taking steps to avoid invasions of privacy.
Photo credit: Stanislaw Mikulski / Shutterstock
-

Apple brings Windows 10 support to Macs with new Boot Camp
Publié: août 13, 2015, 2:18pm CEST par Mark Wilson

Apple has launched a new version of Boot Camp that brings full Windows 10 support. The latest version of Microsoft's operating system cannot be installed on all Macs, but there is a fairly extensive list of models that can run Windows 10.
Boot Camp 6 is gradually rolling out, and brings support to Windows 10 for a number of Mac features including Thunderbolt. Apple explains that it is possible to upgrade an existing Windows 7, Windows 8, or Windows 8.1 to Windows 10, but also provides full instructions for how to start from scratch.
Boot Camp 6 is available for 64-bit Intel Macs running OS X Yosemite, and Apple's support page says that a Windows 10 ISO is needed for the installation. Here Apple also reveals that the updated software brings support for USB 3, USB-C, built-in SD or SDXC card slot, built-in or USB Apple SuperDrive, and Apple keyboard, trackpad, and mouse in Windows 10.
Despite offering Mac users a way to run Windows 10, Apple is still keen to push its own software:
After you install Windows, you can install the latest version of iTunes for Windows to listen to your music or play videos. You'll need to authorize Windows to play music or videos you've purchased from the iTunes Store.
Apple says that the following Macs support Windows 10:
- MacBook Pro (Retina, 15-inch, Mid 2015)
- MacBook Pro (Retina, 13-inch, Early 2015)
- MacBook Pro (Retina, 15-inch, Mid 2014)
- MacBook Pro (Retina, 13-inch, Mid 2014)
- MacBook Pro (Retina, 15-inch, Late 2013)
- MacBook Pro (Retina, 13-inch, Late 2013)
- MacBook Pro (Retina, 15-inch, Early 2013)
- MacBook Pro (Retina, 13-inch, Early 2013)
- MacBook Pro (Retina, 13-inch, Late 2012)
- MacBook Pro (Retina, Mid 2012)
- MacBook Pro (13-inch, Mid 2012)
- MacBook Pro (15-inch, Mid 2012)
- MacBook Air (13-inch, Early 2015)
- MacBook Air (11-inch, Early 2015)
- MacBook Air (13-inch, Early 2014)
- MacBook Air (11-inch, Early 2014)
- MacBook Air (13-inch, Mid 2013)
- MacBook Air (11-inch, Mid 2013)
- MacBook Air (13-inch, Mid 2012)
- MacBook Air (11-inch, Mid 2012)
- MacBook (Retina, 12-inch, Early 2015)
- iMac (Retina 5k, 27-inch, Mid 2015)
- iMac (Retina 5K, 27-inch, Late 2014)
- iMac (21.5-inch, Mid 2014)
- iMac (27-inch, Late 2013)
- iMac (21.5-inch, Late 2013)
- iMac (27-inch, Late 2012)
- iMac (21.5-inch, Late 2012)
- Mac mini (Late 2014)
- Mac mini Server (Late 2012)
- Mac mini (Late 2012)
- Mac Pro (Late 2013)
Photo credit: Andrey Bayda / Shutterstock.com
-

Lenovo BIOS tool prevents clean installs of Windows by downloading crapware
Publié: août 13, 2015, 11:26am CEST par Mark Wilson

Lenovo is no stranger to bloatware, but the latest crapware calamity is cut from a slightly different cloth. In a bid to ensure that its software is installed on its computers, Lenovo BIOSes feature a tool that automatically downloads and installs bloatware even after a clean installation of Windows.
The issue is not entirely new, having been brought to light on Ars Technica's forums, but there is renewed interest in the topic following the launch of Windows 10. Lenovo is making use of a little-known feature called the Window Platform Binary Table which can be used by manufacturers to stealthily install software via the BIOS. The 'feature' is seen by many as amounting to little more than a rootkit, and blame has been laid at the doors of both Lenovo and Microsoft.
The issue was discovered back in May and has generated great interest on the Ars Technica forum in recent days. Few people will be pleased to learn that manufacturers have the ability to push software to their computer even if they have performed a completely clean installation, but this is precisely what is happening with Lenovo.
In this instance, the feature is being used to push Lenovo Service Engine (LSE) software (usually preinstalled on Lenovo systems) to computers. This is a collection of 'anti-theft' and 'system optimization' software which would be classed by many people as junk. Lenovo says that the issue only affects systems produced before June this year, but the company did not stop distributing its LSE bundle in response to complaints about stealth installations. Instead, Lenovo Service Engine is no longer being pushed out to users because it was found to be problematic and insecure.
If you're concerned about having the software installed on your computer, Lenovo has issued a firmware update for laptops, while desktop users can check out instructions for how to clean up their systems.
-

Microsoft Surface Hub shipping slips to 2016
Publié: août 12, 2015, 8:58pm CEST par Mark Wilson

Microsoft today notified customers that Surface Hub orders will not ship until January 1, 2016. The super-sized conference-friendly Surface tablet has been available for pre-order since the beginning of July, and Microsoft had already indicated that the original ship date of September 1 was going to be delayed.
Available in both 55- and 84-inch versions, the Windows 10-powered device has generated a great deal of interest, and this is the reason Microsoft cites for the delay.
Despite the four-month delay, there will be no let-up in pre-orders; the device remains available to order even though it will now not be available until the New Year. The announcement was made with very little fanfare on the Surface Blog where a post from July was updated with the new date. Rather than providing further details, the updated post limits itself to saying:
UPDATE (August 12, 2015): Surface Hub devices will begin shipping on January 1, 2016
While businesses who have placed orders for a Surface Hub already knew that the device would not ship as early as hoped, many would have preferred that the delay would have been shorter. It is unlikely that delaying shipping until next year will harm sales too much as Surface Hub sits in a category of its own, with little -- if any -- competition to speak of.
-

Twitter drops 140 character limit from Direct Messages
Publié: août 12, 2015, 8:39pm CEST par Mark Wilson

As promised back in June, the character limit for Direct Messages on Twitter is being increased. The 140 character barrier is being dropped so messages sent between Twitter users can be much, much longer than before.
The character limit for regular tweets remains the same -- and tweets via SMS are still subject to the same restrictions -- but private conversations can now be much more verbose. The increase will affect Twitter.com, iOS and Android mobile apps, TweetDeck, and Twitter for Mac.
Twitter says that the change allows you to "Speak your mind. All of it". Allowing for lengthier tweets in private conversation shows that Twitter is interested in much more than public tweets, but things remain the same everywhere else. The character increase is far from small; today's change sees the limit increase from a mere 140 characters to a whopping 10,000.
Twitter product manager Sachin Agarwal announced the official start of support for longer private tweets, but gave no indication that we should expect the character limit on public tweets to change any time soon.
The roll out starts today, so make sure to check for app updates, or just be patient if the Twitter website still imposes a limit on your account -- the change is on its way any time now so you can chat away to your heart's content.
Photo credit: tanuha2001 / Shutterstock
-

Sony won't have Windows 10 drivers ready until October or November
Publié: août 12, 2015, 5:58pm CEST par Mark Wilson

If you have a Sony VAIO, you might want to hold off upgrading to Windows 10 for the time being. The company has revealed its schedule for updating drivers and applications to bring Windows 10 support, and there's going to be a wait of at least a couple of months.
Just when your Sony computer becomes Windows 10-ready depends entirely on the version of Windows that was pre-installed. Systems that came with Windows 8.1, Sony aims to push out Windows 10-related updates by October, but if it came with Windows 8 pre-installed, you will have a slightly longer wait on your hands.
Older systems will not have Windows 10 drivers and software until November -- potentially three months after the launch of the operating system. The slowness to release these updates should not really come as a surprise after Sony's announcement that it was leaving the world of computer manufacturing, but it will come as little comfort to those waiting patiently -- or not so patiently -- to upgrade.
Over on the VAIO support pages, Sony says:
We are testing supported models and will be providing the results as quickly as possible. We plan to release Windows 10 upgrade information and, for Windows 8 and 8.1 models, drivers, applications and detailed information on the schedule below based on the operating system originally installed on the PC.
Original Operating System of PC Upgrade information Upgrade instructions & Drivers / Applications Windows 8.1 Preinstalled August 2015 October 2015 Windows 8 Preinstalled August 2015 November 2015 Information regarding Limitation and Issues
Original Operating System of PC Upgrade information Windows 7 SP1 Preinstalled August 2015 There is also a stark warning at the side of the page:
DO NOT UPGRADE YET.
To ensure your VAIO PC works with Windows 10, it is strongly recommended that you wait to upgrade your PC until the drivers are ready.
Of course, there's nothing to stop you from installing Windows 10 if you want to, but there's no guarantee that everything will work as it should.
Photo credit: hhh / Shutterstock
-

People love their mobiles but hate crappy battery life, poor customer service, and endless faults
Publié: août 12, 2015, 4:42pm CEST par Mark Wilson

Stop the presses! People don’t like it when things are rubbish! A new study shows that while we are more attached to our phones than ever, they are an increasing source of frustration and problems. Users have become less tolerant of issues with hardware, bad experiences with customer services, and crashing apps.
The study -- entitled It's Complicated: Mobile Frustrations & Churn -- also found that faulty handsets and poor customer services would be enough to drive nearly a third of people to a new carrier or handset manufacturer. Interestingly, the study also threw up a few surprises, including the revelation that not many mobile users are bothered about photo and video quality.
In fact, just 2 percent of those surveyed in the UK, US, Canada, and Australia indicated that they were most frustrated by the quality of their phone or tablet's camera. Even more surprisingly, just 8 percent of respondents said that low storage problems were their primary concern, reveals the report by Blancco Technology Group.
Handset turnover was found to be faster than ever. 17 percent of people said they buy a new phone every year, or whenever a new flagship is launched. More than a third (35 percent) hang on to their phones for just two to three years. 31 percent of people said they experienced problems with their phone at least once a month, with 38 percent complaining that battery life in their greatest concern.
Handset owners do not like to wait for problems to be looked at. 9 percent of respondents said they would seek help within three hours of running into problems, while 49 percent would wait no more than three days -- many are disappointed, as 38 percent say they have had poor experiences with customer services. The most common course of action when encountering a problem is to attempt to self-diagnose and fix -- there are fears of expensive repairs bills from handset manufacturers or carriers.
The report doesn’t go as far as revealing which carriers or handsets are the most problematic, but it makes for interesting reading nonetheless.
Photo credit: Oleksandr Berezko / Shutterstock
-

Larry Page announces Alphabet and massive Google restructuring with Sundar Pichai as CEO
Publié: août 10, 2015, 11:13pm CEST par Mark Wilson

Sundar Pichai is the new CEO of Google as the company undergoes a huge restructuring. Co-founders Larry Page and Sergey Brin are moving to a new company called Alphabet -- which has a superb URL -- which will serve as an umbrella company for Google and its various projects.
Google itself is being, in Page's words, "slimmed down" and the change is quite an extraordinary one. Page quotes the original founders' letter that was written 11 years go. It states that "Google is not a conventional company", and today's announcement makes that perfectly clear. There's a lot to take in...
Alphabet is, essentially, the new face of Google. Page chose to make the announcement in a blog post that went live after the stock markets closed. This is more than just a rebranding, it is a complete shakeup, the scale of which is almost unprecedented. Alphabet has Page as CEO, assisted by Sergey Brin in the role of president. Putting Pichai at the head of Google is part of improving the focus of the company.
Introducing the new company, Page said:
What is Alphabet? Alphabet is mostly a collection of companies. The largest of which, of course, is Google. This newer Google is a bit slimmed down, with the companies that are pretty far afield of our main internet products contained in Alphabet instead. What do we mean by far afield? Good examples are our health efforts: Life Sciences (that works on the glucose-sensing contact lens), and Calico (focused on longevity). Fundamentally, we believe this allows us more management scale, as we can run things independently that aren’t very related.
He went on to explain that existing Google shares would be converted into Alphabet shares as Google becomes a wholly-own subsidiary of the new company. Two classes of shares will trade on Nasdaq as GOOGL and GOOG.
The new name is going to be hard for some to swallow. Even Page says:
Don’t worry, we’re still getting used to the name too!
Photo credit: Asif Islam / Shutterstock
-

Users are unhappy that Windows 10 automatically sends emails about child account activity
Publié: août 10, 2015, 10:50pm CEST par Mark Wilson

Windows 10, just like its predecessor Windows 8.1, allows for the creation of child accounts that can have limitations imposed upon them. It's a feature that many parents take advantage of, but as more and more people start to upgrade to Windows 10, increasing numbers are complaining about the way in which Microsoft monitors account activity and sends out regular emails about that activity.
The account activity email is optional in Windows 10 -- just as it was in Windows 8.1 -- but it is switched on by default. While many parents like the idea of being able to place restrictions and limitation on a child's Windows account, the "creepy" email that many are seeing for the first time is viewed as a step too far.
Living in an age where concerns about surveillance are greater than they ever have been, having these emails enabled by default is seen by many as a sinister form of spying that they are not comfortable with. On Boing Boing, Windows 10 user Kirk was disturbed to receive an email out of the blue letting him know what his son had been using his computer for:
This weekend we upgraded my 14-year-old son's laptop from Windows 8 to Windows 10. Today I got a creepy-ass email from Microsoft titled 'Weekly activity report for [my son]', including which websites he's visited, how many hours per day he's used it, and how many minutes he used each of his favorite apps. I don't want this. I have no desire to spy on my boy.
The main thrust of the complaint is not the existence of the feature per se, but the fact that Microsoft has not been entirely transparent about what happens to limited accounts during the upgrade to Windows 10. The revelation led to a lively discussion with opinion divided about whether the emails were a good idea or not.
Kirk has a message for younger users of Windows 10:
If you have Windows 10 now, your parents might be getting the same kind of report I did. Don't assume your own computer has your back.
Do you think the emails should be opt in or opt out?
Photo credit: Creativa Images / Shutterstock
-

Google, Facebook, Twitter, Microsoft, Yahoo collaborate to fight child sex abuses images
Publié: août 10, 2015, 9:58pm CEST par Mark Wilson

The Internet Watch Foundation today announced that it is working with some of the biggest names in technology to stamp out child sex abuse images online. Part of the problem with stemming the flow of such images is that once they are removed from one site, it takes little time for them to reappear elsewhere.
Working in conjunction with Google, Facebook, Twitter, Microsoft, and Yahoo, the IWF says that it intends to share image hashes with a view to making illegal images faster to identify. Three different types of hash will be created -- the familiar MD5 and SHA-1, as well as Microsoft's PhotoDNA -- helping to improve rates of detection.
IWF wants to make the hashes available to as many companies as possible so that it can have a greater impact on the content it is trying to eliminate. As well as making it possible to identify images that are already online so they can be deleted, the hashes can also be used to block the upload of known abuse images. The organization says that the system has the potential catalog millions of illegal images.
Announcing the project, the IWF said:
Hashes will only be created from images that the highly-trained IWF analysts have assessed, regardless of whether the image was sourced from a public report, a report from the online industry, an image actively found by our analysts, or an image from the Home Office’s new Child Abuse Image Database (CAID) [...] The more hashes given to the online industry, the greater the protection offered on companies’ online services.
Google, Facebook, Twitter, Microsoft, and Yahoo have already started to use the hash list, and the plan is to make it available to more companies as soon as possible. For now, it is only images that can be identified and hashed, but there are plans to trial a similar program for videos.
Photo credit: Tomislav Pinter / Shutterstock
-

Facebook's privacy settings allow for harvesting data through mobile numbers
Publié: août 10, 2015, 7:50pm CEST par Mark Wilson

If you've added your mobile number to your Facebook account, you might want to reconsider in light of a new security exploit. A software engineer was able to access user data just by entering their mobile number. Profile pictures, names and locations were all accessible even for users who had not made their number public.
There is potential for such harvested data to be misused by malicious parties, as it provides an easy way to link a mobile number to an individual. Reza Moaiandin was able to use a special tool to quickly generate tens of thousands of numbers which, when passed through a Facebook API, fed back the associated user profiles.
As reported by the Guardian, this method of gathering data -- even if it is publicly available -- is open to abuse. Security experts have complained that Facebook had not made it hard enough for people to harvest data in this way. It is something that Facebook users can take steps to protect themselves against, but as things stand Moaiandin says it is like "walking into a bank, asking for a few thousand customers' personal information based on their account number, and the bank telling you: 'Here are their customer details'".
The software engineer has twice reported the problem to Facebook through its bug bounty program but his concerns were brushed aside. Facebook said that it already had measures in place to prevent abuse, and said of his discovery: "We do not consider it a security vulnerability".
Moaiandin disagrees, and says there is much more that could be done. He says that, like Apple and Google, Facebook should introduce an extra layer of encryption as this would obfuscate the data he was able to access. Facebook recently unveiled a privacy checkup tool which it says helps users to ensure that they are not sharing information they do not want to.
If you have added your mobile number to your Facebook account, you can manually configure how it can be used to track you down. Head to the Privacy section of your account and look for the "Who can look you up using the phone number you provided?" and make sure that it is set to something other than Everyone.
Photo credit: JuliusKielaitis / Shutterstock
-

Security is weakened because random numbers are not random enough
Publié: août 10, 2015, 12:44pm CEST par Mark Wilson

A lot of security systems are based on random numbers, prime numbers, or a combination of the two. But generating random numbers is not as random as you might expect -- or hope -- and it relies on sources of broadly random data that can be used as a starting point. The problem is that these sources of data are not large enough.
The entropy of data generated by Linux servers -- which are the backbone of much of the internet -- is, says security expert Bruce Potter, too low. Speaking at Black Hat USA 2015 -- an event which has already seen the unveiling of the Thunderstrike 2 firmware malware and the Stagefright-beating Certifi-Gate Android vulnerability -- Potter warns that the low entropy problem means that seemingly random numbers could in fact be easier to guess or crack than first thought.
Researcher Sasha Moore worked with Potter on a study into random number generation, and the pair were surprised and worried by what they discovered. As reported by the BBC data for random number generation comes from a number of sources, including translating mouse and keyboard movements into binary code. The study found that the data streams generated by many Linux servers not only had low entropy, but also was not tested rigorously enough.
These pools often ran dry leaving encryption systems struggling to get good seeds for their random number generators. This might meant they were easier to guess and more susceptible to a brute force attack because seeds for new numbers were generated far less regularly than was recommended.
Random numbers are used for more than just encryption and data scrambling. They can also be used to randomize the order in which tasks are performed, where data is stored, and many other things that need to be difficult to guess to increase security.
Potter's work uncovered the inner workings of encryption systems used by popular web servers. The previously unknown aspects of the system gave cause for concern. Potter said:
That scared us because when you have unknowns in crypto that's when things go sideways.
With some much of the world's business now conducted online, and all of this reliant on encryption and random numbers, the exposure of any weaknesses in the system that are used could have huge ramifications.
Photo credit: Patricie Malkova / Shutterstock
-

Start menu improvements coming in Windows 8.1 RT Update 3 in September
Publié: août 9, 2015, 2:02pm CEST par Mark Wilson
We already knew that Windows 8.1 RT Update 3 is coming in September, but recent Windows news has been dominated by the release of Windows 10. The update will be pushed out to Microsoft's Surface and Surface 2 tablets as well as other RT devices, and Microsoft Window's 10 FAQ pages have been updated to explain some of the improvements that users can look forward to.
Nothing has changed with regard to Microsoft's position on Windows 10 for RT devices -- this is still not going to happen. Updates to Windows 8.1 RT is the best that users can hope for, and now the company is starting to advertise -- through Windows 10 -- what the update will bring.
On one hand, it is slightly odd to find that Windows 81. RT Update 3 is mentioned in the Windows 10 FAQ. It could be seen as Microsoft using the hype of Windows 10 and having the update ride on its coattails. At the same time, it makes sense that the Windows 10 pages are being used to address questions and concerns that RT users who feel abandoned might have.
In its Windows 10 FAQ, Microsoft poses the question that is on many people's lips 'What about Windows RT?':
If you’re running Windows RT, your device won’t upgrade to Windows 10. We will have an update available in September 2015 that will improve the Start menu and lock screen. Check Windows Update on your Windows RT device to make sure it is ready to download the update when available.
The exact nature of the changes that are coming is not revealed, but Microsoft has already said that some of the features of Windows 10 would be coming to RT. It's not clear that a replica of the Windows 10 start menu will transition to RT, but an approximation of it could well make an appearance.
-

Windows 10 RSAT and Windows Server 2016 Technical Preview 3 coming this month
Publié: août 9, 2015, 12:59pm CEST par Mark Wilson

Microsoft's Gabe Aul has revealed that the company plans to release a new technical preview of Windows Server 2016 later this month. Responding to questions on Twitter, the company's Corporate Vice President and face of the Windows Insider program also said that Windows 10 RSAT will be launched in August.
Unlike the preview builds of Windows 10, previews of the latest edition of Windows Server have been slower to creep out of Redmond. Sysadmins will be keen to get their hands on the latest builds to see just what direction Microsoft is taking with its server software after the decision to delay the launch.
We don’t know anything about what the third technical preview of Windows Server 2016 might include, but it is likely to be little more than a collection of bug fixes and tweaks. It's a little late in the game to expect any major changes to be made.
Remote Server Administration Tools for Windows 10 Technical Preview have not been updated since back in January, so are due a refresh very soon. Designed to work alongside Windows Server, Windows 10 RSAT allows for remote administration of systems.
Aul did not give much away in terms of an exact timetable for releases, but did confirm that both products will be made available before September rolls around:
@LiamBramwell A new RSAT for Windows 10 will be released this month, along with Windows Server 2016 Technical Preview 3
— Gabriel Aul (@GabeAul) August 8, 2015
As soon as more solid details of a release date are made available, we'll let you know.
-

Improvements coming to Twitter for Android as Falcon Pro developer joins the company
Publié: août 8, 2015, 9:03am CEST par Mark Wilson

Joaquim Vergès, the man behind Twitter app Falcon Pro, is joining Twitter. His much loved app will live on, but Vergès will soon be starting work as part of the official Twitter team, helping with the development of the UI.
The announcement came -- of course -- via a tweet. Vergès said that he was going to use Falcon Pro as a testing ground for new features, but explained that he had become frustrated by the limitations of being a third party developer.
This will come as great news to Android users who have become annoyed at the relatively slow pace of development of the official client. We have already seen Twitter acquire Tweetie, integrating many of its features into the main app, and we should see the same happen with Falcon Pro.
The announcement itself was brief and to the point, and congratulatory messages were quick to flow in:
Guys, big news. It’s finally official. I'm joining the @Twitter Android core UI team!
— Joaquim Vergès (@joenrv) August 7, 2015
Keen to assure fans of Falcon Pro that their favorite app was not going anywhere. Those who have paid for the app should not feel that they have been short changed. Vergès followed up his announcement by saying:
Falcon stays with me. IMO It'll be a great place to try new experiments without the slowness of a big company.
— Joaquim Vergès (@joenrv) August 7, 2015
He has not yet given anything away about what he might have in store, but his excitement at being able to work unfettered was clear:
But I've grown tired of all the third party limitations. I want to make a killer official app with full API and a modern UI.
— Joaquim Vergès (@joenrv) August 7, 2015
There are exciting times ahead as Vergès joins Twitter in a little over a week and looks set to get to work immediately.
Photo credit: tanuha2001 / Shutterstock
-

How to find your Windows 10 product key
Publié: août 7, 2015, 10:38pm CEST par Mark Wilson

If you upgrade your computer from Windows 7 or Windows 8 to Windows 10, you probably have no idea what your product key is for the latest version of the operating system. The time may come when you want to perform a clean installation of Windows 10, and this is when you'll need that key.
It is not possible to use your product key for your old version of Windows to activate Windows 10, but during the initial upgrade process this key is converted into a new one. Using a special tool, you can find out the key that has been generated for you so you can make a note of it for future reference.
There are actually numerous tools that can be used to determine your Windows 10 code. One of the more reliable and comprehensive is ProduKey which is available free of charge -- there are 32- and 64-bit versions of the software available, so make sure that you download the correct version for your system.
ProduKey is provided as a compressed file, so unzip it and then run it. In a matter of seconds you'll be provided with the key you need which you can then make a copy of, email to yourself, write down, or backup in some other way for when you need it.
Grab a copy of ProduKey from the Nirsoft website.
Photo credit: koosen / Shutterstock
-

Forget Stagefright, Certifi-Gate vulnerability allows for complete remote control of Android phones
Publié: août 7, 2015, 8:04pm CEST par Mark Wilson

There have been numerous stories in recent days about the threat posed by Stagefright to Android users. A more serious threat has been revealed at Black Hat USA 2015, however -- one that affects hundreds of millions of Android devices. Known as Certifi-gate, a vulnerability has been found in Remote Support Tools which could allow for hackers to take full control of phones.
The security issue was discovered by Check Point, who has notified handset manufacturers of the vulnerability, and launched an app that you can use to see if your handset is affected. Stagefright led to many handset manufacturers announcing a switch to monthly security updates, and some have already issued a fix for Certifi-gate. However, it seems that HTC is a little slow off the mark this time around, particularly when it comes to patching newer phones.
In a statement to CBS News, HTC said: "Working with Google, HTC has already begun rolling the fix into our software, and we will deliver these updates first to the HTC One M9 and the newest HTC Desire products." Check Point has released a full report into Certifi-gate, but if your Android device is found to be vulnerable, there is very little that you can do about it.
Patching is made difficult due to the fact that mobile Remote Support Tools are often pre-loaded onto handset. This means that they cannot be easily removed, and updates can only really be gained through the manufacturer.
Explaining the vulnerability, Check Point says:
Certifi-gate is a set of vulnerabilities in the authroization methods between mobile Remote Support Tool (mRST) apps and system-level plugs on a device. mRSTs allow remote personnel to offer customers personalized technical support for their devices by replicating a device’s screen and by simulating screen clicks at a remote console. If exploited, Certifi-gate allows malicious applications to gain unrestricted access to a device silently, elevating their privileges to allow access to the user data and perform a variety of actions usually only available to the device owner.
Check Point researchers examined the verification methods by which trusted components of the mRSTs validate remote support applications, and discovered numerous faulty exploitable implementations of this logic. This allows mobile platform attackers to masquerade as the original remote supporter with system privileges on the device.
You can download a free copy of the Certifi-gate Scanner app from Google Play to check the status of your phone or tablet.
Image Credit: wk1003mike/Shutterstock
-

Update Firefox right now to squash file stealing bug
Publié: août 7, 2015, 6:11pm CEST par Mark Wilson

Firefox users are being encouraged to upgrade to the latest version of the browser as soon as possible after the discovery of a serious security flaw in the software. Mozilla was quick to patch the security hole which could result in users' personal files being uploaded to a remote server.
Affecting the Windows and Linux versions of Firefox, the security vulnerability stems from the browser's PDF viewer. It allows for the injection of JavaScript that could be used to locate sensitive files and transfer them to a remote server.
The security hole is marked as critical, but Mozilla's Daniel Veditz assures users that "products that don't contain the PDF Viewer, such as Firefox for Android, are not vulnerable". This is not just a hypothetical problem; instances of the vulnerability have been found out in the wild as described in a security advisory notice:
Security researcher Cody Crews reported on a way to violate the same origin policy and inject script into a non-privileged part of the built-in PDF Viewer. This would allow an attacker to read and steal sensitive local files on the victim's computer.
Mozilla has received reports that an exploit based on this vulnerability has been found in the wild.
The company also warns that Windows and Linux users should change passwords and keys associated with certain files and applications. It explains that:
Windows the exploit looked for subversion, s3browser, and Filezilla configurations files, .purple and Psi+ account information, and site configuration files from eight different popular FTP clients. On Linux the exploit goes after the usual global configuration files like /etc/passwd, and then in all the user directories it can access it looks for .bash_history, .mysql_history, .pgsql_history, .ssh configuration files and keys, configuration files for remina, Filezilla, and Psi+, text files with "pass" and "access" in the names, and any shell scripts.
Veditz notes that people who have ad-blocking tools installed may well have been protected against the vulnerability. If you haven't yet updated to Firefox 39.0.3, now is the time to do so.
Photo credit: Evan Lorne / Shutterstock
-

Will Stagefright force all mobile makers to release monthly security updates?
Publié: août 7, 2015, 1:47pm CEST par Mark Wilson

Stagefright took the Android world rather by surprise. As well as catching the industry with its pants down, it highlights a problem of mobile security: it's just not taken seriously enough. In response to the Stagefright vulnerability, both Samsung and Google announced new monthly security update cycles.
Not to be outdone, LG has now followed suit, and it would be surprising if we didn’t see more manufacturers of Android handsets doing exactly the same in the coming weeks. But in announcing its own monthly security update schedule, LG has highlighted another stumbling block for mobile security. Carriers.
For many people, there is quite a delay between the release of a new version of Android, and its availability from their carrier. It could take months before updates are made available to customers, and some handsets are ignored completely. While it is undoubtedly good news that mobile manufacturers are interested in trying to stay on top of security issues, the wording of the announcement begs questioning.
In an email to Wired, LG said:
LG will be providing security updates on a monthly basis which carriers will then be able to make available to customers immediately. We believe these important steps will demonstrate to LG customers that security is our highest priority.
The likes of LG may well start to produce security updates 12 times a year, but how long will it be before they filter down to customers? Carriers will want to run their own tests and checks on updates that are produced, and with the problem of Android market fragmentation, this is something that could take some time. Some handset producers have the luxury of people able to push updates directly to handsets without the need to involve a middleman, but this is certainly not the norm.
The likes of Motorola, HTC et al have yet to indicate whether they will start their own monthly security update releases, but it would be very surprising if this didn’t happen. But as well as the problem of the carrier middleman, there is also the issue of how long handsets are supported. While desktop operating systems are supported for upwards of a decade, the same cannot be said of mobile operating systems.
Despite the fact that there are so many different versions of Android in use -- a problem exacerbated by carrier customizations -- only the most recent tend to receive support. Stagefright affects up to 95 percent of Android handsets, and it's safe to assume that a very large proportion of handsets that are vulnerable stand no chance of being patched.
It's great that handset manufacturers are taking steps to try to improve security, but before we get too excited, we really need assurance from carriers that updates will be pushed out as quickly as possible.
Photo credit: Bloomua / Shutterstock
-

Windows 10 forces app updates on Home users but a September update could change this
Publié: août 7, 2015, 12:57pm CEST par Mark Wilson

Some Windows 10 users have been upset by the fact that updates to the operating system are no longer optional -- without using extra software, at least. Microsoft has now made it clear that the same applies to app updates. Updates to apps will be delivered automatically with no option to skip them.
This is not the first time updates in Windows 10 have caused unrest. As well as the mandatory updates debacle, the fact that updates are shared with other people to speed up delivery also concerned some users. But what has riled Windows 10 Home users about apps updates is the lack of choice and transparency.
As noticed by WinSuperSite, a thread on the Microsoft Community pages feature a question from a user who ask how the grayed out option to disable automatic app updates could be enabled. A reply followed from community moderator Smittychat does not really offer an immediate solution to the issue, but suggests that it's something that might change with an upcoming update to Windows 10 itself:
I believe there is a scheduled update to Windows 10 RTM scheduled for September. It's to deliver a more polished build. Check Settings > Windows Update > Advanced Options to determine if the options have changed after September.
Smittychat goes on to describe the upcoming build as "more polished":
Maybe in September when the more "polished" build is installed this will change.
In the discussion thread, one user complains that "every time I open the store it begins to auto update the apps that I don't want to get updated and jams my Internet connection". This is not the only concern with automatic app updates. There is also the potential for features to be removed from apps before users have received a warning of this and been able to seek out an alternative.
Do you feel forced app updates are a good idea for everyone, or would you prefer the ability to opt out regardless of the version of Windows 10 you're using?
Photo credit: Anton Watman / Shutterstock
-

Microsoft open sources Windows Bridge to bring iOS apps to Windows
Publié: août 7, 2015, 10:46am CEST par Mark Wilson

Microsoft is taking steps to try to ensure that the apps that people want to see on Windows are actually available. We've already seen the company woo developers with tools such as Project Westminster to make it easier to create Universal Windows Apps, and Astoria to help convert Android apps for Windows.
Project Islandwood was the same idea, but for iOS apps -- the idea is that by making it easy to convert apps for Apple's platform into Windows apps, Microsoft can use developers to plug the 'app gap'. To spread the project's net further, it has now been released under the name Windows Bridge for iOS and -- more importantly -- it has been released to GitHub as an open source tool under the MIT license.
The idea of 'bridging' is one that Microsoft has well and truly embraced. Keen to move away from traditional applications towards more portable apps, the company has been taking steps to make it as easy as possible to bring apps from other platforms to Windows. Windows Bridge for iOS taps into the huge readymade collection of apps for Apple's mobile platform. It launches initially as a public preview, with a full release destined for the fall.
While most people will see the project as a way to 'port' apps from one platform to another, Microsoft looks at it slightly differently. Program Manager for Windows Bridge for iOS, Salmaan Ahmed, said in a post entitled 'Let's open this up':
Our goal with the iOS bridge has never been simply to run iOS apps on Windows. Rather, our goal is to help you write great Windows apps that use as much of your existing code and knowledge as possible. We will, of course, continue to work to expand our iOS compatibility, but it’s important to note that there is much more you can do with the bridge.
The move is an important one, as Microsoft is now taking apps more seriously than ever. In championing universal apps, the company demonstrates that it is as keen at creating an app-friendly ecosystem as Apple has shown itself to be. Developers working with Windows Bridge for iOS are not just creating apps for desktop machines running Windows 10, but also mobile Windows 10 devices, Xbox One, and even HoloLens.
Microsoft describes three aims and principles of Windows Bridge for iOS:
- Full Windows API access: Making it easy to use Windows APIs within Objective-C code
- iOS compatibility: Empower developers to reuse as much existing iOS code as reasonably possible
- No sandboxing: iOS and Windows APIs should be able to work together
If you fancy trying out the tool, head on over to GitHub to grab it.
Photo credit: Bloomua / Shutterstock
-

Zimperium releases Stagefright detection tool and vulnerability demo video
Publié: août 6, 2015, 12:46pm CEST par Mark Wilson

We've already looked at the Stagefright vulnerability, discovered by Zimperium, and shown what can be done to deal with it. Affecting up to 95 percent of Android devices, the vulnerability has led to Google and Samsung announcing monthly security updates.
Now the mobile security company has released additional details about how the exploit works. To help explain the vulnerability, a video has been produced which uses a Stagefright demonstration to illustrate it in action. Zimperium has also released an Android app that checks devices for the vulnerability.
Stagefright is a particularly worrying vulnerability as it allows for exploitation without the need for user interaction -- simply receiving an MMS is all it takes. Zimperium has provided details of the exploit to handset manufacturers but warns that it could take some time for patches to be applied to all affected devices.
A free copy of the Stagefright Detector app can be downloaded from Google Play. This reveals whether a device is vulnerable, and indicates whether an OS update is needed. In a blog post, the security company said:
We are working with carriers and device vendors to design solutions to protect users that do not currently have Zimperium zIPS on their phones.
Check out the video below, produced by Stagefright discoverer Joshua Drake, which demos the vulnerability:
-

Reddit decides to be a little less racist
Publié: août 6, 2015, 12:42am CEST par Mark Wilson
Reddit has been nothing short of chaos recently. Users left, staff left, and lots and lots of people got very, very upset. Following on from recent subreddit shutdowns and restrictions, today the site announces that it is bowing to pressure from certain quarters and closing down a number of racist subreddits.
Having culled harassment sections of the site, the latest victims of Reddit's ban hammer are the subreddits /r/CoonTown, /r/WatchNiggersDie, /r/bestofcoontown, /r/koontown, /r/CoonTownMods, /r/CoonTownMeta. The bans come as the site updates its content policy meaning that the six racist subreddits are now in violation of Reddit rules -- and the new rules don't seem to be going down well.
Reddit co-founder Steve 'spez' Huffman broke the news in Reddit's announcement section, and it didn’t take long for hundreds of vocal, vitriolic, and venomous responses to appear. While you might expect the culling of racist content to be broadly welcomed, the announcement actually led for calls for greater transparency and a more equal way of managing other hate communities.
Today we removed communities dedicated to animated CP and a handful of other communities that violate the spirit of the policy by making Reddit worse for everyone else: /r/CoonTown, /r/WatchNiggersDie, /r/bestofcoontown, /r/koontown, /r/CoonTownMods, /r/CoonTownMeta.
He went on to explain a little about the reasons behind the decisions:
Our policies are not changing dramatically from what we have had in the past. One new concept is Quarantining a community, which entails applying a set of restrictions to a community so its content will only be viewable to those who explicitly opt in. We will Quarantine communities whose content would be considered extremely offensive to the average redditor.
Today, in addition to applying Quarantines, we are banning a handful of communities that exist solely to annoy other redditors, prevent us from improving Reddit, and generally make Reddit worse for everyone else. Our most important policy over the last ten years has been to allow just about anything so long as it does not prevent others from enjoying Reddit for what it is: the best place online to have truly authentic conversations.
I believe these policies strike the right balance.
Some people weren't happy with the reasons given for the closure:
It would be nice if for once reddit could just be honest. If you want to ban /r/coontown for being extremely racist, then just come out and say so. You didn't ban them because they exist solely to annoy other redditors, enough of this "we're banning behavior not content" nonsense. You're banning content.
Many commenters questioned why racist subreddits had been singled out, while other hate sections and bigoted subreddits were being left alone. Some pointed to other racist subreddits that "seem to have dodged the bullet", including /r/WhiteRights, /r/AntiPOZi, /r/nazi, /r/TheGoyimKnow, /r/ferguson, /r/GasTheSnoo, /r/KikeTown, /r/Ben_Garrison, and /r/thephilosophyofrape.
As ever, an attempt to balance freedom of speech (as a concept, not a law) with limiting harassment and hateful content appears to have slightly backfired, upsetting many of the more vocal users of the site. Could Reddit have said or done anything that would have made everyone happy? Probably not. But if nothing else, the site serves as a macrocosm of the internet as a whole, perfectly illustrating the difficulty in policing online content.
-

Samsung and Google to release monthly OTA Android security updates
Publié: août 5, 2015, 11:46pm CEST par Mark Wilson

Google and Samsung announced today that they are taking steps to ensure the ongoing security of Android phones and tablets. Both companies said that over the air (OTA) updates will be released on a monthly basis with Google focusing on its range of Nexus devices.
Samsung made reference to the recent StageFright vulnerability in announcing that its Galaxy devices are in line for regular security updates. While Google will be pushing out OTA updates directly, Samsung is currently in talks with global carriers to ensure that updates can be delivered "about once per month".
Google's updates for Nexus devices start to roll out immediately, and will come in addition to the usual operating system updates. Like Samsung, Google refers to StageFright, pointing out that the first security update -- which is rolling out to the Nexus 4, Nexus 5, Nexus 6, Nexus 7, Nexus 9, Nexus 10, and Nexus Player -- features fixes for a number of vulnerabilities including this high-profile security problem.
Announcing the new security update program, Google said:
At the same time, the fixes will be released to the public via the Android Open Source Project. Nexus devices will continue to receive major updates for at least two years and security patches for the longer of three years from initial availability or 18 months from last sale of the device via the Google Store. Security continues to be a top priority and monthly device updates are yet another tool to make and keep Android users safe.
Samsung also sees the value in accelerating the delivery of security updates. Dong Jin Koh, Executive VP of the company said:
With the recent security issues, we have been rethinking the approach to getting security updates to our devices in a more timely manner. Since software is constantly exploited in new ways, developing a fast response process to deliver security patches to our devices is critical to keep them protected. We believe that this new process will vastly improve the security of our devices and will aim to provide the best mobile experience possible for our users.
-

Facebook Live lets celebrities broadcast live video
Publié: août 5, 2015, 11:28pm CEST par Mark Wilson
Facebook has become much more than just a social network for connecting with friends and family, evolving into a way to get in touch with companies and even celebrities. Today the site announces that celebrities are now able to share live video from the Facebook Mentions app directly to fans.
Regular Facebook users need do nothing more than follow the celebrities they are interested in, and any live video that is broadcasting by someone they follow will appear in their news feed. While comparable to the likes of Periscope and Meekat, Facebook Live is not a direct competitor as it is only available to those with verified accounts -- but it also has features that neither of these services offer.
There is already the promise of broadcasts from the likes of Martha Stewart, Michael Bublé, and Serena Williams, but Facebook Live's killer feature -- apart from the massive audience possibilities -- is video archiving. While Periscope and Meerkat delete video streams immediately or after a short delay, it is down to the broadcaster to decide whether a Facebook Live video should be removed or not. By default, live video is stored so that it can be watched back at a later time by those who missed it the first time around.
Facebook Live is introduced as a more immersive way to interact with an audience:
Starting today, public figures can share live video from Facebook Mentions, the app that makes it easy for athletes, musicians, politicians and other influencers to talk with their fans and each other. You can discover these live videos from public figures you follow in your News Feed. You can comment on, like or share the video while watching a live broadcast. You can also see when your friends or other public figures start watching.
It's not clear if Facebook Live will ever filter down to the likes of you and I. For the foreseeable future it's a celeb-only zone.
-

Upgrade to Windows 10 and your kids may no longer be safe
Publié: août 5, 2015, 6:53pm CEST par Mark Wilson

Parents who are upgrading their computers to Windows 10 are warned that the move from Windows 7 or Windows 8.1 will obliterate the safety features used to protect children. You may have spent time putting restrictions in place in a bid to keep your offspring safe when using your computer, but Windows 10 will change these child-friendly accounts into standard accounts with no limitations whatsoever.
The upgrade process wipes out website restrictions, game and app age ratings, time limits, and other parental controls and monitoring options. Unless a parent goes to the trouble of reinstating each of these settings individually, their children will have unfettered computer access. The discovery, revealed by The Register, will come as a surprise to many, but the worry is that many parents will simply be unaware that their children are not protected. And this is far from being the first time Windows 10 has been criticized.
As reported by The Register, Microsoft does explain online that family features need to be re-configured in Windows 10, but it is a process that many will find confusing or just not learn about. This is not the first time that the issue has reared its head; it's something that was noticed by Windows Insiders during the preview testing period of Windows 10. But now that the world at large has access to Windows 10, the problem has the potential to affect a far greater number of people.
Microsoft says that anyone upgrading from Windows 7 or Windows 8 to Windows 10 should receive a notification about performing a Family Safety audit. This is itself something of a convoluted process that involves sending each child an invitation via email, and there are fears that it will be seen as too complicated and not carried out by many. There are also concerns that it is far too easy for a child to convert their account back to a local account.
In a statement, Microsoft said:
We will continue to roll out new Windows 10 Family features over time. We designed Windows 10 as a service, and we’ll keep listening to our customers. If there are ways to make improvements, we will do so.
The Register also published a list of suggestions from one reader who had advice for how Microsoft should fix the problem:
- Check for previous use of Windows Live Family Safety and automatically disable children's accounts until the Windows 10 machine has been properly set up
- Scrap the invitations process for set-up via a PC administrator
- Offering a wizard that guides people through the set-up
Is Microsoft's response good enough? Now do you regret upgrading to Windows 10?
Photo credit: Kylie Walls / Shutterstock
-

Do you regret upgrading to Windows 10?
Publié: août 5, 2015, 10:21am CEST par Mark Wilson

Windows 10 is now with us, and, whether you've made the move from Windows 7 or Windows 8.1, there is a lot to love, but also a lot to hate. With this latest release, there is also one very big difference from previous versions of Windows: it is free of charge.
This is not only likely to encourage more people into making the move to Windows 10, but it also opens up a possibility that many people would simply not have considered before. If you decide that you don’t like Windows 10 (the OS is not without its fair share of problems, after all), you can downgrade to your previous version without ending up out of pocket. The question is, how many people will go -- or have gone -- down this route?
When investing in any piece of hardware or software, there is potential for buyer's remorse. The lack of price tag associated with Windows 10 means that this potential is removed and replaced with the possibility of simple remorse. There is literally no cost or loss involved in rolling back to Windows 7 or Windows 8.1, so if you take umbrage at the way Windows 10 works, or just decide it's not for you, it has never been easier to step back in time.
It might be that you don’t like the way that Windows 10 automatically updates drivers for you -- although if this is your reasons for considering downgrading, there is a workaround. Perhaps you're not keen on the invasions of privacy Windows 10 introduces, maybe you're experiencing error messages when you try to do every day things, or you just can't get sound working. Or it could be that you just feel that Windows just isn’t ready despite all of the feedback-led changes that have been made.
Windows 10 Service Release 1 is supposed to be just around the corner, and for Windows Insiders there is the promise of new builds that could address issues that people may have, but are you willing to stick around to find out if your gripes will be addressed? If you are ditching Windows 10, there's always of the option of running the OS in a virtual machine so you can keep an eye on what's happening while you continue to use your preferred version of Windows.
So, it's over to you. Have you downgraded, will your downgrade, or are you currently toying with the idea? If so... what needs to change to entice you back or keep you from leaving?
Photo credit: durantelallera / Shutterstock
-

Outlook on the web gets a new look, name, and tools to improve efficiency
Publié: août 5, 2015, 12:32am CEST par Mark Wilson
Microsoft today announces a number of changes to the online version of Outlook. One of the biggest updates sees the rollout of a new, cleaner interface which Microsoft says helps to improve efficiency. In addition to aesthetic alterations, there are also a number of new tools that make it easier to manage an inbox.
There is also something of a rebranding taking place. The Outlook Web App (OWA) is no more; say hello to Outlook on the web. The new name is a minor change, however. The big news today are the visual and productivity updates.
A new 'action bar' is visible in the Mail, Calendar, People and Task sections of Outlook on the web, providing easy access to common commands no matter where you are. A UI revamp makes content easier to read, and makes it quicker and easier to get around. Outlook is primarily about email, so it should come as no surprise that there have been a large number of changes to the inbox side of things. A new pinning option makes it possible to keep important messages at the top of your inbox, while Sweep makes it simple to collect together messages from particular senders.
Improvements have been made to the mobile version of Outlook on the web, and the calendar also benefits from a number of tweaks and changes. Many of the changes that have been made are a results of feedback from users and today Microsoft also announced a new way to provide feedback. Outlook UserVoice now includes an Outlook on the web forum, and this can be accessed by clicking the gear icon and selecting Feedback.
While the update rollout starts today, it will first come to users with Office 365 plans that include Exchange Online and have opted into the First Release program. Everyone else can expect to see the update from the first week of September.
-

November Xbox One update brings Xbox 360 backwards compatibility and Windows 10
Publié: août 5, 2015, 12:12am CEST par Mark Wilson

The focus of the launch of Windows 10 so far has very much been on the desktop version of the operating system and the preview builds for Windows Phone handsets. But the latest version of Windows is about creating a Windows ecosystem that embraces a plethora of platforms, and that includes Xbox One.
Microsoft has already given us a glimpse of what is in store for owners of its games console, and today the company revealed that the Windows 10-powered update will arrive in November. As well as bringing Windows 10 to gamers -- including Cortana -- the update will also make it possible to play Xbox 360 games.
Details of the update were given at Gamescom today, and it is backwards compatibility that will have most gamers excited. It does not mean that every single Xbox 360 game ever released will be playable on Xbox One consoles, but scores of titles will get a new lease of life. As well as expanding the library of games that's available and bringing some of the features of Windows 10 to the console, the update has more to offer.
Just in time for the holiday season, the update will also bring DVR functionality to the console. This is part of Microsoft's bid to make Xbox One much more than a simple gaming console, placing it at the heart of entertainment in the home. An exact date for the update release has not yet been revealed, but we at least know that it will be November.
Photo credit: Canadapanda / Shutterstock
-

New Windows 10 preview builds on the way -- time to opt back into Insider updates!
Publié: août 4, 2015, 10:48pm CEST par Mark Wilson

It's now a week since the launch of Windows 10, and if you've missed looking out for the release of new preview builds there's some good news for you. Microsoft disabled preview builds in the immediate run-up to the release of Windows 10, but now you can opt back in.
What does this mean? Now that Windows Insiders have the option of accessing updates from the Fast and Slow rings once again, it's safe to assume that new preview builds are on the way. With the widely-held belief that Windows 10 Service Release 1 is imminent, this is perhaps not entirely surprising -- we may even get a glimpse of Windows 10s first major update.
As reported by WinSuperSite, Microsoft has just made it possible to gain early access to new builds of Windows 10 once again. All you need to do is head to Settings, click Update & security, and click the Advanced options link in the Windows Update section. Under the Get Insider builds heading you can choose between joining the Fast or Slow ring. Should you change your mind, you can always hit the Stop Insider builds button.
There's no word on exactly when a new build might be released, but Gabe Aul suggested on Twitter that there won’t be long to wait:
@elcoxx We'll start delivering builds again before too long, but for now 10240 is the build to be on.
— Gabriel Aul (@GabeAul) August 4, 2015
As before, any builds that hit the Slow ring are going to be more stable than those on the Fast ring, but neither sets of builds are really designed for use on mission-critical computers. If your computer is essential for work, it might be a good idea to stick with the Slow ring, or not bother with Insider builds at all. If you like living on the edge, however... it's an entirely different story.
Photo credit: Anton Watman / Shutterstock
-

Macs are vulnerable to Thunderstrike 2 firmware malware that survives formatting
Publié: août 3, 2015, 11:27pm CEST par Mark Wilson

Macs have long been touted as being immune to viruses and malware -- but there have been plenty of vulnerabilities that show this to be a fallacy. Apple's own claims that its hardware was not susceptible to the same firmware security flaws as PCs served only to encourage people to prove the company wrong.
At Black Hat USA on Thursday, researchers will demonstrate that not only can Macs be remotely infected with malware, but that this malware can survive a user formatting the system. In a talk at the InfoSec event in Las Vegas that focuses on all manner of security topics, Trammell Hudson, Xeno Kovah, and Corey Kallenberg will show that Macs are just as vulnerable to remote attacks as PCs using the Thunderstrike 2 backdoor.
Thunderstrike 2 is impressive in its efficacy. The malware can be remotely installed and can spread between Macs even if they are air-gapped or not networked. The way Thunderstrike 2 locks itself into firmware means that the infection remains in place even if OS X is wiped out and reinstalled; it is also very difficult for security software to detect, let alone do anything about. Xeno Kovah says:
For most users that's really a throw-your-machine-away kind of situation. Most people and organizations don't have the wherewithal to physically open up their machine and electrically reprogram the chip.
The world will get a chance to see the attack in action at Black Hat USA later in the week. The billing for the demonstration says:
This talk will provide conclusive evidence that Macs are in fact vulnerable to many of the software only firmware attacks that also affect PC systems. In addition, to emphasize the consequences of successful exploitation of these attack vectors, we will demonstrate the power of the dark side by showing what Mac firmware malware is capable of.
Apple has previously stated that in order to become infected with firmware malware, direct physical access to a Mac is required. The team behind the revelation is not entirely new to this: it is the same team who demonstrated the LightEater vulnerability that afflicted millions of BIOSes. Although there is a widely-held belief that Macs are more secure than PCs, the counter-argument is that this is simply because of the numbers involved. There are far more PCs in use than Macs, so it make sense for a malware peddler to hit as many system as possible with PC-specific attacks.
Thunderstrike 2 will also be demonstrated at Def Con this weekend.
-

You don't need to use a Microsoft Account to download apps from Window 10's Store
Publié: août 3, 2015, 9:24pm CEST par Mark Wilson
With Windows 10, Microsoft is particularly keen for you to use a Microsoft Account. It's something that was present in Windows 8, and it is still billed as a way to sync settings and apps between computers. While you may be encouraged to use a Microsoft Account, it is not necessary -- you can use a local account, but if you decide to download apps from the Store, you'll be prompted to switch this to a Microsoft Account.
If you're concerned about the privacy implications of using a Microsoft Account, you may want to avoid using it whenever possible. Sign into the Store with a Microsoft ID, however, and you'll find that your local account is converted into a Microsoft account. Here's how to download apps without having to switch.
Fire up the Store using your preferred method -- Start menu, taskbar, or whatever -- and then click the person icon to the upper right of the window, just to the left of the Search bar. Select Microsoft Account in the popup that appears and then enter your email address and password.
You now need to take care.
Microsoft wants you to convert your local account into a Microsoft Account; it is easy to miss, but you do have the option to skip this if you prefer. Rather than entering your password, click the link below the password field that reads Sign in to just this app instead.
You're now free to browse the Store and download apps whilst leaving your local account as a local account.
-

Privacy alert: your laptop or phone battery could track you online
Publié: août 3, 2015, 6:46pm CEST par Mark Wilson

Is the battery in your smartphone being used to track your online activities? It might seem unlikely, but it's not quite as farfetched as you might first think. This is not a case of malware or hacking, but a built-in component of the HTML5 specification.
Originally designed to help reduce power consumption, the Battery Status API makes it possible for websites and apps to monitor the battery level of laptops, tablets, and phones. A paper published by a team of security researchers suggests that this represents a huge privacy risk. Using little more than the amount of power remaining in your battery, it is possible for people to be identified and tracked online.
As reported by The Guardian, a paper entitled The Leaking Battery by Belgian and French privacy and security experts say that the API can be used in device fingerprinting. The API can be used to determine the capacity of a website visitor's battery, as well as its current charge level, and the length of time it will take to fully discharge. When combined, these pieces of information create a unique identifier which can be used like a supercookie.
Supported by Firefox, Opera, and Chrome (but not Internet Explorer or Microsoft Edge), Battery Status API has raised the security hackles of the researchers who say:
We hope to draw attention to this privacy issue by demonstrating the ways to abuse the API for fingerprinting and tracking.
At particular risk are older phones. The age of the battery reduces the battery life, making it easier to generate unique identifiers. What is especially concerning is the fact that users do not need to be warned when the Battery Status API is being used. This is because when drawing up the HTML5 standard, the W3C said:
The information disclosed has minimal impact on privacy or fingerprinting, and therefore is exposed without permission grants.
To overcome the security and privacy issues, the authors of the report suggest that the readings gathered by the API be rounded. They say this would not interfere with the functionality of the API, but would eliminate the problem of tracking. At the moment, nothing more than a simple script is needed to monitor someone's movement from one website to another. The creation of a unique identifier also opens up the possibility of a phenomenon known as respawning. Even if a user goes to the trouble of deleting local-stored cookies, they could instead be remotely stored and reinstate when a user is identified through Battery Status API data.
The researchers also suggest that permission to access the API should be sought from users rather than just allowing its use by default.
Photo credit: scyther5 / Shutterstock
-

ISPs in India told to block access to 857 porn sites
Publié: août 3, 2015, 2:08pm CEST par Mark Wilson

Porn is big business online, but it's also at the center of many a debate surrounding decency, child protection, and censorship. The Indian government has ordered that ISPs in the country block access to more than 800 porn sites in a bid to stop children viewing unsuitable material.
Interestingly, while access to porn is being restricted, it is not being blocked outright. The aim is not to stop adults from viewing pornography but to "protect India's cultural fabric" in addition to protecting children.
Adults with a penchant for porn will still be able to get their fix by turning to VPN tools and services. The government is looking for alternative ways to prevent children from accessing online pornography, and it is believed that the current measures are just a stop-gap until a long term policy is written up.
The Hindustan Times quotes a source at the Indian communications ministry who said:
Certain websites have been reviewed and found to be spreading anti-social activities as hyperlinks from these websites, some of them were pornographic, so we have sent letters to internet service providers to block them. The action has been taken in reference to section 79 of IT Act.
Unsurprisingly, the ban has led to a huge number of complaints. ISPs around the country took action to respond to letters from Department of Telecommunications about implementing blocks, and pornophiles took to Twitter using the #PornBan hashtag to express disappointment at what many regard as censorship and an infringement on rights.
Photo credit: Pavel Ignatov / Shutterstock
-

Sound problems in Windows 10? Here are some workarounds
Publié: août 2, 2015, 1:20pm CEST par Mark Wilson

Windows 10 is now available to all. During the testing period, numerous preview builds were released, each bringing its own set of problems. This post was originally written to help fix audio problems in build 10041, but the suggestions still work in the final release.
If you have problems with the installation of a Realtek driver, don’t get the full audio experience with VIA HD Audio, or have issues with Conexant audio, there's a workaround for you to try.
Let's take a look at these three issues in reverse order. A problem with Conexant audio means that you may hear no sound in Windows 10 even though everything appears to be working correctly. While this is being investigated, Microsoft suggests running msconfig.exe and heading to the Boot tab. Click the Advanced options button, check the Maximum memory box and set the value to 3072.
If you have VIA HD Audio and find that you can only hear sound from certain apps, there's a different workaround for you. Open Playback Devices, right click the audio output device and set it as the default device. With this done, select the device, hit Properties, move to the Enhancements tab and check the Disable all enhancements option.
Finally, if you are plagued with a problematic Realtek audio driver installation -- specifically a 0x000005b4 error -- you can try a workaround published in the Stone Support Library. There's a guide to using Group Policy Editor to give the driver longer to install, or you can download a registry file to put the new settings in place with a couple of clicks. Once this has been done, you can then re-attempt the driver installation.
Photo credit: LDDesign / Shutterstock
-

The insane popularity of proxy site Unblocked shows the futility of web restrictions
Publié: août 2, 2015, 12:16pm CEST par Mark Wilson

Few people like to be told what to do, and this is certainly the case online. If you're told that you're not allowed to visit a certain website, it is only human that you question why -- it may well increase your desire to visit said site. Around the world, governments have taken it upon themselves to try to police the internet. It's something many would describe as an exercise in futility, and it seems they are correct.
The implementation of restrictions on access to certain websites can be seen in many countries, but it is something that the UK government has shown itself to be particularly keen on. So how successful have initiatives to blocks access to the likes of the Pirate Bay, KickAssTorrents et al actually been? Not very. One site that helps users to get around web restrictions is proving more popular than both Skype and Spotify.
You would think that Microsoft's messaging tool and the streaming music website would account for a fairly hefty chunk of web traffic. But in the UK they are both less popular than Unblocked, a site designed to help people bypass web blocks and get to restricted sites. The UK's Conservative government has taken it upon itself to restrict access not only to sites that might provide links to copyrighted software, movies etc, but also to sites that feature hardcore pornography.
But where there's a will there's a way, and people will always find a way to circumvent any access restrictions that may be put in place. This is where Unblocked is really coming into its own. As reported by TorrentFreak, the site is now the 192nd most popular site in the UK. That's a lot of people looking to get around government restrictions.
The top 200 websites are littered with streaming porn sites, as well as big-hitters like Google, The Guardian, and so on. Getting so far up the chart is not easy, and it just goes to show the level of interest people have in accessing blocked content, and the futility in attempting to block it in the first place.
Censorship of the internet has always been a divisive issue. There are those who argue that any form of restriction amounts to censorship, while others say it is only right that certain content is subject to policing. But the global nature of the internet means that any country's restrictions can be bypassed using services like Unblocked. Short of closing down individual sites, it's time to realize that time and resources pumped into trying to control what people can see online is being wasted. It's time for a rethink.
Photo credit: auremar / Shutterstock
-

How to check that Windows 10 is activated
Publié: août 1, 2015, 11:17pm CEST par Mark Wilson

There has been so much confusion surrounding the release of Windows 10 -- is it free or not, what version do you get, who is eligible to upgrade? -- that you may well be wondering if your copy is properly activated. Perhaps you performed a clean install of Windows 10, maybe you upgraded from Windows 7 or Windows 8, or perhaps you’ve remained on the Insider program; you still want to be activated.
It is quite easy to check that you have a legitimate and fully activated copy of Windows 10 installed. Just use the steps below and you can check activation status in next to no time.
If you have upgraded from Windows 7 or 8, you'll be most familiar with the Control Panel. This is still available in Windows 10, and will let you know if you are activated or not. Right click the Start button and select the Control Panel option and then open the System Applet. Look to the lower right hand side of the window to the Windows activation section and you should see the words 'Windows is activated'.
The Windows 10 version of the Control Panel is Settings, and this can also be used to double check that your copy is activated. You can click the Settings icon in the taskbar, or click the Start button and type Settings before clicking the app icon. Click the Update & security icon and then move to the Activation section. Here, beneath confirmation of the edition of Windows 10 you are running, you should also see confirmation that Windows is activated.
-

How to fix 'Device limit reached' errors in the Windows 10 Store
Publié: août 1, 2015, 6:38pm CEST par Mark Wilson

You may have bought yourself a new computer with Windows 10 pre-installed, or you may have manually upgraded your older machines. Whatever route you have taken to Windows 10, the chances are that you will end up in the Store at some point in order to download apps.
We've already looked at what you can do fix the 0x803F7003 error that can plague the Store, but this is not the only issue that can arise. When you try to install an app you may see an error message that reads Device limit reached. Not a problem -- here's what to do.
There are two possible causes for this error. The first is that you genuinely have exceeded the number of devices on which you can install apps. Considering the fact that Windows 10 is free, there's no reason not to install it on every computer you own and it is at this point that you may encounter Windows 10's 10-computer limit -- down from 81 in Windows 8.1. The error message itself is quite helpful:
It looks like you've reached your device limit for installing apps and games from the Store on your Windows 10 device. If you want to install apps and games from the Store on another Windows 10 device, remove a device from the device list.
Start by paying a visit to the device management page at [https:] and remove any devices you are no longer using.
If this does not work -- or you see the error message even though you have nowhere near 10 devices -- you can try the same fix as for error 0x803F7003. Resetting the Store cache should help to resolve the problem.
Hit the Start button (or press the Windows key) and type wsreset. When the command is displayed at the top of the Start menu, right click it and select Run as administrator. You'll probably find that a User Account Control dialog appears and you just need to click Yes here to continue. You should find that you can now download apps.
-

How to fix 0x803F7003 errors in the Windows 10 Store
Publié: août 1, 2015, 2:45pm CEST par Mark Wilson
With Windows 10, Microsoft is pushing apps more than ever, and this means that users are being encouraged to spend more time browsing through the Store. For anyone upgrading from Windows 8 to Windows 10, using the Store will probably be nothing new, but for those moving from Windows 7 to Windows 10, it is a different story.
Just as with any piece of software or service, the Windows Store can prove problematic from time to time. One error that frequently crops up is error 0x803F7003. If you've seen this when trying to download apps from the Store in Windows 10, here's what you need to do to fix it.
The problem stems from an issue with the cache that the Store uses. Rather than being a major cause for concern, a simple cache reset is all that's required. This takes nothing more than running a tool dedicated to this very purpose.
Hit the Start button (or press the Windows key) and type wsreset. When the command is displayed at the top of the Start menu, right click it and select Run as administrator. You'll probably find that a User Account Control dialog appears and you just need to click Yes here to continue. You should find that the Store loads and you can continue to download apps.
-

Chrome has a hidden tab discard option that could solve your memory problems
Publié: août 1, 2015, 12:32pm CEST par Mark Wilson

For many people Google Chrome is their browser of choice. It may be popular, but most users would concede that Chrome has something of a memory problem -- it will gobble up resources like they are going out of fashion. To get around this issue, all manner of extensions have sprung up offering tab suspension -- but there's a hidden Tab Discarding option built in that does the same job.
As revealed by Google's François Beaufort, the Chrome development team is working on bringing the feature, which is already used by Chrome OS users, to the Windows, Linux and Mac versions of the browser. The Discarded Tabs feature works by unloading tabs from memory when resources are running low, and reloading them if and when they are next clicked. If you install the latest nightly builds, this is already available to you -- here’s how to use it.
Tab discarding is the sort of feature that Chrome users have been crying out for. As much as people love Google's browser, its bloating over the years cannot be denied. Bringing better tab management to the browser eliminates the need to rely on extensions to take care of something that Chrome really should be able to do itself.
Writing about the feature on Google+, Beaufort says:
As we speak, the chromium team is adding tab discarding to Windows and Mac OS platforms in the latest chromium build. Linux will follow shortly after. This feature enables least interesting tabs to get automatically discarded when system memory is running low. Discarded tabs are still visible on the tab strip and get reloaded when clicked on.
To enable tab discarding, pay a visit to chrome://flags/#enable-tab-discarding and click the Enable link. That's pretty much all there is to it! You do have the option of taking manual control of discarding tabs by visiting chrome://discards/, so you may want to bookmark that page for future reference.
Oh, and if you were wondering how tabs are chosen as being interesting or not, a Chromium Projects page reveals the order in which tabs are discarded:
- Internal pages like new tab page, bookmarks, etc.
- Tabs selected a long time ago
- Tabs selected recently
- Tabs playing audio
- Apps running in a window
- Pinned tabs
- The selected tab
Photo credit: 360b / Shutterstock
-

Best Buy cashes in on free Windows 10 upgrades
Publié: août 1, 2015, 11:11am CEST par Mark Wilson

It has been mentioned ad nauseum that Windows 10 is free. While retailers would normally make a killing through sales of a new version of Windows, this time around they are missing out. Not a company to shy away from raking in a few bucks, Best Buy has come up with a money-making solution to keep its finance department happy.
The secret formula involves taking advantage of the ignorance of people who are not particularly computer literate, and squeezing them for every cent possible. The chain might not be able to make much money selling copies of Windows 10, but it can sure as hell try to monetize the installation process and training.
If you feel like following Microsoft's on-screen instructions might be a little too taxing for you to tackle on your own, Best Buy is only too happy to relieve you of $29.99. For just shy of $30, the Geek Squad team will install Windows 10 for you. Opt to take a one year subscription to Microsoft Office 365 Personal, however, and the installation will be thrown in free of charge.
But it doesn’t end there.
As Best Buy proclaims, "Windows 10 is the future of Windows". This means there's a lot to learn; whether you're upgrading from Windows XP, Windows 7, or Windows 8.1, much has changed, and much is new. For anyone who feels uncomfortable jumping straight into Windows 10 on their own, Best Buy's Geek Squad is again on hand to help out. For the right price, of course.
A 30 minute in-store introduction to Windows 10 will set you back $29.99. If you'd prefer to take an online tutorial with a chat agent, this is $10 cheaper at $19.99. But the crème de la crème option is one full hour of at-home training from a member of the Geek Squad. The price of having a technician come to your house to show you the ropes? $129.99.
I'll just let that sink in. I'm not sure any more words are needed...
Photo credit: vivairina1 / Shutterstock
-

Facebook uses Lollapalooza to showcase new live streaming feature
Publié: août 1, 2015, 10:00am CEST par Mark Wilson

If you can't make it to Lollapalooza this year, there's no need to be jealous of your friends who are attending. At the music festival, Facebook has started testing a new feature that allows people to live stream events on the social network, taking on the likes of Snapchat head-on.
Music festivals are far from cheap -- a full weekend pass costs $275 and that's before you factor in travel, food, and so on -- so the prospect of a social powered livestream will appeal to many... particularly those to whom the idea of camping is abhorrent. Facebook's Place Tips feature can be used by those in attendance -- including performers -- to post videos, photos and updates that can be enjoyed by those who chose to stay at home.
Place Tips is not a few feature in itself, but Lollapalooza is the first event at which photos and videos have been made widely available. With the ability to see content just from friends, it allows for a very personalized experience which is quite different from the curated offerings from the likes of Twitter and Snapchat.
In an email to the Wall Street Journal, a Facebook spokesperson said:
This Place Tips Lollapalooza experience is just one of the many ways Facebook is trying to help people get the feel of an event when they’re not there.
Real-time coverage of events is something that Facebook is keen to get in on, and the social network will be closely monitoring how popular its Lollapalooza debut proves. The choice of event to give the feature its first outing is quite interesting, perhaps giving an indication of the target market Facebook envisions for future use.
-

For some Facebook users 'hide' may no longer mean hide
Publié: août 1, 2015, 1:26am CEST par Mark Wilson

What do you do if a story appears in your Facebook that you're not interested in? You might just ignore it, or you might try to train Facebook about your preferences by selecting the 'hide' option.
But if you're the sort of person who hides a lot of stories, Facebook might start placing less importance on your dislikes. This might sound counter-intuitive, but Facebook is convinced that it makes sense, saying that for some people opting to hide a story "isn't as strong a negative signal". So who are these people?
Introducing a new update to the way newsfeeds work, Software Engineer Sami Tas, and Engineering Manager Meihong Wang reveal that a small group of people go to the trouble of hiding just about every story that appears in their newsfeed. It is these people for whom Facebook believes that hiding should not necessarily mean that similar stories should be hidden.
To do a better job of serving this small group, we made a small update to News Feed so that, for these people only, we don’t take “hide” into account as strongly as before. As a result, this group of people has started seeing more stories from the Pages and friends they are connected to than in the past. Overall, this tweak helps this group see more of the stuff they are interested in.
Habitual hiders are warned that even if they continue to hide stories, it is likely that they will start to see more appearing in their newsfeeds. As a result of this, page administrators may find that they get more hits than usual.
Photo credit: JuliusKielaitis / Shutterstock
-

Should we all be as pissed as Mozilla about Edge taking over in Windows 10?
Publié: juillet 31, 2015, 11:54pm CEST par Mark Wilson

Microsoft is no stranger to controversy when it comes to web browsers. Internet Explorer has been the butt of jokes for many years, and the company also found itself in trouble in Europe as part of an antitrust case. With the release of Windows 10, history could be about to repeat itself.
Mozilla CEO Chris Beard penned a letter to Microsoft the other day expressing his disappointment that people upgrading to Windows 10 have their default browser choice overridden and changed to Microsoft Edge. While some may feel that Mozilla is whining, it could be argued that the company is right to be pissed -- and Windows 10 users should be just as pissed at the liberties Microsoft is taking.
Of course, there is nothing to stop people from changing the default browser to whatever they prefer but the point is... they shouldn’t have to. Someone upgrading from Windows 7 or Windows 8.1 with Chrome (for instance) installed has already indicated that they have a particular preference when it comes to their web browser -- they installed Chrome. Microsoft should not assume that in upgrading to Windows 10 browsing preferences will change. If a user wants to use Microsoft Edge, they can do so using the taskbar icon. There's just no need to force it upon people.
Microsoft runs a real danger of making Edge something of an unwanted house guest rather than the Internet Explorer replacement it is meant to be. Riding roughshod over the choices that users have already made is no way to make friends and influence people -- as happened with Mozilla, it just rubs people up the wrong way.
Writing to Satya Nadella, Beard said:
When we first saw the Windows 10 upgrade experience that strips users of their choice by effectively overriding existing user preferences for the Web browser and other apps, we reached out to your team to discuss this issue. Unfortunately, it didn't result in any meaningful progress, hence this letter.
We appreciate that it's still technically possible to preserve people's previous settings and defaults, but the design of the whole upgrade experience and the default settings APIs have been changed to make this less obvious and more difficult.
This is something of a theme that runs through Windows 10. Just as it is possible to opt out of the features of the operating system that invade privacy, it is not immediately obvious how to go about it. Does this mean that a lot of people will stick with using Microsoft Edge simply because they don't know how to change the default browser? Only time will tell, but it certainly feels as though we're treading familiar ground here. Microsoft is essential forcing users' hands, and that not something that tends to go down particularly well.
Of course, the obvious comeback is something along the lines of "well, Windows 10 is Microsoft's operating system; it's only right that it is free to do whatever it wants". To a certain extent this is true, but at the same time Microsoft has a moral responsibility to respect the choices that people have already made. Of course Microsoft is free to wipe out any and all program default if it feels inclined, but that doesn’t make it right. There's a big difference between exercising a right, and doing something that is right.
Unlike my colleague Brian Fagioli, I agree wholeheartedly with Chris Beard. He is spot on when he says:
Sometimes we see great progress, where consumer products respect individuals and their choices. However, with the launch of Windows 10 we are deeply disappointed to see Microsoft take such a dramatic step backwards.
It is naïve to suggest, as Brian does, that "the real people this impacts are the ones that don't know how to change their default web browser, and quite frankly, if they don't know how to change back to Firefox, they also probably didn't know how to choose it." Whether done by the user, or through the proxy of a more knowledgeable friend or relative, I assert that it is Microsoft's duty to respect the choices that have been made on a computer.
What is sad is that the people who don’t know how to change the browser may stick with Microsoft Edge simply because they don’t know otherwise. Microsoft's new browser has launched without one of its main selling points -- extensions. We don’t know when this will be added and for those who cannot or do not switch to the likes of Chrome or Firefox (or one of the other alternatives), their experience of the internet is going to be substandard. That's Microsoft's fault, and it's not something that people should be happy to put up with, whether it affects them directly or not.
-

Windows 10 is out, but when will you get it?
Publié: juillet 31, 2015, 8:17pm CEST par Mark Wilson

You won’t have missed the fact that Windows 10 is now out in the wild. The wait is over! Or is it? This is something of a soft launch this time around; not everyone will be getting the upgrade at the same time as it is being staggered.
Microsoft is sending out emails to people who reserved their copy of Windows 10 reminding them that they might have something of a wait on their hands. The email starts by posing the question: "When will my free upgrade arrive?" The fact of the matter is that you might want to stick a pot of coffee on to brew and put your feet up.
Microsoft explains that: "This is the largest software upgrade event ever and we're managing it so everyone has a great experience". This is precisely why the launch is being staggered -- the internet would probably collapse under the sheer weight of traffic if the entire globe tried to upgrade at once! The email continues: "You've already reserved, so your free upgrade is on the way." Ok… but when?!
Your notification to upgrade could come as soon as a few days or in a few weeks.
OK... so the email's not particularly helpful. This will do nothing to calm down those who are impatiently clicking the button to check for the update. It hardly pins down an exact date, after all. The point is, you have not been forgotten. If you want Windows 10, you will get it.
Of course, if your impatience gets the better of you, you can just bite the bullet and use Microsoft's Media Creation Tool. You can try manually triggering the update as well, but there's no guarantee that this will work.
Will you wait it out, or roll your own installer?
-

The real price of Windows 10 is your privacy
Publié: juillet 31, 2015, 6:32pm CEST par Mark Wilson

Windows 10 is a free upgrade, right? Well, surely you know by now that there's no such thing as a free lunch. We're only 48 hours on from the launch of Windows 10 and already the complaining and criticism is underway. One thing that has been brought under the spotlight is privacy under the latest version of Microsoft's operating system.
Some people have been surprised to learn that Microsoft is utilizing the internet connections of Windows 10 users to deliver Windows Updates to others. But this is far from being the end of it. Cortana also gives cause for concern, and then there is the issue of Microsoft Edge, and ads in apps. Is this a price you're willing to pay?
Windows 10 is more closely tied to a Microsoft account than any previous version of the OS. This allows Microsoft to assign an ID number to users that can then be used to track them across different devices, services, and apps. This in turn can be used to deliver closely targeted ads to people. Microsoft has been pushing the mobile first, cloud first philosophy for some time now, and it becomes clear with Windows 10 that the love of the cloud is as much to do with the ability it gives Microsoft to gather useful data as it is about convenience for users.
Without wanting to venture into FUD territory, if you want an idea of just how Windows 10 can be used to gather data about you, take a trip to Privacy in Settings. The number of settings listed here is really quite lengthy -- and just about all of them are enabled by default. The data is almost certain to be anonymized, but the setting labelled "Send Microsoft info about how I write to help us improve typing and writing in the future" will be of particular concern to anyone using their computer to conduct sensitive work.
Then there is location data, the ability of apps to use your camera and microphone, and Cortana's access to your contacts, calendar, and anything else you might care to mention. If this concerns you, go to the Speech, inking, & typing section of Privacy and hit the Stop getting to know me button.
The couple of instructions given in this article highlight another issue. Windows 10 is a new operating system, and things work very differently. Not only are there new privacy settings to consider, but they are in a different place to where similar settings were found in the past. The Control Panel is still there, but a lot of things are now administered through Settings.
Some users have been annoyed to find that Microsoft Edge has been made the default browser, again giving Microsoft the opportunity to gather data. (This is something you can change.)
If you're a Windows Insider who has been working with the various review builds for some months, this may well not be news, but there are a tremendous number of people -- millions upon millions according to Microsoft -- making the switch for the first time. Many of these people know little or nothing about Windows 10, and have no idea of what to expect. Few people who are offered a free upgrade will turn it down, or question why it is free. It seems that the invasions of users' privacy that Windows 10 affords Microsoft is the real price that people are paying.
There has been a trend recently for companies to release transparency reports. Ironically, these were prompted by the activities of the NSA and the concerns raised by surveillance programs; people wanted to know how the companies they deal with were responding to government requests for data. With Windows 10, Microsoft has failed to be completely transparent with users about just what is going on in the background. Sure, the information is out there, but it is hidden away, difficult to interpret, and -- let's face it -- not something that the vast majority of people are going to spend the time to hunt down and digest.
Are you happy to accept that the price of a free operating system is a little bit of yourself? Or will you be taking steps to ensure that your data remains in your control?
Photo credit: Anton Watman / Shutterstock
-

Stop Windows 10 using your internet connection to share updates to other people
Publié: juillet 31, 2015, 12:53pm CEST par Mark Wilson

A lot of things have changed in Windows 10, not least the way in which updates are delivered. Now that Windows 10 has been officially released and is gradually spreading around the globe, more and more people are starting to discover that the latest version of Microsoft's operating system is using more bandwidth than expected.
Windows 10 uses a P2P-style system called Windows Update Delivery Optimization (WUDO) which means that once your computer has downloaded an update it can be shared to not only other computers on your network, but also other people online. While it makes sense to share updates to your own computers, you might well resent giving up your bandwidth to others. Thankfully, it's easy to disable internet-wide WUDO.
In its FAQ, Microsoft explains that WUDO is enabled by default. It is described as being particularly useful for computers with slow or unreliable internet connections, as it allows updates to be downloaded from multiple places at once. As well as Microsoft's own servers, updates -- or parts of updates -- will also be downloaded from other Windows 10 users. In order for this to happen, WUDO has to be enabled, but you might prefer to remain in control of your internet connection and stop it from being used for update sharing in the background.
To disable Windows Update Delivery Optimization, use the following steps:
- Open up Settings and click Update & Security.
- Click Windows Update section to the left and then the Advanced options link to the right.
- Click Choose how updates are delivered.
- You can opt to completely disable WUDO by flicking the toggle switch to the Off position.
- Alternatively, you can continue to share updates you have downloaded to other computers you own but disabled sharing to others by leaving this toggle in the On position and selecting the PCs on my local network option.
That's all there is to it!
-

Silent Circle's ultra-secure Blackphone 2 joins Google's Android for Work program
Publié: juillet 31, 2015, 11:48am CEST par Mark Wilson

The security of mobile communications is of paramount importance to many people, but it is particularly high on the list of priorities for business and enterprise customers. Silent Circle is a company that caters to those concerned with privacy and security, billing its work as the 'world's first enterprise privacy platform'.
The company's original Blackphone generated some interest, and earlier in the year we learned about the follow-up -- the Blackphone 2. Kitted out with a customized version of Android, the security-focused handset is the latest addition to Android for Work, Google's own security-focused program.
In terms of specs, the Blackphone 2 boasts an octo-core processor, 32GB of storage, 3GB RAM, 13MP front camera, 5MP rear shooter, and a 5.5 inch screen. But it is security that's at the heart of the phone. Silent OS allows for the placing of encrypted phone calls, and apps can be downloaded through the locked-down Silent Store.
Silent Circle CEO, Bill Conner said:
Privacy is about being able to decide and control what information to share and how you share it. We're delighted to join the Android for Work program. It's a significant step forward in Silent Circle's development which enables us to deliver privacy and security to a broader enterprise customer base, while meeting their need for the wide-ranging apps and services provided by Google.
The Blackphone 2 was originally earmarked for release in July, but this has now been pushed back to some time in the fall. David Puron, SVP Engineering, Devices said that the second generation of the device has even more to offer customers:
Our Blackphone 2 release this fall will bring support for Google Play and Google Mobile Services to Silent OS, and with support for Android for Work, companies can strike their own balance of control over data and connectivity with established productivity services that are used throughout enterprise.
Silent Circle shared the video below at the beginning of the year, giving a glimpse at the Blackphone 2:
-

Joe Belfiore talks Continuum in Windows 10 Twitter Q&A
Publié: juillet 30, 2015, 10:40pm CEST par Mark Wilson

In an impromptu Q&A on Twitter, Microsoft's Joe Belfiore has revealed more about how Continuum will work on Windows 10 for Phones. He started off by saying that it is a very high-end feature and will require new hardware as it uses dual screens.
Continuum is part of Microsoft's drive to make a uniform experience for Windows 10 users across a range of different devices -- from desktops and laptops, to tablets and smartphones. Belfiore shared pictures of a Xiaomi Mi4 showing how Continuum allows windows to be moved from a desktop to mobile display, giving a tantalizing glimpse of what's to come.
Windows Insiders in China should be able to try out Continuum on their own Xiaomi phones in the next few weeks, but for now we'll just have to make do with the information Microsoft is willing to share about the feature. Belfiore is more than a little upbeat about the potential of Continuum and used his Twitter session to press just how similar apps feel on different devices:
One of the coolest things about Continuum for Phones is how *identical* the Mail/Calendar, Word, Excel, PPT experiences feel to your PC.
— joebelfiore (@joebelfiore) July 30, 2015
He points out that the phone he has shared pictures of is a custom engineering sample, and went on to try to clear up some misconceptions about how Continuum works and its requirements:
Continuum for phones DOESN'T require you to carry a device to connect. It's wireless (BT/Miracast) *or* wired (eg. could have a dock).
— joebelfiore (@joebelfiore) July 30, 2015
The build of Windows 10 that Belfiore is currently using on his Xiaomi Mi4 is described as "a candidate we're testing out to MAYBE flight". We're told that it "needs a bit of time", but at the moment there is no real indication of when a new build will be released.
Is Continuum a killer feature of Windows 10 for you?
-

Windows 10 Service Release 1 may launch next week
Publié: juillet 30, 2015, 9:45pm CEST par Mark Wilson

We know that Windows 10 is the last version of Windows ever -- and this is really another way of saying that Windows will never be finished. Over the coming weeks, months, and years, we can expect to see a near-endless stream of updates to the operating system.
But while a trickle of updates was anticipated, few would have expected that a huge update would be just around the corner. Despite having launched just 24 hours ago, it seems as though the first big update to Windows 10 -- and it's shaping up to be a huge one -- is already looming on the horizon. Windows 10 Service Release 1 (SR1) could be released as early as next week!
According to The Verge, Microsoft's developers have not stopped working on Windows 10 just because the OS has been pushed out of the door. Windows 10 SR1 is a massive collection of patches, fixes, and updates that address the issues that Windows Insiders have complained about, and continue to plague non-Insiders in the RTM build.
Microsoft has already released a 1GB day-one update for Windows 10, but Service Release 1 is shaping up to be even more significant in terms of squashing bugs. Anyone hoping for more new features will be disappointed to hear that SR1 is nothing more than a collection of fixes (albeit a large collection). It is possible that Windows Insiders will be given the opportunity to try out Windows 10 SR1 before everyone else, but The Verge's sources say that early August has been pencilled in as the main release date.
Following this -- perhaps as early as October -- will come yet another big update to Windows 10. This time around, however, new features are expected. Many people were disappointed to learn that Microsoft Edge launched without support for the long-promised extensions, but this will be added in the next major build of Windows 10. Other new features include a new messaging app, and this is something that Insiders will certainly get to try out before everyone else.
Is there anything in particular you want to see in SR1 and later updates?
-

Toshiba announces Windows 10-ready Tecra A50 laptops for SMBs
Publié: juillet 30, 2015, 7:54pm CEST par Mark Wilson

With Windows 10 now out of the starting blocks, a slew of hardware is beginning to appear to take advantage of Microsoft's latest operating system. Adding to its existing SMB lineup, Toshiba today unveils its Tecra 50 range of laptops.
Designed with small businesses in mind, the Tecra A50 can be customized with an Intel Core i5 or Intel Core i7 processor, and features a 15.6-inch display. A user-replaceable battery provides almost 8 hours of power for those on the move, and security is offered by support for Toshiba Cloud Client Manager and Trusted Platform Module (TPM) v1.2. With a starting price of just $729.99, this is an inexpensive system that will appeal to SMBs with a budget.
It's not just software security that's to be found in the Tecra A50. There is also EasyGuard Technology, which offers "multi-tiered security and data protection measures that guard components against accidental bumps". In terms of connectivity, there are two USB 3.0 ports, and one USB 2.0. You'll also find full-size HDMI and VGA ports, Gigabit Ethernet, and an SD Card reader. There's an optical drive and a full-sized keyboard replete with number pad, too.
Toshiba's Carl Pinto says there is a lot for SMBs to investigate:
Small and mid-sized business need more enterprise-class features and performance than ever before, but for a low total cost of ownership. Our line of SMB products not only delivers powerful, secure devices that each meet the varying needs of this segment, but are now Windows 10-ready, enabling businesses and IT departments to take advantage of the new platform as soon as they are ready.
The Tecra A50 range will be available from August; the Tecra A50-C1510 and Tecra A50-C1510W10 will be available for $729.99, while the Tecra A50-C1520 has a MSRP of $799.99. Despite the price, Toshiba offers a guarantee system, that in the event of LCD panel, hard drive, memory, or system board failure, the company will supply a new replacement laptop.
-

PC-to-Xbox One game streaming is in the pipeline for Windows 10
Publié: juillet 30, 2015, 11:50am CEST par Mark Wilson

One of the features of Windows 10 that created ripples of excitement is the ability to stream Xbox One games from the console to a PC. But what about doing things the other way round?
If you like the idea of turning your already-powerful Xbox One into a fully upgradable games PC, you'll soon be able to do just that. Microsoft is currently working on PC-to-Xbox One game streaming, and you might not have to wait too long.
In an interview with The Verge, Microsoft's Phil Spencer said that there are few obstacles to overcome to make PC-to-console streaming a reality, including adding support for using a mouse and keyboard. Microsoft has learned that gamers want greater flexibility and this is a luxury that Windows 10 affords them.
It is relatively simple to bring console games to PC, but giving people the option of playing PC games on their Xbox One is a slightly different matter. Console-to-PC streaming is easy to manage "because we know exactly what you have. It's actually a little more challenging doing the encoding on the PC side to the Xbox, but challenge is good". The range of hardware that’s out there for PC gamers clearly presents something of a challenge as developers need to find a way to bring powerful features to a non-upgradable console.
This is really a continuation of Microsoft's vision of blurring the boundaries between devices, and it will be interesting to see how popular it proves.
-

So you've upgraded to Windows 10... ready to leave the Insider program?
Publié: juillet 30, 2015, 11:07am CEST par Mark Wilson

The wait is finally over. Over the past few months you've downloaded countless gigabytes of Windows 10 related files and now you've had enough. Windows 10 RTM is now installed on your computer and you're happy to stick with a relatively stable version for the foreseeable future.
You've had enough of being a Windows Insider, but how do you stop those pesky preview builds from being downloaded? Thankfully it is very simple to opt out of the Insider program so preview builds will become a thing of the past; here's what you need to do...
While it was fun to get the new builds of Windows 10 during the preview period, you might well feel that it's time to kick back and just enjoy the finished product (not, of course, that Windows 10 will ever be 'finished'). To leave the program just open up Settings followed by Update & Security. Hit the Advanced options link in the Windows Update section and then click the Stop Insider builds button.
That's it. You're out!
Any updates that are rolled out to the Fast and Slow rings will be ignored, and your computer will only receive regular updates. Here at BetaNews we'll let you know whenever an interesting preview build is released, and you can always rejoin the program if there's something you like the sound of.
Photo credit: Ozgur Coskun / Shutterstock
-

Windows 10 launch site launches
Publié: juillet 28, 2015, 11:00am CEST par Mark Wilson

We're just 24 hours away from the launch of Windows 10 (actually, we don’t yet know what time the operating system will be unleashed tomorrow). If the stream of videos coming out the Microsoft camp hasn't whetted your appetite, maybe the new Windows 10 portal will do the job.
Microsoft has launched a new site encouraging people to #UpgradeYourWorld and providing everything a would-be upgrader might want to know about Windows 10. For Microsoft, this is much more than just another software launch; the company is pinning a great deal on the success of Windows 10, and the marketing machine is now going into overdrive.
The Windows 10 launch site is socially-powered as well as housing information from Microsoft. A live map displays tweets from around the world as Twitter users talk about Windows 10 -- just use the hashtag #UpgradeYourWorld or mention Windows 10 to get involved if you want. If you've managed to miss all of the hype so far, the site serves as a place to catch up with everything -- including Microsoft's "10 reasons to upgrade to Windows 10" (see ours here).
If you want to familiarize yourself with the OS ahead of its arrival on your computer, there is a quick-start guide -- which is the same as the one that leaked yesterday. For the completist, there are also all of the videos and screenshots you could possibly want. Hit the Windows 10 launch site to see what Microsoft has in store for you.
-

VeriFyle reveals Cellucrypt, a new multi-layer encryption key management technology
Publié: juillet 28, 2015, 2:16am CEST par Mark Wilson

VeriFyle, the company headed by Hotmail inventor and co-founder Jack Smith, has a new encryption key management technology which it believes will "re-invent how the world thinks about secure sharing and messaging". The major difference is that any object that is shared to the cloud using the system is encrypted for individual users rather than in bulk.
Cellucrypt offers such a high level of security that VeriFyle believes that it "makes illicit bulk-access to customer data virtually impossible." It's a bold claim, but Cellucrypt builds on the traditional public-key system with the addition of password-derived keys.
The encryption technique will be used by VeriFyle's messaging and file-sharing services when it launches later in the year. Cellucrypt has been patented by VeriFyle and will be made available to customers free of charge. Introducing the new encryption technique VeriFyle says:
The patented Cellucrypt technology assigns each data object (e.g. document, note or conversation) a unique encryption key, which is itself encrypted uniquely each time a user shares that object. By encrypting each data object individually for users, Cellucrypt makes illicit bulk-access to customer data virtually impossible.
CEO Jack Smith has high hopes for his company's new technology:
Key management should be invisible to the end-user and it should maximize users' security and peace of mind without burdening them with extra steps and add-on products. VeriFyle is the first all-in-one product that combines advanced key management technology with cloud sharing and messaging. The result is a significantly more secure way to share data.
Photo credit: m00osfoto / Shutterstock
-

Download leaked Windows 10 quick guide here
Publié: juillet 27, 2015, 11:40pm CEST par Mark Wilson

There has been so much information available about Windows 10, it would be easy to think that you know everything there is to know... and the operating system hasn’t even launched yet! Over the past few months, in addition to the official releases, there have been a number of build leaks to whet our appetites.
With just two days to go until launch, the latest leak is a quick-start guide that tells you everything you need to know about Windows 10. There might not be much that Windows Insiders don’t already know, but for everyone else, the guide serves as a great introduction to the most recent version of Windows.
The 14-page guide is available to read in Word Online, but you can also download the document as a PDF. Windows 10 is described as "the best Windows ever", and right at the start Microsoft makes reference to the "free, automatically-enabled updates" that have proved problematic in some instances.
We're also introduced to Cortana, Microsoft Edge, gaming and Xbox features, the built-in modern apps, Windows Hello, and the various security features -- pretty much everything highlighted in Microsoft's video ads for Windows 10 have their own sections in the guide. It's far from being a comprehensive guide to everything Windows 10 has to offer, but for newcomers it serves as a brilliant way to become familiar with the operating system.
Grab your copy of the guide here.
-

Microsoft's latest reason to upgrade to Windows 10 is Continuum
Publié: juillet 27, 2015, 11:37pm CEST par Mark Wilson

Windows 10 is now so close you can smell it. With so many having been more than a little disappointed with Windows 8, Microsoft has to do a lot to convince those that stuck with Windows 7 to make the jump to Windows 10. The latest video Microsoft has released to give the operating system a final push before launch focuses on Continuum.
We've already seen how there are old favorites such as apps, security, and gaming in Windows 10, but people also need new features. Having learned about the likes of Windows Hello, now we are shown how Windows 10's mode-switching Continuum feature could help us.
This is a feature that will appeal to people using hybrid systems such as the Surface Pro -- laptops that can be used in multiple modes. Continuum makes it easy to work with Windows 10 however you happen to be using your computer. No need to manually switch between tablet and laptop mode, Continuum can take care of it for you and ensure that you have the most appropriate UI and tools available.
Microsoft says:
Touch when you want to, type when you need to. Continuum on Windows 10 optimizes your experience for your activity, device and display, so you can do your thing in tablet or desktop mode anytime you want.
Check out the video below and see if the presence of Continuum is enough to make you upgrade to Windows 10 after July 29.
-

Google explains the future of Google+ and improves YouTube comments
Publié: juillet 27, 2015, 6:37pm CEST par Mark Wilson

Since the beginning, Google+ has been seen as a mess. It has been dismissed as the social network for people who don’t actually like to be very social, and Google is only too aware that it needs to step up its game. You may well have wondered if the company knew what it was doing… today Google shares details of what it has planned.
Several months ago, Google announced that it was going to split up Google+ into a number of separate projects -- Hangouts, Photos, and Streams. We've already seen the arrival of Google Photos to replace Google+ Photos (you keeping up?) and now, as well as admitting that it made mistakes, Google gives a taste of what’s to come in the months ahead.
The company says that "while we got certain things right, we made a few choices that, in hindsight, we've needed to rethink". But what does this mean? What is promised is a 'more focused' Google+, and this means chopping Google+ out of other Google services. In future you will be able to use a standard Google account rather than a Google+ profile as your online identity. Current Google+ features will also migrate into other products.
For example, many elements of Google+ Photos have been moved into the new Google Photos app, and we're well underway putting location sharing into Hangouts and other apps, where it really belongs. We think changes like these will lead to a more focused, more useful, more engaging Google+.
What does this mean? An important difference is the fact that, unlike Google+ profiles, Google Account profiles are private and unsearchable. But it doesn’t end there.
Starting today, there are also important changes to commenting on YouTube -- something which has already proved controversial. There is one key change that is likely to divide opinion:
The comments you make on YouTube will now appear only on YouTube, not also on Google+. And vice-versa. This starts rolling out today.
Further down the line the requirement to have a Google+ profile to create a channel, post a comment, or upload a video will be dropped. Ultimately, you'll be able to delete your Google+ profile completely... but:
If you want to remove your Google+ profile, you’ll be able to do this in the coming months, but do not do it now or you’ll delete your YouTube channel
You have been warned!
-

How to stop Windows 10 installing automatic updates
Publié: juillet 27, 2015, 1:41pm CEST par Mark Wilson

One of the more controversial features of Windows 10 is the automatic, mandatory installation of updates. With launch day now just hours away a problem with NVidia drivers has highlighted just why automatic updates have proved so controversial.
Microsoft has previously said that home users will have no choice but to let Windows 10 take care of updates for them. For those concerned about this, the company has a special tool that can be used to block specific updates to Windows and drivers.
Unearthed by ZDNet's Ed Bott, KB3073930 is the tool that many people feel should have been built into Windows 10 as standard. It's not really a tool that Microsoft intended to be used by the majority of people to take control of Windows Updates, it is actually a troubleshooting tool designed for use with the preview builds that have been made available to Windows Insiders. It's not clear whether the tool will continue to work when Windows 10 officially launches in a couple of days' time, but it's certainly an option for now.
The update blocker tool -- called the "Show or hide updates" troubleshooter package -- can be downloaded from Microsoft's support pages where the company describes its purpose:
In Windows 10 Insider Preview, your device is always kept up to date with the latest features and fixes. Updates are installed automatically, with no need to select which updates are needed or not needed. In rare cases, a specific driver or update might temporarily cause issues with your device, and in this case you will need a way to prevent the problematic driver or update from reinstalling automatically the next time Windows Updates are installed.
Using the tool is very simple -- you can use check boxes to indicate which updates and drivers you would like Windows 10 to ignore.
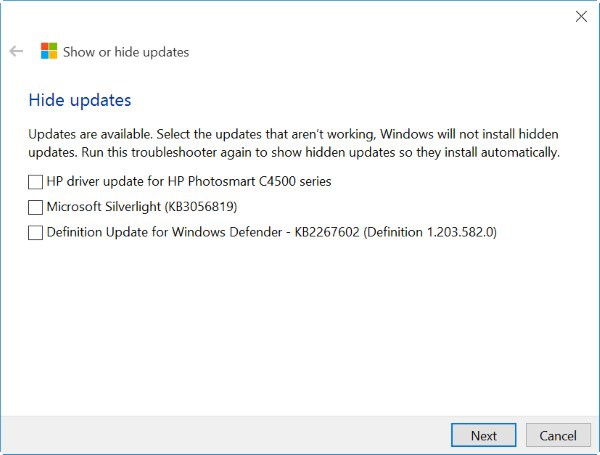
Give the update blocker a try for yourself and see what you think.
-

One year on, Internet.org gives a billion people internet access
Publié: juillet 27, 2015, 12:18pm CEST par Mark Wilson

Mark Zuckerberg's Internet.org has come in for quite a lot of criticism since it launched. Designed to help get the entire world online, it has been argued that the program is in opposition to the idea of net neutrality and many of its backers have pulled out or complained about things since it kicked off.
But in many regards none of this matters -- it is the numbers that are important. Twelve months after the launch of Internet.org, more than a billion people have been connected to the internet free of charge. Moving into year two, the next part of the operation involves scaling things up.
Connecting the unconnected remains at the heart of going forward. The aim is now to get more partners involved and have more operators on board -- this was the reason for launching the Internet.org Platform earlier in the year. Internet.org has already spread into 17 countries, but there are many, many more to tick off the list.
Writing on Facebook, the Internet.org team says:
Internet.org brings new users onto mobile networks on average over 50 percent faster after launching free basic services, and more than half of the people who come online through Internet.org are paying for data and accessing the internet within the first 30 days. These points show that Internet.org is not only a successful tool in helping bring people online, but it is successful in showing people the value of the internet and helping to accelerate its adoption.
But however many people the program gets online, no matter how altruistic the intention may be, it's hard to imagine that Internet.org won't continue to find itself coming under fire from various quarters.
Photo credit: dolphfyn / Shutterstock
-

Windows 10: it's all about the apps, baby
Publié: juillet 26, 2015, 10:00pm CEST par Mark Wilson

From the slew of videos flying out the Microsoft stables over the last week, it's clear that Windows 10 is trying to be all things to all people. The ads we've seen so far have promoted security, Windows Hello, Microsoft Edge, and yet another video has been released today that extols the virtues of the built-in apps.
What's different about this video is that it doesn't really focus on anything that's particularly new and exciting. Many of the Windows apps that are features are not new, so this is clearly a video aimed at those who skipped Windows 8 and stuck with Windows 7 or XP. But it's a good opportunity to take a look at the Photos, Maps, Mail and Calendar, Groove, and Movies & TV apps.
You know the format for the videos now: 48 seconds of pumping-music-backed footage, interspersed with snippy, slightly amusing captions. This time around we take a look at a series of modern apps which Microsoft hopes you'll use to organize your digital life through Windows 10.
There's a palpable sense of excitement on the Windows blog:
We’re three days to our Windows 10 launch! Today, we’re sharing more about the great Windows 10 built-in apps [...] Stay tuned for tomorrow’s post where we’ll be sharing another awesome Windows 10 feature!
Alright, guys... you can put away the exclamation points now.
Take a look at the video for yourself:
-

Windows 10 update KB3074681 causes Explorer crashes
Publié: juillet 26, 2015, 8:11pm CEST par Mark Wilson

In the last few days before Windows 10 is unleashed on a largely unsuspecting world, Microsoft has released a number of updates. These are just regular, everyday updates rather than new builds of the preview, but one of those released over the weekend has been causing problems.
Update KB3074681 was released yesterday (Saturday), and it has been causing issues that result in Explorer crashing. The way updates work in Windows 10 means that there is no way to get rid of the update, so until a patch is released there is little that can be done -- apart from avoiding the crash triggers, that is.
As noted by Richard Hay on SuperSite for Windows, KB3074681 causes Explorer to crash in at least two situations. He found that if the Programs and Features Control Panel is used to try to uninstall or modify a program that is installed, Explorer will die and immediately restart. There is no way to currently use the Control Panel to modify programs on affected computers at the moment.
I have also been able to confirm that opting to enable or disable an active network connection also causes the crash. Irritatingly, I found that I was able to disable the network adapter on my Surface Pro, but when I tried to re-enable it, the Explorer crash bug reared its head. Erk.
So if you have disabled your network adapter since installing the update, what can you do to get it re-enabled? Any time you try to use the Control Panel to enable it, you'll find that Explorer crashes and when it restarts the adapter remains stubbornly disabled. All is not lost; Windows 10 has a troubleshooter that can get things back up and running in next to no time.
- Hit the Windows key, type Troubleshooting and click the Troubleshooting icon.
- Click the View all link to the left of the window.
- Click the Network Adapter link and then click Next.
- Windows 10 will detect the disabled adapter and re-enable it without killing Explorer.
Now... leave it enabled until a new update is released or you're going to have to go through this time and time again!
Microsoft has not issued a statement about the update, nor indicated when a fix will be released -- but with just three days to go until launch, there really isn’t long left.
-

Windows 10's automatic updates for NVidia drivers could break your computer
Publié: juillet 26, 2015, 7:04pm CEST par Mark Wilson

One of the features that has been removed from Windows 10 -- at least for home users -- is the ability to pick and choose when updates are installed. Microsoft has taken Windows Update out of the hands of users so the process is, for the most part, completely automated.
In theory, this sounds great -- no more worrying about having the latest patches installed, no more concerns that a machine that hasn’t been updated will cause problems for others -- but an issue with NVidia drivers shows that there is potential for things to go wrong. Irate owners of NVidia graphics cards have taken to support forums to complain that automatically-installed drivers have broken their computers.
As reported by Gordon Kelly on Forbes, there are many people complaining that updates to NVidia drivers -- which are installed without manual intervention -- are causing problems, and even killing computers. Scores of comments have been left on the GeForce community forum where disgruntled NVidia users have spent the last week and a half voicing their anger at what has happened.
With Windows 10 due to launch on Wednesday, the concerns expressed on the forum could well be echoed in other communities if Microsoft and hardware companies don’t take steps to address the issues. The problems the automatic update causes are quite varied. People are experiencing random crashes after the update has installed, while others have problems with multi-monitor setups. Some games -- including Starcraft 2 and Diablo 3 -- suffer with graphics issues, and some users have found themselves thrown into recovery mode.
Complaints have spilled onto Twitter where users have voiced their annoyance to Gabe Aul:
@GabeAul @Chris123NT @nvidia I agree with Chris, Gabe. You shouldn't be installing graphics drivers automatically. Give us control back.
— Ryan Spooner (@Ry5ter) July 24, 2015
While it is easy to point out that Windows 10 is still yet to be released, the official launch date is now within touching distance and it is widely thought that the current release -- build 10240 -- is the same at the 'RTM' version. Having drivers automatically pushed out to computers around the world is almost certainly going to cause problems; issues with drivers are a fact of life, after all. That there is an issue with a driver is, in itself, nothing astounding. The real concern is that now that updates are not optional, more and more people will be affected whenever a problematic driver is released. Of course, by the same token, 'fixed' drivers will also be received by users faster, but if they are locked out of their systems, this will be small comfort -- and, there's also no way of knowing how long it will take for a patch to be issued.
Part of the problem seems to stem from the fact that NVidia driver updates are handled not only by Windows Update, but also by NVidia's own update tool. This is something that is quite common with numerous hardware and system manufacturers, and it opens up the possibility of there being a conflict between the two update utilities. If their databases are not perfectly in sync, each could believe it has the most recent version of the driver, resulting in an upgrade loop.
Ultimately, the driver update problem is something that Microsoft is going to have to address; it cannot just be ignored. Mark this down as teething troubles if you will, but there's potential for this to become a huge issue. So what to do? Over on Forbes, Gordon Kelly has a couple of suggestions:
Given Windows 10 updates cannot be stopped the most obvious solution is to uninstall third party driver management and hand it all over to Windows Update to avoid clashes. This potentially simplifies matters by providing an all-in-one update service, but it does mean taking away control from specialist companies over their own products.
A second approach is [...] hack it.
Initially this might work, but in April senior Microsoft product marketing manager Helen Harmetz said during a Windows 10 webinar that users who forcibly stopped any Windows 10 updates would eventually have their security updates cut off.
In the meantime, the experience for NVidia users is causing not only frustration, but providing a sub-standard Windows 10 experience. There are posters complaining that "this is the worst driver I've ever used on [an] NVidia card", and pointing out that differing drivers are available through Windows Update and NVidia too, and this is something that could get a whole lot worse when Windows 10 reaches a wider audience.
Have you experienced problems with your NVidia driver updates -- or updates for any other drivers? Do you think it's time for Microsoft to reconsider the idea of forced automatic updates?
Photo credit: 360b / Shutterstock
-

LinkedIn (temporarily) backs down after uproar at contact export removal
Publié: juillet 26, 2015, 11:30am CEST par Mark Wilson

LinkedIn caused a storm a couple of days ago when it removed the option to instantly download contacts. Many users of the professional social network were more than a little irked to discover that while contact exporting was still available, a wait of up to three days had been put in place.
Unsurprisingly, users revolted, having been particularly upset by the fact the change was implemented with no warning or announcement. But the company has managed to turn things around by quickly backtracking on its decision after listening to a stream of complaints on Twitter.
Michael Korcuska, VP of Product Management later explained that the removal of the regular download option had been "part of our ongoing efforts to combat the inappropriate export of member data by third parties." As a result of the vocal outpouring of disapproval, instant CSV exporting is back... for now at least. Writing on Twitter, LinkedIn's customer service team announced the return of the instant download option:
https://twitter.com/LinkedInHelp/status/625055366716329984
But as Korcuska explains, the option is not going to be around in its current form forever. It will disappear again but only when the alternative download method has been sped up. Writing on the LinkedIn blog, he said:
Our goal is to make as much of your data, including connection data, available within minutes. We will keep the CSV connections tool available until we can reach that goal (some other data items will be available in an extended archive that may take longer to process). We will then turn this tool off again, as part of our ongoing anti-scraping efforts.
It's not clear what form future changes will take, or quite when they might be implemented. But, for now, instant contact exporting is back.
Photo Credit: Atelier_A/Shutterstock
-

Kim Kardashian suggests a tweet editing option... Twitter loves the idea
Publié: juillet 25, 2015, 9:35pm CEST par Mark Wilson

Sometimes it just takes someone with a big enough name -- and voice -- to draw attention to something that thousands of others have been saying for a long time. Proving this, Kim Kardashian (of all people) has made a suggestion for a feature that Twitter should adopt: editing. Twitter loves the idea. And when we say 'Twitter', we don’t mean 'people on Twitter' -- we mean Twitter itself: none other than co-founder Jack Dorsey.
Kardashian tweeted to her 33.8 million followers letting them know that she'd got in touch with Twitter to share her idea. In a matter of hours she received tens of thousands of replies, favorites, and replies. If she has husband Kanye West on board, that's another 13.5 million followers.
One reply came from the Twitter CEO who indicated his support for the suggestion. With such a huge following, it's little surprise that Twitter took notice of what Kardashian had to say. It took Dorsey under an hour to response to the tweet.
@KimKardashian great idea! We're always looking at ways to make things faster and easier.
— Jack (@jack) July 25, 2015
Although this is a positive response, there's no knowing if -- or when -- an edit feature might be added. Despite the largely warm reception, some people expressed concerns that giving Twitter users the ability to edit their tweets could end up making respondents look like they supported something they didn’t. Facebook has allowed for the editing of posts and comments, so it's quite feasible that Twitter could follow suit.
Photo credit: DFree / Shutterstock
-

Twitter censors plagiarized tweets that repeat copyrighted joke
Publié: juillet 25, 2015, 7:10pm CEST par Mark Wilson

Can a joke be copyrighted? Twitter seems to think so. As spotted by Twitter account Plagiarism is Bad a number of tweets that repeat a particular joke are being hidden from view. The tweets have not been deleted as such, but their text has been replaced with a link to Twitter's Copyright and DMCA policy.
The joke in question? "Saw someone spill their high end juice cleanse all over the sidewalk and now I know god is on my side." Perform a search for the text and, while you will find several tweeted instances of it available at the moment, there are many examples of tweets that have been censored.
As noted by The Verge, the first appearance of the joke seems to from someone called Olga Lexell. Following this, there are number of tweets that have been obfuscated -- more recent tweets of the joke are visible, but it's possible they will disappear soon. The deleted tweets have been replaced with a standard message from Twitter:
Tweet withheld
This Tweet from @xxxxx has been withheld in response to a report from the copyright holder. Learn more
Plagiarism is Bad spotted the issue earlier today, although it appears to have been going on for some time:
BREAKING NEWS: Twitter is hiding tweets reported stolen. And it's referring to the author as a "copyright holder" pic.twitter.com/DkteWMZ7zg
— Plagiarism Is Bad (@PlagiarismBad) July 25, 2015
Olga responded to the interest that the issue has raised indicating that she had indeed instigated DMCA takedown requests:
If you're wondering why Twitter complied with my copyright takedown requests. pic.twitter.com/MNzZPCHWNc
— uh (@runolgarun) July 25, 2015
What do you make of it all?
Photo credit: aastock / Shutterstock
-

What is Windows Hello all about?
Publié: juillet 25, 2015, 1:55pm CEST par Mark Wilson

Microsoft has talked about a lot of the new features of Windows 10, but something that has only really been mentioned in passing is Windows Hello. A couple of weeks ago we showed you a video of the security feature in action and now a new animated ad has been unearthed that shows the benefits the security feature brings.
Unlike the other videos we've shared in recent days, this video is not one that Microsoft has officially released -- not yet at least. If you're still in the dark about Windows Hello, check it out to find out more.
This animated video is something of a departure from the style Microsoft has used so far. It introduces the "more personal, more secure way to unlock your Windows 10 devices" with a fun, cartoony look. Interestingly, the character at the center of the video is presented as a geek -- as Microsoft is trying to give Windows 10 a broad appeal, this could explain why the footage is yet to be officially promoted.
The video was shared by Richard Hay from SuperSite for Windows and it demonstrates the fingerprint scanning, and facial and iris recognition that can be used to lock down a computer.
[https:] -

Upgrade to Windows 10 build 10240 or lose access to the Windows Store and app updates
Publié: juillet 25, 2015, 12:40pm CEST par Mark Wilson

If you haven't yet upgraded to build 10240 of Windows 10, now is the time to do so. Anyone sticking with an earlier build of the preview will no longer be able to use the Windows Store, and this in turn means they will not be able to update any of the apps they have installed.
Microsoft has been busy promoting Windows 10 this week, providing a number of reasons for people to upgrade from Windows 7 and Windows 8 after July 29, but even before this date the company is keen to move people away from older builds.
You may feel that you can live without access to the Windows Store, but the fact that this means losing access to app updates is something to keep in mind. As the launch of Windows 10 draws ever-closer, app updates are appearing thick and fast -- if you don’t want to miss out, you're going to need access to the Store.
A message on the Insider Hub reads:
The Windows 10 Store team has been making some great fixes and improvements to reliability and performance. To ensure you are able to benefit from these important updates, starting July 24 we will be requiring Insiders who are not running the latest Windows 10 operating system to upgrade their PC; otherwise those affected will be unable to experience the Windows 10 Store. Check Windows Update to make sure you have installed the latest build and the most recent updates.
The 24th having come and gone, now is the time to make the upgrade. Build 10240 is available on both the Fast and Slow rings, so there's really no excuse not to grab it
-

Windows 10 is the most secure version of Windows ever
Publié: juillet 25, 2015, 11:43am CEST par Mark Wilson

If you're looking for a reason to upgrade to Windows 10 next week -- or whenever the upgrade appears for you -- how about the fact that it is the most secure version of Windows ever released? This is the angle Microsoft takes in its most recent video promoting the up-coming operating system.
We've already been treated to a series of videos showcasing some of the highlights of Windows 10. From gaming to multi-tasking, Microsoft has come out with all guns blazing as it prepares to push its latest baby out of the door. Will security enhancements swing it for you?
It is easy to say that each new version of Windows is more secure than the last -- it would be strange to take a step backwards in this department, after all -- but Microsoft uses a new video to back up its claims. Pulled out for particular attention are features such as Windows Defender for tackling malware, and automatic updates to help stave off the latest threats.
The security features of Microsoft Edge are also given an outing. Check out the video below:
-

IFTTT joins the open source community
Publié: juillet 25, 2015, 10:54am CEST par Mark Wilson

It's not that we're (necessarily) lazy, but technology entices us all to find quicker ways of doing things. The internet is something of a behemoth and there are plenty of tools out there that aim to tame it -- one of which is automation service IFTTT.
Harnessing the power of apps, devices, and the cloud, IFTTT has just unveiled five open source projects. Now available on GitHub, the projects can be used by anyone to integrate IFTTT automation in their apps and services.
Earlier this week Microsoft and Google announced new support for IFTTT, and the availability of five open source projects means that we should see support spreading to a wider range of apps an services. The five projects are:
- JazzHands (Objective-C) -- A simple keyframe-based animation framework for UIKit.
- RazzleDazzle (Swift) -- A simple keyframe-based animation framework for UIKit in Swift.
- Kashmir (Ruby) -- A Ruby DSL that makes caching and serialization a snap.
- FASTTTcamera (Objective-C) -- A fast and easy camera framework for iOS with customizable filters.
- Jot (Objective-C) -- An iOS framework for easily adding drawings and text to images.
The open-sourcing of project was announced with little fanfare:
We are huge fans of open source at IFTTT. Lately, we’ve been working hard on a bunch of new open source projects and updates to our existing ones.
Today, we’re officially launching Open Source @ IFTTT -- a collection of our team’s contributions to the open source community.
Check ‘em out, star 'em, and follow us on GitHub for even more.
There may only be five projects to work with at the moment, but the promise of more to come means developers should keep an eye on GitHub to see what the future holds.
-

Huge improvements made to Google Voice transcription accuracy
Publié: juillet 24, 2015, 12:27am CEST par Mark Wilson

If you're a Google Voice user, you'll almost certainly have experienced its frequently insane attempts at voicemail transcriptions. There are times when these offer some hilarious relief in the middle of a dull day, but they also stand in the way of, you know… actually understanding what's been said.
Transcriptions that are not accurate are less than helpful, and Google has taken steps to up its game. Using sample voicemails from volunteers, it has been possible to improve voicemail transcriptions so there are far fewer errors. The new and improved system is available right now, and Google is keen for you to try it out.
By working with voicemails offered up by users, Google has been able to use real world data to bring dramatic improvements to speech-to-text conversion. The development is far from over, and the company says that work continues to make things even better. Google software engineer Zander Danko says:
We asked users if they would kindly share some of their voicemails for research and system improvements. Thanks to those who participated, we are happy to announce an improved voicemail system in Google Voice and Project Fi that delivers more accurate transcriptions. Using a (deep breath) long short-term memory deep recurrent neural network (whew!), we cut our transcription errors by 49%.
If you're yet to try out Google Voice, you can sign up for an account here. For those of you already signed up, have you noticed an improvement?
Photo credit: filip robert / Shutterstock
-

Why should you upgrade to Windows 10? 'Multi-doing' and getting things done
Publié: juillet 23, 2015, 11:42pm CEST par Mark Wilson
This time next week many of us will have upgraded to Windows 10. Until that day, Microsoft continues to publish videos pushing the benefits that the latest incarnation has to offer. This time around we are treated to a guide to 'multi-doing'.
Microsoft explains that this is "all about removing the obstacles between you and 'Done'", and the video is essentially a showcase of all of the tools that help with productivity. From Snap Assist to virtual desktop, Microsoft uses its latest video to show just what Windows 10 can do for you.
The video continues in the vein of its predecessors; bouncy dance music accompanies on screen text urging you to "do (insert-not-particularly-computery-word) things". For anyone who hasn’t been following the preview builds, it serves as a great introduction to what has changed from previous versions.
Improved Snap Assist makes it easier to work with multiple apps and windows, while multiple desktops are on hand to help keep different tasks separate. There's also the Action Center, task view, and more.
Check out the video and see if you agree with what Microsoft has to say about the benefits of Windows 10:
-

HORNET is an encrypted, anonymous web browsing system that destroys Tor's performance
Publié: juillet 23, 2015, 11:10pm CEST par Mark Wilson

With the current concerns about surveillance and privacy, more and more people are turning to anonymizing tools. The existence of unknown numbers of spying tools means that increasing numbers of people are turning to the likes of Tor to keep their online activities private.
But encryption systems such as those used by The Onion Relay have a horrible tendency to slow things down. A new encryption system called HORNET could be a solution. Its creators say that data transfer speeds of up to 93GBps are possible, with much of the acceleration coming from a reduction in the number of hops data has to make around the network.
It might be some time before HORNET is rolled out on any sort of large scale, but things are already looking promising. The academics behind the technology (which is short for High-speed Onion Routing at the Network Layer) published a paper this week outlining the advantages of their system which they say continues to offer robust protection against surveillance. Unlike Tor, HORNET has great potential for scaling up without suffering from the slowdown that blights its better-known counterpart.
The paper concludes by saying:
Our experiments show that small trade-offs in packet header size greatly benefit security, while retaining high performance.
That said, it is worth remembering that things are still in very early stages, and HORNET is yet to be peer-reviewed.
Writing on the Daily Dot, Patrick Howell O'Neill gives a neat summary of how the system works:
The basic architecture of Tor and HORNET are very similar: A group of global relay nodes are used to mix and encrypt Internet traffic in multiple layers—hence the 'onion routing' names— so that by the end of the process, no one is supposed to know where the traffic originated.
HORNET aims for more scalability and efficiency as it pushes the traffic through its network by having the intermediate relay nodes avoid keeping the per-session state (for instance, encryption keys and routing information) and pushing that task to the nodes on either end of the connection. Without that task, nodes can theoretically forward traffic more quickly to a larger number of clients.
Check out the paper in full on the Cornell University Library website.
Photo credit: irin-k / Shutterstock
-

Microsoft thanks you for using Bing Listens to guide its future
Publié: juillet 23, 2015, 7:27pm CEST par Mark Wilson

As shown by the Window Insider program and the development of Windows 10, Microsoft is now all ears. Under Satya Nadella, this is now a company that wants to listen to, and be guided by, its customers. Google may dominate the search arena, but Microsoft is keen for Bing to eat into its market share by giving people what they want.
This is precisely why the Bing Listens program was created, giving people an opportunity to make suggestions about changes and additions they'd like to see made. Today Microsoft not only thanks people for providing feedback, but also reveals some of the suggestions it has acted on. Have your idea been used?
The Bing team reveals that since its launch back in March there have been thousands of ideas submitted and more than 80 percent have been responded to. Among the requests that have been implemented are public transport details, shopping from Bing Images, and synchronization of My Places on Bing Maps with Cortana.
Bing Listens has been updated so you can now see the top three ideas that have been suggested and voted for, and there are plans to make it easier for people to keep track of the suggestions they put forward. The team says:
In the first few months alone, we’ve seen more than a thousand ideas ranging from new ways to earn rewards to adding a custom filter for news, to enabling users to contribute feedback on translation results, and even searching medical related issues.
More than 1 million visitors have been to Bing Listens, with thousands contributing, voting or commenting on the 1500-plus ideas that have been submitted since the launch. The suggestions have been fantastic.
If you want to shape the future of Bing -- or you just fancy seeing the ideas that others have come up with -- take a look at Bing Listens.
Photo credit: Business plus / Shutterstock
-

Microsoft takes steps to tackle revenge porn
Publié: juillet 22, 2015, 11:23pm CEST par Mark Wilson

Revenge porn has become quite a problem online, and Microsoft has now made it easier than ever to report cases. Today the company says that it will happily remove links to revenge porn photos and videos from Bing search results, and has set up a dedicated form to make it easier to get in touch.
Like Google's Right to Be Forgotten, there is little that can be done to remove the offending content from the internet, but Microsoft's action should make it easier to prevent the spread of damaging content. The removal process goes further than just obfuscating links in research results as the company does what it can to help stem the flow of privacy-violating photos and videos.
As well as removing Bing search results globally, Microsoft says that it will also block access to content shared through OneDrive and Xbox Live. The removal service starts off in English for the time being, but there are plans to extend it into other languages.
Writing about the new revenge porn reporting form, Microsoft's Chief Online Safety Officer Jacqueline Beauchere says:
Microsoft remains committed to continuing to work with leaders and experts worldwide on this evolving subject, and we expect to learn a great deal as the process moves forward. In the meantime, our hope is that by helping to address requests and to remove these extremely personal photos and videos from our services, we can better support victims as they work to re-claim their privacy, and help to push just a little further in the fight against this despicable practice.
If you want to report any content you have found, you can do so using the Revenge Porn form.
Photo credit: Rob Hyrons / Shutterstock
-

Microsoft wants you to get your game on in Windows 10
Publié: juillet 22, 2015, 10:43pm CEST par Mark Wilson
Over the last few days, Microsoft has released a series of videos highlighting the latest and greatest features of Windows 10. The latest instalment in the series shows off the gaming capabilities of the operating system. There's a strong focus on Windows 10's integration with Xbox, but there's plenty for PC gamers and those with a more casual interest in gaming.
We've already taken a look at Microsoft's screen recording tool and how it can be used to grab on-screen footage. In its most recent video Microsoft shows how it can be used to record gaming brilliance ready to share with others -- but there's more.
For anyone with an Xbox One and a computer or tablet running Windows 10, game streaming is now a possibility. The new Xbox app brings the full gaming experience directly to the desktop and helps to provide a familiar environment as you move from console to computer and back. As Microsoft says, "whether you’re on your Windows 10 PC or your Xbox One, you’ll always have your gaming life at your fingertips".
For fans of desktop gaming, DirectX 12 is on hand to power the likes of Fable Legends. With the introduction of Xbox Live for PC users, the selection of opponents to play against just got a whole lot larger.
Check out the video to see what Windows 10 can do to improve your gaming experience:
-

Office gains Google Drive and IFTTT support
Publié: juillet 22, 2015, 9:52pm CEST par Mark Wilson
Anyone reliant on Office for their day to day computing just gained two new weapons in their arsenal. Google has created a plugin that adds built in support for Google Drive, and automation fans will be pleased to learn that Office 365 channels have now gone live on IFTTT. But this is not the only new cloud-based tool.
It has long been possible to use Google Drive in conjunction with Office, but it has meant having to use the middleman of a local folder synchronized using the Google Drive app. The new plugin lets you cut straight to the chase and save directly to Google Drive -- handy if you don’t want or need a local copy.
The Google Drive plugin for Office is something that users have been asking for for some time. With the launch, Google says that "people using Office for Windows can now open their Word, Excel and PowerPoint documents stored in Drive, then save any changes back to Drive once they’re done". Grab yourself a copy of the plugin from Google.
Using a series of new Office 365 channels on IFTTT, it is now possible to trigger automatic online events based on things that happen within Office. There are quite a number of options available to users, including a range of readymade recipes. These can be used to do everything from create OneNote entries whenever a new contract is added, backup files automatically to OneDrive, and send notifications to Slack when emails matching certain criteria are received.
-

Kids can now create and customize their own prosthetic arm from Lego
Publié: juillet 22, 2015, 9:27pm CEST par Mark Wilson

Lego is something that is most often used to build models. The versatile little bricks have been keeping children (and adults) entertained for generations, and there have also been plenty of instances of the toy being used for more than just playing. Now, thanks to the work of designer Carlos Arturo Torres, children with a missing limb could build their own from Lego.
It's an idea that merges the worlds of play and entertainment with practicality. The Colombian designer has come up with a modular system which can be used by inventive kids to create elaborate arms that are as functional, as advanced, or as silly as they want.
IKO is a system that helps children to overcome a disability in a fun and creative way. The project is a collaboration between physical rehab center Cirec and the Future Lab section of Lego. Fully compatible with the Lego Mindstorms range, the arm can be programmed and personalized and controlled just like standard prosthetics.
Carlos entered the project into the Core77 Design Awards, and bagged himself a prize in the Open Design category. Going far beyond just fingers and opposable thumbs, IKO can be used to build the robotic arm of kids' dreams, complete with whatever adornments they are able to come up with. Talking about his work, Carlos says:
Using the LEGO system was part of this solution, not just because of its creative content, but most of it its social feature; this is a toy that gathers people around with a single goal: the pride of creation, but in this scenario I found that it transcends to a higher level.
Check out the video and see what you think:
Photo credit: Carlos Arturo Torres
-

You can no longer review apps if you're an iOS 9 beta tester
Publié: juillet 22, 2015, 1:05pm CEST par Mark Wilson

Apple is letting developers and enthusiasts test out beta versions of iOS 9 ahead of launch. While the company is keen on getting feedback for the next version of its mobile operating system (just as Microsoft is with the preview builds of Windows 10), there have been concerns that problems with apps during beta testing has led to a swathe of negative reviews in the App Store.
Developers have complained that problems with iOS betas can cause problems with their apps, rather than their apps being inherently problematic. To address the issue, Apple is placing a ban on App Store reviews from iOS 9 beta testers.
It's a move that has been widely welcomed. Considering the relatively small number of people involved beta testing, and it seems unfair that their reviews could influence the purchasing decision of others using more stable software. Many had called upon reviewers to be sensible in their approach, urging them to take into account the fact that they are running apps on an unfinished operating system and may therefore experience more problems than usual.
But a huge number of low scoring reviews for previously successful apps led to complaints from developers and action from Apple. The problem of negative reviews is something that crops up with every iOS beta, but was made worse this year as Apple opened up the beta program to a wider audience.
Try to post a review from iOS 9 at the moment, and you'll be greeted by the following message:
https://twitter.com/orbuch/status/623724857570758656
It seems that Apple is listening.
-

Windows 10 in action: Cortana and Microsoft Edge
Publié: juillet 22, 2015, 11:49am CEST par Mark Wilson

It's final countdown! Baba ba baaa, baba baba baaaaa! (</Europe mode>) The July 29 launch of Windows 10 draws ever closer, and Microsoft continues to release videos highlighting what's new in a bid to entice people in. The latest installments cover Cortana and Microsoft Edge.
We've already seen a couple of videos from the Microsoft stables, firstly pointing out that the operating system is familiar, and then indicating that it is a new breed for a new generation. Now the company is choosing to focus on what is new -- Windows 10's digital assistant, and the new web browser. Are these enough to convince you?
With Cortana, there is a focus on getting things done -- both personal and business. Perhaps more importantly for those who are yet to experience the tool, we are treated to a series of demonstrations of Cortana in action. The video serves as a handy guide for the completely uninitiated, but also a useful reminder for those more familiar with it just what is possible.
Check out Microsoft's Cortana video:
Much has been said about Microsoft Edge, and many people will be worried about the loss of Internet Explorer. In this video we're given a rundown of everything the new browser has to offer -- writing on web pages, sharing, building up a reading list, distraction-free browsing, and so on.
Take a look at the Microsoft Edge video:
-

New Facebook video controls let you be sexist, ageist or secretive
Publié: juillet 22, 2015, 10:45am CEST par Mark Wilson

Videos on Facebook are big business. As well as drugged up post-dentist footage, there is also huge advertising potential. Now Facebook has announced a new set of options for video publishers -- including the ability to limit who is able to see videos based on their age and gender.
A social network might not be the first place you would think of to try to keep something private, but a new 'secret video' option makes it possible to restrict access to those people who have a direct link. Other new options include the ability to prevent embedding on other sites, but it is the audience restriction settings that are particularly interesting.
For a long time Facebook has been about reaching out to as many people as possible in one hit -- particularly in the case of pages, which are likely to be used for the promotion of businesses and services. But now the social giant provides tools to limit one's audience. It's fairly easy to understand the reasons for implementing age restrictions on video (although there is obviously scope for abuse), but the reasons for gender-based restrictions are less clear.
While Facebook has implemented a real name policy, it is yet to extend this to 'real gender' -- it is near impossible to know if those presenting themselves as male or female actually are.
Introducing the new options, Facebook says that page owners can now:
- Restrict the audience of a video by age and gender (in addition to location and language, which are already available).
- Set an expiration date for a video and retain its insights, even after the video has been removed.
- Publish video directly to the Videos tab for your Page, without distributing to News Feed or Timeline.
- Allow or prohibit video embeds on third-party sites.
Other new tools include an updated uploader, the ability to use custom thumbnails, and video categorization through the use of labels.
Photo credit: R.L.Hausdorf / Shutterstock
-

Does Windows 10 attract or repel you?
Publié: juillet 22, 2015, 2:27am CEST par Mark Wilson

In some ways it only seems like five minutes since the appearance of Windows 8. But at the same time, it feels as though Windows 10 has been a long time coming. While Microsoft has been talking about the upgrade for quite some time, it has only been in recent months that there has been any sense of progress having been made.
Early builds of Windows 10 were a little lacklustre, and even later builds failed to inspire the levels of excitement that Microsoft would undoubtedly want them to do. Any new version of Windows is met with a combination of trepidation, eagerness, and disappointment, and Windows 10 is no different. It's very easy to say that it is impossible to please everyone, but it's certainly fair to say that Windows 10 has proved particularly divisive. Now, as we edge ever closer to launch, the time comes to ask -- what has Microsoft done right, and what is still wrong?
I'm not going to stray into review territory just yet, but when canvassing opinion it makes sense to touch on a few of the operating system's key areas. The development of Windows 10 has seen Microsoft looking for, receiving, and responding to feedback in an unprecedented way -- but has it paid off? Are the changes that have been implemented changes for the better, or has the hive mind made Windows take a turn for the worse?
So what is there to embrace in Windows 10? In many regards, little has changed, but at the same time. The Windows Insider program -- as well as the various leaks that have surfaced -- have given us a great opportunity to familiarize ourselves with the operating system ahead of launch, but it is easy to forget that the vast majority of people will be coming to Windows 10 blind. There have been a lot of testers trying things out, but there are millions more who have no experience at all. July 29 will be the start of a whole new experience.
The Live Tiles that have been ported from Windows Phone still feel a little strange. They appear to have been designed for people suffering from an attention deficit disorder. The Start menu is something that people have been begging for ever since it was culled and replaced with the Start screen. Now it's back and there is a very real danger that Microsoft still has not got it quite right. On the plus side there is the choice between using the Start menu and the Start screen, but the menu is likely to disappoint more than it pleases.
For purists, the Windows 10 Start menu will be an overly large and fussy affair, and the presence of Live Tiles is something that grates. The Start menu has always been somewhere users visit to access apps, files, and folders. Now it is home to information as well. This sound great in theory, but in practice it is far from ideal. Users of the Start menu become accustomed to firing it up, putting it to use as a launcher... and that's it. Now images scroll by, headlines flash up, and all manner of other information is displayed -- if you're willing to stick around and wait for it to appear that is. Spend a little time with Windows 10 and the feeling that the right hand side of the Start menu in general, and Live tiles in particular, is a waste of space and time. Why would you want to spend time lingering in a part of Windows that is historically only a brief stop-over? Your mileage may vary, of course, but the revamped Start menu feels like something of a missed opportunity. It could have been so much more.
One of the biggest features that Microsoft has been shouting about is Edge. The replacement of Internet Explorer is long-overdue, but it's not clear that Microsoft Edge is anywhere near ready. With so few new features in Windows 10, one can't help but feel that it would have made sense to wait a little longer until the browser is fully complete. Perhaps the greatest selling point for Edge is support for add-ons, yet this option will not be available at launch. How many people who rely on add-ons are going to be willing to give Edge another chance further down the line? If you're already invested in Chrome or Firefox, there really is very little reason to move away. It possible that even those moving from Internet Explorer to Microsoft Edge will be tempted to investigate the competition now that concentration has been focused on add-ons and awareness of the possibilities raised.
What else is there? We have a change to the way modern apps run. We have Cortana. There's a virtual desktop manager. There is the much sought after notification system. Is it enough? Has Microsoft listened to feedback enough... or too much?
Over to you.
What are your highs and lows in Windows 10?
-

Check your computer for Hacking Team malware with these essential security tools
Publié: juillet 21, 2015, 7:20pm CEST par Mark Wilson

When Hacking Team was hacked, a massive cache of data was leaked, including the source code for government-strength surveillance tools. Hacking Team warned that the code could have fallen into terrorist hands, but then backtracked slightly to say that any code that had been obtained was incomplete and out of date.
We already know that the company managed to sneak malicious apps into Google Play, and you might be concerned that some of its malware has made its way onto your computer. To help put minds at rest -- hopefully -- Rook Software has released a tool to seek out Hacking Tool malware.
Called Milano, the software is available to download free of charge from the Rook Software website. The company says that its detection utility "contains hashes for 40 Windows executable and library files [which] have been analyzed by Rook Security, and have been deemed to have the highest likelihood of malicious use".
As noted by Slashdot, this is something that is only of use to Windows users. To help Mac owners, Facebook has come to the rescue. It’s open-sourced osquery can be used to scan for backdoors from a variety of sources, and has been updated to include Hacking Team vulnerabilities. Find out more at Facebook’s engineering pages.
-

Huh? Twitter just removed the option to use a background image
Publié: juillet 21, 2015, 10:24am CEST par Mark Wilson
Part of using any social website is customizing the appearance of your account to your liking; now Twitter has bucked the trend and removed that option. As noted by TechCrunch, Twitter users are no longer able to adorn their profile with a custom background image.
It seems like something of a strange move, made all the more odd by the fact that Twitter has not made an announcement about the change. Firing up Twitter, users around the world will today find that their accounts look rather different. It's bright, white backgrounds all the way. So what on earth is going on?
Twitter has not made it remotely clear what the reason behind the decision is, but it is causing a lot of upset today. Speculation is rife that Twitter did not like the fact that colorful, busy, distracting background images would take people's eyes away from advertisements, but it's not clear if this is a contributing factor. Twitter has updated its help pages to indicate that background images will no longer be visible everywhere:
You can customize your design theme so that users who click to view your Tweet detail pages will see it. Other than your theme color, your design theme will not be visible on your profile or Home timeline.
It seems that the change is still taking time to roll out. As noted by TechCrunch, if you change your background image it will initially appear everywhere you would expect it to, but will gradually become limited to key pages.
In a statement Twitter said:
We’re removing background images from the home and notifications timelines on web for all users. Now, background images are only available where logged-in users will see them publicly (Tweet pages, list pages and collections pages). You can find help center content about customizing your design and where it’s visible on Twitter here.
Have you noticed the change in your account?
Photo credit: Deniseus / Shutterstock
-

Twitter launches new Safety Center to educate and protect users
Publié: juillet 21, 2015, 12:22am CEST par Mark Wilson

Over the years Twitter has taken various steps to help users avoid spam, trolls, abuse, and other online problems. Today the social site takes the wraps off the Twitter Safety Center. This is home to advice about staying safe on Twitter and online in general, as well as including links to the various tools that Twitter has to offer.
The Safety Center is divided into three sections -- Tools, Policies, and Enforcement -- and the idea is that users are given the information they need to keep themselves safe. Each of the sections includes advice and guides about improving security, maintaining privacy, and avoiding unwanted content.
As well as help and support for people wanting to protect themselves on Twitter, there are also sections for parents and teachers who will be able to help keep younger users safe. But the Safety Center is not just about staying safe, it's also about making sure you stick to Twitter's rules. To this end, the center includes guides to key policies so you know what you can and can't do -- and what to do if you spot any violations.
Twitter says:
The Safety Center is a resource for anyone to learn about online safety, on Twitter and beyond. This resource is a result of our work with online safety experts who continuously help us to promote good digital citizenship. We’re excited to make this knowledge easily accessible to you via this new site. The Safety Center is organized around Twitter’s tools and policies to address your safety, with sections created especially for teens, parents and educators.
These resources should help you quickly understand how to manage your experience on Twitter and also understand how the community and Twitter take action together when our policies are violated.
Check out the Safety Center and see what it has to offer you.
-

Google+ Photos dies August 1, replaced by Google Photos
Publié: juillet 20, 2015, 11:34pm CEST par Mark Wilson

Wielding its axe above its head, Google today prepares to sever another limb from Google+. It's only a couple of months since Google Photos launched, and we knew back then that the writing was on the wall for the Photos component of Google+. Now we know that the axe drops on August 1.
From this date Google+ Photos will be no more. The service will shut down first for Android users, followed quickly by the web and iOS versions. If you want to continue to take advantage of cloud photo storage, editing, and sharing, you'll need to make the switch to Google Photos.
Google wants to assure users that the process will be as smooth and painless as possible. Google+ Photos may stop working, but any images that have been uploaded will simply be accessible from [photos.google.com] instead. It's a slightly different tool, but there should be no down time.
Google set the countdown timer ticking with an announcement -- predictably enough -- on Google+:
If you’re still using Google+ Photos, now is a great time to make the switch. You may have seen a prompt in Google+ Photos on Android with a link to download the new Google Photos. Don’t worry, all your photos and videos will still be saved and available after you switch to the new, stand-alone Google Photos app. With the new app you’ll still be able to backup, edit, and share your photos and videos, with unlimited storage, automatic organization, and more.
You can find out more about Google Photos on Google's support pages.
Photo credit: 26kot / Shutterstock
-

Microsoft releases emergency security patch for all Windows versions
Publié: juillet 20, 2015, 9:12pm CEST par Mark Wilson

Microsoft has released an off-schedule patch for all currently supported versions of Windows. A serious vulnerability has been discovered in a font driver that could be exploited by a hacker to remotely execute code on a compromised machine.
The problem affects Vista, Windows 7, Windows 8, Windows 8.1, Windows RT, Windows RT 8.1, Windows Server 2008, and Windows Server 2012. Windows 10 is not at risk. Microsoft describes the issue as 'critical' and has pushed an emergency patch to Windows Update.
If you have Automatic Update enabled, things will take care of themselves, but otherwise you will have to manually instigate a download -- or you can download the relevant patch by hand. An advisory notice in the Security TechCenter warns that "the vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts".
The security hole is patched by updating the way Windows Adobe Type Manager Library handles OpenType fonts. Interestingly, Microsoft does not list any mitigating factors for this vulnerability, so the importance of grabbing the update really cannot be overstated.
The vulnerability was discovered by Google Project Zero and FireEye Inc earlier in the month, and Microsoft has acted fairly quickly to address the issue.
Photo Credit: fotoscool/Shutterstock
-

Microsoft's culturally-aware Cortana spreads around the globe ahead of Windows 10 launch
Publié: juillet 20, 2015, 4:39pm CEST par Mark Wilson

Microsoft really is going all-out with its Windows 10 campaigning in the week and a half before launch. The latest carrot to dangle tantalizingly in front of would-be upgraders is the news that Cortana, Microsoft's digital assistant, is spreading into new markets. When Windows 10 launches on July 29, Cortana will be available in the US, UK, China, France, Italy, Germany, and Spain.
Today, Microsoft says that the tool will be made available to Windows Insiders in Japan, Australia, Canada (English), and India in the coming months. Cortana will continue to spread around the world launching in Brazil, Mexico, and Canada (French) by the end of the year. If you were wondering, there's a very good reason that Cortana is not available everywhere from day one.
Microsoft is taking care to ensure that the tool is properly tailored to work in different regions. Feedback suggests that Windows users in different countries are looking for different things from their digital assistant. In the UK, Cortana is slightly self-deprecating, while in China she has been made to sound as though she is smiling as she talks.
The announcement about the expansion was made, of course, by Gabe Aul on Twitter:
Cortana coming to new markets - starting with #WindowsInsiders. [t.co]
— Gabriel Aul (@GabeAul) July 20, 2015
In a blog post, Microsoft reveals the work that is undertaken to ensure that Cortana is perfect for each country:
It is truly a fascinating process to see Cortana evolve for each market. We approach each market rollout with extensive focus groups that answer, “What’s important in a personal assistant in this market?” Based on these research results, we then assemble a local team of creative writers, editors, programmers and voice talent to build a relevant, tailored experience. Voice talent is carefully considered for each market.
Check out Microsoft's video in which the Cortana team talk about how the assistant has been tailored for different countries:
-

Frustration mounts as Microsoft fails to fix Skype's spoof message problem
Publié: juillet 20, 2015, 12:58pm CEST par Mark Wilson

Over on the Skype community pages there are lots of disgruntled Skype users. For a number of weeks now, many users have been plagued with spoof messages from people on their contact list, telling them to visit a Russian website. Others complain that their contacts say their own account has sent out a similar message. Despite the problem having been reported nearly a month ago, Microsoft has still to address the issue.
For now, all the company has to say is "change your password", insisting that a team is working on the issue. The spoofed message includes a shortened URL, so those clicking it have no idea where it leads until it is too late. Rather than offering a full solution, all Microsoft has to suggest is to change Skype passwords -- it seems the company is too busy focusing on Windows 10 at the moment.
Right now, it's not entirely clear what the problem is. Microsoft remains fairly tight-lipped about things but some Skype users have noticed that their account history shows a number of failed login attempts. Perhaps more worryingly are reports that some users say that their account has been sending out spoof messages to their contacts when they are not even logged into their account.
A pinned response from Microsoft reads:
Our engineers are still looking into this.
Meanwhile we'd recommend everyone to change their account passwords for all your Skype related accounts, i.e. also update your Microsoft account password if you linked that to your Skype account. Here's how: https://support.skype.com/en/faq/FA95/how-do-i-change-my-password.
So far, this is the only real advice that Microsoft has given, and it has left a lot of Skype users feeling frustrated. People who use Skype for business are especially concerned not only because of the security implications, but also because it reflects badly on them if their accounts are used to send out these messages to customers and clients.
-

Logitech Collaboration Program makes it easier for remote colleagues to work together
Publié: juillet 20, 2015, 11:01am CEST par Mark Wilson

Today Logitech launches the Logitech Collaboration Program (LCP) with the aim of simplifying collaboration for its customers. With partners including BroadSoft, Lifesize Communications, Vidyo, and Zoom, LCP helps to bring about what Logitech calls the 'anywhere workplace'.
The program features a combination of hardware and software solutions to facilitate remote collaborative work. It allows for the creation of virtual meeting rooms, mobile communication, and videoconferencing as part of a complete collaborative ecosystem.
Products such as the Logitech ConferenceCam Connect are supported by the program, providing a more immersive collaborative experience thanks to remote pan, tilt, and zoom. General manager of Logitech’s collaboration group, Jason Moss, explains that LCP "will focus on an exceptional user experience by enhancing business communications with end-to-end solutions that simply work".
Writing about the program in a blog post, Logitech says:
The goal of seamlessly integrating our offerings is to provide customers with solutions that are easy to deploy and a breeze to use. By working closely together, we aim to deliver advanced product functionality and end-to-end solutions rather than individual products. This way, customers of Logitech and LCP members can enjoy a comprehensive experience.
From huddle rooms to conference rooms to anywhere rooms, we’re working together to make tools that keep people focused and productive anytime, anywhere with plug-and-play solutions that work even better than they look.
More details are available on the Logitech Collaboration Program website.
-

Microsoft goes on the charm offensive with Windows 10 ad campaign
Publié: juillet 20, 2015, 8:18am CEST par Mark Wilson

The countdown to launch really has begun. Microsoft is now pushing Windows 10 with earnest, launching an ad campaign that heralds the arrival of a 'new generation' of Windows. For many, the launch of the latest version of the operating system is something of a rebirth for Microsoft, and this is an idea that is played upon in a child-heavy advert.
This is the launch of Microsoft's global ad campaign which kicks off in the US now, and spreads around the world on July 29. The first installment is heavy on cuteness and works with the idea that Windows 10 is simple enough for a child to use, and will grow up with this generation.
This first ad is only a minute long, and Windows 10 doesn't even make an appearance until the fourth quarter. But when it shows up, we are treated to quick demonstrations of Cortana in action, leaving notes on websites in Microsoft Edge, and... well, that's it actually. There'll be plenty more to come, no doubt.
Writing about the video in a blog post, the Windows team says:
To bring the campaign to life, we see young children from around the world in their natural settings in Morocco, Thailand, Iceland, England and the U.S. Supporting our mission of empowering every person and organization to achieve more, the ads show how technology should be more natural, human and intuitive, and adapt to people’s needs. The key notion – Windows 10 delivers a more human way to do. Enjoy!
Enough waffling... watch the ad and see what you think.
-

Microsoft cites familiarity as a reason to upgrade to Windows 10
Publié: juillet 19, 2015, 7:44pm CEST par Mark Wilson

With just ten days to go to the launch of Windows 10, Microsoft has released a video highlighting reasons to upgrade. Entitled '10 Reasons to Upgrade to Windows 10: IT’S FAMILIAR' (Microsoft's caps), the video is a mere 46 seconds long.
Rather than waxing lyrical about super-exciting features, the video focuses on the fact that anyone moving from Windows 7 or Windows 8.1 is going to feel at home. 'Familiar' is a word that crops up again and again. Microsoft wants you to feel that Windows 10 is a comfortable old pair of slippers ready for you to slip into.
What does Microsoft choose to highlight? The return of the Start menu. The addition of Live Tiles. The fact that Windows 10 is free. Throughout the course of the 46 seconds, you start to get the impression that Microsoft was struggling for content slightly. The video's description neither gives much away, nor explodes with enthusiasm:
Discover why Windows 10 is the best combination of the Windows you already know, plus lots of great improvements you’ll love having. And all of your stuff comes with you, so you’ll be ready to do great things from the get-go.
If you're still sitting on the fence, is the video below enough to push you one way or the other?
-

Windows 10 has a secret screen recording tool -- here's how to use it
Publié: juillet 19, 2015, 6:28pm CEST par Mark Wilson

Windows 10 has not even been released yet, but that's a perfect reason to start unearthing a few secrets. Over the coming weeks and months there will undoubtedly be an endless stream of tips, tricks, and tweaks to try out, but how's this for starters? Windows 10 has a secret screen recording tool that can be used to capture on-screen activity as a video file.
Taking a static screenshot is very simple. You can either hit the Print Screen key, use the Snipping Tool, or turn to one of the countless screen capture tools out there -- many of which are free. When it comes to capturing video, however, it's something of a different story. Before you splash out on a dedicated tool such as Camtasia, you might want to try out Windows 10's hidden tool. It's designed for gamers really, but anyone can use it.
The Game bar is a toolbar which Microsoft meant for gamers to use to capture screenshots of their high scores, as well as video footage of their gaming skills. Despite the name, it is not limited to use within games, and you would be forgiven for having missed it as you browsed through the latest version of the operating system -- you're not going to stumble across it by accident.
Hit the Windows key and G, and a popup will appear asking if you would like to open Game bar -- there are no Yes and No buttons, but check the 'Yes, this is a game' box (you will have to do this the first time you access the screen recorder in any application).

Things are pretty self-explanatory here -- just hit the standard record button to start capturing footage. Hit the button again to stop recording, or you can use the Windows key + Alt + R keyboard shortcut. The Settings button can be used to place a limit on the length of videos that can be recorded -- this helps you to avoid filling up your hard drive if you forget to stop a recording. Videos are saved in MP4 format in the Videos\Captures folder.
You may or may not have realized that this tool is part of Windows 10's Xbox app, and this is where you need to head to adjust more settings. Go to the Game DVR section (the fifth icon from the bottom) and you can access the videos you've recorded, as well as use a basic trim tool to get rid of unwanted sections from the beginning and end.
Give it a try and see what you think!
-

Hacking Team leak shows how to sneak malicious apps into Google Play
Publié: juillet 19, 2015, 9:53am CEST par Mark Wilson
Italian security and surveillance company Hacking Team was most famed for supplying monitoring tools to governments around the world, but a recent security breach revealed the inner workings of the outfit. Sifting through the leaked data revealed not only spying tools and Flash vulnerabilities, but also Android apps with backdoors.
Security experts from Trend Micro found that spyware from Hacking Team was released to Google Play, bypassing checks that are usually performed. BeNews was a fake news apps -- now removed from the store -- that could be used to download remote access software to Android devices running anything from Froyo to KitKat.
Trend Micro reports that the app was designed with the express intention of circumventing Google's malware filtering and checking. The app was even downloaded a few times before removal on July 7. The malicious app exploits a vulnerability to escalate local privileges to install malware and remote access tools. The way the apps makes it into Google Play is rather sneaky.
Apps are vetted on, amongst other things, the permissions they need in order to run. To ensure easy passage into the store, BeNews requested just three permissions. Once installed, the app then used what Trend Micro calls 'dynamic loading technology' to download additional, malicious code, transforming it into a different beast altogether.
The cache of leaked data from Hacking Team not only includes the source code required to build other apps, but also handy how-to guide. While it seems that BeNews was not installed by many people -- perhaps as few as 50 -- the worry is that the source code is now out in the open so it may not be long until copycat apps appear. Hacking Team itself has warned that its tools have ended up in the hands of terrorists.
Photo credit: Maksim Kabakou / Shutterstock
-

No SD card app installations in Windows 10... for now
Publié: juillet 18, 2015, 8:32pm CEST par Mark Wilson

Running out of space and having to shift files and apps to a memory card is a familiar scenario for smartphone users. It's also something that affects tablets, and with the imminent release of Windows 10 talk has turned to how Microsoft's latest operating system with handle things.
The company had previously said that, just like Windows Phone, it will be possible to install apps to an SD card on tablets which have limited space. That said, this is a feature that will be missing from Windows 10 when it launches in eleven days. Microsoft has taken a last minute decision to delay the feature as it's not quite finished.
There has been no big announcement made about the postponement, but Microsoft did respond to questions about the feature from a Windows Insider in its forums. A Windows 10 tester, Olivier Bordes, noticed that the option to change where apps install to is unavailable in French versions of build 10166 and 10240.
In reply, Microsoft said:
We have actually made the decision to postpone the apps on SD functionality to a later release. While I know this feature excited many of us, we didn't feel like it was ready for prime time. Our goal is to delight users with everything that we build, and we truly feel that that is what will happen once we have fully built our vision for this feature.
It's not clear how long tablet users will have to wait to be able to take full advantage of their memory cards, but it's not going to be until some time in August at the very earliest. In all likelihood, the update will be several weeks down the line.
Photo credit: stocksolutions / Shutterstock
-

Robots are becoming self-aware
Publié: juillet 18, 2015, 1:00pm CEST par Mark Wilson

Smartphones might be getting smarter, and the Internet of Things becoming increasingly important, but a large part of the technological future is owned by robots. Human-replacing robots have existed in factories and manufacturing processes for years, but the dream has long been to create a humanoid robot that is 'intelligent' enough to act like a human.
Three robots have been put to the test at the Rensselaer Polytechnic Institute in New York, and scientists showed that one was able to demonstrate self-awareness. We're not quite at the stage of a robot uprising, but it is an important step on the road to improving reasoning and problem-solving in future robots.
The experiment took three Nao robots, and programmed two of them to believe they'd been given a pill that prevented them from speaking. Importantly, none was aware which had been given the 'pill' and which had not. Researchers then asked the robots which pair had taken the pill, and they each tried to respond with "I don't know". Those who were unable to talk remained silent, but the third repeated the phrase. And this is when the magic happened.
Upon hearing its own voice, the robot was quickly able to determine that it had not been silenced by a pill and uttered the words:
Sorry, I know now. I was able to prove that I was not given a dumbing pill.
So not only was the robot able to respond to human input, it also showed that it could recognize itself, and react accordingly.
The full results of the research are due to be presented at the at RO-MAN robotic conference in Japan from August 31 to September 4. Check out the robots in action in the video below:
-

Apple Music won’t work with your iPod Nano or iPod Shuffle -- not even offline
Publié: juillet 18, 2015, 10:15am CEST par Mark Wilson

Apple has made a few big announcements lately, not least of which is the launch of its streaming service, Apple Music. Even more recently came an update to the iPod line including options at the cheaper end of the scale -- the iPod Nano and iPod Shuffle. But if you were thinking about offsetting the cost of an Apple Music subscription with a low-cost iPod, you might want to think again.
Of course the main stumbling block to lack of Apple Music support is the absence of Wi-Fi on the two devices which knocks the idea of streaming on the head. But even if you have an iOS device with an Apple Music subscription, you'll not be able to take advantage of the offline listening option on your Shuffle or Nano. What gives?
Again, the problem is the cheap iPods' lack of Wi-Fi. In order to use Apple Music's offline listening feature, Apple needs to be able to check that an active subscription is in place. Without the ability to get online, this simply cannot be done on a Shuffle or Nano, so offline listen is off the cards.
As noted by 9to5Mac, users attempting to sync offline Apple Music tracks to an iPod Nano or iPod Shuffle are greeted by an error message:
Apple Music songs cannot be copied to an iPod.
It's something that could be addressed in a future update -- Shuffle and Nano owners could be forced to manually 'check in' to their subscription to validate their offline tracks -- but this is not something Apple has announced. DRM's a bitch, eh?
-

Download the latest update to Windows 10 Build 10240
Publié: juillet 18, 2015, 9:20am CEST par Mark Wilson

If you've installed Windows 10 Build 10240, it's possible that you're running near-RTM code. It has been suggested that it is in fact final code, but a new update from Microsoft proves otherwise.
This is not a new build so soon after the other, but a regular, run-of-the-mill update. That’s not to say it's not important -- it is a bug-fixing update which addresses some last minute issues. KB3074665 is listed as a security update, and Microsoft's Gab Aul also describes it as "a package of fixes based on reported issues in 10240".
As we know, Microsoft is forcing updates on Windows 10 users, but you don't have to wait for it to be pushed to your computer. Forced updates can take a little while to propagate, so you can fire up Windows Update in Settings to perform a manual check if you like. The latest patch was announced by Aul on Twitter:
We're releasing an update package on WU for PC build 10240 today. It will install automatically or you can check for updates to grab it.
— Gabriel Aul (@GabeAul) July 17, 2015
A lot of Windows 10 users reported issues with the update failing to complete installation, or taking a very long time to finish installing, but this could be a case of teething problems. The update -- which is "cumulative and includes the last package's security fix" -- is one of the last to be released before the big launch in just a few days' time.
-

Microsoft PhotoDNA helps websites weed out illegal child porn and abuse images
Publié: juillet 17, 2015, 11:33pm CEST par Mark Wilson

Microsoft has released its PhotoDNA tool to help tackle the problem of child abuse images online. The cloud-based tool has been used by law enforcement agencies for some time, and now it is being made available to website owners free of charge.
The spread of child porn images and sexual abuse photos online is prolific, with an estimated 720,000 illegal images uploaded each day. Rather than relying on a team of human workers to track down and remove such photos, PhotoDNA automates the process helping to protect site visitors, protecting website owners from hosting illegal content, and helping in the fight against the exploitation of children.
Despite the large number of illegal images that are uploaded each day, it is still quite a task to hunt them down. Microsoft started work on PhotoDNA six years ago, teaming up with the National Center of Missing and Exploited Children (NCMEC) to help stem the flow of known abuse images. Over the years the technology has developed so it is possible to identify images even if they have been digitally altered or tampered with.
Using hash reference system, PhotoDNA is able to compare the attributes of any given image with those of illegal images to seek out matches. It's a technology that has a huge number of applications, including on social networks and instant messaging services. While some human intervention is still needed, advancement has been such that much of the process is entirely automated and hands-off.
Microsoft released a video introducing the PhotoDNA service:
Photo credit: Vucicevic Milos / Shutterstock
-

Copying CDs and DVDs just became illegal in the UK. Again.
Publié: juillet 17, 2015, 11:01pm CEST par Mark Wilson

The UK has had something of an on-off relationship with CD and DVD ripping. It was illegal, and then it was legalized. But things reverted back. Just last year, ripping was made legal once again, but a High Court ruling today overturned the legislation meaning that disc copiers will -- once again -- be breaking the law.
The government had introduced legislation that permitted people to made copies of audio and video discs they owned, provided it was for personal use. The latest ruling, however, kills the Copyright and Rights in Performances (Personal Copies for Private Use) Regulations 2014 because of a failure to implement a compensation scheme for artists and copyright holders.
The quashing of the regulations means that laws surrounding ripping have taken a step back in time yet again. It had been suggested that the legalization of ripping would have "zero or insignificant" impact on sales and income, therefore negating the need to a set up a compensation scheme. The Musicians’ Union, UK Music, and the British Academy of Songwriters, Composers and Authors disagreed and fought the ruling.
Passing judgement today, Mr Justice Green said:
It is clear that I should quash the Regulations. I make clear that this covers the entirety of the Regulations and all of the rights and obligations contained therein.
It is something that has been welcomed by the music industry, including CEO of UK Music, Jo Dipple:
Last month, the high court agreed with us that the government acted unlawfully when it introduced an exception to copyright for private copying without fair compensation. We therefore welcome the court’s decision today to quash the existing regulations. It is vitally important that fairness for songwriters, composers and performers is written into the law.
In reality, the ruling is largely tokenism. Casual home copying is virtually impossible to police, although largescale ripping factories are a different matter.
Photo credit: gcpics / Shutterstock
-

Apple Pay users could be fined if their battery runs out on the train
Publié: juillet 17, 2015, 10:15pm CEST par Mark Wilson

Apple Pay caused ripples of excitement when it was announced, and just the other day it found its way across the ocean to the UK. The contactless payment method transforms iPhones and Apple Watches into cardless way to pay for low-cost items with little more than a tap.
But if you plan to use Apple Pay to pay for travel by bus, tram, or train in London, it may not all be plain sailing. Using a phone or watch to make a payment is supposed to make life easier, but it could also result in a fine. Transport for London has issued a warning to travelers pointing out that if their battery dies, their journey could prove expensive.
Apple Pay is not unique in that -- obviously -- it can only be used when power is available. An iPhone or Apple Watch is needed, and a dead phone or timepiece is little use to anyone -- including ticket inspectors. Use your iOS device to start a journey and you'd better hope and pray (if that's your thing) that the battery holds out. If you reach your destination with a flat battery, you'll be unable to check out and could end up being charged the maximum possible fare for the route you have traveled. If an inspector is unable to check your device mid-journey, this could result in a fine.
Running out of juice is not the only problem that can arise; Transport for London lists other potential issues. People from overseas or anyone making a payments with a non-UK card may need to factor in an additional transaction fee. If you've linked an American Express card to your Apple Pay account, this cannot be used with Transport for London; make sure you have a backup plan, or you're going nowhere!
It's also worth noting that, unlike other methods of contactless payment, Apple Pay is not instant. Users need to select the payment card they would like to use and authenticate with a fingerprint -- all of which takes valuable seconds. If you receive a call in the middle of making a payment, authorization will be interrupted and you'll have to start again. With a line of people all paying with Apple Pay, a last-minute dash for the train could end in disappointment.
Photo credit: l i g h t p o e t / Shutterstock
-

Reddit kills 'unfettered free speech' with half-hearted censorship
Publié: juillet 17, 2015, 12:54am CEST par Mark Wilson

It's been a tumultuous time at Reddit recently. The self-styled (albeit slightly sarcastically) Front Page of the Internet raised the ire of some users several months ago when it started to impose stronger restrictions on the type of content that could be posted. It started with restrictions on certain types of explicit content, followed by the killing off of harassment, hate, and abuse subreddits.
After the site fired AMA (Ask Me Anything) coordinator Victoria Taylor, there was an uprising. Moderators were unhappy, users were unhappy, and CEO Ellen Pao ended up resigning. As users left in their droves, finding solace in alternatives such as Voat, the site scrabbled to defend itself both to users, employees, admins, and volunteers. Today in an Ask Me Anything session, Reddit co-founder Steve 'spez' Huffman introduced a swathe of new restrictions on what users are allowed to say. In public, at least.
In the AMA session, Huffman starts with a potted history of Reddit and the vision he had for the site. He explains that from the very beginning, he was happy to ban people who posted hateful content "because I don't want that content on our site". As the site grew, intervention started to become impractical. "I didn't have time to pass judgement on everything, so I decided to judge nothing".
This is one of the reasons Reddit gained the reputation it did for 'anything goes'. The truth is, and was, very different. Admins and moderators lurk both in the background and in the crowds ready to jump on anything deemed unsuitable. But the problem is that it has not always been entirely clear what counts as unsuitable. Huffman says:
One thing that isn't up for debate is why Reddit exists. Reddit is a place to have open and authentic discussions. The reason we're careful to restrict speech is because people have more open and authentic discussions when they aren't worried about the speech police knocking down their door. When our purpose comes into conflict with a policy, we make sure our purpose wins.
But the main reason for the AMA session was to introduce new restrictions. Explicitly banned content is as follows:
- Spam
- Anything illegal (i.e. things that are actually illegal, such as copyrighted material. Discussing illegal activities, such as drug use, is not illegal)
- Publication of someone’s private and confidential information
- Anything that incites harm or violence against an individual or group of people (it's ok to say "I don't like this group of people." It's not ok to say, "I'm going to kill this group of people.")
- Anything that harasses, bullies, or abuses an individual or group of people (these behaviors intimidate others into silence)
- Sexually suggestive content featuring minors
The Not Safe For Work category is going to be worked harder. Huffman says that any NSFW content must be flagged as such -- pity the poor bastards who have to check everything -- and this type of content is being made opt-in. NSFW content will not be visible to people not logged into an account, will be hidden from search results, and -- interestingly -- "will generate no revenue for Reddit".
He goes on to say: "We believe there is value in letting all views exist, even if we find some of them abhorrent, as long as they don't pollute people’s enjoyment of the site". The problem is going to be one of subjectivity. Moderators, admins, and users have opinions. When does 'hate' become too extreme. Is it OK to express the desire for an evil dictator to die? At the other end of the scale, who would feel that wishing a child dead is acceptable? It's all about values, context, and perspective.
Who censors the censors? The attempt to move Reddit forward raises just about as many questions as it attempts to answer.
Inviting discussion, Huffman says:
This is what we will try, and if the hateful users continue to spill out into mainstream Reddit, we will try more aggressive approaches. Freedom of expression is important to us, but it’s more important to us that we at Reddit be true to our mission.
As Reddit has been in the news in recent weeks, it has become apparent that the current moderators feel ill-equipped to deal with the content they have to manage. There has been promise of new tools to make their jobs easier, but no word of just what this means and when they will appear.
At the moment it feels as though Reddit is fumbling in the dark. It is a monster out of control and it is almost impossible to rein back in. The AMA highlighted the fact that any form of restrictions and censorship make users question motives. As FSMhelpusall says:
What will keep mods from wrongly classifying comments they don't like as "spam" to prevent people from seeing them?
Remember, you currently have a problem of admin shadowbanning, which was also intended only for spam.
A moderator touches on the problem of the acceptability of different content around the world:
There are sections of the world, and even the United States, where consensual BDSM and kink are illegal.
You can see where this is the type of announcement that raises more than a few eyebrows in our little corner of the world.
At what point do the minority opinion and positions be accepted as obscene, offensive, and unwanted?
BDSM between two consenting adults has been seen and labeled as both offensive and obscene for decades now.
At the moment, things seem very confused. Having previously banned the /r/Fatpeoplehate subreddit, Huffman says:
/r/rapingwomen will be banned. They are encouraging people to rape.
/r/coontown will be reclassified. The content there is offensive to many, but does not violate our current rules for banning.
It's possible that Fatpeoplehate could reappear, but be more closely monitored and made opt-in. At the moment, the policy changes seem ill-defined and rather fluid, but this is part of the reason for the AMA. We are assured that "before we release an official update to our policy we will spell this out as precisely as possible" but one can’t help but feel that Reddit is making it up as it goes along (hate speech is out but the racist /r/coontown subreddit is ok?).
The site looks confused, desperate to save face, and flailing to keep users from leaving.
Photo credit: Gil C / Shutterstock.com
-

Microsoft launches universal app store for Windows 10 [Update: Actually, it's not the unified store...]
Publié: juillet 16, 2015, 9:30pm CEST par Mark Wilson

The launch of Windows 10 is as much about creating a unified Windows experience and a new ecosystem as anything else. Windows 10 for desktops/laptops and for Windows Phone are closely linked and Microsoft wanted to make life easier for developers and users alike when it comes to apps.
To this end the company has launched a web version of its app store, merging the previous Windows Store and Windows Phone Store into one repository. Pay a visit to the online store and it is now possible to browse through the selection of Windows apps and Windows Phone apps in one place. Update: Microsoft contacted BetaNews with more information; see more at the end of the article.
Visually, little has changed from before -- the tile-based interface is exactly what you would expect. The store is now a one-stop-shop for everything Windows 10 related, and the front page is used to highlight some of the most popular apps for both platforms. The everything-under-one-roof approach is something that people have been asking for for some time, and Microsoft has finally delivered.
At the moment, the universal store is only home to Windows 10 and Windows Phone apps, but the presence of an Xbox link suggests that the range will be expanded in the near future. Check out the store for yourself and see what you think.
Update:
Despite our intial excitement, it seems that all is not as it seems. Microsoft has contacted us to clarify what the new web store actually is. A Microsoft spokesperson said:
The Apps on Windows site lets you browse both Windows and Windows Phone apps, but is not the new unified Windows Store. We’ll share more on the Windows Store soon.
-

HP to ship Windows 10 PCs on July 28
Publié: juillet 16, 2015, 12:01pm CEST par Mark Wilson

In the run-up to the launch of Windows 10, there has been come confusion about whether it will be possible to buy a system running the latest OS on the big day. Dell has already made its position clear, and now HP has done the same.
If you want to pick up an HP computer running Windows 10 from a store, you'll have to wait until the beginning of August. But if you order ahead of time, systems will be ready for customers on July 28.
The company has chosen to focus on getting Windows 10 systems out to people who have planned ahead and ordered a system. Those who have had the foresight to place an order via the HP web site will -- or should -- receive their shiny new Windows 10 computers on July 29, Windows 10's launch day. There had been fears that Windows 10 would only be available via download, but two big names have now verified that they are prepared for the big day.
In a statement HP says:
As we get closer to Windows 10 availability, I want to clearly explain how HP will deliver new devices with Windows 10 pre-installed to customers. Right now, a customer can buy select PCs with Windows 10 directly from HP.com and it will ship on July 28th. We are offering free next-day shipping so customers will receive the device on July 29th. Customers will start seeing HP devices running Windows 10 in-store at select retailers beginning August 2nd.
-

Microsoft launches universal app store for Windows 10
Publié: juillet 16, 2015, 10:53am CEST par Mark Wilson

The launch of Windows 10 is as much about creating a unified Windows experience and a new ecosystem as anything else. Windows 10 for desktops/laptops and for Windows Phone are closely linked and Microsoft wanted to make life easier for developers and users alike when it comes to apps.
To this end the company has launched a web version of its app store, merging the previous Windows Store and Windows Phone Store into one repository. Pay a visit to the online store and it is now possible to browse through the selection of Windows apps and Windows Phone apps in one place.
Visually, little has changed from before -- the tile-based interface is exactly what you would expect. The store is now a one-stop-shop for everything Windows 10 related, and the front page is used to highlight some of the most popular apps for both platforms. The everything-under-one-roof approach is something that people have been asking for for some time, and Microsoft has finally delivered.
At the moment, the universal store is only home to Windows 10 and Windows Phone apps, but the presence of an Xbox link suggests that the range will be expanded in the near future. Check out the store for yourself and see what you think.
-

Microsoft Edge gets a huge performance boost in Windows 10 Build 10240
Publié: juillet 15, 2015, 10:20pm CEST par Mark Wilson

So, a possible RTM build of Windows 10 has been unleashed on Windows Insiders, just two weeks before launch day, and just two days after the suspension of build availability. As we're so close to the actual release, it would have been foolish to expect any major new features or changes here, but there have been important tweaks made to Microsoft Edge.
The main reason for build 10240's release may well be to test the upgrade process that will be used by millions of people, but it's also a chance for Microsoft to show off the performance of its new operating system. One thing the company is particularly proud of is just how fast Microsoft Edge, the successor to Internet Explorer, is.
The build number might not be what was rumored to be the first RTM build, but Microsoft is keen to talk about numbers. Gab Aul says that browser optimization has been on-going; now "Microsoft Edge is even better and is beating Chrome and Safari on their own JavaScript benchmarks". Despite referring to Safari-beating performance, only figures for Edge vs Chrome are given:
- On WebKit Sunspider, Edge is 112% faster than Chrome
- On Google Octane, Edge is 11% faster than Chrome
- On Apple JetStream, Edge is 37% faster than Chrome
Performance certainly sounds impressive enough but, of course, the stats are not going to reflect everything that contributes to overall performance. Nor, indeed, is performance the only thing that users are interested in -- stability and features are also key, and it remains to be seen how Edge is received by a wider audience.
-

Wi-Fi Aware could be what the Internet of Things has been waiting for
Publié: juillet 15, 2015, 6:35pm CEST par Mark Wilson
The Internet of Things -- or IoT if you will -- is much more than just a buzzword. It's also much more than 'the next big thing'; it could be fundamental to the future of technology and how we interact with it. When we talk about the Internet of Things, we tend to do so in reference to the home and business -- but there is more to it than that.
There's a lot to consider when it comes to working with data gathered by various sensors built into smart devices, and the most recent game-changer has been unveiled by the Wi-Fi Alliance. Wi-Fi Aware certification has just been opened up with a view to enabling the creation of smart devices that can wirelessly exchange data directly, react to location, and discover other devices. This, rather than a connected fridge or oven, is what is exciting about the Internet of Things.
The difference with Wi-Fi Aware is that data can be transferred without the need for a separate wireless network. There's no need to have a router sitting there waiting to intercept one device's signal and pass it to another -- the two devices can communicate directly without the need to set anything up. It's something that is set for inclusion in mobile phones, but there are plenty of other applications.
While Wi-Fi Aware devices are concerned with location, this is not in terms of longitude and latitude. It is probably more accurate to say that Wi-Fi Aware is about proximity rather than location -- it's not where a device is specifically that's important, but where it is in relation to another device. Just how this technology is used will depend very much on the types of apps that are developed: apps will very much be at the heart of how things proceed.
Perhaps the most obvious use of Wi-Fi Aware is likely to be embraced by retailers. Rather than using loyalty cards, a Wi-Fi Aware enabled phone and app could notify you of e-vouchers you can spend as you walk through the door of the coffee shop. As there is no reliance on GPS, location detection can be more precise and power consumption is greatly reduced -- essential for mobile devices.
It also allows for a highly personalized experience at very little cost. If you're heading to the airport, an app on your phone could not only tell you which desk you need to visit, but could keep you informed about how long you have to wait as you stand in line.
In many ways, Wi-Fi Aware is a development of Bluetooth. That said, this is entirely Wi-Fi-based and as such the range is much greater than Bluetooth. The Wi-Fi Alliance says:
Wi-Fi Aware devices go through a unique process of discovery and synchronization, establishing a common 'heartbeat' that enables very power efficient operation. Devices form clusters and exchange small messages about services available nearby, enabling immediate discovery. Once an interesting service has been discovered, an app can easily initiate a Wi-Fi connection for follow-up activity such as sharing photos or playing a multiplayer game.
There will almost certainly be integration with social networks, but Wi-Fi Aware will likely be integrated into smart devices in the home. There are already a lot of big names -- Intel, Qualcomm, Broadcom, to name but three -- and it will be interesting to see the hardware that emerges in the coming months. The Internet of Things just got personal.
The Wi-Fi Alliance's video serves a good introduction to Wi-Fi Aware:
-

Prevent people printing, copying, and downloading your shared Google Drive files
Publié: juillet 15, 2015, 2:40pm CEST par Mark Wilson

The likes of Google Drive make it easy to collaborate on projects, harnessing the power of the cloud to provide people with access to files. While it's handy to be able to work on files with other people, there are times when you want to ensure that the documents you share are not misused.
With this in mind, Google has now added new permission options to shared files. With the added ability to prevent the copying, downloading, and printing of files, it's now safer to share confidential documents. As Google says, it's "perfect for when the file you're sharing contains sensitive information that you don't want shared broadly or leaked".
Protecting documents, spreadsheets, and presentations by making them read-only is a very simple task. Previously, it was only possible to choose between allowing the people you share files with to edit, comment on, or just view the file. Now, click the Advanced link in the bottom corner of the Share dialog and a new option is available: 'Disable options to download, print and copy for commenters and viewers'.
At the moment the feature can only be accessed through the web version of Google Drive. Google has not yet indicated whether it will be coming to mobile apps, but it seems reasonable to assume that it will migrate at some point as Google says it can also be accessed through the API.
Photo credit: Lichtmeister / Shutterstock
-

Google Cloud Platform gains Windows Server support
Publié: juillet 15, 2015, 11:49am CEST par Mark Wilson

For a long time, Google Cloud Platform has been a Linux-only affair. Now that has changed. Recognizing that many of its customers work in mixed platform environments, Google has added Windows Server support into the mix.
Specifically, Windows Server 2008 R2 and Windows Server 2012 R2 are now supported, after seven months of beta support. During the beta period, Google made a number of Windows-specific tweaks to the Compute Engine virtualization stack.
The company says that Windows Server running on Compute Engine can reach up to 7.5Gbps of throughput thanks to multi queue and generic receive offload support. Microsoft's flexible licensing terms means that existing licenses can be used to run applications in the cloud. Google's Cloud Launcher can be used to deploy servers using ASP.NET or Active Directory and turn to VPN to expand existing systems.
Introducing Windows Server support, Google says:
Making sure Google Cloud Platform is the best place to run your workloads is our top priority, so we’re happy that today Windows Server on Google Compute Engine graduates to General Availability, joining the growing list OSes we support.
Looking to the future, Google also says that it is working with Microsoft to bring support for Windows Server 2016 and Nano Server to Google Compute Engine.
-

Windows 10 is free because... Windows Phone
Publié: juillet 15, 2015, 1:13am CEST par Mark Wilson

Windows 10 is free; that much we know. There was initially some confusion about the length of time for which this would be the case, but one of the biggest questions surrounding the giveaway has been 'why?'. Is Microsoft aping Apple? Does the company feel that the operating system was not good enough to warrant a price tag?
The actual reason is rather interesting, and was revealed in an interview between Satya Nadella and ZDNet's Mary Jo Foley. This is not (really) a bid to compete with Apple, nor is it (particularly) meant to encourage as many people as possible to move away from Windows XP, Windows 7, and Windows 8.1 (although this will almost certainly be a happy side-effect). Rather it is a move to boost the profile of Windows Phone.
A large part of the move towards Windows 10 has been a drive towards a uniform, cross-platform experience. Using Windows 10 on a phone, computer, or games console should feel immediately familiar, and it turns out that phones are key to the pricing decision surrounding Windows 10. Mentioning the Windows Phone 'app gap' is very much treading old ground, but it’s something that Microsoft, like users and pundits, has noticed.
Creating an ecosystem in which universal apps can exist is central to the push of not only Windows 10 for desktops and laptops, but also Windows 10 for phones. Speaking to Foley, Nadella said:
The free upgrade for Windows 10 is meant to improve our phone position.
This is a slightly odd thing to say about an operating system that is, for the most part, destined for laptops and desktop computers.
In Windows 10, Microsoft is pushing the Store more than ever -- something that clearly translates to phones as well as computers. It seems that the thinking is that by presenting the Store prominently, the hope appears to be that users will become used to the idea of downloading apps on one platform and, thanks to the presence of universal apps, titles that exist on the desktop will also be available for phones.
In Windows 10, the store is right there and done in a tasteful way. I want that to translate into success for our developers. That's what's going to get them to write to the phone. If anything, the free upgrade for Windows 10 is meant to improve our phone position. That is the reason why I made that decision. If somebody wants to know whether I'm committed to Windows Phone, they should think about what I just did with the free upgrade to Windows. [...]If you come to Windows, you are going to be on the phone, too. Even if you want to come to Windows because of HoloLens, you want to come to it because of Xbox, you want to come to the desktop, all those get you to the phone.
Will this give Windows Phone enough momentum to gain popularity? That's obviously something that remains to be seen, but Microsoft has said quite plainly that it has no plans to get out of the smartphone business.
Nadella is ambitious:
I want to be able to be present on every mobile endpoint. That's a very explicit core goal. It's not (just) the notion of having our application endpoints, Skype, Outlook, Wunderlist, Sunrise, on every one of the two billion devices. We want to have Microsoft experiences, because to me that's a platform play. It's not like, oh, they're just application endpoints. Guess what is behind those applications? It's One Cloud. It's Office 365, either for the consumer or for the enterprise. There's MSA (Microsoft Account) in there. So to me it's very important to think of our operating system more broadly than some old definition of an operating system. So we want to be in every device, not only have our application endpoints on every device.
Microsoft is looking -- with the help of, amongst other things, Continuum -- to merge the mobile and the desktop. Windows 10 is at the heart of that, and Nadella is pinning a good deal of hope on the idea that it will help to reinvigorate Windows on phones. Now Microsoft is playing the long game, and we'll just have to wait to see if it pays off.
-

Oops! Google accidentally reveals Right to Be Forgotten request details
Publié: juillet 14, 2015, 7:13pm CEST par Mark Wilson

The Guardian has discovered that Google mistakenly revealed more information about Right to Be Forgotten requests than it meant to. The search giant recently released a transparency report which provides scant detail about the number of requests it received in Europe and the sites they related to, but the new discovery goes further.
Critics said the report was not substantial enough, but it seems that a quick glance at the source code is all that's needed to reveal more. While before we knew little more than the fact that more than half of requests are declined, we now have a few extra snippets of information such as learning that over 95 percent of requests come from the general public rather than high-profile people.
When releasing its transparency report, Google chose to highlight some of the more sensational examples of requests it received (such as those relating to sexual content) but there have been calls for far more information to be made available -- as well as suggestions that the Right to Be Forgotten should be extended to the US. Some websites that have had their links removed from Google search results, including the BBC, have chosen to make the censorship public, but for many this is simply not enough -- facts and figures straight from the horse's mouth are preferred.
As revealed by The Guardian, the source code of an archived version of the transparency report goes into more detail than the published report. Since May of last year, Google has received 2,102 removal requests relating to public figures, and 1,025 relating to child protection (22 and 17 percent granted respectively). The figures also reveal how many requests relate to serious crime -- Italy tops the list here, with 11.9 percent of the country’s requests accounted for by crime-related content, compared to France where the figure is just 0.4 percent.
In response to the discovery, Google issued a statement:
We’ve always aimed to be as transparent as possible about our right to be forgotten decisions. The data the Guardian found in our Transparency Report’s source code does of course come from Google, but it was part of a test to figure out how we could best categorize requests. We discontinued that test in March because the data was not reliable enough for publication. We are however currently working on ways to improve our transparency reporting.
So what do we learn from the revelations? The fact that the vast majority of requests come from individuals shows that the Right to Be Forgotten is not being abused by companies to try to improve their online reputation, although at this stage it is not clear whether the individuals contacted Google directly, or used an intermediary.
Check out The Guardian’s report for all the facts and figures.
Photo credit: P.Jirawat / Shutterstock
-

It's your fault Google Photos continues to upload pictures after you uninstall it
Publié: juillet 14, 2015, 9:54am CEST par Mark Wilson

Google's decision to break up Google+ into a number of separate apps and services led to the launch of Google Photos. Just like with Apple's iCloud, the app can automatically upload your images to the cloud ready for sharing, viewing, or just as a backup. You might decide that this automatic uploading isn't for you and opt to uninstall the Google Photos app... but your photos will probably continue to upload in the background.
This is the discovery that many Android users have made; what gives? Is Google being sneaky? The answer's not quite that simple. Before you start freaking out, proclaiming that Google is indeed evil, and wondering how on earth the company thinks it can get away with it, consider this: it's actually your fault.
Nashville Business Journal writer David Arnott is among those who discovered that even after Google Photos has been deleted, photos are still backed up. This is not because Google Photos is being sneaky. Google is not infringing on your privacy. The company is not taking liberties. You opted to have your photos automatically synced to the cloud, and it has absolutely nothing to do with Google Photos -- that's why uninstalling it makes no difference.
"Eh?" I hear you cry.
The uploading of photos is controlled not by Google Photos' settings, but by Google settings. This is clearly something that is going to upset some people -- after all, how are you really expected to know that this is a global, rather than in-app, setting? -- but it's the way things are meant to work. And it's easily addressed if you don’t like the way photos are uploaded on your behalf -- which you may not do if you are on an expensive or limited data plan.
All you need to do is fire up the Google Settings and you can disable the 'Back up photos' option. Simple. It might not be obvious, it might not be entirely clear, but it is by design. Oh... and you might want to check just what has been uploaded in case there's anything you'd rather wasn’t sitting online.
If you think your privacy has been violated, you have no one to blame but yourself.
Photo credit: PathDoc / Shutterstock
-

Hacking Team to conjure up new surveillance software after security breach
Publié: juillet 13, 2015, 11:29pm CEST par Mark Wilson

Following a massive security breach, Italian security firm Hacking Team warned that its government-strength surveillance tools could have fallen into the hands of terrorists. The company advised its customers -- including governments and law agencies around the world -- to stop using its software, and is now launching something of a damage-limitation exercise.
Hacking Team has released a statement indicating that far from giving up and admitting defeat, a new, more powerful version of its software will be released soon. The replacement for Galileo, called Remote Control System 10, is described as a "complete revision" of the old system and "not simply an update". The security firm also stresses that not all of its source code was compromised, only code which is considered obsolete.
The statement, which has more than a slight air of a company trying to save face, is defiant in tone. It describes Hacking Team's surveillance software as the most comprehensive and powerful available. It also goes on to say -- in a bid to wipe aside criticism that has cropped up in recent days -- that its system has only ever been sold to government agencies for "lawful" use. It points out that in the cases of Sudan, Ethiopia, and Russia, business relationships have been brought to an end.
Chief Operating Officer David Vincenzetti said:
While it is true that the criminals exposed some of our source code to Internet users, it is also true that by now the exposed system elements are obsolete because of universal ability to detect these system elements. Today we believe it is extremely unlikely that this obsolete code can be used to surveil cell phones, mobile devices or computer communications. However, important elements of our source code were not compromised in this attack, and remain undisclosed and protected.
He went on to try to allay fears that may have arisen following the breach:
We have already isolated our internal systems so that additional data cannot be exfiltrated outside HackingTeam. A totally new internal infrastructure is being buil[t] at this moment to keep our data safe.
Of course, our top priority here has been to develop an update to allow our clients to quickly secure their current surveillance infrastructure. We expect to deliver this update immediately. This update will secure once again the “Galileo” version of Remote Control System.
And because we have always been committed to being the leading technology company in our field, for months HackingTeam has been building a complete revision of our system. Remote Control System, version 10, will be released in the fall. This is a total replacement for the existing Galileo system, not simply an update. Of course, it will include new elements to protect systems and data considering the impact of the attack against HackingTeam.
Despite what Hacking Team says, it is unknown just who has access to the data that was leaked, and how much of it is actually useful. It makes sense that the company would play down any risks that might exist, after all.
-

Microsoft suspends availability of Windows 10 builds
Publié: juillet 13, 2015, 10:37pm CEST par Mark Wilson

If you haven't already downloaded Windows 10 build 10162 or 10166, you're now too late. Microsoft has suspended the availability of these two builds -- previously available on the Slow and Fast rings respectively -- in the run up to the big launch day in a couple of weeks' time.
As we edge closer and closer to the RTM build of Windows 10, Microsoft is now asking Windows Insiders to stick with the build they currently have installed for the time being. Anyone who hasn’t upgraded to these latest preview builds is out of luck. As well as disabling upgrading through Windows Update, Microsoft is also suspending ISOs and activation.
The reason for the suspension is that Microsoft is readying itself for the big launch and testing the deployment channels that will be used to deliver the final version. The builds that have been released are incredibly close to RTM code, but feedback is still required. Microsoft asks that Insiders continue to use the Windows Feedback tool to report problems -- it's late in the game, but there's still time to fix issues before launch day.
Writing on the Windows blog, Gabe Aul said:
We're suspending the availability of Windows 10 builds briefly while we prepare for that, and the next build that we flight to you will be delivered using the production channels. Starting tomorrow, we will also not be delivering any additional ISOs at this point as we really need Insiders to be using, stressing, and validating our distribution and upgrade processes. We’ll make ISOs available again in the future, but for now we ask you to upgrade your current build via Windows Update once the next build is released.
You still have a few hours to grab the latest preview builds, but this option will disappear in the next 24 hours. After this point, prerelease keys will no longer activate builds, build 10162 ISOs will be taken offline, and anyone checking Windows Update will be told that they are up to date. Microsoft says that the next build to be released will be made available through final production channels, but there's no word on when that might be.
-

Microsoft launches Cortana Analytics Suite to leverage big data
Publié: juillet 13, 2015, 7:37pm CEST par Mark Wilson
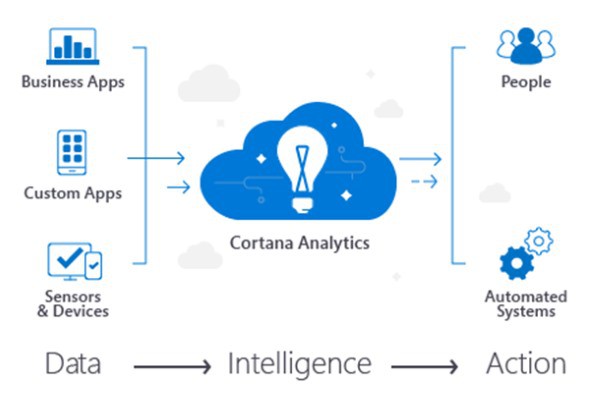
Today at its Worldwide Partner Conference, Microsoft unveiled Cortana Analytics Suite. This is a set of tools designed for business to harness big data and use it to perform relevant, automated tasks. The suite neatly ties together the cloud, big data, and the Internet of Things to create a system that can be put to countless uses.
There are two big clues in the name that help to explain why Microsoft is describing this as a tool that will help to bring about "intelligent enterprise". Automated analytics takes the legwork out of dealing with data from apps, devices, sensors, and more, while Cortana integration means that users can interact with data in a more natural way.
Built after years of research and development, Cortana Analytics Suite uses machine learning and processing in the cloud to take the load off processing large amounts of data and delivering meaningful information to a range of devices. Microsoft predicts that the tools could be used to detect fraud, make customer recommendations, and forecasting.
Microsoft says:
While data is pervasive, actionable intelligence from data is elusive. Our customers want to transform data to intelligent action and reinvent their business processes. To do this they need to more easily analyze massive amounts of data -- so they can move from seeing 'what happened' and understanding 'why it happened' to predicting 'what will happen' and ultimately, knowing 'what should I do'.
Incorporating features such as voice and facial recognition, Cortana Analytics Suite is Microsoft's vision of the future of business processes. The company shared a video showing how Dartmouth-Hitchcock Health System has used Cortana Analytics Suite to bring personalized healthcare to people:
-

How to change Windows 10's title bar color
Publié: juillet 13, 2015, 11:38am CEST par Mark Wilson

Windows 10 introduces a lot of changes. If you're upgrading from Windows 7 or Windows 8.1 (or even from XP or Vista), you're going to find a lot that's new. But in addition to new features, settings, and options, some things have also vanished.
One casualty of upgrading to Windows 10 is the ability to customize the color of title bars. This incredibly simple option has been around for as long as Windows itself, but now it has been sacrificed. That is, unless you are willing to jump through a few hoops. Here's how to change the color of title bars in Windows 10.
Microsoft's decision to have title bars colored an unchangeable white was obviously a conscious design choice, but one that's going to grate with some people. You could turn to a third party customization tool to do the job for you, but there's no need. Take care and follow these steps, and you can colorize your title bars to your heart's content.
Launch File Explorer and navigate to C:\Windows\Resources\Themes. Create a copy of the folder called 'aero' as a backup (within the Themes folder) and click Continue when the Folder Access Denied dialog appears. Check the 'Do this for all current items' option and click Skip at the File Access Denied dialog and then rename your newly created folder to 'Colors' or whatever you prefer -- Windows may complain when you try to rename, so hit Continue to bypass the UAC warning.
Within the folder, locate the file called aero.mstyles and rename it to colors.mstyles -- again, you may have to click through a UAC prompt. Open the en-US folder and rename aero.msstyles.mui to colors.msstyles.mui.
Move back two levels to the Themes folder and copy the aero.theme to your desktop before renaming it colors.theme. Right click this file and use the Open with option to open the file in Notepad. Find the [VisualStyles] section of the code and change the line that reads Path=%ResourceDir%\Themes\Aero\Aero.msstyles to Path=%ResourceDir%\Themes\Aero\colors.msstyles (obviously, adjust accordingly if you opted for a different name earlier). Close and save the file and then double click it -- job done!
To customize the color, head to Personalization in Settings and pick a new accent color in Colors.
If you want to revert back to the original look, just navigate back to C:\Windows\Resources\Themes and double click aero.theme.
Photo credit: faitotoro / Shutterstock
-

Here's how Windows Hello login works in Windows 10
Publié: juillet 12, 2015, 12:38pm CEST par Mark Wilson

One of the more intriguing new features of Windows 10 is Windows Hello. If you're sick of typing a password to log into your account, but don’t want to do away with security altogether, you can use this biometric feature to log in using your face or fingerprint.
Windows Hello works in conjunction with Microsoft Passport to lock down your system, but the facial recognition feature is only compatible with certain hardware. This fact means that it has been hard to try out Windows Hello, but over on SuperSite for Windows Richard Hay got his hands on an Intel RealSense 3D Camera (F200) and recorded a demo of how it works.
While fingerprint recognition is compatible with a number of readers, the Intel RealSense 3D Camera (F200) is the camera specifically mentioned by Joe Belfiore when he introduced Windows Hello earlier in the year. Ray's video shows how quick and easy it is to log in using the camera.
Check out the video to see Windows Hello in action in build 10166 of Windows 10:
Is this a feature you think you'll make use of?
Photo credit: Kostenko Maxim / Shutterstock
-

FTC could probe Apple Music over legality of 30 percent cut from streaming rivals
Publié: juillet 12, 2015, 10:57am CEST par Mark Wilson

The launch of Apple Music has been one of the most controversial for some time. After complaints about the free trial period not generating income for record labels -- a problem seemingly sorted out by the intervention of Taylor Swift -- attention turned to how little the music streaming service paid artists the rest of the time.
Now Apple has a new problem, bringing Apple Music into the limelight for the wrong reasons once again. The Federal Trade Commission is currently considering whether to probe the company for antitrust violations. Reuters reports that the FTC could be on the verge of launching an investigation into the legality of the 30 percent cut Apple takes from other streaming music services such as Spotify.
In fact, it was Spotify that recently brought the issue to public attention. The company emailed its customers to point out that while taking out a subscription through the App Store would cost $12.99 per month, buying direct from Spotify costs just $9.99. Industry insiders say that the FTC has held meetings with a number of "concerned parties", although it is not yet clear whether a formal investigation will be launched.
The 30 percent commission taken by Apple is something that is the norm in the App Store -- there is nothing unusual in the way streaming music services are being treated. But while Spotify has raised the price of its subscription for those making the purchase through the store, others such as Deezer choose to shoulder the cost themselves. While it is possible for any streaming music service to take a leaf out of Spotify's book and widely promote alternative, cheaper ways to take out a subscription, this is yet to happen.
Opinion is divided as to whether an investigation is needed and whether Apple is in the wrong or not. Some argue that the cut it takes is a perfectly acceptable fee for the benefit of promotion through the App Store, while others say it is an unfair abuse of power. At the moment, Apple does not permit companies to promote the non-App Store subscription route from within apps. Apple could find itself embroiled in a court case reminiscent of the ebook price-fixing scandal which only recently came to a conclusion, costing the company $450 million.
Photo credit: FooTToo / Shutterstock
-

Getting started with Windows 10 -- download the essential guide
Publié: juillet 11, 2015, 10:41pm CEST par Mark Wilson

The Windows 10 launch date is now little more than two and a half weeks away. While a lot of people have tried out the various preview builds that have been made available, the majority of people upgrading will be doing so with little to no knowledge of what to expect. Ahead of Microsoft's most important operating system launch for years, Lenovo has published a user guide that will help bring you up to speed.
Quite a lot has changed or been added since Windows 8.1, so there's much to learn. For those people who decided to stick with Windows 7 -- and there are many, many such people -- the jump is even bigger. Lenovo's guide serves as an excellent starting point for learning about what's new, how things work, and what's different. Think Windows 10 101: introducing the Start menu, Action Center, and more.
The 'Starting to use Windows 10' guide is for Lenovo customers, but the 23 page PDF can be downloaded by anyone who's looking for a quick introduction to the operating system. As Windows 10 is still to reach RTM stage, Lenovo has worked with one of the preview builds -- it's possible to make out the desktop watermark in the screenshots -- but everything should still be accurate. (Somewhat more up to date, by the way, is the image at the top of this post. This is a Windows 10 retail boxshot as revealed by WinFuture).
Divided up into six chapters, this is certainly not Windows 10: The Missing Manual, but it's not supposed to be. It's a quick-start guide that covers the essentials so those who have not yet tried Windows 10 do not feel completely lost.
Grab your free copy of the PDF from the Lenovo website.
Image credit: WinFuture
-

Microsoft's 'feeble' enterprise security and virus protection is the worst
Publié: juillet 11, 2015, 2:34pm CEST par Mark Wilson

Tests carried out by independent security labs AV-Test show that Microsoft is at the bottom of the league when it comes to enterprise security and virus protection. The tests pitted 11 security solutions against each other, and Microsoft's Endpoint Protection 2012 from the Microsoft Management Suite System Center 2012 was found to offer the weakest protection.
In both enterprise network security tests and virus detection tests, Microsoft trailed behind the competition in eleventh place. What's particularly concerning is that as the tool tested is bundled software, it's likely that it is precisely what many businesses are relying on for protection.
The efficacy of Microsoft's security software for home users has long been questioned, but security is of even greater concern to business and enterprise customers. The antivirus tests carried out by AV-Test showed that Endpoint Protection picked up just 73 percent of infections, compared to between 95 and 100 percent for the ten opponents. It is ultimately labelled as being "much too feeble in the detection of malware". Products from Bitdefender, F-Secure, Trend Micro, Kaspersky Labs, and Symantec all received flawless scores.
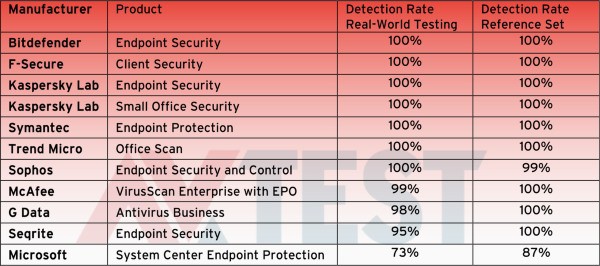
AV-Test's focus on enterprise security throws up Windows 7, which is still very widely used -- over 60 percent of businesses use the operating system. The labs report that just 22 percent of businesses have upgraded to Windows 8.1, and 18 percent are still on Windows XP. But whatever version of Windows is in use, the tests make it clear that switching to an alternative to Microsoft is a very good idea when it comes to security. As the AV-Test puts it:
An economical option for protecting a corporate network is the use of the endpoint module, bundled in the Microsoft Management Suite System Center 2012. The test revealed, however, that this is not to be recommended. The solution was awarded 0 points by the testers in terms of its protection function, and it achieved only 11 out of 18 possible points.
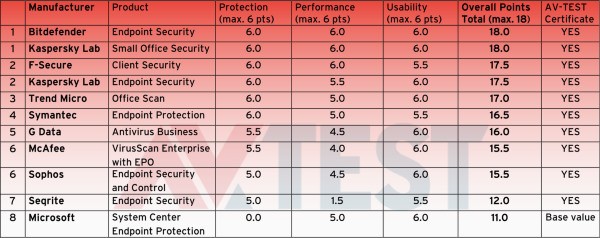
The report says that there is now an excellent range of affordable security suites to choose from -- hit the site to check out the results in full.
Photo credit: ronfromyork / Shutterstock
-

Chrome blocks access to torrent sites
Publié: juillet 11, 2015, 11:41am CEST par Mark Wilson

Chrome users who download torrents may be thinking about switching to a different browser. Google's web browser is now blocking access to a number of big name torrent sites. This is not a case of Google taking the moral high ground about the rights and wrongs of torrenting, but part of the search giant's security program to protect users from "harmful programs".
Starting yesterday, downloaders found that access was blocked to ExtraTorrent and KickassTorrents, although the block was later lifted. The block remains in place for other torrent sites including kat.cr. Upon attempting to visit an affected site, would-be torrenters are greeted by a red, full-screen security warning that advises of the potential danger of the site in question.
As reported by TorrentFreak, Chrome users started to discover that their favorite sites were no longer accessible. ExtraTorrent found that Google had incorrectly labelled something as malware, and after contacting the company, the block was lifted. But for kar.cr visitors and users of some other torrent sites, access is not guaranteed. Try to visit a site that Google has taken objection to and the following warning appears:
The site ahead contains harmful programs
Attackers on kat.cr might attempt to trick you into installing programs that harm your browsing experience (for example, by changing your homepage or showing extra ads on sites you visit).
While it is possible to click through and ignore the warning, the option to do so is slightly obfuscated. A small and easily-missed Details link needs to be clicked followed by another link that indicates your willingness to take the risk and continue to your intended destination. Another option is to disable Chrome's built-in malware protection.
Google has not said that it is particularly targeting torrent sites at the moment, and it seems that the blocks are just part of an on-going security program. It does, however, seem that the blocks are contagious. TorrentFreak reports that some Firefox users are now complaining of similar problems getting to certain torrent sites.
Have you been prevented from accessing any of your favorite sites?
Photo credit: Yuriy Vlasenko / Shutterstock
-

Amnesty International seeks explanation for 'absolutely shocking' government surveillance
Publié: juillet 10, 2015, 11:30pm CEST par Mark Wilson

A court recently revealed via email that the UK government had been spying on Amnesty International. GCHQ had put Amnesty under surveillance -- despite this having previously been denied -- and now the human rights organization wants answers.
In a letter to the UK Prime Minister David Cameron, Amnesty International asks for an explanation for the surveillance. The Investigatory Powers Tribunal's (IPT) email made it clear that GCHQ had been intercepting, accessing and storing communications, something that Amnesty International's Secretary General, Salil Shetty believes "makes it vividly clear that mass surveillance has gone too far".
Amnesty International explains to Mr Cameron that it is deeply concerned about the revelations. The letter says that the victims of human rights abuses that the organization helps will have cause to believe that not only has the government intercepted data about them, but that it may have been shared with foreign governments. More importantly, perhaps, it's something that will be of concern to those considering seeking help from the organization.
Kate Allen, Amnesty UK’s Director said:
It’s absolutely shocking that Amnesty International’s private correspondence was deemed fair game to UK spooks, who have clearly lost all sense of what is proportionate or appropriate. A key measure of a free society is how it treats its charities and NGOs (Non-Governmental Organizations). If Amnesty International is being spied on, then is anyone safe?
The letter calls for a full independent inquiry into the surveillance of human rights organizations, as well as requesting that existing reports into spying be published.
As well as writing to the Prime Minister, Amnesty International has also written to the Guardian. Here, Kate Allen and others point out that the only reason the surveillance came to light is because GCHQ broke rules about how long data could be retained -- if this had not happened, we might have been none the wiser about what had been going on. The letter, co-signed by Shami Chakrabarti, director of Liberty, and Gus Hosein, executive director of Privacy International, asks:
Which other organisations are being spied on? What confidential information was GCHQ looking at? Why was it of interest? Who read it? Was it shared? Is it still going on? How did it come to this?
-

Leaked tool lets you download Windows Phone apps on a PC
Publié: juillet 10, 2015, 6:31pm CEST par Mark Wilson

Something that many Windows Phone users have been asking for is a little flexibility with how apps are downloaded and installed. One particular request is the ability to download apps using a PC rather than with a handset. A new tool leaked by a Microsoft employee makes this possible.
The appropriately-named Windows Phone Assistant is an official Microsoft tool that has been used internally. Nawzil released the software in response to a series of requests from people, granting greater control over apps. The leaked tool is available for anyone to download -- you just need to be running Windows Phone 8.1 GDR 2.
Nawzil says that the app will be of interest to a lot of people, including those who struggle with a slow internet connection. However, he warns that the limited number of phones that were eligible for the GDR 2 update means not everyone will be able to make use of it -- the very reason Microsoft didn’t bother to release it publicly. The availability of the tool was announced on Twitter:
#WindowsPhoneAssistant - Download WP apps on PC and install them on Phone. Requires WP8.1 Update 2 (GDR2). [t.co]
— Nawzil (@Nawzil10) July 8, 2015
If you are lucky enough to have a handset that's running the relevant version of Windows Phone, you, can Download Windows Phone Assistant Direct from Nawzil's website.
(and in case you were wondering, Microsoft has been told about the leak)
-

Twitter removes Vine ads that could trigger epileptic attacks
Publié: juillet 10, 2015, 5:25pm CEST par Mark Wilson

Twitter acted quickly to remove two Vines advertising the network's #DiscoverMusic campaign after warnings from an epilepsy charity. Epilepsy Action advised Twitter that the two ads could be dangerous to those suffering from photosensitive epilepsy.
The charity made a public appeal to Twitter in a tweet, and the company was fast to respond. Communications director Rachel Bremer thanked Epilepsy Action for drawing attention to the ads which were removed. The epilepsy charity was not alone in sending warnings to Twitter -- quite a few concerned tweeters got in touch with the company to point out the problem.
The looping ads featured flashing imagery which could have been harmful to people with certain types of epilepsy -- in the same way that strobe effects at concerts and in movies can be problematic. Speaking to the BBC, Epilepsy Action’s deputy chief executive, Simon Wigglesworth, said: "Twitter's ads were dangerous to people living with photosensitive epilepsy".
A brief online exchange brought the issue to a conclusion:
.@TwitterUK Your #DiscoverMusic Vines are massively dangerous to people with photosensitive epilepsy. Please take them offline now.
— Epilepsy Action (@epilepsyaction) July 10, 2015
The Advertising Standards Authority's regulations forbid the use of imagery that could trigger a reaction in photosensitive epileptics.
-

HoloLens' field of vision isn't quite as impressive as you thought
Publié: juillet 10, 2015, 1:08pm CEST par Mark Wilson

Since Microsoft gave us a glimpse of its immersive HoloLens headset, there has been much pondering about just what to expect from the unit. Until we get an opportunity to go hands on with the new virtual reality cum augmented reality device, we're largely reliant on second hand information about what the experience of using HoloLens is like.
Microsoft has released new footage of HoloLens in action including an almost-first-person perspective that gives an idea of what it's like to wear. What's interesting to note is that, despite the promises of an immersive experience, the field of vision is rather smaller than many people will have expected.
The video shows HoloLens can be used in medicine, with users interacting with holographic 3D models of the human body. As well as the third-person perspective we've already seen, we're also treated to a glimpse of what it is like to look through HoloLens when in use. The wide-angle shots demonstrating what people look like when they’re using HoloLens are great -- it's hard not to be impressed by the three dimensional renderings that hover in front of the user. But step inside the headset, and it's a slightly different story.
With the out-of-body view, you'd be forgiven for thinking that with HoloLens strapped to your head you are transported to another world. Step into the users' shoes, however, and you'll find that this is not actually the case. The new video gives us just the briefest glimpse of HoloLens field of vision. And it is a brief glimpse; blink and you might miss it. Skip to around the 0:41 mark and you can see what the HoloLens wearer sees.

Notice anything? The holographic display does not fill the user's entire field of view, rather there is almost a projected HUD hovering in front of them. It's more like a holographic TV... and that means edges, borders, and things being cut off.
Not that the video gives you long to acknowledge this fact. A second later we zoom back out to third person view so we can see a series of human models in their full, unconstrained glory. Disingenuous? Maybe. It's still hard to say just what HoloLens feels like in use, and it could be that the hovering-screen view works incredibly well... but on the face of it, it is a little disappointing.
Check out the video below and see what you think. Does it cut the mustard?
-

The man who cared about your online privacy has died
Publié: juillet 10, 2015, 11:21am CEST par Mark Wilson

Caspar Bowden, the privacy advocate who was warning about the activities of the NSA before Edward Snowden, has died. The co-founder of the Foundation for Information Policy Research lost his battle with cancer, and tributes have been paid by the world of technology.
Bowden, the former head of privacy at Microsoft, had long-warned about potential backdoors in software and services. He campaigned passionately for the privacy of the individual and voiced grave concerns about the NSA and the FISA Amendment Act. He sat on the board of Tor and was one of the most knowledgeable and well-loved figures on the privacy scene.
Before joining Microsoft in 2002, Bowden was a political technology advisor, and went on to warn that Europe's reliance on cloud computing would be exploited by the NSA in the US. He is said to have suspected the existence of surveillance and monitoring programs long before they were made public, and was a vigorous opponent of any invasion of privacy. He went as far as saying that he no longer trusted his former employer, Microsoft.
The Electronic Freedom Foundation wrote:
We were shocked and saddened to hear of the death of Caspar Bowden [...] Among a community filled with perceptive advocates for a better future, Caspar Bowden stood out as one of the most prescient and the most determined. With a far-reaching knowledge of both policy and technology, he was frequently years ahead of his contemporaries in identifying upcoming issues, and never hesitated to transform his own life and career to better meet those challenges.
Countless individuals from the world of technology and privacy campaigning took to Twitter to express their grief at the loss of a well-loved and much-respected privacy advocate.
Photo credit: Rama / Wikimedia Commons
-

Google updates Android M Developer Preview
Publié: juillet 10, 2015, 1:26am CEST par Mark Wilson

It's not long since we first learned about Android M at Google I/O and today Google launches Android M Developer Preview 2. As the name would suggest, this is a build aimed primarily at developers, giving them an opportunity to ensure their apps are ready to take full advantage of everything the latest version of the operating system has to offer.
Two key changes between Lollipop and Android M are improvements to security and battery life. The second developer preview includes more improvements to permission settings such as how fingerprint authentication works and changes to the way permissions are handled for external storage.
Google is keen for developers to update to the latest preview as soon as possible -- "This ensures that you are building with the latest platform APIs and testing against the latest behaviors". The Bluetooth Stylus APIs have been updated, and new callbacks have been added to the Media API. Some restructuring has been done so some classes have been moved into new packages.
Of course, there are a number of bug fixes, but the build is not without problems. Google warns that the Messenger app does not play happily with the 64-bit emulator, and there are issues sharing YouTube videos. Contact synchronization can be problematic, and there are a number of issues with Android M on Nexus Player.
A full list of changes is available in the changelog.
If you like the idea of trying out the next version of Android before its official release, take a look at our guide to getting it installed on your Nexus device. Grab yourself a copy from the Android M Developer Preview page.
-

Google launches Gmail Postmaster Tools to eliminate spam
Publié: juillet 9, 2015, 11:19pm CEST par Mark Wilson

Spam is a problem that is not going away for anyone who receives email -- and who doesn't? Over the years Google has taken steps to try to reduce the amount of junk that reaches Gmail inboxes and today the company is taking things a step further with Gmail Postmaster Tools and enhanced filter training for Gmail.
Part of the problem with spam -- aside from the sheer volume of it -- is that the detection of it is something of an art rather than a science. It is all too easy for legitimate email to get consigned to the junk folder, and this is what Gmail Postmaster Tools aims to help with. Rather than helping recipients banish spam, it helps senders ensure that their messages are delivered to inboxes rather than filtered out.
Gmail Postmaster Tools are not really for everyone -- it's designed for companies who send high volumes of email. It gives them an opportunity to run diagnostics on their messages and use the data that analysis feed back to come up with better emailing practices. A simple wizard-driven interface guides senders through the process of verifying their identity and help Google to understand that the messages they send are legitimate.
But there's an update for email recipients as well. To help improve the efficacy of spam filtering, Gmail's filters now not only learn from people clicking Spam or Not Spam in their inboxes. Google is bringing the same technology used for Google Search and Google Now so that particularly sneaky junk emails do not slip through the net. Personalization is also improving so spam filters are now far less of a one-size-fits-all option -- Gmail should better understand what you deem to be spam and not just apply the same settings as for everyone else.
Photo credit: Ljupco Smokovski / Shutterstock
-

Prioritize your news feed with updated Facebook controls
Publié: juillet 9, 2015, 4:01pm CEST par Mark Wilson
Add a few friend on Facebook, join a few groups, and follow a few people you know and your Facebook feed can collapse into a jumbled mess. The way Facebook's algorithm works means it's all too easy to see too much stuff you're not really interested in, and miss what you want to see most.
Today the social network is rolling out a new set of options that can be used to gain better control of what you see. The latest update gives prioritization options so you can be certain that you'll always see posts from a particular friend. Will it be enough to please those who are critical of how things work at the moment?
The idea is a very simple one. You can select the friends and pages you are most interested in, and Facebook will ensure that these updates are always pushed to the top of your news feed. But this update is about more than just making sure you see what you want -- Facebook also wants you to see more. The site will make suggestions for pages you might like to follow based on who you currently follow. These are features that have been available to a small group of users for a little while, but are now rolling out to everyone.
Introducing the new features, Facebook says:
We’re always working to improve and personalize your News Feed experience. We know that ultimately you’re the only one who truly knows what is most meaningful to you and that is why we want to give you more ways to control what you see. Last year we announced some new ways to control what you see in News Feed. Today we are announcing even better tools for you to actively shape and improve the experience. We’ve redesigned and expanded Facebook’s News Feed Preferences to give you more control.
The update also makes it possible to unfollow friends so you can avoid posts from certain people but, in Facebook's own words, 'keep up appearances' by remaining friends with them.
iOS users get access first, while Android handsets and the main website will follow very soon.
-

Major threat: Hacking Team warns its spying tools are now in the hands of terrorists
Publié: juillet 9, 2015, 12:54pm CEST par Mark Wilson

Following a massive security breach over the weekend, Hacking Team has issued a warning that its surveillance and remote access software could now be used by anyone -- including terrorists. The Italian security and surveillance firm fell victim to an attack that relieved it of 400GB of company data, including source code for its software.
Whoever was responsible for the security breach made this data available via torrent, meaning that anyone was able to get hold of it. Hacking Team's software is favoured by governments around the world for mounting NSA-style surveillance and monitoring programs and the company has now issued a stark warning: "Terrorists, extortionists and others can deploy this technology at will if they have the technical ability to do so".
Hacking Team says that "a major threat exists" as a result of the source code having been made available online. The security outfit launched an investigation in the wake of the breach and has since determined that "sufficient code was released to permit anyone to deploy the software against any target of their choice".
'Anyone' includes not only the likes of you and I, but also script-kiddies, criminally-minded hackers, and terrorists. The full repercussion of the leak is not yet known, but Hacking Team's technology was sold exclusively to governments and their agencies and this technology is now in the wrong hands. As a result of this, the company says the "ability to control who uses the technology has been lost".
Put bluntly, Hacking Team says:
We believe this is an extremely dangerous situation.
Work is underway to determine if anything can be done to limit any potential damage, but the prognosis is not good. These are tools that were designed to evade detection, to circumvent security measures, and to provide access to just about anything; they were not designed to be reined in. There has been talk recently about governments wanting backdoors to be built in security products, but this is not something that applied to Hacking Team's arsenal:
There have been reports that Hacking Team has 'backdoors' in its systems that would allow us to control the systems remotely. This is simply not true. Clients operate our technology on their own computer systems, and so it is clients who must take action to suspend operations.
For the time being, the majority of Hacking Team's clients have suspended use of its tools and it's now just a case of waiting to see if any group uses the source code for nefarious purposes.
Photo credit: prudkov / Shutterstock
-

Chromecast Ethernet adaptor overcomes Wi-Fi problems
Publié: juillet 8, 2015, 11:07pm CEST par Mark Wilson

Google's Chromecast has gained quite a following of people looking for a cheap, simple way to stream content to their TVs. Part of the device's appeal is its ease of use and extensibility through the use of apps, but it is reliant on a steady Wi-Fi signal. If this represents a problem in your home, there's now a solution.
The new Ethernet Adapter for Chromecast does very much what you would expect -- it adds a wired Ethernet port to Google's streaming dongle. This is great news for anyone with a flaky Wi-Fi signal, or those looking to use Chromecast beyond their router's normal range.
Google's new accessory costs a mere $15 and is a simple adaptor that sits between the Chromecast and its power supply. You'll need to supply your own Ethernet cable but that aside, your $15 gets you everything you need to connect your Chromecast directly to your network.
Google describes it as a "wired connection for hard-to-reach Wi-Fi spots in your home", but it's also a great solution for anyone battling through airwaves crowded with other wireless devices. Supporting speeds of up to 100Mbps the adaptor should also help to improve the reliability of your Chromecast connection.
Hit the Google Store if you want to grab one.
-

Project Westminster is Microsoft's attempt to boost Windows 10 app numbers
Publié: juillet 8, 2015, 5:03pm CEST par Mark Wilson
What do you do if you need to encourage developers to produce more apps for your platform? Make it much, much simpler of course. This is the problem Microsoft has faced for some time now, and in a bid to address the issue it hopes Project Westminster is the answer. With the launch of Windows 10 looming, there's never been a better time to be seen addressing the so-called app-gap.
We learned a little about Project Westminster at Build 2015 earlier in the year -- it basically makes it easy to convert existing web apps into Universal Windows Apps that can run on phones, tablets, and computers. Microsoft is also pushing other projects -- Astoria, Islandwood, and Centennial -- for converting Android and iOS apps, as well as traditional Windows applications into universal apps. Is it enough?
One of the fears with all of these tools is that while they may serve to increase app numbers, they will do nothing to address the small number of apps designed specifically for Windows. As we have seen on mobile platforms, it's very easy to convert a website or web-based service into an app, but web wrappers do not offer anywhere near the same experience as dedicated apps written from the ground up.
Will we see a raft of quick-and-dirty, oh-sod-it-that'll-do conversions popping up in the Windows Store? It's clearly hard to say at this early stage, but it's a very real risk.
With Windows 10 we can see Microsoft venturing into new territory. This is not just a new version of Windows, it's a bid to create a complete ecosystem, to create a Windows experience. Windows 10 is going to be free, we all know that. But part from a few tweaks, nips, and tucks, there isn't really all that much incentive to upgrade from earlier versions. People will -- because it is free -- but Microsoft needs to get the apps in place to complete that experience it is striving for.
Writing on the Windows Blog, Microsoft engineer Kiril Seksenov talks at some length about the benefits of the four platform bridges, focusing mainly on Project Westminster.
Project Westminster embraces "the way of the web" by giving you the opportunity to publish an app while continuing to use your tools, developing your code and deploying to the host you desire. Just enter your app's start page URL and define the app's scope of URLs in the app manifest to create a Universal Windows Platform app. Continue with platform integration by pushing code to your servers, feature detecting for and directly calling Universal Windows APIs.
Microsoft stresses that Project Westminster is "agnostic to the developer workflow that you've chosen", promising that developers "can keep using your favorite code editor, source control and hosting service while developing your website".
But people, all too often, opt for the easy route. We may see app numbers swell in the coming months, but we could also see a growth in the number of low quality web apps quickly converted just for the sake of it. Let's just hope Project Westminster doesn’t turn out to be more like Project Westmonster.
-

Facebook facelift puts women on top
Publié: juillet 8, 2015, 12:48pm CEST par Mark Wilson

Facebook has been busy updating its look. It's very subtle, so you'd be forgiven for missing it. Following on from last week's incredibly understated logo change (just believe us, the font is slightly different) comes an update to the friends icon. A minor thing, you might think, but with the current focus on diversity, it's one that is noteworthy.
The social network comes in for constant criticism; just about everything it does gets a negative reaction. If it's not complaints about Internet.org, it's the company's lackadaisical attitude to privacy. If people are not whining about changes to their news feed, they are questioning censorship. One Facebook designer was unhappy with the way the friends icon pushed a male figure to the front, while the female symbol shrank into the background. So she redesigned it.
Caitlin Winner is a design manager at the social network. Writing on Medium she explains how when browsing through the company's image library, she noticed two things about the female half of the friends icon -- the one that appears to the upper right of your news feed. The isolated version of the female icon had a chip out of her shoulder, while the familiar male-female version featured the man in front of a smaller woman. Winner decided to undertake a redesign, not only removing the chip, but also updating the hair.
But there was something else to tackle:
Next, I was moved to do something about the size and order of the female silhouette in the 'friends icon'. As a woman, educated at a women's college, it was hard not to read into the symbolism of the current icon; the woman was quite literally in the shadow of the man, she was not in a position to lean in.
In the new version of the icon (see above), it is the woman who is in front (sans chip). It's a subtle change, but a small part of a bigger picture. And it sounds as though we might see more minor tweaks in future; Winner is on the lookout for those little cues that can mean so much:
As a result of this project, I'm on high alert for symbolism. I try to question all icons, especially those that feel the most familiar. For example, is the briefcase the best symbol for 'work'? Which population carried briefcases and in which era? What are other ways that 'work' could be symbolized and what would those icons evoke for the majority of people on Earth?
Any pet design peeves that you would like Facebook to take on next?
-

Apple Watch sales are a disaster
Publié: juillet 8, 2015, 11:35am CEST par Mark Wilson

While no official sales figures have been released, analysts suggest that Apple Watch sales figures are dire. The suggestion comes from analysts at Slice Intelligence, with figures pointing to sales now sitting at a fraction of what they were three months ago.
The excitement surrounding any Apple launch means that sales are likely to be high immediately after release, but by anyone's standards Apple Watch sales appear to be a disaster. From a high of around 44,000 sales per week in April, Apple is currently shifting fewer than 5,000 of its wearables each week.
Slice Intelligence used data from shoppers' online receipts to estimate Apple Watch sales since launch day. Even if the estimates are slightly wide of the mark, the general trend will be extremely worrying for Apple. While initial pre-orders looked promising, Apple has not been able to maintain a captive audience with its latest product, as Slice Intelligence's figures show.
The company tweeted a graph showing the declining sales but is yet to publish an accompanying report:
#AppleWatch sales continue to decline in June. #data #Apple pic.twitter.com/Rj1weAzcSa
— Slice Intelligence (@SliceIntel) July 7, 2015
The numbers are broadly in line with sales projections that have been suggested elsewhere, but we'll have to wait a little longer to hear anything official from Apple.
-

No shit! Experts say backdoors and encryption limits are security risks
Publié: juillet 7, 2015, 11:44pm CEST par Mark Wilson

Adding backdoors so governments can access data is a "major security risk". This is the (perhaps slightly obvious) conclusion of security experts and cryptographers writing in a report entitled Keys Under Doormats: Mandating insecurity by requiring government access to all data and communications.
The report from the Massachusetts Institute of Technology’s Computer Science and Artificial Intelligence Lab criticizes plans to allow law enforcement agencies unfettered access to encrypted data through the use of either front doors or backdoors. More importantly it poses the question: "if we want to maintain the security of user information, is this sort of access even technically possible?"
Now that we are all more security conscious than ever before, news that governments around the world -- including the US and UK -- want to limit the strength of encryption that can be used escaped few people. The government wants to be able to access whatever data it wants, whenever it wants, and has tried to force hardware and software manufacturers to build backdoors into their products that it can use.
MIT's report says that calls for law enforcement agencies to be granted "exceptional access" to data fail to take into account the "risks inherent in exceptional access systems". In short, if a backdoor can be used by a government agency, it can be used by someone else; security is massively reduced. We have already seen how a backdoor was exploited by the FREAK SSL flaw -- something that came about because of historic government bans on the use of strong encryption. And just this week Hacking Team -- a security firm used by governments around the world to spy on web activity -- was itself hacked and hundreds of gigabytes of data were made publicly available, highlighting the very real security risks that exist.
The report argues that granting access to encrypted data would prove counterproductive. It "will open doors through which criminals and malicious nation states can attack the very individuals law enforcement seeks to defend". It warns:
...exceptional access would create concentrated targets that could attract bad actors. Security credentials that unlock the data would have to be retained by the platform provider, law enforcement agencies, or some other trusted third party. If law enforcement's keys guaranteed access to everything, an attacker who gained access to these keys would enjoy the same privilege. Moreover, law enforcement's stated need for rapid access to data would make it impractical to store keys offline or split keys among multiple keyholders, as security engineers would normally do with extremely high-value credentials.
It also highlights the problem of the global nature of the internet, asking how countries would interact with each other:
China has already intimated that it may require exceptional access. If a British-based developer deploys a messaging application used by citizens of China, must it provide exceptional access to Chinese law enforcement? Which countries have sufficient respect for the rule of law to participate in an international exceptional access framework? How would such determinations be made? How would timely approvals be given for the millions of new products with communications capabilities? And how would this new surveillance ecosystem be funded and supervised?
The authors suggest that proposals surrounding security backdoors raise more questions than they answer. They say that the onus is on governments to not only prove the need for exceptional access to data, but also to devise the mechanism for access themselves rather than passing the buck to hardware and software manufacturers. As is often the case, this is an issue that boils down to balancing the need for national and international security with personal privacy. It is also important to bear in mind the very great costs that go hand in hand with backdoors and asking the question: is this a price worth paying?
Photo credit: optimarc / Shutterstock
-

Windows 10 Mobile Insider Preview Build 10149 hits Slow Ring
Publié: juillet 7, 2015, 8:28pm CEST par Mark Wilson

Builds of the desktop version of Windows 10 have been released at an accelerated pace in recent weeks, but Windows 10 Mobile users have had far fewer updates to install. A couple of weeks ago, build 10149 was made available to Insiders on the Fast Ring and today it makes its way to the Slow Ring.
Build 10149 has been deemed stable enough to make its way to a larger audience. New features to look forward to include Microsoft Edge, Cortana improvements, updated apps, and plenty of bug fixes.
Microsoft says that tweaks have been made that prevent blurry tiles, and there are updated controls and icons to give a better overall look. This is not necessarily going to be what the final release looks like, but we're getting closer. Other changes include the addition of a flashlight quick action, an updated Photo app, and automatic uploading of camera roll images using OneDrive.
The same warning that applied to the version that hit the Fast Ring remains in place. It may appear that the installation has crashed, but it probably hasn't:
The post-upgrade migration status screen is still missing after upgrading to this build which normally shows you the progress of the post-upgrade migration. After upgrading, the Lock screen will appear frozen without the date and time for up to 10 minutes. Please be patient and let it sit -- eventually the date and time will appear and it will allow you to unlock your phone. If you get impatient and restart or mess with locking/unlocking your phone, you’ll wind up in a funky state -- so just relax and let it do its thing.
The release was given little fanfare, with Gabe Aul tweeting a link to a blog post from two weeks ago:
Windows 10 Mobile build 10149 is now rolling out to #WindowsInsiders in the Slow ring. [t.co]
— Gabriel Aul (@GabeAul) July 7, 2015
The release notes that accompanied the Fast Ring release still apply, and you can check out the Windows Blog for full details of what to expect from this build.
What are you waiting for? Check for updates and start downloading!
-

Pressure mounts on Google to extend Right to Be Forgotten to US
Publié: juillet 7, 2015, 6:29pm CEST par Mark Wilson

The Right To Be Forgotten has proved controversial. A little over a year ago Google was told by a European court that it should accept requests to remove from search results pages that are "inadequate, irrelevant or no longer relevant". Now, calls for the scheme to be extended to the US are growing ever-louder.
Consumer Watchdog not only says that the Right To Be Forgotten should be brought to the US, but also that Google's refusal to do so is an "unfair and deceptive" business practice. The consumer group is writing to the Federal Trade Commission calling for the search giant to be investigated and forced to consider the removal of certain search results. As has been proved in Europe, it's something that is not without controversy.
Reports show that Google actually rejects most requests it receives in Europe, and there have been calls for the company to be more transparent about how it comes to decisions. The Right To Be Forgotten has been incredibly polarizing in Europe, and it's unlikely to be very different in the US. On one hand it is welcomed by those who are looking for a quick fix to the problem of websites that contain information about them they would rather was more difficult to find. On the other, it is something that is accused of amounting to censorship.
The ruling does not mean that data is removed from websites, just that the pages do not appear in Google search results. A number of websites have sprung up that provide information about the URLs that Google has acted upon, and the likes of the BBC track which of their own pages have been affected.
Consumer Watchdog says that the Right To Be Forgotten is an "important privacy option", but striking a balance between personal privacy, freedom of speech, censorship, and general liberty is tricky. The letter to the FTC is critical of Google:
Describing yourself as championing users' privacy and not offering a key privacy tool -- indeed one offered all across Europe -- is deceptive behavior.
Google has already resisted pressure to implement the system in the US, and that's a position that's unlikely to change any time soon. For now, the company is happy to dig in its heels while privacy advocates and freedom of speech proponents battle it out.
Photo credit: Niyazz / Shutterstock
-

Object Theory to create mixed reality apps for Microsoft HoloLens ecosystem
Publié: juillet 7, 2015, 1:25pm CEST par Mark Wilson

Microsoft's take on virtual reality, HoloLens, caused waves of excitement when it was announced a few months ago. Today, a new company founded by a former member of the Microsoft HoloLens Studios team launches to start feeding the ecosystem with a range of apps it is describing not as virtual reality, or even augmented reality, but mixed reality.
Michael Hoffman's Object Theory has been set up with the aim of helping other organizations to build apps that take advantage of what HoloLens can offer. We've already seen how HoloLens can run Windows apps in 3D, and a recent demonstration of Minecraft at E3 thrilled gamers. Object Theory wants to ensure that there is a range of impressive apps on launch day.
To show it means business, the Object Theory website has a holographic mode for anyone who manages to gets their hands on a HoloLens headset (not really, but it does have lots of information!). The enthusiasm is hardly surprising when you consider that within five years, the augmented reality market could pull in $120 billion of revenue; this could be the mobile app explosion all over again.
Hoffman echoes what Microsoft has previously said about the potential impact of HoloLens:
The company was created on the shared belief of the founders that Microsoft HoloLens will have a transformative impact on the way we work, live, and play. With this new platform, our digital life will become more integrated into our physical world than ever before.
Headquartered in Portland, Oregon, Object Theory is looking to work with other companies to create, develop, and launch apps. While gaming and entertainment are expected to be incredibly popular applications of augmented and mixed reality, Object Theory is going to focus on the business and enterprise side of things, hoping to transform the workplace and make the technology work for businesses.
-

Apple wants to control the look of third-party accessory packaging
Publié: juillet 7, 2015, 1:56am CEST par Mark Wilson

Any company wanting to sell its accessories in Apple stores may as well fire some of its designers. Continuing its image-control efforts, Apple is to phase out accessories that are supplied in ugly, non-conforming boxes. Only those accessories that are packaged in boxes co-designed with Apple will be guaranteed shelf space in a store.
Many manufacturers already go to some lengths to mimic the look of official iPhone and iPad packaging, but it won't be long before this is compulsory. A memo sent to retail store staff reveals that accessories from the likes of Incase, Logitech, and Mophie will soon feature the cookie-cutter look that has become synonymous with Apple packaging.
In the coming months, 9to5Mac reports, Apple Store visitors can expect to see more white boxes lining shelves. All packaging will be required to comply with Apple's guidelines that dictate what is aesthetically acceptable in terms of fonts, colors, raw materials, and general style. The move is hardly surprising for a company that is renowned for its anal attention to detail, but there is potential for the consistent look to be confusing.
9to5Mac says:
The company is gearing up to revamp its third-party accessory selection across all of its retail stores by next week by reducing the amount of accessories available in stores to ones sold in packaging co-designed by Apple [...] Over time, Apple will work with more accessory makers to support the new packaging style as it reduces inventory of items that do not fit the new look.
With Apple's plans to create a more uniform look for boxes, improve label consistency, and control the appearance of packaging by being involved in the design process even for third party accessories, there is room for confusion. If all packaging looks similar, customers may start to find it difficult to distinguish between third party and official accessories. For Apple, though, it will help to bring one more side of the business in house, helping to reduce the risk of the design leaks which often stems from accessory manufacturers.
Manufacturers are going to be actively encouraged, or feel compelled, to work more closely with Apple. Whether this turns out to be a good or a bad thing really depends on whether they are left to get on with things without too much interference.
Photo credit: 360b / Shutterstock
-

Social network Facegloria bans swearing, gay content, and sin
Publié: juillet 6, 2015, 6:57pm CEST par Mark Wilson

Need a social network to connect with friends and likeminded individuals? Take your pick; there are dozens to choose from. Facebook remains by far the most popular and, as it is used by real people, it is filled with everything that makes up life -- the good and the bad. In response, a group of Evangelical Christians in Brazil set up Facegloria with the aim of becoming "morally and technically better than Facebook".
Actually the real aim of the site is to promote Christianity -- to the extent that rather than a Like button, there is an Amen button. Think "godbook", if you will. Of course there are restrictions -- religion isn’t meant to be fun, you know. On the list of banned content is violence and pornography, swearing (there are literally hundreds of banned words), anything that violates "biblical principles", and depicting or referring to homosexual activity.
Clearly this is a social network with a particular market in mind, and it has already attracted more than 100,000 users. For now Facegloria is only available in Portuguese, but there are plans to expand into other languages. Speaking to AFP, web designer Atilla Barros said: "On Facebook you see a lot of violence and pornography. That's why we thought of creating a network where we could talk about God, love and to spread his word".
The network is policed by a team of 20 volunteers, on the lookout for any content that could damage the fabric of society. The aim is to attain 10 million users in the next two years, with a boost in numbers expected from an upcoming mobile app.
Just like Facebook, anyone is free to sign up for Facegloria. But if you do, you had better be on your best, most biblical behavior, or you may find that your content is censored, or even that your account is shut down. And if you happen to be a gay Evangelical Christian, you might be best not shouting about it on Facegloria -- save that for Facebook, yeah?
Photo credit: CREATISTA / Shutterstock
-

Laptops to slim down with LG's thinner, lighter LCD panels
Publié: juillet 6, 2015, 5:56pm CEST par Mark Wilson
With portability in mind, laptop owners generally have two key concerns -- weight and battery life. Today LG announces a new range of thin and light LCD panels that will help to reduce the weight and size of laptops of the future.
The Advanced In-Cell Touch (AIT) panels are slimmer than traditional touch screens as they feature embedded touch sensors rather than a separate panel placed on top of the display. The panels will go into mass production in the second half of this year, bringing technology previously used by LG in smartphone screens to larger devices.
Available in 14- and 15.6-inch versions, the AIT panels are full HD units that are slimmer than their predecessors by a full millimeter. Although the company does not reveal any names, LG says that it has agreements in place with several major notebook manufacturers to supply displays. It is also looking to investigate the release of difference sizes depending on demand.
LG says:
The technology eliminates the space needed for a touch function cover glass, and as a result reduces the panel’s thickness by 1 millimeter (approximately 25 percent) and its weight by 200 grams (approximately 35 percent) compared to a conventional 15.6-inch touch-embedded panel with Full HD resolution. It also offers a brighter and clearer screen picture since there is no light loss or light reflection caused by the cover glass. In addition it features an excellent touch response and precise calibration of the touch point even with water drops on the screen.
Also in the pipelines are new panels specifically for pen input. Looking to the end of 2015 and beginning of 2016, we should start to see the arrival of notebooks that are noticeably thinner.
-

First Windows 10 RTM candidate is build 10176
Publié: juillet 6, 2015, 1:45pm CEST par Mark Wilson
With just over three weeks until the launch of Windows 10, preview builds are still popping out left, rights, and center -- some more official than others. Microsoft is beavering away on the final build which will start to roll out on 29 July, and it seems that the RTM version could be signed off as early as this week.
Build tracking site BuildFeed shows that Windows 10 Build 10176 from the th1 branch (a reference to threshold, Windows 10's codename) is now being tested as a release candidate. With a full build string of 10.0.10176.16384.th1.150705-0552, the appearance of this version ties in neatly with a rumor that RTM might be reached this week -- perhaps as early as Thursday.
It has been suggested that the screenshots of the leaked build 10163 contain a hint at when RTM might happen. Wzor's screenshots include an image of the Calendar app which shows 9 July as RTM Sign-Off day. Of course, Wzor is not an official source, but as a leaker has a near-impeccable record of reliability.
With the recent acceleration in build releases, it's possible that Windows 10 Build 10176 will be released to Windows Insiders to try it out for themselves. Even if this does not happen, it's clear that Microsoft is now every much on the home straight, busying itself with the final nips and tucks before the big day rolls around.
-

Hacking Team hacked as tables turn on notorious surveillance company
Publié: juillet 6, 2015, 12:56pm CEST par Mark Wilson

Italian security and surveillance firm Hacking Team appears to have itself fallen victim to a security breach. Hacking Team produces software which is used by governments around the world as part of their surveillance programs. The company has been criticized for facilitating invasions of privacy, and, over the weekend, its Twitter feed was taken over, resulting in its name and profile picture being changed to read Hacked Team.
But this is far from being the end of the story. Whoever is responsible for the security breach also released a torrent file that provides access to 400GB of company data. Included in the cache are emails, source code, and confidential documents. The files reveal who the company has been dealing with including a number of countries known for their oppressive regimes.
Invoices leaked from the stash of documents via the hacked Twitter account show that Hacking Team provided services for countries such as Egypt and Sudan. This includes providing surveillance equipment as well as software for gaining remote access to computers. We've heard a lot about Hacking Team since the explosion of the NSA surveillance debacle. A secret manual published last year showed just how to use the company's various tools to spy on people, get around encryption.
Working through all of the documents that have been leaked since Sunday's breach, CSO reports that Hacking Team's list of customers includes:
Egypt, Ethiopia, Morocco, Nigeria, Sudan, Chile, Colombia, Ecuador, Honduras, Mexico, Panama, United States, Azerbaijan, Kazakhstan, Malaysia, Mongolia, Singapore, South Korea, Thailand, Uzbekistan, Vietnam, Australia, Cyprus, Czech Republic, Germany, Hungary, Italy, Luxemburg, Poland, Russia, Spain, Switzerland, Bahrain, Oman, Saudi Arabia, and UAE.
Hacking Team has gained the attention of human rights groups for its apparent willingness to work with countries engaged in human rights abuse, and those looking to spy on journalists, and people opposed to the government.
The attackers have not been afraid to rub a little salt in the wound. As well as the name change to Hacked Team, the security firm's description was also edited to read:
Developing ineffective, easy-to-pwn offensive technology to compromise the operations of the worldwide law enforcement and intelligence communities.
Control of the account has since been regained.
In addition to invoices, the leaked cache of data also reveals many of the passwords used by clients. With examples such as Passw0rd, Pas$w0rd, and Passw0rd!, it seems clear that security is not viewed with as much importance by all.
Hacking Team was very slow to respond to the attack. Eventually, Christian Pozzi from the company took to Twitter to hit out at the perpetrators. He also defended Hacking Team, suggesting that what was being posted by the attackers was not to be believed, and also tried to discourage people from downloading the data but suggesting that the torrent contained a virus. It's not clear how long it will take Hacking Team to regain control of its accounts, but Pozzi insisted that police are currently investigating. His Twitter account has subsequently been taken offline.
With the number of big governments that seem to be customers of Hacking Team, the fallout from this breach could be huge. As one Infosec associated puts it:
Bad day? Could be worse. It's now someone at @hackingteam's job to call up the Russian secret police and inform them there's been a breach
— Liam (@liamosaur) July 6, 2015
-

Bitcoin wallets vulnerable to double-spending bug
Publié: juillet 5, 2015, 6:49pm CEST par Mark Wilson

The cryptocurrency Bitcoin has not been without its problems. There have been numerous hacks leading to the loss of millions of dollars, and Bitcoin mining tool Epic Scale became embroiled in a crapware scandal with uTorrent. The latest problem to hit the digital currency is a double-spending bug.
As the name suggests, this essentially makes it possible to spend the same Bitcoins twice, and it stems from a problem with a planned upgrade. An issue with some Bitcoin miners means that tests that usually prevent double-spending are not correctly performed. The problem was discovered on 4 July as many Americans were busy celebrating Independence Day.
Double-spending is supposed to be thwarted by a safety mechanism which checks the block chain (or transaction database) to check whether any given Bitcoins have been spent or not. Some Bitcoin miners are now generating invalid blocks, making it impossible to guarantee that currency can’t be spent more than once. The Bitcoin Foundation assures users that all transactions confirmed by 15:00 on 4 July are safe.
An announcement on the Bitcoin website explains:
For several months, an increasing amount of mining hash rate has been signaling its intent to begin enforcing BIP66 strict DER signatures. As part of the BIP66 rules, once 950 of the last 1,000 blocks were version 3 (v3) blocks, all upgraded miners would reject version 2 (v2) blocks.
Early morning UTC on 4 July 2015, the 950/1000 (95%) threshold was reached. Shortly thereafter, a small miner (part of the non-upgraded 5%) mined an invalid block--as was an expected occurrence. Unfortunately, it turned out that roughly half the network hash rate was mining without fully validating blocks (called SPV mining), and built new blocks on top of that invalid block.
Note that the roughly 50% of the network that was SPV mining had explicitly indicated that they would enforce the BIP66 rules. By not doing so, several large miners have lost over $50,000 dollars worth of mining income so far.
Despite adoption by a number of big names -- including Microsoft -- many people remain skeptical of the digital currency. But there are others who believe cryptocurrencies are the future of online, and real world, transactions. With the economy failing in Greece as the country teetering on the verge of crashing out of the EU, some Greeks have converted their money into Bitcoin in an attempt to minimize the risk of devaluation.
At the moment there is no news that the problem has been exploited by anyone, but unless the vulnerability is addressed, it's only a matter of time before this happens.
Photo credit: Lightboxx / Shutterstock
-

DJs and music fans warned iTunes 12.2 could corrupt music libraries and add DRM
Publié: juillet 5, 2015, 2:09pm CEST par Mark Wilson

With the launch of Apple Music came a new version of iTunes. Apple's new streaming music service initially hit the headlines for all the wrong reasons thanks to Taylor Swift, and now it is the turn of iTunes. It's an app that many love to hate, and now there is another reason to dislike the music management tool.
It's not just runners with iPhone and iPod users looking for a musical accompaniment to their daily exercise who use iTunes to organize their music collection, it is also used by professionals. The software is also by DJs to keep their music collections in check, but anyone who relies on their music library might want to heed the warning of website Digital DJ Tips -- "Warning to DJs: Do not upgrade to iTunes 12.2!"
The DJ site warns that those considering upgrading to the latest version of iTunes should rethink, or upgrade with extreme caution. The cautionary notice is quite stark, with would-be upgrading told to consider that iTunes 12.2 could implement "DRM, change your track artwork, alter your tags, and more". Digital DJ Tips is not alone in suggesting that people might want to steer clear of the upgrade -- others have noticed what is being described as a 'bug' as well.
Worrying numbers of users have reported that their music libraries have become corrupt, metadata has gone awry, and album art has become mixed up. But more irritating -- if that's not putting it too lightly -- the iTunes Match feature has caused files to be crippled with DRM. Choosing to sync music to the cloud is something that lots of people will opt to do, and the addition of DRM is something that has irked many.
Digital DJ Tips suggests ignoring iTunes 12.2 for now, or at least making sure that it is all backed up in case anything untoward should happen. The sheer numbers of people complaining about the same issues would suggest that this is far from being an isolated problem, so if you rely on your music collection, you might want to take care. You have been warned!
Photo credit: VGstockstudio / Shutterstock
-

Having problems activating Windows 10? You're not alone
Publié: juillet 5, 2015, 12:36pm CEST par Mark Wilson

Microsoft has been busy over the last seven days, pumping out no fewer than three new builds of Windows 10 to Insiders. Hot on the heels of build 10158 came build 10159, followed swiftly by build 10162.
As these are previews, problems are to be expected, and some users are having trouble activating their copies of the operating system. Despite the fact Microsoft is giving away Windows 10 free of charge, activation is still required and it seems the company still has a few kinks to iron out before launch day on July 29. So what's the deal?
Microsoft is aware of the issue which has arisen because of on-going development of Windows 10, including work that is being done on the activation process itself. Users have complained that they are not only unable to activate Windows 10, but also that it is not possible to change their product key.
Writing on Microsoft Answers in response to queries about the problem, the company said:
We are doing some testing and work on the Activation process. That message is expected and we hope it will go away in the next day. When we have the service back up and running, it should attempt to activate automatically. Until then you can ignore it because I believe other than the UI showing it's not activated, it's not affecting any other use of the system.
Patience, it seems, is all that's required.
Have you experienced activation issues?
-

OnePlus has free Google Cardboard VR headsets for everyone!
Publié: juillet 4, 2015, 12:06am CEST par Mark Wilson

Virtual reality is making a comeback. Forget the atrocious examples we endured in the 90s, now we have the likes of Oculus Rift to delight our senses, and Microsoft is tempting us with HoloLens. Neither of these are particularly cheap, but Google came up with a cheap alternative in the form of Cardboard.
As the name suggests, this is a foldable cardboard unit which can be used to transform a variety of smartphones into a fully-fledged VR headset. While much cheaper than the likes of Oculus Rift and HoloLens, Cardboard is not free... or at least, it wasn't. Ahead of the launch of OnePlus 2, OnePlus is offering its own OnePlus CardBoard for free.
Take a browse through the various Cardboard offerings that are available through Google and you'll find that prices vary wildly. Head over to the OnePlus website, however, and you can grab a headset for nothing more than the cost of shipping -- the headset itself is completely free.
This is OnePlus' own take on Cardboard. The company says:
We applaud Google Cardboard for advancing the dream of bringing VR to homes around the world, but we believe it could be even better. Even more accessible. In typical OnePlus fashion, we didn’t just sit around and talk about how it could be better; we made our own. In addition to the Cardboard 2.0 features, we’ve made a few more improvements.
Despite coming from OnePlus, you are not restricted to using it with just OnePlus handset -- in fact you should be able to use just about any smartphone up to 6 inches in size. The free unit is not just made of run-of-the-mill cardboard, it is specially coated to make it more durable. Order your free Cardboard from OnePlus and you'll receive it some time after July 10 when shipping starts. If you're in the US head here, while UK resident can place their order here.
-

The 2015 Nexus 5 will be built by LG
Publié: juillet 3, 2015, 10:22pm CEST par Mark Wilson

The Nexus range of smartphones has proved a popular way to get a fairly high-end handset running stock Android at a decent price. Previous models have (largely) sold well, and there is always eager anticipation surrounding the next release. One thing people are always keen to know is just who is going to be making the handset.
According to a report by AndroidPIT, it is LG who will be responsible for the 2015 Nexus 5. A spokesperson said that the device is to be based on a yet-to-be-seen prototype rather than the LG G4. Based on previous launches, it's safe to assume that the release will coincide with the launch of the next version of Google's mobile operating system, Android M.
While the Nexus 5 was something of a winner, the larger Nexus 6 was less of a hit. Larger devices have become more common, but 5 inches remains a comfortable, popular screen size. To reinvigorate the Nexus market, sticking to something slightly more populist makes complete sense. It's not yet clear whether the device will retain the Nexus 5 moniker but talking to AndroidPIT, a source close to the development of the device confirmed LG's involvement.
We heard a little about Android M at Google I/O earlier in the year, with changes to security, battery life, and permissions being key features. While there is already a developer preview available, we don’t yet have an exact release date for Android M. While new versions of Android tend to appear in the fall, this time around it is expected to be a little earlier -- August has been hinted at. The Nexus 5 could be launched at the same time, but if not it is sure to be close behind.
-

Your online payments could soon be authorized with a selfie
Publié: juillet 3, 2015, 1:10pm CEST par Mark Wilson

Make an online payment with your credit card and you're probably used to having to enter a password or PIN. But if a trial scheme by MasterCard takes off, this could become a thing of the past. The finance company is testing out a new payment authorization technique including fingerprint scanning and facial recognition.
MasterCard is working with Apple, BlackBerry, Google, Microsoft, and Samsung to introduce the biometric checks. The initial plan is to trial the system with 500 participants before possibly rolling it out on a larger scale. It's something that MasterCard believes will be welcomed by millennials and should simplify the process of making payments from a smartphone.
Demonstrating the system to CNNMoney, it showed how payments could be authorized with a quick touch of a fingerprint scanner, something Apple and Samsung have already implemented. The other option is to use facial recognition. A clear security concern here is that as well as authorizing payments by pointing a cameraphone at one's face, the system might be foiled by simply using a photograph. To get around this problem, users will be required to blink to indicate that they are a real person.
MasterCard says that privacy is maintained by not transmitting or saving images of fingers or faces. Scans are digitized and sent encoded to authorization servers. It's not something that is going to appeal to everyone, but Ajay Bhalla from the company says: "The new generation, which is into selfies. I think they'll find it cool. They'll embrace it".
Other possible authorization techniques include heartbeat pattern checking and voice recognition. But for now, it's the trial of facial and fingerprint scanning to look out for -- you might be using your face to make your next purchase.
Photo credit: Vladimir Gjorgiev / Shutterstock
-

Which version of Windows 10 is right for you?
Publié: juillet 2, 2015, 10:44pm CEST par Mark Wilson
It's not long since Microsoft revealed the various editions of Windows 10 that will be available. We're now in the launch month and the preview builds are rolling out thick and fast to Windows Insiders. But when the big day rolls out, which version should you opt for?
If you're upgrading from Windows 7 or Windows 8, it's a fairly simple process that can be taken care of by Windows Update. For those who have decided to make the upgrade, Microsoft will automatically migrate you to the equivalent version of Windows 10. But if you're running the Home version of Windows, what are you missing out on? Is it worth thinking about going Pro? Microsoft has a handy guide to help you decide.
It's worth having a quick recap of the various upgrade paths that exist. If you're running Windows 7 Starter, Windows 7 Home Basic, or Windows 7 Home Premium, you're eligible to upgrade to Windows 10 Home. If you're running Windows 7 Professional or Windows 7 Ultimate, you're eligible to upgrade to Windows 10 Pro. If you're running Windows 8.1, you're eligible to upgrade to Windows 10 Home. Finally, if you're running Windows 8.1 Pro or Windows 8.1 Pro for Students, you're eligible to upgrade to Windows 10 Pro.
With Windows 10, there are four key versions to consider: Home, Pro, Enterprise, and Education. As shown by Microsoft's Windows 10 version comparison website, all four have the same 'core experiences'. Everyone gets Cortana, virtual desktops, Microsoft Edge, and so on. But if you look at things from a more business-centric view (something which many home users will do anyway), it's a slightly different story. Now the differences between the versions become clear.
It goes without say that Windows 10 Home has the fewest features, but this is unlikely to be a problem for most people. By moving up to Windows 10 Pro, you gain extra such as Bitlocker, Remote Desktop, Enterprise Mode Internet Explorer, and other options. If you need Windows To Go Creator, AppLocker, Credential Guard, and the like, you'll need to opt for Windows 10 Enterprise.
Check out the Windows 10 version comparison website for full details. You can take a look through the online version of the comparison, but Microsoft has also produced a PDF that displays the same information on three pages.
-

UK government illegally spied on Amnesty International
Publié: juillet 2, 2015, 6:43pm CEST par Mark Wilson

A court has revealed that the UK intelligence agency, GCHQ, illegally spied on human rights organization Amnesty International. It is an allegation that the agency had previously denied, but an email from the Investigatory Powers Tribunal backtracked on a judgement made in June which said no such spying had taken place.
The email was sent to Amnesty International yesterday, and while it conceded that the organization was indeed the subject of surveillance, no explanation has been offered. It is now clear that, for some reason, communications by Amnesty International were illegally intercepted, stored, and examined. What is not clear is when the spying happened, what data was collected and, more importantly, why it happened.
The privacy and surveillance debate brought about by Edward Snowden's revelations have centered around the activities of the NSA. Other agencies have also been implicated in mass surveillance programs -- including the suggestion that the NSA passed information to GCHQ. The revelation that an intelligence agency that has been involved in spying on terrorists and criminals has also been spying on a human right groups will cause concern for many people.
June's ruling accepted the fact that GCHQ had been spying on human rights organization, but said that the Egyptian Initiative for Personal Rights and the South Africa-based Legal Resources Centre were who had been subject to surveillance. The amended ruling recognizes that it was Amnesty International who had been spied on, not the Egyptian Initiative for Personal Rights.
The group wrote on Twitter:
Errr... UK's surveillance court - IPT- just wrote to us to 'correct an error' turns out UK gov WAS spying on Amnesty International after all
— AmnestyUK Media Team (@NewsFromAmnesty) July 1, 2015
Salil Shetty, Amnesty International’s Secretary General, expressed disgust at the actions of GCHQ, said:
It's outrageous that what has been often presented as being the domain of despotic rulers has been done on British soil, by the British government. How can we be expected to carry out our crucial work around the world if human rights defenders and victims of abuse can now credibly believe their confidential correspondence with us is likely to end up in the hands of governments?
Shetty went on to question not only the legitimacy of the surveillance, but also the circumstances in which it was made known:
After 18 months of litigation and all the denials and subterfuge that entailed, we now have confirmation that we were in fact subjected to UK government mass surveillance.
The revelation that the UK government has been spying on Amnesty International highlights the gross inadequacies in the UK's surveillance legislation. If they hadn't stored our communications for longer than they were allowed to, we would never even have known. What's worse, this would have been considered perfectly lawful.
This is an interesting point. The Regulation of Investigatory Powers Act actually permitted GCHQ to spy on Amnesty International. However, the agency then stored the data collected for longer than allowed by law meaning it was obliged to come clean about its activities.
Amnesty International is now calling for an independent inquiry into the reasons behind the surveillance.
-

Online disruption after internet backbone cables are cut in CA
Publié: juillet 1, 2015, 11:32pm CEST par Mark Wilson

Vandals have struck in California's Bay Area leading to a disruption to web traffic. The FBI is investigating the incident which occurred when several fiber optic cables were severed in Livermore, around 50 miles east of San Francisco.
The attack took place at about 4.30 am PT Tuesday, and caused problems for ISPs as well as Microsoft Azure. Backbone providers were hit hard, and web users over a wide area suffered from reduced performance. This is far from being the first attack on internet cables in the area, and the FBI is seeking help from anyone with information that could bring the perpetrators to justice.
In the last year, there have been 11 attacks on fiber optic cables and investigations are still on-going. The FBI says that cables have been intentionally severed and calls on those who saw anything to come forward.
"Anyone who may have been in these areas during these times and saw anything either suspicious or related to normal telecommunications maintenance is urged to contact the FBI. The individuals may appear to be normal telecommunications maintenance workers or possess tools consistent with that job role."
At the moment it is not known whether any or all of the attacks are related.
The problem was fixed by last night, but not until countless online and phone services were affected. The Microsoft Azure status website shows an advisory for West US and South Central US:
From approximately 14:45 UTC to 21:45 on 30 Jun, 2015 UTC customers may have experienced intermittent connectivity issues to Azure services deployed in West US and South Central US. Root cause for this issue is attributed to a fiber cuts in the Western US Region. This incident has now been mitigated.
Photo credit: Tatiana Popova / Shutterstock
-

Google apologizes for labeling black people 'gorillas'
Publié: juillet 1, 2015, 6:58pm CEST par Mark Wilson
Google has issued an apology after the automatic tagging feature of its Photos apps labeled a black couple as 'gorillas'. This is not the first time an algorithm has been found to have caused racial upset. Earlier in the year Flickr came under fire after its system tagged images of concentration camps as sports venues and black people as apes.
The company was criticized on social networks after a New York software developer questioned the efficacy of Google's algorithm. Accused of racism, Google said that it was "appalled" by what had happened, branding it as "100% not OK".
Google executive Yonatan Zunger says that the company has now taken steps to ensure that the problem does not arise again. He said that such an issue was "high on my list of bugs you 'never' want to see happen". Google is working not only on improving image recognition technology, but also taking greater care with the wording used in automatic labels.
The problem was spotted by Jacky Alciné who posted a screengrab of the inappropriate labeling on Twitter:
And it's only photos I have with her it's doing this with (results truncated b/c personal): pic.twitter.com/h7MTXd3wgo
— diri noir avec banan (@jackyalcine) June 29, 2015
Speaking to the BBC, a Google spokeswoman said:
We're appalled and genuinely sorry that this happened. We are taking immediate action to prevent this type of result from appearing. There is still clearly a lot of work to do with automatic image labeling, and we're looking at how we can prevent these types of mistakes from happening in the future.
Photo credit: Corepics VOF / Shutterstock
-

O2 has exclusivity and special offers on Surface 3 4G for UK business customers
Publié: juillet 1, 2015, 4:55pm CEST par Mark Wilson

In the last couple of weeks there have been two new Surface models announced. Just a couple of days ago we learned of the new, cheaper Core i7 Surface Pro 3, and just before this the traveller-friendly 4G LTE Surface 3 -- still no news of the Surface 4 or Surface Pro 4, sadly.
In the UK, business and enterprise customers will be able to buy their 4G LTE Surface 3 from O2. The company has a three month exclusivity deal with Microsoft that means this is the only place the 10.8 tablet will be available during this period. As well as being the sole source of the device, O2 has a few deals to entice would-be customers into making a purchase.
Aimed squarely at small businesses, the Surface 3 4G can be bought for as little as £50. This is dependent on signing up for a two-year contract at £27.67 per month and prices exclude VAT. The tablet is available in 64GB and 128GB versions and come with Windows 8.1 pre-installed. As an incentive to buy the tablet, O2 is offering the Surface Pro Keyboard for half price when purchased alongside Office 365 and McAfee Multi Access, or Windows Intune.
The company also announced that it will be stocking the Surface Pro 3. Starting at £707.50, the Pro version of the tablet is available as a 128GB version with 4GB RAM or a 256GB version with 8GB RAM.
O2 Business Director Ben Dowd said:
We're proud to be the first to market in the UK with the Microsoft Surface 3 4G. At O2 we're always looking for ways to give our customers the best in class digital products, services and applications, so they can experience the benefits of having the latest technology at the heart of their business. The Microsoft Surface family is a fantastic example of this and I hope our customers are as excited as we are to start using the new devices.
Business customer can head over to the O2 website to find out more about the Surface 3 4G and the Surface Pro 3. The devices will be available from 3 July.
-

Washington Post implements encryption to protect site visitors
Publié: juillet 1, 2015, 12:33pm CEST par Mark Wilson

Heightened awareness about online security means that more and more websites are using encryption to boost privacy and security. A few weeks after Wikimedia announced it was using HTTPS to encrypt traffic to its site, The Washington Post has followed suit.
It's a move designed to stop snooping on readers' browsing habits. The news outlet explains that it will make it "more difficult for hackers, government agencies and others to track the reading habits". For those concerned about privacy, this will come a good news, but there's a catch; encryption does not apply to the entire site.
To start with, the new security measure only apply to the site's homepage, the national security pages, and the technology policy blog. The rest of the site has not been forgotten; site-wide encryption will roll out in the coming months, although no precise timeframe has been announced. The move to encrypted sites is common in certain areas -- banking, email, shopping, for example -- but, as the Post points out, mainstream news sites have been slow to make the switch.
Writing about the introduction of encryption, the Post's Andrea Peterson says:
Although some smaller online-only outlets, including the Intercept and TechDirt, use https technology by default, The Post is the first major general news organization to roll out the added security measures to all of its readers.
As well as keeping reading habits private, encryption also makes it more difficult for sites to be censored around the world. The site is expecting a slight drop in advertising revenue as a result of the move, as the site will require all advertisers to be secure. The Washington Post's chief digital architect Greg Franczyk said: "Every third party we use on the site needs to be https-compliant, or it either stops working or the browser will warn about it being insecure".
Photo credit: Gil C / Shutterstock.com
-

Microsoft issues a surprise new Windows 10 release -- build 10159
Publié: juin 30, 2015, 11:10pm CEST par Mark Wilson
Hey... wait a minute. Didn't we just get a new build of Windows 10 yesterday? Yes, of course we did. Less than 24 hours ago, Microsoft released build 10158 and today there is something of a surprise announcement for Windows Insiders who are signed up to the Fast Ring: another new preview version in the form of build 10159.
Microsoft has been criticized for the speed at which preview builds have been trickling out, and it seems that the company is listening to feedback. You'll notice that there is only a single digit build increase, but Gabe Aul reveals that this doesn't mean there's nothing to see. As well as more than 300 bug fixes, there is also "one very interesting change".
Aul is being a little cagey about just what is included in build 10159 -- in fact, he's being quite a tease. Pre-empting the release of the build to Fast Ring users he does not elaborate on what the "one very interesting change", but promises that the download will be made available later this afternoon (any clues in the screenshot?). What's the deal with two builds released in such quick succession? Aul explains:
We’d been using 10158 for almost a week and knew it was going to be a strong build, and the data backed that up so we released it yesterday. Hot on its heels though was build 10159, which in addition to more fixes (over 300 of them!), took in one very interesting change. We didn't want to wait with 10158 so we went ahead and released that build while we were still evaluating 10159. As it turns out though, 10159 is also a great build and passes our criteria for the Windows Insider Fast ring.
With build 10158 having only been released yesterday, it's quite possible that you're still in the middle of a download. Microsoft warns that if you are in the middle of downloading build 10158 when build 10159 is published, you may see an error 0x80246017. If this does happen, all you need to do is restart your computer and check for updates once again.
We'll write more about this release as soon as we get our hands on it.
So, what do you make of this new surprise build?
-

Medium.com ditches passwords to increase security
Publié: juin 30, 2015, 10:40pm CEST par Mark Wilson

Remembering all of the passwords required to gain access to all of your online accounts is a pain. You could opt to use a password manager, or you might decide to use the same password for everything. But Blogging platform Medium.com has another option -- just don't use one!
The site has been anti-password for some time; users log into their accounts using an existing Twitter or Facebook account. For people who are not social network users, however, there's a new option. Working in a similar way to the 'I've forgotten my password' system used by many sites, Medium allows users to log in using nothing but their email address -- and says the system is more secure than regular passwords.
Ditching passwords as well as Twitter and Facebook-based logins might seem as though it would open up accounts to unauthorized access, but Medium says that this is far from being the case. Passwords can be very easily compromised, but by emailing time-limited login links to users, Medium thinks it has come up with a solution.
When the time comes to log in, users can request that an email be sent to them. The email contains a unique link that when clicked, logs the users into his or her account. If the link is not clicked within 15 minutes, it expires and each link can only be used once. This means that unless someone else has access to your email account, only you will be able to see the link, and only you will be able to log in.
As well as increasing security, the new login option means that those who shun social networks can use the site, as can those who are unable to use the likes of Twitter and Facebook due to local censorship.
For now the option can be used on the Medium website as well and in the iOS app. Android users will have to wait for an app update to be released -- and this should be happening soon.
Photo credit: shutteratakan / Shutterstock
-

Apple DID conspire to inflate ebook prices, must pay $450 million
Publié: juin 30, 2015, 7:56pm CEST par Mark Wilson

On the same day that Apple Music launched, Apple received some bad news from the 2nd U.S. Circuit Court of Appeals. In a 2 to 1 vote, judges ruled that the company did conspire with publishers to inflate the prices of ebooks sold through iBookstore, agreeing with a 2013 ruling.
The judges found that Apple had violated federal antitrust law in coming to arrangements with five publishers, resulting in book prices jumping from $9.99 to between $12.99 and $14.99. Two years ago US District Judge Denise Cote said that Apple was "central" to a price-fixing conspiracy. The ruling having been upheld today, Apple will now have to pay $450 million.
The case centered around Apple's dealings with Hachette Book Group Inc, HarperCollins Publishers LLC, Penguin Group Inc, Simon & Schuster Inc, and Macmillan. The collective stood accused of working together to push up prices to a level that they were all happy with. Apple's civil liability in the case has been upheld, as has an earlier injunction which places limitations on the agreements the company can enter into with publishers.
Although two judges today found against Apple, one disagreed saying he wanted to overturn the 2013 ruling. US Circuit Judge Dennis Jacobs thought that rather than being anti-competitive, Apple was actually fighting Amazon's market monopoly. He said "Apple took steps to compete with a monopolist and open the market to more entrants, generating only minor competitive restraints in the process".
Photo credit: 360b / Shutterstock
-

Avira wins case upholding its right to block adware
Publié: juin 29, 2015, 7:46pm CEST par Mark Wilson

Security firm Avira has won a court case that can not only be chalked up as a win for consumer rights, but could also set something of a precedent. German company Freemium.com took Avira to court for warning users about 'potentially unwanted applications' that could be bundled along with a number of popular games and applications.
Freemium.com downloads included a number of unwanted extras in the form of browser toolbars, free trial applications, adware, and other crapware. Avira's antivirus software warned users installing such applications; Freemium took objection to this and filed a cease and desist letter, claiming anti-competitive practices. But the court ruled in Avira's favor, saying it could continue to flag up and block questionable software.
Freemium runs a number of download and gaming sites, and its own installer is frequently used in place of a regular setup executable. It is used to install software from partners and advertisers to generate extra funds. The company claimed its ad revenue has dropped by 50 percent since its software had been flagged. The court said that Avira was well within its rights to issue warnings about potentially unwanted components. Freemium was ordered to pay all court costs.
Avira CEO Travis Witteveen said:
This ruling establishes a major legal milestone in the fight against misleading consumers into unintentionally installing unwanted software onto their computers. Earlier this year we established clear guidelines defining unethical software behavior, and defining what our security software will block. We believe in 'freemium' and advertising-supported business models, however they must remain transparent and ethical in their implementation.
Freemium had argued that users were given the ability to opt out of installing extra software, but the court found that opting out was not made sufficiently clear.
Photo credit: zimmytws / Shutterstock
-

Family Safety updated and renamed Microsoft Family ready for Windows 10
Publié: juin 29, 2015, 5:36pm CEST par Mark Wilson

It can't have escaped your attention that we are now on the home straight for the release of Windows 10. With just a month to go, there are a few loose ends to tie up with the operating system itself, but there are also areas of the Windows ecosystem that are receiving attention ahead of the launch. One such component is Family Safety, Microsoft's parental control system.
Now renamed to Microsoft Family, the settings can be used to monitor and restrict what younger computer users are able to do on a computer. As well as the change of name, Microsoft Family is now part of Microsoft Account and there has been a bit of a redesign to make it easier to get around.
It is now easier to restrict access to adult content (it's blocked by default) and to block individual websites. Age ratings have also been updated to make it quicker to prevent the use of unsuitable apps and games. It's not all a matter of simplifying things. Changes to linked accounts mean that if you have linked your children's Family Safety accounts, you will need to manage settings for each device separately. Microsoft recognizes that "this may be painful for some of you" but says that it will help to make account roaming easier.
There's more to come for Windows 10 users as well. On the Microsoft Family FAQ, the company says:
On Windows 10, you'll need a Microsoft account in order to use Microsoft family whether you're part of a family as an adult or a child. When kids are added to a Microsoft family with a Microsoft account, any time they sign in to a Windows 10 device their settings will be applied and their activity will be reported to the adults in their family. Adults can always turn off activity reporting or remove children from the Microsoft family at account.microsoft.com/family.
There are more changes to come in the next few months, and Microsoft recommends keeping an eye on the FAQ for further updates.
Photo credit: Krigerix / Shutterstock
-

Chromecast update moves users to beta channel and breaks apps
Publié: juin 29, 2015, 1:45pm CEST par Mark Wilson

A recent update pushed to Chromecast devices has caused a series of problems for users. One of the most obvious issues is that users who were signed up to the regular, stable update channel found that they had been moved to the beta channel without their permission. Although the problem started to appear a few days ago, Google has been slow to issue a fix.
The update has also caused problems with a number of Chromecast apps including YouTube, Plex, and HBO GO. Not all users have been affected by the issues, and Google insists that only "a small percentage of users" have the issue which is flagged up by a beta/developer string at the bottom of the screen.
There are a few threads on the Chromecast help forums in which users complain about the problems they are experiencing. Google has pushed out an update which has been very slowly rolling out to users. While the update has removed the beta/developer text for some people, not everyone has been as lucky. Google suggested using the Chromecast app to force an update, but apps remain problematic for some.
Problems remain for some users who rely on the Plex app, and YouTube playlists have been plagued by an issue with unwanted disconnections. Other problems that have been reported include a loss of subtitles in HBO GO.
Have you experienced problems with your Chromecast?
-

Apple Music to quadruple iTunes Match limit to 100,000 songs
Publié: juin 29, 2015, 12:23pm CEST par Mark Wilson

Apple Music has managed to cause quite a storm before it even launches, and Eddy Cue has revealed something that will be music to the ears of subscribers. Writing on Twitter he confirmed that Apple Music subscribers will be able to take advantage of an iTunes Match-like feature that allows tracks to be stored in the cloud.
This in itself is nothing new, but the Apple executive also talked numbers. He explained that while Apple Music would have the same 25,000 as iTunes Match to start with, there are plans to increase this fourfold. The jump to 100,000 songs is penciled in as a feature for iOS 9.
The track matching feature of Apple Music is detailed on the Apple Music website. Here Apple explains that it will work in much the same way as iTunes match. It will scan the music libraries of users to see if Apple has the tracks in its own library. Wherever a match is found, the tracks will be made available through iCloud so they can be accessed from any device without using up any local storage space.
The revelation about the upper limit increase came in a Twitter exchange Eddy Cue had with Apple users over the weekend:
@karlfranks @robmsimoes 25k for launch and working to get to 100k for iOS 9
— Eddy Cue (@cue) June 27, 2015
The increase should help to eliminate the appearance of "limit reached" messages -- at least for a while.
-

Microsoft launches new, cheaper Core i7 Surface Pro 3
Publié: juin 29, 2015, 11:41am CEST par Mark Wilson

While we await news of the Surface Pro 4, Microsoft has revealed another model to the Surface Pro 3 lineup. The latest addition is a Core i7 model, bringing the total number of Surface Pro 3s featuring this version of Intel's processor to three.
In all there are now six Surface Pro 3 models to choose from, and the new Core i7 model makes it cheaper to jump into the higher end of the range at a lower cost. While the new model features the same processor and same 8GB of RAM as the very top of the Surface Pro 3 range, storage has been dropped to 128GB to help keep the price down.
Priced at $1,299, the 128GB/Intel Core i7 1.7GHz/8GB RAM Surface Pro 3 costs the same as the most expensive Core i5 version. There are now three very distinct bands to the Surface Pro three range. For those looking for a cheap entry point, the 64GB Core i3 and 128GB Core i5 at $799 and $999 respectively are a good starting point.
Anyone looking for a Core i7 model previously had to part with more than $1,500 for the 256GB/8GB RAM model $1,549) or the 512GB/8GB model ($1,949). Nestling smack in the middle of the two extremes, are the two $1,299 systems. So for mid-range buyers, there is a simple question to answer -- do you want a Core i5 with more storage, or would you prefer the benefit of a Core i7 chip instead?
Head over to the Microsoft Store if you fancy placing an order.
-

Google will eliminate accidental mobile ad clicks
Publié: juin 27, 2015, 10:23pm CEST par Mark Wilson

Ads are part and parcel of being online, but they can be particularly annoying for mobile users. When playing games on a phone or tablet, it's all too easy to accidentally tap an ad you have absolutely no interest in, pulling you out of the game you were playing or the site you were reading. If you've cursed when this happened to you, Google hears you.
The company is taking steps to make the "user experience" of ads a little better. It recognizes that advertisements that get clicked accidentally don't benefit anybody. They end up irritating the clicker, and are unlikely to be of value to the company that placed the ad. With around half of ad clicks being made by mistake, Google is now taking steps to stop this from happening -- great news for users and advertisers alike.
In all, Google is making three key changes to ads that appear on smartphones and tablets, starting off by adding an unclickable border to the outer edges of advertisements. This should help to eliminate clicks that are made by mistake when trying to scroll through a page or click something else near an ad. To ensure that a tap was made on purpose, it needs to be made nearer the center of it.
Some ads can appear on screen unexpectedly -- perhaps on a popup screen. To prevent these from being accidentally clicked, Google is introducing a time delay so that ads are inactive and unclickable for a short time after they first appear.
The final changes tackles problems with in-app popup ads for other apps and games. In the past such an ad feature a clickable app icon which led to the relevant Google Play entry. Unfortunately the "close ad" cross button was part of this icon, making it incredibly easy to interact with the ad when trying to close it. From now on, the app icon will be inactive and a separate button will need to be hit to grab a copy.
Introducing the changes, Google says:
These latest click quality enhancements improve the user experience by keeping them within their desired website or app and not involuntarily taking them to another page. They also benefit advertisers by reducing costs from accidental clicks and improving conversion rates. To date, we’ve seen a 15% average conversion rate lift on display ads by driving more qualified clicks with these updates.
Photo credit: Syda Productions / Shutterstock
-

Anti-trolling site aims to stamp out online abuse, sexism, and homophobia
Publié: juin 27, 2015, 5:55pm CEST par Mark Wilson

The day after the US Supreme Court voted to legalize same-sex marriage in all 50 states, the self-explanatorily named Stop Abuse Online website has launched. While the site has been set up with the intention of combating online abuse and trolling in general, female and LGBT victims are a particular focus.
The aim of Stop Abuse Online is to offer advice to those who find themselves falling victim to abuse -- be it online harassment, stalking revenge porn, or blackmail -- complete with legal tips about how to deal with different circumstances. The site is run by seven voluntary organizations in the UK and looks to bring the same protection to the web that people expect in the real world.
The unstoppable growth in popularity of social networks has served to increase the problem of online abuse as it is now easier than ever to connect with other. It's a problem that affects Twitter and the site recently tripled the size of its own online abuse-tackling team; Google also expanded its Right to Be Forgotten program so that people could request that links to revenge porn be removed from search results.
The Stop Abuse Online's front page explains:
An online life is something many of us take for granted. Smartphones, email, social networking, online dating, chat rooms, blogs, online gaming, Facebook and Twitter – most of us spend part of everyday interacting with others in this online world.
This has vastly increased our ability to share information and views with people around the world. But sometimes these online interactions become abusive and harmful.
Whilst online abuse can affect anyone, women and LGBT people often experience abuse as a result of their sex, gender identity or sexual orientation - or may be targeted for these reasons. The aim of this website is to provide support and guidance to people who are experiencing this type of online abuse.
The site is packed with practical tips about how to deal with online abuse, and stresses that there is a need to strike a balance between freedom of speech and individual human rights. "One person’s right to expression is limited by a balance with another person’s right not to be threatened or abused".
Check out the site which is seeking feedback about how it is doing.
Photo credit: YuryZap / Shutterstock
-

AppleCare+ now covers batteries that drop to 80%
Publié: juin 27, 2015, 12:20am CEST par Mark Wilson

For anyone concerned about their new Apple device, AppleCare+ protection can sound appealing -- even if it might seem expensive in some instances. Today Apple has updated the terms of AppleCare+ for iPhone, iPad, iPod and Apple Watch giving a better deal for people worried about their batteries.
Previously, the extended warranty only covered batteries that would hold 50 percent charge or less. Now this has been updated so that you can request a free replacement within the coverage period if your device's battery is only able to hold 80 percent of full charge. The new terms do not apply to everyone -- it all depends on when you bought your Apple device.
If you bought your iPhone, iPad, iPod or Apple Watch before April 10 2015, you're stuck with the old terms. The only way you're going to get a free battery from apple is if it deteriorates to the point that it is only holding half of its charge. If you bought your device after April 9 2015, you're in luck -- the new 80 percent rule applies to you.
The updated terms read:
If during the Plan Term, you submit a valid claim by notifying Apple that (i) a defect in materials and workmanship has arisen in the Covered Equipment, or (ii) the capacity of the Covered Equipment’s battery to hold an electrical charge is less than eighty percent (80%) of its original specifications, Apple will either (a) repair the defect at no charge, using new parts or parts that are equivalent to new in performance and reliability, or (b) exchange the Covered Equipment, with a replacement product that is new or equivalent to new in performance and reliability. All replacement products provided under this Plan will at a minimum be functionally equivalent to the original product. If Apple exchanges the Covered Equipment, the original product becomes Apple’s property and the replacement product is your property, with coverage for the remaining period of the Plan.
Does this make you more inclined to shell out for extra protection, or are you happy to run the risk?
-

Reddit blocked in China, Wayback Machine blocked in Russia
Publié: juin 26, 2015, 8:54pm CEST par Mark Wilson

It is becoming increasingly common for governments around the world to block access to websites they don’t approve of for one reason or another. The most frequent censor is China, and the latest site to fall victim to the Great Firewall of China is Reddit. If you're not able to pop over to China to check whether the site is blocked, you can use Blocked In China to test whether any site is accessible from within the country.
This is not the only site which people are having trouble accessing. Over in Russia, the Internet Archive -- responsible for the nostalgia-inducing Wayback Machine -- is also blocked. While the blocking of Reddit in China has probably been done on purpose, the same may not necessarily be true in Russia.
China has already blocked access to a wide range of popular sites including Facebook, Twitter, and YouTube. Reddit joins the list of websites that can only be accessed through VPNs or proxies from within China. Take a look at Blocked In China, and you'll see that Reddit access appears to have been blocked in all regions of the country -- Beijing, Shenzhen, Inner Mongolia, Heilongjiang Province, and Yunnan Province. There is a slight irony to Reddit being censored as the site has come under fire for killing certain subreddits and censoring other content.
Despite the apparent block, over on the r/China subreddit, there are a number of claims that the site is in fact working. It's not clear whether this is a matter of a block needing to propagate through the network or not.
GlobalVoices reports that the Wayback Machine -- the site that maintains historic copies of websites for posterity -- is blocked in Russia. It seems as though the block has come about as a result of government legislation designed to clamp down on sites that distribute extremist content. One particular archived page, Solitary Jihad in Russia, calls for the adoption of Islamic sharia law globally -- something the Russia government has taken exception to, and the Russian Pirate Party reports that this page has been added to Russia's blacklist. Unfortunately, because the Internet Archive uses HTTPS connections, ISPs in Russia may not be able to determine which page of the site users are trying to access. As a result of this some people are finding that their ISP has blocked access to Archive.org completely.
Photo credit: Gts / Shutterstock
-

BBC reveals links censored by Google's Right To Be Forgotten
Publié: juin 26, 2015, 6:05pm CEST par Mark Wilson

Google's Right To Be Forgotten gives people the chance to request the removal of search results linking to pages that contain information they believe to be "inadequate, irrelevant or no longer relevant". Google says it rejects more requests than it complies with, but there is still concern that the company is not providing enough detail about what it is doing. There have been calls for greater transparency from the company about the censorship that is taking place.
The BBC has published a list of all of the stories from its own site that have been removed from Google search results. The corporation announced that it wanted to be clear with people about which links has been deleted and plans to update the list each month. It already extends to nearly 200 entries and the BBC explains that while the stories may no longer be shown by Google, they are still available uncensored on the BBC site.
Writing on the BBC Internet blog, Neil McIntosh says that the list was important to maintain the integrity of the BBC's online archives. While the BBC has no issue with correcting or removing information that is incorrect, it regards its archives as "a matter of historic public record" and says that not including factually correct stories in a permanently accessible archive "risks reducing transparency and damaging trust".
At the moment, there are 182 links in the list which started back in July 2014, just after the ruling by the European Court of Justice in the same month which granted individuals the right to request the removal of search results relating to them. The BBC's head of editorial policy, David Jordan said:
It's impossible to have a meaningful debate if you've not got an idea about what's being de-listed.
He said that individual organizations had to decide whether they wanted to follow suit and that he felt it was important for people to be able to get a feel for the type of content that Google was delisting. The BBC revealed that it had made use of Google's appeal process, and this had resulted in the relisting of a story about members of the Real IRA.
You can check out the full list of affected stories on the BBC blog.
Photo credit: mikecphoto / Shutterstock.com
-

Apple starts to cull apps that feature the Confederate flag from the App Store
Publié: juin 26, 2015, 12:15am CEST par Mark Wilson

Following the Charleston shootings in which nine people were killed, debate has raged about whether it is reasonable to display the Confederate flag. A symbol of the South for some, a racist throwback for far more, the flag has already been ditched by the likes of eBay and WalMart. Now Apple has started to clear the App Store of apps that feature the rebel flag.
Developers have been contacted by Apple with a warning that their apps are being dropped because "because it includes images of the confederate flag used in offensive and mean-spirited ways". While this is clearly the case in some instances, the new policy has also affected Civil War games that include the flag for historical reasons.
The use of the flag is now a more sensitive issue than it ever has been, but the move by Apple has taken game developers by surprise. Maxim Zasov of Game Labs -- the company behind Ultimate General: Gettysburg -- said pride was taken in ensuring the historical accuracy of the game. While some developers are considering removing or replacing the Confederate flag with something else, Zasov said that this was not going to happen with Gettysburg, and the game would no longer be available.
Speaking to TechCrunch, Apple said:
We have removed apps from the App Store that use the Confederate flag in offensive or mean-spirited ways, which is in violation of our guidelines. We are not removing apps that display the Confederate flag for educational or historical uses.
It's not really clear how this sits alongside the removal of war games which, arguably, feature the flag for perfectly legitimate reasons.
Is this just another case of PR as Apple latches onto the cause of the moment, or is it indicative of the company doing what it should? The flag being rightly consigned to history, or is it needless censorship in an attempt to look good?
Photo credit: Khvost / Shutterstock
-

Facebook fails to develop a diverse workforce
Publié: juin 25, 2015, 11:34pm CEST par Mark Wilson

Like transparency reports, diversity reports have become quite the fashion at the moment. Companies such as Google, Apple, and Amazon are keen to demonstrate that they are not dominated by white, middle-class men, and that they are open to the full gamut of gender identities and sexualities. Today Facebook released its second diversity report showing that at Mark Zuckerberg's company things haven’t really improved over the last year.
More than half of the workforce (55 percent) is white, and at senior leadership level this jumps all the way up to nearly three quarters (73 percent). The percentage of black workers at the social network is incredibly low -- just 2 percent. The gender balance is largely skewed as we have come to expect. Across the company 68 percent of employees are male, although in 'non-tech' roles women make up 52 percent of the team. For those striving for equality, the numbers make for somewhat depressing reading.
Just as with race, the gender imbalance is more noticeable the further up the company you look. At the top of the heap, 77 percent of employees are men. The number of women employed by Facebook has increased by one percent, but the report describes little more than "positive but modest change". Facebook admits that there is still a long way to go:
While we have achieved positive movement over the last year, it’s clear to all of us that we still aren’t where we want to be. There’s more work to do. We remain deeply committed to building a workplace that reflects a broad range of experience, thought, geography, age, background, gender, sexual orientation, language, culture and many other characteristics. It’s a big task, one that will take time to achieve, but our whole company continues to embrace this challenge.
Facebook is not just saying that it needs to improve things, it is taking steps to do just that. New interviewing techniques encourage hiring managers to spend longer looking for workers to ensure that no one is overlooked. The Facebook University training program is designed to nurture talent in freshman, while employees are all trained to notice unconscious bias and stereotyping.
But, as Facebook says, there's still work to be done.
Photo credit: Vibrant Image Studio / Shutterstock
-

Cloud platform Fasetto shows Google how Undo Send should be done
Publié: juin 25, 2015, 8:38pm CEST par Mark Wilson

A couple of days ago, Google took Gmail's Undo Send feature out of its six year beta period, and brought the option to a wider audience. Although the feature has been widely welcomed, there has also been criticism, particularly about the measly 30 second time limit users are given to change their mind and recall an email. Today Fasetto launched Messaging 2.0 which includes the ability to recall or edit messages or files that have been sent, with no time limits.
Fasetto is a cloud storage platform that offers security features that will appeal to the enterprise, as well as home users. Available for Windows, Android, iOS, OS X, and even Windows Phone, the platform has a focus on security that extends to being completely free of tracking and log files, but it also has a thing or two to teach Google.
The service claims to be the "fastest messaging available cross-platform, cross-device", but in addition to the speed, are the message and file recalling features that are of interest. If a user realizes they have sent a message in error -- possibly revealing confidential information -- it can simply be deleted. It does not matter how much time has elapsed, the ability to delete or edit messages remains available.
The editing feature is also something that will be welcomed by larger companies or teams of collaborators. If a message is sent out to a large number of people that contains incorrect information, one solution would be to send a follow up message explaining the mistake. But there's no guarantee that this message will be noticed or acted upon -- it's entirely possible that some or all recipients will refer back to the original message and take action based on incorrect data. Messaging 2.0 brings the option of editing the original message to eliminate this problem.
Messaging is just one component of Fasetto; cloud storage and file sharing is at its heart. Just as with messages, should a user realize that the wrong file has been sent to someone -- or it has been sent to the wrong person -- it can be quickly deleted from the recipient's device. But can't the recipient just make a copy? Not necessarily. Fasetto allows for restrictions to be placed on files that are sent so they can only be viewed and not downloaded.
Signing up for Fasetto doesn’t cost a thing and includes 10GB of storage as standard. This can be increased to 100GB for $10 per month.
Photo credit: Nobelus / Shutterstock
-

Google bows to pressure to remove eavesdropping extension from Chromium
Publié: juin 25, 2015, 2:42pm CEST par Mark Wilson

Google has removed an extension from its open source browser Chromium after people complained that it had been downloaded without permission and then listened to users through their microphones. The Chrome Hotword extension was used by Chromium to offer "OK, Google" voice activation to the browser.
Privacy advocates were concerned about the potential for eavesdropping, particularly in light of the fact that users were not warned of the presence of the extension. There was also concern that the extension is not open source, so it was not possible to see exactly what it was doing. In response to complaints, Chrome Hotword has now been made an optional component.
With Chromium being open source, users were especially disappointed to see the inclusion of a non-open source element. What was more worrying for some was the fact that Hotword did not appear in the list of extensions visible by visiting chrome://extensions/. Users looking to chrome://voicesearch/ quickly learned that the extension existed, was enabled, and had access to the microphone.
Writing on the Chromium message boards, Google said:
As of the newly-landed r335874 Chromium builds, by default, will not download this module at all.
A binary blob module like this can not be installed by a user via clicking on a link. Such a Native Client module can only be installed by the user deliberately from the Chrome Web Store.
Chromium is open source and it's important to us, as is it is to you, that it doesn't ship with closed-source components, lazily or not.
Is this enough to allay the fears of those concerned with privacy?
-

Apple Music earns artists just 3 cents an hour
Publié: juin 25, 2015, 12:57pm CEST par Mark Wilson

It has been hard to avoid talk of Apple Music over the past couple of weeks. After the initial excitement of the launch, there was much wailing and gnashing of teeth at the revelation that there were no plans to pay artists during the initial three month free trial period.
Never fear, Taylor Swift is here! After complaining on behalf of musicians around the world in an open letter to Apple, Ms Swift managed to convince Apple to change its mind and dip its hand into its pocket. But did this mean that a great deal was offered? Clearly being paid 'something' is better than not being paid at all, but the New York Times reveals that Apple will be paying out just 0.2 cents every time a track is streamed.
If that sounds like very little, well, it is. But sadly it's not unusual. Spotify uses quite a complicated formula to determine how much artists are paid. The company explains that this averages out to a "payout to rights holders of between $0.006 and $0.0084". This still isn't very much, but it is between three and four times what Apple is due to pay. Apple will no doubt, like Spotify does, claim that its streaming service helps to counter piracy and encourage listeners to pay for music they might not otherwise have paid for at all.
It turns the idea of making a 'quick buck' right on its head. If you like the idea of earning money for your favorite band or artist, and opt to listen solely to their material on Apple Music, be prepared to do a lot of listening. To earn your preferred singer or group a miserly dollar, you'll have to listen to 500 tracks.
Assuming an average song length of 3 minutes 30 seconds, if you listened to music non-stop for 1.2 days, Apple would only cough up a solitary dollar. Did someone say 'minimum wage'? To return to the headline, and sticking with the idea of the perfect three-and-a-half-minute pop song, you can squeeze 17 tracks into an hour. This will line your chosen artist's pocket to the tune of 3.4 cents. To put that in perspective, if an artist decided to use Apple Music as a sole income stream, their music would have to be listened to nearly 30,000 times to pay the $9.99 month fee to use Apple Music.
And this is the most valuable company in the world.
It makes you think.
-

Google asks Android developers to show sensitivity to disasters and atrocity
Publié: juin 24, 2015, 10:56pm CEST par Mark Wilson

Today Google revealed an updated version of its Google Play Developer Program Policies. There aren't actually all that many changes or additions, but those that are present are quite interesting. Google is clamping down on the problem of impersonation, making it clearer that it is not permissible to mislead users by imitating other apps, making false claims, or suggesting endorsements that do not exist.
One of the more intriguing changes to the document sees Google calling on developers to show sensitivity to evens such as natural disasters, war, and death. Any apps or other content that attempt to benefit by exploiting such events are explicitly banned.
Google has not revealed what prompted the inclusion of the Sensitive Events section. It is here that it is made clear that: "We don't allow content which may be deemed as capitalizing on or lacking reasonable sensitivity towards a natural disaster, atrocity, conflict, death, or other tragic event."
Speaking to Droid Life, Google said that the updated policy also prevented in-app currencies being moved between apps. The company explains that "to ensure a secure and consistent customer support experience to our users, we’ve introduced a provision which governs the transfer of in-app virtual currencies purchased in an app". In the developer policy document, this is covered by the clause that reads:
In-app virtual currencies must only be used within the app where they were first purchased.
Google also clarified the payment policy that governs paid apps, and in-app purchases in free and paid-for apps.
What all of the changes have in common is that they are designed to protect users in one way or another -- be it safeguarding money, ensuring that people know exactly what they are dealing with, or avoiding the exploitation of disasters.
You can read the full document in Google's developer pages.
Photo credit: RoSonic / Shutterstock.com
-

iOS 9 makes space for updates by deleting apps... and then reinstalling them
Publié: juin 24, 2015, 1:05am CEST par Mark Wilson

It's only a few weeks since Apple announced some details about iOS 9. One feature that grabbed the attention of many people was Apple's move to address the problem of iOS getting a little fat -- it was announced that iOS 9 will need far less free space to perform an upgrade. But if you are running very short of room, there's a new reason to smile.
The second version of the iOS 9 beta was released to developers today and, as noted by 9to5Mac, Apple's mobile operating system features a great new way to handle devices that are low on space. iOS 9 is now able to temporarily delete apps to free up the necessary megabytes, before reinstalling them when the update is complete.
This is clearly something that users have been able to do for themselves, but now the entire process can be completely automated. There's no need to work out how much space you need to free up and calculate the size of individual apps -- iOS 9 can take care of it all for you. To provide the required breathing room update installations call for, iOS will delete however many apps this takes to perform the update and then reinstall the apps complete with their data.
Kaleb Butt screengrabbed what greets updaters who need to temporarily ditch apps:
Well this is new. pic.twitter.com/BQKMDn5D6c
— Kaleb Butt (@Kaleb_Butt) June 23, 2015
This is great news for anyone with a 16GB device, and brilliant for those who hate backing up and manually removing and re-adding apps.
Photo credit: Piotr Marcinski / Shutterstock
-

Undo Send feature promoted from Labs to all Gmail accounts
Publié: juin 24, 2015, 12:03am CEST par Mark Wilson

We've all had occasions when we've sent an email and then, for one reason or another, wished we hadn't. It may have been a message fired off in anger, or a missive you notice is littered with typos. For some time -- six years in fact -- Google has offered a bit of a safety net in the form of the Undo Send Labs feature.
For more than half a decade this was nothing more than an experimental feature, hence its appearance in Labs. But now Google has announced that it is being properly integrated into Gmail for everyone to use. There's no need to enable an experiment option any more, this is now a feature that everyone can access through Gmail's settings.
If you like the idea of giving yourself a little buffer, just head to the General section of Settings in your Gmail inbox. Scroll down until you see the Undo Send option and check the box to enable it. By default you are given a 10 second window in which you can recall an email after you hit Send but you can reduce this to 5 seconds, or increase to 30 if you prefer.
The name is slightly misleading as Undo Send does not actually enable you to pull back an email that has left your outbox. What actually happens is that when you hit Send, Gmail holds off sending the email for whatever period you have specified. This gives you a chance to rethink and hit 'undo', the email will simply not be sent.
As Google explains in a blog post introducing the feature:
'Undo Send' allows people using Gmail to cancel a sent mail if they have second thoughts immediately after sending. The feature is turned off by default for those not currently using the Labs version [...] People currently using the Labs version of 'Undo Send' will have the setting turned on by default at launch.
Is this something you think you'll make use of now it is a fully supported feature?
Photo credit: file404 / Shutterstock
-

Instagram battles Twitter with updated Explore and Search features
Publié: juin 23, 2015, 10:49pm CEST par Mark Wilson
One of the defining features of Twitter is trending topics. It's easy to catch up on what's hot right now, and it's something that Instagram is borrowing in its latest update. The millions of users of the photo service now have access to a new Explore page that includes not only a trending component that highlights events and topics that people are posting about, but also trending tags and places.
These new options make it easier to home in on content of interest, and changes have also been made to Search. You have the option to search Places, Tags, and People separately, or you can use the Top section to search all at once.
The all-new Explore page has been designed to make it faster than ever to find content you like. If you're particularly interested in pictures relating to a certain topic or event, you can quickly home in on them and browse through images, as well as connecting with conversations that are taking place. The updated search tool is all about helping people find what they want to see, but at the other end of the spectrum is another new Explorer feature -- curated content.
There is now a range of curated collections which Instagram uses to surface interesting images relating to a particular theme. Expect to see content from "interesting accounts and places, from musicians and extreme athletes to stunning architecture and gorgeous beaches". The new features are rolling out to Instagram users in the US for now, and a global rollout will follow once the experience has been "fine-tuned".
-

Free, ad-supported Google Play Music takes on Apple Music
Publié: juin 23, 2015, 10:10pm CEST par Mark Wilson

Not willing to be upstaged by Apple Music, Google is launching a free version of its Google Play Music service. To make money, the free version of the service will be supported by advertisements -- forget free trials and the prospect of upsetting artists such as Taylor Swift.
The free version of Google Play Music is starting life in the US and Google is pushing the fact that there are curated radio stations to suit whatever mood you find yourself in. The station features the involvement of some of the Songza team and it is possible to home in on a custom radio station based on genre, mood, decade, activity, or similarity to particular artists.
By opening up Google Play Music to a wider audience -- which offering a free tier will certainly do -- Google says that it is "giving artists another way to earn revenue". While Google will make money through the ads it sells, the ad-supported version of the service is essentially an advert in itself, encouraging listeners to upgrade to the paid-for version.
As well as ads, there are a few limitations to the free version when compared to paid-for subscriptions. Non-paying listeners are limited to skipping six songs per hour, and there is no rewind option -- although it is possible to pause playback. Audio quality of up to 320kps is available but it is not possible to download playlists to listen to offline, or edit the running order.
While US residents can start enjoying Google Play Music on the web free of charge right now, there's no word on when it will be available in other parts of the world. Google says that the free version will be rolling out to Android and iOS users this week.
-

Poll: When Windows 10 launches will you stay a Windows Insider or go RTM?
Publié: juin 22, 2015, 11:34pm CEST par Mark Wilson

If you've been following the news about Windows 10, you can’t have avoided the confusion that arose from Gabe Aul's poorly written (but ultimately updated and clarified) blog post. We now know exactly where we stand. If you have a genuine version of Windows 7 or Windows 8.x you can upgrade to a fully licensed version of Windows 10 for free on July 29. For anyone without a genuine copy of 7 or 8.1, you can legitimately keep running Windows 10 if you are happy to stay on as a Windows Insider.
Of course, even if you upgrade from a valid version of Windows 7 or 8.x, you can still choose to remain a Windows Insider. Just as happens now, this means that you are granted access to pre-release builds on the Fast and Slow rings. Each preview build will be time-limited, but a new version will be released before the previous one expires. So... what will you do? Do you want to stay on the cutting edge of Windows advancements? Or would you prefer to stick with a more stable version of the operating system. There are, of course, pros and cons to both routes.
So far, there has been massive interest in the Windows Insider preview program. It seems that millions of people have been eager to get their hands on the latest bits as soon as humanly possible -- there is obviously the option of downloading the leaked builds that inevitably find their way online, but the program provides a way to stay up to date lawfully. It's interesting that Microsoft has decided to keep the program running after Windows 10 hits RTM, and it will be even more interesting to see how many people embrace the opportunity to stay on board -- was there so much participation simply because it meant being able to try out Windows 10 before release, and will that wane when we reach gold code?
Of course, just as with all previous versions of Windows, security patches and other updates will be pushed out from time to time, regardless of whether you're an Insider or not. But as we all have become used to over the last few months, Insiders who have joined the Fast Ring can expect to continue to receive new preview builds from time to time, while the more stable versions will make their way down to the Slow Ring.
But what is going to prove more important? Having the very latest version of Windows 10, or having the most stable version? We'd like to know what you intend to do.
So, it's over to you. Will you opt for the red pill, or the blue pill? Actually, it's not quite that simple; there are several options available to you:
Note: There is a poll embedded within this post, please visit the site to participate in this post's poll.Cast your vote and leave a comment to explain your decision.
-

Google has a new batch of Android Wear faces for customization fans
Publié: juin 22, 2015, 8:21pm CEST par Mark Wilson

The wearables market continues to grow and there's something of a battle -- just as there is in the smartphone market -- between Apple Watch and Android Wear. Google's wearable OS keeps receiving updates and one of the things that makes it stand apart from Watch OS is the level of customization it offers users.
Today Google unveils 17 new watch faces to add to the existing catalog that already extends to more than 1,500 entries. As ever, the claims of there being something for everyone apply, and there are numerous cultural nods with Terminator Genisys, Hello Kitty, and Angry Birds faces all available for download.
The majority of the faces are free of charge, although two -- ANREALAGE and Gundam RX-78-2 -- have small price tags attached to them. For those looking to match accessories they own, there are faces from Cynthia Rowley, Lulu Frost, and Triwa, and also premium brands such as Bang & Olufsen, Muji, and Kevin Tong.
It's not clear quite what led Google to group together and highlight this particular collection of faces, but you can check them out in Google Play... or in the slideshow below:
-

Lawsuit fights Uber's user location tracking plans
Publié: juin 22, 2015, 8:02pm CEST par Mark Wilson

Uber has faced numerous complaints since its inception in 2010, including suggestions that drivers are not properly vetted. Now the taxi service is facing legal action over plans to track the location of its customers whether the app is running in the foreground or background on their phones.
The new policy is due to come into force on July 15, but the Electronic Privacy Information Center (EPIC) has filed a complaint with the FTC saying that the policy change is unfair and should be investigated by the commission. It will be possible to opt out of this location tracking, but EPIC feels this is unreasonable.
Referring to previous allegations about Uber, EPIC says that the company "regularly abuses its access to customer location data". But it is the proposed changes to user tracking that is now causing concerns. Uber's proposed user privacy statement reads: "We may also collect the precise location of your device when the app is running in the foreground or background. We may also derive your approximate location from your IP address".
In its complaint, EPIC says:
In less than four weeks, Uber will claim the right to collect personal contact information and detailed location data of American consumers, even when they are not using the service. These changes ignore the FTC’s prior decisions, threaten the privacy rights and personal safety of American consumers, ignore past bad practices of the company involving the misuse of location data, pose a direct risk of consumer harm, and constitute an unfair and deceptive trade practice subject to investigation by the Federal Trade Commission.
It is not just location data that Uber is interested in. The proposed policy also refers to the collection of names and details from users' contacts -- something the company has previously said could be useful for "new promotional features". It's not clear quite why Uber wants to continually track user locations, but it could be something to do with potential location-based offers or advertising.
Photo credit: 360b / Shutterstock.com
-

Google empowers collaborative citizen journalism with News Labs
Publié: juin 22, 2015, 5:05pm CEST par Mark Wilson

Google today revealed details of a new project designed to power the world of journalism. News Labs is a joint venture between Google and a number of technology firms and entrepreneurs to make it easier to research and publish stories. It's something aimed primarily at major newsrooms and reporting outlets, but it also features tools that can help to power and promote collaborative citizen journalism.
The search giant has several programs that have been created to make it easier for people to make use of YouTube to deliver and consume news. User-generated news has become increasingly important in recent years, offering not just a wider range of opinion but also unparalleled localization, and Google is keen to be at the heart of it. Newspapers and news websites are far from being the end of journalism; reader interaction adds to the narrative.
Much of what you find online is news, and news comes from a wide range of sources. Any given story may be newsworthy in its own right, but its importance can change with context. In order to place a story in different context, it's vital to have access to data, and this is something Google has in huge quantities. Tools such as Google Trends and Fusion Tables provide access to real-time data and statistics that can be vital for fact-checking and providing context and comparison. News Labs is home to a raft of tools to help with the gathering of information, enhancing stories with visualizations, and sharing stories with a wider audience.
News Labs is not just about providing tools and leaving people to their own devices, however. To encourage as many people as possible to take advantage of the power these tools hold, Google has produced a number of written tutorials and video guides to help them get started. Three specific programs -- First Draft, the WITNESS Media Lab, and the YouTube Newswire -- have collaborative journalism at their heart.
There are also case studies showing how different news outlets have made use of Google's tools and plans to team up with new startups to bring new players to the media arena.
The video below sees Google showcasing some of the tools that can be found in News Labs:
Photo credit: Glinskaja Olga / Shutterstock
-

Sony releasing new 1TB PlayStation 4 in July
Publié: juin 22, 2015, 12:59pm CEST par Mark Wilson

Known as the 1TB PS4 Ultimate Player Edition (or PlayStation 4 Ultimate Player 1TB Edition depending on who you're talking to), Sony is launching a new PlayStation 4 next month. With the ever-growing market for downloadable content, it's difficult to have too much disk space. Recognizing this, Sony is doubling the size of the largest capacity PS4.
The 1TB console will launch next month in the US, Asia and Europe, and the announcement comes just weeks after Microsoft announced a 1TB version of its Xbox One. Gamers in Japan will be able to get their hands on the console by the end of June, but the rest of the world will have to wait until July 15. There's no word on pricing, but Sony has detailed a few other changes that have been made to this version of the console.
Power consumption has been reduced, and the 1TB model uses 8 percent less power than the 500GB version. If you're the type of gamer who carries your console from place to place, you'll be pleased to hear that the weight has been reduced by 10 percent as well. Sony also says that the hard drive bay has a matte finish which -- to use the company's words -- gives the console "a more casual look".
Check out Sony's video which introduces the 1TB PS4 Ultimate Player Edition:
-

What is Facebook not telling us about machiavellian censorship?
Publié: juin 21, 2015, 9:41pm CEST par Mark Wilson

Just a few days ago the Electronic Frontier Foundation published its annual Who Has Your Back report looking at how various technology companies treated customer privacy. The report makes for interesting reading, but it also raises some questions. One question that has cropped up several times is "how the hell did Facebook get a rating of 4 out of 5!?"
As well as rating Mark Zuckerberg's social network in terms of its privacy policies and how it responds to government data request, the EFF also probes the hidden censorship that appears to be going on. There have been numerous examples of blatant censorship from Facebook -- including blocking certain pages in Turkey -- and while this is worrying (particularly when the social network's founder is looking to connect the world to the web with Internet.org) what is perhaps more concerning is the censorship we don't know about. The silent censorship that's going on the in the background.
Facebook is frequently criticized for its attitude to privacy, but in the EFF's 2015 report it was awarded four out of a possible five stars. Although the social network fared relatively well here, it's a very different matter when it comes to censorship. As the EFF points out, take a look at Facebook's Government Requests Report and you'll see that most countries -- take Russia or Turkey for instance -- and among the data that is present you'll see a section headed Content Restrictions. This is censorship by another name.
Take a browse through the data that's presented for each country, and you'll eventually come to the USA. While 'Content Restrictions' in Turkey are justified ("We restricted access to items primarily reported by the Turkish courts (and Access Providers Union) and Telecommunications Authority under local law 5651, which covers a range of offenses including defamation of Ataturk, personal rights violations, and personal privacy") as are those in Russia, the Content Restrictions section is notable by its absence from the United States' page.
There's lots of information (well… some, at least) about Government data requests and National Security Letters, but not the slightest mention of content that has been restricted or censored. What's going on?
Are we supposed to believe that the US government -- considering how concerned it seems to make itself about just about everything else that goes on in the world -- has not asked Facebook to remove any content within its borders? This is so unlikely as to be absurd. Much like Amazon's recent vague and opaque transparency report, Facebook draws attention to certain data by failing to mention it. One can't help but ask what is going on.
Has Facebook been told not to reveal the censorship it is being asked to carry out -- just as it is forced to be absurdly vague about the number of National Security Letters it receives? Or is Facebook pre-emptively self-censoring? EFF correctly points out that we are already aware of the fact that Facebook takes down the accounts of people sent to prison for more than four years -- yet there is no mention of this in the report at all. Why not?
If this data is being left out of the report, what else are we not being told? Can we trust any of the figures Facebook presents to us? Censorship of censorship is Machiavellian, but it is also somewhat pointless. We know that it is happening, so to simply pretend it is not is just absurd. It erodes trust even further and makes us question motives. Transparency reports are all but useless if they are not actually transparent.
Photo credit: alexskopje / Shutterstock
-

Taylor Swift denigrates Apple Music as 'shocking, disappointing'
Publié: juin 21, 2015, 3:44pm CEST par Mark Wilson

There are only a few days until Apple Music launches, but already there is quite a backlash against the music streaming service. It's not just smaller, independent labels that are complaining about Apple's refusal to pay artists any royalties during the initial three month free trial period. Taylor Swift has added her voice to the growing number of complainants, writing an open letter to Apple in which she says she will withhold her new album 1989 from the service.
In the letter, entitled "To Apple, Love Taylor", the singer says that the company's decision not to make royalty payments is "shocking, disappointing, and completely unlike this historically progressive and generous company". Swift is an artist who could afford to shoulder the cost of three months of not being paid by Apple, but she has chosen to make a stand and stick up for those who are less fortunate.
She acknowledges that Apple has been an important partner in helping her to sell her music, but feels that the financial arrangements that will be in place during the free trial period of Apple Music are unacceptable. While recognizing that Apple is ultimately aiming towards paying artists through the paid-for streaming service, Swift says that the current business model is harmful to smaller, up and coming artists.
Writing on her Tumblr blog, she said:
This is not about me. Thankfully I am on my fifth album and can support myself, my band, crew, and entire management team by playing live shows. This is about the new artist or band that has just released their first single and will not be paid for its success. This is about the young songwriter who just got his or her first cut and thought that the royalties from that would get them out of debt. This is about the producer who works tirelessly to innovate and create, just like the innovators and creators at Apple are pioneering in their field…but will not get paid for a quarter of a year’s worth of plays on his or her songs.
She took to Twitter to spread word of the letter:
To Apple, Love Taylor [t.co]
— Taylor Swift (@taylorswift13) June 21, 2015
Echoing sentiments expressed by independent record labels, Swift writes, "three months is a long time to go unpaid, and it is unfair to ask anyone to work for nothing". She calls for the company to rethink its policy before musicians are badly affected by it. She ends the letter by saying:
We don’t ask you for free iPhones. Please don’t ask us to provide you with our music for no compensation.
Photo credit: a katz / Shutterstock.com
-

Reddit refugee camp Voat dropped by German webhost for 'political incorrectness'
Publié: juin 20, 2015, 1:33pm CEST par Mark Wilson

A couple of weeks ago Reddit announced that it was closing down a number of subreddits with harassing subject matter. This came a few month months after a decision to ban content that included images or videos of non-consensual sex. In protest, groups of users switched allegiances and moved to the Reddit clone site Voat.co -- which prides itself on not censoring any content.
Voat.co has been around for a little while, but the site saw its membership swell as former Reddit users jumped ship. Over the last couple of weeks, the "censorship-free community platform" has battled DDoS attacks and was dealt another blow yesterday when its German hosting provider cancelled its contract. The reason given was that the server was being used to host content that is "politically incorrect". But this does not mean that the site is dead.
Hosteurope.de said that "we have received significant information that the content on your server includes political incorrect parts that are unacceptable for us". The company also went on to say that Voat's contract was being terminated "due to the fact that we cannot keep bond of trust to you as our customer". Voat Chief Technology Officer, Atko explained that mere hours before being cut off by the host provider, the site had managed to migrate to a cloud platform.
It is interesting to note the reasons for the termination of the contract. There is no mention of illegal content, just content which has been deemed politically incorrect. This is clearly a very subjective matter, and Atko says that the hosting provider shut down the server "without issuing a warning or trying to talk to us". It is something of a blow for freedom of speech if webhosts start to police the content of the sites they power not because they are breaking the law, but because they just don’t like the content.
Voat is funded by donations, but following a surge in interest in the site, actually removed information about how to donate. Atko thanks all of those who had given money, adding "I feel we have received enough to help us survive for quite some time". For now the site remains up and running, but as Atko says:
We are living in a weird world. We will have to carefully evaluate our long term options of providing a platform of free speech if we are to stay online.
-

Google to block revenge porn from search results
Publié: juin 19, 2015, 8:38pm CEST par Mark Wilson

Google is to start honouring requests to remove links to revenge porn from its search results. In a move that has echoes of the Right to Be Forgotten in Europe, today's announcement indicates that the search giant is now willing to start censoring search results if people request that explicit personal images of them be removed.
This is not supposed to be carte blanche for people to request the removal of any image they are unhappy with -- it is a move designed to target images that might be posted to sexploitation websites with a view to bribing their subjects.
Google says it does not think that this will bring about an end to revenge porn -- the images will still exist online -- but it is a step towards protecting those who find themselves the victims of a humiliation campaign by an ex-partner. The company is yet to provide an online form that can be used to report, but this is due to appear in the coming weeks.
Writing in a blog post SVP of Google Search, Amit Singhal said:
Our philosophy has always been that Search should reflect the whole web. But revenge porn images are intensely personal and emotionally damaging, and serve only to degrade the victims -- predominantly women. So going forward, we'll honor requests from people to remove nude or sexually explicit images shared without their consent from Google Search results. This is a narrow and limited policy, similar to how we treat removal requests for other highly sensitive personal information, such as bank account numbers and signatures, that may surface in our search results.
Google has not revealed details of the numbers of requests it has received so far, or what the scale of the problem of revenge porn is thought to be. The new policy is sure to be welcomed by web users who don’t want to see such content, as well as those who want to protect their own privacy.
Photo credit: Pavel Ignatov / Shutterstock
-

UK CD ripping legislation is unlawful and hurts the music industry
Publié: juin 19, 2015, 7:20pm CEST par Mark Wilson

The casual copying of CDs has been going on for years, but it is only relatively recently that it was made legal in the UK. It was only in the latter half of 2014 that the UK government passed legislation that permitted the copying and ripping of CDs for personal use. Today the High Court in London said that the government's earlier suggestion that ripping would not harm the music industry is incorrect.
When the legislation was passed last year, representatives of songwriters and musicians appealed. They were not unhappy with the legalization of CD ripping, but at the suggestion that financial harm would not be caused and compensation was not needed. Mr Justice Green said that "the absence of a compensation mechanism is unlawful".
The Judge disagreed that the government's suggestion that the change in law would cause "zero or de minimis harm". He said that a couple of assumptions had been made: firstly, that the government suggested that the legislation would only impact upon duplicate sales and would therefore have very little effect, and secondly that the sale price of CDs already had lost sale revenue factored in.
He said that "the conclusions and inferences which have been drawn from the evidence the Secretary of State has relied upon are simply not warranted or justified by that evidence".
UK Music's chief executive Jo Dipple said:
The high court agreed with us that the government acted unlawfully. It is vitally important that fairness for songwriters, composers and performers is written into the law. My members' music defines this country. It is only right that the government gives us the standard of legislation our music deserves. We want to work with the government so this can be achieved.
It's not yet clear what will happen next. A hearing is due to take place next to determine whether the permitting of personal CD copying should be outlawed again, or if some form of compensation scheme should be set up. It has been suggested that a tax could be applied to blank CDs and other media, and these funds could then be divided between members of the music industry.
Image Credit: Feng Yu / Shutterstock
-

Amazing Windows 10 shortcuts to individual Settings
Publié: juin 19, 2015, 2:50pm CEST par Mark Wilson
For anyone who has been using the Windows 10 preview builds, there has been plenty of time to explore the operating system. It's now only a matter of weeks until the final version is released, and whether the gold build will be your first foray into Windows 10, or you're a seasoned tester, there are still plenty of new tricks to learn.
Whatever you use your computer for, you want to be able to get things done as a quickly as possible. In previous versions of Windows, the Control Panel was used to access all manner of options -- now things are split between the Control Panel and Settings. If there are some settings you change frequently, you can create your own shortcuts to jump to them in a couple of clicks; you can also assign keyboard shortcuts to make things even easier. Here's what you need to know...
These are shortcuts in the traditional Windows sense of the word -- icons that you can place on the desktop, Start menu, or taskbar. To create one, use the list below to determine the code you need to access a particular setting and highlight it before copying to the clipboard (you can type it out manually if you prefer, of course!).
Right-click an empty section of the desktop and select New > Shortcut. In the empty text field, paste the code you have copied and click Next. Type a suitable name for the shortcut and click Finish. If you want to take things a step further you can assign a keyboard shortcut to speed things up. Right-click an icon you have created and select Properties. On the Web Document tab, press the keyboard shortcut you'd like to use -- such as Ctrl + Alt + F -- and then hit OK.
Create as many shortcuts as you like, and move them to wherever you find the most useful.
Accessibility Closed captioning ms-settings:easeofaccess-closedcaptioning High contrast ms-settings:easeofaccess-highcontrast Keyboard ms-settings:easeofaccess-keyboard Magnifier ms-settings:easeofaccess-magnifier Mouse ms-settings:easeofaccess-mouse Narrator ms-settings:easeofaccess-narrator Other options ms-settings:easeofaccess-otheroptions Battery and power Battery Saver ms-settings:batterysaver Battery Saver settings ms-settings:batterysaver-settings Battery use ms-settings:batterysaver-usagedetails Power and sleep ms-settings:powersleep Display and user interface Backgrounds ms-settings:personalization-background Colors (display) ms-settings:colors Colors (personaliation) ms-settings:personalization-colors Date and time ms-settings:dateandtime Display ms-settings:display Mouse and touchpad ms-settings:mousetouchpad Personalization ms-settings:personalization Region and language ms-settings:regionlanguage Screen rotation ms-settings:screenrotation Speech ms-settings:speech Start ms-settings:personalization-start Themes ms-settings:themes Typing ms-settings:typing Network and radios Airplane mode ms-settings:network-airplanemode Bluetooth ms-settings:bluetooth Cellular ms-settings:network-cellular Data usage ms-settings:datausage Dialup ms-settings:network-dialup DirectAccess ms-settings:network-directaccess Ethernet ms-settings:network-ethernet Manage Wi-Fi ms-settings:network-wifisettings Mobile hotspot ms-settings:network-mobilehotspot Proxy ms-settings:network-proxy Wi-Fi ms-settings:network-wifi VPN ms-settings:network-vpn Other For developers ms-settings:developers Offline maps ms-settings:maps Optional features ms-settings:optionalfeatures Privacy Account info ms-settings:privacy-accountinfo Calendar ms-settings:privacy-calendar Camera ms-settings:privacy-webcam Contacts ms-settings:privacy-contacts Feedback ms-settings:privacy-feedback Location ms-settings:privacy-location Messaging ms-settings:privacy-messaging Microphone ms-settings:privacy-microphone Motion ms-settings:privacy-motion Other devices (privacy) ms-settings:privacy-customdevices Privacy ms-settings:privacy Radios ms-settings:privacy-radios Speech, inking, and typing ms-settings:privacy-speechtyping System and user Connected devices ms-settings:connecteddevices Family and other users ms-settings:otherusers Lockscreen ms-settings:lockscreen Notifications and actions ms-settings:notifications Proximity ms-settings:proximity Signin options ms-settings:signinoptions Storage Sense ms-settings:storagesense Tablet mode ms-settings://tabletmode/ Windows Update ms-settings:windowsupdate Work access ms-settings:workplace Are there any shortcuts you find particularly useful?
-

It just got a whole lot easier to switch broadband provider
Publié: juin 19, 2015, 1:14pm CEST par Mark Wilson

Moving from one broadband provider to another has long been something of a chore. Starting this weekend (June 20), switchers in the UK will no longer have to go through the hassle of requesting a Migration Authorisation Code (MAC) from their current supplier, as their new ISP will be able to handle the entire process from start to finish.
This should not only help to speed up the process of switching provider, but also eliminate the pestering from ISPs to stay with them. The new rules do not cover all ISPs, just those that use the Openreach network -- this includes major players such as BT, Plusnet, TalkTalk, and Sky -- but it should still make life easier for a lot of people.
It's a move that has been welcomed because it places consumers back in control, and helps to avoid the risk of being talked into sticking with the current package. One problem that has plagued would-be switchers when they have phoned their current ISP is that call center staff often use pressurizing tactics to make people feel as though they should not bother switching.
Cable.co.uk editor-in-chief Dan Howdle said:
The high-profile fights between customers and call center retentions staff that have dogged the news recently have stoked the notion that switching broadband provider is more trouble than it's worth. The new rules mean that (in most cases) you will no longer have to call your existing broadband and/or home phone provider in order to switch. You won't have to deal with a person whose job it is to mix fear-mongering, offers you can't refuse, and flat-out stubbornness in order to get you to stay. And that's a good thing.
The new migration process has been introduced by Ofcom and it is hoped that it will help to keep the broadband market healthy.
Photo credit: asharkyu / Shutterstock
-

FCC votes to subsidize broadband connections for low-income households
Publié: juin 18, 2015, 11:17pm CEST par Mark Wilson
Today the FCC voted in favor of updating its Lifeline program to include broadband. This would mean that households surviving on low incomes would be able to receive help paying for a broadband connection. It might not be as important as electricity or water, but having a broadband connection is seen as being all but essential these days.
From helping with education and job hunting, to allowing for home working, the ability to get online is seen as so vital by some that there have been calls for it to be classed as a utility. The Lifeline program has been running since the 80s, and originally provided financial help to those struggling to pay for a phone line. It was expanded in 2008 to include wireless providers, and it is hoped that this third expansion will help more people to get online.
Announcing the decision to modernize the program, the FCC points out that less than half (48 percent) of households with an income under $25,000 had an internet connection at home. While it could be argued that internet access is possible through smartphones, the commission reveals that half of low income consumers have their mobile connections suspended or cancelled due to financial difficulties.
Broadband has become essential to participation in modern society, offering access to jobs, education, health care, government services and opportunity. Unfortunately, income remains a significant barrier to broadband adoption.
The broadband subsidy would remain at $9.25 and there are plans to "reduce waste, fraud and abuse". A third party would be used to verify the eligibility of households, and it would be required to retain documentation to allow for easier auditing. This would help to take pressure off ISPs, something that could be improved further by the use of subsidies being delivered directly to customers through the use of vouchers.
Photo credit: Denis Rozhnovsky / Shutterstock
-

Apple does more to protect your privacy than Microsoft, Google, and Facebook
Publié: juin 18, 2015, 7:50pm CEST par Mark Wilson

In the Electronic Frontier Foundation's annual Who Has Your Back report, Apple is commended for adopting a "strong stance" on user rights, transparency, and privacy. The 2015 edition of the report is the fifth to have been produced, and it rates a number of tech companies according to how they inform users about their privacy policies and how they respond to government requests for data.
Apple was awarded a full five star rating, faring better than Microsoft (three stars), Google (three stars), and Facebook (four stars). Other companies receiving a five out of five rating include Wikimedia, WordPress, and Yahoo. At the bottom of the heap are AT&T and WhatsApp who received just one star each. Despite a few disappointments, EFF is generally pleased with how tech firms have noted the renewed interest in privacy that now exists.
AT&T and WhatsApp are both criticized for failing to let users know about their policies on government demands for data, as well as data retention policies. AT&T is described as failing to keep pace with the rest of the tech sector, as is Verizon. Apple is singled out for particular praise, with EFF saying, "it has adopted every best practice we’ve identified as part of this report. We commend Apple for its strong stance regarding user rights, transparency, and privacy." Google lost points for failing to reveal more about government data requests and for a lack of transparency about data retention.
In order to earn stars, companies had to prove themselves in a number of areas. The first star has three requirements: that companies require a warrant before responding to requests for data, that they publish a transparency report, and that they clearly explain how they respond to government data requests. Star two is earned by letting users know about government data requests, while the third comes from publicly disclosed data retention policies. The fourth star is earned by disclosing the number of government data requests received and how many were complied with, and the fifth star comes from opposing backdoors and standing up for user rights.
Microsoft found itself on the receiving end of both praise and criticism:
We appreciate what Microsoft has done to stand up for user transparency and privacy, but it still has more work to do. In particular, Microsoft should make clear its data retention policies and disclose what government content removal requests it receives.
In addition to WhatsApp, reddit and Slack were included in the report for the first time this year. Speaking about reddit, EFF said "there's still room to improve" and that the company needed to "take an official stance opposing government mandated backdoors".
You can check out the full report at the EFF website.
Photo credit: Mmaxer / Shutterstock
-

Indie labels 'screwed' by Apple Music free trial deals
Publié: juin 18, 2015, 11:58am CEST par Mark Wilson

With less than two weeks to go until the launch of Apple Music, a report suggests that the company is having trouble enticing smaller and independent labels into signing up to take part. The problem is not necessarily that there is a lack of interest in joining Apple Music, but that the three month free trial period would generate no income for the labels.
Apple Music will make its money through monthly subscription fees, a percentage of which is then shared with record labels. During the three month free trial, Apple will make no money from the music streaming service, and will therefore have no revenue to share. While this is a cost that larger labels might be in a position to absorb, small companies say it could put them out of business.
Speaking to The Telegraph, chairman of industry lobby group UK Music Andy Heath said that smaller labels simply could not afford to take part in the free trial. He said that he was not aware of any independent label having signed up for Apple Music, and this means that music fans will miss out on large catalogs of artists' work. He said:
If you are running a small label on tight margins you literally can't afford to do this free trial business. Their plan is clearly to move people over from downloads, which is fine, but it will mean us losing those revenues for three months. Apple hasn't thought this through at all and it’s not like them. They can't spring a contract like this on us three weeks from release. They are basically putting all the risk on the labels. People will say 'oh but you're on Spotify'. Well yes, but we get paid for that.
Heath says that Apple is looking to branch out into new areas and is, in effect, asking smaller businesses to pay for it. While Apple will be paying out royalties that are above average to labels once the free trial is over, the fear is that this would be too late for some.
It will literally put people out of business. Smaller labels would be completely screwed. Apple just has to move on this.
It seems unlikely that Apple will change its plans so close to launch. While the company could undoubtedly afford to dip into its coffers and bear the cost of the free trial itself while continuing to pay labels, it is more likely that Apple Music will launch without the participation of a number of important, smaller players in the music industry.
-

Apple wants bloggers to pay its legal fees
Publié: juin 17, 2015, 6:17pm CEST par Mark Wilson

The launch of Apple News looks set to upset potential publishers if initial reaction to the service's terms and conditions is anything to go by. Bloggers have complained that they have been spammed by Apple with an email inviting them to join the service. Nothing wrong with that (aside from the unsolicited correspondence), you might say, but the problem is, complainants grumble, that acceptance of terms and conditions is assumed unless individuals actively opt out.
Again, this is not entirely unusual, but one of the terms makes for interesting reading. "If we receive a legal claim about your RSS content, we will tell you so that you can resolve the issue, including indemnifying Apple if Apple is included in the claim". But this is not the only clause that has raised the ire of bloggers.
Would-be publishers also find that they automatically agree to allow Apple to display ads next their content without any payment being made. As well as missing out financially, bloggers also have no control over which ads are associated with their content. The BBC reports that some bloggers are concerned that "they would be bound by the agreement perhaps without ever having seen it or actively consenting to it".
What is perhaps more worrying for content creators is that Apple will simply go ahead and repurpose online articles unless specifically told not to.
If you do not want Apple to include your RSS feeds in News, reply NO to this email and we will remove your RSS feeds.
Anyone who does not see the email (it could well end up in the spam folder or fail to arrive at all) could find that their content is being reused without permission. It's something that blogger Mike Ash has taken exception to. In a blog post entitled I Do Not Agree To Your Terms he says:
First, I want everybody to know about the ridiculous stunt Apple is trying to pull here. I'd have been perfectly happy if they had just sent me an e-mail saying they were going to include my feed, and if I didn't like it I could e-mail to opt out. I'd even be happy if they didn't even give the option to opt out! After all, having an RSS feed in the first place is an implict opt-in to that sort of thing. But trying to dictate terms on top of that while telling me that I automatically agree to them unless I opt out is unacceptable, even if the terms themselves are relatively benign. They should stop doing this, and telling people about what they're doing is the only way I know that might help to make that happen.
Second, I want to declare directly to Apple: I do not agree to your terms. You are, of course, welcome to use my content in any way already permitted by law. I believe that should suffice for your purposes, but if it doesn't, well, too bad. I have no idea if you'll ever see this declaration, but that's just like yours, so I think it's fair.
Apple is yet to issue a statement about the complaints.
Photo credit: 360b / Shutterstock
-

Massive Microsoft shakeup sees Stephen Elop departure
Publié: juin 17, 2015, 5:27pm CEST par Mark Wilson

Microsoft is a company in a constant state of evolution, and today this is perfectly demonstrated by a huge shakeup at the top. Satya Nadella wrote to employees to explain a number of changes to the Senior Leadership Team -- including the departure of Stephen Elop.
The former Nokia CEO and Nadella "agreed that now is the right time for him to retire from Microsoft". A question that can be heard echoing through the company is "did he jump, or was he pushed?" Mark Penn is also leaving the company to form a private equity fund. The reorganization additionally sees the company dividing into three distinct teams to "deliver better products and services our customers love at a more rapid pace".
In an email Nadella reveals that golden boy Terry Myerson will, in effect, be taking over for Elop, the man once destined for the top position at Microsoft. The existing Operating Systems Group and Microsoft Devices Group are being combined into a new division called the Windows and Devices Group. It will focus on Windows as a service as well as the production of Surface, HoloLens, Lumia, Surface Hub, Band and Xbox.
Cloud and Enterprise will continue to be headed up by Scott Guthrie, and will also absorb Microsoft's Dynamics products. Qi Lu remains at the top of Applications and Services Group, and will now incorporate education solutions.
Since his move to the head of Microsoft, Nadella has been pushing the mobile-first, cloud-first vision for the company. Today he outlined three "ambitions" for the company moving forward:
- Reinvent productivity and business processes
- Build the intelligent cloud platform
- Create more personal computing
Also leaving Microsoft are Kirill Tatarinov and Server and Tools stalwart Eric Rudder. Of the four departures, only that of Mark Penn is identified as being unrelated to the restructuring -- he announced his plans to retire from the company earlier in the year. After the reshuffle, the new line up is as follows:
Chris Capossela, Executive Vice President and Chief Marketing Officer (will now also take on responsibility for Dynamics and Education marketing)
Kurt DelBene, Executive Vice President, Corporate Strategy and Planning
Scott Guthrie, Executive Vice President, Cloud and Enterprise
Amy Hood, Executive Vice President and Chief Financial Officer
Kathleen Hogan, Executive Vice President, Human Resources
Peggy Johnson, Executive Vice President, Business Development (will now lead our partnerships with mobile operators around the world)
Qi Lu, Executive Vice President, Applications and Services Group
Terry Myerson, Executive Vice President, Windows and Devices Group
Harry Shum, Executive Vice President, Technology and Research
Brad Smith, Executive Vice President and General Counsel, Legal and Corporate Affairs
Kevin Turner, Chief Operating Officer (will also now take responsibility for the Dynamics sales and partner organization)
Jill Tracie, Chief of Staff
Photo Credit: Asif Islam/Shutterstock
-

Will editorial bias blight a curated Apple News?
Publié: juin 17, 2015, 1:24pm CEST par Mark Wilson

There was a lot of Apple news to digest from WWDC last week. As well as the latest versions of OS X and iOS, we witnessed the appearance of women on stage as Apple tried to do its part for diversity. Apple would probably like us to focus on the likes of the Apple Music and Beats One launches, but really it's another announcement that should be foremost in our minds: Apple News.
On the face of it, this is a simple replacement -- perhaps even just a renaming -- for Newsstand, but it's really much more than that. The key difference here is that content will not only come from media partners, but will also be curated. Apple is now a news editor, and that's extremely dangerous.
There are a number of reasons to be concerned about the fact that Apple will be employing a team of people to control which news stories appear in the News app. Perhaps the most worrying feature of Apple News is that the stories will be handpicked and curated. As noted by 9to5 Mac, Apple is advertising for news editors who are "ambitious, detail-oriented journalists with an obsession for great content". The aim is to "surface great content from a range of high-quality publishers", but what happens when there's a big story that is critical of Apple? Will it be buried? Ignored? Tweaked?
Apple has made much of the human side of news, and the job advertisement says that the successful candidates will need to be able to identify "compelling stories unlikely to be identified by algorithms". It will be interesting to see how the compelling stories that are critical of Apple are handled. As Apple News covers the full gamut of news -- politics, sport, war, finance, entertainment, business, and so on -- it's fair to say that the percentage of potential news stories that might be critical of Apple would be fairly small, but that's not really the point.
Working for Apple is a highly prestigious position. What editor is going to be willing to surface stories that lay into his or her employer simply because the story is compelling? This is the danger of curated news. Bias, opinion, and politics start to creep in. We already seen that media moguls such as Rupert Murdoch are more than happy to use their influence and control of the media to their own advantage, to push the political agenda that benefits them the most. Will the obvious bias of the Murdoch empire be echoed in Apple's editorial choices?
Of course, controlling the news need not be quite as simple as promoting stories that praise the company and ignoring those that are critical. Apple is a business, and it has interests. As a company it cares who is in government. It cares about the outcome of elections. It care about all manner of global issues. Like Murdoch, there will be a strong temptation to push the Apple philosophy through the news it presents to readers. When iOS 9 reviews start to creep out, will Apple News be filled with content that describes how "magical" and "innovative" the latest release is? Will there be any that point out that it is dull and boring? Any that say it has borrowed ideas from Windows Phone and Android? Any that suggest it is a failure?
These are obviously questions that can be leveled at any news outlet or, indeed, individual. But things are -- as ever -- very different with Apple. Organizations are keen to foster good relations with the company in order to get their hands on new Apple products for review. Years can be spent building up a relationship with Apple, and it's famously easy to be ignored or blacklisted by the company. This is also a two-way street. As well as news outlets being unusually inclined to be supportive of Apple, Apple is, understandably, keen to highlight those organizations that sing the praises of its products.
With its News service, Apple has a number of media partners. Will they feel compelled to provide more positive coverage for the company lest their lucrative business partnership be brought to an end? Of course, no news outlet would admit to this -- nor indeed would Apple admit to holding any sort of sway over its partners -- but it is very hard to tell what goes on in board meetings and newsrooms.
These are fears that may amount to nothing, but watch out. Apple's curation of the news could see the company getting political. Will we end up questioning why every single story has been chosen?
Photo credit: Neil Lockhart / Shutterstock
-

Airbus to build 900 satellites for OneWeb to connect the world to the internet
Publié: juin 16, 2015, 1:39pm CEST par Mark Wilson
For some companies, bringing the internet to the entire world is an important part of giving people greater opportunities. Mark Zuckerberg has been pedalling Internet.org for some time now -- even if a lot of people don’t like the scheme -- and now there's a new kid on the block.
Airbus is due to start building more than 900 satellites for OneWeb, a company looking to bring highspeed internet access to billions of people all over the world. The aim is to offer 100 percent coverage of the globe, and there is a great focus on speed. Airbus is hoping to build more than one satellite per day and launch the first batch in 2018.
Unlike Internet.org, the intention here is not to bring free internet access to people, but costs are being kept low. With a set of production values that require the creation of several of the 150kg satellites each day, Airbus says OneWeb "inspired us to develop innovative designs and processes that will dramatically lower the cost in large volumes for high performance space applications".
The company wants to build as many as four satellites per day. Production will start in France, but once an initial batch of ten is complete, manufacturing will switch to the US. The units are much smaller than many of the satellites that are currently used, and it is hoped that when the network is operational it will be able to offer connection speeds comparable to terrestrial fiber.
The project is expected to cost between $1.5 and $2 billion, and is being part-funded by chipmaker Qualcomm and Richard Branson's Virgin Group.
-

Adobe launches stock image service as part of Creative Cloud 2015
Publié: juin 16, 2015, 12:48pm CEST par Mark Wilson
Adobe has carved out a niche for itself as a provider of industry-standard tools for art and design; Photoshop is now so widely used that, like Google, it has become a verb. The company's Creative Cloud suite receives its annual update today, and as part of the update Adobe is also launching its own stock image service.
Adobe Stock is set to compete directly with the likes of Shutterstock and Getty images. Adobe already has something of a captive market. It is very well aware that the very people who tend to use stock images are the same people who use Adobe software -- it just makes sense for the two worlds to collide.
Of course, this is not a free service. Just like its rival, Adobe requires Stock users to sign up for a paid-for package. There are various plans available at different price points, but there's a sweetener for anyone who is a Creative Cloud customer in the form of a 33 percent discount on plan fees; it is also possible to sign up for Adobe Stock without being a Creative Cloud customer.
If you're wondering where all of Adobe's stock imagery is going to come from, cast your mind back to the start of the year and you'll recall that the company bought Fotolia, an existing stock image service. Pricing is competitive, but the economy of scale means that the more images you need, the cheaper it becomes. Purchasing a single image on a whim will set you back $9.99 (or £7.19), but if you are going to download on a more regular basis, the 10-images -per-month package costs $49.99 (or £23.99) with the added bonus that any unused downloads roll over to the next month -- if you're an existing Creative Cloud subscriber, the price drops to $29.99). Heavy users have the option of signing up for the top package that allows for the download of 750 image per month for $199.99 (or £143.99).
The real benefit of signing up for Adobe Stock is the integration with Creative Cloud. Those keen to try out different ideas will be pleased to hear that there's no need to download and pay for a huge image before getting to work. It is possible to download a lower resolution, watermarked version to start with, which can then be replaced with the high res version, complete with edits, at a later time.
-

Minecraft is coming to Microsoft HoloLens, and it looks incredible
Publié: juin 15, 2015, 10:00pm CEST par Mark Wilson

It has been a few months since we first heard about HoloLens, Microsoft's foray into holographic virtual reality. We've already been told that the platform will be able to run Windows apps in 3D, but -- let's be honest -- what people are really looking forward to is the potential for games. Today at E3, Mojang demoed the upcoming HoloLens version of Minecraft.
This is a game that has proved phenomenally successful, and the preview showed off today looks nothing short of incredible. This is a game that is all about the third dimension, and truly takes advantage of what HoloLens has to offer in this department.
Lydia Winters from Mojang announced that HoloLens will include out-of-the-box support for Minecraft. This means that the game can be used in one of two ways -- either projected onto a flat surface such as a wall, or enjoyed in full, immersive 3D as you build the world around you in your living room.
It's the 3D interface that will undoubtedly prove the most popular, but it's easy to switch between the two modes. The HoloLens version of the game can be voice-controlled, but it will be possible for HoloLens gamers to play alongside those playing the regular version. Flying through the virtual world in three dimensions opens up the opportunity to leap into the air or burrow underground.
There's not yet any indication of when we'll be able to get our hands on Minecraft -- we still don’t know exactly when HoloLens will be unleashed.
-

Sony Pictures hack caused accidental broadcast of expletive-filled movie
Publié: juin 15, 2015, 3:15pm CEST par Mark Wilson

When Sony Pictures was hacked last year, one of the primary concerns for the company was the leaking of a number of unreleased movies. But in the UK, there were other consequences, including the daytime broadcast of the movie The Verdict complete with a smattering of four-letter expletives.
Sony Pictures Entertainment's subsidiary company Media Mix Limited owns the TV station Movie Mix, and on 14 December the channel broadcast an edit of the movie peppered with f-bombs. In the middle of the afternoon. The channel's excuse? That the "safe for daytime" broadcast version of the movie had been deleted by hackers.
It is quite common for movies to be cut down into a Suitable Any Time (SAT) version that can be broadcast regardless of the time of day -- such as when kids might be watching. To avoid upsetting people, the "watershed" was created. This is designed to stop the broadcast of strong language before 9 pm. Ofcom (the body that regulates TV and radio broadcasts in the UK) investigated a number of complaints about the showing of the uncut version of The Verdict at such an early time and asked for an explanation.
Media Mix Limited said that it shared computer systems with Sony Pictures. It went on to explain that when Sony was hacked, its own scheduling system was also compromised, leading to the deletion of the SAT version of The Verdict. Programming schedules had to be rebuilt manually, and "human error" was blamed for accidentally replacing the deleted 'safe' version of the movie with the uncut version.
The film was recovered from storage in a form expected to be the SAT version. However, it said that unfortunately due to human error, it was in fact the unedited film which included the two instances of the most offensive language which was retrieved and it was this which was broadcast by mistake.
Ofcom decided to uphold complaints again Media Mix Limited, noting that while the security breach had been a factor in the error, it boiled down to avoidable human error -- the retrieved version of the movie should have been double-checked for compliance with guidelines.
The full report can be read on the Ofcom website -- skip to page 19 for the verdict on The Verdict.
Photo Credit: seanbear / Shutterstock
-

Emoji could be used for your next PIN
Publié: juin 15, 2015, 12:26pm CEST par Mark Wilson
The humble PIN is a common way to secure access to accounts, but it has one major problem -- it is, usually, limited to using the digits 0-9. A UK firm thinks it may have come up with a better solution: emoji-based PINs.
Intelligent Environments' Emoji Passcode system can be used to secure accounts with ideograms. The company argues that Emoji passcodes are not only easier to remember that number-based alternatives, but also more secure. This is thanks to the fact that there is a pool of 44 Emoji to choose from, and research also suggests people find it easier to remember images.
Taking the example of a typical four digit PIN, Intelligent Environments points out that there are 480 more permutations when using Emoji Passcode. The system has already been used in the company's Android digital banking app, and there is interest from other banks that are interested in implementing it as part of their own security procedures.
As well as the increased security, Emoji Passcode has been designed with millennials in mind. David Webber, Manager Director at Intelligent Environments, said:
We've had input from lots of millennials when we developed the technology. What's clear is that the younger generation is communicating in new ways. Our research shows 64 percent of millennials regularly communicate only using emojis. So we decided to reinvent the passcode for a new generation by developing the world’s first emoji security technology.
The video below shows the Emoji passcode system in operation:
The world's first Emoji passcode from Intelligent Environments on Vimeo.
-

Snowden files hacked by China and Russia
Publié: juin 14, 2015, 12:28pm CEST par Mark Wilson

UK secret services say that the encrypted files Edward Snowden held from his time working at the NSA have been accessed by intelligence agencies in China and Russia. The Sunday Times reports that the top secret files have been hacked meaning that British and American spies could be identified and located.
Wanted by US authorities, Snowden has been in hiding for some time now. It is believed that the time he spent seeking refuge in Hong Kong and Moscow may have given security official the opportunity to access the data he held. Although the data was protected, it is thought that the encryption was hacked, and US and UK intelligence services have been "forced to intervene and lift their agents from operations to prevent them from being identified and killed".
The Sunday Times quotes a number of people -- who chose to remain anonymous -- who say that the documents would enable enemies to identify spies and agents because of the information they contain and the techniques they reveal. It is feared that the potential for gaining access to the Snowden's data is the very reason China and Russia offered him asylum.
Snowden is accused of having "blood on his hands" -- a sentiment that is very much in line with those who feel he has acted treasonously. The whistleblower blew the lid off mass surveillance programs undertaken by Western governments, sparking an ongoing debate into privacy and security issues online. The sheer volume of data Snowden leaked means that it is impossible to know everything the documents contain, but there are concerns that potentially damaging information has now fallen into the wrong hands.
-

How to sideload apps in Windows 10
Publié: juin 13, 2015, 7:39pm CEST par Mark Wilson
The sideloading of apps is something that most people associate with smartphones and tablets. If you want to install unofficial apps on your iPhone, Android, or Windows Phone handset, there are things you can do to make this possible. The same is true with Windows 10 assuming you are using build 10122 or newer.
If you want to be able to install apps that are not featured in the Store, all you need to do is enable Developer Mode. As the name would suggest, this is something that will be of particular interest to developers as it makes it possible for them to test out their own apps before they hit the store, but there's nothing to stop anyone from enabling the mode to take advantage of the same feature. Here's what you need to do.
These days, there is no need to mess about the registry or Group Policy Editor -- everything can be handled from within Settings. Open Settings from the Start menu and then click Updates & Security. Move to the For Developers section and select the option labelled "Sideload apps". Windows 10 likes to hold your hand, so you'll be warned that sideloading is potentially dangerous; just click Yes to continue if you're happy to take the risk. If you prefer, you can enable Developer Mode rather than just enabling sideloading -- this unlocks a few extra options as well. If you change your mind at any time, you can easy switch back to regular mode by selecting the "Don’t use developer features" option.
And that's pretty much all there is to it. With either of these settings selected, you'll now be able to download Windows apps from other sources and install them even though they are not featured in the Windows Store.
Photo credit: wavebreakmedia / Shutterstock
-

Wikimedia secures connections with HTTPS encryption by default
Publié: juin 13, 2015, 6:23pm CEST par Mark Wilson
There is a movement calling for the encryption of all web traffic. The cause of this could be laid at Edward Snowden's door, but there's no getting away from the fact that in recent years there is an increased interest in security and privacy. To this end, Wikimedia has announced that it is now using HTTPS to encrypt all of its traffic -- including that to Wikipedia.
We've already seen the US government embrace HTTPS, and companies like Google and Facebook are making it easier to control privacy settings. Apple has hit out at companies that fail to do enough to protect users' privacy, and Wiki media is taking the extra step of also implementing HSTS, just days after Microsoft announced that this would be supported by Internet Explorer 11 under Windows 7 and 8.1.
There has long been the option of accessing the likes of Wikipedia with an HTTPS connection, but the difference now is that encryption is enabled by default. This means that for people accessing Wikimedia sites in certain parts of the world, it will now be much harder for snooping governments to monitor activity; it also makes it more difficult for ISPs to censor content.
Writing on the Wikimedia blog, the foundation said:
To be truly free, access to knowledge must be secure and uncensored. At the Wikimedia Foundation, we believe that you should be able to use Wikipedia and the Wikimedia sites without sacrificing privacy or safety. Today, we’re happy to announce that we are in the process of implementing HTTPS to encrypt all Wikimedia traffic. We will also use HTTP Strict Transport Security (HSTS) to protect against efforts to ‘break’ HTTPS and intercept traffic.
The foundation says that the move has been made in response to increased concerns about government surveillance. The switch to encryption-by-default meant updating not only site code, but also server hardware. The final stages have now been reached, and should be completed within a couple of weeks.
Photo credit: Evan Lorne / Shutterstock.com
-

Amazon publishes opaque transparency report
Publié: juin 13, 2015, 12:54pm CEST par Mark Wilson

Post-Snowden there is great interest in just what involvement the government has with technology firms. There are frequent requests from government agencies for information about users and the likes of Google, Snapchat, and even the NSA itself have all released transparency reports that reveal, in broad strokes, the number of requests for data they have received.
Amazon is the latest company to release a transparency report -- although the term really should be used in the loosest possible sense. The report includes scant details about the number of subpoenas, search warrants, court orders, and national security requests received in the first five months of 2015. The report is so vague as to be virtually meaningless.
As with other transparency reports, the level of detail provided is a disappointing. For each type of request we are simply told how many requests were received, and how many were complied with, partially complied with, or not responded to. There is no breakdown of which areas of Amazon's operation have been the subjects of interest -- the report makes no indication how many of the data requests relate to cloud storage service, and which to retail, for instance.
The title of 'transparency report' remains something of a misnomer, particularly when it comes to revealing information about national security data requests. Here we are not even privy to precise numbers; we're told nothing more than the fact that between 0 and 256 requests were received. No information is provided about the responses given.
Amazon's Stephen Schmidt said:
Amazon does not disclose customer information unless we’re required to do so to comply with a legally valid and binding order. Unless prohibited from doing so or there is clear indication of illegal conduct in connection with the use of Amazon products or services, Amazon notifies customers before disclosing content information.
Where we need to act publicly to protect customers, we do. Amazon never participated in the NSA’s PRISM program. We have repeatedly challenged government subpoenas for customer information that we believed were overbroad.
For what they are worth, here are the figures Amazon has shared:
Subpoenas received: 813
How Amazon responded:
Full response: 542
Partial response: 126
No response: 145Search warrants received: 25
How Amazon responded:
Full response: 13
Partial response: 8
No response: 4Other court orders received: 13
How Amazon responded:
Full response: 4
Partial response: 5
No response: 4National security requests received: 0-249
Non-U.S. requests received: 132
How Amazon responded:
Full response: 108
Partial response: 7
No response: 17Removal requests received: 1
How Amazon responded:
Full response: 1
Partial response: 0
No response: 0The next transparency report is expected at the end of 2015 or beginning of 2016.
Photo credit: Ken Wolter / Shutterstock
-

Facebook factors in article view times to personalize news feeds
Publié: juin 12, 2015, 11:47pm CEST par Mark Wilson

Facebook today announced that it is making another change to the way it determines which stories are displayed in News Feeds. As well as factoring in how many people have liked or commented on a story, the social network will now also take into account how long people spend reading individual articles.
But it's not quite as simple as saying that stories people spend a while looking at are the most popular. Some lengthy visits are the fault of slow connections, for example. Equally, it is not safe to assume that only heavily liked and commented articles are the most read -- there are some stories that do not lend themselves to liking and commenting. Today's change aims to strike a balance between different weightings.
Facebook now keeps a check of how long users spend looking at individual articles compared to how long they spend on others. Despite the change, the site says that Pages are unlikely to see a significant change in distribution. The aim is simply to 'surface' more content that people are interested in reading.
In a blog post, Facebook engineers Ansha Yu and Sami Tas say:
Recently, as part of our ongoing effort to improve News Feed, we asked people to rate their experience and tell us how we can improve the content they see when they check Facebook.
From this research, we learned that in many cases, just because someone didn’t like, comment or share a story in their News Feed doesn’t mean it wasn’t meaningful to them. There are times when, for example, people want to see information about a serious current event, but don’t necessarily want to like or comment on it. Based on this finding, we are updating News Feed’s ranking to factor in a new signal—how much time you spend viewing a story in your News Feed.
You may not see changes to your news feed immediately -- it's rolling out over the next few weeks.
Photo credit: Gil C / Shutterstock
-

Uber puts passengers at risk with a flawed driver-approval process
Publié: juin 12, 2015, 8:58pm CEST par Mark Wilson

Uber, the San Francisco-based private taxi firm, is putting its passengers in grave danger. The company uses a computerized driver sign-up system that can be easily fooled into authorizing drives with fake insurance papers. The transport network exploded onto the scene a few years ago, and a whistleblower claims that it is all too easy to cheat the system making it possible for virtually anyone to sign up to be an Uber driver.
The vulnerability was found to have been exploited in London where there are around 15,000 Uber drivers in operation. The scam has been demonstrated by The Guardian who worked with a whistleblower to fraudulently sign up as a driver. It was achieved using fabricated insurance papers from a made up company with a fake letterhead.
Uber recently cut its fares in a bid to attract more customers, and this was a bill that drivers had to shoulder. It is claimed that in order to save money, some drivers are failing to pay for insurance and use false papers to gain Uber authorization. Working in conjunction with The Guardian, the whistleblower uploaded a fake insurance policy from a non-existent insurance company. Despite the lack of genuine paperwork, he was approved to pick up paying customers.
The driver claims he actually had genuine insurance in place, but uploaded the fake documents to illustrate a point to the wider public. He has since been removed from Uber's books and reported to the police. Uber responded by saying that the illegitimate driver approval was "a unique situation triggered by a deliberate attempt to try and cheat the system" and said that it would implement a limit on which insurers it would allow drivers to use in an attempt to prevent the same thing from happening again.
A spokesperson put the fake document approval down to human error:
We are going through our processes and evaluating them to make sure something like this can’t happen again. It was checked. It was a case of human error. The team involved has been spoken to to ensure our high level of practice has been maintained at all times.
The company stressed that if an accident occurred involving an Uber car driven by someone without the necessary insurance, the incident would still be covered by its separate corporate insurance policy.
-

Google helps you find the best Android phone
Publié: juin 12, 2015, 12:35pm CEST par Mark Wilson

While choosing which iPhone to buy is a fairly simple decision -- there just aren't many options to choose from -- it's a very different matter for Android fans. The wealth of hardware manufacturers producing an endless stream of handsets means that a trip to the phone store, physical or online, can be overwhelming.
Today Google launches a new tool that can be used to home in on the perfect Android handset for you. Answer a few simple questions about the types of thing you need from a phone, and the wide selection of devices will be whittled down to those that are just right for you.
The Which Phone tool asks you to indicate what you will use your handset for, from taking photos and listening to music, to helping with a fitness regime and watching movies. You need to specify at least three requirements, and in most cases you're given the opportunity to go into more detail. If you indicate that you're going to be using your phone to take photos, is that just selfies, or do you need something more advanced?
If you're in the US, you can choose which carrier you'd like to go with, but the phone finder can be used by people anywhere in the world just by indicating that the carrier is not important. You'll then be presented with a list of handsets that match your requirements, complete with a summary of the key specs. The list can be filtered by screen size, carrier, and price range, and you can click through to buy online -- or you can just arm yourself with the information you need to track down the best deal in a local store.
Check it out and see what recommendations Google has for you.
-

Mozilla offers up to $10,000 to security bug hunters
Publié: juin 11, 2015, 11:41pm CEST par Mark Wilson

Bounty hunters can make a killing if they uncover security problems with software. There are lots of companies who will pay out in cold, hard cash to anyone who managed to unearth security vulnerabilities, and Mozilla has announced that it is increasing its top level bounty.
The company is appealing to white hat hackers and security experts to help plug holes in its software, and it is willing to cough up for it. Mozilla's security program had already paid out $1.6 million over the years, and the Client Bug Bounty Program has just been updated so that maximum payout is now $10,000.
There are, of course, a few caveats. Any bug that is reported must be unique if it is to qualify for the bounty payout, and the bug "must be a remote exploit, the cause of a privilege escalation, or an information leak." To prevent the risk of sabotage, code writers are exempt from reporting problems with their own buggy code, and Mozilla Foundation employees are not eligible to submit reports.
Of course, not all reports of security issues will result in a payout, but the top rate has now more than tripled. The previous maximum had been $3,000, and this has now been upped to $10,000, and Mozilla has outlined details of the bounties for different types of vulnerability.
The lowest grade is classed as "medium vulnerability" and will pay out $500-$2500, while the minimum payout for a "high or critical vulnerability" is $3,000. Detail is everything and if you submit a "high quality bug report of a critical or high vulnerability" the payout stands at $5,000; provide details of a "high quality bug report with clearly exploitable critical vulnerability" and you could be in line for a $7,500 reward. The top rate of $10,000 is reserved for a "novel vulnerability and exploit, new form of exploitation or an exceptional vulnerability."
-

Reddit starts killing off harassment subreddits
Publié: juin 11, 2015, 1:11pm CEST par Mark Wilson

Reddit is both famous and infamous. It's a source of news, a platform for disseminating such delights as the pictures that came out of the Fappening, and home to the ever-interesting Ask Me Anything sessions. But like any social website, it also has problems. Like Facebook, Twitter, and other sites, there are issues with spam, trolling, and abuse. Reddit has a particular problem with sections that are dedicated to harassing and abusing groups of people.
Now the site is fighting back. It is taking a proactive approach and removing subreddits whose raisons d'être are the harassment of people. The cull initially sees the removal of five offending subreddits, but the Reddit team explains that only one with a sizeable userbase is affected -- r/fatpeoplehate.
Having stepped up to the plate, Reddit now has a delicate balancing act to perform. It says that it believes in the right to freedom of speech, but also wants to protect security and privacy of users. The aim is to police the site with as light a touch as possible, but the team explains that it has strict rules governing the harassment of others; any subreddits that breach these rules will get the chop. This is certainly not the first time Reddit has stepped in to ban subreddits -- some content fell victim at the time of the Fappening, for instance -- but the proactive stance illustrates that the problem of harassment is now being taken seriously.
In a post explaining the policy, the Reddit team says:
We will ban subreddits that allow their communities to use the subreddit as a platform to harass individuals when moderators don’t take action. We’re banning behavior, not ideas [...] We are continuing to add to our team to manage community issues, and we are making incremental changes over time. We want to make sure that the changes are working as intended and that we are incorporating your feedback when possible. Ultimately, we hope to have less involvement, but right now, we know we need to do better and to do more. While we do not always agree with the content and views expressed on the site, we do protect the right of people to express their views and encourage actual conversations according to the rules of reddit.
Anyone who feels that a particular subreddit should be investigated for problems of harassment is invited to email Reddit to voice their concerns.
Photo credit: Viktorija Reuta / Shutterstock
-

Twitter's block lists make it easier to avoid trolls and spam
Publié: juin 11, 2015, 12:32pm CEST par Mark Wilson

You don’t have to be following too many accounts on Twitter for it to become overwhelming; there is an incredible amount of data created every minute. To make things more manageable, lists make it possible to organize content into different categories so it can be quickly filtered. Today Twitter announces an extension of the lists concept that can be used to tackle spam and trolling.
It is now possible to not only create lists of accounts you would like to block (so you are invisible to them), but also share these block list with others. It's a technique that has already been implemented by some third party Twitter clients, but it is now officially supported. Privacy and abuse have long been issues for Twitter, and this is just the latest move to try to tackle the problem.
Working in a similar way to malware and ad-blocking blacklists, shareable block lists finally present Twitter users with a quick and easy way to block interactions from large numbers of troublesome accounts in one fell swoop. To begin with, users are being invited to start creating and sharing their own lists, but Twitter has not indicated whether it will also release block lists of its own that could be used to filter content.
Introducing the new feature in a blog post, Xiaoyun Zhang, engineer for user safety at Twitter, said:
Today we’re making it possible to share block lists on twitter.com. This new, advanced feature makes blocking multiple accounts easy, fast and community driven. Mute and block are tools to help you control your Twitter experience. While many users find them useful, we also recognize that some users -- those who experience high volumes of unwanted interactions on Twitter -- need more sophisticated tools. That's where this new feature comes in. You can now export and share your block lists with people in your community facing similar issues or import another user's list into your own account and block multiple accounts all at once, instead of blocking them individually.
If you already have a list of blocked accounts, this can be easily exported ready for sharing. The Twitter help center explains how to go about sharing, and the import process is quick and simple.
With a checkered history surrounding trolling and abuse, this could just be the solution Twitter has been looking for that will help to clean up its reputation. But the company has not made it clear if block lists will be policed -- there is clearly potential for the feature to be abused so that legitimate accounts are blocked alongside the less desirable ones. It's early days, and time will be the true test here.
Photo credit: tanuha2001 / Shutterstock
-

Internet Explorer 11 gains HTTP Strict Transport Security in Windows 7 and 8.1
Publié: juin 9, 2015, 9:05pm CEST par Mark Wilson

As the launch of Windows 10 draws ever-nearer, we're hearing more about Microsoft Edge and less about Internet Explorer. Edge (formerly known as Project Spartan) may be the default browser in the upcoming version of Windows, but the browsing stalwart that is IE will live on nonetheless.
Anyone using the Windows 10 preview has had a chance to use the HTTP Strict Transport Security (HSTS) in Microsoft Edge, and today the security feature comes to Internet Explorer 11 in Windows 7 and Windows 8.1. This security protocol protects against man-in-the-middle attacks and is being delivered to users of older versions of Windows through an update in the form of KB 3058515.
With Edge, Microsoft is going to great lengths to bolster security. The inclusion of HSTS is indicative of this, but the company is also keen for Internet Explorer users to feel that they have not been forgotten. Windows 10 may be a free upgrade, but it is fair to say that there will still be a huge number of people who decide to stick with Windows 7 or Windows 8.1. Microsoft feels that this is not a reason to compromise on online security.
Introducing the feature in a blog post, Microsoft explains how it can be used by sites:
Site developers can use HSTS policies to secure connections by opting in to an HSTS preload list, which registers websites to be hardcoded by Microsoft Edge, Internet Explorer, and other browsers to redirect HTTP traffic to HTTPS. Communications with these websites from the initial connection are automatically upgraded to be secure. Like other browsers which have implemented this feature, Microsoft Edge and Internet Explorer 11 base their preload list on the Chromium HSTS preload list.
Microsoft points out that mixed content is not supported by servers offering HSTS. This remains the case with today's update and in both Microsoft Edge for Windows 10, and Internet Explorer 11 for Windows 7 and 8.1 an information bar will appear whenever mixed content is encountered by way of a warning.
Photo credit: Maxx-Studio / Shutterstock
-

Apple Music and Beats One radio launch to shake up audio streaming
Publié: juin 8, 2015, 9:40pm CEST par Mark Wilson

It was not the industry's best-kept secret -- Sony let the cat out of the bag a little early -- but at WWDC today, Tim Cook officially took the wraps off Apple Music. Set to compete with the likes of Tidal and Spotify, Apple's new streaming music service sits neatly alongside iTunes and has the involvement of Dr Dre, Trent Reznor, and Jimmy Iovine to name but three.
Cook stepped into Steve Jobs' shoes for a moment, introducing the famous "one more thing" that has been missing from more recent Apple events. Not a company to hide its light under a bushel, Apple's Music service is not just a music streaming service, but "the next chapter in music". But there's more than just Apple Music; there's also Beats One, Apple's first ever radio station.
The launch of a radio station should, perhaps, not come as a complete surprise. It's a global radio station meaning that everyone, in 100 countries, hears the same thing at the same time -- there is, of course, the slight issue of time zones which could make for some interesting programming decisions. By Apple's own admission, "music has been part of the Apple DNA from the beginning" and it is something that continues to be treated with reverence by the company. Trent Reznor -- he of Nine Inch Nails fame and recent joiner of Apple Creative -- says:
There needs to be a place where music can be treated less like digital bits but more like the art it is, with a sense of respect and discovery
In addition to on-demand streaming for $10 per month (or, probably, £10 in the UK -- yep, the old $ for £ switcheroony once again), Apple Music also features curated content. We already know that Sony views the launch of the service as a "tipping point" and Apple seems to feel the same. This is iTunes on steroids -- all of the tracks you have come to love through iTunes can be streamed or downloaded if you want to be able to listen offline. As you would expect for a paid service, there are no ads, just lots of music tracks and videos.
Rather than relying solely on algorithms as a recommendation engine, Apple promises that recommendations will be provided by music experts. This will make it easy to not only discover new music, but also grab a playlist that is suitable for whatever mood you happen to be in.
But Apple Music is not just a one-way street; it's not just about consumption. It is also a platform through which artists can connect with their fans, and this is something that Apple is really pushing. It's something that will appeal to up-and-coming artists as well as unsigned bands, giving them a way to reach an audience that would otherwise be unavailable.
Apple Music launches on June 30 for OS X and iOS devices, and will find its way to Windows and Android in the Fall. As an incentive to try it out, there's a three month free trial, and in addition to the $9.99 per month subscription package, there's also a $14.99 family package that can be shared by up to six people.
-

iOS 9 public beta coming in July with split-screen apps and improved battery life
Publié: juin 8, 2015, 9:12pm CEST par Mark Wilson

Expectations were high for iOS 9 news at WWDC, and Apple delivered. At the keynote speech at the developer conference we were introduced to the latest version of the operating system that will power iPhones and iPads the world over, with the promise that it has been "refined from the ground up".
What is there to look forward to? Lots. There are updates to Apple Pay, a new News app, updates to Notes, as well as an updated keyboard, split-screen app display, and even a picture-in-picture option. But the news that will get a lot of people excited is that there will be a public beta of iOS released.
Searching has been massively overhauled. There's a new search API, and deeplinking also allows for far better integration with apps as well. When you're using Spotlight, iOS 9 makes intelligent suggestions about apps you might want to use, contacts you may need to get in touch with, as well as highlighting nearby places of interest.
There's a new task switcher that can be accessed by double tapping the home button, and this introduces the idea of full-on multi-tasking -- for iPad users at least. Apps can be layered on top of one another, but there's also the option of splitting the screen 50:50 or 70:30 between two apps you want to be able to see at the same time, while media apps can take advantage of a new picture-in-picture option. Data can be dragged and dropped between apps, opening up the possibility of conducting more "proper work" from an iPad. SplitView is only available on iPad Air 2, while picture-in-picture is supported by iPad Air upwards and iPad mini 2 upwards.
Apple has taken on board complaints that iOS was getting a little fat. The operating system has now been put on a diet and a mere 1.8GB of space is all that's needed to perform an upgrade. Whatever your iOS device is used for, battery life is of the utmost importance. It's something that Apple has focused on in iOS 9, promising up to an extra three hours of life thanks to the introduction of a new low power mode.
Siri has received an interface upgrade and also gains a batch of new features to make it more powerful than ever. There's support for more natural language queries, and it is also contextually aware. This means that you can be in an app and make a request to be reminded about it at a later time, or when you hit home or the office -- Siri will know what you are talking about.
Intelligence is something that Apple is really playing up in iOS 9, looking to create an operating system that proactively adapts to what you do and the way you work. This means that there are location-aware features such as playing music when you get in the car or when you plug in headphones, and if you've set a reminder that involves getting directions, current traffic conditions will be taken into account so that you are reminded to set off in plenty of time.
Notes has been updated, and now includes support for checklists, doodling, and linking to other notes -- handy for working on larger projects. Maps has received quite a big update and now includes details of public transport stops, and highlights nearby places that accept Apple Pay. Interacting with iOS 9 is easier than in previous versions thanks to an improved keyboard that now provides easy access to frequently used options such as copy and paste.
The developer preview of iOS 9 is available today, while the public preview will launch in July. The full release should be expected in the fall, although no specific date has been nailed down.
-

Apple's Newsstand is dead; long live News, baked into iOS 9
Publié: juin 8, 2015, 8:16pm CEST par Mark Wilson
Newsstand is set to disappear from the screens of iPhones and iPads all over the world. At today's WWDC keynote speech, Apple announced the Flipboard-inspired News. A customizable news aggregator, News presents users with a selection of content from media partners that include the New York Times, Conde Nast, and ESPN, and it will be built into iOS 9.
Like Flipboard et al, News learns from the types of media you consume and suggests content you might like to read. Noting the current levels of interest in privacy, Apple stressed that personal preferences and habits will never be shared with third parties. This is a theme that cropped up again and again during the keynote, with strong emphasis being placed on the fact that no data is shared externally and articles are not linked to other Apple services.
Recode reports that publishers will be able to publish apps within the App Store and will be able to push their content directly to them. This helps to avoid the problem that plagues Newsstand that saw new content getting lost and remaining unread. Apple will continue to take a 30 percent stake of developers' app subscriptions, but publishers will retain all of the revenue advertising that News brings in.
Apple is clearly keen for the advertising side of News to take off on an even larger scale. Rather than contend with unsold ad-space, the company is willing to help publishers fill all of their ad slots, for a fee of course. Just as with other similar services, News users can home in on the content they want to see based on either topic or publication. Launching the new app, Susan Prescott, Vice President of Product Marketing said:
The articles can come from anywhere, but the best ones are built in Apple News format.
The success of News will depend largely, it seems, on publishers' willingness to produce articles in the new format. In true Apple style, News articles are described as combining "interactive stories with beautiful editorial layouts, photo galleries, animations, and video". It will be available in United States, Australia, and the United Kingdom.
-

The Apple PR machine wheels out women from the shadows for WWDC
Publié: juin 8, 2015, 2:19pm CEST par Mark Wilson

Diversity is one of the latest buzzwords that tech companies are keen to throw around whenever the chance arises. If you were to knock back a shot of something every time it cropped up in press releases, keynote speeches, and company reports, rates of global alcoholism would shoot through the roof. Now a follower rather than a leader, Apple is ready to jump on just about any bandwagon that happens to be passing.
Google, Microsoft and other companies have recently waxed lyrical about the diverse sexual and racial makeup of their workforces -- it looks great for public relations, after all -- and Apple wants a slice of that pie for itself. It's a company that is highly adept at capturing the zeitgeist; as my colleague Joe Wilcox puts it, Tim Cook is an opportunist. The latest attempt to curry favor with the in-crowd, it seems, is to wheel out a few token women at today's WWDC keynote.
Now don’t get me wrong: clearly it’s a great thing to see more women changing the public faces of companies. Of course we should welcome the fact that women have an equal footing with men in the work place and should applaud companies that encourage the female contingent in the workforce. But actually, should we? Is this not just the way things should be? Women account for around half of the population of the world, does the law of averages therefore not suggest that there should be -- broadly speaking -- a similar percentage of women found in the workplace?
Sadly not. We know from the diversity reports published by the likes of Amazon that companies are still dominated by white men. Google et al are very quick to point out what they are doing to encourage woman not only to work for them, but also to work their way up through the ranks. This is not something that is praise-worthy, it's the natural order of things. The male-dominated work arena -- particularly in the world of tech -- is a duller, sadder place because of the shamefully small number of women working in the industry, with a few notable exceptions.
At today's WWDC keynote we are being told that the speech will feature women. Actual women, in person (where have they been hiding up until now?). Not just another middle-class, middle-ages white guy dressed in black, but a real, walking, talking woman. The cynic in me -- and I have a feeling I'm not alone -- can’t help but feel that this is little more than a case of ticking boxes on a checklist. X percent of gay workers... check! X percent of disabled workers... check! X percent of female workers... oh... hang on... we're a bit short in this department. That doesn’t look good, does it? Let's push someone suitably feminine to the front while it's business as usual in the background.
Let's just hope that whichever woman (or women... let's be optimistic here) are wheeled out for the event do not find themselves in the position for tokenistic reasons. Other tech firms have shown themselves to be keen to be noticeably tackling the 'problem' of a lack of LGBT diversity in the workplace, but there are two dangers here. Firstly that it results in positive discrimination (it should always be the case that the best person for the job gets the job, but that's not to say there isn’t more that could be done to encourage a wider range of people to enter certain fields of work so there is a larger pool to select from) which is never a good idea in the long-, medium-, or short-term.
Secondly, there is the risk that -- and I very much feel that this is what is happening time and time again -- companies use the fact that they employ women (or black people, or gay people, or disabled people, or whatever group of people we happen to be focusing on at the time) as a marketing tool. Yes, obviously -- assuming it happens -- the appearance of women on-stage at WWDC is a good thing. But it shouldn't need to be engineered. When it happens, it shouldn't need to be pointed out. The fact that it is happening at Apple doesn’t mean that Apple is great. It just means that it is doing what it should be doing -- reflecting the naturally diverge nature of humanity and nurturing the skill and talent it finds there.
We should be berating companies that are not diverse rather than lauding those that are. Don’t let Apple chalk this up as a win.
Photo credit: Catalin Petolea / Shutterstock
-

Internet users are powerless to protect their privacy, and they know it
Publié: juin 7, 2015, 7:34pm CEST par Mark Wilson

A paper produced by a team at the University of Pennsylvania confirms something many people have probably thought true for some time: the notion that internet users are unhappy with the way their privacy is undermined by advertisers and online companies, yet feel there is nothing they can do about it.
While marketing companies like to present an image of customers who are happy to hand over personal information in return for certain benefits, the truth is rather different. Rather than dedicating time and energy to trying to stop personal data from being exploited, people are instead taking it on the chin and accepting it as part and parcel of modern, online life. It's just the way things are.
The academics published a report entitled "The Tradeoff Fallacy -- How Marketers Are Misrepresenting American Consumers And Opening Them Up to Exploitation". The report cites a survey, the results of which "indicate that marketers are misrepresenting a large majority of Americans by claiming that Americans give out information about themselves as a tradeoff for benefits they receive. To the contrary, the survey reveals most Americans do not believe that ‘data for discounts' is a square deal".
The modern internet user is very aware of the way things work. They know that they are being used and, while they may not be entirely 'OK' with it, they are willing to put up with the fact in return for some rewards. The realization that there is little point in fighting the system has kicked in, and the mindset has now changed to something more along the lines of "well, if you can't beat the system, you might as well get what you can from it". At least, this is what the marketing companies would have you believe.
There are several ways of looking at people's attitude to online privacy, and it makes sense to use the common example of Google and Facebook. Just about all users know that by using either of these services they are going to find themselves on the receiving end of targeted advertising. This means that habits, hobbies, and demographics factors are being used to build up profiles of users. There are very few internet users who are not aware of this.
There are also a very large number of people who complain voraciously about how terrible a thing this targeted advertising is. A very small minority of complainants will take an active stance and go as far as closing down their Facebook account (let's conveniently ignore the fact that Facebook now, essentially, owns any data that's been added to a profile, active or not, and there's no way to determine how this may be used in future), but most will simply chalk it up foregoing some degree of privacy as the price one pays for using 'free' services.
The likes of Google et al would have you believe that this is a willing exchange, that users are happy to make a small sacrifice to gain access to something. But it seems that this is not actually the case. What is actually happening is that internet users are throwing their hands up in surrender, resigning themselves to the fact that they can do nothing to stop companies from gathering data about them one -- and if it's going to happen, why not use the services anyway?
It is suggested that marketers have greatly misrepresented how people feel about their privacy. In fact people are not happy with the notion of exchanging personal information for rewards and services. When presented with the statement "if companies give me a discount, it is a fair exchange for them to collect information about me without my knowing", the overwhelming majority of people (91 percent) disagreed. Most also disagreed (71 percent) with the statement " It's fair for an online or physical store to monitor what I'm doing online when I'm there, in exchange for letting me use the store's wireless internet, or Wi-Fi, without charge". Frame things slightly differently -- "it's okay if a store where I shop uses information it has about me to create a picture of me that improves the services they provide for me" -- and the figure drops to 55 percent.
But there is a contradiction. Asked if they would be willing to allow a supermarket to collect data in return for a discount on their shopping, 43 percent of people were OK with the idea. The report suggests that the explanation is simple:
Our study suggests a new explanation for what has thus far been misconstrued as "tradeoff" behavior in the digital world: a large pool of Americans feel resigned to the inevitability of surveillance and the power of marketers to harvest their data. People who are resigned do not predictably decide to give up their data.
The report's authors say that most people are so uneducated about the way privacy works online that they have basically given up trying to work out what they can do to protect it. But that's not to say that everyone is happy with how things have turned out. Nearly three quarters of people (71 percent) disagreed with the statement "what companies know about me from my behavior online cannot hurt me."
Internet usage is doing nothing other than increase, and as the Internet of Things grows, the potential for personal data capture is going to explode. How many people know what data wearables share with companies about the wearer, and who is to say what data a connected refrigerator might share and with whom. Will you be reading the smallprint when you buy a fridge to see what you're signing up for, or will you be happy to bag yourself a bargain? Do you care, or have you given up?
Photo credit: MyImages - Micha / Shutterstock
-

Sony Music CEO: Apple WILL launch music streaming service at WWDC
Publié: juin 7, 2015, 4:34pm CEST par Mark Wilson

It has been rumored for as long as we can remember (well... almost...). The idea that Apple would launch a streaming music services -- bearing in mind everything else Apple does -- is something that just makes sense. Now the cat is out of the bag as the rumor is confirmed by Doug Morris, CEO of Sony Music.
The official announcement will come from Apple at its World Wide Developers Conference tomorrow (Monday 8 June), but Morris' statement in an interview in the Midem Music Industry Festival in Cannes is a solid source. He said that the launch will represent a "tipping point" for the industry as music listeners make the move from downloading tracks to streaming them on demand. Just don't expect Apple service to be free.
There are already numerous streaming music services to choose from. Some operate on a free, ad-supported model, while other charge a monthly subscription fee (some, of course, offer a two-tiered system that combines the two models). Spotify has become something of a household name, in much the same way that iTunes has become the go-to services for digital music purchases. Apple is now ready to take its slice of the streaming pie.
Although we won’t know any details about Apple's offering until tomorrow, it looks very unlikely that this will be an ad-supported streaming service. Throughout the interview, Morris indicated time and time again that between ad-supported and paid-for services, his preference is for the latter. This makes sense from a financial point of view, and the very fact that Morris has spoken out is indicative that he actually knows what is going on. Apple would, after all, need the support and partnership of the likes of Sony Music if it is to compete with the other streaming services that are already out there.
He thinks that Apple will kick music streaming to the next level:
[Apple has] $178 billion dollars in the bank. And they have 800 million credit cards in iTunes. Spotify has never really advertised because it’s never been profitable. My guess is that Apple will promote this like crazy and I think that will have a halo effect on the streaming business.
Apple has, understandably, declined to confirm the news at this stage, but we'll have all of the details tomorrow when WWDC kicks off. Expect to see lots of announcements about iOS, OS X, and more over the next few days.
Photo credit: Andrey Bayda / Shutterstock.com
-

UK government switches to Google rather than Microsoft for cloud storage
Publié: juin 6, 2015, 2:51pm CEST par Mark Wilson

The UK's HMRC -- the government department responsible for tax -- is switching allegiances in its choice of cloud storage providers. Her Majesty's Revenue and Customs is switching to Google Apps as more and more departments move away from Microsoft services.
Earlier in the year, the Cabinet Office and Department for Culture, Media and Sport ruled out using Office 365, but found Google offered more suitable collaboration options. As reported by The Register, the move illustrates the government's increased trust in Google's ability to securely store sensitive data offshore.
Microsoft has long been embraced by the UK government for its software needs, with millions of pounds famously spent on end-of-life support for countless official computers still running Windows XP. Just last week it was announced that no more payments would be made for extended support for XP machines, perhaps signalling the end of the Microsoft love affair as the government scrambles to reduce costs to deliver savings promised before the recent election.
A spokesman for HMRC said:
Following a successful pilot, we are planning to roll out Google collaboration tools to more people throughout HMRC later this year. We have carefully considered the protection of customer information and this remains our highest priority.
Google will no doubt be pleased at the news which comes as the search giant faces continued scrutiny in Europe. The company recently updated the way in which users are provided access to their security and privacy settings.
Photo credit: Asif Islam / Shutterstock
-

Forget cables, the Internet of Things could be powered by Wi-Fi
Publié: juin 5, 2015, 8:47pm CEST par Mark Wilson

There is currently a battle underway over the Internet of Things. Samsung has its ARTIK platform while Huawei is pinning its hopes on its tiny LiteOS -- and Microsoft has Windows 10's AllJoyn feature which could prove pivotal in the widespread uptake of the IoT.
There is still plenty of scope for innovation, and it seems that the next great leap forward for connected devices could be the delivery of power over Wi-Fi. A team of US researchers have developed a technique that can be used to power small devices without the need for wires or battery changes.
The potential for power-over-Wi-Fi (or PoWi-Fi) is huge. Wireless signals are now pretty ubiquitous, and it makes sense to try to tap into them for more than just the transfer of data if at all possible. The team published a paper demonstrating that it is possible to power a small surveillance camera wirelessly and it is hoped that the same technique could be used to power sensors and other devices that will interact with systems via the Internet of Things.
Overcoming the problem of power delivery will open up new possibilities for how the IoT could be used. If there's no need to worry about running cables to sensors, or ensuring that cameras can be easily accessed to have batteries changed, it is possible to get a little more creative. PoWi-Fi is the handiwork of Vamsi Talla and others from the Sensor Systems Lab at the University of Washington, Seattle and it could be integrated into routers in the near future.
The team had to overcome a few problems to get the technique to work. Firstly, Wi-Fi signals are only usable when they are broadcasting, and in the case of routers and the like, insufficient voltage is supplied wirelessly when data is not being transferred. The solution to this -- and simultaneously overcoming the problem of interfering with data transfers -- researchers modified a router to continuously broadcast on channels that were not used for other purposes.
In tests, this meant that an unconnected camera was able to gather enough power to take a photograph over a period of 35 minutes. Things are obviously in the very early stages of development but it's a project that's sure to gather momentum and interest very quickly.
Photo credit: dolphfyn / Shutterstock
-

Leaked Windows 10 Build 10135 release notes herald Microsoft Edge and more
Publié: juin 5, 2015, 12:46pm CEST par Mark Wilson
Another set of release notes for Windows 10 have been leaked online by Wzor -- this time for build 10135. Despite being just five increments up from the build that's currently publicly available, there are still a few changes of note, including the official arrival of Microsoft Edge in place of Project Spartan.
As well as the name change for Microsoft's latest browser, the Snipping Tool also receives an update introducing a delayed screen capture option. Skype is now brought front and center thanks to preinstallation on the desktop, and there are all manner of bug fixes.
Wzor's leak shows that both the Photos, Music and Video apps have been updated, and the Calculator app now includes multi-window support. As there is under two months until the launch of Windows 10, this is clearly now an exercise in trimming the fat and tidying up rough edges -- don’t expect to see any ground-breaking new features in the coming weeks.
Of course this is still only a preview, so a number of known issues remain. Among the lingering problems are the retention of cookies in Microsoft Edge's InPrivate sessions until the browser is completely closed, and Cortana remains a cause of crashes on some devices. The Start screen can also be a source of crashes, and there are issues with Developer Tools in both Internet Explorer and Microsoft Edge.
These problems aside, build 10135 also addresses issues that have been picked up during testing, and it's clear that Microsoft now feels it is on the home straight. It's not yet clear whether this build will be made public, but in the run up to launch the release rate of previews does, finally, seem to be accelerating.
-

Microsoft simplifies its service agreements and privacy statements
Publié: juin 4, 2015, 11:50pm CEST par Mark Wilson

When signing up for an online service or installing new software, it's common to be confronted by a privacy statement as well as a service agreement. It goes without saying that few -- if any -- people bother to read through these as they are not only lengthy, but also packed to bursting with legalise. Microsoft wants to change that.
Starting at the beginning of August, the Microsoft Services Agreement and the Microsoft Privacy Statement will be updated so they are easier to understand. Microsoft stresses that the essential content of the documents will not change, just the way it is presented, and the language in which it is written. Covering products as diverse as Bing, Cortana, Microsoft accounts, OneDrive, Outlook.com, Skype and Xbox Live, this is Microsoft's latest bid to be more transparent to customers.
Rather than using confusing terms, Microsoft's new documents are clear and "don't require a law degree to read". The aim is not just to make agreements and statements easier for users to understand, but also to earn the trust of more people. Introducing the changes, Microsot's Horacio Gutiérrez reveals how this will be noticeable:
- Simplicity: These changes bring together a number of previously separate – and often repetitive – documents to make it easier for customers to find and understand the information. Instead of agreeing to separate terms and statements for each service, customers who use more than one Microsoft service will be able to accept once for multiple services and review one privacy statement.
- Transparency: Although we’ve simplified and consolidated the terms and policies, we didn’t want to over-simplify, either. We want to give consumers meaningful information about how we collect and use personal data. Thus, the privacy statement still provides the service-level details our customers need in order to understand the privacy implications of the services they use.
- Privacy: These statements reiterate what we’ve said in the past: We don’t use customer communications to serve targeted ads to customers and we are committed to putting customers in control of their information.
The changes will be implemented before two months is up, so you can expect to receive a series of emails from Microsoft relating to the various services you use.
Photo credit: Sergei Gontsarov / Shutterstock
-

Facebook Lite gives a social fix without eating mobile data
Publié: juin 4, 2015, 10:39pm CEST par Mark Wilson
With its Internet.org project, Facebook is trying to not only spread into new parts of the world by bringing the internet to places where it is not currently available. With a focus on minimal data usage to help keep down costs, it was only a matter of time before a stripped down version of the Facebook app appeared.
Today is the day that Facebook Lite arrives. As the name suggests, this is a data-light version of the familiar Facebook app, and it starts its life on Android devices. It is designed with developing markets in mind, and today it starts the rollout process in Asia before it spreads further around the globe.
The app itself weighs in at a meagre 1MB and has been built from the ground up for limited data connections. Facebook acknowledges that on slower networks it can be a frustrating experience to use the main Facebook app for Android, and Facebook Lite is the answer. It is described as "a new version of Facebook for Android that uses less data and works well across all network conditions".
There is a far simpler look than the full blown version, but it still provides access to all of the essential features that users have come to know and love -- news feeds, status updates, photos, and notifications. Facebook says that in the coming weeks the app will spread to Latin America, Africa and Europe, but for now it is limited to Asia.
-

Yahoo kills Pipes, Maps, and some TV and Music services in prioritization drive
Publié: juin 4, 2015, 9:40pm CEST par Mark Wilson

Yahoo today announced that it is fine-tuning its focus moving forward, and this means that some products and services are being dropped. In its Q2 2015 progress report, the company explains that it looking to dedicate its energy and resources to "search, communications and digital content."
One of the most surprising casualties is Yahoo Maps -- the site will close at the end of June. Despite the closure, maps will still be supported by other Yahoo products such as Flickr, but it illustrates Google's dominance in this arena. Other victims of the cull include Yahoo Pipes, Yahoo Mail on old versions of iOS, as well as Yahoo Music and Yahoo TV in some regions.
From 15 June, Yahoo Mail will no longer be supported for the built-in mail apps for iOS 4 and older -- the mobile web site has to be used instead. From the same date, the syncing of Yahoo Contacts for Mac users is going to be limited to machines running OS X 10.8 Mountain Lion and newer. Yahoo Pipes -- the delightful, visual tool for filtering news feeds and other online data -- will not be supported post-30 August, although existing Pipes will remain available in read-only mode until 30 September.
In the middle of this month Yahoo TV will close in the UK, France, Germany, Spain, Italy and Canada, and Yahoo Music in France and Canada; Spain also stands to lose Yahoo Movies. Yahoo Autos is being shuttered in the UK, France, Germany, Spain and Italy, and the Yahoo Philippines homepage will start to redirect to Yahoo Singapore.
Yahoo's Chief Architect, Amotz Maimon, explained the need to focus on core products:
Part of that focus includes taking a hard look at our existing products and services, and ensuring our resources are spent smartly and with a clear purpose. Ultimately, we want to provide you with the best products, platforms and experiences possible.
Will you mourn the loss of any of these services?
Photo credit: Ken Wolter / Shutterstock.com
-

Microsoft updates Office 2016 on Windows Preview with new features
Publié: juin 4, 2015, 8:06pm CEST par Mark Wilson

Microsoft has released an update for Office 2016 on Windows Preview. It's only a month or so since the public preview of Office 2016 appeared, and Microsoft says that there are already one million people using it. Today's update brings a few new features with a focus on collaborative work.
We first heard about plans for Office 2016 a few months ago, and we've already seen the release of Office 2016 for Mac Preview, as well as Office 2016 IT Pro and Developer Preview. This update sees Microsoft making good on its promise to keep delivering new feature to the Office suite.
One of the collaborative features to be found in this update is Real Time presence. This is a taster of the Real Time Typing feature which is still to be added, and makes it possible to keep an eye on which sections of a document teammates are editing. OneDrive for Business subscribers get to try this out first, but it will be rolling out more widely soon.
Word and Outlook both gain the Bing-powered Insights feature which can be used to look up information about the text in your document online. File sharing has been improved so that it is now easier than ever, and improvements have been made to file version histories.
If you're yet to try out Office 2016, you'll need to sign up to join the preview program -- just as with Windows 10, Microsoft is looking for feedback from preview testers.
-

Apple Watch available from retail stores in two weeks
Publié: juin 4, 2015, 4:53pm CEST par Mark Wilson

When the Apple Watch first went on sale, there was a huge rush to get hold of them. This led to frustration with delayed deliveries, but this could be set to come to an end. Apple’s wearable is due to hit retail stores before the end of June.
Starting on 26 June, in addition to existing countries, the Apple Watch will be available to purchase in Italy, Mexico, Singapore, South Korea, Spain, Switzerland and Taiwan from Apple stores, some Apple Authorized Resellers, as well as online.
In a press release, Apple says that 'some' models of the Apple Watch will be available to buy from Apple retail stores. The company does not elaborate on precisely which version of the strap-on will be on sale, but there’s good news for anyone who is still waiting for their order to ship -- as long as they did not order the 42mm Space Black Stainless Steel model.
Jeff Williams, Apple’s senior vice president of Operations said:
The response to Apple Watch has surpassed our expectations in every way, and we are thrilled to bring it to more customers around the world. We’re also making great progress with the backlog of Apple Watch orders, and we thank our customers for their patience. All orders placed through May, with the sole exception of Apple Watch 42 mm Space Black Stainless Steel with Space Black Link Bracelet, will ship to customers within two weeks. At that time, we’ll also begin selling some models in our Apple Retail Stores.
-

Microsoft revamps Skype for Outlook.com
Publié: juin 3, 2015, 9:00pm CEST par Mark Wilson

It's not long since Microsoft started the rollout of a redesigned version of Outlook.com, and today the company gives Skype for Outlook.com a revamp. The update brings tighter integration between Outlook.com and the messaging tool.
In beta for the time being, the updated version of Skype for Outlook.com aims to make it easier to use the two tools together. It’s the same update that was rolled out on a preview basis to a limit number of users last month, but now it’s being made available to everyone.
Microsoft has not revealed anything about any other new features that might be added to the beta in the future, but for now conversation access and contact management is easier and more refined. Introducing the update in a blog post, Microsoft says:
Clicking on the Skype icon opens the Skype sidebar. From here, you can see which friends are online, view recent conversations and search for people on Skype. If you’re new to Skype, finding contacts is simple -- click on the magnifying glass in the sidebar to search for and add contacts directly in Outlook.com.
Pick up 1:1 conversations or group chats where they left off by clicking on the corresponding bubble on the right. Don’t worry; all of your Skype chat messages are synchronized across all of your devices.
If you want to use Skype for Outlook.com to make audio or video calls, you'll need to install the add-on for your web browser, and you'll be prompted to do this the first time you try to place a call.
The video below highlights some of the new features that are to be found on Outlook.com, including the update to Skype:
-

Microsoft reveals new Windows 10 devices
Publié: juin 3, 2015, 1:32pm CEST par Mark Wilson

Windows 10 is now less than two months away, and today at Computex 2015 Microsoft unveiled the latest range of devices designed with the operating system in mind. Taking to the stage in Taipai, Microsoft's Nick Parker revealed a collection of desktops, laptops, and tablets that will run Windows 10.
The latest version of Microsoft's operating system aims to be all things to all people, and this is something that is reflected in the diversity of devices on show today. In addition to traditional PCs, the 2-in-1 convertible range continues to grow, and there are tablets from a number of Microsoft partners. There's hardware from lots of familiar names, but also from lesser-known companies.
Among the big names is the ASUS Transformer Book T100HA, a laptop with a detachable keyboard, and the gamer-centric, quad-core Intel Core i7-powered ASUS Zen AiO Z240. One of the newest devices is the Dell XPS 15 which features the "virtually borderless" InfinityEdge display that proved so successful in the smaller XPS 13. There's an interesting 2-in-1 from HP that features a detachable, magnetic, hinged keyboard that allows the devices to switch easily between tablet and traditional laptop mode.
Windows Hello is something that Microsoft is keen to show off, and this biometric security feature is supported by a new Toshiba system. The Toshiba Astrea features a face identification and authentication camera that can be used as a means of logging in to your account. Other devices of note include the FoxConn Kangaro. This ultra-portable desktop PC turns a TV into a full Windows PC, and includes a fingerprint reader and offers up to six hours of battery life.
This is just the start of a surge of Windows 10 devices that is sure to explode in the coming weeks and months. Rumors abound about the imminent announcement of a Surface 4 Pro, but Microsoft remains tight-lipped about this for the moment.
-

Tim Cook lashes out at the government, Facebook and Google over privacy
Publié: juin 3, 2015, 1:21pm CEST par Mark Wilson
We live in an age where people are more concerned about and more aware of privacy issues than ever before. Speaking at EPIC Champions of Freedom event in Washington, DC, Apple CEO Tim Cook criticized the government for seeking to implement backdoors into encryption techniques. He also hit out at Google and Facebook with their ad-dependant business models for infringing upon privacy.
He said that Apple wants to be different, saying: "We believe that people have a fundamental right to privacy. The American people demand it, the constitution demands it, morality demands it". Cook was at pains to stress that Apple should be viewed differently to other companies, assuring people that -- unlike others -- the company "doesn’t want your data".
The Apple boss accused the government of trying to undermine people's ability to securely encrypt data -- referring to the calls to either remove encryption from products or make it crackable by intelligence agencies. In his privacy-focused speech, Cook failed to name Google and Facebook directly, but it was clear who some of his remarks were directed at.
We believe the customer should be in control of their own information. You might like these so-called free services, but we don't think they're worth having your email, your search history and now even your family photos data-mined and sold off for god knows what advertising purpose. And we think some day, customers will see this for what it is.
Cook was largely preaching to the converted, but his speech was well-received nonetheless. He has made it clear that he is opposed to proposals from FBI director James Comey that would necessitate the integration of backdoors into security products. He went on to say: "Weakening encryption, or taking it away, harms good people that are using it for the right reasons. And ultimately, I believe it has a chilling effect on our First Amendment rights and undermines our country’s founding principles".
Photo credit: GongTo / Shutterstock.com
-

The new Nokia 105 is Microsoft's cheapest phone
Publié: juin 3, 2015, 11:32am CEST par Mark Wilson

You don't get much for $20 these days, but you can pick up a Nokia 105. This is the latest budget phone offering from Microsoft which sees the company trying to get more people around the world connecting with each other.
Of course, for $20 expectations should not be set too high -- this is an extremely basic phone, but that is very much the point. This is a handset designed as an entry point into phone ownership, and it harks back to the halcyon days of the likes of the Nokia 3310.
Worldwide availability makes it clear that this is not just a handset aimed at the more affordable end of the market, but also at developing nations. The specifications are nothing to get overly-excited about, but this is a phone that's here to get a job done. Forget touchscreens. This handset keeps it old school with a small 1.4-inch display, and navigation is taken care of by a 4-way d-pad and physical buttons.
The Nokia 105 boasts a battery life that modern smartphones can only dream of -- up to 15 days of talk time, and 35 days in standby mode. There are few in the way of fancy extras, but there is an integrated flashlight and FM radio. A dual-SIM version is also available. The ultra-low price tag, coupled with the famous Nokia brand durability, means that this is a phone that is likely to appeal to travelers looking for a cheap second handset to take away with them on vacation or business trips.
-

USA Freedom Act passes unamended, limiting NSA surveillance after Snowden revelations
Publié: juin 2, 2015, 10:59pm CEST par Mark Wilson

Today the US Senate passed the USA Freedom Act without amendments, signalling the start of the significant surveillance reform that has been called for since Edward Snowden blew the whistle on the agency's activities. It had already been determined that the bulk collection of phone metadata was illegal, and the expiry of Section 215 of the Patriot Act at the end of May brought this data collection to an end anyway.
The USA Freedom Act sets in concrete the end of the phone data collection program and is seen as a major victory for privacy advocates. It will come as good news to Snowden himself who will undoubtedly feel a sense of relief that his risk-taking paid off. The bill is still to be signed into law by President Obama, but this is now little more than a formality.
The passage of the USA Freedom Act met something of an impasse last week, after attempts were made to water it down. The proposed amendments were opposed by civil liberties and digital rights groups such as the Electronic Frontier Foundation. Any fears that the powers of the Act would be weakened proved unfounded as, despite efforts by Republicans, Senators voted to pass it in its unaltered form.
Despite vocal opposition from much of the public, Mitch McConnell was eager for the Patriot Act to be extended without amendments, effectively leaving the NSA free to do whatever sort of data collection it wanted. When the Patriot Act was temporarily extended, there were fears that this would continue indefinitely. Obama and his administration expressed their support for the USA Freedom Act and it was a campaign that Rand Paul took up with gusto.
Microsoft was among the first companies to praise the passing of the bill. Brad Smith, executive vice president and general counsel of Microsoft, said:
We commend Congress for taking action to reform government surveillance practices. Today’s vote by the Senate on the USA Freedom Act will help to restore the balance between protecting public safety and preserving civil liberties.
Although the USA Freedom Act is seen as an improvement, many are still concerned that the government and its agencies are still able to covertly collect data about phone and internet usage. Both lauded as a hero and derided as a traitor, the success of the Act is at least partly thanks to Snowden himself. Quite what happens next in terms of surveillance reform remains to be seen.
Photo credit: Rena Schild / Shutterstock.com
-

Facebook expands AI research program
Publié: juin 2, 2015, 10:11pm CEST par Mark Wilson

Mark Zuckerberg's Facebook is more usually associated with social networking, but the company has its fingers in plenty of other pies as well -- including Internet.org. Now the company is expanding its Facebook AI Research (FAIR) program to help with the automatic sorting and analysis of pictures, videos, text, and other data.
Facebook already has research teams looking into artificial intelligence in Menlo Park and New York, and the expansion sees the creation of a new team in Paris. The aim is create system that make it easier to manage the ever-growing quantities of data that are generated day in, day out by Facebook users.
Expanding into Europe is an interesting move for Facebook, which says that it intends to taps into the wealth of research expertise that exists in France. The company has a mutually beneficial arrangement with the French research institute INRIA; as well as setting up study opportunities for researchers and students, there is collaboration on Facebook's own AI programs
Speaking about the new team, Facebook said:
The Paris team will work on ambitious long-term research projects in image recognition, natural language processing, speech recognition, and the kinds of physical and logical infrastructure required to run these AI systems. It’s our hope that this research will ultimately help us make services like News Feed, photos and search even better and enable an entirely new set of ways to connect and share.
It may be some time before the fruits of the research are seen, but work is now well under way to design and build the infrastructures for image recognition, natural language processing, speech recognition projects.
Photo credit: agsandrew / Shutterstock
-

Facebook adds support for OpenPGP email encryption
Publié: juin 1, 2015, 6:47pm CEST par Mark Wilson

Facebook can send out quite a lot of emails to its users in the course of an average day. Notifications can fly in thick and fast letting you know about friend requests, replies to your posts, messages from contacts, and the like, and it's possible -- nay likely -- that these will contain delicate personal information.
To help calm the fear of those with privacy concerns ("why are they using Facebook?", you might well ask) Facebook today announces the introduction of OpenPGP encryption support. This gives users the opportunity to protect communication from Facebook by encrypting it so it cannot be read by unauthorized parties.
This is just the latest move from Facebook as it attempts to curry favor with a user base that has become increasingly concerned with privacy post-Snowden. A few days ago the social network introduced a new security checkup feature, and has previously introduced a secure Tor site for those who want greater security than HTTPS connections offer.
The security team at Facebook says:
To enhance the privacy of this email content, today we are gradually rolling out an experimental new feature that enables people to add OpenPGP public keys to their profile; these keys can be used to "end-to-end" encrypt notification emails sent from Facebook to your preferred email accounts. People may also choose to share OpenPGP keys from their profile, with or without enabling encrypted notifications.
To start using an OpenPGP public key with your account, head to your profile's About page and click the "Add a public key" link. Having pasted in the key you'd like to use, be sure to check the box labelled "Use this public key to encrypt emails that Facebook sends to you", and then click Save Changes. You'll need to set up the feature from the desktop version of the website.
Photo credit: JuliusKielaitis / Shutterstock
-

Windows 10 upgrades: Microsoft gives with one hand and takes with the other
Publié: juin 1, 2015, 3:27pm CEST par Mark Wilson

We now know that there are less than two months to wait until Windows 10 is launched. If you have been working your way through the preview builds, you'll already have a pretty good idea of what to expect in terms of new features -- Cortana, Start menu, notification center, virtual desktops, Continuum, cross-device experience, Microsoft Edge and so on -- but what about the things you're going to lose when upgrading from Windows 7 or Windows 8.1?
The delivery of Windows 10 is not just about bringing new features and tools to desktop, tablets, and laptops; there are also a number of things that are simply going to disappear. Not all of this will matter to everyone, but the stripping out of certain features will come as a blow to some, and it's best to be prepared ahead of time.
Microsoft reveals the details of everything that will be either cut or replaced and one of the first, and biggest, victims is Windows Media Center. This is not new news, but you'll still have to hunt around for an alternative if you are making the jump to Windows 10 and have come to rely on the tool. Relatedly, DVD playback is also being stripped out. That's not to say that DVDs can't be watched in Windows 10, but third-party software will be required.
For Windows Home users, the process of keeping Windows 10 up to date is being taken out of their hands -- Microsoft wants to ensure that everyone is kept completely up to date as quickly as possible. To this end, automatic updates are now the norm for Home users and there is no way to change this. Microsoft does say, however, that "Windows 10 Pro and Windows 10 Enterprise users will be able to defer updates".
Windows 7 desktop gadgets get the chop, as do Solitaire, Minesweeper, and Hearts Games -- although Microsoft Solitaire Collection and Microsoft Minesweeper are available to download as replacements. If you have OneDrive installed as part of Windows Live Essentials, this will be replaced by the built-in version in Windows 10 (so nothing is really lost), and for anyone still rocking a USB floppy drive, you'll need to take the time to download the necessary drivers if you want to continue working with it.
Many of the new features of Windows 10 have limitations on them -- not everything will "just work" out of the box. Cortana is not available globally, and the same is true of Xbox music and video streaming. In order to take advantage of Windows Hello you'll need a "specialized illuminated infrared camera for facial recognition or iris detection or a finger print reader which supports the Window Biometric Framework".
Full details of deprecation and limitations can be found on the Windows 10 specifications website.
-

Google makes it easier to control privacy and security settings
Publié: juin 1, 2015, 1:35pm CEST par Mark Wilson

Taking a leaf out of Facebook's, er, book, Google today unveils a revamped privacy checkup page. Google and privacy are not words that belong in the same sentence for many people, but the search giant wants to change that. Users are invited to answer a series of simple questions to control how their data is stored, collected, and shared.
The company wants to place users back in control, and at the heart of today's announcement is the My Account page which is now central to configuring privacy settings. In the interests of transparency, Google has also set up a page dedicated to revealing how and why data is collected.
The updated My Account page is home to the Privacy Checkup and Security Checkup tools. These make it possible to quickly configure common settings by answering a few questions. Options such as choosing which personal data is made publicly available, changing how ads are personalized, and fine-tuning what information each Google service stores about you, mean that all of your privacy settings can now be accessed in the same place.
The Security Checkup page gives an opportunity to review your account's recovery email address and phone number, as well as checking which devices and services have access to your Google account, and ensuring that nothing untoward is happening with your Gmail account. Back to the subject of privacy, the new Privacy page sees Google laying its cards on the table about how data is collected and used.
Introducing the new features, Google product manager Guemmy Kim said:
Everyday, we make choices that affect our privacy and security online. Most people, however, don’t feel they have the right level of control to make these important decisions. According to a recent Pew study, 93 percent of people think it’s important to control access to their personal information, and 90 percent care about the type of information that’s collected about them. But only 9 percent feel they have "a lot" of control over it. We want to change that.
Are these new changes enough for Google to allay privacy fears?
-

EFF fights abuse of court orders to close sites in the wake of Grooveshark
Publié: mai 30, 2015, 2:52pm CEST par Mark Wilson

The EFF (Electronic Freedom Foundation) has involved itself in lots of online battles -- including the fightback against NSA surveillance, and the drive for net neutrality. The latest fight sees the organization joining forces with web performance and security firm CloudFlare in tackling the site blocking activities of the record industry.
The digital rights group is battling record labels which it says are forcing web firms into becoming the "copyright police". The move was prompted by the closure of Grooveshark, a music website run by one of CloudFlare's clients. It re-opens the question of who is ultimately responsible for the content that appears on sites -- those posting it, those hosting it, or any other company involved in the delivery?
When Grooveshark was closed down, it was done so via a sealed court order. EFF feels this is unfair and that courts are handing out retraining orders that are too far-reaching. It hopes that by bringing the matter out into the open, greater transparency will be encouraged. As things stand at the moment, EFF explains, the court orders mean that "service providers of every kind" can be held responsible for taking down a site -- including the likes of CloudFlare.
Attorney Mitch Stoltz said:
Just because you are providing a service to a website doesn't mean you should be roped into policing it. Copyright holders should not be allowed to blanket infrastructure companies with blocking requests, co-opting them into becoming private trademark and copyright police.
The case was brought before a federal court in an emergency hearing this week. U.S. District Court Judge Alison Nathan ruled that the court proceedings would continue to be sealed, something that EFF and legal firm Goodwin Procter oppose. The judge is expected to come to a decision about whether CloudFlare can be held accountable for access to Grooveshark next week. The argument is that a single court order is insufficient to put "legal responsibilities on the entire Internet."
Photo credit: bogdan ionescu / Shutterstock
-

Life imprisonment for Silk Road creator Ross Ulbricht
Publié: mai 29, 2015, 11:43pm CEST par Mark Wilson

There are lots of online services and sites that quickly become notorious; the Pirate Bay and Napster to name but two. But Silk Road was something in a completely differently league. Found on the dark web, the site acted as a portal to drugs and other illegal goods. It started life back in 2011 and today its founder, Ross Ulbricht is sentenced to life in prison, a year and a half after his arrest.
Ulbricht was found guilty at a jury trial three months ago and today Judge Katherine Forrest said that Silk Road demonstrated he believed he "was better than the laws of this country". She said "this is deeply troubling, terribly misguided, and very dangerous" before handing down the harshest sentence available.
Ulbricht's pleas for leniency fell on deaf ears as he was sentenced for his role in money laundering, conspiracies to traffic narcotics and other charges. Accessed through the Tor browser, Silk Road was seized by the FBI in 2013 having grown into one of the largest online black markets ever known. While famed for the availability of drugs, Silk Road also opened up access to illegal services such as hitmen, prostitutes and more, all paid for with Bitcoin.
The "anonymous market place" was administered by Ulbricht who used the pseudonym Dread Pirate Roberts. Part of the evidence linking him to the site was the fact that he own the PGP signature used to send emails from the Silk Road.
Ulbricht's lawyer said that the sentence is "unfair, unjust, and unreasonable", and promised that there would be an appeal. There have been allegations of FBI corruption throughout the case, including suggestions that agents involved in the site takedown were blackmailers who stole millions of dollars' worth of Bitcoins.
One of Ulbricht's previous defences had been that although helping with the supply of illegal drugs, Silk Road actually helped to protect drug users by ensuring the purity of narcotics. This held no water with prosecutors or the judge, hence the sentence and the order to forfeit $183 million.
Silk Road has already spawned numerous imitators, and it is a site that will go down in history for the impression it has made.
Photo credit: Gil C / Shutterstock.com
-

Brillo is Google's new IoT platform
Publié: mai 28, 2015, 11:24pm CEST par Mark Wilson

Every tech company worth its salt is running to get involved in the Internet of Things; Ubuntu is in on it, and Microsoft has teamed up with more than one company to plant its IoT flag. Today Google unveiled its new IoT platform, Brillo.
Google is not entirely new to the Internet of Things -- it already has its cloud platform in place and has also acquired Nest. Destined for all manner of connected devices, Brillo is a stripped down and streamlined operating system based on Android. Google has not revealed how its size compares to Huawei's LiteOS, but has said that -- like Android M -- there is a focus on security, and the platform will run on Weave.
Sundar Pichai confirmed that rumors about a full-on entry into the IoT with Project Brillo is well founded. Developers will be able to get their hands on a preview of the platform some time in the third quarter of 2015, while a final release is expected in Q4. Although essentially a barebones version of Android, connectivity essentials such as Bluetooth, WiFi and lower power modes are all present and correct. There's also potential for voice interaction with devices.
The basis of the system means that devices that are running Android will be able to automatically detect Brillo and Weave devices. Google describes the upcoming release as an "underlying operating system for the internet of things". This is a reference to the fact that Weave is not Brillo-dependant, and can in fact work on any platform.
Pichai said:
We will have standardized schemas, developers can submit custom schemas, and we will have a Weave certification program to make sure anything that is Weave certified can work together.
Google has not revealed details of any partnership or future products that might come about as a result of Brillo. The acquisition of Nest, however, means that we can almost certainly expect to see more developments in the home automation arena, with more and more tasks becoming controllable from Android phones and tablets.
Photo credit: Ken Wolter / Shutterstock
-

Google Play gets a family-friendly makeover
Publié: mai 28, 2015, 8:59pm CEST par Mark Wilson
All eyes are on Google today, and there are certainly plenty of announcements to take on board. As well as exciting future releases such as Android M, there are also changes to old favorites. Google Play is one stalwart that's in line for an update, and this time around Google has decided to focus on making the store a family-friendly experience.
To allay the fears of concerned parents who are worried about what their kids might stumble across while looking for apps and games, Google is introducing a new Family category. There is a strong focus on making it easier to select content that's suitable for specific age groups and the categorization is available across apps, games, books, movies, and TV shows.
In addition to grouping content together by age group, Google also filters by interest. This should make it easier to help parents find something to keep children of all ages entertained, or even help them to learn something new. If there's one thing that kids love, it's a good character -- who doesn’t know someone who is obsessed with Frozen? If it is the branding of an app, game, or movie is what matters, Google has made it easier to home in on content relating to a particular character.
Advertising in apps for children is something that concerns many people, and Google is only too aware of this. Now any app that is ad-supported is highlighted with a suitable label so the presence of advertising is known in advance. To ensure that younger children are not exposed to unsuitable content, Google has also updated parental controls to make it easier to impose age restrictions and prevent the downloading of paid-for content.
If you don’t see the new features straight away, just be patient; Google says the changes are rolling out over the next couple of weeks.
-

Google reveals Android M with improved security and battery life
Publié: mai 28, 2015, 8:17pm CEST par Mark Wilson

Ready to further facture the Android market, Google today gave us the first glimpse at what to expect in the follow up to Lollipop -- Android M. We're not yet any the wiser about what the M might stand for (Marshmallow? Marzipan? Mars?) but we do know that Google is placing a focus on security improvements, giving users greater control over app permissions, and prolonging battery life.
Battery performance improvements -- if Google is to be believed -- are seriously impressive. The company claims that its Nexus 9 tablet could benefit from twice the battery life currently enjoyed under Lollipop. What else is there to look forward to? The Developer Preview also boasts a new fingerprint reader API, indicating that biometrics are set to become increasingly important in future handsets.
The changes to the way permissions work is something that will be embraced by users who have been begging for finer-grained control for some time now. In Android M, it will be possible to configure permissions on a precise level for individual apps, and it has been made easier to revoke permissions as and when required. The ability to see a list of all of the apps that can access pictures, for instance, is something that places users back in control of their Android devices.
Borrowing an idea from iOS, many app permission will also be set the first time the app is run rather than simply being listed at the point of installation. For example, launch an app that makes use of your location, and you will be given the opportunity to permit or deny this on first launch. If disabling a particular permission reduces the functionality of apps, developers will be encouraged to provide meaningful feedback to users about what features are dependent on which permissions.
Permissions are an important component of perceived security, but something more obvious is facilitated by the fingerprint API. This will enable handset manufacturers to implement fingerprint device unlocking, and app developers to allow users to log into their accounts with a fingerprint rather than a username and password.
Improvements to battery life are what will excite most people, however. These have largely come about through the introduction of a Doze mode which puts devices into a deep sleep, low power mode when not in use. If a handset's sensors are not activated by movement -- such as when a phone is sitting on a desk -- certain apps and processes can be suspended to conserve power.
Other tweaks and changes to look out for in Android M include streamlined sharing so that the apps and contacts that are most frequently shared with are made more accessible. There are also simplified volume controls and easier word highlighting.
-

Facebook ups the ante with new Security Checkup tool
Publié: mai 28, 2015, 3:55pm CEST par Mark Wilson
Security and Facebook are not words that generally sit well together. This is something that the social network is only too aware of, and in recent years has taken various steps to try to improve the security and privacy of individuals' accounts. The latest tool in its arsenal is the new Security Checkup.
At the moment the tool is not being made available to everyone, but those who have been chosen to test drive it will be able to use simple on-screen prompts to change their password, turn on login alerts, and clean up login sessions, all from one handy location.
One of the problems with security on Facebook is that users often do not take the time to look through the settings that are available that could help to keep them protected. By pulling everything together into a single guided process, it is hoped that more people will be encouraged into managing their accounts more carefully.
Introducing the tool test in a Facebook post, Site Integrity Product Manager, Melissa Luu-Van said:
We invest considerable resources to create a safe and secure experience for everyone on Facebook. That means building security technologies directly into our platform that are always working to protect your information, as well as offering tools you can use to increase your account security. Today, we are starting to test a new tool that quickly guides you through a few of the options that anyone can access on their security settings page.
You don’t need to do anything to access the new tool -- if you have been chosen to take part in the test, the Security Checkup will automatically pop up on your screen.
-

AdBlock Plus is deemed legal -- again
Publié: mai 27, 2015, 5:22pm CEST par Mark Wilson

AdBlock Plus has already been in court once this year proving itself to be legal. A German court heard a case brought by a group of TV companies who felt they were getting a poor deal when their ads were blocked.
The internet has something of a love/hate relationship with ad blockers. While surfers love the fact that they clean up the browsing experience, content creators have a source of income crimped. To try to keep everyone happy, AdBlock Plus came up with the idea of Acceptable Ads -- a sort of halfway house between blocking and permitting ads -- and this was something that featured in this most recent court case.
The broadcasters complained that it should not be possible to block ads on websites, and also questioned the legality of the Acceptable Ads initiative (by which certain non-intrusive ads are permitted to appear whilst others remain blocked). The Munich court ruled in AdBlock Plus' favor, leaving the blocking tool vindicated once again.
Ben Williams from AdBlock Plus expressed his delight at the court ruling:
We are elated at the decision reached today by the Munich court, which is another win for every Internet user. It confirms each individual’s right to block annoying ads, protect their privacy and, by extension, determine his or her own Internet experience. This time it also confirms the legitimacy of our Acceptable Ads initiative as a compromise in the often contentious and rarely progressive world of online advertising.
This is the fourth time that massive publishers have brought legal proceedings against our startup. But even with expensive lawyers and bottomless pockets, this was a clear case of users’ rights -- so we felt it was the right time to stand up and draw a line in the sand. Thankfully, the court sided with users and with compromise.
So we’re pleased to say that Adblock Plus will continue to provide users with a tool that helps them control their Internet experience. At the same time we will endeavor to work with publishers, advertisers and content creators to encourage nonintrusive ads, discover new ways to make ads better and push forward to a more sustainable Internet ecosystem.
AdBlock Plus stands by its Acceptable Ads policy and calls on more advertisers to create non-intrusive ads that web users are willing to put up with.
Photo credit: Tashatuvango / Shutterstock
-

Pirate ebook websites to be blocked in UK
Publié: mai 27, 2015, 1:03pm CEST par Mark Wilson

Online piracy is usually associated with music, movies, and software. But the ever-growing popularity of ereaders such as the Amazon Kindle has also led to a burgeoning ebook piracy scene. The UK has been trying to clamp down on piracy recently, and the latest target is a raft of sites offering illegal downloads of ebooks.
We've already seen the government would like to restrict access to some online content such as porn, and torrent sites have been blocked at ISP level. Now a High Court ruling means that a number of big ISPs are to be forced to block access to major ebook sites.
Ebookee, LibGen, and Freshwap all need to be rendered inaccessible by BT, Virgin Media, Sky, TalkTalk, and EE within ten days, reports TorrentFreak. The action comes after an application was made by The Publishers Association which was concerned about the impact piracy sites are having on sales.
In all, ISPs will be required to block Ebookee, LibGen, Freshwap, AvaxHome, Bookfi, Bookre, and Freebookspot which the complainants say comprise 80 percent of pirate material. As with attempts to block access to torrent sites, while restrictions put in place by ISPs will certainly have some impact on ebook piracy, it is not going to eradicate the problem overnight. Simple tools such as VPNs and proxies are all that are needed to bypass ISP blocks.
Photo credit: koya979 / Shutterstock
-

Google revamps age rating system for Android apps in Play Store
Publié: mai 27, 2015, 12:26pm CEST par Mark Wilson

Google's system of rating apps and games in the Play Store has been relatively simple up to now. A rudimentary high, medium, and low labelling format has been used to give a rough indication of the age a particular title is suitable for, but things are about to get a lot more complicated. Developers are now required to answer a questionnaire about their apps so they can be assigned movie-style age ratings.
Sounds simple enough, but this is not a global system; different parts of the world have different views of what is suitable for different age groups. What is deemed acceptable for 15-year-olds in one country might be thought suitable only for over 18s somewhere else. Any app that does not receive an age rating will simply not appear in Google Play.
This is something that developers have had plenty of warning about, but this is the week when the changes take effect. The most important change is that Google is no longer responsible for rating apps itself -- this is now handled by external bodies around the world. The list of companies involved should sound familiar. ESRB, PEGI, Australian Classification Board and others are all bodies that are involved in the rating of video games, and these are the same groups who will be in charge of assigning ratings to apps in the Play Store.
The entire rating system is overseen by the International Age Rating Coalition (Iarc) which works with different groups around the world to implement local ratings. Developers are required to answer a series of questions about their apps -- a process which Iarc chairwoman, Patricia Vance, told the BBC would only take a few minutes -- and the responses provided will be used to automatically assign a rating. Manual checks will be carried out on the most popular apps to ensure that the system is working correctly.
Google provides details of how to submit an app via the Developer Console. The company says:
To help consumers make informed choices on Google Play, we’re introducing a new rating system for apps and games. These ratings provide an easy way to communicate familiar and locally relevant content ratings to your users and help improve app engagement by targeting the right audience for your content.
It warns that developers who fail to submit information about their titles risk having their apps marked as unrated in Google Play, pointing out that such apps may be blocked in some parts of the world.
Photo credit: Jason Winter / Shutterstock
-

Pets are destroying tech
Publié: mai 26, 2015, 7:36pm CEST par Mark Wilson

"The dog ate it" is a classic excuse for failing to deliver homework, but a new study shows that it also explains a good deal of damage to various items of technology. You may well have dropped a phone in the toilet, smashed a tablet on the floor or accidentally obliterated a laptop screen, but it seems our furry friends are just as much to blame as us bipeds.
Figures released by insurance company SquareTrade show that in the last five years, pets in Europe have been responsible for the destruction of £1.5 billion ($2.3 billion) worth of tech. British households have been hit with the highest pet vs tech bills, with cats, dogs and other domestic creature clocking up £358 million in damage.
Dogs destroying phones and cats causing tablet catastrophes are a problem in 14 percent of UK homes. Anyone living in a house where there are both dogs and cats is at particular risk of racking up a bill for replacing technology -- by having both types of critter in the home the chances of damage jumps by 85 percent. With an extra waggy appendage to consider, dogs are prone to flicking phones with their tail, and cat owners will be only too aware of the feline keenness for knocking things off the edges of tables.
Pet expert Arden Moore suggests that we need to spend more time interacting with our housemates to keep them entertained:
Pets have the same range of emotions that their owners do. Just as often as they are happy, they can be jealous, bored or angry. While pet owners may be tempted to pick up their electronic devices the moment they get home, it’s important to give their furry friends just as much attention -- or pet hijinks can become the norm.
So if you spot some teeth marks on your phone, it might be a sign that your four-legged friend is looking for a little more attention.
Photo credit: Vitaly Titov & Maria Sidelnikova / Shutterstock
-

Google starts to show tweets in search results
Publié: mai 26, 2015, 5:23pm CEST par Mark Wilson

Twitter has become more than just a soundboard for those looking to voice an opinion -- although obviously it is still that. It has morphed into a valuable resource for delivering information in real time. This is particularly useful when it comes to keeping up to date with breaking news.
Starting today Google will tap into this wealth of information for its search results. The feature is starting life in Google apps on iOS and Android mobile devices, but will spread its way around the world and to the desktop soon.
Introducing the feature in a blog post, Twitter suggests that when searching for information about celebrities, as well as the usual pages you would expect to see in the results, you will also see tweets they have posted. It’s likely to be something that really comes into its own when looking for details about breaking news stories however, with Twitter tending to be far more up to date and easier to navigate that flicking between multiple news sites.
As the feature is starting out on mobile platforms, it should come as little surprise that there is integration with the Twitter apps. Click a tweet that is highlighted in search results and it will be displayed in the app rather than on a web page.
-

Leaked document shows Europe would fight UK plans to block porn
Publié: mai 25, 2015, 2:13pm CEST par Mark Wilson

Before the UK elections earlier in the month, David Cameron spoke about his desire to clean up the internet. Pulling -- as he is wont to do -- on parental heartstrings, he suggested that access to porn on computers and mobiles should be blocked by default unless users specifically requested access to it. This opt-in system was mentioned again in the run-up to the election as Secretary of State for Culture, Media and Sport, Sajid Javid assured peopled that the party "will age restrict online porn".
But it's not quite that simple. There is the small problem of Europe. A leaked EU Council document shows that plans are afoot to stop Cameron's plans in its tracks -- and with the UK on the verge of trying to debate a better deal for itself within Europe, the Prime Minister is not in a particularly strong position for negotiating on the issue.
Cameron has a fight on his hands, it seems, if he wants to deliver on his promise that "we need to protect our children from hardcore pornography". Documents seen by The Sunday Times reveal that the EU could make it illegal for ISPs and mobile companies to automatically block access to obscene material. Rather than implementing a default block on pornography, the Council of the European Union believes that users should opt in to web filtering and be able to opt out again at any time; this is precisely the opposite to the way Cameron would like things to work.
The subject is written about in a document on the topic on net neutrality. It suggests that users would have to explicitly ask their providers to block access to content, and they should retain the ability to "withdraw this consent at any time". As reported by The Independent, David Carr from the advisory board of the UK council on Child Internet Safety reacted to the document by saying: "The risk is that a major plank of the UK’s approach to online child protection will be destroyed at a stroke".
I, like the EU, have a problem with restricting access to the internet. Any sort of content management system is going to be flawed, that's just the nature of the beast. There is simply no way to ensure that all hardcore pornography websites would be blocked, nor is there any way to guarantee that perfectly inoffensive sites would not be inadvertently blocked. As is so often the case when the emotive issue of 'protecting children' crops up, there seems to have been very little thought put into how such a system could work.
The sheer number of websites that pop up each day means that swatting one site you take exception to is like cutting a head off the Hydra: kill one and two, or more, will spring up in its place. Just as the fight against torrent sites has shown, while it is certainly possible to make access more difficult, it is absolutely impossible to stop people from accessing the content they want to access -- and if teenagers want to access porn, then they will… there are no two ways about it.
To think that the web can be controlled like this is naive to say the least.
Photo credit: alexskopje / Shutterstock
-

USA Freedom Act is blocked but NSA will stop phone data collection anyway
Publié: mai 23, 2015, 10:52pm CEST par Mark Wilson

Privacy advocates in the US -- and, indeed, the world over -- had pinned great hopes on the USA Freedom Act bringing to an end the mass collection of phone records. Hitting the Senate for the second time this year, the Act was blocked in a 57-42 vote.
Section 215 of the Patriot Act expires on 31 May, and it had been hoped that the hype and momentum surrounding it would have helped push the USA Freedom Act through. Despite making through the House of Representative, the Bill failed to reach the 60 vote goal it needed to hit. But as of 1 June, the NSA will still not be collecting phone data. So what happened?
It seems that the NSA has taken on board some of the vocal opposition to its activities. An official from the agency said today: "We did not file an application for reauthorization." This means that when Section 215 expires, indiscriminate collection of phone data effectively comes to an end.
It's something that will be welcomed by groups such as the Electronic Freedom Foundation which says:
Section 215 of the Patriot Act has been wrongly interpreted in secret by the government for years. We commend every Senator who voted against reauthorizing the unconstitutional surveillance of millions of law-abiding Americans.
While the USA Freedom Act may have failed in its bid for success, Mitch McConnell did not manage to arrange a temporary extension to Section 215. This effectively places the Senate at a stalemate, and it means that mass surveillance will come to an end in just over a week. One opponent of the NSA is Paul Rand who took to the floor for a staggering 11 hours on Wednesday. On Twitter he said:
The Senate has refused to reauthorize bulk data collection. I am proud to have stood up for the Bill of Rights. But our fight is not over
— Dr. Rand Paul (@RandPaul) May 23, 2015
Of course the mass collection of phone records is just the tip of the iceberg when it comes to the NSA's activities, and privacy groups continue to fight against all forms of unjustified monitoring, recording and surveillance.
Photo credit: Gil C / Shutterstock.com
-

Amazon decides to start paying tax in the UK
Publié: mai 23, 2015, 9:13pm CEST par Mark Wilson

The issues of big companies paying enough taxes is something that has a lot of people talking at the moment -- governments in particular. Many companies -- including Microsoft, Apple, Google, and others -- take advantage of financial schemes that funnel money through other countries. Now Amazon has announced that it is to start paying corporation tax on sales made in the UK.
Using a scheme similar to the so-called Double Irish, Amazon had been routing transactions for UK-based sales through offices in Luxembourg. The decision to move these sales to the UK means that the company will be able to avoid the possibility of being hit with a hefty bill if the UK government clamps down on the use of such tax avoidance schemes.
For more than a decade the online shopping giant has used Luxembourg as the financial center for its UK sales. Towards the end of 2014, chancellor George Osborne announced plans to fight back against abuse of the tax system, targeting large technology companies among other corporations.
Speaking to the Guardian, an Amazon spokesperson said: "[Amazon is] now recording retail sales made to customers in the UK through the UK branch. Previously, these sales were recorded in Luxembourg".
It is possible that Amazon will start a trend that will be followed by other tech firms. The threat of being hit by a 25 percent tax if found to be diverting profits through other countries could well be enough to get the likes of Microsoft, Google, and Apple to fall in line as well. With Amazon netting £4.71bn ($7.29bn) in sales in the UK, next year's tax return could make for interesting reading.
Photo credit: Joe Ravi / Shutterstock.com
-

Microsoft threatened job cuts to influence UK government IT policy
Publié: mai 22, 2015, 1:29pm CEST par Mark Wilson

By threatening to implement job cuts in affected parts of the country, Microsoft tried to influence UK government IT policy. The company stands accused of trying to blackmail members of parliament when it disagreed with planned IT reforms.
The claims come from Prime Minister David Cameron's former strategy chief, Steve Hilton. He says Microsoft telephoned politicians in areas that the company has research and development departments with the threat of "we will close them down in your constituency if this goes through". And it seems that Microsoft is not alone in this sort of activity.
Hilton says that other technology companies adopted similar tactics in a bid to block policy changes that would not have worked in their favor. This is not the first time Microsoft has had accusations of interference leveled at it. The company has long opposed the adoption of open document standards and Computer Weekly reported last year about apparent threats from Microsoft if politicians spoke in favor of open source software and standards.
Asked by the Guardian about companies trying to exert influence, Hilton said:
I can give you specific examples: the thing I mentioned about IT contracts. Maybe there is someone here to confirm this from Microsoft? When we proposed this, Microsoft phoned Conservative MPs with Microsoft R&D facilities in their constituencies and said, 'we will close them down in your constituency if this goes through'. And we had the same from other tech companies as well … We had the stories from the MPs saying I’ve just had this call from -- sometimes a global CEO -- phoning a Conservative MP, saying we will close down this plant.
The Guardian reports that Microsoft has "nothing to share" on the matter. We have also reached out for a comment and will update the story when we hear back.
Update
We have heard from Microsoft, and a spokesperson says:
We have looked into the nearly decade-old matter and we don't recognise these claims. Fundamentally, it is not how we operate as a business. We have an honest and open engagement with the government and this is how we will continue to work with it.
Photo credit: 360b / Shutterstock.com
-

Hackers leak the sexual preferences of millions of online daters to the dark web
Publié: mai 22, 2015, 1:58am CEST par Mark Wilson
The details of millions of users of Adult FriendFinder -- the dating site with the tagline "hookup, find sex or meet someone hot now" -- have been leaked by hackers. Channel 4 reports that details of nearly 4 million users were exposed on the dark web after a security breach.
As well as information such as names, email addresses, and dates of birth, hackers also gained access to personal information such as users' sexual preferences and details of their willingness to conduct extramarital affairs. The compromised data includes accounts that had been deleted by their owners, and the hackers are now threatening to hit out at victims.
No group or individual has yet claimed responsibility for the hack, but the data has been made available on a dark web forum. Security experts are warning that there is potential for users to be blackmailed by the hackers as it is thought they have the details of government and military personnel.
One of the people whose personal details has been published is Shaun Harper, who says:
The site seemed OK, but when I got into it I realised it wasn't really for me, I was looking for something longer term. But by that time I'd already given my information. You couldn't get into the site without handing over information. I deleted my account, so I thought the information had gone. These sites are meant to be secure.
The owner of the site, which has 63 million users all over the world, says that it has launched an investigation into what happened and is working with law enforcement agencies to get to the bottom of it. FriendFinder Networks Inc says: "We pledge to take the appropriate steps needed to protect our customers if they are affected".
Photo credit: Shutterstock/Nito
-

Google finds security questions are crap because your answers are fake
Publié: mai 21, 2015, 11:04pm CEST par Mark Wilson

Apple and other handset manufacturers might be trying to push users to securing their data with biometrics, but the vast majority of services still rely on the good old password. Lots of sites use the idea of memorable data either as a means of locking down accounts, or as a way to gain access to a forgotten password -- the likes of your mother's maiden name, town of birth, favorite color of underwear, and so on.
Research by Google shows that the security question system is failing, and it should come as no surprise that the blame is laid firmly at the door of the likes of you and I. We already know that people are rubbish at picking passwords, but there is also a problem with the answers they provide to security questions. Answers are either too easy for others to guess, or they are made up -- and people are forgetful buggers prone to failing to remember the answers they dreamt up.
As with passwords, the problem with security questions is that a balance needs to be struck between memorability and security. To overcome the problem of being easy to guess or determine (it is, after all, very simple to find out where someone was born, or what their mother's maiden name is), a lot of people simply make up answers to these common questions. Mother's maiden name? Miami Dolphins. Town of birth? Miami Dolphins. Favorite food? Miami Dolphins. Oh yeah... that's the other problem. Just as people have a tendency to use the same passwords again and again, they also tend to use the same made up answers to questions.
Google researchers analysed the password recovery attempts of millions of users and found that a staggering 40 percent of people were unable to provide the correct answers. This ties in with the idea that people are not giving honest answers, as the entire point of a security question is that the answer is supposed to be something unchangeable and unforgettable.
A paper entitled Secrets, Lies, and Account Recovery: Lessons from the Use of Personal Knowledge Questions at Google, researchers found that questions such as "what is your favorite food?" or "what is your father's middle name?" were, surprisingly simple to guess. Attackers trying to compromise an account, for example, had a 19.7 percent success rate at guessing a favorite food on the first attempt. The difficulty of recalling data such as one's frequent flyer number or library card number are cited as reasons for people simply making up answers. It appears that those lying with their security answers do so not only to make things easier for themselves, but in the mistaken belief that false information will protect their account more.
The conclusion of the paper is that security questions are, to put it bluntly, crap:
We conclude that it appears next to impossible to find secret questions that are both secure and memorable. Secret questions continue have some use when combined with other signals, but they should not be used alone and best practice should favor more reliable alternatives.
This is the reason given for Google only using security questions as a last resort, relying instead on SMS recovery codes in the case of forgotten passwords.
Photo credit: liuwenhua / Shutterstock
-

Hauppauge Digital TV Tuner for Xbox One now available
Publié: mai 20, 2015, 7:39pm CEST par Mark Wilson

A few weeks ago, Microsoft announced the upcoming release of an over-the-air TV tuner for Xbox One owners. Now the big day has rolled around and gamers in the US and Canada can now get their hands on the Hauppauge Digital TV Tuner for Xbox One.
Priced at $59.99, the TV tuner will be welcomed by cord cutters as it brings live over-the-air HDTV or analog TV with no monthly fee. It can be used with any Xbox One including the newly announced white Xbox One with Halo: The Master Chief Collection. It also brings extra features such as the ability to pause live broadcasts, but on the Xbox One this is limited to just 30 minutes.
As well as being subscription-free, the tuner gives Xbox One owners the opportunity to watch TV and play games without having to constantly switch between inputs. It's even possible to use the Snap feature of the console to multitask, catching up on your favorite show whilst playing a game.
The Xbox One SmartGlass app can be used to stream OTA TV broadcasts to Windows, Windows Phone, iOS, and Android devices. There's neat integration with OneGuide so OTA TV listings can be seen in a familiar environment.
The Hauppauge Digital TV Tuner for Xbox One can be purchased direct from the Microsoft store as well as other major retailers. The tuner is also available with a Mohu Leaf 50 antenna for the bundled price of $99.99 which equates to a saving of $30.
-

Huawei's LiteOS Internet of Things operating system is a minuscule 10KB
Publié: mai 20, 2015, 4:12pm CEST par Mark Wilson

Chinese firm Huawei today announces its IoT OS at an event in Beijing. The company predicts that within a decade there will be 100 billion connected devices and it is keen for its ultra-lightweight operating system to be at the heart of the infrastructure.
Based on Linux, LiteOS weighs in at a mere 10KB -- smaller than a Word document -- but manages to pack in support for zero configuration, auto-discovery, and auto-networking. The operating system will be open for developers to tinker with, and is destined for use in smart homes, wearables, and connected vehicles.
LiteOS will run on Huawei's newly announced Agile Network 3.0 Architecture and the company hopes that by promoting a standard infrastructure, it will be able to push the development of internet and IoT applications. Rather than building connected devices, Huawei wants to concentrate on creating tools and platforms that can be used by others to create their own devices. Liu Shaowei, President of Huawei's Switch and Enterprise Communication Product Line, said:
Over the last three years, Huawei has been involved in a number of in-depth technological collaborations with our global industry partners in IoT. We have developed a series of IoT solutions that have already been applied to buildings, electricity meters, vehicles, gymnasiums, factories, retail outlets, and street lights. In line with our approach to provide BDII (Business-driven ICT Infrastructure), Huawei will continue to work with more partners to launch solutions based on our Agile Network architecture for different vertical industries.
Huawei hopes that the operating system will be used in a range of consumer, business and enterprise products, but quite what direction things will be taken in is really down to developers.
Photo credit: 360b / Shutterstock
-

Just about everyone thinks Internet.org is a terrible idea
Publié: mai 19, 2015, 9:43pm CEST par Mark Wilson

Mark Zuckerberg probably thought the world would bow down to him when Facebook announced the Internet.org project. The idea of bringing internet access to those in developing parts of the world seems, on the face of it, to be something of an exercise in altruism. Of course, it's not quite that simple.
Many companies complain that the project goes against the idea of net neutrality -- a claim that Zuckerberg vehemently denies. But now the vocal opposition to Internet.org is getting louder. Privacy group Electronic Frontier Foundation (EFF) has several concerns with the project, and a collective of 67 digital rights groups has signed a letter to the Facebook founder expressing concerns about the approach Internet.org is taking.
Complaints about Internet.org being anti-net neutrality are not the only criticisms being levelled at the project. There is little to argue with about the principle of the venture -- bringing free internet access to those who would otherwise be denied access is certainly a good thing -- but there are serious concerns about the way it has been tackled. EFF says that there is a danger that it "could end up becoming a ghetto for poor users instead of a stepping stone to the larger Internet".
In a bid to ensure that the more basic "feature phones" that are likely to be used to access the internet in some parts of the world are not overwhelmed, Internet.org's guidelines state that bandwidth usage of sites and services should be kept to an absolute minimum. While this makes sense to a certain extent, it does create a two-tier internet: a light, limited version for Internet.org users, and the web that everyone else has access to. Of course some internet access is better than no internet access, but there are also concerns about privacy and security.
The way in which Internet.org traffic is routed through specially designated proxy servers means that it is not possible to access HTTPS sites. You read that correctly: Internet.org will not permit users to access secure websites -- it is also not possible to use TLS or SSL encryption. With all of the interest in privacy that came about following Edward Snowden's NSA revelations, this seems like an astonishingly bad idea -- not that surveillance revelations were needed to make it a bad idea. Why should users have to endure lower security simply because they are accessing the internet for free?
EFF -- and others -- are also concerned that Facebook is essentially setting itself up as a gatekeeper for the internet. As the group explains:
By setting themselves up as gatekeepers for free access to (portions of) the global Internet, Facebook and its partners have issued an open invitation for governments and special interest groups to lobby, cajole or threaten them to withhold particular content from their service. In other words, Internet.org would be much easier to censor than a true global Internet.
The letter to Facebook expresses concerns that "access for impoverished people is construed as justification for violations of net neutrality".
Speaking to the BBC, a Facebook spokesman defended the company's blueprint for free internet access:
We are convinced that as more and more people gain access to the internet, they will see the benefits and want to use even more services. We believe this so strongly that we have worked with operators to offer basic services to people at no charge, convinced that new users will quickly want to move beyond basic services and pay for more diverse, valuable services.
At the moment, Facebook has not expressed any interest in trying to control the type of content that is made available through Internet.org, but the technical limitations -- no support for video, a ban on large images, no VoIP calls, and a lack of JavaScript support -- are seen as being just too limiting. As EFF puts it, it is "less than a true Internet service, but also endanger[s] people's privacy and security".
Effectively acting as a filter to the internet, supported Internet.org sites and services can only be accessed through dedicated Android apps, Facebook itself, and Opera Mini. In order to access content that does not come from Internet.org partners, and to overcome the restrictions Internet.org imposes, users will have to pay for use of a data connection. This is something that net neutrality proponents and equality advocates take issue with.
The letter says:
It is our belief that Facebook is improperly defining net neutrality in public statements and building a walled garden in which the world's poorest people will only be able to access a limited set of insecure websites and services.
This is not a debate that shows any sign of letting up in the near future. Facebook remains adamant that the way it is going about things is the right way, but until privacy, security, and net neutrality concerns are addressed, there are many groups who will continue to take issue with Internet.org -- however well-intentioned it may be.
Photo credit: JuliusKielaitis / Shutterstock
-

Microsoft's VC3 security is encryption for the cloud
Publié: mai 19, 2015, 1:00pm CEST par Mark Wilson

The inexorable move towards the cloud continues apace, and something that remains a key concern is security. Microsoft thinks it may have come up with a solution in the form of Verifiable Confidential Cloud Computing, or VC3, which has been designed to keep cloud data encrypted and secure even when the data is being used to perform calculations.
Described as a "lockbox in the cloud", VC3 keeps data protected by using secure, managed hardware to perform any necessary decryption. Encrypted data is transferred to VC3-managed cloud hardware where it is then decrypted, used in calculations, and then re-encrypted.
It's not quite round the clock encryption, but it's as close as you could really expect. The team behind VC3 explains that with the security in place, any encrypted data is visible only to the authorized owner -- malicious hackers and even the company managing the hardware remain locked out. This offers a levels of protection from the inside, helping to eliminate the risk of disgruntled employees accessing data they shouldn't.
Researchers presented their work in a paper at the 36th IEEE Symposium on Security and Privacy. It's something that will be of particular interest to financial institutions who need to be sure that data sent back and forth has not been interfered with or intercepted. The system offers greater protection at more points than is currently offered, and the team working on VC3 says data remains secure even if a machine becomes compromised.
Check out the video below where Microsoft researchers talk about the importance of cloud encryption:
Photo credit: faithie / Shutterstock
-

Microsoft will keep your emails in check automatically
Publié: mai 18, 2015, 8:05pm CEST par Mark Wilson
Towards the end of last year, Microsoft launched Clutter. It's a tool designed to make it easier to focus on the email that matter by moving the less important ones into a separate folder. It works in a similar way to decluttering tools offered by Yahoo and Gmail, and now it's being rolled out to everyone.
Starting in June, there will be no need to manually activate the feature as it will be enabled by default. If you're not keen on having your emails tinkered with, you can disable it, but Microsoft explains that the aim is to save you time by reducing the amount of chaff you have to sort through to get to the wheaty content that matters.
System administrators who want to stay in control of email now have access to a couple of PowerShell cmdlets. There are key changes that will be visible to the average user as well. Rather than pestering you with constant notifications when emails are moved between folders, Clutter now displays a summary instead. In a post on the Office Blog, the Office team explains:
The existing inbox notifications are being replaced with alerts and summary notifications sent when Clutter is at work. The alerts are sent when new types of emails are moved to Clutter for the first time, you will receive a maximum of one alert per day. The summary notification is sent once per week making it easy to know what Clutter is doing for you.
The update is rolling out in two waves. The first starts on June 1, and the second on June 15.
Photo credit: Sangoiri / Shutterstock
-

Court of Appeals says Samsung's legal payments to Apple should be reduced
Publié: mai 18, 2015, 5:51pm CEST par Mark Wilson

Patent lawsuits in the world of technology are nothing new, and the case between Apple and Samsung resulted in one of the largest fines ever being handed down. Samsung was ordered to pay $930 million in damages after a court found that the company had violated Apple patents with its smartphone and tablet designs.
Today the US Court of Appeals for the Federal Circuit overturned part of the original ruling, saying that the jury was wrong to say that Samsung infringed on Apple's trade dress intellectual property. The exact details of what this will mean are yet to come out, but it should lead to a fairly hefty reduction in Samsung's legal costs.
The case dates back to 2012 and Samsung appealed against the initial ruling. While the findings that Apple's design and utility patents were violated have been upheld, the fact that part of the ruling was found to be incorrect means that the fine will have to be adjusted accordingly. As reported by AppleInsider, today's ruling states:
We therefore vacate the jury's damages awards against the Samsung products that were found liable for trade dress dilution and remand for further proceedings consistent with this opinion.
The full court documents go into some details about the reasons for the decision. It explains that "the requirement that the unregistered trade dress 'serves no purpose other than identification' cannot be reasonably inferred from the evidence" (trade dress patents cover design elements that are functional as well as aesthetic) so a recalculation is in order.
Photo credit: Lisa-Lisa / Shutterstock
-

Apple buys high-precision GPS firm Coherent Navigation
Publié: mai 18, 2015, 2:21pm CEST par Mark Wilson

The accuracy of GPS on iPhones could be on the verge of becoming significantly better. Apple has confirmed that it has acquired GPS company Coherent Navigation, a start-up that specializes in super-precise global positioning systems.
As is usual, Apple remains tight-lipped about future plans, going no further than confirming the purchase in an email. The wheels of activity are already in motion and the Coherent Navigation website has already vanished from the internet.
The accuracy of consumer level GPS is a few feet or a few meters, but Coherent Navigation has a system (High Integrity GPS, or iGPS), that can pinpoint a location to within a few centimeters. Whether we'll see the technology integrated in Apple's mapping software, or used in a future product such as the rumored Apple Car remains to be seen; all Apple has to say at the moment is:
Apple buys smaller technology companies from time to time, and we generally do not discuss our purpose or plans.
Coherent Navigation started life back in 2008, and has worked on various projects over the years including robotics and autonomous navigation. MacRumors -- which broke the story -- notes that a number of Coherent Navigation employees recently started working for Apple. Paul Lego joined the mapping team at the beginning of the year, and co-founders William Bencze and Brett Ledvina entered the Apple fold last month.
Photo credit: best pixels / Shutterstock
-

Streaming video subscriptions will quadruple by 2019
Publié: mai 18, 2015, 12:37pm CEST par Mark Wilson

Online video services such as Netflix and Amazon Prime Video are undeniably popular, but they are set to explode in the next few years. A study published by Juniper Research suggests that in a period of just five years (2014-2019) the number of people subscribing to streaming video services will rocket from 92.1 million to 332.2 million.
Despite what many people may have thought, it is not growing use of mobile devices for entertainment that will be responsible for the increase. The nearly fourfold growth will be driven by the success of the likes of Google's Chromecast and Amazon's Fire TV Stick.
While sales of smart TVs are on the rise, it is the upcycling of old televisions into connected devices that will really fuel the subscription surge. Mobile sales may be high, but when it comes to boxset splurges, viewers still prefer to settle down on the sofa in front of the big screen. The sheer number of ways to push streaming content to TVs -- set-top boxes, games consoles, and plug-in streaming sticks -- means that more and more people are creating their own smart TVs.
The growing market has spawned more players in the field, and this in turn has led to greater competition, helping to push down prices and further increase demand. While North America continues to see huge growth, China and the Far East also stand to fare well, with a predicted quadrupling of video on demand advertising from 2014 to 2019.
Photo credit: scyther5 / Shutterstock
-

Here's how genuine and non-genuine Windows 10 upgrades will work
Publié: mai 15, 2015, 10:38pm CEST par Mark Wilson

Later this summer, Windows 10 will be released. Microsoft has pushed out numerous builds in recent months but details about how the upgrade process will work have been a little thin on the ground. Today Microsoft reveals how users of both genuine and non-genuine versions of Windows 7 and 8.x will be able to upgrade to Windows 10.
We already know that the upgrade process will be simple and Terry Myerson had already suggested that it would be possible to upgrade from a pirated version of Windows for free. Now the differences between the upgrade process for genuine and non-genuine version of Windows are made clear -- and pirates will have to put up with a desktop watermark.
In a post on the Windows blog, Myerson today confirms that the upgrade to Windows 10 will be free for everyone (no mention of a one year timeframe this time), and says that updates will be provided for the "supported lifetime of that device". But what about pirates? If you're running a dodgy copy of Windows 7 or 8.x you'll still be able to upgrade free of charge.
When we can’t verify that Windows is properly installed, licensed, and not tampered with, we create a desktop watermark to notify the user. If you ever encounter this watermark on a new machine, I encourage you to return the device immediately to the retailer from whom you purchased it and request a Genuine Windows device. Non-Genuine Windows has a high risk of malware, fraud, public exposure of your personal information, and a higher risk for poor performance or feature malfunctions. Non-Genuine Windows is not supported by Microsoft or a trusted partner.
If you can put up with a watermark, you still have -- essentially -- a free copy of Windows 10. Though Microsoft has plans to encourage users of non-genuine versions of Windows into going legit. There are no specifics at the moment, but Myerson says:
While our free offer to upgrade to Windows 10 will not apply to Non-Genuine Windows devices, and as we’ve always done, we will continue to offer Windows 10 to customers running devices in a Non-Genuine state. In addition, in partnership with some of our valued OEM partners, we are planning very attractive Windows 10 upgrade offers for their customers running one of their older devices in a Non-Genuine state. Please stay tuned to learn more from our partners on the specifics of their offers.
Presumably there will be a fee involved in turning Windows into a genuine edition, but we'll know more nearer the official release date.
Photo credit: THesIMPLIFY / Shutterstock
-

Facebook rides roughshod over privacy laws
Publié: mai 15, 2015, 7:28pm CEST par Mark Wilson

Facebook and privacy are not words that generally belong in the same sentence, but a Belgian watchdog has expressed surprise at just how little regard for European law the social network shows. The Privacy Protection Commission says "Facebook tramples on European and Belgian privacy laws", and warns users to take action.
Mark Zuckerberg's site is accused to tracking users even if they are not logged into a Facebook account, and sidestepping questions from European regulators. Although the Privacy Protection Commission is not able to impose fines for failure to abide by European law, it is in a position to offer advice -- and the advice to people is to use software to block Facebook's tracking regardless of whether they use the site or not.
The watchdog's report followed an investigation into Facebook's practices, and led to strongly worded criticism of the company. The use of cookies to track people through social plugins (Like and sharing buttons, for instance) gave particular cause for concern, resulting in the Commission calling for an end to the practice as well as the recommendation that people should use privacy software.
With the potential to use tracking information to identify people and target them with advertising, the monetization of even non-Facebook users is frowned upon. A key European law states that sites must gain explicit permission from users before cookies are employed, but this is something that Facebook fails to do.
Facebook also stands accused of failing to comply with the Privacy Protection Commission's investigations, but the company has questioned the watchdog's authority. The Commission would be able to recommend that Facebook is prosecuted for its activities, but would not be able to action this itself. Facebook has said that any tracking of non-users is the result of a bug, but this has done little to calm privacy concerns.
The Privacy Protection Commission is due to publish another report later in the year, and it will be interesting to see whether Facebook has acted on any of the suggestions by then.
Photo credit: dolphfyn / Shutterstock
-

European telecom firms may block all mobile ads, spelling trouble for Google
Publié: mai 15, 2015, 4:11pm CEST par Mark Wilson

Google is facing something of a European revolution as mobile companies consider blocking ads on a massive scale. Israeli company Shine has developed software that blocks mobile ads, and it has gained the attention and support of a number of telecom companies in Europe.
Talking to the Financial Times, one wireless carrier said that the software had been installed at its data centers and could be enabled by the end of the year. With the potential to automatically block most ads on web pages and within apps, the repercussion of the ad boycott could be huge as mobile providers try to wrestle control from the likes of Google.
Blocking ads from Google et al is something that appeals not only to mobile users -- who hasn’t felt irked at the appearance of yet another ad? -- but also the mobile companies themselves. This is not just about keeping customers happy, but also maintaining control over bandwidth usage; in-app ads can be responsible for eating up huge amounts of data. The unnamed European carrier who spoke to the FT said that it was not alone in its ad-blocking plans.
On the face of it, this is something that seems like a win for everyone, but advertising exists for a reason. Sites feature ads as a way to monetize content, and this in turn helps to support sites, apps and services. The disruption caused by an ad blackout could be colossal.
On its website, Shine says:
Ad-tech has gone unchecked, polluting our Web and App experiences with privacy infringing and obtrusive advertising. We work with mobile carriers who are redefining their services to meet the true needs of consumers by offering the power of ad control to millions of subscribers around the world.
At the moment the plan is to provide customers with the ability to opt in to an ad-free experience; it's not clear whether there would be a charge for this. Described as 'the bomb', a system-wide block on ads is designed to "specifically target Google, blocking advertising on its websites in an attempt to force the company into giving up a cut of its revenues," reports the Financial Times. There is a suggestion that ads could be blocked on an intermittent basis simply to get Google's attention and cut better deals for telecoms companies.
Photo credit: phoenixman / Shutterstock
-

Bing follows Google's lead in favoring mobile-friendly sites in search results
Publié: mai 15, 2015, 2:14pm CEST par Mark Wilson

Last month Google announced a series of changes to the way it handled search results on mobile devices, and now Microsoft is following suit. Now there is a focus on promoting those sites that are optimized for viewing on a smaller screen. Microsoft said six months ago that it would start to push mobile-friendly sites, and today this plan is being put into action.
The project started off by simply highlighting mobile-friendly sites to aid identification, but now they will be promoted further up search rankings. If there are two sites rated equally highly for their content, the one which is considered most suitable for viewing on a mobile device will appear higher in results when a search is conducted from a mobile device.
Microsoft says that the new approach "balances the need to improve the ranking for mobile-friendly pages, with the continued focus on delivering the most relevant results for a given query", pointing out that "webpages that are highly relevant to the given query that are not yet mobile-friendly will not get penalized". The transition to the new method of handling search results will not be immediate -- Microsoft expects the rollout to start in a few months.
With Google's dominance of the search market -- both mobile and non-mobile -- any changes made by Microsoft in this field will affect far fewer people. But at the same time it does indicate that web developers are being increasingly encouraged to consider the fact that their sites may be viewed on a range of different screen sizes. Unlike Google, Microsoft goes some way to explain the factors that influence how its search results are worked out.
To be rated as mobile-friendly, sites need to feature large and obvious navigation elements, include text formatted for small screens, require only vertical scrolling, and general mobile browser compatibility is also factored in. Microsoft warns website owners:
There are more factors that we are considering along the lines of mobile friendliness, like the friction that pop-ups sometimes create in navigating to the core content of the page. One important thing to remember -- we depend on access to all the necessary CSS and script files required by your page to make this determination. So, it is important that you allow Bingbot mobile user agents access to download these resources.
-

Microsoft brings searchable handwriting and Apple Watch support to OneNote
Publié: mai 14, 2015, 10:16pm CEST par Mark Wilson
The latest update to OneNote sees the addition of support for Apple Watch as well as the ability to search through handwritten notes. Thanks to handwriting recognition, it is possible to perform a search that looks through not only typed notes, but also those that have been written with a stylus.
The feature is available in the mobile and desktop versions of the app, and Microsoft says that any new handwritten notes that are saved to OneDrive will be automatically rendered searchable in a few moments. Over the coming weeks older handwritten notes will be indexed in the same way so they can also be searched.
Introducing the improvements to handwriting support, Microsoft take the opportunity to highlight the Apple Watch version of the app. In a blog post the company explains that the wearable-bound version of the app has "a strong focus on lightweight interactions and placed a premium on convenience". While typing is possible with an Apple Watch, dictation is by far the easiest way to create notes and it's the method that Microsoft recommends.
If you have OneNote installed on your iPhone, you can use the Apple Watch app to toggle the Watch version on and off. Sticking with the iOS theme, Microsoft has also announced a series of improvements to the iPad version of OneNote, including an updated interface and new swiping options.
-

It's far too easy to steal an Apple Watch
Publié: mai 14, 2015, 8:03pm CEST par Mark Wilson

The problem with a lot of technology is that it acts as a beacon to thieves. Use a phone or tablet in public and you run the risk of having it swiped from under your nose. To overcome this, Apple and Google have built in security features that make it possible to render useless iPhones, iPads and Android devices. The same, however, cannot be said of the Apple Watch.
While the Apple Watch does feature a passcode system that is used as a locking mechanism when the wearable is removed from the wrist, it is incredibly easy to bypass. A thief can grab a Watch, factory reset it and pair it with their own iPhone. The risk of arrest aside -- and, you know, morals -- there is no deterrent to helping oneself to a Watch and claiming it as your own.
Considering Apple already has a security system in place that works perfectly well for its smartphones, it's odd to find that it has not been implemented for the wearable -- particularly when extended warranties are so expensive. In a matter of moments, as demonstrated by iDownloadBlog, it is possible to reset a Watch and pair it with another device so it can be used just like one bought from the store.
Just about the only positive aspect of this story is the fact that performing a hard reset wipes out anything stored on the Apple Watch, so if you are unfortunate enough to have yours stolen, your private data should be safe.
The video below shows just how easy it is to reset an Apple Watch:
-

Leading academics call for greater transparency about Google's Right To Be Forgotten
Publié: mai 14, 2015, 1:35pm CEST par Mark Wilson

Just yesterday Google revealed that it rejects most Right To Be Forgotten requests it receives. In publishing yet another transparency report, the search giant will have hoped to have put to bed any questions that users and critics may have had. While the report may have satisfied some, it did not go anywhere near far enough for one group of academics.
A total of 80 university professors, law experts and technology professionals have written an open letter to Google demanding greater transparency. The letter calls upon the company to reveal more about how Right To Be Forgotten requests are handled so that the public is aware of the control that is being exerted over "readily accessible information".
The letter -- published in the Guardian -- asks Google to reveal more about the type of information that it tends to delist as well as explaining the reasoning behind the decisions. The authors say: "The vast majority of these decisions face no public scrutiny, though they shape public discourse". Not all of the co-signers of the letter view the Right To Be Forgotten in the same way; there are writers who are for it, and some who are opposed to it. But what they all have in common is a desire for more information.
The undersigned have a range of views about the merits of the ruling. Some think it rightfully vindicates individual data protection/privacy interests. Others think it unduly burdens freedom of expression and information retrieval. Many think it depends on the facts.
The letter says that the data provided by Google so far is little more than anecdotal and it is difficult to determine whether information about individual cases that have been made public are representative of others. Any debate about privacy -- which is usually how the Right To Be Forgotten is framed -- needs to be balanced with talking about censorship. This is something else recognized in the letter:
We know very little about what kind and quantity of information is being delisted from search results, what sources are being delisted and on what scale, what kinds of requests fail and in what proportion, and what are Google’s guidelines in striking the balance between individual privacy and freedom of expression interests.
Of particular concern is the fact that Google is, for all intents and purposes, left to its own devices when it comes to implementing the ruling passed down by a court in Europe last year.
Without more detailed information about the processes Google goes through, the academics argue it is impossible to determine whether things are being handled properly. The letter asks for more details about how requests are categorized and dealt with, the type of information that is involved, reasons for the delisting of individual URLs rather than just a statement of delisting, and greater details about the status of complainants -- are they public figures or members of the general public, for instance. Concern is also expressed that, in many cases, "the entire process is silent and opaque" so there is little or no chance to question Google's decisions.
Google has yet to respond directly to the letter, but we have reached out to the company for comment. Speaking to the Guardian, Google said:
Our transparency report is always evolving and it’s helpful to have feedback like this so we know what information the public would find useful. We will consider these ideas, weighing them against the various constraints within which we have to work -- operationally and from a data protection standpoint.
Photo credit: PathDoc / Shutterstock
-

Google stops developers and Mac users installing unofficial Chrome extensions
Publié: mai 14, 2015, 12:36pm CEST par Mark Wilson

Google is extending its block on unofficial Chrome extensions to the developer channel and Mac users. The move is a continuation of the decision taken last year that forced people using the stable and beta channels of the Windows version of the browser to stick with official extensions.
It is a decision which aims to stop people from installing malicious add-ons; Google has previously been criticized for failing to clear out junk quickly enough. With immediate effect, those on the developer channel will have to install extensions from the Store, and the policy will be applied to the Mac version of Chrome in a few weeks. All is not lost for anyone who wants to install unofficial extensions, though.
Google says that since making it more difficult for most people to install non-store hosted extensions, the company has seen requests for help with 'unwanted add-ons' drop by 75 percent. It was originally thought that developers should maintain the ability to install extensions from whatever source they want, but Google changed its mind after malicious software was noticed switching users to the developer channel to install extensions.
Google explained the reason for the move in a blog post:
We originally did not enforce this policy on the Windows developer channel in order to allow developers to opt out. Unfortunately, we’ve since observed malicious software forcing users into the developer channel in order to install unwanted off-store extensions. Affected users are left with malicious extensions running on a Chrome channel they did not choose. As such, starting today we will begin enforcing this policy on all Windows channels. Mac will soon follow, with enforcement for all channels beginning in July 2015.
Anyone who needs to install an extension that is not hosted in the Chrome Web Store can do so by using Enterprise policies. Another option is to install extensions locally for the purposes of testing during development.
Photo credit: 75tiks / Shutterstock
-

Google rejects most Right To Be Forgotten requests
Publié: mai 13, 2015, 5:14pm CEST par Mark Wilson

One year ago, a European court ruled that Google should comply with requests from individuals to remove certain results from search results; it became known as the Right To Be Forgotten. Twelve months after the initial ruling, Google has published a new transparency report that shows it rejects more requests than it complies with.
The Right To Be Forgotten stemmed from a case brought by Spaniard Mario Costeja González who wanted Google to remove search results that pointed to online articles about his home being repossessed. There then followed an influx of requests after Google set up an online form to provide individuals with an easy way to get in touch.
Google's updated transparency report shows that it received a total of 254,271 requests relating to almost a million (922,638) URLs. Of this number, well over half of requests -- 58.7 percent -- were rejected. The least successful country was Bulgeria where just 24.7 percent of requests resulted in a removal, while Germany was the most successful complainant boasting a removal rate of 48.9 percent.
The most popular site flagged up for URL removal was Facebook, with Google's own Google Groups and YouTube also featuring in the top ten. What are the reasons cited for URL removal? There are some interesting cases highlighted by Google including:
A priest convicted for possession of child sexual abuse imagery asked us to remove articles reporting on his sentence and banishment from the church. We did not remove the pages from search results.
-

International access to BBC iPlayer ends in two weeks
Publié: mai 13, 2015, 4:20pm CEST par Mark Wilson
The BBC has announced that access to its iPlayer service from outside of the UK is to end from 26 May. Originally only made available to those living in the UK, the international version of iPlayer provided access to a selection of its content for a monthly subscription.
Those with a subscription have a month to access the content they have paid for, so the final date that iPlayer can be used will actually be 26 June. The timing of the BBC's announcement is interesting, coming just a week after the European Commission revealed plans to break down the barriers of geo-blocking.
The number of streaming media services vying for attention has almost certainly played a part in the BBC's decision, as well the problem of users simply torrenting the shows they want to see. While the paid subscription option may be disappearing, the corporation will be able to do little to stop people outside of the UK from using VPN software to access programmes for free.
The announcement appeared on Twitter as well as on the iPlayer website:
BBC iPlayer (Global) will be closing permanently between 26th May & 26th June 2015. For more info check [t.co]
— BBC iPlayer (Global) (@BBCiPlayerGLBL) May 12, 2015
This will come as bad news to iOS users who had become reliant on iPlayer as a source of entertainment -- this is the only platform it was available on internationally -- but the service's demise has been on the cards for some time now.
-

Terminator Genisys: Revolution is the first Android app you can pre-register for
Publié: mai 10, 2015, 6:44pm CEST par Mark Wilson
To be first in line to download a new app, you need to be quick off the mark. You might hear about a game or app weeks ahead of launch, and it's all too easy to miss the launch date. You might be wondering why it has taken Google so long to do something about it.
For Android users this is now a thing of the past thanks to the introduction of pre-registration. The first title in Google Play to offer this is Terminator Genisys: Revolution. You can now register your interest in the game and you'll be notified when it is released and is ready for download.
The process is pretty simple, and it makes perfect sense for app and game developers as it provides a way to promote a product ahead of launch. There's no need to wait until launch day for supported apps to appear in Google Play as their entry can now be posted ahead of time. To make sure you don’t miss out, just hit the pre-register button and you'll be told:
You're about to pre-register for TERMINATOR GENISYS: REVOLUTION. Pre-registering means that you will recieve (sic) a notification on your device when the app is released. You can unregister by clicking the 'Unregister' button.
Terminator Genisys: Revolution may be the first app in Google Play that you can pre-order, but it certainly won’t be the last.
-

Anonymous Tor Cloud project closes down
Publié: mai 9, 2015, 2:03pm CEST par Mark Wilson

The Tor browser is used by many to stay anonymous online -- and it's something that has been embraced by the likes of WikiLeaks as a way to safely gather information whilst hopefully avoiding the surveillance of the NSA. One lesser known project from the same stables is the Tor Cloud service, and Tor has announced that it is closing down.
Based on the Amazon EC2 cloud computing platform, Tor Cloud provided a way to share computing resources and allow faster uncensored access to the internet. However, the project is plagued with "at least one major bug ... that makes it completely dysfunctional" and after failing to find anyone to undertake the work, the decision was taken to shutter Tor Cloud. This does not mean that Tor itself is dead -- far from it -- and developers are being encouraged to create their own forked versions of Tor Cloud.
It is still possible to manually install Tor bridges on Amazon EC2 and other cloud platforms, but it is now not as simple as it was with Tor Cloud. Any existing instance of Tor Cloud remain unaffected by the closure of the service as all of the necessary settings are already in place. There is still the problem of numerous known bugs, but this is something that users and developers are free to work on.
In a blog post, Tor said:
We have tried to find a new maintainer for Tor Cloud for months, but without success. There have been offers to send us patches, but we couldn't find a Tor person to review and approve them. We encourage everyone who stepped up to start their own cloud bridges project under another name ("Onion Cloud"?), possibly forking the existing Tor Cloud code that will remain available. Tor Cloud is still a good idea, it just needs somebody to implement it.
Photo credit: Charlie Bard / Shutterstock
-

Flickr 4.0 update brings new upload tool and image recognition magic
Publié: mai 8, 2015, 12:53am CEST par Mark Wilson

It has been a while since Flickr (remember that site?) received an update, but today this changes. Flickr 4.0 is rolling out, and it's a massive update. Headlined by Flickr Camera Roll and Uploadr, the update can be enjoyed not only by Android and iOS users, but also those who stick to the website.
There's a tool that makes it easier to get photos up online but, more importantly, tools that make it easier to browse and edit them. Flickr Camera Roll is mouse and touch-friendly browser, there's a greater focus on sharing, and there's a dusting of magic. Magic View is Flickr's new killer feature that can automatically organize your photo collection for you.
Flickr recognizes that things have not always been simple; the blog post introducing the latest version of the site has the slightly self-deprecating title "it’s finally easy to upload, access, organize, edit, and share any photo you’ve ever taken." Browsing has been improved in the Camera Roll, but it's Magic View that Flickr's really proud of.
Automatic organization is a love it or hate it feature, but Flickr's take on things is quite impressive -- on paper, at least. Advanced image analysis is used to identify all your photos that are landscapes, those that feature people, images that have a green hue and so on: no more manual sorting may be required.
Uploadr is a pretty self-explanatory tool for Windows and Mac. Any photos that get added to the location you specify will be automatically uploaded to your Flickr account: simple. Images that are uploaded in this way are added to private galleries and synced between devices without the need for you to intervene. As well as uploading and sharing improvements, image downloading has also been updated with a simple addition: bulk downloading.
Try it out right now and see what you think.
-

Yes, the NSA did act illegally
Publié: mai 7, 2015, 7:45pm CEST par Mark Wilson

It has been hard to avoid talk of the NSA over the past year or so -- Edward Snowden's revelations blew the lid off convert surveillance that has been carried out by the US government. It has been a hugely divisive issue, many heralding Snowden as a hero, others as a traitor and has led people to question whether everyday software might include secret backdoors.
Included in the NSA's activities was the mass collection of metadata about phone calls made and receive by American citizens. Today the US court of appeals ruled that this data collection is illegal. With other countries adopting NSA-style surveillance tactics, the ruling opens up the possibility that the NSA could face further legal proceedings and probes.
It had previously been suggested that the NSA's activities were essentially above the law and could not be assessed through the usual legal channel. This decision was overruled and the American Civil Liberties Union started legal action against James R Clapper the Director of National Intelligence, Michael S Rogers the NSA director, and others. One of the justifications for the NSA's activities has been Section 215 of the Patriot Act, but three judges today said:
We hold that the text of section 215 cannot bear the weight the government asks us to assign to it, and that it does not authorize the telephone metadata program.
The US government's attempt to use the Act as the basis for mass metadata collection is described as "irreconcilable with the statute's plain text." This suggests that the NSA misinterpreted or misapplied the law (deliberately or otherwise) and it raises the question of what happens at the beginning of June when Section 215 expires.
But more interestingly it also opens up the possibility that the NSA could find itself subject to further investigations, and there is a chance that they may not happen behind closed doors. Judges have said that the phone data collection program is too broad and vague, producing a "staggering" volume of information.
Despite today's ruling, the collection of phone data is not going to stop immediately -- or perhaps even at all. The next step is for Congress to review Section 215 and the decision is something the appeal judges say "may (or may not) profoundly alter the legal landscape".
Image Credit: 360b / Shutterstock
-

Android M to be revealed May 28 at Google I/O?
Publié: mai 6, 2015, 10:47pm CEST par Mark Wilson
Countless Android users are still waiting for Lollipop to roll out to their handsets, but already there is talk of the successor -- Android M. Coming up at the end of this month, Google I/O is a developer conference hosted by the search giant in San Francisco and today the full schedule for the event appeared online.
An event on May 28 with the title Android for Work update is of particular interest as there is a strong hint that details of Android M will be revealed. Although it seems that Google may have let something slip a little early -- the session that refers to the next version of Android has since vanished from the schedule, but the description is interesting nonetheless.
Originally pencilled in for 2:30PM on the first day of the event, the session will include talk about the follow up to Android 5.0 Lollipop. The description reads (or read): "Android M is bringing the power of Android to all kinds of workplaces. This opens huge new markets for hundreds of millions of devices to workers at small businesses, deskless workers, logistics and warehousing jobs; all be empowered by adoption of Android devices at Work".
There is a separate session called "What's new in Android" which would seem to be the natural home for news about the latest version of Google's mobile operating system, but all references to Android M appear to have been erased from the schedule now. It's not clear whether this is because Google gave away more than it meant to ahead of the event, or because of a genuine error -- but it's only three weeks until we find out for sure.
Nothing concrete is known about Android M (could it be Mars, Milky Way, M&Ms?) but it is likely that there will be a focus on security in a bid to increase adoption in the workplace. Could we see a demo of Android M in action at Google I/O? Only time will tell...
-

Europe moves to end geo-blocking online content
Publié: mai 6, 2015, 7:40pm CEST par Mark Wilson

While the internet is supposed to be an open-access resource, there is a great deal of content which can only be accessed in certain parts of the world. To comply with licensing rules, broadcasters in particular will often restrict access to their services to specific countries, but in Europe there are plans to bring such geo-blocking to an end.
Described as "a discriminatory practice used for commercial reasons" geo-blocking is derided by the European Commission as little more than a money-making venture. The aim is to create what has been dubbed a Digital Single Market, breaking down barriers and simplifying regulation.
The Commission says that the current system serves both businesses and consumers poorly, and suggests that moving to a Digital Single Market will not only help to create jobs, but also boost the European economy by €415 billion per year. In addition to removing obstacles that stand between consumers and services, the Commission wants to create a more level playing field for digital service providers in Europe.
The move could mean that services such as BBC iPlayer and Netflix are available throughout Europe with the same content in each country. Commission President Jean-Claude Juncker said: "I want to see every consumer getting the best deals and every business accessing the widest market -- wherever they are in Europe".
As part of the Digital Single Market Strategy, a total of sixteen goals for the end of 2016 have been set out. In addition to ending geo-blocking, there's also the promise of easier cross-border e-commerce. Plans to overhaul copyright laws will create a unified European system are likely to be welcomed by consumers, as is a comprehensive review of service providers and how they compete with each other.
Mark Skilton from Warwick Business School said:
The EU’s Digital Single Market initiative aims to redress the balance that has seen US tech giants dominate the online world. The EU’s review of online practices will force companies to define their original service location and bias to help build a level playing field. The Google antitrust case is one such example. The EU is hoping that creating a single digital market will help European companies grow and take on the likes of Facebook, which holds 78 per cent of the social influence market, and Google.
Photo credit: ixpert / Shutterstock
-

Oculus Rift starts shipping Q1 2016
Publié: mai 6, 2015, 2:43pm CEST par Mark Wilson

There's now less than a year until people will be able to get their hands on Facebook's virtual reality headset, Oculus Rift. Writing on Twitter, Oculus VR's vice president of product Nate Mitchell confirmed that the device will begin shipping in the first quarter of 2016.
The announcement was echoed on the official Oculus Twitter feed as well as in an official blog post. While the launch is slightly later than many people had hoped -- initial plans had the release pegged for some time in the latter half of 2015 -- it brings to an end months of guessing.
The company says that the release product will be based on the Crescent Bay prototype that developers have already had a chance to play with, and that pre-orders will start later this year. It's a virtual reality system that the manufacturers say will completely "reimagine what gaming can be", and more details are due to be released next week about full technical specifications.
Nate's announcement on Twitter was met enthusiastically by eager fans:
Extremely excited to announce that the Oculus Rift will be shipping Q1 2016! We can't wait to get it in your hands. pic.twitter.com/TVquKTQJjx
— Nate Mitchell (@natemitchell) May 6, 2015
While based on a previous prototype, Oculus says that the unit features "improved tracking system that supports both seated and standing experiences, as well as a highly refined industrial design, and updated ergonomics for a more natural fit".
There is no word on pricing yet, but this is expected to follow in the coming weeks along with details about games and VR "experiences" that are in the pipeline.
-

France gains sweeping NSA-style surveillance powers
Publié: mai 6, 2015, 1:46pm CEST par Mark Wilson

The French government has voted in favor of greater powers of surveillance, giving it intelligence-gathering capabilities on a par with the NSA. The move came in the wake of the Charlie Hebdo attack which led to the deaths of 12 people and prompted the Je Suis Charlie support campaign.
The new laws allow for NSA-style mass collection of metadata online as well as setting up the National Commission for Control of Intelligence Techniques (CNCTR) to oversee data collection. It has been criticized by some as being the French equivalent of the Patriot Act and the ruling Socialist Party is accused of prying too far into the private lives of normal people in the name of counter-terrorism.
As is to be expected, the move has outraged civil liberties groups as well as -- oddly -- the far right Marion Marechal-Le Pen who said French citizens should not have to choose between security and privacy. As well as setting up the CNCTR to oversee the activities of France's intelligence services, the new laws determine how public complaints will be handled.
As is often the justification for the activities of the NSA and other similar agencies, the French government sold the need for increased surveillance powers off the back of terrorist attacks. The government also said that it wanted to bring the surveillance of modern communication methods into an existing legal framework, but critics say the laws -- which "define the purposes for which secret intelligence-gathering may be used" -- go too far.
The delicate subject matter that prompted the law to be rethought -- cartoons featured in the satirical newspaper Charlie Hebdo that mocked the prophet Mohammed -- means that the privacy versus national security debate has not been split along the usual party political or ideological lines. Left- and right-leaning parties united to vote through the law 438 votes to 86, with notable opposition coming from the Greens and the Left Front.
Outside of government, however, there is vocal opposition to the laws. While there is sympathy for the reasons behind the law change, privacy advocates and civil liberties groups are unhappy with how it has been approached. It's something that Privacy International has described as a "dangerous and broad surveillance bill".
Photo credit: Yulia_B / Shutterstock
-

Microsoft cannot trademark Skype in Europe
Publié: mai 6, 2015, 1:10am CEST par Mark Wilson

It's a name that is, for many people, synonymous with voice and video chats: Skype. But in Europe, Microsoft has just been told that the name of its communication tool cannot be trademarked because it is too similar to that of broadcaster Sky.
Microsoft has previously been forced to rename its cloud storage service SkyDrive to OneDrive, but at the moment there is no suggestion that Skype will have to be renamed. The company has indicated that it intends to appeal against the ruling.
Speaking about the Skype name and logo, the General Court of the European Union said that "conceptually, the figurative element conveys no concept, except perhaps that of a cloud. [It] would further increase the likelihood of the element 'Sky' being recognised within the word element 'Skype', for clouds are to be found 'in the sky' and thus may readily be associated with the word sky".
The case dates back ten years when it was first ruled that Skype was too similar to Sky to be granted a trademark in the European Union. Despite the lack of trademark, other companies would not necessarily be able to create products and services of their own called Skype without fear of repercussions.
Microsoft remains defiant, saying:
The case was not a legal challenge to Skype's use of the mark, it was only against the registration. We're confident that no confusion exists between these brands and services and will appeal. This decision does not require us to alter product names in any way.
-

PlayStation Now subscriptions come to PS3 -- Vita to follow
Publié: mai 5, 2015, 9:21pm CEST par Mark Wilson

Sony is bringing its PlayStation Now game streaming feature to PS3 users. It's something that has been available to gamers with a PlayStation 4 since the beginning of the year, but from May 12, it's something that owners of older consoles will be able to take advantage of.
PlayStation Now allows for the streaming of more than 100 PS3 games, and a 7-day free trial is available for anyone who wants to test the waters. With cloud-based game saves it's possible to start a game on one device, and finish it on another, and Sony says there's more to come.
The announcement was made on the PlayStation blog, and there's the promise that "the subscription will be coming to more devices soon". Writing on the blog, Sony's Jack Buser introduced the feature explaining that one month costs $19.99 and three months costs $44.99. Asked whether PlayStation now will be coming to Vita any time soon, he said "soon".
We have some exciting news: PlayStation Now subscriptions will be coming to PS3 later this May! Now you’ll be able to play a huge library of more than 100 hit PS3 games on PS4 and PS3, as well as select Sony Blu-ray players and TVs, all for one monthly price. That’s an incredible number of games to binge on — and of course, you can play your games across devices with cloud saves.
Sony also highlighted a number of new titles that are coming up this month in a showcase video:
-

Rombertik strikes! In 10 seconds, this computer will self-destruct
Publié: mai 5, 2015, 7:41pm CEST par Mark Wilson

Viruses can be a serious problem and they take myriad forms. Viruses have become increasingly sophisticated over the years, particularly in the methods used to try to evade detection. Now Cisco's Talos security researchers have discovered the Rombertik which goes to extraordinary lengths to avoid analysis.
Researchers managed to reverse-engineer the virus and found "multiple layers of obfuscation and anti-analysis functionality". One sample was found to include code that would destroy the MBR of the host computer if analysis or debugging is attempted.
The effects of a Rombertik can be devastating. Left to its own devices, the malware will sit happily in the background gathering information about online activity, collecting user credentials and feed them back to a remote server. Writing on the Cisco blog, Ben Baker and Alex Chiu explain that while Rombertik's method of propagation -- usually through emails and social networks -- is nothing out of the ordinary, the way it operates is something from a different league.
The infection process starts by Rombertik first checking whether it is running in a sandbox before decrypting and installing itself. Unusually, the virus then installs a second copy of itself but there is a key difference -- the second copy contains the real payload. Rombertik will then check to see that a tool is not trying to block or analyze it, and if it should detect such activity the master boot record will be attacked in a bid to destroy the computer and prevent it from being used.
Talos researchers reveal that the file involved in a Rombertik infection is largely padding. In a file of 1264KB, just 28KB is harmful code while the rest is a combination of unnecessary code, images and extra functions that are not used -- all in a bid to disguise the real payload. To make analysis all but impossible, in the early stages of infection Rombertik writes a random bytes of data to memory 960 million times. Researchers point out that "if an analysis tool attempted to log all of the 960 million write instructions, the log would grow to over 100 gigabytes".
By attacking the MBR of a computer if analysis is detected, Rombertik can effectively kill a computer, throwing it into an endless reboot loop. But what if the MBR cannot be attacked for some reason? To make sure that it still has an impact, Rombertik will then destroy all of the files found in a user's folder. Oh… and if you were thinking, 'oh, I'll just reinstall Windows', as well as destroying the MBR, Rombertik also tinkers with partitions to make it difficult to recover data from them.
Photo credit: Roman Pyshchyk / Shuttestock
-

Apple releases guidelines for third-party Apple Watch bands
Publié: mai 5, 2015, 1:31pm CEST par Mark Wilson

It's been a little while since orders opened for the Apple Watch -- even if anyone who placed an order has quite a wait on their hands -- and now developers are being given the chance to create third-party bands. Apple has produced some detailed guidelines that reveal precisely what is expected of third-party accessories.
For the moment, Apple is only talking about bands, and no mention has yet been made of other third-party accessories such as chargers. Even if you're not a developer thinking of cashing in on the popularity of the Apple Watch, the incredibly detailed design drawings that are provided make for fascinating viewing.
Just as with the iPhone and iPad, Apple has a Made for Apple Watch program which ensures compatibility with its wearable. The guidelines set out the specifications that must be made to ensure full compatibility, and even goes as far as suggesting the materials that should be used in the construction of different components.
Apple has set up a dedicated web site where it describes Bands and Lugs:
Apple Watch bands are easily changed with simple release buttons and lugs that secure the band to the Apple Watch case. When creating your custom bands, refer to the band design guidelines and lug profile. Apple Watch lugs will be available soon through the Made for Apple Watch program.
You can download the guidelines and AutoCAD designs from the same website.
There are already a number of combinations of Apple Watch and bands to choose from, and the launch of a third-party accessory program is only going to see this number increase. There will, of course, be plenty of unofficial third-party bands available, but many manufacturers will be keen to get the official seal of approval from Apple to help boost their sales.
-

Google buys Timeful to bring smart scheduling to Calendar and Inbox
Publié: mai 4, 2015, 11:58pm CEST par Mark Wilson

The latest addition to Google's portfolio is Timeful, Inc. Previously a standalone app for iOS, Timeful is a tool for automatically managing a schedule, using "sophisticated algorithms to suggest the best times to schedule to-dos and habits throughout the day".
There are echoes of Google Now to Timeful, so it's easy to understand why Google was interested in the company. Moving forward we can expect to see the tool integrated into Inbox and Calendar to help with the automatic scheduling of events.
This is something which will sit particularly well in Inbox which already features an email snooze option. Rather than having to decide when you would like to be reminded about a particular email, we should see a time when Google is able to automatically determine the best time to give you a gentle nudge. Look to the Timeful iPhone app description and we're told that "Timeful learns from your behaviors, adapts to your schedule, and personalizes the recommendations the more you use it".
Writing on the Gmail blog, Alex Gawley said:
The Timeful team has built an impressive system that helps you organize your life by understanding your schedule, habits and needs. You can tell Timeful you want to exercise three times a week or that you need to call the bank by next Tuesday, and their system will make sure you get it done based on an understanding of both your schedule and your priorities. We’re excited about all the ways Timeful’s technology can be applied across products like Inbox, Calendar and beyond, so we can do more of the work for you and let you focus on being creative, having fun and spending time with the people you care about.
Google isn't giving any hint about when we might start to see the feature of Timeful integrated into its own products and services, but it shouldn’t be too long before your calendar becomes a little bit smarter.
Photo credit: Brian A Jackson / Shutterstock
-

Google+ Collections lets users curate posts, Pinterest-style
Publié: mai 4, 2015, 11:12pm CEST par Mark Wilson
Google+ is one of the more maligned social networks, but it's clear that Google is not going to give up on it any time soon; far from it. Today the search giant unveils a new feature that is more than a little inspired by Pinterest -- Collections.
The new feature lets users group posts together into collections. This is not just something that makes it easy to manage photos, videos and other content, but also provides a new way to create groups about any given topic. With the option of making collections public, private, or shared with a limited number of people, Collections feel like a natural extension to the way Google+ posts currently work.
At launch, Collections are available to Android and web users, but will make their way to iOS in the near future as well. As with many Google launches, this is one that's rolling out gradually, so if you don’t see the feature just yet, it should be arriving in your account soon -- you'll need to update your Android app to take advantage of it on your phone or tablet. Google says:
Posts in collections you follow will appear in your Home stream, with a link to easily jump right into the collection so you can get to similar content from that author. Collections give you a great way to find more of the stuff you love from the people you follow.
In some ways the Collections feature is similar to existing Communities, but it's rather more versatile. Like Pinterest, Collections can be used for personal benefit, or shared with others as required, and there are not the same administrative headaches that can be involved in managing a community.
-

Facebook launches Internet.org Platform and opens up to more developers
Publié: mai 4, 2015, 1:53pm CEST par Mark Wilson

The aim behind Facebook's Internet.org program is to bring internet access to the wider world. While an undeniably praise-worthy venture, it came in for criticism for going against the principles of net neutrality.
Today the company launches the Internet.org Platform with a view to countering this criticism. The platform opens up Internet.org to more developers, giving them the chance to bring "free basic services" to people around the world. There's also the promise of greater transparency.
While Facebook is keen to get as many developers on board as possible, there are a number of criteria that have to be met. One of the key requirements is that sites and services need to be simple and data efficient. As operators are providing access free of charge, it's important to keep overheads to a minimum, after all. Developers also need to remember that many users will be accessing the internet through fairly basic feature phones, and this limits the types of technology that can be used.
Any developer signing up to take part of the Internet.org Platform needs to keep three things in mind:
- Internet.org is not about promoting individual sites and services, it is supposed to provide access to the internet in its entirety. "Services should encourage the exploration of the broader internet wherever possible".
- Data efficiency is important and there is great importance placed on the need to keep bandwidth usage down. "Websites that require high-bandwidth will not be included. Services should not use VoIP, video, file transfer, high resolution photos, or high volume of photos".
- Websites need to be compatible with basic feature phones and there are guidelines to adhere to. "Websites must be properly integrated with Internet.org to allow zero rating and therefore can’t require JavaScript or SSL/TLS/HTTPS and must meet these technical guidelines".
While these guidelines should help to bring a wider range of sites and services to Internet.org, they are unlikely to quieten the anti-net neutrality claims.
-

WikiLeaks unveils updated anonymous data submission system
Publié: mai 3, 2015, 6:04pm CEST par Mark Wilson

WikiLeaks prides itself on bringing information to public attention that might otherwise stay hidden. In order to get this information out in the open, the organization is reliant on a wide range of sources. The sort of stories which WikiLeaks deals with would often not come to light if those breaking the stories could not be guaranteed anonymity.
A few days ago the Sun newspaper revealed that it was using SecureDrop as a way for people to give anonymous tips about stories, and it was touted at the time as being a WikiLeaks-style tool. Now Julian Assange has announced that WikiLeaks has upgraded its own submission tool to offer even greater security.
Currently running in beta, version 2.0 of the WikiLeaks submission tool is accessible via Tor, just like SecureDrop. Unlike SecureDrop, however, WikiLeaks offers an extra level of security. Rather than forcing would-be submitters to scour the site looking for submission instruction -- something which could be used as evidence against someone -- full bootstrap instructions are included on numerous WikiLeaks pages:
The fact that a source is looking at instructions that are telling them how to submit material could be used as evidence against them if there is an SSL key break. To prevent this, we deploy the full bootstrap instructions and keys on millions of WikiLeaks pages across our full server network. When the "Submit" button is pressed, there is literally zero network traffic as a result, because all these details are downloaded everytime anyone looks at nearly any page on WikiLeaks. We cover the source bootstrap process with our millions of page views by readers.
To help with the processing and verification of any data that is submitted, the system includes an encrypted chat feature. Assange says that "the 2.0 public-facing submission system is an important new method in our arsenal."
-

Microsoft needs to cut the mobile cancer from Windows 10
Publié: mai 2, 2015, 11:19pm CEST par Mark Wilson

In the new world of Microsoft there has been a distinct shift in focus; Satya Nadella has said that the company's focus is a "mobile-first, cloud-first" strategy. This is all well and good -- and in many ways makes a great deal of sense -- but there is a very real danger that Microsoft is focusing too much on these new goals and to the detriment of other areas.
Windows 10 is an excellent case in point. This is an operating system that is destined for a wide range of devices, from phones and tablets to desktops, consoles and IoT devices yet to be devised. But in catering to the mobile side of its dream for the future, Microsoft has lost direction for desktop users and has made far too many compromises.
In particular, Microsoft use of screen space and screen orientations is questionable. Look at build 10074 of the Windows 10 Insider Preview (as it has now been renamed) and many of the concerns I've expressed about previous builds remain. One of my main gripes centers around the fact that, on a desktop, Windows will almost always be used on monitors with a landscape orientation. Of course there will be the odd exception to this but, while I don’t have any hard stats to fall back on, I think I'm safe in saying that most people opt for the widescreen, landscape look.
Is this something that Windows 10 caters to? Not a bit of it. Let's look at a few culprits.
 Want to connect to a wireless network? Hit the network icon in the notification area and you'll be presented with a vertical list of available connections (vertical is a word -- or a notion -- that crops up again and again in Windows 10). What’s the problem with a vertical list? Well, there's nothing inherently wrong, but the way things have been implemented here is terrible. In order to click the network icon, you've already had to move your mouse to the bottom of the screen -- to select an item from the list you then need to move right back up the screen. Not a major hardship, you might say, but it's remarkably inefficient.
Want to connect to a wireless network? Hit the network icon in the notification area and you'll be presented with a vertical list of available connections (vertical is a word -- or a notion -- that crops up again and again in Windows 10). What’s the problem with a vertical list? Well, there's nothing inherently wrong, but the way things have been implemented here is terrible. In order to click the network icon, you've already had to move your mouse to the bottom of the screen -- to select an item from the list you then need to move right back up the screen. Not a major hardship, you might say, but it's remarkably inefficient.The same problem arises with notifications. Move your mouse down to the bottom of the screen and click the notification button and you're presented with a popup that occupies the full height of your screen. Once again, notifications are listed vertically and you can see at a glance anything that needs your attention. But should you need to interact with any of the entries in the list, you'll need to travel back up to the top of the screen -- why not start to populate the list from the bottom up rather than the top down?
This is an excellent example of something that might make sense on a touchscreen device, but is less meaningful on systems operated with traditional peripherals.
While we're looking at the notifications, just check out the size of those buttons at the bottom! It's something I've complained about before, but what gives? I'm all for accessibility, but does Microsoft think we're all blind?
The size of buttons is, frankly just silly. On a small screen, or a touchscreen device, it might make sense to have large, finger-friendly buttons that are easy to hit, but on a regular desktop computer they just look daft and take up too much space. Where's the elegance? Where's the style? Why can buttons not be reduced to small, stylish affairs that don't occupy any more space than they need to? The icons in the notification area manage to convey all of the information they were designed to using very few pixels -- why are other screen elements treated differently?
 There is still far too much of Windows Phone's influence on Windows 10 in evidence for my liking. But it's not just the fact that there's more than a hint of Windows Phone, it's that there's still such a mishmash of styles. The modern icons that are littered here and there are stark, bold, monochromatic -- and, for the most part, huge. Traditional icons, on the other hands are small, colorful, detailed, works of art. Together they look awful. Pick one or the other! The two styles together is an abomination.
There is still far too much of Windows Phone's influence on Windows 10 in evidence for my liking. But it's not just the fact that there's more than a hint of Windows Phone, it's that there's still such a mishmash of styles. The modern icons that are littered here and there are stark, bold, monochromatic -- and, for the most part, huge. Traditional icons, on the other hands are small, colorful, detailed, works of art. Together they look awful. Pick one or the other! The two styles together is an abomination.It's not just about looks, the problems with Windows 10 are also about usability. I work with people in multiple time zones so I'll frequently glance at the extra clocks on Windows to check what time it is in other parts of the world. Pre-Windows 10 it was simple -- just add a couple of extra clocks and you're done. But using the same feature in the Insider Preview once again highlights the terrible influence Windows Phone has had.
Click the system clock and yet another vertical pane flips into view -- quite what Microsoft has against spreading sideways is anyone's guess. Ah... there's the Additional Clocks option. Click it and... what on earth is that?! That's a screenshot from Windows Phone, surely? That's not a feature of Windows 10 -- no one would design a window that looks so much like a mobile app.
As well as looking as though someone has slapped a Lumia handset to your screen, the Alarms & Clocks also demonstrates how space-hungry Microsoft's designs have become. Yep... I'm talking modern apps. These are not new to Windows 10, of course, but their design has certainly not improved. Look to Weather, Calendar, Project Spartan/Edge and the like. Everything is just gigantic! Why not shrink the fonts, put screen elements on a diet and you can fit more information into the same amount of space? Why should I have to scroll around or click through to different sections just because everything is so huge that there's no enough room to show what I want to see?
You see, the problems with Windows 10 are not just about aesthetics, they're about usability. More scrolling and clicking to get around, more mouse travel, these all add up to make simple, every day tasks take longer than they need to. My life has been made harder rather than easier. 'Move with the times, you dinosaur!' I hear you cry, but my complaints are quite valid. I'm having to do more work to achieve the same results. You call that progress?
Windows Phone is an abomination. It has been for... well, forever, really. Let's not ruin Windows 10 by letting this cancer creep onto the desktop as well.
-

A quantum leap into the future of computing
Publié: mai 2, 2015, 6:50pm CEST par Mark Wilson

Year after year computers increase in power. Processors become faster and gain more cores, memory also speeds up and becomes more plentiful. But we're reaching the limits of what can be achieved with current technology -- a real sea change is needed to take things to the next level. Many futurists have set their sights on the possibilities encompassed in quantum computing.
Eschewing the binary states of 1 and 0, bits are replaced with qubits which can hold three states -- on, off, or both at the same time. This introduces the opportunity for much greater computing power, but also introduces more opportunities for errors to creep in. Now IBM engineers have found a new way to detect and correct errors, hopefully creating the building block on which future quantum computers may be built.
In a paper published in Nature, scientists from IBM's Watson Research Center explain that quantum systems are especially susceptible to errors. In addition to the added state, there is the risk of interference of "noise" from outside sources. Until it becomes possible to devise ways to eliminate, correct or ignore the errors that inevitably crop up, the progress of quantum computers is going to be slow.
The authors say that they "present a quantum error detection protocol on a two-by-two planar lattice of superconducting qubits. The protocol detects an arbitrary quantum error on an encoded two-qubit entangled state via quantum non-demolition parity measurements on another pair of error syndrome qubits".
What does all of this mean? In essence, the team has managed to create a lattice between four qubits building a quantum circuit with built-in error-detection. What makes this a real step forward is that it is now possible to detect two types of error at the same time. Rather than looking out for bit-flip and phase-flip errors separately, they can now be picked up at the same time.
The team says that the method they have come up with is also scalable meaning that there is a greater chance for it to be used in real-world, rather than just theoretical, systems. There is still a good deal of work to do, but the outlook is optimistic:
Moving forward, on improving the measurement and gate fidelities in these systems, further expanding the lattice will lead to important studies of different error-correcting codes and the encoding of logical qubits, thereby allowing experimental investigation of fault-tolerant quantum computing. Our results bolster the prospect of employing superconducting qubit lattices for large-scale fault-tolerant quantum computing.
Photo credit: kentoh / Shutterstock
-

Microsoft buys Surface pen technology from N-Trig
Publié: mai 1, 2015, 4:42pm CEST par Mark Wilson
Microsoft has confirmed that it is buying "advanced digital pen technology" from stylus manufacturer N-Trig. The company is behind the Surface pen and the acquisition sees Microsoft bringing more of its hardware production in-house.
The acquisition follows on from rumors that surfaced earlier in the year, and Microsoft has already been working closely with the company for several years now.
Until the acquisition, Microsoft held a share in the Israeli firm N-Trig Ltd. The pen is already used by the Surface Pro 3, and will be available for the Surface 3 which starts shipping this week. Stevie Bathiche from the Surface team envisions great things in the future:
We can't wait to show you what we'll deliver for our Surface Fans in the future. Digital pens have a ways to go to be as good as pen and paper on some dimensions, and we'll get there. But more importantly, adding the ability to capture and share the work you do with a digital pen opens up possibilities that traditional pen and paper just can't match. Today’s investment is another step that will let us push that innovation forward.
-

Antivirus tool stripped of awards after cheating
Publié: mai 1, 2015, 11:59am CEST par Mark Wilson

Antivirus software produced by Qihoo 360 has been stripped of awards by three leading security testers after it was found to have cheated. AV‐Comparatives, AV‐TEST and Virus Bulletin discovered that Chinese company Qihoo 360 submitted one version of its software for testing, but then released a different one.
The publicly released version of the software had a key virus detection engine disabled, resulting in a lower level of protection for users. As a result of the findings, the security testing bodies are not only revoking any awards given to the software this year, but also calling for greater transparency so consumers know what they are getting.
Qihoo 360's software included virus detection of its own and from BitDefender, but only its own was enabled by default. Testers conceded that in-program settings made it possible to enable all available engines, but in real-world scenarios it found that the majority of users stuck with the default settings. Qihoo 360 responded to the allegation by counter-claiming that Baidu and Tencent engaged in similar practices.
In a statement AV‐Comparatives said:
Analysis of products submitted for testing by these companies turned up some unexpected flags within their products, marked with the names of several test labs and implying some difference in product behavior depending on the environment they were run in -- similar flags were also found in Qihoo products. However, no evidence could be found that this gave any significant advantage to either product, and in some cases it even seemed to put them at a disadvantage. Both firms were able to provide good reasons for including these flags in their products.
Qihoo 360 confirmed that a different version of its software was submitted for testing "including enabling detection of types of files such as keygens and cracked software, and directing cloud lookups to servers located closer to the test labs".
Maik Morgenstern, CEO of AV‐TEST, said:
Comparative testing and certification plays an important role in the anti‐malware industry, both for the users and the vendors. Users rely on independent results to make an educated decision regarding their protection software. If vendors start to manipulate the testing process, they are hurting everyone involved.
Photo credit: pockygallery / Shutterstock
-

Microsoft releases Band SDK to developers
Publié: mai 1, 2015, 7:55am CEST par Mark Wilson

In the world of wearables, Microsoft Band may not hold the same gravitas as Apple Watch or the various Android Wear devices, but the company is still trying to get more developers on board -- today launching the Microsoft Band SDK, following on from February's preview release.
With support for Windows Phone, Android, iOS, and full-blown Windows, Microsoft is clearly keen to appeal to as many developers as possible. This full SDK release offers access to all of Band's sensors -- as part of a push to get more third-party apps on the device.
The SDK gives developers the chance to create tiles that display notifications based on information pulled in from the sensors or from connected devices. The software and cloud services giant also appeals to developers in other ways, by, for example, suggesting that personalization options could be used to monetize an app. Introducing the SDK on the Microsoft Devices Blog, Zulfi Alam, general manager of the personal devices division, highlights some of the new features:
- Build apps that support Windows
- Create your own custom layouts for pages on third-party tiles using icons, text, buttons, and barcodes for payment options
- Receive events and button-click callbacks from the Microsoft Band to your phone app. If you press a button on a page inside your tile, your app would know which button was pressed
- Connect to the Band from background tasks
- Tap into calorie subscription from the Microsoft Band
The SDK can be downloaded from the Microsoft Health for Developers website, where sample code is also available.
-

Google's open source addressing system could replace longitude and latitude
Publié: mai 1, 2015, 12:00am CEST par Mark Wilson

Google often decides to go about things in its own way, and is frequently found approaching common problems from a unique angle. The latest candidate to receive the Google treatment is the humble address. Not web addresses or email addresses, but regular postal addresses. So what's the deal?
While street names and numbers usually get you to where you want to go, that's not always the case. You could opt to use longitude and latitude instead, but what sane person wants to do that? This is the very question Google asked before it came up with Open Location Code, an open source addressing system the company hopes developers will latch onto.
Street names and numbers are not always useful, and the same is true of postcodes and zip codes; while common, they are not used in every part of the world, and even when they are, they may not provide the required level of accuracy. Google's Open Location Code is essentially a shortened version of longitude and latitude, and can even be used in conjunction with a partial address to make them even shorter.
For example, 849VCWC8+R9 is the address of Google HQ, and Google points out that this is a similar length to a phone number, and could be easily communicated over the phone or via email. But it can be shortened to CWC8+R9, Mountain View for something that's easier to say and read. So what are the possible applications? It's ideal for giving the location of a remote place that has no landmarks, places at sea, or locations in countries that don’t use a familiar addressing system.
Developers can take a look at the Open Location Code project on GitHub.
Photo credit: Ganibal / Shutterstock
-

Outlook.com API brings add-ons from PayPal, Boomerang, Uber and more
Publié: avril 30, 2015, 11:51am CEST par Mark Wilson

Add-ons are a common feature of traditional, offline applications, but they're becoming increasingly popular in online services. Microsoft is the latest to get in on the action, announcing a batch of new add-ons for Outlook.com, including one from PayPal that makes it easy to make payments via email.
The add-ons were made possible when Microsoft launched the Outlook APIs at Build. They can be used by developers to create plugins with HTML, CSS3, and JavaScript. Microsoft is pushing the "write once, run anywhere" nature of the API that means the same plugin can run in Outlook.com, Outlook Web App and the desktop version of Outlook.
Also showcased was a plugin from Boomerang which can be used to schedule the sending of emails, use your inbox as a reminder tool, and share a calendar with others. An Uber add-on is a rather simpler affair, giving users the ability to set up an Uber ride reminder for calendar events. Microsoft says that the API can be used to create "contextual experiences for Outlook.com and Office 365 users that simplify everyday tasks, helping them get more done without the hassle of switching between multiple applications".
In order to get access to the Outlook API, would-be coders need to sign up for a developer account. With around 400 million active users, Outlook.com is something of an untapped market when it comes to monetization by third parties.
-

Microsoft HoloLens can run Windows apps in 3D
Publié: avril 29, 2015, 10:17pm CEST par Mark Wilson

When Microsoft unveiled HoloLens a few months ago, it came as something of a surprise. It's essentially Google Glass meets virtual reality on steroids, throwing the users into a 3D world filled with holograms, all powered by Windows 10. Today at build 2015, Microsoft showed off some of HoleLens' capabilities.
Something that had been talked about when HoloLens first came to light was the possibility of running regular Windows 10 apps in HoloLens. In a demonstration, Microsoft showed how Windows 10 Universal apps can be used in 3D space, 'projected' onto floors, walls and other surfaces.
It's not yet clear how far we are from seeing a commercial release of HoloLens, but the platform is already creating some interest. A video can be projected onto a wall, a spreadsheet onto a table -- in short, any available surface can be transformed into a workspace. Of course there is also great potential for the platform to be used for gaming, but it is going to be down to developers to determine the future direction of HoloLens.
Microsoft sees the platform being used to walk around three-dimensional designs, and also envisioned uses in the world of medicine. In a video, the company showed how a holographic robot could interact with a user as well as the environment in which it was placed.
Check out the video below which shows how HoloLens can help designers to show off their projects in full 3D.
-

Windows Store to gain subscriptions and phone payments
Publié: avril 29, 2015, 9:27pm CEST par Mark Wilson
Today at Build 2015, Microsoft revealed some exciting changes to the Windows Store -- not least that it will soon be much, much easier for iOS and Android app developers to convert their creations into Windows 10 apps. But this is far from the end of the story, and there are also important payment and subscription options on the horizon.
Microsoft is introducing support for in-app purchasing of subscriptions, providing developers with new ways to monetize their apps. To help make it easier for devs to get money from customers, the ability to pay for purchases with a mobile phone is also to be added.
This payment option is something that will prove popular with users and developers alike. For users, the option to pay for apps and services through a mobile phone bill is something that will be welcomed by those without a credit card, and developers are certain to be pleased with any system that makes it easier for people to pay for their apps. In all, there are 90 carriers on board and Microsoft predicts that this method of payment will prove popular in emerging markets.
System administrators will gain the option of pushing app recommendations to users, as well as distributing business apps to the workforce. Other changes include an updated Windows 10 Microsoft Advertising SDK which brings support for video ads and install tracking, and further monetization is made possible through a new affiliate scheme. Microsoft used the keynote to appeal to developers by highlighting the ease with which Windows 10 apps can be pushed to the full Windows 10 device family.
-

Yahoo might use your ear to unlock your phone
Publié: avril 29, 2015, 2:38am CEST par Mark Wilson

Smartphone security takes a number of forms; you might access your phone with a PIN, your fingerprint, or via facial recognition. But if Yahoo's plans gather momentum, you could be using your ear to unlock your phone in the not-too-distant future. The idea builds on the idea of the unique fingerprint we all have, taking advantage of the capacitive touchscreens that are now a standard feature of phones.
There's no need for special sensors as the way different parts of your ears touch the screen when held in the 'talk' position can be used to uniquely identify you. It's all part of Yahoo's Bodyprint program, which is also looking at how the way you hold your phone could be used as an unlock tool.
It's a technology that could be easily implemented in cheaper handsets, bringing a new level of personal security to smartphones at the lower echelons. The technology can be used to not only permit or deny access to an individual smartphone, but could also be expanded to multi-users systems whereby different people are permitted access to different files.
Yahoo conducted small-scale tests that achieved a 99.52 percent level of accuracy:
We present Bodyprint, a biometric authentication system that detects users' biometric features using the same type of capacitive sensing, but uses the touchscreen as the image sensor instead. While the input resolution of a touchscreen is ~6 dpi, the surface area is larger, allowing the touch sensor to scan users’ body parts, such as ears, fingers, fists, and palms by pressing them against the display. Bodyprint compensates for the low input resolution with an increased false rejection rate, but does not compromise on authentication precision.
Check out the video below to see how Yahoo views the future of smartphone security:
-

ITC rules Microsoft handsets violate patents
Publié: avril 28, 2015, 5:26pm CEST par Mark Wilson

Microsoft could face a ban on importing handsets into the US after a ruling by the International Trade Commission. The ITC found that Microsoft had used technology for which InterDigital owns the patents without obtaining the relevant permission.
Microsoft plans to challenge the ruling, saying "we have a successful track record challenging patent assertion entities that misuse industry standards". It is not the first handset manufacturer to have been hit with legal action from InterDigital, and it could severely hamper future handset sales.
Many of Microsoft's Lumia handsets are made outside of the US, and an import ban would require either a relocation of manufacturer facilities, or a change in the way handsets work. InterDigital owns two patents that govern how a handset powers up and connects to a 3G network without interruption.
The ruling by Judge Theodore Essex is subject to review, and Microsoft's sales and imports remain unaffected in the meantime. The review will be carried out by the ITC, and it is expected to come to a conclusion by the end of August. InterDigital is understandably pleased with the current ruling. Lawrence F. Shay, Executive Vice President, Intellectual Property and Chief Intellectual Property Counsel said:
We're obviously very satisfied with today's ruling, which underscores the strength of InterDigital's portfolio and our long track record of developing and licensing some of the core wireless technologies that have helped drive the growth of our industry. We hope it will form the basis for the final determination by the ITC. We also look forward to continued discussion with Nokia and Microsoft Mobile to achieve a license on fair and reasonable terms.
The case dates all the way back to 2007, and has already been ruled in Microsoft's favor once in 2013. InterDigital appealed, bringing us to the current state of play.
Photo Credit: Asif Islam/Shutterstock
-

Microsoft offers free Skype calls in Nepal, Facebook donates $2 million
Publié: avril 27, 2015, 10:17pm CEST par Mark Wilson

The terrible repercussions of the earthquake in Nepal and the aftershocks continue to be felt. With thousands of people yet to be accounted for, Google and Facebook have already launched services to help connect with people in the affected areas.
Now Microsoft has entered the fray, offering free Skype calls to both landlines and mobiles in Nepal. Starting immediately, Skype users can make calls from within Nepal, or place them to the country regardless of whether they have any credit.
Microsoft took action after the extent of the disruption to the country's communication network became clear. With so many misplaced individuals, plenty of people are trying to let friends and family know that they are okay, as well as those concerned that people they know are safe and well. In a post on the Skype Blog, Microsoft says:
In light of the devastating events that have taken place in Nepal -- and the subsequent impact to the local communications infrastructure -- we are making all Skype calls to landlines and mobiles in and out of Nepal free of charge, with immediate effect.
Since no one knows the full extent of the devastation, we want to help provide people with alternative methods of communication to reach friends and family in the region during this difficult time.
Facebook may have already launched its Safety Check feature for Nepal, and Mark Zuckerberg today announced that Facebook is providing a way for users to make donations to the International Medical Corps -- you should see a donate option at the top of your newsfeed. As well as making it easier for users of the social network to offer financial support, Facebook also offered up some cash of its own:
Facebook will match every dollar donated up to $2 million. Matching funds will be distributed to local relief and rescue organizations working to provide immediate and ongoing relief.
If you want to make a donation, pay a visit to Facebook's Nepal Earthquake Support page.
-

Google wants to buy your patents from you
Publié: avril 27, 2015, 7:13pm CEST par Mark Wilson

Got a spare patent or two lying around, gathering dust and cluttering the place up? Google might be interested in taking those patents off your hands in return for cold, hard cash. Today the search giant announces details of the Patent Purchase Promotion which will run for two weeks in May.
The move is an attempt to "remove friction from the patent market", with the added benefit for Google that it will help the company to expand its patent portfolio. The online patent-selling portal will run from May 8 to May 22 and has been designed to be accessible to smaller players.
As part of the program, patent holders have two weeks in which to submit details of their patents and how much they'd like for them. Google will then spend a month sifting through the submissions, separating the wheat from the chaff and deciding which it wants to splash the cash on. By August it is hoped that the round of purchasing will be done and dusted, and the money and patents will have swapped hands.
In recent years, patents have become huge business for technology companies, and the prevalence of patent trolls means that there is big money to be made. Google has given no indication of the sort of budget it has set aside for this program, nor expressed interest in any particular type of patent. Google says:
By simplifying the process and having a concentrated submission window, we can focus our efforts into quickly evaluating patent assets and getting responses back to potential sellers quickly. Hopefully this will translate into better experiences for sellers, and remove the complications of working with entities such as patent trolls.
Of course, patent buying and selling is still something that is fraught with potential legal issues, and Google advises those who are interested to speak with an attorney.
Photo credit: Olivier Le Moal / Shutterstock
-

The Sun newspaper launches anonymous Tor-based WikiLeaks-style SecureDrop
Publié: avril 27, 2015, 5:28pm CEST par Mark Wilson

The likes of Julian Assange's WikiLeaks have set the standard for blowing the lid on huge stories based on tips from anonymous sources. Whistle-blowers such as Edward Snowden have brought to public attention stories which would otherwise have been kept hidden from the public, and it has been with the help of newspapers such as the Guardian that this information has been disseminated around the world.
Other newspapers are keen to ride on the coattails of those blazing a trail in the world of investigative journalism, and the latest to join the party is The Sun. Today, Murdoch-owned News Corp's newspaper and website launches SecureDrop -- a way for whistle-blowers to anonymously leave tip-offs that can be further investigated.
The cloud service provides a means of getting in touch with journalists at The Sun without giving up anonymity -- something which is particularly important when making revelations about companies and governments. The site provides a basic guide to getting started with the SecureDrop service, starting off with pointing would-be users in the direction of the Tor Browser Bundle. Once downloaded and installed, take a quick visit to nodd5fyasyj4jqgp.onion.
Anyone with information or documents that need to be submitted is invited to do just that. Although the service is anonymous, users are assigned a 7 to 10 word codename -- and the advice is to memorize rather than write it down. Files of up to 500MB can be uploaded to the cloud, and The Sun suggests that users might like to use GPG to add an extra layer of protection. With the codename, it is possible to log back into the same account and check for replies from a journalist.
SecureDrop is being launched at the same time as The Sun's Whistleblowers' Charter, which aims to "uncover the secret stories being kept under wraps by the authorities that YOU have a right to know".
WikiLeaks recognized the launch, suggesting that other sites under the News Corp banner might soon follow suit:
Murdoch's The Sun adopts WikiLeaks methods. Not as good, but close. Likely most News Corp pubs will move to adopt. [t.co]
— WikiLeaks (@wikileaks) April 27, 2015
Talking about anonymous tips, The Sun assures potential users that "our reporter only reads them on a ring-fenced laptop not linked to the Internet". There's also the assertion that "information shared through SecureDrop will go through the same rigorous journalistic process as other tip-offs to ensure it is correct before publication," but it remains to be seen if the service manages to gain the same level of trust as WikiLeaks or the network of sources journalists use.
While it is possible that SecureDrop has been launched with the best of intentions, it could also be seen as a retaliation against legal action taken against The Sun and its journalists after law enforcement agencies tapped reporters' phone without permission.
Photo credit: Imilian / Shutterstock
-

Google and Facebook offer support after Nepal earthquake
Publié: avril 25, 2015, 8:41pm CEST par Mark Wilson

When disaster strikes, technology can often be put to good use. Following the devastating earthquake that struck Nepal this week, Google and Facebook are among the companies helping those in the area, as well as people looking for friends and relatives.
Google's People Finder does very much what it says on the tin. It's a very simple website that enables people to publish requests for information about loved ones, as well as giving those with information somewhere to share it. Facebook's Nepal Earthquake Safety Check provides a similar feature.
Google People Finder can be accessed through mobile devices or computers, and also includes an SMS function to improved accessibility. If you're concerned about someone you know in the area you can search through the People Finder database for information, but if you have information about someone you can add details yourself. Google points out that it "does not review or verify the accuracy of this data."
At the same time, Facebook has launched its Safety Check feature for the earthquake. Like Google's feature, it works two ways. Visit the website and Facebook will let you know if any of the people you are connected to are in the area. If you have had contact from them, you can indicate that they are safe to put others' minds at rest.
Writing on Facebook, Mark Zuckerberg said:
This morning we activated Safety Check for people affected by the earthquake in Nepal. It's a simple way to let family and friends know you're okay.
If you're in one of the areas affected by the earthquake, you'll get a notification asking if you're safe, and whether you want to check on any of your friends.
When disasters happen, people need to know their loved ones are safe. It's moments like this that being able to connect really matters.
My thoughts are with everyone who's been caught up in this tragedy.
The Safety Check tool can also be used by people in the area to broadcast the fact that they are OK.
Photo credit: Vectors.1 / Shutterstock
-

Aggressive Android app ads annoy and interfere
Publié: avril 24, 2015, 10:27pm CEST par Mark Wilson

Avoiding online ads can be fairly easily achieved by installing a tool such as AdBlockPlus, but it's a different matter when it comes to ads in mobile apps. Security researchers at Doctor Web have discovered that a number of Android apps found in Google Play are plagued with aggressive ad modules.
Advertising is considered aggressive if it appears on top of other windows, interferes with the use of applications, and makes normal use of a smartphone or tablet difficult.
This particular breed of advertising module has been used by criminals to monetize free apps, and has been added to the Adware.MobiDash.2.origin category in the Dr. Web virus database. The company warns that malicious activity is not unknown:
Similar to its predecessor, Adware.MobiDash.2.origin starts to perform its malicious activity not right after the installation but after a period of time. This time period is long enough for the user to forget about the potential source of annoying notifications and advertisements, so the malware stays on the device intact.
Dr Web estimates that apps that make use of Adware.MobiDash.2.origin advertising have been installed more than 2.5 million times.
Photo credit: LoveFreedom / Shutterstock
-

Comcast calls time on merger plans
Publié: avril 24, 2015, 7:24pm CEST par Mark Wilson

The planned merger between Time Warner and Comcast has been quashed. Back in February of last year the "most hated company in America" announced that it was planning to join forces with Time Warner to create a technology giant.
Today the company did an about-face, announcing that the merger is now off. The deal would have seen Comcast Corporation acquire Time Warner Cable for $45.2 billion leading to the creation of the largest cable company in the US.
The planned merger had gained the attention of industry regulators, and Comcast failed to present a convincing case that the deal was a good move for consumers. The FCC's Tom Wheeler said that the merger would have stifled innovation and competition. Comcast had originally said that the merger would create "multiple pro-consumer and pro-competitive benefits, including for small and medium-sized businesses".
That excitement was today wiped out with the simple announcement that the transaction agreement had "been terminated".
Comcast Chairman and CEO Brian L. Roberts said:
Today, we move on. Of course, we would have liked to bring our great products to new cities, but we structured this deal so that if the government didn’t agree, we could walk away.
Comcast NBCUniversal is a unique company with strong momentum. Throughout this entire process, our employees have kept their eye on the ball and we have had fantastic operating results. I want to thank them and the employees of Time Warner Cable for their tireless efforts.
I couldn't be more proud of this company and I am truly excited for what’s next.
The collapse of the deal will come as great news for the likes of Netflix who now have a slightly easier battle for customers on their hands.
Photo credit: 360b / Shutterstock
-

Send directions from your desktop to Google Maps on your Android phone
Publié: avril 24, 2015, 12:44am CEST par Mark Wilson

Dedicated satnav units are less popular than they used to be, and this can be attributed in part to the rise of direction-providing smartphone apps like Google Maps and Waze. If you are invested in Google Maps, you may well check out directions on your desktop computer and then have to get them set up on your phone as well.
Today that changes. Google has unveiled a feature that makes it possible to push directions from your desktop computer or laptop to your phone. This eliminates a step and makes the whole process of getting from A to B much easier.
It may seem like a feature that Google Maps should have had for some time now -- after all, Google allows you to sync just about all of your other data between computers and devices. It may have been a long time coming, but the day has finally come and means there's no need to use third party solutions. You can benefit from the larger screen of your computer without the need to pull out your phone.
The feature was launched by Google with little fanfare through a brief post on Google+:
Every minute after you clock out of the office counts. Next time you run errands after work, push directions from your computer to your Android phone and have them ready in hand as you head out the door.
To get started head to Google.com and perform a search for 'send directions'. As long as you are signed into your account, Google knows the location of your phone and you can type in your desired destination. Once you've obtained directions, just hit 'Send directions to my phone' and you're ready to hit the road.
If you find that the feature's not yet available for you, just be patient... it's rolling out right now!
Photo credit: Brian A Jackson / Shutterstock
-

Groupon refuses to pay security expert who found serious XSS site bugs
Publié: avril 23, 2015, 1:24am CEST par Mark Wilson

Bounty programs benefit everyone. Companies like Microsoft get help from security experts, customers gain improved security, and those who discover and report vulnerabilities reap the rewards financially. Or at least that's how things are supposed to work.
Having reported a series of security problems to discount and deal site Groupon, security researcher Brute Logic from XSSposed.org was expecting a pay-out -- but the site refuses to stump up the cash. In all, Brute Logic reported more than 30 security issues with Groupon's site, but the company cites its Responsible Disclosure policy as the reason for not handing over the cash.
The story starts a few days ago when Brute Logic discovered 32 XSS (cross-site scripting) issues affecting Groupon. He says they were particularly serious as they existed at the root of the site and could be easily exploited with a malicious URL. Brute Logic says that the security issue is all the more serious because Groupon stores credit card details, and it would be incredibly easy to craft a spoof Groupon-related URL to trick victims into visiting a fake site.
On April 17 he contacted Groupon to report the problems and heard back almost immediately with a note saying that the company would investigate and report back shortly. The security team then got back saying that it has managed to isolate the issue and would be back in touch once a patch has been produced.
Brute Logic enquired about the level of financial reward that might be offered, and Groupon responded by saying that the bounty was calculated on a case by case basis, promising to "circle back" with details of what could be offered in this instance.
As a contributor to XSSposed.org Brute Logic spoke with people at the site and a reference to one of the security issues ended up being published. This only appeared online for a few moments, and was removed after it was realized it has been published in error. But Groupon is using this as a reason for refusing to pay out.
Groupon's Bug Bounty Program terms say:
We value your input. When properly notified of a security issue we are committed to working with you to understand and remediate verified problems. If you believe you find an issue on our site, we encourage you to report it to us in a private and responsible way. In order to encourage this, we have established a reward program which will pay a bounty for verifiable security issues reported to us through the proper channel.
Brute Logic argues that that an additional 30 problems still existed and very scant details of the security flaw were published for only a very short time. In a further email, Groupon said:
Unfortunately we won't be able to offer you a bounty for this submission. In the future we ask that you respect our responsible disclosure policy and not publicly disclose the vulnerability without properly notification. We noticed that you submitted the vulnerability to xssposed.org.
Understandably Brute Logic is not happy, as his tweets make clear:
32 @Groupon sites affected. They patched them. They refused to pay me. #Bullshit #PleaseRT pic.twitter.com/4j3w2FGFt4
— Brute Logic (@brutelogic) April 22, 2015
He also points out that another company, Sucuri Security, was happy to pay out even after a tweet revealed some details of a security flaw in their product.
Does Groupon's decision seem fair to you, or does it smack of wriggling out of making a payment on a technicality?
Photo credit: Ken Wolter / Shutterstock
-

Bag yourself $15,000 as an Azure or Project Spartan bounty hunter
Publié: avril 23, 2015, 12:35am CEST par Mark Wilson

It's not unknown for technology companies to run bounty programs that reward bug hunters for unearthing problems with software. Discover a security vulnerability and you could be in line for a nice cash bonus. Microsoft is one firm that runs such a program, and today the Microsoft Bounty Program is being expanded -- with a particular focus on Azure and Project Spartan.
Microsoft has already been asking for feedback about Windows 10 Technical Preview, but this is the first time a financial reward has been offered for pointing out security issues with any of its components. The maximum pay-out has been increased to $15,000 USD, so there's more incentive than ever to seek out problems and report them to Microsoft.
As well as Project Spartan and Azure, the bounty program is also opening up to Sway.com. While the online idea-sharing tool and the Azure cloud platform are sure to gain a good deal of attention, the fact that the Internet Explorer replacement is included is especially interesting. This is more than just looking for feedback in the usual sense of the Technical Preview for Windows 10, and it makes it clear just how important Microsoft views Project Spartan.
Announcing the bounty program expansion Microsoft refers to its newest browser as "the onramp to the internet for millions of users" and says that, this time around, security is a top priority. The Spartan bounty program is only running from April 22 to June 22, so you have two months to track down issues. The more severe the bug, the higher the pay-out, and Microsoft also says that the bounties "are tiered by the criticality of the issue reported, as well as the quality of the documentation and how reproducible the issue is".
Photo credit: NLshop / Shutterstock
-

Facebook Hello tells you who's calling before you pick up
Publié: avril 22, 2015, 7:39pm CEST par Mark Wilson
It's easily forgotten with the number of apps available, but mobile phones are primarily designed for making calls on the move -- whodda thunk it? When you receive a call you'll usually see the number of the caller, but this may not be helpful in identifying them before you decide whether to pick up. Facebook's answer to this problem is Hello.
This new app comes from the Facebook Messenger team and aims to tell you more about the person getting in touch with you even if you don’t have their number saved in your address book. Currently available for Android, the dialer app also allows for the blocking of calls from individuals.
Facebook Hello brings free calling and messaging through Messenger, but it is the call management features that Facebook is really pushing. By pulling in information from Facebook users, the app is able to display the caller's number and there's even a built-in spam-filtering feature. If a particular number has been blocked by a lot of other users, it will be automatically blocked for you as well.
The app integrates with Facebook, so you can use it to search for people and businesses. To allay privacy fears, Facebook points out that Hello only has access to information which has been made publicly available on the social network -- perhaps serving as a timely reminder to check your privacy settings.
The video below shows Hello in action -- you can grab a copy of the app from Google Play.
-

Facebook revamps your newsfeed yet again
Publié: avril 22, 2015, 1:53pm CEST par Mark Wilson

Facebook is, once again, making changes to the algorithm that controls what appears in newsfeeds. If you had ever been under the impression that you were going to see a chronological list of status updates from your friends in your newsfeed, numerous changes over the years will have put paid to that notion.
It has been a source of many a social networking grumble, and now Facebook is taking steps to address the issue. Depending on how you use Facebook, you may be connected to not only real-world friends, but also companies, celebrities and even TV shows. Your newsfeed has likely turned into less of a collection of bon mots from your mates and more of a stream of updates from entities you're only vaguely interested in. Now your friends will be given greater priority.
The latest change is Facebook's recognition of the fact that it needs to alter the balance of what appears in newsfeed. There are three key changes in total, starting off with a relaxation of the rule that prevented the appearance of 'too many' posts from the same source. Now, if you are a little light on content, as you continue to scroll through your newsfeed you will start to see multiple posts from the same friends.
Facebook is also adjusting the priority with which posts from your favorite contacts are handled. From now on, "content posted directly by the friends you care about" (although Facebook gives no indication of how this is determined) will appear higher up in your feed. The third and final change demotes notifications about likes and comments your friends have made -- these will still appear in your newsfeed, but lower down.
How do you feel about this latest raft of changes? Is Facebook heading in the right direction or moving further away from what it should be doing?
Photo credit: JuliusKielaitis / Shutterstock
-

HBO cuts off its nose to spite its face
Publié: avril 22, 2015, 4:33am CEST par Mark Wilson

Using proxies to access blocked or region-locked content is nothing new. It's a technique that's often associated with piracy, such as using tools to bypass restrictions placed on torrent sites, but it's far from being the only use. Step outside of the US and it's surprising how many well-known services are no longer available.
HBO Now is an example of a service that is not supposed to be available outside of the US, but with the right tool it is. And this is not a case of people freeloading -- people are willing to pay to view the likes of Game of Thrones. Despite coughing up the cash, non-US HBO Now users are being threatened with having their viewing curtailed.
Viewers outside of the US who have turned to proxies or VPNs to access HBO Now have been hit with an email warning them that they are accessing the service "from outside the authorized service area." There then follows the advice that with a response to the email, the recipient risks getting cut off.
This is an interesting move by HBO. Normally it is piracy that is a problem for broadcasters, people downloading shows without parting with a cent. But here we see people willing to pay a monthly subscription to view their favorite shows. These are people who would rather hand over their cash than hit the Pirate Bay -- but HBO is ready to turn them away.
Of course there is the argument that it is only licensed to provide access to content in certain parts of the world, but this just highlights the absurdity of applying terrestrial licensing to the internet. It just doesn't work. In order to comply with the terms of licensing, HBO is turning away customers simply because of where they live. Who is the winner here? Viewers miss out, HBO misses out on revenue, as do the program-makers. Eager fans are driven to illegal downloads, completely negating any benefit of imposing regional restrictions. HBO has enough clout to agree to wider licensing terms -- it's what viewers want, after all.
But will they listen? Will they hell.
Photo credit: Antonio Gravante / Shutterstock
-

Windows 10 fanboys are Microsoft's developmental laxatives
Publié: avril 22, 2015, 2:25am CEST par Mark Wilson

What do we want? Windows 10! When do we want it? Probably sooner than the development cycle permits! With Windows 10, Microsoft has painted itself to be a benevolent god, ready to bestow gifts from the future on those willing to put up with the 'quirks' of the preview testing process. But the fact that something is free, does not mean that people are not going to complain -- far from it, in fact.
Aside from complaints about the features of Windows 10 itself, one thing that Windows Insiders (an 'exclusive' club has to have a name, after all) cite as a major bugbear is the speed at which new builds are pumped out. Despite the existence of a fast ring, builds are still trickling out painfully slowly. The new 'all-ears' Microsoft listens to its customers. As such the latest email from Gabe Aul promising -- yet again -- that "we're going to send out builds more frequently" comes as little surprise, but is pressure from the Windows 10 fanboys causing Microsoft to rush, and what effect will this have on the final product?
With Windows 10, Microsoft is playing a very dangerous game. This is the first version of Windows for which the company has exposed the development process to scrutiny. It has been presented in the framework of giving users the opportunity to provide feedback and determine the future direction of Windows, but it's fair to say that it has probably exposed Microsoft to greater attention and demands than it was probably expecting. In the face of criticism about the way certain features look or work, Microsoft has responded -- in some cases -- but making populist changes.
Now, following demands from the baying mob, the company has conceded that it needs to produce new builds faster. A new email sent out by Gabe Aul says: "Based on your feedback, we're going to send out builds more frequently to Windows Insiders that have selected 'Fast' preview builds".
Who is in charge here? If customers are driving the pace of development, it's a case of the lunatics running the asylum. Rather than sticking to its guns and keeping development going at a steady pace -- a pace that is needed to ensure quality -- it appears that Microsoft is bowing to pressure and putting the pedal to the metal. Is this good? No -- it's worrying. There's a real danger that Microsoft is really going to rush now and end up pushing out a big steaming pile of shit. The ever-demanding preview testers are effectively developmental laxatives... and we all know what laxative produce.
Of course we know that development doesn't stop when a public preview is pushed out of the door; Microsoft is not sitting back, twiddling its thumbs until a certain amount of feedback is received, but there is a very real danger that the company feels pressure to get the next build into the hands of testers. The latest catalyst to the peristaltic bowel movement that will ultimately plop out a 'finished' version of Windows 10 is the 'slip up' by AMD when the company's CEO revealed Windows 10 will "launch at the end of July."
Way to pile on the pressure!
As my colleague Wayne Williams noted the chances of hitting this deadline -- a mere three months away -- seem painfully slim (well...slenderness is one side-effect of laxatives, after all).
It's very hard to see just how anything approaching a decent version of Windows can be cobbled together in the time that is left. If AMD's announcement is correct, the clock really is ticking now. Of course it is fair to say that even those of us who are part of the Fast Ring, and therefore receiving public builds the fastest, are not exactly on the cutting edge of what's happening with Windows 10. There are several internal rings of development, many of which result in builds that never see the light of day.
Few people who have tried Windows 10 would say that it is anywhere near ready to be unleashed on the general public. There's far more than a bit of spit and polish needed to get Windows 10 up to scratch. There's potential, but there's still a very, very long way to go. It's concerning that Microsoft feels the need to keep its Insiders happy and accelerate the development cycle -- the company has made it very clear that it is most comfortable working at a glacial pace. The faster builds will almost certainly be welcomed -- but don’t forget that we have been promised this before -- but there is a real danger that it will mean compromising quality.
To paraphrase an old maxim: develop in haste, repent at leisure.
Photo credit: Rasulov / Shutterstock
-

AdBlock Plus proves it's not illegal
Publié: avril 22, 2015, 1:50am CEST par Mark Wilson

Online ads are a serious pain in the ass, and lots of people turn to the likes of AdBlock Plus to clean up their browsing experience. Ad blockers are not universally liked, however; many website owners despise the tools. So hated is AdBlock Plus, in fact, that a case was brought against the tool to try to prove that it is illegal.
Now a court in Hamburg has come to a decision, and ruled that AdBlock Plus -- in case there was ever any doubt -- is entirely legal. The plaintiffs in the case alleged that AdBlock Plus should not be permitted to block ads on the websites it owns. The judge presiding over the case disagreed.
The court ruled that AdBlock Plus is well within its rights to provide the option to hide advertisements on websites. The company sees this as setting a precedent and is taking this moment in the spotlight to reach out to content creators to work together to "develop new forms of nonintrusive ads that are actually useful and welcomed by users."
Writing about the case on the company blog, AdBlock Plus' Ben Williams wrote:
It may surprise readers of this blog to know that some advertiser groups believe blocking ads is illegal. They are upset that adblockers impede their multi-billion dollar business (or in this case, euros) of shoveling ads at you whether or not you like it or asked for it. In fact, a group of publishers in Hamburg, Germany was so upset that they actually took Adblock Plus to court.
Today, after a four-month trial, reasonable heads prevailed as the regional court in Hamburg ruled in our favor by declaring that ad blocking is, in fact, perfectly legal. I know, it’s restating the obvious. But it cost us lots of blood, sweat and tears nonetheless.
Photo credit: Ivelin Radkov / Shutterstock
-

Download your Google search history for some amusing reading
Publié: avril 21, 2015, 12:17am CEST par Mark Wilson

Google collects a lot of data about its users -- a lot of data. Much of this data is used for advertising purposes but there's also a lot of data that you might want to make use of yourself... even if it's only for entertainment.
All those searches you performed when you were drunk? These are now available to download! Brace yourself for what could turn into hours of amusement -- or possibly sphincter tightening embarrassment -- as a new addition to Google History means you can grab a copy of this history for posterity, and gain some interesting stats into the bargain.
Pay a visit to Google History and you can browse through your entire search history online; it's kind of like an online version of your browser history. This itself is nothing new, but if you click the gear button to the upper right of the page, a new Download option will be visible. An interesting warning, headed "Please read this carefully, it's not the usual yada yada" will appear suggesting that you don't download this data on a public computer.
Hit create archive and... sit back and wait. You'll receive an email in due course letting you know when your archive is ready to download. It might take a little while to appear, but as you have a bit of time to kill, why not spend it delving into your history? I discovered that I've performed 33,246 searches whilst signed into my Google account and my top search term -- rather inexplicably as I'm not a Transformers fan -- was "tfw2005".
When you've spent a few minutes having a bit of a giggle about your search history, your archive should be ready. It's provided in JSON format and you can use the tool of your choice to perform analysis on the data.
Photo credit: ChameleonsEye / Shutterstock
-

Now you can Direct Message (almost) anyone on Twitter
Publié: avril 20, 2015, 10:43pm CEST par Mark Wilson

Twitter today announces a number of key changes to the way its messaging system works. Until now it has only been possible to exchange a private Direct Message with another user if you both follow each other. This all changes as Twitter introduces the ability to DM anyone as long as they have the feature enabled on their account.
Just last week, Twitter announced that it will use a Dublin-based branch to handle all non-US account data but today's news is all about communication. If you're happy to receive DMs from anyone on Twitter, you can flip the switch on a setting that makes this possible.
Last year Twitter introduced a feature that made it possible to share tweets via Direct Message, but DMs could still only be sent between users who followed each other. If you're happy to receive DMs from all and sundry, pay a visit to the Security and Privacy settings page and enable the 'Receive Direct Messages from anyone' setting. Twitter points out that messaging rules have been changed so that should you receive a DM from someone who does not follow you, you will be able to reply anyway.
But how can you tell if you are able to send DMs to a particular user without just trying and hoping for the best? An update to the iOS and Android apps means that a messaging icon appears on the profile pages of users who have enabled the feature. If you don’t see the changes straight away, just hang on in there as they are rolling out around the global and may take a while to hit your account.
Photo credit: tanuha2001 / Shutterstock
-

Android Wear update brings always-on apps, Wi-Fi support and improved navigation
Publié: avril 20, 2015, 5:14pm CEST par Mark Wilson
Much as Apple would like you to think otherwise, Apple Watch is yet to blow other wearables out of the water. Smartwatches are still something of an emerging technology, but Google has managed to carve out yet another niche for itself with Android Wear. Today the company unleashes an update that aims to make Android-powered watches easier to use.
The first major addition is support for always-on apps. Most Android Wear watches included support for displaying the time round the clock (sorry!) but this feature has now been expanded to other apps. If you're using your watch to get directions or follow a shopping list, you can opt to keep the relevant app active at all times. The update has more to offer too.
Battery-saving is taken care of by only using full-color display when your watch is in a position you might look at it in. The latest update introduces a number of navigation tweaks that Google hopes will make life a little easier. Hands-free navigation makes it possible to scroll through notifications and other data with a deft flick of the wrist.
For those times when you're unable to speak to dictate a response to a message, there's now the option of drawing emojis on the screen. Google has also brought your apps closer to you -- a quick tap of your watch face is all it takes to access what you need. Another change to Android Wear is support for watches with integrated Wi-Fi meaning that -- as long as your phone has a data connection, even if you don’t have it with you -- you'll be able to receive all of your notifications whenever you have a wireless connection.
The update is rolling out now over the course of the next few weeks, and first in line to receive it is the LG Watch Urbane.
-

D-Link says sorry for shoddy security and sloppy patching of its routers
Publié: avril 20, 2015, 1:04pm CEST par Mark Wilson

D-Link has issued an apology to its customers for an on-going security issue with many of its routers. A problem with the Home Network Administration Protocol (HNAP) means that it is possible to bypass authorization and run commands with escalated privileges.
The list of routers affected by the issue is fairly lengthy, and D-Link has already issued one patch. But rather than fixing the problem, last week's update left routers wide open to exactly the same problem. As it stands at the moment, a firmware patch is still being produced for a total of 17 routers. In the meantime, all D-Link has to offer is an apology.
The HNAP issue affects DIR-890L (A1), DIR-880L (A1), DIR-868L (A1), DIR-865L (A1), DIR-860L (B1), DIR-860L (A1), DIR-850L (B1), DIR-850L (A1), DIR-820LW (B1), DIR-818LW (A1), DIR-817LW (B1), DIR-816L (A1), DIR-815 (B1), DIR-600 (B1), DIR-300 (B1), DIR-629 (A1), and DAP-1522 (B1). The problem is listed on D-Link's support pages where it is described thusly:
"An attacker who wishes to gain acces to the router sends an unprivileged HNAP command such as GetDeviceSettings, they append to the command an additional command separated with an "/", which is used as a separator between commands. Any command(s) after the first will be executed unauthenticated. Additionally, additional commands will be passed directly to the underlying Linux system, allowing the injection of arbitrary system commands. The GetDeviceSettings HNAP Command is used to indicate some very common parameters (e.g. the domain name of the HNAP device), as well as to define which HNAP commands are available".
While unhelpful patches have already been issued, D-Link is currently working away on replacement firmware updates. The release dates for these patches is not yet set in stone, but some are due today (20 April), some tomorrow (21 April) and the remainder on 24 April.
In a statement to BetaNews, D-Link said:
Security and performance is of the utmost importance to D-Link across all product lines. This is not just through the development process but also through regular firmware updates to comply with the current safety and quality standards. We are currently working to provide firmware updates to address these issues -- please go to [dlink.com] for updates.
In a separate statement, the company said that it "is deeply apologetic to any users affected by this issue" and advised users to change their admin password and implement a strong password policy.
-

BuzzFeed editorial is controlled by advertisers
Publié: avril 19, 2015, 11:38pm CEST par Mark Wilson

Advertising is unavoidable online. "Ah... but I have AdBlock Plus installed!" I hear you cry. It doesn't matter. You may not see advertising, but it still affects your online experience; this is particularly true if you are BuzzFeed reader. I'm not in the habit of criticizing others in the trade -- and I realize that I'm opening myself up for attack here -- but BuzzFeed is a site filled largely with listicles (lovely words) and churnalism (ditto), headlines sucking up to Google left, right and center.
But for all of the coffee-break-filling articles it pumps out each day, it is the articles that have been deleted that have generated more interest recently. About a week ago one BuzzFeed writer resigned after an article she wrote that was critical of Dove soap ads was pulled. BuzzFeed conducted a review, and this weekend details of the findings came out. It transpires that this is not the first time posts have been deleted because of a conflict of interest between editorial and advertising. BuzzFeed may not be a particularly influential site, but it's worrying nonetheless.
As revealed by Gawker, a memo sent by BuzzFeed's editor in chief Ben Smith to staff shows that over one thousand (1,000!) articles were deleted. Last week, Smith responded to criticism about deleted posts. The post about the Dove ad campaign was restored, as was one post that criticized the game Monopoly written shortly after the game-maker Hasbro started an ad deal with BuzzFeed (the deletion of neither had been advertised) but it was denied that advertiser pressure was to blame:
Appreciate the criticism. We just reinstated two posts and I sent this note to staffers. pic.twitter.com/YodxHiQmt2
— Ben Smith (@BuzzFeedBen) April 10, 2015
The latest memo -- sent to BuzzFeed staff on Saturday -- shows that three posts were deleted after "advertiser complaints." To most reasonable minds, the only justifiable reason for an advertiser to make a complaint to a website about content should be if an error has been made (which can be easily corrected) or if something defamatory is alleged that can be proved false. There may be other possibilities, but what certainly should not be the case is an advertiser taking umbrage at the tone of an article, criticism in an article or something of that ilk, and then using the threat of ad withdrawal to influence whether said posts stay online or not.
But the menu goes into some details about three posts that were deleted and stayed deleted. Mark Duffy wrote an article about Axe body spray that was deleted. The tone was deemed questionable, Duffy was ultimately fired, and Smith assured people that "our editorial team operates independently of advertisers, and I've never based a decision about reporting on an advertiser's needs". Another post by Tanner Ringerud that criticized Internet Explorer was deleted because he had previously worked on a Microsoft ad campaign (hang on -- I thought the two were meant to be independent of each other). Smith explains that "we set up a 'cooling off period' in which he wasn’t allowed to write about any brands he’d worked with for six months" -- so just sort of independent, then.
The third deleted post was written by Samir Mezrahi and included a mixture of positive and negative coverage of various companies. References to Pepsi were pulled because the business side of BuzzFeed is making Super Bowl ad content for the company that would be run on Twitter. If the two sides of BuzzFeed were truly independent, this would not have mattered in the slightest.
To be clear about BuzzFeed's position on writing about ads, Smith says:
We don’t write about ads that are running on BuzzFeed unless they are genuinely newsworthy. Appreciation buzz posts celebrating a fun or cool ad are fine, as are posts critical of ads -- but that content should not be about ads BuzzFeed's business side has created.
Again, if it is not possible to be critical of ads created by the business side of BuzzFeed -- which is supposedly entirely independent of the editorial side, remember -- impartiality is lost. Any content should be game for praise or criticism. Of course, this opens up the possibility of disclosure of association. If a writer used to work for a company and lambasts said company in a post, that's valuable information for the reader to have. It should not mean that the writer is not able to post their article, however.
I have reached out to Ben Smith myself, asking how, in light of the recent revelations, readers can be sure that there is no pressure from advertisers influencing content. I'm yet to hear back, but I'll update this post with ant response I receive.
As regular readers of BetaNews are no doubt aware, here we are not afraid to say what we think. If we like something, it's because it does what it's meant to do and does it well, because it's great value for money, it's sexy, etc. If we don’t like something and give it a bad review it because we think it's crap; it offers poor value for money, is badly made, and so on. We have zero relationship with advertisers to either promote a particular product, nor are we encourage to berate others. What we say is what we think, and that's precisely how it should be.
Of course this means there will be occasional disagreements. Products and services can summon up strong feelings -- both positive and negative -- and it's sometimes the case that among BetaNews staff we don’t feel the same way about something. One of us may love the latest build of Windows 10, while another hates it. Neither writer is being paid by Microsoft or its rivals to promote or condemn, and there is no pressure from an advertising team to give promotional coverage (or even any coverage) to a product or company.
Independence matters. Independence means honesty. Independence means that nothing is out of bounds. At the very least readers should be aware of what influence advertisers have over what they are reading.
Photo credit: PathDoc / Shutterstock
-

Apple must have shares in horse abattoirs
Publié: avril 19, 2015, 7:11pm CEST par Mark Wilson

It's said that just about anything that's broken can be fixed with one of two things. If something moves when it shouldn't, you need duct tape to hold it in place. If it doesn't move when it should, lubricant is what you need. Apple, it seems, has a different approach. Forget screws and clips; these days Apple tech is just held together with glue.
And we’re not talking about just a bit of glue -- we're talking tons of the stuff. Gallons of adhesive pumped into laptops, tablets and phones, holding everything in place and -- ultimately -- making things incredibly awkward to repair. Anyone would think the company had shares in a chain of abattoirs that shipped off horse carcasses to be boiled down into glue. Take the new MacBook Retina for example which featured recently in an iFixit teardown.
It's a device that has created some interest, and a teardown was all but inevitable. Let's cut to the chase: Apple does not build its devices with reparability in mind. In fact, iFixit gave the 2015 MacBook a rating of just 1 out of 10. Ripping into the guts of a MacBook is an entirely different ballgame to get elbow-deep into the entrails of a non-Apple laptop. It used to be that if you delved into your portable's innards, you'd end up surrounded by a sea of screws. Not so much these days.
Unlike many laptop manufacturers, Apple goes to some lengths to discourage user tinkering. If you want something fixed, you're not meant to tackle it yourself, or even seek help from a friend or non-authorized repair shop. These devices are Apple's babies and if something goes wrong, they need to return to the womb rather than going under the knife of an untrained surgeon.
Using tamperproof screws is one way to discourage people from venturing into their MacBooks, and these are employed here. As, it turns out, so are weird assembly/disassembly features that mean it's very, very easy to break something if you do get inside. Remove things in the wrong order, or twist something half a degree too far, and it's time to wave bye bye to your beloved device. But when weird clips and screws are not used, Apple turns to glue.
This is true for the battery. If something goes wrong with your battery, Apple has made it all but impossible to get to the power pack, and even when it is exposed, it is held in place with industrial adhesive. It's one thing to discourage home-meddling, but iFixit shows that Apple seems to be making life difficult for itself. You'd just better hope the battery holds out until you decide to upgrade your MacBook.
Glue holds cables in place, chips where they should be, and covers over whatever they're meant to be protecting. The back of the keyboard is held together with glue for good measure. Glue is cheap, and it's easy to see why it is splashed about so liberally, but it also presents problems. Whether it's done by a MacBook owner or an Apple technician, removing a component held in place with glue greatly increases the risk of damage to it and other nearby electronics.
Glued components are often subjected to torque during removal along with contact with scraping implements, but the alternative -- heating up the glue so it melts -- is equally worrying. That said, glue is not the only problem. iFixit notes: " The processor, RAM, and flash memory are soldered to the logic board."
And then there's the display. This is a completely sealed unit. If somethings goes wrong here, there really is little scope for replacing a damaged component -- it's pretty much a case of replacing the whole thing.
Does the use of glue help to keep costs down? Probably. Does it help to minimize weight? Quite likely. Does it make things really bloody awkward to repair? You betchya!
Photo credit: Katrina Leigh / Shutterstock
-

Twitter moves non-US accounts to Ireland away from the NSA
Publié: avril 18, 2015, 12:32am CEST par Mark Wilson

Twitter has updated its privacy policy, creating a two-lane service that treats US and non-US users differently. If you live in the US, your account is controlled by San Francisco-based Twitter Inc, but if you're elsewhere in the world (anywhere else) it's handled by Twitter International Company in Dublin, Ireland. The changes also affect Periscope.
What's the significance of this? Twitter Inc is governed by US law, it is obliged to comply with NSA-driven court requests for data. Data stored in Ireland is not subject to the same obligation. Twitter is not alone in using Dublin as a base for non-US operations; Facebook is another company that has adopted the same tactic. The move could also have implications for how advertising is handled in the future.
Ireland is widely recognized as having the most relaxed privacy laws in Europe, and this is something which is important for any company looking to monetize user data through advertising. While data that is processed in Europe may be beyond the immediate reach of the NSA, the policy change could also be seen as a way of trying to sidestep future legislation which may make it more difficult for US-based companies to share data about European users with advertisers.
The changes kick in on 18 May 2015 and Twitter briefly explains them in a policy update post:
If you live outside the United States, our services are now provided to you by Twitter International Company, our company based in Dublin, Ireland. Twitter International Company will be responsible for handling your account information under Irish privacy and data protection law, which is based on the European Union’s Data Protection Directive.
If you live in the United States, the services will continue to be provided to you by Twitter, Inc., based in San Francisco, California, under United States law.
Of course avoiding the NSA or making advertising easier are not quite how Twitter explains the reason for the change:
As more people around the world use our services, we’ve expanded our operations to improve how we support our users globally.
It is interesting to see that while San Francisco is used to process US data, Dublin is used to process data from users in every other part of the world. Twitter has also made it clear that users are free to sign up for an account using a pseudonym if they want -- take that, real name policy!
Photo credit: MyImages - Micha / Shutterstock
-

Office Universal apps preview coming to Windows 10 for phones very soon
Publié: avril 17, 2015, 6:49pm CEST par Mark Wilson

Microsoft comes under fire quite often for seeming to favor Android and iOS over its own mobile platforms. Apple and Google's mobile operating system have been first in line for all manner of Microsoft apps and services, and it was much the same story with the mobile versions of Office.
Today Microsoft is taking steps to allay the concerns of Windows Phone users -- you have not been forgotten! Specifically, the company says that the preview version of Office Universal apps will, or at least should, be made available for Windows 10 for phones by the end of the month.
Microsoft has been careful not to pin down a precise date, but if all goes to plan, we should see the apps being made available for download within a couple of weeks. It is described as the 'rounding out' of the Office line-up with a focus being placed on ensuring that the suite is available on as many platforms as possible.
Writing on the Office Blog, general manager for the Office marketing team Jared Spataro said:
Our Office Universal apps are designed for on-the-go productivity. They’re touch-first, built for tablets and phones, and optimized for viewing, quick edits, notes and mark-up. On a tablet, the Universal apps are fast, fluid, and streamlined for an immersive, hands-on experience. They’re fantastic for reading and perfect for touch- and pen-based content creation. On a phone, the Universal apps adapt to the smaller form factor. Commands and controls are moved to the bottom of the screen so you can triage your work and make edits one-handed with your thumb.
We've seen a huge shift in Microsoft interest in mobile recently, and just the other day the Bing app was updated to make it more suitable for single-handed use; now it looks as though Office is following suit.
-

Google cleans up URLs in mobile search results with breadcrumbs
Publié: avril 17, 2015, 4:49pm CEST par Mark Wilson

Google is revamping the way URLs appear in search results on mobile devices. Smaller screens have a tendency to truncate lengthier URLs, and even when this doesn’t happen diminutive screen size can make addresses difficult to read.
To combat this problem, the search giant is introducing a new breadcrumb trail presentation with a view to making the information easy to absorb at a glance. But what does this change actually mean?
What may previously have been displayed as the undeniably unwieldy http://www.google.com/about/company/history is reduced to the far more digestible Google > about > company > history. The move comes as a result of adding support for schema.org structured data as this allows for the easy display of a site name rather than the domain name. It also takes care of the URL conversion process into the more easily readable.
Introducing the change, Google says:
Today we’re updating the algorithms that display URLs in the search results to better reflect the names of websites, using the real-world name of the site instead of the domain name, and the URL structure of the sites in a breadcrumbs-like format.
The company has updated its help pages for developers looking to correctly implement breadcrumb formatting and the site name feature. Breadcrumbing is now rolling out globally, while site name support is limited to the US for now.
Photo credit: vesna cvorovic / Shutterstock
-

Zuckerberg says Internet.org is not anti-net neutrality... but it is
Publié: avril 17, 2015, 12:57pm CEST par Mark Wilson

A few days ago Mark Zuckerberg conducted a Q&A on Facebook. Despite tens of thousands of comments, very little of interest came out of the session -- he works 50-60 hours a week, likes Oculus (surprise, surprise), and he stands behind his Internet.org project which is providing internet access to people all over the world, including those in remote and developing locations. As is to be expected from a Q&A session, Zuckerberg also found that he had criticism levelled at him in addition to questions, including criticisms of his beloved Internet.org.
Some people pointed out that even in the US there is still a digital divide, while others complained that Internet.org goes against the principles of net neutrality. This obviously struck a nerve because the Facebook founder felt the need to defend the program and express his support for net neutrality. My colleague Manish Singh wrote about this, but is Zuckerberg right? Can Internet.org and net neutrality really live happily side by side?
On Thursday, Zuckerberg used an article in the Hindustan Times to defend Internet.org. This made sense because the program is currently rolling out to India and it's understandable that he would want to appease his current target audience. Now he has published the very same text as a post on his Facebook page, which is indicative of one of two things. Either Zuckerberg is so keen that the image of Internet.org is not besmirched that he is willing to bring the story to a wider audience before it spirals out of control, or it could be that he was so genuinely hurt or taken aback by the criticism of his baby that he thought he'd use his position to very publicly defend it.
But does it stand up to scrutiny?
There is one difference between the Hindustan Times article and the post on Facebook: the Times article has a headline. While Zuckerberg's Facebook posts takes a little while to get to the point, the article in the Times makes it clear right from the start: "Net neutrality and universal connectivity must co-exist".
It's an interesting idea, but -- at least on the face of it -- the two ideas oppose each other. The principles of net neutrality suggest that all internet traffic should be treated equally and that no company should be able to pay to give its traffic higher priority. Internet.org does not directly contradict these principles, but it does stray into something of a gray area. The idea driving the net neutrality movement is that we should avoid the creation of a two-tier internet where those willing or able to pay are given priority service, or a better service. But for all its good intentions, this is very much what Internet.org is doing.
It is hard to argue against the well-meaning push to bring internet access to areas where it is not currently available, but it is not providing unfettered access to the internet. Zuckerberg says:
To give more people access to the internet, it is useful to offer some service for free. If someone can’t afford to pay for connectivity, it is always better to have some access than none at all.
This is very much a two-tier internet, There's the internet that most people get to use, and the oh-sod-it-that'll-do internet that's available for free. If that's not a two-tier, divided internet, I don’t know what is.
Yes, it's great that people in developing countries are being given the opportunity to access the internet, but let's not pretend that this is an opportunity of equals. Really, if a country or region is being provided with access to some sites and services, why not provide access to everything the internet has to offer. Who decides what is opened up to users of Internet.org? Zuckerberg says:
By partnering with mobile operators and governments in different countries, Internet.org offers free access in local languages to basic internet services in areas like jobs, health, education and messaging.
Why only basic internet services? This is against the idea of net neutrality. Facebook and Internet.org partners are standing as gatekeepers to the internet for people in developing countries. The zero-rating of some services and sites (making them free to certain users) -- while inherently philanthropic in nature -- is absolutely running against the grain of net neutrality. It is not a level playing field, it is not equal access.
Yes, some access is better than no access, but there is no reason that some access shouldn't be expanded to full access. That's equality. That's net neutrality.
And then there is the problem of hardware. Bringing the internet to remote or poor parts of the world is great, but it's not much use if no one -- or only a small percentage -- living in these areas own devices that can be used to get online. But that's a whole different conversation.
And, ultimately, that's what matters. Conversations. People are now talking about not only net neutrality, but also the rights of people to be able to access the internet. People care, and that’s heartwarming.
Photo credit: cigdem / Shutterstock
-

Instagram is OK with a little nudity, preferably at a distance
Publié: avril 17, 2015, 3:26am CEST par Mark Wilson
Photo-sharing site Instagram has updated its community guidelines to make it clear what sort of images are acceptable. If you were hoping to use your account to supply your followers with a stream of pornography pics, you're out of luck, sadly. Nudity is -- for the most part -- out (we don’t allow nudity on Instagram), including "close-ups of fully nude buttocks"; distant shot of butts are, seemingly OK, as are close-ups of partially clothed cheeks.
Whether we're talking about Twitter, Facebook, Instagram or any of the other countless social networks out there, users frequently fall foul of acceptable content guidelines. Images of nudity and violence are frequently complained about and Instagram's latest guidelines now make it abundantly clear what’s OK and what's not.
As on Facebook, photographs of breastfeeding mothers have been a breeding ground for arguments. Instagram is keen to nip this in the bud. Photos of "women actively breastfeeding" are permitted as are shots of post-mastectomy scarring. It's hard to imagine that there have been many complaints about photographs of naked sculpture or paintings, but Instagram has now made it clear that such shots are fine. Given the general stance on nudity, it probably goes without saying that "content that show[s] sexual intercourse [and] genitals" are off-limits -- and we're not just talking about photos and videos, but also "digitally-created content."
The nudity of children is something that has to be handled delicately. Here Instagram doesn’t have a hard and fast rule -- images of naked children are not covered by a blanket ban. However, Instagram does say:
For safety reasons, there are times when we may remove images that show nude or partially-nude children. Even when this content is shared with good intentions, it could be used by others in unanticipated ways.
There are a number of other topics that are banned, including "offering sexual services, buying or selling illegal or prescription drugs, as well as promoting recreational drug use". The updated guidelines also warn that "videos of intense, graphic violence" may be removed even if they are newsworthy in an attempt to keep the site suitable for everyone.
Instagram may have made its rules slightly clearer, but it almost certainly won't stop people violating them -- or pushing them to breaking point to test the limits.
Photo credit: NLshop / Shutterstock
-

Microsoft makes mobile image searching a (nearly) typing-free experience
Publié: avril 16, 2015, 11:09pm CEST par Mark Wilson
Microsoft thinks that typing on a mobile device is difficult. At the same time it understands that "you love to discover images" on the very same devices. To help make your mobile searches a little easier to conduct, the company is introducing a number of tweaks and changes to the iOS and Android Bing app.
Of course it is not possible to entirely eliminate the need to input words in order to conduct a search, but Microsoft has taken steps to reduce it to an absolute minimum. How has this been done? Enter simple search terms and you're provided with a couple of new ways to drill down to exactly what it is you're looking for with just a few taps.
There are two new options available to help you to hone in on the perfect image. After entering your basic search term (hey, if you're really anti-typing, you could dictate it...) 'bubbling' is used to group together images that fit into a certain category. Search for 'cars' and you might find that they're grouped together by color, model, or year; just tap the appropriately labelled 'bubble' (or button, if you're normal) and your search will be refined accordingly. This process can be repeated to hone in further and further, and you can remove search parameters by tapping the familiar delete X.
There is also a new autocomplete feature that allows for easier search refinement. Decided that your 'car' term is a little vague? Just tap it and you'll see a list of suggestions of alternatives you might want to use instead.
The feature is rolling out right now to all English language users. Check out the video below to see what all the fuss is about:
-

Lost your phone? Just Google it
Publié: avril 16, 2015, 11:38am CEST par Mark Wilson

Becoming reunited with your lost phone just got a whole lot easier. It doesn’t matter if you're alone and don't have access to another phone to ring your cell to see if it has slipped down the back of the sofa. To make life a little easier, Google is rolling out a feature that enables you to conduct a Google search for your phone.
Whether you have mislaid it in the house, or somewhere further afield, Google will help you to track down your beloved handset. You just need to make sure that your phone is updated with the latest version of the Google app and you're ready to go phone hunting. It's a bit like an extension of the feature found in Android Wear, so how does it work?
As we've already alluded, sending out a virtual search party for your phone works like a regular Google search. Fire up your web browser, head to Google.com and type -- you've guessed it -- "Find my phone". Provided you are signed into the same Google account on the computer as on your phone, Google will then work its magic and use your phone's GPS to show you its location on a map.
If the map shows that your handset appears to be very close by, there's a handy 'Ring' option which, you know, rings your phone so you can hear where it is. If you have more than one phone connected to your account, there's a drop down menu so you can select which one you are interested in.
This is a feature that Google has launched with very little fanfare, but it's one that is sure to come in handy for a lot of people at some point in the future. It might not have all of the features of Android Device Manager (there's no remote wiping, for instance), but as a quick 'n' dirty solution, it's great.
-

Google hits back at European antitrust charges
Publié: avril 15, 2015, 2:33pm CEST par Mark Wilson

Google abused its position in Europe to further its own online products, says the European Commission. Following a five-year investigation, Google stands accused of abusing dominance in Europe, violating antitrust laws. EU competition commissioner Margrethe Vestager says that Google gave its own shopping comparison service greater priority over rivals in search results.
The company's mobile operating system is also in the firing line. Android, it is said, has been used by Google to promote its own products and services over those of rivals.The Commission is also launching a formal investigation into Android to determine whether Google acted anti-competitively with its mobile operating system. Attention is focused on Google's bundling of its own apps after forming agreements with hardware manufacturers. Unsurprisingly, Google disagrees.
In fact the company goes as far as to suggest that far from stifling competition, users now have more choice than ever before thanks to Google. It says that the fact it is the most popular search engine should not be used against it. But there is plenty to talk about when it comes to Android antics and search engine shenanigans.
The Commission says that Google used web services to divert traffic to its own services rather than alternatives. Google remains massively dominant in Europe and if the current charges stick the company could face fines that run into billions. If all of this sounds familiar, this is essentially the same case that Google attempted to settle last year, but was unsuccessful in doing so because of objections from European telecoms and ministers.
Vestager said:
In the case of Google I am concerned that the company has given an unfair advantage to its own comparison shopping service, in breach of EU antitrust rules. Google now has the opportunity to convince the Commission to the contrary. However, if the investigation confirmed our concerns, Google would have to face the legal consequences and change the way it does business in Europe.
The complaints against Google shopping date all the way back to 2008 when the Commission says Google's own shopping service was displayed prominently in search results "irrespective of its merits". It is also suggested that Google applied ranking penalties to rival services to push them further down listings, and that as a result of this Google Shopping experienced faster growth than it might otherwise have expected.
The Commission says that Google needs to "treat its own comparison shopping service and those of rivals in the same way", but Google insists there is already thriving competition online. In a graph-heavy blog post responding to the European Commission's complaints, Google appears to deliberately miss the point that's being made. It points to the growth of other shopping services as one of the reasons it must "respectfully but strongly disagree" with the Commission.
Google also stands accused of preventing handset manufacturers from shipping devices with forked versions of Android installed. An investigation is due to start and it will touch on "whether Google has illegally hindered the development and market access of rival mobile applications or services by requiring or incentivising smartphone and tablet manufacturers to exclusively pre-install Google's own applications or services".
Google has been quick to respond to these complaints as well, again pointing to the number of rivals that exist in the arena. It points out that Android is "an open-source operating system that can be used free-of-charge by anyone -- that’s right, literally anyone", again perhaps deliberately missing the point that the Commission is making. The company says "the European Commission has asked questions about our partner agreements. It's important to remember that these are voluntary -- again, you can use Android without Google -- but provide real benefits to Android users, developers and the broader ecosystem," but fails to fully address the suggestions of incentivized exclusivity deals.
The Statement of Objections sent to Google today concludes by saying:
The Commission continues its ongoing formal investigation under EU antitrust rules of other aspects of Google's behavior in the EEA, including the favorable treatment by Google in its general search results of other specialized search services, and concerns with regard to copying of rivals’ web content (known as 'scraping'), advertising exclusivity and undue restrictions on advertisers.
Google says that it is "look[ing] forward to discussing these issues in more detail with the European Commission over the months ahead".
This could be another long, drawn out affair.
Photo credit: Chukcha / Shutterstock
-

Nokia buys Alcatel-Lucent for $16.6 billion, considers selling HERE
Publié: avril 15, 2015, 12:52pm CEST par Mark Wilson

Following on from yesterday's confirmation that Nokia was in talks with Alcatel-Lucent regarding a possible buyout, the Finnish company has now gone ahead with the purchase. Nokia is paying €15.6 billion ($16.6 billion) for the French telecoms equipment manufacturer. The deal is expected to be finalized in the first half of 2016, subject to shareholder approval.
The coming together of forces is very much a forward-looking venture. Nokia says that the combination of Nokia Technologies and FutureWorks with Alcatel-Lucent's Bell Labs will allow for "unparalleled innovation capabilities". Nokia also announced that it has initiated a strategic review of its HERE business, but it is not yet clear whether this will ultimately result in its sale.
The merger will run under the Nokia brand, but research and development will continue to use the Alcatel-Lucent's Bell Labs name. Nokia Technologies will continue to exist as a separate entity, and will work on technologies such as 5G, the cloud, and IP and software-defined networking. Nokia says that the purchase creates a unique portfolio of technologies that will be able to deliver data, voice and video across a range of networks.
In a statement Nokia said:
With more than 40 000 R&D employees and spend of EUR 4.7 billion in R&D in 2014, the combined company will be in a position to accelerate development of future technologies including 5G, IP and software-defined networking, cloud, analytics as well as sensors and imaging.
While speculation may be rife that Nokia is on the verge of branching out into Android handsets, the company is yet to make any indication that this is the case. Nokia Corporation will keep its headquarters in Finland, but has its eye set on expanding further into the United States, China, Europe and Asia-Pacific.
Nokia CEO Rajeev Suri said:
Together, Alcatel-Lucent and Nokia intend to lead in next-generation network technology and services, with the scope to create seamless connectivity for people and things wherever they are.
Our innovation capability will be extraordinary, bringing together the R&D engine of Nokia with that of Alcatel-Lucent and its iconic Bell Labs. We will continue to combine this strength with the highly efficient, lean operations needed to compete on a global scale.
We have hugely complementary technologies and the comprehensive portfolio necessary to enable the internet of things and transition to the cloud. We will have a strong presence in every part of the world, including leading positions in the United States and China.
Together, we expect to have the scale to lead in every area in which we choose to compete, drive profitable growth, meet the needs of global customers, develop new technologies, build on our successful intellectual property licensing, and create value for our shareholders.
Photo credit: Joe Ravi / Shutterstock
-

Nokia could boomerang back into the mobile market with Alcatel-Lucent purchase
Publié: avril 15, 2015, 2:06am CEST par Mark Wilson

At the beginning of the week rumors started to creep out that Nokia was interested in buying Alcatel-Lucent. The story started with a report on Bloomberg and -- rather surprisingly for such rumors -- Nokia decided to not only comment on the rumor, but confirm that it is true.
Details are still rather thin on the ground and there's no hint at a possible timescale for a buyout of the French telecoms firm. What the statement does do, however, is open up the interesting possibility that Nokia could be on the verge of re-entering the smartphone market after offloading the handset side of its business to Microsoft.
Alcatel-Lucent is known for producing, amongst other products and services, cheap handsets. Could this mean Nokia is considering taking a slice of the lucrative developing market pie? Bloomberg speculate that a potential buyout could be funded by the sale of Nokia's HERE mapping division -- with Alcatel-Lucent valued at around $13 billion, Nokia would need to find almost twice the amount of money it received from Microsoft.
In a statement on the company's blog, Nokia said:
In relation to recent media speculation Nokia and Alcatel-Lucent confirm that they are in advanced discussions with respect to a potential full combination, which would take the form of a public exchange offer by Nokia for Alcatel-Lucent. There can be no certainty at this stage that these discussions will result in any agreement or transaction.
Further details will be revealed in the coming days, but this is a buyout that has been talked about for many years now. The fact that "advanced discussions" are now underway is interesting, but we don’t yet know whether talked center around a full purchase, or just the wireless division in a bid to compete with the likes of Ericsson.
Photo credit: 360b / Shutterstock
-

It's your own fault phishing scams are successful
Publié: avril 14, 2015, 11:43am CEST par Mark Wilson

There is no need for cybercriminals to launch sophisticated attacks, or exploit vulnerabilities, to gain access to valuable information; a simple phishing email is all that's needed to convince a worrying number of people to hand over their login credentials. This is just one of the findings of a new security report due to be published by Verizon.
The telco reports that more than two thirds of security breaches involving phishing tactics. The number of people who fall for this type of scam means that phishing remains successful and popular as a means of extracting data from people. In this age of technological enlightenment, it might come as a surprise that more than one in 10 people who receive a phishing email open attachments or click the links they contain.
System administrators will no doubt be vexed to learn that despite their hard work it is user error that is the greatest threat to any computer system. Verizon's Data Breach Investigations Report for 2015 reveals that while scattergun phishing attacks are still used, targeted attacks are increasingly common. Large businesses are frequently targeted simply because of the volume of email they deal with, making it more likely that mistakes will be made and malicious emails will not be recognized for what they are.
By aiming for a company's Achilles' Heel -- dumb, trusting users -- cybercriminals are saved the effort of having to launch more elaborate and sophisticated attacks. As with so many issues that center around technology, a large part of the solution is education. It might be the case that nearly a quarter of phishing email recipients open said messages, but this might be out of nothing more than mocking curiosity; it is the 10 percent of those who click through that are in need of further training.
This is particularly important when you consider that it is not just the personal information of the email recipient that is at risk. Target a large company with a successful phishing attack, and the details of hundreds of thousands of customers could be opened up. Verizon's conclusion is that two-factor authentication is an ideal way to keep data locked down, although the fact that well-publicized vulnerabilities remain unpatched means that this is something that also needs attention.
The report also investigated the threat posed by mobile devices. This is the first year Verizon has included a mobile section in its annual report and the finding are perhaps a little surprising. The majority of mobile threats involve adware, and at the moment there is little evidence of wide scale targeting of corporate users -- which could well be indicative of the emphasis companies have placed on ensuring that smartphones and tablets are secured.
Photo credit: wk1003mike / Shutterstock
-

Windows remains vulnerable to serious 18-year-old SMB security flaw
Publié: avril 13, 2015, 8:38pm CEST par Mark Wilson

A serious security hole leaves millions of Windows users open to attack, making it possible to extract encrypted credentials from a target machine. Researchers at Cylance say the problem affects "any Windows PC, tablet or server" (including Windows 10) and is a slight progression of the Redirect to SMB attack discovered by Aaron Spangler way back in 1997.
Redirect to SMB is essentially a man-in-the-middle attack which involves taking control of a network connection. As the name suggests, victims are then redirected to a malicious SMB server which can extract usernames, domains and passwords. Cylance also reports that software from companies such as Adobe, Oracle and Symantec -- including security and antivirus tools -- are affected.
In a blog post, Brian Wallace explains that Cylance has spent the last month and half working with vendors to help fix the problem, but has now decided to make details of the vulnerability public. A technical white paper explains how the original Redirect to SMB attack worked by sending a URL in the form file://1.1.1.1 -- this would cause Windows to connect to a malicious SMB server at 1.1.1.1, attempt to authenticate, and essentially hand over security credentials.
We uncovered Redirect to SMB while hunting for ways to abuse a chat client feature that provides image previews. When a URL to an image was received, the client attempted to show a preview of the image. Inspired by Aaron’s research some 18 years ago, we promptly sent another user a URL starting with file:// which pointed to a malicious SMB server. Surely enough, the chat client tried to load the image, and the Windows user at the other end attempted to authenticate with our SMB server.
Cylance found no fewer than four Windows API functions that can be used to redirect a user from an HTTP or HTTPS connection to a malicious SMB server. The forced authentication makes it relatively easy to get hold of usernames and passwords, even if they are held in encrypted form. As well as Windows itself, other programs affected by the problem include AVG Free, Internet Explorer, Windows Media Player, BitDefender Free, TeamViewer, and Github for Windows.
Wallace points out that:
Redirect to SMB is most likely to be used in targeted attacks by advanced actors because attackers must have control over some component of a victim’s network traffic.
Malicious ads could also be crafted that would force authentication attempts from IE users while hiding malicious behavior from those displaying the advertising.
Less sophisticated attackers could launch Redirect to SMB attacks on shared WiFi access points at locations such as coffee shops from any computer, including mobile devices. We successfully tested this attack on a home network using a Nexus 7 loaded with all required tools.
Although Microsoft is still to release a patch for the security flaw, Cylance suggests a workaround. By blocking outbound traffic from TCP 139 and TCP 445 you can put an obstacle in the way of authentication attempts that originate outside of your network while retaining SMB capabilities within it.
Photo credit: Ai825 / Shutterstock
-

Pixel pushing -- what's the point in Sharp's 5.5 inch 4K 806ppi screen?
Publié: avril 13, 2015, 6:09pm CEST par Mark Wilson
It is a given that whatever technology you see in front of you will be bettered if not next week, then next month or next year. Processors will get faster, hard drives bigger, laptops thinner and... well, you get the idea. In the realm of mobile devices there was a time when size meant everything. Mobile phone screens grew larger and larger, but then focus started to switch.
Size, it turned out, was not everything after all; it’s the number of pixels that matters. We started to see ppi figures quoted everywhere, Apple even came up with its own label for the pixel density at which pixels became indistinguishable -- Retina Display. This was just the start of the battle of the pixels, though, and now things are starting to get a bit silly. Sharp has announced a 5.5 inch 4K screen which boasts a pixel density of 806ppi. Say, what?
The first question that comes to mind -- well, the second if you count 'say, what?' -- is why? Just... why?
Let's cover the basics. As reported by TechBlog, Sharp's latest screen measures just 5.5 inches from corner to corner and yet boasts a 4K resolution of 3840 × 2160 pixels. The 806ppi screen is due to start mass production in 2016, but it does force us to question the need for such a screen.
Apple's Retina Display devices vary in pixel density from 220ppi (15 inch third generation MacBook Pro) to 401ppi (5.5 inch iPhone 6 Plus). Steve Jobs said that in order to qualify for a Retina Display label, a screen held 10 to 12 inches away from the eyes needed 326ppi -- although there has been debate about whether the figure should in fact be slightly higher.
The point is that Sharp's upcoming display shrinks a 3840 × 2160 display -- a resolution which is four times that of HD video, don’t forget, and normally found in TVs of 55 inches, 65 inches or even more -- right down to a 5.5 inch unit. If a 65 inch 4K television is considered to offer near-unparalleled quality when viewed from several feet away, how close is one going to have to get to a tiny 5.5 inch screen to really benefit from the quality?
While increasing the resolution of displays is logical and understandable, there comes a point when it is simply being done for the sake of doing it. It sounds good on the spec sheet, but what's the real benefit? And that's before we even start thinking about the battery draw a 4K screen is going to have! It would make more sense to invest the time and money in battery research and development rather than creating a new breed of display that brings few tangible benefits. Sharp will now need to wait for battery technology to catch up, the current breed of batteries just won’t cope!
Maybe it's time to start tapping the brakes on mindlessly increasing the numbers and switch the focus to technological changes that will make a real, noticeable difference.
Photo credit: wongstock / Shutterstock
-

Watch Game of Thrones for free on your Xbox 360 or Xbox One
Publié: avril 13, 2015, 3:43pm CEST par Mark Wilson
The wait is now over for fans of Game of Thrones. After a slight break, the first episode of season five aired last night and there were plenty of ways to watch it: HBO NOW for Apple users, or Sling TV to name two legal options, or you could opt to grab a torrent of the first four episodes after they leaked online.
For anyone who wants to see the first episode for free, while staying on the right side of the law, there's another option. Microsoft has announced that the Season 5 premiere is available free of charge to Xbox Live members. There's extra content available too, but you'll have to be quick as S05E01 is only available for a few days.
Microsoft has teamed up with HBO to bring the first episode of the new season of the show to Xbox 360 and Xbox One owners with Xbox Live subscriptions. The free viewing starts right now and it runs until April 16.
When you've enjoyed the episode, there's more to explore. Microsoft says:
And if that’s not enough to get you ready for Season 5, HBO and Xbox have joined forces to bring you a variety of Game of Thrones content in a special experience available this week when you sign into Xbox Live. Preview Season 5 with trailers, pledge your allegiance to a house, go behind the scenes with on-set tours, and test your Westeros knowledge with trivia questions asked by Game of Thrones cast members.
Sadly, if you want to keep watching the rest of the season, you'll have to stump up a little cash. If you want to stick with your Xbox, HBO GO is available for your streaming needs.
-

Unlock a secret dark theme in Windows 10 with a registry hack
Publié: avril 13, 2015, 11:54am CEST par Mark Wilson
Build 10056 of Windows 10 Technical Preview -- which leaked online in the last few days -- has a hidden dark theme. If you have grabbed a copy of this particular build, you'll have noticed that there are a few tweaks here and there such as a resizable Start menu and a redesigned system clock.
But if you're happy to tinker with the registry, you can unlock a whole new look for the operating system, taking Windows 10 to the dark side. It brings to the desktop version of Windows 10 a theme option reminiscent of Windows Phone. Pull on your registry editing pants... we're going in.
Normal warnings apply: registry editing = potentially dangerous, backup your data, your house may be at risk if you fail to keep up repayments, etc, etc. Suitable precautions taken -- or just throw caution to the wind if you are so minded -- head to the Registry Editor: just hit the Windows key, type regedit and press Enter.
Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ Themes\Personalize. You might find that the Personalize key doesn't yet exist, so you may need to add it manually. Now create a new DWORD Value called SystemUsesLightTheme and assign it a value of 0. That's it!
It's not yet clear whether this theme will make it to the final version of Windows 10 in a slightly more accessible way, if it will remain a hidden treat for those in the know, or if it will disappear from future builds. In the meantime, enjoy!
Photo credit: Lucas M
-

Fujitsu and Microsoft announce IoT and M2M partnership
Publié: avril 12, 2015, 11:25pm CEST par Mark Wilson

Much of the focus of talk about the Internet of Things surrounds what the IoT can do for home users. A clever cooker is great, but move up the scale a little, however, and things start to get really interesting. Now teaming up with Miele, Microsoft today announces that it is also partnering with Fujitsu.
The two companies will work together to create IoT based devices to improve the manufacturing of other products. By harnessing the power of IoT and the M2M (machine to machine) platforms, Microsoft and Fujitsu aim to improve production efficiency and help drive down costs.
At Hannover Messe Fujitsu revealed how it has already used a Microsoft Azure database to pull in data from a variety of sources, while the IoT and M2M platforms are used to bring greater productivity and capabilities. As part of what has been dubbed Industry 4.0, Fujitsu and Microsoft's partnership is the perfect demonstration of how technology is being used to streamline systems involving both people and computers.
Fujitsu might not be a company you would most readily associate with agriculture, but it has used Microsoft technologies to help with the mass-production of low potassium lettuce suitable for patients with kidney problems. The system uses the cloud to monitor plants and feed back information to scientists and engineers, as well as computers.
Fujitsu's Hiroyuki Sakai said:
Leveraging the Fujitsu Eco-Management Dashboard solution alongside Microsoft Azure and the Fujitsu IoT/M2M platform, we are able to deliver real-time visualization of the engineering process for big data analytics to improve the entire production process and inform decision-making.
The video below shows how Fujitsu is already taking advantage of the IoT:
Photo credit: bogdanhoda / Shutterstock
-

Microsoft and Miele team up to cook up an IoT revolution
Publié: avril 12, 2015, 9:11pm CEST par Mark Wilson

When people talk about the Internet of Things, there are often semi-joking references to fridges that know when you've run out of milk and ovens that know how to cook whatever you put in them. Forget the jokes; this is now a reality. We've already seen a generation of smart appliances, and Microsoft wants to be part of what happens next.
At Hannover Messe today, Miele -- of oven, vacuum cleaner and washing machine fame -- announces it is working on a new breed of appliances based on Microsoft Azure Internet of Things (IoT) services. What does this mean? Ultimately it means you'll be able to find a recipe online, have the ingredient list and preparation instructions sent to your mobile device, and your smart oven will be automatically configured with the correct settings.
At the industrial fair, Miele revealed that it had completed a proof-of-concept study of Microsoft's technologies and was ready to start building a new breed of smart appliances. Caglayan Arkan, Microsoft's Worldwide Manufacturing and Resources general manager said: "This is just one example of how the Internet of Things and cloud technology are moving from enterprise experiences to personal experiences. Miele is driving a truly innovative home solution that we are looking forward to experiencing in our own kitchens".
Dr. Eduard Sailer, Miele's executive director of Technical Affairs at Miele, said:
This assistance system incorporates temperature charts, times and the machine's special features, such as adding steam, to create the optimum roasting, cooking or baking results. This allows people to get the best results out of their cooking appliances.
Although at the moment there is a focus on food preparation, Microsoft points out that the same technologies could be used in other ways. Other possible uses include generating status report for machines or enabling remote diagnosis of problems.
Photo credit: Brian A Jackson / Shutterstock
-

Microsoft looks after the environment and your wallet with Xbox One energy saving
Publié: avril 12, 2015, 1:44pm CEST par Mark Wilson

Anyone setting up an Xbox One will be presented with the option of enabling the console's energy savings. At the moment, it is the Instant-on feature that is enabled by default, and few people delve into settings to change this later on.
By being upfront with the feature during the initial setup phases, Microsoft gives gamers the opportunity to reduce power consumption and lower electricity bills. As well as easing the impact console ownership has on wallets, it also helps to minimize its environment impact.
Although users are now given a direct and obvious choice between the two settings, it is Energy-saving that appears as the first option. Despite this, in a blog post introducing the new option, Microsoft is quick to point out that there are some comprises to make in switching to Energy-saving mode. As the name implies, Instant-on provides fast startup times, and these are forfeit.
Making the switch also means that updates are not automatically installed in the background, but you will still be notified when they are available for you to download and install -- much as with the Xbox 360. It also kills the "Xbox on" voice command.
Although the energy-saving feature is now being made more prominent than before, Microsoft is still keen to push the benefits of Instant-on:
Only with this setting can you make game or content purchases from SmartGlass or Xbox.com and have the content download automatically to your home console. When factoring the monthly system updates, new features in apps and games and automatic mobile purchase downloads, the Instant-on setting easily saves users countless hours of needlessly waiting.
But there are real savings to be made by becoming a little more energy conscious.
Microsoft explains that with Instant-On enabled, people will pay between $6.50 and $15.50 per year. Switch to Energy-saving mode and this drops to $0.26 to $0.62. The numbers involved may not be huge, but the real point here is taking tiny steps to reducing energy usage -- any financial gain is really just a bonus. Looked at individually the financial and environmental savings may not seem like much, but add up the number of consoles out there and the potential is great.
Photo credit: Bacho/ Shutterstock
-

Apple thinks Apple Watch customers are completely stupid
Publié: avril 10, 2015, 6:48pm CEST par Mark Wilson

Today Apple started taking orders for Apple Watch, and the world is agog. It's online only this time around, so there are no amusing articles about nutters camping outside Apple stores for six months living on noodles and coffee just to be first through the door -- people are, in many cases, buying blind. We've already baulked at the price of the Apple Watch Edition, but today Apple released details of its AppleCare+ extended warranties and, my god, do they make for interesting reading.
There has already been much said about the pricing of the various Apple Watch models -- not least the Apple Watch Edition -- and Apple is sure to make quite a markup on the precious metal version. Not content with raking in the cash through its sales of wrist-bound hardware, Apple is trying to squeeze every last possible cent from its customers. If something goes wrong with your Apple Watch, even if you are covered by the extended warranty, it's going to cost you a pretty penny to get things fixed. If you were foolish (er... lucky) enough to invest in the Edition, the costs are absolutely astronomical.
AppleCare+ for the Apple Watch Sport will set you back $49 for a year. Quite reasonable. The warranty covers not just the Watch, but also the battery, and the magnetic charging cable and power adapter. Lovely! But that's not the end of the story. Should you be unfortunate enough to need to send back your Apple Watch Sport for repair, you'll need to pay a $69 service fee plus tax. Part of the point of buying a warranty is to gain peace of mind against accidental damage -- dropping your device, smashing the screen, and so on -- but the warranty only includes provision for two incidents. After this you'll have to pay for out of warranty repair, or stump up another AppleCare+ fee.
If you've opted for the middle of the road Apple Watch, you'll have to pay a little more: AppleCare+ (for the same hardware, remember, albeit a different chassis) will cost you $69 and any repairs incur a $79 plus tax fee. The policy has all of the same features and caveats as the policy for the Apple Watch Sport, but there's a slight premium to pay.
But then things get really silly.
Anyone who has parted with up to $17,000 for an Apple Watch Edition has already paid through the nose. But Apple's not going to cut any slack when it comes to extended warranties. AppleCare+ for the Apple Watch Edition is $1,500 - regardless of the version you have opted for. Admittedly, this does buy two years' of extended coverage, but here's the killer: if you send back your Apple Watch Edition for repair, there is a $1,000 plus tax service fee. And again, you're only buying coverage for up to two incidents of accidental damage, despite the fact the warranty is for twice as long.
Let's just put this into context. If you manage to smash the screen of your gold Apple Watch Edition or cause some form of internal damage, you'll have to pay $921 (taking tax out of the equation for now) more to get it fixed than if you have precisely the same problem with an Apple Watch Sport. If the thing dies for some reason, it will cost you the thick end of $1,000 to get a replacement for your Apple Watch Edition, compared to $69 for an Apple Watch Sport. Apple has given itself a license to print money. Nice work if you can get it.
Of course, the warranty covers other things. You might, somehow, manage to completely crush your gold Edition. Perhaps you decided to wear it to work for your job as a house builder and dropped a brick on it, or it got run over by a backhoe. Then you get a good deal. You've paid your $1,500 and for just $1,000 plus tax more, you can bag yourself a replacement -- obviously a lot cheaper than buying afresh. But what sort of markup is being made on a gold Apple Watch Edition?
If you were wondering what the cost of out-of-warranty repairs is, MacRumors has the answer: $229 for Sport, $329 for Watch and $2,800 for Edition. Do you risk it, or hand over the cash?
Photo credit: komar_off / Shutterstock
-

Windows 10's unified Store includes apps, movies and music for all devices
Publié: avril 9, 2015, 10:14pm CEST par Mark Wilson
As we get further and further down the road to Windows 10, Microsoft today reveals there will be a major overhaul to the Store. A single unified Store will be used to deliver apps, music, TV shows and movies to everything from desktops and laptops, to mobile devices and Xbox platforms -- the Internet of Things even gets a look in.
Fire up the Store in the Windows 10 Technical Preview and you should now see a Movies & TV section (or Films & TV depending on where you are in the world). This has been present in the beta version of the Store for a while now, but now it actually works. The recently released Music and Video apps will soon be integrated with the Store, and there's more to come.
The latest update is handled server-side, so there's no need to install an update. If you're in one of the 20 supported countries (US, Canada, Mexico, Austria, Belgium (no TV content in these first few just yet), Denmark, Finland, France, Germany, Ireland, Italy, Netherlands, Norway, Spain, Sweden, Switzerland, United Kingdom, Australia, Japan, and New Zealand) you can start renting and buying content right away.
Introducing the latest update to the Store, Microsoft's Brandon LeBlanc said:
The experience you will see today is unfinished and we have a lot more work to do. For example -- you won’t see movie or TV details like cast and crew and you’ll only be able to stream video content right now. But don’t worry -- offline download capability will be coming!
In the coming weeks we'll see the arrival of a Music page, but what Microsoft is ultimately working towards is creating a Store that caters to all of your needs. By unifying the Store experience, Microsoft is taking a leaf out of Apple and Google's books and making it possible to access your content easily no matter what device you are using.
-

Microsoft announces integration between Dropbox and Office Online
Publié: avril 9, 2015, 7:32pm CEST par Mark Wilson

Back in November, Microsoft and Dropbox joined forces to bring Office editing capabilities to iOS and Android users. Now the two companies have taken things to the next level, bringing the same capabilities to the web.
New integration between the ever-expanding Office Online and Dropbox means that it is now possible to create files in Microsoft's cloud-based office suite and save them directly to Dropbox. There's also the option of adding your Dropbox account to Office Online to allow for easy access to files ready for editing.
The merging of the two services will help to make life easier for anyone who finds themselves working in the cloud. As Dropbox points out, you don’t even need access to the desktop version of Office to be able to work with your documents using any computer with an internet connection. The company goes on to say:
We're aiming to make it even faster and easier to work with your Dropbox files from just your browser, so you can save time and be more productive.
Microsoft explains that the new integration is a two-way process. You can add your Dropbox account to Office Online to simplify file management, but you can also use the Open option when previewing Office files in Dropbox. There's no waiting time or rollout process -- the feature is now available to everyone using Dropbox and Office Online around the world right now.
-

Ad-free version of YouTube on the way -- for a price
Publié: avril 9, 2015, 11:20am CEST par Mark Wilson

Google is on the verge of launching an ad-free option for YouTube users. An email sent out to 'YouTube Partners' (or content creators) reveals that the company has plans to unveil a paid-for version of the video service that enables viewers to avoid the irritation of ads.
For content creators, YouTube says the plans offer a new way to pull in the cash: "we'll generate a new source of revenue that will supplement your fast growing advertising revenue". While there is yet to be an official public announcement, the news comes just days after Google came in for criticism for showing "unfair and deceptive" ads in its YouTube Kids app.
It's a venture that will almost certainly be welcomed by a large proportion of YouTube users, as ads are frequently picked out as being the bane of life online -- although many will already be aware that, on the desktop at least, installing the AdBlock Plus extension does much the same job for free. It is interesting to see that Google is sharing the news with content creators first rather than video consumers.
The email says:
Launching a new paid offering will require us to update your terms through your Creator Studio Dashboard -- a process that should feel familiar to anyone who went through a similar process three years ago when we began distributing and monetizing your content on mobile devices. Today mobile represents over half of all watchtime and mobile revenue is up 200 percent in the last year. Just as with mobile, we're confident this latest contract update will excite your fans and generate a previous untapped, additional source of revenue for you.
Google is yet to give an indication of a timescale for its spread into what it describes as "unchartered territories".
Would you be happy to pay to kill the ads?
-

Facebook Messenger breaks away into a brand new dedicated website
Publié: avril 8, 2015, 10:56pm CEST par Mark Wilson
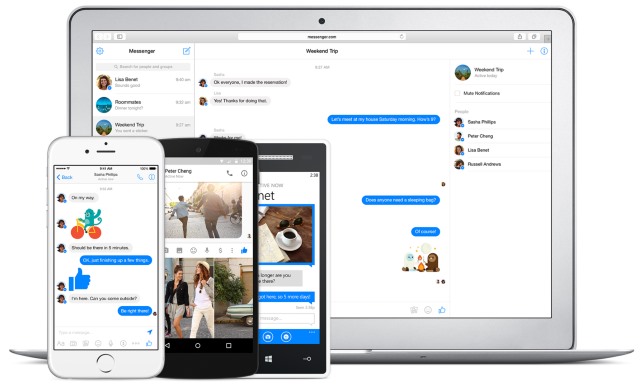
Today Facebook launches a new standalone website for its Messenger service. The separate interface means that it is now possible to chat with your Facebook contacts without having to visit the main Facebook website where you might run the risk of whiling away too much time reading through your timeline as well.
On mobile devices, Facebook has moved users to a dedicated Messenger app rather than allowing them to chat within the main app. By bringing the web-based version of the social network's chat tool in line with the iOS, Windows Phone and Android versions, Facebook has made chatting a distinct feature that can now be conducted completely separately in its own tab.
What is immediately noticeable about the new web interface is how much more room there is than in the old Facebook.com pop-up messaging system. Rather than forcing you to cast your eyes to the lower right hand corner of the screen to see messages as they arrive, Messenger.com offers a full-screen chat experience, and makes it easier to switch between multiple conversations.
Photo and video sharing is included, but there's a killer feature -- one which is likely to convince many people to move their conversations: desktop notifications. One of the problems with conducting chats on Facebook's main website is that there is no visible notification if you browse to another tab or application. They’re not enabled by default, but if you head to Settings in web you can turn them on.
Starting right now, Messenger.com is available to all English speaking Facebook users, and it will roll out in other languages very soon.
-

Intel's RealSense 3D camera could be in your next smartphone
Publié: avril 8, 2015, 5:49pm CEST par Mark Wilson

Intel has managed to shrink its depth-sensitive RealSense 3D Camera to the extent that it could be used in the next generation of cell phones. This is about more than just 3D photography, this is about taking photographs and changing the focus afterwards, as well as bringing Kinect-like gesture support to mobile devices.
Talking at an event in Shenzhen, China, Intel CEO Brian Krzanich demonstrated a much smaller version of its existing technology. So far we have only seen the RealSense 3D camera in laptops such as the Acer Aspire V 17 Nitro, but the miniaturization means that it could be a feature of your next phone or tablet.
Intel has teamed up with an unnamed Chinese company to create the smaller version of the camera, but it is not yet known when it will come to the market. As well as the photographic and gesture control possibilities, the mobile version of the RealSense 3D camera opens up other opportunities currently only found on certain laptops -- touchless interfaces, 3D scanning, and much more. One use Intel highlights is taking photos of a room and converting this into a three dimensional plan that can be used in a CAD or home décor application.
Talking about the device that was shown off, an Intel spokesperson said:
The device which was shown on stage at the Intel Developer Forum was a prototype [...]The device is meant to show the different types of apps, usage models and form factors that RealSense tech can be integrated into and to encourage innovation.
In many ways the idea is similar to those found in Amazon's Fire Phone, although the technology is rather different. While Amazon relies on the presence of multiple cameras, Intel's solution makes use of a single sensor.
Photo credit: Intel
-

Microsoft announces OTA TV Tuner for Xbox One-owning cord-cutters
Publié: avril 8, 2015, 4:04pm CEST par Mark Wilson

These days Xbox is about much more than just gaming and it's a platform that is increasingly appealing to cord-cutters. Microsoft and its partners have gradually increased the number and variety of apps that are available for a diverse viewing experience, but now things have taken a new twist. If the likes of Netflix and HBO are not enough, there's now an over-the-air TV tuner available.
Live TV is something that Xbox One users have been asking for for some time, and Microsoft has teamed up with Hauppauge to come up with the goods. Anyone who is a member of the Xbox One Preview is able to buy the Hauppauge WinTV-955Q and gain access to a wealth of free networks such as NBC and CBS.
The TV tuner -- available from Amazon, Best Buy, GameStop and Micro Center -- will set you back $79.99 (and you'll need to make sure you have an HD compatible antenna), but there are plans to release a cheaper version later in the year. There's no word about a release date just yet, but the Hauppauge TV Tuner for Xbox One will retail for $59.99. Used in conjunction with Kinect, it will be possible to use your voice to control TV, as well as taking advantage of snapping to allow for simultaneously TV viewing and gaming.
The tuner also allows for the pausing of live TV, access TV listing with your Xbox One controller or remote, and stream to Xbox One SmartGlass. If you want to find out what channels you are able to receive, Microsoft recommends visiting the page set up by antenna manufacturer Mohu.
Xbox Wire made the revelation about the new tuner on Twitter where it was met with some enthusiasm:
TV on Xbox Gets More Versatile with Over-the-Air Tuner for the U.S. and Canada [t.co]
— Xbox Wire (@XboxWire) April 8, 2015
While the OTA TV Tuner is only available to residents of the USA and Canada, there is another announcement for people in other parts of the world. The existing Xbox One Digital TV Tuner is spreading to more countries in Europe -- Austria, Belgium, Denmark, Finland, Ireland, Netherlands, Norway, Poland, Portugal, Sweden, and Switzerland -- where it will be available at retail later in the year.
Check out the video below where Major Nelson chats about the device and demonstrates how easy it is to use:
Photo credit: Concept Photo / Shutterstock
-

Google is too slow at clearing crap from the Chrome extension store
Publié: avril 8, 2015, 12:40pm CEST par Mark Wilson

Malware is something computer users -- and even mobile and tablet owners -- are now more aware of than ever. That said, many people do not give a second thought to installing a browser extension to add new features to their most frequently used application. Despite the increased awareness, malware is not something a lot of web users think of in relation to extensions; but they should.
Since the beginning of 2015 -- just over three months -- Google has already received over 100,000 complaints from Chrome users about "ad injectors" hidden in extensions. Security researchers have also discovered that a popular extension -- Webpage Screenshot -- includes code that could be used to send browsing history back to a remote server. Google is taking steps to clean up the extension store to try to prevent things like this happening, but security still needs to be tightened up.
The effects of ad injectors can be varied. It might mean that you see more ads as you browse the web, or it could be that you see ads with a particular origin. But, as in the case of Webpage Screenshot, the payload could be more serious. Security researchers at ScrapeSentry detected a strange pattern in traffic, investigated Webpage Screenshot and detected the malicious code. Google recently announced that it had killed 192 malicious extensions, but it’s clear that not enough is being done to stop malicious code getting there in the first place.
Cristian Mariolini, a security analyst at ScrapeSentry, says:
The repercussions of this could be quite major for the individuals who have downloaded the extension. What happens to the personal data and the motives for wanting it sent it to the US server is anyone’s guess, but ScrapeSentry would take an educated guess it’s not going to be good news. And of course, if it’s not stopped, the plugin may, at any given time, be updated with new malicious functionality as well. We would hope Google will look into this security breach with some urgency.
ScrapSentry's research shows that the extension could be used to send any information that can be seen in a browser tab back to an IP address located in the US.
Google is quick to point out that malicious ad injectors are not specific to Chrome -- they can also be found in Firefox and Internet Explorer. The company says: "We don’t ban injectors altogether -- if they want to, people can still choose to install injectors that clearly disclose what they do -- but injectors that sneak ads into a user’s browser would certainly violate our policies".
On May 1, Google will publish a report based on research carried out with the University of California Berkeley which goes into more detail and aims to "to increase awareness about ad injectors". ScrapeSentry's findings, however, show that there is a need for greater awareness right now, not in a month's time. It's great that Google is taking steps to clear out the crap, but more needs to be done, and faster.
Photo credit: Africa Studio / Shutterstock
-

Microsoft and Getty Images bury the hatchet after legal action and form partnership
Publié: avril 7, 2015, 9:45pm CEST par Mark Wilson

Late last year Getty Images hit Microsoft with a lawsuit for using its images without license in the Bing Image Widget. Getty had complained that Microsoft turned its images into "a vast, unlicensed clip art collection". In a bid to avoid trouble, Microsoft opted to take down the widget and now -- seven months down the line -- it seems that it may just have paid off.
Today, the two companies announced that they are forming a partnership to bring properly licensed images to products such as Bing and Cortana. Technologies from both Microsoft and Getty images will be used together to enrich services on both sides.
Neither company has revealed any specific details about what will be born of the partnership but Getty Images is pleased that properly licensed images can now be provided to Microsoft customers. Craig Peters, Senior Vice President of Business Development, says that his company will "take search experiences to a new level". Most importantly, however, is the fact that photographers will be correctly attributed.
Microsoft's Executive Vice President of Business Development Peggy Johnson says:
This collaboration enables Microsoft users to take full advantage of Getty Images' speed to market, structured metadata and unrivaled content. We look forward to working with Getty Images to provide the next generation of image depth and breadth for our users.
A statement issued by Getty Images implies that Microsoft is getting the best deal out of the new arrangement. Microsoft gains access to Getty Images' APIs that will provide new ways to work with images and metadata.
Photo credit: Marta Paniti / Shutterstock
-

Google reported to FTC for 'unfair and deceptive' ads in YouTube Kids
Publié: avril 7, 2015, 12:49pm CEST par Mark Wilson

A number of consumer groups have filed a complaint with the FTC suggesting that Google is targeting children with "unfair and deceptive" ads in YouTube Kids for Android and iOS. A letter signed by Children Now, Consumer Watchdog, Campaign for a Commercial Free Childhood, and others says that ads are displayed in a way that would not be permitted on broadcast or cable television.
The letter makes three main complaints about the app. The first suggests that Google mixes programming and ads, while another says that the relationship between Google and the manufacturers of advertised products is not clear. The groups ask for the FTC to take action to stop the advertisements.
The YouTube Kids app has only been available for a couple of months, and came shortly after Google announced plans to target children with specially-designed versions of YouTube and Gmail. Another claim made by the letter is that although Google says all of the ads have been carefully vetted to ensure they meet YouTube's policies, a lot of the content in fact violates these policies. It also voices concern at "the large amount of commercial material that was presented as programming".
The groups say that there should be a far clearer distinction between what is advertising and what is programming, as younger children may not be able to tell the difference. There is the complaint that "there is no 'bumper' before the ads as there would be on children's television" as the app plays programming and ads in a continuous stream.
The letter asks a couple of questions in relation to the app's "recommended" sections. "Is Google tracking children’s online viewing habits to make the recommendations? If so, has it given direct notice and obtained verifiable parental consent before tracking them as required by the COPPA Rule?" The presence of a McDonald’s channel in the app in which sections that might be considered advertising are not identified as such is said to "take advantage of children".
The length of ads is also an issue. The letter points out that Google's own policy states that children will only be subjected to non-skippable ads up to 30 seconds in length, or skippable ads up to 60 seconds in length. Despite this promise, there are instances of ads longer than one minute.
Singled out for particular attention are unboxing videos. These are described as program-length commercials which are not identified as ads despite the fact multiple products may be endorsed throughout them.
Google disagrees with the allegations. In a statement to BetaNews, a YouTube spokesperson said:
We worked with numerous partners and child advocacy groups when developing YouTube Kids. While we are always open to feedback on ways to improve the app, we were not contacted directly by the signers of this letter and strongly disagree with their contentions, including the suggestion that no free, ad-supported experience for kids will ever be acceptable. We disagree and think that great content shouldn’t be reserved for only those families who can afford it.
-

Turkey blocks Facebook, YouTube and Twitter; Zuckerberg caves in, Google fights back
Publié: avril 6, 2015, 8:11pm CEST par Mark Wilson

Today Turkey blocked access to a number of websites including YouTube and Twitter. The ban came after the sites published images of a prosecutor being taken hostage at a court in Istanbul earlier in the week. Google has vowed to getting things back up and running, but it's not the same story for everyone.
While a block was also put in place on Facebook, the social network sidestepped the ban by agreeing to comply with a court ruling. This is not the first time Mark Zuckerberg's site has bowed to pressure from Turkey. At the beginning of the year, despite previous claims to stand up for free speech, Facebook bowed to pressure to block pages that insulted or offended the Prophet Mohammad. Now it looks as though history is repeating itself.
Turkish news site Hürriyet reports that a total of 166 websites and individual pages have been blocked by the court order including a number of local newspaper sites. The sites stand accused of sharing terrorist propaganda after publishing photos of the siege carried out by DHKP-C. The group is regarded in many countries as a terrorist organization and it took prosecutor Mehmet Selim Kiraz hostage after taking over a courthouse.
Kiraz was seemingly targeted for his involvement in a case concerning the death of a boy in anti-government protests back in 2013. The photos in questions showed Kiraz -- who was later killed -- with a gun pointing at his head.
A Turkish official said:
The wife and children of prosecutor Kiraz have been deeply upset. The images are everywhere. A request has been made to both Twitter and YouTube for the removal of the images and posts but they have not accepted it and no response has been given. That's why this decision has been taken through a court in Istanbul.
We contacted Googled for a comment and a YouTube spokesperson said:
We are seeing reports that YouTube is blocked in Turkey and we're working to restore the service for users as soon as possible.
Twitter made a similar statement through, unsurprisingly, on Twitter:
We are aware of reports of interruption of our service in #Turkey, and we are working to restore access for our users as soon as possible.
— Policy (@policy) April 6, 2015
But while YouTube and Twitter seem willing to fight to get services restored, Facebook caved in all but immediately. Within hours of being served with the court order that blocked Facebook in Turkey, the social network complied with the country's wishes and removed the photos.
We have also reached out to Facebook and Twitter, but we're yet to receive a response. We'll update this post as soon as we hear anything.
Photo credit: Neil Lang / Shutterstock
-

Snapchat transparency report shows legal requests hit a devilish 666 accounts
Publié: avril 6, 2015, 1:16pm CEST par Mark Wilson

Largely due to the exposés in the media following Edward Snowden's NSA revelations, there is now great interest in security and privacy. From this sprang a new breed of report -- transparency reports detailing the number of data requests legal and governmental agencies made about a particular service.
Google, Facebook, Yahoo, Microsoft and Apple are among the companies who have released transparency reports, and the latest name on the list is Snapchat. As with other similar reports there is a limit to what they are able to reveal, but it does show that various agencies had an interest in no fewer than 666 Snapchat accounts.
The report covers the period November 1, 2014 to February 28, 2015. While it is more usual to wait until six months' of data is available, Snapchat decided to jump the gun slightly "in the interest of transparency". So what does the report tell us? The number involved is actually fairly low.
A total of 375 requests were received, affecting 666 "account identifiers" -- which Snapchat points out refers to things such as username, email address, phone number, and it is probably that multiple identifiers relate to the same account. Data was produced in 92 percent of cases, with search warrants yielding the greatest results -- 96 percent of 172 requests. 89 percent of 159 subpoenas results in the production of data.
As we're yet to hit the all-important six-month mark, there are no details about the number of FISA and NSL requests, but we do know that a total of 28 data requests were made by international governments. The UK tops the chart with 10 requests (three marked as emergency and seven as other), and France is close behind with nine. Overall, data was only produced in response to 21 percent of these requests.
Announcing the availability of this first report, Snapchat says that updates will be released twice a year:
We’re excited to announce our first transparency report, a comprehensive look into the data requests we receive from governments around the world. In this report we detail the number and types of requests each government is making of us.
While the vast majority of Snapchatters use Snapchat for fun, it’s important that law enforcement is able to investigate illegal activity. We want to be clear that we comply with valid legal requests.
Privacy and security are core values here at Snapchat and we strongly oppose any initiative that would deliberately weaken the security of our systems. We’re committed to keeping your data secure and we will update this report bi-annually.
The next report is due in July and will include more information such as "government requests we have received for users’ account information, government demands to remove users’ content, and requests to takedown content for alleged copyright violations".
-

Sony pays out to customers after deceptive PS Vita ads
Publié: avril 6, 2015, 11:52am CEST par Mark Wilson

Sony has started to make settlement payments to PlayStation Vita owners, six months after the Federal Trade Commission found that the company had run misleading ads about the handheld console. If you bought a PS Vita before June 1, 2012 -- and haven’t already returned it for a full refund -- you are in line to receive $25 cash back.
Alternatively, a voucher that can be exchanged for merchandise worth at least $50 is also available. Despite the FTC's findings Sony still "neither admits nor denies liability", the payouts offer some compensation for gamers who feel they were misled.
Anyone wishing to make a claim needs to do so by June 29, 2015 and the form you need to fill in can be found at a specially designed website. The claims stem from a series of ads which suggested players could start a game on a PS3 and pick up from where they left off on a PS Vita console, but this feature was only supported by a small number of games. They also suggested that 3G subscribers could engage in live online games when in fact this was not possible.
The company handling the refunds for Sony explains:
If you purchased a PlayStation Vita handheld game console before June 1, 2012, you may be eligible to receive cash back (or credit on your PSN account) or merchandise worth $50 or more. The Federal Trade Commission has alleged that some SCEA advertisements for the PlayStation Vita during this period were deceptive. Although SCEA neither admits nor denies liability in connection with this matter, SCEA has agreed to settle the dispute with the Federal Trade Commission by offering either cash back (or credit on your PSN account) or merchandise to customers who purchased a PlayStation Vita before June 1, 2012, and who have not returned the product for a full refund.
On the face of it, opting for the merchandise might seem the most appealing, but if you've decided to move on, cash is still available to help soften the blow. The offer is only available to PlayStation Vita owners in the US. Full details are available on https://vitaclaims.com.
-

Microsoft stops Kinect for Windows production... because it's so popular
Publié: avril 5, 2015, 9:36pm CEST par Mark Wilson

Yes, you did read that headline correctly. Microsoft has announced that due to the popularity of Kinect for Windows, the sensor will no longer be produced. While an increase in demand would normally lead to an increase in production, Microsoft is taking something of a different approach.
Rather than maintaining two Kinect product lines -- a model for Xbox One and a model for Windows -- the company will instead sell an adapter that allows the console sensor to be connected to a PC. Microsoft says that this will help to keep things simple and create consistency for developers.
An announcement on the Kinect for Windows blog points out that the Xbox One version of the sensor along with the necessary adapter are available in the Microsoft Store. Had the announcement been made a little earlier, it could have been mistaken for an April Fool, but the Kinect Team explains the thinking behind the decision:
Over the past several months, we have seen unprecedented demand from the developer community for Kinect sensors and have experienced difficulty keeping up with requests in some markets. At the same time, we have seen the developer community respond positively to being able to use the Kinect for Xbox One sensor for Kinect for Windows app development, and we are happy to report that Kinect for Xbox One sensors and Kinect Adapter for Windows units are now readily available in most markets.
Microsoft will continue to support the Kinect for Windows v2 sensor, so anyone who already has the Windows version need not rush out and buy the Xbox One model. Anyone looking to adding a Kinect Sensor to their PC, however, will have to splash out $149.99 on a Kinect for Xbox One as well as $49.99 for the Kinect Adapter for Windows. While the overall cost is much the same as the previous unit on its own, you'll need to make sure your computer has a spare USB 3.0 port.
-

Government should not control access to hardcore porn sites
Publié: avril 4, 2015, 9:37pm CEST par Mark Wilson

Children's access to the internet can be a very emotive issue, particularly when subjects like pornography crop up. In the UK, the General Election is just around the corner and the current ruling party, the right wing Conservatives, are pledging to introduce legislation that enforces age restrictions on access to hardcore pornography sites.
The legislation would be dependent on the party retaining power after the May election, but Secretary of State for Culture, Media and Sport, Sajid Javid says the Conservatives "will age restrict online porn" offering "safety for children and peace of mind for parents". There are just two problems. Firstly, it is completely unworkable, and secondly it is not the government's place to restrict access to the internet using legislation.
Writing on the party's Facebook page, Javid writes: "if the Conservatives win the next General Election, we will legislate to put online hard-core pornography behind effective age verification controls". Right from the start, the plan -- whether you agree with or not -- falls apart. Short of implementing a database of biometric data and requiring internet users to verify their identity with a finger print, blood sample, or something of the sort, there is no age verification system that cannot be side-stepped.
It's incredibly arrogant -- although ultimately naïve -- to think otherwise but Javid thinks he has the solution:
An independent regulator will oversee this new system. It will determine, in conjunction with websites, how age verification controls will work and how websites that do not put them in place will be blocked.
So even though this is an emotive issue which will turn the heads of countless concerned parents, it's a plan that is entirely theoretical. An age verification system has not been designed, presumably because of the impossibility of doing so. You can ask for dates of birth, credit card information, or other forms of ID, but there will always -- always -- be a way to beat the system.
In the UK, websites linked to piracy such as the Pirate Bay are supposed to be blocked at ISP-level. Has this done much to thwart online piracy of music and movies? Of course it hasn’t. It may have stopped a few instances of piracy here and there, but it has also made other people even more determined, fuelling the development of more and more tools that make it easier and easier to bypass ISP restrictions. Exactly the same thing will happen with any porn-busting plans that may be put in place.
Prime Minister David Cameron spoke out about the proposals on Twitter, saying:
We need to protect our children from hardcore pornography. Here's how we'll do it: [t.co]
— David Cameron (@David_Cameron) April 4, 2015
Except there is no explanation of how it will be done. Probably because it can't be done with any reliability. Despite this, hundreds of thousands, perhaps millions of pounds will be spent researching, testing and possibly implementing a system. A system that will not work. A system that uses up valuable money, time and resources that could be put to far better use.
Javid says:
Of course adults should be perfectly free to look at these sites. But if websites showing adult content don’t have proper age controls in place – ones that will stop children looking at this kind of material – they should and will be blocked altogether. No sex shop on the high street would be allowed to remain open if it knowingly sold pornography to underage customers, and there is no reason why the internet should be any different.
The problem is... the internet is different. Politicians, police, and other may wish to think otherwise, but controlling the internet and access to it is all but impossible. Of course this statement will lead to cries of 'well, should we not at least try?' and 'is it not worth it if even one child is prevented from seeing hardcore porn?'. The short answer is: no.
Javid goes on to say:
There will be some who say that this exercise is futile, that websites and children alike will find ways to get around this law. And I agree that there are always people who try to avoid legal restrictions. But we must not let the best be the enemy of the good.
It is right that we act now and do what we can to restrict this content. It is right that we have the same rules applying online as we do offline. And it is right that we do everything we can to protect our children.
The solution to any sort of online problem in relation to children is education and parental. It is down to the education system to teach responsible use of the internet and to provide modern, progressive, forward-thinking sex education. It is down to parents to judge what is right for their offspring to view and to take the appropriate action.
Starting the conversation about restricting access to websites to those concerned with pornography is an easy way to get people on side, but it's also worrying. Look to China and we can see what happens when the government gets involved in controlling the internet. Government has absolutely no place interfering with the internet. All of the talk of protecting children sounds great, but it is delusory to think that any measures that are put in place will be anything other than an expensive waste of time.
We have reached out to Conservative ministers for more information about how the age verification process could be implemented, and we’re waiting to hear back. We'll update this post accordingly when we have more.
Photo credit: Blan-k / Shutterstock
-

Surface AMA reveals all about Surface 3 and nothing about Surface Pro 4
Publié: avril 4, 2015, 6:07pm CEST par Mark Wilson

Microsoft's Surface team took to Reddit to answer a barrage of questions in an AMA (Ask Me Anything) session on the site. Although the team was available for probing for just one hour, scores of questions were fired at them and while nothing ground-breaking was revealed, shrouds of mystery were swept aside.
The upcoming Surface 3 has already managed to generate quite some interest. This is the first non-Pro Surface model that will ship will a full, non-RT version of Windows and it should come as little surprise that many of the questions related to this tablet. If you don’t have the time or inclination to read through the entire thread on Reddit, here are some of the edited highlights.
The standard Surface 3 is due to ship at the beginning of May, but later in the year there is also an LTE model that features an integrated GS chip. The team believes that the pen and active capacitive digitizer are the "best out there" at the moment, but says that improvements can and will be made -- including upping the pen's voltage. On the subject of the pen, the team said the decision was taken to make it available as a separate purchase for two reasons: firstly to keep the price of the Surface 3 as low as possible, as well as giving users the option of buying a pen in their choice of color if they want one.
When it was revealed that the Surface 3 did not have the same 'any angle' kickstand of the Surface Pro 3, but a three-position stand instead, there were some groans of disappointment. But there was thinking behind the decision, and it's tied up with Microsoft's mobile-first philosophy:
We chose to put the 3-position hinges in Surface 3 in order to optimize size and cost of the device. In addition, the 3-position hinges allow the user to flick open the kickstand more easily to the pre-set angles enabling quick operation for on-the go use.
When designing the kickstand, Microsoft's engineers took an interesting approach:
On Surface 3 we defined the sound before we engineered the parts. The sound is created by the materials of the foot snapping onto the magnesium. The hinge snaps the kickstand to the Surface body and imbedded magnets hold it perfectly flat... which gives it the perfect sound.
Anyone looking to get a discount on a Surface 3 purchase will have to enroll in a course -- a 10 percent discount will be available to students through Microsoft Stores on Surface 3 and its accessories. There are currently no plans for a trade-in program, but it’s something that might be considered in the future.
Other snippets and areas of clarification include the fact that Surface 3 supports InstantGo, as well as 4K at 30Hz with Intel X7 Gen8 engine. There's also support for Connected Standby, and after four hours in this mode, the tablet will switch to hibernation. The team confirmed that Windows 10 will be available as a free upgrade to early adopters to the Surface 3.
MMC performance on the Surface 3 is 50 percent of the SSD on Surface Pro 3, and the Pro and non-Pro third generation devices share the same network chip. Surface 3 is a device that Microsoft has designed to be as future-proof as any piece of technology can be:
We built this product to last, and feel amazing about its performance, battery life, usability, etc. Every element of the design is meant to incorporate 'future proofing'. We are super clear our customers expect it from us, and we work hard to be sure you are good with it.
3:2 ratio, this is the future. Once you put this product in your hands you feel the benefits of Windows scaling to 3:2, you will also love the weight distribution on the device as you hold it in portrait to use it to write and read.
And then there's the question that's on everybody's lips -- well, everyone with an interest in Surface devices, that is. Asking on behalf of everyone is Reddit user MichaelEPS5: "What can you tell us about the Surface Pro 4?" Brace yourself for the answer:
Nothing.
Short, sweet and to the point. Microsoft clearly wants us to focus on the Surface 3 for now and not get distracted by devices that are still in the pipeline.
-

Microsoft will no longer enable Do Not Track by default
Publié: avril 3, 2015, 7:26pm CEST par Mark Wilson

Do Not Track will not be enabled by default in future versions of Microsoft web browsers, the company says. The decision comes in response to the latest draft of the World Wide Web Consortium's DNT standard which states "in the absence of user choice, there is no tracking preference expressed".
Microsoft is concerned that if the setting is enabled by default in Internet Explorer or Project Spartan, sites would have a loophole permitting them to ignore a DNT signal. In the future users will need to manually enable the feature, and Microsoft says that clear information will be provided about how to do this.
Do Not Track was implemented in Internet Explorer 10 a couple of years ago, but the changing landscape of web standards means that Microsoft has had to move on to try to avoid confusion and misunderstandings. The change of position means that sites are more likely -- although not guaranteed -- to honor DNT requests due to the fact that they have been purposely selected by users.
In a blog post, Microsoft's Chief Privacy Officer Brendon Lynch said:
Put simply, we are updating our approach to DNT to eliminate any misunderstanding about whether our chosen implementation will comply with the W3C standard. Without this change, websites that receive a DNT signal from the new browsers could argue that it doesn’t reflect the users’ preference, and therefore, choose not to honor it.
Moving forward, users setting up a new PC, installing a new version of Windows or a new version of Internet Explorer will be offered the chance to choose their DNT preference.
Photo credit: Iliana Mihaleva / Shutterstock
-

WikiLeaks leaker Chelsea Manning joins Twitter from prison
Publié: avril 3, 2015, 3:59pm CEST par Mark Wilson

Despite being incarcerated for leaking classified documents to WikiLeaks, Chelsea Manning has joined Twitter. The solider formerly known as Bradley Manning has been approved to receive gender-reassignment hormone therapy, but is not permitted access to the internet.
To get around this restriction, supporters of Manning have set up the @xychelsea account on her behalf. Tweeting is due to start today, and Manning will dictate messages over the phone so "her own candid thoughts and comments" can be shared with Twitter users.
Manning's Twitter profile lists her location as Fort Leavenworth, Kansas, USA, and the hand-drawn profile picture shows her as she would like to appear -- with long hair. Despite permitting gender-reassignment therapy, authorities have said that Manning is not allowed to grow her hair, although this will be reconsidered in the near future once hormone therapy has been administered for a number of months.
Since Manning's conviction in 2013, there has been an online campaign running calling for the whistleblower to be freed. It is likely that the Twitter account will be used as a platform for Manning to communicate with her network of supporters.
Even before the account has been used to post any tweets, it has already managed to collect -- at time of writing -- almost 3,000 followers, a number that is certain to grow in the coming weeks and months.
Update
Having made just four tweets, Manning's follower count has jumped to over 8,500. Things got off to gentle start with the Twitter equivilent of Hello World:
This is my new twitter account =P
— Chelsea Manning (@xychelsea) April 3, 2015
She went on to say that "I'm hoping to stay connected w/ this account as much as poss., but would rather tweet about more meaningful things than not #lessismore". The most recent tweet indicates that Manning may be open to questions, but is yet to respond to any:
It will be hard, but I don’t want this Twitter feed to be a one-way street/conversation
— Chelsea Manning (@xychelsea) April 3, 2015
We are still trying to determine who is actually in control of the Twitter account. We'll update this post if and when we have more information.
Update 2
The Manning Twitter account is being handled by FitzGibbon Media, a Washington DC-based organization whose Twitter profile reads:
Domestic and global communications around cutting edge human rights, env. and progressive campaigns.
-

TrueCrypt doesn't contain NSA backdoors
Publié: avril 3, 2015, 1:50pm CEST par Mark Wilson

A security audit of TrueCrypt has determined that the disk encryption software does not contain any backdoors that could be used by the NSA or other surveillance agencies. A report prepared by the NCC Group for Open Crypto Audit Project found that the encryption tool is not vulnerable to being compromised.
However, the software was found to contain a few other security vulnerabilities, including one relating to the use of the Windows API to generate random numbers for master encryption key material. Despite this, TrueCrypt was given a relatively clean bill of health with none of the detected vulnerabilities considered severe enough to lead "to a complete bypass of confidentiality in common usage scenarios".
NCC's report reveals a total of four vulnerabilities in TrueCrypt, with two of them being marked as severe. The most worrying -- although it must be stressed that the report does not suggest that there is real cause for concern -- stems from the fact that random numbers are generated based on values from a Windows API. Should this API fail for any reason, TrueCrypt may continue to generate keys with the possibility of an element of predictability -- clearly not ideal for encryption software.
Moving forward, the report stresses the importance of improving error handing in the software:
Because TrueCrypt aims to be security-critical software, it is not appropriate to fail silently or attempt to continue execution in unusual program states. More than simply aborting the application, attempt to gather relevant diagnostic information and make it available for submission to developers to diagnose root-causes. This is especially important as it is difficult to fully test code on multiple operating systems and configurations.
With an increased interest in the activities of the NSA, and particularly in the suggestion that hardware and software should have backdoors built in by default, the report comes as good news overall for TrueCrypt users.
Photo Credit: Lightspring / Shutterstock
-

Android malware drops, but there are still nearly 10 million affected devices
Publié: avril 2, 2015, 8:01pm CEST par Mark Wilson

Google says that it is keen for Android to be a secure platform for developers and end users alike. It's not a unique claim; Apple would likely say much the same about iOS, and Microsoft about Windows Phone/Windows 10 for Phones.
To demonstrate how fervently it has been working away at improving security and introducing new security-focused features, Google today published a report looking back on Android security in 2014. Dubbed the Android Security State of the Union 2014, it makes for interesting reading. It includes the revelation that nearly 10 million Android devices have potentially harmful apps installed.
The report starts off by highlighting some of the most noticeable changes made to the Android platform -- the introduction of full-disk encryption, better sandboxing with SELinux-based Mandatory Access Control system, and wider use of hardware protected cryptography. This is all very interesting, but then we're treated to some statistics. Coining the phrase Potentially Harmful Applications -- or PHAs for the sake of brevity (malware by another name) -- Google aims to show how protection has improved over time.
In fact, from the beginning of Q1 2014 to the end of Q4 2014, the number of PHA installations dropped by nearly half. But what does this actually mean? Google throws out some more stats that shed a little light on the matter.
The report suggests that more than a billion devices are "protected with Google Play". Despite this protection, Google admits that fewer than 0.15 percent of Android devices that install software solely from Google Play -- so devices whose owners have not side-loaded apps from other sources -- had PHAs installed. At this stage we're not working with particularly precise figures, but we can estimate that there are around 1.5 million devices with potentially harmful software installed, even though they're only using the official Google source for apps.
But of course there are plenty of people who download apps from other sources, be it Amazon's store, direct from developers' websites, or through less legal channels. Count these devices, and the percentage of devices that have PHAs installed jumps to "fewer than 1 percent". To think that 99 percent of devices do not have potentially harmful software installed is clearly great, but the darker side of the story is that Google is aware of up to 10 million Android devices do have such apps installed.
Considering we're treated to a percentage rounded to two decimal places for devices using only Google Play, it would seem odd that the same treatment would not be given to devices using other sources as well. As such it would seem reasonable to deduce that while the figure is below 1 percent, it's actually very, very close to 1 percent.
Whatever the hard numbers may be, Google says that it has been able to track vulnerabilities and says that "the data does not show any evidence of widespread exploitation of Android devices". The monitoring led to the creation of a total of 79 patches -- 8 low severity, 41 moderate, 30 high (and none rated critical) -- and also showed that an estimated 0.25 percent of devices have rooting apps installed.
Google acknowledges that relying on Google Play is not a guarantee of avoiding PHAs:
Google Play reviews all applications for potential security issues prior to making them available to users. No review process is perfect, and with over 1 million applications in Google Play, there are a small number of Potentially Harmful Applications that do still manage to be published in Google Play.
Photo credit: Kirill__M / Shutterstock
-

Google bans Chinese security certificates
Publié: avril 2, 2015, 3:31pm CEST par Mark Wilson

Google no longer recognizes security certificates issued by CNNIC, China's domain name registry. The news comes after unauthorized certificates were issued for Google domains, and at the time Google said that CNNIC contractor MCS Holdings had issued the certificates.
What was worrying was the fact that MCS Holdings installed private security keys in a man-in-the-middle proxy rather than keeping them secure. MCS said that human error was to blame, but Google is taking no chances. The search giant is, for now at least, no longer recognizing certificates from the agency.
CNNIC is responsible for the security certificates issued for .cn domains, so if you visit any of these at the moment, you will see a warning message -- although there's nothing to stop you from continuing to access the site if you wish. However, it is worth noting that what should ordinarily be considered a secure connection, may in fact not be.
In an update to a blog post from a couple of weeks ago, Google says:
As a result of a joint investigation of the events surrounding this incident by Google and CNNIC, we have decided that the CNNIC Root and EV CAs will no longer be recognized in Google products. This will take effect in a future Chrome update. To assist customers affected by this decision, for a limited time we will allow CNNIC’s existing certificates to continue to be marked as trusted in Chrome, through the use of a publicly disclosed whitelist.
While neither we nor CNNIC believe any further unauthorized digital certificates have been issued, nor do we believe the misissued certificates were used outside the limited scope of MCS Holdings’ test network, CNNIC will be working to prevent any future incidents. CNNIC will implement Certificate Transparency for all of their certificates prior to any request for reinclusion. We applaud CNNIC on their proactive steps, and welcome them to reapply once suitable technical and procedural controls are in place.
It's not currently known when the update will be pushed out to Chrome users, or when Google will publish the whitelist.
-

Surface 3 is Microsoft's chance to take on the iPad
Publié: avril 1, 2015, 11:16pm CEST par Mark Wilson

Microsoft's Surface Pro took many people by surprise. It was a bit of a late entry to the tablet game, but it showed how to do things properly. This was full caffeine, full sugar, full alcohol Windows in tablet form. For those who need a little more flexibility, there's the option of adding a keyboard. With Surface Pro, Microsoft carved out a niche for itself.
It tried to do the same with Surface, and Surface 2, but there was one problem. Windows RT. With the Windows 10 wheels now in full motion, Surface 3 has been pulled out of the bag. Microsoft has made the sensible decision to ditch Windows RT and provide a cut-price tablet with full-blown Windows 8 -- and ultimately Windows 10. This is Microsoft's chance to take on the iPad head to head.
Surface 3 actually offers more than the iPad in many ways. Of course it will be difficult for Microsoft to persuade people away from the church of Apple, particularly if they are currently loyal members of the congregation, but there's plenty to draw people to the Microsoft altar if they're torn between the two camps. Expandability is one key area in which Surface 3 pulls ahead. As well as full blown Windows, there's also a mini DisplayPort and a full blown USB 3.0 port. The latter can be used to plug in a variety of peripherals, but it is more likely to be used to boost storage. If you don’t want to tie up the USB port in this way, there's a microSD card slot. Beat that, Apple!
The starting price for both the iPad Air 2 and the Surface 3 is $499 -- a price point which is affordable and inviting. But what do you get for your money? In terms of storage, a dollar short of 500 gets you just 16GB; with the Surface 3, you're treated to four times this -- 64GB. To get the same amount of storage in an iPad Air 2, you'd have to part with an extra $100. These are both portable devices, so dimensions and weight matter. The iPad Air 2 is slightly thinner than the Surface 3 at 6.1mm compared to 8.7mm, but what's 2.6mm among friends? The Surface is also somewhat weightier at 622g compared to the Apple tablet's 427g. Heavier, maybe, but hardly something that will weigh you down.
In terms of power, processors are what many people focus on. Apple's tri-core (yeah... just had to be different) A8X is clocked at 1.5GHz, and backed up by 2GB of RAM. Microsoft has made the decision to move away from ARM for the Surface 3, opting instead for a quad-core Intel Atom X7-Z8700 processor running at 1.6 GHz and offering a Turbo Boost speed of up to 2.4 GHz. Microsoft's tablet may not set any records in benchmarks, but it's not supposed to. This is not supposed to be a powerhouse tablet, it's a tablet that's realistic about what people 'need' from their hardware.
Of course there will be plenty of people ready to mock the specifications, but think about what most people use their tablets for. In all likelihood, the Surface 3 will be used, like the majority of computers, to browse the internet, check Facebook, send emails and perhaps write the odd document or spreadsheet -- oh, there's a free year-long subscription to Office 365, forget compromising with Pages et al. A quantum computer is simply not needed for simple tasks like this. Even games and most apps that aren't too reliant on 3D graphics will run fine. What's the point in GHz you're not going to use?

Where else does Surface 3 win? The kickstand is a good example. It might not be the highly adjustable version from the Surface Pro 3, but it's still a multi-position stand that should suit most situations. If you want to achieve something similar with the iPad Air 2, you'll need to invest in some sort of case/cover that doubles as a stand. In terms of user experience, it's hard to argue with the Surface 3 for existing Windows users. Running exactly the same operating system as desktops and laptops means that there is no learning curve and no compromises, and the inclusion of a stylus is a nice touch.
We've touched on software in mentioning the inclusion of Office 365, but Surface 3's major selling point is its ability to run any Windows software you care to mention. You might be a fan of Windows Apps from the Windows Store, or you may prefer traditional .exe-based software -- either way, you're covered. The tablet could even be used as a full desktop replacement for the less demanding user; a docking station lets you take advantage of your larger monitor, wired network, and gives you more USB ports.
It's the best of many, many worlds, in a flexible and affordable piece of kit that should do a great job of shaking off the poor image associated with the first two generations of Surface. Apple may not yet be quaking in its boots, but with Surface 3, Microsoft is making slow and steady headway on the inside track.
-

Flickr adds support for public domain photos
Publié: mars 31, 2015, 11:04pm CEST par Mark Wilson

When you stick a photo online, how can you make it clear that you are happy for anyone to use it however the heck they want? By adding support for the Public Domain and Creative Commons 0 designations, Flickr just made things a whole lot easier.
The site has long been home to a raft of images made available under Creative Commons licenses, but now options have been expanded further. If you're happy to forego the copyright you have to your picture, Flickr now lets you become a photographic philanthropist.
It's something that Flickr hopes lots of users will take advantage of. Launching support for the new image designations, it reveals that SpaceX has made score of its photographs available for free for anyone to use, edit, and basically do whatever they want with. You can do the same if you feel so inclined.
Announcing the new categories, Flickr product manager Rajiv Vaidyanathan says:
The default setting on Flickr continues to be All Rights Reserved, but you can change the default for all your photos in your account settings if you’re interested in using Public Domain or CC0. You can also set the designation per individual photo in a variety of Flickr desktop and mobile experiences, such as the Photo Page, Camera Roll, Organizr, Uploadr, etc.
We know these changes will provide more choice for our community and we’re happy to support them on Flickr.
Photo credit: cristovao / Shutterstock
-

Facebook introduces scrapbooks for photos of your kids
Publié: mars 31, 2015, 9:19pm CEST par Mark Wilson
Facebook is about more than being social; it's about presenting a version of yourself to other people. When you share a photo of your meal, you're making a statement: "look at this delicious expensive meal I can afford", "look at the fancy restaurant we're visiting", or "gosh, aren't I healthy for making this salad?". But of course Facebook is not just filled with photos of food -- there are also photos of kids, presenting an image of family life.
Starting today, Facebook is rolling out a new scrapbooking feature designed specifically for pulling together photos of your child. The idea is to make it easier to collect together photos into one place so you can view all of your memories without having to jump from place to place.
In a blog post (with the slightly uninspiring title of "An Optional Way to Organize Photos of Your Child on Facebook" -- sell this stuff! Be proud of it!), father and Facebook product manager Dan Barak introduces the new pilot, explaining that by using a special tag it is possible to add photographs to a customizable scrapbook. As it is likely that it will not just be you taking and managing photographs, you can share ownership of the scrapbook with your partner.
Facebook has created a video that shows off how the feature works:
To help keep the scrapbook truly personal, only you and your partner are able to add photos to it. Only your chosen tag automatically adds a photo to the scrapbook, so you don’t need to worry about friends adding other pictures unvetted.
The feature is rolling out to Facebook on the desktop, on Android and on iOS. To get started with your scrapbook, go to your profile and click About followed by Family and Relationships. You should see an invitation to start a scrapbook, so click Get Started and follow the instructions.
-

Project Spartan: fat, chunky, and devoid of style and features
Publié: mars 31, 2015, 2:54pm CEST par Mark Wilson
After all of the talk, some action. Microsoft has been gentling building the hype about Spartan for some time now, but it's only with the release of Windows 10 Technical Preview Build 10049 that we get to, officially, go hands on. This is the web browser that's replacing Internet Explorer, the default web browser in Windows 10, so it has quite a role to perform.
It's a browser that's "built for the modern web" -- whatever that means -- and it sees Microsoft trying to shed the shackles of IE and move forward. Microsoft has been talking the talking for months, but does Spartan walk the walk? No. Spartan, at the moment, appears to be a joke. Let me elaborate.
Of course there are the usual caveats of "this is pre-release software", "it's an early build", and "it'll all change by the final release". As when I have looked at Windows 10 previews, there will undoubtedly be suggestions that any criticism I may level at Spartan should be delivered to Microsoft rather than aired in public. I'm doing both. Anything I say here is also fed back to Microsoft. This article is a platform for me to share my thoughts with you and to see what you think.
It has been suggested that Microsoft's Technical Preview software is not meant for review. This is not a review, it's a recounting of my experience. It may be the same as yours, it may differ; I'd like to compare notes. If I have problems with Spartan but you don’t, why is that? Is there a difference with our setups, or is it just a peculiarity?
You might think Spartan is brilliant. You're wrong, of course, but I'd still like to hear why.
So what issues do I have with Spartan as it stands? Where shall I begin?
I realize, as I hope I have made abundantly clear, that this is pre-release software. It's meant to be the merest taster of what's to come, and our opportunity to shape the direction in which things might travel. That said, I fail to see why MS bothered with releasing it in its current form; there's nothing to it.
I realize that there's something of a clue in the name Spartan (should we see it as a reference to sparseness, or the city of Sparta rather than yet another Halo link?), but the interface is bare to the point of uselessness. It's like Microsoft just took the Windows Phone version of Internet Explorer and made it bigger. Windows 10 introduced the idea of (lots of) white space, and it's a theme that continues here. There's a place for white space, but here it seems to serve only to make interface elements huge.
Spartan's toolbar is decidedly overweight; let's compare it to Chrome. In the space Chrome houses tabs, the toolbar and the favorites bar, Spartan doesn’t even have room for the tabs and toolbar -- this duo is around 50 percent fatter than the three program elements in Chrome. A bold new design it may be, but it certainly could not be described as anorexic. Everything is so big and chunky. On the plus side, this makes it fat-finger friendly, but it's sure as heck not pretty or an efficient use of space. With everything being so stripped back, options are very few and far between making the browser very hard to personalize.
Apart from a horrible design, image rendering really isn't very good. A quick comparison between the Meet Project Spartan page in both Spartan and Chrome shows that Microsoft's new browser displays images in a fuzzy, smudgy way. It's almost as though really bad anti-aliasing has been enabled; things are so much clearer in Chrome.
Microsoft proclaims that Spartan lets you "do cool things like write or type on a webpage". What is this? A browser for 7 year-olds? Then there are compatibility issues. Google+, for instance, simply doesn’t work -- so much for Spartan switching engines as and when required.
I had been planning a week -- or at least a few days -- of using only Spartan, but at the moment, it's pretty much unusable. I can only hope that it comes on in leaps and bounds because at the moment, it's a joke.
This is meant to be about ditching Internet Explorer. I should be excited... but I need something to be excited about.
-

Syrian Electronic Army hacks Hostgator, FastDomain and more for hosting terrorist sites
Publié: mars 31, 2015, 12:23am CEST par Mark Wilson

It has been a little while since we heard anything from the Syrian Electronic Army, but now the group has made an appearance once again. SEA has hacked five big-name hosting companies -- Bluehost, Justhost, Hostgator, Hostmonster and FastDomain -- all part of the Endurance International Group.
SEA launched the attacks on the five hosts for "hosting terrorists websites" (sic) adding to the list of high-profile names it has already targeted -- a list that includes names such as Skype, Facebook, PayPal, Twitter and Microsoft. No sites were mentioned by name for having gained SEA's attention.
At the moment, it is not clear whether any particular demands have been made of the websites in question. The group took to Twitter to boast of the attacks, posting screenshots of the sites it had managed to commandeer. Bluehost was singled out for particular attention, with a tweet warning: "Next time... we will change the DNS".
Next time... we will change the DNS. #SEA cc @Bluehost pic.twitter.com/Dd9lgOloNB
— SyrianElectronicArmy (@Official_SEA16) March 30, 2015
The Hacker News reports that SEA took control of Bluebox's Twitter account and used it to post tweets, but these have now been removed. The Syrian Electronic Army supports the Syrian President Bashar al-Assad and is well-known for attacking Western websites. For now, it appears that the attacks have come to an end, but there's nothing to say something similar won’t happen again soon.
Photo credit: Duncan Andison / Shutterstock
-

Microsoft brings mobile device management to Office 365
Publié: mars 30, 2015, 9:53pm CEST par Mark Wilson

Microsoft has announced that mobile device management is now available in Office 365 for commercial customers. The feature is built into the office suite and allows administrators to control access to Office 365 data by Android, iOS and Windows Phone tablets and phones.
Security is very much at the heart of Office 365's mobile device management, and it includes a remote wipe feature. For businesses who have embraced the BYOD philosophy, this will bring peace of mind as it allows for the remote removal of Office and associated files even on personal devices.
Of particular interest to many users will be the conditional access options. These make it possible to limit data access to email and documents so that non-compliant and unauthorized devices are cut out of the loop entirely. The feature is powered by Microsoft Intune and Microsoft Azure Active Directory, and can be tailored to suit individual needs.
From a device management point of view, there are great new powers for administrators. Microsoft explains:
You can set and manage security policies such as device-level pin lock and jailbreak detection to help prevent unauthorized users from accessing corporate email and data on a device when it is lost or stolen. Additional settings and rich reporting are also available within the Office 365 admin center so you can gain critical insights about devices accessing your corporate data.
Available at no extra cost, the mobile device management features may prove to be a draw for enterprise customers who are yet to switch to Office 365. The rollout starts today, and it's hoped that the feature will be available worldwide in the next four to six weeks, bringing increased control and security to users.
Microsoft has produced a video that shows off the features and benefits of mobile device management in Office 365:
-

Apple extends its trade-in program to Android, Windows Phone and BlackBerry
Publié: mars 30, 2015, 5:12pm CEST par Mark Wilson

Earlier in the month we reported that Apple was about to start offering gift cards as part of a trade-in program for people buying a new iPhone. The updated program has now gone live so you can take your old Apple device, or non-Apple smartphone to an Apple store, or mail it in to receive credit.
The credit can be used in store or online against the purchase of a new Apple device, and this program expansion is the latest move from Apple to try to tempt users away from other platforms. You can check online to see how much you can expect to receive for your existing phone and decide whether it's worth your while. Hint: it might not be.
It's not an expansion that Apple is making a great deal of fuss about. Head over to the page for a specific Apple store -- such as the San Francisco branch -- and you'll see a small announcement under the "Reuse and Recycling Program" heading, you'll see the description: "Get credit when you recycle your eligible iPhone, iPad, or select smartphone from another manufacturer."
So what are the trade-in values? We got a valuation for a 32GB Samsung Galaxy S5 and Apple's chosen valuation service, Brightstar in the UK, came up with an offer of £144 (around $214). This sounded a little on the low side, so we checked on phone trade-in comparison site SellMyMobile which provided trade-in prices from nine other sites. The valuations ranged from £110 - £185 ($163 - $274), averaging out at £170 (around $251).
On the face of it, the trade-in values are not brilliant. Trading in through Apple means that you are tied into using the company's chosen valuation service. Opt to go it alone and you can check the market and get a better deal -- from a quick check it looks as though it might be worth spending the time shopping around.
-

GitHub hit by its biggest DDoS attack ever
Publié: mars 30, 2015, 1:26pm CEST par Mark Wilson

GitHub is still in the throes of a massive DDoS attack which has blighted the site since Thursday. While the origins of and reasons for the attack is not yet fully known, the fact that two projects relating to Chinese anti-censorship have been targeted speaks volumes.
Now into its fifth day, the attack turned into something of a tug-of-war. Just as GitHub thought it had managed to wrestle back control of the site, a fresh wave was unleashed. The evolving attack is the largest in GitHub's history and engineers "remain on high alert".
The attackers have been using a variety of tactics over the course of the last few days, pursuing different areas of GitHub. The anti-censorship projects appear to have been key targets, and it included a project by Greatfire.org which aims to provide access to services and sites that are banned in China. Only last week GreatFire.org suffered a DDoS attack of its own.
On Friday, the GitHub status Twitter account was used to share some news about the attack:
We've been under continuous DDoS attack for 24+ hours. The attack is evolving, and we're all hands on deck mitigating.
— GitHub Status (@githubstatus) March 27, 2015
The battle against the attackers seemed to going GitHub's way, but the onslaught intensified. A post on the GitHub blog explained:
The attack began around 2AM UTC on Thursday, March 26, and involves a wide combination of attack vectors. These include every vector we've seen in previous attacks as well as some sophisticated new techniques that use the web browsers of unsuspecting, uninvolved people to flood github.com with high levels of traffic. Based on reports we've received, we believe the intent of this attack is to convince us to remove a specific class of content.
At the moment, it would appear that the attacks originate from within China. As reported by PC World, one Chinese blogger has determined that advertising code may have been hijacked and used to pound GitHub with traffic. He found that when he visited Chinese websites, he started to notice JavaScript popups. Further investigation revealed that these were the result of trying to access the previously mentioned anti-censorship projects on GitHib. It looks as though someone has modified the ad tracking code used by Baidu -- the Chinese search giant, comparable to Google -- and used it to launch the DDoS attack.
That said, the attack has not yet been stopped in its tracks as it continues to adapt and change:
The DDoS attack has evolved and we are working to mitigate
— GitHub Status (@githubstatus) March 30, 2015
Photo credit: sibgat / Shutterstock
-

Fake Puush update steals passwords from Windows users
Publié: mars 30, 2015, 12:18pm CEST par Mark Wilson
Screenshot-sharing app Puush has inadvertently infected Windows users with malware. Over the weekend, the Puush server was breached and a fake, malware-infected program update was put in place. This means that anyone updating to version r94 of the software is infected.
The malware tries to grab passwords from infected systems, and was noticed after users complained on Twitter that the latest update had been flagged up by BitDefender. As a precautionary measure, the update server has been taken offline, and a clean update has been made available as a standalone download.
Puush is quick to point out that it is only the Windows version of the app that is affected -- the iOS and OS X apps remain clean. It is not yet clear what happens to passwords that have been collected as tests have not shown them to be sent to another computer. Another update has already been produced, version r100, and this has not only been checked to be clean, but also tidies up after the malware infected r94.
In a statement, Puush said:
The malware may be collecting locally stored passwords, but we are yet to confirm these have been transmitted back to a remote location. We have been running the malware in sandboxed environments and have not been able to reproduce any such behaviour. Even so, we recommend you change any important passwords which were stored on your PC (unless they were in a secure password manager). This includes chrome/firefox saved passwords.
The statement also recognizes the fact that some people may have been put off using Puush. For these users, a cleanup and removal tool is available:
We have created a cleaner for people who do not wish to continue using puush. It is stand-alone and will tell you if you were infected (assuming you have not already updated to r100). You can obtain this here: [puush.me].
-

Snowden's leaks served only to strengthen the NSA's resolve
Publié: mars 29, 2015, 7:19pm CEST par Mark Wilson

Edward Snowden is heralded as both a hero and villain. A privacy vigilante and a traitor. It just depends who you ask. The revelations he made about the NSA's surveillance programs have completely changed the face of online security, and changed the way everyone looks at the internet and privacy.
But just before the whistle was blown, it seems that the NSA was considering bringing its telephone data collection program to an end. Intelligence officials were, behind the scenes, questioning whether the benefits of gathering counter-terrorism information justified the colossal costs involved. Then Snowden went public and essentially forced the agency's hand.
With a massive public backlash against what the NSA had been doing, the agency was obviously keen to defend what it had been doing. Whatever attacks were thrown by privacy advocates, individuals and civil liberties campaigners, the NSA had a trump card. Fighting terrorism. The agency would, of course, never admit that perhaps it was going too far, or that its operations were costing too many millions of dollars; it had to vigorously defend what it had been doing.
The NSA became so wrapped up in defending what it had already been doing, that it managed to convince itself of the worth of continuing its work. After all, if the activities had been justifiable before, do they not continue to be justifiable? The 'threat' of terror attacks is something that has become part of the media and governmental narrative, seared into the public consciousness.
We haven’t been told that terrorist threats had vanished or even diminished; if anything, the threat -- if we're to believe what we're told -- is greater than ever. Throw 'defense of America' into the equation, and you can get away with just about anything. Chuck in a few instances of the word 'terror' for good measure, and you're good to go.
The Associated Press makes the surprising suggestions about the NSA's doubts about what it was doing. The timing is interesting as we are approaching the deadline by which the law authorizes the collection of phone data (June 2015). The NSA has managed to persuade itself of the value of various surveillance programs over the years, and Congress will take quite some convincing if the law is to be changed such that the programs are outlawed.
This is not the first time that it has been suggested that Snowden's revelations had an unexpected side-effect. A data sharing agreement between the NSA and the UK's GCHQ was, essentially, made legal because of the fact that Snowden had made it public. Up until that point it had been illegal for the two intelligence agencies to share information in the way they had been but once the cover was blown it was rather a different story.
It would be very surprising to see the NSA back down now. Even if we were told that phone, email, and other data collection was coming to an end, how many would believe it to be true? It was happening in the background before, who's to say that would not just continue?
Photo credit: Maren Wulf / Shutterstock
-

The FBI wants your computer and mobile to be insecure
Publié: mars 28, 2015, 9:21pm CET par Mark Wilson

You'd think that governments would be encouraging people to keep their computers and personal data safe. Until relatively recently, this has been exactly what the FBI has been pushing -- suggesting that phone users should enable encryption on their handsets. But it seems that there has been something of a change of heart. It's probably Snowden's fault.
Now, as part of an "ongoing website redesign", advice about using encryption and protective PINs has vanished from the FBI website. Forget the security-focused devices such as the Blackphone 2, it appears that the bureau wants your data, and you, to be insecure.
As noted by TechDirt, the FBI website previously included an advice section entitled "safety tips to protect your mobile device". This has now gone, although it can still be seen on the Internet Archive's oh-so-helpful backup. The FBI no longer suggests that phone users enable encryption on their handset to protect their data and their privacy. But this is far from the end of the story.
Speaking on Wednesday, FBI Director James Comey made a call for a ban on encryption. This is not something that came completely out of the blue, it's something he has been pursuing for some time now. Of course it would be a little crazy to just make such a call with no justification behind it, and Comey was ready to pull on heart strings with a doom and gloom vision of a world in which an individual's privacy is seen as being of the utmost importance.
Rather than welcoming a future in which privacy is seen as key, he calls on those who believe in such a vision to imagine something a little darker: a world in which "pedophiles can't be seen, kidnappers can't be seen, drug dealers can't be seen". But this is only one side of the story. The flipside of the coin is that a world in which pedophiles, kidnappers and drug dealers can be seen is a world in which everyone else can also be seen. Nothing to hide, nothing to fear is the common comeback, but that's really not the point.
People are very quick to question this likes of Google when the company tracks user data for targeted advertising and other purposes. But this is something that people, essentially, sign up for. You use Google and you know that your online activities are going to be monitored to some extent. It's a given. Being monitored by the government, however, is an entirely different matter. The very way in which NSA surveillance was carried out demonstrated perfectly that the people collecting data do not know what they're doing or what they're looking for.
With Comey and his ilk pushing for technology company to build backdoors (which we know can be problematic) into all of their products and services that offer encryption. He views encryption as a "huge problem" -- but it's also an incredibly valuable tool for individuals. Encryption with backdoors is as good as no encryption, which is precisely what Comey would like.
Edward Snowden has previously criticized Amazon for failing to encrypt user data (as have others), and with a rise in security attacks, it's little wonder that, on the whole, there is an increased interest in data encryption. The FBI and other organization should be encouraging people to be safer, not pushing for a drop in security simply because it makes surveillance easier.
Photo credit: spiber.de / Shutterstock
-

Slack is tardy to the two-factor authentication party
Publié: mars 27, 2015, 7:34pm CET par Mark Wilson

Following a four-day long security breach back in February, chat and collaboration tool Slack is finally getting two-factor authentication. Last month, the encrypted central user database was accessed by hackers although there is no indication that hashed passwords were decrypted.
Slack insists that no payment information was seen by hackers, and while the breach is far from good news, there is a silver lining: it has forced the company to look harder at security. Starting today, two-factor authentication is available which locks down accounts via the Android, iOS and Windows Phone apps.
Despite the chronology, Slack insists that introducing two-factor authentication is not a response to the "security incident". The company says that the feature "has been in development for the last few months" and is now being released earlier despite the fact it needs "a few small UI tweaks", and has a few "remaining bits of clunky-ness".
An email has been sent out to Slack users which explains:
We are writing to inform you that we were recently able to confirm that there was unauthorized access to a Slack database containing user profile information. We have since blocked this unauthorized access and made additional changes to our technical infrastructure to prevent future incidents. We have made all relevant details available on our blog. No specific action is required of you.
Although the email suggests that no action is required, Slack is trying to encourage users to enable the new security feature.
The new security options do not end there. Slack is also rolling out a Password Kill Switch feature for team owners. This can be used by an administrator to kick all users out of a chat session in the event of a security breach, as well as the ability to force all team-members to change their passwords.
-

Exclusive: Widespread security flaw affects hundreds of UK news sites
Publié: mars 27, 2015, 5:44pm CET par Mark Wilson

A security flaw has been discovered in a number of UK news websites, potentially placing 24.5 million users at risk. The problem was found in websites run by Johnston Press, a UK media group that is responsible for scores of regional news websites.
Just a few days ago we reported about the findings of security researcher Brute Logic. He discovered an XSS vulnerability on Amazon that risked exposing user data and could be used to compromise accounts. Now the same researcher has discovered another cross-site scripting security flaw that could be used to redirect visitors to malicious websites -- and it's worryingly simple to exploit.
Brute Logic found that sites such as Worthing Herald can be easily commandeered. He demonstrated the vulnerability by using a custom URL to generate a popup on Johnston Press websites and explained that the very same technique could be used to redirect visitors to a phishing website. He points out that this type of attack is not detected by the Auditor feature of Google Chrome which is supposed to offer protection against XSS vulnerabilities.
In all, the problem affects hundreds of websites -- both desktop sites and mobile versions -- all seemingly sharing the same IP address. Brute Logic submitted details of the vulnerability to XSSposed, where he remains the top researcher, giving the following description:
The vulnerability is still unpatched putting worthingherald.co.uk users, visitors and administrators at risk of being compromised by malicious hackers. Theft of cookies, personal data, authentication credentials and browser history are probably the less dangerous consequences of XSS attacks.
XSS attacks are becoming more and more sophisticated these days and are being used in pair with spear phishing, social engineering and drive-by attacks.
Brute Logic points out that while it is common for people to worry about high profile websites such as Amazon having vulnerabilities, it's easy to forget about the smaller fish. But as the size of the Johnston Press audience demonstrates, even a security issue with a smaller site has the potential to have a huge impact:
The danger is greater because these companies are less security aware and attacks will be very targeted.
We have reached out to Johnston Press for comment, but at the time of writing we have yet to hear back with a response.
Photo credit: arda savasciogullari / Shutterstock
-

Xbox One April update preview brings voice messaging and more
Publié: mars 27, 2015, 10:36am CET par Mark Wilson

It's time for a new update to roll out to Xbox One consoles around the world, and April's offering has some key changes that are sure to go down well. The headline addition sees the reappearance of a feature that Xbox 360 owners will remember from the previous generation of Microsoft's console -- voice messaging.
Forget time-consuming typing, now a quick double-tap of the Xbox button is all that's needed provided you have the messages app snapped into place. This week's rollout builds on the features that were added to the version that Preview program members gained access to a week ago.
Last week, Microsoft brought a number of improvements to Party Chat, making it easier to get things set up, including configuring privacy options. The latest update makes further improvement with the introduction of dedicated servers for Party Chat, to help overcome the NAT issues that have plagued some users.
Changes have also been made to the What’s On area so that videos, movies, TV shows and game broadcasts are now highlighted. To start with this feature will be available in the US, but it will then expand to Xbox One owners in the UK and Canada. Tweaks to achievement notifications mean that you can now see just what you did to unlock an achievement -- no need to skip back and forth between your game and the achievements app.
Preview users can expect the update any time now, but everyone else will have to wait a little bit longer -- although Microsoft is yet to pin down a release date.
Photo credit: Stefano Tinti / Shutterstock
-

Google has a new data compression extension for Chrome -- do you trust it?
Publié: mars 27, 2015, 2:38am CET par Mark Wilson

A couple of days ago Google launched a Chrome extension that compresses web pages. This is a feature that has been available for the iOS and Android versions of Chrome, but now it has hit the desktop. It's something that will be off interest to people whose ISP puts data caps in place.
Launched on March 23, the Data Saver extension is currently in beta (come on, this is Google… what did you expect?) and it helps to "reduce the amount of data Chrome uses". This might sound appealing, but it does mean that your traffic is routed through Google's own servers. Do you trust Google enough?
Using the extension has obvious plusses. If you have to keep within a data limit, anything you can do to compress pages is to be welcomed. Compressing pages can also have the happy side effect of speeding up load times. Sounds great, yeah? What's not to like about optimized pages? Look to the extension's page in the Chrome Web Store and the description says:
When this extension is enabled, Chrome will use Google servers to compress pages that you visit before downloading them. SSL and incognito pages will not be included.
Very much the same information is provided on the relevant Google support page:
When you're using Data Saver, Google's servers reduce the amount of data that gets downloaded when you visit a webpage. How much data gets saved depends on the type of content on the page. Secure pages (pages that start with https) and incognito pages load without any data savings.
Living in an age of heightened awareness of privacy issues, would you be happy for all of your traffic to pass through Google's servers? Do you have enough trust in the search giant to give it even more chance to scrutinize your online activity?
Photo credit: marekuliasz / Shutterstock
-

LibreOffice moves to the cloud to take on Office Online and Google Docs
Publié: mars 26, 2015, 12:55am CET par Mark Wilson

Four years in the making, LibreOffice is working towards moving online. LibreOffice Online is due to spring from a partnership between IceWarp and Collabora with the aim of competing directly with Google Docs and Office 365. Upon launch, it will be the first cloud-based office suite to offer support for the Open Document Format (ODF) standard.
Based on HTML 5, there's not currently a launch date for LibreOffice Online but IceWarp and Collabora hope to drive competition and innovation by entering the market. The suite is already available for just about every mobile and desktop platform, so the move to the cloud was all but inevitable.
Announcing the new collaboration, Collabora said that it had identified a need for cloud-based document editing and collaboration, and that the LibreOffice Online project would help to improve interoperability between existing services. IceWarp has plenty of experience in this field and its IceWarp Server solution already allows for the online management and viewing of Office documents. Collabora has been a LibreOffice contributor for many years now, and has already put work into an enterprise version of the suite.
In a blog post, Eliane Domingos de Sousa, Director of The Document Foundation said:
LibreOffice was born with the objective of leveraging the OpenOffice historic heritage to build a solid ecosystem capable of attracting those investments which are key for the further development of free software. Thanks to the increasing number of companies which are investing on the development of LibreOffice, we are on track to make it available on every platform, including the cloud. We are grateful to IceWarp for providing the resources for a further development of LibreOffice Online.
With no timeframe for launch yet sketched out, it's a case of 'watch this space' for more news.
-

Microsoft signs letter to congress calling for changes to government surveillance
Publié: mars 25, 2015, 6:51pm CET par Mark Wilson

Microsoft has teamed up with the likes of Mozilla, Silent Circle, Human Rights Watch, the Electronic Frontier Foundation and others, signing a letter to the White House and Congressional leaders that calls for an end to bulk collection of data. Many people and organizations have called for reform to the USA Patriot Act and this letter is the latest attempt to pile pressure on the government to make changes.
Scores of signatories point out that the USA PATRIOT Act Section 215 is due to expire in June, and now is the time to instigate reform. A call is made for greater privacy protection to be put in place when data is collected, as well as for improvements in transparency.
This is something that privacy advocates have been clamoring for for some time now and the number of high profile companies now calling on the government to take notice represents a united front fighting back on behalf of disillusioned customers and clients. The letter also stresses that reforms must allow for the declassification of Foreign Intelligence Surveillance Court decisions.
Writing on the Microsoft blog, Fred Humphries, the company's Vice President, U.S. Government Affairs said, "we understand that governments play a vital role in helping protect our communities, but we must do so in a way that protects the values we cherish. Nearly two years after government surveillance revelations came to light, the U.S. Government still has unfinished business to reduce the technology trust deficit it has created".
The letter concludes by saying:
It has been nearly two years since the first news stories revealed the scope of the United States' surveillance and bulk collection activities. Now is the time to take on meaningful legislative reforms to the nation’s surveillance programs that maintain national security while preserving privacy, transparency, and accountability. We strongly encourage both the White House and Members of Congress to support the above reforms and oppose any efforts to enact any legislation that does not address them.
Photo credit: Lisa S. / Shutterstock
-

Facebook apes TimeHop with On This Day
Publié: mars 25, 2015, 1:46pm CET par Mark Wilson
History. It's so much more reliable than the future. You know where you stand with things that have happened. This is possibly why they are often looked back upon (is that not the only way to view such things?) with such fondness. Unless they were bad things, of course.
Latching on to the general liking for getting moist-eyed and nostalgic, Facebook is rolling out a new On This Day. It's something that borrows heavily from services like TimeHop, and gives users of the social network a new way to check back on the content they've posted. It's something Facebook has experimented with already with its Year In Review, but this is a more wide-reaching feature.
If you've ever wondered what you posted to Facebook 365 days ago, or have been kept awake because you can’t remember what was happening 2 years ago, On This Day could just be the tool you've been waiting for. Conscious that some of this content might be private, Facebook says that posts that are unearthed in this way will only be made public if you explicitly indicate that this is OK.
You can get the ball rolling by heading to the On This Day page or by searching for On This Day within the Facebook app on your phone or tablet. Introducing the feature, Facebook's Jonathan Gheller said:
On This Day shows content from this date in the past. For example, you might see past status updates, photos, posts from friends and other things you’ve shared or been tagged in [...] You can choose to subscribe to notifications so you’ll be alerted when you have memories to look back on. You can also edit and delete old posts, or decide to share your memories with friends.
The feature isn’t available globally just yet, but as the rollout is now under way, it shouldn’t be too long before you see it.
-

Windows 10: Smooth user experience it ain't
Publié: mars 25, 2015, 12:09pm CET par Mark Wilson

Despite months of work, Windows 10 still falls a long way short of what it should be by now. Based on the last time I wrote about Windows 10 in a less than positive way, I'm not expecting great feedback on what I'm about to write. Of course, there is the caveat that we're all using a pre-release version of the operating system and problems are to be expected, but that’s not really the point.
The point is that Microsoft has been working on Windows 10 for quite some time now. Public builds have been a little slow to creep out -- despite promises that things would speed up -- but I'm concerned about how little time there is until the planned release. While there's a lot that right with Windows 10, there's an awful lot that's still very, very wrong.
I know I'm not alone in my disappointment; my colleague Wayne has written about how the operating system fails to meet his hopes. I've been using Windows 10 since it was first made publicly available, and with the release of build 10041 I decided to bite the bullet and move out of the safety of a VMware virtual machine; I installed Windows 10 as the sole operating system on the computer I use for, well, everything. So what are the issues?
I've outlined some of my complaints before, but using Windows 10 as my daily operating system has shifted my focus somewhat, and also highlighted some issues that either didn’t exist in previous builds or just hadn’t cropped up in my day to day usage. The first issue has to be that the UI is just all over the place. The mix of modern and legacy persists, and the jump between the two is quite jarring at times.
For example, the decision to introduce modern-style settings alongside the Control Panel would made sense if there was a degree of logic to having the two co-exist. As it stands, when one decides to change a system setting it's all but impossible to know whether you'll end up working with Settings or the Control Panel -- you get thrown from one to the other in a most nauseating fashion. Let's look at display settings.
I'm using a new operating system, so let's use the new way of changing settings -- i.e. via Settings. Firing up the pseudo-Control Panel from the Start menu and my eyes are assaulted by the monochromatic, outline icons that are more at home in Windows Phone (or Windows 10 for Phones). Even in the latest build, nothing has been done to make Settings elegant. Some will point to the minimalist icon as an example of refinement and elegance, but the hieroglyphs are often difficult to interpret and the amount of white space is astonishing. There is just so much wasted space!
I'm interested in changing my display scaling settings. Nothing helpful to be found in the Display section. Let's click through to Advanced display settings. Still not a setting for me to change, but there is a glimmer of hope in the form of a link labeled "Advanced sizing of text and other items". Woah! Control Panel time! Forget a smooth, uniform experience, here we've been dumped unceremoniously from the modern UI to the legacy look of Windows. I have not the slightest problem with the legacy UI, but from an experiential point of view, the jarring jump is just horrible.
So here we’ve had two UI ideas to contend with. Nothing major, you might say, but inconsistency makes things unpleasant. How about if we try switching wireless networks? What's that experience like?
Click the Wi-Fi icon in the notification area and a Notification Center style pop up appears -- yet another design element! Ah... it seems that I'm on the right network, but things aren’t working as they should. I'll click the Network Settings link to see what I can do. Whoomf! Full screen Settings! I see a list of available connections, so what’s this "Show available connections" link? Let's click it and find out. Huh? A slide out Charms bar network selector? I thought that had been killed -- the Windows + C keyboard shortcut doesn't even work anymore. Weird. Back in Network & Internet settings, there's are lots of links to click in the Related setting section; click something like Network and Sharing Center, Internet options, or Windows Firewall and you're dumped back into legacy view. No fewer than four (!) different UI designs are used. This is cohesive? Insanity.
While I'm complaining about modern stuff (go ahead, call me a dinosaur, but it still seems like a step backwards to me), there's something else that bugs me. Why am I not able to run two instances of a modern app at the same time? I want to look at two PDFs side by side, but it's only possible to view one at a time using the Reader apps. Sure, I can switch between two PDFs open in the app, but not in the same way as switching between open documents in other apps. Rather than being able to Alt-Tab or Windows-Tab through things, I have to use a menu. Inconsistency once again.
I could install a second PDF tool that allows for multiple documents to be displayed side by side, but why should I? Sod it, I might as well install Adobe Reader and use it alongside Windows' own Reader -- at least then I can be consistent with my use of inconsistent interfaces. It takes me back to my previous complaint of Windows 10 being like a rollercoaster ride.
It seems that Microsoft is aware that Windows 10 could be something of a disappointment. So keen is the company to get it installed on as many devices as possible, the company recently announced that there will not be obstacles placed in the way of upgrading from pirated copies of Windows 7 and 8.
But is it all bad news? No. Despite what some people have found, Windows 10 is remarkably stable in daily use -- there's just an awful lot of tidying up still to do. My girlfriend also decided to take the plunge... after all, upgrading is an incredibly simple, pain-free (if rather slow) process. Her first words after completing the upgrade? "God, it's fast. It's like a completely new computer." Whether she stays impressed remains to be seen, but I'm still worried that Microsoft still has a long way to go to get Windows 10 back on track.
Based on how long it has taken Microsoft to get to this point, how confident am I that the niggles will be addressed? Not at all. I'm fully braced for continued disappointment.
-

Microsoft decides sub-10.1 inch devices just aren't professional
Publié: mars 25, 2015, 12:38am CET par Mark Wilson
You've probably heard that size matters, and Microsoft agrees. If you're carrying about a mobile device that measures 10.1 inches or less, the chances are you're not using a "professional" device -- at least this is what Microsoft believes.
10.1 inches, 256.54 millimetres, 25.654 centimetres; this is the new dividing line between what is classed as a personal device, and which is professional. This is interesting to know, but what does it actually mean? For starters, if you fall into the "personal" category, you're entitled to a free copy of Office.
It also means that Microsoft makes a few assumptions about how you use your device. In a post on the Office blog, Kirk Koenigsbauer, corporate vice president for the Office 365 Client Apps and Services team explains that the company has analyzed how its products are used and based Office licensing on this information. Already celebrating 80 million downloads of Office for iOS, Microsoft's aim is to get Office onto as many devices as possible, as exemplified by the availability of free, basic versions of apps for tablets.
Elaborating on Microsoft's view on size, Koenigsbauer says:
Currently, we are also using screen size to delineate between professional and personal use. Based on our research, we are classifying anything with a screen size of 10.1 inches or less as a true mobile device: You’re probably using it on the go, when it's not practical to use a larger computing device such as a PC or a Mac. You probably aren’t using a mouse or a keyboard, instead navigating via touch interface. It’s probably not a 'pro' category tablet that is used for design or presentations. On these devices, the core editing and viewing experience is free, until you get to those premium, subscription features.
There's still a market for paying customers, however. Subscriptions to Office 365 Home and Office 365 Personal grew by 30 percent to 9.2 million in the last quarter, and commercial usage has jumped by 88 percent in a year. Microsoft has also announced that it will be pre-installing more apps on Android devices, but the use of a freemium model means that even though apps may be provided gratis for smaller screens, when the need to create -- rather than just view -- documents arises, it's time for the hand to head to the pocket.
Photo credit: worker / Shutterstock
-

Project Spartan and IE will no longer share rendering engines in Windows 10
Publié: mars 24, 2015, 8:54pm CET par Mark Wilson

It is now a couple of months since Microsoft started talking about Project Spartan, the Internet Explorer successor that's set to become Windows 10's default web browser. Some have suggested that this will lead to the death of Internet Explorer, but today Microsoft confirmed that the two browsers will live on side by side in Windows 10.
At the Project Spartan Developer Workshop, Microsoft went into more detail about the future of the two web browsers. In particular, there is the revelation that previous plans to use a new rendering engine in both Internet Explorer 11 and Project Spartan have been ditched. Internet Explorer will live on in Windows 10, providing legacy support for those who need it, and it will be virtually identical to the version found in Windows 8.1.
The plan had been to introduce a new rendering engine to both Internet Explorer for Windows 10, and Project Spartan, but now things have changed. The new Edge engine will be used solely in Project Spartan, and Trident will be exclusive to Internet Explorer. Microsoft says that this is a simpler browser strategy as it ensures that there is a more consistent experience when using Internet Explorer on Windows 7, 8 and 10.
Program Manager for Project Spartan, Kyle Pflug, said:
Based on strong feedback from our Windows Insiders and customers, today we’re announcing that on Windows 10, Project Spartan will host our new engine exclusively. Internet Explorer 11 will remain fundamentally unchanged from Windows 8.1, continuing to host the legacy engine exclusively.
The decision makes a clear divide between Internet Explorer and Project Spartan. It splits the web into modern and legacy browsers just as Microsoft split apps into modern and legacy camps -- Project Spartan caters for the future, Internet Explorer for the past. Feedback from testers suggested that users failed to see an obvious distinction between the two browsers and now Microsoft has made the difference clear.
Microsoft is keen for as many people as possible to make the switch to Project Spartan, but Internet Explorer 11 will live on to help cope with the "small set of sites on the Web that were built to work with legacy technologies". Businesses that rely heavily on legacy technologies will be able to make Internet Explorer 11 the default web browser using Group Policy, but for home users, the Project Spartan push starts now.
-

Amazon patches huge XSS vulnerability that left user data exposed for two days
Publié: mars 24, 2015, 6:06pm CET par Mark Wilson

A serious XSS vulnerability left Amazon customers in "real danger" of having their accounts compromised. The man who made the discovery is Brute Logic, the current top security researcher at XSSposed.org and "light-gray computer hacker". We spoke to him about the security issue as well as talking about the responsibilities involved in exposing vulnerabilities.
The cross-site scripting vulnerability was discovered on March 21 and was left unpatched for two days. In this time, Brute Logic says there was a real risk that people "could have their Amazon account compromised or had their computer invaded by means of a browser exploit". He says it is the responsibility of sites to fix problems when they are highlighted by the hacking community.
Brute Logic is not, like some hackers, in the habit of holding sites to ransom when a vulnerability is discovered. At the same time, he and other hackers are not out to do the cleanup work for the likes of Amazon. I asked whether he had informed Amazon of the security issue when he discovered it: "Since they do not pay for that, I just reported it to XSSposed.org and tweeted with a mention".
Google's Project Zero came in for criticism recently after Microsoft complained that the search giant's bug disclosure policy did not allow enough time for vulnerabilities to be patched. This led to Google relaxing its policy slightly, but Brute Logic thinks the approach is correct. "I think Google is just 'not being evil'. I like the way they are doing it: it is not Google's problem," he says.
But what of the Amazon vulnerability? It's all well and good to say that users were at risk, but just what does this mean?
This vulnerability let me run JavaScript code (which is responsible for some of the interactive things you can do within a webpage) in your browser. This kind of code can do things like steal your session on a given site (if it has a private area protected by a login) where I can see your credit card number or buy something in your name (in Amazon's case).
This code can also let me redirect your browser (you will not ever see it) to another site, controlled by me, that will identify your browser and select an appropriate exploit to it. If this attack succeeds (based mainly on your lack of browser, Java or Adobe updates), I will have total control over your computer.
In order to make these types of attacks happen, all that's needed is for a victim to click on a specially crafted link, but it is not that difficult once you have a legitimate link from the Amazon website. A fake email or a social network sharing is enough to trick the victim, as that will play on his/her trust in the Amazon reputation.
But what risks were people really at?
Amazon customers were in real danger: it is very easy to launch a massive spam campaign pointing to a link that exploits this flaw.
Brute Logic explained to me that the vulnerability was discovered "by chance. I just use a custom scan from Google results".
So what about the responsibility of someone discovering a vulnerability? How does this tie into describing yourself as a light-gray hacker?
The vulnerability itself has no color: what we did with it is what makes us white, black or gray. I am light gray because I don't care about what white hats call "responsible disclosure", in which they report and collaborate with vendor before making the vulnerability public... unless they pay me well for it. But I don't do anything for money; I refuse to go for the dark side of hacking.
Does the responsibility lie with the person discovering a vulnerability to share it with the world, or with the site or service with the problem?
I think this is a site/service problem. We are forcing the websites to be secure and their owners to stay tuned to what is happening in our hacking community. It is their fault to not take security seriously. We do.
Photo credit: wk1003mike / Shutterstock
-

Microsoft releases Windows 10 SDK tools for developers
Publié: mars 23, 2015, 9:29pm CET par Mark Wilson

It has been a long time coming, but Microsoft has finally released the SDK for Windows 10 -- just ahead of next month's Build. Users have been playing around with various builds of Windows 10 Technical Preview, but this is the first chance developers have had to get hands on with the tools they'll need to create apps for the latest version of Microsoft's operating system.
The Windows 10 Technical Preview tools and Visual Studio 2015 CTP6 can be downloaded by Windows Insiders, and it gives developers the chance to try out the tools and provide feedback with the first technical preview. Templates are provided to make it easy to get started with the development of universal apps, and Microsoft is keen for developers to get to work.
The SDK can be used to create apps that will run desktop computers, laptops, Windows 10 phones, Xbox One and tablets. Tools are available to make it easier to handle different screen size requirements for different device, as well as the option to tailor the control that appear on screen depending on the device that's being used.
Developers will be pleased to see the introduction of a feature that makes it possible to verify whether a particular device supports a given function before making a call for the relevant API. Microsoft says that this will "allow you to adapt your code at runtime to deliver user experiences that feel right on the device it's being run on".
Introducing the new SDK in a blog post, Microsoft's Cliff Simpkins said:
Today I'm excited to announce that we are making the first technical preview of the Windows 10 developer tooling available to Windows Insiders. However, I'd like to point out that this is a preview. Our goal with this release is to give you the opportunity to experiment with the cool new platform capabilities while we continue working to finish Windows 10.
In a separate post, S. Somasega explains that universal apps can be created in C#, VB, C++, or JavaScript and that the tools have been designed to maximize code sharing. Apps developed using the tools can be tested in the Windows 10 Preview or using a Windows 10 Phone emulator. It is not currently possible to test Windows 10 apps designed for Xbox.
Photo credit: 360b / Shutterstock
-

Twitter teams up with Foursquare for location-based tweets
Publié: mars 23, 2015, 8:49pm CET par Mark Wilson

Foursquare (remember that app?) is joining forces with Twitter to make tweets more relevant to specific locations. At the moment it is possible to tag your location in a tweet, but you're limited to mentioning the town or city you find yourself in.
With the new partnership, you'll be able to tag individual locations such as the Starbucks you're sitting in with your iPhone or Android handset. It's a feature that takes advantage of the huge cache of data Foursquare has built up over the years and something that provides yet another way for users to search for data and, importantly, for Twitter to monetize data.
While no real details have been given yet, it's not hard to imagine Foursquare/Swarm-style mayorships being introduced, and the option for businesses to run special offers through the app. It's also a feature that users may well find provides a useful way to share their location with friends.
Twitter has not said exactly when the feature will be rolling out, but references to it already appear in the support documentation:
You can choose to add a location to your Tweets using Twitter for Android, Twitter for iOS, twitter.com or other mobile applications. For example: To give additional location context to your Tweet, you can add a general location label such as "SoMa, San Francisco." In select locations, you may also label your Tweet with the name of a specific business, landmark, or other point of interest. These locations are provided by Foursquare.
Twitter announced the upcoming new feature, unsurprisingly in a tweet, complete with a video that shows off how it will work:
Coming soon! We're working with @foursquare so you can tag specific locations in Tweets: [https:] pic.twitter.com/jATzXvbuV6
— Twitter (@twitter) March 23, 2015
Photo credit: aprilvalery / Shutterstock
-

Sound problems in Windows 10 build 10041? Here are some workarounds
Publié: mars 21, 2015, 12:20pm CET par Mark Wilson

Each build of Windows 10 that is released -- or leaked -- is a step closer to the finished product. We now know that we're building up to a by-the-end-of-summer launch, but there are still plenty of bugs to iron out. Some problems have been fixed but others remain, and if you're having audio issues Microsoft has some suggestions for you.
If you have problems with the installation of a Realtek driver, don’t get the full audio experience with VIA HD Audio, or have issues with Conexant audio, there's a workaround for you to try.
Let's take a look at these three issues in reverse order. A problem with Conexant audio means that you may hear no sound in Windows 10 even though everything appears to be working correctly. While this is being investigated, Microsoft suggests running msconfig.exe and heading to the Boot tab. Click the Advanced options button, check the Maximum memory box and set the value to 3072.
If you have VIA HD Audio and find that you can only hear sound from certain apps, there's a different workaround for you. Open Playback Devices, right click the audio output device and set it as the default device. With this done, select the device, hit Properties, move to the Enhancements tab and check the Disable all enhancements option.
Finally, if you are plagued with a problematic Realtek audio driver installation -- specifically a 0x000005b4 error -- you can try a workaround published in the Stone Support Library. There's a guide to using Group Policy Editor to give the driver longer to install, or you can download a registry file to put the new settings in place with a couple of clicks. Once this has been done, you can then re-attempt the driver installation.
Photo credit: LDDesign / Shutterstock
-

LightEater malware attack places millions of unpatched BIOSes at risk
Publié: mars 21, 2015, 11:05am CET par Mark Wilson
Two minutes is all it takes to completely destroy a computer. In a presentation entitled "How many million BIOSes would you like to infect?" at security conference CanSecWest, security researchers Corey Kallenberg and Xeno Kovah revealed that even an unskilled person could use an implant called LightEater to infect a vulnerable system in mere moments.
The attack could be used to render a computer unusable, but it could also be used to steal passwords and intercept encrypted data. The problem affects motherboards from companies including Gigabyte, Acer, MSI, HP and Asus. It is exacerbated by manufactures reusing codes across multiple UEFI BIOSes and places home users, businesses and governments at risk.
Talking to The Register, Kopvah explained that the problem is made worse because of the fact that very few people take the trouble to update their BIOS. This is something the pair are hoping to change by highlighting the ease with which an unpatched BIOS can be infected with malware.
Introducing the vulnerability, Kallenberg and Kovah said:
So you think you're doing OPSEC right, right? You're going to crazy lengths to protect yourself, reinstalling your main OS every month, or using a privacy-conscious live DVD like TAILS. Guess what? BIOS malware doesn't care! BIOS malware doesn't give a shit!
The malware can be used to infect huge numbers of systems by creating SMM (System Management Mode) implants which can be tailored to individual BIOSes with simple pattern matching. A BIOS from Gigabyte was found to be particularly insecure.
We didn't even have to do anything special; we just had a kernel driver write an invalid instruction to the first instruction the CPU reads off the flash chip, and bam, it was out for the count, and never was able to boot again.
The vunerability is something that has already been exploited by the NSA, but the researchers are encouraging businesses and governments to take the time to install BIOS patches that plug the security hole.
Photo credit: ridjam / Shutterstock
-

Anti-censorship site Greatfire.org suffers massive DDoS attack
Publié: mars 20, 2015, 3:20am CET par Mark Wilson

GreatFire.org, the website with the aim of delivering uncensored news to China, has been hit by a massive DDoS attack. The attack started on March 17 but the anti-censorship site has only just gone public about it and made a call for help.
The organization believes that the attack -- which it calls "censorship by brute force" -- could be a response to an article in the Wall Street Journal. With a peak of 2.6 billion page requests per hour, servers were simply unable to cope with the traffic, knocking GreatFire.org's mirror sites offline.
This is the first time GreatFire.org has ever fallen victim to a DDoS attack, and it is not the only group trying to get uncensored news through the Great Firewall of China -- Reporters Without Borders is also fighting censorship. It is not yet clear who is behind the attacks, but the fingers of blame are pointing towards the Chinese government.
Talking to the BBC, Professor Alan Woodward from the University of Surrey explained that the attackers were bombarding the sites that are normally blocked so they cannot be accessed using any form of circumvention. He said:
"It is difficult not to conclude that someone, most likely a government annoyed that Greatfire has enabled previously censored websites to neuter their censoring technology, has decided to fight back".
One theory for the reason behind the attacks -- other than ensuring blocked sites remain blocked -- is that it may force Greatfire.org to spend money on bandwidth upgrades to cope with the extra traffic and ultimately succumb to the financial pressure. But for the time being the organization has no plans to go under:
overwhelmed at # of messages offering support. please accept our apologies if we r slow to respond - getting our 3 heads above water
— GreatFire.org (@GreatFireChina) March 19, 2015
-

Where did you lose your smartphone? Android Wear can now tell you
Publié: mars 19, 2015, 8:37pm CET par Mark Wilson

Android Device Manger is Google's approach to helping people track down lost smartphones and tablets. Now the feature is rolling out to Android Wear so if you should lose your phone, you can find it with your watch.
At the moment the Android Wear version of the feature is pretty basic; you can use your watch to call your phone. This is great if you have mislaid it nearby, dropped it down the back of the sofa or buried it under some books, but not so helpful if you've left it on the train -- don’t expect to be able to home in on your phone using GPS at this stage.
If you're a fan of voice activation, all you need to do is speak the words "Ok, Google. Start. Find my phone" into your wrist. Should you prefer to go down the touch route, just select the "Find my phone" option from the Start menu.
Google says that Android Device Manager has already helped more than 30 million people find their lost devices, and the spread of the feature to Android Wear will see this number continue to rise. As this is something that is automatically rolling out to all Android Wear devices, you don’t need to do anything other than sit back and wait for it to arrive on your wrist.
-

Opera acquires VPN firm SurfEasy to boost browsing security
Publié: mars 19, 2015, 1:07pm CET par Mark Wilson

Opera Software, the company behind the web browser of much the same name, has acquired SurfEasy, a provider of VPN security. SurfEasy's software bolsters the security of internet users by adding a layer of encryption that helps to protect privacy.
More than this, the software also makes it possible to bypass some online restrictions and to access sites that are region locked. Few details have been revealed yet, but it's possible we could see VPN features integrated into future versions of the desktop and mobile Opera browser.
SurfEasy's aim for the last four years has been to place internet users back in control of their privacy and online freedom. With increased prevalence of spyware, coupled with the surveillance activities of the NSA and GCHQ, security and privacy have been thrust into the public consciousness in recent years.
SurfEasy founder and CEO Chris Houston said:
Over the past few years the dialogue and awareness around online privacy issues has increased dramatically. We are all now very aware just how vulnerable our data is to hacking, monitoring and censorship, regardless of the network or device you’re using to access the web.
Opera CEO Lars Boilesen says that SurfEasy is a neat fit with the Opera philosophy. "Opera has evolved beyond our browser roots and this step will add a critical building block towards a broader portfolio of applications".
-

Electronic payments coming to Facebook Messenger
Publié: mars 18, 2015, 1:36am CET par Mark Wilson
 Facebook is introducing support for sending and receiving money through Messenger. Starting in the US in the next few months, users of the social network will be able to make electronic payments free of charge. While this is not a service that will rival the likes of Apple Pay or PayPal, it provides a way to quickly send money to a friend.
Facebook is introducing support for sending and receiving money through Messenger. Starting in the US in the next few months, users of the social network will be able to make electronic payments free of charge. While this is not a service that will rival the likes of Apple Pay or PayPal, it provides a way to quickly send money to a friend.This is not a payment system that has been completely built from the ground up. It's based on the same backbone that's used to process payments for gamers and advertisers. Security is understandably of paramount importance, and Facebook stresses that as well as encryption and PIN protection for all, iOS users will also be able to take advantage of Touch ID.
In order to send or receive money, you'll need to associate a Visa or MasterCard debit cards with your Facebook account. As Facebook describes the new feature as "a more convenient and secure way to send or receive money between friends" it's clear that there are currently no plans to expand this into a wider payment system.
In addition to the standard security features, Facebook explains that there is a team of anti-fraud specialists keeping an eye out for suspicious activity. Once the roll out is under way, the payment service will be made available to iOS and Android users, as well as people accessing Facebook on the desktop.
Facebook has not revealed plans to launch Messenger payments in other parts of the world, but if it proves successful in the US, it's not hard to imagine it rolling out further.
Photo credit: DollarWoman / Shutterstock
-

Google starts vetting Android apps and implements age rating system
Publié: mars 17, 2015, 11:05pm CET par Mark Wilson

For a long time now Google Play has been home to just about any sort of app imaginable. Apps covering every subject under the sun are available, with quality ranging from atrocious to incredible. To help sort the wheat from the chaff, Google has announced two important changes to the way apps appear in the store.
Apps that are submitted to Goole Play are now subject to a review process, and an age rating system is being introduced to help indicate the target audience for apps. Google says this will help to weed out "violations of our developer policies earlier in the app lifecycle".
For Android users, the new review policy should help to reduce the number of instances of malware in Google Play, but there's also good news for developers. Should an app be denied entry to the store, the Google Play Developer Console now includes greater details about the reason for rejection or suspension. Google says that there will continue to be an emphasis on speed, both in terms of getting apps available in the market place, but also identifying issues so that developers can get to work on fixing them.
For app downloaders, the new age rating system will be of particular interest. Introducing the feature, Google explains:
Today we're introducing a new age-based rating system for apps and games on Google Play. We know that people in different countries have different ideas about what content is appropriate for kids, teens and adults, so today's announcement will help developers better label their apps for the right audience. Consistent with industry best practices, this change will give developers an easy way to communicate familiar and locally relevant content ratings to their users and help improve app discovery and engagement by letting people choose content that is right for them.
The rating system is in keeping with a number of existing systems around the world -- including International Age Rating Coalition (IARC), Entertainment Software Rating Board (ESRB), Pan-European Game Information (PEGI), Australian Classification Board, Unterhaltungssoftware Selbstkontrolle (USK) and Classificação Indicativa (ClassInd). Developers will need to answer a questionnaire about their apps to gain a rating, and apps that are not rated run the risk of being blocked in some parts of the world.
Photo credit: William Perugini / Shutterstock
-

What do you want in a mobile operating system?
Publié: mars 17, 2015, 6:55pm CET par Mark Wilson

I'm not going to open the 'which mobile operating system is best' can of worms -- let's get that clear from the offset. This is not me trying to push my preferred operating system on you, or trying to convince you that you're wrong about the OS you've opted for. This time it's over to you. What you do want?
Do you want things handed to you on a plate, or would you prefer to be granted more control over the operating system on your phone and tablet? Is there mobile platform that meets your needs at the moment, or would you like to combine elements from Android, iOS, Windows Phone and even BlackBerry OS? Just what is it that makes the perfect operating system for your phone or tablet?
We are currently presented with what is essentially a three horse race, with each having its own strengths and weaknesses. Whilst anyone buying a handset has clearly indicated their preference, few would claim the OS installed on their phone is perfect. Whether you've opted for iOS, Windows Phone or Android, you will almost certainly have spent time weighing up the advantages and disadvantages of each before placing your chips on the one that had the most positives and fewest negatives according to your requirements.
But even if you are happy with your choice, you probably had to make the odd compromise here and there.
Maybe you opted for the operating system that came installed on the hardware you could afford, maybe you were swayed by brand image. Perhaps your key concern was the ability access the widest range of apps, or perhaps you needed an app that is only available for one particular operating system. If security is what worries you most, this made have caused you to give one operating system a wide berth.
Do you want to be in complete control of your phone? Looked at through the most objective of eyes it's fair to say that some operating systems lend themselves to personalization and customization more than others. But is this at the expense of security or user experience -- and does it matter? Of course, there is not really a perfect operating system -- what works for one person will not be suited to someone else. Microsoft, Google and Apple all -- obviously -- aim to please as many people as possible with the software they put out, but there's a danger that this means trying to please everyone and ending up pleasing no one.
So… over to you. Does your perfect operating system already exist, or are there changes that need to be made to attain perfection? What elements, if any, would you like to borrow from the competition, or do you think there are key features that are missing from all of the main mobile operating systems? Vent your spleen, spill your vitriol, list your desires, and sing praises in the comments -- I'm interested to learn just what everyone is looking for.
Photo credit: max sattana / Shutterstock
-

No, John Gruber, Apple did not 'basically invent' USB-C
Publié: mars 17, 2015, 12:38am CET par Mark Wilson
Two computers of note have been announced or released in recent days -- the 2015 version of the Chromebook Pixel and the redesigned MacBook -- that feature an all-singing, all-dancing USB-C port. It transfers data, it powers, it makes coffee, it doesn't matter which way round you insert it, and it practically guarantees an orgasm (OK... maybe we got a little carried away).
It’s a progression of USB technology, and one that has been well-received, at least in principle. Who could be responsible for this marvellous technology feat of design? Blogger, Markdown inventor, and owner of Daring Fireball, John Gruber seems to be under the impression that it's an Apple invention. But he's wrong.
In a recent podcast (jump to the 54 minute mark to hear the section we're interested in), Gruber said: "I have heard -- I can’t say who but let's call them informed little birdies -- that USB-C is an Apple invention and that they gave it to the standards bodies … and that the politics of such is that they can't really say that. They’re not going to come out in public and say that but that they did. It is an Apple invention and they want it to become a standard".
He goes on to say:
What I've heard is that it's an Apple invention that was sort of developed alongside Lightning and that they donated, they gave to the standards bodies because they want the industry standard to be thin enough for their devices and they want it to be reversible.
Sorry, to burst your bubble, John, but what you've heard simply isn’t true. You might love Apple, but you can just ascribe inventions to the company. Tacking on the caveat "the politics of such is that they can't really say that" is a bit of a cop out. We could say anything we wanted and tack that on the end of the sentence to cover our asses.
Sadly, it's an idea that's now out there. It has been picked up by the likes of Macrumors, TheTechBlock, and Cult of Mac (but of course) and is already well on its way to becoming an actual part of Apple's history. Repeat something enough, and people will eventually start to think it's true. This is very much what has happened here.
We got in touch with the USB Implementers Forum for clarification. A spokesperson explained that the "USB Type-C Cable and Connector Specification was developed by the USB 3.0 Promoter Group". A full list of contributors to the project can be found in the Universal Serial Bus Revision 3.1 Specification. Skip to page 10 of the USB Type-C Specification Release 1.0 document and you will indeed see that Apple is listed. But so is ACON. And Advanced Micro Devices. And Agilent Technologies Inc. And Cypress Semiconductor, Foxconn, Google, HP, Intel, Lenovo, Nokia, Microsoft, Samsung, Seagate, VIA and many more. Just about every name under the tech sun in fact.
So what are you going on about, Gruber? He has since clarified his position a little:
My comments on The Talk Show about Apple's role in the creation of USB-C were somewhat hyperbolic. It was a brief aside. I certainly didn't mean to imply that no other companies contributed to the final spec. Only that from what I've been told, Apple ought to be getting (and taking) credit as the leading company behind USB-C's innovations. Not that they "invented" it, but that they "basically invented" it. I completely stand by that. But there are a lot of politics involved. One reason Apple isn’t taking more public credit for their role: they truly want USB-C to see widespread adoption; a perception that it’s an Apple technology might slow that down.
I'll also point out that USB-C is a very Apple-like design. It is reversible and thin; because it can handle power, high-speed data transfer, and video, it (obviously, given the new MacBook) allows for a significant reduction in ports on a laptop. Every aspect of USB-C fits Apple's design goals. You can't say that about any previous USB port.
So what if the design of USB-C is very Apple-like? There are Samsung cables that could be described as being very Apple-like. This doesn't mean that the company invented them. Apple does have patent for a reversible USB connector (specifically a Reversible USB Connector with Compliant Member to Spread Stress and Increase Contact Normal Force), but this is different to USB-C. In fact it is more like a traditional Type A USB connector with a couple of tweaks.
Being involved in a project with dozens of other companies -- Apple engineers are outnumbered many, many times over by those from other companies -- is in no way the same as inventing the technology at the heart of the project. What does "basically invented" mean? Nothing essentially. It's something that could be said of any other company or engineer involved in the specification.
"Every aspect of USB-C fits Apple's design goals"? So what? It fits the design goals of lots of other companies too -- that's why it is an official specification adopted by and contributed to by many companies rather than a weird proprietary connector.
There's nothing wrong with loving Apple, John, but don't ascribe things to the company without justification. USB-C was a collaborative effort; it is not Apple's baby.
Photo credit: graja / Shutterstock
-

Apple bribes Android and Windows Phone users to switch to iPhone
Publié: mars 16, 2015, 8:37pm CET par Mark Wilson

Apple may be about to launch a new phone trade-in program in a bid to encourage more people to invest in iPhones. Hand over your old Windows Phone, Android handset -- or even a BlackBerry or aged iPhone -- and you could receive a gift card that can be used as part payment for an iPhone. The news comes from the usually-reliable 9to5Mac where it is suggested that Apple Store employees will place a value on handsets before handing over a gift card in exchange for it.
It's not a completely new venture for Apple; the company has previously run programs to encourage iPhone users to upgrade to the latest version of the handset, but this will be the first time the scheme has been opened up to rival smartphones. While previously this was an incentive to upgrade, this time around it's little more than a bribe.
For many people, choosing a mobile is comparable to one's religion (or lack of thereof) or support for a particular football team. It’s a choice that makes perfect sense to an individual, and can often be difficult to get non-believers to understand. Will a gift card be enough to move people away from their previous handset of choice? Could you be bribed into switch allegiances?
Are things really so desperate at Apple that there's a need to, essentially, pay people to use iPhones? Of course there is no guarantee that the gift card offerings will be a good deal. With countless mobile recycling schemes operating around the world, and sites such as eBay and Gumtree providing access to a market of people willing to pay top dollar for handsets, can Apple expect to compete?
We already know that Android dominates the mobile market. Apple is very comfortably in second place, but it must hurt to see Google performing so well. It hurts so much that the company is willing to resort to bribery in an attempt to grab itself a larger user base. It's a cheap move from a company that would like you to think that it is anything but.
Photo credit: Maryna Pleshkun / Shutterstock
-

Microsoft launches Office 2016 IT Pro and Developer Preview
Publié: mars 16, 2015, 5:57pm CET par Mark Wilson

Hot on the heels of Office 2016 Mac Preview, Microsoft today launched Office 2016 Preview for developers and IT professionals. We've already heard a little about the direction in which the office suite is heading but -- leaks aside -- this is the first time most of the suite has been seen outside of private testing.
Microsoft is a company that is all about previews nowadays; the days of not having a clue what will appear in the next version of apps are gone. There's the disclaimer that "this early build doesn’t yet contain all the features we're planning to ship in the final product", but it's still an intriguing taster of what's to come.
In terms of new features, Microsoft is focusing on business-centric tools for now. The reliability of Outlook has been improved, and RPC-based sync has been replaced with the MAPI-HTTP protocol. There are new email storage management options, faster searching, and support for multi-factor authentication through integration with the Active Directory Authentication Library.
Word, Excel and PowerPoint gain Data Loss Protection to bring them in line with Exchange, Outlook, OneDrive for Business and SharePoint, giving admins the chance to control content creation and sharing. Improvements have been made to device activation controls, there is more efficient update deployment, and there are also new accessibility features.
If you are interested in taking part in the Office 2016 IT Pro and Developer Preview, you can sign up over on Microsoft Connect -- bear in mind that only businesses are likely to be considered.
-

Yahoo introduces On-demand passwords and demoes end-to-end-encryption
Publié: mars 16, 2015, 2:17pm CET par Mark Wilson

The idea of forgetting the password for your email account might seem odd, but it happens. You might be one of those people who signed up for a Yahoo email address years ago, moved on to something better, and now only check in every few months to see if you've missed anything.
To combat the problem of forgotten passwords, Yahoo is introducing a new feature called On-demand passwords. There's no need to battle through the process of answering security questions to reset your password when you forget it; now you can create a temporary password that gets sent to your phone.
Chris Stoner, Director of Product Management, explains that the new feature eliminates the stress and anxiety that goes hand in hand with forgetting a password. It’s an option that’s only available in the US for the time being, but it's hard to imagine that it wouldn’t roll out to other parts of the world if it proved successful. In a blog post, Stoner wrote:
Today, we’re hoping to make that process less anxiety-inducing by introducing On-demand passwords, which are texted to your mobile phone when you need them. You no longer have to memorize a difficult password to sign in to your account -- what a relief!
In order to get the feature set up, you will have to remember your password at least once so you can log in and access your account settings. Head to the Account Security section of settings, activate the On-demand passwords feature, and confirm your phone number.
Yahoo also announced a preview of a new end-to-end encryption system. The feature will come to Yahoo Mail, and it is hoped that it will be implemented by the end of the year. The source code is available on GitHub and the video below was shown at SXSW by way of an introduction:
Photo credit: Brt / Shutterstock
-

Nipples, terrorism, and vivid sexual description -- Facebook's list of banned content
Publié: mars 16, 2015, 12:27pm CET par Mark Wilson

Facebook has updated its Community Standards document, outlining the type of content that is not permitted on the social network. When it's not forcing people to reveal their real names, blocking 'offensive' content, or encouraging users to vote, Facebook is often to be found removing content that has been reported for one reason or another. But what's acceptable, and what's not?
A little while back, the site revealed a simplified version of its privacy policy, and now the Community Standards document has received the same treatment. Facebook has set out the types of pictures that are permissible, along with specifying guidelines for other content. So, what's OK, and what’s not?
Much of what the revamped Community Standards lay out is common sense. Threats to harm others are not tolerated, nor is the promotion of self-harm or suicide, and drug use, terrorism and organized criminal activity are also out. Facebook goes further than just slapping a ban on the promotion of hate against people, also making it clear that content that supports or praises groups, or the leaders of groups, that promote such ideas will not be allowed.
The document includes a whole section entitled 'Encouraging respectful behavior'. Here Facebook lays out its policies relating to nudity, sex, and violence. There is not an outright ban on nudity, but genitals and fully-exposed buttocks are out. Campaigners will be pleased to learn that Facebook will "always allow photos of women actively engaged in breastfeeding or showing breasts with post-mastectomy scarring". Other depictions of breasts that show the nipple are likely to come in for scrutiny.
Facebook says that it is trying to juggle the varying sensibilities that people may have:
Facebook restricts the display of nudity because some audiences within our global community may be sensitive to this type of content -- particularly because of their cultural background or age. In order to treat people fairly and respond to reports quickly, it is essential that we have policies in place that our global teams can apply uniformly and easily when reviewing content. As a result, our policies can sometimes be more blunt than we would like and restrict content shared for legitimate purposes. We apologize for any inconvenience. We are continually re-evaluating how to balance people's interest in expression with the needs of our diverse, global community.
It's not just sexual pictures that are banned -- graphic descriptions of sex also fall victim to the ban hammer. Facebook points out that although the guidelines are now longer than before, the policies themselves have not actually changed -- they have merely been clarified.
Photo credit: Viktorija Reuta / Shutterstock
-

Windows 10 Build 10036 introduces updating via P2P
Publié: mars 15, 2015, 7:21pm CET par Mark Wilson

P2P, or peer-to-peer networking, is usually associated with grabbing illicit copies of movies and albums using BitTorrent (or, of course, those endless Linux distros everyone is downloading...). In Windows 10 Build 10036, however, Microsoft is embracing the technology as an efficient means of delivering software updates to users.
For many years now, using Windows Update to download updates and patches for your operating system has meant download files directly from Microsoft servers. But this new method takes the strain off Microsoft and makes it possible to download some or all of the available updates from other computers.
For businesses running large networks, this could dramatically reduce bandwidth usage. It means that updates could be downloaded on one computer -- or just a few -- and other could grab the updates over the network rather than from the internet. It's a feature that will be of interest to home users with multiple computers, particularly when the time comes to download particularly updates; there will be no need to suck up bandwidth multiple times.
The feature goes further than this, though. As well as introducing the option to download updates from networked computers it also makes it possible to download from other computers online. This is something that will pay off when a service pack or other large update is released. It is at times like this that Microsoft's servers come in for a real hammering, and users frequently complain that updates take too long to download.
Activate the option to "Get updates from more than one place", and Microsoft says that you can "Download apps and OS updates from multiple sources to get them more quickly".
Microsoft has not said anything about the feature yet -- this is, after all, a leaked build -- but security features and verification techniques will have to have been implemented to assuage security fears and to ensure that only legitimate downloads are permitted. The new feature comes two years after Microsoft's acquisition of Pando Networks, a company that developed peer-to-peer technology.
Photo credit: Imagentle / Shutterstock
-

Nope, Microsoft isn't getting into Android with a Cyanogen investment
Publié: mars 14, 2015, 7:18pm CET par Mark Wilson

A little while back rumors surfaced suggesting that Microsoft was on the verge of investing in Android. Not directly, you understand, but via Cyanogen Inc. In August, Cyanogen Inc met with Satya Nadella but it seems that the talks amounted to nothing.
The company is on the verge of raising $110 million of financing, but Microsoft will not be involved. According to a report by Bloomberg, Microsoft will not be contributing to the funding, but could still be interested in perusing commercial ventures with Cyanogen Inc to help push Microsoft apps onto more Android devices.
Bloomberg says that Microsoft is not interested in investing in Cyanogen, and this is likely because the company does not want to shift its focus to far away from Windows 10 and Windows 10 for Phones. While Microsoft has been criticized for not bringing its own apps to Windows Phone fast enough -- it is quite common for iPhones and Android handsets to get new apps faster -- it seems the draw of the larger market of iOS and Android users is too much to resist.
At the moment, as is the norm, no one from either Microsoft or Cyanogen Inc is talking about what is happening, or what may be to come. That said, Bloomberg quotes sources close to the talks as saying that Microsoft is still keen to come to an arrangement that would help to get its software included in Cyanogen's Android builds.
Photo credit: drserg / Shutterstock
-

YouTube adds support for interactive 360-degree video uploads
Publié: mars 14, 2015, 1:19am CET par Mark Wilson

If you've splashed out on a fancy 360-degree camera, you can now use YouTube as a platform to show off your footage. It's something that Google promised back at the start of the year, and it has finally come to fruition. Rather than restricting viewers to watching the action that's happening in one direction, these immersive video allow you to look around in every direction as if you were there.
There are already a number of videos online to check out, and it’s a method of recording that lend itself perfectly to concerts, sporting events and the like. 360-degree videos are best enjoyed through virtual reality headset, but desktop and mobile users have not been forgotten.
For the majority of people who watch 360-degree videos without a headset, simple on-screens can be used to navigate around. Android users can pan around videos augmented-reality-style -- just hold up your phone or tablet running the YouTube app and move it around to change the viewing angle. There are already a number of cameras out there, or due soon, that can be used to shoot 360-degree footage including Bublcam, Giroptic’s 360cam, IC Real Tech’s Allie, Kodak’s SP360 and RICOH THETA.
Google is keen for uploaders to come up with interesting ways of using the technology.
You could let viewers see the stage and the crowd of your concert, the sky and the ground as you wingsuit glide, or you could even have a choose-your-own-adventure video where people see a different story depending on where they look. Only you know what’s possible.
You can test out the immersive 360-degree experience in the video below:
Photo credit: james weston / Shutterstock
-

Oh god... screenshots from Windows 10 build 10036 look worryingly like Windows Phone
Publié: mars 13, 2015, 6:31pm CET par Mark Wilson

OK, I'm starting to get worried now. I've been working my way through each of the public previews of Windows 10 and, on the whole, I've been fairly impressed. Not blown away, but generally satisfied. But some of the recent screenshots that have been leaking out have me a little concerned. -- there's more than just an air of Windows Phone, and that turns my stomach.
Yes, I know that there's meant to be a merging of paths between Windows for phones and Windows for the desktop, but for Microsoft to veer towards the look and feel of Windows Phone is a huge mistake. I only hope that the screenshots currently doing the round from build 10036 are not representative of the build we're waiting to be released.
What am I going on about? Well, we've already seen that Windows 10 is borrowing ideas heavily from Windows Phone. The Start menu has made a welcome return, but it's not The Start Menu we know and love from days of yore -- it's been Windows Phone-ified, all tiles and vertical lists. This is not news, but I should have been more worried earlier on, I think. When the much-talked-about Notification Center reared its head, it happened again. It's like looking at Windows Phone-lite.
Not to worry, I thought... these are just early builds. These things will probably be ironed out, just like those pig-ugly icons. But now images are leaking which show that Windows 10 build 10036 continues the trend. The Wi-Fi network selection window has a new look. You've guessed it... it looks like Windows Phone. Don't believe me? Here's a screenshot posted on OSBetaArchive:
What are you doing, Microsoft? We're meant to be moving forward. Looking to the future, not the past. Have you not learned by now that Windows Phone was a mistake -- people don’t like it. To be fair, they weren’t all that keen on Windows 8.x either (although I'm more enamored than many people are). This in mind, why would you want to sully the look of the next generation of Windows with elements from such a wildly unpopular mobile operating system? It just seems like insanity.
My only hope is that I am not alone. If Gabe Aul's tweets are correct, we should start to see new builds of Windows 10 released more frequently. I hope in the name of all that is just that legions of Windows Insiders complain bitterly not just about the offensively ugly icons, but also the creep towards the look of Windows Phone that's taking place.
Other screenshots from 10036 posted by Wzor show something with a more desktoppy feel to it, but the continued existence of modern apps just adds to the Windows Phone look. Each of these apps adds a little more to the Phoney look and spoils things.
The journey towards the release of Windows 10 has been a complete rollercoaster ride for me. I've loved it, hated it, been ambivalent towards it. But this glacial creep towards Windows Phone is worrying. Windows Phone is a failure, and not without good reason. If Microsoft isn't careful, it'll be signing the death certificate for Windows 10 before its gestation period comes to an end.
Photo credit: Christos Georghiou / Shutterstock
-

CryptoLocker-like ransomware, Teslacrypt, targets gamers
Publié: mars 13, 2015, 5:04pm CET par Mark Wilson

Ransomware is one of the latest tactics used by cybercriminals to extract money from victims. CryptoLocker hit the headlines last year, encrypting the files on infected machines until a ransom was paid. Now the same idea has spread to the world of gaming thanks to Teslacrypt.
Teslacrypt works in much the same way as CryptoLocker, but its raison d'etre is seek out game saves and download content for dozens of popular titles and hold them to ransom. Until victims cough up $500 in Bitcoins, or make a $1,000 PayPal payment, there is no way to access the games.
Despite the similarities to CryptoLocker, security analysts at Bromium say the malware comes from a different group of cybercriminals and doesn’t share any code. Infections come via a compromised gaming site which uses a Flash vulnerability to redirect visitors to the Angler exploit kit. As the site is based on WordPress, Bromium says it could have been compromised using any one of a number of exploits.
Once a computer has been infected, the malware starts its hunt for 185 different file type, more than half of which are associated with games. On the list of targeted titles are Call of Duty, Half-Life 2 and Fallout 3, as well as online games including World of Warcraft and Steam titles.
Bromium Labs' Vadim Kotov said:
Files are targeted by extension. Concretely these are user profile data, saved games, maps, mods etc. Often it’s not possible to restore this kind of data even after re-installing a game via Steam.
While CryptoLocker was cracked so that victims could decrypt their files without having to pay a ransom, this has yet to happen for Telsacrypt.
Photo credit: Phoenixns / Shutterstock
-

Apple releases a public beta of iOS 8.3 -- here's how to get it
Publié: mars 13, 2015, 3:51am CET par Mark Wilson

With Microsoft we've become used to the idea of publicly available preview builds of Windows 10 for desktop and phone. Now Apple is following suit and making iOS 8.3 available as a public beta. This is the first time a public beta of iOS has been released, although Apple has tried the same tactic with betas of OS X.
The beta is in the process of rolling out at the moment, so you may not be able to grab yourself the bits just yet, but you can get yourself in line. What is there to look forward to? Not much at the moment, apart from wireless CarPlay and new emoji. Here's how to grab the beta.
If you haven't done so already, sign up for the Apple Beta Software at the Appleseed website; if you've been testing the previewing builds of OS X, you won't need to do this. It does not matter what device you use to sign up for the program, but you will need to visit it from your iPhone to enrol specifically in the iOS beta program -- if you don’t see the option right away, try again later.
When you’ve signed up for the iOS beta, you'll be invited to download a certificate. Once this is installed check Software Update and you'll find a copy of iOS 8.3 Beta waiting for you to download.
Apple hasn’t really made a fuss about this public beta, and it's not clear how frequently updates will be pushed out, or how long the beta program might run for. Just like Microsoft with Windows 10 Technical Preview, Apple is looking for feedback about iOS 8.3. Install the beta and you could help to shape the future of your iPhone's operating system.
Photo credit: file404 / Shutterstock
-

Windows 10 builds will be released faster to Windows Insiders
Publié: mars 12, 2015, 8:48pm CET par Mark Wilson

The chances of getting a new Windows 10 build this week are starting to look a little thin, but releases are going to be made available more frequently. Writing on Twitter, Gabe Aul said that "we've decided to try to increase pace of Fast", promising that more details would be forthcoming.
Earlier in the week, Aul responded to complaints that new builds were not appearing fast enough, joking that a new release ring called Ludicrous Speed was being considered. Now we've learned that "a good build candidate with some new features" is very close to release.
In his earlier blog post, Aul spoke about balancing speed of releases with the stability of these builds. He mentioned the possibility that slightly "riskier" builds could start to see the light of day if it was decided to increase the rate of output. Today, this ides seemed to come a step closer as he suggested that the more cautious Windows 10 user might want to switch to the slow release ring:
No new build today, but we will be posting an announcement in Insider Hub. suggesting people who want lower risk to move to Slow.
— Gabriel Aul (@GabeAul) March 12, 2015
He went on to say that Microsoft is "Still considering new rings, but for now we've decided to try to increase pace of Fast, and that means letting people know first". There's still an outside chance that the successor to Build 10031 will receive an official release this week, but this is not guaranteed.
What do we have to look forward to? Aul isn't giving much away, but he knows how to push the right buttons to keep people interested:
@GabeAul We have a good build candidate with some new features I think you'll like. Running through our internal rings now.
— Gabriel Aul (@GabeAul) March 12, 2015
So watch this space... you might be updating Windows 10 sooner than you think.
-

Time to migrate to GitHub as Google Code closes
Publié: mars 12, 2015, 7:26pm CET par Mark Wilson

After nine years, Google Code is closing down. Starting today, it is no longer possible to create new projects, and over the course of the coming ten months, the service will be mothballed. Google Code was Google's attempt to help the open source community by offering somewhere to host projects, but the growth of the likes of GitHub and Bitbucket has taken its toll and Google Code has filled up with spam and abuse.
Competition in the world of project hosting has become fierce, and Google feels it's time to pass on the baton rather than fighting for attention. Google has itself moved many of its own open source projects to GitHub. Don't panic if you’re not quite ready to jump ship -- there's still a little time to play with.
While Google has put an end to the creation of new projects, those that are currently hosted on Google Code are safe for the time being. You’ll still be able to upload files and so on, but as of August 2, 2015, the site will switch to read-only mode. From this time you will still be able to access projects, but no editing will be possible. The ultimate deadline is January 25, 2016 when the service closes down. Projects will be available to download as a tarball until the end of the year.
Explaining the closure in a post on Google Open Source Blog, Chris DiBona, Director of Open Source, said:
As developers migrated away from Google Code, a growing share of the remaining projects were spam or abuse. Lately, the administrative load has consisted almost exclusively of abuse management. After profiling non-abusive activity on Google Code, it has become clear to us that the service simply isn’t needed anymore.
Tools are available to help make the process of migration a little easier. Google's preferred option seems to be the Google Code to GitHub exporter tool, but there are also stand-alone tools for switching to GitHub and Bitbucket. DiBona also points out that SourceForge has a Google Code project importer service.
Photo credit: spaxiax / Shutterstock
-

GCHQ does not engage in indiscriminate blanket surveillance
Publié: mars 12, 2015, 6:38pm CET par Mark Wilson

When Edward Snowden blew the whistle on the activities of the NSA, it sparked a global interest in how internet traffic is monitored. The UK's Intelligence and Security Committee of Parliament today published a report into online surveillance carried out by GCHQ, MI5 and MI6 after an 18-month inquiry.
Among the findings is the conclusion that surveillance is legal, but an overhaul is needed to increase transparency. The suggestion that GCHQ's interception of emails "does not equate to blanket surveillance, nor does it equate to indiscriminate surveillance" is likely to be met with skepticism. But what's likely to raise more eyebrows is the revelation that the agency has apparently managed to crack encryption.
While the Intelligence and Security Committee of Parliament found that surveillance was entirely legal, countering allegations that UK laws had been circumvented, the report recognizes that there is a need for change. There is the admission that the "legal framework is unnecessarily complicated and lacks transparency", the suggestion being that the current lack of transparency leads people to be suspicious of all monitoring activities. Bulk surveillance was singled out for particular attention by the inquiry.
It was found that there are three stages of selecting data for viewing: targeting, filtering and selection. The report suggests that this process means that only a very small proportion of collected data is actually read -- something that the NSA said of its dragnet data collection. "Only a very tiny percentage of those collected are ever seen by human eyes". There is also the statement that:
"GCHQ is not collecting or reading everyone's emails: they do not have the legal authority, the resources, or the technical capability to do so".
Despite this, data about entirely innocent people has been collected. It's no good thinking that your private data is safe if you've opted to use encryption, because GCHQ is actively engaged in cracking it:
c) Reading Encrypted Communications
179. Terrorists, criminals and hostile states increasingly use encryption to protect their communications. The ability to decrypt these communications is core to GCHQ’s work, and therefore they have designed a programme of work -- *** -- to enable them to read encrypted communications. There are three main strands to this work:
i) ***;
ii) developing decryption capabilities ***;185 and
iii) ***.186
As this section shows, the report is heavily redacted, and this can make it difficult to fully get a sense of what activities have been taking place. While the report looks to the historic activities of UK intelligence agencies, it looks to the future more than it does to the past.
The main recommendation for moving forward is that the piecemeal collection of acts and laws that govern surveillance should be replaced by a single law. It is suggested that this would help to eliminate ambiguities. Statutory oversight of the use of bulk datasets should also be introduced as the agencies attempt to battle public suspicion.
Photo credit: Gil C / Shutterstock
-

Reporters Without Borders unblocks access to censored websites
Publié: mars 12, 2015, 1:26pm CET par Mark Wilson

Online censorship is rife. In many countries, notably China, citizens are prevented from accessing certain websites at the behest of their government. To help provide access to information and unbiased news, freedom of information organization Reporters Without Borders has set up mirrors to nine censored websites so they can be accessed from 11 countries that blocked them.
As part of Operation Collateral Freedom, Reporters Without Borders is mirroring the likes of The Tibet Post International which is blocked in China, and Gooya News which is blocked in Iran. Mirrored sites are hosted on Amazon, Microsoft and Google servers which are unlikely to be blocked by a censoring country.
While it would still be possible to block access to the mirrored sites, the fact that they are hosted on such popular servers means that there would be massive knock-on effects for other much-used services. Encryption is also in use to help prevent the risk of blocking by keyword.
Reporters Without Borders is waging war on the "Enemies of the Internet" which includes Russia, Kazakhstan, Uzbekistan, Turkmenistan, China, Cuba, Iran, United Arab Emirates, Bahrain and Saudi Arabia. The full list of sites that make up Operation Collateral Freedom are:
- Grani.ru, blocked in Russia
- Fergananews.com blocked in Kazakhstan, Uzbekistan and Turkmenistan
- The Tibet Post, blocked in China
- Dan Lam Bao, blocked in Vietnam
- Mingjing News, blocked in China
- Hablemos Press, blocked in Cuba
- Gooya News, blocked in Iran
- Gulf Centre for Human Rights, blocked in United Arab Emirates
- Bahrain Mirror, blocked in Bahrain and Saudi Arabia
Explaining how access has been opened up, Reporters Without Borders says:
To prevent this blocking, Operation Collateral Freedom is using techniques similar to those developed by GreatFire, an NGO that has carried out several operations of this kind designed to circumvent Chinese censorship.
Access to blocked sites can be restored by using a "website copier" (which copies the content of the censored site to an uncensored server and then keeps updating this "mirror") or by using a proxy.
In Operation Collateral Freedom, we are using both methods, with the mirror site being placed on a strategic server run by a major service provider such as Amazon, Microsoft and Google. The censoring country would be unlikely to block one of these servers because the collateral disruption and damage would outweigh the benefits to be gained from restoring censorship.
The organization is currently renting bandwidth to host the mirrored sites, and is calling for people to spread the word through social media using the hashtag #CollateralFreedom. Donations are being sought to keep the operation running for as long as possible.
Photo credit: alexskopje / Shutterstock
-

Apple Watch launches -- Live blog
Publié: mars 9, 2015, 6:05pm CET par Mark Wilson

So, the clocks have sprung forward and Apple's event is now underway. We'll get to find out more about the highly anticipated Apple Watch, finding out all-important details such as how long the battery is going to last between charges.
The will no doubt be a few surprises along the way, but this is the first change we'll get to see if Apple is really in a position to take on Android Wear. Buckle up... here we go...
What's happening, in reverse order -- start at the bottom and work up!
- Utterly, utterly mad. Completely mental.
- The Edition is a limited edition model. Start saving if you want one. $10,000 is the price tag!
- Next -- "Apple Watch Edition is crafted from 18-karat solid yellow or rose gold."
Apple Watch is the stainless steel version. Prices start at $548 for the 38mm model, $599 for the 42mm version. But these are starting prices. It climbs all the way up to an eye-watering $1,099. - The Sport is the 'affordable' Apple Watch. Two models to choose from here: $349 for a 38mm version and $399 for the 42mm edition.
- Apple could learn from Basis and come up with a charger than can be used while the watch is being worn.

- There are different ranges to the Apple Watch lineup: "Apple Watch Sport has cases made from anodized aluminum in either silver or space gray".
- Oh -- 18 hours of battery life. This is 'typical' usage. I'd be interested to see how this translates into real world usage.
- Apple Watch is a platform -- app developers are going to have to come up with the goods here to help sell it. Apple Watch is undeniably cool, but do you need it? Not by a long chalk. Unless the battery life turns out to be INCREDIBLE, there's really not much reason to supplement your phone with this.
- Use your watch as a hotel keycard? Nice. Until your battery runs out of course...
- If my watch told me to stand up, I would smash it.
- Getting directions via your Apple Watch and using it as a boarding pass for your flight seem cool.
- This is very much about what Apple Watch can do for you, rather than what it is. It feels unfocused, though.
- Apple is keen to make a success of Apple Pay -- double tap the side button on the Apple Watch to pay for something in store.
- I mean... it's a nice idea, but practically speaking? Talking to your wrist? I'll leave that to the kids in the playground, I think.
- Siri is just a tap of the crown away. Get ready to look like a head case by talking to your watch.
- There's a Twitter app, of course.
- We're back.... notifications. If you can get a particular notification on your iPhone, you can get it on your watch. Prepare to be inundated with Candy Crush Saga requests through your Apple Watch.
- This marathon running talk in painful. Make it stop!
- Lots of guffy padding. Cut to the meat!
- Apple Watch will nag you. Not only will it monitor your movement, it'll complain at you if you've been sitting for too long. The machines are rising up, people.
- The touch screen can be used to send drawings to your friends -- what you draw on your screen appears on theirs. I'm sure this won;t be abused in any way whatsoever.
- There's a built in microphone and speaker so you can look like you're in Star Trek and take calls through your watch. Or look like an idiot. Your choice.
- 'Glances' are used to check things on the Watch -- like health monitoring stuff, and the like.

- It tells the time, natch, lots of faces to choose from, and also widgets to allow the Apple Watch to be tailored to your needs.
- "Apple Watch is designed to appeal to a broad range of personal styles. Because what you wear is an expression of who you are."
- "Apple Watch is the most personal device we've ever created."
Watch time!
- The new MacBook will be available in a month -- 10 April -- starting at $1,299.
- Mr Ive is justifiable chuffed with the look of the MacBook. It is a stunner -- although the gold version is not going to be to everyone's taste.
- You expect battery life to be impressive, and you'd be right. Apple promises all day battery. All. Day. Or 10 hours of video playback.
- It's fanless, so no worries about noise, processor uses just 5 watts. These are the facts, folks.
- There's also feedback through the Taptic Engine. A lovely touch. We've seen it in mice, but it's surprising that it has taken so long to come to laptops.
- The entire trackpad is pressure-sensitive. Lots of applications here -- artists will enjoy this.
- The trackpad isn't just big -- it has Force Touch. This means no clickable buttony bits, it's all done with touch. Support for new gestures including the intriguing-sounding Force Click.
- WT actual F? The display is less than 1mm thick!
- LED under every key for even lighting, 12 inch, 2304 x 1440 Retina display. It's a looker.
- It's not just in gold... there's a space gray version too:

- That trackpad looks massive. There's a redesigned keyboard that makes the best possible use of space -- the keys go right to the edge of the MacBook.
- And 13.1mm is pretty darn thin -- 24 percent thinner than the MacBook Air.
- OK. 2 pounds. That's light. Can't argue with that. Lightest MacBook ever.
- Next up.... MacBook. And it's gold. Uber thin and uber light also if Tim Cook is to be believed.
- It's launching in April and there are five apps available right now -- Breast Cancer, Diabete, Parkinson's Disease, Cardiovascular Disease, and Asthma. ResearchKit is open source, so we can expect to see all manner of other apps popping up in the future.
- ResearchKit can be used to help tackle the likes of Parkinsons. It's hard to argue with tech being used for things lik that. Opt-in data monitoring, and you can keep an eye on what's being tracked in real-time. Fair enough, really.
- Expect to see more Apple not just in your car, but in your home, and looking after your health too. Who would have though the iPhone would become a medical research tool?
- Lots of Appley self-congratulatory stuff here. Apple Pay is ace, CarPlay ditto -- and this latter tool will be found in more vehicles very soon.
- Time Cook tells us that (almost) everyone -- 99 percent -- loves their iPhone 6. Will the same be true of Apple Watch? My question, not his.
- Apple TV drops in price to $69 -- becomes all the more tempting for would-be cord-cutters... and everyone else.
- We've heard a lot about what to expect from the Apple Watch. A battery that could need charging after just a few hours of use, apps that have to fulfil their function in 10 seconds. Tim Cook is keeping the tension building. Forget jumping into what everyone is here to hear about, first there's news of a new streaming service -- HBO Now (it goes without saying that this is US-only).
Refresh the page to see the latest updates!
-

Google hit with sexual harassment complaint from ex-employee
Publié: mars 8, 2015, 3:56pm CET par Mark Wilson

A former Google engineer revealed on Twitter this weekend that she suffered sexual harassment whilst working at the company. In a series of tweets, Kelly Ellis said that not only had she been sexually harassed by a male colleague, but that her promotion through the company had been effectively curtailed because she would have been in a position that meant reporting to her harasser.
There is more than a hint of irony at the timing of the revelation. Google would much prefer to be seen encouraging women into technology but Ellis -- who worked on the Google+ team -- dismisses this as nothing more than "PR bullshit". She also says that she was let down by co-workers who failed to back her up.
Ellis spent a good deal of time on Saturday tweeting a series of snippets about her time at Google where she worked from 2010 to 2014. The tweets started with a very blunt statement: "At Google I was sexually harassed by someone who was later promoted to director". Dozens of tweets then followed giving more details about what had happened.
Now working as a software engineer at Medium, Ellis says that the harassment was the main reason she left the company back in July. She says "I don't care if people believe me or not", but, we have to refer to what she says as allegations. She says that Roderick Chavez, another Google engineer, harassed her:
Rod Chavez is an engineering director at Google, he sexually harassed me, Google did nothing about it. Reprimanded me instead of him
— Kelly Ellis (@justkelly_ok) March 7, 2015
Ellis says that she reacted badly to something he said and ended up pouring a drink over his head. Rather than focusing on the harassment that led her to react in such a way, Ellis says that Google's HR department instead concentrated on the humiliation caused to Chavez by being soaked.
"It's taking all of my self control not to grab your ass right now." VERBATIM quote from someone currently an engineering director at Goog
— Kelly Ellis (@justkelly_ok) March 7, 2015
It seems that this is not an isolated incident, and Ellis refers to a male-dominated environment at Google in which she not only felt uncomfortable, but was subjected to inappropriate comments. She took to Google+ to ask former colleagues why they had not helped her out or spoken out. She says she felt trapped and unsupported, and ultimately had to leave Google:
My choices were: speak up loudly, lose my job, burn bridges (which is what I've now done), leave quietly (which is what I did later after realizing it wasn't changing), or not say anything (which is what I initially did).
She also poses the question:
I wonder how many other women don't report or discuss their harassment, for their careers' sake
— Kelly Ellis (@justkelly_ok) January 22, 2015
Kelly Ellis has indicated that she does not intend to speak to the press about the events she has written about, and Google is yet to respond to the allegations. We have reached out to the company for comment, but we're yet to hear back.
Photo credit: Ai825 / Shutterstock
-

Google celebrates women in tech for International Women’s Day
Publié: mars 8, 2015, 3:18pm CET par Mark Wilson

Today is International Women’s Day and in recognition of this Google is celebrating the role women have played, and continue to play, in the world of tech. It's a well-known fact that many technology companies are dominated by men -- as is the case in many industries -- but Google is keen to highlight its own Women Techmakers program.
Set up last year, the program is designed to not only encourage women to enter the male dominated technology sector, but also to promote the visibility of those who are already in place. This month saw the (very quiet) launch of the second Women Techmakers Global Event Series, but today Google wants to speak to the female technology workers of the future.
Google itself has fared fairly well in diversity reports, but there is still a long way to go for the workplace to have a better balance of the sexes. There are undeniable obstacles standing in the way of women climbing the ladder in any industry -- discrimination, inequality, and so on -- but jobs in technology are often seen as being especially dominated by men. Even if companies have an open door policy, there can still be a perception that, as a woman, just getting on the first rung of the ladder is going to be impossible.
This is what Google trying to address today. There's a slightly awkward, patronizing tone to the blog post by Vice President of Engineering Pavni Diwanji, but the overall sentiment is to be welcomed. The idea is that women who have become established in their chosen career send a message out to girls and women who are looking to following their footsteps. The company is encouraging women to submit a video to YouTube using the hashtag #DearMe.
For many young girls, the path to finding themselves is filled with uncertainty. It’s hard to figure out what you want to do or who you want to be when you’re dealing with gossip, self-doubt and pressure from all sides. As part of our International Women’s Day celebration, we’re encouraging you to think back on the advice you wish you’d gotten when you were a young, and to share those words of wisdom with today’s teenage girls. Submit a video letter on YouTube tagged with #DearMe telling your younger self what you wish someone had told you. We’re looking forward to what you have to say.
The idea is to share words of wisdom to one's younger self, but in light of a recent sexual harassment complaint against Google, the choice of hashtag may backfire (more to follow, but #DearMe, indeed).
A number of videos have already been submitted and Google has collected some of them together in a showreel:
-

Sony will only update Xperia Z series Android phones to Lollipop
Publié: mars 7, 2015, 6:46pm CET par Mark Wilson

There is one complaint that is constantly levelled at the Android ecosystem, and that’s the notion that it's a platform that has become very fragmented. For all of Google's bluster about Lollipop, only a tiny proportion of handsets are actually running the latest version of the operating system. This is something that doesn't show signs of changing soon.
Sony has revealed news that will undoubtedly upset many smartphone owners -- only the Xperia Z series is in line for an Android 5.0 upgrade. No Lollipop for the Xperia T2 Ultra, the Xperia M2 Aqua or anything from the E series. A perfect demonstration of why fragmentation is so prevalent. Anyone with a non-Z series Xperia is stuck with KitKat, Jelly Bean or whatever version of Android they may have.
Of course, there will almost certainly be hacked versions of Lollipop available for the eager to install, but for the most part anyone with a slightly older handset is going to miss out on Android 5.0. In fact, it's not really fair to refer to the handsets missing out on the upgrade as "older"; many of those missing out are current generation. But this does make clear that Sony is only really interested in its Z series -- everyone else can just go and whistle.
The news came on Twitter via the official Sony Xperia account:
@roi_rdzdal Hi Roi. The Android 5.0 Lollipop update is only going to be available for the Xperia Z series, we do apologise.
— Sony Xperia (@sonyxperia) March 6, 2015
Predictably, this did not go down well with Sony's followers. Cries of "unfair!" and proclamations of future Sony boycotts followed.
Sony -- just like any other manufacturer -- is free to decide which handsets will receive updates of any sort, but limiting operating system upgrades to a single phone range isn’t doing anyone any favors. It perpetuates the problem of fragmentation, and creates a disillusioned user base. Sony may backtrack on the announcement, but for now the company is sticking to its guns.
Photo credit: gourmetphotography / Shutterstock
-

Reports that uTorrent silently installs Bitcoin crapware are... crap
Publié: mars 6, 2015, 5:41pm CET par Mark Wilson

Sometimes it's easy to be swayed by what's being written online. At the moment there are lots of stories creeping out about the iPad Pro and Apple Watch, none of which are founded in any fact whatsoever. Still, making stuff up, popping it in quotes and attributing it to an anonymous source is great fun, right?
It may be fun, but it's not really fair on the reader. Another story which popped up on my radar today was about uTorrent -- the popular BitTorrent client that's loved and hated in equal measure. Stories on Trusted Reviews, Engadget and the Verge suggest a Bitcoin mining tool called Epic Scale is installed without permission, and is a tricky blighter to remove. There's an easy way to find out; let's just install it.
I've used uTorrent before and I know from experience that running through the installation is something of an exercise in 'spot the crapware'. It has been a while since I used it so I'm interested to see how things have changed.
I grabbed a copy of the latest version of the software from the uTorrent website -- uTorrent version 3.4.2, build 38913. The first screen provides a warning to look out for online scams; how lovely of the developers to care. EULA. I Agree... I guess. Where do I want shortcuts installed? Next... and we're onto the installation proper. After selecting file associations and so on there's my first 'bundled extra'.
Am I interested in Ratking with its offer of '700 fill album' (sic)? Nope. Uncheck the 'Yes, I'd love to check out this download!' box. Next. What's this? Another EULA it would seem. Let's have a quick skim through. Oh… Epic Scale! That's what everyone was banging on about, isn't it? It's described as "a distributed computing platform whereby it combines the unused computer resources of its licensees in order to perform computations for itself and others". Apparently this is the bugger that's impossible to avoid. Oh. I can just click the big Decline Offer button.
Panic over.
Engadget says that there are complaints in the uTorrent forum (which seems to have been pulled offline) that users see no warning about the installation of Epic Scale. I'm not here to defend uTorrent, but from my experience it seems that there is a pretty clear warning. Sure, Bitcoin mining is not mentioned, but it is certainly made clear that there's an optional component that you can either install or avoid.
I've had a check through my system and there is no reference to anything I would not expect or want to find. It seems that, true to my requests during uTorrent installation, nothing extra was installed. I understand the need to monetize free software such as this, and there will be plenty of people who are fooled into installing Epic Scale and other crapware. Ultimately it is their own fault.
As quoted by the Verge, uTorrent says:
We have reviewed the issue closely and can confirm there is no silent install happening... Most likely these users accepted the offer during install. Like many software companies, we have partner offers in our install path and our policy is that they are strictly optional.
It seems the company is right. It seems there is no story. But it makes for good headlines, eh?
-

Facebook's inactive account cull means fewer likes for pages
Publié: mars 6, 2015, 1:45pm CET par Mark Wilson

Like just about any online service, Facebook has a huge number of dead and dormant accounts. It could be that the owner has died, they might have lost interest, or they may be spam accounts that are no longer used. Facebook is now having a spring clean, sweeping aside inactive accounts, and this could have an interesting side effect for page owners.
Accounts that have been purposely deactivated, or memorialized after a death, are currently still factored into the 'like' count for pages. This is set to change, so many page owners should brace themselves for a sudden drop in likes over the coming weeks.
It means that the likes a page is shown as having received should become a better reflection of the number of Facebook users who are actually interested in the service, product or person associated with a particular page. Of course the cull does nothing to address the problem of spam accounts artificially inflating the numbers, but it is a step in the right direction for those keen on greater accuracy.
Explaining the reasons for the change in policy, Facebook said:
Businesses use Page audience data to understand what their followers care about. To make audience data even more meaningful for businesses, we're updating the way Page likes are counted by removing memorialized and voluntarily deactivated accounts from Pages' like counts. This change ensures that data on Facebook is consistent and up-to-date.
The benefits? Facebook suggests two:
- Business results: Removing inactive Facebook accounts from Page audience data gives businesses up-to-date insights on the people who actively follow their Page and makes it easier for businesses to find people like their followers through tools like lookalike audiences.
- Consistency: We already filter out likes and comments generated by deactivated or memorialized accounts from individual Page posts, so this update keeps data consistent.
-

Microsoft and Google working together on Angular 2 JavaScript framework
Publié: mars 6, 2015, 12:34pm CET par Mark Wilson

There are unlikely partnerships, and there are unlikely partnerships -- Google and Microsoft certainly make for strange bedfellows. At developer conference ng-conf in Salt Lake City, Google's Angular team revealed that it has been working with the TypeScript Team from Microsoft to produce Angular 2.
The worlds of TypeScript and AtScript have converged, resulting in the collaborative effort that is Angular 2. The new version of the JavaScript framework will be written in TypeScript and will be used to develop the next generation of web sites and web apps.
Microsoft's corporate vice president of the Developer Division, S. Somasegar, said that the two companies had been working together for several months, and they were now ready to reveal "first fruits of that collaboration". TypeScript, a superset of JavaScript, was first introduced three years ago and few would have expected that Microsoft's development tool would end up as part of a Google project.
Writing on the MSDN blog, Jonathan Turner explains that developers have a lot to look forward to:
We have worked with the Angular team to design a set of new features that will help you develop cleaner code when working with dynamic libraries like Angular 2, including a new way to annotate class declarations with metadata. Library and application developers can use these metadata annotations to cleanly separate code from information about the code, such as configuration information or conditional compilation checks.
We've also added a way to retrieve type information at runtime. When enabled, this will enable developers to do a simple type introspection. To verify code correctness with additional runtime checks. It also enables libraries like Angular to use type information to set up dependency injection based on the types themselves.
You can watch the full keynote speech from the developer conference below:
-

Windows 10 Build 10031 leak shows smaller Start button plus transparency
Publié: mars 6, 2015, 11:31am CET par Mark Wilson
Wzor has come up with the goods again. While many have been disappointed by the lack of new Windows 10 builds in February, appetites have been whetted by a steady stream of unofficial screenshot leaks and even complete builds. Now the Russian leaker has published screenshots from build 10031.
What's new? Microsoft appears to have listened to calls for the introduction of transparency, as the Start menu is now semi-transparent. This is not the only change to the Start menu -- the Start button is also smaller than in previous builds. Could this be the build which is made publicly available in coming days? It's entirely possible.
The screenshots come from the Enterprise version of Windows 10 Technical Preview, and as happened with the last cache of leaked screenshots there's accompanying documentation that reveals what's new. For end users, not a great deal has changed apart from the tweaks to the Start menu; this appears to be another build that's focused on behind-the-scenes tidying up and a bit of spit and polish.
It seems that there is no sign of Spartan in this build, but the leaked release notes reveal a little more about what is going on in the background.
Microsoft seems keen to push touch with Windows 10. While the company would obviously prefer that everyone was using a top of the range Surface Pro 3, it's realistic enough to know that this is not going to happen. As such, this build features a larger detection area around the edge of the touch display to cater for cheaper devices.
There are lots of bug fixes mentioned in the documentation, and changes have been made to the upgrade process for anyone starting off with a Windows 7 machine. If you were hoping for a change to icons in Windows 10, it looks like you're going to be disappointed, by the way.
One of the more notable changes in this build is to the OOBE (out of box experience). Build 10031 sees this switching to a cloud-based focus which means that Microsoft is better able to make changes to it.
We still don’t know when we'll actually get to play around with a new official build, but it shouldn’t be long now!
-

Google Compare tracks down cheap car insurance for US drivers
Publié: mars 5, 2015, 9:28pm CET par Mark Wilson
Referred to variously as Google Compare for U.S. car insurance, Google Compare for car insurance, and Google Compare for Auto Insurance, Google has just added a new string to its bow. The newly launched service lets drivers hunt down the best car insurance deal -- something which UK Googlers have been able to take advantage of for a little while already.
After handing over a few details like address, vehicle stats and the level of coverage required, Google will compare all of the available policies so you can pick the one that suits you the best. Don’t like a quote? Just increase the deductible and a new deal will be calculated for you.
Google Compare is not a completely new service -- Google already provides a way to seek out the best credit card deal -- but the move into car insurance is new and it's a great alternative to manually visiting the websites of dozens of individual insurers. Having gained a quote, you can stick with the online approach and click through to the insurer's website to complete the process, or you can phone up and provide a reference code if you need to speak to someone before parting with your cash.
Google already has a number of national and local insurance firms on board, including MetLife and Mercury, and more will be added over time. The insurance comparison service launches in California to start with, and there are plans to expand it to other states in the future. To get your quote, head over to Google Compare Auto Insurance.
-

Microsoft launches Office 2016 Mac Preview
Publié: mars 5, 2015, 8:30pm CET par Mark Wilson
Microsoft is all about software previews these days. We've seen various preview builds of Windows 10 and Windows 10 for Phones, and now it's time for the next version of Office for Mac. Today Microsoft released Office 2016 Mac Preview, giving Mac users a chance to try out the next version of the office suite ahead of its full launch.
As with the Windows version of Office, and in keeping with the new focus of Microsoft, there's a strong emphasis on the cloud. OneDrive, OneDrive for Business and SharePoint can be used to sync documents between devices, and Microsoft is keen to point out that this is more than just a straight port of PC Office -- the suite has been Mac-ified.
A redesigned ribbon can be found across Word, Excel, PowerPoint, OneNote and Outlook, and the whole UI has been designed to take full advantage of Retina displays. Mac-specific features? Apart from full screen mode, there's also "little Mac affordances like scroll bounce," says Microsoft. But there are lots of new features and improvements to look for in the individual apps.
OneNote has been quite a success story for Microsoft, and the note organization tool receives a welcome update in Office 2016 for Mac. We've already seen Outlook for Mac as a standalone app, but it's also part of the suite. The app everyone knows Office for, Word, gains features such as threaded commenting, while Excel benefits from new data analysis options. PowerPoint gains, among other things, new transitions and an animation builder.
If you fancy taking the office suite for a spin, you can download it here -- as ever, your feedback is encouraged.
-

Hosted web apps could solve Microsoft's Windows Phone problems
Publié: mars 5, 2015, 12:04pm CET par Mark Wilson

Despite my colleague Wayne Williams' eloquent suggestion that the naming conventions used for Lumia devices is part of the reason for the low uptake of Windows Phone, the platform still has a serious problem when it comes to apps. Whether there is a real problem or not, the perception is that Windows Phone -- or Windows 10 for Phones -- is rather lacking in the app department. Fear not... Microsoft has a solution.
Rather than pumping out a glut of new apps of its own, or encouraging developers to produce third-party apps, Microsoft is adopting a slightly different tactic. At MWC 2015 this week the Lumia 640 and Lumia 640 XL were revealed, but Microsoft also announced that web apps will be permitted in the Windows store. Could this be what app-hungry consumers have been waiting for?
Allowing web apps is about more than just helping website owners to convert their site into an app. This is about making the plethora of cloud services available to Windows Phone users without the need for developers who have invested in Android and iOS to spend time developing a Microsoft-specific version as well. I know what you're thinking… web apps are crap, right? But Microsoft is one step ahead.
Microsoft has said that not only will hosted web apps be permitted entry to the store -- so they'll be hosted on developers' servers -- but these apps will be able to make use of universal APIs. This means that the apps will be able to generate notifications, access data on a phone when required, and make use of hardware such as the microphone or camera as and when appropriate; there's even potential for hosted web apps to tie into Cortana.
The move to the cloud means that there is now an astonishing wealth of services to be found online. Of course, these could be accessed through a mobile web browser, but this would create something of a jarring user experience when moving from local app to web app.
It's important to remember that this announcement should not be seen as a way to boost the number of apps in the Windows store. There is a limit to the number of apps that are needed, but there's no denying that Windows Phone/Windows 10 for Phones is lacking apps in certain categories, and quality apps in many of them. Hosted web apps is a quick and dirty solution, but it’s one that could just pay off.
-

Samsung Galaxy S6 and Galaxy S6 Edge unboxing and hands-on videos
Publié: mars 4, 2015, 8:55pm CET par Mark Wilson

Fresh from the unveilings at MWC 2015, Samsung has released official unboxing videos for its two latest Android devices -- the Galaxy S6 and Galaxy S6 Edge. Published on YouTube, the video clocks in at under three and a half minutes -- no epic-length unboxings here! -- and gives us a close-up look at the flagship handsets.
Both devices appear in fairly unassuming, plain white boxes, unadorned with imagery or other distractions, but it's the contents that everyone is interested in. It's the Galaxy S6 Edge that is unwrapped first, and fans of the Galaxy series are sure to be impressed by what they see.
The screen is the undoubted star of the Galaxy S6 Edge and we're immediately treated to a view of using the phone to watch videos. If you've wondered what the point of the curved screen edges is, Samsung demonstrates how when the phone is placed face down, notification lights can still be seen along the length of the device. You're also shown how the curved edge provides easy access to contacts and can alert you to different types of message.
Slightly less exciting is the non-edgy Galaxy S6 -- which is probably why it appears second in the video. The lack of curved screen means that the side of the phone shows off the metal framework rather than notifications, and this is something that Samsung is proud of. Despite the lack of curvature, Samsung is still keen to showcase the S6's high-quality screen... cue close-ups of HD video footage.
You might not be able to go hands-on yourself just yet, but this is a good substitute in the meantime. The video also gives you a chance to see all of the various color options, so check it out below:
-

Apple, Microsoft and Google need just one mobile improvement -- battery life
Publié: mars 4, 2015, 5:45pm CET par Mark Wilson

Let’s face it, you’ve picked the mobile operating system you like. Whether you’ve opted for an iPhone, a Lumia handset or a device running Android, the chances are you’re not going to switch allegiances no matter what others may do or say to try to convince you otherwise. At the same time, few people would argue that their handset of choice is perfect.
You’ve picked your side when it comes to OS, but what about the handset itself? Apple, Samsung, HTC et al keep releasing slightly tweaked versions of last year’s handset, perhaps adding a faster processor, a larger screen and more memory. One thing is constantly overlooked, however -- battery life. And it’s time for things to change.
The quoted statistics for any given phone are all but meaningless because it is impossible to take into account the myriad app configurations and usage patterns that exist. In spite of this, there are probably very few smartphone owners (or tablet owners for that matter) who feel their device's charge lasts for long enough. It would be naive to think that phone manufacturers are not heavily invested in advancing battery technology, but worrying about whether a charge will last the day is something that plagues us all.
Consumers are ever-demanding creatures. Bigger, better and faster is always requested, and it seems that battery technology is failing to keep pace. The faster processor, the bigger screen, the more graphic-intensive games suck up battery power greedily. Use your phone for little more than making the odd call and sending texts, and you'll almost certainly make it through the day without an issue, but factor in web browsing and playing the occasional game of Candy Crush and you could probably watch battery percentage dropping before your very eyes.
There is a solution.
At the moment there is too much focus on creating devices that are wafer thin and feather light. Yet the ever-growing market for rechargeable battery packs and cases with built-in backup batteries shows that many people don’t mind carrying around some extra bulk. If you've opted for a charging case such as those from Mophie, would you not prefer that a larger battery was just built into the phone by default? If you're carrying around a battery pack and a USB cable, would it not be easier if your phone's battery was of a higher capacity to start with?
Of course, it's not quite that simple. Fatten up the iPhone 7 or Galaxy S7 with a bigger battery and -- despite complaints about needing more juice -- there would almost certainly be protests from people unhappy at the extra weight and bulk. So why not make a larger battery optional. Apple has shown that people like a choice of screen sizes, and most manufacturers give consumers a choice of storage capacity. It makes perfect sense to extend this idea of choice to larger capacity batteries.
People who are running few or undemanding apps can opt for regular capacity battery versions of their preferred handset, while those with greater needs could plump for one with a larger battery. It's something that would be made easier and cheaper to achieve if more manufacturers stepped away from the idea of sealed-unit phones with integrated, non-replaceable batteries and made the power pack something that could be easily switched out.
App developers have a part to play as well. There is a lot that can be done to improve the efficiency of apps with code optimization -- too many apps have grown into sprawling, bloated behemoths that need taming. There are also other avenues to investigate such as integrated kinetic charging which could help to keep a battery topped up throughout the day.
Project Ara is an inspiring project from which other manufacturers could borrow ideas. The option of dropping a camera in favor of clipping in a higher capacity battery empowers the customer with choice. The point is that there is much more that could be done to help smartphones make it through the day without needing a charge, even under heavy usage. Now is the time for that more to be done.
Photo credit: Shmizla / Shutterstock
-

What the FREAK? Huge SSL security flaw stems from US government backdoor
Publié: mars 3, 2015, 10:15pm CET par Mark Wilson

Seven hours is all it takes to crack the encryption that is in place on some supposedly secure websites. Security experts blame the US government's ban on the use of strong encryption back in the 1990s for a vulnerability that has just come to light. Named FREAK (Factoring attack on RSA-EXPORT Keys), the flaw exists on high-profile websites including, ironically, NSA.gov.
Restrictions that limited security to just 512-bit encryptions were lifted in the late 90s, but not before it was baked into software that is still in use today. The ban on the shipping of software with stronger encryption apparently backfired as it found its way back into the States. Security experts say the problem is serious, and the vulnerability is relatively easy to exploit.
Browsers can be hijacked and tricked into accessing websites using legacy encryption -- this was the discovery of researchers at Inria in France. There was disbelief that such old protection measures were still being used, but it soon became clear that hackers needed just a matter of hours to exploit the weak security to steal passwords and personal information, or even launch a full-scale attack on a website.
Talking to the Washington Post Matthew Green, a cryptographer at Johns Hopkins Information Security Institute, said that US government had effectively weakened its own security with the earlier ban on the exporting of strong encryption. "When we say this is going to make things weaker, we're saying this for a reason."
The vulnerability could be exploited on vulnerable sites, with encryption cracked in just seven hours. Worryingly, if test samples are correct, more than a quarter of websites that were previously thought to be secure are vulnerable to the problem. In a blog post, Green explains that the vulnerability affects OpenSSL (used by Android) and Apple TLS/SSL clients (used by Safari). He goes on to explain that "the SSL protocol itself was deliberately designed to be broken" and that a man-in-the-middle attack could be easily launched on sites:
The 512-bit export grade encryption was a compromise between dumb and dumber. In theory it was designed to ensure that the NSA would have the ability to 'access' communications, while allegedly providing crypto that was still 'good enough' for commercial use. Or if you prefer modern terms, think of it as the original "golden master key".
In effect, a backdoor put in place by the US government has left countless websites insecure. Green points out that the lengthy list of affected sites includes connect.facebook.net which is used to deliver Facebook's Like button to millions of websites. If this was hijacked, the consequences could be dire.
Patches will almost certainly be on the way, but the final word goes to Matthew Green who sums up the source of the problem quite succinctly:
Encryption backdoors will always turn around and bite you in the ass. They are never worth it.
Photo credit: wk1003mike / Shutterstock
-

iPhone 6 and Surface Pro 3 win at MWC 2015 Global Mobile Awards
Publié: mars 3, 2015, 7:18pm CET par Mark Wilson

MWC 2015 has seen all manner of exciting smartphones, tablets, wearables and other goodies, but the event is not solely about brand new products. It's also a chance to look back on the past year and reflect on the highlights. Today Microsoft and Apple were among the companies picking up gongs for their products.
Both were to be found in the prestigious Best Mobile Handsets and Devices section. Apple's iPhone 6 shared the best smartphone award with the LG G3, and Microsoft Surface Pro 3 picked up the prize for best mobile tablet. Plenty of other awards were handed out in recognition of innovative technology products.
The iPhone 6 and LG G3 fought off competition from HTC One M8, Samsung Galaxy Note 4 and Sony Xperia Z3 in a category where Windows Phone devices were notable by their absence. A Lumia handset was to be found in the Best Low Cost Smartphone category nominee, but it was the Motorola Moto E that walked away with the accolade.
2014 proved to be the year that wearables really started to take off, and Motorola Mobility for Moto 360 claimed the top spot.The Best Mobile Tablet was arguably the most varied of the mobile device categories. Microsoft's tablet-laptop hybrid prevailed over the Apple iPad Air 2, Google Nexus 9, Samsung Galaxy Tab S 8.4 and Sony Xperia Z3 Tablet Compact.
Dennis Meinhardt, director of program management for Microsoft Surface, said:
We're absolutely thrilled to be winning this award. Surface Pro 3 is the world’s most productive tablet, and is a tablet that can replace your laptop. With Surface Pro 3 we have managed to marry the hardware and software to provide the power and performance of a full laptop without compromising the sleek design, lightness, and great battery life that we expect from a tablet.
Did your favorite miss out on an award?
-

Google reneges on its promise of encryption by default for Lollipop devices
Publié: mars 3, 2015, 6:37pm CET par Mark Wilson

Not wanting to be outdone by Apple, when it was announced that iOS 8 would encrypt data by default, Google felt compelled to follow suit. Back in September Google said that in Lollipop "encryption will be enabled by default out of the box, so you won't even have to think about turning it on". But six months is a long time, and it now seems that Google has had a change of heart.
Well, as noted by Ars Technica, many of the Lollipop handsets appearing at MWC 2015 -- including the Samsung Galaxy S6 -- do not have encryption enabled. Of course there is nothing to stop users from manually enabling it, but that's not really the point; the idea was that you "won't even have to think about turning it on". So what gives?
It's all about performance. On-the-fly encryption and decryption eats up valuable processor time, and handsets took a hit in terms of speed. Take a look at a blog post from Google about the release of Lollipop from late October and you'll immediately notice references to "new security features protecting you, like encryption by default" and the assurance that "full device encryption occurs at first boot".
But scroll to the bottom of the post and you'll see that there's an addendum:
In September, we announced that all new Android Lollipop devices would be encrypted by default. Due to performance issues on some Android partner devices, we are not yet at encryption by default on every new Lollipop device. That said, our new Nexus devices are encrypted by default and Android users (Jelly Bean and above) have the option to encrypt the data on their device in Settings ---> Security ---> Encryption. We remain firmly committed to encryption because it helps keep users safe and secure on the web.
Such is the change of heart that full device encryption by default is no longer a requirement for partners according to Google's Android Compatibility Program document (section 9.9 on page 59) it's now optional:
If the device implementation has a lock screen, the device MUST support full-disk encryption of the application private data, (/datapartition) as well as the SD card partition if it is a permanent, non-removable part of the device [Resources, 107]. For devices supporting full-disk encryption, the full-disk encryption SHOULD be enabled all the time after the user has completed the out-of-box experience. While this requirement is stated as SHOULD for this version of the Android platform, it is very strongly RECOMMENDED as we expect this to change to MUST in the future versions of Android.
So there is still a requirement for Samsung et al to support device encryption, but there is no requirement for it to be enabled as initially promised. You'll notice that the Android Compatibility Program document was last updated in the middle of January -- Google didn’t publicize the change, and it's only now that people are starting to notice and question it.
Problems with performance and compatibility are quite reasonable reasons for delaying encryption by default, but Google's lack of transparency is worrying. Following Google's promises back in the latter end of 2014, anyone buying a new Lollipop device would quite reasonably expect that their device is encrypted -- and the uninitiated may not even bother to check. The balance between performance and security is one for users to make for themselves, but Google needs to be open and honest about what is going on.
Photo credit: Daniel Padavona / Shutterstock
-

Embed Twitter-hosted videos on your own site with new widget
Publié: mars 3, 2015, 4:27pm CET par Mark Wilson

It just became a whole lot easier to embed Twitter-hosted videos on websites. A newly launched widget makes it possible to add the video from a tweet to a website without the need to embed the entire tweet. It's a neat-looking solution that makes it simple to embed videos without unnecessary, distracting page furniture.
It works in just the same way as embedding an entire tweet, and it provides a way for Twitter to drive traffic back to its own site rather than other video services, whilst simultaneously making life easier for embedders and helping to pull in followers from other sites.
Embedding a video takes nothing more than clicking the More (ellipsis) button beneath a tweet and then selecting the Embed Video option. The necessary HTML is displayed ready for copying and pasting into the code of a web page or blog post. The way the widget works means that when used outside of Twitter, it is an excellent marketing tool for your Twitter account.
The video player blends neatly into the look of just about any website, and it does more than just house a video. Part of the point of using Twitter as a video-sharing platform is to gain followers, and the video widget helps in this regard. A link to the Twitter account that uploaded the video is displayed to the lower left of the video widget, while to the lower right a Twitter logo provides access to the main text of the tweet along with an all-important Follow button.
Check out the sample below which shows off how the widget looks:
You can now shoot, edit and share video on Twitter. Capture life's most moving moments from your perspective. pic.twitter.com/31JoMS50ha
— Twitter (@twitter) January 27, 2015
-

Android apps crash more than iOS apps
Publié: mars 3, 2015, 1:55pm CET par Mark Wilson

With MWC 2015 underway in Barcelona, the tech world is laser focused on mobile devices at the moment. Whether your mobile device preference is an iPhone, an Android handset or a Windows Phone device, your decision will have been swayed by a number of things -- price, brand reputation, knowledge of the ecosystem, and range of apps. Android may be the most popular choice at the moment, but this appears to be in spite of problems the platform suffers form.
A new report from Crittercism suggests that Android apps crash more frequently than their iOS counterparts. But this is not the only bad news for Google's mobile operating system; the report also finds that the fragmentation of Android persists.
The report from Crittercism -- a company with services that monitors app performance -- looks at the differences between iOS and Android in terms of fragmentation (Microsoft may be disappointed that Windows Phone is not included but, globally, the platform remains relatively insignificant) and app stability. Android fares worse than iOS here.
If you were wondering which types of app are most prone to crashing, Crittercism reveals that photo, video, games and social networking titles are most likely to fall over for iOS users (2.5, 2.4 and 2.1 percent respectively). The categories, and failure rates, are a little different (and higher) on Android -- entertainment, business, photography, and shopping (5.3, 3.4, 3.3 and 3.3 percent).
Apple is singled out for fixing problems quickly. After launch, iOS 8 suffered an app crash rate of 3.3 percent, but this was quickly addressed with updates both from Apple and app developers. The crash rate is now in line with iOS 6 at 2.2 percent, while iOS 7 sits at 2.1 percent. With each iOS release there is a spike in crashing at launch, followed by an ultimate increase in stability. Interestingly, there has been a jump in app crashes on iPhone 4s as developers concentrate their time and energy on newer devices.
The report makes for interesting reading when it looks at adoption rates for the latest version of mobile operating systems. It will come as little surprise that there are more iOS users running the latest version of iOS than there are Android users running the latest version of Android. This is something we probably already knew, but nearly six months after the release of iOS 8, it's worth another look.
Apple's policy of making new versions of iOS available to supported handsets as soon as possible means that there is a very fast adoption rate. So fast, in fact, that it took just 50 days for iOS 8 to account for half of app traffic. We’ve reach the point now that iOS 7 accounts for just 30 percent of app traffic, and iOS 6 and earlier are all but insignificant. Sales of iPhone 6 and iPhone 6 Plus helped to drive this adoption, with the two devices now accounting for 19 percent of app traffic.
It's a very different story for Android. Lollipop may not have been available for as long as iOS 8, but in a little under three months it managed to account for less than 2 percent of app traffic. The bulk of traffic is split between KitKat and Jelly Bean, but Ice Cream Sandwich still features in the charts.
Photo credit: Rashevskyi Viacheslav / Shutterstock
-

Apple Pay security scam nets fraudsters millions of dollars
Publié: mars 2, 2015, 11:48pm CET par Mark Wilson

The big names in tech are falling over themselves to get new payment systems out of the door at the moment. At MWC, Sundar Pichai confirmed Android Pay is on its way, and we've also learned about Samsung Pay from the Barcelona event. The convenience of paying with a smartphone is undeniable, but there are unavoidable security concerns.
Having been adopted by millions of Americans -- and with plans to expand into Europe and beyond -- Apple Pay is serving to highlight important security problems. Lax verification systems used by banks coupled with criminals exploiting stolen credit cards and IDs mean Apple Pay is used to make millions of dollars worth of fraudulent purchases. So how does it work?
The Guardian reports that insufficient security checks are performed by banks when connecting a credit card to an iPhone. In order for a customer to use Apple Pay with their iPhone 6, their bank needs to transmit a digital version of their card to it. In some instances, using information from Apple accounts such as transaction history, banks may automatically approve the addition of a card. Others require additional checks to be performed and, strangely, this is where the problem arises.
Some banks ask for nothing more than the last few digits of a social security number as a means of confirming identity. As social security numbers are often targeted by criminals, this is information that criminals are likely to have, making it all too simple to fraudulently add a credit card to an Apple Pay account and use it to purchase high-value goods... even from Apple stores.
Those executing the scam are careful to take steps to minimize the risk of raising suspicions. A bank might well be wary of authorizing the addition of a credit card when it is being used on the other side of the country to where it's normal activity is centered. By phoning banks ahead of time to let them know of a make-believe vacation or business trip, fraud triggers that would ordinarily be set off when Bob from Detroit suddenly buys a MacBook Air in LA are effectively bypassed.
While this is not a problem with Apple Pay's security per se, it serves to highlight some of the considerations that need to be made before making the switch to such forms of electronic payment. Banks are now taking steps to put additional security measures in place, and Google and Samsung will be paying close attention to how things pan out. Until the problem is addressed, Apple Pay will continue to be an unwitting accomplice to the growing problem of fraud in the US.
-

Microsoft helps enterprise customers move to Internet Explorer 11 and Windows 10
Publié: mars 2, 2015, 10:53pm CET par Mark Wilson

While everyday consumers are important to Microsoft, a decent chunk of its income comes from enterprise customers. This group of users can be slow to upgrade software, and Microsoft is keen to encourage them to upgrade to Internet Explorer 11 before support for earlier versions come to an end in January next year.
The company is only too aware that many people are running web services and apps designed for older versions of Internet Explorer. Laying the groundwork for ultimate upgrades to Windows 10, Microsoft is pushing the Enterprise Mode, the Enterprise Mode Site List and Enterprise Site Discovery feature of IE11 as a way to benefit from security updates and technical support whilst simultaneously paving the way for a Windows 10 upgrade further down the line.
In a blog post, Microsoft's Jatinder Mann and Fred Pullen call upon enterprise users to make the switch from Internet Explorer 8, 9 and 10, explaining that the Enterprise Mode found in Internet Explorer 11 provides backwards compatibility with the IE8 rendering engine. A survey commissioned by Microsoft found that customers who had made the switch to IE11 found it was not only quicker than expected, but also resulted in reduced costs and simplified testing.
New features have been added to Enterprise Mode to help improve compatibility and the MSDN blog post includes full details about how to make the jump to Internet Explorer 11.
We know that upgrading to a new browser can be a time-consuming and potentially costly venture. To help reduce these costs, we introduced the Enterprise Site Discovery toolkit to help you prioritize which sites you should be testing based on their usage in your enterprise. For example, if the data shows that no one is visiting a particular legacy Web app anymore, you may not need to test or fix it. This tool also gives you information on what document mode the page runs in your current browser, so you can better understand how to fix that site if it breaks in a newer version of the browser. This tool is currently only supported in IE11, but we are bringing Enterprise Site Discovery support to IE8, IE9, and IE10 very soon.
Of course this is not just about pushing people to using the current version of Internet Explorer. Having made the transition to IE11, customers are far better placed to make the switch to Windows 10 when it is released later in the year.
-

Blackphone 2 caters to the enterprise, the security-minded and the paranoid
Publié: mars 2, 2015, 5:59pm CET par Mark Wilson

Yep, we know all about the NSA, thanks Edward. Yeah, it's possible (probable?) that a government agent somewhere is listening to or recording your conversations. And yes, even if you're not one of the tin-foil hat brigade, there's a danger that someone could tap into your phone. But you don’t have to be paranoid to want security; there are plenty of companies and enterprise customers for whom security is of the utmost importance.
While much of the news coming out of MWC 2015 has been dominated by Microsoft's Lumia 640, the Samsung Galaxy S6 Edge, and tablets from Sony, there's always room for something a little different. Following on from the security-focused Blackphone, Silent Circle used the Barcelona event to announce the follow-up -- the Blackphone 2.
The privacy-centric company has been working on the "world's first enterprise privacy platform" for some time now and the second generation Blackphone. As you would expect, there's a faster processor than before -- an 8-core beast -- as well as an upgraded 3GB RAM, a larger 5.5 inch screen and a bigger battery than before. Blackphone 2 has a $600 price tag and will be unleashed in July.
Silent Circle is all about security, but security is about more than just a phone that features encryption. There is an entire ecosystem in place starting with the secure PrivatOS 1.1. The latest upgrade to the operating system introduces a feature called Spaces which allows for OS-level virtualization and the ability to keep work and personal apps and data completely separate from each other. These features are also due to rollout to first generation Blackphones through an upcoming update.
There's secure access to the locked down Silent Store, and enterprise admins have an all-important remote lock and wipe option to fall back on. On the software front there's also a new encrypted conference-calling app on top of regular phone calls and messaging. As Silent Circle explains, existing methods of security are simply not enough. It made sense to just start from scratch:
The way we work has evolved. With a growing number of employees now using personal devices to connect to their enterprise networks, traditional approaches to security are no longer enough. Silent Circle is building the world’s first enterprise privacy platform, a unique combination of software, services and devices. Everything we do is designed to help the enterprise achieve real privacy without compromising productivity.
Also arriving later in the year is the Blackphone+. Despite the name, this is not a phone, but an 8-inch tablet. You pretty much know what to expect: this is a Blackphone 2 with a larger screen and the same focus on security. Details are thin on the ground at the moment, but Silent Circle releases a (very) short teaser video:
-

Google+ to split into Hangouts, Photos, and Streams
Publié: mars 2, 2015, 3:53pm CET par Mark Wilson
It's fair to say that of all of the social networks there are to choose from, Google+ is one that has failed to set the world on fire. Facebook may annoy users from time to time but it dominates the social web, and Twitter has carved out a healthy niche for itself as well. But Google is, uncharacteristically, unwilling to give up on Google+ just yet.
In what seems to be an attempt to breathe new life into a flagging product line, Vice President of Google, Bradley Horowitz is taking control. Interestingly he is not looking after Google+ as a whole, just a couple of its branches. Announcing the news, he said that the recent rumors surrounding Google+ splitting up are true.
Talking to Forbes recently, Google's Senior Vice President Sundar Pichai suggested that Photos and Hangouts might soon been separated from Google+, saying, "I think increasingly you'll see us focus on communications, photos and the Google+ Stream as three important areas, rather than being thought of as one area".
Writing on Google+, Horowitz said:
Just wanted to confirm that the rumors are true -- I’m excited to be running Google’s Photos and Streams products! It’s important to me that these changes are properly understood to be positive improvements to both our products and how they reach users.
Judging by the reaction on Google+, the announcement has been very well received. Horowitz's new role, as well as the splitting of Google+ into a trio of services, gained a positive smattering of comment, and many commenters said Horowitz should have been the man at the top of the social network from the beginning. No details have been provided about any changes that might be on the cards, or when we could expect to see evidence of the split.
-

Malware detection in 2014 doubles from 2013 -- 2015 could be even worse
Publié: mars 2, 2015, 3:17pm CET par Mark Wilson
A report from PandaLabs suggests that there were twice as many malware infections in 2014 compared to 2013 -- and China was the hardest hit. Globally, Europe was found to be the area with the lowest rate of infection, and Sweden topped the chart as the safest country. The UK found itself in fourth place with an infection rate of 22.14 percent.
There were certainly plenty of big name security issues throughout 2014. CryptoLocker was just one high-profile example of ransomware, and Trojans continue to be the most common form of infection, accounting for 70 percent of new malware. Viruses tend to be the most commonly known and feared form of infection, but these make up just 12.33 percent of new infections, and a mere 2.7 percent overall.
In total there were more than 75 million new malware samples detected, and Panda Security -- the firm behind PandaLabs -- recorded an average of 200,000 new strains of malware each day. It's not just desktop platforms that are being targeted these days. There is an increased focus on mobile devices, and Android wins itself the unenviable crown for the most targeted mobile OS -- thanks largely to its majority marketshare.
From 2013 to 2014 there has been a huge increase in malware in general (there were actually 2.5 times the number of malware specimens detected rather than a straight doubling), and the fear is that the trend will continue. Luis Corrons, Technical Director of PandaLabs, thinks we have a battle on our hands in 2015:
We live in an Internet-connected world, and as such we are exposed to cyber-attacks now more than ever before. Security threats will increase in 2015, and both companies and home users must prepare themselves to respond to them. It is not a question of whether their security will be compromised but rather when and how, so in this case prevention is key.
Panda Security suggests a number of areas that companies could look at to increase security this year. This includes locking down point-of-sale systems, identifying vulnerable apps that might need updating, and improving traceability so the source of problems can be better identified. The company also suggests that the Internet of Things is the next big cause for concern, pointing to the fact that once a security issue is identified, it is easily exploited as many IoT devices are not updated frequently.
-

Microsoft's Universal Foldable Keyboard loves iOS, Android and Windows equally
Publié: mars 2, 2015, 12:50pm CET par Mark Wilson

Every mobile operating system would have you believe that it has the best built in keyboard. It's clear that plenty of people disagree judging by the number of alternative keyboard apps that exist in the Windows Phone, Apple and Android stores. Sometimes even the best software keyboard isn't good enough, but few people are enamored with the idea of carrying around a full size Bluetooth keyboard.
There are numerous mobile keyboards that are particularly suitable for use with smartphones and tablets, and today at MWC in Barcelona, Microsoft threw its hat into the ring with the Universal Foldable Keyboard. Bearing more than a passing resemblance to a large money wallet, this svelte device connects via Bluetooth to whatever mobile device you happen to be using -- including the newly announced Lumia 640 and Lumia 640 XL.
For extended typing sessions, it's hard to replace a physical keyboard, and this is something that Microsoft has clearly recognized. Looks have been borrowed from the Surface Pro's Type Cover, and if usability is a shared feature as well, things bode well for the Microsoft Universal Foldable Keyboard. It may not transform your phone or tablet into a laptop, but it will certainly help to speed up the typing of lengthy emails and documents.
With all of the announcements flying out of MWC at the moment, full details are creeping out more slowly than the big headline-grabbing news. As such we don’t yet know anything about the pricing or availability of the Microsoft Universal Foldable Keyboard. We've reached out to Microsoft for more details, and we'll update this post when we hear back.
-

Microsoft launches Windows 10-ready Lumia 640 and Lumia 640 XL
Publié: mars 2, 2015, 10:18am CET par Mark Wilson

It was something of a poorly kept secret, but this morning at MWC Microsoft announced the two latest additions to its range of Lumia handsets. News of the Lumia 640 and Lumia 640 XL had already crept out over the weekend thanks to a slightly premature news release that was later pulled, but now the handsets are official and "keeping you prepared for anything".
These may be fairly low-end phones, but there's one thing the handsets are prepared for -- Windows 10. The 5-inch Lumia 640 and 5.7-inch Lumia 640 XL will arrive with Windows Phone 8.1, but are in line for a Windows 10 upgrade. To increase the appeal of the phones, Microsoft is throwing in a one-year license for Office 365, 60 minutes of international Skype calls each month, and 1TB of OneDrive storage. But what about the specs?
These are not powerhouse handsets as the price of €139 to €219 (depending on the model) reveals. The smaller, cheaper Lumia 640 features a 2,500 mAh battery and an 8MP camera. The handset is powered by a 1.2GHz quad-core CPU and features 1GB of memory. The 3G version will cost around €139 (about $155), while the LTE version will be around €159 (about $177). Moving up to the larger Lumia 640 XL, the camera jumps to 13MP, and the battery to 3,000 mAh. The 3G version will cost around €189 (about $211) and the LTE around €219 (about $245). Single-SIM and dual-SIM LTE and dual-SIM 3G will be available.
Microsoft describes the 640 range as being suitable for use at home, at work and on the go, and the bundled services and software certainly help in that department. The year-long Office 365 Personal subscription allows for installation of the office suite on the phone as well as on a tablet and PC, while the 1TB of OneDrive space can be used to expand the phones' storage.
As is customary for Lumia device, these two handsets will be available in a variety of colors. The 5-inch Lumia 640 XL launches in March in matte cyan, orange and black, matte white and glossy white, but if you prefer the Lumia 640, you have to wait until April to buy it in glossy cyan, orange and white, or matte black.
-

Smartphones hit 7 inches as Huawei announces MediaPad X2
Publié: mars 1, 2015, 11:49pm CET par Mark Wilson

The announcements are coming thick and fast from MWC 2015 in Barcelona. As well as the Huawei Watch, Huawei also announced the MediaPad X2. As you might guess from the name, this is a tablet, but dual SIM support means that it is essentially a gigantic smartphone with no less than 7 inches of screen to play with.
And it's more than just the dimensions that are supersized -- the 2.0 GHz Kirin930 64 bit octa-core packs quite a punch. Being a brand new device, it's little surprise that Android 5.0 Lollipop is found pre-installed, and this is supplemented by the third version of Huawei's own Emotion UI. But there is much more to this phone/tablet crossover -- perhaps the first device to genuinely justify the horrific portmanteau phablet.
This is a device that very clearly tries to bridge the gap between tablets and smartphones, and the 323ppi, 1920 x 1200 lends itself to all manner of tasks. Two versions are on the card; one features 2GB RAM and 16GB of storage, the other 3GB RAM and 32GB. Both feature a MicroSD slot that can handle a memory card up to 128GB.
Just 7.18mm thick and weighing at 239g, this is a tablet that could be easily carried around with little trouble, and the hefty 5000 mAh battery means you can last for some time between charges. Huawei is yet to reveal details of pricing and availability, but we do have the full specs to tide us over:
- Height: 183.5mm
- Width: 103.9mm
- Depth: 7.18mm
- Weight: About 239g
- Color: Silver, Gold
- Display: 7-inch 1920 x 1200 FHD IPS LTPS touch display, 10-point capacitive touch screen, 323ppi, 450 nits
- CPU: 2.0 GHz Kirin930 64 bit octa-core CPU, 4 x 2.0 GHz+4 x 1.5 GHz, GPU Mali-T628+ i3 co- processor
- Operation System: Android 5.0, Huawei Emotion UI 3.0
- Memory: RAM: 2GB/ 3GB, ROM: 16GB/ 32GB, MicroSD 128GB
- Network: LTE Cat6: up to 300 Mbps DL / 50 Mbps UL, DC-HSDPA+: up to 42 Mbps DL / 5.76 Mbps UL, Dual 4G SIM connectivity, Dual-antenna Wi-Fi: 802.11a/b/g/n, 2.4/5GHz, Bluetooth: 4.0 (compatible with 3.0 2.1 + A2D, EDR, BLE), MicroUSB 2.0, Cellular Voice, SMS and MMS, AirSharing, Wi-Fi hotspot
- GPS: GPS/A-GPS Location & Navigation
- Connectivity: Model: GEM-702L - GSM: band 2/3/5/8, UMTS: band 1/2/5/8, TD-SCDMA: band 34/39, LTE-TDD: band 38/39/40/41, LTE-FDD: band 1/3/7/8/28, Wi-Fi: 2.4 GHz/5GHz, Model: GEM-703L - GSM: band 2/3/5/8, UMTS: band 1/2/5/8, TD-SCDMA: band 34/39, LTE-TDD: band 38/39/40/41, LTE-FDD: band 1/3/7, Wi-Fi: 2.4/5 GHz
- Sensors: Ambient Light Sensor, Accelerometer, Proximity sensor, Gyroscope, Compass
- Camera: 13-megapixel BSI rear-facing camera, 5-megapixel front-facing camera
- Audio: Dual built-in noise reduction MIC, Receiver and Speaker, DTS sound technology, 3.5 mm stereo headset jack
- Audio formats: MP3/WMA/FLAC/APE/WAV/RA/Ogg/MIDI/3GP
- Video: 1080p full HD video recording and video playback
- Video formats: MPEG-4, 3GP, 3G2, RM, RMVB, ASF, FLAC, APE, MOV
- Battery: 5000 mAh lithium polymer, about 24 days of standby time, about 3.5 hours of charging time, reverse charge function
-

Huawei Watch could be the first smartwatch you actually want to wear
Publié: mars 1, 2015, 9:39pm CET par Mark Wilson

At MWC 2015, Chinese manufacturer Huawei announced its first foray into Android Wear. The company unveiled the rather predictably-named Huawei Watch today, and it's already got tongues wagging around the world. The screen is a 1.4 inch, 400 x 400 pixel AMOLED affair which is, importantly, completely round.
Packing 286 pixels per inch, the Sapphire crystal screen has a higher resolution than the Watch Urbane launched by LG today. The stainless steel case gives the watch a quality look and feel, and the device boasts a bevy of on-board sensors for tracking different activities. What is likely to prove the Huawei Watch's key to success, however, is the fact that it so closely resembles the look of a regular watch.
It's difficult to believe that this is the first smartwatch Huawei has released -- it's seriously sexy, so it seems that biding time has worked in the company's favor. Borrowing from traditional watch design, the Huawei Watch features a crown that can be used to access the app launcher. This can also be accessed by swiping to the left on the screen, while a right swipe calls up a list of frequently used contacts. Customization is a key feature of the watch. There's a choice of black, gold and silver cases, stainless steel and leather straps, and more than 40 built in watch faces so you can create something perfect for you.
In terms of specs, you'll find 4GB of built-in storage, 512MB of RAM and a Qualcomm 1.2GHz processor. There's also a 6-axis gyroscope, a barometer, and a heart rate monitor, while charging is taken care of by a magnetic cradle. It does not matter what Android phone you have, as the Huawei Watch can pair with any one over Bluetooth.
There's no word on pricing at the moment, but here are the full spec to mull over until we have more details:
Size: 42mm diameter by 11.3mm thickness
Color: Silver, Black, Gold
Display: 1.4-inch full circle AMOLED display 400x400, 286ppi Sapphire crystal
Material: 316L Stainless Steel
CPU: Qualcomm APQ8026 1.2GHz
Operation System: Android Wear
Memory: 512MB RAM + 4GB ROM
Network: Bluetooth 4.0/4.1
Sensors: Gyroscope + Accelerometer, PPG, Barometer, Vibration Motor
Audio: Built-in MIC
Battery: 300mAh
-

Thousands of online accounts fall victim to Chinese censorship
Publié: mars 1, 2015, 4:22pm CET par Mark Wilson

Censoring of the web in China is nothing new. Services like Gmail often find they are blocked, and there are constant battles on both sides of the Great Firewall of China to get information in and out of the country. The most recent battleground has been online usernames, and new regulations have come into force that dictate what is acceptable, and what is not.
China has long tried to force internet users to use their real names online and just before the new regulations took effect, more than 60,000 online accounts were deleted because they failed to comply. The Cyberspace Administration of China said that big names including Alibaba and Baidu had removed the accounts which infringed the guidelines for various reasons.
There are various reasons usernames have been deemed unsuitable for use. Some are considered misleading because they impersonate famous people, others have been jumped upon because they are parody accounts. But there are some which have been deleted because they are thought to be engaged in rumor-mongering, pornography, violence and other activities.
The regulations were put in place by the Cyberspace Administration of China, the body which oversees all online content in China. Online services such as Weibo now have dedicated teams working to seek out illegal account names and behavior.
Photo credit: karen roach / Shutterstock
-

IKEA announces furniture with integrated wireless charging for phones
Publié: mars 1, 2015, 12:20pm CET par Mark Wilson

Starting in April, IKEA will start to sell furniture with integrated Qi wireless charging points. The Scandinavian flat-pack furniture store, famous for the likes of the BILLY bookcase, plans to launch a range of home furnishing in North America and Europe, before extending the rollout worldwide.
You might expect that sofas would be a natural home for wireless charging -- just pop your smartphone on the arm so it can power up while you watch your favorite shows -- but in fact it is tables, desk and, surprisingly, lamps which will boast the feature. It's not just phones like the Galaxy Note 3 and Nexus 5 that can take advantage of wireless power, but also tablets like the Nexus 7.
The collection is called HOMESMART, and it hides wireless charging pads into everyday objects, eliminating the spaghetti wiring that plagues all too many homes. Coffee tables, desk lamps, and even floor lamps feature Qi pads, so there's no need to fumble for the end of a cable, just pop your phone down and start juicing up.
Jeanette Skjelmose, Business Area Manager Lighting and Wireless Charging, said:
Through research and home visits, we know that people hate cable mess. They worry about not finding the charger and running out of power. Our new innovative solutions, which integrate wireless charging into home furnishings, will make life at home simpler.
So the tangle of cables could become a thing of the past, but now all of the phones in a house will be fighting for space around a lamp or on a desk.
Photo credit: IKEA
-

Microsoft welcomes weak Consumer Privacy Bill of Rights
Publié: février 28, 2015, 10:12pm CET par Mark Wilson

Late on Friday, the White House released a draft proposal for the Consumer Privacy Bill of Rights Act of 2015. It is supposed to grant greater privacy rights to individuals, and sets out a framework in which codes of conduct can be constructed.
The bill comes in response to growing concerns about the amount of data companies store about their customers and users, particularly online. Government surveillance has brought privacy into the public eye, and this is the government's attempt to be seen to be righting wrongs.
Microsoft's backing of the bill is not to say that the company is in full agreement with every single clause it contains -- and many will be in the same position. As Brendon Lynch, Chief Privacy Officer, says "some will say it goes too far, while others will say it doesn't go far enough – but it's a good place to start the conversation". It's an issues which is likely to divide along party lines -- much like the recent net neutrality vote. Republicans believe the bill oversteps the mark, while democrats feel it does too much for businesses, and not enough for consumers.
At the moment, the bill suggests that companies need to be more transparent about the data they collect and how it is used, as well as suggesting that they should comply quickly to requests for data to be deleted. This sounds great in practice, but it is important to remember that this is only a proposal at this stage, and critics have already pointed out loopholes which could be exploited.
One of the greatest causes for concern is that the bill would enables companies to draw up their privacy policies. There are also interesting little caveats. While the bill implies an increase in customer power to have access to data stored about them, section 106 (a) (2) (A) says that companies will not have to comply if the request is deemed to be "frivolous or vexatious" -- it's not clear who decides whether requests fall into this category or not.
The Federal Trade Commission is critical of the bill, saying it fails to offer "strong and enforceable protections". But this is just the starting point. There is scope for change, and it's entirely possible -- likely, some would suggest -- that the bill won’t make it through Congress as it stands.
Photo credit: solomonjee / Shutterstock
-

Facebook lets you choose a custom gender, now it's time to drop real names
Publié: février 28, 2015, 1:34pm CET par Mark Wilson

Facebook found itself under fire last year for imposing a real name policy. Drag artists, the LGBT community, musicians and other groups were among those who felt they should be able to use a name other than the one that appears on their birth certificate. The social network ultimately backed down, but the whole debacle left something of a bad taste in the mouth.
People are able to use "the authentic name they use in real life" to identify themselves on the site, and Facebook has opened up gender options further. There's no need to feel limited by the male or female labels, or even make a selection from a readymade list -- you can now specify whatever gender you want. But is this enough?
Facebook diversity heralded the feature and also announced that users can use up to ten different gender identities, and can choose the audiences they would like to share each one with. A choice of pronoun is also available, so when birthday time rolls around, friends can be invited to "wish him a happy birthday", "wish her a happy birthday", or the gender-neutral "wish them a happy birthday". The move came about after consultation with LGBT advocacy organizations.
Now, if you do not identify with the pre-populated list of gender identities, you are able to add your own. As before, you can add up to ten gender terms and also have the ability to control the audience with whom you would like to share your custom gender. We recognize that some people face challenges sharing their true gender identity with others, and this setting gives people the ability to express themselves in an authentic way.
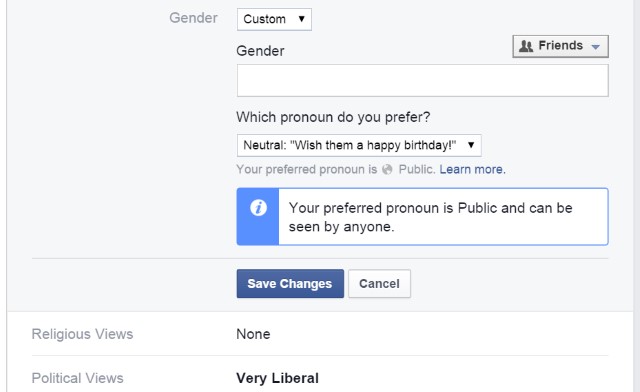
But gender identity is just a portion of anyone's make up. It's time that Facebook offered the same flexibility for names. The social network has accepted the idea that some people find it difficult to share their gender identity with all of their contacts -- the same is true of names. The debate about Facebook's real names policy has a tendency to center around the LGBT community, but this is far from being the only group affected by Facebook imposing the rule surrounding names. Think victims of abuse, victims of crime and so on. These are people who might well want to use a different identity online -- it's not good enough to say that such people should not use Facebook.
One's name is no more or less part of one's identity than one's gender, and just as one may have more than one gender identity according to audience and circumstances, the same is true of names. It has been argued that people who find themselves using different name identity for different parts of their life should set up business pages, but this is not an acceptable solution.
There is the argument that one's real name need to be used to ensure that you are identifiable in case of illegal activity, harassment or the like -- but unless someone using a fake name does something to draw attention to themselves, or is reported by another user, who is to know? It makes as much sense as it would to force people to use a government-verified photo for this profile image.
Of course ultimately, Facebook is free to impose whatever rules and restrictions it likes, and anyone who disagrees strongly enough with them is free to avoid using the site. But that's not the point. Facebook is very keen to be seen as a company that is accepting of everyone -- something it was boastful of when talking about its diverse workforce -- but that's missing the point and giving Facebook too easy a time. The abomination that is Ello sprang to (minor) popularity in protest at Facebook's real name policy and it's clear that the real names policy is something that people care about deeply.
There's no getting away from the fact that Facebook's embracing of different gender identities is a positive thing, but there's still more that can be done. Logically, it makes no sense for Facebook to 'permit' users to express part of their identity in whatever way they wish, but not all of it. Just allow people to identify however the hell they like on the social network; there really is no good reason not to. Judging by the comments that appear beneath Facebook's announcement of the new gender options, I'm far from being alone in my view about the need to eliminate the real name policy. Who's with me?
Photo credit: fieldwork / Shutterstock
-

Twitter triples troll-tackling team
Publié: février 27, 2015, 6:51pm CET par Mark Wilson

Like many social platforms, Twitter is often used by trolls to launch abusive attacks on people. It's something that Twitter has tried to tackle before, but now the company is stepping up its game. Having already made it easier to report abusive tweets, the same tools are being rolled out to simplify the reporting of content relating to impersonation, self-harm and doxing.
Dick Costolo had already promised that Twitter was ready to get tough on harassment, and now we know what he meant. The size of the team handling reports about abuse has been tripled, and this means that five times as many reported tweets are to be investigated.
It is no longer necessary to find yourself on the receiving end of abuse to try to do something about it. Anyone is free to report tweets which could be deemed abusive, as well as those which reveal personal information about people, or in which someone pretends to be someone else. But it is the changes that are happening in the background that Twitter will be hoping make the difference.
A new set of investigative tools and procedures means that Twitter is able to react to reported tweets faster:
While we review many more reports than ever before, we’ve been able to significantly reduce the average response time to a fraction of what it was, and we see this number continuing to drop. We are also beginning to add several new enforcement actions for use against accounts that violate our rules. These new actions will not be visible to the vast majority of rule-abiding Twitter users – but they give us new options for acting against the accounts that don’t follow the rules and serve to discourage behavior that goes against our policies.
Costolo had recently said "we suck at dealing with abuse and trolls on the platform and we’ve sucked at it for years", and this appears to be Twitter's attempt to get back on track. The new features are rolling out globally over the next few weeks starting now, and victims of abuse and other problems will be keen to see what different they make.
Photo credit: Elisanth / Shutterstock
-

FCC votes in favor of Net Neutrality... just
Publié: février 26, 2015, 8:44pm CET par Mark Wilson

The Net Neutrality debate has been rumbling on for quite some time now, but today something of a milestone has been reached. After the campaign gained the support of President Obama, Twitter, and many others, today was the Federal Communications Commission vote on a number of proposals put forward by chairman Tom Wheeler.
It is a victory for Net Neutrality and a great step towards ensuring that the internet remain open and free from controls by companies or government. The policy states, among other things, that ISPs may not charge for prioritization of web traffic. The vote was far from being a landslide. Two Republicans opposed to the policy changes kept the result to a 3-2 vote in favor of the proposals.
While the ban on paid prioritization has been the main focus of much of the net neutrality campaign, it is not the full story. The newly approved rules mean that broadband connectivity will be reclassified as a telecommunications service, introducing greater regulation, and there will be greater control of paid deals between content providers and broadband companies.
As well as being blocked from creating a two-tier internet where certain types of traffic is given greater priority over others, broadband providers will not be permitted to accelerate or block connections for a fee. The definition of broadband has been opened up, so the proposals will apply to mobile providers as well as to companies providing connection through landlines, fiber and the like.
The vote was well-received across the tech industry, and CEO of Xirrus Wi-Fi, Shane Buckey said:
The FCC's decision on net neutrality further validates its goal to provide more affordable and distributed Wi-Fi to the U.S. This foundational step supports IT infrastructure investment to provide more reliable Internet connectivity and improved quality of service for their users regardless of the internet service provider.
But not everyone is happy. The US Telecommunications Industry Association is planning legal action against the changes and Verizon denigrated the vote as "misguided", adding:
Today's decision by the FCC to encumber broadband internet services with badly antiquated regulations is a radical step that presages a time of uncertainty for consumers, innovators and investors.
Opponents of net neutrality have been left licking their wounds but, even in light of the vote, it's unlikely that we have heard the end of this debate yet. Nevertheless, history has been made.
Photo credit: mindscanner / Shutterstock
-

Facebook can put users on suicide watch
Publié: février 26, 2015, 12:07pm CET par Mark Wilson
A few months ago Twitter was criticized for teaming up with suicide prevention charity Samaritans to automatically monitor for key words and phrases that could indicate that someone was struggling to cope with life. Despite the privacy concerns that surrounded Samaritans Radar, Facebook has decided that it is going to launch a similar venture for Compassion Research Day in a bid to prevent suicides.
Working with mental health organizations including mental health organizations Forefront, Now Matters Now, the National Suicide Prevention Lifeline, Save.org, Facebook aims to provide greater help and support for anyone considering suicide or self-harm.
Unlike Twitter's tool, Facebook is not automatically monitoring content that is posted on the social network. Instead, users are invited to get in touch if they notice troubling content from any of their contacts, and Facebook will then reach out with the offer of help, support and tips.
Introducing the feature, Facebook said:
For those who may need help we have significantly expanded the support and resources that are available to them the next time they log on to Facebook after we review a report of something they’ve posted. Besides encouraging them to connect with a mental health expert at the National Suicide Prevention Lifeline, we now also give them the option of reaching out to a friend, and provide tips and advice on how they can work through these feelings. All of these resources were created in conjunction with our clinical and academic partners.
Of course, stumbling across a post that indicates suicidal thoughts can be troubling for the reader as well. With this in mind, Facebook is providing additional tools for anyone who reports such content. Facebook has teams working round the clock to talk to people on both sides of the suicidal thoughts story.
The services are rolling out in the US over the next couple of months, and there are plans to extend the program globally.
-

Samsung's 128-Gigabyte UFS 2.0 memory promises faster smartphones
Publié: février 26, 2015, 10:26am CET par Mark Wilson

Samsung has announced that it has started mass-production of 128 GB ultra-fast embedded memory. Described as an industry first, the memory is based on the Universal Flash Storage (UFS) 2.0 standard and is 2.7 times faster than the commonly used eMMC 5.0.
With performance of 19,000 IOPS (input/output operations per second), the memory offers sequential read and write speeds comparable to SSDs. Despite this, the memory draws half the level of power of existing mobile memory.
Aimed at the high-end smartphone market, Samsung's UFS 2.0 memory is available in 128GB, 64GB and 32GB versions. Current eMMC will continue to exist for mid-range handsets, but the increased speed and reduced power consumption of UFS will see the development of faster phones at the top end of the market with battery life which is far better than what can currently be achieved.
Jee-ho Baek, Senior Vice President of Memory Marketing for Samsung said:
With our mass production of ultra-fast UFS memory of the industry's highest capacity, we are making a significant contribution to enable a more advanced mobile experience for consumers. In the future, we will increase the proportion of high-capacity memory solutions, in leading the continued growth of the premium memory market.
As well as improvements to speed and battery life, there are also space savings to be made. Samsung explains that the ePoP (embedded package on package) memory can be placed directly on top of a logic chip to help keep physical size to a minimum.
-

Google aims to secure enterprise BYOD with Android for Work
Publié: février 26, 2015, 3:21am CET par Mark Wilson

Android has successfully secured its place as the most used mobile operating system. With this in mind it should come as little surprise that more and more people are bringing Android devices into the workplace -- and for IT departments this can be something of a security nightmare. Today Google announces Android for Work with the aim of grabbing the BYOD (Bring Your Own Device) market and making Android more secure and manageable in the workplace.
What does this mean? Work profiles are being introduced to keep business apps and data separate from each other, so employees can use a single device to manage their personal work life. For both employer and employee this brings a number of advantages.
One of the benefits of the BYOD philosophy is that you B your own D. Workers can choose the handset they want to use rather than being issued the same as everyone else, and there's the obvious advantage of having one device to deal with rather than two. While an employee can remotely manage work apps, workers can rest assured that their own personal apps and data are left untouched. This segregation of work and personal data is exclusive to Lollipop devices.
The Android for Work app delivers secure mail, calendar, contacts, documents and browsing to handsets running pre-Lollipop versions of Android. A new store, Google Play for Work, allows for easy deployment of selected apps, and Google has a number of partners on board to help expand the range of supported apps.
Rajen Sheth, Director of Product Management, Android and Chrome for Work, said:
Together with a wide range of management, application and device makers, we believe the Android for Work program provides businesses and workers with the choice and flexibility they need to get things done at work.
Names like BlackBerry, Box, Adobe, Dell, HTC and Citrix will help to bring secure business apps to phones and tablets, and a standardized set of APIs will allow for easy management of new and legacy devices through the same dashboard.
More details are available at the Android for Work website.
-

Microsoft Malware Protection Center helps take down Ramnit botnet
Publié: février 25, 2015, 8:42pm CET par Mark Wilson

Ramnit, a botnet that infected millions of computers around the world, has been tamed, thanks in part to Microsoft Malware Protection Center. The takedown operation was a collaboration between Microsoft, Europol, Symantec and others, and it successfully stopped the malware which worked by disabling virus protection before stealing banking details and personal information from infected machines.
With an estimated 3.2 million computers infected globally, Ramnit has been used by cybercriminals the world over, but the majority of infections were found in Britain. The botnet was brought under control by shutting down several servers used by the group responsible for Ramnit.
Ramnit has been doing the rounds since at least 2010, and Symantec released a removal tool to help people whose computers fell victim. The botnet, which is being described as "module-based malware", remained highly active throughout the years, and Microsoft detected around 500,000 infected machines in the last six months alone.
Wil van Gemart, Europol's deputy director of operations, said:
This successful operation shows the importance of international law enforcement working together with private industry in the fight against the global threat of cybercrime. We will continue our efforts in taking down botnets and disrupting the core infrastructures used by criminals to conduct a variety of cybercrimes.
Ramnit's modular design makes it different -- and more dangerous -- than many other examples of malware. Once a machine has been infected, it is then possible to upgrade the malware to add more features and adapt to attempts to remove it. Being comprised of modules also meant that different elements of Ramnit could be worked on by different coders and optimized according to task. As Microsoft puts it, "Ramnit has a hot pluggable modular framework design that gives it plenty of flexibility to extend new functionality on demand".
Microsoft advises Windows 8 users to run Windows Defender, while anyone with an older version of the operating system can turn to Microsoft Security Essentials.
Photo credit: kentoh / Shutterstock
-

Mobile transfer speeds hit 1Tbps over 5G
Publié: février 25, 2015, 7:36pm CET par Mark Wilson

If you curse the speed of your mobile data connection, prepare to shake with fury, turn green with envy, and yearn for a time machine. Forget 3G, forget 4G; at the University of Surrey in the UK, researchers have harnessed the power of 5G to establish a data transfer rate of one terabit per second.
At this speed it would be possible to download a Blu-ray quality video in under a second, but it's likely to be some time before we have the chance to experience these sorts of speeds via our handsets.
The 5G Innovation Centre may have been able to achieve this staggering data transfer rate, but it could be another five years or more before the technology is ready for the big time. The record-breaking 5G speed is over 65,000 times faster than what can be hit over 4G and was achieved under laboratory conditions, and we're unlikely to see a public demonstration until 2018.
Talking to V3, 5G Innovation Centre director Professor Rahim Tafazolli said that the transfer speed was reached using custom-built hardware over a distance of 100m and was the result of several different lines of development:
We have developed 10 more breakthrough technologies and one of them means we can exceed 1Tbps wirelessly. This is the same capacity as fiber optics but we are doing it wirelessly.
Looking to a future of yet-to-be-imagined applications, Tafazolli explained that one of the aims with 5G is to reduce latency to less than one millisecond.
Photo credit: wk1003mike / Shutterstock
-

Exciting new experimental apps emerge from Microsoft Garage
Publié: février 25, 2015, 5:45pm CET par Mark Wilson

Microsoft Garage is home to all manner of innovative projects from Microsoft employees, and today a new batch of projects has been unveiled. As Garage is a cross-platform venture, there are apps for Windows Phone, Android and desktop Windows, and the myriad tools cover everything from app development to the weather.
On the productivity front, Mouse Without Borders is a name that might seem familiar. Strictly speaking, this is a re-release rather than a new release, and the utility makes it possible to control up to four computers with a single keyboard and mouse by acting like a virtual KVM switch. If this isn’t your sort of thing, there are plenty more tools to explore.
To keep developers happy, there's Developer Assistant and DevSpace. The first tool makes it possible to browse and re-use code snippets in Visual Studio, while the second provides access to Virtual Studio Online projects. While many of the apps -- like Keyboard for Excel which simplifies number entry for Android users -- have something of a businessy feel to them, others are slightly lighter.
Your Weather focuses on China, and provides Windows Phone users with meteorological information. Another mobile app is the aptly-named Picturesque Lock Screen which beautifies the Android lock screens with images from Bing.
Microsoft Garage has come a long way in the few years it has been active. The company says:
Building upon the initial wave of incubation apps launched from the Garage in October, DevSpace, Your Weather, and Join Conference are three of nine projects that continue the momentum from the fall. As eclectic as they are in function and design, the philosophy of the Garage ties them together. Founded in 2009, the Garage acts as a hub for grassroots innovation at the company, connecting people and dissolving traditional boundaries of geographies, organizations and disciplines. This spirit has helped grow the Garage into a community of more than 10,000 Microsoft employees and interns in 36 Garage chapters around the world.
Other business-related apps finding their way out of Microsoft Garage are SquadWatch, which makes it possible to track the location of other people, and Join Conference, a powerful conference calling tool.
Grab any, or all, of the tools from Microsoft Garage.
Photo credit: Andrew Lam / Shutterstock
-

Reddit imposes ban on non-consensual sexual content
Publié: février 25, 2015, 11:25am CET par Mark Wilson

If you want to post naked pictures or videos of people on Reddit without their consent, you only have a couple of weeks to do so. As of March, the site is imposing a ban on content of an explicit nature that the subject has not given permission to be posted.
The cleanup of the site comes hot on the heels of news from Google that explicit content will be banned from Blogger. It also comes in the wake of last year’s Fappening which saw a glut of naked celebrity photos leaked online.
When the images appeared on Reddit, the site was criticized for failing to take action quickly enough. This is something that the announcement acknowledges, saying: "we missed a chance to be a leader in social media when it comes to protecting your privacy -- something we’ve cared deeply about since reddit’s inception. At our recent all hands company meeting, this was something that we all, as a company, decided we needed to address".
In a post on Reddit, the team behind the site introduced the new privacy policy:
No matter who you are, if a photograph, video, or digital image of you in a state of nudity, sexual excitement, or engaged in any act of sexual conduct, is posted or linked to on reddit without your permission, it is prohibited on reddit. We also recognize that violent personalized images are a form of harassment that we do not tolerate and we will remove them when notified. As usual, the revised Privacy Policy will go into effect in two weeks, on March 10, 2015.
Reddit has quite a task on its hands if it is to keep on top of the mass of content that is uploaded each day. Anyone spotting offending content is invited to contact the site via email at contact@reddit.com -- although Reddit is calling for the subjects of pictures and videos to get in touch, not just for people to report content they suspect may be breaching the rules:
If you believe that someone has submitted, without your permission, to reddit a link to a photograph, video, or digital image of you in a state of nudity or engaged in any act of sexual conduct, please contact us.
-

Google unveils a redesign after 1,000 Chrome Experiments
Publié: février 25, 2015, 12:03am CET par Mark Wilson
Chrome Experiments is now entering its sixth year and is home to hundreds of coding experiments that help to make the Internet a more fun and enjoyable place. Ten hundred in fact. To celebrate reaching the milestone of 1,000 experiments, Google is not only launching a new experiment that shows off all of the rest, but also rolling out a redesign.
The redesign is about more than just a new look, it's also about emphasizing the fact that Google wants to be part of every platform available. It's a Polymer-based redesign that works equally well on large-screen-desktops and small-displayed mobiles and is Google's new way to showcase the best in HTML5 and JavaScript.
As part of the celebrations -- if the word is warranted -- Experiment #1000 provides a way to look at every other experiment that is featured on the website. Chrome Experiments has come a long way since its launch back in 2009 when there were just 19 experiments to play with. Now there is a real-time code editor as well as a timeline with selectable tags -- it has been quite a journey.
Picking out some highlights, Valdean Klump from the Data Arts Team said:
Looking back at the old experiments this month has been a joy. Highlights include Mr.doob's classic Ball Pool (one of the original 19 experiments), the first WebGL experiment by Gregg Tavares (try 4,000 fish – this used to be very slow!), and Dinahmoe’s multiplayer audio toy Plink, which combines the Web Audio API with Node.js. At Google I/O in 2012, we released the first mobile experiments, including AlteredQualia’s Multitouch Toy and Dominic Szablewski’s X-Type. And each year afterward, new web technologies appeared, like getUserMedia and the Web Speech API. It's been a wonderful journey.
Originally dreamt up to be a source of inspiration for coders, Chrome Experiments continues to go from strength to strength. If you're yet to check it out, what are you waiting for? Get yourself over to ChromeExperiments.com this instant!
-

Microsoft releases OneDrive API for cross-platform cloud storage development
Publié: février 24, 2015, 7:51pm CET par Mark Wilson

Today Microsoft launches a new OneDrive API, opening up its cloud storage service to a wider range of developers. The API can be used to integrate OneDrive into apps running on Android, Windows, iOS and the web, and there is a focus on efficiency with minimal calls needed to keep files in sync.
The API has already started to roll out to a number of Microsoft apps, and the company is keen to ensure that all developers have access to the same set of tools. There are a number of new features to be found in the API which can be easily added to existing apps and services.
Ryan Gregg, Principal Program Manager for OneDrive said that it takes just a few lines of code to set up basic integration with the Android Picker/Saver SDK and our iOS DocumentPicker contract support. He went on to say:
We are looking forward to working with developers to increase the number of places where users can do more with the files they have stored in OneDrive.
Other features include:
- the ability to retrieve new changes to files and folders to efficiently keep a large set of files in sync with minimal calls
- resumable uploads of files up to 10 GB via file-fragment uploading for working with rich content, like HD videos
- customizable file thumbnail images for delivering a more integrated experience across your app and OneDrive
Developers can browse through the OneDrive API documentation and grab code samples from a dedicated website. The API is already in use by PandaDoc, IFTTT and PicMonkey. A raft of updates are planned for the year ahead, and developers are invited to provide feedback through UserVoice.
-

No sex on Blogger please, we're Google
Publié: février 24, 2015, 11:36am CET par Mark Wilson

Blogger users risk having their blogs removed from public listings if they feature graphic nudity or explicit content. Starting on March 23, any Blogger blog found to contain offending pictures or videos will be converted into a private blog that can only be seen by the owner and those, erm, explicitly invited to see it.
Google emphasizes that no content will be deleted from blogs created before March 23, 2015, but is encouraging blog owners to take action. It's a different story for any blog set up after this date.
Any new blog that is found to house sexually explicit or graphic nude images or video runs the risk of being removed by Google. There is also the threat of unspecified "other action" for sites that violate Blogger Content Policy by hosting adult content, linking to commercial pornography sites, features child abuse imagery or encourage pedophilia.
In the Blogger help pages, Google explains that there could be exceptions to the rule:
We'll still allow nudity if the content offers a substantial public benefit, for example in artistic, educational, documentary, or scientific contexts.
It is not made clear exactly what would constitute 'substantial public benefit', but there will be plenty of bloggers waiting in line to test the boundaries of what is acceptable.
Photo credit: Mingman / Shutterstock
-

Twitter lends its support to Net Neutrality campaign
Publié: février 23, 2015, 8:54pm CET par Mark Wilson

Many prominent groups and figures have given their backing to the fight for net neutrality. Today Twitter reveals why it supports the proposals put forward by the FCC chairman Tom Wheeler, just a few days ahead of a vote that will decide whether they will be adopted by the FCC. The aim is to "protect the open Internet as a place for innovation and free expression".
Twitter's public policy manager, Will Carty, says that protecting the open architecture of the internet is essential for the US to remain competitive and to allow freedom of speech. He says that providing a voice to those who would not otherwise have a platform is at the heart of Twitter, and this is just one of the reasons for supporting the net neutrality proposals.
Central to the proposals are three key ideas: no blocking, no throttling, and no paid prioritization. The aim is to give Internet users greater powers to be able to access legal online content without interference from their ISP. Carty points out that the Internet is a great equalizer in terms of providing access to information, and also a platform for free speech.
In a post on the Twitter blog, Carty said:
This openness promotes free and fair competition and fosters ongoing investment and innovation. We need clear, enforceable, legally sustainable rules to ensure that the Internet remains open and continues to give everyone the power to create and share ideas and information instantly, without barriers. This is the heart of Twitter. Without such net neutrality principles in place, some of today’s most successful and widely-known Internet companies might never have come into existence.
Twitter is especially keen to support rules that prohibit the blocking of legal sites, as well as traffic prioritizing for money. The FCC is praised for "avoiding unnecessary and overly burdensome regulation" and for adopting a 'light touch' regulatory approach.
Photo credit: kentoh / Shutterstock
-

Facebook's privacy policy breaks the law in Europe
Publié: février 23, 2015, 6:32pm CET par Mark Wilson

There are many things that Facebook finds itself accused of on a regular basis. Unfairness to different groups, censorship of content, insensitivity, and endless problems surrounding its attitude to privacy and handling of user data. It seems that concerns about privacy were well-founded as a new report finds that the social network violated European law. Analysis carried out by the Belgian Privacy Commission and ICRI/CIR says that Facebook breaks the law in Europe in a number of ways. As well as placing too many expectations on users to be able to change settings for themselves.
Facebook is also accused of failing to give people the ability opt out of certain privacy-invading features. Back in January, Facebook made some changes to its privacy policies and also introduced simplified documentation. The report found that rather than cleaning up its act, Facebook merely highlighted some of its old, existing practices. The social network is criticized for its "complex web of settings", for failing to explain what is meant when users are told that their data will be used "for advertising purposes", and for not allowing people to opt out of Sponsored Stories and location sharing.
The report also poses an important question: "What are the precise implications of Facebook's extensive data gathering through third-party websites, mobile applications, as well recently acquired companies such as WhatsApp and Instagram?" Facebook's Statement of Rights and Responsibilities stands accused of failing to comply with the Unfair Contract Terms Directive. The report's authors say:
We argue that the collection or use of device information envisaged by the 2015 data use policy does not comply with the requirements of article 5(3) of the EU e-Privacy Directive, which requires free and informed prior consent before storing or accessing information on an individual's device.
While Facebook may argue that users have given consent for their data to be used in a variety of ways, the report disagrees:
To be valid, consent must be "freely given", "specific", "informed" and "unambiguous". Given the limited information Facebook provides and the absence of meaningful choice with regard to certain processing operations, it is highly questionable whether Facebook’s current approach satisfies these requirements.
While users are able to opt out of some features such as the use of personal data in advertisement, the fact that they did not actively opt in means that legally valid consent has not been given. Facebook is also criticized for the inclusion of unfair terms which violate European consumer protection law, and for abusing user data.
In response to the report, a Facebook spokesperson said:
We recently updated our terms and policies to make them more clear and concise, to reflect new product features and to highlight how we're expanding people's control over advertising. We’re confident the updates comply with applicable laws. As a company with international headquarters in Dublin, we routinely review product and policy updates including this one with our regulator, the Irish Data Protection Commissioner, who oversees our compliance with the EU Data Protection Directive as implemented under Irish law.
Photo credit: Gil C / Shutterstock
-

The next Linux kernel is Linux v4.0, codename 'Hurr durr I'ma sheep'
Publié: février 23, 2015, 4:31pm CET par Mark Wilson

In the spirit of democracy, Linus Torvalds recently started a poll on Google+ to decide on the version number of the next Linux kernel. Should it be Linux v3.20 or Linux v.4.0? Well, the people have spoken, and Torvalds has listened -- albeit somewhat reluctantly.
With 56 percent of the vote, v4.0 came out on top, so that's what the next version will be called. Torvalds made the revelation at the same time as announcing the availability of Linux 4.0-RC1. Oh... and it's codenamed "Hurr durr I'ma sheep".
The codename comes from a previous Torvalds poll and the latest version of the kernel includes a number of changes such as fixes to the F2FS file system, DisplayPort audio support for the AMD Radeon driver, improved support for Toshiba laptops, and a host of driver improvements. Torvalds announced the new numbering system in a Git post:
.. after extensive statistical analysis of my G+ polling, I've come to the inescapable conclusion that internet polls are bad.
Big surprise.
But "Hurr durr I'ma sheep" trounced "I like online polls" by a 62-to-38% margin, in a poll that people weren't even supposed to participate in.
Who can argue with solid numbers like that? 5,796 votes from people who can't even follow the most basic directions?
In contrast, "v4.0" beat out "v3.20" by a slimmer margin of 56-to-44%, but with a total of 29,110 votes right now.
Now, arguably, that vote spread is only about 3,200 votes, which is less than the almost six thousand votes that the "please ignore" poll got, so it could be considered noise.
But hey, I asked, so I'll honor the votes.
Photo credit: Neale Cousland / Shutterstock
-

LG launches mid-range Magna, Spirit, Leon and Joy Android phones
Publié: février 23, 2015, 1:30pm CET par Mark Wilson

Mobile World Congress (MWC) kicks off next week, but ahead of the big event LG announces a quartet of mid-range Android handsets. Each of the four phones runs Android 5.0 Lollipop and each is available in LTE and 3G variants -- the former has a metal rear cover, and the latter's is plastic.
The Magna, Spirit, Leon and Joy all share something of a similar look and LG describes the range as combining the "perfect balance of style and usability". At the top of the current batch is the LG Magna, which boasts a 5-inch screen, 1.2GHz or 1.3GHz quad core CPU (exact specs are region-dependent), 1GB RAM and 8GB of storage.
An 8MP rear camera is backed up by a 5MP front-facer, while the removable 2,540mAh battery, LG claims, will get users through a full day even with heavy use. Taking things down a notch is the LG Spirit. Specs are virtually identical, but the screen is slightly smaller at 4.7 inches and the battery shrinks to 2,100mAh. The front camera drops to 1MP and the rear-facer is either 5 or 8 MP depending on the region. The Leon drop things further to a 4.5 inch display and a 1,900mAh battery.
Rounding things off is the smallest of the bunch, the LG Joy, with a screen that measures just 4 inches. As well as featuring a slower processor, this handset is available in a 4GB model indicating that the price should be very low.
The global rollout starts this week, but LG is yet to give pricing details.
Those specs in full:
LG Magna Specifications:
- Display: 5.0-inch HD (294 ppi)
- Chipset: 1.2GHz or 1.3GHz Quad-Core*
- Camera: Rear 8MP / Front 5MP
- Memory: 8GB / 1GB
- Battery: 2,540mAh (removable)
- OS: Android 5.0 Lollipop
- Network: LTE Cat. 4 / HSPA+ 21Mbps
- Size: 139.7 x 69.9 x 10.2mm
LG Spirit Specifications:
- Display: 4.7-inch HD (312 ppi)
- Chipset: 1.2GHz or 1.3GHz Quad-Core*
- Camera: Rear 8MP or 5MP* / Front 1MP
- Memory: 8GB / 1GB
- Battery: 2,100mAh (removable)
- OS: Android 5.0 Lollipop
- Network: LTE Cat. 4 / HSPA+ 21Mbps
- Size: 133.3 x 66.1 x 9.9mm
LG Leon Specifications:
- Display: 4.5-inch FWVGA (220 ppi)
- Chipset: 1.2GHz or 1.3GHz Quad-Core*
- Camera: Rear 8MP or 5MP* / Front VGA
- Memory: 8GB / 1GB
- Battery: 1,900mAh (removable)
- OS: Android 5.0 Lollipop
- Network: LTE Cat. 4 / HSPA+ 21Mbps
- Size: 129.9 x 64.9 x 10.9mm
LG Joy Specifications:
- Display: 4.0-inch WVGA (233 ppi)
- Chipset: 1.2GHz Quad-Core / 1.2GHz Dual-Core*
- Camera: Rear 5MP / Front VGA
- Memory: 8GB or 4GB* / 1GB or 512MB*
- OS: Android 5.0 Lollipop / Android 4.4 KitKat
- Battery: 1,900mAh (removable)
- Network: LTE Cat. 4 / HSPA+ 21Mbps
- Size: 122.7 x 64.0 x 11.9mm
*specification depend on region
-

Windows 10 build 10022 screenshots leak along with 10014 release notes
Publié: février 23, 2015, 12:00pm CET par Mark Wilson
It has been a few weeks since Microsoft released the Windows 10 Technical Preview Build 9926, and Windows Insiders are now champing at the bit for the next version. Mobile users have been kept happy with the release of Windows 10 Technical Preview for Phones, but desktop and laptop users now have some more snippets to whet their appetites.
Over the weekend, screenshots from a couple of new builds were leaked online by the renowned Wzor. First of all we were treated to a glimpse of build 10014, and shortly afterwards images of Windows 10 Professional Technical Preview Build 10022 appeared. Another revelation is a set of release note relating to build 10014. So what do we have to look forward to?
The leaked versions are Russian -- as is so often the case -- and it seems that not a great deal has changed since build 9926. Wzor is a trusted leaker of Windows builds, and the screenshots appear to indicate that the changes in these most recent builds are largely under the hood; there are few discernible visual differences. What is particularly interesting is that the build 10022 leak comes from the fbl_impressive branch of releases, meaning that this is very likely to be the next publicly released preview build.
On Twitter, Wzor introduced the screenshots as being from a "localized Russian version of Windows Professional 10 TP Build 10022.0.150216-2206".
Локализованная русская версия сборки Windows 10 Professional TP Build 10022.0.150216-2206 [t.co] pic.twitter.com/F84vlF0GCN
— WZor (@WZorNET) February 22, 2015
The same source is also responsible for bringing us the release notes for build 10014. The release notes are dated February 11 and were given to Microsoft partners. They confirm the idea that the next public build will focus on improving stability, but there are a couple of notable changes:
- In File Explorer, a maximum of four items can be displayed in frequent folders.
- If OneDrive is set as the default save location, Documents and Pictures will be remapped to the OneDrive versions of these folders.
The list of big fixes is rather lengthier, but there are still a few known issues. Cortana is still a work in progress, the Quiet Hours feature doesn’t yet work, battery levels may be incorrectly reported on portable devices, and so on.
It's not clear if these will have been ironed out in the move from build 10014 to 10022, but it shouldn't be too long until we get to see for ourselves.
Photo credit: Wzor
-

OS X, iOS and Linux have more vulnerabilities than Windows
Publié: février 22, 2015, 7:55pm CET par Mark Wilson

It might come as something of a surprise, but Windows is more secure than not only Apple's iOS and OS X, but also Linux. I'll just let that sink in for a moment...
Windows, the operating system ridiculed for its vulnerabilities and susceptibility to viruses is actually more secure than the supposedly Fort Knox-like Linux and OS X. This startling fact comes from the National Vulnerability Database (described as the "US government repository of standards based vulnerability management data") which details security issues detected in different operating systems and software titles.
The NVD has some revealing statistics for the number of vulnerabilities that were reported in each of the operating systems and GFI Blog has crunched the numbers; many will be surprised to find that Windows is not at the top of the list. In fact, in 2014 it is OS X that was found to be riddled with the greatest number of security problems -- 147 in total, including 64 rated as high severity, and 67 as medium. Also from the Apple stables, iOS did not fare all that much better: 127 vulnerabilities including 32 high and 72 with a medium rating.
The latest version of Windows -- Windows 8.1 -- was found to have 36 vulnerabilities, and its predecessors -- Windows 8 and 7 -- both had the same number. For enterprise users, Windows Server 2007 and 2008 both have 38 vulnerabilities. Windows is reported as having no vulnerabilities of low severity; they cluster under the medium and high labels.
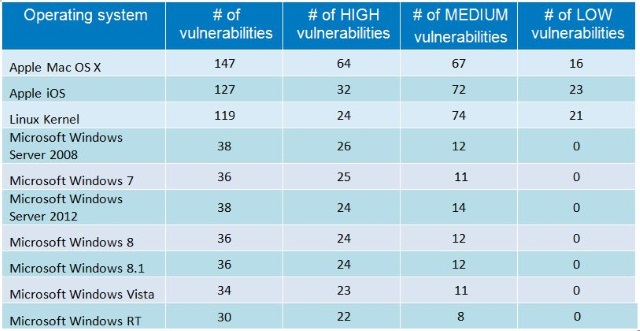
Overall, there has been a huge increase in the number security vulnerabilities in the database. In 2013 the number stood at 4,794, but this shot up to 7,038 in 2014. A lower percentage are rated as high severity, but the number has still increased.
While it is the vulnerabilities linked to individual operating systems that are probably most attention-grabbing, the main problem still lies with third-party software. 83 percent of reported vulnerabilities were to be found in applications, compared to 13 percent in OSes and 4 percent in hardware.
Microsoft might celebrate coming ahead of Apple and Linux in one department, but Internet Explorer was found to be the most insecure web browser. IE had 242 vulnerabilities, compared to 124 in Chrome, and 117 in Firefox.
Photo credit: Olivier Le Moal / Shutterstock
-

Tumblr now classifies all torrent talk as adult content
Publié: février 22, 2015, 5:49pm CET par Mark Wilson

The idea of online censorship is nothing new, particularly when it comes to content of questionable legality. Just last week it transpired that Valve was blocking talk about Kickass Torrents in Steam chat and now Tumblr is engaged in similar activity.
Rather than blocking bloggers from posting about torrents, or stopping people from reading such posts, Tumblr now classifies torrent-related content as 'adult'. This means that many people will not be able to see posts that make reference to torrents unless they change their account settings.
Torrent talk has fallen victim to Tumblr's safe mode setting which was introduced in a bid to help clean up the blogging platform for a wider audience. It's still possible to access such content, as Torrent Freak explains -- all you need to do is hit the padlock icon to the right hand side of the screen to switch off safe mode, and the previously invisible search results will show up once again.
Classifying anything torrent-related as adult content seems a little extreme, although torrent talk on Tumblr does seem to have a more pornographic bent to it than other sites. But whether you're looking for Tumblr blogs that can point you in the direction of the best porn torrents, you want to discuss Linux distros, or you want to talk about the torrential rain you've been enduring, it's good to know that access to such content is just one filter-removing click away.
Photo credit: bofotolux / Shutterstock
-

Suggestions that Twitter is not a valid news source are insane
Publié: février 21, 2015, 4:54pm CET par Mark Wilson

This morning, as I do most mornings, I started my day by firing up my phone and browsing the news headlines in bed. One story caught my attention -- and the reaction to the story in particular. As you'll have discerned from the headline, there were comments that questioned the value of using Twitter as a source of serious news.
The subject of the story doesn't really matter, but for the sake of completeness, it was this one in the Guardian. It's about the backlash that followed a Telegraph article which suggested suicides in newspaper journalists could be attributed to stress stemming from trying to hit commercial targets. This is a story that's not without irony.
So first, a little history.
There had previously been a huge story alleging that a Swiss subsidiary of the HSBC bank had been helping wealthy customers avoid tax. This was big news, covered by websites and newspapers around the world -- but not by the Telegraph. There followed allegations that Telegraph reporters had been discouraged from writing anything negative about HSBC -- interestingly, this happened shortly after the owners of the newspaper secured a £250 million loan from the bank.
The Telegraph's chief political commentator dramatically resigned this week, disgusted at his former employer's "fraud on readers". In an all-out attack on the paper, Peter Oborne made calls for an investigation into the lack of coverage in the Telegraph about the HSBC tax story. With the suggestion that reporters are being leaned on to avoid negative coverage of a bank seen as an ally, it seems slightly ironic, nay hypocritical, to then run a story saying that pressure to hit commercial targets (which would obviously be pushed by managers and editors) could lead to suicide.
And we're not just talking hypothetically. The Telegraph was talking about two real deaths. Two reporters on other newspapers sadly took their own lives, and in addition to the interesting stance on the news, the Telegraph also decided to run the story suggesting the link without naming the reporter responsible for penning it.
Apologies for the rather roundabout introduction, but a little background is needed to understand why there might be a backlash against something that appeared in a newspaper.
It used to be that if readers were shocked, offended, outraged or otherwise upset by a story, they would put pen to paper and write to the editor. This does still happen, but electronic methods of communication have now taken over. Rather than a letter, it's more likely that an email will be fired off. Or, even more likely, an opponent or proponent of a story will take to Twitter to share their views with the wider world. It's the start of the dialog of a story.
Like any dialog, it's a two-way process. Just as people respond to story by venting spleen on Twitter, so reporters and bloggers use Twitter as a source of news and a fount of inspiration. And this is the reason for my lengthy intro. The Guardian story about the negative response to the Telegraph referred to Twitter and quoted pertinent tweets. This, for some reason, upset some readers.
Seriously though, twitter is not news...
What worries me most is the decision of the Guardian to join the trend that regards what a few dozen people say on a "social media" site (Twitter) as the basis for news.
The idea that Twitter should not be used as a source of news seems strange to me. It's just a medium. Any medium through which people communicate can be a source of information, and therefore a source of news. And it's important to remember that news reporting isn’t just about reporting the cold, hard facts that get you from A to B -- analysis, reaction, response, conversation and the like are just as important to the overall understanding of a story.
But people disagree:
We can look on Twitter for ourselves. A journalist who quotes Twitter simply underlines that traditional newspapers are now irrelevant.
In fact this particular comment spurred me to respond:
I'm pretty sure newspapers and Twitter can live side by side... it's not a case of having to pick one or the other.
The same person who prompted me to post a comment also said:
I always think quoting from Twitter is a sad place for a real paper to find itself in. Especislly [sic] when those quoted are just 'randoms.'
Which led me to respond:
That's like disliking vox pops with people on the street. Every 'random' is part of the human collective, and their opinion and input is no more or less valid simply because of the medium through which it was delivered.
I'd go further and say that the two not only live happily side by side, but also feed each other. We've moved on from the idea of the hypodermic needle model. Different media serve each other, and one is not better than another. Platforms such as Twitter mix things up a great deal as they help to give a voice to, well, just about everyone. Perhaps this is why Twitter is not always well-received. There's a lot of crap out there, but it would be foolish to tar every user with the same brush. If you were to see Fox News for the first time and dismiss all television news out of hand because of its blatant bias and absurdity, you'd be doing no one a disservice but yourself.
In the comment on the Guardian article, there was some sense among the madness, however:
Most of Twitter is just irrelevant chatter - but that's because most of what is said anywhere is just chatter... Forget Twitter - it's not important where something is said, it's what was said and by whom. Twitter is not separate from the real world, it is part of the real world - it's just people talking. And some of the conversations are important and newsworthy.
Guardian writers also took the time to reply:
The fact that twitter was the medium they'd used to quote is pretty irrelevant. In this case twitter has just made it easier to get useful quotes: poor journalism is when you cherry pick unqualified tweets, good journalism uses twitter better than that.
I'm interested to gauge opinion. Do you use Twitter as a source of news, or to read reaction to the news? Do you value it more or less than other sources?
Photo credit: turtleteeth / Shutterstock
-

Judge dismisses US antitrust claims against Google search in Android
Publié: février 21, 2015, 1:58pm CET par Mark Wilson

A San Francisco judge has ruled that a class action against Google's alleged monopolizing of searches on Android devices. Gary Feitelson and Daniel McKee brought a case against Google saying that the search giant was being anticompetitive by forging agreements with handset makers that made Google search the default search engine.
The company faces similar charges in Russia where the country's leading search engine, Yandex, has made a similar complaint to the Federal Antimonopoly Service. In Europe Google has just agreed to regular audits to ensure it complies with Data Protection Authority measures in Italy, and Friday's ruling in its favor in the Northern District of California will come as some welcome good news.
Feitelson and McKee complained that when they purchased their phones -- an HTC EVO 3D and Samsung Galaxy S3 respectively -- that "neither Plaintiff was aware that Google search was set as the default search engine on those phones. Further, neither Feitelson nor McKee know if there is a way to change the default search engine setting, nor how to change the default search engine if there is indeed a way to change it". In particular, the pair were unhappy at alleged Mobile Application Distribution Agreements between HTC, Samsung and Google that allowed for the pre-loading of Google apps.
The plaintiffs went on to say that entry into the search market by competitors was rendered all but impossible by Google's dominance. They believed that their phones "would have cost less and had better search capabilities as the result of the competition that would have ensued" if things were made easier for the likes of Bing.
But the court disagreed. District Judge Beth Labson Freeman of the Northern District of California said in her ruling:
There are no facts alleged to indicate that defendant's conduct has prevented consumers from freely choosing among search products or prevented competitors from innovating.
She dismissed antitrust allegations, saying that Google's Android handsets were no different to Apple's iPhones in this regard. She also said that suggestions that Google's search engine stifled competition and limited choice were "entirely too conclusory and speculative".
Photo credit: Sean Locke Photography / Shutterstock
-

Canonical teams up with Amazon and Microsoft to push Ubuntu for IoT
Publié: février 21, 2015, 12:12pm CET par Mark Wilson

The growth of the Internet of Things spreads, and Canonical wants to ensure that Ubuntu is involved. To help with this, the company behind one of the most popular Linux distributions has announced partnerships with Microsoft and Amazon to help facilitate secure cloud infrastructures.
The two companies are to publish their IoT developer APIs on Ubuntu Core so they can be used by Snappy developers in services and apps. The aim is to avoid a market fragmentation, and the new partnerships lay the groundwork to help Ubuntu Core's development deeper into the IoT.
Canonical also announced partnerships with other companies that it is hoped will help give Ubuntu a boost in industrial and telecoms IoT. On the hardware side of things, Cavium will support Ubuntu Core in routers and switches while a move into enterprise is supported by Canonical joining the Industrial Internet Consortium. Speaking about one of the new partnerships, Microsoft's John Chewchuk said:
Smart industrial systems need secure cloud back-ends for data storage and analysis. Microsoft and Canonical are partnering to deliver developer APIs to enable Ubuntu Core for snappy developers. This partnership will simplify cloud-backed device development.
As with any system, there are security concerns surrounding the Internet of Things. To help to minimize the effect of any vulnerabilities that are discovered, systems are in place to help push updates to certified Ubuntu Core when needed. Ubuntu founder, Mark Shuttleworth said:
Certified and supported Ubuntu platforms set the standard for safety and security in connected devices. Device manufacturers who choose Ubuntu Core on certified platforms now have a popular platform that meets corporate and government requirements for security updates and management.
If the Internet of Things is to truly succeed, it is collaborative efforts such as those being spearheaded by Canonical that will drive things forward. Interoperability and guaranteed compatibility not only help to improve uptake rates, but also help to keep costs down.
Photo credit: jules2000 / Shutterstock
-

Need a flashlight in Android Lollipop? Just yell at your phone
Publié: février 20, 2015, 11:10pm CET par Mark Wilson

Who hasn't used their cell phone as a flashlight? Drop your key as you get out of the car at night and it makes sense to reach into your pocket, pull out your handset and search using the light from your screen. If you're really organized you'll have a flashlight app installed, but when you need a source of light quickly, fiddling with the menu can be a little too... er... fiddly.
Well fiddle no more. If your phone is kitted out with Android 5 Lollipop there's no need to navigate menus, or even have a dedicated flashlight app installed. Google has helpfully integrated a flashlight feature into the latest version of its mobile OS which can be activated with your voice.
As revealed by Rita El Khoury over on Android Police, Lollipop introduced the ability to toggle some settings using voice commands. You can add a flashlight toggle button to the pulldown settings drawers, but this is too much like hard work. Next time you're in need of illumination, look no further than Google Now; just holler 'OK Google, turn on flashlight' at your phone, and it will oblige.
Turn on your flashlight in an instant by shouting at your phone
You can also use voice commands to toggle WiFi and Bluetooth, but the feature does not work for all toggle-able settings. Airplane Mode, for instance, refuses to play ball, although you can still access the relevant section of Settings with voice commands.
Let there be light!
Photo credit: Stocksnapper / Shutterstock
-

Google complies with Italian privacy audits
Publié: février 20, 2015, 7:41pm CET par Mark Wilson

Few weeks go by without Google coming under fire for some privacy-related misdemeanor or other. In Italy, however, the search giant has just agreed to comply with measures put in place by the Data Protection Authority. Moreover, the company will be subjected to regular audits to make sure that everything is in order.
Google is required to make improvements not only to privacy notices for its various services, but also obtain consent from users to use their data in research and profiling. The right-to-be forgotten also rears its head again as the authority requires Google to investigate individuals' requests for search listing removals.
Services such as Gmail, YouTube and Google+ will be checked on a quarterly basis to ensure that each has its own specific privacy policy. Google will need to start explaining to its users when data is collected from each of these services and fed into a larger data for the purposes of user profiling. Should any changes be made to privacy policies, Google will have to maintain an easily accessible archive of previous versions to give people a chance to compare them.
The Italian DPA is also demanding that the company makes improvements to its handling of data storage and deletion. Specifically, Google will have to make changes to the processes used to anonymize data and implement a specific time-frame for deleting data from backup systems. The authority is also looking for Google to improve its data storage and deletion mechanisms for users' personal information.
The DPA said that Google has until the beginning of next year to comply:
For the first time in Europe, it will be the subject of regular checks to monitor progress status of the actions to bring its platform into line with domestic legislation. The Italian DPA approved the verification protocol referred to in its order of July 2014 to Mountain View. This marks a shift from the laying down of measures by the DPA to the practical implementation of such measures by Google, which will have to be fully compliant by 15 January 2016.
This is far from the first time Google's privacy policies have come under scrutiny, and the level of interest it attracts in Europe means it is unlikely to be the last.
Photo credit: Chukcha / Shutterstock
-

Google to launch YouTube Kids for Android
Publié: février 20, 2015, 10:42am CET par Mark Wilson

Google is launching a kid-friendly version of YouTube. It's a project we first heard about a few months ago, and now YouTube Kids is about to become reality. But rather than launching as a child-friendly version of the website we've come to know and love, YouTube Kids will start its life as an Android app.
Parents will be pleased at Google's plans, where it will be possible to find carefully selected content that is suitable for a younger audience. Google will be curating videos, but there will be one question that enters the minds of mums and dads around the world: "what if my kid uses 'sex' as a search term".
Google is one step ahead of the game. Should kids conduct searches that are deemed potentially dangerous or that are too adult in theme, a gentle suggestion that the user might like to "try something else" will pop up. Another parental concern is addressed with the inclusion of a time-limiting feature so the app will turn off when it has been used for a while.
The video sharing site has already tried to get 'down with the kids' by introducing support for animated GIFs, but the deliberate targeting of a younger audience is a difference move altogether. Speaking to USA Today, YouTube Kids' project manager, Shimrit Ben-Yair explained how the upcoming app is suitable for children:
Parents were constantly asking us, can you make YouTube a better place for our kids. The images are big as are the tap targets for small fingers, and since most younger children can't type they can search with voice.
Split up in to a number of sections such as TV shows, music and educational videos, YouTube Kids, and partnerships with various content providers will spawn content for the platform. Google has not yet revealed how the service will be monetized -- it's not clear whether ads will be used, or if Google is taking the long view and hoping that child users transition to full-blown YouTube and other services later in life.
-

Google faces anti-trust probe in Russia over Android
Publié: février 18, 2015, 7:48pm CET par Mark Wilson

Google has a new battle on its hands, this time in the form of a potential anti-trust probe in Russia. Yandex, the internet company behind the eponymous Russian search engine, has filed a complaint to the Federal Antimonopoly Service (FAS). Yandex claims that the US search giant is abusing its position by bundling Google services with Android.
It claims that users are forced into using the Google ecosystem including Google Search, and that it is difficult to install competing services on smartphones and tablets. There are distinct echoes of the antitrust lawsuits Microsoft has faced for its bundling of Internet Explorer with Windows.
Yandex is thought to be unhappy after being told that it is no longer able to pre-install its own services on handsets produced by its partners. Calls have been made for Google Search to be disconnected from Android in much the same way that Microsoft was asked to unbundle Internet Explorer. Google has yet to issue a public response, but the Russian company issued a statement saying:
Google's practices relating to Android have been the subject of investigations and lawsuits in many jurisdictions around the world.
Google is the owner of Android, the dominant global mobile operating system. Many believe that Android is an open platform.
In reality, manufacturers of Android-powered devices are locked into the proprietary Google Play application store and closed APIs. In order to install Google Play on their devices, device manufacturers are required to preinstall the entire suite of Google GMS services, and set Google as the default search.
In addition to that, device manufacturers are increasingly prohibited from installing any services from Google’s competitors on their devices.
Yandex is Russia's largest search engine, and its demands are fairly simple:
We believe that user-centric services, such as search, maps, email, etc., should be unbundled from the Android OS. It is essential to return to a level playing field where competition is over quality of products and services rather than bundling and pre-installation.
Google is already facing scrutiny in the US and Europe, and this looks like it could be a battle that runs for some time yet.
Photo credit: Bloomua / Shutterstock
-

HTTP/2 has been approved, bringing the promise of a more efficient web
Publié: février 18, 2015, 1:08pm CET par Mark Wilson

The web could be in line for a speed boost as the HTTP/2 standard edges closer to being finalized. The updated standard will be the first major alteration to the protocol since the late 1990s, and it includes a number of important updates that should help to make life online faster and more enjoyable.
Although HTTP/2 is yet to be published as a completed standard, it is already supported by some web browsers including Chrome and Firefox. However, it won't be until the standard is far more widely adopted that the real benefits will be felt.
The draft proposal for the HTTP/2 standard explains that it will introduce header field compression and allow more simultaneous connections for more efficient use of network resources. As The Next Web suggests, this could also help to reduce the costs associated with running websites and online services by reducing server loads.
In a blog post Mark Nottingham, chair of the IETF HTTP Working Group, said:
The IESG has formally approved the HTTP/2 and HPACK specifications, and they’re on their way to the RFC Editor, where they’ll soon be assigned RFC numbers, go through some editorial processes, and be published.
The move to HTTP/2 should be a relatively painless one as it uses the same HTTP APIs. While some finetuning may be needed, Nottingham explains that HTTP/2 is not a completely new standard, rather about "getting the HTTP we know on the wire in a better way". There are also security benefits thanks to improved security options, and the interesting concept of 'cache pushing' that will make it possible to proactively send data to users' caches for later use.
It’s not yet known how long it might be before HTTP/2 is formally adopted, but the wheels are now very much in motion.
Photo credit: atm2003 / Shutterstock
-

Google pushes Inbox by pulling Sparrow email client from the App Store
Publié: février 18, 2015, 1:38am CET par Mark Wilson

It's not all that long since Google launched Inbox. The 'smart' alternative to Gmail appeared a few months ago and Google tried to get the hype machine going by launching it as an invite-only service, gradually trickling out invites here and there.
Now the search giant is trying a new tactic to encourage people into using the service, specifically Apple users. Google has pulled the iOS and Mac version of the Sparrow email app from the App store; the hope is clearly that Sparrow users will migrate to Inbox.
Although the Mac version of the app can still be grabbed directly from the Sparrow website, iPhone users who do not already have the app installed will find that there is now no way to download it. Google bought Sparrow less than three years ago, but is clearly keen to promote its latest email tool that boasts a snooze feature.
At the moment, Inbox remains invite-only, arguably increasing interest levels and the perceived value. Update has already been reasonably impressive but Android users far outnumber those running iOS. By eliminating an alternative, Google is enticing Apple fans into using Inbox and it will be interesting to see how this is received by fans of the app.
-

UK Police raid popular movie and TV show piracy site
Publié: février 17, 2015, 5:40pm CET par Mark Wilson

Police in London have raided a site providing movies and TV show downloads. Three men have been arrested on suspicion of conspiracy to defraud as well as copyright infringement offenses. The site has not been named, but police describe it as "extremely" popular.
The raid followed an investigation by FACT (the Federation Against Copyright Theft) and resulted not only in three arrests, but also the seizure of computer equipment and financial documents. Although we don’t yet know which site is involved, police say that "it ranked thousands of places higher than a well-known and legitimate film download site".
Talking to TorrentFreak, Detective Sergeant Neil Reynolds said that investigations continued to determine how money raised through the site was being used. While the site was registered to an address in Romania, money brought in from advertising was paid into a UK bank account.
It can be difficult for people to care about copyright laws being broken but the money made from such sites is often spent on funding other crime. We are looking at how much money was made from advertising on this website and where that money went to.
It seems that the site must have been generating a reasonable amount of money as it managed to come to the attention of the London Regional Asset Recovery Team. Comprising revenue and police officers, the team is concerned with financial investigations surrounding profits generated by criminal activity.
Photo credit: pjhpix / Shutterstock
-

Microsoft reveals Office web and mobile apps can use ANY cloud storage service
Publié: février 17, 2015, 4:29pm CET par Mark Wilson
Microsoft's mobile-first, cloud-first strategy continues. In something of a surprise announcement the company reveals that it is launching a new cloud storage partner program meaning that any cloud storage provider will be able to integrate with Office for iOS and Office Online.
The news follows on from Microsoft's partnership with Dropbox in November and while it is just iOS users who will benefit from the new mobile options for now, Office for Android and Office for Windows 10 will also get the same treatment in due course. It's a recognition of the fact that integration with OneDrive is not enough so it shouldn't be long before we see iCloud and Google Drive working with Office.
Opening up the mobile version of Office to third-party cloud storage providers means that the likes of Google, Apple and others will be able to add their cloud services to the Locations picker in the Office apps. Users will be able to open, edit and save files using their preferred cloud service, cutting the ties with Microsoft's offering.
Today's announcement also sees Microsoft opening up Office Online to third-party providers, and Box, Citrix, and Salesforce are already on board. Once developers have signed up to the Cloud Storage Partner Program they will be able to integrate Office Online -- complete with PowerPoint, Word, and Excel document viewing and editing -- into their own apps and services.
Microsoft's corporate vice president for the Office team, Kirk Koenigsbauer said: "these new features represent a big step forward for Office integration into the apps and services that are important to our customers". He added: "Today’s announcements are just one more step on our continuing journey to open up Office in new ways for our customers and partners. Living in a cloud-first, mobile-first world is all about having the flexibility to get things done from anywhere and on any device".
-

Worldwide Equation Group hid undetectable spyware on hard drives
Publié: février 17, 2015, 2:16am CET par Mark Wilson

In a new twist to the on-going NSA story, security firm Kaspersky Lab has discovered that a threat actor of previously unknown complexity and sophistication has been embedding surveillance software on hard drives produced by a number of well-known manufacturers. With names such as Western Digital, Seagate and Toshiba mentioned, and the reach of the spy program stretching to dozens of countries, it's not clear quite how many people may be affected.
Although Kapersky does not go as far as naming the NSA, or even specifying which country is responsible for the advanced surveillance, it seems that the spying campaign is somehow related to Stuxnet -- the tool used by the NSA to attack Iran -- and the Flame group.
The Russian security company uncovered a series of spying programs. It said that it had detected two modules that allowed for the firmware of hard drives to be reprogrammed, and that systems in more than 30 countries had been uncovered by the investigations. Those that have fallen victim include governments, military, energy companies, and even Firefox.
One of the reasons the US government's surveillance activities have been criticized so much is down to the dragnet approach that has been adopted -- data about entirely innocent people is collected as well as 'legitimate' targets. Installing spyware on hard drives allows for slightly more targeted surveillance, but this is unlikely to quell the fears of those concerned about privacy.
A former intelligence worker confirmed to Reuters that the NSA has successfully developed techniques for hiding spyware on hard drives. Director of the Global Research and Analysis Team (GReAT) at Kaspersky Lab, Costin Raiu said:
Once the hard drive gets infected with the malicious payload, it is impossible to can its firmware. To put it simply: for most hard drives there are function to write into the hardware firmware area, but there are no functions to read it back. It means that we are practically blind, and cannot detect hard drives that have been infected by this malware.
With infected machines found in the likes of Russia, Afghanistan, China, Syria and Yemen, it amounts to a massive spying operation. There is the possibility that Kaspersky Lab's discoveries and revelations could have an impact on relations between the West and other parts of the world. Fingers of suspicion will almost certainly be pointed at hard drive manufacturers. While Toshiba, IBM and Samsung offered no comment, Western Digital, Seagate and Micron denied knowledge of the spying programs.
Raiu explains that the coders behind the malware must have had access to the source code of hard drives, although this is something that manufacturers would ordinarily guard ferociously. In what is described as an "astonishing technical accomplishment", the Equation group's ability to "reprogram the hard drive firmware of over a dozen different hard drive brands, including Seagate, Western Digital, Toshiba, Maxtor and IBM" is explained over on SecureList.
There is the promise of more details over the coming days, and this could include some very revealing information.
Photo credit: hadescom / Shutterstock
-

Microsoft leads the way with adoption of first international cloud privacy standard
Publié: février 16, 2015, 6:18pm CET par Mark Wilson

The gradual push of just about everything to the cloud means that security and privacy are of greater concern than ever before. This is true for everyone who makes use of cloud services like OneDrive and Azure, but it is of particular interest to enterprise customers.
Today Microsoft has become the first major cloud service provider to adopt ISO/IEC 27018, the world’s first international standard for cloud privacy. The idea is to ensure that there is a global standard that determines how personal data privacy is handled in the cloud. The standard equips people with a number of assurances.
The code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors -- to give ISO/IEC 27018 its full title -- ensures that customers remain in control of their data. There's a strong focus on leaving the customer not only in control, but fully informed about how data is processed. Customers will be told where their data is stored, how and when it is transferred between places, and who else has access to it -- including access by government agencies where the law permits.
In the case of unauthorized access, the privacy standard requires companies to inform customers, and companies must only process data that could identify customer in accordance with instructions from the customer in question. Any company signing up to the standard will not be able to use customer data for advertising, and are banned from transmitting personally identifiable information over public networks.
Microsoft's General Counsel and Executive Vice President, Legal and Corporate Affairs, Brad Smith, said:
All of these commitments are even more important in the current legal environment, in which enterprise customers increasingly have their own privacy compliance obligations. We're optimistic that ISO 27018 can serve as a template for regulators and customers alike as they seek to ensure strong privacy protection across geographies and vertical industry sectors.
Today's news is just one way we've been working to help strengthen privacy and compliance protections for our customers in the cloud.
Photo credit: Maksim Kabakou / Shutterstock
-

Did the NSA spy on you and pass information to GCHQ in the UK? Here's how to find out
Publié: février 16, 2015, 4:34pm CET par Mark Wilson

It is just about impossible to be an internet user without being aware of the surveillance that has been carried out by the NSA; cheers for the tip, Mr Snowden. While it was the NSA's activities that hit the headlines, governments in other countries used -- and continue to use -- similar surveillance techniques and even share information between each other.
We already know that GCHQ believes that online privacy has never been an absolute right, but this does not change the fact that data sharing between the NSA and GCHQ was illegal before December. Now Privacy International, one of the organizations opposed to such spying, has launched a campaign to help people find out if GCHQ illegally received information about them from the NSA.
It does not matter if you are in the UK, people all over the world are invited to put their names forward for Privacy International to take to court and demand to know whether information was illegally received. Signing up is a simple matter of visiting the Privacy International campaign page and enabling the organization to make a data request on your behalf under Article 8 and Article 10 of the European Convention for Human Rights. Make sure you respond to the confirmation email you receive as well.
The campaign's FAQ explains the reasons for the action:
Intelligence agencies' culture of secrecy have allowed them, for too long, to avoid public accountability. Whether it's secret hearings in closed court rooms or committees equipped only with rubber stamps, intelligence agencies like GCHQ have never been forced to answer to the public for their actions.
We think you have a right to know whether you have been caught up in GCHQ and NSA's illegal intelligence sharing. If so, you have a right to demand that data be deleted. Privacy International wants to help you assert those rights.
As the law has now changed it is not possible to determine whether a governmental agency is currently spying on you. All you will be able to determine is whether the NSA gathered information about you and passed it to GCHQ before December 2014. Privacy International admits it could be years before any information is delivered by the courts, but if you are concerned about your privacy it takes very little effort to sign up.
If you feel uncomfortable handing over your details (which amounts to nothing more than your name, email address and phone number) to Privacy International, there's nothing to stop you from putting in a request of your own, but there is strength in numbers.
Photo credit: 360b / Shutterstock
-

Valve blocks talk of Kickass Torrents in Steam chat
Publié: février 16, 2015, 2:38pm CET par Mark Wilson

If you want to chat about the relative merits of Kickass Torrents, it seems that Steam chat is not the place to do it. The censoring of words deemed offensive is nothing new, but gamers have found that any messages they post which included references to Kickass Torrents or the URL http://kickass.so are stripped.
Like the Pirate Bay, Kickass Torrents has fallen victim to domain name seizures, but even though the site has been taken offline, it would appear that Steam does not want its users to discuss it. A ban on mentioning the site has been described by some gamers as "covert censorship".
It's not clear why Kickass Torrents has been singled out for attention, but the censorship is all the more interesting when you consider that the site has been taken offline. It is understandable that Valve wants to protect its income streams by discouraging users from turning to torrents sites for their game needs, but blocking discussion entirely is something that has not been well-received. The fact that mentions of the site are simply removed from messages without explanation has caused some irritation.
PlayerAttack explains that, at the moment, only one of the various Kickass Torrent mirrors is being blocked. However, links to other URLs for the site are flagged up as being "potentially malicious". Valve has not issued a statement about the censorship, but if we hear back from the company, we'll update this story.
Photo credit: Leigh J / Shutterstock
-

Google relaxes Project Zero bug disclosure policy after Microsoft complaints
Publié: février 16, 2015, 1:15am CET par Mark Wilson

Google managed to ruffle a few feathers recently by disclosing bugs and security problems in widely used software. Project Zero is used to encourage companies to fix issues that have been detected by imposing a 90-day deadline before details of the vulnerabilities are made public.
Microsoft was angered a month ago when Google published details of a security issue in Windows 8.1 just a few days before a patch was due to be released. A few days later, two more bugs were revealed leading to complaints not just from Microsoft but from software users. Now Google has backed down and announced a slight relaxing of its previously strict 90-day disclosure policy.
This is not to say that the 90-day policy is going away, just that there will be a little more flexibility in the future. For example, if the deadline runs out on a weekend or public holiday, it will be rolled over to the next working day. This is something that will go down well with software developers, but the introduction of a 14-day grace period is something that will particularly please Microsoft.
From now on, if a publisher lets Google know that a patch is due for imminent release, the publication of vulnerability details will be delayed for up to a fortnight. The new approach was announced in a post on the Project Zero blog:
We now have a 14-day grace period. If a 90-day deadline will expire but a vendor lets us know before the deadline that a patch is scheduled for release on a specific day within 14 days following the deadline, the public disclosure will be delayed until the availability of the patch. Public disclosure of an unpatched issue now only occurs if a deadline will be significantly missed (2 weeks+).
Of course there will still be plenty of companies who are unhappy with what is seen by many as Google's decision to police coding. Google points out that all vulnerabilities are treated equally: "Project Zero has bugs in the pipeline for Google products (Chrome and Android) and these are subject to the same deadline policy".
Photo credit: NatBasil / Shutterstock
-

Are we really in danger of losing our history to the cloud?
Publié: février 15, 2015, 7:20pm CET par Mark Wilson

If Google's vice president is to be believed, we are in danger of losing an entire generation of information to the digital realm. Look to the history books, and you do just that -- look in a real, physical book. Pictorial histories can be found in photo albums. The works of Oscar Wilde, Samuel Pepys, and Charles Dickens are stored in real, tangible formats.
But now just about everything is stored digitally. Photos are rarely, if ever printed; millions of words are published online each day on blogs, online newspapers, and message boards. These are all important social, political, literary, and historical records. There's no guarantee that the sites, apps and technology needed to access all of these records will still be available in 50 years or more. Could our history be lost to the cloud?
Every day we post reams of information to Facebook and Twitter, and it's usually stuff we have no 'backup' of. Upload a photo and there's a high chance that you have a copy stored on your phone, camera or computer, but the same cannot be said of every bon mot penned. It's easy to deride the contents of social networks as material that we should just forget about, but historians in several hundred years' time may well find it difficult to piece together what it meant to be alive in the late twentieth/early twenty-first century.
Google and other companies have quite a propensity for shutting down services willy nilly -- Helpouts is just the latest in a long line of victims. Speaking at the annual meeting of the American Association for the Advancement of Science, Google's VP, Vint Cerf said:
When you think about the quantity of documentation from our daily lives that is captured in digital form, like our interactions by email, people’s tweets, and all of the world wide web, it's clear that we stand to lose an awful lot of our history [...]We don’t want our digital lives to fade away. If we want to preserve them, we need to make sure that the digital objects we create today can still be rendered far into the future.
We can't be sure that everything we say on Facebook will be accessible next year, let alone in a couple of decades. We have no guarantee that images currently stored as JPEGs will be as easy to open in 2115 as they are in 2015 -- the software horizon is completely unknown. In the relatively short time in which digital documents have become the norm we have already seen a number of once-popular file formats fall by the wayside. Conversion tools are available in many cases, but not in all.
The likes of Word are likely to stick around for longer than any other formats, but there is a danger that we would reach a time when opening certain types of documents requires specialist intervention. Old computer systems and games consoles are consigned to museums. Could the software you are working with at the moment become the Pong of tomorrow?
Storing anything digitally leaves it open to a serious problem -- security. Chuck your data to the cloud, and you're placing a lot of trust in the companies involved to keep your files safe. But if something goes wrong -- from a company closing down, through a hardware failure that wipes out files, to a hack attack -- there is no way of knowing that your cloud-stored information will continue to be available to you.
It's a problem exacerbated by the huge range of mobile apps that are now out there, each storing files in their own unique, often incompatible formats. When it comes to apps for phones and tablets, storing data in the cloud is very much the norm -- it's just the way things are. Too many apps fail to provide a way (or at least an easy or free way) to convert data into another format that would allow it to be used with another piece of software. Patents and IP laws often stand in the way of enterprising programmers from creating their own conversion tools.
This is far from the only concern. The sheer volume of data we all create on a daily basis is staggering
Talking to TechRadar, Mark Whitby, Senior Vice President of Branded Products Group at Seagate Technology, said that our data storage needs are spiralling out of control:
The total amount of digital data generated in 2013 was about 3.5 zettabytes (that's 35 with 20 zeros following). By 2020, we'll be producing, even at a conservative estimate, 44 zettabytes of data annually.
Our data is spiralling out of control. Whether it is stored on hard drives or in the cloud (which ultimately means that it is stored on a hard drive somewhere) we generate countless libraries worth of information every day with no guarantee that it will be accessible in the next century. How much data do you have stored on old 5.25 inch disks, 3.5 inch floppies, or even CD-Rs that are unreadable? It might not just be that you don’t have the drives necessary to read these various types of storage, but that the media is prone to deterioration over time. And this is still where we're relatively in control of it. We have no idea how accessible our cloud data will be further down the line. No idea whatsoever.
CDs we created a few years ago have already become unreadable with age. DVDs and Blu-ray discs will suffer the same fate, and it would be naïve to believe that the hard drives and memory built into so many devices are not prone to the same problem.
The lure of the paperless office means that less and less information is stored on slices of tree, but this is the format that has proved to be one of the most enduring throughout history. Perhaps it's time to dig out the printer, invent in a bunch of ink and start running off hard copies of everything we couldn’t bear to lose.
Right... who's going to print out Wikipedia?
Photo credit: Bruce Rolff / Shutterstock
-

Kaspersky Lab says malware is used to steal millions of dollars from banks
Publié: février 15, 2015, 5:33pm CET par Mark Wilson

However much money you have flowing through your bank account, you probably take measures to keep it secure. You protect your PIN, you use secure passwords for online banking, and ensure that your computer is free from keyloggers and malware. It's only right that you expect your bank to be similarly eagle-eyed about security... right?
A new report from security firm Kaspersky Lab shows that banks' security is not up to the standard that many would expect. In fact Kaspersky says that sophisticated malware has allowed criminals to help themselves to more than $300 million. Has your bank been hit? The affected financial institutions are now aware of the attacks, but non-disclosure agreements and on-going investigations prevent them from being named.
This is not money that has been taken in a single hit. The report, which has been shown to the New York Times ahead of its official publication, shows that money has been syphoned off since the latter half of 2013. Accounts in the US, Europe, Russia and Japan have been targeted, and a variety of techniques have been used to extract money from more than one hundred banks around the world.
The malware has been used to remotely monitor the day-to-day operations of individual banks and employees. More than this, the malicious software enabled criminals to take remote control of banking computers, and this is when the thefts started to take place. Moving money from one account into another would seem like an obvious way to go about stealing money, and this was one of the methods used. But money transferred in this way is easily traceable, the criminals also used different electronic payment systems to send money to fraudulent accounts in other countries.
Perhaps the most audacious method of theft was to simply send instructions to ATMs to dispense money at particular times. All that's needed then is to have someone in place at the right time to collect the cash and move on to the next ATM.
Other techniques included adding 'virtual money' to an innocent target's account and then withdrawing this cash. The New York Times gives an example in which an account with $1,000 in it is artificially inflated to show a balance of $10,000. Cybercriminals could then withdraw the difference of $9,000 without alerting the account holder.
The Financial Services Information Sharing and Analysis Center issued a statement that said:
Our members are aware of this activity. We have disseminated intelligence on this attack to the member... Some briefings were also provided by law enforcement entities.
What will be most worrying to many people, perhaps, is the fact that the attacks have been going on for so long -- and apparently continue to take place. Chris Doggett, managing director of Kaspersky Lab's North American office, said the Carbanak malware helped to keep the attacked under the radar:
This is likely the most sophisticated attack the world has seen to date in terms of the tactics and methods that the cybercriminals have used to remain covert.
Although individual banks have failed to issue statements about the report, President Obama has made a recent call for companies to publicly disclose details of any security breaches that compromises individual's personal or financial information.
Photo credit: Frank11 / Shutterstock
-

Microsoft removes restrictions from OneNote free edition
Publié: février 14, 2015, 9:22pm CET par Mark Wilson
Since its release as a free tool, OneNote has gained a massive following. The note-taking, clip-organizing, jack-of-all-trades tool fits neatly into Office, but can also be used as a standalone tool. Although it has been available free of charge for some time, there were a few features reserved for paying customers -- now this has changed.
Microsoft is making OneNote "even more free" by adding options such as password protection and new audio and video options. All previous restrictions that existed in the free version of the app have been removed.
As well as giving you the ability to secure sensitive notes, a page history feature brings versioning to OneNote. If you're working with other Office files, you can now embed them in your notes, and there are new options for working with audio and video files. An enhanced search tool can be used to track down words in your recordings, and it's possible to take notes whilst recording and jump straight to specific sections when you need to.
Announcing the arrival of the new features, Brad Corob from the OneNote team says:
Today we’re happy to share that we’re adding even more to the free edition. We’re removing all feature restrictions from OneNote 2013. Starting today you’ll be able to access the full power of OneNote on your PC.
Everything must remain in the cloud, however. If you want to take advantage of what OneNote has to offer, you'll have to accept that everything will be stored in OneDrive rather than locally.
You can grab yourself a copy of the app for Windows 7 and Windows 8 from the OneNote website.
-

Google Helpouts to be consigned to history
Publié: février 14, 2015, 6:07pm CET par Mark Wilson

Google is shutting the door on its Helpouts service. Just two and a half years after launching the help and support extension to Hangouts, it has been decided that there just is not enough interest to warrant keeping it running.
Designed as a platform for experts to offer their paid service to people, Helpouts failed to gain the traction needed to make it viable. The shutdown will not take immediate effect, but there's quite a short deadline for users to seek out an alternative.
There are a little over two months until Helpouts is shuttered on 20 April; users are encouraged to download their historical data through Google takeout. The Android app for Helpouts has already been removed from Google Play, although anyone who already has the app installed can continue to use it for the time being.
The closure was announced in a post on the Google Helpouts support pages:
We have some sad news to share: Helpouts will be shutting down on April 20, 2015.
Since launching in 2013, Helpouts has been a home for people to connect with experts on topics they want to learn about or seek advice and solutions to everyday challenges. The Helpouts community includes some engaged and loyal contributors, but unfortunately, it hasn't grown at the pace we had expected. Sadly, we've made the tough decision to shut down the product.
Starting April 20, you'll be able to download your Helpouts history using Google Takeout (available until November 1, 2015).
Payments will still be made to those who have earned money through the service, but Helpouts will completely disappear after 20 April -- the site will not be retained for reference. Google says that the service "hasn't grown at the pace we had expected", but there will still be a number of people disappointed at news of the closure.
Photo credit: Mikkel Bigandt / Shutterstock
-

Cast your vote in Linus Torvalds' Linux version numbering poll
Publié: février 13, 2015, 4:58pm CET par Mark Wilson
When Microsoft launched Windows 10 Technical Preview, the name came as something of a surprise; everyone had been, understandably, expecting Windows 9. Over in the world of Linux, as we know, things work a little differently.
The world of Linux-based operating systems is a fragmented one, but Linus Torvalds -- whose loins were partly responsible for giving birth to Linux -- is asking the community how version numbering should be handled moving forward. Should things be kept simple, or should version numbers just keep getting longer, and longer, and longer, and longer?
Taking to Google+, Torvalds says that there is a danger that 'big numbers' are starting to creep into releases. Should it be nipped in the bud before things get out of control, or should things be left to run their natural course? Judging by the volume and passion of comments on the post, this is something that Linux users feel pretty strongly about -- although there's not exactly a knock-out winner at the moment.
Introducing the poll, Torvalds says:
So, I made noises some time ago about how I don't want another 2.6.39 where the numbers are big enough that you can't really distinguish them.
We're slowly getting up there again, with 3.20 being imminent, and I'm once more close to running out of fingers and toes.
I was making noises about just moving to 4.0 some time ago. But let's see what people think.
So - continue with v3.20, because bigger numbers are sexy, or just move to v4.0 and reset the numbers to something smaller?
You've got two choices: I like big versions, and I cannot lie (currently standing at 43 percent of the vote), and v4.0, 'cause I get confused easily (er, 57 percent, obviously). The vote may have no impact on how version numbering is handled, but you can have your say over on Google+.
Photo credit: Fabio Alcini / Shutterstock
-

Apple boosts iMessage and FaceTime security with two-factor authentication
Publié: février 13, 2015, 1:22pm CET par Mark Wilson

It's something that has been supported by iCloud for a while now. Bringing two factor authentication to iMessage and FaceTime means that messages and video chats are now locked behind an extra layer of protection.
If you log out of your iMessage or FaceTime account, the next time you try to sign in you will be prompted to activate two factor authentication. This means you'll have to log into your account and generate an app-specific password before you can continue.
The security of iCloud had been called into question after a number of high-profile celebrity photo leaks. Until the introduction of two factor authentication, a username and password were all that was required to gain access to an account.
You can set up the extra security feature over on the Apple website, as well as create a Recovery Key in case anything should go wrong.
Photo Credit: Yotka fotoaloja / Shutterstock
-

When you die Facebook will grant your 'legacy contact' access to your account
Publié: février 12, 2015, 9:37pm CET par Mark Wilson

Have you prepared for the day you die? Let people know if you want to be stuck in a hole in the ground, cremated and scattered in an awkward place, or just left at the side of the road to be picked at by passing foxes? While you may have considered what happens to your lifeless meatsack and your worldly belongings, what about things in the digital realm?
Facebook has just taken a step that will make it easier for a designated loved one to take control of your account. Your 'legacy contact' will be able to set up a memorial to you and download your account archive.
If this sounds of interest, and you're in the US, you're in luck. Facebook is now rolling out the Legacy Contact feature so you can make things easier for those you leave behind when you shuffle, run, leap, or fall off this mortal coil. There's no need to worry about how this contact might sully your memory, as there are limits to what they will be able to do.
Once Facebook is informed of your death, your account can be converted to a memorial page and your chosen contact can add a post at the top of your account. They can also change your profile picture and cover photo, as well as respond to friend requests -- although these would presumably only be coming from people who didn’t know you all that well in the first place.
While the legacy contact can, if you choose to let them, download an archive of your Facebook activity, you can be sure that your private messages will be kept out of sight.
To activate the feature on your account, head to settings and click Security followed by Legacy Contact. You'll be guided through selecting your contact and given the chance to send a message to the person in question. While the feature is starting off in the US, there are plans to roll it out further afield. If you'd like to be left alone after you snuff it, you may prefer to have your account deleted
Photo credit: Lane V. Erickson / Shutterstock
-

Microsoft launches Windows 10 Technical Preview for Phones
Publié: février 12, 2015, 8:24pm CET par Mark Wilson

The chances are that you have tried out Windows 10 on your computer already and now -- at long last -- you have the opportunity to try it out on your Windows Phone. Windows Insiders can now grab the first public build of Microsoft's latest mobile operating system and try it out for themselves.
Windows Insiders have been eager to see what Microsoft has done with Windows Phone, and earlier today Gabe Aul cryptically hinted at when the first build would be released. Now it has gone live. As with all preview builds, this is far from a completed product, and there are a few caveats to bear in mind.
First of all, there are a very small number of handsets that are eligible to use the preview for now. In fact, there are just six: the Lumia 630, Lumia 638, Lumia 635, Lumia 730, Lumia 636 and Lumia 830 -- but, pleasingly, the preview is available internationally. There's no mention of some of the big hitters like the Lumia 928, 929 and 930 at this stage. If you're wondering why more high-end phones are not included, Microsoft has an explanation:
We have a feature that will be coming soon called 'partition stitching' which will allow us to adjust the OS partition dynamically to create room for the install process to be able to update the OS in-place. Until this comes in, we needed devices which were configured by mobile operators with sufficiently sized OS partitions to allow the in-place upgrade, and many of the bigger phones have very tight OS partitions.
The second thing to keep in mind is that -- as the company points out -- this is the earliest ever public preview for Windows phones. Just as with Windows 10 on the desktop, Microsoft is looking for feedback but warns Windows Insiders that:
You will encounter bugs. You will see experiences that are clearly just not done yet, and UX that lacks polish at this point. DON’T WORRY! It will improve as we go and new features, stability and performance improvements, and more polished UX will come at each step.
So what's new? In addition to a (somewhat) seamless experience when moving from the desktop to a phone handset, and the ability to work with universal apps on both platforms, Windows 10 Technical Preview for phones boasts:
- Full-size Background Image for Start: We believe phones should be intensely personal -- so we’ve added another option to customize the start screen with a full-size background image.
- More Quick Actions in Action Center: We’ve increased the number of quick actions available to you. Windows Phone 8.1 has four programmable quick actions -- but with Windows 10 you also get an expanded view that can now have up to three rows.
- Interactive Notifications: Notifications are now interactive, allowing you to take action directly like dismissing an alarm, or seeing images for maps. For example, for text messages, when the toast pops, you can quickly reply inline via text or voice.
- Significantly enhanced speech-to-text capability: You can talk to virtually any data field you choose. Your words show up as you speak them – and punctuation appears automatically. This feature is smart enough to understand when to use 'two' -- the number -- instead of 'too' as in 'also'.
- More powerful Photos app: From your very first launch, Photos will show the aggregated set of all your local photos and all your OneDrive photos
There's a lot missing at this stage, and there's clearly a lot of work still to do, but this is the preview that people have been asking for. There are a lot of known issues, but they're being worked on, and new builds will follow in the coming weeks and months.
Introducing this first build in a blog post, Aul explains how to get hold of Windows 10 Technical Preview for phones:
- Join the Windows Insider Program
- Register your device to receive builds as over the air updates
- Builds will come to you automatically as they are ready, after being validated by engineers at Microsoft and used on their own phones
- Use the built-in Windows Feedback app to send us problem reports and suggestions
- Updates will continue all the way up to the final build that goes out to all customers
- You can roll your phone back to the previous OS any time you'd like
So... fire up your Windows Phone and head on over to the Windows Insider website. Joe Belfiore shows off some of what you have to look forward to in a specially-produced video:
-

Microsoft enigmatically reveals release date for Windows 10 for phones
Publié: février 12, 2015, 10:44am CET par Mark Wilson

The Windows Phone Windows Insider App was recently updated, indicating that a mobile build of Windows 10 is imminent -- but when? Answering questions from eager users on Twitter, Microsoft's Gabriel Aul has given some cryptic hints about when the first preview of the successor to Windows Phone 8.1 will be launched.
Over the last few months Microsoft has been popping out new builds of Windows 10 left, right and center. While we now have a pretty good idea of how things are going to look and feel on the desktop, the same cannot be said of mobiles and tablets.
Of course it would be far too simple to just come out with an actual release date, so Gabe decided to tease Twitter users a little. Rather than answering queries about the release date directly, he chose to wind people up by answering in mysterious terms. If you want to know when you can get your hands on a mobile build, you'll have to solve a puzzle.
Make of it what you will, but the release date is somehow wrapped up in the clue 1316:
@callum90ish I love the creative ways you guys try to squeeze me :-) How about a puzzle? This is a REAL answer if you can solve it: 1316
— Gabriel Aul (@GabeAul) February 12, 2015
Joe Belfiore had already made it clear that we should expect a release in February, but no date was pinned down:
Also, we're on track for Insider build coming "in Feb" as Terry said at our 1/21 event. We need to complete internal testing 1st, hang in!
— joebelfiore (@joebelfiore) February 8, 2015
Gabe himself, in response to numerous guesses at the date, caved in a confirmed that we can expect to see the release this month, but would not go into any more detail:
@dey_ritwick All I can say today is "in February". When it comes out, we'll see who gets it right. No one has solved puzzle so far though
— Gabriel Aul (@GabeAul) February 12, 2015
So... start guessing! It seems that no one has managed to pin down the release date precisely yet -- or at least Aul is not saying as much -- but there's only a couple of weeks to wait at the most now.
Update
It's out now!
-

Microsoft confirms that it has acquired calendar app Sunrise
Publié: février 11, 2015, 11:38pm CET par Mark Wilson

Following on from the rumors that surfaced a week ago, Microsoft has confirmed its acquisition of calendar app Sunrise. The Android and iOS calendar app is widely recognized as one of the best that's available, and the announcement marks the latest move in Microsoft's recent productivity focus.
This is the second big acquisition Microsoft has made recently -- just a couple of months ago, the company snapped up email firm Acompli. It also sees Microsoft adopting rather Apple-esque language, referring to "meaningful, beautiful experiences in mobile email and calendaring".
But this is about more than just an interest in productivity; Microsoft is set to do nothing less than reinventing productivity. Rather than starting from scratch and building tools from the ground up, the company has made the decision to jump on established tools that already have a loyal following.
Quelling fears that the app could be shuttered or transformed into an expensive tool, Microsoft said that Sunrise will not only live on, but will remain free. Confirming the acquisition on the Microsoft blog, Corporate Vice President for Outlook and Office 365, Rajesh Jha said:
We are making this acquisition because we believe a reinvention in the way people use calendars on mobile devices is long overdue. Our goal is to better help people manage and make the most of their time in a mobile-first, cloud-first world.
Sunrise founders Pierre and Jeremy also emphasized the fact that the app is here to stay:
Sunrise will remain free and available for iPhone, iPad, Mac, Android and Desktop – we’re not going anywhere [...] Both Sunrise and Microsoft share this vision to make your life a little easier by focusing on time, design, and building experiences that delight you everyday. We can’t wait to show you what we’ve been working on lately :-)
A video posted by the company shows Microsoft’s Steve Clayton talking with the CEOs of Sunrise and Acompli:
Photo credit: Leena Robinson / Shutterstock
-

Google's PerfKit Benchmarker tests the performance of cloud services
Publié: février 11, 2015, 9:03pm CET par Mark Wilson

For both software and data, there is a relentless move to the cloud. But with so many different cloud services to choose from, it can be difficult to decide which one is best. To help make things a little easier, Google today launches PerfKit Benchmarker.
The open-source tool makes it possible to run benchmarks across a variety of cloud platforms, and a dedicated visualization tool, Perfkit Explorer, has been created to help with the interpretation of results. The tool provides essential data to developers who are creating applications in the cloud.
PerfKit Benchmarker can be downloaded from Github, as can Perfkit Explorer. Source code has been released under the ASLv2 license, so anyone is free to participate in the future development of the tools. Unlike other benchmarking tools, PerfKit Benchmarker measures the end to end time to provision resources in the cloud.
This is not something that Google has been working on alone -- in fact there are many companies involved. Introducing the new tool, the Google Cloud Platform Performance Team said:
Over the last year, we’ve worked with over 30 leading researchers, companies, and customers and we're grateful for their feedback and contributions. Those companies include: ARM, Broadcom, Canonical, CenturyLink, Cisco, CloudHarmony, CloudSpectator, EcoCloud/EPFL, Intel, Mellanox, Microsoft, Qualcomm Technologies, Inc., Rackspace, Red Hat, Tradeworx Inc., and Thesys Technologies LLC. In addition, we’re excited that Stanford and MIT have agreed to lead a quarterly discussion on default benchmarks and settings proposed by the community.
PerfKit is described as "a living benchmark framework" which will change over time. With support for Compute Engine, AWS and Azure, the new tools offers a great way to determine which cloud service is the most suitable for different tasks.
Photo credit: OmniArt / Shutterstock
-

Safer Internet Day Google giveaway -- 2Gb of free Drive storage
Publié: février 10, 2015, 6:29pm CET par Mark Wilson
As it's Safer Internet Day today, lots of companies are getting in on the action and doing their bit to encourage people to be a little safer online. One such company is Google, and if you spend a few moments performing a quick security check, you can bag yourself 2GB of Drive storage for free.
There are no trick questions -- it's nothing more than ensuring that your Google account recovery information is up to date. You don’t get the extra space straight away, but you only have to wait until the end of the month for the start of the rollout.
Head over to the Security Checkup page and you can check that your mobile number, recovery email address and security question are all set up correctly. If anything needs changing, this is the time and place to do just that. Click All Done and, well, you're done!
While you're here you can also check your recent account activity -- keep an eye out for anything that looks suspicious -- and disable account access for apps that have been deemed "less secure". You can also check which apps, devices and sites have access to your Google account.
In a blog post Google points out that "Google Apps for Work and Google Apps for Education users are not eligible for the bonus storage but should still consider taking the Security Checkup." If you're a regular Drive user, there's not really any excuse not to take advantage of the offer. What are you waiting for?
-

Google turns virtual doctor with health advice through the Knowledge Graph
Publié: février 10, 2015, 12:07pm CET par Mark Wilson

We're a global nation of hypochondriacs; Google has revealed that 5 percent of search traffic comes from people looking for health and well-being information. To help with any queries you might have about your body and different conditions, the search giant has furnished Knowledge Graph with a raft of medical data.
Got a funny looking rash? Google could help you to determine whether you have something to worry about, or whether it's something that's likely to clear up on its own. Knowledge is power, and medical knowledge is what Google is trying to arm people with to avoid the worry that comes with uncertainty.
The problem with Googling health problem is that, ordinarily, the results that are thrown up are entirely uncurated. You might find some valuable advice, but you are equally likely to find quack advice which is potentially dangerous. The difference with the medical information made available through Knowledge Graph is that real doctors have been involved in information-gathering and fact-checking.
Introducing the feature in a post on the Google blog, Prem Ramaswami said:
We worked with a team of medical doctors (led by our own Dr. Kapil Parakh, M.D., MPH, Ph.D.) to carefully compile, curate, and review this information. All of the gathered facts represent real-life clinical knowledge from these doctors and high-quality medical sources across the web, and the information has been checked by medical doctors at Google and the Mayo Clinic for accuracy.
Of course Google wants to protect its back -- there's no guarantee that data provided through the Knowledge Graph is one hundred percent accurate, and it's certainly not going to be a complete replacement for visiting your doctor. There's the disclaimer:
That doesn’t mean these search results are intended as medical advice. We know that cases can vary in severity from person to person, and that there are bound to be exceptions. What we present is intended for informational purposes only -- and you should always consult a healthcare professional if you have a medical concern.
The feature will be rolling out over the next few days, and can be accessed on phones, tablets and computers -- just ask natural-language questions. For now it's US-only, but there are plans for a wider release as well as information about more conditions and treatments.
Photo credit: Africa Studio / Shutterstock
-

Need a bigger cloud? Microsoft has 100GB of free OneDrive storage for you!
Publié: février 10, 2015, 2:07am CET par Mark Wilson

It's difficult, if not impossible, to have too much storage space. There has been a slow, but steady move to the cloud, and there are numerous names vying for attention, from Google Drive and Mega to OneDrive. Numbers talk, and it's the amount of free space that can sway users to one service or another.
Google has been giving away Drive storage with Chromebooks for some time, and now Microsoft is getting in on the action. Agree to receive promotional emails through Bing rewards, and you can bag yourself an extra 100GB of OneDrive storage completely free of charge for the next two years. If you're in the US, that is. Or if you use a proxy...
It's a pretty straightforward offer. Pay a visit to the Bing Rewards page, click the OneDrive offer and then indicate that you're happy to "receive promotional emails from OneDrive". That’s all there is to it. Oh... it's worth noting that "you can unsubscribe at any time". It's not clear whether this will result in your free storage being removed, so you might want to set up suitable filters to prevent your inbox from filling up with junk.
Once the two years are up, you'll have to stump up the cash for the extra space or lose it, but until then, just enjoy the extra breathing room.
It seems that the offer is only officially available to those within the US, but there's nothing to stop you from using a proxy service to, say pretend you were in the US even if you're not. S'up to you...
-

Imgur Pro is now free for everyone
Publié: février 10, 2015, 12:26am CET par Mark Wilson
It’s a free for all as Imgur Pro goes free for all! The image sharing site is celebrating its sixth birthday by handing out gifts to its users rather than expecting to receive them. As of today, everyone is able to take advantage of unlimited storage on the site, but of course there is a -- very slight -- catch.
You don’t get owt for nowt, and the cost of free in this case is ads. Imgur has long been ad-supported, and now Imgur Pro has gone down the same route. Now that everyone has access to a Pro account, they have access to more than just extra storage space.
If you want to keep track of how popular the images you upload are, you can monitor this using image analytics, and you'll also gain access to extra thumbnailing options. Emails have been sent out to existing Pro subscribers, but the news was also broken in a post on the Imgur blog:
It’s been an amazing six years for Imgur. What began as a simple image uploading service has transformed into a community of the Internet’s most dynamic visual storytellers. Imgur has become the best place to explore, share, and discuss the Internet’s images–and we couldn’t have done it without your support and loyalty. We’re looking forward to many more years of uniting the universe through images with you.
Enjoy the free stuff!
Don't worry if you recently coughed up for a Pro subscription -- you might be able to get your money back. Providing you upgraded in the last 30 days, you are entitled to a full refund. If you're rocking a subscription, your account will remain ad-free until your subscription period runs out.
-

Is evolution rather than innovation the best focus for Apple's iOS 9?
Publié: février 9, 2015, 8:37pm CET par Mark Wilson

Asking someone to switch from their operating system of choice is akin to asking them to switch partners when they’re in a happy relationship. But time and time again, Apple, Google and Microsoft try to attract new users with redesigns, killer features, and headline-grabbing excitement. It's an approach that Microsoft is using for Windows 10, but Apple could use a different tactic with the release of iOS 9.
If you've got an iPad, iPad mini, iPhone 6 or iPhone 6 Plus, the next version of iOS could be slightly lacking in the 'new' department. Reports suggest that rather than taking the wraps off a raft of new features, Apple is instead focusing firmly on improving stability and performance of its mobile OS.
People who have complained that iOS 8 is a little portly will be pleased to hear that iOS 9 will see Apple trying to rein in the size of updates to keep those with less storage space happy -- at least this is the story according to 9to5Mac's sources. But what is more interesting is the idea that Apple is now more concerned with boosting performance and stability, as well as squashing bugs.
That's not to say that there won’t be any new features -- it would be difficult to imagine a new version of iOS being released with little more than bug fixes -- but it looks as though the shift from iOS 8 to iOS 9 might be less marked than moving from Windows Phone 8.1 or Windows 8.1 to Windows 10. It's a little while until we can expect to see the launch of iOS 9, so there's plenty of time for rumors and speculation to mount. As TechCrunch points out, 9to5Mac is usually reliable so even though the source of the information is unnamed, we're probably safe to have some faith in its accuracy.
iOS has recently managed to make inroads into Android's market share and it seems that Apple is now pulling a Microsoft and listening to its customers with a view to delivering what people actually want -- in this case, a solid, reliable OS rather than one dripping with new options or a completely new look. Moving forward Apple's view of software looks like it could more closely follow its attitude to hardware -- it's all about evolution rather than going for all-out innovation.
Photo credit: Ollyy / Shutterstock
-

$1 million prize goes to collision-resistant search and rescue drone
Publié: février 9, 2015, 7:37pm CET par Mark Wilson

A drone designed to help with search and rescue operations has won the top prize of $1 million in the Drones for Good contest. The contest was held in the United Arab Emirates and when we mentioned Drones for Good a couple of weeks ago, we highlighted the Gimball entry from Flyability. It seems it wasn't just us that was impressed with this drone, as Gimball went on to win!
The Swiss drone was designed as "the world's first collision-tolerant flying robot" and it can help with search and rescue operations without fear of damaging itself or people in the area.
Like other drones, Gimball offers incredible maneuverability, but the design here is unique. Surrounded by a geodesic cage which makes Gimball look a little like a flying gyroscope, the rugged framework keeps the drone itself safe from collisions whilst also protecting humans in the vicinity. Team leader Patrick Thevoz said:
We struggled to find funding to develop our search and rescue drone but this UAE Government Summit initiative, Drones for Good, means we can commercially develop our project within a year, and with Flyability able to go where it is dangerous for rescuers, help save lives.
The Drones for Good Award is the first of its kind. It is inspirational, because while there are many awards for academic research there aren't many for the social application of new technology. It allows passionate teams like us to move forward and make this a reality. The Drones for Good Award is a unique opportunity to help people realize that these flying machines are capable of positively impacting society.
The financial prize will be a great help to getting Gimball into production, so it shouldn't be long before we see more in action, helping out where they are needed most.
-

Google snaps up photo backup app Odysee in latest acquisition
Publié: février 9, 2015, 1:43am CET par Mark Wilson

The latest service to be gobbled up by Google is Odysee. Available as an app for iOS and Android devices, Odysee enables users to privately backup and share both photos and videos. In some ways the service is similar to the automatic backup feature provided by Google+, so it is perhaps unsurprising that the Odysee team will be joining forces with the Google+ team.
The mobile apps have been pulled from the App Store and Google Play by developer Nimbuzz Inc, but the service remains in operation for the time being. It's likely that the Odysee API is what sparked Google's interest, and it will be interesting to see how things move forward.
At the moment there's no hint at whether the features of Odysee will be integrated into Google+, or whether new apps and services could emerge. Google has confirmed that it is joining forces with Odysee to TechCrunch. A message on the Odysee website reveals that the service as it is currently known will cease to operate in a couple of weeks' time:
We are excited to share that the Odysee Platform Team will be joining the Google+ Team.
Odysee’s vision was to be the easiest way for everyone to capture unlimited memories and access them everywhere. We are very excited to join Google where we'll continue to focus on building amazing products that people love.
Our deepest thanks to every one of our users. To help you with the transition, the Odysee service will continue till Feb 23rd and soon after that all your photos and videos will be available as a downloadable archive.
If Google is moving into the arena of private photo sharing, it would mark an intriguing switch in focus, and adds fuel to the rumors that the company is considering splitting Google+'s photo features into a separate product.
Photo credit: violetkaipa / Shutterstock
-

How to automatically bypass Windows 10's login screen
Publié: février 8, 2015, 8:42pm CET par Mark Wilson
Like every version of Windows before it, Windows 10 has its share of standout features, and a few niggles here and there. If you're working with the Technical Preview, you may have seen our earlier guide to removing the desktop watermark. But this is not the only thing that can be irritating, you may be frustrated by the requirement to enter your password to login every time you power up.
As with previous versions of Windows, you can configure Windows 10 so that you are logged into your account automatically. This is great if you are the only person using your computer as it shaves valuable seconds off the startup process. If you're sick of typing your password, here's how to bypass Windows 10's login screen and log into your account automatically.
Unlike some tweaks, this particular tip does not require you to delve into the registry or fiddle with key system files. There is a built in feature that can be used to automatically log into a particular user account, but it's pretty well hidden -- you'd be forgiven for not spotting it on your travels through the operating system.
Hit the Start button, or press the Windows key, type netplwiz and then click the entry at the top of the list of search results. If you're feeling old-school, press the Windows key and R to bring up the Run dialog and execute the same command.
In the list of usernames that's displayed, select the entry for your account (if you see more than one that appears to be yours, opt for the one that's an Administrator). Uncheck the option labelled 'Users must enter a user name and password to use this computer'.
When prompted, enter your password -- for what will be the last time -- confirm it, and then click OK. That's it. Once you restart your computer, you'll be automatically logged into your chosen account. Simple!
Photo credit: Nata-Lia / Shutterstock
-

Waiting to take screenshots on Xbox One? The feature is coming soon
Publié: février 8, 2015, 6:06pm CET par Mark Wilson

Taking a screenshot of your gaming prowess on your Xbox One will soon be as simple as screenshotting your desktop on your computer. It's a feature that has been requested for a long time, and promised for almost as long. Now head of Xbox Phil Spencer reveals that work is well under way and the ability to take screenshots should be coming to gamers soon.
The ability to record in-game video is nothing new, but the simple option to grab a screenshot is something that Xbox One owners are still waiting for -- although PS4 owners have enjoed this abilty for a while. With access to development software, Phil Spencer tweeted, er, a screenshot, of the screenshot feature in action.
This is something that's certain to generate a lot of interest, but Spencer has given no indication of when the feature will be ready for primetime. He generated a good deal of interest by tweeting the image which shows that one button press will be used to record video, and another to grab an image of what's onscreen -- great for sharing proof of a high score, or keeping a record of a great move you managed to pull off.
Nice to finally be doing this on my Xbox One dev kit. pic.twitter.com/AgDDWr3ExJ
— Phil Spencer (@XboxP3) February 6, 2015
In response to queries from Xboxers on Twitter, Spencer went on to say that things are still being debugged at the moment, and that the Xbox team would reveal more in due course:
@hybriddialek Team will do a proper intro to the feature when it's ready for preview. UI and activation is all debug right now.
— Phil Spencer (@XboxP3) February 6, 2015
Gamers have been patient so far, and it looks like there's a bit more of a wait to endure.
Photo credit: 360b / Shutterstock
-

Inateck Surface Pro 3 felt sleeve tablet case [Review]
Publié: février 8, 2015, 1:23pm CET par Mark Wilson
![Inateck Surface Pro 3 felt sleeve tablet case [Review]](http://betanews.com/wp-content/uploads/2015/02/surface_pro_3_sleeve_front.jpg)
If you've dropped a few hundred dollars on a Surface Pro -- or even if you're one of the crazy few to have put your faith in Windows RT -- you want to protect your investment. One of the delights of the Surface Pro is that it is pleasingly svelte, even with the keyboard cover connected. So while you'll undoubtedly want to keep your Surface safe and secure, you probably don’t want to wrap it in armor casing that triples its size and weight.
Filling the gap in the market between full-blown laptop case and simple slip cases comes the Inateck Surface Pro 3 felt sleeve. Described variously as a Surface Case Cover, Laptop Bag, Felt Sleeve, Surface Pro 3 Sleeve Case Protection, and a Surface Pro 3 Sleeve, the felt case provides a surprisingly protective home for your tablet, and packs a few pleasing extras.
The case is made of the same soft, thick felt throughout, meaning the screen of your Surface will be secured against scratches whether you have a keyboard cover connected or not. This is not a case that's going to withstand drops from a great height onto concrete, but there's ample cushioning to protect against bumps, scrapes and knocks. This is referred to as a Surface Pro 3 case, but it suits the smaller Surface Pro and Surface Pro 2 just as well -- there's just a little more breathing room with the smaller versions.
![Inateck Surface Pro 3 felt sleeve tablet case [Review]](http://betanews.com/wp-content/uploads/2015/02/surface_pro_3_sleeve_with_surface.jpg)
Slip your Surface into the sexy, felty folds.
In front of the main tablet compartment is another smaller compartment, accessible through a narrower slit. This is ideal for small items such a notebooks, pens, and other relatively flat bits and pieces that you might want to take on the road with you. A flap Velcros in place to keep the contents of these two compartments secure.
Flip to the rear and you'll find two more little compartments. These are just the right size for slipping in a phone or MP3 player, but it's important to remember that there's nothing to keep the contents in place if you turn the case upside down.
![Inateck Surface Pro 3 felt sleeve tablet case [Review]](http://betanews.com/wp-content/uploads/2015/02/surface_pro_3_sleeve_back.jpg)
Extra pockets provide storage for extras you might need to carry.
The case is not without its problems, however. Like all cases of its ilk it suffers with a lack of storage for the bulky charger that's so essential to extended periods of work. With this in mind, you might want to consider this a case you would use only for short trips out with your Surface -- if you're planning a full day away from home working around the clock, you'll need to carry the charger separately, or look to a different case.
On top of this, if you're the type of person who eschews the Surface's trackpad in favor of a mouse, you may be disappointed to find that there's not really room to carry such a peripheral in the case. You could slip a mouse into one of the various pouches, but this would ruin the sleek lines and run the risk of damage. To help overcome this, Inateck includes a small mouse-sized secondary pouch made of the same felt as the main case. This is a nice touch, but at the same time, it's slightly annoying to have to carry something extra.
![Inateck Surface Pro 3 felt sleeve tablet case [Review]](http://betanews.com/wp-content/uploads/2015/02/surface_pro_3_sleeve_with_surface_standing.jpg)
The matching mouse case is a nice touch, but something extra to carry.
For all the talk of Surface, there's nothing to stop you from using the case to house other tablets. The 33.5cm (13.1 inches) by 23cm (9 inches) dimensions are quite accommodating, but there are also specific versions available for 15 inch Macbooks, iPad Airs and iPad minis.
There's an MSRP of $38.99, but at the moment it is possible to buy the sleeve with a $22 discount. Hit the Inateck website to order yours.
-

Thanks to Snowden, NSA-GCHQ surveillance data sharing is now legal
Publié: février 6, 2015, 3:45pm CET par Mark Wilson

A secret UK court has ruled that the UK's intelligence agency GCHQ acted unlawfully by intercepting information gathered by the NSA. Investigatory Powers Tribunal said that because the rules surrounding the UK’s access to the NSA's PRISM and UPSTREAM program data were secret, data sharing between the US and UK was illegal. A case has been brought against GCHQ by Privacy International, Bytes for All, Liberty, and Amnesty International.
But while the IPT said that accessing this information breached human rights laws this is no longer the case. Why? The illegality of sharing data collected through these surveillance programs centered on the very fact that they were secret. In blowing the whistle about what the NSA was doing, Edward Snowden unwittingly made this data sharing legal. Whoops.
The IPT's ruling states that GCHQ's access to NSA data was illegal before December 2014, but after this time the documents revealed by Snowden has brought the sharing of gathered intelligence to the public attention -- it is now legal. The activities of the NSA are now something we are all too aware of. This is largely thanks to the revelations made by Snowden which led to a massive surge in public interest about government monitoring of web usage.
Few would have suspected, however, that the documents leaked by Snowden would end up making the activities legal. The new ruling says that
...prior to the disclosures made and referred to in the Tribunal's Judgment of 5 December 2014 and this judgment the Prism and/or Upstream arrangements contravened Articles 8 or 10 ECHR, but now comply.
So when we didn’t know about what was going on, it was illegal. Now that we do know about it, it's legal. The ethical and legal rights and wrongs of the surveillance have been questioned by many, and today's ruling will do little to silence those opposed to what is going on. Deputy director of Privacy International, Eric King, said:
The only reason why the NSA-GCHQ sharing relationship is still legal today is because of a last-minute clean-up effort by Government to release previously secret 'arrangements'. That is plainly not enough to fix what remains a massive loophole in the law, and we hope that the European Court decides to rule in favor of privacy rather than unchecked State power.
Privacy International and Bytes for All are now calling for the deletion of all data collected before December 2014. The two groups will also continue to fight against GCHQ access to NSA-gathered information, and the ruling is seen as being very bittersweet. James Welch, Legal Director for Liberty, said:
We now know that, by keeping the public in the dark about their secret dealings with the National Security Agency, GCHQ acted unlawfully and violated our rights. That their activities are now deemed lawful is thanks only to the degree of disclosure Liberty and the other claimants were able to force from our secrecy-obsessed Government [...] The Tribunal believes the limited safeguards revealed during last year's legal proceedings are an adequate protection of our privacy. We disagree, and will be taking our fight to the European Court of Human Rights.
Photo credit: Bocman1973 / Shutterstock
-

YouTube's automatic subtitling 'makes absolutely no sense'
Publié: février 5, 2015, 8:05pm CET par Mark Wilson

For the deaf and hard-of-hearing, subtitles are essential. Blu-rays, DVDs and TV shows usually feature subtitling as an option, and it's also something that crops up on streaming media such as YouTube videos. The Google-owned video site attempts to automatically add subtitles to videos, but the feature leaves a great deal to be desired.
You may have noticed this for yourself but if not, vlogger Rikki Poynter would like to bring it to your attention. Rikki, who is hard-of-hearing, complains that YouTube's subtitling is often "completely nonsensical". YouTube acknowledges that it has a long way to go.
Rikki is an active YouTube user and says that the automatic subtitling feature "makes absolutely no sense 99 percent of the time". But the vlogger is not just complaining, she is campaigning to try to get things improved. Talking to the BBC, she explains that because the automatic feature is so unreliable, more video uploaders should add subtitles manually.
The sheer volume of footage uploaded to the site every minute of every day means that YouTube has quite a task on its hands. But product manager Matthew Glotzbach says that the technology is just not quite good enough yet:
Although I think having auto caption is better than nothing I fully admit and I fully recognize that it is by no means good enough yet. It's an area that we've been committed to really from the beginning. Frankly, it's really hard computer science problem that hasn't been solved at that scale yet.
Rikki's campaign is gathering momentum and supporters in growing numbers, and YouTube says that investments are being made to make it easier for corrections to be made to subtitles that go awry.
Check out the video below to see Rikki explaining more about what she hopes to achieve -- and you can also find out how to add subtitles to your own videos:
Photo credit: FMStox / Shutterstock
-

Facebook will urge UK users to register to vote
Publié: février 4, 2015, 7:10pm CET par Mark Wilson

If you're in the UK, your Facebook feed might look slightly different tomorrow (Thursday). In addition to the usual bitching and moaning, cat videos, and lists of eight things you didn’t know about your friends, you may well also see a reminder to register to vote in May's General Election.
Why? Well Thursday 5 February is the excitingly named National Voter Registration Day, and the Electoral Commission has teamed up with Facebook to try to up voter numbers. The idea is riding the wave of interest in politics that swelled around the Scottish referendum on independence, and it is hoped that more young people will be encouraged to register in time to cast their vote at the ballot box.
What's different about 2015's General Election is that it is the first time people are able to register online to vote, although online voting is still a distant dream. While it is possible to register online, research shows that this is something few people realize. With so many people making use of social networks, it seems like the natural medium through which to reach voters. Banners will appear at the top of the newsfeed of those who will be of voting age directing them to register to vote on the Gov.uk portal.
All political parties are keen to attract younger voters, and the Scottish referendum -- a vote in which people as young as 16 could play their part -- showed that there is greater interest in politics from this age group than in the past. For the General Election, however, the voting age remains at 18, and it is people who will be voting for the first time who are particularly being encouraged to register.
To help spread the news further, anyone who does register to vote is invited to share this fact on their newsfeed.
Photo credit: nfsphoto / Shutterstock
-

Grab yourself a free copy of Office for Windows 10 Technical Preview now
Publié: février 4, 2015, 5:47pm CET par Mark Wilson
A couple of weeks ago we learned a little about what to expect from Office for Windows 10. Today Microsoft has made the universal apps for Office for Windows 10 available for download. In order to grab yourself the preview software, you need to be running Windows 10 Technical Preview build 9926 as the apps are being made available through the new Windows Store Beta.
For now, the Word, Excel and PowerPoint apps that make up Office for Windows 10 are available for PCs, laptops and tablets running Windows 10 Technical Preview, but this will open up in due course to phones as well.
Like the Windows 10 Technical Preview, the preview versions of Word, Excel and PowerPoint are available free of charge -- for now. The store listing explains that: "You can use most functionality in Word preview for free. After preview, some functionality will require a qualifying Office 365 subscription".
As revealed two weeks ago, Office for Windows 10 is a series of universal apps. The only reason the apps are not currently available for phones is the fact that Windows 10 has not yet been made available as a preview for such devices. Today's announcement about the availability of the preview builds makes no mention of any changes that have been made in the intervening fortnight, but it's likely that -- just like with Windows 10 itself -- there will be numerous updates in the weeks and months before the official release.
The preview of OneNote was launched at the same time as the build 9926 of Windows 10 Technical Preview, and now you have three new apps to take for a test drive.
-

Can you trust crowdfunding projects? Not in the UK
Publié: février 4, 2015, 4:20pm CET par Mark Wilson

Crowdfunding is now an incredibly popular way for startups and individuals to get the funding to get their projects off the ground. It's certainly an interesting approach to things. Ideas that might not otherwise come to fruition receive the money they need to hit production, further development and so on, and investors get the chance to be involved in something from a very early stage, and possibly reap the benefits when it hits the big time.
But in the UK the Financial Conduct Authority found that most British crowdfunding websites were less than honest with the information shared with potential investors. Specifically, the regulator warns that companies are being selective about the information that is shared with would-be investors, whilst simultaneously underplaying the risks that might be involved.
The Financial Conduct Authority (FCA) warned that some sites using this method of seeking funding misrepresented themselves by deleting negative comments left by others. But the real cause for concern was the finding that many sites were giving investors a "misleading or unrealistically optimistic impression of the investment". The regulator has already introduced concern about "equity crowdfunding" -- this differs from the type of crowdfunding found on Kickstarter as investors expect to get a return on what they put in rather than just settling for incentives.
As well as the dishonesty unearthed by the FCA, there were also concerns that many of the investors who ploughed money into startups had little or no previous experience of investing. Speaking to the Wall Street Journal, chief executive of crowdfunding company Seedrs, Jeff Lynn, said that he expects more than half of the startups (up to 80 percent) using his platform to raise money will fail.
There is talk of European regulation being introduced to help to protect investors, but there is currently no timescale for this.
Photo credit: Andrey_Popov / Shutterstock
-

iOS outsells Android in US for the first time since 2012
Publié: février 4, 2015, 11:52am CET par Mark Wilson

The latest figures published by Kantar Worldpanel show that US sales of iOS devices are outpacing those of Android handsets. Just. Buoyed by the launch of the iPhone 6 and iPhone 6 Plus, Apple saw sales figures rising across Europe, the US and in China, with the smaller of its two smartphones proving to be the best-selling handset in the US.
Overall, iOS devices accounted for 47.7 percent of smartphone sales, just managing to edge ahead of Android which dropped slightly to a 47.6 percent market share. The holiday period was key to this switch in popularity, as the iPhone 6 proved the most popular gift in 2014. But it's not just in the US that Android is losing its grip on the market.
In Europe -- or the five biggest markets, Great Britain, Germany, France, Italy and Spain -- iOS enjoyed a 6.2 percent jump in the share of sales, while Android dropped 3.8 percentage points from the previous year. While Great Britain saw iOS's sales increase by 13.1 percentage points, Android's share of European sales dropped to 66.1 percent.
Carolina Milanesi, chief of research at Kantar Worldpanel ComTech, said: "In the US, Apple iOS overtook Android for the first time since this time in 2012, albeit by the slimmest 0.1 percent margin. While the success of the iPhone 6 and 6 Plus is unprecedented, this quarter’s performance also points to Apple having its strongest portfolio ever. With a range of devices available at different price points in both contract and pre-pay Apple was able to take advantage of a weaker Android offering at the premium end of the market".
Coming in second place behind the iPhone 6, Samsung's Galaxy S5 was the second most popular handset in the US, but Italy was the only European market in which Android sales grew. For Windows Phone, it is pretty much business as usual. Sales remain low in the US (3.8 percent) and China (0.7 percent) and while things look slightly brighter in Europe, a 9 percent share of sales still represents a 1 percentage point drop. There was, however, slight growth for Windows Phone in France and Germany.
Photo credit: charnsitr / Shutterstock
-

'Stop using Windows Server 2003!' says Microsoft
Publié: février 4, 2015, 12:30am CET par Mark Wilson

Microsoft is encouraging users to migrate away from Windows Server 2003. Support for the 12 year old operating system comes to an end in the middle of July, and companies are encouraged to seriously consider moving to Windows Server 2012 R2, Microsoft Azure, or Office 365.
Previously published figures suggest that most of those who are yet to upgrade from Windows Server 2003 will do so before the end-of-life deadline. But this still leaves around a fifth of businesses who have to consider what action to take.
For companies who are yet to put migration plans in place, the timing is now a little awkward. The launch of Windows Server 10 is not too far away so those keen on ultimately making the switch to the latest (and presumably greatest) operating system have a couple of choices.
Firstly, they could continue to use Windows Server 2003 without support until Windows Server 10 RTM makes its way out of the door, or they could jump to Windows Server 2012 R2 as a stop gap measure and then upgrade to Windows 10 in due course -- of course, this involves additional cost.
With Microsoft’s current infatuation with the cloud, it should come as little surprise that Azure and Office 365 are being pushed. In a post on the Microsoft blog, Takeshi Numoto -- Corporate Vice President of Cloud and Enterprise Marketing -- explained the risks associated with sticking with Windows Server 2003 after the support period comes to an end:
Windows Server 2003 instances will, of course, continue to run after end of support. However, running unsupported software carries significant security risks and may result in costly compliance violations. As you evaluate security risks, keep in mind that even a single unpatched server can be a point of vulnerability for your entire infrastructure.
To illustrate just how far we have come in a relatively short period of time, Numoto points out that the power of most modern smartphones far exceeds the minimum system requirements of Windows Server 2003. But demands have also increased. He also goes on to suggest that some customers may be under a legal obligation to upgrade from the aging software:
Important financial and healthcare regulations also include provisions around security: US PCI DSS section 6.1 states that all organizations must “ensure that all system components and software are protected from known vulnerabilities by having the latest vendor-supplied security patches installed,” while HIPAA section 164.308(a)(1)(ii)(B) states that covered entities must “implement security measures sufficient to reduce risks and vulnerabilities to a reasonable appropriate level.” Industry regulations are often country specific, so you should consult your legal, security and audit teams to ensure you understand your compliance landscape.
The costs associated with upgrading server software are not insubstantial, and Microsoft suggests that companies might want to consider replacing physical servers with Hyper-V alternatives.
Photo credit: Macrovector / Shutterstock
-

What's the point of AdBlock Plus if Google, Microsoft and Amazon can pay to bypass it?
Publié: février 2, 2015, 10:31pm CET par Mark Wilson

Ads are pretty much universally hated; in the list of lovable things in the world, ads rank pretty far down. On TV, in movie theaters, in magazines and online, ads are forced upon us and are impossible to avoid. Except that's not true online. Ad-blocking software can be used to filter out the stuff you don’t want to see, making for a happier web browsing experience.
But it turns out that installing an ad-blocking tool like, ooh... I dunno... AdBlock Plus... is not enough to prevent the appearance of unwanted advertisements. Some time ago we learned about the whitelist operated by AdBlock Plus and now the Financial Times reports that that big companies like Google, Microsoft and Amazon have paid to be included on the list so their ads are no longer blocked.
Back in 2013, we learned that advertisers could apply to be included on the whitelist. Just 9.5 percent of those who applied were actually added to the list, and Adblock Plus' Ben Williams explained that "over 90 percent get whitelisted for free". But what about the remainder?
While the Financial Times does not reveal the dollar amounts that are involved, the newspaper was able to confirm that Google, Amazon, Microsoft and Taboola (which the FT says " sometimes serves racy content") have all cut deals with AdBlock Plus so their ads are no longer blocked. Users of the browser plugin can opt out of seeing ads on the whitelist, but Eyeo (the company responsible for AdBlock Plus) is obviously keen for as many users as possible see them.
Much like the idea of net neutrality, there's something of a feeling of inequality about this. While it is claimed that the majority of whitelisted companies have not paid for the privilege, there must be some reason why the big names have coughed up the cash. Could it be that their ads are given greater priority? Are those with the fattest wallets able to punch larger holes in the ad blocking barriers?
Writing for the Financial Times, Robert Cookson says:
The deals, which are confidential but whose existence has been confirmed by the Financial Times, demonstrate that some of the biggest participants in the $120bn online advertising market see the rise of ad-blocking as a material threat to their revenues.
Advertising is key to the survival of many web sites, but when users take conscious steps to control the content they are forced to view using a tool designed for this very purpose, it is only right that there be a greater degree of transparency. Does money talk? Can AdBlock Plus be trusted to respect the wishes of its users?
While there is money to be made by websites through ads, it seems that AdBlock Plus is also able to make a tidy income. Cookson reveals:
One digital media company, which asked not to be named, said Eyeo had asked for a fee equivalent to 30 per cent of the additional ad revenues that it would make from being unblocked.
Is it acceptable to be able to pay to bypass restrictions? Does it matter if users are told one way or the other?
Photo credit: Warner Bros.
-

How to remove the build number watermark from Windows 10's desktop
Publié: février 2, 2015, 4:57pm CET par Mark Wilson
Hundreds of thousands of people around the world are currently running Windows 10 Technical Preview ahead of the official launch. While it's fun to try out a pre-release of the upcoming operating system it does mean having to put up with a few problems here and there, as well as the occasional niggle.
One thing that irks many Technical Preview users is the fact that the current build number is emblazoned on the desktop. It doesn’t really get in the way, but it looks kind of ugly. If you'd like to get rid of this unsightly watermark, there's no need to tinker with the registry or hack files by hand -- there's a nifty tool that will take care of it for you.
The suitably-named Universal Watermark Disabler is available free of charge, and can be used to remove the unwanted text from the lower right hand corner of your desktop. You can enjoy your chosen desktop wallpaper in full, unadulterated glory... Hooray! Start by grabbing yourself a copy of the tweaking tool from the Winaero website and then extract the zip file. If you're using Windows 10 Technical Preview on your main machine, or just don’t want the hassle of reinstallation if anything goes wrong, now's the time to create a backup.
Having taken whatever precautions you deem necessary, right click the UWD executable and opt to run it as administrator. Hit the Install button in the window that appears and then click OK to complete the process by signing out of your user account.
Sign back into your account, and the job's done. Get ready to enjoy your watermark-free copy of Windows 10 Technical Preview! Should you ever want to revert to displaying the build number on the desktop, simply run Universal Watermark Disabler again and select the Uninstall option.
You may find that future build updates bring the watermark back -- just run the tool again and it can be removed.
Photo credit: Zadiraka Evgenii / Shutterstock
-

The ease of upgrading to Windows 10 all but guarantees its success
Publié: février 2, 2015, 1:49pm CET par Mark Wilson

People don’t like change. Well, people don't like change for the sake of change -- if it ain't broke, don't fix it, and all that. But people also don’t like things to stay the same. People are fickle buggers, when you come to think of it, and this is one of the reasons Windows 8 proved to be such a disaster. Windows 10, on the other hand, is almost guaranteed to be a runaway success.
Uptake of the preview builds has already been impressive, but the ease with which it's going to be possible to make the upgrade -- be it from Windows 7 to Windows 10, or from a preview build to the RTM release -- is going to be key to the operating system's success. Why? As well as being fickle, people are suckers for 'easy'; Microsoft has made upgrading to Windows 10 RTM as easy as possible.
Build 9926 of the Technical Preview introduced a new way to upgrade -- through Windows Update. This will, I believe, be key to the success that Windows 10 is almost certain to enjoy. Although Windows 10 Technical Preview has been billed as a release for developers and the like to tinker with, there has been great interest from everyday enthusiasts. For anyone who doesn't want to go to the hassle of fiddling with ISO images, Windows 7, Windows 8 and Windows 8.1 can all be 'upgraded' to the latest build of the Technical Preview through Windows Update.
This is unique in the history of Windows, and the same upgrade model is set to continue when the RTM build of Windows 10 is ready. Add in the fact that the upgrade will be free and it's hard to imagine that most people won't make the jump. Many people who did make the move to Windows 8 (yes, there were a few) are ready to leave it behind -- if they haven't done so already -- and it's certainly time for Windows 7 users to look to the future.
By blending the best bit of Windows 7 and Windows 8 together with some intriguing new options, whilst pushing some of Windows 8's more irritating features into the background, I would be very surprised if we don’t see massive uptake of Windows 10. People are ready for change, but not too much. Windows 8 tried to be revolutionary and failed. Windows 10 is evolutionary and is already being well-received.
But there is still the obstacle of the upgrade process to take care of. Microsoft has spent years pushing the importance of using Windows Update, so it makes perfect sense to use this as the delivery system for Windows 10. From a consumer's point of view it just makes things as easy as possible, eliminating the need to mess about with physical media and the update process for systems running Windows 7 is already being tested to help iron out problems. Keeping things simple is important for everyone involved, and coupled with the lack of a price tag, it's conceivable that many people will be tempted into upgrading to Windows 10 just to see what it's like -- there are so few obstacles standing in the way of an impulse upgrade.
With Windows 10, Microsoft has made two brave decisions. Making the operating system free for all but enterprise users is a surefire way to get people's attention, and delivering the upgrade through a tried and tested channel only serves to grease the wheels further.
-

Obama's proposed overseas earnings tax could hit Microsoft, Google and Apple hard
Publié: février 2, 2015, 12:16am CET par Mark Wilson

It is common practice for companies to take steps to reduce their tax bills. One common technique is to channel money through overseas branches, taking advantage of countries that require payment of little or no taxes. If the President's plans to pull in taxes from multinational companies' overseas earning, the likes of Amazon, Apple, Google and Microsoft could be facing hefty bills.
While the proposed 14 percent tax rate is far lower than the usual 35 percent, it could still top up US coffers by up to $238 billion. In addition to a one off tax payment on money currently held overseas, Obama is looking to slap a 19 percent corporation tax on earnings moving forward.
Large numbers of companies, but particularly technology giants like Amazon and Apple, take advantage of tax schemes in Ireland (among other countries) to slash millions of dollars from their annual tax bills. Ireland had previously announced that it was planning to cut back on the use of such loopholes, and Obama's proposals echo those introduced by the UK -- late last year, George Osborne introduced a 25 percent tax on earnings generated by companies' activities in the UK, but funneled through other countries.
Obama's budget is due to be unveiled on Monday, but details were released to media outlets. Making companies cough up for taxes is something that is likely to go down well with the nation, but just to sweeten things even more the President has outlined how the recouped money will be spent -- helping to fund repairs and expansion of the road infrastructure.
Speaking to the Guardian, an anonymous White House spokesperson said:
These investments would be paid for by closing tax loopholes as part of reforming the business tax rules to level the playing field and make sure everyone pays their fair share [...] After this initial payment, foreign earnings could be reinvested in the US without additional tax, which would [...] encourage firms to create jobs here at home.
The budget is unlikely to be well-received by Republican opponents, but it does continue the theme of the State of the Union address which referred to the idea of wealth redistribution.
Microsoft, Apple, et al are yet to respond to the tax proposals, but we'll almost certainly hear from them in the next couple of days.
Photo credit: JohnKwan / Shutterstock
-

Warning -- Microsoft's new iOS Outlook app is insecure
Publié: février 1, 2015, 8:07pm CET par Mark Wilson

After buying Acompli late last year, Microsoft didn’t take long to rebrand the mobile email app as Outlook and launch Android and iOS versions. But it seems that in the rush to get the app out of the door, Microsoft failed to ensure that it was suitably secure.
In fact, IBM developer René Winkelmeyer suggests that enterprise users stop using the app immediately. He was shocked to discover a trio of security issues in the mobile version of Outlook. Perhaps the most worrying discovery is that users' personal credentials are stored in the cloud -- username and password included.
Winkelmeyer made the discovery after disabling the app and sending himself an email from a second text account. Despite having stopped the app, he received a push notification letting him know of the new email. Investigating further by looking at server logs, Winkelmeyer found that his mail account was being scanned by an AWS IP address without his permission.
Security concerns also surround the fact that Outlook has built-in connectors to OneDrive, Dropbox and Google Drive to allow for easy attachment of files stored in any of these cloud services. But it is also possible to share email attachments through these services -- something that will be greatly concerning for businesses. Malware, anyone?
Completing the trio of security concerns is the fact that the iOS Outlook app does not differentiate between multiple devices used by an individual. You might install the app on an iPhone, an iPad, and an iPad mini -- the same ID will be used each time.
The advice from Winkelmeyer at this stage is simple:
The only advice I can give you at this stage is: block the app from accessing your companies mail servers. And inform your users that they shouldn't use the app.
It is the sharing of user credentials that is particularly concerning, but the sheer number of issues that have been highlighted will make many people think twice about using the app -- Winkelmeyer does have some tips, however. What's interesting is that while the Android version of Outlook is listed as a preview, the same tag has not been applied to the iOS version.
Photo credit: gst / Shutterstock
-

Windows 10 for enterprise will not be free, splits into two upgrade branches
Publié: janvier 31, 2015, 6:06pm CET par Mark Wilson

There aren't many people who don’t like the sound of "free", and this was one of the keywords taken away from Microsoft's Windows 10 event earlier in the month. As build 9926 was unleashed on eager upgraders, Microsoft revealed that it will be free to upgrade to Windows 10 in the first year.
At least this is the case for the average consumer; it's something of a different story for enterprise customers. Microsoft has confirmed that Windows 7 Enterprise and Windows 8/8.1 Enterprise are not versions that will be eligible for a free upgrade -- this is the personification of Windows as a service.
In a blog post, Microsoft explains a little about how Windows as a Service will work, and what it will mean for customers. There's no word on pricing at this stage, but Jim Alkove does reveal a little about how the enterprise version of Windows 10 will be updated and how the update process can be customized to suit individual customer needs. Alkove also announces that there will be two different branches of Windows 10 for enterprise, the Long Term Servicing branches and the Current branch for Business.
But what does this actually mean?
The Long Term Servicing branches have a security focus and will not receive all of the same updates as the consumer version of Windows 10.
To support Windows 10 devices in these mission critical customer environments we will provide Long Term Servicing branches at the appropriate time intervals. On these branches, customer devices will receive the level of enterprise support expected for the mission critical systems, keeping systems more secure with the latest security and critical updates, while minimizing change by not delivering new features for the duration of mainstream (five years) and extended support (five years).
The aim is to ensure that key systems are not taken out of operation by updates that are not completely essential, and are not subjected to updates that have not been fully tested.
The Current branch for Business works in a slightly different way. This branch will be able to access the same updates as consumers, but on a timescale that suits individual businesses. It takes advantage of testing done by Windows Insiders, and updates can be deployed automatically through Windows Update, or via WSUS.
This renewed flexibility is a sign not only of Microsoft listening to its customers, but also the particular ethusiasm for Windows 10 to be more of a success than Windows 8.
Photo credit: woaiss / Shutterstock
-

British army's 77th Brigade to wage psychological war on Facebook
Publié: janvier 31, 2015, 4:47pm CET par Mark Wilson

The British army is creating a new battalion of online soldiers in the form of the 77th Brigade. Hundreds of recruits will make up the division and will engage in "non-lethal warfare" on Mark Zuckerberg's social network from April.
The 77th Brigade will engage in psyops (psychological operations) to try to influence the opinions of civilians in certain parts of the world, as well looking to change the behavior of those engaged in various forms of warfare. The activities of groups such as ISIS (Islamic State) have shown the importance of the internet in general, but social networks in particular, to spreading ideas, messages and propaganda, and this is what the army is looking to manage.
In many ways, what the brigade will be doing is deploying propaganda of its own. It is a very public acknowledgement of the idea that wars are not won solely through violent means, and the army says that it will be using the "traditional and unconventional". An army spokesman said:
77th Brigade is being created to draw together a host of existing and developing capabilities essential to meet the challenges of modern conflict and warfare. It recognises that the actions of others in a modern battlefield can be affected in ways that are not necessarily violent.
Facebook has previously said that it will not block violent videos by default -- although it does pander to requests from some countries like Turkey when it comes to blocking insulting material -- but it has generally steered away from causes with more political leaning. Facebook has clearly been targeted by the army because of its size, reach and popularity, but it is somewhat unusual for the military to become so publicly involved, using the social network as a tool against foes.
As terrorists, guerrilla outfits and intelligence agencies make use of the web, it does make sense for other forces to do so as well. Whether the 77th Brigade turns out to be more than a spin and PR machine remains to be seen.
Photo credit: i4lcocl2 / Shutterstock
-

Jay Z to buy HD music streaming service Tidal
Publié: janvier 30, 2015, 8:41pm CET par Mark Wilson

Rapper Jay Z is spreading his wings outside of the world of hip hop, and venturing into music streaming territory. The musician's company, Project Panther Bidco Ltd is buying the Swedish company Aspiro, the owner of HD streaming music service Tidal for $56m.
The purchase will also see Jay Z acquiring Aspiro's other streaming service WiMP, but it is the quality-focused Tidal that is of particular interest. It will pit Jay Z against the Apple-owned Beats as well as the likes of Spotify.
Both Tidal and WiMP have great potential for expansion. WiMP has been around since 2010, but as it is currently only available in a handful of countries -- Denmark, Germany, Norway, Poland and Sweden -- the ad-free service has a user base of just over half a million. The more recently launched (2014) Tidal loudly proclaims its delivery of lossless sound on its homepage, and it has received positive reviews, despite its relative use.
The quality streaming music market is one that remains relatively untapped, so Jay Z could well have come in on a lucrative business. With subscribers in the US and UK paying a monthly fee of $19.99 (or £19.99) this is a music service for serious music fans and audiophiles who will appreciate the lossless FLAC and ALAC formats that are used.
While the deal has yet to be finalized, the main Aspiro shareholder Schibsted has accepted the offer from Project Panther Bidco Ltd, and Reuters reports that the Aspiro board is united in backing the bid.
Photo credit: landmarkmedia / Shutterstock
-

Windows 10 updates -- new Surface Pro graphic driver, new Windows Phone Windows Insider App
Publié: janvier 30, 2015, 4:42pm CET par Mark Wilson

We're gradually moving towards the official release of Windows 10, but in the meantime we have the Technical Preview to work with -- Build 9926 specifically. As we're only at the preview stage, it is to be expected that there will be a few issues here and there.
The good news is that Microsoft is working on fixing these problems, not just for the eventual RTM release of Windows 10, but also the preview builds. Surface Pro 2 and Surface Pro 3 owners complained about problems with stability when watching videos, and this has been addressed with a driver update.
If you're a Pro user who has been experiencing issues in Windows 10, just hit Windows Update and you'll find an updated Intel graphics driver waiting for you to download and install. The availability of the update was announced with little fanfare by Windows Insider Chief Gabe Aul who got straight to the point:
#WindowsInsiders using Surface Pros with 9926: there is a new graphics driver on WU that should improve stability for you.
— Gabriel Aul (@GabeAul) January 30, 2015
This is not the only Windows 10 related update hitting the downloading servers; there's also an update to the Windows Insider app for Windows Phone. As pointed out on Super Site for Windows, the app doesn't show up if you search the store for it, but you can grab a copy from a direct link.
The previous version of this app was all but useless as it was essentially an internal build, but now it is possible to sign in using a Microsoft account. Nothing is showing up at the moment, but it could mean that we're on the verge of seeing a preview build of Windows 10 released for mobile devices.
-

Doxing: what it is, and how to avoid it happening to you [infographic]
Publié: janvier 30, 2015, 12:49pm CET par Mark Wilson
![what it is, and how to avoid it happening to you [infographic]](http://betanews.com/wp-content/uploads/2015/01/what_is_doxing.jpg)
There are many potential dangers to using the internet, and most people are familiar with the idea of identity theft, unauthorized access to online accounts and the like. But there's another hazard which has come to prominence recently: doxing. The idea is not new, having its roots back in the 90s, but there have been numerous high profile cases of celebrities who have fallen victim to "document dropping".
This involves releasing personal information about someone to the internet -- information that could be embarrassing, personally revealing, or something that the victim would just rather keep to themselves. Interestingly, doxing is not necessarily illegal, but that doesn't mean that the ramifications are not far-reaching.
While doxing is something that is often carried out by hackers, it's not necessarily the case. Nearly all of us publish massive amounts of personal information online, and this can be very easily pieced together and used to gain access to even more data.
It is thought that 2015 is going to be the year in which doxing really hits the headlines, and Studyweb.com has produced an infographic that explains areas of risk, and the steps that can be taken to avoid falling victim.

What is Doxxing and How Can You Avoid It? [Infographic] by the team at studyweb.com
-

If your internet connection isn't at least 25Mbps, it's not broadband
Publié: janvier 30, 2015, 1:00am CET par Mark Wilson

For a long time, the official definition of a broadband connection is one that delivers a download speed of at least 4Mbps. Now the FCC has increased the lower limit so any connection that has a download speed of less than 25Mbps and an upload speed below 3Mbps will no longer be considered a broadband connection.
If you look at your line stats and feel a little let down, you're far from being alone, and the FCC feels your pain. The Federal Communications Commission voted to increase the minimum speed as part of an ongoing effort to push ISPs into offering higher speeds. The reason? The modern web demands it.
The average download speed available in the US is just over 10Mbps, so according to the FCC's new definition, a surprisingly large number of Americans do not have a broadband connection. While the problem is not too bad in urban areas, it's a very different tale for those living in more rural areas. It is hoped that by changing the threshold for what can be described as "broadband", ISPs will increase investment in boosting speeds -- few ISPs would want to be seen offering something other than broadband.
On Twitter, Gigi Sohn from the FCC revealed the figures that will sound familiar to those living in less densely populated parts of the country:
53% of rural Americans, 17% of all Americans don't have access to 25/3 broadband speeds.
— Gigi Sohn (@GigiBSohnFCC) January 29, 2015
FCC Chairman Tom Wheeler used Twitter to share the news and employed a hashtag to indicate his support for increasing speed further:
My colleagues & I voted to increase #broadband speed benchmark to 25/3 Mbps to reflect consumer demand & tech advances #FasterInternetForAll
— Tom Wheeler (@TomWheelerFCC) January 29, 2015
Growing demand for streaming video is partly responsible for greater bandwidth demand, and the relentless increase in image quality means that this is something that is set to continue. While 25Mbps is a marked improvement on 4Mbps, it is still not enough for some; FCC member Jessica Rosenworcel wants to quadruple this figure:
We invented the internet. We can do audacious things if we set big goals, and I think our new threshold, frankly, should be 100Mbps. I think anything short of that shortchanges our children, our future, and our new digital economy.
Photo credit: Sam72 / Shutterstock
-

US firms don't want to hand over source code and provide backdoors to Chinese government
Publié: janvier 29, 2015, 5:37pm CET par Mark Wilson

Technology firms in the US have written to the Chinese government asking for a postponement to the introduction of rules that would oblige companies to hand over source code as well as providing backdoors into hardware and security products sold to Chinese banks. A group of companies wrote to the Communist Party committee on cybersecurity to express disapproval at plans to underrcut the requirements later in the year.
China says that it is concerned solely with cybersecurity and wants foreign technology companies to submit to audits in addition to complying with the other demands. Outside China, the feeling is that the proposed regulations have been designed to either control outside business, or to scare companies out of the market, opening the way for Chinese firms.
There are also suspicions that the requirement for banking hardware and software to have built-in backdoors could have a more sinister purpose. There are concerns that just as the Great Firewall of China has essentially created a split internet, the proposed rules could create a split technology world.
The letter, signed by the US Chamber of Commerce, among others, says the lack of transparency is worrying reports the BBC:
An overly broad, opaque, discriminatory approach to cybersecurity policy that restricts global internet and ICT products and services would ultimately isolate Chinese ICT firms from the global marketplace and weaken cybersecurity, thereby harming China's economic growth and development and restricting customer choice.
There are also fears that technology companies looking to conduct business with Chinese banks would be forced to give up sensitive information and be forced to use Chinese encryption algorithms, potentially reducing security for global customers.
The Chinese government will require that 75 percent of technology products used by institutions in the country are "secure and controllable" by 2019. But more immediately, the rules would require foreign businesses to set up RD departments in China as well as committing to storing all information about Chinese customers on Chinese servers. However, it is China's request for access to data through backdoors that allow for constant monitoring that will be of greatest concern to businesses and their customers.
Photo credit: Augusto Cabral / Shutterstock
-

Google faces a Sisyphean task to remove terrorist content from YouTube
Publié: janvier 29, 2015, 1:16pm CET par Mark Wilson

Too much content is uploaded to YouTube for Google to be able to effectively police users' videos. This is what the search giant said in response to calls for more to be done to counter terrorism-related content on the video network.
Online censorship versus the right to freedom of speech is a battle that has waged online for some time now. Some parts of the world are more prone to censorship than others, and it's an argument that bubbles up from time to time. The debate usually centers around the moral rights and wrongs of censoring content, but the issue of practicality occasionally rears its head as well.
Facebook has shown that when it comes to weeding out fake news stories, it is happy to rely on a little help from users of the social network. While Google adopts something of the same approach by allowing YouTube users to report videos deemed unsuitable for one reason or another, it also actively seeks out illegal content that is uploaded including terrorism-related material.
Google's Public Policy Manager Verity Harding said that every minute of every day, around 300 hours of video is uploaded to YouTube. This works out to 432,000 hours of footage every day, or 18,000 days' worth of video in a 24 hour period. If this content was to be vetted by Google in real time, 2,250 staff members would need to work around the clock watching videos as they are uploaded.
Unsurprisingly, Google thinks that this is expecting too much, making the following comparison when speaking at a European Parliament meeting of the ALDE liberal group:
To pre-screen those videos before they are uploaded would be like screening a phone call before it's made.
European Union's counter-terror chief Gilles De Kerchove recognized the magnitude of the task, and said that it could be made easier by spreading the workload across the continent. He said: "We have to help them, and refer to them, and signal content. Each member state should have a unit with people trained to do that".
Photo credit: Balefire / Shutterstock
-

Microsoft's decision to ditch Surface is a long-overdue mercy killing for Windows RT
Publié: janvier 28, 2015, 10:18pm CET par Mark Wilson

For too long it was the metaphorical unwanted litter of kittens tied in a sack just waiting for someone to ditch it in the river. Windows RT is dead, having enjoyed a cancer-ridden 'life' for longer than many people expected. Microsoft announced that it is no longer going to manufacture Surface devices, all but signing the death warrant for Windows RT.
Hear that sound? No? That's the sound of everyone caring about it. To be fair, the writing has been on the wall for quite some time. Windows RT was always the sickly twin sibling of Windows 8 and now Microsoft has done the decent thing. It might not quite have delivered the lethal shot to the brain yet, but the gun has been cocked. And not before time.
If you're a fan of the Surface Pro -- running proper, full fat Windows -- there's no need to panic; this version of the hybrid laptop is going nowhere (in the positive sense of the phrase). It's just the Windows RT-packing non-Pro version that has been dropped like a hot stone. It's not like there haven't been plenty of clues for some time.
The original Surface was an out and out flop while the follow-up Surface 2 fared little better. When the Surface Pro 3 was released without even a mention of a Surface 3, it really should have become clear to anyone who hadn’t already realized that Microsoft had given up on its limited tablet. As far back as 2013, Microsoft had indicated that the days of having three operating systems -- desktop Windows, Windows RT and Windows Phone -- were numbered. More recently a Microsoft spokesperson said:
We are no longer manufacturing Surface 2; however, those still eager to buy Surface should visit Microsoft Retail Stores, MicrosoftStore.com, third-party retailers and resellers for the latest availability.
I'm not sure people will be beating down shop doors to snap up the last few remaining units. Windows RT was dead in the water from the very beginning, and as the flagship RT devices are killed off there is just going to be a slow, spluttering death until the end of the lifecycle (April 2017 for first generation Surfaces, and April the following year for the second generation).
Microsoft's attempt to muscle in on the tablet market with Windows-lite was misguided. Of course, creating a version of Windows for ARM processors was going to mean making compromises, but there were just too many of them. Part of the problem, once again, was apps. While Google and Apple have a strong infrastructure, a solid ecosystem in place, the same cannot be said for Microsoft with its app stores. Things may have improved somewhat of late, but the damage was already done -- Surface users were left with devices crippled by a lack of apps. The same problems affected Windows Phone, but things have started to improve slightly for phone owners. However, it's too late for Surface and its need for specially made apps.
When talking about Windows RT, one of the virtues of the OS that has been extolled is its 'inability' to be infected with viruses. Well that's just not true. While it is extremely unlikely for RT to be infected thanks partly to the fact that (unless devices are jailbroken) only apps from the official store can be installed -- although that's not to say that a rogue app couldn't slip through the net. There's also the fact that the viruses that affect desktop Windows simply cannot run on RT, but that’s like claiming that Android or iOS can’t be infected with desktop Windows viruses -- it's true, but meaningless.
So RT is breathing its last. There will be few tears shed, and Microsoft will probably mop its brow in relief when it no longer has to consider the disastrous product. Possibly because of the time remaining in the support lifecycle, RT users are in line for an update to their operating system. When Windows 10 is released later in the year there will be an update that offers "some of the functionality of Windows 10". It's not entirely clear what this means -- without further details, it is essentially meaningless. Windows 8 has "some of the functionality of Windows 10", and the statement could be fulfilled by simply updating the calculator in Windows RT to match the one found in Windows 10. I exaggerate, but the point is still a valid one.
The modern Microsoft has shown that it is ready to start listening to its customers, and those customers have said loud and clear that Windows RT is not something they want. It's an operating system that has been on death row for quite some time, and the kindest thing to do now is to pull the plug. Let's put us and it out of our respective miseries and forget it ever happened.
Photo credit: Minerva Studio / Shutterstock
-

Stop jumping to conclusions! Lizard Squad didn't take down Facebook
Publié: janvier 27, 2015, 7:24pm CET par Mark Wilson
Despite many reports to the contrary, there is nothing to suggest that downtime experienced by Facebook, Instagram and Tinder was anything to do with Lizard Squad. Earlier today, the three services were inaccessible for a short while and Lizard Squad took to Twitter to announce the outages.
The tweet, which read "Facebook, Instagram, Tinder, AIM, Hipchat #offline #LizardSquad" was taken as an admission of guilt and reported as such by many, many websites. Even when Facebook announced that the downtime came as a result of a system change by Facebook, site after site continued to report that Lizard Squad was to blame.
This is a group with form. Over Christmas Lizard Squad knocked the PlayStation Network and Xbox Live offline, attacked the Tor network, and also claimed to have helped out with the Sony Pictures hack. But it's also a group of glory hunters. Dismissed by many as little more than a group of skiddies, it is not clear whether the tweet about the network outages was an attempt to claim responsibility, or just drawing attention to the fact:
Facebook, Instagram, Tinder, AIM, Hipchat #offline #LizardSquad
— Lizard Squad (@LizardMafia) January 27, 2015
The number of sites interpreting this as claiming responsibility is staggering -- and there are many big names that have taken it as such. Facebook is very clear about what actually happened:
Earlier this evening many people had trouble accessing Facebook and Instagram. This was not the result of a third-party attack but instead occurred after we introduced a change that affected our configuration systems. We moved quickly to fix the problem, and both services are back to 100 percent for everyone.
Lizard Squad's Twitter feed quickly filled up with shouts of praise and adulation, but it's misplaced. There is precisely zero evidence to suggest that Lizard Squad took down Facebook. Perhaps the tweet was deliberately ambiguous -- the group can easily say they have not claimed responsibility -- but it's almost funny the number of "Lizard Squad did it!" headlines are out there. Ignore them.
-

Facebook is weak and utterly wrong to censor 'offensive' pages in Turkey
Publié: janvier 26, 2015, 8:31pm CET par Mark Wilson

Mark Zuckerberg is a hypocrite. For all of his spiel about being a proponent of free speech, ultimately he is a man all too willing to bow to the demands of a country. Turkey took umbrage at the existence of pages that insulted or offended the Prophet Mohammad and threatened to completely ban Facebook in the country if they were not blocked.
Facebook has now decided to comply with the Turkish demands. Zuckerberg would have us believe that "we never let one country or group of people dictate what people can share across the world", but this is clearly not the case when it comes to upsetting the Islamic faith. This latest move is a political one and shows a lack of strength and conviction.
In Turkey, President Tayyip Erdogan is looking to enforce an Islamic agenda, and the majority of the country is Muslim. Prosecutor Harun Ceylan requested the order to ban Facebook through Golbasi Duty Magistrate Court. A "valid legal request" led to one page being blocked, but now it seems that Facebook is willing to further comply with demands from Turkey.
It's a decision that must, at least in part, be driven by money. Turkey is far from being an insignificant country -- boasting millions of social network users -- and Facebook will be keen to keep as many people happy so that advertisers have more potential customers to target their goods at.
There is no just law that protects against offense. Offense is something that is taken, not given. Facebook users should be free, the world over, to question, mock, ridicule and -- in some cases -- offend. If Facebook decided to block any and all content that was deemed offensive by someone, somewhere in the world, there would be next to nothing left to look at!
While money is almost certainly a key factor in Facebook's decision, the fact that it is the Islamic faith that’s central to the story is probably more important. Islam is the untouchable religion. Express doubt about other religions and you might raise a few eyebrows and rub a few people up the wrong way, but it won't usually result in death or threats from an entire country. Can you imagine the Pope contacting Zuckerberg to block pages that 'insult' (and I use quotation marks because I find the idea of one's beliefs being insulted laughable) Catholicism? It's incredibly unlikely, but Zuckerberg would almost certainly shrug it off and do nothing of the sort.
But when Islam is involved it's a completely different story. Zuckerberg shows himself to be weak, two-faced and hypocritical. He has said that Facebook complies with laws around the world, and the Turkish Penal Code says:
Any person who openly provokes a group of people belonging to different social class, religion, race, sect, or coming from another origin, to be rancorous or hostile against another group, is punished with imprisonment from one year to three years in case of such act causes risk from the aspect of public safety.
And
Any person who openly disrespects the religious belief of a group is punished with imprisonment from six months to one year if such act causes potential risk for public peace.
But both of these articles are open to interpretation. They are worded in such a way to give more leverage to those of a religious bent, but it should be questioned. 'Disrespect' is an all but meaningless term and also a dangerous one in this context.
After the Charlie Hebdo killings Zuckerberg made it sound as though Facebook was going to stand firm and defend users' rights to express their beliefs. It seems this only applies in certain cases and bowing to Turkey undermines any political guff spouted about supporting freedom of speech. You disappoint me, Zuckerberg.
Photo credit: patrice6000 / Shutterstock
-

Turkey to Facebook: ban pages that insult the Prophet Mohammad or we'll block you
Publié: janvier 26, 2015, 2:30pm CET par Mark Wilson

Over the weekend a court in Turkey told Facebook to block several pages that had been deemed to insult the Prophet Mohammad. A court order was delivered to the social network with the threat that if Facebook failed to comply, the site would be completely blocked in Turkey.
Turkey's banging of the religious insults drum comes just weeks after satirical French magazine Charlie Hebdo was targeted for featuring a cartoon that mocked the prophet. At the time Mark Zuckerberg spoke out in support of the #JeSuisCharlie campaign that followed the tragedy, saying that Facebook had previously refused to ban content about the prophet, but it's not clear whether Turkey's threat could make things different this time.
Turkey is just the latest voice to speak up in the on-going freedom of speech debate, and it will be interesting to see how Facebook reacts. The social network frequently finds itself on the receiving ends of requests to block or remove content, and it has previously refused to block violent videos. Speaking out after the killings in France, Zuckerberg told of receiving death threats for failing to block Prophet Mohammad-related content considered offensive.
We stood up for this because different voices -- even if they're sometimes offensive -- can make the world a better and more interesting place.
Facebook has always been a place where people across the world share their views and ideas. We follow the laws in each country, but we never let one country or group of people dictate what people can share across the world.
Zuckerberg has said that he wouldn’t bow to pressure from extremist groups, but it remains to be seen what the reaction to court orders from a largely Muslim country will be. Turkey has a history of blocking access to sites, including Twitter and YouTube so it is not possible to dismiss the court orders as an empty threat. For all of Zuckerberg's pro-freedom of speech blusterings, Facebook does have a track record of complying with many data removal requests.
Update
The BBC is reporting that Facebook has agreed to block the pages in question in Turkey.
Photo credit: kentoh / Shutterstock
-

Windows 10 Technical Preview Build 9926 hands on -- making good on earlier promises
Publié: janvier 25, 2015, 10:55pm CET par Mark Wilson
Windows 10 has been something of a tease so far. There have been hints that it could be a good operating system, protestations that it will be great, but a series of preview builds that have been a little uninspiring. With the release of build 9926, it appears that Microsoft is starting to deliver on its promises. From this release we can see that Windows 10 is actually starting to take shape.
Microsoft is clearly pleased with the progress that has been made because it has simplified the process of upgrading from Windows 7 and Windows 8 -- Windows Update can be used to install the Technical Preview. It might not quite be ready for prime time just yet, but I'm cautiously optimistic even though I've been far from impressed with previous builds. Oh, and before you ask, there's no sign of Spartan just yet. So… what's new and what's improved? Let's take a look.
While things have progressed a great deal over the numerous official and leaked builds, it's important to remember that this is still a preview. Despite what some people may say, this is beyond being an alpha version, but it's not really a beta. Does that make it something in between alpha and beta, or is it something else? A gamma build? Either way, 9926 is a step forward from 9888 -- the march towards 10000 continues apace, and there are real signs of things being pulled together.
For months, Microsoft has talked up Windows 10; build 9926 sees the operating system starting to walk the walk. Microsoft has had to tread a fine line between making sure that Windows 10 is different enough from Windows 7 and Windows 8 to convince users that an upgrade is warranted, but not changing things so much that people feel alienated. This is something that went wrong with Windows 8, and the 8.1 and Update upgrades took steps to fix the jarring move between desktop and modern. What we see now is the result of Microsoft listening to people and acting on it.
The beginning is usually the best place to start, and for many people, this means the Start menu. This has been a bone of contention for some time now. In a bid to please as many people as possible, we're given a Start menu that is a mixture of Windows Phone, the Start screen from Windows 8, and the Start menu that there have been demands for. The Start menu can be enlarged so that it occupies the entire screen.
Windows 10's Start menu has evolved into something eminently usable
This is the version of Windows that's going to be running on EVERYTHING, if Microsoft gets its way. Phone, consoles, laptop, tablets and more. But convertible devices like Surface get particular attention. Continuum takes care of switching the interface to whatever mode is most appropriate to the mode your device is in. When docked or with a keyboard connected you get one mode. Switch to tablet mode and you get a more finger-friendly mode. A simple idea, but it's one that works. It's not clear how many people will make use of this feature, but for those who do have a convertible it is a real boon.
The action center is now home to genuinely useful notification, and this is an area of Windows 10 that is only going to become more useful as more apps tie into it. Sadly, it borrows a lot aesthetically from Windows Phone.
As they develop, Notifications will prove incredibly useful in Windows 10
This is still very much an operating system of two halves. It feels less divided, and while concessions have been made to those who hate modern apps -- they are now easily switched between full-screen and windowed mode and in many ways function just like an old-school desktop application -- the two worlds have not quite merged. Jumping between modern and desktop is far less jarring, the edges have been blurred more, but for anyone who hates the modern side of things, opinions are unlikely to change.
Lines have been further blurred between desktop and modern apps
There is more than a hint of OS X to Windows 10, particularly with the flat, largely borderless look to Windows. There is also what appears to be an attempt to copy the look of iOS's flat icons, but there's work to be done on the color scheme -- the folder icons are just hideous and garish.
Jeez, those are some damn ugly icons! Sort it out!
Cortana is possibly the biggest addition to build 9926. Sadly, I'm in the UK and the feature has not been enabled in my region -- nor have I been able to find a workaround that, er, works. In theory, I'm still to be sold on the value of Cortana. That said, it seems to be something that Windows Phone users have become enamored with and many people are looking forward to it on the desktop. It's possible I'm in a minority, and I'm willing (and happy) to be proved wrong in my cynicism. I just need to get it up and running first!
There are some odd little quirks here and there. In Windows 10, windows can, for the most part, be resized as you see fit, but there are instances where this is not the case. Take the Settings window for instance. At the moment, there are just nine icons in the window. Even though there is blank space beneath the last icon it is not possible to reduce the vertical height of the window -- a minor issue, but an irritating one nonetheless.
There are some things to learn, or remember. The Charms bar is gone. Hit Windows + C -- as I continually do -- and nothing happens. Settings have to be accessed through the Start menu.
There are also a couple of hidden surprises such as a redesigned system tray clock and calendar. This is not enabled by default, but if you fire up the Registry Editor and create a new DWORD (32-bit) value called UseWin32TrayClockExperience at HKEY_LOCAL_MACHINE\Software\Microsoft\ Windows\CurrentVersion\ImmersiveShell you can try out something with a slightly sexier look than the dull tool it replaces.
Hidden redesigned calendar? Don't mind if I do!
If the process of upgrading Windows 7 and Windows 8 to the Technical Preview through Windows Update is anything to go by, it's safe to assume that things should go just as smoothly for those holding off for the final product -- we've already been told that it will be possible to upgrade from the Technical Preview to the RTM release as well.
Talking of Windows Update, this particular Control Panel applet is no more. Of course, it has not been removed completely, but it has been moved to Settings where it can be found under Update & recovery.
Lost Windows Update? Just look to Settings in Windows 10
While you're tinkering with the registry, you might also like to know that there's also a hidden logon screen that you may like to use instead of the default one. Navigate to HKEY_LOCAL_MACHINE\ SOFTWARE\Microsoft\Windows\CurrentVersion\ Authentication\LogonUI\TestHooks and change the value of Threshold to 1. If you change your mind further down the line, just change the value back to 0.
Unlock Windows 10's hidden logon screen to uncover more of Microsoft's love of circles
I've still got some playing around to do, but I'm starting to like Windows 10 more and more. There's still plenty of time for Microsoft to add the final spit and polish, and if done correctly, we could finally lay Windows 8 to rest and move on as if nothing happened. I still find the resemblance that many areas bear to Windows Phone to be a little disconcerting, but maybe it's something I'll get used to -- again, this could be a case of being in a minority that hate the look of Settings.
One thing I have been impressed by is the speed and stability of this build. It's hugely pleasing -- although hardware manufacturers will no doubt disagree -- that Windows 10 will run on the same hardware as Windows 7, and it's something (coupled with the fact that the upgrade will be free) that all but guarantees Windows 10 will be a massive success. I've warmed to 10 a great deal, and I can almost see myself loving it further down the line... thanks, in part, to the fact that the search button can be disabled!
So... over to you now. Does build 9926 cut the mustard? Has it swayed your upgrade decision one way or the other? What else do you feel still needs to be added, removed or refined?
-

How to upgrade from Windows 7 or 8 to Windows 10 via Windows Update
Publié: janvier 25, 2015, 1:54pm CET par Mark Wilson
If you like the idea of trying out the next version of Windows before it is officially launched, Microsoft has made the Windows 10 Technical Preview available for everyone to use. There are various ways to get the preview installed on your computer, but since the release of build 9926, it is possible to upgrade your current Windows 7 or Windows 8 installation to Windows 10 using Windows Update.
This is a much simpler option than downloading the ISO image, but it is an upgrade route that almost encourages people to install the preview build on their everyday computer -- don’t forget that this is not a finished product! We've already looked at how to install Windows 10 in a virtual machine, but if you have a spare machine running Windows 7 or 8, using it as a test bed for Windows 10 just got a whole lot easier.
Although you can download Windows 10 Technical Preview build 9926 through Windows Update, it will not show up by default. First of all you need to install a small update which you can download from the Technical Preview page -- head to this page and click the 'Start upgrade now' button. Take note of the warnings on this page. Although the option to upgrade through Windows Update makes the whole process easier, the page is littered with warnings such as "this is prerelease software", and the more strongly worded:
Remember, trying out an early build like this can be risky. That's why we recommend that you don't install the preview on your primary home or business PC. Unexpected PC crashes could damage or even delete your files, so you should back up everything.
If you're happy to proceed, just run the executable you've downloaded. You may find that Windows Update launches as soon as this installation completes, but if not you should restart Windows and launch Windows Update manually. Perform a check for new updates and rather than the usual patches and fixes, this time you will find that you are offered the Windows 10 Technical Preview as an update.
Hit the Install button and sit back and wait while the download completes and the installation begins.
-

Windows 10 Technical Preview Build 9926 is much better, but there are known problems
Publié: janvier 24, 2015, 1:04pm CET par Mark Wilson
Yesterday, Microsoft took a lot of people by surprise by releasing Windows 10 Technical Preview build 9926 rather earlier than expected. Here at BetaNews we've installed the latest build on various machines -- virtual and real -- having battled with downloads, and now it's time for testing.
We'll be taking a look at this latest build in more depth in future articles, but before we do, it is probably worth pointing out some of the known problems. From playing with build 9926 just briefly it's easy to see that it's a marked improvement on previous releases, but Microsoft has helpfully forewarned users of issues they might encounter.
Of course, we must remember that this is only a preview; problems are very much to be expected and they'll almost certainly be ironed out in the final release. That said, things get off to something of an irritating start for some people who will find that rather than booting straight in to Windows 10, they are instead present with a boot screen. Microsoft explains that this is because of a "bug where a second boot option is persisted to uninstall the Windows 10 Technical Preview and roll back to the previous OS installed". It's just a matter of manually selecting the correct boot option each time, or waiting for 30 seconds for the default option to be selected.
The revamped Start menu has a few potential issues. You may find that the menu fails to launch from time to time, and icon labels can be truncated. One of the most eagerly anticipated features, Cortana, has quite a few problems at the moment. Microsoft points out that complex reminders may not be correctly created, and it is not currently possible to edit reminders. It's worth creating a test reminder as there's a possibility that the first one you create won't be displayed, and completed reminders do not currently move to the History section.
Gamers may experience problems with Xbox Live-enabled games, but Microsoft promises that a fix is in the pipeline. Other issues include the appearance of a battery icon on the lock screen of devices that do not have batteries, pixilation in Remote Desktop sessions, a disappearing Music app, and shorter-than-normal battery life on devices with Connected Standby.
As this is pre-release software, there will undoubtedly be more problems than this, but it's good to know what you're dealing with right from the start. We're still testing out this Build 9926, and you can expect more coverage as we try it out. In the meantime, have you noticed a marked improvement from previous builds?
-

Tweet translations come (back) to Twitter thanks to Microsoft Bing
Publié: janvier 24, 2015, 1:20am CET par Mark Wilson

After introducing the "while you were away" feature to help ensure you don’t miss out on tweets because of, you know, getting away from Twitter from time to time, there's now another feature that will help you to get more from the microblogging site. By teaming up with Bing, Twitter is now able to provide on-the-fly translations for tweets in foreign languages.
This is not an entirely new feature; Twitter has brought a translation to the web and mobile version of its service before, but it disappeared. Now the feature is back. It works in the iOS and Android apps as well as in Tweetdeck and on the Twitter website.
To take advantage of the feature, you'll first need to enable it in your account. Head to your Twitter account settings and in the Content section check the Tweet translation/Show Tweet translation box. That's pretty much all there is too it. But that's not to say that you'll then automatically see everything in your native tongue -- you'll have to click to translate tweets that appear in more than 40 languages.
The relaunch of the feature was given something of a quiet announcement:
We're introducing Tweet translation with @Bing Translator so you can read Tweets in multiple languages: [https:]
— Twitter (@twitter) January 22, 2015
If you spot a tweet in a foreign language, keep an eye out for a little globe icon. Click it, and the translation will appear below the original tweet. Of course, translation may not be perfect. Twitter warns:
"Although Bing Translator relies on advanced translation software to provide Tweet translations, the results still vary and often fall below the accuracy and fluency of translations provided by a professional translator. For this reason, the original text is always displayed above its translation".
Photo credit: ivosar / Shutterstock
-

Bill and Melinda Gates' annual letter says smartphones and mobile banking are key to the future
Publié: janvier 23, 2015, 8:34pm CET par Mark Wilson

Bill Gates is more readily associated with philanthropy than technology these days, but that’s not to say he doesn’t still have more than a passing interest in the world of tech. In their annual letter, Bill and Melinda Gates look 15 years into the future, envisioning a world in which the life in poor countries has improved dramatically.
Technological advancements are key to this vision, and the Gates refer to the importance of mobile banking, cheaper tablets and smartphones, as well as improvements to crops and vaccines. It's 15 years since the Bill & Melinda Gates Foundation was created, and the couple are making a bet that "the lives of people in poor countries will improve faster in the next 15 years than at any other time in history".
The letter makes some interesting predictions about how the next few years are going to pan out, including the suggestion that "better software will revolutionize learning". The fight to get the whole world online continues, and the Gates' envision a world in which everyone has the ability to take online courses to better themselves and improve their lot. It is hoped that funding will help to improve literacy levels, and this is something that will be driven by the availability of cheaper smartphones and tablets.
We think the next 15 years will see major breakthroughs for most people in poor countries. They will be living longer and in better health. They will have unprecedented opportunities to get an education, eat nutritious food, and benefit from mobile banking. These breakthroughs will be driven by innovation in technology — ranging from new vaccines and hardier crops to much cheaper smartphones and tablets — and by innovations that help deliver those things to more people.
But the future also relies on finance. The Gates Foundation stresses the importance of mobile banking to the developing world. It might seem odd to say that the future of poor countries relies partly on citizens' access to mobile banking, but the Gates' letter says that it will enable people to store money more efficiently -- traditional banking is simply too expensive.
This is Bill and Melinda's vision for the future, and it's worth taking a look at the letter in its entirety, as it's an inspiring piece of writing.
-

Drones for Good -- transporting transplant organs, detecting landmines, and wiping out fog
Publié: janvier 23, 2015, 3:08pm CET par Mark Wilson

The humble drone has something of a poor reputation. If it's not seen as a tool for surveillance, then it's a silly toy for those with too much time on their hands to strap a GoPro to and record aerial footage. More recently Amazon has trialled fast deliveries by drone, but a new competition aims to show the incredible things than can be achieved with the unmanned devices.
Drones for Good is an international competition which offers a prize of $1 million for the best and most innovative use of drones. The competition was announced at the Government Summit 2014, hosted by the United Arab Emirates, and has attracted interest from around the world, with entrants from dozens of countries. The list of semi-finalists includes some incredible ideas for how drones could be used to make the world a better place.
In all, there are 19 Drones for Good semi-finalists, and a winner is due to be chosen ahead of the Government Summit 2015 in February, whittled down from more than 800 entrants. Forget ensuring that your latest purchase arrives on your doorstep within the hour, these are ideas that have a humanitarian slant to them -- detecting landmines in warzones, fighting fires that would otherwise be impossible, planting trees, and monitoring the power grid.
Don’t fancy the idea of scaling a skyscraper to clean the windows? You could deploy a drone to undertake the potentially dangerous task. Problems with fog making things dangerous? You need the fog-dissipating drone! In the event of a disaster -- natural or otherwise -- a mapping and tracking drone could be used to help evaluate the scene and track down survivors.
One of the many interesting entries is Flyability, a drone that is described as "the world's first collision-tolerant flying robot" and can help in search and rescue operation. The video below shows the drone in action:
But this is just one of the semi-finalists. It's worth taking a browse through the full list, and some of the ideas are quite inspiring.
-

Windows 10-powered Surface Hub brings interactive whiteboards kicking and screaming into the 21st century
Publié: janvier 23, 2015, 3:03am CET par Mark Wilson

Surface got off to something of a stuttering start, but Microsoft's sort-of-tablet/sort-of-laptop has gained quite a following as it hit the third generation. With the launch of Windows 10 on the cards, the company is now thinking about not just software, but also new hardware formats. We've seen HoloLens, but the device that could transform both work and education is the Surface Hub.
Announced as an 84-inch Surface, it would be easy to dismiss this as a headline-grabbing gimmick, but it's more than that. Much more than that. It's a tool for the office, a tool for enterprise, and a tool for schools and colleges. This is Microsoft showing how Windows 10 can be used for collaborative work, bringing the interactive whiteboard kicking and screaming into the 21st century.
This is Microsoft's game-changing 84-inch Surface powered by Windows 10, and the size is the first indication that this is designed to be used by several people at once. In the conference room, classroom, or boardroom, rather than gathering, hunched around a single tiny laptop, or awkwardly and unreliably sharing a desktop session between several screen, one massive, interactive screen lets everyone not only see what's going on, but also to get involved.
The message that Microsoft is pushing is the idea that working in a group not only helps to boost productivity, but also helps to generate more ideas. This is your new creative hub, and it's a perfect demonstration of how Microsoft is now using joined-up thinking. This is not a case of bolting together a series of independent tools and hoping they work together, rather it is the result of collaboration between the Windows team, the Surface team, the Skype team and the Office team.
And collaboration is very much the name of the game. The large screen -- and it is a LARGE screen -- is perfect for giving presentations, but it comes into its own as an interactive group tool. There's a OneNote-based whiteboard tool that everyone can interact with using their own stylus; this is electronic brainstorming and so much more.
Need to pull in other people who can't get to the office? This is where Skype comes in. Just start a Skype video call and everyone can take part. This is just the beginning. Microsoft is opening up the platform to third party developers who will be able to create all manner of new peripherals and apps:
Microsoft productivity apps like Office and Skype for Business are built in. And with native support for touch, ink and sensors, the hardware will also enable third party developers to develop beautiful, powerful, immersive applications that light up on the big screen and enable groups to be productive together.
The video below shows the Surface Hub in action:
In terms of hardware and specs, the Surface Hub doesn’t disappoint. The display is 4K, and the screen and touch sensor are rated at 120Hz. Microsoft explains that by boosting the touchscreen's framerate twofold, lag and latency are completely eliminated. Xbox Kinect technology is used in conjunction with a pair of full 1080p cameras and a mic array to track people in the room. The Surface Hub will be powered by a choice of fourth generation Intel i5 and i7 processors, and it can be either wall-mounted or moved from room to room on wheeled stands.
There's no word on pricing or release date yet, but it should tie in neatly with the general launch of Windows 10 later in the year. The office and classroom are about to get a whole lot more exciting.
-

Kim Dotcom launches encrypted MegaChat beta, complete with bounty for security flaws
Publié: janvier 22, 2015, 7:52pm CET par Mark Wilson

There was a time when Kim Dotcom was hardly out of the news, but it's been a little quieter for him of late. He popped up recently when he apparently intervened and persuaded Lizard Squad to stop attacking the PlayStation Network and Xbox Live. Dotcom used the opportunity and attention he drew to himself to advertise his Mega storage service, and anyone following him on Twitter can't help but have noticed constant references to MegaChat.
Well, the time for talking about MegaChat is over. The browser-based, ultra-secure chat service that offers end-to-end encryption is now ready for you to talk through. Dotcom refers to it being a Skype-killer, but it remains to be seen just how much trust people are willing to place in the service.
Offering MegaChat as a cloud-based service is hardly surprising when you consider Mega's track record with online services. It's also free of charge, but it's not yet clear whether this could change further down the line, either in the form of a subscription fee or charges for different services. At the moment video calling is available, but this will expand to include text chatting and video conference calls as well.
Dotcom announced the launch on Twitter in his own inimitable style, poking fun at the NSA into the bargain:
3 years ago #Megaupload died 2 years ago #Mega was born 1 year ago the Internet Party Today you get #MegaChat @MPAA @TheJusticeDept @NSA
— Kim Dotcom (@KimDotcom) January 22, 2015
Right from the start it's clear that security is, at least on the face of it, being placed as a top priority. Dotcom tweeted: "#Mega offers a security bounty again. Please report any security flaw to us. We'll fix it and reward you. Thanks for helping".
MegaChat is pitting itself firmly against Skype. Dotcom has previously said that the likes of Skype (meaning US-based services) have no choice but to bow to the demands of the NSA and provide backdoor access -- the implication here is clearly that MegaChat will do no such thing.
If you feel so inclined, you can check out MegaChat through an existing Mega account, or sign up for a new one on the same page.
-

Microsoft shows off Office for Windows 10 and reveals Office 2016 plans
Publié: janvier 22, 2015, 7:26pm CET par Mark Wilson
Microsoft told us a lot about Windows 10 yesterday (it's free!), as well as the future direction of some other interesting projects such as HoloLens and the Spartan browser. We did get a brief glimpse at the touch-friendly versions of Office apps for Windows 10, but today Microsoft also reveals more about the next desktop release -- Office 2016.
In keeping with Microsoft's latest vision, the focus with Office moving forward is "mobile-first, cloud-first". We'll be able to try out Office for Windows 10 very soon as the universal apps are due for release for Windows 10 Technical Preview very soon, and the final version will be pre-installed -- for free -- on phones and small tablets. Some of this we knew yesterday, but talk of Office 2016 is new!
Perhaps the first question that Office users will have is "when will Office 2016 be released". Obviously it's very early days at the moment and a precise date hasn't been pinned down, but Microsoft has pencilled in some time in the second half of 2015 -- so anything from five to 11 months away.
But the next big release for Office is Office for Windows 10, and over on the Office Blog, the Office Product Management team's general manager Julia White shared a series of screenshots showing off the applications. As these are touch apps designed with smaller screens in mind, it should come as little surprise that the interfaces are noticeably cleaner than those currently found in full-blown Office.
Word (pictured above) takes elements of Office 365, but gives them an even more modern twist. A dedicated Read mode strips things back even further for distraction-free reading. Excel (pictured below) boasts a similar look, and White claims that "new touch-first controls shine in Excel, you won’t even miss your keyboard and mouse when selecting ranges of cells, formatting your pie charts or managing your workbooks".
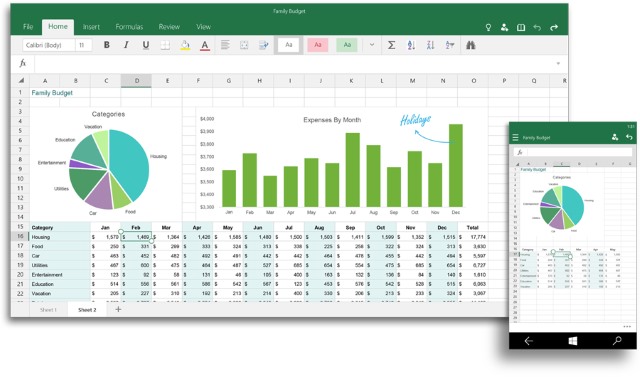
OneNote looks like it has undergone the biggest cleanup; a tabbed interface makes it possible to store a wealth of data in a relative small space. Outlook Mail and Outlook Calendar for Windows 10 (below) draws heavy inspiration from the look of Outlook.com, and this will help to make the transition from web to app easier for people to bear.
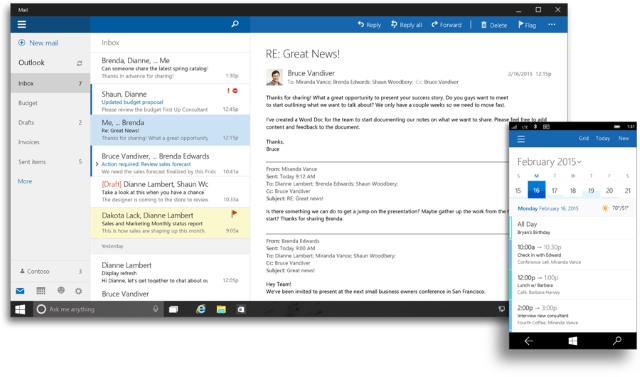
Although it's still not clear exactly when we'll be able to try out Office for Windows 10 for ourselves, things seem to be shaping up very nicely. In the meantime, you can check out the video below to see the software in action, and the Office blog for more screenshots.
-

Microsoft steps into the future with HoloLens, holographic computing meets virtual reality
Publié: janvier 21, 2015, 10:26pm CET par Mark Wilson

Today's Microsoft event was almost entirely about Windows 10 as expected, but there were a couple of surprises too. Among these was HoloLens a virtual reality, augmented reality, Google Glass hybrid that makes use of holograms for a totally immersive experience. We're used to Microsoft offering a unique window on the world, but this is something completely different.
Like Google Glass and virtual reality systems before it, HoloLens relies on a headset, and this is used to overlay holographic object onto physical objects in the real world. Like the idea of a massive monitor filling your living room wall? Rather than splashing out on a colossal screen, HoloLens could make it appear as though you have the screen of your dreams.
Of course there are many more applications, but the real selling point is that it will enable users to interact with objects in three dimensional space. You know those scenes from Minority Report where screens float in the air and can be operated via virtual touch? This is just one of the things HoloLens could bring you.
With HoloLens any object can become a surface onto which digital elements can be virtually projected. Empty spaces can be used to house three dimensional virtual objects which you can interact with in real time -- the design implications are immense.

Microsoft points out that while the headset offers a heads up display, it is completely transparent so you can always see the real world. In actuality, it is the fact that the real world and the HUD are visible at the same time that makes HoloLens what it is. As you work, documents, emails, pictures and models can be projected into the space in front of you. As you work on a DIY project, cook in the kitchen, or undertake countless other tasks, the information you need, the instructions you need to follow can hover in front of your very eyes.
There are endless possibility for gaming, simulations, virtual tours, and so much more. Microsoft explains how the technology transforms your world into a canvas:
Microsoft HoloLens intelligently maps the room you’re in, blending holograms with the environment around you. Pin holograms to physical locations you choose so that your room becomes the canvas for your holographic projects and games. With Microsoft HoloLens, you can interact with holograms and everyday objects together.
HoloLens looks incredibly exciting, but what we've seen so far is a glimpse into the future. You're invited to sign up at the HoloLens website if you'd like to be kept up to date with the latest news.
-

Microsoft introduces Project Spartan, Windows 10's new web browser that replaces IE
Publié: janvier 21, 2015, 9:48pm CET par Mark Wilson
At the Windows 10 event today, Microsoft had a lot to talk about -- not least that Windows 10 itself will be free. But Windows 10 is all about the details, and on top of the likes of Cortana and the new notification center, Corporate Vice President of Operating Systems at Microsoft, Joe Belfiore, also revealed Spartan, the web browser that will replace Internet Explorer in Windows 10.
That's not to say that Internet Explorer is dead and buried. You'll still find the famous blue e icon waiting to be clicked if you want, but Spartan will be the new default browser. So what does Spartan have to offer that will act as a lure away from Chrome and Firefox? To kick things off, there's Cortana support.
In fact Cortana is not just supported, but integrated into Spartan. As you type within the web browser, the digital assistant is on the lookout for key words and phrases so it (or she if you insist) can chime in with helpful information. Think weather, directions, travel data, restaurant information and so on.
There are lots of interesting new features for users to enjoy, including page annotations. Without the need for plugins or extra software, using Spartan you can draw on a website, add comments and share them with others. OneNote syncing makes this a useful tool for research and collaboration.
The likes of Pocket and ReadItLater have proved incredibly popular in recent years, but Spartan goes one better by including a built in reader tool. This can be used to save articles to read later, and the list will be synchronized between devices, including Windows Phone handsets.
While there is a new build of Windows 10 promised for the coming week, it will be a little while until we are able to officially get our hands on Spartan. Belfiore says that it will be made available in the coming months and new features will continue to be added. At this stage we don’t know if the project name of Spartan will stick, or if there will be a new moniker.
-

Microsoft and Yahoo gain ground on Google in search rankings
Publié: janvier 21, 2015, 5:53pm CET par Mark Wilson

In the world of searches, there's one name that rules supreme -- Google. But new figures show that while the search giant is still the most popular way to track down content online, it is starting to lose ground to Microsoft and Yahoo. The latest statistics from comScore are in broad agreement with those published by StatCounter a couple of weeks ago.
Both sets of numbers agree that Microsoft and Yahoo are eating into Google's lead when we look at US searches conducted in December and compare them to November. While Big G will not be happy to see that its grip on the search crown is loosening slightly, the company has little to fear just yet.
In November 2014, Google sites accounted for 67 percent of online searches in the US. Skip forward a month and this drops down to 65.4 percent. Microsoft managed to steal just 0.1 percent of this, taking its share from 19.6 percent to 19.7 percent, but it is Yahoo that managed to take a bigger bite of the pie. A 1.6 percentage point jump from 10.2 percent to 11.8 percent still leaves Yahoo trailing in third place, but it will come as good news none the less.
It's worth noting that these numbers only related to desktop searches, and it's safe to assume that the 12.2 billion searches performed through Google sites would increase if mobile searches were included. Clinging on for dear life are the Ask Network and AOL, managing to retain just 2.0 percent and 1.2 percent of the search market respectively.
Photo credit: Crystal Eye Studio / Shutterstock
-

CloudOn to close after Dropbox acquisition
Publié: janvier 21, 2015, 1:48pm CET par Mark Wilson

Dropbox is one of the most familiar, endearing and enduring names in the cloud, and it is continuing its expansion. The lastest addition to the fold is CloudOn, an Israeli startup with a focus on mobile productivity in the cloud that boasts 9 million users who use the service to edit Microsoft Office documents.
More accustomed to providing cloud storage, Dropbox's most recent acquisition sees the company expanding further into Europe. No details have been released about any money that may have exchanged hands, but news of the acquisition comes just days after Microsoft acquired Israeli company Equivio. So what does the acquisition of CloudOn mean?
In the short term it means that CloudOn is no longer accepting any new users, although apart from this things will continue to operate as normal. But this will be short-lived. CloudOn will close down on March 15, and this is when Dropbox's influence and direction should become more apparent. The CloudOn team announced the acquisition on its website, saying:
Today, we're taking the next step toward our vision of reimagining docs -- by joining the Dropbox team. Our companies share similar values, are committed to helping people work better, and together we can make an even greater impact.
CloudOn sprang up three years ago, and has already managed to expand into 120 countries. With the weight of the Dropbox brand behind it, this number is only going to increase.
Photo credit: Rido / Shutterstock
-

Facebook aims to wipe fake news stories from your newsfeed
Publié: janvier 20, 2015, 10:39pm CET par Mark Wilson

The queen is dead, boys! President Obama has announced he's going to step down! You can rewrite Facebook's privacy policy to your liking! Sick of seeing fake news stories cluttering up your Facebook newsfeed, getting in the way of content you actually want to see? Facebook feels your pain and is taking steps to cut back on the hoaxes.
Stop me if you think that you've heard this one before, but not everything that appears online is one hundred percent true. In fact, there's a huge amount of content that is twaddle, pish, balderdash -- and lots of people fall for it. Facebook is introducing a new feature that lets you report a story as being fake, and if enough other people do the same, the power of crowd sourcing means the story will be culled.
There are plenty of parody news sites out there, but these aren't really what Facebook has in its sights. However, there are journalists who lie, publications that deliberately try to mislead or paint a vulgar picture, and websites who sex up a dull story with things that are simply made up. Many people are able to spot such a story from a mile off and think "I won't share you", but there are plenty who spread hoax or misleading stories around -- and repetition lends credibility to even the tallest of tales.
Facebook is not aiming to censor stories any more than it already does, but the goal is to warn readers that certain posts may not be quite what they seem. It has long been possible to report content for being offensive, containing pornography and so on, but now a new "It's a false story" has been added. If enough people report a story for being false -- which some may argue is a matter of opinion -- a warning flag will be added to the content, as Facebook explains:
To reduce the number of these types of posts, News Feed will take into account when many people flag a post as false. News Feed will also take into account when many people choose to delete posts. This means a post with a link to an article that many people have reported as a hoax or chosen to delete will get reduced distribution in News Feed. This update will apply to posts including links, photos, videos and status updates.
Of course this will not mean that fake stories will immediately start to diminish -- these things take time -- and there is a danger that the feature will be misused to bury certain types of news story, but this is a move to help protect the gullible.
Photo credit: karen roach / Shutterstock
-

The worst passwords in the world -- is yours on the list?
Publié: janvier 20, 2015, 9:05pm CET par Mark Wilson

Did you resolve to increase your security in 2015? If the list of top passwords used in 2014 is anything to go by, a lot of people should have had this right at the top of their list of New Year's resolutions. Security and password firm SplashData has published its annual list of the most common (worst, in other words) passwords that are in use.
If there's anything positive to be taken from this terrifying list of insecurity, it's that 'password' is still not the most used password out there. It only slipped to second place last year to be replaced by '123456'. The top two positions remain the same this year, so there's not really that much cause for celebration. But the list makes for interesting reading, particularly when you consider these (supposedly) security-conscious times we live in.
If you're wondering how the list was compiled, SplashData collected together data about millions of stolen passwords that were posted online. Some of the new entries in the top 25 list are worryingly weak -- that's not to say that this list contains any passwords that would be considered strong by anyone of sane mind, but "access"? Come on, people!
No fewer than ten of the most popular passwords comprise only numbers. Of course, we're not talking about random digits here, but instead predictable patterns such as 123123, 111111, and (snigger) 696969. If that little giggle seemed childish, it's not entirely out of place -- many of the passwords have a rather childish feel to them: "monkey", "master", "superman", and "batman". Urgh.
Here's the full list in all its disturbing, insecure glory;
- 123456 (Unchanged from 2013)
- password (Unchanged)
- 12345 (Up 17)
- 12345678 (Down 1)
- qwerty (Down 1)
- 1234567890 (Unchanged)
- 1234 (Up 9)
- baseball (New)
- dragon (New)
- football (New)
- 1234567 (Down 4)
- monkey (Up 5)
- letmein (Up 1)
- abc123 (Down 9)
- 111111 (Down 8)
- mustang (New)
- access (New)
- shadow (Unchanged)
- master (New)
- michael (New)
- superman (New)
- 696969 (New)
- 123123 (Down 12)
- batman (New)
- trustno1 (Down 1)
Needless to say, if you spot a password you're using listed above, do yourself a favor and change it this instant. After you've punched yourself in the face first, that is.
Photo credit: Maxx-Studio / Shutterstock
-

Microsoft acquires text analytics firm Equivio ready to boost Office 365
Publié: janvier 20, 2015, 8:10pm CET par Mark Wilson

It seems as though there have been quite a few acquisitions by the big names in tech recently, and the latest addition to Microsoft's portfolio is Equivio. The Israeli company specializes in text analytics, focusing mainly on helping other businesses with legal and compliance issues with data, counting the Department of Justice among its clients.
What Microsoft is particularly interested in is Equivio's machine learning technology and information governance tools, and aims to improve the eDiscover feature of Office 365. For any company managing large quantities of data, this will help to make life a good deal simpler, and help to eliminate the need for manually sifting through documents and emails.
Rajesh Jha, Corporate Vice President for Outlook and Office 365, broke the news of the acquisition in a blog post. He explains businesses currently spend too long searching for documents that are relevant to compliance or legal matters and that Equivio uses "machine learning to help solve these problems, enabling users to explore large, unstructured sets of data and quickly find what is relevant".
Text analytics performed by the system make it easier to group documents together and to link them together in ways that would otherwise not be possible. The eDiscover system is already trusted by numerous law firms and Microsoft hopes that by taking control of Equivio, existing tools can be made not only more powerful, but also easier to use.
A post on the Equivio website is glistening with excitement:
When we launched Equivio, we had a vision to deliver innovative text analysis software to the legal market. It’s been an amazing ride. Along the way, our machine-learning technology has transformed the business process of e-discovery. By joining Microsoft, we will now have the opportunity to help many more customers layer these technologies into their standard operational and business practices.
For the time being things will continue as they currently are, but in the months ahead there will be changes coming to Office 365.
Photo credit: Asif Islam / Shutterstock
-

Technology excites developing countries but concerns the developed world
Publié: janvier 19, 2015, 7:18pm CET par Mark Wilson
A poll by Microsoft shows that there are vastly differing views to the technological lives we now lead. While most people believe that technology has made life better in a number of ways, there are key differences in opinion between developing and developed nations.
Countries in which advanced technology is more commonplace -- so-called developed countries -- there is an element of fear and concern that is not found in developing countries. Despite this difference in views, the overall consensus between internet users is that personal technology has had a positive impact.
Perhaps learning from experience, developed nations were found to have more concerns about technology than their less developed counterparts. While developing countries were found to be enthusiastic about the potential benefits of personal technology, people living in developed countries are more likely to be cynical and see problems.
Mark Penn, Microsoft executive vice president and chief strategy officer, said:
Internet users overwhelmingly say that personal technology is making the world better and more vital. But there is a digital divergence in the attitudes of Internet users in developing and developed countries regarding how technology will affect them going forward.
By far the greatest positive impact of technology is an increase in productivity, and the majority of people surveyed in 12 countries thought that it was now easier to start a new business. On the flipside, there were concerns about privacy but there are a number of interesting findings in the full results. In India and Indonesia, people felt fully informed about the collection of personal data -- not a view widely shared.
Technology appears to be shaping the future for developing countries. For example, 77 percent of women in such countries expressed interest working in science, technology, engineering and math, compared to just 46 percent of women in developed countries. In developed countries only a third of people (36 percent) perceived a positive impact on social bond because of technology, while developing nations were rather more optimistic -- 60 percent saw an improvement.
Photo credit: Stuart Miles / Shutterstock
-

North Korea blamed for Sony hack because NSA had been spying since 2010
Publié: janvier 19, 2015, 5:50pm CET par Mark Wilson

When Sony Pictures was hacked, the US was quick to point the finger of blame at North Korea. Security experts may have disagreed, but newly declassified documents show that the NSA had been monitoring the nation as far back as 2010 -- and there are even hints that the US was aware of the possibility of North Korea launching some form of cyberattack.
With the help of allies such as South Korea, US intelligence services were able to tap into North Korean web traffic. The NSA also went as far as installing malware on North Korean computers with a view to monitoring the activity of key systems. New papers published by Der Spiegel show that it is this spying that helped to pin the blame for the Sony attack on NK.
These are just the latest in a raft of documents to be released from the cache collected together by former NSA worker Edward Snowden, and they indicate that the US is readying itself for future cyberwar. But they also lend support to the US government's claim that North Korea was responsible for attacks on Sony Pictures' systems. The US went as far as imposing further sanctions on the country, much to its chagrin.
The New York Times reports that it is information gathered by malware installed by the NSA that ultimately helped to persuade President Obama to publicly accuse North Korea for the attacks. The report also questions why, with such intelligence gathering in place, it was not possible to warn Sony that something was imminent, or to take steps to counter it.
It is questions such as this, as well as doubt about the technical capabilities of North Korea in comparison to the sophistication of the attack, that mean growing seeds of doubt remain about who was really responsible. There have been suggestions that former Sony employees could be to blame, or hackers in China who took steps to try to make it appear that North Korea was responsible.
Photo credit: produktionsbuero TINUS / Shutterstock
-

How to disable Google Chrome's profile switcher button
Publié: janvier 19, 2015, 1:50pm CET par Mark Wilson
If you've joined the beta channel for Google Chrome you'll have seen the browser's profile switcher some time ago. For anyone who has decided to stick with the stable channel it may just have appeared. But what's the point? Nestling in the upper right hand corner of the browser window next to your tabs, you'll see a button with your name on it.
This is not to serve as a name reminder to the forgetful, but to show which Chrome profile you’re signed into. If you've set up more than one profile you can use the menu to switch between them with ease, but if -- like most people -- you only use one, it's a waste of space and looks rather ugly. Here's how to remove the pesky profile switcher button from Chrome.
The menu also provides access to Incognito mode, but as you can access this through the regular Chrome menu, you may well feel that you can live without the button. As with many Chrome tweaks, you're going to need to pay a visit to the chrome:flags page. You'll then need to locate the "Enable the new avatar menu" entry -- just hit Ctrl + F and perform a search for the word "avatar".
Begone! Banish that unwanted button!
Select the Disabled option from the drop down menu under this section and then click the Relaunch Now button that appears at the bottom of Chrome. When the browser restarts, the profile switcher button will have vanished -- pleasing from an aesthetic point of view, but also because it frees up a few extra pixels for tabs.
-

Listen up, Microsoft -- Verizon fixes critical email security flaw in two days
Publié: janvier 18, 2015, 11:00pm CET par Mark Wilson

When it comes to fixing security problems, it's better for everyone involved if a patch can be released as quickly as possible. A few days ago, a critical vulnerability was discovered in Verizon's FiOS app by Randy Westergren when he found it was possible to access the mail account of any Verizon customer with relative ease.
In stark comparison to the unhurried approach adopted by Microsoft to fixing problems identified in Windows -- on more than one occasion failing to hit a public disclosure deadline set by Google -- Verizon acknowledged, investigated and fixed the problem within two days. The problem itself was worrying, but the speed of reaction is impressive.
Back on January 14, Randy discovered that it was possible to not only read the contents of other users' inboxes, but also send message on their behalf. The discovery came about when analyzing traffic generated by the Android app. An API call made clear references to Randy's username, and a quick tweak was all it took to access other people's inboxes.
The security researcher took the time to put together a proof of concept having determined that there was serious cause for concern, and then sent this to Verizon. The company acknowledged receipt of the notification the same day, followed up the next day, and had the problem fixed the next. That's precisely how it should be done: quickly and efficiently. Microsoft could learn a lot.
Google has been berated for publically detailing information about vulnerabilities in Windows, and naming itself arbiter of security. While adopting Google's attitude does run something of a risk of opening up users to danger, having a three month deadline in place to give Microsoft (and other companies -- this is not just about Microsoft) time to patch is more than reasonable. I have applauded Google for continuing to publish details of security problems after first warning Microsoft, and I applaud Verizon for addressing an issue in such a timely fashion.
That's not to say that Verizon is perfect -- far from it many would say. As a commenter on Randy's blog points out, the company's app uses HTTP rather than HTTPS to transmit sensitive data, so perhaps this should be next on the list of things that are given attention.
Photo credit: Gil C / Shutterstock
-

Google reveals two more unpatched Windows security bugs
Publié: janvier 17, 2015, 4:16pm CET par Mark Wilson

Earlier in the week, Google managed to raise the ire of Microsoft by publishing details of a vulnerability in Windows before a patch had been published. Now the same thing has happened again, but this time it's a double whammy. Google Security Research has revealed two more security holes that Microsoft is yet to fix.
Just as was the case a few days ago, Microsoft had been warned about the security problems and Google agreed to keep details private for a period of 90 days. Now the three months is up, details of the security issues have been automatically published, running the risk that users could be targeted.
One of the problems affects both Windows 7 and Windows 8, while the other is regarded a less serious and only affects Windows 7. The Windows 7 security vulnerability is, as pointed by Ars Technica, not regarded as serious enough to warrant a fix from Microsoft, but it's a different story for the second problem that has been exposed -- a problem with the CryptProtectMemory function. This particular problem could lead to user data becoming exposed due to it not being properly encrypted.
There's something of an irony in the fact that while Microsoft kicked up a stink after Google exposed one vulnerability two days before the patch was scheduled to be released, this second serious problem was also due to be fixed in the same Patch Tuesday update. Unfortunately for Microsoft, and possibly for users of Windows, a problem was discovered with the patch itself so it was pulled at the last minute.
This means that, unless Microsoft is willing to release the fix out of schedule -- which it seemed reluctant to do last time around -- users are going to be exposed to the problem until the next Patch Tuesday rolls around in February. But even if the patch release date is pulled forward, details of the problem are now out in the wild and there is potential for this information to be misused.
Microsoft has yet to issue a statement about this particular batch of revelations, but judging by the ire generated earlier in the week, it's safe to assume that the company will be unimpressed.
Photo credit: alexskopje / Shutterstock
-

UK man arrested for Christmas Xbox Live and PlayStation Network attacks
Publié: janvier 16, 2015, 6:47pm CET par Mark Wilson

Cyber crime investigators have arrested an 18-year-old man in the UK for the attacks of the Xbox Live and PlayStation Network that took place over Christmas. This is something that Lizard Squad has claimed responsibility for, but at the moment it is not clear whether the man who has been arrested is associated with the group.
South East Regional Organised Crime Unit (SEROCU) worked in conjunction with the FBI and the UK's National Cyber Crime Unit to home in on the unnamed man believed to have been involved in the DDoS attacks. Thousands of gamers had their Christmases spoiled after the gaming networks were rendered inaccessible, leading Sony to offer compensation to those affected.
Investigators said that cyber crime "is an issue which has no boundaries and affects people on a local, regional and global level", and that numerous electronic and digital devices had been recovered from the man's home in Southport. While the arrest will be seen as a victory, the head of the investigating unit pointed out that there is still a good deal of work to be done.
In a statement, the crime unit said:
An 18-year-old man was arrested this morning (16/1) in Boundary Street, Southport on suspicion of unauthorized access to computer material contrary to section 1 of Computer Misuse Act 1990, unauthorized access with intent to commit further offenses contrary to section 2 of Computer Misuse Act 1990 and threats to kill contrary to Section 16 of Offenses against the person Act 1861.
The arrest is also related to swatting offenses which the unit explains is the act of providing false information to US law enforcement agencies about a threat in a particular place. This is likely a reference to the tweet from a Lizard Squad member that claimed a plane carrying a Sony executive had a bomb on board. Lizard Squad has also claimed involvement in the infamous hack of Sony.
Photo credit: Jinga / Shutterstock
-

War is declared: US and UK to engage in cyber attacks
Publié: janvier 16, 2015, 10:48am CET par Mark Wilson
The US and UK usually get on pretty well, but plans are afoot for the two nations to stage cyberwar on each other. Later this year, Wall Street and the City of London will be subjected to a series of attacks that is being described as "unprecedented".
But this does not signal a breakdown in the "special relationship" that extends across the Atlantic, rather the "war games" are part of a venture between the two countries to help improve security. The aim is to expand information sharing in a bid to stave off real cyber attacks that could be launched by other nations.
The announcement comes soon after the well-publicized hack of Sony Pictures -- an attack which the US government has blamed on North Korea -- and after the UK Prime Minister indicated a desire to be able to access all forms of communication, regardless of encryption. President Obama has also been stressing the importance of cyber security recently, and the two leaders met this week to discuss what could be done to improve technological security.
As part of the operation, cyber cells will be set up in both the US and the UK to improve information sharing and to act as a show of strength to hostile nations. Talking to the BBC, Cameron praised the work of the NSA and GCHQ, but said that cyber security needed to be stepped up. Facebook and Google have been singled out for particular attention -- due in thanks largely to their size and popularity -- and powers are sought that will make it easier for communications to be gathered by governments from these companies.
The ramifications of a genuine attack on the financial sector could have devastating consequences for individuals and countries alike. A recent hack of the Bitstamp Bitcoin exchange resulted in the loss of more than $5 million, so it is little surprise that the first of these staged attacks will involve the Bank of England.
Cyber security is far from being a new issue, though greater importance has been placed on it in recent years. However, security -- as meant by governments -- almost invariably means making compromises in privacy. This is a bitter pill to swallow, but in an attempt to soften the blow, Cameron is quick to stress that it is not just banks and large corporations that are threatened by cyber attacks, but also ordinary individuals and their money.
Photo credit: Bahadir Yeniceri / Shutterstock
-

Marriott hotels back down on plans to block guests' Wi-Fi hotspots
Publié: janvier 16, 2015, 4:16am CET par Mark Wilson

The Marriott chain of hotels has backtracked on its plans to block guests' Wi-Fi hotspots. The group had previously indicated a desire to make use of blocking equipment with a view to increasing security. But the likes of Google and Microsoft saw this as undue interference and decided to fight the plans.
Marriott International went as far as applying to the FCC for permission to use signal blocking equipment, but it has now done a complete 180 and announced that no Wi-Fi blocks will be put in place.
Many opponents believed that, despite claims about bolstering security, the blocking plans were actually designed to encourage guests to pay for internet access in hotels rather than making use of personal connections. It's not all that long -- October, in fact -- since Marriott was fined a total of $600,000 by the FCC for blocking personal hotspots, so the change of heart is perhaps not entirely surprising.
In a statement on the company website, Marriott said:
Marriott International listens to its customers, and we will not block guests from using their personal Wi-Fi devices at any of our managed hotels. Marriott remains committed to protecting the security of Wi-Fi access in meeting and conference areas at our hotels.
But that's not to say that the group isn't going to keep working with the Federal Communications Commission to try to improve network security:
We will continue to look to the FCC to clarify appropriate security measures network operators can take to protect customer data, and will continue to work with the industry and others to find appropriate market solutions that do not involve the blocking of Wi-Fi devices.
Whether this is a case of listening to customers or bowing to pressure from the tech industry, the announcement will please hotel guests who can continue to make use of their own Wi-Fi hotspots without interruption.
Photo credit: Kitto Studio / Shutterstock
-

Ready yourselves, Windows 10 Technical Preview users! Updated program terms ahoy!
Publié: janvier 15, 2015, 11:16pm CET par Mark Wilson
Microsoft has sent out emails to people signed up for the Windows Insider program, informing them that changes are on the way to terms and conditions. These changes will affect anyone who is using Windows 10 Technical Preview which is due for a new build very soon.
There have already been several public preview builds of the next version of Windows, and it is widely expected that the next big update will be unveiled in under a week's time on January 21. "The next chapter" of the Windows 10 story is due -- possibly including a Windows Phone 10 preview -- and it seem that new terms and conditions are needed.
Microsoft's email give nothing away about the changes that are coming, but it could be indicative of a change to the way the preview program works, or it could be because of a new feature of Windows 10. At the moment, the Participation Agreement and Terms of Use document for the Windows Insider Program is dated September 11, 2014. Four months down the line, Microsoft feels it's time for an update.
The email itself is pretty short and doesn’t give anything away:
Hello, Windows Insider –
We hope you are continuing to enjoy the Windows Insider Program.
We'll be sending out more exciting updates and announcements soon. In the meantime, we just wanted to alert you that the Windows Insider Program Terms of Use are changing.
Updated program terms coming soon! We'll post them here, be sure to check back after January 21 to review. Your continued participation in the Program once the terms are live constitutes your acceptance.
Thanks again for helping make Windows better,
The Windows Team
So... is this just legal stuff that will prove to be of little consequence to us users, or do the changes mean something more? Not long until we find out; prepare to download!
-

Facebook at Work unleashed to cater for the office
Publié: janvier 14, 2015, 6:25pm CET par Mark Wilson

For many employers, Facebook is the scourge of the work place -- but this could be set to change with the launch of Facebook at Work. Designed with enterprise users in mind, Facebook at Work is initially going to be made available to a handful of companies and will allow them to create their own social networks.
Sysadmins may have spent endless hours putting blockades in place to prevent workers from wiling away endless hours on Mark Zuckerberg's social network but now the goalposts have been moved. Getting off to a good start, Facebook at Work is not subject to the user tracking associated with regular Facebook, and ads simply do not exist (for now, at least). So what's it all about?
Ultimately, this is a tool for communication. Here the focus is not on growing a friends list, sharing cat videos, and endlessly tinkering with privacy settings. Facebook at Work's primary concern is helping workers to keep in touch with each other. This is something that many businesses already have covered by tools from Microsoft or Google, but Facebook is still keen to muscle in, says the Wall Street Journal.
Apps are launching for both Android and iOS -- Windows Phone is of course ignored as, strangely, are desktop platforms -- and the service aims to not only serve as a messaging tool, but also to replace collaboration applications and project management tools.
The idea of FB@Work -- as it was known back in November, reports TechCrunch -- started out as an experiment in Facebook's London offices. The expansion to a wider pilot program shows that it must have been something of a success, but Facebook has given no hint of when, or indeed if, Facebook at Work might have a full launch. The familiarity of the service will undoubtedly contribute to its success, but Facebook has something of an uphill battle on its hands to convince businesses of the value of Facebook at Work.
Talking to TechCrunch, Facebook's Lars Rasmussen said "Facebook at Work's strength is that we've spent ten years and incorporated feedback from 1 billion active users. All of that is embedded now in the same product but adapted for different use cases. When Mark [Zuckerberg] makes an announcement he just posts it on Facebook at Work".
It remains to be seen whether it will be welcomed so openly elsewhere.
Photo credit: 1000 Words / Shutterstock
-

Facebook should be applauded for not blocking violent videos
Publié: janvier 14, 2015, 1:42pm CET par Mark Wilson

There's a lot of crazy content out there. Social networks fill up with funny footage, music videos, informative clips, and the downright stupid. As with movies, there's also a good deal of graphic content out there too, and some of it finds its way onto Facebook.
In fact, this is one of the complaints that Facebook constantly has to deal with. When people aren’t taking issue with the social network's privacy policy (and trying to make their own amendments to it) there are frequent objections to violent, gory or otherwise offensive videos. Rather than issuing an outright ban and censoring such content, Facebook has adopted a far more sensible, measured approach.
This may be something you have already seen -- the rollout started quietly back in December -- but Facebook has now confirmed that it has started to place warning messages on videos that have been reported by users. Now, videos that are reported and subsequently deemed to be suitable only for an adult audience may not only have a warning message at the start, but such videos will not automatically play in people's timelines as others currently do.
Talking to the BBC, a Facebook spokesperson said:
We also ask that people warn their audience about what they are about to see if it includes graphic violence. In instances when people report graphic content to us that should include warnings or is not appropriate for people under the age of 18, we may add a warning for adults and prevent young people from viewing the content.
Of course, this does not mean that it's now a case of "anything goes" -- the warning messages do not offer carte blanche to post whatever you want and completely disregard Facebook's existing terms of use. Pornography will still be jumped on. Anything which is illegal will still be taken down.
This is a remarkably enlightened move by Facebook, which very recently acquired video compression firm QuickFire. The social network is not unfamiliar with the notion of upsetting people -- as its Year In Review posts showed -- but the Charlie Hebdo shooting led Mark Zuckerberg to speak out in favor of freedom of speech. It's good to see that, within the realms of what has already been deemed legal, Facebook is allowing for something other than the black and white options of "allow everything" or "ban anything seen as offensive".
Now, users have an extra layer of protection. Those of a delicate disposition, the easily offended, the prudish, and the weak of constitution now have a way to avoid content that might upset them. Of course this isn't going to stop people from complaining, but Facebook should be applauded for taking this extra step to shield those who want to be shielded.
The Guardian points out that at the scheme currently only applies to videos that are violent, but as it is a work in progress, it's possible that the warning will roll out to other types of video content as well. Facebook has previously come under fire for removing images of mothers breastfeeding, but there is no reason that the same warning system could not be used in these instances.
Of course, it is not a perfect system. A warning is just a warning, and there will almost certainly continue to be complaints from people who "accidentally" click through, or from parents who are concerned that a warning message acts as a draw rather than a deterrent to their offspring. It's not perfect, but it's a start, and it's a lot better than simple censoring and sanitizing Facebook to cater for the lowest common denominator.
Photo credit: so47 / Shutterstock
-

Google Domains launches as beta service in US
Publié: janvier 14, 2015, 6:17am CET par Mark Wilson
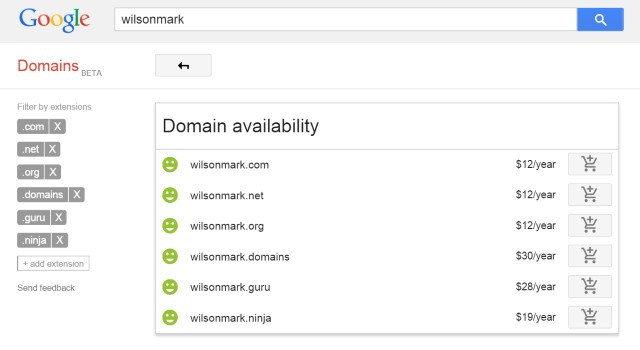
Looking to get involved in yet another area of your online existence, Google today launched a beta version of Google Domains in the US. As the name suggests, this is a domain registration service that Google hopes will be used to manage websites, including Blogger blogs, within the familiar, comfortable arms of Google.
Google Domains has been up and running as a private beta for a little while, but now it has been opened up to the wider public. Although it is available for anyone in the US to sign up for, there's no clue about when the beta tag will be dropped.
If you already have a domain of your own, it can be transferred to Google, but there's also the option of signing up for a new one. There are a number of gTLDs available at the moment, including .com, .guru and .ninja, and there's the promise of more on the horizon. Anyone signing up can take advantage of up to 100 email addresses -- which can also be forwarded to a Gmail address -- and prices start from $12 per year.
Up to 100 sub-domains can be used, and the dashboard allows for advanced control of domains. For anyone unfamiliar with website building, integration with builders services such as Squarespace and Weebly helps to keep things simple. Google hasn't said when Domains will start to roll out to other parts of the world, but this is presumably on the cards for some point in the future.
-

Ban encrypted messaging apps? You'd have to be an idiot to think it workable
Publié: janvier 13, 2015, 9:26pm CET par Mark Wilson

Wherever you are in the world, it's quite likely that your government wants to monitor your communication, be it online or via phone. Following the tragic events in France, politicians have voiced a desire for greater snooping powers. UK Prime Minister David Cameron has suggested that he would ban encrypted messaging tools if he wins the next election.
He has said that he would move to block the use of methods of communication that could not be intercepted and read by security services. With tools such as iMessage, WhatsApp and Snap Chat providing encrypted messaging options, could their days be numbered? Or is this an idiotic and unworkable way of looking at things?
Clearly these are rhetorical questions, the answers being "no" and "yes" respectively. The use of a rhetorical question might seem a little silly, but it's a linguistic device that the Prime Minister employed in a speech about security. As reported by the Independent, Cameron posed the question "in our country, do we want to allow a means of communication between people which […] we cannot read?"
The answer he was obviously hoping would be shouted back at him was "no", but his proposals are unlikely to be welcomed by advocates of free speech and those interested in privacy. The argument that if one has nothing to hide, one has nothing to fear is one that is wheeled out with worrying regularity whenever talk turns to national security and the surveillance that governments so frequently pursue in relation to it.
There are a number of problems with the idea of banning or blocking the use of apps and services that use encryption that cannot be cracked. Firstly, the Prime Minister's suggestion came off the back of the Charlie Hebdo attacks in France. There is (currently) no evidence to suggest that the attacks happened because of authorities' inability to decode encrypted messages, but this is the implication. This is both dishonest and misleading.
Secondly, it is all but impossible to ban anything. Child pornography is banned. Piracy is banned. Both of these things -- and numerous other banned activities -- still take place. The majority of people who use the encryption options offered by messaging services do so out of nothing more than a desire for privacy. People chatting about music, love, life, television, and so on. Of course there are criminals, even terrorists (if we must use the fear-mongering word), who will make use of these methods of communication, but they will also talk to each other in person, send emails, send letters and so on.
WhatsApp et al could be convinced to comply with Cameron's idea of cutting encryption -- these are just the mainstream tools that feature encryption. Are we to think that if the big names stop offering encryption, no one else would consider offering it elsewhere? Are criminals incapable of devising codes and cyphers? The only people who would be affected by the criminalization of using encryption would be criminals too inept to seek out alternatives, and ordinary people just looking for a means of private communication.
We've already seen that the web is virtually unpoliceable. The activities of the NSA have shown that trawling web traffic simply results in the collection of more data than can be feasibly dealt with. Factor in the dark web and it's a whole other ballgame. The likes of Silk Road may have been brought down, but this was possible because of the gathering of intelligence through interceptible web traffic -- mistakes made by those involved in Silk Road essentially. There are almost certainly numerous other Silk Road-like services out there, properly protected and properly encrypted so we, and the authorities, don’t know about them. It's the sort of thing that's publicized on a need to know basis.
To think that banning a particular method of communication will have anything other than a cursory effect on criminal or terrorist activity is naïve in the extreme. The only real effect would be to push things further underground, encouraging a redoubling of efforts to mask activities, to hide communication. The only real victims are free speech, privacy and the ordinary guy/gal on the internet.
Look to China. This is one of the most heavily controlled countries in the world. The Great Firewall of China doesn't stop communication with the outside world. It doesn’t stop Chinese citizens from finding out what's going on elsewhere around the globe. It doesn't stop them from accessing information the Chinese government would rather they didn't. It might make things more difficult, but certainly not impossible. No technological barrier put in place by a government is insurmountable.
David Cameron, you are an idiot if you think that your woolly words hold any weight. Your ignorance would be laughable if it was not so worrying -- nay, terrifying. The technically-minded, the millennials, the intelligent. They all see through the fear-mongering. You're preaching to a dwindling following of the already-converted. You're fighting an invisible and unknown enemy. Wrapping up your megalomania in the guise of protecting the public is starting to fool fewer and fewer people. Your ideas are unworkable and would prove to be just another massive inconvenience.
Of course, this is only an issue should you manage to stay in office and, let's be honest, that's a possibility of shrinking likelihood.
Photo credit: Frederic Legrand - COMEO and Imilian / Shutterstock
-

Is Microsoft about to unleash a Windows Phone 10 preview on an unsuspecting world?
Publié: janvier 12, 2015, 5:16pm CET par Mark Wilson

There's something of an air of excitement surrounding the release of the next version of Windows. The various builds of Windows 10 Technical Preview have delighted, frustrated, aroused, and annoyed in just about equal measure. Whichever side of the fence you fall on, one thing is certain about Windows 10 -- even months before its launch it has got people talking.
There's not long to wait until we get our hands on the next build, but now attention is shifting away from the desktop to mobile devices. There has long been talk of Windows 10 merging mobile and desktop platforms, and the launch of a new Windows Phone app shows that the time could be coming when Windows Insiders see their first glimpse of Windows 10 for phones.
Microsoft has said nothing about a release schedule for the next version of Windows Phone, but we do know that the next public build of Windows 10 is due to be made available for download in just over a week. But the launch of a new app, Phone Insider, for Windows Phone suggests that it might not be long until we start to learn more about Windows' mobile future.
The app description doesn’t give away too much, but links to the Windows Insider program are a pretty clear indication that Phone Insider has been created with the express intension of delivering preview builds to handsets. The description reads:
The Phone Insider application provides registered Windows Insiders the ability to receive pre-release OS updates on their phone, directly from Microsoft. For more information about registering and becoming a Windows Insider visit http://insider.windows.com.
The app itself provides a little extra detail:
This app provides registered users the ability to participate in pre-release phone update program offered by Microsoft. To configure your device so that it will detect pre-release updates, tap find a program below.
We can be fairly sure that this has something to do with the mobile arm of Windows 10 because of the reference to Windows Insider, but at the moment the app does not provide access to any downloads. Microsoft is due to reveal a lot more about Windows 10 in the coming weeks, and at the next event it is looking increasingly likely that we'll hear about a Windows Phone-specific preview program.
Photo credit: Sergey Mironov / Shutterstock
-

Tick tock, tick tock -- Obama says customers need to be told faster about security breaches
Publié: janvier 12, 2015, 4:08pm CET par Mark Wilson

President Obama is calling for more honesty from tech companies when it comes to telling customers about security breaches. Specifically, he wants people to be informed in a more timely fashion whenever a security issue puts their data at risk.
The proposed Personal Data Notification and Protection Act would require companies to contact customers within 30 days of a security breach if personal data has been stolen. The call comes in the wake of several high profile cases in which customers' data was exposed for some time before those affected were informed.
The New York Times reports that Obama will deliver a speech to the Federal Trade commission today in which he will not only ask for companies to update customers faster, but also outline proposals for the Student Data Privacy Act. This would forbid companies from profiting from data collected from students in schools
The White House said: "As cybersecurity threats and identity theft continue to rise, recent polls show that nine and 10 Americans feel they have in some way lost control of their personal information -- and that can lead to less interaction with technology, less innovation and a less productive economy".
As full details of the proposed legislation is yet to be revealed, it is difficult to determine how it will be received and whether there will be much opposition in Congress.
Photo credit: Tang Yan Song / Shutterstock
-

Gotcha! Google angers Microsoft by exposing Windows vulnerability
Publié: janvier 12, 2015, 1:46pm CET par Mark Wilson

At the end of last week, Google took the somewhat unusual step of releasing details of a Windows vulnerability before a patch had been produced. Microsoft is unhappy. Very unhappy. The bug, which affects the 32- and 64-bit versions of Windows 8.1 Update, was publicized as part of Google's Project Zero, but Microsoft is calling it a "gotcha".
So angered was Microsoft that Chris Betz, Senior Director of Microsoft Security Response Center hit out at Google in a strongly worded blog post. Citing the war against cyberattacks, Betz expresses anger that Google made public a security issue about the elevation of privileges in Windows user accounts, saying that companies should "come together and not stand divided".
The vulnerability was not a brand new discovery. Details were published to Google Security Research back in October with a 90-day embargo on it. Once this deadline was hit -- yesterday, 11 January -- details of the security problem were automatically made public. Microsoft is due to publish a fix in tomorrow's Patch Tuesday updates, but details of the problem are now out in the wild, giving attackers a window of opportunity to exploit the vulnerability.
Betz is furious that Google did not give Microsoft time to publish its patch before making the security issue known publicly. He points out that Microsoft believes in Coordinated Vulnerability Disclosure, an agreement by which companies work together to warn each other of security problems in their products in a bid to avert cyberattacks.
Microsoft was warned about the issue by Google -- the company is just annoyed that the publicity fell outside of the release schedule for patches. While Google is of the belief that giving companies a deadline to fix problems before they are made public helps to force security issues to be addressed quickly Microsoft disagrees:
Releasing information absent context or a stated path to further protections, unduly pressures an already complicated technical environment. It is necessary to fully assess the potential vulnerability, design and evaluate against the broader threat landscape, and issue a 'fix' before it is disclosed to the public, including those who would use the vulnerability to orchestrate an attack.
We know that Google told Microsoft about the problem. Betz even tells us that Microsoft requested that things be kept under wraps for another 48 hours, suggesting that there is a danger Windows users will suffer as a result of the disclosure:
Specifically, we asked Google to work with us to protect customers by withholding details until Tuesday, January 13, when we will be releasing a fix. Although following through keeps to Google’s announced timeline for disclosure, the decision feels less like principles and more like a 'gotcha', with customers the ones who may suffer as a result.
He says that in order to address security problems, there is a need to work together, a need for better coordinated vulnerability disclosure. He suggests that Google has been rather selfish in using the Windows vulnerability to gain exposure for itself:
What’s right for Google is not always right for customers. We urge Google to make protection of customers our collective primary goal.
Should Google have waited for the right time in Microsoft's timetable to release details of the vulnerability, or should Microsoft have pushed forward its patch schedule?
Photo credit: Celebrian / Shutterstock
-

Can an 'anonymous' social network using Facebook login ever be trusted?
Publié: janvier 10, 2015, 4:20pm CET par Mark Wilson

Despite its unwavering popularity, Facebook continually finds itself under fire for one thing or another. We've had debate about the social network's real names policy, a raft of people thinking they can rewrite the rules, advertising woes, and constant complaints when changes are made to how timelines operate. But one thing crops up time and time again -- people's desire for privacy.
This may seem rather at odds with use of a social network (there's a clue in the name there), but a new contender thinks it has the answer. Social X describes itself as a social platform where users can set up numerous identities, including an anonymous one. There's one problem -- Facebook credentials are used to sign into Social X, and this is undeniably going to be a massive stumbling block.
Social X was created with the aim of enabling people to freely express themselves and "have honest dialogues without saying too much in their own voices". By default, users are assigned three profiles -- a personal one which pulls in profile picture from Facebook, a professional one which has no image, and an "anonymous" one. Except it's not anonymous is it? Social X is, essentially, an app that runs on top of Facebook. Any data you add to any of your Social X accounts is undeniably, and inextricably linked to your Facebook account.
Your "anonymous" profile cannot be considered such -- at least it is no more anonymous than any other social network. Sure, your name isn't displayed, you can choose any avatar you want, and pick a meaningless name, but you can do that anywhere. Facebook may have a real names policy, but who's to know that your name isn’t Jessica Fletcher instead of Steven Patrick Morrissey?
The point of any social network is to connect with other people, otherwise you might as well climb a mountain and shout at the wind. In the course of discussions, you need to have an idea of who you are dealing with -- is this person who claims to have great medical advice for you really someone you can trust? Even if we accept that Social X offers complete anonymity an online footprint is still built up by anyone participating in a community; it would not be practical for every single message to be completely anonymous, not linked to a user, or there would be no sense of narrative, no flow to a conversation.
Opt to sign up for an account and you'll immediately be met with a Facebook prompt advising you that "Social X will receive the following info: your public profile, friend list and personal description" -- an interesting start to the idea of anonymity.
I asked the CEO of Virtual Artifacts, the company behind Social X, if anonymity was actually possible:
Yes, Social X offers users complete anonymity within Social X communities. They choose a persona before entering a community – which is essentially a room that provides a setting for users to share on a particular topic. Anything they contribute or do in that room will not leak out onto their Facebook profile.
That's not to say that Social X is regarded as a complete solution. Virtual Artifacts recognizes that providing users with three different profiles is potentially problematic:
However, as with all technology, there’s a need to be careful. If a user switches identities in a Social X community, they will reveal a new persona that will be attached to every post they have previously made in that setting.
If anything Social X should be regarded as dangerous. It lures users into a false sense of security about their anonymity whilst at the same time drawing information from another social network eyes suspiciously when it comes to privacy. It could be argued that there is a place for anonymous discussion of certain subjects -- people looking for help and advice with a personal problem might well prefer to do so without revealing who they are -- but when there's a risk of accidentally using the wrong profile, this safety net is all but taken away.
Without a doubt, it is the connection with Facebook that will raise the most eyebrows. I asked how this obstacle had been tackled:
Social X enables users to enter communities connected to Facebook Pages. While a user may enter a Social X community through Facebook, they are not required to disclose their Facebook identity in that community. These communities are basically rooms that give users a place to share about a certain topic. Our patented technology and privacy algorithm allows users to decide how they appear in these rooms. Offering customizable Personal, Professional and Anonymous personas, Social X gives people the power to choose how they represent themselves in a particular community. Content shared through one persona can never pass into another. Equally, a user’s Facebook profile cannot be traced through their Social X persona. Moreover, nothing that is posted through Social X will appear in a user’s Facebook News Feed.
Really, this is not good enough. It's snake oil. We're talking about Facebook being used as a basis for a new platform, and this is not a company anyone in their right mind would associate with anonymity. Social X is no more anonymous than any of the tens of thousands of message boards and newsgroups out there. And don’t think that Social X is offering anonymity in the true sense of the word:
There are many reasons why a user would decide on a certain persona for a specific Social X. For example, someone may wish to use an anonymous identity to share about a sensitive topic, an embarrassing illness or a niche interest. However, if a user was to misuse any of their Social X personas to bully or harass, the person behind that identity -- anonymous or otherwise -- would still be held accountable. Users can report all posts and comments made on Social X and any reported content will be addressed accordingly. We will take appropriate actions against anyone that misuses Social X and acts of bullying or harassment could lead to account termination and the notification of the relevant authorities.
You might not be asked to use your real name, to display a verified photo of yourself, or asked for proof of ID, but don’t for one minute think that you can’t be identified.
Photo credit: Stepan Kapl / Shutterstock
-

Twitter makes predictions for Golden Globe Awards
Publié: janvier 10, 2015, 1:18pm CET par Mark Wilson

What's happening on Twitter is often a fair reflection of what is happening in the world. While it may not represent a perfect cross-section of society, a quick glance at what's being tweeted about -- and the tone being used -- can help to give a sense of the global mood surrounding a subject.
Twitter has been used to predict the outcome of elections, who will win X Factor, and much more; now it's being used to guess movie award winners. The 72nd Golden Globe Awards takes place this weekend, and the numbers have been crunched to see which movies and shows people are talking about the most -- whether these end up as winners remains to be seen, but these are what's on people's lips at the moment.
It should come as no surprise that Game of Thrones has been one of the most talked-about shows since nominations were announced around a month ago. The hit HBO show is the most mentioned entrant in the Best TV Drama Series category, while heading up the Best TV Comedy/Musical Series category is Jane the Virgin.
But it's the movie categories that are of particular interest, as the awards handed out at the Goldenm Globes tend to be an indication of what is going to happen at the Oscars next month. We've already got something of an idea of what the popular choices are thanks to the movies that have been torrented. Twitter is suggesting that Selma and Birdman could snatch the Drama and Comedy/Musical motion picture crowns, but we'll have to wait until tomorrow to see if these predictions are correct.
If you want to catch up with the nominees and follow along on Twitter, a Golden Globes list has been created to help bring all of the relevant accounts into one place.
Photo credit: Fernando Cortes / Shutterstock
-

Microsoft brings new narration accessibility options to Office Online
Publié: janvier 9, 2015, 9:33pm CET par Mark Wilson

Accessibility features in regular applications are now very much par for the course, but it's something of a different matter when it comes to online apps. While a growing number of websites have been designed to better meet the needs of people with sight or hearing problems.
The gradual move to the cloud means there are more and more online apps springing up, but many of them are slow to embrace accessibility options. Today Microsoft announces that Office Online -- the web-based version of its famous office suite -- has gained a number of key accessibility features designed to make it easier to use.
Two new features open up Office Online to more blind and low-vision users. Microsoft points out that the online office suite was designed to comply with WAI-ARIA accessibility standard but now the company is taking things further.
Changes to the Narrator feature introduce descriptions of formatting as well as information about page elements such as headings and tables. The video below shows the updated Narrator in action -- all you need to do is hit Windows and Enter to enable it:
If you use cursor keys to navigate through a document, over the next few weeks a new virtual reading mode is rolling out. Hit Caps Lock and M, and Narrator will read the document from the current cursor position; the video below shows how the tool works:
-

Apple, Google and Facebook lend support and money to Je Suis Charlie campaign
Publié: janvier 9, 2015, 7:17pm CET par Mark Wilson

12 people died in an attack on satirical French magazine, Charlie Hebdo on Wednesday. At time of writing, the situation in France is still unfolding, and technology companies have been quick to show their sympathy for the victims whilst voicing support for freedom of speech.
Google has donated €250,000 (around $300,000) to the targeted Charlie Hebdo title, which is expected to increase its print run more than tenfold for the next issue. The #JeSuisCharlie hashtag has spread across the internet like wildfire as people around the world offer support on Twitter, Facebook and other websites.
As well as financial support, the French version of the Google website is adorned with a black banner, and the French Apple site features a Je Suis Charlie banner. While people worldwide are both grieving and offering sympathy to those affected by the attack, talk around the web has turned to the importance of free speech. It seems that the gunmen were prompted to start their killing spree as a reaction to cartoons featured in Charlie Hebdo that mocked the prophet Mohammed.
Mark Zuckerberg spoke out in a Facebook post, condemning the attacks but also stating that Facebook supports freedom of speech:
Facebook has always been a place where people across the world share their views and ideas. We follow the laws in each country, but we never let one country or group of people dictate what people can share across the world.
Yet as I reflect on yesterday's attack and my own experience with extremism, this is what we all need to reject -- a group of extremists trying to silence the voices and opinions of everyone else around the world.
I won't let that happen on Facebook. I'm committed to building a service where you can speak freely without fear of violence.
My thoughts are with the victims, their families, the people of France and the people all over the world who choose to share their views and ideas, even when that takes courage. #JeSuisCharlie
Another interesting show of support can be found by anyone performing a WHOSIS search on French websites. Users found that the Je Suis Charlie banner appears on WHOIS search results as ASCII art:
ASCII of solidarity. RT @cmdrtaco: Doing a WHOIS on any .fr domain has a secret message. pic.twitter.com/zYfydcrATI
— Andrew McLaughlin (@McAndrew) January 9, 2015
The events in France are truly tragic, but incredible displays of solidarity are coming out of it.
-

Facebook acquires video compression company QuickFire
Publié: janvier 9, 2015, 2:18pm CET par Mark Wilson

Social networks' interest in video show no signs of abating. As talk mounts about a video tool from Twitter, Facebook has acquired video compression startup QuickFire Networks. This acquisition comes just days after the social network acquired speech recognition firm Wit.ai, so 2015 has already been a busy year.
Facebook upset some mobile users by introducing videos that played automatically, and this latest acquisition may go some way to calming those upset by increased data usage. QuickFire boasts using a "proprietary technology that dramatically reduces the bandwidth needed to view video online without degrading video quality".
No details of the deal have been released, but QuickFire broke news of the acquisition on its website. Starting with a simple "We're excited to announce today that we are joining Facebook", company CEO Craig Y. Lee explained that as part of joining forces with Facebook, the company's business operations will come to an end.
Facebook has more than one billion video views on average every day and we’re thrilled to help deliver high quality video experiences to all the people who consume video on Facebook. As part of this, some key members of our team will be joining Facebook and we will wind down our business operations.
A drop in bandwidth usage will be welcomed around the world, but this is particularly true for people struggling with especially slow or expensive connections.
Photo credit: Michal Ludwiczak / Shutterstock
-

Leakers go to great lengths to bring Oscar movie DVD screeners to torrent sites
Publié: janvier 9, 2015, 4:02am CET par Mark Wilson

There are around six weeks to go until the 87th Oscars, and the nominations are due to be announced very soon. TorrentFreak reports that over the last 24 hours there has been a huge jump in the number of big name movies leaked to torrent sites. In the run-up to the movie ceremony preview discs are sent out to critics, reviewers and industry insiders, and it's all-too easy for these to fall into the wrong hands.
We're not talking about dodgy torrents of movies shot on shaky camcorders or mobile phones -- these are DVD quality copies known as screeners. Near perfect copies of the likes of The Hobbit, The Imitation Game, and Birdman, in spite of security and watermarking put in place by movie studios.
The lengths release groups are willing to go to to bring the movies people are looking for to torrent sites is impressive. In a bid to discourage movie reviewers from running off a few copies for friends, or ripping a copy and sharing it online, a number of techniques are employed. Obvious watermarks may be used to make it clear to would-be copiers that a movie could be traced back to them, but sometimes the tactics are rather more subtle.
TorrentFreak quotes a member of the CM8 release group, explaining the hard work they had to do to remove security features from copies of The Hobbit: The Battle of the Five Armies so it could be shared untraceably:
Movie had watermarks visible and invisible ones, had to remove frames to get rid of them. Nothing I haven’t done before. It was hours of work, but it's finally done and here for you to get!
And it's work that does not go unappreciated. In the first day after the initial leak, the movie was downloaded more than half a million times. Other potential Oscar nominees are proving just about as popular, much to the chagrin of the studios who would much prefer downloaders spent money on licensed streamed versions or physical DVDs when there is an official release.
The security measures will continue to be employed, but it's fair to say they will be defeated, no matter how unbreakable they seem at first. Where there's a will, there's a way; where there's infamy, there's determination.
Photo credit: juras10 / Shutterstock
-

Webcloak weaves a secure shroud around the web to keep you safe online
Publié: janvier 8, 2015, 8:13pm CET par Mark Wilson

Kickstarter projects are ten a penny these days, as startup after startup vies for attention and financing. While many projects fall by the wayside, just a handful come to fruition and one of the latest is a handy USB dongle that allows for secure, anonymous web browsing. In just 45 days the campaign reached its target of $60,000, meaning that larger scale production can now go ahead on the line of security-focused USB sticks.
Webcloak is designed as an alternative to the likes of Tor, offering users a secure, self-contained browsing environment. This not only helps to keep browsing anonymous, but also protects against the threat of viruses, and its blend of hardware, encryption and "secure access" software has been designed with ease of use in mind.
The problem with the likes of Tor -- aside from the fact that trust in such services has waned recently -- is that they are perceived as being complex to use, and this immediately presents a barrier. Webcloak has the advantage that it can be easily moved from one computer to another with a minimum of effort. Despite the relatively complex combination of virtualization, sandboxing and security, accessibility is at the heart of the product.
Martin Dawson, Webcloak's founder and chief technology officer said:
Cyber security is a pressing issue for our modern society, which is ever more dependent on the Internet for all aspects of our business and personal lives. Webcloak is a truly revolutionary solution to this growing problem, and we couldn’t be more pleased with the support we’ve received from the Kickstarter community.
The tool has been built from the ground up and features a custom browser environment bolstered by 256-bit AES encryption. IP cloaking is used to help mask users' identity and location, and the USB drive also features SafeVault, a secure file manager that can be used to store personal documents.
There's no word about when the secure USB-based browsing tool will be available to buy, but keep an eye on the Webcloak website for more details.
-

Apple has already raked in $0.5 billion from the App Store in 2015
Publié: janvier 8, 2015, 7:11pm CET par Mark Wilson

We're only eight days into 2015, and Apple is already celebrating bumper sales in the App Store. Buoyed by impressive pre-Christmas hardware purchases, New Year's Day proved to be the biggest day ever for App Store sales. And in the first week of January, Apple enthusiasts spent almost half a billion dollars on apps and in-app purchases.
Sales and income are very much on the rise. Last year was a record-breaker for developers who managed to pull in more than $10 billion in revenue. iPad, iPod and iPhone owners have already helped to earn developers $25 billion, and spending shows no sign of slowing down.
Apple stock rose by more than 3 percent today as the company released details of the App Store earnings, and Apple attributes developers' success in part to the Swift programing language supported by iOS 8. A series of frameworks make it easier than ever to create apps and games that connect with other software and devices.
Eddy Cue, Apple's senior vice president of Internet Software and Services, is more than happy with what he sees:
This year is off to a tremendous start after a record-breaking year for the App Store and our developer community. We're so proud of the creativity and innovation developers bring to the apps they create for iOS users and that the developer community has now earned over $25 billion.
Apple points that sales have not just helped to line its own pockets and those of developers. The Apps for (RED) initiative helped to raise money for the fight against AIDS, with Apple donating $20 million in the last quarter.
Photo credit: AVN Photo Lab / Shutterstock
-

AT&T: Oi, BlackBerry! Redesign the Passport for us. BlackBerry: yeah, OK!
Publié: janvier 7, 2015, 8:12pm CET par Mark Wilson

A few months ago BlackBerry announced the Passport, and the keyword was square. A square screen in a decidedly square body, not to forget the physical keyboard, was a sure-fire way to stand out from the crowd; it's hip to be square after all. But for AT&T, the Passport was just a bit too square.
In fact such was the carrier's dislike of the squareness of the Passport that it asked BlackBerry to redesign the handset. And BlackBerry obliged, producing an AT&T exclusive version of the Passport complete with rounded corners that is more in keeping with the look of the BlackBerry Classic, it was revealed at CES 2015 today.
Aside from rounding off the sharp edges, there's no difference between the version of the Passport available from AT&T, and the version available elsewhere. As AT&T says, "built for productivity, the BlackBerry Passport has been uniquely designed for AT&T users with rounded edges". The handset will be available off-contract for $649.99, while contract options start at $21.67 per month.
Giving a speech at CES 2015, BlackBerry CEO John Chen explained the simple reason for the redesign:
AT&T wanted rounded corners. Some of us are more square. No other reason than that.
As AT&T was the first carrier to launch a BlackBerry device, it's not entirely surprising that the handset manufacturer was willing to bow to the request -- AT&T knows what its customers want. No details have been released about when the rounded Passport will be available, but further launch details will come out in the next few weeks.
-

Mophie Juice Packs power your iPhone 6 or iPhone 6 Plus for longer
Publié: janvier 7, 2015, 7:01pm CET par Mark Wilson

Power -- or running out of it -- is a perennial problem for mobile phone users. As handset screens grow and processors become more powerful, the demand placed on batteries is constantly increasing. It's quite common to hear people complaining that their phone won't last the day without needing a recharge.
Something of a cottage industry has sprung up in third party batteries and charging cases. One name that has been around for some time is Mophie, and at CES 2015 the company took the wraps off three new power cases; two for iPhone 6 and one for iPhone 6 Plus.
The Mophie Juice Pack is available for both iPhone 6, and the larger Plus handset. $99.95 buys you a protective case that not only shuns bumps and scrapes, but also more than doubles the battery life of your phone. A flick of a switch is all it takes to start charging your iPhone via an integrated battery; the iPhone 6 case features a 2750mAh battery while, interestingly, the iPhone 6 Plus version features a 2600mAh battery. The case is available in black, gold and white to match your Apple device.
If 100 percent extra battery life is not enough, how does 120 percent extra sound? If you have an iPhone 6 -- Plus owners miss out for the time being -- the Juice Pack Plus gives a further boost for $119.95, bumping the battery up to 3300mAh. While some people will claim that the latest breed of iPhone has sufficient longevity to obviate the need for additional power, heavy mobile users will always find a way to race through a charged battery. If you find yourself running out of juice towards the end of the day, these cases could help you out.
The Mophie Juice Pack and Juice Pack Plus are available for pre-order right now, and the cases are expected to ship in 3 to 4 weeks.
-

Stop posting your own Facebook privacy notices -- it's completely pointless and looks silly
Publié: janvier 6, 2015, 5:17pm CET par Mark Wilson

It's happening again. Check your Facebook wall and you'll probably find that at least one of your friends has posted a status update indicating that they withdraw the right for Facebook to use the content they've posted to their account. It's written in a pseudo-formal style, and even makes reference to an applicable law. Must be legit, right?
Nope. It's nonsense. Complete and utter twaddle of the most pure and unadulterated kind. By all means post the message to your own wall, but be aware of two things: it will have absolutely no effect on what Facebook is able to do with your information, and it also makes you look a bit silly.
When you joined Facebook -- as Graham Cluley points out -- you agreed to certain terms and conditions. Despite this fact, thousands of users of the social network seem to be under the impression that they are then able to take exception to the way Facebook operates and withdraw permissions already granted. Sorry, bucko, but it doesn’t work like that. It keeps being debunked on Snopes, but still people believe they are free to write laws for themselves.
Let's try an analogy. It's like taking out a loan, signing paperwork that ties you into a repayment package lasting a certain number of years. After making a few repayments you might think to yourself, "the bank is making an awful lot of money out of my interest payment... I'm not happy about this!" Could you then dig out the paperwork you signed when taking out the loan and start making amendments to it? "I hereby declare that I no longer have to pay back any of this money. In fact, the bank owes me money!"
No. The idea is patently absurd, and making one's own changes to Facebook's terms and conditions is no less ridiculous. If penciling in new clauses after a contract had been signed was so simple, we'd all own our houses outright rather than having to pay rent or a mortgage ("I, the undersigned, shall continue to make rent/mortgage payments until I change my mind, and/or say "free house" three times whilst standing on my head, whichever comes soonest").
If you don’t like Facebook's terms and conditions, you have one option open to you -- stop using Facebook. It's that simple. Sadly, this will do nothing to change the way Facebook is free to use any text, images or other content you have already put online (assuming you have an account) -- you’ve already signed away your rights to this. Don’t like it? Tough!
Photo credit: piotr_pabijan / Shutterstock
-

Talking to the wall -- Facebook buys IoT speech recognition firm Wit.ai
Publié: janvier 6, 2015, 1:45pm CET par Mark Wilson

Facebook wants to talk your language. The latest step to achieving this sees Mark Zuckerberg's social networking acquiring speech recognition startup Wit.ai. The startup describes itself as providing "Natural Language for the Internet of Things" and has been doing so for just 18 months.
No details have been released about any money that has changed hands, but the plan is for the Wit.ai platform for remain open for developers to work with. The company is heavily involved in the Internet of Things, and was in line to work with Nest before Google took over.
There's no word yet on just what will come of the acquisition, but it's reasonable to imagine speech recognition being built into Facebook Messenger. That said, Wit.ai is a platform so it's also possible that additional apps will emerge.
Talking to Mashable, Facebook said "Wit.ai has built an incredible yet simple natural language processing API that has helped developers turn speech and text into actionable data. We’re excited to have them onboard".
Wit.ai is understandably upbeat about the acquisition:
It is an incredible acceleration in the execution of our vision. Facebook has the resources and talent to help us take the next step. Facebook’s mission is to connect everyone and build amazing experiences for the over 1.3 billion people on the platform – technology that understands natural language is a big part of that, and we think we can help.
Photo credit: scyther5 / Shutterstock
-

Bitcoin exchange Bitstamp suffers $5 million hack attack
Publié: janvier 6, 2015, 12:19pm CET par Mark Wilson

Bitcoin exchange Bitstamp has been taken offline after a hack attack relieved its coffers of $5 million. A message on the Bitstamp homepage explains that some of the exchange's operational wallets had been compromised, and warned customer to stop making deposits to previously-used addresses.
The attack took place over the week, but details are only now starting to come to light. Although more than 19,000 BTC ($5.2 million) were "lost" as a result of this, Bitstamp assures its customers that any Bitcoins stored up to January 5 are safe, but says that service is suspended for the time being.
As news of the security breach crept out, the value of Bitstamp shares dropped sharply, but the exchange remains hopeful that operations will be back up and running in a few days. Bitstamp co-founder Nejc Kodrič took to Twitter in an attempt to reassure investors that their Bitcoins are safe:
To restate: the bulk of our bitcoin are in cold storage, and remain completely safe.
— Nejc Kodrič (@nejc_kodric) January 5, 2015
Bitstamp's statement explains:
On January 4th, some of Bitstamp’s operational wallets were compromised, resulting in a loss of less than 19,000 BTC. Upon learning of the breach, we immediately notified all customers that they should no longer make deposits to previously issued bitcoin deposit addresses. To repeat, customers should NOT make any deposits to previously issued bitcoin deposit addresses. As an additional security measure, we suspended our systems while we fully investigate the incident and actively engage with law enforcement officials
The exchange goes on to say that the lost money is just a tiny fraction of its Bitcoin reserves, and that work is underway to transfer a secure backup of the site to a safe environment. No timeframe has been given, but this is a bad start to 2015 for Bitstamp and Bitcoin in general.
Photo credit: Lightboxx / Shutterstock
-

2015 -- the year automated malware protection and firewalls become worthless?
Publié: janvier 5, 2015, 11:21pm CET par Mark Wilson

Whether you're a home or business user, one thing you've probably had drummed into you for years is the importance of virus protection, an effective firewall and malware guards. Well, as we start our journey into 2015 such security tools may not be anywhere near as effective as they used to be. Is it worth investing in them at all?
The suggestion isn’t that we should ditch firewalls and malware protection altogether -- that would be insanity. But security expert Ilia Kolochenko says that we need to rethink our reliance on automated security tools.
Kolochenko is CEO of High-Tech Bridge and Chief Architect of ImmuniWeb, and he has looked forward to the year ahead to make a number of security predictions. Perhaps the most interesting is the idea that we will no longer be able to rely on automated security tools to offer the level of protection we need. That's not to say that they won't have their place, just that human intervention is going to be necessary as attacks become more complex and evolve more quickly.
Web Application Firewalls, Web Vulnerability Scanners or Malware Detection services will not be efficient anymore if used independently or without human control. Both web vulnerabilities and web attacks are becoming more and more sophisticated and complex to detect, and human intervention is almost always necessary to fully detect all the vulnerabilities. It's not enough to patch 90% or even 99% of the vulnerabilities - hackers will detect the last vulnerability and use it to compromise the entire website. As a solution to the new threats High-Tech Bridge has launched ImmuniWeb SaaS -- a unique hybrid that uses automated security assessment combined with manual penetration testing.
Kolochenko also believes that we'll see an increase in the number of online problems originating from external sources. It's fair to say that direct attacks that exploit vulnerabilities in sites, apps and services will continue, but there will be an increase in attacks that take other forms. Plugins are seen as being particularly problematic, as is cross-site scripting (XSS), and these are just two examples of security problems that require human intervention.
So while it might not quite be time to ditch the malware tools and firewall entirely, it is time to appreciate that even the best tool is only ever going to offer limited protection.
Photo credit: alphaspirit / Shutterstock
-

Leef iBRIDGE boosts iPhone storage by a colossal 256GB
Publié: janvier 5, 2015, 7:10pm CET par Mark Wilson

Jump on the iDevice bandwagon and one of the first decisions you'll need to make is choosing capacity. This may be determined largely by budget, but what if you run out of space further down the line? Not many people are in a position to just invest in the same device with more space, but Leef iBRIDGE is a neat plug-in solution.
Just as you can expand the storage space of your computer or laptop with a USB drive, Leef iBRIDGE works in much the same way for your Apple device. Available in 16GB, 32GB, 64GB, 128GB and 256GB capacities, the little plug-in modules give you a little breathing room for more music and photos.
The idea itself is not completely new but with a top capacity of 256GB, Leef iBRIDGE has the edge over the competition. It plugs directly into a Lightning connector, and there's also a built in USB port for connecting to a computer -- handy for transferring files between devices. As memory modules go this is quite a looker, with an interesting J shape that hugs the back of your device.
A recent lawsuit shows that many people are unhappy with the amount of storage they have available on their iPhone or iPad, and for those willing to stump up the cash, this could be a great alternative to iCloud storage. In terms of cost, the Leef iBRIDGE is not particularly cheap. Things start off reasonably cheap at the lower end of the scale: 16GB for $59.99 and 32GB for $79.99. 64GB will set you back $119.99, and 128GB costs $199.99. The headline grabbing 256GB version, however, costs a not insubstantial $399.99.
Still, it means you'll never run out of space at a critical time again!
-

Google Cast for audio pumps music to your speakers wirelessly
Publié: janvier 5, 2015, 6:19pm CET par Mark Wilson

We're all familiar with Chromecast, Google's nifty media streaming dongle that makes light work of chucking a video from your computer, phone or tablet to your TV. Fancy doing something similar with audio? Google must have been listening to you because the company has just launched Google Cast for audio.
The idea is virtually the same as Chromecast -- in fact it's based on exactly the same technology -- and it's just as simple to use. Start listening to music on your Android phone or tablet, iPod , iPhone, iPad, Mac, Windows computer or Chromebook and you can throw it to a set of compatible speakers without the need for wires.
But Google Cast for audio is about more than just pushing audio from one device to compatible speakers, soundbars and receivers. Google Cast Ready can connect to the cloud to pull in audio content from the likes of Deezer, Google Play Music, Pandora, TuneIn and more -- all controllable from an app.
Google Cast for audio Product Manager, Tomer Shekel said:
The first Google Cast Ready speakers will first be available in the US this spring from lead brands Sony, LG, and HEOS by Denon with more brands coming later in 2015 with the support of chip makers Broadcom, Marvell, MediaTek and system integrator Libre Wireless.These products will join a growing Google Cast ecosystem, which includes more Android TVs, game consoles and set-top boxes.
The video gives you an idea of what you can expect:
-

Block VPNs? Us? No more than usual, says Netflix
Publié: janvier 5, 2015, 1:57pm CET par Mark Wilson

If you have been experiencing problems accessing Netflix through a VPN recently, it's not because the company has started taking a harder line. Despite an apparent increase in problems connecting to Netflix through a VPN, the company says that it is not handling things any differently to normal.
TorGuard had reported an increase in the number of error messages its users experienced when trying to get their streaming fix, but Netflix is not owning up to clamping down on VPNs and proxies. While TorGuard expressed surprise at the appearance of a VPN-related error message, Netflix insists that it is business as usual.
In a statement to Engadget, the company said that there has been "no change" to VPN handling. A second statement to TheNextWeb, Netflix reiterated this by saying: "Netflix simply uses industry standard methods to prevent illegal VPN use".
So why has TorGuard noticed a jump in the number of problems? There are a few possible reasons. It's possible that Netflix is not being entirely honest about any changes that may have been made. The wording of the statement is vague enough to leave room for there actually having been some policy changes.
Or it could be that TorGuard usage has jumped, bringing it to the attention of an automated system used by Netflix to detect suspicious activity. Whatever the case, VPNs, proxies and other methods will continue to be used to watch Netflix, and eager viewers will always find a way around any blocks that may be put in place.
Photo credit: PathDoc / Shutterstock
-

North Korea says US sanctions after Sony hack demonstrate 'inveterate repugnancy'
Publié: janvier 4, 2015, 5:38pm CET par Mark Wilson

North Korea has reacted angrily to the sanctions imposed on it by the US. President Obama signed an Executive Order putting sanctions in place after an FBI investigation placed the blame for the hack of Sony Pictures firmly at the door of Pyongyang.
North Korea continues to deny involvement in the hack which was sparked by Sony's comedy movie The Interiew in which North Korean leader, Kim Jong-un, is assassinated. The country's state-run news agency issued an angry statement accusing the US of "groundlessly stirring up bad blood".
A spokesperson said: "The policy persistently pursued by the US to stifle the DPRK [North Korea], groundlessly stirring up bad blood towards it, would only harden its will and resolution to defend the sovereignty of the country".
North Korea has offered to conduct a joint investigation into the source of the hack in conjunction with the US, but this offer has been declined. The sanctions that have been put in place instead have been very angrily received:
The persistent and unilateral action taken by the White House to slap 'sanctions' against the DPRK patently proves that it is still not away from inveterate repugnancy and hostility toward the DPRK.
The US has been blamed for the widespread internet outages that North Korea suffered last week, but no official comment has been made about this.
Photo credit: Attila JANDI / Shutterstock
-

Piracy-beating VPN clamp down by Netflix is pointless
Publié: janvier 4, 2015, 12:59am CET par Mark Wilson

Netflix is one of the many websites that can only be accessed in certain parts of the world or has region specific versions. Of course, where there's a will there's a way, and there are numerous tools that can be used to bypass any restrictions that may have been put in place.
Whether using a VPN or a proxy, it's relatively simple to access Netflix from anywhere in the world. Netflix -- or rather the studios whose shows are being "pirated" (if that's the right way of looking at it) -- has had enough. It is fighting back, blocking access to some people who use circumvention measures.
TorrentFreak reports that there has been a jump in the number of VPN and proxy using Netflix users who have started to experience problems accessing the service. In particular, TorGuard -- the popular VPN provider -- has been dealing with users who have seen error messages informing that their Nextflix access has been blocked as a direct result of VPN or proxy use.
At the moment this is little more than a minor irritant. Change settings to change the location you appear to be in, and access is granted again. So it would seem that while Netflix is sometimes able to detect when circumvention tools are being used, whatever method is being used is not perfect. It's not clear whether particular users are being targeted, or users in particular parts of the world, but it appear to be little more than another fence to be hurdled.
A TorGuard spokesman said:
This is a brand new development. Just two weeks ago we received the first report from a handful of clients that Netflix blocked access due to VPN or proxy usage. This is the very first time I’ve ever heard Netflix displaying this type of error message to a VPN user.
As pointed out in the intro, where there's a will there's a way. Any obstacle put in place by Netflix will discourage only a proportion of users. Whatever content is out there in digital form, be it books, software, music, movies, streaming TV, there will be a way to either get it for free, or to connect to content that's not available in your region.
TorGuard seems to think that Netflix is just testing the water, and at the moment it may be that alarm bells are only sounded when there is a spike in the number of users logging in from a particular location. Using VPNs or proxy tools means there is a risk that a huge swathe of people could all appear to be in the same place at the same time, and this could appear suspicious. But this is far from being an insurmountable problem.
Faced with a choice of not streaming the latest episode of your favorite show, or seeking out a new way through the blocks, which route do you think most people would take? But it sounds as though -- as is so often the case -- the hard work will be done by someone else. TorGuard has promised that should Netflix start to aggressively block users, its tool will be updated accordingly.
Just as with torrent sites, Netflix is starting a perpetual game of cat and mouse. The mouse will never be caught, and will continue to find new ways to sneak through the cracks.
Photo credit: Sukharevskyy Dmytro (nevodka) / Shutterstock
-

Ignore Qualcomm's excitement, the Internet of Things hasn’t arrived in homes
Publié: janvier 3, 2015, 9:18pm CET par Mark Wilson
The future is here! We are actually living in the future. The futuristic sci-fi imaginings of the 1960's are not only a reality, they have been bettered, exceeded and trumped. At least that's what we're led to believe. The reality is rather different.
A lot of excitement has been pinned on the Internet of Things -- little more than connected, communicating devices -- but Qualcomm is taking things even further. In a video released ahead of CES 2015, the chipmaker waxes lyrical about not the Internet of Things we're supposed to know and love, but the Internet of Everything. And it's here. Apparently.
The idea's pretty much the same: it's Qualcomm's take on the Internet of Things polished up to add a little extra hype and buzz. The video itself is typical advertising-style guff, all shiny surfaces, beautiful people and white paint as we're treated to a peak into the lives of couple living in a smart, connected house.
A smart water meter is the first thing we're introduced to. It gives a running tally of how much water is being pumped out by the faucet while the lady of house wanders off to take a phone call -- quite why she couldn't remain by the sink isn’t made immediately clear. What's also not made clear is the cost and upheaval involved in getting the water system set up. Replacing faucets is something most people will do when there is a problem with the existing one. Faucets last for years, and the extra cost that would almost certainly be involved in upgrading to smart versions will be a deterrent for many, many years to come.
The same can be said of the smart washing machine that alerts Mr Smart House that the washing cycle has finished -- because just knowing how long a cycle takes to complete is clearly a great chore. A washing machine is not cheap and, like faucets, tend to be part of the family for many, many years. Even if you're in the market for a new one to replace your old unit that’s about to give up the ghost/has died a death, what are you more likely to opt for -- something that similar but perhaps more economical to run than your current machine, or one that's a few hundred dollars more that lets you know when it's done? That's what the beeping is for. And the big display. And common sense.
Oh… Smart Lady is back. The house knows she's left the tap running -- as she probably did. An alert is generated -- because that's what smart houses do; alert you to things, constantly. A text message or alarm is not deemed sufficient. Nope, we need to flash the lights! Hopefully there are no photo-sensitive epileptics in the house, or people chopping vegetables late at night in the kitchen. Flashing lights aren't a good way to alert people to things, it's just bloody annoying and potentially dangerous!
Standing in front of the TV - clearly not a very smart one because it didn’t explode with fury when the occupants of the house left it unattended and unwatched for a few moments, unlike the moaning faucet -- a message pops up as a reminder to take medication. From, of course, a smart pill box.
So smart is the house, and so comprehensive are the warnings, alerts and reminders, that the couples -- poor dumb meat sacks that they are -- have regressed. They no longer have a need to speak with each other. Communications appears to be carried out telepathically or via touch as not a word or hand gesture passes between them. They venture outside, but who knows how long they'll survive out there when they realize that the trees aren’t going to give them directions to the shops, and lamp posts don;t tell them that it's time to use the toilet.
Of course, the house we see in the video is not a typical house -- it's meant to be a showcase of what's possible, and what a small number of people might expect to see and implement in their homes many years down the line. Is it cool? Yeah, kinda. Is it the best use of technology? Arguably not.
Check out the video for yourself and see what you think:
Qualcomm asks "why wait?", to which I say, well, I'm perfectly capable of turning off water, I can remember to take pills if I need to, and having been alive for 35 years I think I'm well-versed in use of a washing machine. Oh yeah, and I'm not replacing hardware that works perfectly well just to add the gimmick of connecting it to other devices. For now, I'll pass thanks. I'm happy with a smartphone, I don’t need more "smart" devices -- I've not regressed to the state of a helpless child yet. And I'm not quite ready to be told off by my house.
Photo credit: charles taylor / Shutterstock
-

Alcatel Pixi 3 comes with a choice of three OSes -- and Android will still win
Publié: janvier 3, 2015, 7:28pm CET par Mark Wilson

When it comes time to buy your next smartphone, will you be swayed by hardware or operating system? Forget iOS for a moment; put Apple's mobile OS out of your mind for right now. Hardware to a large extent determines price, and an upcoming range of budget phones from Alcatel offers an interesting choice.
The Pixi 3 -- that rainbow-colored delight you see above assaulting your eyeballs -- comes with a choice of four screen sizes, and three OS choices. The smallest measures just 3.5 inches, but 4, 4.5 and 5 inch models are also available. But the interesting thing is that each is available with a choice of Android, Windows Phone or, erm, Firefox OS installed.
The hardware is identical for each phone, save for a couple of things. Firstly, obviously, there is the difference in screen size, but the smallest device is 3G only while the remaining three are LTE-compatible. At this stage we know little more about the specs, but more will be revealed at CES 2015 next week.
There have long been rumors -- and even botched examples -- of phones that run two or more operating systems, but that's not what we're seeing here. The choice you make when you buy the phone determines the OS you are stuck with. It's hard to imagine that even when the dilemma of hardware is taken out of the equation that Windows Phone or Firefox OS will prove more popular than Android.
Interestingly, as pointed out by the Verge, there's a chance that Alcatel's upcoming handset could be tied in to a revival of the Palm name. Tellingly, just a couple of months ago the trademark was sold to a company owned by Nicolas Zibell, President, Americas and Pacific at Alcatel One Touch. The Palm website, Palm.com, recently sprang back to life, now redirecting to mynewpalm.com, a site that bears the words Coming Soon.
We'll know more in the next few days.
-

E FUN offers up three super cheap Surface Pro wannabes ahead of CES 2015
Publié: janvier 3, 2015, 2:43am CET par Mark Wilson

It had a bit of a rocky start, but Microsoft's Surface devices have ended up more popular than more people would have imagined. But if there's one complaint that crops up time and time again, it's that the tablet cum laptop is a little on the expensive side -- a Surface Pro 3 could set you back up to $1,949.00 (512GB / Intel Core i7 model).
If you feel priced out of the market, E FUN (nope, us neither) has a trio of cheap alternatives that might suit your pocket. Ranging from $229 to $279, the Nextbook devices include a removable magnetic keyboard and boast touchscreens, and details have been announced ahead of CES 2015.
There are three screen sizes to choose from -- 10.1" 1280x800 IPS, 11.6" 1366x768 IPS, and 12.5" 1366x768 TN -- and these Windows 8.1 devices are powered by a 1.8GHz Quad-Core Intel Atom Z3735F processor. There's 2GB of RAM, and storage is also a little on the light side with just 32GB gracing the smallest device, and 64GB in the two larger-screened models. In all three cases, a microSD card can be used to boost storage.
The keyboard includes a USB port for connecting devices, and you'll find a micro USB port, mini HDMI port and audio jack on the main body. As you’d expect there's also Bluetooth 4.0 and WiFi 802.11 b/g/n connectivity, and cameras on the front and rear. Aimed at everyone "from professionals to students and casual users of any age", the Nextbooks feature a 3-axis sensor for interacting with apps and games.
Jason Liszewski, managing director and VP of sales for E FUN said
We are extremely excited to build on the great success we had launching our first tablets with Windows in the fourth quarter of last year. Our first 2-in-1 tablet with Windows and powered by Intel was one of the best-selling devices by volume throughout the holiday season.
These are clearly budget devices -- $229 for 10.1 inch, $249 for 11.6 inch, and $279 for 12.5 inch -- but the value of the cheapest model is increased thanks to the fact that year's subscription to Microsoft Office 365 Personal is included. Oddly, this offer is not available to anyone buying a larger-screened version.
-

US sanctions North Korea for its role in Sony hack
Publié: janvier 2, 2015, 11:15pm CET par Mark Wilson

Barack Obama today signed an Executive Order imposing sanctions against North Korea following the well-publicized hack of Sony Pictures. The move comes after the "recent cyber-attack targeting Sony Pictures Entertainment and the threats against movie theaters and moviegoers" which the US has pinned on North Korea following FBI investigations.
Although not directly named, the announcement of the sanctions makes clear reference to the movie The Interview which was pulled from theaters following a series of threats. The Executive Order is described as a reaction to attempt to "undermine U.S. cyber-security and intimidate U.S. businesses and artists exercising their right of freedom of speech".
The aim of the sanctions is to isolate entities and individuals that are described as being agents or officials of the North Korean government. Singled out for attention are the Reconnaissance General Bureau (RGB), North Korea's intelligence agency; Korea Mining Development Trading Corporation (KOMID); and Korea Tangun Trading Corporation, responsible for defense research and development programs. Ten individuals are also designated under the Executive Order.
The order signed by President Obama increases financial pressure on North Korea, blocks access to the US financial system, and prevents US companies from trading with the country.
Secretary of the Treasury Jacob J Lew said:
Today’s actions are driven by our commitment to hold North Korea accountable for its destructive and destabilizing conduct. Even as the FBI continues its investigation into the cyber-attack against Sony Pictures Entertainment, these steps underscore that we will employ a broad set of tools to defend U.S. businesses and citizens, and to respond to attempts to undermine our values or threaten the national security of the United States.
North Korea continues to deny involvement in the hack, and suggestions have been made that former Sony-employees may have been involved.
Photo credit: PromesaArtStudio / Shutterstock
-

Sony offers compensation for PlayStation Network DDoS attacks
Publié: janvier 2, 2015, 3:54pm CET par Mark Wilson

You don’t have to be a gamer to be aware that Microsoft and Sony's gaming networks were hit by DDoS attacks over Christmas. Hacking group Lizard Squad found itself on the receiving end of threats from Anonymous after disrupting gamers' holiday fun, and PlayStation owneers found themselves unable to enjoy online games.
To thank its users for putting up with the outage, Sony is offering compensation to PlayStation Network users. As well as extending PlayStation Plus memberships by five days to make up for holiday disruption, the company is also offering all PlayStation Network users a discount code for the PlayStation Store.
All members of the PlayStation Network will be treated to a ten percent discount code that can be used to obtain a one-time discount in the PlayStation Store. The discount can be applied to the full contents of a carts, so the more you buy, the more you save. The codes are not yet available, but will be released "sometime this month".
In a post on the PlayStation blog, Sony said:
Since access to PlayStation Network was impacted during the holidays, we wanted to show our appreciation for your patience by offering all PlayStation Plus members that had an active membership or free trial on December 25th a membership extension of five days. The extension will be automatically applied, so no action is necessary to receive the extension.
With Lizard Squad now offering DDoS attacks for purchase, it's quite likely that Sony will be hit again.
Photo credit: Quka / Shutterstock
-

Apple sued by users who feel iOS 8 is too fat
Publié: janvier 2, 2015, 2:54pm CET par Mark Wilson

It's at this time of year that many people start a diet -- and it's something that Apple might want to think about as well. Two US men are suing Apple because they believe iOS 8 is too big. Or, as the lawsuit puts it, uses an "unexpectedly large percentage of the storage capacity on 8 GB and 16 GB iPhones, iPads and iPods".
Paul Orshan and Christopher Endara complain that Apple failed to warn users that upgrading to the latest version of iOS could mean filling up to 23.1 percent of the available storage space. The lawsuit goes on to suggest that Apple is using the fact that users are likely to run out of space to push its iCloud storage service.
Apple has long been criticized for its low capacity devices, and the loss of up to 1.3GB of space when upgrading to iOS7 to iOS 8 is a hefty chunk to give up. The lawsuit states that users "do not expect this marked discrepancy between the advertised level of capacity and the available capacity of the Devices, as the operating system and other storage space unavailable to consumers occupies an extraordinary percentage of their Devices’ limited storage capacity".
The class action is seeking millions of dollars from Apple because "nothing close to the advertised capacity of the Devices is available to end users". It also points out that in advertising the storage capacity of devices, Apple has used the GB abbreviation to mean gibibytes and not gigabytes. Orshan and Endara also complain that Apple prevent users from adjusting the size of storage partitions, even though it can be achieved through jailbreaking.
The suggestion is that Apple uses a lack of physical storage to push iCloud packages -- "offer[ing] to sell that capacity in a desperate moment, e.g., when a consumer is trying to record or take photos at a child or grandchild’s recital, basketball game or wedding".
Photo credit: Nata-Lia / Shutterstock
-

Want to launch your own DDoS attacks? Just buy them from Lizard Squad
Publié: décembre 31, 2014, 12:21pm CET par Mark Wilson

You know what it's like. You have a niggling desire to launch a DDoS attack on a website but there are a couple of problems. You might not know how to do it, you might not want to run the risk of getting caught, or you might, you know, be too lazy to do it yourself. Never fear, Lizard Squad is on hand to help you out.
The hacker collective hit the headlines over the holidays after taking out the PlayStation Network and Xbox Live. It then claimed to have had a (small) hand in the hack of Sony, but now the aim appears to be to monetize the whole venture. Lizard Squad has launched a service called LizardStresser that could be used to launch DDoS attacks.
Referred to as a "booter", LizardStresser is a service you can sign up for on a monthly or lifetime (five years really) basis. There are a number of packages available that can be used to "stress test" a particular server for anything from a couple of minutes to several hours at a time. As soon as one attack, er stress test, is over, more can be launched straight away at no extra cost, providing you are within the same billing cycle. With monthly fees ranging from just $2.99 up to $69.99, and lifetime subscriptions costing between $29.99 and $309.99, it's all very affordable stuff, ripe for abuse.
Of course, LizardStresser tool is not being directly marketed as a DDoS weapon. Take a look at the terms of service -- yes, even a DDoS tool has such a thing -- and you're told that:
Permission is granted to stress test dedicated servers and networks owned by you. This is the opportunity to make your firewalls better, not to misuse against the law.
Furthermore, the tool may not be used to "intentionally send a ddos flood to an IP address not owned by yourself". All clear? Jolly good.
LizardStresser was launched via Twitter to a flurry of interest:
Our booter is now online & registration is open [t.co]
— R.I.U. Lizard Squad (@LizardMafia) December 30, 2014
The group was quick to boast about the power of the attacks that could be launched:
Without correct power distribution, if you hit a home connection right now, you'll drop the entire city.
— R.I.U. Lizard Squad (@LizardMafia) December 30, 2014
Lizard Squad has previously claimed that its aim is merely to highlight security issues, and the terms of services play up to this idea. But in reality it is hard to pretend that this is anything other than a DDoS for hire available to anyone willing to hand over the cash.
Photo credit: wavebreakmedia / Shutterstock
-

Apple's 14-day returns on iTunes could kill devs and musicians
Publié: décembre 30, 2014, 9:16pm CET par Mark Wilson

From now on, if you buy an app, music track or book from iTunes and change your mind, you can get your money back in the first two weeks, no questions asked -- if you are in the EU, anyway. Distance selling laws mean that a 14-day cooling off period is in place, so it is possible to get a refund on anything bought through iTunes in this timeframe.
It doesn’t matter if you don't like an app or album, something doesn't work as it should, or you just need your money back after an impulse purchase, the cash will be returned to you without question. One the face of it, this is great news for consumers, but the outlook is potential less rosy for app developers, authors and musicians.
A consumer rights directive was passed in 2011, but only came into effect more recently. Apple has updated its terms and conditions in numerous European countries (including the UK), and the new policy includes a "right of cancellation" that reads: "If you choose to cancel your order, you may do so within 14 days from when you received your receipt without giving any reason, except iTunes Gifts which cannot be refunded once you have redeemed the code".
This is a marked change from the way things were dealt with previously; refunds were possible, but Apple would look at each request individually. The new policy effectively means that everything in Apple's digital stores can be bought on a trial basis -- great if you want to try out something new without the risk of being out of pocket, but it's a system that is open to abuse.
Fancy listening to an album? Hand over your cash and it can be yours in a matter of moments. When that final track comes to an end it might be a month until you want to listen to it again -- why not just get your money back and 'buy' it again if you do need another fix. You can basically rent content free of charge.
The same goes for apps and games. You might part with your cash to try out a particular title and then opt to get a refund. Game progress, apps settings and files can be stored in the cloud so the next time you buy it, you can pick up from where you left off.
It might seem cynical to point out the flaw, but it exists, and it will be used. Developers will suffer -- it's unavoidable. In the case of music, there would be nothing to stop you from simply retaining the tracks -- DRM be damned! It will make sales figures very difficult to keep track of, making charts all but meaningless. An app may have been downloaded so many thousands of times, but how many times has it been returned and re-downloaded?
But for developers and artists, it is the potential loss of revenue that's the serious issue here. Smaller developers in particular could really suffer. Most people might think nothing of spending a buck, Euro or quid on an app, discovering it does suit their needs and chalking it up to experience. The developer can learn from any feedback and make changes for future versions, using the income from the initial sales to fund work. But if there is the option of getting one's money back, well... why not? Artists' and developers' pockets will be hit, and development and output are at serious risk of stalling.
What's a win for consumers isn't necessarily a win overall.
Photo credit: Sam72 / Shutterstock
-

Social networks are simply not important in the workplace
Publié: décembre 30, 2014, 7:27pm CET par Mark Wilson

Surveys often reveal facts that are largely common sense, and this is certainly true of a study by the Pew Research Center -- the findings being that is seen as "very important" to workers. Nearly half of the 1,066 people surveyed said internet, email and cell phones made them more productive, while just 7 percent said the opposite was true.
So far, so predictable. But the same study also reveals that just 4 percent of workers feel that social networking sites like Twitter, LinkedIn and Facebook are "very important". These are findings that Facebook would almost certainly disagree with, as would Twitter and LinkedIn, despite reports suggesting that Facebook is valuable to business users.
In most areas of work, employers discourage use of, and even block access to, social networks. It is, of course, not just a case of social networks being seen as poor additions to a worker's arsenal, but also that they serve as a distraction. The same could be said of email -- where there is always time for the occasional personal email throughout the day -- but in terms of importance to getting a job done, social networks rank very poorly.
Part of the reason behind this could be that 46 percent of those questioned said that their employer blocked access to certain websites, or has rules about what employees could post online. While 23 percent of employers encourage workers to promote their company online, the lack of value placed on social media suggests that this promotion is either not being done, or it happens through other channels.
The way social networks are perceived may change if Facebook's plans to launch a business-centric version of the social platform comes to fruition.
Photo credit: Rawpixel / Shutterstock
-

Lizard Squad claims to have assisted with Sony hack: "this is kind of a game for us"
Publié: décembre 30, 2014, 6:52pm CET par Mark Wilson
 To many people Lizard Squad comprises a collection of attention-seeking skiddies looking for their five minutes of fame. To others, they are the group that ruined Christmas by taking down the PlayStation Network and Xbox Live over the holiday period. Of course, it didn't end there. There were then claims of attacks on the Tor network, but the group's impact might be even more high-profile than first thought.
To many people Lizard Squad comprises a collection of attention-seeking skiddies looking for their five minutes of fame. To others, they are the group that ruined Christmas by taking down the PlayStation Network and Xbox Live over the holiday period. Of course, it didn't end there. There were then claims of attacks on the Tor network, but the group's impact might be even more high-profile than first thought.While not claiming full responsibility for the now infamous hacking of Sony, Lizard Squad has said that it provided Sony login details to the people who did. A man identifying himself as a Lizard Squad administrator said that Sony employee details were given to Guardians of Peace (GoP), one of the groups at whom the finger of suspicion is pointing.
The unnamed member of Lizard Squad spoke with the Washington Post and said that while the group "didn't play a large part" in the Sony hack, they were instrumental in helping to get the ball rolling. "We handed over some Sony employee logins to them. For the initial hack".
So what's the point of all the hacks -- Lizard Squad makes it clear that it wants to be seen as a "hacker/hacking group"? The main aim appears to be highlighting the insecure nature of various systems. This is what the PlayStation Network and Xbox Live attack was about:
One of our biggest goals is to have fun, of course. But we're also exposing massive security issues with these companies people are trusting their personal information with. The customers of these companies should be rather worried.
The same is true of attacks on the Tor network. While not the zero-day exploits initially boasted about on Twitter, Lizard Squad was successful in running a large number of nodes on the anonymizing network -- controlling "almost 50 percent of overall Tor network and over 70 percent of exit nodes" at one stage. Again, the point is to "make everyone understand how easy this flaw in Tor is to exploit".
Based in Europe, the group is blasé about being hunted down. "Law enforcement really isn't that big of a deal for us here". There is, unsurprisingly, no hint of what further attacks may take place, but there is the warning that "we're definitely ramping up our activities".
No reference is made to Anonymous' declaration of war on Lizard Squad, but whatever happens next one thing is certain, Lizard Squad finds itself despised not only by those affected by its attacks, but also by its contemporaries.
Photo credit: thailoei92 / Shutterstock
-

Lizard Squad claims to have assisted with Sony hack: 'this is kind of a game for us'
Publié: décembre 30, 2014, 6:52pm CET par Mark Wilson
 To many people Lizard Squad comprises a collection of attention-seeking skiddies looking for their five minutes of fame. To others, they are the group that ruined Christmas by taking down the PlayStation Network and Xbox Live over the holiday period. Of course, it didn't end there. There were then claims of attacks on the Tor network, but the group's impact might be even more high-profile than first thought.
To many people Lizard Squad comprises a collection of attention-seeking skiddies looking for their five minutes of fame. To others, they are the group that ruined Christmas by taking down the PlayStation Network and Xbox Live over the holiday period. Of course, it didn't end there. There were then claims of attacks on the Tor network, but the group's impact might be even more high-profile than first thought.While not claiming full responsibility for the now infamous hacking of Sony, Lizard Squad has said that it provided Sony login details to the people who did. A man identifying himself as a Lizard Squad administrator said that Sony employee details were given to Guardians of Peace (GoP), one of the groups at whom the finger of suspicion is pointing.
The unnamed member of Lizard Squad spoke with the Washington Post and said that while the group "didn't play a large part" in the Sony hack, they were instrumental in helping to get the ball rolling. "We handed over some Sony employee logins to them. For the initial hack".
So what's the point of all the hacks -- Lizard Squad makes it clear that it wants to be seen as a "hacker/hacking group"? The main aim appears to be highlighting the insecure nature of various systems. This is what the PlayStation Network and Xbox Live attack was about:
One of our biggest goals is to have fun, of course. But we're also exposing massive security issues with these companies people are trusting their personal information with. The customers of these companies should be rather worried.
The same is true of attacks on the Tor network. While not the zero-day exploits initially boasted about on Twitter, Lizard Squad was successful in running a large number of nodes on the anonymizing network -- controlling "almost 50 percent of overall Tor network and over 70 percent of exit nodes" at one stage. Again, the point is to "make everyone understand how easy this flaw in Tor is to exploit".
Based in Europe, the group is blasé about being hunted down. "Law enforcement really isn't that big of a deal for us here". There is, unsurprisingly, no hint of what further attacks may take place, but there is the warning that "we're definitely ramping up our activities".
No reference is made to Anonymous' declaration of war on Lizard Squad, but whatever happens next one thing is certain, Lizard Squad finds itself despised not only by those affected by its attacks, but also by its contemporaries.
Photo credit: thailoei92 / Shutterstock
-

Could Android apps save Windows Phone?
Publié: décembre 30, 2014, 2:20pm CET par Mark Wilson

The mobile market is a four horse race... if we're being polite, that is. Really it's a battle between Apple's iOS and Google's Android. BlackBerry desperately neighs about its importance to the enterprise market, while Windows Phone stamps its hooves trying to gain attention as it's hauled off to the glue factory via the knacker's yard.
Microsoft's mobile OS may have gained ground in some parts of the world, but the reality is that it's struggling. Whenever we talk about Windows Phone it feels like the same topic comes up again and again, forcing us to re-tread old ground, bang the same drum. The app situation is dire; it's all but impossible to paint it any other way. But could opening up the ecosystem to Android apps save it from a slow and painful death?
While Windows Phone undoubtedly has its supporters, Microsoft has been flogging a dead horse for some time now. Having invested in the Lumia name, and currently working on bringing its desktop and mobile operating systems closer together, Microsoft clearly has no plans to pull the plug on Windows Phone any time soon. But something definitely needs to be done.
A recurring rumor that Microsoft might be considering adding Android app support to Windows Phone has resurfaced. This is something that may make many ears prick up with interest. The possibility that all of those apps that are currently missing from the Windows Phone Store could just be enough to make people give Windows Phone a second chance. So how likely is this? Could we see the like of Gmail on a Lumia handset (outside of a browser)?
Rumors like this are easy to dismiss as mindless ramblings or wishful thinking, but the rumor comes from a fairly reliable source -- Tom Warren from the Verge. Writing on Twitter he suggests that Android app support is indeed on the way to Windows Phone:
@monkbent @charlesarthur once Windows Mobile is released and eventually supports Android apps then the fate of WP will become clear
— Tom Warren (@tomwarren) December 29, 2014
Interest was piqued among his followers. Questioned about his source, Warren -- usually very dependable when it comes to Microsoft news -- didn't give much away, but added: "I know they're still working on the technical implementation. They wouldn't be doing that for nothing".
Reference to Windows Phone while at the same time reviving the long-dead Windows Mobile moniker, oddly, raised fewer questions. A slip of the tongue or a reference to an as-yet unknown shift in direction for Microsoft's mobile vision? We already know that Satya Nadella's new view is focused on mobile first, cloud first, and that Windows 10 aims to blur the boundaries between mobile and desktop.
Microsoft is not going to throw away its efforts and just ditch Windows Phone, as much as many people think it should -- too much time and money has been invested in it. But there are clearly limits to how much effort can be put into convincing developers that the platform is viable and worth producing apps for. Adding support for Android -- just as BlackBerry did... although perhaps we shouldn't read too much into that! -- could be the Elastoplast Microsoft needs to keep the platform alive, bringing more of the apps people want to Lumia handsets to produce a larger user-base.
On one hand creating a user-base by providing access to Android apps will get Microsoft what it wants -- more users. But on the other, it may not be enough to encourage development specifically for Windows Phone (or Windows Mobile for that matter). Which is more important -- users using the apps they want, or native apps? Where there is already an app crossover, it is often the case that the Android version of an app is better, has more features, looks nicer. Would developers be even less likely to bother producing apps specifically for Windows Phone? Would it mater at the end of the day?
Are collaborations like this a good idea? Windows Phone has been on life support for some time now. Microsoft is unlikely to pull the plug and let its baby die, but it's clear that something needs to be done to prop it up until the operating system has a better sense of direction. Maybe then it will be a serious contender in the race.
Photo credit: Kirill__M / Shutterstock
-

Access to Gmail is blocked in China
Publié: décembre 28, 2014, 11:18pm CET par Mark Wilson

China is one of the more 'interesting' counties when it comes to its attitude to allowing unfettered access to the internet. The Great Firewall of China is famed for the restrictions it places on the online activities of Chinese citizens. New data seems to suggest that Google's Gmail is currently blocked in the country.
Dyn Research, a web traffic research company, reports that Gmail traffic is being blocked at the IP level rendering Google's email service inaccessible within most of China. The disruption appears to have started late on Christmas day and is still on-going.
You can see the drop in traffic for yourself thanks to Google's Transparency Report. The interactive graph shows that there was a sharp drop in Gmail traffic as Christmas day drew to a close. There is a bit of fluctuation for a while, but then there is a prolonged period of flat-lining. There's no sign of things improving.
Speaking to Mashable, Dyn Research's vice-president of data analytics Earl Zmijewski said that "China has a number of ways they can block content. One of the crudest ways is to just block an IP address, and when you do that, you block all the content available at the IP".
A tweet from the company confirmed its findings of an IP level block on Gmail when the site is served from Hong Kong:
@DynResearch confirms China #GFW IP-level block of Google's [t.co] when served from #HongKong pic.twitter.com/uV3Y8pgHTQ
— Dyn Research (@DynResearch) December 28, 2014
Hong Kong is significant as Zmijewski explains that a lot of Chinese Gmail traffic is routed through IP addresses in the region.
China has a history of censoring and blocking web access. News agencies and other online services find that they have a constant game of cat and mouse if they are to evade the firewall or censors. Google has not yet indicated whether it will take any steps to get Gmail up and running in China.
Photo credit: ArtisticPhoto / Shutterstock
-

Apple now lets you rent or buy The Interview from iTunes
Publié: décembre 28, 2014, 9:21pm CET par Mark Wilson

There are few films that have caused as much controversy -- justified or not -- in recent times as The Interview. The Seth Rogen and James Franco movie upset North Korea, was shunned by major cinemas, and earned itself poor reviews when it was screened online and in independent cinemas. Now Apple has announced that the movie can be bought or rented from iTunes.
Apple spokesman Tom Neumayr said simply, "We're pleased to offer The Interview for rental or purchase on the iTunes Store." Anyone who wants to see the movie and doesn't fancy opting for one of the numerous versions available through BitTorrent or other sources, can rent it for $5.99 or buy it for $14.99 -- in the US and Canada, at least.
The Interview was originally destined for a cinema release on Christmas Day, but a series of threats against anywhere screening it led to the opening being put on hold. With estimated costs of $44m, Sony was keen to find a means of distributing and monetizing the movie. Screenings in more than 300 indie theaters brought in over $1 million on the opening day, and the movie was also made available on Xbox Video and Google Play and YouTube.
Apple actually agreed to distribute The Interview at around the same time as Google and Microsoft. The reasons for the delay are not yet clear, but four days on Apple is now ready to make the movie available to renters and buyers. Hit iTunes if the movie is on your must-watch list.
While Sony will be pleased to have the chance to draw in a little money from the movie, the news is not all good for the company. As well as suffering a serious PlayStation Network outage following a DDoS attack, there is also a report from TorrentFreak that suggests the company could be sued for using unlicensed music in The Interview.
Photo credit: Sony
-

Facebook apologizes for miserable, automated Year In Review posts
Publié: décembre 28, 2014, 1:57pm CET par Mark Wilson

You must have seen them whilst browsing your Facebook feed, you probably even have one of your own. Facebook took it upon itself to produce a Year In Review post for users, pulling together photos from throughout the year into one delightful, cheery look back at the previous 12 months. But for some people things weren’t quite so cheerful.
The algorithm that was used to collect photos for inclusion in the posts picked out not only photos of the happy family get-togethers, the unforgettable vacations and so on. Some users were distraught to find that some of the bleaker moments from the year had been highlighted in a presentation entitled "It's been a great year!". Now Facebook has apologized for the upset.
The idea was a fairly nice one. The Year In Review is basically a photo slideshow that picks out what Facebook determines to have been the highlights of your year. As this is entirely automated, an algorithm is used. While we don’t know anything about how the algorithm works, it is safe to assume that the level of interaction with photos had a bearing on whether they were included or not -- that photo from your birthday party with 165 comments is rather more likely to have been featured than the photo of your cat licking its butt that no one noticed.
It's not just happy photos that generate interest though. Post about a tragic life event on your Facebook wall, and you're likely to get a lot of comments from friends and family. A pet may have died, for instance; post a photo to accompany news of the passing, and the sympathetic responses will undoubtedly have flooded in.
One Facebook user, Eric Meyer, was distraught to find that his Year In Review included a photo of his young daughter who lost her battle with brain cancer earlier in the year. In a blog post, Meyer wrote about how he encountered the upsetting juxtapositioning of an image of his dead daughter surrounded by clipart images of people partying.
Where the human aspect fell short, at least with Facebook, was in not providing a way to opt out. The Year in Review ad keeps coming up in my feed, rotating through different fun-and-fabulous backgrounds, as if celebrating a death, and there is no obvious way to stop it. Yes, there's the drop-down that lets me hide it, but knowing that is practically insider knowledge. How many people don’t know about it?
Facebook saw fit to respond. Speaking to the Washington Post, Jonathan Gheller -- product manager for the Year In Review app -- said that he had contacted Meyer to apologize, adding:
[It] was awesome for a lot of people, but clearly in this case we brought him grief rather than joy. We can do better -- I'm very grateful he took the time in his grief to write the blog post.
While the apology is undoubtedly welcome, this case -- and many others like it -- just goes to highlight the fact that once content has been added to social networks such as Facebook, what happens with it is really out of your hands.
Photo credit: Twin Design / Shutterstock
-

Lizard Squad attacks Tor network, ignoring warning from Anonymous
Publié: décembre 27, 2014, 1:18pm CET par Mark Wilson

Lizard Squad, the group believed to be behind the Christmas DDoS attacks on Xbox Live and PlayStation Network now has a new target -- Tor. Just a week ago, the leader of the Tor Project, Roger Dingledine, warned that the anonymizing network could come under attack, and now it seems as though his prediction was correct.
War has already been declared on Lizard Squad by Anonymous, but this does not seem to have been enough to deter the group from its attacks. Reports suggest that more than 3,000 Tor relays have been compromised, and there are fears that this could impact the anonymity Tor was designed to offer.
Yesterday, Lizard Squad announced that it was no longer targeting Xbox Live and the PlayStation Network. It's not clear whether this decision came as a result of Kim Dotcom's intervention but by switching its focus to Tor, the group is certainly trying to draw attention to itself:
To clarify, we are no longer attacking PSN or Xbox. We are testing our new Tor 0day.
— Lizard Squad (@LizardMafia) December 26, 2014
While there have been claims that Lizard Squad is incapable of taking on Tor, it seems that there have been successful attacks. Security researcher Nadim Kobeissi tweeted a screenshot that shows a large number of relays named LizardNSA:
This is what the Tor network looks like right now. pic.twitter.com/0QQAGVTRRI
— Nadim Kobeissi (@kaepora) December 26, 2014
The Tor Project released a statement which seems to suggest that things are under control:
This looks like a regular attempt at a Sybil attack: the attackers have signed up many new relays in hopes of becoming a large fraction of the network. But even though they are running thousands of new relays, their relays currently make up less than 1% of the Tor network by capacity. We are working now to remove these relays from the network before they become a threat, and we don't expect any anonymity or performance effects based on what we've seen so far.
There's something of a war of words underway at the moment as well. Despite the fact that many of the members of Lizard Squad, and the associated Finest Squad, have been doxed (had their personal details published online), the Lizard Squad Twitter feed remains defiant:
Come @ me faggots im undoxable pic.twitter.com/4I1N1mlWai
— Lizard Squad (@LizardMafia) December 27, 2014
-

Anonymous declares war on Lizard Squad after DDoS attacks on game networks
Publié: décembre 27, 2014, 12:29am CET par Mark Wilson

Hacker outfit Lizard Squad was seemingly responsible for the misery of thousands of gamers this Christmas after a series of DDoS attacks were launched on the PlayStation Network and Xbox Live. Mega's Kim Dotcom stepped into the breach and was seemingly -- temporarily -- successful in negotiating with the group and getting them to stop the attacks.
While the gaming networks appear to have come back online for some, this is not enough for Anonymous -- yes, that Anonymous. The international activist group has declared war on Lizard Squad, saying that the hackers have "made an enemy" and warning that "now you are all going down".
Anonymous posted a couple of videos to YouTube in which it -- in its typical dramatic style -- attacked Lizard Squad. While no direct reference is made to the attacks on Sony and Microsoft's gaming networks, the narrator addressed the gaming community as well as Lizard Squad itself. It seems that the declaration of war is about more than just the Xbox Live and PSN DDoS attacks.
In a blog post, Anonymous draws attention to its videos in which the group complains about Lizard Squad's suggestions that Anonymous is working with the FBI. The news was also shared on Twitter, where initial responses fell into two camps -- those complaining that Anonymous didn’t intervene sooner, and those interested to see the fallout of what happens next.
Anonymous Declares War on Lizard Squad Hacker Team. Read Here: [t.co]
— AnonymousArmy (@AnonymousNewsHQ) December 26, 2014
Here's the transcript of one of the videos as the voiceover can be a little hard to make out (this is Anonymous' own transcript, complete with typos):
Greetings Gaming Community & Lizard Squad aka Finest, It has come to our attention that despite our continued warnings you have decided to disregard our requests to stop promoting propaganda such as "Anonymous has joined up with the FBI". The only Anon that ever worked with the FBI is Sabu, the former Lulzsec's leader and now he's know as the biggest traitor and scumbag that shopped hes friends to the police in order to save himself among all Anonymous parties. The Leader of Lizard Squad Jord is also the leader of Finest Squad which is in the same position as Sabu (shopped two of hes friends to the police after hacked by Anonymous and, now is struggling to escape from us). Everything that's happening right now such as "Interview" is a typical brainwashing method of drama in order to save himself. You have made an enemy of Anonymous by saying that we are supporting FBI and now you are all going down!
The first video message to Lizard Squad posted by Anonymous on YouTube:
Just in case one message was not enough, a second video soon followed:
Photo credit: Vincent Diamante
-

PlayStation Network and Xbox Live hit by Christmas hack attack -- Kim Dotcom saves the day
Publié: décembre 26, 2014, 1:53pm CET par Mark Wilson

Gamers were disappointed this Christmas as both PlayStation Network and Xbox Live suffered massive outages. It wasn't long before hacking group Lizard Squad claimed responsibility, but anyone who found an Xbox One or PS4 under their Christmas tree quickly discovered that getting an online gaming fix was impossible.
This is not the first time that Lizard Squad has targeted Sony. At the beginning of December, the group knocked the PlayStation Network and Store offline, but this time Microsoft gamers also suffered. The attack started on Christmas Eve, and continued throughout Christmas Day. Then an unlikely hero saved the day -- Mega's Kim Dotcom.
Both Sony and Microsoft kept would-be gamers updated via Twitter and service status pages, but while both are still currently reporting issues, it seems that a Christmas gift from Dotcom will soon allow for online gaming. The internet entrepreneur intervened and made contact with Lizard Squad on Twitter, bringing about what he calls "a Christmas miracle".
Dotcom, who came to attention with his Mega Upload (then Mega) cloud storage service, managed to negotiate with the hacker outfit and convince it to back down. In a series of private messages, Dotcom offered members of the group 3,000 Mega vouchers -- worth $99 each -- which can be exchanged for 500GB of storage for a year.
A Christmas Miracle. How @MegaPrivacy saved @Xbox & @PlayStation from the @LizardMafia attack. Enjoy your games! :-) pic.twitter.com/qoaZ33eqCi
— Kim Dotcom (@KimDotcom) December 26, 2014
In an extra twist, Kim Dotcom added, "if you leave Xbox Live and PSN alone they will be converted to lifetime". This seemed acceptable to Lizard Squad, but Dotcom warned that "if you attack them again those vouchers will be terminated".
So, if you can't yet get online, it shouldn't be too long before you can.
Photo credit: elisekurenbina / Shutterstock
-

PlayStation Network and Xbox Live hit by Christmas DDoS attack -- Kim Dotcom saves the day [Update: not!]
Publié: décembre 26, 2014, 1:53pm CET par Mark Wilson

Gamers were disappointed this Christmas as both PlayStation Network and Xbox Live suffered massive outages following DDoS attacks. It wasn't long before hacking group Lizard Squad claimed responsibility, but anyone who found an Xbox One or PS4 under their Christmas tree quickly discovered that getting an online gaming fix was impossible.
This is not the first time that Lizard Squad has targeted Sony. At the beginning of December, the group knocked the PlayStation Network and Store offline, but this time Microsoft gamers also suffered. The attack started on Christmas Eve, and continued throughout Christmas Day. Then an unlikely hero saved the day -- Mega's Kim Dotcom.
Both Sony and Microsoft kept would-be gamers updated via Twitter and service status pages, but while both are still currently reporting issues, it seems that a Christmas gift from Dotcom will soon allow for online gaming. The internet entrepreneur intervened and made contact with Lizard Squad on Twitter, bringing about what he calls "a Christmas miracle".
Dotcom, who came to attention with his Mega Upload (then Mega) cloud storage service, managed to negotiate with the hacker outfit and convince it to back down. In a series of private messages, Dotcom offered members of the group 3,000 Mega vouchers -- worth $99 each -- which can be exchanged for 500GB of storage for a year.
A Christmas Miracle. How @MegaPrivacy saved @Xbox & @PlayStation from the @LizardMafia attack. Enjoy your games! :-) pic.twitter.com/qoaZ33eqCi
— Kim Dotcom (@KimDotcom) December 26, 2014
In an extra twist, Kim Dotcom added, "if you leave Xbox Live and PSN alone they will be converted to lifetime". This seemed acceptable to Lizard Squad, but Dotcom warned that "if you attack them again those vouchers will be terminated".
So, if you can't yet get online, it shouldn't be too long before you can.
Update
It seems that Dotcom's efforts were in vain. While the DDoS attacks on PSN and Xbox Live appear to have stopped, the network remain down for many gamers. Kit Dotcom has handed the baton back to Sony and Microsoft:
I tried my best to get Xbox & Playstation back online. Sorry that so many of you are still suffering outages. The ball is now with Sony & MS
— Kim Dotcom (@KimDotcom) December 26, 2014
Activist group Anonymous has now declared war on Lizard Squad.
Photo credit: elisekurenbina / Shutterstock
-

Microsoft and Google team up to fight hotels' personal Wi-Fi hotspot blocks
Publié: décembre 24, 2014, 2:41pm CET par Mark Wilson

Hotels are keen to extract money from guests, and in a bid to try to force them into paying for internet access, the industry is trying to gain permission to block personal Wi-Fi hotspots. Microsoft and Google are usually rivals, but the two companies are putting up a united front to fight these plans.
The American Hospitality & Lodging Association and Marriott International has asked the Federal Communications Commission for permission to use network management hardware that could prevent guests from creating and sharing their own private hotspots. The argument against this is that hotels are essentially requesting permission to block access to unlicensed parts of the wireless spectrum.
The hotel industry is asking the FCC to grant permission for the use of equipment for managing its networks "even though it may result in 'interference with or cause interference' to a Part 1 S device being used by a guest on the operator's property". The argument is that guests could potentially pose a security risk to the network if they are free to create their own hotspots, but the more cynical view -- and one expressed by Google -- is that it is designed to force people into using expensive hotel Wi-Fi connections.
Microsoft agrees, pointing out that "it is illegal to use a cell phone jammer or any other type of device that blocks, jams, or interferes with authorized communication". The company also suggests that hotel guests should be free to set up hotspots using Mi-Fi devices if they want to.
This is a battle that could run for some time, and at this stage there is no indication of which side may come out on top.
Photo credit: lirf / Shutterstock
-

How to use Microsoft's recovery images for Surface and Surface Pro
Publié: décembre 24, 2014, 2:27pm CET par Mark Wilson

If you're thinking of starting afresh with your Surface or Surface Pro in the New Year, Microsoft just made your life a little easier. The company has just released a series of recovery images for Surface devices that can be downloaded and used to restore the Windows tablet to the state it was in when you first bought it.
As this restore feature is something that's built in by default, you might be wondering what the value of these recovery images is. Well, there's always the possibility that your existing recovery image is corrupt, or you may even have freed up some space by wiping it out. Now you can get it back.
Whether you have one of the original Surface or Surface RT devices, or you treated yourself more recently to a Surface Pro 3, there's a download for you. To grab your recovery image, head over to the download page, sign into your Microsoft account and grab yourself the image for whichever Surface you own. You can't just jump in and download whatever you want, you need to provide your Surface's serial number and you'll be offered the relevant download.
With the recovery image safely stashed on your hard drive, dig out a USB drive with 8GB of free space if you're working with a Surface RT or Surface 2, or 16GB in the case of Surface Pros. In Explorer, right-click the drive and format it using FAT32 and then extract the contents of the zip file you downloaded onto the USB drive.
When you decide you want to restore your Surface to its factory-fresh state, turn off your device and insert the recovery USB drive you have created. Press and hold the volume down button and tap the power button to start up your tablet. As soon as the Surface logo appears, release the volume button and then follow the on-screen instructions to complete the process. Full instructions are available at the Surface support site, but the process is fairly straightforward.
-

Rockstar Consortium sells patents for $900 million, ending Android lawsuits
Publié: décembre 24, 2014, 12:34am CET par Mark Wilson

The patent wars are cooling down. Rockstar Consortium's litigation against numerous Android handset manufacturers has come to an end after the group sold 4,000 patents to RPX Corp. The intellectual property risk mitigation company bought the patents for $900 million, ending lawsuits against HTC, LG and Samsung.
Apple, BlackBerry, Ericsson, Microsoft, and Sony formed Rockstar Consortium back in 2011 to purchase around 6,000 patents from the bankrupt Nortel Network Corp for $4.5 billion. 2,000 of the patents had previously been shared between the members of the consortium, and the remainder have now exchanged hands for less a quarter of the original sale price.
Champagne corks will probably be popping at the headquarters of HTC, LG and Samsung, but this is just the latest in a series of patent cases closing down. Apple and Google shook hands and agreed to drop litigation against each other, and Samsung and Apple did the same earlier in the year. While on the face of it it seems as though the consortium has made a huge loss, it is likely to work out cheaper in the longrun -- and RPX will earn money in licensing from the likes of Google and Cicso without the costs associated with legal action.
RPX Chief Executive John Amster said, "I think they were not thrilled at the litigation and thought there was a more efficient way to get fair value for the portfolio. It could have taken many years more of litigation to get the same value." He added: "We commend everyone involved for their leadership and commitment to clearing the risk of the Rockstar portfolio by negotiating a reasonable purchase price in one efficient transaction".
Microsoft said that the news "demonstrates our patent system working to promote innovation". Moving forward it seems as though the battle will be fought on the drawing boards and on the shop floor rather than in the court room, with the hope being that competition will not only help to drive innovation, but also drive down prices.
Photo credit: EDHAR / Shutterstock
-

Windows 8 users can install Windows 10 Technical Preview through Windows Update
Publié: décembre 22, 2014, 8:30pm CET par Mark Wilson
We've seen several builds of the Windows 10 Technical Preview -- some official, some less so -- and there's another big build due in January. If you're interested in Windows 10, it's likely that you have already jumped onto the preview builds and have been updated as and when new versions are released. But as we get closer to the actual launch, the public released builds are going to start to get more exciting.
In January users of existing preview builds will be able to upgrade automatically, or there's the option of downloading an ISO. But Microsoft hasn’t forgotten users of Windows 8, and the company has released a tool that makes it possible to grab January's Windows 10 Technical Preview build through Windows Update.
This is great for anyone who doesn't have a spare computer available to install the build on, or who doesn't want to fiddle about with virtual machines or a clean install. The preparation tool updates your older copy of Windows so that it keeps an eye out for the new Technical Preview build for you. As soon as it is available -- some time in the second half of January -- Windows Update will let you know and give you the chance to install it.
Now this tool is interesting; it indicates a couple of things. Firstly, Microsoft is clearly keen for as many people as possible to try out Windows 10 Technical Preview -- we already know that there are 1.5 million users, but the more the merrier! Secondly, it's obviously that Microsoft wants to make it as easy as possible to install the preview build, and by taking down a small obstacle, more people are likely to try it out.
But -- and perhaps most importantly -- the very fact that Microsoft is providing an upgrade path from Windows 7 and Windows 8 to the Windows 10 Technical Preview demonstrates that the company must have great faith in the upcoming release. The preparation tool's download page emphasizes that Windows 10 is pre-release software, but by making it so easy to jump from an official, stable Windows release to an unreleased -- albeit official -- build shows confidence in the work that has been done.
This next build could be great!
-

Google's latest Transparency Report shows a drop in government data removal requests
Publié: décembre 22, 2014, 8:17pm CET par Mark Wilson

After Edward Snowden blew the whistle on the surveillance activities of the NSA, there has been greater public interest in what data governments are obtaining from technology companies, and what data was subject to censorship and removal. Back in 2010 Google started something of a trend with its first transparency report, and today sees the launch of the latest edition.
Covering the six months from July to December 2013, the latest Transparency Report shows that while there were more requests than the same period in 2012, there has been a drop when compared to the first half of 2013. In all, Google received 3,105 requests to remove 14,637 items, compared to 3,846 requests and 24,737 items in H1 2013, and 2,289 requests and 24,191 items in H2 2012.
Three products feature prominently in the report -- Blogger, Google search and YouTube. Data removal requests hit Blogger the hardest (1,068), but all three showed the same level of decline in request numbers from the previous period. The reasons for removal requests have changed slightly. There was a slight decrease in the number relating to impersonation, and the same is true for reasons of privacy and security. Defamation-related requests jumped by around 10 percent, but there was a sharp drop in the 'Other' category -- 2,359 down to 1,533.
Google's Director of Legal, Trevor Callaghan, said:
Our Transparency Report is certainly not a comprehensive view of censorship online. However, it does provide a lens on the things that governments and courts ask us to remove, underscoring the importance of transparency around the processes governing such requests. We hope that you’ll take the time to explore the new report to learn more about government removals across Google.
While not comprehensive, we are given something of a sneak peak at the types of removal requests that have been made. There was a jump in the number of requests originating from Russia, and in many cases Google complied -- including restricting access to a video that depicted self-immolation of a Buddhist monk, and blocking access to extremist material found in Google Play.
There are some interesting snippets in the Transparency Report, and you can work through all of the information online -- the site has been redesigned to be more user-friendly, so don't be put off if you've been frustrated by the report in the past.
Photo credit: Kirill__M /Shutterstock
-

BlackBerry works with Boeing on secure, self-destructing smartphone
Publié: décembre 22, 2014, 4:27pm CET par Mark Wilson

BlackBerry and Boeing are working together on a new super-secure smartphone. The announcement came at an earnings call at which BlackBerry CEO, John Chen, revealed scant details about the collaboration. What we do know is that the partnership is designed to create a secure device that can be used by US defense and homeland security workers.
Everybody's paranoid nowadays, but the defense sector is one that has a particular need for security. Boomberg reports that the phone is known as the Boeing Black, and it runs on top of BES -- a platform already known and trusted by many enterprise customers.
Talking about the joint venture, Chen said, "We're pleased to announce that Boeing is collaborating with BlackBerry to provide a secure mobile solution for Android devices utilizing our BES12 platform". While he joked that it "is all they allow me to say," this is not the first we've heard about the device.
Earlier in the year a letter to the FCC revealed plans for a self-destructing phone. "Any attempt to break open the casing of the device would trigger functions that would delete the data and software contained within the device and make the device inoperable". Other details in the FCC application include the revelation that the Boeing Black is a dual-SIM phone that can be used to connect to regular and secure networks, as well as an expansion module. Security comes courtesy of Boeing’s PureSecure system.
The phone has already been in development for a couple of years, but there's no hint about when it will hit production.
Photo credit: wk1003mike / Shutterstock
-

Microsoft apologizes for Halo: The Master Chief Collection snafu with a bunch of freebies
Publié: décembre 21, 2014, 10:51pm CET par Mark Wilson

The Halo series has been a massive success for Microsoft on Xbox, and Halo: The Master Chief Collection was an eagerly anticipated launch. But when the remastered game collection hit Xbox One, it didn't take long for gamers to discover a raft of problems with multiplayer games, and a range of glitches that impacted on performance.
Now Microsoft and games studio 343 Industries have apologized for the issues in a way that the companies are hoping will be well-received -- by giving away a batch of free stuff. That's not to say that an accompanying, contemporaneous apology has been issued; instead the freebies are a thank you for gamers' "support and understanding as we worked through issues impacting" the game.
The freebies are not being made available to everyone, just those who bought the game between 11 November and 19 December, but the team has dug deep and put together a collection it is hoped will keep people happy. Head of 343 Industries, Bonnie Ross, said:
Last month, I promised the Halo and Xbox community that addressing the matchmaking issues and other bugs impacting players' experience with Halo: The Master Chief Collection was our #1 priority. We've been working around the clock deploying weekly content updates and numerous server-side adjustments that have shown good results and we’re encouraged by the feedback we're hearing from you.
So... what do you get? To start with, there's a free month of Xbox Live Gold, followed up with an "exclusive" in-game nameplate and avatar. And… well, actually that's it for now, but there's more to follow in spring of 2015. 343 Industries has worked with original Halo developer Bungie and will be releasing a 1080p and 60fps version of the Halo 3: ODST campaign, as well as "re-imagined" version of the Relic multiplayer map for Halo 2: Anniversary.
Lovely stuff, but a simple "sorry" would have been nice as well.
-

Tor network could be attacked and knocked offline this week
Publié: décembre 21, 2014, 7:13pm CET par Mark Wilson

Roger Dingledine, leader of the Tor Project, has warned it could be the subject of an attack this week. In a blog post, he cautioned users that the project had learned that directory authorities might be seized in an attempt to incapacitate the network. Dingledine does not hint at who might be responsible for a future attack, but reassured users that anonymity would be maintained.
Directory authorities are used by Tor clients to help route traffic through the network, ensuring that users remains anonymous at each stage. An attack on directory authorities would probably have little effect to start with, but there is potential to take down the network if enough servers were targeted.
Tor is used by a wide range of people who want to stay anonymous online for a variety of reasons. It enables people in countries who censor the internet to gain access to information that would otherwise be blocked to them, and makes it possible to avoid many forms of surveillance. As with any form of anonymizing technology, Tor is used for bad as well as good, and it is possible that any potential attack is a political statement by a group that is unhappy with some of the activity that is taking place on the network.
Dingledine said:
Tor remains safe to use. We hope that this attack doesn't occur; Tor is used by many good people. If the network is affected, we will immediately inform users via this blog and our Twitter feed @TorProject, along with more information if we become aware of any related risks to Tor users.
We've made it to the end of the weekend without any visible sign of a DDoS attack, but the very fact that an announcement has been made means that suggestive intelligence must be out there. For now Tor is up and running as normal; just don't be surprised if something happens this week to take it offline, even if just for a short time.
-

Reddit (sort of) launches its own nebulous cryptocurrency, Reddit Notes
Publié: décembre 21, 2014, 4:37pm CET par Mark Wilson

We've already heard that 2015 is supposed to be the year of cryptocurrency, and Microsoft recently announced that Bitcoin is an acceptable form of payment. Now Reddit is getting in on the virtual currency action. Kind of. Well, perhaps. The details are vague at the moment, but the intriguingly-named Reddit Notes have been announced.
It comes just a few months after Reddit managed to secure $50 million in funding, and at the time "the investors in this round have proposed to give 10% of their shares back to the community". The birth of Reddit Notes is the start of this payback, but it's not yet clear who will receive them or what they will be used for.
The name has the distinct feel of a cryptocurrency, and Reddit explains that there are "approximately 950,000 reddit notes to divide among active user accounts". The notes can be viewed like shares at this stage, and it's obvious that there will have to be some sort of selection process if less than 1 million shares are to be distributed between users: there are just too many users for everyone to be included.
In a blog post, Reddit explains:
There aren't as many reddit notes as there are accounts, so if you get one, lucky you! Eligible recipients of reddit notes will be determined based on activities before 9/30/14, and we plan to give them away in the fall of 2015. We're still working out details on both the technological and legal aspects of the project, especially regarding how reddit notes will work within existing government regulations.
Reddit Notes are surrounded in ambiguity at the moment -- well, you have to get the hype machine going somehow -- but a basic infographic shows that Reddit Notes can be donated, given, traded, used as payment, or saved. There's no hint about when we might know more, but Fall 2015 is a way off yet, so there's plenty of time for more details to come out.
-

Ad slip-up reveals Apple Pay is about to expand to Europe, Middle East, India and Africa
Publié: décembre 18, 2014, 2:46pm CET par Mark Wilson

Oops! Less than a month ago, Microsoft accidentally let it slip that it was about to acquire email firm Acompli. Not to be outdone, Apple has now let a cat out of the bag a little early as well. A job ad spotted by iClarified shows that the company's Apple Pay service is set to expand outside of the US.
While rolling out outside of the States is not exactly surprising, Apple has given no hints about the timescale it is working to. More and more companies are signing up to get involved with Apple's contactless payment system, and a European launch was all but inevitable -- and now we know for sure.
With growing support from banks, it's looking as though 2015 could be a big year for Apple Pay. The ad posting has now been taken down, but the text was captured by iClarified for posterity. The advertised job is for a support intern to help with business development and contract negotiations.
Apple Pay is a new and exciting area in Apple that is set to expand across Europe, Middle East, India and Africa. Apple Pay will change the way consumers pay with breakthrough contactless payment technology and unique security features built right into their iPhone 6 or Apple Watch to pay in an easy, secure, and private way. The new London-based Apple Pay team will work to drive the roll-out of this technology across EMEIA by working with a variety of internal and external partners, including teams in the US where the product will first launch and the EMEIA organization, as well as Issuers, payment networks and merchants across Europe.
So we're still none the wiser about when we might see Apple Pay spreading through EMEIA, but it certainly seems as though we're edging closer to a wider rollout.
Photo credit: AVN Photo Lab/ Shutterstock
-

Secret CoolReaper backdoor for hackers discovered in Chinese Android phones
Publié: décembre 18, 2014, 1:31pm CET par Mark Wilson

China's monitoring and control of how its citizens access the internet is something that has been going on for some time. Now there is something new for Chinese smartphone owners to worry about. Security researchers at Palo Alto Networks have discovered a backdoor built into millions of handsets produced by Coolpad.
Known as CoolReaper, the backdoor potentially places more than 10 million smartphone owners at risk. The security firm conducted investigations after users complained on message boards about suspicious activity on their handsets. After downloading multiple copies of the stock ROM used on Chinese CoolPad phone, it was found that "the majority of the ROMs contained the CoolReaper backdoor".
A total of 77 ROMs were downloaded, and 64 of them were found to include the backdoor. Unit 42 has published a paper that details the capability of the malware, but users have reported the installation of unauthorized software and popup ads. Interestingly, it is reported that CoolPad deleted message board posts that made reference to these problems. At the moment there is no evidence that CoolPad devices sold outside of China and Taiwan are affected, but this will be off little comfort for those who may be at risk.
What CoolReaper is capable of is concerning, as the research paper explains:
- Download, install, or activate any Android application without user consent or notification
- Clear user data, uninstall existing applications, or disable system applications
- Notify users of a fake Over-the-air (OTA) update that doesn’t update the device, but installs unwanted applications
- Send or insert arbitrary SMS or MMS messages into the phone
- Dial arbitrary phone numbers
- Upload information about device, its location, application usage, calling and SMS history to a Coolpad server
The paper says:
In November a white-hat security researcher identified a vulnerability in the back-end control system for CoolReaper, which allowed him to see how Coolpad controls the backdoor.
The research paper gives a detailed breakdown of the findings and warns:
The known impact of CoolReaper thus far is limited to China and Taiwan, but Coolpad’s position in the market and global expansion plans mean this backdoor presents a threat to Android users all over the world.
While CoolPad is only the sixth largest smartphone manufacturer in the world -- with a global share of 3.7 percent of the market -- it is ranked as the third largest manufacturer in China. The company is gradually expanding into the US and Europe so interest in this backdoor is only going to increase.
So far it's hard to say much about the source of the backdoor. Researchers have determined that it has been around since at least October 2013, but it's not clear whether or not there is a connection to the Chinese government.
Photo credit: lculig / Shutterstock
-

Over 1.5 million Windows 10 Technical Preview users, nearly a third use it daily
Publié: décembre 17, 2014, 11:42pm CET par Mark Wilson

Microsoft's Gabe Aul has given an insight into how the Windows 10 Technical Preview has been received by testers. In a blog post, Aul reveals that there are more than 1.5 million registered Windows Insiders testing out preview builds, and that nearly a third of this number -- around 450,000 -- are using it on a daily basis.
So far there have only been three official preview builds: build 9841, build 9860, and build 9879. There have also been a few unofficial leaks including, 9888 complete with a limited preview of Cortana and more recently build 9901. Microsoft does not shy away from acknowledging the existence of these leaks, but it's not clear if they have been included in the usage figures.
The company is clearly happy with the level of interest in Windows 10 Technical Preview. The spread of the leaked builds around the internet illustrates that there is a huge appetite for a follow-up to Windows 8.1. In the blog post, Aul says that in the course of the preview program, feedback from testers has helped Microsoft to fix more than 1,300 problems.
Aul addresses the disappointment users have expressed about the lack of an official build in December:
We’ve been very hard at work putting together a great build for you that includes a bunch of new features and improvements. As all of those payloads came in we needed to stabilize code, fix any integration issues, and ensure all of the new UX is polished. We’re really focused on making the next build something that we hope you’ll think is awesome. In fact, just so that we have a *daily* reminder to ourselves that we want this build to be great, we even named our build branch FBL_AWESOME.
It's not until the end of the third week of January that a new build will be pushed out, and there are no hints about what we can expect to see: "I'm itching to tell you more about stuff that's coming. You'll see some big things, lots of small improvements, and I hope there will be something for each of you to point to and know your influence was felt and appreciated by us," is all we get for now.
Oh, in case you hadn't heard already, Aul confirms that it will not be possible to automatically upgrade from the leaked build 9901 to the build that comes out in January. Manual upgrades will be possible, but you'll need to wait until the ISO is made available.
-

Microsoft's view of 2015: Internet of Things, security, and machine learning
Publié: décembre 17, 2014, 8:23pm CET par Mark Wilson

Companies are always forward-looking, but it's at this time of year that this is really focused on. Consumers are excited to see what products they'll be able to get their hands on in the year ahead, businesses want to know what services the coming year has to offer, and technology enthusiasts are keen to learn about what projects are in the works.
Today, Microsoft shares its view of which areas of technology are going to be of the greatest importance for businesses in 2015. Corporate Vice President, Enterprise and Partner Group, Susan Hauser believes that security will continue to be strengthened, the Internet of Things will grow, and predictive tools will be more heavily utilized.
With the general focus on the cloud, the increased interest in the Internet of Things is hardly a surprise. Once regarded as something rather nebulous and ethereal, businesses and customers are now starting to see the potential for the IoT. Hauser predicts that what will help to accelerate growth here is increased cooperation between partners, as growing numbers of sensors provide access to "nearly unlimited amounts of data".
Predictions such as Bing's view of what will happen in 2015 are entertaining, but there are far more practical applications for machine learning. Again, this is a growth area whose catalyst has been the explosion of cloud computing and data storage. Hauser predicts that big data will promote the adoption of machine learning across different businesses:
This growth will be driven by three factors: broader access to machine learning, massive computing power connecting systems and services, and the explosion of online data. These developments create more opportunities for organizations to use machine learning for data-driven decision making.
The appearance of security enhancements on a list of predictions was to be expected -- it's something that has always been important and will continue to be. The sheer number of security breaches that occurred in 2014 -- and the costs incurred as a result of them -- have shown that companies still have a lot of work to do in this area. As more services move to and embrace the cloud, customers expect a certain level of security, and Hauser says: "It's clear that businesses need to do more to fight the increasing threat of hackers, do more to protect their businesses and prevent huge losses. We're seeing policy and technology developments that will help businesses beef up security on premises, in the cloud and across mobile devices".
We'll have to check back in a year's time to see how accurate the predictions prove to be.
Photo credit: asharkyu / Shutterstock
-

BlackBerry launches the Classic -- a smartphone with an old-school keyboard
Publié: décembre 17, 2014, 5:30pm CET par Mark Wilson

BlackBerry is not a company that's afraid to do things a little differently, and this is something that's perfectly demonstrated by its latest release. Rather than eschewing the physical keyboard like most smartphones, the BlackBerry Classic embraces it. The square 720 x 720 screen is comparable to that of the BlackBerry Passport, but stands out from mainstream handsets due to its size -- just 3.5 inches -- and unusual aspect ratio.
The look of the handset might be a little dated, and the specs are also something of a blast from the past. Powered by a Qualcomm Snapdragon S4 Plus dual-core processor, the phone has 2GB of RAM, 16GB of storage, an 8MP rear camera, and a 2MP front shooter. And it can be yours for $449 unlocked.
While this may not seem like the most exciting smartphone out there it is important to remember that it is not supposed to be. This is a workhorse of a phone, designed primarily with emailing and web browsing in mind: anything else is just icing as far as BlackBerry is concerned.
With a claimed 22 hours of battery life, the Classic is a phone that BlackBerry clearly wants to last through the day. Speaking about the new device, BlackBerry CEO John Chen said:
We listened closely to our customers' feedback to ensure we are delivering the technologies to power them through their day – and that feedback led directly to the development of BlackBerry Classic. BlackBerry Classic is the powerful communications tool that many BlackBerry Bold and Curve users have been waiting for. It’s the secure device that feels familiar in their hands, with the added performance and agility they need to be competitive in today's busy world.
The Classic runs BlackBerry 10, and includes the Amazon Appstore for access to a wealth of Android apps, as well as BlackBerry World for other apps. The phone is available from today on a contract with a number of providers, or you can buy it unlocked from BlackBerry or Amazon for $449.
BlackBerry has produced a video to show off the Classic:
-

Apple puts sales on hold in Russia as rouble collapses
Publié: décembre 17, 2014, 4:40pm CET par Mark Wilson

The financial crisis in Russia is beginning to have an impact on the rest of the world. The value of the rouble has been fluctuating tremendously, but is generally on a downward trajectory -- it plummeted in value by 20 percent so far this week. For Apple the uncertainty about how things could pan out is too much, and the company has stopped sales of iPads, Macs and iPhones on the Russian version of its online store.
As reported by the BBC, Apple had to increase its prices in Russia last month as a result of the devaluing of the rouble. But now a more drastic step has been taken. Head to the Russian Apple Store now and you're greeted by a virtually blank page rather than the latest tech from the company.
A multi-language message on the website reads: "We'll be back. We're busy updating the Apple Store for you and we'll be back soon". The move is not unprecedented -- Apple closed its Russian online store a few weeks ago, but this ended up lasting for just one day. It's not clear how long the closure will continue this time around.
In a statement, Apple said: "Due to extreme fluctuations in the value of the rouble, our online store in Russia is currently unavailable while we review pricing".
The most likely outcome is that the store will come back online in the next few days with inflated prices, but there's no indication of when this might happen. While the currency fluctuations are understandably concerning for Apple, the company will be keen to get its products back on sale as soon as possible. Bloomberg reports that Apple sold 1.57 million iPhone in Russia in the last year, netting around $1 billion for the company.
Photo credit: FooTToo / Shutterstock
-

Google increases security for desktop Gmail with Content Security Policy support
Publié: décembre 16, 2014, 9:49pm CET par Mark Wilson

Google today revealed a new feature for Gmail that should help to increase inbox security. Newly added support for Content Security Policy (CSP) keeps Gmail extensions in check to ensure that none are malicious or try to interfere with your Gmail session.
It's essentially server-side malware protection for Gmail extensions, and this is just the latest move from Google that aims to increase inbox security. Email security is of interest to everyone online, but it's something that is particularly important to business and enterprise users -- groups Google is keen to keep happy.
Content Security Policy serves as a means of intercepting unsafe code, stopping in its tracks before it has chance to cause any damage or gain access to personal information. Introducing the security feature, Google's Danesh Irani said:
Most popular (and well-behaved) extensions have already been updated to work with the CSP standard, but if you happen to have any trouble with an extension, try installing its latest version from your browser’s web store (for example, the Chrome Web Store for Chrome users).
CSP support has been added to the desktop version of Gmail; Google has not yet indicated if or when the same security feature will be made available to mobile users. Google recently added support for Security Key to Gmail, and has offered HTTPS access for a while now.
Photo credit: Novelo / Shutterstock
-

Twitter could be on the verge of introducing auto-playing video ads
Publié: décembre 16, 2014, 7:20pm CET par Mark Wilson

A little over a year ago, Facebook introduced videos that play automatically. If a report from AdWeek is correct, it looks as though others thought that this was a great idea because Twitter is reportedly considering implementing the same feature. As this is a report that appeared in AdWeek, it should be clear that one of the most likely reasons for introducing the feature would be to increase the visibility of ads.
Just as with Facebook, the concern here is that -- as well as being considered by many as an invasion of, if not privacy, then virtual personal space -- it will lead to an unwanted increase in data usage.
AdWeek cites industry insiders who are quoted as saying: "It's an argument that's happening -- a tug of war". It's likely that Twitter will be very cautious about auto-playing videos. While the site has a need to appeal to advertisers, it has remained popular because of its simplicity. Features such as inline images have been introduced over the years, but Twitter has remained fairly true to its limited-character roots.
Twitter's philosophy has centered around its simple look, and the idea of videos that play automatically when they appear on screen is one that will undoubtedly divide users. At the end of the day, it is likely to be the financial considerations that are the deciding factor. Anything that can be used to grab the attention of a relatively captive audience is going to be embraced by advertisers, and this may be enough to sway Twitter in one direction.
Would autoplay videos be a turn off for you?
Photo credit: woaiss / Shutterstock
-

Apple, Amazon, HP, Verizon and others back Microsoft's fight against US government
Publié: décembre 16, 2014, 6:09pm CET par Mark Wilson

Microsoft is currently embroiled in a legal battle with the US government, and the fight has led to an unlikely alliance between several rival companies. Microsoft was handed a government order requesting access to emails stored at a datacenter in Ireland. The company has been battling the order for several months, and now Apple, Amazon, Verizon, and HP are among the big names lending their support to the fight.
It's not just technology firms who are putting their names forward in support of the challenge of the search warrant. Several global media outlets, including the Guardian, the Washington Post, and CNN as well as numerous trade associations and advocacy organizations have signaled their support for Microsoft.
Microsoft has already appealed against the government order -- and lost -- but it is hoped that the latest move, which sees supporters all filing legal briefs backing Microsoft, will be more successful. The full list of those supporting Microsoft is wide and varied, bringing together technology firms and the likes of the Open Rights Group and the American Civil Liberties Union, representing an almost unprecedented level of cooperation between those who are usually stark rivals.
The level of interest that this case has generated is also quite unprecedented. In a post on the Official Microsoft Blog, the company says:
Seldom has a case below the Supreme Court attracted the breadth and depth of legal involvement we're seeing today. Today’s ten briefs are signed by 28 leading technology and media companies, 35 leading computer scientists, and 23 trade associations and advocacy organizations that together represent millions of members on both sides of the Atlantic.
One of the reasons this has become so high profile -- aside from the fact that Microsoft is involved -- is that, as Microsoft puts it, the case centers around a policy issue that is "fundamental to the future of global technology".
If the US government proved successful in its bid to gain access to Microsoft's datacenter, the implications would be colossal -- and this is precisely why Microsoft is digging in its heels:
We believe that when one government wants to obtain email that is stored in another country, it needs to do so in a manner that respects existing domestic and international laws. In contrast, the US Government's unilateral use of a search warrant to reach email in another country puts both fundamental privacy rights and cordial international relations at risk. And as today’s briefs demonstrate, the impacts of this step are far-reaching.
Photo credit: Junial Enterprises / Shutterstock
-

Microsoft opens up improved Sway Preview to everyone -- no more waiting list!
Publié: décembre 16, 2014, 2:16pm CET par Mark Wilson
It has been a few weeks since Microsoft introduced us to the latest addition to the Office family -- Sway. In fact, as Microsoft points out, the preview was unveiled 10 weeks ago. While the initial preview required anyone interested to join a waiting list, now it's possible to get in on the action straight away; and it seems there has already been great interest in the product.
Microsoft says that there have been 175,000 requests to access the Sway Preview, and the Sway.com website has received over one million visitors. Now anyone with a Microsoft account is able to try out the data collection and presentation tool and check out a batch of new features.
The new Microsoft remains all ears, and there have already been a number of changes to Sway in response to feedback from people who got into the preview early on. Undo and redo might seem like obvious tools to include, but Microsoft explains that feedback from users led to them being introduced faster because of the importance people placed on them. Many of the other changes are focused on text editing.
It's now possible to edit text directly on a Sway canvas, and bullets and numbering are now also included. We've already been told that Sway is a way to "reimagine how your ideas come to life" and it's likely that this will involve several changes of mind when putting together a canvas. Updates have made it easier to re-order a section using drag and drop. Other new features include PDF import, an improved color picker and wider availability of the iPhone version of Sway.
If you're interested in checking out the tool for yourself, sign up for the Sway Preview for instant access.
-

Skype offers free calls from India to US and Canada until March
Publié: décembre 16, 2014, 1:29pm CET par Mark Wilson

Microsoft has an end-of-year present for Skype users in India. Starting now and running until the beginning of March, calls from India to the US and Canada are completely free of charge. Interestingly, this includes calls placed to mobiles as well as to landlines.
Unusually for such an offer, there's no commitment, no free trial and, seemingly, no catch -- just free calls for the next three months. The news comes just after Microsoft unveiled details of its Skype Translator preview, and is just in time for the holiday season when the number of phone calls placed tends to skyrocket.
Over on the Skype website, Microsoft gives some details about the offer, and there are very few limitations. Calls can be up to four hours long -- after this time you can simply hang up and redial if you still need to chat -- and business use, such as in call centers, is prohibited. These points aside, this is a pretty clear cut offer which will be well-received.
Microsoft explains:
From December 16, 2014 (00:01 IST) to March 1, 2015 (00:01 IST) (the Offer Period) use Skype to make free calls from India to landlines and mobiles in the U.S. and Canada (excluding special, premium service and non-geographic numbers).
To take advantage of the offer there's no need to do anything special -- just fire up Skype and start dialing!
Photo credit: Ollyy / Shutterstock
-

Edward Snowden condemns Amazon's 'morally irresponsible' encryption policy -- users don't care
Publié: décembre 15, 2014, 8:19pm CET par Mark Wilson

In a near-perfect example of how there is always more than one way to look at things, Edward Snowden has very different views on Amazon than Amazon users do. On Friday, Snowden appeared -- as ever -- via video link at the surveillance symposium at the Cato Institute. He condemned Amazon's lack of encryption of customers' searches, referring to the practice as "morally irresponsible".
But Snowden's condemnation of Amazon comes at the same time as a study by Bizrate Insights which finds that more than 45 percent of online shoppers trust the site with their payment and personal information. So why the disparity?
As we know from the past twelve months, Edward Snowden is a man with more than a passing interest in privacy. His disdain for Amazon's attitude to encryption has been reported in -- of all places -- the Washington Post. This is interesting because, as pointed out in the article, Jeff Bezos is not only the founder and chief executive of Amazon, but also the owner of the Washington Post.
Snowden is concerned that Amazon goes to the effort of encrypting payments while failing to do the same for customer searches. This means, he says, that the reading and shopping habits of Amazon's customers are open to governmental snooping. While it's unlikely that the government is interested in which books you buy from Amazon, this is not really the point, and Snowden suggests that anyone from ISPs to network providers could see what you're looking for.
At the same time a survey of over 6,200 people carried out by Bizrate Insights showed that while more than three quarters of online shoppers are unhappy with the level of security offered by retailers, Amazon actually fared well in the trust rankings. The online giant found itself in third position, gaining the trust of 45.4 percent of people -- it fell behind PayPal (48.9 percent), and banks and credit unions (72 percent).
Hayley Silver, vice president of Bizrate Insights said:
Among these tech transactional titans, it is those that have low barriers for usage and that have put consumer protection in the forefront that have earned the greatest amount of trust.
Lower down the list, Apple was trusted by just 21.4 percent of those questioned, eBay by 18.7 percent, and Google a mere 12.9 percent.
Photo credit: Ken Wolter / Shutterstock
-

Skype Translator preview breaks down the language barrier
Publié: décembre 15, 2014, 3:51pm CET par Mark Wilson

Microsoft has shown more interest in Skype in recent years, including making it far more web-friendly, and introducing a business-centric version in place of Lync. The latest move is designed to break down more barriers, making it easier for people in different countries to communicate with each other, regardless of the language they speak.
Skype Translator preview is the first step towards making language irrelevant. Rather than relying on interpreters, users can communicate through Skype and translations will be automatically performed. English and Spanish are supported as spoken languages, but there is support for more than 40 written languages as well.
If you need to communicate with people in another country, there's now no need to learn each other's language as Skype can do the hard work for you. Near-instantaneous translation is available whether you are conducting a voice or a text chat, making this a tool that will be of great interest to business users.
Introducing the new Skype feature, Microsoft says:
Skype Translator is a great example of the benefit of Microsoft’s investment in research. We’ve invested in speech recognition, automatic translation and machine learning technologies for more than a decade, and now they’re emerging as important components in this more personal computing era. Skype Translator is the most recent and visible example. Skype Translator relies on machine learning, which means that the more the technology is used, the smarter it gets. We are starting with English and Spanish, and as more people use the Skype Translator preview with these languages, the quality will continually improve.
As we have become used to with the new Microsoft, the company is looking for feedback, and the preview phase will help to improve the accuracy of translations -- there's a little guide to how the recognition and translation process works available here.
Microsoft has already given school children a chance to try out Skype Translator, and the video below shows how they got on while demonstrating the capabilities of the software.
If you're interested in taking part in the program, you can sign up for the Skype Translator Preview.
Photo credit: hobbit / Shutterstock
-

Sony leaks show plans to trick pirates into downloading fake episode torrents
Publié: décembre 14, 2014, 10:24pm CET par Mark Wilson

The hacking of Sony Pictures was quite a revelation. It led not only to the leaking of several yet-to-be released movies, but also the private details of many employees. A cache of documents and information was made available, and as time goes by we get more chance to sift through what's there. The latest revelation comes from TorrentFreak which reports about the Sony Pictures' plans to thwart piracy of its TV shows.
The company's AXN TV network was apparently toying with the idea of using honey traps to trick pirates into downloading fake torrents of popular shows such as Hannibal. The plan was not to just prevent downloaders from getting hold of the videos they were looking for, but also to use torrent sites as a means of free advertising.
If you think this idea sounds somewhat out of leftfield, you're not alone. While AXN Central Europe thought it was a brilliant plan, Sony Pictures had other feelings. The plan was to take advantage of the fact that after popular shows air on TV, there tends to be a flurry of torrent activity immediately afterwards. AXN Central Europe came up with the idea of not just producing fake torrents, but to disguise advertisements as files that users might actually want to download
The idea is simple. We made a promo dedicated to Hannibal which is convincing people in very creative and noinvasive [sic] way to watch Hannibal legally on AXN instead downloading it from torrents. [T]his promo is supposed to be downloaded on the torrents sites, imitating the first episode of Hannibal season 2 but in reality would be only a 60 sec promo. The torrents sites are exactly the place where people just after [the] US premier would be searching for the first episode of season 2. So the success of this project is more than 100% sure.
There are a few problems with the idea -- besides the notion that its success could be "more than 100 percent sure". The first is that most people downloading torrents take great care to ensure that they are downloading the real thing. For each show, there are a number of trusted sources (trusted providers of files, not just trusted sites) to whom downloaders turn. Anyone looking for the latest episode of Hannibal would know where to look, and would likely ignore torrents from other sources.
Secondly, word about fake torrents spreads very quickly. Torrent sites frequently allow for comments to be left so users can comment on audio and video quality and the like. When fake files appear -- as they often do -- they are soon discovered and weeded out. AXN seemingly didn’t realize this.
Thankfully, people at Sony credited web users with more intelligence and shot down the idea. It seems that more concern seems to have centered around the fact that if pirate sites were used for promotion of shows, it would look strange to governments if Sony then tried to close down the same sites for helping with the distribution of copyright material. As one executive put it:
Forget about a site blocking strategy if we start putting legitimate PSAs or promos on sites we’ve flagged to governments as having no legitimate purpose other than theft… PSAs being for public good, etc…
The likes of the Pirate Bay may be struggling at the moment, but any attempts to take advantage of them will clearly have to be better thought through than this idea was.
Photo credit: BUNDITINAY/ Shutterstock
-

Facebook drops Microsoft's Bing in favor of its own search tool
Publié: décembre 14, 2014, 4:32pm CET par Mark Wilson

Bing has been unceremoniously dumped by Facebook. The social network had been using the Microsoft search tool to power its Graph Search platform for some time now, but no longer. While no announcement has been made, Facebook confirmed the news to Reuters.
The lack of official announcement meant that the dropping of Bing was immediately noticed. Facebook does not have a replacement partner in mind -- there is no danger of the social network teaming up with Google -- but will go it alone instead.
It seems that the decision tied in with Facebook's recent updating of its own search tool. A few days ago, the search tool was updated to make it possible to find specific posts rather than users and pages. This made Facebook Search more like a "proper" search engine, and probably led to questions about the value of maintaining links with Bing. But there are other reasons behind ditching Bing.
Facebook issued a statement to VentureBeat in which it explained the switch in focus:
We're not currently showing web search results in Facebook Search because we're focused on helping people find what's been shared with them on Facebook.
While Microsoft will undoubtedly be unhappy with Facebook's decision, it's one that will probably go down well with users of the site. The move is an interesting one, if not one that is entirely surprising. The problem with using Bing to display web search results within Facebook was that it did just that -- display search results from the wider web rather than just Facebook.
This meant that while there was arguably a better experience for users thanks to the extra features, there was a far stronger risk that people would navigate away from Facebook and stop consuming ads. It's not yet clear whether Facebook will start to cast its search net wider, displaying results and pages in a closely controlled built-in browser, but this is certainly something to look out for further down the line.
Photo credit: 1000 Words /Shutterstock
-

Apple customers can now pay online using PayPal
Publié: décembre 13, 2014, 12:08am CET par Mark Wilson

If you're looking for a new way to hand your money over to Apple, you're in luck. It's been a long time coming, but Apple now accepts PayPal payment in both the US and the UK online stores. Accepting this method of online payment is something that customers have wanted for some time, but Apple has previously been reluctant to embrace PayPal.
In fact, PayPal was only recently given the cold shoulder by Apple. The company was ignored when Apple Pay was introduced earlier in the year. It seems that relations between the two companies have improved -- there is money to be made, after all.
Apple has gone further than just allowing customers to purchase their new iPhone, iPad or Mac using money in their PayPal account. The company is promoting PayPal's credit facility, giving people the option of buying now and paying off the balance over 18 months without paying interest.
Things have been a little heated between Apple and PayPal in the past. It's not yet clear whether the bridge-building will extend as far as PayPal becoming an Apple Pay partner, but for now it's something that works in the favor of Apple customers and PayPal's profits.
Photo credit: Sukharevskyy Dmytro (nevodka) / Shutterstock
-

YouTube embraces animated GIFs with new beta sharing feature
Publié: décembre 12, 2014, 10:12pm CET par Mark Wilson

YouTube is a great source of entertainment, but don't you wish that sometimes people would just cut to the chase? There are plenty of videos of epic length, often comprising a massive build up to a short punchline. Why not cut the crap and get to the point?
One way to do this when re-sharing YouTube videos is to convert the interesting portion into an animated GIF, saving viewers time and bandwidth. YouTube itself is getting in on the web's rekindled interest in animated GIFs. A new beta program has been opened up that lets YouTube users transform lengthy videos into snapper clips of up to six seconds in length.
This is essentially a readymade meme creator. Find a video you like -- on a channel that has the feature activated -- and you can select the most pertinent six seconds of footage. You can choose to be even more concise if you like, but you have up to six seconds to play with. But what meme would be complete without a caption? YouTube is on the ball and has included a captioning option for added humorous potential.
Over on the beta sign up page Google explains that: "We are testing this new feature with a handful of creators and look forward to adding new ones soon. Please sign up here to be contacted about the next phase of the Beta test".
There's no word on when, or indeed if, the feature will be made generally available, but anyone who is interested in taking part during the beta phases is invited to put forward their proposals for how they will use the GIF maker. There are two suggested stock replies -- "create GIFs to promote my channel", or "allow fans to interact with my videos" -- but there's also an "Other" option if you'd like to get a little more creative, or amusing, with your reply.
So... prepare yourself for an influx of animated GIFs on your Facebook wall and Twitter feed in the coming weeks and months!
Photo credit: Stuart Miles / Shutterstock
-

File sharing in Google Drive and Docs just got easier
Publié: décembre 11, 2014, 9:50pm CET par Mark Wilson
The gradual but relentless move to the cloud is about more than just making it easier to access files from multiple devices. For many people, particularly business and enterprise users, sharing and collaboration is more important. Today Google has made two small but important updates to Drive and Docs that makes file sharing easier than ever.
Now when you start to type the name of someone you would like to share a file with, you will see their profile picture alongside their name. This mimics the way things work in Gmail, and helps you to check you are selecting the right people.
In a post on the Google Drive blog, software engineer Lev Epshteyn, says: "This can come in handy when you need to confirm that you’re inviting the right contacts, especially if you work with people that have similar names".
Another update which is inspired by Gmail is suggestions. Add two collaborators to a document and suggestions will appear for other people you might also want to consider including. Adding people that have been suggested is a simple matter of clicking their name, so you not only save time typing, but also get reminded of people you might otherwise have forgotten.
The two changes can be found in both Google Drive and all of the Docs editors.
-

Surface Pro 3 is one of the most breakable tablets you can give this Christmas
Publié: décembre 11, 2014, 3:44pm CET par Mark Wilson

We're entering the season of giving and receiving, and it's safe to assume that one of the most popular electronic gifts this year will be tablets. With three key platforms to choose from, various price-points, different sizes, and a bewildering array of manufacturers, which one should you opt for? One factor that's well worth considering is durability.
SquareTrade, a company offering extended warranties on electronic devices, has drop-tested ten of the most popular tablets to see which can handle the abuse. The results might surprise you. Perhaps most startling is how poorly some of the big names fared.
Unsurprisingly, the drop tests confirmed the old adage "the bigger they are, the harder they fall"; larger tablets were found to be more prone to breakage than their smaller cousins. Samsung devices held up well, although results were mixed. The same is true for Apple, but the iPad Mini 3 proved more robust than the larger iPad 2 Air. Microsoft's Surface Pro 3 only just missed out on being rated as the most breakable tablet of the bunch, with only the little known TMAX 9 HD receiving a worse rating.
Here's the full top ten countdown, starting with the least breakable and building up to the tablets that could easily get destroyed. The "breakability score" for each device has been ranked low, medium and high by SquareTrade, and three awards were handed out as well.
- Samsung Tab S 8.4 - 3.3 (low) Least Breakable
- Asus Memo Pad 7 - 3.5 (low) Durable & Budget-Friendly
- Sony Xperia Z3 - 4 (medium) Durable & Water Resistant
- iPad Mini 3 - 4.4 (medium)
- Nexus 9 - 4.5 (medium)
- Samsung Note Pro 12.2 - 5.1 (medium)
- Samsung Tab S 10.5 - 6 (medium)
- iPad Air 2 - 6.1 (medium)
- Surface Pro 3 - 7.6 (high)
- TMAX 9 HD - 8.2 (high)
Check out the video below to see the tests being performed:
Photo credit: solkanar / Shutterstock
-

Microsoft now accepts Bitcoin payments in Windows, Windows Phone and Xbox stores
Publié: décembre 11, 2014, 3:09pm CET par Mark Wilson

We've heard that 2015 could be the year of cryptocurrencies, and now it seems that Microsoft is getting in on the action ahead of the New Year. There is yet to be a formal announcement, but Microsoft now accepts Bitcoin as a form of payment for apps, games and other digital content.
The virtual currency can be used to make purchases in the Windows Stores, Windows Phone Store and the various stores that exist for Xbox. While Microsoft is yet to issue a statement about the acceptance of Bitcoin, a page has been added to its customer support site that gives some details.
The page, entitled "How do I use Bitcoin with my Microsoft account?" explains that "you can now use Bitcoin to add money to your Microsoft account". At the moment, the currency can only be used to make payments within the US, but it is possible that there will be a global rollout further down the line.
In order to make a payment using the digital currency, Bitcoins must first be added to a Microsoft Account and from here the necessary amount can be redeemed. "You can’t use Bitcoin to purchase Microsoft products and services directly at this time," the support page points out.
Microsoft is far from being the first big company to welcome the use of Bitcoin, but its adoption will be seen as a positive move for those pushing for wider acceptance.
Update:
Microsoft has now made an official announcement. Over on the Fire Hose the company explains that starting today, Bitcoin payments are an option -- payments will be processed by BitPay. A Microsoft spokesperson said:
Microsoft is dedicated to providing customers with personalized, integrated and frictionless buying experiences, and Bitcoin represents just one of the company’s investments in offering consumers worldwide flexible payment options, in addition to support for credit cards, PayPal, AliPay, and mobile operator billing. Today we accept payments from customers in over 200 markets worldwide.
Photo credit: Lightboxx / Shutterstock
-

Google News to close in Spain, Spanish publishers to be dropped globally
Publié: décembre 11, 2014, 2:18pm CET par Mark Wilson

Stories about companies going to all manner of lengths to minimize or completely avoid tax payments are nothing new. Google is no stranger to this, and following new legislation in Spain, the company is shutting down the Spanish version of Google News. This is a bid to avoid paying what has been dubbed the "Google Tax".
The Spanish government is about to bring in legislation that would require Google News to make payments to publishers whose content it uses. The news service will close on 16 December, but the consequences go beyond Spanish web users missing out on Google News.
Starting in January, a new copyright law will require sites that republish, or even link to, content from a Spanish publisher to pay the Association of Editors of Spanish Dailies for the privilege. A system of fines will be in place for anyone who fails to comply. Google's decision to close Google News in Spain goes further. Spanish publishers will also be dropped from the global version of Google News.
In a post on the Google blog, Richard Gingras, Head of Google News explains the reason for the closure:
This new legislation requires every Spanish publication to charge services like Google News for showing even the smallest snippet from their publications, whether they want to or not. As Google News itself makes no money (we do not show any advertising on the site) this new approach is simply not sustainable. So it’s with real sadness that on 16 December (before the new law comes into effect in January) we’ll remove Spanish publishers from Google News, and close Google News in Spain.
There is likely to be quite a backlash against the move, but it remains to be seen whether vitriol will be aimed at Google or the Spanish government.
Photo credit: Kichigin / Shutterstock
-

Android Wear users can now download watch faces from Google Play
Publié: décembre 10, 2014, 8:06pm CET par Mark Wilson

Google Play is home to apps for every occasion, books to suit every mood, and movies and music for everyone. Today Google announces that Android Wear users can also download a makeover for their wrist wear from the digital store. Watch faces can now be downloaded from Google Play direct to your chosen wearable.
From the serious to the silly, the cheap-and-cheerful to the utterly stylish, you can transform the look of your smartwatch with just a few clicks. And now that the Watch Face API is available to developers, you can expect to see more and more faces popping up over the coming weeks and months.
There are already a number of faces to choose from, including some themed to tie in with movies and TV shows. Google has also released an update to the Android Wear app to make it easy to browse through the selection that's on offer from the comfort of your phone.
David Singleton, Android Wear's Director of Engineering, points out that the update is rolling out gradually so if you don’t see it just yet, be patient.
Want to know more about watch faces? Check out the video below to sate your desires and learn about the Watch Face API:
-

Bing-powered Insights for Office brings context-sensitive search to Word Online
Publié: décembre 10, 2014, 7:49pm CET par Mark Wilson
Microsoft's current vision is mobile first, cloud first (if two things can be simultaneously first), and this is perfectly demonstrated by what is being done with Office. Office has been pushed to not only mobile devices, but also the cloud and now Word Online gains the power of Bing in the form of Insights for Office.
The new feature makes it possible to perform searches from within Word Online so you can conduct research with fewer clicks. It could be as simple as looking up a definition, or you might be inspired to look up images related to the document you are working on.
But Insights for Office is about more than just basic searching, it's also intelligent. Over on the Bing Blog, Bing Product Management Ryan Gavin uses the example of writing about President Lincoln. If in the course of writing a document about Abe you need to make reference to his birth date, but can't remember exactly when it was, firing up a search engine and performing a manual search is fairly inefficient.
With Insights for Office you can highlight the phrase "Lincoln was born in..." that you have already typed in your document, right-click, select the Insights option and a relevant search will be conducted for you. Information and content is pulled in from Snapshot, Wikipedia, Bing Image Search and other resources, and the order in which results appear depends on the context and content.
Microsoft also announced that Office Online is gaining improved PDF support -- including built-in OCR -- better pagination, and an enhanced Tell Me feature.
-

Intel IoT Platform aims to drive adoption of secure Internet of Things
Publié: décembre 10, 2014, 6:49pm CET par Mark Wilson

The Internet of Things will see an acceleration in adoption if Intel's plans work out. The chipmaker has just unveiled its own Internet of Things platform called, inevitably, Intel IoT Platform. The aim is to create a unified system that makes it easy for manufacturers to securely connect their devices to others.
The platform is essentially a set of protocols that helps to ensure compatibility between devices. Intel has already forged a number of partnerships with a view to accelerating uptake of and interest in the Internet of Things in general, and Intel IoT specifically.
Dell, Accenture and Wipro are just three of the names already on board, helping to create an ecosystem that is "designed to provide a repeatable foundation for devices to deliver trusted data to the cloud". The idea to create a platform that helps to get products to market faster by simplifying the task of working with different devices and data.
The focus on security is particularly important. As the Internet of Things continues to grow, the amount and type of data involved will increase. In a blog post Intel says:
The new offerings and relationships will make it easier for solution providers to move IoT from pockets of pilots to mainstream deployments with a repeatable foundation of building blocks that can be customized for limitless solutions. Data will be unlocked faster to extract meaningful information and value for consumers and businesses.
Intel wants to push "pre-integrated solutions" that can be easily scaled up, and the hope is that by providing more ready-made solutions, more manufacturers will be encouraged to get involved. In a video, Intel's Chris Young talks about the importance of security in the company vision for the IoT:
Photo credit: asharkyu / Shutterstock
-

Forget male and female, Google+ now supports infinite gender identities
Publié: décembre 10, 2014, 1:04am CET par Mark Wilson
What's your gender? For some people it's a simple question -- nothing more than checking one of two boxes. But it can get more complicated than simply indicating that you're male or female. Many people feel that gender is not important and would prefer to keep this information to themselves. This is now a wish that Google respects on Google+.
In fact Google is going far beyond this. Starting today Google+ includes support for an infinite number of gender identifies. So whether you would rather not disclose where you fit onto the gender spectrum, or want to proclaim it outside of the confines of the usual binary options, now you can.
As Google points out in a Google+ post, it has long been possible to select Male, Female or Other as your identity. This trio of options has now been expanded to a quartet, adding a new Decline to state, and Custom settings.
Rachael Bennett from Google said: "Now, the gender field on your profile will contain four entries, Male, Female, Decline to state, and Custom. When Custom is selected, a freeform text field and a pronoun field will appear. You can still limit who can see your gender, just like you can now. We’ll be rolling this feature out for all users over the next few days".
In the wake of the LGBT backlash against Facebook's "real name" policy, attitudes to sexuality and gender identity have been under closer scrutiny than normal. Google recently fared well in a study by the Human Rights Campaign into LGBT equality in the workplace, and this latest move is likely to be well-received.
Photo credit: graphicsdunia4you / Shutterstock
-

The Pirate Bay is offline following Swedish police raid
Publié: décembre 9, 2014, 10:00pm CET par Mark Wilson

The Pirate Bay has hit turbulent seas once again. Earlier today torrent users noticed that the site appeared to be offline. This in itself was nothing particularly unusual -- all sites have occasional downtime -- but it soon transpired that the site was down around the world. The Pirate Bay has already been blocked by many ISPs around the world, but it was clear that this was something different.
Now it seems that the reason for the disappearance of the Pirate Bay is a raid by Swedish Police. And it is not just the main site that's gone -- the same fate became the site's forum (Suprbay.org) and associated sites Bayimg.com and Pastebay.net.
News of the Pirate Bay's initial problem were reported by TorrentFreak, and the site quickly updated its story to include details of the police raid. The site quotes Paul Pintér, a member of the Swedish police involved in IP enforcement. He said: "There has been a crackdown on a server room in Greater Stockholm. This is in connection with violations of copyright law."
TorrentFreak also reports that other torrent sites including EZTV, Zoink and Torrage are down, as is the Istole tracker. These incidents may not be related, but coming at the same time as a raid on the Pirate Bay would suggest that there is a coordinated effort underway at the moment. There have been a number of arrests over a period of months as authorities attempt to clamp down on piracy, including the November arrest of one of the site's founders.
This is far from being the first time the Pirate Bay has attracted the interest of police, and it is not the first time a raid has been carried out. The site has played a long and drawn out game of cat and mouse with authorities around the world, with mirrors and new domains popping up as one is closed down -- there are already mirrors springing up this time around, but it's not clear how long they will last.
Photo credit: Gil C / Shutterstock
-

2015 to be the year of biometrics, wearables, cryptocurrency and streaming
Publié: décembre 9, 2014, 3:13pm CET par Mark Wilson

Coming to the end of 2014, it's time to start looking to what the year ahead may have to offer. After gazing into its crystal ball, Juniper Research has compiled a list of what it expects to be the biggest technology trends of 2015. Topping the list is a focus on security. Juniper Research predicts that there will be greater interest in encryption and tokenization, as cloud storage providers battle to regain customer trust.
The launch of Apple Pay will help to drive an increased interest in biometrics to help with security, but 2015 is also predicted to be the year that wearables really take off. Now that Apple has entered the arena, there should be a greater focus on aesthetics and smaller players will increase in popularity. Tied in with both security and wearables is a predicted jump in the use of NFC -- for payments, authentication, health and more.
Juniper Research's white paper suggests that 2015 will see a marked shift to the consumption of media through streaming services. This is thanks in part to mobile data bundles, and it is predicted that the digital download market "will begin its collapse". There has already been something of a movement towards streaming rather than downloading, so this prediction is not entirely surprising. The same is true of the suggestion that cryptocurrency payments -- such as Bitcoin -- will increase in popularity, again tied to wearables, security and NFC. Perhaps what 2015 is really going to be about is the interoperability of devices and services.
The much-talked about drone is likely to continue to hit the headlines. More than just a system of surveillance, these devices are likely to be widely adopted as delivery systems and used more in filming thanks to a huge drop in prices.
A prediction that will please many is one that suggests that budget smartphones, tablets and phablets will really take off in 2015. We've seen the battle at the top end of the market, and now attention turns to the other end of the scale. This is going to develop into a buyers' market, so we should see some great development in the realm of the budget device. Rounding off Juniper Research's visions for next year are predictions that indoor location awareness will increase in importance, as will web integration and deep-linking of apps.
Photo credit: Vjom / Shutterstock
-

Google Cloud Platform updated to run Windows applications in the cloud
Publié: décembre 9, 2014, 11:05am CET par Mark Wilson

Google has opened up its arms to Microsoft License Mobility for Google Cloud Platform. Product manager Martin Buhr said that customers had been asking for improved support for Windows-based workloads, and now these wishes are being met. There are several key improvements to Google Compute Engine that help to make Windows on Google a reality.
Microsoft License Mobility is the big news, meaning that Google now supports SQL Server, SharePoint and Exchange Server without the need for extra licenses. The second announcement is the availability of a beta version of Windows Server 2008 R2 Datacenter Edition on Google Compute Engine which opens up the opportunity to run Windows applications in the cloud.
The third and final announcement is that a Google Cloud Platform-optimized version of Fusion Labs Chrome RDP has been released. What this means is that it is now possible to create remote desktop sessions from Chrome to allow for use of Windows in Google Compute Engine. In a blog post, Buhr said:
Because Google Developers Console stores and passes the login for the Windows credentials to the RDP app, customers are able to leave the complexity of managing unique user IDs and passwords for each Windows instance to Google.
This is not the end of the story. Google is also working on adding support for Windows Server 2012 and 2012 R2, but why should you pick Google Cloud Platform over Azure? Bhur says:
With awesome features like Local SSD (which also supports live migration), and multiple ways to connect your datacenter to the cloud, Google Cloud Platform is the best place to run your Windows workloads.
-

Barack Obama -- becoming a computer scientist just takes 'a little math and science'
Publié: décembre 8, 2014, 11:02pm CET par Mark Wilson

Today marks the start of the 2014 Computer Science Education Week. As part of this, the second annual Hour of Code is being used to introduce school children to the basics of programming. Students around the world are encouraged to take part in the event which is organized by non-profit Code.org.
The venture has the backing of Barack Obama who is keen to nurture the next generation of coders and computer scientists. And there's no reason to be put off. To quote the president, "becoming a computer scientist isn't as scary as it sounds. With hard work and a little math and science, anyone can do it".
There are lots of big names involved in Hour of Code, including Bill Gates, Mark Zuckerberg and Ashton Kutcher, and donations will be used to fund teachers. Microsoft and Apple are among the companies hosting workshops, and it is expected that more than four million people will take part.
To make the world of programming interesting to as wide and as young an audience as possible, there are tutorials and activities featuring Anna and Elsa from Frozen. There's even the opportunity to create your own version of Flappy Bird -- what more incentive could you need?!
You can check out the full introductory video by President Obama here:
Photo credit: scyther5 / Shutterstock
-

Windows 10 Technical Preview testers should be able to update to the RTM release
Publié: décembre 8, 2014, 5:26pm CET par Mark Wilson

There are positives and negatives to being a tester of early versions of Windows. On one hand it means being able to try out new features before they are officially released, but on the other it means putting up with a variety of problems. Preview builds of Windows used to be all but unheard of, but now anyone can get their hands on early bits to get a taste of things to come.
The preview program for Windows 10 has been slightly different to the way things worked in previous early versions of Windows. This time around it is even possible to upgrade to new builds without the need to reinstall from scratch, and it's looking as though it will also be possible to upgrade to the RTM version when it is released next year.
By the time the finalized version of Windows 10 is released, many Windows Insiders and leak downloaders will have been using the operating system for around a year. Having spent the time getting everything set up to your liking, you may already be dreading the day you need to wipe your hard drive and reinstall from scratch. Well, worry no more -- this time, things are going to be different.
In a Twitter post, Microsoft's Gabriel Aul explained that the intention is to let Windows Insiders upgrade directly to the RTM release when the time comes:
@tomzorz_ @krollTJ Yes, that is our intent.
— Gabriel Aul (@GabeAul) December 4, 2014
Some people may still opt for a clean install, but it looks as though it may not be a requirement.
-

Ralph Baer, Odyssey creator and 'father of video games', dies aged 92
Publié: décembre 8, 2014, 4:47pm CET par Mark Wilson

Ralph Baer, the man credited with helping develop the world's first commercial video games console, died this weekend at the age of 92. He may not have been exactly a household name, but without Baer, video gaming as we know it might have taken a very different turn. Without him, the Xbox One and PS4 might not yet exist.
The German-born electronic fanatic and inventor's work led to the creation of the Odyssey console. The games unit was launched by Magnavox in 1972, managing to pre-date Pong, and Baer went on to invent the first light gun for games as well.
Baer's primitive consoles allowed people to play one of several games, although they were all a variation on the same basic idea. Games could be loaded on cards which served as a forerunner to the cartridges found in later consoles. As well as developing a light gun peripheral, the pioneering inventor also worked on developing games that could be played with others over a network.
Four years ago he was inducted into America's National Inventors Hall of Fame. As well as the Magnavox Odyssey and peripheral, Baer is also known for inventing the light-based game Simon, which requires players to remember and repeat patterns of colored lights.
Photo credit: Twin Design / Shutterstock
-

PlayStation Network and Store hacked and taken offline by Lizard Squad
Publié: décembre 8, 2014, 10:35am CET par Mark Wilson

Gamers today found that they were unable to connect to the PlayStation Network. In what appears to be a hack attack, the gaming network as well as the PlayStation Store were knocked offline. Claiming responsibility this time is the hacking outfit Lizard Squad.
Sony has not revealed any details about what has happened yet, but it's clear that the outage did not come as a result of routine maintenance. Lizard Squad tweeted a message that seemed to claim responsibility for the downtime: "PSN Login #offline #LizardSquad".
This is far from being the first attack on Sony. The entertainment giant has had something of a hard time of thing lately. Prior to the PlayStation Network problems, the company was the subject of a series of high profile movie leaks, and employees' details were also leaked following a hack.
Sony acknowledged the connection problems in a tweeting, indicating that the connection issues were being looking into:
We are aware that users are having issues connecting to PSN. Thanks for your patience as we investigate.
— Ask PlayStation (@AskPlayStation) December 8, 2014
Lizard Squad's tweet is short, but seems to claim responsibility -- and it would not be entirely new territory for the group:
PSN Login #offline #LizardSquad
— Lizard Squad (@LizardPatrol) December 8, 2014
In addition to connection problems with the PlayStation Network, the PlayStation Store was also rendered inaccessible, although it is not clear whether the two problems are related. Anyone visiting the Store at the moment is greeted by a message that reads: "Page Not Found! It's not you. It’s the Internet's fault."
At the moment it appears that the PlayStation Network is back up and running, but the PlayStation store still shows an error message.
Photo credit: Barone Firenze / Shutterstock
-

Windows 10 Build 9888 includes Cortana -- but so bloody what?
Publié: décembre 8, 2014, 12:18am CET par Mark Wilson

It's not long since Windows 10 build 9879 was released and more recently build 9888 leaked online. I'm not going to link to the download as it's not an official release, but it's easy enough to get hold of -- you know where to look, I'm sure. So far the builds that have seen the light of day, officially or unofficially, have been rather light on features, but build 9888 includes what everyone has been chomping at the bit for: Cortana.
Was it worth the wait? Is a voice activated digital assistant appropriate for the desktop? Should anyone care? My answer to all three of these questions is a resounding 'no' -- with some possible exceptions in the case of the last question. Let me elaborate.
Cortana builds on the ideas introduced by Siri and OK Google, bringing voice activation to the desktop. While voice control makes sense on a mobile, I think it's far harder to justify on a desktop platform. Siri and OK Google make it possible to control a phone or tablet hands-free, which is great for when you're driving or doing something else. There's also Cortana in Windows Phone, but this is of interest to around five people.
Talking to one's phone makes a good deal of sense -- it's what the things were invented for, after all. It's also conceivable that using a small, fiddly in-screen keyboard is rather slower than simply giving a vocal instruction for some people. But is it actually useful? Really useful? Outside of those times when it is not practical or possible to operate your phone with your hands, do the likes of Siri really pay their way?
If you're sitting in a coffee shop or library, if you're walking down the street, if you're sitting on a park bench, do you feel comfortable using voice activation to set reminders and so on? "Remind me to call the doctor about that weird-looking rash in the morning!" Cue lots of strange looks. Potential embarrassment aside, we live in an age when we're all more concerned about privacy than ever. Why on earth would you want to bellow your schedule, your text messages and emails, or your search queries into your phone for all to hear? It's madness.
Sure, voice activation is impressive. The fact that it can be done is quite cool… but, really, is it needed? Anyone who has used Siri whilst out and about -- or even just at home -- must have noticed people turning around to see if they were being spoken to. Introduce the idea on the desktop and the problem is the same. "Cortana, remind me to get milk tomorrow." "What's that, love?" comes a call from the next room. "Nothing. Just talking to the computer."
The problem with understanding accents, and dealing with background noise persist. "EVERYONE SHUT UP! I want to set a voice-activated reminder!" Why not just type the thing? That's why the keyboard's there. We learned to type for a reason. Let's not let that skill go the same way as cursive handwriting. There's the problem of misheard commands. If you're not understood the first time around and need to repeat yourself or even manually change what has been interpreted, have you saved any time? Is it really more convenient?
And does no one feel remotely self-conscious about the idea of talking to their computer? The day I start issuing vocal instructions to an inanimate object is the day I hope my loved ones make a call and get me institutionalized.
Microsoft almost made a rod for its own back by announcing that Windows Phone, Xbox and Windows 10 would be converging into a more uniform platform. In saying this, the company all but committed itself to bringing Windows Phone's Cortana to the desktop -- but it's a terrible idea. It's technology for the sake of technology. It's not clever, it's a waste of time.
Photo credit: Stokkete / Shutterstock
-

Xbox is snubbed as Street Fighter V becomes a PC and PS4 exclusive
Publié: décembre 7, 2014, 11:42pm CET par Mark Wilson

The Street Fighter franchise is one that has been quiet for a while now, but Street Fighter V is on the way. Capcom has confirmed that work is currently underway on the latest instalment of the game, bringing an end to months of speculation and rumor. But that is not the end of the news.
It has been revealed that Street Fighter will appear exclusively on PS4 and PC. Owners of Microsoft's Xbox One console will miss out this time around, but there's an interesting feature for anyone who does buy the game on the two supported platforms -- cross-platform play.
This means that PS4 gamers will not be limited to multiplayer games with other Sony gamers; it will be possible to instigate fights between PS4 and PC. It's not clear whether this could have anything to do with why Xbox One has been given the cold shoulder, but gamers will undoubtedly be annoyed to discover that they are going to miss out on such a big title.
A post on the Capcom blog reveals that while there's no release date for the game as yet, it won't be long until we can see it in action:
On December 13th, we will be showing the first live match of Street Fighter V at the Capcom Cup. You’ll definitely want to tune into Capcomcup.com to watch all the action unfold. Currently the release dates for USFIV and SFV have not been announced yet, so I’ll definitely be back with that information and more in the future.
News about Street Fighter V leaked online ahead of this weekend's PlayStation Experience in Las Vegas. Gameplay footage appeared and was quickly pulled, but Capcom seemingly relented as it's available to view once again. When the leaked details first emerged, some gamers expressed hope that Street Fighter V might eventually make its way to Xbox One, but Sony's Adam Boye squashed that idea, saying: "PS4 will be the only console this game ever appears on."
Want to get an idea of what you can expect to see when Street Fighter V launches? Check out the preview footage from the PS4 version:
-

Idaho nurse gains backing of EFF and ACLU in fight against the NSA
Publié: décembre 6, 2014, 8:50pm CET par Mark Wilson

Usually it's the big guys, or at least national and international organizations, that stand up to fight against the government. But on Monday, a nurse from Idaho will continue to fight the case she brought against Barack Obama and government intelligence agencies. Anna Smith says her Fourth Amendment rights were violated when the NSA collected data about her from phone records.
A district court ruled against Smith when she first started to fight the case, but now she has the backing of the Electronic Frontier Foundation (EFF), the American Civil Liberties Union (ACLU) and the American Civil Liberties Union of Idaho.
The original case dates back to June 2013, shortly after the activities of the NSA first came to light. Now the EFF, ACLU, the American Civil Liberties Union of Idaho, and Smith husband have worked together to craft an appeal. The case will be heard at the United States Court of Appeals for the Ninth Circuit and will center on several areas.
One argument is that "neither Smith nor any other precedent authorizes the suspicionless collection of call records in bulk" and that the collection of such data is an invasion of privacy. The appeal also says that the government's mass collection of phone data violates the fourth Amendment and is unconstitutional "because it is warrantless and lacks probable cause".
This is not the first time the Electronic Frontier Foundation has become involved in a case against the government and the NSA, and it is unlikely to be the last. This appeal starts on Monday 8 December at 9:00 AM PST, and we'll be following along to see what happens.
Photo credit: bikeriderlondon / Shutterstock
-

Government surveillance does not breach human rights -- Amnesty International disagrees
Publié: décembre 6, 2014, 7:43pm CET par Mark Wilson

Amnesty International hit out at a court ruling that found communication surveillance carried out by UK secret services did not breach human rights. Amnesty UK and Privacy International brought the case to court following revelations by Edward Snowden that showed GCHQ (UK secret services) and the NSA had been spying on people by monitoring their correspondence.
But a panel of judges found that the actions of GCHQ do not contravene the European Convention of Human Rights. Amnesty said the result was "disappointing if unsurprising" and indicated that it will appeal at the European Court of Human Rights in Strasbourg.
The appeal has to take place in Strasburg because rulings by the Investigatory Powers Tribunal cannot be appealed in the UK. Amnesty International -- in conjunction with Liberty and Privacy International as well as other groups -- says that the dragnet style of surveillance not only breached individuals' right to privacy, but also their freedom of expression.
The judges said:
We have been able to satisfy ourselves that as of today there is no contravention of articles 8 and 10 by reference to those systems. We have left open for further argument the question as to whether prior hereto there has been a breach.
But this is far from good enough for Amnesty International. The organization believes that the ruling is flawed and that powers have been misused. Legal advisor Rachel Logan said:
The government has managed to bluff their way out of this, retreating into closed hearings, and constantly playing the ‘national security’ card. The tribunal has accepted that approach [...] The government’s entire defence has amounted to ‘trust us’ and now the tribunal has said the same.
A statement issued by Amnesty explains that the "secret" nature of the surveillance, coupled with the fact that portions of the case were heard in secret behind closed doors creates a lack of transparency that brings the ruling into question. Logan said:
Since we only know about the scale of such surveillance thanks to Snowden, and given that "national security" has been recklessly bandied around, "trust us" isn't enough.
Photo credit: Tischenko Irina / Shutterstock
-

Cybercriminals steal Bebe Stores customers' credit and debit card details
Publié: décembre 5, 2014, 2:25am CET par Mark Wilson

It's looking like the latest store to fall victim to cybercriminals is women's clothing chain Bebe Stores. Signs of the problem emerged earlier this week when fraudulent charges started to crop up on people's credit cards. What linked each of the victims was the fact that they had shopped in Bebe Stores.
KrebsOnSecurity reports that stolen customer details have been made available for sale on the "cybercrime shop" Goodshop. The timing is interesting as the data seems to have been put up for sale immediately after Black Friday and Cyber Monday -- a period when sales are much higher than normal.
An East Coast bank bought card data from Goodshop and found that they had all been used in Bebe Stores between 18 and 28 November. KrebsOnSecurity points out that what is available to buy "are not cards, per se, but instead data copied from the magnetic stripe on the backs of credit cards".
It's not yet clear quite how many people have been affected by the security breach, nor is it known exactly how the data was obtained. It's possible that malware was used to infect point of sale terminals, but this is yet to be confirmed. There is no suggestion that the Bebe Stores' website has been compromised. Customers whose credit cards have been comprised will have the guarantee of their credit card company to fall back on, but the news is not necessarily as good in the case of debit cards.
Photo credit: Khakimullin Aleksandr / Shutterstock
-

Microsoft Azure RemoteApp launches next week allowing for cloud deployment of apps
Publié: décembre 4, 2014, 8:40pm CET par Mark Wilson

Microsoft Azure RemoteApp has been available since the beginning of the year as a preview service. It's a relatively simple concept (although the technology behind it is rather more complex) that allows for the deployment of Windows apps to the cloud so they can be accessed from anywhere -- even Macs and mobile devices.
Today Microsoft announces that Microsoft Azure RemoteApp will officially launch as a pay-as-you-go service on December 11. Anyone who is already working with the preview will be automatically moved to a 30-day trial version, and after this time a subscription will be needed.
The virtualization service makes it possible for businesses to use a single app on multiple platforms, reducing the time and money that needs to be spent on development and deployment. The ability to host apps on Microsoft's servers helps to reduce costs as well as eliminating the need for multiple platform-specific versions of apps.
Microsoft explains:
Azure RemoteApp provides an effective solution for application delivery: Applications run in the Azure cloud and are accessed through the Microsoft Remote Desktop Protocol (RDP). Your employees can use corporate applications from anywhere and on a variety of devices including iOS, Mac OS X, Android, and Windows platforms. In addition, on the back end, the applications are securely managed, automatically scaling up or down to meet the changing needs of your businesses.
Different pricing structures are available to cater for different needs:
BASIC STANDARD Target user Task worker Information worker Applications Lightweight LOB / data entry applications (e.g. Simple web apps) Productivity applications (e.g. Office) Storage (user) 50 GB 50 GB Starting price (user/month) $10 $15 Hours included in starting price (month) 40 40 Hourly overage rate (Hour) $0.175/hr $0.20/hr Capped price (user/month) $17 $23 Microsoft has produced a video that introduces the various price plans that are available:
-

Creator CI20 is an Android or Linux-powered Raspberry Pi competitor
Publié: décembre 4, 2014, 4:56pm CET par Mark Wilson

Small is beautiful, and this is something that the Raspberry Pi demonstrates perfectly. But now there's a little competition. The Creator CI20 is a new diminutive micro-computer which offers more power than an existing Raspberry Pi, as well as a choice of operating systems -- Android or Linux.
The company behind the barebones computer is another UK chip manufacturer, Imagination, and at just $65, it's a perfect stocking stuffer. Or at least it would be if units were going to ship before January 2015. Like the Raspberry Pi, the Creator CI20 is a fully loaded board designed for use in all manner of DIY computing projects.
Available to pre-order right now, the Creator CI20 boasts more storage, more memory and a faster processor than Raspberry Pi, and the choice of Android 4.4 or Debian 7 Linux is another string to its bow. It's already generating interest from the Linux community, with The Linux Foundation's COO Mike Woster saying:
The excitement around development boards is similar to the early buzz around Linux. Linux development boards, including the one introduced today by our new member Imagination Technologies, are exciting for hobbyists and students with limited resources, as well as extremely promising for engineers and designers during development and beyond.
For a micro-computer, the specifications are really quite impressive:
- Processor: 1.2 GHz dual-core, MIPS32-based Ingenic JZ4780 SoC, 32kB L1 I- and D-cache, 512kB L2 cache
- FPU: IEEE754 Floating Point Unit, XBurst MXU
- Multimedia: PowerVR SGX540 GPU, hardware-accelerated video playback up to 1080p at 60 fps
- Memory: 1 GB DDR3 SDRAM, 4 GB flash memory, 1 x SD card
- Audio: AC97 audio, via 4-pin input/output jack and HDMI connector
- Camera interface: ITU-R BT.645 controller
- Connectivity: 10/100 Ethernet, 802.11 b/g/n, Bluetooth 4.0
- Display: 1 x HDMI up to 2K resolution
- USB: 1 x USB host, 1 x USB OTG device
- I/O peripherals: 2 x UART, 25 x GPIO, 2 x SPI, I2C, ADC, expansion headers, 14-pin ETAG connector
Getting Android running on a MIPS processor is something that a team of engineers worked on "tirelessly", and hobbyists will be keen to get their hands on the device and put it to work in projects. Streaming media is an obvious, if basic, use but there is also scope for home automation and IoT applications. There's even a development platform, FlowCloud, which can be used to build apps.
-

Alabama's LGBT anti-discrimination bill to be named after Apple's Tim Cook
Publié: décembre 4, 2014, 3:05pm CET par Mark Wilson

It's only a few weeks since Tim Cook announced that he is gay and the impact is already starting to be felt. The Apple CEO wrote in Bloomberg Business that "I'm proud to be gay", and his coming out has proved to be inspirational, even in the short time between then and now. Now an anti-discrimination bill in Alabama is to be named after him.
Alabama is in the process of passing a bill that will make it illegal for state employers to discriminate against workers on the basis of their sexuality. Democratic state Representative Patricia Todd is the Alabama's only openly gay lawmaker and she proposed the billing, mentioning Tim Cook's name "in jest".
But it seems that others thought that the Tim Cook association was a good idea, although Todd did hear from Apple who expressed reservations to start with. However, the technology firm then backpedalled and said Cook would be happy to lend his name to the bill. Apple's initial concern stemmed from the "politically sensitive" nature of the bill, but a follow-up call from the company's general counsel, Bruce Sewell, means that the Tim Cook bill is a goer.
Apple issued a statement to Reuters:
Tim was honored to hear that State Rep. Todd wanted to name an anti-discrimination bill after him, and we're sorry if there was any miscommunication about it. We have a long history of support for LGBT rights and we hope every state will embrace workplace equality for all.
There is likely to be Republican opposition to the bill, but Todd hopes that Tim Cook will be able to find the time to come and speak about it, and hopefully sway opinion.
Photo credit: Lester Balajadia / Shutterstock
-

Social networks reimagined as guys -- hipsters, businessmen and kooks
Publié: décembre 4, 2014, 2:03pm CET par Mark Wilson

A little over a year ago, fashion photographer Viktorija Pashuta released images from a photo shoot entitled What If Girls Were Internet Browsers. It was a simple, fun idea in which Internet Explorer, Firefox, Opera, Chrome and Safari were given female personas and represented by models. Now Viktorija has a new project -- What if Guys Were Social Networks.
The idea's very similar to last year's project. Twitter, Instagram, Facebook, Google+, tumblr, Pinterest, flickr and LinkedIn are all anthropomorphized into eight men, each with their own unique look and personality. In the line-up of social networks, all of the major players are represented, but the new kid on the block, Ello, is notable by its absence.
Each character takes on the color palette of the social network they represent, and tries to convey the personality at the same time. Both Instagram and flickr have something of a hipster look and feel to them, while -- unsurprisingly -- LinkedIn is smart and besuited. Twitter is a little kooky and metrosexual, and Google+ stands out thanks to its primary color scheme. The full-sized photo gives a better view.
Pashuta says:
Working closely with the wardrobe stylist, Editor in Chief of Vanichi magazine and one of the models (featured as Instagram) -- together we finalized these looks, making sure we haven’t overlooked any important details to make these characters believable. Even their personalities somehow appeared to be matching the 'soul' of the networks.
What do you make of the idea? Do Viktorija's visions of the social network as guys match your own?
Photo credit: Viktorija Pashuta
-

Technical issue prevents Microsoft from paying Xbox Live Indie Games devs
Publié: décembre 4, 2014, 12:51pm CET par Mark Wilson

The holiday season is probably the worst time to discover that due payments are going to be late, but that's exactly the position independent Xbox game developers find themselves in. Developers awaiting payments for Xbox Live Indie Games on Xbox 360 (Xbox One is not affected) have been told that a problem with Microsoft's payment system has delayed payments to "select developers".
The apology was issued via the ID@Xbox Twitter account late last night, and there are already numerous replies from disgruntled developers. It's not clear exactly what the problem is or why only the Xbox 360 platform has been affected, but these details are of little concern to developers just looking to get paid.
Many developers are annoyed that Microsoft has only issued an apology after the problems became public -- it's something that some complainants say has been going on for more than a fortnight. Microsoft was supposed to send out payments within 45 days of the end of Q3, a deadline that passed two weeks ago.
The full statement reads:
Due to a technical issue in our payment system, we recently learned that some payments to select developers in the Xbox Live Indie Games program on Xbox 360 were delayed. Our partners are important to us and we work hard to help make sure they have a great developing experience. This was an unfortunate error and we are working hard to fix it. We apologize for this incident and anticipate developers will receive payments within the next two weeks.
No details have been provided about the number of developers affected by the issue, or the amount of money involved. We have reached out to Microsoft for further details, and will update this post when we hear back.
Update: We heard back from Microsoft, but the company just reiterated the statement posted on Twitter.
Photo credit: Valentina Razumova / Shutterstock
-

Google to launch kid-friendly versions of its most popular products
Publié: décembre 4, 2014, 1:06am CET par Mark Wilson

Like any company, Google wants to appeal to as many people as possible. Google Docs has been tweaked to increase its appeal to enterprise and business users, and Gmail is constantly primped and poked. Appealing specifically to children is not an entirely new idea for the search giant -- Google Code-In is targeted at 13-17 year olds, for instance -- but now Google is setting its sights on a younger audience.
Talking to USA Today, Vice President of Engineering at Google, Pavni Diwanji explained that the company is looking to create new versions of its products that are "fun and safe for children". Starting next year, the company will launch new versions of existing services, this time aimed at those aged 12 and under.
Google already has its Safe Search Kids search engine ("where Safe Search is always on"), but USA Today reveals that the plan is to take things much further. Details are a little thin about exactly which products are in line for a children-centric makeover, but one thing is clear: Google will have to tread very carefully when it comes to the usual data gathering it carries out on its users. Collecting information about adults is one thing, collecting information about pre-teens is a different matter entirely.
Diwanji said: "We expect this to be controversial, but the simple truth is kids already have the technology in schools and at home [...] We want to be thoughtful about what we do, giving parents the right tools to oversee their kids' use of our products. We want kids to be safe".
Google sees this not just as an opportunity to shares it products with a younger audience, but also to help bring families together. Diwanji said that she is "a big believer in coaching moments for kids, rather than just blocking what they can do. I want to enable trust in them. Thirteen isn't some magical number. I want to teach them what's right and wrong, and bring families together using technology".
It's certainly a move that will prove controversial, but it could also pay dividends for Google in terms of gaining lifelong customers from a new generation of users.
Photo credit: Stylus photo / Shutterstock
-

Facebook tells advertisers how to (very) closely target users this holiday season
Publié: décembre 3, 2014, 2:17am CET par Mark Wilson

Ads are hard to avoid at the best of times, but it has a tendency to get a little worse in the run-up to Christmas. Advertising has become increasingly prolific on social networks, and this is certainly true of Facebook. As we enter the holiday season, Facebook is providing advertisers with advice that will enable them to deliver finely-tuned ads at highly specific sets of users.
If you picked yourself up a new tablets in the Black Friday or Cyber Monday sales, Facebook makes it possible for advertisers to pick you out of the masses. The social network is not only rolling out a couple of new features to help with targeting advertising, but also providing tips for more successful campaigns.
Advertisers want assurances that the ads they post are reaching the right people, and this is something Facebook says it can deliver. Or as a blog post announcement puts it, "advertisers can buy Facebook mobile app ads with highly predictable reach and frequency". Targeting can be incredibly specific: "advertisers can set their app ad campaign to reach 5 million people with a frequency cap of three impressions per person for one week".
What is especially interesting about Facebook's announcement is that it highlights the ability to target people who have bought a new device. It has been possible to target specific devices -- such as iPads or Samsung tablets -- and now the Amazon Fire has been added as a target device. But it is also possible to use the fact that a user has logged into Facebook using a new device as at trigger for delivering certain ads to those users.
Facebook's tips suggest making use of more video ads, so you can probably expect to see more of these cluttering up your timeline in the coming weeks.
How do you feel about this sort of targeted advertising? Assuming some ads are a given, would you rather see generate ads that are likely to be of no interest, or targeted content which may at least be relevant to your needs?
Photo credit: Michal Poracky / Shutterstock
-

Dropbox for Business API set to woo corporate customers with secure cloud apps
Publié: décembre 3, 2014, 12:56am CET par Mark Wilson
While Dropbox for Business is nothing new, there's no getting away from the fact that Dropbox is seen essentially as a consumer level tool. Part of the reason for this -- apart from the occasional security slip-up -- is the fact that it has not been possible to use Dropbox in conjunction with third party tools at an enterprise level. Now this changes thanks to the arrival of the Dropbox For Business API.
The API is yet to be officially announced -- although rumors have been circulating for a little while -- but internal documentation obtained by TechCrunch shows that the launch is imminent, possibly as early as tomorrow (Wednesday December 3rd). Once launched, developers will be able to use the API to produce their own secure Dropbox-based apps and services.
The leaked documents give a glimpse at what could be achieved with the Dropbox for Business API, but a select number of partners have been granted early access to the tools so development will already be underway. TechCrunch reports that Microsoft, Dell and IBM have been working with Dropbox to ensure that their applications and services work with the Dropbox for Business from launch.
Launching the API is something of a shrewd move by Dropbox. Rather than spending the time developing tools of its own and then convincing enterprise customers to put their trust in them, developers are instead being invited to create their own tools that meet their own precise requirements. This not only places customers in greater control, but eliminates the element of compromising that is often part and parcel of using readymade tools.
With a strong focus on security, encryption and rights management, the API will have broad appeal. Security focus will enable companies to produce their own apps that take advantage of Dropbox while adhering to internal security policies.
-

Twitter improves harassment reporting and blocking to boost safety
Publié: décembre 2, 2014, 11:40pm CET par Mark Wilson

Over the years Twitter has come in for a lot of flak for the level of abuse that runs rife on the social network. Now the site is taking action by making improvements to the existing blocking features as well as refining the harassment-reporting facility. With the likes of #gamergate and various other high profile cases, Twitter users have found themselves on the receiving end of vitriol, hatred and abuse.
Today's updates aim to clamp down on these activities, making it easier for users to report problematic tweets and easier for Twitter to respond quickly to problems. There is a particular focus on making life easier to users of mobile versions of Twitter, and the blocking feature is now more prominent in apps.
In a blog post, Twitter explains that it has "made the first of several behind-the-scenes improvements to the tools and processes that help us review reported Tweets and accounts". The idea is not only to make the reporting process simpler for people who receive abusive tweets, but also Twitter users who see the abuse of others.
The Twitter Support account announced the news and provided a video showing how the tweet flagging feature works:
Starting today we're rolling out an improved way to flag abusive Tweets. See how it works. [https:]
— Twitter Support (@Support) December 2, 2014
It's not all about the mobile side of Twitter. Previously, if you wanted to manage the accounts you had blocked -- perhaps you changed your mind about someone and decided to unblock them -- you would have to visit that account to take action. Now there is a dedicated page you can visit within settings -- suitably labelled Blocked accounts -- where you can view and change your blocking settings in one place. Another important change, users you block will no longer be able to even see your account -- previously, block just prevented them from following you and sending you messages.
As ever, a small number of users have been selected as part of the initial rollout, but everyone should see the new features in the coming weeks.
Picture credit: MyImages - Micha / Shutterstock
-

Microsoft Research thinks Haven might be the answer to cloud storage security problems
Publié: décembre 2, 2014, 1:44am CET par Mark Wilson

Storing your data in the cloud requires you to place trust in a company and its service. Whether you're talking about Dropbox, Google Drive or an enterprise level solution, security is of paramount importance. There have been numerous high profile cases in recent months in which data breaches have occurred and private data has been accessed by unauthorized people -- including the NSA et al. It's little wonder that many people are wary of moving entirely to the cloud.
But Microsoft Research may have a solution. A small team of researchers came up with the idea of Haven, a cloud system that introduces the idea of shielded execution. This is a platform designed not just for storing data, but also to securely run cloud-based applications, including those based on legacy code.
Andrew Baumann, Marcus Peinado, and Galen Hunt revealed details of Haven back in October, but today Microsoft research has released a few more details in a rather more accessible form. The beauty of the platform is that it provides in-house levels of security for data and services that are stored and run off-site. It "could allow users to run existing software and data in the cloud with equivalent trust in the privacy and integrity of the data as if it were on-site or in a secure co-location facility".
The trio of researchers are actually part of the operating systems group of Microsoft Research and Haven came about as a result of combining two technologies. Intel SGX had already been developed to run security-centric aspects of applications in encrypted, ring-fenced environments, while Microsoft Research's Drawbridge improved the efficiency of virtualized systems. By merging the two, the team came up with the idea of running Drawbridge within Intel SGX and it was a natural progression to move this to the cloud.
This is not just a technology that will appeal to businesses who are eager to keep their data secure, but also individuals who are keen to protect themselves from surveillance. Andrew Baumann says:
"The cloud provider only ever sees encrypted data, and the only thing the cloud provider could give to the government or some law enforcement body would be encrypted data. There's no way for them to see the raw data".
What's so appealing about the system is that it is very easy to transition existing code to take advantage of the new security features.
"We can take unmodified applications like a SQL database that people already run on their own machines outside the cloud and move them into a secure environment in the cloud. Yes, there's a lot more code in the trusted computing base, but, practically, you end up with a more secure system than if you didn't have it".
As the move to the cloud continues apace, Haven could be the security boost that's needed to improve levels of trust and increase peace of mind.
Photo credit: allepu / Shutterstock
-

Student registrations open for Google Code-In 2014
Publié: décembre 1, 2014, 8:42pm CET par Mark Wilson

Google Code-In has been running for a few years now and serves as a platform for promoting the importance of programming and computer science to students. The current batch of computing student represents the next breed of app coders, website designers and computer experts. Google is keen to encourage teenagers to get involved and today is the day that registrations open for Google Code-In 2014.
One of the aims of the event is to promote the open source community, and encourage 13-17 year olds to get involved in whatever way they can. Google Code-In is a contest but it has been set up in such a way that it simulates working on a real-world open source project.
Participants are invited to sign up to take part and Google stresses that it is open to people who do not consider themselves coders. While this may sound counter-intuitive, the company points out that all computing projects involve much more than just the people producing raw code -- project managers are also needed, as are testers, documentation writers, market researchers, and so on.
Google's Stephanie Taylor says, "this year, students can choose tasks created by 12 open source organizations working on disaster relief, content management, desktop environments, gaming, medical record systems for developing countries, 3D solid modeling computer-aided design and operating systems to name a few".
Since 2010, more than 1,500 students from nearly 80 countries have participated in Google Code-In. This year's contest runs until 19 January. Hit the site to find out more and sign up if you are interested in taking part.
Photo credit: McIek / Shutterstock
-

Microsoft acquires mobile email firm Acompli -- this time it's for real
Publié: décembre 1, 2014, 5:39pm CET par Mark Wilson

As first revealed on BetaNews just before Thanksgiving, a rogue Microsoft blog post seemed to let slip that the company was on the verge of acquiring Acompli. Now it's official. Both Microsoft and Acompli have confirmed that the acquisition is going ahead and the "innovative mobile email apps for iOS and Android" are now in the hands of Microsoft. Seen by many as the mobile app that Outlook.com deserves, Acompli fits neatly into Microsoft's plan to expand further into mobile realms.
Corporate Vice President of Outlook and Office 365, Rajesh Jha says "it's essential to give people fantastic email experiences wherever they go". The existing Acompli app is destined to become integrated into the work already carried out by the Outlook team. While iOS and Android are both mentioned, no reference is made to Windows Phone.
Jha says that the acquisition "will expedite our work to deliver the full power of Office to mobile devices", and Acompli CEO Javier Soltero is similarly excited about the future. It's just 18 months since Accompli burst onto the scene, and it has already managed to carve out a niche for itself and gain the attention of Microsoft.
Our team and products will become part of Microsoft’s ambitious effort to reimagine productivity for the mobile era. 18 months ago we started building a team and a product around the idea that we could make mobile email better. Today that journey continues as part of a larger organization with the technology, talent, and market reach that will help us take the vision of Acompli to hundreds of millions of mobile users across the world.
Soltero goes on to say that talks with Microsoft revolved around the idea of improving Office 365 integration while retaining support for services from Apple, Google and Dropbox. At the moment it is not clear whether Acompli will become an app with a purely Microsoft-driven focus, but there is the promise that "we’ll be sharing more about the exciting product plans we have".
For now, it's business as usual. Acompli can be downloaded for Android and iOS devices right now, but there are sure to be some changes in the coming weeks and months.
-

Permission-free post-loading lets carriers push crap apps to Android handsets
Publié: décembre 1, 2014, 5:04pm CET par Mark Wilson

It used to be that you'd buy a new PC or laptop and have to spend the first hour or so removing all of the crap that the manufacturer had installed. The same idea carried across to mobile phones, particularly in the case of Android handsets, but the key difference is that -- at least without rooting -- many carrier apps can be all but impossible to remove. Now, thanks to "post-loading" the problem is about to get worse.
As the term suggests, post-loading makes it possible for a carrier to push apps to handsets and install them secretly. This is all thanks to Digital Turbine's Ignite system, and the likes of Vodafone, Verizon, T-Mobile and more are listed as clients. Of course, it's all about money or, as Digital Turbine puts it, "maximizing the efficiency of pre and post loading applications on smartphones for more advertising revenue".
The problem -- and this is precisely what it is -- was highlighted recently on XDA Developers, and today Forbes reports on the subject as a well. Post-loading is not just irritating, it's potentially extremely worrying. If apps can be pushed to handsets and installed without the need for user intervention, there is no way to know what permissions a given app has. Follow the usual method for installing an Android app and you're warned about the services it uses and what data it is able to access. If someone else installs an app for you, this privilege -- this right -- is taken away.
The fact that the very reason for Ignite's existence (which appears on handsets as DT_Ignite) is to deliver advertising is cause for concern. Blanket advertising is far less effective than targeted ads, so it's not hard to imagine that the service would make use of information from handsets --installed apps, usage patterns and so on -- to deliver user-specific ads. Add to this the issue of using up space, the fact that most users will be unaware of the presence of these apps let alone know what they might be doing, and there's a privacy nightmare just waiting to explode.
Have you spotted the DT_Ignite app on your phone?
Photo credit: Cienpies Design / Shutterstock
-

Make It Happen! Microsoft wants to help you keep your New Year's resolutions
Publié: décembre 1, 2014, 1:50pm CET par Mark Wilson

The countdown to the end of 2014 is now underway. With less than a month until the arrival of 2015, Microsoft -- specifically Microsoft Lumia -- wants to help anyone making a New Year's resolution to stick to their goals. The idea is simple. Research shows that people are more likely to hold their resolve if they make a public pledge of their intentions. With this in mind, the #MakeItHappen encourages anyone with a goal for 2015 to announce it.
But more than just giving you a public place to announce what you would like for the New Year, Microsoft is also selecting one person a day throughout December and will help them complete their unfulfilled resolutions from 2014.
Having discovered that a huge number of resolutions that were made last year are still to be acted upon, Microsoft points out that it's still not too late to make a difference. There's still a month to make good on the promises you made at the start of the year, and you can give yourself the best possible chance of success with your goals for 2015.
Mark Newton, senior program manager at Microsoft said:
It's almost a given that people will make New Year's resolutions they are unable to fulfill, but this year, we want things to be different. Our global poll reveals a wealth of unfulfilled aspirations for 2014. With the clock ticking, we have dedicated December to helping people #MakeItHappen. Every day in December we will choose one person's 2014 resolution and help bring it to fruition.
The site appears to be down at the moment, but pay a visit to the #MakeItHappen website and you can make a public declaration of what you would like to give up, attain, do, or be in the New Year. There's also a dedicated Facebook page.
In the meantime, check out the video for a few ideas:
Photo credit: marekuliasz/ Shutterstock
-

Just in time for Christmas, Microsoft launches Digital Gift Cards for Windows Phone
Publié: novembre 29, 2014, 10:43pm CET par Mark Wilson

It’s the time of year when attention turns to buying gifts. Black Friday is now out of the way, but there's still Cyber Monday for you to stock up on low-cost presents for yourself and others. There are plenty of electronic devices vying for attention as companies try to tempt you into parting with your cash, but if you're the indecisive type, there's always the trusty fall-back of the gift card.
Keen to give you as many ways as possible to throw your money in its direction, Microsoft has launched Digital Gift Cards for Windows Phone. This is an app that does very much what you would expect, making it possible to buy and share gift cards from the comfort of your Windows Phone. But Microsoft isn’t stupid. The gift cards themselves are not limited to Windows Phone purchases -- they can be used to buy apps, games, movies and music from Xbox and Windows stores.
Great for a last-minute gift, the digital gift cards are emailed out the instant payment is made. Bringing the gift card idea to mobile devices is interesting. Should you find yourself out shopping and unable to locate the perfect gift for your friends and family, you can opt to sort out all of your gift buying over a coffee -- send a batch of gift cards and leave your loved ones to decide what they would like to buy for themselves.
In a fine example of canny marketing, Microsoft is billing digital gift cards as "the perfect 'add-on' for family and friends receiving an Xbox or Windows device". Bought a Windows Phone, Xbox or even a Surface Pro 3 as a gift for someone? Microsoft thinks you might like to "top-up" the present with the gift card as an extra. It's a bit of a cheeky idea, but it makes perfect sense from a money-making point of view.
Of course, this is not just an app that can be used at Christmas -- although the timing is interesting to say the least. It is possible to schedule purchases throughout the year so you don’t forget an important birthday. Is it handy to have a dedicated app for this, or would the existing website have sufficed?
Picture credit: wavebreakmedia / Shutterstock
-

Amazon wants your Cyber Monday money with new deals every 10 minutes, starting now!
Publié: novembre 29, 2014, 5:20pm CET par Mark Wilson

Black Friday is now out of the way, and while there have already been a number of technology deals available, things now get serious as we approach Cyber Monday. As has become the norm, retailers are no longer waiting for the day itself to roll around before trying to lure customers in. Amazon is no different as its Cyber Monday deals start today.
There are, of course, a few headline grabbing offers to be had, but the online giant is looking to maintain shoppers' interest by offering new deals every ten minutes. Don’t see anything that takes your fancy right now? Just stick around, because you never know what may show up in the next batch of deals.
In fact today is the start of eight days of savings in what Amazon has dubbed Cyber week. Interest levels are being kept high by Amazon giving just a taster of some of the deals that are going to pop up (a Sony 40-inch 1080p LED TV for $298, a comparable model form Samsung for the same price). But potential customers are being encouraged to stay on site for as long as possible by the fact that Amazon is not revealing when specific offers are going live.
A new feature of Amazon's Cyber Monday is the Lightning Deals that will pop up in the Amazon app store on Android, iOS and Fire OS. Again, there's no real word about what to expect -- Amazon wants to keep you in the store for as long as possible waiting for the deals to pop up; the hope is obviously that you will end up buying more than you intended to while you wait.
Amazon has special offers in just about all of its store categories -- despite the tradition, it's not just about tech for Amazon -- but there are some great deals to be found in tech and electronic. Acer Chromebook $149, $30 off select Bose headphones, HP 110-430 Desktop and 2371d 23-inch Monitor Bundle for $299.99, and lots of cash-back offers.
So... wait no longer. Head off to the Amazon store and prepare to consume like a good consumer.
Picture credit: Michele Paccione / Shutterstock
-

Social networks told to be honest and stop bamboozling their users
Publié: novembre 28, 2014, 1:07pm CET par Mark Wilson

The UK parliament is calling on social networks such as Facebook and Twitter to simplify their terms and conditions. The Science and Technology Committee has expressed concern that privacy policies and other documents are strewn with legal terms that most people do not read or understand. This means that most social network users are simply not aware that they have agreed for their personal information to be used in various ways -- and are certainly unaware of how it might be used.
The Committee is calling for social networks to make a commitment to explain in very clear terms how personal data is shared and used. It wants to work with the government to draw up a set of standards -- almost a social networking manifesto -- that companies can sign up to.
Facebook has already put forward proposals to simplify its privacy policy in the hope that people will actually read them. But the committee believes there is still a lot of work to do, expressing concerns that these contrasts are "not fit as a mechanism for demonstrating that users have given informed consent for some of the ways companies are now exploiting personal data". What many find particularly worrying is the trend for social networks to hang onto personal information that is not technically required to use the services.
Andrew Miller, chairman of the Science and Technology Committee, said:
Let’s face it, most people click yes to terms and conditions contracts without reading them, because they are often laughably long and written in the kind of legalese you need a law degree from the USA to understand. Socially responsible companies wouldn’t want to bamboozle their users, of course, so we are sure most social media developers will be happy to sign up to the new guidelines on clear communication and informed consent that we are asking the Government to draw up.
At the moment there is just talk of a voluntary code of conduct, but the committee says that it will consider legislation if necessary. As The Next Web points out, the majority of social networks targeted by this venture are based in the US and are covered by US law, meaning that it would be difficult to make the UK guidelines anything other than voluntary.
Photo credit: Ivelin Radkov / Shutterstock
-

Europe votes in favor of splitting up Google and other online companies
Publié: novembre 27, 2014, 11:50pm CET par Mark Wilson

Members of the European Parliament (MEPs) have voted overwhelmingly in favor of breaking up big online companies like Google. While Google is not specifically mentioned, the MEPs aim of "unbundling search engines from other commercial services" to increase competition would clearly impact on the search giant if the resolution is approved by the European Commission.
It's all part of a bid to not help the growth of the EU's digital single market, but also to help boost competitiveness. All very reminiscent of the anti-trust lawsuits that have plagued Microsoft. The vote itself was fairly decisive. 384 voted in favor of the proposed resolution, 174 against, and 56 abstained from voting.
There is concern that large, dominant companies such as Google are overshadowing smaller, emerging firms. While search is one of Google's primary businesses, there is concern that there is "abuse in the marketing of interlinked services by operators of search engines". MEPs are calling upon the European Commission to promote non-discriminatory searches: "indexation, evaluation, presentation and ranking by search engines must be unbiased and transparent".
The power of the search engine is noted, as MEPs highlight the fact that companies are in the habit of exploiting for commercial gain information gathered through searches. The solution? Splitting up large businesses like Google, ultimately "unbundling search engines from other commercial services". There was also a nod to net neutrality as politicians said that "all internet traffic should be treated equally, without discrimination, restriction or interference".
The resolution's aim is not just to help the European economy, but to help get a better deal for customers. The European Parliament believes that problems such as "market fragmentation, lack of interoperability as well as regional and demographic inequalities in access to the technology" currently stand in the way of progress, suggesting that encouraging a more competitive environment would at least help to overcome these obstacles.
Google has not commented on the vote, but the company is not likely to be happy about what might be to come. The Commission will give the company a chance to respond before deciding what action to take.
Photo credit: iQoncept / Shutterstock
-

Does a deleted Microsoft blog post show it's about to buy mobile email firm Acompli?
Publié: novembre 27, 2014, 12:43am CET par Mark Wilson

Web pages can be interesting, transient things; they can be there one minute and gone the next. But while a web page may vanish, that does not mean that all traces of it vanish from the internet. Earlier today an intriguing-looking article popped up in my news reader -- there are many benefits to sticking with RSS feeds: a post on the Microsoft blog with the title "blank post please delete".
Authored by Rajesh Jha, my RSS reader (InoReader) showed that the post's content was very similar to the title -- blank post, please delete. Just a comma added. Interest piqued, I clicked the link to see if there was any more to see. "We're sorry, but we can't find the page you're looking for" announced Chrome. But the URL is curious.
The link took me to a non-existent page on the Official Microsoft Blog formatted to indicate that the post had been made on November 25 -- [blogs.microsoft.com]. But it's those last three words that are particularly fascinating. Microsoft acquires Acompli. Does it? What’s Acompli? Why have I not heard anyone else talking about this?
Acompli, it turns out, is a mobile email app that's available for iOS and Android. An email app with something of a difference as it features an integrated calendar and has been described by the Verge as "the Outlook for iPhone that Microsoft hasn’t yet built". It's easy to see why Microsoft might be interested in acquiring the app and company. A quick look at the Acompli blog revealed nothing, nor did endless web searches.
But this blog post and its intriguing URL did not spring out of nowhere. I contacted Microsoft and -- after something of a delay -- I heard back from a spokesperson who let me know that they were "unable to accommodate [my] request at this time". I've reached out to Acompli as well, and I'm waiting to hear back.
Watch this space. It's not clear if this is a business deal that is yet to happen and someone pushed the button too early, or if something fell through at the last minute. It may amount to nothing -- in which case forget I said anything. But we may soon hear that Microsoft has a new company in its folds -- in which case, you heard it here first!
Photo credit: Ken Wolter / Shutterstock
-

Now Twitter is going to start monitoring which mobile apps you download
Publié: novembre 27, 2014, 12:36am CET par Mark Wilson

Hate 'em, loathe 'em or abhor 'em, it's hard to avoid ads. You know that you're a consumer. Companies exist because you consume, and you are encouraged to consume more and more. To help lead you to consume, you need to be subjected to advertising -- it's all part of the money-go-round of using the web.
Tailored ads are more likely to bring in cash, and social networks are in the business of gathering information about their users with a view to delivering the most laser-focused targeted advertising possible. The latest venture by Twitter involves keeping tabs on the apps you install on your iOS or Android phone or tablet.
This is not quite how Twitter puts it, of course. Collecting information about "occasionally updating the list of apps installed on your mobile device" is all for your own good: "so we can deliver tailored content that you might be interested in" and "to help build a more personal Twitter experience for you".
The app tracking feature -- known obscurely as your "app graph" -- will not be enabled by default on your mobile device if you have previously opted out of web-based ads, but otherwise it will be ticking away in the background. You will get a little warning. An in-app notification will let you know when the feature rolls out to your account.
Twitter says that the information that is gathered will be used to improve the suggestions it makes about who you might want to follow, adding "especially interesting" to your timeline, and to show you "relevant promoted content" -- or ads, as they are better known. If you'd like to switch off the feature head to the Other section of Settings in Android or the Privacy section of Setting in iOS and disable the Tailor Twitter based on my apps option.
Twitter does not go into detail about just what sort of promoted content you might see, but the chances are that if you have a large number of health and fitness apps installed, you're probably not going to see an influx of McDonald's ads.
Photo credit: digieye / Shutterstock
-

EFF joins dozens of groups to create global coalition to fight for net neutrality
Publié: novembre 26, 2014, 7:04pm CET par Mark Wilson

The net neutrality debate has been rumbling on for some time now. Barack Obama even waded into things recently by giving his backing to campaigns that suggest all web traffic should be treated equally. But the US president is far from being the only big name speaking out against the two-tier internet that some providers would like to see created.
Now the Electronic Frontier Foundation (EFF) -- a group involved in many online campaigns and whose tagline is "defending your rights in the digital world" -- is joining forces with other equality advocates, including Greenpeace, to create a global coalition fighting for net neutrality. The latest campaign is a concerted effort to ensure that the internet is not transformed into something that delivers a poorer service to certain customers.
Thus far, the various campaigns for net neutrality have been uncoordinated and designed with slightly differing aims in mind. The idea behind setting up a coalition was to put up a unified front, and the EFF makes it clear that this is an issue affecting not only those in the US, but also people in Europe and other parts of the world.
One of the first tasks of the coalition was to decide on a definition of net neutrality. This chosen definition is:
Net neutrality requires that the Internet be maintained as an open platform, on which network providers treat all content, applications and services equally, without discrimination.
Josh Levy, Advocacy Director at Access, said: "This dynamic coalition shows the importance of net neutrality to every internet user around the world. The open internet remains a crucial driver of education, expression, innovation, health, and creativity; every internet user everywhere deserves equal access to this revolutionary medium. Advocates and decision makers around the world are watching the contentious net neutrality debates in the US and the EU. The decisions made in those regions will set global precedents for how to ensure and protect a neutral, non-discriminatory internet".
The coalition recognizes that ISPs may need to structure traffic in such a way that, for example, voice calls can be placed without interruption, but suggests that this is where traffic shaping should end. "These measures must not be used as a pretext to police communications on their networks, to bestow unfair commercial advantages on their own or particular third-party content, or to create a walled garden where only certain applications, services or protocols are welcome".
Photo credit: albund / Shutterstock
-

Partial refunds for PS Vita customers after Sony’s ‘misleading’ ads
Publié: novembre 26, 2014, 3:02pm CET par Mark Wilson

Sony has been hit with an order to issue partial refunds to customers who bought PlayStation Vita consoles. The Federal Trade Commission found that the company had produced false advertising for the handheld console which suggested that the PS Vita had certain features when in fact it did not. Anyone who bought the console before June 1 2012 is entitled to either $25 cash or credit, or a $50 voucher.
Adverts for the three year old console suggested that players could start a game on a PS3 and pick up from where they left off on a PS Vita console. This feature was only supported by a small number of games. Ads also suggested that 3G subscribers could engage in live online games when in fact this was not possible.
Jessica Rich, Director of the FTC’s Bureau of Consumer Protection, said: "As we enter the year's biggest shopping period, companies need to be reminded that if they make product promises to consumers -- as Sony did with the 'game changing' features of its PS Vita -- they must deliver on those pledges. The FTC will not hesitate to act on behalf of consumers when companies or advertisers make false product claims".
The FTC also found that the PR agency involved with the PS Vita campaign -- Deutsch LA -- had started a marketing drive for the console on Twitter without making it clear that the firm was working with Sony. The full complaint against Sony was quite damning in its suggestion that customers had been misled. A blog post makes it clear that the FTC felt that consumers had been deceived, but it also points out that no framework for issuing refunds has yet been determined.
Photo credit: Barone Firenze / Shutterstock
-

Partial refunds for PS Vita customers after Sony's 'misleading' ads
Publié: novembre 26, 2014, 3:02pm CET par Mark Wilson

Sony has been hit with an order to issue partial refunds to customers who bought PlayStation Vita consoles. The Federal Trade Commission found that the company had produced false advertising for the handheld console which suggested that the PS Vita had certain features when in fact it did not. Anyone who bought the console before June 1 2012 is entitled to either $25 cash or credit, or a $50 voucher.
Adverts for the three year old console suggested that players could start a game on a PS3 and pick up from where they left off on a PS Vita console. This feature was only supported by a small number of games. Ads also suggested that 3G subscribers could engage in live online games when in fact this was not possible.
Jessica Rich, Director of the FTC’s Bureau of Consumer Protection, said: "As we enter the year's biggest shopping period, companies need to be reminded that if they make product promises to consumers -- as Sony did with the 'game changing' features of its PS Vita -- they must deliver on those pledges. The FTC will not hesitate to act on behalf of consumers when companies or advertisers make false product claims".
The FTC also found that the PR agency involved with the PS Vita campaign -- Deutsch LA -- had started a marketing drive for the console on Twitter without making it clear that the firm was working with Sony. The full complaint against Sony was quite damning in its suggestion that customers had been misled. A blog post makes it clear that the FTC felt that consumers had been deceived, but it also points out that no framework for issuing refunds has yet been determined.
Photo credit: Barone Firenze / Shutterstock
-

Windows 10 Build 9879 hits Slow ring, ISO and BSOD fix also released
Publié: novembre 25, 2014, 4:43pm CET par Mark Wilson
With Windows 10 technical Preview, Microsoft is delivering updates to Windows Insiders on two different schedules. People who have opted to join the Fast ring for preview updates already have Windows 10 Build 9879, but today the latest build starts rolling out to those who opted to stay in the Slow ring, or just didn’t know that the faster option was available.
After a couple of weeks' testing on Fast ring guinea pigs, Build 9879 is rolling out to the Slow ring. There have been no changes in the move from Fast to Slow ring, so we know what to expect but Microsoft has taken the opportunity to issue a separate update to fix an issue that caused a BSOD on some systems. But what will please anyone who has been waiting to perform a clean installation of this latest build -- the last public build we'll see until next year -- is the news that Build 9879 has also been made available as an ISO as the Windows Technical Preview November Update.
The majority of testers are using the Slow ring -- Microsoft's Gabriel Aul revealed on Twitter that just 10 percent of users have opted to join the Fast ring. If you have an existing build of the Windows 10 Technical Preview installed you can just sit back and wait for the latest build to roll in. If you're impatient, you can perform a manual check by heading to Update and Recovery in PC Settings and hitting the Check Now button in the Preview builds section.
For anyone looking to work with a bootable ISO to perform a clean install, downloads are available on the Microsoft website, so get downloading. We've already looked at what has been added to build 9879, but as a quick recap, here's what to expect:
- Search and Task View buttons can be hidden without the need for hacking
- New hamburger menu in modern apps
- Changes to window animations
- Changes to OneDrive syncing
- New touchpad gesture support
- Improved MKV support
There's still no sign of Continuum, although a sneak peak is available with a little tinkering.
After installing the latest build -- or if you already have it from the Fast ring -- be sure to check Windows Update for the update that fixes the "0xAB bluescreen".
Photo credit: Patrick Foto / Shutterstock
-

GreatFire.org and BBC punch uncensored news through the Great Firewall of China
Publié: novembre 25, 2014, 1:39pm CET par Mark Wilson

The Great Firewall of China is renowned for the restrictions it places on what Chinese citizens can access online. Free speech advocates have long called for the Chinese government to allow access to the wider web, so people in China can get a better idea of what is going on elsewhere in the world. Now GreatFire.org, working with the BBC, has found a way to deliver uncensored Chinese language news to those on the wrong side of the firewall.
GreatFire.org is an anti-censorship group that monitors web blocking in China and campaigns against censorship. Various techniques for getting around the Great Firewall of China have been publicized in the past, but they have relied on VPNs and other tools that can be complicated to set up. The latest method requires no special tools.
The BBC's Chinese language site was blocked very soon after it launched, cutting off those hungry for news other than that sanctioned by the government. The new method of bypassing censorship uses the "collateral freedom" method to unblock sites using mirrors. The mirror sites are delivered through CDN services like Amazon's CloudFront which are far harder to block.
GigaOM points out that blocking access to "something as widely used as Amazon Web Services (AWS) would be somewhat over-the-top, even for Chinese censors". Microsoft Azure is also used to punch through the Great Firewall.
The timing of the collaboration between the BBC and GreatFire.org is important. Local elections are due to take place in Taiwan, and providing access to uncensored news "gives Chinese netizens a rare opportunity to glimpse how their cross straits cousins elect local officials in a transparent and open democratic process".
Photo credit: karen roach / Shutterstock
-

Thousands of WordPress, Joomla and Drupal sites threatened by CryptoPHP backdoor
Publié: novembre 25, 2014, 3:11am CET par Mark Wilson

A large proportion of websites are built on a CMS rather than raw HTML. Three of the most common are WordPress, Joomla and Drupal, and security researchers at Fox-It warn that site administrators are at risk of being socially engineered into installing the CryptoPHP backdoor on their server.
Distributed through pirated themes and plugins, CryptoPHP's spread is thanks to the light-fingeredness of site admins. It was first detected in 2013 and is still actively spreading. The capabilities of the "well developed" backdoor include remote control of an infected server, and Blackhat SEO -- a form of illegal search engine optimization.
Fox-It warns that thousands of websites have been compromised by CryptoPHP. The threat is so named because it uses s RSA Public Key cryptography to protect communication with servers. A number of sources have been associated with the spread of the backdoor, which is nulledstylez.com, but numerous other sites dealing in pirated plugins and themes that are involved -- including freemiumscripts.com, wp-nulled.com and mightywordpress.com.
Each of the downloads was flagged by the site providing it as being clean from viruses, but Fox-It points out that the versions made available for download differed in that they had been verified as clean by VirusTotal. Upon examining the contents of the pirated downloads, files with different timestamps to the rest were found to include the backdoor hidden in PHP code.
While there is little to stop CryptoPHP infecting other CMSs, WordPress, Joomla and Drupal are the main target due to their popularity. The backdoor installation varies from platform to platform, but in the case of WordPress an extra administrator account is added so that access can be maintained even if the backdoor itself is removed.
Tracing back the activity of CryptoPHP seems to lead back to a Moldavian IP address -- specifically in the state Chisinau. Control centers have been identified in the US, Poland, Germany and Netherlands, and Fox-It has produced a white paper that details how to detect the presence of the backdoor.
Photo credit: Spectral-Design / Shutterstock
-

Google's removal of homophobic 'gay hunting' game was far, far too slow
Publié: novembre 24, 2014, 1:58pm CET par Mark Wilson

This morning there was flurry of activity on Twitter as people became aware of the existence of a game called Ass Hunter on Google Play (link included for the sake of completion, although it's no longer active). There were snorts of indignation, incredulous shakes of virtual heads, and numerous cries for Google to pull the app without delay.
This has now been done. The game, which described itself as a "popular game on hunting gays", encouraged people to "play and do not be gay" is not new. The Android game is (or was) a port of a title that dates back almost a decade, and its appearance in the Play store highlights an importance difference between Google's and Apple's app stores -- the vetting processes involved.
There is one key difference in the way Apple and Google handle apps. Apple pre-vets titles before they hit the App Store. Apps and games have to meet Apple's quite exacting standards before they're allowed through the gates, but it is a very different story with Google. In fact the approach could hardly be more different.
Ass Hunter appeared in the Play Store despite a clause in the Developer Program Policies:
Hate Speech: We don't allow content advocating against groups of people based on their race or ethnic origin, religion, disability, gender, age, veteran status, or sexual orientation/gender identity.
It is not an especially subjective view to suggest that a game in which players are encouraged to hunt and kill gay characters would be covered by the "hate speech" clause. But rather than taking a particularly pro-active stance in weeding out the crap from its store, Google relies heavily on users reporting the titles they deem to be unsuitable in some way.
This is a multi-faceted argument. One way of looking at it is that Google is trying to distance itself from the way Apple operates by not censoring the Play Store. As an advocate of free speech and an opponent of censorship, this is undoubtedly a great thing. At least at face value. But when titles like Ass Hunter appear, things start to get a little more complicated.
The developer, Roman Matrosov, is free to hold and express whatever views he may have. But when these views spill over into the area of incitement to cause harm or commit violence, it's rather a different story. This is why there was such a furore on Twitter:
Dear @GooglePlay, how the hell did you approve a game about killing gay people? #DeleteAssHunter via @tommorris pic.twitter.com/RRHAtZ6Zhs
— Aral Balkan (@aral) November 24, 2014
We reached out to Google for comment about Ass Hunter, but the company was unwilling to shed much light on what had happened. The company said it has a policy of not commenting about individual apps, but went on to say that Ass Hunter had since been pulled from the Play Store. Had the game been submitted to Apple's App Store, the manual checks that are in place would have meant that it would be caught and blocked. Does this amount to responsible publishing, or interfering censorship?
It's great that Google saw fit to remove the game, but the response on Twitter -- the disbelief that such a title would be available in the store -- goes to show that it should not have been there in the first place. This runs counter to my usual anti-censorship stance, but here we’re talking about promoting and encouraging illegal activity (albeit within the confines of a cartoony game) and reinforcing misplaced prejudices.
Which approach do you think works best? Pre-vetting or waiting for issues to be reported?
Photo credit: Aquir / Shutterstock
-

Symantec uncovers Regin, a highly advanced stealth spying tool developed by a nation state
Publié: novembre 23, 2014, 7:53pm CET par Mark Wilson

Security firm Symantec has released details of an advanced cyberespionage it has discovered. Called Regin, the backdoor Trojan is described as having a structure that "displays a degree of technical competence rarely seen". Symantec goes as far as saying that the levels of resources required to create such a highly advanced tool indicate that it was created by a nation state -- although there is no suggestion about who it might be.
The report says that Regin has already been used in mass surveillance programs not by but against government organizations. Symantec estimates that the tool may have been years in development, as it delivers multi-stage attacks, and great lengths are taken to hide each stage. The framework was designed to facilitate long-term surveillance, and the concealment techniques used make Regin difficult to fully understand.
Symantec has published a full white paper about Regin, but gives an overview of the capabilities and threats posed by the malware in a blog post. It seems that the malware has been active since 2008, and a new version was developed in 2013 and a modular approach -- similar to that used by the Flamer and Weevil malware -- makes it easy to tailor attacks to individual targets. Roughly half of infections have been private individuals, but a large proportion are more worrying targets such as telecoms and government agencies.
Strong language is used in Symantec's white paper to refer to Regin:
In the world of malware threats, only a few rare examples can truly be considered groundbreaking and almost peerless. What we have seen in Regin is just such a class of malware. Regin is an extremely complex piece of software that can be customized with a wide range of different capabilities which can be deployed depending on the target. It is built on a framework that is designed to sustain long-term intelligence-gathering operations by remaining under the radar. It goes to extraordinary lengths to conceal itself and its activities on compromised computers. Its stealth combines many of the most advanced techniques that we have ever seen in use.
The capabilities of Regin are concerning to say the least. Password monitoring, remote access, recording of calls (more than a quarter of infections affected telecom backbones), and intercepting email are enough to break any sys admin out in a sweat, but it is the difficulty in detecting the malware that is perhaps the greatest cause for alarm. Once a system is infected with Regin, there is a six stage process that takes place. Every stage is carefully encrypted to hide traces of activity:
The initial Stage 1 driver is the only plainly visible code on the computer. All other stages are stored as encrypted data blobs, as a file or within a non-traditional file storage area such as the registry, extended attributes, or raw sectors at the end of disk.
Full details of each of the stages is provided in the white paper in which Symantec draws comparison with the Stuxnet/Duqu family of malware. The impact that Regin has had, and will continue to have, is difficult to determine but the report points out that the discovery serves as an important reminder that investments are still being made in global surveillance software:
The discovery of Regin serves to highlight how significant investments continue to be made into the development of tools for use in intelligence gathering. Many components of Regin have still gone undiscovered and additional functionality and versions may exist.
You can read the full report on the Symantec blog.
Photo credit: Andrea Danti / Shutterstock
-

Apple and Microsoft both appear in TIME's best inventions of 2014
Publié: novembre 23, 2014, 6:07pm CET par Mark Wilson

It's the time of year -- no pun intended -- when websites and magazines start to reflect over the year that has passed. As we reach the closing stages of 2014, TIME has taken a look back at the preceding months and picked out its highlights from the world of innovation in its annual collection of "the best inventions making the world better, smarter and—in some cases—a little more fun".
There may not be quite the same importance placed on TIME's favorite inventions as its annual person of the year award, but it makes for interesting reading nonetheless. With a print circulation running into millions, it's a publication that holds some influence across swathes of America. Apple and Microsoft make appearances in the list, but there are a few surprise inclusions from the world of tech as well.
Let's get the more obvious inclusions out of the way straight away: Apple and Microsoft. TIME and Apple already have something of a relationship, as the iPad and iPhone versions of the magazine are available free of charge. That in mind the inclusion of the yet-to-be-released Apple Watch is perhaps not entirely surprising. Apple's entry into the smartwatch market is singled out as it "wholly reimagines the computer for the wrist, using a novel interface that combines a touchscreen and physical buttons".
While the Apple Watch neatly falls into the category of invention by virtue of being brand new, the same can’t necessarily be said for the Surface Pro 3. The third generation laptop/tablet hybrid from Microsoft is described by TIME as "more suitable than other tablets for professionals like doctors and businesspeople". While the Surface Pro 3 itself may not be a completely new invention, the redesigned kickstand that overcame many of the problems from the previous two versions could easily be described thus.
One thing stands out about the tech inclusions in TIME's list -- there is a string focus on mobile tech and portability. When it comes to wearables, the Apple Watch is not the only entry; there's also Ringly. This NFC wearable links to a phone to provide notifications about emails, text messages and the like. The mobile theme continues with the Blackphone. Privacy and security concerns are felt around the world of tech as well as in the world at large, and TIME believes that the privacy-focused cell phone -- with security features that would make even Snowdenophiles drool -- is one of the best things to come out of the last 12 months.
An odd inclusion in the list is 3D printing. 2014 could be considered the year that 3D printing exploded in popularity as printers fell into a more affordable price bracket, but it's hard to consider it as an invention of 2014. No "best of" list would be complete without at least one comedy entry, and in this list this accolade goes to the selfie stick. An essential piece of kit for anyone looking to take a selfie from the most flattering angle, the selfie stick is likely to feature highly on the list of popular stocking stuffers this year.
Moving, somewhat, away from mobile devices -- although there are certainly applications here -- TIME gives props to wireless electricity. We've already seen this in its early stages in the form of wireless charge pads for phones and tablets, but if WiTricity gets its way, there's a great deal more to come. We're already getting to the stage where contact with a charging plate is no longer needed, so wireless charging could become as untethered as Wi-Fi. Well ... with a range of a few feet anyway.
The list is something of a mixbag of old and new, product evolution and the genuinely innovative. This could be a reflection of the fragmented tech market that exists more than being a reflection of TIME's peculiarly eclectic taste.
Are your tech favorites on the list, or do you think there have been a few oversights?
Photo credit: Brian A Jackson / Shutterstock
-

Alienware Alpha is the next-gen console ready to take on PS4 and Xbox One
Publié: novembre 21, 2014, 4:36pm CET par Mark Wilson

It must be coming up to Christmas; Alienware, the game-focused arm of Dell, is beginning to ship its new gaming console. The Alienware Alpha is described as the world's first PC gaming console, and it has been designed to blend the power of a gaming rig with the ease of use of a console. With prices starting at $549, gamers have the ability to customize their hardware to suit their needs. The Alpha runs Windows 8.1, and it includes either 4GB or 8GB of RAM, as well as a USB adapted Xbox 360 controller.
The price of the console is bumped up for anyone opting to increase the size of the hard drive or speed of the processor, but the aim here is to blow the Xbox One and PS4 out of the water with raw power.
In all there are four models available. Moving up from the base model involves increasing the hard drive capacity from 500GB to 1TB, and doubling the RAM from 4GB to 8GB while retaining the same 2.9GHz i3-4130T Dual-Core CPU -- this will set you back $699. Pop in a 3GHz Intel Core i5-4590T Quad-Core processor and the price increases to $799, while upgrading to a 2TB hard drive and 3GHz Intel Core i7-4765T Quad-Core processor bumps it up to $899. In all models, graphics are catered for by an NVIDIA GeForce GTX GPU 2GB GDDR5 card. Frank Azor, General Manager of Alienware, said:
We've been working hard this past year to break the mold and develop a system that finally brings hundreds of Steam games, including some really fun indie titles, to TVs. The team and I are excited to finally deliver our vision for big screen gaming and give our fans a console that delivers true next-gen performance with the flexibility to choose how, what and where they want to play.
Alienware is keen to tempt gamers away from the competition, and early adopters placing orders will be treated to a batch of free games including Awesomenauts and Magicka.
Like the Xbox One and PS4, the Alienware Alpha is more than just a console, and the Alpha UI can be used to access movie and music libraries. While this side of things can be controlled using the Xbox 360 controller, the fact that the console is powered by Windows 8.1 means that it functions as a desktop PC with a keyboard and mouse, as well as being an entertainment device for the living room. Find out more and customize your console at the Alienware Alpha website.
-

Twitter now lets you share public tweets via Direct Message
Publié: novembre 20, 2014, 11:35pm CET par Mark Wilson
 You're probably well aware that Twitter features a search option at the top of the page which you can use to track down individuals or topics. Less well-known is the dedicated search page which is the Twitter version of Google (complete with advanced search parameters), albeit one that is -- obviously -- limited to searching within the confines of Twitter itself.
You're probably well aware that Twitter features a search option at the top of the page which you can use to track down individuals or topics. Less well-known is the dedicated search page which is the Twitter version of Google (complete with advanced search parameters), albeit one that is -- obviously -- limited to searching within the confines of Twitter itself.A couple of days ago, this search engine became slightly more useful when Twitter announced that it was indexing every single tweet that has been sent since 2006. Creating a somewhat Shakespearean internet-within-the-internet, Twitter is a valuable resource not only for information but also social commentary. Another update today makes it possible to share any interesting tweets you discover via direct message in addition to the recently added URL sharing option.
These may sound like two fairly minor new additions, but the inability to share URLs with people you follow -- and who follow you in return -- was irritating to many people. It's not exactly a new feature; it's something that used to be possible and was then removed. Now the DMing of URLs has been reinstated so there can be celebrations all round. If you find an interesting story online, it's now easy to share it with your friends.
But the ability to share individual tweets via DM is, as The Next Web suggests, an indication of the growing importance Twitter places on direct messages. Whether there is a desire to compete with the likes of Skype and Google Hangouts is not clear, but it's a nice touch. If you spot a tweet you'd like to enjoy with a friend or two -- but not necessarily go as far as retweeting to all of your followers -- just hit the '...' link beneath the tweet in question and select the Share via Direct Message option. The same option is available in TweetDeck.
-

Google Contributor lets you pay to hide adverts on websites
Publié: novembre 20, 2014, 8:58pm CET par Mark Wilson

Online ads have been seen as the scourge of the web since they were first dreamed up. There are various ways you can avoid them, but they exist for a reason -- to generate revenue. Google may have come up with a solution that keeps everyone happy, website owners and visitors alike. Google Contributor is described as "an experiment in additional ways to fund the web" and it makes it possible to kill ads without killing revenue.
It's invite only at the moment, but once Google Contributor is properly up and running, web users will be invited to make a monthly "contribution". This will enable them to browse participating sites without being bothered by ads; instead you'll see a thank you message or just empty space.
This basically amounts to turning the web into a subscription service, and it appears that Google is looking to keep costs down. Ad-haters can pay between $1 and $3 -- the choice is theirs -- and Google says that "the more you contribute, the more you support the websites you visit". At the moment the list of sites making use of Contributor is pretty small, but there are already some big names on there -- The Onion, Mashable and imgur, for example.
Invites have been sent out to a limited number of people, and if you're interested in paying to cut back on your ad intake, you can add yourself to the waiting list. This new method of website monetization is an extension of the idea of micro-payments that have made in-app purchases such a success. The fact that web users are free to set their own subscription level is likely to be well-received, as is multiple sites being covered by a single payment.
Is this a scheme you'd be happy to pay out for?
Photo credit: IIIadam36III / Shutterstock
-

Microsoft Research makes great strides in automatic image captioning
Publié: novembre 20, 2014, 6:53pm CET par Mark Wilson

Microsoft Research is home to all manner of interesting projects and experiments, and one of the latest that the team is keen to share news about is automatic image captioning. There are no prizes for guessing what this is -- it's very much what it says on the tin -- and the technology has now reached a stage where the automatically generated captions for an image are at least as good as those thought of by people.
A team of just 12 worked on the project, and the results are pretty impressive. The system analyzes an image and identifies its key components. After determining objects and characteristics, these can then be evaluated in relation to each other to help decide what is important, and what can be ignored.
A series of possible image descriptions is then created, and these are ranked according to how much sense they make in natural language, and whether importance has been attributed to the correct components. A post on the Machine Learning Blog gives you the opportunity to see if you can determine which image captions were written by hand and which came from a machine. You might be surprised at just how difficult it is to distinguish between the two!
There are lots of potential applications for this technology, but two of the most obvious are voice control and accessibility options. At the moment it is possible to conduct web searches for images by controlling a computer with your voice, but this is reliant on images having been appropriately tagged and captioned already. If software can be used to automatically caption images on the fly, voice-activated image searches can cast a wider net.
But perhaps a more interesting use of the technology would be to make computers in general, and the internet specifically, more accessible to people with sight problems. Text-to-speech is great for hearing what has been written on a particular page, but what about the accompanying imagery. With automatic captioning, pictures that have been added to an article could be described by text-to-speech software regardless of whether a descriptive caption had been added by the author.
Photo credit: Zmiter / Shutterstock
-

Apple no longer offering 'free' apps in the App Store
Publié: novembre 20, 2014, 6:00pm CET par Mark Wilson

Take a browse through Apple's App Store and you'll notice something interesting: there are no free apps for Mac, iPhone and iPad any more. Or at least you'd be forgiven for thinking that was the case. Rather than trying to entice people into downloading apps by emblazoning a sexy "Free" button next to them, Apple now opts for a more descriptive "Get" button.
This does not mean that free apps now cost money, but it does mean that the apps you download may cost you money further down the line. Confused? The rewording of the download buttons seems to have come about because of regulators in Europe expressing disapproval that apps previously labeled as free could lead to large bills via in-app purchases.
The European Commission had previously suggested that Apple and Google make it clear that apps that appear to be free, could in fact incur charges. This is Apple's way of complying with the suggestion. Rather than creating new labels to cover a wider range of app types -- those that cost money, those that are completely free, those that cost money and can be upgraded through in-app purchases, and those that are free at point of download but include in-app purchases -- the Get button was dreamed up.
Now any app or game which is free to download, regardless of whether in-apps purchases are available, will feature the Get button in the App Store. There have been numerous stories about parents getting hit with large bills after their offspring used their phone or tablet to make in-app purchases without permission, and it's not clear whether this rewording will do much to prevent this from continuing to happen.
Photo credit: newart-graphics / Shutterstock
-

Mozilla, EFF and others join forces to encrypt the web with free security certificates
Publié: novembre 19, 2014, 7:18pm CET par Mark Wilson

It has been a long time coming, but the web is slowly transitioning away from HTTP to HTTPS. Google has done it with Gmail, and Yahoo did the same with its webmail service, and security advocates would like other websites to follow suit. The problem, for smaller sites at least, is the cost involved. But a new venture between Electronic Frontier Foundation (EFF), Mozilla, Cisco, the University of Michigan and IdenTrust will eliminate the cost obstacle when it launches next summer.
The partnership has brought about the creation of Let's Encrypt, a new certificate authority that will provide free security certificates to those who need them. It is hoped that handing out cost-free certificates will encourage more sites to adopt the HTTPS protocol. But Let's Encrypt does not just eliminate the financial hurdle.
The process of setting up and managing certificates is notoriously tricky, and very easy to get wrong. This is something that Let's Encrypt will also take care of by using a software agent to reduce the setup time to under a minute. The tool is still in the development stages at the moment, but you can check it out, and provide feedback on how it works.
HTTPS, EFF freely admits, is not a perfect technology, but it is a marked improved over the standard HTTP protocol which is still very widely used. The certificate authority will be managed by the Internet Security Research Group, and there will be a strong focus on openness, ease and transparency. Certificates will be available to anyone with a domain, and the automated setup means that things can be up and running very quickly. The software behind the process will be open source, and the whole venture is as much about co-operation as it is about security -- ease of use and compatibility are of the utmost importance.
Check out the video below to get an idea of how the software agent will work:
-

Tech companies like Facebook and Google lead the way in delivering LGBT equality in the workplace
Publié: novembre 19, 2014, 3:47pm CET par Mark Wilson

US technology companies are setting a benchmark for those in other sectors to reach for when it comes to LGBT equality in the workplace. These are the findings reported in the thirteenth edition of the Human Rights Campaign (HRC) Foundation’s Corporate Equality Index. The HRC rates workplaces on lesbian, gay, bisexual and transgender inclusion and equality, and this year's report shows that there is now greater awareness and understanding of the transgender community.
The index rates companies using a variety of factors including the presence of non-discriminatory policies, the existence of transgender-inclusion healthcare, and whether or not there are guidelines in place to encourage transgender inclusion. This year there are a record number of businesses attaining a 100 percent rating, and 14 of these fall into the hardware, software and data services areas of the tech sector.
Joining the companies with a perfect score this year are Facebook and Yelp, and Adobe makes an impressive improvement from 90 to 100 percent. Facebook had previously managed to upset the LGBT community with its real names policy. Deena Fidas, director of the HRC Foundation's Workplace Equality Program, said:
Long viewed as thought leaders in business innovation, it's no surprise that computer tech companies continue to be strong leaders in LGBT workplace inclusion. This year, we welcomed two new computer software and hardware companies to the CEI, continuing evidence of the sector's commitment to fairness.
91 percent of Fortune 500 companies include reference to sexual orientation in their non-discrimination policies, while just 61 percent make reference to gender identity. Both figures are up from previous years.
President of the HRC, Chad Griffin, believes that US businesses could teach a lot to other sectors:
Despite 66 percent of all Fortune 500 companies now including gender identity in the employment protections, we know that this does not always translate into everyday inclusion of the transgender community. While many companies are leading the way, our nation's federal non-discrimination protections are lagging behind. Critical cultural shifts need to take place to foster greater inclusion. In this case, our elected leaders should be looking to corporate America for a sterling example of how progress is achieved.
A couple of weeks ago, Amazon published its diversity report which showed the company remains dominated by white middle-class men, although the report revealed nothing about LGBT policies. Next year's HRC report will make for interesting reading as it will, for the first time, include companies' global LGBT policies, not just those in place in US operations.
Photo credit: Rawpixel / Shutterstock
-

Republicans vote against USA Freedom Act that would have limited NSA surveillance
Publié: novembre 19, 2014, 2:19pm CET par Mark Wilson

A bill that could have curtailed the surveillance activities of the NSA has been rejected by the US Senate. The USA Freedom Act was blocked as a bloc of Republican senators voted against the Obama-backed bill. After the Edward Snowden revelations, there have been many vocal calls for the powers of the NSA to be reined in. This was the bill that was supposed to deliver, but right wing opponents referred to it as a "gift to terrorists".
The bill passed the House of Representatives in May and had the backing of many of the biggest technology companies. One of the main aims of the USA Freedom Act was to stop the collection of domestic phone records, but there were also implications for the agency's online dragnet-style data trawling. Now it seems that the fight for privacy starts afresh.
The vote ended up being a fairly close-run thing. Just two votes prevented the bill from moving to the next stages of becoming enshrined, and Senator Patrick Leahy, the Democrat sponsor of the bill blamed "scare tactics" for its defeat. Even support from the White House was not enough to give the bill the push it needed but critics point to the fact that support only came after compromises were made to the scope of the bill.
These compromises centered mainly around a rewording of key passages that left sections of the bill open to wide interpretation. The weakening of the bill -- which many senators who would otherwise have voted in favor of -- led some civil libertarian backers to drop their support.
What happens next could be interesting. In June, Section 215 of the Patriot Act will expire. This is the portion of the Patriot Act that essentially permits the collection of phone records, so this will be the new battleground for privacy advocates. But next on the calendar is the 11 December expiration of the FISA Court order -- it is expected that the Obama administration will grant a further 90-day extension to the order so, for now at least, data collection continues as before.
Ron Wyden, Democratic Senator for Oregon, said, "those who value civil liberties and the US Constitution will not rest until there is true reform that ends this unnecessary overreach". The privacy debate will continue. This battle may have been lost, but the war against surveillance -- whatever form it takes -- continues.
Photo credit: Chris Parypa Photography / Shutterstock
-

PayPal comes to Pebble so you can pay while tracking perambulatory progress
Publié: novembre 19, 2014, 12:58am CET par Mark Wilson

Wearables are starting to come of age, and they're now about much more than just tracking blood pressure and distance while running. Today Pebble continues the expansion of its range of apps with the launch of a dedicated PayPal app. It allow for payments to be made at participating retailers and shows payment notifications so there's no need to rely on a phone.
Pebblers -- as PayPal insists on calling owners of the smartwatch -- now have the ability to make PayPal payments without having to reach into their pockets. The app can be used to pay with a payment code, or to check in to make a payment.
The new payment option comes hot on the heels of a Domino's app that gives Pebble owners the ability to order pizza from their phone. Senior Director of Partnerships and Global Solutions at PayPal, Joel Yarbrough, ponders the evolution of the humble watch:
Did you know the infamous calculator watch has been around since the 1970s? It’s safe to say smartwatches have come a long way since then. And we’re excited to be part of that. At PayPal, we’re working to make shopping easy and seamless so that you are one step closer to walking into a store and being able to place your order and pay without ever reaching into your pocket.
Working together, PayPal and Pebble want you to stop reaching for your wallet, and start using your wrist to pay instead. The new Pebble app is just the latest in a line of apps for wearable devices, such as Samsung's Galaxy Gear range, and Android Wear.
-

IBM Verse aims to transform email with advanced analytics and a social focus
Publié: novembre 18, 2014, 5:30pm CET par Mark Wilson
There are now many names vying to control your inbox. It is not enough to have your email delivered to the inbox of your choice now the battle is to present email in the most understandable, the most accessible, and the least cluttered way possible. IBM Verse is the latest kid on the block, as it looks to divert attention away from Google Inbox and Microsoft Clutter.
Billed as a "new way to work", IBM Verse is more than just another inbox tool -- it is a combination tool that manages email, tasks, collaboration and more. It clearly has enterprise markets in its sights as it brings communication, tasks, sharing and social features under one roof. To further differentiate it from other comparable services, IBM Verse uses advanced analytics to completely tailor itself for individual users.
IBM Verse adapts not only to the way you work, but also the people you work with. It factors in who you work with, how, and when. The default view provides access to an outline view of tasks for the day, a list of contacts you may need to interact with, and brings social elements to the fore. With the likes of Google using data garnered from emails to deliver targeted ads, there is an understandable cynicism surrounding tools like this. Pre-empting this negativity, IBM says:
In contrast to most freely available mail services, we don't mine a user's inbox to target advertising or monetize that data in other ways. This is truly about giving every individual an intelligent assistant to organize and prioritize their most important work and relationships.
This is IBM's vision of the future of work. Tasks are prioritized, there is a strong link between desktop and mobile apps, and the whole idea is based around the people involved in tasks rather than the emails associated with them. As IBM explains, "Rather than replying to a narrow email distribution, project leaders can share their insights as a blog post for their entire project team, with the ability to delegate and track critical actions across individual team members".
To get more of a feel of how IBM Verse works, check out the introductory video:
You can sign up for early access to IBM Verse by visiting the website.
-

Microsoft unveils Office 365 Video for secure enterprise video sharing and streaming
Publié: novembre 18, 2014, 4:43pm CET par Mark Wilson
Microsoft is giving Office 365 users an early glimpse of what it hopes will become the future of enterprise video sharing. Office 365 Video harnesses the power of SharePoint and Azure Media Services to create a tool that gives businesses a one-stop-shop for uploading, sharing, delivering and streaming videos.
A number of possible scenarios are set out by Mark Kashman, a senior product manager in the Office 365 group. From providing employees with access to training videos to delivering CEO messages, this is a flexible tool that has been designed with security and simplicity in mind. Office 365 Video is not expected to launch until early next year, but a sneak peak is available right now.
For anyone who has signed up for Office 365 First Release, the rollout starts now, but general release is still a few months away. It gives organizations a single location to store videos, and there is a strong focus on security at all stages of delivery. Videos can be uploaded in a number of popular formats, and they'll be automatically converted into streamable formats. Office 365 Video aims to provide the best possible experience for anyone watching streaming video, no matter what device they are using, and to this end, multiple versions of the same video are create at different quality levels -- although only the initial upload counts against storage usage.
Office 365 Video adapts video playback according to network conditions and the devices involved. The aim is to provide the highest quality video possible, and checks are performed every couple of seconds to see if quality should be dropped slightly to deliver better performance. Uploaded videos are fed into Office Graph and are discoverable in Delve, with the Delve cards automatically pulling in pertinent information about videos. A page is created for every video that's uploaded, and this features the option to share via Yammer for collaborative work.
This is all part of Microsoft's NextGen Portals for SharePoint which will make it easier than ever to pull in information from a variety of sources, and make it available to a range of devices. As this is an enterprise tool, there are suitable security tools in place to ensure that videos are only accessible to authorized users.
Check out the video below where Microsoft shows how Office 365 video combines the power of SharePoint Online and Azure Media Services:
-

Microsoft gives developers beta access to Bing-powered OneNote Search API
Publié: novembre 18, 2014, 1:27pm CET par Mark Wilson

Microsoft has launched a beta version of the OneNote Search API. The API is a collaboration between the OneNote and Bing teams, and has led to the creation of what has been dubbed a "personal search engine for your private notes and memories in the cloud". As the API is powered by Bing, it brings the same power and features to those looking to perform searches in OneNote.
This means that searches can be filtered according to relevance, spelling mistakes are overlooked, and more. Personal indexing means that searches are limited to just those notebooks that a user has access to, and developers are invited to sign up for beta access right now.
Over on the OneNote Developer Blog, Omar Venado -- a senior program manager at Microsoft -- provides a few details about the API. He points out that during the beat testing phases it may take up to two hours for notes to be indexed but this timeframe should improve further down the line. On the same page, you'll also find the link to sign up for the beta.
As this is only a beta version you can expect much more to be added in future releases. There is already talk of adding the ability to search shared notebooks, and the option to limit searches to a particular notebook. Other promised changes include improvements to relevance and ranking settings, and support for using modification dates as a search parameter.
As ever, Microsoft is looking for feedback, so take the beta for a test drive and see what you think of it.
-

Apple pushes iOS 8.1.1 update to speed up older iPhones and iPads
Publié: novembre 17, 2014, 9:23pm CET par Mark Wilson

It seems that Apple is in update mode today. As well as the launch of the OS X Yosemite 10.10.1 update, today also sees the release of iOS 8.1.1. The focus this time around is not really on delivering exciting new features, or even fixing glaring problems, but keeping owners of older devices happy. Aging iPads and iPhones are in for a treat as there are performance boosts to look forward to.
Pre-iPad 2 owners miss out, but the update is available for iPad 2 and newer a well as iPhone 4s and newer. Apple is yet to publish a changelog for the update, but check for an update on your idevice and you'll see a brief description about what to expect.
iPad 2 and iPhone 4s owners will be happy to see the promise of stability and performance improvements, but reference is also made to unspecified bug fixes. It's not clear if Apple will release more information about what the update includes, but for now we have very little to go on:
This release includes bug fixes, increased stability and performance improvements for iPad 2 and iPhone 4s. For more information on the security content of this update, please visit this website: [support.apple.com].
It is great to see that aging devices are being given the update treatment, and that the update is more than just the usual bug fixes. It seems that any big changes are being saved for iOS 8.2, but the question is, are the performance improvements noticeable?
-

Apple releases OS X Yosemite 10.10.1 update with Wi-Fi and enterprise fixes
Publié: novembre 17, 2014, 8:25pm CET par Mark Wilson

It's only a few weeks since Apple launched Yosemite and there's already an update available. Today, Apple pushes out the OS X Yosemite 10.10.1 update to address issues that had been found in the initial release. This is a fairly minor x.1 update, and there are only ten entries in the changelog for most users, while enterprise users have two more updates and additions.
Described -- of course -- as "recommended for all OS X Yosemite users", the update fixes a problem with Time Machine that made older backups invisible. It also addresses issues with the Notification Center, and problems with entering Japanese text. It "improves the stability, compatibility, and security of your Mac".
Other features of the update include improved Wi-Fi reliability, the elimination of a problem with items not appearing in the App Store, and the correction of issues sending emails through certain providers.
Here's that all-important changelog in full (minus the typo that can be found at the Apple website -- Notification (sic) Center indeed!):
- Improves Wi-Fi reliability
- Improves reliability when connecting to a Microsoft Exchange server
- Resolves an issue that may prevent Mail from sending messages through certain email service providers
- Addresses an issue prevents connecting to remote computers using Back to My Mac
- Resolves an issue where sharing services, Notification Center widgets and Actions may not be available
- Addresses an issue that could cause Notification Center settings to not be retained after a restart
- Addresses an issue that might prevent the Mac App Store from displaying certain updates
- Addresses an issue that could prevent some Mac mini computers from waking from sleep
- Resolves an issue that might prevent Time Machine from displaying older backups
- Addresses an issue that might prevent entering text in Japanese
On the enterprise front, this update to Yosemite fixes a problem that caused the App Store to offer an update to Apple Remote Desktop even when the most recent version was installed. It also adds new options to DNS lookups.
If you have Always Update enabled, just sit back and wait, but otherwise you'll need to manually start the update process.
-

Could Facebook at Work put the work back into social networking?
Publié: novembre 17, 2014, 2:03pm CET par Mark Wilson

There are some people who just can’t get enough of Facebook. Sharing the occasional thought or ponderance is not enough for many who feel the need to live out their entire lives on Zuckerberg's social network. A lot of workplaces -- perhaps sensibly -- block access to sites such as Facebook, but new reports suggest that the social giant is keen to enter the office on legitimate terms with Facebook at Work.
At the moment, Facebook is the bane of network admins' lives as employees find new ways to bypass restrictions that may be put in place. But the Financial Times says that it may soon be welcomed with open arms as a work-centric version of Facebook is rumored to offer Office- and Google-baiting document collaboration, and LinkedIn-aping professional networking.
Although Facebook is yet to issue an official statement about the rumored network, those ever-knowledgeable "people familiar with the matter" say that users will be able to keep their work and personal profile completely separate. This is not a new project; Facebook at Work has been in the works for the past year and a team of engineers is beavering away in London. While LinkedIn has managed to gain a positive reputation in the world of business, the same cannot really be said of Facebook.
Users have been upset by newsfeed experiments as well as Facebook's changing views on the use of real names, but other activities work more in the network's favor. Work with Yahoo to create a secure email standard, providing secure Tor access, and simplifying its privacy policy are steps that will certainly help to ingratiate Facebook with workplaces, but it's clear that any move into the office is a marked change in direction for Facebook. While the current version of Facebook is all about connecting with, and sharing with as many people as possible, companies will need assurances that they are placed firmly in control of the flow of data if they are to embrace Facebook at Work.
But if Facebook manages to pull it off, it would be quite a coup. It would be impressive if the special network was able to make inroads into LinkedIn's user-base -- more so if it was able to eat into Microsoft's and Google's share of the collaborative market. It's clear that Facebook at Work would have to operate in a very different way to the existing site. The Financial Times says:
The company is unlikely to charge for the service, at least initially, which will boost the amount of time spent on the platform, as employees previously banned from using the site in the office may now be encouraged to use it.
But money has to come from somewhere. If Facebook at Work is to succeed, it will need to raise money from either advertising -- which would be off-putting to many workplaces -- or through some form of subscription package.
Photo credit: Twin Design / Shutterstock
-

State Department email system shut down after hacker attack
Publié: novembre 17, 2014, 12:19am CET par Mark Wilson

Reports from Associated Press reveal that the State Department has closed down its email system following a security attack. The news comes after the details of a hack attack on the White House in October were made public. It seems that the email State Department's unclassified email system was attacked at the same time, and technicians are currently working to repair the damage.
It was suggested that last month's White House hack was linked to Russia, but it is not yet clear whether the attack on the email system is part of the same security breach. The email closure is described as "unprecedented", but officials insist that classified data systems have not been affected.
Although the breach took place back in October, the decision to shut down the email system was only taken on Friday. Following the attack on the White House, other agencies such as the US Postal Service and the National Weather Service have also suffered attacks, and a spokesperson said that turning off email was part of a scheduled outage to make improvements to security.
Speaking to NextGov the spokesperson said that State employees' ability to access email and public websites had been interrupted, but went on to say that it was hoped that systems would be back up and running soon. No explanation has been given about why there was such a delay between detecting the attacks and shutting down systems for maintenance.
Photo credit: Sorbis and karen roach / Shutterstock
-

Jony Ive says Apple doesn't aim to make money, hits out at those who copy designs
Publié: novembre 15, 2014, 9:13pm CET par Mark Wilson

Apple's Senior Vice President of Design, Jony Ive, used an interview at London's Design Museum to lash out at design copycats. He touched on many topics, including suggesting that design schools rely too heavily on computers, the "theft" of Apple designs, and explaining why the design of Apple's own products is formulaic.
In conversation with Deyan Sudjic, director of the Design Museum, Ive also said that Apple does not exist to make money. This will come as news to most people -- including, perhaps, Apple itself -- particularly as the company is currently the most valuable brand in the world. He insists that integrity is at the very heart of Apple, and that any money that may come rolling in is merely "a consequence".
The Design Museum is celebrating its 25th anniversary, and Ive is one of the most renowned designers in the world -- he's the sexy, accessible face of the design world. The suggestion that "our goal at Apple isn't to make money" will be hard for many to accept. Of course the company does make money, but for Ive this is just a happy side-effect of what it does:
Our goal is to desperately try to make the best products we can. We're not naive. We trust that if we're successful and we make good products, that people will like them. And we trust that if people like them, they'll buy them. Operationally we are effective and we know what we're doing and so we will make money. It's a consequence.
There's no denying that Apple's and Ive's designs have influenced the direction in which many products have turned in terms of looks. But he's not happy at being influential in this way, and he's far from happy about companies who copy ideas:
It's not copying, it's theft. They stole our time, time we could have had with our families. I actually feel quite strongly about it. It's funny – I was talking to somebody and they said do you think when somebody copies what you do it's flattering? No.
Ive spoke a little about the birth of the Apple Watch, explaining that there are inevitable limitations to small devices strapped to an arm:
The wrist is an amazing place to put technology. You're only going to use it a certain way – you're obviously not going to write a dissertation! But it's very good to see who just texted you, or if you're walking and use it just to see was that left or right. So the watch – just like for telling the time – is very good for these quick in and out things.
He also emphasizes the fact that Apple is about an ecosystem, not just individual products:
One of the biggest challenges that we found was that we wouldn't all be sitting here wearing the same thing. I don't think we want to wear the same thing. Which is why we developed this system not a single product. It's a flexible system, so hopefully it will be appealing, but there's still a very singular idea. We're not just throwing a whole bunch of ideas against the wall to see which one sticks… like some people!
We also learn that the design team is made up of "17 or 18 people" and is unlikely to expand much more. Ive says that "it's wrong to make something different for the sake of being different" so it's safe to assume that there are not going to be any major surprises in terms of the look of new Apple products in the near future.
The (almost) full transcript of what Ive had to say can be found on the Dezeen website.
Photo credit: corund / Shutterstock
-

What a load of number two! Microsoft is the second most valuable company in the world
Publié: novembre 15, 2014, 7:21pm CET par Mark Wilson

A month ago we reported that Apple is the most valuable brand in the world. This ranking was based on figures published by Interbrand, but things have been improving for the Nadella-led company in recent weeks. Since then, Microsoft is creeping up the charts when looked at in terms of market capitalization -- the number of company shares multiplied by the price of a share.
Microsoft now finds itself overtaking oil giant Exxon as it jumps to second place in the global rankings. Apple remains in the top slot. The move up the charts was helped not only by Exxon getting hit by a slump in global oil prices, but also by an increase in Microsoft's share prices.
Shares shot up to $50.04 on Friday -- a 14 year high -- before dropping back slightly to $49.81. This gave Microsoft a value of $410.5 billion, placing it comfortably ahead of Exxon. Despite a share price of $94.90, and a share rise of 24 percent, the oil firm's market capitalization sits at $401.9 billion. While there will undoubtedly be celebrations at Microsoft at the news that the company finds itself second on the podium, there is quite a ways to go if the Redmond-based firm is to catch up with Apple.
The company behind the iPhone and iPad is very comfortably in the lead with a value of $668.2 billion. It's also not clear how long Microsoft will remain at the top of the charts. While the company's value is certainly on the rise, fluctuations in the price of oil were instrumental in overtaking Exxon.
Photo credit: beebrain / Shutterstock
-

Skype for Web beta brings voice and video chats to your browser without plugins
Publié: novembre 14, 2014, 5:44pm CET par Mark Wilson
Installed apps are becoming a thing of the past. Microsoft is just one of a raft of technology companies gradually moving to the cloud and the latest display of this is a new beta version of Skype for Web. The messaging tool has been designed to be used in a web browser without the need for plugins, extensions or other software. At least that is the aim. During the beta stages you'll still have to install a small plugin.
Work being carried out by the Internet Explorer developers should bring plugin-free Real-Time Communications (RTC) to browsers in the near future, and Skype for Web will be able to take advantage of this. The beta is not being made available to everyone straight away, so you'll need to check your account to see if you can try it out.
Head over to the Skype website, sign into your account, and you may find that you are invited to test out the web version. If you have been chosen, you will be able to access your chats and contacts on any computer, and start voice and video chats from your browser with a quick click. It's an idea that is similar to the way Outlook.com users were given the chance to use Skype from their inbox, but now Skype for Web is available as a separate entity.
Just a few days ago, Microsoft revealed that its enterprise communication tool Lync is to be rebranded Skype for Business in the coming months, and it's not yet clear whether the web treatment will transition to the business tool in the same way. As this is a beta, problems are to be expected, and Microsoft points out a few known issues. For now compatibility is limited to Internet Explorer 10 and above, Safari 6 and above, and the latest versions of Firefox and Chrome. You may find that outgoing calls take longer to ring, and Mac users are likely to notice problems with battery consumption.
-

How to enable Continuum in Windows 10 Technical Preview build 9879
Publié: novembre 14, 2014, 3:24pm CET par Mark Wilson
We're now on the third public build of Windows 10 Technical Preview. Build 9879 addresses some of the concerns people had with build 9860 -- including the ability to kill the infuriating Search and Task View buttons without the need for hackery. One of the biggest changes (or at least the most obvious) in Windows 10 is the reappearance of the Start menu, although the Start Screen is still there as an option.
In presentations, Microsoft has made reference to Continuum (a new version of the Start menu), but we're yet to get hands on with it. This changes in Windows 10 Technical Preview build 9879 as it is possible to enable an embryonic (no, rudimentary -- I referred to Windows 10 itself as being embryonic) version of Continuum. Want to take a look at a new Start screen? Here’s what you need to do.
Before you jump in, be warned that this is very, very, very basic. Continuum is not really functioning to any degree, but if you want to get the merest glimpse at what's on the horizon, you can do so. It's easily done, and easily reversed, so you can back out if you decide you'd rather wait.
- Launch the Registry Editor (hit the Windows key and R, type regedit, and then press Enter) and then navigate to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ ImmersiveShell\Launcher
- Click Edit > New > DWORD (32-bit) Value, and name it UseExperience.
- Double-click the newly create item and set the value to 1.
- Click OK, close the Registry Editor and then restart your computer -- or just restart Explorer.
Try it out for a bit, and you'll soon discover that this new version of the Start menu is currently pretty broken; it's prone to crashing and you'll probably end up ditching it. That said, it's interesting to see where Microsoft is taking the Start menu / Start screen hybrid, or at least seeing what ideas the company is toying with.
Tried it and decided it's not for you? Just head back to the same key in the Registry Editor and either delete UseExperience, or change its value to 0.
-

Facebook proposes privacy policy changes in simplified, prettified paperwork
Publié: novembre 14, 2014, 1:25pm CET par Mark Wilson

Facebook gets something of a bad rap when it comes to its privacy policy. Delve into the social network's terms and you're almost certain to find something you disagree with. This is the same with many companies, particularly those with an online presence, but users seem to be continually surprised to discover how their data and activities are being used and tracked. Part of the problem is that -- just like with software EULAs -- very few users bother to read through policies in full.
Mark Zuckerberg's social network is looking to change that. Facebook is introducing Privacy Basics which provides easy-to-follow guides to controlling how your online content is shared with others. But there are also a number of changes proposed to its privacy policy. Facebook is looking for feedback, and assures users that "you’re in charge." But you'll need to be quick -- there's only a week to give your opinion.
One of the obstacles that prevent people from ploughing through privacy polices is the sheer length of such documents coupled with rather impenetrable language. Facebook's new proposed Data Policy is rather a different story -- it has been designed to be accessible. Compare the current policy pages with the suggested updates and the differences are immediately noticeable. Gone is the monochrome dullness, replaced with bright, colorful sectioning, and careful rewording helps to make the policy easier to understand.
This is not to say that you'll necessarily be happy with everything you find in the document, but the point is that you should be able to find information more easily, and better understand the implications.
The updates to terms and policies are introduced in a blog post by Facebook's Chief Privacy Officer, Erin Egan. He explains that Privacy Basics "gives you tips and a how-to guide for taking charge of your experience on Facebook. We're also proposing updates to our terms, data policy and cookies policy to reflect new features we've been working on. And we're continuing to improve ads based on the apps and sites you use and expanding your control over this kind of advertising".
The important thing to remember here is that Facebook -- just like the all-new Microsoft -- is looking for feedback. If you have suggestions for how things could be improved, don’t hesitate to get in touch through the dedicated page.
-

Google Wallet for digital goods to close next year -- PayPal and Apple Pay rejoice
Publié: novembre 14, 2014, 1:46am CET par Mark Wilson

Google has fingers in lots of pies, but in a few short months it will be pulling one of its fingers out of the digital payments pie. As of March 2, 2015 Google Wallet for digital goods will be no more. After three years of fighting off the competition, the search giant has decided to throw in the towel, get out of the digital payments game and leave it to services like PayPal and Apple Pay.
Starting life as a mobile-based payment system compatible with certain smartphones including the iPhone, Google Wallet allowed payments to be made via NFC. It then evolved into a web-based payment service, but never managed to break out of the confines of the US. In a few short months, anyone using the service to make or receive payments will have to turn to one of the alternatives. But what’s with the sudden shuttering?
In fact it is not the full Google Wallet service that is closing down, just the digital goods side of things. Google doesn’t give much away in explaining why the decision was taken to shut up shop. The closure is something of a low-key affair, but a page has been added to the Help section of the Google Wallet site. Here Google says that: "The industry has matured a lot since [Google Wallet launched], providing a number of alternative payment solutions to choose from".
On March 2, 2015 the Google Wallet for digital goods API will be no more. Developers are advised to remove client-side integration code from their websites, delete code that generates JSON Web Tokens, and get rid of the postback code. But this is not the end of the line for Google Wallet. It will still be supported for developers selling apps through Google Play, or who are using the service to process in-app payments.
Interestingly Google is leaving it to merchants to convey the news to users of Google Wallet:
Google Wallet buyers will not be proactively notified. Keep in mind that if you do not remove your integration before March 2, 2015, your buyers will get 404 errors upon checking out with Google Wallet for digital goods API. To preserve your user experience, we highly recommend removing your integration and migrating to another payment processing solution as soon as possible.
As Google Wallet is used to process payments for subscription services, developers only have a few months to decide on an alternative. Google, unsurprisingly perhaps, has no suggestions other than "we encourage you to research payment processing solutions to best fit the needs of your buyers".
Photo credit: PTstock / Shutterstock
-

Google wants US Privacy Act extended to Europe
Publié: novembre 13, 2014, 1:59am CET par Mark Wilson

Privacy is in the news more than ever before, and high-profile companies are falling over themselves to show just how much they care about protecting the rights of their users. We've witnessed all of the transparency reports about government data requests after the Snowden revelations. We've seen Facebook trying to create a safer email standard. We've seen privacy violations by government websites, and we've seen how those in positions of power believe that privacy is not an absolute right.
Google -- ever the master of PR -- thinks that it's time more was done to protect the privacy of internet users; specifically those in Europe. Google feels that the US Privacy Act should be extended to cover citizens of the EU. But what does this actually mean?
At the moment, people in Europe do not have the right to challenge how their data is being used in a US court. This is a right enjoyed by those in the US and Google says that it is only right for it to be extended to people in other parts of the world. US citizens can already challenge the use of their personal data in European Courts, and Google's Chief Legal Officer, David Drummond, explains that the favor should be returned:
"Right now, European citizens do not have the right to challenge misuse of their data by the US government in US courts -- even though American citizens already enjoy this right in most European countries. It's why Google supports legislation to extend the US Privacy Act to EU citizens. The Obama Administration has already pledged its support for this change and we look forward to to working with Congress to try and make this happen".
It's a view shared by Barack Obama who only recently expressed his vision for a free and open internet. The president said that everyone has "legitimate privacy interests in the handling of their personal information", but Google puts it a bit differently. Drummond says that while there are real threats in the world, the balance has "tipped too far in favor of the state and away from the rights of the individual".
European Commission representatives are due to visit Washington DC, but whether this amounts to anything, or if Google's dream becomes a reality, remains to be seen.
Photo credit: ljh images / Shutterstock
-

Get your groove on as Google launches family games for Chromecast
Publié: novembre 12, 2014, 11:28am CET par Mark Wilson

Just in time for Christmas, Google is introducing family games for Chromecast. The diminutive streaming device is more readily associated with watching YouTube videos, but there are a growing number of apps springing up. The latest additions to the selection are a batch of games which can be enjoyed by the whole family.
What's that? The Chromecast has no controller? Far from being a problem, Google sees this as a big advantage: "there's no hassle or expense with extra controllers. Anyone with a phone or tablet can join in". Just as you use your phone or tablet to control media playback, you can do the same to control games, and the built-in sensors found in many handsets mean they work like Wiimote (or Wii Remote if you will insist on proper terminology).
There are already quite a number of titles to choose from, including popular classics such as Wheel of Fortune, Scrabble and Connect Four. For anyone looking for something a little more exciting than a glorified board game, there are slightly more energetic offerings to choose from. You can throw some shapes in Just Dance Now, or if you prefer something more mentally taxing, try something like Big Web Quiz instead.
In a blog post announcing the games, Google also points out that category tabs have been added to the Chromecast Apps page to make it easier to browse through what's available. For more 'traditional' Chromecast entertainment, Showtime Anytime and Starz Play are on hand to pump a constant stream of shows to your TV.
Photo credit: Fotyma / Shutterstock
-

Microsoft launches Clutter to help clear the crap from your Office 365 inbox
Publié: novembre 12, 2014, 2:37am CET par Mark Wilson

Email overload -- it's something that we all suffer with; but what’s the solution? To help make it easier to focus on the emails you need to see and deal with, Microsoft is launching Clutter. It's a tool aimed at Office 365 business customers who want to be able to wade through the rubbish and get to the emails that actually matter.
In many ways, Clutter is Microsoft's answer to Google's Priority Inbox feature for Gmail. It determines which messages are those which you are likely to want to handle later rather than straight away, and moves them out of the way to free up your inbox. Less crap to sort through leads to increased productivity -- at least that's the theory.
The idea is very simple. "Clutter is designed to help you focus on the most important messages in your inbox. It uses machine learning to de-clutter your inbox by moving lower priority messages out of your way and into a new Clutter folder".
It makes use of Office Graph, and maps work relationships before using this information to determine which messages are important and which are not. It 'learns' from the way in which an inbox is used, but it is also possible to manually indicate that particular messages are less important so they will be consigned to the Clutter folder. In a blog post, Microsoft explains the machine learning techniques that are behind Clutter:
It gets smarter over time, learning from your prior actions with similar messages, and assessing things like the type of content and even how you are addressed in the message. The Clutter experience is personalized to each individual and reflects an email experience that adapts to your actions and preferences without you having to do anything. The information Clutter learns from each user’s actions are only applied to that user’s experience and are not shared with anyone else.
As with all such tools, time is the key to success. The longer Clutter is used, the better it becomes at learning which emails are clutter and which are important. It is disabled by default, but it can be enabled through the options menu of the Outlook Web App, and once enabled the effects of Clutter will be seen anywhere you use Outlook -- the desktop app, online, and on mobile.
Rollout of the new tool starts today for customers who have opted into First Release, and it will continue over the rest of the month to other deployments.
Check out the video to get an idea of what Clutter is all about:
Photo credit: TijanaM / Shutterstock
-

Microsoft to kill off Lync and rebrand as Skype for Business
Publié: novembre 11, 2014, 4:33pm CET par Mark Wilson

As part of the simplification of its portfolio, Microsoft is dropping the Lync name as it rebrands the business messaging and conferencing tool. The name will change to Skype for Business in the first half of 2015, and interface tweaks will see the business version of the tools closely mimicking that of the consumer Skype product.
The aim is to create a more uniform experience for people using Microsoft's communication tools at home and in the office. After a decade of Skype, and bearing in mind the success of Lync, it was almost inevitable that the two products would ultimately become one, and that day is now almost here. As Microsoft puts it: "The magic of Skype and the power of Lync are coming together".
Announcing the rebranding, Gurdeep Pall, Corporate Vice President of Skype said: "We are bringing together the familiar experience and user love of Skype with the enterprise security, compliance, and control from Lync to create the most loved and trusted communications platform for doing things together".
As a key component of Office for enterprise, Skype for Business will continue the collaborative drive of Lync. Microsoft promises that in addition to a new interface, there will also be a new server release and updates to the service in Office 365. The business version of Skype will benefit from the addition of video calling and access to the Skype user directory, and the Lync backbone will remain at the core of the product.
Microsoft has a video to introduce Skype for Business:
-

Security breach reveals personal details of USPS employees and customers
Publié: novembre 11, 2014, 1:27pm CET par Mark Wilson

The latest high-profile security breach has exposed the personal details of hundreds of thousand of USPS workers, as well as customers. The attack, which is suspected to originate from China, took place in the middle of September, but details are only just emerging. An investigation by the FBI started straight away and is still on-going.
USPS says that employee information such as "names, dates of birth, Social Security numbers, addresses, beginning and end dates of employment, emergency contact information" was compromised. The security breach also affects customers as call center data was obtained by the attackers, including "names, addresses, telephone numbers, email addresses".
The data of anyone who contacted Postal Service Customer Care Center between January 1 and August 16 is involved, but USPS stresses that there is no need for customers to take any action. It is not clear how many customers have been affected, but with more than 800,000 employees, the ramifications of the breach could be far-reaching.
USPS spokesman David Partenheimer said:
The privacy and security of data entrusted to us is of the utmost importance. We have recently implemented additional security measures designed to improve the security of our information systems, including certain actions this past weekend that caused certain systems to be off-line. We know this caused inconvenience to some of our customers and partners, and we apologize for any disruption.
This will come as little comfort to the employees whose personal data was revealed, but USPS has offered a year of free credit monitoring to help curtail any financial implication of the breach.
China has previously been accused of other security attacks on personal data, so this is far from unprecedented. Globally, there is something of a cold war situation as nations test the technological defenses of other countries. Former NSA general counsel Stewart A. Baker said:
It's perfectly appropriate for us to do everything we can to embarrass and punish the Chinese if they're in our systems, whether or not we're in theirs. It's the case that the US and Russia and other countries are much more cautious about getting caught because they think there are going to be consequences.
USPS said that payment system were not affected by the attack, pointing out that Click-N-Ship, the Postal Store, PostalOne!, change of address, and payments made on usps.com were not compromised.
Photo credit: Leonard Zhukovsky / Shutterstock
-

Obama enters net neutrality debate with four rules for a free and open internet
Publié: novembre 11, 2014, 12:46am CET par Mark Wilson

The net neutrality debate has been raging for some time and Barack Obama has stepped into the fray, voicing his support for a free and open internet. More than this, the president is calling for broadband to be reclassified under Title II of the Telecommunications Act which would give the FCC greater powers of regulation. His statement has come as bad news for cable companies who have expressed a desire to create a two-tiered internet.
But while some providers have suggested that they would like to be able to offer a faster service to customers willing and able to pay more money each month, Obama is calling for a largely unfettered internet. As well as eliminating the idea of fast lanes, he calls for no blocking of legal content, no throttling, and greater ISP transparency.
While proponents of net neutrality will be buoyed by Obama's support for their cause, this is far from being the end of the battle. For everything he has said, the President holds no sway in what actually happens next -- that is in the hands of the independent Federal Communications Commission (FCC). Telecoms expressed surprise and disappointment at Obama's statement -- this stemming from the fact that the FCC could gain greater powers to control prices of broadband provision.
There are concerns that the reclassification of broadband services as "telecommunications services" will introduce new bureaucracy and red tape, and that the existing laws are not easily applied. Net neutrality supporters suggest that these obstacles can be easily overcome, but opponents say that it will serve to stifle innovation. Verizon goes as far as saying that there would likely be legal challenges to reclassification.
Obama's proposed four rules of "no blocking, no throttling, increased transparency, and no paid prioritization" are accompanied by a plea for the FCC to "answer the call of almost 4 million public comments, and implement the strongest possible rules to protect net neutrality". The president's support for the campaign to maintain the democratic nature of the web is a real boost, but at the same time it further politicizes an issue that has already become divided on party lines.
You can check out a video of President Obama's statement below:
The full statement is available to read on the White House website.
-

Facebook is taking over from Google as gatekeeper of the internet
Publié: novembre 10, 2014, 2:37pm CET par Mark Wilson

Google is widely regarded as being one of the controllers of the internet. It is by far the most popular search engine and if a site does not appear in the first few pages of results, it may as well not exist. But Google is far from being the only gatekeeper to the internet; Facebook is increasingly vying for that crown, whilst making efforts to make access more secure through Tor. But what does this mean?
Facebook accounts for a terrifying percentage of web traffic -- it is the second most visited website in the world according to Alexa. This means that it has a huge influence online, giving the social network the opportunity to shape the web and holds great sway in determining which sites, services, and stories rise to popularity. To many people, this influence is all but invisible, and this is perhaps the most concerning part of the story. So how does Facebook's influence present itself?
There have been several high-profile stories in recent times, such as the real name scandal, the on-going battle over whether photos of breastfeeding mothers can be published, as well as the time that Facebook admitted to tinkering with users' timelines in a 'social experiment'. But Facebook is a free service and its business model is at the heart of the way it operates -- it exists to make money. Much of this money comes from ads and Facebook needs to tread a careful line between keeping advertisers happy and avoiding annoying users.
There used to be a time when your Facebook timeline filled up in quite a logical way: it comprises a simple chronological list of status updates from your friends. But factor in shares, pages, sponsored posts, ads, Facebook's own content, and those pesky algorithms that try to promote content that is either of greater interest or likely to be the best money-maker, and things get rather more complicated. Facebook is no longer just a social network, it is a platform. Or, as Felix Salmon puts in in the Guardian, "it is growing into a kind of parallel internet".
Part of the reason for this thinking stems from changes that have been made to the mobile app -- and phone and tablets remain one of the most common ways to access Facebook. You may have noticed that when you click (or tap) a link in the app, that it’s not your default web browser that springs into action, but that the page is rendered within the Facebook app. On the face of it, this is not a problem -- if anything, it should help to improve performance. But there is a more sinister side; it places Facebook in control of the appearance of sites.
Facebook is free to change the layout of stories, strip out any content it doesn't like, even remove ads. The removal of ads from websites might seem like a good idea at first glance, but from the point of view of third-party websites, it's terrible news. Ads exist to generate revenue, and if this is curtailed, smaller websites run the risk of being priced out of the market. Facebook needs to keep its own advertisers sweet, and this is easily done by reducing the chances of stumbling across rival ads.
Keeping people within the Facebook app rather than defaulting to a 'proper' web browser, stops people from being distracted by other sites, making them more likely to see more ads and sponsored content. Already it should be clear that there is scope for abuse here, but there is further cause for concern.
As mentioned before, it would be reasonable to expect that one's timeline would be made up of a chronological list of posts from friends and companies you follow. But, ever fearful that you might miss important content, companies and individuals are given the opportunity to promote their content to ensure that it reaches a wider audience. Left to its own devices, a post might 'organically' only be seen by a couple of dozen people, but for those willing to stump up some cash, the net is cast wider. In many ways this goes against the ideology of the internet. It is supposed to be a democratising tool where everyone is placed on as equal a footing as possible, but in reality it is those with the money who are granted the larger audiences.
With the exception of content which 'accidentally' goes viral, the content promoted by Facebook is limited to that which has been paid for -- smaller companies and individuals without available finances are priced out of the market. This is bad news not only for anyone looking to gain an audience, but it's also bad news for Facebook users who invariably find their newsfeeds clogged with crap such as listicles from Buzzfeed, nonsense health and wellbeing posts, and endless inane videos from the latest viral site.
I may be peering into a bleak and hypothetical future, but the level of control Facebook is starting to gain over what people see online is concerning. Facebook has, thankfully, showed itself to be largely free from a political agenda, but this may not always be the case. If an advertiser is willing to pay for posts with an anti-Obama slant, would the cash talk loudly enough to compel Facebook to promote biased articles? If users start to share content en masse that goes against Facebook's agenda, could it be stifled?
Perhaps referring to Facebook as a 'platform' was incorrect. Maybe it's more like a modern-day broadcaster, What's worrying is that this is a self-governing broadcaster that wields great power, and power without responsibility is a dangerous thing.
Photo credit: Dave Clark Digital Photo / Shutterstock
-

Federal government websites violated the privacy of people looking for AIDS information
Publié: novembre 9, 2014, 3:29pm CET par Mark Wilson

Government websites set to help people gain access to information about AIDS have been leaking the data about its users. Anyone visiting AIDS.gov and making use of the search box will probably be concerned to learn that, until the end of last month, data was transmitted in unencrypted form. The Washington Post points out that this data could be very easily intercepted and used to identify an individual.
We know that web users are more concerned about privacy than ever before -- and little wonder when authorities say that privacy is not a right. We know that there are various ways in which web activity can be monitored, but it seems that the smartphone app associated with AIDS.gov included this feature as standard -- the app collected and transmitted the latitude and longitude of users, again unencrypted.
Following questions from the Washington Post, Miguel Gomez, director of AIDS.gov, said: "We started requiring SSL for the [services] Locator because we understood that information should be encrypted to protect privacy". The Post points out that while encryption has been available "for those who knew how to activate it" since 2013, unencrypted data about people looking for healthcare information has been transmitted since 2010.
AIDS.gov is not the only site which has a history of poor security. Another unnamed site which provides help with locating HIV testing centers, only started to encrypt user data this week.
The lack of encryption was discovered by security researcher Steve Roosa, who was surprised to learn that a government-run service dealing with sensitive health information handled data so poorly. He found that widgets on the pages -- such as Facebook, Twitter and other social elements -- could create cookies that snoopers could easily intercept and use to identify individuals. This would be concerning for any website or app, but when dealing with AIDS and HIV which still -- sadly -- have great stigma attached to them, security is all the more important.
Peter Eckersley from privacy advocates Electronic Frontier Foundation said: "We should be exasperated at the lack of security competence of so many branches of our government, when clearly that government does employ a lot of people who understand exactly how cyber-security works and how to break it".
Photo credit: Imillian / Shutterstock
-

Twitter teams up with Women, Action & the Media to fight online harassment
Publié: novembre 8, 2014, 10:38pm CET par Mark Wilson

Social networks have long been a domain for trolls, but in more recent times there has been an increasing problem with harassment of women. There have been a number of high-profile cases recently, including #gamergate, where women have found themselves targets of vicious attacks online. Women, Action & the Media (WAM!) is a US non-profit whose aimed is to fight for gender equality in the media, and its latest project involves collaborating with Twitter to help fight harassment and abuse.
The project's aim is to better understand how online persecution can be tackled. WAM! explains that "women of color, queer women, trans women, fat women, and other oppressed groups of women are especially targeted and abused", but the Twitter collaboration is design to help any Twitter users experiencing "gendered harassment".
WAM! has set up a simple form that can be used to report harassment on Twitter. Once a few basic checks have been carried out, reports will be escalated to Twitter -- the aim is to get this one within 24 hours -- and complainants will be kept up to date with how their case is being looked at.
WAM! explains:
We're using this pilot project to learn about what kind of gendered harassment is happening on Twitter, how that harassment intersects with other kinds of harassment (racist, transphobic, etc.), and which kinds of cases Twitter is prepared (and less prepared) to respond to. We'll then work with Twitter to improve their responses to the harassment of women on their platform.
Research shows that a quarter of young woman have been sexually harassed online, and slightly more have been stalked. This has led to many women self-censoring in a bid to avoid being attacked. Jaclyn Friedman, Executive Director of WAM!, said:
Were thrilled to be working with Twitter to make their platform safer for women. The disproportionate targeting of women online results in them removing their voices from the public conversation. We’re so glad that Twitter recognizes that the best way to ensure equally free speech for all users on their platform is to ensure that all users are equally free to speak without being targeted by harassment, abuse and threats.
If you have experienced problems on Twitter, or other social networks, you are encouraged to make use of the reporting form, and to share information about the scheme with others.
-

Microsoft thanks Windows 10 Preview testers with three (very) little surprises
Publié: novembre 7, 2014, 8:32pm CET par Mark Wilson

Don't get too excited. Actually, don’t get excited at all. To say thanks for taking the trouble to download a multi-gigabyte image, going to the hassle of setting up a virtual machine or installing a new operating system on a spare computer, for providing feedback on the embryonic Windows 10 Technical Preview, Microsoft has a gift for members of the Windows Insider Program. Three wallpapers.
Yes, you did read that correctly. Three. Wallpapers. Available at resolutions from 1280×1024 all the way up to 4K, the theme linking each of the images is the construction of Windows 10. Microsoft seems to think that a Windows Insider might want to "show your pride about helping us build Windows 10", so the wallpapers give a chance to herald your Insider status to passers-by.
You can grab each of the wallpapers individually -- different sizes of each wallpaper are provided in zip files. But seriously, do not get excited. It's a collection of free gifts, but by God these are dull images! Check 'em out below and download them if your desktop currently looks a little too exciting and needs dulling down a bit.


You shouldn't grumble about something free, but...
Photo credit: PathDoc / Shutterstock
-

Law enforcement agencies swoop on dark net, closing Silk Road 2.0 and other sites
Publié: novembre 7, 2014, 4:04pm CET par Mark Wilson

As concerns about online surveillance mount, more and more people are seeking ways to protect their identities and disguise their online activities. Services such as Tor are increasingly popular as surfers look for ways to maintain their privacy. Facebook even recently got in on the act, providing users concerned about their privacy with a secure .onion address through which to access the site.
While the likes of Tor are often turned to as a means of bolstering security and privacy, there is also a darker side -- the dark net, the dark web -- which is used for more nefarious activities. One site that rose to notoriety was Silk Road, an anonymous online marketplace where just about anything could be bought. Last year, the FBI closed the service, but Silk Road 2.0 soon sprang up out of the ashes. This has now also come to an end as the FBI once again shut down the marketplace with the help of Europol and Eurojust in a coordinated clampdown on the darker side of the web.
The operation was a collaboration between the US and several European countries, and it saw the closure of not just Silk Road 2.0 but also more than 400 other services operating on the Tor network. $1 million worth of Bitcoins were seized, and 17 people arrested, and the action will come as a blow to those who have sought solace in the intricate layers of Tor. Operation Onymous has been running for six months, starting off as an investigation into the sale of guns, drugs and illegal services online.
Head of Europol, Troels Oerting, said:
Today we have demonstrated that, together, we are able to efficiently remove vital criminal infrastructures that are supporting serious organized crime. And we are not 'just' removing these services from the open internet; this time we have also hit services on the dark net using Tor where, for a long time, criminals have considered themselves beyond reach.
Many users of the dark net have thought that their activities were invisible to, and untouchable by, the law, but this latest sting shows that this is not the case. No details have been released about how law enforcement agencies were able to locate individuals through a supposedly anonymous service, and the ripples of concern will be widely felt. When the original Silk Road was closed down, there were suggestions that the FBI had conducted searches without a warrant, so it's safe to assume that extra precautions would have been taken to ensure that everything was done by the letter this time around.
The official complaint against Blake Benthall -- also known as 'Defcon', who admitted to being an administrator at Silk Road 2.0 -- suggests that it was carried out as a sting, with an undercover Homeland Security Investigations agent managing to gain employment. Tackling the problem from the inside may have been the reason for the operation's success rather than cracking Tor. But there will almost certainly be an impact on the Tor network and it's likely that users will begin to lose faith in the security it provides.
-

Streaming video service Hang w/ shares its profits with users -- others take note!
Publié: novembre 7, 2014, 1:01pm CET par Mark Wilson

As a web user it's very easy to feel like just another cog in the financial machine. Visit just about any website and you'll encounter ads. These generate revenue that's needed to pay for developers, writers, servers and so on, but the likes of YouTube, which rely on user-generated content, can quickly generate large profits thanks to the costs to revenue margins. Now video streaming service Hang w/ is bucking the trend and sharing profits with its users.
The platform exists as an iOS and Android app, and enables users to broadcast to users around the world as well as conducting video chats. It has managed to earn itself celebrity endorsement from the likes of Cheech and Chong (oh, yes), 50 Cent, Soulja Boy, Timbaland, and Ultimate Poker, and has helped to drive 22 million downloads for major shareholder MEDL Mobile. Recognizing the fact that it is users creating content, Hang w/ now shares 25 percent of its advertising revenue with users.
To start with, the monetization option is only available in the US, but it will continue to roll out to other parts of the world in the coming weeks. It won't affect all users as ads are only shown before and after a selection of broadcasts. Hang w/ is described as an "experiment in social media" and the decision to share the wealth is just the latest trial. You can sign up for the program, and the more people that watch your broadcasts, the more money you can earn.
CEO Andrew Maltin said:
We believe Hang w/ marks the beginning of a new era in social media. For too long, the creators of content have helped social technology platforms earn billion dollar valuations -- while receiving nothing in exchange. Hang w/ aims to shift that balance so the individual people creating content and driving growth can share in the profits.
This is an interesting move from an online service, and it will be good to see whether it takes off. We're used to either paying to use services, or getting them for free -- being paid to make use of them is something of a novel concept. Rather than remaining merely users, the new scheme essentially transforms those who turn to Hang w/ into shareholders in a publicly owned co-operative.
Photo credit: Jean Lee / Shutterstock
-

Update: Two months lapping up a satellite internet connection
Publié: novembre 7, 2014, 1:00am CET par Mark Wilson

Three months ago I reached the end of my tether. I'm lucky enough to live in one of the most beautiful and unspoilt parts of the UK (it nearly wasn’t part of the UK had the Scottish referendum on independence taken a different turn), but there's one problem: truly awful broadband. There is a 'choice' of one broadband provider who is capable of trickling sub 0.5Mbps connections into houses in the area -- and that's on a good day.
One Twitter rant later, a few emails exchanged with Satellite Internet led to the arrival of two installers to get me set up with a 20Mbps satellite connection. My initial impressions were great. The internet worked as it should for the first time in months. But my fear was that this was just a honeymoon period. So what’s the story nearly three months down the line -- what is it like to live with a satellite internet connection? Were my initial concerns about data usage well-founded?
The simple answer to the question is "partly". My hope was that the arrival of satellite would solve all of my internet related problem, and I could bid a cheery farewell to the copper-based service I so loathe. My experience with satellite has both positives and negatives. I'll start, uncharacteristically perhaps, by looking at the positives.
The first is undoubtedly the speed. I realize that many of my friends, colleagues and contemporaries are enjoying the benefits of 100Mbps fiber-based broadband. This is clearly a world away from the 0.3Mbps I became used to working with, but the 20Mbps I have been experiencing via satellite has been a real eye-opener. Speeds do fluctuate a little, but on the whole browsing the web, downloading files and generally conducting a life online has been a speedy experience.
There are lots of horror stories thrown around about satellite, the first relating to speed. While it is certainly true that there are faster options out there, satellite is for many people, the only route to a speedy connection. The technology has advanced a long way over the years and satellite is now a genuine alternative to traditional broadband. The second concern for would-be users is latency. I am not a gamer -- aside from occasional online board games -- so this did not prove to be a serious issue for me. Anyone looking to hook up a console and play a first person shooter, however, would encounter problems.
The final concern is cost. There's no getting away from the fact that the initial setup costs are a little on the high side. The satellite dish and associated equipment does not come cheap -- £269 (around $425) -- and then there is the cost of installation and activation fee. But this is a one-off (and there is the option of renting equipment if you prefer). From this point forward how much you pay depends very much on the data allowance you want, as well as the speed of access. You can reduce costs by opting for a lower speed, and for a basic package (accessing the internet at 4Mbps with a 3GB data limit -- sufficient for someone just looking to check emails and indulge in a little browsing -- it costs just £9.95 (around $16 per month).
The mid-range package ups access speed to 20Mbps and data allowance to 20GB for £34.95 (around $55), while the top of the range (still limited to 20Mbps but offering unlimited data) will set you back £69.95 ($110) per month. In my previous article, I mention that for a small extra fee (£7 or around $11) it's possible to add unlimited offpeak (11pm to 7am) data. This proved to be well worth investing in. It is easy to forget just how many devices connect to the internet. Between my girlfriend and I there are three laptops, two mobile phones, four tablets, a set top box and numerous other connected devices. It is very, very easy to gulp through a data allowance in next to no time.
To avoid this happening -- or to avoid using the option to pay to reset the data allowance whenever required -- it was necessary to adapt web usage. Having a faster, more stable internet connection did not mean I could spend hours watching videos on YouTube or streaming TV shows on demand. Doing this it would be all too easy to eat the entire month's allowance in a single day without breaking a sweat. Using a satellite connection means being sensible and selective about web usage. It's nice to have the option to reset the counter, but the costs could soon mount up if this is done too many times. With the unlimited off-peak data option in place, I found myself time-shifting web usage. Large downloads could be scheduled, as could torrenting. YouTube use is reserved for post-11pm.
Constantly monitoring data usage is a bit of a pain, and it's surprising how much data certain activities consume. Simple things like browsing Facebook or using messaging tools consume megabytes at a terrifying rate. People on unlimited connections do not give a second thought to sharing videos, downloading app updates, or uploading lengthy animated GIFs -- but I notice every one and see it as something that dents my allowance. I have a fast internet connection courtesy of the dish strapped to the side of my house, but I now view the internet differently than most people.
While the connection is fast -- pages load quickly, downloads stream in at the expected speed -- weather conditions can mess things up. Just as with satellite TV, windy and rainy weather interferes with the signal a little. I'm in Scotland so the weather is a little, er, unpredictable. There have been a couple of occasions when signal has dropped out completely, but when conditions are bad signal levels do drop and performance suffers as a result. Sometimes a modem reset fixed things, while on other occasions it was just a matter of waiting a little while for things to improve.
Would I recommend satellite? For people in my position -- where there is either no cable-based broadband, or alternatives are restrictively slow -- I would not hesitate, and my neighbour is now considering getting a dish as well. The beauty of satellite technology is that coverage is incredibly high; there are few places where it could not be used. There is no requirement for a phone line. Unlike older technology, it is now possible to upload data directly via satellite.
I do not have completely unfettered access to the internet; finances mean that unlimited data is not an option at the moment. I do not experience the internet in the same way as most people I know -- I still have to bend to the will of my connection to some extent, but nowhere near as much as with my appalling landline broadband. I have had to adapt and costs are slightly higher than traditional broadband. But, for me, it's worth it. I'm generally hard to impress, but the connection has -- on the whole -- succeeded. It is not without problems, but my online experience has been improved to an indescribable degree.
Photo credit: Dabarti CGI / Shutterstock
-

WhatsApp adds read receipts as it celebrates fifth birthday [infographic]
Publié: novembre 6, 2014, 3:21pm CET par Mark Wilson
![WhatsApp adds read receipts as messaging app celebrates fifth birthday [infographic]](http://betanews.com/wp-content/uploads/2014/11/whatsapp_birthday.jpg)
A new update has been rolled out to WhatsApp that lets users see when the person they are talking to reads a message. The check marks that appear next to messages to indicate that a message has been successfully sent and successfully delivered now have a third indicator mode. A double blue check mark means that the message has been read.
WhatsApp took the messaging world by storm when it first appeared on the scene. Despite having been found to be one of the most insecure messaging tools out there, it remains incredibly popular with around 600 million monthly users. WhatsApp's impact was such that Facebook parted with $19 billion to buy it, and this month the service celebrates its fifth birthday.
To make it clear how the updated check marks work, WhatsApp's FAQ has been amended with new detail. One grey check means "message successfully sent", two grey checks means "message successfully delivered to the recipient's phone", and two blue checks means "the recipient has read your message". Around the web, particularly on Twitter, WhatsApp users have voiced concern that this could be seen as an invasion of privacy -- no more pretending that you haven’t seen an important message!
The new feature comes as WhatsApp turns five years old. To mark this milestone, Lisa Hallgren of DPFOC has created an infographic highlighting WhatsApp's rise to fame.
-

Electronic Frontier Foundation finds Skype, WhatsApp and more are disappointingly insecure
Publié: novembre 5, 2014, 2:20pm CET par Mark Wilson

Secure communication is something we all crave online, particularly after Edward Snowden's NSA revelations increased public interest in privacy and security. With dozens of messaging tools to choose from, many claiming to be ultra-secure, it can be difficult to know which one to choose and which one to trust. Electronic Frontier Foundation (EFF) has published its Secure Messaging Scorecard which rates a number of apps and services according to the level of security they offer.
It's a fairly exhaustive list that includes numerous well-known names, as well as several more niche products. What is concerning, however, is that many of the most popular tools -- WhatsApp, Yahoo Messenger, Skype, SnapChat, and Facebook chat -- received very low ratings for failing to protect users and their communication data.
EFF's Technology Projects Director Peter Eckersley says: "Many new tools claim to protect you, but don't include critical features like end-to-end encryption or secure deletion. This scorecard gives you the facts you need to choose the right technology to send your message".
The findings of the EFF are worrying. It highlights, for instance, that the desktop version of Yahoo Messenger uses no encryption whatsoever, but many other popular chat tools also scored very poorly.
In testing the tools and services, EFF asked seven key questions: is data encrypted in transit?; is the encryption key accessible to the service provider?; can the ID of the person being spoken with be confirmed?; in the event of encryption keys being stolen, is past communication safe?; can source code be independently reviewed?; is the cryptography used well-documented?; has an independent security audit been performed?
Facebook chat only checked a couple of boxes (in-transit encryption and code auditing), and it was the same story for Google Hangouts and SnapChat. Skype scored points for not only encrypting data, but also keeping it from Microsoft's eyes, but failed in the remaining five categories. Apple's FaceTime fared very well, missing out only on contact identity verification and independent code review. Signal, TextSecure, Silent Phone, CryptoCat, Silent Text, and ChatSecure + Orbot all passed every test, while QQ and Mxit failed on every single count.
The lengthy list of communication tools was chosen to represent those used most frequently. EFF Staff Attorney Nate Cardozo said:
We're focused on improving the tools that everyday users need to communicate with friends, family members, and colleagues. We hope the Secure Messaging Scorecard will start a race-to-the-top, spurring innovation in stronger and more usable cryptography.
Will the findings prompt you to switch to a more secure messaging tool, or are you already confident in the choice you have made?
Photo credit: PathDoc / Shutterstock
-

GCHQ's uncomfortable truth about the web: 'privacy has never been an absolute right'
Publié: novembre 4, 2014, 11:59am CET par Mark Wilson

The head of GCHQ, the UK's equivalent of the NSA, says that the Edward Snowden leaks have helped terrorist organizations such as ISIS who have taken to the web to spread propaganda. Writing in the Financial Times, Robert Hannigan points out that ISIS is the first terrorist group whose members have grown up on the internet. He says that the group has made use of "messaging and social media services such as Twitter, Facebook and WhatsApp, and a language their peers understand" and that the security tools that have popped up post-Snowden makes the work of GCHQ in tracking communication much harder.
This might not come as a surprise, but something else that Hannigan says is likely to raise eyebrows. His assertion that "privacy has never been an absolute right" goes against the grain of what many web users believe, but he suggests that the challenges facing governments and intelligence agencies in fighting back against terrorists can "only be met with greater co-operation from technology companies".
Continuing his singling out of ISIS, Hannigan points out that ISIS hijacked World Cup and Ebola-related hashtags to spread its word wider than ever. He tugs on heartstrings by making reference to the beheading videos spread through Twitter, and illustrates the vitriol clearly felt towards Snowden by sneeringly referring to security and encryption tools that are "Snowden approved". He suggests that US technology companies' services "not only host the material of violent extremism or child exploitation, but are the routes for the facilitation of crime and terrorism".
The customers of these same companies, it is suggested, are aware that services are being misused:
I think those customers would be comfortable with a better, more sustainable relationship between the agencies and the technology companies. As we celebrate the 25th anniversary of the spectacular creation that is the world wide web, we need a new deal between democratic governments and the technology companies in the area of protecting our citizens. It should be a deal rooted in the democratic values we share.
Apparently taking it upon himself to speak for the web at large, he says that "people do not want social media platforms to facilitate murder", which is, of course -- for the most part, at least -- probably true. But it over-simplifies the issue. It is an attempt to legitimize the blanket surveillance that has been carried out by the NSA, GCHQ and associated agencies. Hannigan says that "GCHQ is happy to be part of a mature debate on privacy in the digital age", but the fact of the matter is that the ordinary web user has no say in what goes on in the background.
It's one thing to be opposed to the likes of ISIS, it's quite another to be amenable to having one's entire communication snooped into. GCHQ's sudden decision to enter the privacy debate is interesting, but it's not clear that it will actually amount to anything.
Photo credit: Rawpixel / Shutterstock
-

Certified Ubuntu images float their way into Google Cloud Platform
Publié: novembre 4, 2014, 3:47am CET par Mark Wilson

Working in conjunction with Google, Canonical is launching a public beta of Ubuntu for Google Cloud Platform. These are part of the Certified Public Cloud (CPC) programme which means that the cloud versions of Ubuntu will be updated just about as quickly as the regular ground-tethered versions. Images for Utopic Unicorn, TrustyTahr, and Precise Pangolin releases are now available on Google Compute Engine.
The Ubuntu 14.04 LTS, 12.04 LTS releases benefit from the regular five years of maintenance and security updates, while 14.10 has a shorter shelf-life. Taking Ubuntu to the cloud serves as an alternative to the likes of Azure for anyone looking to venture into cloud platforms without breaking the bank.
As these are beta releases, Google points out that they "are not covered by any SLA or deprecation policy and may be subject to backward-incompatible changes". That said, the lure of readymade "optimised, up to date, fully secure and consistent Ubuntu images" is likely to be enticing to many.
Product manager of Certified Public Cloud, Federico Lucifredi, says:
As more enterprises join start-ups in turning to public cloud environments to run mission critical and scale-out workloads, Google Cloud Platform has quickly established itself as one of the world’s leading contenders for their business. Bringing Ubuntu to Google Cloud Platform is a logical first step in what we believe will be a great collaboration, benefitting developers and enterprises looking for an easy to use, reliable OS for their cloud deployments.
Security has been placed at the highest priority, and Google and Canonical have worked together to ensure that locally-deployed images provide near-instant access to updates and patches as they are released. Head on over to the Google Compute Engine page for details of how to grab the images.
Photo credit: aimy27feb / Shutterstock
-

Microsoft ignores its own Band wearable and gives away Fitbit Flex with the Lumia 830
Publié: novembre 4, 2014, 1:37am CET par Mark Wilson
A lot of wearable devices have accompanying smartphones. The Apple Watch has the iPhone 6, Galaxy Gear ties in with a number of Samsung Galaxy handsets, while the Motorola Moto 360 marries happily to just about any Android phone. Falling into the same works-with-anything camp is the recently announced Microsoft Band.
With a newly launched wearable, you'd think Microsoft would be keen to push it as much as possible. So when the company decided to bundle a wrist-worn device with the new Lumia 830, which do you think it opted for. Yeah... the Fitbit Flex...
Looked at in isolation, it's a pretty good deal -- at least it is if you are in the market for a Windows Phone 8.1 handset. Grab yourself a Lumia 830 from AT&T (ranging from free, through $99.99, to $449.99 depending on the contract you opt for) and you can bag yourself a free Fitbit Flex worth around $100. While this is an older, cheaper wearable than the Microsoft Band, it is nonetheless odd that Microsoft would eschew its own product in favor of a competitor's.
It could be that the deal was arranged long before Band was announced, but it smacks of a lack of faith in the company's own hardware. Initial reviews of the Microsoft Band have been less than glowing. Has Microsoft lost faith in its own wearable already? Part of the thinking is probably that while the Band has been designed to play nicely with not only Windows Phone but also iOS and Android, Fitbit added support for Cortana, making it instantly attractive to Microsoft and its fans.
But there's no getting away from the fact that it just looks a bit weird. Why would Microsoft not want to push its latest hardware rather than someone else's? Band might be slightly more expensive than the Fitbit Flex, but surely some sort of arrangement could be mustered up. Was it down to AT&T rather than Microsoft? Maybe. But Microsoft could have put its foot down. Or maybe Microsoft wants to keep Fitbit sweet, encouraging the use of Microsoft Health.
It could just be an interesting deal, but the Microsoft Band team would probably have preferred support to be thrown behind them rather than the competition.
-

Amazon's Diversity Report shows it is dominated by white males, but photos spin a different story
Publié: novembre 3, 2014, 6:13pm CET par Mark Wilson

Having a web presence means that companies are open to greater scrutiny than ever before. Post-NSA there was huge interest in learning just how much data the likes of Google, Yahoo and Microsoft had shared with the government and its agencies, and the next target for attention has been the racial and gender make-up of these same companies.
We have already seen diversity reports from Twitter and Apple, and now Amazon has thrown its hat into the ring. The Diversity Report's figures show that -- perhaps unsurprisingly -- the company is dominated by white men, particularly in the higher positions. But while the numbers and graphs tell one story, the photographs released by Amazon to accompany the report try to tell a rather different tale.
The report is little more than PR fluff. While padded out with phrases such as "our diverse perspectives come from many sources including gender, race, age, national origin, culture, education, as well as professional and life experience", the stats show that diversity is something that is lacking at Amazon. Globally, the company is 63 percent male and 60 percent white. Move up to managerial level and the figures jump up to 75 percent male and 71 percent white.
Despite the fact the workforce is made up of just somewhere between 25 and 37 percent women, take a look at the report's page on the Amazon website. Notice anything weird? The photos are crammed with women. Forget between a quarter and a third of the staff, if you were to go by what Amazon is presenting in the pictures you would be forgiven for thinking that female employees were at least equal in number to males. There are a number of quotes from female employees. In fact every single pull quote is from a woman. In spite of the very low employment figures, Amazon is quick to herald schemes it has in place to make it "a great place to work for technical women".
It's good that a report has been published, but the spit and polish that has been added to it make it rather disingenuous. The figures state that 40 percent of the company globally, and 29 percent of the company at managerial level is either Asian, Black, Hispanic, or falls into another non-White category. But you wouldn’t know this from looking at the photos. The pictures show a workforce comprising every race imaginable all flashing teeth and sparkle-eyed. The report is honest on one hand, and blisteringly dishonest on the other.

Photo credit: Ysbrand Cosijn / Shutterstock
-

Mozilla to launch a new Firefox-based browser just for developers
Publié: novembre 3, 2014, 12:45pm CET par Mark Wilson

Currently being referred to as something "unique but familiar", Mozilla has a new browser on the way. Based on Firefox, the new web browser has been designed specifically with developers in mind. In a post of the Mozilla Blog, the company explains that the up-coming browser will include built in tools such as WebIDE and the Firefox Tools Adapter.
The browser is due to launch on 10 November and comes after Mozilla looked at Firefox "through a completely new filter to put developers' interests first". The idea of an "independent web" is also being pushed, and Mozilla has commandeered the #ChooseIndependent and #fx10 hashtags to celebrate Firefox's tenth birthday.
Described as being built by developers for developers, the idea behind the new browser is to simply make things easier:
When building for the Web, developers tend to use a myriad of different tools which often don’t work well together. This means you end up switching between different tools, platforms and browsers which can slow you down and make you less productive.
Details are a little thin on the ground at the moment, but Mozilla has published a teaser video to whet the appetites of eager developers. Called simply Firefox Developer Browser -- Teaser Trailer, the video title could be a hint at the name that will be used:
If you're impatient to learn more, you can sign up for the Hacks newsletter and Mozilla will email you as soon as the browser is available.
-

Revealed: the secret guide to encryption, hacking, and surveillance for governments
Publié: novembre 2, 2014, 6:35pm CET par Mark Wilson

There is now great interest in the level of governmental interference that takes place into online activity. Edward Snowden told the world about what the NSA was up to and there are now numerous websites dealing with the revelation that he made. One such site is The Intercept, and it has just published the secret manuals that are supplied to governments who want to use a suite of specialist tools to monitor web users' activities.
Sub-titled "the hacking suite for governmental interception", RCS 9 (or Remote Control System) is a suite of tools from Hacking Team. The Italian security and surveillance company is responsible for providing hacking and monitoring guides and software to a list of countries including Colombia, Korea, Mexico, Nigeria, and Saudi Arabia. RCS itself is "a solution designed to evade encryption" -- the sort of encryption put in place by Google.
RCS 9 -- which goes by the name of Galileo -- is itself no secret. Hacking Team advertizes it on its web site, and there's even a suitably hackery and threatening sounding video explaining what it does. But there is a problem; RCS need to be "installed on the device to monitor". Not to worry -- there's a guide to building a software agent in the manual and details of how to deploy it via USB, email or by force. Once in place, "evidence collection on monitored devices is stealth and transmission of collected data from the device to the RCS server is encrypted and untraceable".
While, at the moment, it seems that RCS is only sold to governments and agencies in certain parts of the world, it's certainly the sort of things that the US and the UK would be interested in. The Intercept reports that Hacking Team has made appearance at homeland security trade shows and conferences. If you like the idea of getting your hands on what amounts to commercial spyware, you're out of luck:
We also understand the potential for abuse of the surveillance technologies that we produce, and so we take a number of precautions to limit the potential for that abuse. We provide our software only to governments or government agencies. We do not sell products to individuals or private businesses.
But as we've seen from the activities of the NSA, there is great potential for governments to abuse such tools, never mind individuals. It's interesting to take a look through the RCS documentation. Despite the terrifying power of the tool, the manual has been written very much with computer novices in mind. There are even instructions about how to close a window by clicking X. But once set up, the tool can be used to record Skype calls, take screenshots, browse through calendars and contacts, record key strokes, and much more.
All readily available to a government near you, to do with just about whatever they want.
Photo credit: Naypong/ Shutterstock
-

NIN's Trent Reznor working with Apple on new, secretive music service
Publié: novembre 1, 2014, 11:18pm CET par Mark Wilson

When he's not busy fronting Nine Inch Nails, Trent Reznor has plenty of solo music projects to work on, as well as countless collaborations with other artists. Talking to Billboard about -- amongst other things -- his upcoming fiftieth birthday, Reznor revealed that he is currently working with Apple on a music venture of some sort. He was unable to give much in the way of detail but we do know that it is "in the world" of music delivery.
Apple is famously secretive about yet-to-be-released products and services, so the fact that Reznor is being tight-lipped at this stage is not surprising. Throughout the course of the Billboard interview he makes several references to music streaming, and it's fairly safe to assume that the up-coming service is in this area.
Trent Renzor has form in the streaming arena. He previously held the position of chief creative officer at Beats Music's, and Apple then acquired Beats. The collaboration between the musician famed for his industrial output and the most valuable brand in the world was all but inevitable. At the same time, he has previously advised his fans to steal his music and given away music in the style of Radiohead and U2. Speaking of the Irish rockers, Reznor understands the backlash that followed giving away Songs of Innocence:
As an artist, when I make a piece of music, I'd like you to know it's out there. I don't want to force it down your throat, but I would like you to know that if you'd like to, you might brush against it -- it exists somewhere... I think the misstep was the wording: If it would've been, "Here it is, if you want it, come grab it..." I am assuming the momentum of that situation led to the oversight in not thinking that people might feel intruded upon.
Talking about his current work with Apple, Reznor explains that it is related to his previous role at Beats. He said that Apple "expressed direct interest in me designing some products with them" and that it "is very creative work that's not directly making music, but it's around music". If you've noticed a drop in output from him recently, that's because the Apple project is taking up his time; it "does mean some compromises in terms of how much brain power goes toward music and creating".
Throughout the course of the interview, Reznor dropped a few more hints that suggest the direction of the Apple project. "I think the right streaming service could solve everybody's problems" is pretty to the point, and a cloud-based music delivery service seems to be what he has in mind:
Ownership is waning. Everybody is comfortable with the cloud -- your documents, who knows where they are? They are there when you need them. That idea that I've got my records on the shelf doesn't feel as important even to me as it used to. I just think we haven't quite hit the right formula yet.
But the question is, can even someone as innovative as Trent Reznor devise a music streaming service that is different enough from what is already out there?
-

Facebook opens up to Tor users with new secure .onion address
Publié: novembre 1, 2014, 10:49pm CET par Mark Wilson

For those who are concerned about their privacy post-Snowden, there are various ways to boost online privacy such as using the anonymizing Tor browser. Browsing the internet anonymously is something that scares the authorities -- there were reports just a couple of months ago that Comcast was threatening to cut off customers who chose to use Tor -- but now Facebook has opened up to the idea.
The social network -- often criticized for its own privacy policies -- has lifted its bans on using Tor, and has created a secure URL ([https:]). This can be used to visit Facebook using any Tor-enabled browser and adds a few extra layers of protection for those looking to stay secure. While the idea of anonymity on Facebook may seem oxymoronic, there is a degree of logic.
One of the key benefits of using Tor is that it enables users to bypass locally enforced censorship and blocks, but until now Facebook has blocked access via Tor. The fact that Tor traffic bounced around the internet multiple times in a bid to disguise its origin, it was often flagged as suspicious by Facebook for appearing like botnet activity. This is no longer the case as the new URL opens up access to the security-minded.
Software engineer Alec Muffett explains that, "Facebook's onion address provides a way to access Facebook through Tor without losing the cryptographic protections provided by the Tor cloud". Accessing Facebook via Tor using the .onion address means connecting directly to Facebook's Core WWW Infrastructure (hence the URL). This allows for direct communication with Facebook, effectively sidestepping browsing restrictions that may have been put in place by local governments, and avoiding any surveillance that might be carried out on traffic that is permitted.
Facebook's Tor-friendly TLD is the first .onion address to be granted a SSL certificate. Muffett says:
We decided to use SSL atop this service due in part to architectural considerations - for example, we use the Tor daemon as a reverse proxy into a load balancer and Facebook traffic requires the protection of SSL over that link. As a result, we have provided an SSL certificate which cites our onion address; this mechanism removes the Tor Browser's “SSL Certificate Warning” for that onion address and increases confidence that this service really is run by Facebook. Issuing an SSL certificate for a Tor implementation is - in the Tor world - a novel solution to attribute ownership of an onion address; other solutions for attribution are ripe for consideration, but we believe that this one provides an appropriate starting point for such discussion.
Despite what some news reports say, this is not a way to stay anonymous on Facebook. You still log into your regular account and use it in the same way. What the .onion URL does is ensure that nothing happens to your data as it travels from your computer to Facebook and back.
-

Apple's Tim Cook is gay -- the fact it needs to be announced shows what’s wrong in tech
Publié: octobre 31, 2014, 12:35am CET par Mark Wilson

The sexuality of people in the public often comes in for scrutiny. Whether we're talking about Michael Stipe coming out at the same time as REM released Monster, Morrissey using Autobiography to give a beautifully tender glimpse into the loves of his life, Ellen DeGeneres revealing her sexual preferences to Oprah Winfrey, or any one of countless other celebrities who chooses to make their sexuality public, where those in the limelight fit onto the sexual spectrum has long been -- and will undoubtedly continue to be -- of endless interest to people.
Writing in Bloomberg Businessweek, Apple CEO Tim Cook, entirely unprompted, has said that he is gay. For many people this will come as no surprise, for most it will be of no consequence, some will take exception to it. But what's interesting is that, in 2014, a man (or woman, for that matter) proclaiming their sexuality, is news. Tim Cook is currently the top trending topic on Twitter.
The whole thing is slightly odd. Tim Cook is CEO of Apple, a technology company loved and hated in just about equal measure, but always regarded with sage admiration. In the realms of the tech world -- which is what we at BetaNews generally concern ourselves with -- what we are interested in is the hardware and software that is pumped out with reassuring frequency, and assessing it in terms of value for money, aesthetics, usefulness and so on. The sexuality of the man at the top matters no more than whether he likes to eat cereal for breakfast or fruit and yogurt.
And yet tech blogs, newspapers, computing websites, social media have lit up at Cook's editorial. I realize there is a slight irony in writing a news article proclaiming that the very thing being referred to may not be newsworthy. But the fact that it is in the news, and so prominently, makes it newsworthy; it's slightly meta in that way.
Cook's sexuality was never a secret as such. As he says, "while I have never denied my sexuality, I haven’t publicly acknowledged it either", and "plenty of colleagues at Apple know I’m gay". It wasn't even an open secret, it was just something that many people assumed, some knew, and most couldn't care about. There has been an incredible reaction to the words "I'm proud to be gay, and I consider being gay among the greatest gifts God has given me". It is an interesting turn of phrase which is sure to set tongues wagging.
Websites have practically fallen over themselves to heap their praise on the announcement. Some, like Neowin, have also questioned whether it should be reported as news, and plenty have labored over carefully chosen words that the writers hope convey how totally cool they are with the notion -- is acknowledging one's sexuality better than "admitting" it? PC Mag seems to suggest that Cook has been mute for a while ("Tim Cook today broke his silence"), and Ars Technica seems to think there has been "debate" about his sexuality. Re/code points out that Cook is "the most prominent openly gay business executive" -- Harvard Business Review says that he is the first CEO of a Fortune 500 company to come out.
Cook says that while he has "tried to maintain a basic level of privacy", he feels that "I've come to realize that my desire for personal privacy has been holding me back from doing something more important". Men and women who work their way to the top of the world of tech often become known for other things. Bill Gates is now more readily associated with philanthropic work than Microsoft -- something Mark Zuckerberg would no doubt like for himself and Facebook. Cook makes it clear that he is not an activist, but says that "if hearing that the CEO of Apple is gay can help someone struggling to come to terms with who he or she is, or bring comfort to anyone who feels alone, or inspire people to insist on their equality, then it's worth the trade-off with my own privacy".
Part of the problem -- if it can be described as such -- with anyone coming out as gay, bisexual, lesbian, transgender, transvestite or as falling into some other group covered by the broad LGBT umbrella, is that all too often it reduces people to fitting into a particular box. Many people's view of Cook will now be forever colored by today's announcement. If this sounds like glib, it is certainly not supposed to. The whole event, and the sickly sweet reactions, is a sad state of affairs, and it just goes to show that the world of technology -- like many other businesses and the world in general -- remains dominated by white, heterosexual, middleclass, right wing men, and any deviation from this is frowned upon, or requires a special announcement followed by acceptance.
Cook's public proclamation was a brave move. Even with the support of friends, family and colleagues, it cannot have been an easy decision. But the very fact that there is such a reaction to something so... normal... is sad. Big love to you, Tim, your anti-discrimination article is inspiring. You're right to be proud. A person can only be proud of two things -- who they are and what they do. You’ve done better than most on both fronts. The fact you're gay simply doesn’t enter into it.
Photo credit: Lester Balajadia / Shutterstock.com
-

Microsoft gives developers new opportunities with Apps for Outlook.com
Publié: octobre 30, 2014, 7:10pm CET par Mark Wilson

At the Inbox Love event in Mountain View, CA, Microsoft revealed the latest way for developers to bring extra functionality to the user. Starting next year, Outlook.com will support third-party apps, known -- uninspiringly -- as Apps for Outlook.com. Just a couple of days ago, Microsoft launched new APIs and SDKs to give developers new options for working with Office 365, and the latest announcement caters for development in the cloud.
Although Apps for Outlook.com will not officially launch until next year, Microsoft is giving developers the chance to start creating apps for the Outlook Web App. Those with a penchant for coding are invited to come up with new, exciting, and productivity-enhancing ways for users to interact with Outlook.com.
Principal program manager for the Outlook team, Pretish Abraham, says:
Whenever a customer reads or composes an email or calendar event, your app could be there, helping them get the job done. If you have a great idea for how our customers should interact with their email or calendar, now is the time to make it happen. Not only are these apps simple to build -- they use open web technologies such as HTML and Javascript -- but you can start building them today.
The benefit of Apps for Outlook.com is that users will be able to take advantage of them without the need for browser extensions or plugins. But more than this, developers will be able to ensure that they are always working with the most recent version of an app without the need for manual updating. Until more details are released, Microsoft suggests developers take a look at Mail apps for Outlook to get an idea of how things will work. Numerous scenarios are suggested, including automatically inserting a map into an email when a user types an address.
-

Samaritans Radar puts Twitter users on suicide watch
Publié: octobre 29, 2014, 11:37pm CET par Mark Wilson

We all go through difficult times, and it can often be hard to cope with what life throws at us. Whether you're going through a particularly tricky patch and feeling low, or you're struggling with depression, it can be helpful to know that there are people you can talk to. But reaching out to people can be hard and it often falls to friends to notice signs of someone in trouble so they can be there when required.
Everyone would like to think they would notice when a friend starts to post worrying messages online, but the sheer volume of content we all consume each day means that it is easy to miss something important. Suicide prevention charity, Samaritans, has launched a new online venture, Samaritans Radar, which monitors the Twitter feeds of those who sign up, looking out for "potentially worrying tweets".
The UK charity explains that the service has been set up because people often use social media to express their innermost feelings, "sometimes in the hope that someone will reach out". Activate the service for your account and it will monitor the tweets of people you follow:
The app contains a special algorithm that looks for specific keywords and phrases that may indicate that someone is struggling to cope. Samaritans Radar then sends you an email if it thinks someone you follow might need some support. If this is the case, Samaritans Radar will offer you guidance on what to do next.
It's a fairly simple idea, but Samaritans Radar looks out for phrases such as "tired of being alone", "hate myself", "depressed", and other undisclosed terms. While the service is well-intentioned, there will be privacy concerns for many people. To try to allay such fears, Samaritans says "Samaritans Radar is activated discreetly and all alerts are sent to you alone -- never to your Twitter friends". This may not be enough to quieten the concerns of those who feel their feeds are now open to additional monitoring.
-

Feedly kills URL shortener to improve speed, security, and privacy
Publié: octobre 29, 2014, 10:47pm CET par Mark Wilson

Back in January feedly -- the RSS reader that tried to fill the gap left by the death of Google Reader -- introduced a URL shortener. At the time it was billed as a "captur[ing] analytics about how people are engaging with the content you are sharing". Ten months later, the news service realized that this could be seen as being overly intrusive and has killed the tool.
The original blog post that heralded the launch of feedly.com/e has been updated to reflect the fact that the shortener is no more. "With hindsight this was a bad idea. We focused too much on feedly's growth versus doing what is right for users and for the Web. Sorry".
The change in direction comes as part of an update to feedly's web and mobile apps. A new blog post goes into a little more detail about the reasons for the change of heart. The company explains that the move is important for transparency, making it clear to users what they are going to see when they click a link.
It is the right thing to do for users, because people who receive those links in emails, SMSs and social media posts will be able to tell by looking at the URL where it leads and who created the content.
This is a move that will almost certainly be well-received by not only advocates of privacy, but also the security-conscious. However, if the boost to security and privacy are not enough, feedly sweetens things even further by pointing out that the move will "shave a few hundred milliseconds from the experience of loading the links".
Photo credit: Pavel Ignatov / Shutterstock
-

Microsoft unveils new Office 365 APIs and SDKs for iOS and Android
Publié: octobre 28, 2014, 2:25pm CET par Mark Wilson

As if giving Office 365 subscribers unlimited OneDrive storage was not enough, Microsoft today has some more news relating to its office suite. Previously only available as previews, a batch of new Office 365 APIs open up new opportunities for developers to tap into Office with their own apps. With APIs available for mail, files, calendar and contacts, there's lots of potential for the future.
One of the first big names to take advantages of the new APIs is IFTTT, the online automation service. The new APIs mean that it is possible for IFTTT to react to things that happen in Office applications -- so it is possible to set up an alert when an email matching certain criteria arrives. There are also updates to the Android and iOS SDKs for developers to work with.
The announcement at TechEd Europe also suggested other usage scenarios for the new APIs -- such as travel apps that connect with users' calendars, and sales apps that integrate with files and emails. Microsoft explains that "these new robust REST-based APIs empower all developers to leverage the more than 400 petabytes of data (as of March 2014) and popular services across Office 365 in any application".
Microsoft is keen for Office to spread to as many platforms as possible, and this is demonstrated by the mobile SDKs. The SDKs will be welcomed by Android and iOS developers who will now find it easier than ever to integrate their apps with Office 365. Rounding off today's batch of developer-pleasing announcements is news about the Office 365 app launcher. Developers will now be able to easily push their apps to the launcher so they appear alongside the likes of Word and Outlook.
-

Beat that Google! Office 365 subscribers get unlimited OneDrive storage
Publié: octobre 27, 2014, 6:19pm CET par Mark Wilson

Microsoft just stoked the fires of the cloud storage wars once again. There have been various updates to OneDrive in recent months. Microsoft lifted the 2GB file size limit all the way up to 10GB, and we showed you how to up your free storage to 15GB. But if you’re an Office 365 subscriber, things just kicked off -- storage limitations are a thing of the past.
Starting today, Office 365 Home, Personal and University plan subscribers have unlimited OneDrive storage. Store as much as you like in the cloud for free. Well, free if you ignore the subscription you've paid, or continue to pay each month. The roll out to the consumer level subscriptions starts today, but you'll need to take action if you're interested.
Unlimited storage will make its way to your OneDrive account eventually, but if you'd like to boost yourself further up the list, pay a visit to the special OneDrive storage page and put your name forward. Microsoft says that the rollout will take place over the course of the next few months, so it's a good idea to get yourself at the front of the queue. Business customers have not been forgotten; the same unlimited storage option will be rolling out to OneDrive for Business customers in the coming days.
Chris Jones, corporate vice president, OneDrive & SharePoint explains that while unlimited storage is great news for Office 365 users, it is just part of the story:
While unlimited storage is another important milestone for OneDrive we believe the true value of cloud storage is only realized when it is tightly integrated with the tools people use to communicate, create, and collaborate, both personally and professionally. That is why unlimited storage is just one small part of our broader promise to deliver a single experience across work and life that helps people store, sync, share, and collaborate on all the files that are important to them, all while meeting the security and compliance needs of even the most stringent organizations.
Run over to the sign up page and put your name forward so you can take advantage of the extra space as soon as possible.
-

The Document Foundation aims to push LibreOffice adoption in the workplace
Publié: octobre 27, 2014, 2:43pm CET par Mark Wilson

Who doesn't like free stuff? Not many people, but there are various definitions of free. Free as in beer, free as in speech, and so on. The open source software movement combines these two ideas, and many more, by making software freely available to anyone who wants to use it, and also affording them the right to tinker with the code and change it in whatever way they want. It's one of the foundations of Linux, and it's a philosophy that -- in increasingly cash-strapped times -- is gaining momentum.
The Document Foundation, creator of the LibreOffice variant of the free OpenOffice suite, today announces that it is joining the Open Source Business Alliance. The aim is to help with the deployment of the free office suite on larger scales within companies and organizations.
There is a reason that Microsoft Office has become an industry standard tool. As well as having the backing of the Microsoft behemoth, there is a great deal of reassurance taken by companies who know that it will "just work". Files that are sent between employees, contractors, and external parties can be opened without problems. Part of the aim of the Open Source Business Alliance is to help ensure compatibility and interoperability so alternatives such as LibreOffice become viable for larger organizations.
The involvement of the Open Source Business Alliance in the LibreOffice ecosystem has already helped to improve compatibility with Microsoft OOXML -- an important factor for any organization considering making the shift from Microsoft. The Alliance's Peter Ganten said:
Open Source Office Software like LibreOffice has always been very important to most of our members, and there is a long and successful history of cooperation between the OSB Alliance and the respective projects. For this reason we are very happy to have The Document Foundation in our organization and are looking forward for a great continuation of our cooperation.
Photo credit: Gilmanshin / Shutterstock
-

Hungary proposes taxing internet usage -- will other countries follow suit?
Publié: octobre 27, 2014, 12:28pm CET par Mark Wilson

You might think that you've already paid enough to get online. You bought your computer (or phone, tablet, whatever...), you pay line rental to your phone provider, you pay your monthly broadband charges, you pay the bill for electricity all of this requires. How does the idea of an extra charge on top of this sound? No? That's the general feeling in Hungary where an "internet tax" has been proposed by Viktor Orban's right wing government.
The Prime Minister proposes taxing internet usage in a similar way to mobile phone companies -- by tracking traffic levels. How much could this end up costing? Well, it could very quickly add up. The draft law suggests a fee of 150 forints (around $0.60) per gigabyte. To put that in perspective, it would cost more than $2 to download the Windows 10 Technical Preview, and around the same amount to upgrade to the latest build 9860.
There is, understandably, something of an uproar about this in Hungary -- the proposed tax in general, that is, not the specific costs of downloading a preview version of Windows. Detractors say that it is the poor who will be hardest hit, and the country has witnessed mass demonstrations in protest. Orban's response to criticism has been to suggest capping the tax at 700 forints per month -- meaning that internet usage beyond 4.6 GB is essentially "free".
Slapping an extra $2.80 on top of internet usage charges might seem like very little, but opponents of the new tax say that it is undemocratic. For many people struggling to make ends meet, $2.80 is a significant chunk of money. But that's not the point, at least it is not the only point. What is particularly concerning here is that this amounts to a tax on the flow of information. The internet is used for many things -- email, job searches, work-related research, and so on. File your taxes online under such a regime and you're basically being taxed for doing so.
There are currently all manner of programs underway at the moment that have the aim of bringing internet access to developing parts of the world. The threat of taxing this fabulous resource is worrying. The internet is something that should be accessible to all, and any plans that put even the smallest of obstacles in the way of those who want to use it should be passionately opposed.
Photo credit: Stuart Miles / Shutterstock
-

How to make Windows 10's Search and Task View buttons die, die, die!
Publié: octobre 26, 2014, 10:17pm CET par Mark Wilson
There's a lot to like about Windows 10, particularly if you're already a fan of Windows 8.x -- there isn’t all that much that's new at this stage. It's not all good news however, and there's also quite a lot to dislike. One thing that has cropped up time and time again in user feedback is the fact that the Search and Task View buttons that appear in the taskbar cannot be removed.
At least, there is no built in option to remove them. Where there's a will, there's a way and some enterprising users of the Technical Preview have found ways to banish the buttons that are seen by many as being pointless.
It's likely that Cortana will at some point be integrated into the search button so it may become more useful in the future. It's even possible that Microsoft will make either or both of the buttons optional. Until that time, you're going to have to do it yourself. Over on the My Digital Life forums, user vali20 has created a simple tool that hides the buttons for you. You'll have to register with My Digital Life to access the files, and then it's a very simple task to hide the unwanted buttons.
Extract the contents of the zip file, and navigate to the \WinTHButtonHider\bin\Debug subfolder and you'll find an executable called, appropriately enough, WinTHButtonHider.exe. Double click it and the two troublesome buttons will vanish; the tweak works in both build 9841 and the newer build 9860. It's not perfect. The buttons remain hidden at all times, but you may find that the bank they occupied reappears when you activate the Start menu, shoving your other taskbar buttons to the right. You'll have to run the program automatically at startup so the buttons are hidden every time you restart your computer.
If you don’t mind getting a little more hands on, the guys over at How-To Geek also have a guide to hiding the buttons with an AutoHotKey script.
Whichever route you decide to go down, hiding the buttons doesn’t mean losing any functionality. The search feature can be accessed by just hitting the Start button or Windows key, and if you're a fan of keyboard shortcuts, the Task View button's function can also be accessed by pressing the Windows key and Tab at the same time.
Photo credit: Zuzana Susterova / Shutterstock
-

Twitter: Your Twitpic photos and videos are safe... for the time being
Publié: octobre 26, 2014, 1:50pm CET par Mark Wilson

After flip-flopping between closing, then not closing, and finally closing, Twitpic has now shut up shop. But that's not quite the end of the story. There had been rumors flying round that Twitter was going to buy the image and video hosting service, but that ultimately amounted to nothing. The latest twist in the story is that Twitpic and Twitter have come to an arrangement that means content that has already been uploaded is safe. For now, at least.
In a statement on the Twitpic blog, founder Noah Everett explains that a deal has been struck with Twitter. What this amounts to is Twitpic handing over the domain and content archive to Twitter. This will keep "the photos and links alive for the time being".
The phrase "for the time being" is interesting. It could be that Twitter and Twitpic simply do not know how long the arrangement will be in place, or it may be that Twitter has plans that will be revealed at a later date. Everett says that "since Twitpic’s user base consists of Twitter users, it makes sense to keep this data with Twitter".
The blog post also explains that the iOS and Android Twitpic apps have been removed from their respective stores, and are no longer supported. The Twitpic site, having been handed over to Twitter, remains online, but only in read-only mode -- it is still possible to delete content if you want. And, of course, the option to export data from your account is still available, and this is something you might want to take advantage of.
It's not clear quite what this means in the long term. On one hand, it's hard to imagine Twitter annoying hundreds of thousands of Twitpic users by just trashing their photos and videos, but on the other hand... well... you just never know.
Photo credit: Thomas Bethge / Shutterstock
-

Streaming music service Deezer buys Stitcher and branches out into talk radio
Publié: octobre 24, 2014, 6:51pm CEST par Mark Wilson

The world of streaming music is dominated by just a few names. Deezer is a relatively new entrant to the US market, and it is now stretching its wings by purchasing Stitcher, the radio and podcasting service. Deezer currently has roughly 16 million users scattered across 180 countries, and this represents great growth potential for Stitcher.
The seven-year-old internet radio service carries content from 40 countries, giving it a catalog of more than 35,000 shows. Diversifying in this way could be Deezer's ticket to success in a somewhat crowded market, where a unique selling point is needed to stand out from the likes of Spotify.
Stitcher says that it is business as usual, but under Deezer, there is great scope for scaling up operations. Adding talk radio to an already vast music collection is seen as the catalyst to take the service to the next level:
We will continue to keep doing what we do best under the Deezer umbrella, and eventually provide even better listening experiences across the globe, combining music and talk. We’re extremely excited about this new adventure, and hope you are too.
In the blog entry announcing the purchase, the Stitcher team says that "we believe we’re just at the dawn of a Golden Age of on-demand spoken audio".
At the moment, there are no details about the amount of money that has changed hands, nor any information about when users will start to see changes to the service.
-

Facebook teams up with Yahoo to create safe email standard
Publié: octobre 24, 2014, 5:01pm CEST par Mark Wilson

A new email standard called RRVS (Require-Recipient-Valid-Since) has been unveiled by Facebook. The new standard comes through the social network working in conjunction with Yahoo, and is designed to protect users against potential account hijacking.
It's now over a year since Yahoo decided that the time had come to start recycling email addresses that had lain dormant and unused. Concerns were voiced that little used email addresses could end up falling into the wrong hands and be used for nefarious purposes. With email addresses used for much more than just email communication -- often doubling up as login credentials -- the need for security in this area is apparent.
Yahoo's email address recycling was something Facebook watched closely. "If a Facebook account were connected to a recycled Yahoo email address, that account could be taken over by the new Yahoo account owner via a password change request if no additional protections were in place," says Facebook software engineer Murray Kucherawy. RRVS is essentially an extension to the SMTP standard which increases security by double-checking when the ownership of a given email address was last known:
Working with our counterparts at Yahoo, we quickly proposed and prototyped an enhancement to email that mitigates this problem. The enhancement inserts a timestamp within an email message to indicate when we last confirmed the ownership of a Yahoo account. If the account changed hands since our last confirmation, Yahoo can just drop the message, preventing delivery of sensitive messages to the wrong hands.
While at the moment the standard only involves Yahoo and Facebook, details have been published so that others can work to combat the problem of account hijacking.
Photo credit: phadventure / Shutterstock
-

Surface generated almost $1 billion revenue for Microsoft last quarter
Publié: octobre 24, 2014, 3:01am CEST par Mark Wilson

Anyone who was under the impression that Surface was a failure for Microsoft need look no further than the latest earnings release for proof that they're wrong. In the quarter ending September 30, Microsoft pulled in $23.20 billion in revenue, and $908 million of this came from the Surface division.
All told, FY15 Q1 represents record first quarter revenue for Microsoft, and it can be at least partly attributed to the influence of Satya Nadella, as well as the restructuring surrounding Nokia Devices and Services. There was a strong performance in the Devices and Consumer divisions, with revenue increasing 47% to $10.96 billion, while commercial revenue rose 10% to $12.28 billion.
The earnings release shows that there are now more than 7 million Office 365 Home and Personal subscribers, and Xbox sales grew by 104 percent to 2.4 million. Phone hardware also fared well, pulling in more than $2.6 billion in revenue. There was growth in a number of other areas including a 128 percent boost in Cloud revenue -- thanks to Office 365, Azure and Dynamics CRM -- and Windows volume licensing revenue rose by 10 percent.
CEO Satya Nadella is understandably pleased with how things are going:
We are innovating faster, engaging more deeply across the industry, and putting our customers at the center of everything we do, all of which positions Microsoft for future growth. Our teams are delivering on our core focus of reinventing productivity and creating platforms that empower every individual and organization.
With the launch of Windows 10 next year, Microsoft will be keen to continue the growth of the operating system's impact on income.
-

Microsoft co-founder Paul Allen pledges $100 million to tackle Ebola
Publié: octobre 24, 2014, 2:46am CEST par Mark Wilson
Saying "the Ebola virus is unlike any health crisis we have ever experienced and needs a response unlike anything we have ever seen," Paul Allen, co-founder of Microsoft, pledged millions of dollars to help tackle the virus. The billionaire philanthropist increased his commitment to "at least $100 million" and called on others to contribute as well.
Ebola has now claimed the lives of more than 5,000 people, and Allen is keen to help fund not only heathcare professionals and treatments, but also the evacuation of international aid workers. Allen's #TackleEbola website is being used as a hub to raise money for a number of individual projects and causes such as household protection kits and hand-washing stations.
The funds will help the U.S. State Department, World Health Organization, and University of Massachusetts Medical School to co-ordinate their efforts to help those in need. Allen made the announcement in a press release as well as on Twitter:
I'm committing at least $100M to #TackleEbola. Join me in helping those responding to this outbreak at [t.co]
— Paul Allen (@PaulGAllen) October 23, 2014
The money has been welcomed by the U.S. Department of State:
We thank Paul Allen and his foundation for their contribution on this crucial issue. We hope that this sets a much needed example for what will be robust and rapid private sector leadership, working in partnership with the U.S. government. Mr. Allen’s #TackleEbola campaign is providing an important catalyst to help us get medical responders to West Africa to fight Ebola at its epicenter. His leadership is timely and greatly augments the work that the U.S. government, international organizations, NGOs, and others are doing on the ground every day.
Paul Allen is not the only figure from the world of technology to get involved in the fight against Ebola. Earlier in the month, Facebook's Mark Zuckerberg donated $25 million to the Centers for Disease Control Foundation.
-

Ello pockets $5.5 million, legally pledges to never feature ads
Publié: octobre 23, 2014, 6:48pm CEST par Mark Wilson
 Out of nowhere, Ello exploded, ninja-style, into the public eye. The social network shot to fame after Facebook's real name policy sent many users scuttling off in search of a new home, and the spartan, "beautiful" (Ello's word, not mine) social network welcomed an influx of new users. In addition to the "use whatever name you want" philosophy, users were happy to find that Ello offered a completely ad-free experience.
Out of nowhere, Ello exploded, ninja-style, into the public eye. The social network shot to fame after Facebook's real name policy sent many users scuttling off in search of a new home, and the spartan, "beautiful" (Ello's word, not mine) social network welcomed an influx of new users. In addition to the "use whatever name you want" philosophy, users were happy to find that Ello offered a completely ad-free experience.Now the lack of ads has been enshrined in law. While pocketing $5.5 million in a new round of venture funding, Ello has converted to a State of Delaware Public Benefit Corporation (PBC). The social network vows to never show nor sell ads, and requires this commitment to transfer to any future owner, should the company be acquired.
In a document signed by Paul Budnitz and Ello's co-founders, the social network responds to "speculation in the press since our launch eleven weeks ago that Ello will someday be forced to allow paid advertising on its network". Despite conceding that the internet is "turning into one giant billboard", Ello remains committed to its "better way" of doing things. Ello explains that in converting to a PBC, it "is legally obligated to take its impact on society into account in every decision it makes".
While Ello enjoyed a massive boost in popularity a few weeks ago, interest seems to have trailed off slightly in more recent weeks. The round of venture funding was headed by Foundry Group, and Bidnitz says that the money will enable Ello to "take [its] time and build rather than rushing ahead and trying to make some money".
-

Windows 10 to include built-in two-factor authentication
Publié: octobre 23, 2014, 1:49am CEST par Mark Wilson

We've looked at the two public builds of the Windows 10 Technical Preview -- the initial, disappointing, embryonic build 9841, and the very slightly less disappointing build 9860 -- but of course the best is still to come. There are many features we expect to find their way into the final build, such as Cortana, and there are sure to be many surprises. One interesting inclusion is built-in two-factor authentication.
The presence of this valuable security feature is revealed by Jim Alkove in a post on the Windows blog in which he talks about the importance of identity protection and general security. He explains that Windows 10 will start to move users away from single factor authentication -- the humble password -- in favor of more secure options.
He is talking specifically about built-in two-factor authentication. This is something that will be of particular interest to business and enterprise customers, but is also of great value to the average consumer. Alkove explains how a cell phone could be used as a login tool:
Once enrolled, devices themselves become one of two factors that are required for authentication. The second factor will be a PIN or biometric, such as fingerprint. From a security standpoint, this means that an attacker would need to have a user’s physical device – in addition to the means to use the user’s credential – which would require access to the users PIN or biometric information. Users will be able to enroll each of their devices with these new credentials, or they can enroll a single device, such as a mobile phone, which will effectively become their mobile credential. It will enable them to sign-in into all of their PC’s, networks, and web services as long as their mobile phone is nearby.
New user credential authentication will be supported by Active Directory, Azure Active Directory, and Microsoft Accounts as standard. Microsoft is keen to move people away from old-fashioned passwords. With other new features such as data loss prevention (DLP) to contain and protect business-related data, and an increased reliance on app signing, Windows 10 is shaping up to be Microsoft's most secure operating system yet.
Photo credit: Johan Swanepoel / Shutterstock
-

Microsoft is killing Xbox Music free streaming
Publié: octobre 23, 2014, 12:33am CEST par Mark Wilson

Microsoft is pushing music fans towards Music Pass by cutting off one supply of free streaming music. On December 1st, the free streaming feature of Xbox Music will be no more, leaving Windows 8, Windows 8.1, and web users looking for new ways to satisfy their music streaming cravings.
In an announcement posted on the Xbox website, Microsoft explains that it wants to encourage music fans into signing up for a paid Xbox Music Pass. The posts explains that there is a free 30 day trial available, but once this is up, the charge is $9.99 per month. Is this likely to fly with users who have been enjoying music for free? That remains to be seen...
An FAQ page has been set up, which explains that MP3s that were uploaded to a user's Xbox Music collection will remain untouched, and any music that has been purchased will also be unaffected. There is potential for missing out on some music; Microsoft points out that some content will not be available through Xbox Music Pass.
There are likely to be a swathe of upset music fans who suddenly discover that their playlists no longer work:
You may continue to view any playlists or collections you created using the free streaming feature, but you can't listen to the music in those playlists or collections unless you purchase the music or an Xbox Music Pass. If you have an Xbox Music Pass, you will still have access to all the music in your playlists, radio stations, collections, and catalog.
Just under six weeks to go, so fill your boots while you can!
Picture credit: Natsmith1 / Shutterstock
-

Kinect apps come to the Windows Store, Kinect SDK 2.0 and adaptor kit launch
Publié: octobre 22, 2014, 10:51pm CEST par Mark Wilson

Kinect has moved on. Once a peripheral that encouraged gamers to dance manically in front of their consoles, it has now evolved into something rather more sophisticated. As part of Kinect's on-going development Microsoft today released Kinect SDK 2.0 following the developer preview program from last November. Developers not only have scores of improvements to enjoy, but they now have the ability to deploy Kinect apps to the Windows Store.
This news goes hand in hand with the release of a new Kinect adaptor. The adaptor makes it possible to take an Xbox One Kinect and connect it to a PC or tablet. There's no need to choose between a Kinect for Windows v2 and Kinect for Xbox One as they both now perform identically.
The $49.95 device is perhaps an indication that the Windows version of Kinect has not proved quite as popular as Microsoft would have hoped. The company is now trying to encourage more developers into making use of the device under Windows and take advantage of all of the Xbox Kinects out there. Microsoft will have to encourage Xbox One users with a Kinect to invest in the adaptor -- there is a something of a saving to be made here.
Starting today, the Kinect Adapter for Windows is available in more than 20 countries, and there are plans to roll it out to more than 40 in total. As with the latest build of Windows 10 Technical Preview, this is another example of the all-ears Microsoft. "We have been listening", proclaims the announcement blog post. These latest movements in the world of Kinect should make life easier for developers and users alike.
-

Google launches Inbox, the smart inbox that 'works for you'
Publié: octobre 22, 2014, 7:45pm CEST par Mark Wilson
Hands up if your inbox is out of control? From that quick show of hands, it's clear that the idea of inbox zero has not caught on globally. We all have more email to deal with than ever before, even if most of it is junk. Google has a new solution to email overload. Inbox. This is, Google is quick to point out, not Gmail, although it is from the same people.
Available for your Android phone and the web, Inbox by Google helps to cut through the crap to ensure that you're free to focus on what actually matters. It expands on some of the ideas already found in Gmail, but is a completely separate tool. This is Google recognizing that people use email not only to communicate with others, but also to organize their lives and keep on top of a schedule.
Email is used to convey all sorts of information, but wouldn’t it be great if they just cut to the chase? This is what Highlights does. By analyzing your messages, Inbox is able to extract pertinent information such as flight times, hotel reservation details, and so on, and highlight this so you don’t have to search for it. If you are the sort of person who finds that emails tend to get buried as more and more messages come through, Inbox has a great feature that could help you out -- reminders.
In fact Inbox offers more than just reminders. You can snooze emails and receive a reminder at a later time; reminders, like emails, can be snoozed if you are busy so you can deal with them at a quieter time. Snoozes can also be put in place so you're not reminded about something until you are in a particular location.
There are also Assists. Your inbox just became a calendar and personal assistant. If you have a reminder to make a call at a particular time, Inbox will provide you with the necessary number, pull up directions if you need to get somewhere, and so on.
Inbox groups similar messages together in bundles, much like the way Gmail currently groups together promotional messages, social email, and so on. The idea behind this is that it makes it easier to jump to certain types of email if they are all found together. Need to check the details of a receipt? They're all together in one place. As you would expect, Inbox's Bundles feature can be trained to cope with email the way you want it to.
The Inbox video serves as an introduction to the app:
But before you get too excited, you need an invite to use the app. Google says that these are being sent out to a select few, but you can request one by dropping an email to inbox@google.com. When you get on board, let us know what you think!
-

Here's what's new in Windows 10 Technical Preview build 9860
Publié: octobre 22, 2014, 3:43am CEST par Mark Wilson
Development of Windows has been criticized in the past for being slow. With the Technical Preview of Windows 10, it's just not possible to level the same complaint at Microsoft. It's only a couple of weeks since we got our grubby little hands on the embryonic build 9841 and tens of thousands of users have provided feedback. Now it's upgrade time. Build 9860 has been pushed out -- through Windows Update, no less... none of this messy ISO malarkey this time around -- so it's time to take a look at the work Microsoft has done.
When build 9841 was released, there was disappointment from many quarters -- including here -- at just how little had changed since Windows 8.1. Jumping up 19 build numbers might not seem like much, but there are now a couple of features that were talked about at the launch of the Technical Preview that were not available in the first release -- but still no Cortana.
On the face of it, little has changed. Fire up PC Settings, however, and you'll see a couple of new tools -- and something else we'll return to at the end of this post. DataSense is a new tool to help stay within data usage limits. It's a continuation of the 'metered connection' idea from Windows 8, and it makes it easy to see how much data has been download over cellular and Wi-Fi connections.
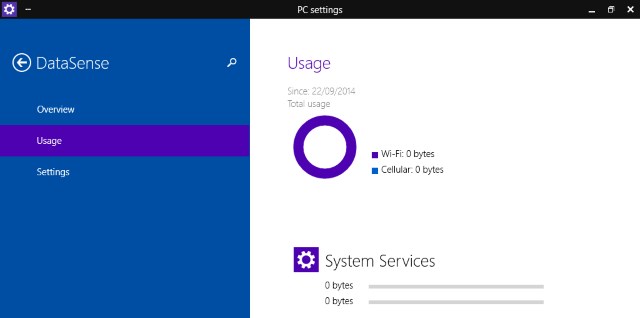
Another new setting is Battery Saver which, as the name suggestions, helps to conserve battery life on laptops and tablets. Both of these features will be familiar to Windows Phone users, and are indicative of Microsoft's merging of platforms.
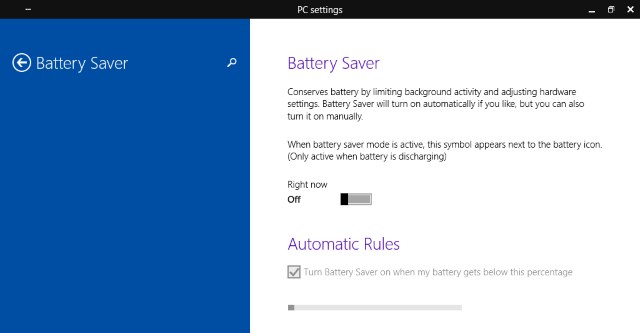
Back at the desktop is the much sought after notification center -- or the Notifications and Actions Center as it is currently known. It serves as a replacement for many popup windows, so you'll see email notifications here as well as information from Explorer and other applications. If an app or web service ordinarily generates some sort of popup notification, you should see them appear here, all collected together in one place from now on.
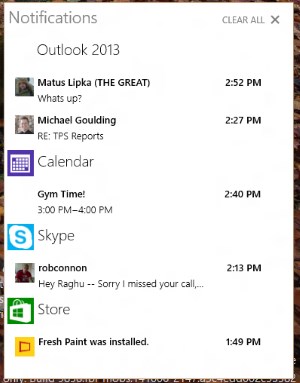
Nothing has changed in the Start menu, but take a browse through All Apps and you'll find a couple of new additions -- DockingController, and PC Settings. At the moment it appears that the former is not working, but will presumably provide access to settings for docking laptops and tablets. PC Settings does work (although there are lots of bits and pieces missing), and seems to be a merging of PC Settings with the traditional Control Panel.
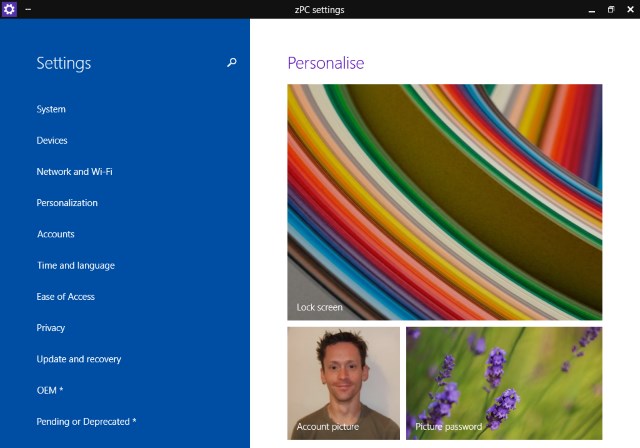
There are also minor tweaks such as new animations that accompany the opening of Windows. Some people suggested that this gives Windows 10 something of an OS X feel -- albeit with a significantly lower number of animation frames -- but really it's just a little eye candy. Windows do not jump out of or into taskbar buttons any more -- the center of the desktop is the start and end point for animations now.
We've already looked at some of the new keyboard shortcuts that were introduced, and in this build there's another shortcut that will be of interest to multiple monitor users. To move a window or application from one monitor to another, just press Windows key + Shift + arrow key.
In the blog post announcing the availability of build 9860, Microsoft's Gabriel Aul gives a little detail about the process involved in getting the build to its public release. Using imagery that conjures up images of the circles of Hell in Dante's Inferno, we are told that there are five rings of development starting with Canary -- where internal daily builds are to be found -- right up to the outer rings which are accessible to those signed up for the Windows Insiders Program. At least there are now five rings of development. Build 9860 has been made available through what is known as Windows Insiders Slow.
The presence of the word 'slow' implies there is a faster option, and indeed this is now the case. For anyone happy to work with less stable builds, it is possible to opt to access the Windows Insiders Fast ring. This means you can get builds that have passed through the Canary, Operating System Group, and Microsoft rings, but may not necessarily have had enough kinks ironed out to be deemed ready for public consumption.
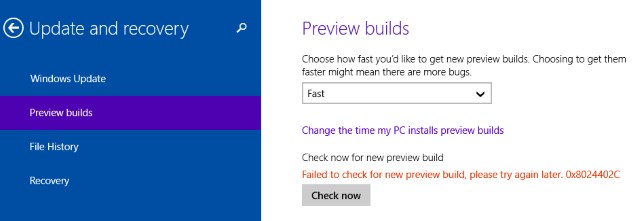
Fancy getting your hands on future builds a little faster? Head to PC Settings, click Update and recovery to the left and then select the Fast option from the Preview builds drop down menu. That's all there is to it.
And that's also all there is to it for Windows 10 Technical Preview build 9860 -- at least on the face of it. It would appear that the majority of the near 7,000 changes have taken place under the hood. Aside from the components that are clearly not finished yet, the build feels solid and stable -- but the same was true of build 9841.
Have you spotted any new features or settings that we've missed?
-

Apple solders RAM into new Mac mini to block memory upgrades
Publié: octobre 19, 2014, 4:24pm CEST par Mark Wilson

This week, Apple unveiled a number of new and updated products. The latest additions to the iPad range were the crowd pleasers, while the iMac with Retina 5K Display was something of a headline-grabber. Yosemite was expected, but the Mac mini refresh came slightly out of the blue.
For anyone looking for a cheap way to get their hands on a Mac, it's a great starting point -- prices start at just $499. But you'd better make sure you select a model with enough RAM when you place your order -- Apple has taken steps that mean it is impossible for buyers to install more memory.
The surprising news was confirmed by Brian Stucki on the macminicolo blog and it will come as a disappointment to anyone on a budget. It's quite common for people investing in a new computer to cut back in certain areas to help keep costs down, and then upgrade further down the line when funds allow. With the new Mac Mini, this is simply not an option. Speculation had been rife that RAM modules were soldered in place, and this was backed up by Stucki:
Confirmed: RAM in the new Mac mini is not user accessible. Hard drive can be replaced/upgraded, though not keeping warranty.
— Brian Stucki (@brianstucki) October 17, 2014
This isn't the only bad news for the would-be upgrader. As well as making double sure you have decided on the right amount of RAM before placing your order, you'd better also have a good hard think about what size hard drive you want. While not impossible to upgrade, Stucki deals another blow:
If people didn't like to hear the confirmation of soldered RAM, wait until they see the foot of the Mac mini with tamper-proof screws.
— Brian Stucki (@brianstucki) October 18, 2014
If you're determined to add more storage, it is possible to do so, providing you don't mind invalidating your warranty.
Does the lack of upgrade possibilities make the Mac mini less desirable, or is it a non-issue?
-

5 essential tips for staying safe online
Publié: octobre 17, 2014, 8:48pm CEST par Mark Wilson

The security of the internet is an on-going concern. Whether you're online for fun, or you're conducting business, there are all manner of pitfalls you may encounter. Issues such as viruses and malware are now widely known about, but these are far from being the only security issues to concern yourself with. Security has been thrown into the limelight once again by high-profile stories like the Fappening, problems with SnapChat, concerns about the Whisper app, and the POODLE SSL 3.0 vulnerability.
A large proportion of companies and individuals are aware of the importance of anti-virus and anti-malware tools, firewalls and the like. Security tools are all well and good, but there's also a lot to be said in favor of changing online behaviors; it's something that the online community and businesses are increasingly coming to understand. Much of what this entails -- taking care about the personal information you share and educating yourself about services before you use them -- is common sense, but it bears repeating.
Jean Dobey is CEO of Virtual Artifacts, a company focused on producing tools that allow for communication, social networking, online payments, and shopping without compromising security. He has a number of tips which can help to protect user privacy and personal information.
1. Be aware of changing privacy policies
When it comes to sharing information through social media platforms and online communication tools, it's worth remembering that what’s private today may be public tomorrow if a site changes its privacy policies. As many sites revise such policies on a regular basis, privacy settings will often only offer a false sense of security.
2. Understand how social media platforms operate
Before you share through a social media platform, take the time to learn how it operates. Many of us place a lot of trust in social media tools without fully understanding the nature of such services. Facebook Lists are a good case in point. Trusting users would be forgiven for thinking that whatever they share through a list made up of their family members would only be accessible to the relations in question. In reality, what you share in a list is accessible to you, the people you’ve added to the list and a hidden audience comprising Facebook and any person or organization that’s paid Facebook to search your content.
3. Be selective with how and what you share
It may sound simple, but you can never be too careful when it comes to sharing personal information online. Apparently straightforward tasks like shopping online or installing an app can force us to expose private or sensitive information -- such as our purchasing preferences, our location or even our lists of contacts. Whether completing a transaction or connecting with someone through social media, it pays to always question who you’re sharing with, what you’re sharing with them, which context you’re sharing in and why. You can then decide what identity or persona you should display to connect with such an audience. In the end, it’s better to exercise a little caution than risk having your private data fall into the wrong hands.
4. Use two-step authentication
It never hurts to add a second stage to the authentication process, particularly when you’re dealing with sensitive personal data. But adding an easy-to-answer security question may only delay, rather than deter, someone. Any resourceful person will easily find your mother’s maiden name, your favorite band or the team you support online. Giving past instead of current information as the answer to a security question can reduce the likelihood of someone gaining access to your account. For example, if the question is ‘In what city or town does your nearest sibling live?’ your answer could be the place they lived ten years ago, instead of their current address.
5. Look at how those close to you, including your children, behave online
Taking the time to educate your children and speak with the other people in your life on the dangers of sharing personal or sensitive information online will not only help to protect their safety, it can also protect your family as a whole. Whether sharing information that could be exploited by others, making purchases online or visiting unsecure sites make sure they understand the potential risks both to themselves and those around them.
These tips may not be the be all and end all of online security, but they are steps in the right direction.
Photo credit: Markus Gann / Shutterstock
-

iMac with Retina 5K display has the world's highest resolution display -- and a hefty price tag
Publié: octobre 17, 2014, 1:07am CEST par Mark Wilson

In addition to the expected iPad Air 2 and iPad mini 3, Apple today announced the latest update to the iMac range. The iMac with Retina 5K display's killer feature is the screen which packs a breath-taking 14.7 million pixels into its 27 inches. With a resolution of 5120 x 2880, the new iMac has two thirds more pixels than a 4K display, and four times the number of pixels found on a regular 27 inch iMac. Despite the colossal number of pixels involved, Apple has switch to ultra-efficient LEDs to keep power consumption, and heat production, down.
The system comes with AMD Radeon R9 M290X graphics as standard, but this can be upgraded to AMD Radeon R9 M295X graphics. This is backed up by 8GB of RAM and a 1TB Fusion Drive, and there is the option of upgrading various components if you're happy to part with a little extra cash.
"A little extra", might not be entirely accurate. The baseline price for the new iMac with Retina 5K display is $2,499. For this money you get a system with a 3.5GHz quad-core Intel Core i5 offering Turbo Boost up to 3.9GHz, 8GB RAM, 1TB Fusion Drive, 2GB graphics card, and -- of course -- the newly unveiled Yosemite. Two Thunderbolt 2 ports each provide a data transfer rate of 20Gbps. But $2,499 is just the starting price; you can pay much, much more if you are willing and able.
Fancy a 4.0GHz CPU? That'll be an extra $150. Bump the RAM up to 32GB? An extra $600. Add a larger hard drive, upgrade the graphics card, and the price soon adds up. Take advantage of all of the possible hardware upgrades -- including adding flash storage -- and the price rockets to $4,547. That's a lot of money, but you get a lot of computer for your cash.
Philip Schiller, Apple’s senior vice president of Worldwide Marketing said:
Thirty years after the first Mac changed the world, the new iMac with Retina 5K display running OS X Yosemite is the most insanely great Mac we have ever made. With a breathtaking 14.7 million pixel display, faster CPU and graphics, Fusion Drive, and Thunderbolt 2, it’s the most beautiful and powerful iMac ever.
If you like the idea of getting your hands on one, head over to the Apple store and have your credit card at the ready.
-

Twitpic really IS closing, and the deadline is tight to back up your data
Publié: octobre 17, 2014, 12:30am CEST par Mark Wilson

Twitpic was closing, then it wasn't. But now the champagne corks have been well and truly push back into the bottle after news of an acquisition turned out to be a false alarm. Users now have just one week to export their photos and data before Twitpic closes for good on 25 October. Company founder Noah Everett used the Twitpic blog to break the news, explaining that the photos and video sharing service will shut up shop in a week's time.
The last month and a half has been something of a rollercoaster ride for Twitpic and its users. After a trademark application dispute, the original closure announcement came on 4 September with the closure planned for 25 September. A lifeline appeared just two weeks later when it was announced that a buyer had been found.
The stay of execution was short-lived, however. Today it has been re-announced that the closure will be going ahead -- a full calendar month after the original closure date.
It's with a heavy heart that we re-announce that Twitpic will be shutting down again. More details on our blog [t.co]
— TwitPic (@TwitPic) October 16, 2014
Over on the Twitpic blog, Everett made the following statement:
It's with a heavy heart that I announce again that Twitpic will be shutting down on October 25th. We worked through a handful of potential acquirers and exhausted all potential options. We were almost certain we had found a new home for Twitpic (hence our previous tweet), but agreeable terms could not be met. Normally we wouldn’t announce something like that prematurely but we were hoping to let our users know as soon as possible that Twitpic was living on.
I’m sincerely sorry (and embarrassed) for the circumstances leading up to this, from our initial shutdown announcement to an acquisition false alarm.
Users are advised that their photos and data can be downloaded from their account page. If you want to safeguard your files, you'd better be quick because the clock is ticking once again.
Photo credit: ronfromyork / Shutterstock
-

Investigation finds 'anonymous' Whisper app secretly tracks user location
Publié: octobre 16, 2014, 8:10pm CEST par Mark Wilson

Following all of the NSA revelations, mass surveillance has increased the general level of paranoia to be found online -- although it could be argued that not all surveillance is bad. With everyone on such high alert it's little wonder that an app that described itself as "an anonymous social network that allows people to express themselves" should be so popular. Whisper encourages users to embrace the supposed anonymity it offers and reveal secrets they would not otherwise feel comfortable sharing.
An investigation by the Guardian found that the app is tracking the location of its users -- even those who have opted out of such tracking. As a result of the Guardian's report, Whisper amended its terms of service and introduced a new privacy policy. But the revelations will cause concern to users of the service, who sent more than 2.5 million messages per day.
Despite the claims of anonymity, Whisper is in fact able to determine the location of users to within 500 metres. Does this matter? Some of the messages posted via Whisper have been found to originate from within the White House -- one that reads "I'm so glad this app is anonymous. The press would have a field day if they knew some of the stuff I post on here", for example. Whisper assures its users that "We collect very little information that could be used to identify you personally" -- which you'll notice is very different to saying no data is collected.
The Guardian learned about the existence of in-house tools that Whisper can use to plot the location of messages on a map. Perhaps most worrying, this includes those users who has explicitly opted out of sharing their location. The privacy statement does state that "we use the information that we collect from you for internal purposes", but few users would expect that their expressed wishes would be directly opposed. The Usage Data section of the privacy documents states that "even if you have disabled location services, we may still determine your city, state, and country location based on your IP address".
The privacy page also now says that using Whisper means that it is possible "to make a determination as to your identity based on the content of your whispers as well as your general location". Whisper reveals that user data if often stored outside of the US: "This may be important to you, as the laws of the United States or such other countries may not be as protective of your personal information as the laws of your jurisdiction."
User location is valuable data, Like many other services, Whisper is keen to provide content that will be of interest to individual users -- this is very hard when dealing with "anonymous" users. But location can reveal a great deal about a user, hence Whisper's keenness to gather such information. The data could also be shared with third parties: "We may also partner with universities or other research institutions or scientists to use the limited information we have in anonymous, controlled research studies".
The Guardian's investigation also found that Whisper was sharing information with the FBI and MI5 for legal reasons, and working with the US Department of Defense to provide data about suicide and self-harm.
Michael Heyward, co-founder and CEO of Whisper, has described the service as "the safest place on the internet". In the light of the revelations, many users might disagree.
Photo credit: Lightspring / Shutterstock
-

When disaster strikes, Safety Check lets people know you're OK... via Facebook
Publié: octobre 16, 2014, 1:19pm CEST par Mark Wilson
In times of natural disaster and chaos, people are increasingly turning to social media for news and updates. But while Facebook is a handy way to keep up to date with the latest news about Ebola, earthquakes, and other problems, it's also a valuable means of checking up on loved ones to make sure they're OK. Now the social network has a new tool that makes it easier than ever to let your friends and family know that you’re safe if you happen to be in or near a problem area.
It’s a simple idea. Facebook uses your statuses and check in details to determine where you are. If you happen to be in a disaster area, a message will pop up in your account or mobile app asking if you're OK. You can then indicate that all is well and your friends and family will be able to see that there is no cause for concern.
If you are with other people, you can also indicate that they are safe so not everyone in a party has to do so manually. Introducing the feature, Mark Zuckerberg said:
Safety Check is our way of helping our community during natural disasters and gives you an easy and simple way to say you're safe and check on all your friends and family in one place.
It's meaningful to be in Tokyo to announce this because the great earthquake and tsunami a few years ago inspired us to build the first version of this for Japan. Now we're glad to have this ready to serve everyone in the world.
There is, of course, a chance that Facebook will incorrectly decide that you re in a disaster area. Facebook explains that, "we'll determine your location by looking at the city you have listed in your profile, your last location if you've opted in to the Nearby Friends product, and the city where you are using the internet." Should your location be incorrectly detected, you can indicate that you are outside of the danger zone.
The feature is starting to roll out globally now.
-

Will.i.am launches Puls -- the smartwatch that's not a watch
Publié: octobre 16, 2014, 12:47pm CEST par Mark Wilson

It's not a watch. It's not a watch. It's not a watch. Despite appearances to contrary (it tells the time and is worn on the wrist for starters...), Black Eyed Peas' singer and tech fiend will.i.am is keen to assure us that his new wristband is most definitely not a watch. Unveiling the wearable, the smart cuff, the wristband -- call it what you will, as long as it's not a watch -- at Dreamforce in San Francisco, he showed off the fact that the Puls (pronounced Pulse, not Pulls) can be used to make calls without the need to be paired with a mobile phone.
It's a device that has been teased for quite some time now. Will.i.am has been seen on many occasions with the band on his wrist, but had resisted giving away too many details. Now we know it is a curved screen device complete with its own SIM card, 16GB of memory and 1GB of RAM, and a Siri/Cortana-bating voice recognition system called Aneeda (I need a...).
We could be seeing the start of a new breed of wearable. While Samsung produces smartwatches that can only be used in conjunction with Samsung phones, and Apple produces the Apple Watch that can only be used in conjunction with an iPhone, Puls has no such reliance. It is a standalone device that can be used to make and receive calls and text messages without the need for a separate handset. There's Wi-Fi and Bluetooth available, and SIM-mirroring means that if you do want to hang onto your phone, you can use the same number on both devices.
As you'd expect from a wearable, Puls is packed with sensors. There is, of course, a touch screen, but accelerometers and GPS are on hand to help with the health and fitness side of things, but there's also an emotion sensor that can allegedly detect the mood of the wearer. Powered by a Qualcomm Snapdragon processor, the Puls runs a forked version of Android and will be capable of playing music and used to run other apps. And that's about all we know. Oh... apart from learning that battery life is a bit, er, rubbish. We're promised five hours of continuous use, so you'll want to make sure you have a charger with you at all times.
At the moment we only know about US and UK launches. In the US the wristband will be carried exclusively by AT&T, while in the UK it will be carried by O2. No pricing or launch date details have yet been announced.
Photo credit: Tech Crunch
-

Parlez-vous l'internet? Google Translate gains new Chrome extension
Publié: octobre 16, 2014, 2:19am CEST par Mark Wilson

The web is truly worldwide, the epitome of globalization and the ever-shrinking world. As much as the McDonaldization of the world means that cultures are on an homogenizing course, there are still plenty of differences to embrace -- language is one of them. Spend just a little time surfing the web and there's a reasonable chance that you'll encounter a foreign language site, or at least a few words and phrases that are beyond your high school French and Latin.
Enter stage right Google Translate. This service of course n'est pas nouveau. In fact Google Translate has been around for ages. Mais maintenant il y a un Chrome extension that makes the translation process easier than ever. Oubliez visiting a dedicated website, now your translation is a mere click away.
Grab yourself a copy of the newly announced Google Translate Chrome extension and you'll be able to quickly translate passages of text or individual words by highlighting and right clicking. This is a handy option if you're reading an article that contains a few foreign words, but you still have the ability to translate entire pages.
Chrome will usually offer to translate web pages that are written in a foreign language, but should this not happen automatically, you can instigate it manually. Rather than highlighting words to translate, just click the Google Translate toolbar button in Chrome and the whole page will be converted to the language of your choice.
Grab a copy of the extension and get translating!
Photo credit: Lemon Tree Images / Shutterstock
-

Google and Asus launch Nexus Player for video, music and game-playing
Publié: octobre 15, 2014, 6:51pm CEST par Mark Wilson

Well... Android Lollipop (née Android 5.0), the Nexus 6 and Nexus 9 were expected, but Google managed to sneak a little 'one more thing' addition to today's batch of announcements. Nexus Player, as you'd probably guess from the name (and certainly from the headline), is a streaming media device. But in addition to catering for all your video and music streaming needs, the device also doubles up as a games console.
In many ways the Nexus Player is an extension of Chromecast -- there is even casting support. Google has teamed up with Asus to bring us a device that not only streams media, but also streams games from phones and tablets. And this aims to be more than a console for casual gamers; there's even a gamepad that's very reminiscent of the Xbox One controller.
The device itself takes the appearance of a big, black period. Google says that "the Nexus Player console is designed to fit beautifully alongside your current home entertainment setup", and it certainly wouldn't look out of place next to most TVs. We've already mentioned the gamepad which owes quite a lot to the Microsoft design team and there's also a remote -- which this time borrows ideas from Roku. The Player is powered by a 1.8GHz quad-core Atom processor which opens up the opportunity to play 3D games.
In the box you'll get a Nexus Player and a remote -- sadly, the controller is going to be sold separately. The remote is a simple-looking affair with just four buttons and a direction ring. Google says that it is suitable for "playing casual games", so it should afford enough control to allow for a quick game of Angry Birds or Candy Crush Saga from the sofa -- and you can then pick up from where you left off on your phone or tablet. The remote is more than a standard buttoned controller. There's also voice activation which can be used for controlling media playback, as well as playing games.
Nexus Player is primarily a streaming media device and there is tight integration with other platforms. Content can be cast from Android, iOS, Windows and OS X, with playback position synced between devices making it easy to switch platforms mid-movie. There's already support for a wide range of apps such as Plex, Netflix and Hulu, but content can also be purchased from the Play Store.
The Nexus Player, like the Nexus 9, is available to pre-order from 17 October and will ship 3 November. Google has confirmed that the Nexus Player with remote will cost $99.99, and will come with $20 of Google Play credit. The optional controller will cost $39.99.
-

Ireland in tax clampdown targeting Microsoft, Apple, Google, and more
Publié: octobre 15, 2014, 4:05pm CEST par Mark Wilson

The Irish government is phasing out the so-called 'Double Irish' finance scheme that currently enables companies such as Google and Apple to slash millions (or even billions) of dollars from their tax bills. The scheme works by companies, regardless of where they may be operating in the world, collecting their profits through an Irish office (where tax is already low), and then funneling the money through a subsidiary company located in another tax haven by means of royalty payments.
Companies, like individuals, are understandably keen to keep their tax bills down as much as possible, and will jump through lots of hoops to reduce the amount of tax they have to pay. Offshore bank accounts, subsidiary companies and the like might sound like the makings of something illegal -- which it can be -- but it's a legitimate way to reduce costs. But the fact that something is legitimate doesn't mean that it's popular. At least it's not something that is popular with governments.
In both the UK and the US, concern has been voiced at the level of tax that has been avoided. It is important to reiterate that tax avoidance is entirely legal; tax evasion is an entirely different matter. No one is suggesting that Google, Microsoft, Apple, et al are involved in anything illegal, but countries are slightly irked that the system has been worked in such a way that respective governments have been unable to collect the amount of tax they would have liked.
Now the heady days are over -- Double Irish arrangements are set to become a thing of the past. Delivering a budget statement, the Irish Minister for Finance, Michael Noonan, said:
Aggressive tax planning by multi-national companies has been criticized by Governments across the globe and has damaged the reputation of many countries. Schemes that exploit mismatches in tax legislation are being heavily scrutinized by the OECD and others and through the Base Erosion and Profit Shifting project they will come to an end over time. The so called "Double Irish" is one of many such schemes.
He went on to explain that the scheme's days are now very much numbered:
I am abolishing the ability of companies to use the "Double Irish" by changing our residency rules to require all companies registered in Ireland to also be tax resident. This legal change will take effect from the 1st of January 2015 for new companies. For existing companies, there will be provision for a transition period until the end of 2020.
While the move will almost certainly upset a lot of companies, it's unlikely there will be a mass exodus from Ireland. With corporation tax set at just 12.5 percent, the country is still an attractive place to do business -- it's rather more than the 0 percent in Bermuda, but much lower than many other countries. The increased costs will almost certainly be passed on to customers, but there are still over five years until this should be cause for concern.
Photo credit: xtock / Shutterstock
-

Tracking and tackling Ebola using mobile phone surveillance
Publié: octobre 15, 2014, 1:11pm CEST par Mark Wilson

Mention web or mobile surveillance, and you're sure to raise a few hackles. But the current Ebola outbreak is showing that the data collected from handsets can be extremely useful. The idea of tackling a disease with 'big data' gathered from mobile phones might seem a little odd, but it's actually an incredibly valuable source of information. Telecom firms such as Orange have been working with data scientists, using anonymized data gathered from phones to track population movement in regions affected by Ebola.
The BBC points out that even in relatively poor countries in Africa, mobile phone ownership is still high. Experts have been able to use this data to determine the best places to set up treatment centers, and it's an idea that has been pounced upon by the CDC.
Used in conjunction with existing data, information pulled from mobile phone masts helps to provide a broad overview of what is happening in any given area. For example, by monitoring mobiles, it would be possible to notice a spike in calls to health and helplines. This could be indicative of a problem in the area so resources could be better concentrated. Mobile phone masts can also be monitored to track changes in population movement -- compare current activity level to historic data and it's easy to see when patterns change.
Monitoring phone and web usage, even when done so anonymously, is generally frowned upon, but so-called 'big data' makes it possible to see trends faster than would otherwise be possible. Hospitals and health centers are tied up treating people and don’t necessarily have the time or resources to report back in real-time about the numbers of people they are treating. Analyzing previously unavailable big data allows for faster responses and better deployment of resources.
The technique is not new -- mobile phone data was also used during the cholera outbreak that followed the Haiti earthquake in 2010 -- but, while it helps to provide valuable data, it's still not quite enough. Frances Dare, managing director of Accenture Health, explains that data from other sources is also needed as well as the ability to successfully analyze it:
Big data analytics is about bringing together many different data sources and mining them to find patterns. We have health clinic and physician reports, media reports, comment on social media, information from public health workers on the ground, transactional data from retailers and pharmacies, travel ticket purchases, helpline data, as well as geo-spatial tracking.
Interconnected systems mean that it is also very easy to track the movement of groups and individuals around the world. Bank details, phone records, social media usage, and information from travel agencies can all be used to follow people from disease prone parts of the world. Should it be suspected that an individual is an Ebola carrier, the task of tracking them down is a great deal easier than it would have been a few years ago.
But the problem with big data is the very fact that it is big. Pulling in information from mobile phones, web searches, and population movement involves working with a massive amount of data. It is comparable to the NSA trawling the web and trying to pick out the few snippets of data that are useful. The analysis of big data is a developing art form, but it's one that's improving all the time. Surveillance and data collection isn’t always a bad thing after all.
Photo credit: Sergey Uryadnikov/ Shutterstock
-

Security alert: Google drops SSL 3.0 after POODLE attack discovery
Publié: octobre 15, 2014, 2:13am CEST par Mark Wilson

Google's security team has discovered a vulnerability in SSL 3.0 which can be exploited to steal secure cookies and other data. The 15 year old technology is still used as a fallback when connection problems occur as it helps maintain backward compatibility, but the security problems mean that Google will start to phase out support. Details of the exploit have been published and Chrome has today been tweaked to disable SSL 3.0 fallback.
Bodo Möller from Google's security team points out that this move will "break some sites" and that they will need to be updated. This does present some compatibility issues, and the advice is to support TLS_FALLBACK_SCSV instead, at least for the time being.
Google explains that SSL 3.0 is an insecure, obsolete protocol that has since been superseded. But even when servers support the more secure TLS 1.0, TLS 1.1 or TLS 1.2, the "protocol downgrade dance" that takes place between servers and clients can be exploited using a POODLE (Padding Oracle On Downgraded Legacy Encryption) attack. Clients and servers will automatically attempt to establish a connection using the most secure protocol supported by each, but should a problem arise the next most secure option will be used, and so on.
An attacker can force this protocol downgrade to take place by preventing the initial connection from taking place, triggering repeated attempts with increasingly less secure protocols. The encryption used in SSL 3.0 is fairly easily cracked and a relatively simple main-in-the-middle attack can then be used to intercept and decrypt secure cookies.
The full effect of the discovery is not yet known, but the fact that such a widely-used -- even if obsolete -- protocol is involved means that large numbers of sites are going to be involved, although it has been suggested that it is older versions of Internet Explorer that are worst affected. Google's security advisory includes advice for system admins looking to ensure the security of their servers.
Photo credit: KPG_Payless / Shutterstock
-

Security firms have created the next dot com bubble by 'scaring their customers'
Publié: octobre 14, 2014, 10:50pm CEST par Mark Wilson

There are too many security firms offering insufficient security. At least that's what Ilia Kolochenko, CEO and founder of High-Tech Bridge thinks. He points to the splitting of Symantec as proof that security companies are struggling, and suggests that the emergence of so many firms competing for attention is the start of a new dot com bubble that could burst at any moment.
Security is important to both home computer users and enterprise businesses. There is a huge amount of money to be made in the field, so it is perhaps little wonder that the number of companies muscling in on the market is on the increase. Kolochenko says that at the end of the century a lot of tech companies sprang up overnight and "most of these businesses were designed to create artificial problems or boost non-existent demand in order to make quick money. They didn't actually solve any real problems". There is a danger that the same could happen in the security world.
Kolochenko thinks we find ourselves in a precarious situation that is on the verge on imploding. He suggests that security firms themselves are to blame:
Some information security companies today solve problems and mitigate risks that probably have the very lowest priority in the business risk list. In order to sell their solutions they create artificial demand, quite often misleading or even scaring their customers with false threats or non-existent risks.
More than ever is now being spent on security, and yet there are still large-scale, well-publicized security breaches. Part of the problem stems from customers relying in third-party security solutions that are not ideally suited for them. Companies are spending money on security, but not the right kind of security. This is something that hackers use to their advantage:
Hacking is about business, money and profit. Black hats will not spend their money and time developing expensive custom-made 0-day attacks when companies have pedestrian vulnerabilities and don’t install patches in a timely fashion.
Spending money on the wrong kinds of security and continuing to fall victim to security breaches could well lead to companies rethinking spending and cutting back in this area. Kolochenko suggests that the swarm of security firms that have developed in recent years could tumble like a house of cards if this happens. The outfits whose current success rides on continuing to create false threats will die out, leaving behind only the genuinely innovative.
Photo credit: klublu / Shutterstock
-

Cloud burst: Dropbox confirms bug deleted user files
Publié: octobre 13, 2014, 4:41pm CEST par Mark Wilson
 There have been various headlines recently about cloud security breaches -- including the celebrity 'event' that shall not be named -- and the latest problem to hit the cloud affects Dropbox users.
There have been various headlines recently about cloud security breaches -- including the celebrity 'event' that shall not be named -- and the latest problem to hit the cloud affects Dropbox users.This time around it's not a security problem, but it does involve losing control of one's files. A problem with the Selective Sync feature of some older versions of the Dropbox desktop app meant that files were deleted rather than synced. It's a problem that Dropbox users have been complaining about for a little while but the cloud storage provider has now confirmed the bug and issued assurances that the problem has been addressed.
The problem seems to arise when the Dropbox application shut down or restarted whilst Selective Sync settings were being applied, but steps have been taken to wipe out the issue. Dropbox has confirmed that the problem stems from older versions of the desktop sync app.
Users on Hacker News quote Dropbox support as saying that "older versions of the Dropbox client had introduced an issue" that led to the deletion of files. The cloud storage company goes on to explain that it has "patched our desktop client so this issue doesn't exist in Dropbox anymore", "made sure all our users are running an updated version of the Dropbox client", and "retired all affected versions of the Dropbox client so no one can use them".
Steps have been taken to recover files that were deleted, but there is no word yet on the number of files that could not be recovered by Dropbox. One user, Michael Armogan, received an email from the company that includes an apology and the news that the problem has been fixed:
We're reaching out to let you know about a Selective Sync issue that affected a small number of Dropbox users. Unfortunately, some of your files were deleted when the Dropbox desktop application was shut down or restarted while you were applying Selective Sync settings.
Our team worked hard to restore files that were deleted from your account. You can see which of your files were affected and whether or not we've been able to restore them on this personalized web page.
We're very sorry about what happened. There's nothing more important to us than making sure your information is safe and always available. Our team has fixed the issue and put additional tests in place to prevent this from happening in the future.
For some Dropbox users, email such as this will be the first they knew of the file deletion problem.
Were you affected by the Dropbox file deletion problem? Did you lose many files or were they successfully restored for you?
-

The battle to wipe out revenge porn continues
Publié: octobre 12, 2014, 11:36pm CEST par Mark Wilson

In the wake of the Fappening, online porn and nudity has been thrust into the public consciousness once again. But porn is about much more than titillating celebrity photos -- even if research shows that we're finding it easier to waste our time online when we should be getting on with work. Revenge porn is on the rise, and steps are being taken to try to thwart its progress. As the Fappening showed us, taking saucy pictures of oneself or partner is far from uncommon. This is fun and exciting in the middle of a relationship, but if that relationship should break down, there's no knowing what could happen to those pictures and videos.
Disgruntled partners may decide to get revenge on their former lovers by sharing those intimate photos and movies online, or it may be obtained by a third party and used as a tool for bribery. Many US states have outlawed the practice, and now the UK is following suit.
New legislation is due to be introduced that will criminalize revenge porn, opening up guilty parties to a potential two year imprisonment. Some have argued that existing blackmail and obscenity laws should be enough, but by explicitly singling out revenge porn as a specific, individual crime, potential loopholes are closed. While revenge porn is most prevalent online, the new laws will also cover printed material.
The law specifically applies to photos and videos that feature people in sexual poses, engaged in sex acts, or displaying their genitals, and it will cover files that are shared by email in addition to those posted online. The Guardian quotes justice secretary Chris Grayling as saying:
The fact that there are individuals who are cruelly distributing intimate pictures of their former partners without their consent is almost beyond belief. We want those who fall victim to this type of disgusting behaviour to know that we are on their side and will do everything we can to bring offenders to justice.
It is legislation that will be welcomed by privacy advocates who have been disturbed by the number of instances of revenge porn being posted to the likes of Facebook and Twitter.
Photo credit: Gustavo Frazao / Shutterstock
-

Windows 10 Technical Preview feedback: what users want to change
Publié: octobre 10, 2014, 5:56pm CEST par Mark Wilson

Microsoft is encouraging people who have downloaded the Windows 10 Technical Preview to provide feedback on the embryonic operating system. The Start menu is something that users have been begging for, and changes to the Command Prompt have been a very long time coming, but just what do testers think of Windows 10 so far? There's still quite some time to go until Windows 10 is released giving Microsoft lots of opportunity to respond to user feedback. This is what Microsoft is all about these days after all.
With help from one of the readers of his Supersite for Windows, Paul Thurrott has pulled together a list of the top ten requests that have been received so far. The methodology may not be entirely scientific, but it does give an interesting insight into how Windows 10 has been received and what people would like to see changed.
The (frankly stupid) dedicated search and taskview buttons top the list of pet peeves. Actually, this is only true when the numbers relating to both buttons are combined, but as both are equally irritating, equally immovable, and equally unhideable, it makes sense to group them together. Next in line appears to come from the aesthetes. There is apparently a general feeling that having the Start menu simply pop into view is not good enough -- testers would prefer there to be an animation effect of some sort. There's a bit of a niggle that Windows 10 users are encouraged into using a Microsoft account rather than a local one, but as this is central to the idea of syncing Windows 10 between computers, requests to make local accounts "easier" to implement are likely to fall on deaf ears.
A reasonable proportion of people giving feedback have suggested that File Explorer should have tabs. This is something that crops up time and time again, and there are a number of third-party tools that can bring this feature to existing versions of Windows. This is not a new request, but it is one that Microsoft has managed to ignore for years. Will the company listen this time around? The inability to activate the Charms bar with the mouse -- something that is probably just a quirk of the preview -- comes in at number 5, followed by a request for a "beautiful boot screen".
Next up is another complaint about the Start menu, this time pointing out that it is not possible to select multiple tiles when the Ctrl key is held down. The mish-mash of desktop vs modern is raised at number 8. The existence of the Control Panel and PC Settings is causing frustration, with many people suggesting that Microsoft should finalize transitioning to the latter. Rounding off the top ten are two more cosmetic requests: that icons should be updated, and that virtual desktops should be able to have different background images.
What's interesting about this list is just how conservative it is (no mention of Cortana? Seriously?). Whether this is an indication that Windows users are not actually all that demanding, or that only a certain type of user is providing feedback is not clear. It seems that only a relatively small number of people have taken the step of giving feedback. Of course it is very early days for the preview at the moment and as time goes by, more and more users should start to try out the preview, and Microsoft may well find that it is inundated with feedback.
The question is, how will it respond?
-

Symantec to follow HP and eBay and split in two
Publié: octobre 10, 2014, 2:40pm CEST par Mark Wilson

There must be something in the air at the moment -- everyone seems to be splitting up. eBay and PayPal decided that it would be better to go it alone, and then HP announced it would be splitting into consumer and enterprise companies. Symantec now reveals that it plans to divide into two independent companies, one focusing on security, and the other on storage.
President and CEO, Michael A. Brown, says that the two markets face their own sets of unique challenges and by splitting in two, each business will have the flexibility needed to respond accordingly.
It means that the storage and security arms of Symantec will be able to operate entirely independently of each other, each able to work with a simpler framework. The split could also mean that one or both of the newly formed businesses are more attractive to other companies who might be interested in a takeover bid.
Brown said: "As the security and storage industries continue to change at an accelerating pace, Symantec's security and IM businesses each face unique market opportunities and challenges. It has become clear that winning in both security and information management requires distinct strategies, focused investments and go-to market innovation. Separating Symantec into two, independent publicly traded companies will provide each business the flexibility and focus to drive growth and enhance shareholder value".
The security business is what Symantec is best known for, and in 2014 it brought in $4.2 billion for the company. The backup and storage side of the company -- or the Information Management Business as Symantec refers to it -- has not fared quite so well, but the hope will be that things will improve with the renewed focus. Once the restructuring is complete, Brown will remain in his position as president and CEO of Symantec, while the new information management business will be headed by John Gannon.
Photo credit: Gil C / Shutterstock
-

Microsoft: Surface is here to stay
Publié: octobre 9, 2014, 6:40pm CEST par Mark Wilson

In a post on the Surface blog, Microsoft has moved to assure businesses that the Surface line is here to stay. We've already heard that the Surface Pro 3 is a success -- although there are no figures to back up this claim -- but Microsoft's failure to launch a third generation RT-based version of the Surface, as well as the disappearance of the long-rumored Surface Mini, raised fears that the line of tablets may not be long for this world. Microsoft is keen to allay these concerns, pointing out not only that Surface is here to stay, but also that it is particularly suitable for businesses.
The post points out that the Surface Pro 3 is a device that's "great for getting things done". There's almost an air of desperation to the blog post in which Microsoft extols the virtue Surface and confirms its commitment to the brand. The selling point is still that the device is a laptop and tablet in one, and post author Brian Hall, General Manager for Surface, is quick to mention a number of big names who have adopted Surface Pro 3.
There is a lot of trumpet-blowing from Hall, but it's not long before the big guns are wheeled out n the form of a statement from CEO Satya Nadella:
We believe a strength of the Microsoft platform for enterprise is the rich ecosystem of hardware and applications developed by our partners, the community at large, and some of our own teams at Microsoft. In particular with Microsoft Surface Pro 3 we are now offering an enterprise-class device that can deliver great end user productivity. Microsoft is putting its full and sustained support behind the ongoing Surface program as one of a number of great hardware choices for businesses large and small.
Microsoft is turning its attention more and more to the enterprise side of its business, and this is just the latest example of this focus. The company is keen to sell the idea of the Windows ecosystem, much as Apple managed with iOS and OS X, and this is a theme that was underlined with the recent launch of Windows 10 Technical Preview. Windows 10, despite being around a year away, is referred to in the blog post, reassuring potential buyers that Surface Pro 3 will be upgradable to the latest version of Microsoft's operating system. It's not clear whether this, coupled with the money-saving Surface Laptop Replacement Bundle will be enough to boost sales of Surface Pro 3, but Microsoft will certainly be hoping so.
Photo credit: Muamu / Shutterstock
-

The internet is a massive waste of time
Publié: octobre 9, 2014, 3:26pm CEST par Mark Wilson

Over the last couple of decades the internet has revolutionized how we work, how we shop, how we communicate, and how we consume media. In most regards it has made life quicker and easier, but it has also brought challenges and side-effects. Technology may have made many tasks simpler, but it has also increased distractions and shepherded in more ways to procrastinate. You've probably noticed that while you can get many things done faster than ever, you spend a great deal of time doing nothing of worth.
In fact, rather than saving money, the widespread adoption of technology could be costing business dearly. Research shows that nearly two-thirds of employees spend work hours browsing sites unrelated to work -- a surprising 3 percent of them spending more than 10 hours a week actively avoiding work online. All of these wasted man hours add up, resulting in an average cost of almost $3,000 for employee each year.
But it's not just websites that are a distraction. Research found that just 14 percent of emails are crucial to work, and 62 percent of people found that dealing with unnecessary messages was one of the down sides of using email as a means of communication. A surprising finding is that, on average, workers spend 4 hours -- or half the working day -- handling emails.
Check out the infographic below to see how technology is wasting time, as well as how it can help.
 Photo credit: Filipe Frazao / Shutterstock
Photo credit: Filipe Frazao / Shutterstock -

Apple remains the most valuable brand in the world
Publié: octobre 9, 2014, 2:08pm CEST par Mark Wilson
 Continuing its run at the top of the charts, Apple is revealed as the most valuable brand in the world. With a massive 21 percent increase over the last 12 months, Apple is now valued at just under $119 billion -- almost double that of Microsoft which finds itself in fifth place with a value of just over $61 billion.
Continuing its run at the top of the charts, Apple is revealed as the most valuable brand in the world. With a massive 21 percent increase over the last 12 months, Apple is now valued at just under $119 billion -- almost double that of Microsoft which finds itself in fifth place with a value of just over $61 billion.The top 100 rankings have been published by Interbrand, and a number of familiar names from the world of tech are to be found in the top 20. Google's value jumped by 15 percent from last year to $107 billion, and the search giant remains in second position.
Apple's valuation is, as the Guardian points out, more than the GDP of countries such as Morocco. This will come as slightly better news to the company than the revelation that it is the top phishing target. The position of the ten most valuable brands remains largely unchanged; the same names jostle for attention at the top of the table. Facebook rocketed up the charts from 52 in 2013 to 29 this year, and managed to increase in value by 86 percent to $14.4 billion.
Despite dropping in value by 8 percent since 2013, IBM holds onto its fourth position slot, followed by Microsoft whose 5 percent boost sees it hanging onto its position from the previous year. Samsung's success with the likes of the Galaxy Note and S5 pushed its value up 15 percent to $45.4 billion. Intel will be disappointed to find that a drop in value of 8 percent (continuing the previous year's 5 percent drop) to $34 billion sees it slipping out of the top ten into twelfth place.
Looking further down the list, Amazon is to be found at 15, enjoying a 25 percent increase in value and jumping up four slots from 2013. eBay continues to increase in value, raising by 9 percent to $14.3 billion, but remain at position 28. The growing importance of Chinese brands -- particularly when it comes to smartphones -- is shown by Huawei's entry into the top 100, making its first appearance at slot 94 with a value of $4.3 billion. Fortunes are less favorable for Nokia which continues to plummet in value losing 44 percent of its value (following a 65 percent drop last year) and sliding from 57 to 98 in the chart.
Photo credit: Everything / Shutterstock
-

UK crime chief wants even more powers to snoop NSA-style
Publié: octobre 9, 2014, 1:49am CEST par Mark Wilson

It has been said that we are living in a post-NSA world. What this really amounts to is that we are now slightly more aware of the level of snooping that has been going on in the background for many years. There has been widespread outrage at the revelations made by Edward Snowden, and there have been similar concerns raised outside of the US. In the UK, the FBI-like National Crime Agency, wants greater powers to monitor emails and phone calls -- and it wants the public to agree to this.
Director General of the NCA, Keith Bristow, spoke with the Guardian and said that the biggest threats to public safety are to be found online. He said that more powers to monitor online data is needed, and suggested that public resistance to this was down to the fact that he had thus far failed to properly explain why such powers are needed.
Bristow seems to be under the impression that if he takes the time to explain why he and his agency need greater powers of surveillance it will be possible to "win public consent" for such powers. On the face of it, this sounds rather more transparent than the beyond-the-scenes surveillance that has been carried out by the NSA, but can it really mean "open" monitoring? The NCS's "snoopers' charter" is unpopular -- there is possibly even less public support for it than there has been for the NSA's activities.
The agency head explains that the public must "consent to losing some freedoms in return for greater safety and security". Of course, it is extremely unlikely that there would be a public vote on whether or not additional monitoring powers should be enforced -- it's just not the sort of things on which there is public consultation. Of course, with the general election just around the corner in May, this is the sort of thing that is likely to feature on the manifestos that are trumpeted over the coming months.
Bristow says that "if we seek to operate outside of what the public consent to, that, for me, by definition, is not policing by consent. The consent is expressed through legislation". It goes without saying that the public has little if any sway in deciding what legislation is put in place, but individual political parties could use the weight of public opinion about privacy and online surveillance to win a few votes. Striking the balance between policing the internet in the interest of public safety, and maintaining the level of privacy that internet users reasonably expect is a tricky one.
But with surveillance now in the public consciousness more than ever before, Bristow and the NCA will have an uphill battle to convince people that indiscriminate mass monitoring is in their interest. Fighting terrorism, paedophiles, organized crime and the like may be valid arguments to some extent, but they certainly aren’t going to win over everyone. And if these problems are seen as sufficiently great to consider mass surveillance programs, it's difficult to see how public opinion will have much bearing on what happens. The idea of watching the many to catch the few -- which many have interpreted as implying everyone is assumed guilty until proven otherwise -- is only going to hold up for so long, no matter how well or how many times it is explained.
Photo credit: Mega Pixel / Shutterstock
-

Microsoft signs pledge to protect student privacy
Publié: octobre 7, 2014, 8:19pm CEST par Mark Wilson

There are few companies who fail to find themselves under the privacy microscope at some point, but Microsoft is one that is the center of attention more than many. Whilst taking steps to allay fear about a keylogger in Windows 10, the company has signed the Student Privacy Pledge, joining big names from the world of education such as Follett, Learnmetrics, and Knovation. The pledge means that Microsoft will use personal information about students to help better tailor learning packages, but it won't be used for advertising, or sold to third parties.
Anthony Salcito, Microsoft's Vice President for Worldwide Education, announced the move at the Future of Privacy Forum (FPF) and the Software & Information Industry Association (SIIA) launched the pledge to help protect students.
Salcito explains:
Student data should be used to improve education and help kids learn, not for other commercial purposes, like targeting kids with advertising. We’re proud to be among the companies announcing today a clear and public commitment to protect the privacy and security of information about school children.
The use of technology in the classroom is something that has been broadly welcomed, as has input and financial support from the likes of Microsoft. But privacy concerns always go hand in hand with any use of technology, particularly when children are involved. Even something as simple as using email to communicate information to or about students is something that is fraught with privacy concerns.
The pledge means that those who sign up to it will:
- Not sell student information
- Not behaviorally target advertising
- Use data for authorized education purposes only
- Not change privacy policies without notice and choice
- Enforce strict limits on data retention
- Support parental access to, and correction of errors in, their children’s information
- Provide comprehensive security standards
- Be transparent about collection and use of data
It already has the backing of not only big-name companies, but also politicians and schools around the US. Mark Schneiderman, senior director of education policy at SIIA, said: "We introduce this Pledge as a clear industry commitment to safeguard the privacy and security of all student personal information. Current law provides extensive restrictions on the use of student information, and this industry pledge will build on and detail that protection to promote even greater confidence in the appropriate use of student data".
Photo credit: racorn / Shutterstock
-

Untwist your panties -- Windows 10's 'keylogger' is nothing to worry about
Publié: octobre 7, 2014, 6:18pm CEST par Mark Wilson

As we all know, Windows 10 Technical Preview is out there and ready for anyone with the time and inclination to try out. Much has been made of the return of the Start menu as well as the new features such as virtual desktops, but over the last couple of days the rumor grapevine has been working overtime.
The big news is that Windows 10 includes a keylogger so that Microsoft can spy on your every action, tracking your every keystroke as you enter usernames, passwords, and bank details. Well, that's not strictly true... despite what some sites would have you believe. So, what then? Windows 10 doesn't include a keylogger? It's not quite that simple.
Check out the Privacy Statements for Windows Technical Preview and you'll see that Microsoft is very upfront about what is going on. Just read the two opening sentences: "Thank you for choosing to participate in the pre-release program for our next version of Windows! The purpose of the program is to enable you to provide usage data and feedback to Microsoft while trying out Microsoft’s pre-release software and services".
So right from the start it is made clear that by using the Technical Preview you'll be providing Microsoft with usage data. But just what does this mean? Handily enough, the privacy statements page breaks it down for us:
- install the Program, we may collect information about your device and applications and use it for purposes such as determining or improving compatibility,
- use voice input features like speech-to-text, we may collect voice information and use it for purposes such as improving speech processing,
- open a file, we may collect information about the file, the application used to open the file, and how long it takes any use it for purposes such as improving performance, or
- enter text, we may collect typed characters and use them for purposes such as improving autocomplete and spellcheck features.
Hold on a minute! What's that last one? "We may collect typed characters"? This is the clause that has upset a lot of people who interpret this as an admission that there is a keylogger built in to Windows 10. We're getting into semantics here, but Windows 10 does not include a keylogger -- at least not in the traditional sense of the word. Microsoft is very open about the fact that data will be collected. It’s very much the point of the preview, after all. Despite my 'meh' reaction to Windows 10 Technical Preview, it's important to remember a few things.
To start with, this is not even a beta release. The preview exists so that Microsoft can not only showcase what's coming up, but also so real-world usage scenarios can be tested. To do this, Microsoft needs data -- lots of data. You might think it unreasonable that Microsoft should collect data entered via the keyboard, but in taking part in the preview program, this is what you have signed up for. Even before downloading the Technical Preview, Microsoft suggests that you "see our privacy statement to learn how we will collect data about your installation and use of the preview to help us improve our products and services".
It's made clear that this is a preview that's suitable if "you're a PC expert or an IT pro" -- it is not something for everyone. Microsoft also points out that you should only be using the TP (oh yes) if you "aren't installing it on your everyday computer". If you fall into these camps, you really should be aware of what a keylogger is, and how you should approach and use pre-release software like this.
How many keyloggers include a description of how collected data will be used? "Microsoft uses data we collect from the Program to operate, improve and personalize the Program and other Microsoft products and services. Some data is stored on your device and some data is transmitted to Microsoft. Microsoft shares some data with our partners to improve how their products and services work with Microsoft’s products and services. We use your contact information to communicate with you, for example, to inform you about the Program, updates, and related products and services. We use information about your preferences to configure Program features. For example, we use information we learn about your interests to help make the ads we show you more relevant, and we use your voice data to improve speech recognition".
The suggestion implicit in referring to a keylogger in Windows 10 is that Microsoft is being underhand. It absolutely is not. Data collection is made explicitly clear right from the beginning. If you've approached the Technical Preview correctly you would be well aware of the logging -- the recent headlines will not have been news. Complaints come from people who do not read small print -- although here it is not "small print", what is going on is made abundantly clear from the very start.
We contacted Microsoft for further clarification about how data is collected and a spokesperson said:
With Windows 10, we’re kicking off the largest ever open collaborative development effort that will change the way we build and deliver Windows. Users who join the Windows Insider Program and opt-in to the Windows 10 Technical Preview are choosing to provide data and feedback that will help shape the best Windows experience for our customers. As always, we remain committed to helping protect our customers’ personal information and ensuring safeguards are in place for the collection and storing of that data. As we get closer to a final product, we will continue to share information through our terms of service and privacy statement about how customer data is collected and used, as well as what choices and controls are available.
Remember, this is Microsoft. It's one of the biggest companies in the world, with millions of pairs of eyes watching its every move -- many of them connected to people ready to pounce the moment a foot is placed out of line. There is nothing untoward going on here. Data collection is to be expected, it is necessary. Microsoft is under far too much scrutiny for even consider misusing collected data in any way, despite what some people have suggested.
I'm all for laying into Microsoft -- but only when it's justified. Cut the company some slack. Move on... there's nothing to see here.
Photo credit: Sergey Nivens / Shutterstock
-

Right to Be Forgotten hits social networks hardest [Infographic]
Publié: octobre 7, 2014, 3:00pm CEST par Mark Wilson

The "right to be forgotten" is something that was expected to take Europe by storm. A court ruling gave people the right to get in touch with search engines like Google and Bing to ask that results relating to them be removed -- assuming they are "inadequate, irrelevant or no longer relevant". One of the services that popped up after the ruling was Forget.me, making it simple to submit removal requests.
Three months down the line, we have access to the first set of figures relating to requests, and they show that social networks are the most affected type of website.
Looking at more than 10,000 removal requests, more than a fifth of the URLs that people have complained about have been on social networks. 21.3 percent of complaints relate to Facebook, Google, YouTube, Twitter, and LinkedIn, but just 8.4 percent of these complaints resulted in a URL being delisted. There were a very small number of complaints about Wikipedia -- just 20 in fact -- and none of them were upheld.
The infographic from Reputation VIP below also shows how press websites and blogs got off very lightly.
-

Microsoft reveals new, cheaper Office 365 subscriptions for SMBs
Publié: octobre 7, 2014, 12:20pm CEST par Mark Wilson

Microsoft is introducing new, cheaper Office 365 subscriptions to businesses in a bid to encourage small businesses into using its office suite. The cost of an Office 365 Personal subscription remains at $6.99 but small to medium-sized businesses -- those with fewer than 300 employees -- are now able to snap up a subscription for just $5 per user per month (which doesn’t match the $1 offer from GoDaddy).
Before you get too excited about this, there is something of a catch. Firstly, there is a commitment to subscribe for a year, and the cheapest package, Office 365 Business Essentials, does not allow for Office's apps -- Word, Excel, PowerPoint, and so on -- to be installed. Opt for the cheap subscription and you're stuck with Office Online.
The subscription still includes 1TB of storage, and 50GB inboxes, but smartphone and tablet versions of the suite are also eschewed at this price. If the idea of signing up for an entire year seems like too much, a monthly, rolling subscription costs $6 per user per month. For businesses willing to pay a little more -- but, again, commit to a year-long subscription -- there is Office 365 Business. For $8.25 you get what most users would expect -- a fully installable version of Office 365 that each user can install on up to five PCs or Macs.
This subscription also provides access to the tablet and smartphone versions of Office, but it does drop a couple of features. Gone are the 50GB inboxes, online meetings, and social networking feature. There is a free trial available, and to drop the annual commitment, the price jumps to $10 per month. Rounding off the new selection of subscriptions is Office 365 Business Premium which costs $12.50 per user per month with an annual commitment, or $15 for businesses who prefer to take things on a month-to-month basis. This most expensive package combines all of the elements of the Business Essentials and Business.
The switch in focus on online-only tools at the cheaper end of the market is an interesting move, perhaps aimed directly at taking on Google Docs. All three new packages recognize the fact that employees work on multiple devices, and Microsoft has taken steps to provide a cross-device Office at an accessible price. Check out the details at the Office 365 for Business page.
-

HP to split into Consumer HP and Enterprise HP
Publié: octobre 5, 2014, 10:15pm CEST par Mark Wilson

HP is on the verge of splitting into two companies. Consumer HP will focus on personal computers and printers, while Enterprise HP's focus will be corporate services and hardware. It's a move that has been talked about for some time now, and it comes just days after eBay Inc revealed that it plans to separate its eBay and PayPal businesses. HP and its investors will be pinning their hopes on the companies performing better as separate entities than as a whole. Similar splits have proved successful as it allows for a more efficient management of resources and a better concentration of efforts.
As part of the split, current CEO Meg Whitman will become chairman of Consumer HP, as well as CEO of Enterprise HP. Consumer HP will gain Dion Weisler as its CEO, while director Patricia Russo will step into the role of chairman of Enterprise HP. Whitman has been widely credited with turning around the fortunes of HP, so all eyes will be on her to see if this latest move proves fruitful.
As reported by the Wall Street Journal, HP talked about the possibility of a division back in 2011, but this amounted to nothing. Following the departure of Chief Executive Léo Apotheker it was decided to keep the business running as a single unit, and a restructuring operation followed in 2012. The company remains one of the biggest shippers of PCs, second only to Lenovo.
HP had previously been expected to ditch its consumer arm to focus on the generally more profitable enterprise business. It remains to be seen whether the previous amalgamation of the money-making printer division with the less profitable PC side of the business manages to hold its own as Consumer HP. Shareholders had previously expressed reluctance to accept a switch to focusing on enterprise ventures, so keeping both sides of HP operational is clearly a bid to keep as many people happy as possible, whilst simultaneously propelling the company forward.
Photo credit: Dragan Jovanovic / Shutterstock
-

HP to split into HP Inc and Hewlett-Packard Enterprise
Publié: octobre 5, 2014, 10:15pm CEST par Mark Wilson

HP is on the verge of splitting into two companies. Consumer HP (or plain HP Inc) will focus on personal computers and printers, while the focus of Enterprise HP (or Hewlett-Packard Enterprise) will be corporate services and hardware. It's a move that has been talked about for some time now, and it comes just days after eBay Inc revealed that it plans to separate its eBay and PayPal businesses. HP and its investors will be pinning their hopes on the companies performing better as separate entities than as a whole. Similar splits have proved successful as it allows for a more efficient management of resources and a better concentration of efforts.
As part of the split, current CEO Meg Whitman will become chairman of HP Inc, as well as CEO of Hewlett-Packard Enterprise. HP Inc will gain Dion Weisler as its CEO, while director Patricia Russo will step into the role of chairman of Hewlett-Packard Enterprise. Whitman has been widely credited with turning around the fortunes of HP, so all eyes will be on her to see if this latest move proves fruitful.
As reported by the Wall Street Journal, HP talked about the possibility of a division back in 2011, but this amounted to nothing. Following the departure of Chief Executive Léo Apotheker it was decided to keep the business running as a single unit, and a restructuring operation followed in 2012. The company remains one of the biggest shippers of PCs, second only to Lenovo.
HP had previously been expected to ditch its consumer arm to focus on the generally more profitable enterprise business. It remains to be seen whether the previous amalgamation of the money-making printer division with the less profitable PC side of the business manages to hold its own as HP Inc. Shareholders had previously expressed reluctance to accept a switch to focusing on enterprise ventures, so keeping both sides of HP operational is clearly a bid to keep as many people happy as possible, whilst simultaneously propelling the company forward.
Photo credit: Dragan Jovanovic / Shutterstock
-

The curmudgeon's guide to Microsoft's embryonic Windows 10
Publié: octobre 4, 2014, 11:16pm CEST par Mark Wilson

It's only a matter of days since Microsoft officially revealed the Windows 10 Technical Preview. This was a revelation with a lot riding on it but it was really something of a tease -- Microsoft didn’t give too much away. We rushed to grab the download, and Wayne showed how to get it up and running in VirtualBox (interestingly, I had to opt for VMware Player, as VirtualBox refused to install the 64-bit version of Windows 10 on my Surface Pro. It ran away from the ISO as though it was infected with ebola). I've had a few days to play about with this release -- I've stuck with a virtual machine for now rather than going all-in with dual-boot -- and I've already had a chance to write a little about the Start menu and the command prompt, but now it's time to delve a little deeper and see what else there is to discover.
Spoiler alert: despite the headline, and indeed my reputation, I don’t hate Windows 10. It just about goes without saying that I'm not head-over-heels in love with it, and there's a great deal I dislike about it, but it does feel... well, just 'nice' really. It's comfortable, familiar, and feels a bit snappier than Windows 8 -- even when running in a virtual machine.
Start as you mean to go on
There's no getting away from the fact that the most immediate and noticeable change in Windows 10 is the Start menu. The Start screen now takes more of a backseat by default and it has been replaced with a somewhat familiar Start menu. As this is one of the first things encountered, it seems like a sensible place to start. If you were hoping for a return to the Start menu of yore, prepare to be disappointed. Rather than reinstating the Start menu from Windows 7, Microsoft has instead created a bizarre amalgam of the Start screen and Start menu. It's a Start menu with Live Tiles. To many people this simply is not going to make sense. The right hand port of the Start menu looks just like a miniature version of the Start screen.
It is possible to remove the right hand section that is populated with Live Tiles to produce something that looks more like the Start menu of old. But don’t be fooled; this is not what it appears. Gone (still) are the fly-out menus that made the Start menu so quick and easy to navigate, replaced instead by a version that re-uses space. You're initially presented with a list of recently used apps, and when you click All Apps (yep -- it's Apps, regardless of modern or desktop status), this list is replaced by the folders of the Start menu. Submenu (like Start All > Apps > Microsoft Office 2013) still don't fly out, but expand in place.
This might seem like a sensible use of space, there is a serious downside. Should you accidentally select the wrong folder, you then need to use the scrollbar (a scrollbar in the Start menu?) to access the right one. It all just seems awkward and I sincerely hope that there are some improvements made here.
Edit: Comments have questioned my references to fly-out menus. Readers have correctly pointed out that these were also not present in Windows 7 -- well... not quite, at least. I blame a slightly failing memeory and the fact that I tweaked my Windows 7 Start menu to display elements such as Control Panel, My Documents, etc as menus rather than links. Excuses aside, I stand by my ascertion that the Start menu is awkward, clumsy, and will fail to please many of those who missed it so desperately in Windows 8.
One of the finest new additions to the Start menu is the permanent power buttons. It’s now much easier and natural to restart and shut down. But overall, the Start menu disappoints, and this sets something of a trend for Windows 10.
More new features
I've already talked about the Command Prompt where there are number of 'experimental' features to play with. It's interesting that such an old feature of Windows is not only still present, but that it has received such attention. With the ability to copy and paste, new window resizing and transparency options, and more besides, it could almost be argued that the Command Prompt has been given more of a makeover than the Start menu. More Microsoft weirdness.
Talking of weirdness, let's look in the taskbar. Next to the Start button, there are two new buttons, the first of which features a magnifying glass. No prizes for guessing that this is a search tool. A dedicated search button. In the taskbar. Forget the fact that whether you are using the Start screen or the Start menu and you could just hit the Windows keys to 'Search everywhere', Microsoft felt the need to add another way to access search. One that is not only right next to the Start button but also cannot be removed or even moved. Don’t like the search button? Tough. You're stuck with it. It will just sit there, glaring at you as it wastes space.
Close, but no cigar
Of slightly more use is the Task View button. On the face of it this is little more than an Alt-tab style task switcher (which it is), but it also gives you access to one of the biggest features of Windows 10 -- virtual desktops.
Virtual desktops have been around for a long time as third party add-ons for Windows, and Microsoft has finally cottoned on to the idea that people find them useful. So now you can set up one desktop for folders and another for apps. Or you can set one for personal and one for business. And so on. At this stage, it's a basic tool. Switching between desktops is a little awkward. You can use keyboard shortcuts or the dedicated Task View button. But there's no overview icon visible at all times that lets you know how many desktops you've set up, or lets you quickly jump to a particular desktop that houses a particular window. It feels like a token effort. Microsoft decided the virtual desktops were needed. Bugger it… that'll do.
Cleaning windows
It looks as if Windows 10 borrows from OS X in a number of areas. This is no bad thing, and contributes partly to the operating system feeling just that little bit nicer than Windows 8 -- although it's hard to say just why it does. Little touches such as tweaks to window shadows, coupled with a slightly more muted palette, give a more professional look to things.
Managing the arrangement of windows has been made a little easier with simple changes to snapping. The screen is now divided up in to four quadrants rather than the previous two panes and this is something that will prove particularly useful on larger monitors.
I've made no secret of the fact that I'm not a fan of Modern apps. I hate, loathe, detest, and abhor them. But if you do feel inclined to use them -- and the Store app is one that just about everyone will have to visit at some point -- there is a slightly less jarring experience. Modern apps can be run in windowed mode, expanding on the ideas brought into Windows 8.1 Update, and allowing for windows to be resized just like any other. A small touch, but one that is likely to please.
Redefined direction
The decision to put such a focus on the touch capabilities of Windows 8 was a mistake. While touch devices are increasingly popular, non-touch computers are still very much the norm. In bringing the desktop back into sharper focus, we see Microsoft admitting that it jumped the gun and tried to push users into a new way of working too quickly. But if Windows 8 was too much of a departure from the norm, Windows 10 sees Microsoft treading water. Yes, this is an early build, but we can’t pretend that Microsoft hasn’t been working on this for quite some time. The company knows that people are expecting something great and, at the moment, Windows 10 is not great. It's OK, but it's certainly not great.
It's fair to say that Microsoft is pitching Windows 10 at Windows 7 users who did not see the point in jumping to Windows 8. Despite protestations to the contrary, this is not a ground-breaking operating system. It's better than Windows 8.x, that's for sure, and there is rather less of jarring jump for anyone who is making the move from Windows 7. It is difficult to understand quite why the Windows 9 moniker was skipped. The decision to just miss out a version number is obviously going to raise questions, and Microsoft has itself implied that this is just too big a release to have a single digital number increase. Is this justified? At this stage, it's a resounding no. There's nothing particularly wrong with Windows 10, but it's not mind-blowing by any stretch of the imagination.
Rather than wheeling in a raft of new features, Microsoft has chosen to focus on making refinements to what was already there while ushering in a couple of headline-grabbers. Far from justifying a jump from Windows 8.1 to Windows 10 as a name, what we seeing at the moment would just about warrant being called Windows 8.2 or Windows 8.1 Update 2. There have been suggestions that the version number came about simply because of potential confusion if other software performs a search for Windows 9*, but this could almost certainly have been worked around.
Of course the comeback to any criticism levelled at Windows 10 is that it is the Technical Preview. Windows 10 will not be released until the second half of 2015, which means we could still have a year to wait -- and an awful lot can happen in 12 months. We're already at build number 9841, and it's fairly safe to assume that we're working up to 10,000 to be the final build. Considering Windows 8.1 Update is build number 9600, we've already jumped 241 to get to where we are with the Technical Preview. If 10,000 is the gold number for the Windows 10 gold master, there are only another 159 builds to go. Considering how little has been achieved so far, it's unlikely there will be any major surprises pulled out of the bag.
Baby steps
But Windows 10 is undoubtedly an improvement over Windows 8.x. In many ways it could, maybe should, be seen as what Windows 8 should have been -- or at least what one of the updates should have made it. As there are definite improvements over both Windows 7 and Windows 8, it's difficult to be too hard on what we find in Windows 10 at this stage, but feelings of disappointment and being underwhelmed abound. A switch in focus to the desktop is very welcome, but after spending a few days working with Windows 10, I can't help but feel it's nothing more than a bit of spit and polish, with an element of style over substance thrown in for good measure.
There is no hint of how this will translate into a cross-device operating system. It has been suggested that Windows 10 will be the OS for desktop, laptop, touch, mobile, and console. For now it feels very much like a desktop operating system and it's difficult to see many changes that will be of interest to users of touch driven computers.
It seems obvious to say that this feels like a work in progress, but Microsoft took the decision to make this release public. Considering the number of complaints there have been about Windows 8, we really should have come further by now. Microsoft has had a long time to work on the successor to Windows 8, and this is what it has come up with; it's disappointing to say the least. We need to see a lot of progress over the coming year -- which will require a massive acceleration in development based on what we've seen so far -- or Windows 10 will fall just as flat as Windows 8, and that would be a huge shame.
-

Keyboard aficionados gain a smattering of new shortcuts in Windows 10
Publié: octobre 4, 2014, 6:13pm CEST par Mark Wilson

While Windows 8 tried to switch the focus to touch input, Windows 10 Technical Preview finds Microsoft seeing sense and realizing that most people still labor away with a mouse and keyboard. Diehard keyboard fans are always keen to learn the latest shortcuts, and the same will be true of Windows 10. We've already seen how Ctrl+C and Ctrl+V can be used to copy and paste at the Command Prompt, but there are a few other new shortcuts to learn. These are largely limited to the new features of Windows 10, and as these are slightly thin on the ground, it's little wonder that there aren’t all that many new keyboard shortcuts to add to your repertoire.
In a post on the Windows blog, Microsoft's Senior Marketing Communications Manager and Chief Windows blogger, Brandon LeBlanc reveals a small number of new shortcuts. While there are -- at this stage at least, very few new keyboard shortcuts, many of them are repurposed from previous versions of Windows anyway, while some are reinstated having been lost in Windows 8.
The existing Windows key + direction arrows shortcut has been expanded so that in addition to left and right snapping, the Up and Down buttons can also be used to snap to upper quadrants of the screen. Alt + Tab is singled out, but while it has been redesigned slightly it functions in much the same way as before. Windows 8 users who missed the Windows key + tab keyboard shortcut will be pleased to find that it makes a return. Hit this keyboard combo to call up the task switcher for accessing not only applications and windows, but also virtual desktops.
Speaking of virtual desktops, you can create a new one by hitting Windows key + Ctrl + D, while a swift hammer blow of death can be dealt with a tap of Windows key + Ctrl + F4. For simple navigation between running virtual desktops, Windows key + Ctrl and the direct keys is the combo you need. If you are taken by the new command prompt, Scott Hanselman has a posted a list of all of the new keyboard shortcuts you can use.
Photo credit: Radu Bercan / Shutterstock
-

In a terrifying future, Facebook could venture into healthcare
Publié: octobre 3, 2014, 8:57pm CEST par Mark Wilson

Facebook gets bashed about privacy concerns, its real name policy, and the proliferation of ads that litter the social network. It's easy to complain about who has access to your photos and status updates, but how would you feel about handing over your private health details to Zuckerberg's baby?
In a move that will strike fear into users of the social network, Facebook is apparently considering branching out into healthcare by providing what are being described as "support communities". The news comes from Reuters which quotes three sources who requested anonymity.
Turning healthcare into a product would be an interesting move for Facebook, and it's one that is likely to get a mixed reception. On one hand the idea of support communities in which sufferers are able to connect with others in a similar position seems like it could be extremely useful. But on the other, Facebook's checkered privacy history means that many people whom the services might be aimed at would think twice, nay thrice, before handing over even more personal information than they already have.
Would-be users of such a service may have fears calmed slightly by Facebook's very recent softening of its real names policy, but there is a big difference between Facebook-run support pages, and the user-run pages that currently exist. The anonymous source suggests that in addition to the support communities, Facebook is also interested in helping people to improve their lifestyle through "preventative care" applications. If this comes to fruition, the privacy and sharing features of such applications will be what makes or breaks the idea. When it comes to healthcare, privacy is of the utmost importance, and there would be obvious concerns about the influence advertisers could have, and the access they might be given to information.
One possible reason for Facebook's apparent sudden interest in healthcare is the surge in organ donation registrations that followed an initiative back in 2012. Facebook's "organ-donor status" program saw organ donor registration soar by 21 times the usual numbers. Facebook has refused to comment on its future plans, it is not clear whether future health services would be a feature of the Facebook website, or would appear under a completely different name -- much like Instagram. But the real clincher is likely to be the policy adopted with regard to anonymity. Just as the sources for the Reuters' story requested that their names be withheld, people looking for information and support with serious conditions are likely to want the assurance of being able to use a pseudonym to protect their identity.
Photo Credit: Gajus / Shutterstock
-

Windows 10: Command Prompt's experimental new features are genuinely useful
Publié: octobre 3, 2014, 5:49pm CEST par Mark Wilson
With the release of Windows 10 Technical Preview you would think that the time would be to look forward rather than backwards. It's a time to embrace the new and exciting, but it's hard not to look back and draw comparisons.
With Windows 10, initial impressions suggest that there may not really have been a need to skip over Windows 9 -- there are no massive surprises to be found. But there are some interesting changes to be discovered in the most surprising of places. In looking backwards, it's hard not to bring MS-DOS to mind, along with its slightly more modern version, the Command Prompt. Forget the redesigned Start menu, virtual desktops and everything else, the Command Prompt is where it's all happening, kids!
Fire up the Command Prompt in Windows 8 (hit the Windows key and R, and then type cmd before pressing Enter), and you'll find that the window remains stubbornly resistant to resizing. The width of the window can be reduced, but there's no way to make it wider. Even if you maximize the window, you're left with a stupidly narrow workspace. This changes in Windows 10. At long last it is possible to resize the Command Prompt window just like any other -- very handy for when you're typing out lengthy commands.
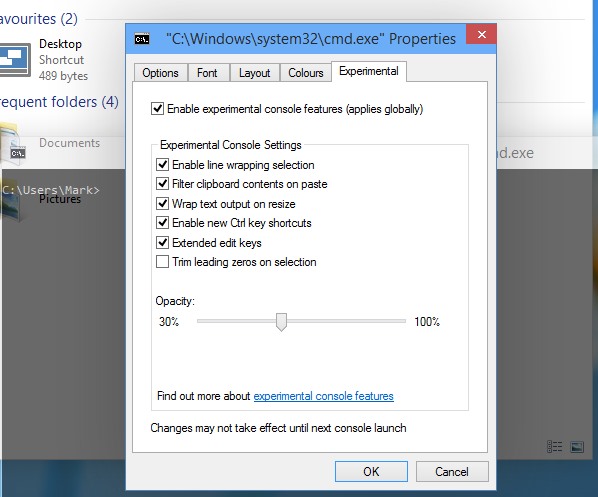
Copying and pasting is one of the most basic functions of an operating system, but it's something that has not been supported by the command prompt. If you've found a lengthy command online that you want to try, using Ctrl+C followed by Ctrl+V seems like the sensible thing to do. In Windows 8, rather than giving you the desired command, you'll find that this simply results in ^V appearing at the Command Prompt. In Windows 10, you can copy and paste just like you would with other apps. It just works as it should do. Typos should be all but eliminated!
There's another interesting feature to experiment with -- and, appropriately enough, it can be found in the Experimental settings section. You can adjust the transparency of the Command Prompt window. Right-click the Command Prompt window's title bar, select Properties, and then move to the Experimental tab. Move the Opacity slider to the left to increase the transparency level, and hit OK to apply the setting. This new option provides a handy way of keeping an eye on what’s going on in the background without having to keep minimizing the windows -- and it's especially useful when you've enlarged the Command Prompt window.
Presumably these features are only classed as "experimental" during the Technical Preview phase, so we'll have to see how many of them make it into the final build, and where they will be accessed. With a new windows transparency setting, it will also be interesting to see if Microsoft decides to make this option available to other applications.
Photo credit: Sergii Korolko / Shutterstock
-

Kill the Start menu and get the Start screen back in Windows 10
Publié: octobre 3, 2014, 2:43pm CEST par Mark Wilson
Since the arrival of Windows 8 there has been a lot of huffing and puffing about the Start screen. Some people love it, but a lot of people yearn for the return of the Start menu. With Windows 10, this is now a reality. If you grab yourself a copy of the Technical Preview you can experience the all-new Start menu for yourself, but you may find that it's not for you.
If you find that you actually miss the Start screen from Windows 8, it's very easy to get it back -- you just need to know where to look.
Getting what you ask for doesn’t always work out as expected, and the new implementation of the Start menu may just not be for you. To get things back to the way they were in Windows 8.x, right-click an empty section of the taskbar and select Properties.
Move to the Start Menu tab and uncheck the box at the top of the window that's labeled "Use the Start menu instead of the Start screen".
Click OK and you'll be prompted to log out of your account to put the new setting in place. Make sure that you've saved any open documents and hit the "Sign out and change settings" button.
When you next sign into your account, you'll be taken to the desktop just as before, but when you hit the Start button, it's the Start screen that will appear rather than the Start menu. Just as in Windows 8.1, you can opt to boot straight to the Start screen if you prefer.
Right-click the taskbar and select Properties before jumping to the Navigation tab. Uncheck the box labeled "When I sign in or close all applications on a screen, go to the desktop instead of Start" and then hit OK.
Job done... Windows 10 in Windows 8 mode!
-

Ransomware is an increasing security concern for IT professionals
Publié: octobre 3, 2014, 12:09pm CEST par Mark Wilson

Ransomware is an increasing security concern for IT professionals
There are always plenty of security concerns causing furrowed brows of IT professionals, but a survey shows that it is ransomware that is causing the biggest headaches at the moment. A survey carried out by Spiceworks and published by Webroot found that 88 percent of professionals had concerns about ransomware, while one third of those questioned had dealt with a ransomware attack first hand. By far the most common strategy for dealing with a device that has been maliciously encrypted is to simply wipe it.
Two-thirds expect the number of attacks to increase in the next year which is particularly concerning when you consider that two thirds of IT professionals know someone who has been affected by ransomware. Despite the threat and attempts to thwart the flow of ransomware with filtering, firewalls, and email scanning, just 44 percent believe their current security set up is "somewhat effective".
Faced with a device that is encrypted by malware and held to ransom, 9 percent of those surveyed would attempt to crack the encryption themselves, while 22 percent would call in encryption experts. The importance of backing up does not seem to have filtered through to the hundreds of people questioned by Spiceworks; while 82 percent of IT professional affected by ransomware would wipe the device in question, just 19 percent would restore data from a backup.
It should come as no surprise that the internet is one of the most common sources of this type of malware, but email and social networks also feature high on the list. A worryingly small 31 percent of IT admins have a specific strategy in place for dealing with ransomware attacks.
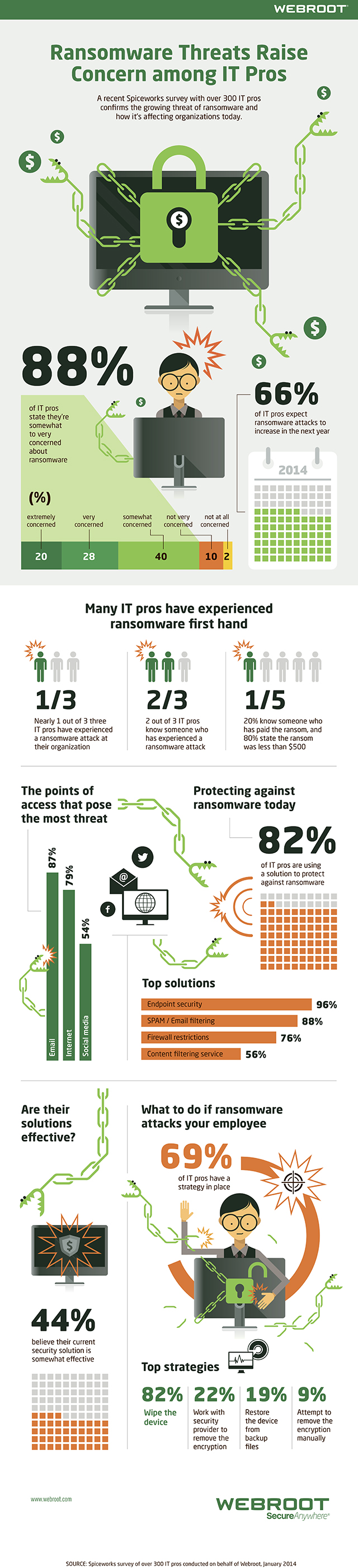
-

UK phone booths become free solar-powered mobile phone chargers
Publié: octobre 3, 2014, 6:14am CEST par Mark Wilson

The red telephone booth is one of the most enduring icons of the UK; but as delightful as their housings may be, the humble payphone has had its day. Coin and card-fed phones are on the verge of being consigned to the history books, while the mobile phone goes from strength to strength. But mobile phones, for all their strength in portability, coverage, and flexibility, have their kryptonite: battery life. In keeping with the environmentally-friendly preference for recycling and reusing rather than trashing, unused phone boxes are being given a new lease on life.
Should you find yourself wandering down London's Tottenham Court Road and notice that your battery is getting a little low, there's a green solution popping up. Phone booths that would have otherwise be left to rack and ruin are being converted into solar-powered charging stations that can be used completely free of charge.
Within the newly-painted boxes -- now a lurid green -- are a series of adaptors to suit a variety of different phones. If your handset needs a boost, just wander in, plug in, and charge up. Few people would be foolish enough to walk away from their phone while they charge, so the company behind the venture, Solarbox, has something of a captive audience to whom to show adverts on a vandal-proof tablet. Advertising comes from the likes of Tinder and Uber, but nearly a third of ad space is reserved for local community projects.
For now there is a single solar-powered phonebox, but more are planned. Five more are currently due to open, with number two expected to be unveiled in January.
Photo credit: Tupungato / Shutterstock
-

Facebook admits it screwed up, but its proposed research guidelines are meaningless
Publié: octobre 3, 2014, 3:49am CEST par Mark Wilson

Facebook is no stranger to controversy, nor is the social network unfamiliar with upsetting its users. It seems as though Zuckerberg's baby has been hitting the headlines for all the wrong reasons lately, and it's not all that long since users vented their fury after it was revealed that their newsfeeds had been manipulated in the name of research. Now the social network says that it was "unprepared for the reaction the paper received when it was published and have taken to heart the comments and criticism" and is now implementing new user research guidelines.
"There are things we should have done differently" may seem like something of a half-hearted admission that mistakes were made, but it's the second semi-apology from Facebook this week. Research into how people use the social network will still continue, but Facebook now says "we want to do it in the most responsible way." So what does this actually mean?
On the face of it, very little. Although Facebook's Chief Technology Officer, Mike Schroepfer, says that researchers will be given clearer guidelines, details are very thin on the ground. There is a promise that any research that involves looking at "deeply personal" content, or includes the study of particular groups of people, then there will be "an enhanced review process before research can begin". There is absolutely no explanation of what this means, no details of what review process -- if any -- has been used up until now, and who will be responsible for conducting the review. A "panel" has been set up to oversee things, but we don’t know whether it is independent, whether its members were elected to post, and so on.
Facebook also promises that its six-week boot camp program will include education about research practices, but without details this is hollow and meaningless. Research will be published online, but one thing is not made clear -- whether users chosen to take part in research will be notified. It's not clear whether users are able to opt out of research, or if individuals are able to request details of the information that has been gathered about them; this in spite of a general trend for web-based firms to become more transparent.
Schroepfer's post ends with the words, "we want to do this research in a way that honors the trust you put in us by using Facebook every day. We will continue to learn and improve as we work toward this goal." It seems there is still a lot to learn.
Photo credit: 1000 Words / Shutterstock
-

Facebook rolls out mobile Like button to iOS and Android app developers
Publié: octobre 2, 2014, 10:41pm CEST par Mark Wilson

As any Facebook user knows, 'liking' content online has become almost second nature. Facebook has Likes, Google+ has +1s, and various other variations exist. But it is Facebook's Like button that reigns supreme -- regardless of the privacy concerns it may raise. Today Facebook is expanding its Like feature so that mobile app developers can take advantage of it. Not just content with giving web users the chance to indicate their approval of a particular Facebook post or online article, it is now possible to 'like' any piece of content within a supported app on iOS and Android.
It's a feature that is likely to be picked up very quickly by game developers, so you can expect to see notifications in the near future letting you know that your Facebook friends like level 118 of Candy Crush Saga. The feature was previewed earlier this year, but is now being made available to any developer who wants to use it. Facebook says:
People using a mobile app can directly Like the app's Facebook Page, or any Open Graph object within the app, and share on Facebook. The mobile Like Button works seamlessly with the Facebook account the person is logged into on their device, allowing people to Like any piece of content, while in your native app.
The news comes after Facebook apologized -- sort of -- to LGBT groups for its heavy-handed enforcement of a real name policy, and this is yet another move by the social network that will be met by disdain and rejoicing in just about equal measure. If the suggestion that players may 'like' individual' levels of games seems a little far-fetched, it is precisely what Facebook suggests as a possible use. Developers may, Facebook proposes, want to display a Like button when a certain stage of a game is reached -- essentially giving gamers a means of bragging about their progress.
It's unlikely that we'll see a sudden raft of Like buttons popping up in apps overnight. Facebook points out that developers "will have to submit your implementation for review via the Status and Review tab in the Dev Tool before the Like Button is live in your mobile app".
Photo credit: Happy Art / Shutterstock
-

Facebook apologizes to LGBT community, 'backs down' on real name policy
Publié: octobre 2, 2014, 4:21am CEST par Mark Wilson

Facebook has issued an apology to "drag queens, drag kings", and the LGBT community for forcing users of the social network to reveal their real names or face having their pages suspended. The social network also bowed to pressure, saying that users will not necessarily have to use their real names in rgw future. Chris Cox, Facebook's Chief Product Officer, made a statement in an online post that admits the negative response to the policy "took us off guard". Why the sudden interest in real names? It seems that one person may have been to blame.
Facebook caused something of a storm of controversy recently when it forced many users to reveal their real names. Large groups of people were affected by this, but it was a number of drag artists who were most vocal in their complaints -- numerous petitions and campaigns, including #MyNameIs, started up. While it was drag queens who hit the headlines, Facebook's sudden enforcement of its long-standing real names policy also affected performers such as musicians -- fans and friends were confused when seemingly new people appeared in their friend list. Despite the backlash Facebook faced, the social network stuck to its gun, remaining adamant that the policy was here to stay, and dismissing complaints out of hand.
Cox explains that "an individual" took it upon themselves to report hundreds of Facebook accounts as being fake. Failing to notice the volume of complaints that one person was generating, Facebook dutifully went through its usual protocol of requesting proof of identify from the reported account holders. The statement clarifies that this has been Facebook's policy for the past decade, but in this instance it resulted in alienating huge swathes of users. Cox also goes on to explain that there has never been a 'real name' policy:
Our policy has never been to require everyone on Facebook to use their legal name. The spirit of our policy is that everyone on Facebook uses the authentic name they use in real life.
Sister Roma, one of the account holders affected by the initial clamp-down, is name-checked in the statement. Facebook recognizes that Sister Roma is Sister Roma -- that is how she is known is day to day life, even if that's not her 'real' name.
This policy will remain in place. Cox injects a little spin by saying that the name policy is "part of what made Facebook special in the first place, by differentiating the service from the rest of the internet where pseudonymity, anonymity, or often random names were the social norm" as well as suggesting that it helps to reduce instances of anonymous bullying. There's a promise that improvements will be made to user verification whilst avoiding "opening up Facebook to bad actors".
It remains to be seen how this apology will be taken by those affected, and whether it is seen by the general Facebook populous as going far enough.
-

Microsoft launches Sway -- Office's new idea collection tool
Publié: octobre 1, 2014, 4:06pm CEST par Mark Wilson

Having unveiled Windows 10 yesterday, Microsoft today welcomed a new addition to the fold in the form of Sway. This is the latest member of the Office family and it's being billed as a way to "reimagine how your ideas come to life". What does this actually mean? In many ways, Sway is an extension of OneNote. It's a web-based way to collect content, store images and text, add videos, and generally piece together everything you might need for a presentation, project, or idea. Sway is currently a preview product and, in keeping with Microsoft's "mobile-first, cloud-first world" there's a strong focus on cross-platform compatibility and cross-device syncing.
Sway is an interesting blend of existing Microsoft products, but it also brings in some new ideas. It's integrated with OneDrive, and has the note-taking features of OneNote. The various templates that can be used to present the data that is collected gives it something of a feel of PowerPoint, but it could also be used for very simple planning and project management like a cut-down, accessible version of Microsoft Project. It's all web-based and Microsoft is touting it as a "new way for you to create a beautiful, interactive, web-based expression of your ideas".
Take photos on your phone, combine them with content written on your computer, drag and drop some images into place, embed a YouTube video, pull in content from social network; Sway aims to make it possible to collect together information from as many sources as possible to create a "new type of interactive 'document' that will look great on any screen and can be shared to anyone, as effortlessly as sending a link". There are some sample documents on Sway.com that give you an idea of what can be created, but the easiest way to get a feel for it is to see it in action.
Check out the introductory video and you'll find Microsoft highlights the cross-platform capabilities of Sway:
As we are now becoming increasingly used to, Microsoft is inviting feedback about Sway. In the early stages, it is an invite-only preview -- you can request an invite by heading over to the Sway homepage.
-

WordPress and other CMSs are 'inherently insecure'
Publié: octobre 1, 2014, 12:27pm CEST par Mark Wilson

A large proportion of websites are not standalone sites in their own right, but creations based on CMSs such as Drupal, WordPress, and Joomla. This is particularly true for personal blogs, but using a CMS as the basis for a site has been increasingly popular among larger companies. CMSs are used because they allow for articles to be posted easily, make it simple for multiple people to contribute to a site, and allow for different users to be assigned different access rights. They can also be extended through the use of plugins, but these self-same extensions are also a security disaster waiting to happen.
Security experts High-Tech Bridge frequently discover vulnerabilities in extensions and plugins for popular CMSs. It is standard procedure to notify the developer before going public three weeks after the discovery -- this provides an opportunity for the problems to be fixed without alerting others who might exploit it. High-Tech Bridge CEO, Ilia Kolochenko, says that CMS security issues are nothing new:
"For upwards of a decade the major CMS platforms such as Joomla and WordPress have been deeply researched by both black and white hat hackers. In the early days SQL injections and code execution flaws were commonplace. In fact, around 90 percent of websites were vulnerable to critical-risk attacks permitting to take control over the website remotely within a dozen of minutes".
A great deal of work has been put into ensuring that CMSs are secure out of the box, leading Kolochenko to say, "I would say that a popular CMS, such as WordPress or Joomla may be considered secure in default installation if they are properly configured, don’t have third-party code and are up to date".
But therein lies the rub. Start to add extensions into the mix, and it's a very different story. High Tech Bridge points out that many plugins are written by inexperienced coders who lack the skills to ensure security. Of course, there are very few vanilla CMS installations out there in the wild -- few people are able to find a CMS that offers all they need without a little help from third-parties. The security flaw in plugins can be at least as serious as any that may have existed in the CMSs themselves in the past. "By exploiting XSS and SQLi flaws in the plugins, the attacker can get at the admin password same as if he were exploiting these vulnerabilities in the core code of the web application".
With a staggering 33,621 plugins downloaded a total of 749,138,518 times in the case of WordPress, the impact of exploiting security vulnerabilities could be huge.
Photo credit: Ingvar Bjork / Shutterstock
-

With Windows 10, Microsoft leaves lots of questions unanswered
Publié: octobre 1, 2014, 12:19am CEST par Mark Wilson

So… we now know that Windows 9 is by far the least successful version of Windows ever, grossing Microsoft a total of $0. But Microsoft is as keen as ever to look to the future, and it's pinning its hopes on the newly revealed Windows 10. At the unveiling in San Francisco we learned quite a lot about the upcoming version of the successor to Windows 8.1 (yep... it's going to sound weird for a long time), but there were also a lot of unanswered questions. It was interesting to see that the demonstration used build 9841 which we have already seen in leak, and in this regard there were few surprises. Between the release of Windows 10 Technical Preview Microsoft still has a lot of work to do, and a lot of people to convince to upgrade.
What do we not yet know? We don’t have a release date, at least nothing that has been pinned down. We know it will be some time in the second half of 2015 -- if everything goes to plan -- but that's quite a big Window. We also don’t know what costs, if any, might be associated with the operating system. It has been suggested that Microsoft would make Windows 10 available free of charge, but nothing official has been said on this front. We have no idea what sort of upgrade path may be available -- would this be Microsoft's opportunity to usher everyone away from Windows XP once and for all? Simply offer a free upgrade to an operating system that addresses the issues users have raised and the security problems associated with an ancient version of Windows should diminish.
One of the hardest battles Microsoft has is convincing people that it is worth upgrading. In showcasing the early build, a great deal of emphasis was placed on upgrading from Windows 7 to Windows 10. A lot of Windows 7 users refused to upgrade to Windows 8 because they didn’t like what they saw. At first glance, Windows 10 is very similar to Windows 8. There are certainly differences there, but taken at face value this is Windows 8 with a few tweaks -- there hasn’t even been a new coat of paint. This is in spite of the fact that Microsoft claims the Windows 10 will be "built from the ground-up".
Why built from the ground up? This is to embrace Microsoft's vision of a "mobile-first, cloud-first world". But the reality is that many people just want an operating system that works on their desktop computer or laptop. They're not necessarily interested in moving from one device to another -- that's quite niche, quite geeky. There's talk of blurring the boundaries betwen desktop Windows and mobile Windows. But who cares? Microsoft is far, far to late to the party with Windows Phone. Mobile users have voted with their cash and shown that iOS and Android are what they want, not a mobile OS offered by Microsoft. So the focus on mobile is curious.
The San Francisco event was, and the Technical Preview is, aimed at enterprise and techy users. But in the home computing market, Microsoft lost a lot of its audience. Gone are the days when every new version of Windows is welcomed with open arms, users are now more discerning, more demanding. People are no longer willing to accept what is handed to them, they expect to be given what they want. This didn’t happen with Windows 8, so it was simply ignored by a lot of would-be upgraders.
Microsoft has, as ever, something of a delicate line to walk. This is a company now obsessed with listening to feedback -- just look to Windows Phone and Xbox One -- but there is a danger in listening to customers too much. Whatever form Windows takes it will, of course, never please everyone, but Microsoft will be understandably keen to satisfy as many people as possible. However users are impatient. Users lose interest. Take too long "getting things right" and there's a strong chance that people will just give up waiting and start looking elsewhere. Rush to hit a deadline and corners will be cut -- we could end up with another Windows 8.
There's a problem of a better cross-device experience, but Apple already has this in the bag. Will people sitting on the fence hold on for (possibly) a year to see if Microsoft can nail it, or jump to the Apple ecosystem which is well-established? The promise that "Windows 10 will run on the broadest amount of devices" is intriguing. When does this happen? Will Windows Phone 8 users be able to upgrade their handsets to Windows 10? Should someone thinking of investing in a new phone hold off until they know whether they have a software upgrade path available to them? With the launch of Windows 10 still some months off, this might seem like jumping the gun but many people hang on to a phone for two years -- and often much longer -- but it's still something to keep in mind.
Upgrade next week only to discover that you've chosen a handset that isn’t getting any Windows 10 love, and you have one less reason to upgrade your desktop operating system. No hints have been made at system requirements, and this is something potential users are going to need to know. There has also been no mention of Cortana, despite the fact many expected the assistant to make an appearance in this version of Windows.
Today's demonstration was very short -- under forty minutes from start to finish. This may have been a very early build, but there really should have been more to show off, more to talk about, more to pique people's interest with. What today showed is that while Microsoft may to be taking steps in the right direction, there's still a long way to go, and the company needs to take care not to get complacent -- users are not going to forget Windows 8 any time soon. Windows 10 needs to impress. We've skipped an entire version number; we need to see something absolutely ground-breaking for that to make any sense.
Photo credit: Sergio Foto / Shutterstock
-

eBay and PayPal to split into separate businesses in 2015
Publié: septembre 30, 2014, 5:35pm CEST par Mark Wilson

A giant of the modern web is to be cleft in twain. eBay Inc is set to split its online payment service PayPal into a separate, independent, publicly traded company; eBay and PayPal will be divided into two in the second half of 2015.
By keeping the auction and payment services at arm's length from each other, eBay will be hoping to breathe new life into the beleaguered selling site. The move comes after a review of the company’s structure and growth strategies by the board of directors, and is described as providing "shareholders with more targeted investment opportunities".
It's around 12 years since PayPal was snapped up by eBay, but it has been decided that it makes more sense for each arm of the business to concentrate on its own field. eBay Inc President and CEO John Donahoe said that the two businesses "will be sharper and stronger, and more focused and competitive as leading, standalone companies in their respective markets".
Although no mention has been made of possible future ventures for either eBay or PayPal, splitting in this way will give the two the opportunity to branch out in slightly different directions. "As independent companies, eBay and PayPal will enjoy added flexibility to pursue new market and partnership opportunities. And we are confident following a thorough assessment of the relationships between eBay and PayPal that operating agreements can maintain synergies going forward. Our board and management team believe that putting eBay and PayPal on independent paths in 2015 is best for each business and will create additional value for our shareholders," said Donahoe.
The move will be welcomed by investors who are keen to see money put to particular uses. Splitting into eBay and PayPal is something that has been talked about for some time, with fuel having been added to the fire when activist Carl Icahn called for the breakup many months ago. But eBay insists that the decision has nothing to do with Ichan's demands. When the split takes place, Dan Schulman from American Express will become PayPal's new CEO.
Photo credit: Chukcha / Shutterstock
-

Google Glass adopted by Edinburgh Airport staff as wearables explode in popularity
Publié: septembre 30, 2014, 3:49pm CEST par Mark Wilson

At the airport, it's normal to see customer service staff equipped with phones, walkie-talkies and perhaps a tablet. Passengers travelling to and from Scotland who pass through Edinburgh airport will soon find that they are greeted by staff adorned with Google Glass. Google's wearable specs are to be trialled in the Scottish airport in a bid to provide more help and information to travelers.
Customer support representatives will be able to call up flight details and answer queries using the head-mounted Android-powered hardware.
Gordon Dewar, Edinburgh airport chief executive, explains: "We're always looking for new and innovative ways to improve the airport experience for our passengers and Google Glass trial is a great example of how we’re thinking out the box".
For now it is just a trial that runs until the end of the year, but if Google Glass proves useful, it could be rolled out on a permanent basis. "The fact it's the first trial of its kind in a UK airport is exciting, as it shows we are leading the way in how we interact with our passengers. Over the next few months we'll be able to establish whether this product is suitable for an airport environment".
The news of the airport's adoption of wearables comes as Juniper Research reveals that over the next three years shipments in this sector are set to quadruple. The report suggests that by 2017, shipments will rise to 116 million units compared to 27 million in 2014. It is predicted to be an incredibly lucrative market, with revenues soaring to an estimated $53 billion in 2019. With big players like Apple finally getting into the sector with the Apple Watch, it certainly seems that the momentum wearables have managed to garner will continue.
Photo credit: Mopic / Shutterstock
-

There is no escape -- with Atlas, Facebook ads follow you between devices
Publié: septembre 30, 2014, 2:20am CEST par Mark Wilson

How much do you hate ads? How much do ads piss you off? Well prepare to turn into an even bigger ball of hate-filled pissed-off-ness when you hear about Facebook's latest ventures in advertising. Few people would argue against the suggestion that Facebook has all but given up any pretence of being a social network and has become little more than a huge cog in a massive advertising machine. Claims have been made that ads are being made more relevant to users, but the truth of the matter is that users are being made more relevant to advertisers. And Facebook now has a whole new way to follow you around the web to make sure you are delivered even more better-targeted ads.
Facebook has been criticized for forcing users to reveal their real names -- information which is as valuable to advertisers as it is anything to do with security -- and there have long been concerns about privacy settings on the site. Users of Facebook may complain that their newsfeeds are cluttered with news and posts at the wrong time, but one of the biggest issues people have with the site is with ad delivery. Last week we learned that Facebook was on the verge of revealing something "more powerful than what Google can currently do" in terms of user tracking. Facebook has now launched Atlas, an ad platform that can track users as they move from desktop to mobile devices -- and it's sure to raise plenty of privacy hackles.
Atlas has been built "from the ground up" to give advertisers a powerful set of tools to push their message to more people. The platform is a response to the fact that "cookies don't work on mobile, are becoming less accurate in demographic targeting" and makes it possible to track users as they move between devices. More than this, "ad tags" and "action tags" make it easier than ever for an advertiser to follow an individual user around the web. If an advertiser wants to "capture the events and understand the paths that lead to desired outcomes", it can do so with ease. There is even the promise of "connecting offline sales to your digital marketing".
Facebook has a number of partners on board -- including Instagram -- meaning that users can be tracked moving not only between devices, but also between services. The extra information that will be afforded to advertisers will enable them to build up even more precise user profiles than in the past, and deliver even more specifically targets ads. On the one hand, it could be argued that this will result in even more relevant ads being displayed, but the privacy implications are rather more worrying. Read through some of the blurb on the Atlas web site, and it's hard not to shrink back with revulsion: "Atlas enhances existing workflows by programmatically sharing media plans, placements and tracking information with partners".
The specificity of ad campaigns that Atlas makes possible completely strips away any last remnants of anonymity -- be it real, or just the sense of anonymity in the crowd -- that may have remained. Facebook just upped the ante when it comes to privacy invasion. You are, now more than ever, the product. Perhaps Ello -- even with its ugliness and threat of paid-for features -- isn't such a bad option after all...
Photo credit: Krasimira Nevenova / Shutterstock
-

Windows 9 download link leaks ahead of Technical Preview launch
Publié: septembre 28, 2014, 1:19pm CEST par Mark Wilson

This week we should finally be able to get our hands on Windows 9 code direct from Microsoft. There are only a couple of days to go until the Technical Preview is officially unveiled at an event in San Francisco, and excitement has been mounting. Slightly ahead of schedule, a page has appeared on the Microsoft website that includes a download link to the 32- and 64-bit versions of the Windows Technical Preview for Enterprise. Intriguingly, the page refers to a version of Windows named Windows TH, but it's not clear that this is actually the name that will be used.
Before you get too excited about grabbing the latest Windows bits, it seems that the page is just a placeholder for now. The download button currently links to a non-updated version of the TechNet Evaluation Center, but a link to the download page that will be used was live briefly. It revealed that the US version of the Technical Preview weighs in at 3.16 GB and 4.10 GB. We've already got a pretty good idea of what to expect from the preview as there have been numerous build and screenshot leaks over recent weeks.
Up until now it has been assumed that the name will be Windows 9, and it is possible that the TH suffix is related to the Threshold codename that has been used thus far. A photo posted by Terry Myerson, Executive Vice President of Operating Systems, gives little away. The photo came in response to name postulations on Twitter by Tom Warren from the Verge and Mary Jo Foley from ZDNet and shows Myerson standing in front of the new Windows logo. His body obscures the all-important part of the name, but Windows 9, Windows X, Windows One, or even just Windows are names that are hotly tipped to be the final moniker.
Windows? @maryjofoley @tmyerson pic.twitter.com/wGa44GpyjE
— Tom Warren (@tomwarren) September 27, 2014
There are no new details or screenshots provided at this stage, but the download page highlights the enterprise benefits of upgrading to the latest version of Windows:
The next version of the Windows client operating system will enable IT professionals to provide users with a familiar experience across multiple devices while enhancing security and manageability. It will also offer new and improved features that enable businesses to: Defend against modern security threats, Elevate employee productivity, Embrace the mobile and cloud era, Enable upgrade without upheaval.
Assuming things haven’t changed dramatically since the build leaks we've already seen, we have a good idea of what to expect. We might not be certain about what the name is going to be, but we know the Start menu, virtual desktops, and a new notification center are three features Microsoft hopes will be seen as an improvement over Windows 8.x.
Will you be installing the Technical Preview as soon as you can, or are you going to hold off until the official launch?
Photo credit: John Fryatt / Shutterstock
-

European airlines to allow the use of phones during flights
Publié: septembre 26, 2014, 8:15pm CEST par Mark Wilson

The European Aviation Safety Agency (EASA) has decided that mobile phones are completely safe to use in-flight, including during take-off and landing. Previous rules required passengers to either switch off phones, or flip them into airplane mode. The EASA's latest decision does not mean that there is an automatic right of mobile use afforded to fliers, but airlines now have the option to permit handset use on their flights. So if you've splashed out on an iPhone 6, bendy or otherwise, you can show it off to your fellow fliers.
While airplane mode blocks the ability to send and receive calls and messages, many passengers have found that they are asked to switch off entirely and refrain from using their handset in any way. The new ruling will arm passengers with more ammunition if they want to argue their case, but it's likely that many European flights will quickly bow to popular demand and permit the use of phones.
Investigations by the EASA found that there is no reason to prevent the use of phones, tablets and other PEDs (personal electronic devices), but individual airlines will undoubtedly want to carry out their own checks. The decision is described by the EASA as "the latest regulatory step towards enabling the ability to offer ‘gate-to-gate’ telecommunication or WiFi services".
An information page about the use of PEDs reiterates that airlines have the final say, and provides the following advice:
- If you are unsure on the use of PEDs, you may check the airline’s website prior to the flight.
- Be reminded that the safety briefing provided by the airline crew is for your benefit. Please pay attention and listen carefully.
- Airline crew may request at any time to switch-off all PEDs and to stow them.
- Passengers have always to follow airline crew instructions as safety is the responsibility of everyone on board the aircraft.
Photo credit: In Tune / Shutterstock
-

Want a free Samsung Galaxy Note 8? Here's how
Publié: septembre 26, 2014, 2:16pm CEST par Mark Wilson

There are lot of ways to get your hands on a free tablet -- stick it on your birthday wishlist, win one in a competition, steal one. But there's also another option: get yourself to university. At least this is a path to a free tablet -- a Samsung Galaxy Note 8 specifically -- if you happen to be a first year student at the University of East London. 4,000 students will be handed a brand new Samsung Galaxy Note 8 when they start their studies. The venture will cost the university £2 million (around $3.25 million), but the vice-chancellor thinks that it is money well-spent.
It might not be the newest tablet on the market, but few students are likely to turn their noses up at the freebie. Professor John Joughin said, "We are delighted to be putting support directly in the hands of our students and providing them with a state-of-the-art learning platform for the duration of their studies", explaining that equipping students with the tablets will create a "level playing field for all of our students".
The hand out is not just about giving students a tablet. The Galaxy Note 8s come pre-loaded with a batch of ebooks about the university and its courses. Providing course books in digital format will not only make it easier -- and rather less muscle-building -- to carry reference material around, but it will also help to reduce the costs students face. Having paid tuition fees, anything that can be done to reduce further expenditure is going to be welcomed.
This time of year is traditionally a very good time for technology sales as students rush to equip themselves with devices to help with their studies. The free tablet deal came about as part of a deal between the University of East London, Samsung, UK ebook platform Kortext, and the JS Group.
-

Bye bye, Facebook. Hello, Ello?
Publié: septembre 26, 2014, 5:30am CEST par Mark Wilson
 It's very easy -- some would say fun -- to bash social networks. MySpace was a very easy target, and Twitter comes in for criticism from time to time, but it's Facebook that tends to bear the brunt of people's ire. Mark Zuckerberg's social (advertising) network hits the headlines quite frequently, but it's been on the lips of many in recent weeks after starting to aggressively implement its "real name" policy. It's something that initially upset drag artists around the world but it's also something that affecting musicians and other artists who have opted to use a stage name. In recent days another name has bubbled to the surface. It's not brand new, but Ello has been hard to avoid over the last few days. What’s going on?
It's very easy -- some would say fun -- to bash social networks. MySpace was a very easy target, and Twitter comes in for criticism from time to time, but it's Facebook that tends to bear the brunt of people's ire. Mark Zuckerberg's social (advertising) network hits the headlines quite frequently, but it's been on the lips of many in recent weeks after starting to aggressively implement its "real name" policy. It's something that initially upset drag artists around the world but it's also something that affecting musicians and other artists who have opted to use a stage name. In recent days another name has bubbled to the surface. It's not brand new, but Ello has been hard to avoid over the last few days. What’s going on?It's clear that the fallout from the drag artist incident that social network users have been seeking out new homes where they are free to be whatever they want to be. This is something that Ello seems to offer. If you want to hide behind a pseudonym, adopt a different online persona, run multiple account under different names, pretend to be someone else, or just smirk at the fact you can call yourself Farty McPoopButt if you feel so inclined, you're onto a winner here.
The site may not be new, but it's certainly in its infancy -- it only sprang into existence this year. Starting life as a "private social network", Ello expanded to a public network. But one with quite a difference: no ads. Ello thinks "ads are tacky" and has committed to remaining ad-free -- so confident are the founders that this will remain the case, a prominent Delete Account button is provide in settings so you can walk away if anything you don’t like should happen.
The page that explains the "no ads" policy does give away a glimpse of what's to come. "Ello is completely free to use". Well that's a good start. "Very soon we will begin offering special features to our users." Sounds good to me... count me in, you cheeky little scamps! "If we create a special feature that you like, you can choose to pay a very small amount of money to add it to your Ello account forever." Ah... there's the rub. Well, one of the rubs.
Ello has an air of Apple to it; old-school Apple, admittedly, but there's a distinctly Apple-y feel to everything. The word "beautiful" is bandied about as if it's an adword. The site is young, but you're given little control over the look and feel of things. The stark simplicity is something that you'll either fall in love with, or loathe with a passion -- much like Apple's products. Ello is like stepping back in time. Forget fancy extras. Forget options. This is stripped-back social networking. At the moment, even the user-base is stripped-back. The fact that Ello is currently invite-only (but getting hold of an invite is not hard) helps to increase intrigue levels, but also create a semi-elitist niche network that will appeal to a certain type of social networker.
Ello is currently riding the wave generated by the public, and celebrity, outcry at Facebook. It's too early to tell whether site with weather the storm, whether it will cope with an influx of new users, or if users will stick around. There's a bit of an echo there at the moment, but word seems to be spreading. Is it cool? Is it hipster? There's a manifesto, comrade. Is it anti-cool? Gawd knows... but it something of a mini-phenomenon at the moment. Maybe it will remain the domain of freaks, geeks, hipsters and musicians.
-

Dear Rupert: Google responds to News Corp, shoots down criticism
Publié: septembre 25, 2014, 11:29pm CEST par Mark Wilson

A week ago, in a letter to the European Commission, News Corps complained that Google is a 'platform for piracy' with 'cynical management'. Today, having gathered together its ammunition, Google responds with a letter of its own. Although News Corp's letter was signed by CEO Robert Thomson, Google's reply starts with the salutation "Dear Rupert" -- addressing CEO Rupert Murdoch -- and the search giant picks apart the complaints levelled at it. One of New Corp's key complaints centered around the idea that Google is riddled with pirated material, and "unlawful and unsavory content", and this is one of the first ideas that Google shoots down.
Countering accusations of being a platform for piracy, SVP Global Communications, Rachel Whetstone, points to the 222 million copyright infringing websites that were delisted last year. The existence of copyright protecting ContentID technology to help detect infringing footage on YouTube is also cited, as is efficiency in weeding out inappropriate contents such as sexual images of children.
News Corp had also complained that Google used its dominant market position to stifle competition, but Google has a response to this as well. "We are not the gatekeeper to the web, as some claim," says Whetstone, going on to point out that Google has lots of competition itself. While Google is somewhat of a Swiss army knife for the web, there are plenty of specialist services and Google's letter rightly points out that many web users jump directly to websites without using the search engine as a middleman.
The letter also addresses some of News Corp's more bizarre accusations, including the notion that Google's certification process for Android apps gives the company "the freedom to develop competing products". Google says that certifying apps is a necessary process to help ensure security and compatibility, and points out that there are competing app stores available for the platform that users are free to turn to. After refuting suggestions that preference is given to YouTube videos in search results, Google takes a swipe at News Corp's complaint that it is leading to a "less informed, more vexatious level of dialogue in our society" -- which is a pretty rich coming from a dangerously rightwing media beast responsible for Fox News.
So now blows have been traded in both directions; the ball is now in News Corp's court. It'll be interesting to see whether there is another letter from the Murdoch empire in a week's time and if this descends into a tit for tat exchange that drags on indefinitely.
Photo credit: wavebreakmedia / Shutterstock
-

BlackBerry Passport aims for longevity with 30 hour battery life
Publié: septembre 24, 2014, 6:26pm CEST par Mark Wilson
Whenever news comes from BlackBerry it feels like a voice from the past calling. Today is no different as the company announces the launch of the BlackBerry Passport, a square-screened phone designed with the corporate market in mind. This might be a phone aimed at business users, but that doesn’t mean there isn’t room for a little joking around: CEO John Chen quipped that the Passport is harder to bend than the iPhone 6 Plus.
The most striking feature of the handset is the 4.5 inch display with its 1400 x 1400 resolution with 453PPI, but nestling beneath this is the Passport's second most interesting feature: the three-line, touch-enabled physical keyboard.
The keyboard and screen complement each other. Opting to install a physical keyboard is something of a unique feature for BlackBerry, and it means that apps are able to make use of the screen in its entirety. The standout aspect ratio -- BlackBerry remains a fans of the squat design rather than the taller, slimmer look favored by most phone manufacturers -- means that there is room for almost twice as much text as on an iPhone; BlackBerry claims 60 characters compared to 33. The screen is not obscured by the keyboard, and the fact that the keyboard doubles as a means of navigation -- thanks touch-sensitivity! -- means that fingers also don’t get in the way. The keyboard is likely to take a little while to get used to as it only has three row of buttons, and the spacebar is rather small.
The Passport runs BB OS 10.3 and is powered by a 2.2 GHz Quad-Core Qualcomm Snapdragon 801 backed up by 3GB RAM. In terms of storage, there's 32GB but a MicroSD slot means that this can be expanded by 128GB. Photographs are taken care of by a 13MP camera but the 3540mAh battery is also noteworthy -- BlackBerry claims it offers up to 30 hours of usage. Apps can be downloaded through either BlackBerry World or the Amazon Appstore.
Anyone looking to get their hands on the BlackBerry Passport can pick up an unlocked version from ShopBlackBerry.com. The handset is available in the US ($599), Canada ($699), UK (£529), France (€649), and Germany (also €649). The phone will also be available on a contract for an expected $249 and by the end of the year, availability is due to extend to more than 30 countries.
Want to know more about the BlackBerry Passport's unique design? Check out the video below for an insight:
-

Google teams up with Endurance to get African and Southeast Asian businesses online for free
Publié: septembre 24, 2014, 4:27pm CEST par Mark Wilson

It's important for any business to establish an online presence, and this is certainly true in emerging markets. It's something recognized by Google, and the company is teaming up with Endurance International Group to help SMBs in Africa and Southeast Asia to launch online ventures.
Google's reputation online precedes it, but Endurance might not be a name that's overly familiar. The company provides hosting, and the new partnership with Google is set to benefit businesses in South Africa, Nigeria, Ghana, Kenya, Indonesia and Malaysia.
There's no shortage of companies looking to help get businesses online, but the difference here is that there are no charges involved. Interested SMBs have access to Google My Business which Endurance will help to get set up. This involves getting businesses up and running on Google Maps, Google+, and getting noticed in search results. There are also paid-for add-ons available such as creating a full blown website rather than just a Google My Business page and the option to get started in ecommerce.
This might all sound a little basic, but you never know what might explode from a small acorn, as the saying goes. Hari Ravichandran, CEO of Endurance said: "Google is stimulating demand for web solutions around the world and Google My Business is a great platform for rapidly getting listed and found online. We expect it will bring many businesses to the web for the first time".
Endurance has history in helping out in emerging markets, having already worked with Google in India on a similar project. The company sees such markets as key to the future of web hosting.
Photo credit: Manczurov / Shutterstock
-

GoDaddy slashes the cost of Microsoft Office 365 to $1 per month for a year
Publié: septembre 23, 2014, 10:20pm CEST par Mark Wilson

People are slowly but surely coming round to the idea of SaaS (Software as a Service), and this is particularly true for businesses. Microsoft is making something of a success of pushing monthly or annual subscriptions for Office 365, but there's still a massive untapped market -- small businesses who are simply not in a position to make additional financial commitments each month. GoDaddy is helping to wipe out this obstacle by offering a package aimed at getting small businesses up and running online for just $1 per month; and the package includes Office 365.
As this is GoDaddy, it should come as no surprise that there is a web-focus to the package. For $1 a month, businesses can bag themselves a custom domain and take advantage of the Website Builder tool as well as site hosting. On top of this, there's round the clock support and $50 worth of Bing credit to help with online promotion. This is already a great value deal, but throwing Office 365 into the mix is going to be too much for many businesses to resist.
Microsoft Office's Product Marketing manager, Kirk Gregersen, said:
Office 365 is transformational for small businesses because it offers the same powerful tools that large companies use, while being affordable and easy for small businesses to set up and manage. We're pleased to continue our partnership with GoDaddy to make it easier and more affordable than ever for small businesses to get online and realize the power and value of Office 365.
The Get Online Today offer is available in the US right now, and it is set to spread around the globe from October.
-

Xbox One launches in India, UK price drops, and Chinese gamers have 'approved games' list
Publié: septembre 23, 2014, 7:30pm CEST par Mark Wilson

It's almost as though we are entering that time of the year when people start thinking about Christmas presents. Game consoles -- like the Xbox One -- are likely to feature pretty high up on wishlists the world over and, out of the blue, there's a raft of Xbox One news spilling out.
It is quite some time since the wraps were taken off the console, but today is the day it finally launches in India. The version with Kinect is available for Rs 45990 (around $755), with the Kinect-free version costing Rs 39,990 (around $655) -- so compared to other parts of the world, the Indian version of the Xbox One is relatively expensive. It will be interesting to see what sort of an impact this has on its popularity.
It’s something of a different story in the UK. Gamers in this part of the world have already been treated to one price drop, and now there's another one. Hit the Microsoft Store or Amazon and you'll find that the Kinect-less version of the Xbox One is available for just £329.99 (around $540). The Amazon deal is particularly interesting as it's the white version of the console and includes a download version of Sunset Overdrive.
So that's a new launch in India and a price drop in the UK. What else is going on in the world of Xbox One? Next on the list is the delayed Chinese launch for the console. Gamers in China now have now less than a week to wait to get their hands on the console on 29 September, but there will be something of a limited number of games to choose from to start with. Despite the fact there are now scores of games available in other parts of the world, the Chinese version of the console launches with just ten titles -- and these are "government-approved" games.
Microsoft has something of a checkered history with the Chinese government, and the company is currently under investigation for antitrust issues. China only recently lifted a 14 year ban on games consoles, so there's a captive market waiting to lap up anything that's released. There's been a long wait -- both for Microsoft and Chinese gamers -- but it's hard to imagine the launch being anything other than a roaring success.
-

Apple: Beats Music to live on, could be swallowed by iTunes
Publié: septembre 23, 2014, 4:41pm CEST par Mark Wilson

When Apple acquired Beats Music earlier in the year, there were obvious fears that the service would shut down. While this type of rumor is often well-founded, it seems fears were misplaced on this occasion: Apple has no plans to shutter Beats Music. A company spokesperson made a statement to the Guardian making it clear that suggestions that the subscription music service is to close down are "not true". But could the brand end up being eaten by iTunes?
Beats Music has not been a runaway success. It has subscribers, but not all that many. With Apple's backing there is a chance that its popularity could increase, but it can be difficult to shake off the reputation of an old name -- Beats Music has singularly failed to reach the celebrated heights of Beats Electronic's headphones. Having spent $3 billion on Beats Music and Beats Electronic, it would be strange if Apple just gave up on a portion of its investment.
While rumors of Beats Music's death may have been overstated, it is unlikely that things will carry on as they are. We already know that Apple has been working on a new music format. It's something that U2 has been working on, and frontman Bono recently revealed his involvement. Very little is known about this music format, but there's nothing to stop Apple from using Beats Music as a launchpad for it -- it could be seen as something of a soft launch.
In fact, both the Guardian and Re/code speculate about whether Beats Music could be rebranded, or even just become a subset of iTunes. Could we see a subscription-based new music format aimed at iPad and iPhone owners? Is it something you'd be willing to cough up for?
Photo credit: Oleksandr Kovalchuk / Shutterstock
-

Adobe snaps up cloud image editor Aviary to fast-track SDK development
Publié: septembre 23, 2014, 4:03pm CEST par Mark Wilson

Seven years after its inception, online image editing service Aviary has been acquired by Adobe. The Photoshop stalwart is no stranger to the cloud, but this latest purchase seems to indicate that the company is looking to expand further in this arena. Pay a visit to the Aviary website and the Adobe branding is already in place -- there's also a new entry on the Aviary company timeline that has been updated to reflect the acquisition. The Adobe-branded Aviary website makes clear the thinking behind the move: "accelerating delivery of mobile apps that integrate with Adobe Creative Cloud".
It seems that the main reason for Adobe's interest in Aviary is the fact that the ornithologically-named firm has developed a number of mobile SDKs. Aviary is already a popular tool, and Adobe is understandably keen to monetize the popularity of cloud apps and mobile services: Aviary is a ready-made package that encompasses both of these ideas perfectly. An announcement by Adobe explains that "the acquisition accelerates Adobe's strategy to make Creative Cloud a vibrant platform for third-party apps, through a new Creative SDK".
The Adobe Creative SDK is yet to see the light of day, and the work that Aviary has already done could well help to speed things along a little. Scott Belsky, vice president of Creative Cloud Ecosystem & Behance at Adobe, said: "Aviary has an exceptional team and technology platform, as well as expertise serving a robust developer ecosystem. We're thrilled to leverage Aviary's technology to make our Creative SDK even more powerful for app developers".
Aviary is understandably upbeat about the latest developments. CEO Tobias Peggs explains that the team can "barely contain [its] excitement" and says that there's a lot to look forward to. "our teams are brainstorming on things that we can accomplish together. We will continue to support and enhance Aviary's SDK as part of Adobe's broader Creative SDK offering. While ensuring no interruption to Aviary's developer community, or their apps’ users, we plan to add additional components and services for developers to incorporate -- such as the ability to save creations to Creative Cloud in Adobe file formats, access Photoshop technology, and connect creativity across devices using the Creative SDK".
-

Facebook to fire news at you faster than ever
Publié: septembre 19, 2014, 4:15pm CEST par Mark Wilson
Part of the point of Facebook, in addition to making it easier to keep in touch with people, is to keep abreast of news. The social network's algorithms are such that you don’t just see a chronological stream of updates from the people, companies, and pages you follow -- stories can 'surface' in a seemingly random order, and may appear some time after they were actually relevant. Facebook is aware that it can deliver posts in something of an untimely fashion, and it's now going to do something about it. It makes a change from forcing users to display their real names...
The social network is rolling out a couple of updates that will help to ensure that stories that appear in your News Feeds are more relevant. There have been complaints that Facebook is slow to start pushing trending topics -- be it sports events or big news stories -- and this is being addressed. Should friends of yours link to, or interact with, a story that is currently trending, it is "more likely to appear higher up in News Feed, so you can see it sooner". You may well have thought that this is how things worked before, but apparently this is not the case.
An announcement from Facebook makes reference to an upsurge in click and shares following tests of this update: "[it] leads to a more than 6 percent increase in people engaging with these stories (e.g., more people share, comment, like or click)". The timing of user interactions is also going to be factored in a more intelligent way in future. If there is a great deal of user engagement early on, Facebook will take this as an indication that other people are also likely to be interested now rather than later, and the story will be pushed to more news feeds.
Facebook advises page managers to make no changes to the way they currently operate:
"We will be rolling out these changes gradually and do not expect posts to see significant changes in distribution as a result of this update. If a Page posts about a trending topic or if a post sees a high velocity of engagement early on that then drops off, that post may begin to see increased distribution early on and less distribution over time. Pages should keep producing great content that is relevant and resonates with their audience".
Have you noticed a change to the timeliness of the appearance of different types of article in your news feed?
Photo credit: Lucian Milasan / Shutterstock.com
-

Panic over! Twitpic is given a stay of execution after a buyer is found
Publié: septembre 19, 2014, 2:46pm CEST par Mark Wilson

Twitpic will no longer close on 25 September as the photo sharing service has found a buyer. There's not yet any word on who is behind the acquisition, but the takeaway news is that photos should be safe as Twitpic will live to fight another day.
Just a couple of weeks ago, founder Noah Everett posted the news that Twitpic was to close following something of a legal tussle with Twitter. But things have taken a turn for the better. After users scrabbled to download their images to ensure they were safe, it now transpires that the service is not going anywhere.
There are very few details available at the moment beyond the fact that an unnamed buyer has stepped forward. It could be Twitter itself, or it could be a third party -- at this stage we just don’t know -- but the last minute reprieve will come as great news to fans of the service. There is less than a week to go until Twitpic was supposed to disappear but a brief announcement appeared on, of course, Twitter, explaining that there was a change of plan.
We're happy to announce we've been acquired and Twitpic will live on! We will post more details as we can disclose them
— TwitPic (@TwitPic) September 18, 2014
It's not clear when we'll find out more about what has happened, as the tweet is all we have to go on at the moment. The most recent entry on the Twitpic blog is still the one from 4 September announcing the closure, but there's sure to be an update in the not-too-distant future.
Photo credit: 1stGallery / Shutterstock
-

Microsoft drops Windows Dev Center fee -- expect a crap app avalanche
Publié: septembre 18, 2014, 7:21pm CEST par Mark Wilson

Free's good, right? Who doesn’t like something gratis? Microsoft has -- sort of -- cottoned onto this idea and dropped the annual fee associated with the Windows Dev Center. The 'sort of' caveat remains because signing up for a Dev Center account is not completely free; there's still a registration fee of $19 to pay, but this is for a lifetime account -- no more annual charges. Announcing the move on the Windows blog, Todd Brix explains that "each of our 600,000+ registered developers will no longer need to pay any additional fees to maintain their account. It’s also a very good time for developers new to the platform to get a Dev Center account and start submitting apps".
Having paid the fee, developers are then free to submit apps to both the Windows Phone Store and the Windows Store. But this is not the only change that's coming to the Dev Center. In what is becoming something of a trend, Microsoft clearly pinned back its ears and made it easier to promote apps and provide offers to users. Improvements to in-app advertising means that campaigns can be more easily run on a global scale and pay outs are made faster.
There are now there different packages available -- Explorer, Expert, and Master -- and developers move through these levels as their apps gain more downloads, earn better ratings, and so on. Each level comes with its own set of benefits, from access to help from experts up to early access to SDKs.
It is, however, the dropping of annual fees that is the big news here. It's no secret that Microsoft has something of an issue when it comes to apps for Windows and Windows Phone. Both in terms of quantity and quality, apps in the respective stores have been found wanting. The dearth of modern and mobile apps is a serious problem, and it's something that Microsoft is obviously keen to address. Cutting the fees associated with developing apps for its operating systems is just the latest carrot Microsoft has to dangle in front of would be developers.
It's likely to lead to a surge in developer numbers, and probably a similar jump in apps, but there is a very real danger that it will be a case of quantity over quality. If anyone can start, and continue, to pump out apps for very little money, the chances are that they will. You know the amount of rubbish that appears in the App Store and Google Play? Expect to see an even bigger avalanche of crap apps sprouting in the Windows Store and Windows Phone Store -- even more than there currently are -- and it's going to further dilute the limited number of decent apps out there.
It's great that Microsoft is trying to lower costs and make app development more accessible, but in making things cheaper, the art of app development is also being cheapened. Of course, there will be some great apps that emerge as a result of this latest move -- but there's going to be much, much more absolute rubbish.
Photo credit: Sergey Nivens / Shutterstock
-

News Corp: Google is a 'platform for piracy' with 'cynical management'
Publié: septembre 18, 2014, 11:04am CEST par Mark Wilson

News Corp, Rupert Murdoch's media behemoth, is the latest source of criticism of Google. Robert Thomson, the chief executive of the company -- responsible for the Times and the Sun in the UK as well the book publisher HarperCollins -- has written to the European Commission to complain that the search giant is "a platform for piracy". Thomson pulls no punches as he lays into Google, saying that the company was in the hands of a "cynical management" and was "willing to exploit its dominant market position to stifle competition".
The letter, addressed to Competition Commissioner Joaquin Almunia, is bitter in tone as Thomson complains of Google's "egregious" practices. It is Google's dominance of the search market that is seen as particularly problematic. News Corps feels that Google's power "increases with each passing day" -- a claim that many have leveled at Murdoch's corporation in the past -- and fears that this "will lead to a less informed, more vexatious level of dialog in our society". But this is far from being the only accusation that Thomson fires at Google.
The company has evolved from a wonderfully feisty, creative Silicon Valley startup to a vast, powerful, often unaccountable bureaucracy, which is sometimes contemptuous of intellectual property and routinely configures its search results in a manner that is far from objective.
It seems that the alleged involvement in copyright infringement is some that is of particular interest to New Corp. "A company that boasts about its ability to track traffic chooses to ignore the unlawful and unsavory content that surfaces after the simplest of searches. Google has been remarkably successful in its ability to monetize users, but has not shown the willingness, even though it clearly has the ability, to respect fundamental property rights".
The letter goes as far as blaming the closure of newspapers on Google:
It is worth pausing for a moment to contemplate how the world of content has evolved, and why five years is an eternity in internet time. Virtually every newspaper in Europe is in the midst of upheaval, and some will surely not exist five years from now, in part because of their own flawed strategy and lack of leadership, but also because the value of serious content has been commodified by Google.
Sadly for News Corp, it is unlikely to find quite as many sympathizers as it might have hoped. For all its failings, Google has helped to open up the internet and provide access to news and content in a way that no other company can claim. News Corp, on the other hand, has thrown up paywalls around many of its sites -- a somewhat understandable move for an organization looking to generate profit, but one that possibly reveals the true motives behind the letter. This is a complaint about the denting of profits rather than genuine concern about Google's market dominance.
Photo credit: ChameleonsEye / Shutterstock.com
-

HooToo TripMate Elite -- the "electronic Swiss army knife" for tech travellers [Review]
Publié: septembre 18, 2014, 1:10am CEST par Mark Wilson
![HooToo TripMate Elite -- the "electronic Swiss army knife" for tech travellers [Review]](http://betanews.com/wp-content/uploads/2014/09/hootoo.jpg) When I first learned about the HooToo it sounded, frankly, a bit nuts. Pitched as an "all-in-one device charger, AC adapter, personal cloud, travel router, Wi-Fi hotspot, and wireless bridge" I was instantly intrigued, but fearful that this was going to be a device that promised the world and delivered little. Was I setting my expectations too low? Before we look at things any further, it's probably worth spending a moment or two decoding what it actually is. One of its more basic functions is a rechargeable USB battery pack complete with two outputs. But there's more to the TripMate Elite. Much, much more.
When I first learned about the HooToo it sounded, frankly, a bit nuts. Pitched as an "all-in-one device charger, AC adapter, personal cloud, travel router, Wi-Fi hotspot, and wireless bridge" I was instantly intrigued, but fearful that this was going to be a device that promised the world and delivered little. Was I setting my expectations too low? Before we look at things any further, it's probably worth spending a moment or two decoding what it actually is. One of its more basic functions is a rechargeable USB battery pack complete with two outputs. But there's more to the TripMate Elite. Much, much more.The 3.2 x 3.2 x 1.0 inch (82 x 82 x 28mm) black box is home to a 6000mAH battery that's perfect for powering up a dead mobile or tablet on the move, but the 7oz (200g) package has plenty more tricks up its sleeve. As it's a portable battery pack, it's hardly surprising to find a couple of USB outputs, one kicking out 1A, the other 1/2.1A. Equally unsurprising -- but no less useful -- is the battery level checker on the adjacent side; tap the button and four blue LEDs let you know the charge level. But what's that next to the charge lights? Internet and LAN indicators? Curiouser and curiouser, said Alice.
Spin back to the edge featuring the USB ports and you'll find confirmation that your eyes did not deceive you. There's also an Ethernet port. What the fudge? This is the router aspect of the increasingly exciting TripMate Elite. If you find yourself in a hotel room where there's only a wired connection, just connect the TripMate to the network and you can share the connection wirelessly to your laptop, phone, tablet and anything else you might have brought with you. Backed up by WPA and WPA2 encryption, everything is kept nice and safe. It also serves as a way to extend the range of a flaky Wi-Fi connection, or to cheekily pay for one connection and share it between multiple devices.
The connection options go a little further. If you have a flash drive or a USB hard drive (up to 4TB) with you and want to share the files between multiple devices, the TripMate Elite can help here too. Plug in your USB storage and you can then connect up to five devices so you can copy files around, share documents, and stream media. Your own personal cloud, as the instruction manual puts it. There are apps available for both iOS and Android to make it easier to access your files from a mobile device. Software is also available for Mac and iOS -- Linux and ChromeOS users miss out for now -- but this is not needed to take advantage of all of the device's features.
Oh, and did I mention the fact that there's a built in two-prong power adaptor so you can plug it straight into the mains without the need for a cable? This is not only handy for charging up the built in battery, but also means the TripMate Elite can function as a replacement for your standard wired mobile charger. As I'm in Scotland rather than the States, I had to ruin the look of the unit by connecting it to a travel adaptor, but it's still a neat and tidy device.
If the features sound good, the price is impressive too. There's an MSRP of $89.99, but the device is currently available for just $59.99 from Amazon, complete with free shipping. There's a similar deal available on Newegg if that’s your preference. Don’t get too excited about it, but in the box you'll also find a little travel pouch to help keep your purchase protected -- it's nothing out of this world, but it's a nice touch.
The PR guff relating to the TripMate Elite describes it as "one easy gadget that keeps all your devices charged, online, and connected to each other". That is precisely what it is, and it does it all tremendously well. It's an outrageously useful device, and an extremely sexy addition to your hand luggage. I'm a cynical bugger at the best of times, but I have been genuinely blown away by this incredible little device. It takes a lot to impress me, so hats off to HooToo for achieving the (almost) impossible.
I'm not a fan of unboxing videos -- and my presentation skills aren't up to much -- but it's worth checking out the introductory video to get a feel for this genuinely impressive piece of kit.
-

Microsoft OneNote gains Android Wear support plus new iOS 8 and Windows Phone apps
Publié: septembre 16, 2014, 9:32pm CEST par Mark Wilson
 Microsoft continues its recent trend of bringing exciting new features to rival platforms by adding Android Wear support to OneNote. The most recent version of Microsoft's note-taking tool -- suitably named OneNote for Android Wear -- and a new iOS 8-friendly version of the app is also due to launch today. If you've invested in an Android smartwatch (you'll have to wait a little longer for an Apple Watch version), taking a note is as simple as uttering "OK Google, take a note" -- but be prepared for a few weird looks when you try this out in a store for the first time.
Microsoft continues its recent trend of bringing exciting new features to rival platforms by adding Android Wear support to OneNote. The most recent version of Microsoft's note-taking tool -- suitably named OneNote for Android Wear -- and a new iOS 8-friendly version of the app is also due to launch today. If you've invested in an Android smartwatch (you'll have to wait a little longer for an Apple Watch version), taking a note is as simple as uttering "OK Google, take a note" -- but be prepared for a few weird looks when you try this out in a store for the first time.To take advantage of the voice-activated features of the app, you will also need to have the main OneNote app installed on your Android phone or tablet. Forget the fact that your smartwatch doesn't have a keyboard -- notes can now be dictated to your wrist in a way that will not in any way make people who may be nearby think you're a little, er, strange. Or, as the Office Blog puts it, "we hope you enjoy using OneNote in a manner even Dick Tracy would envy!"
The first smartwatch-friendly version of OneNote is available free of charge from Google Play, but this is not the only OneNote app on the cards today. We've already mentioned the new iOS 8 app which will hit the App Store at some point today, but Windows Phone users also have an updated version of Office Lens to enjoy.
The app makes it possible to use your smartphone's camera to capture text from papers, posters, noticeboards and the like. These photos are then given the OCR treatment and converted into editable Word documents or PowerPoint presentations. As the Office Blog suggests, it could be used to quickly convert lecture handouts into word files. The video below gives you an idea of what's possible.
-

UK web users are the most likely targets for phishing scams in the world
Publié: septembre 16, 2014, 7:15pm CEST par Mark Wilson

Phishing scams are a problem around the world -- and it's likely that one or more was at least partly responsible for the Fappening -- but it seems that it is more of a problem in some places than others.
Just about all of us have received emails that contain malicious links, but analysis by Proofpoint found that web users in the UK are more than two and a half times as likely to receive phishing mail as those in the US. Germany fairs much better, receiving just a fifth of the number of scam emails as the UK. But these numbers are not the whole story -- phishing emails account for just a portion of unwanted emails.
While Germany did not find itself on the receiving end of too many phishing emails, it did receive more general spam than the UK, France, and the US. Proofpoint chose to use the US as a baseline, and only France found itself on the receiving end of (marginally) less spam. As the security researchers note, this shows that "email accounts in the UK are targeted with a smaller amount of unsolicited email than Germany, France or the US; but as much as five times more of these emails contain malicious URLs."
So just what do these malicious emails contain? Some house links to malware, some to viruses, and others to phishing sites. To help suck in as many victims as possible, the phishing scams emulated the appearance of emails from banks such as RBS (Royal Bank of Scotland). Proofpoint notes that the emails are "simple and of overall good quality", but point outs that one banking email included a disclaimer that seemed to refer to a "you've won a prize" scam email.
The research firm continues to find the same viruses and malware cropping up time and time again. The Dyre Trojan -- made famous through the GameOver Zeus takedown -- is still being delivered through the Upatre downloader.
Photo credit: Stefan Amer / Shutterstock
-

Cheap handsets in India and China fuel huge global surge in smartphone shipments
Publié: septembre 16, 2014, 12:53pm CEST par Mark Wilson

New figures show that global smartphone shipments for 2014 are set to be 19 percent higher than the previous year. Juniper Research reports that handset shipments are forecast to jump from 985 million in 2013 to 1.2 billion this year.
Smartphone popularity continues to rise, and this has been driven -- at least in part -- by the appearance of handsets with bargain basement prices. While the likes of Apple push premium-priced smartphones, emerging markets are lapping up handsets priced at $150 and under.
In fact, Juniper Research singled out two categories of smartphones that are responsible for rocketing sales. "Low-cost Economy" handsets are identified as those costing $75-150, while "Ultra Economy" devices are those priced under $75. Handsets at these prices are available around the world, but it is in emerging markets where the cheaper price points are proving particularly appealing. Chinese manufacturer Xiaomi is singled out for particular attention for its aggressive pricing in India and China, putting up competition for market-leaders Apple and Samsung.
These two manufacturers still account for 45 percent of global handset shipments, despite the higher prices. The established popularity of higher-priced handsets looks set to be diluted by success in emerging markets. Analysts suggest that by 2019 the average price of smartphones will drop to $274. Considering the fact that some handsets are currently nudging towards $1,000, it's clear that cheaper smartphones are going to become increasingly significant.
The shape of the smartphone market is changing rapidly. The report also suggests that sales are starting to stagnate in more established markets as smartphone uptake reaches saturation point. By the end of 2014 it is expected that Far East & China, Indian Subcontinent, Latin America, and Africa and Middle East are likely to account for more than half of smartphone shipments. It's unlikely that Apple and Samsung will produce handsets to compete in the cheaper end of the market, and it's probable that the two-tier pricing will continue around the world. Whether the cheaper manufacturers can expand into more established markets and steal some of the big players' thunder remains to be seen.
Photo credit: Stuart Miles / Shutterstock
-

Comcast could cut off customers who use the Tor browser
Publié: septembre 15, 2014, 5:42pm CEST par Mark Wilson

Last week there were net neutrality protests from a number of big names in the online world. This week there is controversy courtesy of Comcast -- described by DeepDotWeb as "the most hated company in America" -- as the firm apparently declares war on Tor.
The web browser -- one favored by those concerned about their privacy -- has been branded "illegal" by Comcast according to DeepDotWeb and customer reports appearing on the /r/darknetmarkets subreddit (reddit itself having banned subreddits associated with the Fappening). Customers are reporting having been warned that use of Tor is against Comcast's term of use and could result in a termination of service.
Customers have said that Comcast has reached out to them directly and told them to stop using Tor or risk losing their connection. Check out Comcast's Acceptable User Policy, and you'll notice that proxy tools are indeed singled out for attention in the "technical restrictions" section:
"Use or run dedicated, stand-alone equipment or servers from the Premises that provide network content or any other services to anyone outside of your Premises local area network ('Premises LAN'), also commonly referred to as public services or servers. Examples of prohibited equipment and servers include, but are not limited to, email, web hosting, file sharing, and proxy services and servers".
While Comcast customers may be complaining that they are being warned against using Tor, Comcast itself told a different story to Business Insider:
"Customers are free to use their Xfinity Internet service to visit any website or use it however they wish otherwise. Like virtually all ISPs, Comcast has an acceptable use policy or AUP that outlines appropriate and inappropriate uses of the service. Comcast doesn’t monitor users’ browser software or web surfing and has no program addressing the Tor browser. The anecdotal chat room evidence provided is not consistent with our agents’ messages and is not accurate. Per our own internal review, we have found no evidence that these conversations took place".
With two opposing sides of the same story, it can be difficult to know who is telling the truth. But this would be far from the first time internet users have been tarred with the wrong brush. Just last week, TorrentFreak reported about how the BBC was suggesting that ISPs should regard customers who use VPN tools and proxies as "suspicious". The broadcaster is quoted as saying:
"Since the evolution of peer-to-peer software protocols to incorporate decentralized architectures, which has allowed users to download content from numerous host computers, the detection and prosecution of copyright violations has become a complex task. This situation is further amplified by the adoption of virtual private networks (VPNs) and proxy servers by some users, allowing them to circumvent geo-blocking technologies and further evade detection. IIt is reasonable for ISPs to be placed under an obligation to identify user behavior that is 'suspicious' and indicative of a user engaging in conduct that infringes copyright. Such behavior may include the illegitimate use by Internet users of IP obfuscation tools in combination with high download volumes".
How do you feel about ISP interference into web usage? Have you felt the impact of such actions? Would it make you consider switching ISPs?
-

Many UK iPhone 6 pre-orders cancelled after Phones 4u enters administration
Publié: septembre 15, 2014, 1:15pm CEST par Mark Wilson
 Would-be iPhone 6 and iPhone 6 Plus owners are currently wondering whether or not they will receive the handsets they pre-ordered after Phones 4u went into administration.
Would-be iPhone 6 and iPhone 6 Plus owners are currently wondering whether or not they will receive the handsets they pre-ordered after Phones 4u went into administration.On Sunday, the beleaguered retailer threw in the towel after EE decided not to renew contracts. While Phones 4u has said that it will honor orders that have been placed and dispatched, but indicated that orders that are yet to be sent out -- which will include many iPhone 6 orders -- will be canceled, and refunds issued.
EE's move comes shortly after a similar withdrawal by Vodafone, and Phones 4u boss David Kassler explains that: "If mobile network operators decline to supply us, we do not have a business".
In a message signed by the "heartbroken Phones4u Team", customers visiting the company's website are informed of the news and directed to customer support lines:
"Following the unexpected decision of EE and Vodafone to withdraw supply from Phones4U, we regret that we are offline. Please accept our apologies and we will update you as soon as possible".
Store doors are today closed around the country, and a similar message was posted to Twitter:
To our customers, following the unexpected news we are now offline. [t.co] Thank you, The heartbroken Phones 4u Team.
-- Phones 4u (@Phones4u) September 15, 2014
There are currently over 5,500 jobs on the line, and eager iPhone 6 customers have been vocal in their anger. With orders having been placed right up to the weekend, would-be buyers feel that orders should not have been taken. Phones 4u insists that it ceased trading "as soon as practically possible".
Have you been affected by the closure of Phones 4u? Did you manage to track down an iPhone 6 elsewhere?
If you do need to speak to Phones 4u the number you need is 0844 8712253.
Photo credit: JuliusKielaitis / Shutterstock.com
-

Facebook is going to start taking notice of why you hate certain ads
Publié: septembre 13, 2014, 11:56pm CEST par Mark Wilson
Adverts are pretty much universally hated online. Sites can try to justify their presence as much as they like but visitors will still view them with loathing. Among the many complaints levelled at Facebook, the irrelevance of many of the advertisements that appear on users' pages is a major cause of complaints. For quite some time now Facebook has given users the chance to voice a dislike of individual ads -- opt to hide an ad via the official Facebook method and you can indicate that you find it irrelevant, offensive, repetitive, spammy, and so on -- but it has been hard to know just how much notice has been taken of these complaints. Now Facebook wants to assure users that it is listening and that more relevant ads will be displayed.
Hopefully this can be taken to mean "ads that are more relevant" rather than "there will be more ads and they will be relevant", but the point is that Facebook wants to ensure that you see ads that might actually be of interest. Two new updates will help to tailor your ad experience. The first seems like a fairly obvious one:
For years, we have given people the choice to hide an ad so they no longer see it in their News Feed. We’ve also looked at these hides and used them as a signal that other people on Facebook might not want to see that ad. Now, we are going a step further by taking into account the specific reason they didn’t want to see that ad, and use that as a signal to inform whether or not we show the ad to other people.
Again, the wording isn’t perfectly clear, but the implication seems to be that up until now the fact that you indicated that an ad was offensive was not taken into account. Quite why users were asked to specify a reason for hiding an ad was needed (a placebo?) but it's good to hear that it will now be noted and acted upon.
The second update gives great weighting to the reasoning given by people who do not block many advertisements. If someone is usually happy to put up with ads and they're suddenly moved to block one, Facebook will now take that more seriously.
The announcement in the Facebook newsroom includes an interesting snippet of information -- apparently only a few people complain about ads: "These updates are designed to affect the ads that a small set of people give us negative feedback on."
-

Facebook's 'real name' policy is wrong, discriminatory, and potentially dangerous
Publié: septembre 13, 2014, 8:38pm CEST par Mark Wilson
Facebook's policy requiring the use of real names on the social network is not all that new, but it remains controversial. Many users would like to be able to use a nickname (other than the "variation of your real first or last name" permitted by the site), but Facebook continues to insist that forcing the revelation of birth name "helps keep our community safe". Or does it? There's certainly an argument that suggests it makes sense to know who you are dealing with, but this cannot be a one-size-fits-all policy. There will always be exceptions, and this is something highlighted by ReadWrite.
As Selena Larson points out, there are many people who choose to use "pseudonyms online for both safety and personal reasons". And yet the site is trying to force Sister Roma -- a drag artist and member of Sisters of Perpetual Indulgence, a "leading-edge Order of queer nuns" -- to use her birth name rather than what is being regarded as her stage name. Who is Facebook to try to interfere with this? This is the site that only recently was encouraging its users to boost their privacy by checking the settings they had in place. It smacks of giving with one hand and taking with the other.
As reported by the Daily Dot, Sister Roma was this week singled out by Facebook. She explains that: "I was automatically logged out and told my account was suspended because it appears that I'm not using my real name", Sister Roma told the Daily Dot. "I was instructed to log in and forced to change the name on my profile to my legal name". If you head over to Sister Roma's Facebook page now, you'll find that she appears under her birth name of Michael Williams. She has complied with Facebook's demands, but is not happy about it:
In light of the new demand by Facebook that we use our "real" names I am considering shutting down my personal page to concentrate on my "FAN PAGE." I update it an interact as much as I can but I detest the idea of having a fan page. I'm not fucking Britney Spears. I have friends, not fans. At any rate, please follow me there cause this profile may be coming to an end.
There are many people in a similar position to Sister Roma. Countless artists -- musicians, actors, writers -- use a name other than the one that appears on their birth certificate. What level of safety Facebook thinks it is bringing about by forcing these people into using their "real" name on the network is not quite clear. Instances of it are just going to be confusing. Think of Sister Roma, and that's the name that comes to mind, not Michael Williams. Think of Elton John and you don’t first think of Reginald Kenneth Dwight. Sting is not Gordon Matthew Thomas Sumner to many people. U2's Bono is Bono, not Paul David Hewson.
A few weeks ago I asked whether Twitter was right to block accounts that shared ISIS beheading footage. Consensus was that while it might not be "right" to block such content, Twitter is -- of course -- within its right to do pretty much what it wants. Having signed up for an account and agreed to the terms of service, users are bound to certain terms and conditions. But this does not mean that these terms and conditions should not be questioned.
This issue is discriminatory against transgender and other nonconforming individuals who have often escaped a painful past. They've reinvented themselves or been born again and made whole, adopting names and identities that do not necessarily match that on their driver's license.
There is now a petition underway to try to help Facebook see the error of its ways. Whether it pays off is anyone's guess, but Sister Roma's frustrating situation publicizes an important issue. It is often people in the public eye who choose to use a pseudonym. While this is done out of preference, it has the happy side effect of offering a degree of privacy and protection to family members. Ultimately Facebook needs to remember that it is a website -- nothing more. Its approach to privacy over the years has annoyed, irritated and driven away many people, but now is the time for the network to stop throwing its weight around. If I want to be called Rebecca the One-Legged Unicorn on Facebook, why should I not be able to?
Of course, Facebook can impose whatever rules it wants to, but it should also expect to be asked to justify its policies.
-

T-Mobile brings free Wi-Fi calling to its customers, and it's terrible news
Publié: septembre 12, 2014, 4:48pm CEST par Mark Wilson

At its seventh Uncarrier event in San Francisco, T-Mobile unveiled plans to clutter up the internet for everyone -- T-Mobile customers and non-T-Mobile customers alike. On the face of it, things sound great. The T-Mobile Personal CellSpot offers free Wi-Fi calling and "fast data". The Cellspot is essentially a router which can be yours for a deposit of $25 but the difference is that it has been tweaked so that it prioritizes HD Wi-Fi calls over other traffic on the network. If you live in an area with poor mobile reception -- which can be just as frustrating as having to put up with a terrible internet connection -- this might sound like wonderful news, but when you look at the bigger picture, it is really such good news?
Let's try to ignore the fact that in order to get hold of one of the Personal CellSpots, you need to stump up a refundable deposit -- whoever heard of renting their router? -- and ask the first question: who actually needs "HD" phone calls? Pictures are HD, and there really have been very few complaints about the overall quality of voice calls on mobiles over the years. This is just gimmicky and inefficient. T-Mobile CMO Mike Sievert indicated that customers would enjoy the portability of the device -- easy to take on the road and set up anywhere. But how many people take a router away with them? Is this really going to become the norm?
The routing of calls and texts over Wi-Fi is being dubbed "Wi-Fi Unleashed", and T-Mobile CEO and president John Legere explodes with joy talking about it:
"Wi-Fi Unleashed is a game changer. This is like adding millions of towers to our network in a single day. The difference between us and the traditional carriers is that they'll do everything they can to make more money off you. We'll do everything we can to solve your problems, and today, that's about uniting Wi-Fi with our data strong network for unprecedented coverage".
T-Mobile explains that its entire portfolio of phones will be able to take advantage of Wi-Fi calling and texting, and owner of older handsets will be given the opportunity to upgrade. With a suitable phone, any wireless access point that customers can connect to is transformed into a means of making calls and sending texts. Is this really the best use of the internet? T-Mobile customers will eat up acres of internet. Get a bunch of T-Mobilers in Starbucks and they'll just suck up all of the bandwidth that other customers could be using. Expand this idea on a national scale and the gigbytes of data being gobbled up will be staggering.
Of course there's nothing to stop people switching to making regular cellular calls, but how many people will bother? The small print on the T-Mobile website explains that "most devices will not transition between Wi-Fi and the wireless network", and "will not transition between Wi-Fi and the cellular network" -- so if you forget to switch manually, you could find that you're either cut off in the middle of a phone call as you walk down the street, or that you don’t receive any calls or texts as you forgot to switch modes. Snuck into the small print is the announcement that "devices using wireless connections may be vulnerable to unauthorized attempts to access data and software stored on the device". Well that's reassuring, isn’t it?
T-Mobile's announcement also includes the news of a venture with Gogo Air which will enable customers to "text, picture message, even check T-Mobile Visual Voicemail at 30,000 feet". Marvellous! That five hour cross-Atlantic flight can now be punctuated by endless beeping notifications as fliers send photos of the view out of the windows, and awestruck recipients fire off replies whose arrival in-cabin is announced with grating tones. Joy of joy.
So thanks, T-Mobile. Thanks for ruining flights, and for slowing down the internet for everyone.
Photo credit: Ralf Maassen (DTEurope) / Shutterstock
-

Yahoo resisted NSA Prism requests -- US government threatened $250,000 daily fines
Publié: septembre 12, 2014, 1:35pm CEST par Mark Wilson

It's transparency time once again! After Edward Snowden opened the can of NSA surveillance worms, internet users' collected attention has been focused on online privacy. We still don’t know the full extent of the monitoring that took place, but more information continues to leak out. All of the big names -- Google, Apple, Microsoft, Facebook, and the rest -- have slowly trickled out little snippets about government data requests. A new blog post from Yahoo's general counsel Ron Bell sheds further light on the resistance the company put up against requests for data.
Just like Google and Microsoft, Yahoo is keen to let it be known that it tried to stick up for the privacy rights of its customers. A new cache of documents -- stretching to War And Peace baiting 1,500 pages -- from seven years ago shows just how much of a fight Yahoo tried to put on its users' behalves. Way back in 2007, the US government started to request information about users from a number of online companies. Yahoo was one of the companies who -- initially, at least -- refused to comply, and tried to fight the government in court.
Some of the documents that have just been released give an insight into not only Yahoo's attempts to avoid handing over user data, and the company's fight to make the secret court papers publicly available. One particularly interesting little scrap of information included in the paper is the fact that the US government threatened to fine Yahoo $250,000 for failing to comply with requests for information. Not as a one-off fine, but as a recurring, daily fine. A fine of a quarter of a million dollars per day for failing to hand over information about customers.
In his blog post, Ron Bell explains that:
Users come first at Yahoo. We treat public safety with the utmost seriousness, but we are also committed to protecting users' data. We will continue to contest requests and laws that we consider unlawful, unclear, or overbroad.
He also makes it clear the Yahoo continues to fight the US government:
We are still pushing for the FISC to release materials from the 2007-2008 case in the lower court. The FISC indicated previously that it was waiting on the FISC-R ruling in relation to the 2008 appeal before moving forward. Now that the FISC-R matter is resolved, we will work hard to make the materials from the FISC case public, as well.
Photo credit: lculig / Shutterstock
-

Google Drive and Docs gain accessibility options for visually-impaired users
Publié: septembre 12, 2014, 12:56am CEST par Mark Wilson

With a visual impairment, using any software or service can be anything from tricky to impossible. Windows and other operating systems have long included features that make them easier for blind and partially sighted people to use, and now Google is adding similar playing-field-levelling features to Google Drives and Docs. While traditional desktop software has been quick to adopt new methods of opening up to as many people as possible, the same cannot be said of online tools -- Google is looking to change that.
Starting today, Docs, Sheets, Slides, Drawings and Forms all feature support for Alt tags for images, as well as better text-to-voice conversions. Tweaks include support for vocalized spelling correction suggestions, as well as the ability to listen to comments that have been added to shared documents. The arrival and departure of collaborators something else that's now spoken aloud. Changes are also to be found in the many keyboard shortcuts -- additional shortcuts are now available to provide access to a wider range of tools and option than before, including the editing of charts and pivot tables.
Docs is gaining support for Braille displays and Google has put together a series of guides to help newcomers get to grips with a feature that can be a little overwhelming. There are some nice touches such as the option to have Docs read announce the formatting that is in use at the current location so it can be replicated elsewhere.
There's a new accessibility website that gives a full rundown of what’s now available, and in the video below, Google shows off just how helpful the new accessibility option can be:
Photo credit: Pakhnyushcha / Shutterstock
-

Android apps break out of the small screen and jump to Chromebooks
Publié: septembre 11, 2014, 9:20pm CEST par Mark Wilson
A lot of Google services have transitioned to gain the title of "apps", and the same is true of a large number of extensions for the Chrome browser. These online tools are essentially cross-platforms apps that work identically Now Google is taking another step to break out of the confines of making apps available to a single platform. Android apps are, quite rightly, associated with smartphones and tablets, but now a small number of these mobile apps are finding their way onto Chromebook.
The (usually) cheap and cheerful Windows laptop/Mac Book alternative (did someone say netbook?) can now start to benefit from a handful of well-known titles from Android devices. It is very early days but as of today there are four Android apps available to Chromebook owners -- Duolingo, Evernote, Sight Words, and Vine -- but we can expect to see this list expand over time. The quartet of crossover apps were introduced today by Ken Mixter and Josh Woodward. A short blog posts penned by the pair explains that the Chromebook support comes thanks to the App Runtime for Chrome (Beta) project.
Before you get too excited, don't expect to fire up Google Play on your Chromebook and download every app you're using on your phone -- a little work has to be done to ensure compatibility. You can expect to see more apps appearing over the coming months, but you can ask if there's something specific you want. If you have a favorite Android app that you would like to be able to use with a full keyboard on your Chromebook, you can put in a request using a Google form (of course!).
If you missed the announcement that Chromebook users would be able to use Android apps, check out the video below from Google I/O keynote where the feature was introduced.
-

U2 gives away new album to half a billion iTunes Store customers to celebrate iPhone 6 launch
Publié: septembre 10, 2014, 12:33am CEST par Mark Wilson

Apple launch events are normally about getting people to part with their cash rather than giving things away for free. So as not to buck this trend too much, the not entirely inexpensive Apple Watch, iPhone 6 and iPhone 6 Plus were announced but there was also something of a treat for fans of Irish rockers U2. As well as performing at the launch event in Cupertino, Bono and bandmates gave away their new album, Songs of Innocence, free of charge to all iTunes Store users.
This is not the first time U2 has teamed up with Apple. The band was also involved in the launch of early iPod, offering official endorsement to a special edition of the music player. But this is a much larger scale collaboration. Giving away the eleven-track album to more than half a billion people is a big, headline grabbing gesture -- and regardless of your opinion of U2 musically, it's something that's hard to ignore. The album is available for the next five weeks in 119 countries.
Can't be bothered to go and hunt it down? Apple has already done the hard work for you. Just fire up the Music app on your iOS device, head to the Albums tab and you'll find the album ready and waiting for you. Songs of Innocence can also be accessed via iTunes for Mac and PC -- tracks can be streamed or downloaded -- and it can be streamed through iTunes Radio and Beats Music from September 10.
Frontman Bono gushed:
From the very beginning U2 have always wanted our music to reach as many people as possible, the clue is in our name I suppose—so today is kind of mind-blowing to us. The most personal album we’ve written could be shared with half a billion people... by hitting send. If only songwriting was that easy. It's exciting and humbling to think that people who don't know U2 or listen to rock music for that matter might check us out. Working with Apple is always a blast. They only want to do things that haven't been done before -- that's a thrill to be part of.
A nice free gift, or one to skip?
-

Apple revolutionizes mobile payments with Apple Pay
Publié: septembre 9, 2014, 10:59pm CEST par Mark Wilson
 The focus of Apple's event today was the iPhone 6, iPhone 6 Plus, and the Apple Watch, but one of the more understated stars of the show was Apple Pay. This is not hardware, but a new mobile payment platform which Apple is billing as "your wallet, without the wallet". It works in conjunction with the new handsets to provide a new means of contactless payment and it supports credit and debit cards from American Express, MasterCard and Visa. There's backing from the likes of Wells Fargo, Bank of America, and Capital One Bank, and users need to just add their credit or debit card to their iTunes Store account to start paying for goods and services with their phone -- or Apple Watch.
The focus of Apple's event today was the iPhone 6, iPhone 6 Plus, and the Apple Watch, but one of the more understated stars of the show was Apple Pay. This is not hardware, but a new mobile payment platform which Apple is billing as "your wallet, without the wallet". It works in conjunction with the new handsets to provide a new means of contactless payment and it supports credit and debit cards from American Express, MasterCard and Visa. There's backing from the likes of Wells Fargo, Bank of America, and Capital One Bank, and users need to just add their credit or debit card to their iTunes Store account to start paying for goods and services with their phone -- or Apple Watch.A number of big names have already jumped on the Apple Pay bandwagon, including McDonald's, Staples, Disney Store, and Whole Foods Market, as well as the 258 US Apple stores. Apple Pay can also be used in the App Store as well as more than 220,000 locations that support contactless payment. In addition to the benefits of contactless payment, Apple is really pushing the security aspects of Apple Pay. Eddy Cue, Apple's senior vice president of Internet Software and Services says:
Security and privacy is at the core of Apple Pay. When you're using Apple Pay in a store, restaurant or other merchant, cashiers will no longer see your name, credit card number or security code, helping to reduce the potential for fraud.
The new payment system rolls out in October and ties in with Find My iPhone as a security measure. Should your iPhone be lost or stolen, you can easily suspend payments so a bill is not racked up on your behalf. But there's also a great focus on ease and speed. The use of the iPhone 6's NFC antenna means there's no need to touch anything on-screen other than the Touch ID reader -- a payment can be made with a wave of the handset. In the case of the Apple Watch, a quick double tap of the Digital Crown is all it takes, and payment confirmation is provided with a beep and vibrate.
-

Apple announces its first wearable -- the Apple Watch
Publié: septembre 9, 2014, 9:17pm CEST par Mark Wilson

Running counter to many of the rumors circulating ahead of the Cupertino event, Apple today announces the Apple Watch, not the iWatch. Unlike the Moto 360, Apple's offering takes the squarer form adopted by many other manufacturers, but there are differences. Taking design cues from older iPhones -- think 3GS period -- the Watch was relegated to the infamous "one more thing" slot after the iPhone 6 and iPhone 6 Plus were announced. Rather than the unibody design that some had expected, the Apple Watch features six different straps, comes in two sizes (38 mm and 42 mm -- his and hers essentially), and will be available in three different finishes.
Just like the iPhone 6 and iPhone 6 Plus, the Apple Watch's display is made from sapphire crystal but there's something interesting to the right of the screen. More usually found on a traditional mechanical watch, there's a crown -- but this is not used for winding up a spring. Instead, this is a new form of input that can be used to scroll around the interface, zoom in and out, and doubles up as a home button. Despite the squared surround, the Apple Watch's UI is very round in flavor, mimicking the look of a traditional watch.
Tim Cook described the Apple Watch as "the most personal device we’ve ever created", and the screen features an intriguing touch. This is not just a touch sensitive screen, but a display that can distinguish between touches and taps, opening up new possibilities for interacting with apps.
There's haptic feedback courtesy of the Taptic Engine (which can be used to provide map direction so you don’t need to keep looking at the screen), and the device is powered by the S1 system. Like other wearables, there's a raft of sensors on board to track movement, heart rate, and sleep pattern; information which is then fed to the Health app on iPhone and iPad. And this is something potential buyers need to keep in mind -- Apple Watch relies on iPhone, so you'll need to have a handset if you want the wearable (it's compatible with iPhones back to the iPhone 5).
As there's a relatively small screen to work with, there's no keyboard. Instead the Apple Watch suggests messages you might like to use to reply to those you receive and also includes an animated emoji system. Siri is also on hand to allow for voice control, and charging is taken care of by a MagSafe connection. Apps will be what makes the Apple Watch a success -- demonstrations showed the device being used to unlock hotel rooms, and Tim Cook suggested using it as a remote control for the iPhone camera. There's also scope for contactless payment.
There are a lot of options. With six straps, three different finishes, and two sizes, there are numerous combinations to choose from. Factor in customizable watch faces, and the level of personalization is impressive. There's no firm release date yet, but if you were hoping to get one for Christmas, you're out of luck -- the Apple Watch is pegged for launch early next year.
With pricing starting at $349, it's sure to fare well against the competition, but the requirement for an iPhone automatically limits the possible market reach.
So... impressed? Underwhelmed? Blown away?

-

Google Chrome is to blame for a massive increase in online ad blocking
Publié: septembre 9, 2014, 5:30pm CEST par Mark Wilson
 A shocking new report looking at online advertising shows that there has been a huge increase in the number of internet users making use of ad blocking tools. The report describes ad blocking as having gone mainstream, but it also suggests that the loss of ad revenue threatens the life of many websites.
A shocking new report looking at online advertising shows that there has been a huge increase in the number of internet users making use of ad blocking tools. The report describes ad blocking as having gone mainstream, but it also suggests that the loss of ad revenue threatens the life of many websites.Pagefair worked with Adobe putting together the report and found that 4.9 percent of internet users make use of ad blockers, including more than a quarter (27.6 percent) of those in the US.
The figures show that ad blocking is more prevalent among younger web users, with 41 percent of those aged between 18 and 29 employing some form of ad avoidance utility. What is particularly interesting is that from 2013 to 2014, there was a 69 percent increase in the use of ad blockers and this has been fueled at least in part by Google's Chrome browser which saw a huge 96 percent increase in ad blocking.
The report points out the irony of Chrome increasing the interest in ad blocking given that Google's business is built on advertising. Of those who do use ad blocking, 63 percent are Chrome users, while 26 percent make use of Firefox. Opera, Safari, and IE account for 5, 4, and 4 percent of ad blockers respectively. The reasons for blocking ads are quite varied. 45 percent just did not want to see ads, with 30 percent indicating that they are generally too intrusive. 17 percent of ad block users do so because of concerns about privacy and performance.
It seems that ads are viewed as abhorrent by men and women, but male internet users were slightly more likely to take steps to block them. The prevalence of ad blocking can be attributed to internet users' unwillingness to either pay for content or endure pages that are subsidized by advertisements. 80 percent of those questioned indicated a complete unwillingness to pay to avoid ads, but 61 percent of this number refused to see ads that help maintain sites.
Photo credit: Curioso / Shutterstock
-

Porn sites join forces with Reddit, Mozilla, and more in net neutrality protest
Publié: septembre 9, 2014, 4:18pm CEST par Mark Wilson

In one of the strangest joining of forces imaginable, Reddit (of recent Fappening censorship fame), Mozilla (the browser folks) and other well-known names are teaming up with porn sites. The net neutrality debacle is one that has been rumbling on for some time now as more and more ISPs reveal plans to provide faster internet access to those willing -- or able -- to pay more. This creation of a two-tier internet is something that has been met with disgust from many quarters, including lots of big online names.
Tomorrow, 10 September, the likes of Pornhub and Redtube will join Etsy, FourSquare, KickStarter and more in a day of protest.
A number of tech firms have expressed concerns about the prospect of an internet that gives some traffic higher priority. The aim of the protest is simple -- to make it clear that those involved, and lots of others, feel that everyone should be treated equally online; no fast lane and slow lane. If the Federal Communications Commission (FCC) changes the rules on net neutrality, it could mean that internet users have to ensure a second-rate service. Tomorrow's protest is being organized in part by Fight for the Future whose Battle for the Net project advocates online equality.
The protest is highly symbolic. Each of the many sites that has decided to get involved (a list is available on the Battle for the Net website) will adorn itself with "loading" icons to illustrate what a two-tier internet could look like. The icons are purely to make a point; no site will actually slow down, but the aim is to garner as much attention as possible.
The sites that had already signed up for the day of protest were enough to bring information about net neutrality to a wide audience. But the addition of a couple of the biggest porn sites in existence opens things up even more. Time pressures are now mounting. The FCC could come to a decision about how it plans to handle the future of the internet as early as the end of this year.
Photo credit: Lightspring / Shutterstock
-

Twitter tests 'Buy' button to allow purchasing via tweets
Publié: septembre 8, 2014, 6:53pm CEST par Mark Wilson
It has been the subject of speculation for some time now, but today Twitter finally announces that the rumored "Buy" button will soon be making an appearance in timelines. The feature has been made public through a blog post that explains that the button will initially be pushed to "a small percentage of US users", but reassuring everyone else that coverage "will grow over time".
What does this mean? Well, that you will be able to buy things via tweets, essentially.
This is not a feature that will be seen across the entire Twitter network -- at least not for the time being -- it is restricted to the iOS and Android mobile apps to start with. If you see a tweet that mentions something you like the look of, just hit the Buy button to find out more. You'll then be prompted to enter your payment and shipping details, and your order is complete. For future orders, your payment details are securely saved so there's no need to enter them again.
To start with, there is a limited number of partners involved in the scheme including Fancy (@fancy), Gumroad (@gumroad), Musictoday (@Musictoday) and Stripe (@stripe). In the coming weeks you'll be able to buy from the likes of Burberry (@burberry), Eminem (@eminem), The Home Depot (@HomeDepot), Megadeth (@Megadeth), Panic! At The Disco (@panicatthedisco), Ryan Adams (@TheRyanAdams), Soundgarden (@soundgarden), The New Pornographers (@TheNewPornos), and 9/11 Day (@911Day). Musicians feature in the list quite heavily, and this could well be where most of Twitter's Buy button income stream comes from. Bands and artists can sell tickets through Twitter, giving fans the opportunity to ensure a place at the next gig with a quick tap.
Check out the video below for a (very quick) guide to the new Buy button:
-

Calling all RSS fans! Inoreader now supports Microsoft OneNote
Publié: septembre 8, 2014, 5:06pm CEST par Mark Wilson

They said RSS was dead, but when Google decided to close the door on Google Reader, there was a vocal clamoring of disapproval. A flood of tools popped up to filled the vacuum left behind by the absence of Google's service and one that quickly grew in popularity is Inoreader -- thanks, at least in part, to the fact that it can be customized to look and work in much the same way as Google Reader.
No RSS reader worth its salt would be complete without offering integration with a number of other online services of course, and now InoReader benefits from OneNote support.
The addition of OneNote functionality means that it is now possible to share and organize the content you stumble across to Microsoft's note-taking tool. Before you get too excited, there is a slight caveat. In order to take advantage of this new feature you need to have either a Plus or Professional account. If you are puttering away on a free Basic account, you can try out OneNote support for a week by taking advantage of a free trial. The free trial gets a mention in an Inoreader blog post, but you'd be forgiven for missing it.
To enable OneNote integration, hit the settings button to the upper right of the Inoreader page and select Preferences. Move to the Integration section and scroll down until you see OneNote. If you are working with a free account, click the link to commence a seven day trial and then click the Connect With OneNote button. Enter your OneNote credentials and you’re good to go -- at least for a week!
A new OneNote icon will now appear beneath articles you read, and when you click it the article will be saved to OneNote. OneNote is also supported within rules so you can define it as an action -- if articles match certain criteria, you can have them sent automatically to your OneNote account.
-

Facebook celebrates 1 billion daily video views with new view count feature
Publié: septembre 8, 2014, 2:23pm CEST par Mark Wilson
 As demonstrated by the infuriatingly popular #ALS Ice Bucket Challenge phenomenon, video on Facebook is more popular than ever. If you were in any doubt about just how popular these magic moving pictures really are, the social network announces that it is racking up an incredible 1 billion video views every day.
As demonstrated by the infuriatingly popular #ALS Ice Bucket Challenge phenomenon, video on Facebook is more popular than ever. If you were in any doubt about just how popular these magic moving pictures really are, the social network announces that it is racking up an incredible 1 billion video views every day.But have you ever wondered how many other people have wasted their time watching yet another video of crazy Russian drivers, drunken debauchery, or amusing animal antics? Wonder no more! Starting this week, Facebook is rolling out a new feature that shows how many views a particular video clip has received.
This is information that is going to be of most interest to whoever uploaded a video, but it's also a handy way to gauge the popularity of a clip. What? Only 15 people have watched that video? I'm not wasting my time on that -- I'll watch this hilarious footage with its 854,758 views instead, I think! The counter will start to appear from today, and can be found beneath a video preview next to the Like and Comment links.
There have been quite a lot of changes at the social network of late. When it's not trying to clear the crap out of newsfeeds, Facebook is busy helping advertisers pump targeted ads to users based on their connection speed -- and viewing information will be of particular interest to this market. Continuing its trend of not always getting things quite right, the social network introduced a feature that meant videos automatically played as soon as they appeared on-screen. But more recently, having faced criticism for its privacy policies, Facebook started to push a new Privacy Checkup tool which encourages users to double-check that they're not sharing information with too many people.
However, it is video that Facebook is focusing its attention on at the moment. The new view count will appear on videos from both people and Pages, providing they have been made public. If you don’t see it straight away, don’t panic -- it will be with you soon.
-

Microsoft takes down Bing Image Widget after Getty legal action
Publié: septembre 8, 2014, 12:55pm CEST par Mark Wilson
Following a lawsuit from Getty Images Inc, Microsoft has taken the beta version of its Bing Image Widget offline. The stock image firm had complained that Microsoft's widget infringed on copyright by enabling people to embed protected images in websites without attribution or authorization.
In opting to willingly pull the widget, Microsoft may have managed to sidestep at least some of the brunt of the legal action taken against the company. Getty had called for the immediate blocking of the tool and filed a lawsuit at US District Court for the Southern District of New York.
The Bing Image Widget home page includes no explanation, but displays the message: "We have temporarily removed the beta". Getty has previously described the injury caused to the company by the existence of the widget as "incalculable", complaining that Microsoft has turned its vast photo library into "a vast, unlicensed clip art collection".
Contacted by Re/code, a Microsoft spokesperson said: "We have temporarily removed the Bing Image Widget beta so we can take time to talk with Getty Images and better understand its concerns".
We have reached out for further comment, but as this is an ongoing legal matter it is unlikely that we'll learn any more for a little while yet.
-

Reddit bans The Fappening subreddits
Publié: septembre 7, 2014, 11:21pm CEST par Mark Wilson
 Reddit has taken the step of banning the subreddit through which the now infamous Fappening images were made available last week. This follows the decision by 4chan -- the site originally used to leak the images -- to introduce a DMCA policy to help cope with copyright material. The move is unlikely to stem the flow of image sharing -- nor is it likely to prove popular -- but Reddit administrator alienth has posted a lengthy statement explaining the reasons behind the decision.
Reddit has taken the step of banning the subreddit through which the now infamous Fappening images were made available last week. This follows the decision by 4chan -- the site originally used to leak the images -- to introduce a DMCA policy to help cope with copyright material. The move is unlikely to stem the flow of image sharing -- nor is it likely to prove popular -- but Reddit administrator alienth has posted a lengthy statement explaining the reasons behind the decision.Just in case anyone managed to avoid the news, alienth includes a brief summary of the week's events.
"A very shitty thing happened this past Sunday. A number of very private and personal photos were stolen and spread across the internet. The fact that these photos belonged to celebrities increased the interest in them by orders of magnitude, but that in no way means they were any less harmful or deplorable. If the same thing had happened to anyone you hold dear, it'd make you sick to your stomach with grief and anger".
That it has taken Reddit a full week to properly respond to the issue has led to criticism, but the statement explains that things were held up by pressing problems: "First, the amount of traffic hitting this content was breaking the site in various ways. Second, we were already getting DMCA and takedown notices by the owners of these photos. Third, if we were to remove anything on the site, whether it be for technical, legal, or ethical obligations, it would likely result in a backlash where things kept getting posted over and over again, thwarting our efforts and possibly making the situation worse".
The Fappening subreddit -- /r/thefappening -- was a hotbed of activity. The age of at least one of the celebrities depicted in the leaked nude photos meant that it was classed as child pornography, and it seems that this was the tipping point. Reddit makes it clear that "this is where we have drawn a clear line in the sand". There then followed "a game of whack-a-mole"; the laborious task of taking down images only to find them reuploaded. The final decision was to close down the subreddits in question. "It's obviously not going to solve the problem entirely, but it will at least mitigate the constant issues we were facing. This was an extreme circumstance, and we used the best judgement we could in response".
The move was met by something of a backlash of comments, resulting in the creation of a FAQ in which Reddit makes clear that, as far as possible, it wants to remain a neutral platform: "We remove what we're required to remove by law, and what violates any rules which we have set forth". There is also the small issue that the site managed to benefit from an estimated 250 million page views, and commenters are unhappy that Reddit could have benefitted from this.
Photo credit: Konstantin Faraktinov / Shutterstock
-

Watch out! More iPhones stolen than any other smartphone
Publié: septembre 7, 2014, 10:54pm CEST par Mark Wilson

New figures released by the Home Office and published by the BBC show that if you own an iPhone 5, 5C, 5S and 4S in England or Wales, you are most at risk of having your smartphone stolen. If the trend continues, it is likely that the upcoming iPhone 6 will also prove similarly attractive to thieves. Figures show that there were a total of 742,000 phone thefts between 2012 and 2013, and that the largest numbers of theft involved Apple's handsets. Interestingly, despite massively dwindling sales, the next most popular phone to be pocketed by thieves was the Blackberry 9790.
While the iPhone is the most appealing to the light-fingered, the figures show that Apple's claim to be "leading the industry in protecting" seems to be true. New security features introduced in iOS 7 led to a noticeable drop in iPhone thefts, but it still remains the most commonly stolen handset. Apple told the BBC:
Apple has led the industry in helping customers protect their lost or stolen devices since the launch of Find My iPhone in 2009 by allowing customers to remotely set a passcode or erase all their personal data.
With iOS 7, Find My iPhone includes a feature called Activation Lock, which is designed to prevent anyone else from using your iPhone... if you ever lose it. This can help you keep your device secure, even if it is in the wrong hands, and can improve your chances of recovering it.
Looking at the number of thefts is an interesting way to judge the popularity of individual phones, and the drop in iPhone thefts will come as good news to Apple after the celebrity iCloud account compromises that occurred recently. This led the company to further bolster the security of iCloud but the attention this week will turn to the expected launch of the iPhone 6 and iWatch.
Photo credit: Ammentorp Photography / Shutterstock
-

Facebook rolls out Privacy Checkup feature to users around the world
Publié: septembre 5, 2014, 7:31pm CEST par Mark Wilson
We now live in an age where privacy is a key concern. Facebook has long been criticized for its somewhat lackadaisical attitude to the privacy of user data, and over the years various steps have been taken to afford Facebookers greater control over who is able to see their status updates and other data. First announced back in May, the social network is now rolling out its Privacy Checkup feature around the world, giving users the chance to check exactly who they are sharing information with.
The new tool does not really introduce any new features, but it does bring existing security controls to the fore. Privacy Checkup should make itself known over the next few days by popping up when you use Facebook, but it can be accessed whenever you want by clicking the privacy lock icon to the upper right of the page. For some reason, the face of Privacy Checkup is a friendly blue dinosaur, sort of like a prehistoric version of Clippy.
Privacy settings are reduced to three broad categories -- posts, apps, and profile data. In the Your Posts section you can choose which groups of people should be granted access to your status updates -- you can lock it right down, or leave it wide open to the public if you prefer. Move to the Your Apps section, and you can work through the undoubtedly lengthy list of apps you have installed. Privacy settings can be configured for each app individually, and this is also a good time to trim the fat and banish any you no longer use.
The last stage involves configuring the visibility settings to different pieces of personal information. You may decide to share information about your work history with a limited group of friends, or keep your hometown completely private. The controls are not particularly fine-grained, but for anyone who has never given their privacy settings a thought, it's a decent enough start.
Check out the Facebook blog where Product Manager, Paddy Underwood presents a video guide to the checkup tool. He says: "We know you come to Facebook to connect with friends, not with us. But we also know how important it is to be in control of what you share and who you share with".
-

Apple's September 9 event to stream live -- but only to Apple devices
Publié: septembre 5, 2014, 3:15pm CEST par Mark Wilson
It was all but expected, but Apple has confirmed that Tuesday's "special event" will be streamed live online. This in itself is nothing particularly surprising, but the small print at the bottom of the launch announcement page will upset many people -- if you're not already packing an Apple device, you're not invited. "Live streaming video requires Safari 5.1.10 or later on OS X v10.6.8 or later; Safari on iOS 6.0 or later. Streaming via Apple TV requires second- or third-generation Apple TV with software 6.2 or later". Android, Windows, and Linux users are excluded.
At the event, which kicks off at 10am PT on Tuesday at the Flint Center for the Performing Arts in Cupertino, it is expected that Apple will talk about the iPhone 6 -- possibly two sizes -- as well as a wearable device -- which in all likelihood will be the iWatch. Anyone who is not attending the event will have to either fire up a Mac, iPad, iPhone or Apple TV, or wait for news of the announcements to be written up and posted online.
The anticipation surrounding the event -- there's already a countdown timer in place -- really means that Apple has a very easy job on its hands to push any new devices that are launched. On the one hand, limiting the stream to existing Apple users seems like preaching to the converted and limiting the potential audience. On the other, it can be seen as a reward to loyal Apple fans -- a little thank you for their dedication to the brand. However you see it, if you're an Android or Windows user, you're out of luck if you fancied the idea of watching live.
So, if you want to watch the event when it streams on Tuesday, you'd better make sure your iPad or iPhone is charged up! Of course, we'll bring you all of the news of the event here on BetaNews as well.
-

Facebook to target emerging markets with ads tailored to connection speeds
Publié: septembre 5, 2014, 1:47pm CEST par Mark Wilson
Equality for all is a utopian ideal, but Facebook has plans to treat its users differently depending on where in the world they are. Specifically, the social network plans to change the way adverts are delivered to people based upon the speed of their internet connection. In a blog post drearily entitled "In High-Growth Countries, Reaching People Based on How they Connect", product marketing manager Brendan Sullivan reveals details of the plans which will make better use of available bandwidth.
Facebook has analyzed internet usage in developing, growing nations, and determined that the majority of people in these areas get online via mobile networks. The speed of connections can vary greatly from place to place leading to a huge variation in experiences. Mark Zuckerberg is already involved in projects designed to help get more people online, but the company is also concerned about keeping advertisers happy. "High-growth countries" offer great potential for income streams, and companies need to be sure that their ads are being seen by the people they target.
Rather than responding to users' concerns, the new initiative sees Facebook responding to advertisers' requests for "the ability to segment based on network connection type would help them create better ad experiences". What does this mean in practice? As the blog post points out, trying to deliver a video ad to someone accessing Facebook on their phone with a 2G connection is going to be a fruitless exercise -- few people are going to hang about and wait for the video to load. Instead, Facebook plans to detect the speed of the connection that is in use and deliver picture ads or even just a link if it is found to be slow. It allows advertisers to avoid advertising products and services that require a higher speed connection to people in areas with poor internet speeds.
It's something that's already being used to great effect by Vodafone in India. Senior Vice President, Brand Communication, Insights and Online, Ronita Mitra said: "We are excited about the new mobile targeting option on Facebook which allows us sharper targeting to a relevant audience. We hope to see more such technology innovations across the industry".
The "bandwidth targeting" feature is available to use now with the Ad Create tool, Power Editor and the API. To allay any concerns about privacy, Facebook emphasizes the fact that any data used in ad targeting is completely anonymized.
-

Apple takes steps to increase iCloud security post-Fappening
Publié: septembre 5, 2014, 1:00pm CEST par Mark Wilson

It's not a phrase that Apple is using, but the Fappening is a word that very quickly entered the popular lexicon. Once the excitement and titillation factor died down after hundreds of private celebrity photos were leaked on the infamous 4chan (now with added DMCA policy!), attention turned to just how it fappened. Sorry, happened. Attention focused on Apple's security, and the company said it was undertaking an investigation into what it described as a targeted attack. CEO Tim Cook says that new account alerts are to be added to iCloud to help tighten security.
Speaking to the Wall Street Journal about the incident, Cook explained that celebrity accounts had been accessed as a result of phishing scams as well as hackers working out the answers to account security questions. He stressed the company's previous statement that there had not been a security breach and that no passwords had been leaked. Apple, like many other firms, offers a two-factor authentication option, but additional security measures will be introduced.
In the next couple of weeks, iCloud users will start to receive emails and push notifications when an attempt is made to change an account password, when someone tries to restore iCloud data to another device, and when a new device tries to access the account. With just days to go until the unveiling of the iPhone 6, Apple will be keen to divert attention from events such as the photo leaks. While the company is taking steps to bolster account security, Cook also acknowledges that there's more to be done:
When I step back from this terrible scenario that happened and say what more could we have done, I think about the awareness piece. I think we have a responsibility to ratchet that up. That's not really an engineering thing.
It's not yet clear what form facing up to this responsibility will take, but Apple is planning to push two-factor authentication to users more in the future.
Do you think Apple is doing enough? Will the introduction of push notifications really help to improve security?
-

Twitpic is closing. You have three weeks to grab your photos and videos
Publié: septembre 5, 2014, 2:28am CEST par Mark Wilson
 Image and video sharing service Twitpic is closing its doors. Threatened with loss of access to the Twitter API if the company refused to abandon a trademark application, Twitpic has decided it does not have enough clout to take on the microblogging giant. Twitpic founder Noah Everett used a blog post to break the news and give a little background to help explain the move. He stressed that the closure was a difficult decision and thanked users for their support.
Image and video sharing service Twitpic is closing its doors. Threatened with loss of access to the Twitter API if the company refused to abandon a trademark application, Twitpic has decided it does not have enough clout to take on the microblogging giant. Twitpic founder Noah Everett used a blog post to break the news and give a little background to help explain the move. He stressed that the closure was a difficult decision and thanked users for their support.The problem seems to stem from Twitpic's name. Everett explains that the company was contacted by Twitter a few weeks ago and asked to give up on the trademark application. The timing is a little strange because, as Everett points out, Twitpic's name has been in use since 2008, and the trademark application was filed the following year. The company managed to fight opposition from some parties, but it seems as though Twitter dealt the killer blow.
During the "published for opposition" phase of the trademark is when Twitter reached out to our counsel and implied we could be denied access to their API if we did not give up our mark. Unfortunately we do not have the resources to fend off a large company like Twitter to maintain our mark which we believe whole-heartedly is rightfully ours. Therefore, we have decided to shut down Twitpic.
Talking to Fast Company, a Twitter representative said:
We're sad to see Twitpic is shutting down. We encourage developers to build on top of the Twitter service, as Twitpic has done for years, and we made it clear that they could operate using the Twitpic name. Of course, we also have to protect our brand, and that includes trademarks tied to the brand.
Twitpic will close down on September 25. At some point between now and then an export feature will be launched to allow users to grab all of their media files.
Will you mourn the loss of Twitpic? Do you have an alternative lined up?
-

Getty Images fires lawsuit at Microsoft for "massive" copyright infringement
Publié: septembre 4, 2014, 11:43pm CEST par Mark Wilson

Getty Images Inc is suing Microsoft for "massive infringement" of copyright. Microsoft's recently released Bing Image Widget enables people to display images on a website based on search terms. The automatically generated code creates image slideshows and galleries that pull in images from Bing -- Getty's complaint centers around the fact that the widget displays unlicensed images from its catalog that are subject to copyright. The Seattle-based stock image company says that Microsoft has turned the images that can be found online into "a vast, unlicensed clip art collection".
The lawsuit, filed at the US District Court for the Southern District of New York, says that the injury caused to Getty is "incalculable" and calls for the widget to be blocked immediately. The level of damages sought is not specified, but Getty's lawsuit suggests that the company has more than 80 million unique images in its library. Getty has its own image embedding tool, and John Lapham, general counsel for the company, explained to Reuters that it is "only available for non-commercial websites and includes photographer attribution".
He went on to say: "Now you have someone else's picture in full, beautiful display on your website, having never paid for it and with no attribution to the photographer at all". Microsoft issued a statement by email that said: "As a copyright owner ourselves we think the laws in this area are important. We'll take a close look at Getty's concerns".
We reached out to Microsoft for further comment, but have only received the same statement so far. We'll update this story if a further statement is forthcoming.
Photo credit: Wilm Ihlenfeld / Shutterstock
-

Google to cough up $19 million in kids' in-app purchases case
Publié: septembre 4, 2014, 11:05pm CEST par Mark Wilson

Google is to pay out at least $19 million to Android users whose children were tricked into making expensive in-app purchases on smartphones and tablets. The Federal Trade Commission has been investigating mobile purchases for the last three years, and Apple agreed at the beginning of the year to a settlement. Amazon was also investigated and plans to appeal against the charges. In agreeing to repay the money, Google has effectively admitted that apps available in Google Play may be deceptive.
The brunt of the FTC case centers around the idea that it was not made clear to parents that their children would be able to make purchases within apps without authorization. Many of these in-app purchases are to be found in games where players are encouraged into parting with money in return for extra lives, game power-ups, or to unlock new levels. The FTC complained that since 2011 Google had indulged in unfair practices that left parents with bills of hundreds of dollars.
FTC Chairwoman Edith Ramirez said:
For millions of American families, smartphones and tablets have become a part of their daily lives. As more Americans embrace mobile technology, it’s vital to remind companies that time-tested consumer protections still apply, including that consumers should not be charged for purchases they did not authorize.
In 2012, Google did take steps to attempt to keep users informed of purchases. A popup was introduced that required a password to be entered before a purchase could be made, but the FTC found that the password was not required again for 30 minutes. During this time, it was possible to make unlimited in-app purchases, resulting in hefty bills. Google is required to contact all Android users who have made in-app purchases within 15 days of the FTC's order being finalized. Refunds must be made promptly, and if after one year Google has paid out less than $19 million, the remainder must be paid to the FTC.
Photo credit: Sam72 / Shutterstock
-

91 percent of Americans concerned about online privacy -- 7 percent would change their name as protection
Publié: septembre 4, 2014, 7:37pm CEST par Mark Wilson

There are lots of reasons to be concerned about privacy online -- not least the spying carried out by the NSA and other governmental agencies. While some companies are trying to stick up for the rights of their customer, many web users have now taken to censoring themselves. New research by WP Engine shows that the level of paranoia is higher than many people may have thought -- a staggering 91 percent of Americans are concerned about their online privacy. This is interesting in itself, but the steps that web users are willing to take if they feel their privacy is threatened makes for particularly interesting reading.
Of course there are some people who would take things to the extreme, going as far as changing their name in a bid to protect their privacy, but others would take slightly less drastic action. In fact only five percent of those surveyed say they would take no action to protect their privacy. The most common reaction to feeling threatened is to change passwords (79 percent of people), but some would go further, admitting they would consider changing their email address (48 percent) or change their credit cards (48 percent). Well over a third of those surveyed (42 percent) said they would be willing to delete all of their social media accounts. Three percent of people indicated that they would even move house as a result of having their privacy threatened online.
Concerns lie in many areas. Half of those questioned expressed concerns about the locations tracking capabilities of smartphones, and a similar number were worried about storing large volumes of personal information in the cloud. Nearly a third of Americans (30 percent) said that they were particularly concerned about mobile apps, and 57 percent said they would uninstall, or unregister from, apps that proved problematic.
More than half (51 percent) thought the government has access to too much private information, but social networks were highlighted as being worrisome. Two thirds of Americans' online privacy concerns center around social networks, but wearables, online games, and online dating services also had privacy issues.
Has your attitude to online privacy changed in recent years -- and would you go as far as changing your name to protect yourself?
Photo credit: YuryZap / Shutterstock
-

Stop! Don't buy that Xbox One just yet! Free game ahoy!
Publié: septembre 4, 2014, 6:49pm CEST par Mark Wilson

If you were planning on picking a new Xbox One console tomorrow, hold off on that purchase. Wait for a few more days and you can pick up a game worth up to $60 free of charge. This is the latest attempt by Microsoft to boost the popularity of its console and nose it ahead of Sony's PS4. It's likely that this offer will go down well with customers as, apart from the $60 upper price limit, every disc-based game is eligible.
The offer runs from Sunday 7 until Saturday 13 September and it applies to standalone consoles as well as bundles. You could pick up a bundle that already includes a game and still bag yourself another one free of charge. Here's the small print in full, although it's a pretty straightforward offer:
Offer valid September 7-September 13, 2014 at participating retailers with purchase of Xbox One, Xbox One with Kinect, Xbox One Madden NFL 15 bundle, or Xbox One Forza Motorsport 5 bundle. Free game must be a new, disc-based game for Xbox One, maximum retail value $59.99. Not valid for pre-order games. Limit one free game per eligible Xbox One purchase. Cannot be combined with other offers. Refurbished consoles or used games not included. See your local retailer for details.
One thing to keep in mind is that the offer is only available at "participating retailers". There's no way of knowing ahead of time which stores are involved, so you might want to check with your nearby stores before heading out.
Whether you're looking for a cheap stepping stone onto the Microsoft gaming ladder, or you want to pick up a cheap Christmas present, next week could be the best time to do it.
-

Box integrates with Office 365 thanks to new beta tool
Publié: septembre 4, 2014, 2:08am CEST par Mark Wilson
Office 365 users are encouraged into storing their files in one of two locations -- locally or on OneDrive. Microsoft's own cloud storage service is neatly integrated into its office suite, just as it is into Windows 8.1. There are ways to integrate other services such as Google Drive, but today Box launched a beta version of Box for Office 365 in a bid to bring the cloud service to Office. The new beta was announced at Box's BoxWorks event. There are also plans to add Box integration to Office for iPad, although no timescale has been suggested for this.
The idea behind integrating Box into Office 365 is simple, but the beta page explains: "With our new Box for Office desktop app integrations, you can easily open, edit, share and save any file from Box seamlessly within Word, PowerPoint and Excel".
If you want to try out the beta, you can download it free of charge and you will then be able to access your Box account from within Office 365 apps. As you would expect, you can open and save files just as you can with OneDrive, but the beta tool also allows for files to be shared. With a file open, hit the File menu, select Share and then use the Share from Box option.
It's not clear how far off a final version of Box for Office 365 is, but this beta tool is something that will be welcomed by fans of the cloud storage service.
-

Isis Wallet to become Softcard to avoid ISIS extremism association
Publié: septembre 4, 2014, 12:26am CEST par Mark Wilson

When you see the letters ISIS, what is it that you first think of? Is it the Egyptian goddess of health, marriage and love? The Institute for the Scientific Investigation of Sexuality? Or is it the Islamic State of Iraq and Syria, the jihadist group that has been in the news for some time now? It's quite common for there to be unfortunate sharings of names and acronyms, and it's something that Isis Wallet, the NFC payment service, has fallen foul of. To avoid being associated with the Middle East group, the service is being renamed to Softcard.
The rebranding has not come completely out of the blue. Back in July, company CEO Michael Abbott explained: "Recently, we have observed with growing concern a militant group whose name, when translated into English, is Islamic State of Iraq and Syria -- often referenced by the acronym ISIS. We have no interest in sharing a name with a group whose name has become synonymous with violence and our hearts go out to those who are suffering".
The continuing headline-grabbing activities of ISIS have done nothing to dissuade Abbott from the change in name. An announcement on the Isis Wallet, sorry Softcard, homepage reads:
We're changing our name to Softcard.
In a few weeks, Isis Wallet will become Softcard. It's a different name for the same great way to pay.
For now, the existing Isis Wallet website remains but it will be phased out as the new Softcard branding takes over. In fact there is already a Softcard page up and running, although there are still numerous references to the Isis-branded iOS and Android apps.
-

Twitter CEO says it's your own fault you see tweets from people you don't follow
Publié: septembre 3, 2014, 11:43pm CEST par Mark Wilson
 Many Twitter users have become frustrated by a problem with the social network. Increasing numbers of people are finding that they see tweets from people they do not follow. Twitter CEO, Dick Costolo, has an explanation: it's your own fault. He's not talking about promoted tweets or anything like that, but tweets that have been favorited by people you follow. The explanation came over the weekend in a couple of tweets in which Costolo put the appearance of such tweets down to users' impatience.
Many Twitter users have become frustrated by a problem with the social network. Increasing numbers of people are finding that they see tweets from people they do not follow. Twitter CEO, Dick Costolo, has an explanation: it's your own fault. He's not talking about promoted tweets or anything like that, but tweets that have been favorited by people you follow. The explanation came over the weekend in a couple of tweets in which Costolo put the appearance of such tweets down to users' impatience.Freelance science writer Katie Mack pointed out that Twitter feeds now include "random tweets from people others follow, ads, other people's favs". Costolo replied:
@AstroKatie you only see favorites if you pull-to-refresh 2x and there have been no new tweets from accounts you follow either time....
— dick costolo (@dickc) August 31, 2014
All clear? No? Costolo expands on his reponse:
@AstroKatie ...2x request for more content is a strong signal that person wants more content. So the goal is to respond to that well.
— dick costolo (@dickc) August 31, 2014
So you refresh your feed twice in quick succession because you need to feed your tweet addiction. But Twitter doesn't let the fact that the people you follow have not provided any more content to deliver to you stop it. Rather than admitting defeat, Twitter will show you tweets that your followees have favorited -- because no one could just wait a little longer for something new that they might actually want to read, could they?
-

4chan uses the fallout from the Fappening to introduce DMCA policy
Publié: septembre 3, 2014, 7:05pm CEST par Mark Wilson
4chan is notorious at the best of times -- if indeed the site can be associated with such times -- but the Fappening phenomenon has been seen by many as a new low. Apple is undertaking an investigation into what happened to numerous iCloud accounts, but fingers have been pointed at the site where the celebrity photos first appeared. It could be entirely coincidental, but 4chan -- as noted by TorrentFreak -- has just introduced a DMCA policy for the first time in its controversial history. No announcement has been made, but the timing is certainly interesting.
Head over to 4chan's legal page, and you can read through the site's new DMCA policy in full. It explains that content may be removed from the site if it is deemed to contravene copyright law. As the celebrities involved in the recent photo leaks should be able to claim ownership of the copyright of images of them -- or, failing that, the person who took the photos could do so -- it would seem reasonable to assume that 4chan is responding directly to the criticism leveled at it.
What the DMCA policy means is that complainants now have a new point of contact if they want to request the removal of any content. The designated DMCA can be contacted by post at an address in Wilmington, DE, but the policy recommends "sending notices via e-mail for quickest response". Anyone getting in touch must show that the material they would like to have removed "is not authorized by the copyright owner, its agent, or the law".
4chan's new policy, as well as the way content expires on the site, should work in conjunction to help ensure that dubious content does not reappear, or, if it does, it doesn't stick around for long. But the spread of the celebrity photos across the internet shows that it does not really matter where content first appears -- if there is interest in it, it will spread. Well over a million people have download the images via torrent sites, and there's little that can be done to stem this flow of traffic.
-

Toshiba's 7-inch Encore Mini is one of the most affordable Windows tablets yet
Publié: septembre 3, 2014, 6:02pm CEST par Mark Wilson
The tablet market is saturated with cheap Android devices, but there's also a growing number of Windows-powered slates pushing down the average price. The Toshiba Encore Mini is a 7-inch device unveiled at IFA 2014 today and it comes with a price tag of just $119.99.
While this is already a low price, it's possible that retailers will drop the price even further when it ships around September 17. Don’t let the price point fool you -- this is not a Windows RT device; you get fully fledged Windows 8.1. But, of course, compromises have been made.
The quad-core Intel Atom Z3735G processor is backed up by just 1GB RAM, and the multi-touch screen has a resolution of just 1024 x 600. Internal storage is limited to 16GB, but there is a microSD slot that can be used to boost this. There is, of course, wireless connectivity and the ubiquitous front and rear cameras. The specs may be nothing to get too excited about, but the price is enticing, particularly with the Toshiba name attached.
Microsoft's decision to scrap licensing fees for Windows on smaller devices will have helped to drive down the price as much as the corner-cutting, and the Encore Mini is a good investment as a "spare" tablet, or a device to throw in a bag and take on trips. The tablet comes bundled with a one year subscription to Office 365 Personal, and includes 1TB of storage on OneDrive, adding further appeal.
-

LinkedIn introduces data export option and new security features
Publié: septembre 3, 2014, 4:44pm CEST par Mark Wilson
LinkedIn, the social network for professionals looking to stay connected, today introduces a few new features to give users greater control over their accounts. Like Google, Facebook, Yahoo and other online services, it is now possible to check which devices you are signed in on. This is not just something that satisfies a curiosity; the ability to terminate unrecognized sessions means that should you spot that you’re still signed in on a computer you're not using, you can remotely sign out of it -- more importantly, it also makes it possible to boot out anyone who has gained unauthorized access to your account.
You can head to the Settings page of your account and click the See where you are logged in link -- alternatively, you can jump straight to the session management page. The page shows a list of all of the sessions that are currently active and provides details such as the associated IP address, the browser that's in use, and the approximate location of the session. Spot something that you don’t recognize or looks a little untoward? Just hit the Sign out link. You can also sign out of all sessions in one fell swoop if you prefer.
This is a helpful security feature, and the security theme continues in an updated email format. When you make a change to your account, LinkedIn sends out an email to verify that it was you who made the change. Going forward, these emails will also include session information to help users confirm that the email -- as well as the change -- is genuine.
The final option LinkedIn unveils today is the ability download information about your account. This is something that other social networks have offered for some time now, and LinkedIn's take on things is very much what you would expect. In a few clicks you can download all of the information associated with your account including your status updates, activity logs, and search history. On the Settings page of your account, switch to the Account tab and click Request an archive of your data -- or you can just jump straight to the page. Plan ahead if you want your data, though -- the download could take up to 72 hours to prepare.
-

Apple confirms that celebrity accounts were compromised in targeted attack
Publié: septembre 2, 2014, 11:46pm CEST par Mark Wilson
 Since a cache of nude photos of celebrities appeared online, Apple has remained fairly tight-lipped about what may or may not have happened. Right from the start rumors were flying around that Apple's iCloud service may have been comprised or that Find My iPhone may have been to blame. The company said that it was "actively investigating" the suggestions but then things went quiet again. The FBI became involved, but it has been a frustrating 48 hours for anyone trying to find out what happened. Now Apple has issued a statement making it clear that a security attack did indeed take place.
Since a cache of nude photos of celebrities appeared online, Apple has remained fairly tight-lipped about what may or may not have happened. Right from the start rumors were flying around that Apple's iCloud service may have been comprised or that Find My iPhone may have been to blame. The company said that it was "actively investigating" the suggestions but then things went quiet again. The FBI became involved, but it has been a frustrating 48 hours for anyone trying to find out what happened. Now Apple has issued a statement making it clear that a security attack did indeed take place.Entitled Update to Celebrity Photo Investigation the statement reads:
We wanted to provide an update to our investigation into the theft of photos of certain celebrities. When we learned of the theft, we were outraged and immediately mobilized Apple’s engineers to discover the source. Our customers’ privacy and security are of utmost importance to us. After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.
The fact that this is described as a "very targeted attack" should come as some comfort to the average Apple customer, but the company has issued security advice nonetheless. "To protect against this type of attack, we advise all users to always use a strong password and enable two-step verification. Both of these are addressed on our website at [support.apple.com]."
As reported by the Guardian, the individual who posted the photos to 4chan over the weekend posted a message that suggests there could be more photos to come. "I will soon be moving to another location from which I will continue to post". The post goes on to say: "Guys, just to let you know I didn’t do this by myself. There are several other people who were in on it and I needed to count on to make this happen. This is the result of several months of long and hard work by all involved".
With the imminent launch of the iPhone 6 this all comes at a very bad time for Apple. Security issues and account attacks are never good news, but the company would prefer attention was directed elsewhere at the moment.
Photo credit: LittleEvilYor / Shutterstock
-

Office 365 gains new themes option, monthly subscriptions come to iPad
Publié: septembre 2, 2014, 10:49pm CEST par Mark Wilson
Seemingly refreshed after a day off yesterday, Microsoft now hits us with two snippets of Office-related news. iPad users will now be able to sign up to a monthly Office 365 Personal and Office 365 Home subscription from their tablet. Nothing has changed about the subscription model itself, but now if you try to do something in the free version of the Office apps that require a subscription, you can upgrade there and then without having to scuttle off to your computer. You may be reading a Word file free of charge, but if you decide you want to edit it, you can upgrade with a few taps.
As before, Office 365 Personal will set you back $6.99 per month. It can be installed on one PC or Mac as well as one tablet, and bumps OneDrive storage from 15GB to 1TB. For $9.99 per month, Office 365 Home can be installed on up to five computers and five tablets. Microsoft will be hoping that the added convenience will encourage more people into making the jump into a subscription.
On the cards for the desktop version of the office suite is something of a change of look. But this isn’t a new look that's the same across the board, rather an opportunity for companies and individuals to stamp their mark on Office 365. In the coming weeks an update is due to roll out that will enable administrators to create a custom theme to match their brand. By adding a custom logo and selecting a new color scheme, Office can be made to match any company's look.
Keep your eyes peeled for the update -- there's no word on exactly when it will land, but it is on its way.
-

I'm anti-censorship! I won't try to silence those who criticize me
Publié: septembre 2, 2014, 5:42pm CEST par Mark Wilson
 A week ago I wrote about my feelings of ennui towards the iPhone 6, asserting that there was just nothing to get excited about. Some people agreed, but many didn't -- it was to be expected really. What was particularly interesting was not just the discussion that started here in the comments on BetaNews but also that the article spread further afield. It was picked up by Macworld whose resident columnist The Macalope, er, disagreed with what I had to say. You'll notice that I've provided a link to the Macworld article which, despite quoting 46 percent of my post, The Macalope failed to do initially.
A week ago I wrote about my feelings of ennui towards the iPhone 6, asserting that there was just nothing to get excited about. Some people agreed, but many didn't -- it was to be expected really. What was particularly interesting was not just the discussion that started here in the comments on BetaNews but also that the article spread further afield. It was picked up by Macworld whose resident columnist The Macalope, er, disagreed with what I had to say. You'll notice that I've provided a link to the Macworld article which, despite quoting 46 percent of my post, The Macalope failed to do initially.If you take the time to read the Macworld article you'd be forgiven for thinking that I was hurt at having my work pulled apart. Not a bit of it. No, I'm not concerned about being criticized. I've been writing for approaching 15 years now, and I know I'm going to piss people off from time to time. That's not to say that this is necessarily my intention -- in addition to news, I like to share my opinion and there will, of course, be some collateral damage that follows. Despite The Macalope's suggestions to the contrary, this was not designed to be a "link-baity" piece. Like Joe Wilcox, I've written about the importance of writing for the reader rather than writing for Google, and this is an ideology I firmly subscribe to.
But I'll return to this.
My concern with the article from Macworld was not the criticism it levelled at me, nor the vitriol that emerged in the comments -- I'll happily take all that on the chin. What irritated me was the sheer quantity of my work that was quoted. In all, nearly half of my original article was used by The Macalope in his rigorous dissection of my thoughts. It was nice to have been noticed -- even though it wasn't in the best of circumstances -- but it was more than a little irritating to find that Macworld was benefitting from my work without having linked back to my post.
The Macalope justified this by suggesting that my article was nothing more than link-bait and he therefore refused to bite. The point is, it wasn't a link-bait article. At least no more than any other articles on any website are. Anyone who writes anything which is subsequently posted online wants it to be read -- after all what’s the point of writing it otherwise? As such headlines and titles have to be devised to both attract the eye and convey a sense of what the article is about. It's how people decide if they want to read it or not.
I would have been completely in the dark about the Macworld post had someone not tracked me down via Twitter to ask me about it. Alerted to the existence of the article (by someone who didn't appreciate my reference to "those sucking on Apple’s teat"), and the lack of proper citation, I was a little upset. As I said, I was not in the slightest concerned that The Macalope or the readers of the column hated what I had written, or that I was being ridiculed; as an online writer, it's something I open myself up to. But it did seem, well, rude, not to have the decency to link back to the source that served as the inspiration for an article. So I tweeted:
Charming. @macworld ([t.co]) cites 46% of my article ([t.co]) without the decency to link back. The shits.
— Mark Wilson (@MarkWilsonWords) August 30, 2014
Replies from other Twitter users informed me that this is just what I should expect from The Macalope. If he deemed an article to be link-bait, he would not link back. I commented on the article and added a link of my own. This was quickly censored, leading me to complain further on Twitter -- with slightly choice language:
@macworld To be clear, I'm not remotely bothered about being criticized, but no link-back after quoting nearly 50% is full-on shit fuckery — Mark Wilson (@MarkWilsonWords) August 30, 2014
This got me thinking about fair usage. When reviewing or critiquing another piece of work, it is acceptable to quote a certain percentage of it without having to ask for permission. The percentages and numbers of words differ depending on whether you're talking about a book, a paper or an article, but 46 percent of anything is too much. Interestingly, The Macalope agreed:
@MarkWilsonWords @brianfagioli @macworld The fair use argument makes a decent point. It’s not one I’ve had leveled against me to date.
— The Macalope (@TheMacalope) August 31, 2014
A proposal was made. Would I prefer that references to my article be trimmed back, or would I like a link to be added?
@MarkWilsonWords @brianfagioli @macworld Would you rather have the link or fewer words pulled? Sometimes it’s hard to condense.
— The Macalope (@TheMacalope) August 31, 2014
A friend of mine had previously suggested issuing a DMCA takedown notice, but this seemed excessive to me. You may have noticed from my previous writing that I am opposed to censorship -- the idea of censoring someone is abhorrent to me. I don’t want to stop The Macalope, or anyone else, from disagreeing with me, from criticizing me, from belittling my work. Everyone is entitled to an opinion.
This in mind, I asked that a link be added. The Macalope duly obliged, and the column now links back to my article -- albeit it worded with a slight sideswipe ("despite the link-baity-ness of this piece, the Macalope has added the link after the fact because he has pulled so liberally from it").
But that's cool by me. My only aim was proper attribution. Nothing more.
My point is that I practice what I preach. I'm anti-censorship, even if that means people are free to slate me publicly. That's fine. It's a right they have, and I'm happy for them to exercise it. I would rather be disparaged than prevent someone from voicing their opinion.
Photo credit: Imfoto / Shutterstock
-

Apple finally opens up about why it rejects certain apps
Publié: septembre 2, 2014, 1:33am CEST par Mark Wilson
 It may have been something of an unknown quantity for years now. Just why was a particular app denied entry to the App Store? Now Apple -- the company so famed for its secrecy -- has finally laid its cards on the table and revealed the most common reasons apps are rejected. Taking a snapshot from the last week of August, the new Common App Rejections page on Apple's Developer site details the top ten problems that prevent apps from making their way to the App Store. Accounting for more than a quarter of rejections (14 and 8 percent respectively) are apps that do not have enough information and those that exhibit bugs.
It may have been something of an unknown quantity for years now. Just why was a particular app denied entry to the App Store? Now Apple -- the company so famed for its secrecy -- has finally laid its cards on the table and revealed the most common reasons apps are rejected. Taking a snapshot from the last week of August, the new Common App Rejections page on Apple's Developer site details the top ten problems that prevent apps from making their way to the App Store. Accounting for more than a quarter of rejections (14 and 8 percent respectively) are apps that do not have enough information and those that exhibit bugs.Six percent of rejected apps fell foul of terms in the Developer Program License Agreement -- although no further breakdown is given -- and the same percentage of titles were given the thumbs down for not meeting Apple's exacting standards. "Apple and our customers place a high value on simple, refined, creative, well thought through interfaces. They take more work but are worth it. Apple sets a high bar. If your user interface is complex or less than very good, it may be rejected". Apps that are either misleading or similar to other apps, and those with inappropriate names and artwork were also stopped in their tracks, each accounting for 5 percent of vetoed apps.
For developers who are unclear about what they need to aim for with their app, the Common App Rejections page serves as a helpful reminder. Other no-nos include broken links, placeholder content, and ads that do not function as they should. Apps that are little more than "web clippings, content aggregators, or a collections of links" are frowned upon, as are those that mimic the functionality of other apps, and those that fail to offer lasting value.
In all, the top ten reasons for rejection make up 58 percent of those that are rejected. The remaining 42 percent that comprises "Other Reasons" is not detailed further, but the snippet of information, that each one accounts for less than two percent of rejections, means that there are at least a further 21 reasons for an app being knocked back. Speculate away about what they may be!
Photo credit: Fotyma / Shutterstock
-

BBC aims to make programming sexy with new coding TV shows for kids
Publié: septembre 1, 2014, 9:01pm CEST par Mark Wilson

The BBC is looking to create a new generation of code monkeys with a programming push in schools throughout England. Of all the subjects available to study at school, computer science, IT, computing (call it what you will) isn’t exactly, you know, sexy and exciting, but the Beeb is hoping to change that. Back in the 1980s the BBC -- the UK's license free subsidized public service broadcaster -- spearheaded a drive to popularize computing in general, but particularly programming. Three decades later, the new initiative includes plans for not just one, but several programming-themed TV shows aimed at children.
The BBC has already held talks with Microsoft, BT, Google and Samsung, and has managed to sign agreements with between 10 and 20 partners to help with the new endeavor. In addition to the TV shows, there will also be a range of study guides and other material made available at BBC Bitesize, the broadcaster's online education resource. Jessica Cecil, controller of the BBC's coding and digital creative initiative, said: "It's about giving the next generation a chance to shape their world, not just be consumers in it."
While the TV shows will start broadcasting in the fall, the full study program won’t roll out until early next year. The initiative has been designed to be as inclusive as possible, with some components having been designed for children of primary school age -- the full curriculum will follow school kids through their education up to the age of 16. While older children have "algorithms, data representation and binary" to look forward to, the younger ones get started with "debugging programs, writing animation code and explaining how the internet works".
As a public service broadcaster, the BBC is obliged to be impartial, so care has to be taken that any partnerships that may be forged do not become "too close". But the latest venture has been welcomed by Eben Upton, from the Raspberry Pi Foundation. "I think it's a fantastic initiative -- the BBC is getting back to its roots and advocating for computing education in the same way it did in the 1980s, but with all the advantages of doing it with a modern, internet-enabled platform. The bits and pieces I've seen so far look very promising".
Photo credit: Ross Petukhov / Shutterstock
-

Microsoft lifts 2GB file size limit for some OneDrive users
Publié: septembre 1, 2014, 7:11pm CEST par Mark Wilson
 Cloud storage continues to increase in popularity, and as more and more demands are made of the various services that are available, limitations are easy to spot. One limitation that has irked OneDrive users for some time is the fact that it is only possible to synchronize files up to 2GB in size. Over on the OneDrive uservoice page, there have been numerous complaints from users as well as queries about when the limitation might be lifted. A couple of weeks ago Group Program Manager, Omar Shahine explained that: "It’s simply an old limit that we’ve been working on removing for far too long now. The good news is that we are actively working on this".
Cloud storage continues to increase in popularity, and as more and more demands are made of the various services that are available, limitations are easy to spot. One limitation that has irked OneDrive users for some time is the fact that it is only possible to synchronize files up to 2GB in size. Over on the OneDrive uservoice page, there have been numerous complaints from users as well as queries about when the limitation might be lifted. A couple of weeks ago Group Program Manager, Omar Shahine explained that: "It’s simply an old limit that we’ve been working on removing for far too long now. The good news is that we are actively working on this".And work on it they did. Reddit user megaman821 noticed that larger than normal files had started to sync in his account: "I had some 2-3 GB files sitting in my OneDrive and today when I looked they were all synced. I don't know if this is a global rollout or only a few have it. Anyone else have their large files syncing?" The comment thread includes posts from users who find themselves in a similar situation, as well as those who still have the 2GB limit on their account. A quick poll in the BetaNews offices showed that it was certainly not a universal file size limit increase, so we reached out to Microsoft. A spokesperson said:
"As we mentioned on our uservoice, we have started the work to increase the file size limit for all OneDrive accounts. We have started the process with a small number of customers and will continue to roll it out to our full customer base. We will have more to share on this update in the new future, stay tuned to the OneDrive blog".
While only a small number of accounts seem to have been bumped up at the moment, the increase is already being well received. The @biggerthan2gb Twitter account has been tracking the story and noticed the ability to sync larger files just the other day. So, in answer to your question @biggerthen2gb, it's not quite "official", but it will be soon hopefully:
Hey @OneDrive it looks like you removed the 2GB size limit? Is this official now, you should tell people if so :) pic.twitter.com/nWjcRXKjoz
— Bigger Than 2GB (@biggerthan2gb) August 29, 2014
Photo credit: pics4sale / Shutterstock
-

Lumsing Prophet Bluetooth Speaker: a powerful wireless audio solution [Review]
Publié: septembre 1, 2014, 5:00pm CEST par Mark Wilson
![a powerful wireless audio solution [Review]](http://betanews.com/wp-content/uploads/2014/09/lumsing_prophet_bluetooth-300x285.jpg) We seem to have had something of a run on Lumsing products recently, but the focus has been on power -- both in-car and portable. Now it's time for something a little different from the same company: a wireless Bluetooth speaker. It can be used with phones, tablets, laptops and anything else that chucks out a Bluetooth signal; actually, there's a 3.5mm jack, so there is a wired option too. As this is, primarily, a wireless speaker, it should come as no surprise that it features a built in rechargeable battery. Charging comes via a USB port which you can connect to either a computer or a phone charger.
We seem to have had something of a run on Lumsing products recently, but the focus has been on power -- both in-car and portable. Now it's time for something a little different from the same company: a wireless Bluetooth speaker. It can be used with phones, tablets, laptops and anything else that chucks out a Bluetooth signal; actually, there's a 3.5mm jack, so there is a wired option too. As this is, primarily, a wireless speaker, it should come as no surprise that it features a built in rechargeable battery. Charging comes via a USB port which you can connect to either a computer or a phone charger.Let's skirt over the fact that the instruction manual provided with the speaker has a spelling mistake ("Propeht" rather than Prophet) and look at what the Prophet has to offer. This is a budget speaker, but its looks don’t give this away. The disc shape hides two speaker cones, surrounded by a silver trim. Smack in the middle of the speaker grill is a play/pause button which allows for music playback control, and also doubles up as a pick up/hang up button for your phone -- as well as play music from your phone, the Prophet can also be used to make (very loud) hands-free phone calls thanks to the built in microphone.
And the output is quite impressive. The two 5W speakers kick out a pleasing, deep, bassy sound; we're not talking high-end audio, but for a cheapy portable Bluetooth speaker, it does make one's ears prick up. If you're using the Prophet in conjunction with a phone or Bluetooth-enabled MP3 player, there's a little swing out drawer to sit your handset on. It's not ideal as it's a little unstable, but it's a nice touch. You’re not restricted to Bluetooth pairing -- which is very quick and simple -- in addition to the aforementioned 3.5mm jack, you also have the option to use NFC. At around 250g and measuring 120mm in diameter and 32mm in height, the Prophet manages to fall into the portable category.
The volume control at the back of the speaker can be awkward to reach, but there's one rather irritating oversight. While Luming claims 15 hours of battery life between charges, you should expect rather less (unless you listen to music at very, very low volumes); but you won't know when you're going to lose sound as there's no way to check the battery level.
In all, it's something of a confusing piece of hardware. It's clearly cheap (just look at the price tag), but you do get better quality than you might expect when parting with this amount of money. The build quality is more than acceptable, but the plasticky feel does detract from things slightly. The design is not perfect, but the price is hard to argue with… which brings us onto a final point. Just as BetaNews has been rather taken by Lumsing products of late, it seems that shoppers have been too. Usually available for $20 in the US and £20 in the UK, the speaker is currently out of stock on Amazon. Stock is currently available in Japan (¥2,799), but if you want one outside of the land of the rising sun, you'll have to keep an eye open for when shelves are restocked.
-

Microsoft defies court order and refuses to hand over emails to US government
Publié: septembre 1, 2014, 2:10pm CEST par Mark Wilson

Back in July, a New York court ruled that Microsoft should provide access to emails stored at a datacenter in Ireland. The company has been quite vocal in opposing requests to hand over this information, and continues to stand its ground. Although a court order requires the emails to be handed over, Microsoft remains defiant. In a blog post entitled "Your email belongs to you, not us" (forget "all your base are belong to us"), Microsoft's Chief Privacy Officer, Brendon Lynch, reiterates the company's position.
"Microsoft is committed to delivering meaningful privacy protections that build trust with our customers, and we know how much you value the contents of your email. We believe your email belongs to you, not us, and that it should receive the same privacy protection as paper letters sent by mail -- no matter where it is stored. This is the crux of our legal challenge to a U.S. government criminal search warrant for a customer's email stored in our datacenter in Dublin, Ireland".
When the court order was made, there were concerns that the US government was over-reaching the mark by attempting to gain access to data stored in a foreign country. But the recent law passed by the British government that would give the UK just those rights has muddied the water slightly. Microsoft decided to appeal, but prosecutors have now managed to argue that the case is unappealable. In spite of this, Microsoft says that it "will not be turning over the email and plans to appeal. Everyone agrees this case can and will proceed to the appeals court. This is simply about finding the appropriate procedure for that to happen". The company is now effectively defying the court order.
In recent months, Microsoft has been increasingly keen to be seen listening to its customers -- this is the reason cited for the changes that have been seen in Windows Phone and will be seen in Windows 9. With the climate of concern about privacy and surveillance that prevails post-Snowden, Microsoft's stance is understandable and is likely to enjoy continued, firm backing from customers and the tech industry alike. But it is an easy battle to gain followers for. Whatever the outcome, the danger is that it turns into an exercise in vainglory for Microsoft, ever-keen to be seen as the people's champion.
Photo credit: Pavel Ignatov / Shutterstock
-

Could buying Cyanogen give Microsoft some smartphone credibility?
Publié: août 29, 2014, 5:36pm CEST par Mark Wilson
 I'm not going to retread old ground too much here, but there's no getting away from the fact that Microsoft has something of an image problem when it comes to smartphones. But this could be set to change. The word on the grapevine is that Microsoft -- possibly in conjunction with the likes of Yahoo and Amazon -- is interested in joining forces with, or even, buying Cyanogen Inc, purveyor of some of the finest Android ROMs known to humanity. It's a branch of Android favoured by handset owners who live and breathe tweaking, who want an OS custom made to fit them like a well-tailored suit.
I'm not going to retread old ground too much here, but there's no getting away from the fact that Microsoft has something of an image problem when it comes to smartphones. But this could be set to change. The word on the grapevine is that Microsoft -- possibly in conjunction with the likes of Yahoo and Amazon -- is interested in joining forces with, or even, buying Cyanogen Inc, purveyor of some of the finest Android ROMs known to humanity. It's a branch of Android favoured by handset owners who live and breathe tweaking, who want an OS custom made to fit them like a well-tailored suit.Little is known about what form any future arrangement might take, or how far talks have got so far. But we do know that Cyanogen Inc has met with Satya Nadella -- as reported by The Information. It would be interesting to see where this could go. There are two possible avenues that immediately spring to mind. The first -- and probably the least likely -- is that Microsoft might consider creating custom Windows Phone ROMs. This seems somewhat improbable, but there's another option: Microsoft could be looking to muscle in on Google's Android territory. This is not as far-fetched as it might first sound.
We have already seen Lumia devices running Android, and the HTC One (M8) -- a handset most readily associated with Android -- is available in a Windows Phone variant. Microsoft is not completely opposed to the idea of being associated with Android. While Cyanogen is based on Android, it is something of a different beast. As well as customization, there's a strong focus on performance but the number of supported handsets is slightly limited. Talks with Microsoft could mean that we see Cyanogen releases for more devices in the future.
With Windows Phone sales still struggling, and having invested heavily in Nokia, Microsoft is not going to let its baby go down without a fight. The release of Windows Phone 8.1 served as something of a life preserver, but looking to the future Microsoft just has too much ground to make up on Android; if you can't beat 'em, join 'em.
Photo credit: Tashatuvango / Shutterstock
-

Google Authorship comes to the end of the line
Publié: août 29, 2014, 2:30pm CEST par Mark Wilson

Continuing its propensity for terminating projects, Google has decided to kill of its Authorship program. The markup was introduced to provide online writers with a way to link their work to their Google+ profile and have their profile picture displayed in search results. But in its three year lifespan, Authorship did not really manage to take off, and Google Webmaster Tools' John Mueller announced that "we've also observed that this information isn't as useful to our users as we'd hoped, and can even distract from those results. With this in mind, we've made the difficult decision to stop showing authorship in search results".
Head to one of the Google Authorship support pages and you're greeted by the message: "Authorship markup is no longer supported in web search". This is an interesting move, especially considering how keen Google has been to push people into using Google+. Authorship not only enables writers to more visibly stamp their mark online, but also to gain a following. In practice it was found that Authorship did little to help drive traffic and "wasn't always easy to implement".
The move isn't perhaps entirely surprising. As recently as June, authors' profile pictures were stripped from search results on mobile devices and because of Google's desire to create a unified experience on mobile devices and desktop computers, this meant they also disappeared from other search results. Search Engine Land takes an in-depth look at the history of Google Authorship, explaining that back when the service launched, Google was excited at the prospect of helping authors remain associated with their work.
The article speculates that searchers gained little from the inclusion of author photos and bylines -- the thinking being that in a bunch of search results, it is the headline and opening sentence that grabs attention. There have also been studies that show that only a small percentage of sites managed to use the markup correctly. This has ended up being another Google service that has been unceremoniously shown the door after a seemingly endless period of "testing". Who knows what will be next to be trimmed.
As a writer or reader will you mourn the death of Google Authorship?
Photo credit: 1000 Words / Shutterstock
-

Project Wing is Google's drone-based goods delivery system
Publié: août 29, 2014, 12:44pm CEST par Mark Wilson

Drones tend to be associated with surveillance and crowd control, but Google is the latest firm to express an interest in using the unmanned machines as a delivery service. Facebook has previously talked about using drones to "deliver the internet to everyone", and Amazon has also toyed with the idea, but now the search giant wants a piece of the action. The company's development team, Google X, has been beavering away on a delivery system powered by drones, and details of how it works have now been released.
Unlike other drones that tend to take a quad-copter design, Google's take on the idea sees a merging of a plane with a helicopter. Fitted out with a single wing and four propellers which move into different positions when flying, the drones have a housing unit for packages in the center of the wing. The Atlantic has a great deal of background about the project and it looks as though rather than being used to ship things that shoppers have bought, it is more likely to be used to help in disaster areas where aid is needed.
Tests in Australia have already shown that the drone system can be used to deliver "a first aid kit, candy bars, dog treats, and water", but the hope will obviously be that they could be used to deliver other goods quickly and efficiently. Although Google is publicizing its drones, it is still very much a work in progress. Partners are being sought to work with Google, and interested parties are invited to get in touch.
Think the whole thing sounds like a little pie in the sky? Google has a video for all the unbelievers to help show that it is serious.
Photo credit: vipman / Shutterstock
-

California brings in smartphone kill switch legislation to protect handset owners
Publié: août 26, 2014, 10:50pm CEST par Mark Wilson

In California, a bill has been passed that will require smartphone manufacturers to include a kill switch in their handset. The bill states that "any smartphone, as defined, that is manufactured on or after July 1, 2015, and sold in California after that date, include a technological solution at the time of sale, which may consist of software, hardware, or both software and hardware, that, once initiated and successfully communicated to the smartphone, can render inoperable the essential features, as defined, of the smartphone to an unauthorized user when the smartphone is not in the possession of an authorized user". It's a lengthy description, but it means the kill switch that many people have been asking for for so long is becoming a reality in another state
This is not the first time a kill switch bill has been passed -- Minnesota did something similar back in May. The SB 926, Leno Smartphones bill in California is rather more far-reaching and comes partly in response to the statistic that between 30 and 40 percent of robberies in major US cities are smartphone robberies. Once activated, the kill switch will prevent a phone from being registered on a wireless network, and cannot be bypassed even with a hard reset. In the event of theft, a user will also be able to remotely wipe their device to protect any private information they may have stored on it.
Excluded from the bill are second hand phones, and even on phones where the feature is enabled, users will be free to disable it if they want. Handset manufacturers have a great incentive to comply with the bill. Fail to implement the kill switch, a fines of between $500 and $2500 per handset could be handed out -- which soon adds up. Phones produced after January 1, 2015 will be expected to comply with the law, although those produced before this date will be excluded if they "cannot reasonably be reengineered to support the manufacturer's or operating system provider's technological solution, including if the hardware or software cannot support a retroactive update".
It's not clear whether the kill switch will stop or reduce the number of robberies that occur -- or just result in an increase in thefts of older handsets. Phone manufacturers now have the task of producing handsets that are compliant with California law, as well as laws of other states if additional legislation is passed. Questions have been raised about the effectiveness of a kill switch as a theft deterrent. There are also concerns that the average price of handsets will increase, but the need for legislation has been questioned as there is currently a voluntary agreement to between a large number of manufacturers and the CTIA to include kill switches.
Photo credit: cunaplus / Shutterstock
-

V.BTTN is a programmable Bluetooth button that can do anything your phone can
Publié: août 26, 2014, 8:22pm CEST par Mark Wilson
 Think about wearable tech and your mind probably jumps to watches first. V.BTTN is a little different. It's a programmable button that links smartphones, tablets and computers via Bluetooth and it can then be used to trigger all manner of events. Looking for a remote shutter trigger for your smartphone? V.BTTN can do that for you. Need a remote control to start and stop recording? Got that covered too. The device comes from VSN Mobil and is available now for $59.99. It's one of those pieces of hardware billed as having virtually limitless possibilities, but this is one instance where the claim is justified.
Think about wearable tech and your mind probably jumps to watches first. V.BTTN is a little different. It's a programmable button that links smartphones, tablets and computers via Bluetooth and it can then be used to trigger all manner of events. Looking for a remote shutter trigger for your smartphone? V.BTTN can do that for you. Need a remote control to start and stop recording? Got that covered too. The device comes from VSN Mobil and is available now for $59.99. It's one of those pieces of hardware billed as having virtually limitless possibilities, but this is one instance where the claim is justified.What the button does depends entirely on the app you decide to link it to. It's slightly more advanced than just "hit the button" -- there are short and long press options, as well as gesture support thanks to a built-in accelerometer. As standard, V.BTTN is just a button. You can stick it in your pocket or bag and carry it around with you if you like, but there are also a number of accessories.
A wristband turns it into a watch, a clip means it can be attached to clothing or hardware, a keychain option lets you keep the button with your house keys, or you could opt to wear it around your neck on a chain. It's waterproof and robust meaning it should withstand rough handling... which is just as well, as V.BTTN can link with VSN Mobil's V.ALRT personal alert device
In terms of compatibility it has pretty much all of the bases covered -- iOS, Android, Windows, and OS X (Windows Phone even gets a look in!) -- and there's great potential for developers to go to town with it. The SDK is available for developers to work with so the existing range of third party apps should start to grow over the coming months.
-

Software vulnerability patching is far too slow and leaves users at risk
Publié: août 26, 2014, 6:28pm CEST par Mark Wilson

Security holes and vulnerabilities are to be expected, but not enough is being done to patch holes quickly enough. This is the conclusion of Heimdal Security who conducted analysis of software vulnerabilities. The security firm found that while security problems are on the increase, companies are failing to keep pace and issues remain unaddressed for too long. It's something that hackers are taking advantage of, and user data is being left at great risk. Heimdal Security found that between 60 and 90 percent of attacks from hackers take advantage of this fact.
A number of key culprits are singled out for particular attention -- names that will be familiar to most: Oracle Java Runtime environment, Adobe Acrobat Reader, Adobe Flash Player, and Apple QuickTime. The biggest offender, by quite some margin, is Java Runtime environment, blighted by 48 vulnerabilities in 2012, a staggering 180 in 2013, and 90 so far in 2014. According to CVE Details, the average severity rating for all of the vulnerabilities found in each of the four products. Using the CVSS (Computer vulnerability severity system), which rates issue severity on a 1 to 10 scale, the average rating is 7.8 for Java -- and that's the best of the bunch. Adobe's two products were rated 9.2.
So what is being done to address the issues as they are detected? Not enough. CEO of Heimdal Security, Morten Kjaersgaard, says: "Considering the severity and mass of security flaws we see in software released by key vendors, you may think that security gaps should be closed faster. However, our data actually indicates that it can take as many as 12 months between patches for Apple Quicktime to be released." Despite the huge number of security holes detected in its software, Oracle pumps out an update once every couple of months on average. Adobe and Apple fare just about as badly.
All of these products are still widely used. In fact, QuickTime is actually almost three times as popular now as in 2012. But while Apple's media player may only be installed on 33 percent of computers, the two Adobe products and Java Runtime are found on more than 80 percent of systems. Heimdal Security points out that this is particularly worrying as some 27 percent of emails contain malicious URLs which exploit known software vulnerabilities. What is perhaps more troubling is that it is business systems that have been used in the studies. The figures may be slightly different for home computers, but it is business systems that house the most sensitive data in the greatest quantities.
Photo credit: johnkworks/ Shutterstock
-

Twitter may be within its rights to block ISIS beheading content, but is it right?
Publié: août 23, 2014, 8:45pm CEST par Mark Wilson

The subject of US journalist James Foley's recent beheading is obviously a sensitive one, but Twitter's decision to suspend the account of users sharing the video made it about censorship as well as politics. As you are no doubt aware by now, Foley was kidnapped in Syria a couple of years ago, held captive, and on Tuesday a video was released by the Islamic State in Iraq and Syria (ISIS). It shows Foley kneeling on the ground, reading from a script before a masked captor draws a knife, and executes him. It is grisly, horrific, depressing, heart-wrenching, and real. It spread like wildfire across YouTube, Twitter, and countless websites, but it wasn't long before censorship was seen.
YouTube quickly removed the video, but this did not stem the flow. Copies of the video were hosted elsewhere and then posted to Twitter, as were stills from the footage. This is when Twitter stepped in. Posts containing the images or video were removed, and accounts suspended. Dick Costolo, Twitter's CEO, tweeted:
We have been and are actively suspending accounts as we discover them related to this graphic imagery. Thank you [https:]
— dick costolo (@dickc) August 20, 2014
Your first reaction might well be "damn right!", even "why the hell would anyone want to see such a video, let alone share it?". These are valid reactions. But was Twitter right to act as a content gatekeeper in this instance? Of course, the simple answer is "yes". Twitter is free to dictate how its network is used in whatever way it wants. If it decided that the word "the" was banned, there would be little, if anything, that could be done about it. In signing up for a Twitter account, we have all agreed to abide by whatever terms and conditions were in place at the time, any that may be added, and to take account of any changes that may have been made to them. This may sound glib or trite, but it's true. Twitter is able to permit or ban whatever the hell it wants to on its service. But the simple answer is rarely good enough, and it certainly isn't here. There are several things to consider when thinking about possible reasons for Twitter choosing to censor the images. This is, or course, a tremendously distressing time for Foley's friends and relatives so this is one thing to take into consideration. As heartless as this might sound, the fact that a video is distressing is, in itself, not a reason to block it or suspend the associated accounts. The flipside is the good old freedom of speech argument -- what "right" does Twitter have to decide what is acceptable or to set the political agenda? The politics and actions of ISIS may be objectionable to many people, but that does not mean that the group does not have a right to a platform. There is the famous quote from Voltaire biographer Evelyn Beatrice Hall (no, not Voltaire himself):
I disapprove of what you say, but I will defend to the death your right to say it.
This is the paradox of freedom of speech. If you want the freedom to be able to say whatever you want, be it online or through another medium, that freedom also has to be extended to others. Freedom of speech means that people you disagree with, people you hate, people you would prefer dead, have the same freedom as you. ISIS has a right to freedom of speech. But as I said above, Twitter is also free to control who uses its service and for what. It gets slightly more complicated, though. The content of the video could be seen as a call to arms, propaganda, or an incitement to cause violence, and this means it should be treated slightly differently perhaps. In the video, Foley is heard to say:
I call on my friends, family and loved ones to rise up against my real killers -- the US government -- for what will happen to me is only a result of their complacent criminality.
Is this why the video was banned? Because it calls on people to rise up against the US? What was more influential in the decision to censor and suspend accounts -- the desire to stem the flow of extremist propaganda, the fact that it is a violently bloody act, or the fact that it is anti-American? If the aim was to stop people from hearing about ISIS, it clearly failed -- we are still talking about it now. The act took place. A man died in truly horrific circumstances. It should not just be swept under the carpet. This is one of the side-effects of wars, invasions, oppression, terrorism, the "war on terror" -- we cannot pretend that it doesn't happen. We need to know what is going on in the world and events such as this, appalling as they are, serve as a reminder. In the UK, police issued a statement reminding people that "viewing, downloading or disseminating extremist material within the UK may constitute an offence under Terrorism legislation":
After UK police released this statement we rang them to ask if we were now terrorists. Story to follow... pic.twitter.com/u0nJ7b0UR3 — The Register (@TheRegister) August 20, 2014
But the key words here are '"extremist" (a term which is open to interpretation), and "may".
Twitter has a responsibility to allow events to unfold without intervention. The sheer number of people using the site means that it is possible to get a fairly balanced view of what is going on in the world -- do a little research and you should be able to find supporters of every side of just about any story or argument. But for this to work, censorship just cannot happen.
It is also interesting to see how Twitter has decided to take account on this particular occasion. There have been various cases of bullying in the past where the site has refused to intervene. GigaOM points out that Twitter only seems to have taken a hard line with individuals. News outlets posting stills of the video have been left untouched, while individuals' accounts have been closed down. No explanation has been forthcoming from Twitter for this discrepancy. Was the killing of an American what it took to make Twitter prick up its ears.
Do you trust Twitter to vet and edit content for you -- or, more to the point, do you want it to? As soon as one instance of censorship, or editing, is publicized questions are raised about what else is going on that we don’t yet know about. Does Twitter have a political agenda? Should the service be seen as a medium or a publisher?
-

In India it is illegal to like blasphemous online content
Publié: août 23, 2014, 12:39pm CEST par Mark Wilson

In the latest blow for free speech, the government of the southern Indian state of Karnataka has passed legislation that makes it illegal to upload, share, or like content "with a view to hurt religious sentiments knowingly or unknowingly". Let's put aside the odd paradox of being able to have a "view" to do something, but to do it "unknowingly", and look at the history of this. Back in June, Karnataka police warned citizens about the type of things that were covered by the Information Technology Act.
Warning notices appeared in newspapers (of all places):
Citizens are warned not to upload, modify, resend (forward) and like (share) malicious or misleading images, videos and messages through any medium with a view to hurt religious sentiments knowingly or unknowingly. Such persons will be punished under sections 66(A) of the Information Technology Act and 153 (A), 295 of the Indian Penal Code. Citizens are encouraged to information Police Control Room @ 0831-2405231 or e-mail to dcbgm@ksp.gov.in or access facebook (sic) account: Range IGP Belguam.
This is crazy enough. There are several problems with this form of warning, not least that it is directly opposed to the idea of free speech. But more than this, the idea of what is blasphemous, or liable to hurt religious sentiment, is open to debate. New legislation, the lengthily named Karnataka Prevention of Dangerous Activities of Bootleggers, Drug-offenders, Gamblers, Goondas, Immoral Traffic Offenders, Slum-Grabbers and Video or Audio Pirates (Amendment) Bill, 2014, means that citizens can now actually be arrested if they have even committed an offence under the Information Technology Act.
It's not quite clear just how feasible this would be to implement, but it would, technically, be possible to get yourself arrested for, say, talking about the possibility of creating and sharing images of Hindu gods that have been tinkered with in some way to make them "offensive". The so-called Goondas Act ("goonda" is a colloquial term meaning a hired thug) is something of an umbrella act, taking in most of what is already covered by the Information Technology Act, and the Indian Copyright Act.
The whole thing is so loosely tied together that it is open to vastly differing interpretations, and this is worrying. This is the precisely the type of legislation that is open to abuse. Forget, for a moment, the fact that policing the internet is all but impossible -- yes, IP addresses can be tracked, but it is rarely possible to say with one hundred percent certainty who was using a computer at a given time -- and look at the absurdity of the law. A citizen could be arrested for talking about a hypothetical image they might create and share online that could, possibly, offend the religious sensibilities of someone, somewhere.
When did religious sensibilities (or other sensibilities, for that matter) start needing protection? Legislation like this is a roadblock to free speech. Laws that prevent hate crime is one thing, but laws that stand in the way of expressing views because they might be deemed offensive is just insane. It is also the type of law that is open to abuse by governments and officials. More than anything else, it's just worrying. The thought police are out to get you.
Photo credit: Pixel 4 Images / Shutterstock
-

Rebel NSA and GCHQ agents are actually helping make Tor more secure
Publié: août 22, 2014, 5:20pm CEST par Mark Wilson

For anyone looking to stay anonymous online, Tor seems like an obvious option. At the same time, it could lull users into a false sense of security -- after all, this is a network that was, at least in the past, funded by the military and US government -- and conspiracy theories abound that Tor is nothing more than a honey trap to catch the kind of people who have a need for anonymity because of their nefarious activities. The network has evolved over the years and now agencies such as the NSA in the US and GCHQ in the UK are actively seeking out vulnerabilities so they can crack the network. But the relationships are actually far more complex than that.
According to Andrew Lewman, chief of operations at Tor, the same agencies that are trying to break Tor are also posting tips anonymously about the vulnerabilities that have been found -- giving a chance for them to be patched. Talking to the BBC Lewman said:
There are plenty of people in both organizations who can anonymously leak data to us to say -- maybe you should look here, maybe you should look at this to fix this. And they have.
It’s a story that’s somewhat reminiscent of the Edward Snowden story. The NSA worker became so disillusioned with the activities of the agency that he blew the lid off the kind of surveillance that was, and is, taking place. The heightened awareness of web users’ online visibility that followed led to an increase in the number of people taking steps to preserve their privacy. The likes of Tor have long been used to protect the identities of individuals online, and while there are countless entirely innocent users, it is often also used as a gateway to the "dark web” where rather less legal activities take place.
It is the organized crime, paedophilia, and drug dealing that takes place on the dark web that piqued the interest of the NSA and GCHQ. Understandably keen to find a way to catch the criminals making use of the anonymizing capabilities of the network, the agencies set about trying to crack Tor so individuals of interest could be identified. But Lewman has a "hunch" that, just as was the case with Snowden, not everyone working at the agencies is happy about how it is being approached.
As such, the Tor team receives tip-offs from what he believes to be security agency workers on a just about monthly basis. Because Tor is designed to be anonymous, he cannot prove the identity of those providing hints about vulnerabilities that have been detected, but Lewman is convinced:
Obviously we are not going to ask for any details ...You have to think about the type of people who would be able to do this and have the expertise and time to read Tor source code from scratch for hours, for weeks, for months, and find and elucidate these super-subtle bugs or other things that they probably don't get to see in most commercial software … The fact that we take a completely anonymous bug report allows them to report to us safely.
Another NSA whistleblower, William Binney, has informed Lewman that the tips are probably coming because agency workers are unhappy that American citizens are being spied on by their own government. Of course, both the NSA and GCHQ have refused to comment on the suggestions, but this is yet another intriguing twist in the ever more complicated tale of online surveillance and the cat-and-mouse games that are underway.
Photo credit: Giulio_Fornasar / Shutterstock
-

Plans to slap age ratings on online videos are completely and utterly pointless
Publié: août 19, 2014, 12:34pm CEST par Mark Wilson
 Head to the stores to look for real, physical DVDs and Blu-rays, and you'll probably find that there's an age rating on them. Now plans are afoot to bring the same idea to the web. As insane an idea as this may sound, this is actually happening, and it is completely pointless and unworkable. Initially starting off with the involvement of YouTube and Vevo, the scheme is the brainchild of UK Prime Minister David Cameron and will start as a pilot program in October. It's something that is likely to appeal to concerned parents, but the practicalities are a rather different matter.
Head to the stores to look for real, physical DVDs and Blu-rays, and you'll probably find that there's an age rating on them. Now plans are afoot to bring the same idea to the web. As insane an idea as this may sound, this is actually happening, and it is completely pointless and unworkable. Initially starting off with the involvement of YouTube and Vevo, the scheme is the brainchild of UK Prime Minister David Cameron and will start as a pilot program in October. It's something that is likely to appeal to concerned parents, but the practicalities are a rather different matter.Announcing the ratings plan, Cameron said: "We shouldn't cede the internet as some sort of lawless space where the normal rules of life shouldn't apply. So, in as far as it is possible, we should try to make sure that the rules that exist offline exist online. So if you want to go and buy a music video offline there are age restrictions on it. We should try and recreate that system on the internet".
No details have been given about just how the scheme will work -- probably because it won't work. As I see it, there are two possible outcomes, neither of which will have any of the effect Cameron was hoping for. If videos are simply assigned ratings, viewers will know ahead of time the type of content they are likely to be letting themselves for: a PG-rated music video is going to be more "suitable" for a younger audience than a video rated 18 or X.
For the prudish, it could be a helpful system that will guide them away from content they might be upset by, but the labels also serve as a beacon to children. An 18 or X label just screams "here be swearing, nudity, and all sorts of other fun things". This is clearly the reverse of the effect that Cameron is hoping for, but it's a likely outcome. Make a fruit forbidden and it becomes all the more enticing. Factor in the inability of websites to verify ages, and video ratings are purely FYI.
The second possible route is that -- assuming there are actual checks and real legislation in place -- sites will become inundated with kids creating fake accounts that indicate they are over the age of 18 or 21. In a video store, should a shopkeeper (in the UK, at least) sell an 18-rated movie to someone under the age of 18, there are fines that can be handed out. How would this work online? There are millions of kids online who have become used to the idea of virtually unfettered access to the internet. If they want to get hold of something, they will. It's that simple. Unless the likes of YouTube and Vevo are threatened with fines, what incentive is there for these companies to actually police their users? None.
How is it policeable? The internet is a global entity, and laws surrounding what is deemed acceptable for different age groups around the world differ from country to country. A video rated PG in Europe might be an 18 in the US and vice versa. It's a scheme that's going to create nothing but confusion and bureaucracy. And what does bureaucracy mean? Cost increases. Cost increases that have to be passed on to users in one form or another.
Oh, and the really funny thing. Cameron's proposal only covers music videos. On just about every level it is completely and utterly pointless. It is nothing more than yet another politician trying his damnedest to appear to be doing something, protecting families, and upholding values. In the pilot, there are only two sites involved, and three major record labels (Sony, Universal and Warner Music). This may cover many bases, but it is certainly not going to have the entire video output of the music industry covered. It's a waste of everyone's time.
Pointless, posturing poppycock.
Photo credit: yavuzunlu / Shutterstock
-

Satellite broadband finally opens up the internet to me
Publié: août 18, 2014, 4:05pm CEST par Mark Wilson

A few weeks ago I complained bitterly about my atrocious internet connection. The impact of a deathly slow and unnervingly unstable connection is hard to overstate. Tension and frustration chez Wilson reached boiling point. Nerves were frayed and tempers short. But as I sank into the bleak, hellish broadband abyss, a hand reached out to save me. The hand was extended by the suitably named Satellite Internet who took pity on me having read of my plight. A trial of satellite broadband was duly offered, and I don’t think I could have said "yes, please" faster. It's something I've considered before, but the startup costs had put me off.
Satellite Internet's service uses Astra satellites, the same ones used to deliver satellite TV to Europe. This means that a smaller dish than you might expect is needed. Forget the monster installations you may have seen in people's gardens in years gone by, these days the dishes have shrunk to something that's just about the same size as those used for TV broadcasts. Installation was delayed due to my trip to the Isle of Skye (which, incidentally, has blisteringly fast internet considering it's a tiny island connected to the mainland with a small bridge), but this morning two installation engineers arrived at 8:00, having travelled more than two hours to reach me.
Within about an hour, we were up and running. Chunky lengths of coax wound their way into the house and a gigantic satellite modem nestled under the stairs. Within moments I hit the first stumbling block. The installers left, telling me that everything was up and running and demonstrated the working connection on their own laptop. But after they'd gone, my own laptops wouldn’t connect... largely because there was no wireless network visible. Ah... need to plug in the router (not supplied). After a couple of false starts, a connection! Web pages flew in, I felt like a bird uncaged. Any fears I had about satellite being, well, a bit rubbish, evaporated.
There is a slight delay between clicking a link and a page loading, but it is only very slight, and once the transfer is underway it's all systems go. A couple of test downloads finished very quickly, and a speed test revealed that I was enjoying 12.55Mbps download speed. The speeds are nothing compared to fiber connections, but it's a huge jump for me. The connection is supposed to be up to 20Mbps, and I'm not sure if there'll be an increase, but it's entirely possible that previously suffocated apps and devices started to suck up the available bandwidth like oxygen.
This is something I'm going to have to keep a close eye on. Speeds are great, but there are limitations. The package I'm on at the moment costs £22.95 per month (around $38) and includes 10GB of data at up to 20Mbps. Once this limit is reached, it's still possible to use the internet, just at a rather reduced speed of 256kbps -- time to curb those downloads. It is possible to buy a bolt-on called FreeZone which opens up more options. For £7 extra per month (around $11) the package adds unlimited overnight traffic that doesn’t count towards the overall monthly limit -- time to start scheduling!
Is it all good news? Not entirely. Living in such as remote part of the world means that it is not only my telephone-based broadband that suffers -- mobile signal is also something of a rarity. There are literally no networks that offer a signal at my home address, and this meant that there was really no reason for me to move away from Orange/EE. After much tooing and froing several months ago, Orange/EE sent me a signal booster to plug into my router. It's a 3G box that essentially allows for text messages and phone calls to be made through an internet connection. The recommended minimum connection speed for using the booster is supposed to be 2Mb. As I have mentioned before, my broadband connection was crippled at 0.3Mbps on a good day. But the box worked. Sort of.
When I say it worked, what I really mean is that the box would kick out a signal around fifty percent of the time, frequently losing sync and falling over. When connected, the laughable internet speed meant that -- of course -- it was impossible to make or receive phone calls; the phone would ring so I'd know a call was coming, but the audio had a distinctly underwater feel at best. Text messages worked fine, so it was worth keeping the box plugged in just for that. With satellite up and running, I was keen to see if I would, at long last, be able to make voice calls on my mobile at home.
No such luck.
Just as gamers bemoan the latency of satellite broadband, so the signal box decided to throw a hissy fit. A quick call to customer service revealed that the relatively high latency of the connection meant that the signal booster would not be able to sync with the server and would therefore be unusable. Drat and darn! Still... it seems like a small price to pay for an internet connection that is not only (in early tests, at least) rock solid stable, but also fast.
Of course, it's very early days. I'm just a few hours into using the connection, but I'm already sold. The internet is enjoyable rather than a pain, pleasurable rather than a chore. I'll write a little more about my experiences in the coming weeks, but based on my early impressions -- assuming you can stomach the initial set up costs, and don’t mind monitoring your web usage a little -- I'm sold.
-

EarlyClaim reserves usernames so you don’t end up with a crappy handle
Publié: août 17, 2014, 10:57am CEST par Mark Wilson
You never know when the next Twitter is going to crop up. When a new service like Pinterest, Vine, or Skype appears, if you're not quick off the mark there's a high chance you'll miss out on your preferred username. You want MarkWilsonWords? Sorry, that went ages ago… you'll have to settle for MarkWilsonWord09868. Getting stuck with a crappy username sucks, but it's very hard to monitor all of the new services that pop up so you can bag your ideal name as early as possible. This is something that EarlyClaim can help with.
It's a free service that seeks out new startups and reserves a username on your behalf -- you just say what handle you'd like, and EarlyClaim does the hard work for you. For businesses, it is important to have a brand identity that is the same across different social networks (who is going to take notice of Coca Cola 1897 on Facebook?) but it's also something that is valuable to individuals. How many times have you signed up for a site only to find that you're unable to secure the username of your choice and had to opt for something far inferior? Every time you use that service there is a constant reminder that you weren't fast enough at signing up.
EarlyClaim is described as a "ground zero for online identities". The service trawls the web for new startups, actively seeking out new sites -- startups are also invited to get in touch with EarlyClaim to get involved. In either case, startups register to use the API and EarlyClaim can then reserve your desired username for a few days. You also have the option of reserving a second and third choice of username, and this will be used should your first choice be deemed unsuitable by a particular site. To take advantage of this feature, you need to spread the word about EarlyClaim by sharing a personalized link through social networks.
If you're worried about becoming inundated with endless spam, the site claims that "EarlyClaim.com digests all out-bound communication, emails and messages from the startups, funneling them into a single daily digest email to each user’s personal email".
-

Constantly turned on -- the bleak reality of being permanently connected
Publié: août 16, 2014, 1:06pm CEST par Mark Wilson

We expect, and are expected, to be contactable at any given moment -- and indeed we often expect the same of others. Send a text, and you expect a response. Pen an email, and you expect to receive one in return, and fast. Hit up someone on Google chat and an all-but-instant reply is all but expected. Maybe this doesn’t sound like you, but I can guarantee that you fit on the spectrum, and also that the people you are in contact with make the same demands of you. When did this change? It used to be that you'd call a landline number and if you didn’t get a reply you might just try again a few hours later. The fact that we now carry mobiles with us virtually 24/7 means that it is weird if someone doesn't answer the call.
They can’t be busy! Try again! Still no reply? Send a text. And an email. And an IM. If it was limited to office hours, it might be understandable -- and bearable -- to some extent, but there has been a massive slip in end-times. It is acceptable to send emails to someone at any time of day. You may have woken up at 3 in the morning and thought of something relating to work, or even just something that made you laugh, and felt the need to share it immediately. The recipient, in all likelihood, will be alerted to this email on a smartphone or tablet if they don’t happen to be sitting at their computer. At 3 in the morning, it might not wake them up, but at, say, 8pm how likely is it that the email will be ignored? The recipient's working day just got extended by several hours.
We don’t switch off enough. How many of us check our phones for messages the moment we wake up, and it's also (one of) the last thing(s) we do before finally succumbing to sleep. The fact that we have a phone all but grafted to our bodies around the clock means that we know the second someone is trying to get in touch with us. If your phone buzzes, vibrates, pings, or bongs, how many times do you ignore it compared to the number of times you look at the screen instantly? That unread email could be the one that changes your life, after all. But rather than helping us, this constant connectivity is killing us; not literally perhaps, let's not take things too far.
Constant connectivity means constant distractions. You might be trying to write a letter on your computer, only to be distracted by an endless barrage of emails and instant messages. You can try to turn a blind eye to them, but they continue to pop up. Your phone continues to buzz away next to the keyboard. Your concentration is broken, albeit it ever so slightly. You lose your train of thought as you ponder whether you should look to see who that text message is from, or switch to your inbox to see if anything important has come through. The letter ends up taking three times as long to write as it should. Have you got the will to ignore the notifications?
At the end of a hard day, you might settle down to watch a movie. But how far away is your phone? When an alert pops up, do you wait until the end of the movie to check it, or do you end up trying to "multitask" by reading and replying whilst continuing to watch out of the corner of your eye. Multitasking doesn’t happen. We unitask. We switch between two or more tasks back and forth, back and forth, and each time it takes a brief time to get back into the swing of what we were doing. We've reached a point where it is almost considered rude not to reply to an email or other message instantly. Technology has made it possible to supply an instant reply, but it comes at a great price.
The line previously dividing work and leisure time has blurred, some say. I say it has all but disappeared (this is not a diatribe against current employers, merely an observation). The constant connection, be it enforced, chosen, or accidental, is exhausting, draining, and counter-productive. We spend more time getting less done. More time working on multiple things at the same time to the detriment of all of them. Less time resting, more time in go, go, go mode. It's great to be turned on, but there's a lot to be said for being turned off from time to time. Disconnect. Set limits. Stick to them. Make people wait. Live life. Make technology work for you, not the other way round.
Photo credit: ponsulak / Shutterstock
-

Edward Snowden can stay in Russia for at least three more years
Publié: août 7, 2014, 3:09pm CEST par Mark Wilson

The enfant terrible of the tech world, and the thorn in the side of the NSA, Edward Snowden has been granted permission to stay in Russia for a further three years. The former NSA analyst turned whistle-blower sought exile in the country a year ago and on August 1st he was granted an extension. The three-year residency permit was approved a week ago, but has only just been made public by Snowden's lawyer. Anatoly Kucherena explained that Snowden himself would hold a press conference as soon as possible, reported Russia Today.
The US has tried to force Russia to hand over Snowden so he can face charges in his home country, but for the time being, he will be able to stay where he is. If he feels inclined, the permits allows for him to travel abroad for up to three months, and he is free to travel wherever he wants within Russia. Although he has not expressed an interest in doing so, Snowden would be eligible to apply for permanent residence in Russia in five years' time.
More than a year after the initial revelations, the effect of Snowden's leaks are still being felt. He managed to single-handedly turn the world's attention to surveillance and increased public interest in the transparency of online firms. His actions have divided opinion, with some seeing him as a traitor who put the United States at risk, while others have applauded his actions for bringing to light the secretive activities of government agencies.
Photo Credit: Tashatuvango / Shutterstock
-

Google makes it easier to unsubscribe from email lists
Publié: août 7, 2014, 12:46pm CEST par Mark Wilson
Gmail is undergoing another change, but this time it's a fairly minor tweak -- and one that is likely to be broadly welcomed. Unsubscribing from mailing lists is about to become simpler. Rather than having to hunt through the small print at the end of an email, or scouring the text for a hidden link, you'll soon find the unsubscribe option right at the top of emails. Announced via the official Gmail Google+ page, Google describes the change as "a win for everyone".
The new feature is not something that mailing list creators need to opt into, or indeed do anything about at all. Providing an email features an unsubscribe link somewhere in its text, Gmail will automatically add it to the top of a message next to the From field. Google explains that "when a sender includes an 'Unsubscribe' link in a Promotions, Social or Forums message, Gmail will surface it to the top", so it's not clear if the feature will work with every single mailing list.
The comments on the Google+ post are positive for the most part, but there are also concerns. One commenter asks "what's to stop somebody crafting a malicious unsubscribe URL?" Others have suggested that senders might simply stop including unsubscribe links in their emails. This would seem unlikely as it would probably result in emails being flagged as spam. Some Gmail users have indicated that this feature has been available in their inbox for some time already, so it's possible there was a soft launch. But now the feature is official so if you don’t see it yet, you should do very soon.
Photo Credit: TACstock1 / Shutterstock
-

Dating site OkCupid freely admits lying to its customers
Publié: juillet 29, 2014, 1:49pm CEST par Mark Wilson

There was widespread condemnation of Facebook when it was revealed that the social network had been manipulating users' newsfeeds as part of a social experiment. Official complaints may have been made but it doesn’t seem to have served as a lesson for other websites. Now it transpires that OkCupid -- the dating website whose slogan is "We use math to get you dates" -- has been fiddling the figures in a series of experiments on its users. The weird thing is, the site is openly bragging about it.
In a blog post unashamedly titled "We Experiment On Human Beings!", founder Christian Rudder writes that "OkCupid doesn’t really know what it’s doing". Seems like something of an odd admission. The blog post details three experiments the dating site conducted on its subscribers. There must have been more because the post is prefaced with the words "Here are a few of the more interesting experiments OkCupid has run." Does "interesting" just mean "less controversial"? Who knows?
So is the openness to be welcomed, or should we view it a little more cynically? It just about goes without saying that I would suggest the latter. Transparency is great, but sometimes what is revealed is far from savory. Some of the experiments listed are fairly innocuous -- hiding pictures so users have to base their opinions on words, for example -- but telling people they are compatible when OkCupid's "math" actually says otherwise is a little different. That's blatantly lying to people, and that's never right. The results of the experiments are tedious to most people outside of OkCupid, but the mere existence of the experiments is fascinating.
The timing is a little weird. On Monday, a tweet from the OkCupid account proudly proclaimed "The OkCupid blog is back! New post up now...", while a tweet from Christian was similarly excited: "Very happy to announce the first OkCupid blog post in three years". Why bring the blog back from the dead after so long? It might be slightly late to ride the wave of controversy surrounding Facebook's experimenting, but it's an attention grabbing story which captures the zeitgeist. It's said that there's no such things as bad publicity -- which I would argue is nonsense -- but advertising a stunt like this is a sure fire way to get noticed. What’s that, Christian? You have a book coming out in September? Interesting stuff.
Facebook's experimentation was bad enough. We have enough to worry about without having the added concern that what we're seeing -- even when it is from our friends -- has been processed through some third party filter. But OkCupid is a different matter. The site may be free, but it's dealing with people's hearts, minds and lives. Christian Rudder may think himself tremendously clever for crunching the numbers and gaining all of this free publicity for his book, but the argument that "if you use the Internet, you’re the subject of hundreds of experiments at any given time, on every site... that’s how websites work" just doesn't cut it. Of course websites try things out, different designs and layouts, new features, different types of content and so on, but that's really not quite the same things as lying to users.
Is OkCupid off the hook for being retrospectively honest? Not in my book. It's probably covered in some small print somewhere, but it's still unethical and dishonest, and it breaks my heart.
Image credit: Piotr Krzeslak / Shutterstock
-

Wilson's Weekend Whine: slow connections are dividing the web -- and making me mad
Publié: juillet 28, 2014, 12:37am CEST par Mark Wilson

The inspiration for this weekend's whine, along with the reason for its slight delay are one and the same thing. An appallingly slow (often non-existent) internet connection. Well, actually it's a combination of things, a slow internet connection being just one of them. Most people -- myself included in the past -- don't give a second thought to living online. Web pages are there ready be accessed on demand. Movies are just waiting to stream. Facebook and Twitter posts stream by. And so on. At least that's how it should be. If you live out in the sticks, it's a very different story -- and it stops me from banging about Edward Snowden and the NSA.
Look at the headlines and you’d be forgiven for thinking that everyone in the "developed world" is working with a blisteringly fast connection. Forget cables, we just have our brains connected directly to the internet. But we don’t. Here in the UK, there is a very noticeable digital divide, and I know it's a similar story in many other parts of the world. I've been fairly lucky in the past. Moving house at the turn of the millennium happily coincided with the arrival of broadband in the area. Hooray! 4Mbps of downstream -- more than acceptable nearly 15 years ago. A house move later, and things jumped to 8Mbps.
Across the pond
I then spent some time in the US. This meant dealing with Verizon rather than BT, and accepting a drop in speed to 3Mbps or thereabouts. Several months later, returning to the UK, a move to Scotland was on the cards. But not just "Scotland", "middle-of-virtually-nowhere Scotland". Mobile signal was a little flaky, but a surprisingly speedy "up to 8MB" broadband connection was available. Great for everyone in the area, but essential for people like me who work from home. The next move, despite involving relocating from somewhere very rural to somewhere on the edge of decent-sized town, meant dropping back to 3Mbps. The drop wasn't too much to shoulder, but there was a noticeable increase in drop outs, unreachable websites, and general frustration. But nothing could prepare me for what was to come next.
Yet another house move, and things took a turn for the particularly rural. An area where there are fields filled with sheep and cows in every direction, clumps of trees on the horizon, and only one neighbour, sounds -- and indeed is -- idyllic, but it comes with drawbacks. Chez nous had zero mobile signal. Not a bit. But worse than this, particularly for a technology journalist working from home, is the fact that the term "broadband" here refers to a connection that is *up to* 0.5Mbps. And when my ISP says "up to" you can almost hear them laughing as they say it. In reality, it means battling with a connection that operates at 0.3Mbps on a good day. Downhill with a tail-wind.
It's hard to describe how frustrating working with such an antiquated connection is. Simple online tasks that should take seconds, spread out to take minutes or hours. It is not possible to multi-task. You want to look at two web sites? Forget loading one in a background tab because that just means that the first tab won’t load at all! Streaming video? What's that? YouTube is reduced to looking like a flickbook operated by an arthritic old man, only able to flick between pages once a minute -- and who needs to take a lie down to recover from the exertion of turning three in succession.
F*&%!
I'm a person not averse to swearing. In fact it's something I embrace. A good, loud, full-bodied curse is great for the soul. But I don’t think I have ever sworn so much in my life. The internet is not just slow -- it is frequently completely unusable. Literally. Take this past week for instance. There have been three days when there has been no internet connection whatsoever. Countless phone calls to my ISP resulted in line tests revealing no problems, and probing showing that we should be able to connect at the blistering speed of 0.38Mbps. There was a beautiful irony in talking to a customer service robot who insisted that everything was working as it should. I was asked on several occasions to perform a speed test on the line, which led me to report back that the speed tests were inaccessible. With three different routers.
Now, after spending virtually the whole of Sunday on the phone battling, explaining, arguing, and trying to remain calm as I was told time and time again that everything was fine, the connection seems to be back up and running -- but for how long? And when I've spent my day dealing with people who don’t understand the difference between an internal and an external IP address, I do wonder how qualified they are to help.
The reason for my terrible internet connection -- and through which I am expected to write things online -- is that not only is the Wilson-plus-partner-and-cats abode way out in the middle of the Scottish countryside, but that the internet hardware in the area is positively ancient. Serving a total of under one hundred people, the local telephone exchange is simply not able to deliver broadband of about 0.5Mbps -- minus a bit for distance, minus a bit more for contention, and a bit more for noise, and a bit more for good measure. Never mind... we don’t have long to wait until the equipment is upgraded, do we? What's that? 2017, you say? W T actual F?! (and I stand by my use of the oft-maligned interobang there).
The remote location means that my current ISP has a monopoly. They own the cables and it's up to them when the system is upgraded. Cable and fiber just aren’t going to happen. The only vaguely realistic alternative is broadband via satellite, but this has hefty setup fees and ongoing charges. Restrictively hefty.
He over-speeds and he never gets pulled over...
Heading to coffeeshops, libraries, and other public hotspots -- even just browsing the web on a phone's data connection in town -- is a revelation. Pages that refused to appear at home flash up in an instant. I realize I am far from being alone. For each person gloating over the fact they have a 100Mbps connection, there are dozens more still stuck in the dark ages of dialup speeds -- literally in many cases, although thankfully not mine. And web pages are just not created for people with slow connections. Massive images, embedded videos, fat and lazy code. All these things slow down the internet for everyone, but it's only really noticed on the really slow connections.
How many web designers *really* think about optimizing their sites for everyone. It's all too easy to assume that everyone connects to the web at 10Mbps or more, and create all-singing, all-dancing sites to take advantage of all of this bandwidth. But the reality is that many, many people do not have such connections, and that means missing out on a lot the web has to offer. Spotify, YouTube, even the likes of Imgur are all but out of bounds to me -- I just don’t have the time or patience to wait for pages to load. There are tools and browsing that can compress pages, optimize browsing and so on, but there's a whole lot more than can be done to make the internet more accessible to all.
And despite all this, I continue to live my life online. The internet is my entertainment (not my sole form, of course), my job, a hobby, my research tool, and so much more. But I feel like a second class citizen of the web. The internet is my livelihood, but I have to bend to its will rather than it to mine. That's not right.
Photo credit: Djomas / Shutterstock
-

Forget.me now handles 'right to be forgotten' requests for Bing as well as Google
Publié: juillet 23, 2014, 2:05pm CEST par Mark Wilson
Back in May, the EU Court of Justice ruled that people have a "right to be forgotten" from search results. Google fairly quickly set up an online form to allow complainants to put forward their case for censoring their appearance in results. It didn’t take long for Microsoft to follow suit, and Bing users were soon afforded the same option.
Forget.me was one service that offered to take care of Google removal requests for people, and at the time CEO Bertrand Girin promised that "if Bing and Yahoo get their Right to be Forgotten forms in order, we’ll be able to provide you with the possibility of submitting your URL to all three search engines at the same time." For Microsoft, that day has come.
Forget.me can now be used to submit removal requests to Bing as well as Google. The service not only saves those with complaints from having to hunt down the relevant forms on Google and Bing's sites, but also eliminates the need to submit two requests -- one form can be used to submit requests to both search engines at the same time. There's no word on when support for Yahoo will be added, but the ball is very much in Yahoo's court for now.
Just how valuable the removal of links will prove to be remains to be seen. The court ruling has proved controversial, with many media outlets complaining that it amounts to little more than censorship. While the ruling does not require publishers to delete or amend any pages that contain "inadequate, irrelevant or no longer relevant" information, the onus has been place on search engines to remove links to them -- the content still exists and can still be accessed, just not via specific searches.
The "right to be forgotten" was heralded as a victory for privacy from some quarters, but the removal of search results has also been shown to be ineffective. Individuals may feel a sense of personal victory when results are removed, but sites like Hidden From Google are making a point of highlighting the pages that have been removed. With many websites drawing attention to articles that have been hidden from searchers, attempts to censor the web may actually have the reverse of the intended effect -- highlighting information that someone was trying to conceal.
-

Do Not Track is bolstered by EFF's Privacy Badger extension
Publié: juillet 21, 2014, 11:40pm CEST par Mark Wilson

Online security and privacy are hotter topics than ever. Just this weekend, Edward Snowden made an appearance at the Hope X 2014 hacker event, and called for those in attendance to help make encryption tools easier to use. Another fierce advocate of online privacy is the EFF (Electronic Frontier Foundation), and today the group released a beta version of Privacy Badger, a beautifully named extension for Chrome and Firefox designed to stop a number of tracking techniques used online. The idea of tracking cookies is something that will be familiar to most, but tracking takes many forms, including advertising and social media. Privacy Badger aims to block this tracking.
Peter Eckersley, EFF Technology Projects Director, said: "Widgets that say 'Like this page on Facebook' or 'Tweet this' often allow those companies to see what webpages you are visiting, even if you never click the widget's button. The Privacy Badger alpha would detect that, and block those widgets outright. But now Privacy Badger's beta version has gotten smarter: it can block the tracking while still giving you the option to see and click on those buttons if you so choose".
The beta release follows an alpha version which was unleashed three months ago. So far, an estimated 150,000 people have installed the extension and the latest version introduces a feature that offers further protection and social widgets. But rather than just blocking 'Like' and 'Tweet this' buttons, Privacy Badger actually replaces them with benign yet functional versions -- so you can still 'like' an article you have read, but now you can do so without revealing more about your online reading habits.
EFF is a supporter of Do Not Track and in many regards Privacy Badger can be seen as an extension of this. "Users who install Privacy Badger aren't just getting more privacy and a better browsing experience for themselves -- they are providing incentives for improved privacy practices and respect for Do Not Track choices across the Internet", said Eckersely. With many companies choosing to ignore Do Not Track requests, this extension provides a way to send a clear message to guilty parties.
Grab the extension from the EFF website.
-

Wilson's Weekend Whine: Snowden's call for online encryption is sad but necessary
Publié: juillet 20, 2014, 9:58pm CEST par Mark Wilson

It was quite a coup for HOPE (Hackers On Planet Earth). At the 2014 hacker event, Hope X, in New York City this weekend, Edward Snowden delivered a speech to those in attendance, advocating the use of encryption online. The former NSA analyst was not at the event himself -- he's still holed up in Moscow -- but he called on those present to help to protect privacy online. Speaking via a video link Snowden said: "You in this room, right now have both the means and the capability to improve the future by encoding our rights into programs and protocols by which we rely every day".
It was a great piece of work keeping the presentation a secret. There were, of course, fears that Snowden's appearance would somehow be thwarted: "We had to keep this bombshell quiet til the last minute since some of the most powerful people in the world would prefer that it never take place." There were certainly risks involved, but it was a risk worth taking. "[Snowden's] revelations of the massive NSA surveillance programs confirmed the suspicions of many and shocked those who haven’t been paying attention".
Speaking to the Guardian last week, Edward Snowden said that "Any communications that are transmitted over the internet, over any networked line, should be encrypted by default. That’s what last year showed us." Having helped to enlighten the world about online surveillance, Snowden has now expressed something of a shift in focus. The whistle has been well and truly sounded. Now is the time for something to be done. The hissing and moaning is all well and good, but now there is a call to arms. However loudly and frequently complaints are made, the chances of invasive surveillance programs coming to an end are pretty slim. But this does not mean we have to accept things lying down. Snowden is calling for the development and adoption of easy to use techniques to counter surveillance.
One of the most obvious options here is to embrace encryption. Governments "don't like the adoption of encryption. They say encryption that protects individuals' privacies, encryption that protects the public’s privacy broadly as opposed to specific individuals, encryption by default, is dangerous because they lose this midpoint communication, this midpoint collection".
Encryption. "That is what a lot of my future work is going to be involved in", Snowden promised at Hope X. There's no word on quite what form this will take, but his vocal opposition to what has been taking place made it clear that this is a man with a great deal of fight left in him. He will undoubtedly push for a system that is accessible for all, cheap and simple to implement, and difficult to circumvent.
Many people have said that internet users should expect their communication to be monitored, intercepted, violated. But why? The simple fact that surveillance is possible -- and, at the moment, relatively simple -- is not a justification. Nor is the assertion that terrorist attacks could be stopped. "Could" is the key word here. A large number of crimes could be prevented ahead of time if the government was to intercept every single letter sent through the postal system. It would be a mammoth task, for sure, but is it something people would stand for? Of course not. If it transpired that all of our phone bills, credit card statements, birthday cards, love letters, and anything else you sent or received through the mail was being read or scanned by the government there would be complete outrage. Would the fact that organized crime might be reduced soften the blow for you? Would that be enough for you to permit all of your paper-based mail to be read and stored? I sincerely hope not. I hope you all value your privacy, and indeed dignity, more than that.
But this is precisely what is happening online. It's communication in a different form, so why is the interception of electronic mail and other web traffic seen as more acceptable than intercepting regular mail? For me, there is no difference whatsoever -- aside from the fact that it is rather easier for agencies to secretly intercept electronic communications. If you learned your letters were being read, you would either stop sending them, or devise a code that you could use to communicate privately. It's heartbreakingly sad that we need to do the same online, but we do. This is not a matter of hiding your data from the government because you have something to hide, it's about protecting a basic human right: the right to privacy.
As Snowden said to the Guardian: "What last year's revelations showed us was irrefutable evidence that unencrypted communications on the internet are no longer safe and cannot be trusted. Their integrity has been compromised and we need new security programs to protect them. Any communications that are transmitted over the internet, over any networked line, should be encrypted by default. That’s what last year showed us". Snowden took unbelievable risks in making contact with the media with his initial revelations, but hopefully things will become easier for future whistleblowers. Also discussed at Hope X was SecureDrop, a system that can be used by those with information to share it with the media. Again, it is desperately sad that a system like this needed to be devised, but the need is there.
I'll leave the final word to Hope X who sums things up beautifully: "We are humbled to have [Edward Snowden] in our program, and hope the day will come when he's not confined to a video link and able to be as free as he is helping all of us to be".
Photo credit: soliman design/Shutterstock
-

New competition! Win a year's subscription to Office 365 Home
Publié: juillet 19, 2014, 6:01am CEST par Mark Wilson
 In the second of our (hopefully) regular competitions, we have quite a treat for you. You've read the headline so you should know what's up for grabs, but if you missed it, the prize is a year's subscription to Office 365 Home worth $99.99.
In the second of our (hopefully) regular competitions, we have quite a treat for you. You've read the headline so you should know what's up for grabs, but if you missed it, the prize is a year's subscription to Office 365 Home worth $99.99.Microsoft has very kindly donated a full subscription for us to give away, but this is more than just one copy of the world-famous office suite -- you can install Office 365 Home on up to five PCs or Macs, as well as five tablets. Enough for all the family!
So what's in the virtual box?
- The latest and most complete set of Office applications -- Word, Excel, PowerPoint, Outlook, OneNote, Access and Publisher
- An additional 20 GB of OneDrive cloud storage, nearly three times the amount available with a free OneDrive account
- 60 free Skype world calling minutes per month to call mobile phones, landlines or PCs around the world
- Future upgrades, so you always use the latest time-saving technology
You can find out more about features of the suite at the Office 365 Home page. With more than 4.4 million subscribers to Office 365 Home, the winner of this competition will be in great company.
We'll keep the competition open for a couple of weeks so the closing date will be the end of the day on Saturday 2 August (23:59:59 to be precise). Enter after this time, and your entry will be ignored.
Just like last time, entering the competition takes nothing more than leaving a comment below. Make sure you're signed into your Disqus account so we have a way to get in touch -- the winner will be selected at random and contacted shortly after the closing date. A license code and instructions will then be sent out via email so you can enjoy your prize straight away.
Good luck!
Photo credit: iQoncept/Shutterstock
-

Snowden: Facebook is allowing the government to see your messages
Publié: juillet 19, 2014, 12:49am CEST par Mark Wilson

In a lengthy interview with the Guardian, NSA whistle blower Edward Snowden spoke with editor Alan Rusbridger about his extraordinary rise to infamy. Currently in exile in Russia, he talked about how he disseminated documents about the activities of the NSA to numerous countries: "Once you start splitting them over jurisdictions and things like that it becomes much more difficult to subvert their intentions. Nobody could stop it". He remains defiant. He may be an outlaw but "it’s been vindicating to see the reaction from lawmakers, judges, public bodies around the world, civil liberties activists who have said it’s true that we have a right to at least know the broad outlines of what our government’s doing in our name and what it’s doing against us".
He explains how during his time working as an NSA analyst, he learned about previous surveillance programs run under George W Bush. Programs that were deemed unconstitutional and, having been closed, forced the US government to assume new executive powers that were then used "against the citizenry of its own country". For Snowden the power of the state is worrying:
So when we think about the nation we think about our country, we think about our home, we think about the people living in it and we think about its values. When we think about the state, we’re thinking about an institution. The distinction there is that we now have an institution that has become so powerful it feels comfortable granting itself new authorities, without the involvement of the country, without the involvement of the public, without the full involvement of all of our elected representatives and without the full involvement of open courts, and that’s a terrifying thing.
The ever shrinking costs of technology is cited as a reason to further fear the surveillance programs. When it becomes cheaper to store data than it is to sift through it and work out what is actually valuable, it is held onto for a long time. The NSA, for instance, is able to hang onto information about individuals for five years before having to apply for an extension. While there has been an outpouring of global disgust at Snowden's revelations, he feels the backlash against the government would be even stronger if the impact of surveillance programs were better understood.
You have a tremendous population of young military enlisted individuals who, while that’s not a discredit to them, may not have had the number of life experiences to have felt the sense of being violated. And if we haven’t been exposed to the dangers and risks of having our privacy violated, having our liberties violated, how can we expect these individuals to reasonably represent our own interests in exercising those authorities?
It has long been alleged that the internet companies who have decried the NSA have actually been willing partners. Snowden says that the financial arrangements that exist between surveillance agencies and internet and telecommunication companies is kept entirely secret -- "at a much greater level than for example the names of human agents operating undercover, embedded with terrorist groups".
Talk about the NSA has become so commonplace that it is easy to forget the huge numbers of entirely innocent people whose privacy has been invaded in recent years -- and Snowden insists that the big names have been (maybe still are being) fully compliant.
Agencies are provided with direct access to the contents of the server at these private companies. What it means is Facebook is allowing the government to get copies of your Facebook messages, your Skype conversations, your Gmail mailboxes, things like that.
It seems there is not really a need to be concerned that the government is hacking into private accounts, rather than access is being openly provided on demand.
[The government goes] to the company and they say: "You're going to give us this. You're going to give us that. You're going to give us that.” And the company gives them all of this information in a cooperative relationship. If Facebook is going to hand over all of your messages, all of your wall posts, all of your private photos, all of your private details from their server the government has no need to intercept all of the communications that constitute those private records.
The world of a surveillance worker is painted as something slightly dirty and sordid. After all, that's precisely what it is. Young men are "thrust into a position of extraordinary responsibility", and the sharing of individuals' private data is common:
In the course of their daily work they stumble across something that is completely unrelated to their work, for example an intimate nude photo of someone in a sexually compromising situation but they’re extremely attractive. So what do they do? They turn around in their chair and they show a co-worker. And their co-worker says: "Oh, hey, that’s great. Send that to Bill down the way.” And then Bill sends it to George, George sends it to Tom and sooner or later this person's whole life has been seen by all of these other people. Anything goes, more or less. You’re in a vaulted space. Everybody has sort of similar clearances, everybody knows everybody. It’s a small world.
Snowden calls for companies to adopt a policy of encrypting clients' data. Governments "don't like the adoption of encryption. They say encryption that protects individuals' privacies, encryption that protects the public's privacy broadly as opposed to specific individuals, encryption by default, is dangerous" because it interferes with their ability to easily intercept data.
While the world's attention has been focused primarily on the US, there are similar surveillance programs taking place around the world, including in the UK. Snowden points out that UK residents actually have a worse deal because "their ability to communicate and associate without monitoring and interference is not strongly encoded in law or policy. And the result of that is that citizens in the United Kingdom and citizens around the world who are targeted by the United Kingdom, by the UK government, by UK systems, by UK authorities, they’re at a much greater risk than they are in the United States".
The debate about ongoing surveillance programs is going to keep us busy for quite some time to come -- there are just no signs of a let up. "It happens automatically, pervasively, and it's stored on databases, whether or not it's needed."
-

Bing offers complainers a right to be forgotten from search results
Publié: juillet 18, 2014, 12:26am CEST par Mark Wilson

If you live in Europe and don't like the fact that Binging yourself throws up results you'd rather didn’t appear, Microsoft has created a form you can use to request removal of these links from searches. (Yeah, ok…Bing doesn't really work as a verb in the same way as Google. Lesson learned.) Not all that long ago, Google was forced to consider censoring search results that people considered to be out of date, incorrect or irrelevant -- it's a ruling that has been dubbed the right to be forgotten. A form was set up to make it easier for people with complaints to get in touch, and now Microsoft has followed suit and created a Request to Block Bing Search Results In Europe form.
Filling in the form is absolutely no guarantee that a search result will be removed -- and it is important to remember that this is only about removing links from search results, not removing actual content. Or, as Microsoft puts it in the form:
We encourage you to provide complete and relevant information for each applicable question on this form. We will use the information that you provide to evaluate your request. We may also consider other sources of information beyond this form to verify or supplement the information you provide. This information will help us to consider the balance between your individual privacy interest and the public interest in protecting free expression and the free availability of information, consistent with European law. As a result, making a request does not guarantee that a particular search result will be blocked.
If you have a complaint, you'll need to prove who you are and that you are an EU resident. Interestingly, the form also asks complainants "are you a public figure (politician, celebrity, etc.)?" and "Do you have a role or expect to have a role in your local community or more broadly that involves leadership, trust or safety". It's not clear how much of a bearing this information has on how a request is dealt with, but there are just four reasons a block request can be made: if information is inaccurate or false, it is incomplete or inadequate, it is out-of-date or no longer relevant, or it is excessive or otherwise inappropriate.
Photo credit: Gustavo Frazao/Shutterstock
-

Google does a 180 and allows fake names on Google+
Publié: juillet 16, 2014, 5:50pm CEST par Mark Wilson

Google is no stranger to upsetting people, and it certainly managed to do this back when Google+ launched three years ago. The social network that finds itself the butt of many jokes has long been criticized for forcing users to reveal their real names. But this policy is no more.
As well as reversing the real name requirement, Google has also apologized for the restrictions that have been in place over the past three years. The change of heart was announced, of course, in a Google+ post, and has been welcomed by the + community.
The post sees Google admitting that its policies were restrictive. "When we launched Google+ over three years ago, we had a lot of restrictions on what name you could use on your profile. This helped create a community made up of real people, but it also excluded a number of people who wanted to be part of it without using their real names". It is, however, interesting to note that the post has been made by an unnamed Google employee. The irony is saccharine-sweet.
But the big news is that the name restrictions have now been lifted. "Over the years, as Google+ grew and its community became established, we steadily opened up this policy, from allowing +Page owners to use any name of their choosing to letting YouTube users bring their usernames into Google+. Today, we are taking the last step: there are no more restrictions on what name you can use".
The post concludes by apologizing for the change in policy taking so long to come. "We know you've been calling for this change for a while. We know that our names policy has been unclear, and this has led to some unnecessarily difficult experiences for some of our users. For this we apologize, and we hope that today's change is a step toward making Google+ the welcoming and inclusive place that we want it to be".
And just so you know that complaints you may level at Google do not go unheeded, the company thanks users for "expressing your opinions so passionately".
Photo Credit: RTimages/Shutterstock
-

Hidden From Google shows the 'right to be forgotten' is pointless
Publié: juillet 16, 2014, 2:06pm CEST par Mark Wilson

It's a little while since a European Court of Justice ruling forced Google to start removing search links to certain articles. Dubbed the "right to be forgotten", the ruling led Google to create an online form making it easier for people to get in touch about search results relating to them thought to be "inadequate, irrelevant or no longer relevant". But just like those requests from celebrities to stop publishing compromising images online, it seems like asking for search links to be censored serves only to highlight the existence of the web pages they correspond to.
The court's decision that people should be able to request that information about them be removed from Google searches came after Spaniard Mr Costeja González took exception to links to stories about a series of old debts he had. There are now few people who follow news about Google who are not aware that Mr González has a less than perfect credit history. It's not clear whether he regards the ruling as a personal victory, but the appearance of Hidden From Google is sure to ruffle the feathers of many who have submitted similar removal requests to the search giant.
The site exists for one very simple reason:
"The purpose of this site is to list all links which are being censored by search engines due to the recent ruling of "Right to be forgotten" in the EU.
This list is a way of archiving the actions of censorship on the Internet. It is up to the reader to decide whether our liberties are being upheld or violated by the recent rulings by the EU".
Hidden From Google comprises a simple "list of search results omitted, erased, or censored" by Google. Numbers are fairly small at the moment, but visitors are encouraged to submit links they discover. Dear Mr González's story is recorded for posterity, and there are other stories from around Europe. Among them, the tale of an archaeology specialist who tried to steal toiletries from a shop in Oxford, UK. Hidden from Google helpfully links to a story about why the story was removed -- the newspaper in question labels the right to be forgotten as "censorship and open to abuse by criminals and the powerful who will try to hide information from the public".
The appearance of a site like Hidden From Google was just about inevitable. It perfectly demonstrates the futility of censoring search results, and it will be interesting to see how the complainants react to their removal requests being advertised.
Image Credit: Maxx-Studio/Shutterstock
-

1 million users affected by CNET.com hack
Publié: juillet 15, 2014, 11:59am CEST par Mark Wilson
News and review website CNET has been targeted by a team of Russian hackers called W0rm. CNET's servers were hit over the weekend, but details have only just been released.
Although CNET has not given a concrete confirmation of exactly what happened, the site explains that a representative of W0rm claims to have stolen a database containing the usernames and passwords of over a million users. It seems a security hole in the Symfony PHP framework was exploited, and it is not yet clear what the fallout could be.
On Twitter, user @rev_priv8, a W0rm representative whose profile description reads "Research & Development", taunted CNET with a message and picture apparently showing the database source code:
https//w0rm.in/cnet.com.tar.gz cnet hacked, here is src of www. pic.twitter.com/ggkaNF3VfE
— w0rm (@rev_priv8) July 12, 2014
A Direct Message conversation followed an invitation to get in touch:
#cnet i have good protection system for u, ping me.
— w0rm (@rev_priv8) July 14, 2014
If the conversation is to be believed, the hacks appears to have been a bid to highlight security issues rather than to make money. CNET asked whether anyone was interested in buying the database. To which came the broken-English response: "Yes. But I principled that something would not sell it if rasprostronenie [distribute] source code -- a step to improve safety. SNET [sic] sale bd for me crime, information about the sale move to the aggravation of the situation around hacking". There was apparently a threat to sell the database for a single Bitcoin, but this was merely to gain attention.
So is there cause for concern? The problem has now been resolved, and CNET quotes Robert Hansen of White Hat Security as saying "CNET readers might not be at risk". This in itself may not sound particularly reassuring, but he goes on to say "W0rm was careful not to give the full path to the actual exploit, and informed the general public that the compromise occurred".
-

Wilson's Weekend Whine: Snowden is right to be disgusted at UK 'emergency surveillance bill'
Publié: juillet 13, 2014, 11:48pm CEST par Mark Wilson

When we talk about surveillance online, it is almost always with reference to the NSA and activities in the US. But US citizens are far from being the only web users affected by surveillance. The NSA has long arms, but there are also similar activities going on in plenty of other countries. This week in the UK, the government is pushing through legislation that requires phone and internet companies to store information about customers' communication, and to hand it over to authorities on request. What made this particularly unusual was the fact that this was classed as emergency surveillance legislation with little to no debate and, more importantly, no public consultation whatsoever. Edward Snowden has plenty say on the matter, likening the British government to the NSA.
The legislation covers not only UK-based companies, but also those based in other countries who have gathered data about UK customers. It is in direct opposition to a recent European court ruling that said retention of data was a violation of European law. This in itself would be reason for any surveillance-related laws to be debated, but the government chose instead to use emergency measures -- usually reserved for times of war or disaster -- to push through laws it knows will prove unpopular. As we are now used to hearing, the surveillance is not about recording phone calls, or storing individual emails and text messages, but about retaining the related metadata -- who contacted who, when, for how long, from where, and so on.
But as we have already seen in the US, this dragnet style of surveillance means that the lives of countless innocent people are impacted upon. Point the finger at everyone and you’re sure to catch a criminal. Still holed up in Russia, former NSA worker Edward Snowden spoke with the Guardian in a mammoth seven hour interview. During the interview he compared the British government's legislation to something that could have been written by the NSA:
"The NSA could have written this draft. They passed it under the same sort of emergency justification. They said we would be at risk. They said companies will no longer cooperate with us. We're losing valuable intelligence that puts the nation at risk."
Prime Minister David Cameron has tried to justify the legislation which has angered privacy and civil liberties groups. "Sometimes in the dangerous world in which we live, we need our security services to listen to someone's phone and read their emails to identify and disrupt a terrorist plot. As prime minister I know of examples where doing this has stopped a terrorist attack". If this sounds like familiar scaremongering, it should. It's nothing we haven't heard before -- it’s the same words from a different mouth.
"We face real and credible threats to our security from serious and organised crime, from the activity of paedophiles, from the collapse of Syria, the growth of Isis in Iraq and al-Shabaab in east Africa". Yeah -- we’ve heard it all before, David. Would you like to read my mail before it drops through my letterbox as well? Or would gathering the metadata about who has written to me be enough? Deputy Prime Minister Nick Clegg bowed under pressure, but was quick to defend himself. "I have only agreed to this emergency legislation because we can use it to kickstart a proper debate about freedom and security in the internet age". But the legislation has been widely condemned as a "stitch-up by the elite".
There is simply no justification for blanket surveillance. It does not make sense in any world. The number of man hours, the amount of expense, the number of false leads, the sheer volume of data is staggering. My opinion is divided when it comes to Edward Snowden. I applaud what he has done -- it was an extremely brave move to essentially stand up to the US government as a one-man army -- but I do find that he is something of an odd figurehead for privacy. But this is just a personal thing. Snowden is a modern day hero, and he has forced more people to do what they do not do often enough -- question authority and those in power. When something is done either in your name or for your benefit, it is only right that you have a say in how things are tackled. With both the NSA's activities and the UK government's "emergency" legislation (I feel from this point forward, I have to wrap that word in quotes lest I legitimize the government's actions).
Snowden speaks complete sense when he says the government is looking to get new laws in place "immediately without any debate, just taking their word for it, despite the fact that these exact same authorities were just declared unlawful by the European court of justice". But more important is the question he poses: "Is it really going to be so costly for us to take a few days to debate where the line should be drawn about the authority and what really serves the public interest? If these surveillance authorities are so interested, so invasive, the courts are actually saying they violate fundamental rights, do we really want to authorise them on a new, increased and more intrusive scale without any public debate?"
We are very much in the dark about what is happening. Limp-wristed references to national security, foreign threats and the like are meaningless (how many illegal wars have been started with any of these given as justification?). As Snowden says, "What's extraordinary about this law being passed in the UK is that it very closely mirrors the Protect America Act 2007 that was passed in the United States at the request of the National Security Agency, after the warrantless wire-tapping program, which was unlawful and unconstitutional, was revealed".
For all the talk of living in a democracy, the fact that laws like this can be passed with no public consultation is unbelievable. The public is not being properly informed about what is happening, what the implications are, and what, if anything, they can do to get involved. For this to be happening in modern politics is a disgrace. I'm with Snowden on this one -- I'm fucking furious. I know I'm not alone, and I can only hope that a groundswell of opposition to mass surveillance and data retention as used by the NSA and UK government will force those involved to engage in meaningful debate.
Final thought
As you may have noticed, the weekly roundup of the week's news is no more. In its place will be -- as you have probably discerned from the headline -- a weekly whine. During the week there is plenty of time for news, while the weekend brings more time for reflection and analysis... and I can usually find something I'm less than happy about. Feedback is, as ever, welcome -- thoughts on content, ideas for what to cover, et cetera.
Image Credit: Nomad_Soul / Shutterstock
-

Is Russia on the verge of creating its own controlled, closed internet?
Publié: juillet 5, 2014, 10:07pm CEST par Mark Wilson

The idea of a closed internet is hardly new; turn your eyes to East Asia, and the Great Firewall of China looms large. The Chinese government is well known for the control it likes to exert over the levels of access its citizens have to the internet, and there have been numerous well-publicized cases of censorship and access being restricted to pages that refer to certain events in the county's history. The country is highly defensive of its image, and goes to great lengths to fight off western influence -- including going as far as banning Windows 8 on government computers lest machines furnished with Microsoft's most recent operating system be used for spying on the People's Republic of China. Now it looks as though Russia could be going down a similar route.
Russian parliament has just passed a law that requires internet companies to store data about Russian citizens within the county's boundaries. The move can be viewed in a couple of ways. It is no secret that the Russian government, and Vladimir Putin in particular, is no fan of social media -- social networks were used by Russians to voice their disapproval at Putin's activities. It is thought that the move to contain citizen's data without Russia is a bid to create a Russian version of China's closed internet.
While the Kremlin insists that the laws -- which could come into play in the third quarter of 2016 -- are aimed at improving data protection, it is being viewed more suspiciously by others outside of the government. The concern centers around the fact that the government will retain the right to block or close down sites that do not comply with the law. This means that social networks like Facebook and Twitter will have to store their data in Russia rather than at data centers elsewhere in the world or risk missing out entirely on the Russian market.
Russia has something of an interesting relationship with many other countries, most notably the US. After Edward Snowden fled the States, he managed to obtain asylum in Russia, placing something of a strain on American-Russian relations. Having blown the whistle on NSA activities, Snowden has changed the face of the internet forever. He is held up as a hate figure by many, but lauded as a hero by others. His revelations about the activities of the NSA served only to make Russia more suspicious of the US.
Russians will no doubt be happy to ensure that their personal data is not being stored in the US. But bringing things in-house could mean giving up access to a democratic, free internet. Whether there will ultimately be a Russian firewall in place remains to be seen, but -- assuming the laws are passed by the upper parliamentary chambers as well as Putin himself -- it certainly looks as though Russians could end up losing access to parts of the internet the government doesn’t like.
Image Credit: Reidl / Shutterstock
-

The most popular stories on BetaNews this past week: June 29 -- July 5
Publié: juillet 5, 2014, 10:34am CEST par Mark Wilson
 Something of a quieter week this week -- perhaps because of Independence Day and preparations there for. Still, there was plenty of news to keep us busy, including the NSA releasing a transparency report -- for what it's worth. Facebook found itself in the firing line after it transpired that the social network had been conducting psychological experiments by meddling with users' newsfeeds. Security is an on-going concern in technology, but it's something we have tendency to think about only in relation to computers and smartphones. One of the latest targets for malware and attacks is the power grid, and it's hard to tell what sort of havoc could be wreaked.
Something of a quieter week this week -- perhaps because of Independence Day and preparations there for. Still, there was plenty of news to keep us busy, including the NSA releasing a transparency report -- for what it's worth. Facebook found itself in the firing line after it transpired that the social network had been conducting psychological experiments by meddling with users' newsfeeds. Security is an on-going concern in technology, but it's something we have tendency to think about only in relation to computers and smartphones. One of the latest targets for malware and attacks is the power grid, and it's hard to tell what sort of havoc could be wreaked.Microsoft tried to do its bit for security -- arguably in a misguided fashion -- by taking control of dynamic DNS service No-IP, and accidentally taking out a number of legitimate sites in addition to those malware-related ones -- the intended targets. In more positive Microsoft news, enhancements were made to Office 365's collaboration options. Windows Phone is still struggling in the smartphone market, but Microsoft will be hoping that this month's launch of Windows Phone 8.1 will help to improve things -- will the addition of folder support be enough? Looking further into the future, Joe pondered what Microsoft should do with Nokia. He also decided to give Windows another chance, helped along by his new Surface Pro 3.
Maybe Joe's renewed interest can do something to reverse Windows 8.x's decreasing popularity. Perhaps a rebrand is in order; it looks like dropping the Surface name might be on the cards, so why not extend the idea to Windows? Looking to other sales, Samsung's Galaxy S5 is doing "quite well" -- and there's now an S5 mini on the way. But the news is not so good when it comes to wearables -- the Woz has ditched his Samsung smartwatch.
We asked whether Google Glass will ever gain mainstream popularity -- almost half of you said you had no interest in wearable tech, and smartglasses in general got the thumbs up from just 13 percent of you. There are lots of companies vying for attention in the smartwatch market, but Samsung has made it clear that it doesn't care about an Apple smartwatch. Despite rumors to the contrary, Google has said it has no plans to kill the Nexus line, but next on the company's list of launches is Android TV. Plex users will be pleased to hear that the streaming media service will be available on Android TV right from the launch.
Have a restful, fun-filled weekend, and we'll continue to pump news and other delights in your direction.
-

Facebook faces official complaint over deceptive newsfeed experiment
Publié: juillet 5, 2014, 5:37am CEST par Mark Wilson

The revelations about Facebook's emotional experiment with users' newsfeeds back in 2012 has seen the social network fighting off a torrent of criticism. Users were upset to learn that the content of their newsfeed may have been manipulated as researchers tried to determine the effects exposure to positive and negative newsfeed content had on users' subsequent output. Now an official complaint has been lodged against the social network by thee Electronic Privacy Information Center. Epic filed a complaint with the US Federal Trade Commission, alleging that "the company purposefully messed with people’s minds".
There are several lines of attack in the complaint, but the main thrust is that Facebook neither obtained permission from the 700,000 affected users, nor informed them about what was happening. Epic also complains that Facebook failed to warn users that their data would be shared with researchers at Cornell University and the University of California. The complaint points out that "at the time of the experiment, Facebook was subject to a consent order with the Federal Trade Commission which required the company to obtain users' affirmative express consent prior to sharing user information with third parties".
Despite the level of interest the experiment has garnered, the complaint does not make many demands -- just that Facebook should be forced to make publicly available the algorithm used to generate newsfeeds, and also "provide such other relief as the Commission finds necessary and appropriate". The suggestion is that Facebook and the research teams not only failed to follow ethical protocols, but also ignored Facebook's own Data Use Policy. The policy that was in place at the time of the experiment stated that "We use the information we receive about you in connection with the services and features we provide to you and other users like your friends, the advertisers that purchase ads on the site, and the developers that build the games, applications, and websites you use". It goes on to say that no data will be shared without first obtaining permission.
Epic notes that Facebook changed its policies after the experiment was conducted in January 2012, to allow for user data to be used for "data analysis, testing, research and service improvement" -- fairly broad terms which could cover the experiment, or variant thereon in the future. Facebook and the researchers ended up analyzing over three million posts, although the fact that computers rather than human anlayzers were used was seen as keeping the research in line with Facebook policies.
Epic's complaint makes reference to the many, many vocal opponents to Facebook's actions, citing numerous forum comments and Twitter posts. Some highlights include a tweet from @kissane_sxsw who said "Get off Facebook. Get your family off Facebook. If you work there, quit. They're f*cking awful," and @RalphPici who tweeted "It's sad in a pathetic way that @facebook doesn't get that its [sic] about trust and that they betrayed user trust #FacebookExperiment."
Facebook is yet to respond to Epic's filing of a complaint, but COO Sheryl Sandberg offered a sideways apology about the study on Thursday, saying "We never meant to upset you. It was poorly communicated," she said. "And for that communication we apologize."
What outcome would be acceptable to you? Can Facebook do or say anything to put right what it has done wrong?
Image Credit: Sarawut Aiemsinsuk / Shutterstock
-

NSA under the microscope -- agency releases "transparency" report
Publié: juin 28, 2014, 10:13pm CEST par Mark Wilson

NSA, Snowden, spying, yadda, yadda, yadda. This story is old, I know, but it goes on. The activities of the NSA and other government agencies have forced the online world to look very closely at how its data is being used, and how the companies handling it operate. Just about every online company worth its salt has gone out of its way to bemoan the NSA, their need to comply with data requests from the agency, and their inability to reveal everything they want to about what the NSA is asking about.
We have seen "transparency reports" from Google, Microsoft, LinkedIn and numerous other companies. But as suggested by my use of quotes, and as alluded to in the opening paragraph, there have been (severe) limits to the levels of transparency we have seen. "Quite opaque" might be a better description. Still, with the world and its dog falling over one another to release the most details, most comprehensive, and most self-congratulatory report, we probably should have predicted that pressure on the NSA would reach a point at which it felt forced to show its own hand. That time has come. The microscope has been turned around, and the security agency is now laying bare its own facts and figures.
The "Annual Statistics for Calendar Year 2013" report is not exactly a willing publication. On the first page, the agency suggests that, left to its own devices, the report would not have seen the light of day: "President Obama directed the Intelligence Community to declassify and make public as much information as possible about certain sensitive U.S. Government surveillance programs while protecting sensitive classified intelligence and national security information". This is not even a case of trying to improve public relations or boost the agency's image, more something that is done -- not even out of a sense of duty -- out of obligation.
You can take a browse through the report on the NSA's Tumblr page. Here you'll find the delightfully obtuse "Annual Statistics for Calendar Year 2013 Regarding Use of Certain National Security Legal Authorities", and the figures make for interesting, if not particularly revealing, reading. For instance, we learn that there was just one single section 702 FISA order issued. This affected as "estimated" 89,138 targets (a surprisingly precise figure for an estimate), but this is not as clear as one might expect.
The NSA explains that "the term 'target' has multiple meanings. For example, 'target' could be an individual person, a group, or an organization composed of multiple individuals or a foreign power that possesses or is likely to communicate foreign intelligence information that the U.S. government is authorized to acquire by the above-referenced laws." This renders the figures all but meaningless, especially when we factor in the data requests we're not allowed to know about. But knock yourself out with meaningless stats: 19,212 National Security Letters sent out, 38,812 requests for information, 1,767 FISA orders, and so on.
This is not the face of a new NSA. This is the same organization dealing with the same levels of obfuscation, misdirection, and fudge. Plus ça change, plus c'est la même chose.
So, what do you make of it all. Has the NSA struck the balance between keeping people happy and maintaining national security, or is the agency just paying lip service to advocates of transparency?
Image Credit: 360b / Shutterstock
-

The most popular stories on BetaNews this past week: June 22 -- 28
Publié: juin 28, 2014, 1:15pm CEST par Mark Wilson
 The battle for dominance between Microsoft and Google continued, with Microsoft offering a huge storage boost for Office 365 and OneDrive users. This was quickly trumped by Google later in the week at 1/0 2014, when the company announced unlimited storage for Google Drive for Work users. Microsoft is basking in the glory of being heralded as cooler than Apple by Joe -- and stunts like offering cashback deals to sway MacBook Air owners into switching into Surface Pro 3 certainly helps. Microsoft opened a new store on Long Island, while Google branched out into new territory with a trial run of a new domain registration service. Microsoft also ventured into new waters with its first Android smartphone, the Nokia X2.
The battle for dominance between Microsoft and Google continued, with Microsoft offering a huge storage boost for Office 365 and OneDrive users. This was quickly trumped by Google later in the week at 1/0 2014, when the company announced unlimited storage for Google Drive for Work users. Microsoft is basking in the glory of being heralded as cooler than Apple by Joe -- and stunts like offering cashback deals to sway MacBook Air owners into switching into Surface Pro 3 certainly helps. Microsoft opened a new store on Long Island, while Google branched out into new territory with a trial run of a new domain registration service. Microsoft also ventured into new waters with its first Android smartphone, the Nokia X2.In something of an interesting twist, Microsoft opted to use Opera Mobile as the default web browser. Opera is also returning to Linux after the surprise release of Opera 24 Developer. Linux Mint 17 "Qiana" KDE was also released. Linux also managed to hit the headlines for facilitating the hacking of Google's Nest thermstats. If this hasn’t put you off, Logitech added support to its Harmony remotes.
Security news, you say? How about the revelation that there are still a terrifying number of servers lying vulnerable to the Heartbleed exploit. Need a little more? It turns out that the CryptoLocker ransomware is still out there, and mobile malware in general is on the increase. New Trojans have been uncovered by Kaspersky Lab that affect iOS and Android devices. Windows Phone doesn’t tend to get mentioned when security problems crop up, but that may change -- the ease with which the handset can be made means that more vendors are interested in the devices.
Smartphones may be more popular than ever, but this is not something that website designers seem to be taking into account. More than a quarter of websites are not mobile-friendly, leaving tablet and smartphone users with a sub par experience. Returning to I/O briefly, Google revealed Android Auto as well and merging the worlds of Android and Chrome OS. Of course, there was also Android L which HTC promised to bring to its flagship handsets -- if you want to get it installed on your Nexus 5 or 7, we had a guide to doing just that.
Amazon's Prime Music service fared well in its first week of existence… well some form of entertainment was needed after Facebook died for a full 30 minutes -- imagine! We took a look at what can be learnt from the outage.
Good weekends, all.
Image Credit: vinz89 / Shutterstock
-

Google brings out the big guns -- unlimited storage for $10 per month and Office editing
Publié: juin 25, 2014, 9:25pm CEST par Mark Wilson

At I/O 2014 Google announced that more cloud storage will be made available to space hungry users. Google Drive for Work has a price tag of $10 per month and includes not just more cloud storage, but unlimited cloud storage. Well, there is one limitation; individual files cannot exceed 5TB, but this is, for all intents and purposes, a deal that is unlimited by most people's understanding of the word. As the name suggests, this is a product that is aimed at businesses, but at this price it is hard to imagine that there won’t be swathes of home users looking to take advantage of the package.
A few months back, Google slashed the cost of its cloud storage packages, but today's news is something quite different. Worries about security may be allayed by the news that Drive, Gmail and Calendar data will be encrypted at data centers. IT admins will also be able to audit and control options, that means internal security policies can be implemented as required.
The Drive storage announcement from Google comes just after Microsoft increased the amount of free storage provided to OneDrive users, as well as bundling 1TB of cloud storage with Office 365. But Google is also trying to lure Office users away from the grips of Microsoft. Slides is Google's take on PowerPoint, but the big news for Google Docs users is support for editing Office documents.
This is big news for home users and businesses alike. In a direct attack on Office Online, Google is giving users the ability to edit Word and other Office documents online free of charge. New files can be saved in Word format, addressing one of the biggest limitations of Google Docs -- and bringing Quickoffice to Chrome will help to create a new online experience for users. This is Google wrestling back control of the web and the workplace.
Photo Credits: l i g h t p o e t/Shutterstock
-

The most popular stories on BetaNews this past week: June 15 -- 21
Publié: juin 21, 2014, 2:26pm CEST par Mark Wilson
 This is the week of the Surface Pro 3. Brian had already attended the launch event earlier in the month, and has provided an essential list of hardware and software purchasers need to grab for the best all round experience -- he even goes as far as suggesting that it's better than a MacBook Air. Even before launch there was an update available for the tablet-cum-laptop, and there was also news that the Intel Core i3 and i7 models would be shipping earlier than previously expected. But not all of the products we looked at this week were quite so "every day". There was the wifi doorbell complete with camera, and also the prospect of charging your phone wirelessly with your pants -- yes you did read that correctly.
This is the week of the Surface Pro 3. Brian had already attended the launch event earlier in the month, and has provided an essential list of hardware and software purchasers need to grab for the best all round experience -- he even goes as far as suggesting that it's better than a MacBook Air. Even before launch there was an update available for the tablet-cum-laptop, and there was also news that the Intel Core i3 and i7 models would be shipping earlier than previously expected. But not all of the products we looked at this week were quite so "every day". There was the wifi doorbell complete with camera, and also the prospect of charging your phone wirelessly with your pants -- yes you did read that correctly.The Windows Phone market is dominated by Nokia, but a new batch of handsets has been unveiled by Indian manufacturer Micromax. If Android is your mobile OS of choice, you may be thinking about venturing into the rooted world. This week a new tool was released that makes the process as quick and painless as possible, opening up a whole new breed of apps and options. Joe decided to take a walk on the wild side and adopt the Nokia Lumia Icon as his phone of choice. In the Android arena, a new contender entered -- the Amazon Fire Phone. Will a kill switch be added? Microsoft and Google have agreed to add it to their mobile operating systems.
Whatever your preferred phone choice, do you side with the 88 percent of Brits who are under the impression that their phones are being tapped? Whether you are paranoid or not, more speed is on the way as the foundations for 5G networks have been set. For anyone concerned about privacy, the news that online mapping services such as those offered by Microsoft and Google will be allowed to use higher resolution satellite images will be enough to send them scurrying under the bed covers.
When it wasn't busy going offline -- just for about half an hour all over the world -- Facebook was softening its guidelines surrounding photos of breastfeeding. The #FreeTheNipple campaign proved a success in the end. This was far from being the only social network-related news. LinkedIn is going to be in court at some point in the future after a judge found it had violated the privacy of users by "spamming" their contacts. Twitter managed to make its way into the headlines as well after the company reinstated a series of tweets and user accounts that had previously been deemed blasphemous. An interesting patent case has made it clear that simply applying an existing idea to computers does not make it patent-able -- patent trolls beware.
No week's roundup would be complete without its fair share of security news, and this week is no different. Hackers discovered a sneaky way to double their money through PayPal but better news came from Avast who released an Android app to remove ransomware -- and it might be just as well because batches of phones have been leaving factories pre-infected with malware. New figures showed that using dating apps could be a security risk, but there are security problems on the desktop as a fifth of businesses refuse to upgrade from Windows XP. But as it turns out, it's the users who are the biggest security risk.
That's all for this week. Pleasant weekends all round!
-

US Supreme Court squares up to software patent trolls with stricter rules
Publié: juin 20, 2014, 2:36pm CEST par Mark Wilson
A ruling by the US Supreme Court could change the way patents are assigned in the future. A case between New York-based CLS Bank International and Australian company Alice Corp found judges unanimously agreeing that software patent was invalid because it was simply an existing idea transferred to a computer. In order to qualify for a patent, an idea must be unique, and the court ruled that the simple addition of a computer application is not enough.
CLS Bank International had complained that Alice Corp had applied a "generic computer implementation" to a patent owned by the bank, rendering it invalid; the court agreed. "The representative method claim does no more than simply instruct the practitioner to implement the abstract idea of intermediated settlement on generic computer", the ruling states.
The ruling could help to stamp out the problem of patent trolls -- or non-practicing entities, as they are sometime known -- as it would force companies to come up with completely unique ideas. Trolls have become a serious issue for the tech industry, with many companies stockpiling patents in the hope that they will be able to force big companies into buying them. Software patents have been something of a sticking point for many years, and there have long been complaints that patents have been issued that are too vague. Similarly, it has previously been very easy for companies to take an existing idea that has been patented by someone else, add a tech twist, and call it their own.
The BBC points out that the US has the "most generous approach" to patents. In Europe software patents can only be awarded to software products that address technical problems. In the US "business methods" can be patented, and software falls into this category. The case has been very closely watched by the tech industry. The decision that combining a set of pre-existing ideas into one product without adding more features, or taking an existing patent and "computerfying" it, does not qualify for a new patent could have wide-reaching ramifications.
Photo Credit: Feng Yu/Shutterstock
-

Microsoft, Google to include kill switch in Windows Phone, Android
Publié: juin 20, 2014, 11:47am CEST par Mark Wilson

Both Microsoft and Google have agreed to add a kill switch their mobile operating systems. Following an agreement with the New York Attorney General, the next versions of Windows Phone and Android will include a feature that will render handsets useless if they are stolen. The attorney general, Eric Schneiderman, published a report yesterday outlining the importance of such a feature, and revealed that two of the biggest names in technology are on-board.
It's something that authorities have been calling for for some time now, citing the sheer number of mobile phone thefts taking place around the world. Schneiderman's report points to Apple as proof of the efficacy of a kill switch. Thefts of iPhones dropped by 17 percent in New York City after the introduction of a remote wiping and locking feature. The Secure Our Smartphones report took fire at Samsung. The company had opted not to include a kill switch, and thefts of Samsung handsets jumped by 40 percent in NYC. "Reactivation Lock" has since been implemented on a small number of new Galaxy handsets.
But while a kill switch can act as a serious theft deterrent -- "An activated kill switch converts an easy-to-sell, high-value multimedia device into a jumble of plastic and glass, drastically reducing its street value", says the report -- there are also security concerns. There is potential for the mechanism to be hijacked so the kill switch could be activated by a hacker or malicious user. It is likely that it will also be possible to block the kill switch signal -- perhaps by activating airplane mode until a workaround can be implemented.
The Save Our Smartphones initiative started one year ago as a joint venture between Eric Schneiderman and San Francisco District Attorney George Gascón. The Major of London, Boris Johnson, joined the project as co-chair, and in recent months various US states have pushed through kill switch legislation.
Photo Credit: Mark Dyer/Shutterstock
-

Amazon takes on Apple and Google with Fire phone
Publié: juin 18, 2014, 10:51pm CEST par Mark Wilson

Amazon today unveiled the latest entrant to the smartphone race -- the Fire phone. The handset continues the Fire name that is more readily associated with Amazon's range of Android tablets, and it has a few tricks up its sleeve to make it stand out from the competition. A press event in Seattle brought to an end weeks of rumor and speculation as the phone, which features Dynamic Perspective that allows for maps and other images to be displayed in three dimensions, was revealed.
Run by four ultra-low power specialized cameras and four infrared LEDs, Dynamic Perspective has numerous uses. One application makes it possible for users to gain a different perspective on an image or object on screen by moving their heads. In games, a move of the head can be used to switch views, and there is scope for unique navigation options within apps. Some applications are slightly simpler, and mimic those found in other handsets such as Samsung's Galaxy range. For example, auto-scroll allows for easy reading of lengthy documents and web pages without the need for swiping.
Extending on the phone's name, and conjuring up images of Nathan Fillion in a TV series of the same name, the handset runs a service called Firefly. Hoping to trump Siri and Google Now, Firefly recognizes groceries, books, and songs, allowing for easy ordering from Amazon (but of course), as well as food labelling, paintings, and more, to enable users to find out more information with ease. "Firefly recognizes a hundred million different items in real-world situations", said Jeff Bezos, the founder and CEO of Amazon. The Firefly SDK, as well as the SDK for Dynamic Perspective are being made available so its likely capabilities will quickly extend in both of these areas.
In terms of specs, the Fire phone features a 4.7-inch screen powered by Adreno 330 graphics, a 2.2GHz quad-core Snapdragon 800 processor, and backed up by 2GB of RAM. Photography comes courtesy of a 13MP camera complete with an f2.0 lens. The front facing camera is just 2.1MP, but both are capable of capturing 1080p HD videos. Just like its tablet big brothers, Fire phone runs Android.
 Taking on Google Drive and Apple's cloud storage, Amazon Fire phone owners will be able to take advantage of unlimited photo storage on Amazon Cloud Drive. If this is not enough of a draw, phones taken on contract include a 12-month Amazon Prime subscription, providing access to streaming music, movies and TV, and offering benefits such as faster shipping on Amazon orders.
Taking on Google Drive and Apple's cloud storage, Amazon Fire phone owners will be able to take advantage of unlimited photo storage on Amazon Cloud Drive. If this is not enough of a draw, phones taken on contract include a 12-month Amazon Prime subscription, providing access to streaming music, movies and TV, and offering benefits such as faster shipping on Amazon orders.But it is Amazon's existing infrastructure and set of services that could be the deal-breaker for buyers. Just like the Kindle Fire tablet range, the May Day button is available for when help is needed, and there's integration with Fire TV -- and other Miracast-enabled devices -- to allow for second-screening of videos. And of course Amazon's vast array of digital and physical goods are just a few taps away.
The Amazon Fire phone launches July 25 and will be available exclusively on AT&T. The 32GB model will cost $199 on a two-year contract, or starting at $27.09 per month. Double the storage to 64GB and you'll have to part with $299 on a two-year contract, or $31.25 per month. Pre-orders start now!
-

Twitter reinstates tweets that mock the Prophet Muhammad and depict Koran burning
Publié: juin 18, 2014, 5:49pm CEST par Mark Wilson
 Twitter has reversed blocks it placed on numerous tweets and accounts in Pakistan that were deemed "blasphemous" and "unethical", including some that featured anti-Islamic content, depictions of the Prophet Muhammad, and photos of the Koran burning. Pakistani authorities complained to Twitter back in May, and the social network "made an initial decision to withhold content in Pakistan".
Twitter has reversed blocks it placed on numerous tweets and accounts in Pakistan that were deemed "blasphemous" and "unethical", including some that featured anti-Islamic content, depictions of the Prophet Muhammad, and photos of the Koran burning. Pakistani authorities complained to Twitter back in May, and the social network "made an initial decision to withhold content in Pakistan".But after the Pakistan Telecommunication Authority failed to provide the additional information that Twitter requested, the accounts and tweets have been restored.
Twitter issued a statement to Chilling Effects, a website that publishes cease and desist notices that have been issued to companies:
We always strive to make the best, most informed decisions we can when we're compelled to reactively withhold identified content in specific jurisdictions around the world. On May 18, 2014, we made an initial decision to withhold content in Pakistan ... Consistent with our longstanding policies we provided notice to all of the affected account holders and published the actioned takedown requests on Chilling Effects to maximize transparency regarding our decision. We have reexamined the requests and, in the absence of additional clarifying information from Pakistani authorities, have determined that restoration of the previously withheld content is warranted. The content is now available again in Pakistan.
The Pakistani complaints -- which are available to see on the Chilling Effects website -- cite Pakistan Penal Code as the reason for numerous accounts and tweets being deemed ban-worthy. Accounts held by users who tweet pictures of the Prophet Muhammad -- while such depictions are not banned by the Koran, it is something forbidden by many Islamic leaders -- were included in the initial ban. Accounts like "draw Muhammad" and "Let's Draw Muhammad!" are among those who voice support for "free speech and freedom of artistic expression".
The Pakistan Telecommunication Authority politely asked that Twitter block a series of "Blasphemous URLs", "Blasphemous links", and "Unethical links", but the ban was in place for just one month. The decision by Twitter will be viewed quite differently around the world. For many it will be a victory for free speech, while others will find it as offensive as many did the original content. The fact that some of the accounts and tweets mentioned, as well as others, remain blocked outside of Pakistan, highlights the problems of the global nature of life online, and the problem of policing across borders.
Image Credit: Jandrie Lombard/Shutterstock
-

LinkedIn to face lawsuit for spamming users' email address books
Publié: juin 15, 2014, 6:25pm CEST par Mark Wilson

A judge in the Northern District of California has paved the way for a lawsuit against the social network LinkedIn for violating the privacy of its users. The complaint was that LinkedIn "violated several state and federal laws by harvesting email addresses from the contact lists of email accounts associated with Plaintiffs’ LinkedIn accounts and by sending repeated invitations to join LinkedIn to the harvested email addresses". It relates to the fact that LinkedIn not only used the address books of those signing up for accounts to tout for business by sending out an email to that effect, but also sent follow-up email if there was no response.
US district judge Lucy Koh ruled that while users granted permission for LinkedIn to access their contact list it is this 'spamming' that is likely to land the company in court again. The judge outlined the process users were complaining about, explaining that LinkedIn sent an email to connected in users' address books -- albeit with initial permission -- sends the same email a week later if the recipient has not joined LinkedIn, and a third email if another week passes without a signup.
Further complaints stemmed from the fact that "the only way a LinkedIn user can stop the two follow-up endorsement emails (assuming the user found out about the initial emails in the first place) from going out to the email addresses harvested from that user’s external email account is for the user to individually open up each invitation from within his or her LinkedIn account (which LinkedIn has intentionally made difficult to find within the user’s account) and click a button that allows the user to withdraw that single invitation". This means it could take several hours to individually cancel hundreds, or even thousands, of emails that were scheduled to be sent out.
The complainants pointed out that LinkedIn's Help Center pages are filled with complaints from other users about the emails. Some users said that "LinkedIn knew about flaws in its process but nevertheless took no action". One of the plaintiff's main causes for concern is that their contacts would regard the emails sent out by LinkedIn as being indicative that they endorsed LinkedIn, as well as being seen as being so enamored with the network as to spam on its behalf. This 'spamming' is seen as having the potential to damage the reputation of the user the emails were sent on the behalf of -- it could "injure users' reputations by allowing contacts to think that the users are the types of people who spam their contacts or are unable to take the hint that their contacts do not want to join their LinkedIn network".
The judge also pointed out that some of the wording used during the signup process was misleading. "By stating a mere three screens before the disclosure regarding the first invitation that 'We will not... email anyone without your permission,' LinkedIn may have actively led users astray". Koh also suggests that LinkedIn has violated California law by associating users' names and images advertising for further business.
No date has yet been set for further court hearings.
Image Credit: Gil C / Shutterstock
-

#FreeTheNipple campaign leads to breastfeeding nipple-shot ban reversal by Facebook
Publié: juin 15, 2014, 5:12pm CEST par Mark Wilson
 Facebook comes under fire for all manner of things -- it's just part and parcel of being a social network. When users are not up in arms at the site's privacy policies, they are found voicing their disapproval at the types of content they're not allowed to publish on their timelines. There are lots of types of pictures that are frowned upon, and parents were upset to find that many of the photos they posted fell foul of Facebook's moderators. Facebook's Community Standards have never included a stated ban on breastfeeding pictures, but those that included glimpses of nipples were often swiftly removed. A well-publicized campaign that used the hashtag #FreeTheNipple seems to have had the desired result.
Facebook comes under fire for all manner of things -- it's just part and parcel of being a social network. When users are not up in arms at the site's privacy policies, they are found voicing their disapproval at the types of content they're not allowed to publish on their timelines. There are lots of types of pictures that are frowned upon, and parents were upset to find that many of the photos they posted fell foul of Facebook's moderators. Facebook's Community Standards have never included a stated ban on breastfeeding pictures, but those that included glimpses of nipples were often swiftly removed. A well-publicized campaign that used the hashtag #FreeTheNipple seems to have had the desired result.As noticed by The Independent, there has been a softening of views as Facebook Moderators are now encouraged to consider the context in which nipples appear in photographs. The Community Standards state "Facebook has a strict policy against the sharing of pornographic content and any explicitly sexual content where a minor is involved. We also impose limitations on the display of nudity". But there is the caveat that "we aspire to respect people’s right to share content of personal importance, whether those are photos of a sculpture like Michelangelo's David or family photos of a child breastfeeding".
Further clarification is given on Facebook's help pages. Under the heading "Does Facebook allow photos of mothers breastfeeding?", comes the reply that "Yes. We agree that breastfeeding is natural and beautiful and we're glad to know that it's important for mothers to share their experiences with others on Facebook. The vast majority of these photos are compliant with our policies. Please note that the photos we review are almost exclusively brought to our attention by other Facebook members who complain about them being shared on Facebook".
Facebook has confirmed the change in policy to both The Independent and The Verge but has not issued any comment on the change of heart. Considering the publicity the #FreeTheNipple movement managed to gain, it's hard to imagine that the change cannot be at least partly attributed to the work of campaigners.
-

The most popular stories on BetaNews this past week: June 8 -- 14
Publié: juin 14, 2014, 5:38pm CEST par Mark Wilson
 Eyes were focused on Microsoft as the company held an Xbox One press conference at E3 2014, with the focus being very much on games. Not to be outdone, Sony also held a press conference at the event. Consoles from Sony and Microsoft are still largely reliant on traditional controllers -- dull! But the SteelSeries Sentry Eye Tracker is something to, almost literally, keep an eye on as it allows for controlling games with your peepers. PS4 users have the arrival of YouTube to look forward to, and Chromecast owners will soon be able to stream files from VLC.
Eyes were focused on Microsoft as the company held an Xbox One press conference at E3 2014, with the focus being very much on games. Not to be outdone, Sony also held a press conference at the event. Consoles from Sony and Microsoft are still largely reliant on traditional controllers -- dull! But the SteelSeries Sentry Eye Tracker is something to, almost literally, keep an eye on as it allows for controlling games with your peepers. PS4 users have the arrival of YouTube to look forward to, and Chromecast owners will soon be able to stream files from VLC.In security news, AVG publicized details of yet another OpenSSL flaw. While less serious than other vulnerabilities that have been discovered recently, it's still something of a cause for concern. We're still feeling the fallout of the Zeus botnet, and F-Secure set up an online testing tool that can be used by anyone to check for the infection. One tactic used to attack websites is bombarding them with comment spam, and new research shows that 80 percent of such spam is generated by less than a third of site attackers.
The latest big-name site to suffer a DDoS attack was Feedly, which found itself held to ransom, and it was amusing to learn that hackers are just as bad with their password choices as the rest of us. With so many security problems online, perhaps the best option is to take a leaf out of the book of those who choose not to connect. Windows security experts revealed that changes have been made to Windows 8.x files ,while the same file remained untouched, and potentially insecure, in Windows 7. But even with all of the security worries in the headlines, it is still hardware failure that is responsible for the highest levels of data loss.
LG's G3 carried across many ideas from its predecessor, and Brian took a look at the handset in his review -- he was particularly taken with the camera's laser focusing. He also got the chance to get hands on with the new Samsung Galaxy Tab S. Motorola released a 64GB version of the Moto X, giving users greater potential for storing apps and music. Windows Phone users have a new lockscreen feature to look forward to, but if you're more of an iOS fan, the aluminium (or aluminum, if you prefer) Kloqe case is well worth a look. There have long been rumors that a larger iPhone is on the cards, and new evidence came to light that suggests it is all but certain. Whatever your smartphone of choice, running out of power is always a concern. Grab yourself a Lumsing LUM-008-01 Power Bank and you can keep your devices powered for longer. But if remembering to take a USB cable out with you is too much, pop one on your keyring so it's always available when you need it.
In the UK, .uk domain registrations opened up, with more than 50,000 takers on launch day -- it seems they were not put off by the fact that any website registrant must publicize their name and address if they make money from ads on their sites.
That's another week under our belts -- good weekends all round!
Image Credit: vinz89 / Shutterstock
-

The most popular stories on BetaNews this past week: June 1 -- 7
Publié: juin 7, 2014, 8:43am CEST par Mark Wilson
 The biggest news of this week came from Apple which held a keynote speech at WWDC in San Francisco. One of the major announcements was the unveiling of iOS 8 which will be making its way to iPhone and iPads around the world sometime in the Fall. There was a lot to take in, including "Hey, Siri", HealthKit and iCloud Drive. OS X also got a new lick of paint with Yosemite, with beta versions made available for immediate download. There was also an intriguing change to the App Store Review Guidelines that suggests the doors may be opened to virtual currencies such as Bitcoin.
The biggest news of this week came from Apple which held a keynote speech at WWDC in San Francisco. One of the major announcements was the unveiling of iOS 8 which will be making its way to iPhone and iPads around the world sometime in the Fall. There was a lot to take in, including "Hey, Siri", HealthKit and iCloud Drive. OS X also got a new lick of paint with Yosemite, with beta versions made available for immediate download. There was also an intriguing change to the App Store Review Guidelines that suggests the doors may be opened to virtual currencies such as Bitcoin.Windows 7 continues to grow faster than Windows 8.x, but if you're looking for an alternative to Windows, Linux Mint 17 "Qiana" could be worth a try. Windows XP is still managing to hang on it there for the time being. Microsoft celebrated the news that Windows Phone is becoming increasingly popular -- if not with developers -- particularly when security is important; which is just as well, because reports suggest that handsets need to be made more secure for enterprise. Microsoft also had cause for celebration after helping the FBI to take down the Zeus botnet.
The HTC One just became slightly more affordable as a version not constructed entirely from metal was launched and Samsung announced its first Tizen smartphone. The same company pushes the size boundaries with the Galaxy W which seems unsure whether it is a tablet or a phablet. HP embraced Android by releasing a laptop running Google's mobile operating system, and ASUS is also keen to get in on the Android party, unveiling a number of tablets running the OS. It's all just part of the Android Army's march forward, says Joe. On the subject of Android, 4.4.3 KitKat was released.
Google's other mobile operating system is also spreading around the world as the HP Chromebook 11 launched in nine more countries, but are the models built without Google's involvement of quite the same standard? For the security-conscious, Google's End-To-End encryption extension is worth a look. There are new features coming to Internet Explorer, and hopefully by the time it arrives the world will have been saved from the Cryptolocker ransomware. We also learned that fans of online pornography are likely to be using the latest version of Microsoft's web browser.
Demonoid returned and Pirate Bay founder is arrested as torrenting hits the headlines for the first time in a while. In the UK, the copying of digital media was legalized meaning that -- at long, long last -- music fans who create MP3 copies of their favorite albums are no longer the breaking the law. The backlash against the activities of the NSA continues, and this week Reset The Net called for users to take control of their online privacy by using encryption tools. The question remains… is Snowden a hero or a villain?
Image Credit: vinz89/Shutterstock
-

Queen's speech proposes life sentences for cyber criminals in the UK
Publié: juin 5, 2014, 12:25am CEST par Mark Wilson

Edward Snowden is on the run, living in exile as a means to evade the long arm of US law. The United States seems keen to have him prosecuted for leaking documents that have arguably put national security at risk. He acted in good faith, but has been branded a cyber criminal. Today in the UK, the Queen gave her annual speech -- well, it's really a speech written by the government, but dear Liz reads it out so she gets to call it hers -- and she revealed that cyber criminals could face life sentences for their endeavors, and that existing punishments for digital crimes cold become harsher.
Singled out for particular attention are those "cyberattacks which result in loss of life, serious illness or injury or serious damage to national security, or a significant risk thereof". Those committing such acts could be put behind bars for life. But the proposals do not end there. The aging Computer Misuse Act could be updated, so that criminals that cause "a significant risk of severe economic or environmental damage or social disruption" incur a 14 year term compared to the current 10.
Some of the proposals have come in for criticism. Some see the sentences as too harsh, but there are other potential problems too. Security experts employed to test the defenses of a company's network, could find their probing activities to be criminal. It creates an odd paradox, in which people who investigated the Heartbleed bug for example, are not looked at as heroes, but criminals.
Speaking to the Guardian, Trey Ford from penetration-testing firm Rapid7 said: "it's concerning that the law designed to protect people from cybercrime also penalizes activity designed to identify areas of cyber risk".
Whether there would be any possibility for plea-bargains to reduce the sentences, or even get off entirely, is not clear. Best tread carefully, just in case...
Photo Credit: Bob Orsillo/Shutterstock
-

The new industrial revolution -- machines rise up to become our equals
Publié: juin 4, 2014, 2:53pm CEST par Mark Wilson
The Internet of Things is just the latest buzzword that is being used to push all manner of products. Let's cut to the chase -- it's just about "stuff" (other than obvious things like computers and phones) connecting to the internet. Nothing more than that. But this dismissive-sounding definition is not meant to undermine the importance or the significance of the IoT. We've spent the last 20 years or so getting used to the idea of accessing the web, harnessing what it has to offer, exploiting it in various ways and finding all manner of methods of using it to make life easier, more entertaining, and more profitable. The evolution of the Internet of Things sees this taken to the next level.
We are on the cusp of a new industrial revolution. Many would say that the wheels are already in motion. The tired -- very, very tired -- example of what the Internet of Things is about, is the prospect of owning a fridge that will be aware of when you run out of milk, and then either alert you or place an order on your behalf. This is a very simplistic view of things, but it is the communication between devices that will be the hallmark of things to come. Inter-device communication, or machine-to-machine (M2M) connectivity. Devices that can be left to their own devices (ahem) are approaching in ever-growing numbers, and there are advantages to be gained.
A report by Westbase Technology shows just what could be gained from the spread of M2M technology, and shows that we may not have to wait all that long to start reaping the benefits. More than just a technology, M2M is predicted to become an industry in its own right -- one worth an estimated $950 billion globally by 2020. We're not quite at the stage that machines and devices are becoming sentient, but there are growing legions of hardware that can be left to self-manage whilst serving us.
Huge savings are to be made through employing machines that can report back to us without the need for human interaction. Think security monitoring, access rights and early warning systems. Think automation -- we don’t need to sit in front of a machine to ensure that it does its job; it just does it. Now it is becoming increasingly feasible for one machine to tell another what to do, to respond to the environment and other variables. Realtime feedback can be used to increase efficiency, maximize profit and minimize the need for unreliable humans.
We're reaching the stage at which computers and machines are not minions to be controlled by us; they are our equals and will increasingly be found working alongside us, making decisions and being trusted with responsibilities. But ultimately the machines will continue to serve us, rather than us them -- assuming there is not a robot uprising.
The infographic below shows how the M2M industry could pan out over the next decade in Westbase Technology's vision of the future.

Courtesy of: Westbase TechnologyPhoto Credit: Arjoe /Shutterstock
-

Dirty desktops and titillating tablets -- the browsers you use to get a porn fix
Publié: juin 4, 2014, 12:56pm CEST par Mark Wilson

Porn has always been big business, and online porn accounts for a staggering proportion of web traffic. The availability of always-on internet connections in the home, and near blanket use of internet-enabled mobile phones and tablets, means that it is now easier than ever to get a porn fix if you feel the urge. But have you ever wondered how all of this porn is being accessed? Well… wonder no more! Porn site (you don’t say!) PornHub conducted research after Gizmodo expressed an interest in seeing which browsers were most used by consumers of porn, and the figures make for interesting reading.
It perhaps comes as no surprise that desktop browsers prove the most popular. Some 51 percent of Pornhub's traffic comes from people using desktop computers. But, without wanting to put too many unpleasant images in your head, this leaves 49 percent of porn perusal that is enjoyed on mobile phones and tablets. You know, those devices that are easily transported to a quiet room and are rather easier to hold in one hand than a laptop...
For now, let's stick with the desktop stats. It is here that Chrome rules supreme, gobbling up 44.4 percent of Pornhub's traffic, Internet Explorer coming second with 23.2 percent, and Firefox just behind with 20.1 percent. Bringing up the rear is Opera with 2.6 percent of porn traffic, while Safari accounts for 7 percent. But on mobile platforms, it's Apple's browser that takes the crown. Looking at portable porn, Safari occupies well over a third of the mobile porn browsing market -- 38.2 percent. Android stock browser -- yes, it is used -- accounts for 29.4 percent, while Chrome comes in third place.
Focusing in on tablets, it seems that iPad users are the most interested in pornography -- 73 percent of PornHub's tablet driven traffic comes from Safari. Dirty iPad owners! Chrome takes second place with just 13.6 percent, and BlackBerry even manages to make an appearance, eating up… wait for it… 0.69 percent of traffic. On the desktop, Internet Explorer may account for less than a quarter of PornHub traffic, but those who are using this browser are keen to keep up to date it seems; more than half of users are using Internet Explorer 11.
We'll leave you to take a look through the most popular search terms -- there's nothing too horrific here, but before looking through the list at work, keep in mind that these are searches relating to porn! -- but there are further interesting breakdowns of browser usage. Safari users may be responsible for lots of porn traffic, and this is because they are a picky bunch who have to look at lots of pages to find something they like. On the desktop, Safari users look at an average of 9 pages per visit (more than any other browser), and the figures are very similar on mobiles and tablets, although the browser is beaten into second place in both instances.
The most, er, easily satisfied users? On the desktop it's Opera users who are done and dusted the quickest -- 7 minutes and 31 seconds -- while on mobile devices, it is Android users who finish last. Or first, depending on how you look at it...
Photo Credit: Feel Photo Art/Shutterstock
-

Google offers End-To-End encryption with new alpha Chrome extension
Publié: juin 4, 2014, 2:04am CEST par Mark Wilson
Today, Google took the wraps off a new security tool for Chrome users. Currently available as an alpha release, End-To-End is an extension for Google's browser that offers... well... end-to-end encryption for data arriving in and departing from Chrome. As this is only an alpha version, the extension is not currently available in the Chrome Web Store, but Google has made the code available so the privacy-conscious and security-minded can take it for a test drive.
Based on OpenPGP and a newly developed, JavaScript-based crypto library, End-to-End can be used to encrypt, decrypt, digitally sign, and verify signed messages. Google is keen to receive feedback -- discover a problem and you could cash in, thanks to the Vulnerability Reward Program. In a post on the Google Online Security Blog, Stephan Somogyi, Product Manager, Security and Privacy explains that "we recognize that this sort of encryption will probably only be used for very sensitive messages or by those who need added protection. But we hope that the End-To-End extension will make it quicker and easier for people to get that extra layer of security should they need it".
Releasing the source code for a project such as this is a risk, but it is one that Google recognizes. The project home page acknowledges that there is nothing to stop people from compiling the code and submitting it to the Chrome Web Store, but implores "please don’t do this". Eventually, End-To-End will receive an official release, but in the meantime the team is asking that the code is used responsibly:
The End-To-End team takes its responsibility to provide solid crypto very seriously, and we don't want at-risk groups that may not be technically sophisticated — journalists, human-rights workers, et al -- to rely on End-To-End until we feel it's ready. Prematurely making End-To-End available could have very serious real world ramifications.
Security has become a real headline grabber over the last couple of years, and on June 5 Reset the Net aims to encourage and educate web users about online security and privacy. Tools such as End-To-End are welcomed with open arms.
Image Credit: Graham Stewart / Shutterstock
-

Apple opens the door to Bitcoin and other virtual currencies
Publié: juin 3, 2014, 12:19pm CEST par Mark Wilson

Yosemite! Woo! iOS 8! Yay! New way of programming! Huzzah! These were the obvious highlights of Apple's WWDC keynote yesterday, but as the dust settles there are some additional interesting tidbits emerging. As this was a developer conference, it should come as no surprise that the announcements and revelations have the most immediate impact on developers -- but things will also filter down to users. One change that was not given any fanfare at the WWDC is an alteration to Apple's App Store Review Guidelines which paves the way for virtual currency support.
The guidelines themselves are surprisingly easy to read -- this document is nothing like an EULA! But if you'd like to cut to the chase, jump to 11.17 in the "Purchasing and currencies" section. Here you'll find the advice that "Apps may facilitate transmission of approved virtual currencies provided that they do so in compliance with all state and federal laws for the territories in which the app functions". There is no reason that this possible virtual currency support should not include Bitcoin, although the currency has not been specifically mentioned.
Bitcoin has had something of a rocky journey of late, having been banned in both Russia and Thailand. There was also the high-profile story of missing Bitcoins at the Mt. Gox exchange, and there have been problems with Bitcoin mining apps in Google Play. Developers will need to tailor their apps to comply with local law, so a future app that supports the transfers of Bitcoins would have to be changed if it were to be used in Russia, for instance.
The policy change does not mean that Apple is going to be accepting Bitcoin as a method of payment for app purchases, but it does open the door for Bitcoin shopping apps, wallets and the like. Apple had previously pulled a number of Bitcoin wallet apps from the App Store, and other apps that allow for the transfer of Bitcoins were also squashed or forced to change. We could see a number of apps emerging that bring PayPal-like options to Apple using Bitcoin fans. On the other hand, it could be that Apple has plans to unveil its own virtual currency at some point in the future. There's also the possibility of a virtual currency from the technology entrepreneur that many love to hate, Kim Dotcom.
Photo Credit: Kostsov/Shutterstock
-

HP wants you to forget Chrome OS and embrace the Android laptop SlateBook
Publié: juin 2, 2014, 12:43pm CEST par Mark Wilson

At the cheap end of the laptop market, there isn’t really all that much choice at the moment. Chromebook has the bargain basement side of things covered, but this is not an OS that works for everyone. Android is, by quite some way, the most popular operating system on phones and tablets, so it makes sense that it should also prove popular on a laptop, right? This is what HP is hoping, at least, as it launches its new SlateBook, a 14 inch, touchscreen laptop that runs Android.
Launching July 20, the SlateBook has a price tag of $399 and includes a full-sized keyboard in addition to a 1080p touchscreen. As this is a device running Android, it should perhaps come as no surprise that battery life is fairly high. The quoted nine hours is fairly impressive and this is being touted as an entertainment device. To back up this claim, in addition to the longevity of the battery, four speakers from the Apple-acquired BeatsAudio provide what is described as "the best-sounding, richest audio on a notebook".
The SlateBook is 16mm thick and weighs 3.7lb and benefits from an impressive array of ports for an Android device. In addition to a microSD card reader and HDMI out, there's also a single USB3.0 port and two USB2.0 ports. 16, 32, and 64GB models are available. Powered by a 1.8GHz NVIDIA Tegra 4 mobile and running Jelly Bean, HP hopes that user will take to working Android using a keyboard and trackpad as well as a touchscreen.
Despite the price, HP has not scrimped on the touchscreen -- this is a full HD 10-point capacitive screen, rather than a cheaper five-point model. And it's the touchscreen that could really make this laptop a success. Running Android, being able to interact via touch is something that many users will expect -- and it make perfect sense as this is how the OS was designed to be used -- and it could be something that has held back the sales of cheaper Chromebooks running Chrome OS sans touch.
-

Pirate Bay founder arrested as Demonoid returns from the dead
Publié: juin 2, 2014, 11:11am CEST par Mark Wilson

The Pirate Bay saga is one that has been running for a number of years now, and the latest chapter sees one of the founders arrested in Sweden. Peter Sunde had been on the run for two years after failing to make an appearance having been sentenced to two years in prison. He had been handed an eight month term for aiding and abetting breach of copyright laws, although those associated with the site have long-maintained that they should not be held responsible for the sharing copyrighted material as no data was stored on the site.
Sunde had been sought by Interpol and his arrest coincided with the eight-year anniversary of the police raid of Pirate Bay servers. He had been living in hiding in Berlin, but having family in Sweden meant that he often returned to the country. Torrent news website TorrentFreak reports that the arrest was a joint operation between Swedish and Polish law enforcement agencies.
Despite a series of high profile legal battles with the site, and blocks being put in place in many countries, the Pirate Bay continues to survive. Bouncing from one server to another as and when required, and endless proxy services providing access to people who find that their ISPs have put obstacles in the way.
In related news, that stalwart of the torrent world, Demonoid, is back online. Many users who already have accounts registered with the site received emails over the weekend letting them know the good news. The site -- which reappeared at its original home of demonoid.ph -- is also currently accepting new registrations. Just how long the site manages to stay online this time around remains to be seen.
Image Credit: Palto/Shutterstock
-

The most popular stories on BetaNews this past week - May 25 -- May 31
Publié: mai 31, 2014, 2:13pm CEST par Mark Wilson
 No week would be complete without a little Windows news, and this week was no different. A registry hack emerged that should make it possible to receive updates for the no-longer-supported Windows XP right up until 2019. Microsoft later spoiled the fun by pointing out that it could lead to problems as the updates that would be made available as a result of implementing the hack would not be designed for regular desktop versions of Windows XP.
No week would be complete without a little Windows news, and this week was no different. A registry hack emerged that should make it possible to receive updates for the no-longer-supported Windows XP right up until 2019. Microsoft later spoiled the fun by pointing out that it could lead to problems as the updates that would be made available as a result of implementing the hack would not be designed for regular desktop versions of Windows XP.Last week we were wondering why it took eBay quite so long to warn users to update their passwords after a security breach earlier in the year. This week we discovered that it was because the company was under the impression that no user data had been accessed. Apple forgot to renew its SSL certificate, and in another Apple-related security story, a hacker managed to take control of iOS and Mac devices, and hold them ransom. To console itself, the company then splashed the cash on Beats Music -- Joe pondered whether this was just another indication of Apple's lack of innovation.
While the development of technology continues apace, all too often it is held back by a lack of investment by government. I argued that governments around the world need to realize the importance of tech to the progress of the world, and invest in it accordingly. We've not heard much about the NSA for a while, but an Edward Snowden interview caused the agency to deny that Snowden tried to voice his concerns about the methods internally before going public about the organization's surveillance activities. Snowden is the enfant terrible of the technology world, but had he been a hacker rather than a whistleblower, he could possibly have taken a leaf out of LulzSec's book and aided the FBI in return for a get-out-of-jail-free card. Online legal issues are rarely cut and dried, and things get more complicated when the likes of Wil Wheaton say they don’t mind if you pirate their TV shows anyway.
Irony struck when security firm Avast fell victim to a hacker, affecting 400,000 user accounts, and a slightly smaller scale hack of Spotify led to a single user's data being accessed. Google is trying to boost the security of Chrome by only permitting the installation of browser extensions via the Chrome Web Store. When the company wasn't concerning itself with security, it was busying itself with driverless cars and launching Chromecast in more countries. The search giant also created a form to allow users to ask to be forgotten in line with an EU ruling.
After the Surface Pro 3 launch, LG's G3 event had a lot to live up to. Brian was there and was, as ever, impressed with what he saw. Alan decided to work exclusively from a Chromebook while Joe celebrated his two year anniversary with Google's laptop.
Good weekends all round. Same time next week etc.
Image Credit: vinz89/Shutterstock
-

Google gives in, sets up 'forget me' form following EU ruling
Publié: mai 30, 2014, 3:22pm CEST par Mark Wilson

A couple of weeks ago, a European court ruling said that internet users had a "right to be forgotten". Google was at the center of the test case, and the internet giant expressed disappointment at the court's decision that individuals should be able to request that their details be removed from search results. Now a removal request form has been created for those looking to clear their name from search queries.
In order to use the form, individuals are required to provide a "valid form of photo ID". It is then possible to request that information that is "inadequate, irrelevant or no longer relevant, or excessive in relation to the purposes for which they were processed" be removed. Google has already made it clear that it found the court ruling "disappointing", and the company says that submitting a request is no guarantee of having details removed from search results.
"We will assess each individual request and attempt to balance the privacy rights of the individual with the public's right to know and distribute information. When evaluating your request, we will look at whether the results include outdated information about you, as well as whether there's a public interest in the information," the form explains. While the aim is to balance "the privacy rights of the individual with the public’s right to know and distribute information", there are a few exceptions mentioned right from the offset -- "information about financial scams, professional malpractice, criminal convictions, or public conduct of government officials".
The form only covers European countries and it's possible that it will change over time. "This form is an initial effort. We look forward to working closely with data protection authorities and others over the coming months as we refine our approach", says Google.
But one thing is certain: the task of balancing personal privacy, public interest, and censorship is going to be a tricky one, and Google is likely to be inundated with requests from people who are unhappy about appearing in search results.
Image Credit: Lane V. Erickson / Shutterstock
-

NSA: Edward Snowden did not raise surveillance concerns internally
Publié: mai 30, 2014, 1:12pm CEST par Mark Wilson

In an interview with NBC earlier in the week, Edward Snowden -- ever a thorn in the side of the NSA -- defended his decision to leak documents to the press, saying "Sometimes to do the right thing, you have to break a law". The whistleblower has long insisted that his revelations were born of a desire to help his country, and claims that he previously tried to voice his concerns about the US government's surveillance tactics through official channels.
Speaking in Wednesday's interview, Snowden said "I actually did go through channels, and that is documented. The NSA has records, they have copies of emails right now to their Office of General Counsel, to their oversight and compliance folks, from me raising concerns about the NSA’s interpretations of its legal authorities". This is something disputed by the NSA who released details of a brief email exchange between Snowden and the Office of General Counsel.
The emails show Snowden querying whether Executive Orders or federal law took precedence. The NSA claims that this is nothing more than Snowden "asking for an explanation of some material that was in a training course he had just completed", going on to say this is the only relevant record to be found that supports his claims. The Office of General Counsel's reply to the email states that Executive Orders have the "force and effect of law", but "cannot override a statute".
It may seem like a minor point, but it is one that it important. One of Snowden's justifications for his leaks is that he thinks "it's really disingenuous for the government to invoke and sort of scandalize our memories [of 9/11], to sort of exploit the national trauma that we all suffered together and worked so hard to come through to justify programs that have never been shown to keep us safe, but cost us liberties and freedoms that we don't need to give up and our constitution says we should not give up". If there was a confusion between orders passed down by the White House and law passed by Congress the argument is that the NSA's activities were illegal.
The NSA is insistent that the short email exchange is not proof of Snowden voicing concerns internally. The agency goes further saying, "We have searched for additional indications of outreach from him in those areas and to date have not discovered any engagements related to his claims".
There are unsurprising claims of a government cover-up. Snowden's legal advisor, Ben Wizner said: "This whole issue is a red herring. The problem was not some unknown and isolated instance of misconduct. The problem was that an entire system of mass surveillance had been deployed -- and deemed legal -- without the knowledge or consent of the public. Snowden raised many complaints over many channels. The NSA is releasing a single part of a single exchange after previously claiming that no evidence existed".
This game of verbal tennis is likely to continue for months and years to come. Edward Snowden may have rattled governmental cages with his actions, but public opinion of his decisions remains divided. Surveys show that people in the 18-29 age bracket believe he served the public interest, and those in older age groups are more likely to feel he should face criminal prosecution.
Photo Credit: ollyy/Shutterstock
-

Caught as a hacker? Helping the FBI is your get-out-of-jail-free card
Publié: mai 28, 2014, 1:05pm CEST par Mark Wilson

LulzSec is an infamous, famous and notorious name in the technology world. The small collective made a name for itself by attacking high-profile websites such as Fox.com and government sites, but all of this was interrupted when founding member Sabu (or Hector Xavier Monsegur to his mother) was arrested three years ago. Originally facing a jail sentence of more than 26 years for his hacking work, Sabu is now a (relatively) free man having earned himself a get-out-of-jail-free card by working with the FBI since his arrest to help identify other hackers.
Although a judge in New York passed a sentence of seven months, Sabu had already spent this length of time incarcerated so all that is left is one year's supervision. The leniency comes thanks to the fact that Monsegur agreed to continue to work undercover in the hacking community, supplying the FBI with information about activities and individuals. Among those he helped authorities to prosecute were Jeremy Hammond -- one of the most-wanted cybercriminals in the sights of the FBI -- who was jailed for leaking emails to WikiLeaks.
Switching sides did little to improve Sabu's reputation in the hacking community where he is unpopular to say the least. He is credited with helping to hold back Anonymous, and preventing millions of dollars of losses by having "provided, in real time, information about then-ongoing computer hacks and vulnerabilities in significant computer systems".
Judge Loretta Preska praised Sabu for his "truly extraordinary cooperation". Sabu's work with the FBI was revealed some time ago, and this led to him and his family having to be relocated. The hatred leveled towards the hacker-cum-helper is obvious from the statement given to the Guardian by an Anonymous spokesperson:
Monsegur is, first and foremost, a criminal; the FBI’s cyber crime task force are his co-conspirators. While operating under their supervision, Monsegur committed numerous felonies which should in no way be excused due to his protected informant status. The FBI continues to use captured informants, who commit egregious crimes in pursuit of reduced sentences, for the sole purpose of creating "examples" to frighten the public. They do this with the hope of pacifying online dissent and snuffing out journalistic investigations into the US government’s misconduct.
The court documents relating to Sabu's case make for interesting reading. The presentence report makes clear that the potential sentence is 259 to 317 months in prison and explains that Sabu's role is that of a "rooter", or one who analyzed code "for vulnerabilities that could then be exploited". It goes on to describe the work he did for the FBI, explaining that prior to this case he had no criminal history.
It is interesting to see how technology related crime is treated rather differently to other varieties. The show The Blacklist may have elements of truth to it, but you don’t hear of (m)any murderers managing to sidestep jail time by helping the authorities to avoid other murders or put other murderers behind bars -- I choose murder as an example largely due to the comparable jail terms that may be handed down. It's indicative of the disconnect between law enforcement and the technologically minded. It makes sense to take down criminal organizations from the inside, but a more usual technique would be to infiltrate an organization with a mole rather than turning an existing member against his own.
Does this show that the FBI is unable to nurture skilled workers of its own, or is it a canny way of using the best tools available? How much sense does it make that a crime deemed worthy of 26 years or more behind bars can be erased by less than three years of work? Perhaps it shows that the FBI et al are running sacred of the likes of LulzSec and are willing to cut just about any deal imaginable to make inroads. It certainly shows that there are very different rules in place when a threat is perceived against government organizations. It is unlikely that Anonymous will be quaking in their collective boots despite court claims that Sabu "contribut[ed] greatly to law enforcement's understanding of how Anonymous operates" as it is an outfit that is able to adapt far faster than the FBI.
Image Credit: Twin Design/Shutterstock
-

Technology and politics -- two paths that need to cross to enable progress
Publié: mai 25, 2014, 10:55pm CEST par Mark Wilson

In the world of politics, the wheels of change move slowly; very slowly indeed. Parties and those in power have a vested interest in maintaining the established order, and any attempts to buck the status quo are usually fairy fiercely opposed. Contrast this with the technological world where there are new innovations made every single day -- even at the weekend! Technology doesn’t run out of money and leave an entire nation on the verge of collapse. Technology is not interested in race, class, sex, sexuality or other characteristics. It is certainly true that technology is largely driven by a desire to generate profit -- we are, for the time being, living in a capitalist world, after all -- but it is profit born of fulfilling people's needs and desires.
Can the same be said of politics? To a large extent politics is self-serving. There's still an interest in generating a profit, but it is for the benefit of the few. Technology serves the masses, and has the potential to serve and benefit all. Of course, the term "technology" is rather broad. For the purposes of this article, I'm going to use it to refer to computers, the internet, smartphone, the cloud, electronic/connected devices, robots and the like. For all the gestures to democracy and choice, politicians are, for the most part, interested in serving certain sections of society. There are of course those parties and politicians who are able to take a wider view, have an interest in helping those at the bottom as much as those at the top, and value all people equally.
Being as it is non-sentient (for now, at least), technology is democratic, non-discriminatory. And empowering. It is something that the world, nations, groups and individuals are able to embrace and use to further their cause, better themselves and help other people. Can the same be said of modern politics? Compared to many parts of the world, the US, the UK and many other countries get a pretty good deal. These are not countries -- all joking aside -- in which people are ruled by dictators. Polling stations are places where every man and woman is free to express their views and do their little bit to change the destiny of the country they call home.
But, as mentioned above, the political world is a painfully slow one. A party that promises something that ultimately wins over the people and gets them into power, will find that promising and delivering are two very different things. Laws take an age to get through all of the various stages of voting that need to be navigated to bring them into being, and it is often the case that the legislation that is passed is a pale imitation of what was originally proposed, a watered-down version that tries to please everyone and ends up disappointing all. But by this point, it’s time for the next election and the whole shebang starts all over again.
Look again to the world of technology. This is a world that changes minute to minute. Being both profit-driven and fragmented, it is possible to keep a far larger number of people happy -- and, really, how many people have complained about processor speeds increasing, new devices being released, new software being developed and so on? You might not be overly interested in technology, but you can opt in to whatever degree you want. You can choose to be on the cutting edge, take things a little more slowly, or even take no active position.
It's easy to forget just how democratizing technology can be. It may seem trite to look at the likes of the smartphone and even Twitter as being tools of democracy or the political process, but they are. In order to be an informed citizen able to make educated decisions about who to vote for, information is needed. In regimes where society's access to information is controlled, access to the outside world is vital. This is a communication process that works both ways. In closed societies, it can be all but impossible for the outside world to know what is going on. This might not be a problem ordinarily, but when abuse arises there are obvious advantages to those affected being able to get a message out.
Access to the web provides access to information. This is important not just for the political process, but also for education in general -- and there are few people who would argue with the idea that an educated world is a better world. Love or loathe politics, it is a part of your life. Politics and technology need to join forces to help with progress to a better world -- for all. But governments are slow to adopt technology. They are unwilling to invest in the money that is needed to bring universal internet access to the world... not several years down the line, but right now, when it matters.
Governments will always find money to invest in weapons of war, to fight for oil, to pay back loans that have been taken from other countries, and so on. But how do these budgets compare to the money that is put towards technology? How many politicians have embarrassed themselves with tech gaffes; referring to "the Twitter" or "going on the email"? Governments spend money on technology, but not in the right way. The wrong people are asked to install computer systems which then end up costing billions more than can be justified. But spending billions on a broadband infrastructure for all? Billions on ensuring every child has a computer? Billions supporting hardware and software companies? Dream on!
It is false economy not to invest in technology. Technology is the future. Technology is people. Technology absolutely matters -- just about more than anything else. There's little that technology cannot improve, and it is disconcerting that the world of politics is seemingly so out of touch with what is going on and how to help things progress. Politics and technology should be running and skipping hand in hand into the sunset. Technology is not just about playing Angry Birds, creating ever higher resolution monitors, making porn available on every device imaginable. Technology is about people's life, and it matters one hell of a lot.
Being driven by profit and popularity, technology knows about efficiency, it knows about moving forward quickly, and it knows about competition. It could probably learn a thing or two from politics, but the tech world has more to teach politicians, the democratic process, and the people in power. Bill Gates hasn’t quite made the move from tech to politics, but he has shown how technology can be used to better the world. We need more figureheads like this -- and they don’t have to be super-rich like Gates -- but how many will be willing to pick up the baton?
This is where politics and government come into play. The importance and value of technology, its nurturing and development, need to be embraced and encouraged by government. Without this, the disparity between what people want and what politicians offer will only get wider. There are very few people -- wherever they live -- who are happy with who is in power, or are pleased with the way things are going. What’s needed is a revolution. There are charismatic, intelligent, personable technologists out there who are far better positioned to, if not run the world, steer it in the right direction. The world stagnates while technology continues apace. The two worlds need to converge so we can accelerate progress.
Image Credit: LANTERIA / Shutterstock
-

The most popular stories on BetaNews this past week: May 18 -- May 24
Publié: mai 24, 2014, 3:14pm CEST par Mark Wilson
 It should come as no surprise that this week's big news was Microsoft's Surface Pro 3 unveiling. Brian had been looking forward to the NYC event and was at the event to get hands on with the new device. There's certainly a lot to love about Microsoft's third generation tablet, but there is that price to consider. If you like the look of what you see, the device is available for pre-order right now -- and if you're undecided between the Surface and a MacBook Air, Mihaita compared the two. Maybe you're one of those who thinks it’s a niche product.
It should come as no surprise that this week's big news was Microsoft's Surface Pro 3 unveiling. Brian had been looking forward to the NYC event and was at the event to get hands on with the new device. There's certainly a lot to love about Microsoft's third generation tablet, but there is that price to consider. If you like the look of what you see, the device is available for pre-order right now -- and if you're undecided between the Surface and a MacBook Air, Mihaita compared the two. Maybe you're one of those who thinks it’s a niche product.The Surface Mini failed to make an appearance, but there are still lots of other tablets to choose from -- although they are yet to make much of an impression in higher education, unlike Chromebooks which have found their way into Welsh schools. Will Microsoft's tablet manage to attain the longevity of Apple's iPad? You'd be forgiven for thinking that hell itself had frozen over at the news that work is underway that will make it possible to run Android and iOS apps side by side on the same device.
Could Google kill off the Nexus brand as well as Google+ as well? Joe is among those who think it would be a bad idea. Following last week's "right to be forgotten" ruling, Google prepared an online tool to deal with requests and also managed to earn itself a 100 percent rating for protecting user data. Another 100 percent rating could be assigned to Norton after the company offered a guarantee that all viruses will be removed from the systems of Norton Small Business customers.
But of course there was plenty more going on as well. China upset Microsoft by slapping a ban on the use of Windows 8 on government PCs while German gamers were able to get their hands on Wolfenstein for the first time -- albeit a version free from Nazis. More censorship was to be found in the App Store where a marijuana growing game was shown the door. On the review front, I took a look at a touchscreen monitor that failed to win me over, and Brian played around with a PC with a difference.
The latest security problem found eBay telling it's user to reset their passwords after a database breach and it wasn't long before the company came under fire for the way things were handled. Security issues were found in the Outlook.com Android app which left emails and attachments easily accessible in unencrypted form. Online, Microsoft expanded its 22tracks music site, and Any.DO finally gained a web app.
Another week under our belts, here's to a restful weekend in preparation for another busy seven days.
-

Sad news for springers -- Springpad shuts up shop June 25
Publié: mai 23, 2014, 6:04pm CEST par Mark Wilson

Data organization wars have claimed a victim. Springpad, the notebook service designed to help users "get inspired, get organized, get more done" is to close. After six years of helping people store notes, recipes, project ideas and more, Springpad will close in just over a month. The world of note taking tools, managers and general information organizers has become crowded. The likes of Evernote, OneNote and even Google Keep have all been vying for attention in recent years, and there are only so many users to go around.
The closure rumors started last night with the Verge citing the oft-mentioned "person familiar with the company's plans", but now it has been confirmed. In a blog post the Springpad team confirms what hundreds of thousands of users hoped and prayed would turn out to be untrue -- as of June 25, the service will cease to function. At this stage no reasons are being given for the closure, but it will leave users scrabbling to find a new home for their data.
From the shut off date, the Springpad website will be unavailable and the syncing features of the various mobile apps that exist will also cease to function. The main concern for most users will be what they can do about their data. Any data that is currently stored offline in apps will remain safe, and an export tool is in the pipeline to allow for the creation of backups ready for importing into another service.
"Please know that it is our top priority to help you during this transition. Amidst current rumors we wanted to confirm the news and give you all of the information possible at this time. We are putting the final touches on a new export tool that will allow you to take your data with you. This will include an improved backup file that you can save and use to reference your notes in the future in addition to the option to migrate your data".
Will you be sad to see Springpad disappear? Do you have a new home in mind for the data you have accumulated over the years?
Image Credit: Evdokimov Maxim/Shutterstock
-

Facebook listens to feedback and tightens up privacy settings -- a bit
Publié: mai 23, 2014, 12:01am CEST par Mark Wilson
Privacy. It's something that we're all concerned about, particularly online. Facebook is one of many companies that comes in for scrutiny and criticism for the way it handles user privacy, and there have long been complaints about the fact that statuses and uploaded photos are made publicly accessible by default. Today that changes. After years of pestering, Facebook has listened to its user base and changed the default visibility setting to "Friends only". At least this is the case for brand new users.
Anyone signing up for a new Facebook account -- can there be many people left who do not yet have one? -- will be able to avoid accidentally sharing private photos with the world. "Going forward, when new people join Facebook, the default audience of their first post will be set to Friends. Previously, for most people, it was set to Public," says Facebook in a blog post. The first time a post is made, users will be asked whether it should be made public or limited to a smaller audience. If no selection is made, it will default to Friends.
This is good news for newcomers to Facebook, but the social network has something in store for existing users as well. In the coming week a Privacy Checkup tool will be rolled out across the network, aimed at helping people to ensure they are sharing content with "the right people". The checkup will guide Facebookers through reviewing the privacy settings of their profile as well as double checking the apps they have installed and, of course, checking the default sharing settings.
Changes are on the cards for mobile users, and Android and iOS users will find that "audience selectors" have been simplified. This is something that will be available to new and old users alike. Unfortunately, the choice between friends and public is as good as it gets for now. Finer tuning is not possible -- for default settings, at least -- but this is likely to be seen as a step in the right direction. "Everything about how privacy works on Facebook remains the same" states the network's announcement. Whether this is good or bad is really a matter of personal opinion.
-

Warning to Android users -- Outlook.com app stores emails unencrypted
Publié: mai 22, 2014, 4:54pm CEST par Mark Wilson

Reverse engineering apps is an interesting field of work. On one hand, it can be used by software engineers to determine how an app works so they can copy it. On the other, the method can be used by those with malicious intent to track down weaknesses that can then be exploited. But there's also a third hand. Reverse engineering can also be used to highlight security problems with a view to not only alerting those affected, but also addressing the problem.
Researchers at Include Security, whilst practicing their reverse engineering skills, turned their attention to the Outlook.com app for Android and discovered a potentially worrisome security issue.
The team found that the app -- which was produced by Seven Networks rather than Microsoft itself -- stores emails and attachments in the Android file system without encryption or security. This fact could be exploited by maliciously coded third party apps which would be able to read the unencrypted subject lines and body text of email, as well as accessing attached files. Email attachments being saved automatically to the /sdcard/attachments folder by default means that they can be accessed by anyone with physical access to the Android device, as well as any specially coded app.
Even if PIN protection is in place, a backup email database is stored in an easily accessible location in the file system, completely unencrypted. The researchers found that the PIN feature merely blocks access to the app's GUI, leaving emails and attachments just as vulnerable as ever to any slightly determined malicious user or app. It is possible for Android Debug Bridge to read the data on all devices, but the processes is even easier on those that have been rooted. Once the database file has been accessed, its contents can be very easily extracted and read.
Include Security says "We feel a key security and privacy attribute of any mobile messaging application is the ability to maintain the confidentiality of data stored on the device the app runs on". The security team recommends that Android users ensure that USB debugging feature of their device is disabled (Settings > Developer Options > USB debugging) as well as considering implementing full disk encryption. It is also recommended that user change the folder that is used to store email attachments.
It is worth noting that Include Security alerted Microsoft to the security issues back at the beginning of December. The response was that "users should not assume data is encrypted by default in any application or operating system unless an explicit promise to that effect has been made". The same statement was issued last week when the researchers contacted the company again.
How do you feel about this? Is it reasonable for a user to expect that their private data would be kept secure by default?
We have reached out to Microsoft for the company's reaction to the findings, and we'll update the post when we receive a response.
Update: Microsoft has responded, and a spokesperson had this to say:
"Microsoft is committed to protecting the security of your personal information. We use a variety of security technologies and procedures to help protect your personal information from unauthorized access, use, or disclosure. For people using the Outlook.com app for Android, applications run in sandboxes where the operating system protects customers’ data. Additionally, customers who wish to encrypt their email can go through their phone settings and encrypt the SD card data. Please see Microsoft’s online privacy policy for more information".
Image Credit: weerapat kiatdumrong/Shutterstock
-

Finally! Task and todo list manager Any.Do gains a web app
Publié: mai 22, 2014, 2:09pm CEST par Mark Wilson
Today is a day of celebration for fans of Any.Do -- the todo list and task manager for iOS, Android and Chrome. Some four years after its inception -- and after many, many demands from the service's user base -- Any.Do has, at long, long last, gained a web app. Founders Omer Perchik, Yoni Lindenfeld, and Itay Kahana have successfully avoided a brouhaha from users by finally delivering what they describe as "the number one most requested feature by our users".
Any.Do has proved incredibly successful on mobile platforms -- as well as in Google's web browser -- amassing more than 10 million users. Perchik says: "Web is a huge market we haven't even touched yet. There's a world of people who haven't considered us because they need a full web experience, right on their computer screens" of the launch. "We're conquering mobile, now it's time to break out in a broader market".
The move to the web from mobile device is the reverse of the route taken by many services, but it means that people using Any.Do to keep their lives in order can now do so from their web browser as well as through the app. The online interface is sparse yet effective, much like the mobile apps, and offers a selection of views that allows for tasks to be grouped by project or due date. There's Planning Mode for getting tasks organized across folders, and Focus Mode for homing in on what's coming up in your schedule.
Sign up for the web app by paying a visit to the new page.
-

German gamers get Nazi-free version of Wolfenstein: The New Order
Publié: mai 21, 2014, 2:10pm CEST par Mark Wilson

Germany and Nazism have history; one doesn’t have to be much of a history buff to know that. But the aftershocks of Hitler's Germany are still being felt; the country is still rather sensitive, shall we say, about the whole idea of the Nazis. So touchy, in fact, that as part of post-World War Two denazification the display of Nazi symbols (or "use of symbols of unconstitutional organizations") is illegal. This presents an issue for the game Wolfenstein which concerns itself largely with escaping from Nazis, killing Nazis, tracking down Nazis... there are lots of Nazis involved. Ultimately this meant that the popular game series was banned from Germany since it was first conceived back in the early 80s.
The latest installment in the series, Wolfenstein: The New Order, is set in the 1960s after a Second World War won by the Nazis. But this time around the game got a German release -- yesterday in fact. Bethesda's Pete Hines said last month that Germany has "a thing about Nazis", describing the country as "a little touchy" about the subject. So how was the release possible? This is not because the country has relaxed its laws -- the display of Nazi-related material can still result in a three year jail term -- but because the game has been censored.
Germany is getting a version of Wolfenstein: The New Order which is different to that released in any other part of the world (apart from Austria which is subject to similar censorship). Hines said: "In Germany, we've removed all Nazi symbols and references. Unlike films and other works of art, video games in Germany are forbidden to use such symbols and references as they are classified in Germany as toys and not media art".
Copies of the game are "geo-locked" meaning that uncensored versions of the PC game could not be used in Germany or Austria. Such is the censorship that the Nazis -- so central to the very idea of Wolfenstein -- simply do not exist, morphing instead into The Regime. Censorship may be rife, but Bethesda has some heartening words for oppressed gamers: "the levels of violence and action remain the same as in the international version". Well, that's good to know isn’t it?
-

Hanns G HT231HPB: an entry-level touchscreen monitor let down by Windows 8.1 and itself [Review]
Publié: mai 21, 2014, 12:32pm CEST par Mark Wilson

I have no problems with touchscreens in general, no problem at all. I can't imagine using a non-touchscreen phone any more, and I have tablets of all shapes and sizes coming out of my ears. Touchscreens make sense, they are intuitive, they are fun to use. In the right situation, at least. I bang on about being a very happy Surface Pro owner (not as yet a Surface Pro 3), but how often do I take advantage of the fact that it has a touchscreen? Very rarely. I might jab the screen every now and then to switch apps, I may even mess about with handwriting recognition from time to time, but despite my love of the device, a keyboard/trackpad/mouse combo is my preferred choice.
I use my Surface Pro as a laptop, and perhaps this is where my issues stem from. To me it makes little sense to reach over the keyboard to interact with the screen when a far more energy and time efficient trackpad flick does the job just as well. Used as a tablet, it would be a different story, but to me the Surface Pro range is not about amalgamating the best of laptops and tablets, it's about having a fancy laptop. But I digress. My point is that I have yet to be convinced of the value of touchscreen laptops (when used as laptops), and the idea of touchscreen monitors for desktop computers just seems like a step too far.
Of course, touchscreen monitors for non-tablet computers are nothing new, not by a long shot -- they are to be found in restaurants and at countless POS in stores, for instance. But for everyday desktop computing do they make sense? At a POS touchscreens make the life of a cashier easier by reducing the necessary interaction to a series of taps. This works for a number of reasons. Firstly, cashdesks in stores are set up so the screen is correctly positioned, and there's no awkward keyboard getting in the way. There's also the fact that the software being displayed on the screen has been designed for use with a touchscreen monitor.
So, the Hanns G HT231HPB. Technically, it is pretty impressed, but it has a number of obstacles to overcome right from the start. Picture how you sit at your desk. You're in a chair, knees under a table top, keyboard in front of you, the monitor positioned 18 inches or more away from you. Is this an arrangement that lends itself to interacting with your monitor by touching it? I can only speak from personal experience, but I sit more than an arm's length away from the screen. To tap it I would not only have to lift my hand until it is level with the lower half of my face, but also lean forward. Every time I want to tap something or swipe something or drag something. Every. Single. Time. I'm here to use my computer, not get an arm workout.
Marx would have us fighting against the bondage of the machine, but here we find that we have to bend to the will of the screen. We have to adapt the way we work to reap any benefits. A touchscreen monitor used in conjunction with a desktop computer requires more work and effort on the part of the user. This is not what computing is about. With a 23 inch screen, there's a lot of arm movement -- interacting with Windows is akin to conducting an orchestra.
But the HT231HPB is intriguing. Rather than a regular foot stand, support comes from a fold out stand at the back. This can be used to position the monitor in a traditional near-vertical orientation, but it can also be folded back so the screen is at a much shallower angle -- think laptop with the lid opened almost all the way. But again this creates work and requires effort. Used in the laid-back mode, the monitor transforms almost into a tablet, but without any of the benefits of a tablet due to the need to be tethered to a base station.
It is possible to use Windows 8's onscreen keyboard in this mode, allowing you to dispense with your oil-based physical peripheral, but it's a strange and rather uncomfortable experience, resulting in back-, hand- or wrist-ache -- and, of course, Windows' built-in keyboard leaves a lot to be desired. I can see the monitor appealing to that strange breed of workers who have taken to conducting their toil in a standing position, but even then the monitor feels as though it should be an all-in-one rather than just a monitor. It's just awkward.
There appears to be little reason for the Hanns G HT231HPB to exist. It's one of those devices that seems like a great idea at the time, a fabulous impulse buy -- but it's a purchase that's likely to bring about a severe case of buyer's remorse. At £199.99 (or equivalent throughout Europe), it's not a hugely expensive 23-incher by any stretch of the imagination when you factor in the touchscreen side of things, but you're paying for a feature which I would argue is let down by not just the fact that a computer needs to be connected, but the fact that Windows 8's touchscreen experience on the desktop is a car crash. Keep in mind that this is not a tablet, but a monitor designed to use with a computer.
In all likelihood you're going to be using the monitor to interact with, apart from Windows itself, desktop apps -- unless you're one of the small number of people who can endure modern apps on the desktop. This does not a happy computing experience make. Traditional apps do not lend themselves to touchscreen use which means your touchscreen interactions are going to be limited to Windows-specific activities. How much time do you spend on such tasks? How much of your money is that worth?
For your money you get the 23 inch 10 point multi-touch screen, made up of 1920 by 1080 pixels. We're looking at a full HD display here, but the quality isn’t actually that high. There's a fuzzy look to things -- which could be due to the use of a TN rather than IPS panel -- but the response time of 5ms is reasonable as is the contrast ratio of 1000:1. There are built-in speakers which do the job but there are issues with the control buttons which being hidden around the back of the unit make configuration a nightmare task. The energy usage level of 26W is pleasing but, sadly, this is one of the few highlights.
Factor in the cheap feel of the unit, and this is one to miss -- it does at least serve to highlight the absurdity of desktop touchscreen monitors. It might appeal to a poor, struggling graphic designer, but regret will ultimately ensue.
-

Hanns G HT231HPB: an entry-level touchscreen monitor let down by Windows 8.1 and itself
Publié: mai 21, 2014, 12:32pm CEST par Mark Wilson

I have no problems with touchscreens in general, no problem at all. I can't imagine using a non-touchscreen phone any more, and I have tablets of all shapes and sizes coming out of my ears. Touchscreens make sense, they are intuitive, they are fun to use. In the right situation, at least. I bang on about being a very happy Surface Pro owner (not as yet a Surface Pro 3), but how often do I take advantage of the fact that it has a touchscreen? Very rarely. I might jab the screen every now and then to switch apps, I may even mess about with handwriting recognition from time to time, but despite my love of the device, a keyboard/trackpad/mouse combo is my preferred choice.
I use my Surface Pro as a laptop, and perhaps this is where my issues stem from. To me it makes little sense to reach over the keyboard to interact with the screen when a far more energy and time efficient trackpad flick does the job just as well. Used as a tablet, it would be a different story, but to me the Surface Pro range is not about amalgamating the best of laptops and tablets, it's about having a fancy laptop. But I digress. My point is that I have yet to be convinced of the value of touchscreen laptops (when used as laptops), and the idea of touchscreen monitors for desktop computers just seems like a step too far.
Of course, touchscreen monitors for non-tablet computers are nothing new, not by a long shot -- they are to be found in restaurants and at countless POS in stores, for instance. But for everyday desktop computing do they make sense? At a POS touchscreens make the life of a cashier easier by reducing the necessary interaction to a series of taps. This works for a number of reasons. Firstly, cashdesks in stores are set up so the screen is correctly positioned, and there's no awkward keyboard getting in the way. There's also the fact that the software being displayed on the screen has been designed for use with a touchscreen monitor.
So, the Hanns G HT231HPB. Technically, it is pretty impressed, but it has a number of obstacles to overcome right from the start. Picture how you sit at your desk. You're in a chair, knees under a table top, keyboard in front of you, the monitor positioned 18 inches or more away from you. Is this an arrangement that lends itself to interacting with your monitor by touching it? I can only speak from personal experience, but I sit more than an arm's length away from the screen. To tap it I would not only have to lift my hand until it is level with the lower half of my face, but also lean forward. Every time I want to tap something or swipe something or drag something. Every. Single. Time. I'm here to use my computer, not get an arm workout.
Marx would have us fighting against the bondage of the machine, but here we find that we have to bend to the will of the screen. We have to adapt the way we work to reap any benefits. A touchscreen monitor used in conjunction with a desktop computer requires more work and effort on the part of the user. This is not what computing is about. With a 23 inch screen, there's a lot of arm movement -- interacting with Windows is akin to conducting an orchestra.
But the HT231HPB is intriguing. Rather than a regular foot stand, support comes from a fold out stand at the back. This can be used to position the monitor in a traditional near-vertical orientation, but it can also be folded back so the screen is at a much shallower angle -- think laptop with the lid opened almost all the way. But again this creates work and requires effort. Used in the laid-back mode, the monitor transforms almost into a tablet, but without any of the benefits of a tablet due to the need to be tethered to a base station.
It is possible to use Windows 8's onscreen keyboard in this mode, allowing you to dispense with your oil-based physical peripheral, but it's a strange and rather uncomfortable experience, resulting in back-, hand- or wrist-ache -- and, of course, Windows' built-in keyboard leaves a lot to be desired. I can see the monitor appealing to that strange breed of workers who have taken to conducting their toil in a standing position, but even then the monitor feels as though it should be an all-in-one rather than just a monitor. It's just awkward.
There appears to be little reason for the Hanns G HT231HPB to exist. It's one of those devices that seems like a great idea at the time, a fabulous impulse buy -- but it's a purchase that's likely to bring about a severe case of buyer's remorse. At £199.99 (or equivalent throughout Europe), it's not a hugely expensive 23-incher by any stretch of the imagination when you factor in the touchscreen side of things, but you're paying for a feature which I would argue is let down by not just the fact that a computer needs to be connected, but the fact that Windows 8's touchscreen experience on the desktop is a car crash. Keep in mind that this is not a tablet, but a monitor designed to use with a computer.
In all likelihood you're going to be using the monitor to interact with, apart from Windows itself, desktop apps -- unless you're one of the small number of people who can endure modern apps on the desktop. This does not a happy computing experience make. Traditional apps do not lend themselves to touchscreen use which means your touchscreen interactions are going to be limited to Windows-specific activities. How much time do you spend on such tasks? How much of your money is that worth?
For your money you get the 23 inch 10 point multi-touch screen, made up of 1920 by 1080 pixels. We're looking at a full HD display here, but the quality isn’t actually that high. There's a fuzzy look to things -- which could be due to the use of a TN rather than IPS panel -- but the response time of 5ms is reasonable as is the contrast ratio of 1000:1. There are built-in speakers which do the job but there are issues with the control buttons which being hidden around the back of the unit make configuration a nightmare task. The energy usage level of 26W is pleasing but, sadly, this is one of the few highlights.
Factor in the cheap feel of the unit, and this is one to miss -- it does at least serve to highlight the absurdity of desktop touchscreen monitors. It might appeal to a poor, struggling graphic designer, but regret will ultimately ensue.
-

China bans Windows 8 from government PCs with twisted logic, and embraces Linux
Publié: mai 21, 2014, 3:11am CEST par Mark Wilson

Microsoft may have been granted permission to launch its Xbox One console in China in September, but a decision by the Chinese government could impact severely on sales of Windows 8. China's official state news agency, Xinhua reports that the latest version of Microsoft's operating system will be banned from governmental computers, although there are to be no restrictions placed on home computers. The reason for the ban on Windows 8? Well it's not quite clear, but it's put down to something to do with energy-saving -- although this seems unlikely.
The website of China's Central Government Procurement Center posted an 'Important Notice' entitled, catchily, "Agreement to supply information about the class of energy-saving products complement the mandatory tender notice". A list of criteria then follows including, at number 5 "all computer products are not allowed to install Windows 8 operating system". This is slightly at odds with the news agency's suggestion -- the official news agency, remember -- that Windows 8 is being banned from new government PCs in "a move to ensure computer security after the shutdown of Windows XP".
The agency goes on to point out that Windows XP currently enjoys a 70 percent market share in China. Just last month, support for the now-decrepit operating system came to an end, and Xinhua goes on to say that the Windows 8 ban is "a move to ensure computer security after the shutdown of Windows XP". So far we have two explanations for the ban. Any more to add to the pot, anyone? In fact the news agency has another one for you to mull over. One of the side-effects of the end of support for Windows XP was "arousing [sic] safety concerns and appeals for domestically designed OS".
The story continues: "the Chinese government obviously cannot ignore the risks of running OS without guaranteed technical support. It has moved to avoid the awkwardness of being confronted with a similar situation again in future if it continues to purchase computers with foreign OS". This makes it sound rather more like a matter of mistrusting foreign software than safety or energy-saving concerns. Xinhua then reveals what is perhaps the real reason for banning Windows 8 -- the government wants to build its own Linux-based operating system: "China will focus on the development of its own OS based on Linux".
Energy-saving? Security? Paranoia? Promoting home-grown coding talent? Laying the groundwork for a wider rollout of a government-built OS? You decide.
Image Credit: Hung Chung Chih / Shutterstock
-

With Surface Pro 3 and no Mini, Microsoft delights and disappoints
Publié: mai 21, 2014, 2:04am CEST par Mark Wilson

Today's Microsoft event in New York City was something of a mixed bag with its fair share of highs and lows. There was an obvious highlight -- the Surface Pro 3. It was a highlight for two reasons. Firstly, despite expectations to the contrary, this was in fact the only device to be announced today. Secondly, at least in terms of looks and specification, it's bloody amazing. But there were at least a couple of low points. No Surface Mini, and the frankly bonkers, nuts, crazy, mad Surface Pro 3 pricing.
The Pro side of Microsoft's Surface range has long been criticized for being a little on the pricey side, but the third generation takes things to the extreme. At the top end of the scale -- a rather juicy sounding Intel Core i7 device packing 8GB RAM and 512 GB of storage -- you'll need to save up an astonishing $1,949. Panos Panay made a great deal of noise about how this is the tablet that can replace your laptop. For that price, I should flippin' well hope so. For that price I can buy a top of the range laptop and still have enough left over to buy a decent tablet. I could even venture into Apple territory if I was feeling a little saucy...
Sure, there are cheaper models available, starting off with the 'entry level' version with Intel Core i3, 4GB RAM and 64GB of storage -- but even this will set you back $799. That's a lot to ask for a bottom of the range device. A heck of a lot. Yes, it's sleek and sexy looking, but Microsoft is already facing an uphill battle winning people over to Windows 8.1. Could this be the reason Windows 8.1 Update lowered the system requirements for the operating system? And don’t forget -- the price you pay for the Surface Pro 3 is only the start. For the asking price you get a tablet. But this is meant to be able to replace your laptop.
What do laptops have? Keyboards! While a cheap and cheerful wireless keyboard can be picked up for a few dollars, if you're really going to show your Surface love, you're going to need a Type Cover. Yours for a mere $129.99. So the price of an entry-level Surface Pro 3 jumps up to $929.98. That's a lot of f-oldin' money; no two ways about it. At the top end of the market you're looking at over two grand for a fancy tablet. That's a lot of Nexus 7s or iPad minis!
But still I love it. There is so much right about Surface Pro 3 that it is possible to forgive the pricing insanity. I'm not going to rush out and buy one -- my first generation Surface Pro serves me well, thank you very much -- but the point is… I want to. Microsoft may not have quite reached the aspirational highs of Apple products, but Surface Pro 3 is getting there. It is expensive, but it knows and doesn’t give a damn. If you want this baby, you’re going to have to pay for it!
With this iteration of the Surface Pro, Microsoft has introduced a lot of enticements. The new screen ratio is very appealing. Widescreen may be very a la mode, but Surface Pro and Surface Pro 2 did take things to the extreme. The 3:2 aspect ratio provides a more comfortable resolution, and the 2160x1440 is not short of a pixel or two. Nine hours of battery life (obviously a theoretical maximum), may not quite be the all-day performance everyone hopes for, but it's getting there.
I'm quite enamored with the SP3 -- as I've decided to call it, recalling days of XP Service Packs -- but is it enticing enough to compel me to upgrade from my first gen model? Well, yes, it is -- but there's a catch. The screen looks incredible, the kickstand is a great leap forward from the single position unit I use, and the whole thing is thinner, lighter, and generally lovelier.
But as lovely as all of these features are, I'm not sure there is quite enough to draw me in. The undoubted stumbling block is the price. I fear heavy narcotics may have been involved in dreaming up those figures. My problem is, what 'extra' would I be getting for my money -- is that worth it. And, sadly, it's not. My trusty Surface Pro is a workhorse -- but there's little that the top of the range SP3 can do that I can't already. The (slight) extra turn of speed and additional storage space is not worth two grand of my money? Microsoft is going to have a battle on its hands convincing significant numbers of people that it's a worthwhile investment. In truth, it is worthwhile, but it is a colossal outlay for what is, ultimately, just a very nice laptop -- and one that, despite protestations to the contrary, does involve making compromises. Microsoft wants to simultaneously compete with everyone and no one with the SP3, but it really ends up being a very expensive gamble for anyone who is tempted.
Image Credit: Rob Byron / Shutterstock
-

The most popular stories on BetaNews this past week: May 11 -- May 17
Publié: mai 17, 2014, 12:34pm CEST par Mark Wilson
 The past week was one dominated by privacy and security related stories. A court ruling in Oracle's favor means that the company is able to claim copyright protection for APIs subsequently used by Google in Android. The long term effects of the ruling are yet to be understood, but they could certainly be far-reaching. Privacy hit the headlines again as SanDisk works on a self-encrypting SSD, and Google was told that users can request that information about them be removed from search results -- of course it didn't take long for the requests to start rolling in.
The past week was one dominated by privacy and security related stories. A court ruling in Oracle's favor means that the company is able to claim copyright protection for APIs subsequently used by Google in Android. The long term effects of the ruling are yet to be understood, but they could certainly be far-reaching. Privacy hit the headlines again as SanDisk works on a self-encrypting SSD, and Google was told that users can request that information about them be removed from search results -- of course it didn't take long for the requests to start rolling in.New research shows that there has been an increase in online suspicion, indicated by a huge increase in the levels of encryption used. The UK government approved the use of Samsung KNOX devices which could help to allay fears about BYOD. Google announced GAME -- Google Apps Message Encryption -- to provide end-to-end encryption for email outside of the Gmail ecosystem.
LG unveiled the latest additions to the G Pad range and ARCHOS announced the Android-powered laptop, the ArcBook. Catering for both ends of the marker, Motorola took the wraps off the low(er)-end Moto E as well as the 4G enabled Moto G and we had a hands-on with the cheaper device. If you're in the market for a new handset, new research shows that -- perhaps unsurprisingly -- battery life is a key factor in deciding which to go for -- Joe suggests that price is also a very important factor. For a glimpse of what might be to come in the handset market, look no further than LG's G3 teaser. The first Windows Phone 8.1 devices went on sale, and HTC unveiled the HTC One Mini 2. It wasn't just phones that were launched this week, Samsung also announced the learning-friendly Samsung Galaxy Tab 4 Education.
Gmail started testing a new interface, added public transport support to Maps in the UK, and Twitter introduced a mute feature to enable users to silence tweets from people they don’t want to hear from. Firefox users could see the appearance of extra ads in their browser if plans to introduce sponsored landing pages come to fruition), and there are also plans to add DRM support to the browser. In the meantime, AdBlock Plus users have to contend with the fact that the add-on hugely increases memory usage. For web users for whom aesthetics are important, D-Link's new colorful router might be of interest.
Microsoft changed its mind again and pledges to give Windows 8.1 users another month to install Update, and the company was also celebrating the fact that Office for iPad has been downloaded an impressive 27 million times in just a month and a half. The company also created a cross-platform app that runs not only on Windows, but also on, of all things, Firefox OS. Gamers have a new Xbox One bundle to consider as Microsoft launched the Kinect-free version of the console.
That’s another week ticked off. Time for a couple of slightly slower days before things kick off again.
Image Credit: vinz89/Shutterstock
-

Google Apps Message Encryption keeps enterprise communication secure
Publié: mai 15, 2014, 3:18pm CEST par Mark Wilson

Just yesterday we were looking at how there has been an increase in the level of encrypted traffic online, and today Google announces the launch of Google Apps Message Encryption (GAME). Google is partnering with Zix Corporation to bring fully encrypted communication to enterprise customers even when emailing contacts outside of Google's infrastructure. Emails sent to Google servers have been encrypted by default for a little while now, but the new launch means that emails sent to the likes of Yahoo and Outlook.com will also be encrypted.
As this is a third-party solution provided by Zix Corporation, Google is not offering full customer support for it, but a quick start guide has been published. Available for $35 per user, GAME enables Google Apps customers to not only ensure that the emails they send are encrypted, but also gives the option of setting up custom bounce messages for emails that are sent to unauthorized users who attempt to send encrypted emails.
Emails that are earmarked for encryption are routed through Zix Corporation's "Zone" data center, encrypted using ZixPort, and sent on to the recipient. Chairman and CEO of ZixCorp, Rick Spurr, said: "In the midst of growing awareness regarding data threats, it's more important than ever that companies have a reliable solution for the secure exchange of valuable customer and corporate data".
But of course this is not just an announcement that will come as good news for those concerned about privacy in these times of heightened awareness, it is also going to come as music to the ears of SMEs looking to ensure the security of their data. It's not something that's completely new by any means -- there are plenty of third-party solutions available such as PGP -- but being baked right into Google Apps is hugely advantageous.
Image Credit: Melpomene/Shutterstock
-

UK government gives the nod to secure Samsung KNOX devices
Publié: mai 15, 2014, 1:00pm CEST par Mark Wilson

Public sector workers in the UK will soon be able to use Samsung handsets after the UK government gave the greenlight to devices running Samsung KNOX. The Communications and Electronics Security Group (CESG) tested the KNOX platform and the government has now published End User Devices (EUD) Security Guidance for Samsung KNOX on certain handsets and tablets. It's not clear whether this paves the way for a new wave of BYOD for government workers, but it is certainly a possibility.
Samsung is pleased with the announcement, and Injong Rhee, Senior Vice President of KNOX Business, IT and Mobile Communications Division, says "Samsung devices with KNOX are already extensively deployed globally across the private sector but now with this significant recognition, government agencies across the UK will be able to adopt Samsung KNOX enabled Galaxy smartphones and tablets setting the scene for other governments to follow".
Secure communication is of paramount importance for governmental work, and this will be seen as a feather in the cap for the handset manufacturer. "We are pleased that our KNOX enabled devices have been cleared for use by the UK Government, and are confident given the period of intensive testing that the robust capabilities of KNOX act as a credible security solution for government agencies," said Graham Long, Vice President of the Enterprise Business Team in the UK and Ireland. "We are committed to working more closely with government departments and agencies that need to maintain high levels of security and data confidentiality on their mobile devices".
At the moment, the Samsung Galaxy Note 3, the Galaxy S3, the Galaxy S4 and the Galaxy S5 running Android 4.3 are covered by the guidance, but other Android 4.2.2 devices have already been approved. The announcement comes a full year after the US Department of Defense and Defense Information Systems Agency published a Security Technical Implementation Guide about KNOX, okaying the use of approved Samsung devices by defense staff.
Image Credit: Anan Chincho / Shutterstock
-

Is AdBlock Plus killing the web? Massive memory usage is dragging Firefox down
Publié: mai 15, 2014, 11:51am CEST par Mark Wilson
 As something of a browser butterfly, I like to keep an eye on what's happening with browsers other than the one I'm currently using fulltime. Like many tech journalists (and non-journalists for that matter), I gave up on Internet Explorer quite some time ago, opting for Firefox initially. I also dabbled with Opera and Waterfox, amongst others, but for a number of years it was Firefox that delivered web pages to me. Sadly, I noticed that things started to slow down. New versions were more bloated and sluggish, and in the search for better performance, I ended up with Chrome. I've been a Chrome user for years now, but I was recently spurred into trying out Firefox once again.
As something of a browser butterfly, I like to keep an eye on what's happening with browsers other than the one I'm currently using fulltime. Like many tech journalists (and non-journalists for that matter), I gave up on Internet Explorer quite some time ago, opting for Firefox initially. I also dabbled with Opera and Waterfox, amongst others, but for a number of years it was Firefox that delivered web pages to me. Sadly, I noticed that things started to slow down. New versions were more bloated and sluggish, and in the search for better performance, I ended up with Chrome. I've been a Chrome user for years now, but I was recently spurred into trying out Firefox once again.Quite where the impetus came from, I'm not sure -- just one of those "let’s see if anything's changed" moments, I guess. Apart from little quirks like the refresh button being on the "wrong" side of the program window, Firefox seems pretty decent. I was impressed by the sharpness of the display for starters -- I had forgotten that Chrome handles high DPIs very poorly. As I'm using a Surface Pro running at 1920 x 1080, running at 150 percent DPI scaling is essential (I don’t have microscopes for eyes!) and Chrome makes everything look slightly blurry... not enough to put me off -- I'm still using it, after all -- but Firefox was a revelation!
Performance-wise, I found there to be little difference between Chrome and Firefox. No exhaustive tests were performed, though from general usage everything "felt" about the same. So I stuck with Chrome. I'll put up with the blurriness for now -- although now it's at the forefront of my mind, it would be nice if Chrome devs pulled their thumbs out and got it sorted. It's been going on for years now, and it really shouldn’t be hard to fix. Other browsers cope with high resolution displays without problems. The point of all of this is that Firefox suddenly entered my life after years of absence, so what happened last night struck me as interesting.
Scanning through Twitter whilst nodding off in bed, I spotted a tweet from journalist Ed Bott:
Loading TechCrunch in Firefox uses 194 MiB of RAM. With AdBlock Plus, it uses 417 MiB. Jeez. [https:]
— Ed Bott (@edbott) May 14, 2014
Having previously had concerns about Firefox and Chrome's memory usage, this piqued my interest. So this morning I fired up Firefox. One tab open -- BetaNews, of course -- finds memory usage sitting at around 184MB (Chrome, for comparison, eats up about 112MB for the same). OK, so let's get AdBlock Plus installed to check out these claims.
Instantly, memory usage for Firefox rocketed to 383MB -- so more than doubling -- although it did drop slightly to 350MB after a few minutes. It was a very different story in Chrome where installing the same extension seemed to have no effect on memory usage whatsoever. Weird.
Over on the Mozilla blog, the numbers are crunched. Just having AdBlock Plus installed in Firefox increases memory usage by 60MB or more, and an extra 4MB per iFrame found on websites -- which can really mount up. The problem is being attributed to the fact that AdBlock Plus is loading a colossal stylesheet for each and every iFrame.
As reported by Martin Brinkmann on Ghacks, the problem can be partially alleviated by using a custom blocklist rather than one of the defaults, but the issue has still been logged as a bug on Bugzilla. Other options, of course, include not using an adblocker at all, or using one of the countless alternatives.
For many people this will be seen as another reason to avoid AdBlock Plus. While the add-on's website proclaims that its aim is "making the web a better place", it appears to be doing much the reverse. There has long been an argument that blocking advertisements hurts websites, curtailing valuable revenue streams and, ultimately, affects the viability, longevity and even content of sites. But it also seems that the add-on is hindering many people's online experience, and possibly Firefox's usage figures.
Computers may have more memory than ever before, but reliable memory management is still important. How many people will have installed Firefox, unquestioningly installed AdBlock Plus on a friend's recommendation, only to find that performance was so poor that they have returned to Internet Explorer, Chrome or wherever else they came from? How many people just labor on, putting up with poor performance assuming that's just the way things work?
What has your experience of AdBlock Plus been? Do you find it to be a memory hog in Firefox or other browsers?
Image Credit: alexsvirid/Shutterstock
-

Denizens of a distrustful dystopia: huge surge in online encryption post-Snowden
Publié: mai 15, 2014, 3:03am CEST par Mark Wilson

The revelations made by Edward Snowden have irreversibly changed the face of the internet. There is now suspicions at every turn, every site and provider is the subject of questioning, and web users are warier than ever before. The use of encryption to hide the content and nature of online activity is nothing new, but it seems that it is very much on the increase. As reported by TorrentFreak, analysis from Sandvine shows that there has been a global increase in the use of encryption.
The figures have been reached by looking at the levels of SSL traffic over the past year, and these show that in North America, during peak hours, encrypted traffic just about doubled. In Europe the increase is even more marked, jumping fourfold so that it now accounts for over six percent of peak time traffic. Europe appears to have a greater interest in encryption than North America, with the latter's SSL traffic accounting for 3.8 percent of peak time traffic.
These are interesting numbers in their own right, but when you consider that in North America, over 31 percent of peak time traffic is accounted for by Netflix, and over 12 percent by YouTube, the levels of SSL traffic are even more significant. And it's a story that is repeated in other parts of the world. It is obviously not always the case, however traffic encryption is often used to disguise piracy, it is likely that at least some of the increase can be attributed to the heightened awareness web users have of their online visibility.
Security issues such as Heartbleed, coupled with the activities of the NSA, Snowden's revelations, and so on have brought online security, and the subject of privacy, to the fore. It is fascinating to watch the web evolving, its users becoming more savvy, becoming increasingly unwilling to accept things at face value. The lack of trust in online privacy and security is at once worrying and heartening.
This is the face of web users taking control. This is the face of users fighting back.
Have you felt the need to turn to encryption to protect your privacy or to hide what you're doing online?
Image Credit: produktionsbuero TINUS / Shutterstock
-

Privacy victory: Google told that people have a 'right to be forgotten' online
Publié: mai 13, 2014, 6:03pm CEST par Mark Wilson
 If you Google yourself, do you stumble across information you would rather wasn't online? Those naked photos of you cavorting in the garden or a snippet from a drunken rant in an online forum could be sitting there for all to see. The page in question may have gone, but that's not to say that you won’t still appear in Google search results.
If you Google yourself, do you stumble across information you would rather wasn't online? Those naked photos of you cavorting in the garden or a snippet from a drunken rant in an online forum could be sitting there for all to see. The page in question may have gone, but that's not to say that you won’t still appear in Google search results.Obviously there are situations in which this could be detrimental to your reputation, and it's understandable that you might want something done about it. Following a case presided over by the European Union Court of Justice in Luxembourg, judges have ruled that, in certain circumstances, people may ask a search operator to remove data about them from search results.
It is being referred to as the "right to be forgotten" and comes after a Spanish man was unhappy to find that information about the repossession of his house appeared in search results. Mario Costeja González discovered that when his name was used as a search term, searchers were directed to newspaper articles about the auctioning of his house as part of proceedings to recover debts he owed back in 1998. He complained to Agencia Española de Protección de Datos (AEPD, the Spanish Data Protection Agency) that the public availability of the information was an infringement of his privacy. Mr Costeja González had asked that the newspaper be forced to remove the article from its website, however this request was denied.
He had also requested that Google "remove or conceal" from search results as the proceedings "had been fully resolved for a number of years and that reference to them was now entirely irrelevant." The AEPD ruled that Google Spain and Google Inc should indeed remove the listings, but Google appealed to the Spanish High Court and the case was in turn referred to the European Union Court of Justice.
In its ruling, whilst recognizing that search engines are making available information that has already been published online, the court stated that Google can be seen as "processing" data even if the search results "concern material that has already been published as it stands in the media". The important part of the ruling is that:
"The Court holds that the operator is, in certain circumstances, obliged to remove links to web pages that are published by third parties and contain information relating to a person from the list of results displayed following a search made on the basis of that person’s name. The Court makes it clear that such an obligation may also exist in a case where that name or information is not erased beforehand or simultaneously from those web pages, and even, as the case may be, when its publication in itself on those pages is lawful".
It is not clear quite what these "certain circumstances" are, it will almost certainly be down to the judgment of individual courts, the point is that the doors have now been opened. The ruling does not suggest that websites other than search engines should be forced to remove content that individuals object to. The ruling makes it clear that it is not the availability of the information that is potentially problematic, but the ease with which search engines make it possible to piece together data about someone that would otherwise have been far harder to connect: "this information potentially concerns a vast number of aspects of his private life and that, without the search engine, the information could not have been interconnected or could have been only with great difficulty."
It also makes clear that a balance needs to be struck between an individual's right to privacy and the interest of other internet users: "inasmuch as the removal of links from the list of results could, depending on the information at issue, have effects upon the legitimate interest of internet users potentially interested in having access to that information, the Court holds that a fair balance should be sought in particular between that interest and the data subject’s fundamental rights, in particular the right to privacy and the right to protection of personal data".
Referring to whether an individual may wish data "relating to him personally to be 'forgotten' after a certain time", the ruling states that there could be cause for the links to be erased. This is particularly true if "the data appears to be inadequate, irrelevant or no longer relevant, or excessive in relation to the purposes for which they were processed and in the light of the time that has elapsed". The first port of call for anyone with concerns about a set of search results is going to be the search engine itself, but court action may be required if an agreement cannot be met.
Google is not particularly happy about the ruling, saying that being asked to remove search results in this way amounts to censorship. Freedom of speech campaigners are inclined to agree, though privacy groups see this as a victory for individuals concerned about their online information.
Image Credit: SoulCurry/Shutterstock
-

Twitter's mute function lets you silence talkative tweeters
Publié: mai 13, 2014, 1:59am CEST par Mark Wilson

It is said that Twitter is the social network for those who suffer from verbal diarrhoea, and it's certainly true that you have to be slightly selective about who you follow if you are to avoid drowning in an avalanche of overwhelming drivel. But even if you do pick and choose who appears in your timeline very carefully, there may be times when you want certain people to just shut up. You could stop following them, or even go as far as blocking them, but this might be seen as taking things a little too far. Twitter's new mute function could be the solution to the problem you didn’t know you had.
Announced in a post on the Twitter blog, Product Manager Paul Rosania says the feature is being rolled out to not only the web version of Twitter, but also the official iOS and Android apps. In many ways, muting is a watered down version of blocking a user and it could prove useful in certain circumstances. You may have some friend who is watching a show you've yet to catch up with. To help avoid spoilers, you could mute their tweets until you're up to date; the same idea rings true for sporting results, and other big announcements.
Muting a user is very simple, and you can do it in one of two ways on the website. The first option is to visit a user profile, click the gear icon and select Mute from the menu that appears. The second technique is to click the More link at the bottom of an individual tweet and then select Mute. As you would expect -- and hope -- people you mute will not be notified of the fact that you have virtually silenced them, and you can unmute just as easily whenever you want. If you head over to the profile of someone you've muted, a red speaker icon will be displayed: click this and they will be unmuted.
When muted, the tweets the tweeters you have singled out will not appear in your timeline. You also no longer receive push or SMS notifications from them. Unlike with blocking, muting a user has no effect on another user's ability to see and interact with your tweets. A muted user can retweet your tweets, for instance, but you won’t be told about it.
So if you've encountered someone who has thrown a Twitter tantrum, rather than flinging insults back and force, why not try cooling off with a little enforced silence courtesy of the new mute option?
Image Credit: Nomad_Soul / Shutterstock
-

API ruling in Oracle's favor could have far-reaching consequences
Publié: mai 12, 2014, 7:29pm CEST par Mark Wilson

In something of a surprise twist on Friday, a court ruled that Oracle is entitled to copyright protection for its Java APIs. This is a case that has been rumbling on for some time now after Oracle sued Google for implementing the APIs into Android, and the implications could be far-reaching. It almost goes without saying that Google will appeal the ruling, although no announcement has actually been made to this effect. The decision that "we conclude that the declaring code and the structure, sequence, and organization of the 37 Java API packages at issue are entitled to copyright protection" seems fairly cut and dried, but the real consequences are yet to be felt.
Back in 2012, it had been decided that there was not a problem with Google, or anyone else, writing code that performed the same function as existing APIs -- this is essentially what Google had to do when implementing the Java APIs in Android -- with the judge at the time stating that "duplication of the command structure is necessary for interoperability". But the latest ruling turns this on its head, which is not good news for Google. "We therefore reverse the district court's copyrightability determination with instructions to reinstate the jury's infringement verdict. Because the jury hung on fair use, we remand Google's fair use defense for further proceedings consistent with this decision".
Oracle is understandably upbeat about the decision ("we are extremely pleased that the Federal Circuit denied Google's attempt to drastically limit copyright protection for computer code"), and Google rather less so ("we're disappointed by this ruling"). But the ruling has divided opinion in the legal and technology worlds. On the one hand it is easy to understand Oracle's keenness to protect its code and work, but on the other -- as many people have pointed out -- there is the question of interoperability to take into account.
What the ruling means is that even by writing its own code, Google has still infringed upon Oracle's copyright. Google's own code calls on functions that have the same names as functions in Java -- this is to help improve interoperability. While it had previously been decided that keeping names the same was important for interoperability and was therefore not a creative element but a functional one, the latest ruling says that function names can also be subject to copyright infringement.
A precedent was set back in 1992 when Sega lost a case after it tried to prevent a game maker producing "unauthorized" titles for its Genesis console. Back in the nineties it was decided that the functions and commands needed to run the game on the console were not copyrightable, but the ruling in the Google case is completely the reverse of this.
As has been suggested over on Vox there are huge potential implications. Citing the example of the Samba project which makes it possible to share files from a Linux machine to Windows, Vox pointed out that an existing set of Windows code was reverse-engineered, and the functions were then duplicated to bring the same functionality to Linux -- and in turn it was carried across to OS X.
This could just be the tip of the iceberg. There have been countless patent cases over the years, and if a case such as the one between Google and Oracle is seen to be profitable in one way or another, we could see a whole new batch of court cases in the coming years. And ultimately, it is going to be end-users who lose out. APIs are essential to the smooth running of so many pieces of software. To make them copyrightable is akin to making protocols such as HTTP or FTP copyrightable. It just makes little sense.
Image Credit: Anneka/Shutterstock
-

Ads in your browser? Sponsored landing pages could appear in Mozilla
Publié: mai 12, 2014, 1:33pm CEST par Mark Wilson

Using the internet and being subjected to advertising very much go hand in hand. Sites have server bills to pay as well as other costs, and this is offset by displaying ads as a means of generating income. This is something we're all used to, and it's generally accepted as the price we have to pay. With the spread of mobile apps, the notion of advertisements within software becomes more and more popular, but, while not entirely unknown, it's not a notion that really translated to the desktop. But this could be set to change if Mozilla's experiments with in-browser advertising come to fruition.
Of course, referring to it as advertising would be a little off-putting, so the word 'sponsored' is being thrown around in its place. What's all this about? Well, back in February Mozilla's Head of Content Services, Darren Herman, posted a blog entry outlining the company's 'Directory Tiles' idea. What this amounted to was a suggestion that in future versions of Firefox, the new tab page could feature "sponsored content from hand-picked partners" as well as links to site based on location. Herman gave the reassurance that "sponsored tiles will be clearly labelled as such" but, ultimately, it still amounts to in-browser advertising.
Perhaps unsurprisingly, there was something of a backlash from users about this. In fact, such was the tide of discontent that Vice President of Firefox, Johnathan Nightingale has stepped in to try to clear things up a little. "A lot of our community found the language hard to decipher, and worried that we were going to turn Firefox into a mess of logos sold to the highest bidder; without user control, without user benefit. That's not going to happen. That's not who we are at Mozilla".
It almost goes without saying that there is a "but". And it's a "but" that will do little to calm concerns. "But we will experiment. In the coming weeks, we’ll be landing tests on our pre-release channels to see whether we can make things like the new tab page more useful". Sell-outs! Comes the cry from the Mozilla community. But hold on. "These tests are not about revenue and none will be collected". See? There was nothing to be concerned about! It's about adding value for the user! "Sponsorship would be the next stage once we are confident that we can deliver user value". Wait… what’s that? So it's not about revenue, but sponsorship would be the next stage. That's cleared that up then!
Windows 8.1's blurring of the boundaries between desktop and mobile software, and it is not unknown for modern apps to include ads. But the worry is that the browser will become overrun with "sponsorship". Mozilla would like to allay these fears. "We'll keep listening for feedback and suggestions to make this work better for you. Because that’s who we are at Mozilla," says Herman. Part of the justification given by Nightingale for revamping the new tab page was that it "isn't delivering any value for [new Firefox users]", pointing out that it is unpopulated and stark -- opening up Nightingale to questions from commenters such as "did you get previous complaints about a new tab being empty?"
If Mozilla is going to introduce advertising to Firefox, it should at least have the decency to be honest about it. This is not about adding value, or improving the user experience. It is about trying to bring in money and testing the water to see if users will let it slide or not. Claims such as "in the coming weeks, we’ll be landing tests on our pre-release channels to see whether we can make things like the new tab page more useful" just sound disingenuous.
Image Credit: iQoncept / Shutterstock
-

The connected car -- AVG warns of security and privacy concerns
Publié: mai 11, 2014, 1:10am CEST par Mark Wilson

The "internet of things" is one of those catch-all terms that has become one of the latest buzzwords to be bandied about hither and thither. It is often used to conjure up images of an online oven, connected kettles and web-enabled waffle makers, and is referred to as something that is yet to be. So used is this term, that it's easy to forget that it's something that already exists -- just ignore the absurd name and you simply have a collection of devices that connect to the internet for a variety of reasons. But having any device connected to the internet has advantages and disadvantages, and this is something that security experts AVG recognize only too well.
Take cars for instance. Things have advanced in leaps and bounds in recent years, to the point that the traditional key is no longer needed, and apps can be used to check vehicle stats -- who needs dials and in-car displays, eh? Just as owning a car has changed dramatically in the past couple of decades, so has the problem of car security. Numbered are the days of a brick through the window, a screwdriver or coat hanger slipped down the side of the window, and touching together a couple of wires to make a getaway in just a few minutes.
Cars are now incredibly computer-heavy, and while this initially led to an increase in security and user-friendliness, it also led to a new breed of car thief. The computers used to add all manner of fancy features to new vehicles also serve as new points of entry for the technically minded thief for whom the prizes are ever more valuable. "Connected vehicles" are just as at risk as less technically advanced cars, and it's a problem that is likely to do nothing but get worse.
In a post on the AVG blog, Tony Anscombe -- AVG's "Senior Security Evangelist" -- points out that with a predicted 50 billion connected devices by 2020, it's time to look seriously at vehicular security. He says that while car hacking currently means that it is possible to be relieved of your vehicle by a techno-thief, there's also potential for something slightly more sinister.
This is not just a matter of security; there is also privacy to consider. As Anscombe points out, the connectivity of cars "potentially gives manufacturers access to data we may consider to be private, whether that's our music and navigation data or more personally, our location, family information and potentially other sensitive information. So the physical loss of the car could in fact be coupled with the loss of personal privacy".
It was, and is, the desktop computer that was the source of concern, and this spread to smartphones as the popularity of handsets increased. Now "cars are becoming the smartphones of the future" as a new generation of drivers expects and demands the same level of connectivity. In shows such as Person of Interest and Intelligence we have seen depictions of the remote control of vehicles, and this is something that AVG is concerned about. "What if car hacks were malicious, and the goal was to meddle with your car’s driver system to adjust the braking, cruise control or steering?" Forget going to fill up with gas, you may have to pull in to install the latest virus definitions and security updates.
Anscombe says that AVG wants to be at the forefront of working with car manufacturers to develop effective security techniques. But perhaps the way ahead is to realize that there is no need for everything to be connected. Is the internet of things being oversold?
Image Credit: haveseen / Shutterstock
-

The most popular stories on BetaNews this past week: May 4 -- May 10
Publié: mai 10, 2014, 1:46pm CEST par Mark Wilson
 What's that? It's the end of the week already? How did that happen?! Things got off to a slightly slow start, but it ended up being another jam-packed seven days. Microsoft was criticized for continuing to patch Windows XP after support was supposed to have ended, but it does seem as though usage is starting to decline. Interestingly, it is Windows 7 that suffered from a higher malware infection rate according to Microsoft's Security Intelligence Report. Windows 8.x is still struggling to gain a large audience and Wayne looked at why this is the case -- maybe a smartwatch would be a smart move.
What's that? It's the end of the week already? How did that happen?! Things got off to a slightly slow start, but it ended up being another jam-packed seven days. Microsoft was criticized for continuing to patch Windows XP after support was supposed to have ended, but it does seem as though usage is starting to decline. Interestingly, it is Windows 7 that suffered from a higher malware infection rate according to Microsoft's Security Intelligence Report. Windows 8.x is still struggling to gain a large audience and Wayne looked at why this is the case -- maybe a smartwatch would be a smart move.The effects of Heartbleed are still being felt, and ExtraHop Networks had some advice during a Q&A session. Symantec unveiled its security roadmap for Advanced Threat Protection, and Dropbox discovered a vulnerability that led to the company pulling access to hyperlinked files. Many big names came together to try to make passwords more exciting -- give it up for World Password Day!
It wasn't just security that was hitting the headlines this week, but also privacy. Yahoo announced that it will stop honoring Do Not Track requests while John McAfee launched Chadder, a secure messaging app for those willing to run their private chats through a service owned by the founder of McAfee. A new series of emails showed that Google was rather friendly with the NSA a couple of years ago.
Joe's love affair with Chromebooks continues, now taking in the Dell Chromebook 11 and there was more Chromebook action from Lenovo with the N20 and N20p which we'll be looking at in more depth as soon as we can. Joe also looked at the success of Chrome OS before keeping us abreast of everything that was happening at the Google-Intel event and then suggesting that things are not evolving fast enough.
Mihaita took a look at VLC for Windows Phone, there was rejoicing as Windows Phone users learned they would be gaining a file manager and figures showed that millennials are more reliant on their phones than ever. Showing that mobile operating systems need not be limited to mobile devices, AOC launched two Android-powered desktops. But on mobile phones it is Android that remains the most popular, successfully staying ahead of Windows Phone and iOS. Brian showed us that it can still make financial sense to build your own computer rather than buying off the shelf, looking at the AMD AM1 platform.
Prize for weird idea of the week is awarded to Amazon for teaming up with Twitter to allow tweeters to add goods to their shopping cart through the social network -- the company also introduced Sunday deliveries in more US cities. Award for best use of technology to increase laziness levels goes to the D-Link Wifi Smart Plug. Netflix managed to cause confusion with its latest price change.
Enjoy your weekend, and if you're a gamer just think -- you could be playing a new version of Unreal Tournament soon! Hopefully it will be a little less controversial than Nintendo's Tomodachi Life.
Image Credit: vinz89/Shutterstock
-

Windows XP use declines steadily but security concerns mount
Publié: mai 9, 2014, 5:32pm CEST par Mark Wilson

It's now a month since support for Windows XP came to an end, and we've already had our first exciting little post-XP incident. When a security flaw was discovered in Internet Explorer, an out-of-band patch was released for XP users despite Microsoft's previous claims that no more such updates would be issued. A month on seems like a good time to assess the lay of the land for the operating system, and that's precisely what security firm Secunia has done.
Looking at the install base for Windows XP, Secunia found that there has been an extremely steady decline in usage from the beginning of the year. According to Secunia's numbers, XP could be found on 22 percent of US PCs between January and December of 2013, but this dropped to 18 percent in the period January to February this year. It is possible that this marked drop could be attributed to people finally coming to terms with the idea that XP was no longer being supported and deciding to move on. But things start to slide further as we move into April.
One week after XP's end-of-life, usage dropped to 17 percent, and just one week later it dropped a further percentage point to 16 percent. Four weeks after the end of support for XP, the operating system was to be found on just 15 percent of US computers. This coming "Patch Tuesday" will be the first one after the Internet Explorer patch was released recently and Secunia is warning that as time goes by, Windows XP users will "be a 'free-for-all' to hackers".
Kasper Lindgaard, Secunia's Director of Research and Security said: "Come Tuesday, Microsoft will be patching some vulnerabilities in Windows, and it is realistic to assume that at least one of these will also affect Windows XP". And this is where the concern lies. "We can expect to see exploits in the wild for vulnerabilities in XP because it is End-of-Life, private users will not receive patches from Microsoft". It is not as though this notion has come out of the blue, but the severity of the Internet Explorer problem means that XP users and security experts are looking at the situation with renewed interest.
"We will see a rise in attacks," warns Lindgaard. "Future patches to the other Windows operating systems will be reverse engineered by hackers, seeking to discover which vulnerabilities were fixed by Microsoft, and subsequently -- if applicable -- modified to work against Windows XP". It's not clear whether Microsoft will back down from its "no more support" stance again, but with the Internet Explorer issue, the company has set a precedent -- and possibly made a rod for its own back.
Image Credit: Jirsak/Shutterstock
-

Nintendo says no same-sex marriage for Mii
Publié: mai 9, 2014, 1:09pm CEST par Mark Wilson

Real life sims are very easy to get wrong -- just look at The Sims, for instance -- and Nintendo's latest venture into this branch of gaming, Tomodachi Life, demonstrates this perfectly. Taking a collection of Miis (Nintendo's sickly sweet customizable avatars) and dumping them on an island, the game presents players with a "world full of possibilities". The game's website proclaims, "in Tomodachi Life, populate your very own island with the Mii characters of family, friends or anyone else you can think of!" As long as the Miis are not gay that is.
Yes, in the Disney-like world of Nintendo, same-sex relationships are not possible. You're free to do pretty much anything you like in the game, but when it comes to striking up a relationship and getting virtually married, it's boy-girl action only. Homosexuality simply does not exist in Nintendo's little bubble, and this is something that was noted by one gamer who then launched a campaign on Twitter to try to get the gaming giant to change its ways. Tye Marini 's Miiquality Twitter account was started to try to persuade Nintendo to rethink the game and allow for lesbian and gay relationships.
The Nintendo 3DS game has been available in Japan since December, and it has already proved popular. It was hoped that the Twitter campaign would force Nintendo to change its mind about LGBT relationships ahead of the game's European and North American launch in June. But the Mario factory has declined, saying that "the relationship options in the game represent a playful alternate world rather than a real-life simulation. We hope that all of our fans will see that 'Tomodachi Life' was intended to be a whimsical and quirky game, and that we were absolutely not trying to provide social commentary".
But for campaigners, this simply doesn't cut it. Claims of being "whimsical and quirky" and not intending to "make any form of social commentary" cannot be used as get out of jail free cards. Could the same excuses be given for introducing casual racism into a game? The reasons given are not good enough, and the Miiquality campaign, thankfully, continues. All may not be completely lost, as Nintendo has at least states to the campaign: "We will continue to listen and think about the feedback. We're using this as an opportunity to better understand our consumers and their expectations of us at all levels of the organization".
The issue does highlight the problems associated with simply transplanting a game from one country and introducing it to another unchanged. In Tomodachi Life's homeland of Japan, gay marriage is not legal -- in the UK and US (for the most part) it is. But again, these cultural differences are no excuse.
-

New UK measures to combat piracy are far weaker than hoped for by copyright owners
Publié: mai 9, 2014, 12:09pm CEST par Mark Wilson

A new deal could be struck between ISPs and representatives of the music and film industries in UK in a bid to combat online piracy. But the proposed scheme does not go anywhere near as far as had been hoped by the BPI (British Phonographic Industry) and the MPA (Motion Picture Association). Four of the country's biggest ISPs -- BT, Sky, TalkTalk and Virgin Media -- have come together to create the Voluntary Copyright Alert Program (Vcap) which has the aim of educating downloaders of pirate material of the error of their ways. As the name suggests, the program is completely voluntary.
There have been years of debate on the topic, and the BBC has seen documentation that shows ISPs will be doing little more than sending out letters to those suspected of downloading pirated material. The letters are described as having an "educational" tone, while the industry bodies had been calling for warning letters to be sent out alerting downloaders to the possibility of legal action. They had also asked for access to a database of web users known to have downloaded pirated material.
The venture will be financed mainly by the MPA and BPI who will pay each of the ISPs up to 75 percent of the costs of setting up the scheme, as well as paying up to 75 percent of annual running costs. As the expense of getting such a scheme and the on-going costs have been cited as a major obstacle for many ISPs -- particularly the smaller ones -- it is likely that more and more providers will get on board now that these have been reduced.
There will obviously be concerns about customer privacy with any such system, and it will need to be approved by the Information Commissioner's Office before it can be put into action. The proposal is that copyright holders will be provided with a monthly report outlining the number of letters that have been sent out, but details about customers' identities will not be passed on. Interestingly, there are limits on the number of letters -- or "alerts" -- that can be sent out. Each customer can receive no more than four letters or emails (none of which will make reference to possible legal action or other consequences) and between the four ISPs, a maximum of 2.5 million alerts may be sent out annually.
ISPs have previously described any attempts to monitor and warn their customers about piracy as "unworkable", but this time around a consensus seems to have been reached. Whether it proves to be workable remains to be seen.
Image Credit: Valeriy Lebedev/Shutterstock
-

Twitter bolsters security with password reset and suspicious login improvements
Publié: mai 9, 2014, 1:55am CEST par Mark Wilson

Security is always important, but now that we find ourselves in a post-Heartbleed world, it seems that there is more importance than ever being placed on passwords and the safety of online accounts. The constant advice, that we should be using unique passwords of ever-increasing complexity for each service we use, means that there is a greater chance of forgetting our login details. This is something that Twitter recognizes with a couple of account safety changes that are being introduced today.
A new password reset procedure lets you choose whether reset details should be sent to your registered email address or phone number. Having a choice is helpful in case you no longer use the email address you registered with, or if you have switched phone numbers. Choice is good! Mobile users will also find that the reset process has been improved, and Twitter helpfully provides some tips to aid with selecting a strong new password.
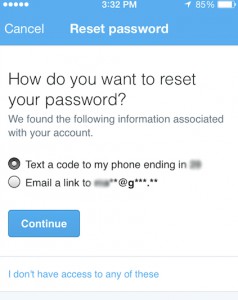 Changes are also being made to better identify suspicious logins -- account logins that may not be you. Using information such as your login history, your location and the device that is being used, Twitter's algorithms have been designed to detect unusual logins. Should a login be determined to be suspicious -- even if the correct password has been used -- you'll be asked (or whoever is trying to access your account) to provide some personal details or answer a security question before access will be granted. Of course, there is a possibility that someone else may be able to correctly answer these questions, so a warning email will be sent out to give you the opportunity to reset your password.
Changes are also being made to better identify suspicious logins -- account logins that may not be you. Using information such as your login history, your location and the device that is being used, Twitter's algorithms have been designed to detect unusual logins. Should a login be determined to be suspicious -- even if the correct password has been used -- you'll be asked (or whoever is trying to access your account) to provide some personal details or answer a security question before access will be granted. Of course, there is a possibility that someone else may be able to correctly answer these questions, so a warning email will be sent out to give you the opportunity to reset your password.Are you pleased to see that Twitter is taking steps to protect your account? Do you feel the new procedures go far enough? Tell me in the comments.
Image Credit: leungchopan/Shutterstock
-

Weapon up! Unreal Tournament to return as free, crowd-sourced game
Publié: mai 9, 2014, 1:51am CEST par Mark Wilson

Remember Unreal Tournament? Remember the hours (days?) you invested in it? Well, it's back! Or at least it will be soon… It's a game that we've heard nothing of for some time now, but Epic is wheeling out the classic title for a new airing. This time around, the gaming community is being called upon to contribute. In a post on the Unreal Engine Blog, Steve Polge says, "work on the future of Unreal Tournament begins today, and we're happy to announce that we're going to do this together, with you".
What does all of this mean? To cut to the chase, a new version of Unreal Tournament is, as of right now, being developed. Yippee! The UT community is a passionate one, and the new project is going to take full advantage of this. This is a collaborative project and the finished product will call upon the input of fans, Unreal Engine 4 developers, and Epic. If you fancy getting involved -- be it to contribute code, artwork, or just ideas -- you are free to do so.
Speaking of free, this is exactly what the game will be when it is complete: "it will be free. Not free to play, just free". Unfortunately, an actual release could be some ways off. As the blog post points out, development is starting completely from scratch and will include Windows, Mac and Linux versions of the first person shooter. Epic is very much playing this by ear. It's a unique project "and we don't yet have everything figured out". It's unlikely to be a smooth journey -- "things will probably definitely go wrong from time to time, and when they do, we'll have to work through them together".
Combining the skills and input of a dedicated community is sure to produce something of a crowd-pleaser. But it is not being done just for the love of it. While the game will be made available free of charge, the project will still need to be paid for. To this end, in-game purchases will be made available:
"We'll eventually create a marketplace where developers, modders, artists and gamers can give away, buy and sell mods and content. Earnings from the marketplace will be split between the mod/content developer, and Epic. That's how we plan to pay for the game."
The whole project is an extremely interesting way to tackle the development of a new game, and it will certainly be one to watch. Like the idea of getting involved? Sign up for a free Unreal Engine 4 community account and keep an eye on the forums.
Imaged Credit: BlueSkyImage / Shutterstock
-

6 tips to increase company security post-Heartbleed from LastPass CEO, Joe Siegrist
Publié: mai 8, 2014, 1:06am CEST par Mark Wilson

Heartbleed was a security nightmare that caught the technology world unaware and unprepared. There was a good deal of panicking in the immediate aftermath, but looking back a month down the line there is a lot to learn from what happened. But perhaps the most important thing is what happens moving forward.
Post-Heartbleed, Joe Siegrist, CEO for LastPass has a series of tips for companies to help protect data and improve privacy.
1. Acknowledge that company passwords are a problem
Passwords are one of those things that we all know we should do better but many secretly feel helpless to do anything to change. Insecure sharing of passwords is rampant in organizations, and due to the burden of password requirements and password changes, employees default to the easiest passwords they can remember and get on with their lives.
The first step is for leadership to recognize that there's a password problem, and that it poses a serious security risk to your organization.
2. Get a plan in place
It's one thing to tell everyone that they have to update their passwords, and then force those changes on them. It’s another thing to give them tools and a framework that enables them to painlessly make those changes and follow best security practices going forward.
This is where an Enterprise password management system is critical. It is nearly impossible for employees to follow best password practices without one. Not only that, but employee productivity is bolstered by having a tool that fills passwords for them, keeps them from having to call the helpdesk to reset passwords, and enables them to manage everything from one secure portal. With a system like LastPass Enterprise, the team can implement both password vaulting and SAML Single Sign-On in one secure place. Committing to a password manager helps the company get a plan in place and map out how to implement password security improvements.
3. Enforce policies that support your security goals
Once you have deployed a password management system, you can spend time reviewing the policies and security restrictions available to help your organization gently enforce security standards. For example, LastPass policies can be set to disallow access from outside the company office, or other trusted locations -- and policies can be both inclusive and exclusive, so that everyone but a few can be given a separate set of restrictions. Policies allow you to enforce strong master passwords, restrict mobile access, disallow use of features like exporting, and more. The key is to create a customized security environment that meets your compliance needs.
4. Prioritize updating critical accounts
LastPass makes it easy for admins and employees alike to understand where they are using weak or duplicated passwords for their online accounts, and helps with the process of creating strong new passwords. Admins who manage a shared account can prioritize those critical updates, while employees can take responsibility of their logins that need updating. The LastPass Security Check helps both employees and admins keep an eye on progress and work towards concrete goals.
5. Enable multifactor authentication
Multifactor authentication adds a layer of protection to LastPass accounts by requiring that a user complete an extra step before being given access to their account. Typically this means providing data from something you have access to like a device that generates a one-time code or a mobile app that generates a temporary code or biometrics such as a fingerprint scan. LastPass Enterprise simplifies the deployment of multifactor authentication and integrates seamlessly with a range of options. Companies can choose the methods that work best for their devices and environment.
6. Do a password sweep
The password management system you put in place is only as good as your employees' adoption of it. Consider doing a "password sweep", and walk around the office to see if any passwords are posted in plain sight -- perhaps posted on a cork board or written on a white board. Save all of these data points to the password manager and share them through that system.
Imaged Credit: soliman design / Shutterstock
-

Microsoft, McAfee and more join forces to promote security with World Password Day
Publié: mai 7, 2014, 5:55pm CEST par Mark Wilson

Security is fun! Security is sexy! In fact, passwords get so many hearts pounding that World Password Day had to be dreamed up just to create an outlet for the outpouring of emotion associated with them. This may be stretching things a little, but today really is World Password Day, a global movement involving McAfee, Microsoft, Dell, Acer, Lenovo and numerous other big names to educate the world about... passwords! I jest a little, but this is a day with a serious message -- we are all incredibly reliant on passwords, but too many of them are just not strong enough.
Head on over to the website and you'll find all manner of tools designed to stress the importance of strong passwords, and to promote good practices. Things get off to a fairly gentle start with a typing game in which you're invited to type common passwords and blast them out of the sky. There are also tools and tips from each of the companies involved in the project. Microsoft has a password checker that will test the strength of your password, McAfee (now nothing to do with John McAfee!) has a Heartbleed vulnerability checker, while Dell has the handy tip that one shouldn’t type one's password into the username field.
Michelle Dennedy, chief privacy officer at McAfee, said: "Our goal this World Password Day is to educate consumers on ways they can proactively protect their identities, and other personal information and assets, through a series of simple steps".
We’ve been talking about World Password Day here at BetaNews, and the claim made on the website that "90 percent of all passwords are vulnerable" certainly set our minds racing. Brian was prompted to ask "how do I get one of the 10 percent unhackable passwords?" Fair question! But the fact of the matter is that we can all do something to improve our password security. I'm not sure how well the suggestion that people might want to "host a #passwordday party in your classroom" will go down, but every little bit helps, I guess.
Head on over to the site to see if there's anything you can learn.
Photo Credit: Dr. Cloud/Shutterstock
-

Emails suggest that Google was a willing partner with the NSA
Publié: mai 7, 2014, 12:44am CEST par Mark Wilson

Dear old Google. Dear, dear old Google. In the fallout from the NSA revelations, the company has been falling over itself to try to appear open and transparent about the relationship it had with the security agency during its surveillance program. But a series of emails dating back to 2012, obtained by Al Jazeera America, show that things were rather different than the picture that has been painted thus far. Google -- and other web companies who have, for whatever reason, cooperated with the NSA -- has made it seem as though they were unwillingly forced into taking part in NSA activities, but things may not be quite what they seemed.
Recently, a NSA lawyer made it clear that Microsoft, Google, Yahoo and others were fully aware of the levels of data collection that were being performed. This flies in the face of the earlier claims that these firms were completely ignorant of what was happening. You might have thought that such mass surveillance would be illegal, but no, this was absolutely fine according to a federal judge.
As more details came to light, largely thanks to Edward Snowden, web users started to ask questions about what had really been going on, and company after company suddenly started to feel guilty and tried to appease this guilt by publishing details about the data that had been handed over to the US government and other governments around the world.
The insistence has always been that data has only been handed over when there was a legal requirement to do so -- "Oh, pity us! Our hands are tied!" But the emails obtained by Al Jazeera give a different side of the story. The emails are between Google's Sergey Brin and Eric Schmidt, and NSA Director General Keith Alexander and the latter, in June 2012, writes:
"About six months ago, we began focusing on the security of mobility devices. A group (primarily Google, Apple and Microsoft) recently came to agreement on a set of core security principles. When we reach this point in our projects we schedule a classified briefing for the CEOs of key companies to provide them a brief on the specific threats we believe can be mitigated and to seek their commitment for their organization to move ahead … Google's participation in refinement, engineering and deployment of the solutions will be essential".
The emails were released after a Freedom of Information Act request and are not particularly incriminating -- they probably would have not been released if they were deemed *too* damaging -- they do show that Google was far from strong-armed into NSA meetings. In one cheery email to Alexander, Brin says "looking forward to seeing you next week". Following a meeting between Google and the NSA, Schmidt emailed Alexander to say "so great to see you! … Would love to see you another time".
See it as a business-like politeness if you will, but there is still a rather more cheerful and friendly tone to the messages than we might have expected, and the relationship between Google and the NSA is a bit more friendly than we have been previously led to believe.
Image Credit: Lorelyn Medina / Shutterstock
-

Paranoid? Enough to place your privacy in the hands of John McAfee?
Publié: mai 6, 2014, 12:47pm CEST par Mark Wilson

Remember McAfee? You know, the company whose AV software you couldn't remove from your computer fast enough after picking up an off-the-shelf model? The firm was founded by the now infamous John McAfee, although he has not actually been associated with it in anything other than name for quite some time now. In fact he has become better known for a series of bizarre incidents that saw him accused of manufacturing drugs, mentioned in association with a murder and becoming a fugitive who was concerned that the police were going to kill him.
Sounds like the sort of person you'd like to make an app for your phone? Well, the man is back and this time he, or at least his company Future Tense, has come up with Chadder -- yet another messaging app. But this is a messaging app with a difference. The focus is, allegedly, on privacy, security and encryption. The company's motto is "Say what you want! ⋇⊮ ≩⋉⊱∪≀ ⋘≫≯⋌∹∦ ≎⋡⋔∪≙∼≉{] (We can’t see it anyway!)". My, those symbols really do trip off the tongue.
The Google Play listing warns that "This application is in beta! We published it quickly and there is not a lot of features" [sic] but at the same time panders to the concerns of those who worry about their online activities coming to haunt them. "Aren’t you sick of hearing about safety online because everything you post is permanent?" No, not really, but do continue.
"With Chadder you have no more worries!" None at all?! Wow! That’s quite a claim there! "We have a state of the art way to make sure we can never see your information!" Oh, you just meant in relation to the app, not life in general. That's a little disappointing. "As developers we have worked to create an application that has security fully built in vs. just laid on top". Built in sounds good to me too. "The goal is to build an application that is fun and easy to use that happens to be private!" Hold on… I thought the privacy side of this was the most important aspect. You've got me all confused now.
This is, ultimately, just a messaging app, but the use of encryption -- the decryption key for which is only, apparently, available to participants in a conversation -- is being touted as a unique selling point, although the app is free. Lexi Sprague, founder of Etransfr, who has partnered with Future Tense to release the app, said: "Chadder is here to prove that young people want privacy just as much as adults do... it is about giving privacy and control back to the user without scaring them off with complicated log in and messaging processes. The team […] believes there needs to be a balance between usability and privacy!"
If you fancy chancing your luck with the app, you can grab a copy for Android and Windows Phone -- yep, Windows Phone gets the app before iOS. You might also want to take a look at the Future Tense website which is a wonderful exercise in scaremongering using broad strokes. All very amusing stuff. Oh... while you're at it, take a peek at the John McAfee website -- hilarious stuff.
But the question is, would you be willing to place your privacy in the hands of John McAfee?
Photo Credit: CREATISTA/Shutterstock
-

Do Not Track: Stop using Yahoo if you're concerned about privacy
Publié: mai 5, 2014, 4:24pm CEST par Mark Wilson
 It has been mentioned here and there, but to be honest I am very surprised that more of a stink has not been kicked up about Yahoo's announcement last week. Quietly slipped into a blog post by the slightly ironically named Yahoo Privacy Team, the web firm announced that "Do Not Track settings will no longer be enabled on Yahoo". Yep, sod privacy, Yahoo is more concerned with delivering "A Personalized Experience" -- Yahoo's capitalization, not mine.
It has been mentioned here and there, but to be honest I am very surprised that more of a stink has not been kicked up about Yahoo's announcement last week. Quietly slipped into a blog post by the slightly ironically named Yahoo Privacy Team, the web firm announced that "Do Not Track settings will no longer be enabled on Yahoo". Yep, sod privacy, Yahoo is more concerned with delivering "A Personalized Experience" -- Yahoo's capitalization, not mine.Do Not Track has been around for a few years now -- interestingly, Yahoo was one of the first companies to start using it -- and it makes it possible for users to prevent websites from monitoring their online activities. It's a feature that is supported by a number of browsers, either as a built in option, or one that can be added through the use of an extension, and it is something that has been welcomed by privacy groups all over the world.
Yahoo's justification for the change of heart is laughable:
"Here at Yahoo, we work hard to provide our users with a highly personalized experience. We keep people connected to what matters most to them, across devices and around the world. We fundamentally believe the best web is a personalized one".
There is also the claim that "we have yet to see a single standard emerge that is effective, easy to use and has been adopted by the broader tech industry". There may be an element of truth in this but really -- so bloody what? Defining a standard becomes far harder if the self-proclaimed "first major tech company to implement Do Not Track" changes its mind about whether to use it or not.
Of course, it has absolutely nothing to do with tailored advertisements does it? The blog post points out that "users can still manage their privacy on Yahoo while benefiting from a personalized web experience" (via the Yahoo Privacy Center), but how many Yahoo users are -- honestly -- going to do this? It would require them to a) know that something had changed that they need to take action on, b) know that it is possible to do something to protect their privacy, c) know how to do it, and d) actually get around to doing it.
It is worrying that Yahoo can just decide to ignore a privacy feature that has been implemented in numerous forms. Users who have opted to use Do Not Track have -- in most cases, at least -- done so for a particular reason: they value their privacy. For Yahoo to ride roughshod over that is just plain rude. These are not the actions of a company that values its customers for anything more than an income stream.
Yahoo is being sneaky and underhanded. It is also being incredibly dishonest in its reasoning for the change. At least it would be possible to offer begrudging respect to the company if it came out and said "This Do Not Track thing is really hitting our income from ads, we need to ditch it", but the announcement is both very quietly made and -- I would suggest -- is far from giving users the full story.
I'm neither a user nor a fan of Yahoo, so the change has little, if any, immediate impact on me. But the worry is that other firms will follow suit and the privacy of the individual will be further eroded. Too many companies seem keen for us to forget that privacy is a right, and giving it up should not be the price we are expected to pay to use the internet.
Image Credit: Pixel Embargo / Shutterstock
-

The most popular stories on BetaNews this past week: April 27 -- May 3
Publié: mai 3, 2014, 9:36am CEST par Mark Wilson
 Security news a-go-go once again this week, starting off with a massive security flaw that was discovered in Internet Explorer. The problem affects everything from Internet Explorer 6 to 11, but it was Windows XP users who were particularly at risk due to the fact that Microsoft has ended support for the operating system and is releasing no more security patches. At least that was the case before this problem came to light, causing the company to change its mind and give users one more hit of update goodness.
Security news a-go-go once again this week, starting off with a massive security flaw that was discovered in Internet Explorer. The problem affects everything from Internet Explorer 6 to 11, but it was Windows XP users who were particularly at risk due to the fact that Microsoft has ended support for the operating system and is releasing no more security patches. At least that was the case before this problem came to light, causing the company to change its mind and give users one more hit of update goodness.While Microsoft's latest security whoopsie did leave Microsoft licking its wounds a little, there was cause for celebration for OneDrive for Business users as storage was boosted to 1TB -- and the cloud is becoming ever more important with predictions suggesting 50 billion online devices by 2020. Microsoft was also able celebrate finally having a launch date for the Xbox One in China. In other security news, AOL email service was hacked leading to the leaking of customer data and a new report suggested that just about every website dealing in pirated material is also home to scams and/or malware.
Apple updated its MacBook Air lineup with a new batch of processors (Joe wasn't impressed although he did like the new ad campaign rather more) and was probably pleased to find that its iPhone was still in second place in the mobile market behind Android. Windows Phone still trails in third place, and now the likes of the Lumia 1020 face additional competition from Samsung's Galaxy K Zoom. At an event in NYC, the Core i3 Acer C720 Chromebook was unveiled and Brian was on hand for a hands-on.
Fans of Hulu who live outside of its catchment area and have come to rely on VPN tools to tap into the streaming service were disappointed to find that their efforts had been noticed and blocks put in the way. There are plenty of other services to choose from, however, and many of them are featured in Alan's cord cutting guide. Cord cutting is becoming very popular by all accounts. If you're looking to get fit rather than be entertained -- although you may not necessarily separate the two -- Amazon's new Wearable Technology store may be of interest. Sprint teamed up with Spotify to give customers access to a free music trial.
Reviews were slightly thin on the ground this week, but I took a look at the 360 Case for iPad and Nexus 7, as well as the world's slimmest soundbar. Brian decided that Google+ is brilliant while I argued that Google was exercising a little too much control over web content, encouraging websites into featuring certain types of article. A pleasing round of comment ensued -- that is what this is all about after all... engaging and interacting.
This week was the 50th birthday of BASIC -- it's impressive that five decades on the programming language is still viewed with such fondness.
See you next week for more!
Image Credit: vinz89/Shutterstock
-

Degrees of protection -- 360° Case for Nexus 7 and the iPad family
Publié: mai 2, 2014, 2:08pm CEST par Mark Wilson

Tablets are über cheap these days. It seems as though just about every electronics company has them flying off the production lines. But even if you manage to pick up a cheap tablet, you still want to keep it protected -- no one wants to end up with a screen that is scratched to the point of being unusable, or a body that's smashed to smithereens. The need to protect is even greater if you have handed over a few hundred dollars / pounds for something from the Apple family, and there are all manner of cases to whet the appetite of those keen to keep things safe.
One such offering is the 360° Case from Everything Tablet (operating in the US and Canada as well as the UK) which features a folio-style wrap-around design. I took a look at the Nexus 7 model and my previously svelte 7 incher was transformed into something resembling a leather-bound personal organizer from the 80s. Such is the price one pays for protection, I guess.
At the moment Nexus 7 users have a rather limited choice when it comes to colors for the case. There's Black Carbon, with which it is all but impossible to go wrong, and then there is orange. And holy heck, is it orange! iPad users have a wider palette from which to make their selection -- Baby Blue, Baby Pink, Black Carbon, Gun Metal Grey, and Orange -- and just about the full gamut of Apple tablets is covered. The iPad 2, 3 and 4 cases will set you back £22.99 ($22.99), the iPad Air jumps to £29.99 ($29.99), the iPad Mini drops to £19.99 ($19.99), and the lower price is what Nexus 7 owners are expected to part with as well. The pricing is good, but yet again it is disappointing to see UK consumers getting worse deal, ultimately ending up paying a massive premium -- $22.99 equates to £13.63, for instance, and while there are state taxes to factor in, an extra £9.36 (or $15.79) is difficult to justify. Maybe the US and Canada is just getting a really great deal, but being in the UK I can’t help but feel like I'm getting the dirty end of the stick.
That minor rant out of the way, the case itself is pleasing to use, but not the best I've ever come across. The cover of the case is held in place with an elasticated band. A magnetic catch or other form of closing mechanism would have been preferable because there's huge potential for catching the strap on the content of a bag when the tablet is pulled out for use. Open it up and the smart cover activates the screen -- at least it does most of the time -- and the tablet can then be used in a number of ways. Hold the case in portrait mode and you can use your tablet in the case as if reading a book, but there is scope to fold the cover all the way round the back.
Flip round to landscape mode and you'll find a groove running along the front edge of the inside of the cover that can then house the bottom edge of the tablet. This is a great 'tent' style mode for watching movies or making use of a Bluetooth keyboard. But here's the interesting bit. The 360° part of the case's name stems from the rotatability of the portion that holds your tablet in place. It can rotate through a full 360°, but really it's just to allow you to switch between a hands-free portrait and landscape mode. The angle is a little shallow when flipped to the vertical position, but it is still more than usable.
The case feels robust and, aside from access to buttons and speakers, there are few exposed parts that could get scratched or damaged. I'm not sure how much rotating the case will stand for months or years to come, but the rotator cuff, including its off two-inch hole that makes it look as though it has been blasted at close range with a firearm, is certainly a weak point.
While the 360° gives a generally decent viewing angle and will protect against bumps and scrapes, it also feels rather awkward to use, making the tablet experience more annoying than enjoyable -- and this is something no case should do.
-

World's thinnest soundbar: Humax STA–1200 BSW packs a punch
Publié: mai 2, 2014, 12:27pm CEST par Mark Wilson

Whether you've been following Alan's guide to cutting the cord and have opted to ditch your traditional TV service in favour of something web-based, you're keen on sticking with your cable or satellite setup, or you're a gamer, sound is incredibly important to any setup. You could opt to go down the 5.1 (or even 7.1) surround sound route, but all too often this will involve trailing cables around the room in somewhat untidy fashion.
In recent years there has been something of a surge in interest in soundbars -- single units that pump out pseudo-surround -- and there is a huge range to choose from. Many are big and bulky, but the latest offering from Humax -- of set top box fame -- has something of a unique claim to fame: it is, allegedly, the slimmest soundbar in the world.
The first time I read the dimensions for the Humax STA-1200 BSW, it just didn’t make sense. I didn't go quite as far as whipping out a tape measure or making up a dummy unit out of cardboard, but I did plenty of guestimating of size with much waving of arms whilst muttering (something along the lines of) "that can't be right!" Anorexia references are probably in bad taste, but I'm not one for worrying about such things and it's been typed now -- I'm not going back to delete it. Good taste or bad, this is a soundbar that is positively waif-like: 1200mm wide by 37mm tall by 20mm deep. Yep -- no typos there, this is a soundbar that has dimensions that are not dissimilar to a broom handle. There's also a sub to take into account, but this is hardly of mammoth proportions.
Dotted along the length of the soundbar are four speakers, pumping out 80W of power. The sub is a passive unit that provides 100W of bass backup. There's a frequency range of 40Hz-40KHz (or 40Hz-14KHz, depending on whether you trust the online brochure or the user manual), which is more than acceptable. Despite the unit's diminutive size, it really does throw out some decent sound. Controls are basic -- there are no equalizer settings to play with, for instance -- but the bass boost option and "surround" feature both yield impressive results. Audio is rich and clear, but it would be nice to be afforded a little more in the way of tweaking options. Switching through the small number of settings can be achieved using the mini remote control, or the pleasing touch controls on the bar itself.
Aesthetically, the Humax STA-1200 BSW is a good looking piece of kit and it wouldn't look out of place under any large screen TV or monitor. The styling is such that the soundbar can "blend in" with most setups, and you can choose between using a wall bracket or a desk-mounted stand. The wall bracket keeps things neat and tidy, but the stand gives more flexibility in terms of positioning.
The stand itself, whilst entirely functional, is a very basic and plasticky affair. Whilst not exactly flimsy one can’t help but feel that it wouldn’t take much to snap it in two -- if you have a couple of cats stalking the house, or perhaps kids, you may feel similarly concerned. Left to its own devices it's going to come to no harm, but it almost has the look and feel of a 3D printed model -- it is something of a low point.
In terms of inputs, things are a little limited. In fact there are only two wired options: optical or 3.5mm jack. While this will allow for connection to most devices, audiophiles may well rue the dearth of inputs. There is one other option however -- the Humax STA-1200 BSW also functions as a wireless speaker thanks to built-in Bluetooth support. Great for streaming music from a phone or tablet, using the soundbar as a Bluetooth speaker is very simple to get up and running... and it's just kinda cool, really. Pairing is a breeze and output via Bluetooth 3.0 is more than passable.
So… is this the best soundbar you could get for £200 (it's currently UK only)? Possibly not. Is it £200 well-spent? Almost certainly. This is a unique beast whose looks and stature belie the power and punch that lurks beneath the surface. For fans of minimalism looking for sleek style without having to make too much of a compromise, this is a great option. And hey, it is also referred to as the Blade, which is kinda sexy. Maybe we'll see a surge in sound blades this year...
-

Surprise, surprise -- almost every piracy website features cyber scams
Publié: avril 30, 2014, 12:55pm CEST par Mark Wilson

Many people think nothing of grabbing the latest episode of Game of Thrones, Blacklist -- or whatever the current show du jour may be -- via one of a seemingly endless number of sites that provide access to pirated material. If you've ever visited such a site, you'll be aware that there is always something of a payload. You'll find advertisements -- usually of a pornographic nature -- fake chat windows, misleading links and all manner of other nasties. For the web-savvy, this is nothing new, but for every tech-minded torrent aficionado who is able to traverse through the online ghettos with an element of safety, there are countless others who are less well informed. And the world of pirate material is a dangerous one for the novice.
While this may not be news in itself, the figures involved are really quite surprising. A report published by The Industry Trust reveals that virtually every one of the most popular sites used to download or stream pirated films and TV shows are riddled with malware or credit card scams -- a staggering 97 percent. The report goes on to suggest that 75 percent of people who have made use of such a site have then experienced problems with their computers. The study was limited to 30 of the most frequently used pirate sites, and monitored them over a two week period. Just one site was found to be free from malware or credit card scams.
The methods used to trick unwitting users are often quite crude -- fake 'play' buttons that link to malicious download rather than the desired video -- but the results can be deeply worrying. 17 percent of visitors to pirated sites lost personal data, while 14 percent were exposed to unwanted violent or explicit material. Nearly a third of visitors ended up with a virus infection, and 39 percent were inundated with popups.
You would be forgiven for thinking that in this day and age there was sufficient wariness coupled with common sense to mean that fake links and malware were problems that were easily avoided or solved. But it's easy to forget that huge swathes of internet users are still reasonably unaware of the digital dangers that exist. The increased security afforded users by anti-malware tools and browsers themselves helps to protect many people, but keeping up to date is important -- something that the less technically minded are not necessarily inclined to take care of.
Just as a spammer mass-mailing hundreds of thousands of random people with promises of riches in return for a small processing fee need just a tiny fraction of recipients to turn a profit, so just a very small number of torrent users or downloaders of pirate material need to be tricked into clicking the wrong link or need to be running an insecure browser. Each user with lowered security or a lack of knowledge about web security is a microscopic cog in a catastrophic plan.
Image Credit: SOMMAI / Shutterstock
-

AOL hacked -- 'significant number of user accounts' compromised
Publié: avril 28, 2014, 10:47pm CEST par Mark Wilson

The latest big name company to fall victim to a security breach is AOL. In a post on the company blog, the AOL security team reveals that it is currently working with "best-in-class external forensic experts and federal authorities" to investigate unauthorized access to the network. Suspicion was raised by a marked increase in the number of spam emails sent via spoofed AOL Mail addresses, and an investigation was immediately launched.
AOL says that a "significant number of user accounts" are affected and that the breach involves accessing information associated with these accounts. It seems that those responsible for the security breach have been able to gain access to email addresses, postal addresses, and address book contact information, as well as encrypted versions of passwords and answers to security questions.
It is estimated that two percent of email accounts are involved in the spoofing incident, but AOL is quick to point out there is currently no reason to believe that the encryption used to secure passwords and security answers has been broken. There is also "no indication that this incident resulted in disclosure of users' financial information, including debit and credit cards, which is also fully encrypted".
AOL is advising both its users and employees to change their password as well as their security questions and answers. In the meantime, "AOL is notifying potentially affected users and is committed to ensuring the protection of its users, employees and partners and addressing the situation as quickly and forcefully as we can".
Further information to follow as we learn more.
Image Credit: chevanon / Shutterstock
-

Microsoft gives OneDrive for Business users 40 times more storage space
Publié: avril 28, 2014, 10:21pm CEST par Mark Wilson

Free storage space is very common, and it's available from the likes of Dropbox, Google and countless others. Microsoft's OneDrive also gives users a certain amount of free online storage space, and today business users receive a massive boost -- a forty-fold increase in capacity. OneDrive for Business storage is being boosted from 25GB to 1TB per user, and the same is true for Office 365 ProPlus customers.
Microsoft is putting ever-increasing faith in the cloud, particularly for its business users. "The cloud is about breaking down walls between people and information. Not building a new set of islands in the sky", states the Office blog. There's a third announcement too: "we’ll help organizations migrate data to OneDrive for Business". It's not quite clear exactly what this entails, but it certainly sounds good for anyone who has their data hosted elsewhere.
The blog post states that "smart businesses are now choosing partners that have a holistic, comprehensive and connected set of cloud offerings", suggesting that Microsoft is one such partners that businesses should be choosing. The recent launch of OneDrive for Business as a standalone product means that it is now accessible to more users than ever before, and the latest offering is going to make it seem even more attractive.
Image Credit: Andrey tiyk / Shutterstock
-

The most popular stories on BetaNews this past week- April 20 -- April 26
Publié: avril 26, 2014, 3:30pm CEST par Mark Wilson
 After weeks of negotiations, changes to terms and all sorts of other shenanigans, Microsoft finally completed its acquisition of Nokia's Devices and services arm. Developers, and the eager average user, have now had a little time to play with Windows Phone 8.1, and Mihaita is one person who feels it is a big step in the right direction. The release of Microsoft Remote Desktop for Windows Phone 8.1 is something that will be welcomed by owners of Microsoft handsets who need to access their computers on the move.
After weeks of negotiations, changes to terms and all sorts of other shenanigans, Microsoft finally completed its acquisition of Nokia's Devices and services arm. Developers, and the eager average user, have now had a little time to play with Windows Phone 8.1, and Mihaita is one person who feels it is a big step in the right direction. The release of Microsoft Remote Desktop for Windows Phone 8.1 is something that will be welcomed by owners of Microsoft handsets who need to access their computers on the move.Another release -- not software this time -- Microsoft's fiscal announcement showed that the company had $20.4 billion revenue It wasn't just Microsoft sharing financial figures this week -- Apple also revealed its latest accounts for Q2. And Microsoft joining forces with Nokia was not the only new marriage -- Microsoft and AOL also came together in a new content deal. Joe waxed lyrical about the Surface platform, suggesting that Microsoft needs to do more to promote it -- and a new campaign aims to draw in a new audience using everyone's favorite… cake! And with the Chromebook 2 being delayed, Microsoft stands a chance to gain more ground.
There has been a gradual move to cloud-based services over the last few years, and while this has made it much easier to access data and apps from a wider variety of devices, the number of security attacks is on the increase. Over the last couple of weeks Heartbleed has been hitting the headlines a lot, and in the fallout it is time to reflect on what has been learned from the experience. One thing we do know is that Android handsets are just as vulnerable as other devices, but in non-Heartbleed news, cross-platform goodness prevailed as Adobe Air made its way to Android.
There was a lot going on on the media front this week. Alan was more than a little impressed with the Amazon Fire TV and compared it to the Roku 3 and Google TV. A new deal with HBO means that Amazon Prime customers will gain access to a wide range of exclusive content. Need even more content? Chromecast users gained access to an extra 100 channels courtesy of PlayOn. Had enough of streaming videos and need something else to entertain you over the weekend? Check out Google's new time travel feature for Street View
Enjoy your end of week break -- expect to find a stream of news flying your way over the next seven days.
-

Microsoft's Nokia Devices and Services acquisition completes Friday April 25
Publié: avril 21, 2014, 7:02pm CEST par Mark Wilson

It was said to be happening in April, but as the month drags on it was starting to seem less and less likely. Now, however, we have a solid date for the finalization of Microsoft's acquisition of the Devices and Services arm of Nokia -- Friday, April 25, in case you missed it in the headline. In a post on the Official Microsoft Blog, Microsoft's General Counsel and Executive Vice President, Legal and Corporate Affairs, Brad Smith is "excited" to announce the date of the deal closure.
As Smith says, the "completion of this acquisition follows several months of planning" but for those outside of the companies it feels as though machinations have been rumbling away forever -- in reality it is only seven months. Back in September, it was announced that Microsoft wanted to purchase Nokia's Devices and Services business for $7.2 billion, taking on thousands of Nokia employees and providing the handset manufacturer with some patents.
The closure ties in quite neatly with the release of Windows Phone 8.1, and Microsoft is looking forward to accelerating "innovation and market adoption" for these handsets, but also to "introducing the next billion customers to Microsoft services via Nokia mobile phones".
There have been a few changes to the details of the deal since it was first brokered. Nokia's Korean manufacturing facility was originally going to be taken over by Microsoft, but this is no longer the case. However, it has been decided that Microsoft will take over the management of not only Nokia.com, but also Nokia's social media sites. Microsoft will also take on Nokia's 21 Chinese workers rather than leaving them to continue working under Nokia.
Image Credit: Tanjala Gica / Shutterstock
-

The most popular stories on BetaNews this past week: April 13 -- April 19
Publié: avril 19, 2014, 2:13pm CEST par Mark Wilson
 It's nearly a week since Microsoft ended support for Windows XP, but there are still around a quarter of Avast customers who plan on sticking with the old dog a little longer. What is perhaps more shocking is the revelation that over one fifth of those surveyed had no idea that support was coming to an end! For those living more on the cutting edge, good news came for Chrome users who found that their browser of choice gained support for Office Online. Microsoft may be leaving users of Windows XP out in the cold, but this is to be expected after so long. Users of Windows 8.1 who have opted to forego the pleasures of installing the recently released Update will find that their operating system is also not supported, as no further security updates will be made available until the confusingly named Update is used to update Windows 8.1 to Windows 8.1 Update. Got it? Good! Some business users who had trouble grabbing the download have been granted slightly longer.
It's nearly a week since Microsoft ended support for Windows XP, but there are still around a quarter of Avast customers who plan on sticking with the old dog a little longer. What is perhaps more shocking is the revelation that over one fifth of those surveyed had no idea that support was coming to an end! For those living more on the cutting edge, good news came for Chrome users who found that their browser of choice gained support for Office Online. Microsoft may be leaving users of Windows XP out in the cold, but this is to be expected after so long. Users of Windows 8.1 who have opted to forego the pleasures of installing the recently released Update will find that their operating system is also not supported, as no further security updates will be made available until the confusingly named Update is used to update Windows 8.1 to Windows 8.1 Update. Got it? Good! Some business users who had trouble grabbing the download have been granted slightly longer.Post Build, following Microsoft's announcements about universal apps for Windows 8.1 and Windows Phone, app prices are changing -- but consistency seems to be an issue. The hotly anticipated Windows Phone 8.1 was released to developers, but Mihaita was on hand with a guide that allows anyone to grab themselves a copy of the latest update. If you're on the lookout for a new Android handset, Joe puts forward a compelling argument in favor of the HTC One M8.
When it comes to home entertainment, around a tenth of people intend to "cut the cord" in the coming year. Comcast customers who are planning on going down this route will be heartened by the news that their ISP’s speed tests have improved, making for a more enjoyable streaming experience. Roku fans have a new search tool to use on Android and iOS, and two new keyboards look set to make life easier for those with home theater setups. The Logitech Harmony Smart Keyboard now offers support for Amazon Fire TV, while Microsoft's All-in-One Media Keyboard makes light work of controlling media from the sofa.
Writing for websites opens one up to all manner of problems, but one of the most common is choosing between tailoring content for readers or for Google. I argue that it is readers who should be placed first, but there needs to be a much wider change in attitudes if writers are to cater to their audiences rather than bowing down to Google and bending to its every whim. The news was that Google is trying to coerce websites into using encryption by threatening lower searching ranking for those who don't. Misplaced power? You decide. Other Google news saw Gmail users gaining the ability to insert auto-backup photos into their emails.
The security world may have been abuzz about Heartbleed over the last couple of weeks, but the current trend for BYOD is also an on-going cause for concern. On the subject of Heartbleed, anonymizing web service Tor was still feeling the bite -- there are concerns that a large number of nodes that make up the network are running vulnerable versions of OpenSSL. Taking them offline would reduce the network in size by around 12 percent. If you're not concerned about security risks, Nokia Lumia 2520 have something else to worry about -- being shocked by their device's charger.
Earlier in the month there was outrage that Brendan Eich had been appointed as the CEO of Mozilla. His views on gay marriage meant that he was not destined to remain in the position for long. This week, a new interim CEO was put in place who will hopefully stick around for slightly longer. In similar news, the appointment of Condoleezza Rice to the Dropbox board of directors caused something of a stir, and the cloud storage firm took steps to try to calm concerns raised by users. In rather less controversial news, Dropbox also expanded its operations into Asia Pacific.
Well, that’s another week worked through. Enjoy Easter if that's your thing, and we'll see you next week for more of the same in the way of newsy goodness.
Image Credit: vinz89/Shutterstock
-

Amazon and Samsung launch custom Kindle for Samsung service
Publié: avril 17, 2014, 7:46pm CEST par Mark Wilson

Not content with already having a Kindle app for Android devices, Amazon has joined forces with Samsung to launch Kindle for Samsung. The slightly unnecessary venture brings a new custom ebook service to owners of devices from the South Korean firm and launches on the Galaxy S5 immediately. Other Samsung Galaxy handsets and tablets will gain access to the app shortly afterwards, providing they are running Android 4.0 or newer. Of the millions of books and magazines that will be available through the service, more than 500,000 of the titles will be exclusives.
At the same time as the Kindle for Samsung launch, the two companies are also launching Samsung Book Deals. This enables Galaxy owners to obtain up to 12 free ebooks per year, making a selection from a choice of four each month. With the promise that "each book is chosen specifically for Galaxy smartphone and tablet users from a wide selection of prominent titles", there should be something for everyone.
Vice President, EU Kindle, Jorrit Van der Meulen said: "Were thrilled that Samsung has chosen Kindle as their eBook provider. People around the world will have instant access to the best digital bookstore and reading experience, including more than half a million titles that are only available from the Kindle Store, and innovative features like Whispersync, Time to Read and much more".
Samsung is similarly upbeat about the joint venture, saying "We are delighted to be able to deepen our long-standing relationship with Amazon and offer Kindle for Samsung as the perfect app for reading on a smart device. With this service we demonstrate our commitment to creating and broadening key content partnerships that deliver rich and personalized experiences for our customers".
The lure of a free book each month is obviously attractive, but one can't help but feel that a device-specific version of Kindle is somewhat superfluous to requirements. Time will tell whether it is a valuable partnership.
Photo Credit: connel/Shutterstock
-

Post Heartbleed, Tor could significantly reduce capacity -- but is it enough?
Publié: avril 17, 2014, 7:00pm CEST par Mark Wilson

It seems that there have been few big names left unaffected by the Heartbleed bug in OpenSSL. Google may have rushed to patch the flaw, but the number of websites and services that fell foul of the discovery is staggering. It seems that even stalwarts of security are finding themselves in troubled waters, and this includes anonymizing service Tor.
Put very simply (very, very simply!), Tor works by not only encrypting data that is transferred online, but also bouncing it around a number of servers, making it all but impossible to trace to a particular user or computer. It transpires that some of the Tor nodes that are used in the process are running versions of OpenSSL that are vulnerable to Heartbleed, and this has led to calls for the affected nodes to be closed down. Writing to the Tor mailing list, developer Roger Dingledine suggests that up to 12 percent of the network's capacity may be lost if all of the vulnerable nodes are taken offline.
Security and anonymity are at the very heart of Tor, so it is understandable that users would want steps to be taken to eradicate such a well-publicized flaw. Reducing capacity by an eighth would be a serious step to take, but Dingledine has already built up a list of nodes that should be rejected due to their vulnerable status. This is a list that is almost certain to grow: "I/we should add to this list as we discover other relays that come online with vulnerable openssl versions".
But the problem with Tor is the very fact that it is anonymous. It is something of an untamed beast, and while not quite running out in the wild, it is difficult to determine the exct size of the network or to work out exactly which areas of it are affected. It is a mammoth task to hunt down all of the nodes that are running Heartbleed-prone versions of OpenSSL. But there is also the fear that this could be a case of closing the stable door after the horse has bolted. If vulnerable nodes have already been discovered and exploited, the inner workings of Tor could have been investigated. It is very hard to tell whether any lasting damage has been done, but faith is likely to wane as a result, anyway.
Image Credit: Ase / Shutterstock
-

Nokia issues warning for potentially shocking Lumia 2520 charger
Publié: avril 17, 2014, 3:27pm CEST par Mark Wilson

Nokia is warning owners of the Lumia 2520 tablet that they should stop using the European and UK versions of the AC-300 charger. The warning affects customers in Austria, Denmark, Finland, Germany, Russia, Switzerland and UK, with tablets owners being warned to "suspend use of the charger until further notice". At the moment there is no word on whether or not a full recall will be made, but the problem also affects the Lumia 2520 travel charger that was available in those countries and the US.
Unlike other charger problems that have emerged in recent times, Nokia's warning does not relate to an overheating issue, but the risk of electric shock. This time it has been determined that in "certain conditions" -- which Nokia does not specify -- the charger's plastic cover could work loose and come off, exposing internal components that "pose a hazard of an electric shock if touched while the plug remains in a live socket".
Nokia says that around 30,000 chargers are affected by the problem, including some 600 travel chargers sold in the US. The company points out that the chargers were manufactured by a third party and stresses that there have been no reported incidents as a result of the findings:
"While there have been no confirmed consumer incidents related to this potential quality issue, product quality and safety are top priorities at Nokia. We apologize to the owners of the Lumia 2520, and we are working with urgency to minimize the inconvenience".
For the time being, sales of these chargers have been halted, and customers are advised to keep an eye on the announcement page for further information. Owners of the Lumia 2520 find themselves in something of an awkward position as the charger features a unique design, eliminating the possibility of 'borrowing' a charger from another device. The 2520 has fairly impressive battery life… but not that good.
-

New CEO ahoy! Mozilla grows a Beard… will balls follow?
Publié: avril 15, 2014, 9:25pm CEST par Mark Wilson

Emerging from what it describes as an "unexpected leadership transition", Mozilla announces its new CEO, albeit an interim replacement. The vacancy opened up a couple of weeks ago after the departure of Bendan Eich following outrage from developers that someone opposed to gay marriage should be placed at the head of a company. The pitchfork wielding and flaming torch brandishing mob, got their way as Eich "stepped down".
It's not really clear whether he jumped or whether he was pushed -- what is publicly announced is not necessarily representative of what has taken place behind boardroom doors -- but there's now a new man at the top. Announced with the Mozilla Blog, Chris Beard's appointment is apparently something that had been under consideration for some time: "we began exploring the idea of Chris joining the Board of Directors some months ago." Executive Chairwoman Mitchell Baker described Beard as someone who has "been actively involved with Mozilla since before we shipped Firefox 1.0, he’s guided and directed many of our innovative projects, and his vision and sense of Mozilla is equal to anyone’s".
It is possible that Beard will become the CEO proper in due course. He "is the right person to lead us through this time and he is a strong candidate for CEO", but only time will tell whether he manages to hold onto his position for more than the eleven days Eich managed. What is interesting about the blog post is that Baker says "Mozilla needs to act quickly and decisively", which is ironic when you consider how indecisive it was about Eich. He's in as CEO. Oh, no! People don't like the views we've known about for years. He's out.
Maybe, when Chris Beard's successor is found, Mozilla will be slightly more strong-willed and stick to its decision rather than bending to the will of the baying masses. It is certainly true that Eich's views are objectionable to many -- myself included (although I would defend his right to hold those views) -- but so what? His views on sexuality had no bearing on his ability to do the job he was appointed to do. If Chris Beard expresses the view that he opposes the idea of a meat-free diet should I, as a vegetarian of approaching two decades, have the right to demand his head? Well… yes, I have that right, and the right to express my dislike of his views, but as a reasonable human being I can see that views on vegetarianism are simply not going to affect someone's work. Unless they happen to be appointed head of an abattoir.
Let's just hope that Chris Beard, or the fulltime CEO who fills his shoes further down the line, doesn't have any skeletons in his (or her) closet, or Mozilla may have to grow some balls and just keep them in place lest we descend into a never-ending game of hunt the new CEO.
Image Credit: auremar / Shutterstock
-

Google is a bully, but that's not necessarily a bad thing
Publié: avril 14, 2014, 4:31pm CEST par Mark Wilson
 Google has a lot of mud thrown at it, and while a lot of it slides off, there is a good proportion that sticks. There are a variety of accusations levelled at the search giant -- evil, self-serving, monopolistic, nosey, invasive, overbearing, corporate, et cetera, et cetera -- but could it be that the power the company wields is actually a good thing? Could Google use the sway it holds over website owners to make the web a better place? But before we start praising Google, there's no harm in sticking the boot in first, eh?
Google has a lot of mud thrown at it, and while a lot of it slides off, there is a good proportion that sticks. There are a variety of accusations levelled at the search giant -- evil, self-serving, monopolistic, nosey, invasive, overbearing, corporate, et cetera, et cetera -- but could it be that the power the company wields is actually a good thing? Could Google use the sway it holds over website owners to make the web a better place? But before we start praising Google, there's no harm in sticking the boot in first, eh?For many people, Google is a bully. In the constant search for page views, ranking in Google matters -- it matters a lot. My colleague Joe Wilcox argues that writers should write for themselves and their readers rather than Google -- something I would strongly advocate -- but until this notion gathers momentum, there are still countless bloggers panicking themselves silly about what impact the latest search algorithm changes will have on their position in search results. It can be a constant game of catch-up, requiring endless changes to optimize content for maximum visibility -- all too often at the expense of readability and reader experience.
In some ways Google has killed the web. In a bid to stand out, stories have to use ever-more sensational, tabloidistic headlines ("Oh, j'accuse, monsieur Wilson!"). There's the old tale that "dog bites man isn't new, man bites dog is". Battling for attention leads to increasingly eye-ball-grabbing ideas, more extreme content, with the real story, the real narrative, the human element getting lost along the way. In this method Google can be seen as shaping the web in a negative way -- although, as Joe would argue (and I would agree), there is no need to chase for Google's approval.
Whatever your opinion of Google, there is something that's undeniable. Google has power. Lots of power. What if it were to use that power for good? In many ways it already does: there are lots of charitable ventures and numerous very worthy programs underway, for example. Google has been one of the many web companies pushing for greater transparency about government spying online (although it has been suggested, including by myself, that this is something of a public relations exercise, and not entirely altruistic). A report in the Wall Street Journal suggests that Google might now try to push websites into using encryption -- almost inevitably in return for better rankings in search results.
Websites that use encryption protect their users by making it more difficult to spy on activity and it's something that advocates of online privacy have been pushing for some time. If Google lends its support to a campaign, it is likely to gain far more attention than might otherwise have been the case. But, Google being Google, as soon as the company gets involved, suspicions are raised. "What is it after?" "What's in it for Google?"
It does show the power that Google has to shape the present and future of the web. Whether for the greater good or for its own interests, all the company needs to do is dangle the carrot of improved search rankings -- or, conversely, brandish the rod of Being Shunned By Google -- and website owners will bend to the company's will in droves. Encouraging the adoption of encryption is something that should be welcomed, but it does raise some interesting questions about the politics of interacting with Google. To quote a T Reznor, Esq., "Bow down to the one you serve. You're going to get what you deserve".
So what do you think? Is it OK for Google to flex its muscles and abuse its power for the good of the web? Do the ends justify the means? Or can Google just never be trusted?
Photo credit: jcjgphotography /Shutterstock
-

The most popular stories on BetaNews this past week: April 6 -- April 12
Publié: avril 12, 2014, 10:13am CEST par Mark Wilson
 Microsoft was in the headlines this week not for launching new products but for, finally, bringing an end to support for Windows XP. Yes, the now ancient and decrepit -- although still much loved and used -- operating system is no more. It will be interesting to see how long it manages to survive now it has been officially dropped -- some are suggesting that a move to Linux might be in order, or even a switch to Chromebook. But, of course, it hasn’t all been about XP. After the announcements at Build, Joe Belfiore revealed on Twitter that developers will be able to get their hands on Windows Phone 8.1 in the "first part of April".
Microsoft was in the headlines this week not for launching new products but for, finally, bringing an end to support for Windows XP. Yes, the now ancient and decrepit -- although still much loved and used -- operating system is no more. It will be interesting to see how long it manages to survive now it has been officially dropped -- some are suggesting that a move to Linux might be in order, or even a switch to Chromebook. But, of course, it hasn’t all been about XP. After the announcements at Build, Joe Belfiore revealed on Twitter that developers will be able to get their hands on Windows Phone 8.1 in the "first part of April".There is also renewed interest in Windows 8.1 following the release of Update, and Microsoft published a guide to making the most of the new features and options. Will the operating system be viewed as fondly as XP in years to come? Only time will tell. Working in conjunction with Google, Microsoft also gave a new and improved YouTube experience to Xbox One owners.
It has been an interesting week on the security front. Derrick looked at the question of whether Apple devices really are safer and more secure than their rivals. There have been a large number of high-profile security breaches in recent months, but the flaw found in OpenSSL is probably one of the most wide-reaching -- although Google was quick to jump in and get to work getting things sorted out , so were we right to worry ? Something of a man after my own heart, Derrick donned his cynical cap, investigating why 3D TV in the home has turned out to be such a damp squib.
I’ve said it before, and I’ll say it again: I’m not a fan of wearable tech. But that aside, will.i.am’s soon-to-be-launched smartwatch is sure to generate a good deal of interest; it certainly seems to have the looks to make it stand out from the crowd. There are promising things ahead for other mobile devices, thanks to Qualcomm’s announcement about the Snapdragon 810 and 808, but the new processors are not expected to hit smartphones and tablets until the first half of 2015. For now, handset lovers will have to content themselves with the likes of the HTC One (M8) which, despite the silly name, turns out to be a superb piece of kit.
This has been a slightly quieter week than normal, but hopefully things will pick up again over the next seven days. In the meantime -- enjoy the weekend!
Image Credit: vinz89/Shutterstock
-

The most popular stories on BetaNews this past week: March 30 -- April 5
Publié: avril 5, 2014, 10:01am CEST par Mark Wilson
 It's difficult to deny Microsoft at least some of the limelight this week as the Build developer conference generated some interesting news. Bringing Windows version numbers in line with each other, Windows Phone 8.1 was finally revealed, complete with a notification center and Siri-like Cortana. The highly anticipated Windows 8.1 Update (which you may have heard something about) was official unveiled and given a launch date of April 8. Wayne, for one, liked what he saw.
It's difficult to deny Microsoft at least some of the limelight this week as the Build developer conference generated some interesting news. Bringing Windows version numbers in line with each other, Windows Phone 8.1 was finally revealed, complete with a notification center and Siri-like Cortana. The highly anticipated Windows 8.1 Update (which you may have heard something about) was official unveiled and given a launch date of April 8. Wayne, for one, liked what he saw.Microsoft came over all open source, making the Roslyn compiler as well as WinJS freely available. Brian was pleased with the tech giant's latest moves, proclaiming Microsoft is now back. Build also gave us a sneaky glimpse of an upcoming, but as yet unnamed, version of Windows that features the return of the Start menu -- all of this chopping and changing is getting confusing. Maybe next on the list of things to do with Windows will be getting rid of those apps and features that should have been killed some time ago.
While Build may have been the big event of the week, it was also the exciting named World Backup Day which has the aim of encouraging computer users to safeguard their files. If you have considered using Dropbox as an online backup medium, you may have been concerned to learn that the company was issuing DMCA notices to users about files they had stored privately. But Dropbox was quick to respond, explaining that an automated system tracked down duplicate files on the network, and assuring users that their documents were not being looked at.
Another big date this week was April Fools' day. Traditionally the day on which all sorts of practical jokes are played, Brian was far from impressed by one of Google's offerings -- and then a couple of days later, much the same feature was unveiled as being genuine. Suggestions that the US government could save a fortune by changing the font used on printouts were not a joke, but some people did question the amount of money that could saved.
If a recent report is correct, more than half of people surveyed said they felt that the web was an unsafe place to voice opinions -- I'd better watch out, in that case! The deadline approacheth for the end of support for XP, and while many people are resolving to stick with their preferred operating system, it seems that those who are moving away from the aging software are migrating to Windows 7 rather than Windows 8. Little wonder, then, that Windows 8.x is faring so badly.
In security news, Internet Explorer was found to be the web browser that offers the best protection against social engineering attacks, but this will be of little consolation to victims of ransomware which is becoming increasingly common. Neither is it much help for owners of routers that are vulnerable to attack.
The mobile market is one that is dominated by a handful of names, but in Europe it is Motorola that is starting to gain ground. In an interesting twist, BlackBerry announced that it was no longer in love with T-Mobile and that its handset would no longer be available through the mobile operator. Turkey continued its attack on freedom of access to the internet by intercepting Google's Public DNS. Whether it was a matter of freedom of speed, gay rights, the vocal majority winning, or someone just looking to save face, after the furore surrounding Brendan Eich, the CEO of Mozilla, stepped down from his position at the top.
There were also a couple of birthdays this week. Microsoft was founded an astonishing 39 years ago, and Google celebrated the tenth anniversary of Gmail... and... that's your lot! Time to relax with a nice glass of something strong.
Oh... one last thing. If you have a Nest Protect smoke alarm, you might want to invest in an alternative. Safety concerns have led to the device being taken off sale and a key feature has been remotely disabled. Maybe a double is in order...
Join us for more of the same over the next seven days.
Image Credit: vinz89/Shutterstock
-

Nest halts sales of smoke and carbon monoxide alarm amid safety concerns
Publié: avril 4, 2014, 1:12am CEST par Mark Wilson

When people invest in a smoke alarm, it is done with the intention of making the home safer. Should a fire start during the night, for instance, it's good to know that there's something there to alert you. While most smoke alarms are fairly basic affairs, there are some more advanced models available, including from Nest Labs -- the company behind intelligent thermostat controls and the Nest Protect smoke alarm. But there are safety concerns about the device which could mean that the sounding of an alarm is delayed, leaving owners to burn to a crisp in their beds. Perhaps.
In a message on the Nest website, the company's CEO Tony Fadell explains that a feature of the smoke alarm is being disabled and the sale of units is to be stopped. Nest Protect -- which has the tagline "Cares for your family as much as you do" -- includes a feature called Nest Wave. The idea is that should you accidentally set off the alarm by burning the toast, you can shut it up by waving your hand in front of the device. The problem is that the feature can be, to use Fadell's words, "unintentionally activated".
Citing a "unique combination of circumstances", the CEO explained that recent laboratory tests had led to the discovery that the alarm could be accidentally silenced -- but insists that Nest is "not aware of any customers who have experienced this". As a precautionary measure, Nest Wave has been disabled. Visit the product page and you can read the following description of the feature:
No more frantically swinging towels at the smoke alarm to quiet it down. If there’s a nuisance alarm, just stand under Nest Protect and wave your arm to hush the alert. As you wave, your hand should be 2 to 8 feet away from the alarm.
But on the main Nest page, Nest Protect is now listed as being "temporarily unavailable".
There's no word on exactly when the product will go on sale again, but it looks like it is some time off.
Once we have a solution that ensures Nest Wave works as intended, we will update our software to turn this feature back on. This will only happen after extensive testing and once we have received approval from safety agencies in the the US, Canada and UK. We expect this to take at least two or three months and we’ll continue to update you as we have more information.
Customers who are unhappy with the news are able to return their Nest Protect for a full refund.
Image Credit: Dale A Stork / Shutterstock
-

Stop Google+ broadcasting the number of profile views you've received
Publié: avril 2, 2014, 4:37pm CEST par Mark Wilson
It has often been said that making use of any social network is an exercise in vanity or narcissism. The likes of Facebook, Twitter, Google+ and other similar tools give anyone a platform to voice their views, concerns, complaints and anything else they feel inclined to get off their chest. But what matters about each of these social networks -- for the vane narcissist, at least -- is the number of people who are actually reading the words that are published. Unburdening online can be a wonderfully cathartic experience, but all the better if it is read by tens of thousands of people rather than just hundreds.
Each network gives you its own way to keep track of your potential audience. On Facebook, it's easy to keep track of the number of friends you have, while on Twitter it's the number of followers that's important -- as well, of course, as the coveted blue verified badge. Similarly on LinkedIn, it is easy to see how many people you’re connected to, and in the case of Google+ you can check how many people have circled you. But then there is the matter of how these figures translate into actual views.
Yesterday, Google started to roll out a new feature to Google+ users -- the ability to see how many times your profile and content have been viewed. If you’re using Google+ for business purposes, this can be a useful way to keep track of what type of content is pulling in the most pairs of eyes, but it's also a great way to feed the ego... just watch the counter creeping up each day. Of course, there is also potential for the number to be rather soul-destroying, but I'm sure that's not the aim.
If you notice that there's a view count in your profile and you'd rather it vanished -- these numbers can be embarrassing, after all -- it's easy enough to get rid of it once and for all.
- Click the Home button to the upper left of your profile page and click the Settings link in the menu that appears.
- Scroll down to the Profile section and clear the checkbox labelled "Show how many times your profile and content have been viewed".
That's all there is to it!
-

LinkedIn 'hacking' tool Sell Hack no longer exposes user email addresses
Publié: avril 2, 2014, 11:50am CEST par Mark Wilson
One of the great things about social networks is that it is possible to connect with people without the need to share email addresses. This means that you can remain "friends" with someone on Facebook, but not get to the point where you're handing out your email address and worrying about checking your inbox. The same is true of LinkedIn, but the difference with this "professional network" is that you're probably connecting with a larger number of people you would rather didn’t have your personal contact details. This comforting level of security was wiped out by Sell Hack.
This free browser extension -- available for Firefox, Chrome and Safari -- could be used to expose the email address associated with any LinkedIn account, regardless of whether you are connected to the person you are, essentially, spying on. Perhaps understandably, this caused a degree of upset and resulted in LinkedIn sending a cease and desist notice to the extension's developers. Sell Hack adds a "Hack In" button to social network pages which, when clicked, reveals the email address used by the account owner to create their page.
At least this was the case. Sell Hack has bowed to pressure and has announced in a blog post that "SellHack plugin no longer works on LinkedIn pages". But it's far from being all bad news for the team. The media coverage has created a storm of interest, and on 1 April "we had more signups today than in our first 60 days combined".
The post also explains that "we are building a better product that does not conflict with LinkedIn’s TOS" and anyone signing up for a new account with the service receives an email that says "we received a letter from LinkedIn and decided to suspend the service until we are compliant with their terms of use. Don’t worry, we’re already working on a solution". To counter claims that Sell Hack is "sneaky, nefarious, no good, not ‘legitimate'", the developers insist that "we only processed publicly visible data from LinkedIn based on your profile permissions".
For the time being it seems as though Sell Hack has been stopped in its tracks, but it's unclear how long this will be the case. The level of interest surrounding the story is fascinating -- over the past 48 hours there have been countless articles and blog posts about Sell Hack. With Sell Hack's insistence that it only uses publicly visible data in its analysis, it's difficult to see quite where all of the upset comes from. Commenters have suggested that LinkedIn is upset because the tool "erodes its business model for LinkedIn premium".
In an email to BetaNews, LinkedIn said: "There were a few news outlets that erroneously reported that premium LinkedIn members get access to email addresses. That is false... There are a number of different premium subscriptions LinkedIn members can get. One of the things premium members get are InMails. [These] are one-to-one messages between LinkedIn members. Those InMails don’t give you anyone’s email address though. The reason we issued Sell Hack a cease and desist was because it was violating our Terms of Service and our User Agreement".
So what do you make of it? Is (or was) Sell Hack really a privacy concern, or has it been stamped upon for potentially stemming a flow of income for LinkedIn?
-

Switching to Garamond could slash US government printing costs by almost a quarter
Publié: mars 31, 2014, 10:36pm CEST par Mark Wilson

A Pittsburgh teenager has worked out that the US government could slash millions from its costs by making a simple change to IT policy. Suvir Mirchandani's suggestion is laughably simple, but it is one that should hold water -- although I'll admit to not fully following through with the math to determine the precise levels of savings that could be achieved. Suvir proposes that a move away from the most commonly used fonts, such as Times New Roman, in favour of a lighter typeface such as Garamond could reduce the US government's printing costs by a colossal 24 percent.
There can be few printer owners who have not cursed the price of ink -- it is one of the costs of ownership that can creep up on the unsuspecting printer user. You might think that the paperless office was, if not here, well on its way to arriving. It's something that has been talked about for years now, and there has been a general move toward eliminating some paper versions of documents in favour of electronic copies. But there are still an unbelievable number of printed documents out there.
With a printing budget of $1.8 billion each year, any savings that could be made by the government could very easily mount up. Suvir had already managed to calculate that his school district's printing costs could be reduced by $21,000 each year, he was challenged to scale up his project to see how much could be saved by the federal government. The numbers are somewhat mindblowing. By doing nothing more than printing documents in Garamond, federal government could slash its costs by $136 million each year.
If this is not impressive enough, factor in state governments and the figure jumps to $370 million. There's potential to take things even further. If printer manufacturers switch focus to quantity rather than quality, printer owners could expect to get more documents per dollar of ink; in addition to using a lighter font, defaulting to draft mode rather than the highest quality print setting could cut costs even more.
But of course, there is also a change in user mindset needed. There are still huge numbers of people printing out emails and other documents when an on-screen version would suffice. Naturally, there are times when a hard copy is essential, but a faster move to digitization is needed. Suvir's work shows the financial savings are there to be made, and there are also environmental concerns to factor it.
So -- do your bit... switch to Garamond in draft mode!
Image Credit: komar_off / Shutterstock
-

5 features of Windows that need defenestrating -- including IE
Publié: mars 29, 2014, 11:27pm CET par Mark Wilson
 Defenestrating? Pretentious? Moi?! How could you?!
Defenestrating? Pretentious? Moi?! How could you?!Don't get me wrong, I love Windows. A fanboy I am not -- I'll quite happily pick holes in Microsoft's operating system -- but for the most part I do love it. While I have a great deal of time for Windows, it doesn’t mean there isn't room for improvement. By this I don’t mean that Microsoft needs to bring back the Start menu or start copying features from OS X or Linux, rather that it's time to have spring cleaning. In just over a week, Windows XP will be consigned to the OS graveyard, but what about Windows 8.1? The latest version of Windows doesn't need to be killed, but there are lots of features that need to be put out of their misery.
So, here I stand, bolt gun in hand, ready to administer swift and ruthless justice to those elements of Windows that are just pointless, that have outstayed their welcome, or have been done so much better by someone else. It's not just a rock star who can throw things out of windows, you see.
1. Paint
It's almost too easy a target, but there is just no reason for the existence of Paint. It can be used for no level of artist work (unless you're one of those odd people with far too much time on their hands who like to post YouTube videos demonstrating how to replicate the Mona Lisa in Paint in a mere 86 hours) -- it's not even useful for screenshots as the Snipping Tool is available for anyone unwilling to investigate the plethora of more powerful alternatives. This is a good opportunity to plug Paint.net a surprisingly powerful little image editor which actually started life at Microsoft. It broke free and evolved into something wonderful -- perfect for quick and dirty day-to-day editing.
2. Compatibility mode
Be decisive. What do you want to use -- an old app or the latest version of Windows? Pick your side and stick with it... none of this halfway house stuff for ancient apps that really should be moved on from. OK? Oh, alright, a slight concession. If you have an old app that you really, really, really can’t live without, set up a virtual machine and keep it separate from everything else. But honestly, you should be able to find an alternative. Decide which decade you want to live in, and act accordingly.
3. Disk Defragmenter
Seriously, who bothers with defragging these days? Things have improved a little over the years, but the offering found in Windows is still so slow, cumbersome and limited compared to other tools that are out there, it's hardly worth bothering with even if you do feel that way inclined. There's a move towards SSDs these days and -- although there is ongoing, tedious debate about it -- it's not really a good idea, or even worth, defragging them. Another one to consign to the history books.
4. Internet Explorer
A controversial choice? No. Internet Explorer is a fat, behemoth of a beast struggling to catch up with the browsers that overtook it in terms of features, power and security years ago. There have been at least two historical instance of Internet Explorer causing a stink, and each time it managed to escape execution. The early days of IE's integration into Windows upset many people, but it was allowed to stay. In later years, Microsoft was forced to offer users a choice of browsers -- this was the right move, but it didn’t go anywhere near far enough. Internet Explorer is a relic from times gone by. It is under-powered, limited and lacks support for the kind of basic extensions we just expect to find elsewhere. It is a lazy browser that offers the bare minimum and nothing more. Users shouldn't have to settle for this -- there's plenty of choice out there and Internet Explorer being the default browser just gets in the way of enabling the discovery of alternatives. Kill it. Kill it with fire.
5. WordPad
Sure, it's come a fair way since the days of Write, but WordPad is still fairly pointless. Sure, it can be used to view Word documents, but why not just build in a file viewer -- remember the likes of QuickView Pro? Yeah, it's arguably more powerful than Notepad (although I'd argue that Notepad is infinitely more useful), but damn it's limited. It's a half-hearted effort, and you can’t help but feel that Microsoft shouldn’t have bothered. Just for the space-hungry interface it deserves to be dragged through the streets and shot at dawn.
I could go on, but I'd be in danger of talking myself out of liking Windows. I realize that the answer to my dislike of many of the features I have singled out would be to ignore them; but that's not the point. These are the very features that are holding Windows back. It needs to break free from the shackles of the past and become something new and exciting. Forget fancy new interface changes -- built in tools matter more.
How about you? Are there any features of Windows that you would condemn to Room 101?
Image Credit: Joyce Vincent / Shutterstock
-

The most popular stories on BetaNews this past week March 23 -- 29
Publié: mars 29, 2014, 2:55pm CET par Mark Wilson
 Microsoft has flirted with Apple's iPad on a couple of occasions this week. Early on in the week there was the case of a 12-year-old girl who wanted nothing more than an iPad Mini. Microsoft stepped in and managed to convince her that the Surface 2 was the way ahead. Way to spin! But this was not the big Microsoft-iPad news. In a move that many saw as almost sacrilegious -- but one that was welcomed by just about the same number -- Microsoft Office, finally, made its way onto iPad. This wasn't the only release from Microsoft this week -- the source code for early versions of MS-DOS and Word for Windows was made publicly available. Having faced criticism for the way it approached a recent investigation, Microsoft pledged that it would no longer read customer emails during the course of an investigation without getting law enforcement involved.
Microsoft has flirted with Apple's iPad on a couple of occasions this week. Early on in the week there was the case of a 12-year-old girl who wanted nothing more than an iPad Mini. Microsoft stepped in and managed to convince her that the Surface 2 was the way ahead. Way to spin! But this was not the big Microsoft-iPad news. In a move that many saw as almost sacrilegious -- but one that was welcomed by just about the same number -- Microsoft Office, finally, made its way onto iPad. This wasn't the only release from Microsoft this week -- the source code for early versions of MS-DOS and Word for Windows was made publicly available. Having faced criticism for the way it approached a recent investigation, Microsoft pledged that it would no longer read customer emails during the course of an investigation without getting law enforcement involved.Windows XP may be in its death throes, but this isn't going to stop people from using it. To help keep these hardy fellows safe, Malwarebytes announced that it would keep its users protected for life. It's not just XP that Microsoft is lowering into the grave, Office 2003 also finds itself six feet under. As the door on XP closes, another one opens -- or closes, depending on how you look at it. The purchase of Nokia's Devices and Services division is due to close in April after initially facing some delays.
While Joe bemoaned the DRM crippling of his music collection, fears were mounting that changes to tax laws in the UK and Europe could lead to an increase in the cost of digital downloads. But while the cost of apps and MP3s might be on the up, the cost of life in the cloud is dropping -- hooray!
This weekend sees the first gay marriages taking place in the UK, but in the world of software developers boycotted Firefox after it was suggested that the new CEO is opposed to same-sex nuptials. Security was breached at Basecamp when a huge DDoS blocked access to the site which found itself held to ransom by the attackers.
HTC took the wraps off the latest additions to the One range -- the HTC One (M8), and Mihaita felt the accompanying ad was a little cocky. Odd happenings in South Korea saw the Galaxy S5 being sold by mobile operators two weeks ahead of the official launch. To help young people save up the money needed to invest in a new handset, Spotify introduced a new lower pricing structure for students. Facebook, on the other hand was throwing cash around like it was going out of fashion, chucking $2 billion on virtual reality startup Oculus VR.
This was an interesting week for wearable tech. I previously talked about (ok, moaned about) the pointlessness of most wearable tech, inadvertently pre-empting Google's defense of Google Glass. In sticking up for a product that hasn’t even launched yet, it did feel as though Google was suffering from a case of "the lady doth protest too much", but a few days later it all became clear as the company announced it was joining forces with the firm behind Ray-Ban. It's almost as though Google has been laying the groundwork... but then I am a big cynic! But as if to prove it's not just me who likes to view things slightly skeptically, Alan suggested that Apple has already lost the wearable race to Android.
Mice reviews don’t come around all that frequently these days, but then you turn your back for a little while and two come along at once. Alan took a look at the Rapoo T120P Touch Mouse complete with its wheel-less scrolling zone featuring haptic feedback. At the rather less fancy end of the spectrum, I looked at the Microsoft Wireless Mobile 1850 Mouse, coming to the conclusion that it was very much what you would expect from a low-cost Microsoft mouse -- cheap, cheerful, effective.
One of the odder stories of the week was that Kim Dotcom -- yes, him -- is embarking on a political career, with a manifesto that focuses mainly on freedom online. There is no hope for humanity. The policies may be of interest to those in Turkey who have found that both Twitter and YouTube have been blocked. Some interesting changes to the law in the UK mean that CD and DVD ripping will soon be legal.
Slipping into sarcasm mode, I revelled in the fact that a new viewing option in Gmail makes "promotional emails" more prominent. Rejoice, one and all!
Gazing into my crystal ball I can foresee another hectic week ahead. I'm off to have a lie down in preparation.
Image Credit: vinz89 / Shutterstock
-

The cheap, cheerful and lovable Microsoft Wireless 1850 mouse [Review]
Publié: mars 27, 2014, 4:20pm CET par Mark Wilson

What can you get for $15 these days? Not a lot, really. A few Starbucks, perhaps, a burrito and a couple of slices? Or you can get yourself a cheaper, almost throwaway, replacement mouse to chuck in your laptop bag. This is the bill that the Microsoft Wireless 1850 fits. The mouse was announced just recently, and we've got our hands on one to put through its paces. To cut to the chase, this is a perfectly acceptable mouse, but it ain't going to blow your mind.
This is a mouse designed with the pocket in mind in more ways than one. Yes, it's super low-cost, but it's also super lightweight; and I mean that both in terms of mass and features. Oh, at this point it's worth highlighting something I touched upon the other day when talking about the price of digital downloads. While in the US this mouse costs $14.95, over here in the UK it has a £16.99 price tag. Sure, US buyers have to factor in taxes, but $14.95 should translate into about £9, so the trip across the ocean from One Microsoft Way has resulted in the price almost doubling!
Still, whatever way you look at it, this is a cheap mouse, you just happen to get a better deal if you find yourself on the right side of the Atlantic. While a range of colors is promised for later in the year, Flame Red, Orchid Pink, and Pantone Purple (plus Wool Blue for the US market), it is the Coal Black that's available at the moment. At first glance, this is a simple mouse. At second, third and indeed fourth glance, it is also a simple mouse. But there's nothing wrong with that. Nothing at all. This is a mouse that's here to get a job done with no unnecessary messing about.
The symmetrical design means it can be grasped by right-handed users and southpaws with equal comfort, while the ambidextrous out there will be able to throw the mouse between hands with gay abandon. The mini USB wireless receiver slips into a perfectly-sized cutout in the battery compartment, but there's none of the fancy magnetic holding it in place, just good old friction.
The peripheral does feel good in the hand, but while the scrollwheel is comfortable to use, it does have a slightly cheap feel to it. This isn’t a sense one gets from the mouse on the whole, also it is clearly a basic, plasticky affair. The wheel is rubbery, but has no textured grip. It's a personal thing, but I prefer my scrollwheels to have a bit of grip rather than being smooth.
Ultimately this is a mouse that achieves what it sets out to. It is cheap, comfortable and portable. It's light enough and small enough to take around without it being too noticeable and -- perhaps more importantly -- it's cheap enough that you're not going to shed any tears if it should get mislaid. It's basic, but gets the job done. Literally. The pointer moves around the screen and everything!
-

Kim Dotcom takes on politics and Bitcoin with the Internet Party
Publié: mars 27, 2014, 10:57am CET par Mark Wilson

Kim Dotcom -- the man behind the infamous MegaUpload, and then Mega -- has been out of the spotlight for a little while, but now he's back with renewed strength. This time around he's not trying to launch a new service, but a new branch of his career. Not content with bringing free cloud storage to the masses, Dotcom is now venturing into politics, launching the Internet Party in New Zealand. He finds himself in an interesting position as he is currently fighting extradition to the US where he faces charges of infringing copyright.
As the name suggests, the Internet Party is concerned primarily with what's happening online. The party has a fairly simple mission statement. "The Internet Party was founded on the spirit of the Internet, to get an open, free, fair, connected and innovative society". It is described as "a party that will give you faster, cheaper Internet, create high-tech jobs, protect your privacy, and safeguard our independence".
There are lots of other web-related aims in the party's sights -- cheap and unlimited broadband for the whole of New Zealand, the introduction of a government-sponsored digital currency (watch out Bitcoin!), reforming copyright laws, and stopping online spying and data collection. It's very much the sort of thing you'd expect to see, although there are also policies relating to New Zealand's independence, and the environment.
This is not the first time we have seen the web spawn a political career. In Sweden, the Pirate Party was set up in 2006 to promote the reform of copyright laws. With New Zealand going to the polls in September, we'll probably be hearing a lot more from Mr Dotcom over the next six months. At the moment -- although it is obviously very early days, things are not looking too promising, with just 17 percent of those polled indicating that they might vote for the Internet Party... but Dotcom sounds quite happy with the numbers:
#InternetParty tracking well at 17%! :-) #NZPol [t.co] [t.co]
— Internet Party (@InternetPartyNZ) March 27, 2014
Obviously, the Internet Party is limited to New Zealand, but if Dotcom's party ran for election in your country, would he get your vote?
-

Spam emails just not quite annoying enough? Google has the solution!
Publié: mars 27, 2014, 12:51am CET par Mark Wilson

Spam's great, isn't it? I know I just can’t get enough of it. I particularly love the in-your-face, unavoidable stuff that grabs my attention and ultimately has nothing to offer. Love it. This is one of the reasons I was indescribably happy when Gmail introduced its tabbed inbox feature. While some people saw it as a way of keeping their inbox clear, I saw it rather differently. Now I can see all of that level spam -- sorry, I mean "promotional emails" -- in one place: the handily named Promotions tab.
But there are too many emails that are just too subtle. They don’t grab my eyeballs and try to wrestle them from my head. Well, let joy be unbounded, Google has come up with the solution I've been looking for! It's like the company has been reading my mind! I've lost count of the number of times I've thought, "you know what's missing? Really big, graphic versions of my emails. If that was implemented, my spammy desires could be so much more effectively sated!"
Be still my beating heart!
No longer will I have to content myself with reading mere subject lines for emails companies have taken the time and effort to specially tailor to my needs and interests, oh no. Now I can enjoy the full graphical glory of a grid view which shows off the products these companies are so eager for me to see. This all comes thanks to a new experimental Gmail feature that you can request be added to your account. Check it out below and revel in its beauty for yourself:
Wow! Not just promotional marketing emails, but huge, gargantuan thumbnails showing off all of those products I just can’t wait to throw my hard-earned money at. But wait... it doesn’t end there. As Google kindly points out in a helpful blog post, "grid view also comes with infinite scrolling". So I can just keep scrolling and scrolling and scrolling and scrolling? An endless stream of aspirational images for all the products under the sun. I feel quite faint with delight!
If you're as excited at the prospect as I am, get yourself over to the special signup page to put your name down for the 'field trial'.
Disclaimer: Please do not attempt to replicate these levels of sarcasm at home. BetaNews cannot be held responsible for the consequences of doing so.
Image Credit: Sadovnikova Olga / Shutterstock
-

Keepin' it virtually real -- Facebook buys Oculus VR for $2 billion
Publié: mars 26, 2014, 2:56am CET par Mark Wilson

It has been a day of purchases today. If Intel purchasing wearable tech outfit Basis was not enough, everyone's favorite social network (or something like that), Facebook has splashed the cash on virtual reality startup Oculus VR. In a deal worth $2 billion, Mark Zuckerberg's company will hand over $400 million in greenbacks, in addition to 23.1 million Facebook shares. The purchase comes just weeks after Facebook bought messaging service Whatsapp for $19 billion.
Oculus VR is most readily associated with gaming, but Zuckerberg is more interested in the communication potential. Millions of people use Facebook to keep in touch with friends, family, celebrities and companies, but the firm wants to take things further. "We have a lot more to do on mobile, but at this point we feel we're in a position where we can start focusing on what platforms will come next to enable even more useful, entertaining and personal experiences", says Zuckerberg in a statement on Facebook.
The Facebook CEO goes on to briefly explain virtual reality to the uninitiated, but then switches back into excited mode. Forget the blocky, Tron-like polygon worlds that epitomized the early days of VR, "the incredible thing about the technology is that you feel like you're actually present in another place with other people". But the plan doesn’t seem to be to take Oculus VR too far away from gaming, at least initially. "We're going to focus on helping Oculus build out their product and develop partnerships to support more games".
Moving forward, things sound intriguing. "After games, we're going to make Oculus a platform for many other experiences. Imagine enjoying a court side seat at a game, studying in a classroom of students and teachers all over the world or consulting with a doctor face-to-face -- just by putting on goggles in your home".
Oculus is similarly upbeat about the purchase. In a blog post that refers to a meeting with Facebook a couple of months ago, the company explains that "we discovered the two teams shared an even deeper vision of creating a new platform for interaction that allows billions of people to connect in a way never before possible". If you're having trouble seeing the link between the two companies, the Oculus team has a simple explanation: "Facebook understands the potential for VR. Mark and his team share our vision for virtual reality’s potential to transform the way we learn, share, play, and communicate". There's also the promise to "see you in the Metaverse!"
With the money exchange and back-slapping out of the way, it will be curious to see how things progress. It's already looking as though the Oculus community is reacting rather less positively -- accusations of selling out, predictably, abound -- than Facebook fans who seem excited about what's to come.
Image Credit: Nejron Photo / Shutterstock
-

Google teams up with Ray-Ban to gain some cool for Glass
Publié: mars 25, 2014, 3:06pm CET par Mark Wilson

After trying to drum up more interest in Glass by dispelling some myths believed to have built up around the wearable tech, Google is looking to push things even further, gaining a little cool cred by teaming up with Luxottica the group behind well-known names such as Ray-Ban and Vogue. Teaming up with such a premium brand could be key to the success or failure of Glass, and Google is keen to push Glass as being the next step in the gradual evolution of eyewear.
At the moment, there are more than forty different looks for Glass (once the various frames, colors and styles are factored in), but it is hoped that the new partnership will result in even more designs. Love them or not, Ray-Ban and Vogue are names you will be quite familiar with, and it seems as though this is something that Google is keen to latch on to -- although it is, of course, a household name in its own right. "Luxottica understands how to build, distribute and sell great products that their clients and consumers love -- something we care deeply about at Glass, too," purrs Google on its Google+ page.
But it is the infrastructure that Luxottica already has in place that is likely to be of particular interest: "Luxottica’s retail and wholesale distribution channels will serve us well when we make Glass available to more people down the road".
Will the tie-in with a luxury brand be the move that increases interest? It's difficult to say at this stage, but it is interesting to note that Google chose to announce the partnership with the high-end name just days after spending time trying to cast off the label of being expensive. "Glass is only for those privileged enough to afford it" is the myth Google was keen to get rid of. Is entering into a relationship with a company responsible for expensive brands the best way to back this up? Perhaps not. Or maybe it's an indication that there will be various models of Glass available when it gets a full launch -- one for the everyday person, and one for those with slightly deeper pockets.
Image Credit: javi_indy/Shutterstock
-

UK digital download tax will cripple sales and damage the industry
Publié: mars 24, 2014, 1:19pm CET par Mark Wilson
 Last week in the UK, the announcement of the new budget for the country was closely watched as citizens kept an eye on whether they'll be paying more for beer and whether taxes are going up or down. There's a lot to talk about in George Osborne's 2014 budget, but this is not the place to discuss most of what it involves. One thing is of interest for technology enthusiasts, though. The cost of digital downloads -- meaning ebooks, music and apps -- could be set to rise as the chancellor (the guy holding the purse strings) closes a tax loophole.
Last week in the UK, the announcement of the new budget for the country was closely watched as citizens kept an eye on whether they'll be paying more for beer and whether taxes are going up or down. There's a lot to talk about in George Osborne's 2014 budget, but this is not the place to discuss most of what it involves. One thing is of interest for technology enthusiasts, though. The cost of digital downloads -- meaning ebooks, music and apps -- could be set to rise as the chancellor (the guy holding the purse strings) closes a tax loophole.At the moment, companies offering digital downloads are able to avoid paying taxes in the UK by routing them through another country where taxes are lower. This is not a new technique, and there is nothing illegal about it. It is a loophole that has been exploited for many years, but now plans are afoot to close it off. What is this likely to mean? Well, it should come as no surprise that, ultimately, it's probably going to lead to higher prices for people in the UK.
The document reads:
The government will legislate to change the rules for the taxation of intra-EU business to consumer supplies of telecommunications, broadcasting and e-services. From 1 January 2015 these services will be taxed in the member state in which the consumer is located, ensuring these are taxed fairly and helping to protect revenue.
As things stand at the moment, UK consumers already -- generally speaking -- pay more for digital downloads. A $0.99 price tag in the US usually results in just swapping the dollar sign for a pound sign for UK sales; $0.99 becomes £0.99. At the current exchange rate $0.99 equates to £0.60, so there's already quite a nice bit of extra profit being generated from the UK market.
The plan is to make UK tax payable in whatever country sales are made. With VAT (Value Added Tax) currently standing at 20 percent, sellers will either have to take quite a hit on a nice little profit, or pass the extra costs onto consumers. If tax becomes payable in the UK for digital downloads, it is unlikely that the costs will simply be absorbed by companies -- it is far more likely that they will be passed onto the buyer. So in spite of the fact that a game that costs $0.99 in the US costs significantly more in the UK, it looks as though the pricing difference could become even more marked.
On the face of it, the extra money raised from taxes would be good news for the UK economy. It is estimated that in 2012, the treasury missed out on around £1.6 billion on tax that could have been applied to digital goods. But the £0.99 price point is important psychologically. Raising prices never goes down well, but breaking the £1 barrier is something consumers are liable to struggle with, mentally if not financially. There is potential for the government to rake in millions through this form of taxation, but there is also the risk that the price increases will lead to a drop in sales, hurting developers, authors, musicians and the movie industry. Is that a price worth paying?
Photo Credit: gosphotodesign/Shutterstock
-

As wearables flounder, Google struggles to dispel Glass 'myths'
Publié: mars 22, 2014, 3:49pm CET par Mark Wilson
 I have not hidden the fact that I'm yet to be sold on the idea of wearable tech. A post about smartwatches failing to take off lead to some interesting discussions, and many people leapt to the defense of watch 2.0. Judging from the comments, it seems that there is some love for wearable devices, but it still doesn't appear to be translating into sales. It's not just wearables fans who are quick to defend the honor of their beloved devices, the manufacturers are doing so as well. Google is the latest proponent of strapped-to-the-body-tech, which is hardly surprising considering the company's vested in the market with Glass.
I have not hidden the fact that I'm yet to be sold on the idea of wearable tech. A post about smartwatches failing to take off lead to some interesting discussions, and many people leapt to the defense of watch 2.0. Judging from the comments, it seems that there is some love for wearable devices, but it still doesn't appear to be translating into sales. It's not just wearables fans who are quick to defend the honor of their beloved devices, the manufacturers are doing so as well. Google is the latest proponent of strapped-to-the-body-tech, which is hardly surprising considering the company's vested in the market with Glass.Google Glass has received a bad rap, or so Google seems to think. Not happy to sit back and let the rumormongering run its course, Google has instead written a blog entry aiming to dispel some of the "awesome urban myths" (their words, not mine) that have built up around the technologically advanced spectacles. Considering this is a product that is yet to receive a full public release, it is interesting to see that Google already feels the need to stick up for its baby. But that said, this is a device that has seen the term "glass-holes" coined, even before launch.
Google is concerned that while "Myths can be fun, but they can also be confusing or unsettling... and... can morph into something that resembles fact." Well. We couldn't have that now, could we? Although admitting that it is "flattered by the attention", the company is also looking to assuage fears that may have built up surrounding Glass, lest sales take a hit when the device does finally hit the shelves.
The first myth is that Glass is "the ultimate distraction from the real world". This would seem hard to argue against -- it is precisely why Glass users have been banned from using the devices whilst driving. Google is under the impression that lots of people believe that Glass is constantly recording video in a privacy-invading fashion. This is not the case, which will come as a relief to many people, but one of the reasons cited is that "the battery won’t last longer than 45 minutes before it needs to be charged". Well that’s reassuring. Privacy fears can be allayed -- because battery life sucks.
Another "myth" is that Glass users are technology-worshipping geeks. This one is hard for Google to wriggle out of. By its very nature, Glass is geeky. Take exception to the term "technology-worshipping geeks" all you like, but that is the target audience. Google is free to dress things up however it wants, but it’s a geeky gadget. End of story. However, there’s still a long way to go. As Google stresses, Glass is a prototype device and "in the future, today's prototype may look as funny to us as that mobile phone from the mid 80s".
There are various other myths that are picked apart, including that slightly contentious argument against the claim that "Glass is only for those privileged enough to afford it". Well of course it is. This is true of any piece of tech, but when the price tag is $1500, it becomes an aspirational item -- most people just don’t have that sort of money lying around waiting to spend on something unnecessary. But according to Google, this hefty price "doesn’t mean the people who have it are wealthy and entitled. In some cases, their work has paid for it. Others have raised money on Kickstarter and Indiegogo. And for some, it’s been a gift." Well that makes me feel much better! Thanks for that, Google! Here Google admits that the price is high enough that those interested have to raise money by asking for donations, or have someone else buy it for them. Someone better off. Someone "privileged enough to afford it".
It is interesting to see -- regardless of whether you are excited about Google Glass or not -- that Google is having to defend its product before it has even officially launched. It is an odd state of affairs, but Google almost certainly has the advertizing nous and hype-building wherewithal to whip would-be customers up into a frenzy before it is ready for the mainstream… whatever that means. But the company needs to be careful that it hasn’t peaked too soon, however. Glass has been on people's lips for a couple of years already and there's still no word on when a final version might be ready. Interest levels can only be maintained for so long before customers start to wander off, distracted by other shiny toys.
Image Credit: David Huntley Creative / Shutterstock
-

The most popular stories on BetaNews this past week March 16 -- 22
Publié: mars 22, 2014, 2:24pm CET par Mark Wilson
 Not a good week for Microsoft this week. Things kicked off as Mozilla shunned the Windows Store by opting to stop development of a modern version of Firefox and then things got a little awkward following the investigation of an employee involved in leaking information about Windows. The company then came under fire for accessing the email account of an individual, despite its claims that "Outlook and Hotmail email are and should be private".
Not a good week for Microsoft this week. Things kicked off as Mozilla shunned the Windows Store by opting to stop development of a modern version of Firefox and then things got a little awkward following the investigation of an employee involved in leaking information about Windows. The company then came under fire for accessing the email account of an individual, despite its claims that "Outlook and Hotmail email are and should be private".There was better news as an LTE version of Surface 2 went on sale opening up a new income stream for the company and new mobile computing opportunities for customers. More good news for users came when OneNote was not only released for Mac, but also made free for all platforms. Mihaita wasn't overly impressed with the Mac version, though.
It seems like a while (sort of) since the NSA received a mention, but the organization managed to sneak back into the headlines after claiming that its data collection operations were carried out with the full knowledge of the tech companies involved. Google flipped the switch to make Gmail HTTPS-only, encrypting communication to help evade such snooping.
In Europe plans are afoot to settle on a universal mobile phone charger design to help cut down on waste and eliminate the need to find the 'right' charger for a particular handset. One phone that is unlikely to change its charger without being forced to do so is the iPhone, and this week Apple introduced an 8GB iPhone 5c while retiring the iPad 2.
As Google announced details of wearable Android devices, I argued that there is just no interest in smartwatches. While waiting for wearables to take hold of the public imagination, the company is happy with launching Chromecast in a further 11 countries. Oh, and if a streaming device powered by Google doesn’t do it for you, smart TVs powered by Opera are one alternative you may be interested in. Google has already cut the price of Google Drive storage, which could well signal the start of a cloud storage price war -- hopefully the beneficiaries will be the likes of you and I.
Price cuts were far from being the order of the day for Pandora One customers who saw a jump in subscription prices. Netflix came under attack for a couple of reason this week. Joe lambasted the streaming outfit's personalized suggestions for limiting choice rather than expanding it. Brian, however, had rather more to get off his chest, suggesting that the company should pay a toll to ISPs by way of compensation for the bandwidth gobbled up by its customers.
In the world of security, printers may not be the first thing you think of, but HP launched a new touch-to-authenticate system for enterprise customers using NFC. Security is a serious business, and new figures suggest that worldwide the cost of malware is $500 billion. With the end of support for Windows XP approaching on the horizon, security firm Avast warned that this presents a serious security issue.
Same time next week? See you then! Expect more fun and frolics over the next seven days...
Image Credit: vinz89 / Shutterstock
-

Smartwatches -- the harsh truth is that no one cares
Publié: mars 21, 2014, 1:15pm CET par Mark Wilson

OK, maybe that's a slight exaggeration. But wearable devices are really struggling to get off the ground, at least in the UK. All of the excitement that surrounds smartwatches that can be used to read email, VPN into a home computer, check vital stats, set off The Bomb, or tell the time (imagine!) -- maybe a couple of these are a little far-fetched -- seems to be little more than manufacturers' fluff and guff. The wheels of the marketing machine have been whirring away furiously, but it has had very little effect. With a population of approaching 65 million people, only a very tiny proportion of the nation has seen the need to invest in a smartwatch -- below 1 percent in fact.
Figures from Kantar World Panel show that a lowly 0.9 percent of UK consumers have put their hard-earned money towards a smartwatch. Other statistics to come from the research are of little surprise. Almost three quarters (72 percent) of smartwatch owners are male, and 56 percent are aged under 35. There are a small number of names associated with smartwatches, and the spread is fairly evenly distributed. At the top of the heap is Samsung with a 32 percent share, followed by Sony with 21 percent and Pebble with 18 percent. There is obviously a leader, but with the numbers being so low, percentages are very easily swayed.
It could be argued that smartwatches are a relatively new technology, and all we're witnessing it a slow uptake rate. This is true to some extent, but the idea of a smartwatch is one that has appealed for decades. The allure of being able to speak FBI-style into a wrist-mounted device is something that was conjured up in all manner of sci-fi books and movies. But the reality has proved to be very disappointing. Devices are expensive and limited (again, an accusation that could be levelled at many newer devices) and this has been noted by consumers. The consumer votes with his (I'll stick with 'his' for want of a gender-neutral third person singular) wallet. And when it comes to smartwatches, the wallets have remained firmly in pockets.
My colleague Alan noted around a year ago that the watch in general is on the decline. Dumb watches are still available but they are far less common than a decade or two ago. Smartwatches face an uphill struggle to gain any sort of foothold. But it seems like consumers are not completely opposed to the idea of wearable tech. Fitness bands are twice as popular, although this still only amounts to ownership by 18 percent of the population.
Writing this in Word 2013, it is interesting to note that the word 'smartwatch' is flagged up as being incorrectly spelled. It is a word that may be in the tech lexicon, but it is yet to infiltrate general vocabulary. Is there a reason smartwatches are struggling to gain mass popularity? Price probably plays a large part in this. It is interesting to note that Samsung is leading the pack at the moment, despite the fact that its Galaxy Gear smartwatches need to be used in conjunction with a Samsung phone.
But ultimately the problem is that there are simply no compelling reasons to part with your cash. What benefit does a smartwatch offer over the ubiquitous smartphone? Devices with a specific purpose -- like fitness bands -- have a reason to exist, but the majority of smartwatches seem to have been created just for the sake of it. With smartwatches usually merely parroting the functionality of a smartphone (albeit in a very limited fashion), what is the point? Ultimately there is none. And this is a message that consumers are sending to manufacturers loud and clear by keeping their cash for other things.
I don't doubt that if the rumored iWatch ever makes an appearance, things will pick up dramatically, but the prospect of yet another crowd-pleasing-but-ultimately-disappointing idevice is one that fills me with dread.
Smartwatches were dead before they even began. Expensive, limited functionality, awkward screen, universally ugly designs; it's no wonder sales are so low.
Photo Credit: Robnroll/Shutterstock
-

NSA lawyer says data collection occurred with tech firms' 'full knowledge and assistance'
Publié: mars 21, 2014, 1:22am CET par Mark Wilson

The NSA story isn't new. Scratch that. It's not really a story; it's a saga. Just when it seems safe to feel that there can't possibly be any more revelations to knock us sideways... oops... there's another little surprise for you! Just a week ago, I argued that Google's encryption of Chinese web searches amounts to little more than a PR exercise, designed to try to get the disgruntled user back on its side. This is not something that is related to the NSA revelations. When we found out that the likes of Facebook, Microsoft, Google and Yahoo (to name but a few) had been handing data over to the US government, all of these companies were falling over themselves to appear to be doing everything they could legally do to let their customers know what had been happening with their data.
Of course, it's not just the UK that has this problem, although that’s certainly where the attention has been focused -- the UK had (or possibly has) its own Optic Nerve program which was used to spy on webcam chats. The story we have heard time and time again is that these companies did not know what was going on. That the government had been collecting data without their knowledge. There were concessions that in some cases, FISA requests had been received but there were limitations on what could be publically revealed. Each company tried to outdo the others by appearing to reveal as much data as it could as quickly as humanly possible.
But it looks as though these big-name tech companies may have just been playing dumb. Despite the protestations that the PRISM program was essentialy a government backdoor into numerous online services about which the owners have no knowledge, this is very likely not the case. All those company sound bites in which they denied knowledge of the existence of PRISM and other such programs, in which collaboration with the government was repudiated, may just have been shown to be what many people believed from the very beginning. Complete nonsense.
Rajesh De, the NSA general counsel, has revealed that all of the data collected by the NSA was done with the full knowledge of all of the companies involved. All of the big names have denied knowledge of any surveillance program. But De says "Prism was an internal government term that as the result of leaks became the public term. Collection under this program was a compulsory legal process, that any recipient company would receive." Asked outright whether surveillance was carried out with the "full knowledge and assistance of any company from which information is obtained" he gave the simple, single-word response "yes".
This clearly flies in the face of what we have been told thus far. Over the coming days there will undoubtedly be endless protestations from the companies involved. The line of defense will almost certainly be that they are ignorant. The best we can hope for is that the companies will complain that their hands were tied, and they were not legally permitted to admit the help they were providing. It does make it increasingly difficult to know who to trust.
A couple of months ago, President Obama promised reforms to government surveillance, but it's anyone's guess just what this will amount to. What is said and what is done can be two very, very different things.
Kurt Cobain once drawled "just because you're paranoid, it don’t mean they're not after you". It's a line that is often used (or a variant of it) by conspiracy theorists to defend their seemingly crazy ideas. But maybe the conspiracy nuts were right all along. Well, maybe not all of them. Edward Snowden still comes across as an unlikely hero, but his whistleblowing keeps gaining in significance; it has turned out to be a veritable Pandora's box. It makes you think. Tim Berners-Lee's idea for a bill of rights for the web looks ever more appealing. Part of the proposed bill of rights is about access to the web, but it is also about the rights of those online. This would surely involve the right to know what the bloody hell is going on with our private data and communication. But ultimately, there is just no way of knowing what's going on in the background, and that’s a disgusting state of affairs.
Image Credit: Mark Carrel / Shutterstock
-

Cloud storage price wars! First blood to Google!
Publié: mars 18, 2014, 10:43pm CET par Mark Wilson
 And so it begins. The price war in the cloud. There are few tech companies that would not like you to store all of your files in the cloud, and there are several big names vying for attention. The obvious contenders for the crown are Microsoft with SkyDrive (sorry, OneDrive), Dropbox and Google Drive -- of course there are plenty of others, but these are the names that trip readily off the tongue. As computer users we have become increasingly comfortable with the idea of storing files online; in fact we almost demand it. If an app or service does not offer cloud storage, there are instant complaints about the lack of between device syncing.
And so it begins. The price war in the cloud. There are few tech companies that would not like you to store all of your files in the cloud, and there are several big names vying for attention. The obvious contenders for the crown are Microsoft with SkyDrive (sorry, OneDrive), Dropbox and Google Drive -- of course there are plenty of others, but these are the names that trip readily off the tongue. As computer users we have become increasingly comfortable with the idea of storing files online; in fact we almost demand it. If an app or service does not offer cloud storage, there are instant complaints about the lack of between device syncing.But cloud storage does come at a cost. On the face of it, online storage is available free of charge. All of the big names -- and many of the smaller ones -- provide gigabytes, in varying quantities, of space gratis. But for cloud storage to be truly useful, everything needs to be stored there. The 5GB of free space from one provider is not to be sniffed at, but 5GB disappears very quickly. Opt to store all of your photos online, for instance, and the gigabytes will very quickly be eaten up.
But never fear! If you need more space, you may have it. But at a price, of course. Unlike hard drive space, this is not storage space you are buying outright (usually, at least), but renting. In this regard it quickly works out to be a tremendously expensive way to house your files. Of course there are the added benefits of being able to grab your files from any device but it is down to the individual to decide whether this is a price worth paying. Just as it costs more to rent a house than to buy outright, it cost more to rent cloud storage each month or year.
But Google is kicking off a price war. In the battle for users, the search giant has drawn first blood by slashing its pricing. There is yet to be any reaction from the likes of Microsoft, but it is hard to image that this will not descend into all-out war. By cutting the prices of its storage, Google is sending a clear message to its competitor -- take us on if you dare!
The price cut is obviously going to appeal to users old and new. Been considering investing in a little more space? Now's the time to do it! Not quite sure which cloud storage provider to go for? Google's lower price certainly makes it more attractive! But what is the real price? Yep... I'm going to bang the privacy drum again! We already know about online spying, government data requests and the like, but there are millions of users -- myself included -- who are happy to store all manner of personal files in the cloud ready to be poked and prodded by god-knows-who. Is this the price we’re willing to pay for the ability to sync files between computers or automatically backup photos from our phones?
The cheaper option for everyone would be to invest in a NAS drive and configure it for remote access. Terabytes of data could be yours for a fraction of the cost of big name cloud storage. There's also the huge advantage that you are placed firmly in control of how and when data is accessible. Whether you're looking to keep things private, or need the option to share with others, just how far you take it is entirely up to you. You don’t even need a network drive. Dust off that old laptop that is being used to prop up the wonky table, and with the right software (free of course), you can make its hard drive, and any USB drives you choose to connect, accessible online.
Will I go down this route? Probably not. I'm lazy. I use Google Drive because it's there, it's easy and it works. I could have ended up using OneDrive, Box.net or something else, but Google snared me first, and I'm yet to hear a particularly compelling reason to switch allegiances. Integration with so many services and apps means that Google has managed to worm its way into my life -- and the lives of countless others -- like a rampant cancer. There have been numerous incentives along the way to help sweeten the deal, and the decision to stick with Google has been made slightly easier thanks to being 'given' an extra 100GB of storage for doing nothing more than being in possession of a Chromebook. Thanks Google!
I have no idea if Google is looking through my files. They probably wouldn't tell me if they did, but I haven't got the time, energy or inclination to sift through the clauses of the user agreement. Based on our knowledge of government data requests, if government bodies are poking their noses into my affairs, Google would probably not be able to tell me anyway. I'll probably see a few tailored ads, but so what? I'll cope.
How do you make your files available to other computers? Or, indeed, do you need to? Perhaps you're happy sticking with locally stored files, email them between computers as required? One thing is for sure, though: Google making the first move in the price wars that are almost certain to come has all but guaranteed its ultimate dominance.
Image Credit: Burlingham / Shutterstock
-

Mozilla's Metro move shows that modern apps belong in the mortuary
Publié: mars 16, 2014, 4:15pm CET par Mark Wilson
 Just a few days ago, Mozilla announced that it would not bother releasing a modern version of Firefox for Windows 8.x -- this in spite of the fact that a team of developers have been working on it for over a year. It seems that the company behind the famous foxy browser regards the modern interface with just about as much disdain as everyone else. So much contempt, in fact, that it can't even bring itself to use the proper terminology: "I know [Metro is] not what Microsoft calls it anymore, but it remains how we talk about it in Mozilla", sneers Johnathan Nightingale, Vice President of Firefox.
Just a few days ago, Mozilla announced that it would not bother releasing a modern version of Firefox for Windows 8.x -- this in spite of the fact that a team of developers have been working on it for over a year. It seems that the company behind the famous foxy browser regards the modern interface with just about as much disdain as everyone else. So much contempt, in fact, that it can't even bring itself to use the proper terminology: "I know [Metro is] not what Microsoft calls it anymore, but it remains how we talk about it in Mozilla", sneers Johnathan Nightingale, Vice President of Firefox.Despite acknowledging that Mozilla is no longer "tiny" (far from it, really), Nightingale says that the company needs to focus its attention on those projects that will have the most impact. According to StatCounter, Firefox still manages to grab over 20 percent of the desktop browser market, dropping very slightly to just over 19 percent once tablets are factored in. But moving forward, there will simply be no more work carried out on the modern version of the browser. It is being abandoned like the runt of a litter.
This is a big blow to Microsoft. Undoubtedly the Redmond firm will try to downplay it, but there is no getting away from the fact that this is a big name snubbing the modern side of Windows 8.x. Losing such a well-known face is a big deal, no matter how you look at it. Firefox is the third most popular desktop browser, and losing the third largest player in the market is huge. Some will say that Microsoft's Internet Explorer and Google's Chrome will benefit from this news -- which is true to a certain extent -- but the real news is that modern apps are dead. Microsoft may be pushing modern hard, but it's a very difficult thing to sell.
Adoption levels are very low, and this is something that Mozilla recognizes. There is more interest in web browsers than ever before -- this is a side-effect of the amount of time we now spend online -- and both Mozilla and Google have long made available beta, and even alpha, versions of their browsers for those who just have to live on the cutting edge. Everytime a new build is released, download servers strain under the traffic of browser updates -- yet with the modern version of Firefox, Nightingale claims that there are fewer than 1000 active daily users.
Mozilla is a company that does its research. It has been in this business for years, after all. For such a big player to completely drop support for a particular platform should be seen as what it is -- a terrible blow for Microsoft. Users may bemoan the fact that they're extremely unlikely to see a modern-friendly version of Firefox, but it is Microsoft that should be licking its wounds. After more than a year of work and investment, Mozilla sees it as a better option to simply walk away "than the real costs of investment in a platform our users have shown little sign of adopting".
The problem with modern apps is that they are pale imitations of their desktop siblings. Users have become accustomed to being able to tinker with software, getting right under the hood and changing every setting imaginable. This is simply not possible with modern apps. Modern apps are watered down shadows of their former selves. They are an embarrassment to the world of software. It's time to consign them to the digital graveyard.
Windows RT users may be making use of modern apps, but this is because there's no choice. Based on comments on my previous vitriolic ejaculations, I'm fully anticipating defensive comments proclaiming the brilliance of modern apps and decrying 'outmoded' desktop software; I'm ahead of you. But the numbers speak for themselves. Modern apps are a disaster. A complete and utter unmitigated disaster. Mozilla knows it. Microsoft knows it. We all know it really. A few more people just need to admit it publicly so we can move on and get things sorted out.
Image Credit: Vibrant Image Studio / Shutterstock
-

The most popular stories on BetaNews this past week March 9 -- 15
Publié: mars 15, 2014, 4:26pm CET par Mark Wilson
 This is the week that saw the web celebrating its 25th birthday and Tim Berners-Lee took the opportunity to call for a web bill of rights, which I argued is essential for the future of democracy.
This is the week that saw the web celebrating its 25th birthday and Tim Berners-Lee took the opportunity to call for a web bill of rights, which I argued is essential for the future of democracy.Another week means a fresh batch of security concerns. In Europe, users were warned of the dangers of connecting to public wifi hotspots, while a new report found that cybercriminals are becoming increasingly sophisticated in their techniques. Ian was on hand with advice for anyone trying to tackle or avoid viruses.
Here at BetaNews we have put Google under the microscope more than once. Brian revealed how the company is offering money in return for Google Apps referrals while Joe suggested that the end of Chromebook -- and indeed PCs in general -- is on the cards; although users can get a 60-day free trial of Google Music.
This was far from being the end of Google coverage this week. Subtle changes to Google's search results page made ads slightly less obvious, but this isn't necessarily the good news you might think. The search giant also announced that it would be encrypting searches in China. Sounds great, but I viewed it as a cynical marketing move benefiting no one but Google. Joe felt much the same about something else Google-related. Following a price cut for Google Drive storage, he pondered whether the convenience was worth the loss of freedom involved in getting in bed with Google.
After I complained that the Windows 8.1 update is rubbish, Brian disagreed, saying that it was time for the moaners to grow up and stop whinging. If you're really struggling with the Start screen, Wayne compiled a list of the best Start menu replacement tools to keep you happy.
Being offered an incentive to buy a phone, a computer or a piece of software is nothing particularly new, but if you've been putting off buying an Xperia Z2, the lure of a free Sony Bravia TV just might be enough to sway your decision. If you've already got yourself an iOS device the release of iOS 7.1 adds CarPlay support as well as new camera settings and speeding up of performance. Samsung busied itself mass-producing 20 nanometer 4Gb DDR3 memory for both PCs and mobile devices and also working with Microsoft on a wireless charging system.
It's not just buying a new phone that gets you something free. Getty Images announced that its pictures would be made available free of charge to anyone looking to use them for non-commercial purposes. In the world of media, Netflix released new details of which ISPs offer the best performance while at CeBIT the UK Prime Minister announced plans for an ultrafast 5G mobile network.
If you're looking for something fun to end the week, check out the updated Hitchhiker's Guides to the Galaxy game which was rereleased for the book's 30th anniversary. Oh, and if you're looking to bring in a little money with a skill you have, check out Fiverr which has just found its way to Android.
Enjoy the weekend, and sit back while more news comes your way.
Image Credit: vinz89 / Shutterstock
-

Google's Chinese web encryption is nothing more than PR and posturing
Publié: mars 14, 2014, 11:15am CET par Mark Wilson
 We are spied upon. Someone, somewhere, knows what you have been doing online. It might be your snooping friend taking a look at your browsing history, or it might be that weird looking guy on the next table in the coffee shop watching your every click. It might be advertisers using cookies, or it could be your own government. This is now just about expected; it is part and parcel of using the internet. In some parts of the world, access to the internet is not only monitored, but also restricted and controlled. But it didn’t used to be like this, and it needn't stay like this.
We are spied upon. Someone, somewhere, knows what you have been doing online. It might be your snooping friend taking a look at your browsing history, or it might be that weird looking guy on the next table in the coffee shop watching your every click. It might be advertisers using cookies, or it could be your own government. This is now just about expected; it is part and parcel of using the internet. In some parts of the world, access to the internet is not only monitored, but also restricted and controlled. But it didn’t used to be like this, and it needn't stay like this.In some regions the idea of mass spying is a relatively recent concept. The activities of the NSA, GCHQ and other government organizations are something only the most recent generation of internet users is "used" to -- for the rest us, it is at best an unpleasant sea change, and at worst just the tip of the iceberg. As it was revealed that governments were not only spying on citizens' online activities but also getting other companies involved by requiring them to hand over user data, big names such as Microsoft, Google, and Apple were falling over themselves to appear to be going out of their way to reveal everything they could about the demands made of them. It was the PR machine in action, trying to make the best of a very, very bad situation.
Few companies are more adept at trying to get people on its side than Google. Forget "don't be evil", these days it is more about saving face -- "don’t appear to be evil". The company's latest move is to start encrypted searches that are conducted in China. This is a country famed for the restrictions it places on internet usage, and the Great Firewall of China and government interference with the web are the worst kept secrets online.
Like Google, China is keen to maintain a particular image. Rather than engaging in an expensive and ineffective PR campaign, the country has chosen a different route: wrestling control of the internet from the people so it is completely in control of what people are able to access. Don’t like that awkward event in your history? Just pretend it didn’t happen! No one will notice! Chinese control of the internet is widely condemned around the world and there are frequent calls for "something to be done about it".
Google's announcement that it is to encrypt Chinese searches seems like a great idea -- people in China should be able to access the wider web and evade governmental intervention. At least that's the theory. Google is fooling itself if it thinks the Chinese government won’t be able to find a way to close this loophole; it may already have done so. I'm not saying that Google and others should just sit back on its heels and do nothing, but it is very difficult not to view this move cynically.
Speaking to the Washington Post, Percy Alpha, the founder of Great Firewall of China monitor group GreatFire.org said "It will be a huge headache for Chinese censorship authorities. We hope other companies will follow Google to make encryption by default".
This is the way it looks, but we have no way of knowing what is happening in the background. China could very easily stop the encrypted searches from working -- it has legions of technicians specializing in just this. It may do this, or it may not. A more sinister possibility is that "encrypted" searches are allowed to continue unfettered, but the Chinese government closely monitors the activities of individuals. This is dangerous. We have no way of knowing whether Google is in cahoots with the Chinese government -- on the face of it, it appears that the company is helping out the Chinese nation, but trust is at an all-time low.
When talking about the US government monitoring of online activity, we are constantly told by Microsoft, Google, Yahoo et al that there are limits on what we can be told. I'm quite sure that the US government has placed heavy restrictions on what online companies are able to reveal, but because there is so much going on out of sight, we just have no way of knowing whether we're not being told what’s going on because the government prevents companies from revealing more on pain of death, or whether this information is not being revealed because it would look bad for the companies involved. No company wants to be revealed as being on the receiving end of huge payouts for handing over user data, for instance.
What's happening in China is the other side of the same coin. The NSA revelations have seen companies scrabbling to save face, but now Google is trying to use the situation in China as a public relations exercise. The irony is that while the company is keen to appear to be helping those in China, it is rather less keen on taking steps to avoid the long arm of the US, UK and other governments. What is it one rule for one set of users, and another for others? It doesn't make sense and it smacks of PR and posturing.
Forgive me, but I can't just take all of this at face value.
Photo Credit: rangizzz/Shutterstock
-

Hey, Google! Please be open and honest with your search ads
Publié: mars 13, 2014, 8:38pm CET par Mark Wilson
 It may not be a new season, but it's time for a Google makeover nevertheless. This time around it is the search results page that has been given a lick of paint, although you might be forgiven for not quite being able to put your finger on what's changed. You'll almost certainly notice that things look a bit different, but the details may escape you. The changes were put in place yesterday, having been heralded on Google+ by Google search designer Jon Wiley who explains that the subtle changes are to bring the desktop look more in line with that used on mobile devices.
It may not be a new season, but it's time for a Google makeover nevertheless. This time around it is the search results page that has been given a lick of paint, although you might be forgiven for not quite being able to put your finger on what's changed. You'll almost certainly notice that things look a bit different, but the details may escape you. The changes were put in place yesterday, having been heralded on Google+ by Google search designer Jon Wiley who explains that the subtle changes are to bring the desktop look more in line with that used on mobile devices.The size of search result titles has been boosted, and the underline that was present has now been removed. Wiley says that "we've […] evened out all the line heights [which] improves readability and creates an overall cleaner look". This all sounds great in principle. After all, as Wiley points out, it helps to make "the multi-device experience more consistent". But it also ushers in a few concerns.
For some people (I'm talking specifically about the people who have commented on Wiley's Google+ post), the absence of underlines is a little disconcerting. While it may seem like a very small change, it could take some getting used to. Some people have complained that search results are harder to pick out without the guide of an underline. You would think that the larger font would help here, but this is also not going down well with some searchers.
Others have noted that there are weird inconsistencies between web browsers, with the look in Firefox being described as having "horrible" typography. User Wood Whittler gives a simple review: "It looks crap. Pure and simple".
But perhaps the most worrying aspect of the redesign is that ads sort of blend in with search results. Yes, there's a little Ad label there but... yellow on a white background? Come on! You can try a bit harder than that! Many people were unhappy with ads being, er, added to search results, but it is more bearable when they are obvious. Sure, ads appear at the top of search results, but not every search causes ads to be displayed. It's not possible to just train yourself to mentally filter out the top couple of results, because sometimes these will be real results that you might want to click.
I would go so far as to describe the redesign as dishonest and misleading. Users are essentially being tricked into accidentally clicking on ads that are, all too frequently, virtually indistinguishable from regular results. It's sneaky and mean-spirited. Ads may not be disappearing any time soon -- this I can live with -- but Google should at least have the decency to make them obvious.
Photo Credit: Ryan Rodrick Beiler/Shutterstock
-

CeBIT: UK Prime Minister backs development of insane-speed 5G networks
Publié: mars 10, 2014, 11:36pm CET par Mark Wilson

Mobile users are just getting around to upgrading their handsets to take advantage of 4G networks, but this simply is not fast enough. UK Prime Minister, David Cameron, spoke at CeBIT announcing that the country will join forces with Germany to develop the successor to 4G -- the uninspiringly-named 5G. The PM announced a deal with Germany which will help to push forward with the development of a mobile broadband network that will offer download speeds up to 1,000 times those currently available on 4G.
To put this kind of speed in perspective, as the Prime Minister explained, an 800MB movie (or any other type of file for that matter) could be download in a single second. One second. For the best part of a gig of data. On a mobile device. Who is going to say no to that? Ultimately, the adoption rate will be determined by the costs involved -- mobile tariffs, suitable handsets, data charges, and coverage -- but before any of this becomes an issue, 5G needs to be, well, invented really.
In the UK, King’s College University in London and the University of Surrey will join forces with Germany's University of Dresden to help ensure that neither country gets left behind in the digital race. Cameron is keen for the UK to become the "most digital nation" in the G8 and has to help convince anyone who has doubts, he also pledged a big chunk of funding for the "internet of things".
Toasters, refrigerators and other everyday devices connecting to the internet is already a reality, and by boosting funding to the tune of £45 million, Cameron is keen to be seen investing in what many think of as "The Next Big Thing". The Prime Minister is certainly talking the talk: "see the Internet of Things as a huge transformative development - a way of boosting productivity, of keeping us healthier, making transport more efficient, reducing energy needs, tackling climate change".
Researchers at Gartner have predicted that by 2020, there will be 26 billion devices connected to the internet of things. Let's just hope someone comes up with a better name long before then!
Image Credit: asharkyu / Shutterstock
-

Discover the answer to life, the universe and everything 30 years on
Publié: mars 10, 2014, 10:04pm CET par Mark Wilson

Gamers of yore will remember the delight that could come from playing a text-based computer game. Forget pushing polygons around the screen as fast as a GPU's legs can pump, these were games where words were king. Back in 1984, the Hitchhiker's Guide to the Galaxy game took the gaming world by storm and now, thirty years later the BBC has resurrected the classic title in an exclusive online version that's free for anyone to play.
This accessible and hilarious sci-fi classic translated well into a game, and whether you missed it the first time around or you like the idea of reliving the mid-80s, warm up your keyboard and prepare to type your way to victory -- and immense frustration. This is not the first time the game has been revived, but this time around there is an HTML5 version to enjoy and there are some comedic touches right from the start. The game developers decided to replace the $, % and ^ symbols with symbols for the Altarian Dollar, Flanian Pobble Bead and the Triganic Pu, "not because they are needed in the game, but just because we felt like it."
As was the case with the 20th anniversary edition, the 30th birthday release has been tarted up with a few sparse graphics -- but don't expect to see anything to rival Titanfall! It is described as a "wonderful piece of interactive fiction", and this is a very fitting description. It's a game that simply has to be experienced, and you would be doing yourself a disservice if you didn’t go and test it out this very instant!
To revel in a little nostalgic gaming, head over to the BBC mini-site for the game, and you can get started straight away. If you would like to be able to save your progress, you'll need to create an account with the BBC (which is free). We found that the game didn’t play nicely with all browsers -- Chrome seemed to have trouble, for instance -- but it's worth persevering if you do run into a problem. Just bear in mind the introductory caution: "A word of warning. This game will kill you frequently. It's a bit mean like that."
-

Europol warns users of WiFi hotspot security risks
Publié: mars 9, 2014, 10:00pm CET par Mark Wilson

Europol, the law enforcement agency for the European Union, is warning that people should exercise extreme caution when using WiFi hotspots when out and about. Citing an increase in the number of "man-in-the-middle" attacks on such connections, the head of Europol's cybercrime division, Troels Oerting, said that public WiFi connections are being used to "steal information, identity or passwords and money from the users who use [them]". The advice is to not necessarily stop using public networks, but to avoid using them for anything that involves transmitting personal data.
Singled out for particular attention is online banking, which Oerting suggests people should do "from home where they know actually the wi-fi and its security" rather than in a coffee shop. Europol is currently working with several member states of the European Union following in an increase in the number of WiFi network attacks.
It is a relatively simple task to intercept data that is being transmitted over an open network such as those found in public places like libraries and hotels, meaning it is easy for personal information to fall into the wrong hands. Usernames and passwords can be gathered in addition to other data that could be exploited by a criminal, and very little equipment is needed.
The numbers of people who seek out free WiFi connections in towns and cities, many of whom have little or no knowledge of internet security, shows no signs of declining. An investigation by the BBC found that the problem of "evil twin" networks was very prevalent, and would-be surfers could be easily tricked into connecting to a fake network in which their activities can be monitored. But even on a supposedly secure network it is possible, with the right snooping software, to track virtually all online activity. The investigation also found that mobile apps broadcast a great deal of information including username, passwords and contact details, and these could also be grabbed with special tools.
As with many online problems, the solution comes in the form of education. Opting to use secure networks is part of the solution, but even this is not completely infallible. The best attitude for anyone to adopt is to use only networks that are encrypted, stick to using mobile data connections rather than WiFi, or just wait until you get home -- and turn off the auto-connect feature on your phone and tablet so you don’t automatically get put online when you're in range of a network you have connected to before.
Image Credit: watcharakun / Shutterstock
-

Getty Images makes its pictures available for free -- but what’s the real price?
Publié: mars 9, 2014, 7:52pm CET par Mark Wilson

You can't argue with free can you? The absence of a price tag makes just about anything seem more attractive, and the latest company to join the freebie party is none other than Getty Images, that bastion of photos whose pictures you cannot fail to have seen in newspapers, magazines and on websites. Previously only available to those willing to cough up the cash, Getty Images' new Embed Images tool can now be used by any to... well... embed images into web pages and blog posts. And there are literally millions to choose from.
Sounds great, right? You must have found yourself struggling to find a royalty free image to use in a blog post, ultimately settling for working with something less than ideal -- after all, you wouldn’t just "borrow" an image from another site, would you? Now you can simply head over to the Getty Images site and, assuming you're not going to use pictures for commercial purposes, start browsing for and using whatever photos take your fancy. Hoorary!
Or maybe not.
Getty Images may be free, but you're not able to just download images and use them however you want. Rather than downloading images, you are required to embed them using code supplied by Getty Images. This might not seem like an issue -- it's a small price to pay for 35 million free images -- but consider this. Who knows what happens in a year's time? That image you have embedded on the front page of your website could just vanish. It's unlikely that Getty Images itself will disappear any time soon, but the same cannot be said for individual images.
Depending on how Getty's image database is set up, there is also the possibility that an image could be replaced by something completely different. We are, of course, talking hypothetically, but who's to say that the lovely landscape scene you spent forever choosing won't turn into a shot of a lingerie-clad lady? But the fact that the delivery of images is reliant on embedding code opens up somewhat more sinister possibilities. Ads.
The very fact that code is used to embed images means that it would be easy to deliver additional content. A Getty Images overlay or watermark is not entirely unexpected, but there would be nothing to stop other overlays being added, including advertisements. The embed code for images is difficult to interpret. A photo of a monkey on the phone has the address src="http://betanews.com//embed.gettyimages.com/embed/169937758?et=F12UYuHMs06DZOEVeIkKmg&sig=hSTP-g5TRomSqtiDuQch2nT78DjmX0TlFADxCxx9vYg=". The image reference number is 169937758, and there's no way of knowing what the additional code is used for.
The point is, images are entirely managed server-side, meaning that the person using them gives up control. Is this a price you're willing to pay?
The change in business model could also have implications for photographers. Image providers who once received a cut of income whenever their images were used now find that control has been wrestled from them as well. This in turn could mean that photographers are less willing to supply Getty Images with their work, which could ultimately mean that quality drops. Is that a price anyone should be happy with?
Image Credit: AntonSokolov / Shutterstock
-

The most popular stories on BetaNews this past week March 2 -- 8
Publié: mars 8, 2014, 6:22pm CET par Mark Wilson
 It's been a busy week for Microsoft -- and not necessarily for the reasons the company might have expected. For anyone unwilling to wait until April to receive Windows 8.1 Update, a few methods emerged that made it possible to grab a copy of the eagerly awaited update ahead of the official launch. While some of these options appear to have been stopped in their tracks, where there's a will there's a way, and numerous users -- my good self included -- jumped on the downloads as soon as possible. Some were impressed while others -- yep, me again! -- were not. Perhaps it is little wonder that Windows XP usage continues to grow faster than that of Windows 8.x. This lead to analysts suggesting that the decline of the PC will be slowed rather than avoided by the continued popularity of XP.
It's been a busy week for Microsoft -- and not necessarily for the reasons the company might have expected. For anyone unwilling to wait until April to receive Windows 8.1 Update, a few methods emerged that made it possible to grab a copy of the eagerly awaited update ahead of the official launch. While some of these options appear to have been stopped in their tracks, where there's a will there's a way, and numerous users -- my good self included -- jumped on the downloads as soon as possible. Some were impressed while others -- yep, me again! -- were not. Perhaps it is little wonder that Windows XP usage continues to grow faster than that of Windows 8.x. This lead to analysts suggesting that the decline of the PC will be slowed rather than avoided by the continued popularity of XP.Windows 8.1 Update wasn't that only Microsoft download that was on the agenda this week. Brian had details of how Windows RT users can update their copies of Office 2013 to SP1. At the top of Microsoft, a quick reshuffle saw a change of faces in a number of key positions as well as the departure of some well-known characters. Skype rolled out to Outlook.com around the world and gained HD video calling as well. It is normally Microsoft that is to be found on the giving-end of a smeary advertising campaign (hello, Scroogled), but after the Oscars it was Nokia poking fun at Ellen DeGeneres' blurry selfie that was taken on a Samsung device.
When not being mocked in tweets, Samsung was busy unveiling the Chromebook 2 which will be available in 11.6-inch and 13.3-inch variants. Benchmarks seemed to show that Samsung has stopped 'tweaking' performance when testing software is detected, meaning that benchmarks are now more reliable. Samsung also managed to hit the headlines -- yes, again! -- by launching its Milk music service for Galaxy owners. Yahoo and BlackBerry (who?) announced plans to experiment further with mobile advertising. Oh, talking of BlackBerry, OneDrive also arrived in the platform.
As a writer, it is quite common to be accused of being a fanboy. Express a like for something and you're clearly being paid by the company in question, offer criticism and you'll find yourself on the receiving end of hate letters (not literally sent through the mail, though). This made me wonder about the fanboy phenomenon and to ask whether brand loyalty was becoming a thing of the past. One field in which fanboys certainly still exist is the world of Linux, and if you fancy getting in on the action, the Linux Foundation has a series of free courses to help you get started.
Anyone looking for money to get a project off the ground can take heart from the fact that crowdfunding site Kickstarter has helped countless campaigns to the tune of a total of $1 billion since it launched. Windows Phone users felt the benefit of the arrival of Facebook Messenger.
In-car entertainment took a turn for the fruit-flavored as Apple announced CarPlay to make it easier for iPhone owner to listen to music, use maps and make calls in their vehicles. Entertainment in the home is made a little easier thanks to the latest additions to Logitech's Harmony range, including a keyboard and mobile app. Rokua launched the Stream Stick, a direct Chromecast competitor complete with a now-familiar casting option.
That's it for this week. As ever... much more coming up over the next seven days.
Image Credit: vinz89 / Shutterstock
-

Windows 8.1 Update is the final nail in the coffin
Publié: mars 7, 2014, 6:49pm CET par Mark Wilson

Windows 8.1 Update. Windows 8.1 Update 1. Windows Feature Pack. Windows 8.1 Service Pack 1. Call it what you will, the big update to Windows 8.1 is just around the corner and it promises much. Or at least it did. It was revealed yesterday that it was possible to get hold of the update ahead of schedule with a quick and simple registry edit -- or by downloading the necessary files from the numerous mirrors that quickly sprang up -- and it appears that this is final code; the RTM version that will hit Windows Update for the masses very soon. Was it worth the wait?
This update was Microsoft's chance to put things right, to win back people who hated Windows 8 and have failed to be won over by 8.1. I make no secret about having a love-hate relationship with Windows 8.x. There have been parts of Windows 8 -- particularly the Metro/modern side of things -- which I disliked from day one, but for the most part I have been able to just avoid using them. Microsoft has even acknowledged that people want to avoid the Start screen whenever possible, and has provided tips on how to do so.
Like many others, I jumped through the necessary hoops, grabbed the required files from Windows Update and I'm now running Windows 8.1 with the Update installed. I boot straight to the desktop, so what's the first noticeable change having installed the update? Oh, there's a bright green icon screaming for attention in the taskbar. What’s all that about? Ah… the Store link. Great. That'll come in handy for all of the modern apps I don’t install. But as I've noticed it, why not give it a click and see if anything else is new. As we knew from earlier leaks, modern apps now have a pseudo titlebar like 'legacy' apps (sidenote -- why in the name of sweet hell are they 'legacy' apps? Legacy? They're the most commonly used apps!). Except it's not visual all of the time and it doesn’t act like other titlebars.
In a regular app (I am, henceforth, refusing to use the word 'legacy') one can use the titlebar to drag and drop apps to new positions. Not with modern apps. In regular apps, right clicking a titlebar displays a context menu. Not in modern apps. Again Microsoft gets it wrong. In trying to clear the boundaries between modern and regular apps, the company has merely succeeded in highlighting just how different they are and creating a strange experience for anyone unfortunate enough to find that they use both types.
The lack of Start menu is something that sits uncomfortably with many users. The release of Windows 8.1 addressed the issue to some degree by reintroducing the Start button, but this was not really enough. The new update makes another tweak. The Start button is still present, and clicking it still brings up the Start screen. The change is that the taskbar remains visible when the Start screen appears; it's almost like having a full-screen Start menu. But move the mouse to click on something and… wait… what’s that? The taskbar has disappeared? WTF?!
For anyone with a preference for working in desktop mode, this disjointed weirdness merely exacerbates a problem that has been present for some time -- the idea that Windows 8.x just doesn't seem to know what it wants to be. The strange hybrid beast that has been created is worse than the Frankenstein's monster it has has been likened to. It's just a bloody mess. Accusations of being bolted together are nothing new, but it is astonishing that Microsoft can consider this a completed product and be happy to put its name to the update. This was meant to be the one update to rule them all -- in reality it has just fucked things up. There is really no politer way to put it.
There have been complaints, whinges and grumbles about the fact that the Start screen has not featured a shutdown option. Well, fear not! This is addressed in the Update! Oh wait… no it's not. My mistake. Yes, there is now a shutdown option, but it is very awkward and the 'workflow' of getting to it is just absurd. Click the Start button at the bottom left of the screen. If the Start screen is configured to go to App view you will then need to switch to the other screen. Then the power icon is visible, nestled in the upper right hand corner of the screen -- the opposite bloody corner to the Start button! Do you not believe in efficiency, Microsoft?! -- which can finally be tapped or clicked to restart or shutdown. I need a lie down after that.
Windows 8.1 Update is a Band-Aid holding together an already patched up operating system. There had better be some seriously impressive plans in store for Windows 9 -- or maybe even another update to the 8.x range -- because Microsoft is putting its famous franchise in danger of becoming even more of a laughing stock than it currently is. And yet I continue to use it! Is there something wrong with me? When will I start to listen to my own advice and spend more time with OS X and Chrome OS? The Update is a joke. It smacks of Microsoft desperately scrabbling to correct its mistakes and failing -- dramatically -- to do so. This is a poor patch for a broken operating system. Go home Microsoft, you're drunk.
Did you bite the bullet and install the Update? Did it live up to expectations (did you have high ones?) or was it a disappointment?
Image Credit: Fer Gregory/Shutterstock
-

Cover up your bits! Vine bans porn
Publié: mars 7, 2014, 6:27pm CET par Mark Wilson
 The internet is awash with porn. If you want to find something a little titillating, have a taste for the weird, or just want some good old fashion hardcore, you don’t have to look too far to satiate that desire. But if you have been looking to Vine to get your kicks -- and seriously, there must be some better places to look! -- you're going to have to turn your attention elsewhere, as a complete porn ban has been put in place.
The internet is awash with porn. If you want to find something a little titillating, have a taste for the weird, or just want some good old fashion hardcore, you don’t have to look too far to satiate that desire. But if you have been looking to Vine to get your kicks -- and seriously, there must be some better places to look! -- you're going to have to turn your attention elsewhere, as a complete porn ban has been put in place.It does not matter if you want to share porny videos of yourself with a loved one privately, everything that falls into the category of "Pornography and Sexually Explicit Content" is outlawed. Vine's terms of service state in no uncertain terms that "You may not post Content that... Is pornographic or sexually explicit", and the Vine Rules make it abundantly clear what is permitted and what is not.
Further clarification is provided in an updated support article where it is explained that "explicit sexual content" is defined as "depictions of sex acts, nudity that is sexually provocative or in a sexual context, and graphic depictions of sexual arousal". This encompasses all of the obvious things such as the performing of "sex acts" (solo and in company), imagery that focuses on exposed genitals (although exposed genitals are not necessarily banned), aroused genitals under clothing and animations depicting the same. Vines that show the "use of sex toys for sex acts" is not permitted, although this is probably already covered by the ban on sex acts in general.
But Vine is not completely opposed to people showing off the human body. Nudity, in certain contexts, is deemed acceptable. Non-sexual nudity is OK -- such as breastfeeding -- as well as "artistic" nudity and nudity in a documentary context -- with the oddly specific example of nude protesters. A slightly contentious inclusion on the banned list is "clothed sexually suggestive dancing".
So now you know where Vine's values lie. Let's see how long it is before people start pushing it to the absolute limit en masse.
Image Credit: Aquir/Shutterstock
-

Yahoo takes data visualization startup Vizify under its wing
Publié: mars 6, 2014, 10:42am CET par Mark Wilson
 Yahoo has been splashing the cash once again, this time placing its bets on Vizify, a company set up to make it easier to create visualizations from social media data.
Yahoo has been splashing the cash once again, this time placing its bets on Vizify, a company set up to make it easier to create visualizations from social media data.The outfit has been up and running since 2011, but as a result of Yahoo's acquisition the service will be "sunsetted". It seems that the startup has been swayed by the idea of teaming up with Yahoo with a view to expanding its audience to one of hundreds of millions and will now be working closely with the search giant on projects that are yet to be revealed.
A Yahoo spokesperson said that "we have found in Vizify a company that shares our passion for visualization technology and the user experience" (echoing an almost identical statement on the Vizify website) and that Vizify's five-person team will join Yahoo in San Francisco. While it is not yet clear exactly what the new venture will mean, it is likely that search results will benefit from new visualization tools, but there could be other ideas in the offing.
So what does all of this mean for Vizify users and users-to-be? Well, as of right now, no new signups are being accepted, either free or paid-for. Anyone who has signed up for a paid-for account will be eligible to receive a refund, and users who purchased a domain through the service will be provided with details about how to take ownership of their domains without incurring any additional charges.
As has become the norm when an online service closes, users will be provided with the option to backup their data and keep it for posterity. "For all bioholders, free and paid, we’ll be providing a way for you to opt-in to 'archive' a snapshot of your current bio that will remain live at the same URL through September 4, 2014". An email containing additional details will be sent out to users in due course.
Image Credit: PathDoc/Shutterstock
-

Time for honesty -- Samsung seems to have stopped fiddling with benchmark figures
Publié: mars 5, 2014, 11:39pm CET par Mark Wilson

Benchmarks are important. With so much choice in the world of computers, smartphones and tablets, a key factor for potential buyers to bear in mind is raw performance. A few months back benchmarking stalwarts Futuremark took the unusual step of delisting a number of handsets produced by HTC and Samsung after tests appeared to show that the phone artificially boosted performance when they detected benchmarking software was running. Now it looks as though this apparent cheating has come to an end.
Back in October, results published on Anantech showed how a number of popular phones seemed to be cheating the system, giving consumers a false representation of real-world handset performance. Now, according to new tests carried out by Ars Technica it would appear that handsets are behaving in a far more reasonable fashion after being updated to KitKat.
When tests were performed on a Samsung Galaxy S4 and Samsung Galaxy Note 3 running Android 4.3, the questionable benchmark results were noticeable. But running the same tests under Android 4.4 yielded somewhat different results. Rather than detecting the presence of a benchmarking tool and putting the pedal to the metal with every single available core, processors were only used when it was necessary. It almost goes without saying that suspicious minds were still firing. John Poole from Primate Labs ran the tests and while the results appeared to show a lack of figure massaging, he was initially skeptical.
No artificial speed boost was found. He "did not detect a boost under 4.4.2, which leads me to believe that Samsung has disabled the benchmark boost in Android 4.4.2. I was concerned that the boost became more sophisticated and was able to evade the detector." But it does appear that benchmarking tools are now treated in just the same way as any other app, rather than being singled out for special treatment.
What do you make of this? Is it too little too late? Perhaps you don’t care whether benchmark results are inflated and are quite happy to judge performance for yourself. Do you think Samsung's reputation has been damaged by the whole debacle... and is this move enough to save face?
Image Credit: Barbol / Shutterstock
-

Where have all the fanboys gone? Is brand loyalty dead and buried?
Publié: mars 5, 2014, 2:21am CET par Mark Wilson

This is a personal account of the way I have noticed the technology markets changing over the years. It is not gospel, and you are welcome (encouraged, if you like) to disagree… It's not all that long ago that brand loyalty was a given; it was almost the default setting for many people. If you got into computing -- and it was something you "got into" rather than just having as part of your life -- you stuck loyally to whatever brand you chose at the start. We could go back to the 70s and look at the birth of personal computing, but as this is my personal account, we'll have to start in the 80s.
I did just manage to sneak into the 70s -- being born in 1979 puts me in the difficult-to-comprehend position of being 34 years old but having seen five decades -- but an interest in computing didn't emerge until some time in the late 80s. I remember there being several computing camps: BBC, Amstrad, Spectrum, Vic and Commodore to name a few. My decision was made for me at an early age when my dad decided to invest in a Commodore 16 Plus 4 (the Plus 4 referring to the fact that the OS featured four built-in applications including a spreadsheet tool, the absurd simplicity of which was not lost on me even at a young age).
The Commodore was laughably basic -- in retrospect, I'm fairly sure I realized this at the time -- but it did give me a chance to cut my programming teeth. Hitting secondary school, I was introduced to the wonders of the PC and my dad decided it was time to switch to a new platform. The Commodore, which had to be plugged into a television rather than a monitor, was found wanting and ultimately left to gather dust in a cupboard. There was much excitement amongst my circle of friends about the system we would be getting. It was at the time of the first breed of Pentium processors, the speed of which just could not be conceived!
Our family, however, opted for the next model down; a 486 DX2-66 running, unsurprisingly, at a blistering 66MHz and packing a mindblowing 16Mb RAM. All for around £1500 -- probably about $3000 with the exchange rate at the time. Starting off with Windows 3.11 and progressing through Windows 95 to 98, this was a workhorse used for my father’s business, as well as homework, surfing the web on a 56k modem (straight in at the top end of dial up speeds!). Knowing a few dodge characters, even in the days before BitTorrent and the like, it was still possible to obtain early builds of Windows, and I remember eagerly installing Memphis, Nashville and other builds whose names now escape me -- yes, I could venture towards Wikipedia, but where's the fun in that?
I loved Windows. I loved being able to tweak the hell out of it. I remember editing config.sys and autoexec.bat files, delving into the registry and tinkering with .ini files. I was hooked. Among my friends, PCs were very much the norm. Macs were not unheard of, but they were outrageously expensive and the preference of… well… freaks, really. It was Windows all the way through school. It was just expected that this is what you would use. It was a little strange at university being offered the choice of Macs or PCs! I had used Macs a few times -- they were hardly difficult, after all -- and they did make a nice change every now and then.
It wasn’t until starting my first (proper) job at the age of 21 that I encountered what would now be known as fanboys. Working in publishing, writing about computers meant using a PC day in, day out, and spending just about every waking hour with likeminded people. Despite working for countless PC titles -- including an official Windows Me title (stop sniggering!) -- it was interesting to encounter the design and art teams who not only used Macs, but lived, breathed and staunchly advocated the use of them.
Letters from readers were quite vitriolic in their support for, or hatred of, Macs or PCs. Back then it was just not possible to like both. There was, of course, Linux, but this was considered seriously weird! It was around this time that smartphones started to emerge… or what would come to be known as such. If desktops and laptops were polarizing when it came to operating systems, it was nothing to what was to come in the world of cell phones. There was a lot of choice to start with. Palm, BlackBerry, Windows Mobile and, of course, Android and iOS.
Again, you chose your camp and stuck to it doggedly. I'm nothing of a sports fan, but it could be likened to picking your team. Whether you make your choice based on where you live, a family history, or a colour preference, it was your choice to the death. Everything else was rubbish, used by idiots -- but the chances were that your choice of desktop operating system did not match your mobile OS.
The explosion of the mobile market is when brand loyalty started to fragment I think. Microsoft devotees who were evangelical in their support of Windows were swayed by Android or by iOS. And this is where things start to get a little odd. There are lots of mobile fanboys. Who hasn’t heard someone defending their choice of handset? And just saying "I prefer this" is not enough. You have to be willing to die for your mobile operating system.
But while Windows continues to rule the desktop, Microsoft is yet to make serious inroads into the mobile market. You might now be a Windows XP fanboy (or just a supporter, if you prefer), but the chances of being a Windows Phone fanboy are, well… slim, shall we say. Mobile and desktop have created a couple of unique markets. Despite the fact that just about everyone uses desktop and mobile platforms there are very few people who could be -- honestly -- labelled as Microsoft fanboys. The chances are that you use Windows as your primary operating system, but it’s likely that you use Android or iOS on your phone or tablet.
Of course, there are some people who survive using just Microsoft products; it is not impossible. Apple users are the most likely to be ardent fanboys (if we must continue to use the term, let's at least agree that it’s not a term of criticism or praise, merely descriptive). Apple may not be the leader of either desktop or mobile platforms, but there's a decent crossover. The same can probably be said of Windows Phone. If you use a Windows Phone, I think it is fair to say that it is unlikely you use OS X or Linux! But in both cases it is hard to argue with the suggestion that numbers are low.
So maybe fanboys do still exist, but they have changed. And the companies who have the fanboys are the ones to blame. Microsoft's Windows Phone has still failed to win many fans, and the same can be said of Chromebook, despite Google's dominance in so many other areas. What do companies need to do to enjoy the brand loyalty of the past? Does it still exist in pockets, or have consumers been empowered by choice? I know that I am not alone in using iOS, Android, Windows Phone, ChomeOS, OS X, Linux and Windows. Variety is the spice of life! Of course I have my favorites, but I would never class myself as a fanboy (this in spite of the fact that, as some are undoubtedly aware, I write for other sites and publications, some of which have a particular leaning to them). My needs change and I will use the best tools for the job. I'm yet to find one company that caters to all of my needs and I would be interested to hear whether I am in a minority or completely alone.
Image Credit: marekuliasz / Shutterstock
-

Yahoo and BlackBerry worm further into your life with mobile ads
Publié: mars 4, 2014, 1:39pm CET par Mark Wilson

There are few people who like ads. Sure, they can be works of art -- certainly there are some advertisements that are infinitely better than a lot of the dirge pumped out by television networks -- but while advertisements on television can be fairly easily avoided (thank you TiVo -- other PVRs are available!) it is a different matter on a computer or mobile device. "Opting" to watch a mindblowing ad for Apple, Guinness or Honda is one thing, but to have unavoidable -- and usually crappy -- advertisements forced upon you whilst browsing the web or using an application is an entirely different matter.
There are groups of people who are happy to endure these adverts because they fund apps, and make it possible for developers to provide their hard work free of charge -- you may fall into this group and have perhaps been able to configure an automatic ad filter for your eyes. But there are larger legions for whom ads are just plain, damned irritating. In some instances it is possible to pay to avoid them, but this is not always the case. If BlackBerry and Yahoo get their way, advertisements are going to become rather more noticeable.
Both companies have announced plans to increase ads on mobile platforms -- ads which follow you no matter where you are. BlackBerry's troubles are well-documented and the need to generate income is understandable. BBM users may find that ads are starting to appear in the messaging tool -- particularly in beta builds. It's not yet clear if or when this will roll out to non-beta versions, but for the time being the ads will appear in the Invites section of BBM as "sponsored invites" and in the Updates section as "sponsored channel posts".
Yahoo is doing something similar in a bid to increase the number of app downloads. A spokesman for the company said: "We're testing in-stream ad opportunities with an initial group of advertisers who have mobile apps and want to connect directly with audiences across Yahoo mobile apps and sites. The purpose of these native ads is to help brands drive downloads of their mobile apps. These tests will begin to appear across all of our properties where in-stream ads run on iOS and Android devices". It's interesting to note that that there is no mention of Windows Phone.
What do you think about the prevalence of ads? A necessary evil or just seriously bloody annoying? Would you switch sides if a service or app you currently use suddenly introduced ads?
Image Credit: Drazen/Shutterstock
-

The most popular stories on BetaNews this past week February 23 -- March 1
Publié: mars 1, 2014, 4:34pm CET par Mark Wilson
 Webcam porn! Spying! Cell phones! Bitcoin controversy! Just another normal week in the world of tech news! Bitcoin exchange Mt Gox disappeared offline amid concern about missing millions and then filed for bankruptcy. After panic spread through Mac users following the discovery of a serious SSL bug in Mavericks, Apple released an update that plugged the hole -- but it was also discovered that iOS 7 has a keylogging vulnerability. Microsoft released Service Pack 1 for Office 2013, but anyone using Office 365 will need to force the installation of newer updates in order to reap the benefits.
Webcam porn! Spying! Cell phones! Bitcoin controversy! Just another normal week in the world of tech news! Bitcoin exchange Mt Gox disappeared offline amid concern about missing millions and then filed for bankruptcy. After panic spread through Mac users following the discovery of a serious SSL bug in Mavericks, Apple released an update that plugged the hole -- but it was also discovered that iOS 7 has a keylogging vulnerability. Microsoft released Service Pack 1 for Office 2013, but anyone using Office 365 will need to force the installation of newer updates in order to reap the benefits.Security updates are all well and good for operating systems and applications, but it will do little to protect you against the wandering eyes of government agencies. As if everything we have already learned about the activities of the NSA et al, this week's revelations about what the UK's GCHQ has been getting up to is sure to raise ire. Not content with logging emails and web searches, the UK intelligence agency apparently spent a number of years tapping into the webcam chats of millions of Yahoo users. There may be little good news in this revelation, but it was at least slightly amusing to find that the surveillers were rather taken aback by the amount of pornographic content they encountered. It makes ya proud!
The Mobile World Congress took place this week, bringing official news that Update 1 will be released for Windows 8.1 this spring, while Microsoft's announcement about a new batch of partners fueled speculation that devices running both Android and Windows Phone could be on the agenda. In other mobile news, Lenovo unveiled three more S-series phones and Nokia took the wraps off a new line of Android handsets -- with Microsoft revealing that Skype would be made available for the range.
As Sony launched waterproof phones and tablets in the form of the Xperia Z2 and Xperia Z2 Tablet, Microsoft was digesting the bittersweet news that Windows Phone was managing to increase its market share in the US, but stalling in the rest of the world. In a bid to maximize its share of the desktop market, reports suggested that Microsoft is considering cutting the cost of Windows licenses for OEMs. New devices were forthcoming from HP with the ElitePad 1000 G2 and ProPad 600, as well as the convertible Pavilion x360.
Samsung added to its product line with the unsurprisingly named Galaxy S5 -- and the reception was a little muted. Something of a blast from the past, BlackBerry raised its head to let the world know it is still alive, announcing details of the upcoming Z3 and Q20 smartphones. Mobile users in the US can celebrate the news that phone unlocking is now legal, although the hoped for legalization of bulk unlocking that might help to drive down is yet to happen.
Alan decided it was time to move on, cutting the cord on his cable and satellite subscriptions -- could you do the same? If not, there's always Roku's WWE network to fall back on, or Qplay from TiVo. Another option would be to invest in Apple TV, which this week was revealed to have earned Apple $1 billion. Nice work if you can get it.
Another week down, we’re already into March -- a month that holds great promise… lots to come in the week ahead!
Image Credit: vinz89 / Shutterstock
-

A somewhat rewarding hobby -- Apple TV nets $1 billion in sales
Publié: février 28, 2014, 10:26pm CET par Mark Wilson

Once dismissed as little more than a hobby for Apple, Apple TV seems to have quietly gathered momentum. Talking at a shareholder meeting in Cupertino, CEO Tim Cook revealed that the company has managed to net over $1 billion through the devices, leading him to quip "it's a little more difficult to call it a hobby these days." It's difficult to tell just how many sales this translates into as the figure includes content sales as well as device sales.
But while $1 billion may sound impressive, it is a drop in the ocean compared to the billions that Apple rakes in from its other product lines. The last figure released suggested that over 13 million apple TV boxes had been sold by May last year, but the sales figures released today relate to the fiscal year that ended in September. For anyone thinking about jumping on the bandwagon, Apple has a new incentive -- a $25 iTunes gift card for anyone who buys a set-top box by 5 March.
On Twitter, analyst Horace Dediu from Asymco described Apple TV as Apple's fastest growing hardware line, estimating a year on year boost of around 80 percent. But with Apple saying that the figures include both hardware and content sales, it's very difficult to say just where the growth lies. Initial reports about the shareholder meeting suggested that Tim Cook's announcement meant that 10 million units had been sold in the fiscal year.
But factoring in money made from content sales makes it impossible to tell -- until Apple is a little more open about sales figures, that is. According to Peter Kafka at re/code, Apple has confirmed that hardware and content sales contribute to the $1 billion. It could be the case that 2013 saw a massive surge of interest in Apple TV in terms of new adopters, but it is also possible that hardware sales are low and the majority of the money is coming from content. There has been no official word about an update to Apple TV, but it would be surprising if new hardware does not make an appearance some time this year.
Image Credit: mehmetcan / Shutterstock
-

Spotify agrees to block user-created Ministry of Sound playlists
Publié: février 28, 2014, 3:28pm CET par Mark Wilson
 Spotify is all about streaming music, creating playlists and sharing them with others. Who doesn't relish the idea of creating the ultimate mixtape and sharing with not just their best friend, but the whole world? Music fans love it, and so do the musicians who earn royalties from making their work available.
Spotify is all about streaming music, creating playlists and sharing them with others. Who doesn't relish the idea of creating the ultimate mixtape and sharing with not just their best friend, but the whole world? Music fans love it, and so do the musicians who earn royalties from making their work available.But Ministry of Sound felt a little differently about things. Back in September, the dance brand took Spotify to court, claiming that the music streaming service was refusing to delete playlists created by users that mimicked the tracklisting of Ministry of Sound releases.
The two companies have now managed to come to an out of court agreement, but there are very few details to go on at the moment. The reasoning behind the lawsuit is not quite what you might expect. Spotify was not allowing users to stream any music for which the relevant licenses had not been obtained: there is no question that Spotify was making payments to the appropriate record labels. What Ministry of Sound took exception to was the creation of playlists that were identical to compilation albums it released -- and streaming rights were only available to the original label.
It could be that Ministry of Sound felt irked at the fact it was not able to benefit from making its own music compilations available and therefore felt that no one else should be able to either. It could certainly be argued that Spotify could be seen to be benefiting from the Ministry of Sound brand. The argument is MoS owns the copyright for the compilation it has created regardless of whether individual tracks may be streamed legally -- the order in which tracks appear is what is subject to copyright just as much as the tracks themselves.
Neither company is being particularly vocal about the terms of any deal that has been reached, but head of licensing business affairs at Spotify, James Duffett-Smith said "Spotify and Ministry of Sound are pleased to have reached a resolution on amicable terms". A similarly unrevealing statement was made by Lohan Presencer from Ministry of Sound: "Ministry of Sound welcomes Spotify’s willingness to work together to reach an agreement".
It has been suggested that Spotify will not remove the offending playlists that have been created, and no users will be banned from using the service -- after all, there is nothing wrong with creating a custom playlist for personal use. But these playlists will not appear in search results, and other users will be prevented from following such playlists.
Image Credit: Krasowit/Shutterstock
-

How to force Office 365 to upgrade to Service Pack 1
Publié: février 27, 2014, 8:16pm CET par Mark Wilson

Service Pack 1 has just started to roll out to Office 2013 users, but Office 365 users have been left out in the cold. You might think that as a subscriber your software is kept constantly updated -- and this is true to a point. But talking to Paul Thurrott, Microsoft reveals that a "handful of updates are totally new in SP1" and these have not all made their way to Office 365 yet. Unless you follow the little trick that Paul has shared, that is.
Unlike many applications Office 365 does not have a built-in means of forcing an update check -- so we have to force a forced update! The steps are very quick and simple to follow, and you can grab yourself a copy of SP1 in next to no time.
- Launch the Office 365 program of your choosing.
- Click the File tab and select the Account option.
- Click the Update Options button to the right and then select Disable updates.
- If a User Account Control dialog appears, click Yes.
- Click the Update Options button again, and then select Enable updates -- again, click Yes in the UAC dialog.
A notification area popup should let you know that updates are being downloaded and you'll be running SP1 before you know it!
-

UK's Optic Nerve program spied on millions of Yahoo users' video chats -- found porn
Publié: février 27, 2014, 6:58pm CET par Mark Wilson
 It sounds like something from a James Bond film -- or something from a creepy news story about a landlord stalking one of his tenants -- but the headline relates to a real story. We're all only too aware of the activities of the NSA and other governmental agencies monitoring the telephone and internet activities of people around the world, but the latest revelations see things taking a turn for the seriously sinister.
It sounds like something from a James Bond film -- or something from a creepy news story about a landlord stalking one of his tenants -- but the headline relates to a real story. We're all only too aware of the activities of the NSA and other governmental agencies monitoring the telephone and internet activities of people around the world, but the latest revelations see things taking a turn for the seriously sinister.The UK intelligence agency GCHQ, between 2008 and 2010, tapped into the webcam chats of millions of Yahoo users.
A report in the Guardian reveals that, just as has been the case with other instances of surveillance, monitoring was carried out indiscriminately and that the agency gathered all manner of material, including that of a sexual nature. The data gathering was not just carried out in the UK; this was a global operation that is revealed in secret documents obtained by the UK newspaper.
Yahoo was chosen for monitoring by GCHQ because "Yahoo webcam is known to be used by GCHQ targets". Surveillance involved capturing an image every five minutes, and the reason for this is partly attributed to a lack of storage space, but also to comply with human rights legislation. We have heard many references made to metadata in the course of the NSA revelations, and this is a phrase that crops up here too. Agency staff were apparently limited to conducting bulk searches of just metadata, but the documents reveal that "webcam images associated with similar Yahoo identifiers to your known target" were also shown in results.
In true Person of Interest style, it appears that GCHQ was attempting to automate the process of searching for wanted targets by making use of facial recognition. But facial recognition would not be enough to deal with all of the nudity encountered by the agency in its spying. Sounding slightly prudish, one document includes the realization that "it would appear that a surprising number of people use webcam conversations to show intimate parts of their body to the other person".
Pornographic content seems to have presented something of an issue for GCHQ, with the agency discovering that webcams could "sometimes be used for broadcasting pornography" and an impressive 3 to 11 percent of captured content featuring "undesirable nudity". The good news -- if there can be any good news from a story that reveals webcam chats were being recorded -- is that disciplinary action hung over anyone caught disseminating any "offensive material" that may have been intercepted.
Yahoo insists it was completely unaware of the activities of GCHQ, issuing a statement to that effect:
We were not aware of, nor would we condone, this reported activity. This report, if true, represents a whole new level of violation of our users' privacy that is completely unacceptable, and we strongly call on the world's governments to reform surveillance law consistent with the principles we outlined in December. We are committed to preserving our users' trust and security and continue our efforts to expand encryption across all of our services.
While for now it is Yahoo that is the center of attention, the documents reveal that GCHQ was also considering monitoring Kinect cameras connected to Xbox 360s.
It's hard to imagine how the surveillance revelation could get much worse, but as there are new surprises just about every month, perhaps we should brace ourselves for the revelation that our smartphone cameras are constantly recording every single thing we do. At least that would go some way to explaining flaky battery life...
Image Credit: 06photo/Shutterstock
-

Chameleon virus spreads between wireless access points like the common cold
Publié: février 26, 2014, 6:30pm CET par Mark Wilson

The latest breed of virus is airborne. We're not talking about a 24 hour bug that does the rounds at the office, but a computer virus. A team of researchers at the University of Liverpool, UK, demonstrated how a virus known as Chameleon was able to spread undetected over Wi-Fi by exploiting vulnerabilities in access points.
For town and cities where there are large numbers of routers and access points in close proximity, this represents a serious security risk as there is potential for a terrifying number of infections to be made in very little time.
The spread of the virus has been likened to the spread of the common cold, and it takes advantage of known weaknesses. What is particularly worrying about the spread is that it is very difficult to detect. "When Chameleon attacked an AP it didn’t affect how it worked, but was able to collect and report the credentials of all other Wi-Fi users who connected to it," says Alan Marshall, Professor of Network Security at the University. "The virus then sought out other Wi-Fi APs that it could connect to and infect".
Tackling the spread of such viruses is far more complex than those that take a more traditional form. Antivirus tools are only effective against viruses that can be detected on hard drives, in memory, or in network traffic, but in the case of Chameleon it is the Wi-Fi network itself that is infected. Just as the common cold can be carried by someone without them exhibiting any symptoms, so Chameleon can move from host to host until it finds one that can be fully infected.
It is not just fixed access points that pose a risk. Routers and other networking equipment are in plentiful supply in urban areas, but factor in mobile devices and there is then potential for the infection to spread even further afield. Professor Marshall explained that many businesses are likely to have advanced security measures in place that could thwart the spread of such a virus, but this is less likely to be the case for smaller businesses and individuals.
Full details of the research have been published online and are available for anyone to read, and the next move is to create firmware for access points that will be resistant to this type of attack.
Image Credit: Pressmaster/Shutterstock
-

US House of Representatives approves bill legalizing phone unlocking
Publié: février 26, 2014, 2:51pm CET par Mark Wilson

Do you rue the day you signed up with your phone provider? Maybe you've found a better offer elsewhere and want to take your cell phone to another company. Now, if you're in the US, you are able to -- legally -- unlock your mobile and take it to whatever network you like. The bill was approved yesterday, having been brought about by a massive petition that gathered over 100,000 signatures. A 2012 ruling made unlocking illegal by closing a DMCA exemption loophole that had been permitted in 2006 and 2010.
In other parts of the world it is common practice to unlock phones and move them between providers, so it's understandable that US residents felt they were getting a poor deal. Now the bill has been approved, handset owners are able "to legally unlock their cell phones so that they can use it on other cellular networks." But this does not mean there is going to be a free-for-all; unlocking must be carried out "without violating anti-circumvention provisions".
But the bill does not go as far as some people would like. The provision that "this bill does not permit the unlocking of cell phones for the purpose of bulk resale" is understandable up to a point, but there is also the risk that this serves to push up the price of handsets. There are also limits on the type of device that can be unlocked -- for now at least. Bill H.R. 1123 now permits the unlocking of phones, but a decision is yet to be made about tablets.
This is not to say that tablet unlocking will not be made legal at some point in the future, but for now the bill "directs the Librarian to study the issue of unlocking other cellular devices (e.g. tablets) and enact a rulemaking for these devices". It will be interesting to see just how quickly tablet legislation changes -- really there is no reason for them to be treated any differently to cell phones.
The bill is likely to be broadly welcomed by consumers, but for Public Knowledge, an organization fighting for consumer rights, it does not go far enough. A statement on the Public Knowledge website explains that the group "supported a previous version of the bill that did not draw a distinction between cell phone unlocking and bulk cell phone unlocking".
Sherwin Siy, Vice President of Legal Affairs at Public Knowledge said:
We're glad that the bill will allow Americans to unlock their phones. However, language recently added to the bill could be interpreted to make future unlocking efforts more difficult. We're disappointed that the House was unable to reach a compromise that would have prevented such barriers and still met the objectives of helping consumers.
It's clear that more needs to be done to prevent copyright law from interfering with consumers' rights and picking winners and losers between business models. There is bipartisan support for such an approach to reform and we're hopeful that the bill will be improved in the Senate.
Businesses will see the bulk unlock caveat as a serious obstacle and, ultimately, it means a worse deal (or at least not as good a deal as could be conceived) for consumers as well.
What do you make of it all? Is it a step in the right direction, or a watered-down piece of legislation?
Photo credit: Brian A Jackson/Shutterstock
-

Bitcoin exchange Mt. Gox is offline 'in light of recent news reports'
Publié: février 25, 2014, 6:48pm CET par Mark Wilson

One of the largest Bitcoin exchanges that exists, Mt. Gox, is currently offline. It is not entirely clear what the full story behind the disappearance of the site is, as the situation is still evolving. There have been rumors of Bitcoin theft, but nothing has yet been verified. Mt. Gox vanished off the face of the internet, and initially visitors saw nothing more than a blank page but a statement has since been added to the site.
Pay a visit to the Mt. Gox website now and you'll be greeted by a message explaining that the site is currently not operational:
Dear MtGox Customers,
In light of recent news reports and the potential repercussions on MtGox's operations and the market, a decision was taken to close all transactions for the time being in order to protect the site and our users. We will be closely monitoring the situation and will react accordingly.
Best regards,
MtGox Team
The Twitter feed for the Tokyo-based Bitcoin exchange site is now devoid of tweets, although the account remains active and currently has over 28,000 followers.
A document purporting to be a "crisis strategy" paper from the company has been circulating online, although its authenticity has yet to be confirmed. The document refers to almost 750,000 missing Bitcoins and suggests that a rebranding to Gox.com may be on the cards. Over the weekend Mt. Gox resigned from the board of directors at the Bitcoin Foundation, but it is unclear whether this is related to what else is happening at the moment.
In a statement emailed to Reuters, Mt. Gox CEO Mark Karpeles said: "We should have an official announcement ready soon-ish. We are currently at a turning point for the business. I can't tell much more for now as this also involves other parties".
As and when further details emerge, we'll update this post.
Image Credit: Lightboxx/Shutterstock
-

Mark Zuckerberg addresses MWC 2014 -- looks to get the world online
Publié: février 24, 2014, 6:58pm CET par Mark Wilson
Mark Zuckerberg spoke at the Mobile World Congress today, saying that there needs to be some "pretty dramatic changes" to help to get more people online, pointing out that most people in the world simply do not have access to the internet. The Facebook founder has already launched Internet.org with a view to getting more people online around the globe and this is referred to as an "an on-ramp to the internet" -- he wants to get a billion people online in the next five years.
Zukerberg's goal is fairly simple. He feels that there are a number of basic services -- he mentions weather and messaging specifically -- that everyone should have access to, and this is what Internet.org provides. He admits that Facebook is not able to connect everyone without help, and suggested the possibility of working with more partners in the future. It seems as though this is a venture that Zuckerberg has taken a broad view with. At the moment it is a venture that is losing money, but this is not an example of martyrdom: "If we do something good for the world, eventually we'll find a way to benefit from it".
One of the problems with keeping costs down is the volume of data involved, and the project is keen to improve efficiency. Zuckerberg explains that a year ago the average Facebook users ate through 14MB of data each day, but that with various optimization techniques, including tweaking images, this has plummeted to just 2MB. The aim is to get this number down even lower, helping to reduce costs for carriers.
He says that in order to succeed, additional partnerships are needed. The activities of the NSA are cited as making the industry work more closely together, but at the same time as being "not awesome" -- something which will be widely viewed as an understatement. Rounding up with a Q&A session, Zuckerberg spoke of the recent purchase of WhatsApp, saying that the aim is to make no changes to it at all.
What do you think? Are weather reports and messaging what the world needs, or are there other things to focus on first?
-

HP boosts its mobile business device portfolio with ElitePad 1000 G2 and ProPad 600
Publié: février 24, 2014, 4:32pm CET par Mark Wilson

There have been a lot of interesting announcements made at MWC this year, and HP is one of several companies making it clear that business users have not been forgotten. The new HP ProPad 600 has been unveiled alongside an upgraded HP ElitePad 1000 G2, and both have been designed with mobile computing in mind.
Both tablets run Windows 8.1 and the ElitePad 1000 G2 picks up where the HP ElitePad 900 G1 left off. The hardware is impressive enough, but there is a strong focus on battery life and portability.
Battery life is helped by the inclusion of a Qualcomm GobiTM 4G LTE modem, and weighing in at just 1.5lbs and measuring a mere 9.2mm thick, this is one tablet that won't build up your muscles. The tablet is driven by a 64-bit Intel AtomTM Quad-Core processor, backed by 4GB RAM and a choice of 64GB or 128GB of storage. Prices start at $739, and this includes a 1900 by 1200 WUXGA screen featuring Corning Gorilla Glass 3. HP points out that with an aspect ratio of 16:10, there is 5 percent more screen real estate than with the more standard 16:9 aspect ratio.
The ProPad is available from March and while there is currently no pricing information for the HP ProPad 600, this will be announced ahead of the launch in April. This time around there's 64GB of internal SSD storage, but this can be boosted by up to 32GB with a microSD card. As with the ElitePad 1000 G2, there's a 10 inch 1900 by 1200 WUXGA display, and a 2MP front facing camera as well as an 8MP camera on the rear for HD photography needs.
A Micro USB 2.0 port is joined by a Micro HDMI port and the weight of just 1.44lbs make this another easily transported device. The 8380 mAh battery gives up to 8.5 hours of video playback, and the fanless design keeps everything nice and quiet. 4GB RAM is available for the 64-bit model, while the 32-bit version has 2GB.
-

Sony announces Xperia Z2 smartphone and Xperia Z2 Tablet, er, tablet
Publié: février 24, 2014, 11:10am CET par Mark Wilson

There's already a lot of news coming out of the Mobile World Congress, Barcelona, and Sony is using the 2014 event to launch the latest additions to the Xperia range. The Xperia Z2 is a waterproof handset that is being billed as "the world’s best camera and camcorder". This is a claim backed by the inclusion of a 20.7 MP sensor, a 5.2 inch HD screen and the ability to capture video in 4K. Sound is recorded with digital noise canceling, and image stabilization is borrowed from Sony's existing range of camcorders and can reduce ambient noise by up to 98 percent.
The phone is driven by a Qualcomm Snapdragon 801 processor with 2.3 GHz quad-core Krait CPU as well as the Adreno 330 GPU. To ensure maximum shooting time, Sony saw fit to include a 3200 mAh battery, and power-saving technology is used to automatically switch off any phone features that are not being used.
Of course, the hardware is important, but Sony is also including updated software. The new Xperia camera apps allow for video recording at 120 frames per second, depth of field adjustment and a range of augmented reality effects. Sony has designed the device to feel good in the hand, using an aluminum uni-body to produce a slim device that has a smooth finish.
There are no prizes for realizing that the Xperia Z2 Tablet is essentially a larger version of the Xperia Z2. This tablet is touted as the slimmest and lightest waterproof tablet in the world, and is all but identical to the Z2 in terms of specs. The larger display -- a 10.1 inch screen -- is a Live Color LED panel that offers more natural images, and is squeezed into a case that's just 6.4mm thick, weighing in at 426g (the LTE model is 13g heavier). A 6000mAh battery provides up to 100 hours of video playback.
The Xperia Z2 and Xperia Z2 Tablet will be available around the world in March.
-

Lenovo adds three new handsets to the S-series -- something for every pocket
Publié: février 24, 2014, 9:50am CET par Mark Wilson

Whether you're looking for a phone whose battery will last all day, a handset that can push pixels around the screen faster than others, or looks are more important to you, Lenovo is hoping to sway your custom its way with the latest additions to the S-series range of smartphones. Starting at the cheaper end of the scale, the S660 is set to cost $229 and is aimed at "value seekers". Packing a 4.7 inch screen, the handset's key selling point is the battery life, but the brushed metal finish is sure to turn some heads as well.
Moving up market slightly, we come to the S850 which has been built for "fashion-conscious users". The 5 inch screen is found on the front of a thin and light body which is available -- interestingly -- in a choice of pink or white, and will set buyers back $269. The phone is driven by a MTK quad-core processor and with 13 MP rear and 5 MP front cameras, this is a device that looks set to impress with its all-glass exterior.
But the most noise is being made about the S860 -- the handset for all-day, uninterrupted usage. Priced at $349, the phone has a high definition 5.3 inch screen and Lenovo is pushing a claimed 24 hours of talk time, as well as a standby time of forty days. In fact, Lenovo seems to think that there is so much battery capacity that a micro USB cable is provided that can be used to charge other devices! In terms of raw power, there's a quad core processor, as well as 2GB RAM.
Liu Jun, executive vice president, Mobile Business Group, Lenovo said, "The new S860, S850 and S660 smartphones perfectly complement the full range of mobile devices available to consumers around the world, letting consumers easily pick the Lenovo smartphone that’s right for them. Customers told us they wanted a great user experience without sacrificing performance, so we built these new smartphones for style, blazing fast processing speeds, and integrated Lenovo apps".
All three handsets are due to go on sale in "select markets" from June.
Photo Credit: anaken2012/Shutterstock
-

The most popular stories on BetaNews this past week February 16 -- February 22
Publié: février 22, 2014, 1:54pm CET par Mark Wilson
 Another week, another spate of security related news. In the latest of a recent run of high-profile hacks, Kickstarter announced that it had been hacked, and it was discovered that ASUS routers could be sharing files with more people than users intended. Google is looking to bolster online security with its latest acquisition -- audio-based authentication outfit SlickLogin, while Microsoft's latest partnership with DocuSign looks set to make digital signatures in Office simpler and more secure. If you were under the impression that app security was generally increasing, think again; a new study shows that an almost unbelievable 96 percent of applications have security issues.
Another week, another spate of security related news. In the latest of a recent run of high-profile hacks, Kickstarter announced that it had been hacked, and it was discovered that ASUS routers could be sharing files with more people than users intended. Google is looking to bolster online security with its latest acquisition -- audio-based authentication outfit SlickLogin, while Microsoft's latest partnership with DocuSign looks set to make digital signatures in Office simpler and more secure. If you were under the impression that app security was generally increasing, think again; a new study shows that an almost unbelievable 96 percent of applications have security issues.Brian got his hands on the Lenovo Miix 2 and was reasonably impressed by what he saw. He also unboxed the much touted Nokia Lumia Icon and found it to be not dissimilar to the 928 -- no bad thing. Anyone looking for an entry-level 4G smartphone now has the Android-based Samsung Galaxy Core LTE to look forward to, complete with "Jelly Bean Plus".
While Microsoft celebrated Outlook.com's first birthday, Sony was celebrating hitting 5.3 million PlayStation 4 sales as well as becoming the most popular console in the US in January. New entertainment options will be finding their way to Amazon Prime thanks to a new deal with MGM -- get ready for some Silence of the Lambs! -- and smart TV owners are set to benefit from a new partnership between Opera and TiVo which will bring a new selection of apps..
Microsoft's ad campaigns took a turn for the weird as the company apparently branded Surface 2 purchasers idiots, and also officially rebranded SkyDrive as OneDrive as well as relaunching Web Apps as Office Online. Google seemed to be suggesting that Glass owners are also a little daft, feeling the need to provide a list of dos and don'ts for buyers. The week was rounded off by Facebook parting with a not insignificant $19 billion for WhatsApp.
It has been a little quiet of late, but news seems to be gradually picking up after something of a slow start to the year -- hopefully the trend will continue, and we'll have a busy week ahead of us!
Image Credit: vinz89 / Shutterstock
-

96 percent of applications have security vulnerabilities -- and it's getting worse... or better
Publié: février 20, 2014, 11:55am CET par Mark Wilson
 Publishing its Application Vulnerability Trends Report, Cenzic states that virtually all of the applications it tested had at least one security vulnerability. A staggering 96 percent of apps exhibited security issues, and it looks as though things are on a downward spiral.
Publishing its Application Vulnerability Trends Report, Cenzic states that virtually all of the applications it tested had at least one security vulnerability. A staggering 96 percent of apps exhibited security issues, and it looks as though things are on a downward spiral.In a similar report published last year, it was found that the median number of flaws was 13; this year it has increased to 14. So it appears as though things are getting worse... but is this the full story?
This is something that will be of particular concern where employees are increasingly bringing their own laptops and tablets into the work environment rather than relying on company-supplied and controlled devices. Especially worrying is the rise in security problems in mobile devices. Cenzic found that more than 80 percent of mobile apps had "excessive privileges" or violated privacy. The move to the cloud has been broadly welcomed, but it has also brought with it a range of problems.
An increasing number of web services and applications are in use, and there are concerns about how many are sharing sensitive, private data with third parties. In fact, almost a quarter of the security problems found related to such "information leakage" as Cenzic rather quaintly puts it. There have been a number of very high profile security issues in recent months -- Target, Adobe, etc -- affecting millions of people around the world, highlighting just how important security is. It is also proving incredibly costly, with companies generally responding retrospectively rather than proactively bolstering security; all at a global cost of $300 billion.
But while these figures may not sound all that great, there are signs of improvement. Despite the increased number of problems with mobile apps, and the slight jump in the median number of flaws, there is an overall downward trend. Back in 2012, an almost unbelievable 99 percent of applications were found to have security vulnerabilities, so things have improved to the tune of three percentage points. Cenzic points out that there is a shortage of "skilled application security professionals", so brush up on your skills and you could make yourself highly employable.
Image Credit: micic/Shutterstock
-

Sony shifts 5.3 million PS4s and takes number one spot
Publié: février 18, 2014, 4:10pm CET par Mark Wilson

Ten days ago, the PlayStation 4 passed something of a landmark -- selling 5.3 million units. Figures also shows that the PS4 was the top selling console in the US in January. Hitting the number one spot is based on data from NPD Group, while the overall sales numbers come from Sony's own record of sales in North America and Latin America, as well as in Europe and Asia.
Andrew House, President and Group CEO of Sony Computer Entertainment Inc said "I am thrilled that so many customers around the globe have continued to select PS4 as the best place to play throughout and beyond the holiday season. We are delighted that according to the NPD Group's latest data, PS4 was January's top-selling console in the United States. The PS4 system's momentum just keeps growing stronger".
With the PS4 due to launch in Japan on 22 February, these sales figures are almost certain to gain a massive boost towards the end of the month. But Sony already seems to have gathered some impressive momentum, managing to sell almost as many units in a few months as Nintendo managed with the Wii U in a year.
Microsoft will be licking its wounds, with the Xbox One having been beaten into second place. Sales of the Microsoft console have been a little disappointing, and in January, just over half the number of Xbox Ones were sold as PS4s
-

Google acquires SlickLogin, the sound-based security startup
Publié: février 16, 2014, 6:28pm CET par Mark Wilson

Google is delving into its wallet once again, fishing out a little cash and going on a spending spree. This time around, it is Israeli startup SlickLogin that is being put in the shopping cart. You may not have heard of the company, and that’s because its services haven't even launched yet, but it is looking to revolutionize two-factor authentication. Additional layers of security are being added by every website worth its salt, and SlickLogin has an interesting alternative to the traditional password.
Like many other two-factor security systems, this makes use of smartphones -- but in a somewhat different way. Rather than generating a unique code that is emailed out and needs to be typed into a website, SlickLogin is audio-based. A unique sound is generated and played through a computer's speakers. So far, so weird. To make things more interesting, and probably more secure, the sound is inaudible thanks to being ultra-sonic, and an app on a smartphone placed near the speaker picks up the sound and completes the authentication process.
The acquisition is announced on the SlickLogin website, where the three-man team (comprising Or, Ori and Eran), make a statement under the heading SlickLogin Joins Google:
We started SlickLogin because security measures had become overly complicated and annoying.
Our friends thought we were insane, but we knew we could do better. So we set out to improve security while still making it simple for people to log in.
Today we`re announcing that the SlickLogin team is joining Google, a company that shares our core beliefs that logging in should be easy instead of frustrating, and authentication should be effective without getting in the way. Google was the first company to offer 2-step verification to everyone, for free - and they're working on some great ideas that will make the internet safer for everyone. We couldn`t be more excited to join their efforts.
No details have been given about how much money has changed hands. It is quite possible that the SlickLogin team will simply be absorbed into Google, but we'll update you when we hear more about it.
Image Credit: Bagiuiani / Shutterstock
-

Kickstarter is the latest hack victim -- regains control and issues belated apology
Publié: février 16, 2014, 1:07am CET par Mark Wilson

It seems to be hacking season at the moment, with new high profile victims hitting the headlines just about every day. The latest target is Kickstarter. The website, which exists to help projects raise the funds they need to get off the ground, was hacked on Wednesday, but details of the attack -- along with an apology -- have only just been made public. If you're wondering why is has taken so many days for Kickstarter to speak out, the company has pre-empted your question and supplied a FAQ: "We immediately closed the breach and notified everyone as soon we had thoroughly investigated the situation".
In a statement on the Kickstarter website CEO Yancey Strickler explained that the company had been contacted by law enforcement officials and alerted to the activity of hackers. It's not clear what users are likely to find more alarming, the fact that the site was hacked in the first place, or the fact that it was not Kickstarter that noticed, but a third party.
Few details have been given about the number of accounts that were affected, but Kickstarter admits that hackers gained access to "usernames, email addresses, mailing addresses, phone numbers, and encrypted passwords". Unauthorized activity was detected on just two accounts following the security breach, and these have now been secured. Strickler is quick to point out that passwords are encrypted, but conceded that "it is possible for a malicious person with enough computing power to guess and crack an encrypted password, particularly a weak or obvious one".
Users are being advised to change their passwords, and a reminder is displayed in a banner at the top of the page on the first visit after the attack. Kickstarter says that its security has already been bolstered since Wednesday, but there seem to be even more fortifications planned as more security improvements are to be introduced in "the weeks and months to come".
Are you concerned by the recent state of attacks that have been launched on big websites, or is it to be expected?
Image Credit: SFerdon / Shutterstock
-

The most popular stories on BetaNews this past week: February 9 -- February 15
Publié: février 15, 2014, 1:46pm CET par Mark Wilson
 It is usually Bill Gates who is heralded for his philanthropy, but according to the Chronicle of Philanthropy, it is Facebook's Mark Zuckerberg who is currently the most generous. In another change from the norm, malware threats to OS X, Linux and Android have increased, showing it is not just Windows that is prone to attack. As if to prove this, Mac malware has been discovered that has been designed to steal Bitcoins from victims. Factor in all of Apple's devices and the company managed to sell more units than Windows PCs are sold, although this revelation caused quite some debate.
It is usually Bill Gates who is heralded for his philanthropy, but according to the Chronicle of Philanthropy, it is Facebook's Mark Zuckerberg who is currently the most generous. In another change from the norm, malware threats to OS X, Linux and Android have increased, showing it is not just Windows that is prone to attack. As if to prove this, Mac malware has been discovered that has been designed to steal Bitcoins from victims. Factor in all of Apple's devices and the company managed to sell more units than Windows PCs are sold, although this revelation caused quite some debate.Twitter found itself in the headlines after the James Dean estate tried to gain control of a fan's James Dean-related account. Twitter has already spoken out about the shackles binding companies from being open about government data requests -- companies are practically falling over themselves to add their names to the list -- and Dropbox is in agreement. The European Commission has expressed a desire to wrestle some control of the internet from US hands voicing fears that too much influence was being exerted,
Mozilla has unveiled part of its plans to steal back users from Chrome. Firefox accounts work much like Google ones allowing data to be synced between devices. After months of speculation, rumors and leaks, the Nokia Lumia Icon finally got an official release date on Verizon -- which will add to the 1 billion smartphones that shipped in 2013.
Performing remote tasks from a Windows Phone just got easier thanks to the release of Putty, and in other mobile news HTC has posted disappointing Q4 results and has announced it would be focusing on cheaper handsets in the future. Chromebook users stand to benefit from Windows applications thanks to a venture between Google and VMware. When making calls on the move, Google just made it a little easier to keep in touch with your nearest and dearest, with a new voice dialling option that recognized common relationships. Hulu has joined forces with CBS to bring a range of classic shows to the streaming service, and DirecTV channels have found their way onto Roku devices.
Wayne was not overly impressed with Windows 8.1 Update 1, ruing the lack of a Start menu, while Joe suggests that Microsoft has approached Windows 8 in completely the wrong way. In slightly more cheerful news for Microsoft, the company has managed to sell 200 million Windows 8 licenses -- although it is worth noting that this includes OEM sales -- and the FAA has approved pilots' use of Surface 2. Mihaita has pondered whether Microsoft should embrace legacy apps into the Windows Store. But it's not all about Microsoft and Windows; laptops running Ubuntu are being handed out to students in Pennsylvania.
Another seven days of news coming up!
-

VoIP service Viber snapped up for $900 million
Publié: février 14, 2014, 8:43pm CET par Mark Wilson
The world of VoIP services is one packed with various names bustling for attention. One of the biggest names in the game is Viber, which started small but grew impressively as it spread across platforms -- now it has grown to the point that it is deemed worthy of handing over $900 million. At least that is the view of Rakuten, the Japanese firm behind Play.com and the Kobo eReader that agreed to part with this not insubstantial sum of money for an outright purchase of Viber Media Ltd.
With around 280 million registered users, Viber could be quite a money-maker for Rakuten who explained that the service has a "rapidly growing numbers of users, especially in emerging countries". With its fingers already in various online pies -- ebooks, shopping and streaming media through Wuaki.tv -- Viber represents yet another string to Rakuten's bow as the company "aims to be the global number one internet services" provider.
The purchase of Viber strengthens the firm's digital portfolio and it is likely that the VoIP tool will be incorporated in the "Rakuten Ecosystem" and will probably benefit from integration into the Super Points reward program that is already in place.
Rakuten chairman and CEO, Hiroshi Mikitani, said "I am tremendously excited to welcome Viber to the Rakuten family. Viber delivers the most consistently high-quality and convenient messaging and VoIP experience available. Viber has introduced a great sticker market and has tremendous potential as a gaming platform. [It] understands how people actually want to engage and have built the only service that truly delivers on all fronts".
Are you an existing Viber user? Are you excited or concerned about what the future might hold following the acquisition?
Image Credit: Brian A Jackson / Shutterstock
-

Microsoft celebrates selling more than 200 million Windows 8 licenses
Publié: février 14, 2014, 12:15am CET par Mark Wilson
Very little has been said about sales figures for Windows 8 of late, but today Tami Reller, Microsoft's executive vice president of Marketing outed the most recent number of sales during a webcast. Reller revealed that 200 million Windows 8 licenses have now been sold. This is an impressive increase from the last sales figures of 100 million back in May 2013, but sales of the latest version of Microsoft's operating system remain slower than its predecessors.
The 200 million licenses do not include volume license sales, but the number does include sales to the public as well as those to OEMs. A doubling of sales in under a year is not to be sniffed at, but it will probably do little to calm the vocal groups keen to bash Windows 8's success. Ultimately the speed of sales is still a little slow. While more than 40 million licenses were sold in the month after Windows 8's release, this was not sustained.
Sales are a little on the disappointing side when compared to those of Windows 7. While Windows 8 has taken almost 15 month to pass the 200 million landmark, Windows 7 raced past this, selling 240 million licenses in its first year of availability.
It's not clear whether Microsoft was waiting until the 200 million mark was passed before announcing sales figures again, or indeed if there will be further, more regular announcements.
But one thing is for sure -- champagne corks had to have been popping when that magic number was reached.
Photo credit: Kesu/Shutterstock
-

TV show uncovers lost 'Steve Jobs time capsule' after 30 years
Publié: février 13, 2014, 6:53pm CET par Mark Wilson

Time capsules are a cool idea, and they're something many of us put together at school. A box, tin, jar or other container to house keepsakes, momentos, favorites things and other objects that capture the zeitgeist. After 1983's International Design Conference in Aspen, Colorado, the organizer decided to create a time capsule on a larger scale -- a 13 foot pipe that looked a little like a torpedo. Into it were a range of goodies from attendees and presenters. Steve Jobs threw his Apple Lisa mouse and the capsule was dubbed the Steve Jobs Time Capsule.
The plan was to unearth it in the year 2000 -- that iconic year that was seen to hold such promise and power before it arrived -- but it was lost thanks to a combination of landscaping, poor memory and a lack of mapping. The TV show Diggers brought the capsule above ground for the first time in 30 years back in September, but video footage of the excavation has only just been released.
The passing of Steve Jobs makes the video all the more poignant, but there's a great deal for 80s enthusiasts to get excited about as well.
In addition to the beer (not strictly related to the 80s, I'll admit), the capsule also contained a Rubik's cube and an 8-track of the Moody Blues. But without a doubt, it is the iconic mouse placed in the capsule by a truly iconic man that is the star of the show.
The episode of Digger in which the capsule features airs on National Geographic on February 25 at 10 pm ET. Check out the video!
-

Rise of the mobile -- Apple devices outsell Windows PCs
Publié: février 13, 2014, 11:46am CET par Mark Wilson
 Apple overtakes Microsoft! That’s not a headline you'd expect to read, and when you look at sales of Macs versus Windows desktops, Macs and Windows laptops, or any combination of these, it is Windows devices that are always going to come out on top. But look at things from a different angle and it is a very different story. In Q4 2013, the number of Apple devices sold exceeded the number of Windows PCs sold around the world.
Apple overtakes Microsoft! That’s not a headline you'd expect to read, and when you look at sales of Macs versus Windows desktops, Macs and Windows laptops, or any combination of these, it is Windows devices that are always going to come out on top. But look at things from a different angle and it is a very different story. In Q4 2013, the number of Apple devices sold exceeded the number of Windows PCs sold around the world.This is an interesting demonstration of the notion that mobile devices are very much on the increase. Compared to Windows PCs, Macs account for a very small percentage of computer sales, but once sales of iPads, iPods and iPhones are factored in, Apple overtakes PCs -- not by much, but it is still significant. It is also worth noting that while Windows Phone is widely derided for poor sales, once these smartphones are included, Windows devices return to the top of the charts -- but again, not by much.
Obviously it is not usual to compare the sales of mobile and non-mobile devices achieved by one company to just non-mobile sales made by another, but these figures do make for interesting reading.
As analyst Benedict Evans notes: "This is a pretty good illustration of the scale of mobile: Apple limits itself only to the high end of the mobile market but still sells more units than the whole PC industry".
It appears that users' reliance on traditional desktop software is starting to diminish, which will come as good news for Microsoft keen to push Surface 2 devices running Windows 8.1 (RT).
Photo Credit: sukiyaki/Shutterstock
-

1 billion smartphones ship in 2013, Android and iOS still dominate
Publié: février 12, 2014, 8:51pm CET par Mark Wilson

According to figures released by International Data Corporation (IDC), 2013 was the year that smartphones really took off -- a staggering 1 billion units shipped. As has been the case for some time, it is Android and iOS that continue to dominate, with Google's mobile operating system claiming a 78.1 percent market share, and Apple's 17.6 percent. As has been the norm, Windows Phone found itself in third place, although it did manage to increase its market share to 3 percent.
The figures are based on shipments in the fourth quarter of 2013, and when compared to the same period in 2012, Android and Windows Phone both made gains while iOS lost some of its market share. Jumping from 70.3 percent of the market in 2012, Android's growth was impressive, while iOS dropped 3.3 percentage points from 20.9 percent. Looked at in terms of percentage points, Windows Phone's jump from 2.6 to 3.0 percent of the market, it still represents an improvement of more than 13 percent.
It is interesting to see how market shares changed throughout 2013. While Android and iOS shared 93.8 percent of the market for the year, in the Q4 the market share was 95.7 percent. Ramon Llamas, Research Manager with IDC's Mobile Phone team said: "Clearly, there was strong end-user demand for both Android and iOS products during the quarter and the year. What stands out are the different routes Android and Apple took to meet this demand. Android relied on its long list of OEM partners, a broad and deep collection of devices, and price points that appealed to nearly every market segment. Apple's iOS, on the other hand, relied on nearly the opposite approach: a limited selection of Apple-only devices, whose prices trended higher than most. Despite these differences, both platforms found a warm reception to their respective user experiences and selection of mobile applications."
Here is the smartphone OS market share, with shipments, in Q4 2013.
Here is the smartphone OS market share, also with shipments, for 2013.
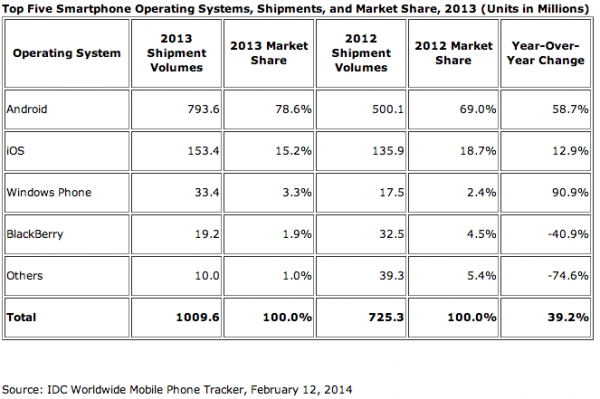
It seems that the cheaper smartphones are becoming more popular with handsets costing below $200 accounting for 42.6 percent of global shipments. Taking this into account it’s easy to understand Android's continued growth -- there are numerous handsets that fall into this price category. While Apple has released the cheaper iPhone 5c, it is still more expensive than a lot of Android devices. The number of manufacturers releasing Android phone means that there is much more competition, helping to drive prices down.
Photo Credit: bloomua/Shutterstock
-

Google and VMware join forces to bring Windows apps to Chromebook via the cloud
Publié: février 12, 2014, 8:18pm CET par Mark Wilson

Chromebooks may be increasing in popularity, particularly in business, but they still have a long way to go before they catch up with Windows-based laptops. One of the factors holding back Chromebook is, both obviously and ironically, Chrome OS. It is a perfectly capable operating system for anyone locked into the Google ecosystem, but it has one failing -- for many people, at least -- it will not run Windows applications. But all this is set to change thanks to a new venture between Google and VMware.
VWmare is a name long-associated with bringing one platform's apps to another using virtualization, and now it is pushing its DaaS platform (or VMware Horizon Desktop as a Service Platform for Service Providers to give it its full, unabridged title) as a way to bring Windows applications to Chromebook users. As this is something that will be available on a subscription basis, it is likely to appeal to businesses rather than individuals, but it does break down another obstacle for anyone with two minds about Chromebook.
Amit Singh, President of Google Enterprise, claims that "Google Chromebooks can save businesses about $5,000 per computer when compared to traditional PCs", but this does not eliminate the need many people still have for Windows software. VMware's Horizon DaaS platform delivers Window applications, and even a full desktop experience, via the cloud. As Google puts it, "this means you can work with Chromebooks and connect to a Windows experience running VMWare Horizon View".
Businesses keen to get their hands on the technology can contact Google for "on-premise service", but an app will be made available in the Chrome Web Store.
If you're a Chromebook user is this something you're interested in, or could it tempt you away from your traditional laptop to Google's take on things? Or are you happy to keep Windows apps on Windows computers, and use a Chromebook to work with other apps and services?
Image Credit: Iaroslav Neliubov / Shuttstock
-

Europe calls for less US influence over the internet
Publié: février 12, 2014, 6:34pm CET par Mark Wilson

The US is used to being a dominating force in the world -- this is true in sport, politics, economics, and many other areas -- but the European Commission thinks there should be less US influence over the internet. There are concerns about the level of control the United States has over the technologies and protocols that underpin the internet. One area for concern is ICANN which operates on behalf of the US government yet exerts control over procedures that have global effects.
There is also concern that Europe does not currently have enough sway over the internet. Neelie Kroes, commissioner in charge of telecommunications policy, said: "Europe must contribute to a credible way forward for global internet governance. Europe must play a strong role in defining what the net of the future looks like."
US surveillance of the internet sent shockwaves around the world and caused tensions in the relationship between the US and Europe. Following revelations by Edward Snowden about the web monitoring activities of the US, there was widespread uproar. The European Union had initialy said that an agreement to grant US agencies access to European data would be ended, but it was ultimately maintained.
A vote is due to take place to determine whether Europe-based servers should be used to store data that is gathered online, but the real aim is to try to make the internet less US-centric. A careful equilibrium needs to be struck if a globally balanced internet is to be created, but care needs to be taken that other governments don’t exert too much control -- we've already seen what has happened in China.
Image Credit: alexmillos / Shutterstock
-

Who's your daddy? Google voice dialling lets you call and text family with ease
Publié: février 12, 2014, 11:23am CET par Mark Wilson

You know how sometimes it just seem like too much hassle to scroll through your contact list to place a call or send a text to someone? Well, no more! There's no need to update your app, but Google's Search tool for Android has been enhanced with a new voice-dialing feature. The app now lets you use phrases such as "OK, Google, call mom" or "OK, Google, send a text to dad" you can... well... place a call to your mom or compose a text message to send to your dad.
Before you start panicking that Google has started spying on your family and is now aware of the relationships you have with each of your contacts, fret not! This is not an entirely automated feature -- you will need to specify which of your contacts is your mom, your dad, and so on. If you try to call your mother using the vocal command before having set up your relationship, you will be prompted to choose which of your contacts gave birth to you -- on subsequent utterances, the call will be placed straight away.
The new feature was announced on the official Google Google+ page (sorry for the stutter) and it seems to be the kind of timesaving option that will go down very well with mobile users who are ever more concerned about efficiency. At the moment you are limited to using keyword vocal shortcuts for standard familial relations, and there is support for different variants -- mum, mom and mother for example.
It's not clear whether things will be extended further to include quick-call options so you can quickly telephone your best mate or your boss. Of course, there's nothing to stop you from creating a contact called "boss", but for now we'll have to make do with a faster way of getting in touch with our immediate relations.
Good feature?
Photo Credit: pashabo/Shutterstock
-

Mark Zuckerberg is the most generous man in the US
Publié: février 10, 2014, 6:05pm CET par Mark Wilson

According to the Chronicle of Philanthropy, Facebook founder Mark Zuckerberg and his wife, Priscilla Chan, were the most generous US philanthropists last year. In 2013, the couple donated 18 million Facebook shares to the Silicon Valley Community Foundation, amounting to some $992.2 million. The Chronicle of Philanthropy put together a list of the top fifty most generous donors in 2012, ranked according to the size of individual donations.
The list is concerned only with gifts and pledges of cash and stock to non-profit organizations and it might be surprising to find that the Bill & Melinda Gates Foundation is not at the top spot -- in fact, it does not appear in the list at all. This is explained by the publication:
"Some of America’s biggest charitable donors don’t appear on the current Philanthropy 50 even though they were still writing big checks to charity. That’s not because these philanthropists aren’t giving. The Chronicle’s rankings are based on new commitments donors made to their foundations and to other non-profits in 2013 and do not count payments on past pledges of foundation grants".
The explanation of how the list was compiled does include some details of the Gates' generosity. In 2013, the couple donated $181.3 million to their foundation, but this was part of a $3.3 billion pledge made in 2014 -- and it is interesting to note that the Gates' have now donated more than this. All told, the list of the top 50 most generous donors gave more than $7.7 billion to worthy causes.
Image Credit: Ivelin Radkov/Shutterstock
-

HTC posts disappointing Q4 earnings and shifts focus to cheaper handsets
Publié: février 10, 2014, 4:42pm CET par Mark Wilson
 HTC is a brand that has fallen from the lofty heights it enjoyed just a few years ago. Today, the company releases fourth quarter earnings and the figures do not make for particularly happy reading.
HTC is a brand that has fallen from the lofty heights it enjoyed just a few years ago. Today, the company releases fourth quarter earnings and the figures do not make for particularly happy reading.On the positive side of things, the results show HTC managed to break even -- this is good news having suffered losses throughout 2013. It's not great news as profits stand at just NT$0.31 billion, but it's certainly better than a loss.
It looks as though the company is willing to learn from its mistakes, and at the same time as releasing its financial results, HTC's CEO, Peter Chou said: "We will continue to stay focused on making the best smartphones and building a compelling mid-range portfolio. Meanwhile, we are going to communicate better with consumers".
This is a sentiment echoed by Cher Wang, HTC co-founder, who said to Reuters last week: "The problem with us last year was we only concentrated on our flagship. We missed a huge chunk of the mid-tier market". It is fair to say that the One range is what HTC is known for, and this is made up of higher-end handsets. Although the HTC One and all of its offshoots were very well-received by critics, this failed to translate into sales.
By adjusting focus and tapping into a slightly lower area of the market, HTC may be able to regain the position it commanded not too long ago. It is likely this was a decision that was difficult to make -- few companies want to be seen taking a step down the ladder -- but it is one that could pay off. Offering cheaper handsets will enable HTC to make better headway in developed and emerging markets, but only time will tell how long it takes to pay off.
-

Twitter needs to stand its ground over James Dean legal action
Publié: février 9, 2014, 9:39pm CET par Mark Wilson

Legal threats on Twitter are nothing new, but it is usually Twitter users who are the subject of litigation. In the case of the @JamesDean account, however, it is Twitter itself found on the receiving end of legal action. Acting on behalf of the James Dean estate, celebrity licensing agency CMG Worldwide is attempting to wrestle control of the Twitter account -- which is currently being used to tweet quotes by and about the star -- from the hands of its current owner.
The complaint says that Twitter is breaching trademarks owned by James Dean Inc by placing "objectionable content" online. CMG Worldwide has been in touch with Twitter to ask that the account activity be stopped, and that contact details for the account owner be handed over. Twitter has refused both requests. It is hard to see how the James Dean estate could have suffered "immeasurable and irreparable" damage. It is also interesting to note that the complaint suggests that unless the account activity stops, then James Dean Inc "will continue to be irreparably harmed and suffer actual damages in an amount as yet undetermined". There is no suggestion of what irreparable damage has actually been caused.
Fan pages exist all over the web, and any company, individual or representative that tries to take fans to court does the fans and themselves a great disservice. It would be a very different matter if a user on Twitter was tweeting defamatory statements about the actor, but this is not what is happening here. CMG Worldwide complains that Twitter and the owner of the @JamesDean account falsely represent James Dean Inc. This is precisely why verified accounts exist. The @JamesDean account is not verified, and there would be nothing to stop CMG Worldwide from creating one of their own which Twitter would presumably be only too happy to verify.
The existence of "real" verified accounts, and unofficial fan accounts are to be found all over Twitter. The fact that a celebrity has a particular name does not automatically entitle them to their first choice of Twitter handles -- sorry to be the bearer of bad news. There are countless famous people who have had to "settle" for a less than perfect handle -- the addition of words such as "real" or "the" are common -- but gaining a verification logo makes it clear to everyone that the account is what it appears to be.
The complaint that the use of the James Dean trademark is "knowing, intentional, willful, malicious, and unauthorized" is certainly open to debate. Take a look through the @JamesDean timeline and see for yourself. Not liking something that has been said does not necessarily mean that it is actionable in court. There are certainly issues with some Twitter accounts where fans, or those with malicious intent, do pretend to act on behalf of a celebrity -- both alive and dead -- but this is certainly not the case here.
CMG Worldwide claims to be acting to protect the James Dean image, but in treating fans so poorly its actions are reflecting very badly and will do more damage to the James Dean estate, name and legacy than a fan's Twitter account. It's unclear why this particular account has attracted attention -- at the time of this writing it has just over 8,000 followers (including Yoko Ono, interestingly). Twitter's stance so far has been to do nothing, but it has responded to previous complaints:
We've researched the reported account and determined that it is not in violation of Twitter's Trademark Policy. The account is not being used in a way that is misleading or confusing with regard to its brand, location or business affiliation. Twitter does not have a username registration policy. Users are free to select any name for their account, provided they do not violate Twitter's Terms of Service or Rules.
This could be a case that rumbles on for a while, but I for one will be hoping that Twitter does not back down. How do you feel?
-

The most popular stories on BetaNews this past week: February 2 -- February 8
Publié: février 8, 2014, 1:50pm CET par Mark Wilson
 The biggest news of the week has to be the appointment of Satya Nadella as CEO at Microsoft, which brought to an end weeks of speculation and rumor. Bill Gates also stepped down as chairman. A leaked version of Windows 8.1 Update 1 appeared online giving us all a sneak peek of what we can expect to see in the upcoming release -- including context menus on the Start screen, a new enterprise mode in Internet Explorer, and different ways of working with modern apps. Ahead of this big release, it was Windows XP that was showing growth rather than Microsoft's latest operating system.
The biggest news of the week has to be the appointment of Satya Nadella as CEO at Microsoft, which brought to an end weeks of speculation and rumor. Bill Gates also stepped down as chairman. A leaked version of Windows 8.1 Update 1 appeared online giving us all a sneak peek of what we can expect to see in the upcoming release -- including context menus on the Start screen, a new enterprise mode in Internet Explorer, and different ways of working with modern apps. Ahead of this big release, it was Windows XP that was showing growth rather than Microsoft's latest operating system.In other Microsoft news, Xbox One's first big update was revealed to be coming up on 11 February. Sony announced that it was selling its VAIO business to enable it to focus its attention on mobile devices. Business and individuals who rely on 37signals' products found that the company was not only changing its name, but also dropping all of its services apart from Basecamp. There was another blow for Bitcoin as the online currency was effectively banned in Russia.
It was another big week for security news as eBay and PayPal came under attack from the Syrian Electronic Army. HP released a report into enterprise security threats, showing that applications are often incredibly insecure. Orange customers in France discovered that their personal data had been stolen from the company's website, and Google and various other web-based companies released additional information about government data requests that had been received, although there was still very little given away. Twitter took a stand, saying that the new rules on transparency just are not enough.
A new service called Forgotify launched, helping music fans to discover new tracks that had never been listened to by anyone on Spotify. If videos are more your thing than audio, I showed you how to enabled the center-aligned version of YouTube with a quick cookie hack. As news of the UK launch of Google's Chromecast crept out, developers were finally able to get their hands on the Chromecast SDK which should lead to an increase in the number of apps available -- but none that are porn-related. Google also released the red Nexus 5 into the wild.
Google announced Chromebox for Meetings, making it easier for companies to hold video conference calls. Super Bowl Sunday was part of a big weekend for sports fans, and many big companies took it as an opportunity to show off their products and services with big-budget commercials. Among them was Microsoft's offering which showed how technology has empowered people. Facebook celebrated its tenth birthday, and Google started the process of trying to improve user trust by vetting YouTube views to weed out artificially inflated figures.
That's it for this week!
Image Credit: vinz89 / Shutterstock
-

Russia implements an outright ban on Bitcoin
Publié: février 7, 2014, 8:05pm CET par Mark Wilson
 You might think that Russia has just about enough on its plate at the moment, what with having the Winter Olympics to host and fending off global accusations of homophobia, but the Central Bank of Russia has found the time to slap a ban on Bitcoin. This is not the first country to outlaw the online currency -- it's something that has already been done by Thailand and it's being considered by others.
You might think that Russia has just about enough on its plate at the moment, what with having the Winter Olympics to host and fending off global accusations of homophobia, but the Central Bank of Russia has found the time to slap a ban on Bitcoin. This is not the first country to outlaw the online currency -- it's something that has already been done by Thailand and it's being considered by others.The General Prosecutor of the Russian Federation looked into "the so-called virtual currencies" phenomenon and found that there was a risk of Bitcoin being used for money laundering. The damning ruling refers to Bitcoin and other similar currencies as "money substitutes". Citing Article 27 of the Federal Law, the General Prosecutor said that "the official currency of the Russian Federation is the ruble", going on to say that money issued in other forms is prohibited.
"Certain distribution received anonymous payment systems and kriptovalyuty [virtual currencies], including the most famous of them -- Bitcoin -- are money substitutes and cannot be used by individuals and legal entities." Despite Russia's reluctance to use Bitcoin, the currency has been welcomed by the US, Europe and many other parts of the world.
Russia's ban seems to stem partly from the fact that Bitcoin purchases can be all but anonymous, and concerns have also been expressed about the security of the currency.
Image Credit: Blan-k / Shutterstock
-

LinkedIn to spend $120 million on job-seeking site Bright
Publié: février 7, 2014, 12:25am CET par Mark Wilson

The social network for professionals, LinkedIn, is to acquire Bright, a job-search site that matches employers with potential employees. This is a purchase that makes a lot of sense for LinkedIn, the Facebook of the working world, helping to make it even easier for people to connect across industries. While LinkedIn has around 11 years of experience under its belt, Bright is more a newcomer, having only launched three years ago.
It seems like a perfect pairing. LinkedIn members have their resumes online as part of their profiles. Bright makes use of resumes to link people to jobs. It just seems to make sense. The three year old site is being purchased for what LinkedIn describes as "approximately $120 million, subject to adjustment". This total comprises 73 percent stock and 27 percent cash. The deal is expected to conclude by the end of Q1 2014.
Bright says that it uses "data science to enable the labor market to operate more efficiently" and the decision to join LinkedIn came about "because of what we lacked -- the ability to apply this technology across the entire economy". Founder of Bright, Eduardo Vivas, said: "We're excited to join LinkedIn because the company shares a similar vision and is equally obsessed about using data and algorithms to connect prospects and employers".
LinkedIn already has some experience in trying to pair users up with jobs. As well as suggesting other users who may be known to you, the site also suggests jobs that may be of interest. Over the coming years, and using the technology honed by Bright, the site will be able to suggest more jobs that are even better suited -- employers and employees alike should feel the benefits. LinkedIn's Deep Nishar mused: "What LinkedIn does best is connect talent with opportunity at massive scale". It looks as though that scale is only going to increase.
Image Credit: Maxx-Studio / Shutterstock
-

Google launches Chromebox for Meetings -- Hangouts on steroids for businesses
Publié: février 6, 2014, 10:31pm CET par Mark Wilson

Actual, real-life meetings are just so passé! In fact I have hardly met up with any of the people I work with in person -- we are living in the digital age, man! But the likes of Skype and FaceTime show that there is still an interest, even a need, for virtual face-to-face time, and this is particularly true for businesses. Conference calls are easy to set up on the phone, but there are times when it really does help to see what’s going on at the other end. Today Google takes the wraps off its solution: Chromebox for meetings.
As you would expect from Google, and probably guess from the name, this is a box running ChromeOS. Powered by a 4th generation Intel Core i7 processor, there are four USB 3.0 ports as well as HDMI and DisplayPort++ connections, and network connectivity is provided by an Ethernet port as well as an 802.11 a/b/g/n WiFi adaptor. Also provided is an HD camera, a mic and speaker combo, and a remote control.
In a sense, this is Hangouts on steroids, brought to enterprise -- it's basically a fancy, and none too cheap -- video-conferencing system. Coming from Google, the integration with Google apps is to be expected. Meetings can be controlled from an online management console, and participants can be invited to a meeting through Google Calendar. Not everyone involved has to have a Chromebox for Meetings of their own, as meetings can be joined by anyone with a Gmail account.
So far, Dell and HP are also on board, with the latter announcing their first Chromebox for Meetings today. For the time being there is only the ASUS device available, priced at $999. To start with, this is a US-only product, but there are plans to launch in Australia, Canada, France, Japan, New Zealand, Spain and the UK. The purchase price includes $250 for the first year's "management and support fee", but this is an extra annual fee that will have to be paid for continued usage. Only time will tell whether this new system manages to replace the humble telephone conference call, or indeed a simple webcam.
-

Sony sells VAIO, cuts 5,000 jobs and exits PC manufacturing
Publié: février 6, 2014, 12:18pm CET par Mark Wilson

Sony is pulling out of the PC business and is selling the VAIO brand to Japanese investment fund Japan Industrial Partners (JIP). The announcement came after industry speculation about what might be happening in Sony's future after the company responded to rumors that it was in talks with Lenovo about a possible sale by saying that it was looking to "address various options for the PC business". No details about the fees involved have yet been revealed, but it is hoped that an agreement will be reached by the end of March.
Citing "drastic changes in the global PC industry", Sony's announcement came as the company revealed its financial results for Q3 2013. Analysis of the results showed that the "target of returning the TV and PC businesses to profitability will not be achieved within the fiscal year ending March 31, 2014", hence the need for reform. This means that Sony will now concentrate "its mobile product lineup on smartphones and tablets". An estimated 5,000 jobs will be lost.
Once the transfer of business to JIP is complete, Sony will completely stop designing and developing PC products, although there is a promise that "customers will continue to receive aftercare customer services". But even though the VAIO brand will live on under the new owners, it will not -- at least initially, be a global venture. "The new company is expected initially to concentrate on sales of consumer and corporate PCs in the Japanese market and seek to optimize its sales channels and scale of operations, while evaluating possible further geographic expansion."
There has long been talk of the death of the PC industry, and this move from Sony is going to do little to restore hope. With an expected $1.08 billion loss for 2013, it is clear that Sony's hand was being forced into taking drastic action. For many people, VAIO is a name synonymous with quality, but there is a strong chance that it could disappear from many markets forever. Whether new owners JIP are able to establish enough of a foothold in Japan to expand with a global relaunch is something that remains to be seen, but many will see this as an ominous sign of things to come for the rest of the PC industry.
Image Credit: testing / Shutterstock
-

37signals becomes Basecamp and drops all but its eponymous product
Publié: février 5, 2014, 4:49pm CET par Mark Wilson
 The name 37signals may not mean much to people outside of tech and business circles. This is a company that produces something that is better known than its own name: Basecamp. The very fact that 37signals is primarily, or even solely, associated with Basecamp seems as good a reason as any to consider a rebrand, and this is precisely what the company is doing. While some people content themselves with blowing out candles on a cake, 37signals celebrates its tenth birthday by renaming itself Basecamp.
The name 37signals may not mean much to people outside of tech and business circles. This is a company that produces something that is better known than its own name: Basecamp. The very fact that 37signals is primarily, or even solely, associated with Basecamp seems as good a reason as any to consider a rebrand, and this is precisely what the company is doing. While some people content themselves with blowing out candles on a cake, 37signals celebrates its tenth birthday by renaming itself Basecamp.But it does not end there. In addition to taking a new name from its popular online collaboration and project management tool, the company is switching its focus so that Basecamp is its only product. The announcement appears on the company's website, explaining that the decision will allow all energies to be channeled into the tool that gained greatest success:
Moving forward, we will be a one product company. That product will be Basecamp. Our entire company will rally around Basecamp. With our whole team -- from design to development to customer service to ops -- focused on one thing, Basecamp will continue to get better in every direction and on every dimension.
While Basecamp has exploded in popularity, the company itself has remained relatively small, employing just 43 people. With over 15 million people using Basecamp, it is understandable that the small team wants to avoid spreading themselves too thinly. "We've released so many products over the years, we've become a bit scattered, a bit diluted".
But what of the company's other projects? There are several to consider: Ta-da List, Writeboard, Backpack, Campfire, The Job Board & Gig Board, Highrise, Sortfolio, Know Your Company, and We Work Remotely. It seems that there are no concrete plans at the moment. Several ideas are being thrown around for the time being. Other projects could be turned into individual companies in which Basecamp will retain partial ownership, or they could be sold to a new owner in their entirety. The final option is to shift the products into "maintenance mode" which means that existing users can continue to work with them in the way they have become used to, but there will be no further development -- but security fixes and minor updates would still be released.
How do you feel about this? Are you a Basecamp user who welcomes this tighter focus?
Photo Credit: wanphen chawarung/Shutterstock
-

Google slips into the red with a new Nexus 5
Publié: février 4, 2014, 9:53pm CET par Mark Wilson

There's a new Nexus in town -- not a Nexus 7 or a Nexus 8 or a Nexus 10, but a slightly updated Nexus 5. The difference? This time around it is purely cosmetic. No hardware changes of any description, just a new coat of paint. The latest addition to the Nexus 5 range is the red variant -- but not just any red, a capitalized Bright Red, no less. This new release supplements the previously available black and white versions, bringing the color total to three.
As the only change that has been made is to the hue of the handset, it should come as no surprise that there has been no change to pricing either. The 16GB model can be picked up for $349, while the 32GB model will set you back an extra $50 at $399. The Nexus 5 is the phone that was eagerly anticipated, but proved to be slightly disappointing when it finally arrived on the scene -- to Brian, at least -- but it is still one that manages to pique people's interest.
Nexus 5 in red will take no one by surprise. There have been rumors pretty much since the initial launch, and more recently there have been numerous leaked images of the handset in its new clothes. It does almost feel as though the Nexus 5 is taking a cue from Nokia's Lumia palette but this is not necessarily a bad thing -- the new color choice is likely to increase appeal. Red has numerous connotations, but it is likely to appeal equally to both male and female users.
Google may be able to cash in on other associations the color red has. It is interesting to note that the new model is being made available just ten days ahead of Valentine's Day -- how romantic! Of course there are plenty of sports teams who have red kits, it may appeal to surgeons as well as those who lean to the left -- onward, comrades!
If you fancy getting your hands on the new shade, head over to Google Play to place your order.
-

Google releases details of FISA data requests -- for what it's worth
Publié: février 4, 2014, 3:02am CET par Mark Wilson

Trying to claw back its reputation of not being evil, and riding the wave of public interest in the surveillance activities of the government, Google releases some additional details about the government data requests it has received. Just last week, the Department of Justice announced that companies would be permitted to reveal more information about the requests made of them. Google has now updated its Transparency Report to include statistics about Foreign Intelligence Surveillance Act (FISA) requests.
Until recently, Google and other companies had been blocked from revealing any information about FISA data requests, causing them to group together to file a lawsuit in a bid to overturn this barrier. Today's report released by Google follows on from last week's agreement with the DoJ and includes details of requests made under the Foreign Intelligence Surveillance Act. For advocates of government transparency this sounds like a victory for freedom of information, but sadly it amounts to very little.
On the face of it, it looks as though Google has gone beyond what might be expected of it, releasing details of data requests dating all the way back to the period January to June 2009. Restrictions put in place by the Department of Justice mean that "providers must wait six months before publishing statistics about FISA requests". So as it stands, there are only figure up to January to June 2013. The July to December 2013 period cannot be published until six months after the end of this period -- so July 2014.
But the figures that have been released are very vague. Google has been prevented from releasing exact numbers and indeed precise details about the types of requests that have been received. The figures are shown in chunks of 1000, so for every six month period we can see that Google received between 0 and 999 requests -- this covers both content and non-content requests. Getting slightly more specific, we can see that there were between 0 and 999 users or accounts affected by the non-content requests, but there is far more fluctuation when it comes to requests relating to content. The most recent figures show that between January and June 2013, between 9,000 and 9,999 requests were filed -- down from between 12,000 and 12,999 in the previous period.
Google is still hoping to be able to publish more detailed information in the future. Richard Salgado, Legal Director, Law Enforcement and Information Security said: "We want to disclose the precise numbers and types of requests we receive, as well as the number of users they affect in a timely way. That’s why we need Congress to go another step further and pass legislation that will enable us to say more. You have the right to know how laws affect the security of your information online. We’ll keep fighting for your ability to exercise that right by pushing for greater transparency around the world."
Are the published figures of any interest or value, or do you think a lot more needs to be done to make the reports worthwhile?
Photo Image: jocic / Shutterstock
-

Google Cast SDK opens up Chromecast to developers -- more apps on the way!
Publié: février 3, 2014, 8:18pm CET par Mark Wilson

Today, Google launches the developer preview of Google Cast SDK, allowing for the development of apps for the company's plug-in-and-forget-about-it streaming unit. In a post on the Chromium Blog, Engineering Manager John Affaki, explains that developers will find it easy to make existing mobile and web apps ready for use with Chromecast as the SDK allows for easy integration. In addition to the Chrome extension, the SDK is also available for Android and iOS.
The lack of new and exciting apps that offer Chromecast support has partly contributed to the fact that Google's streaming device has not really caused the explosion of excitement that it should have done. Google will be hoping that by making the SDK available, developers will start to integrate the API into existing apps that are suitable for taking advantage of second screen casting.
Developers will be able to self-manage the publication of apps through developer console, and Google has produced some documentation to help with getting started. Resources include a design checklist as well as numerous sample apps. Everything developers need to get started can be found on the Google Cast website.
Check out the introductory video below, and keep your eyes open for -- hopefully -- some exciting releases over the coming weeks and months.
-

Security breach exposes personal data of 800,000 Orange users
Publié: février 3, 2014, 4:01pm CET par Mark Wilson
 2014 is not proving to be a very good year for security -- and it is not just down to the Syrian Electronic Army. Hundreds of thousands of Orange customers in France have had their personal details exposed after hackers managed to procure a mass of unencrypted data from the My Account section of the orange.fr website.
2014 is not proving to be a very good year for security -- and it is not just down to the Syrian Electronic Army. Hundreds of thousands of Orange customers in France have had their personal details exposed after hackers managed to procure a mass of unencrypted data from the My Account section of the orange.fr website.The attack was carried out on 16 January, but details are only coming to light some two weeks after the security breach.
Orange France says that less than 3 percent of its customers were affected, but this still amounts to some 800,000 people. Hackers were able to gain access to unprotected data including names, addresses, phone numbers and other account details, although Orange insists that passwords remain safe and the integrity of accounts has not been compromised. The company recognizes that the information gathered by hackers could be used to launch a large-scale phishing attack and it has directed customers to a support page explaining how to avoid falling victim.
Customers received an email from Orange France on 23 January providing a warning to be wary of phishing attacks, but no reference was made to the data breach. A subsequent email revealed some details about what had actually happened, and speaking to PCInpact, Laurent Benatar, technical director of Orange France said that sensitive information such as bank account details were obscured and therefore unusable.
As yet there are no reports of any phishing attacks having been launched on customers, but this in itself will do little to reassure customers. Many will be asking questions such as why data was stored in an unencrypted state, and why customers were not alerted sooner.
Image Credit: alexskopje/Shutterstock
-

Syrian Electronic Army strikes again! PayPal and eBay come under attack
Publié: février 3, 2014, 12:18pm CET par Mark Wilson

There have been a lot of website compromises in 2014 despite the fact we're only just into February. Now it looks as though the Syrian Electronic Army is at it again. This time it is eBay and PayPal who found themselves in the crosshairs, as some users discovered that they were redirected to sites that announced the hack, praised Syria and chided the US government.
It might seem obvious that the Syrian Electronic Amy was behind the attack, but in case there was any doubt, the group used their Twitter feed to claim responsibility.
The message on the sites read "Hacked by Syrian Electronic Army! Long live Syria! Fuck the United States Government", although it was slightly hard to read what with being hidden behind a Syrian flag comprising red and white zeroes and ones. It seems as though the attack was short-lived, and PayPal claims that aside from the inconvenience of not being able to access their account, users were not placed at any risk.
Talking to security analyst Graham Cluley, PayPal issued a statement:
We were not hacked. For under 60 minutes, a very small subset of people visiting a few marketing web pages of PayPal France, UK and India websites were being redirected. There was no access to any consumer data whatsoever and no accounts were ever in any danger of being compromised. The situation was swiftly resolved and PayPal’s service was not affected. We take the security and privacy of our customers very seriously and are conducting a forensic investigation into this situation.
At time of writing, the Syrian Electronic Army's Twitter account has been suspended, but it will probably not be long before it reappears in one guise or another. It is not clear why the SEA chose PayPal and eBay in particular -- it may just be a matter of both being high profile sites which will gain greater coverage.
Were you affected by the hack? Does it worry you that so many big-name sites are falling victim to one form of attack or another in recent weeks?
Image Credit: Aquir/Shutterstock
-

How to enable the hidden, experimental, center-aligned version of YouTube
Publié: février 1, 2014, 5:49pm CET par Mark Wilson
YouTube, like many other websites, undergoes changes, and it has taken on a number of guises over the years. Some looks have lasted for a long time, while others have been shorter lived. There are also experimental looks, not all of which end up being released, but even when a redesign is rolled out, it can take a while to make its way around the world. Currently in the experimental stage is a center-aligned layout which includes a cleaned up interface a new menu and a few other tweaks.
In the new design, a top navigation bar is now locked to the top of the screen, remaining in place while the rest of the page scrolls. There is a customizable carousel and a new Upload button encourages visitors into sharing. It's not yet clear quite when this new interface will be officially released to a waiting world, but it's something you can enable now; all it takes is a quick cookie tweak.
You'll need to fire up YouTube and then access your web browser's dev console and the method varies slightly from one browser to another.
- In Chrome, press Ctrl + Shift + J
- In Opera, press Ctrl + Shift + J
- In Internet Explorer, press F12 and move to the Console section
- In Firefox, press Ctrl + Shift + K
Select and copy the code below before pasting it into the console.
document.cookie="VISITOR_INFO1_LIVE=LlWIQlLwL_Y; path=/; domain=.youtube.com";window.location.reload();
Hit the Enter key and then close the console. You should find that the page automatically reloads with the new, cleaner interface in place.
Should you change your mind and decide you prefer the old look, return to the console and enter the following code to reverse the change.
document.cookie="VISITOR_INFO1_LIVE=; path=/; domain=.youtube.com";window.location.reload();
Do you like the new look, or are you sticking with the old interface?
-

Forget Spotify -- discover never-before-heard music on Forgotify
Publié: février 1, 2014, 2:51pm CET par Mark Wilson

Like the internet itself, Spotify is a fantastic resource, but it is one which remains somewhat unexplored. There are darker reaches that are yet to be visited by anyone, and who knows what sort of gems might be lurking there waiting to be discovered? You could spend endless hours trawling the length and breadth of what's available online in the hope of stumbling across something new and exciting. You could do that, or you could get someone else to do the hard work for you.
With Forgotify, the idea is simple. It's a streaming music site, but not quite like the others you may have tried. Any music you find through Forgotify is guaranteed not to have been listened to by anyone else on Spotify. Spend a little time playing random tracks and you could find something truly amazing -- of course, you will undoubtedly have to endure a load of absolute drivel, but there will be some utterly delightful tracks in every genre as well.
Getting started could hardly be easier. Just head over to the site and click the Start Listening button -- you will need to log into your Spotify account to hear anything. You can share the tracks you like (or want to publicly ridicule!) or just skip to the next track whenever you're ready. On about my tenth listen, Carroll Baker's "Wichita" from the album "I'd Go Through It All Again" -- sadly nothing to do with Glen Campbell's "Wichita Lineman" -- started, and a few clicks later I was listening to "Termite One One" by Lol Coxhill.
Set aside a little time for this site as it quickly becomes addictive. Gems I found include Louise Huebner's "The Self Fascination Ritual For Increased Power" from the album "Louise Huebner's Seduction Through Witchcraft". She is, in case you are unaware of her, the only "officially appointed official witch in the entire cosmos". That's the sort of stuff you can expect to enjoy!
Give it a try and let us know if you come across anything weird, wonderful or brilliant!
-

The most popular stories on BetaNews this past week: January 26 -- February 1
Publié: février 1, 2014, 2:44pm CET par Mark Wilson
 Phew! Well it seems that 2014 is finally in full swing -- the past seven days have been the busiest in a while. It was a busy week for security. A piece of malware came to light that was using Windows computers as a means of infecting the Android devices connected to them. Yet another security breach meant that the credit card details of Michaels customers were compromised.
Phew! Well it seems that 2014 is finally in full swing -- the past seven days have been the busiest in a while. It was a busy week for security. A piece of malware came to light that was using Windows computers as a means of infecting the Android devices connected to them. Yet another security breach meant that the credit card details of Michaels customers were compromised.While the computing world worries about whether or not the NSA is reading their email or recording their phone calls, school children in Britain learned that their computing activities are being monitored in the classroom. There was celebration as companies such as Microsoft and Google won a lawsuit that means they are now able to reveal more information about US Government data requests.
Online, Wikipedia's new voice archive got underway, and the policing of Twitter came under the spotlight as Courtney Love won her case after a lawyer claimed to have been libeled by the singer on the microblogging site. On the subject of the law, there was an outbreak of hatchet burying. Samsung and Google came to an agreement about the use of patents, and Samsung also made arrangements with Ericsson. After upsetting British broadcaster Sky over the naming of SkyDrive, Microsoft reveal the new name for its cloud storage service -- OneDrive.
Google decided to rid itself of Motorla but managed to hang on to a lot of patents. Tablet sales slowed and Windows Phone sales remain low. The State of the Union address was covered by Fox News and in conjunction with Bing it was possible to gauge live reaction to what was being said. Bing has also been used to see if there is a link between location and search traffic for the Denver Broncos and the Seattle Seahawks.
In the BetaNews newsroom, there was a lot of talk about switching operating systems. Mihaita completed his transition from Windows to Mac and loved it. Brian thought that anyone looking to migrate away from Windows XP should consider moving to Linux, but I wasn't so sure that this was a good idea. For anyone concerned about moving to Windows 8.1, Microsoft helpful collected together some tips to help wary users avoid the Start screen.
In the world of entertainment, Beats Music extended its free trial period, but there was a slight delay for the Windows Phone app. Yamaha and Spotify joined forces so that Spotify Connect will work with a wider range of devices. Ever wondered if you might be spending too much time on Facebook? A new tool from TIME magazine helps you to find out for sure. You may have noticed an increasing need for instant gratification, it turns out that you can put the blame at technology's door.
I need a lie down after all that! More of the same over the next seven days, I'm sure. If you need something fun to unwind, take a look at Build with Chrome -- a great new tool from Google that lets you play with LEGO online.
Image Credit: vinz89 / Shutterstock
-

From Windows XP to Linux? -- you'd have to be mad!
Publié: janvier 31, 2014, 12:20pm CET par Mark Wilson
 It has been suggested that the people who are still hanging onto Windows XP after all of these years are going to continue to do so once support officially ends in April. Microsoft is obviously keen to herd people towards Windows 8.1, but there is a good deal of resistance. Some have proposed Linux as a viable alternative; to me, this seems like a completely nonsensical "upgrade" path. Brian managed to cause quite some excitement yesterday when he wrote that Windows XP refugees should migrate towards Linux rather than considering the latest version of Windows. Without wanting to fall out with Brian, I think he's plain wrong.
It has been suggested that the people who are still hanging onto Windows XP after all of these years are going to continue to do so once support officially ends in April. Microsoft is obviously keen to herd people towards Windows 8.1, but there is a good deal of resistance. Some have proposed Linux as a viable alternative; to me, this seems like a completely nonsensical "upgrade" path. Brian managed to cause quite some excitement yesterday when he wrote that Windows XP refugees should migrate towards Linux rather than considering the latest version of Windows. Without wanting to fall out with Brian, I think he's plain wrong.One of the reasons many people cite for not wanting to upgrade to Windows 8 or 8.1 is that they don’t want to have to deal with the Start screen. They have become used to things working in a certain way and, while not perhaps entirely resistant to change, need a little encouragement into seeing the value of things. Brian suggests that one of the reasons to switch to Linux is that "you get to learn something new." If this is supposed to be an attractive element of Linux, then users may as well spend the time getting used to Windows 8.1.
Sure, there are plenty of differences between Windows 8.1 and XP, but at its heart it is still the same version of Windows we have known for years. There are a few new techniques and features, but for the most part everything works as you would expect it to and can be found where you would expect. The same certainly cannot be said of Linux. That's not to say that the likes of Ubuntu are impenetrable -- far from it -- but for those uncomfortable with change for whatever reason, there's certainly a steeper learning curve to navigate for Linux than Windows 8.1.
Brian suggests that one of the perceived stumbling blocks for moving to Linux is a lack of software. He goes on to describe the various alternatives to commonly used apps. But this is the problem. Someone who has stuck with Windows XP for more than a decade, probably using Office XP as well, isn’t going to want to have to learn how the likes of LibreOffice operate. Learn a new operating system and relearn how to use all of your apps? Is this likely to appeal to the average home user? I'm familiar with various Linux distros, but when it comes to helping out my mum over the phone, I know it would be a heck of a lot easier telling her how to do things in the slightly unfamiliar environment of Windows 8.1 than the completely alien territory of Linux. Put simply, Linux would scare my mother -- and I don’t think she's alone.
The low system requirements of Linux are often cited as a great bonus. In fact, there isn’t that great a difference between Windows and Linux here. The requirements for Ubuntu are a 700MHz CPU and 512MB RAM. Windows 8.1 requires a 1GHz processor and 1GB RAM. Hardly a massive difference. It has even been suggested that when Update 1 is released for Windows 8.1, system requirements will be even lower. OK, you're not going to be fully at full pelt on these sorts of machines, but if you're the type of person still hanging onto Windows XP, you're probably not on the cutting edge of technology running the most demanding software anyway.
Something that is swept under the carpet is that fact that Linux often just doesn't play nicely with some hardware. This is something I know from personal experience! If you can't get a key piece of hardware to work, Linux is not going to be for you.
Of course there will be some people who do have an ancient computer that is simply not up to the task of running Windows 8.1. This is to be expected. Things do not last forever. The computer you spent however many hundred dollars on back in the 90s is no more invincible than any other piece of electronic equipment. Ultimately your old CRT TV died -- or will die. If you want to continue to watch TV, a new one will be required and it will have to be a flatscreen. Things move forward. Things change. That's just the way it is. Yes, it's going to upset some people, but the march of progress always leaves a few casualties in its wake.
In all of the debate, it is easy to forget one thing. You could just stick with Windows XP. Computers around the world aren't going to suddenly explode and become unusable in April. My suggestion is if you can, upgrade to Windows 8.1. This might mean parting with a little cash to get a new computer, but it is possible to pick up something halfway decent for very, very little these days. If you simply can't bring yourself to do this, or really can't afford to, just don’t worry about it. Keep using XP. You'll be fine.
Photo Credit: cunaplus/Shutterstock
-

Microsoft doles out some tips to help you avoid the Start screen in Windows 8.1
Publié: janvier 29, 2014, 9:35pm CET par Mark Wilson
Today on the Windows Experience Blog, Microsoft has done something a little odd -- admitted that the Start screen "can take some time to get used to". But more than this, the blog post by Kirsten Ballweg outlines five tweaks that can be used to "make Windows 8.1 feel more familiar". Given that the first line of the post is "Windows 8.1 looks a whole lot different than Windows 7 or Windows XP", it appears that Microsoft is conceding that Windows 8.1 just isn't everyone's cup of tea.
The solution? A series of tips to help make the latest version of Microsoft's operating system feel more like a version that is several years old! The first tip is interesting. Rather than suggesting the ways in which the Start screen could aid productivity, rather than pointing out all of its cool features, users are advised to simply bypass it. Microsoft has given up trying to sell the new features of Windows to users, opting instead to show how they can be avoided -- after all "the desktop we all know and love is still there".
Tip two highlights another way to simply avoid using the Start screen: pinning shortcuts to the taskbar. There's a slight change of tack for the third tip, but it is one that's fairly inconsequential. Tip three lets you know how to use the same background on your desktop and on the Start screen. So here the Start screen is being gently ushered in, but it's hardly a power tip! I'm not convinced it really fits into the theme of making Windows 8.1 "more familiar" either. The fourth tip is more nonsense -- using a PIN or picture to sign in rather than using a password. If anything this makes Windows 8.1 less familiar as it's a new technique, but we'll skip over that.
But don’t worry... we're back on form for the final tip. You know all those modern apps that Microsoft harped on about for so long? Forget 'em! You don’t want to use the modern version of Internet Explorer, do you? Tip five shows you how to ensure that Microsoft's browser always opens in desktop mode. Yet another tip that seems to go against everything Microsoft was pushing in Windows 8 and 8.1. There is a nod to the "value" of the Start screen in a bonus tip, but overall the post feels almost like an admission of defeat.
It's like Microsoft is saying "yeah, we know you don’t like all of this modern stuff... let's just forget it's there shall we?" Whether this is an indication of what we can expect to see in Windows 8.2 and Windows 9 remains to be seen. What do you make of it?
Image Credit: Semmick Photo / Shutterstock
-

Wikipedia's celebrity voice archive gets underway with the help of Stephen Fry
Publié: janvier 28, 2014, 12:55am CET par Mark Wilson

Wikipedia. It's one of the cornerstones of the internet. It's a global resource which has quite a reputation and has spawned numerous copycats and offshoots; the latest addition to the wiki canon is the Wikipedia Voice Intro Project (or WikiVIP). As you may have guessed from the name, this is a project concerned with audio -- voice recordings specifically. The Wikipedia entries for celebrities and notable figures are to be spruced up with the addition of audio clips.
The first name to enter the vocal history books is Stephen Fry, a man known for his love of technology as much as his comedy, general knowledge and general loveliness. This month he recorded a ten second clip ("Hello, my name is Stephen Fry, I was born in London, and I’ve been in the entertainment business, well I suppose since 1981") which now appears on his Wikipedia page.
Audio clips can be found in the right hand summary panel, and are being made freely available. This means that they are available for free download, and can be embedded in websites and used in other projects.
The number of articles featuring vocal clips is going to expand over the coming weeks and months, and it seems fitting that another name to be given the audio treatment is World Wide Web inventor, Tim Burners-Lee.
As noted by the Guardian, the BBC is also working in conjunction with Wikipedia to extract audio clips from a number of existing recordings. This is likely to help bolster the number of recordings for historical figures.
Which voices do you think should be next in line for documenting on Wikipedia?
-

Policing Twitter -- can the existing legal system cope with the technological age?
Publié: janvier 26, 2014, 8:00pm CET par Mark Wilson

Twitter is rarely out of the headlines, but this week two legal cases surrounding the social network slash micro-blogging service brought it to attention for slightly different reasons than normal. On one side of the Atlantic a couple fell foul of the law for using Twitter to make threats to a feminist campaigner, while on the other a celebrity managed to avoid prosecution for libel after managing to plead ignorance about the falsity of a claim made online.
For a court case victory, it was announced in a very restrained, quiet way... particularly when you consider that the victor was none other than Courtney Love. The celebratory tweet reads simply "I can't thank you enough Dongell Lawrence Finney LLP, the most incredible law firm on the planet. We won this epic battle. #justiceprevails", and the decision to use Twitter was slightly ironic considering the fact that the court case stemmed from a previous tweet made by Ms. Love.
Ms. Love had posted a tweet suggesting that her former lawyer had been "bought off". Rhonda Holmes took exception to this and tried to sue Love for $8 million on the basis of harm caused to her reputation. There were several mitigating factors for the judge to consider, perhaps the most important of which is that Love apparently posted the tweet under the impression that it was a private rather than public message. The second is that Love deleted the tweet as soon as she realized that it was in fact public.
The third factor is that Love believed what she tweeted to be true -- although this in itself cannot be used as a libel defence. The speed with which the offending tweet was deleted dramatically reduced the number of people able to view the statement. Ultimately, a jury at Los Angeles County Superior Court decided that Holmes had not been defamed and Love won the case. Questions have since been asked about whether tweets should be treated as opinion rather than a statement of fact, and afforded greater freedom of speech status.
Meanwhile in the UK, two people have been jailed after using Twitter to make violent and sexual threats to a feminist campaigner who has been calling for the images of more women to appear on bank notes. The man and woman from the North East of England eventually pleaded guilty to "improper use of a communications network" -- a law that can be used to cover menacing, threatening, obscene and indecent messages, with the interesting note that it is "irrelevant whether [such a message] was received" (sending being the crime). Could this have been tackled with another law rather than one specific to a communication network? Simply making a threat would be enough to warrant prosecution. Shouting a threat does not result in an "improper use of a voice" prosecution.
So what does all of this demonstrate? Perhaps the first thing that's clear is that laws have not been able to evolve quickly enough to take into account the ever-changing face of technology. Does it matter that these cases stem from statements made online -- is it really any different to statements made through other mediums? The immediacy of the internet means the impact can not only be greater, but also felt sooner. At the same time, it is much easier and faster for mistakes to be rectified when necessary -- something that is very different from the case of libellous statements printed in newspapers.
It is probably fair to say that few people fully think through the implications of what they publish online (comments posted in response to this and other articles could be used as the basis for a libel case, for instance) -- and even fewer would regard using Twitter as "publishing" in the traditional sense. But does this matter? Ignorance of the law can rarely be used to avoid conviction, and while there may not always be a specific law that covers every possible eventuality online, there are certainly laws that can be bent to fit. Is this good enough, or should new laws be drafted to ensure that there is no room for confusion? As ever, the international nature of the internet presents the biggest obstacle. Which country's law takes priority when there is a disagreement between what is on the two statutes of nations involved in a case?
Image Credit: carol.anne / Shutterstock
-

British school children subjected to NSA-style surveillance
Publié: janvier 26, 2014, 5:39pm CET par Mark Wilson

The idea of being monitored, spied upon, surveilled, call it what you will, is something we are gradually becoming used to. CCTV cameras abound, we now know that our private communication could be intercepted at any time, and god only knows what else is going on unbeknownst to us. The plots of Person of Interest look positively tame compared to what is actually happening. Look, a whole introductory paragraph about modern-day surveillance and not one reference to Big Brother, 1984 or George Orwell. Oh ... damn.
But it seems that it is not just potential terrorists, criminals and other ne'er do wells who might feel concerned about who is reading their emails and monitoring their online activity. Hundreds of schools up and down the UK are actively monitoring the online communication of pupils using methods not too far removed from those employed by the NSA on a global scale.
The monitoring is performed using software from Impero Solutions, enabling schools to very closely monitor how pupils are using the school network. Many schools have implemented policies that place restrictions on the types of websites that can be accessed from school computers, but the latest techniques go even further. The e-safety feature of Impero Solutions Education Pro package constantly monitors network communication for a customizable list of keywords. This enables schools to be on the lookout for problems with bullying, but also to monitor students who might be at risk of self-harming or committing suicide. The same software has also been used in the US to help combat gangs.
The software can be tweaked as required, but it looks out for obvious keywords as well as slang and acronyms that might be used to try to disguise threats. We're all aware of text speak like PMSL, LOL and BRB, but this is a constantly evolving lexicon that can include terms such as DIRL meaning die in real life, and other such bleak phrases. As pointed out by the Guardian the software can be tailored as required, but can be on the watch for seemingly innocent words such as Bio-oil which could be indicative of self-harm -- this is a product traditionally used to treat post-pregnancy stretch marks, but has found a new market more recently.
While there are probably few pupils who are particularly welcoming of the monitoring, it is clearly something that has value. Being able to look out for tell-tale signs that a depressed student may be on the brink of taking things too far is something that has simply not been available to previous generations. In a sense it is a microcosm of the NSA's activities, but this use of technology is likely to be viewed rather more favourably than indiscriminate global web surveillance.
As is so often the case, context it everything. Looking at how technology can be used to help protect children and ease social problems just goes to show that surveillance is not necessarily a bad thing -- but it is open to abuse and needs to be monitored. Which raises the question ... who watches the watchers?
Image Credit: Tatyana Vyc / Shutterstock
-

The most popular stories on BetaNews this past week - January 19 -- 25
Publié: janvier 25, 2014, 2:32pm CET par Mark Wilson
 Handset news aplenty this week. The Nokia Lumia 929 appeared for sale in China, and also showed up on Verizon's US website under the Nokia Lumia Icon name before quietly disappearing. None of this did anything to improve Windows Phone sales for Nokia which were found to be disappointing. Figures released this week showed that phablets are going to become increasingly popular as user look to merge smartphones and tablets in to a single device. It will probably come as little surprise that in the next few years it is predicted that mobile apps will be the most used software. Samsung Galaxy Note 3 owners were disappointed to find that upgrading to KitKat killed their ability to use third party accessories.
Handset news aplenty this week. The Nokia Lumia 929 appeared for sale in China, and also showed up on Verizon's US website under the Nokia Lumia Icon name before quietly disappearing. None of this did anything to improve Windows Phone sales for Nokia which were found to be disappointing. Figures released this week showed that phablets are going to become increasingly popular as user look to merge smartphones and tablets in to a single device. It will probably come as little surprise that in the next few years it is predicted that mobile apps will be the most used software. Samsung Galaxy Note 3 owners were disappointed to find that upgrading to KitKat killed their ability to use third party accessories.Ahead of the release of Update 1 to the operating system, Microsoft finally got around to releasing a guide to mastering Windows 8.1. So keen is Microsoft for you to learn more about Windows 8.1, a second batch of guides was released later in the week. And while you're becoming an expert Windows 8.1 user, Microsoft would like you to take a second look at Internet Explorer and rethink its web browser.
Microsoft fixed yet more problems with the Surface 2 via another update, but a new portable entered the fray as Toshiba's Chromebook became available for pre-order. An interesting debate about the future of Facebook was sparked by a Princeton paper.
Looking to be entertained? The Smart TV Box is an Android-driven media player released this week. If streaming media if your thing, the fastest broadband connection in the world could be what you need -- assuming you can speed-watch movies. Music fans gained a new service in the form of Beats Music, and while Android and iOS users could listen to their favorite artists straight away, Windows Phone users are still waiting. This wasn't just a week of new releases; LogMeIn Free was killed off, with users being herded towards the paid version of the software.
Anyone upset at the activities of the NSA is unlikely to have been placated by President Obama's proposed surveillance reform, which could ultimately amount to nothing. The annual list of popular passwords was released showing we're little better at taking steps to keep ourselves protected. Perhaps this is what contributed to the theft of the credit card details of millions and millions of South Koreans.
Two birthdays this week, so we'll finish on a happy note by wishing many happy returns to Vine which turned one, and the Mac which is now 30. Happy birthday to both!
Image Credit: vinz89 / Shutterstock
-

Happy birthday to the Mac! 30 years and still going strong
Publié: janvier 24, 2014, 1:40pm CET par Mark Wilson

Today is a day of celebration. Entering one's 30s is something of a milestone. It’s a time to look back at achievements, gather thoughts and see where the future is going to take you. 1984 was a big year. It's a year that will be permanently associated with George Orwell, the birth of my sister (happy birthday for today, by the way! Oh, and apologies for revealing your age!) and the first Mac. Three decades ago today, as my mum and dad were welcoming their daughter into the world, the technology world was welcoming the arrival of the Macintosh.
The Apple homepage has been taken over by a birthday message to the company's baby. Click through and there's a special mini-site that features a timeline of Mac evolution over the years. The intro page is both celebratory, forward-facing and a call to arms:
In 1984, Apple introduced the world to Macintosh. It was designed to be so easy to use that people could actually use it. And it came with a promise -- that the power of technology taken from a few and put in the hands of everyone, could change the world. That promise has been kept. Today, we create, connect, share, and learn in ways that were unimaginable 30 years ago. Imagine what we can accomplish in the next 30 years.
The mini-site is about more than just the Mac itself, but also the "generation of innovators who continue to change the world" that Apple claims the computer launched. It makes for interesting viewing, and is sure to bring waves of nostalgia washing over you.
Check out the celebratory video that acts as a marvelous reminder of what Apple has brought to us over the last 30 years -- all condensed into a bite-sized three minute chunk, complete with Moby and various other artists.
What are your memories of Mac? Have you divided your time between Mac and Windows, or are you a one OS kind of person?
-

If Facebook is like a disease, I don't mind getting infected
Publié: janvier 24, 2014, 1:35pm CET par Mark Wilson
 Facebook has been in the news over the past few days after a report suggested that the social network is spreading in a similar way to a virus. Like all epidemics, the report suggests, the rate of infection will ultimately drop off, leading to the suggestion that by 2017 the social network will have shed 80 percent of its users. To which I -- and many others of reasonably sound mind -- cry "nonsense!" The catchily titled "Epidemiological modeling of online social network dynamics" paper published by, of all places, Princeton University puts forward the idea that Facebook users are set to abandon the social network in droves in the coming years.
Facebook has been in the news over the past few days after a report suggested that the social network is spreading in a similar way to a virus. Like all epidemics, the report suggests, the rate of infection will ultimately drop off, leading to the suggestion that by 2017 the social network will have shed 80 percent of its users. To which I -- and many others of reasonably sound mind -- cry "nonsense!" The catchily titled "Epidemiological modeling of online social network dynamics" paper published by, of all places, Princeton University puts forward the idea that Facebook users are set to abandon the social network in droves in the coming years.Things don’t get off to a good start. In explaining the methodology, authors John Cannarella and Joshua A. Spechler say they will use "epidemiological models to explain user adoption and abandonment of OSNs [online social networks], where adoption is analogous to infection and abandonment is analogous to recovery". The abstract gets off on the wrong foot by suggesting that Facebook "is just beginning to show the onset of an abandonment phase" -- a wonderfully vapid term with no grounding in, well, anything really. It's easy to pick holes in papers that have slight flaws, but right from the start it is almost too easy here.
It is worth taking a read through the paper in its entirety. It's only eleven pages long -- much less if you discount the meaningless graphs and citations -- but it's a perfect example of approaching something from the wrong angle, and bending the facts to suit what you set out to prove. It is twaddle. Nonsense. Tosh. Flim flam. Drivel. Crap. So why are we talking about it? Well, any paper that makes such drastic sounding suggestions about the future of such a successful institution -- for this is what Facebook has become -- is bound to attract attention. Indeed that was almost certainly the intention. It pains me slightly to fall into the trap of advertising a report apparently designed to bring short-lived fame to the authors. But just in case the authors do genuinely believe what they've written, it's worth spending the time blowing their absurdities out of the water.
The analogy drawn between Facebook and disease epidemics is, put simply, wrong. Sure, there may be similarities in the way epidemics spread and mutate and how social networks increase in popularity around the world, but this certainly does not mean that their full lifecycles are comparable. The paper looks at the rise and fall of MySpace which seems to fit the spread and decline of infectious disease quite nicely. But so what? MySpace got things wrong. It peaked too early. It was purchased by a company with no clue what to do with it. Competitors did things better. It did not fall into decline because of a natural lifecycle. It failed because it was terrible. Facebook could be seen as the cure.
Disease dies out for a few reasons. It might be countered by medicine. To stick with the stupid analogies, this could be seen as a rival service emerging to kill off Facebook. The chances of this happening are just so slight, it's not even worth considering. It's like suggesting that Coca-Cola will lose 80 percent of its customer base following the arrival of a cheeky startup. A disease could kill off everything it infects. If there are no hosts left for the infection, the infection dies. Facebook cannot have too many users. More users is in no way going to contribute to any decline in Facebook's success -- this could be nonsensical.
Facebook didn’t really need to enter the fray, but it chose to respond to the paper, doing an excellent, and amusing, job of demonstrating that it is possible to use the same methodology to prove whatever you like. Myth busted. Fewer people are performing Google searches for Facebook? This means there's less interest in the site, says the paper. Or maybe the millions upon millions of users have the site bookmarked, or are able to remember the URL between visits, eliminating the need to search for it. Visit any website and you're probably going to see a button to 'like' the article you're reading or share it with your friends. People don’t need to search for Facebook -- it does a good job of seeking people out on its own.
But what is worrying is the number of online publications who have reported about the paper as if it was peer-reviewed. It is in no way a scientific study. The figures have not been exactly plucked out of the air, but they have been thrown at the page like discarded runes in the hope that some meaningful pattern would emerge. It didn't ... but that didn’t stop the paper from being published anyway.
Love it, like it or loathe it, Facebook is not going to disappear or lose its users in droves. It's simply not going to happen. Facebook is going nowhere -- and I mean that in a good way.
Photo Credit: Brian A Jackson/Shutterstock
-

Fastest ever broadband test achieves a staggering 1.4Tb/s
Publié: janvier 23, 2014, 2:15pm CET par Mark Wilson
 In trial run by BT (British Telecom) and Alcatel-Lucent in London, UK, a data transfer rate of 1.4Tb/s has been achieved. This certainly sounds fast, and Alcatel-Lucent is claiming that it is the highest data transfer speed ever achieved using commercial-grade hardware.
In trial run by BT (British Telecom) and Alcatel-Lucent in London, UK, a data transfer rate of 1.4Tb/s has been achieved. This certainly sounds fast, and Alcatel-Lucent is claiming that it is the highest data transfer speed ever achieved using commercial-grade hardware.What could you do with an internet connection of this speed? If you felt so inclined you would be able to download no less than 44 HD quality movies in a single second. One. Single. Second.
What makes the tests particularly interesting is the fact that they were carried out using an existing fiber link rather than a new, dedicated line. The speed was achieved by increasing channel density on the fiber connection, helping to boost transmission efficiency by more than 42 percent. The new technique involved using a new "flexible grid" infrastructure called Flexgrid, and it demonstrates that significantly faster broadband speeds could be offered to home and business users without the need to upgrade the existing network.
This is something that is going to be welcomed by both ISPs and customers as it means that faster speeds are possible without a huge price hike. Just to show that the speeds were not limited to very short distances, the tests were performed over a 410km connection between London and Suffolk. Perhaps most importantly, as well as being incredibly fast, the data transfer was free from errors.
Dr Tim Whitley, BT's MD of Research and Innovation said: "BT has a long history of leading innovation in telecommunications, from the earliest days of the electric telegraph to today’s global fiber networks. These trials continue that tradition, as we work with Alcatel-Lucent to push the boundaries of fiber technology, allowing us to support the ever increasing bandwidth required by our customers, and deliver new and exciting services which rely on fast, data-hungry applications".
It might be a while before connections of this speed start to filter down to the average user, but it certainly looks like the future of broadband is bright. And very, very fast.
Photo Credit: Keo/Shutterstock
-

Woah there! Samsung Galaxy Note 3 KitKat update stops third-party accessories working
Publié: janvier 23, 2014, 12:43am CET par Mark Wilson

You would think that the rollout of an Android update would cause mass delight. There are usually ripples of excitement as a new device receives the latest version of Google's mobile operating system, and this has certainly been the case with KitKat. But some owners of the Samsung Galaxy Note 3 are finding that the update has a rather unfortunate side-effect -- third-party accessories no longer function.
There are various threads popping up on XDA with users complaining that cases, such as those from Spigen, are no longer working correctly. Specifically, the S-View feature appears to have stopped working for many people -- this is the feature that makes it possible to view a portion of the handset's screen through an aperture in the protective case so it is possible to keep an eye on notifications without having to open up the cover.
A few months back, there were rumors flying around that Samsung was thinking about implementing a means of blocking the use of third-party accessories, and it seems that it could be becoming a reality. Various solutions have been put forward, including transplanting magnets and identification chips from other accessories, but for anyone willing to root their device, XDA users have found that installing the Xposed framework mod can help, but there are potential issues associated with going down this route.
There has, as yet, been no official statement from Samsung, and it's therefore not clear whether this accessory blocking is here to stay, whether it is a mistake, or if there could be a change of heart. But for the time being it looks as though a number of cases no longer function as they should. Have you upgraded your Samsung Galaxy Note 3 to KitKat and been affected by the problem? Are you planning to ask for a refund on your case, take it up with Samsung, or try one of the workarounds?
-

LogMeIn Free is no more -- look elsewhere for your free remote access needs
Publié: janvier 21, 2014, 8:15pm CET par Mark Wilson
 Need a free remote access tool? Any day now your number of choices drops by one as the free version of LogMeIn will soon be no more. In a statement posted to the management section of its website, LogMeIn announces that LogMeIn Free is "going away".
Need a free remote access tool? Any day now your number of choices drops by one as the free version of LogMeIn will soon be no more. In a statement posted to the management section of its website, LogMeIn announces that LogMeIn Free is "going away".Like a gentle parent euphemistically softening the blow about a departed pet or loved one having "gone to sleep", LogMeIn is using this terminology to usher in the news that if you want to keep using its products, you're going to have to pay.
After ten years of service, the free tool is vanishing as LogMeIn unifies its "portfolio of free and premium remote access products into a single offering". As you will have guessed by now, "this product will be a paid-only offering". So what does this mean for existing users? The free tool is not being shuttered with immediate effect. Notifications are gradually being sent out to users starting today.
Once a notification is received, users have a seven day grace period in which to decide whether to upgrade or not. During this period the app will remain free, but unless you upgrade to a LogMeIn Pro account, you will then lose access to your remote machines through the tool.
Anyone who has the iOS or Android version of LogMeIn Ignition installed on their phone or tablet will be offered discounts "as well as generous terms to ease the transition".
A FAQ has been set up but there is little that can be added to the statement -- a tool that once was free is no more. It is likely that there will be something of a migration away to one of the many free alternatives that still exist, but LogMeIn is going to remain an appealing choice for companies and individuals looking for support options.
Are you affected by this announcement? Will you be upgrading or looking elsewhere?
Photo Credit: gst/Shutterstock
-

Dr Dre launches Beats Music to deliver the right tune at the right time
Publié: janvier 21, 2014, 3:57pm CET par Mark Wilson
 What's that? Another music streaming service? Another one?! You could be forgiven for having this reaction to the news that Dr Dre's Beats Music is now available for iOS and Android; this is a market that is already rather saturated, and music lovers are not exactly short of options when it comes to picking a service to satiate their audio needs. So any new service vying for attention has to have something rather unique to offer if it is going to stand out from the competition.
What's that? Another music streaming service? Another one?! You could be forgiven for having this reaction to the news that Dr Dre's Beats Music is now available for iOS and Android; this is a market that is already rather saturated, and music lovers are not exactly short of options when it comes to picking a service to satiate their audio needs. So any new service vying for attention has to have something rather unique to offer if it is going to stand out from the competition.Beats Music does have a unique selling point. It is a service that is about more than just streaming music, it aims to deliver the right music according to the time of day, what you are doing and where you are. Is this sort of stream tailoring enough to win over music fans? Only time will tell, but Beats Music certainly has a fight on its hands if it is to wrestle users away from the existing services that have been established for some time.
Dr Dre's Beats brand has already made something of a name for itself, and the Dre association may be enough to help Beats Music gain momentum from launch. But this is not the only name associated with the service; Jimmy Iovine, Luke Wood, Trent Reznor, and Ian Rogers are also involved. Featuring a catalog of over 20 million songs, Beats Music offers curated music. Forget creating your own playlists, the app can do it for you.
Whether you're looking for a workout playlist, something to relax to, a motivational soundtrack, or something completely different the aim is to provide the perfect tracks time and time again. In addition to this, there are also ready-made playlists from publications such as Mixmag and Pitchfork.
Beats Music is available for iOS as well as Android, and there is a Windows app in the pipeline. This is a subscription service that will set you back $9.99 per month, but there is a seven day free trial available and a special deal means that AT&T customers can use the service without charge for three months.
-

The rise of the phablet -- shipments to hit 120 million by 2018
Publié: janvier 21, 2014, 12:42pm CET par Mark Wilson

The phablet. It's a device with a silly name, but it's a market that is gaining massive momentum. Analysis by Juniper Research suggests that the number of larger-screened devices that ship will rocket by 600 percent by 2018. Projected figures show shipments jumping from around 20 million devices in 2013, to 120 million five years later. But taking into account the loose definition of a phablet it is possible that the figures could be even higher.
In fact there is no "official" definition of a phablet, at least in terms of the size of screen a device must sport in order to qualify for the title. Juniper Research acknowledges that phones with very large screens are increasingly common, with many high-end handsets featuring 5 inch - 5.5 inch displays. For the purposes of its report, Juniper Research uses the term phablet to refer to handsets that have a screen size between 5.6 inches and 6.9 inches.
Although the research suggests that phablets will increase in popularity at both the high and low ends of the scale, it is expected that the devices will hold particular appeal in poorer countries. While this may sound counter-intuitive, the dual-functionality of a phablet -- replacing both a smartphone and a tablet -- could actually make more financial sense for people with a lower disposable income.
Juniper Research expects that established names such as Nokia and Samsung will dominate the upper end of the market, while lesser-known manufacturers will focus on emerging markets. The paper also suggests that just how things play out in the phablet market will be heavily influence by whether Apple gets involved or not. As things stand at the moment, dominance in the phablet arena looks to be a battle between Android and Windows.
Photo Credit: Tanjala Gica/Shutterstock
-

IT worker steals credit cards details of almost half of South Koreans
Publié: janvier 20, 2014, 6:30pm CET par Mark Wilson
 As data theft goes, it has to go down as one of the largest and most audacious acts in history. The numbers may not be the highest -- although it's still a very hefty figure -- but looked at in terms of percentage of population, it is staggering.
As data theft goes, it has to go down as one of the largest and most audacious acts in history. The numbers may not be the highest -- although it's still a very hefty figure -- but looked at in terms of percentage of population, it is staggering.The work of a single person led to the credit card details of an incredible 20 million South Koreans, or almost half of the country's population, being stolen and sold onto marketing companies.
The Korean Financial Service Commission (FSC) announced that a contractor working for Korea Credit Bureau, a credit rating service, managed to make copies of customer information including data, credit card details and social security numbers.
Details were taken from the servers of credit card firms KB Kookmin Card, Lotte Card, and NH Nonghyup Card, and sold on to telephone marketing companies. The contractor has been arrested along with the managers of the other companies involved.
Referring to the "latest accident", the regulating FSS said that "the credit card firms will cover any financial losses caused to their customers". It is not yet clear whether any of the stolen customer details have been used, but there is certainly potential for a very large insurance bill as a result of the incident.
Reports coming out of South Korea suggest that the data was stored in an unencrypted form and was stolen by simply copying it onto a USB drive. An investigation is currently underway but in the meantime, millions of South Koreans will be checking their credit card statements rather more closely than usual.
Photo Credit: Brian A Jackson/Shutterstock
-

The spying game: Obama announces watered-down NSA surveillance reforms -- but will we see any difference?
Publié: janvier 18, 2014, 2:14pm CET par Mark Wilson

Unless you have been living under a rock for many months, you couldn't help but be aware of the activities of the NSA. They certainly knew what you were up to, even when you were hiding under that rock. Campaigners have been calling for reform ever since Edward Snowden blew the lid off previously secret surveillance of telephone calls and web activity of millions of users in America and around the world. In an address at the Justice Department, President Obama gave details of some reforms to surveillance, but at the same time remained defensive of the National Security Agency.
Referring to surveillance (or spying, if you will) carried out in the 1960s, Obama said: "In the long twilight struggle against communism, we had been reminded that the very liberties that we sought to preserve could not be sacrificed at the altar of national security". The speech continued, making the obligatory nods to terrorism, "weapons of mass destruction" and September 11th; all very emotive stuff. This heartstring tugging was cited as the reason the intelligence community in general -- including the NSA -- needed to up its game. They "suddenly needed to do far more than the traditional mission of monitoring hostile powers and gathering information for policymakers."
But for all of the justification given for the actions of the NSA et al, Obama used his speech to hold his hands up to the "more pronounced... risk of government overreach" and admits to having been opposed to "several practices, such as warrantless wiretaps". He freely admitted that intelligence agencies had access to a "powerful tool", whilst conceding that "collection and storage of such bulk data also creates a potential for abuse".
He almost boasted that "the power of new technologies means that there are fewer and fewer technical constraints on what we can do" -- seemingly failing to understand that this is precisely what people take issue with. Snowden was name-checked, albeit in passing: "I'm not going to dwell on Mr. Snowden’s actions or his motivations". Obama did voice his disapproval of the revelations, indicating that he thought that they revealed US methods to adversaries.
But it would be hard to ignore the fact that there is a trust issue that needs to be worked on. US citizens are understandably upset that phone activities have been indiscriminately logged, and it seems absurd that the NSA is collecting far, far more data than it can sift through and make use of. Obama used the speech as a self-congratulatory tool, repeating assurances that the NSA was only interested in national security and that work was already underway to make reforms to the way the organization works.
But, unsurprisingly, the reforms go nowhere as far as many people would have wanted. It was obvious that this would be the case before the speech was even made, but when caveats are announced ahead of news of reform ("We cannot prevent terrorist attacks or cyberthreats without some capability to penetrate digital communications, whether it’s to unravel a terrorist plot, to intercept malware that targets a stock exchange, to make sure air traffic control systems are not compromised or to ensure that hackers do not empty your bank accounts"), you know things are going to be disappointing.
Obama also attempted to humanize the NSA -- "the NSA and other intelligence agencies are our neighbors. They’re our friends and family" -- but this was just an exercise in softening up before the real meat of the speech was delivered. So what’s on the agenda? Annual reviews of what the intelligence agencies are doing. One would hope that in the fast-paced world of tech, things would be reviewed more frequently than this anyway. A promise of greater transparency is an empty gesture. It means nothing. We will still only be told what the US government wants to share, which essentially amounts to little or no change.
One vaguely promising proposal is that an independent third party will be called on to participate in "significant cases" in the Foreign Intelligence Surveillance Court. But there are problem here. Who decides which cases are deemed significant enough to warrant the involvement of these third parties? And who chooses them? How independent are they really? Data collected about communications between US citizens and those in other countries in certain circumstances will be restricted, but who will police this? Obama also promises that the secrecy surrounding "national security letters" demanding information from companies will be reduced and "more information" will be made available to the public... although it's not quite clear exactly what this actually means in practice.
In reference to the bulk collection of bulk telephone metadata, Obama waxed lyrical about the importance of such a program. A new program will be implemented -- at an unspecified time -- that "preserves the capabilities we need without the government holding this bulk metadata". What this means is that phone companies or third-parties will retain the data and will have to hand it over to the government on request. Plus ça change, plus c'est la même chose.
What has been promised is that only phone calls that are two steps removed from numbers associated with known terrorist organizations will be parsed; at the moment, three stages of removal are deemed permissible. Obama also made the rather empty announcements that he was ordering the development of new techniques that produce the same results as the current program, but without the need for the government to retain metadata.
But the question that needs to be asked is, will anything actually change? It may be that the reforms that have been announced do not go anywhere near as far as many wanted and hoped for, but how will we know if the smaller changes that have been announced are actually implemented? The world went for years living in blissful ignorance about the activities of the NSA. Is the leopard really likely to change its spots overnight? Whether things remain precisely as they are, or change even slightly, it is very unlikely that we'll ever really know what's going on. The NSA and other government agencies have already lost the trust of America, and indeed the world. There's an uphill battle if that trust is to be regained.
Do the proposals go anywhere near far enough in your view?
Photo Credit: bofotolux/Shutterstock
-

The most popular stories on BetaNews this past week - January 12 -- 18
Publié: janvier 18, 2014, 1:16pm CET par Mark Wilson
 Now that CES 2014 is completely out of the way (although there was still time for me to pick my favorite tech from the show), it's back to business as usual. For many a company, business as usual means security issues, and Microsoft suffered at the hands of The Syrian Electronic Army. Again. The earlier security issues at Target were found to be far worse than first thought, affecting an estimated 100 million customers, and a potential security flaw was identified in Starbucks' mobile apps. For the antivirus side of protection, Kaspersky's Internet Security was named product of the year by AV-Comparatives.
Now that CES 2014 is completely out of the way (although there was still time for me to pick my favorite tech from the show), it's back to business as usual. For many a company, business as usual means security issues, and Microsoft suffered at the hands of The Syrian Electronic Army. Again. The earlier security issues at Target were found to be far worse than first thought, affecting an estimated 100 million customers, and a potential security flaw was identified in Starbucks' mobile apps. For the antivirus side of protection, Kaspersky's Internet Security was named product of the year by AV-Comparatives.Hoping against hope that new tech isn’t embraced for the sake of embracing new tech, I pondered the need for curved screens. In the mobile world, KitKat started to roll out to the Samsung Galaxy Note 3 and also announced the company somewhat deceptively named Galaxy Tab3 Lite, which is in fact no lighter than the non Lite version, other than in terms of hardware specs.
Google's latest acquisition turned out to be Nest, the firm behind smartphone-controllable home heating systems and advanced more alarm. Does this mark the beginning of Google taking over even more of our lives? Brian asked whether it was possible Google could learn too much about us as a result. Whether this is the case or not, if you let Google know that you’re looking for royalty free images that you are free to reuse, the search engine now makes it easier to home in on them, while the addition of an activity stream feature to Google Drive makes it possible to see who has made what changes to files.
When Twitter accounts weren't being hacked, the website was undergoing a makeover to bring it in line with the mobile apps. Twitter served as inspiration for Tumblr as the site "borrowed" the idea of @ mentions. Facebook did something similar by introducing a new trending topic feature.
Helping to make life easier for international travellers, Microsoft added a new speech-to-speech translation option to Bing. It seems as though Microsoft was in a helping mood this week. A new partnership with GW Micro makes it easier for users with visual impairments to enjoy the benefits of Office with the help of a little extra software. Upgrade time finally rolled around for anyone still running the preview version of Windows 8.1, so get downloading if you haven’t done so already.
Windows XP users can celebrate the good news that their beloved operating system will receive anti-malware updates for a year longer than previously planned. Microsoft itself was celebrating after it was revealed that Xbox One sales outstripped the PS4 in December.
These were some of the highlights from this week. Let's see what the next seven days have to offer!
Image Credit: vinz89 / Shutterstock
-

Facebook copies Twitter and introduces trending topics
Publié: janvier 16, 2014, 9:18pm CET par Mark Wilson
It's starting to feel as though the myriad of social networks that exist are homogenizing. As one site introduces a feature, it is not long before the rest follow suit. Now it is Facebook's turn. Occasional leader, but often a follower, Facebook now boasts a trending topics feature. Simply known as Trending, the new feature borrows the idea used by Twitter and countless news websites to provide a constantly updating list of topics that people around the world are talking about.
In fact, Trending acts as a sort of blend between Twitter's Trends feature coupled with content suggestions. This is not a straight list of the subjects that are proving most popular around the world, but, theoretically, the list should be personalized with content that you have an interest in. That’s the theory at least.
Subjects that have been picked out for highlighting at the upper right hand corner of your account page include a brief description that lets you know why the topic is trending. Click through and you'll be able to see a list of posts relating to that topic.
Facebook says that the feature is rolling out in a select number of countries, although there is no word on precisely which countries are included and what sort of timescale is involved. Mobile apps will not be getting the feature for the time being, but it is on the cards for some point in the future.
Have trending topics hit your account yet? How does it sit with you -- something you'll make use of, or is it something to ignore?
-

Samsung adds the bigger, heavier Galaxy Tab3 Lite to its 7-inch tablet line-up
Publié: janvier 16, 2014, 3:21pm CET par Mark Wilson

There's no shortage of choice when it comes to 7-inch tablets, and Samsung is extending the selection even further with the release of the Galaxy Tab3 Lite. As you've probably discerned from the not-particularly-enigmatic name, this is a device closely based on the original Galaxy Tab3, albeit in a thinner lighter design. Or so you might think. Despite the name, the Tab3 Lite is not smaller in terms of dimensions or mass. In fact it is both larger and heavier than its predecessor. Here, 'Lite' refers to trimming back on the hardware spec.
Looked at in terms of size, it looks as though the Tab3 Lite has gained a little over the holiday period. The Lite model is more than 3mm wider, over 5mm taller and 10g heavier. The new device is 2mm thinner than the Tab3, but it is the other specs that make for interesting reading. A 2 Megapixel rear camera replaces the 3 Megapixel unit, while on the front you'll find that the camera has disappeared entirely.
This exercise in trimming the internal fat spares the screen and the processor which remain the same at 1024 x 600 and 1.2 GHz Dual Core respectively. This is backed up by 1GB of RAM and 8GB of storage, and there's a Micro SD slot which adds support for up to 32GB of extra storage. Battery capacity is another victim of the cull, dropping from 4000mAh to 3600mAh.
In terms of connectivity, all of the usual suspects are present -- Wi-Fi b/g/n, 3G (HSPA+ 21/5.76) and Bluetooth 4.0, as well as GPS. Running Android 4.2 Jellybean, the Samsung Galaxy Tab3 Lite is available in a choice of black and white. There's no word on pricing or launch date as yet, but this looks to be Samsung's entry-level, budget 7-incher.
-

Why I hope curved screens don't become the norm
Publié: janvier 12, 2014, 6:10pm CET par Mark Wilson

One of the most memorable presentations given at CES this year saw Samsung showing off its latest curved screen TV. Sadly for the tech giant it was Michael Bay's on-stage brain fart that most people took away from the talk (if I can just leave you with the delightful image of taking away someone's fart with you...), but Samsung would much rather we concentrated on the display technology it was showcasing. It excited a great many people, and for some it is seen as the way ahead and something we could see a lot more off. I sincerely hope we don't, particularly on the desktop.
Why? There are lots of reasons that I am opposed to the idea of curved screens, particularly when used for TVs and monitors -- smartphones are slightly different, but I'm not too keen on that either. Curved screens are not really a brand spanking new technology; there have been curved cinema screens for a number of years now, and I can see the benefit of the curve in this setting. Used in a theater the curve eliminates the problem of trying to find a seat right in the center because it matters far less where you are in relation to the screen. Everyone gets an equally good view of the action. It is a democratizing technology. So why am I down on it?
While the initial lure of curves is appealing, the hype surrounding curved screens does not really stand up to close scrutiny. As with any newish technology, curved screens are more expensive than their flat counterparts. This is to be expected, but the costs can be justified if there are sufficient advantages to making the investment. Sadly, this is precisely where curved screens fall down. On the desktop screens often need to be viewed by more than one person at a time, or a single operator may wish to be able to see the screen from different parts of the room.
This is where viewing angles are important and it is something that flat screen producers have been trying to maximize over the years. It is also reduced by curving a screen. Why would you want to limit your range of vision? Sitting in front of a laptop, generally speaking, viewing angles are less important (but please, no damned curved screen laptops!) but desktop users should be free to enjoy as wide a viewing angle as possible. Curving the screen and reducing it would seem like a backwards step.
With a flat screen it is easy to position your screen so it avoids reflecting that window behind you. With a curved screen it is far, far easier to pick up unwanted reflection to distract you from what you are actually meant to be looking at. Distortion is also an issue. The effect of screen curvature on an image may be minimal, but why compromise for the sake of embracing a new technology. Can you see designers working with a curved screen (just like all those curved drawing boards, eh?) and compensating for distortion as they sketch out ideas?
It's not all that long ago that we were using curved screens of a different kind -- older CRT monitors were rather convex. I remember working on a tiny 14-inch CRT display which, although not quite goldfish-bowl-like, certainly had a discernable distorting curve to it. Look at yourself in the back of a spoon. Go to a hall of mirrors at the fair. Curvy means weird-looking. Even as a teenager 20 years ago, I remember yearning for flat screens free from the need for image correcting pin-cushion and barrel controls. Why are we now taking a step back in time?
So here's hoping monitor manufacturers don’t jump on the bandwagon and start producing curved monitors en masse. Curved screens have their place, and the desktop is not that place.
Photo Credit: holbox/Shutterstock
-

My favorite product from CES 2014 [Mark]
Publié: janvier 12, 2014, 1:41pm CET par Mark Wilson

There has been a lot of talk about 2014 being the year of wearable tech. I'm yet to try out Google glass, but I can see its appeal -- providing the price drops a little! -- yet what interests me are smart versions of existing things we already wear. (I will grant you that Glass kind of falls into this category, but not everyone wears glasses) There have been quite a lot of smart watches over the last year, but they have a tendency to be rather ugly, bulky, or require an additional, specific device in order to function correctly. Yes, Galaxy Gear, I'm pointing at you.
But things are starting to evolve quite nicely. The new Pebble Steel is a spectacular smart watch that overcomes the looks issue that has blighted other models. The three models -- black leather, stainless steel and black matte -- all look great, and don’t stand out for the wrong reasons. This is a smart watch that looks like a watch rather than a smart watch, and this is where wearable technology stands or falls. An incredible piece of technology should be capable of just blending in and getting on with its job rather than jumping up, grabbing your eyeballs and demanding LOOK AT ME!
At $249, the Pebble Steel may not be exactly cheap, but it's also not extortionately expensive. The ability to use it in conjunction with just about any modern phone is a serious boon, and the range of apps and notifications that's available is impressive. I'm known for my pessimism, skepticism, nay, occasional nihilism, but Pebble works for me. It outpaces other smart phones in many areas, starting off with the fact that it is genuinely useful in so many ways.
It's not just a pedometer. It's not just about music. It's not just about notifications. It does all of this and more. It works with Android and iOS, and it is also fantastically customizable. Looks are important, but not necessarily in the way you might think. I want my tech to blend seamlessly into my life -- and ideally not attract the attention of potential muggers! -- but I also want massive functionality. Pebble Steel has all of this and more, including an impressive multi-day battery thanks to the e-ink display. Fantastic stuff, and I'm looking forward to seeing even more great things from this fabulous device.
-

The most popular stories on BetaNews this past week: January 4 -- 11
Publié: janvier 11, 2014, 9:13pm CET par Mark Wilson
 This was a week dominated by CES, and there were a huge number of announcements about upcoming hardware. Lenovo took the wraps off the (slightly) heavyweight ThinkPad Tablet 8, but any excess weight was countered by the ultra-light ThinkPad X1 Carbon ultrabook. HP's range of business desktops even included one device running Android, while Nvidia's new Tegra K1 promises much for the mobile market.
This was a week dominated by CES, and there were a huge number of announcements about upcoming hardware. Lenovo took the wraps off the (slightly) heavyweight ThinkPad Tablet 8, but any excess weight was countered by the ultra-light ThinkPad X1 Carbon ultrabook. HP's range of business desktops even included one device running Android, while Nvidia's new Tegra K1 promises much for the mobile market.Competitor Qualcomm revealed two processors designed for entertainment while Pure's Connect platform opens up the possibility of using any streaming music service with its wireless speakers. Smart TVs are set to benefit from the addition of Roku software, but it seems that the technology du jour is 4K, with a new 4K laptop from Toshiba joining the streams of 4K TVs and monitors.
Germaphobics can celebrate the launch of Antimicrobial Gorilla Glass which will keep your mobile screen sanitary. Mobile workers can also benefit from the extended battery life of 14 hours from the Samsung ATIV Book 9 2014 Edition. The company also launched a couple of 12.2-inch tablets, the Galaxy NotePRO and TabPRO. CES saw several transforming computers, and I had enough of the genre.
Android, iOS and Windows Phone may have more serious competition in 2014 as a new batch of partners joined forces to push Firefox OS, and mobile devices got a whole lot tougher with the launch of the Panasonic Toughpad FZ-M1. Taking a step away from all of the interesting releases, one of the highlights of this year's CES for many people has to be Transformers' director Michael Bay making something of a spectacle of himself after suffering from what appeared to be a combination of stage-fright and autocue issues.
Google was up to its usual tricks again, starting off by taking onboard another small company -- this time, Android app Timely's developer. Shortly after this, the company managed to annoy Gmail users by introducing a feature that makes it possible for any Google+ user to email a Gmail user -- but thankfully this can be disabled. Yahoo did a good job of upsetting a few people as well, spreading malware via advertisments. Amazon, on the other hand, did a good job of keeping its customers happy.
Facts and figures from the week revealed that the PS4 is far outselling the Xbox One, over $10 billion was spent in Apple's App Store, and the top gadgets of the year were announced.
Well… it's been a busy one. If you're looking for a little light relief (so to speak...) take heart from the German court ruling that said streaming 'pirated' porn videos is not illegal. Nice if you like that sort of thing!
Image Credit: vinz89 / Shutterstock
-

How to disable Gmail's new email via Google+ option
Publié: janvier 10, 2014, 7:37pm CET par Mark Wilson

Google recently made an interesting change to Gmail, making it possible for users to send messages to anyone in their Google+ circles. If the prospect of receiving emails from people you don’t know concerns you -- they don’t even need to know your email address -- you might like the idea of locking down your account. Thankfully, Google has made it quite simple to put restrictions in place. So if you'd like to avoid a possible influx of unsolicited emails, here's how to go about it.
Before we get started, it's worth pointing out that you may not see these settings in Gmail yet. This means that the feature has not been enabled for your account yet -- which means you don’t need to worry about receiving messages in this way anyway!
- Log into your Gmail account, click the cog icon to the upper right of the page and click the Settings option.
- Make sure you're on the General tab, scroll down and locate the Email via Google+ section.
- Use the drop down menu to choose who should be allowed to send you emails via Google+ -- choose between any Google+ user, people in your extended circles, people in your immediate circles, or no one.
- When you're happy with the selection you have made, scroll down to the bottom of the page and click the Save Changes button.
You can always go back and change the setting again should you feel the need, but it's good to see that you can knock this feature on the head if you don’t like it.
-

Watching pirated porn streams is not illegal says German government
Publié: janvier 10, 2014, 1:09pm CET par Mark Wilson
 Dealing with copyrighted material online has long been something of a legal minefield. Whatever your moral position on enjoying copyrighted movies, music, and other content without paying for it, there is usually little argument about whether or not it is actually illegal.
Dealing with copyrighted material online has long been something of a legal minefield. Whatever your moral position on enjoying copyrighted movies, music, and other content without paying for it, there is usually little argument about whether or not it is actually illegal.While downloading copyrighted movies from FTP servers, via BitTorrent, or using other means is widely regarded as breaking the law, things are not seen in quite such black and white terms when it comes to streaming content.
Sports fans will be aware that it is possible to tap into live streams of football matches that are being shown on pay-per-view channels. The same is true of pornographic content -- a field in which there is a vast amount of money to be made. Don't feel like paying to get your rocks off? Hunt around and you'll probably be able to find free access to a porno stream that would otherwise set you back a few dollars.
RedTube is a streaming video site, with a focus on "adult content", that found itself being taken to court by a team of lawyers representing porn producers. Copyright holders were upset that their content was being shared online through the site and lawyers duly issued cease and desist letters. The case rumbles on but there has been an interesting little tidbit thrown up. The German Ministry of Justice has said that the "viewing of a copyrighted stream without permission is not in itself an act of copyright infringement".
This appears to make a legal distinction between streaming content and downloading it -- one is legal, the other is illegal. But it is not the end of the story. The case is still to work its way higher into the legal system and the outcome is ultimately to be decided by the European Court. It's difficult to say what the result will be, but if streaming copyright content is deemed legal, it sets an interesting precedent that could have far-reaching consequences. Of course, there is still the question of whether the creation of the stream is legal, or whether the copyright permits potential mass viewing in this way. It will be fascinating to see how this plays out.
Does the ruling make sense to you? If you were the copyright holder -- of porn or other content -- would you be happy that your work could be streamed free of charge without the chance to prosecute those who view the material?
Photo Credit: SFerdon/Shutterstock
-

Gmail lets you email Google+ users without exchanging email addresses
Publié: janvier 9, 2014, 8:39pm CET par Mark Wilson

Assuming you're a Gmail user you'll be aware that there's rarely a need to type out an email address in full. Once a contact is in your address book, you can start typing a name into the To field and suggestions will pop up as you type. But what about those people whose email address you don’t actually have? You may have connected with someone on Google+ but start to type out an email and you suddenly realize you don’t have an address to send to. D'oh! However a new feature that's rolling out could see this frustration becoming a thing of the past.
What’s the solution? Google is keen on integrating Google+ with as many products and services as possible, and now this is spreading to Gmail. You've probably got a large number of contacts on Google+ (well… maybe you have some... Google+ isn't that unpopular!), but it doesn’t necessarily mean that you have their email address. Over the next few days, when you start to type the name of a recipient in the To field, Google+ contacts will be displayed as suggestions in addition to entries from your address book.
This essentially makes it possible to email people regardless of whether you have their email address or not. This is obviously a two-way process and other people are able (or may be able -- of which more in a moment) to send emails to you. Emails that are sent to Google+ users whose email address you do not have are treated slightly differently to regular emails. If you are emailed by someone who is in your circles, the message will appear on your Primary tab. Messages from anyone not in your circles are demoted to the Social tab.
Senders who are not in your circles are only able to message you once -- at least until you respond or add them to your circles. If you receive a message from someone and ignore it, you'll never hear from them again. But there is still obviously potential for this new system to be abused, and it is likely that over the coming weeks there will be a raft of spam delivered until the kinks are ironed out.
It goes without saying that privacy is a major concern, but Google is already a step ahead. The new feature is announced in a blog post by product manager David Nachum and he explains that email addresses are not shared when messages are sent via Google+ in this way. It is also possible to choose who is able to email you -- any Google+ user, only people in your immediate circles, people in your extended circles, or no one.
You may not see the feature at the moment, but you'll receive an email when it is rolled out to your account.
What do you make of the idea of being able to email anyone on Google+? Does it seem like a good one, or is it misguided?
Photo Credit: Lipowski Milan/Shutterstock
-

Stop with all the transforming, just decide what kind of device you want to be!
Publié: janvier 9, 2014, 11:17am CET par Mark Wilson
 It seems that these days it is not enough for a laptop to just be a laptop, or a tablet to be a tablet. I'm not talking about the strange new breed of devices that are capable of running Windows and Android, or the rumors that handsets running Windows Phone and Android might see the light of day (haha! Can you imagine?). I'm talking about the devices that seem to be trying to become best friends with Michael Bay, transforming between multiple modes.
It seems that these days it is not enough for a laptop to just be a laptop, or a tablet to be a tablet. I'm not talking about the strange new breed of devices that are capable of running Windows and Android, or the rumors that handsets running Windows Phone and Android might see the light of day (haha! Can you imagine?). I'm talking about the devices that seem to be trying to become best friends with Michael Bay, transforming between multiple modes.It's not really a new concept. We've already looked at Lenovo's Yoga 11S which can be bent into four different positions. The same company also has the Flex range which has fewer Transformer-like capabilities, but is still more than just your average laptop. At CES 2014 Toshiba decided to up the ante, taking the wraps off a 5-in-1 device.
Call me old fashioned, call me a stick-in-the-mud -- hell, you can call me worse than that if you like -- but what's wrong with a tablet being a tablet, a laptop being a laptop, and never the twain shall meet?
Sure, there will be time when you think, "yes, I really must rip the keyboard from this laptop, flip out the kickstand and watch a movie on my angled screen. No other method of viewing will suffice!" But seriously, how much better an experience is this than just watching in laptop mode?
You might like the idea of a laptop that converts into a tablet. But opting for a multi-purpose device almost always means having to make compromises. Why not just invest in a laptop and tablet? They're cheap enough these days and it is, genuinely, pretty hard to buy a really crappy product. The current fad for transform-a-devices is just that -- a fad. It's a passing phase that (I'm hoping) consumers will discover to be little more than a drop of marketing magic.
You don’t need these devices. A product with a rotation, detachable keyboard, a screen that flips around into every conceivable position is not fancy or clever, it's silly. It's the Ferrari of computers, indicative of owners making up for failings in other areas of their lives.
Not only do you end up paying more for the devices, there is more scope for things to go wrong. A detachable keyboard is all too easy to forget or lose. And more moving parts in the form of hinges and swivels means there is more scope for something to break.
Be decisive. Do you want a laptop or a tablet? Buy it! Feeling flush? Buy both. But don’t fall for these absurd hybrid transformers. No compromise, comrades!
Photo Credit: anyunov/Shutterstock
-

Nokia taunts Samsung after Michael Bay fluffs his lines
Publié: janvier 7, 2014, 7:54pm CET par Mark Wilson

Michael Bay -- yes, he of Transformers fame -- managed to get Samsung some attention with his performance at CES 2014... but not necessarily the sort of attention the company was hoping for. The idea behind the director's appearance was that he would showcase Samsung's latest range of curved-screen TVs. As a director, Bay probably has an eye for such details. He would seem to be well-positioned to extol the virtues of the new ultra-high definition. But it seems that speech making is not a forte of his. A mini-meltdown saw him fleeing the stage after an apparent auto-cue problem.
After attempting to "wing it", Bay fluttered off stage muttering "I'm sorry". He appeared incredibly uncomfortable from the moment he started speaking, but it wasn’t long before he said that the text was "all off". The situation was handled slightly more professionally by the Samsung representative who tried to cajole Bay into explaining how the curved screen would enhance the viewing experience -- but to no avail.
Of course, the world was quick to laugh and ridicule -- this was to be expected. But now Samsung's rival Nokia is joining in on the fun. In a tweet earlier today, the Finnish hardware manufacturer posted a message to Samsung that read "Pro tip for presentations: Save key talking points on OneNote in case the teleprompter fails. CC @S4TE". Accompanying the text was a photo of a Nokia handset running OneNote, itself used to keep a handy guide to giving a presentation.
It's not quite Scroogled, and it's all meant -- we think -- with the best intentions… but that doesn’t detract from the fact that it's funny. As laughing at others' misfortunes often is.
Oh, and if you managed to miss the incident, check out the video below to enjoy it in all its glory.
-

New raft of partners to help push Firefox OS in 2014
Publié: janvier 7, 2014, 11:44am CET par Mark Wilson

Firefox OS may have been with us since last year, but it's yet to make any sort of headway into the market. At CES, a new batch of partners has been unveiled which it is hoped will propel Firefox OS to mass popularity. Just as Android is not limited to use in phones and tablets, so Firefox OS has applications in other areas, and this is something demonstrated by the latest partnership with Panasonic. Working with Mozilla, the company will produce Firefox OS-powered smart TVs.
But of course there is great scope for Firefox OS to be used as a mobile platform, and this has already been explored to some extent. ZTE has produced a phone running Mozilla's operating system and in the coming year the company will be developing a "new Firefox OS line to give users more choice". But the success of an operating system is not just about getting customers on board -- developers are also vital.
To this end, Mozilla is launching a new contribution program in conjunction with Foxconn. This will enable more developers to get their hands on reference hardware so they are better able to create their own OS builds. For now the program is focusing on the development of Firefox OS for tablets -- the reference hardware is a 10-inch device with 16GB of storage and 2GB RAM.
Mozilla has also forged a new partnership with VIA with a view to developing Firefox OS for a range of new devices. Starting off with APC Paper -- an extremely interesting low-cost computer with a recycled cardboard case -- the company is releasing the source code online so the development community can help track down bugs and assist with taking things further. Think Raspberry Pi. But in a cardboard box. That looks a bit like a hardback book.
Could this be the year that Android's mobile crown is threatened? And is Mozilla the one who will gain ground?
-

New breed of Antimicrobial Gorilla Glass fights germs as well as scratches
Publié: janvier 6, 2014, 8:09pm CET par Mark Wilson

Corning Gorilla Glass is well known for its ability to fend off scratches, but the latest version has a new trick up its sleeve as well -- germ-fighting capabilities. Hypochondriacs and neurotics around the world rejoice! Touching your phone need not be the disgusting, bacteria ridden vomit-fest it has been up until now! Getting touchy feely with phones is something we have become used to over the years, and while it's probably easy to pull up some statistics to prove the notion that your toilet is more sanitary than your phone, it's safe to assume that your handset is a swarming mess of unpleasantness just waiting to transfer all manner of disease, infection and other unthinkable things.
All this could be a thing of the past thanks to Corning’s Antimicrobial Gorilla Glass. Made with ionic silver, an antibacterial agent, Antimicrobial Corning Gorilla Glass retains the toughness its predecessors became famous for. Think of what your phone goes through. Everything your hands come into contact with end up touching your phone. It's put down on all manner of surfaces, shoved into pockets with unmentionable disgustingness lurking in the depths. It's not hard to imagine a Petri dish-like bacterial colony building up and wreaking havoc.
Corning's senior vice president and general manager, James R. Steiner said:
"Antimicrobial Gorilla Glass inhibits the growth of algae, mold, mildew, fungi, and bacteria because of its built-in antimicrobial property, which is intrinsic to the glass and effective for the lifetime of a device".
This is all great news of course, but don’t forget to wash your hands anyway! It would be nice to see if these new breed of Gorilla Glass could be incorporated into the entire body of a phone rather than just the screen, but this is something we'll be able to monitor over the coming months.
Image Credit: Julien Tromeur / Shutterstock
-

Pinterest faces trademark battle in Europe over use of name
Publié: janvier 6, 2014, 1:12am CET par Mark Wilson

What comes to mind when you hear the name Pinterest? It's probably the famous content sharing site that enables users to pin their online finds to a virtual pinboard. But a British firm has proved in court that it registered the Pinterest trademark in Europe two months before the more famous Pinterest had even registered the name in the US. Premium Interest -- which feasibly shortens to Pinterest -- is a news aggregation service based in London founded by Alex Hearn.
The startup registered the Pinterest trademark in Europe in January 2012, but it wasn't until two months later that Pinterest filed for the trademark in the US. The ruling was made by the European Commission’s Office for Harmonization in the Internal Market, Trade Marks and Designs Division "rejected in its entirety" Pinterest's claim to the name in Europe. The court made its decision back in November, but the ruling has only just been made public.
The full court ruling can be found online at the Office for Harmonization in the Internal Market website if you don’t mind spending a few minutes registering for a free account. It's fairly heavy going legalese, but the documents do point out that while Pinterest was active as early as 2010, evidence submitted referred to the service as "sudden craze" and point out that it took some time for Pinterest to become recognized.
Despite taking into account the global nature of the internet, the paper states that Pinterest "seems to be based in the United States of America" and that there were "no indications regarding the relevant territory of the United Kingdom and the awareness of the relevant public in respect of the non-registered mark".
What could this mean in the long term? Well, it's unlikely that the Pinterest you had actually heard of will be disappearing anytime soon. What is more likely is that the service will change its name in Europe, or money could change hands with Premium Interest. For now, Premium Interest's court costs of €300 will have to be paid by Pinterest.
Photo Credit: tlegend/Shutterstock
-

Google takes Timely alarm clock developer Bitspin under its wing
Publié: janvier 4, 2014, 7:13pm CET par Mark Wilson

Google may have just announced the closure of Flock and Bump, but it's not all about closures -- there are also acquisitions taking place as well. The latest addition to the Google fold is Bitspin. The name of the company may not be immediately familiar, but this is the company behind the Android alarm clock app Timely. At this stage it is not clear whether the company has been bought outright by Google or if there is a partnership in the cards, but there is certainly something afoot.
An announcement on the Bitspin website says:
We're thrilled to announce that Bitspin is joining Google, where we'll continue to do what we love: building great products that are delightful to use.
For new and existing users, Timely will continue to work as it always has. Thanks to everyone who has downloaded our app and provided feedback along the way; we truly appreciate all your support.
Timely is an interesting alarm app that allows for alerts to be synchronized between multiple Android devices. Set an alarm on your phone and it will also sound on your tablet; mute or cancel an alarm, and it will be silenced on all devices. It's a simple concept, but one that works wonderfully well.
This is very likely why Google is interested in the firm. At this stage we do not know if Google intends to keep the Timely app up and running, plans to close it down, or if it will be incorporated into a future version of Android, but we'll update the post as soon as we hear more.
-

The most popular stories on BetaNews this past week: December 29 -- January 4
Publié: janvier 4, 2014, 2:29pm CET par Mark Wilson
 The start to any new year is always slow, and 2014 is no different. As the tech world struggled to shake off its New Year hangover, it was a pretty quiet week. The pace should start to pick up again, though, as CES is just around the corner!
The start to any new year is always slow, and 2014 is no different. As the tech world struggled to shake off its New Year hangover, it was a pretty quiet week. The pace should start to pick up again, though, as CES is just around the corner!The New Year wasn't the only cause for celebration; it was also Linus Torvalds' 44th birthday. Tablet makers were popping the champagne corks as it was revealed that such devices were among the most popular Christmas presents. Microsoft was also celebrating Windows 8 gaining a 10 percent market share, but Windows 7 also continues to grow in popularity.
The BetaNews team continued the theme of looking back over the previous year whilst also looking forward to making the most of the New Year with a series of tech resolutions. Alan shared his favorites from the year, ending by saying he's looking forward to the Nexus 10. Joe's list was home to a quite eclectic mix of hardware. In drawing up my list of favorite products, I found that I use a great deal of Google hardware and software! I've committed to a series of resolutions for 2014. How are they going? Well… pretty well so far, but we are only four days into the year! Mihaita also made a raft of resolutions, and Wayne tried to keep things realistic. Ian, however, decided to buck the trend and drew up a list of non-resolutions.
It isn't just the BetaNews team that is looking forward to the year ahead, Google's Eric Schmidt also delivered a number of predictions about what we might see. If Kaspersky Labs' prediction is correct, 2014 could see the internet being divided up along international boundaries. Whether this will do anything to stop attacks such as those launched by Syrian Electronic Army on Skype remains to be seen.
Google went on another culling spree, and announced that Bump and Flock will be dropped at the end of January. After the news that Winamp was to close, a buyer has been found in the form of Radionomy. On the other side of the coin, streaming music service HypedMusic fell victim to the RIAA and shut up shop. Interestingly, music download sales are on the decline.
Some people sending back a Surface Pro 2 for repair received a nice surprise when it was revealed that Microsoft was quietly upgrading the processors.
With all of the holidays out of the way, it's back to business as usual. We're looking forward to finding out what CES has to offer, and expect to read all about it right here!
Image Credit: vinz89 / Shutterstock
-

Google does it again -- kills Bump and Flock
Publié: janvier 3, 2014, 9:39pm CET par Mark Wilson

It's becoming quite a trend with Google. Buy up an interesting company or service, sit on it for a little while… and then shut it down. The latest victims of Google's seemingly never-ending cull are Flock and Bump. Bump was only acquired back in September, but it is already on the kill list. At the time of the acquisition, there was debate about whether the service might be rebranded, but as of the end of January it will be no more.
Bump was, in its day, quite an innovative tool, seen by many as the precursor to NFC. It enabled files to be quickly transferred between devices by bumping them together. Flock was a similar tool, but concerned solely with photo sharing. However as of 31 January, both apps will disappear from view, as announced in a blog post by CEO and co-founder of Bump, David Lieb:
Back in September, we announced that the Bump team was joining Google to continue our work of helping people share and interact with one another using mobile devices.
We are now deeply focused on our new projects within Google, and we've decided to discontinue Bump and Flock. On January 31, 2014, Bump and Flock will be removed from the App Store and Google Play. After this date, neither app will work, and all user data will be deleted.
If you have data stored in either app, don’t panic. As Lieb explains in his blog post, you'll be able to grab a copy of it:
We've taken much care to make sure that you can retain any data you have in Bump and Flock. At any point in the next 30 days, simply open either app and and follow the instructions for exporting your data. You’ll then receive an email with a link containing all of your data (photos, videos, contacts, etc) from Bump or Flock.
It is possible that we have not completely seen the end of Bump and Flock yet; they could still re-emerge in a new guise. Lieb makes reference to Bump's "new creations at Google", so there could well be another announcement in the pipeline.
Image Credit: IkeHayden / Shutterstock
-

Google does it again -- kills Bump and Flock
Publié: janvier 3, 2014, 9:39pm CET par Mark Wilson

It's becoming quite a trend with Google. Buy up an interesting company or service, sit on it for a little while… and then shut it down. The latest victims of Google's seemingly never-ending cull are Flock and Bump. Bump was only acquired back in September, but it is already on the kill list. At the time of the acquisition, there was debate about whether the service might be rebranded, but as of the end of January it will be no more.
Bump was, in its day, quite an innovative tool, seen by many as the precursor to NFC. It enabled files to be quickly transferred between devices by bumping them together. Flock was a similar tool, but concerned solely with photo sharing. However as of 31 January, both apps will disappear from view, as announced in a blog post by CEO and co-founder of Bump, David Lieb:
Back in September, we announced that the Bump team was joining Google to continue our work of helping people share and interact with one another using mobile devices.
We are now deeply focused on our new projects within Google, and we've decided to discontinue Bump and Flock. On January 31, 2014, Bump and Flock will be removed from the App Store and Google Play. After this date, neither app will work, and all user data will be deleted.
If you have data stored in either app, don’t panic. As Lieb explains in his blog post, you'll be able to grab a copy of it:
We've taken much care to make sure that you can retain any data you have in Bump and Flock. At any point in the next 30 days, simply open either app and and follow the instructions for exporting your data. You’ll then receive an email with a link containing all of your data (photos, videos, contacts, etc) from Bump or Flock.
It is possible that we have not completely seen the end of Bump and Flock yet; they could still re-emerge in a new guise. Lieb makes reference to Bump's "new creations at Google", so there could well be another announcement in the pipeline.
Image Credit: IkeHayden / Shutterstock
-

Microsoft under attack -- Syrian Electronic Army hack Skype's blog, Twitter and Facebook
Publié: janvier 2, 2014, 7:27pm CET par Mark Wilson

The Syrian Electronic Army is no stranger to the headlines, and the group's latest exploits have gained it further attention. This time the target is Microsoft, specifically Skype. The SEA target the Skype Twitter stream, as well as Facebook page and blog in what may be the first high-profile hack attack of the New Year.
The group defaced the blog with a message to Microsoft that read "Hacked by Syrian Electronic Army.. Stop Spying!". A message posted on the Skype Facebook page read "Don't use Microsoft emails (hotmail,outlook), They are monitoring your accounts and selling the data to the governments."
A tweet posted by the group through the Skype twitter account said "Stop spying on people! Via Syrian Electronic Army @Official_SEA16 #SEA cc @FBIPressOffice spr.ly/6019di9c". The fact that the FBI Press Office was "cc'd" in on the tweet is likely to be a reference to NSA surveillance.
All of the accounts are now back in the control of Microsoft. The breach was acknowledged by Microsoft in a tweet that reads: "You may have noticed our social media properties were targeted today. No user info was compromised. We’re sorry for the inconvenience." So if Microsoft is to be believed, this was simply an exercise in defacement, nothing more.
Image Credit: JMiks / Shutterstock
-

My tech resolutions for 2014 [Mark]
Publié: décembre 30, 2013, 10:04am CET par Mark Wilson
 Well, that's another year out of the way! It's customary at this time of year to make resolutions... for some people at least. It's something I've always shied away from, but this year is going to be different.
Well, that's another year out of the way! It's customary at this time of year to make resolutions... for some people at least. It's something I've always shied away from, but this year is going to be different.I don’t smoke anymore, I don’t need to lose weight, and I'm unlikely to take over the world in the next twelve months. But when it comes to tech, there is room for improvement, so here are my New Year's resolution that I will, truly, try to stick to.
Backing up stuff
Working as a tech journalist for the last 13 years, I've lost count of the number of times I tell people to ensure they make regular backups of their data. Do I practice what I preach? Er... no. But this year, this will change. My network drive will be put to better use. I'll need to invest in a couple (a few?) terabyte drives to hook up as extra storage, but I will -- I promise -- backup all of my computers on a schedule. And my phones and tablets.
Stop slagging off Windows Phone
I've bitched and moaned about Windows Phone. Quite a lot actually. My opinion hasn’t changed, but now I'll shut up until Windows Phone 8.1 is released. It is what it is for now, and hopefully it will get better.
Stop pretending I'm going to use Linux
My desktop PC is set up to dual boot between Windows 8.1 and Ubuntu. The number of times I've felt the need or urge to boot into Linux can be counted on one hand. Now is the time to wipe out that OS, eliminate the boot menu that I almost always forget is there and stick to using Windows. That particular PC didn’t play too nicely with Ubuntu anyway.
Embrace Chromebook
I don’t know quite why, but I don't use my Chromebook anywhere near as much as I should. I've managed to accumulate three different machines through 2013 and none of them are used enough. The Chromebook 11 is lovely and deserves to be pulled out more frequently. I shall endeavor to do so.
Sort out my passwords
This is kind of like my backing up. There is a distinct lack of practicing what I preach here too. I used to have a solid password policy in place and, while I was not perfect at changing passwords on a regular basis it did at least happen every now and then. I've got out of this habit and this needs to change. Facebook and Google are two that need particular attention -- I make use of Facebook and Google login whenever it's an option, so I really should try to bolster my security here.
There are probably more, but I think five resolutions will do for now -- I don’t want to set myself up for failure! How about you? What are your resolutions for 2014, both tech and non-tech?
Photo Credit: Kozini/Shutterstock
-

My favorite tech products of 2013 [Mark]
Publié: décembre 29, 2013, 10:26am CET par Mark Wilson

This past year has been incredibly busy, and a huge amount of hardware has passed through my hands. Some of it has impressed, a lot has disappointed, but a handful was great enough to make it to my list of favorites for the year.
While I've tried out a great deal of software, this has been a year in which it has been hardware that has caught my eye. So here it is: my favorite tech from 2013.
Nexus 7
I'm almost -- but only almost -- tired of banging on about the Nexus 7. I simply love it. I had problems with it to start with, in the form of touchscreen issues, but a couple of software updates sorted this out. Now I'm left with what is, in my mind, the finest 7 inch tablet on the market. I used to be attached to my phone, but now it is my tablet that is never far from my hand. Whether I'm in bed, on the sofa, in the kitchen or out and about, the chances are the Nexus 7 is just an arm's length away.
Of course it's used for email, web browsing, video, social networking and gaming, but it's also my go-to tool when cooking -- it's an awful lot easier to find room for this diminutive device on cluttered worktops than a laptop. This is one tablet I just can't recommend enough.
KitKat
 Having said that 2013 has been dominated by hardware, KitKat also impressed me. This is a highly polished version of Android and the performance boost included, make it worthy of installation. Better integration with Google Drive, built in Quick Office, Chromecast support, app sandboxing, and improved apps make this one OS upgrade not to skip.
Having said that 2013 has been dominated by hardware, KitKat also impressed me. This is a highly polished version of Android and the performance boost included, make it worthy of installation. Better integration with Google Drive, built in Quick Office, Chromecast support, app sandboxing, and improved apps make this one OS upgrade not to skip.Chromebook 11
 Chrome has been my browser of choice for a good couple of years now -- Firefox fell out of favor a little while back -- so the move to Chromebook seemed like a natural one. Google's changes to browser apps made the idea of a Chrome-based browser feel far more natural and in terms of looks, there's no denying that the Chomebook 11 is going to turn a few heads.
Chrome has been my browser of choice for a good couple of years now -- Firefox fell out of favor a little while back -- so the move to Chromebook seemed like a natural one. Google's changes to browser apps made the idea of a Chrome-based browser feel far more natural and in terms of looks, there's no denying that the Chomebook 11 is going to turn a few heads.Cheap enough to throw around without worrying, and light enough to chuck in a bag without getting weighed down, this is a perfect traveling companion with one of the best keyboards I have used in a long time.
Chromecast
 This was something of a slow-burner for me. I was first introduced to Chromecast at the same time as the Nexus 7, and I was initially somewhat indifferent to it. But I did try it out and learned to love it. Recent updates such as the addition of Plex mean that Chromecast is now permanently plugged into my TV and gets pretty much daily use. Movies and webpages can be thrown from laptops, tablets and phones, and the ability to view YouTube videos on a larger screen is great for sharing. Worth every penny.
This was something of a slow-burner for me. I was first introduced to Chromecast at the same time as the Nexus 7, and I was initially somewhat indifferent to it. But I did try it out and learned to love it. Recent updates such as the addition of Plex mean that Chromecast is now permanently plugged into my TV and gets pretty much daily use. Movies and webpages can be thrown from laptops, tablets and phones, and the ability to view YouTube videos on a larger screen is great for sharing. Worth every penny.Kindle Fire HDX
The Nexus 7 may be my favorite Android tablet, but the Kindle Fire HDX -- specifically the 8.9 inch model -- comes a very close second. I have previously eschewed dedicated e-readers. A brief flirtation with the Sony Reader some years ago left me apathetic to this genre of device, but the HDX rekindled (sorry!) an interest. The Amazon experience takes a little getting used to, but that screen! Wow! Books are a delight to read on this perfectly proportioned and well-balanced device. I was impressed from the second I powered it up, and this has not waned.
HTC One
 I have long been a fan of HTC hardware and the One range won me over again. The HTC One mini is impressive enough, but the flagship One really steals the smartphone crown. For me the One Max is a little too large, but this is personal preference. Build quality is simply stunning, and I would not hesitate in recommending this handset to anyone on the lookout for an Android phone.
I have long been a fan of HTC hardware and the One range won me over again. The HTC One mini is impressive enough, but the flagship One really steals the smartphone crown. For me the One Max is a little too large, but this is personal preference. Build quality is simply stunning, and I would not hesitate in recommending this handset to anyone on the lookout for an Android phone.This is a phone that feels like it belongs in your hand. The aluminum body is cool -- in more than one sense -- and the screen is mind-blowingly good. HTC Sense has been refined once again, creating a stylish and enjoyable experience that is wondrous to work with.
Looking back over the list I can see that it is fairly Android heavy. This is perhaps a little odd as I spend more time using Windows than anything else. An honorable mention goes to Office 365 which, between Windows Mobile, Mac, laptops, desktops, and Android devices, I have installed on seven or eight devices. I'm not yet fully convinced by the mobile edition of the office suites, but for desktop and laptop use, it is -- for me -- the best version, and best value version, of Office so far.
I hope that 2014 brings me a fresh batch of tech to get excited about. We may see a preview of the next update to Windows, hopefully the release of Windows Phone 8.1 and a new round of wearable devices -- maybe Google Glass will become affordable!
Image Credit: zmkstudio / Shutterstock
-

The most popular stories on BetaNews this past week -- December 22 - 28
Publié: décembre 28, 2013, 12:56pm CET par Mark Wilson
 This hass been a much quieter week than usual with Christmas meaning that many companies have been on a virtual shutdown. But there has still been a bit of activity over the past seven days. We've reached the end of the year and the BetaNews team finds itself in a reflective mood. Mihaita was the first to pick his favourite tech products of the years, and Wayne wasn't far behind. Brian also got in on the action and Ian shared his thoughts as well. Bing also took a look back at the year, putting together a list of the top ten homepage images of 2013.
This hass been a much quieter week than usual with Christmas meaning that many companies have been on a virtual shutdown. But there has still been a bit of activity over the past seven days. We've reached the end of the year and the BetaNews team finds itself in a reflective mood. Mihaita was the first to pick his favourite tech products of the years, and Wayne wasn't far behind. Brian also got in on the action and Ian shared his thoughts as well. Bing also took a look back at the year, putting together a list of the top ten homepage images of 2013.A delay at UPS meant that the delivery of many Christmas presents was held up, but if the delivery man did manage to make his way to your door in time to bring you a Surface 2, Brian has a guide to getting started. Alan was also on hand to help anyone who was the lucky recipient of a Kindle Fire HDX or a Google TV. Many people will have received, or bought themselves, a Windows 8.1 PC: Wayne had the info you need to get started.
UK porn filtering has been put in place by ISP BT. It is possible to opt out of the filtering, but problems have already emerged with non-porn websites falling victim to blocking. The Pirate Bay continues to not only prove as popular as ever, but also manages to sidestep any attempts to block access to it. For anyone concerned with government interference in internet usage, Edward Snowden had a message delivered to the UK on Christmas day: indiscriminate spying on citizens needs to stop. Sadly, a US judge has deemed the recording of phone data to be legal. Alan Turing, the genius who helped crack the Engima code, was granted a pardon having been convicted of homosexuality back in 1952.
If your resolution for the New Year is to get fit, Samsung Galaxy Gear could give you the motivation you need, but the new ads seem to highlight how it can be used for more creepy things. Probably not quite the message Samsung wanted us to take away from it! Anyone looking to try something a little different should take a look at Canonical's latest project that allows for dual booting between Android and Linux.
That’s it: we've made it to the end of another year (assuming you subscribe to the Julian calendar). 2013 was a cracker, and we'll be here throughout 2014 to bring you the best in news, reviews, fun and analysis
Image Credit: vinz89 / Shutterstock
-

Surprise, surprise! Federal judge says NSA's mass surveillance is legal
Publié: décembre 27, 2013, 11:31pm CET par Mark Wilson

The NSA's indiscriminate collection of telephone data has been ruled as legal by a federal judge in New York. Judge William Pauley ruled that the National Security Agency's activities do not violate the constitution. Just last week, another federal judge suggested that the collection of phone records was likely to violate the US constitution and a White House review panel has already recommended that President Obama stops the NSA in its tracks.
The American Civil Liberties Union (ACLU) had brought a case to court challenging the NSA program, but Judge Pauley's ruling put an end to this. It looks like there could be something of a battle ahead, and the latest ruling opens up the possibility that the matter will be settled by the US Supreme Court. Referring to the fourth amendment, Judge Pauley said that whether it "protects bulk telephony metadata is ultimately a question of reasonableness."
With different judges taking opposing sides of the argument, there could be a rocky road ahead. The judge said that "while robust discussions are underway across the nation, in Congress and at the White House, the question for this court is whether the government’s bulk telephony metadata program is lawful. This court finds it is."
It is the dragnet style of data gathering that irks many people, but this was not seen as an issue by Judge Pauley. "This blunt tool only works because it collects everything," he said, but this is precisely the issue that raises hackles. It is already known that the NSA is collecting more data that it is reasonably able to handle. This is not enough to sway Judge Pauley who said:
"The ACLU argues that the category at issue -- all telephony metadata -- is too broad and contains too much irrelevant information. That argument has no traction here. Because without all the data points, the government cannot be certain it is connecting the pertinent ones. There is no way for the government to know which particle of telephony metadata will lead to useful counterterrorism information. Armed with all the metadata, NSA can draw connections it might otherwise never be able to find."
The ACLU has already said that an appeal will be lodged, but this is a case that is going to rumble on for quite some time to come.
-

Facebook? What’s that, granddad? Teenagers fall out of love with Zuckerberg's social network
Publié: décembre 27, 2013, 6:44pm CET par Mark Wilson

Once the darling of the social networking world, it looks as though Facebook is falling out of favor. At least that seems to be the case with teenagers. An extensive and ongoing study into social media finds that huge swathes of 16 to 18 year-olds are abandoning Facebook and jumping ship to the likes of Instagram, Twitter, and Snapchat. In total, nine different regions are being studied over a course of 15 months.
As Professor of Material Culture at University College London, Daniel Miller says, Facebook is now uncool. Mum and Dad are now not only using the social network (which is an immediate nail in the coffin), but actively encouraging their kids to share details about what they're doing: "Parents have worked out how to use the site and see it as a way for the family to remain connected".
While the likes of Whatsapp have exploded in popularity none of the alternatives which are attracting younger users offer quite the same set of options as Facebook. Instagram is great for sharing photos, but in terms of organization and interaction, it is found wanting. Snapchat and Twitter have their plus points, but lack a lot of functionality.
Which social networks do you align yourself with? Have you found that your preferences have changed over the years or do you stick ruggedly to whichever network you first used? I was something of a lurker on Facebook for a couple of years before becoming fully immersed in it. At 34, I probably fit neatly into the average demographic and I like the network because it offers a nice combination of instant communication and slower, laid-back newsy style.
Twitter was more of a slowburner for me. Again, I signed up for an account pretty much as soon as it was possible to do so, and then did little for some time. Twitter bemused me, and I couldn’t see the point. Then I experimented and found that it blended blogging, instant messaging and news delivery in one neat package. I'm now in love. Force me to choose two networks to use and Twitter and Facebook would win without question, but choosing between these two to pick a winner would be hard.
Photo Credit: Suzanne Tucker/Shutterstock
-

Edward Snowden calls for an end to spying in Christmas address to the UK
Publié: décembre 26, 2013, 1:42pm CET par Mark Wilson

At this time of year in the UK it is traditional for the Queen to record a message to the nation. Broadcast on TV at 3pm just as everyone is recovering from Christmas lunch, she looks back over the year in a speech which usually has a reflective tone. In recent years there have been numerous alternatives to the Queen's speech, with broadcaster Channel 4 giving a platform to the funny, the controversial, the meaningful and the strange. Whilst not necessarily anti-monarchy, it is a broadcast that is certainly non-monarchist, and frequently of a more left-wing bent. This year, Edward Snowden used it as a mouthpiece.
The 30-year-old former NSA worker who blew the cover off the secret surveillance that is being carried out on web users all over the world. He is currently living in Russia where he sought asylum having fled from the US earlier in the year after threats of espionage charges. The two minute long address makes reference to the book 1984, with Snowden saying that George Orwell had forewarned us of such dangers but said that the spying techniques described in the classic work were nothing compared to what actually exists now.
"A child born today will grow up with no conception of privacy at all," Snowden says, warning that "they'll never know what it means to have a private moment to themselves." Snowden may not be the best figurehead for the anti-NSA campaign: he has a tendency to come across as rather smug, self-satisfied and arrogant. But cut through this and what he says is correct: "Privacy matters". Security matters, of course, but at what price? Snowden points out that the discussion that is now taking place following the revelations he made will determine how much trust we can place in governments and technology.
Ultimately, what Snowden and his supporters are looking for is an end to indiscriminate mass surveillance:
"Together we can find a better balance, end mass surveillance and remind the government that if it really wants to know how we feel, asking is always cheaper than spying."
Quite what 2014 holds for us in terms of surveillance remains to be seen, but it's unlikely that -- whatever the global backlash -- the NSA will cease its dragnet-style activities any time soon.
In some parts of the world, it is possible to watch Snowden's Christmas message on the Channel 4 website, but have a look around YouTube and you should also be able to find a copy.
-

Grandfather of computing Alan Turing granted posthumous royal pardon
Publié: décembre 24, 2013, 11:17am CET par Mark Wilson
 Dr Alan Turing, the mathematician who helped to crack the Enigma code during the second world war, has been granted a royal pardon 59 years after he took his own life. His crime? Homosexuality. In spite of his role in code cracking -- which is widely regarded as having helped to shorten the war -- he was convicted for engaging in homosexual activity, and underwent experimental chemical castration as "cure" and punishment in 1952. Two years later he killed himself aged just 41.
Dr Alan Turing, the mathematician who helped to crack the Enigma code during the second world war, has been granted a royal pardon 59 years after he took his own life. His crime? Homosexuality. In spite of his role in code cracking -- which is widely regarded as having helped to shorten the war -- he was convicted for engaging in homosexual activity, and underwent experimental chemical castration as "cure" and punishment in 1952. Two years later he killed himself aged just 41.It was the illegality of homosexuality that meant Turing's relationship with a man led to a criminal record, and this in turn meant that he was no longer permitted to continue his work at GCHQ (Government Communications Headquarters). The UK's justice secretary, Chris Grayling requested the pardon which was then granted under the Royal Prerogative of Mercy. Grayling said:
"Dr Alan Turing was an exceptional man with a brilliant mind. His brilliance was put into practice at Bletchley Park during the second world war, where he was pivotal to breaking the Enigma code, helping to end the war and save thousands of lives. His later life was overshadowed by his conviction for homosexual activity, a sentence we would now consider unjust and discriminatory and which has now been repealed."
The pardon has not come completely out of the blue as there has been a long running campaign to clear Turing's name. Two years ago, former UK Prime Minister Gordon Brown apologized for the "appalling treatment" Turning has received and calls have been made for a pardon for some years. The campaign received the backing of names such as Professor Stephen Hawking and Richard Dawkins. Pardons are usually only granted when it later transpires that someone convicted of a crime is in fact innocent. As Turning engaged in homosexual activity (or "gross indecency" as it was termed), he was, technically speaking, guilty.
While the pardon has been welcomed by many, for others it is not enough. Turing is just one of many people convicted under a law that does not exist anymore. His high-profile work led to a high-profile campaign to clear his name, but it does nothing for the less well-known people convicted of the same "crime". We can thank Turing not only for the work he did during the war, but also for paving the way for modern computing. This is not really the place for debate about the rights and wrongs of a 61 year old conviction, but Richard Dawkins makes good point on Twitter: "Overturn a conviction" sounds a lot better than "pardon". "Pardon" implies that #Turing did something wrong in the first place.
Anyway -- thanks Mr Turing.
-

The UK's porn filtering shows that a rethink of child protection is needed
Publié: décembre 22, 2013, 8:48pm CET par Mark Wilson

Just last month Google and Microsoft came together in an unlikely pairing. This was not a software venture, but a bid to help tackle the problem of child porn online. UK Prime Minister David Cameron has said on numerous occasions that ISPs needed to do more to not only block access to torrent sites -- despite the fact they can be used for perfectly legal downloads -- but also to make it more difficult for children to access pornography. Four major ISPs either already have porn filters in place, or have plans to roll them out.
TalkTalk's filters have been in place for a few years now, Sky's were recently launched and Virgin is piloting a scheme due for full scale roll out at some point in 2014. In the past few days, BT switched on its filters, falling in line with government requests for access to legal porn to be made opt-in -- i.e. blocked by default. So is this having the desired effect? Well, it's very early days, but there are a few observations to be made already.
Firstly, the porn filters apply to new users. Anyone joining BT for internet access will find that the porn filter is in place by default, and they'll have to phone up to get the block lifted if they find that it is interfering with their ability to access the content they want to see. Secondly, it has been very quickly revealed to be a "sledge hammer to crack a nut" solution to a problem -- it may be working to some extent, but there are also some unwanted side effects.
The idea of the filter is to prevent children from -- innocently or otherwise -- viewing online porn. But if there's one thing we know about children, it is that if they want to access something, they will do so. Knowledge of proxies and filter bypassing tools are no longer the domain of the technically-minded -- it is the norm. PirateBay is blocked? So what! A quick re-route and 30 seconds later the site is accessible again. Hooray! The same is true for porn or anything else that may be blocked.
Talking about children and pornography in the same breath is always going to raise a few hackles (even if we're not talking about child porn per se), but any form of filtering is flawed from the start. My fear with filtering is that categorization of sites -- the millions and millions of sites that exist -- is all but impossible. Tests carried out by BBC TV show Newsnight found that with 68 test porn sites, TalkTalk -- the longest running filter -- failed to block 7%. With new sites popping up every day, shifting servers, changing names and disguising themselves, achieving 100 percent porn blocking is all but impossible.
But there is a more worrying concern: that these filters block more sites than they are meant to. And this is exactly what is happening. The porn filters that have been put in place are also blocking access to genuinely useful sites. Sites such as sex education programs, pages about getting help with domestic abuse, and even a rape help center. What is worse? Allowing a child to access porn, or preventing them from accessing sites they might need? It seems the two are not mutually exclusive.
We run the risk of creating another Great Firewall of China, a two-tier internet. Yes, children should be sheltered from adult content, but a less drastic solution needs to be found. If Microsoft and Google can work together, why not ISPs? The government understanding of the role of the internet, and appreciating children's knowledge of it, is sadly lacking. If the web is to be filtered a proper, fully funded taskforce needs to be behind it, not a disparate group of ramshackle ISPs all working independently on different systems.
It's great that David Cameron and BT bosses can go to sleep with a smile on their faces in the belief that they're doing something to help. But do the disadvantages outweigh the benefits -- is this the best approach?
Image Credit: alphaspirit / Shutterstock
-

The most popular stories on BetaNews this past week -- December 15 - 21
Publié: décembre 21, 2013, 2:10pm CET par Mark Wilson
 This is the final roundup before Christmas and the penultimate one of 2014. Things are very much starting to wind down for the year, and the world of tech is starting to go into something of a hibernation mode. But that's not to say that there hasn't been a fair select of big stories over the past seven days. If you're dreading the prospect of traveling across the country to meet up with family, Microsoft may have a solution -- just turn to Skype instead!
This is the final roundup before Christmas and the penultimate one of 2014. Things are very much starting to wind down for the year, and the world of tech is starting to go into something of a hibernation mode. But that's not to say that there hasn't been a fair select of big stories over the past seven days. If you're dreading the prospect of traveling across the country to meet up with family, Microsoft may have a solution -- just turn to Skype instead!Valve's highly anticipated Steam OS was made available to the public as a beta, so gamers can create their own rigs. Gamers with a lots of spare cash floating around might prefer to opt for a solid gold Xbox One -- but the price tag is an eye-watering £6000 (around $9,800)! For those to whom quality matters, Amazon's announcement that all new shows in 4K Ultra HD will come as great news. For entertainment at slightly lower resolution, Redbox Instant made an appearance on the Kindle Fire HDX -- a tablet that I was quite enamored with. Roku 3 users can also celebrate the arrival of YouTube for their video entertainment.
After last week's debate about whether the Start menu should return to Windows, I wondered aloud about how much customers should be listened to by companies. Wayne warned us all that time is running out to upgrade from Windows 8.1 Preview.
Security problems hit the headlines this week as Target found itself falling victim to a breach that exposed the details of some 40 million customer card transactions. The government often requests that websites be taken down in the interests of national (and international) security and Google announced the number of requests it had received in the first half of 2013. Wayne took a look at improving privacy in Windows 8.1 and I revealed a new technique that allows for the decryption of files by listening to the sounds your computer makes when accessing them.
LG took the wrapping paper off its latest phablet, the Gx which is a direct competitor Samsung's Galaxy Note 3. Fancy one under your Christmas tree or do you have something else in mind? In the world of Apple, Mavericks 10.9.1 hit the download servers which fixed, amongst other things, problems with the Mail app. The Mac Pro was also released for anyone with a bundle of spare cash, and Joe was impressed with Apple's current marketing video. Nokia's new ad for the Lumia 2520, on the other hand, is slightly out of leftfield.
It's the time of year when companies like to look back over the past twelve months, and this year is no different. I look back at some of the let-downs of 2013 while Google took a look back at what 2013 brought us in its annual Year-End Zeitgeist video. The company also recalled the HP Chromebook 11 charger because of an overheating problem.
But forget overheating, this is the season for some overeating! Have a great Christmas and we'll have one more roundup before 2013 comes to a close -- finish off with something fun: a full-sized car built from Lego.
Image Credit: vinz89 / Shutterstock
-

Shhh! The noise your computer makes could be used to decrypt your files
Publié: décembre 20, 2013, 2:36pm CET par Mark Wilson
 It's probably not something you need worry about in relation to your personal files just yet, but according to a newly published paper (the snappily titled "RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis") it appears that it is possible to extract 4096-bit RSA decryption keys by listening to the sounds made by a computer.
It's probably not something you need worry about in relation to your personal files just yet, but according to a newly published paper (the snappily titled "RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis") it appears that it is possible to extract 4096-bit RSA decryption keys by listening to the sounds made by a computer.This might sound like the talk of someone paranoid, but it is actually more feasible than you might first think. And the paper has been penned by no less than Adi Shamir, the co-inventor of the RSA algorithm.
Shamir, working with Daniel Genkin and Eran Tromer from Tel Aviv University, proved that the sound generated by a laptop could be picked up with a mobile phone or a more distant microphone. Described as an acoustic cryptanalysis key extraction attack the technique exploits the fact that the vibration of hardware when used, and when dealing with different RSA keys different sound patterns are produced.
This is due to the fact that power usage alters dramatically when performing different tasks, and the resulting high-pitched tones can be detected with the right equipment. Tests showed that an RSA decryption key used by PNU Privacy Guard could be determined in an hour.
A mobile phone with a suitable app installed could be easily placed near a victim's computer, or there is even the possibility of remotely accessing a victim's own mobile to use it against them -- we're getting into the realms of Person of Interest now. So should you be concerned? Unless you're dealing with life-and-death data, probably not. Government bodies may want to take note, but for the average computer users there's probably not too much to lose sleep over.
Worryingly, decryption via sound is not the only means of extracting data. The trio of authors also found that it was possible to perform an attack by measuring the electric potential of the chassis of a computer. The paper suggests that this data could be gained by merely touching the case, or gathered from a USB, Ethernet or VGA cable.
All of this has an air of espionage about it -- making it simultaneously fascinating and disturbing!
Image Credit: Volodymyr Krasyuk/Shutterstock
-

Crowd-funded car built from Lego runs on air at up to 20km/h!
Publié: décembre 20, 2013, 10:40am CET par Mark Wilson

If you had access to 500,000 pieces of Lego (yes, they are Lego bricks or pieces, not Legos!) what would you build? When Steve Sammartino, an American entrepreneur, joined forces with "crazy Romanian teenager" Raul Oaida the answer seemed obvious -- build a full sized car capable of hitting 20km/h. Sammartino and Oaida met online, came up with the wacky idea for the plastic vehicle and tweeted to ask for help with funding.
The tweet lead to the birth of the Super Awesome Micro project. Having read the tweet -- "Anyone interested in investing $500 - $1,000 in a project which is awesome and a world first tweet me. Need about 20 participants" -- Ford Australia pledged some funding, as did some other investors, and the project was able to get off the ground.
The car is propelled by four air-powered engines and 256 pistons. Believe it or not, the car is constructed almost entirely from Lego with the exception of the wheels -- which does make for a rather uncomfortable-looking seat. The half-million bricks took a year and a half to form into the drivable car, and the delicate construction was shipped from Romania to Australia.
The engine is described as "fragile" however it packs enough punch to not only move the car, but also an adult driver. You can check out a video of the car in action at the BBC News website (which doesn't allow embedding, sadly). So sit back, enjoy the gentles strains of Madness (which will make sense when you watch the video) and prepare to be slightly blown away by what two people have managed to create from little plastic bricks.
-

Need to switch to a different Office 365 plan? Now you can!
Publié: décembre 19, 2013, 8:45pm CET par Mark Wilson

One of the problems facing an organization investing in subscription software is determining what package to opt for. It makes sense to keep things as cheap as possible and plump for the lowest priced package, but what happens when your business expands and your needs grow? Microsoft is looking to make things a little easier for Small Business users who find that their needs change over time, making it possible to easily jump to the Midsize or Enterprise plans.
The Switch Plans program also makes it possible for Midsize Business subscribers to switch to an Enterprise plan. This is a great option for businesses whose employee numbers swell faster than expected, or for those who discover that they need access to additional features and options that are not available on the plan they originally chose.
There's no need to deal with Customer Service as everything can be handled from within admin center -- just head to the Purchase page and look to the Licenses section. Full details of the available upgrade paths can be found on the Office support pages.
There are a few points worth noting before rushing ahead and upgrading. Firstly, Microsoft recommends that you backup all information before proceeding. Next, anyone who has a vanity domain needs to remove it from Office 365, switch plans and then re-add it. Finally, you need to bear in mind that plan switching is a one-way process; upgrading is simple, but downgrading is not possible.
Image Credit: donskarpo / Shutterstock
-

What have been the biggest disappointments of 2013?
Publié: décembre 18, 2013, 3:30pm CET par Mark Wilson
 It's that time of year once again. Approaching the end of another 365 and a quarter days cycle puts us all in a reflective mood. It's not uncommon to look back at what has happened in the previous 12 months and pick out the highlights of the year. It's also quite common to look forward in anticipation of what the coming year might have to offer. But how about something a little different, something a little more downbeat? What have been your lowlights and disappointments? There's no need to end the year on a high, after all!
It's that time of year once again. Approaching the end of another 365 and a quarter days cycle puts us all in a reflective mood. It's not uncommon to look back at what has happened in the previous 12 months and pick out the highlights of the year. It's also quite common to look forward in anticipation of what the coming year might have to offer. But how about something a little different, something a little more downbeat? What have been your lowlights and disappointments? There's no need to end the year on a high, after all!I am one of those people still devastated at the loss of Google Reader. Both as a journalist and as someone who simply devours news from all manner of sources, this was my go-to service for getting my daily -- well, hourly… oh, OK, five minutely -- fix of headlines from hundreds of websites. Double disappointment came when I thought an ideal solution was to be found in Feedly, but slow updates and a pricing structure I found objectionable meant that this soon fell by the wayside. Disappointment number two. Still, it helped me to discover InoReader -- every cloud, and all that.
Back to disappointments. Windows 8.1 did a great deal to address some of the shortcomings of Windows 8. I'm pretty happy with it -- although I have argued for the Start menu to be reinstated -- but it still left a lot of people wanting more. The update to Windows Phone 8 was a massive let-down for me. It was always meant to be a fairly minor update, but I clung to the hope that there could be a few surprises in there to make the OS vaguely usable.
Few people could honestly say that they're not at least slightly disappointed at the actions of the NSA and government agencies around the world. The biggest disappointment is two-pronged, however. First, it is very unlikely that things are going to change in the foreseeable future, nor is there likely to be an increase in transparency. Secondly, I think it is likely that this is just the tip of the iceberg. Edward Snowden has revealed a great deal about the kinds of activities that have been taking place, but it would be foolish to think that surveillance does not run even deeper and is even more prevalent than we already know.
Back on the hardware front, Apple's latest offerings in the form of the iPhone 5s (the less said about the 5c, the better, I think) and the iPad Air demonstrated a company caught treading old ground. I was initially excited at the prospect of the new iPhone, but on closer inspection, it enveloped me with an overwhelming sense of ennui. Thinner iPad? Meh.
This was not the only handset to disappoint. Many people felt let down by the Nexus 5. It was a phone that promised so much and ultimately delivered just enough. A phone that has no major issues, but proved to be far from mind-blowing. I could list more disappointments, but I think it's time to turn it over to you.
Oh -- how could I forget? -- I still don’t have the hoverboard I was promised by Marty McFly.
So, what have been your low-points of the year? Are there any releases that left you in tears, or are you mourning the loss of any online services? Offload below... it'll make you feel better.
Photo Credit: Leszek Glasner/Shutterstock
-

Should companies stick to their guns or give in to customer demands?
Publié: décembre 16, 2013, 10:47am CET par Mark Wilson

The customer is always right, right? As a customer it is understandable that this old adage seems like something set in stone, but looked at from a company's point of view things are rather different. A large proportion of customers are in fact idiots. While it is reasonable to expect a company to listen to what its customers have to say, does this risk stifling innovation as customers demand that things be done a certain way?
Here on BetaNews we've had a little debate about whether Microsoft should reintroduce the Start menu. Despite the number of people calling for its return, Brian does not think it is a good idea saying that "the company should ignore these customers, even if they are the majority". I am of the opinion that it would be good to at least make it optional, particularly for enterprise customers.
In my mind, if there are a huge number of users making the same demand, it would seem to imply that something needs to change. This is something that Twitter recognizes. Just a few days ago the social network made a significant change to the way its blocking feature worked. It essentially meant that blocking someone no longer meant that they were blocked in the sense that most people would understand. Users were upset. Users voiced their disapproval. Twitter listened and reversed the changes.
Should this be seen as a sensible case of listening to the customer, or is it more like caving in? It would be a bold company that just went ahead and did whatever the hell it wanted to, but there is a fine line to walk. A company that acts upon every demand made by customers is doomed to failure.
So what’s the answer? When there are areas of contention -- such as with the Start menu -- who should get the final say about what happens. Should a company stubbornly stick to its guns and do what it thinks is best, or should it take into account what paying customers think? Would it make sense to have polls to see what the majority of people want done? The danger with going down this route is that it would be open to abuse; online polls can be sabotaged, for example.
How would you tackle balancing customer demands and development of a company's ideas?
Photo Credit: ollyy/Shutterstock
-

Get your hands on Valve's SteamOS beta right now!
Publié: décembre 14, 2013, 9:07pm CET par Mark Wilson

Anyone who fancies the idea of building their own gaming box can head over to the Valve website can grab themselves a beta copy of SteamOS. The Linux-based operating system is available for anyone to download free of charge and coincides with the shipping of 300 prototypes of Valve's Steam Machine devices to specially selected testers. The OS and boxes have both been designed with pure gaming in mind -- but the system requirements are quite specific.
The download weighs in at 960MB, and there are reports that the servers are struggling as legions of eager gamers hit the link. But before you rush over to the site and start the download for yourself, take a moment to check whether your rig is up to the task. You'll need a 64-bit processor, but both Intel and AMD will do the job equally well, and 4GB of RAM is also required.
Strangely, the installation of the operating system requires a hard drive of at least 500GB, but then the requirements start to get even more specific. UEFI boot support is a must as is an NVIDIA graphics card, although support for AMD and Intel cards is promised for the future.
The 960MB download can be used to get the operating system up and running using the Debian installer -- SteamOS is based on Debian GNU/Linux (specifically the 'wheezy' (stable 7.1) distribution). Full instructions are available on the Steam community website, and you should prepare yourself for something of an involved process; click and run this ain't. If you’d like a slightly easier time of things, you should instead grab the 2.4GB system restore image which can be extracted to a 4GB USB drive. Be warned though -- using this method requires you to have a 1TB hard drive.
When you're up and running, you'll be able to play native Steam games as well as stream games running on another computer. Let us know how you get on creating your SteamOS gaming platform -- best of luck!
-

The most popular stories on BetaNews this past week -- December 8 - 14
Publié: décembre 14, 2013, 1:46pm CET par Mark Wilson
 Things are starting to get festive, and that means there's also a lot going on. This past week has been quite a busy one! It might not come as a surprise, but the figures are in -- Windows 8.1 is not performing anywhere near as well as Windows 7 in terms of sales. Part of the reason for the slower adoption could be the Start screen and the absence of the Start menu. There has been some debate here at BetaNews about the possibility that the Start menu could make a return. Brian is very much opposed to the idea, I think it's probably a good idea, particularly for business users, while Wayne showed us how to get the Start menu back right now.
Things are starting to get festive, and that means there's also a lot going on. This past week has been quite a busy one! It might not come as a surprise, but the figures are in -- Windows 8.1 is not performing anywhere near as well as Windows 7 in terms of sales. Part of the reason for the slower adoption could be the Start screen and the absence of the Start menu. There has been some debate here at BetaNews about the possibility that the Start menu could make a return. Brian is very much opposed to the idea, I think it's probably a good idea, particularly for business users, while Wayne showed us how to get the Start menu back right now.The backlash against NSA surveillance continues, and now Microsoft, Apple, Google and a number of other big names have joined forces and written to President Obama asking for reform. Joe was not impressed. To help protect user accounts, Microsoft beefed up security.
Wayne jumped ship, leaving behind Samsung as he fell back in love with the iPhone. Microsoft is keen for customers to switch from Gmail to Outlook.com and released a tool to make it easier than ever -- and Alan had a guide to doing it. Yahoo suffered an outage that lasted for a few days, leaving users confused and upset. Some YouTube uploaders were upset when their video game footage uploads were slapped with copyright warnings.
The Nokia Lumia 2520 was found to have a more impressive screen than the Surface 2, and Android users were warned to be on the watch for a nasty piece of malware that could lead to hefty phone bills. Factory images for Android 4.4.2 were released for people to get their hands dirty with.
To help you get in the festive mood, Rdio launched a series of holiday stations and playlists. The service was also updated to make it available in more countries. If you're looking for other forms of entertainment this holiday season Google's update to Chromecast -- including support for Plex -- will keep you supplied with all the streaming media you could need. If you have visitors coming for Christmas, you could use Google Maps and Photo Spheres to create a 3D map to give interactive directions thanks to a new update.
This wasn't the only 3D update this week -- Microsoft also made improvements to PhotoSynth. If you're on the lookout for a quick last-minute present, the LG G Pad 8.3 is worth a look, as is the white Nexus 7. In the market for a new laptop? Try Dell's new Chromebook on for size. Twitter took a look back at what has happened in 2013.
That's it for this week. The coming seven days are sure to be busy... as we all panic with online Christmas shopping!
-

YouTube slaps copyright violation notices on game footage videos
Publié: décembre 13, 2013, 4:19pm CET par Mark Wilson
 A number of YouTube users who post game walkthroughs and feature footage from games in other ways are finding that their content is being flagged for copyright violation. It seems that uploaders are falling victim to YouTube's automated ContentID system which is responsible for weeding out all manner of copyrighted material. What is interesting is that videos are not being removed from YouTube, but are unable to earn money from advertisements, leading to a loss in revenue for a lot of people.
A number of YouTube users who post game walkthroughs and feature footage from games in other ways are finding that their content is being flagged for copyright violation. It seems that uploaders are falling victim to YouTube's automated ContentID system which is responsible for weeding out all manner of copyrighted material. What is interesting is that videos are not being removed from YouTube, but are unable to earn money from advertisements, leading to a loss in revenue for a lot of people.Uploaders are warned that their videos are still viewable but told that the flagged video's copyright is owned by someone else. What is confusing is the fact that the companies named in relation to the warnings do not actually seem to be the copyright holder. For example, VentureBeat cites the case of warnings being handed out for videos featuring footage from the game Metro: Last Light.
In this instance, the copyright holder is Deep Silver but the copyright warnings that were issued made reference to a YouTube channel called 4GamerMovie. Deep Silver issued a statement explaining that anyone issued with a warning should dispute it, saying that they were working with YouTube to resolve the "various issues that have plagued the YouTube gaming community".
Major game publishers such as Capcom, Blizzard and Ubisoft have also voiced support for video uploaders and said that the copyright violation claims have not necessarily been instigated by them. In a tweet, Capcom said "YouTubers: If you are receiving content matches, please dispute them so that we can clear any false claims".
It is worth noting that while the uploading of game footage is, technically, a violation of copyright, it is something that is usually overlooked by game publishers as videos posted essentially serve as free advertising.
Have you been affected by the copyright warnings? Are you going to roll over and take it, or are you going to dispute it?
Photo Credit: Archiwiz/Shutterstock
-

Stop being so bloody-minded, Microsoft -- bring back the Start menu!
Publié: décembre 12, 2013, 8:21pm CET par Mark Wilson

Unlike my colleague Brian Fagioli, and many other disillusioned users, I think Microsoft made a serious mistake when the Start menu and button were removed from Windows 8. The company practically admitted as much when Windows 8.1 saw the reintroduction of the Start button. But this was simply not enough. Windows is all about the Start menu, and for many people the Start button and Start menu are so inextricably linked that to have either without the other just makes no sense.
Sure, we have the Start screen in Windows 8.1 and from it you can achieve pretty much what you were able to do with the Start menu. But it is not the same. Windows 95 was all about the Start button and the Start menu that it conjured up. Yes, we may be the thick end of 20 years down the line, but this is at least partly the point. We have had almost two decades to get used to a particular way of working. It would be strange if there wasn’t a backlash against something we have become so used to.
Brian, like many others, is under the impression that the modern interface and associated modern apps are the future of Windows. I disagree. I think they are important and will play a role in the future of Windows, but they are far from being the end of the story. It has been suggested that those who don’t like the Start screen should just suck it up and learn to live with it, but what about the millions of enterprise and business users all over the world?
Microsoft is obviously keen for as many people as possible to upgrade to the latest operating system -- both home and corporate users. Windows 8 and Windows 8.1 are such a sea change from Windows 7 and its predecessors that training is needed to acclimatize workers to the new OS. Laugh at this if you like, but it is true. Windows 8 and Windows 7 are completely different beasts, and for the average office worker it is not going to be a case of sucking it up and learning to live with it, there is a serious learning curve.
It is IT departments that have to deal with training employees. Companies have to foot the bill for this and lose countless man hours as staff disappear on training days and work more slowly in the new UI. I'm surprised a bigger, louder stink isn’t being kicked up.
There are already rumors circulating that the Start menu could make a return in Threshold -- although even more recent speculation suggests that there could even be an update to Windows 8.1 next year that brings a 'mini-Start' with it. This could mean that Start menu lovers no longer have to rely on third party solutions to get back the feature they so love.
Of course, the blame for all of this lies firmly at the door of modern apps.
The point of modern apps is that they are supposed to be touch-friendly. Everything is big and ready for jabbing with a fat finger. This means that interfaces are bigger, uglier, and there is less room for useful buttons. Complex pieces of software such as Office -- think spreadsheets and databases -- simply do not translate to this medium. So-called 'legacy' apps are needed, and they are going to be needed for a very long time. Businesses are not going to drop them and neither are a huge proportion of home users.
And if this is the case, a 'legacy' system is needed for accessing these apps. This is what the Start menu is. It was designed, tweaked, did its job wonderfully... and was then unceremoniously dropped. Being anti-Start screen is not the same as being opposed to progress. The Start screen has its place… but it is not for everyone. It would be madness to think that after so long doing things a particular way, something so radically different (and the Start screen really is quite different) would be embraced without question.
So, come on Microsoft. Wake up out of this slumber. Yes, there is a place for modern. It's on Surface. It is not for the desktop. Desktop users need the Start menu and the great degree of control and accessibility it provides. Stop being so bloody-minded, admit Modern just isn't for most people, and do something about it.
Image Credit: Pavel Ignatov / Shutterstock
-

2013 -- the year Twitter earned our respect?
Publié: décembre 12, 2013, 6:32pm CET par Mark Wilson

It's not all that long ago that the idea of posting news, thoughts and ideas on a social network (or "micro-blogging service" as it is infuriatingly referred to) that imposed a limit of 140 characters on posts seemed absurd. Now Twitter is so commonplace that any company, or even TV show, worth its salt has its own account. The word hashtag entered the technical lexicon a little while ago, but such is Twitter's dominance that it is now spoken aloud: hashtag yousoundstupid.
2013 has been a big year for Twitter, perhaps most notably due to it starting to trade on the NYSE. But there have also be great strides made in how Twitter is used. Of course it is still home to vainglorious, the trolls and celebrities, but 2013 is also the year in which Twitter proved itself to be genuinely useful.
'Useful' Twitter accounts -- such as those that give advance warning of severe weather, natural disasters and the like -- are nothing new, but 2013 saw the introduction of Twitter alerts. A number of well known organization such as the American Red Cross, World Health Organization and FEMA signed up to take part in a program designed to help disseminate emergency information. Alert tweets can be pushed to phones or sent via SMS to ensure they are read. Alerts now come to you rather than you having to seek them out.
A blog post looking back at the year mentions various national and international events that have been advertised or shared via Twitter -- the search for the Boston bombers, the death of Glee's Cory Monteith to name but two. In fact a tweet by Monteith's co-star, Lea Michelle earned itself the title of the Golden Tweet for being the most retweeted post of the year.
Twitter has become more serious and more respected -- it has been even used to help pick Time's person of the year. As a source of news it offers a degree of instantaneousness that is just not possible through other media.
But of course there is a lot more to the service than emergencies, news and death announcements. Twitter has put together a site that makes it possible to look back at some of the highlights of the year at Year On Twitter. Here, custom timelines can be used to view the most popular news and entertainment posts, showbiz tweets and those that have been deemed "inspirational".
Of course, no look back on the year would be complete without a montage, and Twitter duly obliges in this reflective video. Here's to 2014 in tweets.
-

Government surveillance needs to be reformed, say Google, Microsoft, Apple, and others
Publié: décembre 9, 2013, 1:33pm CET par Mark Wilson

Headlines about government surveillance of web usage all over the world have been difficult to avoid this past year. Since Edward Snowden blew the whistle on activities by the NSA, both companies and web users have been asking for greater transparency in data collection and there have been endless calls for dragnet data collection to be stopped completely. It is often the case that when confronted with a common enemy, some unlikely alliances are forged. This is certainly true with the NSA, and now Apple, Google, Microsoft, Facebook, Yahoo, LinkedIn, Twitter and AOL are all coming together to present a united front and push for legal reform.
The collective has written an open letter to President Obama and congress, warning that "the balance in many countries has tipped too far in favor of the state and away from the rights of the individual". There has been quite a backlash against the number of requests for data that the US government has made of companies, and the letter makes it clear that the eight companies that have joined forces are not happy:
For our part, we are focused on keeping users’ data secure -- deploying the latest encryption technology to prevent unauthorized surveillance on our networks and by pushing back on government requests to ensure that they are legal and reasonable in scope.
Microsoft has also said that there is a risk that consumers will be discouraged from using the internet. "People won’t use technology they don't trust. Governments have put this trust at risk, and governments need to help restore it". A similar line is taken by Yahoo CEO Marissa Mayer who says: "Recent revelations about government surveillance activities have shaken the trust of our users, and it is time for the United States government to act to restore the confidence of citizens around the world".
The letter invites President Obama to take a look at the Reform Government Surveillance website where the consortium calls for five principles to be put into action: Limiting governments’ authority to collect users’ information, oversight and accountability, transparency about government demands, respecting the free flow of information, and avoiding conflicts among governments.
From these principles, it is clear that the companies not only want restrictions put in place, but also want to be allowed to tell their customers about requests for data made by government.
What do you make of this? How likely do you think it is that government will start to take notice now that eight big names are working together?
-

The most popular stories on BetaNews this past week -- December 1 - 7
Publié: décembre 7, 2013, 12:12pm CET par Mark Wilson
 The tech world seems to be slowling down slightly in the run up to Christmas, but there have still been a lot of stories over the past seven days. There are sure to be a whole new raft of sales to look forward to both before and after Christmas, but if the Thanksgiving sales are anything to go by they may not offer as good a deal as first appearances would have you believe. Whether you bag a bargain or not, it looks as though tech presents are going to be as popular as ever this year -- and if you buy a Windows device, you'll get a free gift card.
The tech world seems to be slowling down slightly in the run up to Christmas, but there have still been a lot of stories over the past seven days. There are sure to be a whole new raft of sales to look forward to both before and after Christmas, but if the Thanksgiving sales are anything to go by they may not offer as good a deal as first appearances would have you believe. Whether you bag a bargain or not, it looks as though tech presents are going to be as popular as ever this year -- and if you buy a Windows device, you'll get a free gift card.After Microsoft tried comparing the Surface to the iPad Air, Amazon decided to follow suit -- guess which was more popular! Microsoft kept its fire trained on Google, taking a swipe at the Chromebook. Tablet makers may be pushing their product in the run up to Christmas, but PC shipments have suffered the largest decline ever. New computers will have an updated USB connection in the near future. USB type C brings to an end a problem that has plagued anyone who has ever plugged in a USB cable -- this generation can be plugged in either way up!
Microsoft was probably feeling a little upset that Windows 8 and 8.1 are still faring quite poorly in terms of usage. Despite the fact that it is now fairly old, Windows 7 is still growing at a faster rate than its successors. For anyone unhappy with Windows 8.1, there is now Threshold to look forward to. There was better news on the browser front as Internet Explorer managed to retain well over half of the market. The Office 365 Student Advantage program went live meaning that thousands of educational institutions will be able to offer the suite to their students. Microsoft looks set to earn itself a place in more people's good book by promising to do more to protect user data from government spying by implementing new encryption methods and more.
We're approaching the end of the year, so expect to see lots of 'best of' lists and reflections of the past twelve months in the next three weeks or so. In this vein, Bing revealed the most popular search terms from the year -- Beyoncé Knowles was the most searched for person, while Big Bang Theory bagged the title of most searched for TV show.
Dell announced its new 4k monitors-- Brian has one, so expect to see a review soon! On the subject of reviews, I pondered the worthlessness of banning bad reviews. Brian was less than impressed with 'irregular activity' on the PlayStation network and decided to return his PS4.
Online, Apple bought Twitter analytics firm Topsy Labs, although there is no news on how it will be used. Speaking of news, Facebook wants to help deliver more news than memes and is updating News Feeds accordingly. If you have invested in a 4k monitor, you'll want some HD content to view, and if you're a PlayOn or PlayLater user, HD is now available for streaming.
In other news, Google updated searching on Android devices, and the sale of HTC's One mini was blocked in the UK after a judge found the device infringed on Nokia patents. Another legal wrangling saw the FTC charging an app developer with deceiving users after it was revealed that Brightest Flashlight Free collected user location and device ID data.
That's it for this week. Another -- hopefully busier -- seven days coming up!
Image Credit: vinz89 / Shutterstock
-

Got a faulty Chromebook 11 charger? You can soon buy a new one for $19.99
Publié: décembre 7, 2013, 12:47am CET par Mark Wilson

A few weeks ago Google's Chromebook 11 was removed from sale after an overheating problem was found with some chargers. No recall was ever announced, but users were advised against using the supplied charger in favour of another Micro-USB charger of their own. In fact, both Google and HP have been very quiet since the announcement, but now a new Chromebook 11 charger has appeared in Google Play.
The charger is not currently available; it is listed as 'Coming soon'. It also has a $19.99 price tag associated with it (or £14.99 if you're in the UK). This is a very simple piece of equipment, as illustrated by the short and sweet product description: "Keep your HP Chromebook 11 topped up with an extra charger."
Except this would not be regarded as an extra charger by anyone who has been told to stop using their original one. It would be regarded as a replacement. And not a cheap one at that. This is a very basic Micro-USB charger, and $19.99 does seem to be pushing the limits of acceptability a little. It will certainly not go down well with disgruntled Chromebook 11 owners if it turns out that this is the price they have to pay for a new charger that does not overheat.
The image on the Google Play listing shows that the charger is of a different design to the one originally supplied with the Chromebook. This time around it is branded with a Chrome logo, but the specifications are the same.
Google has made no announcement about the new charger, but this could change in the coming days. We've reached out to the company for clarification about whether or not those affected by an overheating charger will be expected to pay for a replacement or not, and we'll update this post when we hear something back from them.
Update: In a brief reply, Google told us "we are working with the Consumer Product Safety Commission to identify the appropriate corrective action, and will provide additional information and instructions as soon as we can".
-

FTC charges Android flashlight developer with leaving users in the dark about data usage
Publié: décembre 6, 2013, 2:13pm CET par Mark Wilson
 The permissions screen that pops up during the installation of an Android app has become the new EULA. Very few people bother to read through what is on screen before clicking through and going ahead with the installation -- you could be signing your life away for all you know!
The permissions screen that pops up during the installation of an Android app has become the new EULA. Very few people bother to read through what is on screen before clicking through and going ahead with the installation -- you could be signing your life away for all you know!Apps will let you know if they make use of your location, have access to your contacts, could send messages on your behalf and numerous other things. But in the case of Brightest Flashlight Free it turned out that the app was not only sharing users' location and device ID information with third party advertisers, but it was doing so secretly.
The company behind the app, GoldenShores Technology LLC, has been charged by the Federal Trade Commission (FTC) with deceiving its customers. You would think that this would have a negative impact on the app's popularity, but take a look at the Google Play listing and you'll find that, astonishingly, it still has a 4.8 out of 5 rating. It could be the case that news of the charges have yet to filter down to users, so we could well see this rating tumble when you consider that advertisers had the ability to learn precisely where in the world users were located, and tracked which ads they clicked on.
The complaint by the FTC alleged that "the company’s privacy policy deceptively failed to disclose that the app transmitted users’ precise location and unique device identifier to third parties, including advertising networks. In addition, the complaint alleges that the company deceived consumers by presenting them with an option to not share their information, even though it was shared automatically rendering the option meaningless".
GoldenShores Technology LLC has made a settlement with the FTC which means that all personal information that has been collected has to be deleted. The app will also be required to inform users how, when and why information is collected about them in the future. Founder of the company, Erik M. Geidl, has been ordered to allow the FTC to access advertising material and compliance documentation for the next five years, and also needs to notify the commission if he starts a new business or leaves GoldenShores Technology.
Do you take the time to read through EULAs and grant the permissions asked for by the apps you install? Should more be done to make software agreements easier to understand, and what steps can be taken to prevent developers from lying about what their apps actually do? Is it reasonable to expect every app to be tested before it is allowed to appear in an app store ready for download? Apple has a fairly strict review policy in place, but this has not stopped a few rogue apps slipping through the net. Do you have any ideas how these things could be better policed in the future?
Image credit: dmitrieva/Shutterstock
-

Facebook wants to ditch the meme and focus on news delivery
Publié: décembre 3, 2013, 2:57pm CET par Mark Wilson
 Facebook was never really meant to be about news. It is a social network that's about keeping in touch with people. But companies quickly cottoned onto the site as a valuable tool for reaching out to customers, delivering information about product launches, app updates and other news. Despite the fact that Facebook users are invited to update their "status", anything that is posted appears in the "News Feed" of others. Now Facebook is trying to make your News Feed more about news.
Facebook was never really meant to be about news. It is a social network that's about keeping in touch with people. But companies quickly cottoned onto the site as a valuable tool for reaching out to customers, delivering information about product launches, app updates and other news. Despite the fact that Facebook users are invited to update their "status", anything that is posted appears in the "News Feed" of others. Now Facebook is trying to make your News Feed more about news.There have been endless complaints about the order in which posts are displayed in the News Feed, and the presence of ads, but this latest update has been brought in to help further separate the wheat from the chaff. Having conducted a survey, Facebook has come to the conclusion that its users are more interested in seeing high quality content than countless images of cats and bastardized Keep Calm posters.
"Starting soon, we’ll be doing a better job of distinguishing between a high quality article on a website versus a meme photo hosted somewhere other than Facebook when people click on those stories on mobile. This means that high quality articles you or others read may show up a bit more prominently in your News Feed, and meme photos may show up a bit less prominently".
But it doesn’t end there. Facebook is not only keen to provide you with links to a high quality story to keep you educated, informed and entertained, it wants you to keep reading non-meme content. Should you click a link to a story that has been deemed to be of suitably high quality you will start to see more related links to stories that are either in a similar vein, or from the same source.
The updates will also see Facebook trying to increase users' interactions with stories. How often have you posted a comment on something you've stumbled across, but then don’t bother to check back to see if people you know are also posting comments? In the near future, posts that have received new comments -- particularly those commented on by your friends -- will be bumped to the top of your newsfeed.
What do you make of the changes? Are you happy that Facebook tries to deliver content it thinks you'll be interested in, or would you rather be left to your own devices?
Photo Credit: Sebastian Kaulitzki/Shutterstock
-

Apple starts feeling social, buys Twitter analytics firm Topsy Labs
Publié: décembre 3, 2013, 1:26pm CET par Mark Wilson
 Apple is a company that, generally speaking, likes to keep itself to itself -- but that's not to say it doesn't like to keep its finger on the pulse and learn about what others are talking about. This is demonstrated perfectly by the company's latest purchase. This time around Apple has invested a reported $200 million in Topsy Labs, a social media analytics firm that specializes in monitoring trends on Twitter.
Apple is a company that, generally speaking, likes to keep itself to itself -- but that's not to say it doesn't like to keep its finger on the pulse and learn about what others are talking about. This is demonstrated perfectly by the company's latest purchase. This time around Apple has invested a reported $200 million in Topsy Labs, a social media analytics firm that specializes in monitoring trends on Twitter.Topsy has access to every single tweet sent since Twitter inception back in 2006, making it the most extensive database of the micro-blogging service. The information available through Topsy is the sort of data that would prove immensely useful to advertisers, but at this stage it is not clear just how Apple intends to use the information. Topsy Labs' tool can be used to monitor trends on Twitter, check the topics that are being discussed, as well as determining the success and impact of online campaigns.
In addition to being useful for advertising, information gathered through Twitter would enable Apple to make better use of this and other forms of social media. The ability to analyze Twitter in real-time is a valuable tool for any company, but it is certainly something that one the size of Apple would be able to put to a variety of uses.
There is potential for integration with existing services such as Apple TV. It is easy to imagine Twitter data being used to make program recommendations based on users' Twitter activity and the other Twitter users they interact with. But perhaps the most obvious use for the data is for advertising. Analysis of social media data is just one way in which ads can be better targeted at specific groups, and this could be something we see developed in future iOS and OS X apps -- but only time will tell.
This is far from being the only purchase Apple has made recently. In the past fortnight we have also seen the company buy PrimeSense, the firm behind the 3D motion detection technology used in the Kinect for Xbox.
Photo Credit: Sebastian Kaulitzki/Shutterstock
-

The most popular stories on BetaNews this past week - November 24 -- 30
Publié: novembre 30, 2013, 1:36pm CET par Mark Wilson
 It being the week of Thanksgiving, anyone looking for a bargain will have been eagerly anticipating Black Friday. The big names did not disappoint including Microsoft who had special prices on Surfaces. If you were undecided between buying a Surface or an iPad, Microsoft compared the two devices so you don’t have to -- and there are no prizes for guessing which comes out on top! If you give or receive giftcards as presents this year, they can now be used to pay for things through PayPal checkout.
It being the week of Thanksgiving, anyone looking for a bargain will have been eagerly anticipating Black Friday. The big names did not disappoint including Microsoft who had special prices on Surfaces. If you were undecided between buying a Surface or an iPad, Microsoft compared the two devices so you don’t have to -- and there are no prizes for guessing which comes out on top! If you give or receive giftcards as presents this year, they can now be used to pay for things through PayPal checkout.Microsoft's Scroogled campaign may not be in the spirit of the season, but it continues apace. In one advert, the services of Pawn Stars were called upon to take a pop at Google's Chromebook -- Alan was less than impressed. Brian, however was pleased to be the recipient of a surprise, unadvertised mug having placed an order via the Scroogled store, and Joe is a big fan of the campaign. Speaking of Chromebooks, Acer announced an ultra-cheap touchscreen device in the form of the C720P.
In another ad campaign, Microsoft aims its barrels at the Samsung Galaxy Tab 3 while speculation mounts about whether Windows RT might be on the verge of disappearing.
It may be the time of year when most people are thinking about presents and turkey, but at Time magazine it is when the Person of the Year is considered. There are a little under two weeks until the announcement is made, and the magazine is looking to Twitter for suggestions -- there's still time to nominate your suggestion if you're quick! Virgin's Richard Branson came out as the latest supporter of Bitcoin, saying that it will be possible to use the virtual currency to pay for a trip to space on Virgin Galactic.
It's not quite clear what may come of it, but Apple this week purchased PrimeSense, the company behind the Xbox's Kinect unit. Following on from the recent launch of the Xbox One, Microsoft responded to disappointed gamers who found themselves with a problematic console by saying that the issues are being looked into and that those affected by the problem will be entitled to a free game download. For anyone who does have a working console, Microsoft released a voice and gesture cheatsheet to help users learn the new commands.
The Samsung Galaxy Grand 2 was introduced as the latest addition to Samsung's phablet range, although it is certainly not the largest devices to fall into this category. Samsung and HTC were delisted from Futuremark's 3DMark app after suspicions that the two companies were artificially boosting device performance when benchmarking software was running. For anyone on a budget who doesn't want to make too many compromises, the Moto G from Motorola looks like and interesting option. This wasn't the only cheap handset unveiled this week -- Nokia also announced the Lumia 525.
Following the recent rollout of KitKat to various Nexus devices, the HTC One Google Play edition also received the update. Elsewhere, Google has promised to make changes to the way the new Google+ commenting system works on YouTube.
This was a week in which we looked at quite a few pieces of hardware. Alan was impressed with the Kindle Fire HDX noting a number of improvements over its predecessor. Looking at peripherals, Brian was rather taken with the Feenix Nascita 2014 gaming mouse and Dimora mousepad. Looking for a cheap monitor? AOC's 27-inch e2752She could be what you’re looking for.
I entered whinge mode, complaining about the prevalence of online spoilers for TV programs -- bah humbug!
With Thanksgiving out of the way, this week should be even busier: bring it on!
Photo Credit: vinz89/Shutterstock
-

Family Guy **spoilers** highlight the problem of the web ruining TV
Publié: novembre 26, 2013, 7:15pm CET par Mark Wilson

***Warning! There are no spoilers ahead!***
Whether you're a fan of Family Guy or not, you can’t help but have heard that there has been a big storyline -- there was no need to seek out the news, you could just sit back, let it wash over you and absorb it by osmosis. I love Family Guy and I'll admit to getting seriously pissed off at a friend of mine who spilled the beans on Facebook. No warnings, he just straight out announced what had happened in the show. What a bastard! But he wasn't the only one.
Browsing through Twitter and Facebook, I encountered countless references to what had transpired. Sure, in the Family Guy circle, it was big news (I'm saying nothing about it whatsoever. I don't want to ruin it for anyone who has, somehow, managed to avoid the news). But this seemed to spread like wildfire… it was incredible to watch (the spread, not the show -- which I still haven’t seen!).
I'm not a sports fan, but I've known people who have had to work when an important sporting event has taken place. The world cup or something. Means nothing to me. But I can understand that if soccer is your thing, if that gets you excited and you know you're going to miss watching the match, you're relying on a recording to get your fix. You'd probably drive home without listening to the radio, run into the house without speaking to anyone, switch on the TV making sure to avoid news channels and then fire up the recording. If anyone revealed the score to you ahead of time, you'd probably kill them.
With Family Guy, it wasn’t just social networks that were problematic (there are tools like Spoiler Shield which can block reveals there). Major websites were in on it as well -- even big-name newspapers (yes, the Guardian, I'm looking at you). Discussion of shows that have been on TV the previous night are very common, but there is an unspoken rule about not giving anything away, at least not in the first couple of paragraphs -- and certainly not in the headline. It's a simple thing, but it prevents casual browsers from finding out something they shouldn't. But here I was finding that everything was being given away in headlines!
Some sites "tried". They included the word "spoiler" in their headline. Great, you might think. But in almost every case, the first sentence gave away some or all of what had happened, or there was a prominent image which did the talking instead. What is wrong with people? An event in a cartoon was being treated as if it was news. Sites were falling over themselves to report what had happened and to analyze it in detail.
It highlights a problem with modern TV viewing. Being based in the UK, I'm used to shows airing in the US first and having to wait a little while to see them over here. Well, obviously there are ways and means (where there's a will there's a way), but that’s another discussion for another article. It's not as big a problem as it used to be. Major shows used to air months ahead of UK broadcasts and fans of shows like Lost had to avoid reading articles that gave the game away.
Shows are now broadcast at much the same time, or are made available through different channels at the same time. But very little viewing is done live these days -- almost everything is timeshifted. This means that there is nearly always going to be someone who has seen the show before you. TV can be timeshifted, the internet can't. We're not talking about revealing who Rosebud was -- this is a film that's 72 years old. Revealing storylines for shows that are on now is very different.
Sure, the internet is free to be used by anyone for anything, to voice whatever they want. But at the same time, there are unwritten protocols. Leave a little to the imagination. The internet doesn’t have to be about instant gratification (whatever form that may take), or getting all the information in the world delivered into your eye holes at the fastest possible speed. Allow people to take their time, delight in their own discoveries. In short, don't spoil the fun.
So, please, in future, don't be a bugger -- keep your mouth shut and still your wavering fingers before they type anything they shouldn't.
Photo credit: mast3r/Shutterstock
-

Motorola Moto G available to buy now in US for just $179
Publié: novembre 26, 2013, 6:19pm CET par Mark Wilson

Motorola's answer to Apple's iPhone 5c and Google's Nexus 5, the Moto G, is available to order now, starting at $179. Despite coming in at just "one third of the price of current high-end phones", this is an entry-level smartphone that still manages to pack a punch. There's a 4.5-inch display and a quad-core Qualcomm Snapdragon 400 processor, and Motorola is claiming all-day battery life. It is the GSM version that is available now, and in January it will be possible to buy the CDMA model in the US as well.
It has already been launched in a number of territories including Brazil, Mexico, Chile, Argentina, Peru and parts of Europe, but now the US is getting some Motorola loving too. Buy direct from Motorola and the handset is free from contract, has no SIM lock, and has an unlockable bootloader -- a tweaker's dream! At 1280 by 720 HD, 329 ppi, the Moto G's screen is above and beyond what you might expect to find on a handset around this price.
The phone is comparable to the iPhone 5c and goes as far as adopting similar multi-colored casing options. There are Shells, Flip Shells and Grip Shells which can be snapped into place to stamp your rainbow-esque mark on the phone. The $179 price is for the 8GB version, but there is also a 16GB model available for $199. The storage is bolstered for two years by 50GB of space on Google Drive.
The Moto G initially ships with Android 4.3 -- which Motorola describes as "the most up to date Android of any phone in its class" -- and there is a guaranteed upgrade to 4.4 KitKat in early 2014. And this is pure, unadulterated Android, "no skins to clutter or slow the experience and great performance" as Motorola puts it.
Place your order now and handsets will ship from 2 December. While you wait to get your hands on a G, check out the ad that showcases some of the highlights.
-

Futuremark delists 'suspicous' HTC and Samsung handsets from 3DMark benchmarking app
Publié: novembre 26, 2013, 11:36am CET par Mark Wilson
 A total of six Android devices from Samsung and HTC have been delisted by Futuremark after suspicions were raised about their performance in 3DMark benchmarks. Although no specific details are given about why the handsets were removed, concerns surrounded the performance of particular phones.
A total of six Android devices from Samsung and HTC have been delisted by Futuremark after suspicions were raised about their performance in 3DMark benchmarks. Although no specific details are given about why the handsets were removed, concerns surrounded the performance of particular phones.It comes after Samsung code appeared to detect the presence of benchmarking software and seemingly increased GPU frequency to achieve higher results. A new version of the Android app implements the delistings.
In a statement on its website, Futuremark explains that people rely on accurate and reliable benchmark results in order to objectively compare devices. The company goes on to say that it has very clear rules about how a device may interact with its software, saying that it should be treated in exactly the same way as any other app. This is precisely what Samsung had previously been accused of: detecting running benchmark software and artificially boosting performance.
The full statement reads:
People rely on Futuremark benchmarks to produce accurate and unbiased results. That's why we have clear rules for hardware manufacturers and software developers that specify how a platform can interact with our benchmark software. In simple terms, a device must run our benchmarks without modification as if they were any other application.
When a device is suspected of breaking our rules it is delisted. 3DMark scores from delisted devices should not be used to compare devices. Delisted devices appear unranked, and without scores, at the bottom of the 3DMark Device Channel and the Best Mobile Devices list on our website.
The affected handsets are the HTC One, HTC One Mini, Samsung Galaxy Note 10.1 Exynos 5 Octa, Samsung Galaxy Note 10.1 MSM8974, Samsung Galaxy Note III Exynos 5 Octa, and the Samsung Galaxy Note III MSM8974.
It is fair? Should it have been done sooner? Do you put any stock in benchmarks or do incidents like this make you distrust them?
Image Credit: Konstantin Faraktinov/Shutterstock
-

Apple buys PrimeSense: Could Macs or AppleTV get their own Kinect?
Publié: novembre 25, 2013, 6:00pm CET par Mark Wilson

Using a peripheral to interact with your computer is so passé. Xbox One and Xbox 360 owners have the Kinect to dance in front of, and PlayStation gamers have a camera that can be used in much the same way. PC users can turn to the likes of Leap Motion if they like the idea of eschewing traditional forms of control, and an increasing number of smartphones can recognize eye and hand movements. Now it looks as though Apple is joining the party by buying 3D motion detection specialists PrimeSense.
This may not be a firm that sounds all that familiar, but you're almost certainly aware of the Israeli company's work -- Kinect for the Xbox. Yep, you read that correctly. Apple is buying the firm behind one of the most interesting and innovative features of Microsoft's game console. While no details of the purchase have been revealed, and no mention made of any money that may have swapped hands, PrimeSense has confirmed that the purchase is going ahead.
We asked whether the sale was happening and what we could expect to see in the future from the joining of forces. In a brief statement, the company responded with "We can confirm the deal with Apple. Further than that, we cannot comment at this stage".
So what can we expect to see as a result of this purchase? Well the most obvious result would be the addition of gesture-based control to Apple TV, but it needn't end there. The same technology could also find its way into iPhones and iPads -- Samsung has implemented facial and motion detection into various handsets, and it would make sense for Apple to follow suit. Motion detection has, thus far, been mainly implemented for living room devices, so it will be interesting to see whether Apple continues down this route or decides to concentrate on mobile device, or even Leap Motion-style desktop control.
How would you make use of 3D motion technology? Have the big players missed any tricks that would make your life easier?
-

The most popular stories on BetaNews this past week - November 17 -- 23
Publié: novembre 23, 2013, 2:21pm CET par Mark Wilson
 Sony PlayStation 4 hit the stores and Brian not only took a look at the brand new console, but also cracked open the case and slipped a larger hard drive inside. Brian wasn't alone in his love of the PS4, more than a million people also bought a console on the day of launch. But not everyone was happy as many units were found to suffer from a Blue Light of Death problem that rendered them unusable. Raspberry Pi was also celebrating its sales figures as more than two million were shifted since its launch last year.
Sony PlayStation 4 hit the stores and Brian not only took a look at the brand new console, but also cracked open the case and slipped a larger hard drive inside. Brian wasn't alone in his love of the PS4, more than a million people also bought a console on the day of launch. But not everyone was happy as many units were found to suffer from a Blue Light of Death problem that rendered them unusable. Raspberry Pi was also celebrating its sales figures as more than two million were shifted since its launch last year.In a rare show of unity, Microsoft and Google joined forces to help tackle the problem of online child pornography. At the same time, Microsoft took its Scroogled campaign to a new level by releasing merchandise (although Joe was impressed). Elsewhere online, Twitter introduced Twitter alerts to the UK and Ireland to help provide people with critical information in an emergency.
In a week that culminated in the launch of the Xbox One, Microsoft shuffled out a rather smaller release in the form of Office Remote for Windows Phone which allows for remote control of PowerPoint presentations. While there still are very (very) few official Google apps for Windows Phone, there are no shortage of companies producing apps to fill the gap, and the latest Gmail replacement is Metromail. Roku owners enjoyed the arrival of PlayCast which brings Chromecast-like functionality to the devices. On Android, Google unveiled Newsstand.
The sales of Nokia's handset arm to Microsoft was finalized, but this wasn't the only news in the world of portable devices. Some big name app made their way onto Windows Phone in the form of Waze and Instagram. Google promised to improve the security of Android devices and the Kindle Fire HDX was updated.
If you were looking to upgrade your Nexus 4, 5, 7 or 10 to KitKat, Mahiata revealed everything you need to know. I'm a Surface Pro user and I would easily choose to keep using it over the iPad Air, but Wayne was of the opposite opinion.
Other highlights from the week: Apple won a not-insubstantial $290 million from Samsung, the Ouya console gained support for external storage, and Amazon Prime became a giftable commodity.
Xbox One may have been the biggest new release of the week -- oh, and Logitech managed to sort out Harmony remote support just in time -- but the door finally closed on WinAmp, the audio player (and later, cloud service) than millions of music lovers grew up on.
More of the same over the next seven days!
Photo Credit: vinz89/Shutterstock
-

Coin -- the only card you'll need in your wallet
Publié: novembre 22, 2013, 12:48am CET par Mark Wilson

Take a look at your wallet. How many debit cards, credit cards and loyalty cards do you have? If it's anything like mine it is probably bursting at the seams with an inch or more of plastic cards. Reach the checkout in a store and you may well have ended up red-faced as you rummage for the right payment and loyalty card. With Coin, all of this could come to an end. The idea of a catch-all replacement that combines multiple cards into one is not new, but thus far solutions have taken the form of mobile apps. Coin is different -- this is a real card that acts as many.
Coins have a tendency to weigh down your pockets, but this Coin is a single lightweight unit. The card features an integrated display which you can use to view the last four digits of a stored card along with the expiration data and CVV so you, and the person you hand the card to, knows which of your stored cards you are using. You may well have used a mobile app that replaces loyalty cards, and Coin is taking this idea to the next level.
In fact, there is a mobile app (for iOS and Android to start with, with the possibility of a Windows Phone version if there is sufficient demand), and it is used to manage the physical Coin card. You can load an unlimited number of your cards into the app, and you will then need to transfer them to the Coin using a supplied dongle. Up to eight cards can be stored on the Coin at any one time, and you can cycle through them with a quick button press -- this is where the display comes in handy.
The mobile apps serves a handy second purpose -- it can alert you if you are parted from your Coin. This is helpful if you accidentally leave the Coin at the checkout, but there is also the option of deactivating the card after a pre-defined length of time in case it is stolen.
It's difficult to believe, but Coin really is just about the same size as a regular credit card. If you were thinking that this is a chunky piece of kit, think again…it will slip into your wallet beautifully as it is a mere 0.84 mm thick. Incredibly, it can even be used in an ATM.
Coin is due to hit the market some time in 2014, priced at $100. If you're keen to get your hands on one as soon as possible, and like the idea of saving some money, there are a limited number of Coins available for just $50. You might usually feel that it's good to have a heavy moneybag, but Coin lightens your wallet in a very good way.
Want to learn a little more? Check out the Coin website, as well as the introductory video:
-

Office Remote turns Windows Phone into a presentation controller
Publié: novembre 19, 2013, 1:19am CET par Mark Wilson

Microsoft Research's latest app makes it easier than ever to give a presentation without having to hunch over your laptop. Like the idea of wandering the stage gesticulating wildly as you skip between PowerPoint slides? Fancy being able to scroll through Word and Excel documents without the need to find your mouse? This is what Office Remote has been designed for. This is a simple app for Windows Phone, but one that will be welcomed with open arms by anyone who has to give presentations as part of their job.
The app is described by Microsoft as transforming a cell phone into a "magic wand" and it untethers presenters so they are free to walk the stage and interact with their audience. While the most obvious app to use Office Remote with may be PowerPoint, it can be used with Word and Excel too -- the 2013 and 365 versions of the office suite are supported (although not the RT version of Office).
If you've created a presentation that includes speaker notes, these notes can be displayed on the screen of your Windows Phone, but there are also those all-important controls for advancing to the next slide. A virtual laser point is available for pointing out interesting elements of a slide. In a post on the Windows Phone blog, Office program manager Bert Van Hoof said:
You can start your PowerPoint presentation, advance the slides, see your speaker notes, and control an on-screen laser pointer with a touch of your finger -- all from your phone. You can also navigate between Excel worksheets and graphs, and control data slicers from the palm of your hand. And you can scroll through a Word document or quickly jump to specific sections or comments.
Grab yourself a copy of the app from the Windows Phone app store. You'll also need a copy of the desktop add-in.
Image Credit: gielmichal / Shutterstock
-

PlayStation 4 users suffer Blue Light of Death -- Sony may have a fix
Publié: novembre 18, 2013, 3:57pm CET par Mark Wilson

Yay! The PlayStation 4 is out in the wild! Yippee! Oh…. It's broken. Boo! Sound familiar? Think back to the Xbox 360 and Microsoft was blighted by the infamous RRoD (Red Ring of Death) that signified cooked hardware. It's looking as though the much anticipated launch of the PS4 is suffering a similar fate as more and more users complain about consoles that will not turn on, and exhibit nothing more exciting than a pulsing blue light -- the imaginatively name Blue Light of Death, or BLoD.
Sony may have been rubbing its hands with glee as more than a million consoles flew off the shelves in the first day on sale, but things very quickly took a turn for the worse. Take a look at the PlayStation 4 support forums and you'll find a large number of complaints from disgruntled gamers annoyed at the fact their console is not working. The hashtag #PS4broken has been trending on Twitter on and off as users take to the web to voice their annoyance.
So what's the issue? At the moment it is not entirely clear. Quite a lot of users are complaining about their PS4 being DoA and Sony has issued a troubleshooting guide that it hopes will alleviate the problem for a lot of people. A post in the support forum from Sony suggests that there are at least four possible causes for the blue light issues:
This blinking light issue could indicate any number of causes including but not limited to:
- TV compatibility
- Issues with PS4 power supply
- Issues with PS4 hard drive
- Issues with other PS4 hardware
There then follows a brief troubleshooting guide which includes checking that the console hard drive is correctly seated. Other suggested fixes include restarting the console in safe mode and reinstalling the system software, but Sony does say that investigations are on-going into the source of the issues.
How have you got on with your PS4? Are you enjoying a new generation of gaming, or do you find yourself lumbered with an expensive paperweight?
-

Google and Microsoft work together to block access to child porn
Publié: novembre 18, 2013, 12:46pm CET par Mark Wilson
 To help fight the problem of child pornography online, Google and Microsoft are joining forces to block access to illegal content in the UK and then globally. Writing in the Daily Mail, Google's Eric Scmidt explains how new search filtering techniques now prevent more than 100,000 search terms relating to child pornography from returning any results. The filtering is starting in English speaking countries, but will soon roll out to more than 150 languages.
To help fight the problem of child pornography online, Google and Microsoft are joining forces to block access to illegal content in the UK and then globally. Writing in the Daily Mail, Google's Eric Scmidt explains how new search filtering techniques now prevent more than 100,000 search terms relating to child pornography from returning any results. The filtering is starting in English speaking countries, but will soon roll out to more than 150 languages.He explains that Google and Microsoft have worked with law enforcement agencies for many years and are proactively involved in the removal of illegal images. More than 200 extra employees have been assigned the tasks of developing new technologies over the last three months. This is very much a joint venture between the two companies, and Schmidt recognizes the input of Microsoft, saying that the company "deserves a lot of credit for developing and sharing its picture detection technology".
Google's primary weapon in the fight against child porn is blocking access to it -- it would be difficult for the company to stop such content from being created, but Schmidt is keen to make it clear that everything possible is being done to prevent its dissemination. As well as cleaning up search results, Google is also aiming to deter web users from seeking out child porn in the first place. When a search is placed using one of more than 13,000 child porn related queries, warnings are displayed about the illegal nature of such content, and links are provided to organizations that offer help and support.
Schmidt points out that automatically detecting and removing questionable images is very difficult. "Computers can't reliably distinguish between innocent pictures of kids at bathtime and genuine abuse. So we always need to have a person review the images." To help prevent the sharing of images that are detected, each is assigned a unique ID that makes it possible to rank it online -- this is something that Microsoft has been heavily involved in. Google engineers at YouTube have also developed technology that can be used to track videos of child abuse, and Google aims to share this with other companies in future.
It is great to see companies who are essentially rivals working together like this, especially for such an important cause. But there are fears that any blocking methods will always be open to circumvention and there is the risk of pushing things further underground and making them even more difficult to police. It is a tremendously difficult topic, but Google and Microsoft are taking steps in the right direction.
Photo Credit: Arcady/Shutterstock
-

Get your hands on a free Nexus 7 courtesy of Google
Publié: novembre 17, 2013, 11:40pm CET par Mark Wilson

Fancy getting your hands on a Nexus 7 without having to part with any cash? If you've been on the lookout for a 7-inch Android tablet, Google has a contest that may well be of interest. Providing you live in the US, you can take part in a photo competition to bag yourself either a free Nexus 7 or a $50 Google Play gift card. Sound tempting? All you need to do is take a photo of an arrangement of things that matter to you -- that's all there is to it!
The competition is not actually new as three draws have already taken place -- but there are only a couple of days left to try your luck with the final one. A reminder was issued on Google+ and while the introduction on the main competition page suggests that photos need to include an Android device, read on a little and you will discover that this is not actually a requirement for entry -- but make sure you don’t include a rival product in the shot though, as "non-Nexus or Android devices (phones/tablets) may not be shown in entry".
There have already been three draws and the fourth and final one is due to end on 19 November. The first prize is a 16GB Nexus 7 worth $229, and there are also five 2nd prizes of $50 Google Play gift cards. Keep in mind the usual small print that any photos submitted may be used by Google in promotional material, and could be edited in some way.
So what are you waiting for? Get creative, get snapping and in just a few days you could be richer to the tune of a new tablet or gift card.
Entry is simple. Just head over to the competition page, enter your details and upload a picture -- there's a file size limit of 2GB so you're free to upload just about the largest, highest resolution image you can lay your hands on. Good luck!
-

The most popular stories on BetaNews this past week -- November 10-16
Publié: novembre 16, 2013, 2:12pm CET par Mark Wilson
 It would be a strange week if Google didn’t steal a few headlines, and this week saw the introduction of new quick actions to Gmail as well as the launch of a series of online tools to help with the aftermath of the Philippines typhoon. Changes were also made to attachments in Gmail so it is now possible to download files directly to Google Drive. After the launch of the Nexus 5 -- which Brian was not blown away by -- Google also started to roll out Android 4.4 to Nexus tablets -- Mihaita was on hand with a guide to manually upgrading for anyone who did not want to wait for the OTA update to arrive. The news wasn't so good for the Chromebook 11 which was taken off sale after problems with overheating chargers. Google won a court battle after a judge ruled that the scanning of books is not illegal.
It would be a strange week if Google didn’t steal a few headlines, and this week saw the introduction of new quick actions to Gmail as well as the launch of a series of online tools to help with the aftermath of the Philippines typhoon. Changes were also made to attachments in Gmail so it is now possible to download files directly to Google Drive. After the launch of the Nexus 5 -- which Brian was not blown away by -- Google also started to roll out Android 4.4 to Nexus tablets -- Mihaita was on hand with a guide to manually upgrading for anyone who did not want to wait for the OTA update to arrive. The news wasn't so good for the Chromebook 11 which was taken off sale after problems with overheating chargers. Google won a court battle after a judge ruled that the scanning of books is not illegal.This week it was revealed that while BitTorrent still accounts for a large proportion of web traffic, and usage has actually increased in Europe, in the States there has been a drop in traffic. Anyone who seeks entertainment through other channels will be pleased by the fact that Roku streaming boxes can now be used to access Disney and ESPN channels. The Netflix channel was also updated with a new look.
Apple's iPad mini with Retina display was officially launched after last month's announcement -- but is it anything all that special? If you feel Apple's offering is slightly out of your price range, Hanspree launched a super-budget 13-inch tablet for just $318. New research revealed that by 2017 our smartphones could outsmart us but this will be little comfort for Microsoft who finds that Windows Phone still trails in third place behind iOS and Android.
For anyone who works during the week -- which, frankly, is most people -- placing online orders means planning to be home to receive deliveries. Things just got easier for Amazon Prime customers after Amazon announced Sunday deliveries for certain parts of the US.
Black Friday is lingering on the horizon, and there are sure to be plenty of bargains to be snapped up. If you've been holding off getting a Surface tablet, now could be the time to jump on board as Best Buy is lopping a massive $150 off the regular price, dropping it down to under $200. Intel also published a holiday buying guide for anyone struggling for gift ideas. There's not long left until the Xbox One is released and to keep the hype going, Microsoft showed off SkyDrive running on the console.
Online, Twitter introduced custom timelines and the previously US-only ad platform was opened up to businesses in the UK, Ireland and Canada.
Facebook announced the Facebook Login API which can be used by developers to log into apps, share data and more, all using a Facebook profile. Great news for European travelers came as the European Commission OK'ed the use of 3G and 4G data connection on flights.
So, this week we had the PlayStation 4 and next week there's the Xbox One to look forward to. It promises to be another packed seven days!
Photo Credit: vinz89/Shutterstock
-

Data on a plane gets the greenlight -- European Commission likes the idea of in-flight Facebooking
Publié: novembre 15, 2013, 6:11pm CET par Mark Wilson
 Following the lead of US airlines, the European Commission gives the go-ahead for the use of 3G and 4G services during flights. The Commission is permitting the use of UMTS and LTE data connections on aircraft above altitudes of 3,000 meters in the European Union (EU). Up until now, only 2G (GSM) usage has been allowed and the decision paves the way for passengers to make use of high speed data connections, although the decision about whether to permit this on individual flights lies with airlines.
Following the lead of US airlines, the European Commission gives the go-ahead for the use of 3G and 4G services during flights. The Commission is permitting the use of UMTS and LTE data connections on aircraft above altitudes of 3,000 meters in the European Union (EU). Up until now, only 2G (GSM) usage has been allowed and the decision paves the way for passengers to make use of high speed data connections, although the decision about whether to permit this on individual flights lies with airlines.The Commission's announcement makes it clear that the decision does not translate into an automatic right for passengers to use data connections, at least partly because aircraft need to be adapted.
This EU decision creates the possibility for airlines -- rather than a right for passengers -- to allow use of smart phones and tablets during flights. But, in order for this service to work, airlines must install specific hardware on board each concerned airplane.
As the decision has only just been announced, no airlines have yet expressed that they will permit in-flight data usage. As this is something that passengers have been pushing for for many years, it would seem likely that most, if not all, will install the necessary hardware.
There will obviously be some cost involved in upgrading aircraft, and there is the possibility that this cost will be passed on to travellers -- perhaps in the form of paid-for internet access. Anyone using their smartphone during a flight can also expect to pay the usual roaming charge to their network provider.
Are you happy about the decision? Is in-flight data something you'll make use of?
Photo Credit: auremar/Shutterstock
-

FCC calls for phone unlocking to be made much, much easier
Publié: novembre 15, 2013, 5:13pm CET par Mark Wilson
 The head of the Federal Communication Commission (FCC), Tom Wheeler, is calling for phone providers to pass rules that will make it easier for handset owners to unlock their devices. In a letter to Steve Largent, president and CEO of CTIA The Wireless Association, Wheeler says that "enough time has passed, and it is now time for the industry to act voluntarily or for the FCC to regulate". He goes on to call for the unlocking policy to be put in place before the December holiday season.
The head of the Federal Communication Commission (FCC), Tom Wheeler, is calling for phone providers to pass rules that will make it easier for handset owners to unlock their devices. In a letter to Steve Largent, president and CEO of CTIA The Wireless Association, Wheeler says that "enough time has passed, and it is now time for the industry to act voluntarily or for the FCC to regulate". He goes on to call for the unlocking policy to be put in place before the December holiday season.Wheeler is concerned that despite eight months of collaboration between CTIA and the FCC to make changes to CTIA's Consumer Code, these changes are yet to be made. The FCC is asking for five specific rules to be put in place to make it easier for consumers to unlock their phones.
- Provide a clear, concise, and readily accessible policy on unlocking.
- Unlock mobile wireless devices for customers, former customers, and legitimate owners when the applicable service contract, installment plan, or ETF has been fulfilled.
- Affirmatively notify customers when their devices are eligible for unlocking and/or automatically unlock devices when eligible, without an additional fee.
- Process unlocking requests or provide an explanation of denial within two business days.
- Unlock devices for military personnel upon deployment.
These all seem like reasonable demands -- it amounts to allowing customers to unlock their phones, be informed about the process involved and for unlocking to be carried out in reasonable time without cost.
According to Wheeler's letter, it is just the third point that is proving problematic. He does not expand on whether it is the automatic unlocking of devices that is the stumbling block, the request that customers be notified of unlocking eligibility, or the requirement for there to be no fee.
It remains to be seen if anything will happen in time for the holiday season as requested, but the ball is very much in CTIA's court now.
Photo Credit: arbalet/Shutterstock
-

Gmail for iPad gets a slick new look
Publié: novembre 14, 2013, 10:52pm CET par Mark Wilson
There's nothing stopping tablet owners from making use of mobile websites, but apps are where it is at. Gmail has a perfectly serviceable website, but the app does make many tasks easier to perform. Today, Google takes the lid off a completely redesigned version of its iPad app which has been designed to make it easier to do more, whether you choose to work in landscape or portrait mode.
Despite the fact that this release is, based on version number at least, a small move forward -- this is version 2.7182 -- there are a lot of changes, some cosmetic, some functional. Landscape mode benefits from the addition of a new navigation bar that can be used to switch between accounts and categories. This is essentially an iPad friendly version of the tabbed inbox that has been introduced online.
Just as with online tabs, each category has its own message count, but this is a feature you'll either love or hate. Switch to portrait mode and you'll see a full screen preview of messages. This is a clean, uncluttered look that still manages to provide access to frequently used features. Working in portrait view gives a larger message composition window.
Google is also claiming "improvements to scrolling performance" and the announcement posted on the Gmail blog also touts "several iOS 7 visual updates on both iPad and iPhone". You can grab yourself a copy of the app from the App Store.
-

Judge rules Google's scanning of books is not illegal
Publié: novembre 14, 2013, 7:57pm CET par Mark Wilson
 There is nothing wrong with Google scanning millions of book and making that text available as snippets in search results. This is the ruling made today by a judge in New York, bringing to an end an eight year legal battle between Google and The Authors Guild in conjunction with several specific authors. Starting back in 2004, Google has scanned more than twenty million books -- and permission was not obtained from the copyright holder in many cases.
There is nothing wrong with Google scanning millions of book and making that text available as snippets in search results. This is the ruling made today by a judge in New York, bringing to an end an eight year legal battle between Google and The Authors Guild in conjunction with several specific authors. Starting back in 2004, Google has scanned more than twenty million books -- and permission was not obtained from the copyright holder in many cases.A class action lawsuit was launched against Google back in 2005, but in New York, U.S. Circuit Judge Denny Chin has ruled that there is no copyright infringement and that Google's book scanning qualifies as fair use. Among the named writers were former New York Yankees pitcher Jim Bouton, The Trouble with Thirteen author Betty Miles, and legal author Joseph Goulden.
All three, and others, complained that Google was making their work available without permission and without payment. The works were scanned as part of the Google Books program, although the majority of the books that were scanned were out of print. While it was, and indeed still is, possible to perform searches that reveal snippets of text from the books, entire books are never made available in this way.
While performing different searches will reveal different snippets that can be used to piece together the bulk of a book, Judge Chin noted that searchers:
"...would be able to obtain at best a patchwork of snippets that would be missing at least one snippet from every page and 10-percent of all pages..."
The full ruling is available to view online, where it is possible to see Judge Chin's recognition that Google Books has become an important tool for libraries, librarians and cite-checkers. He likens the book snippets to the display of thumbnail previews of photographs, and says "in my view, Google Books provides significant public benefits". In short, the case against Google has been completely dismissed.
How do you react to this ruling?
Image Credit: Feng Yu / Shutterstock
-

Twitter advertising opens its doors to businesses in UK, Ireland and Canada
Publié: novembre 14, 2013, 6:55pm CET par Mark Wilson
 It's only been a week since its IPO, but Twitter's development is not going to end there. Previously only available to US businesses -- or those willing to grovel -- Twitter's ad platform is now being made available to small to medium sized business in the UK, Ireland and Canada.
It's only been a week since its IPO, but Twitter's development is not going to end there. Previously only available to US businesses -- or those willing to grovel -- Twitter's ad platform is now being made available to small to medium sized business in the UK, Ireland and Canada.It's a simple idea: put some money up front and this will be used to fund Promoted tweets that will reach a wider audience or even target specific types of users.
In a blog post, product manager Ravi Narasimhan says: "It takes a just few minutes to get started with Twitter Ads. If you can Tweet, you can advertise on Twitter -- all you need is a Twitter account and a credit card. You’re in control of your ads, the audience you want to reach, and of course your budget. Best of all, you will only be charged when people follow your Promoted Account or retweet, reply, favorite or click on your Promoted Tweets. You are never charged for your organic Twitter activity".
Twitter does offer quite a unique platform for advertisers, making it possible for small businesses and individuals to manage their own ad campaigns without the need for help from third parties. This obviously keeps costs down, but also enables businesses to use knowledge of their target customer to spend money in a way that makes sense.
As you would expect, there's a hashtag to follow -- #TwitterSurpriseEgg -- as well as dedicated Twitter accounts that can offer support: @TwitterSmallBiz and @TwitterUKI_SME.
Will you be making use of Twitter's advertising platform to promote your business, or have you already had experience of it in the US?
Photo Credit: bikeriderlondon/Shutterstock
-

Google Chromebook 11 no longer on sale after charger overheating problems
Publié: novembre 13, 2013, 10:42pm CET par Mark Wilson

Google and HP are, at least temporarily, stopping the sale of the Chomebook 11. Announced in a joint statement on the Google Blog and HP's Next Bench blog. The cessation of sales is blamed on overheating chargers. No recall has yet been declared, but Chromebook owners are told to stop using the charger supplied with the device.
The statement reads: "Google and HP are pausing sales of the HP Chromebook 11 after receiving a small number of user reports that some chargers included with the device have been damaged due to overheating during use. We are working with the Consumer Product Safety Commission to identify the appropriate corrective action, and will provide additional information and instructions as soon as we can".
It goes on to say:
"In the meantime, customers who have purchased an HP Chromebook 11 should not use the original charger provided with the product. In the interim they may continue using their HP Chromebook 11 with any other Underwriters Laboratories-listed micro-USB charger, for example one provided with a tablet or smartphone. We apologize for the inconvenience".
At this stage it is not clear whether there will be a product recall, but we have contacted Google for clarification and will update this story when we hear back. The final paragraph of the statement is interesting. In similar situations, there are not many manufacturers who would advise -- or even be able to advise -- using a third party charger. The emergence of this problem is clearly not good news for Google or Chromebook owners, but it shows that the decision to use a micro-USB charger was probably a smart move.
-

Google updates Gmail with Google Drive support for attachments
Publié: novembre 12, 2013, 7:19pm CET par Mark Wilson
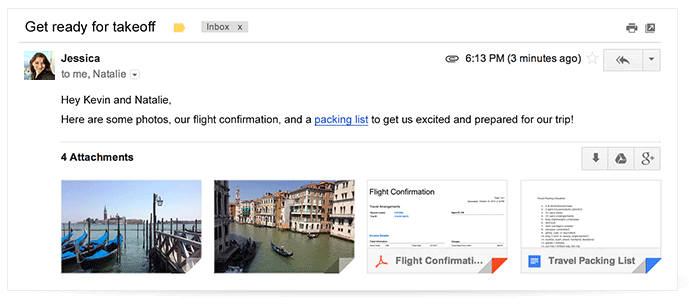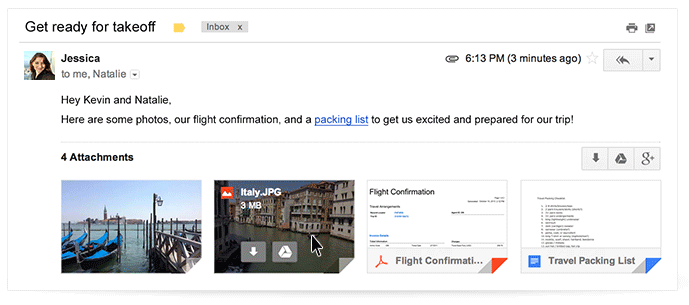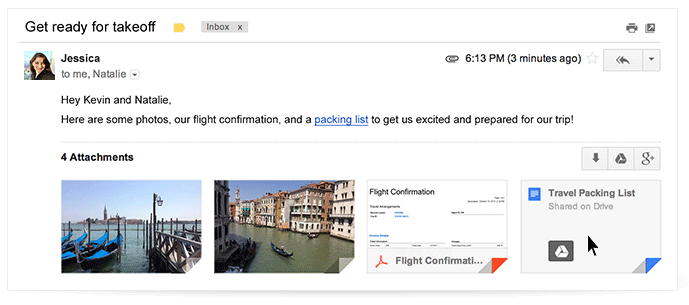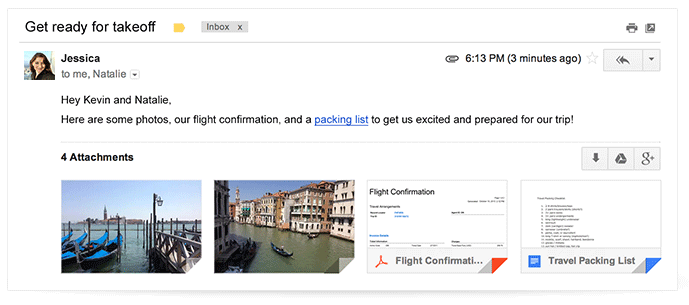
When you're sent an email with an attachment you probably do one of two things. You might preview the file in your browser, or you might download it to your hard drive. If you want to be able to access the file on other computers without having to track down the original email again, you may then take the extra step of uploading it to Google Drive. But it's all too easy for attachments to end up getting lost on the desktop or a catch-all Downloads folder.
This is something Google may be able to change with the latest addition to Gmail. Now there is no need to click an attachment to view a preview -- supported file types (including images, PDFs and videos) are automatically previewed as small thumbnails. You can still click them if you would like to see a larger preview, but this is not the only change that has been made. When an email has multiple attachments, it is now possible to scroll through them slideshow-style.
This is great for dealing with several images at once, but it is also handy for other types of files. When previewing files there are two new download buttons. The button featuring a Google Drive icon does what you'd expect: it lets you save the file directly to your Google Drive account to bypass having to manually upload it. It's even possible to choose which folder the file should be added to.
Files can be downloaded individually from the preview screen, or you have the option of downloading them all at once using the "Save all to Drive" button in your email. Regular, local downloads are still possible, and these are catered for by the button featuring an arrow. The announcement was made in a post on the official Google blog where it is explained that the features will be rolling out to Google users over the coming week.
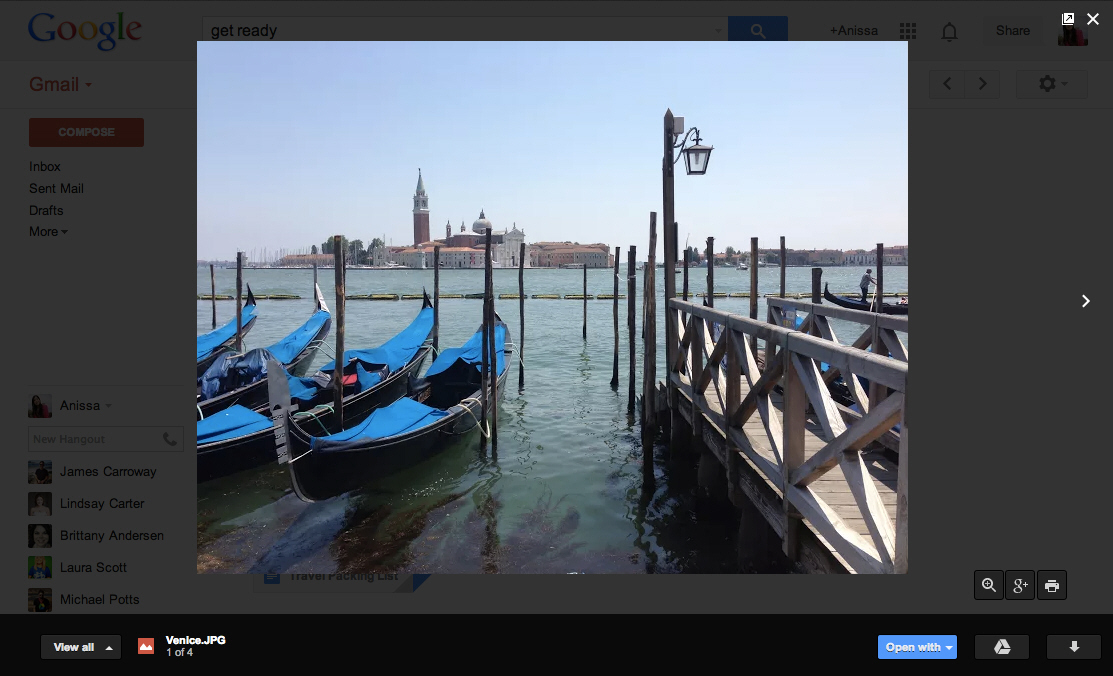
-

iPad mini with Retina display sees Apple preaching to the converted
Publié: novembre 12, 2013, 1:27pm CET par Mark Wilson

Five words, 25 letters, all indicating the latest addition to Apple's growing iPad family. Let's try to skirt over the name that extends to almost Tolstoyan lengths before we get too bogged down in it. But it does bear mentioning that this is a name no one is going to use; this is the iPad mini, perhaps the 'new' iPad mini to help differentiate from its predecessor. However it's not just the official title that's big… there's that price tag too.
While the price is not a new revelation -- we knew about it when the new iPad mini was announced a few weeks back -- now that the latest model is actually available to purchase, it seems a good time to reassess it. Head over to the Apple website and you can pick up the diminutive tablet for $399. And that's just the base price.
The fat end of $400 gets you the 16GB model, progressing through $499 for 32GB and $599 for 64GB, all the way up to $699 for 128GB. What's that? You want a data connection as well? That'll be an extra $130, please. These prices are, in my opinion, off the scale. They are insane. The big selling point for this latest version of the iPad -- so important a change that it is crowbarred into the awkward name -- is the Retina display. The screen is what Apple is using to push this tablet.
But how special is it? Look at what is one of the iPad mini's closest rivals, Google's Nexus 7. Apple's device has 0.88 inches on the Nexus 7's 7.02 -- 7.9 inches compared to 7 -- but it does have a higher resolution -- the Nexus 7 offers 1920x1200 while the iPad mini is 2048x1536. At first glance it might seem like this is a significant difference, but break it down into pixels per inch and it becomes far less significant. It turns out that Apple boasts 326ppi while Google has 323.
With these small differences, surely the prices are fairly close? Nope. The Nexus is $170 cheaper for the 16GB model and a staggering $230 cheaper for the 32GB version. 32GB is the largest Nexus 7 available, and it is the only model that comes with a data option. What do you pay for this privilege? Not $130 extra, that's for sure -- just $80.
Taken at face value, the iPad mini offers a screen that is less than an inch larger than the Nexus and a meager 3ppi more. Is this worth the extra $170, $230 or $280? I can't see that it is. What is sickening is that people will pay this kind of money for what is really a very ordinary tablet. But it's clear that Apple is preaching to the converted here. With a starting price of $399, this is a purchase that will appeal to those who are already ingrained in the world of Apple, but for anyone just looking for a rough-seven-inch tablet, it's obvious which is going to be more attractive.
For newcomers, the price is going to be seriously offputting. If you already own a full-sized iPad and want a smaller model without incurring the expense of re-purchasing apps for a different platform, the mini might make sense, but for the most part Apple is pricing itself out of the market. Apple's hardware has long had a reputation for being expensive, and this latest round of pricing does nothing to shake off this idea.
Has the price put you off, or are you willing to pay more to be part of the Apple world?
-

BitTorrent usage increases in Europe, drops in US
Publié: novembre 12, 2013, 11:00am CET par Mark Wilson
BitTorrent still accounts
 for a massive proportion of Internet traffic, but it looks as though the global spread is switching somewhat. According to data published by Sandvine, BitTorrent traffic has dropped significantly in North America. While the protocol accounted for more than 31 percent of traffic five years ago, today this has plummeted to below 10 percent.
for a massive proportion of Internet traffic, but it looks as though the global spread is switching somewhat. According to data published by Sandvine, BitTorrent traffic has dropped significantly in North America. While the protocol accounted for more than 31 percent of traffic five years ago, today this has plummeted to below 10 percent.The Global Internet Phenomenon Report found that BitTorrent now accounts for just 7.39 percent of traffic in North America, a drop of 20 percent. Conversely, in Europe, BitTorrent traffic has increased to 17.99 percent. Interestingly, during peak hours, 48 percent of European upstream traffic is accounted for by BitTorrent.
On the whole, there has been little change in the amount of data transferred online using a fixed line over the past six months. The average North American user had a monthly data usage of 44.5GB and an increasing percentage of this is made up by 'real-time entertainment', or streaming movies and music. In this particular area, Netflix was responsible for the bulk of traffic. In Europe, data usage on the whole is much lower, with the average user consuming just 7.3GB of data.
While there has been little change in fixed line data usage, mobile data has increased. A jump in average usage from 390.1MB to 443.5MB represents an increase of 13.5 percent. The type of traffic generated by mobile users is rather different, with a strong focus on Facebook, YouTube and HTTP.
Photo Credit: JMiks/Shutterstock
-

Google launches tools to help with Philippines typhoon aftermath
Publié: novembre 12, 2013, 10:28am CET par Mark Wilson
To help with the emergency in the Philippines after Typhoon Yolanda (Haiyan) struck, Google launches a series of tools to assist those affected by the disaster. The website can be used by anyone looking for friends or relatives who have been lost, as well as by those who have information about the whereabouts of individuals. With information very hard to get hold off in the area, this is a valuable service to those hunting for loved ones.
It is possible to visit the site and perform a search for anyone using their full name, or just part of it. Where possible, details about whether the individual has been located alive and well are provided, although there is the disclaimer that "Google does not review or verify the accuracy of this data". To help keep the people database up to date, anyone with information is invited to share information about people they know to be alive.
Google's typhoon page is also home to a constantly updated map that provides information about shelters, relief centers and other places that will be of help to victims. Website owners are encouraged to spread the word by embedding the map in their own site, and Google links to organizations such as the Red Cross who are accepting donations to help with the relief effort.
In addition to the main site, there is a mobile version available, and there are also SMS-based options available:
You can also search with SMS by texting 2662999 (Globe), 4664999 (SMART), 22020999 (Sun), or +16508003977 with the message Search [name]. For example, to search for Joshua, text Search Joshua.
This is far from being the first time that Google has stepped in to lend a hand following a natural disaster, and just recently the company donated 17,000 Nexus 7s to Hurricane Sandy communities.
-

Gmail gains more quick actions buttons to speed up common email tasks
Publié: novembre 12, 2013, 12:57am CET par Mark Wilson
Google continues to make changes and improvements to Gmail, and the latest addition is a raft of new quick action buttons to help speed up common email tasks. The idea of quick action buttons is not completely new; if you make use of Google Calendar, you have probably noticed that it's possible to indicate whether or not you'll be attending an event you are invited to by making a selection from a drop down menu that appears in the subject line.
Now Google is extending the number of quick action buttons that are available so it is possible to do even more without even having to open an email. The idea behind the buttons -- as you'd probably guess from the name -- is to save time. There are some emails which do not really require you to read them, they simply require some form of response. When you receive a calendar invitation you can probably tell what your response is going to be from the subject line -- so the RSVP quick action button enables you to accept or decline the invitation with a couple of clicks.
There are several new options that help to speed up various tasks. Booked a restaurant via OpenTable? If you need to make a change to your reservation, you can do so using a quick action button without the need to open an email. Quick and simple. If you receive an email letting you know that a Google Docs file has been shared with you, why bother clicking the email to open it and then tracking down the link to access the file? Use the quick action button and you can open the file in a flash.
The lists of buttons also allows for the writing of product reviews, accessing uploaded YouTube videos and much more -- and more are being added all the time. Google has been criticised in the past for scanning emails, and Microsoft recently used this in a pro-Outlook.com ad campaign, and while these additions will do little to extinguish these fires, it does help to save time when dealing with certain emails.
-

The most popular stories on BetaNews this past week -- November 3-8
Publié: novembre 9, 2013, 12:09pm CET par Mark Wilson
 Another busy week with more news than you could shake a stick at. Following the release of KitKat, Google was riding high as figures revealed that Jelly Bean is now installed on more than half of Android devices. It’s a similar story for Microsoft. Its previous operating system, Windows 7, is still the most popular while growth for Windows 8 and 8.1 remains slow. It was better news for Windows Phone which is making serious inroads into Android and iOS's share of the mobile market in Europe, and even managed to overtake Apple in Italy.
Another busy week with more news than you could shake a stick at. Following the release of KitKat, Google was riding high as figures revealed that Jelly Bean is now installed on more than half of Android devices. It’s a similar story for Microsoft. Its previous operating system, Windows 7, is still the most popular while growth for Windows 8 and 8.1 remains slow. It was better news for Windows Phone which is making serious inroads into Android and iOS's share of the mobile market in Europe, and even managed to overtake Apple in Italy.It seems that more people want to be able to use the latest and greatest version of Android, and following the announcement that the Galaxy Nexus would not receive a KitKat update, a petition was quickly launched to try to change Google's mind. Showing that the march of progress will always leave casualties, Google announced that Internet Explorer 9 will no longer be supported by Google Apps, and Windows 7 users gained Internet Explorer 11. To push the launch, Microsoft unveiled a new Anime ad campaign focusing on the browser's improved security.
In the world of apps and services, Google launched Helpouts, a help-based version of Hangouts that can be used to give or receive help for free or for a fee. Dropbox may be branching out into new territory with its purchase of Sold, and BitTorrent Sync received an update that brings speed improvements and better iOS support. Digg announced a video only category and Microsoft made a number of key improvements to Office Web Apps.
Google upset YouTube users with the introduction of a new commenting system, and the company looked to tighten up security in Chrome by making users install extensions through the official web store.
While Fedora Linux celebrated its tenth birthday, Canonical was busy trying to shut down a website for using the Ubuntu name and logo. The FAA lifted a ban on the use of electronic devices on flights, and Amazon celebrated with a quick Kindle sale.
Things took an interesting turn at BlackBerry when the expected sale to Fairfax Financial Holdings fell though and CEO Thorsten Heins' imminent resignation was announced. Over at Twitter, things were very much looking up as the company debuted on the NYSE and share prices quickly rocketed.
Fuel buyers in the UK could soon see video adverts tailored to them as they fill up thanks to face recognition software. This might not go down too well as research by Outlook.com found that most people in the UK are opposed to the idea of email scanning to deliver targeted ads. Microsoft started to take advantage of the public's desire for privacy, and launched an anti-Google campaign focusing on email scanning. Apple was the latest company to reveal details of government data requests they have received.
Joe took a look at the iPad Air and was impressed by the evolution of a product into something he felt could be a serious laptop replacement. Brian was rather less taken with the Lenovo Yoga Tablet 10 which he liked the look of but ultimately felt was slow and underpowered. The eagerly anticipated Kindle Fire HDX started shipping, and Nokia's latest Windows Phone handset, the Lumia 1520, became available for pre-order. Another piece of Microsoft hardware was showcased as the company released a video showing what the Xbox One is like to use.
That's it for now -- same time next week?
Photo Credit: vinz89/Shutterstock
-

Google takes control of Chrome extensions: Chrome Web Store a must for Windows
Publié: novembre 8, 2013, 6:35pm CET par Mark Wilson
 The days of some third party extensions for Chrome may be numbered. While most people will head to the Chrome Web Store as their first port of call for downloading extensions to add new features to the browser, this is far from the only means of obtaining add-ons.
The days of some third party extensions for Chrome may be numbered. While most people will head to the Chrome Web Store as their first port of call for downloading extensions to add new features to the browser, this is far from the only means of obtaining add-ons.But at the start of the new year, all of this is set to change. If you stick with the stable or beta channel of the browser, you'll be limited to installing extensions from the official repository only.
Announced in a blog post, Chrome's Engineering Director Erik Kay, says:
Starting in January on the Windows stable and beta channels, we'll require all extensions to be hosted in the Chrome Web Store. We'll continue to support local extension installs during development as well as installs via Enterprise policy, and Chrome Apps will also continue to be supported normally.
Referring to what it calls "bad actors", Google points to extensions that have abused the silent installation option to add malicious code to Chrome. The blog post reveals that a leading complaint about Chrome for Windows is the replacement of the New Tab page by extensions. By forcing the use of the Chrome Web Store as the sole source for extensions, Google is better able to police what is out there.
Assuming developers take the appropriate action, there should be no issues for extensions that are currently hosted outside of the Chrome Web Store. Google advises that "you should migrate them as soon as possible. There will be no impact to your users, who will still be able to use your extension as if nothing changed. You could keep the extensions hidden from the Web Store listings if you like. And if you have a dedicated installation flow from your own website, you can make use of the existing inline installs feature".
Good move with safety in mind, or will it stifle the development of extensions?
Photo Credit: Andrea Danti/Shutterstock
-

Canonical tries to stop fan website using Ubuntu name and logo
Publié: novembre 8, 2013, 12:51pm CET par Mark Wilson

Canonical, the team behind Ubuntu, finds itself the subject of criticism after contacting an Ubuntu related website and asking that the domain name be changed. Fix Ubuntu was created by Micah Lee to provide Ubuntu users with instructions about how to disable the web component of the desktop search tool. Lee was emailed by Canonical to request that he not only stop using the word "Ubuntu" in the domain name, but also refrained from using the logo.
The reason? Canonical's email suggests that the name and use of logo could cause confusion among Ubuntu users:
Unfortunately, in this instance we cannot give you permission to use Ubuntu trademarks on your website and in your domain name as they may lead to confusion or the misunderstanding that your website is associated with Canonical or Ubuntu.
Lee has reproduced the full text of the email in a blog post and explains that he has decided to remove the logo. The domain name, however, remains the same -- for now at least. To help make things a little clearer and to avoid the confusion that Canonical is clearly so worried about, Lee has added a little disclaimer, seemingly written with tongue planted firmly in cheek (or blood boiling, perhaps):
Disclaimer: In case you are either 1) a complete idiot; or 2) a lawyer; or 3) both, please be aware that this site is not affiliated with or approved by Canonical Limited. This site criticizes Canonical for certain privacy-invading features of Ubuntu and teaches users how to fix them. So, obviously, the site is not approved by Canonical. And our use of the trademarked term Ubuntu is plainly descriptive -- it helps the public find this site and understand its message.
There are numerous other unofficial Ubuntu websites that use the word Ubuntu in their domain name including the popular OMG Ubuntu. Lee intends to continue to use the domain, arguing that use of the name falls under "nominative use". There could well be a stream of communication over the coming days and weeks, but if the responses to Lee's blog post are anything to go by, Canonical has not won itselfs any new fans with this move.
-

Gramohorn II amplifies your HTC One in a retro-style
Publié: novembre 8, 2013, 12:38pm CET par Mark Wilson

Phones are great for music, but in most cases the built in speakers are a bit subpar; quality might be decent enough, but if you're looking for a punch of volume, speakers are going to be needed. Or maybe not. If you're an HTC One owner looking for something a little different -- and have a wad of spare cash lying around -- the Gramohorn II could just be of interest. It brings not one, but two gramophone inspired horns to amplify your music without the need for power.
3D printing is all the rage, and the Gramohorn II is the latest accessory to be produced in this way. There are plaster- and metal-based versions available, but whichever one you opt for, you're going to need to have deep pockets. The plaster-based model is the cheaper of the two, but "cheaper" is very much a relative term. There are 22 color choices and five metallic finishes but only 100 will be produced.
There's a bit of a wait -- 3-4 weeks from ordering -- but if you're quick, there's still time to get one for Christmas. What's that? Oh, the price? Yeah… it's quite an expensive stocking-stuffer. This double horned beauty will set you back £999 (around $1,600). If you happen to be in the mood for spending even more money, the metal-based version could be what you're looking for.
Again this is 3D printed, but this time it is with a bronze-infused stainless steel powder. Gold, silver and bronze finishes are available, but there are only ten of each. There probably won't be too many people standing in line in front of you though, as the price tag is an eye watering £4,999 (a shade over $8,000). The horn is only available for the HTC One and only amplifies volume by up to 50 percent -- but it'll certainly be a talking point for guests!
-

Apple joins the party and reveals details of government data requests
Publié: novembre 6, 2013, 12:30pm CET par Mark Wilson
 It's becoming a familiar story. A big name company decides to reveal figures about the number of requests for data that have been received from the government, apologizing straight away for the lack of detail it can provide. Microsoft has already done it, as has LinkedIn and Google. The latest figures come from Apple, and they make for interesting reading.
It's becoming a familiar story. A big name company decides to reveal figures about the number of requests for data that have been received from the government, apologizing straight away for the lack of detail it can provide. Microsoft has already done it, as has LinkedIn and Google. The latest figures come from Apple, and they make for interesting reading.The report starts off by stating that Apple is revealing as much information as it is legally allowed to, and then immediately goes on the defensive:
Perhaps most important, our business does not depend on collecting personal data. We have no interest in amassing personal information about our customers. We protect personal conversations by providing end-to-end encryption over iMessage and FaceTime. We do not store location data, Maps searches, or Siri requests in any identifiable form.
It also goes on to say that the company is unhappy with the reporting restrictions that are in place and, like every other company that has revealed similar figures, expresses a desire for increased transparency.
The report differentiates between requests made about users and requests made about devices. It points out that when a phone is lost or stolen, it may be reported to the police and a request may come as a result of this. But it is the '"account requests" that everyone is interested in -- personal details about users and their usage. Apple says that it usually hands over little more than details about a user's iTunes or iCloud account, but in "extremely limited circumstances" hands over other content such as photos.
Unsurprisingly, it is the US government that made the most requests, asking for details about more than 2,000 accounts. But there is an interesting note at the end of the document.
Apple has never received an order under Section 215 of the USA Patriot Act. We would expect to challenge such an order if served on us.
Had Apple received such a request, it would not be permitted to say either way. This means two things. Firstly that the company has not received any Section 215 request. Secondly -- and more interestingly -- should this note disappear from future reports, it could be indicative of the fact that such requests have been received. Interesting stuff.
Photo credit: Jirsak/Shutterstock
-

Google planning to use your Google+ profile image for caller ID
Publié: novembre 6, 2013, 11:57am CET par Mark Wilson
 Google is going to start displaying Google+ Photos as caller ID images from early 2014. The new feature will be enabled by default for anyone who has a verified phone number associated with their Google account.
Google is going to start displaying Google+ Photos as caller ID images from early 2014. The new feature will be enabled by default for anyone who has a verified phone number associated with their Google account.This means that should you get a call from someone you have circled on Google+, but have not added to your phone's address book, you will still be able to see who they are -- or at least be able to see whatever their most recent Google+ profile image is.
For the time being, the feature will be limited to Android 4.4 KitKat users, and is enabled on the recently announced Nexus 5. The revelation is made in a post by Google's Attila Bodis and is described as the "coolest part of the new Caller ID by Google feature my team worked on". Google says:
Coming in early 2014, users who have verified their phone number and have discovery turned on will have their names and Google Profile photos display whenever they call you, or you call them (it’s great if a new friend who hasn’t been saved in your contacts yet calls you).
Users do have the ability to opt out of this by heading to the phone numbers section of account settings.
There will obviously be many people who are concerned about the privacy side of this, but there are advantages as well. As Bodis points out, it can be helpful in determining who is calling you and help you to decide whether to answer or not. Phone numbers are cross-referenced against Google Places listings to help you identify businesses.
Photo credit: Bizroug/Shutterstock
-

Microsoft is at it again! New campaign targets Google's email scanning
Publié: novembre 5, 2013, 6:41pm CET par Mark Wilson
Microsoft is no stranger to trying to stick the knife into the competition, and the company's latest campaign, Keep Your Email Private, is no different. This is not just an ad campaign, but rather an entire microsite that has been set up to demonstrate how much better Outlook.com is than Gmail. The reason? There is only really one put forward for consideration -- Google's scanning of emails.
This in itself is nothing new. We have known for a long time that Google scans the content of emails with a view to delivering targeted ads. It’s not something that everyone is happy with, but we know all about it, and if you don’t like it, you're free to move away from Gmail. But Microsoft is now exploiting this fact in a bid to attract people to Outlook.com.
Unlike Gmail, Outlook.com keeps your privacy private. You won’t see ads based on keywords from your personal email. Your email is nobody else's business. But Google makes it their business. Even if you’re not a Gmail user, Google still goes through your personal email sent to Gmail and uses the content to sell ads.
There is a little '"infomercial" in which Microsoft explains how Gmail's scanning works -- except it doesn't really make it clear that the scanning is anonymized and private data is not revealed to any third party.
Microsoft explains Google's email scanning:
There are lots of statistics quoted about how much people dislike the idea of email scanning ([keepyouremailprivate.com]) as well as the ubiquitous petition which visitors are invited to use to voice their disapproval.
There's also a suitably amusing advert to help drive home the idea of personal privacy.
Are these tactics underhanded, or has Google left itself open to this sort of criticism? What's your view?
-

Dropbox gets Sold!
Publié: novembre 5, 2013, 12:35pm CET par Mark Wilson
 Dropbox is a name that's usually associated with online storage where it finds itself pitted against the likes of Google Drive and Microsoft's SkyDrive. But now the company could be branching out in a new direction with the purchase of Sold, one of the simplest online selling services ever invented.
Dropbox is a name that's usually associated with online storage where it finds itself pitted against the likes of Google Drive and Microsoft's SkyDrive. But now the company could be branching out in a new direction with the purchase of Sold, one of the simplest online selling services ever invented.Sold existed as an iOS and Android app and the idea was that a user uploaded a photo and brief description and everything else was taken care of by Sold -- no worrying about determining the best price or calculating postage. Or as Sold put it "doing all the dirty work for" users. There are no details about what will happen to Sold now that it has been, er, sold, but for now the site has been effectively shut down.
A statement on the Sold website reads: "As of today, our service will no longer be accepting new items".
The statement goes on to say:
We decided that the move to Dropbox couldn’t be better -- their roadmap includes exciting new experiences which align perfectly with our ethos of creating products that positively affect people. Going forward, the Sold team will continue working together to build these experiences, shaping the future of Dropbox for their 200M strong user base. It’s an opportunity too good to pass up.
At this stage it is not clear whether Sold will relaunch under a different guise, will be absorbed into Dropbox, or whether it will just vanish. But whatever happens, Dropbox has gained itself an interesting service or a number of new additions to its staff. Either that or it has just shut down the competition because of a future venture.
Image credit: Mmaxer/Shutterstock
-

Google launches new Hangouts-inspired assistance service, Helpouts
Publié: novembre 5, 2013, 11:58am CET par Mark Wilson
 As promised back in August, Google launches Helpouts, an online video help service based on the idea of Hangouts. Or as Google puts it, "real help from real people in real time". There are numerous online help repositories -- Yahoo Answers et al -- but the thinking behind Helpouts is to make things live and instantaneous.
As promised back in August, Google launches Helpouts, an online video help service based on the idea of Hangouts. Or as Google puts it, "real help from real people in real time". There are numerous online help repositories -- Yahoo Answers et al -- but the thinking behind Helpouts is to make things live and instantaneous.If you have a sudden yearning to make a soufflé, forget hunting through score of recipes sites for the best method, get someone to show you step by step.
It's kind of like having your mum, dad, best friend, knowledgeable uncle and local handyman on tap whenever you need them. Of course, this all comes at a price. Those offering help are able to charge for their services, while anyone looking for help can browse through the experts and make a choice based on price, the ratings of other users and availability.
Hangouts is very much a two-way street. If you are an expert in any given field, you can offer your help to the online community. And of course there is the opportunity to make a little money. You have the option of charging by the hour (which conjures up some interesting images) or per session, and everything is taken care of through Google Wallet. There is potential for Helpouts to be used to offer one-off help sessions as and when required, or ongoing lessons.
The beauty of Helpouts is its simplicity. It is a wonderfully simple idea -- using a webcam to show someone how to do something seems blindingly obvious -- but this is the first time it has really been implemented in such a way as to be accessible and workable. It's early days at the moment, and there are a limited number of categories of help, but this will expand over time. To help instill confidence, there is a full money back guarantee for anyone who is not completely happy with their experience.
There are already some well-known names involved -- Weight Watchers, Sephira and Rosetta Stone to name but three -- but anyone is free to offer their help, and charge for it. If you fancy earning some cash by sharing your knowledge, head over to the signup page.
Check out the video to get an idea of what Google thinks you could be using the service for.
Image credit: iQoncept/Shutterstock
-

CEO Heins steps aside as BlackBerry calls off sale
Publié: novembre 4, 2013, 4:43pm CET par Mark Wilson
 BlackBerry CEO Thorsten Heins is to resign from his position at the head of the company, and the board of directors is also facing a reshuffle. The struggling mobile firm was set to be sold to a consortium lead by Fairfax Financial Holdings for $4.7 billion but that plan, announced last month, has now fallen through.
BlackBerry CEO Thorsten Heins is to resign from his position at the head of the company, and the board of directors is also facing a reshuffle. The struggling mobile firm was set to be sold to a consortium lead by Fairfax Financial Holdings for $4.7 billion but that plan, announced last month, has now fallen through.BlackBerry instead intends to raise $1 billion in fresh funding from a group of investors including Fairfax.
The purchase was still on the table until today which was the deadline by which Fairfax had to raise the funds needed for the buyout. But it seems as though talks surrounding the purchase, which came after the announcement that BlackBerry would be looking into "strategic alternatives", have now been abandoned. Instead, the Canadian firm is looking to raise $1 billion from institutional investors with Fairfax set to buy $250 million of the subordinated debentures. BlackBerry said the debentures would be convertible into common shares at $10 and it is hoped that this will be enough to turn around the company's fortunes.
On a short term basis, Heins will be replaced by John Chen, former chairman and CEO of Sybase Inc. Mr Chen will take on the role of Interim Chief Executive Officer until a full time replacement can be found. He will also take on the role of Executive Chair of BlackBerry's Board of Directors and will oversee the strategic direction, strategic relationships and organizational goals of BlackBerry. Prem Watsa, Chairman and CEO of Fairfax, will be appointed Lead Director and Chair of the Compensation, Nomination and Governance Committee.
Barbara Stymiest, Chair of BlackBerry's Board, said:
Today's announcement represents a significant vote of confidence in BlackBerry and its future by this group of preeminent, long-term investors. The BlackBerry Board conducted a thorough review of strategic alternatives and pursued the course of action that it concluded is in the best interests of BlackBerry and its constituents, including its shareholders. This financing provides an immediate cash injection on terms favorable to BlackBerry, enhancing our substantial cash position.
John Chen is under no illusions about the magnitude of the task ahead of him:
I am pleased to join a company with as much potential as BlackBerry. BlackBerry is an iconic brand with enormous potential -- but it's going to take time, discipline and tough decisions to reclaim our success.
While the deal is all but done, it does still need to be approved by the Toronto Stock Exchange.
Photo credit: iamharin/Shutterstock
-

In UK supermarket Tesco, the adverts are watching you
Publié: novembre 4, 2013, 12:24pm CET par Mark Wilson
 After the launch of its own brand tablet, the Hudl, UK supermarket Tesco is hitting the headlines for another reason. We are all used to the irksome familiarity of watching adverts on TV and online, they are hard to avoid. But the retailer is turning things on their head slightly by introducing advertisements that watch customers.
After the launch of its own brand tablet, the Hudl, UK supermarket Tesco is hitting the headlines for another reason. We are all used to the irksome familiarity of watching adverts on TV and online, they are hard to avoid. But the retailer is turning things on their head slightly by introducing advertisements that watch customers.Well, that's not strictly true, but it's an interesting way of looking at what is happening. Just as the likes of Google tailor advertisements to web users, Tesco is looking to ensure that the ads its customers see are relevant. The fuel stations found at many branches of the supermarket are soon to be home to personalized ads courtesy of Amscreen.
Amscreen is run by Simon Sugar, son of Lord Alan Sugar (he of Amstrad and The Apprentice fame) and the new venture showcases the company's OptimEyes technology. This is a face-recognition system which is to be rolled out around the UK, but rather than being used to identify individuals, it will be used to identify "key traits" in those nearby. The system is able to pick up various data such as age and sex but it also takes into account the time of day.
So should the system detect a man on his way to work in the morning, it will display advertisements believed to be pertinent to him. Should a woman be detected, advertisements deemed to appeal to her will be displayed instead. It's certainly an interesting use of technology, but it's also one that is going to have privacy advocates up in arms.
Photo credit: IdeaStepConceptStock/Shutterstock
-

The most popular stories on BetaNews this past week -- October 27-November 2
Publié: novembre 2, 2013, 12:13pm CET par Mark Wilson
 This week Google put an end to all the speculation and finally launched not only the Nexus 5 but also the new version of Android -- KitKat. There were no great surprises as there had been so many leaks prior to launch that we knew pretty much everything there was to know, but it was good have the rumors confirmed. Expect a full review in the very near future. The Nexus 5 comes with KitKat preinstalled, but it will also be available as an upgrade for a number of other handsets. As it this wasn't quite enough for Google, the company also donated 17,000 Nexus 7s to communities affected by Hurricane Sandy.
This week Google put an end to all the speculation and finally launched not only the Nexus 5 but also the new version of Android -- KitKat. There were no great surprises as there had been so many leaks prior to launch that we knew pretty much everything there was to know, but it was good have the rumors confirmed. Expect a full review in the very near future. The Nexus 5 comes with KitKat preinstalled, but it will also be available as an upgrade for a number of other handsets. As it this wasn't quite enough for Google, the company also donated 17,000 Nexus 7s to communities affected by Hurricane Sandy.After the recent announcement, the iPad Air went on sale, and Logitech was ready with a series of cases.
The Nexus 5 wasn't the only handset unveiled this week. Not to be outdone by Samsung's Galaxy Round, LG announced its curved mobile, the G Flex. Can't find a phone you like? Motorola may have the solution for you. Project Ara is the company's latest venture, enabling mobile users to build their own handset with a modular design. Nokia may have impressive-looking sales figures for Lumia handsets, but it does look as though growth is starting to slow down for the handset manufacturer -- Samsung, however, gained a larger share of the market than ever. Whatever your handset of choice, it looks as though you may be able to start using it on flights.
Microsoft celebrated 10 years of OneNote, while Wayne took a look at some of the issues that have irked him with Windows 8.1. Microsoft also celebrated the fact that Internet Explorer has been found to be better at defeating social engineering attacks. Twitter introduced changes to the way images are displayed prompting fears that it could lead to prominent ads in users' timelines. Sick of that super-lengthy URL for your Google+ profile? Rejoice as custom URLs start to rollout to everyone!
RSS reader Feedly, who benefited from a massive influx of new users when Google Reader shut down, reintroduced its lifetime subscription package. This time, however, the price has increased by more than 300 percent to $299. In other online news, social sharing site Buffer came under attack and was temporarily taken offline. Going the way of Google Reader and numerous other services, iGoogle breathed its last as it was shuttered.
In other security news -- this time, news that could have far wider-reaching consequences -- a firm specializing in AI managed to reliably crack CAPTCHA codes. Following on from last week's security breach at Adobe, it was revealed that the number of accounts affected was much, much higher than first thought -- no less than 38 million users.
PlayStation 3 owners now have a new streaming service available to them in the form of Redbox and Plex users now have Cloud Sync to enjoy allowing for remote access to cloud-synced media files. Need a bit more streaming media? Pandora also found its way onto Android tablets and support was added to Chromecast.
On the hardware front, Brian was highly impressed with 50 Cent's SMS Audio Sync headphones. After its #betterway campaign, Lenovo launched its Yoga Tablet complete with integrated kickstand. Owners of Dell Latitude 6430u ultrabooks started to complain of a rather unpleasant smell emanating from their devices.
On that delightful note, we'll bring this roundup to a close! Here's to another week of exciting releases and announcements.
Photo Credit: vinz89/Shutterstock
-

Android 4.4 alert! Google takes the wrapper off KitKat
Publié: octobre 31, 2013, 8:29pm CET par Mark Wilson

Just in time for Hallowe'en, Google takes us all out of our misery and officially launches Android 4.4 -- or KitKat as it is rather sweetly known. As with the Nexus 5, we have known pretty much what to expect from KitKat for a little while now. Google's blog post heralding the arrival of the latest version of the OS is a little understated and doesn't give much away.
One thing is particularly interesting. Rather than blowing its own trumpet and boasting about rafts of new features -- although this will probably follow -- Google has chosen to highlight the fact that Android 4.4 can run comfortably on devices with as little as 512MB RAM. The blog post points out that it is not just the operating system that has been put on a diet (ironic when you consider the origins of the name) but all Google services such as YouTube and Chrome.
We'll have a full look at KitKat as soon as we can, but for now we can look forward to the immersive mode that removes distractions when watching a movie, a global contact search feature and a new launcher for Nexus 5. KitKat also features an updated version of Hangouts which includes support for SMS and MMS in addition to chat and video calling.
KitKat will come preloaded on the new Nexus 5, but will also be made available for Nexus 4, 7, 10, the Samsung Galaxy S4 and HTC One Google Play edition devices over the coming weeks. Notable by its absence from this list is the Galaxy Nexus -- it looks as though this device is entering its twilight years.
But for everyone with a compatible smartphone or tablet, expect to receive an OTA update in the near future. Unlike the Nexus 5, there's going to be no shortage of KitKat to go around.
-

Google officially announces the Nexus 5 -- launch date: now!
Publié: octobre 31, 2013, 7:33pm CET par Mark Wilson

Ending months of rumors and speculation, Google puts all of our minds at rest and announces that the Nexus 5 not only exists (as if we didn’t already know following all of the leaked images!) but is launching now.
It does seem like an age since we first (apparently) caught a glimpse of this phone in a Nexus 7 video, but now we know it to be true. The Nexus 5 is here, and it looks like it's everything we could have hoped it would be.
So many leaks have sprung over the past few weeks that there is little we don’t already know about Google's latest phone. As the name suggests, this is a device sporting a 5 inch screen (well 4.95 inches, but it's as near as damn it) in-keeping with the naming convention used for the Nexus 7 and Nexus 10.
As expected, there are 16 and 32GB versions, and they'll be priced from $349 and available to buy in the US, Canada, UK, Australia, France, Germany, Spain, Italy, Japan and Korea. The smartphone will be sold through Google Play, Sprint, T-Mobile, Amazon, Best Buy and RadioShack. Black and white models are available, but here are those all-important specs in full -- this time entirely confirmed!
- 2.3 GHz Qualcomm Snapdragon 800 processor
- Adreno 330, 450 MHz GPU
- 5 inch full HD screen complete with Gorilla Glass 3
- Android 4.4 KitKat
- 1.3MP front camera
- 8MP rear camera
- 2,300 mAH battery with up to 17 hour talk time
- Weighs in at 130g or 4.59oz
You can find out more at Google Play -- hit the link to view the new Nexus 5.
-

The numbers increase: 38 million user accounts affected by Adobe hack
Publié: octobre 30, 2013, 6:03pm CET par Mark Wilson

Back at the start of the month, Adobe reported that the company’s network had suffered a breach and that as a result the accounts of 2.9 million customers had been compromised. Sounds bad? It's worse than first thought. And not just a bit worse; much, much worse. Upon further analysis of the figures Brian Krebs of KrebsOnSecurity puts the numbers at 38 million user accounts.
We reported the security breach at the time, and it is amazing to discover that the figure of 2.9 million affected users is in fact more than ten times as high. So how could the figures have been misread to such an extent? Apparently, many of the directories of data were password protected, making it difficult to give precise numbers at the time.
In fact it was not just user accounts that were compromised. Source code for a number of Adobe applications -- including Acrobat, Reader and Photoshop -- was also obtained. As recently as this weekend, an unencrypted file seemingly containing data from Adobe appeared on AnonNews.org; an encrypted version of the file had previously been made available but security firms were unable to crack the password.
A spokeswoman for Adobe, Heather Edell said that the investigation is ongoing and that the attackers gained access to "many invalid Adobe IDs, inactive Adobe IDs, Adobe IDs with invalid encrypted passwords and test account data". She went on to say:
"So far, our investigation has confirmed that the attackers obtained access to Adobe IDs and what were at the time valid, encrypted passwords for approximately 38 million active users. We have completed email notification of these users. We also have reset the passwords for all Adobe IDs with valid, encrypted passwords that we believe were involved in the incident—regardless of whether those users are active or not.
We believe the attackers also obtained access to many invalid Adobe IDs, inactive Adobe IDs, Adobe IDs with invalid encrypted passwords, and test account data. We are still in the process of investigating the number of inactive, invalid and test accounts involved in the incident. Our notification to inactive users is ongoing.
We currently have no indication that there has been unauthorized activity on any Adobe ID account involved in the incident."
Have you been contacted by Adobe to let you know that yours is one of the affected accounts? Share your experiences in the comments.
Photo Credit: David Evison/Shutterstock
-

Google donates 17,000 Nexus 7s to Hurricane Sandy communities
Publié: octobre 30, 2013, 1:06pm CET par Mark Wilson

It may be a year since Sandy struck, but the effects of the storms are still being felt. To mark the anniversary, Google is donating 17,000 Nexus 7 tablets to communities still feeling the impact of the hurricane. The devices, worth a total of $2.7 million, have been donated to community centers, libraries and other centers in the affected areas in New York.
The tablets were donated to the non-for-profit service the New York State Community Action Association who worked with the Port Authority of New York and New Jersey to store and distribute the devices. The Nexus 7s will be used in a number of ways including being loaned out as e-readers in areas where libraries are yet to re-open.
Small businesses and libraries will be able to use the tablets in training, while community centers can use them to help with communication and to improve technology skills.
Susan Molinari, Vice President for Government Relations at Google said:
We believe that technology can and does play a compelling role in rebuilding communities to make them more resilient and stronger. Increasingly, more and more people are using technology and the Internet to educate themselves or provide for their families. Our hope is that these tablets will be a resource to do just that.
The website of New York Governor, Andrew M. Cuomo, includes a spreadsheet that lists all of the locations where tablets can be found.
-

Twitter makes photos and videos more prominent -- ads to follow?
Publié: octobre 30, 2013, 12:29pm CET par Mark Wilson
Very little fanfare is being made about it, but Twitter is changing the way photos and videos are displayed in timelines. When someone you follow tweets a picture or video, there's no longer any need to click a link to see what the tweet is referring to -- previews are displayed right there in the timeline. To see a larger version, you'll still need to click or tap through, but at least you'll be able to get an idea of whether it is worth doing so ahead of time.
In a blog post entitled "Picture this: More visual Tweets", the new feature is explained, and a Vine video shows it in action. The video also shows how mobile users benefit from the addition of easily accessible replay, favorite and retweet options.
The switch to image previews is helpful in some regards, but it is also likely that this is a sign of something else -- more prominent timeline ads. Adverts are far more likely to be seen if users do not have to click through to view them, after all. Users of the official Twitter mobile apps, as well as Tweetdeck, have the option of disabling the image preview feature, but this is not possible for anyone using the website.
The new features are rolling out to the web version of Twitter right now, but mobile users will need to download updated versions of the Twitter app from Google Play for Android and the App Store for iOS.
-

Google+ Hangouts and Photos gain a raft of new options
Publié: octobre 29, 2013, 11:25pm CET par Mark Wilson

Google is in the process of rolling out a series of new features to Google+ Hangouts and Photos, many of which have been designed to save users time. Hangouts gains a new option that enables broadcasters to schedule Hangouts On Air, while a management page in the form of the Control Room can be used by moderators to eject unruly participants should the need arise.
Video call quality sees improvements not only to quality, but also to automatic lighting adjustment. It doesn’t end there for Hangouts. The chat tool also gains the ability to send and receive SMS as well as location sharing. But it is Photos that sees the largest number of changes and additions. Something that will please mobile users who have enabled the autobackup feature is the introduction of full sized backups (rather than scaled) and background syncrhonization.
Google is all about searching. Another enhancement to Photos sees the search giant showing off its image recognition technology. Thousands of everyday objects are recognized making it possible to very quickly track down all of your photos featuring trees, for example. Improvements have been made to Auto Enhance and it is now possible to gain greater control over the edits that are made, or even disable the feature entirely for certain albums.
There are more automatic options to play with for photographers looking to find interesting ways to share their snaps. Three new features have been added to Auto Awesome: Action, Eraser and Movie. For anyone who likes to get more hands on, a new HDR filter is being added to Snapseed, while the $149 Nik Collection benefits from the addition of the Analog Effects Pro package.
Features are being gradually rolled out. Some will appear in the next few days, while others -- such as the new On Air features -- will take a few weeks to become widely available.
Image Credit: Aleksandra Kovac / Shutterstock
-

AI firm Vicarious cracks CAPTCHA codes
Publié: octobre 28, 2013, 4:09pm CET par Mark Wilson
 CAPTCHA are a thorn in the side of web users. Those almost indecipherable string of letters and numbers that are meant to help websites determine that you are a human rather than a spambot often cause more frustration for users than anything else, and they have now been cracked.
CAPTCHA are a thorn in the side of web users. Those almost indecipherable string of letters and numbers that are meant to help websites determine that you are a human rather than a spambot often cause more frustration for users than anything else, and they have now been cracked.Vicarious, a California-based AI team, reveals that it has been able to develop algorithms that can successfully solve CAPTCHAs from the likes of Google, Yahoo and PayPal.
The cracking of CAPTCHAs by machine is nothing all that new, but Vicarious is reporting an extremely high success rate -- the algorithm is successful in up to 90 percent of cases. The company goes as far as saying that "this advancement renders text-based CAPTCHAs no longer effective as a Turing test". The Turing test -- introduced by Alan Turing, one of the old-masters of computing -- was developed to test whether a computer could pass itself off as a human being.
The algorithms were not developed specifically with a view to cracking CAPTCHAs (which stands for Completely Automated Public Turing test to tell Computers and Humans Apart), but it is one of the capabilities of the Recursive Cortical Network (RCN) technology pioneered by Vicarious. The techniques used differ from other methods that have been used to bypass CAPTCHAs in the past.
Vicarious co-founder D. Scott Phoenix says: "Recent AI systems like IBM’s Watson and deep neural networks rely on brute force: connecting massive computing power to massive datasets. This is the first time this distinctively human act of perception has been achieved, and it uses relatively minuscule amounts of data and computing power. The Vicarious algorithms achieve a level of effectiveness and efficiency much closer to actual human brains".
This could have huge security implications although Vicarious is planning for its technology to be used in "robotics, medical image analysis, image and video search, and many other fields". Could this be the end of the CAPTCHA? What methods should we use next to prove that we're human and not an advanced computer?
Photo Credit: Maen Zayyad/Shutterstock
-

Samsung shows off its curves in new Galaxy Round ad
Publié: octobre 28, 2013, 1:12pm CET par Mark Wilson

Flat screens are so yesterday; curves are where it is at these days. Not content with constantly increasing the size of phone displays, handset manufacturers are now looking for a new twist. Both LG and Samsung have decided that curves are the way ahead. LG has officially announced the G Flex following on from the Galaxy Round that was revealed by Samsung just a few weeks ago, but it is the Samsung handset that is highlighted in a new ad.
As the Galaxy Round is destined for the Korean market, it should come as no surprise that the commercial is in Korean. This matters little as the looks of the phone speak for themselves. The advertisement demonstrates various curved objects that sit neatly in the hand to highlight that a great design decision has been made. Oddly, most of the objects shown -- an egg, a hand, a lemon, a glass -- are convex in curvature, so it's not really a direct comparison with how the handset will sit in the palm.
The Galaxy Round is curved differently to the G Flex. Both handsets have concave displays, but while the LG G Flex is curved along the short edges, Samsung has opted to curve the Galaxy Round along the length instead.
When Samsung's handset was unveiled a few weeks ago I asked whether curved screens are a gimmick or are genuinely useful. Now we have two handsets that are curved along different axis, the next question is... which is better, horizontal or vertical curving?
-

Social sharing service Buffer is hacked -- temporarily takes itself offline
Publié: octobre 27, 2013, 12:46am CEST par Mark Wilson

The latest web service to fall victim to a hack attack is Buffer, the social sharing tool that can be used to schedule posts to multiple social networks. Although it looks as though customers' passwords and billing details are safe, the problem was noticed late Saturday morning when spam type posts started to appear on users' Facebook and Twitter accounts. The Buffer team has been quick to take action and notified users via Facebook.
Buffer co-founder Leo Widrich posted saying "hey everyone! We greatly apologize for this big mess we've created. Buffer has been hacked." Shortly after this Facebook postings were disabled in a bid to stop the spread of spam and Buffer assured users that "We're continuing to work on this and trying to investigate and fix".
Buffer's Twitter feed is also being used to keep users up to date with what's happening, although at the moment it appears there is no word on the source of the problem or how many users have been affected. An email update was sent out to everyone who is signed up with Buffer and in it, "Joel and the Buffer team" explained a little about the situation:
"I wanted to get in touch to apologize for the awful experience we've caused many of you on your weekend. Buffer was hacked around 1 hour ago, and many of you may have experienced spam posts sent from you via Buffer. I can only understand how angry and disappointed you must be right now.
Not everyone who has signed up for Buffer has been affected, but you may want to check on your accounts. We're working hard to fix this problem right now and we're expecting to have everything back to normal shortly."
A Twitter update from Joel soon after this revealed that Facebook and Twitter access tokens had been compromised and an investigation is underway to determine how it happened. When things are back up and running, users will need to connect their Facebook and Twitter accounts to Buffer.
Were you affected by this? Did you notice spam posts being sent out on your behalf?
-

[Update -- fixed!] Social sharing service Buffer is hacked -- temporarily takes itself offline
Publié: octobre 27, 2013, 12:46am CEST par Mark Wilson

The latest web service to fall victim to a hack attack is Buffer, the social sharing tool that can be used to schedule posts to multiple social networks. Although it looks as though customers' passwords and billing details are safe, the problem was noticed late Saturday morning when spam type posts started to appear on users' Facebook and Twitter accounts. The Buffer team has been quick to take action and notified users via Facebook.
Buffer co-founder Leo Widrich posted saying "hey everyone! We greatly apologize for this big mess we've created. Buffer has been hacked." Shortly after this Facebook postings were disabled in a bid to stop the spread of spam and Buffer assured users that "We're continuing to work on this and trying to investigate and fix".
Buffer's Twitter feed is also being used to keep users up to date with what's happening, although at the moment it appears there is no word on the source of the problem or how many users have been affected. An email update was sent out to everyone who is signed up with Buffer and in it, "Joel and the Buffer team" explained a little about the situation:
"I wanted to get in touch to apologize for the awful experience we've caused many of you on your weekend. Buffer was hacked around 1 hour ago, and many of you may have experienced spam posts sent from you via Buffer. I can only understand how angry and disappointed you must be right now.
Not everyone who has signed up for Buffer has been affected, but you may want to check on your accounts. We're working hard to fix this problem right now and we're expecting to have everything back to normal shortly."
A Twitter update from Joel soon after this revealed that Facebook and Twitter access tokens had been compromised and an investigation is underway to determine how it happened. When things are back up and running, users will need to connect their Facebook and Twitter accounts to Buffer.
Update
Buffer is now reporting that the problem has been fixed and that security has been bolstered. The service is now operating as normal, but users will need to reconnect their Facebook and Twitter accounts.
Were you affected by this? Did you notice spam posts being sent out on your behalf?
-

RSS reader Feedly pushes preposterous pricing for Pro package -- $299!
Publié: octobre 27, 2013, 12:22am CEST par Mark Wilson

It is now four months since Google Reader shut up shop. At the time, Google cited a declining interest in the product and many people were quick to suggest that RSS was a technology past its sell-by date used by very few. But this seems to be contradicted by the staggering number of Google Reader alternatives that popped up to cater for the large numbers of RSS fans who bemoaned the loss of Google's tool.
One tool that quickly gained a large following is Feedly. In fact, so many people switched to Feedly that servers were unable to cope, and the service briefly collapsed under the weight of its own popularity. This was a temporary blip and things were soon back up and running. I was one of thousands of people who made the jump -- in fact I had a period of crossover using Feedly and Google Reader simultaneously to help ease the transition -- and things went fairly well.
Moving from one service to another is never easy. Feedly is not a replica of Google Reader and works in a slightly different way -- there is a slight learning curve and adjustment period. Like Reader, it is web-based but has APIs that can be used to access feeds through third party apps. Great stuff. Best of all it was free. All was (relatively) well with the world.
Back in August, Feedly Pro was introduced. This did not so much introduce new features, rather strip them out of the free version and ask users to pay for them. Searching for instance: something that is key to managing any large amount of information -- precisely the reason RSS exists. $5 a month, or $45 a year, also gained subscribers SSL, easy integration with Evernote and "premium support". A limited number of people were also able to snap up a $99 lifetime subscription.
Then the lifetime option vanished. But now it's back! There's a difference though -- the price has gone up a little. If tripling can be counted as "a little" that is. $299 for a lifetime subscription. Let me repeat that:
$299 for a lifetime subscription.
Break this down and you'll find that you do not start to benefit from this until you have been a Feedly user for more than six and a half years. At this point it works out cheaper than having opted for a regular $45 a year subscription.
But who is going to be willing to stake nearly $300 and gamble that the company is still going to be active nearly seven years down the line. Google Reader and some of the alternatives that aimed to replace it just go to prove that nothing is forever. Six and a half years is an incredibly long time in the internet world -- anything could happen and $300 is a big investment in such a transient market. On Twitter, Feedly claims that the lifetime subscription option was re-introduced "as a response to businesses asking simpler payment" (sic) -- it seems rather like an exercise in generating a quick income to me.
What does going Pro get you these days? In addition to new sharing options, a say in what features are added to future versions and full article searching, a Pro account also gets you Speed Boost -- faster updates. Pay up and your feeds are refreshed 30 percent faster than those using a free account. Feedly Pro also speeds up the update frequency for "smaller sites" so those feeds with "fewer followers" are updated four times faster. Fewer than what is not made clear.
It has been suggested that RSS is only used by journalists, bloggers and the news-obsessed. This is only partly true, but even if it was the complete truth it would still mean that a very large number of people are still reliant -- or at least keen on using -- RSS feeds. The nature of my work means that I am keen on top of news, but even if I was in a different job, I would be equally news obsessed.
I am starting to feel as though Feedly has taken advantage of Google Reader refugees. The regular, free accounts that drew people in to start with are becoming more and more limited as well as slower. It smacks of bad practice and I'm loathed to continue using the service. I would rather use something free, but I would be willing to pay for something I deemed worthy. Feedly keeps moving the goalposts, though, and this does not fill me with confidence.
How do you feel about RSS? Do you still use it? Does Feedly's Pro subscription model represent good value to money to you?
-

The most popular stories on BetaNews this past week -- October 20-26
Publié: octobre 26, 2013, 9:31am CEST par Mark Wilson
 Apple took center stage this week. At a special event the new iPad Air, iPad mini, Mac Pro and a raft of free software were all revealed, and we liveblogged through the whole thing. Not to be outdone by Microsoft, Apple decided to give Mavericks away free of charge along with iWork and iLife. But it was the iPad Air and mini that stole the show, sharing the same innards as the recently announced iPhone 5s, but boasting a redesigned exterior -- at least in the case of the Air.
Apple took center stage this week. At a special event the new iPad Air, iPad mini, Mac Pro and a raft of free software were all revealed, and we liveblogged through the whole thing. Not to be outdone by Microsoft, Apple decided to give Mavericks away free of charge along with iWork and iLife. But it was the iPad Air and mini that stole the show, sharing the same innards as the recently announced iPhone 5s, but boasting a redesigned exterior -- at least in the case of the Air.Of course, no tablet launch would be complete without matching cases. There was also the interestingly designed Mac Pro which looks delightful and is a serious powerhouse, but has a price tag to match. After the big launch of the iPhone 5s, Apple showed off the latest addition to the iPhone range in a TV commercial.
It has been a week of mixed fortunes for Microsoft this last seven days. After the launch of Windows 8.1, Internet Explorer 11 users were disappointed to find that Google was not working in the browser. A quick tweak saw that it was fixed, however. Surface RT users looking to upgrade to RT 8.1 had a slightly rough time and Microsoft ended up pulling the update from the Windows Store before quietly fixing the problem and re-issuing the update. We also showed you how to grab the Windows 8.1 ISO without the need for an MSDN subscription.
Surface 2 went on sale this week and Microsoft targeted musicians with the intriguing Surface Music Kit. The company also made a move to get rid of stock of the previous generation Surface Pro by dropping the price.
Google launched a series of tools aimed at promoting freedom of speech around the world while at the same time ruffling some feathers by experimenting with banner ads in search results. It was the end of an era as torrent website isoHunt shut up shop. In other online news Yahoo acquired image recognition startup LookFlow.
Despite later deciding to spend a week using only Microsoft products, Brian was more than a little impressed with the Acer C720 Chromebook.
Moving on to smartphones, Windows Phone users gained a new alternative browser in the form of Maxthon and Mihaita was keen to highlight why you might want to try out a Microsoft/Nokia handset. Following the release of Update 3 last week, new larger Windows Phone handsets were showcased. Nokia also unveiled its new Windows RT 8.1 tablet, the Lumia 2520. In a break from the norm, LG released its first Firefox OS phone, the Fireweb.
That's it for this week. The next seven days promise to be action-packed... there's a distinct possibility that Google may have a word or two to say about the Nexus 5. We have our ears to the ground.
Photo Credit: vinz89/Shutterstock
-

Google breaks its promise and experiments with banner ads
Publié: octobre 24, 2013, 1:08pm CEST par Mark Wilson
 Google's ad-supported model is one that we're now all familiar with. Spend any amount of time online and, unless you have installed some form of ad-blocker, you'll see text advertisements littering numerous websites you visit, including in your search results.
Google's ad-supported model is one that we're now all familiar with. Spend any amount of time online and, unless you have installed some form of ad-blocker, you'll see text advertisements littering numerous websites you visit, including in your search results.Sponsored search results are nothing new, but Google is now experimenting with large banner ads which show up when certain searches are performed.
A banner ad for Southwest Airlines was first spotted by web firm Synrgy who quickly shared the discovery on Twitter. The new ad program is being described as a "small experiment" and is currently only visible to a limited number of users in the US. Many of Google previous advertising models have been fairly unobtrusive, so this "experiment" marks quite a change in focus.
But more than that, the introduction of banner ads -- if it does become widespread -- would also be a u-turn for Google. Back in 2005, following a $1 billion investment in AOL, the search giant promised that banner advertisements would never appear in search results. The company could not have been much clearer in its wording: "There will be no banner ads on the Google homepage or web search results pages. There will not be crazy, flashy, graphical doodads flying and popping up all over the Google site. Ever".
The appearance of any banner advertising is clearly in direct opposition to the promise made eight years ago.

How do you feel about this? Have you spotted any banner ads yet?
Image Credit: Everett Collection/Shutterstock
-

Yahoo acquires image recognition startup LookFlow -- Flickr to benefit
Publié: octobre 24, 2013, 12:38pm CEST par Mark Wilson

One of Yahoo's most popular and successful products is Flickr. Adding to its list of acquisitions, the company is now taking LookFlow under its wing.
This California-based startup, which specializes in image recognition technology, is joining forces with Yahoo to "build a new deep learning group". It is likely that we'll see image based searching added to Flickr in the near future.
Yahoo has not released a statement of its own, but the LookFlow website has been taken offline and is now home to a message from the team: "We built LookFlow as an entirely new way to explore images you love -- combining delightful user experiences with the latest advances in machine learning. Flickr is the largest collection of images we love. They share our passion for creating phenomenal experiences & technology to help you discover those images".
It goes on to say: "We couldn't be more excited. Fret not, LookFlow fans. Keep an eye out for our product in future versions of Flickr -- with many more wonderful photos and all that Flickr awesomeness!"
It is not yet clear just what chances we can expect to see at Flickr, but there are certainly changes afoot.
-

Apple announces the thinner, lighter iPad Air and new iPad mini
Publié: octobre 22, 2013, 8:50pm CEST par Mark Wilson

It was a feature-packed morning of announcements where it seems as though Apple was going to give away everything for free. Sadly the freebies are limited to software and the new range of hardware has to be purchased in the regular way. The big news for tablet fans is the iPad Air. Borrowing its name -- in part at least -- from the MacBook Air range, thinner and faster are the adjectives of the day.
Phil Schiller said: "Thinner, lighter, more powerful than ever before, and incredibly, excitingly new that it deserves a new name: iPad Air". Boasting the same A7 processor as the recently announced iPhone 5s, the iPad Air is just 7.5mm thick and weighs 1 pound -- compare this to 9.4mm and 1.4 pounds for the previous model. Despite the thinner design and smaller battery size, we can still expect 10 hours of usage from the tablet which offers up to eight times the performance of the original iPad, and up to 72 times the GPU performance.
Silver and white, and space gray and black models are available from 1 November with prices starting at $499 for the Wi-Fi-only 16GB model. If you want a cellular data connection, the price jumps to $629. The iPad 2 remains on sale for $399.
The iPad mini is also sure to cause some excitement. This miniature model really is just a shrunken version of its bigger brother. The screen may be smaller but it is now a Retina display which boasts the same number of pixels as the iPad Air. Inside, there's the same A7 processor, up to four times faster graphics than its predecessor and the same 10 hour battery life.
The color choices are the same as with the iPad Air (silver and white, and space gray and black), and the 16GB Wi-Fi-only model starts at $399. The original iPad mini remains on sale for the reduced price of $299. It's still more expensive than the likes of the Nexus 7 and the Kindle Fire HDX, but the gap is closing.

-

Live Blog: Apple Special Event -- iPad 5, iPad Mini and more
Publié: octobre 22, 2013, 5:45pm CEST par Mark Wilson
 It's only a matter of weeks since the last big Apple event at which the iPhone 5s and iPhone 5c were announced. Today we have another event to look forward to and while we're not absolutely certain of what's going to be unveiled, the clever money is on the iPad 5, a new iPad mini, new Mac and release details for Mavericks.
It's only a matter of weeks since the last big Apple event at which the iPhone 5s and iPhone 5c were announced. Today we have another event to look forward to and while we're not absolutely certain of what's going to be unveiled, the clever money is on the iPad 5, a new iPad mini, new Mac and release details for Mavericks.Who knows… maybe there'll even be "one more thing"!
We'll be live blogging the announcements as they come. Things kick off at 1PM EDT/10AM PDT, and we'll be here until the end.
All updates will be in reverse chronological order (all times are EDT). The latest ones are first and first ones are last. You will need to hit the refresh button in order to see the newest updates.
2:22PM -- "We couldn't be prouder to present all of them to you in time for the holidays" -- I bet!
2:18PM -- Same colors as the iPad Air. Starts at $399 for 16GB model. Original iPad Mini still available for $299. Lots of covers to choose from. Why don't we see an ad for it, eh?

2:16PM -- Jonny Ive video out of the way... time to talk iPad Mini. As expected Retina display on the 7.9 inch screen. 2048 x 1556 pixels -- same as the iPad Air. Same processor too.

2:10PM -- Break out the stats. 7.5mm thick (thin)GPU 72x faster than predecessor. "Screaming fast". 10 hour battery life, 5MP iSight camera, new FaceTime HD camera, dual microphones, Siri. Silver and white / space gray and black. Starts at $499 16GB wifi, add cellular $629 - ships November 1. iPad 2 $399.
2:07PM -- Schiller breaks the news. iPad Air -- super thin, narrower bezel. Weighs in at a mere 1 pound. Same A7 processor as the iPhone 5s.

2:04PM -- Cook praises the creativity of iPad users. Hooray for tablet-fiends. Let's have a video to celebrate our awesomeness!
2:01PM -- iPad has a 81% share of the tablet market.
2:00PM -- One hour in and we're onto iPad. 170 million of them have been sold!
1:57PM -- Apple sticks two fingers up to Microsoft. iWorks and iLife are free and available today. "Biggest day ever for apps".
1:54PM -- iWorks demo. Even with the best will in the world, the demo projects look awful! We'll let them off as they're working live. Document collaboration is shown off -- again it's cringe-worthy stuff, but shows the potential for simultaneous working on files.
1:52PM -- Interactive charts is the only change that's mentioned. Keynote gains new transitions and effects.
1:50PM -- iWorks rewritten from the ground up for Mac. New UI in Pages makes formatting easier on iPad.
1:45PM -- GarageBand gets additional tracks and a new look -- up to 32 tracks on iPad. Everything syncs through iCloud. Cringe-worthy music demo time. But the app's free so that's great new -- available from today.
1:42PM -- App time. Eddy Cue shows off iPhoto. Photobooks come to iPad so you can design and order a printed photobook from your Apple tablet.
1:37PM --Rundown of endorsements for Mac Pro from industry professionals. Price is $2999 -- available by year end. May not be as quiet as a mouse, but it is as quiet as a MacBook Mini at 12dB.

1:33PM -- Now the trashcan-like Mac Pro. Fastest mac processor ever. Fastest memory - 1866MHz DDR3. Dual workstation graphics. Up to 12GB VRAM. Flash-based storage which is ten times faster than any hard drive. Thunderbolt 2 aids expandability.
1:30PM --15 inch model. Crystalwell quad-core process, but down to 8 hours battery life. $1,999 -- 2GHz, 8GB, 256 GB SSD. Available now.

1:27pm -- MacBook Pro updates. 13inch MacBook Pro now weighs just 3.46lb and is 0.71 inches thick. Iris graphics, Intel Taswell and up to 9 hours of battery life. Starts at $1299 -- 2.4 GHz, 4GB 128GB SSD.
1:25PM -- Download now! It's free! Works with Mac back to 2007, can even upgrade from Snow Leopard.
1:24PM -- Mavericks is FREE!
1:23PM -- Quick demo of maps and demo is done.
1: 21PM -- Changes to Safari - top sites reader view, accelerated scrolling.
1:19PM -- Oh the hilarity! Notification from wife about untucked shirt. Reply from the notification. Nice.
1:18PM -- Interactive books including videos in iBooks. Demo of tags -- just in case you couldn't work out how to use them.
1:16PM -- Tags in Finder. Better notification system. New apps -- maps with multi-touch, turn-by-turn directions. Demo time!
1:12PM -- Mavericks; Craig Federighi waxes lyrical. Highlights improved battery life and memory usages.
1:11PM --Cook describes competition as confused. Swipe at Microsoft for making tablets into PCs and PCs into tablets. Apple, however has direction and has products to show off.
1:10 PM -- More facts and figures. Over a million apps in the App Store with more than 60 billion downloads.
1:08PM -- iOS 7 is the biggest software launch ever. 64% of iOS devices are running the latest version.
1:06PM -- more indulgence as video of the iPhone launch day is shown.
1:04 PM -- Tim Cook is excited. Apparently. Quick recap of what's happened over the last few weeks with the iPhone range. Biggest iPhone launch ever. Back-slapping all round.
1:02 PM -- Lovely twinkly piano. Tron-esque dots and lines make up a monochromatic intro.
1:00 PM -- "If everyone is busy making everything how can anyone perfect anything?"
12:58 PM -- As per Apple's request, our phones are now set to silent mode as we await the fun that's to come.
12:10 PM -- We don't have much to go on yet. Invites for the event are swathed in pastel colors. The tag line is "We still have a lot to cover". Are we looking at a range of iPads in different colors, or could the rumored Surface-style cover be one of the things that's under wraps? Less than an hour until we find out!
-

Microsoft pulls Windows RT 8.1 update from Windows Store
Publié: octobre 19, 2013, 9:17pm CEST par Mark Wilson
 Just about everyone with a desktop, laptop or even a Surface Pro running Windows 8 has been busy updating to Windows 8.1 over the past couple of days.
Just about everyone with a desktop, laptop or even a Surface Pro running Windows 8 has been busy updating to Windows 8.1 over the past couple of days.But things aren’t so rosy for anyone with a Surface RT. After a number of users took to Microsoft forums to complain about problems updating their tablet/laptop hybrids to the latest version of Windows, the update was pulled from the Windows Store.
Moderators explained the removal of Windows 8.1:
Windows RT 8.1. Microsoft is investigating a situation affecting a limited number of users updating their Windows RT devices to Windows RT 8.1. As a result, we have temporarily removed the Windows RT 8.1 update from the Windows Store. We are working to resolve the situation as quickly as possible and apologize for any inconvenience. We will provide updates as they become available.
The problems come as something of a blow to Microsoft which has been enjoying positive feedback and pushing the operating system update in a couple of new ads. It's not clear how many people have been affected by the issue, but Microsoft is likely to be breathing a sigh of relief that it is only the RT variety of 8.1 that is proving problematic as usage levels are far lower than regular Windows.
No detailed explanation has been given, but if there is any further news, we'll update this post accordingly.
Have you had trouble updating your copy of Windows RT? Take some comfort in the fact that Microsoft is looking into it.
-

The most popular stories on BetaNews this past week - October 13 -- 19
Publié: octobre 19, 2013, 1:03pm CEST par Mark Wilson
 This was another week in which Microsoft managed to steal the show, this time with the public release of Windows 8.1. Here at BetaNews we were fully prepared for the upgrade and showed off what's new. While we're generally impressed with the update, there's still a little room for improvement. Of course the Start menu (or lack thereof) is still a sticking point, but you can get this back. The operating system update was preceded by a raft of updates to Window's built in apps.
This was another week in which Microsoft managed to steal the show, this time with the public release of Windows 8.1. Here at BetaNews we were fully prepared for the upgrade and showed off what's new. While we're generally impressed with the update, there's still a little room for improvement. Of course the Start menu (or lack thereof) is still a sticking point, but you can get this back. The operating system update was preceded by a raft of updates to Window's built in apps.Windows 8.1 may be where it's at right now, but there are still plenty of people running Windows XP. Google announced that Chrome users on XP would be supported for a year after the OS is retired.
Anyone in the market for a new portable computer might be considering a Surface 2, or Surface Pro 2 to run Windows 8.1 should be aware that these are two very different beasts as one runs Windows RT, although this may not be immediately obvious to everyone.
This was not the only release from Microsoft this week. Just days after celebrating the third birthday of Windows Phone, Update 3 (formerly GDR 3) was released. There was nothing groundbreaking to be found, but this was already expected, and we installed it as soon as was possible. The freebies from Microsoft didn’t end there -- it was also announced that students will be able to get their hands on Office 365 completely free of charge from December.
A final software release saw an update to Visual Studio being made available at a time-limited low price. There's not long to go until the Xbox One is launched, and Major Nelson himself showed off some of the upcoming gaming hardware. In other Microsoft news, BetaNews was issued with a DMCA takedown notice for linking to old software on the Microsoft website.
OS releases were not limited to Microsoft: Ubuntu 13.10 Saucy Salamander was also unleashed onto desktops and mobiles. Microsoft decided to make it easier to access Windows PCs from Android and iOS devices with its mobile Remote Desktop apps.
Not wanting to be left out of the burgeoning phablet market, HTC unveiled the latest addition to the One range: the HTC One Max. This 5.9 inch monster retains the look of the original device and borrows the fingerprint reader idea from the iPhone 5s. Other hardware of note from this week included the Lenovo Miix 2, a tablet which includes full-blown Windows 8.1 for just $299 -- no sign of RT here. Brian was impressed with the LG G2.
The keenly anticipated Nexus 5 was, whoops! accidentally-on-purpose (?) revealed in Google Play only to quickly disappear. Amazon started shipping the 7-inch Kindle Fire HDX some time after it had been announced. Apple noticed that some drives in MacBook Airs were at risk of failure, and issued a recall.
In the online world Twitter decided that DMs should be made available to everyone while music streaming service Rdio branched out into videos with a documentary. Yahoo decided to catch up with other email providers and make HTTPS enabled by default. To tie in with the release of Windows 8.1, a Facebook app was finally released for Microsoft's desktop OS.
Stay tuned over the next seven days, they're sure to be busy. We might hear something more about the Nexus 5 from Google, and Apple has an event on Tuesday which is likely to include new iPads, new MacBook Pros and availability info for OS X 10.9 Mavericks...
Photo Credit: vinz89/Shutterstock
-

Microsoft uses DMCA to force BetaNews and others to remove old software listings
Publié: octobre 19, 2013, 12:29am CEST par Mark Wilson

Microsoft is using an interesting technique to ensure that websites such as BetaNews (or FileForum in particular) list only the latest versions of its software. Rather than just contacting websites who link to software that is no longer available, Microsoft is invoking the Digital Millennium Copyright Act (DMCA) to force websites to remove the links. BetaNews has been contacted by Google after one such complaint from Microsoft.
In the complaint -- which can be read on the Chilling Effects website -- Microsoft refers to our listing for Microsoft Project (although the page is no longer live). Microsoft contacted Google who in turn contacted us to say that "Google has been notified, according to the terms of the Digital Millennium Copyright Act (DMCA), that some of your materials allegedly infringe upon the copyrights of others".
Google goes on to say that "we are in the process of removing from our Google Search results the materials that allegedly infringe upon the copyrights of others". In this instance the FileForum listing for Microsoft Project simply linked to a Microsoft page -- one that also no longer exists. So why the takedown notice? Why go down a legal route rather than simply making contact?
It's understandable that Microsoft wants to promote its latest software, but to suggest that a page linking to the original product page for an older version of software is copyright infringement makes little sense. It smacks of forcing the hand of website owners. There are plenty of instances of copyright infringement for which the DMCA is entirely applicable, but to use legal measures to block pages featuring links to non-existent software would not appear to be one of them.
The quicker, easier, cheaper and -- and, frankly, friendlier option -- would have been to make direct contact with us and ask for an updated link to be posted, or to set up a redirect that automatically took visitors to the page for the latest version of Microsoft Project. Forcing websites to link to the most recent version of an application or none at all is not what the DCMA was designed for.
Image Credit: Africa Studio / Shutterstock
-

Apple starts recall of MacBook Air flash storage drives
Publié: octobre 18, 2013, 6:10pm CEST par Mark Wilson
 Apple is recalling 64GB and 128GB flash storage drives after discovering that the units are at risk of failure. Affected system were sold between June 2012 and June 2013, and there is a free replacement program in operation for anyone who finds they have one of the potentially failure-prone drives. There is a firmware update available that can be used to determine whether or not your MacBook Air is affected.
Apple is recalling 64GB and 128GB flash storage drives after discovering that the units are at risk of failure. Affected system were sold between June 2012 and June 2013, and there is a free replacement program in operation for anyone who finds they have one of the potentially failure-prone drives. There is a firmware update available that can be used to determine whether or not your MacBook Air is affected.A MacBook Air Flash Storage Drive Replacement Program has been set up and this directs MacBook Air owners to download a firmware update from the Mac App Store. The MacBook Air Flash Storage Firmware Update 1.1 can be used to test your drive and, if necessary, you'll be redirected back to the replacement program page.
It's not clear quite how many units could be affected, but an entire year's worth of MacBook Airs means that there could be a large number of people at risk of losing their data. For anyone who finds that their drive is one of those that may fail, a free replacement is available from Apple stores or authorized service providers.
Apple is clearly taking the matter seriously, and the announcement includes a stark warning:
"If your drive is affected, we strongly recommend that you do not install any operating system updates or new applications. We also recommend backing up your data on a regular basis until you receive a replacement drive."
So if you're a MacBook Air owner, head to the Apple website to see if you need to do anything.
Image Credit: NatUlrich / Shutterstock
-

Google shows off $349 Nexus 5 in Play store -- for a few minutes, anyway
Publié: octobre 18, 2013, 3:55pm CEST par Mark Wilson

Google's Nexus 5 is a hotly anticipated handset, and over the past few weeks there have been numerous leaked images purporting to show what the device looks like.
Now it looks as though the speculation can come to an end after Google accidentally listed the device in the Play store, complete with pricing details. The temporary listing -- which has now been removed -- showed the 16GB model costing $349, and featured the tagline "capture the everyday and the epic in fresh new ways".
The "accidental" listing may not have been live for long, but it was up long enough for screengrabs to be captured and full sized images to be downloaded. These were quickly shared on Twitter by many people including Marques Brownlee. The listing itself did not give away much, but the image does seem to show that Android KitKat 4.4 has a new camera and folder icon -- it's interesting to note that the clock is set to 4:40.
Google has been something of a leaking bucket recently, with all manner of rumors about the upcoming mobile circulating around online. At this stage we're still not even sure quite when the official release date is, but it is almost certainly just around the corner now. Whether the Google Play listing of the Nexus 5 was an accident or part of the advertising hype is not clear, but the Google+ page for KitKat has been teasing followers for the last few days as well.
 On Tuesday 15 October, a date that many had thought may have seen some sort of announcement, a photo was posted with the caption "Everybody dance now!" -- seemingly a reference to the C&C Music Factory hit released on 18 October 1990 (and a song that was 4 minutes and 4 seconds long). The following day, a photo of the words "This is it" was posted with the caption "Sometimes you have to look for the signs…". This could be a reference to Michael Jackson's This Is It movie which has a 28 October release date. But then there's the album of the same name that came out on the 26th!
On Tuesday 15 October, a date that many had thought may have seen some sort of announcement, a photo was posted with the caption "Everybody dance now!" -- seemingly a reference to the C&C Music Factory hit released on 18 October 1990 (and a song that was 4 minutes and 4 seconds long). The following day, a photo of the words "This is it" was posted with the caption "Sometimes you have to look for the signs…". This could be a reference to Michael Jackson's This Is It movie which has a 28 October release date. But then there's the album of the same name that came out on the 26th!It's all too much to deal with! It looks as though we may now know the starting price for the Nexus 5, but we're still a little in the dark about when we might get it. But in the meantime, Google is doing an excellent job of keeping interest levels high... it's certainly working on us!
How about you? Are you looking forward to the Nexus 5 and KitKat?
-

Microsoft brings Windows to Android and iOS phones and tablets
Publié: octobre 17, 2013, 11:52pm CEST par Mark Wilson
Microsoft's big release of the day may be Windows 8.1, but it doesn't end there. The desktop operating system may have stolen the headlines today, but Microsoft also recognizes the importance of mobile devices. The company is not only concerned with its own devices, realizing that Apple and Android still dominate the mobile arena. But this does not mean that mobile users do not need access to Windows PCs -- hence the release of Microsoft Remote Desktop for iOS and Android.
The prospect of running Windows on an Android or iOS device may be a little way off yet, but it can be achieved via remote access -- which has the handy side effects of making it possible to access files, apps and anything else that might be needed whilst away from your computer. There is no shortage of remote desktop apps in the App Store, but Microsoft's offering aims to keep things simple. As you would expect, this is an app -- free of course -- that can be used to control a Windows PC from an iPhone, iPad, iPod touch or Android device.
Weirdly, there is no Windows Phone version yet, but if you are an Apple or Android owner, you're in luck. Using the remote desktop protocol means there's no need for extra software to be installed on the desktop machine, you just need to know the IP address in order to establish a connection.
That feature list in full:
- Access to remote resources through the Remote Desktop Gateway
- Rich multi-touch experience with remote desktop protocol (RDP) and RemoteFX supporting Windows gestures
- Secure connection to your data and applications with breakthrough Network Layer Authentication (NLA) technology
- Simple management of all remote connections from the connection center
- High quality video and sound streaming with improved compression and bandwidth usage
- Easy connection to external monitors or projectors for presentations
So if you fancy the idea of controlling your PC from your phone or tablet (or you have a need to), take this app for a test drive and see how it compares to the myriad remote access apps there are to choose from.
-

What's still wrong in Windows 8.1
Publié: octobre 17, 2013, 12:54pm CEST par Mark Wilson

Before you recoil, a brief disclaimer. I love Windows 8.1. In its own right, it is a great operating system, and a massive jump forward from Windows 8. There have been lots of little changes and additions -- and some not so small -- that have collectively transformed Windows 8 into something that can be taken seriously. But it's not perfect. Microsoft has taken steps to address the concerns of users moving from Windows 7 and earlier, but there is still room for improvement.
A gripe of mine -- and one shared by many people -- is the existence of the Modern UI. While it may make sense on dedicated tablets, for desktop users, it creates an odd, disjointed experience. Microsoft has seen fit to make it possible to boot straight to the desktop so you would think that if you were not a fan of the Modern UI, it would be possible to avoid this side of things completely. But no.
Double click an image and it defaults to opening in the image viewer app. Why? The same is true for other file types, even if there is a built in desktop app. Being able to avoid the Start screen at boot is a good start, but there needs to be a "just bloody well disable everything related to Modern UI" setting. I'd enable it in a heartbeat.
The Windows Store does little to promote apps. The Store is much maligned for its range, breadth, depth and quality of apps. Sure, the accusation of having a lot of crappy apps is one that could be levelled at any operating system -- Windows Phone, iOS, Mac and Android stores are all guilty -- but the ratio of good to bad is worryingly low. This is obviously a subjective opinion to some extent, but the high number of incredibly low scores awarded to apps seem to back it up.
System settings could do with an overhaul. They are all over the place at the moment. There are three different sections available in the Charms bar that can be used to change settings: Control Panel, Personalization and Change PC Settings. Users shouldn’t need to remember where a particular setting needs to be changed -- this is why the Control Panel is divided up into a number of applets. There's no need to break things up further.
Shutdown should be easier to access. Closing down Windows through the Charms bar is just convoluted and strange, but there's a new option now. Right click on the Start button and select the option you need from a sub-menu. Right click? That's something reserved for access to more obscure settings, it's not something many people ever do. And why make that menu so ugly? For shutting down you're given two choices: the nice looking Modern way that takes a swipe followed by three taps, or the ugly way which is quicker, but will seem alien to a lot of users.
This next one is a minor gripe. Windows Experience Index. Why remove it? Why? It wasn't doing any harm. Yes, it wasn't the most in-depth benchmarking tool ever invented, but it was reassuring to see that Microsoft was giving your setup a stamp of approval and good to see what was holding back optimum performance.
Despite my dislike of the Modern UI, I often have occasional reason to use the Charms bar. A degree of transparency would be nice here to avoid hiding what's going on on-screen. And what’s the point of the huge pop up date and time panel? As we're back on the subject of Modern UI elements, let's just admit that the Start screen is awkward, right? All that screen space and yet it's still necessary to scroll to see everything that's installed? Makes no sense. The Start menu made sense. The menu opened up to submenus so you could drill down to what you needed quickly and easily. Now whenever I find I need to launch an app I've not pinned to the taskbar, I have to play the "hunt the shortcut" game. Silliness.
Despite all this, I still love Windows 8.1. It has been installed as my main operating system from the moment preview versions were made available. Microsoft has listened to its customers, and I hope it will continue to do so. I look forward to seeing what Windows 8.2 has to offer. Are you happy with the way things have ended up, or do you think there's still room for improvement?
-

Facebook releases official app for Windows 8.1
Publié: octobre 17, 2013, 12:11pm CEST par Mark Wilson
Facebook fans running Microsoft's tiled OS need no longer turn to third party solutions -- the official Facebook app is now available in the Windows Store.
It has been a very long time coming, but the social network finally has its own official app, arriving just in time for the release of Windows 8.1. The app has the look and feel of Modern UI apps and includes a live tile that is used to display updates.
The app itself is a fairly simple affair, with the interface divided into three sections. It will look familiar to anyone who has used mobile versions of the app before, with links to different sections of your account appearing in a sidebar to the left of the screen -- the same sidebar that slides out from the left in mobile versions. To the right, you'll find the chat sidebar while the central section is occupied by your newsfeed.
It is possible to have the app running in the background at all times so you can receive notifications of messages and events as you get on with other things.
Being a Modern UI Windows 8.1 app, there's support for Snap view so status updates can be seen as you work in desktop apps. There are no settings to choose from within the app. If you try to visit Account Settings or Privacy Settings you'll be taken out of the app and transported to the Facebook website.
You need to be running the RTM version of Windows 8.1 (or the full version when available) if you want to install the app. Grab yourself a copy of it from the Windows Store.
-

Windows XP users get a year of Chrome support after OS retires
Publié: octobre 16, 2013, 6:05pm CEST par Mark Wilson

It has served us well, but Windows XP is now considerably into old age; it's time to be put out to pasture. Microsoft is retiring the game-changing operating system on 8 April 2014 but this does not mean that people will not try to hang onto their beloved operating system for as long as possible.
One issue that XP diehards are going to face is support for apps. This is an old operating system, and it's not really reasonable to expect software manufacturers to keep pumping out new releases and updates. But just how long can you expect to receive updates and support? Google has nailed its colors to the mast in announcing that Chrome for XP will be supported for at least a year after Windows XP is retired.
In a blog post, Mark Larson, Director of Engineering and Superintendent of Public Safety for Google Chrome says: "We recognize that hundreds of millions of users, including a good chunk of current Chrome users, still rely on XP. Moreover, many organizations still run dozens or even hundreds of applications on XP and may have trouble migrating. Our goal is to support Chrome for XP users during this transition process. Most importantly, Chrome on XP will still be automatically updated with the latest security fixes to protect against malware and phishing attacks".
Are you one of the people who will cling onto Windows XP until the bitter end? What happens when Chrome is no longer supported and updated -- are you happy to keep using an unpatched browser?
Image Credit: JohnKwan /Shutterstock
-

Yahoo realizes it’s the 21st century -- plans HTTPS as default for Mail
Publié: octobre 15, 2013, 10:49pm CEST par Mark Wilson
 Email encryption for Yahoo Mail may not seem like major news. In fact, Yahoo introduced the use of HTTPS as an option earlier in the year. This was not only several years after the likes of Gmail and Hotmail (and now Outlook.com), but also an optional security feature. But now security campaigners can breathe a sigh of relief; in just three short months, email encryption will be enabled by default in Yahoo Mail.
Email encryption for Yahoo Mail may not seem like major news. In fact, Yahoo introduced the use of HTTPS as an option earlier in the year. This was not only several years after the likes of Gmail and Hotmail (and now Outlook.com), but also an optional security feature. But now security campaigners can breathe a sigh of relief; in just three short months, email encryption will be enabled by default in Yahoo Mail.The news comes from Jeffrey Bonforte, SVP of Communication Products who says in a blog post that "at Yahoo, we take the security of our users very seriously". It will come as great news to not only Yahoo users, but also the Electronic Frontier Foundation (EFF) who wrote a letter to Marissa Mayer back in November expressing their concerns about the (then) absent HTTPS option.
It is already possible to force the use of SSL encryption, but as of 8 January 2014, the option will be enabled by default.
"Starting January 8, 2014, we will make encrypted https connections standard for all Yahoo Mail users. Our teams are working hard to make the necessary changes to default https connections on Yahoo Mail, and we look forward to providing this extra layer of security for all our users."
In the meantime, if you want to help to increase your security, don’t forget that you can head to the Security section of your account settings and select the Use SSL checkbox.
Image Credit: ktsdesign / Shutterstock
-

At what age should children be allowed to use the internet?
Publié: octobre 15, 2013, 10:27pm CEST par Mark Wilson

The internet is an amazing tool, especially for children looking to learn. It is essentially the world's biggest library available 24 hours a day, seven days a week. But the web also has a darker side, and parents have to ask themselves the question "when is the right time to let my child go online?" Or, as Director of Online Safety at Microsoft, Kim Sanchez puts it "How old is too young to go online?".
This is a far more complicated problem than it used to be. It is not all that long ago that the average household had no more than one computer, which may not have been connected to the internet. Now, however, we live in a time when households could have multiple computers. There might still be one shared "family" computer, but it is also very common for children to have their own computer or laptop. There are also phones and tablets to think of. Pester power is an incredible thing, and it’s a strong parent who is able to resist giving into demands for a tablets when "all my friends have one".
Parents do have a very tricky balancing act to perform. On one hand it would be foolish to deny a child access to the most valuable educational resource available, but on the other, particularly with younger children, it is something that has to be monitored. Everybody is busy nowadays, and this is certainly true for parents. How many people with children have the time to sit down with their offspring as they do their homework online, ensuring that they don't stray from the beaten track? Some do, but far more are just not able to.
For those times when parents are not able to supervise computer usage, software solutions are available -- Windows includes Parental Controls for instance. But this does not really help with the problem of ensuring that children know how to use the internet "properly" and safely. Kim Sanchez's blog post puts forward some simple tips to help keep children safe online.
According to research carried out by Microsoft, 94 percent of parents permit their children to use one or more online device or service. The average age at which parents said they were happy for independent, unsupervised internet access is a slightly surprising eight years old. How does this fit in with your thinking? With the right education, do you think this is an acceptable age for children to be let loose online?
29 percent of parents said they would allow their children to use a mobile phone without supervision, while 40 percent were happy with the idea of unsupervised computer use. The survey found that people without children of their own expressed stricter views than parents -- 19 percent of parents of children aged between seven and 10 were happy for them to use social networks, compared with eight percent of non-parents.
If you fancy taking the survey for yourself, head over to the How Old is Too Young To Go Online website.
As a non-parent, I do find it hard to know quite where to fall with this. I am of the firm belief that education, as ever, is the key to success. A combination of schools and parents have a responsibility to teach children not only how to use the internet, but how to do so safely. I'd be interested in hearing your thoughts.
Image Credit: Pressmaster / Shutterstock
-

Twitter now allows you to receive DMs from anyone
Publié: octobre 15, 2013, 3:06pm CEST par Mark Wilson
 Twitter is changing the way direct messages work. Up until now DMs could only be exchanged between people who were following each other. But now all that changes as Twitter is making it possible for users to opt to receive direct messages from any of their followers, regardless of whether they are following them in return.
Twitter is changing the way direct messages work. Up until now DMs could only be exchanged between people who were following each other. But now all that changes as Twitter is making it possible for users to opt to receive direct messages from any of their followers, regardless of whether they are following them in return.The setting is switched off by default, but once enabled you can receive direct messages from any one of your followers.
It's a feature that is gradually rolling out, but if you head to the Settings and look in the Account section, you'll see -- or will soon see -- a new setting labelled "Receive direct messages from any follower". This might sound reasonably self-explanatory, but the description lets you know exactly what this means: "Generally, you must follow someone before they have the ability to direct message you. If you check this option, any Twitter user that follows you will be able to send you a DM, regardless of whether you decide to follow them back".
The whole idea of Direct Messages is that it allows private conversations to take place between people who know each other. Rather than using the @name method of mentioning people which will then show up publicly for anyone with access to your timeline to see, DMs are kept off the record. You indicate your willingness to receive direct, private messages from your followers by following them back. What could be simpler? Why change it?
On one hand it makes it easier for companies to exchange messages with customers via Twitter without having to do so publicly. On the other, it is also open to abuse. If you opt to enable the setting, it is quite likely that you will soon by followed by a raft of companies who will deliver spam straight to you via direct message.
Do you have this new setting yet? Is it a feature you'll be enabling, or do you fear it will open the floodgates for unwanted messages?
Photo Credit: Anke van Wyk/Shutterstock
-

The most popular stories on BetaNews this past week: October 6 -- 12
Publié: octobre 12, 2013, 12:57pm CEST par Mark Wilson
 In another busy week, Microsoft continued to promote Internet Explorer 11 by showing off some of the new features that will be available to Windows 8 users. At the same time, the company released a tool that lets Windows 7 users block the update. Microsoft also announced that it would speed up the approval process for apps submitted to the Windows Store, so initial certification can be complete within five days.
In another busy week, Microsoft continued to promote Internet Explorer 11 by showing off some of the new features that will be available to Windows 8 users. At the same time, the company released a tool that lets Windows 7 users block the update. Microsoft also announced that it would speed up the approval process for apps submitted to the Windows Store, so initial certification can be complete within five days.Moving away from the desktop, champagne corks were popping as it was revealed that Raspberry Pi has sold 1.75 million units. After the launch of Mavericks, Mihaita was taken with his MacBook Air, and I was quite impressed with the Tesco Hudl -- although it's not going to be replacing my Nexus 7 any time soon.
Security companies AVG and Avira were both left licking their wounds after their websites were hacked and replaced with pro- Palestine messages. These are two companies more used to helping keep computer users secure, while Adblock Plus's aim is to help strip out the ads to make being online a more enjoyable experience. For the first time, the company explained a little about how its whitelisting process works. Staying with the online theme, Amazon launched a new payment scheme "Login and Pay with Amazon".
There was quite a lot happening on the hardware front this week as well. Acer announces the C720 Haswell Chromebook to rival the new Chromebook 11. There are interesting things in store for mobile devices as LG mass-produces flexible displays for the first time, while Samsung launched a curved-screen phone in Korea. T-Mobile decided to slash the costs of travelling abroad with a phone by giving customers free global data and texts. We don't know exactly what it is yet, but Lenovo is teasing us with a new ad campaign that promises a #betterway for tablets.
A new Auzre-based personalized radio service emerged in the form of Omny, but if TV is more your style, celebrate in the fact that HBO has now come to Google Play. While you're busy streaming music and video, give a thought to people in parts of the world where internet access is prohibitively expensive. This is something the Alliance for Affordable Internet wants to rectify. Sticking with the online theme, Microsoft started a push in the UK to promote Bing, suggesting that it is more popular than Google.
Google Maps regains multi-destinations in a move that will please people who were confused by the removal of this feature, and in an on-going saga, the YouTube app was removed from the Windows Phone Store... again. In a side note, happy birthday to Windows Phone, which celebrated its third anniversary this week, while Microsoft updated the Outlook Android app, adding server-side searching, alias support and more.
It's not long since GTA V was released, but the game has already broken seven world records. If your idea of entertainment is listening to music rather than stealing cars, the BBC's launch of Playlister may be of interest. The new service makes it possible to tag music tracks you listen to on a radio stream and then create a printable playlist, complete with track and artist details. If TV's more your kind of thing, Twitter and Comcast's See It service can be used to set program reminders via tweets.
What will the next seven days hold? Only one way to find out… sit back and wait while the week comes right at you!
Photo Credit: vinz89/Shutterstock
-

Happy birthday Windows Phone! 3 years old today!
Publié: octobre 12, 2013, 12:13am CEST par Mark Wilson

It is three years ago today that Windows Phone first saw the light of day. Microsoft's mobile operating system has now been with us for a full 36 months, when Windows Phone 7 took the baton from Windows Mobile. There isn’t much in the way of celebration from Microsoft, and the anniversary was quietly ushered in by the company's Joe Belfiore in a tweet:
Happy Bday, "MetroUI"! 3 yrs ago today WP7 launched. In just a few countries on just one chip with only a handful of apps...
The move from Windows Mobile to Windows Phone was about much more than just a new name; it also heralded the arrival of the MetroUI. This interface developed over the years and is still to be found in Windows Phone 8 as well as other Microsoft products such as Xbox, Office and, of course Windows 8 -- albeit under the new moniker of the Modern UI.
The operating system has its lovers and its haters, but there is no denying that Windows Phone is incredibly significant. It has come a long way in three short years, and there are sure to be great developments ahead -- including the possibility of running on tablets.
Windows Phone... we raise our glasses to you.
Image Credit: Robyn Mackenzie / Shutterstock
-

Skin and protect your Nexus 7 [Review]
Publié: octobre 11, 2013, 1:39pm CEST par Mark Wilson
The Nexus 7 has gone down well with the team here at BetaNews (despite a few teething problems) and it's proving popular with a lot of other people as well. Part of the tablet's appeal is that it offers great value for money. But just because something is relatively cheap, it does not mean that it should not be looked after.
Whatever phone or tablet you have, there are countless protective skins to choose from and also various ways in which to stamp your mark on your mobile device. With a couple of Nexus 7's (Nexi?) to take care of, I thought I'd take a look at some of the options that are available. The official sleeve has been available for a while and the official case has been unveiled. At $50 it's worth seeing what else is out there as well.
Poetic GraphGrip -- $14.95

The GraphGrip is available in six colors in total, including a fairly unpleasant pink. I opted to look at the rather more stylish, and Goth-friendly, black. This is a simple silicon case that envelopes your Nexus and is robust enough to offer protection against bumps and drops. The screen is left exposed but the front ridge is big enough to largely avoid scratches should the tablet land facedown.
All of the ports are freely accessible and the GraphGrip feels great in the hand. It does not add too much weight or bulk, but being silicon does mean that it has a grippy, rubbery feel to it that make slipping in an out of a bag or pocket a little awkward.
MiniSuit Keyboard Stand Case -- $24.95

When looking at this particular case, my first experience was not great. For some reason the wake/sleep function was not working -- I tried it with two Nexus 7s, both of which worked just fine with other cases -- but the replacement functioned as it should.
Once up and running with the case, it feels like taking a step back in time. The fat leather case is reminiscent of 1980s business organizers -- it's good-retro and bad-retro at the same time. And another thing… it's big. Your Nexus just about triples in thickness, and the other dimensions are rather extended as well.
At least part of the reason for the extra bulk is the inclusion of a Bluetooth keyboard. This is not unpleasant to use, but it's not the best keyboard in the world by any stretch of the imagination. The keyboard itself sits on a separate leather base which can be removed from the case if required, but is held in place with magnets when it is in position.
There's a pop-out stand on the back to prop up your tablet for a decent viewing angle, but there's no room for adjustment. The Nexus can be tricky to use in the case as the leather hold area has a tendency to get in the way a little, making it hard to use the very edge of the touchscreen. All that leather simultaneously gives the case a quality feel whilst making you feel a little like a "stereotypical 1980s businessman". It does the job fairly well though -- function wins over style here.
Poetic SlimLine -- $16.95

This is actually the case I have ended up using the most, despite the fact that it is probably the cheapest looking of the bunch. As the name would suggest, what the case has in its favor is its svelteness -- it adds just a few millimeters to the thickness of the tablet.
This is a magnet case which wakes and sleeps the Nexus inside as it is opened and closed. There are three magnets that snap the cover into place, but these do not run down the full length of the open edge, just the bottom half. You might think that this is a slight oversight, but in fact it makes the case easier to open. The top right edge has just enough movement to it to make it easy to flip open with a finger.
The portion of the case that the tablet fits into is pleasingly sturdy. This hard section feels robust and grabs onto the Nexus with reassuring firmness.
The cover doubles as a stand so your Nexus can be propped up for watching videos or typing. But what lets the case down is the material. While it is entirely functional, it looks and feels very cheap. It put me in mind of old plastic coated notebooks from the 1980s -- or maybe even 1970s! Luxury is certainly not the word.
dbrand Skins -- $20

If you're more interested in changing the look of your tablet than keeping it protected, a skin may be what you're looking for. Dbrand has a series of colored, metal-effect, wood-effect and carbon fiber skins to choose from. There are versions available for numerous phones and tablets and each is precision cut with apertures for earpieces, speakers, cameras etc.
With 15 different designs to choose from, you should be able to find something you like, but be warned: getting the skins installed is not a ten second job. The skins are described as having "the most precise fit on the market". This means that you have to take great care to line everything up correct before sticking the skin in place -- there's even a video to guide you through the process!
Once the adhesive has made contact, the skin is secured in place by heating with a hairdryer. This is a little disconcerting and another time you'll need to take care with these skins -- no one wants to melt their tablet!
The skins do offer a little protection, but only really to the front and back -- the sides do not get a look in. The screen is very slightly protected due to the thickness of the skin, so you could place your Nexus facedown on a flat surface without risk of scratching. Overall, the look is pretty good, but installation is fiddly, and protection levels are low.
Poetic StrapBack -- $19.95

This is another relatively slim case which again offers sleep/wake support. This time, however, the cover is held in place with a clip rather than magnet -- it feels solid, but it's also slightly annoying and it means it's not possible to flick the case open quite so quickly and easily.
Why the name? Open the cover all the way and there's a strap you can slip your hand through to help avoid dropping your tablet. The case itself has a cotton fibre exterior and brushed cotton finish on the inside. Oh, and there's a pen holder too, weirdly. Maybe it's for a stylus, but the Nexus 7 doesn’t come with one.
The StrapBack's nifty secret extra is the way it doubles up as a stand. The portion of the case that the Nexus clips into folds in half. This allows the tablet's left hand edge (of the bottom as it will become in landscape mode) to rest in one of two ridges for the preferred viewing angle. There's no protractor at hand, but I'm estimating 45 and 60 degree angles.
Buttons and ports remain easily accessible, and while there are some parts of the Nexus left exposed, the case does provide protection all the way around including at the all-important corners.
Conclusion
Of these five (plus a previously reviewed Asus case), I have the Poetic SlimLine and StrapBack in use at the moment. I'm not completely decided which I'll end up sticking with -- and there are plenty more to look at! -- but these two will do for now.
Are there any cases or skins you have been particularly impressed with?
-

Which way? That way? Lenovo says there's a #betterway for tablets
Publié: octobre 11, 2013, 11:32am CEST par Mark Wilson
 There is not a lot to go on at the moment, but Lenovo is teasing us with the promise of something interesting that's coming at the end of the month. Head over to the company's website or Facebook page and you are greeted by the promise that "A #betterway is coming".
There is not a lot to go on at the moment, but Lenovo is teasing us with the promise of something interesting that's coming at the end of the month. Head over to the company's website or Facebook page and you are greeted by the promise that "A #betterway is coming".A date of 30 October is mentioned and visitors are invited to "Join the Event" or sign up for more information. There's also a nice-looking cropped close-up of a brush aluminium case.
The #betterway hashtag is suggested as a solution to what Lenovo describes as "tablet hassle" -- how to go hands-free. Further hints are provided on Facebook which has the tagline "It's time for a tablet that can hold its own". Take a look at Lenovo's Twitter stream and the company suggests that battery life is going to be key.
While the launch date of whatever it is that Lenovo currently has under wraps is given as 30 October, click through to the event page and Lenovo proclaims that all will be revealed on the day before. "It's time for a new tablet to take shape. Join Lenovo at our livestream as we unveil a #betterway on 29th Oct".
The wheels of the advertising machines are already rolling and there is a short video for us to mull over. Entitled "Hot glue and magnets? A #betterway is coming", the video shows magnetic letters being stuck to the back of a tablet which is then stuck to a refrigerator door. What could it all mean?
-

Stop! Microsoft releases Internet Explorer 11 Blocker Toolkit
Publié: octobre 11, 2013, 10:10am CEST par Mark Wilson
 So… you don’t want Internet Explorer 11 in Windows 7, eh? What are you going to do? Block it! Ahead of the release of the completed version of IE11, Microsoft is giving Windows 7 users the chance to avoid automatically updating. The Internet Explorer 11 Blocker Toolkit can be used to prevent the web browser from being pushed as an "important" update when it is released.
So… you don’t want Internet Explorer 11 in Windows 7, eh? What are you going to do? Block it! Ahead of the release of the completed version of IE11, Microsoft is giving Windows 7 users the chance to avoid automatically updating. The Internet Explorer 11 Blocker Toolkit can be used to prevent the web browser from being pushed as an "important" update when it is released.IE11 comes as an integral part of Windows 8.1 (Windows 8 users can currently only get it by upgrading) and a Release Preview of the browser was made available for Windows 7 three weeks ago. There's no official word on when the finished version of IE11 for Windows 7 will see the light of day, but it's likely to be fairly soon.
While most web browser updates are welcomed with open arms, updates to Internet Explorer tend to be received rather differently, especially by businesses who have large fleets of computers to worry about. Many companies will want to test out the browser internally to check both security and functionality before unleashing it on employees. The blocking toolkit buys some extra time by preventing Windows Update from automatically installing the latest version -- but it will not stop manual updating.
A note in the Microsoft Download Center points out:
Even if you used the Blocker Toolkit to block Internet Explorer 8, Internet Explorer 9, or Internet Explorer 10 from being installed as a high-priority or important update, you will still need to use the Internet Explorer 11 version of the Blocker Toolkit to block Internet Explorer 11 from being installed. There are different registry keys used to block or unblock automatic delivery of Internet Explorer 8, Internet Explorer 9, Internet Explorer 10 and Internet Explorer 11.
So if you'd rather stay in control of when your web browser is upgraded, grab yourself a copy of the Internet Explorer 11 Blocker Toolkit which can be used in both Windows 7 and Windows Server 2008 R2.
-

T-Mobile customers gain unlimited international data and texts… for free!
Publié: octobre 10, 2013, 12:00pm CEST par Mark Wilson
 T-Mobile is taking the wraps off the next stage of its "uncarrier" program, revealing that from the end of October anyone on its Simple Choice plans are going to get something for free. Not just any old something. Free text and free unlimited data. It doesn't end there. The free offers work on a global scale, meaning that international data and texts will be free in more than 100 countries.
T-Mobile is taking the wraps off the next stage of its "uncarrier" program, revealing that from the end of October anyone on its Simple Choice plans are going to get something for free. Not just any old something. Free text and free unlimited data. It doesn't end there. The free offers work on a global scale, meaning that international data and texts will be free in more than 100 countries.John Legere, president and CEO of T-Mobile US, Inc. says "Today's phones are designed to work around the world, but we're forced to pay insanely inflated international connectivity fees to actually use them. You can't leave the country without coming home to bill shock. So we're making the world your network -- at no extra cost".
The deal will be available to new customers from 20 October, but existing T-Mobile users will have to wait until 31 October. This is great news for international travelers who do not want the hassle of buying a new SIM card locally, or having to ensure that they are in the best tariff for every country they visit.
It's not all good news, though. Look at the small print and you'll see that data speeds are limited to 2G rates and tethering is not an option. There's also the rather vague warning that the "service may be terminated or restricted for excessive roaming or misuse".
The program also sees the cost of calling from the 100+ Simple Choice countries cut to a maximum of 20 cents per minute. However, the prospect of unlimited data may well encourage travellers to investigate VoIP tools such as Skype.
-

Are you a Bing-er or a Googler? Brits can take the test!
Publié: octobre 10, 2013, 10:21am CEST par Mark Wilson
 In the red corner, Bing. In the blue, Google. But which is better? Microsoft launches the Bing It On campaign in the UK to enable web searchers to choose which results are best. Google is such a ubiquitous online tool that it has become a verb and entered the dictionary; it is the search engine that automatically springs to mind for most people when they need to research something.
In the red corner, Bing. In the blue, Google. But which is better? Microsoft launches the Bing It On campaign in the UK to enable web searchers to choose which results are best. Google is such a ubiquitous online tool that it has become a verb and entered the dictionary; it is the search engine that automatically springs to mind for most people when they need to research something.But this does not mean that there is not room for a little competition, and this is something that Microsoft is keen to exploit with its latest campaign.
The Bing It On website can be used to perform a web search using both Bing and Google at the same time -- but it is not immediately revealed where the results are coming from. You'll be shown the two sets of results side by side and asked to vote on which you prefer. After five searches you'll be told whether you are a Bing-er or a Googler.
Brian Kealy, Head of Search for Microsoft UK, says:
We've removed all branding and other visual triggers from the results at www.bingiton.com so people’s decisions on which they feel are more useful will be based purely on the content delivered to them. We're confident in the quality of Bing's results and we believe many people will be surprised by the outcome of the challenge.
Microsoft carried out a series of blind tests involving 1,000 people. The Redmond, Wash. company says that 53 percent of those tested indicated a preference for Bing, 34 percent preferred Google and 13 percent were undecided. These results are a little, erm, surprising to say the least. Figures from StatCounter Global Stats for the last three months show that Google accounts for nearly 90 percent of searches worldwide, and takes around 67 percent of the search market in the US, while Bing gets just over 4 percent. Bing's share in the UK increases slightly to just under 7 percent, but Google retains much the same share.
So where does this disparity come from? One set of figures shows that Google is many times more popular than Bing, while the other suggests that close to twice as many people prefer Bing's results.

Where do you fit into the stats? For me, Google won four out of five rounds. Take the test for yourself and let us know which service engine comes out on top for you.
Image Credit: Lightspring/Shutterstock
-

Google Slides gains widescreen presentations and editable slides
Publié: octobre 10, 2013, 12:51am CEST par Mark Wilson
 Presentations are loved and loathed in just about equal measure. A great presentation helps to drive a message home; a bad one makes a meeting drag on forever. PowerPoint may be the king of presentations, but the online office tools that are available in Google Drive also have a good following. Now Google has recognized the fact that monitors are almost universally widescreen these days, adding the ability to create widescreen format slides in presentations.
Presentations are loved and loathed in just about equal measure. A great presentation helps to drive a message home; a bad one makes a meeting drag on forever. PowerPoint may be the king of presentations, but the online office tools that are available in Google Drive also have a good following. Now Google has recognized the fact that monitors are almost universally widescreen these days, adding the ability to create widescreen format slides in presentations.The change in aspect ratio may seem like a minor feature, but it is immensely useful. Be gone foul borders! Presentations can now make use of every pixel of your display, or give a full cinema experience when projected to a larger audience. Widescreen slides have not just been introduced, they have been made the default setting -- and there are 16:9 and 16:10 formats to choose from.
This is not the only change that has been introduced. Google now also allows you to edit the theme of a series of slides. By making a change to the master slide, it is now possible to very quickly apply presentation-wide settings in just a few clicks -- great if you need to change something and don’t fancy the idea of working through each slide individually. The slides layouts contained within a theme can be customized as well.
If you've created a custom theme that you're particularly proud of, share it on Google+ using the hashtag #mygoogleslides and you could find that it gets featured on the Google Drive page.
Are you a fan of Google Drive's tools? Are they reaching the point that they can be used as replacements for the likes of Office?
Image Credit: Tomnamon / Shutterstock
-

Tesco Hudl -- the budget tablet with great aspirations [Review]
Publié: octobre 6, 2013, 3:16pm CEST par Mark Wilson

Many people are settling into the idea that a 7 inch screen is the ideal size for a tablet. The extra screen space provided by a 10 inch model sounds great in theory, but it does result in a device that is slightly more cumbersome to take from place to place. Looked at in terms of portability, 7 inches is perfect -- large enough to make most tasks easy, but small enough to easily slip into a bag, if not necessarily a pocket.
The slightly smaller size also makes an important difference to the price tag, and there is a burgeoning market for tablets of this size. It is interesting to see that as the screens of phones gradually get larger and larger, the general trend for the tablet is to shrink -- the two are on a collision course!
Price is an important factor for many people looking for a portable device. Apple's iPad and iPad Mini, and certainly Microsoft's Surface, are beyond the means of someone looking for something cheap and cheerful.
 Without doubt, it is the Nexus 7 that has dominated this corner of the market, certainly in recent months, but there is a lot of competition. This is great for anyone looking for a tablet as it means there is a great deal of choice, and there is also something of a price war as manufacturers compete for attention by driving prices down.
Without doubt, it is the Nexus 7 that has dominated this corner of the market, certainly in recent months, but there is a lot of competition. This is great for anyone looking for a tablet as it means there is a great deal of choice, and there is also something of a price war as manufacturers compete for attention by driving prices down.UK supermarket Tesco may seem an unlikely contender, but it is the latest company to enter the market. The Hudl has been designed from scratch, and with a price of just £119, it will immediately appeal to anyone looking to get hold of a tablet for as little as possible. In fact, bought in conjunction with coupons through Tesco's Clubcard loyalty scheme the price is driven down to below £100. No details are provided about who has helped with the design and manufacturing process, but Tesco says that it has worked with a partner in China that "also manufacturers well-known products for Microsoft, HP, BlackBerry and Sony".
Stop Me If You Think You've Heard This One BeforeOverall, Hudl specs should sound fairly familiar -- there are a few devices which fall into much the same bracket. The screen should be the starting point when talking about any tablet. Here we have a 1440 x 900 resolution, working out at 243 pixels per inch -- compare this to the Nexus 7's 1900 x 1200 and 323 ppi.
The display looks nice, but it's hard to get much more excited about it than this. Everything looks sharp enough, but even with the brightness turned up all the way, the image is still a little dark and murky. It's fine looked at in isolation, but as soon as it's compared to other recent mobile devices, it looks rather less impressive.
 Despite the low price, the Hudl features a quad-core 1.5GHz processor. For day to day tasks, this is just fine, but to avoid disappointment, you shouldn't expect too much from it.
Despite the low price, the Hudl features a quad-core 1.5GHz processor. For day to day tasks, this is just fine, but to avoid disappointment, you shouldn't expect too much from it.Running the Ice Storm benchmark in 3DMark yielded a good-looking picture, but there was noticeable judder and frame drop. Even in the least demanding benchmarks, the framerate dropped to 7 fps at times -- although it was generally above this. Overall, 3DMark assigned the tablet a rating of 2.5 out of 5 with a score of 3528, compared to 3.5 out of 5 and 4454 for the Nexus 7. The average frame rate of 21.2FPS for the Hudl compared to the Nexus 7's 50.2.
Shifting up to the Ice Storm Extreme test, the tablet really started to struggle. The average framerate drops to 12.2, and an overall score of 2747 earns the tablet 2.5 stars out of 5. The Nexus 7 receives a 5 out of 5 rating for a sore of 6988. Taking things even further with the Ice Storm Unlimited test, the Nexus 7 scores and impressive 10597, while the Hudl trails behind with just 3916.
So bona to vadaBut this is not really what this tablet is designed for, nor is it likely to be what buyers are expecting from it. Spend £100 on a tablet and it's not likely you're going to be using it to play the latest, greatest and most demanding games. Available in multiple colors -- in addition to the covers -- this is a tablet that will certainly appeal to children.
On the software front, the Hudl is running Android 4.2.2 and the OS has been tweaked with a few Tesco specific tools. There is an extra onscreen button in the bottom left hand corner -- this T icon provides access to Tesco's range of online services including shopping, loyalty card details and banking.
Blinkbox is installed as standard, and there's also Clubard TV with free movies and TV programs. Being free, the selection is a little limited, but free is free. The homescreens are filled with Tesco widgets that can be used to place online orders and get account details, and there are helpful tutorials which are useful for first time tablet users.
This is being touted as a family tablet, and there is guidance to help parents set up controls and restrictions to stop kids from accessing anything they shouldn't.
In terms of hardware, the Hudl impresses. The slightly bubbly, rounded body has a retro 70s feel to it and, coupled with the rubbery back, it feels great in the hand. The weight is more than the Nexus 7 at 390g, but it's still not too heavy. Physical buttons for power and volume are pleasingly raised and there's a mini HDMI output for connecting to a TV.
The harsh truth of the camera eyeThere's only 16GB of built in storage, but the microSD slot means this can be expanded to 48GB very easily and cheaply. What really lets the Hudl down are the cameras. Both the front and rear cameras are awful -- this in spite of resolutions of 2MP and 3MP each, which should be enough to take reasonable pictures. Images are noisy and low quality, but they are sufficient for video chats when no other options are available.
The tablet feels nice and robust -- it seems as though it should withstand family life -- but there are soft touch cases available for £15 each, or leather versions for £20 to add some extra protection. There are other accessories available including an in-car charger and a mini-HDMI to HDMI adaptor.
This is clearly a tablet for non-demanding users. Performance is hampered slightly by the 1GB of RAM, but everything else is pretty much up to par. Dualband wifi is practically a given these days, and audio quality is decent.
The Hudl is no powerhouse, but it’s far from being something to dismiss out of hand. You get a lot of tablet for your money -- and it's a great present for younger children who don't need the raw power of more expensive alternatives. Look at it as 'my first tablet' or 'my backup tablet' and you won't be disappointed.
-

The most popular stories on BetaNews this past week: September 29 -- October 5
Publié: octobre 5, 2013, 8:31am CEST par Mark Wilson
 This has been a week with a lot of news about operating systems. As we near the official release OS X Mavericks went GM and was made available to developers, while in the world of Linux Red Hat Enterprise 5.10 was also unveiled. Windows 8.1 was made available for pre-order, but a study of sales figures revealed that Windows 7 continues to grow faster than Windows 8. Ahead of his retirement sometime in the next twelve months, Microsoft's Steve Ballmer was punished for poor performance with a bonus reduction, with first generation Surface sales partly to blame.
This has been a week with a lot of news about operating systems. As we near the official release OS X Mavericks went GM and was made available to developers, while in the world of Linux Red Hat Enterprise 5.10 was also unveiled. Windows 8.1 was made available for pre-order, but a study of sales figures revealed that Windows 7 continues to grow faster than Windows 8. Ahead of his retirement sometime in the next twelve months, Microsoft's Steve Ballmer was punished for poor performance with a bonus reduction, with first generation Surface sales partly to blame.Things look better for Surface 2 and Surface Pro 2, with reports of the tablets selling out -- this is perhaps not surprising when Delta Airlines has bought 11,000 of the devices for its pilots. As well as looking forward, Microsoft also came over a little nostalgic, choosing to show off the capabilities of Internet Explorer 11 with a revived version of the classic Windows 95 game Hover.
After last week's look at the usability of Windows Phone, we took a second look at the Pfeiffer report to address some of the queries it raised. Windows Phone may have fared poorly in this particular test, but sales are improving in Europe. In software developments, Google announced AdMob for Windows Phone.
Speculation was rife about the possibility of Android and Windows Phone making an appearance on HTC devices, and the Windows Phone version of Facebook was updated. This was far from being the only Facebook news as Graph Search was extended (much to the concern of those worried about privacy), and status updates were made editable with the possibility for hilarious results.
Not to be left out, iOS felt the benefit of the arrival of online radio and music promotion platform Earbits. In less pleasing news, investigations into benchmarking found that Samsung may have been massaging the figures to help make its devices look better.
In the world of security Adobe suffered a breach that resulted in the theft of millions of customer records, while Evernote aimed to increase security by adding two-factor authentication. Yahoo showed that it was serious about security by offering a reward of up to $15,000 for vulnerability a bug reports. The company also bolstered defenses with new second sign in and App Password features. Better known for helping to speed up file sharing, BitTorrent revealed a new secure messaging service.
Staying with the web, the BFI announced a new movie streaming service and Chromecast users felt the benefit of the arrival of Hulu. Microsoft gets the final words this week as the company revealed more details about Smart Files in Windows 8.1's integrated SkyDrive. Ahead of the release of the latest version of the operating system, the Start button was highlighted in the company's latest ad campaign.
Back again in seven days after what promises to be another busy week.
Photo Credit: vinz89/Shutterstock
-

Skype promises better message syncing and continued mobile improvements
Publié: octobre 5, 2013, 1:16am CEST par Mark Wilson
 In a blog post that looks forwards as well as backwards, Skype lays out details of planned improvements for the desktop and mobile versions of the app. Mark Gillett applauds the technological improvements that have been made over the past year and also gives a glimpse of the changes we can expect to see in the year to come. The post acknowledges that a large proportion of Skype usage is on mobile devices, and a number of mobile-friendly changes are revealed.
In a blog post that looks forwards as well as backwards, Skype lays out details of planned improvements for the desktop and mobile versions of the app. Mark Gillett applauds the technological improvements that have been made over the past year and also gives a glimpse of the changes we can expect to see in the year to come. The post acknowledges that a large proportion of Skype usage is on mobile devices, and a number of mobile-friendly changes are revealed.One particularly noteworthy feature specific to mobile users is the promise that chat synchronization across devices will be improved. This is something that anyone who used Skype on multiple devices will have noticed can be a problem. Send a large number of text based messages from the desktop version of Skype and when you launch Skype on another computer or a phone, you'll currently find that there can be quite a delay as message history is downloaded. While no details are provided, Gillet says:
"We are working to synchronize chat message status across all of your devices so you will know the current status of all of your chats on every device you use to interact with Skype. This capability will be rolling out across clients over the next few months".
Mobile users look set to reap the benefits of efficiency improvements. The blog post makes reference to the battery-saving "sleep" mode which enables Skype's cloud backbone to take care of the bulk of the work, taking the strain off handsets. No further specifics are given, but further improvements in this area and account security are mentioned.
Microsoft has put a lot of work into Skype since acquiring it, and this shows no sign of slowing pace.
Image Credit: Oleksiy Mark / Shutterstock
-

Just how much trust can you put in benchmarks? Is Samsung tricking us?
Publié: octobre 2, 2013, 1:57am CEST par Mark Wilson

Benchmarks are important. The quoted figures for any piece of hardware are all well and good, but potential buyers need to know how a hard drive, processors, computer, tablet or smartphone really performs. After all, two processors with a clock speed of 3GHz do not necessarily perform equally well, and it is only through testing that it is possible to determine which one comes out on top. Few people have the means to go out and compare two similar pieces of hardware, so this is where benchmarks prove useful.
People use smartphones and tablets for different things. One person might be happy being able to take notes and make phone calls, while someone else might be looking for a 60fps hi-def gaming experience. Here benchmarks matter. It is important to be able to accurately compare devices using reliable figures. If you want to know how quickly phone A shifts pixels around the screen compared to phone B, it is important that the tests are performed in the same way, and are carried out fairly.
This might seem like stating the obvious. It makes sense that benchmarks are only really meaningful if direct comparisons can be drawn between two sets of results. We need to know that each device has been tested in the same way.
Back in July, many people felt suspicious about the benchmark performance of Samsung's Galaxy S4.
It looked very much like code had been written in such a way that performance was increased when benchmarking software was running. These weren't just paranoid or unfounded claims from Samsung detractors; the company went as far as explaining the anomaly by saying that the GPU frequency of the S4 was increased from 480MHz to 533MHz when "running apps that are usually used in full-screen mode, such... certain benchmarking apps". Samsung insisted that the changes were "not intended to improve certain benchmark results".
This may be the case, but it does render benchmarks all but meaningless. The point of a benchmark should be to try to replicate real world scenarios so users can know what to expect in terms of performance -- knowing how well hardware can run benchmarking software is, in itself, useless information.
But it looks as though this may not have been a one-off. And it is Samsung that is in line for questioning again. This time around it is the Samsung Galaxy Note 3 which has been put through its paces, by Ars Technica.
Eyebrows were raised when the Note 3 fared significantly better in benchmarks than the similarly specced LG G2.
Both devices feature the 2.3GHz Snapdragon 800 but Ars Technica's benchmarks found that the Note 3 scored higher -- and not just a bit higher... up to 20 percent higher -- than the G2. Ars Technica did a little digging and seems to have discovered that when certain benchmarking tools are running, Note 3 performance is increased. Perhaps more importantly, the team found a way to disable the alleged optimization so it was possible to see what difference it made (this essentially involved running a renamed version of a benchmarking tool to trick the Note 3 and prevent it from "realizing" benchmarking software was running. This is how the apparent 20 percent difference was found.
You might well wonder what the fuss is about. Surely it makes sense to have a device running at full pelt whenever possible. To a certain extent that is true, but it is not representative of real usage. All apps should be treated equally. Sure, games may make use of different CPU modes than, say, a simple email app, but there are few people who would want a benchmarking app to be treated differently to any other app.
It is understandable that a phone or tablet manufacturer would not want their device to be running flat out all of the time -- it would lead to massive battery usage and heat generation -- but there is a big difference between power conservation and fiddling the figures.
Consumers need to be able to put their trust in benchmarks. If performance is adjusted specifically when testing software is running, it means that there is not a level playing field and makes it impossible to accurately compare devices. As in so many walks of life, it is transparency that is needed. If figures are being manipulated in any way it does not matter as long as we know about it. If we know about it we can make further adjustments for ourselves so we can compare in a meaningful manner.
How do you feel about this? How much attention do you pay to benchmark results? Do they sway your buying decisions?
Image Credit: iQoncept / Shutterstock
-

Samsung Galaxy Note 3 and Gear ad shows off devices' potential
Publié: octobre 1, 2013, 7:39pm CEST par Mark Wilson

We are now just days away from the launch of the Samsung Galaxy Note 3 and Galaxy Gear. If you're yet to be caught up in the hype and excitement, Samsung's first commercial for the two devices could help to whip you into a frenzy. There's a slight cinematic quality to the ad which is… well… take a look for yourself. "Different" is perhaps the word.
The advertisement finds us following an artist as she uses the two devices to help her prepare for a dance performance in the evening. We see the star of the ad flick through My Magazine whilst getting ready to leave the house before showing off the Air Command and Action Memo feature when making a note of an interesting event advertised on a poster in town.
The disclaimer that continually flashes up at the bottom of the screen warning "Screen Image Simulated. Sequences Shortened" might be a legal requirement, but they hardly seem necessary. The Note 3 may be a speedy beast, but the team behind the advertisement have done a very poor job of making the screen look realistic -- we know the image has been pasted into place, not just because we're told, but because it is blindingly obvious from the substandard color-matching.
But, hey... this is about devices not editing techniques!
The Gear makes an appearance as an email notification appears on its screen before being checked in full on the Note 3. Memographer is then used to record an inspiring video and our heroine starts to prepare for the evening's performance, transforming a shop into a makeshift stage.
We are then shown S Finder in action as it is used to locate a video called Sweet Dream -- then the music kicks in (a peculiar rendition of the Eurythmics' Sweet Dreams (Are Made of This) and human puppets dance onstage. Of course there are people in the enthralled crowd equipped with their own Note 3s recording the performance. We're treated to a final feature showcase as recorded video is dropped into a message for sharing to highlight Multi Window and Drag & Drop.
One thing that's worth noting... at no point are we treated to the sight of Samsung's colossal 5.7-inch beast being slipped casually into a pocket. There were simply no pockets large enough, it would seem.
-

Facebook adds posts, status updates and more to Graph Search
Publié: octobre 1, 2013, 1:18am CEST par Mark Wilson
Facebook's Graph Search is being updated to include more information from the social network. The personalized search engine previously allowed for searching of people, photos, places and interests when it was launched back at the beginning of the year. Now posts from you and your friends as well as status updates can be included in searches allowing you to get even more specific about what you're looking for.
Also included in the update is the ability to search for status updates, photo captions, check-ins and comments. There are various ways in which searches can be used to hone in on the content you're looking for, and natural language searching is the order of the day. Want to see the posts your online contacts have made about Microsoft's latest operating system? Just search for "posts about Windows 8.1 by my friends". Results can be limited by date as well, so you could search for "posts about Nexus 7 from the last month".
As with the previous incarnation of Graph Search, this updated version will not enable you to see content that has not been shared with you. Just as before, the tool respects privacy settings so -- in theory at least -- your searches should only return results that include data that has been shared with you or made publicly available. The announcement comes hot on the heals of another addition to Facebook which makes it possible to edit statuses after they've been posted.
The initial roll out of Graph Search back in January was a beta that gradually spread across the network. This time around, the updated options are only being made available to "a small group of people who currently have Graph Search". Facebook says that improvements will be made based on user feedback.
Test out the tool at the Graph Search page.
-

The most popular stories on BetaNews this past week -- September 22-28
Publié: septembre 28, 2013, 10:34am CEST par Mark Wilson
 Microsoft held an event in NYC to launch the Surface 2 and Brian was live-blogging. The full video of the launch is available to view online as are advertisements that show off the tablets' versatility. Microsoft is pinning a lot on the updated product after the first generation suffered from poor sales. There were no great new features, but there is a redesigned kickstand, a healthy speed boost, new dock and updated covers -- Brian was particularly impressed by the Blades.
Microsoft held an event in NYC to launch the Surface 2 and Brian was live-blogging. The full video of the launch is available to view online as are advertisements that show off the tablets' versatility. Microsoft is pinning a lot on the updated product after the first generation suffered from poor sales. There were no great new features, but there is a redesigned kickstand, a healthy speed boost, new dock and updated covers -- Brian was particularly impressed by the Blades.Anyone buying a Surface 2 or Surface Pro 2 earns themselves a SkyDrive upgrade. Purchase a new device and your online storage gets upgraded to 200GB, but the same amount of space is available for $100 per year. Moving away from Surface-related news, Microsoft turned its guns on Google Docs, highlighting user complaints to demonstrate the superiority of Office 365.
After last week's launch, Apple's iPhone remained in the headlines. Selling 9 million units in the opening weekend seems impressive on the face of things, but all may not be as it seems. It came as no great surprise that the top of the range iPhone 5s proved more popular than its cheaper counterpart, but the device's fingerprint reader was shown to be "hackable" with a printer and some glue.
Back on the desktop, Apple launches four new iMacs and also lost a patent case relating to the click wheel on iPod Classics.
It has been a week of mixed news for BlackBerry. The beleaguered company found a potential buyer, and then went on to announce massive losses when its financial results were published. The figures had been widely anticipated and had been preceded by the cancellation of a previously scheduled conference call with analysts.
A few new tablets were announced or released this week including a cheap offering from UK supermarket Tesco. New Kindle Fires boasting faster performance and better screens were also unveiled. For owners of Android phones and tablets, Android Device Manager was updated to include the option of remotely adding password protection to a device, and Mihaita showed how to achieve the same in Windows Phone. A report suggested that Windows Phone is the most unusable mobile OS available was published and lead to some lively debate in the comments!
In the Linux world, Gnome 3.10 was released and SteamOS, Valve's take on home media streaming, was also unveiled. Sticking with the media streaming theme, Roku updated its line of boxes and Netflix boosted video quality.
There was quite a lot happening online over the last seven days: Google changed YouTube commenting to be Google+ powered and Yahoo's email recycling program backfired slightly when it resulted in private data being handed over to the wrong people. Gmail suffered an unscheduled outage, and it was also revealed that some people are perfectly happy to remain cut off from the web.
That's it for now. Here's to another seven action-packed days.
Photo Credit: vinz89/Shutterstock
-

Microsoft to allow apps to be installed on up to 81 devices
Publié: septembre 28, 2013, 1:35am CEST par Mark Wilson
Microsoft announces that it is dramatically increasing the number of devices users are able to install apps on. At the moment there is a limit of five devices, enabling customers to install the apps they have bought on multiple devices with the same user account. While you might think that five devices is enough for most people, some developers and customers wanted more. Microsoft listened and has increased the app roaming limit. Massively.
Five devices just not enough? How does 81 sound? Yep… 81 devices. Microsoft says it is responding to the demands made of it -- "since we launched Windows 8, we heard growing feedback from many developers and from our most enthusiastic customers that the limit of 5 was not enough for their needs. Developers asked for more flexibility in implementing their business models, and customers wanted to run those apps on the variety of tablets, laptops and desktops they owned".
Although the figure appears to be derived from the version number of Windows 8.1, the new limit will be in place for users of both Windows 8 and Windows 8.1 from 9 October.
If developers are concerned that this will lead to a reduction in income due to app "sharing", Microsoft points out that APIs exist that can be used to place a limit on the number of devices that can access a service simultaneously.
Is 81 enough for you?
-

Microsoft highlights Reading List ahead of Windows 8.1 launch
Publié: septembre 28, 2013, 12:13am CEST par Mark Wilson
There are only three weeks to go until the release of Windows 8.1 and Microsoft is laying the groundwork by highlighting some of the new features and apps that are to be found in the update. The latest app to be picked out is Reading List -- Microsoft's answer to the list of Pocket and ReadItLater. The app has been designed to make it easier to save online articles to read at a later time without the need to bookmark it.
Reading List differs from RSS readers such as Feedly in that articles are stored on an individual basis. And while it is well suited to "bookmarking" articles you find on websites that you would like to return to, it can also be used to bookmark content from other apps. Just like other "read it later" tools, the real advantage comes from the fact that content is synchronized between devices.
If you're catching up on the news on your home PC before heading off to work, lengthy articles can be added to your Reading List so you can finish it off on your laptop or Surface on your journey to the office. Using Reading List means taking advantage of Windows 8.1's Charm bar. Swipe in from the right -- with a finger or mouse -- select the Share option and then choose Reading List.
But it's not just a handy way to sync articles between devices -- Reading List is also a great way to collate related information when researching a project. It's not an option that is going to completely replace the traditional idea of bookmarking sites, but it serves as an excellent complementary method.
Are there any particular features you're looking forward to in Windows 8.1? If you've already updated you operating system, how does Reading List compare to other similar tools you've used in the past?
-

BlackBerry reports almost $1 billion loss in Q2 fiscal results
Publié: septembre 27, 2013, 5:09pm CEST par Mark Wilson
 As expected, BlackBerry is reporting a quarterly loss of nearly $1 billion as the struggling firm releases its fiscal results for the second quarter. The company managed to ship 3.7 million handsets, giving a revenue of $1.6 billion. This is a drop of 49 percent from the first quarter ($3.1 billion) and 45 percent down on the same period last year ($2.9 billion). Overall, there are operating losses amounting to $965 million.
As expected, BlackBerry is reporting a quarterly loss of nearly $1 billion as the struggling firm releases its fiscal results for the second quarter. The company managed to ship 3.7 million handsets, giving a revenue of $1.6 billion. This is a drop of 49 percent from the first quarter ($3.1 billion) and 45 percent down on the same period last year ($2.9 billion). Overall, there are operating losses amounting to $965 million.A large proportion of the units shipped were BlackBerry 10 handsets sent out to wholesalers and mobile firms, and profits from these will not be counted until sold to customers. In Q2, 5.9 million smartphones were placed in customers' hands, and this includes handset shipments from previous quarters. The poor results had been widely predicted, and BlackBerry cancelled its scheduled conference call.
BlackBerry is pinning much of its losses on an unsold inventory of Z10 handsets ($934 million) as well as "pre-tax restructuring charges" of $72 million. But there is no denying that the fact that the company's revenue has all but halved in three months is a disaster.
Thorsten Heins, President and CEO of BlackBerry said "We are very disappointed with our operational and financial results this quarter and have announced a series of major changes to address the competitive hardware environment and our cost structure. We remain a financially strong company with $2.6 billion in cash and no debt. We are focused on our targeted markets, and are committed to completing our transition quickly in order to establish a more focused and efficient company".
BlackBerry remains in talks with Fairfax, who emerged as the only potential buyer interested in taking on the company.
Image Credit: Ilya Andriyanov / Shutterstock
-

Office of Fair Trading says games should not encourage in-app purchases by children
Publié: septembre 27, 2013, 12:06pm CEST par Mark Wilson

The Office of Fair Trading (OFT) is calling on the games industry to avoid pressuring children into making in-app purchases in games and potentially running up large bills. Back in April, an investigation began into the ways in which children are pressured into making in-app purchases. 38 web and app-based games thought to appeal to children were looked at, and the results of the investigation are available in the Children's Online Games report.
The OFT aimed to determine whether the way in-app purchases were presented could be considered "misleading, aggressive or otherwise unfair". As a result of the investigation, the OFT has drawn up a set of eight proposed principles that apps and games should follow. The principles include clearly and prominently informing app users about the potential for costs to be incurred through the app. It is suggested that users should be able to fully understand the current and future costs associated with any app they download.
The proposed principles also suggest that app developers should make a clear distinction between free and paid-for content. There are concerns that the wording of links to premium content is such that costs are not made clear. A clear distinction should also be made between real-world payment with money and in-game purchases with virtual money, the OFT suggests. Principle six states that games should not employ practices that are "aggressive" or "have the potential to exploit a child’s inherent inexperience, vulnerability or credulity".
The final principle states that payments should not be taken unless authorized by the payment account holder. This would mean that a child using their parents' phone or tablet should not be able to make purchases without the parent being aware of it. The OFT suggests that a password be entered every time a purchase is made, and that account holder consent should not be "assumed" through the use of an opt-out system or any other means.
To help parents who are concerned that their children might rack up hefty in-app charges, the OFT has put together a series of video guides that demonstrate how to disable or password-protect in-app purchases. There are guides for BlackBerry, Android, iOS 6 and 7, and Windows Phone, as well as details of how to disable roaming before heading off on a trip abroad.
Feedback on the proposals can be left until 21 November 2013.
Image Credit: Yarkovoy / Shutterstock
-

More than half of tech professionals would take a pay cut to work from home
Publié: septembre 26, 2013, 10:13pm CEST par Mark Wilson
Working from home is something of a luxury, but it's also not easy -- this is something I know from personal experience. I've been a home worker for around a decade now, but it does take some getting used to. Tell people that you work from home and there's usually a look of jealousy in the eyes the ones who have to stay behind at the office each evening. Home working means being able to pick your own hours, not having to deal with the daily commute, and not having to do the coffee round, but would you be happy to pay for the privilege?
 We already know that most people would rather work from home than have to trudge to the office every day, but a new report from GetVoIP reveals that taking a pay cut would be an acceptable compromise for most tech professionals. A survey of 501 workers shows that 53 percent would be willing to earn a smaller pay check each month if it meant they could work from the comfort of their own home.
We already know that most people would rather work from home than have to trudge to the office every day, but a new report from GetVoIP reveals that taking a pay cut would be an acceptable compromise for most tech professionals. A survey of 501 workers shows that 53 percent would be willing to earn a smaller pay check each month if it meant they could work from the comfort of their own home.But just how much of a pay cut? On average, workers said they would accept a $6,764 reduction in their annual salary, or 7.9 percent (based on average tech earnings as determined by Dice.com). Some people were willing to take a bigger cut. More than 6 percent would accept a 31 percent cut -- willing to lose almost a third of their income to work from inside their own four walls.
The figures show that we're keener on the idea of working from home than a couple of years ago. Back in 2011, 35 percent of those asked said a pay cut would be a fair price to pay to work from home, while in 2008, 37 percent felt the same way.
Of course this leaves 47 percent of those questioned who answered "none" when asked "How big of a pay cut would you take in order to work from home?" This could mean they simply have no interest in telecommuting, or the benefits of homeworking are insufficient to warrant earning less money.
Image Credit: Roobcio / Shutterstock
-

Microsoft announces Surface 2 and Surface Pro 2
Publié: septembre 23, 2013, 7:29pm CEST par Mark Wilson

At an event in New York, Microsoft reveals the successor to the Surface RT and Surface Pro -- the predictably named Surface 2 and Surface Pro 2 (interesting to note that the "RT" is gone from the former's name) -- and Brian Fagioli was live-blogging from the event. So what do we have to look forward to from the product refresh?
The first generation Surface tablets suffered poor sales and came in for criticism from many quarters, so there is certainly room for improvement.
Microsoft is claiming that the Surface Pro 2 is faster than 95 percent of laptops currently on the market. In terms of raw figures, there is a performance boost of 20 percent and a graphics performance improvement of 50 percent.
Inside there's a Haswell chip which goes some way to explaining the claims that the second generation Surface Pro not only runs more quietly and cooler than the original, but also boasts a 75 percent improvement in battery life. This is boosted further by the addition of the Power Case accessory, resulting in two and a half times the battery life of the original Surface Pro.
The kickstand of the original Surfaces meant that it was tricky to use away from a flat surface, but this has been changed so there are now two positions to choose from, making it easier to use on the lap like a laptop.
 A docking station is something that many people felt was lacking from the Surface lineup, and this has been rectified with version 2. The Surface Docking Station not only adds power, but also three USB 2.0 ports, one USB 3.0 port, Ethernet, audio in and out and Mini DisplayPort. Other accessories were also announced, including improved versions of the Type and Touch covers. The Type Cover 2 is available in two colors, is thinner than the original and is also backlit.
A docking station is something that many people felt was lacking from the Surface lineup, and this has been rectified with version 2. The Surface Docking Station not only adds power, but also three USB 2.0 ports, one USB 3.0 port, Ethernet, audio in and out and Mini DisplayPort. Other accessories were also announced, including improved versions of the Type and Touch covers. The Type Cover 2 is available in two colors, is thinner than the original and is also backlit.The Touch Cover 2 has more sensors than the first version, opening up the possibility of touch gestures in addition to typing. The keyboard cover is more rigid as well as being thinner and it is backlit just like the Type Cover 2.

The Surface 2 is the cheaper, entry level model. There are improvements to be found here too. Again, it's faster and lighter. Although RT is no longer part of the name, this model still runs Windows RT, now on an upgraded full HD display. The Surface 2 comes bundled with Office 2013 RT and pricing starts at $449. Both the Surface 2 and Surface Pro 2 upgrade SkyDrive users' storage to 200 GB, for free.
The baseline pricing figures look good, with the Surface 2 starting at $449. This is for the 32 GB version, and there's also a 64 GB model available. The Surface Pro 2 starts at $899 for a 64 GB version with 4 GB RAM and there is a 128 GB model with the same memory capacity. There are also 256 GBand 512 GB versions backed up with 8 GB RAM -- full details of all prices have not yet been confirmed. But the prices soon add up. The Touch Cover 2 costs $119.99, and the Type Cover 2 costs $129.99. Like the idea of the Power Cover? This will set you back $199.99 and you'll have to wait until 2014 to get your hands on it. The Docking Station has the same price and estimated release date.
Both Surface 2 devices are available from 22 October, but pre-ordering starts tomorrow, September 24 at 8 AM EDT. For now, the pre-order site is home to information about the devices.
-

Tesco launches low-cost Hudl tablet to compete with Nexus 7
Publié: septembre 23, 2013, 1:15pm CEST par Mark Wilson

UK supermarket Tesco launches its own 7-inch tablet undercutting the price of just about everything else on the market. The Hudl may be cheap (just £119), but the specs are surprisingly high -- the budget price doesn’t seem to have meant having to make too many cutbacks. A 1.5GHz processor powers a 1440 by 900 display, and the 16GB of integrated storage can be expanded through the use of the microSD slot. The tablet runs Android 4.2.2 and Tesco wants it "to open up a world of entertainment and connectivity to all". It is priced well to compete with the likes of the Nexus 7.
Heading to the supermarket may not be where you'd first think to buy your next tablet, but Tesco's new Hudl is likely to change that. The tablet has been designed to be very family friendly; it looks approachable and has been configured so that parents are guided through the process of setting it up for use by children. The Hudl will be available in four colors -- red, blue, black and purple.
At first glance things look very much like any other tablet, but look to the lower left of the screen an there's a Tesco T. This is more than just a branding logo -- tap the icon and users can gain access to Tesco services such as on-demand films through Blinkbox, shopping, banking and more.
The tablet is likely to fly off the shelves thanks to the low asking price, but any narrow profit margins will surely be offset by the range of accessories that are going to be available. There are 6 soft touch cases and two leather cases to choose from, and a bumper case designed specifically for children. A Micro-HDMI to HDMI cable can be used to turn the tablet into a media streaming device for the family.
Tesco says that many people who do not yet own a tablet "feel that the technology is too expensive or intimidating". The Hudl is already incredibly cheap, but further savings can be had by Clubcard holders (Tesco's loyalty scheme) which will bring the price down to less than £100.
The Hudl is not available just yet -- Tesco is whipping up a little hype and interest ahead of the on-sale date -- but it can be picked up in around 1,000 Tesco stores, as well as online, from 30 September.
-

iPhone 5s Touch ID bypassed with a fake fingerprint
Publié: septembre 23, 2013, 11:39am CEST par Mark Wilson
 Just days after the launch of Apple's iPhone 5s, German security and privacy group Chaos Computer Club, claims to have found a way to bypass the Touch ID fingerprint reader. The group says that this demonstrates that "fingerprint biometrics is unsuitable as an access control method" but the "hack" is longwinded enough to mean that it is unlikely to be of concern to most people.
Just days after the launch of Apple's iPhone 5s, German security and privacy group Chaos Computer Club, claims to have found a way to bypass the Touch ID fingerprint reader. The group says that this demonstrates that "fingerprint biometrics is unsuitable as an access control method" but the "hack" is longwinded enough to mean that it is unlikely to be of concern to most people.The Chaos Computer Club (CCC) goes as far as explaining precisely how it managed to bypass Touch ID using a fake fingerprint fabricated from a photo of a print.
The group has previously shown how easy it is to fake fingerprints using original prints left on glass surfaces. Bypassing the security of the iPhone 5s uses very much the same method, but relies on a higher resolution fake to help fool the high resolution sensor found on the phone.
So how does it work? CCC says that the hack can be accomplished with "materials that can be found in almost every household". After dusting a suitable fingerprint left on a glossy surface, the print is photographed, touched up and laser printed out onto a transparent slide. The toner from the laser printer gives a slightly raised representation of the fingerprint which can then be used to create a fake fingerprint. The secret ingredient? Wood glue.
The glue is smeared over the printout and lifted off when it dries. To help trick the iPhone's sensor, the latex fingerprint is then breathed upon to give it the slightly moist feel of a real finger and it can then be used to unlock the phone.
Have doubts about whether it could work or not? Check out the demonstration video on YouTube :
Does this concern you or is this a hack we don’t need to worry about?
Image Credit: NREY/Shutterstock
-

The most popular stories on BetaNews this past week -- September 15-21
Publié: septembre 21, 2013, 7:43pm CEST par Mark Wilson
 Apple stole the limelight from just about everyone else this week. The big news was, of course, the release of the iPhone 5c and iPhone 5s. Just about as soon as online orders opened up, delays in shipping started to lengthen; Joe was somewhat skeptical about the limited supplies.
Apple stole the limelight from just about everyone else this week. The big news was, of course, the release of the iPhone 5c and iPhone 5s. Just about as soon as online orders opened up, delays in shipping started to lengthen; Joe was somewhat skeptical about the limited supplies.Before the new hardware hit the stores, iOS 7 was released to mixed reviews -- I hated it, Wayne loved it. A couple of security holes were found in the operating system including one that allowed for Siri to be used to post messages and access phone details even on locked handsets. There was also a new iOS 7 inspired look for iCloud and the addition of a bookmark syncing option.
It hasn’t all been about iOS -- Windows Phone users got a chance to download Angry Birds Star Wars 2 early. Research revealed that tablets are used mainly for fun and this is probably true for anyone looking to buy one of NVIDIA's newly announced tablets. Fans of custom ROMs for phones and tablets will be excited at the revelation that CyanogenMod has become a company in a bid to not only boost interest but also steer the project forward in a meaningful direction.
Microsoft pulled a series of anti-iPad ads which it admitted were off the mark and then busied itself with a redesigned logo for Bing and a new look for the search tool. The update was not made available to everyone immediately, and Mihaita tired of staggered roll outs. Bing's iOS app was also updated to add support for the latest version of the mobile operating system.
Elsewhere, Microsoft revealed Windows 8.1 pricing and also made Windows 8.1 Enterprise RTM available to Technet and MSDN subscribers. Internet Explorer 11 Release Preview for Windows 7 also came blinking into the sunlight.
The Motion Picture Association of America complained that Google doesn’t do enough to stop piracy, and I expressed some views on the way piracy is perceived. Brian shared research that showed that searches for celebrity women can lead to malicious sites, while Microsoft said that users need to do more to protect themselves when online. This is entirely understandable when it has been found that a terrifying number of people use public wifi connections to carry out work-related tasks.
Apart from new phones from Apple, a few other pieces of hardware were scrutinized this week including new Panasonic headphones and the colossal Droid Maxx. Alan found that the Logitech T630 touch mouse took a little getting used to.
Not wanting to be left out of the headlines, Google bought Bump and also started to roll out a new look navigation menu. If you’re not yet able to access it, there's a handy trick you can use to force it to appear. Whether through altruism or in an attempt to steal some of Apple's thunder, Google also made QuickOffice available free of charge to iOS and Android users.
Busy week! We all need a day off to recover...
-

Motion Picture Association of America blames Google for online piracy
Publié: septembre 21, 2013, 12:11am CEST par Mark Wilson
Piracy is a problem, a big problem. A few days ago I wrote about the consequences of piracy and the fact that it is far more than just the copyright holder who is affected. While I believe that piracy should be viewed as something other than theft, it is obviously still wrong. The label "wrong" sounds almost belittling, but there are few people who would deny it is an issue that needs to be tackled.
The obvious targets when cracking down on piracy are the people who are illegally downloading music, movies and software they are not entitled to, but this does not really nip things in the bud. Piracy is a very complex issue, and as with any complex issue a scapegoat is needed. The Motion Picture Association of America is understandably keen on stemming the flow of illegally downloaded films and it is pinning the blame, at least partly, on Google.
The MPAA commissioned research into how web searches lead to the discovery of pirated content to see whether algorithm changes implemented by Google last year were proving effective. The findings make for interesting reading, but one thing is clear -- the MPAA doesn’t think Google et al are doing enough. Google in particular finds itself in the crosshairs as the research found that 82% of web searches that lead to copyright infringing material came from Google.
This in itself is not surprising in the least. Google is the biggest search engine. Pick any topic -- porn, MP3, illegal movie copies, torrents, software cracks -- and just by virtue of being the world's largest and most popular search engine, it is highly probable that most traffic comes via Google. But does this matter? The fact that Google can be used to find illegal content is just an unfortunate "side effect", isn’t it… in much the same way that a library could be used to discover interesting ways to poison an enemy without detection?
But the MPAA feels that Google should be doing more. The organization points out that 58 percent of searches that include illegal content in the results do not include obvious terms to track down such content -- in many cases just searching for the name of a TV show is enough to reveal the location of downloadable copies. The report, entitled Understanding the Role of Search in Online Piracy, doesn’t just single out Google -- it does make passing reference to Bing, Yahoo and "others" -- but the search giant is clearly the MPAA's main target.
Google has spoken out several times in the past, and this month has published a report of its own: "How Google Fights Piracy". The company is especially keen to point out that it believes that search engines in general (and Google specifically) are not key factors in driving traffic to sites that either host or provide access to pirate material; in fact, big name torrent sites have said that only a small proportion of traffic comes via Google.
This is not to say Google is not taking steps against piracy but, as stated in the report, "search engines do not control what content is on the web." The search giant has made changes to the way it works so that terms closely associated with piracy do not feature in suggested results of autocomplete lists. Google also pushes some sites further down the list of results -- or "makes legitimate alternatives more visible" in its words.
Certain sites can be filtered from search results, but this is done retroactively. Sites that are removed are under investigation following a removal request. There have to be investigations because site reporting is open to abuse, and Google "reject bogus infringement allegations, such as removals for political or competitive reasons." Details of removal requests are even published for all to see.
Is it right to demand that Google do more? I don’t think so. Mock the "don't be evil" motto as much as you like but Google's heart is, generally speaking, in the right place. The MPAA should take some responsibility itself. The existence of sites offering illegal content is not Google's fault -- it is a product of an industry that demands more and more money of consumers. Find new, innovative, flexible and cheap ways for consumers to access the content they want, and piracy will be reduced. It really is that simple.
Piracy will never be eliminated. However cheap something is made, the prospect of getting something for free will be too much for some people to resist. There will always be some degree of piracy -- the MPAA needs to accept this. It also needs to accept that it can itself do more -- in conjunction with the movie studios it represents -- to help reduce the problem. Education and price are key areas for attention.
Google is a tool, and tools can be misused. Google may do no evil, but that does not mean it cannot be used for evil. A breadknife is another tool -- one designed with a perfectly innocent purpose in mind, but one that can also be used for more nefarious things. When there is a fatal stabbing -- something that happens with worrying frequency -- there are not calls for knife manufacturers to make their products safer or to start running programs to educate consumers about safe knife use. Why should Google be treated any differently?
So long as the search engine is not actively promoting piracy, there is a limit to the level of responsibility the company can be expected to have for how its tools are used. It is not reasonable to expect Google to police the internet. Even responding to complaints the company receives (57 million pages were the subject of removal requests in 2012) is an absurdly large job. The number of man-hours involved is incredible.
The MPAA shouldn’t expect other people to fix its problem for it.
-

Siri security flaw leaves some locked iPhones open to abuse
Publié: septembre 20, 2013, 10:26pm CEST par Mark Wilson

The number of people who are running iOS 7, either by buying a new iPhone or by downloading the update from Apple, is high. Very high. But shortly after the excitement of the new operating system, a security flaw with Siri emerges -- and it's not one to be taken lightly. Security firm Cenzic reveals details of a vulnerability that enables anyone to bypass the lock screen of an iPhone using Siri.
The voice activated assistant is better known for providing answers to questions and allowing for hands-free operation of iPhones. But Cenzic researchers show that it can also be used for more sinister purposes. You would think that when your phone is locked it should not be possible to do anything, besides answering calls, until you unlock it.
But Cenzic Security Engineers, Abhishek Rahirikar and Michael Yuen found that it is possible to use Siri to use phone functions that really should be inaccessible when a device is locked -- such as the ability to post Facebook and Twitter updates, viewing call records and even send emails. This means that, in theory, should your iPhone be lost or stolen, someone else could use it to post messages on your behalf.
The ability to make calls from a locked phone could be seen as being useful to a legitimate owner of a phone. Cenzic says that the vulnerability demonstrates that "there is a thin line between security and convenience" and has called on Apple to remedy the problem. I've reached out to Apple to get their side of the story, and I'm awaiting a response.
A video has been posted to YouTube showing how the vulnerability works. It may seem that Siri first refuses to post a Facebook status update and then just gives in on the second request, but Abhishek Rahirikar explains that "you need to give right command, and Siri does not think whether the phone is locked or not, it carries out the action. This is true for some commands that we think should have some restrictions."
The problem is not restricted to iOS 7; it is also to be found in iOS 6.1.4.
Check out the YouTube video to see the vulnerability for yourself:
Image Credit: lucadp / Shutterstock
-

Buying your iPhone 5s or 5c from Apple? Expect to wait a while!
Publié: septembre 20, 2013, 3:08pm CEST par Mark Wilson

The iPhone 5s and iPhone 5c are now here -- or they will be in a bit. Anyone with an older device that isn't too old is able to update to iOS 7 -- the jury is out about whether it is a step in the right direction or not -- but if you're looking for the full iOS 7 experience running on the latest hardware, the new iPhones are a must-buy.
Even on launch day it looks as though buying direct from your mobile provider, or joining the queue at your nearest Apple store might be the quickest way to get your hands on a new phone. Opt to make a purchase direct from Apple's website and you'll probably find that you have quite a wait on your hands.
It doesn’t seem to make much difference where you are in the world. Unless you were fast with your mouse finger, there's a high chance you'll have to wait until next month until your phone even ships. In the US, many iPhone models have a lead time of seven to ten business days, while in the UK, many handsets have an unspecified dispatch date of some time in October.
The fact that supplies are low should come as no great surprise -- it happens after the launch of virtually every new Apple product. But it's not really clear whether Apple was ill-prepared for great demand, whether there is greater demand than expected, or if supplies are being purposefully limited to help keep the hype going.
So how did you get one? Were you one of the enthusiasts waiting in line for the doors to open, or are you relying on an online order? Which proved to be the faster option for you -- direct from Apple online or going through your mobile supplier?
Image Credit: luminaimages /Shutterstock
-

New My Yahoo aims to make the internet personal again
Publié: septembre 19, 2013, 8:03pm CEST par Mark Wilson
Not content with its new logo, Yahoo is now pushing the personal homepage with the relaunch of My Yahoo. It's a blast from the past in many ways. The personalized portal is something that had virtually died off, but Yahoo is keen to dust it off, give it a polish and entice people back into using it.
If you’re the kind of person who likes to be able to access everything in one place, the resurrected My Yahoo just may well appeal. "Resurrected" might not be the right word. My Yahoo never really went away, it just faded into obscurity and everyone forgot about it. But now it's back with knobs on -- and quite a lot of purple.
Google may have dropped iGoogle, but Yahoo has its arms open wide to receive anyone looking for a new home for their online widget. And widgets are what it's all about -- widgets to display email, news, weather, news feeds, headlines and more. There's nothing new to shout about, just a new look that Yahoo is keen to share on its blog.
My Yahoo is great if you like to get your data in snippets or bite-sized chunks. Want to see a few of the tweets from people you follow but don’t fancy visiting Twitter? There's a widget for that. Like the idea of seeing a tiny portion of the unread email waiting for you in your inbox? Ditto. Things not feeling quite commercial enough? Why not change the look of your own My Yahoo with a theme from your favorite band (or brand)?
Still need convincing? Let Yahoo's video work its magic on you:
Do you feel the need for a personalized introductory page to access the web or are you more comfortable with a selection of tabs?
-

7 things I HATE about iOS 7
Publié: septembre 19, 2013, 2:14pm CEST par Mark Wilson
 So… it's here. iOS 7 has lumbered its way onto hundreds of thousands of iPhone and iPads all over the world -- mine included. My iPad 2 may be slightly aging, but it still does the job for me. I've yet to find a compelling reason to upgrade to a more recent model, but the prospect of a major OS upgrade is always exciting.
So… it's here. iOS 7 has lumbered its way onto hundreds of thousands of iPhone and iPads all over the world -- mine included. My iPad 2 may be slightly aging, but it still does the job for me. I've yet to find a compelling reason to upgrade to a more recent model, but the prospect of a major OS upgrade is always exciting.I'd read great things about iOS 7 previously, but having never taken the step of jailbreaking my tablet, I had not been able to try it hands-on. The download from Apple's servers was going to be my first proper experience of the update.
In all, the process took about 3 hours. I fared better than a lot of people, but I still experienced multiple failed downloads as everyone in the world (it seemed) tried to grab the update at the same time. Quite why the failed download had to start from scratch each time is beyond me, but if that's the way it works, that's the way it works.
So I now have an iPad 2 loaded with iOS 7. What do I think of it? Well, it's early days, but my first impressions are far from good. It didn’t take long to come up with a list of 7 things I hate about iOS 7.
1. The beauty has gone from iOS. The word "beautiful" -- which is attached to virtually anything Apple releases -- does not apply here. I'm not anti-change, don’t get me wrong, but the system icons are just ugly. Inexcusably ugly. Crafted from a palate that is simultaneously garish and pastel -- I don’t know how they did it! But it's not just the icons… there's just so much blank space! We've got all of these pixels, so why not fill them up with something useful?
2. iOS 7's app switcher seems to have copied the method I had so much trouble with in Windows Phone 8. What was wrong with the old method? Double tap the home button and a handy list of recent apps adorned the bottom of the screen. This is still the case, but icons are now super spaced out so more swiping is needed to access apps that you used a while ago. The new switcher has introduced more work.
3. Accessing spotlight. Why change this?! I was perfectly happy with swiping from left to right on the homescreen and I've built up memory muscle. Now I need to remember to swipe down. But not from the top of the screen… oh no. From the MIDDLE of the screen on the homescreen. In what world does that make sense? This is a perfect example of change for the sake of change. What does a left to right swipe on the homescreen now do? Nothing. Absolutely nothing. At the very least, the down-swipe-in-middle-of-homescreen could have been used to supplement the old method. Why replace it?
4. The keyboard. Still no swipe typing? And it's huge! This might sound good, but the keyboard takes up half the screen (nearly) while actually featuring very few keys. And the lack of customization here is surprising. The iPad is marketed as a tool that can be used for everything. It certainly can’t be used for extended periods of typing -- the keyboard is just too limited. Need to type the percentage symbol? Should be quick and easy, right? Nope. You first have to tap the .?123 key to switch to symbol mode. Then realize that the symbol you need isn’t there. So you tap the #+= button to switch to the second symbol mode. There's little in the way of intelligent grouping here. The iOS keyboard is a law unto itself and stuck in the Dark Ages.
5. The camera app. There are just too few settings. And what the heck is the point of the square mode? The burst mode seems kind of pointless to me. There are going to be very few circumstances in which it is going to be possible to fire off series of rapid-fire shots without the pictures looking terrible -- there just isn't time for focusing.
6. Near Me in the App Store. Why would I care which apps have proved popular with people near to my current location? Why would this be useful? Apart from being in the same place, what are the chances of me having anything else in common with someone who just happens to be in my environs? Gimmicky and pointless.
7. The built in apps. You would think that Apple -- no stranger to producing software -- would be able to produce a halfway decent selection of built-in apps. But even though we've reached iOS 7 (yes, 7!), Apple's own apps are still awful. The Notes app is a joke, the calendar little better. Apps such as the Clock -- the Timer element in particular -- just make such bad use of the available space. Reminders looks like it was designed in 1992. I could go on, but I feel I need to lie down.
 It's a shame. I dearly wanted to love iOS 7. The iPhone 5c and 5s announcements got me excited about Apple again -- which is odd as many people were deriding the company for its lack of innovation. I was seriously considering getting back into the world of iPhone (it's a while since I owned my 3GS), but I'm not sure I could live with the OS full time.
It's a shame. I dearly wanted to love iOS 7. The iPhone 5c and 5s announcements got me excited about Apple again -- which is odd as many people were deriding the company for its lack of innovation. I was seriously considering getting back into the world of iPhone (it's a while since I owned my 3GS), but I'm not sure I could live with the OS full time.I may change my mind. The iPad 2 is currently serving as a testbed -- I may grow to like it more over time, but at the moment iOS 7 turns me off just about as much as Windows Phone. I'm just glad I didn’t have to get tied into a 2-year contract to find out I didn’t like the OS!
My colleague Wayne Williams lists seven things he loves about iOS 7 here. If you've upgraded to the new OS, what's your view of it? Do you love it, hate it, or are you undecided? Leave your comments below.
Photo Credit: Arcady/Shutterstock
-

Update your iPhones and iPads! Apple releases iOS 7
Publié: septembre 18, 2013, 7:07pm CEST par Mark Wilson
 Anyone who manages to get their hands on an iPhone 5c or iPhone 5s on Friday will find that it comes with iOS 7 pre-installed. But if you’re not planning on investing in new hardware, head over to Apple's update server right now and you can grab yourself an upgrade free of charge.
Anyone who manages to get their hands on an iPhone 5c or iPhone 5s on Friday will find that it comes with iOS 7 pre-installed. But if you’re not planning on investing in new hardware, head over to Apple's update server right now and you can grab yourself an upgrade free of charge.The OS revamp is available as of 10am PST / 6pm BST, and if you jump on the download straight away you may well find it a slow and frustrating experience as the world and its dog tries to do exactly the same. But hang on in there... it'll be worth the wait.
There's a great deal to explore in the latest version of Apple's mobile OS, and it is the new look that is the immediate eye-catcher; one that Apple has brought to iCloud as well as iOS. This time around there is a flatter, layered look that is quite a change from previous versions, but this is an OS that is about much more than just looks. Apple has taken a leaf out of Google's book and added a new control center which provides easy access to frequently used settings such as Wi-Fi, brightness and camera.
There are also plenty of new features to explore. The Notification Center keeps you up to date with everything you need to know from your calendar and other apps, while AirDrop simplifies the process of sending files from one device to another. There's better multi-tasking, an improved version of Safari, enhanced Siri, and free web radio in the form of iTunes Radio. Wayne looked at more of the changes when iOS 7's release date was announced.
So, can you get the upgrade? As has been the case with previous iOS releases, Apple has not forgotten people who have had its devices for a few years. Numerous older products are eligible for upgrade -- Phones all the way back to iPhone 4 are in line for the update, although iPod touch users need to be packing a fifth generation model. For iPad owners, it is only people with first generation devices that are out of luck -- iPad 2, Retina display iPads, and iPad minis are all supported.
So… what are you waiting for? Well, you could just wait for your device to offer you the upgrade in due course, but where’s the fun in that?! Fire up your iOS device, head to Settings and tap Software Update in the General section. It might take a while, so crack open a cold one while you wait. Enjoy!
-

LinkedIn throws its hat into the ring -- wants to be more transparent
Publié: septembre 18, 2013, 6:23pm CEST par Mark Wilson
 It seems that every online company is in a sharing mood at the moment. Facebook has already come clean about the data requests it has received from the US government, Microsoft wants to tell us more and Google is really keen on the idea. The latest company to express concern about the restrictions on reporting about government data requests is LinkedIn.
It seems that every online company is in a sharing mood at the moment. Facebook has already come clean about the data requests it has received from the US government, Microsoft wants to tell us more and Google is really keen on the idea. The latest company to express concern about the restrictions on reporting about government data requests is LinkedIn.In a "Letter to the LinkedIn community", Vice President, General Counsel, and Secretary of LinkedIn, Erika Rottenberg, not only announces the publication of the social network's Transparency Report for H1 2013, but also expresses "great disappointment and frustration" at the limitations on what can be reported. Rottenberg reveals that she has written to the FBI to ask that LinkedIn be permitted to release additional data about requests that have been made.
In the letter, Rottenberg points out that there are "significant concerns among both the American people and the global community about the privacy of Internet communications, activities, and personal data". She also refers to the requests made by LinkedIn to disclose "information regarding the total number of national security-related requests, including FISA and NSL [National Security Letters] related requests, if any, and the number of members affected by these requests" and asks that the FBI reconsider its position.
LinkedIn wants to "disclose the information that we believe our members and the broader public are entitled to receive".
Rottenberg also reveals that LinkedIn has filed an amicus brief in which the company argues that gagging orders restricting the publishing of information about national security letters are a violation of the First Amendment.
The transparency report itself does not contain a great deal of information -- it is very much the type of thing we have already seen released by other social networks. The report does reveal that in the first half of 2013 information was requested for less than 0.00005 percent of LinkedIn accounts. As has become the trend, it is the US government that is revealed as making the most requests. In the first six months of 2013, 70 requests affecting 84 accounts were made -- and data was provided by LinkedIn in 57 percent of cases.
In fact, it looks as though LinkedIn has provided very little information in response to government requests. Only the US and Denmark made successful requests. The UK government requested data relating to four accounts, but no data was released. You can take a browse through the figures for yourself by viewing the online report.
Photo Credit: Syaheir Azizan/Shutterstock
-

Any.do bridges the web-desktop divide with new Chrome app
Publié: septembre 18, 2013, 2:01pm CEST par Mark Wilson
 There can be few of us who don’t rely on a todo list of one form or another to manage our increasingly hectic schedules -- and there are certainly plenty of tools to choose from. To help juggle deadlines and manage my time, I've long relied on Any.do, starting off with the iOS app and then migrating to the Android version and Chrome extension. Now there's a new tool to play with: the Any.do Chrome App.
There can be few of us who don’t rely on a todo list of one form or another to manage our increasingly hectic schedules -- and there are certainly plenty of tools to choose from. To help juggle deadlines and manage my time, I've long relied on Any.do, starting off with the iOS app and then migrating to the Android version and Chrome extension. Now there's a new tool to play with: the Any.do Chrome App.Google recently celebrated Chrome's fifth anniversary with a push of apps for the browser, and Any.do is just the latest big name to find itself included in the For Your Desktop section of the Chrome Web Store. As there was already an extension available, what’s the point of a separate Chrome App?
The key advantage is the ability to work offline. This is great for anyone using a laptop out and about as there is no need to have an active Internet connection to add new appointment reminders. As soon as a connection is available, anything that has been created offline will be synced to the cloud and made available to other devices you have associated with your account.
There are a couple of other points worth noting. Firstly, the app supports dictation, so if you don’t fancy typing out a reminder you can simply say it aloud.
Secondly, because the Any.do app now runs in an entirely separate window it appears more like a regular app and there are also handy keyboard shortcuts.
The app can be downloaded from the Chrome Web Store now. Take it for a test drive and see what you think!

Photo Credit: Brian A Jackson/Shutterstock
-

Apple gives iCloud.com an iOS 7 makeover
Publié: septembre 18, 2013, 12:30pm CEST par Mark Wilson

Today is iOS 7 day! But there is more than just a new operating system for your iPhone, iPad and iPod to look forward to; Apple also has a redesigned iCloud website for you to use. Unsurprisingly the new design takes heavy inspiration from the look of iOS 7, mimicking the floaty, layered styling that graces the new mobile OS.
Log into your account and you'll immediately be greeted by a muted, blurry background, over the top of which various icons appear to float. Apps including Mail, Contacts, Calendar, Notes, Reminders and Find My iPhone all now sport the iOS 7 look, but the beta editions of Pages, Numbers and Keynote retain their older design. It looks as though there might still be a little work to do -- not all icons have been redesigned, for instance.
There have been a lot of redesigns in the tech world recently. Google's flat logo is appearing on its sites for many people, Yahoo has a new logo, and Bing just revealed a new look for its news site as well as a new logo. With iOS 7 being such a radical departure from the previous versions of the OS, it makes perfect sense for Apple to give the rest of the product line a similar feel.
If you’re keen to try things out, you may have to wait for a bit as iCloud appears to be groaning under the weight of traffic as millions of iOS users back up their data in preparation for the big upgrade.
What do you think of the new design for iCloud?
-

Microsoft wants you to do more to stay safe online
Publié: septembre 17, 2013, 8:00pm CEST par Mark Wilson
 Microsoft is no stranger to finding itself on the receiving end of complaints about security issues that are found in Windows and its other software. But now the Redmond company is turning the tables on consumers, saying that they need to do more to secure their own computers. Microsoft's research shows that Internet users are taking fewer precautions when they're online.
Microsoft is no stranger to finding itself on the receiving end of complaints about security issues that are found in Windows and its other software. But now the Redmond company is turning the tables on consumers, saying that they need to do more to secure their own computers. Microsoft's research shows that Internet users are taking fewer precautions when they're online.This is based on declining Microsoft Computing Safety Index (MCSI) scores over the last couple of years. The MCSI system was developed in 2011 as a way to measure the security savviness of web users. The system takes into account whether users do common things such as installing anti-malware software, enabling a firewall and keeping software up to date. It also factors in whether users are aware of the importance of using secure websites, using unique passwords and taking care of the personal information they share online.
It's not all bad news. The research shows that we're generally getting better at ensuring the basics are covered -- using secure networks, installing protective software and (not that there's any bias in the research, you understand) using a genuine version of Windows. But it certainly seems as though there is room for improvement in other areas -- areas Microsoft has called Technical and Behavioral.
What do these areas encompass? They include taking a more proactive approach to security by doing things such as PIN protecting a phone, changing social networking settings, and learning more about what can be done to stay safe.
But one thing is clear... better education about staying safe online is needed. The findings reveal that some people are actually more secure than they thought they were, but this seems to be as a result of luck rather than good judgment. For example, only 40 percent of people thought they had a firewall in place, but when guided through checking settings, it transpired that 78 percent were actually protected by a firewall.
If you're interested in seeing how you fit into the statistics you can take part in a survey which will assign you a couple of scores -- one for general computing safety and one for mobile safety. For anyone who's interested, I scored 37 and 48 respectively, and Microsoft suggested I "take it up a notch".
Photo Credit: Maxx-Studio/Shutterstock
-

The most popular stories on BetaNews this past week -- September 8-14
Publié: septembre 14, 2013, 4:18pm CEST par Mark Wilson
 Big news came from Apple and Microsoft this week. Microsoft seemingly had a change of heart; having previously said that Windows 8.1 RTM would not be made available before its official launch date, the company announced that it would be released to people with TechNet and MSDN subscriptions.
Big news came from Apple and Microsoft this week. Microsoft seemingly had a change of heart; having previously said that Windows 8.1 RTM would not be made available before its official launch date, the company announced that it would be released to people with TechNet and MSDN subscriptions.The same group of people also gained access to the pre-release version of Skype. Microsoft was clearly in a very giving mood this week as the company also announced that it was giving free copies of Office 365 to non-profit organizations.
But it was Apple with the really big news. As well as revealing that iOS 7 will be available on September 18, the long-awaited new iPhones were also unveiled. The iPhone 5c is Apple's colorful addition to the iPhone line-up, while the higher end iPhone 5s benefits from a 64-bit processor, new camera options and, of course, that fingerprint reader. Pre-orders were opened soon after the announced launch.
Not content with what's available to buy now, Ian looked further into the future to see what we could expect from the word of tech in the year ahead. Joe revealed the latest range of Chromebooks will be based on Haswell chips.
Social networking giant Facebook revealed not only that possibility that public posts could start to appear in TV broadcasts, but also that we should brace ourselves for the arrival of auto-playing video ads. AVG announced CrowdControl, a new tool managing privacy settings on Facebook.
This was also a week of offense. AT&T caused ripples with an ill-advised ad-campaign that featured 9/11 imagery on the anniversary of the tragedy. IN the UK, the domain name registry Nominet asked for input from customers to determine whether potentially offensive domain names should be banned.
Mihaita spent some time this week looking at life online. As well as embracing Just Delete Me's easy method closing down online accounts, he was also pleased that Microsoft finally added IMAP support to Outlook.com.
Tablet users could be in line for a boost in storage space -- Seagate's 500GB Ultra Mobile HDD indicates a move away from SSDs where space is traded off for speed. On the subject of mobiles, Brian got a little vocal about the issues he has with Android, while I voiced my dislike for a lot of what I found in Windows Phone 8. Mihaita looked at how Google is shunning Microsoft's mobile OS by delivering uglier interfaces to WP users accessing its online services.
Moving to the desktop, Wayne opined about the installation process of Windows 8.1. He also showed his age (sorry, Wayne!) reminiscing about his punk days, as Google celebrated the music of The Clash. Also on the musical front, Google rolled out an update to Music All Access that allows for better personalization of the service.
We already knew that the PlayStation 4 is not too far off, but Sony also announced the PlayStation Vita TV. Essentially a Chromecast-style media streaming unit, the Vita TV also allows for the streaming of PS4 games from one room to another. Anyone already packing a Roku streamer now has a new Android app that allows for video to be streamed from Android to Roku.
These are just some of the highlights from this past week. The next seven days promise to be at least as busy!
Photo Credit: vinz89/Shutterstock
-

Facebook to increase your mobile data usage with automatic video playback
Publié: septembre 13, 2013, 8:05pm CEST par Mark Wilson

A new feature is rolling to Facebook mobile, a feature that has been designed to provide "an easier way to watch video". "How could a video possibly be made easier to watch?", you may well ask. "All it takes is a quick tap to start playback!" The new feature will play videos as soon as you see them in your news feed -- no need for a tap.
Videos start playing silently and if you're not interested in watching you can just keep scrolling by. But if a video does take your fancy, how do you think you view it with sound and in full screen mode? That's right… you tap on it. Just like you do at the moment. The feature is not yet available to everyone, but if you don’t see it in your account on your mobile handset, you can check out a video of what it looks like in action.
You may well be pleased to hear that the feature is not yet being made available to advertisers -- the initial rollout is limited to video posted by individuals, bands and musicians. Sadly this is probably not going to be the case forever. Facebook says "we'll continue to explore how to bring this to marketers in the future".
When advertisers' videos play automatically in your newsfeed, there are a couple of side effects, neither of them particularly appealing. Firstly, you are forced into watching at least a snippet of a video you may well not be interested in. Obviously we do not yet know just how video ads with auto playback will be implemented, but if they work anything like the way regular auto playback videos do, ads are about to get a whole lot more intrusive.
But the second side-effect is more worrying. For a video to play automatically, it has to be downloaded or streamed on the fly. If a video is one you are not interested in viewing, the download is carried out needlessly. And remember, the automatic playback option is on mobile devices. There you may well be paying for data usage -- so you are effectively going to be paying to view advertisements.
It is one thing to have an app or service that is supported by advertisements; users have the option of ignoring them or taking notice as they prefer. But to force people to pay for extra bandwidth usage is below the belt. It's good to hear (or not) that videos do play silently, but that's not really the point. It looks as though mobile Facebook users will need to keep a close eye on their data usage, or a quick browse of their newsfeeds could turn out to be expensive, particularly when roaming.
Credit: Vectorlib-com/Shutterstock
-

Twitter explains why you and your friends may see different site features
Publié: septembre 13, 2013, 7:28pm CEST par Mark Wilson

When you use Facebook and Twitter, everyone's looking at the same website and has access to the same set of tools, right? Wrong. In the case of Twitter, users who have verified accounts have access to different tools and options and the same is true for different levels of users on other sites and social networks. But it seems that even two average Twitter users could find that they have a different experience from each other on the site.
In a blog post entitled "Experiments @ Twitter", Twitter's Vice President of Engineering, Alex Roetter, says that experimenting with new features and options may mean that two people see different versions of Twitter. Roetter explains "it’s rare for a day to go by when we’re not releasing at least one experiment", referring to both the website and mobile clients.
Providing access to different options is nothing unusual -- it's something that Google and Microsoft frequently indulge in. Where you are in the world is most often the determining factor in which version of a site you see, but it does not sound as though this is the case with Twitter.
When Roetter says "you may see some features that your friend doesn’t see, or vice versa", there is no reference made to countries. Tests are carried out with small groups of users to help to decide which features should be officially released. I contacted Twitter to find out what criteria they use when selecting testers for experimental features, and Carolyn Penner told me that selections are random rather than being based on location.
In the meantime, I'm interested to hear if anyone has been granted early access to a feature that was later made public, or whether you got to try out some great new options that were dropped.
Image Credit: YanLev / Shutterstock
-

Facebook closes Social Fixer's page -- owner warns other businesses
Publié: septembre 12, 2013, 5:15pm CEST par Mark Wilson
Social Fixer is a browser extension available for Chrome, Firefox and others. It exists to make Facebook a more pleasurable experience, by ironing out annoyances and adding extra features. In theory this means Facebook users are happier and therefore use the site more -- everyone's a winner. The tool is free and over the course of four years its developer, Matt Kruse, built up a following of hundreds of thousands of users. Now Facebook has wiped that out.
The Social Fixer tool still exists and still offers the same options as it did before, but it no longer has a Facebook presence. Back on 2 September the Social Fixer Facebook Page (which is still inaccessible) was "unpublished" by Facebook. The reason specified was that the page had been flagged up for spam -- this is something Matt vehemently denies ever engaging in.
This in itself is nothing particularly out of the ordinary. Pages do get temporarily suspended from time to time, and it can be done by mistake. But what is more interesting is what happened yesterday, 11 September, following an appeal. This time Facebook completely removed the Social Fixer page entirely, citing a violation of "community standards".
The page had over 330,000 likes but these have now been lost forever. The support group was used by over 13,000 people, but this has now been closed as well.
In a blog post entitled "Beware: Your Business Is At The Mercy Of Facebook!" Matt explains his experiences and warns other businesses who use Facebook to be aware of the possibility of page removal.
The case of Social Fixer is probably unique. It is free of charge, although donations are accepted, and the extension website does feature advertisements, but it is understandable why Facebook might take umbrage at its very existence. Social Fixer has its own website and is not exactly reliant on Facebook but the social network is where many people turn to for support from any product or company.
I've reached out to Matt to try to get some more details about what is happening now and next, and I'm waiting to hear back from him -- I'll update this article as and when I do.
In the meantime, what do you think about this? Assuming Matt has not been spamming users, what justification could Facebook have for closing down the pages? Do you use Facebook as a point of contact for your business, and does this worry you? Obviously Facebook is, ultimately, free to close any pages it wants for whatever reason -- but is this right?
-

AT&T causes offense with 9/11 Twin Towers ad for BlackBerry Z10
Publié: septembre 11, 2013, 9:47pm CEST par Mark Wilson
 AT&T finds itself on the receiving end of an internet backlash after tweeting an advertisement for the BlackBerry Z10 that used 9/11 imagery. On the anniversary of the tragedy that saw the Twin Towers fall, the US phone giant posted the ad on Twitter -- the tweet has since been removed -- which featured the Tribute in Light memorial under the heading Never Forget. A similar post was also made on Facebook -- this has too been removed.
AT&T finds itself on the receiving end of an internet backlash after tweeting an advertisement for the BlackBerry Z10 that used 9/11 imagery. On the anniversary of the tragedy that saw the Twin Towers fall, the US phone giant posted the ad on Twitter -- the tweet has since been removed -- which featured the Tribute in Light memorial under the heading Never Forget. A similar post was also made on Facebook -- this has too been removed.The ill-advised marketing move has backfired however. The company's Twitter feed is now filled with vitriolic responses from those sickened by the imagery. Search Twitter for AT&T and there are tweets from thousands of users who can only be described as being seriously pissed and deeply offended. On the BetaNews team, New Yorker Brian said that it was horrible and that he hated it.
The original tweet, after being removed, was followed a few hours later by a tweeted apology. This time AT&T's words had a rather different tone to them: "we apologize to anyone who felt our post was in poor taste. The image was solely meant to pay respect to those affected by the 9/11 tragedy".
Both #NeverForget and #september11 were trending topics throughout the day, and many have berated AT&T's advert as being in poor taste. The cell provider is far from being the only company to make reference to 9/11 today (there have been countless tweets of memorial from many big names), but it is one of a very small number who had the gall to try to profit from the tragedy by using it in advertising.
-

Google loses appeal in Street View Wi-Fi collection case -- right or wrong?
Publié: septembre 11, 2013, 6:36pm CEST par Mark Wilson
 Google faces claims for damages from people who had personal data collected from their wireless networks as the company gathered information for its Street View service. Google had previously claimed that emails, usernames and passwords had been collected unintentionally, but the appeal ruling means that the company is not exempt from liability under the federal Wiretap Act.
Google faces claims for damages from people who had personal data collected from their wireless networks as the company gathered information for its Street View service. Google had previously claimed that emails, usernames and passwords had been collected unintentionally, but the appeal ruling means that the company is not exempt from liability under the federal Wiretap Act.Back in 2010, Google admitted that data such as network SSIDs and MAC addresses were collected along with photos. In this blog post the company denied that it pulled "payload data" (essentially the data that is being sent over the networks) but it was later revealed that "Google did indeed collect (and store) this information from unencrypted Wi-Fi networks". A full report is available to read online. Google was required to delete this data, and indeed did so.
But this did not stop the court cases from groups of people who felt that their privacy had been invaded. Google tried to claim that its collection of data was exempt from the Wiretap Act but this was rejected because "data transmitted over a Wi-Fi network is not an 'electronic communication' that is 'readily accessible to the general public'". The ruling in the Joffe vs Google case can be read in full online -- including the reminder that Google was found to have collected 600GB of data transmitted over wireless networks in 30 countries.
Google has thus far had little to say on the ruling, but a spokesperson told me, "We are disappointed in the Ninth Circuit's decision and are considering our next steps".
The court decision led to some lively debate here at BetaNews. I'll leave things anonymous for now, but it was suggested by one member of the team that there was no problem with Google gathering data from a public place assuming there was no encryption to bypass. Another argument that cropped up was that Google could not be considered to have been wiretapping as it collected the data without meaning to.
The counter argument was that Google should have been fully aware of exactly what data it was collecting whilst travelling the streets of the world. Breaking the law by accident, or unintentionally, is still breaking the law -- and it's only right to expect an appropriate punishment to be handed out.
The appeal ruling says it would be "absurd" to consider emails and other data sent over an unencrypted network to be "readily accessible to the public", so it is fair to assume that software had to be written that was capable of harvesting this specific information.
We'd be interested to hear what you make of it all. Should Google be penalized for the "unintentional" collection of data? Is data transmitted over an unsecured Wi-Fi connection fair game?
Image Credit:ronfromyork/Shutterstock
-

Google files amended transparency petition in push to publish FISA order details
Publié: septembre 11, 2013, 2:32pm CEST par Mark Wilson

Google's unofficial motto has long been 'do no evil' and the company is keen to be seen to stick to it. Jumping into bed with Nestle may have raised a few eyebrows and rattled a few cages, but in a blog post, Richard Salgado, Director of Law Enforcement & Information Security, and Pablo Chavez, Director of Public Policy and Government Affairs show the search giant is eager to stay on the right side of customers.
Google has filed petition in the US Foreign Intelligence Surveillance Court asking that they be allowed to publish details of FISA orders. The petition is very similar to others that we have seen in recent months in the wake of the NSA surveillance revelations, and is really just a follow-up to the We Need To Know letter from back in July in which a number of leading companies wrote to, amongst others, President Obama to "urge greater transparency around national security-related requests".
The newly amended petition doesn't really ask for much that's new. It reads "Google Inc respectfully moves this Court for a declaratory judgement that Google may disclose statistics regarding Google's receipt of orders issues by the Court, if any, without violating the FISA or FISC Rules of Prodcedure".
Google also requests a "public oral argument" of the amended motion so that "this issue of public concern is debated and decided with the utmost transparency". This is the key part of the amended transparency petition -- that a public debate be carried out rather than discussions behind closed doors.
So is this more aggressive move by the search giant to reveal more about data requests in the public interest, or in Google's?
Image Credit: Raywoo/Shutterstock
-

9 reasons why Windows Phone 8 leaves me cold
Publié: septembre 10, 2013, 2:28pm CEST par Mark Wilson

Just like Brian (despite his niggles), Android is my mobile operating system of choice. I was once a diehard iOS user -- my old iPhone 3GS is still one of my favorite phones of all time -- but I've also been known to experiment with other mobile platforms.
Back in the days before smartphones, I had handsets from Nokia, Sony, Samsung, LG and numerous others that have been lost in the mists of time. My first smartphone was a rebranded HTC handset going under the guise of an Orange SPV M3100. It ran Windows Mobile, had a slideout keyboard and was amazing.
This was my first experience of a mobile phone operating system from Microsoft (I'd previously owned some device or other running Windows CE and also had an iPaq handheld at some point), and I loved it. One of the most enjoyable things about it was the fact that it was so customizable.
Don’t like the look of the default skin? Sure, you could download another one -- often at a cost -- but there was great fun to be had in rolling your own. It was glorified webpage design, but it meant that I could transform my homescreen into whatever I wanted. I then had a brief blip. Something I'm not proud of. I bought a BlackBerry. I actually quite liked it. But… moving on.
Then I switched to my beloved iPhone. I loved it. iOS was unlike anything I'd ever used before and it was special enough for me to overlook the rather restrictive nature of the OS. iOS is an impressive piece of software, but after two years I was ready to try something new -- although I still keep my hand in with my iPad.
Jumping ship to Android is probably the best move I ever made. I'll freely admit to being something of an Android fanboy. I realize it's not a perfect operating system, but for me it comes pretty damn close. Sure, there are still restrictions I'm not overly happy with -- the need to root to perform certain tasks is irritating (although I do appreciate the reasoning behind it) and extreme customization is more difficult than it should be.
But Android is still the mobile OS for me. I use it on an HTC Sensation, HTC One mini, Sony Tablet S and a Nexus 7. I love it, and I'm not ashamed to admit it.
Recently I branched out to Windows Phone 8 after a Nokia Lumia 928 came my way. Was it going to be a chance to relive the days of working with Windows mobile? In a word "no". I am in disbelief. I am staggered that this operating system exists in 2013.
What’s wrong with it? Where shall I begin?
- Why is the notification bar not visible at all times? I don’t just want to see the time, I want to be able to see my battery level and signal strength, as well as checking whether I'm in silent mode without the need to swipe down.
- Outrageously awkward method of toggling wifi/data/GPS etc on and off. If I want to toggle a setting like this, I want to be able to do it in a couple of taps, not by navigating to Settings and hunting down what I need.
- App switching. In stock Android switching to a recently used app is simple. Press the button, swipe down, tap app. Job done. In Windows Phone 8 it's a case of tap and hold the back button, only to be presented with an "icon" for each recent app that takes up virtually the entire screen -- which means too much scrolling if the app I'm looking for is not the last one I used. I realize this is not too dissimilar to switching on other devices, it's the size of app icon that grates.
- No Google-made apps. OK, none might be putting it a bit strongly (there is one, but it only acts as a link to Google Search), but the lack of Google apps is a serious drawback. I realize that this is not Microsoft's fault, but it irritates me anyway.
- Apps in general. It's almost too easy a target, but the selection of apps in the Store is nothing short of pitiful. Any app store is populated by a massive majority which are, put simply, utter crap -- it's to be expected. But the low overall number of apps available for Windows Phone means that the small number of halfway decent ones that there are just get lost.
- No push/pull email for the Google profile. My email has to be checked on a schedule? Which century are we living in here? Seriously!
- Notification system. Live tiles are not a good way to let me know that I have a new direct message on Twitter, 57 emails to read, and various interactions on Facebook. If I'm reading a website and want to see how many new notifications there have been since I last checked, I don’t want to leave what I'm doing and head to the home screen to find out -- that's just insane.
- Why are games treated differently to apps? I install an app and it appears, obviously, in the apps list that appears with a left swipe. Great. If I want to access games, they are locked away in their own section. I'm not much of a gamer, but I do like the occasional puzzler to pass the time. Yes, games shortcuts can be pinned in place, but why should I have to go through this extra step? Games are meant to be fun, not hard work! Playing games may be fun, but intuitive it ain't!
- Screen rotation. Why is this not a system wide setting? If I want to browse the web with Internet Explorer whilst lying on my side, the page 'helpfully' rotates for me, and there's no way to override it -- short of using a different browser or jumping back to my Android phone.
How is an operating system this bad allowed to exist in this day and age?
It's a great shame. The Lumia 928 is a lovely piece of hardware; the screen is nothing short of gorgeous. I'm a fan of the slightly retro, cubist look of the handset, and the camera is fantastic. But the software is just dire, dire, dire.
Microsoft produces operating systems. Admittedly some are worse than others (Windows Me?), but Windows Phone really has taken me aback. What the hell is Microsoft thinking?
Photo Credit: filipw /Shutterstock
-

F*@K me! Nominet may block 'offensive' words in domain names
Publié: septembre 10, 2013, 12:30pm CEST par Mark Wilson
 You know how the internet is meant to be one of the few remaining forums in which you’re free to speak your mind? That could be set to change in a slightly concerning way. You might think that if you have your own website you're free to say pretty much whatever you want (legality providing), but the UK's domain name registry, Nominet is looking into the possibility of blocking offensive words from domain names.
You know how the internet is meant to be one of the few remaining forums in which you’re free to speak your mind? That could be set to change in a slightly concerning way. You might think that if you have your own website you're free to say pretty much whatever you want (legality providing), but the UK's domain name registry, Nominet is looking into the possibility of blocking offensive words from domain names.Perhaps the first question to ask here, is "who decides what is offensive?", and Nominet is not only reviewing its domain registration policy but also asking for input from the public. In its review document, Nominet explains that until now it has "intentionally taken a non-restrictive approach to the words and phrases that may be used in a domain name". The organization goes on to say that it has not "made any value judgement as to the use to which domains are put, or whether they might be offensive or in poor taste" but cites the Republic of Ireland and China as examples of countries in which some restrictions are in place.
Back at the end of July, Nominet was contacted by the Department for Culture, Media and Sport and discussions took place about the possibility and practicality of blocking offensive words from domain names. From the exchange of correspondence, it does seem as though the policy review has very much been prompted by Government intervention.
Nominet point out that "defining whether something is offensive is a subjective judgement" and cites a couple of examples which might lead to problems. The oft mentioned Scunthorpe problem raises its head once again, and Nominet also suggests therapist.co.uk is a domain that could be read in more ways than one.
Indeed, consider www.psychotherapist.co.uk. Does this refer to the helpful services of a psychotherapist, or is it the home of a more sinister website Psycho The Rapist?
Feel strongly about it one way or the other? Let Nominet know what you think by completing its online survey.
Photo Credit: K. Faraktinov/Shutterstock
-

Now your public Facebook posts could appear on the news!
Publié: septembre 9, 2013, 1:10pm CEST par Mark Wilson
Facebook is making it easier for news outlets such as BskyB, CNN and NBC to integrate conversations from the social network into their broadcasts. Using the Public Feed API, broadcasters are now able to display a real-time feed of posts that contain a specific word. Considering that, according to Facebook's own figures, last week's kick-off of the new NFL season resulted in over 20 million likes, comments and shares, that's a lot of data to be dealing with.
There is also the new Keyword Insights API which can be used to determine how many posts mentioned a particular term in a specified timeframe. But the API goes further than this, also making it possible to filter results -- allegedly anonymously -- based on gender, age and location. At the moment both of these APIs are only being made available to a limited number of partners, but the list is certain to grow over time.
For news shows looking to find new ways to interact with their audience, this is a great announcement. Now, rather than just presenting viewers with the news, programs can pontificate about how viewers from different parts of the country feel about a given story. A lot of people like the idea of hitting the headlines, but this is unlikely to be what they had in mind.
What is interesting to note is that, as you'd probably guess from the name, the Public Feed API can only be used to access public posts, but no such limitations are mentioned in relation to the Keyword Insights API.
The blog post that Facebook uses to announce the new "feature" -- referred to, almost comically as "tools for surfacing conversations" -- is also home to an interesting little infographic that shows the number of Facebook interactions generated by various TV programs.
So… what do you think? Should we have been expecting something like this to happen? Does it seem like a reasonable implementation of Facebook's terms of service? Anyone planning on storming away from the social network in a stroppy protest?

-

The most popular stories on BetaNews this past week
Publié: septembre 7, 2013, 7:21pm CEST par Mark Wilson
 Looking at the biggest stories on BetaNews from September, 1 - 7, 2013. This was a week packed with news from IFA in Berlin -- lots of big announcements to whet our appetites for the coming months. LG's G Pad was revealed as a potential competitor to the Nexus 7 and iPad mini, while Acer was found to be proudly showing off its new R7 notebook complete with innovative Ezel hinge that allows for a range of working positions.
Looking at the biggest stories on BetaNews from September, 1 - 7, 2013. This was a week packed with news from IFA in Berlin -- lots of big announcements to whet our appetites for the coming months. LG's G Pad was revealed as a potential competitor to the Nexus 7 and iPad mini, while Acer was found to be proudly showing off its new R7 notebook complete with innovative Ezel hinge that allows for a range of working positions.IFA was also where Samsung unveiled the Galaxy Note 3 as well as the Galaxy Gear smartwatch which will allow us all to live out our Star Trek dreams. It wasn't long before Note 3 pre-orders were being taken. If you've noticed that phones are getting bigger and bigger, the same is certainly true of tablets -- the Panasonic Toughpad 4K is a staggering 20 inches from corner to corner.
Not quite a tablet, but not really a PC, HP's 23- and 27-inch ENVY Recline TouchSmart PCs were announced, while Lenovo revealed the new Vibe X smartphone and S5000 tablet.
The old adage tells us that as one door opens another one closes. This week it was China that shut the door on Yahoo while the door of opportunity opened up as Microsoft bought Nokia's phone arm from the Finnish company. This wasn’t the only purchase in the news: Vodafone also sold its share of Verizon Wireless for a healthy $130 billion.
An interesting partnership also emerged between Microsoft and the NFL while Yahoo tried to keep itself in the headlines by revealing its new logo. Two updates to Bing this week changed the way video search results are displayed as well as unleashing a new-look version of Bing News.
In the world of software, Spotify revealed details of its stream-music-to-your-speakers-or-devices service Connect. Canonical announced that Ubuntu downloads will now default to the 64-bit version rather than 32-bit -- Brian felt this had been a longtime coming.
Google took a lot of people by surprise by announcing that the successor to Jelly Bean would not be Key Lime Pie as previously expected, but KitKat. Brian and many others were not impressed.
Fans of ebooks had an unusual amount of news to digest this week. Amazon announced its Matchbook service which offers cheap or free e-versions of physical books purchased through Amazon. Amazon was also proud to show off its new Kindle Paperwhite, while Apple lost a lawsuit relating to price-fixing in the ebook market.
Moving to the desktop, Chrome celebrated its fifth birthday. To welcome becoming old enough to go to school, Google released Apps for desktop, further blurring the boundaries between offline and online apps.
We already knew the release date of Sony's PlayStation 4, and Microsoft finally revealed when eager gamers can get their hands on the Xbox One -- November 22. To help stir up interest, a new advertisement was aired.
By its very nature, this new roundup looks back in time, but Bristol University is looking to the future. Anyone wishing to see where the future of computing could lead might like to take a look at the university's quantum computer simulator.
Phew! A busy week... time for the next seven days of fun!
Photo Credit: vinz89/Shutterstock
-

Taste the future -- try out a cloud-based quantum computer
Publié: septembre 6, 2013, 7:27pm CEST par Mark Wilson
 A taste of the future of computing is available from the Physics department of the University of Bristol. The limits of traditional computers are being reached and new technology is needed if things are going to develop at any sort of reasonable pace in the coming years. Quantum computing could just be the way ahead, and the UK university has produced Qcloud, an online quantum computer that you can play with for free.
A taste of the future of computing is available from the Physics department of the University of Bristol. The limits of traditional computers are being reached and new technology is needed if things are going to develop at any sort of reasonable pace in the coming years. Quantum computing could just be the way ahead, and the UK university has produced Qcloud, an online quantum computer that you can play with for free.Mere binary is too limiting, but a quantum computer is not restricted to working with 1s and 0s. Rather than the two states associated with a regular bit, a quantum bit (or qubit -- not to be confused with the Brighton Rock character, Cubitt) is capable of being in multiple states simultaneously. Forget "on" and "off", each qubit can be used to hold multiple pieces of data at the same time.
It is likely that quantum computing will prove pivotal in the development of computing, and if you fancy the idea of trying out such a machine, you can do so with the online simulator. Before you get too excited, quantum computing is still very much in its infancy -- what's being done here is technically very impressive, but at the moment it's not going to enable you to play Grand Theft Auto.
The University of Bristol does have a real -- albeit relatively simple -- quantum computer, whose processor will be available for use from 20 September. But before you fire off your registration, it's a good idea to dabble with the simulator to get a feel for how things work.
It's a bit of a step up from coding Basic or tinkering with Powershell, but who knows where it might lead. With two weeks to go until the real processor is made available, try out the simulator first and get your head around the notion of working with qubits and measuring superposition and entanglement.
Photo Credit: agsandrew/Shutterstock
-

Judge bars Apple from price-fixing deals with ebook publisher
Publié: septembre 6, 2013, 6:10pm CEST par Mark Wilson
 Apple says it will appeal against a court ruling that bans the company from entering into deals with publishers that could allow ebook prices to be fixed or inflated. The case was raised by the Department of Justice and judge Denise Cote's decision is very much in line with what they were seeking. The Cupertino, Calif.-based company is banned from entering into agreements with five named publishers in ways that might restrict ebook prices.
Apple says it will appeal against a court ruling that bans the company from entering into deals with publishers that could allow ebook prices to be fixed or inflated. The case was raised by the Department of Justice and judge Denise Cote's decision is very much in line with what they were seeking. The Cupertino, Calif.-based company is banned from entering into agreements with five named publishers in ways that might restrict ebook prices.Having been found to have conspired with publishers to prevent retailers (rather than publishers or Apple) from setting ebook prices, Apple fell foul of antitrust legislation. The company is required to wipe out a controversial 'most favoured nation' clause in its contracts that effectively ensure that Apple's ebook prices would always match the lowest price available online. Restrictions are in place for different lengths of time for various publishers, ranging from two years in the case of Hachette, to four years for Macmillan.
Apple is also banned from retaliating against or punishing any publisher for refusing to enter in an ebook agreement. Deals and agreements have not been banned with any publisher, but there are important restrictions now in place. In addition to all of this, Apple will spend the next two years under the supervision of a third party monitoring committee.
The judge's ruling will remain in place for five years, but there is potential for this to be extended if deemed necessary. It is hoped that it will ultimately lead to lower prices for consumers, although it's not clear how long it might take the price drops to trickle down and be noticeable.
The ruling can be read in full on the website of the United States District Court for the Southern District of New York.
Photo Credit: koya979/Shutterstock
-

Google celebrates Chrome's 5th birthday with Apps for the desktop
Publié: septembre 5, 2013, 11:05pm CEST par Mark Wilson
Five years. That's how long it is since Chrome was unleashed on an unsuspecting world. Five years and we've already made it to version 29! There will undoubtedly be a few glasses charged in celebration, but Google is also taking this special date as an opportunity to reveal a "new breed of Chrome Apps". Head to the Chrome Web Store and you'll find a new section: For Your Desktop.
Working online with web apps has become increasingly common, but traditional desktop apps are still more popular. Now Google is looking to blur the boundaries between the two, making web apps much more like desktop software. The key thing to note here is that the apps that are found in this section do not -- after the initial download process of course - require an internet connection: they can be used in offline mode.
The news is something that will be music to the ears of Chromebook users (a club I have just joined, having come into an Acer C7), but it's also something that's available to Windows users. Linux and Mac owners haven’t been forgotten, but support for these platforms is still in the pipeline.
So what's so special about this new generation of Chrome Apps? In addition to allowing for data syncing through the cloud, there's also the option of working in offline mode. To help mask the fact that you're really working in Chrome browser elements are hidden from view, and any apps you do use are automatically kept up to date.
But perhaps the most useful feature is the Chrome App Launcher. This is only available for Windows at the moment, and is installed in the taskbar after your first Chrome App is installed. Any Windows 8 user missing the Start menu could seek sanctuary here as it acts as a simple launcher for Chrome Apps as well as providing access to the Store and app options.
Full details can be found at the Google Chrome blog and the apps collection can be found in the For your Desktop section of the Chrome Web Store.
-

Bing News hits the headlines with a modern makeover
Publié: septembre 5, 2013, 7:51pm CEST par Mark Wilson
Today Microsoft refreshes the look of Bing News, giving the site a modern makeover that’s more in keeping with the look of Windows 8 and Windows Phone. But the redesign is about more than bringing products in line with each other, the new layout is "built for touch" recognizing the ever-increasing popularity of touchscreen devices -- not just phones and tablets, but also the likes of the Surface Pro and Yoga.
The new look not only embraces touch, but also takes into account the fact that many people use different devices to access the internet -- switching between a phone, tablet and computer is far from uncommon these days. With this in mind, the site now better adapts to different screen sizes.
At first glance the revamped Bing News page is not a million miles away from the look of Windows 8's Start screen but navigation is, for the most part, kept to vertical rather than horizontal movement. The changes are not all cosmetic, and there are a few additions to page content.
The big new feature is Trending Topic which highlights the biggest stories not just from Bing, but also Twitter and Facebook. Perform a search using Bing News, matching stories are highlighted in the news carousel. If you head over to the site and don’t yet see the new look, keep checking back as it may take a little while for the changes to rollout globally.
-

Samsung Galaxy Note 3: new 5.7-inch monster phone packs a punch
Publié: septembre 5, 2013, 2:04am CEST par Mark Wilson

At IFA in Berlin, Samsung takes the lid off its giant screened smartphone -- the Galaxy Note 3. It use to be the case that as technology developed, devices became smaller -- colossal Walkmans were replaced by more svelte models, chunky Discmans by portable players barely bigger than the disc they were playing. There was a time when the fashion for cell phones took a similar route, but the current propensity for larger screens shows that this no longer rings true.
Samsung's Note range has long taken the idea of a large screened smartphone to the extreme, but the third generation pushes things even further. Equipped with a whopping 5.7 inch screen, the third iteration of the phone is thinner than its predecessor at just 8.3 millimeters, and also lighter at a mere 168g. The Super AMOLED display, boasting a resolution of 1920 x 1080 risks being something of a power sucker, but it's backed up by a 3,200mAh battery.
With an impressive 3GB of RAM and a 2.3Ghz quad-core processor (in the 4G version) or 1.9GHz Octa Core (in the 3G edition), speed is not an issue. The 32GB or 64GB of internal storage is expandable through the MicroSDXC card slot, which might well be needed considering the 13 megapixel rear camera (complete with 4k video recording) and 2 megapixel front facer.
The Note 3 will be available in three colors -- black, white and pink -- and at launch there will also be dozens of colored covers available. These smart covers feature an aperture which reveals a portion of the screen so you can keep an eye on the time and app notifications. The phone -- or phablet as such large devices have been sickenly dubbed -- has a soft-feel back and boasts an updated S Pen. The last version of the stylus includes support for a range of new gestures and navigation options.
As you would expect with a new release, the Note 3 runs Android 4.3. The launch date is set for September 25 in more than 140 countries, although the US launch is slightly later, in October.
-

Amazon introduces 'All-New' Kindle Paperwhite for easy-on-the-eye reading
Publié: septembre 4, 2013, 12:06pm CEST par Mark Wilson

The Kindle Paperwhite is the most successful e-reader ever, and Amazon is updating the range with the sixth generation of the Kindle family. It's the "All-New" prefix that aids identification, but aside from the name, there's a new display, faster processor and a raft of new features for readers to use. In terms of appearance, there are few differences to its predecessor, but the display is where things are most noticeable.
New display technology gives a higher contrast ratio and Amazon claims that pages are "virtually indistinguishable from a physical book". No new version would be complete without an extra turn of speed, and the latest Kindle Paperwhite doesn't disappoint, offering a processor running 25 percent faster than in the previous model. The touchscreen has been upgraded with a tighter grid to help improve sensitivity and accuracy.
But it's not all about the hardware -- new features also abound. Amazon claims battery life stretches to eight weeks, and weighing in at just 7.3 ounces (207 grams) -- 30 percent lighter than the iPad Mini -- it's light on the pocket in at least one way. If you're the kind of person who likes to skip back and forth in a book, Kindle Page Flip enables you to do just that without losing your place.
Other new features include enhancements to the Vocabulary Builder and the new In-Line Footnotes. There's more to come as well. Kindle FreeTime is something that may well be welcomed by parents. It turns reading into a game for kids, letting them earn achievements by way of encouragement. Also in the pipeline is integration with Goodreads, which means you'll be able to keep an eye on what your friends are reading.
The Wi-Fi only and 3G + Wi-Fi versions of the e-reader are available for pre-order for $119 and $189 respectively. The price of the Wi-Fi only Paperwhite does come with some baggage. Shell out $119 and you'll have to put up with onscreen advertisements. Pop an extra $20 in Amazon's pocket and you'll be freed up from seeing these "special offers".
While pre-ordering is already an option, there is a bit of a wait to endure. The Wi-Fi only model is due to ship on September 30, but if you've got your eye on the 3G model, you'll have to hold out until November 5.
-

Nymi NFC bracelet brings 3-factor authentication to your devices -- for a price
Publié: septembre 3, 2013, 10:50pm CEST par Mark Wilson
 We've already seen an NFC (Near Field Communication) ring and it looks like a full complement of body adornments may soon be available. The latest addition to the jewelry box is an NFC bracelet from Nymi which will, when it sees the light of day, give owners the ability to unlock their smartphone with their heartbeat.
We've already seen an NFC (Near Field Communication) ring and it looks like a full complement of body adornments may soon be available. The latest addition to the jewelry box is an NFC bracelet from Nymi which will, when it sees the light of day, give owners the ability to unlock their smartphone with their heartbeat.This might sound a little wacky but, just like your fingerprint, your heartbeat has a unique pattern to it meaning it can be used to uniquely identify you. Being a bracelet, the Nymi is worn around the wrist and when you need to authenticate to unlock your phone, a simple press of the sensor on top is all it takes. Of course, you need not limit yourself to unlocking your phone. The bracelet could also be used to replace car keys, make payments in stores and to open hotel doors.
It's simple, but also an incredibly powerful three-factor authentication system. Two-factor authentication has become incredibly common now, with Facebook and Twitter jumping on that particular bandwagon. But here things are taken up a notch. To unlock a device you not only need to have physical access to the Nymi bracelet, it needs to be able to detect your heartbeat -- specifically your heartbeat, not just a heartbeat -- and you need to have the device registered to the bracelet.
It seems like a nice idea -- particularly from a security point of view -- but there are issues. The first is price. The NFC ring Brian looked at cost just $20; this bracelet is four or five times that price depending on when you buy it. The Nymi worked with a proximity sensor so -- and, yes, I realize that this is kind of the point of NFC -- you have to be very close to whatever it is you're looking to unlock.
Fancy getting your hands on one? If you're quick, you can pre-order a bracelet for $79, but once the first 25,000 have been snapped up, the price jumps to $99. Quite how long it will take that number to sell isn’t clear, but even if you pre-order right now, you won't get your hands on the goods until some time in early 2014.
-

Sweet! Google unwraps the next version of Android: KitKat
Publié: septembre 3, 2013, 10:13pm CEST par Mark Wilson
 In something of a surprise move, Google announces that the successor to Jelly Bean will not be Key Lime Pie as everyone was expecting but… KitKat. There are no details of just what Android 4.4 will have to offer, or when we can expect to see it, but the new KitKat website promises to "make an amazing Android experience available for everybody".
In something of a surprise move, Google announces that the successor to Jelly Bean will not be Key Lime Pie as everyone was expecting but… KitKat. There are no details of just what Android 4.4 will have to offer, or when we can expect to see it, but the new KitKat website promises to "make an amazing Android experience available for everybody".The name might seem like something you would expect to hear announced on April 1, but this is no joke. The Nestlé website confirms that the next version of Google's operating system will be named after the "popular chocolate and wafer confectionery".
But the joint venture is likely to lead to some raised eyebrows in the technology community (ignoring the fact that KitKats are really a snack rather than a dessert). John Lagerling, director of Android global partnerships says that the name change decision came when Google "realised that very few people actually know the taste of a key lime pie", but many are going to see it as a marketing move.
The marketing machine is now rolling into motion. Nestlé is already in the process of producing 50 million specially branded KitKat bars which will give chocolate lovers the chance to win a range of prizes including Nexus 7s and Google Play credits.
Nestlé says that the partnership is part of the company's latest move to "leverage digital technology and online content to get closer to its consumers to better understand and cater to their preferences". Whether this is a reference to the sharing of customer data is not clear, but the joint forces of two such gigantic companies certainly raises some questions.
What do you make of the name change? An interesting surprise or a money-making marketing move? Who stands to gain the most from this venture -- Google or Nestlé?
-

LG G Pad 8.3 aims to take on iPad Mini and Nexus 7
Publié: septembre 1, 2013, 11:31am CEST par Mark Wilson

Forget the iPad, LG wants you to give the G Pad some love -- the G Pad 8.3 specifically. The company is not new to the world of tablets, though it has been some time since its last foray into the arena. The South Korean manufacturer posted a teaser video on YouTube just a few days ago but a new announcement reveals more details and confirms the imminent release of the successor to the Optimus Pad, the G Pad 8.3.
The tablet -- which surely deserves to be known as the Mexican horse tablet (El Gee Gee Pad) -- is due to debut at IFA in Berlin in the next few days, with a release pegged for Q4 2013. But it's the specs that really matter, and LG has unveiled a full breakdown of what we can expect from its latest handheld device.
Unsurprisingly fitted out with an 8.3-inch screen, the tablet boasts a better-than-full-HD display running at a resolution of 1920 x 1200. This is backed up with a quad-core Qualcomm Snapdragon 600 processor clocked at 1.7 GHz, and a more than respectable 2 GB of RAM. Built in, you'll find 16 GB of storage space, 5.0 MP rear camera, 1.3 MP front camera, a healthily-sized 4,600mAh battery, all powering Android 4.2.2 Jelly Bean.
Weighing in at 338 g, the G Pad will be available in black or white, and boasts a number of LG-specific features. KnockON is an alternative to the regular power button and can be used to turn the device on and off by double-tapping the display. This may be a tablet that hasn't really been designed for making phone calls or sending and receiving text messages, but the QPair feature allows for pairing with a smartphone. Once that is done, phone calls and text messages received on the phone will also appear on the tablet.
There's no news at the moment about whether this will remain a Wi-Fi-only device, or if a data-friendly version will also be available. We'll keep an ear to the ground, but all will be revealed -- including pricing details -- at IFA in the coming days.
-

The most popular stories on BetaNews this past week
Publié: août 31, 2013, 7:49pm CEST par Mark Wilson
 Looking at the biggest stories on BetaNews from August, 25 - 31, 2013. For the second week running, Microsoft managed to steal many of the headlines. After going gold, RTM, or however Microsoft now wants to refer to it, Windows 8.1 was released to OEMs. Depsite reaching this important milestone, developers were… irked, shall we say, to learn that they will not be able to get their hands on the completed code until it is released in October. At least that would be the case had the bits not leaked online very quickly. It was a Chinese version that was made available for unofficial download first, but an English version wasn't far behind.
Looking at the biggest stories on BetaNews from August, 25 - 31, 2013. For the second week running, Microsoft managed to steal many of the headlines. After going gold, RTM, or however Microsoft now wants to refer to it, Windows 8.1 was released to OEMs. Depsite reaching this important milestone, developers were… irked, shall we say, to learn that they will not be able to get their hands on the completed code until it is released in October. At least that would be the case had the bits not leaked online very quickly. It was a Chinese version that was made available for unofficial download first, but an English version wasn't far behind.I have previously pondered the popularity (or otherwise) of the Surface Pro, and this week Derrick stood firmly behind Windows RT positing five reasons it is destined to succeed.
In the mobile arena, the security of Android came under the spotlight – tests revealing varied performance between mobile security apps. Another study found that third-party Android app stores are rife with malicious code.
Apps appearing in Google Play may be safer, but two fifths of those released are virtually abandoned, receiving no updates at all. Rarely a man to mince his words, Brian wondered whether Android has lost its way, lambasting Google for slowly stripping away features from both hardware and software.
Many of us are still smarting from the loss of Google Reader, and the service that many people flocked to, Feedly made its Pro service available to all. Alan wondered why anyone would feel inclined to pay for RSS, and it’s a question I'm inclined ask as well.
Anyone already paying for a SkyDrive Pro account got a nice surprise this week as Microsoft announced that 25GB of space would be available to all employees using a business account. Everyone else can take advantage of the newly added OCR feature that can be used to grab text from photos.
Nintendo crept out of the shadows with a release that took many by surprise. The 2D version of the 3DS handheld -- called, inspiringly, the 2DS -- drops a dimension and trims the price tag. Another hardware release this week came in the form of the European and Asian Nexus 7, but there's still no news from Google about whether touchscreen issues have been addressed once and for all.
My Nexus came on a trip away with me, making me think about the importance of battery life in mobile devices. Looking to a future release, case maker Poetic may have dropped a clanger when they seemingly revealed the name and release date of the next iPhone.
Facebook lost a lawsuit that will see the social networking site pay out $20m. The site also revealed details of the government data requests it has received from around the world and proposed a series of changes to the way it handles user data.
The debacle about the NSA/government/world-and-dog collecting data about internet users continues to rumble on, and the week was rounded off with the unlikely alliance of Microsoft and Google. The two firms are working together to try to force the government to allow them to reveal more about the data requests that are being made of them. A PR move doomed to failure? Only time will tell.
-

Microsoft and Google (don’t really) want to tell you more about government data requests
Publié: août 31, 2013, 12:54pm CEST par Mark Wilson

Sounds nice, doesn't it? Two big names have listened to the concerns of the people that matter -- their customers -- in the wake of the NSA debacle, and want to share more information with the public about precisely what information the government is asking them to hand over. If only it were that simple.
In a blog post on TechNet, Microsoft General Counsel Brad Smith reveals that both Microsoft and Google filed lawsuits back in June to try to force the government to permit them to publish details of data requested under Foreign Intelligence Surveillance Act (FISA) orders. Smith says they [the two companies] believe they have a "clear right under the US Constitution to share more information with the public".
Despite weeks of negotiations with government lawyers, talks have amounted to nothing. According to Smith, on six occasions the government was granted more time to respond to the lawsuit, but nothing has come of it.
My colleague Brian Fagioli wondered aloud, on group chat, why the company has agreed so many times to grant the government more time to respond to the lawsuits. "After three attempts, did they not get the message?", he pondered. I can see his point to some extent, but at the same time Microsoft and Google find themselves in an awkward position.
If they keep giving the government more time to reply, people will complain that they are bowing to pressure, or not being hard enough on authority. Give up trying after three attempts and people would complain that they had given in too easily. It's a classic case of damned if they do and damned if they don't.
At the same time, continually making the requests could be seen as being a fool's errand. The government is so unlikely to change its mind about what data can be released it is practically pointless to ask about it. It's all too easy for catch-all "national security" reasoning to be bandied about.
So what's all the fuss about? Microsoft's blog post points out that the government will "begin publishing the total number of national security requests for customer data for the past 12 months and do so going forward once a year". But that's not enough. Smith believes it is vital to "publish information that clearly shows the number of national security demands for user content, such as the text of an email".
He goes on to say, "And unless this type of information is made public, any discussion of government practices and service provider obligations will remain incomplete". When he says, on behalf of Microsoft and Google, "with the failure of our recent negotiations, we will move forward with litigation in the hope that the courts will uphold our right to speak more freely", you can almost foresee the shoulder-shrugging and hand-wringing as they sigh, "well, we tried!"
Even if Google and Microsoft get what they are fighting for, it will be something of a Pyrrhic victory. We already know that the lawsuits have been dragging on for at least a couple of months; that's not cheap.
If they manage to "force" the government to be more transparent about collection of and use of data, do they not realize that the same demand will very likely be made of Google and Microsoft by their customers?
If Microsoft and Google reveal more information about the data they've already shared with the government, is this going to make customers more or less trusting of the companies?
Yes, this is obviously a PR campaign. The likes of Google and Microsoft get a lot of bad press (as well as good) so it should come as no surprise that they're keen to come across as the good guys, fighting for the average man on the street.
But to me it just comes across as misguided and ill-judged. It's a PR campaign doomed to backfire. Freedom of speech is one thing -- and it's something I'm a keen advocate for -- but to play the "constitutional right" card in this instance feels cheap, and undermines the whole debate surrounding the secret collection of data.
Microsoft and Google need to appreciate that what they're asking of the government could well be demanded of them. Is that a price they're willing to pay?
I have reached out to Google for a statement on the matter, and will update this post accordingly.
Photo Credit: mikute/Shutterstock
-

Nexus 7 comes to Europe and Asia -- O2 reveals details of 4G model
Publié: août 28, 2013, 6:24pm CEST par Mark Wilson
Some weeks after the US release of the Nexus 7, Google’s 7 inch tablet has found its way to eager customers in other countries. In Europe, the UK, France, Spain and Germany get a little bit of Nexus love, while in Asia it is Japanese tech-heads who can now get their hands on the 7-incher everyone is talking about. As has become the norm with many gadgets, prices are comparatively higher than in the US.
There are 16GB and 32GB Wi-Fi versions available and UK customers can expect to pay £199 and £239 respectively. In France, Germany and Spain, prices are pegged at €229 and €269, while Japanese Nexus fans can expect to be parted from ¥27,800 and ¥33,800 apiece.
At the moment there is no news regarding whether different firmware has been included to help overcome the touchscreen and GPS issues that many people had been experiencing with their devices. The new Nexus 7 can be purchased directly from Google Play, complete with free shipping, but it is also available from other stockists such as Amazon.
In the UK, mobile provider O2 has revealed details of the upcoming 4G version. The 32GB 4G Nexus 7 is available to pre-order now for £319.99 and will ship ready for launch day on September 13. Anyone pre-ordering through O2 will also receive a free case for their tablet.
Have you received your Nexus 7? Have you experienced any of the problems that have been reported with the tablet so far?
-

Tech festival -- a long weekend in the mud shows battery life needs to improve
Publié: août 28, 2013, 2:31pm CEST par Mark Wilson
 For me, virtually any trip out of the house means loading up on various pieces of tech. I, obviously, cannot leave the house without my phone -- my trusty HTC Sensation has been with me for two years -- but there are usually other things to consider as well. While my phone is great for picking up my emails on the move and staying in touch with people via IM, Facebook etc, it’s far from ideal for doing any work.
For me, virtually any trip out of the house means loading up on various pieces of tech. I, obviously, cannot leave the house without my phone -- my trusty HTC Sensation has been with me for two years -- but there are usually other things to consider as well. While my phone is great for picking up my emails on the move and staying in touch with people via IM, Facebook etc, it’s far from ideal for doing any work.Depending on where I’m going, and how strong I’m feeling, there are various other pieces of kit I can take with me to make things easier. My Sony Tablet S is easier to type on than my phone, thanks mainly to its larger screen, but it’s not something I like to use for extended periods of time. I could take my laptop with me, or the MacBook Pro, which are great to work on, but rather weighty to hump from place to place.
This weekend my girlfriend and I headed off to the Leeds Festival after she won tickets in a last minute competition. This wasn’t necessarily a festival either of us would have chosen to attend, but free tickets and the prospect of seeing Johnny Marr (his performance of Smiths tracks brought a lump to the throat), Eminem, the Strypes and Nine Inch Nails was too good to refuse.
Throwing gear into the car for a long weekend in a festival field was part of the story, but then there were communication, entertainment and work devices to think about. Neither of us could be without a phone so these had to be packed -- all three of them (long story), complete with wall and USB chargers. I needed to be able to work whilst away -- yes, even when at a festival -- so I added my Surface Pro to the bag, again, complete with charger.
This didn’t seem like quite enough, so a Nexus 7 was thrown into the mix as well. Campsites can be noisy places, you end up getting woken up at strange hours and never know when a little music or video entertainment might be needed! At home I’ve become used to using a Poetic StrapBack case and this seemed to lend itself well to getting thrown in a bag and offering a decent viewing experience with its multi-angle options.
Power Up
The two year old battery in my HTC Sensation has seen better days -- I’m lucky if it gets me through the day. It’s well overdue a replacement, but it’s just one of those things I never get round to. Because of this, charging facilities were needed. Festivals often have charging stations, but these tend to be extortionately priced. So I armed myself with a cigarette lighter USB adaptor and a selection of USB cables.
An inverter could have been used to power the Surface Pro, but I’m always worried about draining the car battery -- especially when stuck in a muddy field four hours from home -- so I was relying on the device’s battery life to hold up. Wi-Fi connections tend not to be particularly prevalent at festivals, and Leeds was no different. This left me reliant on my phone’s data connection for web access. This could be shared to my other devices using tethering but this meant additional battery drain.
To help with charging up whilst walking around the festival and watching bands, I popped an emergency USB charger in my bag. This was a great way to ensure that I didn’t run out of charge whilst out and about, but with the Surface Pro’s battery life hovering around the four hour mark, something was going to have to give.
What ended up giving was our will. Rather than risk running out of battery on site, we decided to drive away from the festival during the day at times when there was little happening. This served a dual purpose. Firstly we could escape to a pleasant bathroom with porcelain toilets! But it also meant that we would run off to Starbucks (yes, I know, I’m sorry) to take advantage of free Wi-Fi and power points.
In Need of a Boost
But what this highlighted for me is that battery life is what mobile device manufacturers need to address next. Speed is great -- no one wants a sluggish phone, tablet or computer. Likewise, it’s lovely to have a super high resolution display. Having used my Surface Pro with its 1920 x 1080 resolution, switching back to a netbook with the same sized screen but a resolution of 1024 x 764 made for an unbelievably blocky experience. The Nexus 7 has the same massive resolution, but crammed into a 7 inch screen.
At some point there needs to be a shift in attitude. Are we more interested in displays that are made up of invisible pixels, or do we want devices that can be used for longer? Of course, there will be advances made in battery technology that will mean devices can be powered for greater periods of time, but I think it’s likely that this will just lead to bigger screens, higher resolution displays, and faster devices making greater demands of them.
If battery life is to improve we need to be realistic about what we want from a device. Is a screen that includes more pixels than your eye can detect really necessary? Do you need a screen so bright that watching a movie gives you a sun tan? Or would you prefer to go back to the good old days when a phone could last several days without a charge.
I don’t want to have to carry around extra battery packs, endless cables and secondary devices to act as a backup. I don’t think I’m asking too much -- just to be able to go away for a couple of days without having to panic about where I’m going to get power from. Who’s with me?
Image Credit: Sealstep/Shutterstock
-

Facebook reveals details of government data requests from around the world
Publié: août 28, 2013, 12:13am CEST par Mark Wilson
 We’ve known for a while that governments around the world have been gathering data about Internet users, monitoring online communication via instant messaging, email and much more. Numerous websites and social networks have received requests from government bodies for information relating to their customers and users. Now, Facebook reveals for the first time just who has been asking for data.
We’ve known for a while that governments around the world have been gathering data about Internet users, monitoring online communication via instant messaging, email and much more. Numerous websites and social networks have received requests from government bodies for information relating to their customers and users. Now, Facebook reveals for the first time just who has been asking for data.The Global Government Request Report covers the first six months of 2013, and is introduced with the words "Transparency and trust are core values at Facebook". Although the report is not especially detailed -- it is likely that it was not legally possible to be -- it does show which countries have asked for data, the number of requests each country made, the number of user accounts inquired about, and (perhaps most interestingly) the percentage of requests that Facebook was legally obliged to comply with.
Colin Stretch, Facebook’s General Counsel, says that "government transparency and public safety are not mutually exclusive ideals… each can exist simultaneously in free and open societies". But he is also keen to stress that Facebook is not quick to bow to just any request. "We scrutinise each request for legal sufficiency under our terms and the strict letter of the law…we fight many of these requests.... and we frequently share only basic user information, such as name".
Unsurprisingly, it is the US government that has made the most requests for data, and has a high success rate for getting what it asks for. Strangely, however, while request numbers for the likes of the UK, Spain, Taiwan and Germany are precise (1,975, 479, 229 and 1,886 respectively), things are much more vague for the US – 11-12,000 requests.
Of the 20-22,000 user accounts asked about, the US government managed a 79 percent hit rate. Other countries were more successful with their requests – Albania got information from 83 percent of its requests, Hong Kong 100 percent (although there was only one request) and Taiwan was successful with 84 percent of its requests. Some governments were left disappointed, with Uganda, South Africa, Russia, Serbia and Bangladesh among those who had their requests completely denied.
Facebook takes the opportunity to point out its guidelines for responding to data requests. The company states that, while this is the first report into requests, it is not going to be the last, and that it hopes "to be able to provide even more information about the requests we receive from law enforcement authorities" in future.
Image Credit: Skylines / Shutterstock
-

Facebook to pay out $20m to users in 'Sponsored Stories' case
Publié: août 27, 2013, 10:17pm CEST par Mark Wilson
 A US judge rules that Facebook must pay out $20m as the Fraley vs Facebook class action draws to a close. The lawsuit was taken out by users of the social network whose pictures were used without consent in "Sponsored Stories" advertisements. While up to 150 million Facebook members were affected, only approximately 614,000 who filed a claim will receive any money.
A US judge rules that Facebook must pay out $20m as the Fraley vs Facebook class action draws to a close. The lawsuit was taken out by users of the social network whose pictures were used without consent in "Sponsored Stories" advertisements. While up to 150 million Facebook members were affected, only approximately 614,000 who filed a claim will receive any money.It’s hardly a massive windfall. The $20m is to be divided not only between the successful claimants, but also used to pay for lawyers and administrative costs. Users will be paid $15 each -- not even enough to buy half of a share in Facebook.
This is likely to come as a disappointment to those involved in the case who could have expected to receive up to $750 in statutory damages for a violation of California Civil Code 3344.
Judge Richard Seeborg said that "it is far from clear that [the plaintiffs] could ever have shown they were actually harmed in any meaningful way". He also went on to say that if all complainants (meaning all 150 million affected members) were to recover the full theoretical amount, this could "threaten Facebook’s existence" as costs could spiral beyond $12bn.
The lawsuit dates back to 2011 when Facebook users who 'liked' a company on the site found that their names and images where being used in advertisements. The ruling has also made a new demand of Facebook -- that its Statement of Rights and Responsibilities is changed so that users are warned of any potential use of their data.
Photo Credit: tlegend/Shutterstock
-

More than two thirds of US adults have home broadband -- three percent still on dial-up
Publié: août 27, 2013, 12:01pm CEST par Mark Wilson
 Mark Zuckerberg may be keen on making the internet accessible to everyone in the world but it appears even in the US there is still a little way to go. A report by Pew Research reveals that while 70 percent of US residents over the age of 18 have a high-speed broadband connection at home, access is not as prevalent as the Facebook founder would doubtless like.
Mark Zuckerberg may be keen on making the internet accessible to everyone in the world but it appears even in the US there is still a little way to go. A report by Pew Research reveals that while 70 percent of US residents over the age of 18 have a high-speed broadband connection at home, access is not as prevalent as the Facebook founder would doubtless like.The research center’s Internet & American Life Project has monitored broadband usage since 2000 when dial-up connections accounted for 34 percent of access and just three percent of adults used a broadband connection. Increased availability of Internet access means that 73 percent of US adults now have some form of connection at home, compared to just 37 percent 13 years ago.
Although broadband usage has increased fairly steadily, three percent of Americans are reportedly still struggling on with dial-up. Perceived cost as well as a lack of interest are the reasons cited by the 27 percent of people who have no form of home Internet connection, says the report’s author Kathryn Zickuhr.
Besides having a need for, or interest in, using the web, the main factors determining whether a household is connected or not are found to be age, education and income. Broadband adoption rates are highest among the over 50s, college graduates and those from household with an income of $50,000 and above.
The research also finds that more than half of US adults (56 percent) have a smartphone, although these individuals were not included in the "broadband" connection figures. Analysis of the research reveals that 32 percent of people who do not have a broadband connection do have smartphone that could be used to get online.
Image Credit: anyaivanova/Shutterstock
-

The most popular stories on BetaNews this week
Publié: août 24, 2013, 8:05pm CEST par Mark Wilson
 Perhaps the biggest news from the last seven days -- at least in part because it came as such a surprise to most people -- was the announcement that Steve Ballmer intends to resign from Microsoft within the year. The CEO is planning to step down as soon as a suitable replacement is found, but there has been speculation that Ballmer may have been pushed rather than opting to jump.
Perhaps the biggest news from the last seven days -- at least in part because it came as such a surprise to most people -- was the announcement that Steve Ballmer intends to resign from Microsoft within the year. The CEO is planning to step down as soon as a suitable replacement is found, but there has been speculation that Ballmer may have been pushed rather than opting to jump.Getting my hands on a Surface Pro for the first time gave me an opportunity to try out Windows 8 as a touchscreen operating system. Despite loving the Surface in general, I pondered whether the use of the same version of Windows 8 as on desktop machine may have been what's stopping Microsoft’s convertible devices from becoming more popular. At the same time, Brian fell in love with the Lenovo Yoga, citing Windows 8 as one of the computer’s strengths.
Lenovo cropped up elsewhere in the news as the firm teamed up with Pokki in a deal that will see the Start menu replacement software pre-installed on a number of systems.
It was a busy week for gamers, with the eagerly anticipated PlayStation 4 finally being assigned a solid release date. Not to be outdone, Microsoft revealed details of the upcoming Xbox One’s games line-up, announcing that 38 percent will be platform exclusives. Anyone looking to break into the world of game development is likely to find it a little easier after Microsoft launched ID@Xbox for indie developers.
Ashton Kutcher’s role as Steve Jobs has come in for some criticism, including from Robert X Cringely. While not unimpressed with the film on the whole, Robert feels that much of the essence of Jobs is overlooked. Also falling slightly short of the mark was the Ubuntu Edge campaign. The indiegogo fund-raiser ended up a massive $20m short of its $32m target.
Receiving something of a mixed reaction, and adding to last week’s commercials, were Microsoft’s Office 365 ads which put one of Brian’s loves, the Lenovo Yoga, up against the iPad in the classroom -- you can guess which came out on top.
Mark Zuckerberg joined forces with a number of key players in the Internet and mobile market to set up Internet.org. The project has been created with the goal of making the Internet more widely available, particularly to people in developing countries.
Two months after Google purchased Waze, the partnership is finally starting to trickle through. Incidents reported by Waze users not only appear in the Waze app, but also in Google Maps -- Waze users can also benefit from the addition of Google searching within the app.
Microsoft’s Outlook.com hit the headlines several times this week. After problems with the site, the access issues appeared to be fixed, but then re-emerged for some users. Microsoft said sorry, and then went on to add not only new alias management options to the site, but also officially released Skype for Outlook.com.
The company also announced an ad-free version of Bing for schools. No prizes for guessing the name of this service -- Alan revealed it to be, rather unimaginatively, Bing for Schools.
Photo Credit: vinz89/Shutterstock
-

The most popular stories on BetaNews this past week
Publié: août 24, 2013, 8:05pm CEST par Mark Wilson
 Perhaps the biggest news from the last seven days -- at least in part because it came as such a surprise to most people -- was the announcement that Steve Ballmer intends to resign from Microsoft within the year. The CEO is planning to step down as soon as a suitable replacement is found, but there has been speculation that Ballmer may have been pushed rather than opting to jump.
Perhaps the biggest news from the last seven days -- at least in part because it came as such a surprise to most people -- was the announcement that Steve Ballmer intends to resign from Microsoft within the year. The CEO is planning to step down as soon as a suitable replacement is found, but there has been speculation that Ballmer may have been pushed rather than opting to jump.Getting my hands on a Surface Pro for the first time gave me an opportunity to try out Windows 8 as a touchscreen operating system. Despite loving the Surface in general, I pondered whether the use of the same version of Windows 8 as on desktop machine may have been what's stopping Microsoft’s convertible devices from becoming more popular. At the same time, Brian fell in love with the Lenovo Yoga, citing Windows 8 as one of the computer’s strengths.
Lenovo cropped up elsewhere in the news as the firm teamed up with Pokki in a deal that will see the Start menu replacement software pre-installed on a number of systems.
It was a busy week for gamers, with the eagerly anticipated PlayStation 4 finally being assigned a solid release date. Not to be outdone, Microsoft revealed details of the upcoming Xbox One’s games line-up, announcing that 38 percent will be platform exclusives. Anyone looking to break into the world of game development is likely to find it a little easier after Microsoft launched ID@Xbox for indie developers.
Ashton Kutcher’s role as Steve Jobs has come in for some criticism, including from Robert X Cringely. While not unimpressed with the film on the whole, Robert feels that much of the essence of Jobs is overlooked. Also falling slightly short of the mark was the Ubuntu Edge campaign. The indiegogo fund-raiser ended up a massive $20m short of its $32m target.
Receiving something of a mixed reaction, and adding to last week’s commercials, were Microsoft’s Office 365 ads which put one of Brian’s loves, the Lenovo Yoga, up against the iPad in the classroom -- you can guess which came out on top.
Mark Zuckerberg joined forces with a number of key players in the Internet and mobile market to set up Internet.org. The project has been created with the goal of making the Internet more widely available, particularly to people in developing countries.
Two months after Google purchased Waze, the partnership is finally starting to trickle through. Incidents reported by Waze users not only appear in the Waze app, but also in Google Maps -- Waze users can also benefit from the addition of Google searching within the app.
Microsoft’s Outlook.com hit the headlines several times this week. After problems with the site, the access issues appeared to be fixed, but then re-emerged for some users. Microsoft said sorry, and then went on to add not only new alias management options to the site, but also officially released Skype for Outlook.com.
The company also announced an ad-free version of Bing for schools. No prizes for guessing the name of this service -- Alan revealed it to be, rather unimaginatively, Bing for Schools.
Photo Credit: vinz89/Shutterstock
-

Tumblr ‘hack’ leads to a spate of undeletable posts
Publié: août 22, 2013, 12:10am CEST par Mark Wilson
 Tumblr is downplaying a suspected hack attack that left users facing the appearance of a series of undeletable posts in their blogs. Reports of problems spread through Tumblr itself as well as Twitter. The problem is not just that posts are undeletable, but also that they were not created by the blog owners.
Tumblr is downplaying a suspected hack attack that left users facing the appearance of a series of undeletable posts in their blogs. Reports of problems spread through Tumblr itself as well as Twitter. The problem is not just that posts are undeletable, but also that they were not created by the blog owners.While some of the content is fairly tame, some users have complained about the appearance of pornographic posts. Researchers at ThreatTrack Security Labs are advising users to change their account passwords, as bloggers are left facing not only undeletable posts, but many also finding themselves unable to access their dashboards.
Details are currently scant, and it is unclear whether there has been a security breach or if there is some other issue. Tumblr took a while to make any sort of public announcement, but did eventually tweet a message saying that "Our engineering team is working quickly to repair an issue causing incorrect posts to appear on a small number of affected blogs".
Christopher Boyd from ThreatTrack Security Labs reached out to Tumblr support, but only received a cookie-cutter response – "Our engineers are aware of this issue and are currently working on a fix. We hope to have the problem resolved shortly. Thanks for your patience".
Are you a Tumblr user affected by the issue? Share your experiences.
-

Microsoft targets parents of back to schoolers with new Office 365 ads
Publié: août 21, 2013, 5:58pm CEST par Mark Wilson
 Microsoft is on something of a roll with advertisements at the moment. After taking a swipe at iPads and Google, the latest round of ads, this time for Office 365, takes a slightly different approach -- tugging on the heartstrings of parents about to wave offspring off to university.
Microsoft is on something of a roll with advertisements at the moment. After taking a swipe at iPads and Google, the latest round of ads, this time for Office 365, takes a slightly different approach -- tugging on the heartstrings of parents about to wave offspring off to university.The two advertisements examine father-son and mother-daughter relationships and push the collaborative and cloud-working features to be found in Office 365.
The commercials are slightly in-your-face with their delivery, but while Office 365 University is mentioned, at no time is it shown on-screen. Both advertisements take much the same approach, with a slightly awkward conversation taking place between a teenager about to head to college, and a parent keen to hide the fact that they are going to miss their child.
If it all sounds a little sickly sweet, well… it is a bit. But the ads also show that Microsoft has a heart as well as a sense of humour. While both parents and students say one thing out loud, on-screen captions reveal what both are really thinking. See what you make of them.
The Stoic
The Empty Nester
-

Mark Zuckerberg launches Internet.org to help bring web access to the whole world
Publié: août 21, 2013, 1:49pm CEST par Mark Wilson
The Internet is thought of as being a global infrastructure that breaks down barriers, blurs physical boundaries and renders distance meaningless. But for two thirds of the world, Internet access is just not available, and this is something that Facebook founder Mark Zuckerberg wants to change.
Working in conjunction with Ericsson, MediaTek, Nokia, Opera, Qualcomm and Samsung, Internet.org is an initiative that aims to help bring web access to the five billion people who are not yet connected.
If this seems like a huge venture, you'd be right and the founders accept that it is a "goal too large and too important for any one company, group, or government to solve alone". However, by pooling resources and expertise, it is hoped that headway can be made.
Internet.org’s commendable aim is set out in a humbling and inspiring mission statement which recognizes three main obstacles to global Internet availability -- cost, bandwidth and suitable business models.
The project partners plan to work together to help develop lower cost technologies and hardware that can be used around the world; the role of the mobile operators who are involved is clearly key. Whether Internet access is delivered through a computer, a smartphone or a device yet to be imagined, bandwidth is needed, and in many parts of the world this is at a premium.
Internet.org wants to help improve the efficiency of data delivery, in part through the use of new compression techniques. But even once this has been done, there is the issue of giving people access to the Internet. This is where the third phase comes into play, helping to enable as many people as possible to make use of the web, regardless of where they are and what language they speak.
The prospect of getting 5 billion people online is quite a daunting one. It is not something one person or one company could tackle alone, so this new partnership makes a great deal of sense. If Mark Zuckerberg and friends manage to work their magic, the Internet could become a truly global beast.
-

Sony announces PS4 release date
Publié: août 21, 2013, 10:48am CEST par Mark Wilson
 At a press conference at Gamescon, Sony revealed the information that hundreds of thousands of gamers have been waiting to hear -- the official launch date of the PlayStation 4.
At a press conference at Gamescon, Sony revealed the information that hundreds of thousands of gamers have been waiting to hear -- the official launch date of the PlayStation 4.And there’s not all that long to wait. In just over three months, on November 15 to be precise, the eagerly anticipated console will be made available in the US and Canada.
As is usually the case, other parts of the world have slightly longer to wait – but not too long. The European and Latin American release date has been set for a fortnight later on November 29. Pricing has been pegged at $399.99, undercutting the Xbox by $100, but it is unlikely that this price difference will sway many people away from their console of choice.
But games are what it’s all about. Microsoft has already revealed its list of titles and unveiled its ID@Xbox indie developer program, and now Sony announces PS4 buyers will have 33 titles to look forward to by the end of December, with at least 180 other games already in development.
While there has been no official date announced for the release of the PS4’s rival, Xbox One, Microsoft has said that its console will be on sale some time in November as well. The Xbox One and PS4 are both already available for pre-order.
-

ID@Xbox gives indie developers the chance to sell games directly on Xbox One
Publié: août 20, 2013, 5:34pm CEST par Mark Wilson
 Becoming a developer for platforms such as iOS and Android is relatively simple, but the same has not always been true for anyone looking to break into the world of serious gaming. Microsoft is keen to help out, and the new Independent Developers @ Xbox (ID@Xbox) program aims to make it possible for small-scale devs to work in the same arena as the big players.
Becoming a developer for platforms such as iOS and Android is relatively simple, but the same has not always been true for anyone looking to break into the world of serious gaming. Microsoft is keen to help out, and the new Independent Developers @ Xbox (ID@Xbox) program aims to make it possible for small-scale devs to work in the same arena as the big players.At Gamescon, Microsoft today unveils details of the program and Director of ID@Xbox, Chris Charla, is keen to welcome the next generation of developers who will usher in a new breed of games. The scheme will enable developers to publish their own games on Xbox One and gain access to the same development kits and resources that are already available to leaders in the market.
The option of appearing in the Xbox One Store alongside big titles is something that is going to appeal to any developer looking to get noticed, and ID@Xbox does not seem to be a cut-down offering for small-time game companies. Chris Charla points out that through the program, all developers have access to the same features including Achievements, Gamerscore, Kinect and Xbox SmartGlass.
At the moment the program isn’t open to just anyone interested in trying their hand at game development. Microsoft is currently looking for "professional independent game developers who have a proven track record of shipping games". But looking at the longer term, the firm is keen to push the idea that "anyone with a retail Xbox One will be able to develop, publish, and sell their game". Of course, the company will be "evaluating each developer application individually on its own merits".
More details about the program can be found at the ID@Xbox website where it is also possible to register as a developer.
-

Surface Pro -- is Windows 8 the biggest failing of this expensive tablet?
Publié: août 20, 2013, 9:16am CEST par Mark Wilson
 Almost every time I have written about Microsoft in the past, I have been accused of being on the company's payroll when I write something positive, or being a hater out to bash the firm when I write something negative. Fair warning to anyone inclined to make such accusations (and a slight spoiler); this is one article in which I am going to sit firmly on the fence.
Almost every time I have written about Microsoft in the past, I have been accused of being on the company's payroll when I write something positive, or being a hater out to bash the firm when I write something negative. Fair warning to anyone inclined to make such accusations (and a slight spoiler); this is one article in which I am going to sit firmly on the fence.Let’s get one thing out of the way to start with. I quite like Windows 8. It’s not perfect and I have my complaints, but it is my primary operating system on three computers, and has been for some time. Until now, my only experience of Windows 8 has been on a traditional desktop and a laptop -- this means I have only interacted with the OS using a combination of a keyboard, mouse and trackpad.
Perhaps this is why I have developed a universal loathing for everything modern/Metro related in Windows 8; navigating with a keyboard and mouse seems clunky, slow, unintuitive, and awkward. Getting my hands on a Surface Pro gave me a chance to put a theory of mine to the test.
Since Windows 8 was first released, I had the feeling that it was a poor hybrid. As far as I’m concerned, there is little wrong with Windows 8’s traditional desktop mode. But used on a regular desktop machine, it has always felt to me that the 'modern' side of things was tacked on almost as an afterthought.
Maybe that’s not quite it. Perhaps what I’m trying to say is that the 'modern' aspects of Windows 8 felt to me like a half-finished mobile operating system. It was clearly designed with touchscreen devices in mind but it was bolted onto standard Windows regardless.
For me this conjured up two possibilities. Firstly that Windows 8 proper just wasn’t different enough to Windows 7. By adding the 'modern' facet, users are presented with a choice, with the perception of added value -- hey, it’s almost like two operating systems for the price of one!
But the modern/Metro/mobile side of things -- even though I had only previously looked at it from a desktop point of view -- seemed underpowered. It lacked the finesse of iOS. It lacked the punk rock attitude of Android. It was fluffy, cutesy, clumsy and… big. It felt as though Microsoft did not have enough faith in this side of the operating system to release it as a product in its own right, be that because of an underlying reliance on standard Windows architecture or due to the mobile aspect being under-developed.
For me, it basically made Windows 8 feel slightly directionless. It couldn’t quite decide what to be, so it tried to be everything. I’d long wondered if using the same operating system on a touchscreen monitor or a tablet would change my mind. A Surface Pro (I veered firmly away from Windows RT) came into my possession, so it was time to find out.
On the Surface
There’s certainly a lot to like about the Surface Pro. In terms of build quality it is hard to fault. It is a delightfully solid piece of hardware, albeit it verging on the heavy side. As an iPad and Android tablet owner, the size and weight difference is quite noticeable. Still, considering this is essentially a notebook/ultrabook, it’s more than forgivable.
The screen is just lovely. Packing a resolution of 1920 x 1080 into the same physical space as my Samsung NC10, which did 1024 x 768, makes things look wonderfully crisp and bright. The touchscreen itself is -- perhaps obviously -- intuitive. Being familiar with iOS and Android probably did nothing to help here, everything just works pretty much as you would expect.
I’m not much of a fan of on-screen keyboards, and my Android tablet has been used as testing ground for more keyboard apps than I care to remember. The stock Windows keyboard is about as unpleasant as they come, so I was pleased to have access to a Touch Cover and Type Cover.
Both keyboard/cover hybrids work in the same way, snapping magnetically into place and providing a full-sized keyboard that doubles up as a screen-protecting case. The Touch was too unpleasant to use. The flat keys offered no tactile feedback and required precise finger positioning that was not easy with no guiding key edges to work with.
The Type keyboard is far better in my opinion, more closely resembling a laptop keyboard. But there is a slightly odd keyboard layout and some strange decisions have been made. The left Shift key is too small, the arrow keys are badly positioned and whoever thought it was a good idea to drop the Prt Scr key is in need of serious interrogation.
It was great to be able to navigate through Windows without using a mouse. Launch Explorer with a prod. Scroll through files with a drag. But on numerous occasions it was obvious that the bulk of Windows is not ideally suited to touchscreen operation, and this is certainly true for a lot of apps.
Switching out of desktop mode was a different story. Here apps have been designed with finger pokes in mind. Interface elements are larger and easier to hit without having to think about it too much -- but this does come at the expense of features. There are few 'modern' apps that are not mere shadows of their desktop counterparts.
So have I been sold on 'modern' Windows 8? Well, I can see its appeal a little more clearly, but for me it still doesn’t quite work. Just like Windows 8 tries to be everything to everyone, so I get a very similar feeling about the Surface Pro.
The software means that it is not as great to use in tablet mode as either Android or iOS, but at the same time you are able to use all of the apps you are familiar with. Used in laptop mode, neither of the keyboards I tried out were perfect -- the Touch Cover particularly so -- and the fold out stand meant that it was difficult to use on my lap. I had to find a surface to use my Surface.
Summing Up
So yes, I do like the Surface Pro. I’m not sure I’d go so far as to say I love it, but it has won me over. That said, whether used as a tablet or a laptop, it feels as though compromises are being made. I haven’t decided which mode works best yet, but my preference for regular Windows 8 coupled with on-screen-keyboard-phobia found me switching to laptop mode more often than not.
It’s a shame. Surface Pro could be a great tablet. As much as I like Windows 8, I can’t help but feel this is really what has prevented Surface from taking off. Oh, that and the absurd original price tag.
-

Latest Microsoft ad targets students while dissing iPads
Publié: août 20, 2013, 12:27am CEST par Mark Wilson
 In a recent ad Microsoft levelled its guns at Google, but this time around it is Apple who finds itself in the crosshairs. The thinly veiled attack pits the Lenovo Yoga against Apple’s iPad in a bid to win favour in time for the ‘back to school season’.
In a recent ad Microsoft levelled its guns at Google, but this time around it is Apple who finds itself in the crosshairs. The thinly veiled attack pits the Lenovo Yoga against Apple’s iPad in a bid to win favour in time for the ‘back to school season’.The advertisement is set in a lecture hall and finds the lecturer’s audience divided into three distinct camps -- old-school pen and paper fans, iPad users, and a solitary student with a convertible Windows device. As the cue comes to start taking notes, the Windows user casually stops playing the word game she was engrossed in, flips the Yoga into ‘notebook’ mode and starts typing.
Meanwhile, the other students scrabble to attach keyboards, stands and other peripherals to their iPads, panic as pens fail to work, and even email Microsoft-girl to ask for a copy of her notes.
As well as highlighting the flexibility of convertible, hybrid devices such as the Yoga, the ad also manages to focus on the multitasking capabilities of Windows 8. Not bad going for a 30-second commercial.
YouTube commenters have been quick to point out that the advertisement compares products that are in completely different price brackets.
-

Google gives us all a laugh and raises money for charity with the Hangout Comedy Club
Publié: août 15, 2013, 10:23pm CEST par Mark Wilson
 Right now in Edinburgh, the Fringe festival is taking place. Billed as the world's largest arts festival, this three week long extravaganza is home to the weird and the wacky, the silly and the serious, the new and the inventive. But what it's really known for is comedy; it's where many household names took their first steps on the road to fame, and huge numbers of big names come back year after year.
Right now in Edinburgh, the Fringe festival is taking place. Billed as the world's largest arts festival, this three week long extravaganza is home to the weird and the wacky, the silly and the serious, the new and the inventive. But what it's really known for is comedy; it's where many household names took their first steps on the road to fame, and huge numbers of big names come back year after year.Thousands of shows take place in bars, basements, theatres, on street corners -- just about anywhere you can think of. The Fringe is famous the world over, and the Scottish capital swells in size as performers and fans travel from not only around the UK, but from all over the world. Sadly, not everyone who wants to make it to the festival is able to do so. Google thinks it has the answer in the form of the Hangout Comedy Club.
If you can't make it to a comedy show -- whether you're in Scotland or somewhere further afield -- Google can bring the shows to you. You can take a seat, for free, in the audience of live comedy shows where a string of comedians are hosting Hangouts.
Laugh along with the audience, from the comfort of your own home; that's the idea. But just as when you're at a "real life" comedy show, there are bound to be some hecklers in the front row. In fact, it could be you! At each online show a small number of Hangout participants will be given the opportunity to interact with the comedian.
So if you're looking to get your ribs tickled, head on over to the Hangout Comedy Club YouTube channel. Things kick off 10pm BST, August 15 and if you like what you see, you can make a donation to Comic Relief, a charity raising money for people in need all over the world. Hook up your webcam and microphone, get the Google+ Hangouts plugin installed, and get ready to have a giggle.
-

Is there a bad batch of Nexus 7s? Users complain of touchscreen issues and more
Publié: août 15, 2013, 12:28am CEST par Mark Wilson
 If you're in the US, you've had access to the Nexus 7 for a few weeks now. I'm in the UK which means that, technically, I have to wait until August 28 for the release on my side of the Atlantic. But the nice chaps at Google saw fit to wing a unit my way so I wouldn't have to wait. Lovely.
If you're in the US, you've had access to the Nexus 7 for a few weeks now. I'm in the UK which means that, technically, I have to wait until August 28 for the release on my side of the Atlantic. But the nice chaps at Google saw fit to wing a unit my way so I wouldn't have to wait. Lovely.I was already aware of the experiences of my colleague Alan Buckingham who, stateside, had received his Nexus some time before me. He was understandably disappointed to find that the tablet he was sent was unusable; it would not boot.
I do not think either of us thought much of this, nor anyone else who heard about it. Bad devices happen, it's just one of those things. Alan was sent out a replacement which proved problem-free. I eagerly anticipated the arrival of mine.
It's quite common for there to be problems with a new device. I'd go as far as saying it is reasonable to almost expect a few teething problems with brand new devices, particularly if you're an early adopter. Recently my colleague Joe Wilcox started an article looking at the Nexus 7's impact on the iPad mini with the words 'Rest in peace, iPad mini. Google killed you', but for everyone who is happy with the 2013 version of the Nexus 7, there are plenty who have cause for complaint.
Considering the thousands of miles the package had to travel to sunny Scotland, mine arrived at my door quite swiftly. Tearing open the box I was greeted by the sight of a shiny Nexus 7, accompanied by a Chromecast. The latter was very quickly set up and put to use, but it wasn't long before my attention, and that of my girlfriend, turned to the tablet.
But the excitement was somewhat short-lived. I was pleased to find that I was not plagued by Alan's unbootable device issue, but it promptly became clear that something was amiss.
Browsing through websites or using Google maps, I found that my view would zoom in and out in a seemingly random fashion. Most irksome. But it didn't end there. Writing emails, typing documents, playing games... anything that involved using the onscreen keyboard, or just using the touchscreen in general, yielded unexpected results.
Trying to type a simple sentence took forever just because I spent so much time backtracking to correct mistakes that had crept in. These were not typos I'd made, rather random keypresses introduced by an unknown gremlin.
"No biggie", I thought, "I'll just try out my Bluetooth keyboard for now". No joy. The keyboard, which worked -- and indeed continues to work -- perfectly with a couple of Android phones and an iPad, just refused to communicate with the Nexus. It appeared to be successfully paired, but typing was fruitless.
Looking around online it soon became transparent that I was far from alone. Perform a search for "Nexus 7 2013 Bluetooth problems" or "Nexus 7 2013 ghost taps" and you'll find countless disappointed Nexus owners gnashing their teeth.
Threads on the Google product forums stretch to many, many pages. There are people complaining of unbootable devices and GPS issues, but by far the biggest bugbear is touchscreen problems. Download the app YAMTT (Yet Another MultiTouch Test) from Google Play. If you're in possession of one of the problematic Nexus 7s (Nexi?) you will see ghost taps appearing as you place your fingers on the screen.
Perhaps the obvious thing to do is to try a factory reset. This shouldn't really be necessary with a brand new device, but it's worth a shot. Lots of people have tried doing this with no success. OK, plan B. Maybe it's a faulty unit... Take it back/send it back and swap it for a new one. Again, this is a route lots of people have gone down, with some forum users claiming to be on their sixth or seventh Nexus 7, each exhibiting the same problems.
This has obviously caused immense frustration among users. Sure, the new Nexus 7 is one of the cheapest tablets of its class, but that's not the point. Spend a couple of hundred dollars on a device and it's not unreasonable to expect it to work.
But what has annoyed people the most - certainly in the Google forums - is the fact that Google remained silent about things for so long. The fact that so many people appeared to be affected by the same issues would seem to indicate that there was a serious problem with the unit, but Google was saying nothing - despite raging speculation the company has not even made an announcement stating whether the thinking is that the problem is hardware or software related.
Finally, Paul Wilcox from Google entered the arena. He didn't have much light to shed on the situation, but at least he had something to say: "The Android team is aware of this issue and investigating. I'll post an update when there's new information to share".
So, some weeks after release there are still many, many Nexus 7 owners who do not possess a tablet they can reliably use. Problems do happen. Product launches are not always perfectly smooth, but what's irritating here is the lack of communication. The Nexus 7 had a high profile launch, and to avoid addressing the issue head on, and publicly, smacks of deception. Something is wrong when no one is willing to step up to the plate and face the public.
Of course it is not practical to expect every single forum post to get a response from someone in the know, but some sort of update about what's going on is needed. To do otherwise is rude, disrespectful and terrible public relations.
I'm amazed that anyone has the perseverance to try six different units -- in the same position I think I would have given up after three and started to save up for one of the slightly more expensive alternatives.
I'm currently awaiting the arrival of my first, and hopefully only, replacement Nexus. I sincerely hope the second unit is free from problems. I love the idea of the new Nexus 7 and, in theory, it has a great deal in its favor. But obviously it needs to work.
At the moment speculation is all there is -- and there's a lot of it. We don't even know if there is a hardware or software problem, whether a firmware update is all that's needed, or if there may be a recall. This is a poor show from Google. I'm disappointed in how things have been handled and I know I'm not the only one.
I'd be very interested in hearing how others who jumped on the Nexus bandwagon have got on. Did you get a unit that works flawlessly the first time or do you count yourself amongst the growing number of disgruntled customers?
-

Ready your hard drives -- Windows 8.1 gets an official release date
Publié: août 14, 2013, 4:01pm CEST par Mark Wilson
 A couple of days ago my colleague Wayne Williams looked at the new features in the latest leaked build of Windows 8.1 and now, hot on the heels of that, comes the announcement of the official release date for the OS refresh.
A couple of days ago my colleague Wayne Williams looked at the new features in the latest leaked build of Windows 8.1 and now, hot on the heels of that, comes the announcement of the official release date for the OS refresh.Set your alarm for 4am Pacific Time October 17 as this is when the much-anticipated update to Windows 8 will be unleashed on an eager public.
The announcement comes from Brandon LeBlanc on the Windows blog where he explains that the update will be made available free of charge to existing Windows 8 users through the Windows Store. The post also reveals that Windows 8.1 will be available preinstalled on new machines from October 18.
The final build number is not yet known, but we have already reached build 9471, showing there have been several version jumps from the official available preview (build 9431), and with just two months until the official release, it is unlikely that we'll see any noteworthy changes -- it's really just a case of ironing out the creases and adding a little spit and polish at this stage.
So, add the date to your calendar and set aside a couple of hours on the big day. Don’t forget that if you're already using the preview release of Windows 8.1 you're going to need to reinstall all of your apps afterwards.
Will the release of a finalized version of Windows 8.1 compel you to upgrade if you've been putting it off so far, or are you happy sticking with Windows 7 or XP?
-

Received a badly formatted email on your mobile? 75 percent of you will delete it
Publié: août 14, 2013, 11:30am CEST par Mark Wilson
 A survey by Constant Contact shows that mobile devices are more important than ever, particularly to those under the age of 30. The study reveals that 80 percent of smartphone owners say it is "extremely important to be able to read emails" on their mobile devices. But marketers take note -- if an email doesn’t display correctly, it's highly likely it will just get deleted.
A survey by Constant Contact shows that mobile devices are more important than ever, particularly to those under the age of 30. The study reveals that 80 percent of smartphone owners say it is "extremely important to be able to read emails" on their mobile devices. But marketers take note -- if an email doesn’t display correctly, it's highly likely it will just get deleted.High mobile email usage is hardly a revelation in itself, but the way the figures break down is interesting. Predictably it is the 18-30 age bracket that has the highest mobile usage, with 88 percent of users turning to their mobile for emails.
Move up through age ranges and the number starts to drop, but not as much as you might think; 85 percent of 30-39 year olds, 74 percent of 40-49 year olds and, perhaps most shocking of all, 71 percent of those aged between 50 and 59, and 66 percent of those over 60.
There are very few people, it seems, who have not used their mobile device for reading emails. In the youngest age range, more than half (52 percent) use a mobile device as their primary source for email -- move up an age bracket and this only drops slightly to 48 percent.
There are slight variations between platforms. iPhone owners are more likely to open emails on their mobile (82 percent), compared to users of other mobile brands (72 percent).
But what is interesting about the research is the way in which it demonstrates how emails need to take mobile viewing into account. We all complain about the amount of spam we receive, but marketing emails play an important role in the economy -- cast a wide net and a few new customers are sure to be picked up at virtually no cost.
Sadly for advertisers, a massive 75 percent of those surveyed said that they are highly likely to delete emails they are unable to read on their smartphone. The viewing of emails on smaller screens is something marketers need to take into account. I've stopped counting how many press releases, product announcements and other emails I've received that are just not suited for easy reading on the screen of my Android phone.
I'll persist though. It's very rare that an email actually cannot be viewed on my mobile, although it may be awkward. If things are too difficult to make out, or require too much zooming and scrolling, I'll save the message for later and look at it on my computer. It looks as though I'm in a minority however.
With almost half of respondents (49 percent) saying they are likely to click on links contained in emails sent to them by businesses, maybe it's time for high mobile usage to be looked at differently. It's not just a way for developers to sell apps, or for consumers to be able to access the web on the move. Mobile users have changed a lot over the years; perhaps it's time for advertisers to try to keep pace.
Photo Credit: bloomua/Shutterstock
-

Internet Explorer is the latest browser to get the Adblock Plus treatment
Publié: août 13, 2013, 9:39pm CEST par Mark Wilson
 It might come as a surprise, particularly if you are a Chrome, Opera or Firefox user, but Adblock Plus has not been available for Internet Explorer until now. Microsoft's web browser is the latest to gain the option to block advertisements. An experimental version of the plugin was released for IE a couple of months ago, but today sees the release of the official, final version.
It might come as a surprise, particularly if you are a Chrome, Opera or Firefox user, but Adblock Plus has not been available for Internet Explorer until now. Microsoft's web browser is the latest to gain the option to block advertisements. An experimental version of the plugin was released for IE a couple of months ago, but today sees the release of the official, final version.The add-on has been a long time coming to Internet Explorer, and fans of the browser are likely to welcome it with open arms. If you've used the extension in other browsers, you'll have a good idea of what to expect -- although the name is something of a give-away.
Windows 8 users may be disappointed to find that there is no support for the modern or Windows RT versions of the browser, just the desktop edition. The modern version's lack of support for any extension -- at least at the moment -- means this is unlikely to change any time soon.
After installing the add-on, you'd be forgiven for thinking the installation has failed; there is no obvious way to access Adblock Plus. Make sure you have the status bar enabled and you'll be able to access the extension's options. It's also worth bearing in mind that even the Adblock Plus website admits that "there is still much room for improvement".
So, if you're an Internet Explorer user who is tired of seeing advertisements littering the web pages you visit, head on over to the Adblock Plus website and grab yourself a copy. But don’t forget, websites like BetaNews rely on advertising to some extent to stay alive. There are plenty of sites who go over the top, but don’t forget to add us to your whitelist!
Photo Credit: Quka/Shutterstock
-

BlackBerry considers selling itself to help boost BB10 sales
Publié: août 13, 2013, 1:26pm CEST par Mark Wilson
 The days of the CrackBerry are well and truly over. Years of declining sales as smartphone users move to iPhones and Android devices for their telecommunication needs has left the Canadian company floundering. In Europe, BlackBerry handsets account for just 2.2 percent of smartphone sales. In the face of stiff competition in a fierce market, BlackBerry is considering a potential sale in a bid to turn around the company's fortunes.
The days of the CrackBerry are well and truly over. Years of declining sales as smartphone users move to iPhones and Android devices for their telecommunication needs has left the Canadian company floundering. In Europe, BlackBerry handsets account for just 2.2 percent of smartphone sales. In the face of stiff competition in a fierce market, BlackBerry is considering a potential sale in a bid to turn around the company's fortunes.BlackBerry has seen its market share steadily dropping off over the years. In the second quarter of 2013, this stood as just 2.9 percent, down from 4.9 percent in the same period the previous year. A lot of hope was pinned on the launch of the BB10 platform and IDC's research shows that the company has benefited from steady progress since its release.
Putting itself up for sale is not the only option available to BlackBerry. The company's board of directors is also considering other possibilities such as "…possible joint ventures, strategic partnerships or alliances…". Chairman Timothy Dattels said that "…now is the right time to explore strategic alternatives".
BlackBerry is keen to stress that there are currently no assurances about what might happen and the "exploration of strategic alternatives" may not result in a transaction. The company has said that news of further developments will not be announced until such a time that the board of directors approves a specific transaction, or brings the explorations to a formal conclusion.
Whether BlackBerry's reliance on business customers has worked against it is open to debate. But the ever declining market share certainly seems to indicate that the company has failed to adapt to a fast-changing market. Remember the PlayBook? No, thought not.
Just what happens next is unclear -- and we may know nothing more for some time. BlackBerry's largest shareholder, Fairfax Financial, has said that it has "no current intention of selling its shares".
Photo Credit: Slavoljub Pantelic/Shutterstock
-

CheapCast transforms an Android device into a Chromecast device for free
Publié: août 13, 2013, 11:55am CEST par Mark Wilson
 Google's Chromecast streamer may not yet have set the world on fire but it is earning itself quite a following. Part of the device's appeal is its low price -- just $35 for a fairly capable plugin streaming unit -- but there are times when only free will do. CheapCast is a free app that turns virtually any Android phone or tablet (running Android 2.2 or above is the only requirement) into a Chromecast.
Google's Chromecast streamer may not yet have set the world on fire but it is earning itself quite a following. Part of the device's appeal is its low price -- just $35 for a fairly capable plugin streaming unit -- but there are times when only free will do. CheapCast is a free app that turns virtually any Android phone or tablet (running Android 2.2 or above is the only requirement) into a Chromecast.The app is a fairly early beta, but in terms of replicating what Chromecast has to offer, it does a reasonably good job. CheapCast does nothing, yet, to address many of the complaints about Chromecast -- such as the inability to easily stream local content -- but it does mimic the Google device's casting capabilities for the likes of YouTube and Google Play.
Setup takes a matter of moments: download and install the app and you're good to go. There are no settings to concern yourself with, but if you have a spare Android device lying around you may want to enable the option to automatically start CheapCast on boot.
Fire up YouTube on your computer and, much like with Chromecast, you can opt to stream a video to the second screen. The key difference is that the $35 dongle connects neatly to the HDMI socket of your TV and can draw power from an available USB port. The chances are you'll have to invest in an adaptor if you want to connect your old phone to your TV, unless you don’t mind watching on a smaller screen.
So is this a Chromecast killer? Not by a long chalk. I'm prepared to cut it some slack as it’s a beta app, but there's still a way to go. Add features like easy streaming of network media, and this free app could make a dent in Google's potential income. At the very least, it's worth giving the app a shot to see how an actual Chromecast could fit into your life. It's free… you've got nothing to lose!
The name might need some work though -- CheapCast is something of a misnomer at the moment. The app is free, and 'free' and 'cheap' are not really synonymous. Sure, there's the cost of the required Android device to factor in as well as the potential cost of an adaptor if you want to view on your TV, but… oh, I'm just being picky now.
-

IFTTT gains New York Times channel to help automate news delivery -- but Pipes it ain't
Publié: août 13, 2013, 12:03am CEST par Mark Wilson
 Web automation service IFTTT just gained itself a new channel, adding support for no lesser an establishment than the New York Times. This means that if you don’t want to have to keep checking the NYT website to see when there is a new article in the Science section, you no longer need to. In a couple of steps it's possible to create a recipe that will send you an SMS, email or some other form of alert.
Web automation service IFTTT just gained itself a new channel, adding support for no lesser an establishment than the New York Times. This means that if you don’t want to have to keep checking the NYT website to see when there is a new article in the Science section, you no longer need to. In a couple of steps it's possible to create a recipe that will send you an SMS, email or some other form of alert.As with many of IFTTT's other channels, the New York Times has various possible triggers. In addition to the addition of an article to a particular section, recipes can also check for popular' articles, Critic's Pick movie reviews, new additions to the Best Sellers list and the addition of new events.
But perhaps the most useful trigger is the one that can be used to send out an alert -- or perform some other action -- when an article matching your specified search terms is found.
The channel may have just gone live, but there are already more than 70 readymade recipes to choose from, and this is a figure that's likely to increase over the coming days.
IFTTT continues to grow, both in terms of the number of online services it supports and the number of users. Its popularity can be attributed, at least in part, to its undeniable ease of use. It may not be the most powerful web automation site out there, but it is probably the one that is easiest to get started with.
But, for me anyway, IFTTT will always remain the poor cousin of the oft-overlooked Yahoo Pipes. Yes, there is a steeper learning curve -- there's no getting around that -- but it is infinitely more flexible. Lending itself to so many applications, I've whiled away many a happy hour creating the ultimate custom newsfeed -- and it's something I've implemented on my own website to automatically pull in stories from the various websites I write for; it saves me from having to manually post links to my work.
That's not to say IFTTT doesn’t have its place. It's still something I've been known to turn to, and I've even used it in conjunction with Pipes. It's user-friendly automation for the masses, and that's not something to be sneered at.
-

By the Numbers is Microsoft's already-out-of-date new infographic website
Publié: août 12, 2013, 4:19pm CEST par Mark Wilson
Do you wonder how many Windows 8 licenses Microsoft has sold? Are you kept awake at night trying to calculate how many minutes are spent speaking on Skype globally each day? Intrigued to learn how many pageviews MSN gets each month? Well fret no more! The answers to all of these ponderings and plenty more besides can be found on Microsoft's new By the Numbers website.
In a break from the usual look of Microsoft sites, the modern styling of Windows 8 is used here to produce an interactive infographic that does an excellent job of blowing Microsoft's trumpet. The tiled interface mimics that found on Windows 8's Start screen, but the difference here is that live tiles are used to display key statistics about various areas of Microsoft's business.
For what is essentially an exercise in lauding itself, Microsoft by the Numbers is a good-looking site. It's a great bit of branding, but whether it will do much to convert skeptics to the Start screen remains to be seen.
There are some interesting figures highlighted. Apparently SkyDrive is home to 11 billion photos, and one in seven people use Office. There are also a number of rather sillier figures to lighten the mood -- if you care how much pizza and cola are consumed on the Microsoft campus each year, prepare to put your mind at ease as this valuable data is revealed.
Despite the declaration that the data "is current as of August 11, 2013" a lot of the figures quoted are already a few months old. The usage number for Bing, for instance, is based on comScore research in June. The sales figures for Windows 8 are also a little dated. Unless sales have seriously plateaued, the 100 million licenses proclaimed to have been shifted is likely to be rather higher -- this landmark was actually reached some three months ago. It would be great if the site could get updated on a regular basis.
There are no useful statistics available for Windows Phone -- the number of apps available in the App Store is pointed out, but what we're interested in is how many are downloaded, and how much money is being made. The lack of any sort of reference to Surface is also worth noting; this may change, but from the infographic, it's as though the platform just doesn't exist!
For anyone who prefers their stats in a more traditional form, the data is also available as a rather less exciting, and decidedly less interactive, PDF file.
-

Apple wins patent case that could lead to a ban on certain Samsung products
Publié: août 10, 2013, 1:11pm CEST par Mark Wilson
 The Apple and Samsung battle continues to rumble, and less than a week after a proposed ban on the sale of iPhones and iPads was overturned, another ruling has -- at least for the time being -- gone Apple's way. The US ITC has upheld a previous ruling dating back to 2011 that found Samsung has infringed various Apple patents, potentially leading to a US ban on various devices from the South Korean company.
The Apple and Samsung battle continues to rumble, and less than a week after a proposed ban on the sale of iPhones and iPads was overturned, another ruling has -- at least for the time being -- gone Apple's way. The US ITC has upheld a previous ruling dating back to 2011 that found Samsung has infringed various Apple patents, potentially leading to a US ban on various devices from the South Korean company.The ruling found that Samsung had violated two patents relating to Apple's iPhone. The first patent (often referred to as the "Steve Jobs patent") relates to the use of a touchscreen interface as means of interacting with a device using one or more fingers. The second patent relates to the design of an audio socket that can determine the type of microphone or headset that has been plugged into it.
But, as happened last week, there is potential for the ruling to be overturned. President Obama has 60 days to review the Commission’s ruling, and the ban is on hold until a final decision is made.
There is no word on exactly which Samsung product would be affected by a ban, but as the initial case dates back two years, it is likely that older products would be involved.
One thing is for sure...this is one court drama that looks set to run and run for sometime to come.
-

Quick! Grab your Google Latitude data before it's too late!
Publié: août 9, 2013, 8:20pm CEST par Mark Wilson
 The latest horse to be sent out to pasture from Google's stables is Latitude. Little notice was given when the service's retirement was revealed -- albeit quite quietly -- back in July. In a blog post about the latest version of Maps, Google mentioned in passing that "Latitude and check-ins will be retired. These features will no longer be a part of the new Google Maps app, and will stop functioning in older versions by August 9".
The latest horse to be sent out to pasture from Google's stables is Latitude. Little notice was given when the service's retirement was revealed -- albeit quite quietly -- back in July. In a blog post about the latest version of Maps, Google mentioned in passing that "Latitude and check-ins will be retired. These features will no longer be a part of the new Google Maps app, and will stop functioning in older versions by August 9".Pay a visit to the About Latitude page and you will indeed see confirmation that Google will close "Google Latitude, Latitude for iPhone, the Latitude API, the public badge, the iGoogle Gadget, and the Latitude website on August 9". Well the date is now upon us. The end is nigh.
But if you're quick -- and we mean quick -- you can still back up your Latitude data through Google Takeout. If you have other Google data that you'd like to download as an archive you can pick and choose what you'd like to include in your backup, but you can also jump right in and create a Latitude only archive.
So if you’re keen to maintain access to all of the location data previously stored in Latitude, saddle up and get moving -- the clock is ticking!
Image Credit: Triff / Shutterstock
-

Mobile ads find their way to Google Maps for iOS and Android
Publié: août 9, 2013, 12:42pm CEST par Mark Wilson
 Ads are prevalent and all but unavoidable online these days, and in a bid to keep software free and fund development, in-app advertisements are increasingly common.
Ads are prevalent and all but unavoidable online these days, and in a bid to keep software free and fund development, in-app advertisements are increasingly common.The latest kid to the party is Google Maps for iOS and Android. Perform a search for a restaurant, coffee shop, or other establishment, and you may well find that the bottom of your mobile is adorned with an ad for a related business.
The AdWords-powered addition sees the arrival of advertisements that feature the names and ad text for a, hopefully, relevant business.
Tapping through reveals the address, contact details and directions.
There's no way to opt out of the ad service, but if you're looking for a particular type of establishment and the adverts are related, this is one example of advertising that could prove genuinely useful.
-

Twitter tracks your tweets so advertisers can monitor sale performance
Publié: août 9, 2013, 12:44am CEST par Mark Wilson
 Twitter teams up with Datalogix (DLX) in a new program that enables brands to track the impact that their tweets have on sales. Referred to as "offline sales impact", the program can be used to see just what effect promoted and regular, "organic" tweets have on the number of units shifted from shop shelves.
Twitter teams up with Datalogix (DLX) in a new program that enables brands to track the impact that their tweets have on sales. Referred to as "offline sales impact", the program can be used to see just what effect promoted and regular, "organic" tweets have on the number of units shifted from shop shelves.The precise process involved is not revealed, but the program sees Datalogix send Twitter a list of hashed email addresses which is then compared to a list of email addresses associated with Twitter accounts.
Data is anonymized through the use of ID numbers, and where a match is found between the two lists, Twitter shares details such as views of, and clicks on, a brand's tweets. Partners can then use this information to compare sales between groups of people who saw tweets and those who didn't.
Twitter insists that user privacy is respected and that there is no way that advertisers can gain access to data that would identify anyone or what they have bought. But if you're still concerned about your privacy, it is possible to opt out of the program.
But even with an opt-out page, just how to ensure that your anonymized data is not handed over to advertisers, is not immediately obvious. Head down to the Choice section, click the final "click here" in the last sentence referring to "direct mail, online, mobile and analytic products".
Image Credit: VladKol / Shutterstock
-

Ofcom wants to make broadband switching quicker and easier in the UK
Publié: août 8, 2013, 11:04pm CEST par Mark Wilson
 Switching broadband providers should be easy -- the emphasis is very heavily on the word "should" here -- but in practice this is often not the case. There may be issues getting hold of the necessary authorization code, or the dreaded period of downtime as one ISP takes over from another. All this could be set to change, for the UK at least, if Ofcom's proposed new measures have the desired effect.
Switching broadband providers should be easy -- the emphasis is very heavily on the word "should" here -- but in practice this is often not the case. There may be issues getting hold of the necessary authorization code, or the dreaded period of downtime as one ISP takes over from another. All this could be set to change, for the UK at least, if Ofcom's proposed new measures have the desired effect.To help make the transition as smooth and seamless as possible, Ofcom is eliminating one potential bottleneck. Now customers looking to switch need do nothing more than contact the ISP they would like to move to. There's no need to get in touch with the current ISP who may drag their heels, the new provider can now take care of the entire process on behalf of the customer.
The new process will apply to switching landline telephone providers as well as ISPs, and steps are also being taken to help avoid a loss of service during the changeover. In addition to this, steps are proposed that will help to prevent customers from having their broadband service switched by accident or without their consent.
Other proposals include making it easier for home movers to take over the existing line of their new property, and ensuring that providers keep records of customer consent for switching. Ofcom is also keen that customers are better informed by ISPs about factors such as early termination fees.
Details of precisely how the new measures will work are still to be finalized, but the timetable for getting everything in place stretches some way into the future. The initial consultation period will come to an end at the beginning of October 2013, details should be finalized by the start of 2014, and then the new switching process should be implemented within a year.
Image Credit: Zsolt Biczo / Shutterstock
-

Facebook’s algorithm update: who benefits most? Facebook, users or advertisers?
Publié: août 8, 2013, 1:05am CEST par Mark Wilson
 Success on Facebook is as much about the quality of posts as it is about the quantity of posts. Research by Expion into the social network finds that user engagement with brands has declined despite an increase in the number of posts from the top 50 retailers.
Success on Facebook is as much about the quality of posts as it is about the quantity of posts. Research by Expion into the social network finds that user engagement with brands has declined despite an increase in the number of posts from the top 50 retailers.The list includes such names as Tiffany & Co, Walmart and Amazon who are responsible for a good deal of the site's ad revenue and the findings go some way to explaining not why the news feed algorithm has changed, but also why Facebook announced it so publicly.
Advertising is only effective if users are engaged, and Expion's report found that retail brands experienced the slowest period of growth in the first half of 2013 for two and a half years. This is in spite of the fact that there were more posts made by the biggest retailers.
But Facebook is actually benefitting from the poor growth period as companies are spending more money on advertising and promoted posts. This has resulted in Q2 2013 pulling ad revenue of around $1.6B, and analysts suggest there will lead to higher quality posts as retailers vie for attention in an already saturated market.
High quality brands were found to post to Facebook far less frequently, but this resulted in relatively high user engagement. In the first half of 2013 Tiffany & Co made 186 posts resulting in almost 29,000 "fan actions" (commenting, sharing etc.) for each one, compared to Walmart who made 1,034 posts while benefiting from just under 11,500 fan actions each; five and a half times the number of posts, but less than half the impact with each one.
It's not just luxury brands that fare well on Facebook, the type of content posted is also important. Images make up 80 percent of posts from retailers, with videos accounting for a mere three-percent.
Basic status updates -- the reason most people use Facebook -- make up a tiny one-percent of retailers' posts. The preference for graphical posts is understandable as they are 28 percent more popular with site users.
Facebook is obviously keen for advertisers to see results from the ads they pay for. By increasing the amount of time users spend on the site, the number of posts and ads that are seen by each Facebooker increases. This is one of the reasons Facebook algorithm tweaking is so significant.
The seemingly selfless act of helping Facebook users to see more posts that they might previously have missed actually ensures that more of these ads are seen, keeping retailers happy and the money rolling in.
Of course it is not just the big names that are important to Facebook -- smaller brands are also key. They may spend less in advertising but they remain important cogs in a larger machine.
Expion's research found that from 11am to 2pm ET was hone to the most successful posts, but 8am to 11am also did very well. As brands look to reach larger global audiences, local time zones become meaningless.
It may previously have been difficult for a small company with limited resources to arrange for posts to be made at the most effective times, but the changes now mean that time of posting is now a less significant factor in whether an individual post is seen or not.
So the algorithm change looks to benefit lots of people in different ways. The average Facebook user gets to see more of the content that is relevant to them, businesses on the network have an easier time not having to worry so much about time zones, and big name, big money advertisers are kept happy due to increased page time and user engagement.
It will be interesting to see if Facebook users notice the changes or whether they will appear subtly.
Image Cedit: Gonzalo Aragon / Shutterstock
-

Vodafone's 4G network hits London 29 August
Publié: août 7, 2013, 6:12pm CEST par Mark Wilson
 Vodafone reveals that its 4G network will be made available to mobile users in London on 29 August, with several other key cities being added to the list by the end of the year. SIM-only tariffs, with a 12-month contract, start at £26, matching the cheapest tariff offered by O2.
Vodafone reveals that its 4G network will be made available to mobile users in London on 29 August, with several other key cities being added to the list by the end of the year. SIM-only tariffs, with a 12-month contract, start at £26, matching the cheapest tariff offered by O2.The mobile firm has teamed up with Spotify and Sky Sports to provide content to subscribers. Anyone signing up for a 4G package will be able to choose between a Spotify Premium or Sky Sports Mobile TV bundle, gaining access to music and live sport. Both bundles are provided free of charge for the first six months, but after this Sky Sports Mobile TV costs £4.99 per month, and Spotify Premium £9.99 per month.
The key benefit of 4G is speed of downloads -- and for many people this will mean downloading more than they have done in the past. Vodafone has a Data Test Drive option that will enable users to determine which data package they should sign up for.
For three months, users are free to download as much as they want at no extra cost; at the end this period Vodafone will let them know which package would be most suitable for that level of usage.
Non-Londoners have slightly longer to wait to join the network. 4G is coming to Vodafone customers in Birmingham, Bradford, Coventry, Edinburgh, Glasgow, Leeds, Leicester, Liverpool, Manchester, Newcastle, Nottingham, and Sheffield by the end of 2014, and the company aims to have 98 percent coverage of the UK in the next couple of years.
Photo Credit: stefanolunardi/Shutterstock
-

Average UK broadband speed quadruples in five years
Publié: août 7, 2013, 5:15pm CEST par Mark Wilson
 Throughout the UK internet users are benefiting from accelerating access speeds according to research by Ofcom. The average residential broadband speed now clocks in at 14.7Mbit/s -- around four times the speed back in November 2008 when figures were first published.
Throughout the UK internet users are benefiting from accelerating access speeds according to research by Ofcom. The average residential broadband speed now clocks in at 14.7Mbit/s -- around four times the speed back in November 2008 when figures were first published.Of course, these are average figures, and the majority of web users will find that their actual connection speed is well above or below 14.7Mbit/s. One of the key factors influencing obtainable speed is location. Customers in rural areas were found to have download speeds that were less than half of those enjoyed by customers in urban areas -- 9.9Mbit/s compared to 26.4Mbit/s.
The increase in average speeds has been driven largely by a surge in the availability of "super-fast" connections -- those offering speeds of 30Mbit/s and above. In particular, Plusnet’s "up to" 76Mbit/s and Virgin Media’s "up to" 120Mbit/s cable service are likely to have bumped up the numbers. This type of connection is more widely available in urban areas, and this will come as no surprise to anyone living out in the country.
Despite the fact that average broadband speeds are increasing faster in rural areas than anywhere else, the difference in download speeds between urban and rural areas is greater than ever. This can be attributed to the availability of significantly faster services in towns and cities. "Super-fast" connections are available to rural dwellers, but far less widely.
The research also revealed that internet access speeds are fairly stable throughout the day. It seems that the days of web access slowing to a crawl in the evening are gone, although speeds do still drop off -- but only down to 88 percent of full speed on average.
If you fancy crunching the numbers yourself, the full report is available at the Ofcom website where you'll also find some analysis of the figures.
-

Read all about it! Facebook reveals details of its news feed algorithm
Publié: août 7, 2013, 12:34pm CEST par Mark Wilson
 It's one of the mysteries of life. It may not quite rank up there with who shot JR or why the word "monosyllabic" has so many syllables, but there can be few Facebook users who have not wondered why particular stories appear where they do in their news feed. Now, Facebook reveals details of the secret algorithm that determines how content is ranked.
It's one of the mysteries of life. It may not quite rank up there with who shot JR or why the word "monosyllabic" has so many syllables, but there can be few Facebook users who have not wondered why particular stories appear where they do in their news feed. Now, Facebook reveals details of the secret algorithm that determines how content is ranked.According to the social network there are around 1,500 stories waiting for the average user to see upon logging into their Facebook account. Few people have the time to scroll through all of them, with research showing that users manage to work through just over half of the stories. Prioritization is needed and this is where the algorithm comes into play.
The secret formula takes into account not only how frequently users interact with each other, but also how popular a post is proving globally and whether users have expressed an interest in similar content. This enables Facebook to pull out around 300 posts it thinks you're most likely to want to read.
But the algorithm post is about more than how things have and do work; for the algorithm is changing. To help ensure users don’t miss out on stories, older items will be pushed further up news feeds -- assuming they are gaining sufficient likes and shares from other Facebook users, that is.
Tests have shown that this change results in a 'like' increase of between 5 and 8 percent -- great news for anyone, or any business, using Facebook to interact globally as it helps to minimize the problem of working in different time zones.
So in a nutshell, the news from Facebook is old is the new new.
Photo Credit: Brian A Jackson/Shutterstock
-

Windows Phone App Studio beta makes a developer of everyone
Publié: août 7, 2013, 2:13am CEST par Mark Wilson
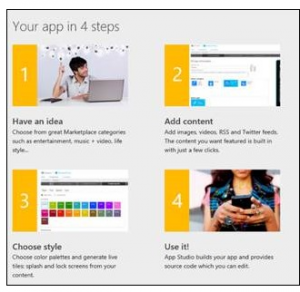 The app market is crazily busy. With so many thousands of apps to choose from, a developer looking to get noticed needs to come up with something pretty special. But the people with the best ideas aren't necessarily those with coding skills, and funds available to individuals and startups are usually limited. The solution? Make app development as easy as possible. Enter Windows Phone App Studio.
The app market is crazily busy. With so many thousands of apps to choose from, a developer looking to get noticed needs to come up with something pretty special. But the people with the best ideas aren't necessarily those with coding skills, and funds available to individuals and startups are usually limited. The solution? Make app development as easy as possible. Enter Windows Phone App Studio.The online service is a new beta tool that can be used to create Windows Phone apps in a few simple steps. The idea is to keep things as simple as possible so even new developers should be able to create an app fairly quickly. No coding knowledge is required as this is all taken care of automatically. There are a number of templates available into which content such as text, video and RSS feeds can be dropped.
Windows Phone App Studio beta is available to anyone who wants to try it out, not just old hands at the game. The simplified registration process means that anyone and everyone is free to sign up for an account, register a phone to use as a test platform and work with up to two apps. Microsoft is touting the tool as not only a means for new developers to get started in the world of app creation, but also as a way for more seasoned coders to create prototypes very rapidly.
The Windows Phone Developer Blog also announces a new "Click to Chat" feature for registered developers, as well as the addition of Costa Rica, Cyprus, Kazakhstan, Lebanon, Malta, and Trinidad and Tobago as supported markets.
Fancy the idea of getting into the Windows Phone App Studio beta website? Now is your chance to get creative and publish the next big thing.
-

Apple announces takeback program for dodgy iOS power adapters
Publié: août 6, 2013, 12:44pm CEST par Mark Wilson
 Ahead of its August 16 launch, Apple reveals details of a takeback program that aims to replace third-party power adapters with authentic units. Concern over the safety of third-party and counterfeit adapters for iPhones, iPads and iPods prompted the scheme, and Apple says any adapters handed in will be "disposed of in an environmentally friendly way".
Ahead of its August 16 launch, Apple reveals details of a takeback program that aims to replace third-party power adapters with authentic units. Concern over the safety of third-party and counterfeit adapters for iPhones, iPads and iPods prompted the scheme, and Apple says any adapters handed in will be "disposed of in an environmentally friendly way".So what's the incentive for just giving your current adapter to Apple? Well aside from that warm, fluffy feeling that comes from knowing that you're helping to do your little bit for the environment rather than just adding to landfill, Apple has another carrot to dangle.
Don't get your hopes up -- Apple is not going to be offering free replacements. But the program will enable anyone who is interested in getting hold of a genuine power adapter to do so for the reduced price of $10 (or the worldwide equivalent).
No safety testing is offered, so if you have a third-party adapter you have concerns about, the program will not enable you to find out if it is dangerous. Rather you get to hand over your old adaptor and buy a shiny, new genuine one for a discounted price.
Users are limited to one adapter per iOS device, and the program runs until October 18, 2013. You'll need to take your power adapter and iPhone, iPad, or iPod to an Apple Retail Store or participating Apple Authorized Service Provider.
Full details and links to find your closest stores, can be found at the announcement page.
Photo Credit: Wayne Williams
-

Could Twitter's verified accounts be the answer to stopping tweet threats?
Publié: août 5, 2013, 5:56pm CEST par Mark Wilson
 We've talked about Twitter and the subject of policing the Internet quite a bit recently. It's not just us. Countless websites, newspapers, blogs and TV news channels have debated just what can be done to stop the problem of online abuse.
We've talked about Twitter and the subject of policing the Internet quite a bit recently. It's not just us. Countless websites, newspapers, blogs and TV news channels have debated just what can be done to stop the problem of online abuse.Part of the problem is that Twitter is -- as is the case with much of the Internet -- largely anonymous; or at least that's what most users think. They must think that, or they would not behave so stupidly and recklessly online. The reality is that, unless someone has taken measures to cover their tracks through proxy servers or other masking techniques, it's not really all that difficult to link an online message to, if not an individual person, at least an individual machine -- with the help of ISPs and other parties.
But maybe there is a simpler solution. The way things stand at the moment, it takes moments to sign up for a Twitter account, and there's nothing to stop you from signing up for thirty accounts if you feel the need or desire. Why might you want so many? Well, lots of people use Twitter professionally as well as personally. The person in charge of a company's official Twitter feed is likely to want their own personal account as well, and a lot of companies maintain multiple Twitter accounts for various purposes.
Multiple accounts can also be abused. A seemingly respectable person who uses Twitter to share thoughts and ideas may well have a darker side. There is nothing to stop them from opening up a second "trolling" account that is used for nothing more than stirring up trouble or harassing others.
Twitter already has a system in place that could be adapted to combat the problem: Verified accounts. These badges of authenticity are currently reserved for celebrities, politicians, journalists and other public figures. This does not mean that spoof, parody and out and out fake accounts do not exist, but the presence of the blue tick helps to reassure followers that a tweet from Stephen Fry really is from Stephen Fry. Tweets from me really are from me as well, by the way, although my account is devoid of the tick.
The way things stand at the moment, there is no way to reach out to Twitter and apply for a verified account -- unlike Google+ which allows anyone to request verification (you'll probably get turned down, but there's no harm in asking, eh?). Twitter is not especially open about who gets verified, what level of celebrity is required, and whether being an advertiser has any bearing on things, but one thing is clear: it will contact you, not the other way round.
The number of verified accounts is very small. You can keep an eye on the latest additions to the elite club by following @verified and there are some interesting and surprising accounts in the list. If you feel you or your company is deserving of verification, there's no point in trying to contact Twitter. Save your typing fingers the effort -- it's not worth the time. There are countless websites that claim to offer advice about how to get verified; ignore them. If you have to ask to be verified, you probably don't deserve or need to be.
Perhaps Twitter should consider looking at verified accounts in a completely different way. Rather than using it as a means of helping users to avoid being duped by fake celebrities, maybe it should be a compulsory part of signing up for an account. If you've handed over government issued identification papers during sign-up (driving license, passport etc) to prove who you are, you're significantly less likely to start sending out death threats -- unless you're stupid.
Of course this opens up all manner of privacy concerns. If formal identification was a requirement for creating a Twitter account -- and Twitter would be free to make this compulsory -- it would have be made abundantly clear that personal data such as address and date of birth would only be used when absolutely necessary (so only when tracking down those who have committed crimes or abused other users).
Twitter knowing exactly who each user really is would wipe out many, many problems that exist on the network, but is this getting a little too close to having an online ID card? Maybe, but it's an idea worth considering. It's another idea to throw into the pot and mull over. It's not an ideal solution perhaps, but it's certainly no worse than anything else that’s been suggested.
-

Obama overturns ITC ban on the sale of various iPads and iPhones
Publié: août 4, 2013, 12:03am CEST par Mark Wilson
 In a letter to the International Trade Commission chairman, the Honorable Irving A Williamson, the Obama administration vetoes an earlier ITC ruling that was due to block the sale of a number of Apple products. The original ruling came in June and was to prevent the sale of various products including certain models of the iPhone 4 and the iPad 2.
In a letter to the International Trade Commission chairman, the Honorable Irving A Williamson, the Obama administration vetoes an earlier ITC ruling that was due to block the sale of a number of Apple products. The original ruling came in June and was to prevent the sale of various products including certain models of the iPhone 4 and the iPad 2.The letter from Ambassador Michael Froman explains that having reviewed the information surrounding the patent dispute between Apple and Samsung, he had decided to "disapprove the USITC's determination to issue an exclusion order and cease and desist order". Under section 337 of the Tariff Act of 1930 the President is obliged to evaluate decisions made by the Commission during a 60-day review period, and in this instance the authority was passed to the USTR.
The reason for Ambassador Froman's overturning of the ban? It is based on his "review of the various policy considerations discussed [in the letter] as they relate to the effect on competitive conditions in the U.S. economy and the effect on U.S. consumers".
The letter concludes by saying that the vetoing of the ban does not mean that Samsung, as patent holder, was not "entitled to a remedy" but that the company was free to "continue to pursue its rights through the courts".
You can read the letter in full -- and revel in all its delightful legalese -- at the USTR website.
Photo Credit: BMCL/Shutterstock
-

Android Device Manager tracks down your lost phone
Publié: août 2, 2013, 9:02pm CEST par Mark Wilson
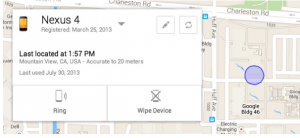 We've all done it -- put our hands to our pocket only to discover that the phone we thought was pressed close to our body is in fact missing. But where? That's the question. Android Device Manager is Google's latest solution to help you hunt out your hidden handset.
We've all done it -- put our hands to our pocket only to discover that the phone we thought was pressed close to our body is in fact missing. But where? That's the question. Android Device Manager is Google's latest solution to help you hunt out your hidden handset.You could get a friend to call your phone -- that would seem like the obvious thing to do. But it's no help if you have put your phone into silent mode. Android Device Manager is able to call your phone and make it sound, even if the volume is turned down, so you can quickly determine if your Droid is nestling down in the back of the sofa or in the back of your car.
Of course, it may well be that carelessness struck a little further afield. Never fear, a map is available to show the location of your device. If you are concerned about security, a remote wiping option will keep data away from prying eyes.
Before you get too excited, Android Device Manager is not yet live. It's due some time this month, so if you have lost your phone you'd better hope that your battery holds out, and silent mode is not enabled. Just keep an eye on the official Android Blog (or here!) for updates.
-

Multiple personality tweeters rejoice -- Windows 8 app gets multi-account support
Publié: août 2, 2013, 1:23pm CEST par Mark Wilson
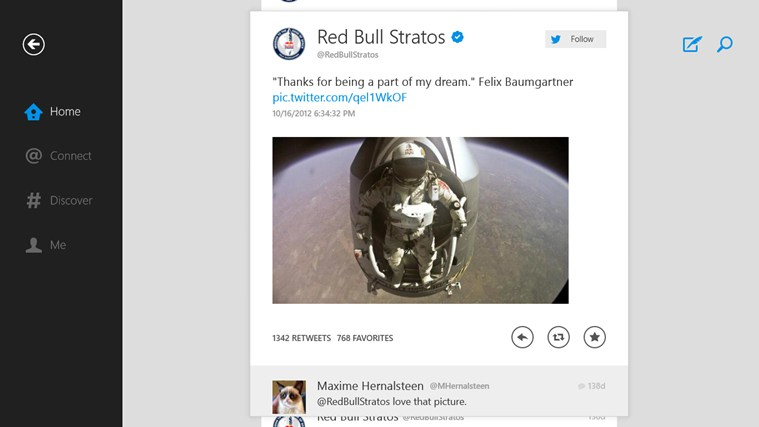
It may not be an update that will set the world on fire, but it's one that will be welcomed by anyone who manages a personal and a work Twitter account. The Window 8 version of the app now includes support for multiple accounts, so there's no need to keep signing in and out.
This is good news not only for tweeters who use Twitter for business and pleasure, but also those who just like to maintain more than one persona online. Other additions to the app include list support for easier management of the accounts you follow.
If you've already got the app installed, a quick trip to the Windows Store will bring you up to date, while new users can grab a copy for fresh installation. Oh, and if you are a completely new user, account sign up is now available in the app as well.
-

Samsung explains why some Galaxy S4 benchmarks appear 'optimized'
Publié: juillet 31, 2013, 6:28pm CEST par Mark Wilson
 On Tuesday AnandTech published a report that suggested some sort of "trickery" was being used by Samsung to boost device performance when benchmarks are run. The Korean electronics manufacturer responded to the claims today, and while it does not deny that performance is adjusted when benchmarking tools are running, it refutes the suggestion that changes to the frequency of the Galaxy S4's GPU during benchmarking are "intended to improve [these] results".
On Tuesday AnandTech published a report that suggested some sort of "trickery" was being used by Samsung to boost device performance when benchmarks are run. The Korean electronics manufacturer responded to the claims today, and while it does not deny that performance is adjusted when benchmarking tools are running, it refutes the suggestion that changes to the frequency of the Galaxy S4's GPU during benchmarking are "intended to improve [these] results".Investigations started after a post on the Beyond3D forum claimed that the GPU speed was usually limited to 480MHz but increased to 532MHz when certain whitelisted apps were running. Benchmarks using older testing apps gave worse performance results than newer ones for user frogblast.
AnandTech carried out various tests and found that GPU frequency was indeed capped at 480MHz when running a variety of games -- but when running GLBenchmark 2.5.1 this increased to 532MHz. So what could account for this 10 percent difference? Digging deeper, AnandTeh unearthed an intriguingly named string (BenchmarkBooster) in the benchmark APK. Alarm bells did ring.
Samsung's response is interesting. The company does not deny that there is a change in the GPU frequency, explaining that it does indeed have a maximum operating frequency of 533MHz (yes, 533, not 532MHz). The statement goes on to say that GPU frequency is "lowered to 480MHz for certain gaming apps that may cause an overload, when they are used for a prolonged period of time in full-screen mode".
It concludes by saying that "maximum GPU frequency of 533MHz is applicable for running apps that are usually used in full-screen mode, such as the S Browser, Gallery, Camera, Video Player, and certain benchmarking apps, which also demand substantial performance.
"The maximum GPU frequencies for the Galaxy S4 have been varied to provide optimal user experience for our customers, and were not intended to improve certain benchmark results".
-

Newspapers in a digital age: moving with the times and charging for it
Publié: juillet 31, 2013, 4:00pm CEST par Mark Wilson
 For most of us the digital revolution started some time ago. Working in journalism for nearly 15 years means that I have seen things change enormously, but even back in the late 1990s it was clear that the web was where it was at -- or where it was going to be. Newspapers and magazines have had to adapt to fight for ever-decreasing audiences in a changing market. But not everyone has been moving at the same pace, or has quite the same idea about how things should work.
For most of us the digital revolution started some time ago. Working in journalism for nearly 15 years means that I have seen things change enormously, but even back in the late 1990s it was clear that the web was where it was at -- or where it was going to be. Newspapers and magazines have had to adapt to fight for ever-decreasing audiences in a changing market. But not everyone has been moving at the same pace, or has quite the same idea about how things should work.The ease of self-publishing and the low overheads associated with running a website, in conjunction with the always-on, instant updateability of the internet has seen the sales of newspapers and magazines dropping off. Most titles have gone with the flow and have developed an online presence, but the need for publishers to make money is at odds with the widely held belief that everything online should be free.
A newspaper really does need to have a website. It is expected of it. But when you're trying to sell real, physical newspapers for actual money, the prospect of making the same content available online free of charge seems counter-intuitive. But this is exactly what many British newspapers did for many years.
Obviously money needs to be made, and advertising plays an important role here. To help bring in additional revenue some newspaper sites started to charge for access to major stories -- taking out a subscription provides access to additional content. But when something has been available free of charge for so long, a switch to a subscription model can be hard for readers to swallow.
Of course, the erection of paywalls is far from restricted to the UK. In the US, the Wall Street Journal makes some of its content available to all, while a good portion is left so it can only be read by subscribers. There is a very similar setup at the New York Times.
Subscription models are nothing new and they have proved to be flexible. When Hurricane Sandy hit, both sites dropped their paywalls to provide free access to information.
One of the biggest supporters of paywalls is the Murdoch group. The Times -- one of the most respected newspapers in the world -- now just gives a taster of articles for free, with full access being limited to paid-up subscribers.
It should come as no surprise that other titles from the same stable chose to go down the same route, and the Sun -- still the UK's most popular newspaper -- is the next in line to disappear behind a paywall.
In an astounding piece of editorial, the Sun sets out its manifesto and explains its view of the state of the nation.
There is nothing remotely unusual about a newspaper nailing its colours to the mast, but here there is a slightly different approach. The article starts by focusing on changing technology, the prevalence of tablets and smartphones and the widespread availability of broadband. For the rest of the publishing world, this is not news, but the Sun sees these wonders as being 'just around the corner'.
So why the sudden interest in technology? Why so keen to be seen to embrace the change that it brings? Perhaps unsurprisingly it is because of other changes. Sun+ is the Sun's subscription-based online portal. It is a massive change for a big website that has been free for many years. Whether audience figures fall, rise or remain constant is something only time will tell, but I see the paper's lauding of technology rather more cynically.
The declaration that "we love gadgets, we love the freedom and the fun they bring, we love apps" doesn’t sound sincere -- it sounds out of touch, old fashioned, and several years too late. It sounds like your great-grandmother pretending to be interested in your computer.
 The Sun's rebranding has a feel of a Trojan attack (in the historical sense, not a virus attack). The editorial spouts purple prose about the paper's support for Britain and everything it believes to be great about it. It purports to be on the cutting edge of what's happening (despite apparently referring to "lightning fast broadband" as a "giant leap" that is "just around the corner". It tells the readers what they want to hear… and then sneaks in the fact that access to its content will no longer be free.
The Sun's rebranding has a feel of a Trojan attack (in the historical sense, not a virus attack). The editorial spouts purple prose about the paper's support for Britain and everything it believes to be great about it. It purports to be on the cutting edge of what's happening (despite apparently referring to "lightning fast broadband" as a "giant leap" that is "just around the corner". It tells the readers what they want to hear… and then sneaks in the fact that access to its content will no longer be free.So excuse me if I look at this with a slightly jaded eye. Yes, technology is marvellous, exciting, liberating, democratizing and so much more. But to feign interest in it just to rake in the money seems wrong.
Do you, or are you willing to pay for access to news online? You know that there will always be at least some free news available, but how would you feel if your preferred source starting charging? Would you cough up, or move on?
Photo Credit: fuyu liu/Shutterstock
-

Google puts us in a spin with 360-degree Views
Publié: juillet 31, 2013, 12:51pm CEST par Mark Wilson
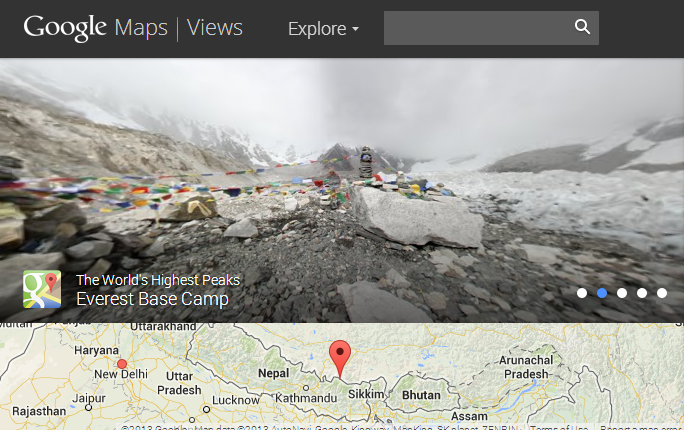
Google is touting its new Views community as the latest way to add Photo Spheres to Google Maps. These 360-degree photos can be captured with Android 4.2 devices and help to give an immersive online experience of a location -- think Street View but with a personal twist.
Views gives users a new way to share their photos so they are not just left forgotten on an SD card. The site can be used to work with any panoramic shots you've taken, or you can import them from your Google+ account.
The community is a simple affair, but it's an interesting central repository for managing your Views -- it also makes it easier to browse through the panoramas that have been uploaded by other users.
Google Maps & Photo Sphere product manager Evan Rapoport waxes lyrical on the new launch in a blog post here.
-

Is Twitter's introduction of an abuse reporting button really workable?
Publié: juillet 30, 2013, 1:17pm CEST par Mark Wilson
 It is said that there is no such thing as bad publicity, but the PR department at Twitter might well be feeling otherwise at the moment. After coming under fire for using fabricated tweets in promotional material Twitter has been in the headlines after the company faced calls to do more to combat abusive tweets.
It is said that there is no such thing as bad publicity, but the PR department at Twitter might well be feeling otherwise at the moment. After coming under fire for using fabricated tweets in promotional material Twitter has been in the headlines after the company faced calls to do more to combat abusive tweets.Threats of death and rape do not make for pleasant reading, but it is something that has happened to a number of Twitter users. The most recent victims to speak out -- Caroline Criado-Perez, who successfully campaigned for Jane Austin to appear on British bank notes, and UK MP Stella Creasy -- led to a grassroots campaign for Twitter to do more to police its micro-blogging service.
Bowing to pressure, Twitter has announced that an abuse reporting option will be added to the web and Android versions of its apps -- it is already available in the iOS app and on the mobile website.
I have opined about the futility of trying to police the web, but it is clear that something needs to be done to prevent illegal activity. Making death threats in the real world is illegal, and there is no reason for Twitter, or the Internet in general, to be any different.
The difficulty comes from finding a way to make online laws work. It is all well and good having an international law that makes threatening others online illegal. But if a death threat is made against someone, how do the relevant authorities go about tracking down the perpetrator? Sure IP logs can help to some extent, but it's very easy to create an online account using false credentials and to spoof an IP address.
It is impractical to think that Twitter could self-police. If there is one thing we have learned from the NSA debacle it's that gathering activity data about non-specific users generates more information than can be practically dealt with.
So it is left to other users to do the policing. The introduction of a 'Report abuse' button seems like a good idea, but it is going to be open to abuse. See a tweet you disagree with? Report it as abuse. Fallen out with someone and want to get back at them? Report all of their tweets as abusive. This seems petty, but it's very likely that this is exactly how things will pan out.
And if the abuse reporting button is to be of any use at all, Twitter will have to spend time and money properly investigating every single report -- regardless of whether it was a report of a serious crime, or a petty squabble between two people.
Then there is the problem of the boy who cried wolf. There will undoubtedly be people who misuse any means of reporting problems -- just as people misuse the emergency services number -- but should someone who does this be blacklisted? What if that same person is then the subject of legitimate threats?
The whole idea of policing any aspect of the internet is a tricky one. No one has yet come up with an ideal approach, but the very fact that so many people are now talking about it is a step in the right direction. Perhaps a crowd-sourced solution will emerge from all of the unpleasantness and debating.
Photo Credit: Oleksiy Mark/Shutterstock
-

Thailand bans Bitcoin -- company suspends trading in the country
Publié: juillet 30, 2013, 12:06pm CEST par Mark Wilson
 Thailand has ruled that use of the online currency Bitcoin is illegal. Bitcoin Co Ltd was going through the process of registering with the necessary government agencies in order to operate legally. Having initially ruled that Bitcoin is not a currency, Bank of Thailand now says that due to a lack of existing applicable laws, numerous Bitcoin activities are now illegal.
Thailand has ruled that use of the online currency Bitcoin is illegal. Bitcoin Co Ltd was going through the process of registering with the necessary government agencies in order to operate legally. Having initially ruled that Bitcoin is not a currency, Bank of Thailand now says that due to a lack of existing applicable laws, numerous Bitcoin activities are now illegal.A statement on the Thai Bitcoin website explains that it now illegal to buy and sell Bitcoins within the country. In addition to this, the buying and selling of goods and services for Bitcoins is outlawed, as is sending and receiving Bitcoins from anyone outside of Thailand.
While this does not prevent Bitcoin Co Ltd from trading in Thailand, it imposes such restrictions on its operations that the company has "no choice but to suspend operations until such as time that the laws in Thailand are updated to account for the existence of Bitcoin".
The bank has said that it will reconsider the situation in the future, but did not specify a timeframe.
Photo credit: ppart/Shutterstock
-

On the futility of blocking porn and torrent websites, Immunicity style
Publié: juillet 28, 2013, 6:44pm CEST par Mark Wilson

Pornography has been in the news a great deal, and David Cameron's bid to make online porn "opt-in" has sparked a fierce debate in many quarters. The apparent aim of the proposed measure is to protect children and the responsibility has been moved squarely to the door of ISPs, just as with access to torrent sites. But is this fair?
The Internet is an important element of democracy. It should be a tool for free speech, free access to information and the ability to communicate worldwide free of charge. Freedom is at the heart of it. Creating a two-tier Internet in which some people are able to access all content, and others can only access a portion of it flies in the face of what the world wide web is all about. It is also dangerous.
If the aim of web censorship is to protect children, those aiming to offer the protection should be aware that those same children are not only very tech savvy, but also very fast learners. Put any restriction in place -- be it the requirement to use a password, the need to prove age, or forcing people to opt in -- and it will never be long before a method of circumvention is discovered.
A petition of the government, signed by tens of thousands of Internet users, not only asks that ISPs not be forced to block content, but also suggests that to implement such blocking would be inadvisable.
The petition posits the idea that bad parenting is the root cause of children accessing objectionable content. No one is suggesting that unrestricted access to illegal content such as child pornography should be provided, but for legal pornography (whatever one's view of it) it is suggested that education and good parenting are more important.
It's not difficult to follow the argument. Ultimately it should be parents who are responsible for how their children use computers and what they access online. This could take the form of physical monitoring of younger children, using control software where necessary, but parents also need to be teaching their offspring about responsible use of the Internet.
The proposed introduction of mandatory porn filters at ISP level seems ill thought out. If the idea is to stamp out online pornography by reducing its audience, this is likely to fail. It is possible that by making access to pornography opt in, web users will be embarrassed into not accessing it -- the idea of phoning the support line to ask "can you make porn appear on my PC?" is not one that is going to fill many people with delight.
But I would have not the slightest qualm about phoning my ISPs and requesting access to porn. Not because I am interested in accessing porn, but because I do not want my Internet access to be restricted. In filtering out porn, how could I be sure that whoever is doing the filtering is not also blocking access to other things, be it through a sense of morality, or by simply miscategorizing something?
I want unfettered access to the Internet. I am not willing to accept anything less than that, and certainly not because parents are unable to educate their children about how to be responsible online.
But even if porn blocks are introduced, they will very quickly -- or even instantly -- be proved moot. The likes of the Pirate Bay are now blocked by many ISPs. Has this done much to reduce overall levels of piracy? No. This is because of the speed at which the Internet is able to react to anything that is thrown at it. Your site has been taken down? Just launch a mirror somewhere else. Even if your site is blocked completely in certain countries, users are able to make use of proxy servers to bypass any restrictions that may be put in place.
The likes of Tor make it possible to access content that has been blocked, and while this and other tools are relatively simple to use, things look set to get a great deal easier.
Immunicity is the latest weapon in the anti-censorship arsenal. It is described as "simple Internet circumvention", and even for the non-technically minded, things are kept as simple as possible. It's little more than another proxy server, re-routing web traffic to bypass restrictions, but it has been designed with the average person in mind. It doesn't matter if users don't even know what proxy is, one setting change -- explained in words of very few syllables -- is all it takes.
The service is free and currently unblocks access to a huge range of torrent sites. And Immunicity is scaleable. Should porn blocking be introduced, it takes a very minor tweak server-side for access to be enabled. Anything that is or may be blocked can be made accessible in an instant.
So, Mr Cameron, you are free to attempt to block access to any section of the Internet you like, it will ultimately amount to very little. Playing the moral gatekeeper for the nation is not a role that will win many fans -- and there's always a way to get past the guard at the door.
Photo Credit: Pressmaster/Shutterstock
-

Now TV box is cheap alternative to Apple TV for UK viewers, but with a catch
Publié: juillet 26, 2013, 1:29pm CEST par Mark Wilson
 Like the idea of Apple TV but feel the hardware is a little expensive? Today Sky releases its Now TV Box to UK fans for the ultra-low price of £9.99. This is significantly cheaper than Apple's flagship streaming device, and even manages to undercut Google's Chromecast. With the price tag including not just the device itself, but also delivery, there's got to be a catch, right?
Like the idea of Apple TV but feel the hardware is a little expensive? Today Sky releases its Now TV Box to UK fans for the ultra-low price of £9.99. This is significantly cheaper than Apple's flagship streaming device, and even manages to undercut Google's Chromecast. With the price tag including not just the device itself, but also delivery, there's got to be a catch, right?The WiFi streaming box provides access to on-demand content from the broadcasters such as Sky, BBC and Channel 5, including sports and movies. There's also the option of using apps such as Spotify and Facebook to transform a regular TV into a smart TV. So far, so couch potato.
For the hardware to be so cheap, it has to be subsidised in some way -- and therein lies the rub. A subscription to Now TV/Sky package is required. There's a free 30-day trial of the Sky Movie Pass available, and at the end of the trial period the standard price is £8.99 per month for the first three months, jumping up to £15 per month in month four.
Sports fans have a Sports Day Pass option. For £9.99 this provides access to six Sky Sports channels for 24 hours -- not a cheap route for serious sporties to go down as this adds up to almost £300 per month if unlimited access is required.
Find out more at Now TV.
-

Suck it up -- you're still going to get spied on after House votes for continued NSA surveillance
Publié: juillet 25, 2013, 8:22pm CEST par Mark Wilson

A move to close down NSA surveillance of US phone records bites the dust after a vote at the House of Representatives. The closely fought battle ended with a nail-bitingly tight vote that saw 217 votes against limiting the Agency's data collection abilities and 205 for.
Republican Justin Amash looked to end the indiscriminate collecting of phone records that was brought to light by whistleblower Edward Snowden. Rather than looking to simply stop the NSA's actions, the proposed amendment took a slightly different approach and aimed to block funding instead.
The voting makes for interesting reading with both sides of the political spectrum seemingly split. Voting for the amendment were 94 Republicans and 111 Democrats, while the 217 votes against were made up of 134 from Republicans and 83 from Democrats.
As interesting and close as the vote may have been, it ultimately means one thing: the NSA remains free to collect whatever data it wants.
Image Credit: Peeradach Rattanakoses/Shuttstock
-

Twitter says sorry for faking tweets from real user accounts
Publié: juillet 25, 2013, 8:09pm CEST par Mark Wilson
 Advertising rarely proves popular, but Twitter has made something of a boo-boo with its latest venture -- one that has led to the microblogging site having to apologise to three of its users.
Advertising rarely proves popular, but Twitter has made something of a boo-boo with its latest venture -- one that has led to the microblogging site having to apologise to three of its users.The company mocked up a series of tweets from three genuine Twitter accounts, and used them in a promotional blog post. All without the account owners' knowledge or consent.
In the fake tweets, @Neil_Gottlieb, @WilliamMazeo, and @subhash_tewari each supposedly made reference to commercials they had seen. The problem was none of the trio had watched the commercials nor tweeted about them.
Understandably, this has upset people, not least the three individuals who found that their names were being used to promote Twitter's TV ad targeting service. The blog post has since been amended to remove the offending content. An apology now appears at the top of the page reading "An earlier version of this blog post included an image with mock Tweets from real users of our platform".
It goes on to say, "This was not OK. Once we became aware of this mistake we took it down immediately. We deeply apologize to the three users included in the earlier images". Twitter also apologised to the three individuals in a tweet reading "Hey @Neil_Gottlieb, @WilliamMazeo, @subhash_tewari -- so sorry about the confusion earlier today. We're fixing the problem now".
Does Twitter's use of accounts in this way concern you? Is the apology enough?
Image Credit: fotoscool/Shuttstock
-

Google Translate adds handwriting support and tries to make sense of your scrawl
Publié: juillet 25, 2013, 1:09pm CEST par Mark Wilson
 Why type it when you can write it? Google Translate users can now scribble symbols using a new handwriting input tool. While this is unlikely to be a faster option for translating a lot of languages, it does prove useful for inputting certain foreign characters. Want to find out what that Russian or Chinese phrase means? Don’t bother trying to work out how to input these characters via your keyboard, just draw them.
Why type it when you can write it? Google Translate users can now scribble symbols using a new handwriting input tool. While this is unlikely to be a faster option for translating a lot of languages, it does prove useful for inputting certain foreign characters. Want to find out what that Russian or Chinese phrase means? Don’t bother trying to work out how to input these characters via your keyboard, just draw them.This is an option that has been available to users of the Google Translate Android app for a little while, but it's now also available to desktop users. Things are a great deal easier if you have access to a graphics tablet, but the onscreen handwriting input panel can also be used in conjunction with a mouse.
Analysis of whatever you scrawl into the input box works much like predictive texting -- a number of possibilities are listed to choose from and an instant translation is provided.
Support currently stretches to 45 languages, and not all of them are symbol based. This is handy for those occasions that require the addition of an all-important accent or other embellishment that could completely change the meaning of a word.
Oh, and if you find that handwriting input is not immediately obvious, just look beneath the regular input panel, click the keyboard icon there, and the option will present itself.
-

SwiftKey Cloud brings trending phrases, sync and backup to your swipe-friendly keyboard
Publié: juillet 24, 2013, 12:08pm CEST par Mark Wilson
 Typing is just so passé; swiping is very much where it's at these days. SwiftKey's latest Android beta adds interesting new cloud features that can be tested for free during the beta phase. What’s new? Backup and sync options mean that dictionaries can be synchronized between multiple devices, and upgrading your phone need not result in having to start from scratch.
Typing is just so passé; swiping is very much where it's at these days. SwiftKey's latest Android beta adds interesting new cloud features that can be tested for free during the beta phase. What’s new? Backup and sync options mean that dictionaries can be synchronized between multiple devices, and upgrading your phone need not result in having to start from scratch.But perhaps the most interesting feature is the introduction of trending phrases. Whether you're writing in English, Spanish, French, Portuguese or Brazilian Portuguese, SwiftKey analyzes trending topics on the likes of Twitter to help bolster its dictionary and provide better suggestions.
The beta version also builds on SwiftKey's lauded next-word prediction and auto-correction. The app analyzes and learns from the user's personal writing style so the suggestions provided are more personally tailored and less generic. Gmail, Facebook and Yahoo Mail can all be used as sources for analysis, giving SwiftKey a good chance of learning how you use language.
If you're already a paid-up SwitftKey user, all of these cloud features will be added to version 4.2 of the app, but everyone is free to try them out in the beta which can be downloaded from the SwiftKey website -- separate versions are available for phones and tablets.
-

YouTube announces Geek Week -- Dr Who and cosplay fans rejoice!
Publié: juillet 24, 2013, 11:12am CEST par Mark Wilson
 Geeks looking for their fix of programming have something of a treat in store thanks to YouTube’s upcoming Geek Week. The video site has teamed up with the UK's Channel Flip and the US channel Nerdist to showcase over 100 of the geekiest, most sci-fi packed channels known to man. It will also be "unveiling new videos, series premieres and creative collaborations".
Geeks looking for their fix of programming have something of a treat in store thanks to YouTube’s upcoming Geek Week. The video site has teamed up with the UK's Channel Flip and the US channel Nerdist to showcase over 100 of the geekiest, most sci-fi packed channels known to man. It will also be "unveiling new videos, series premieres and creative collaborations".YouTube Geek Week runs from August 4-10, starting with Blockbuster Sunday which will kick things off with a look at the icons and heroes of geek culture.
As the week goes on, there's all sorts of fun to look forward to. Global Geekery Monday brings a celebration of Doctor Who as well as (British kids of the 80s rejoice) a brand new episode of the cult classic Knightmare.
Other highlights for the week include a look at stunts and experiments on Brainiac Tuesday, the superhero packed Super Wednesday, games galore on Gaming Thursday and a super-nerdy Fan Friday -- featuring not only cosplay, but also (we kid you not) sci-fi themed cooking.
Of course, no geek event would be complete without something collectable to show off. Check out the Geek Week channel in the run-up to the big event where you’ll be able to collect badges through Easter eggs. Full details are available at the YouTube blog.
Photo credit: Gow27/Shutterstock
-

Microsoft explains how SkyDrive keeps bandwidth usage to a minimum
Publié: juillet 23, 2013, 12:11pm CEST par Mark Wilson
 The release of Windows 8.1, complete with the more tightly interwoven SkyDrive, brings Microsoft's cloud storage service to the fore. In a new blog post, Mona Akmal from the SkyDrive team explains how the service is able to make files available on all of your devices without eating up too much bandwidth. How is this done? It's largely down to "placeholder" files.
The release of Windows 8.1, complete with the more tightly interwoven SkyDrive, brings Microsoft's cloud storage service to the fore. In a new blog post, Mona Akmal from the SkyDrive team explains how the service is able to make files available on all of your devices without eating up too much bandwidth. How is this done? It's largely down to "placeholder" files.The obvious solution to making all SkyDrive files available on all of your devices would be to simply sync everything. But when it comes to tablets and phones, it is entirely possible that the amount of available local storage is far lower than the amount of cloud storage space that has been used. Placeholders are essentially "ghost" files that take up a fraction of the space of the original.
These placeholders can be moved, renamed and deleted, the contents of folders can be browsed -- all without having to download the contents in their entirety. When a file is open it has to be completely downloaded, but this is not done until necessary to help speed things up. Mona's blog entry shows an example in which a 5.8GB file stored on SkyDrive occupies just 185MB locally.
But this is not the only new technique employed by SkyDrive. Cloud storage services are often used to store digital photos, and these are files that rarely have meaningful names -- you really need to be able to see what you are working with. Rather than fully downloading images just in case they may be needed, thumbnail pre-fetching is used to give a sneak peak of what images look like.
As with other files, images can be moved, renamed and deleted, and they are only downloaded when viewed at full size or when edited. The claim is that the combination of placeholders and the new smart thumbnail means that access to all files can be provided to your cloud content even though locally synced content takes up just 5 percent of the space of the equivalent files on SkyDrive.
This, coupled with well implemented offline access, demonstrates just how seriously Microsoft now is taking the move to the cloud. You can read the post in full at the Windows blog.
-

Apple Developer site STILL down four days after 'intruder' prompts database rebuild
Publié: juillet 22, 2013, 12:16pm CEST par Mark Wilson
 The Apple Developer site remains inaccessible after a security breach on Thursday. The company is quick to point out that personal information accessed in a database was encrypted, but goes on to say the possibility that personal data had been accessed could not be ruled out. Apple is taking the intrusion very seriously it seems.
The Apple Developer site remains inaccessible after a security breach on Thursday. The company is quick to point out that personal information accessed in a database was encrypted, but goes on to say the possibility that personal data had been accessed could not be ruled out. Apple is taking the intrusion very seriously it seems.The fact that the site is inaccessible is down to Apple rather than being the direct result of an attack. Apple states that as soon as it was aware of the breach, the site was purposely taken down. This initially saw the site replaced with a message informing visitors that the site was down for maintenance, but was later replaced with a message from Apple that goes into more detail.
The message now apes the email that was sent to developers over the weekend, with Apple revealing more about what is happening "in the spirit of transparency". The site is offline while the compromised database is rebuilt, server software is updated and the developer system is overhauled.
Anyone attempting to access the iOS or Mac sections of the Apple Developer site is greeted by a message from Apple stating "We'll be back soon". No timeframe is given for when things will be back up and running, but developers with memberships expiring during the downtime are assured that their apps will remain in the App Store until things are sorted out.
Developers with any concerns about their accounts are encouraged to contact Apple through the company's website.
-

We want to wipe out child porn online, but can it actually be policed?
Publié: juillet 21, 2013, 9:30pm CEST par Mark Wilson
 Filtering web content is always something of a sticky topic, and there are two very vocal sides to the argument. In the blue corner (red and blue are not being used in a political sense here -- if only because the blue represents right-wing parties in the UK and the more left-leaning in the US) we have those who advocate freedom of speech online, the right for anyone to say whatever he or she wants. In the red corner are those who feel that there is a need for policing, control and regulation.
Filtering web content is always something of a sticky topic, and there are two very vocal sides to the argument. In the blue corner (red and blue are not being used in a political sense here -- if only because the blue represents right-wing parties in the UK and the more left-leaning in the US) we have those who advocate freedom of speech online, the right for anyone to say whatever he or she wants. In the red corner are those who feel that there is a need for policing, control and regulation.It is certainly a difficult balance to strike. It would be all but impossible to draw a baseline level of sensibilities that should be catered to -- whatever form of control may be put in place will be seen as draconian in its severity by some, and pathetically lenient by others.
There are many subjects that are open to debate. Freedom of religious expression means that everyone is free to not only express, but also support and promote their beliefs. This is true even when different religions are at odds, and the same rings true for political beliefs. The western world looks on almost in a state of disbelief at what passes for the internet in China.
ISPs around the world are under constant pressure from various sides to censor, filter and police what their customers are able to access. Copyrighted material is removed from websites quite frequently, but it does very little to combat piracy. Attempting to stop anything on the internet is a virtually impossible task. The infrastructure is already in place so that any restrictions that are introduced are easily bypassed -- unless a country does take the extreme step of setting up its own Great Firewall of China.
As most of the world is (fairly) democratic, few countries would like to go this far; so it is left to ISPs and web hosts to manage things. In the UK, Prime Minister David Cameron is calling on internet companies such as Facebook and Google to do more to tackle online pornography. Google has already offered to invest heavily in cleaning up porn and developing a hashing technique that will make it easier to track images as they spread across the web.
But who should be held responsible for content that is deemed unsuitable or illegal? The person who posted it? There are different laws in different countries to consider. The hosting company which essentially makes the content available? This would be a gargantuan and prohibitively expensive operation, particularly for smaller companies. How about ISPs for ultimately delivering content to individual computers? You may as well take things further and start suing monitor manufacturers for providing a technology that could be used to display all manner of illegal content.
Then there is the Scunthorpe problem to consider. For the uninitiated, Scunthorpe is an English town. Nothing extraordinary in this, but the name does include a four-letter word that has fallen foul of many an over enthusiastic obscene word filter.
This is obviously not something that relates directly to the issue of porn, but it does raise the issue of context. Nudity is not always porn, nor indeed are images of children, even naked children, something that should be viewed as 'wrong'. How many photos do your parents have of you as a children? Hundreds, no doubt.
I'm willing to bet hard cash that a proportion of these feature you in some state of undress -- mum and dad always take snaps of their kids in the bath, cavorting naked in the garden, or skinny dipping at the beach. These are not porn, are they? Upon bringing a new partner to meet your parents, these photos may be pulled out as a bit of fun. How different is this -- really -- to sharing the same images on Facebook?
Well, it probably wouldn’t last long on Facebook as virtually all nudity is quickly stamped out, but the same photos could be shared on a personal website and little would be thought of it. It is about context. A photo of a child in the bath included in a gallery of childhood photos is quite innocent; include the same image in a gallery that also features more illicit images and it's a different matter entirely.
But things aren’t always that black and white. The notion of context is something that is quite subjective. An image that is completely innocent, pure and savoury to the majority of people could be something quite titillating to someone else.
Of course, there are organized child porn rings involved in terrible cases of abuse, and I want in no way to diminish the seriousness of such crimes. Governments are keen to be seen to be doing something about anything that stirs up strong emotions in the electorate.
It is very easy for David Cameron to call for 'something' to be done, but in merely making this demand he -- and others like him -- are demonstrating that they are out of touch and really don't understand what is involve in monitoring web content. Something we learned from the NSA debacle is that so much data is being collected that it is impossible to do anything with most of it, so you're back to relying on content being reported, or randomly picking on websites to see if there is objectionable content.
There is no easy solution. Politicians calling on companies to police something as inherently unpoliceable as the internet amounts to little more than passing the buck. It seems there is no perfect answer.
A policed web is something that should be eyed with suspicion, while something entirely unmanaged runs the risk of becoming anarchic -- although the same could be said of conversations, or letters. Nothing that falls between these two extremes is going to please everyone, but those in power need to be seen to be doing something meaningful rather than using emotive subjects to score points.
Photo Credit: InnervisionArt/Shutterstock
-

Ubuntu Forums falls victim to hack attack -- 1.8m passwords stolen
Publié: juillet 21, 2013, 7:22pm CEST par Mark Wilson
 Well, it's happened again. If it's not the NSA spying on internet users, then someone else is always ready to spoil the fun. Yet another website has fallen prey to hackers, putting the personal details of hundreds of thousands of users at risk.
Well, it's happened again. If it's not the NSA spying on internet users, then someone else is always ready to spoil the fun. Yet another website has fallen prey to hackers, putting the personal details of hundreds of thousands of users at risk.This time around, it is Ubuntu Forums that has been affected -- visit the site and you're greeted by the announcement that the forums are down for maintenance before some details of the security breach are revealed.
The bad news is that the user names, email addresses and passwords of every single one of the site's 1.8 million users have been nabbed.
The attack took place at 20:11 UTC June 20, starting with the defacement of the front page to advertise a Twitter account (@Spuntn1k_) and included text that read: "None of this "y3w g0t haxd by albani4 c3blr 4rmy" stuff. Straight up, you dun goofed. It’s as simple as that".
It is unclear whether the owner of the Twitter account in question is responsible for the attack, but that account no longer exists.
Canonical is keen to stress that it is only Ubuntu Forums that have been breached and that the passwords were stored as salted hashes, not plain text. Ubuntu One, Launchpad and other Ubuntu/Canonical service accounts remain unaffected.
As Ubuntu Forums points out, a key concern stems from the fact that many people rely on the same username and email address for multiple sites and services. The advice in that instance is to change your login credentials on other sites, and keep an eye on Ubuntu Forums for updates.
Photo Credit: JMiks/Shutterstock
-

Ubuntu Forums falls victim to hack attack -- 1.8 million passwords stolen
Publié: juillet 21, 2013, 7:22pm CEST par Mark Wilson
 Well, it's happened again. If it's not the NSA spying on internet users, then someone else is always ready to spoil the fun. Yet another website has fallen prey to hackers, putting the personal details of hundreds of thousands of users at risk.
Well, it's happened again. If it's not the NSA spying on internet users, then someone else is always ready to spoil the fun. Yet another website has fallen prey to hackers, putting the personal details of hundreds of thousands of users at risk.This time around, it is Ubuntu Forums that has been affected -- visit the site and you're greeted by the announcement that the forums are down for maintenance before some details of the security breach are revealed.
The bad news is that the user names, email addresses and passwords of every single one of the site's 1.8 million users have been nabbed.
The attack took place at 20:11 UTC June 20, starting with the defacement of the front page to advertise a Twitter account (@Spuntn1k_) and included text that read: "None of this "y3w g0t haxd by albani4 c3blr 4rmy" stuff. Straight up, you dun goofed. It’s as simple as that".
It is unclear whether the owner of the Twitter account in question is responsible for the attack, but that account no longer exists.
Canonical is keen to stress that it is only Ubuntu Forums that have been breached and that the passwords were stored as salted hashes, not plain text. Ubuntu One, Launchpad and other Ubuntu/Canonical service accounts remain unaffected.
As Ubuntu Forums points out, a key concern stems from the fact that many people rely on the same username and email address for multiple sites and services. The advice in that instance is to change your login credentials on other sites, and keep an eye on Ubuntu Forums for updates.
Photo Credit: JMiks/Shutterstock
-

Pipe exits beta and lets Facebook users swap files up to 1GB in size
Publié: juin 5, 2013, 2:13pm CEST par Mark Wilson
Facebook is great for sharing thoughts, links, complaints and pictures with your friends, family and colleagues but, until now, there has been no easy way to share files through the social network. Pipe is a Facebook app that has undergone private testing for some time, but is at last available for everyone to use. Once installed, Pipe will let you send files of up to 1GB in size to your Facebook friends.
The app works by setting up a P2P connection between you and anyone you decide to share a file with. Ordinarily, file transfers are carried out in real-time, but if you want to send a file to a friend who is not currently online, it will be securely stored until they are available. This reduces the size limit right down to 100MB but it is possible to send an unlimited number of files in this way.
Any type of file can be sent through Pipe and users are not restricted to sharing files with friends who are already using the service. You can share a file with anyone you like and they will be prompted to install the app before they will be able to download the item.
This app is well worth checking out even if it's just for the sake of nostalgia -- there's an 8-bit Mario vibe to the website and Facebook page -- and the promo video also features some delightfully retro music.
-

Is your anti-malware software doing its job? AMTSO launches tools that may reveal all
Publié: juin 5, 2013, 9:55am CEST par Mark Wilson
 The importance of having virus and malware protection installed is something that is drummed into every computer user. There are countless security tools to choose from these days, and numerous reviews to help you to decide between them. But how can you be sure that the software you have opted to use is doing its job properly?
The importance of having virus and malware protection installed is something that is drummed into every computer user. There are countless security tools to choose from these days, and numerous reviews to help you to decide between them. But how can you be sure that the software you have opted to use is doing its job properly?AMTSO (the Anti-Malware Testing Standards Organization) has a series of tools that can help you to find out whether your computer really is protected. Does the fact that your system seems to be free from malware mean that your security software is offering suitable protection, or that you have just been lucky so far?
If you want to check the state of your defences, the AMTSO website is home to a series of testing tools. These are relatively simple affairs which will check to see whether your browser, operating system and other software are configured to block malicious and drive-by downloads, phishing attacks and more.
In the past, AMTSO has come under fire for having a membership that appeared to be comprised mainly of anti-virus companies. Over the last year the organization has tried to improve its reputation.
But the online tools seem simplistic at best and little advice is given about what to do if your computer fails any of the tests. A positive result could be reassuring, or a placebo -- there's little way of knowing. Take a look for yourself and see what you think. Do you view the tests as cynically as me?
Photo Credit: Svinkin/Shutterstock
-

UK court says yes, your tweets can be libellous -- is this right?
Publié: juin 4, 2013, 9:01pm CEST par Mark Wilson
 British libel law is a veritable minefield and the difficulty of policing many aspects of the internet mean that websites and social networks have often been treated rather differently to newspapers and magazines. But a court ruling means that this is set to change. A judge has ruled that a 46 character tweet made by Sally Bercow, wife of the Speaker of the House of Commons, John Bercow, is indeed libellous.
British libel law is a veritable minefield and the difficulty of policing many aspects of the internet mean that websites and social networks have often been treated rather differently to newspapers and magazines. But a court ruling means that this is set to change. A judge has ruled that a 46 character tweet made by Sally Bercow, wife of the Speaker of the House of Commons, John Bercow, is indeed libellous.The tweet read "Why is Lord McAlpine trending? *Innocent face*". For the uninitiated, Lord McAlpine is the former Deputy Chairman and Party Treasurer of the Conservative Party and he denied claims that he was involved in alleged sexual abuse at a Welsh foster care home in the 70s and 80s.
News reports back in November made reference to a "leading Conservative from the time" although no one was officially named as the party in question. Social networking sites being what they are, tongues were soon wagging (and fingers tapping) and it wasn't long before Lord McAlpine's name was being bandied about. During this time, Mrs Bercow tweeted the offending seven-word post.
A leading British newspaper went onto name Lord McAlpine as the previously unnamed politician, but added the detail that the abuse victim had since realized that he had been wrong about the identity of his abuser. Various broadcasters and publishers made out-of-court settlements with Lord McAlpine, but Sally Bercow ended up in court, with the ultimate decision by High Court Justice Sir Michael George Tugendhat being that her tweet is defamatory.
The decision appears to hinge on Bercow's use of the phrase "innocent face" which Justice Tugendhat thought would be understood by many Twitter users to be ironic. But the fact that her 56,000 or so followers were expected to have a similar political leaning to Mrs Bercow and would have linked it with the concurrent abuse story served as the final nails in the coffin.
Libel law is always a source of vigorous debate. The definition of defamatory words is that "words are defamatory of a claimant if they refer to that claimant and they substantially affect in an adverse manner the attitude of other people towards the claimant, or have a tendency so to do".
Here there is no question that the claimant is the subject of the tweet -- Lord McAlpine is directly named. But the matter of whether the tweet itself is defamatory is interesting. The words themselves are in no way defamatory -- they say nothing -- but their context and timing makes a big difference.
There is also the problem of the "rule of repetition" to keep in mind. Anyone repeating a defamatory statement is treated in exactly the same way as the person making the original statement. In a largely unregulated arena such as Twitter, where retweeting someone else's post is nothing more than a click away, the potential for a huge number of libellous statements to be made in a short space of time is immense.
Balancing freedom of speech online -- or in any format -- with other rights is incredibly difficult. But in the instance-response world we now live in, it's all too easy for an off-the-cuff remark to either be taken out of context, or taken too far. We live in an age of litigation, and while I understand fully Lord McAlpine's desire to take this case to court, I fear that this ruling sets a worrying precedent.
There is the danger that critical, comedic, satirical or ironic tweets would result in legal action. Were I defamed I would rush -- well, not rush, saunter gently perhaps -- to get legal advice, but I'd like to think I'd take a balanced approach to things. Faced with a tweet along the lines of Bercow's assumptions have to be made in order for it to be deemed defamatory.
The law is often subjective, but when dealing with tweets that are 140 characters or fewer, there's too much margin for things being misconstrued. We're starting to walk a dangerous line with rulings such as this.
How do you think Twitter should be policed -- or should it be policed at all? Whose rights are more important -- the subject of an opinion or the one voicing it? Share your thoughts and experiences below.
Photo credit: stockpix4u/Shutterstock
-

Bing to be integrated into Windows 8.1 for web and local searches
Publié: mai 31, 2013, 8:16am CEST par Mark Wilson
The upcoming release of Windows 8.1 has been the subject of countless column inches over recent weeks with the main focus being on the return of the Start button. But changes are also afoot for searching, with Bing being tightly integrated into the operating system to provide a rich and flexible search experience.
The Bing development team is working closely with the Windows team to produce a utility that can be used to search globally and locally. Windows' integrated search tool has evolved over the years into something that can be used to search not only files but also shortcuts.
When Windows 8.1 is unleashed the Bing-powered search tool will try to guess what it is you're looking for and provide a list of suggestions.
Call up the search screen and type "Morrissey", for instance. As well as locating music files you may have stored on your hard drive from the ex-frontman of The Smiths' back catalogue, you'll also be provided with links to Morrissey related websites, documents you may have stored in the cloud and more. Windows 8.1's search will also query apps, settings, online videos and so on, when appropriate.
The aim is to help reduce the number of searches that need to be performed. Search results are actually rather more general, casting a wider net with a view to providing access to everything you might need. Search for a city name and you'll be shown links to local events, the weather forecast, photos of the area and more.
Blurring the boundaries between the web and the PC is something that Microsoft has been doing for years. Derrick Connell, Corporate Vice President of Bing, sums it up in saying that searching is not only "something that’s just there when you need it" but also "beautiful as well as functional".
-

Google gets it terribly, terribly wrong with Gmail tabs and makes me angry
Publié: mai 30, 2013, 8:43pm CEST par Mark Wilson
 Like many Gmail users, I greeted the news of the introduction of tabs to the interface with a degree of anticipation -- now it was just a matter of waiting for the feature to roll out so I could try it for myself. Earlier today I was randomly signed out of my Gmail account, and after signing back in and checking the settings menus, I could see that tabs were now available to me. Excitement was short-lived, however; it quickly became apparent that this new feature is a disaster.
Like many Gmail users, I greeted the news of the introduction of tabs to the interface with a degree of anticipation -- now it was just a matter of waiting for the feature to roll out so I could try it for myself. Earlier today I was randomly signed out of my Gmail account, and after signing back in and checking the settings menus, I could see that tabs were now available to me. Excitement was short-lived, however; it quickly became apparent that this new feature is a disaster.On the face of it, there's a lot to be said in favor of adding tabs to one's inbox. The idea is that emails that match certain criteria are automatically sorted so your inbox is easier to manage. I have an enormous number of filters configured that sort and label messages but the prospect of having a series of tabs to access certain types of mail was definitely appealing.
So, what does Google think would be useful tabs to have as default? Forums, Updates, Promotions, Social and Primary, it seems. As there are only five tabs, each covers a multitude of sins. Forums will, supposedly, capture emails relating to groups and forums, as well as housing your mailing list subscriptions. Social -- unsurprisingly -- groups all social networking messages together.
Promotions is fairly self-explanatory -- all of your offers, marketing mail (aka secondary spam) should end up here. But then things get a little odd. The Updates tab displays messages that are determined to be receipts, bills and statements. Everything else gets lumped together in the Primary tab.
OK, so these tabs may not be quite what you were expecting, but they can be customized, right? Right? Nope. The idea of tabs appealed to me at first as I thought I would be able to customize them to filter out emails from specific websites or people -- such as a Family tab. But no. Google has decided that these are the only five tabs I can have and that I cannot rename them or create any more.
This is not the only problem. Tabs are completely unintuitive. When a new message is received from Facebook, for example, Gmail determines that this is a Social email and filters it accordingly. A notification appears in the Social tab to let me know that there is an unread email, but nowhere else. Because the message has bypassed my Primary tab, my Inbox label is not updated with a new message count.
If I happen to be browsing my starred messages, I am not informed of the arrival of a new mail. Why? Oh, one thing I haven't mentioned yet is that tabs disappear when you are anywhere other than the inbox. But there's more. Or less. Depending on how you look at it.
The new message notification on each of the tabs does not tell you how many unread messages you have in this tab. Rather it lets you know how many new messages have arrived since you last visited that tab. This means that should I see that a number of messages are on my Social tab, click that tab to see them but then navigate elsewhere before actually reading any of the messages, the message count is zeroed.
There are unread messages on my Social tab, but I am not told how many -- I have to go and look. You might think that the craziness would end there, but it doesn't. Gmail does a spectacularly bad job of determining where emails should go. It is possible to re-categorize emails to different tabs, but only when you are in the inbox or on a tab. Email cannot be categorized from folder or label views, which means it is nowhere near as user-friendly as it should be.
 But the biggest problem is undoubtedly the way in which the unread mail count has altered. I want to see at a glance how many emails I have yet to read -- I don’t want to have to look at five different tabs. The terrible automatic categorization -- an inexact science, easily on a par with spam not being correctly identified -- means I really don't know when I have unread messages to attend to.
But the biggest problem is undoubtedly the way in which the unread mail count has altered. I want to see at a glance how many emails I have yet to read -- I don’t want to have to look at five different tabs. The terrible automatic categorization -- an inexact science, easily on a par with spam not being correctly identified -- means I really don't know when I have unread messages to attend to.The five unread messages listed on the Social tab, are they emails that relate to Facebook and Twitter, or has that important work email I've been waiting for been misidentified? I have no way of knowing without looking at each tab manually thereby negating any timesaving their introduction was meant to bring about. The hoops you have to jump through to see everything in one place really beggars belief.
I love Gmail. I really do. It's not perfect, and there is a lot of room for improvement, but it gets so much right that I'm willing to cut it a little slack. But now things are starting to go awry. Tabs are a seriously bad idea. Yes, they are optional, but they are so close to unusable that hardly anyone is going to persevere with them to see if they improve with time.
Change is good -- it should be encouraged and embraced -- but change needs to be for the better and it needs to have direction and purpose. Some of the recent changes to Gmail make me wonder just who is making the decisions and who the target audience for the various features is.
Part of the problem is the fact that Gmail now offers so many different ways to organize and navigate emails. Labels are handy, as are folders (especially the more recent nesting option) and priority inbox -- in theory at least -- makes it easy to focus on the emails that are most important.
But it doesn’t end there. Multiple inboxes can be displayed when Priority Inbox is enabled, conversations view can be used to group together related messages and line spacing can be adjusted to suit your liking.
Having choice is nearly always a good thing, but Google is taking it to the extreme with Gmail. It's getting to the point that there are just too many options to choose from. It's a mess. I moved away from Hotmail years ago, seeking refuge in Gmail's cleaner, tidier interface. But now Google's webmail is starting to anger me. It's starting to be frustrating to use. I don't think I'm alone in feeling this way.
What do you think? Relieve yourself of your splenetic juices in the comments below.
Oh… if you were wondering. Tabs have now been disabled in my account.
Photo Credit: Roger Jegg - Fotodesign-Jegg.de/Shutterstock
-

Pre-order Verizon BlackBerry Q10 in black or white, and get it for June 6
Publié: mai 30, 2013, 5:05pm CEST par Mark Wilson
 Touchscreen phones are just about the default choice these days, but there are still some users for whom a real QWERTY keyboard is an absolute must.
Touchscreen phones are just about the default choice these days, but there are still some users for whom a real QWERTY keyboard is an absolute must.If you're one of these people, get ready to smile -- Verizon is now accepting pre-orders for the BlackBerry Q10.
The phone packs a 3.1-inch Super AMOLED touch display, dual-core Qualcomm CPU and 2GB of RAM, and if you order it now you could have it in a week's time. Anyone happy to sign up for a two year contract can snap up the phone for $199.99, but commitment-phobes will have to part with $599.99 for the month-to-month option.
Not put off by the price? Whizz over to the Verizon website to place your pre-order and get your hands on it by June 6.
-

Apple to pay out $53m in iPhone 'water damage' lawsuit
Publié: mai 29, 2013, 1:31pm CEST par Mark Wilson

153,000 iPhone and iPod owners are in line for a payout from Apple after the company agreed to a $53 million settlement to a 2010 lawsuit. The class action suit concerned malfunctioning devices that the Cupertino, Calif. based company claimed had been damaged after coming into contact with water.
A "liquid damage policy" allowed Apple to deny warranty coverage if the liquid indicator inside the device changed color from white to pink or red, "proving" contact with water.
However, although the indicators were designed to show the presence of water, it was later found that heat could also cause the damning color change.
Documents filed at the US District Court for the Northern District of California state that the money will be held in a fund and shared between the members of the class-action suit. Successful claimants can expect to receive around $200 -- $300 each from Apple.
The settlement is still to be approved by the court, but is unlikely to face further obstacles.
Photo Credit: morrison77/Shutterstock
-

One third of UK web streamers pirate film, TV and music
Publié: mai 28, 2013, 11:38pm CEST par Mark Wilson
 We all know that the internet is home to illegal software, music, movies and much more. It may seem like an impossible task to put figures to piracy levels, but a report by Ofcom, the independent regulator for the communications industries in the UK, has done just that. The Online Copyright Infringement Tracker report found that a staggering 30 percent of regular downloaders of media did so illegally.
We all know that the internet is home to illegal software, music, movies and much more. It may seem like an impossible task to put figures to piracy levels, but a report by Ofcom, the independent regulator for the communications industries in the UK, has done just that. The Online Copyright Infringement Tracker report found that a staggering 30 percent of regular downloaders of media did so illegally.The report looked at the period from November 2012 to January 2013 and analyzed UK consumption of online music, film, TV programmes, books, games and software. Compared to the previous three months, the percentage of web users accessing any of this type of content increased from 57 percent to 60 percent.
But the really interesting figures are concerned with piracy. The results are based on anonymous questionnaires in which 18 percent of participants admitted to indulging in some form of online copyright infringement.
Narrowing down the numbers to include only those who streamed or downloaded media, makes the findings particularly intriguing. 33 percent of movie watchers enjoyed films illegally, while 26 percent of music lovers got their singles and albums from illegal sources. Authors and publishers fared slightly better, with a mere 8 percent of digital book downloads taking place illegally.
Those indulging in online theft of this nature were more likely to be male and aged under 34, and the reasons for illegally downloading or streaming media was that such content was free, convenient and quick.
By far the most popular means of obtaining illegal content was through the use of P2P service, and uTorrent had the largest following, accounting for 20 percent of illegal downloads.
Despite the apparent increase in piracy, there was also an increase in the number of people who claim to pay for all of their online TV watching, as well as those watching a mixture of free and paid-for content.
As the study only looked at internet users aged 12 and over, it's entirely possible that the real figures are even higher. While some of those questioned said they would be discouraged from illegally downloading files if their ISPs wrote to them, 16 percent said nothing would stop them.
If you fancy crunching the numbers yourself, the full report is available for download from the Ofcom website.
Would you be honest about your online activities if questioned? Share your thoughts in the comments.
Photo Credit: Didecs/Shutterstock
-

Spy on the world's web searches with a Google Trends screensaver
Publié: mai 24, 2013, 7:01pm CEST par Mark Wilson

Google is all about searching. Well… not "all" about, but it's what the company is known for. Any firm that logs information about how customers are using its services are usually berated, but Google Trends can provide a fascinating insight into how the rest of the world is using the internet. This tool has been available for a while but there's now a sexy new full screen mode available -- and you can turn it into a screensaver.
If you've ever been curious about what people in other parts of the world are searching for, head over to the full screen visualization tool and you can find out. At the bottom of the screen you can choose from one of several countries, or opt to see an overview of global searches.
By default you'll be shown a single search at a time, displayed on a background in one of Google's four colors. Want to see more? Whizz your mouse up to the upper left of the page and hover over the 3x3 grid icon that appears. In the popup you can then select a number of search tiles that should be displayed -- each shows a different search term, and the display can become quite mesmerizing.
As you change country and tile options, you may well notice that the URL in the address bar changes. Each setting change results in a unique URL, and this can be exploited to turn Google Trends into a rainbow search screensaver. When you've chosen a view you like, copy the address to the clipboard.
Turning a web address into a screensaver isn’t something that's built into Windows, but there's a great free screensaver tool hosted on Google Projects. Download a copy of Web Page Screensaver (it's free), and move the .scr file to C:\Windows\System32.
The screensaver can then be configured from the Display Control Panel -- right-click the desktop and select Personalize before clicking the Screen Saver icon at the lower right of the window. Select Web-Page-Screensaver from the drop down menu, click Settings and paste the URL you copied earlier.
Now when your computer is idle, global web searches will be displayed on your screen. It's hardly an incentive to get on with work, but it looks cool and is an interesting way to keep up with what’s happening in the world.
There are various other search visualization options available on the Google Trends page.
-

On your marks, get set... GO Launch Dev Team releases Android Next browser
Publié: mai 24, 2013, 4:01pm CEST par Mark Wilson
 The Android web browser market is a packed one, and users are almost spoiled for choice. If you're a fan of Firefox, Chrome or Opera on your main computer, there's an accompanying mobile version for you to work with, and there are plenty of others as well.
The Android web browser market is a packed one, and users are almost spoiled for choice. If you're a fan of Firefox, Chrome or Opera on your main computer, there's an accompanying mobile version for you to work with, and there are plenty of others as well.The GO Launcher Dev Team is best known -- it should go without saying -- for the Android launcher GO Launcher EX, but it has now branched out and is bringing its stylish looks to a web browser -- Next Browser.
Like many of the other apps from the same team, Next Browser has a clean, Holo look but it is the features that are going to make or break it. The app borrows ideas from many of its existing competitors, including tabbed browsing, a speed dial screen, a combined search and URL bar, and bookmark syncing.
Support for plugins means that the browser's feature set can be further extended and this is something that is sure to make Next Browser extremely popular, especially as more and more add-ons are released.
Voice searching is available, but this is not the only means of interacting with the browser. There is good use of gesture support in the app. Swipe down to close a tab, swipe left to access extensions, and swipe right to access Next View. This handy page provides a quick overview of headlines and stories from various websites.
Could this be the browser to rule them all? Maybe not, but it's a decent alternative to the big names and shows great signs of promise.
Next Browser is available free of charge from Google Play.
-

Android users rejoice! BBC iPlayer 1.7 brings support for your 10-incher
Publié: mai 24, 2013, 12:48pm CEST par Mark Wilson
 A week ago BBC iPlayer finally made its debut on Windows Phone 8, but the existing Android version has been far from forgotten about. BBC iPlayer 1.7 has hit Google Play and now boasts support for 10 inch tablets.
A week ago BBC iPlayer finally made its debut on Windows Phone 8, but the existing Android version has been far from forgotten about. BBC iPlayer 1.7 has hit Google Play and now boasts support for 10 inch tablets.While owners of larger tablets previously had to pay a visit to the iPlayer website, UK viewers can now enjoy their favorite programmes directly in the app. If you're nursing a smaller 7-incher, there's no need to feel left out. The UI for more diminutive tablet and phones has been updated with a few tweaks as well.
Anyone holding out for the video downloads that are already enjoyed by users of the iOS version of the app may take heart in the update description. Developers state that "work continues" on this feature, although no timeframe is suggested.
The app can be downloaded free of charge from Google Play.
-

Google X acquires flying turbine company Makani
Publié: mai 23, 2013, 4:10pm CEST par Mark Wilson
 Google may be most readily associated with the Internet, apps and mobile devices, but the company has many more strings to its bow. Google X -- the secretive research and development division best known for Project Glass and the driverless car -- has acquired Mikani Power, a green energy company that generates power with flying turbines.
Google may be most readily associated with the Internet, apps and mobile devices, but the company has many more strings to its bow. Google X -- the secretive research and development division best known for Project Glass and the driverless car -- has acquired Mikani Power, a green energy company that generates power with flying turbines.Ground-based wind turbines are common all over the world, but Mikani Power takes a slightly different approach. Using wings fitted with miniature turbines it is possible to generate power with a series of self-piloted kites. Successful tests have been conducted on a 30kW prototype model, with plans to scale up to 600kW in the future.
By placing turbines at an altitude of between 250 and 600m, it is possible to harness more consistent wind power. The manoeuvrability of the wings means that they can adapt and reposition according to weather conditions, and easily land if wind speeds become too high -- a problem that can lead to traditional wind turbines becoming damaged.
The acquisition is not completely out of the blue. Since 2006, Google has invested a total of $15m in the company.
-

Sweet! Official new themes give Windows 8 a global makeover
Publié: mai 20, 2013, 10:19am CEST par Mark Wilson
 Desktop themes are so often catered for by third party tools that it’s easy to forget that Windows has built in support for theme packs. If you’re short of inspiration, don’t trust your own photography skill, or just can’t be bothered to browse Flickr for a new image, a new batch of themes direct from Microsoft could be what you need to breathe new life into your desktop.
Desktop themes are so often catered for by third party tools that it’s easy to forget that Windows has built in support for theme packs. If you’re short of inspiration, don’t trust your own photography skill, or just can’t be bothered to browse Flickr for a new image, a new batch of themes direct from Microsoft could be what you need to breathe new life into your desktop.There are five new themes in total, four of which have a travel connection. The Alaskan Landscape theme features photography from Kyle Waters -- a total of fifteen images. There is more of a seasonal feel to two New Zealand Landscapes themes.
The Queenstown theme is cool and wintery, while the One Tree Hill theme is far more summer inspired. Both themes showcase the work of photographer Ian Rushton. Continuing the seasonal theme, and completing a previous collection, is Swedish Spring.
Rounding off the new download selection is something rather more cartoony. The Delectable Designs theme offers a tasty selection of desktop images inspired by snack time -- cupcakes, cookies, coffee and more are all on hand to help you build up an appetite
The new themes, and others, can be downloaded from the personalization section of the Microsoft website, but you can find out more about the new releases at the Windows Experience Blog.
-

Photoshop for free? Adobe Photoshop Express hits Windows 8 and RT
Publié: mai 18, 2013, 7:10pm CEST par Mark Wilson

Not content with free versions of its cut-down photo editing software for iOS and Android, Adobe has released Photoshop Express for Windows 8 and RT. As this is available free of charge, it should come as little surprise that the app does not afford users access to an unfettered range of professional level image editing tools, but for quick and dirty tweaks and fixes, there are plenty of options.
Taken a wonky photo? Getting things straightened up takes just a couple of taps and swipes. There are also tools for removing red eye, adjusting color levels and tweaking shadows and highlights. If you don’t feel like doing the hard work yourself, you can always turn to the auto-fix option to help take care of common issues in an instant.
Simple controls appear as they are need to reduce clutter and helping to keep the interface as friendly and approachable as possible. With photo editing reduced to moving a slider here and there, things don’t really get much easier than this.
As changes are made to an image, there’s a useful View Diff toggle that can be used to compare before and after versions of a photo. The obligatory sharing options are all present and correct.
As is becoming increasingly common with free apps, the selection of bundled tools can be added to through in-app purchases. The Looks and Noise Reduction packs can be used to access additional filters and image improvement options, but it will set you back $4.99.
If you fancy trying out the app on your photos, it can be downloaded free of charge from the Windows Store.
-

eBay for iOS update includes new UI and registration via driver's license
Publié: mai 17, 2013, 3:25pm CEST par Mark Wilson
 The iOS versions of eBay’s app have been updated with a redesigned interface and a raft of other changes. The latest release improves on the stripped back UI that was available in previous versions and larger photos can now be accessed. As before, there are versions of the app available for iPad (which is version 2.3.0) and iPhone (which has reached version 3.0.0).
The iOS versions of eBay’s app have been updated with a redesigned interface and a raft of other changes. The latest release improves on the stripped back UI that was available in previous versions and larger photos can now be accessed. As before, there are versions of the app available for iPad (which is version 2.3.0) and iPhone (which has reached version 3.0.0).But there’s more than a new look to the latest version of the app. If you’re one of those people who has yet to create an eBay account, the signup process just got a whole lot easier -- if you’re in the US, that is. Forget time-consuming form filling, you can now sign up for an account with a quick scan of your driver’s license.
Improvements have been made for buyers and sellers alike, and anyone looking to grab a last-minute bargain will find that scope for sniping is now more accessible. There are better filtering options so sellers can be sorted by their feedback rating and seller can now more easily list items that are similar to those they already have for sale -- no more starting listing from scratch.
eBay users in both the US and UK can now buy multiple items faster than before thanks to a new option. It is now possible to checkout multiple items at the same time so there’s no need to skip back and forth between pages as much.
You can find out more and download a free copy of the app by paying a visit to the eBay for iOS review page -- there are separate versions available for iPhone and iPad.
-

iTunes 11.0.3 offers faster performance and improved MiniPlayer views
Publié: mai 17, 2013, 12:37am CEST par Mark Wilson
Loved and loathed in just about equal measure, iTunes is installed on a huge number of computers around the world. It has been a while since the last update, but now iTunes 11.0.3 has been unveiled and there are a few important changes that make it worthy of installing, including new MiniPlayer views.
In the initial update to iTunes 11, many users were disappointed to find that the progress bar has vanished from the MiniPlayer. In the most recent update, this has been reinstated and it is also possible to have album art displayed while playback controls are hidden.
Album art can also be displayed in songs view and improvements have been made to the handling of multi-disc albums. To make those compilations, concept albums and other multi-parters easier to manage, iTunes now treats them as a single album rather than two or more.
These are the most obvious changes, and all of them are cosmetic ones that should be immediately apparent. Apple also claims that this latest update helps to improve performance for people with large music libraries. There are no figures to elaborate on what constitutes a large library, but faster searching and sorting is promised.
You can find out more and download a copy of the app -- which is available for OS X and Windows -- by paying a visit to the iTunes review page.
-

TweetBackup shuts up shop, recommends Norton Ditto as replacement
Publié: mai 16, 2013, 6:37pm CEST par Mark Wilson
 If you were thinking of signing up for a TweetBackup account to create an archive of your Twitter account, it is now too late. Having been bought by Backupify around two and a half years ago, the project has been sidelined, and no new registrations are being accepted. So where does this leave anyone who has come to rely on the service?
If you were thinking of signing up for a TweetBackup account to create an archive of your Twitter account, it is now too late. Having been bought by Backupify around two and a half years ago, the project has been sidelined, and no new registrations are being accepted. So where does this leave anyone who has come to rely on the service?Although there are no new sign-ups, TweetBackup is not just going to vanish in a puff of smoke. Existing users will be able to log into their accounts until June 28 2013 but after this time it will no longer be possible to access your backup -- so be sure to download your data before this date.
So what are you supposed to do if you’ve become reliant on TweetBackup? As the service closes down, it does so with the recommendation that users check out Norton Ditto. This is another free backup service, but one that is not focused solely on Twitter.
Norton’s offering can be used to automatically backup not only your Twitter account, but also Facebook and Gmail. All of this can be done on a schedule so even the forgetful Twitter user can rest assured that their data is kept safe.
And of course, there’s always the option of manually downloading your Twitter archive; just head over to the Settings side of your account and hit "Request your archive".
Photo credit: Vitezslav Valka/Shutterstock
-

Google makes it easier to send money through Gmail
Publié: mai 16, 2013, 5:26pm CEST par Mark Wilson
Think about how to send money electronically and it’s probably PayPal that springs to mind first. But if Google gets its way, Google Wallet is about to become much more popular. For anyone in the US, Google Wallet is now integrated into Gmail meaning that it is possible to send money as easily as sending an email.
Sending money works in much the same way as attaching a file to a message -- you can attach payment to an email just as you would an image or other file. You may not see it just yet -- Google plans to roll the feature out over the next few months -- but once activated you’ll see a $ button at the bottom of the Compose window. It’s clear that Google is making electronic payments as simple as possible to help the company take a bigger share of the electronic payment pie.
If you have money in your Google Wallet, sending money is free of charge as is the case when making transfers directly from your bank account. The payment system can also be used to make debit and credit card payments using cards you have associated with your account, but these will incur a 2.9 percent fee per transaction. As you would expect, receiving money is free.
Should you start to get impatient with waiting for the feature to be enabled in your account, check with people you know to see if they already have access to it. As soon as someone else sends you money, email based payments will be enabled in your own Gmail account as well.
-

Google's new Hangouts messaging system makes it easier to keep in touch with friends
Publié: mai 16, 2013, 11:12am CEST par Mark Wilson
 There were a lot of big unveilings at Google I/O -- an overhaul of Google+, updated maps, an on-demand music streaming service, and much more. But perhaps one of the most intriguing revelations was Hangouts.
There were a lot of big unveilings at Google I/O -- an overhaul of Google+, updated maps, an on-demand music streaming service, and much more. But perhaps one of the most intriguing revelations was Hangouts.This name may well seem familiar, but it now refers to a unified messaging system that caters for iOS, Android and Chrome users. There are apps and extensions available for each of these platforms, and the idea is to bring all Google related communication into one place.
This means that Hangouts serves as a replacement for not only its namesake service, but also Google+ Messenger, Google Talk and the original Hangouts video chatting service. In some respects this could be seen as Google’s answer to FaceTime.
So at its heart, Hangouts is a messaging app, but it does go well beyond the basics. In addition to regular text based chats, there is the option of performing video chats, sharing files and sending one of scores of newly designed emoticons. As the name would suggest, Hangouts has the potential to be used as a group hangout for several people and it’s easy to invite other people to join a conversation once it is under way.
As this is a cross-platform messaging system -- and it’s likely that many users will be working with a browser extension as well as a mobile app -- synchronization is extremely important. In Hangouts, it is not just messages that are synched, but also notification. This means you won’t be pestered by the same alert on multiple devices and you’ll be able to see your entire chat history no matter which device you have been using.
You can find out more and download a copy of the apps and extension by paying a visit to the Hangouts review page.
-

BBC iPlayer ‘app’ hits the small screens of Windows Phone 8
Publié: mai 15, 2013, 12:44pm CEST par Mark Wilson
 BBC iPlayer has long been the go-to service for catching up on TV and radio shows. The web-based version has been available for years, and iOS and Android users have their own mobile versions to use on phones and tablets. Having been promised back in March BBC iPlayer is now available for Windows Phone 8.
BBC iPlayer has long been the go-to service for catching up on TV and radio shows. The web-based version has been available for years, and iOS and Android users have their own mobile versions to use on phones and tablets. Having been promised back in March BBC iPlayer is now available for Windows Phone 8.In terms of functionality, there’s little to differentiate this from its Apple and Google counterparts. The app has been a long time coming, but in reality the BBC iPlayer app is little more than a wrapper for the mobile iPlayer website.
Both TV and radio content is available, and users can browse through programming using an EPG-style schedule, search through categories or check to see what is proving popular with other users. There is support for playing the radio in the background as well as Live Tiles.
Anyone still holding out for a release for Windows 7.5 should stop holding their breath -- such an app has been ruled out due to platform limitations. Head of BBC iPlayer, Dave Price, explains:
We've been unable to provide the same quality playback experience as on Windows Phone 8. This led to the joint decision not to make BBC iPlayer available on Windows Phone 7.5.
But if you are packing a Windows Phone 8, the app can be used to catch up with the last seven days of programming over Wi-Fi or 3G.
To get your fix of BBC programming, you can download a copy of the app from the Windows Phone store.
-

Hey, Gmail users, Mailbox for iOS is now available, without reservation or waitlist
Publié: avril 21, 2013, 4:37pm CEST par Mark Wilson
 Gmail shows little sign of becoming any less popular, but any iOS user will find that dealing with a Gmail account on an Apple device is not the most pleasant experience. Mailbox was released to help address this fact and proved so popular that newcomers were greeted by a lengthy waiting list before they could get started. The app has now been updated in a number of key areas and, perhaps most importantly, anyone is free to jump right in and get started without the need to wait on a reservation list.
Gmail shows little sign of becoming any less popular, but any iOS user will find that dealing with a Gmail account on an Apple device is not the most pleasant experience. Mailbox was released to help address this fact and proved so popular that newcomers were greeted by a lengthy waiting list before they could get started. The app has now been updated in a number of key areas and, perhaps most importantly, anyone is free to jump right in and get started without the need to wait on a reservation list.This is obviously great news for people who have been waiting to try out the app, but there is also plenty for existing users to take advantage of. One of the major standout features of the app from its inception was the way in which emails could be dealt with using little more than a swipe; swipe one way to delete or mark as read, and the other way to snooze.
The snooze feature has been enhanced in this latest release. Just as before it is possible to hide emails that you do not want to deal with immediately, but you are now able to deal with multiple messages simultaneously. The actual snoozing process has also been improved so that the options you are provided with are appropriate to the time of day and the day of the week.
Another noteworthy change means that when in the neat conversation view, you can view email addressed by double tapping a message bubble. The latest update includes all of the big fixes and performance improvements you would expect. Check out Mailbox and see if its unique snoozing option can help you to achieve inbox zero and better manage your messages.
You can find out more and download a copy of this free app from the Mailbox review page.
-

Clover 3 adds tabs and additional navigation features to Explorer
Publié: avril 15, 2013, 2:02pm CEST par Mark Wilson
 What’s the one thing that is missing from Windows Explorer? Actually, there’s probably more than just one thing missing, but what is the most obvious? Tabs. They are now so ubiquitous in web browsers that it’s unlikely you give them a second thought; they’re just there and you use them. Why should your file browser be any different? This is an anomaly that the developers of Clover felt had to be put right with the latest release.
What’s the one thing that is missing from Windows Explorer? Actually, there’s probably more than just one thing missing, but what is the most obvious? Tabs. They are now so ubiquitous in web browsers that it’s unlikely you give them a second thought; they’re just there and you use them. Why should your file browser be any different? This is an anomaly that the developers of Clover felt had to be put right with the latest release.Aside from the addition of tabs to Explorer -- which means that it is possible to deal with multiple folders in a single window -- there are a number of other changes in this latest released. For anyone concerned with aesthetics, support for themes means that the look of the program can be completely changed.
But there are more important changes that are worth noting. To allow for easier navigation of files, new methods of interaction have been added. The folder bookmarking system has been updated so that by middle-clicking on a bookmark it is possible to load a folder in a foreground tab, and bookmarks can now be exported and imported.
This is a handy option to have available if you use Clover on more than one machine, but it also serves as a useful backup mechanism.
 Another navigation option allows a double click to be used to skip up a directory level. Forget seeking out the Up button, now you can simply double click in an area of white space to jump to the parent of the current folder.
Another navigation option allows a double click to be used to skip up a directory level. Forget seeking out the Up button, now you can simply double click in an area of white space to jump to the parent of the current folder.Clover stands apart from many of the tools that are used to enhance Explorer in that it does not try to go too far. It focuses on doing a small number of things and doing them well.
You can find out more and download the latest version at the Clover review page.
Photo Credit: Milena_Bo/Shutterstock
-

Everything.me launcher dynamically adapts to what you’re doing right now
Publié: avril 12, 2013, 7:43pm CEST par Mark Wilson
 Unlike iOS, Android devices can be very easily customized without the need to jailbreak or root them. This means that there is an ever-growing market in third-party launchers that enable phone and tablet users to try out a variety of new ways to access the apps they have installed on their device. While cosmetically different and packed out with a range of extra features, most launcher are generally fairly similar, but this same cannot be said of Everything.me which adapts itself according to what you are doing and where you are.
Unlike iOS, Android devices can be very easily customized without the need to jailbreak or root them. This means that there is an ever-growing market in third-party launchers that enable phone and tablet users to try out a variety of new ways to access the apps they have installed on their device. While cosmetically different and packed out with a range of extra features, most launcher are generally fairly similar, but this same cannot be said of Everything.me which adapts itself according to what you are doing and where you are.The idea is simple. Launching apps and accessing information is now seen as being the same thing. Looking for a recipe you have stored in an app you use? Type ‘recipe’ and a list of corresponding apps will show up. In addition to this, you’ll also be shown a list of related websites so you can check out other recipes online. Breaking down, or at least blurring, the barriers between local apps and online services is an interesting approach.
There’s also scope for tailoring search results to your current location. Look for restaurants and you’ll be able to find out what is nearby. As well as ensuring that you have easy access to the information you’re looking for, Everything.me also changes the appearance of your phone according to what you’re doing. Perform a search for ‘football’ and your background will change to the NFL logo.
A launcher that dynamically adapts to what you’re doing can take a little getting used to; it feel strangely unintuitive to start with, but it doesn’t take long to become second nature. It’s really just a matter of retraining that memory muscle.
But there is another option available in the form of smart folders, and these act as a sort of hallway house between dynamic homescreens and a more traditional folder-based launcher. Select a category -- such as a shopping -- and any apps that you have that fall into this category will be automatically added to the folder along with a list of associated online resources. Create a ‘social’ folder and you’ll find that Fourquare, Twitter, Facebook etc are all automatically grouped together for you.
Everything.me is currently in beta but can still be downloaded from Google Play.
-

Jam with Google Play Music Manager
Publié: avril 5, 2013, 2:29am CEST par Mark Wilson
 The cloud is now used for many things, from simply storing documents, to create and editing files online. Google Play, in addition to many other things, offers a place to store up to 20,000 tracks that can then be listened to online or with a range of mobile devices. This number relates only to songs from your "personal collection" and is in addition to any purchases you make. Google Play Music Manager is the tool you need to get everything up and running.
The cloud is now used for many things, from simply storing documents, to create and editing files online. Google Play, in addition to many other things, offers a place to store up to 20,000 tracks that can then be listened to online or with a range of mobile devices. This number relates only to songs from your "personal collection" and is in addition to any purchases you make. Google Play Music Manager is the tool you need to get everything up and running.Install and launch the app, sign into your Google account and you’ll be asked where you current music collection is stored. There is support for iTunes and Windows Media Player, but there’s also the option of just opting to work with files stored in My Music, or any other folder for that matter. If you have your music scattered across multiple folders, you can add them all to your Google library.
Once your library has been created, you can opt to have any new files that you add to these folders automatically uploaded. This ensures that you always have access to all of your most recently ripped CDs and other music acquisitions without the need to remember to manually sync anything.
Even if you have a relatively small music collection of just a few hundred tracks or so, you’re possibly envisioning a very lengthy wait while all of your music is uploaded for you. Well, unless you have particularly eclectic tastes, you should find that things happen much faster than you might expect -- if Google already has a copy of a track you own available online, there’s no need for it to be uploaded.
In practice, however, just how long it takes for your collection to be made available online will depend on its size, the types of music you like, whether your music files are ripped or purchased as well as the speed of your internet connection. The web interface for the music player is comparable to an online version of iTunes. It is a little limited, but it gets the job done.
You can create playlists, listen to albums in their entirety or pick out individual tracks. In addition to the usual browse by album option, a large library can also be searched or you can filter tracks by artist, genre or alphabetize them.
Google Play Music Manager is available free of charge for Windows, OS X and Linux.
Photo Credit: CREATISTA/Shutterstock
-

Microsoft releases SkyDrive 3 for iOS
Publié: avril 3, 2013, 7:01pm CEST par Mark Wilson
 There’s certainly no shortage of cloud storage services to choose from these days and Microsoft’s SkyDrive provides a fairly generous 7GB of space free of charge. The latest version of the iOS app sees compatibility extending to include not only the iPhone 5, but also the iPad Mini, and there are also a few new features to explore.
There’s certainly no shortage of cloud storage services to choose from these days and Microsoft’s SkyDrive provides a fairly generous 7GB of space free of charge. The latest version of the iOS app sees compatibility extending to include not only the iPhone 5, but also the iPad Mini, and there are also a few new features to explore.The latest release comes after Apple blocked updates to the app following Microsoft’s launch of a subscription model. This could be one of the reasons that it is now not possible to sign up for a SkyDrive account from within the SkyDrive app -- if you have an account already you’ll be able to sign in straight away, but if you need to create one, you will have to head over to the website to do so.
Perhaps the most obvious change, although by no means the largest, is the new icon sported by the app. This new look continues through the UI, with a darker, cleaner feel now replacing the slightly dated look of the previous version.
There have been improvements made throughout the SkyDrive app which mean that there is now better support for not only opening the files you have stored online in different apps you may have installed, but also better support for saving files from apps to SkyDrive.
Other changes mean that full resolution photos can be downloaded and there is the usual selection of bug fixes.
If you have an iPhone or an iPad, you can download a free copy of the SkyDrive app and take advantage of Microsoft’s cloud storage service.
-

New Evernote supports Windows 8 Modern UI
Publié: octobre 27, 2012, 12:19am CEST par Mark Wilson
Evernote for Windows 8, a dedicated app designed to take advantage of the new Windows 8 Modern UI, is now available. It’s completely separate from Evernote for Windows Desktop 4.5.9, the traditional desktop app that has also been updated today.
Both apps were joined by the first dedicated Windows build of related Evernote app, Skitch, which release influenced the major new features in Evernote for Windows Desktop 4.5.9.
Evernote for Windows 8 is installed through the Windows Store, and is accessed through the new Windows 8 Start screen via its dedicated shortcut tile. The app is designed to take full advantage of the stripped back, minimalist Modern UI interface, presenting a user’s notes in a clean, easy-to-read way.
As is to be expected with Modern UI apps, Evernote for Windows 8 is also extremely touch-friendly, making it simple to swipe between notes and access various program options. Things are more awkward with a mouse and keyboard, but users can still opt for the desktop version instead, which is more fully featured, and has been refreshed to version 4.5.9.
Evernote for Windows Desktop Updates
The emergence of Skitch as a desktop app has formed the key improvements to be found in Evernote for Windows Desktop 4.5.9. Users can now create Skitch notes directly in Evernote via the New Note dropdown menu, which launches Skitch. Images within existing notes can also be edited directly in Skitch by right-clicking them and choosing Markup with Skitch.
The integration goes the other way too, with new Skitch notes appearing in your Evernote desktop. Skitch notes are differentiated by a pink bar inviting users to both open and edit the note back in Stitch.
The new update also simplifies the process of sharing notebooks with others -- when the user opts to share a notebook, a pop-up window will appear with all the options needed to set up the shared notebook, from managing permissions to inviting other users or creating a public link.
Evernote’s latest update is also rounded off by a series of undocumented stability improvements that Evernote promises will make the “app more reliable than ever”.
Evernote for Windows 8 and Evernote for Windows Desktop 4.5.9 are both available as freeware downloads. An Evernote account is required to save notes and sketches.
-

Before buying Windows 8, use Upgrade Assistant
Publié: octobre 26, 2012, 4:01pm CEST par Mark Wilson

It is here. After months of waiting, beta releases and consumer previews, Windows 8 has finally hit the shelves and download servers. If you’re considering upgrading the next thing you need to consider is whether your computer is up to the task, whether all of your hardware is going to be compatible and how many of your applications are going to need to be upgraded. These are all questions that can be answered by the Windows 8 Upgrade Assistant.
As Windows 8 is the first version of Windows to be made available as a download, it should come as no surprise that once you have run through the Upgrade Assistant you will be invited to purchase the latest version of the operating system. Compared to previous versions of the assistant, the Windows 8 specific release seems to take rather more time over system analysis during which all of your hardware and software will be checked.
The assistant will then let you know what is deemed fully compatible with Windows 8, what is not going to work and highlighting anything that needs your attention -- this includes pointing out that if you currently use Windows to watch DVDs you’re going to need to install a suitable app if you switch to Windows 8.
The final stage of the assistant asks whether you would like to transfer all of your files, apps and settings, just your files or nothing, and it will then suggest which version of Windows 8 is most suitable for your needs. More than this, you are able to order and download your copy so you can get started with Windows 8 straight away. Clearly this is a great marketing ploy by Microsoft, but it is also very helpful for consumers who just want to jump and get started right away.
You can find out more and download a free copy of the program by paying a visit to the Windows 8 Upgrade Assistant review page.
-

Use Clover to add tabs to Windows Explorer
Publié: octobre 25, 2012, 5:17pm CEST par Mark Wilson
 The introduction of tabs to web browsers is arguably one of the most useful innovations that have been made. Advances in security and performance are all great, but tabs make a real difference to the usability of browsers, making multi-tasking a great deal easier. Clover is a free Windows add-ons that enables you to take advantage of this very same feature in Explorer so you can navigate between your folders in tabs rather than having to have multiple windows open.
The introduction of tabs to web browsers is arguably one of the most useful innovations that have been made. Advances in security and performance are all great, but tabs make a real difference to the usability of browsers, making multi-tasking a great deal easier. Clover is a free Windows add-ons that enables you to take advantage of this very same feature in Explorer so you can navigate between your folders in tabs rather than having to have multiple windows open.The addition of tabs to Explorer may seem like a fairly minor change, but it is amazing just how much of a difference it can make. If you’re a fan of the way tabs work in Firefox, Chrome, et al, you’ll love the similar way in which Clover works. All of the shortcuts you have become used to can be used here -- Ctrl+T to open a new tab, Ctrl+W to close it, Ctrl+Tab to move the next tab etc.
Just as with your browser you can drag and drop tabs to re-order them, and you can access additional options -- such as re-opening closed tab, closing all of the tabs to the right of the current one -- by right clicking a tab. You can also create duplicates of any open tab, and create bookmarks so that you can access your favorite folders faster than ever. Another browser style feature means that it is possible to ‘pin’ tabs so that they are always available.
The Bookmarks toolbar is optional, but it certainly comes in very handy. It enables you to have instant access to all of your most frequently used folders so you don’t need to battle with Explorer’s tree structure all of the time. One area in which Clover stands apart from the competition is in that it is an add-on rather than a standalone app; as such you can still access a tabbed version of Explorer without having to launch a different program.
You can find out more and download a free copy of the add-on by paying a visit to the Clover review page.
Photo Credit: NinaMalyna/Shutterstock
-

IOBit Advanced SystemCare 6 Pro review
Publié: octobre 24, 2012, 4:41pm CEST par Mark Wilson

Tweaking performance is something that virtually every Windows user is interested in. There are various degrees to which performance tweaks can be applied, starting with simple things such as ensuring that there are not too many programs configured to start when Windows launches, to more advanced options such as tinkering with services and the registry.
Whether you are a newcomers to system tweaking or a more seasoned user, turning to a third party-tool -- rather than doing all of the legwork yourself -- not only helps to save a good deal of time, but also helps to reduce the risk of making mistakes that could have disastrous consequences; edit the registry incorrectly and you could find that you have an unbootable system on your hands.
There is a seemingly endless number of programs available, both free and paid for, that claim to make it easier to tweak your computer or deliver better results than manually tweaking. IOBit Advanced SystemCare 6, available as a Free or commercial Pro version, is an all-encompassing utility that aims to satisfy the demands of the power-user whilst remaining accessible to those who are less experienced.
Things get off to a very warm and friendly, hand-holding start with the appearance of a helpful, although perhaps not strictly necessary, introductory tutorial. The app and its interface are really fairly self-explanatory, but it’s still nice to find that absolute beginners are being catered for.
Simple or Expert?
We’ve mentioned that this is an app that is suitable for beginners and experts alike, and it’s easy to switch between Simplified Mode and Expert Mode -- by default the app works in simplified mode after installation, so anyone new to the world of tweaking is not going to be thrown in at the deep end and left wondering what to do.
Taken at face value, Simplified Mode is a very dumbed down version of the app. Whether this is a ploy to make the Expert mode more appealing is open to debate, but being presented with a single Smart Scan button when working in basic mode is going to quickly drive most users to switch to Expert mode.
In Simplified Mode it is still possible to access individual components of the tweaking suite by clicking the Quick Settings link at the bottom of the screen, but this is tucked out of the way at the bottom of the screen so that the option to switch modes is more prominent.
Getting Tweaked
For the remainder of this review, we’re going to concentrate on the Expert component of the app and it is almost inconceivable that this is not where most users will end up heading -- it is where the guts of Advanced SystemCare are to be found after all.
Once you are working in the more advanced mode, there are three sections of settings to work through: Care, Toolbox and Turbo Boost. In the Care section you’ll find twelve different collections of settings ranging from privacy checking to registry cleaning.
Each of these individual components can be added to the overall scan, which can include as many or as few of these options as you like. Sadly, there are no additional options to be found in each section, they are either enabled or disabled. Or at least that is that way it seems to start with.
While it may appear that the only option available to you is to select or deselect a component, hover over a section heading and a previously hidden settings icon will appear. Here you can access the main settings screen from which you can configure the options you would like to use. Although this does enables you to set up the program to your liking, it is not the most intuitive aspect of the program. This may be expert mode, but it is no excuse for poor interface design.
Free vs Pro
There are plenty of free tweakers to choose from, and IOBit Advanced SystemCare 6 adds to this number, However, there is also a Pro version of the program available that gives you access to a number of additional tools and options. The claims associated with upgrading to the Pro edition of the app are slightly vague – doubling of PC speed, tripling of internet speeds, and cleaning the registry ‘more deeply’ – but the decision to part with some cash will unlock a many more options.
It is difficult to say whether the Pro version of the program is worth the money. There is no denying that it helps to make life a little easier when it comes to tweaking, but there are no ground-breaking settings revealed that a true "pro" would not be able to change anyway. However, autocleaning options and scheduled boot-time optimization are certainly useful.
Away from the main program interface, integration with Windows means that some options can be accessed from the right click menu in Explorer. For example you can right click a file and have it securely deleted from your hard drive according to the settings you have already configured.
Summing Up
Tweaking tools are something of a difficult breed of software to judge. The results that can be expected will vary massively from one computer to another. What cannot be denied is that IOBit Advanced SystemCare 6 Pro certainly helps to make life easier. You do not need to remember where all of the important settings are to be found in the registry or which area of the Control Panel you need to visit to optimize different aspects of your computer. The software lists for $29.99, for Windows 2000, XP, Vista, 7 and 8.
Verdict: Fairly average tweaking tools that bring nothing out of the ordinary but gets the job done with no nonsense.
We Like: Accessible to all levels of computing ability, reasonable results may be noticed.
We Don't Like: Some settings are rather unintuitive, vague claims of program benefits, Pro price is a little high.
Photo Credit: Dino O./Shutterstock
-

Use WinMetro to bring Modern UI to older Windows
Publié: octobre 23, 2012, 3:50pm CEST par Mark Wilson

Microsoft may have changed the name of the interface formerly known as Metro to Modern Interface, but that does little, if anything, to stop consumers and software publisher from continuing to use the original moniker. As such, one of the apps that brings the look of Windows 8 to older versions bears the name WinMetro.
Regardless of the technical appropriateness of the name, WinMetro is a handy utility for anyone impressed with the aesthetics of Windows 8 but who is not looking to make the jump from the current operating system. While the tool is not a replacement for the Start menu in the strictest sense of the word -- it is not possible to remap the Windows key to bring it into view for instance --- the application is a neat overlay that brings you the look and feel of Windows 8 at no cost.
There are two components to WinMetro, the Start Screen and a side bar. The Start screen can be used to access your most frequently-used programs, but it is also home to a series of widgets. These are slightly limited, but the ability to view the weather forecast, news headlines and slideshows is an almost identical replica of what is to be found in Windows 8.
There are numerous aspects of the Windows 8 interface that are missing, but everything that is here looks great. The controls for volume look great but, just as in Windows 8, they are slightly fiddly to access. In many respects the look of WinMetro is cleaner and easier to read than Windows 8, and you might well find that it sates your interface upgrade needs until you decide whether to make the jump to Windows 8 or not.
You can find out more and download a free copy of the app by paying a visit to the WinMetro review page.
-

Start Screen Pinner does for Windows 8 what the name implies
Publié: octobre 19, 2012, 4:02pm CEST par Mark Wilson
 The release of Windows day is mere days away and the release rate for tools geared up for the latest version of Microsoft’s operating system is accelerating. One of the most controversial aspects of Windows 8 is the new Start Screen, and this is a feature that many tweaking tools concentrate on. This is certainly the case with Start Screen Pinner which, as the name suggests, makes it easy to pin almost anything to the Start Screen.
The release of Windows day is mere days away and the release rate for tools geared up for the latest version of Microsoft’s operating system is accelerating. One of the most controversial aspects of Windows 8 is the new Start Screen, and this is a feature that many tweaking tools concentrate on. This is certainly the case with Start Screen Pinner which, as the name suggests, makes it easy to pin almost anything to the Start Screen.Start Menu tweakers are tools that crop up fairly frequently, and there are plenty of utilities that have been designed to make the Start Screen of Windows 8 easier to use by reinstating the Start button. Start Screen Planner is slightly different in that it provides you with a way of adding new shortcuts to the Start Screen rather than changing the way it work or the way in which you access it.
This is a very simple tool -- it is tiny and does not even need to be installed -- but it provides you with an incredibly easy way to add links to almost any item to your Start Screen. This include files, folders and libraries that you use frequently and want to be able to access easily, but there is also the option of adding more useful shortcuts to system tools such as individual Control Panel applets.
Many users who have tried out the preview releases of Windows 8 have found that the new Start Screen is a little awkward to use. Start Screen Pinner does nothing to change the way it works, but it does help to make it a great deal easier to add more useful shortcuts that will enable to get around your computer more quickly.
You can find out more and download a free copy of the app by paying a visit to the Start Screen Pinner review page.
-

Google Calendar releases as separate Android app -- get it NOW!
Publié: octobre 18, 2012, 5:31pm CEST par Mark Wilson
 Android users running Ice Cream Sandwich and Jelly Bean can now take advantage of a new standalone version of Google Calendar. The move brings the product/service more in line with Gmail, Google Play and others that have been separate apps for some time now, and the split sees the introduction of some interesting new options that could well be enough to persuade users away from other calendar apps.
Android users running Ice Cream Sandwich and Jelly Bean can now take advantage of a new standalone version of Google Calendar. The move brings the product/service more in line with Gmail, Google Play and others that have been separate apps for some time now, and the split sees the introduction of some interesting new options that could well be enough to persuade users away from other calendar apps.The calendar app previously was limited to a number of devices, notably Nexus, but now it is available to anyone running the right version of Google mobile operating system. While the standalone app is nothing groundbreaking, there are a few noteworthy tweaks, starting with the fact that there is now a snooze function for those occasions when you are busy with something else but still want to be reminded of an upcoming appointment.
Talking of reminders, it is very easy to configure multiple reminders for any entry in your calendar -- these can take the form of emails or notifications -- and you can also browse up to a year into the past by default. There is a lovely pinch-to-zoom option in the calendar that enable you to zoom in to see more detail on a particular day and the quick, canned responses to invitations are a great touch.
HTC users might want to hold back on the celebrations for the time being as there are problems with a number of devices at the moment with this release. This is hopefully something that Google will address in future updates, but for now you may find that certain views do not work or notifications may not sound, among a variety of other issues. These niggles aside, anyone without an HTC device is in for a treat and even HTC owners might want to get the app installed so they can be notified when updates are released.
You can find out more and download a free copy of the app by paying a visit to the Google Calendar review page.
-

Uniblue PowerSuite 2013 build 4.1.4.0 adds startup manager and resource optimizer
Publié: octobre 18, 2012, 2:12pm CEST par Mark Wilson
 Looking to tweak Windows? There are plenty of tools to choose form if you don’t fancy the idea of editing the registry, but you have to sort the wheat from the chaff in order to find something half decent. The world of tweaking tools is divided into two camps: utilities that are free and those that are not. Paying for a program is not necessarily an indication of quality, and with PowerSuite Lite 2013 you have the option of sticking with the free version or paying a bit for a range of extra tools.
Looking to tweak Windows? There are plenty of tools to choose form if you don’t fancy the idea of editing the registry, but you have to sort the wheat from the chaff in order to find something half decent. The world of tweaking tools is divided into two camps: utilities that are free and those that are not. Paying for a program is not necessarily an indication of quality, and with PowerSuite Lite 2013 you have the option of sticking with the free version or paying a bit for a range of extra tools.Whichever route you decide to go down, the latest build 4.1.4.0 introduces two important new enhancements -- a PC startup manager and PC Resource Optimizer. The free, lite version of the program features the PC Resource Optimizer component and, when enabled, this component of the suite aims to improve the performance and responsiveness of your system by balancing processor and disk resources so demand is never too high at any given time.
This is the sort of claim that is easy to view with suspicion, as you should, and results will vary from one computer to another, but in tests we found that it did seem to make a noticeable improvement to the general feel of the running of Windows. If you’ve parted with the cash for the Pro version of the program you can take advantage of the PC startup manager, and there’s a clue in the name as to what you can expect here.
This, oddly, is a less impressive update to the tweaking suite, but it does, as you have probably guessed, make it possible to manage the programs that start automatically with Windows. In itself this is nothing out of the ordinary, but the ability to view Startup shortcuts, registry autoruns and more all in one place is a helpful timesaver. The program can be used with all versions of Windows from Windows XP all the way up to Windows 8.
The commercial Pro version offers access to many more tools such as the new PC startup manager, registry defragging, system tweaking, junk file removal and much more. You can buy the Pro version from the Downloadcrew Software Store for $29.95.
To test the free Lite version, pay a visit to the Uniblue PowerSuite 2013 download page.
-

Need to restore your PC? Try Windows Post-Install Wizard
Publié: octobre 17, 2012, 3:51pm CEST par Mark Wilson
 The prospect of reinstalling Windows is not one that many people relish, particularly if it is something that needs to be done on a regular basis, to numerous machines, or both. Part of the problem is that getting everything set up how you want it to be is that once Windows itself is up and running, there is still a great deal to do in terms of configuring the operating system to your liking as well as installing the applications you need.
The prospect of reinstalling Windows is not one that many people relish, particularly if it is something that needs to be done on a regular basis, to numerous machines, or both. Part of the problem is that getting everything set up how you want it to be is that once Windows itself is up and running, there is still a great deal to do in terms of configuring the operating system to your liking as well as installing the applications you need.Whether you are someone who frequently wipes the hard drive to start afresh, or you are an admin looking after several computers that need to be refreshed from time to time, Windows Post-Install Wizard is a tool that exists to help make your life easier. The seemingly simple task of cleaning up a system by installing the operating system from scratch can very easily turn into a chore that takes up and entire day -- until your create your own custom installation disc that is.
Windows Post-Install Wizard enables you to place your copy of Windows, all of the application you want to install as well as any registry tweaks and scripts all on one disc. This has a few advantages, but the two key bonuses are the fact that you only need to carry a single disc with you rather than a great stack of CDs, and the setup process can be automated so that once Windows has finished installing, your chosen apps will also be installed and your chosen options and settigns will be put in place.
There’s no getting away from the fact that getting Windows Post-Install Wizard configured is a bit of a pain and something of a lengthy process, but this is a small price to pay for the time it will save you in the long run. This is not necessarily a tool that you’ll be able to pick and use straight away, but there is a fairly detailed manual included with the app that should help to get you up and running, and it’s worth spending some time reading through this. You’ll be glad you did as the next time you have to reinstall Windows, it will be done in a fraction of the time.
You can find out more and download a free copy of the app by paying a visit to the Windows Post-Install Wizard review page.
Photo Credit: AISPIX by Image Source/Shutterstock
-

SnapPea manages your Android device from Windows
Publié: octobre 12, 2012, 5:55pm CEST par Mark Wilson
Looking for a way to better manage the contents of your Android phone or tablet? SnapPea is a free tool, currently in beta, that could meet your needs. Regardless of whether your device was provided with its own management software, which is found wanting in the vast majority of cases, you can use the program to connect to your device to perform backups, transfer data and browse through images and other files.
You’ve probably found that keeping on top of your contacts on your phone can be a pain – with SnapPea you can take advantage of your computer’s mouse and keyboard to make changes, additions and backup more quickly and easily than ever before. Similarly, the program can also be used to browse through your text messages in a simple yet sleek interface, but more importantly it gives you the ability to send text messages from within Windows.
While many mobile phone operators provide a backup tool on various tariffs that can be used to safeguard contacts and other data, SnapPea provides you with a more hands-on option. The program can be used to automatically backup contacts, text messages and photos every time you connect your phone or tablet to your computer so there’s no need to worry about manually transferring data.
You can also use SnapPea to manage your app -- removing those you no long need, moving apps between internal storage and a memory card and even downloading new apps from Google Play and other stores. It’s also possible to mirror the display of your device on your PC monitor – useful for showing of photos on a larger screen – and take screenshots. This is a valuable tol even if only used as a backup utility, but there are plenty more options that make this well worth a look.
You can find out more and download a free copy of the app by paying a visit to the SnapPea review page.
-

Save big on these October software treats
Publié: octobre 11, 2012, 10:00pm CEST par Mark Wilson

September was crazy month for new software. Whether this was the rush to get new products on-sale before the Windows 8 launch or the traditional Q3 pre-Christmas release schedule, or a combination of both, you may have missed one of these important releases.
Creating PDF files used to be an incredibly expensive operation but this is no longer the case. Nitro Pro 8 is an advanced PDF creation and editing tool which is available at a 20-percent discount -- just $95.99. For a limited period of time, you can get the previous Nitro Pro 7 for only $59.99, saving 50 percent from MSRP. There are also multi-user versions of Nitro Pro 8, so you can buy for your business and save further.
Digital Content Creation
There are some great savings to be made on music creation and video editing software, with the latest versions of MAGIX software available at an impressive discount. MAGIX Music Maker 2013 could be yours for just $44.99 -- saving you 25 percent off the MSRP and bringing you the app’s all-new interface. Also from MAGIX, is the powerful video editor, MAGIX Movie Edit Pro 2013, available for $48.99, saving 30 percent from MSRP and receive a free bundled copy of Video Sound Cleaning Lab worth $59.99, for FREE!
MAGIX is not the only company with video editing software available; you’ll also find various titles from Cyberlink, such as PowerDirector 11 Deluxe, a professional level editing package that is available for $59.99, saving you 14 percent off the MSRP. If you want to take your video editing even further, there is also CyberLink PowerDirector 11 Ultra, which is available for 20 percent off the MSRP -- just $79.95. The next step up takes you to CyberLink PowerDirector 11 Ultimate, which, at 15 percent off, costs just $109.99.
For the most demanding of user, there is also the most feature-packed version -- CyberLink PowerDirector 11 Ultimate Suite. This edition includes ColorDirector and AudioDirector and could be your for just $219 -- 12 percent off the MSRP. There are also discounts available on upgrade versions of the software. CyberLink PowerDirector 11 Ultra UPGRADE costs just $53.99 -- or 10 percent off the MSRP -- while CyberLink PowerDirector 11 Ultimate UPGRADE costs $69.99, also saving you 10 percent . Exclusive to the Downloadcrew Software Store, PowerDirector 11 Ultra (or higher) is bundled with CyberLink MediaEspresso 6.5, worth $39.95, for FREE!
There are also a number of other programs available from Cyberlink that are not concerned with video editing. PhotoDirector 4 is the latest version of the impressive photo editing and organizational tool and you could own a copy for the bargain price of $89.99, representing a 10 percent saving off the MSRP. To help to you take control of colors within your videos, CyberLink ColorDirector 1.0 could be what you need. Replacing and adjusting colors is made easy in this tool which is available for $112.99 -- or 13 percent off the MSRP. Also available is Cyberlink AudioDirector 3 -- $112.99, or 13 percent off the MSRP -- and this can be used to work with your video soundtrack. If there are a number of Cyberlink products that you are interested in buying, you should take a look at Cyberlink Director Suite. This suite includes PowerDirector, PhotoDirector, ColorDirector, AudioDirector and more, and is available at a 13-percent discount for just $259.99.
PC Protection
In the store you’ll also find the latest 2013 versions of the most popular security tools, including AVG Anti-Virus 2013. This industry standard antivirus tool is available for the massively discounted price of $9.95 which saves you a colossal 75 percent off the MSRP. For a more complete security solution, take a look at AVG Internet Security 2013, which includes an added firewall, spam filter and more -- all for just $17.99 or a 67-percent discount. The most complete security package comes in the form of AVG Premium Security 2013 Complete Bundle, which includes four separate applications worth a total of $130 but you can buy the collection for a 69-percent discount for just $39.95.
Another discounted product from AVG is PC TuneUp 2013, which helps you to eek extra performance from your machine. This great utility costs as mere $12.99, or a saving of 68 percent off the MSRP. Returning to the security theme, BullGuard Internet Seurity 2013 can be used to protect up to three computer for just $19.95 -- saving you an impressive 67 percent. Virus protection is available from the same company in the form of BullGuard Antivirus 2013, and you can save 50 percent off the MSRP when you buy the software for $15. More security software is available at half price -- Avira Internet Security 2013 costs just $30, while the 3-PC version features an even better 56 percent saving at just $39.99.
Bringing this roundup to a close are a series of tools that enables you to protect and optimize your computer to keep things running smoothly, and as you would expect, these are all tool that are compatible with Windows 8. If you’re looking for a solid, reliable backup tool, look no further than True Image 2013 by Acronis, which costs just $37.49, saving your 25 percent from the MSRP. If you want to take care of your hard drive rather than just securing its contents, take a look at O&O Defrag 16 Professional, which costs just $23.95.
One final tool that we’d like to draw your attention to is TuneUp Utilities 2013, which enables you to boost the performance of your computer for just $22, saving you 55 percent off the MSRP.
Of course, all these recent new releases can be found in the Downloadcrew Software Store along with a host of other offers -- take a look and see what else you can find.
Photo Credit: Michael C. Gray/Shutterstock
-

Turn your tablet or phone into a second monitor
Publié: octobre 10, 2012, 4:01pm CEST par Mark Wilson
 If you use, or have ever used, a multi-monitor computer, you’ll know just how useful a setup it can be. Have the extra space afforded you by double the usual number of monitor enables you to see more at once, work more quickly and be more productive -- but it can also be expensive and requires you to have a desk large enough to hold two monitors comfortably. If you have a mobile device, however, you can use iDisplay to gain an extra monitor from your existing hardware.
If you use, or have ever used, a multi-monitor computer, you’ll know just how useful a setup it can be. Have the extra space afforded you by double the usual number of monitor enables you to see more at once, work more quickly and be more productive -- but it can also be expensive and requires you to have a desk large enough to hold two monitors comfortably. If you have a mobile device, however, you can use iDisplay to gain an extra monitor from your existing hardware.The name of the software might imply that this is something that will only be of interest to Apple hardware owners, but in fact it can be used in conjunction with an iOS or Android phone or tablet. Your mobile device does no need to be physically connected to your computer -- the desktop version of the client software is available for both Mac and PC -- which opens up new opportunities.
This is an app that would seem to be more useful for tablet owners, particularly when used in conjunction with a vertical stand, but there is a also great scope for using with a phone. While the smaller screen of a phone means that you’re unlikely to want to use it to display complex spreadsheets from your desktop computer, it can be used to house program panels and controls to help free up space -- for example, in an image editor, you could move some of the controls to your phone’s screen to gain a larger work area on your monitor.
If you ever find yourself needing to give a presentation, iDisplay can also be used in mirror mode. This means that you can share the display of your PC or Mac with a number of iOS or Android devices so your audience can get a great view of whatever you are doing. When used In regular mode, you can easily switch between portrait and landscspe mode, and app can bemoved between displays with a quick shortcut.
You can find out more by paying a visit to the iDisplay review pages – iDisplay for PC, iDisplay for Mac, iDisplay for iOS and iDisplay for Android.
Photo Credit: CLIPAREA l Custom media/Shutterstock
-

LibreOffice 3.6.2 stomps bugs dead
Publié: octobre 4, 2012, 5:34pm CEST par Mark Wilson
 With more and more computer users counting the pennies, the move to lower cost and free software gains momentum. Microsoft Office may still be the world’s most popular office suite, but there is a growing user base that has turned to one of the free alternatives that have been gathering strength in recent years. LibreOffice is one such suite, and the latest version addresses a series of known bugs and helps to improve stability.
With more and more computer users counting the pennies, the move to lower cost and free software gains momentum. Microsoft Office may still be the world’s most popular office suite, but there is a growing user base that has turned to one of the free alternatives that have been gathering strength in recent years. LibreOffice is one such suite, and the latest version addresses a series of known bugs and helps to improve stability.Although there are no major new features or options to be found in LibreOffice 3.6.2 – this crown was taken by the 3.6 release -- there have been improvements in a number of areas which increase the overall stability of the program and make it a piece of software that more businesses are likely to look to as a free office suite. 3.6.2 includes bug fixes for both the Windows and OS X versions of the suite.
Among the changes are several crashes fixes in different areas of the suite, and correctly an error with older versions of the Javas Runtime Environment. Problems with saving and opening files in different formats have been address, as have issues with the word count and PDF creation features.
Other fixes include changes to the way footnotes are displayed when the mouse is hovered over them -- they are now shown on a single line for ease of reading -- as well as addressing a problem that caused LibreOffice to crash when opening Lotus 123 files. Additional spreadsheet related fixes include changes to the pasting of data between cells and various issues that had been found with pivot tables.
You can find out more and download a free copy of the program by paying a visit to the LibreOffice review page.
Photo Credit: ARENA Creative/Shutterstock
-

Dropbox 1.5.34 experimental previews new menu, Retina Display support
Publié: septembre 26, 2012, 4:22pm CEST par Mark Wilson
 The desktop client for the ever-popular cloud storage service Dropbox has been updated with a new experimental build. There are a number of new features to explore in this latest release, but the most obvious is the newly redesigned menu. This is a neater affair than in previous versions, providing an overview of the latest activity as well as access to additional options.
The desktop client for the ever-popular cloud storage service Dropbox has been updated with a new experimental build. There are a number of new features to explore in this latest release, but the most obvious is the newly redesigned menu. This is a neater affair than in previous versions, providing an overview of the latest activity as well as access to additional options.These extra features include pausing files transfers, as well as sharing and restoring files. The new menu is only available to OS X and Windows users -- anyone running Linux misses out for the time being -- and Mac users also benefit from new Retina Display support as well as a new batch of great-looking icons.
Other changes in this latest experimental build also include a number of other changes that are pertinent to Mac owners. In addition to Retina Display support, there is now also support for Mountain Lion’s Notification Center and the use of Python 2.7 means that performance has been improved; there are also faster startup times for anyone working with a large number of files in their sync folders.
The Windows version of the client benefits from a range of fixes including problems with the tray icon and camera uploads in Windows 8. Many of these new features and changes will eventually find their way in to the official, stable version of the software, but for now they are only available anyone willing to test the waters of the experimental release.
You can find out more and download a free copy of the app by paying a visit to the Dropbox Experimental Edition v1.5.34 review page.
Photo Credit: RAJ CREATIONZS/Shutterstock
-

BullGuard Internet Security 2013 gets new look, improves detection
Publié: septembre 21, 2012, 6:18pm CEST par Mark Wilson
 BullGuard Internet Security 2013, the latest version of its online security suite, is now available. Comprising antivirus, firewall, spam filter, parental controls and more, the suite aims to cover more than most other comparable tools and the latest version features a dramatically redesigned interface which is cleaner and sharper than in previous versions, making it easier focus on the task in hand.
BullGuard Internet Security 2013, the latest version of its online security suite, is now available. Comprising antivirus, firewall, spam filter, parental controls and more, the suite aims to cover more than most other comparable tools and the latest version features a dramatically redesigned interface which is cleaner and sharper than in previous versions, making it easier focus on the task in hand.Virus detection rates are improved with the addition of Behavioural Detection, which helps to identify unknown threats by monitoring activity and helps to bolster the regular signature based scanning. Security is further enhanced by the inclusion of a firewall and spam filter, but this is a security suite that bills itself as a tool that not only makes your PC impenetrable, but also provides a number of associated utilities.
In addition to the standard security tools, the suite also includes 5GB of free online storage -- this is a suite that goes far beyond the basics. While protection is certainly the main focus of the suite, the inclusion of a Tune Up section that can be used to free up disk space and optimize performance, along with a Parental Control tools means that it also caters for other needs as well.
Although it is only something you will do once, the installation process is unnecessarily convoluted. The initial download is deceptively small and it transpires that this is just a setup tool for the online installer. Despite the fact that the installer then goes online to download the very latest version of the program, once this is installed there is another wait while updates are downloaded -- this is something that could be avoided by simply ensuring that the ‘latest’ version of the installer has the most recent definitions built in.
You can find out more and download a free 60 day trial of the program by paying a visit to theBullGuard Internet Security 2013 review page.
-

HDClone 4.2 Free supports Windows 8
Publié: septembre 20, 2012, 4:27pm CEST par Mark Wilson
 The release of a new operating system often means that there is renewed interest in migration and backup tools and this is certainly the case with the imminent release of Windows 8. Hard drive cloning tool HDClone 4.2 Free is the latest app to be updated with support for the latest version of Microsoft’s OS, and there are a number of other improvements that have been made to this utility.
The release of a new operating system often means that there is renewed interest in migration and backup tools and this is certainly the case with the imminent release of Windows 8. Hard drive cloning tool HDClone 4.2 Free is the latest app to be updated with support for the latest version of Microsoft’s OS, and there are a number of other improvements that have been made to this utility.While the free version of the program is more limited than its big brothers -- there are also Basic, Standard, Professional and Enterprise editions available for anyone whose needs are a little more demanding -- there’s still enough here to cater for most people’s requirements.
Speed improvements that allows for data to be copied at up to 30 MB/sec mean that cloning can be achieve faster than in previous versions of the program. There are also two important new additions that help to ensure support for as wide a range of hard drive technologies as possible. The first new feature of the free version of HDClone is full support for GPT.
There is also the added option of booting from UEFI BIOSes for anyone working with hardware that support this technology. Despite these changes and additions, you’re still limited to working with ATA, SATA or USB drives as there is no support for SCSI, Fireware or even USB 3.0 drives.
You can find out more and download a free copy of the program by paying a visit to the HDClone 4.2 Free review page.
Photo Credit: Sergey Mironov/Shutterstock
-

Ashampoo UnInstaller 5 cleans better than ever
Publié: septembre 19, 2012, 6:14pm CEST par Mark Wilson
 Removing unwanted software from your hard drive should be easy, but there are countless reasons why the process may prove problematic -- even if this just boils down to a badly written uninstaller. This is the very reason there are so many dedicated software uninstaller tools available, and one of the biggest names in the field is Ashampoo. The company has just released Ashampoo UnInstaller 5, which expands on its predecessor by improving the removal of apps that are no longer required.
Removing unwanted software from your hard drive should be easy, but there are countless reasons why the process may prove problematic -- even if this just boils down to a badly written uninstaller. This is the very reason there are so many dedicated software uninstaller tools available, and one of the biggest names in the field is Ashampoo. The company has just released Ashampoo UnInstaller 5, which expands on its predecessor by improving the removal of apps that are no longer required.While the program can be used to uninstall any program on your hard drive, it works best when used to remove those that have been installed after Ashampoo UnInstaller 5 itself. The latest version of the software includes an improved installation monitor which checks precisely what changes an installed program makes to your computer so they can be easily reversed when the time comes to remove it.
But even in the case of previously installed software, UnInstaller can monitor the uninstallation and check for leftover files and registry entries to help clean things up for you. This latest version also sees the addition of a number of general maintenance tools, which are not necessarily a reason to buy the program but are a nice extra. Tools available include a drive cleaner, defragmenter, files eraser and more.
Slightly ironically, the initial installation of the program also tries to lever in a browser toolbar -- a prime candidate for uninstallation on most people’s computers. Thankfully, the toolbar is optional but it is selected for installation by default, which is a little disappointing.
You can find out more and download a free trial of the program by paying a visit to the Ashampoo UnInstaller 5 review page.
Photo Credit: Goydenko Tatiana/Shutterstock
-

Emsisoft Anti-Malware 7 boasts two scanning engines
Publié: septembre 19, 2012, 3:12pm CEST par Mark Wilson
 The threat from viruses and malware is one that not only continues, but shows no signs of slowly down. The need for protective software has not gone away, and what could be better than install an anti-malware tool to help keep yourself safe? How about a security tool that boasts not one but two scanning engines? Take a look at Emsisoft Anti-Malware 7 -- in addition to Emsisoft’s own malware scanner, there is now a new second scanning engine from BitDefender.
The threat from viruses and malware is one that not only continues, but shows no signs of slowly down. The need for protective software has not gone away, and what could be better than install an anti-malware tool to help keep yourself safe? How about a security tool that boasts not one but two scanning engines? Take a look at Emsisoft Anti-Malware 7 -- in addition to Emsisoft’s own malware scanner, there is now a new second scanning engine from BitDefender.There is a strong focus on performance with this release. Emsisoft has optimized its own scanning engine, and new settings have been added that enable users to configure how the software should make use of processors. What this amounts to is being able to choose how many cores should be used to run the scanner as well as increasing or decreasing the number of active threads, increasing program priority and making use of advanced caching techniques to help speed things up.
Emsisoft aims to ensure that users are protected against threats as soon as possible by offering hourly updates. While definition updates tend to be fairly small anyway, this is being billed as a way of speeding up protection by breaking down updates into smaller incremental downloads. As is now the norm, there is an online network through which users statistics are shared to allow for better malware definitions and advice to be provided.
Experienced users will know very much what to expect from the program, but newcomers are politely guided through the process of checking for and fixing problems and then activating the settings that will provide on-going protection against malware, malicious web sites and even unknown threats.
You can find out more and download a free trial of the program by paying a visit to the Emsisoft Anti-Malware 7 review page.
Photo Credit: njaj/Shutterstock
-

Make September a time to remember with these software sales
Publié: septembre 19, 2012, 1:33am CEST par Mark Wilson
 Everyone loves to save a little money here and there, but when the timely bargains result in an alliteratively name month -- September savings -- so much the better!
Everyone loves to save a little money here and there, but when the timely bargains result in an alliteratively name month -- September savings -- so much the better!Brand new to the store this month is the much-anticipated TuneUp Utilities 2013. You can save 50 percent from TuneUp Utilities 2013 [3-PC], ideal for installing on three home computers. If you have a single PC, save even more with TuneUp Utilities 2013 [1-PC]. There is also TuneUp Utilities 2013 [UPGRADE] designed to enable previous users to upgrade, at a discount. Finally, a TuneUp Utilities 2013 + AVG Internet Security 2013 [1-PC] bundle will safeguard and maintain a single computer.
A well respected name in the security world is AVG and you’ll find a great selection of tools in the store at great prices. Again, these are the latest tools from the 2013 range, starting off with AVG Internet Security 2013 Complete Bundle, an exclusive bundle of tools (AVG Internet Security 2013, AVG PC TuneUp 2013, AVG Family Safety and AVG Mobilation Pro) which could be yours for just $49.95 -- a massive saving of 66 percent off the MSRP. In a similar vein is AVG Premium Security 2013 Complete Bundle, which also includes four AVG products -- AVG Premium Security 2013, AVG PC Tuneup 2013, AVG Family Safety and AVG Mobilation Pro [four AVG products] -- and is available as an exclusive bundle at the discounted price of $39.95, as 69-percent saving. AVG is famed for is virus protection software and the latest version of its flagship product is AVG Anti-Virus 2013 [1-PC, 1-Year], which keeps you PC free from unwanted malware at a 75-percent discount -- just $9.95. We’ve already mentions a couple of bundles that include AVG’s Security suites, but these are also available separately.
AVG Internet Security 2013 [1-PC, 1-Year] is available for just $17.99 -- saving you 67 percent -- while AVG Premium Security 2013 [1-PC, 1-Year] offers additional security options for the slightly higher price of $22.99 -- this is another saving of 67 percent off the MSRP. Demonstrating that AVG is not just a one-trick pony, AVG PC TuneUp 2013 [1-PC, 1-Year] is all you need to keep boost the performance of your computer for just $17.99 (a saving of 55 percent off the MSRP), but for just a little more, you could optimize three separate computers with AVG PC TuneUp 2013 [3-PC, 1-Year] -- just $19.99 and a 67-percent saving. Whichever AVG tool you go for, you not only get the benefit of the very latest levels of protection, but also a thoroughly modern look inspired by the Windows 8 interface.
More security software is available from Bitdefender; again, there is a brand new 2013 range of titles. There’s a saving of 71 percent off Bitdefender Total Security 2013 [1-PC, 1-Year] which includes a strong antivirus engine, intelligent two-way firewall, capable spam filter -- all for just $19.99. If you want to keep your computer safe for even less, look no further than Bitdefender Internet Security 2013 [1-PC, 1-Year], which still packs a punch for just $14.99 saving you 70 percent off the MSRP.
Many homes have more than one computer and keeping them all protected can get expensive. However, if you invest in Bitdefender Internet Security 2013 [3-PC, 1-Year] can be used to ensure the safety of three PCs for just $29.95. Every computer should have at least an antivirus tool installed, and it’s hard to find something that’s better value than Bitdefender Antivirus Plus 2013 [1-PC, 1-Year] which costs just $6.95 with a reduction of 83 percent. You can save a fortune protecting all of the computes in your home with 74% off Bitdefender Antivirus Plus 2013 [3-PC, 1-Year] -- a mere $12.95 to protect up to three computers.
If you like the idea of getting musically creative but you’re not sure quite where to start, MAGIX Music Maker 2013 is the latest version of the instantly accessible music tool. With hundreds of samples and loops to work with and the ability to create projects with up to 99 tracks, there is great flexibility in a wonderfully easy to use program that could be yours for a 25 percent at just $44.99. Also from MAGIX is the video editing software MAGIX Movie Edit Pro MX. For just $45.99 -- a saving of 34 percent -- you can gain access to everything you need to edit and optimize your home videos ready for sharing with others.
MAGIX Movie Edit Pro MX Plus is also available for anyone looking to take things to the next level. There’s a 30 percent saving off the MSRP giving you access to extra special effects, additional tracks and much more for just $69.99. If you buy CyberLink Media Suite 10 Ultra for just $99.95 -- saving you 23 percent -- you can get a copy of PowerDirector 10 Ultra, for FREE! There’s another top deal to be found in the form of Xara Photo & Graphic Designer 2013. With 44 percent off the MSRP, this great tool which is a cross between an image editor, DTP package and an illustration app, could be yours for just $49.99.
Finishing off this selection of the latest and greatest offers are two tools from O&O, both of which place you in control of your hard drive. O&O DiskImage 6 Professional is an amazing backup and cloning tool that you can own for just $14.50 -- half the recommended price -- while O&O Defrag 15 Professional is also available at a 50-percent discount, also just $14.50.
Of course there are plenty of other special offers for you to take advantage of, so head over to the Downloadcrew Software Store to see what you could be tempted by.
-

Oracle VirtualBox 4.2 improves VM management
Publié: septembre 13, 2012, 6:32pm CEST par Mark Wilson

Oracle has released a major update to VirtualBox taking it up to version 4.2. The virtualization software is available for Windows, Linux and OS X, and now includes a new VM Group features that makes it easier to manage related virtual machines by organizing them together in groups. Users are able to utilize several virtual machines simultaneously either through the GUI, using various APIs or through command line tools.
VirtualBox 4.2 has a number of improvements to networking components, starting with increasingly the maximum supported number of network cards for a virtual machine from eight to 36. This is not the only improvement that has been made to networking as it is now also possible to place limits on network usage by any virtual machine. If a network is being used for other things, this traffic shaping is a valuable way to prevent unwanted slow-down in other areas.
Other networking improvements see the introduction of support for VLAN tagging, allowing for more flexibility in real and virtual network environments. The latest version of the open-source virtualization software now includes a range of new startup options that can be used to automate the launch virtual machine on a host device. Virtual machines can be configured to start automatically with a host device allowing for unattended launching of virtual environments.
The relatively recent release of Mountain Lion and the upcoming release of Windows 8 means that the inclusion of support for these latest operating system should come as no surprise, and there is also support for Oracle Linux 6.3
You can find out more and download a free copy of the program by paying a visit to the VirtualBox 4.2 review page.
Photo Credit: Angela Waye/Shutterstock
-

Opera 12 beta RC supports Retina Display
Publié: septembre 13, 2012, 1:39pm CEST par Mark Wilson
 Retina Display support continues to be added to more and more applications as they are updated, and the latest update is for Opera 12.10 beta. This is one of the headline features of the latest build, but there are also a range of bug fixes as well as an update core – although it should be noted that this is a beta release.
Retina Display support continues to be added to more and more applications as they are updated, and the latest update is for Opera 12.10 beta. This is one of the headline features of the latest build, but there are also a range of bug fixes as well as an update core – although it should be noted that this is a beta release.The addition of Retina Display support helps to improve the appearance of web pages, particularly for text. Graphics, on the other hand, will appear slightly blurry unless the page administrator has taken the step of using double resolution images. The interface of the browser has also be updated with a new skin which includes new higher resolution icons.
Updates to the libvpx library help to improve the performance of WebM videos but the majority of other changes are minor bug fixes. There is a somewhat strange change to version numbering which means that Opera has moved from ’12.50 internal’ to ’12.10 beta RC’ – this has the knock-on effect of meaning that automatic updating from Opera Next to 12.10 is not possible, but a manual install over the top is not a problem.
You can find out more and download and free copy of the program by paying a visit to the Opera 12.10 review page. There’s also a separate dedicated 64-bit build.
-

ViStart 8 gives back what Microsoft took from Windows
Publié: septembre 11, 2012, 1:37pm CEST par Mark Wilson
 If you have tried out any of the preview releases of Windows 8, you may well have joined the thousands of users who are mourning the loss of the Start menu. Microsoft’s decision to drop this staple element of Windows has caused frustration, confusion and disbelief in equal measure, but with the help of ViStart 8, you can bring back an old favorite to Windows 8, but there’s also a lot to look forward to if you have an older version of Windows.
If you have tried out any of the preview releases of Windows 8, you may well have joined the thousands of users who are mourning the loss of the Start menu. Microsoft’s decision to drop this staple element of Windows has caused frustration, confusion and disbelief in equal measure, but with the help of ViStart 8, you can bring back an old favorite to Windows 8, but there’s also a lot to look forward to if you have an older version of Windows.One of ViStart 8 key selling points -- although the app is actually free -- is that it supports skins. These provide you with a quick and easy way to completely transform the look of the Start menu. You may think that the program has done very little when you first install and run it in Windows XP, Vista or 7, but as you explore the range of skins that are available, you’ll discover that there are varying layouts to choose from.
While ViStart 8 can be used in all versions from Windows from XP upwards, the fact that it can be used to bring the Start menu back to Windows 8 is likely to be welcomed by most people. If you want to get the best of both worlds, it is possible to install a Metro-style (although obviously we don’t use that word any more…) skin to create a fusion between the Windows of today and tomorrow.
Skinning and Windows 8 support may be the biggest news here, but there’s also fast file searching from the Start menu, instant shortcut indexing, and system tray access to various shutdown options. Take care during the installation as there are a couple of potentially unwanted extras bundled with the app. Just remember that you can click the Decline button to avoid installing them without affecting the installation of the main program.
You can find out more about the software and download yourself a free copuy by paying as visit to the ViStart 8 review page.
-

Get Aero on Windows 8
Publié: septembre 7, 2012, 5:11pm CEST par Mark Wilson
 Hot on the heels of the RTM version of Windows 8, a swathe of tools that can be used to either emulate the appearance and features of the latest version of the operating system, or tweak Windows 8, have emerged. Windows 8 Transformation Pack 6.0 and Windows 8 UX Pack 6.0 both fall into the former camp. Something that has annoyed many long-term users: Microsoft dropped Aero from the latest release -- with these tools you can regain it.
Hot on the heels of the RTM version of Windows 8, a swathe of tools that can be used to either emulate the appearance and features of the latest version of the operating system, or tweak Windows 8, have emerged. Windows 8 Transformation Pack 6.0 and Windows 8 UX Pack 6.0 both fall into the former camp. Something that has annoyed many long-term users: Microsoft dropped Aero from the latest release -- with these tools you can regain it.Now that the final release version of Windows 8 has been unveiled, many of the changes that have been are fairly minor updates that bring this duo of tweaking tools in line with the very latest code. In the Transformation Pack this means that wallpapers from the RTM version of Windows 8 are now available, and changes have been made to the use of the Segoe font family for better compatibility. Elsewehere you’ll find the very latest icons, buttons, boot screen and more, so you can get the full Windows 8 look.
Although Aero has been officially dropped from Windows 8, with the transformation pack you can bring it back. Version 6 of the tool sees the Metro Desktop UI and Aero’s auto-colorization being used by default. Things have also been updated in the UX pack. Again there are changes that bring the Windows 8 emulator more in line with the release version of the operating system, but there have also been problems fixed.
The program launcher will no longer ask for administrative rights every time it is started, and the Start orb has been updated to give it a better look and feel. For a fully immersive Windows 8 experience, the Charms Bar is now available as well.
You can find out more and download free copies of the programs by paying a visit to the Windows 8 Transformation Pack 6.0 and Windows 8 UX Pack 6.0 review pages.
-

Tweak your PC with Puran Utilities
Publié: septembre 5, 2012, 3:30pm CEST par Mark Wilson
 Just how involved would you like to be with the process of cleaning up and maintaining your computer? If you’re reading this, there’s a fairly high chance that you like to get pretty hands on, but there will still be occasions when time is short and you need a quick-and-easily solution to get the job done quickly. Puran Utilities is a free utility suite that has both bases covered with an impressive selection of more than 20 tools that you can use individual or in combination with each other.
Just how involved would you like to be with the process of cleaning up and maintaining your computer? If you’re reading this, there’s a fairly high chance that you like to get pretty hands on, but there will still be occasions when time is short and you need a quick-and-easily solution to get the job done quickly. Puran Utilities is a free utility suite that has both bases covered with an impressive selection of more than 20 tools that you can use individual or in combination with each other.These tools cover everything from check your hard drives and registry for problems, removing unnecessary software, rendering deleted files unrecoverable and much more. Many of the optoins available may sound like tools that are already built into Windows, but this is not the case for all of them. Windows has lacked a file wiping tool for years, and a registry cleaner is similarly noticeable by its absence, but even if you view Puran Utilities as a repository of simple tools, it is useful to have everything available in one place.
The Gaming PC and Minimal PC shortcuts make it possible to create and switch between different system profiles so you can ensure that maximum system resources are available when you need them the most – such as when you are planning to play games. But the main focus of Puran Utilities is performance and maintenance and this is something made available to everyone thanks to the wizard that will guide less confident users through a simple step by step performance improvement regime.
Each of these utilities can be used on their own whenever you need them, but for on-going maintenance, the automated option may be of interest. Here you can opt to run a number of tools on a regular schedule with a view to avoiding problems and maintaining performance. The range of options available here may not be exhaustive, but there is more than enough here to rival similar apps that have a price tag attached to them.
You can find out more and download a free copy of the app by paying a visit to the Puran Utilities review page.
Photo Credit: zimmytws/Shutterstock
-

BBC iPlayer for iOS now downloads TV shows
Publié: septembre 4, 2012, 9:05pm CEST par Mark Wilson
iPhone, iPod and iPad users who take advantage of the streaming capabilities the BBC’s iPlayer app now have a new feature to play with -- the ability to download programs and store them on your phone or tablet for up to a month. This is a move that will be welcomed by travellers as it opens up the chance of downloading a batch of programs at home over a Wi-Fi connection to avoid racking up expensive data usage bills while away from home.
There is promise of an Android version of the updated app in the pipeline, but for the time being this is something that can only be enjoyed by iOS users. The newly added offline mode is a great addition to the app, which had already been updated to allow for programs to be streamed over a data connections as well as when connected to Wi-Fi. While the change is undoubtedly beneficial, it does come with limitations.
These should come as no surprise to anyone who has downloaded programming content from the BBC before. Once you have downloaded a particular viewed, it is yours to keep for 30 days. However, once you start watching it you then have just seven days to work through it. These far from hamper the usefulness of the app but there is the somewhat peculiar fact that while TV programs can be downloaded for offline playing, the same is not true of radio shows.
The actual process of downloading is very simple. You can browse through the available programming in the usual way and tap the Download button that is now to be found adorning the pages of individual shows. This will add the currently selected program to the download queue and the download will take place as soon as you are connected to a wifi network.
You can find out more and download a free copy of the app by paying a visit to the BBC iPlayer review page.
-

Three tools to tame Windows 8
Publié: septembre 1, 2012, 5:58pm CEST par Mark Wilson
 Users of Windows are known not only for their love of tweaking, but also for their love of knocking the product they use -- how many people who use nothing but Windows do nothing but complain about the way it looks or works? The release of a new version might be seen as a time for Microsoft to address the issues and annoyances that have plagued their customers, but for many upgraders, the switch to Windows 8 brings a new batch of things to get irritated about.
Users of Windows are known not only for their love of tweaking, but also for their love of knocking the product they use -- how many people who use nothing but Windows do nothing but complain about the way it looks or works? The release of a new version might be seen as a time for Microsoft to address the issues and annoyances that have plagued their customers, but for many upgraders, the switch to Windows 8 brings a new batch of things to get irritated about.While some of the new irritants are fairly major, such as the relegation of the Start menu, other more cosmetic issues are something that can be more easily addressed through the use of third party tools. Winaero produces a collection of tools designed with tweakers in mind, specifically those who are running Windows 8. If you’re the kind of person who tires of their desktop wallpapers quickly, Desktop Background Tuner provides you with a means of customizing the rotation of a series of images to help keep things interesting.
This is a very simple tool, but gets the job done very effectively, and the same can be said of Aero8Tuner. As the name suggests, this is a tool that enables you to tweak the Aero settings that are used by Windows 8 so you can adjust the overall hue of windows as well as enable High Contrast mode if you have trouble viewing different con-screen elements.
One final tool from the same stables is Tiny Windows Borders for Windows 8, and this makes it possible to tame the size of window border which many users have found to be excessive. Just like the previous tool, this can be used without the need for installation an d it enables you make changes to registry settings without having to directly edit the registry yourself. Just use a simple slider system to reduce the size of borders, or increase it if you feel so inclined, and you’re done.
You can find out more and download free copies of these handy utilities by visiting the Desktop Background Tuner, Tiny Windows Borders for Windows 8 and Aero8Tuner review pages.
-

Troubleshoot your PC with Power Eraser 3.1 and Bootable Recovery Tool 5.1
Publié: août 29, 2012, 4:30pm CEST par Mark Wilson
 With effective antivirus software installed, you can protect yourself against a range of online threats such as viruses, spyware and other malware. But there are some forms of malicious software that manage to evade detection by even the newest and completely updated protection tools. In this situation, you may feel as though there is nothing left to do but to format your hard drive and start from scratch, but Norton Power Eraser 3.1 and Norton Bootable Recovery Tool 5.1, both updated yesterday, prove otherwise.
With effective antivirus software installed, you can protect yourself against a range of online threats such as viruses, spyware and other malware. But there are some forms of malicious software that manage to evade detection by even the newest and completely updated protection tools. In this situation, you may feel as though there is nothing left to do but to format your hard drive and start from scratch, but Norton Power Eraser 3.1 and Norton Bootable Recovery Tool 5.1, both updated yesterday, prove otherwise.You may have noticed popup windows that you do not seem to be able to eliminate, but there could be countless other symptoms indicating that something is wrong with your computer. But before you reach for the installation disc for Windows, grab yourself a copy of the latest version of Norton Power Eraser, which can be used to scour your hard drive for instances of malware that may not otherwise be detected.
Once the scan is complete, you’ll be invited to remove anything that is thought to be suspicious. The tool’s approach is rather aggressive and you may well find that there are a few false positives flagged up, but these can be reversed if problems arise. Should you find that Norton Power Eraser has not be successful in cleaning up your computer, all is still not yet lost as you can try your luck with the newly updated Norton Bootable Recovery Tool.
This is a free tool for anyone who has another registered Norton product, and it is designed to help in situations when a malware infection means that the usual scanners do not run correctly. The tool can be run from CD, DVD or USB drive and is ideal if you are not able to boot into Windows. You’ll be guided through every stage of the process of booting your computer in a safe state before scanning and cleaning up any infections that exist.
You can find out more and download the software by paying a visit to the Norton Power Eraser 3.1 and Norton Bootable Recovery Tool 5.1 review pages.
Photo Credit: zimmytws/Shutterstock
-

Chrome for iOS adds Facebook, Google+ sharing
Publié: août 23, 2012, 12:29pm CEST par Mark Wilson
 Just like Firefox, Chrome rockets through version numbers as though it is going out of fashion. Although Google’s foray into the world of web browsers for iPhone and iPad is fairly recent, Chrome for iOS already is version 21. The latest release is a relatively minor one, but there is still one feature that brings the browser in line with other more socially aware apps.
Just like Firefox, Chrome rockets through version numbers as though it is going out of fashion. Although Google’s foray into the world of web browsers for iPhone and iPad is fairly recent, Chrome for iOS already is version 21. The latest release is a relatively minor one, but there is still one feature that brings the browser in line with other more socially aware apps.The big news in this release: addition of new sharing options. Found a website that you think your friends will love? There is no need to copy and paste the URL into an email as there are now new sharing options built directly into the app. A new popup menu lets you share pages through Google+, Facebook, Twitter or via email.
While this may seem like a fairly inconsequential addition to the app, it makes sharing much quicker and easier. Other changes sees problems with blank pages appearing in Incognito mode addressed and other issues that have been reported by users have also been fixed.
Other changes that have been made to the app are mostly bug fixes and performance improvements. Problems with sync sign in are now accompanied by ‘more actionable’ error messages and problems with language detection during the welcome tour have also been addressed.
You can find out more and download a free copy of the app by paying as visit to the Chrome for iOS review page.
-

Benchmarking tool AIDA64 now supports Windows 8
Publié: août 22, 2012, 5:42pm CEST par Mark Wilson
 Want to know the specifications of a computer? You could look at the manufacturer’s website, but you’ll probably find that there is a limit to the level of detail provided. Similarly, if you want to know how fast your machine is, there is little point relying on figures quoted by the manufacturer, if you want to know how it performs in the scenarios you are using it in. AIDA64 is one of the most advanced benchmarking and diagnostic tools available and the release of version 2.60 sees the addition of support for Windows 8 as well as the latest hardware.
Want to know the specifications of a computer? You could look at the manufacturer’s website, but you’ll probably find that there is a limit to the level of detail provided. Similarly, if you want to know how fast your machine is, there is little point relying on figures quoted by the manufacturer, if you want to know how it performs in the scenarios you are using it in. AIDA64 is one of the most advanced benchmarking and diagnostic tools available and the release of version 2.60 sees the addition of support for Windows 8 as well as the latest hardware.Benchmarks are a great way to see how one system compares to another, and they also provide a means of checking exactly what difference, if any, tweaks and hardware upgrades make to the performance of your computer. There is support for a massive range of hardware, so whether you are using an aging machine, or something more cutting edge, you should be able to find out everything you need to know.
The latest update adds support for not only for the RTM version of Windows 8 and Windows Server 2012 but also additional hardware -- after all, hardware is the focus of the application. Benchmarks optimized for VIA Nano X2 and QuadCore processors have been added, including the VIA VX11 platform. AMD A-Series Trinity APUs are now also supported meaning that there are specific benchmarks for this hardware as well as all of the detailed specifications you could ever need.
The August update to the software means that the program is now able to provide GPGPU information for Direct3D Compute Shader, AMD Stream, nVIDIA CUDA, and OpenCL devices, now with APP SDK 2.7, CUDA 5.0 and OpenCL 1.2 updates. Various other hardware models have been added to the list of supported devices, and there have also been fixes to RAID member enumeration and RAID SMART support for Intel RAID controllers.
You can find out more and download a free trial of the program by paying a visit to the AIDA64 review page.
Photo Credit: Dudarev Mikhail/Shutterstock
-

Norton Mobile Utilities Lite for Android packs premium, paid upgrade
Publié: août 22, 2012, 3:41pm CEST par Mark Wilson
 Symantec is a company with many strings to its bow but is most often associated with security software. Those with long memories will remember Norton Utilities, a tweaking tool for Windows that Symantec bought. The Norton name lives on and Norton Mobile Utilities revives the Utilities genre for Android users. The tool is designed to help your Android device more efficiently, and the release of version 2.0 of the app sees it splitting into two branches -- free, and paid-for premium versions.
Symantec is a company with many strings to its bow but is most often associated with security software. Those with long memories will remember Norton Utilities, a tweaking tool for Windows that Symantec bought. The Norton name lives on and Norton Mobile Utilities revives the Utilities genre for Android users. The tool is designed to help your Android device more efficiently, and the release of version 2.0 of the app sees it splitting into two branches -- free, and paid-for premium versions.The free version of the app, now referred to as Norton Mobile Utilities Lite, gives users greater control over memory usage, making it easy to terminate apps to free up resources. There are a number of informational components to the app, and these will tell you everything from how much battery life you have left, details of the hardware you are using and how much storage space you have available.
While it may be interesting to know the speed of your phone’s CPU, there are also more useful options available in the app. You can monitor your data usage and configure alerts that will sound when you reach a particular level to help you avoid receiving a hefty bill from your service provider. There are also many options that are really just duplicates of those already available in Android, such as freeing up space by uninstalling apps or moving them to your memory card, but these options are now available in one place and tied together with a neat user interface.
If you expect the tweaking options that were available in the old Windows version of Norton Utilities, you’re going to be somewhat disappointed. By upgrading to the full version of the app for $9.99, you gain access to features such as automatic battery profiles. It is also possible to configure automatic resource management so that running apps are terminated on a schedule to help keep things running smoothly.
You can find out more and download a free copy of the app by paying a visit to the Norton Mobile Utilities review page.
-

Sizester gets photos just right for sharing
Publié: août 21, 2012, 1:26am CEST par Mark Wilson
 Before you share images via email, Facebook, or some other online means, the chances are that you have to spend time resizing them. This may be to overcome size restrictions (in the case of email attachments) or to reduce upload time (when you are sharing via social networks). Sizester is a great low-cost tool that lets you resize and share from the same place, helping you to get your images online faster than ever.
Before you share images via email, Facebook, or some other online means, the chances are that you have to spend time resizing them. This may be to overcome size restrictions (in the case of email attachments) or to reduce upload time (when you are sharing via social networks). Sizester is a great low-cost tool that lets you resize and share from the same place, helping you to get your images online faster than ever.This is a small app that loads and operates incredibly quickly, making it a far cry from slow and cumbersome image editors that you may be used to. While it’s not free of charge, the asking price is very low and the ease with which it enables you to get your images online more than makes it worthwhile. It includes just the features you need to get the job done so you are not overwhelmed with unnecessary options.
You can work with images on an individual basis, or in batches, and there are couple of ways in which you can reduce the size of your pictures. Resizing can be achieved by using a slider to choose from one of ten pre-defined size, or you can shrink images based on percentages. You can also specify an exact height or width of image you would like, and you can then use a slider to choose an image quality. You can also crop images with a couple of clicks.
If you change your mind about the settings you have chosen by looking at the preview, there is an multi-level undo feature available. The Upload button beneath the preview window gives you instant access to a number of social networks, such as Twitter and Facebook as well as image services like Flickr and Smugmug. You can also send the resized images as email attachments from within the app, and save them as new files so you can use them in other projects.
You can find out more and download a free trial of the program by paying a visit to the Sizester review page.
Photo Credit: Alberto Zornetta/Shutterstock
-

Sky+ 4 turns your iPad into a TV remote
Publié: août 16, 2012, 9:53am CEST par Mark Wilson
When you’re watching TV the remote control seems to have a life of its own, often resulting in it disappearing when you decide you want to switch channels. Being somewhat larger than a standard Sky remote, your iPad is far less likely to go missing, so wouldn’t it be great if you could use the tablet you’re using to check emails while you watch TV to control your Sky+HD box? The release of Sky+ 4.0 means that this is exactly what you can now do.
Getting up and running is very simple -- just make sure that your Sky+HYD box and your iPad ate connected to the same network and you’re ready to go. While the app itself is not new, many of its existing features have been updated and there are plenty of new options that have been added as well. The big new feature is remote control. Using gestures you can control the playback of whatever you’re watching, tapping to play and pause, and swiping to skip back and forth.
This is by far the biggest new feature of the app, but there’s more too. You can also connect to your Planer and schedule programmes to record, check what you have lined up for recording and add reminders. The TV guide has been improved so that navigation is easier than ever and you can tab on the icon for a channel to switch your TV to that station. It would have been good to see more of these feature implemented in the iPhone version of the app, but the extra screen space of a tablet makes all the difference.
In addition to this, there is also an improved search tool that can be used to search for programmes from within the planner as well as when looking at TV listings. There have been general improvements to the look, layout and navigation side of things; whether you are an existing user of the app, or you’re yet to try it out, this is a great tool to supplement your TV viewing.
Note -- this app is only available in the UK.
You can find out more and download a free copy of the app by paying a visit to the Sky+ 4.0 review page.
-

RealPlayer for Android exits beta
Publié: août 15, 2012, 5:24pm CEST par Mark Wilson
 Remember RealPlayer? The media player that was once, quite some time ago, one of the go-to media players for online media disappeared into relative obscurity, shouldered out of the limelight by the likes of Silverlight and HTML5 video. For desktop platforms, RealPlayer has all but vanished, but it is trying to make headway into the mobile market. RealPlayer for Android is out of beta and officially released.
Remember RealPlayer? The media player that was once, quite some time ago, one of the go-to media players for online media disappeared into relative obscurity, shouldered out of the limelight by the likes of Silverlight and HTML5 video. For desktop platforms, RealPlayer has all but vanished, but it is trying to make headway into the mobile market. RealPlayer for Android is out of beta and officially released.Rather than just audio and video, RealPlayer for Android can also be used to play slideshows of photos, but movies and music are really where it’s all at. There is support for playlists so you can create mood music for every occasion and access it with ease. Aside from RealVideo and RealAudio, support for which can be added through and in-app purchase, the app can playback any file that is supported by your phone or tablet.
The interface is neatly set out and a handy widget is available so you can control media playback from the home screen; you can also control playback when your device is locked. RealNetworks’ online focus means that a variety of sharing options should come as no surprise; in addition to sharing through your favorite social network, there is also support for lastFM scrobbling so you can let others know what you are listening to.
The app does suffer a little from trying to be a jack of all trades -- it does a reasonably good job of acting as a music player, a video player and a photo viewer, but it does not excel in any of these areas and there are better apps available for each of these tasks. That said, if you are someone who abandoned RealPlayer some time ago, this might be the time to give the name a second chance as this mobile app is a different beast to the desktop tool of days gone by.
You can find out more and download a free copy of the app by paying a visit to the RealPlayer for Android review page.
-

Mountain Growl gets more from OS X 10.8 notifications
Publié: août 15, 2012, 2:15pm CEST par Mark Wilson
Growl is an excellent notification system for OS X that makes it easy to keep an eye on the status of a range of different applications without the need to switch between apps. But there is one problem, particularly for anyone who is keen to jump on the latest version of OS X -- there is currently no support for Mountain Lion and its new Notification Center. Mountain Growl can help here.
The Notification Center is in line with the same feature that is found in iOS and is the latest in a series of changes to OS X that blurs the lines between the mobile and desktop versions of Apple’s operating system. If you have been a Growl user, you’ll have noticed that when you upgraded to Mountain Lion that you have to endure Growl notifications alongside those from the Notification Center.
Once you have Mountain Growl installed, this is no longer the case. This free app can be used to push Growl notifications to the Notification Center so that they will appear with all of your other notifications. This unification plugs the gaps until a fully Mountain Lion compatible version of Growl is released.
All of this works well, but there is one slight drawback. All of the notifications are generated are sent by Growl itself, so this is the icon you will see next to individual entries in the Notification Center, this is a minor quibble, however, and Mountain Growl is well worth a look.
You can find out more and download a free copy of the app by paying a visit to the Mountain Growl review page.
-

Auslogics BoostSpeed 5.4.0.0 supports Windows 8, IE10
Publié: août 10, 2012, 4:41pm CEST par Mark Wilson
 Who doesn’t love a good tweaking tool? Everyone likes the idea of being able to boost the performance of their computer without having to shell out on potential expensive hardware and Auslogics BoostSpeed is an extremely accomplished utility that enables you to do just this. The latest version of the program is a major upgrade that sees not only added support for Windows 8 and Internet Explorer 10 but also new options that make the app and even more powerful tool for cleaning up and optimizing your computer.
Who doesn’t love a good tweaking tool? Everyone likes the idea of being able to boost the performance of their computer without having to shell out on potential expensive hardware and Auslogics BoostSpeed is an extremely accomplished utility that enables you to do just this. The latest version of the program is a major upgrade that sees not only added support for Windows 8 and Internet Explorer 10 but also new options that make the app and even more powerful tool for cleaning up and optimizing your computer.The imminent release of Windows 8 is big news for all software developers, and the latest release of Auslogics BoostSpeed not only supports the operating system, it also allows for control of Metro processes as added new tweaks to the Tweak Manager (Yes, we know Microsoft dropped the Metro name). The existing cleanup tools have been enhanced so you will notice that there are new categories available in the Registry Cleaner, Track Eraser and Disk Cleaner making it easier than ever to protect your privacy and delete sensitive data -- these improvements extend to the wiping of USB drives.
As well as deleting unwanted files, the program can also be used to uninstall software that is no longer needed. There are occasional problems with uninstallers that do not do their job properly, and the Force Remove function has been improved here to help you to remove such troublesome apps. To help to boost the speed of your internet connection, there is an improve Internet Optimizer component. Other updated features include support for the latest version of all popular web browsers, including fixes to problems specific to Internet Explorer 9.
Of course, there are also the usual range of bug fixes to be found as well as corrections to errors that had been found in language files. There’s an added bonus as well; a single purchase of the program means that you are able to install the software on up to three computers so you can keep all of the machines in your home optimized. Auslogics has also updated the free version of its Disk Defrag tool, again with added support for Windows 8 and addressing a number of known issues.
You can find out more and download a free trial version of the program by paying a visit to the Auslogics BoostSpeed 5.4.0.0 review page.
Photo Credit: Lilya/Shutterstock
-

Pixelmator 2.1 supports Retina Display, iCould sync
Publié: août 10, 2012, 12:01pm CEST par Mark Wilson
 If you’re looking for a powerful image editing tool, the likes of Photoshop are going to spring to mind first. But there are plenty of much lower cost tool available that are more than adequate for the job, and one of these app is Pixelmator. This is an image editing package that has been around for some time, and the seemingly minor update to version 2.1 brings about the introduction of a number of important new features and options.
If you’re looking for a powerful image editing tool, the likes of Photoshop are going to spring to mind first. But there are plenty of much lower cost tool available that are more than adequate for the job, and one of these app is Pixelmator. This is an image editing package that has been around for some time, and the seemingly minor update to version 2.1 brings about the introduction of a number of important new features and options.It makes sense for any image editing app to offer the best possible visual performance, and this is something that is greatly helped by the addition of support for Retina Display. This means that you can view the images you are working on greater detail than ever before and the UI is also made more accessible due to the clearer buttons and toolbars. There’s also support for Mountain Lion now, but there are more changes and additions to explore.
Any image editor worth its salt includes a range of special effects that can be applied to your own images, and five new ones have been added here -- Vintage, Miniaturize, Black and White, Rain, and Snow. To make it easier to browse through these and the other effects that are available, there is a new Effects Browser. This enables you to preview special effects and try out ideas before applying them.
New alignment guides are on hand to help you to position objects in your projects, but one of the most interesting new features is iCloud integration. This is great if you find that you are regularly working with more than one Mac as it allows for automatic synchronization of your work between machines. This is a nice touch that saves you the effort of having to manually transfer files between computers.
You can find out more and download a free trial of the app by paying a visit to the Pixelmator review page.
-

Your Windows programs can PlayOnMac
Publié: août 9, 2012, 8:55pm CEST par Mark Wilson
 So, you’ve made your choice between Mac and PC and decided that OS X is the operating system for you. But whatever personal choice you may have made, there are various reasons why you might need to turn to Windows software from time to time. While it is less common with big-name applicaions these days, there are still numerous titles that are not available for OS X. If your work requires you to use such a program, PlayOnMac could be just what you have been looking for.
So, you’ve made your choice between Mac and PC and decided that OS X is the operating system for you. But whatever personal choice you may have made, there are various reasons why you might need to turn to Windows software from time to time. While it is less common with big-name applicaions these days, there are still numerous titles that are not available for OS X. If your work requires you to use such a program, PlayOnMac could be just what you have been looking for.Working much like the likes of Wine -- in fact the software is based on Wine -- this is an emulation tool that enables you to run Windows software on your Mac. This is not a unique piece of software by any means, but PlayOnMac is designed to be easier to use than Wine, and it does not have a price tag like the comparable Parallels does.
While you could simply copy or download any Windows executable to your Mac, and test it to see if it will work, if you’re looking for guaranteed results, browser through a list of supported apps is better. By installing software from this list you are not necessarily going to find that a particular app or game will run perfectly at top speed, but it should at least be largely problem free.
The range of supported programs is fairly wide, but it is not exhaustive. Performance issues, particularly with any software that is heavily dependent on graphics, such as games, are not unknown, but PlayOnMac still acts has a handy, wallet-friendly solution to a problem that faces many Mac users who have made the transition from Windows to OS X.
You can find out more and download a free copy of the app by paying a visit to the PlayOnMac review page.
-

Heat up August with one of these software bargains
Publié: août 9, 2012, 4:23pm CEST par Mark Wilson
 The Downloadcrew Software Store is a great place if you’re looking for a software bargain, but with so much to choose from, it can be difficult to know just where to begin. Security and tweaking is a very good place to begin, and you can save 77 percent off the MSRP when you buy AVG Premium Security Complete Bundle for just $29.95. This exclusive deal gives you everything you need to keep yourself safe online and include four great AVG products.
The Downloadcrew Software Store is a great place if you’re looking for a software bargain, but with so much to choose from, it can be difficult to know just where to begin. Security and tweaking is a very good place to begin, and you can save 77 percent off the MSRP when you buy AVG Premium Security Complete Bundle for just $29.95. This exclusive deal gives you everything you need to keep yourself safe online and include four great AVG products.Everyone wants to get the best possible performance from their computer and this is something that AVG PC Tuneup 2012 [1-PC, 1-Year] could help with. For just $8.95 -- saving your 78 percent off the MSRP -- you cn tweak and optimize your system in next to no time, and there’s an even better deal availbale if you want to take care of multiple computers. AVG PC Tuneup 2012 [3-PC, 1-Year] gives you the same great tuneup options, but it can be installed on up to three computers. This could be yours for just $10.95, saving you 78 percent. AVG Internet Security 2012 Plus Bundle is another great selection of four AVG products that could be your for just $29,95 -- saving you a massive 80 percen off the usual MSRP of $149.
You can also save 80% off PC Tools Internet Security 2012 when you spend just $9.95 on this security suite that includes virus, spyware and spam protection as well as a firewall. Another security tool available at a great discount is Kaspersky Internet Security 2012 [5-PC, 1-Year], which could be used to protect all of the computers in your house for just $34.95 -- saving you 73 percent. You might also want to take a look at Bitdefender Total Security 2013 [1-PC, 1-Year]. This new release include virus protect, a firewall, parental controls and much more, and it could be yours for just $19.99, saving you $49.96!
In the store you will also find a number of deals on creative software and utilities, starting with CyberLink Media Suite 10 Ultra which can be your for such $99.95 (a saving of 23 percent off the MSRP) and includes a free copy of PowerDirector 10 Ultra. You can also buy CyberLink PowerDirector 10 Ultra separately and this includes not only a 35 percent saving but also $89 worth of free software. If you’re looking for disc software, you can save 82% off the MSRP of Roxio Creator 2011 when you buy it for just $17.99 -- Roxio Creator 2011 Pro is also available at a saving of 81 percent for just $24.99.
Bringing this month’s highlights to a close are four more impressive tools. If you need to safeguard your data, look no further than Genie Backup Manager Pro 9. This powerful yet easy to use program will set you back just $39.95 -- a saving of 43 percent off the MRSP. Performance improvements are so important to most computer users, it is worth mentioning the excellent Auslogics BoostSpeed 5 which, for just $14.95, a savings of 70 percent -- enables you to boost the performance of your system without the hassle of selecting endless option.
In a similar vein is TuneUp Utilities 2012, which comes complete with a lifetime license that can be used on up to three computer and features a massive 64-percent discount, bringing the price down to just $17.99. The program is also availbale with security software if you buy the TuneUp Utilities 2012 + avast! Pro Antivirus 7 bundle. This will cost you just $19.95 -- saving a colossal 78% of the MSRP of the two tools -- and enables you to protect and optimize your machine. It’s also worth noting that if you added Extended Download Insurance to your order, you’ll also receive a free copy of CyberLink Media Suite 9 Centra worth $69.95.
Of course, these are just some of the highlights from the Downloadcrew Software Store -- take a browse and see what else you can find.
Photo Credit: iQoncept/Shutterstock
-

Don't download, make a Mountain Lion install disk
Publié: août 9, 2012, 2:12pm CEST par Mark Wilson
 Like its predecessor, Apple’s most recent version of OS X, Mountain Lion, has been made available in the app store. From Apple’s point of view this helps to dramatically reduce production costs, and these saving can then be passed to customers who reap the benefits of cheap upgrades. But what the online installer model fails to take into account is that many people have to work within monthly download limits put in place by their ISP -- this is something that Lion DiskMaker can help with.
Like its predecessor, Apple’s most recent version of OS X, Mountain Lion, has been made available in the app store. From Apple’s point of view this helps to dramatically reduce production costs, and these saving can then be passed to customers who reap the benefits of cheap upgrades. But what the online installer model fails to take into account is that many people have to work within monthly download limits put in place by their ISP -- this is something that Lion DiskMaker can help with.Whether you have a single computer to upgrade, or want to bring your entire fleet of Macs up to date with Mountain Lion, it is quite possible that downloading a large installer could push you over your monthly limit, possibly resulting in hefty charges. If you have more than one computer you would ordinary have to download the installer separately for each machine. You might think that you could simply copy the installer but this is not easily achieved.
The problem is that once you have run through the installer, it will be automatically deleted preventing you from using it again. With this in mind, you should ideally use Lion DiskMaker before you perform an upgrade to Mountain Lion; you will only have to download the installer once. As well as saving your time and bandwidth, going down this route means that it is possible to upgrade computers that are not connected to the Internet.
The app can be used to create your own offline installer disk using an 8GB USB drive, SD card or a dual layer DVD. If you don’t mind taking a hands-on approach, this is something you could achieve with OS X’s built in Disk Utility, but Lion DiskMaker simplifies the whole process and takes care of everything for you.
You can find out more and download a free copy of the tool by paying a visit to the Lion DiskMaker review page.
-

Roundup – 22 updates and new downloads to kick off August
Publié: août 7, 2012, 3:46pm CEST par Mark Wilson
The end of July and the beginning of August have seen the release of a number of important apps and updates. If you’ve found it hard to keep to speed with what has been going on in the world of software, this roundup is here to help. SoftMaker FreeOffice 1.0.3340 is a free alternative to Microsoft’s office suite that is capable of producing Office compatible documents as well as PDFs. The news that Windows 8 has been released to manufacturers has rekindled interest in all things Metro, and Immersive Explorer 0.1.1 Alpha extends the look and feel of the Windows 8 Start menu into a fledgling replacement for Windows Explorer. If you’re more interested in storing your documents in the cloud, Google Drive 1.3.3209 has been updated, providing you with access to several gigabytes of free online storage and the ability to sync with your computer. While you’re online, you may well visit Facebook from time to time, and Facebook Messenger for Windows 2.1.4590.0 is a handy free tool that can be used to chat with contacts, monitor status updates and more all from a neat sidebar on your desktop.
Regardless of whether you have a Netgear router or not NETGEAR Genie 2.2.26.50 can be used to take care of it. NETGEAR Genie 2.0.25 (mobile version) is always available so you can use your Android or iOS mobile to perform tasks such as controlling your media and running speed tests. To make your life online easier, you need a decent web browser, and Opera 12.01 FINAL and Opera 12.01 FINAL 64-bit have both been released, with improved performance and better HTML5 support. If you’re more of a Google fans, Google Chrome 21 FINAL and Google Chrome 21 Portable provide you with everything you need including an all-new API for high-quality video and audio communication.
There must have been times when you have wanted to print out what you can see on your screen and have had to use and image capture tool to capture the desktop before printing it; Hardcopy 2012.08.01 enables you to simply print in one step. To help you get things done faster, Send To Toys 2.7 enables you to add new options to the Send To menu so you can work with files more easily, while Windows Games Tweaker 2.0 is on hand for when you need a little light relief, opening up new options in Windows’ built in games. Everyone likes to get the best from their computer, and this is something that iolo System Mechanic Free 11 can help you with. This advanced tweaking and maintenance tool can clean up and optimize your system and is also available in a number of paid for versions that boast extra features – iolo System Mechanic 11, iolo System Mechanic Pro 11 and iolo System Mechanic Premium 11. Anyone who has made the jump to Mountain Lion should take a look at Mountain Tweaks 1.0.2 which can be used to tweak the latest version of OS X.
Moving onto apps with a media slant, DVD Author Plus 2.32 can be used to burn all types of not only data CDs and DVDs, but also video discs. If you want to be able to access a vast library of online videos ready for streaming to your iPad, look no further than Amazon Instant Video 1.0 (US only) assuming you’re a paid-up Amazon member. We’ve already mentioned screen capturing, and this is something that Jing 2.7 has been designed for. Available for Mac and PC, the program not only captures your desktop but can also record video, enables you to share image on social networks and automatically upload via FTP, and much more. Whether you’re creating a web site and need to keep bandwidth in mind, or you need smaller images to attach to an email, PNGGauntlet 3.1.2 can be used to reduce the size of PNG images without compromising on quality.
That’s it for another week. Join us again in another seven days for the next roundup.
-

Flutter gives you (basic) gesture control of media via your webcam
Publié: août 6, 2012, 11:21pm CEST par Mark Wilson
Gestures are where it's at these days, with the Kinect add-on for Xbox 360 and the motion controls of the Wii allowing for direct interaction with games and other software. Even mobile devices such as Android and iOS phones and tablets are making greater use of gestures rather than just for menus and buttons. Touchscreen displays for Mac and PC make gesture interfaces possible in Windows and OS X, but Flutter enables you to use your webcam to interact using gestures.
As you can tell from the version number (currently 0.1.185), this is a very early version of the software and things are a little limited at the moment – but that’s not to say that it is not still worth taking a look at. At the moment, Flutter can be used to control your media player, enabling you to use basic hand gestures to start and pause music or video playback.
Currently this is the only supported gesture – a simple holding of the hand in front of your web cam is used to both pause and resume playback – but there are plans to add more gestures. It can be used with Spotify, Windows Media Player, iTunes, QuickTIme and VLC, and in future releases support will be added for YouTube, Netflix, Pandora and Hulu. The great thing about the app, despite its obvious limitations, is the fact that the program you are controlling does not have to be in the foreground.
Next time you receive a phone call while you are working and listening to music, there’s no need to bring the media player in front of every other running app before hunting for the pause button. Instead you can just hold your open palm in front of your webcam and playback will pause until you repeat the motion. Once gestures for track skipping and volume control are added this will be a great app, but for the time being it is still a curiosity that’s worth investigating.
You can find out more and download a free copy of the app by paying a visit to the Flutter review page.
-

Makeover OS X 10.8 with Mountain Tweaks 1.0.1
Publié: juillet 30, 2012, 1:37pm CEST par Mark Wilson
 There are no operating systems that are free from irritations and, despite its largely warm receptions, Apple’s latest OS X release, Mountain Lion is no exception. When Lion released Lion Tweaks was on hand to allow users to tweak and customize the OS and there is now an updated version available in the form of Mountain Tweaks. This is a free tool that enables you to change numerous settings to tailor OS X to suite your needs.
There are no operating systems that are free from irritations and, despite its largely warm receptions, Apple’s latest OS X release, Mountain Lion is no exception. When Lion released Lion Tweaks was on hand to allow users to tweak and customize the OS and there is now an updated version available in the form of Mountain Tweaks. This is a free tool that enables you to change numerous settings to tailor OS X to suite your needs.Tweaking tools have always been incredibly popular, but it is usually Windows users that reap the benefits of utilities designed to allow for easy changes to regular and hidden changes to the operating system. Lion Tweaks was an impressive tweaker made available for OS X Lion, and this latest release sees the app updates to add support for Mountain Lion. Mountain Tweaks can in fact be used under both Lion and Mountain Lion, but there are some settings specific to the latter.
Of course, OS X is customizable to a certain degree out of the box, but Mountain Tweaks opens up a number of new options. Using the tool you can unlock OS X’s hidden FTP server, ensure that hidden files are main visible and choose whether the Library folder should be displayed or not. If unnecessary animations irk you, you can disable the animations that are used on windows and mail and change the look of Contacts and Calendar.
You can customize the appearance of the dock as Launchpad and decided whether or not permanent scrollbars should really be permanent on display. Other options include the ability to enable TRIM support., enable Airdrop on older hardware and disable Gatekeeper. Some tweaks are practical, others visual, but you’re sure to find plenty that you’ll want to implement.
You can find out more about the app and download yourself a free copy by paying a visit to theMountain Tweaks review page.
-

Cool the summer heat with one of these 24 software downloads
Publié: juillet 29, 2012, 5:46pm CEST par Mark Wilson
 It’s the end of another month and the end of another busy week of software releases. If you’ve been too caught up with other things to keep an eye on the titles that have been hitting the download servers over the past seven days, this roundup will bring you up to speed.
It’s the end of another month and the end of another busy week of software releases. If you’ve been too caught up with other things to keep an eye on the titles that have been hitting the download servers over the past seven days, this roundup will bring you up to speed.Tomahawk 0.5.5 is a social media player that enables you to play your local music collection as well as tracks from the web, and also enables you to browse through the collections of your friends. If you’re keen to share your musical taste with your friends, look no further than ON AIR 4.0.0.834, which will automatically update your Skype status with the track you are currently listening to.
If you’re on the lookout for new music, RipTunes 1.0 can be used to rips YouTube videos into MP3 tracks and you can stream this to all of your home computers using Serviio 1.0. This advanced DLNA server can also be used to stream video and photos across your network.
Everyone wants to ensure that their computer runs at peak performance and without problems and this is something for IObit Advanced SystemCare 5.4.0.257. This suite of tools can be used to secure, optimize and maintain your computer, while Webroot System Analyzer 8.0.1.194 is a program that can be used to quickly and easily analyze problems with your computer. Keep things running smoothly is important, but privacy and space-saving are also concern for many people. CCleaner 3.21 and CCleaner Portable 3.21 can be used to help in both of these areas but also assists in boosting the performance of your computer by cleaning up after a huge number of programs that you may have installed. SmartPower 1.4.2 is another interesting tool which can be used to control exactly when your computer powers on and off, helping you to save electricity and ensure that your machines are available when you need them most.
For anyone who doesn’t mind getting a little hands-on with their system maintenance, FreeFixer 0.63 is a useful tool to help identify and remove unwanted and unnecessary software. This is a helpful utility in the fight against malware and a great addition to your security arsenal.
Paragon Partition Manager 12 Free and Paragon Partition Manager 12 Home are updated versions of Paragon’s powerful partitioning tools. The free version is great for day-to-day partition formatting, creating and resizing partition, while the Home edition gives you access to more advanced options such as backing up and data moving. Sticking with the hardware side of things, MultiMonitorTool 1.0 32-bit and MultiMonitorTool 1.0 64-bit superbly supplement Windows display Control Panel and makes it easy to move program from one screen to another and much more.
Moving to life online, Comodo IceDragon 13.0.3.0 is a newly release browser built on a Firefox core and designed with security in mind. The release of Mountain Lion also saw the release of Apple Safari for Lion 6, which includes a new unified search and address bar and a new offline reading feature. Users of Windows looking to emulate some of the features of OS X should take a look at Mission Control / Expose Clone W7 4.00 Beta, which does exactly what the name suggests.
This has been quite a hectic week for Android releases, starting off with G Cloud 1.0.3. This is a cloud based backup solution for your mobile device that includes 1GB of free storage, with more available for a price. If you’re looking for an easy way to manage your Android phone or tablet from your computer, look no further than AirDroid 1.0.8, which enables you to connect to and control your device through a web browser.
For anyone keen on getting more from their Android device and computer working in tandem, DeskNotifier 1.1.1 and DeskNotifier for Android 1.1.0 can be used together to receive notification from your phone or tablet within Windows. We’ve already mentioned a few media related tools in this roundup, but VLC (NEON version) 0.0.2 is an early version of the famous media player made available for Android. One final Android tool this week is Hideman 1.0 for Android which can be used to spoof your IP address and overcome country specific restrictions on web site access; there is also a Windows version of the tool available in the form of Hideman 1.8.
That’s it for another week -- join us in another seven days for the next roundup, and keep checking Downloadcrew for all the latest releases.
Photo Credit: Rafaël Croonen/Shutterstock
-

ON AIR Skypes music details as you listen
Publié: juillet 25, 2012, 9:24pm CEST par Mark Wilson
 Most people are keen to share their unquestionably excellent musical taste with everyone they know, and what better way to go about it than through a chat client. ON AIR is a plugin for Skype that enables you to share details of the music you are currently listening to by having your Skype status message automatically changed whenever a new track plays.
Most people are keen to share their unquestionably excellent musical taste with everyone they know, and what better way to go about it than through a chat client. ON AIR is a plugin for Skype that enables you to share details of the music you are currently listening to by having your Skype status message automatically changed whenever a new track plays.As well as track information, your Skype status can also be customized through the use of text, links and emotions. The plugin includes an extensive history section that keeps a record of all of the tracks you have been listening to.
There is currently support for 33 different media players, so unless you are using something fairly obscure, you should find that you are able to make use of ON AIR. If you are concerned about broadcasting details of everything you play in your media players, it is possible to choose to have the plugin ignore those of your choice. In this way it is possible to have ON AIR monitor what you’re playing in, say, VLC, but ignore the more embarrassing music you may choose to play in Windows Media Player.
In addition to changing your Skype status, ON AIR also proves to be useful at a more local level. Whenever the currently playing track changes, a pop up will appear with details of exactly what it is. You can then click this pop up to view more details about the artists, such as lyrics to songs, discography details and more.
You can find out more and download a copy of the free plugin by paying a visit to the ON AIR review page.
Photo Credit: CREATISTA/Shutterstock
-

Use AirDroid to manage your Android, no cable required
Publié: juillet 24, 2012, 6:58pm CEST par Mark Wilson
 Want to get some photos off your Android phone or tablet but don’t have your USB cable with you? Looking for a way to send SMS messages from your computer? Want to copy and paste text between your Android device and computer? These are just some of the things that AirDroid could help you with.
Want to get some photos off your Android phone or tablet but don’t have your USB cable with you? Looking for a way to send SMS messages from your computer? Want to copy and paste text between your Android device and computer? These are just some of the things that AirDroid could help you with.This free app enables you to use your web browser to connect to and control your Android device on a Mac or a PC running Windows or Linux. Connect your computer to your phone or tablet -- there’s no need for a desktop program to be installed -- and you can do this on both your personal computer and those in public locations. You can establish a connection in a matter of seconds by firing up the app on your mobile device and then visiting the URL you are provided with. After entering the password you’ve been given, you’ll be presented with an online desktop that you can use to browse and manage your Android device.
There are various ways in which you can move different types of file between your phone or tablet and computer. The integrated file browser supports drag and drop to make moving files around as easy as possible, and there are also dedicated ‘apps’ that can be used to work with photos and music. You can play music from your Android device with or without copying first and even change ringtone and alarm notifications.
Also available are a call log manager as well as a messaging component. This can be used to not only browse through the messages you have received, but also to reply to text messages using your computer keyboard. You can also use the browser interface to install and uninstall apps, check how much free spacey you have available, and use a shared clipboard to copy text between devices.
Despite the fact that this is only a beta tool, it is already very accomplished. If you have an Android device this is a must have app which is quite unique in its range of features and ease of use. You can find out more and download a free copy of the app by paying a visit to the AirDroid review page.
-

Want the benefits of Firefox but more security? Try Comodo IceDragon 13.0.3.0
Publié: juillet 23, 2012, 5:52pm CEST par Mark Wilson
 Going online means having to decide which web browser you’re going to use to find your way around the Internet. If security is your primary concern, a new browser just entered the arena and vies for attention. If Comodo IceDragon sounds familiar, you’ve probably been put in mind of Comodo Dragon, the security focused web browser based on Chromium. IceDragon is very much the same idea but this time around there is a Mozilla core.
Going online means having to decide which web browser you’re going to use to find your way around the Internet. If security is your primary concern, a new browser just entered the arena and vies for attention. If Comodo IceDragon sounds familiar, you’ve probably been put in mind of Comodo Dragon, the security focused web browser based on Chromium. IceDragon is very much the same idea but this time around there is a Mozilla core.Comodo have recognized that not everyone wants to use the same web browser just to get the benefits of added security, and Chrome is not a browser that suits everyone. The unveiling of a Mozilla based version of the same tool opens up a world of more secure web browsing to a wider audience. If you are already a Firefox user, you’ll be pleased to find that your bookmarks history, passwords and more can be imported into IceDragon.
The browser has a great looking interface, but it is security that is the really important feature. Just as with Comodo Dragon, here you have the opportunity to use Comodo Secure DNS. This helps to ensure that the sites you visit are not malicious and because this is a Firefox-based browser you can continue to use all of the browser extensions that you have become used to over the years.
There is a Site Inspector tool built into the browser and this can be used to check the safety and validity of any web site you may be concerned about. This is a helpful feature if you have decided against using Comodo Secure DNS, but it also acts as an extra line of defence if a site raises your suspicions.
You can find out more and download a free copy of the web browser by paying a visit to theComodo IceDragon review page.
-

Mission Control / Expose Clone brings some of OS X's best UI features to Windows
Publié: juillet 23, 2012, 2:42pm CEST par Mark Wilson
When it comes to subtly, Mission Control / Expose Clone will win no prizes for its name -- however, it may well impress in its ability to bring a great feature of OS X to Windows users. Ordinarily, Windows allows you to navigate between open windows and program using the task bar or by pressing the Win + Tab or Alt + Tab keyboard shortcuts. With Mission Control / Expose Clone installed, you can add Ctrl + Tab to your shortcut collection to access this great utility.
The program brings you some of the features of Exposé and Mission Control, enabling you to quickly access and overview of all running programs and open windows on a single desktop. Just as well your Alt + Tab between programs you can see a live preview of open windows, but things are kept beautifully neat thanks to the way the screen is arranged. Just like Mission Control, the program will automatically create stacks of windows from the same program -- so all of your Word documents are grouped together.
If you don’t mind getting your hands dirty tinkering with configuration files, you can even set up the program so that multiple applications are all grouped together, such as all open browser windows or all image related tools. Getting the program up and running is not too taxing, but the fact that it is currently in beta is made abundantly clear by the fact that there is not only no installer but that you are left to create a manually Startup shortcut if you want the program to start with Windows.
This minor complaint aside, this is a great tool that not only looks good, but functions well and could genuinely help to improve your workflow. It can be used as a simple Alt + Tab replacement, but the wealth of keyboard and mouse shortcuts that are on hand mean that this is a much more powerful utility than it might first appear to be.
You can find out more and download a free copy of the program, by paying a visiting to the Mission Control / Expose Clone review page.
-

Thunderbird 15 Beta 1 debuts Australis UI
Publié: juillet 19, 2012, 3:05pm CEST par Mark Wilson
 After the furore surrounding Mozilla’s recent announcement that it’s to place its email client, Thunderbird, into an “extended support release”, the launch of Thunderbird 15.0 Beta 1 was always bound to attract attention. And it’s certainly turning heads, thanks to the official debut of a redesigned user interface.
After the furore surrounding Mozilla’s recent announcement that it’s to place its email client, Thunderbird, into an “extended support release”, the launch of Thunderbird 15.0 Beta 1 was always bound to attract attention. And it’s certainly turning heads, thanks to the official debut of a redesigned user interface.Thunderbird 15 Beta 1 also debuts two noticeable new features in addition to the revamped user interface, extending the global search tool to cover the Chat module, plus implementing the “do not track” feature that debuted in Firefox last year.
The most obvious change in Thunderbird 15 will be the implementation of a new, curvaceous user interface called Australis. This introduces itself immediately with the rounded tabs at the top of the screen, but extends to redesigned lines, a repositioned toolbar and categorized filters, and has the effect of bringing the user interface up to date.
Revamped user interface aside, there are two notable new features. The unified global search now covers the chat module, which supports Facebook, Twitter and Google Talk among others, while the “Do not track” option introduced in Firefox has been added to Thunderbird too. This option, accessible from the Web Content tab in the Security section of Thunderbird’s Options screen, is of less relevance to email users, but may stop some emails from tracking the user, but only if they’ve signed up for the voluntary code of practice.
Going forward, Mozilla plans to split Thunderbird into two separate code bases, with Thunderbird ESR being maintained by Mozilla and Thunderbird being handed over to the open-source community to develop further. Thunderbird ESR will be updated every six weeks for stability and security only, and its changes rolled into whatever new build of Thunderbird has been developed in that timeframe. It means that while the long-term future of Thunderbird is uncertain, in the short to medium term it remains a viable email client for its 20 million user base.
Thunderbird 15.0 Beta 1, which installs over the top of any existing stable Thunderbird release, is available now as a free, open-source download for Windows, Mac and Linux.
Photo Credit: Gina Sanders/Shutterstock
-

Access OS X and Windows partitions with Paragon NTFS & HFS+ Beta
Publié: juillet 19, 2012, 12:47am CEST par Mark Wilson
 Owners of Android devices who work with both Macs and PCs should take a look at NTFS & HFS+ Beta. This newly unveiled app from software developer Paragon helps to overcome compatibility issues that you may have experiences with your cell or tablets and PC and Mac. Despite the fact that this is an early beta, it is an interesting tool.
Owners of Android devices who work with both Macs and PCs should take a look at NTFS & HFS+ Beta. This newly unveiled app from software developer Paragon helps to overcome compatibility issues that you may have experiences with your cell or tablets and PC and Mac. Despite the fact that this is an early beta, it is an interesting tool.If you are an Android owner with a Mac, you may well have formatted a memory card as an HFS+ drive. This is not ordinarily a problem, until the time comes when you want to access the files on a PC. Similarly, if you are a PC users, formatting a drive using NTFS could lead to problem with your Mac.
Providing you have rooted your Android device, this free app can be used to mount both HFS+ and NTFS formatted drives so you can use them without having to worry about compatibility issues. It is a simple tool that does its job well, although it could be argued that this is merely providing a feature that should have been included in the Android operating system as standard.
You can find out more and download a free copy of the app by paying a visit to the Paragon NTFS & HFS+ Beta review page.
Photo Credit: Balandina G/Shutterstock
-

Manage all your social networks in one place with AVG MultiMi
Publié: juillet 18, 2012, 2:15pm CEST par Mark Wilson
 Social networks are great tools, but there are now so many of them it can be something of a nightmarish task keeping on top of all of them. Using the likes of Facebook, Twitter and LinkedIn should be fun and rewarding, but if you use more than three or four networks things can quickly spiral out of control and become unmanageable. AVG MultiMi has now left beta and enables you to manage all of your social networking needs from one place.
Social networks are great tools, but there are now so many of them it can be something of a nightmarish task keeping on top of all of them. Using the likes of Facebook, Twitter and LinkedIn should be fun and rewarding, but if you use more than three or four networks things can quickly spiral out of control and become unmanageable. AVG MultiMi has now left beta and enables you to manage all of your social networking needs from one place.With support for Facebook, Twitter, LinkedIn, Flickr, YouTube and countless email services, whatever your online life includes, there’s a high chance that it’s supported by MultiMi. If you have used the beta version, you’ll notice that there has been something of an interface overhaul but there are also a range of new options. There is now support for Google Reader although there is also a built in RSS reader, and if you are a Read It Later user who has migrated to Pocket, there’s support for this service too.
There are impressive performance gains that come about largely because of the shift from using Internet Explorer as the built in browser to using Chromium instead. MultiMi not only enables you to see all of your social networking and social media in one place, it also helps to make it much easier to share content between accounts. Drag and drop can be used to copy text, image and more from, say, Twitter to an email, or from an email to Facebook.
The program enables you to quickly jump to all of the messages you have been sent regardless of which network it was sent through and there are similar shortcuts that can be used to view all of your photos, videos and more. This is particularly useful when working out your calendar as it is possible to view all of the events and appointments from all of your various calendars. You can also see the full activity of each of your contacts in one place -- click on a friend’s name and you can see what they have been posting on Twitter, Facebook and YouTube without the need to keep switching accounts.
You can find out more and download a free copy of the program by paying a visit to the AVG MultiMi review page.
Photo Credit: d3images/Shutterstock
-

Keep your PC healthy with IObit Advanced SystemCare v6 Beta
Publié: juillet 17, 2012, 9:32pm CEST par Mark Wilson
 System optimization and maintenance tools are not exactly thin on the ground, but there are some names that are far more worthy of attention than others. One such name is IOBit, and their newly released Advanced SystemCare v6 Beta is the latest in a line of tools designed to help make it easier to look after your computer. If you’ve used the program before you’ll immediately notice that the beta boasts a new look, but there is far more to explore besides the aesthetics.
System optimization and maintenance tools are not exactly thin on the ground, but there are some names that are far more worthy of attention than others. One such name is IOBit, and their newly released Advanced SystemCare v6 Beta is the latest in a line of tools designed to help make it easier to look after your computer. If you’ve used the program before you’ll immediately notice that the beta boasts a new look, but there is far more to explore besides the aesthetics.This is a tool that has all of the bases covered, from simple things such as deleting invalid shortcuts and cleaning up junk files, to defragmenting drives and the registry and even offering protection against malware and online threats. There are various components that can be called on whenever you need them, but one of the key advantages of using Advanced SystemCare v6 Beta over other similar tools is the fact that there is on-going monitoring and maintenance carried out for you.
In this latest beta, the performance monitoring engine has been overhauled to ensure more efficient optimization and the program itself is smaller as lighter than ever before. The Turbo Boost feature that was present in the previous version of the program can still be used to optimize your system for different tasks, and it has been improved along with the registry fixing component. Depending on the number of options you would like to see, you can choose between working in simplified or expert mode.
The expend toolbox that is available in Expert mode has been improved and there are now more options to choose from than ever before. The Registry Fix and Vulnerability Scanning sections have been updated to ensure better performance, and overall this is an accomplished update to an already impressive product. Despite the fact that this is a beta, it already seems stable enough and is well worth taking a look at.
You can find out more and download a free copy of the program by paying a visit to the Advanced SystemCare v6 Beta review page.
-

Move apps among virtual desktops with Dexpot 1.6
Publié: juillet 17, 2012, 2:40pm CEST par Mark Wilson
Virtual desktops are a great alternative to having multiple monitors installed to gain more space to work with. Dexpot is a virtual desktop management tool and it has just been updated to include and impressive new interactive preview screen that can be used to move windows and program between desktops, and even perform more advanced options such as creating copies of windows. There’s also a portable edition of the same version of the app available Dexpot Portable.
The preview window also features support for mouse and keyboard controlled zooming, but one of the most intriguing new features is the Window catalog. This displays all of the windows that are included on a desktop as a series of tiles and if you start dragging windows around Dexpot will automatically switch to full screen preview mode. Old favorites such as the desktop manager and desktop preview have also been redesigned.
A big step forward sees the addition of support for multiple monitors. If you have two or more screens connected to your computer, you can now use Dexpot to gain even more workspace. There are advanced optoins such as the ability to exclude a particular monitor from being used by the program so you can keep content static when required. To help make virtual and real desktops easier to differentiate, you can choose to have a different background to each desktop or for the desktops of a particular monitor.
In addition to all of this, there are also new keyboard shortcuts that make it easier than ever to interact with the program and access frequently used options. If you find that you use Dexpot in a number of different ways and have set up various profiles, these can now be loaded via shortcuts to allow for easy switching. New support for hot corners is another quick shortcut to accessing the features you use most.
You can find out more by paying a visit to the Dexpot and Dexpot Portable review pages.
-

Panda Cloud Antivirus 2.0: Security gain, without PC resource pain
Publié: juillet 16, 2012, 7:17pm CEST par Mark Wilson
 Virus protection is a must for all computer users and in addition to the level of security that such software provides, it is also important to bear in mind the impact that such protection programs can have on your system. It is all well and good having a program that protects you from every known virus, but there is little point in it if running the software causes your computer to slow to a crawl. Panda Cloud Antivirus Free 2.0 takes the strain off your computer by ensuring that all of the hard work is done for you in the cloud.
Virus protection is a must for all computer users and in addition to the level of security that such software provides, it is also important to bear in mind the impact that such protection programs can have on your system. It is all well and good having a program that protects you from every known virus, but there is little point in it if running the software causes your computer to slow to a crawl. Panda Cloud Antivirus Free 2.0 takes the strain off your computer by ensuring that all of the hard work is done for you in the cloud.This in itself is nothing new, but version 2.0 of the program, available in both free and paid for varieties, brings a number of changes, additions and enhancements that make this worth a second look if you have previously dismissed it. Probably the biggest change in this particular release sees the inclusion of the behavioral analysis engine that was previously only available to Pro users in the free edition of the software as well.
One of the highlights of the cloud-based antivirus tool is that your computer is freed up to do other things. This is still the case in version 2.0, only more so as scans speed up even further. There is still a fairly major incentive to upgrade to the Pro version (currently $29.95). Not only does this grant you access to customer support, but it also includes a new firewall component. The free version of the program also includes a new USB immunization component that prevent flash drive based programs from running automatically -- there’s also a process monitor that enables you to keep an eye on what is running in the background at all times.
As is becoming increasingly common, the installation of the software also includes a toolbar that claims to offer additional security options, as well as changing your search provider and start page. Thankfully, provided you take care during the installation process, it is possible to avoid these annoyances, leaving you with just the useful software you are interested in. If you can ignore this minor annoyance and concentrate solely on the protection aspects of the program, Panda Cloud Antivirus Free 2.0 is an impressive piece of kit.
You can find out more by paying a visit to the Panda Cloud Antivirus Free 2.0 review page.
Photo Credit: Jirsak/Shutterstock
-

Grab 34 exciting software downloads released this week
Publié: juillet 14, 2012, 7:15pm CEST par Mark Wilson
 The second week of releases for July is a little different from other weeks in that there has been a greater number of Mac releases than usual. TRIM Enabler 2.2 is a great free tool that helps to improve the life of SSDs, and the latest version of the app includes support for a wider range of drives. Lion is proving to be the most popular version of OS X yet, and Lion Tweaks 2.0.1 is a free tweaking tool that can be used to customize the operating system and eliminate irritations, while CrystalClear Interface 2.7.4 enables you to completely change the appearance of OS X through the use of skins. If you want to be sure of a secure web connection whether you are at home or out and about with a laptop, Hotspot Shield 2.61 is a free proxy tool that protects your privacy and enables access to blocked web sites.
The second week of releases for July is a little different from other weeks in that there has been a greater number of Mac releases than usual. TRIM Enabler 2.2 is a great free tool that helps to improve the life of SSDs, and the latest version of the app includes support for a wider range of drives. Lion is proving to be the most popular version of OS X yet, and Lion Tweaks 2.0.1 is a free tweaking tool that can be used to customize the operating system and eliminate irritations, while CrystalClear Interface 2.7.4 enables you to completely change the appearance of OS X through the use of skins. If you want to be sure of a secure web connection whether you are at home or out and about with a laptop, Hotspot Shield 2.61 is a free proxy tool that protects your privacy and enables access to blocked web sites.No week would be complete without its fair share of browser updates, and this week is no different in that respect. Chrome 21.1.1180.41 Beta is an interesting peak into the future of Google’s browser, and there is also a portable version of the software available in the form of Google Chrome Portable 21.1.1180.15 Beta. If you're keen to see what the future holds for Chrome, there is also Chrome 22.0.1201.0 Dev and again there is a portable version available -- Chrome Portable 22.0.1201.0 Dev.
If you’re a fan of Opera, Opera Next 12.50 ‘Marlin’ build 1497 and Opera Next 12.50 ‘Marlin’ build 1497 (64-bit) give a preview of what to expect from upcoming releases.
OneClick Chrome Extension 1.1 is a great extension for Chrome that eliminates the need for a torrent client, making it possible to download torrents just as you would any other file. Privacy is a concern for everyone, and Disconnect for Chrome 3.4.0 makes it easy to avoid website tracking, while Malwarebytes’ Anti-Malware Free 1.62 is a free yet fully featured malware protection tool.
Cloud storage is currently all the rage -- something that is unlikely to change in the near future -- and Dropbox 1.4.11 provides a handy way to keep files in sync on your computer; Dropbox Experimental Edition v1.5.8 is something of a preview of changes and additions that may be made in future releases. Microsoft SkyDrive 2012 v16.4.6003 has also been updated, this time with a new logo and enhance status window to keep you informed as to what is happening.
Whether you encode your own videos, download them from the Internet, or are given them by friends, you need to ensure that you have the correct codecs installed. This is where a codec pack is particularly handy, and means that you do not need to worry about downloading individual codecs. K-Lite is a well-respected collection of codecs available in a number of different versions -- K-Lite Codec Pack Full 9.0.2, K-Lite Codec Pack 64-bit 9.0.2, K-Lite Codec Pack Mega 9.0.2, K-Lite Codec Pack Basic 9.0.2 and K-Lite Codec Pack Standard 9.0.2.
BurnAware Free 5.0 could be used to copy your videos onto CD or DVD, but it can also create all manner of other discs. The latest release is a fairly major upgrade that adds support for more file systems as well as a number of improvements and enhancements. Additional features and options can be found in the paid for versions of the program -- BurnAware Home 5.0 and BurnAware Professional 5.0.
A disc burning tool could be used for backup purposes, but a dedicated tool is a better idea. Acronis True Image Home 2012 (Update 2.1) v15.0.7133 includes an improved scheduling feature, better archive management and much more. If you’re more concerned with recovering data than backing it up, Recuva 1.43 could be what you are looking for; there’s also a portable version available -- Recuva 1.43 Portable.
Speccy 1.17 is a great tool for anyone who needs to find out detailed information about their compute, and the latest version has improved support for all of the latest hardware. Speccy 1.17 Portable is also available for fans of portable apps. Uniblue PowerSuite 2013 can be used to optimize the performance of your computer, and the new 2013 release boasts a new interface as well as a new free Lite edition.
Finishing up this week’s roundup are a couple of tools aimed at helping you to get work done. LibreOffice Productivity Suite 3.5.5 is a free alternative to the likes of Microsoft Office while EssentialPIM Free 5.0 can be used to help organize your contacts, emails, notes and much more. EssentialPIM Free Portable 5.0 is a portable version that could be copied to your USB drive, while EssentialPIM Pro 5.0 offers a wider set of features for an upgrade fee.
That’s it for another week. Join us again in seven days’ time for a quick catch up on the preceding week’s releases.
Photo Credit: Rafaël Croonen/Shutterstock
-

Get organized -- EssentialPIM 5.0 comes to Android, iOS
Publié: juillet 9, 2012, 11:21pm CEST par Mark Wilson
 Everyone needs to keep their life organized and any tool that can help with this is welcome. One such piece of software is EssentialPIM, which has just been updated to version 5.0. The headline new feature: synchronization with both iOS and Android devices; a companion Android app is available for download from Google Play, while an iOS app is expected in the App Store in the near future. But this is not the only new feature in this handy PIM which bears quite a resemblance to Microsoft Outlook.
Everyone needs to keep their life organized and any tool that can help with this is welcome. One such piece of software is EssentialPIM, which has just been updated to version 5.0. The headline new feature: synchronization with both iOS and Android devices; a companion Android app is available for download from Google Play, while an iOS app is expected in the App Store in the near future. But this is not the only new feature in this handy PIM which bears quite a resemblance to Microsoft Outlook.The app can be used to manage your contacts, calendars, email accounts, notes, passwords and much more. Available in Free, Portable and Pro varieties, the program has been updated to include support for multiple SMTP servers as well as the ability to configure an unlimited number of identities in the mail component.
A slightly redesigned interface means that it is now possible to open several dialogs simultaneously thanks to the fact that most windows are now independent from the main program window. To make it easier to navigate between contacts, a new letters bar has been added, and message starring makes it easier to highlight emails you would like to be reminded of in the future.
The Pro version of the program includes a range of extra features and additions that are not found in the Free edition. This includes new templates for creating todo lists and appointments, and a new one-way synchronization option with Outlook. When a one-way sync is performed with Outlook, WebDAV, Google or another online service, there is now the option to choose between removing or leaving items that do not match in both locations.
You can find out more and download a free copy of the program by paying a visit to the EssentialPIM Free 5.0, EssentialPIM Free Portable 5.0 and EssentialPIM Pro 5.0 review pages.
Photo Credit: Blend Images/Shutterstock
-

Keep your PC healthy with Uniblue Powersuite 2013
Publié: juillet 9, 2012, 7:08pm CEST par Mark Wilson
 System optimization tools are ten-a-penny, but those that are worthy of note are few and far between. One tool that falls into the noteworthy camp is Uniblue Powersuite, which has just been updated to version 2013. This comprehensive suite of optimization tools has received a major facelift that makes its various components easier than ever to navigate and provides you with helpful information about the health of your system.
System optimization tools are ten-a-penny, but those that are worthy of note are few and far between. One tool that falls into the noteworthy camp is Uniblue Powersuite, which has just been updated to version 2013. This comprehensive suite of optimization tools has received a major facelift that makes its various components easier than ever to navigate and provides you with helpful information about the health of your system.The redesigned interface finds the suite’s tools divided up into three main sections -- speed tools, system optimization and disk optimization -- but there is also a general Overview section that gives you a quick insight into the state of your computer. The Speed Tools section covers all of the basics such as CPU management to better balance CPU load as well as improveing the launch times of various programs by caching the resources they use. There’s also a proactive thumbnail generator that eliminates the need to Windows to create image thumbnails on the fly.
Moving to the System Optimization section can be used to apply a huge range of tweaks to your system -- these are basically registry edits that are applied on your behalf -- as well as performing fairly standard actions such as killing unnecessary startup items. You can also use this section of check for driver updates, remove invalid registry entries and defragment the registry.
Finally, the Disk Optimization section includes a number of options to help free up space and improve performance. You can claim back many megabytes by removing unnecessary files and old backups – as well as using file compression -- and then take advantage of a defragmentation tool which is more advanced than the utility that is built into Windows.
While you are using the free Lite version of the program you only have access to the tools in the speed section, but it does give you a good taste of what the suite as a whole is capable of. By upgrading to the Pro version of the program, as well as unlocking all of these extra tools, you also gain the ability to schedule the program to run a system scan on a regular basis. You can find out more and download a free copy of the Lite edition of the program by paying a visit to the Uniblue Powersuite 2013 download page.
Photo Credit: Levent Konuk/Shutterstock
-

Celebrate July with one of these 19 software downloads
Publié: juillet 8, 2012, 10:45pm CEST par Mark Wilson
 The halfway point of the year has come and gone, and as we slide our way through the calendar, there are more and more software releases to keep track of. If you’ve been busy through the first week of July, here are some of the highlights that you may have missed.
The halfway point of the year has come and gone, and as we slide our way through the calendar, there are more and more software releases to keep track of. If you’ve been busy through the first week of July, here are some of the highlights that you may have missed.Starting off this week’s selection of titles are a number of tools with a connection to the Internet. Connectify Lite 3.5 is a great free tool that can be used to turn your laptop onto a WiFi hotspot that can be used by other laptops or mobile phones. If you want to use the Internet as a platform for your photography, jAlbum 10.8 can be used to share your photos online. ShareMeNot is a browser extension that can be used to prevent social networking buttons from tracking you line -- it is available as ShareMeNot for Firefox 2.0.1 and ShareMeNot for Chrome 1.0.
Users of Microsoft’s Outlook PIM can turn to Microsoft Outlook Configuration Analyzer 2.0.0 to check the software for problems, while WSUS Offline Update 7.4 makes it easy to keep Office and Windows up to date. Microsoft’s .NET Framework is behind a huge range of tools, and .NET Framework Setup Verification Utility can be used to check your installation for problems that may be preventing other tools from running properly.
For more entertaining tasks, MediaMonkey 4.0.6 makes it easy to manage your music collection so you can always find what you want to listen to. VLC Media Player 2.0.2 (32-bit) and VLC Media Player 2.0.2 (64-bit) are releases aimed at Mac users as the latest version of the media player supports Retina Display.
Do you find that Windows Explorer is a little lacking for you, EF Commander 8.50 is a competent replacement with a raft of helpful built-in utilities, and Z-Cron 4.9 is an advanced task scheduling tool that far exceeds the capabilities of Windows’ own built in tool.
If you’re looking to gain a little extra space to work with, Dexpot 1.5.18 is an interesting virtual desktop manager, complete with impressive 3D transitions. Back to tools which make it easier for you to work with files, Attribute Changer 7.10 is all you need to change time stamps, file attributes and more, while IObit Smart Defrag 2.5.0.1160 places you in full control over your hard drives, with the latest version adding support for Windows 8.
Security is important whatever you happen to use your computer for, and USB Safeguard 6.0 Free is a handy tool that can be used to encrypt the contents of your USB drive so that its files cannot be accessed by other people. To help stay safe online, Comodo Dragon 20.0 is a Chrome based browser with a keen focus on security, but no support for extensions.
If you’re more concerned with taking care of the files you have stored on your hard drive, backing up data is absolutely essential. Genie Backup Manager Home 9.0 inclues everything you need to secure your data with impressive performance and rich feature-set.Genie Backup Manager Professional 9.0 includes additional encryption options, advanced scheduling and other features that will please the more discerning securer of data.
That’s it for another week. We’ll be back in another seven days to help you keep up to speed with the week’s releases.
Photo Credit: Kudryashka/Shutterstock
-

Get a dark menu bar that matches OS X's cosmic desktop
Publié: juillet 6, 2012, 3:30pm CEST par Mark Wilson
Unlike Windows computers, Macs tend to have something of a uniform look to them. Sure, you can move the dock around the screen and choose a new background image, but there just isn’t the same tweaking and customization community that exists for Windows. MenuBarFilter is a free tool that brings basic, if much welcome, customization of the menu bar to OSX.
This is a tiny utility that you need simply unzip, copy to your Applications folder and then add to your list of login Items. Once this has been done, the menu bar will no longer be silvery grey with black text, but the exact opposite. The light text on a dark background look is not only somewhat classier than the default colors, it is also in keeping with how things are in iOS.
It is not just changing the appearance of OSX that makes the tool appealing, the new look afforded by the dark version of the bar is easier on the eye a serves as less of a distraction. It is an item of screen furniture that you have become used to over the years -- you know where it is and what it’s for, so there’s no need for it to draw attention to itself with a light color scheme.
Installing MenuBarFilter gives you a look that is more in keeping with iOS and also prevents the menu bar from being an unnecessary distraction. With the darker colors in use, it can blend in better with your monitor, but whatever your reasons for install the tool, you get a great new look for your desktop that oozes style.
You can find out more and download the free utility by paying a visit to the MenuBarFilter review page.
-

USB Safeguard password-protects your stick
Publié: juillet 5, 2012, 11:23am CEST par Mark Wilson
 Data security is of the utmost importance, but it is usually the files stored on our hard drives or transmitted over the Internet that we are primarily concerned with. It’s likely that you have at least one USB drive that you use o move files from one computer to another, perhaps transporting files between home and office. If you were to lose the drive, there is not only the irritation of not having access to the files you need, there is also the concern that whomever finds the drive will be able to vie your private data -- this is something that USB Safeguard can help with.
Data security is of the utmost importance, but it is usually the files stored on our hard drives or transmitted over the Internet that we are primarily concerned with. It’s likely that you have at least one USB drive that you use o move files from one computer to another, perhaps transporting files between home and office. If you were to lose the drive, there is not only the irritation of not having access to the files you need, there is also the concern that whomever finds the drive will be able to vie your private data -- this is something that USB Safeguard can help with.As you’ve probably guessed from the name and the scenario we have set up, this is a program that can be used to protect the files you have chosen to store on a USB drive. This is a tiny portable app, weighing in at less than 100KB, but it is none the less powerful. While there is a paid version of the app available that can be used to protect drives of up to 16TB in size, there is also a free version that can be used on drives up to 2GB.
While this may not seem like much, it is still more than enough to keep your valuable data safe. Word documents and spreadsheets are not necessarily very large, so a 2GB drive could be used to store a very large number of them. These could contain all manner of private data including financial information which could be misused by anyone else that was to gain access to the drive. You can also use the software to protect images on camera memory cards.
USB Safeguard enables to you password protect your drive so that it cannot be accessed by anyone who does not know it. The data on your drive is protected on the fly with 256-bit AES encryption to help avoid the risk of passwords protection being bypassed. Quick to use and easy to implement, this is a fantastically useful program.
You can find out more and download a free copy of the app by paying a visit to the USB Safeguard review page.
Photo Credit: Brian A Jackson/shutterstock
-

ShareMeNot protects your privacy from prying social networks
Publié: juillet 3, 2012, 5:49pm CEST par Mark Wilson
 Most people who have used the Internet for any length of time are only too aware that websites are able to track their online activities by using cookies. This information is incredibly useful to advertisers, but there are steps you can take to help protect yourself. With the ever increasing popularity of social networks there is a new breed of tracking in the form of Like buttons -- and this is something that ShareMeNot can tackle.
Most people who have used the Internet for any length of time are only too aware that websites are able to track their online activities by using cookies. This information is incredibly useful to advertisers, but there are steps you can take to help protect yourself. With the ever increasing popularity of social networks there is a new breed of tracking in the form of Like buttons -- and this is something that ShareMeNot can tackle.There are very few Internet users who do not have a Facebook account, but there are numerous other social networks such as Google+, LinkedIn and many more. Many of these have their own site integration buttons that you have no doubt seen adorning the pages of many sites you visit -- they will give visitors the options of "Liking the current page on Facebook, or sharing it via some other means.
This in itself sounds useful, but the truth of the matter is that even before you click one of these buttons, it is likely that the various social networks know where you are online. This is where ShareMeNot comes into play. This is an extension that is available for Chrome and Firefox and it effectively blocks the functionality of these social networking buttons unless you explicitly choose to use them.
Being placed in control over how social networks make use of information they are able to gather about you is something that is out of your hands to some extent, but it is possible to limit what information they have access to. ShareMeNot is not just a tool for the paranoid – it is useful for anyone that has privacy concerns. As there are undoubtedly going to be sites for which you do not mind sharing information, you have the option of setting up a list of exceptions, but with the extension installed the default setting ensures that data is not shared – unless you say otherwise.
You can find out more and download yourself a copy of the browser extension by paying a visit to the ShareMeNot for Chrome or ShareMeNot for Firefox review pages.
Photo Credit: Lakhesis/Shutterstock
-

IObit Advanced SystemCare with Antivirus 2013 mini-review
Publié: juillet 2, 2012, 2:23pm CEST par Mark Wilson
 Security is a key concern for all users of Windows, but coming a close second is a desire to get the best possible performance. IObit Advanced SystemCare with Antivirus 2013 is an all-in-one suite that has both the security and performance bases covered along with a fair smattering of maintenance thrown in for good measure. The program is divided up into five main sections and in all there are dozens of tools on hand to help you to take care of your computer.
Security is a key concern for all users of Windows, but coming a close second is a desire to get the best possible performance. IObit Advanced SystemCare with Antivirus 2013 is an all-in-one suite that has both the security and performance bases covered along with a fair smattering of maintenance thrown in for good measure. The program is divided up into five main sections and in all there are dozens of tools on hand to help you to take care of your computer.The antivirus component of the suite offers real-time protection against all manner of threats, but you also have the option of running manual scans, both quick and full, whenever you feel the need. Any files you receive via email are automatically scanned for signs of infection as are any files you download while browsing the Internet. Everything you would expect to find in an AV tool is available here -- scanning whenever you need it, quarantined of suspicious files, automatic updates and whitelisting of trusted files.
IObit has combined their existing Malware Fighter anti-malware engine with Bitdefender Antivirus to offer dual-protection against the latest threats. If you have an existing security suite, you can install Advanced SystemCare with Antivirus in “compatibility mode” and analysis your system on-the-fly, when you want a second choice security analysis of your PC.
The next component of the suite is Quick Care and here you will find a series of tools for fixing a range of problems with your system. These includes everything from fixing problems with the registry, checking for malware and fixing broken shortcuts. There are also options to remove your internet history and to free up disk space by removing unnecessary files. A nice touch is the ability to automatically shut down your computer once all of these tasks have been performed, meaning that it is an ideal thing to do at the end of the day.
More in-depth options are available in the Deep Care section that is essentially a more thorough version of the options found in the previous section and includes additional settings such as defragging of hard drives. The Tool Box section provides you with access to a massive selection of programs that give you full control over various aspects of your computer. Included here are a registry and disk cleaner as well as optimization tools to help speed up your network connection, boost startup times and recover deleted files.
If there is an accusation that could not be levelled at IObit Advanced SystemCare with Antivirus 2013 it is that it is short of tools. There is a good balance of tools that are automated compared to those that require you to manually configure settings. This means that whatever your level of computing expertize you can expect to gain something from this valuable suite.
If you’d like to try out the software for yourself before buying it, you can download a trial version from the Downloadcrew page.
-

Celebrate the half-year with one of these 24 software downloads
Publié: juillet 1, 2012, 11:09pm CEST par Mark Wilson
 We’ve reached the beginning of July but shouldn't forget June, which ended with a swatch of updates and releases.
We’ve reached the beginning of July but shouldn't forget June, which ended with a swatch of updates and releases.Security is always a priority like these: avast! Free Antivirus 7.0.1451 is the free version of the AV tool, with avast! Pro Antivirus 7.0.1451 also featuring the same new Emergency Updater and improvements to sandboxing. Also available is avast! Internet Security 7.0.1451 which includes not only virus protection, but also a firewall, web filtering and more. Another free firewall is available in the form of the newly updated ZoneAlarm Free 10.2.64.0 and if you want virus protection as well, you might want to take a look at ZoneAalarm Free Antivirus + Firewall 10.2.
Free Studio 5.6.2 provides users with a staggering number of utilities for dealing with media files including converting videos between formats, downloading streaming video formats and burning media files to disc. If you’re interested in just the audio side of things,
Audacity 2.0.1 is a feature-packed audio-editing tool that can be used to work with music files and voice recordings. Popular video codec pack K-Lite has been updated to add support for all of the latest video formats and you can choose between K-Lite Codec Pack Standard 8.9.5,K-Lite Codec Pack Basic 8.9.5, K-Lite Codec Pack Mega 8.9.5 and K-Lite Codec Pack Full 8.9.5 depending on how many different formats you need to be able to play.
Returning to the security theme, Bitdefender Antivirus Plus 2013 has also been updated with a new security widget, better protection of online banking, better parental controls and much more. For a more complete security solution, Bitdefender Total Security 2013 also includes a firewall, spam protection, while Bitdefender Internet Security 2013 is a slightly lower cost version of the suite.
IObit Advanced SystemCare with Antivirus 2013 v5.5.2.270 is the latest release from IObit which sees the addition of an antivirus components to the maintenance suite that also includes tools to helps optimize the performance of Windows.
A lot of releases at the moment add support for Windows 8, and this is the case with both CCleaner 3.20 and CCleaner Portable 3.20.
Keeping your system in good shape means keeping it up to date and this is something that Secunia PSI 3.0 FINAL can help with by keeping your applications current.
If you’re looking for a combined FTP and web server tool,Serva 2.0.0 32-bit is a great free option released this week, and there’s also Serva 2.0.0 64-bit.
Google has been in the news quite a lot this week and one reason is the release of Google Chrome 20 FINAL. Also unleashed was Google Chrome 20.0.1132.47 Beta and Google Chrome 21.0.1180.15 Dev which fixes a problem experienced by Mac users with the Intel HD 4000 graphics chip.
Join us again in another week’s time for a catch up with all of the latest releases.
Photo Credit: Rafaël Croonen/Shutterstock
-

VLC 2.0.2 now supports MacBook Pro Retina Display
Publié: juin 30, 2012, 7:57pm CEST par Mark Wilson
Popular media player VLC has been updated to version 2.0.2 and despite the minor version number increase, the changes should be immediately noticeable. The big news here is addition of support for Retina display so if you have invested in a new MacBook Pro, this is one app that will enable you to take full advantage of the enhanced screen.
Retina display support means that not only can video itself be seen in much better quality, but also that subtitles and any other overlays for a particular file can be displayed at a much higher resolution. This is clearly a release that will be of most interest to OS X users, and in addition to the new display option, a number of known problems have also been addressed. Blu-ray playback has been improved and issues that users had experienced with rotating, cropping and zooming with video have also been fixed.
Additional changes and additions include better support for compressed file formats and H.264 webcam output. Previous versions’ problems with HTTP access through a proxy and issues with certain file types have also been addressed. The on-going development of VLC, particularly for OS X, means that this continues to be one of the most impressive and feature-packed media players available.
Audacity, the free, cross platform audio editing tool has also been released. Again, there is not a very big increase in version numbering, but Audacity 2.0.1 is still worth a look thanks to the number of big fixes that are included, but there are also new effects and features to explore. For Mac users, there is now compatibility with VoiceOver screen reader.
You can find out more and download free copies of the programs by paying a visit to the VLC and Audacity review pages.
-

Save big on these June software deals
Publié: juin 20, 2012, 3:01pm CEST par Mark Wilson
 We’ve made it to June -- the year just seems to be flying by! -- and with each passing month there are more and more great offers in the Downloadcrew Software Store. In fact, there are so many great offers to be found that we thought that we had better collect together some of the highlights to make things a little easier for you.
We’ve made it to June -- the year just seems to be flying by! -- and with each passing month there are more and more great offers in the Downloadcrew Software Store. In fact, there are so many great offers to be found that we thought that we had better collect together some of the highlights to make things a little easier for you.Starting things off are two disc burning tools from Roxio.Roxio Creator 2011 is available for just $19.99 (a saving of 80 percent off the MSRP) while its big brother Roxio Creator 2011 Pro could be yours for just $24.99, instead of $105. These immensely powerful media suites include everything you need to create CDS, DVDS and Blu-rays containing video, audio and data.
There are a number of security products to be found on sale in the store, including Kaspersky Internet Security 2012 [5-PC, 1-Year]. This security suite costs just $39.95 (a saving of 64 percent) and can be installed on five computers, while Webroot Internet Security Essentials 2011 [3-PC] includes a firewall, antivirus tool and spyware detection for just $4.95 (saving you a massive 92 percent) as well as a free upgrade to SecureAnywhere Essentials 2012.
The same upgrade offer is available if you buy Webroot Internet Security Complete 2011 [3-PC] which could be your for just $9.95 instead of the usual price of $79.95. From the same company is Webroot AntiVirus with SpySweeper 2011. This great security tool costs just $4.95, a saving of 88% off the MSRP, and includes a free upgrade to SecureAnywhere Antivirus 2012! There are also deep discounts from the Bitdefender range of security software.
If you feel like getting creative with your music, photos and videos, look no further than the special offers on CyberLink products. You can save 30 percent off the regular price of CyberLink PowerDirector 10 Ultra when you buy it for just $69.95 and this immensely powerful suite includes everything you need to create your own stunning videos. In addition to saving $30, you will also receive $89 worth of complementary software (CyberLink MediaEspresso 6.5 and Travel Pack 2).
The previous version of PowerDirector, PowerDirector 9 Ultra64 is still available and can be snapped up for the bargain price of just $29.95 -- saving your 70 percent off the MSRP of $99.95.If you buy CyberLink Media Suite 10 Ultra at a 23 percent saving for just $99.99, you’ll also a free copy of PowerDirector 10 Ultra worth $99.95 in this Downloadcrew store, world exclusive CyberLink-approved offer.
We’ve already mentioned some security tools that can be found in the store, and there a several special offers that you can take advantage of if you’re looking for products from AVG. AVG Internet Security 2012 Plus Bundle is available at an 80 percent discount for just $29.95, while AVG Premium Security Complete Bundle could be yours for 77 percent off the MSRP -- just $29.95. AVG is most famous for its antivirus software, and if you have spent your time up until now working with the free version of the program, there has never been a better time to upgrade to a paid-for version. AVG Anti-Virus 2012 [1-PC, 1-Year] has been massively reduced to just $4.95 – a saving of 88 percent off the MSRP of $39.99 -- giving you a great and cheap way to keep your computer protected. Just to show that AVG is not only concerned with security, AVG PC Tuneup 2012 [3-PC, 1-Year] costs just $16.00 instead of $33 and could help to boost the performance of up to three computers.
To finish off the selection of special office this month, you’ll find a number of programs that have been designed to help improve the performance of your system. TuneUp Utilities 2012 is great value for money as not only can it be installed on three computers, it also features a lifetime non-expiring license – all for the bargain price of $16.99. For just a little more, TuneUp Utilities 2012 + avast! Pro Antivirus 7 could be yours. For just $19.95, a huge 78% off the MSRP, you can secure and boost your computer.
The final two products for the month both some from Auslogics. Auslogics Disk Defrag Pro 4 is on sale at half the usual price at just $14.95, and Auslogics BoostSpeed 5 is another great deal which sees you saving 70% off the MSRP when you buy this great performance and maintenance tool for just $14.95.
Of course, this is just a selection of some of the great offers you can find in the store. To take a look at the full range of what’s available, head on over to the Downloadcrew Software Store.
Photo Credit: iQoncept/Shutterstock
-

Rev up this week's 20 exciting software downloads
Publié: juin 16, 2012, 5:29pm CEST par Mark Wilson

There are a number of worthy highlights this week, including the long awaited Opera 12 release, iTunes support for iOS 6 devices and a relatively major update to Skype for Windows and Mac.
The major release this week must be Opera 12. After months of beta-testing, the browser is finally available, along with an interesting twist, in the form of the first native 64-bit build. Whether a 64-bit version of a web browser makes a huge difference is another matter entirely. Opera 12 ships with numerous speed improvements, including basic support for hardware acceleration. It’s not all good news though as gone are the widgets and other features such as Opera Voice. Download Opera 12, Opera 12 (64-bit) and the separate Opera Portable 12, which you can take on the road.
Skype 5.10 is a relatively major update for the Windows edition, despite the version number. Leaving aside the debate about adverts in Skype-to-Skype audio calls, the new version brings a single contact list for your Facebook and Skype contacts, the ability to pin your favorite contacts to the top of your contacts list, plus backwards-compatible video rendering, for older PCs that do not support hardware acceleration. Skype 5.8 for Mac also received a major upgrade with support for better handling of Skype calls from mobile phones, improved screen sharing, as well as a refined contacts list.
Security-wise, Norton Power Eraser 3.0.0.21 received a big update this week. This powerful portable tool can be used alongside your existing security software to find, seek and removal problematic malware. AppRemover 2.2.26.1 is a very different tool that will remove stubborn security software, whilst Kaspersky Security Scan 2.0 is a simple tool that will find and notify of potential security issues (but won’t fix them). Bitdefender Parental Control Beta is new software you can use, as a parent to restrict your children’s access to the internet, plus monitor their behaviour. Note there’s a separate Bitdefender Parentral Control Beta (64-bit).
VMware Player 4.0.4 is free software you can use to host a virtual operation system. Ideal if you want to test the latest Linux distribution or Windows 8 Release Preview. You can’t create a virtual host in Player, but you can within VMware Workstation 4.0.4, also updated this week. If you’re a Mac user, VMware Fusion 4.1.3 was updated and made available this week.
Apple announced the developer preview of their iOS 6 mobile operating system this week and an updated iTunes 10.6.3 and separate iTunes 10.6.3 (64-bit) to allow users to manage their iOS 6 devices (if you’re lucky enough to be able to get hold of iOS 6). Free Studio 5.6.1 is a powerful 47-in-1 multimedia suite, with a host of conversion tools, whilst other DVDVideoSoft titles were updated, including Free Disc Burner 3.0.11, Free WebM Video Converter 5.0.13, Free AVI Video Converter 5.0.13 and Free Audio Converter 5.0.13.
WinRAR 4.20 (32-bit) and (64-bit) was updated this week, along with the general-purpose archive management tool, PeaZip 4.6. Also available as a 64-bit build and portable version.
Finally, if you have you have any downtime, take a look at 0 A.D. r11863, which is an alpha of an historical RTS game, with superb graphics for a free game.
Photo Credit: nito/Shutterstock
-

O&O DiskImage 6.8 supports Windows 8
Publié: juin 12, 2012, 4:45pm CEST par Mark Wilson
 Berlin-based O&O Software has announced a major update to its Windows back-up and restore tool. O&O DiskImage 6.8.1 Professional, also available in 64-bit, boasts full Windows 8 support, plus promises faster performance in key areas.
Berlin-based O&O Software has announced a major update to its Windows back-up and restore tool. O&O DiskImage 6.8.1 Professional, also available in 64-bit, boasts full Windows 8 support, plus promises faster performance in key areas.Version 6.8.1 also takes into account third-party power settings, ensuring it stays on for the whole backup process, plus streamlines and simplifies key parts of the program in response to customer and partner feedback.
O&O DiskImage 6.8.1, which is a free update for registered users of version 6.0, builds on the new features introduced in O&O DiskImage 6.0. These included support for file-based backups, the ability to restore backups to different hardware platforms, and support for forensic-based images for the purposes of data recovery.
Version 6.0 also introduced support for converting DiskImage drive images to and from Microsoft VHD format for use in virtual environments. The latest update promises faster VHD file creation in addition to its raft of other performance tweaks and improvements.
O&O DiskImage 6.8.1 Professional 32-bit and O&O DiskImage 6.8.1 Professional 64-bit are both available as free trial downloads for PCs running Windows XP or later, including the latest Windows 8 Release Preview. The full Professional version can be purchased for just $23 through theDownloadcrew Software Store.
Photo Credit: Sergey Mironov/Shutterstock
-

Uh-oh, Windows blue screened and you don't know why? WhoCrashed answers
Publié: juin 11, 2012, 11:05pm CEST par Mark Wilson
 When Windows dies it’s not always easy to determine just what caused the problem. Sometimes you may be lucky and find that you are shown a helpful error message that singles out the culprit, but for most BSoDs and crashes you’ll end up with an error code that is all but impossible to interpret. In many cases you will find that Windows simply restarts, giving you no opportunity to find out what has caused the problem. Install WhoCrashed and you should be able to learn so much more.
When Windows dies it’s not always easy to determine just what caused the problem. Sometimes you may be lucky and find that you are shown a helpful error message that singles out the culprit, but for most BSoDs and crashes you’ll end up with an error code that is all but impossible to interpret. In many cases you will find that Windows simply restarts, giving you no opportunity to find out what has caused the problem. Install WhoCrashed and you should be able to learn so much more.After or during crashing, Windows will generate a crash dump file that could help you to find out just what the problem is. However, finding, reading and understanding these dump files can be a problem on its own. WhoCrashed Home Edition is a free program that will automatically scan your hard drive for the presence of crash dump files and let you know which drivers are likely to be responsible.
Having identified the culprit that led to the Windows crash, you are then in far better position to set about the task of diagnosing and fixing the issue. You can easily check for updates that may be available for the device in question and you should hopefully find that this addresses the problem. The crash dump analysis can also reveal program files that have caused issues and you can use this information to choose to update or uninstall problematic software.
While WhoCrashed is not a perfect program, it makes things a great deal easier than blindly trying different options. You should find that you are pointed in the right direction pretty much every time, and even if a direct solution is not offered, you have been provided with the data you need to carry out your own investigations.
You can find out more and download a free copy of the app by paying a visit to the WhoCrashed Home Edition review page.
Photo Credit: Roger Jegg - Fotodesign-Jegg.de/Shutterstock
-

Take those online videos to go with Wondershare vDownloader
Publié: juin 7, 2012, 4:45pm CEST par Mark Wilson
 There are countless websites that feature hours of streaming video that you can watch whenever you have an Internet connection. But what about those times when you are not able to get online? If you are going on a trip and want to ensure that the children have something to watch on a laptop or tablet, Wondershare vDownloader is a tool that can be used to grab a load of videos in advance and load them onto the device of your choosing.
There are countless websites that feature hours of streaming video that you can watch whenever you have an Internet connection. But what about those times when you are not able to get online? If you are going on a trip and want to ensure that the children have something to watch on a laptop or tablet, Wondershare vDownloader is a tool that can be used to grab a load of videos in advance and load them onto the device of your choosing.Saving videos from some websites is easy enough -- just right click a link and save the target file to your hard drive. With other sites things are a little more tricky, you may need to examine source code and determine the link needed to download a file. And then there are some sites that make it all but impossible to save a copy of a video you have come across. Whether you’re looking to make it quicker and easier to download videos, or you want to be able to save copies of those videos that are hard to get, Wondershare vDownloader is a valuable, and free, tool.
The service is available as a browser plugin that can be used with Internet Explorer, Chrome and Firefox, which is great if you’re looking for a seamless way to browse and download video. When you are working your way through the likes of YouTube, you need simply click the newly added Download button that is added by the extension. You also have the option of copying and pasting links into the program itself which is a good option if you want to queue up a number of downloads .
There are various uses for this app. You might just fancy the idea of having your own copy of a video you like, but it can also be useful for getting hold of offline footage that can be viewed when you don’t have an Internet connection, or could be transferred to a different device. The number of sites that Wondershare vDownloader can be used with is impressive -- Hulu, YouTube, Vimeo, Facebook and many more -- and there is a built in player than can be used to watch the videos that you add to your library.
You can find out more and download a free copy of the app by paying a visit to the Wondershare vDownloader review page.
Photo Credit: cybrain/Shutterstock
-

Start off June with one of these 23 software downloads
Publié: juin 2, 2012, 8:24pm CEST par Mark Wilson
 By far the biggest releases of the past week come from Microsoft. The up-coming Windows 8 is now really not too far away and you can check to see whether your computer is going to be able to run it by downloading yourself a copy of Microsoft Windows 8 Release Preview Setup. This simple little tool can also be used to obtain a product key that can be used to install Microsoft Windows 8 Release Preview (32-bit) or Microsoft Windows 8 Release Preview (64-bit).
By far the biggest releases of the past week come from Microsoft. The up-coming Windows 8 is now really not too far away and you can check to see whether your computer is going to be able to run it by downloading yourself a copy of Microsoft Windows 8 Release Preview Setup. This simple little tool can also be used to obtain a product key that can be used to install Microsoft Windows 8 Release Preview (32-bit) or Microsoft Windows 8 Release Preview (64-bit).Whether you are using the very latest version of Windows or a slightly older one, security is of the utmost importance, and ZoneAlarm Free 10.2.47.0 is a free firewall that helps to protect your internet connection, while IObit Advanced SystemCare 5.3.0.246 is a complete security suite with added optimization options. From the same stables, there is also IObit Advanced SystemCare with Antivirus 2012 (v5.5.2) Beta 2 add virus protection in this preview release.
Cyberlink upgraded its product line with the release of CyberLink PowerDirector 10 Deluxe (build 1703), which has been updated with improved processor support -- third generation Intel Core i5/i7 and second generation AMD APU 4000 and 5000 series -- along with improved stability and performance. Also available is CyberLink PowerDirector 10 Ultra (build 1703), which also includes native 64-bit support, 3D options and more. As well as video editing, Cyblerlink also produces video and DVD playback software. CyberLink PowerDVD 12.0.9380.1620 Pro can be used to play DVDs, Blu-rays, as well as a wide range of online content; CyberLink PowerDVD 12.0.9380.1620 Ultra is also available and includes DLNA Digital Media Controller and Renderer.
If you have photos to work with rather than videos, the updated Adobe Photoshop Lightroom 4.1 may be what you’re looking for. The latest release adds new Color Fringing corrections, the ability to work with HDR TIFF files as well as support for Adobe Revel.
Struggling to keep on top of your inboxes? EmailTray 4.0 is an email prioritization tool that ensures that you are only notified about the most important emails that hit your inbox while lower priority messages and spam are filtered out. If you’re looking to kit out your computer with software to enables you to get to work, you could do much worse than installing LibreOffice Productivity Suite 3.5.4, and TED Notepad 6.0.2 is a great replacement tool for Notepad completed with nine built in clipboards for easy copying and pasting of text.
In a similar vein, Notepad++ 6.1.3 plugs the gap that exists between the likes of Notepad and fully fledged word processors, with support for large files, recognition of various coding languages and much more -- there’s even a portable version available in the form of Notepad++ Portable 6.1.3.
Anyone looking to benchmark their system or just find out more about hardware and software should take a look at the updated AIDA64 2.50, which now features SensorPanel graphs and gauges, and support for Intel 330 and OCZ Vertex 4 SSD. This week there have also been a few releases that help you to make better use of your monitors.DisplayFusion 4.0.1 is a great tool if you have two or more monitors in place, providing you with shortcuts for moving programs and windows between screens.
Dexpot 1.5.17 and Dexpot 1.5.17 Portable are more suitable if you only have one monitor, as it gives you virtual desktop to work with – up to twenty, in fact! If you’re reading this article, you undoubtedly have an interest in software, and Sandboxie 3.70 is a great way to ensure that new software doesn’t affect the rest of your system by giving you the option of sandboxing apps. The penultimate app for this week,
BlueStacks App Player 0.7.0 (beta) can be used to run Android apps on your PC. If you need a break from working with apps, why not play a game? Space Invaders OpenGL 0.6.1 is a great way to relive your youth by returning to the virtual arcade.
That’s it for this week’s roundup.
Photo Credit: Victor Correia/Shutterstock
-

Take control of your inbox with EmailTray for Windows or Android
Publié: mai 31, 2012, 3:45pm CEST par Mark Wilson
 The need to prioritize emails is an idea that has been around for some time, starting with spam filtering that aimed to reduce the amount of junk reaching your inbox. Google and other email providers have made further advances by highlighting emails believed to be more important than others you receive based on content, sender and previous correspondence. EmailTray provides you with even more control by automatically filtering your mail into high priority, lower priority, no priority and spam.
The need to prioritize emails is an idea that has been around for some time, starting with spam filtering that aimed to reduce the amount of junk reaching your inbox. Google and other email providers have made further advances by highlighting emails believed to be more important than others you receive based on content, sender and previous correspondence. EmailTray provides you with even more control by automatically filtering your mail into high priority, lower priority, no priority and spam.This is a desktop app that can be used to check as many email addresses as you want providing you are working with POP3 or IMAP accounts, but all of your email is made available in one place. The program analyzes your email messages as they arrive and filters them in to inboxes of different priorities. Emails that are sent by people with whom you regularly communicate with will be assigned a higher priority than other emails, and all of your mail is sorted into ‘Top priority’, ‘Low priority’, ‘No priority’ and Spam.
Notifications can be customized so that you are only warned about the arrival of the most important email and do not waste your time looking through unimportant messages, and you can define rules of your own so that email from certain contacts or messages that include certain words are always sent to spam or prioritized as necessary. The program also checks through the spam folders of your email accounts to ensure that the spam filters of your email providers have not been too rigorous.
The reduction in email notification is very welcome, and the program seems to do an excellent job of correctly determining how different emails should be dealt with. As an added bonus, EmailTray provides you with more information about anyone you receive emails from by pulling in information from their Facebook and LinkedIn profiles. The Android version of the app includes all of the features of the Windows edition of the software and is also available free of charge.
You can find out more and download a copy of the app by paying a visit to the EmailTray or EmailTray for Android review pages.
-

Deskspace turns your desktop into a 3D virtual cube
Publié: mai 30, 2012, 6:21pm CEST par Mark Wilson

You don’t have to have too many programs running to start to find the amount of space available on your desktop to be a little tight. Rather than rushing out to buy a larger monitor, you might want to think about trying a virtual desktop tool. There are plenty of these apps to choose from, many of which are very similar top each other, but DeskSpace stands out from the crowd with a delightful 3D interface.
The program provides you with six virtual desktops, each of which is the face of a cube. You can navigate from desktop to desktop by dragging your way around the cube faces in three dimensions, but you also have the option of jumping straight to a particular workspace by using a keyboard shortcut or a menu. This is not the first time that a three dimensional concept has been used in virtual desktops, but here it has been beautifully implemented.
The animation effects when moving from one desktop to another are impressively smooth and fluid, and the fact that each of your virtual desktops can be assigned its own background image helps with fast identification. As well as a unique background, each desktop can have its own set of shortcuts that will be loaded every time you have the program running -- this is a great way to give each desktop a specific purpose.
Applications and windows can be easily moved between virtual spaces by just moving them to the edge of the screen. Although there are free tools available that provide you with extra work space, this is an app that is worth considering paying for -- take the trial version for a test drive and you’re sure to fall in love with it. DeskSpace is surprisingly light on system resources, and you will find that it works well even on older computers, laptops and slower hardware.
You can find out more and download a trial version of the app by paying a visit to the DeskSpace review page.
-

Here's an iOS app for our UK readers -- HMRC Tax Calc
Publié: mai 29, 2012, 2:50pm CEST par Mark Wilson

How much tax are you going to be paying over the coming year? It’s not always the happiest news, but it’s the sort of things that it is certainly best to know in advance -- rather get the bad news now than get a nasty surprise further down the line. HMRC Tax Calc is a free app for iOS from HMRC which can be used to work out how much tax you’re going to be paying from your wages each week or month as well as showing you what this means for your annual tax bill.
The app is designed for people whose tax situation is fairly simple -- if you have anything other than a tax code of 810L or a National Insurance letter A, you’re going to have to look elsewhere to have your tax calculations done for you. All you need to do it tap in your gross pay or wages along with how many hours a week you work, and everything else will be done for you. At a glance you can see how much of your earnings are tax free and where all the rest goes.
It is understandable that you would want to know what is happening to any of your pay that does not end up in your pocket or bank account. HMRC Tax Calc also includes a section that reveals just how your taxes are being spent – this is a nice touch that makes for interesting reading regardless of whether you use the app for its main purpose of estimating your tax bill.
In reality, this is a very basic app, and the HMRC web site is a far better source of tax advice. However, it’s a helpful tool to have to hand when you are looking around for a new job as you can quickly see what a base salary translates into when tax and National Insurance are taken into account. The capabilities of the app are going to be expanded, and there is scope for this to be transformed into something very impressive, but it is still worth taking a look at in the meantime.
You can find out more and download a free copy of the app by paying a visit to the HMRC Tax Calc review page. Note, this app is only suitable for UK tax payers.
-

Take one of these 27 downloads out for a spin
Publié: mai 27, 2012, 7:08pm CEST par Mark Wilson
 May is coming to a close, and as June beckons there are still countless software releases to keep track of. If you’ve had trouble keeping up with everything, this handy roundup is here to bring you up to speed.
May is coming to a close, and as June beckons there are still countless software releases to keep track of. If you’ve had trouble keeping up with everything, this handy roundup is here to bring you up to speed.This past week saw the release of WikidPad 2.1_01, a wiki-style text editor that can be used to capture thoughts and ideas -- stored locally or exported as an HTML file to upload to the web. If you need to store reminders of things you need to do and appointments you need to attend, PNotes 9.0.107 is a great sticky note tool that may be able to help you out. There’s also PNotes Portable 9 for anyone who likes the idea of running the same program from a USB drive. If pictures are more important to you than words, Juicebox 1.0.2 can be used to create a stunning gallery to show off your digital photos -- all in HTML5 glory.
The week was than usual on the browser update front, but there there were still important advancements for Chrome and Pale Moon. Google Chrome 20.0.1132.17 Beta hit the download servers as the browser’s march up the version numbering system continues, but there is little to report aside from a range of bug fixes -- if you want to keep your browser on a USB drive, look no further than Google Chrome Portable 20.0.1132.11 Beta. If you want an even more up to date version of Google’s browser, the Dev channel is for you and Google Chrome 21.0.1145.0 Dev and Google Chrome Portable 21.0.1145.0 Dev are the latest releases in this area.
The Firefox 12-based browser Pale Moon has also seen an important update this week which brings in smoother scrolling, better memory handling and improved stability. Various versions of the browser are available -- Pale Moon 12.1, Pale Moon x64 12.1, Pale Moon 12.1 Portable and Pale Moon x64 12.1 Portable.
O&O is a company that produces a large number of handy utilities and if you have a few of them installed, O&O LaunchPad 3.0.107 is a great way to access them all. The famous system cleanup tools CCleaner has received a couple of updates, CCleaner 3.19 and CCleaner Portable 3.19, which eliminates User Account Control warnings and adds support for new applications. While you’re looking at cleaning up and optimizing your computer, take a look at Defraggler 2.10413 and Defraggler Portable 2.10, both of which offer speed improvements of up to 30 percent on previous versions.
To help you to keep an eye on your hardware, Acronis Drive Monitor 1.0.0.566 can be used to check the health of your hard drives, and ESET Rogue Applications Remover 1.0.1.1b (32-bit) and ESET Rogue Applications Remover 1.0.1.1b (64-bit) are valuable tools for looking after your system and protecting it from malicious software.
If you have a keen interested in privacy and security, Free Hide IP 3.7.9.8 is a simple way to help stay anonymous online by masking your real IP address. Privacy concerns also exist offline, and Encryption Wizard 3.3.3 is an easy to use yet powerful utility that enables you to encrypt files on OSX, Windows and Linux machines, while Eraser 6.0.10 can be used to ensure that the files you delete cannot be recovered.
To help you to manage the files you do want to keep, Total Commander 8.0 FINAL is an advanced alternative to Windows Explorer that can handle local and remote files and has been updated to include an improved image viewer. If you want to store your important files online, Wuala “Wollishofen” build 401 enables you to do so securely, with the latest version adding customizable filters for synchronization and backup as well as numerous other bug fixes and improvements.
The final updates for this week’s roundup are for anyone looking to run virtual copies of operating systems -- VirtualBox 4.1.16 includes a range of minor fixes, and VirtualBox Extension Pack 4.1.16 adds even more options to an already powerful virtualization tool.
Remember to keep one eye on Downloadcrew Giveaway, Serif PagePlus 11, previously sold for $99.99, which ends May 27.
That’s it for this week. We’ll be back in about seven days’ time with another roundup.
Photo Credit: corepics/Shutterstock
-

Get Serif PagePlus 11 for free while you still can
Publié: mai 25, 2012, 7:41pm CEST par Mark Wilson
 Serif is a name long associated with powerful yet easy-to-use software, and these are both terms that applyto PagePlus 11. This is an extremely powerful desktop publishing application capable of producing professional looking newsletters, brochures and other documents using a series of design tools.
Serif is a name long associated with powerful yet easy-to-use software, and these are both terms that applyto PagePlus 11. This is an extremely powerful desktop publishing application capable of producing professional looking newsletters, brochures and other documents using a series of design tools.If you have been put off using DTP software in the past because you have found that it is either too complicated for day-to-day use, or too simplistic for quick projects, this could be the program you have been looking for and you can get a copy for yourself without having to part with any money. Serif PagePlus 11 originally sold for $99.99.
Using a wide range of features, templates and wizard, even potentially complex documents, such as trifold menus, can be put together in a flash. Many of the wizards that are available can be completed in a matter of moments, and you are guided through the entire process. You can keep things very simple and just change the text to reflect your personal requirements, or you can get a little more hands-on and customize the stock images and logos that are used.
A great feature of PagePlus 11 is its support for layers. Just like in an image-editing package, you can store different parts of your document on different layers, showing and hiding them as and when required. A really useful option sadly lacking from many desktop publishing programs is the ability to work with PDF. PagePlus 11 enables you to not only export the documents you create to the popular PDF format, but also to import existing PDF so they can be edited.
While there is a strong set of utilities that are geared towards the graphic side of document creation, the text-editing and layout controls are also very impressive. You’ll also find that there is excellent image support both in terms of the range of different formats that can be imported and the selection of editing tools that are included.
There are just so many features for you to explore in this versatile program that it is difficult to know quite where to begin. You can find out more about this amazing piece of software by paying a visit to the Serif PagePlus 11 review page.
To take advantage of this great giveaway, you’ll have to head over to the Downloadcrew Giveaway page between Friday May 25 and Sunday May 27.
Photo Credit: Adem Demir/Shutterstock
-

Google Search gets big iOS makeover
Publié: mai 25, 2012, 3:56pm CEST par Mark Wilson
 Google is the go-to search engine for most people, so the existence of a dedicated mobile app should come as no surprise. There has been a tool available for iOS for some time but the release of Google Search 2.0 sees the introduction of a completely redesigned app that not only boasts a new interface and new features, at least if you have an iPhone, but also easier access to other Google searches such as Gmail, Docs and Calendar.
Google is the go-to search engine for most people, so the existence of a dedicated mobile app should come as no surprise. There has been a tool available for iOS for some time but the release of Google Search 2.0 sees the introduction of a completely redesigned app that not only boasts a new interface and new features, at least if you have an iPhone, but also easier access to other Google searches such as Gmail, Docs and Calendar.As before, it is possible to conduct searches by typing, using your voice or taking a photo with your camera and using Google Goggles. There have been improvements made to the speed of autocomplete suggestions so you should find that results are available faster than ever and you can take advantage of a preview pane that slides in from the side to view individual page results. Switching between search results and pages takes nothing more than a swipe, and this gesture can also be used to switch search modes, such as moving between a standard search and an image search.
To make it easier to find relevant text, there is a magnifying glass icon that can be used to perform a search for text on a page, saving you having to read through endless passages to reach what you’re looking for. When you’re looking for images, there is a great new look to work with. You can switch to a full screen grid view of results that provides a great overview of what Google has found for you. This makes for a much clearer way of browsing through results, but also gives you a better view of individual images you choose to view.
Google Search was already an impressive tool, but the latest update transforms it into something sleek and stylish. If you are an iPad owner, there is far less to look forward to in terms of new features -- nothing more than the ability to save images to the camera roll -- but iPhone users should jump on this update as soon as they can as it is a major advancement.
You can find out more and download a free copy of the app by paying a visit to the Google Search 2.0 review page.
-

Symantec releases free iAntivirus for the Mac
Publié: mai 24, 2012, 1:10pm CEST par Mark Wilson
 While there are still Mac users who will proclaim that their systems are immune to viruses and malware, recent high-profile virus infections show that this is simply not the case. Even for anyone still convinced that their computer is immune to viruses, if a Mac is on the same network as a PC, it can easily be used to pass a virus to a Windows-based machine. This is just one of the reasons that Mac virus protection is much more important than many people believe, and Symantec’s newly released iAntivirus is a free tool that could help to bolster security.
While there are still Mac users who will proclaim that their systems are immune to viruses and malware, recent high-profile virus infections show that this is simply not the case. Even for anyone still convinced that their computer is immune to viruses, if a Mac is on the same network as a PC, it can easily be used to pass a virus to a Windows-based machine. This is just one of the reasons that Mac virus protection is much more important than many people believe, and Symantec’s newly released iAntivirus is a free tool that could help to bolster security.If you have used any of Symantec’s security software for Windows, taking a look at the antivirus tool that has been released for OS X is going to come as a little bit of a shock. Minimal is a word that best describes not only the app’s interface, but also its feature set. Rather than on-going background protection against viruses and other forms of malware, all that is on offer here is on-demand scanning -- although you do have the choice of performing a scan of your entire system, your Home folder or other locations.
In addition to this, you can drag and drop files you are unsure about onto the app window to perform a quick scan of just these files, but there are very few options to work with. This could be viewed as a good or a bad thing as it helps to keep the software simple to use, but it also means that important security features are lacking. Anyone that is more used to antivirus tools sitting quietly in the background taking care of business will need to change their ways of thinking if they install this app as the lack of background checking means that the onus is on the user to start any scans.
Should anything untoward be detected, potentially dangerous files are quarantined so they are unable to cause any damage. You have the option of attempting to repair the files, deleting it, or just restoring it to its original location. There is one intriguing feature to be found in iAntivirus -- the option of scanning your Facebook wall for malicious links that could be harmful to you and your online friends. This is a nice touch, but hardly a deal breaker.
You can find out more and download a free copy of the application by paying a visit to the iAntivirus review page.
Photo Credits: maraga/Shutterstock
-

Create HTML 5 photo galleries with Juicebox
Publié: mai 23, 2012, 10:59pm CEST par Mark Wilson
 Looking for an impressive way to show off your digital photos? Juicebox may be just what the doctor ordered. This free Adobe AIR app can be used on Macs as well as PCs running Windows or Linux and whatever platform you use to create your gallery, you can be sure that it’ll look great on both desktop and mobile platforms. The app has been designed specifically with online photo galleries in mind, and despite the fact that stunning HTML5 galleries can be created, you do not need to know a single line of coding.
Looking for an impressive way to show off your digital photos? Juicebox may be just what the doctor ordered. This free Adobe AIR app can be used on Macs as well as PCs running Windows or Linux and whatever platform you use to create your gallery, you can be sure that it’ll look great on both desktop and mobile platforms. The app has been designed specifically with online photo galleries in mind, and despite the fact that stunning HTML5 galleries can be created, you do not need to know a single line of coding.One of the problems that faces anyone looking to create an online gallery is finding a way to ensure that your photo slideshows look good on a number of different devices and platforms, particularly taking into account mobile devices with smaller screens. This is not a problem with Juicebox -- you can simply choose a design and layout that you would like to use and it will be automatically scaled to suit different screen sizes. From an end-user’s point of view, navigation is made wonderfully easy thanks to support for not only mouse and keyboard controls, but also touch screen navigation.
The beauty of Juicebox, aside from the fact that it is so easy to create great-looking galleries that can be viewed on countless devices, is the everything is just so simple to get up and running. You do not need to worry about resizing images as this is all taken care of for you. If you have already uploaded images to Flickr, you do not need to spend time downloading them and then re-uploading them: they can be used in their current online form by Juicebox.
There are some gorgeously simple yet effective gallery layouts to choose from, and all of the necessary code is generated for you ready to copy and paste into the code of your web site. If your demands are a little higher – such as the ability to add background music to your galleries or the option of creating a random playback order – you have the option of upgrading to the Pro version, but for all intents and purposes, the free version is perfect for most people.
You can find out more and download a free copy of the app by paying a visit to the Juicebox review page.
-

Do you use Gmail and want to know more about your contacts? Try Rapportive
Publié: mai 23, 2012, 6:10pm CEST par Mark Wilson
 We all now communicate with people through so many channels that it is often difficult to put names to faces. You may know someone on Twitter and Facebook but when you receive an email from them you do not necessary make a connection between the two. This is where Rapportive can help, by providing you with extended information about the contacts you receive emails from in your Gmail inbox.
We all now communicate with people through so many channels that it is often difficult to put names to faces. You may know someone on Twitter and Facebook but when you receive an email from them you do not necessary make a connection between the two. This is where Rapportive can help, by providing you with extended information about the contacts you receive emails from in your Gmail inbox.Rapportive is available as a browser extension for Chrome, Firefox and Safari and appears as a right-hand side panel whenever you look at individual emails. The extension pulls in information from social networks such as Twitter, LinkedIn and more to provide you with a more detailed profile of your contacts, and by connecting the service with your social networking accounts you can build up even more detailed information.
There are a few other extensions that do much the same job as a Rapportive, but none do it quite as neatly and quickly. A wealth of information is made available to you, but the side panel is not in the least bit obtrusive. It’s great to be able to see at a glance what someone looks like, where they are based and get a reminder about what other services you may have used to interact with them.
The very bottom of the side panel gives you the opportunity to save notes about your contacts and this is purely for your benefit -- you do not need to worry that any disparaging thoughts you type are going to be seen by your colleagues. One thing that is definitely worth mentioning is the fact that the Rapportive panel is not only packed with helpful information, it also replaces the advertisements that normally appear to the right of your inbox.
You can find out more by paying a visit to the Rapportive review page.
Photo Credit: Archipoch/Shutterstock
-

Protect your accounts with Sticky Password
Publié: mai 22, 2012, 7:03pm CEST par Mark Wilson
 The ever-present need for security means that every account that you have online, and probably on your computer as well, needs to be protected with a username and password. If you have taken the wise step of ensuring that all of your passwords are different, this will undoubtedly mean that you have an incredible number of passwords to remember.
The ever-present need for security means that every account that you have online, and probably on your computer as well, needs to be protected with a username and password. If you have taken the wise step of ensuring that all of your passwords are different, this will undoubtedly mean that you have an incredible number of passwords to remember.Sticky Password is a free tool that can store all of your passwords in a secure database and save you having to remember them by automatically filling in login information for you. Sticky Password 6.0 has just been released and there’s a lot to look forward.
To start with, there is a completely overhauled interface and added protection against malware extracting passwords from the clipboard. When you need to come up with a new password for an account you are creating, rather than relying on your own collection of letters, numbers and symbols, you can instead turn to the built in password generator which has now been enhanced with a history option. It is always a good idea to change your passwords from time to time and there is a reminder option built into the app to encourage you to do so.
Sticky Password will highlight potential security problems by pointing out accounts that have weak passwords. To make it easier to store information in the program’s database, it will automatically save usernames and password you use to create new accounts, and it is possible to define a different default web browser that should be used with different accounts -- great if you use different browser for specific tasks.
Not all of the accounts you use require you to use a password and there is now support for accounts that enable you to log in with just a username or email address. There have been plenty of other changes and additions to the latest version of the app including highlighting of login fields, and a new context menu in Internet Explorer that provides access to autofill actions.
The free version of the app does have some limitations to entice you into upgrading to the paid-for Pro version, but they are minor enough that the free version is still well worth taking a look at. The free version only allows you to create a single user account, and there is support for up to 15 online and program accounts. You can install the software as a normal program, but there is also the option of using it as a portable app so you can take it from machine to machine on your USB drive.
You can find out more and download a free copy of the app by paying a visit to the Sticky Password 6.0 review page.
Photo Credit: marekuliasz/Shutterstock
-

Security dominates mid-May's 27 software downloads
Publié: mai 20, 2012, 7:11pm CEST par Mark Wilson
 Halfway through May and the software release schedule shows no sign of abating, and beta releases stand out over the past week. Some of the biggest releases come from security experts Norton, which updated 2013 public betas. Norton AntiVirus 2013 v20.0.0.106 beta, Norton Internet Security 2013 v20.0.0.106 beta and Norton 360 2013 v20.0.0.106 beta provide an early look at what to expect from the upcoming security line, and all of these tools are free during the beta testing period.
Halfway through May and the software release schedule shows no sign of abating, and beta releases stand out over the past week. Some of the biggest releases come from security experts Norton, which updated 2013 public betas. Norton AntiVirus 2013 v20.0.0.106 beta, Norton Internet Security 2013 v20.0.0.106 beta and Norton 360 2013 v20.0.0.106 beta provide an early look at what to expect from the upcoming security line, and all of these tools are free during the beta testing period.But Norton is far from the only name in the security world, and ESET Smart Security 6 Beta (32-bit) includes not only antivirus protection but a firewall and interesting anti-theft features for laptop users; there’s also a 64-bit version of the program available -- ESET Smart Security 6 Beta (64-bit).
From the same company also comes ESET NOD32 Antivirus 6 Beta (32-bit), which focuses on the key security areas of checking for viruses, malware and rootkits. Again, there are anti-theft features built in and there is a 64-bit version of the program available -- ESET NOD32 Antivirus 6 Beta (64-bit).
For computers that are already infected with viruses or malware, Emsisoft Emergency Kit 2.0 Beta is a great tool to have in your software collection, and the latest version of the program is faster than ever at cleaning up machines.EraserDrop Portable 2.1.1 is a different type of security tool that enables you to securely delete files so that they cannot be recovered, all using a program that runs from a USB drive.
Cloudfogger 1.1.1349 is a free tool that enables you to encrypt your data including both local files and those held in cloud storage accounts such as Dropbox.
As well as security tools, a number of interesting utilities released this week. Auslogics Disk Defrag 3.4.3.0 is a fantastic free way to keep your hard drive in great shape, while Auslogics BoostSpeed 5 is a low-cost tool that helps to boost the performance of almost any computer in a few easy steps. Cloud System Booster 1.0.0 FINAL takes something of a different approach to system optimization, using shared, cloud-based information to provide fixes and tweaks for any situation.
Life online would be difficult without a web browser, and Google Chrome 19 was one of the biggest releases last week. The latest version of the browser to reach the stable channel features new synchronization options that can be used to sync tabs, extensions and more between computers -- there is also a USB drive friendly version available in the form of Google Chrome Portable 19.
If you’re looking to improve your security online, HTTPS Everywhere for Firefox and HTTPS Everywhere for Chrome are tools that will ensure that you use the secure HTTPS version of a web site whenever one is available. If you are happy to take a hands-on approach to security and want a quick and easy way to change your DNS settings, DNS Jumper 1.0.4 could be just what you’ve been looking for.
Moving onto the selection of new creative releases: Xara Photo and Graphic Designer MX 8.1 is your one-stop-shop for photo editing, desktop publishing, illustration, web graphics and much more, while Xara Designer Pro X 8.1 builds on this theme with the added ability to create web sites. Any Video Converter Free 3.3.8 is a useful tool to have installed whether you are preparing video for use online, or just want to ensure that videos can be viewed on any given device, enabling you to convert between formats quickly, easily and for free.
Three others are a bit of a mixed bag. Toolwiz FlipBook 1.4.0.0 continues the creative theme to some degree by enabling you to convert any text file into a self-executing, three dimensional ebook. For programmer, web developer, or anyone just looking for a more advanced text editor than Windows’ Notepad, PilotEdit Lite 5.6.0 is well worth a look, while Producteev 1.0.1.0 is a great little task management tool that is available for a variety of platforms so you can keep on top of your to-do list from a range of devices.
That’s it for this week. Join us in another seven days to catch up on the latest software releases.
Photo Credit: Kheng Guan Toh/Shutterstock
-

FeedDemon 4.1 drops Google Reader sharing features
Publié: mai 17, 2012, 5:45pm CEST par Mark Wilson
 It’s a strange day when some of the biggest news about the latest release of an application is a feature's removal, but this is the case with the latest version of FeedDemon. Some months ago, Google announced plans to make changes to its Reader service and this has ultimately led to FeedDemon removing the sharing features that relied on this particular service, but Google+ mostly been picks up the slack. The most recent version of FeedDemon also has a number of other changes and additions that are worth mentioning.
It’s a strange day when some of the biggest news about the latest release of an application is a feature's removal, but this is the case with the latest version of FeedDemon. Some months ago, Google announced plans to make changes to its Reader service and this has ultimately led to FeedDemon removing the sharing features that relied on this particular service, but Google+ mostly been picks up the slack. The most recent version of FeedDemon also has a number of other changes and additions that are worth mentioning.The program has long featured a recommendation engine that can point you in the direction of stories, articles and feed that you might well find interesting, and this has been improved to ensure greater relevance. When you use the built in browser to view web pages, a new Ctrl+0 keyboard shortcut is available that can be used to revert to a 100 percent zoom level. If you have the Pro version of the program – as opposed to the free Lite version – you also have a new newspaper style Photo Strip view to make use of.
If you have found the program has been slow to start you should now find that things are slightly faster, and there are a number of other bug and problem fixes that are worth mentioning. When you opt to hide all of the buttons on a toolbar, that toolbar now becomes hidden itself rather than remaining visible with no buttons, and the new tab page now includes handy Most Visited and Recently Closed options.
Other issues that have been addressed include problems with an incorrectly displayed system tray icon, problems with using the Send to Twitter and Send to Delicious options and more. To overcome compatibility problems with Internet Explorer 9, transition effects have now been removed, and there are the usual range of spit and polish changes that you would expect to find in any release.
You can find out more and download a copy of the app by paying a visit to the FeedDemon review page.
Photo Credit: nasirkhan/Shutterstock
-

Flipboard 1.9 for iOS lets you listen while you look
Publié: mai 17, 2012, 5:20pm CEST par Mark Wilson
 iOS app Flipboard has already earned itself something of a name as a great way to aggregate multiple social networks and news media into a single, more easily managed stream. The latest version of the iPhone and iPad app sees the introduction of support for audio as well as the more usual text and image based content. Audio content can be scanned through just as you would the rest of your feeds, but it can also be played in the background while you continue with your browsing.
iOS app Flipboard has already earned itself something of a name as a great way to aggregate multiple social networks and news media into a single, more easily managed stream. The latest version of the iPhone and iPad app sees the introduction of support for audio as well as the more usual text and image based content. Audio content can be scanned through just as you would the rest of your feeds, but it can also be played in the background while you continue with your browsing.There is support for SoundCloud, NPR (National Public Radio) and PRI (Public Radio International), which gives you the opportunity to listen to a wide variety of podcasts, radio broadcasts and more. By connecting Flipboard with SoundCloud you can listen to sounds that have been created or shared by your friends. There is a whole new audio category for you to explore and this interesting change in direction for the social networking tool.
Just as with anything else you consume through Flipboard, the sounds you encounter through the app can be shared through the likes of Facebook, Twitter and other services. Just where the audio addition will lead remains to be seen. There is almost undoubtedly be online radio stations that are designed specifically for a Fliboard audience, and it won’t be long before artist start to use the app as a medium for collaborative or crowd-sourced work. The future looks and sounds exciting.
The latest update also improves accessibility options, and it is now possible to use the VoiceOver feature of iOS to listen to articles rather than having to read them. There is also a new fully localized Japanese version of the app as well as support for Readability. This last addition supplements the existing support for Instapaper and provides users with another option for time-shifting their reading.
You can find out more and download a free copy of the app at the Flipboard review page.
-

Secure your connections with HTTPS Everywhere
Publié: mai 17, 2012, 3:24pm CEST par Mark Wilson
 When browsing the Internet you may well have noticed that some of sites you visit are secure, while others are not. While HTTPS is most often used for secure shopping and banking web sites, there is no reason that connections to other pages should not be encrypted to help improve privacy and security. If this is something that has concerned you, HTTPS Everywhere could be just what you have been looking for.
When browsing the Internet you may well have noticed that some of sites you visit are secure, while others are not. While HTTPS is most often used for secure shopping and banking web sites, there is no reason that connections to other pages should not be encrypted to help improve privacy and security. If this is something that has concerned you, HTTPS Everywhere could be just what you have been looking for.This free browser extension can be used to ensure that a secure connection is used whenever available. There are a huge number of websites that offer support for encrypted HTTPS connections, and yet will default to sending visitors to the regular, unencrypted HTTP version of the sites. HTTPS Everywhere uses a series of specially written rules to redirect your browser, provided you are using Chrome or Firefox, to the secure version.
There are number of remade redirection rules included that add support for a number of major web sites, but you can also define your own rules to add support for others that you may make use of. Support is a little hit and miss so you will have to experiment with the XML files used to write rules to see what you can come up with, but this is an easily enough process providing you don’t mind getting a little hands-on.
HTTPS Everywhere is currently available for Google Chrome and Mozilla’s Firefox browsers. While Firefox users have a stable version of the extension to work with, the Chrome version is currently in beta but it still a handy tool to have installed. It is not a magic solution that will wipe out all security concerns that are involved in using the web, but it is help additional layer of protection that seems to work well and as compatibility improves, it will only become more useful.
You can find out more and grab yourself free copies of the extension by visiting the HTTPS Everywhere for Chrome or HTTPS Everywhere for Firefox review pages.
Photo Credit: Jimmi/Shutterstock
-

SyncBackSE 6.1 is chock full of bug fixes
Publié: mai 16, 2012, 12:35am CEST par Mark Wilson
 SyncBackSE is a solid, reliable backup tool that has fared well in tests and compares very well to expensive alternatives. Version 6.1 of the software has just been released, and besides the addition of a Russian translation and new email options, there are a host of updates and fixes to explore. There are very few new features in the latest release, but the ability to view FTP and email communication messages has been added.
SyncBackSE is a solid, reliable backup tool that has fared well in tests and compares very well to expensive alternatives. Version 6.1 of the software has just been released, and besides the addition of a Russian translation and new email options, there are a host of updates and fixes to explore. There are very few new features in the latest release, but the ability to view FTP and email communication messages has been added.On the problem fixes front, an issue that saw file and folder filtering check boxes unnecessary checked has been addressed. If you found that backups included unnecessary operations such as the creation and subsequent deletion of empty directories, you should find that this is no longer a problem, and when you view the application history you will now find that the list starts with the newest events rather than the oldest.
There are numerous updates featured in this particular release including a redesigned history grid and users who have configured SyncBack to start automatically with Windows will be pleased to find that they are no longer prompted for a password. If you are creating remote backups via FTP, should a 451 error be encountered, the program will try to establish contact again rather than simply timing out.
Other changes and fixes include addressing a problem with copying open or locked files, along with improved detection of junction or mount points that relate to missing or disconnected. If a backup operation will results in the contents of a folder being wiped out, a warning will be displayed in advance to ensure that this is what is meant to happen. With all of these fixes and changes to an already impressive backup tool, this is one utility that is well worth taking a look at.
You can find out more and download a free trial of the app by paying a visit to the SyncBackSE review page.
Photo Credit: Modella/Shutterstock
-

Chrome 19 arrives with tab syncing -- get it now!
Publié: mai 15, 2012, 7:16pm CEST par Mark Wilson
 Google just pumped out another stable release of its web browser as Chrome 19 sees the light of day. It seems as though new browser releases are becoming an almost daily occurrence these days, so what can you expect from Google’s latest offering? Well the big new feature to be found in this release is tab syncing -- and this is as self-explanatory and awesome as it sounds.
Google just pumped out another stable release of its web browser as Chrome 19 sees the light of day. It seems as though new browser releases are becoming an almost daily occurrence these days, so what can you expect from Google’s latest offering? Well the big new feature to be found in this release is tab syncing -- and this is as self-explanatory and awesome as it sounds.In many regards Chrome is playing catch-up with Firefox here, as Mozilla’s web browser has featured the ability synchronize tabs for some time now. Chrome 19 takes very much the same approach so that whenever you are signed into your Google account any tabs you have open are automatically synced to the cloud. When you switch computers you can then access any tabs you had open on another machine by accessing the Other devices menu of the new tab page.
The feature works with all flavors of Chrome regardless of whether you are using Linux, Windows, OS X or even Android. You could be working on a project in the office before heading off home to continue working. Rather than remembering the names of the sites you have been looking at, or emailing yourself links, Chrome 19 ensures that you will have the same tabs available on your home computer so you can pick up where you left off.
And while tab syncing is undeniably great, it doesn’t end there. The same sync service is also used to synchronize your browsing history, bookmarks, themes and app settings between devices. It is also possible to synchronize browser extensions, helping you ensure that you have a uniform browsing experience no matter what computer you are using.
If you have followed the development of Chrome through the beta channels, these sync options are nothing new, but it’s great to see such a useful feature making its way out to the stable version. It almost goes without saying that the latest release also includes a bunch of bug fixes so if you have been experiencing problems with your browser, you should find that troublesome issues have been addressed with this release.
You can find out more and download a free copy of the app by paying a visit to the Google Chrome 19 review page.
-

Don't miss one of the week's exciting 25 software downloads
Publié: mai 13, 2012, 7:57pm CEST par Mark Wilson
 The second week of May has passed, and it was as busy as ever in the world of software. If you haven’t kept your finger on the pulse, we have put together this roundup to bring you back up to speed.
The second week of May has passed, and it was as busy as ever in the world of software. If you haven’t kept your finger on the pulse, we have put together this roundup to bring you back up to speed.Windows users looking to bring one of the features of OS X to their PCs will be interested in TweakNow DriveShortcut 1.0.0, which can be used to automatically create desktop shortcuts whenever removable media is inserted. If you’re looking to clean up your hard drive, the release of GeekUninstaller 1.0.0.2 is very timely, while EASEUS Todo Backup Free 4.5 has been updated with support for Windows 8 -- if you want to protect your valuable files. In a similar vein is Acronis True Image Home 2012 (Update 2) v15.0.7119, which has been enhanced with a number of tweaks and new features.
The last week saw fewer web browser updates than usual, but Opera 11.64 FINAL did see the light of day, although there are few noteworthy changes.TweetDeck 1.4 has also received a minor update.
Ad-Aware Free Antivirus+ 10.1 is a more major release with improvements made to the virus scanning engine, enhancements made to the firewall and changes to the real-time protection feature. Another security tool that has been updated is Bitdefender Total Security 2013 Beta 32-bit and Bitdefender Total Security 2013 Beta 64-bit, which are previous version of the suite that includes a firewall, spam filtering, secure browsing and much more.
If you use work with audio or video, there are some new releases that may interest you, starting with Ultimate Encoder 7 Free, which can be used to rip CDs and convert files between formats. AirServer 0.9.0 is an interesting tool that enables you to stream the output of your iPad to your PC, while SopCast 3.5.0 is a great online media tool that enables you to, amongst other things, create your own online TV station and watch broadcasts from all over the world. To help you to make the most of your media collection, Plex Media Center 0.9.5.2 (beta) is an all-in-one tool that enables you to pull in all your media files from network locations and enjoy them on your PC or TV, and Plex Media Server 0.9.6.1 is available to help you to get everything set up.
This week also saw the release of trial versions of the CS6 range of applications from Adobe. Fireworks CS6 is a staggering powerful image editor designed with web creation in mind, while the latest version of Adobe’s flagship image editor, Photoshop CS6 really needs no introduction. Adobe is famous not only for its image editing tools, but also software for creating content for the web. Dreamweaver CS6 features the same redesigned and refined interface that can be found across the rest of the CS6 range, while Adobe Flash Professional CS6 is available for anyone who doubts the future of HTML5. For video-editing fans, Adobe Premiere Pro CS6 is a staggeringly powerful tool that includes almost everything you could ever imagine using, while Adobe Illustrator CS6 is a versatile vector drawing tool that can be put to countless uses.
But Adobe is far from being the only company producing image editing software, and Pixelitor 1.1.2 is a surprisingly feature-packed editor that is available completely free of charge. Also free is GIMP 2.8.0 FINAL, which has undergone a huge makeover and is now more approachable than ever -- there’s even GIMP Portable 2.8.0 ready to copy onto your USB drive for use on the move. Topping off this week’s roundup is Apache OpenOffice 3.4.0, which is the latest version of the free office suite that has, amongst other enhancements, been given a speed boost for better performance.
That’s it for this week. There’ll be another roundup in seven days’ time, and in the meantime you can keep checking out Downloadcrew for details of all the latest releases.
Photo Credit: yavuzunlu/Shutterstock
-

Use TweakNow DriveShortcut to display disks on Windows desktop
Publié: mai 11, 2012, 12:15am CEST par Mark Wilson
 Sometimes it is the smallest of things that makes the biggest differences -- it can be little touches that matter the most. Users of OS X and many flavors of Linux will be used to the appearance of a desktop icon when an external drive is plugged in or an optical disc is inserted. This little feature may seem minor, but it is also immensely useful. By installing TweakNow DriveShortcut, you can bring the same feature to Windows.
Sometimes it is the smallest of things that makes the biggest differences -- it can be little touches that matter the most. Users of OS X and many flavors of Linux will be used to the appearance of a desktop icon when an external drive is plugged in or an optical disc is inserted. This little feature may seem minor, but it is also immensely useful. By installing TweakNow DriveShortcut, you can bring the same feature to Windows.This is a great alternative, or supplement to Windows’ own built-in AutoPlay feature as it enables you to more easily access drives when you want rather than having the contents automatically displayed after insertion. The most common use for the program would be to create desktop shortcuts for CDs and DVDs as they are inserted, but it can also be used to automatically create shortcuts for USB drives.
TweakNow DriveShortcut runs in the background, constantly monitoring your computer for the appearance of new drives and this also includes removable hard drives and network drives. To make the shortcut icons easier to locate, you can opt to always use the same location for individual icons, and the program can easily set to start with Windows so there is no need to remember to launch it manually.
It is not just removable media that the program can be used with -- it also provides a quick and easy way to enable or disable shortcuts to fixed drives that you have installed. While not quite as useful as the way drives are handled in OSX, this is a handy utility that brings an interesting feature to Windows.
You can find out more and download a free copy of the app by paying a visit to the TweakNow DriveShortcut review page.
Photo Credit: Sergii Korolko/Shutterstock
-

Ad-Aware Free Antivirus+ 10.1 advances, leaves Windows 2000 behind
Publié: mai 9, 2012, 3:15pm CEST par Mark Wilson
 The jump to version x.1 of a program may not seem like particularly big news, but with the release of Ad-Aware Free Antivirus+ 10.1 there is a surprising amount to take in. For anyone who has taken the security step of installing more than one antivirus tool, you should now find that, which Norton and AVG at least, Ad-Aware no longer produces a BSOD, but there have also been more important changes to the engine of this antivirus and firewall tool.
The jump to version x.1 of a program may not seem like particularly big news, but with the release of Ad-Aware Free Antivirus+ 10.1 there is a surprising amount to take in. For anyone who has taken the security step of installing more than one antivirus tool, you should now find that, which Norton and AVG at least, Ad-Aware no longer produces a BSOD, but there have also been more important changes to the engine of this antivirus and firewall tool.A major concern with any antivirus tool is the impact it has on your system and in the latest release there have been tweak made to the scanning engine that mean that schedule scans are performed faster than in the past. The program has already undergone something of a makeover but there have now been additional improvements made so the app as a whole feels generally snappier – this is in addition to faster scan completion.
On the firewall front, programs that have been deemed as trustworthy are now added to the white-list and there is now better support for 64-bit versions of Windows for both the firewall and antivirus side of the application. Users of Windows 2000 will be disappointed to find that their operating system is no longer supported, and this comes as results of changes that have been made to improve the reliability of system drivers.
A problem that meant multi-user systems were plagued with requests for a license key when switching between accounts has been addressed and the program is now able to detect a wider range of tracking cookies. This minor version increase is a great move forward for Lavasoft, as their famous security software makes increasing steps towards catching up with the competition that overtook it in recent years.
You can find out more and download a free copy of the program by paying a visit to the Ad-Aware Free Antivirus+ 10.1 review page.
Photo Credit: alexskopje/Shutterstock
-

Start May off right, with one of these 27 downloads
Publié: mai 5, 2012, 5:40pm CEST par Mark Wilson

They say April showers bring May flowers, and perhaps that's true of software, particularly supporting the cloud. For sure, the month started with lots of new applications to explore.
There has been a recent resurgence in interest in cloud storage following the unveiling of Google Drive, but if you are looking for a way to secure data you have backed up to the cloud, Cloudfogger 1.1.1291 may be just what you have been looking for. Unimpressed with Google Drive et al? Check out Amazon Cloud Drive 0.3.28 which can be used not only store files but also backup your MP3 purchases. Last week’s stable release of Dropbox has been followed up with Dropbox 1.4.2 to address problems. Proving that you don’t have to have an Internet connection around the clock the benefit from the internet, GMapCatcher 0.7.7.2 enables you to cache online maps for offline viewing.
There are numerous tools that can convert video between formats, and Hybrid 2012.5.3.1 is a free utility that gives you a great deal of control over the process. If you prefer to watch online video, Miro 5.0 FINAL is a powerful streaming suite that enables you to pull in clips and shows from all manner of sources. Sticking with the more traditional browser-based method of viewing online, Turn Off the Lights for Firefox 2.0.0.81 and Turn Off the Lights for Chrome 2.0.0.81 are browser extensions that make it easier to focus on your videos without distraction.
If music is more your thing, Freemake Music Box 0.9.3 is a free service that enables you to stream music to your computer freely and legally. Spotify 0.5.0 for iPad enables those with a Spotify Premium account to stream music to their Apple tablet, while the newly released Skype for iPad 4.0 can be used to keep in touch with friends and colleagues while taking advantage of new video options.
Sticking with the mobile device theme, Bitdefender Power Tune-up 1.3.209 Android enables you to squeeze every last drop of battery life from your Android-based phone or tablet.
Anyone working with two or more monitors at a PC can take advantage of DisplayFusion 4.0, which provides you with a great deal of control over your multi-monitor setup.
There has been a selection of interesting release o the productivity front. If you have ditched Adobe Reader, Foxit Reader 5.3.0 may be the PDF tool you have been looking for, and LibreOffice Productivity Suite 3.5.3 has been updated to bring even more value to this free office suite. Should you be more interested in performance tweaking that productivity, you should check out Ashampoo WinOptimizer Free 1.0.0 which enables you to fix problems with your computer and speed it up with just a few clicks of the mouse.
No roundup would be complete without a few browser updates and this week is no different. Pale Moon 12.0 is a speed optimized version of Firefox that includes all of the latest stability and security fixes of Mozilla’s browser and is also available in other varieties. Pale Moon Portable is available for copying to a USB drive, while anyone with a 64-bit system should take a look at Pale Moon x64 and Pale Moon x64 Portable.
You may also be interested in checking out Waterfox 12.0 which is also designed for 64-bit systems. When you’re online it is important to stay safe, and this week has seen the release of a number of handy security tools.
ZoneAlarm Free Antivirus + Firewall 10.2 is dual-head security suite that protect your computer on two fronts, while BitDefender USB Immunizer 3.0 is a handy addition to any system that prevents malware from auto-running from USB drives.
We may not yet be halfway through 2012, but the 2013 products are already with us. Norton Internet Security 2013 beta, Norton AntiVirus 2013 betaand Norton 360 2013 beta all boast new interfaces, but little in the way of new features, and Norton Bootable Recovery Tool 4.5 has been released to enable you to disinfect your computer even if Windows won’t boot.
That’s it for this week’s roundup. Join us again in a week’s time for another catch up on all of the best releases from the preceding seven days.
Photo Credits: James Thew/Shutterstock
-

Foxit Reader 5.3 improves by nips and tucks
Publié: mai 3, 2012, 5:55pm CEST par Mark Wilson
 The PDF format is commonly used to deliver documents online, and people increasingly discover that there is no need to use a bloated piece of software such as Adobe Reader to open them. Foxit Reader is one lighter weight alternative that prides itself not only on the speed and performance it offers, but also the security features. The Read Out Loud feature has been updated with a new Read from Current Page option as well.
The PDF format is commonly used to deliver documents online, and people increasingly discover that there is no need to use a bloated piece of software such as Adobe Reader to open them. Foxit Reader is one lighter weight alternative that prides itself not only on the speed and performance it offers, but also the security features. The Read Out Loud feature has been updated with a new Read from Current Page option as well.Foxit Reader 5.3 adds support for viewing RMS-protected PDF that have dynamic watermarks, and there are also a number of other changes, improvements and additions in this latest release. When the program is used to view a document that is too large to print on regular-sized paper, you can now take advantage of the new Tile Large Pages option in the print dialog that makes it possible to split such large pages over several pieces of paper in the style of a poster.
When you view PDF files in full-screen mode it is possible to reposition the toolbar to the location of your choice. In previous versions of the program, this custom position was forgotten when exiting full-screen mode, but it is now retained for the next time you make the switch. The ribbon-style toolbar that is gracing an increasing number of programs is not new to Foxit Reader, but the new toolbar button to switch between mode with a click is a helpful new addition.
Other changes to this minor update include changes to the way in which updates are provided, easier selection of text and improved highlighting. If you are using the app to view PDFs on a web site, the download progress bar has been tweaked so that it is displayed before document content, and when you are working with multiple PDFs in tabs, you now have the option of using cursor keys to switch between documents.
You can find out more and download a free copy of the program by paying a visit to the Foxit Reader 5.3 review page.
Photo Credit: ssuaphotos/Shutterstock
-

Use multiple monitors with Windows 8
Publié: mai 3, 2012, 3:20pm CEST par Mark Wilson
 Working with multiple monitors is a great way to improve productivity, but it is a completely different way of working that can take a little getting used to. DisplayFusion is a utility that makes it easier to work with multi-display setups, and version 4.0 of the app includes a raft of new feature that will help you to get even more from your monitors, starting off with support for the Windows 8 Consumer Preview.
Working with multiple monitors is a great way to improve productivity, but it is a completely different way of working that can take a little getting used to. DisplayFusion is a utility that makes it easier to work with multi-display setups, and version 4.0 of the app includes a raft of new feature that will help you to get even more from your monitors, starting off with support for the Windows 8 Consumer Preview.As standard Windows will only display the taskbar on one monitor, but it can be added to all of them with DisplayFusion. Any program that is shown on a particular screen will have a taskbar button on the corresponding screen and in the latest version of the program, Jump Lists are now available. There is also newly added support for icon profiles that can be used to quickly re-arrange desktop icon according to what you are doing.
HotKeys have been available for a while, making it easy to interact with programs and windows, but the setup tool has now been revamped to make it easier to customize these shortcuts. There have also been changes to the way Aero coloring is picked so the color is now based on the wallpaper that is selected or the application that is currently active. If you’re looking for new wallpapers, Google Image Search, Bing Image Search, and deviantART have been added as online providers.
For corporate users, ADMX Group Policy templates are available for centralized control in Active Directory environments, and support for right-to-left languages has been added. There is also the usual selection of bug fixes and performance improvements, and whether you are an existing DisplayFusion user or you’re yet to experience the program, this is an update that is well worth taking a look at.
You can find out more and download a free trial of the app by paying a visit to the DisplayFusion 4.0 review page. There is also a free version of the program available.
Photo Credit: corepics/Shutterstock
-

Spotify comes to iPad -- get it now!
Publié: mai 2, 2012, 4:59pm CEST par Mark Wilson
 Fans of Spotify need no longer endure a blown up app designed for the smaller screen of the iPhone, thanks to the release of a dedicate iPad version of the app, today. Spotify 0.5.0 has been a long time coming and, as you would expect, there is support for the Retina display of the new iPad. There has been a shift in focus with this release, as the app now makes it easy to discover new music rather than simply enabling you to listen to things you have already found.
Fans of Spotify need no longer endure a blown up app designed for the smaller screen of the iPhone, thanks to the release of a dedicate iPad version of the app, today. Spotify 0.5.0 has been a long time coming and, as you would expect, there is support for the Retina display of the new iPad. There has been a shift in focus with this release, as the app now makes it easy to discover new music rather than simply enabling you to listen to things you have already found.The interface has been given a gesture-friendly overhaul and the screen is divided into two sections that allow for easy navigation of playlists, friends and news, while providing a clear display of the information you are looking for. The newly released app is comparable to its desktop counterpart, providing access to almost the same set of features, although there is no support for the likes of last.fm and other apps at the moment; this is likely to be something that is added in the future.
New features in this version include gapless playback -- which is ideal if you are using Spotify to provide a party soundtrack -- as well as crossfading for seamless transitions between tracks. There’s also AirPlay functionality so you can stream music to other devices. There are lots of nice touches throughout the app such as the way search works. As you start to type the name of an artist or song, there is live updating with results shown from both your existing library and tracks you are yet to discover.
As you would expect, there are also a number of fixes to address problems that have been discovered, and this is by far the most impressive version of Spotify for iOS to date. As with previous versions of the software, it can only be used in conjunction with a Spotify Premium account and you have the option of signing up for a free 48 hour trial if you do not already have one.
You can find out more and download a free copy of the app by paying a visit to the Spotify 0.5.0 review page.
-

Bitdefender USB Immunizer protects your PC from flash drive malware
Publié: mai 1, 2012, 6:15pm CEST par Mark Wilson
 There are a number of ways in which a virus or malware infection can find its way onto a computer, and if USB drives are used to transport files from one machine to another, this represents a security risk that could be exploited by malicious software. Part of the problem arises from the fact that USB drives can be configure to autorun just like optical media, but this is something you can tackle with Bitdefender USB Immunizer.
There are a number of ways in which a virus or malware infection can find its way onto a computer, and if USB drives are used to transport files from one machine to another, this represents a security risk that could be exploited by malicious software. Part of the problem arises from the fact that USB drives can be configure to autorun just like optical media, but this is something you can tackle with Bitdefender USB Immunizer.This free tool is not new, but it has undergone an overhaul that makes it easier to work with multiple USB drives and enables you to prevent USB drives from being automatically launched. This is achieved by creating a read-only autorun.inf file in the root of the drive, which is left blank so that it serves no real function. Because the file is read-only, it cannot be edited by malware looking to launch itself when your USB drive is plugged in.
Relatedly, the fact that an autorun,inf file exists means that another one cannot be created, so there is no way malicious program can be made to run without your permission. Should you decide that you ever want to use your USB drive in conjunction with a legitimate autorun.inf file you will need to delete the one that the app creates. Because of the security measures that have been put in place, you will need to delete the existing file using a computer running Linux or OS X.
The most recent update to the app features a redesigned interface that makes it easier to protect several USB drives in one fell swoop, and there is also the ability to automatically prevent all drives from autorunning. This works by simply disabling the system wide autorun feature, and while this is something that you could do manually, it is a handy addition to a useful security tool.
You can find out more anjd download a free copy of the program by paying a visit to the Bitdefender USB Immunizer review page.
Photo Credit: chien321/Shutterstock
-

Have frequent Skype crashes ruined your relationships? Try the iOS update
Publié: mai 1, 2012, 5:05pm CEST par Mark Wilson
 iOS users now have an updated VoIP app to work with following the release of Skype 4.0 for iPad and Skype 4.0 for iPhone. The latest version focuses mainly on stability and accessibility improvements, but there are also a few other enhancements and new features to enjoy. There’s a new sign in screen in addition to a number of minor UI tweaks.
iOS users now have an updated VoIP app to work with following the release of Skype 4.0 for iPad and Skype 4.0 for iPhone. The latest version focuses mainly on stability and accessibility improvements, but there are also a few other enhancements and new features to enjoy. There’s a new sign in screen in addition to a number of minor UI tweaks.Anyone who finds the app prone to crashing should be happier with this new version. Skype promises generally-improved stability, and auto-restart in the event of a crash. This is hardly a ringing endorsement for a chat tool, but it’s a step in the right direction. Surely, it's better than untimely disconnects during an important video chat.
While the app can be used with and device running iOS 4.3 or higher, if you want to use it to make video calls you’ll need a device with a front-facing camera. If you have used Skype on a desktop platform, you’ll be aware that it is possible to re-position video windows when you are in the middle of a call. Skype 4.0 brings the same option to iOS -- meaning that you are now able to move your video preview window.
The UI changes are little to get overly excited about, amounting to little more than a slight redesign to the messaging and contact sections of the app as well as minor movements to app elements. Some iPhone users are reporting problems with Bluetooth headsets so if you are currently using such a headset, you might want to think about holding off updating your software until Skype addresses this.
You can find out more by paying a visit to the review pages for of Skype 4.0 for iPad and Skype 4.0 for iPhone.
-

What timing, avast! Free Antivirus for Mac exits beta as OS X security concerns escalate
Publié: avril 30, 2012, 5:19pm CEST par Mark Wilson

Macs have been in the news more than normal recently. The Flashback Trojan shows the platform is just as prone to viruses and malware as Windows and other operating systems. Many Mac users believe -- wrongly, it might be added -- that OS X is immune to malware and does not need any form of protection. The latest high-profile infestation highlights the need for Mac security tools and; with almost uncanny timing, avast! Free Antivirus for Mac has exited beta and gone gold.Software from avast! has been available for Windows for quite some time, and the Mac version of software is based on the same protection engine. The app is broken down into three basic areas -- File System Shield, Mail Shield and Web Shield -- and if you have used the Windows version of the tool, you’ll know pretty much what to expect. As is becoming increasingly common, this security tool takes advantage of community reporting to improve the analysis of suspicious files, helping to allow for faster responses to emerging threats.
Individual files can be scanned for infection by dragging them onto the app interface, but you also have the option of running scans of your entire system, including removable media and network locations. The Web Shield works in conjunction with the WebRep browser plugin -- available for Safari, Chrome and Firefox -- helping to protect against malicious phishing web sites as you spend time online.
Unlike some security software, when avast! say that their software is free, they mean that it is free. This is true for both home users and businesses, which is great news for any small company looking to keep costs to a minimum while maintaining the security that is so important.
You can find out more and download your free copy of the program by paying a visit to the avast! Free Antivirus for Mac review page.
Photo Credit: Jirsak/Shutterstock
-

Say goodbye to April with one of these 36 downloads
Publié: avril 29, 2012, 7:40pm CEST par Mark Wilson
 Cloud was the big news this past week, and there were exciting developments in the world of online storage. After what seems like years of waiting, Google Drive 1.0 finally released, extending the idea of Docs and providing users with the opportunity to store any files they want online and keept them synched with their computers. There’s also a mobile version of the app available, Google Drive for Android 1.0.77, that enables access toyour files on the move.
Cloud was the big news this past week, and there were exciting developments in the world of online storage. After what seems like years of waiting, Google Drive 1.0 finally released, extending the idea of Docs and providing users with the opportunity to store any files they want online and keept them synched with their computers. There’s also a mobile version of the app available, Google Drive for Android 1.0.77, that enables access toyour files on the move.Ubuntu One 2.0.3 has nothing whatsoever to do with the operating system of the same name, but provides you with 5GB of free space for storage and backups. Cloud storage stalwart Dropbox 1.4.0 has been updated and finally becomes stable, as well as adding batch uploading and importing of photos Meanwhile, Microsoft released Microsoft SkyDrive 2012 v16.4 and Microsoft SkyDrive 2.0 iOS with reduced storage levels.
For managing the space on your local hard drive, IObit Uninstaller 2.2 enables you to keep things neat and tidy by removing unnecessary program and toolbars, while CCleaner 3.18 and CCleaner 3.18 Portable provide you with more advanced cleanup options. If you find that Explorer is too limited for your file management needs, XYplorer 11.00 provides you with a dual-paned interface and a host of feature that make it easy to work with files and folders – albeit at a price.
VirtualBox 4.1.14 has been updated for anyone looking to virtualize an operating system, fixing a range of known issues whileVirtualBox Extension Pack 4.1.14 adds handy extra features such as a USB 2.0 controller.
It was a big week for Mozilla browsers with the release of Firefox 12 FINAL and Firefox 12 Portable 12, which have now moved into the stable channel, although there isn’t a great deal to look at in terms of new features. Firefox 13 Beta features a redesigned New Tab pages, while Firefox Aurora 14.0a2 adds support for Windows 8’s Metro interface. Firefox Nightly 15.0a1 (32-bit) and Firefox Nightly 15.0a1 (64-bit) give glimpses of the future of Firefox, although they are not recommended for the faint-hearted.
For anyone who is keen to keep an eye on the latest interface changes coming in future versions of Mozilla’s web browser, Firefox 15.0a1 UX (32-bit) and Firefox 15.0a1 UX (64-bit) should interest. Mozilla is about more than its web browser, and Thunderbird 12 FINAL keeps the version numbering in line with Firefox and both this standard app and the portable version, Mozilla Thunderbird Portable 12.0, include search improvements and more.
There were a number of noteworthy security releases this past week, including Emsisoft Anti-Malware 6.5.0.11, which keeps your computer free from unwanted nasties and includes speed improvemens as well as new plugins for Outlook.
Norton Identity Safe 2012.6.0.72, Norton Identity Safe iOS 1.0.50 and Norton Identity Safe Android 1.0.1 are new, free tools from Symantec that can be used to securely store passwords in an encrypted database and quickly enter personal information into online forms. Not content with updating SkyDrive and announcing a future update to the public preview of Windows 8, Microsoft have also release Microsoft Security Essentials 4 FINAL [32-bit] and Microsoft Security Essentials 4 FINAL [64-bit], which boast improved performance and is available free of charge for small businesses.
Getting a little more creative, CyberLink Media Suite 10 Ultra is a staggeringly feature-packed suite that comprises no less than eleven separate tools for viewing, editing, managing and sharing your media collection. If you encode videos yourself, you will know exactly what format it is in, but you may well encounter other videos online that won't play back. This may well be because you do not have the necessary codecs installed and this is where codec packs are useful; released this week were K-Lite Codec Pack Basic 8.7.0, K-Lite Codec Pack Standard 8.7.0, K-Lite Codec Pack Mega 8.7.0 and K-Lite Codec Pack Full 8.7.0.
The final releases in this week’s roundup will be of interest to mobile users. Twitter 4.2 for iOS and Twitter 3.2.0 for Android have been updated to feature better push notifications as well as a redesigned Discover section. If you’re using social media for professional purposes, LinkedIn for iOS 5.0 will be of interest as it is now a universal app and also features iOS calendar integration.
This has been a particular busy week for releases, and the coming seven days look like being just as exciting. Our next roundup kicks of May goodies.
Photo Credit: CCimage/Shutterstock
-

Cobian Backup 11 exits beta, adds new features
Publié: avril 29, 2012, 12:42am CEST par Mark Wilson
 Looking for a backup tool? There is plenty of choice for even the pickiest of software connoisseurs. Aside from the irritating aspect of having to actually get a backup job set up, one thing that puts many people off safeguarding their valuable data by backing it up is the cost of the necessary software. Cobian Backup 11 is one of a number of free backup tools vying for users’ attention and it boasts an impressive array of features.
Looking for a backup tool? There is plenty of choice for even the pickiest of software connoisseurs. Aside from the irritating aspect of having to actually get a backup job set up, one thing that puts many people off safeguarding their valuable data by backing it up is the cost of the necessary software. Cobian Backup 11 is one of a number of free backup tools vying for users’ attention and it boasts an impressive array of features.If you have followed the app's development, the move to version 11 introduces a number of new features as well as tweaks to existing favorites. There is now support for AES encryption, better remote management and the ability to use tasks within groups. The important thing to remember with any backup regime is that your files are only truly safe if you back them up regularly. Rather than relying on memory, it is better to have an automatic schedule in place, and this is definitely something that Cobian Backup can help you out with.
The range of scheduling options is impressive and there are various new system events that can be used as triggers rather than just relying on dates and times. For example, you may choose to run a backup at startup, or on the third Tuesday of the month, or before computer suspension. If you have configured multiple backups -- you may want to backup music files and image separately, for instance -- one task can be used as trigger for another.
Other enhancements see the addition of the ability to limit the number of differential backups that are retained, meaning that you are able to place restrictions on the amount of space that has to be set aside to house backups. With features such as FTP backups, both as source and destination, strong compression and encryption and much more besides. It’s easy to be put off the idea of using free software, particular for something as important as backing up data, but this is a tool that deserves serious attention.
You can find out more and download a free copy of the program by paying a visit to the Cobian Backup 11 review page.
Photo Credit: Raimundas/Shutterstock
-

Delete something accidentally? Try Wise Data Recovery
Publié: avril 26, 2012, 3:59pm CEST par Mark Wilson
 How many times have you done it? After deciding to spring clean your computer you empty the Recycle Bin only to realize that it contained some files that you meant to copy out. Or you may be browsing through files over the network and delete some files on another machine, bypassing the Recycle Bin altogether. We have all found ourselves needing to restore files that have been deleted in haste, and this is something that Wise Data Recovery can help with.
How many times have you done it? After deciding to spring clean your computer you empty the Recycle Bin only to realize that it contained some files that you meant to copy out. Or you may be browsing through files over the network and delete some files on another machine, bypassing the Recycle Bin altogether. We have all found ourselves needing to restore files that have been deleted in haste, and this is something that Wise Data Recovery can help with.The name of the program is about as descriptive as you could hope for, and this is an example of an app that does precisely what you would expect it to. There are no fancy extra features to be found here, but what this free recovery tool does, it does well and makes everything as simple as possible. Scans of hard drives are performed surprisingly quickly and you can tell at a glance what chance you have of restoring the data thought you might have lost.
Wise Data Recovery enables you to browse through recoverable files in their original folder structure, although you may find that folder names have been obliterated, and uses a traffic light system to let you know the status of any file. Files marked with a green icon are in good condition and should be recoverable without problems while those with a yellow icon are in a poor condition. This may mean that you are able to recover some data from them, but anything that has been assigned a red icon is unrecoverable.
There is also a search option on hand to help you to track down files that include certain words and you can either work through files restoring them on an individual basis, or you can selected large number to recover at the same time. For a free tool this seems like an impressive program and in tests it was able to successfully recover files that had been deleted some time ago. If you have lost data, this is well worth taking a look at.
You can find out more and download a free copy of the program by paying a visit to the Wise Data Recovery review page.
Photo Credit: Dirk Ercken/Shutterstock
-

Norton Identity Safe secures Android, iOS, OS X and Windows passwords
Publié: avril 25, 2012, 6:44pm CEST par Mark Wilson
 You’ve no doubt noticed that a huge number of websites require you to log into an account before you can do anything useful. This could be your banking site, a forum, a social network, or almost anything else imaginable and in all likelihood you have a huge number of passwords to remember. Some people simply use the same password for everything, but this has obvious security implications. Norton Identity Safe is one possible solution that rivals tools such as KeePass and 1Password as it stores all of you log in details in a secure database.
You’ve no doubt noticed that a huge number of websites require you to log into an account before you can do anything useful. This could be your banking site, a forum, a social network, or almost anything else imaginable and in all likelihood you have a huge number of passwords to remember. Some people simply use the same password for everything, but this has obvious security implications. Norton Identity Safe is one possible solution that rivals tools such as KeePass and 1Password as it stores all of you log in details in a secure database.The app is available for Windows as well as iOS and Android and, providing you make sure you download the software before 1 October 2012, it is completely free of charge. Although there is a regular program installation to run through, the app is really a browser plugin for users of Windows and OS X, and it is compatible with Internet Explorer, Chrome, Firefox, Safari and Opera. As all of your password are stored in one place, you will obviously need to create a strong password to keep everything secure, and there is a two-step approach to this.
Firstly, you need to sign into an existing Norton account, or create a new one if you do not already have one, and you then have to create a separate password for Identity Safe itself. It’s no good trying to cheat here as you are not allowed to use the same password as for your account, and you will be guided through the process of making a suitable strong password – not too short, a mixture of upper and lower case letter, and including numbers and symbols.
Once this has been done you can start storing your usernames and password, and Identity Safe will then automatically fill in login forms whenever you call on it to do so -- auto-form filling also extends to address, credit card details and the like. Because data is stored in the cloud it can be automatically synchronized between devices so you never have to remember passwords -- however many different machines you use. It’s somewhat disappointing to find that it is not possible to successfully import passwords that have already been saved in your web browser.
There are also mobile versions of the app available for Android and iOS and while these offer many of the same options as the desktop version, there are a few differences. Firstly, you need to have setup the desktop version in advance so the mobile app can pull in password information from the cloud. The iOS app is really a replacement for the built-in browser and it will enable you to access the passwords you have stored in your account and similar options are available to Android users. It is also possible to check the safety of web sites and any pages that are deemed unsafe will be automatically blocked.
You can find out more and download a free copy of the software by paying a visit to the review pages -- Norton Identity Safe, Norton Identity Safe for iOS and Norton Identity Safe for Android.
Photo Credit: bicubic/Shutterstock
-

Google Drive arrives -- and what a shock, it's really an upgrade for Docs
Publié: avril 24, 2012, 8:42pm CEST par Mark Wilson
 One of the most eagerly anticipated online storage services -- and one of the worst kept secrets in computing -- has finally seen the light of day. Google Drive has, at long last, been unveiled after years of rumors and speculation, working in much the same way as the likes of Dropbox and providing users with 5GB of cloud storage free of charge.
One of the most eagerly anticipated online storage services -- and one of the worst kept secrets in computing -- has finally seen the light of day. Google Drive has, at long last, been unveiled after years of rumors and speculation, working in much the same way as the likes of Dropbox and providing users with 5GB of cloud storage free of charge.In many ways, the release of Google Drive can be seen as more of an update to Google Docs, and this is clear for Android users who will find that their Google Docs app will update and become Google Drive.
In terms of online use, working with Google Drive is virtually indistinguishable from Google Docs and any files you have already created in Docs will have been transferred across ready for you to use. All of the usual search and sorting options are available, and there are also a few cool extras such as OCR that can be used to convert your PDF files and images into a format that can be searched.
As you would expect, there are a couple of desktop app available, one for Mac and one for Windows, and there is also an Android app for free download in Google Play. There will be an iOS version of the app released at some point in the future, but there may be a delay in it hitting the App Store as it makes its way through Apple’s vetting process. The desktop app is a simple affair that enables you to synchronize your online files with your Mac or PC, while the mobile app enables you to access any of the files you have stored or synched online.
5GB is a reasonable amount of storage space to get started with, but if you feel like it’s not going to be enough, there are a number of upgrades for you to choose from. You can get 25GB for $2.49 a month, 100GB for $4.99 a month, or even 1TB for $49.99 a month, and these are prices that compare very well with the competition.
You can find out more and download a free copy of the app by paying a visit to the review pages – Google Drive for Mac and PC and Google Drive for Android.
-

Minor update adds more languages to jAlbum 10.6
Publié: avril 24, 2012, 7:18pm CEST par Mark Wilson
 Web album creator jAlbum has been updated to version 10.6 with a range of bug fixes and feature enhancements. Mac users can now take advantage of a native file chooser that can be used to add folders and images to an album, but there are also numerous tweaks and updates to the Windows and Linux versions of the app to take a look at.
Web album creator jAlbum has been updated to version 10.6 with a range of bug fixes and feature enhancements. Mac users can now take advantage of a native file chooser that can be used to add folders and images to an album, but there are also numerous tweaks and updates to the Windows and Linux versions of the app to take a look at.One of the great things about jAlbum is that skins can used to create a completely unique look for your online albums, helping to avoid the risk of looking like everyone else's. This minor update includes an updated version of the Turtle skin, but most of the changes are under the hood. Translators have been hard at work providing updated text in Brazilian Portuguese, German, English, Swedish, French, Spanish, Finnish, Slovak, Polish, Slovenian, Romanian and Korean, and language information is now added to published albums.
Other changes include the ability to sign out of your account and leave your license active and a slightly modified way to activating a software license. While none of the changes and additions are particularly ground-breaking, these are merely polishing tweaks to an established and accomplished app that provides users with a powerful and flexible way to create galleries to show off their digital photographs.
As you would expect from any program update, there are also a range of bugs fixes including one that prevented certain PNG files from being processed. If you have experienced problems with the code generated by jAlbum, you should hopefully find that these issues have been addressed in the latest release as there have been a number of changes made to fix specific errors.
You can find out more and download a free trial of the app by paying a visit to the jAlbum 10.6 review page.
Photo Credit: marekuliasz/Shutterstock
-

Opera 12 gets opt-in hardware acceleration
Publié: avril 24, 2012, 3:22pm CEST par Mark Wilson
 It is only a week since Opera 12 added support for cameras, and since then two new builds have been released that push the development of the browser even further. Performance is of utmost importance for every computer user, and the latest builds of Opera Next have been improved with the implementation of hardware acceleration. Interestingly, hardware acceleration is an opt-in feature.
It is only a week since Opera 12 added support for cameras, and since then two new builds have been released that push the development of the browser even further. Performance is of utmost importance for every computer user, and the latest builds of Opera Next have been improved with the implementation of hardware acceleration. Interestingly, hardware acceleration is an opt-in feature.A new DirectX backend is available instead of OpenGL and the hardware acceleration is used to not only improve the rendering time for pages, but also boosts the speed of the user interface. In addition to the performance gains that come from the implementation of this new feature, overall performance of the browser has also been tweaked and stability problems arising from the use of plugins have been addressed.
Opera has supported right-to-left (RTL) web pages for quite some time now, and the latest snapshot bring the same support to the program interface. If you have your language set to Arabic, Farsi, Hebrew or Urdu the RTL UI will be loaded for you automatically, effectively creating a mirror image of what is usual displayed, with the order of menus and buttons reversed.
A somewhat more minor change to the browser is the new icon. The change is nothing major, amounting to little more than a bit of spit and polish, but it is another step along the road to completion.
You can find out more and download a copy of the latest version of the browser by paying a visit to theOpera Next 12.00 build 1385 review page. There’s also a 64-bit version of the browser available.
-

TweakNow HD-Analyzer reclaims hard drive space
Publié: avril 20, 2012, 2:00pm CEST par Mark Wilson
 Have you ever wondered where all of the space of your multi-gigabyte, or even terabyte, drive has disappeared to? The voluminous hard drive you installed a year ago seemed like it would last you forever filled up all too quickly. While there’s nothing to stop you from manually working your way through the contents to determine what could be removed to free up space, TweakNow HD-Analyzer is a free tool that could make the decision-making a little easier.
Have you ever wondered where all of the space of your multi-gigabyte, or even terabyte, drive has disappeared to? The voluminous hard drive you installed a year ago seemed like it would last you forever filled up all too quickly. While there’s nothing to stop you from manually working your way through the contents to determine what could be removed to free up space, TweakNow HD-Analyzer is a free tool that could make the decision-making a little easier.If you are running short of space, perhaps before starting a video editing project or something else similarly space-hungry, it makes sense to home in on the files and programs that are currently occupying the most space. This is something that TweakNow HD-Analyzer can help you with, performing and in-depth analysis of your hard drive and highlighting the largest files and folders so you can easy delete them or move them to an alternate location.
Scan results are ordered so that not only are the largest files listed at the top of the information panel, but a bar chart system is used to give a visual idea of how much space is being used. That’s really all there is to the app -- it is a simple yet effective tool for tracking down the megabyte munching files that you may want to remove. In a matter of moments you can track down the largest files or discover which of the programs you have installed are occupying space you could be put to better use.
If you want to get a little more hands-on with the program, there are options that open up possibilities. You may only be interested in weeding out the largest video or audio files that you have stored on your hard drive. It is possible to specify which files types should be recognized by TweakNow HD-Analyzer so that these types of file are highlighted in the results list.
You can find out and download a copy of this free tool by paying a visit to the TweakNow HD-Analyzer review page.
Zadorozhnyi Viktor/Shutterstock
-

Bypass cumbersome iOS settings with Bluetooth OnOff
Publié: avril 19, 2012, 3:44pm CEST par Mark Wilson
 Something that irritates many iOS users, and drives a large number of them to go as far as jailbreaking their phones and tablets, is the fact that Apple is so strict about what apps are able to do. The guidelines for getting into the App Store mean that it is not possible for any app to replicate an existing feature of iOS, nor access system settings in any way that Apple deems inappropriate. Despite this, Bluetooth OnOff has found its way in to the App Store, providing easy access to Bluetooth settings.
Something that irritates many iOS users, and drives a large number of them to go as far as jailbreaking their phones and tablets, is the fact that Apple is so strict about what apps are able to do. The guidelines for getting into the App Store mean that it is not possible for any app to replicate an existing feature of iOS, nor access system settings in any way that Apple deems inappropriate. Despite this, Bluetooth OnOff has found its way in to the App Store, providing easy access to Bluetooth settings.Due to battery draining, it is not a good idea to leave Bluetooth enabled when it is not being used. With this in mind, it is strange to find that in order to switch Bluetooth off, Apple makes users jump through a series of hoops in a process that takes several taps. Bluetooth OnOff is a simple little utility that reduces this to a one or two tap process so if you need to enable Bluetooth for a quick gaming session, you can do so in around a second.
Bluetooth OnOff can be used in one of two ways. The first option is to launch the app and then manually select the option to enable or disable Bluetooth, but by adjusting app settings you’ll find that there is a better option available. The app can be set up so that Bluetooth is switched on or off as soon as the app is launched, reducing the amount of time it takes to switch settings even further.
The app features a built in chatting option, but in all likelihood this is just a façade to help get a hady utility through to the store. If you’ve been frustrated by Apple’s restrictions but don’t fancy the idea of jailbreaking your iOS device, this may just be what you have been waiting for -- and at this low price you have very little to lose in testing it out for yourself.
You can find out more about the app by paying a visit to the Bluetooth OnOff review page.
-

So long Read It Later, Hello Pocket
Publié: avril 18, 2012, 1:15pm CEST par Mark Wilson
 Do you find that you never have time to read the articles you discover online? In the past you may have turned to Read It Later to bookmark a site so that you can refer back to it later, but now there is a new analogy to work with. Read It Later has been re-launched as Pocket, so you can now ‘pocket’ those stories you don’t have time to read right now and save them to your online account ready for when you have more spare time.
Do you find that you never have time to read the articles you discover online? In the past you may have turned to Read It Later to bookmark a site so that you can refer back to it later, but now there is a new analogy to work with. Read It Later has been re-launched as Pocket, so you can now ‘pocket’ those stories you don’t have time to read right now and save them to your online account ready for when you have more spare time.The rebranding is more than just a change of name; there are also new features that you can take advantage of as well as a redesigned interface. Whether you are surfing the web in your preferred browser, or you discover an interesting link on Twitter or Facebook, Pocket enables you to quickly and effectively bookmark pages, images and videos so you can easily access them later. Content can be saved using a browser extension or using the dedicated iOS or Android apps.
Whichever method you use to save, your content is synched to your account so it can be accessed from any device with an Internet connection. Spend a little while working with the service and you’ll no doubt find that you very quickly build up a pretty extensive list of articles you have saved. To make it easier to root through them, you have the option of filtering content by type as well as using the search tool to home in on a particular article based on title or URL.
The redesigned interface has something of a familiar feel to it as it boasts a Metro-inspired tile based look. This is all very neat and distraction-free, and when you clip any article for reading later you can view just the content of the article itself without the unnecessary page furniture of the web site it came from. With support for a massive range of apps as well as various browser extensions, Pocket has improved upon the already impressive options available in Read It Later.
You can find out more and download a free copy of the app for iOS and Android by paying a visit to the Pocket review page. There are also browser extensions available for Chrome and Firefox.
-

Smile for the camera, Opera Next is watching you
Publié: avril 18, 2012, 12:31pm CEST par Mark Wilson
 Things continue to develop apace in the world of Opera, with the latest snapshot of Opera Next showcasing camera support. The latest addition to the browser means that developers will now be able to use JavaScript to access webcams, which opens up new levels of interactivity with web pages -- everything from using your webcam as a color picker to simplifying the process of uploading a picture of yourself.
Things continue to develop apace in the world of Opera, with the latest snapshot of Opera Next showcasing camera support. The latest addition to the browser means that developers will now be able to use JavaScript to access webcams, which opens up new levels of interactivity with web pages -- everything from using your webcam as a color picker to simplifying the process of uploading a picture of yourself.There are obvious privacy concerns when web pages are allowed to access webcams, but Opera Next ensures that users are kept informed about what is going on and are given the chance to block or permit connection as they see fit. Whenever a page attempts to access your camera you are warned by the appearance of a popup that gives you the opportunity to block or allow the site on a permanent or one-off basis.
Websites are also able to make use of a site visitor’s location and changes have been made to Opera’s tabs to allow this information to be conveyed to the user. Whenever a site is making use of an attached camera or is using location information, badge icons are displayed in the relevant tab. Simple tab-based controls can then be used to make further changes to permission settings as and when required.
As this is a very early snapshot of a future release of Opera, it is only reasonable to expect that there are going to be a few problems here and there. That said, things are already looking good and there are a few demonstration web sites that can be used to test out the capabilities of the new camera support -- take a look at Photo Booth, Polaroid, Color Picker, Explode and Speedo for samples.
You can find out more and download a free copy of the app by paying a visit to the Opera Next review page; there is also a 64-bit version of the program available.
Photo Credit: alterfalter/Shutterstock
-

WinZip 16.5 gets Office-like ribbon, AMD speed boost
Publié: avril 17, 2012, 2:36pm CEST par Mark Wilson
 Stalwart of the file compression world WinZip has received a major upgrade that sees the introduction of a number of new features along with other enhancements and performance improvements. WinZip 16.5 has a strong focus on performance with a completely upgraded 64-bit engine as well as improved performance when used in conjunction with AMD processors.
Stalwart of the file compression world WinZip has received a major upgrade that sees the introduction of a number of new features along with other enhancements and performance improvements. WinZip 16.5 has a strong focus on performance with a completely upgraded 64-bit engine as well as improved performance when used in conjunction with AMD processors.Anyone with AMD Fusion processors and AMD Radeon GPUs will see the speed, but the overall performance of the app as a whole feels snappier. There is also a new look for the program, and the facelift helps to breathe new life into an archiving tool that many people have been using for a decade or more. The ribbon-style toolbar takes inspiration from the likes of Microsoft Office and gives a more streamlined feel while providing access to a huge range of features and options.
As well as the new interface and enhancements, there are also new options to enjoy. If you’ve already been using WinZip to take care of your backup procedure, there is now the ability to burn these backups directly to Blu-ray discs -- provided you are using the Pro version of the program. It’s not just backups that have benefited from a storage space boost; if you have created a large file that you want to share with others, you can do so using the ZipSend cloud service rather than trying to rely on email attachments.
The potential for improvement in WinZip is slowly reducing, but this particular release shows that there was still a little that could be done. It’s difficult to see just where the software is going to move forward from here aside from further improvements to performance, but this latest release show that there is still plenty of life left in the granddaddy of compression.
You can find out more and download a free trial of the app by paying a visit to the WinZip 16.5 review page.
Photo Credit: Arkady/Shutterstock
-

Keep out prying eyes with Wise Folder Hider
Publié: avril 12, 2012, 2:15pm CEST par Mark Wilson
 You don’t need something to hide to have something to hide. Whether you share your computer with others, or your machine is situated somewhere that other people may be able to access it, there’s a high chance that it has files stored on it that you would like to keep private. Documents relating to personal and financial issues are the sorts of files that should be kept away from unauthorized eyes, and Wise Folder Hider Beta is a free tool that makes it easy to do just that.
You don’t need something to hide to have something to hide. Whether you share your computer with others, or your machine is situated somewhere that other people may be able to access it, there’s a high chance that it has files stored on it that you would like to keep private. Documents relating to personal and financial issues are the sorts of files that should be kept away from unauthorized eyes, and Wise Folder Hider Beta is a free tool that makes it easy to do just that.There are various ways in which you can make sensitive files more difficult to access, but this handy security tool helps to make things as simple as possible. Protecting the files you would rather other people were not able to see take little more than signing into the program account you have created and then dragging and dropping the relevant files and folders onto the program interface -- this can be done on an individual basis, or you can choose to hide a whole bunch in one go.
The files and folders you select will be completely hidden from view until you access the program and opt to make them visible again. For extra protection, you can also choose to add a password to your hidden files in case you step away from your computer and forget to lock your hidden files. The fact that there is support for user accounts opens up the possibility of every user of a single computer working in the same Windows user account while still retaining the ability to keep their own documents private.
Wise Folder Hider Beta can also be used to prevent unauthorized access to any USB drives you have attached to your computer. In just the same way as for files and folders, you can choose to make a particular drive invisible. By taking this simple step, you make it much more difficult for someone else to access the data stored on the drive, or to use it to store their own personal documents. The program is currently in beta, but it seems stable and reliable – and it’s completely free of charge.
You can find out more by paying a visit to the Wise Folder Hider Beta review page.
Photo Credit: Kheng Guan Toh/Shutterstock
-

Geekbench 2.3.0 supports Ivy Bridge, dumps Power Mac
Publié: avril 11, 2012, 1:59pm CEST par Mark Wilson
 For anyone that is interested benchmarking the performance of their computer, be it a Mac, PC, Linux machine or a mobile device, Geekbench is a simple, low-cost tool that provides you with all of the tools you need. Benchmarking tools are often used by fans of overclocking and tweaking to see what difference can be made to performance, but they can also be helpful for revealing helpful information about the hardware in mobile phones and tablets.
For anyone that is interested benchmarking the performance of their computer, be it a Mac, PC, Linux machine or a mobile device, Geekbench is a simple, low-cost tool that provides you with all of the tools you need. Benchmarking tools are often used by fans of overclocking and tweaking to see what difference can be made to performance, but they can also be helpful for revealing helpful information about the hardware in mobile phones and tablets.If you are interested in benchmarking performance, it is likely that you are running recent hardware. As such, it is little surprise to find that the latest version of Geekbench drops support for PowerPC Macs. The fact that this is hardware that is no longer supported by Apple and the ever dwindling numbers of remaining users mean that this was really inevitability, and the day has now finally come.
Obviously there is nothing to stop PowerMac users from sticking with an older version of the app, but as of now development in this area has now ceased. But the app continues to grow and develop in other areas. In addition to new support for Ivy Bridge processors, there is also better support for 2009 MacBook Pros. Other changes include the ability to use a Pro license for a portable version of the app.
It is also worth noting that there are iOS and Android versions of the app available. For iOS users the app is not really able to reveal a great deal of information, but the Android version is somewhat more useful. In addition to revealing basic information about the hardware and OS you are working with, your mobile device can also be assigned an overall rating by testing the performance of memory, floating point operations and much more.
You can find out more by paying a visit to the Geekbench 2.3.0 review page. Separate versions are available for Android devices and for the iPad/iPhone.
-

Chrome 19 beta syncs tabs everywhere -- get it now!
Publié: avril 10, 2012, 11:05pm CEST par Mark Wilson
 Most of us now use at least two devices to connect to the Internet and while this freedom of connectivity is great in many respects, there are also problems associated with it. One of the most infuriating aspects of moving from browsing the web on one computer to using another device is that you will lose the web sites you were looking at. This is something that is addressed in the latest beta version of Google Chrome 19, which features the synchronization of tabs between devices. The feature extends to other devices a capability available with Chrome for Android Beta.
Most of us now use at least two devices to connect to the Internet and while this freedom of connectivity is great in many respects, there are also problems associated with it. One of the most infuriating aspects of moving from browsing the web on one computer to using another device is that you will lose the web sites you were looking at. This is something that is addressed in the latest beta version of Google Chrome 19, which features the synchronization of tabs between devices. The feature extends to other devices a capability available with Chrome for Android Beta.If you are working on your computer at work and then head home, there is no longer any need to send yourself an email with links to the websites you have been looking at during the day. Instead, assuming that you have the beta version of Google web browser installed on both machines and you are signed into your account, when you get home you need look no further than the ‘Other devices’ menu on the new tab page.
In this menu you will find a list of all of the tabs you have opened on other machines and you can load them up with just a further click. As an added bonus, the browsing history for individual links is preserved so you can still track back through your browsing trail without the need to worry about which computer you are using.
As well as this handy tab synchronization, the latest beta version also features the usual range of tweaks and bug fixes. Problems with NVIDIA GPUs with 3D graphics have been fixed as have issues with incognito windows. It’s a shame that it’s not possible to easily install the beta version of the browser alongside an existing installation of the stable release version, but it does seem remarkably stable in its own right.
The web browser is available for Windows, Mac and Linux, and you can find out more by paying a visit to the Google Chrome 19 Beta review page.
-

Start April right, with one of these 17 downloads
Publié: avril 9, 2012, 6:01am CEST par Mark Wilson
 We now find ourselves well into Spring, so what better excuse is needed to start spring cleaning your computer? You can set about doing this manually, but it’s easier if you turn to a dedicated tool to take care of system maintenance.
We now find ourselves well into Spring, so what better excuse is needed to start spring cleaning your computer? You can set about doing this manually, but it’s easier if you turn to a dedicated tool to take care of system maintenance.iolo System Mechanic Free 10.8.3.51 is a free tool that can be used to delete unnecessary files, defrag your hard drive, clean out the registry and much more. If you’re someone that takes a keen interest in the smooth running of your computer, you probably have some form of application monitoring software installed, and Bad Application 1.0 is a simple little utility that will enable you to test these out, checking what happens with crashed and hung applications.
UserAssistView 1.02 is an interesting tool that can be used to keep an eye on which programs have been running, while WSCC 2.0.4.0 enables you to easily update, manage and use any Sysinternals and NirSoft utilities you have installed.
Another new system utility this week is Microsoft Fix it Portable, which provides a number of handy diagnostic tools in a program that does not need to be installed. As well as maintaining the performance of your computer, it is important to backup the data you have stored on it; this is something that Genie Timeline Free 2012 v3.0.1 can help with, enabling you to automatically safeguard your valuable files.
Should you be a little more demanding of your backup software Genie Timeline Home 2012 v3.0.1 allows for more frequent backups as well as a disaster recovery mode for any time you are unable to boot into Windows. Another step up the product line take you to Genie Timeline Professional 2012 v3.0.1, which gives you greater control over which files are backed up as well as making use of encryption.
Everyone has a series of digital photos stored on their hard drive, but how many of us actually put them to any use? With MAGIX PhotoStory on DVD MX (v11) installed you can transform your snaps into sophisticated slideshows that you can share with your friends and family. With a huge range of special effects and transitions to choose from and the ability to not only burn projects to disc, but also upload to the web, there’s plenty of scope for creativity here.
MAGIX PhotoStory on DVD MX Deluxe 11 is also available with even more options and templates for you to experiment with. From the same company is MAGIX MP3 deluxe MX (v18) which includes all of the tools you need to manage a music collection of any size. If talk of Windows 8 has got you hankering for a new look for your operating system,
Windows 8 Transformation Pack 4.0 and Windows 8 UX Pack 4.0 are available to help you get the look of the next version of Windows free of charge.
LibreOffice Productivity Suite 3.5.2 is a great office suite for any looking for a spreadsheet, word processor and more without the need to part with a penny, and it is a piece of software that keeps improving with every release. If you’re more in the mood for fun, Simutrans 111.2.2 may be up your street -- it’s an intriguing twist on the sim genre which places you in charge of a transportation network. Fans of the Amiga platform will likely be interested in checking out WinUAE 2.4.0, which is a free Amiga emulator for Windows that can be used to run all manner of old games and software.
If you’re more interested in trying out the latest and greatest, VirtualBox 4.1.12 (build 77245) may be more what you’re looking for, enabling you to install virtual operating systems within Windows so you can try out different versions and platforms.
The week ahead is sure to be packed with a plethora of great new releases, so keep an eye on Downloadcrew and join us next week for another roundup.
Photo Credit: treasure dragon/Shutterstock
-

Keep your PC fit with these April software bargains
Publié: avril 6, 2012, 7:55pm CEST par Mark Wilson
 Looking to save some money on your software purchases? Look no further than the Downloadcrew Software Store this April, where you’ll find all manner of bargains on everything from security tools to audio and video editing programs.
Looking to save some money on your software purchases? Look no further than the Downloadcrew Software Store this April, where you’ll find all manner of bargains on everything from security tools to audio and video editing programs.Genie Timeline Professional 2012 is an exciting new release that simplifies and automates the backup of your computer and you can save a massive 50-percent off the MSRP when you buy this invaluable tool for just $29.95. In the store there are also a number of tools suitable for anyone looking to get creative with audio and video files. A top deal is available for CyberLink PowerDirector 10 Ultra, a powerful video editing application that brings professional level tools to the home user -- you can save 30 percent when you buy the program for just $69.96.
If you already have an older copy of PowerDirector, you may be interested in saving 33 percent off CyberLink PowerDirector 10 Ultra UPGRADE ($39.95 instead of $59.95), and both packages include an extra $69 worth of software. If you’re more interested in boosting the sound of your audio files, there’s a colossal saving of 83 percent off MAGIX Audio Cleaning Lab v17 deluxe which you can buy for the ridiculously low price of $9.99.
April sees a number of special offers on security software, starting with a 75 percent off avast! Pro Antivirus 7. If you are an existing user of the free version of the program, upgrading will cost you just $9.99 and you’ll gain access to a whole range of extra features in the Pro release.
A great new release this month is Kaspersky PURE 2.0 Total Security, which will help to keep your computer safe. With virus protection, a firewall and much more, you can protect up to three computers for just $39.99 -- a saving of 60 percent. This is not the only security tool that’s on offer in the store; there’s also a 68-percent savings off PC Tools Spyware Doctor with Antivirus 2012, just $12.99, and 70 percent off PC Tools Internet Security 2012 - $14.95 instead of $49.95.
With Kaspersky Internet Security 2012 [3-PC, 1-Year] you can protect all of your home computers and save 64% when you buy the software for $28.95 instead of $79.95. If you have more computers to consider, there’s a great saving of 69 percent off Kaspersky Internet Security 2012 [5-PC, 1-Year] which is reduced from $129.95 to just $39.95.
There are also a number of security tools from AVG on offer this month, starting with 93 percent off AVG Anti-Virus 2012 [1-PC, 1-Year] which is available for the unbelievably low price of $2.95 -- if you been considering upgrading from the free version of AVG’s antivirus tool, there has never been a better time to do so. From the same company there is also AVG Internet Security 2012 Plus Bundle which includes four fantastic security products for just $29.95 -- saving you an amazing 80 percent off the MSRP of $149.
There’s also a great saving of 79 percent to be made on AVG Premium Security Complete Bundle. This bundles includes everything you need to keep you and your computer save and costs just $24.95. One final offer from AVG is for AVG Internet Security 2012 [4-PC, 2-Year] which can be you for just $24.99 -- a saving of 64 percent off the MSRP. This is a powerful suite that includes not only virus protection but also parental controls, online backup, a firewall and much more.
Rounding up this month’s offer highlights is a selection of helpful utilities that will help you to keep your computer running at peak performance. Auslogics BoostSpeed 5 is an immensely powerful tool that can be used to improve the performance of your system in just a few steps -- all for just $9.95. this price includes a three PC licence, meaning that the 80-percent savings represents even better value for money.
If you want to keep your hard drive in good shape, look no further than Auslogics Disk Defrag Pro 4. This amazing defrag tool can be installed on up to three computers and at just $9.95, you can save 67 percent off the MSRP. There are numerous performance boosting tools available for Windows, but when it comes to value for money, it’s hard to beat TuneUp Utilities 2012.
This program costs just $14.99, saving you 70 percent off the MSRP, but the fact that it can be installed on up to three computers and includes a lifetime, non-expiring license makes this an incredible deal. If you have more machines that you would like to tend to, take a look at TuneUp Utilities Business Edition 2012, which includes a five PC, lifetime license for the same price -- $14.95 instead of $83.95.
These are just some of the highlights for this month -- there are plenty more bargains to be found if you head on over to the store.
Photo Credit: iQoncept/Shutterstock
-

Taposé gives iPad split personality
Publié: avril 5, 2012, 7:25pm CEST par Mark Wilson

Much has been made of Taposé in recent days, with a great detail of attention being focused on the new iPad app being based on the failed Microsoft Courier project. But it is important to look at this as a piece of software in its own right.
Taken at face value, this is an app that could easily been seen as trying to be all things to all people, but the simple fact: it is a fully-featured tool. Packing notes, maps, word processor, web browser, drawing tools and much more, this is an app that can turn its hand to many tasks.
Taposé is surprisingly flexible, and when used in portrait mode it is a versatile app that can be used for everything from drawing plans, collecting together ideas for a project, keeping notes and much more. The set of tools you are presented with means that Taposé can easily replace several apps and can save you a great deal of app switching. But it is when you switch to working landscape mode that the app becomes particularly interesting.
On its side, Taposé splits your iPad screen in two and enables you to run a different component of the app on each side. So you might use one side to browse the web for research, and use the other to make notes in the word processor. This is handy, but you can also drag and drop elements from one side to the other, so if you come across a web site you would like to make a note of, you can drag and drop it into a document and a snippet will be instantly added for you.
All of this is made even more useful thanks to the fact that Taposé is cloud aware. You are provided with 400MB of online storage space which opens up the possibility of collaborative work. There is also talk of Android and web-based versions of the app, so you will be able to access your data from a number of different devices in the future.
The app isn’t perfect, but it is interesting and it is worth investing $2.99 to see where this intriguing piece of software goes.
You can find out more by paying a visit to the Taposé review page.
-

Keep your hard drive in shipshape with Uniblue MaxiDisk
Publié: avril 3, 2012, 8:29pm CEST par Mark Wilson
 Taking care of your computer can easily turn into a full time job, so it makes sense to delegate at least some of the responsibility to a third party tool. Uniblue PowerSuite is an impressive collection of maintenance tools that can be used to manage the registry, keep drivers up to date, clean out junk files and much more. The latest addition to the suite is MaxiDisk, a defrag tool that makes it simple to keep your hard drive shipshape -- and there are a few extra options to investigate as well.
Taking care of your computer can easily turn into a full time job, so it makes sense to delegate at least some of the responsibility to a third party tool. Uniblue PowerSuite is an impressive collection of maintenance tools that can be used to manage the registry, keep drivers up to date, clean out junk files and much more. The latest addition to the suite is MaxiDisk, a defrag tool that makes it simple to keep your hard drive shipshape -- and there are a few extra options to investigate as well.At its heart, MaxiDisk is a fairly basic defragmentation tool, but if all you have used in the past is the one that is built into Windows, it is a great leap forward. The analysis process is completed faster than Windows’ defragmenter and you are provided with basic information about the layout of the data on your drive, along with an indication of whether or not defragging is required. The re-organization of files on your disk is something that unavoidably takes time, but it is something that is well worth doing.
There is also a system cleanup tool that can be used to track down junk files that can be remove as well as out of date backups that you may no longer need. The program also offers to compress the largest files on your drive to free up more space. While these are all useful options, they are somewhat oddly positioned after the defragging section in the program interface when it would make much more sense to perform these tasks first.
The final section of the program enables you to decompress any of the files you chose to compress, and it also details information about your computer -- but nothing you cannot determine through the Control Panel. You also have the option of scheduling defragmentation to save you from having to do this manually. Looked at on its own, MaxiDisk is a fairly basis tool ,but when considered as a new component of a larger suite, it’s a great addition.
Whilst Uniblue release a new tool, they appear to have silently cancelled RegistryBooster, which was always one of their more controversial tools. All references to RegistryBooster has disappeared from theUniblue website.
You can find out more and download a free trial of the program by paying a visit to the Uniblue MaxiDisk review page.
Photo Credit: Raimundas/Shutterstock
-

Want Windows 8 Metro without the upgrade? Skin it!
Publié: avril 2, 2012, 3:39pm CEST par Mark Wilson
Fancy the idea of using the Windows 8 UI but don’t feel like going as far as installing the consumer preview version of the OS? Look no further than a transformation pack to give your operating system a makeover and a completely new look. If you’re working with Windows 7 you can use Windows 8 UX Pack 4.0, while Windows 8 Transformation Pack 4.0 can be used in everything from Windows XP and up. Both apps bring the look and feel of Windows 8 to your desktop with no need for complex tweaking.
The two skinning app’s version numbers have been brought in line with each other, and there are a number of changes to investigate. Windows 8 UX Pack 4.0 now better mimics the look of Windows 8 thanks to the switch to using the Segoe UI font and inclusion of all of the desktop wallpapers from the Windows 8 Consumer Preview.
There are the usual big fixes that you would expect to find in a new software version, and there are also changes to the Start button and UI to bring the program more in line with Windows 8.
Windows 8 Transformation Pack 4.0 has undergone more of an overhaul, including the addition of the same Segoe font. Anyone who has trouble working with the new interface now has an alternative in the form of the Charms Bar which enables you to try out another of the features of Windows 8. Problems with colorization in Windows 7 and Vista have been addressed, and there are new logon screens, system tray icons, Start buttons and more.
If you’ve not experimented with transformation packs in the past, these tools offer a great introduction. UX Pack works, incredibly, without modifying and system files, but Windows 8 Transformation Pack has been tweaked and primped to be safer and more reliable than ever. You may have been put off by flaky skinning tools of old, but these are two tools that not only give your computer a completely new look, but manage to do so in a simple and impressive way.
You can find out more by visiting the review pages for Windows 8 Transformation Pack 4.0 and Windows 8 UX Pack 4.0.
-

37 downloads you shouldn't miss this week
Publié: avril 1, 2012, 5:05am CEST par Mark Wilson

Another week -- month, actually --- is behind us and a huge number of software releases to keep track of. If you feel like you may have missed out on some of the biggest releases, this roundup is here to get you back up to speed.
iolo System Mechanic Free 10.8.3.51 is a great free tool for optimizing your system, but if you’re more concerned about protecting your privacy by securely deleting files, take a look at Disk Wipe 1.5. Auslogics Disk Defrag 3.4.1.0 is a free utility to replace Windows’ defragmentation tool which now offers better stability and performance. There’s also a Pro version of the program available –Auslogics Disk Defrag Pro 4.0.1.50. Infamous system cleaner CCleaner 3.17.1689 and CCleaner Portable 3.17.1689 feature improved cookie options, better support for Chrome and a host of other fixes and enhancements.
BurnAware Free 4.8 is one of the most recent apps to be updated with support for Windows 8, while Xara Web Designer MX 8 is an advanced web design tool, but if you need something a little more powerful, take a look at Xara Web Designer MX Premium 8. As well as creating your own websites to put online, you should also be able to enjoy other people’s sites.
When you’re using the internet, security software is always important, and Ad-Aware Free Antivirus+ 10 FINAL and Kaspersky PURE 2.0 Total Security can help you with this.
For anyone that takes a keen interest in their computer, AIDA64 2.30 can reveal everything you need to know about your hardware and software -- there’s also AIDA64 Business Edition 2.30 which includes a number of extra handy options. If you own an iPhone, iPad or iPod, Apple iTunes 10.6.1 (32-bit) and Apple iTunes 10.6.1 (64-bit) have been released.
This is largely a bug fixing release, and there are no new features of note. If you’re more of a fan of Android devices, BlueStacks App Player 0.6.3 (beta) is an interesting tool that makes it possible to install Android app within Windows.
The week saw a number of releases from Adobe, focused around its two big internet tools. Adobe Flash Player for Internet Explorer 11.2 (32-bit) and Adobe Flash Player for Internet Explorer 11.2 (64-bit), which is the latest version of the browser plugin for IE users. If you’re using a different browser, Adobe Flash Player for Other Browsers 11.2 (32-bit) and Adobe Flash Player for Other Browsers 11.2 (64-bit) have been released offering improved performance thanks to the software taking advantage of GPUs. Also released by the company is Adobe Air 3.2 which includes impressive performance improvements thanks to better compression support.
We’ve already looked at a few security tools, but there have been a number of releases from AVG starting with AVG Premium Security 2012 SP1 (v12.0.2126). This latest service pack adds the ad tracker blocking as well as protection against spoofed wifi networks and there’s also a service pack for the company’s famous AV tool, AVG Anti-Virus 2012 SP1 (v12.0.2126). There’s also a free version of the tool available -- AVG Anti-Virus Free Edition 2012 SP1 (v12.0.2126) -- and a lower cost version of the main security tool in the form of AVG Internet Security 2012 SP1 (v12.0.2126). One final update form AVG this week is AVG LinkScanner Free Edition 2012 v12.0.2126 which keeps you protected by blocking potentially dangerous web sites.
There are often weeks that seem to be dominated by web browsers, and the week past is no different. Google Chrome 18 FINAL sees a new version of Google’s browser entering the stable channel and there is also a portable version available in the form of Google Chrome Portable 18.0.1025.137 Beta. The new stable release means that there is now Google Chrome 19.0.1084.1 Dev for anyone who likes to be at the cutting edge, and Google Chrome Portable 19.0.1077.3 Dev is available if you want to pop the browser on a USB drive. The release of a new version of Chrome means that there is also a new version of speed and security optimized variantComodo Dragon 18 FINAL, while Apple Safari 5.1.5 is a more minor release.
If this does not give you enough choice for browsing the web, take a look at Opera Next 12.00 build 1351 or Opera Next 12.00 build 1251 (64-bit). Neither version offers huge difference from their predecessors, but the march of development continues -- but Opera 11.62 FINAL now provides better HTML5 support and a raft of other improvements.
There isn’t a new version of Firefox just at the moment, but Pale Moon 11.0.1 and Pale Moon x64 11.0.1 are the latest version of the Firefox 11 based browser, bringing various improvements including better HTML5 and CSS3 support.
Join us again end of the week for another app-packed roundup.
Photo Credit: Trudy Simmons/Shutterstock
-

Protect your deleted data with Disk Wipe
Publié: mars 29, 2012, 5:36pm CEST par Mark Wilson
 Whether you’re concerned that files you have stored on a USB drive might be recovered by someone else after they have been deleted, or you are selling your computer and want to ensure that none of your personal documents can be accessed, almost everyone has a need to securely delete data at some point. Simply deleting files is not enough as there are all manner of tool in existence that can be used to restore them, but Disk Wipe is a free, easy to use app that helps to ensure that when a drive is formatted, none of its data is recoverable.
Whether you’re concerned that files you have stored on a USB drive might be recovered by someone else after they have been deleted, or you are selling your computer and want to ensure that none of your personal documents can be accessed, almost everyone has a need to securely delete data at some point. Simply deleting files is not enough as there are all manner of tool in existence that can be used to restore them, but Disk Wipe is a free, easy to use app that helps to ensure that when a drive is formatted, none of its data is recoverable.It is not just hard drives that the app can be used to secure. If you have stored private documents on a USB drive or have photos or other files stored on a memory card, the same app can be used to completely format any FAT, FAT32 or NTFS drive that can be accessed from within Windows. In addition to the secure file wiping, Disk Wipe also provides you with a good deal of information about the drives it detects, such as the number of sectors, the manufacturer and serial number.
The entire wiping process is wizard-based and you’ll be guided through each step of selecting a new file system and choosing which wiping method should be used. The method of wiping that you choose can have a huge bearing on how long the process takes, so if you are wiping a removable drive you may want to decide between whether you want to continue using your computer for other tasks, and you can choose to run wiping processes at different priority levels accordingly.
Being a portable app means that Disk Wipe does not need to be installed and can be added to your USB drive for transporting from machine to machine. This may not be a tool you use on a regular basis, but its ease of use it something you will welcome when the time comes. More advanced users will appreciate the inclusion of a hex view that can be used to view information about a drive and you can jump straight to particular clusters with the simple search tool.
You can find out more and download a free copy of this great security tool by paying a visit to the Disk Wipe review page.
Photo Credit: Anneka/Shutterstock
-

Undo tweets with Windows 8-inspired MetroTwit
Publié: mars 28, 2012, 12:18am CEST par Mark Wilson

Inspired by the look of Windows Metro, MetroTwit is a unique-looking, clean Twitter client that oozes style and simplicity. The app has just hit version 1.0, having already proved itself to be worthy of note in the beta stages. The official release sees the addition of a number of important new features including highly configurable filtering that helps you to ensure that your stream is not cluttered up with tweets you are not interested in.
In a similar vein to TweetDeck, the MetroTwit interface includes multiple columns that can be used to display different aspects of your Twitter account, and there is great integration with Windows 7 that sees notification area popups revealing direct messages and other interactions.
A feature that will be welcomed by many users is the undo tool. Whether you change your mind about a tweet you posted in haste, or notice an embarrassing spelling mistake, you can take a step back in time in a couple of clicks.
As with previous versions of the client, MetroTwit is fast and is, on the whole, a nicely rounded package that can greatly enhance your Twitter experience.
If you’re wary of shortened URLs, just hover your mouse over one and the complete URL will be revealed, while when it comes to catching up with a stream you haven’t looked at for a while, you can take advantage of infinite scrolling so you do not have to manually load more tweets when you reach the end.
The free version of the app is ad-supported, but if you start to find this too irritating, there’s always the option of upgrading to the Plus edition, although at $16, this does make for something of an expensive Twitter client. Going down the paid-for route does open up another new feature of the app – support for multiple Twitter accounts.
While MetroTwit is an interesting and good looking app, it may be hard to justify this cost when there are free alternatives that can already be used to sign into more than one Twitter account simultaneously.
You can find out more and download a free copy of the Twitter client by paying a visit to the MetroTwit review page.
-

Yell 'Wahoo' and download 64-bit Opera 12 alpha right now!
Publié: mars 26, 2012, 9:29pm CEST par Mark Wilson
 The development of Opera continues apace and for anyone wanting to try out the very latest features of the browser, there's a new version to install. The latest build of Wahoo (the codename for Opera 12) is available for the first time as a 64-bit release for both Mac and Windows users and the latest snaps shot also features improved support for HTML 5 and CSS3. As with previous builds of Opera 12, it is possible to install this alongside your current stable version of the browser so you can try it out while maintaining the version you have become used to.
The development of Opera continues apace and for anyone wanting to try out the very latest features of the browser, there's a new version to install. The latest build of Wahoo (the codename for Opera 12) is available for the first time as a 64-bit release for both Mac and Windows users and the latest snaps shot also features improved support for HTML 5 and CSS3. As with previous builds of Opera 12, it is possible to install this alongside your current stable version of the browser so you can try it out while maintaining the version you have become used to.Opera changed the way plugins are handled, to make the move to 64-bits. Plugins now run in a separate process to the browser itself, known as OOPP or Out of Process Plugins, which also not only help to improve overall stability, but the security of Opera as well.
The move to OOPP also means that it is possible to run 32-bit plugins in a 64-bit browser, and Mac users will find that there is now a universal binary available that includes both 32- and 64-but versions rather than making them available separately.
The two other major points of interest are the improved support for HTML5 and CSS3. This particular build sees support for HTML5 drag and drop, and while this is still something of an emerging standard, it’s good to see that work is taking place to ensure the best level of support possible. On the CSS3 front, there is now experimental support for CSS animations as well as updated support for transitions.
At the heart of the browser there is a new Presto core that gives the rendering engine a complete overhaul. If you’ve yet to try out some of the more experimental versions of web browsers that are being released, this is an excellent opportunity to do so.
Despite the fact that it is still fairly early days for Opera 12, things are already shaping up well. For a full list of changes in this release, head on over to the Opera Desktop Team blog and the Opera Developer News blog.
You can find out more and download a free copy of the program by paying a visit to the Opera 12 review page.
-

Our gift to you -- Ashampoo Photo Commander 9
Publié: mars 25, 2012, 7:57pm CEST par Mark Wilson
 If you own a computer, there’s a pretty high chance that you also own a digital camera, and this means that you probably have a large number of photos on your hard drive. Unless you have been particularly fastidious in renaming all of your images as you copy them from memory cards, your photo collection may well be a disorganized mess.
If you own a computer, there’s a pretty high chance that you also own a digital camera, and this means that you probably have a large number of photos on your hard drive. Unless you have been particularly fastidious in renaming all of your images as you copy them from memory cards, your photo collection may well be a disorganized mess.Now you can stop hunting for a solution as we’re giving away a free copy of Ashampoo Photo Commander 9 worth $49.99! It’s worth noting that this is a full current product.
You’ll no doubt have guessed from the name that this is an application that places you in command of your photos, and this applies to a number of areas. The program not only provides you with the tools you need to keep your images organized and easy to locate, but also features a range of editing tools, both basic and advanced, that can be used to get the very best from your digital photography collection.
Not all of your photos will need serious editing carried out on them, and for these images you can make use of the Common and Quick-Fix sections of the program. Here you will find all manner of everyday editing options such as rotating and cropping as well as the ability to apply a range of effects and filters. For common problems such as red-eye there are one-click solutions available, but if you want to get a bit more hands on, you have the option of switching to a more advanced editing mode to access additional features.
One of the most useful features of the editing window is the two-pane view that makes it easy to compare an original image with the edited version you are working on. But one of the major components of Ashampoo Photo Commander is the organizational aspect which can be used to group and tag images for easy locating.
In addition to all this, the program can also be used for creative ventures, and there are a number of templates and wizards on hand to help you to create everything from calendars to slideshows. You can find out more about this fantastically powerful tool by paying a visit to the Ashampoo Photo Commander 9 review page.
To take advantage of this amazing giveaway, you’re going to have to quick because it’s only available for 24 hours. You can claim your free copy of the program by heading over to the Downloadcrew Giveawaysite between 00:00 and 23:59 on Monday 26 March – Central European time and equates to 7 pm EDT Sunday 25 March to 6:59 pm EDT Monday 26 March.
Photo Credit: Laborant/Shutterstock
-

23 downloads you shouldn't miss this week
Publié: mars 24, 2012, 9:07pm CET par Mark Wilson
 Another busy week of software releases is behind us and, in case you managed to miss some of them, we’ve collected some of the most-compelling titles together into this week’s roundup.
Another busy week of software releases is behind us and, in case you managed to miss some of them, we’ve collected some of the most-compelling titles together into this week’s roundup.If you spend time installing a lot of the programs we highlight here, you’re going to need a suitable launcher to help you manage them. Winstep Nexus 12.20 is a stylish dock for Windows that provides easy access to all of your apps. The software is perfectly complimented by Winstep Xtreme 12.20, which enables you to completely customize the appearance of your desktop with skins and widgets that can be as adventurous as you like.
Anyone looking to make Windows easier to use rather than making it prettier will like Mayhem Developer Preview, which can be used to automate frequently performed tasks using scripts, while Mouse Switcher 1.0.0 is an interesting tool that allows for program switching with the mouse wheel.
Typically there are normally a fairly large number of web browser updates, but this week was much quieter than usual. Pale Moon 11.0 is the latest version of the speed optimized Firefox variant, based on v11. This time around you’ll find improved HTML5 and CSS support as well as page rendering speed improvements. If you have a 64-bit version of Windows, you should take a look at Pale Moon x64 11.0, while if you like keeping your software on a USB drive to take with your rom computer to computer, you’ll be interested in Pale Moon 11.0 Portable and Pale Moon x64 11.0 Portable.
Security and Sync
Whatever browser you’re using to surf the internet, you need to keep safe, and ZoneAlarm Free 10.1.101.000 is a free firewall that keeps you protected against hackers and malicious software.
This has been a great week for utility fans, starting off with Wise Disk Cleaner Free 7.11, which can be used to free up disk space and IObit Advanced SystemCare 5.2.0.223 FINAL that provides you with a series of tools to help optimize and maintain your computer.
If you’re one of the millions of people who flock to Twitter each day, TweetDeck 1.3 has been updated to include support for more picture services, better list management options, new columns and much more. TweetDeck is a Twitter client that is available for multiple platforms.
If you work with multiple devices you should check out SugarSync, which enables you to keep your files synchronized between devices with ease. SugarSync 1.9.50 is available for Windows and Mac, and there is also SugarSync for Android 3.5.1 and SugarSync for iOS -- the iPad version has received and impressive makeover that makes it even more appealing.
Convert and Create
Fancy getting away from it all for a while? Look no further than Microsoft Flight 1.0, the free flight sim that enables you to explore the island of Hawaii.
The final selection of tools this week are all related to video and image files. Light Image Resizer 4 is a quick and dirty tool that reduces batch image editing and resizing to a minimum of steps.
Adobe Photoshop CS6 beta is an exciting preview of the next version of the world-famous image editing tool that includes a number of content-aware features and more than enough tweaks, enhancements and additions to make this the most impressive version of Photoshop for quite some time.
On the video front, Freemake Video Downloader 3.0.1 is a free tool that makes it possible to download video files from all manner of streaming web sites, while Freemake Video Converter is on hand to enable you to convert these, and almost any other video into a range of different formats.
Download and Do
Miro 5.0 RC1 is a similar tool that not only allows for video downloading, but also provides you with a dedicated program interface for managing all of your on- and offline video content.
If you’re more of an offline video viewer, VLC Media Player 2.0.1 FINAL has been updated to include Blu-ray support for Mac users as well as a range of enhancements for other platforms.
One final program worth pointing out this week is Close All Windows 1.3 which will make it easier to close a number of programs in one fell swoop. Join us again next week for another roundup of Mac, Windows, Android and iOS software.
Remember to keep one eye on Downloadcrew Giveaway. On Monday Ashampoo Photo Commander 9 will be available, on Wednesday AIDA64 Extreme Edition and on Friday, another full commercial application, which will be confirmed next week.
Photo Credit: ArtisticPhoto/Shutterstock
-

SugarSync 3.0 gets darker look, improves iPad features
Publié: mars 23, 2012, 2:11pm CET par Mark Wilson
 A huge proportion of us are now multi-device users. In addition to our home computers, there is also a work machine to think about and to this you can add other mobile devices such as iPads and Android phones. Almost without realizing it, we have become used to living in the cloud and web-based email services such as Gmail, and online office tools such as Google Doc, have made it possible to access our emails and files on any device with an internet connection.
A huge proportion of us are now multi-device users. In addition to our home computers, there is also a work machine to think about and to this you can add other mobile devices such as iPads and Android phones. Almost without realizing it, we have become used to living in the cloud and web-based email services such as Gmail, and online office tools such as Google Doc, have made it possible to access our emails and files on any device with an internet connection.There is no reason that the same philosophy should not be applied to files, and this is something that SugarSync aims to address. The latest version has been redesigned from scratch, bringing a new look and ways of working for anyone who managed to get their hands on a new iPad.
SugarSync is one of a growing number of synchronization tools that can be configured to ensure that the files you need are always available no matter which device you are using. Available for iOS, Android, Windows and OS X, it does not matter how many different systems you own, you should be able to keep everything in sync.
The app itself is nothing new, but iPad users have an updated version to install which has a lot in store. The light-colored, chunky look of the previous interface has been replaced by a darker, sleeker look that is sure to win over many people, but of course any app is about much more than just good looks.
The interface has been redesigned to help make it easier to get things done faster than before. This starts with simple things such as the addition of photo and video backup links to the start screen, but there is a general change of focus that should enable you to get more done in the app faster than ever. This is helped in part by the app’s new look which takes full advantage of the available screen space and reduces the amount of wasteful white space that is on view.
A slick three-dimensional view is used so you can stack open folders on top of each other and view the contents of more than one at the same time and also jump back and forth with your navigation far more easily than before. There is also improved support for gestures, but the core features of synchronization, sharing, downloading, media access, such as streaming of your music files, and file backups are at the very least equal to the like of Dropbox, and in many instances exceed the capabilities of the competition.
You can find out more and download a free copy of the app by paying a visit to the SugarSync for iOS review page. If you user other platforms you should also take a look at the SugarSync for Windows/Mac and SugarSync for Android reviews.
-

Need to decompress files fast? Try Unarchiver 3 for OS X
Publié: mars 22, 2012, 3:14pm CET par Mark Wilson
 Compressed files are not always used for the space savings reasons they were initially created for, but they are still very important. The widespread availability of high-speed Internet connections means that the size of downloads is far less important than used to be the case, but many downloads are still supplied in one of the many compressed formats that are available. OS X includes integrated support for a number of formats but if you want to be able to extract the contents of more archives The Unarchiver has been updated to version 3.0 with support for more compressed files types than ever before.
Compressed files are not always used for the space savings reasons they were initially created for, but they are still very important. The widespread availability of high-speed Internet connections means that the size of downloads is far less important than used to be the case, but many downloads are still supplied in one of the many compressed formats that are available. OS X includes integrated support for a number of formats but if you want to be able to extract the contents of more archives The Unarchiver has been updated to version 3.0 with support for more compressed files types than ever before.As you’ve probably guessed from the name of the app, this is a piece of software that is concerned solely with the decompression of archives, so if you’re looking to compress files you’re going to need to look elsewhere. In the software world there is a general trend towards jack-of-all-trades utilities, so it is slightly unusual to come across an app that does just one thing -- thankfully, The Archiver does it well, so it can be let off the hook somewhat.
The app is so unobtrusive that once you have had it installed for a while you could be forgiven for forgetting of its existence and believing that its features were part of OS X. What this particular update brings is support for an extra swathe of new formats including WinZip’s .zipx ads well as Linux formats such as ar and deb. Existing support for extracting files from disc images has been expanded to include MDF, NRG and CDI files and there is now also the option of extracting images and sounds from SWF files.
If you’re a fan of The Unarchiver, or find that you become one, you may also be interested in checking out The Archive Browser (http://archivebrowser.c3.cx/) from the same company. This application is a handy addition to your archival arsenal, making it easier to browse and preview the contents of compressed archives without the need for decompression. This tool is not free of charge and it is The Unarchiver that is likely to join the ranks of essential apps that you use every day.
You can find out more and download a free copy of the app by paying a visit to the review page for The Unarchiver.
Photo Credit: Modella/Shutterstock
-

Miro 5 media manager available as release candidate
Publié: mars 21, 2012, 5:30pm CET par Mark Wilson

There are countless websites that provide streaming content, either in an episodic or less structure form. Add to this the media files you already have stored on your hard drive and you have a lot of audio and video to contend with. Miro is a powerful media player that can be used to play local files, but is also geared up to playing online content from the likes of YouTube and Hulu. The application itself is nothing new, but the release candidate of version 5 of the program gives a tantalizing taste of what’s to come.
While there is a leaning towards video in Miro, the release candidate helps to highlight that it can be used for other media as well. If you have a hefty MP3 collection on your hard drive, Miro can be used to listen to your favorite albums and while you’re doing so, you can take advantage of the application’s ability to go online and retrieve the correct album art and information for any track or albums that are incorrectly labelled.
If you are a music fan, you’ve probably got an iPod or similar player that you take with you when you go out and about. Updating MP3 players can be a nightmarishly slow task, but Miro 5 helps to speed things up with accelerated automatic synchronization and automatic format conversion. There is not shortage of sites and services looking to sell you MP3, and if you’ve been on the lookout for another, support has now been added for eMusic.
Windows users have an updated backend to look forward to, but the release candidate has also be made available for OS X. For most people, Miro is all about streaming video, and this is still very much at the application’s core. While many of the changes and additions that are to be found in the program are music-centric, there is also the new option to download high definition videos from Vimeo.
You can find out more and download a free copy of the app by paying a visit to the Miro 5 RC1 review page.
Photo Credit: olly/Shutterstock
-

Apple device users, 'Cloak' your identity on public hotspots
Publié: mars 21, 2012, 1:21pm CET par Mark Wilson
 Free WiFi is more prevalent than ever and the popularity of mobile devices means that more and more of us are connecting to these free networks using laptops, tablets and mobiles. In these situations, using their own computer, most people would not give a second thought to security.
Free WiFi is more prevalent than ever and the popularity of mobile devices means that more and more of us are connecting to these free networks using laptops, tablets and mobiles. In these situations, using their own computer, most people would not give a second thought to security.But if you’re using your MacBook, iPhone or iPad in a public place with free Internet, such as a coffee shop, it is possible for someone to tap into your connection and steal your private data. Cloak is a security tool for Apple fans that makes securing these connections quick and easy.
There are numerous ways in which you can secure your computer’s connection when you are using public WiFi, but if you don’t fancy getting your hands dirty with network configuration options, Cloak may just be the tool you have been looking for. This is a VPN service that prevents your private data from simply being transmitted for anyone to intercept. Instead, data is encrypted and routed through secure servers to help keep you protected against potential data and identify theft.
Of course, it is not just your web browser that makes use of a web connection -- instant message apps, file sharing tools and more are also prone to attack. Cloak can help protect all of these by securing your Internet connection as a whole, and the great thing is that you do not even have to remember to activate it. As soon as an insecure connection is detected, Cloak springs into action. The service makes use of secure server located all over the world, and you’ll be automatically connected to whichever one will offer you the best performance.
As you might well expect, this is the kind of service that offers different subscription levels. There is a free version available and this has certain restrictions associated with it. If you opt for the free service you are limited to 1 GB of traffic or two hours of connection time in any month. Should you need more than this, you’re going to have to part with some cash.
There are two paid-for subscriptions available, both of which offer unlimited time online but still feature caps on monthly traffic. The Productive package is available for $8 a month and includes 20 GB of data, while the Powerful package gets you 50 GB of data for $15 a month.
You can find out more and download a free copy of the app by paying a visit to the Cloak review page.
Photo Credit: Tyler Olson/Shutterstock
-

Get CryptBox 2012 for free, but hurry!
Publié: mars 20, 2012, 11:53pm CET par Mark Wilson
 Whether you share your computer or not, you should probably think about encrypting some of your private documents. Files relating to your finances, work and personal life can reveal a great deal of information about you, and it is not just a matter of wanting to maintain personal privacy. Identity theft is a serious problem, and if your personal details fall into the wrong hands, there is no way of knowing just how it will be used.
Whether you share your computer or not, you should probably think about encrypting some of your private documents. Files relating to your finances, work and personal life can reveal a great deal of information about you, and it is not just a matter of wanting to maintain personal privacy. Identity theft is a serious problem, and if your personal details fall into the wrong hands, there is no way of knowing just how it will be used.CryptBox 2012 is an immensely powerful encryption tool that can be used to secure your data and you can grab yourself a free copy in today’s giveaway.
The program employs government standard 256-bit AES encryption that can be applied to individual files, whole folders or even complete drives -- you can even encrypt the drive on which Windows is installed. Everything can be configured using a series of wizards and in a matter of minutes you will be able to set up all of the encrypted safes that you need. These can be used to not only store files, but also to install portable apps that can then be used on any computer without the need for installation.
CryptBox is travel-friendly in other ways too, making it possible to store an encrypted safe on a USB drive so you can benefit from the same security on other computers. If you want to avoid having to take too much on the toad with you, you could opt to use your iPod as the storage location.
You do not have to have something to hide to want to use security software such as this, you just need to have an interest in your own privacy and safety. It is important to remember that it is not just the files that you have saved that could be used against you in some form or other, but also those that you thought you had deleted.
It is all too easy to recover files that have been deleted, so erasing a sensitive document is not necessarily enough to prevent other people from accessing it. CryptBox includes a file shredder tool that not only delete files from your hard drive, but overwrites the space they occupied to block potential recovery attempts.
In order to unlock CryptBox 2012, a full current product worth $29.95, you will need to apply for a serial number. Launch the program after installation and enter your name and email address when prompted to do so, before clicking the ‘Get free unlock code now’ button. Within a few moments you will receive and email containing the required unlock code that will enable you to continue using the program free from restrictions.
As with all of the Downloadcrew giveaways, the free download of CryptBox 2012 is only available for a limited period. You have just one day -- from 00:00 to 23:59, Central European Time, on Wednesday March 21 -- to get hold of your copy head over to the giveaway page now. For Americans that's 7 pm EDT March 20 to 6:59 pm EDT March 21. Grab it while you can.
Photo Credit: BL/Shutterstock
-

AirCover protects your phone and files via the cloud
Publié: mars 19, 2012, 7:41pm CET par Mark Wilson
 Protection software is something that most people will most readily associate with desktop and laptop computers, but even owners of mobile devices such as cell phones and tablets have to take care. It is not just viruses, something that can affect Android users, that mobile device owners have to worry about. It is the risk of losing a device or having it stolen.
Protection software is something that most people will most readily associate with desktop and laptop computers, but even owners of mobile devices such as cell phones and tablets have to take care. It is not just viruses, something that can affect Android users, that mobile device owners have to worry about. It is the risk of losing a device or having it stolen.Besides the value of the device itself, there is also the data it contains to consider. If you have concerns in any of these areas, AirCover is a free tool for iOS and Android that could help to give you peace of mind.
Apple already offers a tool that can be used to locate a lost iOS device, and there are various similar apps available for Android, but AirCover offers a more complete level of protection, particularly for Android users. In addition to the device tracking and online backup options, the Android version also includes virus protection, system optimization and privacy protection options. This enables you to control the level of access individual app have to the data store on your device as well providing you with tools to free up memory and resources.
While the iOS version of AirCover does not offer all of the helpful protection features available to Android users, it does have a helpful Battery Doctor component that enables you to monitor the life of your battery in different usage scenarios.
Both editions of the app have a safety feature that will appeal to parents. Family Safety can be used to track the location of a phone using GPS, but it can also be configured to automatically generate an alert if the phone strays beyond a pre-defined region -- great if you have told your kids not to stray too far from home.
It is worth noting that in order for device location features to work correctly, it will be necessary to enable GPS. As anyone who has ventured away from a power source for any length of time will attest, this can be a serious drain on your battery. This means that should you find that your phone or tablet does become lost or stolen, you will have a limited timeframe in which to do something about it – obviously this is not the fault of the app, but it is still worth bearing in mind.
You can find out more by paying a visit to the AirCover review page.
-

Thunderbird 12 beta -- rapid release, few changes
Publié: mars 17, 2012, 5:15pm CET par Mark Wilson
 The house of Mozilla is pumping out application updates faster than ever, and while we have now become used to the accelerated release schedule of Firefox, and indeed other browsers, this is not the only app to be given the fast-track treatment.
The house of Mozilla is pumping out application updates faster than ever, and while we have now become used to the accelerated release schedule of Firefox, and indeed other browsers, this is not the only app to be given the fast-track treatment.Mozilla’s email client, Thunderbird has also been moved onto the same rapid release cycle and this means that there are new alphas and betas to look forward to more frequently. Whether you’re only interested in running the most stable version of the software, or you’d prefer to try out the latest and greatest features as soon as possible, there is a version of the application for you.
It is not very long since the main release branch hit version 11 and this meant that the beta channel was also due for a refresh. Thunderbird 12.0b1 has now been released, but despite the jump from version 11 to 12, there really isn’t all that much that has changed on the surface. The only new feature to speak of comes into play when performing global searches, and you will now see message extracts in your search results.
There have been some minor changes to the way in which newsgroup and RSS subscriptions are handled, but apart from this the latest beta is really a bug fixing release -- you can see a full list of fixes in the changelog. The minor nature of the update means that this beta seems stable enough for day to day use, but it’s worth remembering that if you already have Thunderbird 11 installed, this will replace it.
Just as Firefox has a somewhat more experiment Aurora version which will be welcomed by anyone keen to try out the very latest features, albeit in software that is not necessarily completely stable, so Thunderbird has an alpha version called Earlybird. This can be installed alongside your current version of Thunderbird, so you can test out the latest version without compromising stability.
You can find out more and download a free copy of the email client beta by paying a visit to theThunderbird 12.0 Beta review page.
Photo Credit: Gina Sanders/Shutterstock
-

Get the luck of the Irish with one of this week's 32 downloads
Publié: mars 17, 2012, 5:09pm CET par Mark Wilson
 Apple's iPad dominated news about hardware this week, but there was still plenty else going on in the software world.
Apple's iPad dominated news about hardware this week, but there was still plenty else going on in the software world.If you’re running Windows but like the idea of trying out different operating systems, or just installing a different version of Windows without the need for dual booting, VirtualBox 4.1.10 (build 76836) may be what you’re looking for. When you’re running virtual system in this way you can use VirtualBox Extension Pack 4.1.10 to add extra features such as better USB performance and networking booting.
You may be more interested in boosting the performance of your real rather than virtual computer, and IObit Advanced SystemCare 5.2.0.223 FINAL is a well-balance system optimization and maintenance suite that enables you to do just that. To stay in control of your system and make the best possible use of available resources, take a look at Task Manager DeLuxe 1.1.0.0, which is an enhanced version of the tool that is built into Windows.
No roundup would be complete without its fair share of browser updates, and this week we have seen a bumper batch of releases. Firefox 11 FINAL has seen few updates besides improved synching but it has moved to the stable channel and there is also a portable version available -- Firefox Portable 11.0.
Users of 64-bit versions of Windows can take advantage of the speed, stability and security of Waterfox 11.0 while anyone who wants to take a glimpse into the next version of Mozilla’s browser need look no further than Firefox 12 Beta. Should you fancy peering further into the future, there is also the alpha version of the browser -- Firefox Aurora 13.0a2. Although yet to be classed as stable, there are a number of interesting new features such as a new tab page and other interface changes.
For fans of the very latest releases, Firefox Nightly 14.0a1 (32-bit) and Firefox Nightly 14.0a1 (64-bit) are testing grounds for more experimental features and are only recommended for more advance users. Firefox 14.0a1 UX (32-bit) and Firefox 14.0a1 UX (64-bit) provide a glimpse of what you can expect even further down the line and includes features that may or may not find their way into the main release branch such as a new home tab. If security is a concern for you,Comodo Dragon 17.5.2.0 is a security focus browser that is based on Google Chrome that is worth checking out.
Mozilla is most famous for its web browser, but the company also has an email client in the form of Thunderbird 11 FINAL. This latest version includes better handling of tabs and improved importing of data from Outlook, while Thunderbird 12.0 Beta includes enhanced global searching and range of bug fixes.
 Just as there are beta and alpha versions of Firefox, the same is true of Thunderbird, and if you’d like to see where the email client is heading, Mozilla Earlybird 13.0a2 gives you a good idea. One final release from Mozilla this week -- Mozilla SeaMonkey 2.8. This internet suite includes not only a web browser and email client, but also an HTML editor and more. And finally on the browser front, Apple Safari 5.1.4 boasts drastically improve JavaScript performance.
Just as there are beta and alpha versions of Firefox, the same is true of Thunderbird, and if you’d like to see where the email client is heading, Mozilla Earlybird 13.0a2 gives you a good idea. One final release from Mozilla this week -- Mozilla SeaMonkey 2.8. This internet suite includes not only a web browser and email client, but also an HTML editor and more. And finally on the browser front, Apple Safari 5.1.4 boasts drastically improve JavaScript performance.When online it is important to stay safe, and a number of security tools released this week. Comodo Internet Security Premium 2012 v5.10 is a free security suite that includes antivirus and firewall protection -- but you can also download and install these components separately: Comodo Antivirus 2012 v5.10 and Comodo Firewall 2012 v5.10.
Keeping software up to date is an important factor in ensuring the security of your computer, and SUMo 3.0.0 is a free tool that checks your system and lets you know if any of your applications are out of date and points up in the directions of any available downloads.
Using a computer involves working with files, and if you use more than one computer you may need a way to transfer files between machines. Bitdefender Safebox 1.0 provides a free and secure means of doing just this, enabling you to encrypt files and store them online in a secure account so only you can access them.
When it comes to working with local files, an advanced search tool is essential for anyone who creates a large number of documents. Instant File Search Professional 1.3 is a powerful search tool that harks back to the search tool that used to be found in Windows.
If you have files on your hard drive that you would like to convert into PDF format, look no further than Nitro PDF Reader 2.3 32-bit or Nitro PDF Reader 2.3 64-bit which, despite being available free of charge, are packed with incredible feature that leave you in control of the PDF creation process.
 This week’s big hardware release may have been the new iPad, but if you have an iPhone, you’ll want to take a look at iPhone Backup Extractor Free 3.3.5 which can be used to backup and restore data from your phone -- in fact, despite the name, it can be used with any iOS device.
This week’s big hardware release may have been the new iPad, but if you have an iPhone, you’ll want to take a look at iPhone Backup Extractor Free 3.3.5 which can be used to backup and restore data from your phone -- in fact, despite the name, it can be used with any iOS device.A handy utility for your desktop computer is Restarter 2.0 which, as the name suggests, can be used to automate the restarting of programs -- such as when they crash or you close them accidentally. The final batch of tools in this week’s roundup are all audio utilities, starting with Audacity 2.0 FINAL -- the update that has been six years in the making!
Audiggle 3.0.0.2 takes an idea that will be familiar to owners of iOS and Android devices. If you’ve ever struggled to identify a song, this is an app that will be able to reveal the name of a track you hear on the radio or TV. And if you’re a fan of online radio, streamWriter 4.0.0.0 is an extremely useful tool that can be used to record two stations at the same time and even automatically split recordings into individual tracks.
Remember to keep one eye on Downloadcrew Giveaway this coming week. On Monday we’re giving away Ashampoo WinOptimizer 8 (yes, it’s a repeat, but it was the first offer we ran when we launched “Giveaway” in December) and two other full apps lined up for next week which will be confirmed and announced on Monday.
That’s it for this week. There are another seven exciting days of releases ahead of us… join us this time next week for another roundup.
Photo Credit: Home-lab/Shutterstock (top)
-

Kindle 3.0 for iOS supports iPad Retina display
Publié: mars 15, 2012, 10:05pm CET par Mark Wilson
 The iPad has not really taken off as a platform for ebooks yet. Thus far the screen resolution has been high, but still no match for the various e-ink screens available on dedicated ereaders. All this could well change with the release of the new iPad, tomorrow, thanks to its high-resolution Retina display that packs more pixels than ever before.
The iPad has not really taken off as a platform for ebooks yet. Thus far the screen resolution has been high, but still no match for the various e-ink screens available on dedicated ereaders. All this could well change with the release of the new iPad, tomorrow, thanks to its high-resolution Retina display that packs more pixels than ever before.Kindle for iOS is among a host of apps being updated to take advantage of the increased resolution.
The new version helps to ensure that books and magazines look as crisp as ever but there are few other updates or improvements to enjoy. Despite the version number increasing to 3.0, perhaps to match the third generation of the iPad, aside from the Retina display support, the only other changes to be found here are a redesigned library and a new cloud view.
This last feature makes it possible to access all of your ebooks in the cloud, combining the collections you have amassed across your various devices. You are presented with what basically amounts to two separate libraries -- the publications that are on your device, and those that you have acquired but are still online. Books stored in the cloud can be easily downloaded to your device.
There is also a new look for the library on iPad, while iPhone users have a grid view to work with. Pitted against the likes of iBooks, the Kindle iOS app is still found slightly lacking but the the higher resolution is certainly welcome. This is first app update that could see the new iPad transformed into a more viable platform for ebooks.
You can find out more and download a free copy of the app by paying a visit to the Kindle for iOS review page.
-

Windows 8 tweaks are among the week's best downloads
Publié: mars 11, 2012, 1:14am CET par Mark Wilson
 Apple dominated news the second week of March, but, not to be outdone, Microsoft released a couple of interesting tools that are well worth a look. Microsoft Research Cliplets 1.0.1 32-bit is a quite unique program that can be used to create something very impressive from your video clips. In short you can select a short video file and choose an area that should be played as normal while the remainder is montionless. You can come up with some very eye-catching results, and if you’re using a 64-bit version of Windows you should take a look at Microsoft Research Cliplets 1.0.1 64-bit.
Apple dominated news the second week of March, but, not to be outdone, Microsoft released a couple of interesting tools that are well worth a look. Microsoft Research Cliplets 1.0.1 32-bit is a quite unique program that can be used to create something very impressive from your video clips. In short you can select a short video file and choose an area that should be played as normal while the remainder is montionless. You can come up with some very eye-catching results, and if you’re using a 64-bit version of Windows you should take a look at Microsoft Research Cliplets 1.0.1 64-bit.You may have taken the plunge and installed Windows 8 Consumer Preview. Microsoft Device Center Beta 32-bit is available to help you to take full advantage of the Windows 8 specific features of Microsoft keyboards and mice. Again, if you are using a 64-bit version of Windows, there is a version for you in the form of Microsoft Device Center Beta 64-bit.
On the subject of Windows 8, the absence of a Start button is something of a controversy. Start8 0.85 is a free tool that restores the Start button to its rightful place and provides you with easier access to shutdown options. In a very similar vein is ViStart 7.0 (build 3821) which can be used to enhance the Start menu in any version of Windows but, perhaps most importantly, restore it in Windows 8.
Whatever version of Windows you happen to be using, you may well have found that Explorer is a bit limited for your needs. Q-Dir 5.00 32-bit is a fully featured alternative tool that boasts a four pane view that makes it easier than ever to work with multiple folders. Q-Dir 5.00 64-bit is also available and both versions can be installed in Windows 8.
Everyone loves to tweak their computer with a view to getting a performance boost or just changing the way a particular aspect of Windows works. TweakNow WinSecret 2012 v4.0.0 has been updated with added support for the Windows 8 Consumer Preview and now includes even more tweaks that you can apply to your system.
Turning our attention to life online, Adobe SWF Investigator 0.6.1 is a free tool that can be used to dissemble SWF applets so you can see how they work and adapt them to suit your needs. Using the Internet need not mean putting together your own website, and this week there have been a couple of communication tool released. Skype Voice Changer 1.2 is a fun little app that lest you change the way you sound in voice conversations in Skype, while Facebook Messenger for Windows 2.0.4447 enables you to keep up to date with all that’s happening in your Facebook account without the need to visit the site.
 To help keep you safe when you’re online, Kaspersky Internet Security 2013 Beta gives an early glimpse of what to expect when the security suite gets an official release in the near future.
To help keep you safe when you’re online, Kaspersky Internet Security 2013 Beta gives an early glimpse of what to expect when the security suite gets an official release in the near future.Another big-name release this week is Adobe Photoshop Lightroom 4 FINAL, which is a professional level digital darkroom that can be used to help keep your photo collection organized -- and throws a range of editing tools into the mix to boot. While much of the week’s news has been focused on Apple’s hardware releases, there has also been an update to its software.
Apple iTunes 10.6 32-bit adds support for 1080p HD movies and TV shows in the App Store, as well as fixing issues with iTunes match. Users of 64-bit operating systems should take a look at Apple iTunes 10.6 64-bit.
If you’re in the market for software that helps to make your computer easier to use, Chameleon Shutdown 1.1.1.30 is a handy utility that enables you to shutdown, restart and hibernate your computer on a schedule or timer. Finally this week is Dropbox Folder Sync 2.5. This is a great free tool that makes it possible to control which of your folders are synchronized with Dropbox.
That’s it for the time being. Join us over the next seven days for even more software releases, topped off with another roundup this time next week.
-

Our gift to you: Ashampoo Burning Studio 2012
Publié: mars 9, 2012, 12:58am CET par Mark Wilson
 Burning discs has become so fundamental to computing that practically every computer produced in the last decade has a disc burner of some sort built in. But in order to make use of your burner, you’re going to need some suitable software. Windows includes some very basic support for disc burning, but if you want to do much more than copy files from your hard drives onto a recordable disc, you’re going to have to look elsewhere.
Burning discs has become so fundamental to computing that practically every computer produced in the last decade has a disc burner of some sort built in. But in order to make use of your burner, you’re going to need some suitable software. Windows includes some very basic support for disc burning, but if you want to do much more than copy files from your hard drives onto a recordable disc, you’re going to have to look elsewhere.The software that is supplied with CD, DVD and Blu-ray recorders is often complicated and packed with endless features you’ll never use. Ashampoo Burning Studio 2012 is a user friendly burning tool that strikes the perfect balance between ease of use and depth of features.
We’re giving away a free copy of the application, worth $49.99, so you can venture in the world of disc creation without having to break the bank or spending too much time learning to use complex options. Despite the absence of a price tag, you’ll undoubtedly be impressive by the power of the program.
In addition to support for CD creation, you can also use the software to burn your own DVDs and Blu-ray discs -- if you are using Ashampoo Burning Suite to create compilation or any other type of disc, there are handy tools available to enable you to design and print custom covers with ease.
You also have the option of creating images of existing discs, or burning images you alreasdy have onto the appropriate type of disc. A great use for recordable media such as DVD-R discs is backing up your data, and Ashampoo Burning Suite 2012 has a simple but effective backup tool built in to allow you to do just this. Among the suite other handy tools include a CD ripping option, and the ability to create movie discs from pre-prepared folders.
To get your full, free version of Ashampoo Burning Studio 2012, simply head to the Downloadcrew Giveaway website, download a copy of the software, and request a unique serial code.
Note, this offer is only valid from 00:00 Central European Time, Friday 9th March 2012 (that's 6 pm ET March 8), through to Saturday 23:59. You must activate your software during this promotional period.
Photo Credit: AISPIX by Image Source/Shutterstock
-

Save 54% on CyberLink PhotoDirector 3
Publié: mars 8, 2012, 10:03pm CET par Mark Wilson

CyberLink is a company that is synonymous with software that is incredibly powerful yet also incredibly easy to use. When it comes to the arena of photo editing, there are a number of extremely high-end tools to choose from, and these have a tendency to not only be very complicated to use, but also restrictively expensive. The same cannot be said of CyberLink PhotoDirector, which includes all of the powerful tools you would expect to find in a professional image editing tool, but it is far easier to use than the likes of Adobe Photoshop.
We thought we’d let you in on a deal which will get you the latest PhotoDirector 3, which is retailing with a $149.95 MSRP for only $69.95, saving you a huge 54 percent. Read on.
The latest version of the photo program is CyberLink PhotoDirector v3; this usually sells for $149.95 and you can find out more in our review. The application’s predecessor, CyberLink PhotoDirector 2011 is still available however, and this is a very capable tool in its own right. But choosing to buy this previous version does not mean you have to miss out on the latest and greatest features -- in fact, it means that you are making a great saving. This is because when you buy CyberLink PhotoDirector 2011 for just $69.95, you will automatically receive a free upgrade to v3, effectively shaving more than half off the regular MSRP.
If you have already tried out the 2011 version of the program, you will find that v3 is a major advancement on an already very capable product. There is a strong focus on workflow, and this is something that will be welcomed by keen amateur photographers as well as professionals. The program interface is divided up in to five main sections, the first of which can be used to catalog and organize your images, while the Edit and Adjustment section can be used to tweak and enhance your shots. Slideshow and Print sections are also available for you to make the most of your edited images.
There is support for RAW image formats -- something that will appeal to the more professional end of the market -- and when it comes to organizing your image collection, you can use tags and flags to categorize images and make them easier to find and filter. As well as giving you the opportunity to manually adjust every aspect of your photos, there are also a number of presets available to help you to get results as quickly as possible. There is also a batch processing option and a number of advanced tools such as the background and object removal features.
You can find out more by paying a visit to the CyberLink PhotoDirector v3 review page and to take advantage of the special upgrade offer, pay a visit to the Downloadcrew Software Store. Hurry though, this offer is limited to the remaining 2011 serial codes remaining in stock and will end March 31.
-

Save big bucks on creative and security software
Publié: mars 8, 2012, 3:53pm CET par Mark Wilson
 Everybody loves a bargain, and if you’re on the lookout for software at a great price, look no further than the Downloadcrew Software Store where you’ll find something to suit every taste and budget throughout the month of March.
Everybody loves a bargain, and if you’re on the lookout for software at a great price, look no further than the Downloadcrew Software Store where you’ll find something to suit every taste and budget throughout the month of March.Perhaps you need to squeeze the last ounce of performance out of your computer; there are a number of applications that can help you out, starting with Auslogics BoostSpeed 4. For just $9.95, a saving of 80 percent off the MSRP of $49.95, you can speed up your start times, clean out the clutter from your hard drive and more. When taking care of your drives, Auslogics Disk Defrag Pro 4 provides a complete defragmentation solution, and it is currently available for 67 percent off the MSRP of $29.95 at just $9.95. Other performance enhancing tools worth taking a look at include TuneUp Utilities 2012 [3-PC non-expiring lifetime licence] which can be installed on up to three computers and costs just $14.99 (70 percent off the MSRP of $49.95) and IObit Advanced SystemCare 5 PRO [3-PC], which is also discounted by 70 percent from $39.95 to $11.95.
Computers do need some care and attention from time to time, but they are also valuable tools that can be used for all manner of creative ventures. Although CyberLink PhotoDirector 3 was released earlier this month, you can still buy CyberLink PhotoDirector 2011 for only $69.95, saving 54 percent from the v3 MSRP. More importantly, you’ll also receive a free upgrade PhotoDirector 3 direct from CyberLink. Bargain.
If music is more up your street, MAGIX has a tool for you. MAGIX Music Maker MX (v18) is on offer for just $39.99 – a 33 percent saving off the MSRP of $59.99 -- and includes everything you need to create music from scratch working with loops, samples and special effects. Should you want to take things even further, MAGIX Movie Edit Pro MX (v18) features even options to help you to make the most of your home movies and you can save 34% off the usual selling price of $69.99 when you buy the software for $45.99.
Getting creative doesn’t necessarily meaning having to be musically or artistically talented. You can get creative by doing little more than making a compilation CD of your favorite music, or collecting together your favorite photos to create a slideshow. Roxio Creator 2011 Pro is a power suite of disc burning tools that can be used to create all manner of CDs, DVDs and Blu-ray discs. For just $29.99 – a saving of 77 percent off the usual price of $129.99 – you can create your own custom movie discs, backup data, and much more.
O&O UnErase 6 Personal is a great tool for anyone who has been a little careless emptying the Recycle Bin or has fallen victim to a virus that has deleted files. The program can be used to recover files that might otherwise have been lost and you can save 76 percent off the MSRP $29.00 when you buy the program for just $6.95. If you have recently bought or you are thinking about buying a new computer Laplink PCmover Professional & SafeErase Bundle may be just what you have been looking for. You can buy the software for just to $39.95, saving 53 percent off the MSRP of $84.95, and this includes a three computer license.
The importance of having adequate security software installed cannot be overstated, so it should come as no surprise that there are a number of security tools available. Webroot Internet Security Complete 2011 [3-PC] is an antivirus tool, malware blocker, spam filter, firewall and ID theft protector. All of this comes at the bargain price of $9.95 – saving 88 percent off the usual price of $79.95 -- and you can install the software on three computers.
 If you’re needs aren’t quite as high, take a look at Webroot Internet Security Essentials 2011 [3-PC]. Again, this software can be installed on three computers and include virus, malware and firewall protection all for just $4.95, representing a saving of 92 percent off the MSRP of $59.95 -- as an added bonus, there’s also a free upgrade to SecureAnywhere included, from Webroot!
If you’re needs aren’t quite as high, take a look at Webroot Internet Security Essentials 2011 [3-PC]. Again, this software can be installed on three computers and include virus, malware and firewall protection all for just $4.95, representing a saving of 92 percent off the MSRP of $59.95 -- as an added bonus, there’s also a free upgrade to SecureAnywhere included, from Webroot!Other security tools include AVG Premium Security Complete Bundle, which is made up of Quick Tune, AVG PC Tuneup 2012, AVG Family Safety 2012 and AVG Mobilation all for the incredible price of $29.95, a saving of 77 percent off the MSRP of $130. An even greater saving of 80 percent is to be found off the usual price of AVG Internet Security 2012 Plus Bundle, which can be used to protect up for four computers for just $29.95 instead of $149.00.
Another big name in the world of security is Kaspersky, and there are savings to be made here too. Kaspersky Internet Security 2012 [1-PC, 1-Year] is a comprehensive security suite that includes antivirus, web site checking, banner ad blocking, and much more for 68 percent off the MSRP $59.95 at just $18.95. if you have more than one computer to think about, look no further thanKaspersky Internet Security 2012 [5-PC, 1-Year] which includes five license and is available at 69 percent saving off the usual price of $129.95 – just $39.95!
 Rounding off March’s marvellous selection of money saving offers are more tools from some of the biggest names in computer security. BullGuard Internet Security 12 [3-PC, 1-Year, 10GB backup] can be yours for just $9.99, saving you 85 percent off the usual price of $65.95. the app is a powerful security suite that includes virus protection but also boast 10GB of online storage space that you can use for backups. From the same company is BullGuard Antivirus 12 [1-PC, 1-Year], which is a straightforward antivirus tool that can be bought for 77 percent off the MSRP of $29.95 for just $6.99.
Rounding off March’s marvellous selection of money saving offers are more tools from some of the biggest names in computer security. BullGuard Internet Security 12 [3-PC, 1-Year, 10GB backup] can be yours for just $9.99, saving you 85 percent off the usual price of $65.95. the app is a powerful security suite that includes virus protection but also boast 10GB of online storage space that you can use for backups. From the same company is BullGuard Antivirus 12 [1-PC, 1-Year], which is a straightforward antivirus tool that can be bought for 77 percent off the MSRP of $29.95 for just $6.99.AVG is a company usually associated with security, but AVG PC Tuneup 2012 [1-PC, 1-Year] helps to keep your computer in good shape. Available at a 66 percent discount for just $11.99 the app includes a series of optimization tools that can boost the performance of your computer. If you’re looking for online storage, look no further than AVG LiveKive [25GB storage] which gives you a generous 25GB of online space for just $14.95 – this is 70% off the usual price of $49.99.
These are just some of the highlights from the Downloadcrew Software Store. There are plenty more bargains to be found, so pay a visit to the store to see what takes your fancy.
Photo Credit: iQoncept/Shutterstock
-

Get Skype 5.6 for Mac now!
Publié: mars 7, 2012, 3:32pm CET par Mark Wilson
 Mac owners with Skype installed have a new version of the chat tool to install, and despite the small increase in the version number, there’s actually a lot packed in.
Mac owners with Skype installed have a new version of the chat tool to install, and despite the small increase in the version number, there’s actually a lot packed in.One of the biggest improvements in Skype 5.6 for Mac is the addition of automatic updates -- this is something that will be welcomes by anyone who likes to ensure that they always have the very latest version installed. It is an important security measure, too, as it means that any problems that have been detected with previous versions can be fixed automatically.
After something of a delay, there is now support for full-screen mode in OS X Lion, which leaves you free to focus on chats without the distractions of any desktop furniture. Skype has been constantly improving the way that group and conference calls are handled, and this latest update is no different, with interface tweaks and feature enhancements included in this latest version.
Most notable for group chats is the dynamic mode that is available in group video calls. In this mode, the video window of whichever participant is talking is automatically moved to the top of the screen -- this can make conversation much easier to follow when there are several people involved, particularly if you are not overly familiar with them. It is now also possible to disable the auto gain feature of your microphone which had led to background noise problems in some conference calls.
Another new feature makes it possible to delete individual messages from within conversations and delete entire conversations from your chat history. As you would expect, there are also a number of bug fixes, including problems with the selection of contacts, issues with call ending and problems with USB headsets, as well as an issue that mean chat messages become invisible after clearing chat history.
You can find out more and download a free copy of the app by paying a visit to the Skype 5.6 for Mac review page.
-

You CAN have a Start button on Windows 8 Consumer Preview
Publié: mars 6, 2012, 11:57pm CET par Mark Wilson
If you’ve installed Windows 8 Consumer Preview, you can’t have missed a glaring omission. The familiar Start button is gone, something that has fazed many users who have taken the plunge and decided to test drive Microsoft’s next operating system.
If you're feeling lost. There is hope. Start8 is a remarkably simple, yet nonetheless remarkable, free tool that can be used to restore the Start menu.
The app does not bring back the original Start menu, but a facsimile, and a good one. The presence of a standard Start button means that accessing the applications you have installed is made significantly easier.
Many people who have installed Windows 8 have been confused by the empty space that appears to the far left of the taskbar, and Start8 beautifully fills this gap and improves the ease of use of Windows 8. You have a choice of Start buttons to boot.
Start8 not only provides you with a Start button that can be used to access the new-style Start menu when you click it with the left mouse button, there are also handy options available from the right click menu. It is now easier to access the shutdown section of the new Start menu, so shutting down or restarting your computer is now easier than before. The reinstated Start button also provides easy access to the Run dialog and the ability to search your installed applications.
Living without the Start button is something that some users will find that they get used to over time and are able to get used to the new way of working. But for anyone for whom this button has become such an integral part of Windows, its removal is counterintuitive. Start8 is one remedy.
You can find out more and download a free copy of the app by paying a visit to the Start8 review page.
-

Be creative with one of these 21, exciting downloads
Publié: mars 3, 2012, 6:46pm CET par Mark Wilson

It has been another very busy week in the world of software releases and we’ve collection together 21 of the biggest titles that you may have missed; there’s something for everyone here, no matter what you use your computer for.
This has been a big week for anyone looking to get a little creative with their computer. CyberLink Video and Photo Creative Collection 2.0 is a powerful collection of tools that includes all you need to work with your photo and video collections. Comprising PowerDirector and PhotoDirector, you can edit all of the images and footage you have capture with your digital camera ready to use in a range of projects.
CyberLink PhotoDirector 3 FINAL is also available as a standalone product and has been greatly enhanced from previous versions, now boasting a number of advanced features such as lens correction. If you are someone who has an extensive photo collection on your hard drive, look no further than MAGIX Photo Manager MX (v11) Deluxe which includes everything you need to browse, view, edit and organize your images.
This week also saw the release of tools for anyone looking to get creative online. If you have a website and have been thinking of using it to showcase videos, flowplayer 3.2.7 is a stunning streaming video player that can be customized in a huge number of ways and is available free of charge, even for commercial use.
For the home user wanting to show off digital photos online, Jalbum 10.4 makes it easier than ever to create an online gallery for your web site; there are a range of styles and templates to choose from so you can find something to suit your existing site.
Any mention of the Internet always leads to thoughts about security, and Norton Internet Security 2012 v19.5 (60-day) is an impressive virus protection tool (and much more ) that is not only available as a generous 60 day trial, but is also compatible with the Consumer Preview of Windows 8. Norton is not the only name in the security arena, and Panda Cloud Antivirus Free 1.5.2 is a different style of security tool that take full advantage of the cloud to offer reliable, constantly updated protection.
Skype Launcher 1.6.5 is a handy tool for home and business users alike, making it possible to sign into multiple Skype accounts at the same time -- a great way to keep your work and personal life separate.
 Moving away from Internet based programs, Speccy 1.16 is an excellent utility to help you to discover everything you need to know about your computer. Whether you need to find out the exact specification of your machine ready to sell it, or you need to check the model number of a piece of hardware, this is the tool for you; there’s also Speccy 1.16 Portable for portable software fans.
Moving away from Internet based programs, Speccy 1.16 is an excellent utility to help you to discover everything you need to know about your computer. Whether you need to find out the exact specification of your machine ready to sell it, or you need to check the model number of a piece of hardware, this is the tool for you; there’s also Speccy 1.16 Portable for portable software fans.Software is just as important as hardware, and Secunia PSI 3 (beta) is a helpful tool that enables you to ensure that all of your software is kept up to date, overcoming problems that old software can be plagued with.
Your hard drive is one of the most important components of your computer, and you need to take care of it and manage it properly. Paragon Hard Disk Manager 12 Suite can be used to partition your drive into manageable chunks, defragment it to keep it running smoothly and recover data if something goes wrong. More demanding users need look no further than Paragon Hard Disk Manager 12 Professional, which adds support for dynamic volumes as well as virtual machine support and task scheduling.
If Mac users have felt a little neglected of late HandBrake 0.9.6 is now available. Despite the minor version number increase, there is actually a great deal that has been added to this powerful video conversion tool, including support for more decoders ad support for Lion -- there’s also a Windows and Linux version available.
Mac users can also take a look at SnagIt for Mac 2.0. This is a staggerly powerful screen capture tool that can now be used to record desktop videos as well as grabbing screenshots – again, there is also a Windows version available in the form of SnagIt 11.0.
 Not to be overlooked: Microsoft released a swathe of beta and preview products, starting with Microsoft Windows Server 8 Beta. Of greater interest to the majority of computer users areWindows 8 Consumer Preview 32-bit and Windows 8 Consumer Preview 64-bit, which enable you to take the next version of Windows for a spin before it is released later this year. Despite being a Consumer Preview, both the 32- and 64-bit versions of the operating system are shaping up extremely well although compatibility with all hardware and software is not guaranteed.
Not to be overlooked: Microsoft released a swathe of beta and preview products, starting with Microsoft Windows Server 8 Beta. Of greater interest to the majority of computer users areWindows 8 Consumer Preview 32-bit and Windows 8 Consumer Preview 64-bit, which enable you to take the next version of Windows for a spin before it is released later this year. Despite being a Consumer Preview, both the 32- and 64-bit versions of the operating system are shaping up extremely well although compatibility with all hardware and software is not guaranteed.These versions of Windows are provided in ISO format and will need to be burnerd to DVD, but you can also take a look at Windows 8 Consumer Preview Setup. This is a great alternative to the ISO download as it enables you to use a system checker to test for possible compatibility problems and then automatically download and install the preview if you would like to -- all of this with a wonderfully sleek installation process.
Software developers may also want to take a look at Microsoft Visual Studio 11 Ultimate Beta ISO, which can be used to produce applications and even publish directly to the Windows Store.
Join us again at the same time next week for another software roundup.
Photo Credit: Joseph S.L. Tan Matt/Shutterstock
-

Protect your Android with COMODO Mobile Security & Antivirus Free 1.1
Publié: mars 2, 2012, 7:28pm CET par Mark Wilson
 Viruses are something that are most readily associated with the Windows platform, but the increased popularity of mobile devices means that operating systems such as Android have become targets more recently. It’s easy to question the need for antivirus software for your cell phone, and if the software had a price tag attached to it, you might be right to view it with some degree of suspicion.
Viruses are something that are most readily associated with the Windows platform, but the increased popularity of mobile devices means that operating systems such as Android have become targets more recently. It’s easy to question the need for antivirus software for your cell phone, and if the software had a price tag attached to it, you might be right to view it with some degree of suspicion.But Comodo Mobile Security & Antivirus Free for Android is available free of charge and comes from the reliable security firm Comodo -- and it’s packed with extra features, making it well worth a look.
As you have probably guessed from the name of the app, one of the main components of this security tool is the antivirus feature. Just as you would expect on your PC, the app provides real-time protection, constantly checking the files you access and the apps you install, looking for signs of infection. You can also choose to manually scan individual files, or all of your device’s memory as well as taking advantage of the scheduled scan option.
But it doesn’t end there. There are a number of additional tools and options that can be used to help protect your privacy and security. Android is commonly installed on cell phones and it can be used to effectively filter the SMSes and phone calls you receive. You can easily configure a black and white list of blocked and permitted numbers, and you can also use keyword filtering to block text messages that you would rather did not make its way to your inbox.
Continuing the privacy theme, Private Space is a secure storage location for the text messages, contacts and numbers you would rather other people do not have access to.
As an added bonus there is also a software and process manager that can be used to not only keep an eye on what is running on your Android, but also enabling you to close down anything that looks suspicious or is using too many system resources. This is a quick and easy way to help optimize the optimize the performance and stability of your device, and while it does duplicate an option found within the Android OS, it is handy nonetheless.
You can find out more and download a free copy of the app by paying a visit to the Comodo Mobile Security & Antivirus Free for Android review page.
-

Recover deleted photos with EaseUS Mac Photo Recovery Free
Publié: mars 2, 2012, 1:58pm CET par Mark Wilson
 The panic that sets in after emptying the Trash folder only to realize that it contained files you actually needed is a feeling that can only be match by the one that arises after hard drive fails and you realize you have no backup.
The panic that sets in after emptying the Trash folder only to realize that it contained files you actually needed is a feeling that can only be match by the one that arises after hard drive fails and you realize you have no backup.Losing certain files through user error, hardware failure or some other problem can cause inconvenience and lead to a great deal of work, but when it comes to photos and other images files, it is often the case that replacing files is simply not possible. EaseUS Mac Photo Recovery Free is a data recovery tool that may be able to help.
Unlike many other data recovery tools, this app from EaseUS has been designed to recover a very limited number of file types. It can be used to recover data from a regular hard drive, or removable media such as USB drive or memory cards providing it is BMP, JPG, PNG, TIF or MP3 file you are looking for.
The actual scanning process is relatively fats, although this will obviously depend on the size of the drive involved as well as the number of files. The selection of file types is arguably a little strange; the image formats make sense as they are commonly used, and the software is billed as a photo recovery tool. The added support for MP3 audio files is a bonus, but it would have made more sense for this to have been a video formats such as MPEG.
Hardware failure or a virus attack may have led to the loss or damage of drive partitions. EaseUS’s tool can be used to recover such partitions and get back the files that were stored on them. Once a scan has been performed, you can browse through the folder structure of the files that can be recovered and take advantage of the built in file preview so you can check what an image looks like without having to rely on the file name alone.
EaseUS Mac Photo Recovery Free can be used with Leopard, Snow Leopard and Lion, but if you need to recover files other than those that have been mentioned, you’ll need to upgrade to the standard version of the app. Costing $89.95, this could be regarded as being a little expensive, particularly for a piece of software you would not use very often (preferably no more than once), but at the same time, it is difficult to put a price on irreplaceable files.
You can find out more and download a free copy of the app by paying a visit to the EaseUS Mac Photo Recovery Free review page.
Photo Credit: pav197lin/Shutterstock
-

Snagit -- capture videos as well as screens
Publié: février 29, 2012, 12:02am CET par Mark Wilson
 Screen capture can be as simple as hitting the Print Screen key on your keyboard, but if you’re slightly more demanding you’re going to have to look elsewhere for a more advanced tool than those built into your operating system.
Screen capture can be as simple as hitting the Print Screen key on your keyboard, but if you’re slightly more demanding you’re going to have to look elsewhere for a more advanced tool than those built into your operating system.Snagit is one such a screen capture tool that has carved out something of a name for itself on both Mac and PC, and can be used to grab entire screens, individual windows, capture on a delay and much more. The release of Snagit 11 and Snagit for Mac 2.0 sees a major new feature, the ability to capture video as well as stills, added to the Mac version, while Windows users have a number of key improvements and new features to enjoy.
It has long been possible to capture shots of your desktop in a number of ways, but the new screen recording option opens up new opportunities. The app can be used to record demos and reviews, and these can be posted to the likes of Facebook and YouTube all from within the application.
Anyone who has used previous version of Snagit will be aware of just how versatile a tool it is when it comes to capturing the contents of your desktop in still images, and now this has been extended to video.
There have also been a number of enhancements to the standard stills capturing process. If you are capturing a full desktop, or a very large window, the preview canvas is now automatically scaled so that the image is visible in its entirety.
The Mac version of the app also adds the ability to capture still images using a web cam, but whatever type of capture you are working with, whether on a Mac or PC, there are a range of new stamps that can be used to highlight sections of an image -- and of course there is the usual selection of editing tools to work with.
The images you capture can be uploaded to Facebook, Twitter and Evernote, but even those that you choose to keep stored only locally can be tagged and stored in your library for easy retrieval in the future.
An all-important spell check has been added so you can avoid embarrassing mistakes in presentations and there are easier resizing options as well as better canvas handling. In terms of look and feel, there’s little to differentiate between this and its predecessor, but this is no bad thing.
You can find out more and download a free trial of the software by paying a visit to the Snagit 11 and Snagit for Mac 2.0 review pages.
-

Use CCleaner? CCEnhancer 3.0 makes it better
Publié: février 27, 2012, 6:54pm CET par Mark Wilson
 Just as with your home, it is a good idea to have a spring clean of your computer from time to time. By sifting through the buildup of files that accumulates on your hard drives, you can easily free up significant amounts of disk space and help to boost not only performance but also privacy and security.
Just as with your home, it is a good idea to have a spring clean of your computer from time to time. By sifting through the buildup of files that accumulates on your hard drives, you can easily free up significant amounts of disk space and help to boost not only performance but also privacy and security.Anyone looking to automate the process of clearing up the crud that accumulates over can turn to CCleaner to delete file usage histories, remove superfluous registry entries and more. CCEnhancer 3.0 is a free third-party extension to the program that provides support for even more applications.
In all, CCEnhancer adds support for more than 500 extra programs, vastly extending the already impressive capabilities of the original program. In practice, there is very little involved in taking advantage of CCEnhancer. Launch the app and you will be presented with a window featuring a Download Latest button; click this and the latest support definitions will be downloaded for you, in much the same way as downloading virus definitions for your AV software.
You should find that the program is able to automatically locate your copy of CCleaner and apply the definition updates for you, but if you have installed to a strange location, you may find that you need to point it in the right direction. CCEnhancer 3.0 offers improved support for the portable version of CCleaner and the fact that CCEnhancer itself does not require installation means that it can be easily copied onto the same USB drive as the main cleanup tool and kept up to date whenever needed.
If you feel like getting your hands dirty, you can even go so far as editing the winapp2.ini file yourself to add support for even more programs. This may not be an option that appeals to everyone, but software developers wanting to cleanup after their own programs, or anyone using little known titles has this available to them. It’s worth pointing that that CCEnhancer is in no way associated with CCleaner, so compatibility cannot be guaranteed if the main program is updated in the future -- it is still an impressive tool worth adding to your maintenance toolkit.
You can find out more and download a free copy of the app by paying a visit to the CCEnhancer 3.0 review page.
Photo Credit: Goydenko Tatiana/Shutterstock
-

Adobe brings Photoshop Touch to iPad
Publié: février 27, 2012, 3:53pm CET par Mark Wilson

It has been some time since Adobe announced plans to release an iPad-specific version of the image editing tool Photoshop, and that day is finally here. Adobe Photoshop Touch arrived today, joining a surprising number of software announcements coming out of Mobile World Congress.
Photoshop Touch is a latecomer to iPad. Adobe released an Android tablet version in November.
There was already Photoshop.com Mobile, which could be used on an iPhone or iPad, but this is the real deal -- an astonishingly powerful version of the world famous digital photo manipulation tool. It should come as little surprise that this is resource hungry beast, so anyone with a first generation iPad is out of luck; you need to be toting an iPad 2 running iOS 5 to run this app.
Weighing in at $9.99, this app is one of the more expensive in the App Store, but this is a seriously impressive tool. Far more than just a fingerpainting app for your tablet, there is a huge selection of powerful tools that you also find in the desktop version of Adobe’s software. You are limited to working with images with a maximum resolution of 1600 x 1600, but you are free to work with layers, adding drop shadows, image blending and the usual array of filters and effects.
The majority of iPad apps are simple enough affairs that require little introduction -- in most cases you should be able to pick up an app and get started with it straight away -- but whether you are familiar with the desktop version of Photoshop or not, it’s worth spending a little while working through the selection of tutorials that have been included, just to familiarize yourself with the slightly different method of working.
Equipped only with fingers, you might imagine that it would be difficult to perform tasks such as selecting objects to work with. In reality, working with the Scribble Selection tool followed by the Refine Edge tool, things are much easier than you might first think.
The ability to work with layers is Adobe Photoshop Touch’s strong point, but the option of move, skewing, rotating and resizing selections is also very useful. There are also features that are unique to the iPad, such as Camera Fill which enables you to use the iPad’s camera to create backgrounds and textures.
There are a number of ways in which to get images into the app ready to work with. Of course you have the option of snapping a photo with your camera, but you can also import images you have uploaded to Facebook. If you have made use of Adobe Creative Cloud, this can also be used as an import source, and you even have the ability to use an integrated version of Google Images to grab images from the internet.
Quirks such as an inability to open PSD files, although you will find that you are able to open Photoshop Touch files on your desktop computer, are going to prove irritating to some, but on the whole this is a well-polished product worthy of the Photoshop name.
You can find out more and purchase a copy of the app by paying a visit to the Adobe Photoshop Touch review page.
-

BeatBlaster gives your iPad a new Hi-Fi makeover
Publié: février 25, 2012, 6:48pm CET par Mark Wilson
 The large screen of the iPad means that it is ideally suited for use as a movie player, but there is no reason that it cannot also be used to listen to music. BeatBlaster is a great looking music playing app that not only enables you to listen to your iTunes library on your iPad, but enables you to do so using a retro styled Hi-Fi.
The large screen of the iPad means that it is ideally suited for use as a movie player, but there is no reason that it cannot also be used to listen to music. BeatBlaster is a great looking music playing app that not only enables you to listen to your iTunes library on your iPad, but enables you to do so using a retro styled Hi-Fi.There are few people that still make use of a traditional Hi-Fi these days, but by popping your iPad into a dock and hooking it up to a set of speakers, you can take a step back in time while benefitting from great sound quality.
The main view of the app is that of a Hi-Fi, complete with a graphic equalizer, basic playback controls and links to other aspects of the app. For many people, watching the bounce of a graphic equalizer was a great accompaniment to listening to music but if this does not appeal, BeatBlaster has another couple of options available to you. You can also switch to Turntable mode in which you can watch digital vinyl spinning while you listen, or you can watch a pair of speaker cones pumping.
There’s no denying that this is a stylish looking app, but this does not mean that features have been scrimped on. As well as listening to the music collection you have synchronized with iTunes, you can also use the app to listen to online radio stations. When you are listening to music you can click through to read song lyrics or artist information and comprehensive sound controls are available whatever you are listening to.
You may be thinking that if you have your iPad connected to a dock and a set of speakers, it is going to be awkward to switch tracks. If you’re planning to settle down on the sofa for a music session and don’t want to have to get up to keep switching tracks, there is a companion app available for iPhone -- BeatBlaster Remote. As you might have guessed from the name, this simple little app, which is available free of charge, can be used to control the playback of BeatBlaster using a Bluetooth connection
Used together, this is a great combination, and you can find out more by paying a visit to the BeatBlaster review page and the BeatBlaster Remote review page.
-

Hit 'Enter' and get one of these 23 exciting software downloads
Publié: février 25, 2012, 6:40pm CET par Mark Wilson
 February may be the shortest month of the year, but the list of software releases over the past seven days is just as long as ever. This week we have collected together 23 key releases that may have escaped your attention, and as no roundup would be complete without at least one security tool, what better place to start that with Avast! Internet Security 7 FINAL.
February may be the shortest month of the year, but the list of software releases over the past seven days is just as long as ever. This week we have collected together 23 key releases that may have escaped your attention, and as no roundup would be complete without at least one security tool, what better place to start that with Avast! Internet Security 7 FINAL.Offering virus protection, a firewall, web filtering and remote assistance, this is a very comprehensive suite, but there is also Avast! 7 Free FINAL for anyone who would like a decent level of protection without having to part with any money.
Once you have a secure internet connection, you can make safe use of online services such as Google Docs, and gExplore 1.0 is on hand to enable you to interact with your online documents in a handy Windows-style interface.
If you’d like to squeeze a little extra performance from your computer without having to perform any upgrade, TweakNow PowerPack 2012 v4.0.0 may be just what you have been looking for. Including tools that enable you to boost Windows’ memory management as well as customizing the appearance and function of not only your operating system, but also applications you might have installed such as Office.
For anyone more interested in system maintenance, CCleaner 3.16 is an incredibly useful tool to help clean up your hard drive and ensure your privacy by clearing up after programs such as Chrome, Firefox, and Adobe Acrobat -- there’s also improved support for Windows 8.
Talking of the next version of Microsoft’s operating system,Windows 8 Start Screen Full 3.0 is a free transformation tool that brings the Metro interface to users of older versions of Windows. If you’re stuck with Windows 7 for the time being, Start Orb Mover 1.0 is a self-explanatory tool that makes it possible to move the Start button to a new location.
If you take your computing serious and want to keep up to speed with the file and folder permissions that are in place, look no further than NTFS Permissions Reporter Free Edition 1.0.0 which can tell you precisely that.
Using your computer should also be fun, and many, many people use their machines to watch movies and listen to music. If you’re having trouble playing a particular file or you’re looking to standardize your media collection, SUPER 2012.50 can be used to convert just about any audio or video file into a different format.
While Windows includes its own media player in the form of Windows Media Player, VLC 2.0.0 is far more feature packed, and features a new interface for Mac users as well as Blu-ray support. There is also a portable version of the app available, VLC Media Player Portable 2.0.0, while any who wants to see what to expect up future releases of the media player should check out VLC Media Player Nightly 2.1.0.
 We’ve already mentioned a couple of tweaking and maintenance tools, but IObit Game Booster 3.3 is also worth taking a look at. This free tool makes it easy to free up system resources so they can be put to better use by games, while PC Wizard 2012.2.0 enables you to get the lowdown on the hardware you are running so you can see if you meet the minimum requirements for a particular game as well as determining what setting are in place for your devices.
We’ve already mentioned a couple of tweaking and maintenance tools, but IObit Game Booster 3.3 is also worth taking a look at. This free tool makes it easy to free up system resources so they can be put to better use by games, while PC Wizard 2012.2.0 enables you to get the lowdown on the hardware you are running so you can see if you meet the minimum requirements for a particular game as well as determining what setting are in place for your devices.Tweaking and upgrading your system can produce some impressive performance improvements, but speed boosts can be hard to quantify without running some form of tests. Auslogics Benchtown 1.1.0.65 is a free tools that enables you to benchmark your computer so you can see how it compares to your friends’ machines, while Geekbench 2.2.7 is a paid-for, but low cost, benchmarking tool which is not only easy to use but also incredibly fast.
There has also been the usual selection of web browser updates starting withPale Moon 9.2. This Firefox inspired web browser is also available as a portable app, Pale Moon 9.2 Portable, and there is also Pale Moon x64 9.2 and Pale Moon x64 9.2 Portable for users of 64-bit versions of Windows.
Fans of 64-bit software can also take advantage of Waterfox 10.0.2 which is also based on Firefox code -- the latest version of which has just been transformed into a portable app in the form of Firefox Portable 10.0.2.
The next version of Mozilla’s browser, Firefox 11 Beta 4 is also available with improved synching options and other tweaks.
That’s it for this week; there’ll be another round the same time next week.
Photo Credit: Steven Newton/Shutterstock
-

Blast to the past with Midway Arcade for iOS
Publié: février 24, 2012, 10:26pm CET par Mark Wilson
 Anyone who grew up in the `70s and `80s will remember the lure of the arcade and the thrill of pumping coin after coin into a machine to have one more go on a tricky level. Games have come a very long way since the days of Defender and Spy Hunter, but these are classic titles that still have appeal.
Anyone who grew up in the `70s and `80s will remember the lure of the arcade and the thrill of pumping coin after coin into a machine to have one more go on a tricky level. Games have come a very long way since the days of Defender and Spy Hunter, but these are classic titles that still have appeal.While recent games such as Need for Speed and GTA have found their way onto the iOS platform, iPads and iPhones are perfect devices for a little retro gaming. Enter Midway Arcade to enable you to relive your youth or discover it anew.
The app takes the form of a virtual arcade that you can walk through and choose the cabinet at which you would like to play. You can choose between Spy Hunter, Rampage, Joust, Root Beer Tapper, Defender, Arch Rivals, Air Hockey, Arcade Basketball, Pool or Roll Ball, each presented in its original form complete with the original graphics and sound.
The virtual arcade is a nice touch, and the ability to play ten of the most famous games of all times for the insanely low price of 99 cents should be enough for anyone. You can also earn tickets playing the Arcade classics Air Hockey, Arcade Basketball, Pool, and Roll Ball which you can then exchange for prizes. But with arcade games such as those found in the Midway Arcade selection, it’s all about highscores. To this end, there is integration with Game Center so you can compete against your friends as well as the rest of the world.
As is becoming increasingly common, your game collection can be expanded through in-app purchases. The ten games that are included should keep you busy for a while, but if you want more titles to entertain you. The first game pack includes NARC, Total Carnage and APB, while the second pack includes Gauntlet, Gauntlet II and Wizard of Wor -- and there’ll undoubtedly be more to come in the future.
You can find out more and purchase a copy of the app by paying a visit to the Midway Arcade review page.
-

LibreOffice Productivity Suite 3.5.0 review
Publié: février 21, 2012, 6:03pm CET par Mark Wilson
 There aren’t many things in life that you can say are completely free. In the case of free software, you often find that you must make some sort of compromise, whether it be putting up with a limited version of a commercial application, enduring advertisements, or simply having to work with something that is less than impressive in terms of standards. Almost every computer user has need for an office suite, or at least some component of it, at some point, if not every day of their lives.
There aren’t many things in life that you can say are completely free. In the case of free software, you often find that you must make some sort of compromise, whether it be putting up with a limited version of a commercial application, enduring advertisements, or simply having to work with something that is less than impressive in terms of standards. Almost every computer user has need for an office suite, or at least some component of it, at some point, if not every day of their lives.Microsoft Office may be the most widely-installed suite, but for the average user it is expensive and unless a copy came pre-installed on your computer, you may not feel inclined to part with that amount of money. This explains the increased interest in free alternatives, and one such suite is LibreOffice Productivity Suite, which has just hit the milestone release number of 3.5.0.
It is fair to say that an office suite is not the most exciting piece of software anyone is going to install, but it is something vital to so many people and it is important that it does its job well. One of the reasons Microsoft Office is so popular: It's feature-packed and caters to almost any requirements you may have. When you start to look at free alternatives, you’ll often find that quality starts to slip and important features get dropped.
These are not charges that can be leveled at LibreOffice, which is just about as riddled with features as you could possibly hope. Should you be unfamiliar with the suite, this particular set of office programs comprises a word processor, spreadsheet, drawing tool, presentation application, a database and an equation editor.
Fully-loaded Suite
It is impressive to see that a database tool has been included, and while this is not something that everyone will need no corners have been cut. For many people, the cornerstone of any office suite is the word processor, and LibreOffice’s offering is suitably adorned with everything you would expect. On-the-fly spell checking has become a fairly standard feature of modern word processors and while grammar checking is sometimes available, it is often slow and unreliable. The latest version of LibreOffice introduces a faster checker and improved handling of errors to help make it clearer what issues have been detected. Recent changes to the handling of headers and footers make these document components even easier to work with.
But an office suite is about more than the word processor, and the spreadsheet tool is just as important. Calc is an extremely competent program that is Excel compatible and now boasts support for documents that contain up to 10,000 sheets.
Elsewhere in the suite you’ll also find the presentation tool Impress, drawing and logo creation app Draw, and Math the equation and formulae editor. Each of these programs has very much the same look, so once you have spent time using any of them, you’ll immediately feel at home in any of the others.
Speedy Development
This is an office suite that has come a long way in a relatively short space of time. Breaking away from OpenOffice has led to a faster development cycle, which in turn has mean that it has been possible to address issues long causing problems for users in different ways.
Something that has long deterred serious writers from making the switch to LibreOffice was the lack of a live word count. This might seem like a minor point, but when you need to write to a word count, you want to be able to focus on getting the words down on the page rather than having to keep checking through menus to see how many more words you have left to work with. The addition of a live word count to the latest version is a small but important change, and just goes to demonstrate that such a little thing makes such as big difference, and is an excellent example of listening to the target audience.
In the past, if you wanted to keep up to date with the latest version of the suite, it meant performing a manual check online to see if anything new had been released. Arguably one of the most useful additions to the software is the update availability notifier; when a new release hits the servers, the program will let you know so you can update your program straight away.
LibreOffice does fall down slightly in terms of looks. The toolbars are a little cluttered and the design of some of the buttons a too busy, and the aforementioned live word count, while useful, has been oddly implemented so a separate window needs to be kept open to monitor a changing word count.
The way the installer works is interestingly different to other apps and recognizes the fact that making the switch from one office suite to another is a big step. On the one hand, the installer informs you that it could be used as the default handler for Word, Excel and PowerPoint document -- but importantly, does not steal file associations by default -- and also points out the fact that if you are only trying out the suite you might want to leave this option disabled. This is a small touch, but it irons out an annoyance that has plagued too many other programs in the past.
Cross-platform Compatibility
A big plus point for LibreOffice: it is available for Windows, Mac and Linux. Cost-conscious computer users may have opted to go down the Linux route to save money on hardware and software, and this suite is available for users of this operating system. But if you are working in a multi-platform office environment, or want a reliable way to collaborate on projects with people using different systems, this is a great way of ensuring a level playing field on which everyone has access to the same tools and options and does not have to worry about incompatibility issues.

Overall, this is an office suite that comes highly recommended. The decision to break away from the main OpenOffice product has led to a faster development cycle and this has resulted in the impressive product we now see before us.
Choosing an office suite is quite a personal affair, and it is not possible for one suite to cater to the needs of every user. LibreOffice Productivity Suite 3.5.0 achieves an excellent balance of everyday features that are intuitive and more powerful options that will be welcomed by businesses and power users.
Whether you are currently in the market for a new office suite or not, this is well worth taking a look at as you may just be swayed. However, it is worth noting that this release (version 3.5.0) is recommended for power users. The Document Foundation recommends that less technically minded users and businesses hold off updating for the time being.
Photo Credit: Liv friis-larsen/Shutterstock
-

Catalog Blu-rays, DVDs and DivX videos with Movie Label 2013
Publié: février 20, 2012, 7:45pm CET par Mark Wilson

While digital video formats are more popular than ever, most people still have large collections of DVDs and Blu-rays. One of the many advantages of digital video formats is that they are easily stored on removable hard drives and can be searched and cataloged in a variety of way.
Movie Label 2013 is the latest version of a movie cataloging tool that has been designed to place you firmly in control of your DVD collection, storing more information than is possible in the majority of similar tools that are available.
At its most basic, the application can be used to create a simple database of all of your DVDs and Blu-rays so even if you choose not to have your discs out on display you’ll never lose track of what you own. But this is an app that can also be used to catalog your DivX video files in the same way and keep track of which discs you have lent out to other people.
One of the biggest problems with any sort of cataloging software is the data entry side of things, but Movie Label 2013 makes things nice and easy – you can either scan the bar code of a disc and the data will be downloaded for you automatically, or you can perform searches that will populate data fields for you.
If all of this sounds like nothing special, the app has plenty of tricks up its sleeve. There are data fields that are simply not found in any other app and this is what sets Movie Label 2013 apart from the competition. Not only are you able to store details about the cast of shows and movies but you can also save information such as the type of equipment used on a shoot and attach details of awards that have been won -- this is great if you ever want to track down all of the movies starring a particular actor that have been nominated for Oscars. Additional options such as filming locations, advanced searches, a wonderfully redesigned program interface and a high level of customization mean that this is perfect for any self-respecting movie buff.
Weighing in at $39.95, it could be argued that Movie Label 2013 is a little on the expensive side -- but bear in mind that there is also a professional version available for almost double the price at $69.95 if you want to install the program on up to three computers, export data and create your own reports -- but it is pretty powerful.
Movie Label 2013 goes far beyond any other comparable tool, and while there is nothing to stop you from knocking up a more basic database in Access, this is far more feature-rich and good looking than anything most people would be capable of producing.
You can find out more by paying a visit to the Movie Label 2013 review page.
Photo Credit: Leigh Prather/Shutterstock
-

Sky Satellite TV app for Android arrives -- on 7 phones only!
Publié: février 20, 2012, 6:35pm CET par Mark Wilson
 Subscribers to UK satellite TV provider Sky have just gained a new way to watch TV. Sky Go is a free app from the broadcaster that enables subscribers to access various channels on their Android phones at no additional cost. This is something that has been available to iPhone and iPad users for some time, and Android users now have the same option, although there is slightly patchy support for different devices.
Subscribers to UK satellite TV provider Sky have just gained a new way to watch TV. Sky Go is a free app from the broadcaster that enables subscribers to access various channels on their Android phones at no additional cost. This is something that has been available to iPhone and iPad users for some time, and Android users now have the same option, although there is slightly patchy support for different devices.In fact the app, at time of writing, is only compatible with seven handsets, all of which are phones -- it's not a great start. There is currently no support for any tablets, nor indeed support for any devices running Ice Cream Sandwich. This is something that will hopefully be addressed in future updates to the app as in the coming month there are Ice Cream Sandwich update scheduled for a number of the currently supported phones. A lack of support for larger screen tablets also seems like a serious oversight when the app is concerned solely with watching television.
The channels that you have access to depends on the type of Sky subscription you have, but there are total of 22 channels to choose from. This includes a number of sports and movie channels as well as arts, news and general entertainment. The app can be used over a WiFi or a data connection, but with a recommended minimum continuous connection speed of 500Kb per second this is likely to be something you only use when in range of a wireless network.
There are a few other restrictions to keep in mind before you get too excited about the app. If you live outside the United Kingdom or the Republic of Ireland, you’re not going to be able to make use of Sky Go and if you have rooted your phone, you are again out of luck. Despite a number of issues, if you are a Sky users, this app is a free perk so you may as well take a look to see if it could enhance your viewing experience.
You can find out more by paying a visit to the Sky Go review page.
-

What's in a week? 23 downloads you may have missed
Publié: février 19, 2012, 6:15am CET par Mark Wilson
 There has been a great deal of activity in the security software department this week, starting with the release of Avast! 7 Free (beta2), a preview of what to expect from the upcoming antivirus tool. Interesting features such as the Reputation Service to check the safety of files and websites, and Remote Assistance for remote problem fixing, mean that this is worthy of your attention. From the same company comes another beta tool in the form of Avast! Internet Security 7 (beta2) which takes the security of your computer even more seriously.
There has been a great deal of activity in the security software department this week, starting with the release of Avast! 7 Free (beta2), a preview of what to expect from the upcoming antivirus tool. Interesting features such as the Reputation Service to check the safety of files and websites, and Remote Assistance for remote problem fixing, mean that this is worthy of your attention. From the same company comes another beta tool in the form of Avast! Internet Security 7 (beta2) which takes the security of your computer even more seriously.Norton is a well-known name in the security arena and Norton 360 v6 FINAL is a complete suite of tools including a firewall, password manager and phishing protection as well as handy bonus features such as backup and system optimization.
Microsoft may be best known for producing Windows, but it is also responsible for a range of security tools. Microsoft Malicious Software Removal Tool (32-bit) 4.5 and Microsoft Malicious Software Removal Tool (64-bit) 4.5 are malware detection and removal utilities that do not offer real-time protection but are still useful tools nonetheless.
If you’re looking to boost your privacy as well as your security, look no further than Private Browsing 2.0, which can be used to add a number of privacy tools for Firefox, including FlashBlock and AdBlock.
Talking of web browsers, there have been a number of updates in this area, too. Google’s ever accelerating browser development continues with the release of Google Chrome 17.0.963.56 FINAL, and Mozilla shows no signs of slowing down either. The recently released final version of Firefox 10 has just been updated to Firefox 10.0.2 FINAL, while Firefox 11 Beta 3 is available if you would like to get a preview of what is coming up in a few weeks’ time.
If you’re running a 64-bit version of Windows, Waterfox 10.0.1 is a 64-bit version of Firefox that enables you to take full advantage of your hardware.
Of course, you do not need a web browser in order to use the Internet. While there are a number of online services available, they can often be accessed outside of a browser, and if you are a Google Docs user, you can take advantage of gExplore 1.0 to access your online files in a handy app.
The Internet can be a great source of video files, and in order to play back these files you will need to ensure that you have the correct codecs installed. K-Lite is a codec collection that is available in a number of forms -- K-Lite Codec Pack Basic 8.4.0, K-Lite Codec Pack Standard 8.4.0, K-Lite Codec Pack Full 8.4.0 and K-Lite Codec Pack Mega 8.4.0 – and covers almost every video and audio format imaginable.
 For anyone who is interested in getting the most form their computer rather than just using it, there have been a number of interesting releases. PC Wizard 2012.2.0 is an immensely useful utility that can be used to find out everything you could possibly need to know about the hardware and software you have – a great tool when it comes to diagnosing problems and upgrading your system.
For anyone who is interested in getting the most form their computer rather than just using it, there have been a number of interesting releases. PC Wizard 2012.2.0 is an immensely useful utility that can be used to find out everything you could possibly need to know about the hardware and software you have – a great tool when it comes to diagnosing problems and upgrading your system.Ashampoo WinOptimizer 9 FINAL is, as the name suggests, a powerful collection of utilities designed to help you to boost the performance of your computer, perform maintenance tasks and much more. If you prefer not to part with any cash and are happy to work with the tools that are included with Windows, Windows 7 in a Box 1.0.0.0 provides easy access to a variety of accessories.
Backup, backup, backup should be the mantra for any computer user, and to make life a little easier in this department, Paragon System Backup 11 is a reasonably priced backup tool that enables you to easily, and automatically, backup your valuable files. But first you need to have created some files to backup, and if you’re in need of a word processor, spreadsheet, database or presentation tool, look no further than the update offshoot of Open Office, LibreOffice Productivity Suite 3.5.0 FINAL.
All of your PDF creation and editing needs can be catered for with Nitro Pro 7.2.0.12 [32-bit]. and there is also a 64-bit version of this PDF software available in the form of Nitro Pro 7.2.0.12 [64-bit]. The discovery of bugs and security holes mean that it is important to keep all of your software fully up to date.
Rather than manually checking countless websites to see if there are any updates available, take a look at updated Downloadcrew UpdateScanner 2.0.0.2 Beta which can do all of the hard work for you.
The past seven days have been busy and the coming week is shaping up to be similarly exciting – check back this time next week for another roundup.
-

WinZip comes to iOS
Publié: février 16, 2012, 8:04pm CET par Mark Wilson

It has taken rather a long time, but the stalwart of file compression,WinZip, has finally released a version of their famous archive handling tool for iPhone and iPad. Available completely free of charge, the app can be used to open compressed files and preview their contents, and while the restrictions of iOS mean that this is not as complete a compression tool as many people would hope, WinZip for iOS is still a welcome addition to the App Store.
Where the app proves particularly useful is in the way it enables you to view zip files that have been emailed to you. Whether you are working with the email accounts you have configured in the mail app, or you are using a web based service such as Gmail or Hotmail, the app can be used to view the contents of zip file attachments. It does not matter if the zip files you want to view are encrypted; providing you have the necessary password, these can be opened as well.
It’s a shame to see that there isn’t support for any other compressed formats, but for the most part it is fair to say that the zip format is still the most frequently used for day to day purposes. There’s also no support for the creation of archives, but the lack of a traditional file browsing structure, for most iOS users, means that this is largely unnecessary anyway.
The features that are present all work well. The interface used to browse through the contents of compressed files is impressive enough and there is built in support for the previewing of a number of common file types including PNG, GIF and JPEG images as well as DOC, TXT, PDF and many more. This universal app is a fairly basic tool, but the things it does , it does well.
You can find out more and download a free copy of the app by visiting the WinZip for iOS review page.
-

WinOptimizer 9 improves Registry and hard-drive cleanup
Publié: février 15, 2012, 7:36pm CET par Mark Wilson
 Tweaking and performance boosting tools for Windows are not exactly difficult to come by, and there are countless free tools available. With the proliferation of free software, you may wonder why you would want to spend money on a program that claims to improve the performance of your computer. Take Ashampoo WinOptimizer 9 for a test run and we think you’ll find that it is worth parting with your cash for -- it will even provide you with proof that it is doing its job.
Tweaking and performance boosting tools for Windows are not exactly difficult to come by, and there are countless free tools available. With the proliferation of free software, you may wonder why you would want to spend money on a program that claims to improve the performance of your computer. Take Ashampoo WinOptimizer 9 for a test run and we think you’ll find that it is worth parting with your cash for -- it will even provide you with proof that it is doing its job.Performance enhancing software often makes all sorts of claims about what can be achieved, but Ashampoo WinOptimizer puts its money where its mouth is and provides you with benchmarking options so you can test performance before and after and see what difference it makes. You can get as hands-on as your feel comfortable with, or you can take advantage of the various one-click optimization options that have been designed to automate many common tasks. If you’ve tried system boosting software in the past and have wondered if any speed benefits you notice are for real or just the result of the placebo effect, the benchmarks available here should speak for themselves
What’s New?
The introduction of a HDD Inspector analyzes the S.M.A.R.T. values of your hard drive and will identity and warn of potential failure, whilst a new cleaning tool will remove redundant entries and generally keep your Registry in check. Improvements to the user-interface, including four new visual themes enable you to choose from a blue, white and two different black themes.
The sheer number of modules that make up the suite is impressive and not all of them are focused on performance and benchmarking. You’ll also find tools that can be used to free up hard drive space, tweak the appearance of functionality of Windows as well as enabling you to perform various file operation such as splitting, joining, undeleting and securely erasing. There are also a number of nice little touches such as an easy to use context menu editor, a tool for saving the position of desktop icons and an AntiSpy module for preventing Windows from ‘phoning home’.
There are a couple of things to note about the installation of the program. Firstly, it is important to be aware that the installer includes the Ask toolbar, so ensure that you select the custom installation option if you would prefer that this was not added to your web browser. The second thing to be aware of is that the software will initially install as a ten day trial, but this can be extended to 30 days by registering for a free trial code from within the program.
You can find out more and download a free copy of the app by paying a visit to the Ashampoo WinOptimizer 9 review page.
-

Get Laplink PCmover Express for free
Publié: février 13, 2012, 9:59pm CET par Mark Wilson
 You got a new PC, and you're excited. Only then you realize how much work is involved setting it up. Chances are your old computer held a very large number of personal files that you will want to transfer to the new machine. It is also likely that you have a number of settings in place that you have become used to, and the task of reinstating all of these could be a very lengthy one.
You got a new PC, and you're excited. Only then you realize how much work is involved setting it up. Chances are your old computer held a very large number of personal files that you will want to transfer to the new machine. It is also likely that you have a number of settings in place that you have become used to, and the task of reinstating all of these could be a very lengthy one.This is where Laplink PCmover Express can help, and you can take advantage of a free copy of the program worth $29.95. For 24 hours, so do hurry.
As well as enabling you to transfer files and settings, the application can also be used to transfer up to three of your favorite applications and associated settings. If you have spent an age configuring Microsoft Office to suit your needs and don’t fancy the idea of running through the entire process again, this is a real timesaver.
You are guided by a wizard from start to finish and there are numbers of ways of making the actual transfer of data --you can choose between making a network transfer via Ethernet cable, utilizing a USB cable, or using media such as CDs, DVDs or USB drives.
Application Transfer
When it comes to transferring programs, there are a number of advantages when compared to the usual route of re-installing from scratch. Firstly, there is no need to track down your original installation discs, and if you no longer know the location of your product serial numbers, you do not need to worry about this either.
As we have mentioned, transferring applications also means that your settings are transferred and the fact that the transfer of software can be done at the same time as your files means that everything can be moved across in one fell swoop.
Should you need to migrate more than three installed applications, take a closer look at PCmover Professional.
You may think that this is not a program that you will use all that often -- you may not be planning to buy several more computers, for example -- but even if you only use it once, you will have saved yourself not only a great deal of time, but also a lot of effort and stress. And as you are doing so because of this giveaway, all of these bonuses come completely free of charge.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site and grab your copy of the program. Be quick as the offer is for February 14 only, and expires at 23:59 Central European Time (for Americans, that's starting at 5:59 pm ET February 13).
Photo Credit: dny3d/Shutterstock
-

Count `em, 19 downloads you shouldn't miss this week
Publié: février 12, 2012, 12:26am CET par Mark Wilson
 This week has seen an impressive number of releases, so many that you may have missed one or two. In this roundup we’ve collected together some of the highlights starting with a selection of mobile app. OneNote Mobile has been available to iOS users for a little while now, but the app has just made its way to the Android platform. Offering synchronization with your computer and a comprehensive selection of options, this is a great way to manage notes, lists, to-dos and more.
This week has seen an impressive number of releases, so many that you may have missed one or two. In this roundup we’ve collected together some of the highlights starting with a selection of mobile app. OneNote Mobile has been available to iOS users for a little while now, but the app has just made its way to the Android platform. Offering synchronization with your computer and a comprehensive selection of options, this is a great way to manage notes, lists, to-dos and more.If your children have an Android mobile or they have access to yours, you can turn to Norton Safety Minder 2.3 to place restrictions on how the Internet can be used and monitor the web pages that are visited. Should you be in the market for a new web browser for your mobile, look no further than Chrome for Android Beta 0.16.4130.199, which is available for Ice Cream Sandwich devices and compares well to the desktop version of Google’s browser, even at this early beta stage.
Burners, PDFs
Moving back to your desktop, BurnAware Free 4.6 is a free disc burning tool that can be used to create your own CDs, DVDs and Blu-rays, including data, music and video discs. If you share your computer with others, it is likely that each user has his or her own preference when it comes to system settings. To avoid users to battling over what screen resolution should be used, Carroll 1.12 makes it possible to choose a different resolution for each user, automatically applied at startup.
This week also saw a number of releases from Nitro PDF. Nitro PDF Reader 2.2.1.14 (32-bit) is a great alternative to heavyweight applications such as Adobe Reader, and there is a 64-bit version available in the form of Nitro PDF Reader 2.2.1.14 (64-bit). Nitro Pro 7.0.2.8 [32-bit] and Nitro Pro 7.0.2.8 [64-bit] are the tools you need if PDF creation and editing for your business. While a little on the pricey side, it is still cheaper than many of its rivals.
Security
The importance of keeping your computer protected against viruses and other forms of malware can never be overstated. Lavasoft Ad-Aware Free 10.0.155 Beta is a free beta version of Lavasoft’s popular security tool. A redesigned interface and improve real-time protection make this well worth checking out.
This is not the only beta security tool released this week; Avast! 7 Free (beta) is another virus protection tool that includes cloud based updating and reporting. From the same company comes the latest version of Avast! Internet Security 7 (beta), which benefits from many of the same improvements and offers even greater protection.
Spybot will be a familiar name to anyone who has been using a computer for a while, and Spybot -- Search & Destroy 2.0 beta 5 is the latest version. It proved to be a little problematic in testing, but you may have a better experience.Boxcryptor 1.2 was also released, and this is an interesting file encryption tool that can be used in conjunction with your preferred cloud based storage service to secure the files that you are storing online.
Browsers
This week also saw a number of important browser releases. After the recent release of Firefox 10, Firefox 10.0.1 FINAL keeps the ball rolling with a number of minor changes. For anyone who wants to stay a little ahead of the game,Firefox 11 Beta 2 offers a few small additions, but there’s little to get too excited about at this stage. While Firefox can be installed on any system, if you want to take full advantage of a 64-bit operating system, look no further thanWaterfox 10.0 which is based on the latest Firefox code and you can install 64-bit versions of Flash and other plugins.
In other browser news, Chrome 17 became the latest stable release of Google browser as Chrome 17 FINAL hit the servers. Improvements include a new Javascipt engine, better protection against malicious files and much more. Google Chrome 18.0.1025.11 Beta was also released, giving users a chance to check out the future direction of the browser.
The past week has brought numerous programs that you might want to check out, and there’s plenty to look forward to in the week ahead. As well as the usual selection of tools, utilities and other apps, there’s also a great giveaway on the Downloadcrew Giveaway site . On Friday 10 February we gave away a free copy of Paragon System Backup 10.5 SE, a great backup tool worth $29.95. On Monday 13 February there’ll be a fantastic competition with the opportunity to win one of 50 copies of Auslogics Disk Defrag Pro 4, while on Tuesday 14 February, you can grab yourself a free copy of Laplink PCmover Express.
Join us the same time next week for another catchup of the biggest software releases.
Photo Credit: ArtisticPhoto/Shutterstock
-

Our gift to you: Paragon System Backup 10.5 Special Edition
Publié: février 10, 2012, 12:15am CET par Mark Wilson
 Backing up data is something that every computer user needs to do, but many people simply never get round to -- it is one of those chores that is just too easy to put off. There are a few obstacles that put people off: the time it takes to configure backup software and the amount of money it costs to invest in one are probably the main ones. With today’s special giveaway, you can eliminate both of these issues and safeguard your valuable data by grabbing a free copy of Paragon System Backup 10.5 Special Edition, worth $29.95.
Backing up data is something that every computer user needs to do, but many people simply never get round to -- it is one of those chores that is just too easy to put off. There are a few obstacles that put people off: the time it takes to configure backup software and the amount of money it costs to invest in one are probably the main ones. With today’s special giveaway, you can eliminate both of these issues and safeguard your valuable data by grabbing a free copy of Paragon System Backup 10.5 Special Edition, worth $29.95.The beauty of working with this particular backup tool, aside from the fact that it can be yours completely free of charge, is that it is so incredibly easy to use. Paragon System Backup 10.5 Special Edition will automatically check your system and determine which of your available hard drives has sufficient free space to be used to store backups -- as such, it is a good idea to ensure that you have any USB drives connected so they can be analyzed. Once this has been done, the program will automatically create a snapshot of your system, getting the protection process underway immediately.
From this point onwards, your backup will be constantly updated so you do not need to worry about manually creating new ones every time you create new files. Having these tasks taken care of for you leaves you free to simply get on and use your computer without having to think about the backup process -- everything is done for you automatically.
If you do want to get a little more hands on, you can opt to change how frequently your backup is updated, choose to exclude certain types of file from the backup. Should you ever need to make use of the backup you have created, you can choose between restoring a snapshot in its entirety, or browsing through the contents and selecting the individual files you are interested in.
Free Registration
Please note that in order to unlock Paragon System Backup 10.5 Special Edition, you will need to obtain a serial number. After downloading the software, start the installation process and click the Registration link to the right of the dialog to be taken to the registration web site. Enter all of the details requested of you and click the Submit button -- a few moments later you will receive an email contains your code. Return to the installation program and you can continue with the setup process -- just enter the Product Key and Serial Number you have been provided with and click OK (it is a good idea to copy and paste the codes to avoid the risk of typing mistakes).
The installer can also be used to create a recovery disc that you can use should you ever need to restore your data but find yourself unable to boot into Windows in the usual way. To do this, select the Recovery-Disc option from the installer and then click Next. You can then choose between burning the necessary files directly to a recordable CD or DVD, and creating an ISO image of the disc that you can burn at a later time.
When you need to make use of the disc, you just need to remember to configure your computer to boot from the DVD drive and you’ll have access to the recovery tool that will help you to get your data back where it should be.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, grab your copy of the program and get a free serial code. Be quick as the offer is for February 10th only, and expires at 23:59 Central European Time. (Americans, as we post, it's already tomorrow CET, so don't wait. Get it now!)
Photo Credit: Modella/Shutterstock
-

Save big on security software in February
Publié: février 8, 2012, 5:20pm CET par Mark Wilson
 February is a great month if you’re looking to bolster the security of your computer as we have an amazing selection of offers available on AVG products in the Downloadcrew Software Store. Whether you are looking to protect a single computer, or several, we have deals on the most appropriate software for you so you can save money whatever your needs.
February is a great month if you’re looking to bolster the security of your computer as we have an amazing selection of offers available on AVG products in the Downloadcrew Software Store. Whether you are looking to protect a single computer, or several, we have deals on the most appropriate software for you so you can save money whatever your needs.For complete, all-round security, look no further than AVG Internet Security 2012 Complete Bundle, which includes an incredible five AVG products -- (AVG Internet Security 2012, AVG PC Tuneup 2012, AVG LiveKive (complete with 25GB of storage), AVG Family Safety 2012 and AVG Mobilation). This exclusive bundle is available for just $34.95, saving 82 percent of the MSRP of $198.
You may feel that you do not need each of these products, and if this is the case AVG Premium Security Complete Bundle may be more along the lines of what you are looking for. Including four AVG products (AVG Premium Security 2012, AVG PC Tuneup 2012, AVG Family Safety 2012 and AVG Mobilation) you can save 77 percent off the MSRP when you buy this package for just $29.95 instead of $130.
Family and Small Business Security
If you have more than one computer that you need to protect, look no further than AVG Internet Security 2012 [4-PC, 1-Year] which can be installed on up to four computers and includes updates for a year. Usually sold for $69.99, Downloadcrew Software Store customers can take advantage of a 64 percent discount and grab the bundle for just $24.99. But many people only have one computer to think about, in which case, AVG Internet Security 2012 [1-PC, 1-Year] is ideal. You can get your hands on a copy for just $12.99, saving 76 percent off the MSRP and making an even greater saving than back in January.
As well as small businesses, it is increasing common for households to have more than one computer -- there may be a shared family computer as well as a couple of laptops use by the kids, for example. For such homes, AVG Family Safety 2012 [3-PC, 1-Year] offers excellent peace of mind, enabling you to protect your computer and control how users access the internet. The program was originally sold for $19.99, but at the new price of $7.95 you can save 60 percent.
Whilst AVG is mainly associated with security software, this is not the only string to the company’s bow. AVG PC Tuneup 2012 [1-PC, 1-Year] has been reduced in price by 66 percent from $34.99 to $11.99. With this program installed you can boost the performance and stability of your computer, but if you have more than one machine in need of regular maintenance, take a look at the 3-PC version of AVG PC Tuneup 2012. A one year license used to cost $49.99, but this has now been reduced to $19.99, saving you 60 percent.
Tune up Your PC
Security and performance tend to be the biggest concern for any computer user, and you can kill two birds with one stone by investing in the special TuneUp Utilities 2012 + AVG Internet Security 2012 package. Bought together, you can save a colossal 80 percent off the usual selling price of $114.98, now reduced to just $22.95, You can also choose purchase the system optimization software on its own,TuneUp Utilities 2012 [with 3-PC, lifetime license] has been further reduced to just $16.95 -- saving of 66 percent off the usual price of $49.95. If this doesn’t already sound like an amazing deal, bear in mind that TuneUp Utilities includes a lifetime license and will not expire or require renewal like many rival products.
The store also features a number of other system optimization tools, many of which are available at impressively discounted prices. Your hard drive is one of the most important components in your computer, and it is imperative to keep it in good shape. Rather than relying on Windows’ built in drive management utilities, take a look at Auslogics Disk Defrag Pro 4.0, which makes light work of defragmenting hard drives and maintaining maximum performance. Forget the MSRP of $29.95, you can save 33 percent and buy a copy for just $19.95.
There’s an even bigger saving to be made if you buy O&O Defrag 14 Professional. This drive management tool was cheap enough when it cost $29, but a massive 79 percent discount brings this price down to just $5.95. Also from O&O comes O&O DiskImage 6 Professional which can be used to create an image of your drives for backup purposes. Pick yourself up a copy for half price when you take advantage of the discounted price of just $14.50.
Spyware Catchers
Returning to the security theme, we also have a number of special offers on BitDefender software. Bitdefender Total Security 2012 [1-PC, 1-Year] includes not only anti-virus protection but also a firewall, file encryption, parental controls and much more. The MSRP is $69.95, but you can buy a copy for just $14.99 saving 79 percent. Bitdefender Internet Security 2012 [1-PC, 1-Year] is another powerful security tool, this time available at 74% discount for just $12.99.
If you want to keep multiple computers protected, Bitdefender Internet Security 2012 [3-PC, 1-Year] is reduced by 70 percent to $14.99, and if you’re looking for just virus protection, you can save 80 percent off Bitdefender Antivirus Plus 2012 [1-PC, 1-Year]when you buy the software for the astonishingly low price of $4.95.
There are also a number of security bargains from Webroot available in the store. Webroot Internet Security Complete 2011 [3-PC] is priced to clear at just $9.95, saving 88 percent off the MSRP of $79.95. Another advanced security suite is available in the form of Webroot Internet Security Essentials 2011 [3-PC] and at just $4.95 – a saving of 92 percent! This is one bargain that’s difficult to turn down. Both of these products also include a free upgrade to the new SecureAnywhere, offering even greater value for money.
The reductions in the store in February are not just focused on security and optimization software. If you want to make the most of the media files you have on your computer, look no further than CyberLink PowerDVD 12 Pro. This brand new release normally costs $79.95, but now you can snap up a copy for just $69.95, saving you 13 percent. Also from Cyberlink is PowerDirector 10 Ultra when you buy this software for just $79.95 saving 20 percent off the MSRP of $99.95, you can also benefit from a free copy of CyberLink MediaEspresso 6.5.
Finishing off this roundup of bargains is a special Laplink PCmover Professional & SafeErase Bundle. This includes three licenses for PCmover which can be used to move files and settings to a new computer, as well as SafeErase which makes it easy to securely wipe your hard drive. If you’re thinking of buying a new PC and selling your old machine, this is a great bundle, at with a price tag of just $39.95 you can make a saving of 53% off the MSRP.
These are just some of the highlights from the Downloadcrew Software Store. There are plenty more bargains to be found, so pay a visit to the store to see what takes your fancy.
Photo Credit: Julien Tromeur/Shutterstock
-

Waterfox 10 -- 64-bit browsing for your Windows PC
Publié: février 7, 2012, 5:10pm CET par Mark Wilson
 When it comes to operating systems, 64-bit is becoming increasingly popular. The ability to access additional, and ever-more-important, memory is a big draw, as is the added security and stability. But despite a general move to 64-bits for OSes, there is still relatively little 64-bit software that has been written to take advantage of them -- well, Windows. This is also true in the browser arena, but it is something that is being addressed by Waterfox 10, a 64-bit version of Firefox.
When it comes to operating systems, 64-bit is becoming increasingly popular. The ability to access additional, and ever-more-important, memory is a big draw, as is the added security and stability. But despite a general move to 64-bits for OSes, there is still relatively little 64-bit software that has been written to take advantage of them -- well, Windows. This is also true in the browser arena, but it is something that is being addressed by Waterfox 10, a 64-bit version of Firefox.While it is true that there are already 64-bit versions of Firefox available, this is only the case in the less stable Nightly and Aurora channels, and this is not something that everyone will be comfortable using. It is also worth noting the existence of Pale Moon, which is another Firefox-based web browser that also has a 64-bit version available. Waterfox is fully 64-bit and is based on the latest Firefox code -- this means that the two browsers are all but identical, save for the color and labeling of the Firefox/Waterfox menu button.
As the browser is based on the very latest Firefox code, you are able to take full advantage of all of the newest features. The updated navigation bar includes an intelligent forward button that is only displayed when it might be needed, and optimized code means that the program has a smaller footprint and improved performance. If you’ve made the move to a 64-bit version of Windows and like using Firefox, there’s simply no reason not to take Waterfox for a test -- there is not even any configuration to worry about.
There are a few things to remember when using the 64-bit Waterfox browser. Firstly, you will find that some of the plugins you have become used to in Firefox will not work. You will need to download special 64-bit versions of the likes of Flash and Java, which you can find on the Waterfox downloads page. You should also note that if you already have Firefox installed, Waterfox shares the same user profile files. This means that should you decide to uninstall either browser, you should ensure that you do not opt to remove personal data or your settings will be lost.
You can find out more and download a free copy of the web browser by paying a visit to the Waterfox 10 review page.
-

GooReader: When you need Google Books to go
Publié: février 1, 2012, 6:05pm CET par Mark Wilson

Google Books is a gigantic and ever-expanding online library of books and magazines that can be used to read classic titles free of charge as well as to purchase new releases in all manner of categories. But you may be one of the many people who have found that the interface for the website and the way you interact with books leaves a little to be desired. Enter GooReader, a desktop app that enables you to browse your books both on and offline.
You can take advantage of a handy interface that makes it easy to navigate through the pages of your books and you can also zoom in and out, which is great if you are using a laptop with a smaller screen, and perform searches. All of the books you have purchased can be accessed from within the app and organization of your library is delightfully simple. When it comes to lengthy tomes or even an average sized novel, bookmarks can be used to quickly jump the place you left off.
But probably the most useful feature of GooReader is the ability to create a local library of books. This means that you can choose a selection of books and they will be downloaded so they can be accessed offline. This is a great option if you want to take books on the road with you, and the overall look and feel of the application means that the reading of ebooks is made an immensely pleasurable experience.
Should you feel that the ability to convert your books into PDF format would be useful, there is also a paid for version of the app available. In additional to this PDF conversion option, providing you are not working with DRM protected books, you can also take advantage of an interface that is not adorned with advertisements. Other than these two features, the paid-for and free versions of the software are identical, but the extra options will set you back $19.95.
You can find out more and downloads a free copy of the app by paying a visit to the GooReader review page.
Photo Credit: Tischenko Irina/Shutterstock
-

Quick ‘n’ Easy Web Builder lives up to its name
Publié: février 1, 2012, 5:25pm CET par Mark Wilson
 Creating a website is something that many people feel an urge to do but, as with many things, the perceived steep learning curve is enough to put most folks off the idea. In reality, it is actually quite simple to create web site -- obviously, the greater your knowledge the more impressive site you can create -- and there are a number of WYSIWYG editors to choose from that mean you do not need to know HTML, CSS or any other form of coding.
Creating a website is something that many people feel an urge to do but, as with many things, the perceived steep learning curve is enough to put most folks off the idea. In reality, it is actually quite simple to create web site -- obviously, the greater your knowledge the more impressive site you can create -- and there are a number of WYSIWYG editors to choose from that mean you do not need to know HTML, CSS or any other form of coding.Coming from the team behind WYSIWYG Web Builder, Quick ‘n’ Easy Web Builder is a cross-platform website creation tool that shows great signs of promise.
The WYSIWYG Web Builder application was original written for Windows, leaving Mac and Linux users out in the cold. Rather than setting about the somewhat arduous task of porting the existing product from one platform to another, Quick ‘n’ Easy Web Builder took inspiration from WYSIWYG Web Builder and built a new app from the ground up -- this time compatible with not only Windows but also Mac and Linux.
Despite the somewhat cutesy name, this is a powerful tool. The cross-platform nature of the app means that it is ideal for collaborative teams working in environments where not everyone is necessarily using the same type of system. There are decent numbers of templates to choose from if you’re stuck for ideas, but you can also start from scratch, using the toolbox to drop page elements into place and the Property Inspector to customize objects and settings.
Sites can be published from within the app so there’s no need for a separate FTP client, and the interface is a tidy affair that provides access to all of the tools you need while leaving a decent working area visible. As this is only a release candidate rather than a completed product, there are a few aspects of the app that need a little fine-tuning. There is currently no option to zoom in and out of pages nor is it possible to work in full screen mode. Options such as importing HTML and fairly standard tools such as spell checker are still to be added, but hopefully these will make into the completed software.
You can find out more and download a free version of the app by paying a visit to the Quick ‘n’ Easy Web Builder review page.
-

30 software downloads you need this week
Publié: janvier 28, 2012, 6:47pm CET par Mark Wilson
 We’ve reached the end of the first month of 2012 and this has been another busy week for software releases. If it seemed a little quiet on the browser updates recently, things changed this week with the release of Opera 11.61 FINAL as well as Opera Portable 11.61. Fans of cutting edge software may be more interested in Opera Next 12.00 build 1256, which is the first update to the beta channel of Opera for quite some time.
We’ve reached the end of the first month of 2012 and this has been another busy week for software releases. If it seemed a little quiet on the browser updates recently, things changed this week with the release of Opera 11.61 FINAL as well as Opera Portable 11.61. Fans of cutting edge software may be more interested in Opera Next 12.00 build 1256, which is the first update to the beta channel of Opera for quite some time.When browsing the Internet, speed is often the most important consideration, and Pale Moon is a speed optimized version of Firefox that includes support for extensions. This week saw the release of not only Pale Moon 9.1 and Pale Moon x64 9.1, but also portable versions in the form of Pale Moon x64 9.1 Portable and Pale Moon 9.1 Portable.
Of course, using the Internet does not have to be about simply consuming other people’s website, you may have considered creating an online presence for yourself. This is made incredibly easy with MAGIX Website Maker MX, which can be used to create Flash-based sites even if you have never experimented with Flash before. Whether you are looking to create a site to showcase your digital photos or videos, or you want to create an online store with PayPal support, you’ll find everything you need here. If all of this sounds like hard work, you can always use the internet for entertainment, and TapinRadio 1.51.1 enables to find, listen to and record a massive range of online radio stations.
For all of your offline media needs a codec pack will help to ensure that you do not encounter any video or audio files that you are unable to play. If you already have a version of the K-Lite Codec Pack installed, you should take a look at K-Lite Codec Pack 8.2.0 Update, which includes a number of new additions. If you are yet to discover just how useful a codec pack can be and you need to start from scratch, look no further than K-Lite Codec Pack Mega 8.2.0, K-Lite Codec Pack Basic 8.2.0, K-Lite Codec Pack Standard 8.2.0 or K-Lite Codec Pack Full 8.2.0, which will help you to play a wide range of media formats.
Whether or not you are using your computer to access the Internet, you will make use of a variety of programs. To help make these easier to manage, take a look at Stardock Tiles 1.00, which makes it incredibly easy to organize and navigate through your running applications. Also updated this week were CCleaner 3.15 and CCleaner Portable 3.15, which help you to optimize your system and protect your privacy, with even greater support for a wider range of programs in these latest versions.
Fans of tweaking software will no doubt be impressed with Advanced System Tweaker 0.9.6 (beta) which can be used to tweak and customize your system in a range of ways -- this particular app is extendable through the use of tweaking add-ons that is a nice touch. For day-to-day maintenance of any system, Defraggler 2.09.391 provides you with a great way to ensure that your hard drive is free from fragmentation -- and if you’re constantly moving from one computer to another Defraggler Portable 2.09 can be popped on a USB drive.
It is a good idea to take an active interest in your computer’s hardware, but this is certainly the case if you have overclocked your system. Open Hardware Monitor 0.4.0 is a free tool that can be used to monitor the temperature of your graphics card, processor and hard drive so you can ensure that you aren’t pushing things too far.
 If you are more interested in software than hardware, take a look at Speccy 1.15.309, which will tell you everything you need to know about not only the hardware you have, but also the software you have installed; there’s also Speccy Portable 1.15 available for fans of portable software.
If you are more interested in software than hardware, take a look at Speccy 1.15.309, which will tell you everything you need to know about not only the hardware you have, but also the software you have installed; there’s also Speccy Portable 1.15 available for fans of portable software.It is important to keep an eye on how your computer is being used, but this is especially true in the case of shared computers. History Viewer 4.8 enables you to monitor how other users have been making use of the internet and USB drives so you and easily check for unwanted activity. Hardcore computer users should take a look at Microsoft Desktop Player 1.0.0 (beta), which provides access to library of white papers, podcasts and webcasts that may be of interest.
This week has also seen a number of releases that will be of interest to anyone who uses their computer for work. Computers are expensive enough to start with, so anything that can be done to reduce on-going costs is to be welcomed. LibreOffice Productivity Suite 3.4.5 is a free office suite that includes everything you need to create a range of business and personal documents, and LibreOffice Portable 3.4.5 is also available if you would like to keep your office software on a USB drive to take with you.
If you’re looking for a way to collaborate on work or just store notes online, look no further than Evernote 4.5.3. Developer and anyone with a serious interest in computers and operating systems will be interested in VMware Player 4.0.2 and VMware Workstation 8.0.2, which can be used to run virtual machines on your computer so you can work with older versions of Windows or even install the likes of Ubuntu without the need to have access to a second machine.
That’s it for this week’s highlights. There is sure to be an impressive swathe of releases to look forward to over the next seven days and our roundup will be available this time next week to bring you up to speed on anything you may have missed.
Photo Credit: Sebastian Kaulitzki/Shutterstock
-

Don't miss the end-of-January software sale
Publié: janvier 27, 2012, 5:24pm CET par Mark Wilson
 You can find plenty of bargains at Downloadcrew Software Store, but there have been even greater savings to be had this month. If you’re thinking about investing in some new software, now is the time to do so -- these special offers will end when we reach the end of January.
You can find plenty of bargains at Downloadcrew Software Store, but there have been even greater savings to be had this month. If you’re thinking about investing in some new software, now is the time to do so -- these special offers will end when we reach the end of January.The holiday season is now a month behind us, so it’s time to think about organizing all of those photos you took during family get togethers. CyberLink PhotoDirector 2011 may be just what you’ve been looking for. This is a seriously powerful photo editing tool that includes support for RAW images and boasts a range of features to rival Photoshop. Buy the software now for just $44.95, a savings of just 55 percent off the MSRP, and you will receive a free upgrade to PhotoDirector 2012 v3 when it releases in February.
You may well also have video files you want to take care of and if this is the case, take a look at CyberLink Video & Photo Collection 1.0. For $99.95, a 33-percent savings, you can grab yourself a super powerful photo and video editing package which includes a range of incredible 3D effects.
You may have decided to treat yourself to a new computer for 2012, and whether or not the case, it is worth investing in some software to help keep your system running at peak performance. Look no further than TuneUp Utilities 2012 [3-PC, 1-Year], which will help to keep your system optimized -- and you can save 62 percent off the MSRP when you buy the software for just $18.95. Small businesses can make an even greater 75 percent savings when buying TuneUp Utilities Business Edition 2012 [5-PC, 1-Year] for just $19.95.
Security is going to be more important than ever this year. To help fight the threat of viruses, look no further than AVG Anti-Virus 2012 [1-PC, 1-Year]. For an amazingly low price of $5.95 (saving you a staggering 85 percent off the usual price) you can get yourself a copy of this highly acclaimed antivirus tool. For just a little extra, AVG Internet Security 2012 [1-PC, 1-Year] offers AV protection as well as parental controls, online backup and more -- all for just $12.99.
For AVG’s ultimate protection package AVG Premium Security 2012 [1-PC, 1-Year] is available for just $19.99. This includes the added bonus of identity protection and Quick Tune optimization to help speed up your system, and all for 71 percent off the MSRP. If looking after the performance of your computer is of interest, AVG PC Tuneup 2012 [1-PC, 1-Year] is available at the discounted price of $11.99, and if you have more than one computer to take care of, you should take a look at AVG PC Tuneup 2012 [3-PC, 1-Year], which you can buy for just $19.99 – saving you 60 percent.
Looking for online storage? AVG LiveKive 2012 [UNLIMITED storage]includes all of the cloud storage you could possibly need and you can save yourself a massive 70 percent when you buy an unlimited package for just $14.95.
Sticking with the security theme, Bitdefender Antivirus Plus 2012 [1-PC, 1-Year] is available at the bargain basement price of $4.95 -- a gigantic 80 percent savings. You might also be interested in Webroot Internet Security Complete 2011 [3-PC], which can be used to protect up to three computers against viruses, spam and ID theft. The low price of $9.95 represents a huge 88 percent savings off the usual MSRP, and an even greater saving is to be found with Webroot Internet Security Essentials 2011 [3-PC] with a 90 percent saving bringing the price down to just $5.95. Both of these program include a free upgrade to Webroot SecureAnywhere.
A new year is as good a time as any to learn a new skill or take up a new hobby. If you’ve ever fancied the idea of becoming a DJ, we have just the software for you. MAGIX Digital DJ 2 is available at the discounted price of $29.99, saving you 40 percent, and is a powerful music tool can be used to mix tracks like a pro on a set of digital decks. More creative software is available in the form of MAGIX Music Maker MX, which you can snap up at a 33-percent discount for just $39.99.
With a huge collection of samples, loops and effects to work with, you’ll find that it’s incredibly easy to create something truly impressive that you can share online with others. You can save more than one third off the MSRP when you buy MAGIX Movie Edit Pro MX for just $45.99, and when you do so you are equipping yourself with everything you need to edit and enhance your home video footage.
Anyone looking to protect valuable data should look at Genie Timeline 2.1 Professional, which is an innovative backup tool that makes it easy to safeguard your valuable files. Available for just $9.95, you can save 83 percent off the MSRP when you buy this great tool today. Multi-computer households can take advantage of an 83-percent savings off Uniblue PowerSuite 2012, and for just $19.95 you can equip yourself with an advanced tweaking and optimization tool.
Finally for this roundup,Laplink PCmover Professional v6 is a great tool for anyone making the move to a new computer. For a mere $29.95 (a saving of 50 percent), you can buy this incredibly useful tool that will help you to move your files, programs and settings from one computer to another with a minimum of effort.
Don’t forget, these special offers expire at the end of January, next Tuesday, so be quick and take advantage while you can. These are just some of the highlights from the store – there are plenty more bargains to be found so head over to the Downloadcrew Software Store to see what you can pick up today!
Photo Credit: iQoncept/Shutterstock
-

CCleaner 3.15 improves like a well-aged wine
Publié: janvier 26, 2012, 5:30pm CET par Mark Wilson
 Popular system cleanup and optimization tool CCleaner has been updated with a range of improvements and a smattering of new features. CCleaner 3.15 sees support for the cleaning of a range of new applications including Freemake Video Downloader, Camtasia Studio and Ashampoo Burning Studio. As you would expect from any app update there are also a number of bug fixes as well as a small range of additional options.
Popular system cleanup and optimization tool CCleaner has been updated with a range of improvements and a smattering of new features. CCleaner 3.15 sees support for the cleaning of a range of new applications including Freemake Video Downloader, Camtasia Studio and Ashampoo Burning Studio. As you would expect from any app update there are also a number of bug fixes as well as a small range of additional options.In terms of new features, you will find that there is newly added support for Chrome Canary, including the ability to clear search data from the omnibox. The ability to remove items from the Recycle Bin is nothing new, but there is a new option to filter Recycle Bin deletion to only those files that were added more than 24 hours ago. This is a useful way to claw back a few extra megabytes of space while retaining the option of restoring some of the files you have deleted.
There have been a number of enhancements to existing features, and you will find that the cleaning of Firefox’s history has been improved and the way in which file sizes are detected has been updated. Further improvements have been made to the Driver Wiper component which now provides better feedback when operations complete. Whether you have been experiencing problems with CCLeaner or not, the bug fixes means that this is well worth installing, and the extra features are a bonus.
There is also a portable version of the app available for anyone looking for software to add to their USB drive. This version of the application does not differ from the regular edition of the software, besides the fact that it does not need to be installed, and includes all of the same new options, features and bug fixes.
You can find out more and download a free copy of the app by paying a visit to the CCleaner review page.
-

Kingsoft Office 4.3 for Android mini-review
Publié: janvier 25, 2012, 6:46pm CET par Mark Wilson
 There are a number of tools that computer users will install by default on their Mac or PC -- an email client, web browser, media player and an office suite. Make the move to a mobile platform such as iOS or Android and the range of apps you need changes slightly. Most phones and tablets will comes with a number of apps pre-installed including a calendar, messaging tool, web browser and various other tools. One thing that is generally left out of the mix is a mobile office suite.
There are a number of tools that computer users will install by default on their Mac or PC -- an email client, web browser, media player and an office suite. Make the move to a mobile platform such as iOS or Android and the range of apps you need changes slightly. Most phones and tablets will comes with a number of apps pre-installed including a calendar, messaging tool, web browser and various other tools. One thing that is generally left out of the mix is a mobile office suite.There are plenty of suites to choose from, but the vast majority of them cost too much and many users are disappointed to find that the app they choose to try out is too limited for their needs. Kingsoft Office is something of an anomaly -- an extremely powerful and feature-packed Android office suite that is available for free.
As you would expect from any productivity app, Kingsoft Office can be used to open and edit documents that have been created in Microsoft Word, including the more recent XML-based formats for Word, Excel and PowerPoint, including encrypted files. Your documents can be stored locally or in the cloud -- box.net or WebDAV -- and performance is reassuringly fast.
When it comes to opening files that you have already created, there is a great preview screen that can be used to navigate through documents before you open them. Rather than browsing through fiddly folders, full screen previews are displayed that you can easily swipe through to find the file you need. There is also an excellent file explorer that can be used to browse through all of the documents stored on your Android device, including text and PDF files that can be opened in the suite.
One of the problems with many mobile office suites, aside from the cost that many people are unwilling to pay, is that going down the mobile software route usually means making feature compromises. While Kingsoft Office is no mobile replica of Microsoft Office, it certainly is one of the most complete tools. Ability to use features such as headers and footers, adjusting line spacing, add comments and much more, mean that this is probably the most comprehensive mobile office app available.
Ease of Use
When working with spreadsheets, you can freeze panes to aid navigation and display charts and shapes. The navigation of spreadsheets is something that has long proved tricky but it is something handled with panache in Kingsoft, and the option of quickly switching to full screen mode is very useful. It is easy enough to type in documents using the on-screen keyboard, there is also the option of using a Bluetooth to make extended sessions of typing more comfortable. Standard keyboard shortcuts for copying and pasting can be used when working with an external keyboard.
One of the problems that any mobile office suite faces: Expectation there will be a large number of options and these would ordinarily be housed in monitor width toolbars, like the desktop. While this is easy enough for Mac and Windows application, mobile apps do not have the luxury of such screen space and also have to be geared up for use in two different orientations. Kingsoft Office uses a familiar toolbar system that would not look out of home in Microsoft Office, but makes them scrollable.
This technique means that it does not matter whether you are working in portrait or landscape mode, it is still possible -- easy, even -- for access a large number of toolbar buttons. The size of the buttons means that they are easy to identify and press, but it does also have the side effect that, particularly in portrait mode, a limited number are displayed out without having to scroll, and it is possible to 'forget' that the remaining buttons exist.
Mobile phone users are unlikely to turn to Kingsoft Office as their primary office tool -- there is no getting away from the fact that a desktop suite will always be easily to use and boast more powerful features -- but tablet owners have a particularly great tool on their hands. The screen space available on tablets means that spreadsheets are very easy to work with and more of a text document can be seen at any one time.
The ability to view and play presentations means that the suite could be used as a valuable tool for business meetings, but it is also the sort of app that home users will find countless uses for. Free software is often dismissed as being inferior to commercial apps, but here is an example of a free app that is at least as good as the paid-for competition.
-

Get more from screen captures with WinSnap 4.0.1
Publié: janvier 25, 2012, 1:32pm CET par Mark Wilson
 Capturing what’s on your desktop can be as simple as hitting the Print Screen key and pasting the contents of the clipboard into an image editing app. But you’ll notice that it is not possible to capture everything; the cursor cannot be included in grabs and many dialogs disappear when Print Screen is pressed. WinSnap is a powerful screen capture tool that includes a number of handy options, with the latest version bringing support for the capturing of native Aero shadows.
Capturing what’s on your desktop can be as simple as hitting the Print Screen key and pasting the contents of the clipboard into an image editing app. But you’ll notice that it is not possible to capture everything; the cursor cannot be included in grabs and many dialogs disappear when Print Screen is pressed. WinSnap is a powerful screen capture tool that includes a number of handy options, with the latest version bringing support for the capturing of native Aero shadows.WinSnap is now able to capture the shadow that is added to windows and object by Windows, but in cases where this is not possible, post-capture shadowing can be added for you. Screen capturing has many purposes, but it is often used to highlight information. To make this easier, WinSnap includes a number of annotation tools that can be used to draw shapes and arrow on your grabs as well as adding text. To the same end, there are also a number of effects to choose from. If you want to highlight a particular area of a screen capture, you can opt to grey out the rest of the image, or blur it slightly.
A number of different keyboard shortcuts can be created to allow for a variety of capture modes -- full screen, active window, sizeable region, and various others. You can choose whether or not to include the cursor in your captures -- while useful, this may not be an option you always want to use -- and the ability to place a delay on captures means that it is possible to grab objects that would normally disappear when a hotkey was pressed.
To allow for more impressive presentation, there is an intelligent cropping mode available. This is particularly useful when cropping screen captures that include Aero shadows as it means that shadows can be re-added at the edge of a crop to give a more professional finish. If you are using your captures in other programs, WinSnap preserves any areas that are transparent to eliminate the need to capture multiple versions of the same shot so you can piece something together. Add to this the ability to add watermarks, custom cursors that can be moved around as separate objects, and a decent price point, and you have yourself a very accomplished screen capture tool.
You can find out more and download a free trial of the app by paying a visit to the WinSnap review page.
-

17 downloads you shouldn't miss this week
Publié: janvier 21, 2012, 8:15pm CET par Mark Wilson
 This has been another busy week for software releases, so it would not be surprising if some gems had escaped your attention. This is exactly why we put together these weekly roundups, bringing you a selection of the best software from the preceding seven days. If you’re a fan of software and trying out the latest and greatest titles, you’re undoubtedly going to be interested in ensuring that you have the latest versions of all your favorite programs installed. Downloadcrew UpdateScanner 2.0.0.1 Beta is a free tool that keeps you informed about when new versions are released so you don’t have to keep checking manually, as well as bringing you special offers, the latest software news and free giveaways.
This has been another busy week for software releases, so it would not be surprising if some gems had escaped your attention. This is exactly why we put together these weekly roundups, bringing you a selection of the best software from the preceding seven days. If you’re a fan of software and trying out the latest and greatest titles, you’re undoubtedly going to be interested in ensuring that you have the latest versions of all your favorite programs installed. Downloadcrew UpdateScanner 2.0.0.1 Beta is a free tool that keeps you informed about when new versions are released so you don’t have to keep checking manually, as well as bringing you special offers, the latest software news and free giveaways.It has been a surprisingly busy week when it comes to software designed with businesses in mind. As any modern company will be all too aware, having the right tool for the job can make life so much easier, and this is particularly true when it comes to the world of work. Managing a large team of people working on a project can be difficult, but Revolver Office 9.0.0 Preview is here to help make things easier. Bringing email together with project management, employee and resource assignment and much more into a single package, this is the perfect tool for any business looking to stay ahead of the competition.
Many businesses include not only Macs and Windows based PCs, but also computers running Linux. If you are looking for a cross platform office suite that can be used by everyone, look no further than the updated, and free, LibreOffice Productivity Suite 3.4.5. In a similar vein is Lotus Symphony 3.0.1 -- again available for all three platforms – providing you with a Microsoft Office compatible suite comprising spreadsheet, word processor and presentation tool.
Whatever your line of work, or maybe even just for fun, you may well have thought about creating a website. Rather than plumping for an expensive and complicated top-of-the-range title, why not give CoffeeCup Free HTML Editor v9.7 a try? This free tool is an HTML based editor that is perfect for anyone will a little experience of web site creation, and support for HTML5 and CSS3 means that you are able to experiment with all of the latest techniques. There’s even a code-cleaner on hand to optimize your site by tidying up your HTML.
No site would be complete without images, and if you’ve tried GIMP but found the interface a little intimidating, you should take a look at GIMPshop 2.6.11. This is a beautified version of the powerful image manipulation tool that you can use free of charge. If you’re working on a site or want to share images or ideas with friends or co-workers, overcoming email attachment limits can be a pain. Share by BitTorrent (alpha) is a free personal torrent client that can be used to share files of any size quickly and easily.
As well as sharing files, the Internet is a great platform for communication, and Skype for Windows 5.7.0.137 Beta is a great way to keep in touch with other people. The latest beta brings improved video calling and Facebook support and is available for Mac and PC.
You’ve probably found that when you’re online you tend to visit the same websites again and again. To make it easier to switch between sites and programs you may be using, take a look at Pokki 0.245 Beta, which can be used to transform your favorite websites into desktop apps.
If you’re looking for entertainment online, you can download a wide range of book from Google Books. Google Books Downloader 1.6 is a free tool that enables you to convert these files into different formats so you can use them on different devices more easily. This week also saw the release of Apple iTunes 10.5.3.3 (32-bit) and Apple iTunes 10.5.3.3 (64-bit) which adds support for interactive iBooks synchronization.
O&O AutoBackup 1.0.106 (32-bit) and O&O AutoBackup 1.0.106 (64-bit) are 32- and 64-bit tools that can help you to ensure that your valuable data is kept safe at all times, while NexusFont 2.5.7 enables you to not only install and view fonts, but also keep them backed up. If security is a concern – which it is for many people -- Hardwipe 1.5.0 enables you to prevent the restoration of files you delete from your hard drive by overwriting them a number of times with random data. Another form of protection is provided by this week’s final title, Real Temp 3.70, which enables you to monitor the temperature of your processor so you will know if you have taken overclocking too far.
Join us again the same time next week for another roundup of the week’s releases.
Photo Credit: treasure dragon/Shutterstock
-

Quick Look: iBooks Author
Publié: janvier 19, 2012, 11:38pm CET par Mark Wilson

Apple’s iPad has fairly quickly become a great tool for the workplace and in education and the company’s latest bid to revolutionize the market is with ebooks. Ebooks themselves are nothing new, but the existence of touchscreen devices such as the iPad means that the opportunities available to readers through interactive multimedia book are now greater than ever. iBooks Author is a free Mac app that can be used by anyone to create iPad friendly ebooks that can include a variety of widgets such as photo galleries, videos, KeyNote presentations, 3D objects and more.
This is more than just an ebook creation tool for Mac, it is a complete solution that enables you to work through the entire process from initial concept to design and layout before ultimately publishing and making available online. To help get you started, there are a number of different templates to choose from and then it is just a matter of dropping material in place and performing any customizations you want.
You can start by replacing the dummy text that each template contains and you can then set about the task of adding more content such as image, tables, charts and widgets. It is widgets that really open up the potential of books created in iBooks Author as they make it possible to include a wide range of interactive elements in your publications -- everything from videos and animations to photo galleries and more.
The ability to add voiceovers means that you can cater for the visually impaired while all readers can benefit from an immersive multimedia ebook experience.
The books that are created can either be given away free of charge, or they can be sold through the iBookstore. In either case publications need to be vetted by Apple before they can be made available through the book store and you need to be aware that anything made available through iBooks cannot be made available elsewhere.
Whether used for vanity publishing, producing material that will be of benefit to students or creating reports and other documents, iBooks Launcher makes it easier than ever to not only create some truly impressive pieces of work, but also to present them to as large an audience as possible.
You can find out more and download a free copy of the app by paying a visit to the iBooks Author review page.
-

Share: Your personal torrent client
Publié: janvier 18, 2012, 4:55pm CET par Mark Wilson
 When it comes to sharing files, there are a number of options available to you. If you want to share files with someone nearby, it may make sense to pop them on a USB drive and physically deliver them. For smaller files it is possible to make use of email, but things get trickier when larger files are involved. You could go as far as uploading files to your own web space or even setting up your own FTP server, but this is something that few people would want to go to these lengths. Share is a free tool that enables you to overcome these problems and share files of any size.
When it comes to sharing files, there are a number of options available to you. If you want to share files with someone nearby, it may make sense to pop them on a USB drive and physically deliver them. For smaller files it is possible to make use of email, but things get trickier when larger files are involved. You could go as far as uploading files to your own web space or even setting up your own FTP server, but this is something that few people would want to go to these lengths. Share is a free tool that enables you to overcome these problems and share files of any size.Coming from BitTorrent, it should come as no surprise to learn how Share works. It is essentially a personal torrent client that makes it possible to allow people of your choice to connect to your computer and access the files you have chosen to share; this is a great example of personal P2P. having created an account, files can be shared by using nothing more than drag and drop, and all you need to do is to select who you would like to share them with.
Sharing can be made into quite a social experience thanks to the ability to comment on files that are being shared. This is a great option if you are using the service to share files relating to a work project as it allows for a degree of collaboration. The fact that Share is available for both Mac and PC means that it is opened up to a larger audience and the ability to create groups for sharing means that sharing files with the same people time and time again is made as fast as possible.
Share is currently an alpha version, so it’s still somewhat experimental, but things are already looking promising. Just as with more major torrent clients such as uTorrent and the like, there will undoubtedly be claims that Share is a tool that could be used for piracy. While this is true to some extent, there are also numerous legitimate uses to which the service can be put. If you’ve found yourself wondering how you are going to share a large video you have shot, this could be the solution you have been looking for.
You can find out more and download a free copy of the app by paying a visit to the Share review page.
Photo Credit: Modella/Shutterstock
-

21 downloads you shouldn't miss this week
Publié: janvier 14, 2012, 5:24pm CET par Mark Wilson
 We’re only just through the second week of January, but the number of software releases is just as fast as ever. There have been so many applications hitting the servers over the last seven days, we wouldn’t be surprised if you had missed some here and there. This is why we have put together this handy roundup to get you back up to speed.
We’re only just through the second week of January, but the number of software releases is just as fast as ever. There have been so many applications hitting the servers over the last seven days, we wouldn’t be surprised if you had missed some here and there. This is why we have put together this handy roundup to get you back up to speed.If you want to keep in touch with friends, family and colleagues, look no further than Skype for Windows 5.7.0.137 Beta. The latest beta version of this chat client fixes a number of problems that have been found, but Mac users have more to look forward to in Skype for Mac Beta 5.5. The latest beta includes an improved call interface that makes it easier to mute calls, add new people to a conversation, and share files and video.
There are a number of web browsers to choose from these days, and one up and coming star is Pale Moon 9.0.1. The latest release is an impressively speed-optimized custom build of Firefox and there is also a 64-bit version available in the form of Pale Moon x64 9.0.1. Fans of portable apps should take a look at Pale Moon 9.0.1 Portable and Pale Moon x64 9.0.1 Portable, which can be popped onto a USB drive. Another web browser update worth checking out is Google Chrome 17.0.963.33 Beta which enables you to check out just where Google’s alternative to the likes of Firefox is heading.
Many people use their computers to manage a digital photo collection, and Adobe Photoshop Lightroom 4 Beta 32-bit and Adobe Photoshop Lightroom 4 Beta 64-bit can be used to make this easier. The latest beat version of this handy utility makes it possible to not only browse and manage photos as well as editing and enhancing them. Adobe may be well known for its photo editing software, but PhotoFiltre 7 is worth a look. This surprisingly powerful photo editor can also be found in a portable form -- PhotoFiltre Portable 7.
If you have spent any time creating a work of art or touching up your photo collection, you should definitely think about backing up your files. O&O AutoBackup 1.0.106 (32-bit) is a wonderful free backup tool that enables you to put your external hard drive to good use and if you are working with a 64-bit version of Windows, you should try O&O AutoBackup 1.0.106 (64-bit) instead. It is important to keep all of your files backed up but FavBackup 2.1.3 provides a quick and easy way to back up the settings and data for your web browser. Hardwipe 1.5.0 is a handy security tool that can be used to completely eliminate the files you want to delete.
If you are used to working with an iOS or Android device, the idea of gestures will be familiar. StrokesPlus 1.2.3 enables you to create gestures that can be used in any Windows application to help automate common tasks. To make it easier to work with your applications and get to work faster, Windows 7 App Launcher v0.0.9.1 makes it easy to quickly launch multiple programs at the same time. If you want to customize the look of your computer, Rainmeter 2.2 makes it possible to completely alter the appearance of Windows with skins, gadgets, widgets and much more. On a more practical note, CDBurnerXP 4.4.0.2905 includes everything you need to create your own CDs and DVDs, including audio discs. Also in the musical category is TuneSync Server 2.0 which can be used by Android users in conjunction with Notpod 1.4.1 to wirelessly transfer your iTunes music collection to your Android device.
That’s it for this week -- there’ll be a plethora of downloads to look forward to in the week ahead and another roundup in seven days.
Photo Credit: Sean Gladwell/Shutterstock
-

Need Microsoft Office on iPad? Try OnLive Desktop
Publié: janvier 13, 2012, 3:36pm CET par Mark Wilson
 While there are a lot of claims made about how tablet computers such as the iPad could be used as complete replacement for desktop computers, there are a number of obstacles that get in the way of this. There are a number of mobile versions of well-known desktop applications available, but these tend to be far more limited than the software you are used to using and there is also the problem of transferring files between devices to bear in min. These are problems that OnLive Desktop can help with, providing iPad users with a fully functional version of Microsoft Office to work with.
While there are a lot of claims made about how tablet computers such as the iPad could be used as complete replacement for desktop computers, there are a number of obstacles that get in the way of this. There are a number of mobile versions of well-known desktop applications available, but these tend to be far more limited than the software you are used to using and there is also the problem of transferring files between devices to bear in min. These are problems that OnLive Desktop can help with, providing iPad users with a fully functional version of Microsoft Office to work with.This is not a standalone office suite, nor is it a remote access tool in the traditional sense -- rather it is something of an amalgamation of these two ideas. OnLive Desktop provides you with a Windows 7-style interface along with a remotely hosted version of Microsoft Word, Excel and PowerPoint, which is a million miles away from the office suites that can be found in the App Store. Here you are working with a remotely hosted version of Office, which means that you have access to the full gamut of features.
No cloud-based service would be complete without a smattering of storage space, and OnLive Desktop comes complete with 2GB of space that you can use to save your files. Microsoft’s famous Office suite translates well to the iPad’s touchscreen and while iPhone users may feel left out by the lack of support for their device, the smaller screen would simply be too awkward to work with.
The free version of the app is well worth taking a look at, but for anyone looking to carry out serious work on an on-going basis is going to want to consider upgrading to one of the paid-for services. Opting for a Pro account, at a cost of $9.99, will not only give you more storage space to the tune of 50Gb, it also comes with priority access to the OnLive servers. In addition to this, you have the option of installing additional software, also you are not given a free rein and OnLive do have some restrictions in place. There are also enterprise package available and these can be customized to suit your needs.
You can find out more and download a free copy of the app by paying a visit to the OnLive Desktop review page.
-

Save big on security software and system utilities
Publié: janvier 13, 2012, 12:54pm CET par Mark Wilson
 January is traditionally a tight month for finances after all of the expenses of Christmas, but it is also the time of year when there are great bargains to be grabbed. Head over to the Downloadcrew store and you’ll find all manner of great deals with huge savings to be made on big name software.
January is traditionally a tight month for finances after all of the expenses of Christmas, but it is also the time of year when there are great bargains to be grabbed. Head over to the Downloadcrew store and you’ll find all manner of great deals with huge savings to be made on big name software.You may have decided to put yourself through a new health regime for 2012 and there’s no reason your computer shouldn’t be given the same treatment. Look no further than TuneUp Utilities 2012 [3-PC, 1-Year], which will help you to keep your system optimized and you can save 62 percent off the MSRP when you buy the software for just $18.95. Small businesses can make an even greater 75 percent savings when buying TuneUp Utilities Business Edition 2012 [5-PC, 1-Year] for just $19.95.
If you have resolved to make more of your digital media collection in the new year, CyberLink PhotoDirector 2011 may be just what you’ve been looking for. This is a seriously powerful photo editing tool that includes support for RAW images and boasts a range of features to rival Photoshop. Buy the software now for just $44.95 -- a saving of just 55 percent off the MSRP -- and you will receive a free upgrade to PhotoDirector 2012 v3 when it is released in February. You may well also have video files you want to take care of and if this is the case, take a look at CyberLink Video & Photo Collection 1.0. For $99.95 – a saving of 33 percent -- you can grab yourself a super powerful photo and video editing package which includes a range of incredibly 3D effects.
2012 is a year in which security is going to be more important than ever. To help fi8ght the threat of viruses, look no further than AVG Anti-Virus 2012 [1-PC, 1-Year]. For an amazingly low price of $5.95 (saving you a staggering 85 year off the usual price) you can get yourself a copy of this highly acclaimed antivirus tool. For just a little extra, AVG Internet Security 2012 [1-PC, 1-Year] offers you AV protection as well as parental controls, online backup and more -- all for just $12.99. For extra peace of mind, AVG’s ultimate protection package AVG Premium Security 2012 [1-PC, 1-Year] is available for just $19.99. This includes the added bonus of identity protection and Quick Tune optimization to help speed up you system, and all for 71 percent off the MSRP.
If looking after the performance of your computer is of interest, AVG PC Tuneup 2012 [1-PC, 1-Year] is available at the discounted price of $11.99, and if you have more than one computer to take care of, you should take a look at AVG PC Tuneup 2012 [3-PC, 1-Year] which you can buy for just $19.99 -- saving you 60 percent. Looking for online storage? AVG LiveKive 2012 [UNLIMITED storage] includes all of the cloud storage you could possibly need and you can save yourself a massive 70 percent when you buy an unlimited package for just $14.95.
Feel like trying your hand at DJing? MAGIX Digital DJ 2 may be just what you have been looking for. Available at the discounted price of $29.99, saving you 40 percent, this powerful music tool can be used to mix tracks like a pro on a set of digital decks. Sticking with the creative theme, MAGIX Music Maker MX is available at a 33 percent discount for just $39.99. with a huge collection of samples, loops and effects to work with, you’ll find that it’s incredibly easy to create something truly impressive that you can share online with others. You can save more than one third off the MSRP when you buy MAGIX Movie Edit Pro MX for just $45.99, and when you do so you are equipping yourself with everything you need to edit and enhance your home video footage.
Returning to the security theme, Bitdefender Antivirus Plus 2012 [1-PC, 1-Year] is available at the bargain basement price of $4.95 -- a gigantic 80 percent savings. You might also be interested in Webroot Internet Security Complete 2011 [3-PC], which can be used to protect up to three computers against viruses, spam and ID theft. The low price of $9.95 represents a huge 88 percent saving off the usual MSRP, and an even greater saving is to be found withWebroot Internet Security Essentials 2011 [3-PC] with a 90 percent savings bringing the price down to just $5.95. Both of these program include a free upgrade to SecureAnywhere.
Anyone looking to protect valuable data should take a look at Genie Timeline 2.1 Professional is an innovative backup tool that makes it easy to safeguard your valuable files. Available for just $9.95, you can save 83 percent off the MSRP when you buy this great tool today. Multi-computer households can take advantage of an 83% saving off Uniblue PowerSuite 2012 as for just $19.95 you can equip yourself with an advanced tweaking and optimization tool. Finally for this roundup, Laplink PCmover Professional v6 is a great tool for anyone making the move to a new computer. For a mere $29.95 (a saving of 50 percent), you can buy this incredibly useful tool that will help you to move your files, installed applicationsand settings from one computer to another with a minimum of effort.
Don’t forget, these are just some of the highlight from the store – there are plenty more bargains to be found so head over to the Downloadcrew Software Store to see what you can pick up today!
Photo Credit: Gunnar Pippel/Shutterstock
-

Sync files to USB drives with O&O AutoBackup -- download free for January
Publié: janvier 12, 2012, 4:19pm CET par Mark Wilson
 O&O AutoBackup is a (temporarily) free backup and synchronization tool that can be used to safeguard your valuable data by creating a copy on a removable USB or Firewire drive. Unlike many backup tools, this particular offering from O&O Software benefits from being incredibly easy to get up and running, in addition to its free availability.
O&O AutoBackup is a (temporarily) free backup and synchronization tool that can be used to safeguard your valuable data by creating a copy on a removable USB or Firewire drive. Unlike many backup tools, this particular offering from O&O Software benefits from being incredibly easy to get up and running, in addition to its free availability.You can choose to backup an entire drive, a selection of folder or use wildcards to specify particular types of file that should be included, and there are numbers of options when it comes to choosing how your files should be handled. You can opt to simply copy files from one location to the other or you can choose to copy only new and changed files. The third option is to go down the synchronization route so any files that have already been removed from the source drive will also be deleted from the removable drive.
When it comes to run the backup or synchronization job, you can opt to run it on a manual basis, or you may prefer to use the automatic option so you backup is updated every time you connect the USB drive you are working with. That’s really all there is to it -- backing up data is kept as simple as it possibly can be.
For the month of January, O&O AutoBackup is available completely free of charge, but you will need to apply for a free registration code in order to unlock the software. To do so, pay a visit to the registration page, enter your email address and click the ‘Request free license’ button. A serial number will be emailed out to you and you will be given the opportunity to enter this during the installation of the program. Take advantageof this offer while you can – from 1 February, this will revert to being a paid-for product.
You can find out more and download a free copy of the program by paying a visit to the O&O AutoBackup 1.0.106 (32-bit) review page (http://www.downloadcrew.com/article/26596-oo_autobackup_32-bit). There is also a 64-bit version of the software available which you can download from the O&O AutoBackup 1.0.106 (64-bit) review page.
Photo Credit: Brian A Jackson/shutterstock
-

'Hardwipe' Windows PC data
Publié: janvier 12, 2012, 2:58pm CET par Mark Wilson
 When it comes to your computer, security takes a number of forms. There is the threat of viruses and spyware to consider, the importance of securing accounts with strong passwords and there is also the security of your files to bear in mind. You might think that when you delete the files you no longer need they are gone forever, but there are a variety of tools can techniques that can be used to recover data that has been ‘removed’. Hardwipe is a free tool that can be used to boost your security by overwriting files multiple times to dramatically reduce, or even eliminate, the ability to recover files.
When it comes to your computer, security takes a number of forms. There is the threat of viruses and spyware to consider, the importance of securing accounts with strong passwords and there is also the security of your files to bear in mind. You might think that when you delete the files you no longer need they are gone forever, but there are a variety of tools can techniques that can be used to recover data that has been ‘removed’. Hardwipe is a free tool that can be used to boost your security by overwriting files multiple times to dramatically reduce, or even eliminate, the ability to recover files.The program can be used in a couple of ways, either to wipe a drive in its entirety or delete selections of files. When it comes to wiping a drive, you must use the main program interface to select the drive you are interested in as well as selecting the options that should be used, but when it comes to deleting individual files and folders, Windows’ right click menu provides access to the wiping option.
Files can be overwritten anything from once to 35 time depending on the sensitivity of your data or your level of paranoia, but you should expect most of the multi-wipe options to take quite some time -- although it is possible to adjust the priority at which the program runs. Whether you are wiping a drive completely or just deleting a large number of files, you can opt to have Windows automatically shut down so you do not need to sit at your computer waiting for the process to finish.
Another handy option is the ability to wipe free space that has already been created by deleting files in the usual way or using other software. This option to clean up the potential security risks from the past is a nice touch, as is the feature that makes it possible to wipe data that has been stored in Windows’ swap file.
Hardwipe is not the only secure deletion tool that is available – in fact there are quite a few to choose from – but it benefits greatly from the fact that it is not only free of charge but also incredibly easy to use. If you want to protect your privacy if you are passing on hardware to another owner, this is a great way to keep your data secure.
You can find out more and download a free copy of the app by paying a visit to the Hardwipe review page.
Photo Credit: megainarmy/shutterstock
-

PhotoFiltre 7 is an accomplished photo-editng tool
Publié: janvier 11, 2012, 2:01pm CET par Mark Wilson
 Photo editing and manipulation tools are not exactly in short supply but those that get the balance between the number of features and ease of use are few and far between. Despite featuring an interface that is somewhat off-putting to start with, PhotoFiltre 7 is an extremely accomplished tool with the latest update adding support for both layers and transparency – these are options that were previously only available in the more advanced PhotoFiltre Studio.
Photo editing and manipulation tools are not exactly in short supply but those that get the balance between the number of features and ease of use are few and far between. Despite featuring an interface that is somewhat off-putting to start with, PhotoFiltre 7 is an extremely accomplished tool with the latest update adding support for both layers and transparency – these are options that were previously only available in the more advanced PhotoFiltre Studio.While the interface is perhaps the most well organized, it is more appealing than the likes of the GIMP. This freeware image editor is probably PhotoFiltre’s closest competitor in this particular software arena and while neither app is going to win any prizes for the most attractive or well-designed interface, PhotoFiltre definitely has the edge over its rival -- and while the interface is a little on the cluttered side, it does mean that many options are easily accessible through the wide range of toolbar buttons on display.
Being a freeware tool, it should come as little surprise that this is a slightly limited app. PhotoFiltre 7 is in fact a slightly cut down version of the commercial app PhotoFiltre Studio X. There are obviously a number of features that have been omitted from this free version of the tool, but it is still accomplished enough to mean that it is well worth checking out.
As the app’s home page points out ([photofiltre-studio.com]), should you remain allergic to layers, the older PhotoFiltre 6.5.3 is still available for download. You can find out more and download yourself a free copy of the latest version of the progam by paying a visit to thePhotoFiltre 7 review page.
Photo Credit: Laborant/Shutterstock
-

January 10 giveaway -- East-Tec Eraser 2011
Publié: janvier 10, 2012, 1:46am CET par Mark Wilson
 Your computer can reveal a great deal of information about you and if other people have access to your machine, it would be all too easy for this data to fall into the wrong hands. Simply deleting files you no longer need is not enough as there are numerous tools that can be used to restore anything that has been erased -- even from a drive that has been formatted. This is where East-Tec Eraser 2011 can help, making it possible to securely wipe information from your computer so that it cannot be recovered.
Your computer can reveal a great deal of information about you and if other people have access to your machine, it would be all too easy for this data to fall into the wrong hands. Simply deleting files you no longer need is not enough as there are numerous tools that can be used to restore anything that has been erased -- even from a drive that has been formatted. This is where East-Tec Eraser 2011 can help, making it possible to securely wipe information from your computer so that it cannot be recovered.The application is broken down into a series of different section, with the main interface making it easy to securely delete any files you no longer need. You can simply drag and drop files onto the program window before choosing how secure the wiping should be -- this ranges from deleting and overwriting with random data to the Gutmann method, which is very slow but renders files completely unrecoverable, even using hardware tools.
East-Tec Eraser 2011 can also be used to wipe deleted emails, securely empty the Recycle Bin and scrub free space. Scheduling can be used to ensure that secure deletion takes place on an automatic basis without you having to remember to do so manually. There are also tools on hand that can be used to clear the tracks that other programs store about you. This extends far beyond just wiping your browser history, enabling you to wipe recent file logs in scores of applications. With the ability to securely wipe your entire hard drive, the application can come in handy for when you are thinking of selling an old computer and do not want to risk your data.
It is worth noting that the application will initially install as a 15-day trial but you can obtain the full, unrestricted version of the software by clicking the Free Registration button at the startup screen. After providing your name and email address you will need to click the confirmation link in the email that is sent out to you. Click the Get Free Key button on the page that loads and you will be given a serial number that you should select and copy. Return to East-Tec Eraser and click the Enter Key link before entering your name and pasting the code into the Key field. Hit OK and you’re ready to start using the program.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, log in (or create a free account if you don’t have one already), grab your copy of the program and get a free serial code. Be quick as the offer is for January 10th only, and expires at 23:59 Central European Time.
Photo Credit: Zadorozhnyi Viktor/Shutterstock
-

21 downloads to ring in the new year
Publié: janvier 7, 2012, 6:51pm CET par Mark Wilson

We might all be feeling slightly sluggish after overindulging throughout the holidays, but the software release schedule continues apace. Your thoughts may have already turned to Windows 8 and if you’re yet to try out the Developer Preview, PCmover Windows 8 Beta Assistant is here to make things easier for you. If you have been put off by the idea of having to set up a virtual a machine or updating your existing installation because of the prospect of transferring your files and installing all of your favorite software, this handy utility can help to automate the process.
Whether you’re upgrading Windows or not, everyone needs a backup tool, and EASEUS Todo Backup Free 4.0 fits the bill perfectly. You can backup individual files and folders or entire partitions, and you can create incremental backups to save space. If you’re sticking with your current version of Windows for the time being, SharpKeys 3.5 enables you to disable keys on your keyboard that you do not use or find that you press accidentally -- a much easier option that editing the registry. You may well be more interested in customizing the look of your computer rather than customizing the way your hardware works, and this is something that Kuvva 1.1 can help with, making it possible to automatically change your desktop wallpaper on a schedule.
It has been a fairly busy week for web software and we have seen the release of Google Chrome 16.0.912.75 FINAL as well as Google Chrome 17.0.963.26 Beta, which moved from the Developer to the Beta channel. Both versions of the app offer speed improvements over previous releases as Google’s web browser development shows no signs of slowing down. There is an interesting browser available in the form of CoolNovo 2.0.0.4, which is an enhanced version of Chrome packed with extra features, although these can be added to Chrome with plugins. For those PDFs you invariably encounter online, Foxit Reader 5.1.4 can be used to not only view these portable files but also edit and annotate them.
When it comes to editing audio files, tools such as Audacity may spring to mind, but Wavosaur 1.0.6 is well worth a look. The app can be used to record, edit and process audio, while RarmaRadio 2.64.3 enables you to listen to Internet radio stations, including the option of recording multiple stations simultaneously. If you’re interested in online radio, Clementine 1.0 is a cross-platform radio player that can be used on Windows, Mac and Linux, complete with support for Spotify, Grooveshark and SKY.fm. You may be more interested in television, and TVNations 1.0 can be used to watch hundreds of streaming TV channels from around the world. TV and radio have their place, but book are here to stay, and Adobe Digital Editions 1.7 enables you to read and manage your ebook collection on your computer.
For many people, listening to music means working with an iPod. If you are one of the many people who are not keen on iTunes, look no further than Floola 2012, which can be used to manage your digital music collection. One of the problems with any form of media is that it often means battling with file formats.Free Studio 5.3.3 is a handy tool that can be used to convert video and audio files between formats, while Freemake Video Converter 3.0.1.3 focuses on enabling you to work with video files including downloading from YouTube, converting between formats and burning to disc. The YouTube downloading component is available as a separate tool asFree YouTube Download 3.0.20, and Freemake Music Box 0.9.0 opens up a world of online music that you can listen to legally and free of charge.
It is important to take care of your computer if you want to gain the best possible performance from it. Your hard drive is something that needs particular attention. UltraDefrag Portable 5.0 (32-bit) is a replacement for the built in defrag tool found in windows, and 64-bit OS users can turn to UltraDefrag Portable 5.0 (64-bit). The final tool in this week’s roundup is IObit Advanced SystemCare 5.1 FINAL which includes a huge number of tools to help boost the performance, stability and security of your computer. AS new uninstaller component complements the existing registry and hard drive cleaners along with numerous other maintenance tools.
There are plenty of tools here to keep you busy over the week end -- join us again next week for more top releases.
-

Thinking about the BIG upgrade? Try Laplink PCmover Windows 8 Beta Assistant
Publié: janvier 7, 2012, 6:24pm CET par Mark Wilson
 While the release of a new operating system is generally quite exciting, even computer users who are keen to have the latest and greatest version of Windows installed are filled with a slight sense of dread at the prospect of the installation. While the installation process for Windows 8 is one of the fastest and easiest yet, there is still the problem of having to install the apps you need and transferring all of your files. PCmover Windows 8 Beta Assistant from Laplink helps to ensure that things go as quickly and smoothly as possible by enabling you to more easily migrate your existing files, settings and user profiles.
While the release of a new operating system is generally quite exciting, even computer users who are keen to have the latest and greatest version of Windows installed are filled with a slight sense of dread at the prospect of the installation. While the installation process for Windows 8 is one of the fastest and easiest yet, there is still the problem of having to install the apps you need and transferring all of your files. PCmover Windows 8 Beta Assistant from Laplink helps to ensure that things go as quickly and smoothly as possible by enabling you to more easily migrate your existing files, settings and user profiles.PCmover has been around in various versions for some time now, but this beta release has been designed specifically with the pre-release versions of Windows 8 in mind. It can currently be used to make the move to the Developer Preview version of Windows 8, but it will also work with the Beta version when that it released in the near future. For reasons best known to Laplink, there is only support for 64-bit versions of Windows, both as source and destination operating system, and it can only be used with Windows 7; there is no support for XP or Vista.
Whether you want to install Windows 8 on a second computer and move files and settings from an existing Windows 7 computer, you are upgrading from Windows 7 or Windows 8, or you are working in a virtual environment, the app offers a number of ways to complete the transfer. The wizard-driven interface makes it easy to select exactly what you would like to transfer, but there is an undo option if you change your mind about anything, and choose how the transfer should be performed. You can use a network connection, transfer cable or removable media.
It’s a shame that just a large section of the Windows market has been effectively cut out here, but for anyone currently working with a 64-bit version of Windows, this tool could be a real timesaver. If you have used a previous version of the app to migrate to Windows 7 or Vista, there are no surprises, just an accomplished tool that has been updated to support the latest version of Microsoft’s operating system.
You can find out more and download a free copy of the app by paying a visit to the PCmover Windows 8 Beta Assistant review page.
-

Got iPad and need Microsoft Office? Try CloudOn
Publié: janvier 6, 2012, 6:36pm CET par Mark Wilson
 There are a number of Office compatible office suites to choose from in Apple's App Store, so anything that wants to stand out from the crowd needs to offer something special. After a brief appearance followed by a rapid vanishing act, CloudOn for iPad has returned to the App Store. What makes this app different from any of the other suites you could choose to install? Well, not only is it free of charge, but the suite is not only Office-compatible, it is a cloud-based version of Microsoft’s flagship suite.
There are a number of Office compatible office suites to choose from in Apple's App Store, so anything that wants to stand out from the crowd needs to offer something special. After a brief appearance followed by a rapid vanishing act, CloudOn for iPad has returned to the App Store. What makes this app different from any of the other suites you could choose to install? Well, not only is it free of charge, but the suite is not only Office-compatible, it is a cloud-based version of Microsoft’s flagship suite.The app integrates with Dropbox that is used to store all of your documents, and you have access to Word, Excel and PowerPoint. The app interface is almost exactly the same as using the desktop version of Office, but working with an on-screen keyboard is vastly different to typing in the usual way. It is unlikely that you will want to use the app for extended periods of typing, but the ability to review existing documents and make changes to spreadsheets, presentations and text documents in a familiar environment is big news.
While CloudOn is a great tool, it suffers from the same problem as any cloud-based app. The stuttering launch of the app just goes to highlight the failing of working with software and services that are not remotely installed -- overwhelming demand, server issues and other problems could make it impossible to access your files so, in the early stages of OnCloud’s life it might be advisable to avoid using it for anything that is mission-critical.
The cloud-based nature of CloudOn also works in its favour as it greatly simplifies the process of transferring files from your iPad to your Mac or PC -- just log into your Dropbox account and your files will be immediately available. The documents you are working on are saved and synchronized automatically so the latest version of files is always available on Dropbox. Many users will have privacy concerns about the fact that the CloudOn app so it might be advisable to avoid using it for sensitive files, but until an official iPad version of Microsoft Office this is a pretty decent tool.
You can find out more and download a free copy of the app by paying a visit to the CloudOn review page.
-

January 6 giveaway: Auslogics Registry Defrag
Publié: janvier 6, 2012, 1:40am CET par Mark Wilson
 It is important to keep your computer in good shape if you are going to get years of use from it and there are various techniques that can be used to ensure that you are getting the best possible performance from your hardware. While it is fairly easy to use the various tools that are built into Windows to keep your hard drive optimized, when it comes to the registry it is something of a different story. Windows includes a tool that can be used to edit the registry, but nothing that enables you to optimize it. This is precisely where Auslogics Registry Defrag can help and today we’re giving you a free copy of this powerful app worth $19.95.
It is important to keep your computer in good shape if you are going to get years of use from it and there are various techniques that can be used to ensure that you are getting the best possible performance from your hardware. While it is fairly easy to use the various tools that are built into Windows to keep your hard drive optimized, when it comes to the registry it is something of a different story. Windows includes a tool that can be used to edit the registry, but nothing that enables you to optimize it. This is precisely where Auslogics Registry Defrag can help and today we’re giving you a free copy of this powerful app worth $19.95.Auslogics has a great reputation for producing powerful maintenance tools, and Registry Defrag falls very neatly into this category. The registry is an area of Windows that many people do not feel comfortable tampering with -- and with good reason, as any incorrect changes could have disastrous consequences for your computer. But just like your hard drive, your registry is prone to fragmentation as software installation and uninstallations leading to bloating and an increase in size that impacts negatively on performance.
Whether you have a cutting edge computer or you are working with a slightly older machine, Auslogics Registry Defrag is a valuable tool that can make a real difference to performance. Turning to this dedicated tool is a far better option than trying to battle with the registry yourself. Windows’ huge database is an unwieldy beast to battle with and if you make incorrect changes or deletions you could render your system unusable. Registry Defrag automatically create a System Restore point so in the unlikely event that something goes wrong you can reverse the changes.
The fact that Windows is making constant reference to the registry means that it is important to keep it optimized. Auslogics Registry Defrag will eliminate unnecessary entries and reduce the overall size of the registry to keep things running as smoothly as possible and maximizing the amount of RAM available to applications. As an added bonus the app can be installed on up to three computers with a single license, so you can maintain all of the computers in your household with the same tool.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, log in (or create a free account if you don’t have one already), grab your copy of the program and get a free serial code. Be quick as the offer is for January 6th only, and expires at 23:59 Central European Time.
Photo Credit: Sergey Mironov/Shutterstock
-

Turn your Android into a second PC monitor
Publié: janvier 5, 2012, 4:02pm CET par Mark Wilson
 Anyone who has worked with a dual monitor setup will be aware of just what a productivity boost the extra screen space can be. The ability to have more than one application visible in full screen mode enables you to view more information at any one time is incredibly useful and it something that everyone should try. But whether you have a couple of monitors sitting on your desk or not, ScreenSlider enables you to gain a little extra space using your Android device.
Anyone who has worked with a dual monitor setup will be aware of just what a productivity boost the extra screen space can be. The ability to have more than one application visible in full screen mode enables you to view more information at any one time is incredibly useful and it something that everyone should try. But whether you have a couple of monitors sitting on your desk or not, ScreenSlider enables you to gain a little extra space using your Android device.The app can be used with either tablets or phones, and while both are useful options, tablet owners undoubtedly get a better deal thanks to their larger screens. ScreenSlider simply requires that you install the free app on your Android device as well as the desktop software on your PC and the software will then automatically detect your phone or tablet over your wireless network from your computer. You can drop any program window onto the display and take advantage of it whilst sat at your desk or move further afield --providing you stay within range of your network.
Performance is not high enough to allow for your new wireless monitor to be used to stream video from your computer but it is useful for housing your web browser or inbox. The cheaper version of the app is slightly limited, but the installation does include a 30-day trial of the extra features that are to be found in the Pro version, including pinch-to-zoom gesture support, the ability to use the Android keyboard to enter text as well as the handy ability to transfer files between your computer and Android device.
It’s a shame to see that there is no support for Mac users at the moment, but hopefully this is something that will be addressed in the future. As it stands, ScreenSlider is an interesting utility. Android phone users are unlikely to find that the extra two or three inches of screen space can be put to much use, but tablet owners will find that they already have a second or third monitor in their possession, and this is screen space that can be genuinely useful.
You can find out more and download a free copy of the app by paying a visit to the ScreenSlider review page.
-

Dolphin Browser HD 7 for Android mini-review
Publié: janvier 4, 2012, 3:58pm CET par Mark Wilson
 Whatever operating system you look at, it is fair to say that most people fall out of love with the default web browser pretty quickly. Windows users will find that they migrate away from Internet Explorer, while Mac owners are likely to adopt an alternative to Safari. The same is true for mobile platforms and when it comes to Android devices there is no shortage of web browsers to choose from. Dolphin Browser HD is one alternative browser that has gained an impressive following not only on iOS devices, but also on Android.
Whatever operating system you look at, it is fair to say that most people fall out of love with the default web browser pretty quickly. Windows users will find that they migrate away from Internet Explorer, while Mac owners are likely to adopt an alternative to Safari. The same is true for mobile platforms and when it comes to Android devices there is no shortage of web browsers to choose from. Dolphin Browser HD is one alternative browser that has gained an impressive following not only on iOS devices, but also on Android.This is a mobile web browser that got off to something of a slow start. When it was first released it was an interesting alternative to the likes of mobile Safari and Opera Mini but it has developed over a relatively short period of time into some seriously impressive. Being designed for touchscreen devices means that the browser takes advantage of gestures to make it easier to perform common operations such as moving back and forwards between pages. Support for gestures means not only that web navigation is made a great deal easier, it also frees up screen space that would otherwise have been occupied by a toolbar full of buttons.
Gestures can be customized so they can be used to access your favorite websites more easily. There is also a slide-out panel hidden to the left of the screen that can be revealed by swiping from left to right. The Quick Access panel that appears contains links to all of your bookmarked sites and also enables you to bookmark the current site as well as adding it to the Speed Dial screen. You can also access the settings screen, browsing history and theme settings -- this means that things are nicely accessible, but not cluttering up your screen.
Bookmark Syncing
It is possible that you have more than one Android device, or that you also use Dolphin Browser on an iPad or iPhone as well. The latest version of the browser includes Dolphin Connect, which enables you to synchronize settings and bookmarks between devices so you can move from one to the other seamlessly. This is not a feature that is unique to Dolphin, but it is well implemented. Something that many mobile web users will be pleased to see is that there is support for add-ons. Extra features such a PDF viewer, translation tool, password manager, Twitter tool and much more can be add by browsing through the fairly extensive selection of available add-ons. Once you have any add-ons installed, they can be accessed by swiped right to left to reveal another side bar.
As you would expect, there is support for tabbed browsing -- and the way this is handled can be configured through Settings -- and the Opera-style Speed Dial screen provides easy access to your most frequently used web sites. Another interesting option is Webzine, which provides a mobile friendly view for a range of social networks and blogs such as Twitter and Facebook. Working much like a social network app and RSS reader combination, this features provides a great way to interact with web sites without unnecessary distractions.
If you spend any time browsing the Internet on your Android phone or tablet, you owe it to yourself to get Dolphin Browser HD installed as soon possible. This is a browser that is just worlds away from almost all of the competition -- once you have tried it you will find it very difficult to use anything else. The fact that it is available free of charge is impressive and removes any obstacle that might otherwise prevent you from trying it out. It’s fair to say that not every aspect of the app is immediately intuitive, hiding setting away in the side panel is a little confusing to start with, but once you get used to the way the browser works, this is quickly forgotten.
It is easy to jump on a bandwagon and proclaim any new app as the latest and greatest, but Dolphin Browser has been slowly evolving into its current incarnation. The browser was not perfect when it was first released, and it’s still not quite there yet, but it is getting very close. You’ll find it difficult to find a more capable browser in the Android Market at the moment.
-

MAGIX Music Maker 17 Silver is yours, free download just for a day
Publié: janvier 2, 2012, 11:34pm CET par Mark Wilson
 You may well have entertained the thought of using your computer to create music, but knowing just where to start can be a serious stumbling block. Unless you are already a musician, the majority of the music creation titles that are available are pretty complicated to use and can be very off-putting to anybody looking to get started. To help make things a little easier for you, we’re giving away a free copy of MAGIX Music Maker 17 Silver, worth $19.95, which can be used to create impressive musical works with loops, samples and more.
You may well have entertained the thought of using your computer to create music, but knowing just where to start can be a serious stumbling block. Unless you are already a musician, the majority of the music creation titles that are available are pretty complicated to use and can be very off-putting to anybody looking to get started. To help make things a little easier for you, we’re giving away a free copy of MAGIX Music Maker 17 Silver, worth $19.95, which can be used to create impressive musical works with loops, samples and more.As anyone who has used MAGIX software will be aware, Music Maker 17 Silver is a delightfully easy to use program, but this does not make it any the less powerful. You are provided with a computer-based four track recording studio to work with, and while four tracks may not sound like much this is a versatile tool that lends itself to experimentation, and you will find that you are able to create something truly impressive quickly and easily.
There is a selection of loops and samples for you to work with, with examples from a number of music genres and the option of using a range of different instruments. These form the building block of your musical creations, and creating your first track is a simple matter of dropping these samples into place on the timeline and arranging them however you like. You can then start experimenting with the special effects and filters in a bid to create something truly unique.
If you are a musician, MAGIX Music Maker 17 Silver can be used to compliment your instrument. You can use the application to record yourself playing, giving you the ability to create your own loops and samples that can be used in future projects. Whatever sort of creation you come up with, you can export the results to an MP3 file which can be easily burned to disc or shared online with others.
Once you have the program downloaded and installed, you will need to register the software in order to use it free of charge. The first time you launch the MAGIX Music Maker 17 Silver, click the registration link and either sign into or create a new MAGIX online account. Once you have provided a valid email address, you will be provided with a serial number that can be pasted into the registration screen of the application.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, grab your copy of the program and get a free serial code – but act fast, the offer goes live for 24 hours, between January 2 at 23:59 and January 3 at 23:59, Central European Time.
Photo Credit: Pavel K/Shutterstock
-

Kuvva gives your PC a fresh new look every day
Publié: janvier 2, 2012, 3:33pm CET par Mark Wilson
 Your desktop wallpaper may be something you don’t give much thought to, but whether you have chosen to stick with a stock image, or have adorned your desktop with a photograph of loved ones or a favorite place, this is an image you are going to be seeing on a daily basis. It is easy to become bored of constantly seeing the same image, and being bored is not a mood that is conducive to being productive, whatever you are meant to be doing. Kuvva is a free app that helps to alleviate the boredom by providing you with a new wallpaper every day.
Your desktop wallpaper may be something you don’t give much thought to, but whether you have chosen to stick with a stock image, or have adorned your desktop with a photograph of loved ones or a favorite place, this is an image you are going to be seeing on a daily basis. It is easy to become bored of constantly seeing the same image, and being bored is not a mood that is conducive to being productive, whatever you are meant to be doing. Kuvva is a free app that helps to alleviate the boredom by providing you with a new wallpaper every day.This is not exactly a new idea as there are numerous wallpaper changing applications available; but Kuvva is a little different. Rather than relying on your providing a series of images that can be rotated as your desktop wallpaper, Kuvva gets its images from an online repository that is constantly updated by artists, designers and photographers. The app takes care of changing your wallpaper for you, so when you switch on your computer in the morning you can be greeted by a new and inspiring work of art.
The app requires you to set up an online account at the Kuvva website, and this means that it is possible to configure various preferences. Desktop wallpapers you are keen on can be favorited so you can easily activate them again if you decide you want to see a particular image again. It is also possible to create sets comprising images you would like to group together -- based on theme, color scheme or anything else you feel appropriate.
Kuvva is available for both Mac and PC and is a great way to give your machine a fresh new look each day. While there are a limited number of artists and pictures to browse through at the moment, as Kuvva gains momentum it looks like it is going to grow into something impressive. And if you are a budding artist or photographer, you could use this as a platform for you work -- check it out to see how it could help you.
You can find out more and download a free copy of the app by paying a visit to the Kuvva review page.
-

Freemake Music Box: Streaming, no subscription required
Publié: décembre 30, 2011, 2:59pm CET par Mark Wilson
 When it comes to listening to music on your computer you have a number of options. You can just play a CD, or you may have taken the trouble of ripping your existing music collection so that all of your favorite tracks are available on your computer. You could stream music using the likes of Last.fm, or you could listen to streaming radio stations from all over the world. But all of these options have their limitations -- if you don’t have a CD with you you can’t listen to it, working on different computers means that you might not have access to your music collection and radio stations may not necessarily play what you want to hear. Enter Freemake Music Box.
When it comes to listening to music on your computer you have a number of options. You can just play a CD, or you may have taken the trouble of ripping your existing music collection so that all of your favorite tracks are available on your computer. You could stream music using the likes of Last.fm, or you could listen to streaming radio stations from all over the world. But all of these options have their limitations -- if you don’t have a CD with you you can’t listen to it, working on different computers means that you might not have access to your music collection and radio stations may not necessarily play what you want to hear. Enter Freemake Music Box.This is a free app that enables you to stream free music to your computer without the need to create an account or set up a subscription. The tiny app -- it’s only 1MB in size -- can be downloaded and installed in a matter of moments and after performing your first search you can be listening to music in seconds. You can search for your favorite band or jump straight in to find a particular track.
If you are looking to create a perfect soundtrack to accompany your work, numerous tracks can be built up into a playlist that you can listen to however you want -- and if you step away from your computer you will be able to pick from where you left off. The app itself is very simple and streamlined; it is not bursting with features, but it doesn’t need to be. It does what it set out to do – providing access to a wealth of free online music -- and it does it very well.
There are already a number of enhancements planned for future versions of the app -- as it stands, Freemake Music Box has not even reached version 1.0 yet. In the, hopefully not too distant future, we can look looking forward to using a web based version of the app as well as synchronizing playlists between computers. It is early day for this music app, but things are already shaping up well. The fact that only legal music is available will be attractive to anyone keen on avoiding getting into trouble, and everyone can benefit from the fast searches and extensive music database there is available.
You can find out more and download a free copy of the app by paying a visit to the Freemake Music Box review page.
Photo Credit: Dmitry Naumov/Shutterstock
-

LogMeIn Free for iOS mini-review
Publié: décembre 29, 2011, 6:53pm CET par Mark Wilson
In both the home and work environment, there are numerous uses for remote access tools. For home users, the ability to not only access the files stored on a computer housed in another room but also take full control of it as if you sit in front of it can save a great deal of legwork reviewing a document you need to read or checking the status of a download, all without having to run up and down stairs. Used for work, the possibilities are almost limitless. Network administrators can control their entire network from almost anywhere -- homeworking becomes a possibility for a far larger number of people; the list just goes on and on. There are a number of remote access tools available for iOS, LogMeIn is not only one of the best known, it is also one of the best. And the great news is that it is now completely free of charge.
The app was previously available for $30, and while many people could see the benefits of using such a powerful and useful tool, the price was a little off-putting. With the launch of a free version of the app, which is mercifully light in the restrictions department, the world of VPN has opened up to a whole new audience who are now able to take advantage of remote access from a well-known name without having to part with any cash.
The free version of LogMeIn is a universal app, and while the app can be installed on both iPhones and iPad, tablet owners are in for a treat with a version of the software that has been optimized for use on a larger screen. This is obviously a great advantage when remotely connecting to a computer as it is likely to have a display that is at least 17 inches in size. This is not to say that LogMeIn is not a good app when used on an iPhone; the interface has been designed in such a way that navigations and remote use are perfectly usable on the smaller screen.
The app can be used to take remote control of your Mac or PC, assuming that you have installed the necessary client software and your computer is switched on. Working with an iPhone, after logging into your account, you can see a small portion of your desktop at any one time, unless you adjust the zoom level, and you can then pan around using a fixed mouse cursor and onscreen mouse buttons. This system takes a little getting used to, but after a few minutes you will find that it work well and allows for easy navigation of your files and desktop.
Remote Desktop Access
Whether you are using an iPhone or an iPad, an onscreen keyboard is available that can be used to type in remote apps so you really can use your remote computer as if you were sitting in front of it. Things do get a little cramped on the iPhone’s screen when the keyboard is activated, but it’s hard to see how this could be avoided. The extra screen space available to iPad users means that the remote access experience is even more pleasing. The larger screen means that your remote desktop can be viewed at a larger size and the virtual mouse cursor can be moved around the screen rather than having to move a desktop aperture as on the iPhone. When the keyboard is activated, a larger section of your desktop remains visible, which is a great help.
The app can be used to access both Macs and PCs, and although this free app does not include an integrated way to transfer files from one device to another, the overall experience is very good. Some additional features are available if you decide to upgrade to a LogMeIn Pro account, and these can be unlocked via an in-app purchase should you decide that you need them. Paid-for features include the ability to stream audio and HD video as well as support for printing to AirPrint compatible printers. There are also additional file management options, such as the ability to transfer photos and other files to and from your iPhone or iPad, as well as the My Cloud Bank feature taht provides access to cloud storage services.
While these are features that are going to be useful, or even essential, to some people, they are features that the majority of potential remote computer users could live without. Even if you find that you cannot possibly do without the ability to transfer photos from your iPhone to your computer, for example, there are ways around these minor limitations if you still do not feel inclined to part with any money. You could simply email files from your phone to an email address that you can remotely access on your computer and you can then save the image to that computer, where you are free to work with it in whatever way you want.
The slightly more basic feature set of the free version of LogMeIn exceeds that found in other similar tools and provides the quality and reliability that we have come to expect from LogMeIn.
The possibilities for remote computing are wide and varied. Whether you want to be able to access your files when you are on the move or would like to be able to provide remote assistance more easily, the fact that there is now a free version of LogMeIn available means that there has never been a better time to implement such as system for yourself. Grab yourself a copy of LogMeIn Free for iOS from the App Store to see what all the fuss is about.
-

Improve your PC's performance with this end-of-year software sale
Publié: décembre 28, 2011, 4:28pm CET par Mark Wilson
 Late December is traditionally the time of year to snap up a bargain in the post-Christmas sales, and there is no shortage of special deals to be found in the Downloadcrew Software Store. Take a browse through the store and you will find everything from security software to video editing tools -- there really is something for everyone. With huge savings of up to 83 percent off some of the best software available, you’d better hurry because these offers expire on December 31, 2011.
Late December is traditionally the time of year to snap up a bargain in the post-Christmas sales, and there is no shortage of special deals to be found in the Downloadcrew Software Store. Take a browse through the store and you will find everything from security software to video editing tools -- there really is something for everyone. With huge savings of up to 83 percent off some of the best software available, you’d better hurry because these offers expire on December 31, 2011.For anyone looking to watch videos on their computer, CyberLink PowerDVD 11 Ultra is a versatile media player with support for a huge range of video formats and discs, including 3D formats. You can save 45 percent off the MSRP when you buy the software for just $45. Also from CyberLink is CyberLink PowerDirector 10 Ultra which you can buy for just $69.95, saving 30 percent off the MSRP. This powerful program can be used to edit video, including 3D formats, and it comes bundled with a free copy of CyberLink MediaEspresso 6.5 worth $39.95.
From the same company comes CyberLink PhotoDirector 2011, which you can buy for just $44.95 -- a saving of $55 or55 percent. This is a high-end photo correction and image editing tool that includes most of the features found in the likes of Adobe Photoshop. You can buy the 2011 version of the software now and you will receive a free update to PhotoDirector 2012 -- release ETA February 2012. If you’re feeling creative, you may also be interested in CyberLink Video & Photo Collection 1.0, which you can buy for $99.95, saving 33 percent.
Low-cost Security
We all know how important it is to keep our computers secure and with a massive 83 percent saving off AVG Anti-Virus 2012 [1-PC, 1-Year] which you can buy for just $6.95. AVG is a company famous for its security software and there are more titles available in the store. AVG Family Safety 2012 [3-PC, 1-Year] can be used to place restrictions on computer use to keep your children safe, and you can save 60 percent when you buy the software for just $7.95. Another security tool from the same company is AVG Internet Security 2012 [4-PC, 1-Year] which you can buy for just $19.95 (a saving of 64 percent off the normal MSRP). AVG isn’t just about security. AVG PC Tuneup 2012 [1-PC, 1-Year] is available for just $11.99 (saving you 66 percent off the usual price of $34.99) and can be used to boost the performance of your computer in a few easy steps.
If performance boosting is what you’re after, you can save 62 percent off the MSRP of TuneUp Utilities 2012 [3-PC, 1-Year] when you buy it for just $18.95. The program lets you optimize, and customize your computer as well as freeing up space and fixing problems for you -- and it can be installed on up to three computers. If you need to improve the performance of more computers, look no further than TuneUp Utilities Business Edition 2012 [5-PC, 1-Year] which you can buy for just $34.95, saving you 58 percent off the MSRP.
The Downloadcrew Software Store is home to even more system tweaking tools, including IObit Advanced SystemCare PRO 5 [1-PC, 1-Year], which is available at the discounted price of $7.95 - a saving of 60 percent. This app can be used to take care of your registry, improve your computer’s boot time and much, much more. You may also be interested in Auslogics Boostspeed 5 [3-PC, 1-Year]which can be used to boost startup times, remove the junk from your hard drives, improve security and more. You can save a massive 70% when you buy the software for just $35. Other performance improving software worth checking out includes O&O Defrag 15 Professional which is available for just $14.50 (that’s half price!). From the same company there is also O&O DiskImage 6 Professional which can be used to create a comprehensive backup of your computer and is available at 50% of the MSRP for just $14.50.
More Discounts Through December
Returning to the security theme, you can keep your computer free from unwanted infections using Emsisoft Anti-Malware 6 [1-PC, 1-Year]. This powerful antivirus and anti-spyware tool is available for just $9.95, saving you a colossal 75 percent off the MSRP. Emsisoft also produce Emsisoft Online Armor Premium Firewall 5 [1-PC, 1-Year]and you can also save 75 percent off this program when you buy it for just $9.95. If you’re looking for a security suite, you may be interested in Kaspersky Internet Security 2012 [3-PC, 1-Year]which can be used to protect up to three computers and is available for just $29.95, saving you 63 percent off the MSRP. If you just want an antivirus tool, look no further than Kaspersky Anti-Virus 2012 [1-PC, 1-Year] which will keep your computer safe for just $19.95, saving you 60 percent off the MSRP.
Continuing the discounts on security software, you can save a gigantic 74 percent off Bitdefender Internet Security 2012 [1-PC, 1-Year] when you buy the powerful suite for just $12.99. Also available is Bitdefender Antivirus Plus 2012 [1-PC, 1-Year] which can be used to keep your computer free from viruses for the ultra-low price of $6.95 -- this is a huge 72 percent saving when compared to the usual selling price of £24.95.
Rounding off the highlighted discounted are a series of programs from MAGIX, starting with MAGIX Xara Web Designer 7 Premium. You can save 10 percent off the MSRP when you buy the software for $44.99, and you are then ready to set about creating a professional looking web site without the need to type a single line of HTML. Other creative ventures can be tackled in MAGIX Xara Photo & Graphic Designer 7, which is available at a 50 percent discount for just $44.50 and includes everything you need to not only editing your photos, but also create vector images and illustrations from scratch. If you want to get a little musical, you can save $40, or 40 percent off MAGIX Music Maker MX Premiumwhen you purchase this powerful music creation tool for just $59.99. Also from MAGIX is MAGIX Movie Edit Pro MX Plus which is available at the discounted price of $59.99, saving your 10 percent.
Don’t forget that these prices are only valid until the end of December, days away, so grab them while you can. These are just some of the highlights to be found on special offer -- to browse through other bargains, pay a visit to the Downloadcrew Software Store.
Photo Credit: Semisatch/Shutterstock
-

One day giveaway -- Auslogics File Recovery 3
Publié: décembre 27, 2011, 9:49pm CET par Mark Wilson
 New Years is nearly upon us and it's around this time that many of us start to think about trying to shed a few pounds. The arrival of a new year is a good reason to get back into shape after over-indulging, and with today’s giveaway you can also help to get your hard drive back into good shape by recovering files you may have accidentally deleted. We’re giving away a free copy of Auslogics File Recovery 3 worth an amazing $49.95 and this can be used to recover all manner of files -- not only hard drives but also memory cards.
New Years is nearly upon us and it's around this time that many of us start to think about trying to shed a few pounds. The arrival of a new year is a good reason to get back into shape after over-indulging, and with today’s giveaway you can also help to get your hard drive back into good shape by recovering files you may have accidentally deleted. We’re giving away a free copy of Auslogics File Recovery 3 worth an amazing $49.95 and this can be used to recover all manner of files -- not only hard drives but also memory cards.The application is compatible with all 32- and 64-bit version of Windows from XP and upwards, and it can be installed on up to three PCs -- great for households with more than one computer. It does not matter what format you have used for your drive -- FAT32, FAT16, NTFS and other formats are all supported -- you can scour your hard drives for recoverable files in a number of ways. If you would like to check to find out just what could be recovered, you can opt to perform a scan to reveal all files that could possibly be recovered.
But if you are looking for a specific file that you have accidentally deleted, you can speed things up by performing a search with a range of filters in place. When it comes to recovering files you can do so on a file-by-file basis, or you can select entire folders or even all files of a particular type; this is a great option if you are recovering photos from a camera card that has been accidentally formatted. If you can’t remember the name of a file you are looking for, file previews are available for a number of files type to help you to identify what you are looking for.
Recover or Wipe
Enabling you to get back valuable files that you may have thought lost forever makes this an incredibly useful tool. Auslogics File Recovery 3 can also be used to securely delete files that you would rather no one else was able to see. The Disk Wiper tool can be used to wipe and overwrite previously deleted files so they cannot be recovered, while the file shredder component makes it possible to quickly and securely delete files you are sure you do not need and also do not want anyone else to be able to recover.
So whether you have lost some valuable data and need to get it back, or want to ensure that sensitive documents do not fall into the wrong hands, Auslogics File Recovery 3 is a powerful utility that could be just what you have been looking for.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, log in (or create a free account if you don’t have one already), grab your copy of the program and get a free serial code -- but act fast, the offer is for December 28th only, and expires at 23:59 Central European Time.
Photo Credit: Sergey Mironov/Shutterstock
-

Our Christmas gift to you -- IObit Malware Fighter PRO -- 24 hours only, so hurry
Publié: décembre 25, 2011, 1:56am CET par Mark Wilson
 Today we are excited to bring you a free copy of IObit Malware Fighter PRO worth $19.95 to help keep your computer protected against malware in the New Year. But you’ll need to be quick -- this free gift to you is only available for 24 hours, so make sure you head over to the Downloadcrew Giveaway site before 23:59, Central European Time, December 26th.
Today we are excited to bring you a free copy of IObit Malware Fighter PRO worth $19.95 to help keep your computer protected against malware in the New Year. But you’ll need to be quick -- this free gift to you is only available for 24 hours, so make sure you head over to the Downloadcrew Giveaway site before 23:59, Central European Time, December 26th.Malware is a serious problem for anyone that uses the Internet, and as it is not a problem that shows any signs of abating, the best thing you can do is to ensure that you are adequately protected. IObit Malware Fighter PRO is an advanced malware protection tool that weeds out spyware, rootkits, keyloggers, Trojan, spyware and all manner of other nasties that may have found their way onto your system. As well as ben able to hunt down and remove known malware, an advanced heuristics engine means that the program is able to detect new malware by looking out for signs of suspicious activity.
Cloud Protection
To ensure that you are completely protected against all of the latest threats, IObit Malware Fighter PRO uses information gathered from other users of the program and shared through the cloud to ensure that the malware definitions can be updated and disseminated as quickly as possible. While it is important to keep your computer and its data secure, no one would want this to be at the price of performance. Thankfully, IObit Malware Fighter PRO is very light on system resources so you should find that it does not impact on day to day computing.
In reality, IObit Malware Fighter PRO is more of a security suite than a security tool. It includes the regular scanning component, but there are also a number of other important utilities built in. Startup Guard ensures that no malicious processes start with Windows while Browser Guard ensures that no software makes changes to the settings of your web browser. There are also checks in place to ensure that unknown file you open do not cause any damage, that USB drives you connect to yoru computer are not carrying infected files, and that cookies are not shared without your knowledge. This really is a complete security package.
To take advantage of this special giveaway, go to the Downloadcrew Giveaway site, log in (or create a free account if you don’t have one already), grab your copy of the program and get a free serial code – but act fast, the offer is for December 26th only, and expires at 23:59 Central European Time.
Merry Christmas! And look out for more giveaway offers next week!
-

Celebrate Christmas with one of these 29 downloads
Publié: décembre 24, 2011, 9:30pm CET par Mark Wilson
 Almost everyone has been busy over the past week making some form of preparation for Christmas and the holiday season. But despite the general pace of the world winding down slightly, the pace of software development continues with its usual speed. Mozilla has been particularly busy this week, releasing numerous updates to its Firefox web browser. The main release branch for the browser has hit version 9. Firefox 9.0.1 FINAL includes numerous tweaks to performance as well as changes to the way add-ons are handled. Startup times have been improved as has the general performance and stability of the browser.
Almost everyone has been busy over the past week making some form of preparation for Christmas and the holiday season. But despite the general pace of the world winding down slightly, the pace of software development continues with its usual speed. Mozilla has been particularly busy this week, releasing numerous updates to its Firefox web browser. The main release branch for the browser has hit version 9. Firefox 9.0.1 FINAL includes numerous tweaks to performance as well as changes to the way add-ons are handled. Startup times have been improved as has the general performance and stability of the browser.If you like to try out something before most people, Firefox 10.0 Beta has also been updated as has the somewhat more experimental and alpha-like Firefox Aurora 11.0a2. For anyone who wants to be right on the cutting edge of browser development, the nightly builds of Firefox have also entered a new phase. Firefox Nightly 12.0a1 (32-bit) includes a range of interface enhancements and Firefox Nightly 12.0a1 (64-bit) brings the same experimental version of the browser to users of 64-bit systems. Even more interface changes can be found in Firefox UX 12.01 UX (32-bit). The UX branch of Firefox includes a more streamlined toolbar and a new tab page amongst other new features. 64-bit users should take a look at Firefox UX 12.01 UX (64-bit).
Continuing the Firefox theme, Waterfox 9.0 is a version of the browser designed specifically for 64-bit versions of Windows. It is based on the current stable version of Firefox so if you have become used to how this browser works but want to take advantage of 64-bit goodness, this is well worth checking out. It doesn’t end there for Mozilla. There are no more versions of Firefox for you to play with, but Mozilla Thunderbird 9.0 FINAL has been released. This is an email client and RSS reader that is evolving well over time, and if you take a liking to it, you should also check out the Mozilla Lightning 1.1 FINAL add-on that adds a calendar component to the program.
While your web browser may be one of the most used applications, when it comes to hardware your hard drive is your most important component. If you have taken the step of upgrading your drive to solid-state, Intel SSD Toolbox 3.0.2 can be used to optimize its performance. Seagate SeaTools for Windows 1.2.0.6 can be used with any type of hard drive -- and not just those produced by Seagate -- to check for problems and repair damaged sectors. If you’ve ever wished that it was possible to use your iPhone or iPod more like a removable hard drive, iExplorer 2.2.1.3 could be just what you’ve been looking for as it makes it possible to copy files to and from your device with ease.
Sticking with iOS devices, iPadian 0.2 is an interesting free tool that makes it possible to run iPad apps -- albeit a very limited selection -- on your desktop computer using an Adobe AIR app. PhotoScape 3.6 is a program for anyone looking to enhance their digital photos and is an editor that does not require a degree to use it. Despite its ease of use, this is a powerful app, but if you are a little more demanding, you may want to take a look at CyberLink PhotoDirector 3 Beta which includes not only the advantage of photo editing options but also media management tools and much more.
System Maintenance
System maintenance tools have always been popular and one particularly popular tool is CCleaner 3.14, which has improved support for cleaning up after Internet Explorer. Should you prefer to keep all of your maintenance apps available on a USB drive, there is also a portable version available in the form of CCleaner Portable. Two interesting new tools were unveiled this week. JetBoost 1.0 makes it possible to boost the performance of your computer by terminating unnecessary processes, while JetClean can be used to free up disk space, optimize memory usage and optimize your registry.
Fans of special offers should definitely check out IObit Advanced SystemCare PRO 4 is an amazingly powerful system maintenance tool that you can grab completely free of charge. Originally sold for $19.95, you can grab your copy of the app free of charge from Downloadcrew.
In addition to system maintenance, system security and protection are also incredibly importance. Toolwiz TimeFreeze 1.2.0.55 is a free tool that extends the idea of Windows’ system restore facility, making it possible to freeze the state of your computer and restore it should unwanted changes be made. If you like to be involved in the process of protecting your files, look no further than Paragon Backup & Recovery 2012 Free. This immensely powerful backup tool can be used to backup data to removable media, as well as local hard drives, and you can schedule your backups so you don’t need to remember to manually create them.
System security often includes using passwords, and Password Security Scanner 1.0 can be used to check the strength of the various passwords you have stored on your computer. This is a great way to hone in on potential security holes in your system, enabling you to make the necessary changes quickly and easily. Comodo Internet Security 5.9 is a free security suite that includes antivirus and firewall protection. If you don’t want to install a complete security suite, you can install the components individually -- Comodo Antivirus 5.9 and Comodo Firewall 5.9.
Rounding off the security tools for this week are BufferZone Pro 4.0, which enables you to run your Internet tools in a sandboxed environment to avoid the risk of sharing private information or falling victim to viruses and malware. VirtualBox 4.1.8 is a system virtualization tool that can be used for the same security purposes, but it can also be used as a test bed for running alternative operating systems or running software without affecting your main OS.
Remember to keep one eye on our Downloadcrew Giveaway website over Christmas. Extra special discounts and, on Christmas Day, IObit Malware Fighter 1.2 PRO, worth $19.95, free for one day only! More free full apps available next week, too.
This is the penultimate software roundup of 2011, so all that remains is for us to wish you a Merry Christmas!
Photo Credit: Vladimir Melnikov/Shutterstock
-

Microsoft SkyDrive for iOS mini-review
Publié: décembre 22, 2011, 7:26pm CET par Mark Wilson

Despite having its own mobile platform to support, Microsoft is still understandably keen to keep its fingers in other pies, particularly those tasty iOS desserts. As such it should come as no surprise that there is an app that can be used to access the files you have chosen to store in the cloud in your SkyDrive from your iPhone, iPod or iPad. There is now no shortage of online storage services to choose from, but from the offset this is one that will prove popular with anyone looking to not only store files online, but to benefit from integration with other Microsoft services such as Hotmail.
SkyDrive itself is not all that new a service, but the iOS app is. This means that it is now possible to interact with your SkyDrive account in two ways. Not only can you access the files that you have already uploaded, you can also upload files whilst you are out and about. Ultimately this makes it possible to take photos with your iPhone camera and rather than having to email to yourself or sync with your computer, you can upload the images so that they can be accessed from any computer. This is also a great way to share images with others, but this can also be achieved by attaching them to an email from within the app.
While the SkyDrive app is certainly useful, it is not without its problems. If you want to upload more than one image or file, you are likely to become frustrated by the fact that each one will need to be uploaded individually. The inability to transfer multiple files simultaneously is a strange oversight, but hopefully something that will be addressed in future versions. There are also limitations on the types of file that can be previewed within the app and it would have been nice to be able to edit your files online. Again, this is something to add to the wish list for future releases.
Where SkyDrive falls down when compared to the likes of DropBox is in the lack of OS integration. The app really is standalone that is handy for viewing your files, and provides you with the option of sharing them, but if you want to actually do anything with your files, you’re out of luck. There is no option to open files in a different app, so while you can view the images you have uploaded to your SkyDrive, you are not able to load them into the iOS version of Photoshop for a little editing, and if you have an office suite installed, these can also not be used.
This lack of support for third party apps works both ways. There is no way to create a document in an app you have installed and then upload it to SkyDrive. The only options you have are to upload photos and videos that you already have stored on your device. These are limitations that need to be remembered before investing too much time in the app -- if you intend to work primarily with photos and video, it may be just what you have been looking for.
When working with photos, the images you have uploaded are previewed in a well-presented form. The ability to create folders from within the app makes it easy to organize pictures and other files. Unfortunately, it is not possible to create files directly in your SkyDrive. The fact that the service comes complete with 25GB of free storage is obviously a major draw, and the ability to access files on the move is definitely useful.
It is shame to see that the app is, while handy, is not something that could be described as essential. There are too many little niggles that get in the way of this being a great app. With a few tweaks here and there, there is plenty of potential for this to develop into something special, but at the moment, it is not really all that impressive.
You can grab yourself a free copy of the app by paying a visit to the SkyDrive page.
-

Save a bundle on PC security software
Publié: décembre 22, 2011, 3:01pm CET par Mark Wilson
 The New Year is almost upon us and for many people this means it’s time to think about making New Year’s resolutions. Whether you subscribe to the idea of setting yourself such goals or not, the arrival of a new year is as good a time as any to consider the security of your computer. And with Christmas only just around the corner, you could head on over to the BetaNews Downloadcrew Software Store to buy a present for yourself and your computer -- you’ll find all manner of essential security tools available at heavily discounted prices.
The New Year is almost upon us and for many people this means it’s time to think about making New Year’s resolutions. Whether you subscribe to the idea of setting yourself such goals or not, the arrival of a new year is as good a time as any to consider the security of your computer. And with Christmas only just around the corner, you could head on over to the BetaNews Downloadcrew Software Store to buy a present for yourself and your computer -- you’ll find all manner of essential security tools available at heavily discounted prices.If there is one piece of security software that everyone should have installed it is an antivirus tool. It is possible that you already have the free version of AVG’s virus protection tool installed, but for a mere $6.95 you could upgrade to the full commercial edition of AVG Anti-Virus 2012 -- a huge saving of 83 percent off the MSRP. Offering protection not only against viruses and malware, the program can also check links for malicious downloads, scan incoming emails and protect against identity theft. In addition to this, you can benefit from instant messaging protection, priority support and more frequent program updates.
You can take your security to the next level, take a look at AVG Internet Security 2012 [1-PC]. For just $19.95, a savings of 64 percent, you can take advantage of all of the virus protection features of AVG Anti-Virus, but also parental controls, online backup and Internet optimization. Unlike many other security titles, this is one that will not have a negative impact on system performance, thanks to a raft of software optimization that has been carried out to make the program as streamlined as possible. As increasing numbers of households have more than one computer, multi-license purchases make more sense and could mean saving even more money. There is also a four user license version of this program available; why not move up to the 4-PC 1-Yr for only $24.99 -- AVG Internet Security 2012 [4-PC, 1-YR]?
AVG Premium Security 2012 is the next step up the security ladder, and in addition to all of the tools found in AVG Internet Security there are also system performance enhancing options. In a couple of clicks you can clean up the registry, remove junk files and optimize your hard drive. There’s also the Identity Alert component which ensures that your credit card details and other private data aren’t being shared over the Internet. You can grab a copy of the app for 50 percent off the MSRP at just $34.99.
Everyone wants their children to reap the benefits of being able to access the Internet, but it is also important to keep them safe online. This is precisely how AVG Family Safety 2012 can help and you can buy a copy of this software for 60 percent off the MSRP at just $7.95. The program can be installed on up to three computers at no additional charge, and it includes tools that enable you to monitor and control how your children use the Internet. This includes blocking access to websites you deem unsuitable, preventing the use of certain programs and even monitor IM and email communication.
The security of your computer and children is very important, but you may be interested in securing your files. Using AVG LiveKive 2012 [UNLIMITED], you can store your files online with unlimited storage space, and even store multiple versions of the same files. Available for the massively discounted price of $19.95 – a 75 percent savings -- this is definitely one not to miss.
Essential Security Software
AVG is just one of the big names you can save money on. Bitdefender Internet Security 2012 [1-PC, 1-Year] is available at a 74 percent discount for just $12.99. The suite offers virus protection, spam filtering, malware blocking, file encryption and parental controls, all wrapped up in one neat interface. If you are only interested in virus protection, Bitdefender Antivirus Plus 2012 [1-PC, 1-YR] can keep for computer safe for just $6.95 -- saving 72 percent off the MSRP.
Emsisoft Anti-Malware 6 will add an extra layer of protection to your existing security software for the bargain price of $9.95 – saving your 75 percent off the MSRP. The application includes virus and malware protection and will even warn you about the presence of suspicious software and files rather than just those that are definitely malicious. From the same company comes Emsisoft Online Armor Premium Firewall 5 which adds an important layer of protection to your Internet connection. Buy the program for just $9.95, a saving of 75 percent off the MSRP, and you can take control of the traffic to and from your computer. The rule based system makes it easy to control which if your installed programs are permitted to access the Internet.
Keeping your computer secure is very important, but everyone wants to get the best possible performance from their hardware. IObit’s Advanced SystemCare PRO 5 enables you to achieve all of this in one handy package. For just $7.95 --saving you 60 percent -- you can protect your computer against viruses and malware and use an arsenal of tools to keep your system in good shape. There’s a registry cleanup and defragmenter, a file shredder, memory optimization and much, much more.
Other security tools worth casting your eyes over when considering your purchases are Kaspersky Internet Security 2012 [1-PC, 1-YR] and Kaspersky Anti-Virus 2012 [1-PC, 1-YR]. The former is available at a 67 percent discount for just $19.95 and provides real-time protection against viruses and malware as well as IM protection, a phishing filter, parental controls and a virtual keyboard to help avoid keyloggers. Kaspersky Anti-Virus 2012 [1-PC, 1-YR] offers real-time and on-demand virus protection as well as email scanning and rootkit protection.
So no matter what type of protection you are looking for, the Downloadcrew Software Store has something for you. There are also plenty of other non-security related bargains to grab.
Note that many of these deals will end December 31 2011, so hurry!
Finally, keep one eye on the new Downloadcrew Giveaway. This brand new website will bring you the occasional full software giveaway, sandwiched between super-cheap further discounted products.
Photo Credit: Ye/Shutterstock
-

Facebook for iOS 4.1 mini-review
Publié: décembre 20, 2011, 3:13pm CET par Mark Wilson
 Facebook for iOS has been something of a staple installation for iPad and iPhone owners. The app has undergone various developments over the years, including finally getting a dedicated iPad app. As the Facebook website has evolved, so the app has changed to reflect new features and now, as the app hits version 4.1, it seems to have come of age. The most recent addition to the Facebook website is the new timeline component and this is just one of the latest features of Facebook for iOS 4.1.
Facebook for iOS has been something of a staple installation for iPad and iPhone owners. The app has undergone various developments over the years, including finally getting a dedicated iPad app. As the Facebook website has evolved, so the app has changed to reflect new features and now, as the app hits version 4.1, it seems to have come of age. The most recent addition to the Facebook website is the new timeline component and this is just one of the latest features of Facebook for iOS 4.1.Strangely, at time of writing, the timeline feature is not yet supported on iPad, but it is something that iPod and iPhone users can already take advantage of. If you have already activated your own timeline, you will need to use version 4.1 of the app in order to see it and the timelines of other people who have activated it -- you can go here to get your timeline in place before the fullscale rollout.
For some time, the Facebook app has been significantly more usable than the mobile version of the social networking website, and this has done nothing but improve over the years. Development has been such that using the iOS app no longer feels like you are missing out on any of Facebook’s features, and in many respects it is actually more enjoyable to use than the standard web site.
Speed of operation is important for any mobile app and this is something that has been gradually improved. Not only in terms of raw performance, but the way in which the interface is laid out means that is now faster than ever to navigate the site and perform common tasks such as commenting on other people’s content, uploading images and checking in to locations.
The slide out left hand navigation pane is one of the greatest changes that has been made to the app. From here it's possible to access every aspect of your Facebook profile, from your timeline and messages, friends list and groups, and much more. Perhaps most importantly, it is possible to add links to favorite sections of Facebook so you can jump to them quickly and easily -- as well as saving space by cutting out those that you do not use very often.
The ability to make use of lists is a great way to manage a large friends list, and support for apps means that working with a Facebook app need not mean missing out on the things you make use of on the main website. The search feature makes it easy to track down individual friends and the way the navigation bar works means that it is possible to break away from reading status updates and other news to upload an image or do something else with your account without losing where you got to.
This is one app that has long been described as essential and frequently tops the charts for popularity. In the past this has been as much because the app was pretty much the only specially designed way to access Facebook from your mobile, but now it is this coupled with the fact that it is also a well-developed app that finally provides an enjoyable experience.
You can grab yourself a free copy of the app by paying a visit to the Facebook for iOS page.
-

Get into the holiday spirit with one of these 15 festive downloads
Publié: décembre 16, 2011, 7:34pm CET par Mark Wilson

Christmas is very nearly upon us, and over the past couple of weeks we have been collecting together some of the best festive offerings available. Whether you’re looking for some seasonal games to keep the kids (or yourself) entertained, a festive app for your iPhone, or something to give your desktop a more Christmassy look, there’s something here for you. In this round up we take a look at some of the software you may have missed.
For fans of simple strategy games Christmas Troubles -- Tower Defense Game 1.0 is a great way to get into the festive spirit. With fun graphics and instant appeal, this is a game that’s suitable for all ages. If you’re more of a puzzler, Christmas Puzzle 1.0 is a festive take on the classic game Bejewelled, while Christmas Crisis 1.3.9 is a vertical scroller in which the aim is help Santa deliver his presents all over the world.
Despite the very similar name, Christmas Eve Crisis is a platform game that’s also a race against the clock, but a different game nonetheless. From the same stables comes Chicken Invaders 4.1: Ultimate Omelette Christmas Edition, which features wonderfully quirky graphics in a game that finds in a Chicken and Christmas inspired take on the classic Space Invaders; yes, it’s silly, but it’s a huge amount of fun.
Christmas is all about fun, but this doesn’t mean you have to limit yourself to festive games. Desktop Christmas Tree Collection is a great way to brighten up your desktop with a series of animation Christmas trees and snow globes -- you can choose to add just one, or go over the top with a Christmas tree forest.
Another great way to customize your computer is Christmas Living 3D Fireplace Screensaver which features a stunning crackling log fire, while Christmas Icon Packs provide you with the opportunity to customize your desktop with a series of Christmas icons.
If a screensaver isn’t quite your thing, DesktopSnowOK 1.61 may be what you have been looking for. This cool utility transforms your desktop into a snow scene featuring customizable snow flakes that flutter from the top of your monitor.
To quickly transforms the look of your entire desktop, look no further that the official Microsoft Holiday Lights Theme Pack, which feature a new color scheme, desktop backgrounds and more. Anyone who fancies getting creative need not feel left out as the selection of Christmas fonts can be used to create everything from Christmas cards to name tag or posters.
You may be looking forward to getting an iPhone or iPad for Christmas, but if you already have one, there are a number of apps you might want to check out in the run up to the big day. PopOut! The Night Before Christmas 1.3 is a delightful animated book of the classic Christmas poem that will be loved by kids and anyone feeling nostalgic.
A Charlie Brown Christmas 2.0 will be loved by fans of Chuck and the gang as the famous Peanuts tale receives and receives an iOS makeover with stunning graphics, sumptuous audio and a wealth of interactive elements that will keep you entertained for hours. iOS gamers have not been forgotten.
Piggly Christmas Edition 1.0.0 is a fun platformer in which you must help Mrs Piggly collect a variety of treats to feed her family. There is also an iPad version available in the form of Piggly Christmas Edition HD 1.0.0.
If you weren’t already excited about Christmas, there’s plenty here to get you in the mood. Have a browse through the downloads and you’re sure to find something you like.
-

BBC iPlayer now truly available for iPhone
Publié: décembre 14, 2011, 12:52am CET par Mark Wilson
While the BBC’s iPlayer has been available to iPhone users for some time, until now it has only been through a web browser. The latest update to the iOS iPlayer app means that there is now an app that can be used to watch the programs you have missed from the BBC’s channels -- this brings the same option that has been available to iPad users who have been able to take advantage of a dedicate app for a number of months.
While most people will be happy to be able to watch programs at home using a wireless Internet connection, the new iPhone app also allows for broadcasts to be streamed over a 3G connection. Adaptive bitrates are used to ensure the best possible quality for your connection speed but the option of using a 3G connection opens up the possibility to incur hefty data charges nonetheless.
One of the key draws of iPlayer is that it enables you to browse through programming from the past seven days and watch anything that takes your fancy, but it is also possible to watch live broadcasts as well as listening to live radio. If there is a particular show you want to ensure you don’t miss out on, the app can be used to add it to a list of favorites for easy access.
Providing your iOS device - be it an iPod, iPhone or iPad -- has been updated to iOS 5, there is also support for AirPlay which means that it is now possible to stream content to your TV. But it is the 3G streaming that is the real headline grabber, as well as the fact that the app is now iPhone compatible. Similar features are promised for the Android version of the app in the near future.
You can find out more and download a free copy of the app by paying a visit to the BBC iPlayer review page.
-

Don't miss even one of this week's 20 exciting downloads
Publié: décembre 10, 2011, 5:31pm CET par Mark Wilson
 It may only be the second week of December, but the Christmas feeling has already taken over. Software publishers are still releasing software throughout the festive season and we’ve collected together twenty of the biggest titles from the past seven days that you may have missed.
It may only be the second week of December, but the Christmas feeling has already taken over. Software publishers are still releasing software throughout the festive season and we’ve collected together twenty of the biggest titles from the past seven days that you may have missed.Whether you get a new camcorder for Christmas, or you’re using an existing camera to capture the seasonal excitement on film, CyberLink PowerDirector 10 Ultra (build 1129a) includes everything you need to edit, burn and share your footage. If your needs aren’t quite as high, you could opt for the slightly cheaper, but still powerful, CyberLink PowerDirector 10 Deluxe (build 1129a).
While there is a general trend for programs to become bigger and bigger with each release, the portable software movement aims to achieve the reverse. As well as providing powerful tools that require very little space, these tools can also run from a USB drive without the need for installation. PortableApps.com Platform 10.0.1 FINAL is a major update to the portable software suite that enables you to create your own custom USB utility drive. If you’re looking to take care of your computer, Toolwiz Care 1.0.0.118 is a free optimization tool that can be used to clean up your hard drive, manage your registry and much more.
In the same vein, Sysinternals Suite 2011.12.05 is a comprehensive suite of system utilities that can be used to control startup programs, manage running processes, check for rootkits and other malware -- there are more than sixty tools in total. Feel the urge to fee up a bit of hard drive space? IObit Uninstaller 2.1 can help you out in the this department, helping you to remove programs that would otherwise remain undeletable. While you’re keeping your system in good shape, you could turn to DriverMax 6 to make sure that you have all of the latest drivers installed for your hardware, and Norton Power Eraser 2.5 Beta returns us to the portable theme, offering you the opportunity to check your system for malware.
On the subject of security, creating a secure password for your Windows account and the various web sites you use is essential. If you are struggling to come up with something suitably secure, look no further than Awesome Password Generator 1.0.0.824 which can be used to generate hundreds of passwords in one fell swoop. Once you have created your passwords you can rest assured that your online life is safe and you can venture onto the web without worries.
When you encounter a PDF file that you would like to read, make sure that you have Foxit Reader 5.1.3 installed to enable you to do so without the need to use a slow and bloated app. You can also use the updated Evernote 4.5.2 to store notes online ad share them with others, but if all of this sounds too much like hard work, you can relax with a game of Sea Battle 3.0.
Increasing numbers of people are realizing that using the Internet need not mean using Interner Explorer or even Firefox, and Opera 11.60 FINAL with its refined look and excellent performance shows just why alternative browsers are proving so popular.
But using the Internet is about much more than just visiting web sites and sending emails. If you want to download large files, it is often more efficient and faster to use BitTorrent to do so. You could use the official client, BitTorrent 7.6 or you could use the lightweight alternative uTorrent 3.1 which now includes a built in media player in addition to a number of performance improvements.
For many people, the Internet is all about social networking and the all-new TweetDeck 1.0 FINAL sees the tweeting tool not only exiting beta but also leaving behind its days as an Adobe AIR app.
 Fancy getting a little creative with your computer, take a look at Skin Pack Installer System 3.0 (32-bit). This will enable you to not only create your own themes and skin packs for Windows, but also to wrap them up in an installer so you can easily share them with others. If you are using a 64-bit version of Windows, you’ll need to install Skin Pack Installer System 3.0 (64-bit) instead.
Fancy getting a little creative with your computer, take a look at Skin Pack Installer System 3.0 (32-bit). This will enable you to not only create your own themes and skin packs for Windows, but also to wrap them up in an installer so you can easily share them with others. If you are using a 64-bit version of Windows, you’ll need to install Skin Pack Installer System 3.0 (64-bit) instead.Chances are you will take lots of photos over the coming weeks. Rather than leave them sitting on your hard drive, why not use the updated Jalbum 10.2 to create an impressive digital photo gallery. If you’d like to share your Christmas photos online -- a great option if you have friends and family overseas – Google Picasa 3.9 could be what you’re looking for. Despite the small version number increase, this is a fairly major update to Google’s photo sharing tool which adds the ability to share through Google+ as well as providing you with more photo editing options.
That’s it for this week. Join us again in seven days for another roundup and look out for a special Christmas-specific roundup next week.
-

Tune up your PC this holiday with these smart savings
Publié: décembre 10, 2011, 4:44pm CET par Mark Wilson
 Taking care of your computer means that it will serve you well and hopefully delay the need to upgrade your hardware for as long as possible. The festive season is now upon us, which means over-indulging in the food and drink departments and generally failing to look after ourselves. But this does not mean that our computers also need to be neglected.
Taking care of your computer means that it will serve you well and hopefully delay the need to upgrade your hardware for as long as possible. The festive season is now upon us, which means over-indulging in the food and drink departments and generally failing to look after ourselves. But this does not mean that our computers also need to be neglected.If you’re feeling the pinch after splashing out on Christmas presents for friends and family, our great sale prices on optimization and maintenance software means that you will still be able to keep your system in top shape. There are a number of tools to choose from, all of which are very gentle on the pocket.
TuneUp Utilities 2012 is available at the hugely discounted price of $18.95 -- that’s 62 percent off usual price of $49.95. This versatile tool can be used to not only optimize your computer by cleaning up the registry and removing unwanted software, but also to free up disk space, fix problems you may be experiencing and tweak system settings to give Windows a more personal feel. If the price sounds like a great deal, it’s about to get even better: the software can be installed on up to three PCs so you can take care of all of the computers in your household.
If you run a small business, and have more computers that need attention, TuneUp Utilities 2012 Business Edition [5-PC] may be more what you have been looking for. The software can be installed on up to five computers and you can save 58 percent off the usual selling price of $83.95 by grabbing yourself the software for just $34.95.
AVG may be a name that is more readily associated with antivirus software, but AVG PC Tuneup 2012 is a power program for tweaking your computer. It replaces the PC Analyzer module that ships with AVG Internet Security 2012 or AVG Anti-Virus with more comprehensive options for boosting the registry and taking care of your system in other ways. A single license version of the program can be purchased for just $14.99 (a saving of 57 percent off usual price of $34.99), but there is also a 2-PC license version available for just $21.49 -- a saving of 52 percent off usual price of $44.99.
IObit Advanced SystemCare PRO 5 is a tool that can be used to not only optimize, but also protect your computer. In addition to a range of tools that can be used to boost performance and improve stability, the program can also be used to check for and remove malware. You can save a massive 60 percent off usual price of $19.95, so for $7.95 this is great value for money.
Auslogics Bootspeed 5 is also super cheap through December, with 70 percent off the usual $49.95, bringing the price down to just $14.95. This is for a 3-PC license so you can boost the performance of all your machines for less than $5 each. The program includes tools to help you to optimize your hard drive, take control of browser addons, manage startup programs and much more.
Another great bargain to snap up this month is Uniblue PowerSuite 2012. Usually available for $119, you can grab this great set of maintenance tools for a mid-blowing $19.95 -- saving a gigantic 83 percent. The suite is made up of three individual tools, DriverScanner, RegistryBooster and SpeedUpMyPC. These individual components ensure that your drivers are up to date, your registry is fully optimized and enabling you to tweak a huge number of system settings to boost performance. Everything you could possibly need can be found here from tools to control third-party apps’ use of processor time to internet connection optimization.
And as this is the season of giving, you can expect some presents to come your way courtesy of Betanews’s Downloadcrew, in addition to great savings. Later this month, we’ll be giving you some full free commercial software as part of a brand new website. More details to follow soon!
-

Cure rogue touchpad contact
Publié: décembre 5, 2011, 9:25pm CET par Mark Wilson
 There has been a general theme of downsizing when it comes to laptops. While this has helped to make computers more easily portable than ever before, it has also exacerbated a problem long plaguing laptop users: Rogue touchpad contact. Not everyone is an adept touch typist and for many people this means looking at the keyboard whilst typing. Should the palm of your hand stray on the touchpad, you may not notice until a large portion of text has been overwritten or typed in the wrong place. This is something that Touchpad Blocker can help you with.
There has been a general theme of downsizing when it comes to laptops. While this has helped to make computers more easily portable than ever before, it has also exacerbated a problem long plaguing laptop users: Rogue touchpad contact. Not everyone is an adept touch typist and for many people this means looking at the keyboard whilst typing. Should the palm of your hand stray on the touchpad, you may not notice until a large portion of text has been overwritten or typed in the wrong place. This is something that Touchpad Blocker can help you with.A laptop should is supposed to mean freedom -- to work wherever you choose. You could pop a mouse into your laptop bag so avoid the problem of working with a touchpad, but this is just something else to remember, something else to carry around, and something else to lose. Touchpad Blocker is a free app that enables you to intercept and block accidental touchpad touches to prevent them from interfering with your typing.
This makes Touchpad Blocker different to other applications that have been designed to help with the same problem. Other programs have a tendency to allow the touchpad to be completely disabled but Touchpad Blocker does a good job of only blocking it when needed. This works by disabling the touchpad whenever the keyboard is being used and for a short period of time afterwards.
You also have the option of configuring keyboard shortcuts that can be used to disable the accidental tap detection, but a shortcut can also be used to enable or disable the touchpad altogether for times when this is more appropriate. The features of the program may sound simple, but if you have ever been frustrated by the positioning of your touchpad, this is a seriously useful tool.
You can find out more and download a free copy of the tool by paying a visit to the Touchpad Blocker review page.
Photo Credit: nito/Shutterstock
-

Don't miss one of this week's 18 exciting downloads
Publié: décembre 4, 2011, 2:00am CET par Mark Wilson
 In the run up to Christmas the release of top-notch software shows no signs of abating. Microsoft unveiled the latest version of its free system security tool, Microsoft Security Essentials 4 Beta with a slightly redesigned interface and faster operation. This handy tool can prevent malware infections, but a side-effect of being hit by a virus could be the deletion of files. Whether this has happens to you or you have just accidentally deleted some documents, Recuva 1.42 could help you to get them back. There is also a portable version of the app available; Recuva Portable 1.42.
In the run up to Christmas the release of top-notch software shows no signs of abating. Microsoft unveiled the latest version of its free system security tool, Microsoft Security Essentials 4 Beta with a slightly redesigned interface and faster operation. This handy tool can prevent malware infections, but a side-effect of being hit by a virus could be the deletion of files. Whether this has happens to you or you have just accidentally deleted some documents, Recuva 1.42 could help you to get them back. There is also a portable version of the app available; Recuva Portable 1.42.Prey 0.5.3 continues the security theme, offering protection for your laptop. Should you be unfortunate enough to lose your portable computer this tracking software can locate your machine via the Internet. Once you recover your laptop, you may want to install Touchpad Blocker 2.1.0.27, which enables you to temporarily disable the touchpad when you are typing to prevent accidental mouse movement.
While Ihe internet can be used to retrieve a lost or stolen laptop, it can also be used for more entertaining purposes. Antenna 1.5 is an Adobe AIR app that can be used to listen to and record online radio station while Spotify 0.6.5 has been updated to make it even easier to stream the music of your choice to a wide range of devices. Spotify 0.8.0 Beta has also been released with support for third-party apps.
If you have fancied spinning some discs as a DJ, MAGIX Digital DJ 2 could be right up your street. The app can be used to work with your MP3 collection, mixing tracks and creating the perfect party soundtrack. Beginners can take advantage of the auto-mix feature, but more seasoned music makers can plug in their professional equipment for even greater control.
Working with music files can be fun, but videos can be a frustrating experience, particularly when it comes to battling with codecs or playing files back on different devices. Freemake Video Converter 3.0.0 is a free tool that can be used to quickly and easily convert videos between formats and optimize them for playback on a number of popular devices including iPod and PSPs.
MyPaint 1.0 is a free digital painting app that can be used to tap into your creative side. With a powerful selection of tools and a range if different brushes to choose from, you can create a masterpiece with ease. If words are more up your street, but you find that you are too easily distracted by the features, Writemonkey 2.3 is a word processor that cuts down on the clutter to leave you free to focus on your writing. RootsMagic Essentials 5.0.0.2 is a program for budding genealogists, with the free version giving you a gentle introduction to the world of family trees.
No week would be complete without a little tweaking, and Ultimate Windows Customizer v1.0.1 is a combined tweaking and customization tool for Windows 7 and Vista. A familiar name to anyone who has used Windows for any length of time will be CCleaner 3.13, with the latest version adding an add-on manager for Internet Explorer and numerous enhancements. Fans of portable software can investigate the same tools in CCleaner Portable 3.13. The penultimate tool in this week’s roundup is Cyberduck 4.2, a FTP client that can be used to upload and download files, manage a website and more.
There’ll be another software roundup the same time next week. To make sure you don’t forget, take a look at Free Alarm Clock 2.5 so you can set yourself a reminder.
-

Antenna turns your PC into an Internet radio
Publié: décembre 2, 2011, 8:02pm CET par Mark Wilson

When it comes to listening to the radio, the Internet means that you are no longer limited to listening to what you are able to pick up through your set’s antenna. There are a huge number of radio stations broadcasting online and while this means that there is no shortage of choice, it does mean that it can be difficult to find something you like unless you know about it in advanced. Antenna is a free Adobe AIR app that takes a new approach to internet radio.
Tracking down a new station to listen to is a wonderful interactive process that can be approached in a few ways. If you already know the name of station, you can simply perform a search for it, but if you would like to find something new, you can browse through the interactive map where pushpins are used to represent radio stations.
Alternatively, you can use the icon-driven interface to filter radio station based on the country they are broadcasting from or the language they use. Of course, there is the usual option of browsing through stations that fall into the genre of your preference, and an online chat facility is available to enable you to chat with other listeners and exchange details about your favorite stations.
If a station you like is not available through the app, you can adds its URL so you can use Antenna to listen to it in future, and the option to rate and bookmark stations provides you with additional filtering options and easy access to stations you like. Antenna also enables you to record streaming radio, although we did find that this was occasionally a bit hit and miss. Minor niggles aside, this is a great looking app that’s well worth checking out.
You can find out more and download a copy of the app by paying a visit to the Antenna review page.
-

Protect your kids online with AVG Family Safety
Publié: décembre 1, 2011, 5:19pm CET par Mark Wilson
 Anyone with children will know that it can be difficult to police use of the Internet. The fact that you have young children means that you are naturally concerned about web content, and many parents would love to be able to use the Internet with their offspring to ensure that they don’t stray into unwanted territory.
Anyone with children will know that it can be difficult to police use of the Internet. The fact that you have young children means that you are naturally concerned about web content, and many parents would love to be able to use the Internet with their offspring to ensure that they don’t stray into unwanted territory.But in reality, this is often impractical as there are few people who have the time spare to be able to monitor their children, however much they may want to do so. AVG Family Safety is a software alternative to a parent’s watchful eye, making it possible to not only monitor but also control what your children use the Internet for.
The app comes from the company more readily associated with antivirus software, but it has ventured into numerous other areas of life online, too. Tackling the issue of Internet access control is a tricky battle, but AVG Family Safety has a number of tools that can be used in combination to meet the needs of you and your family. You can control access to websites based on URL or content type, and place restrictions on when the Internet can be used. If there is an attempt to access blocked content, alerts can be sent out in the form of emails or SMS (in the United States).
Obviously there are problems associated with blocking websites. The first major issue: In order for a website to be blocked based on subject matter or content they must be checked and categorized - the sheer number of websites that exist mean that this is somewhat impractical. The program offers the chance to block or permit access to sites in a large number of categories, and settings can be manually configured or you can use the pre-defined age settings to speed things up. Similar age restrictions can be used to control access to online media. Industry standard age rating systems are supported so you can choose the type of music your children can listen to and the type of streaming video they can watch; it is also possible to block access to online games, but again this is dependent on ratings having been assigned to them.
AVG Family Safety can also be used to filter web searches, so you can choose to block certain keywords in a number of popular search engines including Google, Yahoo and Bing. If there are websites you are aware of that you would prefer your kids did not access, you can add them to a blacklist that will be blocked without question. Conversely, it is also possible to set up a whitelist, and anyone looking to be particularly restrictive with the Internet may want to use this option. This is a great way to introduce younger children to the Internet as it enables you to specify a list of sites that are permitted to be accessed. Providing other settings are correctly configured, it is possible to only allow access to sites that appear in this list, and this means that children can be left to use the Internet unattended safe in the knowledge that they will not be able to venture to other sites.
Having a computer connected to the Internet means more than having to think about what is going on in a web browser; there are also chat clients and social networking clients to consider. AVG Family Safety includes the option to prevent programs of your choice from running, and this including proxy tools that could be used to bypass any restrictions you may have put in pace. It is also worth taking a look at the iOS version of the app, AVG Family Safety 10.1.7, which enables you to place restrictions on how the Internet is used on your iPhone or iPad.
Multiple Profiles
Many households have more than one child, and with this in mind AVG Family Safety includes the option to create multiple profiles each of which can have settings of their own. This is great for home in which there are children of different ages for whom different levels of restriction and control are needed. Another interesting option is the ability to restrict the times at which the Internet can be used. To avoid the risk of your children changing the Windows clock to bypass this, the time restrictions are implemented using an online time server.
In terms of configuration, AVG Family Safety is hard to criticize. All of the settings you could possibly need are easily accessed, but you may find that getting things fine-tuned to your liking may take some time. As well as putting restrictions in place, the software can also be used to monitor how the Internet is being used. AVG Family Safety can log not only the websites that are visited, but also the searches that are performed, so even if you decide to give your children unfettered access to the Internet you can still keep an eye on what they’re up to online. You can also log instant messaging conversations and check logs that will reveal which programs have been used and for how long.
A very nice touch is the ability to view all of the program logs and even change application settings online. This means that you are able to monitor and control Internet usage even when you are not at home. AVG Family Safety is easy to use, even if satisfactory configuration could take a little while to complete. It is a tool that not only offers peace of mind but also helps to keep children safe without being too intrusive. The annual fee covers up to three computers making this great value for money.
AVG Family Saftey lists for $19.95 and runs on Windows XP, Vista or 7.
Photo Credit: NinaMalyna/Shutterstock
-

Microsoft drops Windows Security Essentials 4 beta -- pick it up now!
Publié: décembre 1, 2011, 1:54am CET par Mark Wilson
 Microsoft has released a public beta version of its Windows Security Essentials package, giving users a sneak glimpse of what to expect from future releases. There are not a huge number of changes to speak of, but the release is an important advancement for a home-user friendly security suite that has gained a large following since it debuted. Windows Security Essentials 4 beta is available right now to anyone with a Windows Live ID.
Microsoft has released a public beta version of its Windows Security Essentials package, giving users a sneak glimpse of what to expect from future releases. There are not a huge number of changes to speak of, but the release is an important advancement for a home-user friendly security suite that has gained a large following since it debuted. Windows Security Essentials 4 beta is available right now to anyone with a Windows Live ID.There are some minor interface tweaks to be seen in the application, but it is the improvements to performance and the detection process that are most interesting. One of the concerns with running any security software is the potential for it to impact on system performance -- and this is one reason why many people simply do not bother installing security software. Performance tweaks help to reduce the strain on your system while it is protected.
But the purpose of the program is to offer protection against a range of threats and in addition to the general performance enhancements, there are improvements made to the detection engine. No security app is able to promise 100 percent protection, but Windows Security Essentials 4 improvements bring great levels of protection to Windows users.
There is a strong focus on ease of use, and as well as the redesigned and cleaned up interface, changes have also been made to the way the app handles threats that are detected. The program now deals with a greater number of threats automatically without the need for user intervention, and there is also the ability to configure on-demand and scheduled system scans in addition to the all-important real-time protection.
You can find out more and download a free copy of the app by paying a visit to the Microsoft Security Essentials 4 Beta review page.
Photo Credit: Julien Tromeur/Shutterstock
-

Got iPhone and administer a network? You need iPRTG 3
Publié: novembre 29, 2011, 7:26pm CET par Mark Wilson
 If you maintain a server or network, you understand the importance of being able to monitor it around the clock. There are a number of tools available that can be used to keep an eye on your network whilst on that network, but there will be numerous occasions when you are away from the office but still need to check that things are running smoothly. PRTG Network Monitor is one such network monitoring tool, but for when you are out and about you can turn to iPRTG 3 to use your iPhone or iPad to remotely monitor your network.
If you maintain a server or network, you understand the importance of being able to monitor it around the clock. There are a number of tools available that can be used to keep an eye on your network whilst on that network, but there will be numerous occasions when you are away from the office but still need to check that things are running smoothly. PRTG Network Monitor is one such network monitoring tool, but for when you are out and about you can turn to iPRTG 3 to use your iPhone or iPad to remotely monitor your network.iPRTG enables you to view information about the state of your network and while the interface has been optimized for viewing on the screen of iOS devices, iPad users undoubtedly get a better deal, with the larger screen making it far easier to work with data. Depending on the size of your network you may choose to navigate through the app in different ways. It is possible to use network sensors as jump points, so you can, for example, quickly navigate to the device with the lowest uptime or the most free disk space.
It is something of a shame that iPRTG is focused almost entirely on network monitoring, and that there is so little scope for interacting with your network. As the app has clearly been designed to help on those occasions when you are out so you can monitor what is going on, it is rather unfortunate that it is not possible to respond to any alarms that may be raised by the network.
Relatedly, it is also a shame that iPRTG is not able to deliver push notifications about network events -- you are able to view alarms and alerts in the app, but only by manually checking them. The app can also be used to access the PRTG web interface which provides access to additional reporting and analysis options.
You can find out more by paying a visit to the iPRTG review page.
-

Don't miss one of this week's exciting 18 downloads
Publié: novembre 20, 2011, 1:37am CET par Mark Wilson
 Another busy week software releases has passed, and chances are you missed something. Fear not, we have collected together some of the highlights of the past seven day in another handy roundup so you can catch up.
Another busy week software releases has passed, and chances are you missed something. Fear not, we have collected together some of the highlights of the past seven day in another handy roundup so you can catch up.VMWare released a series of updates to it virtualization software, starting with VMware Workstation 8.0.1. The app can be used to run virtual copies of Windows and Linux and the latest version includes graphics performance improvements as well as support for Ubuntu 11. VMware Player 4.0.1 is the free version of the virtualization tool for Windows while VMware Fusion 4.1 is more a major upgrade for Mac users, which supports full screen mode in Lion, improves performance of virtual machines and much more.
But you may well be more interested in looking after your standard copy of Windows rather than a virtual one, and this is where IObit Advanced SystemCare 5 FINAL can help. The updated system optimization tool includes real-time optimization in the form of ActiveBoost while the re-written program uses fewer resources. Sticking to the system utility theme, Quick Erase 0.4 makes it possible to quickly and easily erase files you would rather were not seen by anyone else -- for whatever reason. There are twelve secure deletion options to choose from, helping to ensure that the files you delete stay that way.
If you are more interested in ensuring that your files are backed up rather than deleted, BurnAware Free 4.2 may be right up your street. This free CD, DVD and Blu-ray burning tool can back up data, burn ISO images and create audio discs. Also on the creative front, Microsoft Expression Encoder 4.0 SP1 captures video from a variety of sources, before editing and converting it for viewing on a range of devices, including online broadcasts. This is an example of a program that can be made as simple or as complex as you like, and while it is possible to get results fairly quickly, there are plenty of options here for anyone who wants to get a little more involved.
Skype for Windows 5.7 Beta and Skype for Mac 5.4 Beta both received updates this week, adding the ability to conduct video chats with your Facebook contacts amongst other enhancements. The group chat options of Skype is ideal for conducting online meetings. Whether you are conducting on- or offline-meetings, PointerStick 1.0 is a valuable tool. This free utility provides a large onscreen pointer that can be used to draw attention to thing you want to demonstrate.
The week was quieter for browser updates -- Waterfox 8.0 released. This is a browser for users of 64-bit Windows who can’t wait for the 64-bit version of Firefox as it is based on Firefox code and is virtually indistinguishable from the more common 32-bit version of Mozilla’s browser.
 The Internet can be used for business and pleasure, and when used for entertainment, Game Downloader 2.5 can point you in the direction of dozens of downloadable games. We’ve already mentioned one disc burning tool, but Hamster Free Burning Studio 1.0.9.9 is also worth a mention if only for its pleasingly customizable interface. On the subject of eye-candy, Horloger 1.0 FINAL is an attractive desktop clock for Windows users that will appear familiar to HTC Sense users -- good-looking and functional.
The Internet can be used for business and pleasure, and when used for entertainment, Game Downloader 2.5 can point you in the direction of dozens of downloadable games. We’ve already mentioned one disc burning tool, but Hamster Free Burning Studio 1.0.9.9 is also worth a mention if only for its pleasingly customizable interface. On the subject of eye-candy, Horloger 1.0 FINAL is an attractive desktop clock for Windows users that will appear familiar to HTC Sense users -- good-looking and functional.For music fans Apple iTunes 10.5.1 (32-bit) and Apple iTunes 10.5.1 (64-bit) were both updated, adding support for iTunes Match in the United States. If video is more your thing, Freemake Video Downloader 3.0.0 makes it possible to download streaming video from an extensive list of supported sites, while a blast from the past RealPlayer 15 adds the ability to track your friends’ Facebook videos.
Whatever type of software you are looking for, there’s something here from the past week for everyone.
-

New Skype betas add Facebook video chat
Publié: novembre 18, 2011, 1:06am CET par Mark Wilson
Skype’s integration with Facebook is nothing new, but the latest beta version of the cross-platform chat and VoIP tool takes this to a new level. Skype for Windows 5.7 Beta and Skype for Mac 5.4 Beta bring further advantages to connecting your Facebook account with your Skype one. Now, as well as being able to make use of Facebook chat from within the app, it is now also possible to conduct Facebook video chats.
This can all be carried out from within Skype itself without the need to visit the Facebook web site -- just as it has been possible to conduct text-based chats with your Facebook contacts, the same is now possible with face-to-face VoIP calls. Improvements have been made to Skype’s video rendering, which helps to give a smoother overall experience, and there are a number of other new features to explore.
Another improvement in the Facebook arena is better handling of online status. Now, if you indicate that you are away in Skype, this fact will be relayed to not only your Skype contacts, but you’re your Facebook friends. Sticking with the video chat side of things, you now have the ability to share your screen when conducting a group chat.
This means that in addition to sharing your webcam footage, you can choose to share the content of your entire desktop, or just the contents of a single application window -- a great option for remote meetings. Skype is used in a huge number of different ways, and a new push-to-talk feature opens up even further possibilities -- of course, there will be occasions when you want to appear offline in Skype but remain online on Facebook, and this is also possible.
You can find out more and download a free copy of the beta software by paying a visit to theSkype for Windows 5.7 Beta or Skype for Mac 5.4 Beta review page.
-

Adobe apps turn Android into artist's canvas
Publié: novembre 17, 2011, 12:59am CET par Mark Wilson

Adobe is a name associated with design tools, and it has long been associated with desktop software that can be used to create everything from websites and product designs to page layouts and perfect photos. But in recent years there has been a huge interest in mobile devices, and while handheld devices are a little limited when it comes to being used as design tools, the same cannot be said of tablets. The larger screens found on tablets have been put to great use in Adobe’s latest Android apps -- Adobe Photoshop Touch, Adobe Proto and Adobe Debut.
Adobe Photoshop Touch is, perhaps unsurprisingly, a touchscreen compatible version of the company’s flagship image editing tool. The selection tool has been redesigned to make it easier to control with just a fingertip, and the usual raft of filters and effects can be found here to help enhance images on the move. For most people, this app will be the one that appeals most from Adobe’s new range of Touch Apps.
For designers, Adobe Debut can be used to present ideas to clients, while Adobe Proto can be used to draw up design prototypes -- the naming convention could not be accused of being illogical. Each has the feel of being a tool designed specifically with touchscreen mobile devices in mind, rather than just being a knocked together ports of existing software. Debut can be viewed as a presentation tool that can be used to show off designs that have been created on your Mac or PC, while Proto can be used to create wireframe mockups of apps, pages and web sites – these can be interactive so you can get an idea of how things will work as well as how they will look.
Each of the tools can be used in conjunction with Adobe Creative Cloud, which makes it possible to upload files from your desktop to an online storage location and then access them on your tablet -- but this is obviously dependent on being able to pick up an Internet connection on your Android.
Weighing in at $9.99, these are not cheap apps, but they have heritage. Adobe is one of the few companies that can justify charging such an amount for a mobile app, but the software still needs to live up to the price tag. With its foray into the iOS market, Adobe had a chance to test the waters with its mobile apps. The tools that are now available for Android are well evolved apps that are surprisingly developed considering the 1.0 version numbers.
You can find out more about these apps by paying a visit to the review pages -- Adobe Photoshop Touch, Adobe Debut and Adobe Proto.
-

Tick Tock, here's a new Windows clock
Publié: novembre 16, 2011, 6:53pm CET par Mark Wilson
 Finding out what time it is need not mean relying on Windows’ built in clock, which is functional, but ultimately pretty ugly. Horloger, on the other hand, is a beautiful flip clock that will look great on any desktop. The look may appear familiar to mobile owners as widgets with a similar style are also available for the likes of Android, but this is a take on the genre that has been designed with Windows users in mind.
Finding out what time it is need not mean relying on Windows’ built in clock, which is functional, but ultimately pretty ugly. Horloger, on the other hand, is a beautiful flip clock that will look great on any desktop. The look may appear familiar to mobile owners as widgets with a similar style are also available for the likes of Android, but this is a take on the genre that has been designed with Windows users in mind.The stylish clock feels simultaneously old-fashioned and ultra-modern, and there are small and large versions available -- you can also choose from a few other skins, but the default is probably the best looking. Rather than being forced to keep your clock tethered to the lower right hand corner of the screen, Horloger can be placed anywhere on your desktop.
One of the advantages of using Windows’ own clock is the fact that it is tucked out of the way and does not obscure anything you may have open on your screen. If you have decided to position your flip clock somewhere more central, you have the option of making it transparent so that things in the background can still be seen. With the option of displaying the date as well, this is a seriously stylish and useful utility.
You can grab yourself a free copy of the clock app by paying a visit to the Horloger review page. If this clock doesn’t suit your particular tastes, you might want to take a look at Vector Clocks or even the Vector Clock Designer if you’d like to come up with your own.
-

Hamster Free Burning Studio: Make discs without hassle
Publié: novembre 15, 2011, 6:38pm CET par Mark Wilson
 It’s fair to say that a disc burning tool is one thing hardly in short supply, so it would be natural to wonder why another might be needed. While there are all manner of advanced burning suite available, anyone starting out in disc burning for the first time tends to get forgotten. This is something that Hamster Free Burning Studio aims to address, bringing the option to create and copy discs to everyone.
It’s fair to say that a disc burning tool is one thing hardly in short supply, so it would be natural to wonder why another might be needed. While there are all manner of advanced burning suite available, anyone starting out in disc burning for the first time tends to get forgotten. This is something that Hamster Free Burning Studio aims to address, bringing the option to create and copy discs to everyone.The interface is the first thing you will notice about the app -- it is far from being the complex and often confusing beast that Nero has become; Hamster Fre is just delightfully simple. Despite this apparent simplicity, you can use the program to create CDs, DVDs and Blu-rays using your own files or ISO images, or you can create direct copies of discs.
Switch to ‘compact mode’ and this is just about as simple as you could expect them to get. A disc shaped window appears and lets you know what type and capacity of disc you are working with, and you can then simply drag and drop files into place. Hit the burn button when you’re ready and everything is taken care of for you.
There are five different color themes to choose from, and while this may not be adeal-breaking for many people looking for a disc burning tool, for those taking their first tentative steps into disc creation, this is one extra touch that helps to make Hamster Free Burning Studio that little bit more appealing.
You can find out more and download a free copy of the program by paying a visit to the Hamster Free Burning Studio review page.
-

Apple releases iTunes Match to US subscribers
Publié: novembre 14, 2011, 8:57pm CET par Mark Wilson

Apple has pushed out the latest version of its media player and management software -- iTunes 10.5.1. The latest version of the app is not big news in itself, but the release coincides with the much anticipated launch of iTunes Match, in the US market at least. The service has been expected for some time, but a series of delays pushed the release date back slightly. Now, at long last, iTunes Match is here.
The subscription service will set you back $25 per year and enables you to access your entire music collection in the cloud. The latest version of iOS has seen Apple expressing a greater interest than ever before in life in the cloud and this foray means that it will now be possible for those willing to stump up the annual fee to access their music collection from any internet connected device without the need for manually copying of files.
However, Apple's cloud servers are failing to meet demand, with widespread reports iTunes Match isn't available (we've had troubles, too).
All of the music available from iCloud is provided in 256-Kbps AAC DRM-free format. It does not matter if your original files were of a lower quality, anything you download with iTunes Match will be upscaled for you. For the time being, iTunes Match is only available in the United States, and you will need to upgrade to the latest version of iTunes in order to use the service.
You can wait for your copy of the software to offer you an update at some point in the next few hours or days, or you can manually download the latest version. Head over to the Apple iTunes 10.5.1 (32-bit) or Apple iTunes 10.5.1 (64-bit) to grab yourself a copy.
-

You need this week's 32 downloads
Publié: novembre 13, 2011, 3:43am CET par Mark Wilson

The nights are drawing in, but the pace of software release shows no sign of slowing down. It has been another busy week in the app world with a number of important releases including Uniblue PowerSuite 2012. This handy suite of tools includes everything you need to boost the performance of your computer, and if you don’t feel the need for quite such an extensive selection of utilities, you can pick and choose which you would like to use as there are also individual releases available. Uniblue RegistryBooster 2012 takes care of optimizing the registry, while Uniblue DriverScanner 2012 ensures that all of your drivers are up to date and Uniblue SpeedUpMyPC 2012 includes a huge range of options for boosting the performance of Windows.
If you like to get hands on with your computer, creating partitions is a great way to help keep different types of data separate from each other, and this is something that Parted Magic 11.11.11 can help with. This bootable Linux-based disc can be used to create and manage partitions in a range of file systems, and could be used to configure a dual boot system. Going down this route is not something that suites everyone though, and if you’d like to try out some of the new features of Windows 8, the Windows 8 Simulator Beta 1.0 enables you to do so without having to install a new operating system. You may prefer to simply get the look of Windows 8 without having to go to too much trouble, and this is something that you can do with Pulmon 2.0. This transformation pack gives you a take on the Metro interface of Windows 8. Should you decide that you would prefer to actually install the developer version of Windows 8, you will need to burn the image file to disc, and this can be achieved with the updated BurnAware Free 4.1.1.
Almost everyone has need for an office suite and if you don’t fancy shelling out on the likes of Microsoft Office, LibreOffice Productivity Suite 3.4.4 is available free of charge to cater for your word processing, spreadsheet and database needs. It may be the case that your writing requires a more powerful tool than a standard word processor and this is where Scrivener for Windows 1.0.1 FINAL can help, proving you with advanced word organization options that are ideal for lengthier documents including books.
Apple Store 2.0 for iOS has been updated to allow for in-store reservations as well as adding the ability to pay for good in an Apple store using your Apple account. If you use iTunes but don’t have a lot of love for Apple’s software, iTuner – The iTunes Companion can help to make it easier to use by providing access to common options from the system tray. Streaming media can be downloaded using URL Snooper 2.30.01 which reveals the web addresses you need to grab music and video files, and the updated Trillian 5.1 enables you to chat with friends on multiple platforms with newly added support for Skype. When you’re online with your iOS device, look no further than Hotspot Shield VPN 1.0.1, which compresses data to reduce data uses and also encrypts your data to help protect your privacy.
It has been a busy week for updates to web browsers, with Google releasing the latest version of Chrome -- Google Chrome 15.0.874.120 FINAL and Google Chrome Portable 15.0.874.120. New versions of the next version of the web browser, including a portable version were also released – Google Chrome 16.0.912.36 Beta and Google Chrome Portable 16.0.912.36 Beta – while anyone looking to peak further into the future can do so by installing Google Chrome Portable 17.0.932.0 Dev. To slightly less fanfare, Opera 11.60 (Tunny) Beta 1 was also released.
Not to be left out, Mozilla has unleashed a raft of releases including the all new Firefox 8 FINAL which is also available as a portable app – Firefox Portable 8.0.Firefox 9 Beta was also updated with more speed improvements, while Firefox Aurora 10.0a2 starts to see the introduction of interface changes. For those who like to be right on the cutting edge of browser development, there is Firefox 11.0a1 32-bit (Nightly) and Firefox 11.0a1 64-bit (Nightly) to test out, as well as Firefox 11.0a1 UX and Firefox 11.0a1 64-bit UX for those that are feeling even more adventurous.
But it is about more than web browser updates for Mozilla, and the latest version of the accompanying email client was also unveiled. Mozilla Thunderbird 8.0 FINAL does not have many new features worthy of note but there is also a portable version available in the form of Mozilla Thunderbird Portable 8. Rounding off this week’s well-rounded roundup is Mozilla Lightning 1.0 FINALwhich is a Thunderbird extension that adds a calendar option to Thunderbird to transform it into more of an Outlook-style PIM.
-

Make iTunes work better for you
Publié: novembre 11, 2011, 2:45pm CET par Mark Wilson
 iTunes is a piece of software that is loved and hated in equal measure. There is no getting away from the fact that it is a powerful and impressive media management program, but it is also slow to use and has something of a space-hungry interface. This is something that iTuner aims to address, enabling you to take advantage of the power of iTunes without actually having to battle with the interface.
iTunes is a piece of software that is loved and hated in equal measure. There is no getting away from the fact that it is a powerful and impressive media management program, but it is also slow to use and has something of a space-hungry interface. This is something that iTuner aims to address, enabling you to take advantage of the power of iTunes without actually having to battle with the interface.The tool is a small system tray utility that not only provides access to basic playback controls but also to manage your media library. Keyboard shortcuts can be used to start and stop playback, skip between tracks and adjust volume, as well as show lyrics and jumping in the main iTunes application for those occasions when it simply cannot be avoided.
This in itself is handy enough, but there is more to iTuner than just that. The utility can also clean up your music library by removing files that do not work and deleting duplicate tracks and empty folders. You can convert tracks between formats, export playlists, and copy files to removable media as well as synchronizing with an MP3 player, all from the comfort of the system tray.
Even if it is used just for the basic playback controls, iTuner is a useful tool and the pop up that appears when the track changes is a nice touch. But the extra options offered by the program, and the fact that it is available free of charge, mean that this is an essential tool for anyone with an iOS device or who works with iTunes.
You can find out more and download a free copy of the app by paying a visit to the iTuner review page.
Photo Credit: olly/Shutterstock
-

Get more from Windows with Uniblue's 2012 tools
Publié: novembre 10, 2011, 6:59pm CET par Mark Wilson
 We’re approaching the end of 2011, so it should come as no surprise that developers are pushing out their 2012 products. Uniblue is a company synonymous with system utilities, and the newly announced 2012 product lines bring a number of important updates to all of the key programs. SpeedUpMyPC 2012,DriverScanner and RegistryBooster are all available as individual tools, but there is also the money saving PowerSuite 2012 which incorporates each of these utilities into a single suite.
We’re approaching the end of 2011, so it should come as no surprise that developers are pushing out their 2012 products. Uniblue is a company synonymous with system utilities, and the newly announced 2012 product lines bring a number of important updates to all of the key programs. SpeedUpMyPC 2012,DriverScanner and RegistryBooster are all available as individual tools, but there is also the money saving PowerSuite 2012 which incorporates each of these utilities into a single suite.As the name hints at fairly strongly, SpeedUpMyPC is concerned with boosting the performance of Windows. This is achieved by optimizing network and hard drive settings, amongst other things, and you are guided through the whole optimization process. Additional performance boosts can be achieved by turning to Uniblue RegistryBooster 2012 which can be used to defragment, trim and optimize the registry. There’s also DriverScanner which automates the process of keeping your system’s drivers up to date.
Each of the tools is useful in its own way, and represents decent value for money, but opting for the PowerSuite package makes the best financial sense as it combines RegistryBooster, SpeedUpMyPC and DriverScanner. All of the programs that make up the suite have been updated to some extent, some more than others, and there is a great sense of unity when they are used together. While it’s not exactly an essential upgrade for anyone who already owns the 2011 versions of any of the programs, for new-comers it’s a great way to get more from Windows.
It’s important to note that Uniblue ship their products as a function-limited demo, meaning you need to pay for a license before you can utilize the functions in full. Existing Uniblue customers will be able to download and install the latest 2012 build using their existing licenses.
You can find out more and download free very limited trial versions of the programs by paying a visit to the review pages for Uniblue PowerSuite 2012, Uniblue RegistryBooster 2012, Uniblue SpeedUpMyPC 2012 and Uniblue DriverScanner.
-

Clean up iTunes with Real Networks Rinse
Publié: novembre 3, 2011, 12:10pm CET par Mark Wilson
 Apple’s iTunes may not be everyone’s favorite music player or media management tool, but for millions of iPod, iPad and iPhone owners it is the software they use to work with their music collection. We have all experienced problems with MP3s to one degree or another -- a library littered with duplicate tracks, albums that have no ID3 tags, tracks with misspelt name to name but a few -- and this is something that Real Networks’ Rinse can help with.
Apple’s iTunes may not be everyone’s favorite music player or media management tool, but for millions of iPod, iPad and iPhone owners it is the software they use to work with their music collection. We have all experienced problems with MP3s to one degree or another -- a library littered with duplicate tracks, albums that have no ID3 tags, tracks with misspelt name to name but a few -- and this is something that Real Networks’ Rinse can help with.This is an Adobe Air application that can be used to analyze and fix your music library, comparing the information attached to your files with an extensive online database. If you are the sort of person who likes to remain in control of what is happening with your computer, you may want to work through your music collection one track at a time, confirming any suggested changes that Rinse comes up with.
But if you have a particularly gigantic music collection, or if you simply don’t fancy the idea of sitting in front of your computer confirming every change, you have the option of working in automatic mode. Rinse can also prove useful if you have used other music management tools in the past only to discover that your music genres have gone awry.
If you have been plagued by missing album art or multiple copies of the same track, Rinse makes it easy to get things back in order. The application does nothing that you could not achieve manually, but it will save you a great deal of time and effort if you leave it to work its magic. The tool is a little on the expensive side at $39, but the results it comes up with are impressive.
You can find out more and download a copy of the program by paying a visit to the Rinse review page.
-

Spookify your desktop with Halloween Skin Pack
Publié: octobre 31, 2011, 4:30pm CET par Mark Wilson
Everyone loves to give their computer a makeover from time to time, and Halloween is as good a reason as any to seek out a new desktop theme. While there’s nothing to stop you from heading out with your digital camera and snapping a suitable shot, or even getting creative in the likes of Photoshop, it is a great deal easier to let someone else do the hard work for you; this is where a Halloween Skin Pack could give you the new look you have been looking for.
More than just a new background image -- although this is a part of the skin pack -- the Halloween Skin Pack includes a number of options for spookifying your desktop. Providing you have the relevant third party tools installed, you can customize your login screen, Start menu, icons, and much, much more.
The diminutive size of the initial download is slightly deceptive as during the installation process you will need to be connected to the Internet to download all of the required components. If you have not already patched your system to allow the installation of unsigned themes, this option is available during the installation to enable you to completely change the look of Windows.
All of the icons and images have been produced to a very high standard, and the number of programs you need to get full advantage of the skin pack is fairly extensive. Thankfully, you do not need to worry about checking that you have all of them installed as this is all taken care of for you automatically. Run through the installer and after a quick reboot, you will be greeted by a Halloween inspired desktop.
You can download the skin pack by paying a visit to the Halloween Skin Pack review page -- there’s also a 64-bit version available.
-

Scare up one of these 25 downloads released this week
Publié: octobre 29, 2011, 8:07pm CEST par Mark Wilson
 It’s the end of October, but the relentless release rate of software shows no sign of abating. The last seven days have been at least as busy as usual, so it would not be surprising if you managed to miss a few titles here and there. Thankfully, we’ve had our finger on the pulse and have compiled a roundup to help you get up to speed. One of the biggest releases of the week is undoubtedly Google's browser, which has come out of beta with the release of Chrome 15.0.874.106 FINAL. As well as speed and stability improvements, there is also a redesigned tab interface that fans of portable apps can take advantage of.
It’s the end of October, but the relentless release rate of software shows no sign of abating. The last seven days have been at least as busy as usual, so it would not be surprising if you managed to miss a few titles here and there. Thankfully, we’ve had our finger on the pulse and have compiled a roundup to help you get up to speed. One of the biggest releases of the week is undoubtedly Google's browser, which has come out of beta with the release of Chrome 15.0.874.106 FINAL. As well as speed and stability improvements, there is also a redesigned tab interface that fans of portable apps can take advantage of.When online it is important to keep yourself protected and a firewall is a great first line of defense. ZoneAlarm Free 10.1.056.000 can help to control the flow of traffic to and from your computer. There are many types of files you will encounter online, and one of the most common if the humble PDF. If you’d prefer to steer clear of the big names, Foxit Reader 5.1.0 wll cater for your needs perfectly.
For both on and offline music listening on your computer, Winamp 5.622 is an old favorite that has seen something of a resurgence in interest recently. Android users can work with Winamp for Android 1.2 and keep their music collections synchronized between mobile and desktop computers. If you have a Mac, the new WinAmp For Mac Sync 0.7.1.85 Beta brings the same offline music and online radio playback complete with the ability to synchronize wirelessly with other devices and import an existing iTunes library.
When it comes to music, you may decide that you would like to create a more traditional CD from your library, and this is something that BurnAware 4 Free. This free disc burning utility can be used to create audio discs, burn disc images and much more, and there are also two paid-for versions of the program available – BurnAware Home 4.0 and BurnAware Professional 4.0 with the former adding the ability to create copies of discs and the latter adding support for multiple disc burners.
If you’d prefer to work with videos rather than other types of file, DVDStyler v2.0 should be right up your street. There is also a portable version of the app available in the form of DVDStyler Portable v2.0 and both can be used to create impressive looking DVDs from almost any video file you may have on your hard drive. iSpring Free 6.0 is a handy tool that can be used to convert a PowerPoint presentation into a Flash document ready to use online or on a presentation disc.
We’ve already mentioned the somewhat old-school Winamp which is enjoying a revival, and the same could be said of WinZip 16.0. The latest version of the program makes it easier to work with and share very large archives and the new 64-bit engine provides improved performance. A more lightweight zip tool can be found in PeaZip 4.1 (32-bit) andPeaZip 4.1 (64-bit). There are also portable versions of the app available -- PeaZip Portable 4.1 (32-bit)and PeaZip Portable 4.1 (64-bit). For management of other files on your hard drive, for those occasions when Windows Explorer simply doesn’t cut it,Explorer++ Portable v1.3.2 32-bit is a powerful, portable alternative. The tabbed interface makes it easy to work with multiple folders simultaneously and owners of 64-bit systems can take advantage of Explorer++ Portable v1.3.2 64-bit.
 If you’re more concerned with improving the performance of your computer and keeping things running smoothly, CCleaner 3.12 is a complete cleanup tool that can help you to keep your system in shape. There’s also a portable version available -- CCleaner Portable 3.12 -- which can be popped on your USB drive to move from one computer to another. Whether you are tweaking your system or not, AIDA64 2.00 is a great tool to help you to benchmark your computer to see how it compares to other setups. Tweaking of a different kind is available in 7 Taskbar Tweaker 3.0 which enables you to make a number of important changes to the way the Windows’ taskbar works, while Windows 8 BluePoison 2.1 is one of the first tweaking tools available for Windows 8.
If you’re more concerned with improving the performance of your computer and keeping things running smoothly, CCleaner 3.12 is a complete cleanup tool that can help you to keep your system in shape. There’s also a portable version available -- CCleaner Portable 3.12 -- which can be popped on your USB drive to move from one computer to another. Whether you are tweaking your system or not, AIDA64 2.00 is a great tool to help you to benchmark your computer to see how it compares to other setups. Tweaking of a different kind is available in 7 Taskbar Tweaker 3.0 which enables you to make a number of important changes to the way the Windows’ taskbar works, while Windows 8 BluePoison 2.1 is one of the first tweaking tools available for Windows 8.That’s another busy week out of the way -- the coming seven days are sure to be just as hectic, so there’s lots to look forward to.
-

AVG LiveKive 2012 review
Publié: octobre 29, 2011, 12:01am CEST par Mark Wilson
 Cloud storage has come a long way in recent years, and the ever-increasing number of mobile device means that more and more people are finding different ways to make use of it. The importance of backing up valuable data, coupled with the widespread availability of high-speed broadband connections means that cloud storage is ideally suited to safeguarding files you need to protect, not only helping to avoid the risk of data loss, but also making it possible to access your files from other computers.
Cloud storage has come a long way in recent years, and the ever-increasing number of mobile device means that more and more people are finding different ways to make use of it. The importance of backing up valuable data, coupled with the widespread availability of high-speed broadband connections means that cloud storage is ideally suited to safeguarding files you need to protect, not only helping to avoid the risk of data loss, but also making it possible to access your files from other computers.AVG is a company best known for its antivirus software, but AVG LiveKive sees it branching out into another area of security -- backups. Traditionally, this practice is something that has involved the use of a separated hard drive partition or perhaps a dedicated drive, but the feasibility of storing files online brings a number of benefits. As you are using remote storage, you do not need to worry about running out of space in quite the same way as when using a local hard drive, and the option of remotely accessing files that have been backed up from a machine other than the one from which the backup from created opens up even more opportunities.
Unlike some backup software, LiveKive gets off to a good start by being instantly accessible. Rather than having to battle with complicated configuration screens, getting the software setup is reduced to a simple wizard that makes things as easy as possible. Used at its most basic, you can simply tell LiveKive to backup various type of files, such as a videos and music, and files stored in a number of key locations will be automatically included in any backup that is created.
There is also a more advanced mode available that can be used to more precisely control just what is backed up. It is also possible to create a backup schedule so your files are automatically uploaded to your online storage space on a regular basis, but you have the option of timing it so it will not happen at a time when you are likely to need your Internet connection for something else. To help keep the size of uploads to a minimum, incremental backups can be created so that only changed or new created files need to be uploaded rather than creating the backup from scratch each time.
Store and Share
While LiveKive is ostensibly a backup utility, the service has a couple of additional tricks up its sleeve. Data synchronization is also available, so as well as backing up the files you have stored on multiple computers, such as your desk top and laptop, it is also possible to ensure that the same files are available in each location. Add to this the ability to share files online with other, avoiding the need to battle with email attachment size limitations, and it won’t take long for LiveKive to prove its value to you.
If you’re unsure as to whether the service is suitable for your needs, there is a free starter version available that includes 5Gb of storage space without the need to part with any money. As well as Windows and Mac versions of the software, there are also versions available for iOS and Android devices so you can access the documents you have stored in the cloud whilst you are away from your desktop computer.
The cross-platform support offered by the software is particularly interesting, and with the exception of Linux users, no operating system has been left out. It is likely that you will find that if you use LiveKive as your main backup solution, the 5GB of storage space provided free of charge will not be enough. Thankfully, upgrading to 25GB or even unlimited storage space is relatively cheap -- $49.99 and $79.99 respectively. Backing up data is something that the majority of computer users realize they need to do, but many simply don’t get round to it. But when backing up is made as simple as with AVG LiveKive, there is simply no excuse for not protecting your valuable data.
You can download a free copy of the app by paying a visit to the AVG LiveKive desktop version page or the page for the mobile version of AVG LiveKive.
-

Uh-oh iTunes, WinAmp comes to OS X, syncs with Android
Publié: octobre 27, 2011, 4:53pm CEST par Mark Wilson
 WinAmp used to have a huge following back in the days when MP3 was still something of a new format, and the increased popularity of the Mac and Android platforms seems to have brought about something of a resurgence. While Windows users have long enjoyed the player, Mac users have not been so lucky. All this changes with the release of a beta version of the Mac player along with an important update for users of the Android version of the app.
WinAmp used to have a huge following back in the days when MP3 was still something of a new format, and the increased popularity of the Mac and Android platforms seems to have brought about something of a resurgence. While Windows users have long enjoyed the player, Mac users have not been so lucky. All this changes with the release of a beta version of the Mac player along with an important update for users of the Android version of the app.The curiously names WinAmp for Mac Sync Beta not only indicates that the Mac software is currently in beta testing, but also that there is a strong focus on synchronization. While the player can be used to listen to your locally stored music library, it can also be used to keep your iTunes library synchronized as well as synching music with your Android device.
The great thing about Android syncing: it can be done wirelessly so there’s no need to hunt around for that elusive USB cable. Synchronizing music in this way makes it easy for anyone who has tired of working with iTunes to make the switch to a different player with a minimum of fuss, and the Android version of the music player is well worth checking out as well.
In addition to music, you can also choose to synchronize videos. But while these are all important updates, WinAmp is still WinAmp at heart -- it is basically a lightweight music player that can be used to listen to music stored on your hard drive or to stream online radio and much more.
You can find out more and download free copies of the apps by paying a visit to the WinAmp for Mac Sync Beta review page and the WinAmp for Android review page. An updated WinAmp for Windows is also available.
-

Get tabs in Windows Explorer
Publié: octobre 26, 2011, 5:54pm CEST par Mark Wilson
 Windows Explorer is an incredibly useful tool for managing your files, making it possible to open, copy and move documents in folders quickly and easily. But the file management tool that is built into Windows is not without its limitations -- why there is a market for replacement tools. One of the greatest, yet simplest, innovations in the humble web browser was the addition of tabbed browsing, and Explorer++ brings the same handy feature to your file manager.
Windows Explorer is an incredibly useful tool for managing your files, making it possible to open, copy and move documents in folders quickly and easily. But the file management tool that is built into Windows is not without its limitations -- why there is a market for replacement tools. One of the greatest, yet simplest, innovations in the humble web browser was the addition of tabbed browsing, and Explorer++ brings the same handy feature to your file manager.Just as tabbed browsing makes it easier to work with multiple websites simultaneously, so a tabbed file manager makes it easier to work with multiple folders at the same time. Rather than having a huge number of individual windows open when copying or moving files from one folder to another, or simply working with documents stored in different locations, Explorer++ enables you to make do with a single program window.
This feature in itself is enough to make Explorer++ worthy of note, but the application has much more to offer. Perhaps most important, this is a portable app, which means it can be easily popped onto a USB drive and transported between computers without the need for installation -- so if you are working on someone else’s machine, you can continue to work in a familiar environment and reap the benefits of the program you have become used to.
To make it easier to jump to folders you make use of on a regular basis, Explorer++ can create bookmarks, and there is support for more advanced file operations such as splitting and merging as well as secure deletion. Additional feature include advanced search options, and a hugely customizable interface. While the program can be used as a standalone portable app, if you find that you are sufficiently enamoured with the program, it can be installed as complete replacement for Explorer.
You can find out more and download a free copy of the app by paying a visit to the Explorer++review page. There is also a 64-bit version of the program available.
-

Need to lock down Firefox? Try Dell KACE Secure Browser
Publié: octobre 24, 2011, 1:51pm CEST par Mark Wilson
 One way to stay safer online is to run your browser in a sandbox, where it’s isolated from your main PC: even if you’re infected by something unpleasant, this greatly limits the damage that malware can do.
One way to stay safer online is to run your browser in a sandbox, where it’s isolated from your main PC: even if you’re infected by something unpleasant, this greatly limits the damage that malware can do.You don’t have a sandbox? Then one simple alternative is to download and install Dell KACE’s free Secure Browser, which essentially provides a virtualized version of Firefox 3.6.13.
Launch the program and it looks just like regular Firefox, but any process activities are virtualized, so if you’re infected by malware then it can’t (for instance) add Registry keys to launch itself automatically in future.
Secure Browser looks out for processes being launched via the browser, too, so if malware tries to launch a particular program it won’t happen until you explicitly give your permission.
Enable the Network Access Control option and you can additionally lock down the browser by specifically allowing or blocking particular sites.
You can still add browser favorites, or install your preferred Firefox extensions, just as normal. And you should be able to install and run Secure Browser alongside a regular Firefox installation without causing any problems. (This worked for us, but Firefox Profile management is a tricky business, so we’d recommend you back up your existing Firefox setup before installing Secure Browser, just to be safe.)
And if, despite all this, you still think you’ve been hit by a malware attack, then you can always hit the Reset button (click the leftmost button on the Secure Browser toolbar, click Reset). This will close all programs running in the virtualized session, delete all download files and so on, essentially restoring the Secure Browser to its default settings (although your favourites and home page can optionally be preserved).
There are some issues with the Secure Browser, too, most notably that it comes with an old version of Firefox: not ideal, security-wise. This seems to be easily fixed, though: we simply copied our existing Firefox installation to the appropriate Dell folder (C:\Program Files\Dell\Secure Browsers\Secure Browser (Firefox 3)\Firefox\Files\C\Program Files\Mozilla Firefox) and it was ready to go right away.
You don’t get the configurability here to match up with Sandboxie or Comodo’s sandboxing technology, then. Still, Secure Browser is straightforward, free and very easy to use, so if you’d like a browser sandbox without the usual hassles then it’s well worth a closer look.
-

Unlock Windows 8 hidden features with BluePoison 2.1
Publié: octobre 23, 2011, 7:20pm CEST par Mark Wilson
 Many Windows users are keen on tweaking their operating system and this is even truer when a big interface change is made. The public release of the Windows 8 Developer Preview means more people than usual are getting sneak peek at the upcoming version of Microsoft’s operating system, during its earlier stages of development. Windows 8 BluePoison is a free tool that unlocks a number of hidden features.
Many Windows users are keen on tweaking their operating system and this is even truer when a big interface change is made. The public release of the Windows 8 Developer Preview means more people than usual are getting sneak peek at the upcoming version of Microsoft’s operating system, during its earlier stages of development. Windows 8 BluePoison is a free tool that unlocks a number of hidden features.Moving through the options in the application, you can opt to revert to the old style Start menu and access the Applications folder, which are normally hidden as well as enabling the snap feature on small displays.
But if you are interested in seriously changing the look of Windows 8, the Themes section will interest. Here you can choose from a number of new themes. BluePoison can also be used to download and customize a leaked version of the upcoming Office 15, which we recommend against.
You can find out more and download a free copy of the app by paying a visit to the Windows 8 BluePoison review page.
-

15 downloads you shouldn't miss this week
Publié: octobre 22, 2011, 8:25pm CEST par Mark Wilson
 It has been another busy week in the world of software releases, so we wouldn’t be at all surprised if some titles escaped you attention. Some of the highlights from the last seven days include WebSite X5 Free, which is a surprisingly effective free template-based web editor that has been designed for beginners looking to create their first site. With a huge range of stylish templates to choose from and a built-in FTP client, there’s everything you need to start and finish your perfect site.
It has been another busy week in the world of software releases, so we wouldn’t be at all surprised if some titles escaped you attention. Some of the highlights from the last seven days include WebSite X5 Free, which is a surprisingly effective free template-based web editor that has been designed for beginners looking to create their first site. With a huge range of stylish templates to choose from and a built-in FTP client, there’s everything you need to start and finish your perfect site.If looking after your computer is more up your street OSForensics 1.0.1001 may well be of interest. This powerful tool can be used to unearth a wealth of information about your system including details of hardware that is or has been connected, and while there are limitations in the free-for-personal-use version it could still furnish you with the information you need to help overcome all manner of problems.
When it comes to analyzing your computer, there is more than one tool that may be of interest.Speccy 1.13 can be used to check all manner of hardware details such as the type of memory you have installed, but there is much more to this versatile tool. If you are the sort of person who helps out friends and family to fix problem with their computers, the updated Speccy Portable 1.13 will be a handy addition to your USB drive. For people who like to listen to music while they work at their computer, Volume Concierge 1.0.0.0 is a handy utility that can be used to automatically adjust system volume depending on the time of day so you can avoid annoying others as you work late at night or early in the morning.
O&O SpeedCheck 2.0.45.0 is a system optimization tool that analyzes the state of your hard drive and determine whether it is worth performing a potentially lengthy defragmentation. For on-going system maintenance, there are times when it is necessary to manually terminate applications that may have become unstable If you fancy the idea of using a tool that’s easier and faster to access than Windows’ Task Manager, take a look at Task ForceQuit Pro 1.0.0.0.
MailStore Home 5.0 is a free email archival tool that can be used to keep on top of an ever-growing amount of communication. The latest version of the app includes a completely redesigned interface and an automatic configuration mode that helps you to get up and running as quickly as possible. If you are more concerned with dealing with your incoming mail, Mozilla Thunderbird 8 Beta 3 is the latest version of Mozilla’s email client which is undergoing the same rapid development cycle as the Firefox browser
Of course, there has also been the usual raft of updates to web browsers. Pale Moon x64 has now reached version 7.0.1, offering huge performance improvements over the previous release, while Firefox 8.0 Beta 4 gives an interesting preview of what’s coming up in the next version of the Mozilla web browser. Opera has also been updated, with Opera Next 12.00 build 1116 and the same is true of the Internet Explorer based Maxthon. Maxthon 3.2.0.1000 blends the best aspects of Internet Explorer, Chrome and Safari to create a feature-packed browser that boasts a real turn of speed.
 When you’re out and about and want to make use of the Internet, you will need to know where the nearest wifi hotspots are, ad this is something that Hotspot Shield 2.09 can help with. Whether you’re browsing the Internet at home or out of the house, you will undoubtedly have to contend with numerous web sites and programs that require the use of password. If you have a tendency to forget your login information, KeePass 2.17 can take care of things for you.
When you’re out and about and want to make use of the Internet, you will need to know where the nearest wifi hotspots are, ad this is something that Hotspot Shield 2.09 can help with. Whether you’re browsing the Internet at home or out of the house, you will undoubtedly have to contend with numerous web sites and programs that require the use of password. If you have a tendency to forget your login information, KeePass 2.17 can take care of things for you.What type of software tends to tickle your fancy, there is sure to be something here for you to try out over the weekend.
-

Remember the Milk for Android Review
Publié: octobre 22, 2011, 6:35pm CEST par Mark Wilson
 When it comes to to-do apps and reminder tools, Android is the perfect platform thanks to its mobile nature and the various synchronization options that are available to ensure that the same data is available on your PC or Mac. So ideal is the platform for this type of app, there is no shortage of titles that have been designed to help you to keep your life in order, avoid missing deadlines and appointments, or keep track of things you need to do and buy. Even before days of iOS and Android, Remember The Milk was available as an online app and the level of control the service provides over your to do list is unparalleled.
When it comes to to-do apps and reminder tools, Android is the perfect platform thanks to its mobile nature and the various synchronization options that are available to ensure that the same data is available on your PC or Mac. So ideal is the platform for this type of app, there is no shortage of titles that have been designed to help you to keep your life in order, avoid missing deadlines and appointments, or keep track of things you need to do and buy. Even before days of iOS and Android, Remember The Milk was available as an online app and the level of control the service provides over your to do list is unparalleled.The iOS app has been available for the iPhone and iPod for a little while now, but the update to version 2 for Android has seen the software evolve into a free app that brings the same powerful options that have been available to iOS devotees for so long a time. The interface has been given a major overhaul, but it is the fact that anyone with a Remember The Milk account -- both free and paid-for -- can now make use of the app free of charge that is the real headlines news.
When created, tasks and reminders can be easily organized into categories to allow for easier sorting in future by assigning them to lists. To make it even easier to manage very extensive lists of things you need to remember, additional fields can be added to individual entries including tags, location information, web links and more. As you would rightly expect from any to-do app worthy of note, Remember The Milk allows for different priority levels to be assigned to tasks so that you can see at a glance what you need to be focusing on next.
Despite the huge range of options available in the app, the interface remains remarkably uncluttered and allows for easy navigation. By default you are greeted by the list of tasks you have to complete today, but links are available so you can see what needs to be done tomorrow and in the week ahead. You can also view all of the lists you have created and this makes it easy to separate the tasks that you have created that are related to work, and those that are more personal in nature, but it can also be used to manage large project by breaking them down into a series of smaller sub-tasks.
Other options come into play when you have assigned a task to a particular location. This can then be used as another method of sorting all of your incomplete tasks, but you also have the option of using location services to determine if you have anything on your to-do list that could be done in the surrounding area -- for shopping this can be a real time-saver as it is all too easy to drive home only to realize that there was one more shop you needed to visit. Depending on how you work and what you are using the app for, you may want to adjust the search radius for what qualifies as 'nearby'. By default this is set to 1 kilometer, but can be reduced to as little as 250m or increased to up to 50km.
Keeping in Sync
It is hard to find any complaints with the app -- it's so well thought out. If there is one minor niggle it would be using Remember The Milk with a standard, free account; you are limited to synchronizing once every 24 hours. Upgrading to a Pro account also adds support for push notifications and badges, and this can make it easier to monitor how many tasks you have left to complete.
For everyday use, such as shopping lists and reminders for doctors’ appointments and the like, this should not be an issue, although it does mean that you have to plan ahead with your syncs. Of course, the premium subscription allows unlimited synchronization, but this does come at a cost -- albeit a fairly low one. The homescreen widgets that are also available with a Pro account are available mean that you can monitor your to-do list at a glance, while the app in never far away for when you need more detail or more control.
In many ways, Remember The Milk for Android is something of a strange app, particularly for a web-based service. Rather than simply complementing or replicating the options that are available at the RTM website, the app actually makes the service easier to use. If you have signed up for a Remember The Milk account in the past but have been put off by the way in which the website works, downloading the app will enable you to completely re-evaluate the service and see it in a new light.
Many people will find it difficult to get excited about what is essentially a to-do app, but until you have tried out Remember The Milk, it is hard to understand just how much better it is when compared to other similar tools. The range of options available is simply unrivalled, and this is coupled with a delightful ease of use that actually manages to make tasks management a pleasure.
You can download a free copy of the app by paying a visit to the Remember The Milk page.
-

WebSite X5 Free: sophisticated but limited
Publié: octobre 21, 2011, 4:01pm CEST par Mark Wilson
 Creating a website from scratch can be a tricky business, and one that many people simply do not have the time or, so they may think, ability to see through. But it does not matter if you are unable to type of a line of meaningful code, there are still a number of tools available that can help you to create an online presence. While template-based WYSIWYG web editors are not going to be the most suitable tool for businesses or more advanced users, they do have their place, and WebSite X5 Free is the latest contender vying for the attention of would-be web masters.
Creating a website from scratch can be a tricky business, and one that many people simply do not have the time or, so they may think, ability to see through. But it does not matter if you are unable to type of a line of meaningful code, there are still a number of tools available that can help you to create an online presence. While template-based WYSIWYG web editors are not going to be the most suitable tool for businesses or more advanced users, they do have their place, and WebSite X5 Free is the latest contender vying for the attention of would-be web masters.The program is perfectly suited to anyone looking to create their first website, or a small group or club looking to break into the online world without breaking the bank. The sites that can be created are not staggering works of beauty, but the templates are of a reasonably high standard, and the sites that can be created are impressive enough and not your usual fare and have a more modern feel than is often the case with such applications.
The fact that there are three more advanced versions of WebSite X5 available indicates that this particular version of the program has been designed with the beginner’s market in mind. You re limited to creating sites that are made of up to ten pages, and while this does not sound like a lot, for many purposes it will prove to be just enough. This is not a website that you are going to use to run a huge business, but it could help you to create something to promote a small local venture or share thoughts on a hobby or interest you have.
If you’re looking to create an advanced website or anything beyond a relatively simple collection of pages, this is not the web editor for you, but WebSite X5 Free does not pretend to be anything other than what it is – a simple, no-nonsense application that makes it as easy as possible to create a web site and get it online. The fact that there is a built in FTP client helps to keep thing simple for anyone starting out in web site creation, keeping the number of tools needed to an absolute mimimum.
You can find out more and download a free copy of the program by paying a visit to the WebSite X5 Free review page.
-

Adobe Reader finally comes to iPad, iPhone
Publié: octobre 18, 2011, 6:39pm CEST par Mark Wilson
 While iOS has supported Portable Document Format for some time, there has been no official app from the king of the PDF, Adobe. With the release of Adobe Reader for iPhone and iPad, this has now changed. As you would expect, the app provides support for the opening of PDF files that have been created on other platform, including those that have been password-protected, and PDF portfolios.
While iOS has supported Portable Document Format for some time, there has been no official app from the king of the PDF, Adobe. With the release of Adobe Reader for iPhone and iPad, this has now changed. As you would expect, the app provides support for the opening of PDF files that have been created on other platform, including those that have been password-protected, and PDF portfolios.Lengthy files can be easily navigated using bookmarks and text searching, and a thumbnail preview section at the bottom of the app makes it easy to jump to a specific page without having to scroll through a document in its entirety. It’s good to see that the iPhone and iPad versions of the app are, apart from the differences in screen size, indistinguishable from each other.
Support for comments and annotations means that by viewinging a PDF on a mobile device you are not missing out. You can choose between working through your documents in single page mode, or opt to use continuous scrolling mode instead for uninterrupted reading.
The ease with which files can be shared means that security is now of the utmost importance, and anyone creating sensitive PDFs will be pleased to find that there is support for 256 AES encryption and password protection. When it comes to working with your files, PDF can be printed out using AirPrint or shared with others by emailing from within the app.
You can find out more and download a free copy of the app by paying a visit to the Adobe Reader for iOS review page.
-

Taptu ties together professional and social news feeds
Publié: octobre 15, 2011, 12:16am CEST par Mark Wilson
With a range of social networks to choose from, each with their own timeline or news feed available, coupled with blogs and news websites, many Internet users have a huge amount of information to wade through each day. If you don’t fancy the idea of visiting each of your preferred news websites and blogs individually, or cluttering up your phone or tablet’s home screen with endless social networking apps, Taptu may be of interest as it makes it possible to access all of your social network and news feeds in one place.
You can quickly and easily add your Facebook account to the app so you can keep track of news that is posted in this way, as well as using the app to keep an eye on your timeline as it fills up with comments and pictures from your friends. Similarly, you can add your Twitter account to make it easy to keep up to date with the tweets of everyone you follow from the same place.
There is also the option of importing news feed from Google Reader as well as browsing through stories selected by Taptu. So far, so so. But what makes Taptu interesting is the fact that it lets you create a mass-up of the information that you have chosen to access through the app to create a completely customized timeline that draws from multiple sources. If you are particularly happy with a customized feed you have created you can share it with others.
News stories and posts you discover through the app can be shared via Facebook and Twitter, or you can make use of Instapaper or Read It Later to keep a record of stories you would like to read at a later time. The interface is slick and good-looking, albeit a little slow at times, proving that style and content can live happily side by side.
You can find out more and download a copy of the app by paying a visit to the Taptu for iOS or Taptu for Android review pages.
-

MAGIX PC Check and Tuning 2012 review
Publié: octobre 13, 2011, 4:56pm CEST par Mark Wilson
 When it comes to optimizing the performance of your computer it is possible to take a very hands-on approach and get involved in editing the registry and checking that you do not have too many startup programs running. But this is not something that everyone has time for or, indeed, the inclination. PC Check and Tuning 2012 is the latest in a series of system maintenance utilities from MAGIX, and it can be used in a quick, one-click mode -- or you can get more involved if you like.
When it comes to optimizing the performance of your computer it is possible to take a very hands-on approach and get involved in editing the registry and checking that you do not have too many startup programs running. But this is not something that everyone has time for or, indeed, the inclination. PC Check and Tuning 2012 is the latest in a series of system maintenance utilities from MAGIX, and it can be used in a quick, one-click mode -- or you can get more involved if you like.The one-click mode can be accessed by launching this option from the Start menu, but it is also available in the main program itself. This mode will check for updates for drivers and software you have installed as well as performing a variety of optimization tasks, such as deleted unnecessary files or removing startup items. The program will also check and optimize the registry as well as seeing whether services you don’t need are running.
But many more advanced users will feel more comfortable being a little more in control of what is going on with their computer, and this is where the relatively self-explanatory "Increase performance", "Free up memory", "Performance check’", "Configure Windows", "Info -- My PC" and "Save power" sections come into play. Starting with "Increase performance", you are afforded a greater degree of control over the optimization process than if you simply rely on the one-click option. Each of the various optimization components can be run separately, so if you’re just looking for a quick fix you may choose to skip over the defragmentation of your hard drive until you have a little more time available.
The ‘"Free up memory" section deals with hard drive space rather than RAM, and it includes tools that enable you to uninstall programs, delete unnecessary files, securely delete data and wipe your Internet history. To enable you to tell how your computer is performing, the "Performance check" section is essentially a series of benchmarks, not entirely dissimilar to the system rating provided by Windows itself. This enables you to not only check how your system compared to other machines, but also to monitor what a difference the tweaks you apply make and see what effect hardware upgrades have.
Moving to the "Info -- My PC section", it is possible to discover everything you could possibly want or need to know about your computer. This component will give you a breakdown of the hardware you are working with as well as detailing the software you have installed. You can also use this section to monitor running processes, analyze and optimize your running services and keep an eye on how often you have used PC Check and Tuning to tweak your system.
The final section, "Save power", is only likely to be of interest to laptop and netbook users, as it enables you to balance power-saving options and performance to achieve the perfect blend of speed and battery life. The suite also has a few hidden extras such as the option to clean up the New sub0menu of the Windows context menu, and the ability to recover files that have been deleted - assuming, of course, that they have not been securely deleted.
MAGIX PC Check and Tuning represents great value for money, but it is something of a shame that some particularly useful tools are hidden away in a menu that many users may never investigate. The software lists for $39.99/£29.99 and is available for Windows XP, Vista or 7.
-

One day before iCloud and iOS 5, Apple drops iTunes 10.5
Publié: octobre 11, 2011, 11:29pm CEST par Mark Wilson
 The attention of Apple fans has been focused on the imminent release of iPhone 4S on October 14, but before that there is iCloud and iOS 5 -- tomorrow. To make the most of both, a new version of iTunes is needed. iTunes 10.5 includes iCloud support as well as a number of other important additions.
The attention of Apple fans has been focused on the imminent release of iPhone 4S on October 14, but before that there is iCloud and iOS 5 -- tomorrow. To make the most of both, a new version of iTunes is needed. iTunes 10.5 includes iCloud support as well as a number of other important additions.iTunes in the Cloud is part of the new level of connectivity that is to be found in iOS 5, and it means that any music or video purchases you make are synced online and can be accessed from any of your computers or iOS devices. Tied into this idea are automatic downloads; when you purchase music from iTunes Store, it will automatically sync to your other computers and iOS devices.
Apple also has added the capability to redownload apps, music and television shows you have purchased in the past -- and the usual synchronization process has been simplified thanks to the addition of WiFi syncing. Providing your iPhone, iPod or iPad is on the same network as your computer that has iTunes installed, synchronization will automatically take place wirelessly.
The release of iTunes 10.5 also paves the way for iTunes Match, which will be available in some countries on a subscription basis. As an added bonus, downloaders may also be pleased to see that it will now possible to grab a copy of iTunes independently of QuickTime. There are still a few hours before the release of iOS 5, so now is as good a time as any to get your copy of iTunes bang up to date.
You can find out more and download a copy of the app by paying a visit to the iTunes 10.5 review page. There are versions available for both the 32- and 64-bit versions of Windows as well as for OS X.
-

Strip back and take control of Android with CyanogenMod 7.1
Publié: octobre 11, 2011, 4:35pm CEST par Mark Wilson
 One of the joys of Android is the fact that users are not fenced in in quite the same way that iOS users are. It is possible to install a wider range of software on your device with fewer worries. If you want to take things to the next level, CyanogenMod is a replacement for your existing Android OS that has been stripped back and optimized to provide a balance between performance, stability and customization.
One of the joys of Android is the fact that users are not fenced in in quite the same way that iOS users are. It is possible to install a wider range of software on your device with fewer worries. If you want to take things to the next level, CyanogenMod is a replacement for your existing Android OS that has been stripped back and optimized to provide a balance between performance, stability and customization.The firmware is built around Android 2.3 and while the interface is nothing flashy, the focus is on speed rather than looks -- but you still have the option to use themes. The unique tweaks and options include the ability to swipe notifications off the screen, while the built-in music player boasts the simplicity and ease of use of an iPod. Support for customizable gestures means that it is easier than ever to control playback.
Gestures are also put to good use on the lockscreen where swipes can be used to not only unlock your device, but also switch on the flashlight and toggle sound. New in this version of the ROM is the ability to use Touch to Focus when taking photographs and it is also possible to change the way focusing works as well as using a timer to take group photos.
Security is important for any mobile user just as it is for desktop computer users, and CyanogenMod makes it possible to take control of permissions that have been granted to apps. While this is something that should be used with caution, it is also places users firmly in control. There is also an interesting Phone Goggles tool, referred to by the developers as ‘drunk mode’, in which phone calls and messaging features can be disabled until mathematical captchas have been solved.
There is a huge amount to explore in this firmware, and while it is something that novice users should perhaps shy away from, it is well worth a look.
You can find out more and download a free copy of the firmware by paying a visit to theCyanogenMod review page.
-

Opera Next build 1090 is here -- get it now!
Publié: octobre 11, 2011, 1:03am CEST par Mark Wilson
 The Next branch of Opera’s development has been updated to build 1090, with a number of interesting changes that see alterations to the skin’s appearance and improvements made to the plugin installation process. Of course, there is also the usual swathe of bug fixes and performance enhancements, and despite the fact that this is a fairly early glimpse of the next version of the browser, it already seems surprisingly stable and polished.
The Next branch of Opera’s development has been updated to build 1090, with a number of interesting changes that see alterations to the skin’s appearance and improvements made to the plugin installation process. Of course, there is also the usual swathe of bug fixes and performance enhancements, and despite the fact that this is a fairly early glimpse of the next version of the browser, it already seems surprisingly stable and polished.There are a number of changes that can be summed up as polishing -- icons and buttons have been updated as has the badge graphic. The overall size of the skin has been reduced in terms of file size, and the padding around some screen elements has been adjusted to improve alignment.
Problems stemming from Opera’s automatic updating have also been addressed, helping to avoid issues that crop up after updating. The plugin installation wizard has been tweaked so it is now possible to hide the plugin installer progress window, and crashes that occurred in previous builds have also been fixed.
Opera Next is available for Mac, Windows and Linux is shaping up well and the accelerated development cycle is comparable to that of Firefox. Across all platforms there are minor yet noticeable changes including tweaks to colorization in Windows and Linux to better match the color schemes of the two operating systems.
While this build is generally stable, it should be remembered that it is still only a development version. You can find out more and download a copy of the browser by paying a visit to the Opera Next review page.
-

Chrome Remote Access Beta: Have mom install it right away
Publié: octobre 10, 2011, 3:15pm CEST par Mark Wilson
 Anyone who has tried to provide computing assistance over the phone will know just how frustrating an experience it can be. Without the ability to interact with a problematic computer, it can be hard to diagnose just what the problem is, and having to rely on someone else to explain what the issue is can be all but useless. There are a number of remote access tools that can be useful in these circumstances, but Chrome Remote Desktop Beta is an extension for the Chrome browser that brings remote access to the web browser.
Anyone who has tried to provide computing assistance over the phone will know just how frustrating an experience it can be. Without the ability to interact with a problematic computer, it can be hard to diagnose just what the problem is, and having to rely on someone else to explain what the issue is can be all but useless. There are a number of remote access tools that can be useful in these circumstances, but Chrome Remote Desktop Beta is an extension for the Chrome browser that brings remote access to the web browser.The extension can be used from a Windows, OS X or Linux based machine, and the only requirement is that both computers involved need to have both Google Chrome and the extension installed. As things stand, Chrome Remote Desktop Beta is unlike many other remote access tools in that someone needs to be in front of both the host and client computers.
This is because an authentication code needs to be generated and provided to the other party in order to grant access. This is an understandable security steps that should be praised, but it does mean that the extension cannot be used to take remote access of your own home computer when you are in the office.
However, as a tool for providing remote assistance, this is an impressive extension. If you find that you are frequently providing telephone support to your friends and family, you might want to start insisting that they have this extension installed ready for when they next need your help.
You can find out more and download a free copy of the extension by paying a visit to the Chrome Remote Desktop Beta review page.
-

25 downloads you may have missed this week
Publié: octobre 8, 2011, 8:09pm CEST par Mark Wilson
 While much of the IT world has been focused on news about the iPhone 4S and iOS 5, there has been a huge number of other newsworthy releases in the past week.
While much of the IT world has been focused on news about the iPhone 4S and iOS 5, there has been a huge number of other newsworthy releases in the past week.Related to portable devices such as a the iPhone is Freemake Video Converter 2.4.0, which makes it easy to convert videos between formats and, in particular, convert them optimized for viewing on a specific device. The app can also be used to rip non-copy-protected DVDs and to share your videos using YouTube. From the same company is Freemake Video Downloader 2.2.0 which can be used to download videos from the likes of YouTube and Dailymotion, and Freemake Audio Converter 1.1.0 which, much like its video related sibling, can be used to convert audio tracks from one format to another.
Pale Moon 7.0.1 has been released and this Firefox-based web browser is even faster than its predecessor, and this is a browser that already offered impressive performance. When you are online, it is important to keep safe, and a trio of tools from Webroot aim to do just this. Webroot SecureAnywhere Essentials 2012 v8.0.0.40 is a cloud-based anti-virus tool that is incredibly light on resources while including handy features such as sandboxing of apps. Also released were Webroot SecureAnywhere Complete 2012 v8.0.0.40 and Webroot SecureAnywhere AntiVirus 2012 v8.0.0.40.
Other security software released this week includes Emsisoft Anti-Malware 6 FINAL which offers vastly improved performance of the scanning engine when compare to previous versions.
If you’re looking to secure your data, look no further than the updated Wuala “Hirslanden” build 370,which now includes 2GB of free online storage space.
Spend any amount of time online and it won’t be long until you encounter a site that uses Flash. This week Adobe released updated versions of its Flash Player browser plugin -- Flash 11. There is a 32-bit version available for Internet Explorer, the 64-bit version of Internet Explorer, as well plugins for other 32-bit browsers and 64-bit browsers. The company also released Adobe AIR 3.0.
While OS X Lion has already seen the light of day and iOS 5 is not far off, Windows 8 is still some ways away. If you can’t wait to get the look of the upcoming operating system take a look at the updated Windows 8 Transformation Pack 2.0 and UX Pack 3, which enable you to mimic the look of the very latest preview version.
If you’re feeling a little more adventurous and fancy installing the Developer Preview, VMware Player 4.0 offers better hardware support for virtual machines, while VirtualBox 4.1.4 makes better use of system resources for improved performance.
 There has also been a series of releases from disc burning and multimedia specialists Nero. Nero Burning ROM 11 is a the company’s flagship burning tool that allows for the creation of all manner of discs, while Nero Video 11 allows for advanced yet easy editing of videos that can then be used in a range of projects. Both of these two and many more can be found in the Nero 11 suite. The final release from Nero this week is Nero Kwik Media 11.0, a media management suite capable of handling all your images, music and video files.
There has also been a series of releases from disc burning and multimedia specialists Nero. Nero Burning ROM 11 is a the company’s flagship burning tool that allows for the creation of all manner of discs, while Nero Video 11 allows for advanced yet easy editing of videos that can then be used in a range of projects. Both of these two and many more can be found in the Nero 11 suite. The final release from Nero this week is Nero Kwik Media 11.0, a media management suite capable of handling all your images, music and video files.Rounding off this week’s releases is a collect of free office tools from Kingsoft. Kingsoft Writer Free 2012 is a fully-featured Microsoft Word-compatible word processor that can be used completely free of charge, while Kingsoft Spreadsheets Free 2012 caters for the needs of spreadsheet users.
Rounding off the free tools is Kingsoft Presentation Free 2012 and all of the tools can be downloaded as part of the Kingsoft Office Suite Free 2012 if you would like to use all of them.
-

Nero updates flagship digital media software
Publié: octobre 6, 2011, 6:00pm CEST par Mark Wilson
 The Nero range of disc burning tools has been updated, and there’s something for everyone in this comprehensive suite of utilities. The company’s flagship Nero Burning ROM allows for the importing of files from the updated Nero MediaBrowser while SecurDisc Surface Scans make it easy to verify burn projects, but it is in the main Nero suite that the bigger changes are to be found, and the various tools that make it up.
The Nero range of disc burning tools has been updated, and there’s something for everyone in this comprehensive suite of utilities. The company’s flagship Nero Burning ROM allows for the importing of files from the updated Nero MediaBrowser while SecurDisc Surface Scans make it easy to verify burn projects, but it is in the main Nero suite that the bigger changes are to be found, and the various tools that make it up.One common use for the Nero suite is backing up data, and there have been a number of improvements in this area. As well as support for NAS drives as a backup location, there is now support for incremental backups of your drives as well as the option of creating 1:1 file copies. Related to safeguarding your data, NeroRescue Agent can now be used to work with partitions that have not been assigned a drive letter.
Nero Video now includes the option to import video clips directly from the Nero MediaBrowser, and if you have already started working with videos using Windows Live Movie Maker these projects can be imported into the program without fear of losing the work you have done so far. To help make your videos more exciting, there are now more audio and video effects to choose from and enhanced performance comes thanks to hardware acceleration with a wider range of graphics cards.
For when you are working with videos, Nero Recode also includes a number of useful enhancements. To make it easier to re-encode videos for playback on particular devices, there are now more re-defined profiles available but you also have the option of creating your own if you want to frequently save videos using the same settings. There are also new options for ripping both video and audio from DVDs as well as improved support for batch video conversion.
Other changes and additions across the suite include the ability to create and order photos products such as cards and calendars from within Nero Kwik Media, and Facebook video sharing.
-

Get the Windows 8 look and feel on XP, Vista or 7
Publié: octobre 6, 2011, 5:14pm CEST par Mark Wilson
 Even though the developer preview of Windows 8 is publically available, there will be some people who are keen to try out the upcoming operating system without having to go to the effort of setting up a dual boot system or wiping out their existing installation. This is where transformation packs can help, and the Windows 8 Transformation Pack 2.0 and UX Pack 3.5 have just been released with a view to making the task of mimicking Windows 8 easier and more impressive than ever.
Even though the developer preview of Windows 8 is publically available, there will be some people who are keen to try out the upcoming operating system without having to go to the effort of setting up a dual boot system or wiping out their existing installation. This is where transformation packs can help, and the Windows 8 Transformation Pack 2.0 and UX Pack 3.5 have just been released with a view to making the task of mimicking Windows 8 easier and more impressive than ever.In a matter of moments, the transformation tools enable you to turn your copy of Windows XP, Vista or 7 into a very close match to the look of Windows 8. The pack makes use of genuine Windows 8 resources to give an authentic finish, and this updated version includes changes to UI fonts, as well as the very latest icons navigation buttons and other interface components.
Closely related is the release of UX Pack 3.5. You have the choice of using the Aero, Aero Lite or Metro theme, complete with desktop widgets, and an authentic update version of the Start Orb. The updated version also includes new desktop wallpapers as well as new themes and users tiles.
Used together, the results that can be achieved with these two tools is genuinely impressive. Whether you are looking to get the Windows 8 look, or just fancy the idea of giving Windows a facelift, this is a great way to do so.
You can find out more by paying a visit to the Windows 8 Transformation Pack 2.0 and UX Pack 3.5 review pages.
-

Adobe Photoshop Lightroom 3.5 released -- get it now!
Publié: septembre 30, 2011, 1:32pm CEST par Mark Wilson
 Adobe has released an update for Photoshop Lightroom, bringing it to version 3.5 and adding support for an increased range of digital cameras. The update supports more high-end cameras' RAW output.
Adobe has released an update for Photoshop Lightroom, bringing it to version 3.5 and adding support for an increased range of digital cameras. The update supports more high-end cameras' RAW output.The list of newly supported cameras includes models from Fuji, Nikon, Olympus, Ricoh, Panasonic and more, and the same cameras are now also supported by the Camera Raw plug-in 6.5 for Photoshop. As well as adding new hardware support, Lightroom 3.5 also adds a number of enhancements and fixes bugs.
Performance issues when using the arrow keys to make adjustments have now been addressed, while problems with preview caching that plagued earlier versions of the program have also been addressed. Users of Lightroom 3.4.1 will have experienced issues with GPS Altitude metadata, but this is no longer a problem.
But it is not just problems with Lightroom itself that this latest update addresses, there are built-in optical correction options for various lenses. If you have been using various lenses manufactured by Canon, Hasselblad , Sony and others, Lightroom can now automatically fix known image defects that can creep in.
Among the newly supported cameras
- Fuji FinePix F600EXR
- Olympus E-P3
- Olympus E-PL3
- Olympus E-PM1
- Panasonic DMC-G3
- Panasonic DMC-GF3
- Phase One IQ140
- Phase One IQ160
- Phase One P40+
- Phase One P65+
- Sony Alpha NEX-C3
- Sony SLT-A35
The list above and below are direct from Adobe's website
Among the newly supported lenses
Lens Mount Lens Name Canon Canon EF 14mm f/2.8 L USM Canon SIGMA APO 120-300mm F2.8 EX DG OS HSM Hasselblad Hasselblad HC 2.2/100 Hasselblad Hasselblad HC 2.8/80 Hasselblad Hasselblad HC 3.2/150 Hasselblad Hasselblad HC 3.2/150N Hasselblad Hasselblad HC 3.5/35 Hasselblad Hasselblad HC 3.5/50-II Hasselblad Hasselblad HC 3.5/50 Hasselblad Hasselblad HC 3.5-4.5/50-110 Hasselblad Hasselblad HC 4/210 Hasselblad Hasselblad HC 4.5/300 Hasselblad Hasselblad HC Macro 4/120-II Hasselblad Hasselblad HC Macro 4/120 Hasselblad Hasselblad HCD 4/28 Hasselblad Hasselblad HCD 4-5.6/35-90 Nikon Nikon AF Zoom-Nikkor 80-200mm f/2.8D ED Nikon Nikon AF-S NIKKOR 24mm f/1.4G ED Nikon Nikon AF-S NIKKOR 35mm f/1.4G ED Nikon Nikon AF-S NIKKOR 50mm f/1.8G Nikon SIGMA APO 120-300mm F2.8 EX DG OS HSM Pentax SIGMA 85mm f/1.4 EX DG HSM Sigma SIGMA 85mm f/1.4 EX DG HSM Sony SIGMA 85mm f/1.4 EX DG HSM Sony TAMRON 18-270mm F/3.5-6.3 Di II PZD B008S Sony TAMRON SP 70-300mm F/4-5.6 Di USD A005S You can find out more and download a free trial of the program by paying a visit to the Adobe Photoshop Lightroom 3.5 review page.
-

Adobe Photoshop Elements 10 released
Publié: septembre 29, 2011, 4:09pm CEST par Mark Wilson
 Adobe has updated Photoshop Elements to version 10, and there are a huge range of features to enable you to view, organize, manage and edit your digital photos. For many people, using a photo editing package is all about adding special effects to images, and there are dozens of new effects to choose from here.
Adobe has updated Photoshop Elements to version 10, and there are a huge range of features to enable you to view, organize, manage and edit your digital photos. For many people, using a photo editing package is all about adding special effects to images, and there are dozens of new effects to choose from here.If you’re having trouble using any of the tools you find in the program, Guided Edits are on hand to provide you with assistance. While these may not help you to produce the best possible results, it is a good way to get an introduction to any tools you are not familiar with so you can see just what they are capable of.
There are a number of other interesting options such as the ability to search for objects in your image library. For example, select a picture of a cat and you will be shown a list of all the other library images that also feature cats. It is now easy to apply effects to just a portion of an image and there are a host of templates available for creating online image galleries and printed material.
As is almost obligatory these days, social networking gets a look in, and it is now possible to tag your photos using your Facebook friends list, then share your favorite images online. If you’re using Photoshop Elements to work with video clips, they can be uploaded to YouTube from the Organizer, and there is even support for full HD.
You can find out more and download a free trial of the program by paying a visit to the Adobe Photoshop Elements 10 review page.
-

Skype for iPad, iPhone now supports Bluetooth headsets
Publié: septembre 28, 2011, 5:52pm CEST par Mark Wilson
 Skype’s iPhone app proved to be incredibly popular, and the recently released iPad version soon picked up a healthy following as well. Both versions of the app have been updated to include support for Bluetooth devices while the iPhone version has a new anti-shake feature designed to eliminate wobbly footage when conducting a video call.
Skype’s iPhone app proved to be incredibly popular, and the recently released iPad version soon picked up a healthy following as well. Both versions of the app have been updated to include support for Bluetooth devices while the iPhone version has a new anti-shake feature designed to eliminate wobbly footage when conducting a video call.Bluetooth support has been enabled for iPhone 3GS and 4 users as well as for the iPad 2 and fourth generation iPods. This opens up the opportunity to use headsets to make and receive hands-free calls.
iPhone 4 users can take advantage of the new image stabilization feature that kicks in when the rear camera is in use. This makes it more enjoyable for other parties involved in a video call to see what’s going on without having to endure sea sickness-inducing camera shake.
Another update to both the iPad and iPhone versions of the Skype app sees the introduction of advertisements. Anyone who has Skype credit available will not see ads, and the same is true for anyone with a calling or premium subscription -- everyone else has to view them.
It is worth noting that to avoid potential problems such as slow contact syncing and a misreported loss of Skype credis, it is a good idea to delete your existing version of the app before installing the new one rather than simply updating in the usual way.
-

AVG Anti-Virus Free for Android has your back
Publié: septembre 27, 2011, 7:15pm CEST par Mark Wilson
 PCs are certainly the most common target for virus attacks, but this does not mean that other platforms are immune. The increased use of mobile devices means that platforms such as Android devices are prone to virus infection and antivirus software is now available to help counter this. AVG is most famous for its desktop virus protection software, but Anti-Virus Free is also available for Android and its aim is to protect your mobile in a number of ways.
PCs are certainly the most common target for virus attacks, but this does not mean that other platforms are immune. The increased use of mobile devices means that platforms such as Android devices are prone to virus infection and antivirus software is now available to help counter this. AVG is most famous for its desktop virus protection software, but Anti-Virus Free is also available for Android and its aim is to protect your mobile in a number of ways.As you might expect, the app provide virus protection on a real-time basis as well as enabling you to scan on a schedule or manually. Surfing the web is the source of many threats, and to this end the app includes phishing and malware protection. But Anti-Virus Free also goes far beyond this, and includes a number of handy extra tools and utilities.
If your phone is lost or stolen, there are a couple of remote tools that will be of interest. The app can be used to remotely switch on GPS and then broadcast the location of your phone so you can go and pick it up. Remote locking is also available so you can prevent a thief or anyone that should find your phone from running up a huge bill or prying into your personal information.
While AVG’s focus is understandably on avoiding virus infection and other threats, data protection is also important. There is a beta version of a backup utility that can be used to backup you text messages, contacts and other data while a task management tool is available to enable you to kill apps and processes that become problematic.
You can find out more and download a free copy of the app by paying a visit to the Anti-Virus Free review page.
-

WebM Video Converter is an absolute doddle to use
Publié: septembre 27, 2011, 6:15pm CEST par Mark Wilson
 Converting video from one format to another can be a real chore. Whether you are looking to reduce the size of a video file so you can more easily add it to your website, or if you need to have a file in a particular format so you can play it back on your chosen media device, almost everyone will have to battle with video formats and conversion software at some point. Free WebM Video Converter is a free tool that may just be able to make your life a little easier.
Converting video from one format to another can be a real chore. Whether you are looking to reduce the size of a video file so you can more easily add it to your website, or if you need to have a file in a particular format so you can play it back on your chosen media device, almost everyone will have to battle with video formats and conversion software at some point. Free WebM Video Converter is a free tool that may just be able to make your life a little easier.There are a large number of applications available that can be used to convert video files from one format to another, many of them are rather expensive and complicated beasts. Free WebM Video Converter is different as it is completely free of charge and an absolute doddle to use. There is no need to fiddle with complex menus or tweak endless options, with Free WebM Video Converter successful video conversion can be achieved in just a few mouse clicks.
The fact that the program is available free of charge does not mean that you have to make compromises about the video formats you are able to work with. Even if your digital camera captures footage in an obscure format, support for the likes of .ivf, .ts, .ogv, .mts, .tod and .mod, in addition to the usual .avi, .mov, .3gp and more, means that you can work with your videos without worries.
The actual conversion process is incredibly simple, and once you have selected the file you would like to work with, you can then select a name, destination and tagging options. After selecting a video format, you can use a drop down menu to choose from one of a number of presets before getting the conversion underway. It is possible to batch convert a number of videos at once and your computer can be scheduled to switch off when this is complete for overnight processing sessions.
You can found out more and download a free copy of the program by paying a visit to the Free WebM Video Converter review page.
-

Weekly roundup: 17 downloads you won't want to miss
Publié: septembre 25, 2011, 1:25am CEST par Mark Wilson
 Another busy week of software updates has passed. What could you possibly have missed?
Another busy week of software updates has passed. What could you possibly have missed?Right Click Enhancer 2.0 is a handy tool that gives you the chance to add new option to Windows’ context menu. There are a number of pre-defined examples that you can add by simply selecting from a list, or you can go to the effort of creating menu links of your own as well as adding and removing entries from the Send To menu.
It has been another busy week for Windows 8 tools, with both Windows 8 Transformation Pack 1.0 and UX Pack 3.0 seeing the light of day. The former can be used to give the look and feel of Windows 8 to any previous version of Windows from XP upwards, while the latter has been designed specifically with Windows 7 users in mind. As we wait for the completed version of Microsoft’s next operating system to be released, there is Microsoft WebMatrix 2 Beta from the same stables to take a look at. The tool can be used to create a website using any of a number tool including Joomla!, WordPress and Drupal.
If you prefer to build your websites from scratch, or you are involved in application design, WireframeSketcher 2.7.0 is likely to be of interest. The program is a sketchy, doodle-style way of piecing together web layouts and interface ideas quickly and easily, and it is available for not only Windows but also Mac and Linux. For anyone with a website of their own looking for a way to display photographs effectively, Jalbum 10.0 is an impressive tool. In next to no time you will be able to put together a photo gallery that can be easily added to your existing site or blog, and support for xmp metadata means that image information can be shared between applications.
Moving into the field of system tools, WinBuilder 082 can be used to create custom Windows boot discs. Ideal for creating diagnostic and fix-it discs, handy extra tools can be added to your disc that can be helpful in fixing a problematic computer. Autoruns 11.0 enables you to easily, and freely, analyze and fix startup problems. This Microsoft tool can be used to probe startup files and processes so you can determine where problems stem from before setting about the task of fixing them.
On the subject of system maintenance and improvement, O&O Defrag 15 -- available in both 32- and 64-bit versions -- makes it easy to keep your hard drive in good shape. The program can be used to automatically defrag your hard drive on a schedule, while Explorer integration means that individual files can be defragmented when required. The move to version 15 brings dramatic program performance improvements in a program that could dramatically improve the performance of your system.
 PeaZip 4.0 is a free archiving tool that can be used to open and create a variety of compressed files formats. As well as the usual performance enhancements and big fixes, the latest version of the program adds thumbnail support for images contained in archives. There is also a 64-bit version of the program available.
PeaZip 4.0 is a free archiving tool that can be used to open and create a variety of compressed files formats. As well as the usual performance enhancements and big fixes, the latest version of the program adds thumbnail support for images contained in archives. There is also a 64-bit version of the program available.On the browser front, there has been the usual flurry of activity. Comodo Dragon 14.0 is the latest version of the Chromium based web browser, focusing one performance and security. Google Chrome 15.0.874.24 Beta, Google Chrome 16.0.889.0 Dev and Google Chrome 14.0.835.186 FINAL all saw the light of day, as did Firefox 7.0 Beta 6.
SecretSync 1.261, despite the version number, finally came out of beta this week. The free version of this tool, will enable you to encrypt up to 2GB of data using your Dropbox account. You can also use other backup/synchronization tools such as SugarSync or SpiderOak. Alternatively use the free TrueCrypt to encrypt your Dropbox content.
Finally, take a look at the freeware Free Studio 5.2.1. This toolbox offers you a a suite of video and audio conversion tools and, from what we’ve told, this won’t be free for much longer. Grab it now whilst you can.
-

Comodo Dragon: Better browsing security with less bloat
Publié: septembre 23, 2011, 6:54pm CEST par Mark Wilson
 Spending time browsing the Internet can be fulfilling, but it can also be fraught with dangers. Every web browser claims to have a wealth of security options built in, Comodo Dragon goes a little further aiming to not only ensure that life online is as safe as possible, but also that the experience is not dogged by poor performance. Based on a Chromium core, Comodo Dragon is a bloat-free browser that balances speed and security.
Spending time browsing the Internet can be fulfilling, but it can also be fraught with dangers. Every web browser claims to have a wealth of security options built in, Comodo Dragon goes a little further aiming to not only ensure that life online is as safe as possible, but also that the experience is not dogged by poor performance. Based on a Chromium core, Comodo Dragon is a bloat-free browser that balances speed and security.The installation of the browser gives you the option of installing a portable version of the application, while the option to import your history, password, cookies and other settings from your current browser means that it makes switching easy.
Installing the software also enables you to use Comodo SecureDNS, not only with the web browser, but with any application that connects to the Internet. This makes it easier to avoid malicious websites without the need for additional software, and thereby eliminating the strain on your system. The browser’s clean and uncluttered interface is a pleasure to use, but it is the peace of mind Comodo Dragon offers that is particularly appealing.
There is enhanced certificate security and the now obligatory private browsing mode, here known as Incognito mode. Cheap domain-only SSL certificates are highlighted, alerting that you may be visiting sites that do not have the most scrupulous security. A small memory footprint is impressive, and the fact that the browser is free means that even if you already have multiple browsers installed, Comodo Dragon is still worth checking out.
You can find out more and download a free copy of the secure web browser by paying a visit to the Comodo Dragon review page.
-

WireframeSketcher: user interface mock-ups made fast and easy
Publié: septembre 21, 2011, 2:07pm CEST par Mark Wilson
 The days of using a drawing board are not quite behind use, and when it comes to sketching out a quick idea for a website, or even a program interface, it is quite common to reach for a pen and paper rather than a computer. But this may change if WireframeSketcher has anything to do with it. This is a design application that makes it easy to create rough mockups for websites and applications.
The days of using a drawing board are not quite behind use, and when it comes to sketching out a quick idea for a website, or even a program interface, it is quite common to reach for a pen and paper rather than a computer. But this may change if WireframeSketcher has anything to do with it. This is a design application that makes it easy to create rough mockups for websites and applications.Whether you are designing for the Internet, Windows, Mac or mobile platforms, WireframeSketcher can be used to quickly knock up an interface. The program can be used on solo projects, but there are also tools for collaborative work. There is an extensive library of page and interface elements that can be dragged and dropped onto your workspace to create an interface design in moments.
The app is something of a dream for designers. One of the problems with working with pen and paper is that it can look somewhat unprofessional when the time comes to present ideas to prospective clients, while creating fully-fledged mockups in a graphics package can be extremely time-consuming. The semi-hand-drawn look of WireframeSketcher is cute and appealing, but means that it is easier to focus on layout and basic ideas rather than the finished look of a product.
Basic behaviors can be added to interfaces so it is possible to try them out rather than just look at a theoretical layout. The free download is a trial version of the program which allows for use of all features. Any files you export from the application with be watermarked and a reminder dialog will be displayed each week.
You can find out more and download a free copy of the app, pay a visit to the WireframeSketcher review page.
-

Share 1-minute clips with Klip Video
Publié: septembre 20, 2011, 9:05pm CEST par Mark Wilson
 If you have an iOS device, be it an iPhone, iPod or iPad, you are equipped with everything you need to not only watch, but also record video footage. Just like photos, half of the fun of shooting videos is sharing the content with other people and for many people this will mean turning to YouTube. But having test driven Klip Video for iOS, this may soon change.
If you have an iOS device, be it an iPhone, iPod or iPad, you are equipped with everything you need to not only watch, but also record video footage. Just like photos, half of the fun of shooting videos is sharing the content with other people and for many people this will mean turning to YouTube. But having test driven Klip Video for iOS, this may soon change.The app can be used to record with the front or rear camera of your device and the integrated video editor can be used to trim the footage down to a clip that is one minute in length. While there is no limit on the number of files you can upload, the length of one minute cannot be exceeded, and this helps to keep Klip Video fresh and lively.
Of course, the app is not just about sharing your own videos, you can also browse through clips that have been uploaded by other people. just like Facebook and YouTube you are free to leave comments on videos, and Twitter-style hash tags can be used to follow videos of a particular theme.
Klip Video feature a couple of interesting navigation options; shake your device to preview all of the video thumbnails at the same time, and swipe an individual clips to control playback speed. To ensure the best possible performance, video streams are constantly analysed and the image quality is adjusted according to the available bandwidth.
You can find out more and download a free copy of the app by paying a visit to the Klip Video review page.
-

17 downloads you may have missed this week
Publié: septembre 18, 2011, 4:13am CEST par Mark Wilson
 Another week, another slew of software releases and app updates. The undoubted headline stealer is the release of the Developer Preview of Windows 8, but there have been plenty of other releases worthy of investigation for anyone not interested in Microsoft’s up-coming operating system. Available in both 32- and 64-bit varieties, the Microsoft Windows 8 Developer Preview is freely available for anyone to install, not just developers -- although there is also a version available that includes developer tools.
Another week, another slew of software releases and app updates. The undoubted headline stealer is the release of the Developer Preview of Windows 8, but there have been plenty of other releases worthy of investigation for anyone not interested in Microsoft’s up-coming operating system. Available in both 32- and 64-bit varieties, the Microsoft Windows 8 Developer Preview is freely available for anyone to install, not just developers -- although there is also a version available that includes developer tools.While the successor to Windows 7 is showing great signs of promise, it’s probably not a good idea to use it as your main operating system or use it for handling any mission critical data. But for seasoned users and anyone keep to keep on the cutting edge of software development, the preview gives you a chance to try out the Metro interface and a redesigned Explorer interface.
While you could set up a dual boot system to test drive Windows 8, you could also turn to VMware Workstation 4 or VMware Fusion 4 to install the operating system in a virtual environment. VMware Workstation 4 is a virtual machine manager for Windows and this latest release includes support for up to 64GB of RAM, HD audio and USB 3.0. There have been a number of visual chances to the program interface, with a new machine library replacing the old favorites sidebar and an update fullscreen toolbar provides access to more options than before.
Mac users need look no further than VMware Fusion 4 to cater for their virtualization requirements. The program can be used to host Linux and Windows operating systems so you can run software that is not available for OS X. The latest version of the virtualization tool brings Lion support that enables you to add Windows apps to Launchpad, and there is enhanced general and graphics performance. VMware Fusion 4 can also be used to host virtual copies of Lion, Snow Leopard and Leopard.
Windows users with safety in mind will have been heartened by the release of Paragon Backup & Recovery 11 Home which makes it easy to backup selected folders of your data or create an image of drives in their entirety. Having created a backup, should you find that your computer is rendered unbootable, a bootable restoration disc is available to help get your data back where it should be.
Being a computer user can be a frustrating experience, particularly when it comes to diagnosing and fixing performance issues and other problems. The updated release of Soluto may be able to help, using a connected cloud community of user data to diagnose and fix everything from serious system crashes to slow start times. Aside from fixing problems and gaining a speed boost, security is one of the primary concerns of any PC users. ESET 5 is a suite of tools that includes realtime virus protection as well as a firewall, parental controls, spam filtering and more. Security analysis is enhanced through the use of the cloud based Live Grid that is used to assess the threat level of different files and programs.
 Dexpot 1.6 beta is a great tools for anyone who feels they are running out of screen space. Rather than investing in a larger monitor, the applications enables you to take advantage of virtual desktops to maximise the amount of screen real estate available to you. The latest version of the app includes support for multiple monitors and enables you to configure individual applications to open on a particular desktop or monitor.
Dexpot 1.6 beta is a great tools for anyone who feels they are running out of screen space. Rather than investing in a larger monitor, the applications enables you to take advantage of virtual desktops to maximise the amount of screen real estate available to you. The latest version of the app includes support for multiple monitors and enables you to configure individual applications to open on a particular desktop or monitor.And no week of software releases would be complete without the usual selection of browser updates. Pale Moon 6.0.2 is the latest version of the speed-optimised browser based on Firefox 6 which is well worth a look. Other browser updates released this week include Firefox Portable 7.0 Beta 4 , Firefox 7.0 Beta 5, Opera Next 12.00 build 1065, Google Chrome 15.0.874.15 Dev, Google Chrome Portable 14.0.835.163 Beta, and Google Chrome 14.0.835.163 Beta.
-

Cheetah Sync wirelessly connects Android and PC
Publié: septembre 16, 2011, 2:26pm CEST par Mark Wilson
 Synchronizing files between devices usually entails one of two methods. The first involves establishing a physical connection between the two devices so that the contents of folders can be compared, while the second option takes advantage of cloud storage to act as an intermediary store for files. Cheetah Sync for Android eliminates the need for the middleman and allows you to synchronize files over your wireless network.
Synchronizing files between devices usually entails one of two methods. The first involves establishing a physical connection between the two devices so that the contents of folders can be compared, while the second option takes advantage of cloud storage to act as an intermediary store for files. Cheetah Sync for Android eliminates the need for the middleman and allows you to synchronize files over your wireless network.The app is available free of charge from the Android Market and in order to use it you will also need to download a copy of the desktop software for your Mac or Windows PC. You can then set about the task of configuring folder pairs and Cheetah Sync will take care of the rest for you. If you regularly work with more than one computer, you can choose to synchronize to multiple machines and there are advanced options for controlling filtering and resolving version conflicts.
Cheetah Sync offers a great way to keep the photos you take with your Android’s camera in sync with your main photo library on your computer. Rather than having to manually copy files into place, or using complicated software, automatic synchronization means that the photos you take can be copied into place for you so they are ready and waiting in the folder you would expect.
Of course, the same idea can be extended to any file type so documents are always where you need them. But you are not limited to using the app for standard synchronization -- it can also be used as a valuable automatic backup tool that takes the hard work out of safeguarding your data.
You can find out more and download a free copy of the app by paying a visit to the Cheetah Sync review page.
-

Manage your money with Manilla
Publié: septembre 16, 2011, 9:15am CEST par Mark Wilson
 Whatever sort of life you lead, there is no avoiding finances. We all have some form of bills to pay each month and bank accounts of one sort or another to keep track of. Keeping on top of what’s coming in and what’s going out and when can be tricky, often meaning having to visit one website after another, each with their own login requirements. Manilla is a great online service that enables you to access details of all your accounts and bills from one place. There are also apps available for iOS and Android devices.
Whatever sort of life you lead, there is no avoiding finances. We all have some form of bills to pay each month and bank accounts of one sort or another to keep track of. Keeping on top of what’s coming in and what’s going out and when can be tricky, often meaning having to visit one website after another, each with their own login requirements. Manilla is a great online service that enables you to access details of all your accounts and bills from one place. There are also apps available for iOS and Android devices.The Manilla website is almost obscenely useful. At its most basic you can use the service to monitor the various bank accounts you have, making it possible to get all of your balances in one place without the need to log into multiple websites. For this reason alone, Manilla is well worth checking out, but the fact that the service could also save you money by helping you to avoid late fees is also a great draw.
You can configure accounts for all of your monthly bills -- from your phone and internet to electricity and gas -- and the app can then be configured to send you reminders whenever a bill is due. Bills can then be marked as paid so you do not lose track of where you are with your outgoings. But it is the amount of time Manilla can save you each month that is so impressive -- the simple marvel of being able to view so much of your financial information in one place cannot really be appreciated until you’ve tried it out.
If you want to view more details about any of your bills, the Manilla app has a built in document viewer that can be used to open PDF and other files. Other handy features include support for Living Social and Groupon so you can be sure that the coupons you have bought will not be left forgotten to expire unused.
You can find out more by paying a visit to the Manilla for iOS and Android review pages.
-

Facebook for Android lags iOS version
Publié: septembre 16, 2011, 7:32am CEST par Mark Wilson
 It was only last week the iPhone version of Facebook was updated; the Android app followed suit this week. The Android app is not quite as fully featured as the iOS version, but the update brings a number of important improvements that bring it in line with the features of the Facebook website.
It was only last week the iPhone version of Facebook was updated; the Android app followed suit this week. The Android app is not quite as fully featured as the iOS version, but the update brings a number of important improvements that bring it in line with the features of the Facebook website.The big news here is the mirroring of the privacy controls that can be found on the Facebook website. When making a post, it is now possible to choose its visibility and choose whether location data should be attached to it. The same options are available when tagging images and sharing content online.
Much of your time in the app is likely to be spent looking at the News Feed page, and this has been updated in a number of ways. iPhone users, and users of a wide range of other apps, will be familiar with a downward swipe gesture being used to update the current view. This can now be used in Facebook for Android to check for new posts. Swiping left and right can also be used to navigate between images when browsing a gallery.
Facebook for Android does not quite have the polish, nor indeed quite the same feature set, as the iOS version, but it is a great step in the right direction. Some users have found that updating to this version of the app leads to stability problems, but these can be overcome by removing any existing version of the app before installing this one.
You can find out more and download a copy of the app by paying a visit to the Facebook for Android review page.
-

Stream TV anytime, anywhere with OrbLive
Publié: septembre 14, 2011, 6:50pm CEST par Mark Wilson
 Few people could imagine a TV viewing life that involved the rigid scheduling of a few years ago. The advent of devices such as Tivo and services such as Hulu and Netflix means that TV programms can be watched whenever it suits you. But while it can be useful to be able to timeshift you viewing in this way, OrbLive, used in conjunction with Orb Caster, can be used to stream video from your PC or Mac or your iOS or Android device.
Few people could imagine a TV viewing life that involved the rigid scheduling of a few years ago. The advent of devices such as Tivo and services such as Hulu and Netflix means that TV programms can be watched whenever it suits you. But while it can be useful to be able to timeshift you viewing in this way, OrbLive, used in conjunction with Orb Caster, can be used to stream video from your PC or Mac or your iOS or Android device.Videos can be watched away from your computer without the need to synchronize files -- all that is required is that the streaming software be installed and your computer be left switched on. With these two conditions met, install the OrbLive app on your mobile and you’re good to go. The ability to stream your existing video library from one device to another is great news, but it doesn’t end there.
The Orb applications can also be used with Hulu and Netflix so you can search for your favorite shows wherever you are -- streaming can also be achieved over the internet, not just over your own network. The apps can also be used as an elaborate means of streaming video to your TV. Providing you have the necessary cables, you can stream video form your computer, that may be located in the office, to your mobile, and view the footage on your large-screen TV in the bedroom.
Of course, it is also possible to stream music as well as accessing photos. This not only means the content of your iTunes library, but music you have stored in any other folders. When it comes to working with photos, you can browse through images stored in folders as well as those in your Flickr and Facebook account. But it doesn’t end there. If your computer has a TV card installed, or a web cam connected, the Orb software can also be used to view and control these devices.
While the desktop software is available free of charge, the mobile apps will set you back $9.99. You can find out more and download the software by paying a visit to the Orb Caster review page and the OrbLive review page.
-

Released this week: 29 must-see downloads
Publié: septembre 10, 2011, 6:05pm CEST par Mark Wilson
 This has been another busy week in the world of software releases, and there has been more news than normal in the field of security; both AVG and Norton products have been unveiled. AVG Internet Security 2012 is a step up from the free antivirus tool that many people will be familiar with, adding a number of handy protection tools to the equation including parental controls and online backup. Anyone looking for extra security, should look no further than the premium version of the program which offers protection against identity theft as well as system tuning tools.
This has been another busy week in the world of software releases, and there has been more news than normal in the field of security; both AVG and Norton products have been unveiled. AVG Internet Security 2012 is a step up from the free antivirus tool that many people will be familiar with, adding a number of handy protection tools to the equation including parental controls and online backup. Anyone looking for extra security, should look no further than the premium version of the program which offers protection against identity theft as well as system tuning tools.AVG also updated its flagship virus protection software, AVG Anti-Virus -- both the free and paid-for versions, with the latter providing additional checks for downloaded files amongst other things – and there is now a strong focus on minimizing the use of system resources whilst maintaining security. The company’s Rescue CD app, designed to fix problems with unbootable system, was also update, including the USB flash drive version.
But security news is about more than AVG -- the 2012 range of Norton security products was also released. Norton Anti-Virus 2012 is now faster and sleeker than previous versions of the app, while still offering great levels of protection. The cloud philosophy is used in the Download Insight 2.0 feature to share details about potential dangerous files between Norton users, while the full security suite Norton Internet Security 2012 features an updated firewall and the same refined interface and improved performance.
It doesn’t end there. The free avast! anti –virus software was also updated, as was its paid-for big brother avast! Internet Security. So whether you are looking for free security software for your computer, or you are willing to part with a few cents, there is plenty to choose from at the moment. Tackling security from a different angle is the updated version of O&O DiskImage which hit version 6. The latest enhancements include the option to backup individual files while the Machine Independent Restore feature enables you to restore a backup to a new computer, and you now have the ability to created backups of virtual partitions.
Moving away from security software, Screenshot Captor was updated to show that taking a screenshot can be much improved if you move away from simply pressing Prnt Scr. Converting videos and audio files can be a painfully time-consuming and complicated process, potentially involving the use of several different tools. The updated Free Studio, however, helps to make things easy as possible by bundling a whole load of converters into one handy tool. If you’re looking to convert video to watch on your iPod or PSP, or you like the idea of creating a DVD from YouTube footage, look no further.
 If you like the idea of getting creative, Corel PaintShop Photo Pro X4 is a cut above the competition. There are more than 75 improvements and new features in total, including a redesigned workspace that makes it easier to work the way you find best -- the addition of dual monitor support is something that will be welcomed by graphic workers everywhere.
If you like the idea of getting creative, Corel PaintShop Photo Pro X4 is a cut above the competition. There are more than 75 improvements and new features in total, including a redesigned workspace that makes it easier to work the way you find best -- the addition of dual monitor support is something that will be welcomed by graphic workers everywhere.IObit Uninstaller 2.0 has been released to make it easier than ever to remove unwanted software from your hard drive. The Forced Uninstall option makes it possible to wipe out even the most troublesome of programs, while the dedicated Toolbar section enables you to quickly find out what unwanted add-ons you have to remove. There is also a portable version of the app available for use on the move.
Finally, a number of updates to the major web browsers. Chrome 13 FINAL, Chrome Portable 13, Chrome 14 beta, Chrome Portable 14 beta, Chrome 15 dev, Firefox 6.0.2 FINAL, Firefox Portable 6.0.2, Firefox 7.0 beta 4, Firefox Portable 7 beta 4 and Opera Portable 11.51 were all updated in the last week. Opera Next v12.00 (build 1060) is an early preview of the next generation Opera, whilst Maxthon 3.17.1000, a web browser that mixes the best of Chrome and Internet Explorer, was made available. If you’re a Chrome fan, make sure you check out Comodo Dragon 13.2.
-

Imitate Windows 8 with Mosaic Desktop
Publié: septembre 10, 2011, 2:22am CEST par Mark Wilson
 As the launch of Windows 8 draws closer and closer, and increasingly tantalising details creep out about the operating system, the number of tools that enable you to mimic the look or copy the features of the next version of Windows also increases. One such tool is Mosaic Desktop. which enables you to bring the look of the redesign to your Windows 7 computer.
As the launch of Windows 8 draws closer and closer, and increasingly tantalising details creep out about the operating system, the number of tools that enable you to mimic the look or copy the features of the next version of Windows also increases. One such tool is Mosaic Desktop. which enables you to bring the look of the redesign to your Windows 7 computer.The tiled interface can be used to display a range of information -- from the date and time to the state of your inbox. There are a number of tiles that can be added to the interface, some of which show information about your computer, while other pull in information from the Internet. In order to add new tiles to the basic set that is included by default, you need to pay a visit to the Mosaic ‘store’.
Here you can choose from tiles that provide access to the Control Panel or the desktop, make it easy to interact with your Hotmail or Gmail accounts, or keep an eye on the weather. Mosiac Desktop can also be used as a launcher tool, as it is possible to add program and web site shortcuts to the interface to provide easy access to those that you use most frequently.
It is worth bearing in mind that this is beta software, and in tests it did prove to be a little unstable at time. That said, if you just can’t get enough of Windows 8, it is worth taking a look at and keeping an eye open for future updates.
You can find out more and download a free copy of the tool by paying a visit to the Mosaic Desktop review page.
-

Wi-Fi Finder for Android and iOS hunts down hotspots
Publié: septembre 8, 2011, 5:17pm CEST par Mark Wilson
 If you have an iPhone or an Android phone, the chances are that you frequently connect to the internet using a 3G connection. The same is true for some iPad users, although there are more WiFi-only Apple tablets in circulation. Whether you are working with a device that only offer WiFi connectivity, you are out of range of a 3G signal or you just need faster Internet access, there are numerous reasons you might want to find a wireless Internet connection when you are out and about, and this is something that Wi-Fi Finder can help with.
If you have an iPhone or an Android phone, the chances are that you frequently connect to the internet using a 3G connection. The same is true for some iPad users, although there are more WiFi-only Apple tablets in circulation. Whether you are working with a device that only offer WiFi connectivity, you are out of range of a 3G signal or you just need faster Internet access, there are numerous reasons you might want to find a wireless Internet connection when you are out and about, and this is something that Wi-Fi Finder can help with.The app is available for iPhone, iPad and Android, and native versions have been released for each type of device. If you do have a 3G connection, you can use the app online and check in the area for the availability of wireless networks. The database of hotspots includes both free and paid-for networks and you can use filtering to track down particular types of establishment offering WiFi -- you might want to avoid hotels, for instance.
A map and contact details is provided to help you get within range of the network and with a database covering over 140 countries, Wi-Fi Finder is great for use at home and abroad -- it is certainly worth installing before you head off on holiday or on a business trip.
This in itself is useful enough, but the app can also be used in offline mode. It makes sense that at least some of the times you are trying to find a wireless Internet connection, you may well be without an Internet connection of any sort. If you find yourself in this predicament, the offline database can be used to search for available networks; this can also be useful if you are planning a trip and want to check where you will be able to get online on your journey.
Even if you only use it a couple of times, this is an app that deserves your attention. Find out more and download a free copy of the app by paying a visit to the Wi-Fi Finder for iPhone/iPad and Wi-Fi Finder for Android review pages.
-

iOS Calendar shoot-out: Calvetica vs Weave
Publié: septembre 8, 2011, 2:19pm CEST par Mark Wilson
 The simple fact that iPhone, iPod and iPads have been designed specifically with portability in mind, they are perfectly suited for use as task management tools. As you are likely to have your iOS device with you at all times, it makes sense to store details of upcoming appointments, information about the projects you are working on, and to keep track of everyday data such as income and expenditure. Two of the most well received iOS apps in this category are Weave and Calvetica. We decided to put them head to head to see which comes out on top.
The simple fact that iPhone, iPod and iPads have been designed specifically with portability in mind, they are perfectly suited for use as task management tools. As you are likely to have your iOS device with you at all times, it makes sense to store details of upcoming appointments, information about the projects you are working on, and to keep track of everyday data such as income and expenditure. Two of the most well received iOS apps in this category are Weave and Calvetica. We decided to put them head to head to see which comes out on top. From the offset Weave is at a major advantage by virtue of being free. This gives the app instant appeal, and the fact that trial versions of iOS app do not exist, save for so-called ‘lite’ versions of apps, it is more likely to be installed by someone browsing the App Store.
From the offset Weave is at a major advantage by virtue of being free. This gives the app instant appeal, and the fact that trial versions of iOS app do not exist, save for so-called ‘lite’ versions of apps, it is more likely to be installed by someone browsing the App Store.But the absence of a price tag is not the only thing that works in Weave’s favor. The way the app works in unlike other comparable tools. There are plenty of nice little touches such as the option to turn off reminders on particular days of the week, which means that if you choose to take a couple of days off here and there, you can do so without having to worry about be pestered about deadlines you need to hit.
On the downside, there is no iPad version of Weave, and this means that iPad users have to endure the magnified mode that blights non-universal apps. This is not a problem that affects Calvetica; it is a universal app that looks good on the large or smaller screen. Or at least that is the way it would seem to start with. The iPad version of Calvestica makes excellent use of space and manages to convey a huge amount of information without ever looking cluttered.
The same cannot be said when the app is viewed on an iPhone or iPod; the screen restraints mean that it is simple not possible to show all of the information you have recorded about appointments and tasks. There is little that can be done to change this but it does mean that the iPhone and iPad version of Calvetica are almost different apps, and iPad users definitely get the better deal.
Calvetica is clearly designed with the power user in mind, and support for a wide range of gestures means that app navigation and accessing common features is quick and easy. Whether you are creating events or tasks, you can add notes, location information and more, and these details can be used to perform searches when you need to home in on certain information. Natural language style configuration of repeating events is interesting and unique, and the speed of event creation is incredible.
Choosing an app for any purposes is a very personal thing, and an app that is perfect for one person could not be more unsuitable for someone else. Weave and Calvetica are both very capable apps, and they both take dramatically different approaches to the age old problem of keeping on top of your tasks and events. Weave is undeniably simpler but it is perfectly designed to handle specific, keys pieces of information and presents it in a beautifully accessible form. Calvetica is somewhat more feature-rich, but this will not necessarily be to everyone’s tastes. The app you choose will depend very much on your individual circumstances, but in either case you are going to have a valuable tool at your disposal.
To help make your decision, pay a visit to the Weave or Calvetica review pages.
-

Facebook 3.5 for iOS adds privacy controls but no dedicated iPad app
Publié: septembre 7, 2011, 5:02pm CEST par Mark Wilson
 The good news: Facebook 3.5 for iOS is available, packing some new privacy controls. The bad news: There's still no dedicated iPad app. For now we’ll have to content ourselves with a less major updates. The v3.5 app reflects some of the privacy changes that have been made to the Facebook website, as well as bringing in tagging and location options.
The good news: Facebook 3.5 for iOS is available, packing some new privacy controls. The bad news: There's still no dedicated iPad app. For now we’ll have to content ourselves with a less major updates. The v3.5 app reflects some of the privacy changes that have been made to the Facebook website, as well as bringing in tagging and location options.New privacy settings are in place that can be configured to control who will be able to see and comment on the posts you make. You can choose to make posts public, limit them to your friends list or a particular group you have already set up. The settings you choose for a particular post remain in place until you change them for a future post, so be sure to check before making more status updates.
It is now also possible to tag people in photos and posts, while the location option means that you can broadcast your current location with your status update, although you do have the option of choosing to check into somewhere completely different.
If you find that clicking a link in a friend’s status takes you to an external website, it is now possible to share links you find interesting whilst in web view. Other minor updates include changes to the appearance of profiles and group walls and there is the usual quota of bug fixes and performance improvements.
You can find out more and download a copy of the app by paying a visit to the Facebook for iPhone review page.
-

IObit Uninstaller 2 nukes pesky toolbars and anything else you don't want
Publié: septembre 7, 2011, 4:31pm CEST par Mark Wilson
 Hard drives are larger and cheaper than ever before, meaning there is less of a need to reclaim disk space for reasons of capacity. But there is still a market for disk cleanup and uninstaller software. It's a perception thing: switching from the idea of looking at such tools as freeing up megabytes to instead regarding them as clearing up the mess left behind by other programs; it’s then easy to see their worth. One such utility is IObit Uninstaller 2.0, which comes with the added benefit of having being free.
Hard drives are larger and cheaper than ever before, meaning there is less of a need to reclaim disk space for reasons of capacity. But there is still a market for disk cleanup and uninstaller software. It's a perception thing: switching from the idea of looking at such tools as freeing up megabytes to instead regarding them as clearing up the mess left behind by other programs; it’s then easy to see their worth. One such utility is IObit Uninstaller 2.0, which comes with the added benefit of having being free.Windows includes a dedicated section of the Control Panel to help make it easier to remove software you have decided that you no longer need, and used in conjunction with an application’s own uninstaller things generally go smoothly. But can you really be sure that all traces of the program you just nuked has been completely wiped out? The obvious program folder may have disappeared, but what about entries that may have been added to the registry, or files that have been added to system folders?
There are also those troublesome apps that simply refuse, for reasons unknown, to uninstall in a tidy fashion. IObit Uninstaller can help to ensure that when you opt to remove a program form your hard drive, it really is completely eradicated. The program automatically creates a System Restore point in case anything goes wrong, before allowing the normal uninstall routine to run through its paces. Once this is complete, a scan of your computer will reveal any remnants that have been left behind and give you the opportunity to eliminate them. Should you encounter any software that does not want to play ball when it comes to removal, a forced uninstall option is available.
Unwanted browser toolbars are not only irritating, they can also prove tricky to remove. IObit Uninstaller has a dedicated section that lists any toolbars that may have found their way onto your system, and provides you with the same cleanup options to wipe them out. If you are having trouble deciding what to remove from your hard drive, browsing through the Rarely Used section may reveal a few potential candidates and the Batch Uninstall option helps to speed up the process of removing several programs without having to separately start the uninstaller for each app you no longer need.
You can find out more and download a free copy of the program by paying a visit to the IObit Uninstaller 2.0 review page.
-

Move over GarageBand and make room for MAGIX Music Maker MX
Publié: septembre 6, 2011, 11:40pm CEST par Mark Wilson
 Music creation software has something of a poor reputation, with many people regarding it as being expensive to buy and complicated to use. This is a reputation that MAGIX is trying to change with its Music Maker program, and the latest version, MAGIX Music Maker MX goes a long way to achieving this aim. While the program is incredibly simple to use, the music creation you produce using the software can be made as basic or as complex and involved as you like.
Music creation software has something of a poor reputation, with many people regarding it as being expensive to buy and complicated to use. This is a reputation that MAGIX is trying to change with its Music Maker program, and the latest version, MAGIX Music Maker MX goes a long way to achieving this aim. While the program is incredibly simple to use, the music creation you produce using the software can be made as basic or as complex and involved as you like.Used at its most basic, MAGIX Music Maker MX provides you with 64 audio tracks onto which you can arrange a series of samples to create the skeleton of a musical composition. If you want, you can leave things as they are, but even the least musically minded of people could not resist tinkering with special effects, dropping in a few loops here and there, and then there is the drum machine to play with. Before you know it, you have become fully engrossed in the process of putting together a piece of music -- and it does not matter that you’ve never picked up an instrument in your life.
Creating music using the building blocks of readymade loops and samples is the easiest way to get started with the program, and even in this way it is possible to create something quite impressive. With samples covering everything from hip hop and rock to dance and electronic, there’s sure to be something that inspires you. A wide range of drum and melody loops means that a completed track is never far away.
Of course, to get the most from the application, it is necessary to take things to the next level, and MAGIX Music Maker MX has a fairly gentle learning curve that enables you to take things at your own pace. You can learn how to use individual components of the music suite and each will enable you to come up with something new that can be added to your current project. One such a component is the Lead Synth which is an analog synthesiser that can be used to create your own melodies. Used in conjunction with a selection of realistic Vita Solo instruments, the results can be stunning.
Dance To Your Own Beat
Few tracks would be complete without some sort of percussion being present, and this is where the Drum engine comes into its own. Whether you are looking for a basic beat to keep things going, or you like the idea of recreating a classic drum sound, all the tools you need are available to enable you to do so.
The MX part of Music Maker’s name stand for Media eXchange and is a reference to the fact that it is now easier than ever to share tracks between different MAGIX products. For example, if you use Music Maker to record yourself playing an instrument, there may be unwanted background noise. It is now quick and simple to transfer the recording to Audio Cleaning Lab for enhancement before passing it back for use in your music project. Music Maker need not just be about creation stand-alone music; it can also be used to create soundtracks for videos. If you have a video project that you have been working on in Movie Edit Pro, it can be imported into Music Maker so you can get to work.
While the program is very easy to get started with -- if you are not the most musically minded of users, one of the best ways to learn about the various tools is by trial and error -- there are a number of online video tutorial that can point you in the right direction if you get stuck at any point. But the point is that MAGIX has made its name by producing software that makes potentially complicated things, such as music creation, simple for anyone to try their hand at.
Premium Edition
While the standard version of the program is packed with features, there is even more to work with in MAGIX Music Maker MX Premium. If you were worried that the 64 audio tracks available to you in the standard version of the software, the Premium version gives you 96 top work with as well as a wider range of effects, samples and instruments. BeatBox Plus is an enhanced version of the MAGIX drum machine, while tools such as the analog compressor and high quality synthesiser allows for great experimentation. To help with the process of creating loop and samples, a dedicated audio editor as well as a MIDI editor are available. Going Premium also unlocks the ability to work with 5.1 surround sound and includes a mastering suite to help with the production of CDs.
Whether you opt for the standard or premium version of MAGIX Music Maker MX, you are investing in a quality program that will service your music creation needs well. You can find out more and download a free trial of the program by paying a visit to the MAGIX Music Maker MX download page. The software runs on Windows XP/Vista/7.
-

Want something other than Mobile Safari? Try Dolphin Browser
Publié: septembre 2, 2011, 4:55pm CEST par Mark Wilson
 The choice of browsers for iOS is hardly overwhelming, so any new additions are always welcome. Dolphin Browser is the latest contender to vie for mobile Internet users’ attention and it has a number of unique features that make it well worth a look. The headline feature is support for gestures, but there is also desktop style tabbed browsing, an impressive smart address bar and space-saving sidebars that can be used to access bookmarks and app options.
The choice of browsers for iOS is hardly overwhelming, so any new additions are always welcome. Dolphin Browser is the latest contender to vie for mobile Internet users’ attention and it has a number of unique features that make it well worth a look. The headline feature is support for gestures, but there is also desktop style tabbed browsing, an impressive smart address bar and space-saving sidebars that can be used to access bookmarks and app options.There are already a handful of Safari replacements available, including the iOS version of Opera, so Dolphin is going to have its work cut out for it to stand out from the competition. The fact that the app is available free of charge certainly works in its favor, but it is the way the interface has been implemented, particularly the way in which you interact with it, and the intelligent use of available screen space that makes Dolphin Browser interesting.
Support for gestures means that valuable screen space that would otherwise be dedicated to navigation buttons can be reclaimed, and an all-important full-screen mode means that every millimeter of space can be used. This is particularly important at the moment for iPad users as there is only an iPhone/iPod version available; there is currently no universal app or dedicated iPad app at the moment.
The gestures make it easy to jump back and forth between pages as well as to the top and bottom of pages -- a much faster option than scrolling through lengthy web pages. There are a number of default gestures built in as standard, but you also have the option of creating your own. Taking inspiration from Opera, Dolphin Browser includes a Speed Dial feature for accessing common websites easily, and the idea is extended to the webzine component that can be used to quickly access your Facebook and Twitter accounts as well a news feeds.
Hidden sidebars can be called up with a simple swipe to the left or the right, with the former providing access to your bookmarks. A right hand swipe brings up the app’s toolbar where, amongst other things, you can configure program options. This is a refreshing change to the approach taken by other browsers, but the crowning glory of Dolphin Browser is the address bar. Autocomplete pulls in entries from your bookmarks as well as your browsing history and there is also a menu entry that makes it easy to perform searches; there are also handy buttons to add common domain suffixes.
You can find out more and download a copy of the app by paying a visit to the Dolphin Browser review page.
-

Use these tools to get the Windows 8 look now
Publié: septembre 2, 2011, 1:49pm CEST par Mark Wilson
 Windows 8 is just around the corner and it seems that almost every week there details emerge about just what can be expected from the latest version of Microsoft’s operating system. With every new Windows that is announced, there follows a rush to mimic the look and features long before the software hits the shelves, and things are no different with Windows 8.
Windows 8 is just around the corner and it seems that almost every week there details emerge about just what can be expected from the latest version of Microsoft’s operating system. With every new Windows that is announced, there follows a rush to mimic the look and features long before the software hits the shelves, and things are no different with Windows 8. There are a number of skins and customization packs available that can be used to get the Windows 8 look, including Omnimo for Rainmeter, but if you prefer the idea of getting a little more hands on, there are a range of tools you can use to mimic the elements of Windows 8 you most like the look of.
While transformation packs have their place, they are a little impersonal and tend to present you with a standard set of options. Going down the manual route means that you can add and change precisely what you want. At the heart of any version of Windows is Explorer, so it makes sense to make this your starting point. Windows 8 brings the Ribbon that Office users have become familiar with, and this can be almost perfectly replicated using Styler and a suitable skin. Using the ribbon skin, Windows 8 toolbar goodness is not far away.
Windows 8 also features a re-designed Start button and this is something that has been difficult to tweak in the past. StartOrbz is a free tool that changes this, and used in conjunction with the Windows 8 Start Orb you can quickly and easily match the look of Windows 8′s button. There is also Windows 8′s new Metro interface to consider and by using Metro Home you can add customizable weather and date gadgets to your desktop just like in Windows 8.
If you would like a more involved desktop makeover to mimic Windows 8, Zetro VS may be just what you have been looking for. The skin closely replicates the flat look of the Metro UI and also includes a re-designed Start menu as well as Windows 8 desktop images. Whether you want to go the whole hog or not, you can use a great looking wallpaper from the latest beta of Windows 8 to brighten up your desktop. This isn’t the only Windows 8 inspired theme that is available, and you may also like to take a look at Aero Lite with Glass.
All of the customization options we have looked at so far enable you to change the way Windows looks once you have logged into your user account. But by installing Windows 7 Logon changer you can customize your computer right down to the login screen. This is something that would normally require tinkering with system files, but with this application installed, it is a simple matter of selecting an image by browsing from the program interface, or taking advantage of the context menu option that will enable you to select any image you would like to use.
Of course, there are plenty of other tools that can be used to take your desktop customisation even further -- there really is no limit to the level of personalisation you can achieve. However far you want to take it, you’re sure to be able to find something to keep you going until Windows 8 finally sees the light of day.
-

Finally, Adobe offers PDF creation app for iOS
Publié: août 31, 2011, 4:50pm CEST par Mark Wilson
 Adobe has been a little slow venturing into the world of iOS software, but the release of Adobe CreatePDF sees it further branching out onto the platform with one of its most well-known services -- the creation of PDF files. iOS is not a platform you would naturally associated with a task such as creating PDFs, but Adobe feels that there is sufficient demand to justify a dedicated app; and quite a pricey one at that.
Adobe has been a little slow venturing into the world of iOS software, but the release of Adobe CreatePDF sees it further branching out onto the platform with one of its most well-known services -- the creation of PDF files. iOS is not a platform you would naturally associated with a task such as creating PDFs, but Adobe feels that there is sufficient demand to justify a dedicated app; and quite a pricey one at that.For $9.99 Adobe CreatePDF offers to create PDF files of the same standard as Adobe Acrobat. This sounds great in theory, even if the price tag is somewhat eye-watering, but there are some issues that need to be borne in mind. Firstly, as the name subtly suggests, this is an app concerned solely with the creation of PDFs. If you are looking to view PDF files you have created or downloaded, you’ll have to look elsewhere.
The app can be used to convert a limited number of files formats to PDF, including .psd, .doc, .xls and .jpeg. The ability to convert files is dependent on Adobe CreatePDF’s support for that app; if the app you use to open a particular file is not supported, you will not be able to convert that file type. In spite of the popularity of Apple’s own iWork office suite, Adobe does not allow Numbers or Pages documents to be converted. Also missing is the ability to edit PDFs, or even open them.
The number of people that rely solely on their iOS device for business is fairly limited, as is the range of formats supported by the app. Adobe CreatePDF is a nice idea -- in fact it is a little strange that it has taken Adobe so long to release such an iOS app -- but this feels like it has almost been released for the sake of releasing a mobile version of a popular tool. The price and limitations do not work in the app’s favour and it is unlikely to win too many fans.
You can find out more and download a copy of the app by paying a visit to the Adobe CreatePDF review page.
-

Infected PC won't boot? Try Dr Web LiveCD
Publié: août 26, 2011, 5:58pm CEST par Mark Wilson
 Antivirus and anti-malware software are essential for any computer users, but there are times when your defenses are down. You may have reinstalled your operating system or had to disable your security software for some reason. If you find that for these or other reasons your computer has become seriously infected with malware, perhaps to the point that it will not boot, Dr Web LiveCD is on hand to help you to get things back in order.
Antivirus and anti-malware software are essential for any computer users, but there are times when your defenses are down. You may have reinstalled your operating system or had to disable your security software for some reason. If you find that for these or other reasons your computer has become seriously infected with malware, perhaps to the point that it will not boot, Dr Web LiveCD is on hand to help you to get things back in order.As the name suggests, this is a live CD that can be used to boot an otherwise inaccessible computer with a view to retrieving files and fixing problems. Dr Web LiveCD downloads as a disc image that needs to be burned to CD and once this disc has been created it can be used to boot into a Linux environment that can be used to remedy a range of computer problems.
A virus scanner can be run to check your computer for signs in infection, removing or quarantining any suspicious files. There are also a number of other built in applications such as a web browser and an email client that can prove useful while you continue to fix your computer. More advanced users familiar with Linux have the option of booting into a command line version of the operating system, but most people will be more comfortable using the GUI.
At the very least, the live CD gives you the opportunity to access the files you have stored on your hard drive and therefore enables you to copy them to another location to help keep them safe. Even if this is all you are able to do before you have to reinstall Windows, Dr Web LiveCD is a valuable tool, but you’re likely to find that it is much more useful than that.
You can find out more and download your free copy of the disc image by paying a visit to the Dr Web LiveCD review page.
-

Annotate your photos with Skitch for Android, iOS
Publié: août 23, 2011, 5:25pm CEST par Mark Wilson
 It has been a busy few days for Evernote recently. Less than a week ago the company acquired the Mac application Skitch, and this was quickly followed by a big update to the Evernote iOS app. Just as the main Evernote notetaking app is available on a range of platforms, so Skitch is available not only for Mac but also for Android, making it possible to add annotations and doodles to the photos you take.
It has been a busy few days for Evernote recently. Less than a week ago the company acquired the Mac application Skitch, and this was quickly followed by a big update to the Evernote iOS app. Just as the main Evernote notetaking app is available on a range of platforms, so Skitch is available not only for Mac but also for Android, making it possible to add annotations and doodles to the photos you take.Skitch enables you to use a number of text and drawing tools to add information to photographs you have taken. This could take the form of useful notes about a snap you took on holiday, such as the name of a restaurant or attraction you liked, or it could be notes to help someone else understand what is visible in an image.
Of course, the app can also be used for less serious pursuits and the ability to upload doodles to Facebook and Twitter means that countless images of moustachioed and bespectacled relatives are sure to be found online.
Evernote has also released an update to its iOS software. An app x.1 upgrade is not normally something to get too excited about, but the introduction of Evernote 4.1.0 has quite a lot in store. iPad users in particular get a good deal -- a new three-finger gesture can be used to navigate between notes, and an overhauled interface makes things not only better looking than ever, but also somewhat easier to use.
It is now possible to select multiple notes for deleting or sharing, and both iPhone and iPad versions of the app include the option of searching within notes. Also new is the ability to add rich text lists, links and style to notes and support for shared notebooks means that the iOS version of the app is now far more useful when it comes to collaborative work.
You can find out more about Skitch and download a free copy of the app for your Android by paying a visit to the Skitch review page. If you already have Evernote installed on your iPhone or iPad, check the App Store for updates, or you can find our more or download a copy of the app by paying a visit to the Evernote review page.
-

Need More from Windows 7? Try Explorer Toolbar Editor
Publié: août 22, 2011, 4:06pm CEST par Mark Wilson
As you browse the contents of your hard drive in Windows Explorer, you will no doubt have noticed that depending on the type of folder you have selected, different buttons are displayed in the toolbar. While Windows generally does a pretty good job of determining what you might want to do with a particular type of file, it is not always right. Explorer Toolbar Editor enables you to choose which buttons you would like to have on display and when.
For example, when you are browsing through folders containing music, or performing searches of these folders, it is likely that you will either want to listen to these files or burn them to a disc so it makes sense to have the relevant buttons on display in the toolbar. However, if you would prefer different buttons to be displayed, or you would like these buttons to be displayed for other folder types, Explorer Toolbar Editor enables you to makes the necessary changes without having to edit the registry.
Even if you are happy with the default buttons that Microsoft has chosen to display in the toolbars, it is possible that they do not appear in an order that works for you. Again, this is something that Explorer Toolbar Editor can help with. In a few mouse clicks you can easily move the more commonly used buttons to a more prominent position, remove those that you never use and add any that are missing.
The application also allows for customization of the Explorer toolbar that appears when no files or folders are selected. While it makes sense to have cut and paste buttons when selecting files, when nothing is selected, there are probably more useful buttons to display. Any changes you make can be easily reverted if you change your mind or make mistakes, but the software is likely to stay on your hard drive as it can prove a real boost to productivity as the tools you need are always right where you need them.
You can find out more and download a copy of this free utility by paying a visit to the Explorer Toolbar Editor review page.
-

Did you miss these 26 software downloads last week? Get them now
Publié: août 22, 2011, 3:58am CEST par Mark Wilson
It was such a busy week -- what with Google planning to buy Motorola Mobility and HP killing TouchPad -- you could easily have overlooked a momentous number of new software releases. As the new week begins, we look back on what you might have missed during the last one.
The major release last week was more about the migration of Mozilla Firefox 7 from Aurora to the Beta channel, rather than the recent announcement that Firefox 6 is now stable. Firefox 7 is a bigger update, with much improved memory management and a host of similar features. Read through the blog announcement for more information. In addition to Firefox 6 going stable and Firefox 7 entering beta, Firefox 8a2 hit the Aurora channel, whilst the first preview of Firefox 9a1 hit Nightly. None of the planned UI enhancements have been implemented in this first alpha of Firefox 9 and, for OS X Lion users, these recent Firefox updates may leave you disappointed. The full screen mode does not place Firefox on a separate space and the scrollbars do not mimic the new bars introduced in the new operating system.
For OS X Lion users, we’d recommend Chrome 14, which moved in to the Beta channel recently. This build provides full support for gestures, the new scrollbars and proper full screen via Mission Control. The latest v14 beta also ships with a print preview for Mac users -- although it doesn’t always work very well. For serious users, the recent Chrome 15 Dev is updated overnight to give you the very latest features, and bugs.
Mozilla pushed out their Thunderbird 6 release last week and you’ll struggle to find many new features. Thunderbird 6 is based on the updated Gecko 6 engine, supports Windows 7 jump lists and ships with further stability and performance improvements. Expect Thunderbird 7 to hit the beta channel within days. There’s also a separate Thunderbird 6 Portable edition, which can be used on a temporary machine and removed without requiring installation.
The popular file synchronization and backup tool, Dropbox 1.1.40, was made available this week and the primary change is Finder support for OS X Lion. If you’re a serious user, take a look at the Dropbox Experimental Edition v1.2.27 which contains bleeding edge features, security enhancements, but also can be unstable. Talking of synchronizing content, take a look at the free Air Playit Sever 1.0.1 which will enable you to setup and stream video from your computer to your iPad or iPhone. You could setup an old PC as your media server, install Air Playit and be able to show video wherever you are located. You’ll need to install Air Playit for iPhone and the separate version for your iPad, so you can view the streamed content.
Skype launched a brand new app this week, Skype WiFi 1.0. This free app for your iPhone or iPad enables you to use pre-purchased Skype credits to pay for WiFi access whilst you are on the road. The idea here is that you do not need to get your credit card out and pay via your iPad when you’re away from the office. You might also want to take a look at Viber for iPhone/iPad or Viber for Android, which is another free app that will enable you to make calls via your 3G or WiFi network, which is always going to prove cheaper than paying for regular calls from your mobile provider.

Before you start streaming video to your iPad, you may want to convert the content to a format more suitable. MediaCoder 2011 R8, which is available for 32-bit and 64-bit PCs, is one of the better free conversion tools. Avidemux 2.54 is another, again provided with separate 32-bit and 64-bit builds. You might also want to look at Free Studio 5.1.7, which is a collection of conversion tools for video and audio. VidCoder 1.0, again available in 32-bit and 64-bit editions, was finally given a stable 1.0 release.
IObit Advanced System Care 5 beta 1 was made available for public beta testing this week, whilst the existing ASC v4 was upgraded to 4.1 at the same time. iolo System Checkup 3 (which is a brand new tool, despite the v3 tag) is a recent release which enables you to manually optimize your system, rather than allowing the app to sit in the background taking up precious system resources. Similar tools, Tweak Me! 1.2.0.3, TuneUp Utilities 2011 v10.0.4320 and Auslogics BoostSpeed 5.1.1 were made available this week.
Lastly, take a look at a couple of these Chrome extensions. Click&Clean for Chrome 7.6.0.0 gives you one-click access to a range of cleaning, history removal and other tools to get the most from Chrome. IE Tab for Chrome 2.7.14.1 enables you to run the Internet Explorer engine in Chrome, which is interesting for developers and for websites that are still designed specifically for IE, such as your bank. Note that this extension will only work with the Chrome for Windows, for obvious reasons.
-

Viber vies for Skype’s free-calling crown
Publié: août 19, 2011, 2:30pm CEST par Mark Wilson
There is no shortage of VoIP apps available for both Android and iOS platforms, but most of them fall down in one of several ways. The first sticking point that can mar an otherwise perfect app is the presence of advertisements. If these are not present it is likely that you will need to purchase credits in order to make call or send messages. Add to this the possibility for an app to just be bad, and any VoIP app vying for attention has to be something pretty special to avoid criticism. Viber falls into this latter category, being as it is, free, well designed, free from advertisements and lacking the requirement to purchase credits.
As a VoIP app, Viber is pretty much what you would expect. It enables you to send text messages and make phone calls using a WiFi or data connection. If you have the app installed on a phone, you can use it to keep in touch with people without racking up a huge bill and without eating into your monthly call and text allowance; if you have it installed on a non-Phone device, you can add phone functionality free of charge.
Unlike some other VoIP and messaging app, in order to use Viber you do not need to send messages or make calls to a special number or address for your contact. Providing they already have the app installed you can use Viber to keep in touch with people using their regular mobile number. This may seem like a minor thing, but it saves a great deal of hassle, particularly if you have a lengthy address book.
The app’s interface ties in neatly with the Android and iOS messaging and phone system to the extent that it is easy to forget that you are using a third party tool. Spend a little while working with the app and you’ll quickly come to realize that this could be a serious contender to Skype’s crown. There are still improvements to be made in the fields of stability, call quality and customization option, but things are looking very good already.
Viber is available for iOS and Android. You can find out more and download a free copy of the app by paying a visit to the Viber review page.
-

LinkedIn for iOS gets a much needed makeover
Publié: août 17, 2011, 2:18pm CEST par Mark Wilson
By Mark Wilson, Betanews
Previous versions were notable for being unimpressive. The release of LinkedIn 4.0 for iOS looks set to change the app's reputation, with a less-cluttered and more Mac-like UI.
-

Got Dropbox? And Android Phone? Try Dropsync
Publié: août 16, 2011, 4:01pm CEST par Mark Wilson
By Mark Wilson, Betanews
Rather than requiring you to visit the Dropbox website and edit files online or download them manually, Dropsync is a two-way synchronization tool for Android.
-

Beta This! Symantec tests new security software for Android
Publié: août 12, 2011, 4:05pm CEST par Mark Wilson
By Mark Wilson, Betanews
The mobile app includes expected anti-malware protection plus other goodies, like locating lost phones or disabling the device when SIM card is removed.
-

Apple tool solves Leopard to Lion Migration woes
Publié: août 12, 2011, 2:18pm CEST par Mark Wilson
By Mark Wilson, Betanews
Mac OS X Leopard's Migration Assistant lacks what you need to get your applications, data and settings on to newest version Lion. Finally, Apple has a solution.
-

Lion Tweaks takes control of OS X 10.7 features from Apple and gives it back to you
Publié: août 9, 2011, 4:25pm CEST par Mark Wilson
By Mark Wilson, Betanews
While Lion has generally received good reviews, there are still a number of aspects that have caused irritation to users who have upgraded from Snow Leopard and this is something that Lion Tweaks can help with.
-

Got Lion but feel insecure? Symantec releases two compatible beta security apps
Publié: août 8, 2011, 3:45pm CEST par Mark Wilson
By Mark Wilson, Betanews
Mac OS X 10.7 broke many programs that ran just fine under Snow Leopard. Developers are scrambling to update or release compatible applications. Two new Norton anti-malware apps join them.
-

MAGIX Music Maker 17 -- Silver edition is free
Publié: juin 28, 2011, 10:57pm CEST par Mark Wilson
By Mark Wilson, Betanews
This cutdown version of the paid product limits the number of audio channels to four and sample musical styles to three. That's OK, because appeal lies in ease of use coupled with surprising versatility and power.








-

Opera Next clears clutter from the browser UI
Publié: juin 23, 2011, 4:55am CEST par Mark Wilson
By Mark Wilson, Betanews
Project Featherweight brings a fresh new look to the browser interface. The rather minimalist interface features a completely redesigned set of icons for the toolbar which are more muted in style that in previous released. The result is a sophisticated look and feel that already feels polished.








-

Look to the heavens and fight malware with Panda Cloud Antivirus 1.5
Publié: juin 22, 2011, 1:16am CEST par Mark Wilson
By Mark Wilson, Betanews
Panda leverages the processing power of remote computers to improve scanning time.








-

Webian Shell: Full-screen browser replaces Windows, Mac OS
Publié: juin 21, 2011, 1:03am CEST par Mark Wilson
By Mark Wilson, Betanews
Do you spend most of your time in the browser and perhaps are considering Google Chromebook? You can achieve the same experience with your current computer.










![WhatsApp adds read receipts as messaging app celebrates fifth birthday [infographic]](http://betanews.com/wp-content/uploads/2014/11/whatsapp_infographic_small.jpg)