Canaux
108470 éléments (108470 non lus) dans 10 canaux
 Actualités
(48730 non lus)
Actualités
(48730 non lus)
 Hoax
(65 non lus)
Hoax
(65 non lus)
 Logiciels
(39066 non lus)
Logiciels
(39066 non lus)
 Sécurité
(1668 non lus)
Sécurité
(1668 non lus)
 Referencement
(18941 non lus)
Referencement
(18941 non lus)
éléments par Sead Fadilpašić
BetaNews.Com
-

Facebook Workplace Chat gets a desktop app
Publié: octobre 28, 2017, 8:29am CEST par Sead Fadilpašić
Facebook has expanded its Workplace enterprise suite with the launch of a real-time desktop comms offering called Workplace Chat. Even though it is called Workplace Chat, the PC app offers much more than just text-based communication. It also offers video chat with a co-worker or a group, screen sharing and file sharing. It also includes features like message reactions, @mentions, and gifs that "keep the conversation fun but focused," and may soon also offer group video chat. This desktop app joins web and mobile clients. It has been a year since Facebook first introduced Workplace and it released a few numbers on… [Continue Reading] -

Nvidia releases GPU Cloud container registry
Publié: octobre 27, 2017, 8:29pm CEST par Sead Fadilpašić
Nvidia has marked a new step forward in AI development with the release of its Nvidia GPU Cloud container (NGC). The NGC helps developers make their first steps into developing deep learning by allowing free access to a "comprehensive, easy-to-use, fully optimized deep learning software stack." However at the moment, the cloud-based service is available immediately "to users of the just-announced Amazon Elastic Compute Cloud (Amazon EC2) P3 instances featuring NVIDIA Tesla V100 GPUs." The company said it is planning on expanding support to other platforms "soon." No dates mentioned, though. "The NVIDIA GPU Cloud democratizes AI for a rapidly expanding… [Continue Reading] -

GDPR makes businesses concerned about cloud storage
Publié: octobre 26, 2017, 2:51am CEST par Sead Fadilpašić
More than nine in ten (93 percent) of companies worry about storing their data in the cloud, once GDPR kicks in, new research has claimed. A report from cloud solutions provider Calligo polling 500 IT decision-makers in companies with more than 100 employees, found than 91 percent of respondents worry how the new rules will affect cloud services. Less than one in seven (14 percent) said they were worried about meeting obligations under new privacy laws. For 41 percent, security and breaches are the biggest concern. When it comes to cloud services, almost half (46 percent) worry about the complexity of GDPR,… [Continue Reading] -

Mastercard opens blockchain API to developers
Publié: octobre 25, 2017, 11:37pm CEST par Sead Fadilpašić
Mastercard has opened up its blockchain technology to developers who want to test their own solutions. The company is looking to spur on development in the B2B space, saying that its technology is designed to increase speed, transparency and costs in cross-border payments. "By combining Mastercard blockchain technology with our settlement network and associated network rules, we have created a solution that is safe, secure, auditable, and easy to scale," Mastercard Labs executive vice president Ken Moore said in a blog post. "When it comes to payments, we want to provide choice and flexibility to our partners where they are able to seamlessly… [Continue Reading] -

UK banks don't want to deal with crypto companies
Publié: octobre 25, 2017, 2:50am CEST par Sead Fadilpašić
British banks are reportedly staying away from companies that handle cryptocurrencies According to the FT, the ambition of British banks to be see as a global hub for the fast-growing fintech sector are being questioned as companies that wanted to do business in the UK are now being force to opt for other countries like Poland or Gibraltar. According to companies working with cryptocurrencies, banks often see the new currencies as means of doing illegal business, following many reports that trade being carried out on the dark web is being done in this way. "The moment you mention crypto to a bank,… [Continue Reading] -

AWS and Nokia team up to make cloud migration easier
Publié: octobre 23, 2017, 11:13pm CEST par Sead Fadilpašić
AWS and Nokia are joining forces on a new partnership deal aiming to make cloud migration easier, and SD-WAN services for enterprises better overall. On top of that, the two technology giants will also work together on developing 5G and IoT use cases, combining their expertise to push forward future development. There are four major areas of collaboration between the two companies: first, they will be building a new 5G and edge cloud strategies and guidance, which includes reference architectures; second, they will be looking to commercialize IoT use cases using AWS Greengrass, Amazon Machine Learning, Nokia Multi-access Edge Computing (MEC) and the… [Continue Reading] -

Google officially introduces Data Loss Prevention API
Publié: octobre 23, 2017, 4:25pm CEST par Sead Fadilpašić
Google has just released a new API that helps organizations protect and regulate sensitive data. The Data Loss Prevention (DLP) API, which has been in beta since March, has now been unveiled, together with a couple of new features. The features include redaction, masking and tokenization. The API can enforce the principle of least privilege, or need-to-know access to data to production applications and data workflows. Its service can work with any data source or storage system. "Google Cloud DLP API enables our security solutions to scan and classify documents and images from multiple cloud data stores and email sources," said… [Continue Reading] -

HPE drops the cloud server business
Publié: octobre 23, 2017, 2:50pm CEST par Sead Fadilpašić
HPE could be saying farewell to the cloud server business after reports that the company will no longer sell low-end servers to some of its biggest clients, including the likes Microsoft and Amazon. The move seems to have a financial motive, as it can be extremely hard to turn a profit selling low-end servers in this way. Although HPE sells a lot of servers, the big players in the field, who buy these servers at bulk, are capable of negotiating huge discounts, making profits almost non-existent. To make matters even worse, most of them, including Google or Amazon, reach out to contract… [Continue Reading] -

Many businesses remain unprepared for GDPR
Publié: octobre 21, 2017, 3:23am CEST par Sead Fadilpašić
A shockingly large proportion of businesses have no idea how to behave when GDPR comes into play, a new report by the DMA has claimed. More than half of marketers surveyed (56 percent) believe they’re on the right track, with four percent actually saying they’re ahead in their plans of being compliant by May 2018. Another 17 percent are behind their current plan -- up from 11 percent in May this year. The report says that in the last year, "awareness and preparedness among marketers has risen." More than three quarters (77 percent) now rate their awareness as good, with just less… [Continue Reading] -

Privacy Shield gets EU's nod of approval
Publié: octobre 20, 2017, 2:46am CEST par Sead Fadilpašić
Last year’s framework which organized how Washington uses and protects data from EU citizens gets the nod of approval of the European Union this week. The EU-US Privacy Shield, a data pact which replaced the old Safe Harbor agreement, went through its first annual review. The general conclusion is that the United States has lived up to its promise to better protect data from EU citizens when they are transferred over the Atlantic. Failure to do so could have suspended the Privacy Shield, but as things stand now, it is not going to happen. This will be good news for… [Continue Reading] -

Cisco's new AI-based enterprise services can predict IT failure
Publié: octobre 19, 2017, 9:38pm CEST par Sead Fadilpašić
Cisco has just announced a new set of services that aims to predict potential troubles in a company’s IT department. Powered by artificial intelligence, the Business Critical Services and High-value Services offerings will anticipate IT failures, mitigate risks, reduce maintenance costs and assist organizations in keeping necessary skills to keep digital transformation going. Business Critical Services "goes beyond basic optimization to deliver more capabilities," Cisco says, adding that analytics, automation, compliance and security by Cisco Advanced Services’ tech experts are among those capabilities. This will enable a more secure, more efficient and agile technology environment. With Business Critical Services, human errors should be… [Continue Reading] -

Microsoft launch comparison tool for AWS and Azure
Publié: octobre 19, 2017, 2:09am CEST par Sead Fadilpašić
Microsoft has released a new tool to help IT decision makers understand the differences and similarities between Azure and Amazon Web Services easier. The tool is called Cloud Services Map. Both Amazon and Microsoft have increased their cloud offerings by a significant margin in the last couple of years. That makes tracking the differences, advantages and disadvantages of the two platforms reserved for only the most cloud-savvy among IT decision makers. That, as it turns out, isn’t good for anyone. So Microsoft wants to simplify the analytics process, laying out the pros and cons and helping customers plan their cross-cloud… [Continue Reading] -

Financial services to boost security investment on account of breach risks
Publié: octobre 19, 2017, 12:09am CEST par Sead Fadilpašić
Virtually every second global financial services organization was a victim of a data breach sometime in the past, according to a newly released Thales report. The 2017 Thales Data Threat Report, Financial Edition, says 49 percent of financial services organizations suffered a breach, with a fifth (21 percent) being breached more than once. Nine in ten (90 percent) feel more vulnerable to such incidents. As a result, more than three quarters (78 percent) are spending more to protect themselves. Almost all (92 percent) will deploy advanced tech, such as IoT, big data or cloud services, with 73 percent doing so before… [Continue Reading] -

IBM speeds up international payments with new blockchain-based service
Publié: octobre 18, 2017, 2:01am CEST par Sead Fadilpašić
IBM has looked to take the pain out of transferring currency across territories with the creation of a new cross-border blockchain payment solution. Built in partnership with KlickEx Group and Stellar.org, the solution should improve efficiency and reduce the cost of global payments for both consumers and businesses. The solution is based on IBM’s blockchain technology, allowing clearing and trade settlements on a single network and in real-time. International payments, however, have long been a problem, as they’re expensive, fallible and time-consuming. When it comes to transactions in multiple currencies, sometimes it can take weeks before they are fully processed. IBM says… [Continue Reading] -

Iran may have hacked the UK Parliament
Publié: octobre 17, 2017, 11:01pm CEST par Sead Fadilpašić
It seems to be Iran, and not Russia, who is behind last summer's cyber attack against the UK Parliament. At least that’s what The Times is reporting, and it’s backing its claims with "secret intelligence assessment." If that truly is the case, this would be Iran’s first foray into cyber-warfare. When it comes to possible motives behind the attack, it’s all still in domain of speculation. From looking into UK’s interests to try it to make any concessions, to scouting for advantages in trade, to changing the direction of the nuclear deal. It is the latter, however, that’s got everyone worried. According… [Continue Reading] -

HP announces 3D metal printing plaform
Publié: octobre 17, 2017, 2:14am CEST par Sead Fadilpašić
HP has looked to breathe new life into the 3D printing industry with the announcement of a new metal printing platform. Announcing the news, HP's president of 3DP business, Stephen Nigro, called the launch a "major step for HP 3D printing aspiration." The company hopes that the release of this new platform will "transform 3D metal printing into more mainstream, high-volume production. 3D metal printing is currently available for more specialized, high-value products." Speaking at the HP Securities Analyst Meeting in Palo Alto, Nigro also said next year HP will be introducing full color 3D printing, as well. He added that HP… [Continue Reading] -

AWS and Microsoft announce deep learning library Gluon
Publié: octobre 16, 2017, 9:13pm CEST par Sead Fadilpašić
Microsoft and Amazon Web Services have joined forces to make machine learning accessible to a greater number of developers. With that in mind, the duo has launched an open-source deep learning library called Gluon. The library will work as an interface where developers will be able to create prototypes, build, train and deploy ML models for either cloud or mobile apps. In the joint press release, the two companies have said that Gluon is more concise and easier to understand, compared to competing programs. It also said prototyping will be faster, and developers will be able to test neural network models without… [Continue Reading] -

Google and IBM launch open-source security tool for containers
Publié: octobre 16, 2017, 7:56pm CEST par Sead Fadilpašić
Google and IBM, together with a few other partners, released an open-source project that gathers metadata that developers can use to secure their software. According to an IBM blog post, the goal of the project is to help developers keep security standards, while microservices and containers cut the software supply chain. Grafeas was built as a container security API. IBM, on the other hand, will add its own container scanning tool, Vulnerability Advisor, into Grafeas. IBM said it will be a "central source of truth," when it comes to enforcing security policies. The API will collect the metadata defining a user’s software… [Continue Reading] -

Fear of cyber attacks holding Office 365 adoption back
Publié: octobre 14, 2017, 12:42am CEST par Sead Fadilpašić
Businesses in the EMEA region re increasingly using Microsoft’s Office 365 solutions, but they’re doing it with a dose of fear from cyber-attacks and similar malicious actions. This was concluded in the new Barracuda Networks report, entitled Office 365 Adoption: Drivers, Risks and Opportunities. Based on a poll of more than 1,100 organizations in EMEA, the report says almost two thirds (62 percent) are now using Office 365. This is a jump from last year’s 50 percent. Of those that still don’t use the service, almost half (40 percent) said they’re planning to do so in the future (49 percent… [Continue Reading] -

Microsoft releases Windows 10 Fall Creators Update SDK
Publié: octobre 13, 2017, 8:30pm CEST par Sead Fadilpašić
Microsoft took the Windows Developer Day as an opportunity to release a couple of new features and announce some fairly big changes to some of its best-known platforms Among the biggest things announced are the launch of the Windows 10 Fall Creators Update SDK. With the new SDK, which was in preview until now, developers will be able to submit everything they do, including apps, games and updates, to the Microsoft Store. Microsoft says the Fall Creators Update SDK, which can be downloaded from this link, "provides 1000s of new capabilities and improvements." The other big announcement is that Windows Store… [Continue Reading] -

Accenture leaves highly-sensitive data on unsecured servers
Publié: octobre 12, 2017, 8:22pm CEST par Sead Fadilpašić
Accenture has confirmed that highly sensitive company data was left sitting on an unlocked cloud server. The tech giant confessed that a huge database, including hundreds of gigabytes of data for the company’s enterprise cloud offering, was left on four unsecured Amazon S3 servers. The data included highly sensitive passwords and secret decryption keys, which could have inflicted significant damage on both the company and its clients. To put things into perspective, Accenture’s clients are Fortune 100. The data was uploaded in such a way that anyone who knew the servers’ addresses could have walked in and taken the data. Chris Vickery,… [Continue Reading] -

Brexit impact on UK jobs market may be overestimated
Publié: octobre 12, 2017, 6:07pm CEST par Sead Fadilpašić
New reports are arguing that Brexit may not have such a major effect on the UK's tech sector as previously imagined. Research released by Tech City UK and Nesta claim that foreign workers are more likely to have come from outside the EU, meaning that losing EU-based workforce may not be as "dangerous" for businesses as previously thought. Based on an analysis of 1.7 million workers in the digital space, it says that 13 percent are not from the UK. Out of that number, just over half are from outside the EU. In London, foreign workers from the EU accounted for 11 percent… [Continue Reading] -

Top banks teaming up for a blockchain-based syndicated loans platform
Publié: octobre 10, 2017, 12:32am CEST par Sead Fadilpašić
Seven of the world's top banking groups, including HSBC, ING and BNY Mellon are joining forces to create a platform for syndicated loans based on blockchain technology. The blockchain service will be provided by R3 (a popular blockchain consortium) and Finastra (a UK financial software company). The service starts with Fusion LenderComm, an online marketplace that will use blockchain’s distributed ledger technology to reduce cost and improve on the efficiency and transparency of loans with multiple lenders. So far, the work in the syndicated loans was done manually. "The community of banks already on board covers approximately 10 per cent of the… [Continue Reading] -

IT spend will reach $3.7 trillion in 2018
Publié: octobre 5, 2017, 8:25pm CEST par Sead Fadilpašić
Global spending on IT is expected to grow 4.3 percent next year, according to new estimates from market analyst Gartner. Gartner says spending is expected to hit $3.7 trillion next year, up from $3.5 trillion. The growth will be fueled mostly by communications services, followed by software spending which will see an increase of 9.4 percent next year, to a total of $387 billion. This year, it grew 8.5 percent. Spending on IT services will grow four percent this year, to $931 billion, and more next year -- 5.3 percent, up to $980 billion. What’s also interesting is that Gartner predicts growth… [Continue Reading] -

Oracle announces blockchain-based enterprise service
Publié: octobre 5, 2017, 2:04am CEST par Sead Fadilpašić
During the Oracle OpenWorld event, Oracle announced its entry into the world of blockchain with a new enterprise-oriented service. It is fully-managed, and built on the open-source Hyperledger Fabric project. Prior to announcing the project, Oracle joined forces with IBM in building a blockchain service. "There are not a lot of production-ready capabilities around Blockchain for the enterprise. There [hasn’t been] a fully end-to-end, distributed and secure blockchain as a service," Amit Zavery, senior vice president at Oracle Cloud said. Zavery says this project will help businesses interested in blockchain, a hit-the-ground-running start. That is achieved by taking the basics… [Continue Reading] -

Equifax was aware of vulnerabilities prior to data breach
Publié: octobre 4, 2017, 9:03pm CEST par Sead Fadilpašić
The total number of people affected by the recent Equifax breach has risen after more details came to light. According to new reports, the number of affected customers has now hit 148 million -- meaning that an additional 2.5 million people have been impacted. However the number of customers hit in some markets may be less than previously thought -- as the report claims that only 8,000 Canadians were affected, not the 100,000 originally reported. During a testimony in front of the Congress, former Equifax CEO Richard Smith said both humans and technology is to blame for the breach. Apparently, Equifax knew about… [Continue Reading] -

Oracle to add AI capabilities to cloud apps
Publié: octobre 4, 2017, 7:21pm CEST par Sead Fadilpašić
Following the introduction of "adaptive intelligence" earlier this year, designed to improve customer experience (CX), Oracle has now introduced a new offering that builds on that idea. During the Oracle OpenWorld event, the company announced that it will be adding its AI-powered capabilities to the bulk of its cloud applications, including Enterprise Resource Planning Cloud, Human Capital Management Cloud, Supply Chain Management Cloud, as well as the Oracle Customer Experience Cloud applications. Similar to what Salesforce has done with its Einstein, Oracle will be looking to help its clients make better use of both customer and business data. "We have the broadest… [Continue Reading] -

Equifax data breach may be state-sponsored
Publié: octobre 3, 2017, 9:12pm CEST par Sead Fadilpašić
The Equifax hack that saw data of millions of Americans compromised might as well have been state-sponsored, new media reports have claimed . As the investigation unfolds, reports have started coming out that some elements of the attack point to a state-sponsored play, although nobody is pointing any fingers. Bloomberg says the hack might have been initiated by a less experienced group, but it seems as they had handed over the baton to a more "sophisticated" team somewhere along the line. Researchers have said that some of the tools used in the hack were of Chinese origin, and that the hack itself… [Continue Reading] -

SEC goes after two ICOs over fraud
Publié: octobre 3, 2017, 7:11pm CEST par Sead Fadilpašić
Bitcoin and other cryptocurrencies may be set to face more scrutiny from law authorities following a landmark case in the US. The Securities and Exchange Commission (SEC) has raised its first ICO-related lawsuit, charging businessman Maksim Zaslavskiy with fraudulently running two initial coin offerings (ICOs). The ICO is an unregulated investment practice in which companies take investors’ cryptocurrency in exchange for "crypto-tokens." This practice has already been banned in China and South Korea recently. The SEC has been issuing warnings that ICOs are a good platform for scammers. Zaslavskiy was, according to the SEC, selling unregistered securities and issuing digital tokens or coins… [Continue Reading] -

BlackBerry is on the road to recovery
Publié: septembre 29, 2017, 8:14pm CEST par Sead Fadilpašić
Rumors of BlackBerry's death may have been somewhat premature. The company just revealed its latest financial results, showing significant profits. The former smartphone giant posted a stronger-than-expected second quarter, after, according to BlackBerry, its "complete transformation to a software company." The company reported a Q2 profit of $19 million, with its shares rising seven percent in Thursday premarket trading. Analysts expected BlackBerry to "break even" on revenue. "We achieved historical highs in total software and services revenue and gross margin, as well as the highest non-GAAP operating margin in over five years, reflecting our complete transformation to a software company,"… [Continue Reading] -

Chinese investment firm buys Imagination Technologies
Publié: septembre 26, 2017, 11:47pm CEST par Sead Fadilpašić
Leading UK technology company Imagination Technologies is being acquired by a Chinese investment firm in a multi-million pound deal. CBFI Investment Limited (owned by Canyon Bridge) is shelling out £550m to acquire the hardware maker, based in Kings Langley just outside of London, the parties confirmed late last week. The CBFI Investment Limited (newly incorporated company owned by the Canyon Bridge Fund) and Imagination’s board of directors agreed on a recommended cash acquisition by which the entire Imagination’s issued and to be issued ordinary share capital will be acquired by CBFI. The price agreed is 182 pence per Imagination share. CBFI won’t… [Continue Reading] -

Google introduces zero-touch enrollment tool for Android devices
Publié: septembre 26, 2017, 12:39am CEST par Sead Fadilpašić
Employees given one of the most popular choices of Android smartphones can now expect their devices to arrive preconfigured, meaning they can use them out of the box without the typical tedious -- albeit necessary -- setup process. A new tool rolled out by Google, called zero-touch enrolment, aims to result in less work for both administrators and end-users. Admins will be sure all corporate policies are always in place, and end users only need to log in to start using their new smartphone. As of today, the deployment method is available from Google’s zero-touch carrier partners, including BT and Deutsche Telekom in Europe, Verizon,… [Continue Reading] -

Ransomware attacks affect five percent of SMBs
Publié: septembre 25, 2017, 5:54pm CEST par Sead Fadilpašić
Five percent of all small and medium-sized companies in the entire world were victims of a ransomware attack in 2016 alone, with the money paid out to reclaim data reaching new highs, new research has revealed. Datto's new State of the Channel Ransomware Report found that an estimated $301 million (£222 million) was paid to ransomware hackers from 2016-2017. The report, which was based on a poll of more than 1,700 managed service providers that work with more than 100,000 SMBs, also found that 99 percent of respondents believe the number of ransomware attacks will increase in the next two years. The financial strain… [Continue Reading] -

Moving IT operations to the cloud is good for the bottom line
Publié: septembre 22, 2017, 11:23pm CEST par Sead Fadilpašić
UK’s businesses are earning less because they lack cloud skills, a new report by Rackspace and the London School of Economics claims. The report also says that the lack of these skills is also hindering creativity. The report, called The Cost of Cloud Expertise, is based on a poll of 950 IT professionals. Two thirds (64 percent) said they’re losing out on revenue due to the lack of required cloud expertise. The same amount said they need to invest more in the workforce. Even more, 67 percent, said their organizations could bring more innovation if they knew how to use cloud to… [Continue Reading] -

Over one million phishing websites are created every month
Publié: septembre 22, 2017, 10:22pm CEST par Sead Fadilpašić
Every month, almost 1.5 million new phishing websites are created. This is according to a new report by Webroot, showing just how big of an industry phishing really is. The Webroot Quarterly Threat Trends Report says that 1.385 million new phishing sites are created every month. May was the busiest of them all, with 2.3 million sites created. The report also says these sites are getting more sophisticated and harder to detect, while the goal always remains the same -- to trick the unsuspecting visitor into giving away personal information. The interesting thing about these sites is that they stay up very short --… [Continue Reading] -

Toshiba sells chip unit to Bain Capital for $18bn
Publié: septembre 22, 2017, 2:48am CEST par Sead Fadilpašić
Toshiba has finally confirmed it will be selling its troubled chip unit to Bain Capital in a deal worth $18 billion. As revealed by Reuters, the deal, the equivalent to two trillion yen, brings an end to a prolonged bidding process which has lasted around eight months, and seen Toshiba flirt with a number of major organizations as it looked to offload its memory chip division. US firm Bain Capital's acquisition is backed by a consortium of domestic and foreign investors, most notably Apple, Seagate and Dell, which will both provide financial support, as well as Toshiba itself, which will reinvest 350.5 billion… [Continue Reading] -

Two billion data records were stolen or lost in 2017 so far
Publié: septembre 22, 2017, 12:46am CEST par Sead Fadilpašić
Almost two billion data records were either lost or stolen in the first half of this year, according to a new report by Gemalto. The company found that 1.9 billion records were lost or stolen during the first half of 2017 -- more than in the whole of last year, and equivalent to 10,439,560 records per day -- or roughly 3,000 whilst you read these few sentences. There have been 918 reported data breaches in the first six months of this year, which is a jump from 815 that we had in the same period last year. Out of all those, 22 breaches have… [Continue Reading] -

AI will boost productivity and collaboration
Publié: septembre 20, 2017, 3:54pm CEST par Sead Fadilpašić
Not everyone sees artificial intelligence as the destroyer of worlds or, in milder cases, destroyer of jobs. Many people, particularly Millennials, are confident AI will instead create new jobs in the future. That's is according to a new report by analyst firm CCS Insight, which found that many workers believe AI will automate mundane work tasks and boost productivity and collaboration applications. The report, which polled more than 650 employees, found that more than half believed this profound change will happen within three years. A larger portion, however (70 percent), believe this will happen within the next decade. CCS Insight's vice president… [Continue Reading] -

UK SMBs spend up to £3 million a year on technology upgrades
Publié: septembre 19, 2017, 8:10pm CEST par Sead Fadilpašić
UK SMBs are shelling out huge amounts of money on upgrading their technology every year, potentially hindering investment elsewhere, new figures have claimed. A report from American Express and the Center for Economics and Business Research (CEBR) found that on average, SMBs spend roughly £200,000 each year on new technologies. Their spending has a range from £225,000 (micro-businesses with less than nine employees) to £3 million, for SMBs with 50+ employees. On average, about a fifth of the company’s expenditure goes on new technology. The biggest cut, roughly a quarter, goes on hiring new people. "Running a business can be an expensive… [Continue Reading] -

Microsoft adds Confidential Compute to Azure cloud platform
Publié: septembre 19, 2017, 1:26pm CEST par Sead Fadilpašić
Microsoft has revealed a major new addition to its Azure cloud platform, aimed at keeping user data safe. The feature, called Confidential Compute, will make sure the data is being encrypted even when it’s being computed on in-memory. So far, it’s been encrypted while stored or while in transit on a network. Microsoft says this feature will make sure data stays away from prying eyes, including hackers, government warrants or even Microsoft itself. There will be two modes to the feature -- one built on virtual machines, and the other using Software Guard Extensions (SGX). Both allow apps to enclose parts… [Continue Reading] -

Facebook's new AI research lab opens in Montreal
Publié: septembre 19, 2017, 12:33pm CEST par Sead Fadilpašić
Facebook is opening another AI research lab as it looks to expand its artificial intelligence capabilities. The company's fourth dedicated AI lab is following the footsteps of Google and Microsoft by being located in Montreal, Canada. The lab, which will initially number just ten employees, plus interns, should rise to 30 in a couple of years, will be led by Joelle Pineau, an associate professor at Montreal’s McGill University. Pineau will keep her academic position. "I love that job, but there comes a time when you're up for a new challenge and finding out about a new way of doing… [Continue Reading] -

Public cloud security is a concern for most IT pros in UK
Publié: septembre 16, 2017, 1:22am CEST par Sead Fadilpašić
An overwhelming majority of the UK’s IT professionals (90 percent) have their worries when it comes to securing the public cloud, according to a new study. Research by Bitdefender found that 90 per cent of British professionals had concerns around the security of public cloud. A fifth (20 per cent) also said that their business doesn’t have security measures set up for sensitive data outside the company infrastructure. Bitdefender found that only half of the organisations surveyed said that cloud migration expanded their threat landscape 'significantly,' and a fifth encrypts migrated data. The survey covered 1,051 IT security professionals from large companies… [Continue Reading] -

It will be easy for businesses to comply with GDPR, UK's digital minister says
Publié: septembre 15, 2017, 4:46pm CEST par Sead Fadilpašić
UK's new Data Protection Bill, aimed to "encourage innovation while protecting privacy," was published this week. Digital minister Matthew Hancock took the opportunity to call all businesses to become compliant with GDPR before the deadline of May 25, 2018. In an opinion piece published on City AM, Hancock said the new laws are built on the existing ones and it shouldn’t be too hard for businesses to get used to them. "Any organization’s data protection framework that’s compliant with the existing rules should be in a good position to take the step up to being compliant with the new laws. They add… [Continue Reading] -

Google Chrome will stop trusting older Symantec certificates
Publié: septembre 14, 2017, 10:39pm CEST par Sead Fadilpašić
Chrome will stop trusting any security certificates issued by Symantec, Google has confirmed. In a blog post, Chrome Security's Devon O’Brien, Ryan Sleevi and Andrew Whalley say that certificates from the security firm will be "distrusted," starting with version Chrome 66. This affects all certificates issued before June 1, 2016. At the same time, Symantec is working with webmasters to switch to Digi Cert certificates, after the company bought the firm's failing web security business. Chrome 66 is expected to arrive in June next year, so the final shutdown should expected with Chrome 70 next October. This will, as Google puts it,… [Continue Reading] -

Oracle plans massive job cuts in Europe
Publié: septembre 14, 2017, 6:51pm CEST par Sead Fadilpašić
Oracle is reportedly planning major job cuts across Europe as it readies for a company-wide reorganization. According to The Register, Oracle is looking to shift its hardware support division into Romania. Confirmed by 'multiple insiders' the report states the process has already begun, although the deadline for migration differs from country to country. There seems to be a total of 424 Oracle employees in Europe that work on hardware support. With 137 already in Romania, that leaves us with 287 people outside the country that might lose their jobs. The majority (77) are based in Germany, with Spain (67), France (55),… [Continue Reading] -

Google plans to appeal €2.42bn EU antitrust fine
Publié: septembre 13, 2017, 7:40pm CEST par Sead Fadilpašić
Google will appeal the EU fine of €2.42 billion for abusing its dominant position in the market, reports have claimed. The US giant was fined earlier this year for abusing its monopoly in search engine and shopping comparison services. Google said it respected the EU Commission's ruling, but that it disagrees. A spokesman for the EU commission said: "The commission will defend its decision in court," however it is expected to take years for the Luxembourg-based general court to rule on Google's appeal. The European Commission fined Google on June 27 this year in what is the largest ever fine imposed on… [Continue Reading] -

Intel will discontinue WiGig laptop docks
Publié: septembre 13, 2017, 3:20am CEST par Sead Fadilpašić
It looks as if Intel's idea of a wireless docking station for laptops was a bit short-lived. The company recently announced that it will discontinue its WiGig laptop docks and as of September 29 will no longer take orders, and as of December 29 will no longer make shipments. This came as a surprise for many, especially given that laptops are becoming thinner, and easing out as many ports and slots as possible. The WiGig wireless docking station came with five USB ports, a landline, HDMI and DP ports. It had up to 4.7Gbps of bidirectional bandwidth and had cost… [Continue Reading] -

Europe wants tech giants to pay higher taxes
Publié: septembre 13, 2017, 12:20am CEST par Sead Fadilpašić
Tech giants like Google or Amazon might end up paying a lot more tax in Europe, if a new EU initiative goes through. A debate concerning whether tech giants should pay taxes wherever they produce value has been scheduled for September 15. So far, they are only paying taxes where they are physically present. This has led to businesses going into countries with different tax incentives. Google, for example, has its EU headquarters in Ireland, which helped it dodge taxes in France. Now, after a joint letter addressed to the European Union's presidency and Commission, and written by finance ministers of France, Germany,… [Continue Reading] -

Google announces Dedicated Interconnect for enterprise users
Publié: septembre 12, 2017, 9:31pm CEST par Sead Fadilpašić
Google has revealed a new way for enterprise users to connect to its cloud platform. Dedicated Interconnect revolves around a few useful perks. Onboarding is easy through manageable, high-bandwidth and secure network, reducing the cost for enterprises and offering increased security by avoiding public internet routing. Google says Dedicated Interconnect is useful for businesses that want to extend their corporate data center network as part of a hybrid cloud deployment. Google also said the new feature is "ideal for data and/or latency sensitive services." These may be retail or financial services, but others, as well. "Accessing GCP with high bandwidth, low… [Continue Reading] -

Microsoft Azure is the preferred cloud for Adobe Sign
Publié: septembre 11, 2017, 11:10pm CEST par Sead Fadilpašić
Microsoft and Adobe are expanding on their partnership and further integrating their respective solutions to help people work more efficiently. After the integration of Adobe Experience Cloud, Microsoft Azure and Microsoft Dynamics, the time has come for Adobe Sign and Adobe Document Cloud to integrate with Microsoft's Office 365 suite in general. Thus, Adobe Sign, the company's e-signature solution, is now Microsoft preferred across the company's portfolio, Office 365 included. Microsoft Teams, on the other hand, is now the preferred solution for Adobe Creative Cloud, Document Cloud and Experience Cloud. Also, Microsoft Azure is now Adobe's preferred cloud platform for Adobe Sign.… [Continue Reading] -

Many UK businesses don't know if they are GDPR compliant
Publié: septembre 8, 2017, 2:04pm CEST par Sead Fadilpašić
Every fifth business in the UK has "no idea" if their corporate policies are enough to comply with the upcoming General Data Protection Regulation (GDPR). This is according to a new report by Citrix, which investigates the obstacles companies in the UK are still facing when it comes to complying with GDPR. The report says there are three major roadblocks --data sprawl, a huge influx of personal customer information and uncertainty around data ownership. "The GDPR will do far more than strengthen data privacy rights. The regulation will set a high bar for responsibility and accountability – and not one that… [Continue Reading] -

HPE acquires Cloud Technology Partners
Publié: septembre 8, 2017, 2:29am CEST par Sead Fadilpašić
Hewlett-Packard Enterprise (HPE) has announced it is acquiring Cloud Technology Partners, a born-in-the-cloud services company. Financial terms of the deal were not disclosed. Cloud Technology Partners helps sophisticated IT organizations move to the cloud. It does it by determining optimal apps for both public and private clouds. The company also executes migrations and help clients transform their organizations as needed. Cloud Technology Partners helps clients build new and disruptive solutions that revolve around IoT, Big Data and Machine Learning. Also, it helps clients achieve governance, risk and regulatory compliance. "Businesses today live in a Hybrid IT world. Achieving business outcomes requires putting each workload in… [Continue Reading] -

Vodafone and Onecom announce IoT partnership
Publié: septembre 7, 2017, 11:25pm CEST par Sead Fadilpašić
Onecom and Vodafone have signed a five-year deal aimed at expanding the choice of IoT services available to UK businesses. The two companies will jointly "develop, launch and manage" a range of tools going forward. Onecom, a unified communications platform, will deploy Vodafone’s global IoT managed connectivity, platform and services, so businesses can use connected solutions within their organizations. Onecom will also develop its own IoT services that will be boosted by Vodafone’s IoT connectivity and global platform. Aaron Brown, chief operating officer at Onecom, noted that the company is committed to seeing IoT services as a major focus of… [Continue Reading] -

Internet of Things adoption adds higher storage requirements
Publié: septembre 7, 2017, 5:51pm CEST par Sead Fadilpašić
IoT devices are generating huge amounts of data, and it’s leaving a mark across the enterprise IT industry. That's according to a new report by analyst firm 451 Research, whose The Voice of the Enterprise: IoT -- Workloads and Key Projects report says a third of organizations is planning on increasing their storage capacity. Three in ten (30 percent) will increase network edge equipment, while almost the same number (29.4 percent) plans on increasing server infrastructure. And finally, off-premises cloud infrastructure will also be getting a boost in 27.2 percent of the companies surveyed, all in the next 12 months. Spending on IoT… [Continue Reading] -

Microsoft at the forefront of enterprise SaaS market
Publié: septembre 4, 2017, 10:17pm CEST par Sead Fadilpašić
Enterprise SaaS market has seen growth of almost a third (31 percent) compared to last year. That's according to the latest research from Synergy Research Group. Its Q2 data says the market almost hit $15 billion in quarterly revenues. The highest growing segment was "collaboration." Looking at the leaders in the market, Microsoft seems to be at the forefront, after overtaking Salesforce last year. Synergy Research Group says it was on track for further growth even before it decided to acquire LinkedIn, and that the acquisition only gave it a "further boost." After Microsoft and Salesforce, follow Adobe, Oracle and SAP,… [Continue Reading] -

Okta adds two-factor authentication
Publié: septembre 2, 2017, 1:24am CEST par Sead Fadilpašić
Okta has recently made three major announcements. First, it introduced new developer product toolkit capabilities, allowing developers to add Okta’s identity-driven security solution to their own applications with ease. This has been announced during Oktane, its user event in Las Vegas. New features include easy and secure authentication, rapid customization and branding, out-of-the-box workflows, as well as securing APIs that are exposed to third-party developers. "Millions of new applications are built every year. Identity components like authentication and user management are required for every single one of these experiences -- be it a web app like MGM Resorts International’s MLife website,… [Continue Reading] -

The PC is still king in the office
Publié: août 30, 2017, 5:52pm CEST par Sead Fadilpašić
Desktop computers remain the primary means of work for the majority of the workforce, but this may not be the case for long. A new report from Spiceworks examining the current usage of, and future investments in business PCs and mobile devices in the US, UK and Canada titled The Future of the PC says 60 percent of employees still use desktops as their primary working device. PCs are followed by laptops (27 percent), thin devices (five percent), tablets (three percent), smartphones (two percent), and 2-in-1s (two percent). However, the future seems brighter for the laptop than the PC. Investments… [Continue Reading] -

HP and Deloitte team up to give 3D printing a boost
Publié: août 30, 2017, 12:22am CEST par Sead Fadilpašić
Deloitte and HP are joining forces to give their digital manufacturing services and 3D printing services a little push. The partnership will see HP’s 3D printers become part of the digital supply chain in more large-scale manufacturing environments. The goal of the joint effort is to help businesses speed up product design, as well as to create a more flexible manufacturing supply chain and production services (for example, prototyping). By using 3D printing for prototyping, manufacturing will be faster and more efficient, and at the same time cheaper and with less waste. The two companies hope this makes large enterprises more competitive… [Continue Reading] -

Apple will open two data centers in Iowa
Publié: août 29, 2017, 8:18pm CEST par Sead Fadilpašić
Apple has announced it is planning to build two new data centers in Waukee, Iowa. Reuters reported that the two new data centers "will create hundreds of jobs for people in Iowa from construction to engineering," Apple CEO Tim Cook said, although it was left unclear how many of those jobs will remain once the data center is actually built. The new facility will set Apple back $1.375 billion, although $207.8 million will be received in incentives approved by the Iowa Economic Development Authority and Waukee city council. The company will buy 8.09 square km of land in Waukee, some 30… [Continue Reading] -

PC sales will continue to decline
Publié: août 29, 2017, 12:06am CEST par Sead Fadilpašić
Once again, analysts have predicted a grim, grim future for the PC. According to the latest IDC forecasts, PC sales will fall from the 435.1 million units seen in 2016 to 398.3 million in 2021. That's a five-year compound annual growth of -1.7 percent. According to Loren Loverde, IDC's VP for Worldwide Personal Computing Device Tracker, things could turn (somewhat) around, but that depends on a couple of moving targets. "Shipments could pick up if accelerators like economic conditions, adoption of gaming, VR, and Windows 10 speed up," Loverde said, before adding: "even in the best case, overall growth would… [Continue Reading] -

Semi-autonomous truck convoys will hit UK highways by the end of 2018
Publié: août 28, 2017, 10:52am CEST par Sead Fadilpašić
Small groups of semi-autonomous trucks will be tested on major highways in the UK by the end of 2018. According to the UK government, Transport Research Laboratory (TRL) has been awarded a contract to test vehicle convoys. These convoys, consisting of up to three trucks, will be traveling in formation, with the leading truck controlling breaking and acceleration. At first, the tests will be done on test tracks, but before 2018 ends, we can expect these truck convoys to hit the motorways. The leading vehicle will be controlled by a human driver. Humans will also control the steering in trucks behind -- just not acceleration and… [Continue Reading] -

Microsoft wants you to beta test Windows 10 S
Publié: août 25, 2017, 11:52am CEST par Sead Fadilpašić
Microsoft has announced a major shake-up in the testing for Windows 10 S. The software giant has announced that its new OS can now be tried out by all members of the Windows Insiders program. Interested testers need to have run Windows 10 Pro or Enterprise to be able to install it. Keep in mind that this is a beta, so it might be wise to back up any and all files before proceeding. "By exclusively using apps in the Windows Store and ensuring that you browse safely with Microsoft Edge and keeps you running fast and secure," Microsoft said in its announcement blog. "It is… [Continue Reading] -

Cyber-security is an investment, not a burden
Publié: août 22, 2017, 1:33am CEST par Sead Fadilpašić
CEOs across the UK are increasingly seeing cyber-security not as a burden, but rather an investment opportunity, a new study has claimed. The KPMG CEO Outlook 2017 report, based on a poll of 150 CEOs in the UK, found that 70 percent considered investing in cyber-security an opportunity to find new streams of revenue. The report also found that cyber-security is increasingly falling under the CEOs’ agenda, signaling a shift from CIOs and CISOs. More than three quarters (77 percent) of CEOs agreed with the statement: "I am personally comfortable with the degree to which mitigating cyber risk is now part of my… [Continue Reading] -

Hackers can disable your car's safety systems
Publié: août 21, 2017, 5:17pm CEST par Sead Fadilpašić
Hackers could disable a modern car's airbags and other safety systems, putting the driver and the passengers at grave risk, according to a new warning. Researchers from security firm Trend Micro have revealed a flaw that could allow the controlling network of a connected car to be overloaded, allowing possible hackers to compromise key systems in the vehicle, including safety aspects. Trend Micro's report claims that hackers could, with relative ease, overload the controller area network (CAN) standard, which the company says is used in "practically every light-duty vehicle currently in circulation today." The system, which was developed in 1983… [Continue Reading] -

Data leak exposes 1.8 million US voters' private information
Publié: août 21, 2017, 11:23am CEST par Sead Fadilpašić
A supplier of US voting machines has confirmed a major data leak that has seen the details of more than 1.8 million voters in the state of Illinois exposed. The leaked data includes full names, addresses, dates of birth, social security numbers (albeit partial), as well as party affiliations. In some cases even ID numbers and driver license numbers were exposed. The breach was exposed by a security expert from UpGuard. Jon Hendren noticed that an Amazon Web Services device wasn't password protected. The company, Election Systems & Software (ES&S), posted about the leak on its website. It was said that the FBI… [Continue Reading] -

Microsoft reveals Azure Event Grid
Publié: août 18, 2017, 3:00pm CEST par Sead Fadilpašić
Microsoft has revealed a new Azure feature aimed at helping developers that build event-based applications. Azure Event Grid is built to help devs that create event-based and serverless applications with a higher level of abstraction. That way, worrying about infrastructure, provisioning or scaling, becomes a thing of the past, according to Microsoft. "We're seeing many apps in Azure being developed around events," said Corey Sanders, Director of Azure Compute. He explained that this includes IoT, mobile apps, as well as aps that initiate business processes. He also said that Azure Functions/serverless and Azure Logic apps are what drives the need for… [Continue Reading] -

AWS Macie is a security service based on machine learning
Publié: août 16, 2017, 9:00pm CEST par Sead Fadilpašić
Amazon Web Services has launched a new machine learning service aimed at helping organizations protect their sensitive data in the cloud. Macie's general premise is quite simple: it analyzes data on the S3 storage service, and is capable of identifying names, addresses, credit card numbers, driver licenses or social security numbers, stuff like that. It then monitors that data and keeps an eye out for anomalies. It can't independently conclude if the leak is malicious or not, but once it identifies that there is a leak it will send out notifications. Macie also comes with a centralized dashboard that is able… [Continue Reading] -

Researchers hack a computer using malware injected into DNA
Publié: août 15, 2017, 11:04pm CEST par Sead Fadilpašić
Security researchers have managed to infect a computer with malware embedded in a strand of human DNA. The news sounds like a science-fiction writer's dream, but when biologists want to handle large amounts of DNA samples, they need to digitize them and process them on their computers. But the software that they use to process these samples is usually open-source and often doesn't follow security best practices. So if, by some arcane magic, a DNA sample that needs to be digitized carries a malicious code would it be able to infect a computer? The answer is a definitive yes. "We analyzed open-source… [Continue Reading] -

HPE and NASA sending a supercomputer to space
Publié: août 15, 2017, 3:59pm CEST par Sead Fadilpašić
The computers the human race currently work with aren't built for space, and can't last long in off-planet environments. Astronauts aboard the ISS need new machines every month, as the old ones get destroyed by various factors that don't exist on Earth, like solar flares, radiation, subatomic particles, and irregular cooling. Considering that SpaceX is currently preparing for a mission to Mars, it is paramount that the astronauts that eventually head out there have durable, working machines. Now, HP has announced it is working with NASA to create such a computer. The HPE Apollo Spaceborne Computer is going to be lifted into… [Continue Reading] -

Manufacturers are cybercriminals' biggest target
Publié: août 11, 2017, 5:06pm CEST par Sead Fadilpašić
Cyber-attacks all over the world are becoming increasingly sophisticated, according to a new report by the NTT Group company. According to the same report, these attacks are also growing in frequency. The Global Threat Intelligence Center (GTIC) 2017 Q2 Threat Intelligence Report says cyber-attacks were up by 24 percent globally, in the second quarter of 2017. Manufacturers are still the number one target for cybercriminals. The report says 34 percent of all documented attacks were against manufacturers. It was also says that they appear in the top three targets in five of the six geographic regions globally. Phishing is the biggest… [Continue Reading] -

Security challenges slow down innovation in the financial sector
Publié: août 10, 2017, 10:29pm CEST par Sead Fadilpašić
Organizations in the financial services sector are forced to innovate in order to stay relevant. At the same time, innovation is being slowed down by the need to keep data and applications safe, putting organizations in this vertical in quite a tough spot. This conclusion was given out in a new report by Claranet. The report says that striking the right balance between innovation and security is becoming a "key competitive differentiator" in the sector. The report itself is based on a poll of 138 IT and digital decision makers in financial services. Among those, more than half (57 percent) said… [Continue Reading] -

Most people never change their router's password
Publié: août 8, 2017, 8:16pm CEST par Sead Fadilpašić
How often do you change your Wi-Fi password? According to electronics retailer reichelt elektronik, not often enough. Its latest report claims that more than half of users, 55 percent to be exact, never changed it. That leaves them quite vulnerable to cyber-attacks, the report adds. The survey, based on a poll of 1,000 UK adults, says the majority (85 percent) know that they need to protect their Wi-Fi networks with a password. However, once set up, most never change it. Less than a quarter (22 percent) keep it for more than two years at a time. Just 10 percent change their Wi-Fi… [Continue Reading] -

Facebook uses neural networks to translate posts
Publié: août 8, 2017, 2:34am CEST par Sead Fadilpašić
Facebook has revealed it is harnessing the power of AI to support its growth across the world. The social media giant, which has over two billion users worldwide, is now using neural networks for to automatically translate content in foreign markets. In a blog post detailing the switch, Facebook says it went from using phrase-based machine translation model to neural networks, and so far has seen an 11 percent increase in the accuracy of machine translation. The biggest disadvantage of a phrase-based model was that it broke down sentences into individual words or phrases. When translating them, the system could only consider a couple… [Continue Reading] -

Oracle upgrades its most-popular cloud services
Publié: août 7, 2017, 11:34pm CEST par Sead Fadilpašić
Oracle has announced several new upgrades to some of its most popular cloud applications. The company says that the releases will help organizations everywhere "grow faster, differentiate from competitors and better serve their customers." The latest release offers new features across Oracle Supply Chain Management (SCM) Cloud, Oracle Customer Experience (CX) Cloud Suite, Oracle Enterprise Resource Planning (ERP) Cloud and Oracle Human Capital Management (HCM) Cloud. The company also says all Oracle Cloud Apps have gotten an enhanced user experience through personalisation, offering improvements to productivity, insights and collaboration. Thus, the Oracle SCM Cloud aims at improving the supply chain. Oracle CX Cloud… [Continue Reading] -

UK outsourcing market spend reaches £5.2 billion in 2017
Publié: août 4, 2017, 11:35am CEST par Sead Fadilpašić
The UK outsourcing market has enjoyed some of its strongest performance for several years, according to new figures released today. The latest Arvato UK Outsourcing Index, revealed that the first six months of 2017 has been the most successful since 2012, with £5.2 billion worth of outsourcing deals in this time. Financial services companies have accounted for more than half of the total contract value -- 55 percent, or £2.9 billion. There was also a "steep increase in spending by UK businesses." Companies have signed contracts worth £4.5 billion in the first half of this year, equalling to a year-on-year rise of 95 percent.… [Continue Reading] -

Facebook Messenger chatbots help companies boost sales
Publié: août 3, 2017, 9:18am CEST par Sead Fadilpašić
Chatbots on Facebook's Messenger have helped companies increase their sales more than expected, meaning the technology could soon become widespread. The news was announced during Facebook's F8 keynote, with its VP of messaging products David Marcus discussing a number of big-name brands such as Sephora, SnapTravel and Tommy Hilfiger. Sephora has allegedly seen an 11 per cent increase in booking rates through the Sephora Reservation Assistant. The bot also helped increase in-store sales, as well. Those consumers that booked an in-store service via Messenger usually spend more than $50. SnapTravel has seen $1 million in hotel bookings in less than a year, since… [Continue Reading] -

Facebook buys AI startup Ozlo to improve Messenger
Publié: août 3, 2017, 2:32am CEST par Sead Fadilpašić
Facebook has acquired an AI start-up as it aims to strengthen the artificial intelligence capabilities of its Messenger platform. The start-up in question is called Ozlo. It is based in Palo Alto, California, and has roughly 30 employees, the majority of which will be joining Facebook in either Menlo Park, California, or Seattle, Washington. Financial details of the deal were not disclosed. What makes this AI technology stand out from the rest is its alleged possibility to answer questions with more than a simple "Yes" or "No." It is allegedly capable of reading and understanding text and context, and capable… [Continue Reading] -

Blockchain technology is an integral part of FinTech's future
Publié: août 2, 2017, 10:30pm CEST par Sead Fadilpašić
Blockchain technology is perceived as "critical" for the future of financial services companies, a new report by Cognizant has shown. A poll of more than 1,500 financial services executives from more than 500 companies worldwide found that 91 percent saw implementation of blockchain technology to be critical for the firm’s future. However, the report found that there is still "significant uncertainty" on how the blockchain system will develop. Essentially all respondents (98 percent) believe blockchain will save them money. Roughly 75 percent expect revenues to grow five percent after implementation. Half (46 percent) think it will help with transparency, 40 percent… [Continue Reading] -

Wi-Fi chip vulnerability affects one billion Android and iOS devices
Publié: août 1, 2017, 9:27pm CEST par Sead Fadilpašić
Millions of smartphones around the world could have been affected by a Wi-Fi security flaw, security researchers have claimed. Broadcom's mobile Wi-Fi chips hid a vulnerability on them which could have allowed malicious actors to potentially attack a billion Android or iOS devices. Fortunately, the vulnerability, which was demonstrated at the recently held Black Hat conference by security researcher Nitay Artenstein, has now been patched. Artenstein developed malicious code which he could transmit through the air, probing nearby devices. Once a device with the BCM43xx family Wi-Fi chipset was found, the code could rewrite the firmware that controls the chip, allowing… [Continue Reading] -

Russia tried to spy on Macron campaign using fake Facebook accounts
Publié: juillet 28, 2017, 8:57pm CEST par Sead Fadilpašić
This is why you never accept Facebook friend requests from people you don't know, kids. Reuters has reported that Russian agents created two dozen fake Facebook accounts to try and infiltrate and spy on campaign officials working for Emmanuel Macron during his presidential campaign. The news was apparently confirmed by "a US congressman and two other people briefed on the effort." Facebook has "detected spying accounts in France and deactivated them." It used a combination of improved automated detection and stepped-up human effort to find sophisticated attacks. Reuters says Facebook suspended up to 70,000 accounts, and the social media giant did not… [Continue Reading] -

Intel discontinues Arduino 101 development board and Curie module
Publié: juillet 28, 2017, 12:02am CEST par Sead Fadilpašić
Intel has revealed a significant scaling back in its hardware offerings. The company has announced it will stop making its Arduino 101 board as well as the Curie module, both of which offered low-cost computing solutions. Anyone looking to get their hands on the Arduino 101 has until September 17 to order one, with Intel confirming it will fulfill orders through to December 17 this year. As for Curie, it will be available until January 17, next year, with fulfillments continuing until July 17, 2018. The Curie Open Developer Kit will no longer get updates, and the forum will be open until… [Continue Reading] -

Ransomware victims paid over $25 million to recover files
Publié: juillet 27, 2017, 6:46pm CEST par Sead Fadilpašić
Ransomware victims have paid more than $25 million in the past two years to get their data back, a new study by Google has shown. The report, made by researchers at Google, Chainalysis, UC San Diego, and the NYU Tandon School of Engineering, followed the trail of cryptomoney through the blockchain, allowing researchers to get a birds-eye view of the ransomware world. A total of 34 ransomware families were tracked, but only a handful made most of the profit. This includes Locky, whose epidemic forced more than $7 million in payments. Locky was the first ransomware to split payment and encryption… [Continue Reading] -

Alphabet Q2 2017 by the numbers: $26 bn revenue, $3.5 bn profit
Publié: juillet 27, 2017, 2:18am CEST par Sead Fadilpašić
There are four key areas where digital businesses can make a significant profit, and Google's parent company Alphabet appears to be gaining in all four of them according to its latest earnings report. In a recent call to reveal its results, Alphabet said revenue rose 21 percent to $26 billion, in the second quarter of 2017. Net income was $3.5 billion. The four areas where Alphabet made significant earnings are mobile ads, video streaming, artificial intelligence and the cloud. For mobile ads, revenue rose 18 percent, to $22.7 billion. The biggest driver of this growth was paid clicks, which rose 52 percent.… [Continue Reading] -

Fruitfly malware starts infecting Macs
Publié: juillet 27, 2017, 12:17am CEST par Sead Fadilpašić
A new version of the Mac malware dubbed Fruitfly has been spotted in the wild, and it’s unclear if the latest macOS is vulnerable to it or not. This is according to former NSA hacker and chief security researcher at Synack, Patrick Wardle. He told ZDNet that the malware, which was first revealed back in January, can take full control of an infected machine, including files, camera, screen, and peripherals. According to the report, the malware has been found on "hundreds of Macs." Fruitfly has been in existence for a number of years before it was finally uncovered this January, because “current… [Continue Reading] -

Many businesses believe they're GDPR-compliant: The reality says otherwise
Publié: juillet 26, 2017, 10:13pm CEST par Sead Fadilpašić
A new study has claimed that, contrary to what they may think, many businesses are struggling to be ready for GDPR. According to The Veritas 2017 GDPR Report, a third (31 percent) of respondents believe their enterprise is in line with the regulation’s key requirements. On the other hand, when they were asked about specific GDPR provisions, their answers have shown that they’re most likely not compliant. Veritas says that just two percent actually seem to be in compliance. "With the EU’s General Data Protection Regulations (GDPR) less than one year away, organizations around the world are deeply concerned about the… [Continue Reading] -

Intel: Qualcomm uses the courts to destroy its competition
Publié: juillet 25, 2017, 11:15pm CEST par Sead Fadilpašić
Intel has weighed in on the legal sparring between Apple and Qualcomm, accusing the latter of (ab)using the courts to destroy any competition it has. The American chipmaking company accused Qualcomm of competition squashing on Thursday, issuing a public statement to the US International Trade Commission. The Commission asked for the statement, as it investigates Qualcomm’s accusations that Apple’s iPhones infringe six Qualcomm patents. Intel basically said that Qualcomm is looking to "stave off" any competition from its only competitor. "Qualcomm did not initiate this investigation to stop the alleged infringement of its patent rights; rather, its complaint is a transparent effort to… [Continue Reading] -

CEOs should be held accountable for cyber attacks and data breaches
Publié: juillet 25, 2017, 9:15pm CEST par Sead Fadilpašić
CEOs should be the ones responsible in case of a cyber-attack and a data breach in an organization, according to a new report by Tripwire. Polling Infosecurity Europe 2017 attendees on who should be held accountable in such a scenario, 40 percent said CEOs. CISOs are the second in line with 21 percent of answers, while 14 percent would blame the CIO. Tripwire says CEOs should be aware of the "basic principles of security," and remembered the example of former Yahoo CEO Marissa Mayer, who forfeited her cash bonus following a breach. However, CEOs shouldn’t be the only ones holding responsibility for… [Continue Reading] -

Citrix Workspace arrives on Google Cloud Platform
Publié: juillet 25, 2017, 3:11am CEST par Sead Fadilpašić
Citrix cloud users will now be able to manage secure digital workplaces on the Google Cloud Platform. The partnership was announced by Citrix late last week as the latest extension of the long-term relationship between the two companies. The new offering brings cloud delivery of apps and desktops to enterprise customers. The two companies also announced new integrations between Citrix ShareFile and Google G Suite, available as of late last week. These integrations will enable follow-me-data for Citrix Workspace solutions users. There’s a new ShareFile plug-in, allowing sharing files via Gmail in a (more) secure way. The ShareFile connector to Google… [Continue Reading] -

Microsoft Q4 FY2017 by the numbers: $24.7 billion revenue, $7 billion profit
Publié: juillet 25, 2017, 12:11am CEST par Sead Fadilpašić
Microsoft has beaten analyst expectations once again with better than expected quarterly earnings. The Redmond, Wash.-based giant has released its latest quarterly earnings, for Q4 FY2017, showing a non-GAAP revenue of $24.7 billion and GAAP earnings of $0.83 per share. Non-GAAP operating income sat at $7 billion. Wall Street’s analysts predicted $24.3 billion in revenues, representing a seven percent year on year growth. In terms of earnings per share, analysts expected $0.71, a three percent increase compared to the previous year. The biggest gainer for Microsoft was Azure cloud computing platform. Although overall growth slowed slightly, the division still saw increases… [Continue Reading] -

Bank of England supports FinTech startups
Publié: juillet 22, 2017, 3:18am CEST par Sead Fadilpašić
The Bank of England has allowed access to settlement accounts in the real-time gross settlement system (RTGS), the media reported this week. Apparently, this move should blow some wind into the sails of innovative fintech companies, boosting competition. The bank has said that it is now offering access to non-bank payment service providers (PSP), meaning direct access to the UK’s sterling payment system is now possible. This move, however, is not Bank of England’s alone -- the UK’s Financial Conduct Authority (FCA), has been helping the bank develop this framework for non-bank PSPs to access RTGS, together with HM Revenue and Customs and HM Treasury.… [Continue Reading] -

London Stock Exchange trials blockchain for shares in Italy
Publié: juillet 22, 2017, 1:21am CEST par Sead Fadilpašić
London's Stock Exchange is set to start using blockchain to improve transparency for shareholding information among unlisted businesses. According to a news report by CityAM, the London Stock Exchange Group (LSEG) will use Hyperledger Fabric, one of the open source blockchain frameworks hosted by The Linux Foundation to make info on private SMEs digital. The end goal is to draw more mature investors. Borsa Italiana, the Italian stock exchange, will kick off the trial by conducting a small test using blockchain to hold a shared registry of shareholder transactions and records. Only issuers, investors and regulators (authorized personnel) will have access to it.… [Continue Reading] -

One in 10 UK businesses moved to the cloud
Publié: juillet 21, 2017, 10:17pm CEST par Sead Fadilpašić
A tenth of all UK businesses have moved entirely to the cloud, according to a new Breaking Barriers 2020 report from Fuze. The report is based on a poll of more than 900 CIOs, and claims that the UK keeps lagging behind North America and the rest of Europe in terms of adopting cloud services. The report compares the UK with American firms, 45 percent of which have fully made the migration to cloud. What Fuze sees as a positive move is the fact that almost half (49 percent) adopted some form of formal cloud initiative, either partially or fully. A… [Continue Reading] -

The biggest challenge to adopting IoT? Identifying ROI
Publié: juillet 21, 2017, 8:19pm CEST par Sead Fadilpašić
The biggest challenges companies have with implementing IoT technologies is not security but rather identifying ROI. This is according to a new report by Canonical, entitled Defining IoT Business Models, which polled 360 IoT professionals, including devs, vendors and enterprise users, more than half (53 percent) say "quantifying ROI and providing a clear use case" is currently their biggest challenge. So, it’s currently more important than the lack of available infrastructure (40 percent), or the need for improved device security (45 percent). The report also states that a third (34 percent) of IoT pros think "quantifying the business benefits" should be their… [Continue Reading] -

Dow Jones server leaks personal info of 2.2 million customers
Publié: juillet 20, 2017, 3:05am CEST par Sead Fadilpašić
Private information of more than two million customers of the Dow Jones publishing agency have been exposed online. According to the IB Times, a configuration error on the Dow Jones & Co. cloud storage server led to sensitive information including names, addresses, account information, emails and the last four digits of credit cards for almost 2.2 million people becoming available to anyone with an Amazon Web Services Account. The flaw itself was first spotted by cybersecurity researchers from UpGuard back in June. The researchers said the number of affected users might reach four million. According to UpGuard’s Director of Cyber Risk Research,… [Continue Reading] -

Qualcomm CEO: Apple dispute will be settled out of court
Publié: juillet 20, 2017, 1:05am CEST par Sead Fadilpašić
Apple and Qualcomm might be fighting hard in the courtroom, but that's not where the battle is going to end. That's according to the latter company's CEO, who believes the issue will most likely be settled out of the court. Speaking at the Fortune's Brainstorm Tech conference recently, Qualcomm CEO Steve Mollenkopf said disputes with Apple are "nothing new. Those things tend to get to resolved out of court and there's no reason why I wouldn't expect that to be the case here." At the same time, there was no talk on a possible resolution, and Mollenkopf asked for no… [Continue Reading] -

Google wants to get devs to embrace quantum computing
Publié: juillet 19, 2017, 12:41pm CEST par Sead Fadilpašić
Google wants developers and scientists to build tools and write code for its quantum computer, and is making its high-powered platform available online. According to a Bloomberg news report, Google is aiming to commercialize quantum computers, and turn them into an extremely powerful cloud-computing service. In its report, Bloomberg cities a Google presentation slide which details the company's "Embryonic quantum data center," as well as the ProjectQ -- an open-source effort to get devs to write code. "They’re pretty open that they’re building quantum hardware and they would, at some point in the future, make it a cloud service," Peter McMahon, a… [Continue Reading] -

The cost of recovery from a security breach? Over £1 million for UK businesses
Publié: juillet 19, 2017, 3:39am CEST par Sead Fadilpašić
A business in the UK would need to spend over £1 million to recover from a security breach, new research has claimed. According to the 2017 Risk:Value report from NTT Group, UK companies have to pay more than the global average of £1 million, which has gone up from the previous report’s estimate of $907,000. The report is based on a poll of 1,350 non-IT business decision makers, scattered across 11 countries, 200 of which were from the UK. The results have shown that businesses would need roughly 80 days to recover from an attack, almost a week longer from the 74-day global average,… [Continue Reading] -

How large would the financial losses get in case of a global cyber attack?
Publié: juillet 18, 2017, 5:15pm CEST par Sead Fadilpašić
A global cyber-attack could be as expensive as a major natural disaster, a new report has claimed. Analysis by Lloyd’s of London compared the effects of a hypothetical global cyber-attack to the super storm known as Hurricane Sandy that hit the US coast in 2012, in terms of the financial impact. A major attack could result in financial losses of up to $53 billion, close to the total cost of the 2012 storm. That's according to noted banking group Lloyd’s of London, which teamed up with risk-modeling firm Cyence to look at several potential cyber-attack disaster scenarios. Apparently, insurers are… [Continue Reading] -

The cloud, IoT and SDN create the biggest complications on enterprise networks
Publié: juillet 15, 2017, 12:20am CEST par Sead Fadilpašić
Cloud adoption is still the "most vexing factor" in increased network complexity, according to a new report by Kentik. The report, based on a poll of 203 IT professionals attending the Cisco Live 2017 annual conference, says cloud adoption is followed by IoT, SDN, and networks functions virtualization (NFV). It also says that most organizations still aren’t ready for network automation, even though machine learning is seen as "important technology for network management." More than a third (36 percent) of respondents said cloud adds the greatest network complexity to their organizations. They can still improve operational visibility for cloud and digital… [Continue Reading] -

Industrial control security practitioners 'working blind' to protect their network
Publié: juillet 14, 2017, 10:19pm CEST par Sead Fadilpašić
Four out of 10 industrial control security practitioners don’t have proper visibility into their ICS networks. This is according to a new study by the SANS Institute. Based on a poll of ICS practitioners and cybersecurity stakeholders across various verticals, including energy, manufacturing, oil and gas, the report says that 40 percent of defenders are actually working blind to detect a cyber attack. And by "working blind" the report refers to finding out where the attack is coming from and trying to remediate it in a "reasonable" amount of time. "That statistic is even scarier," the report says, "when you… [Continue Reading] -

Millennials prefer to work in the office, not remotely
Publié: juillet 13, 2017, 9:36pm CEST par Sead Fadilpašić
Contrary to popular belief, the majority of workers under the age of 35 -- millennials -- actually prefer office life to working remotely, a new report has found. According to research by Maintel, who polled 1,000 employed adults in the UK aged 18 or over, there are a couple of reasons for this. One is that the younger workforce needs face-to-face support of experienced workers. It backs such claims up by the fact that among the older workforce (55 and above), just 19 percent prefer office life to remote work, and that 28 percent said it was challenging to find other… [Continue Reading] -

Consumers want online retailers to provide two-factor authentication
Publié: juillet 13, 2017, 12:22am CEST par Sead Fadilpašić
In today’s fast-paced world, one might think consumers value speed more than anything. In case of online banking, however, this is not the case. Instead, consumers would rather have more security than speed. This is according to a new report by MYPINPAD, the company that enables multi-factor authentication for touchscreen devices. The report, entitled Consumer Trust and Mobile Payments Growth, states consumer would very much like multi-factor authentication implemented. When asked what online retailers could do to improve trust, 40 percent would love to use cardholder PIN, 50 percent would like to see a combination of PIN and biometrics, while just… [Continue Reading] -

Many businesses believe they can be hacked
Publié: juillet 12, 2017, 8:08pm CEST par Sead Fadilpašić
Businesses aren’t investing enough to protect their businesses from data breaches. What’s more, even the funds they are investing are going down the wrong path. New research from digital security firm Gemalto found that, despite the increasing number of data breaches and nearly 1.4 billion data records being lost or stolen in 2016, the vast majority of IT Professionals still believe perimeter security is effective at keeping unauthorized users out of their networks. Almost all (94 percent) of the companies surveyed said that they see perimeter security as effective, while 65 percent aren’t extremely confident (down from 69 percent last… [Continue Reading] -

SMBs lack clear plans on cyber-attack aftermaths
Publié: juillet 12, 2017, 12:55pm CEST par Sead Fadilpašić
There’s plenty of talk on how small and medium-sized businesses can and should protect themselves from cyber-attacks. However, when it comes to the aftermath of a cyber-attack, things are awkwardly quiet. This is according to a new report by PolicyBee, which says cyber recovery is not really in the minds of SMB owners. This is despite a third of those surveyed saying that they think a cyber-attack is inevitable, with a further quarter believing it is "likely" to happen. Yet, three quarters (74 percent) haven’t put aside any budget to deal with the aftermath, and over four in ten (43 percent) say… [Continue Reading] -

Consumers have a 'false sense of security' when using public Wi-Fi hotspots
Publié: juillet 12, 2017, 2:46am CEST par Sead Fadilpašić
Brits still use public Wi-Fi for things they should not, a new report by Norton by Symantec claims. By doing so, they’re putting a lot of their personal information at risk. The report says most consumers have a "false sense of security" when using public Wi-Fi. Almost two thirds (65 percent) feel safe when they use public Wi-Fi, and less than a fifth (19 percent) use a VPN. While online, on a public Wi-Fi, one in 12 admit watching porn. Out of those people, a quarter (24 percent) are doing it at work, while 47 percent have done it in… [Continue Reading] -

Microsoft replaces Jim DuBois as CIO with Kurt DelBene
Publié: juillet 12, 2017, 12:46am CEST par Sead Fadilpašić
Last week we reported how Microsoft is laying off thousands of its workers as it shifts its focus towards cloud a bit more. It was reported, on multiple occasions, that it will be sales jobs, and mostly abroad, that will be nixed. However, new media reports are now painting a different picture. Among those that left the company is Jim DuBois. DuBois, who left the company last Friday, was Microsoft's chief information officer. He was named CIO in 2013. Prior to this position, he's held various positions in Microsoft, since 1993. According to Geekwire, he will be succeeded by Kurt… [Continue Reading] -

IT decision makers concerned budget cuts will affect security
Publié: juillet 11, 2017, 12:20am CEST par Sead Fadilpašić
Almost two thirds of IT decision makers in the UK (61 percent) think budget cuts will leave a mark on their IT investment abilities. This is according to a new report by Sungard Availability Services, which also reported that almost half (48 percent) of those surveyed expressed worries that their security could also be affected by budget cuts. What makes these results even more interesting is the fact that the UK, besides Canada, is a country least concerned with issues of being compliant with security regulations. Less than a third (32 percent) of UK IT departments see it as one of… [Continue Reading] -

Kaspersky BitScout tool lets security researchers collect forensic information
Publié: juillet 10, 2017, 9:02pm CEST par Sead Fadilpašić
Just like in a real-life crime scene, forensic evidence for cyber-crimes must not be tampered with. That's why sometimes investigations take too long -- forensic researchers need a lot of time to reach the crime scene and extract malware samples without compromising evidence. Kaspersky Lab identified this as a huge pain point in the combat against cyber-crime, and has since released a tool to help all researchers do their work faster and with more precision. The tool, named BitScout, allows researchers to "remotely collect key forensic materials, acquire full disk images via the network or locally attached storage, or simply remotely assist… [Continue Reading] -

Microsoft confirms thousands of job cuts
Publié: juillet 10, 2017, 5:35pm CEST par Sead Fadilpašić
Earlier last week, rumors emerged about Microsoft laying off thousands of workers as it reorganizes and focuses even more on cloud computing. The Redmond giant has confirmed these speculations. CNBC has reported that Microsoft is preparing "thousands of layoffs," mostly in sales, and mostly abroad. In total, less than 10 percent of the workforce will be laid off, and out of those that will have to look for a new job, 75 percent are outside the US. "Microsoft is implementing changes to better serve our customers and partners," a Microsoft spokesperson told CNBC. "Today, we are taking steps to notify some employees that their… [Continue Reading] -

Petya attackers make $250,000 demand
Publié: juillet 8, 2017, 2:41am CEST par Sead Fadilpašić
Criminals behind the recent Petya/NotPetya attack have made a fresh ransom demand as they look to continue their mayhem A post on online hub DeepPaste said to be from the attackers is demanding 100 bitcoins ($250,000) to decrypt anything that's been affected by the recent attack. Motherboard managed to get in touch with one of the individuals claiming to be from the group. They tried the decryption on a file, and after a two-hour wait, it was successful. However, Prof Alan Woodward from the University of Surrey told BBC News that this doesn't necessarily mean the key could decrypt everything. "Once the PC's MFT… [Continue Reading] -

Cyber attacks against UK businesses rising sharply
Publié: juillet 7, 2017, 10:40pm CEST par Sead Fadilpašić
There has been a significant increase in the amount of cyber-attacks targeting UK’s businesses in the second quarter of 2017, a new report has claimed Research by business ISP Beaming found that the number of online attacks rose significantly in the three months from April to June. During this time, 65,000 attacks were recorded -- a 52 percent increase compared to Q1 2017. The majority of these attacks (68 percent) targeted connected devices such as security cameras and building control systems, but the report also found a "substantial increase" in attacks against company databases. The report says that each UK business has witnessed 105 attempts… [Continue Reading] -

Smart device shipments will fall in 2017
Publié: juillet 7, 2017, 3:37pm CEST par Sead Fadilpašić
Global shipments of smart devices including PCs and smartphones are set for a surprising decline this year, according to new Gartner figures. Shipments will hit 2.3 billion this year, representing a 0.3 percent decline compared to the year before, the analyst firm said, before returning to growth next year. According to the report, the devices market is steady for the first time in many years. "Overall, the shipment growth of the device market is steady for the first time in many years," said Ranjit Atwal, research director at Gartner. "PC shipments are slightly lower while phone shipments are slightly higher… [Continue Reading] -

VCs still investing in UK's tech sector despite Brexit risks
Publié: juillet 7, 2017, 2:59am CEST par Sead Fadilpašić
The UK's tech sector is continuing to see high levels of interest in spite of the risks associated with Brexit, new figures have revealed. In fact, the nation attracted more investments in the last six months than it has in any six months in the last decade. Also, London kept its place as the biggest tech city in Europe, ahead of rivaling European cities Berlin, Dublin, Paris or Stockholm. In the first half of 2017, venture capitalists pumped in £1.3 billion into the UK's tech sector, with London alone accounting for £1.1 billion of that. “For a technology business looking to… [Continue Reading] -

Many IT projects failing in UK
Publié: juillet 6, 2017, 12:15am CEST par Sead Fadilpašić
A huge number of IT projects currently being undertaken in the UK are doomed to fail, new research has claimed. Over three in ten of all IT projects in the country could fall short of expectations, according to a new Axelos report, based on a poll of 182 project managers. The report states that 31 percent of UK IT projects failed last year, with some of the most common issues including large changes to the project brief, to unrealistic timeframes, to the lack of understanding of the risks, to projects being resourced with the wrong people, to no clearly defined goals, to… [Continue Reading] -

Microsoft shutters Windows App Studio
Publié: juillet 4, 2017, 11:13pm CEST par Sead Fadilpašić
Microsoft is killing Windows App Studio, its web-based app development tool. The news was announced late last week by the Windows Apps Team. However, don't be too alarmed -- the Redmond giant has already prepared a replacement. Windows App Studio has long been the go-to place when it comes to the first steps in app development. Starting as a Windows phone app, it transformed over the years and became available for desktop operating systems, including Windows 10. Now, however, it is getting replaced by the Windows Template Studio, which is already available. The new program is an extension of Visual Studio and… [Continue Reading] -

Microsoft structural changes could lead to thousands of layoffs
Publié: juillet 4, 2017, 5:45pm CEST par Sead Fadilpašić
Microsoft is set for a major reorganization as it moves to focus more on selling cloud services, and less on selling traditional software, according to new reports. A report by the The Wall Street Journal, claims that the Redmond giant has kicked off "structural changes" first proposed in 2014, when Satya Nadella took over the company. These changes apparently won't affect Microsoft's day-to-day business, but could, possibly, result in thousands of layoffs in the near future, particularly in the company's sales team. Microsoft is playing catch up with Amazon and its AWS, while Google and its cloud services are increasingly breathing… [Continue Reading] -

Video calls are more effective than voice calls
Publié: juillet 4, 2017, 3:00pm CEST par Sead Fadilpašić
Almost three quarters (72 percent) of workers in the UK and US agree that video calls are a more effective work communication channel than voice calls. According to a new report by Kollective entitled Generation Now, almost two thirds (64 per cent) of workers now trust a message more if they see a person actually delivering it. Six in ten of the 2,000 workers surveyed across the US and UK also found visual content easier to consume, the study said, and almost half (46 percent) can’t be bothered to read long emails or documents, the report stated. "In general, videos have a better… [Continue Reading] -

London behind other UK cities in 4G and broadband speeds
Publié: juillet 4, 2017, 2:35am CEST par Sead Fadilpašić
London's 4G and broadband speeds are slower than many smaller cities across the UK, a fact labelled 'quite embarrassing' according to a new study. A report by the London Assembly (which can be found on this link), found that London's connectivity is lower than that in York, Coventry and Edinburgh. In some areas, like Rotherhithe in Southwark, there are "not-spots" and "digital deserts" (places with no connectivity at all). Chair of the Regeneration Committee, Navin Shah, says the situation is "frankly embarrassing in some areas," according to The Register. The capital is also ranked 30 out of 63 when it comes to higher broadband… [Continue Reading] -

China bets on AI to boost productivity and empower employees
Publié: juillet 3, 2017, 11:34pm CEST par Sead Fadilpašić
China is reportedly set to beef up its AI capabilities as it looks to boost and improve its tech talent. According to a Reuters report, this is all part of a soon-to-be-announced national Artificial Intelligence plan, which was allegedly confirmed by a senior Chinese official speaking to China Daily. The goal of the project is apparently to use AI to boost productivity and give more power to the employees. The country will release a number of different artificial intelligence development projects and research papers. It was also said that more resources will be allocated to make sure talent is nurtured. According to Chinese minister… [Continue Reading] -

Google users starting to embrace voice search
Publié: juillet 3, 2017, 10:30pm CEST par Sead Fadilpašić
Those people who have started using mobile voice search in the last six months are the most frequent voice adopters, according to news coming out of Google UK. More than four in ten (42 percent) are using it daily, compared to those that started using it more than four years ago, where it’s frequently used by a quarter. According to the report, the adoption curve is "getting to a point where brands and agencies need to start taking it seriously." With the help of voice, 75 percent are searching more frequently than before. However, voice isn’t exactly "killing" text search… [Continue Reading] -

Few UK consumers trust councils' ability to handle their data
Publié: juillet 1, 2017, 2:12am CEST par Sead Fadilpašić
Slightly over half (53 percent) of local authorities in the UK are ready to take on a cyber-attack, according to a new report by PwC. When it comes to local authority leaders, 35 percent are confident their staff are well equipped to deal with such an attack. Three quarters (76 percent) of UK CEOs are concerned about cyber threats, and almost all (97 percent) said they’re currently addressing cyber breaches that are affecting business information or critical systems. From the consumers’ point of view, things aren’t looking any better either. A parallel survey of 2,000 consumers conclude that just 34 percent… [Continue Reading] -

SMS-based mobile marketing will target 37.2 million Brits in 2017
Publié: juillet 1, 2017, 12:11am CEST par Sead Fadilpašić
When it comes to mobile marketing, there is a lot of room for growth among UK businesses, according to a new report from Textlocal. The report, based on a poll of 1,000 users, says Britain has roughly 80 million active mobile users, but just 50 percent of businesses are using SMS for marketing. However, that is about to change. SMS-based mobile marketing is expected to rise, from 37.2 million customers this year, to 48.7 million before we reach 2020. If this trend continues, SMS marketing is set to become the fastest growing marketing channel in the UK. Ofcom’s numbers are saying… [Continue Reading] -

The 'slow-burn' cost of a cyber attack
Publié: juin 30, 2017, 10:10pm CEST par Sead Fadilpašić
Businesses have been warned that they may be hit for damages in multiple ways after being affected by a cyber-attack. A new report by Lloyd's of London says there are two different costs linked to a cyber-attack: a one-off cost, and a "slow-burn" effect. The one-off cost is the visible one -- notifying customers, paying ransom, paying for public relation expenses, things like that. But there is also the "slow-burn," which can sometimes even be more expensive than the one-off price, and that includes things like loss of customers, fall in share price, or reputation damages. "There is a lack of understanding as… [Continue Reading] -

AI could boost UK's GDP by 10 percent by 2030
Publié: juin 30, 2017, 2:59am CEST par Sead Fadilpašić
Artificial Intelligence (AI) is set to provide a major boost to the UK’s GDP over the next decade, new research has claimed. A new report by PwC says that by 2030, the country’s GDP could see a boost of around 10 percent thanks to AI -- equivalent to around £232 billion. For PwC, this makes AI the biggest commercial opportunity today. In its biggest part, these gains will come from an increased consumer demand, which will result in a greater choice of products, more personalization and lower prices. To a somewhat lesser extent, improvement in productivity will also drive GDP gains. "Much of… [Continue Reading] -

UK workers optimistic about automation
Publié: juin 30, 2017, 12:58am CEST par Sead Fadilpašić
Every second office worker in the UK (48 percent) is optimistic about what automation technologies will do to their workplace in the future. The only problems are that it’s expensive and infrastructure is lacking. This is according to a new report by Capgemini, based on a poll of more than 1,000 UK office workers. Four in ten (40 percent) believe machine learning will have a positive impact, while 32 percent said the same for robotics. Only 10 percent said automation might have a negative impact. Almost half (47 percent) have seriously thought about how automation can support their departments on a daily… [Continue Reading] -

VMware will release security solution for virtual machines
Publié: juin 28, 2017, 11:48pm CEST par Sead Fadilpašić
VMWare is finally going to release its security solution for virtual machines, and according to the company's senior VP, it could be released in the third quarter of this year. Speaking at a global roadshow in Melbourne, Australia, Jeff Jennings said the product (which will probably be called App Defense) will be looking at the "context of a virtual machine." In a nutshell, here’s what we can expect: a solution will first look at a virtual machine and analyze executables that are supposed to run inside it. It will network the infrastructure the VM will touch on, analyze which ports… [Continue Reading] -

More than 8 million Brits work from home
Publié: juin 28, 2017, 7:08pm CEST par Sead Fadilpašić
More than eight million of British employees now work at home for at least one day per week -- equivalent to almost a third (31 percent) of the entire working British populace. The news comes from Virgin Media, which based its conclusions on a study of 2,006 employees. The report says homeworkers are bringing in £167 billion to the UK economy every year, and that number will only continue to grow. This year, homeworkers spend 10.2 billion hours working from home, which represents a 26 percent increase compared to 2012. Among those that still don’t work from home, many would love to… [Continue Reading] -

London phone booths to feature Wi-Fi, charging station and access to local services
Publié: juin 28, 2017, 4:14pm CEST par Sead Fadilpašić
BT is going to replace payphone kiosks in London with a replacement that it says can be "the phone boxes of the future." According to a Mobile Europe news report, the new InLinkUK units will be smaller than traditional payphone boxes, will provide ultrafast Wi-Fi, a charging station, access to maps and local services, a business phone directory and real-time, context specific information such as weather updates and London Underground tube times. BT also says the services will be free and paid for by advertising revenue, but added that users will have to register for them. "This is the phone box of… [Continue Reading] -

European carriers worry new EU data rules could harm innovation
Publié: juin 27, 2017, 7:07pm CEST par Sead Fadilpašić
The European Telecommunications Network Operators’ Association -- ETNO -- and the GSM association have warned that upcoming EU rules governing how businesses use data could slow down innovation and growth in the industry. The proposed updates to ePrivacy rules could also mean businesses such as telecom operators in the EU might no longer be able to use data to improve customer experiences. ePrivacy rules, which first came into force at the beginning of the century, are now being revamped to by the EU as part of its Digital Single Market reforms. The latest draft was submitted by MEP Marju Lauristin, and… [Continue Reading] -

What your startup needs to grow fast
Publié: juin 27, 2017, 12:02am CEST par Sead Fadilpašić
If you want to succeed as a start-up, you need to excel in three key categories: design thinking, open thinking and platform thinking. This is according to a new report released by Alfresco Software, which analyzed what separates winners from losers in the digital world. Based on a poll of 328 senior-level IT executives, the report says that 64 percent of those companies that excel in the three categories above usually "report significant annual growth." On the other hand, 43 percent of companies that are still developing their capabilities in one or two of the key areas are reporting different. Design… [Continue Reading] -

Businesses spend $2,300 to deal with a malware attack
Publié: juin 23, 2017, 11:38pm CEST par Sead Fadilpašić
To remedy a malware attack businesses need to shell out, on average, $2,300 per attack. This is according to a new report by Arbor Networks. The report, produced in partnership with research organization 451 Research, says spear phishing attacks are still most successful of all the different methods of entry. However, they won’t stick with spear phishing if it doesn’t work. They will use whatever is cheap, free or available as long as it works. Financial and identity frauds are losing popularity, the report says, as cybercriminals move towards more profitable and less complex strategies. "We have produced a very… [Continue Reading] -

One in three UK businesses has a digital executive
Publié: juin 23, 2017, 8:05pm CEST par Sead Fadilpašić
More than a third of the largest companies in the UK now have a digital executive whose sole task is to pull a competitive advantage from digital transformation efforts. With a 35 percent adoption rate, it is much higher than the global average of 19 percent. This is according to a new report by Strategy&, PwC’s strategy consulting business. All around the world, however, businesses are realizing the potential of having a dedicated digital executive. Two years ago, only six percent of companies have had a digital leader hired. The report, based on an analysis of the top 2,500 public companies… [Continue Reading] -

Cyber attacks and regulations don't change businesses' digital transformation plans
Publié: juin 23, 2017, 2:50pm CEST par Sead Fadilpašić
Businesses looking to digitally transform won’t be intimidated by cyber-attacks or data protection regulations, according to a new report by Advanced. Based on a poll of more than 500 senior executives in UK organizations, Advanced says organizations are concerned, but won’t give up. Security (82 percent) and data protection (68 percent) of cloud solutions top the list of concerns, but 80 percent of them won’t quit digitally transforming. A third (33 percent) say they’re experienced in the cloud and will consider it for new projects. Another third (37 percent) have recently launched cloud projects for the first time. Businesses do,… [Continue Reading] -

AMD reveals new GPU line for servers
Publié: juin 22, 2017, 11:58pm CEST par Sead Fadilpašić
AMD has revealed three new GPU server accelerators, promising a "dramatic increase" in performance, efficiency, and ease of implementation for deep learning and HPC solutions. The new line of GPU server accelerators comprises of Radeon Instinct MI25, Radeon Instinct MI8, and Radeon Instinct MI6 and will be paired with AMD’s open ROCm 1.6 software platform. The Radeon Instinct MI25 accelerator is based on the "Vega" GPU architecture and comes with 14nm FinFET process. AMD says it is "the world’s ultimate training accelerator for large-scale machine intelligence and deep learning datacenter applications." The Radeon Instinct MI8 accelerator, based on Fiji architecture,… [Continue Reading] -

Retailers will lose $71bn due to payment fraud
Publié: juin 22, 2017, 2:47am CEST par Sead Fadilpašić
Retailers are facing losses of up to $71 billion globally as the number of fraudulent card-not-present (CNP) transactions rises hugely within the next five years. A new report from Juniper Research has revealed that a number of different factors are driving the increase in fraud, including the US shifting towards EMV cards, delays in 3DS 2.0 and click-and collect fraud methods. The report, entitled Online Payment Fraud: Emerging Threats, Key Vertical Strategies & Market Forecasts 2017-2022, claims many retailers still see cyber-security solutions as too expensive. Juniper Research believes they will be underprepared for frauds when EMV gets introduced in the… [Continue Reading] -

Amazon and Microsoft lead IaaS market
Publié: juin 21, 2017, 11:46pm CEST par Sead Fadilpašić
Market analyst Gartner has released a new magic quadrant that visualizes how cloud companies are currently sitting in the market. According to the report, Amazon and Microsoft are the sole leaders of the market, with the rest far, far behind. Amazon Web Services is leading the charge. Microsoft is (sort of) trailing, but it is still considered a leader in the IaaS market. Google is considered "visionary," but it is on the very border of becoming a leader. Other companies that fell under the "visionaries" category are Alibaba Cloud, IBM and Oracle. Yes, Oracle. Gartner says it is still not a market… [Continue Reading] -

Connectivity issues hurt productivity the most
Publié: juin 21, 2017, 9:44pm CEST par Sead Fadilpašić
More than two thirds (67 percent) of small and medium-sized business in the UK see internet problems as their biggest productivity roadblock, new research has found. According to a new report by Storey that surveyed 500 SME decision-makers across the UK, more than three quarters (76 percent) of businesses see productivity as a top priority in their office, while 69 percent are certain that improving office layout and design can do wonders on their productivity. More than half (52 percent) of SME managers spend anywhere between 11 and 40 hours every month administrating their workplace. More than a fifth (21 percent) spend… [Continue Reading] -

Consumers ignore security risks for free Wi-Fi
Publié: juin 20, 2017, 9:59pm CEST par Sead Fadilpašić
A growing number of British consumers are using their neighbors' Wi-Fi, sometimes even without permission, because they can't afford their own. This is according to a new report by Santander, which also says that the price of phone and broadband services has increased hugely over the past ten years. Fourteen percent of Brits (roughly seven million people) will use their neighbor’s Wi-Fi without permission, or go to a café and use the internet there without actually buying anything. They will also take advantage of free, open Wi-Fi networks whenever possible. The advantages of a free internet outweigh the security concerns, the… [Continue Reading] -

Digital solutions make up nearly half of a company's revenue
Publié: juin 20, 2017, 3:48pm CEST par Sead Fadilpašić
Digital solutions are becoming an increasingly profitable operation for many businesses, generating almost half of revenue (47 percent) for most major organizations, according to a new report. That's according to Pure Storage which surveyed 9,000 businesses in 24 countries and in three regions (US, EMEA, Asia Pacific), and found that digital transformation is "no longer a buzzword" but is, in fact, actually happening right now. But despite clear progress, businesses are still being held back from becoming "truly digital," the company says, with the biggest roadblocks being technical complexity, and a strategic uncertainty from an infrastructure standpoint. On average, businesses are running… [Continue Reading] -

Tech disruption will destroy jobs
Publié: juin 19, 2017, 9:13pm CEST par Sead Fadilpašić
The head of one of the UK's biggest advertising firms believes new technology will destroy jobs in the future. "I happen to be in the camp of people who think that technology disrupts, and will destroy, jobs," says Sir Martin Sorrell, CEO of WPP, speaking at London Tech Week. Discussing online activity and marketing, Sorrell added that the internet will simplify the business significantly within the next few years. "It's shortening the supply chain and getting rid of what I used to call, the tyranny of geography." The supply chain in the media and advertising system "is the most complicated… [Continue Reading] -

Unencrypted USB drives putting UK businesses at risk
Publié: juin 19, 2017, 5:00pm CEST par Sead Fadilpašić
UK businesses are putting almost no effort into securing the data they keep on USB drives, which is not in line with what GDPR demands, potentially putting them at risk of being hit with huge fines. That's according to data storage firm Kingston, which concluded after polling 480 employees from companies in various industries. The storage solutions company says a fifth (20 percent) of companies don't plan on improving their security posture. More than 80 percent of USBs employees use in the UK don't use hardware-based encryption. More than a quarter (27 percent) of these drives are used to store sensitive data.… [Continue Reading] -

Cloud security services will be a $5.9bn market in 2017
Publié: juin 16, 2017, 10:55pm CEST par Sead Fadilpašić
Cloud-based security services saw a huge increase during the last 12 months, according to the latest figures from Gartner. In a new report, Gartner says cloud-based security services will reach $5.9 billion this year, representing a 21 percent growth compared to the year before. Overall growth for the cloud-based security services are outpacing the total information security market and by 2020, Gartner believes cloud-based will hit $9 billion. The driving force behind this immense growth are small and medium-sized businesses (SMB). They are becoming increasingly aware of security threats and are willing to invest more to protect themselves. They also see cloud deployments… [Continue Reading] -

Salesforce reveals AI-powered Einstein Analytics
Publié: juin 16, 2017, 3:55pm CEST par Sead Fadilpašić
Salesforce has revealed the launch of its most advanced CRM analytics platform yet. Called Einstein Analytics, this platform leverages artificial intelligence to the analytics workflow, allowing users to automatically create CRM insights. The AI will also be able to recommend actions which improve customer service and boost sales, as well as helping optimize marketing campaigns. Salesforce says that the platform will come with role-specific KPIs, providing users with an "intuitive, self-service way" to gain access to newest data from any device. One of the tool’s main features is called Einstein Discovery -- which conducts thousands of statistical checks to check the validity of… [Continue Reading] -

UK consumers increasingly prefer biometric authentication
Publié: juin 16, 2017, 2:56am CEST par Sead Fadilpašić
New research has shown that biometrics is quickly becoming the preferred method of authentication among British consumers. A report from Mastercard/University of Oxford report, has found that more and more of us across the UK are happy to use biometric security processes such as iris scans or fingerprint authentication. The news has been welcomed by Fujitsu, which has been at the forefront of biometric development for some time. Commenting on the report, Anthony Duffy, the company's director of retail banking, UK and Ireland at Fujitsu, says the findings show that biometrics are "coming of age." "Biometric solutions have been used overseas for… [Continue Reading] -

Most UK managers support remote working
Publié: juin 15, 2017, 10:55pm CEST par Sead Fadilpašić
More than a third (34 percent) of business managers and HR professionals in the UK are not satisfied with the technology they work with every day. This is according to a new report by IDC and Cornerstone OnDemand, which analyzed if UK workplaces are supplying the latest tech to their employees to help them work better. The report is based on a poll of 1,469 European business managers and HR pros. It also states that another third (34 percent) of respondents in the UK see legacy systems as their biggest roadblock to development and growth. Despite not providing the latest and… [Continue Reading] -

More than half of shopping-related searches come from mobile devices
Publié: juin 15, 2017, 8:55pm CEST par Sead Fadilpašić
For the first time ever, consumers all over the world carried out more shopping-related searches on their mobile phones than on their computers. Data from the new Salesforce Q1 2017 Shopping Index analyzed the shopping habits of more than 500 million consumers in 27 countries, with smartphones coming out on top for the first time. "A couple years ago, if you were browsing Facebook on your phone and saw a jumper you wanted to buy, you had to wait until you got to your computer to log on and purchase it. However, now, with the evolution of mobile, we can easily search… [Continue Reading] -

BlackBerry lets Android and iOS developers embed BBM into their apps
Publié: juin 14, 2017, 6:48pm CEST par Sead Fadilpašić
Developers building enterprise apps for Android and iOS can now embed BlackBerry's messaging system with ease, the company has announced. The Canadian firm has released an SDK for its famous BBM app, which it hopes can bring secure communications services for users around the world. The SDK is focused towards enterprise users, coming with a cost of $29 per user per year, if just using the messaging capability. Those looking for more advanced features will have to shell out $79 per user per year. Those advanced features include read receipts, message editing or file sharing. "Since announcing our limited release… [Continue Reading] -

Industroyer is more dangerous than Stuxnet
Publié: juin 13, 2017, 8:05pm CEST par Sead Fadilpašić
Remember Stuxnet, the worm that wreaked havoc across Iran's nuclear facilities? Security researchers from ESET say that they have discovered an even bigger threat, which is being called Industroyer. According to the company's report, Industroyer is built to "disrupt critical industrial processes," and was recently used in an attack in Ukraine, causing the city of Kiev to lose power for an hour. According to ESET, Industroyer uses "industrial communication protocols used worldwide in power supply infrastructure, transportation control systems and other critical infrastructure systems, such as water and gas." So in theory, Industroyer can be used for much more than disrupting the… [Continue Reading] -

Farming needs technology to feed the globe
Publié: juin 12, 2017, 7:29pm CEST par Sead Fadilpašić
Farmers need to embrace advanced technologies such as the IoT in the next few years in order to support the growing human population, new research has claimed. With the global population set to reach 11 billion by the end of the century (according to UN estimates) and climate change set to affect agriculture, changes are required in how we source and grow food, analyst firm Beecham has said. Report co-author and chief research officer, Saverio Romero, cites the UN Food and Agriculture Program, saying global production of food, feed and fiber will need to increase by 70 percent by 2050, to meet… [Continue Reading] -

UK businesses are 'happy to lose' data
Publié: juin 12, 2017, 1:08pm CEST par Sead Fadilpašić
Almost three quarters of UK businesses (72 percent) are "happy to lose" more than 24 hours’ worth of data after a cyber-incident, new research shows. According to a report by Disaster Recovery, 13 percent of companies have never backed up their data, while 43 percent lost vital information in the last two years. The report also says that the number of businesses that protect their data on a continual basis jumped eight percent year on year to reach 29 percent. However, Disaster Recovery stresses that the report was created just days after the WannaCry incident, so there was an increased… [Continue Reading] -

Server shipments and revenue are down
Publié: juin 10, 2017, 1:12am CEST par Sead Fadilpašić
Global server revenue dropped 4.5 percent in the first quarter of 2017, according to the latest updates from Gartner. Shipments were also down 4.2 percent compared to the first quarter of last year. Looking at the global server market, Hewlett Packard Enterprise (HPE) is still leading the charge, based on revenue. It posted more than $3 billion in revenue, with a total share of 24.1 percent for Q1 2017. Dell EMC held on to second place with a 19 percent market share, as the only vendor to experience growth this year. In terms of server shipments, Dell EMC has a 17.9… [Continue Reading] -

Pay attention to benefits to attract talented developers
Publié: juin 9, 2017, 2:42pm CEST par Sead Fadilpašić
Stack Overflow released a new report that details the needs and motivations of today's developers. With 98.6 percent of developers in employment, and just 9.5 percent actively looking for a new role, the new report aims to help businesses attract talent. The newly released Q2 2017 Developer Ecosystem report: the Employment Trends & Insights edition concludes that: Agile is the fastest growing keyword in the job search Developers don’t always get the benefits they want They also feel underpaid Remote work is important They don’t just work in software companies and startups Their priorities change over time As a keyword, "agile" is… [Continue Reading] -

People expect Internet of Things to grow
Publié: juin 9, 2017, 2:26am CEST par Sead Fadilpašić
The huge growth of the Internet of Things shows no signs of slowing down in the next few years, new research claims. A report released today by Pew Research Center and Elon University’s Imagining the Internet Center has found that 85 percent of people believe that the world is set to become a more connected place than ever before. The research itself was inspired by the ever-growing number of cyber attacks like the most recent WannaCry one. More than 1,200 experts were asked questions regarding IoT and the future of the human race, and 15 percent believe more people will choose… [Continue Reading] -

Botnet activity rises by 69 percent
Publié: juin 9, 2017, 12:25am CEST par Sead Fadilpašić
PhishMe has released its latest malware trends report for Q1 2017, concluding that botnets are on the rise, it is unusually quiet on the ransomware front, and cyber criminals are tapping into international trends. The report, entitled 2017 Q1 Malware Review, is based on an analysis of 749 sets of phishing emails delivering nearly 10,000 unique malware samples supported by over 14,000 online resources. First -- botnets. There has been an increase of 69 percent in botnet activity. These botnets are led by the Ursnif malware, allowing cyber criminals access they need to kick off long-term intrusions. Other tools are also used… [Continue Reading] -

IBM builds 5nm chip with better performance and energy efficiency
Publié: juin 8, 2017, 2:12am CEST par Sead Fadilpašić
We haven't even seen 7nm chips in mass production, however, IBM has already announced that it has managed to build a 5nm one. What's even more important than its size, is the fact that it is much, much faster than the 7nm one. How faster, you ask? Well, 7nm chips can hold 20 billion transistors. These 5nm chips can hold as much as 30 billion transistors. The building process is similar (ultraviolet ligthography), but the transistor design was replaced with stacks of nanosheets. IBM says these chips will be much faster than anything we have today, and that's a given. But… [Continue Reading] -

Insider threats putting many financial services at risk
Publié: juin 7, 2017, 7:54pm CEST par Sead Fadilpašić
The majority of financial services are at risk of insider cyber threats because their mainframe environments have blind spots, according to Compuware. The company's latest research claims that organizations such as banks keep the majority of the sensitive customer data on the mainframe, as they consider it the securest in the entire enterprise. However, they are not monitoring it close enough to truly understand what those with privileged access are doing with that data. Polling 400 CIOs, 66 of which were from the financial sector, the report says more than three quarters (78 percent) of CIOs admitted to knowing of a… [Continue Reading] -

Impersonation attacks rising sharply
Publié: juin 7, 2017, 5:34pm CEST par Sead Fadilpašić
The number of impersonation attacks rose by 400 percent this quarter, new research has revealed. According to a new report by Mimecast, attacks where malicious actors carefully impersonate C-level executives, employees or business partners are on the rise. Mimecast says the technique, which tricks recipients into initiating wire transfers or sending other sensitive or highly monetisable data, is being exploited at an "alarming rate" and can lead to "significant financial loss." It cites the FBI, saying since October 2013 and December 2016, more than $5.3 billion were lost due to these types of scams. Between January 2015 and December 2016,… [Continue Reading] -

New malware could be as dangerous as WannaCry
Publié: juin 6, 2017, 6:34pm CEST par Sead Fadilpašić
Security researchers have warned that more dangerous malware has been released from the recent NSA dump that resulted in the WannaCry ransomware outbreak. Experts at Secarma have revealed that the attack could be hiding another malicious package, which could be as dangerous as WannaCry. The exploit is called "ExplodingCan," and it is capable of infiltrating "fully patched Windows 2003 servers offering IIS 6.0, under certain conditions." Secarma claims that some 375,000 systems worldwide could be affected, including telecoms, banking, educational and government institutions. "After WannaCry hit, people were asking what is going to be the next attack. We've been analyzing the dump… [Continue Reading] -

Data protection fines double in UK
Publié: juin 5, 2017, 9:06pm CEST par Sead Fadilpašić
UK companies were hit with fines totaling over £3.2m last year after falling foul of data protection laws, a new report reveals. Analysis of figures from the ICO by PwC found that the 35 fines handed out in 2016 were almost double of the previous year, despite repeated warning that the new GDPR regulations are just a year away. According to the report, 23 enforcement notices were issued last year, representing a 155 percent jump compared to 2015. PwC noted that the UK, along with Italy, was one of the most active regions when it comes to regulatory enforcement in… [Continue Reading] -

Insurance companies increasingly relying on machine learning
Publié: juin 2, 2017, 5:24pm CEST par Sead Fadilpašić
More than half, 54 percent, of almost 200 insurance executives recently confirmed that their company was using machine learning for predictive analytical modeling. They confirmed it to analytics solutions firm Earnix, which used the information to release a report entitled Machine Learning -- Growing, Promising, Challenging. Of those that are deploying this new tech, almost three quarters (70 percent) say they were using it for risk modeling. Demand models and fraud detection were also mentioned. Earnix says this means machine learning will bring "significant change" to the industry in the next three to five years. Most companies have already realized measurable benefits,… [Continue Reading] -

Data quality can impact software development
Publié: juin 2, 2017, 2:03am CEST par Sead Fadilpašić
The quality of your company's data can have a major effect on the software deployment, new research has claimed. According to a report by Delphix, poor data quality is to blame for roughly 15 percent of software defects, with higher-level data a major factor in faster application development. The report, entitled State of Test Data Management, also says that many IT firms admitted to compromising data quality, despite the fact that the ability to bring high-quality software to market is considered "critical" to business success. Businesses are adopting agile and DevOps methodologies to improve innovation, but when it comes to… [Continue Reading] -

Intel announces Core X processor lineup
Publié: juin 1, 2017, 10:03pm CEST par Sead Fadilpašić
The battle for the title of the most powerful PC processor in the world has just become even bloodier. Intel has announced its first 18-core processor at Computex in Taipei, officially named i9-7980XE The 7980XE, which will cost from $1,999, represents the very top of Intel's high-end offerings, marking the eighth generation of its Core processor chips. This is a processor built for the most demanding of desktop users, with Intel saying that many different industries will find things to love about the new chip, particularly those carrying out CPU heavy tasks such as video editing or coding. Besides this… [Continue Reading] -

Why UK businesses can't take full advantage of Office 365
Publié: juin 1, 2017, 2:22am CEST par Sead Fadilpašić
The advantages of Office 365 are being hindered by poor connectivity, bandwidth and latency issues, according to new reports coming out of Zscaler. As it turns out, Office 365 is a great service with many benefits which businesses all over the UK are very well aware of. However, due to issues with connectivity and latency, many organizations can't take full advantage of the service. According to Zscaler, almost two thirds (64 percent) have reported network and cost issues. More than half (58 percent) had to increase their bandwidth, while 65 percent upgraded their firewalls as they prepared to deploy Office… [Continue Reading] -

The cost of cyber attacks will rise to $8 trillion in five years
Publié: mai 31, 2017, 10:21pm CEST par Sead Fadilpašić
Cyber attacks will cost businesses across the world $8 trillion in the next five years, according to a new Juniper Research report. Just to put things in perspective, India's entire GDP crossed $8 trillion two years ago. The report says that we'll hit that threshold very soon due to higher levels of Internet connectivity, and inadequate enterprise-wide security. Juniper's report, entitled The Future of Cybercrime & Security: Enterprise Threats & Mitigation 2017-2022, says the number of personal data records stolen this year will hit 2.8 billion, and is expected to hit five billion, almost double, by 2020. Businesses are trying… [Continue Reading] -

China's QR codes changing the way young people perceive money
Publié: mai 31, 2017, 7:01pm CEST par Sead Fadilpašić
QR codes are "changing social behavior" in China, according to a new story published on the South China Morning Post. As a payment technology, QR codes are going through a renaissance in mainland China, where mobile payments are now 50 times greater than those in the US. Mobile payments in the States have reached $112 billion last year, the report states, calling on a Forrester Research report. A single QR code is capable of storing 300 times more data than a traditional one-dimensional code. iResearch claims payments made via mobile devices in China reached 38 trillion yuan. "China has started… [Continue Reading] -

Technology will completely transform healthcare
Publié: mai 30, 2017, 9:00pm CEST par Sead Fadilpašić
Medical workers in the UK are confident that new technological solutions will be able to completely transform their industry for the better, a new survey has found. Advances in technology which allow faster information flow and better solutions will contribute to making jobs much easier, according to a report from Epson. The report says big data will help improve diagnosis and treatment success, with 3D printing particularly considered a "revolutionary force." Knowledge sharing between specialists will also improve thanks to new collaboration technologies. Waiting times will be cut, 3D printing organs and cells will speed up medical processes, and remote… [Continue Reading] -

Cisco and Microsoft team up on Internet of Things solutions
Publié: mai 30, 2017, 3:52am CEST par Sead Fadilpašić
Cisco has made a couple of interesting announcements in its IoT space, including a new hardware platform and a collaboration with Microsoft on hybrid IoT solutions. There are three new components to the Cisco IoT Operations Platform: Connection Management at Scale, Fog Computing and Data Delivery. Connection Management at Scale is a platform which will help businesses manage an ever-expanding amount of IoT devices. Fog Computing is there to make sure "data processing and device control happens at the right place for each job," and Data Delivery allows organizations to collect, collate and act on the data their systems are… [Continue Reading] -

Security providers should consider offering DDoS protection as a service
Publié: mai 30, 2017, 1:52am CEST par Sead Fadilpašić
Need a new business idea? How about you start offering DDoS protection as a service? What, you think it wouldn't work? Think again. A new report by Corero Network Security says it could work out nicely. Out of its respondents, 82 percent see a "clear business opportunity" in providing DDoS protection as a service to its customers. Also, 93 percent see providing DDoS mitigation in relation to other types of security services as "high priority." This is up 10 percent compared to last year. A third, 37 percent, see it as more important, and half, 56 percent, see it as… [Continue Reading] -

Consumers expect mobile devices to transform
Publié: mai 26, 2017, 10:16pm CEST par Sead Fadilpašić
When Microsoft says we'll be holding much more than a mere smartphone in our palms in a few years, they weren't exaggerating. A new Gemalto survey says that by 2025, consumers expect mobile devices to become much more than what they are today. They expect the mobile device to be their ID tool, maybe even their passport. They expect the device to autonomously control their home, they expect to use it as a payment tool, and as a banking device, as well. For the report, Gemalto polled 2,000 consumers in the USA, UK, France, Germany, China and Brazil. Almost half… [Continue Reading] -

UK businesses want to increase adoption of cloud services
Publié: mai 26, 2017, 5:18pm CEST par Sead Fadilpašić
The adoption of cloud technologies in a company is becoming a key function of many company’s technology strategy. Almost nine in ten (88 percent) of UK businesses have adopted cloud to some extent, the report says, adding that two thirds (67 percent) of users expect to increase the adoption of cloud services in the near future, according to a new report by the Cloud Industry Forum (CIF) CIF’s report, however, concludes that there is a discrepancy in opinions between IT decision makers and their business counterparts. Almost three quarters (73 percent) of ITDMs think cloud is being driven by their… [Continue Reading] -

XData ransomware starts wreaking havoc
Publié: mai 26, 2017, 1:40am CEST par Sead Fadilpašić
The dust hasn’t even settled around WannaCry, another ransomware appears. This one was detected by ESET and identified as Win32/Filecoder.AESNI.C. Security researchers dubbed it XData ransomware. It appears mostly in Ukraine (96 percent of cases). The outbreak seems to have started on May 17, reaching its peak on May 19. ESET says that it has been tracking the malware since early December last year, when the version Win32/Filecoder.AESNI.A first appeared. Some decryption keys for this variant have been published on the BleepingComputer.com forum. This ransomware seems to be going around through a Ukranian document automation system used in accounting. ESET… [Continue Reading] -

Most UK businesses feel vulnerable to cyber threats, despite increased security spending
Publié: mai 25, 2017, 11:12pm CEST par Sead Fadilpašić
According to Thales' new report almost two thirds (63 percent) of businesses in the UK increased their cyber security spending this year, which is a jump from last year's 54 percent. However, despite this, 43 percent were breached last year (Thales fails to mention the percentage difference compared to a year earlier, though). More than four fifths (84 percent) still feel vulnerable to threats, with 20 percent feeling "very" or "extremely" vulnerable. There are some strange conclusions in the report, too. For example, the majority of businesses are using traditional cyber security methods, like network and endpoint security solutions. On… [Continue Reading] -

Executives are the most at risk employees when leaving the office
Publié: mai 24, 2017, 10:15pm CEST par Sead Fadilpašić
Four in ten organizations in the US and Western Europe believe C-level executives are the most at risk of cyber attacks when working outside the office. That's according to research by iPass, whose Mobile Security Report 2017 says that coffee shops and cafes are the riskiest venues (42 percent), followed by airports (30 percent), hotels (16 percent) exhibition centers (seven percent) and airplanes (four percent). The report is based on 500 responses from organizations in the UK, US, Germany and France. More than nine in ten (93 percent) say they are worried about security, with 47 percent saying they are "very" concerned (up… [Continue Reading] -

CISO salaries topping €1 million in Europe
Publié: mai 24, 2017, 2:31am CEST par Sead Fadilpašić
Now might be a good time to consider that job as a chief information security officer you always wanted, because salaries are skyrocketing. Thanks to an ever-increasing number in breaches, and the damage these breaches are causing, businesses in Europe have begun offering much better salaries to their CISOs. A CityAM report says CISO salaries are topping €1 million, and that the importance of the issue has given CISOs a place in the boardroom. "CEOs have started to lose their jobs over data breaches and the financial impact of some individual data breaches now runs into the tens or hundreds… [Continue Reading] -

Businesses worry about long-term data storage
Publié: mai 24, 2017, 1:30am CEST par Sead Fadilpašić
Businesses fear that, with the speed at which technology changes, they won't be able to read their corporate data in the near future. And that seems to be a big issue, as many businesses want to be able to read its archived data for at least 50 years in the past. This is according to a new report released recently by Crown Records Management. Files created in Word Perfect or Lotus 123, or multimedia content stored in the .MOV format, are in danger of becoming obsolete. Anything stored on floppy drives, as well. More than nine in ten share the same… [Continue Reading] -

Microsoft working on DNA-based data storage
Publié: mai 23, 2017, 5:51pm CEST par Sead Fadilpašić
Quantum computing is not the only large leap in computing the human race is currently working on, there's also the crazy and amazing research in storing data in DNA. According to media reports, Microsoft is now planning on building, "an operational storage system based on DNA working inside a data center," by the next decade. The DNA storage machine, or whatever it will be, should be the size of a large, 1970s-era Xerox copier, but could fit every movie ever recorded inside a volume smaller than a sugar cube. The problem, as it usually is with new technology, is that… [Continue Reading] -

Google Cloud IoT Core helps businesses manage data and devices
Publié: mai 23, 2017, 2:06am CEST par Sead Fadilpašić
Google has announced the launch of a new service to help businesses handle large volumes of data created by their IoT devices. IoT Core will look to take on the likes of AWS and Microsoft, although a company's spokesperson says that Google is not playing catch up. Instead, the company says it is catering to customers who were demanding such a feature, as an increasing number of companies are dealing with larger volumes of data, as more and more IoT devices come into the fold and start working. Google Cloud IoT Core's main task would be to simplify data management.… [Continue Reading] -

Customers prefer bots over humans for support
Publié: mai 23, 2017, 12:05am CEST par Sead Fadilpašić
People are now more receptive of bots in customer support services, a new report by LivePerson has concluded. Consumers would rather talk to a bot than to a human, and usually rate the interaction with the digital helpers as a great one. Even though the general opinion of bots was that they were implemented by companies to cut costs, it is now being realized that it was also (or even more) about the speed of service. More than half (52 percent) of consumers globally would not rate the customer service as "excellent," if they were forced to wait on the… [Continue Reading] -

Tech-savvy workers increasingly common in non-IT roles
Publié: mai 22, 2017, 6:55pm CEST par Sead Fadilpašić
IT professionals are becoming an increasingly common presence outside of the traditional IT departments, new research has found. According to CompTIA, it seems executives are calling for specialized skills, faster reflexes and more teamwork in their workers. According to the report, a fifth (21 percent) of CFOs say they have a dedicated tech role in their department. Those roles include business scientists, analysts, and software developers. There are also hybrid positions -- in part technical, but also focused on the business itself. "This isn’t a case of rogue IT running rampant or CIOs and their teams becoming obsolete," says Carolyn April, senior director,… [Continue Reading] -

More businesses are becoming familiar with GDPR, but fines are still likely
Publié: mai 20, 2017, 2:00am CEST par Sead Fadilpašić
Even though the GDPR is just a year from coming into force, the majority of businesses are still unprepared. This is according to new research from Compuware, which says businesses are risking huge non-compliance fines. Some businesses, truth be told, have made progress since last year. The most progress has been made on the knowledge front -- 67 percent of European and 88 percent of US organizations with EU customer data are informed on GDPR. This is up from 55 percent and 73 percent respectively, last year. UK businesses, unfortunately, are least prepared to comply with the General Data Protection… [Continue Reading] -

APT3 hacking collective has ties to Chinese government
Publié: mai 20, 2017, 12:44am CEST par Sead Fadilpašić
Cybersecurity experts from Recorded Future think the cybercrime group we know as APT3 is on the Chinese Ministry of State Security’s payroll. It bases its conclusions on the work of "intrusiontruth," a group claiming to have investigated some of the most important APT actors. Analyzing APT3’s C&C infrastructure, it came across two names, Wu Yingzhuo and Dong Hao, who allegedly registered many of the domains that the threat actors had used. Both names are also shareholders for a China-based security firm Guangzhou Boyu Information Technology Company, or Boyusec. According to the Washington Free Beacon, Boyusec worked with Huawei to create… [Continue Reading] -

Demand for microservices skills is growing
Publié: mai 19, 2017, 9:13pm CEST par Sead Fadilpašić
Job positions that require skills in so-called "microservices" have seen a huge boost to increase by 133 percent in the last year. According to a new report by Rackspace, this has made such positions among the most popular IT jobs on the market today. The report also says that roles related to Agile Software Development are also up 16 percent in the last year. Google’s Kubernetes has seen "meteoric" growth in demand among engineers, jumping 919 percent since last year. Docker is also seeing continued interest over the course of the last 12 months, as well. The demand for DevOps… [Continue Reading] -

Adylkuzz malware mines Monero to generate revenue
Publié: mai 19, 2017, 6:50pm CEST par Sead Fadilpašić
A new form of malware is targeting innocent victims in order to mine cryptocurrency for its creators. Adylkuzz, which targets the Monero cryptocurrency, stays hidden within an infected machine, and does not give visual warnings or interfere with users’ files. Security firm Bitdefender, which first spotted the malware, says the best way to protect yourself is to keep your operating system up to date, to disable the Server Message Block service on the computer if patching is impossible, and back up any and all data to offline hard drives. Anyone can create cryptocurrency through a process called mining. It is… [Continue Reading] -

IT leaders want to adopt unified communications systems
Publié: mai 19, 2017, 12:13am CEST par Sead Fadilpašić
Enterprise communications are set to see a major overhaul within the next five years, according to a new report. Research from Fuze found that almost six in ten (59 percent) of companies have prioritized adopting new communication technology. Based on a survey of 900 IT leaders, the report says 64 percent are looking to cut the number of communications apps to remove complexity. Two thirds (64 percent) are also looking to move their communications completely into the cloud. Sixty-three percent will have adopted a unified communications system by 2022, and 62 percent think video will replace voice-based comms by 2022.… [Continue Reading] -

Many senior executives do not know GDPR is coming
Publié: mai 18, 2017, 11:12pm CEST par Sead Fadilpašić
More than four fifths (84 percent) of small business owners in the UK, and almost half (43 percent) of senior executives in large companies have no idea what GDPR is and that it’s coming. That's according to Shred-it’s Security Tracker research, which also found that roughly one in seven (14 percent) of small business owners, and 31 percent of senior executives know what the fines of not complying with the GDPR are. This is despite the fact that 95 percent of senior executives and 87 percent of small business owners claim to have some understanding of their industry’s legal requirements.… [Continue Reading] -

IT pros are feeling stressed at work
Publié: mai 18, 2017, 8:37pm CEST par Sead Fadilpašić
The road to becoming an IT professional is often thought to be a lifelong process, however, new research claims that this is not the case. A new report from Spiceworks, entitled "A Portrait of IT Workers," says 41 pe cent of IT pros in the UK consider themselves "accidental" and that they ended up in their career via a "non-traditional" route. The report, which covers areas including the career plans and education levels of IT professionals, found that a third (33 percent) of the UK’s IT job force don’t have a college or a university degree. They are also more pessimistic… [Continue Reading] -

VMware to deliver Horizon Cloud on Microsoft Azure
Publié: mai 18, 2017, 1:34pm CEST par Sead Fadilpašić
VMware has announced two major announcements with Microsoft and Samsung. The cloud infrastructure and business mobility firm has announced it will now deliver VMware Horizon Cloud on Microsoft Azure, helping its customers migrate to Windows 10 faster. VMware virtual desktops and applications are now also available to Azure enterprise users. VMware says this move will "help support the company’s cross-cloud strategy" offering customers a couple of infrastructure options for virtual desktops and apps. The company also says customers will be offered flexibility to move between different platforms, if need be. For Samsung, the partnership aims to simplify Internet of Things… [Continue Reading] -

US considers laptop ban on European flights
Publié: mai 15, 2017, 11:19pm CEST par Sead Fadilpašić
The Trump administration is considering a further expansion of the ban on using laptops on commercial flights to cover European travel. According to Reuters , the US government is reviewing how to make sure lithium batteries that get stored in the luggage don’t explode during flights. Reuters says that the expansion will affect flights on United Airlines, Delta Air Lines and American Airlines Group. Both US and European officials have said that they’re waiting on the US Department of Homeland Security to make an announcement, but it is not yet clear as to when that might happen. DHS and airline… [Continue Reading] -

Brexit has a major impact on UK tech jobs
Publié: mai 15, 2017, 11:12am CEST par Sead Fadilpašić
We don't have to wait any longer to see the effects of Brexit on the tech job market in the country -- Hired.co.uk already has some data for us. And it's exactly as you might have imagined it. According to the hiring site's report, the number of foreign tech workers in the UK is now down 50 percent. The rate at which foreign workers are now accepting UK-based roles has also dropped by a fifth (20 percent). But it’s not just the employees that are declining offers, businesses are also sending out less. The percentage of UK-based companies that send job… [Continue Reading] -

Automation will transform accountants' jobs in the next five years
Publié: mai 13, 2017, 12:51am CEST par Sead Fadilpašić
Do you think automation will change your job in the next five years? Accountants seem to think so. Pretty much every accountant believes their work will be either partly or completely automated by 2022. A new report by FreeAgent says 96 percent of accountants agree with this claim, and just three percent say they don’t think automation will change their work. Almost two thirds (62 percent) of those accountants participating in the survey for the report also say they don’t believe they will be performing the same tasks they do today in the next five years. But they are getting… [Continue Reading] -

Enterprises that don't embrace automation will cease to exist
Publié: mai 12, 2017, 9:04pm CEST par Sead Fadilpašić
Automate or perish. That is essentially what a new study by BMC Software, an IT solutions for the digital enterprise company, is saying. It polled IT decision makers for its new report and came to the conclusion that almost three quarters (73 percent) agree with the above-mentioned statement. ITDMs believe that those organizations which fail to adapt automation within the next five years will cease to exist in 10. More than nine in ten (92 percent) said that demands for new sources of revenue, unique competitive advantage, and operational excellence are creating "enormous pressure to compete digitally" to earn the… [Continue Reading] -

One in four European businesses don't know GDPR is coming
Publié: mai 11, 2017, 7:23pm CEST par Sead Fadilpašić
Every fourth European company has no idea GDPR is coming its way. Consequently, they don’t know about the dangers and the draconic fines that follow those that don’t comply with the upcoming regulation. This is according to a new report by IDC Research, based on a poll of 700 European companies. More than half (52 percent) don’t know what the impact on their organization is. Even among those that were aware of GDPR, the findings aren’t what they should be. Every fifth company (20 percent) still hasn’t started preparing for the GDPR, even though it’s just a year away. Almost… [Continue Reading] -

Majority of UK workers blindly open email attachments
Publié: mai 11, 2017, 4:29pm CEST par Sead Fadilpašić
Come on, people. We’re almost halfway through 2017, and you’re still opening shady email attachments? Glasswall Solutions seems to think so. As a matter of fact, its new report says UK workers are "too trusting" of email attachments. More than half, 58 percent, "blindly" open email attachments from unknown sources. Three quarters, 75 percent, recognize how often they get shady emails. Just 16 percent thinks they should be worried about a cyber-attack. More than two thirds (69 percent) fear data theft, while 41 percent are afraid of losing a network, or a system. Only a quarter (24 percent) is afraid of… [Continue Reading] -

Digital transformation is powerful, but also dangerous
Publié: mai 11, 2017, 11:03am CEST par Sead Fadilpašić
More than two thirds of network managers in the UK consider the digital strategy an important part in tackling competition. However, almost half (49 percent) look at legacy technologies as something that’s holding them back in this endeavor. This is according to a new report by Axians UK, released earlier today. Digital transformation is serious business. It’s essential to delivering a satisfying customer experience, yet if done poorly, could force companies into administration. As digital strategy becomes a priority for more businesses, network changes that are necessary to sustain secure and agile businesses are being missed, the report states. "Organizations… [Continue Reading] -

Automation, IoT and VR will improve sales and customer experiences
Publié: mai 10, 2017, 8:29pm CEST par Sead Fadilpašić
Retail, wholesale and manufacturing companies are turning to Internet of Things (IoT), Automation and Virtual Reality (VR) to drive sales and improve customer experiences. This is according to a new report by global ecommerce consultancy firm Salmon, which says almost two thirds (61 percent) of European companies in above mentioned industries are investing and believing in IoT. For over a third (35 percent), enabling IoT is among the biggest business priorities for the next year. More than half (53 per] cent) are looking to take advantage of voice interface technology in the next five years. Almost six in ten (59… [Continue Reading] -

UK businesses spent £1.74bn on IT outsourcing in Q1 2017
Publié: mai 10, 2017, 10:21am CEST par Sead Fadilpašić
Companies are ramping up investment in digital transformation, and it’s showing. This is according to a new report by Arvato, which says Q1 2017 was the strongest in the last five years when it comes to the UK’s private sector outsourcing market. During Q1, businesses have agreed deals worth £2.42 billion. The Arvato UK Outsourcing Index, created in partnership with NelsonHall, says this is the "largest private sector spend since Q4 2011." In total, businesses spent £1.74bn outsourcing IT, with more than two thirds (68 percent) going on new projects. Commitment to the improvement of customer experiences led to an… [Continue Reading] -

Technology won't fully replace in-store workers, retailers believe
Publié: mai 10, 2017, 2:07am CEST par Sead Fadilpašić
There will still be people working in the stores of the future, but technology is still going to make a profound impact on the retail industry. This is what retail workers think about how their job will transform in the near future. According to a new report by Epson, 70 percent of retailers think technology will never be able to fully replace people in stores, but it will revolutionize the shopping experience. Four in ten (40 percent) think they’ll no longer hold stock. Instead, they will create customized products on demand. Sixty-seven percent think automatic ID of customers will create… [Continue Reading] -

Barclays announces new controls for debit cards to fight fraud
Publié: mai 10, 2017, 1:06am CEST par Sead Fadilpašić
Barclays is fighting back against fraud by offering its users more power over when and how their debit cards can be used. According to its announcement, customers will be able to instantly turn a card "on" or "off," disallowing remote purchases. They will also be able to set their own daily ATM withdrawal limits through the Barclays Mobile Banking app. The new controls are part of the £10 million nationwide drive to increase the public’s awareness of financial fraud risks. "Fraud is often wrongly described as an invisible crime, but the effects are no less damaging to people’s lives," says Ashok Vaswani,… [Continue Reading] -

Governments are the biggest targets for cyber attackers
Publié: mai 9, 2017, 11:04pm CEST par Sead Fadilpašić
Cyberattacks against the government sector increased by 100 percent in 2016, rising up to 14 percent, according to a new report by Dimension Data. The financial sector has also seen a dramatic increase in the number of attacks, from three percent in 2015 to 14 percent in 2016. The manufacturing sector is now on third place with 13 percent of all attacks while retail, which used to be the number one target, fell to fourth place with 11 percent. Poor retail. This data was published in Dimension Data’s Executive’s Guide to the NTT Security 2017 Global Threat Intelligence Report. The… [Continue Reading] -

Financial organizations are having trouble finding documents
Publié: mai 9, 2017, 10:04pm CEST par Sead Fadilpašić
Pretty much every organization in the financial sector, 96 percent of them, struggles to find documents in the workplace. This is according to a new report by M-Files, saying financial sector organizations need to be better at protecting their information. M-Files was quick to throw words like "putting customer data at risk" or "GDPR" around, too. The report claims that almost two thirds (62 percent) of respondents have had to recreate an existing document, because they failed to find it on the corporate network. Just below half (46 percent) say employees use file sharing apps, and 27 percent say their… [Continue Reading] -

Netrepser malware targets government agencies
Publié: mai 9, 2017, 6:49pm CEST par Sead Fadilpašić
Researchers at cyber security firm Bitdefender recently unveiled a new targeted attack and named it Netrepser. What makes this threat different from other APTs (advanced persistent threat) is that it was built with readily available software tools. The goal of Netrepser, according to Bitdefender, is to steal data from government agencies. No information on which agencies were targeted. Netrepser uses multiple methods to get its tiny digital hands on the victim’s information, from keylogging, to password theft, to cookie theft. At the very heart of this tool is a "legitimate, yet controversial" recovery toolkit provided by Nirsoft. Nirsoft provides apps… [Continue Reading] -

UK businesses will spend £37bn on failing agile projects
Publié: mai 5, 2017, 8:31pm CEST par Sead Fadilpašić
Businesses in the UK will waste £37 billion on failed agile IT projects in the next 12 months, according to a new report from 6point6. The report is based on a poll of 300 UK and US CIOs. They were asked about their experiences with agile, and how its principles are being applied and executed. More than half of CIOs (53 percent) see agile development as "discredited," and three quarters (75 percent) don’t even want to defend it any more. Seventy-three percent of CIOs think agile IT is its own industry now, and 50 percent consider it an "IT fad."… [Continue Reading] -

Verizon sells 29 data centers to Equinix for $3.6bn
Publié: mai 3, 2017, 8:16pm CEST par Sead Fadilpašić
Global data center company Equinix has bought 29 data centers, along with their operations, from Verizon Communications. Approximately 250 Verizon employees will also become Equinix employees in the process. The deal, worth $3.6 billion, will be completed in all cash. It includes more than 1,000 customers, 600 of which are net new. Verizon will now, consequently, become a substantially larger customer. It also includes roughly a million square meters of data center space. Thanks to the acquisition, the company will also be moving into three new markets, Bogotá, Culpeper and Houston. Equinix says the acquisition further broadens its capabilities by strengthening… [Continue Reading] -

Big data will be a $76bn market by 2020
Publié: mai 3, 2017, 5:41pm CEST par Sead Fadilpašić
Big Data is now a $57 billion market, according to a new report from SNS Research. Entitled The Big Data Market: 2017 - 2030 -- Opportunities, Challenges, Strategies, Industry Verticals & Forecasts, it says that vendors will be earning from hardware, software, and professional services revenue. What’s more, the report says the investments are expected to grow at a CAGR of roughly 10 percent over the next four years, reaching $76 billion by the end of 2020. As companies around the world work to revitalize their economies, they will be incorporating different legislatives, trying to capitalize on the opportunity of… [Continue Reading] -

Ransomware's biggest target is the healthcare sector
Publié: mai 1, 2017, 5:12pm CEST par Sead Fadilpašić
Ransomware grew 50 percent in just a year, according to a new report by Verizon. The Verizon Data Breach Investigations Report (DBIR) is based on the analysis of 79,000 security incidents and 1,945 confirmed data breaches, across 79 countries. According to the report, ransomware also grew in popularity, and by a large margin. In 2014, it was the 22nd most common malware variety. Fast-forward two years, and now it’s fifth most common. The healthcare sector is under greater threat than all others, it was also added, as 72 percent of all malware incidents targeted this sector. More consumers than ever are… [Continue Reading] -

Hajime botnet controls nearly 30,000 devices
Publié: mai 1, 2017, 1:10pm CEST par Sead Fadilpašić
Hajime, a mysterious IoT botnet, now controls almost 300,000 devices, according to a new report by Kaspersky Lab. The report also states that the botnet's true purpose is still unknown. Kaspersky says the malware, whose name means "beginning" in Japanese, first appeared in October 2016. Since then it has evolved into a decentralized group of compromised machines that discretely perform either spam or DDoS attacks. The interesting thing is Hajime does not have an attacking code or capability. It just has a propagation module. It attacks pretty much anything that's connected to the internet. However, it fancies digital video recorders,… [Continue Reading] -

IT leaders will struggle to meet future demands
Publié: avril 28, 2017, 7:50pm CEST par Sead Fadilpašić
When it comes to meeting future demands, IT leaders in the UK are lagging behind those in Germany and the US. This is according to a new report by Brocade, entitled Global Digital Transformation Skills Study. The report is based on a survey of 630 IT leaders in the US, UK, France, Germany, Australia and Singapore. It says that organizations are "at a tipping point" -- a point in time when technology demands are just about to outstrip the skills supply. Consequently, those that train their staff now and prepare for the future in that respect are the ones that are… [Continue Reading] -

Many businesses don't have a digital transformation strategy
Publié: avril 28, 2017, 2:36pm CEST par Sead Fadilpašić
Four out of five business leaders think their industry will get positively disrupted by digital transformation within the next three years. This is according to a new report recently released by Microsoft and Harvard Business Review Analytic Services. "A vast majority (80 percent) of the 783 survey respondents believe their industry will be disrupted by digital trends," the report states. "And most of those (84 percent) said their industry has either passed the inflection point of disruption or will pass it by 2020 -- just three years away." However, the report states that the race is still on. "Companies that form… [Continue Reading] -

WeWork launches store for services and software
Publié: avril 27, 2017, 6:00pm CEST par Sead Fadilpašić
WeWork wants to make sure you never leave it, and it's trying to keep you as a customer by releasing its own tools store. Called Services Store, the new offering gives users simple access to a wide variety of tools and apps, and sometimes even exclusives. Once logged in, users can search, purchase and download a wide variety of enterprise apps. They can also leave reviews for different products, to help others find the perfect app for their business. The platform was built by WeWork, in cooperation with quite a few partners: Salesforce, Lyft, Upwork, Zendesk, Xero, Slack, Amazon Web Services,… [Continue Reading] -

Most businesses will migrate to Windows 10 by the end of 2017
Publié: avril 27, 2017, 3:46pm CEST par Sead Fadilpašić
Businesses will move to Windows 10 faster than they have moved to previous operating systems, according to a new report by Gartner. Surveying businesses everywhere, Gartner believes 85 percent of businesses will have migrated to Windows 10 before the year ends. First of all, Gartner’s research director Ranjit Atwal says the time to evaluate and deploy Windows 10 has come down, from 23 months to 21 months. Large businesses that are yet to start the migration, are delaying because of legacy applications. "Large businesses are either already engaged in Windows 10 upgrades or have delayed upgrading until 2018," Atwal says. "This… [Continue Reading] -

Four million Brits can't work from home because of poor connectivity
Publié: avril 27, 2017, 1:49am CEST par Sead Fadilpašić
If your telecom's poor connectivity is preventing you from working from home, you're not alone. There are four million Brits suffering from the same woes, according to new research from uSwitch.com, the price comparison and switching service. In the past year, almost half (43 percent) of employees in the UK have worked from home at least once. Among the younger workforce, those aged 18 - 34, the percentage jumps to 55. Yet, 58 percent have suffered from slow speeds and poor call quality. The problems were so pervasive that 46 percent of those with issues believe they can no longer… [Continue Reading] -

Many UK SMBs don't have a succession plan
Publié: avril 26, 2017, 6:51pm CEST par Sead Fadilpašić
More than half (52 percent) of small and medium-sized businesses in the UK’s IT sector have no idea what they’d do if key staffers decide to quit. This is according to a new report by the Aldermore Future Attitudes, which claims these businesses are lacking a succession plan. The report puts things in a dangerous perspective -- 22 percent of SME IT businesses see senior executives leaving as their biggest business threat. Another fifth, 21 percent, are worried their entire team would leave. Out of those 48 percent that do have a succession plan, 46 percent have confirmed this includes "ensuring… [Continue Reading] -

UK companies losing money due to inadequate communication and collaboration tools
Publié: avril 26, 2017, 2:07am CEST par Sead Fadilpašić
Inefficient communications and poor collaboration costs UK companies £8,000 per employee, every year, according to a new report by enterprise communications company Mitel. That means that a business with 500 employees or more could be losing more than £4 million every year. Looking into productivity within the workplace, Mitel’s new report also says that employees lose nearly a day every week due to inadequate communications capabilities. On average, a fifth of the working day is lost to emails. That costs businesses roughly £2,000 per employee, per year. The report falls in line with recent ONS figures, which claim that people… [Continue Reading] -

Many business apps with open source code have unpatched vulnerabilities and license conflicts
Publié: avril 25, 2017, 10:06pm CEST par Sead Fadilpašić
Apps that come with open-source code are putting organizations at risk, according to a new report by Black Duck. As you might imagine, many companies are using apps with open-source code. Black Duck’s Center for Open Source Research & Innovation analyzed 1,071 apps audited during 2016 and found that 96 percent of them had open source. Of those, more than 60 percent had open source security vulnerabilities. In the financial industry, there were 52 open source vulnerabilities per application. Sixty percent had "high-risk" vulnerabilities. In the retail and e-commerce industry, there was the highest proportion of apps with high-risk open… [Continue Reading] -

Hackers are going for your healthcare data
Publié: avril 25, 2017, 10:05pm CEST par Sead Fadilpašić
Every eighth person in England has had their healthcare data breached. This is the conclusion of a new report just released by Accenture. Based on a poll of 1,000 people it says that more than half of those who experienced a data breach (56 percent), were in fact, victims of medical identity theft. The report also says that these data breaches are fairly expensive, too. On average, more than three quarters (77 percent) have had to pay roughly £172 in out-of-pocket costs, per incident. Pharmacies are the most usual places where breaches occur. Hospitals, urgent care clinics, physician’s offices and retail… [Continue Reading] -

Consumers don't trust tech companies with their data
Publié: avril 25, 2017, 3:10pm CEST par Sead Fadilpašić
There is a high degree of mistrust when it comes to the technology sector managing people’s personal data. This is according to a new report from the Chartered Institute of Marketing (CIM), that got released late last week. According to the report, just six percent of the public trusts businesses in the technology sector to handle their personal data responsibly. Fast moving consumer goods sector is the worst (one percent), followed by media and the publishers (two percent). Financial services (34 percent), pharmaceuticals (25 percent), and professional and business services (16 percent) are at the other end of the spectrum.… [Continue Reading] -

The biggest threat to enterprise security? People
Publié: avril 25, 2017, 12:14am CEST par Sead Fadilpašić
People are the biggest threat when it comes to enterprise cyber-security, not technology or processes. This is according to a new report by The Institute of Information Security Professionals (IISP), which says there are a couple of ways people are putting organizations at cyber risk. The first, and most obvious one, is not being careful enough when opening links in emails, downloading attachments and visiting threat-carrying sites. The second one, less obvious, is the lack of technical skill. And finally, the third one, is the risk from senior business stakeholders making "poor critical decisions around strategy and budgets." Despite all… [Continue Reading] -

Riverbed buys Xirrus
Publié: avril 24, 2017, 8:12pm CEST par Sead Fadilpašić
Riverbed recently announced it's buying Xirrus for an undisclosed sum of money. The former is a company that builds SD-WAN products and generally looks to improve and optimize WANs. Xirrus, on the other hand, builds next-gen Wi-Fi networks. With the new acquisition, Riverbed will be able to offer its customers "the power of unified connectivity and policy-based orchestration that spans the entire distributed network -- WAN, LAN/WLAN, data center and the cloud." Xirrus will also be offered through Riverbed as a standalone enterprise WLAN solution. "Xirrus is a strategic acquisition for Riverbed, providing us with a leading enterprise-grade Wi-Fi solution,… [Continue Reading] -

Most Brits can't explain what ransomware is
Publié: avril 24, 2017, 5:28pm CEST par Sead Fadilpašić
Despite the fact that the media is constantly buzzing with stories of successful ransomware attacks, the general public in the UK is largely unaware of the threat. Backup experts Acronis polled Brits, and in their report it says that 60 percent of respondents would not be able to explain what ransomware actually is. Sixteen percent "just heard of it," while seven percent say they could "definitely" explain what ransomware is. Fifteen percent "probably could" Acronis also says that this lack of awareness is "matched by data insecurity" among respondents. More than two thirds (69.6 percent) feel "worried" about their personal data… [Continue Reading] -

Live linear streaming will be more popular than TV in the next five years
Publié: avril 24, 2017, 1:17pm CEST par Sead Fadilpašić
Live-linear streaming over-the-top video (OTT) will surpass traditional broadcast TV within five years, a new report by Level 3 Communications, Streaming Media and Unisphere Research says. It’s based on a poll that says 70 percent of respondents agree with the claim. The report, entitled OTT Video Services Study, polled almost 500 media industry professionals. More than a quarter of respondents expect OTT year-on-year revenue to grow as much as 25 percent, while around half expect growth to be anywhere between 30percent and 50 percent. For almost 66 percent of respondents, OTT-related services will account for more than a quarter of… [Continue Reading] -

Mastercard introduces card with built-in fingerprint scanner
Publié: avril 22, 2017, 1:50am CEST par Sead Fadilpašić
Mastercard has unveiled a new card that comes with a fingerprint scanner, allowing consumers to make purchases without the card ever leaving their hands. It builds on fingerprint scanning technology currently available in smartphones, and can be used at EMV terminals worldwide, the company says. The technology was tested in South Africa, in two separate trials. One was with Pick n Pay, while the other one was Absa Bank, a subsidiary of Barclays Africa. The process is simple. You go to your financial institution and enroll for the card. Once registered, your fingerprint is converted into an encrypted digital template… [Continue Reading] -

Oracle products now available through Docker store
Publié: avril 21, 2017, 9:49pm CEST par Sead Fadilpašić
Oracle’s databases, middleware and developer tools are now available in the Docker Store marketplace, thanks to a new partnership between the two companies, announced yesterday. Available via the Docker Certification Program, the tools allow developers to quickly build cloud-native applications using Docker Enterprise Edition as their container platform. The Certification Program is a framework, allowing partners to integrate and certify their technology to the Docker EE platform. The new offering is effective immediately. It allows developers to pull images of Oracle products in Docker and start testing and deploying enterprise apps fast. The solutions included in the partnership are Oracle… [Continue Reading] -

Businesses forget good security practices in DevOps environments
Publié: avril 21, 2017, 12:40am CEST par Sead Fadilpašić
Many organizations don’t enforce proper security measures in their DevOps environments, putting both the company and the product at risk. This is according to a new report by Venafi looking into security practices among DevOps adopters. Using the same passwords for multiple machines or not even bothering to secure communications between machines are some of the most common issues, usually among organizations in the middle of adopting DevOps practices. However, even organizations that say their DevOps practices are "mature" still make these rookie mistakes. Just over half (53 percent) of respondents in the middle of adopting DevOps claim security measures… [Continue Reading] -

Microsoft and Rambus optimizing DRAM for cryogenic temperatures
Publié: avril 20, 2017, 6:00pm CEST par Sead Fadilpašić
Rambus and Microsoft are working together on developing systems that optimize memory performance on cryogenic temperatures. This is the second time the two companies are teaming up, following the initial collaboration back in December 2015. According to Rambus, the new partnership aims to "enhance memory capabilities, reduce energy consumption and improve overall system performance." The two companies are now looking to develop systems to improve energy efficiency for DRAM and logic operation at temperatures below minus 180 degrees Celsius, ideal for high-performance supercomputers and quantum machines. "With the increasing challenges in conventional approaches to improving memory capacity and power efficiency,… [Continue Reading] -

Fujitsu announces six new enterprise devices
Publié: avril 19, 2017, 6:35pm CEST par Sead Fadilpašić
Fujitsu has announced six new enterprise devices on six different product series, offering faster machines and more security. There's the new 10.1-inch Arrows Tab Q507/P-SP tablet, a new Notebook Lifebook, two ESPRIMO models, a 17.3-inch Celsius H970 mobile workstation, and the Futro MU937 mobile notebook device (which Fujitsu claims is the world's lightest). What's particularly interesting about the Arrows device is that, for the first time, it comes with Fujitsu's Biometric Authentication Slide Passport functionality. This biometric authentication service allows users to log in using the palm of their hand. “With the simple action of sliding your hand along the guides displayed on… [Continue Reading] -

Lloyds Bank offers Windows Hello facial and fingerprint recognition
Publié: avril 18, 2017, 8:03pm CEST par Sead Fadilpašić
Lloyds Bank customers will soon be able to log into their accounts through fingerprint scanners and facial recognition technology, rather than typing in passwords. According to the bank, it has teamed up with Microsoft to bring the Windows 10 authentication technology to its customers. The biometric authentication technology, which Microsoft named Windows Hello, uses a combination of infrared technology and advanced software to identify the user in various lighting conditions. It was also emphasized that fraudsters can’t bypass the security measure by using a photograph. "With customer experience and security at the forefront of our minds, we are keen to… [Continue Reading] -

UK businesses face nearly 500 attacks a day
Publié: avril 15, 2017, 3:14am CEST par Sead Fadilpašić
OK, so, Beaming says UK businesses suffered, on average, 43,000 cyber-attacks in the first quarter of 2017 -- each. If this number sounds way too big, then it would be even more interesting to hear that this is actually seven per= cent lower than what was going on in the same period last year. Breaking the numbers down, Beaming says each business gets attacked 474 times per day. Almost all of these attacks, 92 percent of them, are targeting Internet of things devices, such as networked security cameras or building control systems, as these IoT devices can be controlled remotely, over… [Continue Reading] -

Marketers underestimate GDPR's ramifications
Publié: avril 13, 2017, 2:21am CEST par Sead Fadilpašić
Awareness of the GDPR has gone up, but B2B marketers are still falling behind and underestimating the impact of the new regulation, according to a new report by the DMA. More than a quarter of businesses (28 percent) still feel unprepared, which is just a two percent decrease, compared to earlier numbers. The number of marketers that have a "good" awareness about GDPR has risen 13 percent, to 66 percent in total, the report claims. B2B marketers, however, are at the both ends of the spectrum. More than a quarter (26 percent) of marketers believe their companies are still unprepared… [Continue Reading] -

UK national weather service has new mainframes that can perform 23,000 trillion calculations a second
Publié: avril 11, 2017, 10:35pm CEST par Sead Fadilpašić
Met Office, the UK’s national weather service, has a new IT solution, thanks to a partnership between the service, IBM and Computacenter. It will allow the Met Office to process greater volumes of weather data faster. Currently, the service collects and safeguards around 200 million weather observations every day. The new environment includes two new mainframes with 44 cores, and 200 terabytes of attached storage. This solution will allow the Met Office to perform more than 23,000 trillion calculations per second. The platform is based on two IBM z13 LinuxOne mainframes and IBM hybrid storage systems. "Every day, our weather… [Continue Reading] -

Global IT spending will reach $3.5 trillion in 2017
Publié: avril 11, 2017, 10:34am CEST par Sead Fadilpašić
Worldwide IT spending will jump another 1.4 percent this year, according to a new report by Gartner. The report says IT spending is expected to hit $3.5 trillion this year. A quarter before, the increase was 2.7 percent, but the difference occurred mostly due to the strengthening of the US dollar. "The strong US dollar has cut $67 billion out of our 2017 IT spending forecast," says John-David Lovelock, research vice president at Gartner. "We expect these currency headwinds to be a drag on earnings of US-based multinational IT vendors through 2017." There will be a slight grow in the… [Continue Reading] -

Accountants are embracing artificial intelligence
Publié: avril 10, 2017, 10:03pm CEST par Sead Fadilpašić
Despite the popular belief that artificial intelligence is coming to take your jobs away, accountants would love some robotic help to get them through the day. This is according to a new report by Sage, which says 96 percent of accountants are confident about the future of accountancy as well as their role in it. Despite welcoming change, more than two thirds of respondents (68 percent) expect their roles to change through automation, in the future. Here’s what accountants are expecting from automation: almost four in ten (38 percent) see number-crunching as their number one frustration. Thirty-two percent still use… [Continue Reading] -

London's Square Mile gets free Wi-Fi
Publié: avril 10, 2017, 6:37pm CEST par Sead Fadilpašić
The heart of London’s financial district -- The Square Mile -- is getting free public access WiFi, a new press release from O2 states. The telecoms operator also says this is a multimillion-pound project, one of the largest investments in wireless infrastructure in London, so far. O2 will be working with Cornerstone Telecommunications Infrastructure, which was awarded a 15-year contract to build and maintain City of London’s wireless network. The network itself will be fully operational by autumn 2017, and will allegedly be "more technically advanced" than those found in other global financial centers like New York. That means users will be able to… [Continue Reading] -

Wiping out ransomware after an attack? Some UK businesses not confident they can do it
Publié: avril 8, 2017, 1:20am CEST par Sead Fadilpašić
A third (36 percent) of companies in the UK that have been victims of a ransomware attack are not "very confident" they managed to completely eradicate the malware from their systems, according to a new report by Citrix. The report also shines new light on just how prevalent and dangerous ransomware attacks really are. One in three UK businesses have had more than 100 of their devices affected by ransomware recently. Almost half of large businesses have suffered a successful ransomware attack, but, despite it, more than 10 percent don’t have a formal ransomware policy set up. What’s more, almost… [Continue Reading] -

IT departments need to transform to stay relevant
Publié: avril 8, 2017, 12:17am CEST par Sead Fadilpašić
IT environments require either moderate or significant transformation if they are to meet business requirements over the course of the next five years, a new report says. The report by 451 research, entitled "Voice of the Enterprise: Cloud Transformation," says that 80 percent of organizations agree IT departments need disrupting to stay relevant. That disruption may include moving workloads to the cloud or spending more on cloud solutions. Almost a quarter (22 percent) of businesses adopted the "cloud first" approach, the report also says, adding that IaaS (infrastructure as a service) is the fastest-growing cloud model. That’s why choosing the… [Continue Reading] -

Jailbreaking puts mobile users at risk
Publié: avril 7, 2017, 9:10pm CEST par Sead Fadilpašić
Mobile users frequently stray from official app stores when looking for new mobile applications, putting themselves under increased risk from malware, ransomware and other malicious actors. This is according to a new report by RiskIQ, which says that users in the UK are a bit more "conservative," and a bit more on the safe side compared to mobile users in the US. The report, entitled "Appsession: Is our appetite for mobile apps putting us at risk?" is based on a poll of 2,000 mobile users -- 1,000 in the UK and another 1,000 in the US. It says that 14 percent… [Continue Reading] -

Purple announces free Wi-Fi solution for businesses
Publié: avril 7, 2017, 5:34am CEST par Sead Fadilpašić
Purple wants to disrupt the market by offering a free license Wi-Fi solution. It has called the service Purple Free, and claims it delivers "more advanced functionality than other paid-for-utility WiFi solutions" out there. The service allows businesses and venues to acquire a seamless guest Wi-Fi service, while keeping the Corporate Data Protection Policy in mind. Businesses can expect a "simplistic login," branded splash pages and "a glimpse of' Purple's customer insights." Commenting on the new free product, Gavin Wheeldon, CEO of Purple, says: "Purple Free is sure to cultivate fresh opportunities and cement our place as the leader for Wi-Fi and… [Continue Reading] -

Brits willing to trade privacy for safety
Publié: avril 7, 2017, 12:34am CEST par Sead Fadilpašić
Two thirds of the UK’s general public would feel more safe if digital communications were unencrypted, according to a new report by Cable.co.uk. The argument? If the government could access our communications, it would be able to intercept messaging between terrorists plotting new attacks. Out of 2,000 UK adults polled for the report, less than a fifth (18 percent) say they believe the general public’s privacy is more valuable than organizations having power to access messages sent through apps like WhatsApp. Half (51 percent) say removing encryption would make them feel safer while 25 percent say they’d feel less safe,… [Continue Reading] -

Digital technologies disrupting manufacturing
Publié: avril 6, 2017, 9:34pm CEST par Sead Fadilpašić
Digital technology is disrupting the manufacturing sector, but it seems as it is not afraid of it. As a matter of fact, the manufacturing industry seems to be embracing new technology and is excited to see what the future holds. This is according to a new report by Fujitsu, entitled Fit for Digital, which takes a closer look at the UK’s manufacturing sector. Nine in ten (90 percent) of those polled for the report say the manufacturing sector has already been digitally disrupted, and even more (95 percent) expect it to be disrupted even more in the future. For 90 percent… [Continue Reading] -

UK businesses without a website are losing a lot of money
Publié: avril 6, 2017, 9:31am CEST par Sead Fadilpašić
There are almost two million small and medium-sized businesses in the UK that don’t own a website, and combined they’re losing £343 billion every year. This is according to new research by Approved Index, which claims SMEs without websites (a total of 1.98 million of them) are missing out on £173,769 per business, per year. Smaller businesses would benefit the most from introducing a website, the research claims, a total of £106 billion per year, to be exact. The biggest losers are those operating in the retail, transport and the food industry. There are more than 330,000 SMEs without a… [Continue Reading] -

Malware creators reuse decades-old code
Publié: avril 6, 2017, 3:19am CEST par Sead Fadilpašić
Security researchers from Kaspersky Lab and Kings College London have uncovered similarities between Turla attacks from 2011 and 2017 and an ancient advanced persistent threat that was used two decades ago to launch an attack against the US government's network. The researchers (Juan Andres Guerrero-Saade and Costin Raiu from Kaspersky Lab and Thomas Rid and Danny Moore from Kings College London) have taken logs of Moonlight Maze, an attack that happened in the late 90's, from a now retired IT admin whose server has been used as a proxy to launch the attacks. Looking at the logs, the researchers uncovered that… [Continue Reading] -

Fujitsu and Oracle unveil new servers with 'world's highest per CPU core performance'
Publié: avril 6, 2017, 1:30am CEST par Sead Fadilpašić
Fujitsu and Oracle have teamed up to deliver new, ulta-fast servers, as they give cloud computing and digital transformation another push forward. Named SPARC M12, these servers come equipped with an all-new SPARC64 XII processor. Fujitsu claims this processor allows the SPARC M12 server to "achieve the world's highest per CPU core performance." There are two models available for the new servers, the SPARC M12-2, and the SPARC M12-2S, which can be expanded to a maximum of 32 processors. "In recent years, as the Internet of Things (IoT), big data and artificial intelligence (AI) have become more prevalent in companies… [Continue Reading] -

Security researchers uncover new global cyber espionage campaign
Publié: avril 6, 2017, 12:19am CEST par Sead Fadilpašić
There is a new, global cyber espionage campaign, and this one demonstrates a "new level of maturity." This is according to a new report by PwC and BAE, released after consultation with other cyber security experts, including the UK's National Cyber Security Center. The report claims this new cyber espionage campaign targets businesses through managed services IT providers. So basically, the group behind the attacks targets only a few, and through them targets the many. The group behind the attacks is called APT10, and PwC believes only a small part of its total operation has been uncovered. There has been… [Continue Reading] -

We'll create 163ZB of data by 2025
Publié: avril 5, 2017, 9:19pm CEST par Sead Fadilpašić
The amount of data we are about to create in the next eight years will swell up to 163ZB, according to a new Seagate report. That is also ten times as much as we have created last year. Interesting (and quite expected) thing is that it’s not the consumers that will create all this data, but businesses instead. According to the report, by the time we reach 2025, three quarters (75 percent) of the world’s population will be interacting with digital data one way or another. In eight years, an average person will interact with a connected device almost 4,800 times… [Continue Reading] -

One in three consumers lost data due to ransomware
Publié: avril 5, 2017, 12:38am CEST par Sead Fadilpašić
Users are generally unaware of the dangers of ransomware attacks, and that makes them mostly clueless about how to prepare for one. This is according to a new report by Acronis. The report is based on a survey conducted in the US, UK, Australia, Germany, France and Japan. With users being as they are, ransomware was quick to become one of the most serious malware threats out there. It is expected that $5 billion will be extorted this year, alone. And according to former FBI counter-terrorism operative Eric O’Neill, cyber criminals are attacking everyone, businesses and consumers included. The survey… [Continue Reading] -

IT modernization leads to lower costs and higher revenue
Publié: avril 4, 2017, 9:05pm CEST par Sead Fadilpašić
IT modernization is essential to addressing the needs of modern digital businesses, according to a new report by Avanade. The report is based on a poll of 800 IT decision makers in organizations scattered all over the world. On average, IT decision makers believe that by modernizing IT, they could boost their company’s revenue by as much as 14 percent. That’s almost $1 billion a year, Avanade says. But it’s not just about boosting revenue -- it’s also about cutting costs. Costs could be cut by more than 13 percent. Most ITDMs (80 percent) believe that by ignoring the latest trends… [Continue Reading] -

Next public safety networks will use 4G LTE
Publié: avril 4, 2017, 12:50pm CEST par Sead Fadilpašić
AT&T has been chosen for a very lucrative contract, to build and manage a nationwide public safety network for first responders in the US. Ingo Flomer, Public Safety product manager at Cobham Wireless, says the network itself won't be operational this year but rather in 2018. "Although there will not be an operational LTE public safety network in place this year, it is likely that the standards and regulations will be implemented in advance of a possible 2018 deployment." Flomer also added that 4G LTE is very likely to become the long-term solution for public safety networks. "We can expect other… [Continue Reading] -

Citrix launches Receiver client for Samsung Galaxy S8 DeX
Publié: avril 3, 2017, 11:26pm CEST par Sead Fadilpašić
Citrix wants a part of that tasty Samsung Galaxy S8 DeX cake, and it just announced a new software client to make sure it gets it. The newly announced Citrix Receiver is a free to download client which allows users fast access to XenDesktop and XenApp installations. The client allows users to access applications, desktops and data easily and securely, the company says. "While many people use their smartphones for business, they usually turn to a laptop or desktop when they need to use Windows or browser-based apps," says Maribel Lopez, founder and principal analyst, Lopez Research. "Even though VDI… [Continue Reading] -

Security researchers uncover phishing attack with very high success rate
Publié: avril 3, 2017, 2:38pm CEST par Sead Fadilpašić
A new and "very aggressive" airline phishing attack was just spotted, and it's one with such a high success rate that even security experts are baffled. It was spotted by Barracuda, and it says that this new attack has a success rate of 90 percent. The attack combines impersonation, advanced persistent threats and phishing, giving the attackers long-term stealth access to a myriad corporate networks. Barracuda did not say who is behind the attack, but it did reveal that the attackers' usual targets include logistics, shipping, manufacturing, and pretty much any other industry which requires a lot of travel. The attacks are… [Continue Reading] -

Many UK businesses cancelled GDPR preparations due to Brexit
Publié: avril 3, 2017, 10:47am CEST par Sead Fadilpašić
Here's a facepalm moment for you this morning -- a quarter of UK businesses stopped preparing for the GDPR thinking the regulation won't apply once the UK leaves the EU. The GDPR, or General Data Protection Regulation, has been ratified by the UK and will come into force on May 2018 -- which will almost certainly be before the UK leaves the EU. Even if the UK leaves before, however, the GDPR will still apply for all companies wanting to do business with the EU. Crown Records Management has polled IT decision makers in the UK, and came to results which… [Continue Reading] -

Microsoft launches English-speaking chatbot in India
Publié: mars 31, 2017, 10:40am CEST par Sead Fadilpašić
Microsoft has released yet another chatbot, and this one is aimed specifically at the Indian market. Named Ruuh, the chatbot is said to enjoy chatting about Bollywood, music, humor, travel and browsing the net. It is available only in India and only in English, at least for now. It was launched on February 7, with Microsoft filing for a trademark on March 15. "At Microsoft, we're focused on helping people and organizations achieve more through new conversation models," a company spokesperson told ZDNet. "We're excited about the possibilities in this space and are experimenting with a limited pilot program of… [Continue Reading] -

Amazon unveils Connect contact center solution
Publié: mars 30, 2017, 11:11am CEST par Sead Fadilpašić
Amazon has announced a new contact center solution aimed to "power millions of customer conversations." The solution, named Amazon Connect, is a cloud-based offering, with customers paying by the minute of usage. It all starts with the "Virtual Contact Center" solution, integrated deep within AWS. According to Amazon, it only takes a couple of minutes to set the feature up and it requires no special training to use. Payment by the minute goes on top of telephony costs, a pricing model AWS uses in its cloud services, too. What's also interesting here is that Amazon is partnering up with what should… [Continue Reading] -

Businesses lose 44 data records every second
Publié: mars 30, 2017, 12:37am CEST par Sead Fadilpašić
Before you are done reading this article, there will have been more than 2,500 digital records stolen. This is according to a new report by Gemalto, which was released to show just how unprepared UK's businesses are for cyber risks. Gemalto says that in 2016 1.37 billion data records were compromised. That basically means 3,776,738 records every day, 157,364 every hour, 2,623 every minute, or 44 data records every second. To make things even worse, Gemalto claims the amount of compromised data almost doubled (86 percent increase) since 2015. The US is a "clear leader" when it comes to the number of… [Continue Reading] -

Internet outages cost the UK economy £7 billion in 2016
Publié: mars 28, 2017, 8:20pm CEST par Sead Fadilpašić
Organizations in the UK have had a total of three days of Internet outages in 2016 each, according to a new report by Beaming. The UK economy lost £7 billion because of it, while companies lost productivity and had to cover for extra overtime. More than 75 percent of companies polled for the report say they experienced at least one connectivity failure that stopped them from accessing crucial services. In 2016, on average, a company suffered four outages, waiting six hours for each one to be fixed. Some companies managed to use the downtime to get other tasks done, while… [Continue Reading] -

AI will make and break the job market
Publié: mars 28, 2017, 6:51pm CEST par Sead Fadilpašić
There’s a heated debate going on whether artificial intelligence will cause people to lose jobs or create new jobs instead. Well, IT consultancy firm Infosys has weighed in on the debate, releasing the results of its own survey. Basically, the firm says jobs will be both lost and created, so workers should not be too worried as long as they’re willing to re-train. However, companies will have reasons to rejoice as AI will boost their revenue, significantly. UK companies, on the other hand, need to do a lot of work, as they’re lagging behind the competition. Four in five companies that… [Continue Reading] -

Outdated programs main cause for security incidents
Publié: mars 28, 2017, 4:32pm CEST par Sead Fadilpašić
Did you update Flash on your PC? How about Java? According to cybersecurity firm Avast, you probably didn't -- and that's the number one cause of cybersecurity incidents. Avast just released a new report, entitled Avast PC Trends Report January 2017, which is based on insights from the company’s AVG TuneUp product, and says that more than half (52 percent) of the most popular PC applications have outdated installations on consumers' devices. That way, Avast claims, people are exposing their data to cybercriminals, as their machines become vulnerable to malware and ransomware. Drawing intel from 116 million Windows machines worldwide, here are… [Continue Reading] -

Businesses want rugged two-in-one devices
Publié: mars 27, 2017, 1:10pm CEST par Sead Fadilpašić
Organizations are very much interested in equipping their mobile workforce with detachables, according to a new report by Panasonic. Released during CeBIT 2017, it says detachable devices with screens ranging from 12 to 13.3 inches are in the "sweet spot," when it comes to screen size. The second key element to a well-built device is ruggedization. Entitled Why Tablets Can Successfully Transform your Business, the report is based on a poll of 1,203 IT decision makers and line-of-business managers. For 60 percent of respondents, tablets are high on their priorities list for this year. Among those that have already made… [Continue Reading] -

Machine learning pays well in the UK
Publié: mars 24, 2017, 11:44am CET par Sead Fadilpašić
If you are a developer looking to earn some serious cash, you might want to consider becoming a machine learning specialist. According to a new report by Stack Overflow, entitled "Developer Hiring Landscape Report," machine learning specialists earn 24 percent more than what’s the average among developers on the British Isles. That's £56,851 a year. The report also says developers will continue to be a high-earning bunch, regardless of what language they specialize in. The UK national average salary for last year was £28,000, while developers earned £44,000, or 45 percent more. Almost all of developers (94 percent) are partially self-taught,… [Continue Reading] -

What challenges do Industrie 4.0 projects face?
Publié: mars 23, 2017, 4:33pm CET par Sead Fadilpašić
Algorithms are at the heartbeat of Industrie 4.0 projects, according to Gartner, and that’s going to result in 30 percent of Industrie 4.0 projects sourcing algorithms from leading algorithm marketplaces by 2020. That means a jump of less than five per cent, compared to what we currently have in the market. Industrie 4.0 is a German Federal-Government-sponsored initiative to create smart manufacturing that is gaining broader support as a framework for connected, smart products and systems. "Industrie 4.0 projects are facing two significant challenges," says Thomas Oestreich, managing vice president at Gartner. "First -- in the connected world of cyber-physical systems… [Continue Reading] -

The role of IT decision makers in purchasing new technology
Publié: mars 23, 2017, 2:45pm CET par Sead Fadilpašić
IT decision makers (ITDM) in the EMEA region serve as their company's "gatekeepers" and primary influencers, when it comes to choosing new technology purchases for the company. This is according to a new report by Spiceworks, which digs deeper into the roles of ITDMs and business decision makers (BDMs) when it comes to purchasing new technologies. The study, "ITDM vs. BDM: Tech Purchase Superheroes," says BDM’s role is to "give final approval for technology funds and purchases." It also says more than 80 percent of ITDMs evaluate and recommend technology solutions, compared to less than 40 percent of BDMs. "Although… [Continue Reading] -

Three UK suffers new data breach
Publié: mars 22, 2017, 8:26pm CET par Sead Fadilpašić
A couple of bizarre incidents happened to Three users in the UK recently, and the media are suspecting the company might be facing a new data breach. According to a report by The Guardian, some customers, logging into their accounts, were "presented with the names, addresses, phone numbers and call histories of strangers." On Three’s Facebook page, there is a couple of complaints of users saying they were presented with other people’s details when they logged into the my3 service. "Why do I have someone else’s details when I log onto my3?" wrote Dazz Burns. Another user, Mark Thompson, said:… [Continue Reading] -

Businesses make automated security a part of DevOps
Publié: mars 22, 2017, 7:38pm CET par Sead Fadilpašić
Mature development organizations make sure automated security is built into their DevOps practice early, everywhere and at scale, according to a new report by Sonatype. The report, entitled 2017 DevSecOps Community Survey, is based on a poll of 2,292 IT professionals, and also says IT organisations continue to struggle with data breaches. There was a nearly 50 per cent increase in breaches, compared to SonaType’s 2014 survey. Two thirds of respondents (67 per cent) have described their DevOps practices as "very mature" or "of improving maturity." In almost half of the cases (47 percent), traditional development and operations teams see… [Continue Reading] -

IBM announces price-competitive cold storage solutions
Publié: mars 22, 2017, 5:09pm CET par Sead Fadilpašić
IBM is jumping on the cold storage bandwagon, offering a service and trying to take Amazon, Microsoft, and Google a piece of their pie. The company recently announced the launch of IBM Cloud Object Storage Cold Vault, which basically stores data that only needs to be accessed every once in a while. There will also be a cold storage service with "pay as you use" model, called IBM Cloud Object Storage Flex, coming later this year. With Amazon, Microsoft and Google already firmly positioned in this market, IBM figured the best way to compete is to brutally lower its prices.… [Continue Reading] -

ARM introduces new architecture for artificial intelligence and machine learning
Publié: mars 22, 2017, 10:55am CET par Sead Fadilpašić
ARM, the Cambridge-based microprocessor company has just announced a new processor architecture that it promises will give a significant boost to artificial intelligence and machine learning technology. The new technology, announced this Tuesday, is called DynamIQ and ARM describes it as "probably the biggest micro-architectural shift since ARM announced 64-bit ARMv8-A in 2011." This "monumental shift in multicore microarchitecture" is not the processor itself -- new Cortex-A processors will be built by ARM’s partners, both of which will be announced later this year. It is a foundation of all future processors to come. Why is this so important? Because these… [Continue Reading] -

IBM announces Hyperledger Fabric-based Blockchain-as-a-service
Publié: mars 21, 2017, 11:11am CET par Sead Fadilpašić
It was a big day for IBM today, as it unveiled its first Blockchain-as-a-service. Unveiled at the Interconnect conference, this commercial blockchain service is based on the open-source Hyperledger Fabric 1.0, built by The Linux Foundation. In a nutshell, IBM Blockchain allows customers to build their own secure blockchain networks. It took the company a year to bring it from the initial announcement to a finished product. Blockchain is a technology built to track the movement of bitcoin. It is completely transparent, and virtually impossible to fiddle with. With IBM Blockchain, companies could build their own networks, share the information within… [Continue Reading] -

SAS: Open source software comes with hidden costs and problems
Publié: mars 20, 2017, 9:52pm CET par Sead Fadilpašić
Open source technologies are great for organizations, but they're far from perfect. As a matter of fact, many of the open source technologies in use today come with hidden costs and problems. This is according to a new report by SAS, which was created on a poll of 300 executives across the UK and Ireland. These costs and problems mostly revolve around training staff, as well as recruiting, or replacing employees with essential data science skills. That's why it's ideal -- at least according to SAS -- to keep the ratio between open source and proprietary technology 40 to 60… [Continue Reading] -

Seven year-old Linux vulnerability now patched
Publié: mars 20, 2017, 8:33pm CET par Sead Fadilpašić
An old vulnerability was just discovered in the Linux kernel, potentially allowing hackers to gain privilege escalation, or cause a denial of service. The vulnerability was quickly fixed and there have been no signs of it in the wild, although that does not necessarily mean it went unnoticed. According to Positive Technologies expert Alexander Popov, the CVE-2017-2636 vulnerability is seven years old and has affected the majority of popular Linux distributions, including RHEL 6/7, Fedora, SuSE, Debian, and Ubuntu. Alexander Popov found a "race condition in the n_hdlc driver that leads to double-freeing of kernel memory, which can be exploited… [Continue Reading] -

Employees are a major security risk, say IT pros
Publié: mars 20, 2017, 8:00pm CET par Sead Fadilpašić
Almost a third of companies have suffered either data loss or a security breach because their employees use mobile technologies to work. This is according to a new report by Apricorn. The company polled 100 IT decision makers in the UK for the report. Almost half (44 percent) expect mobile workers to expose their company’s data to risks of breaches and theft. Nearly half of respondents also agree that employees are the biggest security threat to their company. As all of this is happening, companies are still confused, as most of them don’t know how to adequately enforce security policies.… [Continue Reading] -

Consumers know apps are insecure, but they do little to protect themselves
Publié: mars 20, 2017, 4:44pm CET par Sead Fadilpašić
Once again, an urban myth turns out to be true. People know mobile apps can be targeted by hackers, they fear the scenario, yet they’re doing very little to protect themselves from such potential attacks. The confirmation was released by F5 Networks, in a study into the UK’s app-centric society and consumer behaviors. Almost three in five fear the Facebook app is a target for hackers. A quarter (23 percent) would not purchase a voice activation system such as Alexa, and more than a third (39 percent) would not purchase smart locks over fears of hacking. Yet, this doesn’t stop… [Continue Reading] -

Qualcomm: Snapdragon is more than a processor, it's a platform
Publié: mars 20, 2017, 8:16am CET par Sead Fadilpašić
Qualcomm no longer refers to Snapdragons as processors, but rather as a platform. It says it is changing the terminology because "Snapdragon is more than a single component, a piece of silicon, or what many would misinterpret as the CPU." According to Qualcomm, the Snapdragon is an anthology of technology, composed of hardware, software and services. Looking at it that way, the word "processor" is unsuitable, and therefore had to be nixed. The Snapdragon platform, the company claims, takes the offerings beyond a single chip. "While the single processor form factor is truly a system-on-a-chip (SoC), housing custom technology like an… [Continue Reading] -

Amazon makes it cheaper to build and host Alexa skills
Publié: mars 17, 2017, 6:27pm CET par Sead Fadilpašić
Thousands of Alexa developers can now build and host most Alexa skills for free using Amazon Web Services (AWS), thanks to a newly released Amazon program. Previously, developers have had at their disposal the AWS Free Tier, offering a million AWS Lambda requests and a total of 750 hours of Amazon Elastic Compute Cloud (Amazon EC2) -- monthly, for free. However, exceeding these limits also meant monthly fees. Developers with a published Alexa skill can now apply for a $100 AWS promotional credit, and can get another $100 every month, which basically means it’s now free to build and host most… [Continue Reading] -

Cyber security spending to reach $90bn in 2017
Publié: mars 17, 2017, 4:06pm CET par Sead Fadilpašić
This year, the cyber-security focus is shifting from prevention only, into detection and response territory. This is according to a new Gartner report, which also says cyber-security spending will hit the $90 billion mark this year. That’s actually a 7.6 percent increase year-on-year. Spending will keep on growing, Gartner says, up to $113 billion in 2020. What’s interesting is that this shift has created new security product segments, including deception, endpoint detection and response, and software-defined segmentation. There’s also cloud access security brokers, or user behavior analytics. Besides making businesses spend more on security, it’s also making them spend less… [Continue Reading] -

UK cloud adoption rises five percent
Publié: mars 17, 2017, 10:22am CET par Sead Fadilpašić
The overall cloud adoption rate in the UK now stands at 88 percent, according to a new report by the Cloud Industry Forum. The report also states that there has been a five percent increase year-on-year, and an 83 percent increase since 2010, when the first stats were taken. What’s also interesting in this report is that two thirds (67 percent) of users expect to increase their cloud service adoption over the coming year. A "vast majority," the report claims, will maintain a hybrid IT estate for some time. Small and public sector organizations have a higher percentage of cloud adoption,… [Continue Reading] -

Most businesses consider artificial intelligence essential to being competitive
Publié: mars 16, 2017, 9:17pm CET par Sead Fadilpašić
A new report by Tata Consultancy Services has shown just how profound of an effect artificial intelligence already has, and will have, on businesses everywhere. The "Getting Smarter by the Day: How AI is Elevating the Performance of Global Companies" study says 84 percent of companies worldwide see AI as "essential" to being competitive. Another half (50 percent) see the technology as "transformative." Two thirds (67 percent) of IT departments are adopting AI, mostly to detect security intrusions and deliver automation. This has made them the biggest adopters of AI today. North American companies were the leading investors in AI… [Continue Reading] -

Cyber espionage is the biggest security threat for businesses
Publié: mars 16, 2017, 6:29pm CET par Sead Fadilpašić
European and US businesses see cyber espionage as the biggest threat to their security, according to a new report by Trend Micro. The report says that organizations in the West are under "increasing pressure" from groups looking to get their hands on some sensitive data. In relations to the accusations that the Russians have been interfering with US elections, there’s an interesting stat: a large percentage of countries with recent, or upcoming polls, say they had been subjected to cyber espionage attacks in the last 12 months. The US (20 percent), Italy (20 percent), France (18 percent), The Netherlands (16… [Continue Reading] -

Nearly half of UK's tech workers looking for a new job
Publié: mars 16, 2017, 2:19pm CET par Sead Fadilpašić
Just above half (58 percent) of UK workers believe it’s possible for them to get their dream job, according to a new report by Hired. The interesting thing about this stat is that the global average is significantly higher -- 70 per cent. The similar statistic is with people that already believe they have their dream job -- globally, 44 percent of them think so, compared to 35 percent in the UK. And it gets worse. Tech workers in the UK are twice as likely to hate their jobs compared to their peers in the US and Australia, and almost half (41 percent) are… [Continue Reading] -

Cyber security spending highest for financial institutions
Publié: mars 14, 2017, 8:03pm CET par Sead Fadilpašić
Banks and other financial institutions spend three times the amount non-financial organizations are spending on cyber security, a new report by Kaspersky Lab has shown. According to the Financial Institutions Security Risks research from Kaspersky Lab and B2B International, cyber security is a high priority for financial institutions, as they're coming under increased pressure from the government, top management and customers. It was said that almost two thirds (64 percent) of all financial institutions will improve their IT security, regardless of the return on investment. Banks are mostly getting ready for the full takeover of mobile. More than four in ten… [Continue Reading] -

Most employees use smartphones for private tasks during work hours
Publié: mars 14, 2017, 7:43pm CET par Sead Fadilpašić
Smartphones, even personal ones, are no strangers to the workplace. With the increase in adoption of BYOD initiatives, more and more employees are using their smartphones for everyday job tasks. However, according to a new report by LaptopsDirect.co.uk, British workers are also using personal smartphones for private communication, during work hours, as well. Out of 2,012 UK adults polled, 98 percent of IT workers said they used their smartphone during working hours. More than three quarters (78 percent) regularly text, 59 percent talk, and 52 percent use apps like WhatsApp or Facebook. Nine percent have sent a Snapchat. The report… [Continue Reading] -

Microsoft and Nvidia unveil HGX-1 hyperscale GPU accelerator
Publié: mars 13, 2017, 7:37pm CET par Sead Fadilpašić
Blueprints for a new hyperscale GPU accelerator have been introduced recently, jointly by Microsoft and NVIDIA. The two companies are saying the accelerator would "drive AI cloud computing." The accelerator is called HGX-1 hyperscale GPU. It is released in conjunction with Microsoft’s Project Olympus, as an open-source design. The two companies are equalling HGX-1 to ATX (Advance Technology eXtended), saying HGX-1 willl do to cloud-based AI workloads what ATX did for PC motherboards. It creates an industry standard, making market demand easier to fulfil. Microsoft and NVIDIA are hoping the new accelerator will find its application in autonomous driving, personalized… [Continue Reading] -

One in five websites uses insecure SHA-1 certificate
Publié: mars 10, 2017, 5:32pm CET par Sead Fadilpašić
More than a fifth (21 percent) of all websites are still using an insecure certificate, which is leaving them open to different types of cyberattacks. This is according to a new report from cyber security experts Venafi. The report says many sites are still using the SHA-1 certificate, which means they’re vulnerable to man-in-the-middle attacks, brute force attacks and collision attacks, all of which can expose the site’s sensitive data. This means extra danger for people providing financial, or sensitive information to sites. Venafi says there has been improvement since November 2016, when more than a third (35 percent) of… [Continue Reading] -

Avaya sells networking business to Extreme Networks
Publié: mars 10, 2017, 3:48pm CET par Sead Fadilpašić
Extreme Networks agreed to acquire Avaya’s networking business for roughly $100 million. Avaya, a company that went private in 2007, is struggling with bankruptcy. It filed to restructure under Chapter 11 bankruptcy protection in January. It also said it was looking for ways to monetize some of its assets. Extreme Networks said Avaya’s networking business is in line with its strategy for growth, and that it will help broaden its portfolio across different verticals. "Furthermore, we expect the Avaya business to generate over $200 million in annual revenue, increase our market share and offer new opportunities for our customers," says Extreme… [Continue Reading] -

HPE buys Nimble for $1bn
Publié: mars 9, 2017, 10:02pm CET par Sead Fadilpašić
Hewlett Packard Enterprise (HPE) says it came to an agreement with Nimble Storage to acquire it for approximately $1 billion in cash. HP Enterprise should assume, or pay out, Nimble’s unvested equity awards, with a value of $200m, at closing. According to Wall Street Journal, the deal has roughly a 41 percent premium to Nimble’s $700m market value. In the first nine months of last year, Nimble reported revenue of some $286 million, up roughly 23 percent compared to the year before. A partner to both HPE and Nimble, Veeam’s VP of Global Alliances, Andy Vandeveld, believes it’s a good deal for… [Continue Reading] -

TeamViewer unveils web conferencing solution for enterprises
Publié: mars 9, 2017, 7:45pm CET par Sead Fadilpašić
TeamViewer is looking for a piece of Amazon Chime's pie as it introduces a competitor, Blizz by TeamViewer. It is a dedicated web conferencing and collaboration solution, aimed at the needs of small and medium sized businesses and mid enterprise organizations. The product is available right now, and comes in three plans with different functionalities. Among the key advantages of Blizz by TeamViewer, the company singled out the possiblity of starting meetings instantly, being secure, allowing up to 300 participants, dialing in via a telephone line, and HD videocalls. "We felt there was a lack of innovation in the web conferencing… [Continue Reading] -

IBM Q is the first initiative to build commercial quantum computing systems
Publié: mars 8, 2017, 3:10pm CET par Sead Fadilpašić
Your business will finally get the chance to use a quantum computer to do... well, whatever a business could use a quantum computer for. IBM has just announced IBM Q -- "an industry-first initiative to build commercially available universal quantum computing systems." Its systems and services will be delivered via the IBM Cloud platform, and IBM believes it could be used to "deliver solutions to important problems where patterns cannot be seen because the data doesn’t exist and the possibilities that you need to explore to get to the answer are too enormous to ever be processed by classical computers." It is… [Continue Reading] -

Kaspersky discovers StoneDrill wiper malware
Publié: mars 8, 2017, 11:28am CET par Sead Fadilpašić
Security researchers from Kaspersky Lab have found a very powerful malware, one which is capable of completely wiping the contents of a disk. Announcing the finding, the security company says the malware, which it dubbed StoneDrill, was found on just two machines so far, one in the Middle East, and one in Europe. The researchers claim StoneDrill is both similar and "very different and more sophisticated" than another wiper malware -- Shamoon 2.0. They actually stumbled upon StoneDrill while investigating Shamoon 2.0. At this time, researchers still don't know how the malware is propagated, but they do know how it works: "Once on… [Continue Reading] -

Microsoft Azure Blueprint helps public organizations move faster to the cloud
Publié: mars 7, 2017, 10:17am CET par Sead Fadilpašić
Microsoft is looking to help public sector organizations cut on the time needed to get Microsoft Azure up and running. According to a new announcement it has made, it will now take organizations hours, instead of weeks, to get things rolling. The company has revealed a blueprint that "reinforces its cloud security principles," and a UK official template for creating workloads in Azure and Service Bus Premium Messaging. Microsoft Azure Blueprint is reinforcing cloud security principles that were laid out by the UK government’s National Cyber Security Centre. The company says it is now easier and quicker for organizations to store large… [Continue Reading] -

Small businesses aren't sold on SaaS
Publié: mars 4, 2017, 9:10am CET par Sead Fadilpašić
Three quarters (75 percent) of large businesses now consider SaaS tools an essential part of their business. This is according to a new report by GoCardless, based on a poll of more than 1,000 senior decision makers. Small businesses aren’t that convinced though, with every second company sharing the same thoughts on SaaS. The report claims that product updates and payment flexibility are considered the main advantages of SaaS, as compared to traditional software. More than a third (37 percent) of senior decision makers say regular updates sold them on SaaS, while 31 percent say it was the convenience of… [Continue Reading] -

Nearly 3 million UK businesses experienced a cyber-security incident in 2017
Publié: mars 3, 2017, 8:04pm CET par Sead Fadilpašić
More than half of businesses in the UK were victims of cybercrime last year, according to a new report by Beaming. The report says that 2.9 million UK firms, or 52 percent, experienced some form of cyber-security incidents, costing them £29.1 billion. Most common incidents included virus infections and phishing attacks. Both of them have an equal share of attacks -- 23 percent. Less than a fifth (18 percent) went on hacks and data breaches. The report also states that the bigger the company, the bigger the chances of a cyber-attack. Almost three quarters (71 percent) of organizations with 250 employees… [Continue Reading] -

Microsoft Azure Stack Technical Preview 3 is now available
Publié: mars 3, 2017, 9:39am CET par Sead Fadilpašić
Microsoft has announced an extension of Azure technologies on-premises, as well as a couple of Azure Stack updates. According to a blog post announcing the new features, the updates will enable organizations with hybrid cloud environments to have the same flexibility and innovation capability to match their business objectives and app design. Organizations looking to create new apps, or re-work their current ones, on both cloud and on-premises environments, now have three unique hybrid cloud scenarios on offer. Consistent hybrid application development. Organizations get to choose from a "worldwide pool of talent," meaning they can get productive on day one, and… [Continue Reading] -

Enterprises with heavy mobile use are more profitable
Publié: mars 1, 2017, 12:09pm CET par Sead Fadilpašić
There’s a new research report that says companies whose employees use mobile devices for multiple things are more productive than those with limited usage. It was commissioned by Synchronoss and conducted by Sapio Research. The report says that 38 percent of enterprises use mobility solutions for basic tools like email and calendar. Such enterprises are 15 percent less productive and almost a third (29 percent) less profitable than those with more advanced mobile capabilities. Those capabilities include file sharing, data analytics, app integrations and multi-factor authentication. It was also said that these companies don’t have a firm requirement to secure… [Continue Reading] -

Most financial businesses in the UK worry about the effects of disruption
Publié: février 28, 2017, 7:58pm CET par Sead Fadilpašić
More than three quarters (78 percent) of financial organizations in the UK worry about what digital disruption can do to their industry, according to a new Fujitsu report. The company claims this makes the financial industry the most concerned one, compared with retail, public and manufacturing, and utility sectors. The report, entitled Digital: Co-creation in the Age of Disruption, says most C-suite execs (80 percent) see digital disruption as an exciting opportunity, with 92 percent thinking they need to evolve to stay relevant. Even though the majority seems positively excited about digital disruption, 56 percent believe their business will not… [Continue Reading] -

SoftBank makes massive investment in WeWork
Publié: février 28, 2017, 5:16pm CET par Sead Fadilpašić
SoftBank is looking to invest between $3 billion and $4 billion into WeWork. According to a CNBC report, the deal is "close to finalizing". At first, there will be a $2 billion primary tranche, followed by a secondary round worth anywhere between $1 and $2 billion. CNBC also says there is a "tender offer" for WeWork insiders, around $44.10 per internal share. If the deal goes down, WeWork would be valued at more than $20 billion, increasing its value by $3 billion after the last investment round. WeWork’s spokesperson did not want to comment on the reports, while SoftBank is… [Continue Reading] -

Cyber attacks cost the UK economy £1.9 billion
Publié: février 27, 2017, 8:42pm CET par Sead Fadilpašić
Eighteen percent of UK businesses have been the target of a cyber-attack in the last 12 months, according to a new report by Altodigital. These attacks cost the economy £1.9 billion. Back in 2013 33 percent of companies were hacked, so Altodigital sees the current figure of 18 percent as a "welcome improvement." Each individual attack cost more than £2,000 last year. These hacks equated to five to seven days of downtime for UK businesses, and 89 percent of staff was affected. Despite the evident progress, there are still a few things organizations are doing wrong. Forty-one percent don’t have… [Continue Reading] -

Social media makes phishing attacks easy
Publié: février 27, 2017, 2:27pm CET par Sead Fadilpašić
People like getting friend requests on social media, and hackers are using that to launch successful phishing campaigns. This is according to a new report released by phishd by MMR InfoSecurity. After reviewing simulated attack campaigns targeting almost a million users, phishd by MMR InfoSecurity says that social media is the most effective lure to have victims clicking email links. Almost a quarter of users clicked a link to be taken to a fake login screen. Out of that number, more than half (54 percent) provided user credentials, and 80 percent downloaded a file. Financial lures, like the ones where… [Continue Reading] -

Most executives fear competition from disruptors
Publié: février 24, 2017, 7:15pm CET par Sead Fadilpašić
Almost two thirds (65 percent) of C-suite executives believe four in ten (40 percent) of today’s Fortune 500 companies won’t exist in 10 years’ time. This is according to new research from ChristianSteven Software, conducted by GITNS. It is based on a poll of more than 500 C-suite executives across the United States and Europe. It also says that more than half (53 percent) of those surveyed say they fear competition from industry disruptors. Still, nine in ten (91 percent) say they are hopeful about the future of technology in their business. "Our study allowed us to take a close look at the business… [Continue Reading] -

Employees who embrace BYOD feel judged
Publié: février 24, 2017, 6:27pm CET par Sead Fadilpašić
There is a strange side-effect to the Bring Your Own Device initiative, and one that's slowing it down. Apparently, many employees refrain from bringing their own devices to work for the fear of being judged. No, not because their devices are old or slow, but because others will think they're using them for personal instead of professional reasons. Yes, that's a real fear, and it's quite prevalent. According to Nudge Rewards just 40 percent of employees feel trust is not an issue when using BYOD. Just a quarter (23 percent) say they are actively encouraged to use mobile devices in the workplace. A third… [Continue Reading] -

Dropbox releases open-source Slack bot
Publié: février 24, 2017, 2:29pm CET par Sead Fadilpašić
Dropbox is looking to tackle unauthorized access and other security incidents in the workplace with a chatbot. Called Securitybot, it that can automatically grab alerts from security monitoring tools and verify incidents with other employers. The company says that through the use of the chatbot, which is open source, it will no longer be necessary to manually reach out to employees to verify access, every time someone enters a sensitive part of the system. The bot is built primarily for Slack, but it is designed to be transferable to other platforms as well. It works quite simple, too. As soon… [Continue Reading] -

Public cloud services market will reach $246.8 billion in 2017
Publié: février 24, 2017, 11:38am CET par Sead Fadilpašić
The global public cloud services market is expected to grow 18 percent this year, according to Gartner’s latest report. Totaling $246.8 billion (up from $209.2bn last year), the growth will mostly come from IaaS, which is expected to grow 36.8 percent and reach $34.6 billion. The growth will also be fueled by SaaS (20.1 percent increase, to $46.3 billion). "The overall global public cloud market is entering a period of stabilization, with its growth rate peaking at 18 percent in 2017 and then tapering off over the next few years," says Sid Nag, research director at Gartner. "While some organizations… [Continue Reading] -

Organizations failing to address security pain points
Publié: février 23, 2017, 7:53pm CET par Sead Fadilpašić
Cyber-attacks against organizations in 2017 will continue to be as successful as they were last year, because organizations aren't addressing the pain points they had last year, a new report says. Fujitsu's "Blind spots and security basics -- letting your guard down could cost you in 2017" report says that attacks over encrypted channels will continue to be missed, due to the lack of SSL inspection capabilities. The rise in attacks against enterprises using Microsoft PowerShell will continue, because many organizations lack adequate protection for malicious use. As it’s already part of the Windows system, it is easier for attackers… [Continue Reading] -

Windows botnet spreads Mirai malware
Publié: février 23, 2017, 6:30pm CET par Sead Fadilpašić
Security researchers from Kaspersky Lab are currently investigating the first Windows-based spreader for the Mirai malware, something that can have huge implications for companies that invested heavily in IoT. The spreader was apparently built by someone with "more advanced skills" than those that had created the original Mirai malware. This, Kaspersky Lab says, has "worrying implications for the future use and targets of Mirai-based attacks." It is richer and more robust than the original Mirai codebase, even though many of its components are "several years old." Its spreading capabilities are limited, as it can only deliver from an infected Windows… [Continue Reading] -

Most CRMs don't generate revenue according to managers
Publié: février 23, 2017, 5:24pm CET par Sead Fadilpašić
Less than a fifth (17 percent) of customer relationship managers believe their CRM is generating revenue. This is according to a new report by marketing technology company Wiraya, based on a poll of 500 CRM managers. Despite not having a great image, CRM is still perceived as a key business driver in a third of businesses. The problems, according to the report, lie in the fact that many lack a clear direction and customer insight to support their goals. Without these things, it’s hard to create direct business profitability. The report speaks about three levels of CRM maturity: Traditional, Adhoc… [Continue Reading] -

Windows 10's strong security will make mobile devices a more attractive target
Publié: février 23, 2017, 11:03am CET par Sead Fadilpašić
As enterprises move to Windows 10, and take full advantage of the advanced security features offered in the operating system and in Microsoft Edge, cyber criminals will increasingly look towards the mobile ecosystem for exploits. This is according to Fujitsu's latest report, which believes 2017 will see an even bigger increase in attacks against the mobile world. "Individuals now have multiple smart devices, many of which hold vast amounts of personal and business data due to modern storage capabilities and, as such, attackers will continue to develop innovative attacks against mobile platforms with mobile ransomware demanding payment for the return… [Continue Reading] -

European enterprises engage with startups to innovate
Publié: février 22, 2017, 7:51pm CET par Sead Fadilpašić
European businesses are among the world's most active when it comes to finding innovation through start-ups. This is according to Samsung's new report, The Open Economy. According to it, businesses are changing the way they’re innovating, and are focusing on bringing in and collaborating with young and inspiring start-ups. Out of the five countries with the highest number of large companies engaged with start-ups, four are in Europe, the report states. Almost all European corporations surveyed (97 percent) have carefully analyzed the need for open innovation. Not all have acted on their findings just yet. Just as with other new technologies… [Continue Reading] -

Changing business models will create 'ultra freelancers'
Publié: février 22, 2017, 2:53pm CET par Sead Fadilpašić
With the significant and imminent changes in the way we do business a new type of freelancers will emerge, according to Samsung. Called "ultra-freelancers", this type of workers will "connect deeply within multiple organizations simultaneously, working with multiple corporate data sets but fiercely protective of the privacy of their own data." These ultra-freelancers will be mostly Millennials, a cohort that is taking full advantage of the new technologies and the open economy. Samsung’s new report, "The Open Economy," says "60 percent of independent workers in Europe are highly satisfied with the flexibility that being a freelancer offers, and just 14 percent… [Continue Reading] -

Security must be a priority in smart offices
Publié: février 21, 2017, 6:05pm CET par Sead Fadilpašić
Businesses all over the globe are faced with a tough challenge: to make their "smart offices" as secure and safe as possible. This is according to a new report by Samsung, which says that by 2021, there will be 7.3 billion connected IoT devices. Each device also represents a security challenge, so it will be "critical" to secure each and every one. Samsung says businesses have up to three years to secure themselves, otherwise they’re risking being left behind as the market moves forward. The business landscape is facing significant changes, with a "highly dispersed workforce" that wants to work… [Continue Reading] -

Europe leads in business collaboration
Publié: février 21, 2017, 10:20am CET par Sead Fadilpašić
The way people do business will drastically change in the next three to five years, and Europeans are leading the way. This is according to a new report by Samsung, which investigates key trends impacting the workplace culture. This new business model we’re all about to embrace Samsung dubs the Open Economy. Basically, it revolves around high levels of collaboration between companies, contractors and partners, while retaining industry-standard security levels. The report calls upon WIPO’s Global Innovation Index, which claims European countries occupy eight out of the top ten slots. Getting this high level of collaboration means adopting new structures, technologies… [Continue Reading] -

IBM and Visa want your IoT devices to double as point of sale terminals
Publié: février 20, 2017, 11:23am CET par Sead Fadilpai
IBM and Visa want every Internet-connected device you own to be its own point of sale. The two companies announced the industry’s first collaboration to achieve this, through IBM’s Watson for IoT platform and Visa’s token technology. Visa is currently powering 60 percent of the entire world’s payments and IBM’s Watson really needs no particular introduction. For example, you could be using your car to pay for gas. No cash, no cards, no phones. Or, your running sneakers could be able to purchase you new ones, when these sense they can no longer be used. "IoT is literally changing the world… [Continue Reading] -

IT departments dealing with 'unrealistic expectations' in project assignments
Publié: février 17, 2017, 7:23pm CET par Sead Fadilpašić
Just half of IT departments managed to complete all of the projects that they were assigned during last year, a new report by MuleSoft claims. Based on a survey of 951 IT decision makers, MuleSoft’s Connectivity Benchmark Report 2017 says there is a widening IT delivery gap that is to blame for these results. According to the report, IT departments are faced with "unrealistic expectations" of what can be achieved with the resources that they have available. One of the ways to fix the issue is by pursuing an API strategy. It would allow for faster innovation and less pressure on… [Continue Reading] -

New macOS malware steals passwords and iPhone backups
Publié: février 17, 2017, 9:58am CET par Sead Fadilpai
Cyber security firm Bitdefender says it has recently uncovered a new type of malware which targets macOS users. The company says that the malware, which it has dubbed Xagent, is capable of stealing passwords, taking screenshots and grabbing iPhone backups stored on the machine. Bitdefender says it still can’t be absolutely certain of who is behind the malware, but all evidence points in the direction of the APT28 cybercrime group. The company says this group uses the same dropper / downloader, as well as the same control center URLs. On top of that, Bitdefender says same artifacts have been hardcoded in the binary… [Continue Reading] -

Most UK businesses will be ready for GDPR
Publié: février 16, 2017, 6:42pm CET par Sead Fadilpašić
Whoever gets to enforce GDPR on businesses is going to have their hands full starting May next year. According to DMA, 26 percent of marketers believe their businesses are unprepared for the General Data Protection regulation, and just two thirds (68 percent) believe they will be compliant in time for the deadline, which is May 2018. In the second edition of DMA’s "GDPR and you" series, it says that two thirds of marketers (66 percent) have "good" awareness, up from 53 percent in June last year. Also, the marketers’ "personal" feeling of preparedness increased significantly -- from 49 percent to 71… [Continue Reading] -

Ford makes $1bn investment in Argo AI to research and develop self-driving car tech
Publié: février 16, 2017, 12:17am CET par Sead Fadilpašić
One of the world’s largest car manufacturers, US-based company Ford, plans to invest $1 billion to research and build artificial intelligence for its vehicles. Ford states that it will invest $1 billion in the Argo AI startup within the next five years, which will focus on building and developing self-driving car technology. At the beginning, Argo AI will build AI technology for Ford, exclusively, but after a few years it will do so for other manufacturers as well. This move is Ford’s biggest effort so far to enter the race for the car of the future, that Silicon Valley companies… [Continue Reading] -

UK tackles attacks with new National Cyber Security Center
Publié: février 15, 2017, 6:16pm CET par Sead Fadilpašić
The UK is getting a national center to combat cyber attacks, and it's the Queen who gets to open it. The National Cyber Security Center (NCSC) will reportedly be opened in central London by the Queen, accompanied by The Duke of Edinburgh and Chancellor Philip Hammond. The NCSC is part of intelligence agency GCHQ and has already tackled 188 attacks in the last three months. It will look for holes in sites belonging to the public sector, will tackle spoof emails and pull phishing sites down. Commenting on the announcement and claims that the NHS is the biggest target, Michael… [Continue Reading] -

European businesses are not prepared to handle a cyber attack
Publié: février 15, 2017, 10:57am CET par Sead Fadilpašić
More than half of companies in the UK, US and Germany (53 percent) are not prepared to face a cyber-attack. This is according to a new report by specialist insurer Hiscox, which has polled more than 3,000 companies for the report. The Hiscox Cyber Readiness Report 2017 looks at four areas -- strategy, resourcing, technology and process -- and ranks companies based on such criteria. Most companies score fairly well for technology, but less than a third (30 percent) reach the "expert" score in their overall cyber-readiness. The report says 35 percent of UK businesses that were targeted in the past 12… [Continue Reading] -

Brits will spend €27bn on mobile devices in 2017
Publié: février 15, 2017, 1:03am CET par Sead Fadilpašić
This year, the UK will spend more than £27 billion on mobile devices, new figures from VoucherCodes.co.uk and the Center for Retail Research show. This means there will be a 26 percent jump compared to last year. Consequently, online retail sales will also grow, by 11.5 percent compared to 2016. British shoppers are expected to be quite the spenders this year, spending a total of £1.428.39 per head online. That’s a third higher than the EU average of £1,003.54. The report also found that almost three quarters (71.5 percent) of the UK population are now considered e-shoppers. Combined, they’re expected… [Continue Reading] -

IT decisions makers and executives don't agree on cyber security responsibility
Publié: février 14, 2017, 10:03pm CET par Sead Fadilpašić
There’s a severe disconnect between IT decision makers and C-suite executives when it comes to handling cyber attacks. Namely, both believe the other one is responsible for keeping a company safe. This is according to a new and extensive research by BAE Systems. A total of 221 C-suite executives, and 984 IT decision makers were polled or the report. According to the research, a third (35 percent) of C-suite executives believe IT teams are responsible for data breaches. On the other hand, 50 percent of IT decision makers would place that responsibility in the hands of their senior management. Cost… [Continue Reading] -

Robots could take over almost 250,000 jobs in the next two decades
Publié: février 7, 2017, 3:29pm CET par Sead Fadilpašić
The everlasting debate over whether robots will take our jobs or not continues. London-based think tank Reform weighted in, and most humans aren't going to like it. It recently said that almost 250,000 jobs in the public sector could be replaced by robots in the next two decades. This will mean billions of pounds in savings for businesses and organizations, but also a loss of steady jobs for many people. Approximately 130,000 Whitehall administrators (90 percent of them) could be replaced by robots by 2030. This would save roughly £2.6bn. Another 90,000 NHS admins, and 24,000 GP receptionists could also… [Continue Reading] -

Most banks aren't confident they can detect a data breach
Publié: février 3, 2017, 10:08am CET par Sead Fadilpašić
Consumers are quite confident banks and insurers can keep their data safe, but these organizations aren’t that sure. A new report by Capgemini has shown that financial institutions lack a significant amount of confidence when it comes to data protection. Just one in five (21 percent) of financial service organizations admitted they’re "highly confident" they could detect a data breach. On the other hand, 83 percent of consumers trust banks and insurers with their data. Looking at the UK specifically, the figures didn’t change much. More than four-fifths (82 percent) of consumers trust financial institutions. The institutions, however, severely lack… [Continue Reading] -

Server downtime: What are the costs?
Publié: février 2, 2017, 11:39am CET par Sead Fadilpašić
Server downtime -- it happens. Most large companies have at least once experienced the frustration that is having their servers down, whether it’s for a few minutes, hours or even days. It’s regarded as a part of life, something that happens that you can’t quite prevent, but in fact, server downtime costs companies millions of dollars yearly, either in lost business or in the distraction and psychological toll it takes on employees who have to deal with the problem. But actually, these can be prevented by avoiding common server issues, implementing agile working practices and creating a plan should emergencies happen.… [Continue Reading] -

Dropbox introduces Smart Sync and Paper
Publié: février 1, 2017, 12:30pm CET par Sead Fadilpašić
Dropbox has announced "significant product updates", introducing Smart Sync (some of you might know it as Dropbox Infinite), and Paper. The company says the introduction of Smart Sync and Paper will boost team productivity and improve collaborative processes, end-to-end. First up is the Smart Sync. Dropbox calls it an "industry first", cross-platform, on-demand cloud storage solution. It offers intuitive storage, allowing users to sync all the content from their computers to their Dropbox accounts. Together with Dropbox team folders, the company wants to become a "centrally manageable, secure hub for teams to work together." Smart Sync is available to Dropbox Business… [Continue Reading] -

Cisco acquires intelligence software company AppDynamics
Publié: janvier 30, 2017, 12:12pm CET par Sead Fadilpašić
Tech giant Cisco has announced that it is buying AppDynamics, a privately-held application intelligence software company headquartered in San Francisco. The deal is worth $3.7 billion, and will be completed in cash and assumed equity awards. Rowan Trollope, Cisco’s senior vice president and general manager of its Internet of Things and Applications Business Group said it became much harder to keep enterprise apps running and performing well. With the importance apps have nowadays, and with AppDynamics being a cloud application and business monitoring platform, it will be a great addition to Cisco, as well as Cisco’s clients. "The combination of Cisco and… [Continue Reading] -

Demand for security pros in UK rises by 46 percent
Publié: janvier 27, 2017, 12:30pm CET par Sead Fadilpašić
To say that IT security professionals in the UK are in demand would be a severe understatement. A new report by Experis says there has been an increase of 46 percent in the demand for both permanent and contract IT security professionals. The report, entitled Tech Cities Job Watch, says companies are putting more emphasis on long-term investments. There has been a 52.9 percent surge in demand for permanent staff, year-over-year. From Q4 2015, to Q4 2016, the demand had risen "just" 15.3 percent. The increase in demand has also affected IT security pros’ salaries. Annual IT security permanent salaries… [Continue Reading] -

Security is more important than availability in app development
Publié: janvier 26, 2017, 5:18pm CET par Sead Fadilpašić
Security is now the top priority for app development, surpassing availability, a new report by F5 Networks states. The State of Application Delivery report is based on a poll of more than 2,000 IT, networking, application, and security professionals worldwide. Looking at how they are deploying and managing their applications in a rapidly evolving landscape, the report also says that organizations in the EMEA region (Europe, Middle East, Africa), expect more than three quarters (76 percent) of their apps in the cloud this year. The average organization in this region also plans on deploying 18 app services in the next… [Continue Reading] -

Most UK businesses still unaware of GDPR
Publié: janvier 24, 2017, 8:11pm CET par Sead Fadilpašić
Despite the fact that the media has dulled its teeth and worn out its keyboards, talking and reporting about the General Data Protection regulation (GDPR), less than half (47 percent) of businesses in the UK are aware of it. What’s more, just four in ten (40 percent) are fully aware of the NIS Directive. Both documents will be coming into effect in 2018, and will significantly change how we do business online. A new report, discussing the issue, also says just a third (33 percent) of businesses are ready to meet both regulations. The report was created and published by… [Continue Reading] -

Almost half of UK CEOs not assessing AI's impact
Publié: janvier 24, 2017, 5:54pm CET par Sead Fadilpašić
UK CEOs aren’t giving artificial intelligence (AI) and automation the right attention, and that’s putting the entire country’s economy at risk. This is according to a new report by PwC, which was published at the World Economic Forum in Davos. It says that almost half (47 percent) of UK’s CEOs are not addressing the impact AI and automation can have on their organisation. To put things into perspective, in Germany, the number stands at 19 percent. In the US, it's 32 per cent, and in China it's 31 percent. Globally, 31 percent aren’t addressing AI, at the moment, leading PwC… [Continue Reading] -

One in three workers expect some tasks to be automated soon
Publié: janvier 24, 2017, 11:56am CET par Sead Fadilpašić
Workers are ceding responsibility for learning new skills to their employers, according to a new report by BMC. After polling 3,200 office workers in 12 countries, it was concluded that workers like the idea of enhancing their work lives through technology. However, 40 percent don’t think they’ll be able to keep up with the pace of change, and 88 percent say the responsibility of innovative cultures lies in the hands of their employers. Paul Appleby, EVP of Digital Transformation at BMC, says: "The massive digital disruption we are experiencing is forcing societies and businesses to create new learning environments to… [Continue Reading] -

Hacking group uses Google services to control malware
Publié: janvier 20, 2017, 11:26am CET par Sead Fadilpašić
Carbanak, a powerful cyber-crime group, is using certain Google services as command and control for its malware and other malicious elements. The news was released by cybersecurity firm Forcepoint this week. Forcepoint uncovered a trojanized RTF document, which, once ran, will "send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services." Each infected user gets a unique Google Sheets spreadsheet, allowing the attackers to "manage" each victim. This approach allows the group two key advantages. One, it allows them to hide in plain sight, and, two, it’s highly unlikely that organizations will be blocking Google services by default,… [Continue Reading] -

Younger workers are a major security threat to enterprises
Publié: janvier 19, 2017, 6:59pm CET par Sead Fadilpašić
It is now normal for technology companies, media and telecom companies to be victims of either fraud or cyber-attacks, a new Kroll report says. Almost four-fifths (79 percent) of companies were victims of fraud in the last year, with physical assets or stock being most sought after (35 percent). Cyber-attacks were no less dangerous, with 77 percent claiming to have been victims. These attacks are mostly virus or worm infections. What’s particularly interesting in the report is that it’s not the outside threat that’s most dangerous, but the inside one. Both current and former employees, together with third parties, were… [Continue Reading] -

Few consumers believe it's their job to secure their data
Publié: janvier 18, 2017, 8:30pm CET par Sead Fadilpašić
Gemalto has just issued a report which clearly shows how lenient we are when it comes to protecting our private data on the Internet. In short, we are very quick to give companies our personal data, we want them to safeguard it, but we’re pretty certain they’re doing a terrible job at it. Gemalto has polled 9,000 consumers in the following countries: Australia, Benelux, France, Germany, Russia, UAE, Saudi Arabia, India, Japan, United Kingdom, and United States. Almost three quarters (70 percent) claim organizations are responsible for securing customer data. Just 30 percent believe the responsibility lies with them. Almost a… [Continue Reading] -

UK will face a shortage of three million highly skilled workers
Publié: janvier 18, 2017, 10:47am CET par Sead Fadilpašić
By 2022, the UK could be missing approximately three million highly skilled workers, according to a new annual CEO survey by PwC. The report says that, by that time, there will be 15 million high-skill jobs in the country. This state will actually come as a result of automating low-skill, routine tasks, which will place more emphasis on higher-skill, agile roles. Another interesting conclusion is that more than nine million people could be chasing four million jobs. This is according to the government’s State of the Nation report. The Open University is warning that something needs to change, as soon… [Continue Reading] -

Few UK retailers confident about their customer experience
Publié: janvier 17, 2017, 11:03am CET par Sead Fadilpašić
Retailers are seriously lacking confidence when it comes to delivering a seamless, connected experience across channels. This is according to a new report by SAP and PwC. The report, based on a poll of 300 retailers and more than 2,000 consumers, says less than a fifth (17 percent) of retailers are confident in their capabilities. More than six in ten agree siloed business units are hurting their efforts, and a third say they are having trouble implementing the "single view of the customer". Just eight percent have successfully done this, the report claims. Retailers are faced with four key challenges,… [Continue Reading] -

Amazon introduces new job training program in UK
Publié: janvier 16, 2017, 5:54pm CET par Sead Fadilpašić
Amazon has steadily been expanding the scope of its cloud storage business AWS beyond hosting websites and apps for businesses and today the company announced its latest venture aimed at increasing IT skills training in the UK. During an event in London, the company announced its new training and job placement program, re:Start. Amazon's new service, that was built in partnership with the UK's Ministry of Defense, the Prince's Trust and QA consulting, is geared toward educating young adults and military veterans and their wives. At launch re:Start will only be available in the UK though the company may expand it… [Continue Reading] -

UK companies take too long to reach to Internet disruptions
Publié: janvier 16, 2017, 10:20am CET par Sead Fadilpašić
Internet disruptions, in their biggest part, are taking place outside a company’s network, a new report by Dyn claims. The report also says having poor visibility beyond "company walls" makes it harder for those companies to react on time. More than half (57 percent) of all Internet disruptions UK companies faced in the last year happened outside company networks. These companies need double the time to react compared to companies in the US. A quarter of businesses (25 percent) say it’s either "extremely" or "very difficult" to monitor and identify when a disruption occurs outside their network. Another third (31 percent) say it’s… [Continue Reading] -

UK companies take too long to react to Internet disruptions
Publié: janvier 16, 2017, 10:20am CET par Sead Fadilpašić
Internet disruptions, in their biggest part, are taking place outside a company’s network, a new report by Dyn claims. The report also says having poor visibility beyond "company walls" makes it harder for those companies to react on time. More than half (57 percent) of all Internet disruptions UK companies faced in the last year happened outside company networks. These companies need double the time to react compared to companies in the US. A quarter of businesses (25 percent) say it’s either "extremely" or "very difficult" to monitor and identify when a disruption occurs outside their network. Another third (31 percent) say it’s… [Continue Reading] -

European businesses are not ready for ransomware attacks
Publié: janvier 13, 2017, 11:56am CET par Sead Fadilpašić
Ransomware was the number one way hackers attacked businesses in 2016, a new report by Radware confirms. Entitled Global Application and Network Security Report 2016-2017, it says 49 percent of European businesses confirmed cyber-ransom as the biggest motivator last year. That basically represents a 100 percent increase compared to a year before, when it stood at 25 percent. A quarter of IT pros in Europe say they fear either a partial or full outage, following a cyber-attack. Another quarter (23 percent) fear data leakage, or data loss, while 18 percent are worried about a ruined reputation. Another seven percent worry… [Continue Reading] -

IT spending will increase by 2.7 percent in 2017
Publié: janvier 13, 2017, 8:37am CET par Sead Fadilpašić
Gartner has tweaked its IT spending predictions for 2017, and now says the three percent increase in spending is not exactly realistic. It's going to be less -- 2.7 percent to be exact, which is still a positive prognosis, keeping in mind we're talking about growth. The reduced spending is mostly to blame on the "wait-and-see" approach many companies are taking, caused by political and economic uncertainty. In total, Gartner believes $3.5 trillion will be spent on IT technology this year, mostly on new technologies like cloud or AI. Software will be dominating the spending, while hardware will "remain flat".… [Continue Reading] -

Citrix acquires Unidesk for its layering technology
Publié: janvier 12, 2017, 9:37am CET par Sead Fadilpašić
Citrix has announced that it has acquired Unidesk, a company that created layering. The technology allows for the separation of Windows applications from the operating system. The value of the acquisition was not disclosed. What we do know, however, is that we can expect a much tighter cooperation between Microsoft and Citrix. "Unidesk has been recognized by customers and industry analysts as the clear leader in application layering, offering multiple unique advantages that streamline secure app delivery and VDI deployments and make them easier to manage", says Jeroen van Rotterdam, senior vice president of Engineering at Citrix. "By incorporating Unidesk technology into… [Continue Reading] -

Cyberattacks against IoT devices tripled in 2016
Publié: janvier 11, 2017, 2:37pm CET par Sead Fadilpašić
It only takes one successful cyber-attack to seriously hurt a company, so it’s shocking to see that UK businesses suffered, on average, almost 230,000 cyber-attacks in 2016. This is according to Beaming. The ISP says a third of attacks was targeting company databases, but two thirds were, in fact, attacking connected devices, such as security cameras or building control systems. Such devices can be controlled remotely, through the internet. The volume of attacks against IoT devices grew 310 percent in the first and final quarter of 2016, and by the end of the year, more than 90 percent of attacks were against… [Continue Reading] -

One in three companies plans to embrace DevOps by 2019
Publié: janvier 11, 2017, 10:16am CET par Sead Fadilpašić
Almost half of large organizations (47 percent) have a DevOps approach to at least some, if not all, of their projects. This is according to a new report by Redgate Software, entitled State of Database DevOps. The company says it has polled 1,000 SQL Server professionals all over the globe, with more than half working at companies with 500 employees or more. Another third (33 percent) is planning on adopting a DevOps approach within the next two years. What’s also interesting is that the bigger the company, the bigger the adoption rate. It went up to 59 percent for professionals working at companies… [Continue Reading] -

Insurance company replaces claim workers with AI
Publié: janvier 6, 2017, 1:11pm CET par Sead Fadilpašić
We keep hearing how artificial intelligence won't leave people jobless, but instead will leave them with more time to tackle more demanding issues. However, if a Japanese insurance company is any indicator, that story doesn't hold water. Fukoku Mutual Life Insurance Company just announced that it will "replace 34 claim workers with IBM's Watson Explorer". So yeah, 34 white-collar employees got replaced by an AI. Watson, an artificial intelligence system that's been making plenty of headlines lately, will be tasked with reading medical documents, and then using that information to determine payouts. It will base its conclusions on the injury involved,… [Continue Reading] -

Intel unveils 7th-generation processors for desktops and high-end laptops
Publié: janvier 5, 2017, 11:50am CET par Sead Fadilpašić
Mobile devices might be the hottest thing nowadays, but PCs are still important for many people, and Intel knows it. The company has announced new series of processors aimed at desktop computers and performance laptops. The S series is designed for desktops. The H series is meant for high-end laptops and mobile workstations. The Y-series is for ultra-thin machines, and the U-series for ultraportables. As one might expect from new processors, these chips are expected to be faster, and consume less energy. Intel is comparing its latest S-series i7-7700K CPU to the old i7-4770K, saying it's 25 percent faster. It's worth noting that i7-4770K… [Continue Reading] -

Smart machines will become mainstream in the enterprise by 2021
Publié: décembre 20, 2016, 3:19pm CET par Sead Fadilpašić
If Gartner’s right, smart machines will become a business mainstream by 2021. Its new report, entitled "Smart Machines: Consulting and System Integration Services Market Forecast and Opportunities", says smart machines will see a 30 percent adoption in the next five years among large enterprises. Gartner says cognitive computing, artificial intelligence (AI), intelligent automation, machine learning and deep learning are all considered "smart machines". By becoming mainstream, smart machines will open up an entirely new industry, which is expected to be worth approximately $29 billion (£23.3bn) by 2021. Organizations in the consulting and system integration business will help organizations with strategic… [Continue Reading] -

Only one in three consumers install firmware updates right away
Publié: décembre 20, 2016, 11:23am CET par Sead Fadilpašić
Less than a third (31 percent) of consumers in the UK perform firmware updates on their devices as soon as they become available, a new report by Ubuntu Core, a Canonical company working on connected devices, says. Four in ten (40 percent) have never updated the firmware on their devices, ever. This leaves them extremely vulnerable to attacks, as firmware updates are also designed to patch security holes. What’s also interesting is that a significant number of consumers don’t even think it’s their responsibility to keep their devices up-to-date and protected. A quarter (22 percent) thinks software developers should worry about it,… [Continue Reading] -

Having mainframe problems? You're not alone
Publié: décembre 16, 2016, 5:52pm CET par Sead Fadilpašić
Enterprises that rely on mainframe are having a hard time delivering applications as fast as they need to, a new report by Forrester and Compuware has shown. Nine in ten (90 percent) of enterprises are having these issues, the report says, adding that it is a serious issue, as the majority of new business initiatives include the mainframe. Almost half (48 percent) have moved some apps off the mainframe, which resulted in security issues, higher costs, poor performance and project delays. More than four in ten (41 percent) are trying to work around the mainframe, resulting in greater complexity, more… [Continue Reading] -

HP unveils security solutions for business laptops
Publié: décembre 16, 2016, 1:05pm CET par Sead Fadilpašić
HP has just announced a new security solution, called the Sure Start Gen3, and a new laptop series, the EliteBook 800 G4 series. These new notebooks will be shipped with the security solution, which is why HP is calling them the "world's most secure and manageable PC". The solution handles the computer's BIOS, and makes sure no tampering can occur on that microlevel, whatsoever. "HP Sure Start Gen3 will help prevent such attacks by automatically detecting tampering attempts with the BIOS (both in pre-boot and run-time), notifying the user of a problem and restoring the BIOS to its original pristine… [Continue Reading] -

UK IT pros believe Brexit will not impact their career
Publié: décembre 16, 2016, 11:27am CET par Sead Fadilpašić
It seems that Brexit fears, at least when IT is concerned, have been largely unsubstantiated. A new report by Dice says IT experts have reasons to feel optimism as they head into 2017, based on a poll of 1,000 tech professionals. Just under a quarter (22 percent) feel optimistic about the future of the tech job market. More than half (53 percent) don't think Brexit would have a negative impact on their career plans. Almost one in ten (nine percent) are now "much more optimistic". One in five (19 percent) believe Brexit will have a positive impact on the country’s tech sector… [Continue Reading] -

Businesses believe IoT can drive customer engagement
Publié: décembre 15, 2016, 8:21pm CET par Sead Fadilpašić
Every fifth business is planning on adopting the Internet of things (IoT) to help address customer demand, and improve engagement. This is according to a new report by analytics firm SAS. These companies are mostly focused on improving front-end processes and efficiency. Only after tackling these issues will they focus on internal processes. Just under one fifth (17 percent) say the main benefit of IoT was improved customer services, as well as an enhanced digital offering. For a third (30 percent), applying design thinking (designing through user experience) is very important. More than a third (36 percent) think IoT will improve end-user experience,… [Continue Reading] -

There's no off switch for IT managers during the holidays
Publié: décembre 15, 2016, 3:46pm CET par Sead Fadilpašić
The lack of skilled workers in the IT industry is putting pressure on IT professionals in more ways than we'd previously imagined. A new report, recently released by Unified Security Management and AlienVault says IT managers that will take days off during the holidays will actually spend them worrying about work. The "good news" is -- less than a third (29 percent) will actually take time off during the holidays. The rest will just keep on working. The report is based on a poll of 464 IT professionals, and aims to better understand how the skills gap effects those currently… [Continue Reading] -

Employees' bad security habits put businesses in danger
Publié: décembre 9, 2016, 7:49pm CET par Sead Fadilpašić
Employees have poor security practices and use completely unsecured private devices for work, putting their organizations at huge risk of cyber-attacks, a new report by WinMagic says. After polling workers in the UK, the report says more than four in ten (42 percent) use private devices for work, accessing corporate data and e-mail accounts. More than half (52 percent) use private accounts, including enterprise file sharing services (EFSS), which they use to either store or access corporate files. Only a third (34 percent) say they had never done so. Laptops, smartphones and USB devices are the top three personal devices used for… [Continue Reading] -

Many of UK's NHS trusts continue to rely on Windows XP
Publié: décembre 9, 2016, 9:05am CET par Sead Fadilpašić
Nine in ten NHS trusts still rely on Windows XP, even though Microsoft stopped supporting the platform with new patches and security fixes a year and a half ago. This information was released by Citrix, and it is based on a Freedom of Information (FoI) request. Out of 63 trusts Citrix reached out to 43 responded, and 90 percent say they still use Windows XP. What's also interesting is that 24 of them -- more than half of those that responded -- have no idea when they'll migrate to a newer operating system. Migrating to a newer operating system is… [Continue Reading] -

Senior leaders holding new tech adoption back
Publié: décembre 8, 2016, 12:42pm CET par Sead Fadilpašić
IT managers in UK organizations believe their senior leaders are intentionally holding back the adoption of new technologies, as they fear that could endanger their position within the company. This is according to a new report by global cloud communications provider 8x8, which surveyed 260 IT managers in UK organizations. Almost half (45 percent) of IT managers are suspicious senior leaders are holding technology back for reasons of "self-preservation". Same IT managers, a third of them (34 percent), believe their company is making full use of the latest technology. Among C-suites, that percentage is up to almost a half (49… [Continue Reading] -

HP announces printer security services
Publié: décembre 7, 2016, 1:47pm CET par Sead Fadilpašić
HP has redesigned the way it protects printers, setting a new industry standard, the company announced in a press release this week. Its new Secure Managed Print Services (MPS) offer "advanced" security professional services and solutions, as well as expanded core delivery capabilities, which now include a new remote fleet security management service. The company also says it will be pre-configuring its print devices for security. The services part of the deal will see companies outsourcing security to save IT resources. Among the offerings are Print Security Implementation Service (HP provides specialized security support technicians), Print Security Advisory Retainer Service… [Continue Reading] -

Insurance companies hesitate to leverage big data -- but things are changing
Publié: décembre 6, 2016, 6:46pm CET par Sead Fadilpašić
Insurance companies are mostly reluctant to use big data analytics to rate their customers’ driving habits, but the trend is slowly picking up pace, a new report by PTOLEMUS Consulting Group says. The report is based on an analysis of the world’s 27 largest usage-based insurance (UBI) policies, including those of Admiral, Allianz, Allstate, AXA, Generali, Desjardins, Direct Line, State Farm, The Hartford, UnipolSai, Uniqa and Zurich. It says the number of UBI policies reached 14 million at the end of Q3 this year, but things are still slow. Global telematics insurer Progressive still uses a temporary device and doesn’t… [Continue Reading] -

Tape backups are too expensive
Publié: décembre 6, 2016, 4:10pm CET par Sead Fadilpašić
It’s almost 2017 and many organizations are still using tape to archive their data. According to a new report by Kroll Ontrack, that can be challenging, risky and expensive. After polling 819 IT administrators, more than a quarter (27 percent) don’t have clear insight into which information is being backed up on legacy tapes. It can also be quite costly. Survey respondents have said that maintaining legacy tape backup solutions can cost anywhere between £8,000 and £1 million. The biggest drivers of cost are storage, maintenance and staff. All in all, almost 40 percent want to terminate their maintenance contracts… [Continue Reading] -

One in three enterprises is not ready for digital transformation
Publié: décembre 6, 2016, 12:16pm CET par Sead Fadilpašić
A third of enterprises, globally, are completely unprepared for the process of digital transformation, a new report by global data, market research and advisory firm Ovum says. Six in ten (60 percent) of enterprises say that the process of digital transformation is "well advanced" or "in progress". However, just seven percent say the process is "complete". The financial services sector seems to be spearheading the charge, with 60 percent of enterprises saying the process is "well advanced". Retail banks, as well as payment, insurance and financial markets, are most advanced. The retail sector considers itself least prepared. "The uneven maturity of digital… [Continue Reading] -

CA Technologies buys enterprise automation company Automic
Publié: décembre 5, 2016, 8:29pm CET par Sead Fadilpašić
One of the largest independent software companies in the world, CA Technologies, has announced it is acquiring enterprise automation company Automic. The parties signed a definitive acquisition agreement last Thursday, for a transaction that’s worth approximately €600 million (roughly £507m). The deal has been unanimously approved by both boards of directors, and is expected to close in the fourth quarter of CA’s fiscal 2017. Automic is an enterprise automation company selling ONE -- it’s automation platform. The platform provides business process automation, application release automation and infrastructure workload automation. It is based in Vienna, Austria, and employs approximately 650 people in Europe,… [Continue Reading] -

Social engineering attacks are a real threat to most organizations
Publié: décembre 2, 2016, 4:45pm CET par Sead Fadilpašić
Social engineering, as a method of cyber-security attacks, is very popular and quite widespread, according to a new report by cybersecurity firm Agari. It had polled 200 professionals from healthcare, government, financial services and education sectors. Six in ten (60 percent) of security leaders say their organization either was, or "may have been" a victim of at least one targeted social engineering attack, on the last year alone. Two thirds of those attacks (65 percent) led to employees’ credentials getting compromised. Financial accounts were breached in 17 percent of attacks. Almost nine in ten (89 percent) of respondents say they noticed either… [Continue Reading] -

Ransomware attacks to decrease in 2017
Publié: décembre 1, 2016, 5:34pm CET par Sead Fadilpašić
Ransomware is expected to deflate a bit next year, but hackers won’t be resting on their laurels, that’s for sure. Instead, they might just move to dronejacking, for a "variety of criminal or hacktivist purposes". This is according to McAfee Labs, whose new report, the McAfee Labs 2017 Threats Predictions Report, identifies 14 cyber-security trends to watch in 2017. Based on the opinions of 31 Intel Security thought leaders, the report says we can expect a decrease in both volume and effectiveness of ransomware in the second half of 2017. Windows vulnerability exploits will also continue downwards, but infrastructure and… [Continue Reading] -

Deutsche Telekom hack affects 900,000 customers
Publié: novembre 30, 2016, 11:39am CET par Sead Fadilpašić
German telecommunications giant and T-Mobile parent company Deutsche Telekom was the victim of a cyber-attack over the weekend, which left some 900,000 users affected, the company confirms in a blog post. This weekend, a hacker (or more likely, hackers) infiltrated the company, and tried to infect users' home routers with malware. Deutsche Telekom said its network was not affected "at any time". "The attack attempted to infect routers with a malware but failed which caused crashes or restrictions for four to five percent of all routers", the company says. The telecoms company says it had implemented a series of measures to the network,… [Continue Reading] -

UK businesses unprepared for virtualization security challenges
Publié: novembre 28, 2016, 8:29pm CET par Sead Fadilpašić
For UK companies with at least 1,000 PCs, virtualization is a "strategic priority", however, they are yet unprepared for all the different security challenges this approach brings. This is according to a new report by Bitdefender. Surveying 153 IT decision makers in the UK, working in such companies, the report says hybrid infrastructures are the major common architecture in enterprise environments, as CIOs all over the world being to increasingly adopt them. The report sheds some light on the biggest fears and concerns IT decision makers have with the new infrastructure approach. Most (75 percent) fear the possibility of a… [Continue Reading] -

One in four Wi-Fi hotspots is a security nightmare
Publié: novembre 28, 2016, 12:19pm CET par Sead Fadilpašić
A quarter of the world's Wi-Fi networks are so insecure that the only thing stopping hackers from abusing them is their own lack of will. This is according to a new, extensive research by security experts at Kaspersky Lab, which have analyzed more than 31 million public Wi-Fi hotspots all over the world. Basically, 25 percent aren’t using any type of encryption or password protection, meaning the information going through these networks is wide open for everyone to see. Another three percent are using WEP, which is a protocol that can be cracked "within minutes, using tools that are freely… [Continue Reading] -

UK bank will let customers withdraw cash using their smartphone
Publié: novembre 24, 2016, 5:39pm CET par Sead Fadilpašić
UK bank Barclays is testing a new feature for cash withdrawals which should eliminate skimming at ATM machines, the BBC reports. The idea is similar to contactless and mobile payment systems -- you wave your smartphone close to an ATM machine and, when prompted, type in your PIN code in either the smartphone or the ATM. The bank says that way it will make it much harder to hijack card details. The new feature is being tested for Android-powered devices only, with iPhones being out of the picture. Apple has limited the use of iPhone NFC chips to their own Apple… [Continue Reading] -

Kaspersky: DDoS attacks are a smokescreen
Publié: novembre 24, 2016, 4:49pm CET par Sead Fadilpašić
Distributed denial of service (DDoS) attacks make a lot of noise, and according to a new Kaspersky Lab report, that’s exactly what hackers are using them for. As businesses are preoccupied with handling DDoS attacks, hackers use the opportunity for another, more targeted, and more deadly type of attack. Basically, DDoS is nothing more than a smokescreen. The conclusion comes in Kaspersky Lab’s report, which polled businesses about their cybersecurity experiences. More than half (56 percent) say DDoS is being used to cover something else. In more than a quarter (29 percent) of attacks, DDoS has been part of the tactics.… [Continue Reading] -

Tech salaries are up in the UK
Publié: novembre 24, 2016, 12:44pm CET par Sead Fadilpašić
The technology skills gap is working well for those already in the industry, as the salaries for these positions in the UK just keep going up. According to a new Dice report, tech jobs have seen an increase of five percent, on average, in salaries, in the last 12 months. The highest average pay was spotted for program managers, with these positions getting a six percent increase in salaries, up to £78,847 for permanent roles. Contractors have day rates of £600 now, 1.5 percent up compared to last year. The biggest jump, however, goes to security analysts and senior java… [Continue Reading] -

Symantec acquires LifeLock for $2.3bn
Publié: novembre 22, 2016, 11:24pm CET par Sead Fadilpašić
Security firm Symantec is buying US identity theft protection services company LifeLock, Reuters has reported. The deal is worth $2.3 billion (£1.87bn), and it is claimed that this is Symantec’s way of amping up sales at its Norton cybersecurity unit. According to the report, Norton is still profitable, but its sales are in decline for one simple reason -- mobile. Norton comes preloaded on a large number of traditional computers, but people are turning more towards mobile devices. "Norton had been declining with the declines in PC market share. This acquisition brings $660 million in revenue to the consumer business and… [Continue Reading] -

People don't understand how they get infected with malware
Publié: novembre 22, 2016, 2:30pm CET par Sead Fadilpašić
A new Kaspersky Lab report says a lot of us end up with viruses on our machines, but we just don't know how. But, in fact, we very much do. Here are the report's figures. Almost half (42 percent) of internet users have either come across or have been targeted by malware online. A fifth of those (22 percent) have fallen victim to it, and almost a third (29 percent) have "no idea how it ended up on their device". Just after that, the report says this: "The study found the highest number of infections happen when people visit suspicious… [Continue Reading] -

The paperless office is a dream
Publié: novembre 18, 2016, 3:58pm CET par Sead Fadilpašić
After last month’s report from AIIM, which said we were actually inching closer to a paperless office thanks to the unrelenting digitization, a new report from Danwood now says exactly the opposite. Not only are we not moving towards the paperless office, but away from it, and worse of all -- it’s digitization’s fault. After surveying 1,000 office workers, almost half (46 percent) say they print something every day and 84 percent say this is an "important aspect of work". So how does this relate to the digital transformation? Well, increased digitization means organizations are getting a lot of information,… [Continue Reading] -

Microsoft plays nice with the EU to buy LinkedIn
Publié: novembre 18, 2016, 2:11pm CET par Sead Fadilpašić
According to the European Commission, Microsoft has made commitments to appease EU antitrust regulators regarding its $26 billion acquisition of the professional social networking site LinkedIn. The company announced its plan to acquire the site in June for $26 billion, in its largest acquisition to date. The deal would allow Microsoft access to LinkedIn's large user base and would give it an edge in providing cloud-based services -- such as Office 365 -- to businesses. Last week, EU regulators expressed concerns regarding the deal and the company was forced to make concessions in order to gain approval for its acquisition… [Continue Reading] -

UK businesses are not keen to embrace AR
Publié: novembre 17, 2016, 5:01pm CET par Sead Fadilpašić
Businesses are reluctant to accept augmented reality, a new survey by ISACA has shown. The main reasons for this reserved stance is that they don’t believe the benefits are bigger than the risks of implementing the new technology. The findings were published in ISACA’s new report, entitled IT Risk/Reward Barometer, which polled 363 UK professionals. Less than a fifth (18 percent) currently believe the benefits of AR are bigger than the risks, and 40 percent say that both organizations and consumers should be "very concerned" about the privacy risks that go with the implementation of augmented reality tech. The biggest fear is… [Continue Reading] -

Wi-Fi is more important than sex
Publié: novembre 17, 2016, 2:08pm CET par Sead Fadilpašić
Which of these would you consider a daily essential: sex, chocolate, alcohol or Wi-Fi? If you depressingly chose the fourth and final answer, then you probably are a mobile professional, according to a new iPass report, the iPass Mobile Professional Report 2016. The report surveyed 1,700 mobile professionals, and 40 percent of them choose Wi-Fi. Thirty-seven percent choose sex, 14 percent chocolate and nine percent chose alcohol. When asked why they gave such answers, three quarters (75 per cent) say having Wi-Fi improves the quality of their life. Almost two thirds (63 percent) prefer using Wi-Fi over mobile data, and three quarters… [Continue Reading] -

CEOs not deemed responsible for cyber-security -- but they should be
Publié: novembre 17, 2016, 12:47am CET par Sead Fadilpašić
Chief executive officers in the UK are still far from being considered responsible for keeping their organizations safe from cyberattacks, according to a new report by NCC Group. The report, which the risk mitigation and cybersecurity company just released, is based on a poll of 200 UK board of directors, where they were questioned on cybersecurity. Just 13 percent say the managing director was responsible for cyber risks in their company. Also, just nine percent named the financial director. The biggest burden is still on the shoulders of CTOs and CIOs -- 52 percent. "Boards continue to pass the cyber buck by… [Continue Reading] -

SMBs hold on to their hardware longer than enterprises
Publié: novembre 15, 2016, 6:39pm CET par Sead Fadilpašić
Smaller and medium-sized businesses would rather wait a couple years longer before upgrading their systems, compared to large enterprises, a new survey by memory and storage company Crucial shows. Out of 350 IT decision makers in the UK, US, Germany and France, more than half (52 percent) say their company has a hardware refresh cycle of about three to four years. Large organizations replace systems every two years or so (23 percent) while small organisations wait four years or more (22 percent). The reason behind upgrades is always the same -- their current systems are no longer good enough. Sometimes, businesses would… [Continue Reading] -

Employees want flexibile hours more than a company car
Publié: novembre 11, 2016, 6:27pm CET par Sead Fadilpašić
It's been a while since remote working became a reality, but this latest survey into the matter showed that it is now becoming the norm. As a matter of fact, employees would rather have flexible hours and the possibility of mobile working than a company car, according to BT. A total of 1,500 workers in the UK, Germany, France and Spain were polled for the report, and 67 percent confirm the claim regarding the car. For 76 percent, flexible working is one of the top three priorities in their company. But mobile working is far from perfect -- current technology… [Continue Reading] -

Microsoft patches Windows flaw reported by Google
Publié: novembre 10, 2016, 3:26pm CET par Sead Fadilpašić
Microsoft has kept its promise and delivered a vulnerability patch for its Windows operating system, for a flaw, revealed by Google, which allowed attackers to gain full control of a targeted system. Releasing the details in a security bulletin, Microsoft says the flaw in the Windows kernel "could allow elevation of privilege if an attack logs onto an affected system and runs a specially crafted application that could exploit the vulnerabilities". Once an attacker gains control of the system, they can install other malicious applications which would allow even easier access, eliminating the need for the original flaw. "To exploit… [Continue Reading] -

SMBs find cash increasingly expensive to manage
Publié: novembre 9, 2016, 6:12pm CET par Sead Fadilpašić
Businesses are moving faster towards a cashless society because it's cheaper than handling "real" money. This is according to a new report by Sage, integrated accounting, payroll and payment software provider. The company’s latest report says small and medium-sized businesses are losing £9.4bn each year through cash payments. A quarter (24 percent) say that staff members stole some cash, a third (34 percent) believe human error had them losing money, and more than half (56 percent) claim they spend at least an hour every week counting and sending money to the bank. All these reasons are giving businesses strong arguments… [Continue Reading] -

Women in tech earn 9 percent less than men in UK
Publié: novembre 8, 2016, 6:48pm CET par Sead Fadilpašić
Women in the UK's tech industry earn nine percent less money than men, according to a new report by Hired. In salary terms, that's approximately £5,000 a year in difference. The worst part is the UK is leading the way globally, when it comes to gender pay gap in the technology sector. The US has a gender pay gap of 8 percent in the tech sector, Canada 7 percent, and Australia has the lowest gap -- five percent. Hired's report also says that it's not just about the pay. Getting promoted and being part of the boardroom is also more challenging… [Continue Reading] -

IT pros earn less in UK than Australia and New Zealand
Publié: novembre 4, 2016, 11:52am CET par Sead Fadilpašić
A new survey has revealed that IT professionals working in Australia and New Zealand (ANZ) earn a substantially higher salary than their counterparts in the UK and Ireland. Computer Weekly and TechTarget's Salary Survey 2016 APAC found that the average salary of ANZ IT pros was between £50,000 and £94,000 a year. In order to learn more about IT salaries in the region, 450 IT professionals from Australia, New Zealand and Southeast Asia were questioned regarding how much they earned annually. A similar survey conducted in the UK and Ireland by Computer Weekly found that IT professionals in those countries… [Continue Reading] -

Kaspersky tells ransomware victims not to pay up
Publié: novembre 3, 2016, 9:54am CET par Sead Fadilpašić
If your organization ever gets infected by ransomware (and there are good chances it will) it is better not to pay up because you probably won’t get your data back, even if you do pay the ransom. This is according to a new report by security firm Kaspersky Lab, which urges organizations to instead report the incident to the authorities. It bases its conclusions on a couple of research results -- more than a third (36 percent) of organizations pay the ransom, but around 20 percent still don’t get their files back. Approximately 17 percent of organizations have been victims… [Continue Reading] -

DevOps can make apps more secure
Publié: octobre 28, 2016, 2:41pm CEST par Sead Fadilpašić
Pretty much all IT operations professionals (99 percent) agree: adopting a DevOps culture can improve application security. This is according to a new report by Hewlett Packard Enterprise. The report, titled Application Security and DevOps Report 2016, also emphasizes that just a fifth (20 percent) of respondents test their application’s security during development, and 17 percent are using no technologies whatsoever to protect their apps. The conclusion of the report is simple: there is a significant disconnect between perception and reality of secure DevOps. "Our research shows that both security leaders and developers believe that the DevOps movement has the… [Continue Reading] -

Businesses find IoT devices hard to secure
Publié: octobre 24, 2016, 9:32pm CEST par Sead Fadilpašić
Internet of things (IoT) is expected to make an enormous impact on pretty much every industry in the upcoming months and years, but it seems as organizations don’t really know how to secure their devices. This is according to a new report by ForeScout Technologies, which surveyed 201 senior IT decision makers in the UK, Germany, Austria and Switzerland. First, the report says the threat surface is going to increase dramatically. An average business will operate 7,000 IoT devices in the next 18 months, which is "far more" than what the average company is used to securing and defending. Second,… [Continue Reading] -

Hackers use old SSH vulnerability to attack Internet of Things devices
Publié: octobre 13, 2016, 7:28pm CEST par Sead Fadilpašić
There is a 12 year old vulnerability in OpenSSH that hackers are now using to attack Internet of Things (IoT) devices and remotely generate traffic. Akamai Technologies' researchers Ory Segal and Ezra Caltum have identified the old vulnerability and dubbed it SSHowDowN Proxy. The researchers say hackers are using it to target CCTV, NVR, and DVR devices, satellite antenna equipment, networking devices such as routers or hotspots, and internet-connected NAS devices. These devices are being used to mount attacks against "a multitude of Internet targets and Internet-facing services, such as HTTP, SMTP and Network Scanning", researchers say. It is also… [Continue Reading] -

Cloud apps give businesses a 'huge' competitive advantage
Publié: octobre 12, 2016, 7:36pm CEST par Sead Fadilpašić
Businesses in Europe that have sent at least one of their core business areas to the cloud now have a "huge" competitive advantage over their peers, according to a new report by Frost & Sullivan. The company says businesses that have adopted a cloud-based approach for either accounting, customer relationship management (CRM) or enterprise resource planning (ERP) are reaping the benefits of their (r)evolutionary approach. The report is based on a poll of 600 senior IT decision makers from a cross section of industries throughout Europe. "For businesses in Europe, cost savings are not the main driver for moving to… [Continue Reading] -

Few businesses are prepared for GDPR
Publié: octobre 12, 2016, 6:12pm CEST par Sead Fadilpašić
The GDPR is drawing ever closer, but organizations which will be directly affected by it still don't know how to approach the new regulation, a new study by Dell shows. Ever since it was unveiled that the General Data Protection Regulation will come into effect in May 2018, surveys have been done to see if companies are preparing themselves for it, and if they will be ready to comply with it in time. Never have these reports shown positive or encouraging results, and the new one by Dell is no different. Still, organizations aren't even close to being prepared. More… [Continue Reading] -

IT pros struggle with AI and intelligent systems
Publié: octobre 11, 2016, 8:02pm CEST par Sead Fadilpašić
Almost nine in ten (88 percent) IT professionals say that their organization invested in some form of intelligent solutions, be it smart business apps, whole systems or bots. The information was presented in a new research report from Ipswitch. The report also says that more than three quarters (78 percent) can’t fully grasp the challenges and threats of deploying such systems themselves. For more than two thirds (78 percent), it is challenging (58 percent say it is a challenge, and 19 percent say it is "extremely hard" to do). However, businesses aren’t giving up, as more than a third (35 percent) see it as crucial to stay… [Continue Reading] -

YouTube makes it easier to create video ads
Publié: octobre 11, 2016, 2:31pm CEST par Sead Fadilpašić
YouTube has announced a new platform which will make creating video ads for the site easier. The number of visits, as well as visit duration, have gone up lately, and the company wants to cash in on the momentum. The new offering is called YouTube Director -- a solution to help businesses create a professionally-looking ad in no time. There are two ways to do it: the YouTube Director for Business app and the YouTube Director onsite service. The former, free and currently only available in iOS, helps businesses create an ad through a custom template. With a step-by-step walkthrough, the… [Continue Reading] -

Consumers don't want to use more apps due to security concerns
Publié: octobre 10, 2016, 8:45pm CEST par Sead Fadilpašić
The fact that people are afraid to use more apps because of security reasons is costing the UK economy billions. To be more precise, £2.5 billion this year, £3.2 billion the next. This is according to a new report by Rackspace, which says that 36 percent of consumers are reluctant to use more apps for security reasons. Privacy is also a huge issue for 33 percent of consumers in general -- rising up to 37 percent among the older population. More than a quarter (26 percent) said a failure in an app prevented them from doing something important. "Our research… [Continue Reading] -

Identifying hackers is harder than you think
Publié: octobre 10, 2016, 7:33pm CEST par Sead Fadilpašić
One of the main reasons why hackers and other malicious actors are so hard to locate is not the fact they're really good at hiding their location -- it is because they're exceptional when it comes to faking things. They fake their locations, their working hours, language, infrastructure, toolkits -- even their own groups. Hackers are going extreme lengths to make sure people looking for them are actually in for a wild goose chase. These conclusions were released by security researchers at Kaspersky Lab who tried to tackle the issue of misleading both victims and security researchers. "The attribution of… [Continue Reading] -

Fewer businesses investing in big data
Publié: octobre 7, 2016, 4:02pm CEST par Sead Fadilpašić
Market analyst company Gartner has issued a report that says that investment in big data is up, but fewer companies are actually planning on investing in this field. While 48 percent of companies have invested in big data in 2016, up three percent compared to the year before, the percentage those who plan on investing within the next two years is down from 31 to 25 per cent. According to Paul Cant, EMEA head of enterprise solutions operation for BMC Software, businesses are giving up on big data because they failed to implement it properly and are not really reaping… [Continue Reading] -

Ransomware becomes biggest security threat on Android
Publié: octobre 7, 2016, 3:02pm CEST par Sead Fadilpašić
Android users, beware. Ransomware for your favorite mobile operating system is picking up -- it's now the main threat in the US, UK, Germany, Denmark and Australia, in the first half of 2016. These are the figures from security organization Bitdefender. Its report claims the Android SLocker ransomware family accounts for almost half of all mobile malware reported by infected devices in the first half of 2016 in Denmark. In Germany, it's at 25 percent, in Australia 21.54 percent and 16.48 percent in the UK. The US has had the least troubles so far, sitting at 16 percent. The ransomware… [Continue Reading] -

Worldwide device shipments fall by 3 percent
Publié: octobre 7, 2016, 10:34am CEST par Sead Fadilpašić
Worldwide shipments for devices including PCs, tablets, smartphones and mobile phones, are expected to decline three percent this year, according to a new report by market analysts Gartner. The company says this will be the second consecutive year of decline, as the global devices market fell by 0.75 percent in 2015. "The global devices market is not on pace to return to single-digit growth soon", says Ranjit Atwal, research director at Gartner. "Growth is on pace to remain flat during the next five years. All segments are expected to decline in 2016, except for premium ultramobiles and utility mobile phones (entry… [Continue Reading] -

Open source IT pros are in high-demand in Europe
Publié: octobre 6, 2016, 8:40pm CEST par Sead Fadilpašić
Open source employees in Europe have it good, especially when we compare that market to the rest of the world. This is according to a new report by Dice and The Linux Foundation. The report says that out of 1,000 European respondents 60 percent believe it would be fairly easy to find a new job this year. Globally, the figure stands at about 50 percent. "Demand for open source talent is growing and companies struggle to find experienced professionals to fill open roles", says Bob Melk, president of Dice. "Rising salaries for open source professionals indicate companies recognize the need to… [Continue Reading] -

Mastercard rolls out biometric payments in Europe
Publié: octobre 6, 2016, 8:34pm CEST par Sead Fadilpašić
MasterCard has just rolled out a new feature that should simplify online shopping, without making any compromises in security. The feature, called Identity Check Mobile, allows users to use biometrics like fingerprint scanning or facial recognition to verify their identity before making a purchase, eliminating the need for passwords or PIN codes. At the moment, the technology is being introduced in 12 European countries: the UK, Austria, Belgium, Czech Republic, Denmark, Finland, Germany, Hungary, the Netherlands, Norway, Spain, and Sweden. Worldwide rollout is expected next year, although no specific dates have been given. MasterCard says current identity verification methods often… [Continue Reading] -

Paper use in the office is declining
Publié: octobre 5, 2016, 6:56pm CEST par Sead Fadilpašić
Our offices are still not entirely paper-free, but we're slowly getting there. This optimistic prediction has been published in a new report by AIIM, entitled Paper-Free in 2016, Are we there yet?. According to it, the amount of paper going into offices is declining, while digital inbound documents are increasing, for two thirds of business executives. The report launches as part of the run up to World Paper Free Day (WPFD) 2016, AIIM says, taking place on November 4. "The once elusive concept of paper-free business operations is today a real possibility and real progress has been made over the… [Continue Reading] -

Some UK businesses don't know what ransomware is
Publié: octobre 5, 2016, 6:20pm CEST par Sead Fadilpašić
More than one in ten (11 percent) of all UK organizations have never even heard of ransomware, Trend Micro claims. Another 20 percent don't know how the malware works. Yet, more than four fifths, or 82 percent to be exact, consider malware a threat. This general lack of knowledge about ransomware best reflects in how the organizations in question think ransomware originates. A third (33 percent) of them know it comes from malicious email attachments. However, a quarter (24 percent) believe ransomware infections come from clicking a link in an email, and 14 percent think it happens if you simply… [Continue Reading] -

Microsoft's bot platform has 45,000 developers -- more than Facebook's, less than Google's
Publié: octobre 4, 2016, 8:47pm CEST par Sead Fadilpašić
Facebook, Google and Microsoft are currently locked in a battle over which bot platform will have more developers, and currently it's Google that's winning -- but it's not that simple. Just before releasing its chat app Allo, Google acquired API.ai, a bot-building platform through which developers can make bots for various platforms. API.ai is currently being used by 60,000 developers, according to VentureBeat, putting Google at the top of the pack. Considering that it has just only acquired the start-up, it’s easy to argue that the company didn’t really do much to hit that milestone. Facebook and Microsoft, on the other hand, have been… [Continue Reading] -

Big Data and IoT leave businesses more vulnerable to cyber attacks
Publié: octobre 4, 2016, 7:52pm CEST par Sead Fadilpašić
In the next three years, there will be more cyberattacks than there were in the past five, a new report by the Economist Intelligence Unit (EIU) claims -- it points the finger at the growth of IoT. The report says that out of 200 operators of critical infrastructure worldwide, 80 percent say the proliferation of IoT and Big Data is making them more vulnerable to cyberattacks. Telecom and IT services are the most vulnerable types of companies, as an attack would create the most damage, followed by banking institutions. "The increasing connectedness of critical infrastructure is improving the quality and reach of services, but it… [Continue Reading] -

Apple loses patent cases to VirnetX again -- will have to pay $302.4 million
Publié: octobre 4, 2016, 5:37pm CEST par Sead Fadilpašić
"Third time's the charm", VirnetX is probably now thinking, as a US court has, for the third time, ruled that Apple has infringed the company’s patents. A federal judge in Tyler, Texas ruled on Sunday that Apple must pay $302.4 million (£235.10m) for infringing VirnetX’s patents in services like FaceTime and iMessage. Back in 2010, VirnetX was awarded $368.2 (£286.25m), but the ruling was partially overturned because it wasn’t exactly clear how the jury calculated the damages. The second time, earlier this year, the court ruled Apple should pay, setting the figure at $625.6 million (£486.37), but that ruling too was… [Continue Reading] -

Microsoft will build a data center in France
Publié: octobre 4, 2016, 9:04am CEST par Sead Fadilpašić
Microsoft has announced that its investments in cloud computing in Europe exceeded $3 billion, as it plans to open a new data center in the country next year. Besides making this announcement, Microsoft has also released a new book, entitled A Cloud for Global Good, containing policy recommendations for things like data protection. The company’s CEO, Satya Nadella, says the investment comes as a result of a "growing demand" from both European customers and partners. "Building a global, trusted, intelligent cloud platform is core to our mission to empower every person and organization on the planet to achieve more. There’s never been a better time… [Continue Reading] -

Same hacker collective may be behind the biggest data breaches
Publié: octobre 3, 2016, 5:56pm CEST par Sead Fadilpašić
You know that Yahoo breach that just happened recently? The one where 500 million credentials were stolen? Well, a highly respected security researcher claims the hack was done by the same group that breached MySpace, LinkedIn, Badoo, VK.com, and a few others. The researcher in question is Andrew Komarov, and he told The Register that not only did the same group do all these things, but the number of breached Yahoo accounts is probably a billion. Double what was reported. Komarov says the group, referred to as "Group E", is a "small Eastern European hacking outfit" that makes money by hacking… [Continue Reading] -

Enterprises' favorite cloud solution is IaaS
Publié: septembre 28, 2016, 8:52pm CEST par Sead Fadilpašić
Just over half of enterprises (51 percent), which decide to deploy a cloud solution, opt for Infrastructure-as-a-Service (IaaS), over Platform-as-a-Service (PaaS) or Software-as-a-Service (Saas). This is according to a new report by Intel DCM, based on a survey of 204 US-based IT managers, directors, software engineers and DevOps responsible for overseeing their enterprise cloud strategy. The report also states that DevOps teams spend most of their time monitoring complex environments in their organization. That includes tuning infrastructure, and remediation analysis. Besides Software-as-a-Service, and Platform-as-a-Service, IaaS is considered a main category for cloud computing services. It provides virtualized computing resources, over the… [Continue Reading] -

Customers lose trust in hacked businesses
Publié: septembre 28, 2016, 11:29am CEST par Sead Fadilpašić
If your business gets hacked, expect to lose a significant portion of your customers -- for good. This is according to a new report released by Alertsec, the cloud-based encryption company. Its Brand Perception Study, based on a poll of 1,200 Americans, says 17 percent of women and 11 percent of men would permanently lose trust in a hacked company. Almost a third (29 percent) would need months to return while a further 22 percent would need only one. Men are also more likely (16 percent) to switch brands after a hack than women (6 percent). For more than a third… [Continue Reading] -

Microsoft teams up with Adobe in the cloud
Publié: septembre 27, 2016, 7:21pm CEST par Sead Fadilpašić
At the Microsoft Ignite event, the Redmond, Wash.-based software giant announced a new cloud partnership with none other than Adobe. This one works both ways. On one side, Microsoft "will make Adobe Marketing Cloud its preferred marketing service for Dynamics 365 Enterprise edition", and, on the other side, Adobe will "make Microsoft Azure its preferred cloud platform for the Adobe Marketing Cloud, Adobe Creative Cloud and Adobe Document Cloud". Interestingly enough, Adobe has so far used Amazon Web Services, but it was left unclear if this means Amazon is getting the boot or not. "Business leaders in every industry are focused… [Continue Reading] -

Yahoo is still vulnerable
Publié: septembre 27, 2016, 5:26pm CEST par Sead Fadilpašić
The first thing you should do after getting your home or apartment robbed is, obviously, change the lock. Yahoo doesn’t seem to think so, as the same practices that were in place when it got breached are still being used according to a new report by Venafi. What’s more, its practices have for years been known as unsecure. Venafi puts it simply: if you’re a Yahoo user, you should be worried about this. Here’s what it did (or, didn’t do): most importantly, 27 percent of certificates on external Yahoo sites haven’t been changed since January 2015. "Replacing certificates after a breach… [Continue Reading] -

Millennials want to share personal data -- but not for free
Publié: septembre 27, 2016, 11:01am CEST par Sead Fadilpašić
Sharing for the sake of it won't suffice among millennials, a new study has shown. But if there are certain benefits to be had, well, that is now a completely different story. Business intelligence company SAS, together with research agency Future Foundation, came to these conclusions after extensive research. It says millennials, which it also calls "Data Generation" (16 - 34 year-olds), expect a "hyper-personalized service from brands". They are willing to use their personal information as bargaining chips to get a better experience from businesses. According to the report, 67 percent are willing to share their information with the… [Continue Reading] -

Few users are concerned about their online security
Publié: septembre 26, 2016, 8:07pm CEST par Sead Fadilpašić
Just 21 percent of Internet users feel threatened by anything online, including malware, viruses, fraud, etc. At the same time, 29 percent have actually fallen victim to cybercriminal schemes, out of whom eight percent have had an account hijacked, and 22 percent have had malware on their devices. On top of it all, a total of 60 percent of all people online use protection, in form of a cybersecurity solution for all devices accessing the internet. These figures were unveiled by Kaspersky Lab which has, together with B2B International, released a report on the current level of cyberthreats faced by… [Continue Reading] -

Russian hacker collective targets over 85 leading US companies
Publié: septembre 26, 2016, 6:10pm CEST par Sead Fadilpašić
A group of hackers speaking Russian and using Russian servers are out hunting for American companies' user credentials, an exclusive story published on The Epoch Times claims. This group, allegedly not tied to any government and basically operating on its own, is targeting "at least" 85 companies, including Amazon, American Airlines, AT&T, Best Buy, Wells Fargo, DropBox, Dunking Donuts, Ebay, GoDaddy, Uber, Match.com, McDonald’s, Office Depot, PayPal, Pizza Hut, Steam, and Apple Pay. Epoch Times broke the news after being approached by darknet investigator Ed Alexander, who apparently saw hackers "capturing card numbers and full identities", including answers to personal… [Continue Reading] -

Apple acquires machine learning startup TupleJump
Publié: septembre 26, 2016, 10:19am CEST par Sead Fadilpašić
Apple is on a mission to buy virtually every machine learning start-up it stumbles upon. The latest "victim" in its shopping spree is an Indian-US company called TupleJump. The news was first broken by TechCrunch, and even though Apple is yet to confirm the acquisition there are signals out there to back such an event. First things first. Apple did give a statement, and a pretty vague one that is arguably open for interpretation. "Apple buys smaller technology companies from time to time, and we generally do not discuss our purpose or plans". Second signal is TupleJump’s website -- it… [Continue Reading] -

Most employees don't want to share passwords
Publié: septembre 23, 2016, 8:53pm CEST par Sead Fadilpašić
For many people, both business owners and employees, remote working is the future of business. It’s at the very heart of business transformation, together with cloud computing, automation and artificial intelligence. However, a new poll by OneLogin seems to suggest that certain workers aren’t really fond of the idea of remote working. Half of full-time workers believe employees below mid-manager level shouldn’t be allowed remote access to the corporate network. This remote access refers to both work-owned devices (47 percent) and private devices (54 percent). More than a quarter (27 percent) of those polled believe only senior management should have… [Continue Reading] -

BT to offer customers Microsoft Azure services
Publié: septembre 23, 2016, 7:32pm CEST par Sead Fadilpašić
British telecommunications company BT has announced a new offering, expanding the cloud choice for its customers. BT Computer for Microsoft Azure allows BT’s customers to order Microsoft Azure together with BT’s cloud. With the new offering, according to BT, customers will be able to create hybrid cloud infrastructure with a single service wrap, on a single bill. “Hybrid cloud has become a major focus for many large enterprises as they choose a variety of cloud solutions to suit their complex business needs. In fact, BT research suggests that 90 percent of its largest customers expect to be using a combination… [Continue Reading] -

Office workers want the latest technology, or else they'll quit
Publié: septembre 23, 2016, 4:03pm CEST par Sead Fadilpašić
Business owners, pay attention. If you don't step up your technology game, your employees might leave you. This is according to a new global report from Dell and Intel, entitled Future Workforce. Based on a poll of 4,000 full-time employees all over the world, it tried to understand how modern technologies are shaping the office world. Even though the majority of UK workers are happy with their jobs, almost half think new technologies are not being fully used. Twenty percent of employers are actually ready to quit their jobs if technology isn't up to date. When it comes to face-to-face… [Continue Reading] -

Education will shift away from classrooms in the future
Publié: septembre 22, 2016, 8:56pm CEST par Sead Fadilpašić
Classrooms could be a thing of the past by 2025, according to new research by Polycom. Its Education in 2025 -- Technology Innovation survey takes a closer look at education and technology and has some interesting takeaways. While almost two thirds (64 percent) of respondents believe students engage with content primarily in the classroom, just a quarter (25 percent) believe that will still be the case in ten years' time. More than half (53 percent) of education professionals believe real-time video collaboration and mobile devices will be the number one way students will engage with content in 2025. At the moment, however,… [Continue Reading] -

Homes are getting smarter, but not more secure
Publié: septembre 22, 2016, 12:10pm CEST par Sead Fadilpašić
Smart homes aren’t something that’s going to happen in "the near future" -- smart homes are happening today. They’re no longer reserved for the early adopters or geeks, too. In some places, they’ve reached the "tipping point" -- they’re basically mainstream now. This is according to a new and fairly extensive research by the non-profit prpl Foundation. In its study, The prpl Foundation Smart Home Security Report, it surveyed 1,200 people in the UK, US, France, Germany, Italy and Japan, and concluded that people should be more careful with their home routers. Comparing them with the front door, the foundation says home routers are… [Continue Reading] -

Number of data breaches rises by 15 percent
Publié: septembre 22, 2016, 10:06am CEST par Sead Fadilpašić
The number of breaches and their severity are both growing, a new report by digital security company Gemalto is saying. Titled Breach Level Index, it says there has been 15 percent more data breaches in the first half of 2016, compared to the last six months of 2015. A total of 974 data breaches were reported worldwide, amassing 554 million compromised data records, in the first half of 2016. It is also interesting that in more than half of cases (52 percent), the number of compromised records were not disclosed at the time of reporting. Looking specifically at the UK, there… [Continue Reading] -

Businesses spend nearly $3 billion a year on mobile connectivity
Publié: septembre 21, 2016, 1:11pm CEST par Sead Fadilpašić
The cost related to mobile connectivity through roaming, pay-on-demand Wi-Fi and free Wi-Fi is costing businesses in Europe and North America at least $2.91 billion every year. This is according to iPass, provider of global mobile connectivity. The cost is high because, as the report puts it, mobile professionals have an "insatiable need for connectivity". When traveling and working on the go, they spend on average 6GB every month. The report has an interesting conclusion -- free Wi-Fi is not always as free as you’d think. These connections, being available to everyone, can often be slow, unresponsive and crowded. Business… [Continue Reading] -

DDoS attacks rarely strike businesses just once
Publié: septembre 20, 2016, 4:58pm CEST par Sead Fadilpašić
A company is rarely attacked by a DDoS (distributed denial of service) just once. If it happens once, it will probably happen again, which is why constant preventive measures are required, if a company wants to keep their online services operational. These are the results of a new report by Kaspersky Lab. Entitled Corporate IT Security Risks 2016, it says that one in six companies were victims of DDoS attacks in the past 12 months. The majority of those attacks were aimed against construction, IT and telecommunications companies. Almost four out of five (79 percent) reported more than one attack,… [Continue Reading] -

Ransomware is lucrative: Attacker's profits near $100 million
Publié: septembre 20, 2016, 10:55am CEST par Sead Fadilpašić
Hackers are increasingly targeting healthcare institutions with malware because of their poor cyber-security posture, reliance on legacy IT systems, third-party services and the need to access information as soon as possible in order to deliver great patient care. These are the conclusions released in a new report entitled McAfee Labs Threats Report: September 2016. It says that hospitals paid almost $100,000 (£75,500) to a specific bitcoin account. In the first half of 2016, one "actor" (it could be a single hacker, but more likely a group) apparently received $121 million in ransomware (189,813 bitcoin), targeting various industries. This actor, according… [Continue Reading] -

Dell announces Latitude 13 3000 Series convertible laptop
Publié: septembre 19, 2016, 10:06pm CEST par Sead Fadilpašić
Dell has announced a new hybrid device to help small businesses with tight budgets. The convertible laptop, a Latitude 13 3000 Series 2-in-1 comes with a few important features which budget devices usually lack, like the USB Type-C port or Windows Hello support. The new device, available now on Dell's online store, comes with a starting price of $699 (£530). "Staying abreast of the latest form factors and solutions is critical in today’s competitive business landscape", wrote Raza Haider in a blog post, announcing the new device. "Specifically, the growth of 2-in-1 devices are revolutionizing the way workers perform day-to-day jobs,… [Continue Reading] -

HP launches new ProBook 400 G4 laptops
Publié: septembre 19, 2016, 8:50pm CEST par Sead Fadilpašić
HP has announced a new series of laptops aimed for small business owners whose employees are style-oriented millennials. Truth be told, if you're a bit older, but would still like a fairly cheap, well-designed laptop, there's nothing stopping you from getting your hands on the new HP ProBook 400 G4 Series. It comes with the latest seventh-generation Intel Core processor, or seventh-generation A-Series APUs from AMD. Its graphics are powered by the NVIDIA GeForce 930MX, and is paired with 16GB of RAM. It has full HD displays, USB-C ports, and enterprise-grade security. Most importantly, the company significantly improved its battery… [Continue Reading] -

European workers vulnerable to social engineering attacks
Publié: septembre 19, 2016, 6:46pm CEST par Sead Fadilpašić
Hackers are using social media to gather information about their next victim. They use that information to form sophisticated strategies and deliver advanced threats into networks. These are the results of a new Blue Coat Systems report, based on a poll of 3,130 workers in various industries in Great Britain, France and Germany. Key takeaway from the report is that user behavior has not improved much since last year. This year, 42 percent of respondents say they only accept friend requests from people they know. This is down one percent, compared to a year before. Just as last year, 60 percent… [Continue Reading] -

Ads drive most Internet traffic in Europe
Publié: septembre 16, 2016, 8:42pm CEST par Sead Fadilpašić
With all the buzz and fuss over ad blockers and how they hurt the internet we know today, it's interesting to see just how much traffic these ads actually drive. As it turns out, more than you'd expect. According to a new report by Adobe Digital Insights, more than two thirds (68 percent) of all European traffic is driven by ads. General traffic is also growing. In Europe, more than half (54 percent) of sites grew their traffic in the last three years. Also, mobile advertising is catching up. Personal advertising, an ads strategy which seems to be working quite… [Continue Reading] -

IBM Cloud adds mobile security service
Publié: septembre 16, 2016, 7:11pm CEST par Sead Fadilpašić
When it comes to corporate IT security, one of the biggest pain points is the mobile device. With almost every employee having one, and many bringing their own, the cyber-attack surface increases dramatically, putting corporate data at huge amounts of risk. Now, IBM is stepping into the game with a service of its own, which aims to protects mobile devices, via IBM Cloud. The mobile-security-as-a-service, called IBM MaaS360, aims to help IBM’s clients address local data protection standards. It is currently in operation in the US, Germany and Singapore, with France and India already in the works. They will be… [Continue Reading] -

One in 50 employees could be a malicious insider
Publié: septembre 16, 2016, 11:22am CEST par Sead Fadilpašić
If your company counts 50 people, at least one of them might be a malicious insider, according to new studies. Imperva has released a report which says that 36 percent of surveyed companies suffered a security incident involving malicious insiders in the past year. One in every 50 employees is considered to be a malicious insider. Another interesting finding is that not all malicious insiders are disgruntled former employees looking to inflict some damage as they close the door on their way out. There are people who are using their position to transform confidential data into a second stream of… [Continue Reading] -

Cost of a cyber-attack will soon reach $1 million for large businesses
Publié: septembre 15, 2016, 8:07pm CEST par Sead Fadilpašić
We are coming closer to the point where a cyber-attack will cost every large business more than $1 million. According to a new Kaspersky Lab report, a single cyber-security incident now costs a large business, on average, $861,000. Small and medium-sized enterprises (SME) pay ten times less, on average -- $86,500. The new report also stresses, once again, how costs go up the longer the threat remains unseen. For an SME, it will have to pay 44 percent more to recover from a week-old attack, compared to the one spotted on the first day. Among large companies, the percentage sits at… [Continue Reading] -

Microsoft Outlook app gets Sunrise features
Publié: septembre 15, 2016, 1:47pm CEST par Sead Fadilpašić
Sunrise is dead, long live Sunrise! Once considered the best mobile calendar app to ever grace us with its presence, it got acquired by Microsoft and is now officially retired. But Microsoft has taken its best features and reincarnated them into its Outlook app's calendar, and the general feeling is overall quite positive. The updated Outlook, which is available now, comes with a couple of changes. Interesting Calendars is one of the new features, which allows Outlook to connect with businesses, TV shows and similar. That way, your calendar will have automatic updates on your favorite sports events, next episodes of that… [Continue Reading] -

Dell EMC sells Enterprise Content Division to OpenText
Publié: septembre 14, 2016, 4:12pm CEST par Sead Fadilpašić
Dell EMC continues to offload unwanted divisions within the new company, and the latest victim is its Enterprise Content Division (ECD), including Documentum. They have been acquired by enterprise information management company Opentext.com, for $1.62 billion (£1.22bn). The transaction is still subject to regulatory approvals, and is expected to close within 90 to 120 days. All software, associated services, and employees of ECD will be integrated into OpenText. OpenText hopes to "further strengthen its vertical offerings, customer base, managed services, and geographical coverage". The acquisition was made with the help of Barclays, which served as a financial advisor to OpenText and also provided… [Continue Reading] -

IBM introduces new servers for AI workloads
Publié: septembre 14, 2016, 11:55am CEST par Sead Fadilpašić
IBM introduced a series of new servers dubbed "x86 killers". The devices, designed to give a significant boost to artificial intelligence, deep learning and advanced data analytics, were picked up by the Chinese telecommunications company Tencent, and IBM claims the results are basically out of this world. "A large cluster of the new IBM OpenPOWER servers was able to run a data-intensive workload three times faster than its former x86-based infrastructure", IBM says in a press release. "While reducing the total number of servers used by two-thirds". The first of the three, and obviously the flagship server, is the IBM… [Continue Reading] -

BlackBerry launches new subscription-based Android apps
Publié: septembre 13, 2016, 7:59pm CEST par Sead Fadilpašić
Canadian telecommunications company Blackberry announced new services for its Android Hub+ platform this week. Besides the Hub, Calendar and Password Keeper, which were available earlier, another six apps are now available for Android users, for both Marshmallow and Lollipop versions of the operating system. These apps include Contacts, Tasks, Device Search, Notes, and Launcher, all part of Blackberry's productivity suite. They are available for a free 30-day period, after which they'll cost 99 cents per month. Hub, Calendar, Password Keeper, and Launcher will remain free, but with ads. The platform has also gotten a few updates, Blackberry says in a blog… [Continue Reading] -

Microsoft adds guest access to Office 365
Publié: septembre 13, 2016, 4:29pm CEST par Sead Fadilpašić
Microsoft keeps adding new features to its Office 365 suite, and now it has made easier for people outside a group to collaborate on files. A new feature, for Office 365 groups, allows people who aren't staff members, or members of a particular group, to join in and collaborate. Group owners can now use the web version of Outlook to invite non-staff members in. "We are rolling out guest access functionality in phases. Starting today, group owners can add guests to a group in Outlook on the web", it says on the Microsoft blog. Microsoft says that it doesn't matter which… [Continue Reading] -

New version of RAA ransomware only goes after business users
Publié: septembre 12, 2016, 2:39pm CEST par Sead Fadilpašić
A new version of the RAA ransomware was found recently by security researchers at Kaspersky Lab. This one, written completely in Jscript, seems to be targeting business users exclusively, the researchers claim. It comes as they all do: through an email with the malicious attachment. This one, however, comes in a password-protected zip file. This method does two things: Makes it harder for anti-virus software to recognize the malware Makes it seem more legitimate to the victims The email usually says something about "overdue payment order from a supplier", to trick the victim into opening the attachment. The second biggest change… [Continue Reading] -

PayPal teams up with Mastercard for in-store payments
Publié: septembre 9, 2016, 9:43pm CEST par Sead Fadilpašić
Just days after announcing a similar deal with Visa, PayPal has now announced it has come to an agreement with MasterCard, as well. This will allow customers to use PayPal to pay in stores, it was said, through the use of smartphones and contactless payment cards. According to multiple media reports, this deal actually means losses for PayPal in the short term. Wall Street Journal reported that PayPal is "shifting away from promoting free bank transfers to fund customers' transactions and toward the networks, which charge a fee". But with strong competition coming from the likes of Apple or Stripe,… [Continue Reading] -

Box users will soon be able to edit Google documents
Publié: septembre 9, 2016, 2:43pm CEST par Sead Fadilpašić
During BoxWorks 2016, the annual Box conference taking place in San Francisco, the enterprise content platform announced it is teaming up with Google to make working and collaborating in the cloud simpler and easier. Box will become third-party content repository for Google Docs, Google Sheets and Google Slides, it was unveiled during the conference. Once the new offering is available, it will enable Box users to create and edit Google documents directly from its cloud services. The two companies will also work together on Google Springboard -- the search engine for files stored across the Google Apps suite. The collaboration… [Continue Reading] -

Box and IBM team up to increase productivity in cloud workflows
Publié: septembre 9, 2016, 11:33am CEST par Sead Fadilpašić
Thanks to a new partnership between Box and IBM, Box users will be getting a new workflow solution which will allow any business users to build, manage and track custom and pre-built workflows. The new solution, called Box Relay, will be a part of the "all new Box", to be presented during BoxWorks 2016, Box's annual San Francisco conference. Box says the new offering will help users be more productive, regardless of if it's about automation in user onboarding, budget streamlining or asset approving. The product will reduce IT dependency, make processes seamless across the extended enterprise, reduce time needed… [Continue Reading] -

GoDaddy acquires ManageWP for its WordPress management tool
Publié: septembre 8, 2016, 4:34pm CEST par Sead Fadilpašić
Internet domain registrar, and web hosting company GoDaddy, has announced that it has acquired ManageWP. ManageWP is a WordPress dashboard, allowing webmasters to manage multiple WordPress sites from a single dashboard. "GoDaddy is serious about investing in WordPress and ManageWP is by far the leading tool for managing WordPress sites", says Jeff King, SVP of Hosting at GoDaddy. "Together, we’ll bring ManageWP to the scale of GoDaddy, helping web designers and developers save thousands of work hours and touch millions of websites globally, no matter where they are hosted". Even though financial details of the agreement were not disclosed, ManageWP… [Continue Reading] -

EE rolls out 4G LTE Cat 9 in UK
Publié: septembre 7, 2016, 11:09am CEST par Sead Fadilpašić
UK carrier EE has launched a new layer of extra capacity for its 4G network to help high-end smartphones use their full potential, which will make smartphones "faster on EE than any other UK network". EE has also said that it will make Cat 9 devices faster. Cat 9, or Category 9 4G, is capable of supporting 450Mbps download speeds, and devices such as HTC M10 or the Samsung Galaxy S7 are capable of achieving these speeds. "There’s no point having the latest smartphones on a network that can’t support the top speeds the device is capable of", says EE CEO Marc… [Continue Reading] -

Enterprises moving to hybrid cloud
Publié: septembre 6, 2016, 4:10pm CEST par Sead Fadilpašić
Cloud computing seems to be a feature of successful businesses, but still a lot of workloads remain on premises, a new study by IBM suggests. More than 1,000 C-suite executives from 18 industries were interviewed, face-to-face, to come to this conclusion. In 78 percent of cases, cloud initiatives are either "coordinated" or "fully integrated", which is a significant jump, compared to 34 percent we had in 2012. More successful the company is the higher the percentage too. On the other hand, 45 percent of workloads remain, and are expected to remain, on premises. "Enterprises are moving to the cloud, especially… [Continue Reading] -

Microsoft now leads the SaaS market
Publié: septembre 6, 2016, 11:45am CEST par Sead Fadilpašić
Microsoft is now the overall leader in the software-as-a-service (SaaS) market, beating Salesforce by a tiny margin. However, not everything is as straightforward as it seems. According to Synergy Research Group, Microsoft, even though late to the party as usual, now holds 15 percent of the SaaS market, while Salesforce, the leader so far, has 14 percent share. In the first quarter of 2016, both were tied at 14 percent each. The funny thing is, Salesforce doesn't even rank in all the different aspects of SaaS. It holds the dominant position in customer relationship management (CRM), true. But Microsoft ranks number one… [Continue Reading] -

Most enterprise workloads will be in the cloud by 2018
Publié: septembre 5, 2016, 8:55pm CEST par Sead Fadilpašić
More than four out of ten (41 percent) of all enterprise workloads all over the world are either on a private or public cloud. By the time we reach 2018, the number will have risen to 60 percent, according to a new report by 451 Research. The cloud-first approach is already common, the report says. More than a third (38 per ent) of all enterprises polled for the report say they already have such a policy. Europe is leading the way, with 42 percent of organizations having such a policy. On-premise private clouds as well as software-as-a-service models are most… [Continue Reading] -

IT pros don't use all their annual leave due to work pressure
Publié: septembre 5, 2016, 8:26pm CEST par Sead Fadilpašić
IT professionals are most likely, out of all working people, not to use their entire annual leave, according to a new Robert Walters Career Lifestyle Survey. This is mostly because they are under pressure to deliver new projects on tight deadlines, and to keep their projects safe from cyber-attacks. Almost half (44 percent) of IT pros polled during research said they had not used their entire annual leave, compared to the average of 36 percent. "In the last year, IT professionals working in cyber security have seen a particular spike in demand for their skills, driven by several data breaches… [Continue Reading] -

Cyber-attacks costing the UK economy £147 billion a year
Publié: septembre 3, 2016, 12:59am CEST par Sead Fadilpašić
Apparently, 1.8 million of UK’s businesses have been victims of a cyber-attack, and that costs the country’s economy more than £147 billion, in the last year alone. This is according to a new report by Gareth Bacon, GLA Conservative London Assembly, entitled Safe & Secure: Protecting London’s data. Pretty much all businesses affected by these security breaches -- 99 percent of them -- are small businesses, counting 249 employees, or less. With that in mind, the report proposes a Mayoral Standard for data security, helping London consumers and businesses protect themselves from cyber-attacks. Basically, it would force companies to keep… [Continue Reading] -

Dell - EMC merger will close September 7
Publié: septembre 3, 2016, 12:09am CEST par Sead Fadilpašić
Dell and EMC will finalize their merge on September 7, following China's regulatory approval, the two companies announced earlier this week. The new company, named Dell Technologies, will start working as soon as the merge is complete. China's Ministry of Commerce (MOFCOM) approved the merger, after EMC shareholders did the same on July 19. "This is an historic moment for both Dell and EMC. Combined, we will be exceptionally well-positioned for growth in the most strategic areas of next generation IT including digital transformation, software-defined data centre, converged infrastructure, hybrid cloud, mobile and security", says Michael Dell, chairman and CEO… [Continue Reading] -

UK businesses report 88 percent more breaches
Publié: septembre 2, 2016, 7:59pm CEST par Sead Fadilpašić
It's not that there are less data breaches lately -- it's that they're not being disclosed. That's basically what Huntsman Security is saying, after it requested data about error and breaches in security through the Freedom of Information Act. Between April 2015, and March 2016, a total of 2,048 incidents were reported to the Information Commissioner’s Office (ICO). This represents a jump of 88 percent, as the year before, there were a total of 1,089 reported incidents. "Unfortunately, this is not the full story. The average organization is subject to multiple breaches, of which only some will be detected, so… [Continue Reading] -

Dropbox 2012 hack exposes 68 million accounts
Publié: septembre 2, 2016, 10:23am CEST par Sead Fadilpašić
Remember how Dropbox asked all those that haven't changed their passwords since 2012 to do so now? Remember how they said they did it for no particular reason, just as a precaution? Turns out, it was much more than that. As a matter of fact, back in 2012, more than 68 million accounts were hacked. "The list of email addresses with hashed and salted passwords is real, however we have no indication that Dropbox user accounts have been improperly accessed", the company’s head of trust Patrick Heim confirms in a blog post. "We’re very sorry this happened and would like to… [Continue Reading] -

Analytics and data are the most sought-after IT job skills
Publié: septembre 2, 2016, 3:53am CEST par Sead Fadilpašić
Data and analytics are some of the most important new skills you, as an employee, can have today. This is according to Alteryx, whose new report dives into the most important skills and competencies in the workforce today. That being said, data and analytics have surpassed some interesting skills, like multilingualism. Knowing a second language isn’t really that important any more, even though a 2014 report suggested otherwise. The Alteryx report, entitled The Business Grammar Report, also says data is no longer "confined to the IT department or technical specialists". Just 15 percent of UK businesses are still doing it… [Continue Reading] -

Cisco buys container-as-a-service startup ContainerX
Publié: septembre 1, 2016, 9:07pm CEST par Sead Fadilpašić
Cisco wants to transform into a software company and to further move towards that goal it announced the acquisition of CointainerX, a small start-up formed by engineers from Citrix, Microsoft and VMware. The container-as-a-service business creates virtual containers for data centres, for Windows and Linux. The financial details of the agreement were not disclosed. ContainerX didn’t try to hide the excitement. Writing a blog post, co-founder and CEO Kiran Kamity says the company will continue developing a "comprehensive cloud-native stack" for customers. "The Cisco team has been extremely supportive of our plans to accelerate product development as we strive to build… [Continue Reading] -

Most websites have security vulnerabilities
Publié: septembre 1, 2016, 11:28am CEST par Sead Fadilpašić
Dangerous vulnerabilities are present in a large number of today's websites, and the percentage is only going to keep on growing, according to a new report by Acunetix. The automated web application security software company released its annual Web Application Vulnerability Report 2016, based on 45,000 website and network scans, done on 5,700 websites over the past year. The results are worrying. More than half (55 percent) of websites have at least one high-severity vulnerability, representing a nine percent growth compared to last year's report. More than four fifths (84 percent) have medium-severity vulnerabilities. There has been a small, "encouraging"… [Continue Reading] -

HP announces trio of cloud-oriented business products
Publié: août 31, 2016, 11:08pm CEST par Sead Fadilpašić
HP has launched three new products to help businesses move their workloads into the cloud computing environment easier. The trio includes the t630 Thin Client, ThinPro 6, and VMware Blast. The t630 Thin Client allows for the streamlining of current cloud-based deployments, comes with next generation, x86 quad-core systems-on-a-chip developed by AMD, and offers AMD Radeon graphics. The ThinPro 6 is powered by a 64-bit Linux operating system, and comes with a tool-less BIOS update, allowing simple upgrades, both locally and remotely. And finally VMware Blast is based on H.264, or MPEG-4 Advanced Video Coding (AVC) standard, and improves both mobile… [Continue Reading] -

How much does it cost to start a business in UK?
Publié: août 31, 2016, 7:27pm CEST par Sead Fadilpašić
How much money do you think it needs to kickstart a business in UK? A couple of thousands? Maybe go straight into five figures? Wrong. According to a new report by cloud accounting software provider FreeAgent, you probably don't need any money. The company surveyed micro-business owners and freelancers in the UK, and according to the results 44 percent of business starters required no funds at all. Almost the exact same percentage (43 percent) used their personal savings, and that was enough. Four percent borrowed money from friends or family, two percent used either credit card or bank loan, while… [Continue Reading] -

Your personal data is worth less than $1
Publié: août 31, 2016, 11:24am CEST par Sead Fadilpašić
There's a new calculator online which will tell you exactly how much your digital data is worth. This tool, created by Totally Money, asks you to name the price for 13 different data types, including email address, health condition, or credit rating. After giving your price, the calculator then tells you the real price. The whole project was basically designed to show people just how easy and cheap it is for companies to buy your personal data. Following the release of the calculator, the company also did a survey of 1,000 UK adult consumers. Forty percent of Facebook users, for… [Continue Reading] -

Security experts want passwords to be put out to pasture
Publié: août 29, 2016, 9:18pm CEST par Sead Fadilpašić
Russian internet giant Mail.ru has been hacked once again, and some 25 million accounts associated with forums run by the company have been compromised. Among the data that was stolen are usernames, passwords (easily crackable, according to Secure CloudLink), email addresses, phone numbers, birthdays and IP addresses. Security firm Secure CloudLink says theft of this kind of data is worrying, especially with IP addresses involved, as hackers could find a person’s real life address. For the security company, this is yet another proof we need to move away from passwords and into more modern solutions. "Given the severity and regularity… [Continue Reading] -

Google slows down Fiber deployment, may switch to wireless
Publié: août 29, 2016, 1:58pm CEST par Sead Fadilpašić
Google is scaling back a project because it's too expensive for the company. No, really, something is too expensive for Google. The project in question is Google Fiber, the fiber-to-the-premises service currently being developed and deployed in the US. According to a report by The Information, Google has basically failed -- it only has 200,000 subscribers at the time, and knowing that it set a goal of five million by the end of 2015, it's obviously not enough. Instead of fiber, the company will shift its focus towards wireless technology, as it's much cheaper. It was also said that the unit,… [Continue Reading] -

Mozilla wants EU copyright law reform
Publié: août 29, 2016, 10:39am CEST par Sead Fadilpašić
Mozilla has called out the European Union, asking it to reform its copyright laws. The current one, according to the organization, is holding innovation and economic development down. Writing a blog post on the topic, Mozilla CIO Katharina Borchert says EU’s copyright laws are stopping great ideas in their tracks. "The internet brings new ideas to life every day, and helps make existing ideas better. As a result, we need laws that protect and enshrine the internet as an open and collaborative platform", Borchert says. "But in the EU, certain laws haven't caught up with the internet. The current copyright legal… [Continue Reading] -

Businesses struggle to prevent data breaches
Publié: août 20, 2016, 9:21am CEST par Sead Fadilpašić
Data breaches are everywhere, and companies feel they’re not doing a good job at preventing them. They are, however, taking steps to try and counter the trend. This is according to a new report by business documents management organization M-Files Corporation and the Association for Information and Image Management (AIIM). According to the report, more than a third (38 percent) of organizations have suffered at least one data breach in the past 12 months. Almost a third (31 percent) feel their company isn’t doing all it can to protect sensitive information, and 36 percent say their company doesn’t have a "formally… [Continue Reading] -

Smart plugs have major security issues
Publié: août 19, 2016, 9:10pm CEST par Sead Fadilpašić
Plugging things into a smart electrical plug might not be the wisest of choices at the moment, because they could easily be hacked, putting both your physical and digital life at risk. This is according to a new report by Bitdefender, which says that smart electrical plugs could be hacked, and the attacker could not only gain access to your personal data, but also reprogram the plug. If these plugs control your security systems or medical devices -- it could spell a whole lot of trouble. There are two crucial problems with such devices, according to the report. First, the… [Continue Reading] -

Nvidia slams Intel for fudging CPU vs GPU benchmark results
Publié: août 19, 2016, 5:18pm CEST par Sead Fadilpašić
Intel’s recent claims that CPUs are better than GPUs when it comes to deep learning on neural networks has sparked a rebuttal from Nvidia. In case you don’t know what this is all about, here’s a short recap: Machine learning is currently a really big deal. It’s a huge market with untapped potential in many industry verticals, which is why a lot of different companies are trying to get in on the action. It is widely taken as a fact that GPUs are a better solution than CPUs when it comes to deep learning, because neural networks require low precision computation,… [Continue Reading] -

Security researcher accuses Microsoft of 'sneaky data mining' in Windows 10
Publié: août 19, 2016, 11:03am CEST par Sead Fadilpašić
Ah, you can never get enough paranoia nowadays, can you? Security researcher Mike Patterson -- founder and CEO of security analytics organization Plixer -- says Microsoft's Windows 10 sends encrypted data from your machine every five minutes, and there’s basically very little you can do to stop it. Even when he opted out of everything he could find, regarding data transfer, the OS still continued to do it. The weirdest part about it is that you can’t really determine what is being sent. The content was encrypted so that it is impossible to know what’s going out, essentially hiding this information from the… [Continue Reading] -

UK tech salaries continue to grow
Publié: août 18, 2016, 9:25pm CEST par Sead Fadilpašić
Salaries for tech jobs in the UK are still rising in the second quarter of the year, despite the fact that the number of jobs in the industry is slowly declining. This is according to a new report by Dice, the online career site for the technology community. Together with Watch, it lists the most wanted jobs and skills in the industry. The two companies say cloud and security skills are still most wanted, both in permanent and contract roles. Most wanted skills in Q2, for permanent roles, were agile software development, SQL, JavaScript, .NET, C#, Java, CSS, Linux, project management,… [Continue Reading] -

Finance organizations rely too much on spreadsheets
Publié: août 18, 2016, 7:53pm CEST par Sead Fadilpašić
Pretty much every finance organization in London (97 percent of them) is worried about how reliant it is on spreadsheets. These are the results of a new research by finance function solutions provider, Accountagility. The worry stems from faults experienced when using it for both planning and reporting, as four out of five (80 percent) of organizations have had such experiences. Just under half (49 percent) also consider a problem the fact that manual effort is needed to both validate and analyze Excel data. "Our research reveals that this problem is not just limited to The City, but is an issue… [Continue Reading] -

Users know the risks, but connect to Wi-Fi hotspots anyway
Publié: août 18, 2016, 11:34am CEST par Sead Fadilpašić
People are risking a lot when they connect to a free Wi-Fi, which is particularly important knowing how many people use mobile devices for work. According to a new report by NordVPN, a company selling VPN services, Wi-Fi networks can be hacked easily and attackers could steal valuable data, including corporate information, credit card information or identities. "Hackers often position themselves as Wi-Fi hotspots and easily steal personal information of each individual that logs in", says NordVPN. "In addition, identity thieves have lately been using wireless sniffers, a software designed to intercept and decode data when it is transmitted over a… [Continue Reading] -

Cisco Meeting Server enables Skype for Business users to connect with other platforms
Publié: août 17, 2016, 9:09pm CEST par Sead Fadilpašić
Skype for Business users have had a pretty rough time connecting with other platforms (like Cisco or Avaya), but that’s no longer the case as the Cisco Meeting Server gets released. Cisco's new product will allow Skype for Business users to easily connect to users on other platforms by clicking a link. The company believes its product will completely reshape office collaboration, and the impact will be "huge". "Connecting should not be hard. But it has been, because certain vendors’ technologies have not played well with standards-based technologies, like Cisco’s industry-leading video systems. We just fixed that, and the impact is huge", says… [Continue Reading] -

Blockchain startups raise $290 million worldwide
Publié: août 17, 2016, 7:29pm CEST par Sead Fadilpašić
Blockchain and bitcoin start-ups have raised almost $300 million in funding in the first half of 2016, Juniper Research claims. This goes to show just how important the new way of doing business and paying for goods and services is. There are more than 30 startups in the world which Juniper looked at for this research. Juniper look at more than 30 startups across the globe for this research, which have raised a total of $290 million. A large part ($165m) went to just three companies: Circle ($60 million), Blockstream ($55 million) and Digital Asset Holdings ($50 million). According to the… [Continue Reading] -

Salesforce acquires data analytics startup BeyondCore
Publié: août 17, 2016, 10:03am CEST par Sead Fadilpašić
Salesforce has announced it is buying data analytics startup BeyondCore. In a tweet posted earlier this week, Marc Benioff says: "I am thrilled announce @Salesforce has acquired @beyondcoreinc to enhance the AI capabilities of Analytics Cloud". Financial details of the acquisition were not disclosed, but we do know that BeyondCore will integrate into Saleforce’s Analytics Cloud, and will leverage its AI knowledge. At Salesforce, BeyondCore will be uniquely positioned to further magnify our impact on the world of analytics as part of the Analytics Cloud, extending smart data discovery and advanced analytics capabilities across the entire Salesforce Customer Success Platform", writes Beyondcore CEO Arijit Sengupta. "Of… [Continue Reading] -

Oracle has a database of 400 million business profiles -- and it's now for sale
Publié: août 16, 2016, 8:39pm CEST par Sead Fadilpašić
Oracle is now the third of the big technology companies that is selling business profiles. The company just announced on its website that it is selling a database containing 400 million business profiles. "Oracle Data Cloud today launched the largest business-to-business (B2B) audience data marketplace to help make programmatic and data-driven B2B marketing easier", says Oracle. What does this actually mean? You can use the database to "reach buyers and decision makers at specific companies to align B2B marketing and sales efforts" or "build audiences based on companies that have purchased a specific enterprise solution in the past". You can also "digitally… [Continue Reading] -

GM tried to buy Lyft
Publié: août 16, 2016, 4:53pm CEST par Sead Fadilpašić
General Motors (GM) currently holds some nine percent stake at Lyft, the US ride-sharing startup. However, according to new reports, firstly coming out of The Information, GM was interested in purchasing the other 91 percent, as well. How much money would that be? Well, if nine percent is $500 million, the entire company would be around $5.5 billion. Lyft, apparently, turned the offer down and instead wants to go for another round of funding. The speculation is that all of this comes as a result of the recent teaming up with Frank Quattrone’s Qatalyst Partners, a Silicone Valley group "known for selling companies". As for GM’s… [Continue Reading] -

US businesses slowly embracing Privacy Shield agreement
Publié: août 16, 2016, 3:47pm CEST par Sead Fadilpašić
The new program that replaces the Safe Harbor agreement is being picked up by US companies, but very, very slowly. In the first two weeks since the US Department of Commerce started accepting applications for the Privacy Shield transatlantic data transfer program, just 40 companies have been certified. Another 200 applications are currently being reviewed, so we can expect this number to increase, although it’s still far, far away from the 4,000 companies certified for the Safe Harbor agreement. "The first joint annual review will therefore be a key moment for the robustness and efficiency of the Privacy Shield mechanism… [Continue Reading] -

Malware hits 20 major hotels, customer data may be stolen
Publié: août 16, 2016, 11:10am CEST par Sead Fadilpašić
As many as 20 hotels in the US have been hit by malware, and fears are spreading that customer data, including credit card information, was stolen. According to a Reuters report, hotels under attack include Starwood, Marriott, Hyatt and Intercontinental -- all part of the HEI Hotels & Restaurants. The malware was developed specifically to target it and collect credit card data from its systems. The malware was found two months ago, on payment systems used all over these hotels -- in restaurants, bars, lobbies, and spas. The number of people affected is hard to estimate, as many people used… [Continue Reading] -

New key hack exposes 100 million Volkswagen cars
Publié: août 15, 2016, 1:58pm CEST par Sead Fadilpašić
Back in the day, people had to walk into a bank in order to rob it. They also had to walk into a car in order to steal it. Nowadays, people rob banks from the comfort of their home (or their parents’ basements), and it’s only a matter of time before they start hijacking cars the same way. According to a couple of researchers, whose work has been covered by Wired recently, we’re already halfway there -- a new vulnerability has been found which allows hackers to remotely unlock 100 million Volkswagen cars. Yeah, you read that correctly -- 100 million vehicles from… [Continue Reading] -

Apple gets green light to build Irish data center
Publié: août 15, 2016, 11:23am CEST par Sead Fadilpašić
After months of back and forth, Apple has finally gotten the approval to build its first data centre in Ireland. The approval was given by the Irish planning body -- An Bord Pleanala -- last week, despite being opposed by a couple of individuals and local businesses. The planning body said the 197-hectares data center, to be built in a forest on the west coast of Ireland, will significantly boost local economy. The opposition says the building will have a negative effect on the local wildlife, and could have a negative effect in terms of flooding. The data center’s energy consumption… [Continue Reading] -

Consumers apps better made than enterprise apps
Publié: août 12, 2016, 10:17pm CEST par Sead Fadilpašić
Consumer grade is the new enterprise grade, a new survey by ScaleArc says. The annual survey among IT decision makers has revealed that consumer apps seem to be much better than enterprise apps, because they’re faster, and more reliable. "It is clear that consumer grade is the new enterprise grade", says Justin Barney, president and CEO of ScaleArc. "IT decision-makers who build enterprise apps recognize that they, and the general public, have a better experience on their personal apps than their work apps. We’ve all lost patience with websites and apps that don’t offer optimal performance". A vast majority of… [Continue Reading] -

Asian countries lag behind in data storage security
Publié: août 12, 2016, 7:23pm CEST par Sead Fadilpašić
Asian nations are not very secure places to keep your digital data, a new report by secure data centre Artmotion suggests. The report was built on data from the UN, World Economic Forum and Transparency International, among other groups. Titled Data Danger Zones, it ranks more than 170 nations on how good they are at keeping data secure. Switzerland was ranked first. But looking at Asian countries is where things get particularly interesting. Singapore has a risk score of 1.9 percent, and is considered the safest Asian nation. Hong Kong, Taiwan and South Korea also made it in the top 15,… [Continue Reading] -

Notebook shipments are 'healthier', says TrendForce
Publié: août 12, 2016, 5:11pm CEST par Sead Fadilpašić
Notebook shipments have returned to a somewhat "healthier" state, but the second half of the year, which is traditionally seen as the "peak" in shipments, is expected to be weaker than usual. These are the highlights of a new report by market analysts TrendForce. Total number of notebook shipments for the first half of 2016 hit 74.18 million units, representing a four percent decline compared to the year before, and TrendForce sees this as a return to a more healthy state. However, September usually marks the beginning of a new cycle, when consumers upgrade and re-stock on their notebooks, as the… [Continue Reading] -

Many students are interested in starting a business
Publié: août 11, 2016, 10:33pm CEST par Sead Fadilpašić
A third of students are either considering starting a business, or already have one, new research from Santander Universities says. This equates to a total of 518,000 students, who generate £913 million every year, the report adds. However, it’s not (just) money that motivates these people. Instead, they’re more interested in pursuing a hobby or personal interest (70 percent). Financial gain is only placed second (58 percent), right before work experience (26 percent). The average yearly turnover is £13,213, which is almost double compared to a year before. The number of student entrepreneurs has also increased by more than a… [Continue Reading] -

PC users install Windows updates, but don't patch programs
Publié: août 11, 2016, 8:09pm CEST par Sead Fadilpašić
Microsoft is doing its part protecting its users from hackers, but it can’t do everything on its own. According to new figures released by Secunia Research in its Country Reports, covering Q2 2016 for 12 countries, the number of unpatched Windows machines is on the decline. Compared to Q1 this year, when 6.1 percent of systems were unpatched, only 5.4 percent are not up to date now. Same time last year, the figure was 10.3 percent. "The decline in unpatched Windows operating systems is remarkable and encouraging", notes Kasper Lindgaard, director of Secunia Research at Flexera Software. "It will be interesting to see if… [Continue Reading] -

Samsung Pay vulnerability can enable fraudulent payments
Publié: août 11, 2016, 5:13pm CEST par Sead Fadilpašić
During the recent Defcon hacking conference, held last week in Paris, a hacker demonstrated how he could make fraudulent payments through Samsung Pay. Samsung says it knew of this and considers it an acceptable risk. It claims the method is almost too difficult to pull off, and no different than fraud methods we see today with credit cards. Before letting you decide if new payment systems should have the same flaws as the old ones, let’s dive into what the method really is. According to the hacker, Salvador Mendoza, an attacker could intercept Samsung Pay tokens (codes generated by the… [Continue Reading] -

Most smart car vulnerabilities can be easily exploited
Publié: août 11, 2016, 10:26am CEST par Sead Fadilpašić
Remember that cyber-experiment when a couple of hackers managed to take control over a speeding car in the middle of the highway? Well, IOActive has published a study, entitled Commonalities in Vehicle Vulnerabilities, after three years of testing, and the results are quite scary. It tested a "leading vehicle manufacturer", discovering that half of the found vulnerabilities could allow hackers either partial or full control over the target vehicle. What’s more, almost three quarters of these vulnerabilities could be exploited quite easily, which makes IOActive conclude that they most likely will be exploited. Half of the vulnerabilities found (50 percent) are deemed "critical"… [Continue Reading] -

Intel buys machine learning startup Nervana
Publié: août 11, 2016, 8:00am CEST par Sead Fadilpašić
Intel is buying machine learning start-up Nervana, and it’s paying some serious money for it. According to multiple media sources, the 48-person start-up was acquired for a stunning $408 million (£312m). Nervana is an artificial intelligence company which is looking to integrate AI beyond the usual software -- it wants to squeeze it into the chips themselves. And who better to team up with to achieve that goal than Intel -- one of the biggest chipmakers in the world. But the deal isn’t around consumer electronics, it’s about chips in data centers. According to Intel vice president Jason Waxman, data… [Continue Reading] -

Data loss and theft is on the rise
Publié: août 11, 2016, 7:09am CEST par Sead Fadilpašić
There has been a "sharp increase" in the number of lost and stolen corporate data in the past two years, according to a new report by the Ponemon Institute and Varonis Systems. But it’s not as straightforward as you’d think. The new report, titled Closing Security Gaps to Protect Corporate Data: A Study of U.S. and European Organisations, says that 76 percent of respondents experienced either data loss, or theft, in the past 24 months. The results are based on a poll of 3,027 employees in the United States, United Kingdom, France, and Germany, including 1,371 end users and 1,656 IT and IT… [Continue Reading] -

Micro announces UFS 2.1 3D NAND mobile storage chip
Publié: août 11, 2016, 6:39am CEST par Sead Fadilpašić
Micron has announced a new 3D NAND chip for mobile devices, claiming it will give your smartphones more storage capacity and possibly even reduce the use of SD cards. The memory technology, based on the Universal Flash Storage (UFS) 2.1 standard, will come at first as a 32GB solution. The company promises its module will offer users seamless HD video streaming, higher bandwidth gameplay and faster boot up time. "Micron continues to advance NAND technology with our introduction of 3D NAND and UFS products for the mobile segment", says Mike Rayfield, vice president of Micron’s mobile business unit. "The improved… [Continue Reading] -

Kaspersky finds advanced cyber-espionage malware that hid for five years
Publié: août 10, 2016, 7:43pm CEST par Sead Fadilpašić
Kaspersky Lab's security researchers have found a new cyber-espionage malware, most likely built by a nation-state to use against other states' organizations. Dubbed "ProjectSauron", it is "particularly interested" in accessing encrypted communications. The malware hunts such communications down using an "advanced modular cyber-espionage platform", comprised of a number of different and unique tools. Researchers say traditional compromise indicators are "almost useless" in this case, because ProjectSauron has noteworthy avoidance patterns. It customizes its implants and infrastructure for each individual target, and never recycles them, meaning it’s extremely hard to notice it. ProjectSauron looks as it was created by an "experienced… [Continue Reading] -

Hackers compromise Oracle's point-of-sale unit
Publié: août 10, 2016, 12:36pm CEST par Sead Fadilpašić
Another day, another major data breach. This time it’s Oracle’s MICROS, its point-of-sale division, that got hurt. According to security researcher Brian Krebs, who first disclosed the breach in a blog post (you can read it here), chances are that a Russian organized cyber-crime group is behind this. The group, called Carbanak, is believed to have inserted malicious code in the company’s software and, apparently, 700 internal systems were compromised as a result. According to Oracle, "certain legacy MICROS systems" were affected, and the hackers were onto the company’s customer support portal for credit card payment systems. Oracle is now… [Continue Reading] -

Brexit has little impact on UK's IT jobs market
Publié: août 9, 2016, 2:58pm CEST par Sead Fadilpašić
The Brexit vote is yet to make a more significant impact in the UK’s tech job market, according to a new Dice report. The career site for the tech community surveyed 1,200 UK tech professionals and recruiters, and found that people are generally not making any dramatic movements because of Brexit. It says that just above a fifth (22 percent) changed their career plans since Brexit. While more than half think a positive vote on the referendum would have a negative impact on the UK’s tech job market, 44 percent say they’re now looking for a new job in the EU. Out of… [Continue Reading] -

Airbnb's valuation reaches $30 billion
Publié: août 9, 2016, 11:18am CEST par Sead Fadilpašić
Airbnb, the home rental startup, is raising another $850 million (£651m), according to a new report by Bloomberg, at a valuation of $30 billion, making it the second most valuable start-up, right behind the $68-billion-worth car-sharing Uber. The document, filed with the state of Delaware, does not show who the investors are, and Airbnb has yet to make a comment. It currently has more than 1,500,000 listings in 34,000 cities and 191 countries. Business Insider reports that the state of New York has passed a bill which will prevent people from advertising short-term rentals. That basically means Airbnb will not be able to do… [Continue Reading] -

Companies not using IoT data to create 'actionable insights'
Publié: août 8, 2016, 7:06pm CEST par Sead Fadilpašić
There is a "clear disconnect" between vision and the ability to execute that vision among companies that want to use Internet of Things (IoT) devices to collect data and act on them to improve product quality. Those are the results of a new study by LogMeIn’s Xively, entitled Simplifying the Complexity of IoT. It has an interesting point: more than half of surveyed companies are collecting data through their IoT devices, yet a third use it to create "actionable insights", benefiting both themselves and their customers. On the other hand, almost two thirds (61 percent) say product monitoring features are a "key… [Continue Reading] -

UK workers would like a six-hour workday
Publié: août 8, 2016, 11:50am CEST par Sead Fadilpašić
Some 11 million workers in the UK would very much like to see a six-hour workday, according to a new report by remote working solutions company, TeamViewer. TeamViewer says workers believe a six-hour workday would improve their work - life balance, and reduce their stress levels. Productivity is also expected to increase. The work - life balance thing is really important; for 79 percent, it’s more important than salary. Even more (82 percent) believe employees should be offered work flexibility, without them having to sacrifice their career for it. Almost three quarters (72 percent) agree flexibility makes them more effective,… [Continue Reading] -

Business apps are not ready for EU's GDPR rules
Publié: août 5, 2016, 5:49pm CEST par Sead Fadilpašić
Time is relentless. The GDPR is moving ever closer, while at the same time apps aren’t. And that’s a huge problem for businesses, because if apps are not GDPR-compliant, they’re not GDPR complaint. That can mean huge fines, possibly even the end of businesses. The fact that apps are far away from being GDPR compliant came as a result of a new and extensive study by Blue Coat Labs. The company analyzed more than 15,000 enterprise cloud applications in use and 108 million enterprise documents stored and shared within them. Cloud apps included Dropbox, Slack and Salesforce, all being rapidly… [Continue Reading] -

Business apps can greatly benefit from flash storage
Publié: août 5, 2016, 10:14am CEST par Sead Fadilpašić
Here’s an interesting thought -- if you don’t use flash storage, you risk reputation damage. Interesting conclusion, right? Well, this is basically what data management company NetApp is saying in its latest report. NetApp claims that almost a quarter (23 percent) of businesses risk damaging their reputation because they do not support business-critical applications with flash storage. The report is based on a poll of 1,000 IT decision makers. They say that features such as processing of payments, customer relation management (CRM) tools, and email marketing systems are key business applications, used by 40 percent, 36 percent, and 35 percent of IT… [Continue Reading] -

Most businesses experience four monthly disruptions
Publié: août 4, 2016, 8:16pm CEST par Sead Fadilpašić
Internet performance management company Dyn says businesses are still under a lot of disruptions, which severely hurts their internet performance, resulting in unsatisfied customers. The company polled 100 IT senior IT leaders from enterprises across the United States, and released the results in a report titled "Constant Website Disruptions Demand a New Kind of Performance Management". More than three quarters (78 percent) reported suffering at least four disruptions each month, and pretty much all of them (99 percent) say their websites were either "stagnant", or "slower" last year. Yet, those companies that use internet performance management, are "2.3 times more… [Continue Reading] -

Application control is a solid defense against ransomware
Publié: août 4, 2016, 7:17pm CEST par Sead Fadilpašić
Application control, such as greylisting, paired with selective local admin rights management, is 100 percent effective against ransomware and unwanted file encryption. This is according to CyberArk Labs’ new report, based on the analysis of more than 23,000 real-world samples from common ransomware families, such as Cryptolocker, Petya and Locky. More than 30 different malware families were tested, and the results posted in the report entitled Analyzing Ransomware and Potential Mitigation Strategies. The greylisting method was compared to the effectiveness of other, known strategies, such as anti-virus software which relies on blacklists. "Ransomware has emerged as a credible and opportunistic… [Continue Reading] -

AI will boost fintech revenue by 960 percent
Publié: août 4, 2016, 4:17pm CEST par Sead Fadilpašić
Earnings created by the use of artificial intelligence (AI) in financial technology (fintech) will skyrocket in the next five years, according to new reports by Juniper Research. The researchers have said that, by 2021, we should expect a jump of 960 percent, with revenues hitting $17 billion (£12.95bn). There are two main reasons behind such a significant jump in the near future, Juniper says. The first one is the fact that machine learning used to be way too expensive, and computationally time-intensive be hit the mainstream. That is no longer the case. The second reason is that access to extensive… [Continue Reading] -

Ransomware makes up half of all malware
Publié: août 4, 2016, 8:47am CEST par Sead Fadilpašić
Ransomware is no longer a quick and easy way for cyber-criminals to get their hands on some money. It is now considered a "permanent fixture on the threat landscape" -- at least according to PhishMe’s Q2 2016 Malware Review. The security experts’ new report says ransomware now accounts for 50 percent of all malware configurations, meaning it is now a mature business model. It also says it shows no outward signs of diminishing. There are three key trends which have been previously recorded, but are now considered "firmly established", by PhishMe, and those include Encryption Ransomware, Rise in evasion techniques,… [Continue Reading] -

Microsoft SharePoint remains 'underused' in spite of improvements
Publié: août 4, 2016, 2:47am CEST par Sead Fadilpašić
SharePoint continues to be an "underused" piece of software, despite Microsoft adding new features in hopes to increase the uptake. These are the results of a new survey by independent information management analysts, AIIM. The company polled 274 respondents, asking if they’re aware of what SharePoint has to offer. Less than half (43 percent) said they were "somewhat aware", while 29 percent said they had "no awareness at all". SharePoint is a piece of software enabling its users to collaborate on files, storing and synchronising group work files. Yet the report, entitled "The Impact of SharePoint -- 2016", states that… [Continue Reading] -

Cyber security is not a priority for most UK businesses
Publié: août 2, 2016, 9:41pm CEST par Sead Fadilpašić
Despite the constant warnings experts keep giving out to businesses concerning cyber-security, UK’s firms won’t be prioritizing it in the next 12 months. This is according to a new quarterly survey by Close Brothers. Its key takeaway is that 63 percent of companies decided not to invest in better security, while the other 37 percent decided to do so. The biggest problem with these results is that they show how UK’s businesses are not in line with the upcoming GDPR (General Data Protection Regulation). The GDPR, kicking off in mid-2018, will dictate how companies use and share their customers’ data, as well… [Continue Reading] -

Advanced technology is not in the cards for small UK businesses
Publié: août 2, 2016, 8:00pm CEST par Sead Fadilpašić
The UK might be a leader in advanced technology, such as driverless cars or 3D printing, but the majority of small organizations in the country don’t believe they’ll be using advanced technology any time soon. Those are the results of a new study by Axa Insurance. Just 20 percent (one in five) plan to migrate to the cloud in the next five years. Just six percent expect to adopt "smart technology", and eight percent believe they’ll be owning a driverless car by 2020. Another advanced technology -- 3D printing -- is also losing popularity, hard. Last month, the first 3D… [Continue Reading] -

Tesla acquires SolarCity in a $2.6 billion deal
Publié: août 2, 2016, 12:30pm CEST par Sead Fadilpašić
Tesla is buying SolarCity, a company selling solar power systems for homes and businesses. The electric car maker will shell out $2.6 billion (£1.97bn). Tesla’s founder and CEO, Elon Musk, is the same person that is also chairman and the largest stakeowner of SolarCity. So basically, Musk is merging his two companies into one which will offer "end to end clean energy solutions". SolarCity was founded by Musk’s cousins, CEO Lyndon Rive and director Peter Rive. You’ll have a business that will sell solar panels for you to generate clean electricity, Powerwall batteries where you’ll be able to store excess energy, and… [Continue Reading] -

US and UK facing IT 'talent crisis'
Publié: août 2, 2016, 7:44am CEST par Sead Fadilpašić
Both the UK and the US are in serious need of cyber-security talent, as there are hundreds of thousands of job vacancies in this industry that won’t be filled any time soon. This is according to a new report by Intel Security and CSIS, which polled businesses all over the world. There is a "talent crisis" in Australia, France, Germany, Israel, Japan, Mexico, US and UK. According to the report, titled Hacking the Skills Shortage, 82 percent of respondents said there is a shortage is cyber-security skills, and 71 percent said this shortage is directly to blame for damage caused… [Continue Reading] -

Communication issues growing concern for enterprises
Publié: août 2, 2016, 5:44am CEST par Sead Fadilpašić
Here’s an interesting finding: the number of downtime incidents, which prevent staff to work from their usual offices or access business-critical systems, has seen only a tiny drop -- five percent, compared to 2014. But the nature of these incidents has changed -- dramatically. According to Sungard AS’s new report, communication-related failures have "jumped by a third" and now account for 25 percent of all total invocations. Consequently, communication issues have, for the first time ever, been named as the top reason UK business invoke recovery services. But if the number of incidents remained pretty much the same, and communication-related issues jumped,… [Continue Reading] -

Security pros find it hard to measure ROI on spending
Publié: juillet 29, 2016, 8:51pm CEST par Sead Fadilpašić
The majority of IT security experts actually struggle to measure the return on investment in security measures, Tenable Network Security says. Based on a survey of 250 IT security professionals, conducted during the Infosecurity Europe 2016 summit, it says that the majority can only measure the return on less than 25 percent of their security spend. What’s more, just 17 percent were confident their investments were being distributed properly. "It’s undisputed that security is one of the top priorities for organizations across the globe", says Gavin Millard, EMEA technical director, Tenable Network Security. "However, our research revealed that many organizations… [Continue Reading] -

Russia becomes main target for DDoS attacks
Publié: juillet 29, 2016, 6:42pm CEST par Sead Fadilpašić
There has been a huge increase in the number of DDoS (distributed denial of service) attacks in the second quarter of this year, a new research report by security experts Nexusguard says. According to Nexusguard’s Q2 2016 Threat Report, there has been more than 182,900 attacks in Q2 this year, with the majority falling onto Russia. Yes, Russa has become the number one target country for DDoS attacks, with its Starlink internet provider soaking up more than 40 percent of the DDoS attacks measured over a two-day period. The average length of such attacks has gone from minutes to hours.… [Continue Reading] -

Dropbox launches AdminX dashboard for business users
Publié: juillet 29, 2016, 3:36pm CEST par Sead Fadilpašić
Dropbox has just announced AdminX, a new dashboard aimed at helping IT admins better manage Dropbox Business users. AdminX, which has been in development since last year, will have a couple of new features, including new versions of folders for both individuals and groups. With a more tier-style permission system across the board, it will tighten up security, and the permissions will be managed from AdminX. Enhanced file sync controls are also coming, which will allow admins to choose which files to sync locally, and which not to. That basically means files will be modified depending on the device they’re being… [Continue Reading] -

Financial services need to beef up crime protection and prevention
Publié: juillet 28, 2016, 8:30pm CEST par Sead Fadilpašić
Financial services need to rethink crime protection and prevention because the current measures are simply not cutting it, according to PwC. In the company’s new paper, it examines the industry to find out to what extent it is complying with the latest rules and regulations, whether it is investing heavily in protection and prevention, and what are the results. Basically, financial institutions have always been, and it seems as they will continue to be, cyber-criminals’ most wanted target. They are under intense scrutiny by regulators, and they are investing heavily in both protection and prevention. As a matter of fact, "the level of… [Continue Reading] -

Businesses are less high tech than they think they are
Publié: juillet 28, 2016, 5:39pm CEST par Sead Fadilpašić
Here’s an interesting prospect: the majority of companies that consider themselves high-tech have not invested nearly enough to become digital businesses. That is according to a report just released by Accenture, a global professional services and consulting company. Titled Accelerating Digital Performance in High-Tech, it says that just nine percent, out of 55 companies surveyed, are "digital high performers". The companies that were surveyed do a wide variety of businesses, from smartphone manufacturing, to telecoms equipment, software, and a "range of other high-tech products and services". What’s more, almost half (40 percent) say they haven’t even tried building their digital… [Continue Reading] -

How IT teams of the future will look
Publié: juillet 28, 2016, 4:25pm CEST par Sead Fadilpašić
IT teams will look completely different in the next five years, according to professional IT resourcing company Experis. The company has released a new report, titled Tomorrow’s Tech Teams, in which it polled 1,000 IT workers and 200 senior IT managers. Six in ten (59 percent) believe the traditional IT department doesn’t exist in modern business. IT teams of the future will look differently, with regards to contingent workers, skill sets, age and gender balance. The change is fueled mostly by the pressure to deliver additional services, such as cloud computing, strategic input for decision-making, or mobile apps. In order… [Continue Reading] -

Xen hypervisor has 'fatal' security vulnerability
Publié: juillet 28, 2016, 10:53am CEST par Sead Fadilpašić
Security expert Jérémie Boutoille from Quarkslab says that he has found a critical bug in the Xen hypervisor. The open-source hypervisor, which has the likes of Amazon, and IBM on its cloud clients list, has had a bug which could lead to potential privilege escalation. The bug, identified as CVE-2016-6258, affects all versions of Xen. However, only PV guests on x86 hardware should be worried. Hardware virtual machine (HVM) and ARM guests are deemed invulnerable. "Running only HVM guests will avoid this vulnerability", the researcher said in an advisory posted on the Xenbits website. In theory, the bug would allow… [Continue Reading] -

AMD unveils workstation Radeon Pro WX Series graphics cards
Publié: juillet 27, 2016, 8:57pm CEST par Sead Fadilpašić
We have a lot of news coming out of AMD’s kitchen, including new GPUs, an open-source rendering engine, and a new solution for large dataset applications. First in line is the Radeon Pro WX Series of professional graphics cards, aimed at modern content creation and engineering. It is based on the Polaris architecture, and AMD says it was built with open-source software in mind. The new cards are "designed for creative professionals and those pushing the boundaries of science, technology and engineering". A total of three cards were unveiled. The Radeon Pro WX 7100 GPU, created for engineering and media… [Continue Reading] -

Future ransomware will be scary-dangerous
Publié: juillet 27, 2016, 12:57pm CEST par Sead Fadilpašić
Here is a scary prospect. Ransomware that hides in a corporate network, analyzing it and multiplying itself until it is found on every machine in an organization. Only after it has contaminated every machine in a network will it activate, in a coordinated attack, bringing an entire company’s business to a screeching halt, until a large sum of money is paid to the attacker. Such an idea is not yet reality, but it’s not far from it, either. Cisco’s Midyear Cybersecurity Report says it is only a matter before we hit this milestone, mostly because ransomware has become the most… [Continue Reading] -

Teradata buys Big Data Partnership
Publié: juillet 26, 2016, 8:28pm CEST par Sead Fadilpašić
US-based data analytics company Teradata has acquired UK-founded Big Data Partnership. Maria Wagner, investment director at Beringea hopes the deal will serve as an inspiration to British startups that the global market is still open to them, despite Brexit results. Founded in 2012 by Mike Merritt-Holmes, Pinal Gandhi and Tim Seears, Big Data Partnership’s goal is to help businesses use the power of complex data. Two years ago, they got £1.2 million in a Series A funding, which was led by Beringea, transatlantic venture and growth investor. In a Series B round, in May 2015, Beringea again led to a total… [Continue Reading] -

Total iPhone sales will exceed one billion mark
Publié: juillet 26, 2016, 5:42pm CEST par Sead Fadilpašić
Just days after it was reported that Facebook has a billion people using Messenger, a similar thing will happen with Apple. The company has either already, or will very soon, sell its one billionth iPhone. In the last reported quarter (Q1 2016), it was unveiled that the company had sold a total of 987 million iPhones in the seven years since its inception. Some 40 million had been sold in the quarter alone, and according to Financial Times, analysts expect at least another 40m quarter ahead. And that, ladies and gentlemen, gives us a billion. "Microsoft wanted to put a… [Continue Reading] -

Here are the tools ISIS relies on to stay online
Publié: juillet 25, 2016, 8:48pm CEST par Sead Fadilpašić
Ever wonder how groups such as ISIS remain active online, no matter how hard people, or groups like Anonymous, try to kick them out? Data and intelligence firm Flashpoint asked the same question, and came up with six tools they use in their digital operations. The answers were published in a new research report titled Tech for Jihad: Dissecting Jihadists’ Digital Toolbox. "Jihadists’ reliance on technology for survival is a proven, powerfully motivating force, pushing the community to constantly learn, adapt, and advance through various technological tools", says Laith Alkhouri, a co-author of the report and the director of Middle… [Continue Reading] -

US government could save billions by modernizing its technology
Publié: juillet 25, 2016, 2:27pm CEST par Sead Fadilpašić
The US government could save $5.8 billion in technology cost, and at the same time modernize and improve the efficiency of its systems. This is according to the Information Services Group, a technology insights, market intelligence and advisory services company. Today, at the headquarters of the General Services Administration, it released a report, together with the Commission on IT Cost, Opportunity, Strategy and Transparency (IT COST). The report says that $55.9 billion, from the total $81.6 billion FY2017 budget for IT spending (approximately 75 per cent) goes to Operations and Maintenance. At the same time, $18.7 billion goes to development,… [Continue Reading] -

DDoS attacks are getting worse
Publié: juillet 22, 2016, 7:20pm CEST par Sead Fadilpašić
Just a couple of days after a horrendous DDoS attack took down Pokemon GO servers for a day, Arbor releases its new report on the state of DDoS around the globe, which basically says things are only getting worse. The reasons are still the same -- DDoS attacks are simple to launch, cheap and easy to obtain, for anyone "with a grievance and an internet connection". Over the past 18 months, Arbor detected an average of 124,000 DDoS attacks a week. The peak size jumped a stunning 73 percent compared to 2015, up to 579Gbps. Just in the first six months… [Continue Reading] -

Apple patches Stagefright-like vulnerability on iOS, OS X
Publié: juillet 22, 2016, 1:21pm CEST par Sead Fadilpašić
An equivalent to Android’s Stagefright vulnerability has recently been spotted on iOS and OS X devices. It has since been patched, and security experts from Sophos are urging all Apple users to patch up as fast as they can to protect themselves from the serious flaw. For those who are unfamiliar with it, Stagefright (in its multiple version) allowed a hacker to take over a victim’s Android smartphone by sending a message with an image or a video file. Long story short, it had something to do with the way Android managed images, and pretty much every Android version you… [Continue Reading] -

Most EMEA businesses are happy with Windows 10
Publié: juillet 22, 2016, 10:56am CEST par Sead Fadilpašić
Windows 10 is now used in 39 percent of businesses in the EMEA (Europe, Middle East, Africa) region, according to a new report by Spiceworks. Titled "Windows 10 Adoption: Sprinting out of the Gate", it reveals that the highest adoption rate is among companies with more than 250 employees -- 51 percent. Software, manufacturing and energy industries are where Windows 10 is most used. People are generally satisfied with the OS, too, which is a big weight off Microsoft’s chest, knowing that some previous versions got some nasty comments. Eighty-four percent of companies with Windows 10 said they were satisfied with the OS. Still,… [Continue Reading] -

Brexit will not make GDPR mandatory in UK
Publié: juillet 21, 2016, 8:07pm CEST par Sead Fadilpašić
Another day, another Brexit story. It’s going to be years before we stop hearing the various implications and results of the recently held UK referendum on leaving the European Union. This time, it’s about private data and its sharing to third-parties, by private companies, without users’ consent. Currently, users need to opt-out of data sharing if they don’t want businesses sharing and/or selling their data to third parties. These features are usually squeezed away somewhere in a tick box, or in the end-user license agreements, where it’s easily overlooked. The upcoming GDPR (General Data Protection Regulation) is going to change… [Continue Reading] -

Too strict mobile security can frustrate employees
Publié: juillet 21, 2016, 5:49pm CEST par Sead Fadilpašić
Executives are dancing on a thin line between state-of-the-art security for their company, and just overdoing it, frustrating their employees. This is according to a new report by BlackBerry Limited, which says that, as executives fail to implement the highest levels of security possible, they’re opening up their business to various vulnerabilities, mostly in the mobile segment. There’s an interesting survey following it -- 82 percent of executives said mobile security precautions cause "at least some frustration among employees" and is even being lined with hindered productivity. Overall, 44 percent believe too much security prevents people from doing their job.… [Continue Reading] -

Brexit vote doesn't affect UK jobs market
Publié: juillet 21, 2016, 1:03pm CEST par Sead Fadilpašić
The results of the Brexit vote don’t seem to have an immediate effect on the British job market, especially in the IT industry, according to a Morgan McKinley report. The global professional services recruiter also says that it still might be too early for a definitive conclusion. IT jobs in London were off to a slow start at the beginning of 2016, but that’s usually how things go in January and February. Interestingly enough, the slow period moved into the second quarter of 2016 in most sectors, and it wasn’t before the very end of the quarter that we saw… [Continue Reading] -

Average ransomware demand doubles in six months
Publié: juillet 21, 2016, 11:55am CEST par Sead Fadilpašić
Remember that recent article I wrote about how people value their online data much more than what extortionists are asking for when they hit them with ransomware? Well, extortionists seem to have caught on. Newest research paper from Symantec tells us that the average ransom demand is now £525, up from £223 at the end of last year. What’s more, the number of demands spiked to 56,000 in March, which is double the normal rate. Looking at new variants of ransomware, discovered this year, all but one were crypto-ransomware. Last year, 80 percent of new variants discovered were crypto-ransomware. The… [Continue Reading] -

Retailers believe social media is key for future growth
Publié: juillet 20, 2016, 10:03pm CEST par Sead Fadilpašić
Retailers consider social media extremely important for future growth, a new report states, adding that all of them use at least one social media channel. SAP’s new report, based on a face-to-face survey with retailers and SMEs between April and May 2016, reveals that almost a third (29 percent) of respondents use more than three social media channels. Facebook, LinkedIn and Twitter are considered the most popular, but Pinterest and YouTube are not that far behind. "Every customer we engage with has an interest in social media", says EJ Jackson, SVP & GM of SAP Anywhere. "The number using social media… [Continue Reading] -

Machine learning, big data analytics and Internet of Things skills are in high demand
Publié: juillet 20, 2016, 8:28pm CEST par Sead Fadilpašić
Both virtual and augmented reality, machine learning and big data analytics, as well as the Internet of Things, are the most in-demand skills, according to a new report by Packt. The report, titled "Skill Up", polled more than 11,500 worldwide developers and IT professionals. Besides identifying the most sought-after skills, it also says that security is one of the highest-paying industries in 2016, especially for freelancers. Bash, Perl and Scala are programming languages which will earn you most money, and online training is still a great way to acquire new skills. Python remains the "tool for all trades in 2016",… [Continue Reading] -

Businesses can minimize software costs by 30 percent
Publié: juillet 20, 2016, 3:03pm CEST par Sead Fadilpašić
Businesses can cut software costs by 30 percent if they stick to software management best practices, Gartner has announced -- research director Hank Marquis says potential savings are just "too large to ignore". Companies will spend $332 billion on it in 2016, so yes, it is a pretty big deal. There are three best practices organizations can use to achieve these savings: optimizing software configurations, recycling licenses and using software asset management (SAM) tools. "Automated software license optimization is a relatively new discipline and most organizations are at lower levels of maturity", says Marquis. "The variety of license entitlements also makes it tough for… [Continue Reading] -

Internet of Things and virtual reality will become essential to office life
Publié: juillet 19, 2016, 4:48pm CEST par Sead Fadilpašić
If your office technologies are not up to today’s standards, millennials are going to dump you. Seriously, almost half (42 percent) of people in that age group are willing to quit their job for this reason. The revelation is made in the Future Workforce Study, released by Dell and Intel. In it, it says that employees don’t really consider today’s workplaces "smart", even though they believe offices should definitely move in that direction. The two companies say the addition of both Internet of Things (IoT) and VR will soon be essential to office life. More than half believe their office… [Continue Reading] -

IT security pros shouldn't try to 'prevent everything'
Publié: juillet 18, 2016, 5:18pm CEST par Sead Fadilpašić
A new survey by Countercept by MWR InfoSecurity highlights all the frustrations IT security experts are experiencing as they’re trying their best to protect their company’s assets and employees. The survey, conducted during Infosecurity Europe, asked 301 IT security professionals about their company’s ability to detect and deter cyber-attacks. A third doesn’t believe they have the skills, manpower or technology to detect attacks "that matter". The report doesn’t say which types of attacks matter, and which not, although it rounds them all under those that "do damage". It did say, however, that an increased threat landscape, with laptops, tablets, smartphones,… [Continue Reading] -

Older Brits like to shop on tablets
Publié: juillet 18, 2016, 12:24pm CEST par Sead Fadilpašić
Tablets might have a rough time ahead of them, but if you ask UK’s consumers, aged 55 and above, they’re quite nice to use for shopping. That’s according to a new report by Bronto Software, which says that twice as many people in this age group (22 percent) use tablets for shopping, compared to their US (11 percent) and Australian (11 percent) peers. The UK has more tablets (60 percent), compared to the US (57 percent) or Australia (54 percent), and Brits use it for shopping more frequently (34 percent) compared to these two countries (25 percent and 19 percent, respectively).… [Continue Reading] -

Microsoft will release Azure Stack in mid-2017
Publié: juillet 15, 2016, 9:12pm CEST par Sead Fadilpašić
Microsoft has announced that its Azure Stack offering won’t be released before mid-2017. What’s more, it will come in appliance form, with just a few vendors -- so far only Dell, HPE and Lenovo -- being mentioned. Announcing the news in a blog post, corporate vice president for Enterprise Cloud, Mike Neil, says the decision has been made following months of feedback gathering. The feedback had shown that customers want a fast, and simple solution, instead of installing and configuring Azure Stack systems themselves. "To best meet these requirements, we will prioritize delivering Azure Stack as turnkey integrated systems in the initial… [Continue Reading] -

Printers can let hackers take control of Windows PCs
Publié: juillet 15, 2016, 7:26pm CEST par Sead Fadilpašić
Security researchers from Vectra Networks discovered a serious vulnerability in Windows which allows hackers to take control over complete computer networks through vulnerable printers. The report didn’t say which versions of the operating system are affected, but the patch is already issued and you can find it here and here. Everyone who has a printer attached to their system is strongly advised to patch ASAP. "This particular vulnerability enables an attacker to exploit the ease with which Windows machines connect to printers on networks", says Günter Ollmann, CSO of Vectra Networks. "While most devices require specific user or administrative permission before software… [Continue Reading] -

Ransomware victims pay less than they expect
Publié: juillet 15, 2016, 4:07pm CEST par Sead Fadilpašić
If you’re a cyber-criminal looking to enter the ransomware game, but not sure how much money you should demand for the unlocking of a victim’s files, don’t worry. Kaspersky Lab has done the research for you. The security firm, together with B2B International, says people value their smartphone data, on average, at $682. In 39 percent of cases, the figure exceeds $1,000. On the other hand, cyber-criminals which have managed to lock a victim’s device through ransomware, usually demand $300. "These figures explain why so many people are willing to pay extortionists, and once again, demonstrate the need for preventive protection measures… [Continue Reading] -

Facebook's 13,000 employees will use Microsoft Office 365
Publié: juillet 15, 2016, 7:51am CEST par Sead Fadilpašić
Facebook has signed a deal with Microsoft to use some of the software giant’s cloud-based productivity tools. Facebook’s 13,000 employees will use some of Microsoft's Office 365 services, such as email and calendar, while other services, like Skype for Business or Yammer, will not be used as directly compete with Facebook’s own. As a reminder, Facebook has recently developed Facebook at Work, a communications platform which allows co-workers to share content through the company’s well-known interface, but which also offers the security and admin features a professional environment would require. Before inking the deal, Facebook’s employees have been using on-premise… [Continue Reading] -

Shadow IT responsible for cyber attacks
Publié: juillet 15, 2016, 3:51am CEST par Sead Fadilpašić
Shadow IT has always been considered a huge risk to an enterprise’s cyber-security efforts, but now we have a new survey which supports the claim and shows the scope of the problem. The report, recently released by Tenable Network Security, says that both German and UK-based companies acknowledged shadow IT as a problem, but the former reported more cyber-attacks. That being said, 88 percent of IT decision makers in UK and German companies believe shadow IT makes them more vulnerable, with 65 percent of Germany-based respondents saying the use of shadow IT directly lead to a cyber-attack in the past… [Continue Reading] -

Robots can't understand advanced business processes
Publié: juillet 14, 2016, 9:51pm CEST par Sead Fadilpašić
In a time when some really intelligent people are expressing fears over intelligent robots, the worst thing you can do is tell a bunch of scientists that robots that smart can’t be made. Yet, that’s pretty much what shared services professionals said when they were polled by robotics and automation specialists Redwood Software, together with Shared Services Link, the online community for finance, shared services and outsourcing leaders. Out of more than a 100 polled, 67 percent said they plan on using robotic process automation in the next 12 months, 52 percent agree that they can "understand basic finance processes", while just… [Continue Reading] -

Many companies continue to rely on Windows Server 2003
Publié: juillet 13, 2016, 10:04pm CEST par Sead Fadilpašić
It seems that the constant expert warnings that legacy software should be avoided aren’t really resonating with businesses across the world. According to a new report by Spiceworks, more than half (53 percent) of companies all over the world have at least one instance of Windows Server 2003. That wouldn’t be much of an issue if the operating system’s EOL (end of life) date wasn’t a year ago (July 14, 2015). After that date, Microsoft has officially ceased supporting the product, stopped releasing patches and new updates, which means that companies still using Windows Server 2003 are actually putting themselves at a lot… [Continue Reading] -

CEO fraud scams target more than 400 businesses every day
Publié: juillet 13, 2016, 4:49pm CEST par Sead Fadilpašić
More than 400 businesses get targeted by CEO fraud scams every day, a new report by security researchers Symantec says. CEO fraud is a type of scam in which cyber-criminals target financial staff, often posing as CEOs or other executives, and request large money transfers. Even though it sounds too simple to work, its success rate is actually quite high, and relies mostly on putting financial staff under a lot of pressure through a sense of urgency, not giving them enough time to think things through. From those 400 daily targets, small and medium-sized businesses (SMB) are the biggest target… [Continue Reading] -

Enterprises leave vulnerable industrial control systems exposed online
Publié: juillet 12, 2016, 9:08pm CEST par Sead Fadilpašić
Industrial control systems (ICS) are not supposed to be connected to the Internet, Kaspersky Lab says, as it opens a sea of opportunities for hackers. Such systems are run by energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and drink, governmental, financial and medical institutions, and should be, for the sake of security, run in a physically isolated environment. However, Kaspersky Lab says that is not the case, and that it has found 13,698 ICS hosts exposed to the Internet, which very likely belong to large organizations. More than nine in ten (91.1 percent) host remotely-exploitable vulnerabilities,… [Continue Reading] -

UK wants mandatory insurance for self-driving cars
Publié: juillet 12, 2016, 7:14pm CEST par Sead Fadilpašić
Autonomous driving is an exciting prospect, but it’s not without its problems and ethical dilemmas. Recently, two Teslas were involved in accidents (two separate incidents), and in one of them the driver was killed. Such exciting technology also begs the question: who’s to blame when two autonomous vehicles collide, and what happens if someone gets killed in the process? The UK, which has stated on multiple occasions that it wants to be the global leader in autonomous vehicles, is tackling the issue from the insurance perspective. The UK government has launched a new consultation, under which autonomous cars could be insured. The… [Continue Reading] -

Brexit will impact IT spending in UK and Europe
Publié: juillet 12, 2016, 10:16am CEST par Sead Fadilpašić
Global IT spending is expected to be flat this year, hitting $3.41 trillion (£2.63tr), market analysts Gartner says. But an important factor hasn’t been taken into consideration. Gartner says the global IT spending will be up from last quarter’s 0.5 percent negative growth. These changes are mostly driven by fluctuations in currency, so it should be business as usual. However, the forecast was made assuming the UK would not vote to leave the European Union. As we all witnessed, that surprise move has shaken global economy, so different outcomes are now also a reality. "The current Gartner Worldwide IT Spending… [Continue Reading] -

Researchers store music video in DNA strain
Publié: juillet 11, 2016, 9:16pm CEST par Sead Fadilpašić
Researchers from Microsoft and the University of Washington managed to store a high-definition music video by OK Go into a DNA strain. This is actually much more serious than it sounds. A team of scientists and researchers stored 200 megabytes of data on a molecular strand, and thus set a new record. A bunch of data was added, including digital versions of works of art, the Universal Declaration of Human Rights in more than 100 languages, the top 100 books of Project Guttenberg and the non-profit Crop Trust’s seed database. Knowing IoT and Big Data are on the way, having a… [Continue Reading] -

Google's looking for 10 UK startups that 'think big'
Publié: juillet 11, 2016, 7:28pm CEST par Sead Fadilpašić
Google wants to help UK’s young start-ups make it big, and it’s kicking off a start-up camp to make it happen. A nationwide search has kicked off, with the goal of finding 10 start-ups "who think big". Applications are now open and will remain so until July 29. The 10 start-ups that do get selected, will have access to "bespoke support", including insights from London’s most experienced mentors and investors. The residential program will take place at Google’s space for start-ups, Campus London, and should kick off on Monday, August 22. At the moment, Google’s mentors are on the road,… [Continue Reading] -

Google acquires media streaming and monetization platform Anvato
Publié: juillet 11, 2016, 12:29pm CEST par Sead Fadilpašić
End-to-end video streaming and monetization platform Anvato announced recently that it has been acquired by Google, and that it will be joining the Google Cloud Platform team. Anvato is a video processing software solution, offering encoding, editing, publishing and distribution of videos on various platforms. The company’s clients include NBCUniversal, MSNBC, CBS, Univision, HGTV, Bravo and Fox Sports, and they use their services to power live streams, to edit videos directly in the cloud, and insert ads. The end-to-end service for both publishing and monetization is not something Google has on its platform, TechCrunch reports. "With OTT [over-the-top] adoption rapidly… [Continue Reading] -

Microsoft launches AppSource and Dynamics 365 enterprise apps
Publié: juillet 8, 2016, 10:52pm CEST par Sead Fadilpašić
Microsoft has introduced new business apps and services aimed to be intuitive, deliver helpful assistance, and improve the lives of their users. The new offerings are called Dynamics 365 and AppSource. Dynamics 365, available this fall, will unify the current CRM and ERP solutions into a single cloud service, with new apps to better manage specific business functions. Power BI and Cortana Intelligence are also integrated, to offer customers predictive analytics and prescriptive advice. Dynamics 365 will be deeply integrated with Office 365. AppSource is an application store, where businesses will be able to find and try out line-of-business SaaS apps from Microsoft… [Continue Reading] -

Microsoft COO Steve Turner will be Citadel Solutions' next CEO
Publié: juillet 8, 2016, 6:56pm CEST par Sead Fadilpašić
Steve Turner, Microsoft’s chief operating officer, and an important figure for the past 11 years, is leaving the company. With July’s end, Turner will abandon ship and join Citadel Solutions as its chief executive officer. Citadel Solutions is a division of Citadel LLC. Turner has been in charge of Microsoft’s worldwide sales, field, marketing and service organizations, and has been in charge of more than 51,000 people. He is also a member of Microsoft’s inner-circle senior leadership team. Following Turner departure, Microsoft says there basically won’t be a successor. Instead, it will disperse Turner’s responsibilities across a number of managers. Citadel said Turner will assume the CEO… [Continue Reading] -

Our private data is worth less than we think
Publié: juillet 8, 2016, 1:15pm CEST par Sead Fadilpašić
Brits think their personal data is really, really valuable. There is nothing wrong with that, and private data should be valued highly, and guarded as such. However, once criminals get a hold of such data, they’ll sell it for such a low price you simply won't believe. According to a new TotallyMoney.com report, based on a poll of 1,000 consumers, we value an email address at £983. In reality, it is being sold for five pence. A similar thing is with the browsing history. Its actual price on the black market is a ridiculous £0.0014. On average, we value it… [Continue Reading] -

Mozilla is working on a StumbleUpon-like feature
Publié: juillet 8, 2016, 10:38am CEST par Sead Fadilpašić
Mozilla has announced the creation of a new content recommendation system, which hopes will help people find better and more relevant content, easier. The new product is called Context Graph, and the company’s VP of Products, Nick Nguyen, describes it as a "better forward button". "The largest button on a modern browser is the back button. Trips to the web are short. Enter a search, get a result, click back, then try again", Nguyen writes in a Medium blog post. "This feels backwards (forgive the pun!). What if there was a better forward button?". Nguyen goes on explaining how the system will… [Continue Reading] -

Government IT pros overconfident about detecting insider threats
Publié: juillet 7, 2016, 5:45pm CEST par Sead Fadilpašić
Federal government IT professionals are overconfident in their ability to detect insider threats, endpoint security firm Tripwire has found. Analyzing the confidence of IT experts regarding their efficiency in seven key security controls, it polled 763 professionals from various industries. Almost a third say they would not be able to detect every time a non-privileged user attempted to access files. Almost three quarters (73 percent) assume their system would generate an alert or email within hours if a user inappropriately accessed file shares. "More and more, information security is about protecting sensitive data", says Tim Erlin, director of IT security and risk strategy… [Continue Reading] -

Facebook malware infects 10,000 users in two days
Publié: juillet 7, 2016, 10:37am CEST par Sead Fadilpašić
A new malware was spotted by security researchers at Kaspersky Lab, targeting Facebook users. According to the researchers’ new report, there have been 10,000 victims in two days. The malware has two stages: firstly, an unsuspecting victim gets a message from a Facebook friend, saying they had mentioned them in a comment. But when the victim clicks to see the comment, they instead download a bunch of malware, including a Chrome add-on which can take over the victim’s Facebook account, once they log back in. After that, anything is possible, including privacy settings changes, data extraction, and so on. The… [Continue Reading] -

Cost is not the main reason behind cloud adoption
Publié: juillet 6, 2016, 11:29pm CEST par Sead Fadilpašić
The notion that cloud computing solutions are being driven primarily by reduced costs, and that they’re causing IT teams to shrink everywhere seems to be significantly in the myths area. A new report by Six Degrees Group (6DG) points out that there are other, more important reasons, businesses opt for cloud solutions, and that teams are not necessarily shrinking, but reshaping mostly. Almost a third (31 percent) of respondents in the report say balancing cost management and value is their priority, and 23 percent are focused only on value. Cost is cited by just 15 percent of respondents. In terms of shrinking IT teams, yes,… [Continue Reading] -

IT teams of the future will have non-tech members
Publié: juillet 6, 2016, 6:43pm CEST par Sead Fadilpašić
Leadership, understanding of business objectives and project management are the three most important skills among businesses, a new report by IT resourcing company Experis says. In the report, entitled "Tomorrows Tech Teams", it was also said that IT teams will see an influx of people from a non-tech background, further complicating the existing IT skills shortage. For almost every IT leader, out of 200 that were questioned, the ability to learn new skills is as important as those that workers have today. According to those surveyed, future-proof IT teams will support continuous learning, and will have a training strategy responsive… [Continue Reading] -

Workers at fault for most cyber attacks
Publié: juillet 6, 2016, 12:08pm CEST par Sead Fadilpašić
Here’s another solid proof of what security experts have been buzzing about in the past few years -- that people are the single greatest cyber-security threat to businesses. This time, proof comes from Transputec and Business Continuity Institute, which have polled 369 business continuity professionals from all over the world into enterprise cyber-security. The results are clear. Among the companies targeted by cyber-criminals, in 60 percent of cases they were hit by either phishing, or social engineering. Spear phishing was mentioned 37 percent of times. The costs of these attacks "varied greatly", from less than €50,000 (£42,500, 73 percent of… [Continue Reading] -

Academics create algorithm that can detect if you're lying in emails
Publié: juillet 6, 2016, 11:07am CEST par Sead Fadilpašić
A lie has no legs, the saying goes, but when you’re online, you don’t need legs. You can cruise through the Internet, lying to people free of the little signals which could give you away, such as body language. This is a topic academics from the Cass Business School tackled, ultimately creating an algorithm that can detect lies in an email. I’m totally serious. It works by detecting "linguistic cues of deception". The paper, "Untangling a Web of Lies: Exploring Automated Detection of Deception in Computer-Mediated Communication" will be published in Journal of Management Information Systems. For example, liars tend not… [Continue Reading] -

BMW, Intel and Mobileye team up to make self-driving vehicles
Publié: juillet 6, 2016, 8:40am CEST par Sead Fadilpašić
It seems that the recent tragedy in which a person was killed while riding an automated Tesla vehicle isn’t discouraging car makers from pursuing their dream of fully autonomous vehicles on our roads. BMW Group, Intel and Mobileye have teamed up to bring fully autonomous vehicles to mass production within the next five years. That’s quite the triumvirate. The three companies, which have announced their partnership on July 1 at the BMW Group Headquarters in Munich, have recognized the scope of the challenge at hand, and said that they’ve created a set of milestones to track their progress. First, they’ll demonstrate an… [Continue Reading] -

Bitcoin is a 'safe haven' in a period of economical and political instability
Publié: juillet 6, 2016, 2:40am CEST par Sead Fadilpašić
Bitcoin’s transaction value has increased drastically over the past year, mostly because of both political and economic instability we’ve been witnessing in the past few years, according to a new Juniper Research report. Total value of the cryptocurrency’s transactions is expected to hit $92 billion (£69.3bn) this year, up from less than $27 billion in 2015. If you were hesitant on investing in the cryptocurrency, this new report, entitled "The Future of Cryptocurrency -- Deep Dive Data & Forecasting 2016-2021" should could give you the crucial nudge. It says chances are its value will go up, even more. Firstly, the report explains why… [Continue Reading] -

Video conferencing increases productivity
Publié: juillet 5, 2016, 10:21am CEST par Sead Fadilpašić
Video collaboration increases productivity and improves both business and personal relationships, according to video conferencing technology company Lifesize. The company polled its users and says that 99.2 percent of respondents find video conferencing boosts relationships both in and out of the office. No word on how many people were polled, though. Also, 91.7 percent of respondents say it is easier to get their point across when they can see the other person on video, and 77.7 percent say their productivity jumped, and their work-life balance improved. "Frost & Sullivan research findings are in line with the Lifesize survey results. The… [Continue Reading] -

Office workers find printers more important than PCs
Publié: juillet 4, 2016, 4:57pm CEST par Sead Fadilpašić
If you’d asked me what the most used item in the office is, I’d probably tell you the watercooler. But, according to new research, the most important one is the printer. Yes, the printer is more important than the computer. Or the pen. Or the stapler. The research was conducted by Danwood on 1,000 office workers. Out of that thousand, 81 percent cited the printer as the most important, followed by pens (73 percent), staplers (71 percent) and computers (70 percent). Almost half of the workers polled (46 percent) said print something every day, with 80 percent saying they need… [Continue Reading] -

Box launches Shuttle service for speed up data migration
Publié: juillet 1, 2016, 5:04pm CEST par Sead Fadilpašić
Box wants enterprises all over the world to migrate their data to the Box cloud, and it has now launched a new service to help them achieve that goal. The service, named Box Shuttle, enables businesses the migration of millions of files in a secure and timely fashion. Announcing the new product, the company said early feedback was "extremely positive". Box Shuttle offers a couple of services to businesses looking to go into the cloud, including planning and strategy (every business gets an individualized migration plan with key milestones), content analysis and lifecycle assessments (the company helps businesses decide which data… [Continue Reading] -

Box launches Shuttle service to speed up data migration
Publié: juillet 1, 2016, 5:04pm CEST par Sead Fadilpašić
Box wants enterprises all over the world to migrate their data to the Box cloud, and it has now launched a new service to help them achieve that goal. The service, named Box Shuttle, enables businesses the migration of millions of files in a secure and timely fashion. Announcing the new product, the company said early feedback was "extremely positive". Box Shuttle offers a couple of services to businesses looking to go into the cloud, including planning and strategy (every business gets an individualized migration plan with key milestones), content analysis and lifecycle assessments (the company helps businesses decide which data… [Continue Reading] -

Home alarms let users keep default credentials
Publié: juin 30, 2016, 6:08pm CEST par Sead Fadilpašić
German investigative journalists from the c’t magazine said many home security systems come with a huge vulnerability which can put every home using the system at risk. The vulnerability, however, is nothing fancy in hacking terms -- it’s pretty obvious and straightforward, but frequently overlooked. You see, similar to Internet routers, these home security systems are configured through a browser, and many come with easily crackable passwords like "1234" or "admin1234". These passwords are easily changed when setting up the system, but because the setup doesn’t require a password change by default, many users simply don’t do it. "When registering… [Continue Reading] -

Most enterprises use Internet of Things devices
Publié: juin 30, 2016, 11:12am CEST par Sead Fadilpašić
Even though IoT is an emerging industry, it is already being used by 65 percent of enterprises for business purposes, 451 Research claimed on Wednesday. According to the research company’s report, there are a couple of device types being used to gather valuable data: Datacenter IT equipment (51 percent) Camera and surveillance equipment (34 percent) Datacenter facilities equipment (33 percent) Smartphones and other end-user devices (29 percent) Manufacturing businesses collect 49 percent of data from factory equipment, while healthcare organizations take 49 per cent of data from medical devices. The data itself is split into three categories: Gathered from machines… [Continue Reading] -

IT pros training CEOs to spot phishing attacks
Publié: juin 29, 2016, 7:09pm CEST par Sead Fadilpašić
Out of 300 IT professionals attending the Infosecurity Europe conference, almost half (49 percent) believe their CEO has fallen victim to a targeted phishing attack. The results have been published in a new paper by unified security management and crowd-sourced threat intelligence company, AlienVault. More than three quarters (82 percent) still worry their CEO might be vulnerable to such attacks, but many fail to educate their CEOs and help them spot them. Less than half (45 percent) are training everyone in their organization, including the CEO, to spot phishing attempts, 35 percent offer such training to "most employees", while 20… [Continue Reading] -

Public Wi-Fi is unsecure
Publié: juin 29, 2016, 4:51pm CEST par Sead Fadilpašić
People are aware of the risks that come with using Wi-Fi, but generally believe public hotspots, like those on airports, are secure. Those are the results published in Norton’s latest Wi-Fi Risk Report 2016, which said 64 percent of UK’s adults assume public Wi-Fi is safe enough to use. However, Norton says this couldn’t be further from the truth. "We know many consumers believe that using a password to access public Wi-Fi means their information is safe, but that’s not necessarily the case", said Nick Shaw, vice president and general manager at Norton EMEA. By using these networks, people often… [Continue Reading] -

Workers find meetings productive
Publié: juin 29, 2016, 11:01am CEST par Sead Fadilpašić
You’ve probably heard it a million times, how meetings are actually a waste of time and do little good. You’ve also heard how people usually browse social media and look at the ceiling during these meetings, and that it would be more productive watching paint dry. Turns out, this couldn’t be further from the truth. Unified communications solutions company ShoreTel conducted a research into what the current workforce thinks about meetings, and the overall opinion is vastly positive. "Only 11 per cent of global respondents found meetings 'a waste of time'", it says. Almost half (40 percent) believe meetings were… [Continue Reading] -

Security researchers find major vulnerabilities in Uber
Publié: juin 28, 2016, 6:22pm CEST par Sead Fadilpašić
A group of hackers from a security company in Portugal managed to hack into Uber and get their hands on a bunch of data that should remain hidden. The team of three experts, Vitor Oliveira, Fábio Pires and Filipe Reis from Integrity, found a total of six flaws: they managed to use promotion codes, found private emails using UUID, found users’ phone numbers, created driver accounts, validated them, found where you went, who your driver was, and who you are and, ultimately, date of the trip, driver name and picture, the ID and the cost of the trip. The route map… [Continue Reading] -

IBM Summit will be the world's fastest supercomputer
Publié: juin 28, 2016, 2:59pm CEST par Sead Fadilpašić
After it was reported that China has the world’s fastest supercomputer, IBM unveiled a few details about its upcoming behemoth, which is already branded as the computer that will dethrone the Chinese Sunway TaihuLight. IBM's supercomputer is called Summit. It is expected to reach US Department of Energy’s Oak Ridge National Laboratory in early 2018, and should have a quarter more computational power than originally intended. Originally, the machine should have been capable of 150 petaflops. Instead, it will be capable of 200 petaflops. The Chinese Sunway TaihuLight is capable of 93 petaflops, 124.5 at peak performance. The deal is reportedly worth $325 million.… [Continue Reading] -

Intel Security is up for sale
Publié: juin 28, 2016, 10:07am CEST par Sead Fadilpašić
Intel is looking for a buyer for its Intel Security. Intel Security, previously called McAfee, was bought from the security firm McAfee back in 2011 for $7.7 billion (£5.75bn). Intel rebranded the company as Intel Security, and aimed to implement its security features at chip level, giving cyber-security a whole new dimension. It seems, though, six years later, the plan had failed. Intel Security is still an important company, doing valuable work, which is why Intel is expected to sell it for a lot more than it paid for it. Still no word on how much that might be, but IBTimes.co.uk… [Continue Reading] -

Crucial introduces NVDIMM persistent server memory
Publié: juin 27, 2016, 6:56pm CEST par Sead Fadilpašić
There’s a new type of server memory which might speed up backup restore and recovery, as well as help with salvaging any data left unsaved during a power outage. Memory and storage upgrade company Crucial has announced its Nonvolatile DIMM (NVDIMM) server memory. The company says this type of memory is a better choice for servers because it offers better read and write speeds than HDD or SSD disks, allowing for speedy backups and recoveries. "NVDIMM is a persistent memory solution for companies who have valuable data they need to protect in case of a power outage", said Michael Moreland, worldwide product… [Continue Reading] -

Businesses get used equipment and third-party maintenance
Publié: juin 27, 2016, 10:57am CEST par Sead Fadilpašić
More than half of IT decision makers opt to go for third-party maintenance (TPM) and pre-owned equipment, to cut costs and take advantage of improved support independent maintenance providers offer. It was also said they’ve had a "positive experience" with prior-generation hardware. The news was published by Curvature, an IT infrastructure solutions provider, which polled 500 IT decision makers. Out of the 500 respondents, 60 percent use TPM, and 53 percent decide to purchase pre-owned equipment. "Navigating through today’s complex landscape, IT buying decision makers face growing challenges. They need to take into account capabilities and quality of technology as well… [Continue Reading] -

Think twice before accepting LinkedIn invitations from strangers
Publié: juin 24, 2016, 2:07pm CEST par Sead Fadilpašić
Have you ever wondered if someone on LinkedIn is not really who they say they are? I’m not being paranoid here, this is a legitimate question. If your answer is "No", you’re not alone. A vast majority of people never wonder if there are fake accounts requesting to connect on the professional social network, and almost a quarter accept requests from people they don’t really know. This is a pretty big problem, according to Intel Security CTO, as accepting requests from people you don’t know opens you up to many risks, such as phishing or scams. Raj Samani, CTO EMEA… [Continue Reading] -

DevOps can help bridge the gap between software companies
Publié: juin 23, 2016, 7:23pm CEST par Sead Fadilpašić
High-performing organizations are widening the gap against low-performing ones, a new report on DevOps suggests. Entitled 2016 State of DevOps Report, it was released by Puppet and DORA (DevOps Research and Assessment), and is considered one of the largest, most comprehensive and longest-running studies on the topic of DevOps. High-performers deploy 200 times more frequently and have 2,555 times faster lead times. They recover 24 times faster from failed changes and have three times lower change fail rates. The report also said high-performers spend 22 percent less time on unplanned work and rework, and are able to spend 29 percent more time on… [Continue Reading] -

'No-cloud' policy to soon go extinct
Publié: juin 23, 2016, 4:24pm CEST par Sead Fadilpašić
Within the next four years, the extreme "no-cloud" policy among businesses will be as rare as "no-internet" policy is today, Gartner predicts. By 2020, however, not everything will be cloud-based, but companies having absolutely nothing in that respect will be almost extinct. "Aside from the fact that many organizations with a no-cloud policy actually have some under-the-radar or unavoidable cloud usage, we believe that this position will become increasingly untenable", says Jeffrey Mann, research vice president at Gartner. "Cloud will increasingly be the default option for software deployment. The same is true for custom software, which increasingly is designed for some variation of… [Continue Reading] -

Millennials would trust tech companies with money transactions
Publié: juin 23, 2016, 9:43am CEST par Sead Fadilpašić
There’s a new report suggesting that banks need to seriously consider innovating, if they don’t want to hand over their business to tech companies. The report, entitled "Are Banks Losing The Innovation Game?", was released by financial regulatory framework compliance experts, Neopay. It is based on a poll of 2,000 UK adults on their experience with high street banks and tech companies. Here’s the deal: the younger audience would rather trust a tech company with their e-money than a bank. Now, knowing that eCommerce is rising fast, it’s time for banks to start reacting, even faster. Almost half (41 percent)… [Continue Reading] -

Businesses want to spend more money on making apps
Publié: juin 22, 2016, 8:51pm CEST par Sead Fadilpašić
Businesses want to increase their spend on mobile app development, but we’re still a long way to go before that spending becomes more relevant, a new study by Gartner has shown. According to the market analysts’ report, overall app development budget allocated to mobile is 10 percent, a two percent decrease compared to the year before. However, almost half (42 percent) of organizations plan to increase their mobile app development spend by an average of 31 percent this year. "Demand for mobile apps in the enterprise is growing, but the urgency to scale up mobile app development doesn’t yet appear… [Continue Reading] -

Most UK businesses plan to introduce digital services
Publié: juin 22, 2016, 5:05pm CEST par Sead Fadilpašić
IT pros are feeling the pressure of digital transformation, as nearly 90 percent of UK’s businesses are looking to introduce digital services. According to CloudTalent, an Avanade company specializing in IT strategic advisory services, this challenge is greater than anything IT teams faced before. Of the surveyed IT decision makers going through digital transformation just 40 percent believe they’re making good progress, and a third (34 percent) are near the end of the process. Two thirds said they need to hire specialist IT consultants, while 94 percent say they’d already used their services before. Half are planning to place a larger… [Continue Reading] -

Big data management salaries see 8 percent rise in UK
Publié: juin 22, 2016, 2:30pm CEST par Sead Fadilpašić
If you were thinking about switching careers in order to start earning bigger money, you might want to consider a career in big data management. Reports started coming in that salaries for this position jumped eight percent this year, more than what the Bank of England forecast (three percent). Professional IT resourcing firm Experis also says that 5,148 advertised jobs in Q1 were in the big data segment, with 87 percent being in London. Other tech cities are closing the gap though, with Manchester, Leeds and Birmingham being notable examples. But it’s not just about the potential big data brings… [Continue Reading] -

Most UK tech workers against Brexit
Publié: juin 22, 2016, 9:10am CEST par Sead Fadilpašić
The tech industry is not really hyped about the UK’s potential abandoning of the European Union, according to new reports by market analysts. Juniper Research just released a new report which says that almost two thirds (65 percent) of UK’s tech employees believe Brexit would not have a positive effect on the global tech industry. There are multiple reasons why a positive outcome of Brexit would have a negative impact on the tech world, with two standing out. According to the surveyed, the UK would have a harder time attracting and recruiting talent from the European Union (70 percent). More… [Continue Reading] -

UK government wants to fine companies for data breaches
Publié: juin 21, 2016, 12:32pm CEST par Sead Fadilpašić
Even though the TalkTalk hack happened last October, it’s still sending ripples through the cyber-security world. The Department for Culture, Media and Sport has given a number of recommendations, following the breach. Among the recommendations is the idea of fining companies that fail on cyber-security, as well as the idea of linking the CEO’s pay to effective cyber-security. It should be easier for consumers to get compensation if their information was compromised in an attack, and the government should run a public awareness campaign about the dangers of the cyber-world. Companies that fail to report on data breaches on time… [Continue Reading] -

Majority of consumers will embrace digital assistants like Google Now and Siri
Publié: juin 21, 2016, 10:15am CEST par Sead Fadilpašić
Like it or not, we’re all going to have Batman’s Alfred Pennyworth soon. In a digital format, that is, but nonetheless an assistant. This was concluded by research specialists Gartner, which said that by 2019, at least a quarter of households in developed countries will use the services of a digital assistant, either on a smartphone, or in a standalone device. That will be the primary interface in interacting with connected home services, moving us into the "post-app" era. "In the not-too-distant future, users will no longer have to contend with multiple apps; instead, they will literally talk to digital… [Continue Reading] -

Hackers selling more than 70,000 compromised servers
Publié: juin 17, 2016, 7:22pm CEST par Sead Fadilpašić
Pssst! Hey, kids, wanna buy a remote desktop protocol server, cheap? I guess I should say "Вы хотите купить сервер?" Security researchers from Kaspersky Lab say they’d found a global forum, run by a Russian-speaking group, where hackers could buy access to compromised servers for as little as $6 (£4.25) per server. The forum, called xDedic, currently lists more than 70,000 of these servers for sale. Many provide access to "popular consumer websites and services", the researchers say, and some even have protocols installed for direct mail, financial accounting and point-of-sale (PoS) processing. These servers could be used as launching… [Continue Reading] -

The app generation wants to work in an office
Publié: juin 17, 2016, 5:59am CEST par Sead Fadilpašić
A new report by business communications provider Fuze challenges everything we think we know about the office of the future. While there’s been much talk about mobile and flexible working, and how the office is essentially dead, Fuze’s research states the exact contrary -- office will remain strong, if not stronger than before. This conclusion is based on a survey of 2,500 teenagers, aged 15 – 18, about what they consider essential for their future jobs. Surprisingly, having an office space where they can meet and collaborate with other people is very important. More than two thirds (69 percent) said… [Continue Reading] -

Average data breach cost rises to $4 million
Publié: juin 16, 2016, 7:42pm CEST par Sead Fadilpašić
The average cost of a data breach has jumped 29 percent since 2013, a new report by IBM Security and the Ponemon Institute says. This brings the figure up to $4 million per breach. The number and the severity of these incidents keeps on growing, the two companies said in the report. There have been, according to the report, 64 percent more reported security incidents in 2015, than the year before. As the complexity of the attack rises, so does the cost. Breaking the numbers down, it was said that a single compromise record costs the company $158. Among highly… [Continue Reading] -

App collusion is not a myth anymore
Publié: juin 16, 2016, 12:28am CEST par Sead Fadilpašić
Up until today, app collusion for malicious purposes has been in the domain of myths and urban legends, but according to a new report by Intel Security, no more. The security firm released its latest security report, entitled McAfee Labs Threats Report: June 2016, in which it says that it had found some apps capable of app collusion. For those unaware of the term: app collusion is a practice in which two (or more) apps are commanded by a cyber-attacker, and work together to extract valuable information from a smartphone. It requires for one app (example -- a banking app)… [Continue Reading] -

Major websites are vulnerable to advanced bots
Publié: juin 15, 2016, 4:32pm CEST par Sead Fadilpašić
Pretty much every top website, in retail, financial services, consumer services, OTA members (Online Trust Alliance), news and media, and top US government agencies, is vulnerable to advanced bots, new research says. Bot detection and mitigation company Distil Networks, analyzed 1,000 top websites in these verticals, and how they behave against crude, simple, evasive and advanced bots. All of the verticals performed quite well against crude bots, (75 percent in consumer services, 70 percent in government, 65 percent in financial services, 64 percent in news and media, 78 percent in retail and 67 percent in OTA members), but when it… [Continue Reading] -

IT vs security pros: Handling appsec
Publié: juin 15, 2016, 9:29am CEST par Sead Fadilpašić
A new report into corporate app security, conducted by runtime application security visibility and protection company Prevoty, shows significant discrepancies between IT and security professionals, when it comes to app security. The report, entitled "The Real Root Cause of Breaches -- Security and IT Pros at Odds Over AppSec", is based on a poll of more than 1,000 IT and security professionals and says there are major divides in how these two groups handle app updates, app security tuning and backlogging. Half of IT professionals update an app every one to six months, while half (52 percent) of security experts do… [Continue Reading] -

EMEA businesses too slow to detect a data breach
Publié: juin 14, 2016, 9:51pm CEST par Sead Fadilpašić
It takes businesses in the EMEA region (Europe, Middle East, Africa) three times longer than businesses elsewhere in the world to detect a breach, mostly because they’re forced to detect such hits themselves instead of relying on outside help. Those are the general conclusions of the first Mandiant M-Trends EMEA Report. The report, released by security experts FireEye, is based upon the statistics collected during investigations in the region, done by Mandiant’s leading consultants in 2015. The report says that EMEA businesses need, on average, 469 days to detect a breach. High number, knowing that globally it takes about 146… [Continue Reading] -

Microsoft sells 1.1 million Surface units in Q1 2016
Publié: juin 13, 2016, 8:20pm CEST par Sead Fadilpašić
Two-in-one and pro slate devices have earned their vendors higher revenue, managing to stabilize average selling prices, a new report by Strategy Analytics says. The report, entitled "Global Tablet Vendor & OS, Unit & Value Market Share by Region: Q1 2016", says Microsoft and Apple sold more than a million of their pro slates last quarter. What’s more, most mobile-first and smartphone vendors now have pro slates with an optional keyboard, or 2-in-1 tablets in stock, to "sate growing demand for these converged computing devices". And here I was, thinking the tablet market was done for. I guess there’s still… [Continue Reading] -

IT pros: Cloud apps are as secure as their on-premise counterparts
Publié: juin 13, 2016, 6:39pm CEST par Sead Fadilpašić
For the first time ever, the majority of cybersecurity professionals believe cloud-based apps are as secure as on-premise apps. Those are the results of a new survey conducted by Bitglass, among 2,200 cybersecurity experts. According to the report, entitled The Rise of Purpose-Built Cloud Security, 52 percent of those surveyed said they found cloud-based apps as secure as their on-premise counterparts. The most interesting thing is that this percentage has jumped from 40 percent same time last year. But just because apps are believed to be secure, it doesn’t mean businesses are. The report also says that user behavior, such… [Continue Reading] -

Dell launches new PowerEdge servers
Publié: juin 13, 2016, 3:23pm CEST par Sead Fadilpašić
Dell has announced that it has upgraded its 13th generation PowerEdge four-socket server portfolio. The new servers, designed with big-data and real-time analytics in mind, offer more flexibility, scalability and manageability. This includes four new offerings: the PowerEdge R830 and PowerEdge R930 servers, PowerEdge FC830 -- a full-width, four-socket compute node for the Dell PowerEdge FX architecture -- and PowerEdge M830 blade server. All servers now come with better processors (Intel Xeon E5-4600 v4 and Intel Xeon E7-8890 V4 for the PowerEdge R830 and PowerEdge R930, respectively). The PowerEdge R930 holds the world record result on the standard benchmark for… [Continue Reading] -

Two in three commercial apps with open source code have security vulnerabilities
Publié: juin 13, 2016, 10:34am CEST par Sead Fadilpašić
"If you’re using open source, chances are you are likely including vulnerabilities known to the world at large". This is a quote taken from the latest open source security report released by software company Black Duck. The company analyzed more than 200 applications that are based on, or partially use, open source material, over a six-month period. The results are that 67 percent of them have vulnerabilities, and every application has at least five vulnerable components. It was found that more than 10 percent have the Heartbleed vulnerability, and almost 10 percent POODLE. LogJam and FREAK were present at almost… [Continue Reading] -

Many UK workers don't know what ransomware is
Publié: juin 10, 2016, 6:38pm CEST par Sead Fadilpašić
It seems all that talk by security experts how employee education is the best way to protect a business from a cyber-attack has fallen on deaf ears. A new study by ISACA, based on a poll of 2,000 UK consumers, says that more than half of those haven’t gotten any cyber-security awareness training, at all. Here is what having no cyber-security training gets you: more than a third (36 percent) of employees not being able to spot a phishing email, 19 percent falling for a phishing scam, and 33 percent choosing a speedy internet over a secure one. The report,… [Continue Reading] -

Three in four apps do not meet GDPR requirements
Publié: juin 10, 2016, 2:59pm CEST par Sead Fadilpašić
Using cloud apps in a business environment, be it Shadow IT or not, is going to be risky business in a couple of years, as a vast majority of today’s widely used apps do not comply with the upcoming rules and regulations of the EU GDPR. GDPR, or general data protection regulation, is a EU-crafted document aimed at regulating the corporate use of data, and how businesses must act in order to ensure maximum safety of customer data used, as well as privacy. It will come into force in less than two years. Cloud access security broker Netskope, researching deeper… [Continue Reading] -

European workers use cloud services for whistle blowing
Publié: juin 9, 2016, 7:41pm CEST par Sead Fadilpašić
Wait until you hear what employees in Europe are using cloud services for. Oh, boy. Blue Coat Systems has polled more than 3,000 workers in France, Germany and the UK, asking them about their cloud usage habits, and, as it turns out, some employees use such services (Dropbox, Box, Office 365, Slack, LinkedIn, Facebook, Gmail, etc.) to store data before starting a new job, for corporate espionage, whistle-blowing and even "personal protection". Eight percent of employees said they stored data to be later used for whistle-blowing, and those employees are most usually HR professionals (17 percent). "This research highlights the behavioral… [Continue Reading] -

Number and frequency of DDoS attacks rising
Publié: juin 9, 2016, 6:06pm CEST par Sead Fadilpašić
The number, and the frequency of DDoS attacks (distributed denial of service) continues to grow, a new report by content delivery network (CDN) services provider Akamai Technologies says. The company said its DDoS mitigation platform, the Akamai Intelligent Platform, mitigated 4,500 DDoS attacks during the first quarter of 2016, representing a 125 percent jump, compared to the same period last year. Almost all attacks were based on reflection attacks using stresser/booter-based tools. More than half of attacks (55 percent) were against gaming companies, with 25 percent targeting the software and tech industry. The report also highlights a new record in… [Continue Reading] -

Older workers can handle new technology
Publié: juin 9, 2016, 4:41pm CEST par Sead Fadilpašić
The stereotype of older people having trouble using new technology is nothing more than that -- a stereotype. At least, according to a new report by Dropbox and Ipsos Mori. The two companies surveyed more than 4,000 workers aged 55 and more about their use of technology in the workplace. The results will most definitely be surprising to some. Older workers use, on average, 4.9 forms of technology per week. An overall average is 4.7. They also find using technology in the workplace less stressful than their younger colleagues. Only a quarter of this workgroup found tech in the workplace stressful,… [Continue Reading] -

Majority of web services and mobile APIs are unsecure
Publié: juin 8, 2016, 9:01pm CEST par Sead Fadilpašić
More than 60 percent of web services, or mobile app APIs have at least one high-risk vulnerability, which can potentially lead to a compromised database. Those are the results of a new and comprehensive report by High-Tech Bridge, summing up the trends in web security for the past six months. The report also says that in case a website is vulnerable to cross-site scripting (XSS), it is also vulnerable to other critical flaws, in at least 35 percent of cases. Other vulnerabilities include SQL injection, XXE or improper access control. When it comes to HTTPS encryption, 23 percent of websites… [Continue Reading] -

People spend less time on social networks
Publié: juin 8, 2016, 6:16pm CEST par Sead Fadilpašić
The amount of time people spent in apps of social media networks in the first three months of 2016, in nine major countries in the world, has dropped "dramatically", a new report by digital market intelligence company SimilarWeb says. Facebook, Twitter, Instagram and Snapchat have all seen significant drops in the amount of time people in the US, UK, Germany, Spain, Australia, India, South Africa, Brazil and Spain have spent in Q1 2016, compared to the same period a year before. Image-sharing network app Instagram has seen the biggest drop (23.65 percent year-on-year), followed by Twitter (23.44 percent), Snapchat (15.74… [Continue Reading] -

Businesses that don't allow card payments are making customers' life difficult
Publié: juin 7, 2016, 9:15pm CEST par Sead Fadilpašić
People like paying with plastic and those businesses that don’t enable easy card payment methods risk destroying themselves, a new survey suggests. According to a report by Worldpay, 60,000 of small and medium-sized businesses (SMB) in the UK are "making life difficult" for those that dislike carrying cash around and they’re risking ruining their own businesses because of it. A quarter (25 percent) of consumers have started avoiding businesses that don’t take cards, the report says, with a further 30 percent saying they only use cash when it’s "absolutely necessary". Almost two thirds (60 percent) of people aged 24 -… [Continue Reading] -

Responsive websites trump mobile apps
Publié: juin 7, 2016, 7:53pm CEST par Sead Fadilpašić
GovInsider recently did an interview with Ben Terrett, the former head of design at the UK Government Digital Service (GDS), about the GDS’s success in the digital realm. The two discussed mobile apps, why websites are better, and what needed to be done in order to have a successful digital project. Terrett said the problem with mobile apps is that they are a huge undertaking -- not only is it expensive to make an app (or multiple apps, or an app ecosystem) but also to support it and update it following various software changes. Apps are "very expensive to produce, and… [Continue Reading] -

There's no confidence in Internet of Things security
Publié: juin 3, 2016, 8:34pm CEST par Sead Fadilpašić
During the IOActive IOAsis event in San Francisco, security professionals were asked on their opinion on the state of security among Internet of Things (IoT) devices, and the results are not encouraging. According to the IOActive Internet of Things Security Survey, based on this poll, almost half (47 percent) of respondents felt less than 10 percent of IoT devices have appropriate security measures. Almost nine out of ten (85 percent) believe less than half of IoT devices are secure. What’s even more depressing is that 63 percent of these people also think IoT has better security measures than other devices. Everyone… [Continue Reading] -

Human error and data breaches go hand in hand
Publié: juin 3, 2016, 5:11pm CEST par Sead Fadilpašić
There have been significantly more data breaches this year, compared to the year before, new figures from Egress Software Technologies suggest. The company cross-checked data from security breaches in the past three years and says that 66 percent of the business sectors surveyed reported an increase in data breach occurrences. It would have been even higher if healthcare organizations haven’t had "just" a 13 percent increase. Attacks against insurance firms jumped 317 percent, general businesses 157 percent, solicitors and barristers 127 percent, and even charities at 109 percent. But perhaps even more worryingly, the report says that human error accounted… [Continue Reading] -

Server shipments increase, revenue declines
Publié: juin 3, 2016, 9:08am CEST par Sead Fadilpašić
Gartner has released new figures about the state of server shipments worldwide, and even though growth has been recorded, that’s not real a success story yet. According to its figures, global servers shipment increased 1.7 percent year-on-year, but revenue declined 2.3 percent. The research company says this means that servers which were being sold same time last year were more expensive than the ones being sold now. "Although revenue declined, the first quarter of 2016 continued with a trend of low-level shipments growth on a global level with a variation in results by region", says Jeffrey Hewitt, research vice president at Gartner.… [Continue Reading] -

Internet of Things devices will surpass smartphones by 2021
Publié: juin 2, 2016, 7:59pm CEST par Sead Fadilpašić
Before we reach 2021, there will be more internet-connected devices (IoT) than smartphones, Ericsson said in its latest Mobility Report. Projected growth of these devices is 400 percent in the next five years, with a total of 16 billion devices expected by that time. One of the main drivers of adoption will be regulatory requirements, Ericsson argues, saying that things like smart utility meters will be leading the charge. Paired with a growing demand in internet-connected cars, and you get a significant spike in adoption. "IoT is now accelerating as device costs fall and innovative applications emerge. From 2020, commercial… [Continue Reading] -

Expect to lose data when your SSD fails
Publié: juin 2, 2016, 9:48am CEST par Sead Fadilpašić
As more people are switching from HDDs (hard disk drives) to SSDs (solid state drives), more data loss is occurring, a new report by Kroll Ontrack suggests. SSD disks might be solid in their state, but don’t seem to be more reliable than HDD disks. Still, it doesn’t stop their popularity growth. Out of 2,000 global respondents to the Kroll Ontrack survey, 92 percent are using SSD technology, with more than a third (38 percent) having experienced an SSD failure. Of those failed disks, almost a quarter (23 percent) lost data. "Businesses and consumers continue to move toward SSD technology",… [Continue Reading] -

New API helps open-source developers 'become license-aware'
Publié: juin 1, 2016, 8:28pm CEST par Sead Fadilpašić
The Open Source Initiative (OSI), the steward of the Open Source Definition (OSD), announced today it has created a machine readable publication of OSI approved licenses. According to the organization, the API will allow third parties to "become license-aware", giving businesses everywhere the means to determine if a license is open source or not. The Open Source Initiative considers this the next "logical step" and quite important, knowing all the copyright and license legal battles going on nowadays, and how expensive they can be. Open Source Lead at GitHub, Brandon Keepers offered, "A canonical, machine-readable source of license metadata is… [Continue Reading] -

420 million mobile device users block ads
Publié: juin 1, 2016, 2:39pm CEST par Sead Fadilpašić
Businesses whose revenue come from mobile ads will seriously have to consider an alternative, because news just came in about a significant rise in mobile ad blocking usage. According to a new report by PageFair, a start-up helping publishers get around ad blockers, and mobile app tracking company Priori Data, there has been a 90 percent rise in mobile ad blocking usage, compared to the same period last year. That amounts to a total of 420 million mobile users, worldwide, or every fifth person. Interestingly enough, this is a trend most popular in the Eastern part of the world --… [Continue Reading] -

New Microsoft Ventures to invest in promising startups
Publié: juin 1, 2016, 10:36am CEST par Sead Fadilpašić
Microsoft has today announced a new department designed to invest into disruptive start-ups in their early phases. The department, led by Nagraj Kashyap (corporate vice president) and executive vice president of business development Peggy Johnson, holds the name Microsoft Ventures. This is not to be confused with the "old" Microsoft Ventures. That arm, now called Microsoft Accelerator, helps start-ups with technology and expertise, but rarely cash. Microsoft Ventures will look for early-days start-ups in cloud, security and machine-learning markets, those that can complement their Azure cloud services, among other things. Basically, Ventures will sit somewhere between the Accelerator, and larger… [Continue Reading] -

SWIFT hack affects 12 more banks
Publié: mai 31, 2016, 5:51pm CEST par Sead Fadilpašić
Earlier reports of a couple of banks using the SWIFT (Society for Worldwide Interbank Financial Telecommunication) system being hacked are now paired with new reports saying that additional 12 banks using the same system might have fallen victim to the attack. According to security researchers FireEye, which have been investigating the matter, "numerous" other banks have contacted them, including banks from the Philippines, and New Zealand. Even though the majority of these attacks were thwarted, approximately $81 million made it to the Philippines and ended up at casinos, where its trail is lost. At the same time, SWIFT warns that… [Continue Reading] -

Hacker offers 427 million MySpace passwords for just $2,800
Publié: mai 31, 2016, 11:29am CEST par Sead Fadilpašić
You know your website isn’t worth much when a database of 427 million stolen login credentials are being sold online for roughly $2,800 (£1,920). Yep, that’s what happened to MySpace over the weekend. But Myspace not being worth much nowadays is not the news. Possibly the biggest login credentials theft, is. Reports say that a hacker going by the name Peace is selling this huge database online, in the dark web marketplace called The Real Deal. He’s asking for six Bitcoin. It is hard to say if the database is legitimate or not. It seems like the person behind this database is the same… [Continue Reading] -

CEO falls for email scam, loses $47 million
Publié: mai 31, 2016, 7:17am CEST par Sead Fadilpašić
An airplane parts manufacturer has fired its CEO after the poor guy got scammed, costing the company €42 million ($47 million). "In the supervisory board meeting, held on May 24, 2016, Mr. Walter Stephan (CEO) was revoked by the supervisory board as chairman of the management board of FACC AG with immediate effect for important reason. The supervisory board came to the conclusion, that Mr. Walter Stephan has severely violated his duties, in particular in relation to the 'Fake President Incident'. Mr. Robert Machtlinger was appointed as interim CEO of FACC AG". The 'Fake President Incident' the announcement is referring… [Continue Reading] -

Lazarus may be responsible for Bangladesh Central Bank hack
Publié: mai 30, 2016, 6:51pm CEST par Sead Fadilpašić
The group that tried to steal a million dollars from the Vietnamese Tien Phong Bank, managed to steal $81 million from Bangladesh's Central Bank, and managed to steal $12 million from a bank in Ecuador, also attacked a bank in the Philippines. However, it remains unclear if the group actually managed to steal any money from this bank or not. What we do know, though, is that all these attacks seem to be pointing at the same hacking group, known as Lazarus. That is the conclusion security experts came to, after analyzing the source code of the malware used in… [Continue Reading] -

Citrix to offer cloud services through Microsoft Azure
Publié: mai 30, 2016, 5:36pm CEST par Sead Fadilpašić
Citrix and Microsoft announced recently that they will be expanding their partnership. More precisely, Citrix will use Microsoft’s Azure as its cloud. Besides Azure, they will also integrate Citrix XenMobile and NetScaler into Microsoft’s Enterprise Mobility Suite. Once the partnership kicks in, Citrix customers will get the opportunity to manage Windows 10 images on Azure, through XenDesktop virtual desktop infrastructure. The only condition is that you need a licensed, per-user Windows 10 Enterprise. The cooperation works both ways. Citrix wants to help its customers deploy more virtual apps and desktops, while Microsoft is looking to boost the installation of Windows… [Continue Reading] -

Financial services believe blockchain is the biggest innovation since the Internet
Publié: mai 27, 2016, 2:01pm CEST par Sead Fadilpašić
Blockchain is the most important innovation since the creation of the internet, almost two thirds (60 percent) of global financial services retailers with some knowledge of the technology said. That’s a bold claim. And that’s exactly why the fact that more than a third (35 percent) of all global respondents said they had never heard of the technology is even more scary. Among those that have heard of it, 23 percent said they had no understanding of what blockchain actually is. The study was conducted by Marketforce, on behalf of business applications provider Pegasystems and information technology provider Cognizant. It… [Continue Reading] -

Toyota bets on Uber
Publié: mai 26, 2016, 7:26pm CEST par Sead Fadilpašić
Ahh, the battle in the car industry is heating up. Quick, everyone, grab your popcorn! After both Lyft and Gett found investors in the form of General Motors and Volkswagen, respectively, it is Uber’s turn to get funded, and the car making company with the pleasure is none other than Toyota. The news broke out on Bloomberg’s Technology site, although it didn’t say how big the investment was. Both Uber and Toyota are keeping quiet about the matter, but it seems as the investment is not astronomical. "The Japanese automaker has no interest in taking a big position in the ride-sharing… [Continue Reading] -

Nearly half of European workers use personal devices for work
Publié: mai 26, 2016, 6:39pm CEST par Sead Fadilpašić
Shadow IT, or stealth IT, is a practice still commonly used by European workers, according to a new Fuze report. It means employees are using either hardware or software that has not been directly approved of by the IT department, risking security breaches. The report, entitled "App Generation report", argues that 40 percent of employees are using their personal devices for work. The same goes for software and apps. The survey includes answers from 5,000 workers and 2,500 teens across Europe. Besides mobile phones, 32 percent of workers in the UK use their own laptops for work, and 21 percent… [Continue Reading] -

One in three drivers don't know their car has connectivity features
Publié: mai 26, 2016, 11:47am CEST par Sead Fadilpašić
Pretty much every car will have connectivity features within the next four years, but consumers are still unaware of the benefits this new technology brings. Thirty-nine percent of drivers are unaware their car has connectivity features, at all. Manufacturers are also unsure how to use the opportunity to open new revenue streams, busting the doors wide open for technology giants. Those are the results of a new study conducted by TNS and the BearingPoint Institute. It includes 3,700 owners of connected cars in Europe. One of the highlights of the report is that people are very excited about new features,… [Continue Reading] -

Business leaders: Anticipating future tech trends is not in our job description
Publié: mai 25, 2016, 7:33pm CEST par Sead Fadilpašić
Business leaders understand the importance of data analytics, and will do what it takes to make sure their company’s data needs are met. However, they don’t think they should be anticipating future trends in order to take full advantage of any upcoming opportunities. Those are the results of a new study conducted by The Economist Intelligence Unit (EIU), and sponsored by Microsoft Cloud. The study is entitled Transforming Business, and says that 67 percent of survey respondents (including IT leaders, HR leaders, finance and sales & marketing people), are "somewhat" or "very" confident about their department’s ability to use data.… [Continue Reading] -

Millennials realize social media mistakes could damage their career
Publié: mai 25, 2016, 5:30pm CEST par Sead Fadilpašić
That half-naked butt-selfies millennials sometimes take on top of their washing machine in the bathroom are coming back to haunt them, as they start looking for their first (or new) job, a new survey says. The survey by cyber-security firm Norton and recruitment firm Reed says UK millennials (18 - 34 year-olds) are now concerned how their social media activity might interfere, and damage, their professional careers. Sixteen percent are worried they might have work-related issues thanks to their social media activity, and almost every other hiring manager (48 percent) said they’d found something online that had stopped them from… [Continue Reading] -

Mobile security is not a concern for European workers
Publié: mai 24, 2016, 2:40pm CEST par Sead Fadilpašić
Businesses in the UK, as well as elsewhere in Europe, are not really worried about security, as their employees increasingly use company mobile devices, new research has shown. Secure identity solutions firm HID has revealed that 77 percent of employees in the UK aren’t concerned about mobile security, highlighting a pretty high level of confidence in they have in mobile security. Looking at Germany, the percentage stands at 82. Overall, 74 percent of European workers are confident about using corporate mobile devices. "These results underline how mobile users in the workplace are confident in the ability of their companies to keep… [Continue Reading] -

Hackers using bot armies for financial gain
Publié: mai 23, 2016, 1:53pm CEST par Sead Fadilpašić
A new security report by digital identity company ThreatMetrix says hackers are using a large army made out of "automated cyber robots", or bots, for financial gain. Their Q1 2016 report, entitled Q1 Cybercrime Report, says there have been 311 million bot attacks detected and stopped in this year’s first quarter. Although the report fails to mention exactly how these bots are utilised to earn their masters money, it mentions two types of attacks: "loud and fast" and "low and slow". It says that fraudsters first buy large batches of login credentials on the dark web, and test them to… [Continue Reading] -

Consumers don't trust companies with their data, but they're willing to share personal info
Publié: mai 20, 2016, 8:32pm CEST par Sead Fadilpašić
Consumers in the EMEA region (Europe, Middle East, Africa) are fairly skeptical about companies keeping their data safe, but are willing to share personal information to get something in return anyway. Those are the results of a new and extensive research by F5 Networks, which had asked more than 7,000 consumers in UK, Germany, France, Bene, United Arab Emirates, Saudi Arabia and Poland about their online shopping habits, and data attitudes. Almost three quarters (70 percent) of consumers fear data they share with private companies would end up in the wrong hands. Just above two thirds (64 percent) are afraid… [Continue Reading] -

European IT departments want to invest in cloud and security
Publié: mai 20, 2016, 5:26pm CEST par Sead Fadilpašić
Another confirmation of the heading IT departments are taking this year comes to us from tech giants Toshiba. After an extensive research into business practices in IT departments across Europe, it was found that cloud-based solutions (56 percent) and data security (50 percent) remain the biggest areas of investment for IT departments in the country this year. The research shows results of a poll of 400 senior IT decision makers in the UK, France and Germany. Software updates are the biggest challenge when managing multiple devices at scale, for companies in both the UK (36 percent), and Germany (39 percent).… [Continue Reading] -

European workers still find fax machines 'essential'
Publié: mai 20, 2016, 4:36pm CEST par Sead Fadilpašić
Europe is considered an old continent by many standards, but when it comes to what workers there find essential, that’s where the oldness really kicks in. Apparently, workers in the EU still find fax machines "essential" to office life. As a matter of fact, they find it more important than tablets, or smartwatches. Those are the results of a survey done by business communications technology provider Fuze. It asked 5,000 employees about the technologies still used in the office. So, for example, the fax machine is "essential" for 30 percent of workers in the UK, 39 percent in Germany and… [Continue Reading] -

Ultramobiles are a glimmer of hope in a shrinking PC market
Publié: mai 20, 2016, 12:02pm CEST par Sead Fadilpašić
PC vendors are definitely in a pickle, as the market size everywhere continues to shrink, but there are areas of the industry that are still profitable, market analysts Gartner have said. PC sales have recorded one of its lowest quarterly growth rates in Q1 2016, but ultramobiles are growing, and that’s where the focus should probably be. Ultramobiles (tablets, thin and lightweight PCs, convertibles) are expected to grow 16 percent, to $34.6 billion, compared to 2015. Gartner predicts the ultramobile premiums will soon hold the largest part of the PC market in terms of revenue, forecast at $57.6 billion. "The… [Continue Reading] -

IBM creates faster, longer lasting memory technology
Publié: mai 19, 2016, 7:59pm CEST par Sead Fadilpašić
IBM’s researchers have found a way to build computer memory that’s incomparably faster to anything we have today. Besides being that much faster, it’s also more enduring and dense. Sounds a bit like science fiction, doesn’t it? The new technology is called PCM, or phase-change memory, and it revolves around storing three bits of data per cell. It doesn’t lose data when powered off, and it can live through "at least" ten million write cycles (average USB stick can endure some 3,000 cycles). The company said the new technology’s application is wide. It can be used as storage, as RAM memory… [Continue Reading] -

IT departments need to contribute more to digital transformation
Publié: mai 19, 2016, 2:30pm CEST par Sead Fadilpašić
Everyone agrees IT departments need to play a bigger role in the process of digital transformation. Those are the results of a new and extensive survey by The Economist Intelligence Unit and SAP. The survey asked more than 800 senior executives from various industries, with more than half being IT leaders, about the process of digital transformation. Key highlight of the report is that there’s a "distinct lack of strategic co-ordination around digital transformation". It was said that business departments (29 percent of cases) are more likely to lead digital transformation initiatives than the IT function (22 percent). Everyone agrees this should change,… [Continue Reading] -

ARM buys imaging company Apical
Publié: mai 19, 2016, 11:22am CEST par Sead Fadilpašić
British chip maker ARM has announced that it has acquired Apical, an imaging and embedded computer vision company. The deal, worth $350 million in cash, was closed on Tuesday, May 17, the company said. Apical’s products are used in smartphones everywhere (1.5 billion, according to ARM), and in 300 million other devices, all over the world, including IP cameras, digital cameras and tablets. After the acquisition, its products will be used in ARM’s "next generation vehicles", security systems, robotics, mobile and other consumer, smart building, industrial or retail application. These devices will be able to "understand and act intelligently on… [Continue Reading] -

Trojan hijacks search results to generate advertising revenue
Publié: mai 18, 2016, 8:53pm CEST par Sead Fadilpašić
There’s a Trojan out there that forces infected computers to automatically click on advertising banners. By doing so, its creators are earning money while businesses paying to be seen are just burning a hole in their budgets without achieving anything. Those are the results of a new report by security firm Bitdefender, which has identified the Trojan as Redirector.Paco. According to the company’s press release, the Trojan has, since 2014, infected 900,000 machines. It’s most present in India, Malaysia, Greece, the USA and Italy, and works like this: once a machine is infected, its internet configuration settings are changed so… [Continue Reading] -

China’s security reviews target foreign tech products
Publié: mai 18, 2016, 11:19am CEST par Sead Fadilpašić
The Chinese government is quietly scrutinizing foreign technology products sold in the country, the New York Times has reported. According to the report, executives from companies like Apple are being called in by a Cyberspace Administration of China committee to explain, in person, things like encryption and data storage. There are multiple reasons why the Chinese government would do such a thing. First and foremost, to see if the products are secure and its users are not being spied upon. Other countries do that as well, but according to the report – not for wide consumer electronics. Another reason for… [Continue Reading] -

UK will introduce digital driver's license in 2018
Publié: mai 17, 2016, 7:00pm CEST par Sead Fadilpašić
The days when you forget your driver’s license and ending up paying a fine for it might soon be a thing of the past, as there are people out there working on a paperless version of the license. According to a BBC report this week, the UK’s Driver and Vehicle Licensing Agency is working on such a project, and there’s already a prototype in place. A photo of the prototype was tweeted recently by CEO Oliver Morley. As it turns out, the digital driver’s license is based on the Apple Wallet app for the iPhone and it will, at least… [Continue Reading] -

No UK tech unicorn is publicly in favor of a Brexit
Publié: mai 17, 2016, 4:22pm CEST par Sead Fadilpašić
This morning I wrote a report on how just a third of UK’s companies actually have a plan in place in case the country leaves the European Union, following the Brexit referendum in some six weeks’ time. At the same time, Guardian reached out to UK’s unicorn companies -- those valued at more than a billion dollars -- about their opinion on the Brexit, and those that were willing to speak were firmly against the UK leaving the European Union. The majority, however, either didn’t want to comment, or remained neutral. Out of 14 unicorns that UK has, five were… [Continue Reading] -

98 percent of Brits are happy with their bank
Publié: mai 16, 2016, 9:02pm CEST par Sead Fadilpašić
Pretty much everyone in the UK is satisfied with their banks and the services those banks offer, Juniper Research confirmed this week. According to the market analysts' research, 98 percent of those surveyed said they were either "happy", or "quite happy" with their service. Juniper failed to mention the size of the group it surveyed, though. But what it did mention is that banks are now faced with a couple of new challenges -- mobile access and contactless payment. Mobile access is now considered a "key pillar of a bank’s offering", and 31 percent of users would consider switching banks if… [Continue Reading] -

7-Zip gets an update to fix major security vulnerabilities
Publié: mai 16, 2016, 11:16am CEST par Sead Fadilpašić
Security researchers from Talos have written a bunch of fancy words on their blog here, which basically say 7-Zip has a couple of serious security flaws. Everyone’s up in arms about it, too. There are two major security flaws found in the program, one which allows hackers to remotely execute code (basically run programs from afar), and the other one which can lead to heap corruption or buffer overflow. But the problem is not just 7-Zip having problems, the problem is also that other people use 7-Zip in their own software, meaning many more applications now have this problem. Everyone… [Continue Reading] -

Barclays will introduce Android mobile payment service
Publié: mai 13, 2016, 7:08pm CEST par Sead Fadilpašić
UK bank Barclays has announced it will soon roll out its own contactless payment service for its Android-using customers in the country. All Barclays customers with an NFC-enabled Android smartphone will be able to pay for things the same way they pay with a contactless card. For purchases of up to £30, all they need to do is tap their smartphone at the payment terminal, the same way they’d tap a contactless card. For purchases of up to £100, customers would need to tap in their PIN code. The new feature, dubbed Contactless Mobile, will come as a part of… [Continue Reading] -

IT pros too confident about detecting ongoing cyber-attacks
Publié: mai 13, 2016, 2:19pm CEST par Sead Fadilpašić
Endpoint detection and response company Tripwire and Dimensional Research conducted a research, and asked 763 IT professionals from various industries about their security practices, and if they felt confident they could detect an ongoing cyber-attack. The two companies announced that the majority of IT experts felt overconfident in their abilities to detect an ongoing threat and remove an unauthorized device from their network. Eighty-seven percent of IT pros questioned said they could remove an unauthorized machine from their network within minutes or hours. Director of IT security and risk strategy at Tripwire, Tim Erlin, said there is a difference between security… [Continue Reading] -

Publishers to lose $27 billion by 2020 thanks to ad blockers
Publié: mai 12, 2016, 6:41pm CEST par Sead Fadilpašić
Publishers are set to lose $27 billion by 2020 thanks to ad blockers such as AdBlock Plus, a new report by Juniper Research says. Keeping in mind that the digital advertising spending worldwide sits at $197.48 billion (expected to grow to $252bn by 2018) according to Statista, that means ad blockers will account for almost 10 per cent of total digital advertising market. Ouch. The report, entitled Worldwide Digital Advertising 2016 - 2020, says ad blockers are only going to get stronger, more sophisticated, and used by more people. Millennials are at the forefront of ad blocker adoption, it was… [Continue Reading] -

Businesses open to hiring ex-hackers to beef up security
Publié: mai 12, 2016, 10:22am CEST par Sead Fadilpašić
The Hollywood scenario where people hire ex criminals to do their bidding, as no one else seems to have the necessary skills, has been replicated in real life, according to a new report by cyber-security service provider SecureData. SecureData says more than a third of businesses (34 percent) would have no problems hiring an ex hacker to compensate for the lack of in-house cyber-security skills. I just wonder how you classify someone as an "ex hacker". Whatever the definition may be, the situation is obvious -- there’s a serious lack of skilled security experts, and businesses need to handle it,… [Continue Reading] -

Only a solid strategy can unlock the cloud's benefits
Publié: mai 10, 2016, 4:35pm CEST par Sead Fadilpašić
Switching to a cloud-based solution, either public, private or hybrid, can result in reduced cost, better data security and improve the overall bottom line, but only if it comes with a solid strategy, VMTurbo says. The application performance control platform company says businesses will fail to realize the benefits of a cloud-based approach to business without a proper strategy. It has come to that conclusion following a poll of 1,368 organizations, where 57 percent said they had no multi-cloud strategy, 35 percent no private cloud strategy, and 28 percent no public cloud strategy. Besides not having a strategy, it was… [Continue Reading] -

Lenovo will make enterprise harware in Europe for EMEA customers
Publié: mai 10, 2016, 12:22pm CEST par Sead Fadilpašić
Chinese tech maker Lenovo has announced that it will start building enterprise hardware for its EMEA (Europe, Middle East, Africa) customers in Europe. That way, customers can expect lower prices (sort of) and faster delivery times. Lenovo’s manufacturing partner Flex will be building a full range of x86 server products, including assembly, as well as storage and networking options, at the Sarvar site in Hungary. Fully integrated racks will also be available. According to a press release following the announcement, production will start this Summer, and will complement the production of the ThinkServer product line, among other products. Customers can… [Continue Reading] -

Security concerns keeping IT pros up at night
Publié: mai 10, 2016, 12:10am CEST par Sead Fadilpašić
Security is still the main reason IT professionals are up at night, new reports from BCS, The Chartered Institute for IT say. BCS has asked 444 IT experts about their thoughts and fears revolving their company in 2016. The results, released in the 2016 Digital Leaders survey, show a mix of "predictable" and "thoughtful" ideas, as the BCS puts it. Security is still the number one issue, though, with the Internet of Things (IoT) devices just adding to the existing cyber-risks. "This is the fifth year that we have conducted the research helping us to build a picture that is… [Continue Reading] -

Microsoft invests in cloud company Pivotal
Publié: mai 9, 2016, 8:37pm CEST par Sead Fadilpašić
It was reported on Friday morning that Microsoft has invested in Pivotal, a San Francisco-based cloud-computing company. Besides Microsoft, Ford was also announced as a major investor. The media reported that Pivotal’s Series C funding round hit $253 million, with Ford contributing with $182.2 million. It is not known exactly how much money Microsoft poured into the company. We do know, however, that the company’s value now sits at $2.8 billion. Other investors include General Electric, EMC, and VMWare. "This relationship builds off what was already a strong relationship", Forbes quotes Pivotal CIO Marcy Klevorn saying. "We are re-positioning the… [Continue Reading] -

IT departments need to adapt faster to change
Publié: mai 9, 2016, 7:20pm CEST par Sead Fadilpašić
The fast-changing IT environment of today is forcing companies to reconsider their approach to IT, as they believe that can help them stand out in the crowd of their competitors. However, the process is quite challenging. Those are the general conclusions of a new research released by managed services provider Claranet. The research polled 900 IT decision makers in the UK, France, Germany, Span, Portugal and the Benelux about fast changing business models and in 46 percent of cases it’s very challenging. A year before, 35 percent of those surveyed thought it to be a challenge, showing how demanding the… [Continue Reading] -

Demand for open source talent on the rise
Publié: mai 9, 2016, 10:16am CEST par Sead Fadilpašić
Open source talent is in high demand when it comes to recruiting new technology experts, and this trend is only going to grow, new reports say. According to the latest 2016 Open Source Jobs Report, 59 percent of hiring managers will increase the number of open source talent in their organization within the next six months. What’s more, 65 percent of managers said this part of their business is set to grow more than any other, and 79 percent said they’re doing more to keep their current professionals. DevOps seems to be the most wanted skill, with 59 percent of… [Continue Reading] -

Google's AI is reading love novels to give 'humanized' answers
Publié: mai 7, 2016, 2:07am CEST par Sead Fadilpašić
Soon enough, you can expect Google’s AI to start sending you love letters. And judging by the information you are just about to read, those might be some of the best love letters ever written, in the history of robotkind. Or humankind. Or both, I guess. Here’s what’s going on. Google says its AI engine’s answers to human questions are too factual. Imagine the answers as being purely robotic. Subject, predicate, adverbial clause. Google, on the other hand, wants those answers to be more human -- it wants the robot to be able to answer the same question in different words,… [Continue Reading] -

What's the most popular ransomware?
Publié: mai 6, 2016, 2:02pm CEST par Sead Fadilpašić
Ransomware is something like the digital version of Kanye West -- everyone hates it, but its popularity just keeps on growing. And it takes your money for things you really don’t want to buy. The news about the rising popularity of ransomware was confirmed by security firm Kaspersky Lab, which released its quarterly report into the state of malware. According to the Q1 report, the company reported 2,900 new malware modifications in the quarter, representing a 14 percent increase compared to a quarter before. The most popular ransomware in Q1 was Locky, Kaspersky Lab confirms, which has been seen trying to… [Continue Reading] -

Tech companies could disrupt financial industry
Publié: mai 5, 2016, 3:24pm CEST par Sead Fadilpašić
People would gladly take banking services from tech companies such as Google, Amazon or Facebook, a new survey has shown. According to a new Europe-wide study by Fujitsu, the digital transformation keeps disrupting the financial industry, and if traditional service providers fail do adapt on time, tech disruptors will step in. For the poll, Fujitsu asked 7,000 consumers about their interaction with banks and insurers. Traditional payment is still the most popular, with 44 percent of consumers reporting using it, but 32 percent have already embraced mobile devices as payment services, 22 percent are using wearable devices, and 20 percent… [Continue Reading] -

Nearly half of OS X devs want to learn Swift
Publié: mai 5, 2016, 11:00am CEST par Sead Fadilpašić
Almost a quarter (25 percent) of OS X developers don’t use file sharing in the cloud -- at all, according to a new survey. German-based Fournova surveyed more than 7,000 OS X developers in more than 100 countries to see which tools, services and technologies are the most popular ones. Of those developers that do use cloud for file sharing, Dropbox is the number one solution, with Google Drive being the leading intranet and documentation solution. Besides a quarter of developers not using cloud, the report also says Full-Stack Web, Mobile, and Web Frontend are the most popular areas for… [Continue Reading] -

Wearables are likely source for security breach
Publié: mai 4, 2016, 7:32pm CEST par Sead Fadilpašić
The Internet of Things (IoT) opens up a sea of new opportunities for revenue and growth, but it is also a security challenge, IT pros have said. If the new Spiceworks IoT report is to be believed, 85 percent of IT professionals in the EMEA region (Europe, Middle East, Africa) believe IoT will create new security and privacy issues in the workplace. The report highlights a shift in direction for companies deploying IoT solutions, as two years ago it was bandwidth which was the biggest issue for businesses. Now, it’s security. Yet, only 25 percent of businesses in the EMEA… [Continue Reading] -

Just 30 percent of UK companies experienced a security breach in 2015
Publié: mai 4, 2016, 4:13pm CEST par Sead Fadilpašić
Almost a half (43 percent) of UK companies did not experience a security breach in 2015, a new report suggests. Released by IT management software provider SolarWinds, it includes answers from 109 IT practitioners and managers from small, medium-sized and large UK companies. According to them, just 30 percent suffered a breach last year. Quite surprising. More than a third (39 percent) said they feel less vulnerable than they did a year ago, while 27 percent said they felt more vulnerable. The time needed to detect a threat decreased for 42 percent of companies, while 18 percent said it increased.… [Continue Reading] -

Hackers now targeting victims with country and culture-specific malware
Publié: mai 4, 2016, 11:32am CEST par Sead Fadilpašić
Hackers are targeting specific countries with their malware now, new research from security firm Sophos shows. The security firm analyzed millions of devices worldwide and has come up with the conclusion that it seems to be more lucrative if the malware is specifically designed to target certain cultures or countries. Scams are also getting harder to notice, as hackers now counterfeit different company logos and invoices perfectly. You could be getting an electricity bill or a speeding ticket that is, in fact, a scam attempt. "You have to look harder to spot fake emails from real ones", said Chester Wisniewski,… [Continue Reading] -

Outdated Java, QuickTime installations on the rise in UK
Publié: avril 28, 2016, 11:40am CEST par Sead Fadilpašić
UK’s citizens are getting more diligent when it comes to patching and updating their Windows-operated computers, new survey by Flexera Software’s Secunia Reports team says. QuickTime users, on the other hand, aren't as vigilant. According to the team’s Country Reports, the number of unpatched Microsoft Windows operating systems is on the decline. At the end of the first quarter of 2016, the number sits at 6.1 percent, where last year at this same time, it was at 11.5 percent. QuickTime 7.x users, on the other hand, are lagging behind. The number of users with unpatched software is now at 61 percent,… [Continue Reading] -

Companies invest more in DDoS protection
Publié: avril 27, 2016, 6:10pm CEST par Sead Fadilpašić
Pretty much every company out there has been, or will be a target of a DDoS attack. A new report by real-time information services provider Neustar, entitled The Threatscape Widens: DDoS Aggression and the Evolution of IoT Risks, released this month, says it’s no longer the question of "if" or "when" a company will be DDoSed -- it’s how often and how long will it last. According to the report, 73 percent of companies were attacked in 2015, with 82 percent of those attacked suffering multiple attacks. Out of that number, 45 percent said they were attacked six times, or… [Continue Reading] -

Why ATMs are easy to hack
Publié: avril 27, 2016, 12:24pm CEST par Sead Fadilpašić
Security researchers claim ATM machines are usually not that difficult for hackers to penetrate. Once they’re inside, they can steal money, or banking details from unsuspecting victims. Now, researchers from Kaspersky Lab have investigated what makes ATMs such an easy target for hackers, and came to two conclusions: both software and hardware are easy to access and temper with. According to the researchers, ATMs are usually based on outdated systems (usually Windows XP), which makes them vulnerable to either malware attacks or exploits. In many cases, ATMs communicate with banking infrastructure through an old, unsecure XFS standard. "The problem is… [Continue Reading] -

EE plans to cover the whole of the UK with 4G
Publié: avril 26, 2016, 10:50am CEST par Sead Fadilpašić
Mobile operator EE said it will cover the entire UK (well, 95 percent of it, at least) with 4G connectivity by 2020. It also said it will shut down its customer call centers in India and create 600 new jobs in the UK and Ireland. The announcement comes after EE landed a contract with the Government, under which it will replace the Airwave radio network and eliminate blinds spots, or 'not-spots' in connectivity, The Telegraph reported recently. Currently, about 60 percent of the country is covered in 4G, with mostly rural areas being in the dark. This must quickly be… [Continue Reading] -

Merchants are not security savvy
Publié: avril 21, 2016, 8:29pm CEST par Sead Fadilpašić
More than a third (38.5 percent) of merchants don’t even know what type of risks new technologies such as mCommerce bring. They most likely wouldn’t recognize a fraud threat even if they were right in the middle of it. Those are the conclusions written in the new 2016 Mobile Payments & Fraud Survey, released by Kount. The figures are quite a surprise, knowing that mobile fraud increased by 81 percent between 2011 and 2015. "Despite awareness that the mobile channel poses a greater risk than standard eCommerce, businesses are taking a blanketed approach to their security strategies", said Don Bush,… [Continue Reading] -

Free Wi-Fi hotspots are a major security threat for businesses
Publié: avril 21, 2016, 11:27am CEST par Sead Fadilpašić
Free Wi-Fi hotspots are the biggest security threat for mobile workers, according to new reports. The recently released iPass Mobile Security Report says that 62 per cent of organizations are banning their mobile workers from using free Wi-Fi hotspots, with another 20 percent planning on doing the same in the future. For 94 percent of surveyed companies, free and open Wi-Fi hotspots are a "significant mobile security threat". "Wi-Fi is a disruptive technology that has changed the way people work, but in recent times it has also introduced formidable mobile security concerns", said Keith Waldorf, VP Engineering at iPass. "Being… [Continue Reading] -

Internet of Things will extend to running shoes
Publié: avril 19, 2016, 4:16pm CEST par Sead Fadilpašić
Your next running shoes will probably be connected to the internet, IoT-style. Footwear branding, labeling and RFID solutions firm Avery Dennison Retail Branding and Information Solutions (RBIS) and IoT firm EVRYTHNG announced today they’re teaming up to give more than 10 billion apparel and footwear products a "unique digital identity". Yes, they’re putting IoT chips into shoes. The products should hit the market within the next three years. The two companies believe this will be the largest number of IoT-connected devices in a single deal, ever. They will be powered by the Janela Smart Products Platform, for digital identity and data management… [Continue Reading] -

Kaspersky introduces Industrial CyberSecurity solution
Publié: avril 18, 2016, 7:15pm CEST par Sead Fadilpašić
Security firm Kaspersky Lab today announced a new, specialized security solution, aimed at critical infrastructure and industrial facilities. The solution, called Kaspersky Industrial CyberSecurity, is built to protect technological processes in industrial environments from cyber-attacks because, as the company says, these threats now have the potential to cross the realms, from the virtual one into the physical one, threatening not only businesses, but humanity and nature, as well. The solution is aimed for today’s industrial facilities such as nuclear power plants, refineries and assembly lines, facilities which require, as Kaspersky puts it, "faultless continuity and consistency of the technological process".… [Continue Reading] -

UK bosses support a six-hour workday
Publié: avril 18, 2016, 11:20am CEST par Sead Fadilpašić
When workers say they’d love a six-hour workday, no one finds it particularly shocking. Ask them for a two-hour workday and you’ll hear similar responses. But when bosses and HR people also start supporting the idea, that’s when we really start to listen. And believe it or not, a new survey says bosses and HR people really do support the idea. According to a survey commissioned by Crown Workplace Relocations, 75 percent of employees were for a six-hour workday. In London, the figure rose to 78 percent. Among bosses, 60 percent said they’d consider introducing such practice. In London, the… [Continue Reading] -

British workers don't know their privacy rights
Publié: avril 15, 2016, 10:48am CEST par Sead Fadilpašić

British workers are mostly unaware about their privacy rights at work, a new survey suggests. Security firm Comparitech.com has polled 1,000 employees living in the UK, and according to the poll, 53 percent don’t believe bosses should be allowed to read their private communications during working hours.
What’s more, 36 percent said bosses aren’t allowed, legally, to read such emails and texts, while 13 percent said they’d quit their job if they found out their bosses were reading their private communications.
However, Comparitech.com reminds everyone of the January European Court of Human Rights (ECHR) ruling, which said bosses can review any messages sent during working hours.
"Many staff members won’t be clear what the policy is regarding bosses reading their emails unless they’ve read their employment contract in detail -- and by then it may be too late", said Lee Munson, researcher at Comparitech.com.
The company also said every worker should be careful when signing their contracts, and should check to see what the contract says about the use of social media and private communications in general.
"The study proves that people need to be more vigilant in knowing their rights in the workplace by thoroughly checking their contracts for reference to use of social media, personal email and chat at work, especially if they send private messages at work and are concerned about them being read".
Comparitech.com also says if you’re in doubt, assume all emails you send and receive from a corporate email account will be read. If you really must send a private message, make sure to use an encrypted emails service. The best solution would be to use a personal device, with a personal account, through a personal network, and not the corporate Wi-Fi.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Syda Productions / Shutterstock
-

IT pros would switch jobs for better training opportunities
Publié: avril 14, 2016, 7:51pm CEST par Sead Fadilpašić

More than a third of IT professionals in the UK (36 percent) haven’t gotten any professional training through their employers in the last three years.
At the same time, pretty much everyone (97 percent of IT pros everywhere) says that knowing the latest skills is essential to them getting their work done. Those are the results of a new survey conducted by the global freelancing site Upwork.
IT managers are also aware of the issues. Ninety-five percent of them know updated skills are essential, but they’re having all kinds of trouble getting there. For 70 percent, technology moves too fast to always keep up with the latest, while for 49 percent, budgets restrictions are holding them back.
What’s more, 44 percent cite time limitations, while 33 percent prioritize other business responsibilities.
But IT managers should really consider investing in trainings and courses, as 89 percent of IT workers said they’d consider leaving their position for better training opportunities elsewhere. This not only means businesses could keep their workers, but they’d also attract new talent, as well.
"IT managers recognize the value in having a well-trained workforce but other business priorities and tight budgets mean training is often neglected", said Rich Pearson, SVP of Marketing at Upwork. "As a result, workers often feel stifled in their jobs, which can have negative effects on performance, morale and loyalty. To alleviate these pressures in-house teams face, businesses shouldn’t be afraid to look beyond their four walls and capitalize on independent professionals with proven expertise in the specific technical skills they need".
"Both training and finding staff with the right skill set is a real challenge for a growing business like ours", said Philip Lilliefelth, Pansofica Founder. "It’s imperative we keep up with evolving skills but upskilling our staff can be expensive and time-consuming, especially given the pace of change. Using freelance specialists who take it upon themselves to stay up-to-date with technical skills solves this problem, we are able to source the desired skill set immediately without major overheads – which in many cases is more suitable for start ups with budget constraints".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Javier Brosch/Shutterstock
-

IT workers will not put up with pirated software
Publié: avril 14, 2016, 6:51pm CEST par Sead Fadilpašić

Workers in the IT and telecoms industry are more prepared to blow the whistle on illegal activities in the office than any others, a new report suggests.
The report, released by BSA | The Software Alliance, looked at unethical and illegal practices in the office, relating mostly to the use of unlicensed and pirated software.
According to the report, 38 percent of UK workers would report their boss for such activities, jumping to 50 percent in the IT and telecoms industry. Out of 2,000 employees questioned, ten percent suspect their boss is up to no good. This figure jumps to 23 percent with workers in the IT and telecoms industry.
"With a third of workers willing to blow the whistle on illegal or unethical IT practices, businesses need to make sure their house is in order before it’s too late", says Sarah Coombes, managing director at BSA EMEA. "Our research shows that employees aren’t willing to put up with any practices that breaks laws or put their ethics into question. As a result we’ve seen a dramatic increase in whistleblower reports we’ve received in the last year".
What’s even more interesting is the fact that 42 percent said they’d do it for moral reasons, while just seven percent said they’d do it for a financial reward.
BSA encourages people to report unlicensed product use, and offers rewards for information which leads to a legal settlement. This year, BSA will launch the 2016 Fact or Fiction campaign, warning UK businesses about the dangers of using unlicensed software.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Marcos Mesa Sam Wordley / Shutterstock
-

Cyber-criminals run things like a business
Publié: avril 13, 2016, 8:42pm CEST par Sead Fadilpašić

This cyber-crime thing has gotten to a point where we now really need a digital Batman to fix everything. Security firm Symantec has recently released its Internet Security Threat Report, revealing that cyber-criminals are almost as good as state-sponsored attackers.
They’re highly skilled, well-organized and structured like a business. Here’s what Kevin Haley, director at Symantec Security Response says:
"Advanced criminal attack groups now echo the skill sets of nation-state attackers. They have extensive resources and a highly-skilled technical staff that operate with such efficiency that they maintain normal business hours and even take the weekends and holidays off. We are even seeing low-level criminal attackers create call center operations to increase the impact of their scams". Yeah, I only have Sony Entertainment left to hack this week, then I can go to Bora Bora for a couple of days.
Zero-day vulnerabilities are on the price nowadays. Advanced groups will either take advantage of them, or sell them on the open market. Symantec says that the number of zero-day vulnerabilities discovered in 2015 more than doubled, to 54, breaking records along the way. Compared to a year before, this represents a 124 per cent jump.
The report also sheds some light on data theft, saying that more than half a billion personal information records were either stolen, or lost, last year. Encryption is now used by cyber-crooks to keep data hostage, a practice also known as ransomware. Scam is also making a comeback, with fake tech support centers (a 200 percent increase last year) being the most popular one.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: alphaspirit/Shutterstock
-

Hackers love Microsoft's PowerShell
Publié: avril 13, 2016, 5:46pm CEST par Sead Fadilpašić
PowerShell, a scripting language inherent to Microsoft operating systems, is largely used to launch cyber-attacks, a new report suggests.
The Unified Threat Research report, released by next-generation endpoint security (NGES) firm Carbon Black, says that 38 percent of incidents reported by Carbon Black partners used PowerShell.
During investigations last year, 68 percent of the company’s responding partners encountered PowerShell, and almost a third (31 percent) reported getting no security alerts before the investigation of incidents related to the scripting language.
The majority of attacks (87 percent) were clic-fraud, fake antivirus programs and ransomware, but social engineering techniques are still the favorite.
"PowerShell is a very powerful tool that offers tremendous benefit for querying systems and executing commands, including on remote machines", said Ben Johnson, Carbon Black’s chief security strategist and cofounder.
"However, more recently we’re seeing bad guys exploiting it for malicious purposes it because it falls under the radar of traditional endpoint security products. This often causes tension between the IT and security professionals. PowerShell gives the bad guys a lot of power because it’s part of the native Windows operating system, which makes it difficult for security teams. On the other hand, PowerShell helps IT guys automate various tasks. The two departments need to come together and strike a balance between IT automation and security".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Box customers can now choose where to store their data
Publié: avril 13, 2016, 10:49am CEST par Sead Fadilpašić

Online file sharing company Box today announced a new service, allowing businesses to store their cloud data across Europe and Asia.
The service, announced at the Box World Tour Europe, is called Box Zones, and it will allow Box customers to choose whether they want to store their data in Germany, Ireland, Singapore or Japan.
"Businesses today are more connected, collaborative and global thanks to the power of the cloud", said Aaron Levie, co-founder and CEO of Box. "Yet for many companies, local laws and regulations have forced them to make technology tradeoffs that limit their success and place a drag on employee productivity and collaboration. Box Zones will help power digital transformation for enterprise customers across Europe and Asia and accelerate our international presence".
The company also said that the new feature will not interfere with any of the existing ones, with features like watermarking, granular permission controls and comments and tasking, staying. Deep integrations with Office 365 and Salesforce are also here to stay.
"Security is the top priority for AWS and our customers. With the recent launch of Box KeySafe running on AWS, Box offers companies of all sizes greater control over their business-critical, sensitive content, and furthers that mission with today’s introduction of Box Zones", said Terry Wise, vice president of Worldwide Partner Ecosystem, Amazon Web Services.
"We believe customers should have the freedom to choose where and how their data is stored. With Box Zones leveraging Amazon Simple Storage Service (Amazon S3), customers can better meet the highest levels of security and regulatory compliance required in their respective geographies".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wavebreakmedia/Shutterstock
-

Software-defined data center adoption will grow in 2016
Publié: avril 12, 2016, 7:15pm CEST par Sead Fadilpašić

Business and IT executives in the UK and the US (62 percent) expect a higher adoption of software-defined data centers (SDDCs) this year, but the projection for faster deployment is slightly higher in the UK (67 percent), compared to the US (64 percent).
Those are the results of a new study conducted by security, compliance and control software company HyTrust, and co-sponsored by Intel. The study takes a look at the issues and trends among businesses migrating to the cloud and software-defined data centre.
There are some sharp differences between businesses in the two countries, regarding SDDC, with 30 percent of UK’s businesses expecting greater tangible benefits and return on investment (ROI), compared to 56 percent in the US.
Adoption for network virtualization is expected among 23 percent in the UK, and at 56 percent in the US, while adoption for storage virtualization is expected among 31 percent in the UK, and 58 percent in the US.
There is also a sharp difference between the two countries in the better alignment of security strategies built to address SDDC -- 14 percent have aligned their strategies in the UK, compared to 48 percent in the US.
Even though security is still the number one issue stopping businesses from deploying all of their apps to the cloud, the report suggests signs of optimism.
When asked if security will be less of an obstacle to greater SDDC adoption by the end of this year, 68 percent in the UK and 69 percent in the US say "Yes".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: sellingpix/Shutterstock
-

Jaguar Land Rover is building an Uber competitor
Publié: avril 12, 2016, 6:21pm CEST par Sead Fadilpašić

Jaguar Land Rover has announced the launch of a new business, which is basically an Uber competitor. According to the company’s press release, the new technology start-up called InMotion will "build apps and on-demand services to overcome modern travel and transport challenges".
The start-up will soon start testing a couple of different services related to car sharing and car ownership. The testing will take place in North America, Europe and Asia "in the coming months".
InMotion will first conduct a global, in-depth research about the current state of travel and transportation markets, and then will go for closed, real-world experiments. Once it decides on the "most effective" approach to the problem, it will proceed to build and beta test a product.
"With the development of new apps and on-demand services, InMotion provides us with an opportunity to provide engaging and invaluable experiences to both new and existing customers globally", said Adrian Hallmark, group strategy director at Jaguar Land Rover. "As a start-up business, InMotion combines the flexibility and pace needed to compete in the ever-changing mobility sector. It allows us to react quickly to new tech and ever-changing customer demands".
Financial Times says that the new start-up will also build valet parking solutions, as well as insurance products. It has employed former Google employees to make this happen and, according to the report, will throw "hundreds of millions of pounds" if it comes up with technology that demands investment.
The division will be based in London, and will be completely independent from the rest of the company.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Contactless payments market to reach $95 billion by 2018
Publié: avril 12, 2016, 10:41am CEST par Sead Fadilpašić

The global value of contactless payment market will reach almost $100 billion by 2018, a new study by market analysts Juniper Research says.
According to the research, entitled Contactless Payment: NFC Handsets, Wearables & Payment Cards 2016 - 2020, the market will hit $95 billion in two years, up from $35 billion in 2015.
The research says wearable devices, such as smartwatches and smart wristbands will be important for the market, but not crucial. Wearables as a whole would not account for more than two percent of non-card contactless payments by value in 2018.
On the other hand, smartphones will be extremely important. The research says the nine million Apple Watches that were sold in 2015 were "dwarfed" by NFC-capable iPhones. It also said that such devices pose a higher security risk.
With vendors embedding security measures within their devices, the report argues this spells trouble for mobile network operators. Samsung, currently the only Android OEM with its own contactless payment service, is being followed by Xiaomi, ZTE and Lenovo.
"Most operator-led pilots and commercial ventures have now closed down", says research co-author Nitin Bhas. "Apple’s entry into NFC gave the industry a much needed boost, and could well be seen as the tipping point for the technology, but at the same time it sounded the death knell for the mobile operator projects".
The whitepaper, NFC ~ No Contact Required, is available to download from this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: s4svisuals/Shutterstock
-

EMC wants to sell Documentum
Publié: avril 8, 2016, 9:09pm CEST par Sead Fadilpašić

The EMC-Dell deal never stops to capture headlines, and today is no different. The media have reported that EMC is looking to sell Documentum, its enterprise content management platform.
Documentum was acquired by EMC in December 2003, when it cashed out $1.7 billion for it. The platform is a part of EMC’s Enterprise Content Division (ECD) business unit.
Bloomberg was the first to start reporting how EMC is looking to sell Documentum, although it failed to mention the price. It did, however, said that the company would be very interested in selling software assets Sonicwall and Quest, all together for a price of about $4 billion.
According to multiple media reports, Documentum has an annual turnover of $600 million, and has a 30 percent profit margin. The sources are, according to Bloomberg, very acquainted with the subject matter, but would like to remain anonymous as the discussions aren’t public.
The Dell-EMC merger was announced on October 12, 2015. Back then, Dell announced it would be acquiring the company in a cash-and-stock deal valued at $67 billion. This is the biggest acquisition to ever happen in the tech industry.
However, such a large acquisition has left Dell is significant debt, which is why it is looking to offload non-core assets to mitigate the cost of the merger. According to The Register, Dell’s services business was sold to NTT Data Corporation in March for $3 billion.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Consumers do not trust Internet of Things
Publié: avril 8, 2016, 4:50pm CEST par Sead Fadilpašić
Even though consumers see tangible benefits of the Internet of Things (IoT) adoption, many have their doubts regarding security, trust and safety, and that could seriously hurt the adoption of the new technology.
Those are the results of a new study conducted by global mobile trade body Mobile Ecosystem Forum (MEF). The Global Consumer Survey asked 5,000 mobile users in eight markets about the future of the connected world.
Globally, 60 percent of consumers are worried about the new technology, especially in the emerging markets such as Brazil, India and South Africa (66 percent). The biggest concerns are trust (62 percent) and security (54 percent), followed by physical safety (27 percent), and not being able to fix the technology (24 percent).
Ten percent said they couldn’t see the benefits of a world filled with IoT devices.
"Whilst this survey shows that consumers are excited about a future connected world, it also clearly identifies the need for the industry to consider how such technology and services are rolled out when it comes to building a trusted relationship with consumers", said Rimma Perelmuter, CEO of MEF.
"The business opportunities surrounding IoT are clear, but only if industry heeds the lessons of the broader mobile ecosystem when it comes to the paramount importance of building consumer trust at the outset. Our 2016 Global Consumer Trust Report demonstrated the demand for transparency in mobile apps and services with 64 percent saying it’s important to be told when an app is collecting and sharing personal information. This new report reaffirms the need for all stakeholders in the ecosystem to take action now to secure a viable future for such technologies".
The full report detailing how consumers perceive IoT can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Global IT spending will reach $3.49 trillion in 2016
Publié: avril 8, 2016, 10:33am CEST par Sead Fadilpašić

IT spending, worldwide, will decline 0.5 percent this year, Gartner forecasts. The market analyst firm says this year’s forecast totals $3.49 trillion, down from $3.50 trillion which were spent in 2015. Last quarter’s forecast was 0.5 percent growth, and these new changes are mainly due to currency fluctuations, Gartner says.
"There is an undercurrent of economic uncertainty that is driving organizations to tighten their belts, and IT spending is one of the casualties", said John-David Lovelock, research vice president at Gartner. "Concurrently, the need to invest in IT to support digital business is more urgent than ever. Business leaders know that they need to become digital businesses or face irrelevance in a digital world. To make that happen, leaders are engaging in tough cost optimization efforts in some areas to fund digital business in others".
Device markets (PCs, laptops, ultramobiles, mobile phones, tablets and printers) will continue to shrink, and sales will continue to drop this year. At the same time, the spending on data centers and enterprise software will continue to grow.
The device market is forecast to decline 3.7 percent. "The underlying reasons are a combination of factors and are geography-specific, and the worsening economic conditions in many countries only serve to amplify the impact of these factors", Gartner says in the press release.
Spending on data centers will reach $175 billion in 2016, representing a 2.1 percent increase, compared to a year before. Spending on enterprise software is expected to hit $321 billion globally this year, a 4.2 percent increase from 2015.
The full Gartner report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: beeboys / Shutterstock
-

For $500 you could look through your competitor's email
Publié: avril 7, 2016, 5:37pm CEST par Sead Fadilpašić

So you want to snoop through your competition’s email? Yeah, we can make that happen, but it’ll cost ya! How much? You’d be surprised. Secure Works’ researchers have dug deep into a popular cyber-crime forum to find out how much it costs to hire a hacker to do your dirty work, and the results, somewhat surprising, have been published in the Secure Works report.
Apparently, the luxury of reading your competitor’s email will cost you $500 (£353). To make things even better, the hacker will not change the email’s password or anything, so it will be pretty darn hard for the victim to realize they're being spied upon.
And if you’re interested in someone’s social media account, or private emails such as Gmail, Hotmail, Yahoo!, that’s gonna cost even less -- a stunning $129 (£91).
Despite these surprisingly low prices, and I’ll show you some more below, the researchers say that hackers have also developed a sense of entrepreneurship:
"Prices and goods are not the only way sellers are distinguishing themselves. There also continues to be a focus on salesmanship. Compared to the report last year, our security experts noted this time around that many hackers were expanding their working hours to include weekends and even promising to be available 24 hours a day", the report says.
Credit cards are also quite popular -- American Visa can be bought for $7, while Visa Classic and MasterCard will set you back $15. Asian cards (Visa Classic and MasterCard Standard for Japan and Asia) with Track 1 and Track 2 data cost $50.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: phadventure / Shutterstock
-

Barclays announces Apple Pay support
Publié: avril 6, 2016, 2:50pm CEST par Sead Fadilpašić

Apple Pay is now available to Barclaycard and Barclays customers, the bank has announced. "We are passionate about helping customers access services and carry out their day to day transactions in the way that suits them", said Ashok Vaswani, CEO of Barclays UK.
"As part of this, we have developed a range of digital innovations that allow people to choose how, when and where they bank and make payments. Adding to the existing choice, from today both Barclays debit and Barclaycard credit card customers can use Apple Pay to make payments with their Apple device across the UK".
The new payment method, whose popularity is growing by the second, is supported by these devices: iPhone SE, iPhone 6 and beyond, Apple Watch, iPad Air 2, iPad mini 3, iPad mini 4 and iPad Pro.
According to the press release, there are more than 400,000 contactless locations in the UK, across the London transport network and within participating retailers’ apps.
"Since we introduced contactless to the UK in 2007, it’s changed the way consumers make everyday purchases by cutting out the hassle of handling cash", said Amer Sajed, Interim CEO of Barclaycard. "With Barclaycard and Barclays bringing Apple Pay to our customers, we can now offer the widest choice of ways to make and take payments in a way that’s most convenient for them".
Contactless payment is gaining ground in the UK. According to latest figures by Visa Europe, contactless payments have seen an increase in use of 237 percent year-on-year.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Only a third of businesses have proper DDoS protection
Publié: avril 6, 2016, 10:19am CEST par Sead Fadilpašić

Among the biggest cyber-threats to businesses nowadays are phishing, patch exploitation, trojans and DDoS (Distributed Denial of Service), yet new figures show that a quarter of companies don’t have an anti-DDoS protection set up.
Those are the results of a new survey by security firm Kaspersky Lab and B2B International. According to their research, approximately half of businesses surveyed understand the risks cyber-attacks pose, not just to their financials, but also to their reputation. Approximately, the same percentage also thinks being protected from DDoS attacks is an important cybersecurity requirement.
But, there is the 24 percent of companies that don’t use this type of protection, and 41 percent that use it, only partially. "It turns out that just 34 percent of companies are fully protected against this widespread threat", the security firm said.
To make things worse, the majority of companies with no protection fall into the "risk group" -- businesses most frequently attacked. Those include the media (36 percent), healthcare and education, both at 31 per cent.
"It’s important to take DDoS attacks seriously as they can be just as damaging to a business as any other cybercrime, especially if used as part of a bigger targeted attack", said Russ Madley, head of B2B, Kaspersky Lab.
"The ramifications caused by these types of attacks can be far-reaching and very impactful as they’re able to reach deep into a company’s internal systems. Organizations must understand that protection of the IT infrastructure requires a comprehensive approach and continuous monitoring, regardless of the company’s size or sphere of activity".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

HP and Nvidia team up to offer Z Workstations with VR Ready systems
Publié: avril 5, 2016, 7:58pm CEST par Sead Fadilpašić

HP and Nvidia are teaming up to offer developers an easier time building virtual-reality content. The joint effort will see HP’s Z Workstations upgraded with Nvidia's VR Ready systems, equipped with Quadro professional GPUs.
The new systems, which can come with up to two NVIDIA Quadro M6000 24GB cards, support the Scalable Link Interface (SLI), GPU Affinity API and VR Synchronization technologies, doubling the rendering power of even the most demanding VR applications and practically eliminating image tearing.
The two companies are confident the new systems can provide ultra-high frame rates and low latency, even with the most demanding of data sets. Certified configurations include the HP Z240 Workstation with NVIDIA Quadro M5000, HP Z640 Workstation with NVIDIA Quadro M6000 and the HP Z840 Workstation with dual NVIDIA Quadro M6000 graphics.
"We are embarking on a new frontier that will change how content producers and artists develop the most immersive, visually stimulating content available", said Jeff Wood, vice president, Worldwide Product Management, Workstations and Thin Clients, HP Inc. "HP Z desktop workstations with NVIDIA graphics are the ideal combination for this new content creation era".
"VR is expanding beyond gaming to revolutionize fields across everyday life — like medicine, architecture, education, product design and retailing", said Bob Pette, vice president, Professional Visualization, NVIDIA. "Our VR Ready initiative makes it easy for professional users to adopt VR technology to make better, more informed decisions and perform their best work".
Pricing starts at $4,363 (£3,057), the companies added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Rommel Canlas/Shutterstock
-

IT pros have bad security habits
Publié: avril 5, 2016, 5:50pm CEST par Sead Fadilpašić

Double standards, double standards everywhere. Our IT bosses might force us to change our passwords every so often, but they rarely change their own credentials, even though theirs offer administrative privileges.
Those are the results of a new survey conducted by cyber security vendor Lieberman Software. The company had asked 200 IT professionals at RSA Conference 2016 about their password changing habits.
More than half (55 percent) of IT pros force their users to change their passwords more often than they do, and 10 percent of them never change their administrative credentials at all. Seventy-four percent change admin passwords on a monthly or less frequent basis.
"Administrative passwords are the most powerful credentials in an organization -- the keys to the IT kingdom", said Philip Lieberman, president and CEO of Lieberman Software. "The fact that 10 percent of IT professionals admitted that they never change these credentials is astounding. It’s almost like an open invitation to hackers to come in and stay a while. In the meantime, the intruders are nosing their way around the network. They can anonymously help themselves to information and remain undetected until it’s too late".
But that’s not all -- in 36 percent of cases, passwords are shared among the IT staff, and 15 percent of IT pros said that if they are to leave their company now, they would still be able to remotely access it with the same credentials later on.
"Given that insider threats are one of the biggest concerns for CISOs, knowing that more than a third of IT professionals share privileged passwords is ludicrous", Lieberman continued. "The same can be said about so many ex-employees who can still access administrative credentials. Automated privileged access management solutions can prevent these types of cyber threats related to unsecure credentials".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Pixelbliss/Shutterstock
-

Reducing costs is a growing priority for IT departments
Publié: avril 5, 2016, 4:12pm CEST par Sead Fadilpašić

IT departments in businesses across Europe are still focused on saving money, and not on adding value to the company, or innovating to support further growth. Those are the results of a new survey by Vanson Bourne on behalf of Claranet.
Polling 900 European IT leaders, it was unveiled that despite growing IT budgets, these departments are still looking to cut costs and save money. Today, 46 percent said reducing cost was the top priority, compared to 34 percent a year before. For 29 percent, new revenue streams were their core activity, and for 25 percent, that was increasing customer loyalty.
"European IT budgets are growing, which would suggest there’s a recognition within businesses of the importance of IT, however time and resources are still not being spent on more forward-thinking projects that can generate more revenue in the long-term", said Michel Robert, Claranet’s UK managing director.
It is clear from the data that the focus on cost reduction and ‘keeping the lights on’ we witnessed in last year’s report has been maintained and, for many, has actually increased. It goes without saying that costs are important, but it’s critical that IT departments can reposition themselves internally as enablers of business agility and innovation, rather than as cost centers", added Robert.
"Any business looking to digitally transform their processes must have the right partners and suppliers in place to carry out those standard tasks universal to IT departments. By working with a managed service provider, CIOs can effectively outsource this work and spend more time working on strategy and revenue-generating activities", concluded Robert.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: tomertu/Shutterstock
-

Consumers would trust PIN authentication for online transactions
Publié: avril 4, 2016, 10:35am CEST par Sead Fadilpašić

Nine in ten (90 percent) of frequent online shoppers are confident that PIN is a good authentication method for mobile commerce transactions. Those are the results of a recent survey by myPINpad, provider of multi-factor authentication technology for touchscreen devices.
Following the survey, the company has released a new report, entitled PIN: From Brick to Click, which takes a closer look at the PIN, and if consumers are ready to use it on their smart devices the same way they use it, for example, at ATM machines.
The short answer is -- yes, they are. The report also says more than 40 percent of all e-commerce in the UK is now carried out on a mobile phone, or a tablet.
"Banks’ ability to invest in innovation is in many cases inhibited by the need to maintain legacy systems, and by the overhead of regulatory compliance", said myPINpad CEO, Phil King. "But, for over 30 years, PIN had been used at ATMs and consumers are familiar with entering a four-digit code to access their bank account. Its introduction in the UK reduced face-to-face fraud by 69 percent. We are now firmly embedded in the age of digital commerce. Having taken the PIN from ATM to the store, consumers are now ready to take the PIN into the digital age".
Security compliance now requires an effective authentication system, especially with financial institutions involved in payment transactions. Their duty is to have a quality system in order to prevent money laundering and reduce fraud.
"They must now balance all of this with not just maintaining but improving the consumers’ experience", the company says.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: mtkang / Shutterstock
-

Brits would share their data with tech companies for financial gain
Publié: avril 1, 2016, 9:24pm CEST par Sead Fadilpašić

Brits would love to share personal data with companies, for the promise of monetary gain. Not only that, but they’d give companies access to their connected home habits, if that means they’d get paid for it.
Those are the results of The Global Internet of Things Smart Home Survey. Sixty-three percent would share data about their daily habits, 61 percent would give companies access to their connected home devices, and 77 percent would do it to get bonus tax credits.
At the same time, they’re quite worried about the security implications smart homes bring. Ninety-one percent fear hackers taking control of home devices and using those devices against them.
The "virtual babysitter" device is something the majority doesn’t want in their home. Also, three quarters are anxious about the number of passwords required to keep a smart home safe.
"Smart homes produce a wealth of data about the way we live and by leveraging this data, companies have the potential to improve how we go about our daily lives", said Simon Hunt at Intel Security. "People are aware of how valuable this data is for third party companies, but this data is not just valuable for these companies it’s also like gold dust for hackers. In the rise of the Internet of Things, security has to be addressed from the outset to prevent the smart home hackers. When done right, security can unlock the benefits IoT promises to deliver".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Lucia Pitter/Shutterstock
-

Losing selfies is a major concern for the majority of smartphone users
Publié: avril 1, 2016, 3:48pm CEST par Sead Fadilpašić

Mobile memory experts Leef quizzed the UK population to see just how important smartphones are for them, and how often they back such devices up. It turns out, not so frequently. As a matter of fact, some people don’t even know what backing up actually means.
So here’s the thing. The quiz polled 1,000 smartphone users across the country, and more than half would be terrified of losing their smartphone, mostly because of "their selfies and other irreplaceable photos from their smartphone", the Leef report says.
The percentage jumps even higher, to 62 percent, among the younger population, aged 16 - 24. The older generation has more fears of losing their contacts, and still rarely backs up their devices. On top of it all, five percent don’t know what "backing up" means.
"Increasingly often people are having great moments and photo opps blighted by the ‘memory full’ pop up on their phone. As we rely on our phones more and more, backing them up is vital!",said David Smurthwaite, partner at Leef. "If you don’t back your phone up because you are worried the cloud in unsafe, or you can’t be bothered with a clumsy web of cables -- search for a better solution! You don’t want to be left kicking yourself because you’ve lost years’ of precious content...".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Vladimir Gjorgiev / Shutterstock
-

Many Brits now do not trust online banking
Publié: avril 1, 2016, 6:51am CEST par Sead Fadilpašić

Almost half of people living in the UK (48 percent) fear either their identities, or their banking data will be stolen. Those are the results of a new survey from financial technology company Intelligent Environments. According to the report, the fear is well founded, with 20 percent of Britons being victims to some type of cyber-crime, either identity theft or bank details theft.
The report reveals a cybersecurity map of Britain. In it, it says that Birmingham is most concerned with cybersecurity, with 57 percent fearing banking information theft, and 59 percent identity theft. Birmingham is followed by Newcastle and Cardiff.
But perhaps the most important revelation of the report is that people are refraining from using online banking in the first place, thanks to security threats. Twenty-two percent don’t trust digital banking apps, and 12 percent don’t trust online banking. Another seven percent have given up on online banking having been victims to an attack.
"People are more on edge these days, and with good reason", says managing director of Intelligent Environments, David Webber. "High profile hacking attacks on organizations like Ashley Madison, Bitdefender and TalkTalk as recently as six months ago have put the issues at the top of people’s minds, and as a result they are rightfully concerned about their security online. Of course, banking data is always going to be a primary concern as it’s particularly attractive to hackers. We’re therefore calling on banks to play a more active role in educating customers on how best to keep themselves and their financial information safe while they’re online".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: mama_mia / Shutterstock
-

The right PC can improve job satisfaction
Publié: avril 1, 2016, 4:53am CEST par Sead Fadilpašić

Do you want satisfied workers? Give them a well-designed PC, a good and secure mobile device, and let them work when they want to, where they want to. Those are, in a nutshell, the results of a new research by Redshift Research, which had polled 1,016 people, across France, Germany, the UK, Italy, Netherlands, Spain and Switzerland.
For 90 percent of IT decision makers, device security is a current concern, because in the last 12 months, a quarter of Europe’s businesses have been breached. That has resulted in less than a third (32 percent) being completely confident in the level of security offered by their current devices.
The report also says that PC design is important -- for 69 per cent of IT decision makers it must allow for mobility, and 77 percent believe it can improve job satisfaction.
"The way that we’re seeing our customers use their business devices is continuing to evolve and is resulting in greater collaboration, mobility and productivity for users", said John O’Reilly, director of Corporate, Enterprise & Public Sector and Personal Systems at HP. "However, this new way of working also presents a real challenge for IT decision makers in ensuring that their devices remain secure whilst being able to provide beautiful, stylish products that match the productivity and design demands from their employees".
In case you were wondering what might be wrong with their current PC setup, that’s mostly unattractive design (27 percent), and short battery life (25 percent).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Zurijeta / Shutterstock
-

Businesses want their infrastructure in the cloud, but it will take time
Publié: mars 31, 2016, 4:43am CEST par Sead Fadilpašić

IT management software firm SolarWinds recently polled 166 IT practitioners, gaining valuable insights into business cloud adoption, security concerns and new and valuable skill sets. The results are quite interesting -- 92 percent said cloud adoption is important to their business, while 27 percent said it was "extremely important".
However, despite cloud technology growing rapidly, businesses are not eager to place their entire infrastructure in it -- 43 percent believe half or more of their infrastructure will be in the cloud within the next three to five years. Sixty percent believe their organization will never fully migrate.
Still, companies want at least some of their infrastructure "up there", with just nine percent saying they have no infrastructure in the cloud.
Last year, the number of businesses not yet in the cloud at all was at 18 percent, this year it’s six percent, giving clear signals that business transformation begins with the cloud.
"The findings of this year’s study paint a clear picture: cloud adoption is nearly ubiquitous, but it’s not now and will not in the foreseeable future be suitable for all workloads, and even if it were, very few if any companies would convert all of their existing applications to run in the cloud", said Joel Dolisy, CIO of SolarWinds.
"The resulting dynamic -- one set of critical on-premises services connected with another set of services in the cloud -- is hybrid IT. And at the center of this evolution is the IT professional who needs to ensure always-on performance of applications, devices, networks and systems -- regardless of location. They need to be empowered with the support to gain the skills and tools required to properly manage hybrid IT environments, which in turn will allow businesses to truly unlock the potential of the cloud".
The full report, entitled IT Trends Report 2016: The Hybrid IT Evolution, can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wavebreakmedia/Shutterstock
-

IT budgets will mostly go towards buying mobile devices, security
Publié: mars 29, 2016, 3:01pm CEST par Sead Fadilpašić

IT budgets for businesses in the US will be mostly spent on security, and mobile devices allowing employees remote working, a new survey has shown.
According to a new survey by Wakefield, 30 percent of US businesses will spend most of their IT budgets on network and data security, and 28 percent will spend it on mobile devices allowing employees to work remotely.
The survey has polled 509 US small business owners, and business decision-makers at companies with 500 or fewer employees.
Other survey answers have shown that the average employee uses a printer approximately 10 times a day, and that the printer is the most common device in a company (84 percent), followed by a scanner (75 percent).
It was also interesting to see how often people bluff when faced with new technology. According to the report, 51 percent of people questioned have pretended to know more about how to operate a device than they actually did, a number which grows to 61 percent among millennials.
The report tops things off by exploring how many people take a real vacation -- completely isolating themselves from any and all work activity. Twenty-three percent of people questioned have never taken a real vacation, and among companies with 50 employees and less the number jumps to 36 percent.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Syda Productions / Shutterstock
-

ESET discovers 'unique' self-protecting USB trojan
Publié: mars 26, 2016, 5:45am CET par Sead Fadilpašić

ESET has detected an undetectable malware. The security firm recently said to have discovered what it now calls Win32/PSW.Stealer.NAI, also known as the USB Thief.
The malware is designed to steal data and is, according to the firm, basically undetectable. It cannot be copied or reverse-engineered, making it extremely difficult to detect or analyze.
However, the vast masses of the internet are pretty safe -- it’s bound to a single USB device, preventing it from leaking from the target systems. ESET’s malware analyst Tomáš Gardoň said it looks as this malware was designed for "targeted attacks on systems isolated from the internet".
What makes it difficult to discover is that it behaves as a plugin source of portable applications or just a library -- DLL -- used by the portable application. ESET gives an example: if an app like Firefox portable is executed, the malware is run with it.
"This is not a very common way to trick users, but very dangerous. People should understand the risks associated with USB storage devices obtained from sources that may not be trustworthy", warns Tomáš Gardoň.
Explaining the technical details of the malware on its blog, ESET says this self-protecting multi-stage malware is very powerful, mostly as it leaves no traces of ever being present on a system. "After the USB is removed, nobody can find out that data was stolen", it says, adding that it currently "just" steals files, but could be redesigned to do pretty much anything else.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: andriano.cz/Shutterstock
-

Instagram is taking advantage of Twitter's weakness
Publié: mars 26, 2016, 1:45am CET par Sead Fadilpašić

A new report on the global state of social media confirms what everyone’s been talking about lately -- Twitter is struggling and Instagram is taking full advantage of it.
The report, entitled simply "Social", is the product of GlobalWebIndex, and it is a compilation of the latest trends in social networking.
It shows some interesting stats, including the fact that 92 percent of online adults have a social platform. What’s more interesting, the average adult, aged between 25 and 34, is spending 2h 12 m on social media daily.
"Younger groups, women and the lower income quartile devote the most time to networking", the report says.
Growth issues Twitter has been facing for quite some time now may be down to the very essence of what the network is used for, the report suggests. Social networks are usually used to stay in touch with friends (44 percent), and less to keep in touch with the latest news (27 percent).
Instagram is taking advantage of Twitter’s limping, closing in on the gap -- it has retained the title of the fastest growing network, even though only 35 percent of online adults actually have an Instagram account.
Facebook is still king of the social media, with 85 percent of all online adults globally having an account on at least one of the company’s services.
Snapchat has turned out to be quite the disruptor of the social media space. According to the report, 61 percent of Snapchatters use the service to send messages, and 42 percent to actually send a photo.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Tech industry sides with Apple in San Bernadino iPhone case
Publié: mars 25, 2016, 1:44am CET par Sead Fadilpašić

The tech industry is on Apple’s side when it comes to the dispute with FBI over the unlocking of the San Bernardino shooter’s iPhone.
This was, once again, confirmed through a research done by security vendor AlienVault. According to the company’s survey, which polled 1,500 IT security professionals, 33 percent support FBI, while the rest think unlocking the phone will do nothing but weaken overall product security.
Almost two thirds (63 percent) believes Apple should not give in to FBI’s demands.
But the opinion the surveyed have on overall security is what’s dismal here -- almost two thirds believe the government is already so intrusive and pervasive in its surveillance that it’s impossible to have a private conversation on any device.
Moreover, 34 percent believe the government should monitor mass communications for national security purposes.
"We are clearly at a turning point in the history of Internet surveillance and suspicions among those in the know are running high. IT and security professionals can see straight through the public arguments being made about the Apple case", said Javvad Malik, security advocate at AlienVault.
"Many seem to view it as a power grab by the FBI, and an attempt to gain significant new powers that could undermine the communications infrastructure used by us all. But whatever the underlying motives may be, the outcome of this case will clearly have broader implications on future government attempts to access encrypted information, and the development of legal frameworks for state surveillance powers, such as the Investigatory Powers Bill in the UK".
The FBI recently uncovered an iPhone 5c belonging to the San Bernardino shooter. The iPhone is locked and the authorities have no way of unlocking it to see if the phone has any leads on potential accomplices or future plans.
The government asked Apple to help them unlock the iPhone, and has even gone as far as to ask phone makers to build special backdoors so that law enforcement agencies could have access to the devices.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shutterstock/ymgerman
-

Losing customer trust is a major concern for DDoS targets
Publié: mars 24, 2016, 9:44pm CET par Sead Fadilpašić

The loss of trust and confidence of customers is the most damaging consequence of a DDoS (distributed denial of service) attack, a new survey by Corero Network Security says.
In the annual survey, entitled DDoS Impact Survey, losing trust is the most damaging consequence for 50 percent of those surveyed, followed by lost revenue, for 34 percent. The surveyed include IT decision makers (ITDMs), network operators and security experts that were present at the recently held RSA 2016 conference.
"Network or website service availability is crucial to ensure customer trust and satisfaction, and vital to acquire new customers in a highly competitive market", said Dave Larson, COO at Corero Network Security. "When an end user is denied access to Internet-facing applications or if latency issues obstruct the user experience, it immediately impacts the bottom line".
Larson also said that even DDoS attacks which are not large-scale by nature, can be devastating to business. They can impact network performance, ultimately ruining user experience. What’s even more troubling is that such attacks are usually used as a diversion for a more malicious attack.
"Industry research, as well as our own detection technology, shows that cyber criminals are increasingly launching low-level, small DDoS attacks", said Larson. "The problem with such attacks is two-fold: small, short-duration DDoS attacks still negatively impact network performance, and—more importantly, such attacks often act as a smokescreen for more malicious attacks"
"While the network security defenses are degraded, logging tools are overwhelmed and IT teams are distracted, the hackers may be exploiting other vulnerabilities and infecting the environment with various forms of malware", added Larson.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

IT pros: Security budgets are not growing fast enough
Publié: mars 24, 2016, 4:59am CET par Sead Fadilpašić

As an answer to the ever increasing threats of cyber-attacks, the security budgets across various industries are growing, a new survey by The Institute of Information Security Professionals (IISP) suggests.
However, the rise in budgets is not enough to tackle the problem.
The report is based on answers of more than 2,500 members of the institute, working in security across various industries, including a significant proportion at Senior/Lead/CISO level.
In it, it says that for more than 75 percent of members the security budgets have increased, with another 15 percent saying their budgets have stayed the same. Still, 60 percent of respondents said that the budgets were still lagging behind the rise in the level of threats.
"In times of financial pressure or instability as we have seen in recent years, security is often seen as a supporting function or an overhead", said Piers Wilson, Director at IISP. "Security budgets are hard won because they are about protection against future issues, so are a good indication of the state of risk awareness in the wider business community. While it is good news that businesses are increasing investment, it is clear that spending on security is still not at a level that matches the changing threat landscape".
Another problem, once again, is in the shortage of staff. But that, the report says, doesn’t just mean the shortage of actual people -- it also means the lack of required skills and experience necessary. That’s why training and development are among the most important elements for the industry’s future.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Andy Dean Photography/Shutterstock
-

French media goes on the offense against ad-blockers
Publié: mars 23, 2016, 6:00pm CET par Sead Fadilpašić

French media is bringing the fight to ad blocking software. According to a report by The Guardian, a number of local outlets are preventing readers who run ad-blockers from accessing their content.
The sites, some of which are major media publications, are part of a trade association representing online businesses. They’re saying that by using ad blocking software, users are depriving the companies of valuable revenue sources, killing the business.
"For our 400 journalists to provide you each day with high-quality, reliable and varied news each day ... we must be able to rely on advertising revenue", The Guardian cites a message from Jerome Fenoglio, the editor-in-chief of French daily Le Monde.
Le Monde was joined by sports daily L’Equipe and Le Parisien, as well as Deezer, a France-based music streaming service. Even though Le Monde does allow the visitors through, after communicating this message to them, others require users to disable the software.
Ad blocking is a huge, and quite a debatable trend. On one hand, users are enjoying the possibility of an interruption-free online experience, while on the other hand, advertising is what makes a lot of online content free.
Yahoo also recently announced it won’t allow access to its email service to anyone using an ad blocker. On the other hand, whistleblower Edward Snowden once said that "it’s your duty" to use an ad blocking software.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Brian A Jackson/Shutterstock
-

Keyless entry makes car theft easy
Publié: mars 23, 2016, 4:24pm CET par Sead Fadilpašić

Thieves can probably steal a bunch of cars with ease, if they are equipped with keyless entry. Those are the results of a new study done by a group of German car security researchers, looking into just how secure the technology is.
According to a news report by Wired, keyless entry for cars is not secure at all. As a matter of fact, out of 24 different cars, from 19 different manufacturers, all have been easily hacked through a method of amplifying the signal from the key fob in the house.
Not only can thieves unlock your car, but they can also drive it away, apparently.
"This clear vulnerability in wireless keys facilitates the work of thieves immensely", the ADAC website says about the new research. "The radio connection between keys and car can easily be extended over several hundred meters, regardless of whether the original key is, for example, at home or in the pocket of the owner".
These are the cars that were successfully hacked: Audis A3, A4 and A6, BMW 730d, Citroen DS4 CrossBack, Fords Galaxy and Eco-Sport, Honda HR-V, Hyundai Santa Fe CRDi, KIA Optima, Lexus RX 450h, Mazda CX-5, MINI Clubman, Mitsubishi Outlander, Nissans Qashqai and Leaf, Opel Ampera, Range Rover Evoque, Renault Traffic, Ssangyong Tivoli XDi, Subaru Levorg, Toyota RAV4, and Volkswagens Golf GTD and Touran 5T.
The worst part is, the hack itself wasn’t expensive at all. The researchers spent approximately $225 (£157) on their attack device.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: SpeedKingz/Shutterstock
-

Demand for IT security pros is rising in UK
Publié: mars 23, 2016, 4:29am CET par Sead Fadilpašić

The tech talent shortage the UK is faced with nowadays is no small problem, as the demand for IT security experts reaches new heights.
According to a new research by recruitment finance provider Sonovate, IT security professionals are currently the most wanted workers in the UK’s growing jobs market.
The growth for such roles has reached 19 per cent -- a new year-on-year high, and is expected to reach 30 percent over the course of 2016. Besides the IT security roles, user experience (UX) roles are also in demand (17 percent year-on-year growth), as well as Architecture (five per cent).
Looking at IT security alone, consultants, network security engineers and analysts are most wanted, with 52 percent, 26 percent, and 24 percent respectively.
"IT security has always been important for companies looking to protect their business interests -- something which has only been reinforced by the recent spate of high-profile data breaches and cyber-attacks. In addition, changing attitudes to work have resulted in a burgeoning contractor market", said Richard Prime, co-CEO and co-founder of Sonovate.
Prime added: "There’s a real appetite for high-quality contractors at the moment. This research says one thing loud and clear: it’s a great time to be an IT security recruiter, especially one with an eye for opportunity".
The lack of tech talent is a big issue in the UK nowadays, with Stack Overflow recently reporting how recruiters, with their lack of knowledge of the industry, are more of a nuisance than any help.
The full report by Sonovate can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Manczurov / Shutterstock
-

Some UK developers believe recruiters lack IT knowledge
Publié: mars 22, 2016, 11:29pm CET par Sead Fadilpašić

The shortage of tech talent in the UK is not as straightforward as we thought -- it’s not just about the country not having enough actual people. The problem is also in the recruiters, a new and comprehensive study suggests.
The study was done by the Stack Overflow website for developers, and surveyed more than 56,000 people living in 173 countries. According to the survey, 73 percent of developers in the UK are either actively looking for new jobs, or are "open to new opportunities".
Approximately six percent of those looking for work said the recruiters were the most annoying part of the job hunt, mostly because of their "lack of knowledge about the industry".
"The 2016 Stack Overflow developer study reveals that the majority of UK developers are in fact open to new career opportunities, but at the moment some recruiters simply do not know how to attract and engage with developers, which in this market is a big problem. It's vital that recruiters are given the right tools to develop their knowledge and understanding of how developers work. At Stack Overflow, we are committed to bridging the gap and driving this change", commented Angela Nyman, director of International Marketing at Stack Overflow.
The report also says UK developers are among the highest paid in Europe, with an average annual salary of £45,387. When job hunting, their top priorities are salary, culture and a good work/life balance.
Gender equality is still far off, with just 5.5 percent of UK respondents being female, but it seems as there are better times ahead: 24 percent of females currently have less than two years’ experience, compared to 12 percent of males.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: garagestock/Shutterstock
-

Downtime costs more than ransomware
Publié: mars 22, 2016, 11:58am CET par Sead Fadilpašić

You might think that having to pay for files locked by ransomware is costly, but it’s the downtime that actually hurts a business more.
Those are the results of a new survey conducted by cloud IT services company Intermedia. The survey, entitled 2016 Crypto-Ransomware Report, polled nearly 300 expert IT consultants about the current trends in malware.
According to the report, many firms do not have a business continuity plan, which would help them continue working while under a cryptolocker attack. Instead, they suffer costly downtime, with 72 percent not being able to access their files for two days, and 32 percent for five days, or more.
The results are obvious -- data recovery costs, reduced customer satisfaction, lost sales and, as Intermedia puts it, "traumatized employees".
There are two other important trends spotted in the report. One is that ransomware no longer targets just individuals and small firms -- it’s also targeting bigger businesses now. Almost 60 percent of businesses targeted by ransomware have more than 100 employees, and 25 percent have more than 1,000.
The second important trend is that ransomware is a growing industry. Walter Chamblee, director of Information Technology at Signaturefd.com, said, "Ransomware attacks are on the rise and are growing in complexity. Without the right protection measures in place, ransomware can be majorly disruptive to a business. In these cases, it’s the user downtime and the hassle for IT that’s far costlier, even if you pay the ransom".
The full report can be found on this link
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Jean Lee / Shutterstock
-

Email marketing works
Publié: mars 18, 2016, 7:05pm CET par Sead Fadilpašić

You might be annoyed by the constant marketing you’re getting in your email, but that’s only because research shows that the method works. Not only does it work, but it’s working better than (almost) ever.
Email marketing software provider Sign-Up.to released its new annual Email Marketing Benchmark Report, looking at how successful email marketing campaigns are. It employed some serious numbers into its results -- more than a billion emails across 29 industry sectors, looking at various parameters such as click through rates, open rates and so on.
The report says that the average open rate of marketing email jumped 1.8 percent year-on-year, to 24.88 percent. This also means the average open rate has been growing for seven consecutive years. The best performers come from the Legal/Accounting sector, TV/Radio/Film and the Government.
Click-through rates also jumped 9.3 percent to 3.42 percent, returning to the highest level since 2010, the report says. Mobile is also jumping, with open rates on mobile devices increasing 1.2 percent year-on-year, to 54.59 percent. Unsubscribe rates (0.52 percent) showed a 5.5 percent decrease from the 2015 figures.
"Our 2016 Email Marketing Benchmark Report continues to indicate that the benefits of email marketing are growing", said Matt McNeill, brand director, Sign-Up.to. "Overall, the report shows that brands that take the opportunity to understand and profile their audience and offer relevant, timely and valuable messages are rewarded with better open rates, improved levels of engagement and ultimately greater customer loyalty".
"Most reports available to UK businesses provide global figures or focus on large companies. It’s important for us to provide a viable benchmark for SMEs in the UK. We want to help them make the most of their assets and our report shows that focusing on areas like mobile responsive design, automation and precision targeting can dramatically increase their rates of success".
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Pavel Ignatov/ Shutterstock
-

Want the best customer support? Use Facebook
Publié: mars 18, 2016, 5:59pm CET par Sead Fadilpašić

Facebook is the number one channel for people looking to get answers from retailers’ customer service in the UK, a new study shows.
According to the Eptica Multichannel Customer Experience study, Facebook is the channel through which retail customer service answers most frequently and most accurately, followed by email. Twitter came in third, with pretty poor results.
The study looked at 40 "leading" UK retailers, split into four sectors (food and wine, consumer electronics, entertainment, and fashion), and sent them questions on the three channels, mimicking customer interaction.
The study says that UK retailers could successfully answer 59 percent of questions asked via Facebook, 55 percent on email and 45 percent on Twitter. Only 10 percent responded on all three platforms.
Despite solid results over email, more and more retailers seem to be switching off from the channel. Today, 88 percent of retailers offered email to non-customers, 10 percent down from a year before.
Across the pond, the results are somewhat different. In the US, retailers answered, successfully, to 73 percent of emailed questions, 54 percent of questions on Facebook, and 20 percent on Twitter. Things aren’t looking good for the micro-blogging site, on both sides of the Atlantic.
"Retailers on both sides of the Atlantic seem to be adopting fundamentally different strategies when it comes to customer service", said Olivier Njamfa, CEO and co-founder, Eptica. "What the Eptica research demonstrates is that retailers in the UK and US are focusing on specific channels, rather than adopting a truly multichannel approach that delivers high levels of service, whatever the customer’s channel of choice. Companies need to learn from each other and deliver a consistent experience if they are to thrive in increasingly global markets".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: nevodka / Shutterstock
-

The majority of teens do not want a career in engineering
Publié: mars 17, 2016, 9:00pm CET par Sead Fadilpašić

Teens understand the importance of technology and engineering for the future of the world, but aren’t really interested in pursuing a career path in the industry, a new research says.
A new study by the Elizabeth Prize for Engineering says that 82 percent of teenagers, aged 16 and 17, believe engineering is a key part in the future of innovation. On the other hand, only 21 percent are interested in pursuing a career in these fields.
What’s also interesting is that money, position, job security and material things in general is not what drives these kids -- it’s the benevolence that’s in focus here. Approximately 36 percent of kids questioned said they’d go into technology to build innovations to change the world.
So what exactly would they be changing?
Climate change and depleting energy resources is the top priority for 70 percent of them. They feel engineering could solve these issues within the next 20 years.
The report also says that STEM subjects (science, technology, engineering and math) still have a reputation of being hard, which is also a reason why some of the kids decide to avoid it, girls in particular.
Nigel Whitehead, group managing director at BAE Systems, said: "Our sector needs to work together to overcome some of the outdated stereotypes and old-fashioned notions that engineering isn’t a career suitable for women. We must do more to show all young people -- and their parents -- that engineering is a great career choice. We need to be bolder about the importance of Stem subjects".
The full report can be found on the Computer Weekly site, here.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Pressmaster / Shutterstock
-

Over two thirds of businesses want to cut SIEM costs
Publié: mars 17, 2016, 4:12pm CET par Sead Fadilpašić

Security information and event management (SIEM) systems are placing extra weight on companies’ budgets, a new study suggests.
According to IT auditing software company Netwrix Corporation, 69 percent of companies are looking to reduce SIEM bills.
For the study, entitled The 2016 SIEM Efficiency Survey, the company studied the opinions of 234 large enterprises using SIEM solutions for security and IT infrastructure monitoring.
The results show that SIEMs are quite expensive, mostly when it comes to maintenance and support. Looking at what drives the cost of SIEM ownership up, the need to hire and train more SIEM analysts scored highest (4.8).
"In the past few years, SIEM solutions have become a cornerstone of organizations’ security policies. Although SIEM solutions are widely used in the enterprise sector, the study shows that companies are not completely satisfied with the high costs and level of visibility provided by SIEM", said Alex Vovk, CEO and co-founder of Netwrix.
"The tendency we see today is that most companies are not ready to put up with considerable expenses and limitations. The companies are looking for ways to solve this problem and finally understand what is going on in their IT infrastructures. IT auditing can become a perfect solution to overcome these drawbacks and provide complete visibility, while decreasing IT costs".
The survey also says SIEM is necessary for better security threat awareness, that excessive data could be worse than the lack of data and that reports on data are sometimes too difficult to understand.
The full survey can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: tomertu/Shutterstock
-

Majority of IT pros support Apple in legal fight with FBI
Publié: mars 17, 2016, 10:21am CET par Sead Fadilpašić

Encryption is a must-have in today’s digital communications, IT pros agree, adding that what the government is (trying to) achieve with surveillance could mean the death of privacy altogether.
Those are the results of a new survey conducted by security firm AlienVault. It surveyed the attitudes of more than 1,500 IT (including security) professionals about today’s privacy, and came up with interesting results -- 34 percent believe the government should be able to eavesdrop on communications for the purposes of national security.
Among the general population, that number sits at 60 percent -- almost twice as much.
Looking at the FBI - Apple debate, some IT pros believe FBI is using the opportunity to set a new legal precedent, with the majority (63 percent) supporting the tech company.
AlienVault suggests this might be the case because IT pros have more knowledge and can see the bigger picture of what government surveillance at this level might bring. They believe the government could start prosecuting people for crimes they admitted to in private conversations. People could also stop doing business with US firms, as they’ll stop trusting them.
"Those in the IT and security industries are uniquely positioned to comment on privacy, because they understand the tools and processes that are frequently used to circumnavigate security protocols", says Javvad Malik, security advocate for AlienVault.
"We often find that the same vulnerabilities used by intelligence agencies to spy on global citizens can also be exploited by criminals to steal your passwords. This gives them a unique perspective on privacy debates and explains why they often have quite different views when compared to the general public".
Stronger encryption was the best way to protect online privacy, they said, with just 34 percent thought tougher legislation was the way to go. Some even suggested you shouldn’t mention sensitive information in digital communications at all.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: TK Kurikawa / Shutterstock
-

Symantec introduces website encryption service
Publié: mars 16, 2016, 8:30pm CET par Sead Fadilpašić

Symantec today announced the global release of a new product which will help companies encrypt user data on their websites.
The new product is called Encryption Everywhere, and it will be offered through hosting providers. According to a press release following the announcement, there will be a couple of levels of encryption and general protection the new service will offer, but Symantec would love to see every "legitimate" website in the world have at least the basic level of encryption by 2018.
The security firm says there are a couple of reasons why webmasters should encrypt the data on their sites: first, it will help protect their customer data, which should be enough in its own right. But besides keeping the business safe, it will also do good for the company brand. Also, Symantec says Google and "other browsers" have announced they’ll push unencrypted websites down in search ranking results.
"There are almost a billion web sites today, yet only about three percent of those sites are encrypted, which means cybercriminals have been able to make a good living off of the web’s lack of security", said Roxane Divol, senior vice president and general manager, Website Security, Symantec. "Symantec is about to change the game for cybersecurity with Encryption Everywhere. It’s time to secure every legitimate website and win back security on the internet for every business and consumer. That’s why Symantec is making it easy to secure any website from the very moment it is registered or renewed, starting with free, basic encryption all the way through to complete website security solutions".
Encryption Everywhere will be demonstrated during the World Hosting Days conference in Rust, Germany March 15-18.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: jijomathaidesigners / Shutterstock
-

Dropbox moves away from AWS, now stores 90 percent of user data
Publié: mars 16, 2016, 6:52pm CET par Sead Fadilpašić
Look at Dropbox, all grown up and moving away from home. The company has announced that it is now using, almost entirely, its own custom-built infrastructure to hold data.
Dropbox says this is an important milestone, as it moves away from Amazon Web Services it relied on before. Still, it will continue to partner with Amazon, when "it makes sense for our users", Dropbox says.
Writing a blog post on the milestone on Monday, Dropbox’s Akhil Gupta said the company now hosts 90 percent of all data. "We’re excited to announce that we’re now storing and serving over 90 percent of our users’ data on our custom-built infrastructure".
Cloud hosting service company Dropbox keeps two kinds of files: file content and metadata about files and users. While metadata about files and users was always kept on Dropbox’s custom servers, files themselves were stored on Amazon.
But as the company grew, and more users flocked to its service, it became clear that a custom-built infrastructure was the way to go.
"As the needs of our users and customers kept growing, we decided to invest seriously in building our own in-house storage system. There were a couple reasons behind this decision. First, one of our key product differentiators is performance. Bringing storage in-house allows us to customize the entire stack end-to-end and improve performance for our particular use case. Second, as one of the world’s leading providers of cloud services, our use case for block storage is unique. We can leverage our scale and particular use case to customize both the hardware and software, resulting in better unit economics".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Google's Single Sign On adds support for Microsoft Office 365, Facebook at Work, Slack and more
Publié: mars 16, 2016, 10:26am CET par Sead Fadilpašić

Besides being the super poplar search engine, email provider, work and collaboration services provider, Google is also used, by a number of different services, as an identity provider.
It allows people to register and log into different online services using their Google account. Now, the company announced it’s expanding the feature to add a number of new services, some of which are direct competitors.
There’s a total of 14 new pre-configured options, including Microsoft Office 365, Facebook at Work, New Relic, Concur, Box, Tableau, HipChat and Slack. You can find out more on this link.
The company says it’s not just about being able to log into services with Google, it’s also about using the company’s security measures, especially when going mobile.
"Google’s identity services provide even more security on mobile when combined with Google Apps enterprise mobile management controls like password strength, lock screen requirements and app management", says Shashank Gupta, a product manager for Google Apps for Work.
"These can work in tandem with the increasing number of mobile security options, from hardware such as fingerprint readers, to software such as Google’s Smart Lock. Our Google Smart Lock features are available to all Google Accounts, including those used at work, and we provide identity services and enterprise mobility management (EMM) as part of Google Apps for Work at no additional cost".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Most IT pros are unprepared for data migration failure
Publié: mars 14, 2016, 6:16pm CET par Sead Fadilpašić

Among businesses, data migration seems to be a much bigger issue than previously thought. Those are the results of a new report by Vision Solutions, entitled 2016 State of Resilience.
It gathered responses from more than 2,000 CTOs, CIOs and other IT leaders all around the world, from North America, Latin America, Europe, Africa and the Middle East, and looked at various data trends including migration, HA/DR, cloud and data sharing.
One of its key findings is the fact that almost half of global IT leaders experienced a migration failure -- a trend which saw a 20 percent increase between 2014 and 2015. Seventy percent of IT professionals all over the world failed to calculate how much migration downtime cost them.
It was also said that 85 percent either had no recovery plan or weren’t completely confident their plan was complete.
There has been more data loss than a year before, while the use of hardware-based storage solutions and software-based storage solutions were evenly split (35 percent both ways).
A quarter of IT professionals said they will include a third-party in their future plans, be it either managed services, cloud or DRaaS.
"Even one imbalance in the IT system -- which includes data, applications, hardware, networks, external vendor software and partners -- can be the tipping point between an organization’s success and failure", said Alan Arnold, Vision Solutions executive vice president and chief technology officer.
"In a world where data insights lead business growth, it’s essential that IT leaders take a close look and identify the best tools and solutions to ensure resilience".
The full Vision Solutions report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: bahri altay/Shutterstock
-

Only half of businesses believe eCommerce maximizes profits
Publié: mars 4, 2016, 1:46pm CET par Sead Fadilpašić

A recent poll into the state of eCommerce has unveiled that half of businesses believe their eCommerce sites help them be as profitable as possible.
The results were released late last week in the 2016 State of the Digital Commerce report, published by Salesforce eCommerce integration company CloudCraze.
The report surveyed 340 IT and marketing professionals across business to business, as well as business to consumer industries. The goal was to reveal any opportunities and challenges digital brands and legacy commerce system users are facing today.
Besides saying that half of the businesses believe eCommerce helps them be profitable, it was also unveiled that 70 percent of companies have spent more than $1 million (£710,000) on their website. Moreover, 30 percent have spent more than $2 million (£1.42 million).
For almost a half (44 percent), it took more than a year to implement the current site.
The final point of the report is that quickly updating evolving needs, scaling to the changing market and getting a holistic view of the customer are the top three pain points for brands.
The full report can be accessed via this link.
While you’re at it, you can also take a look at the seven handy tips on how to boost your eCommerce business.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Nonnakrit/Shutterstock
-

German startup has greener data center than Facebook and Google
Publié: mars 4, 2016, 10:24am CET par Sead Fadilpašić

You might think Apple or Google have the greenest datacenters, but it’s actually a German startup called Cloud&Heat that takes the crown.
The company said it managed to realize the lowest energy consumption and has "undercut Google’s optimum value by 40 percent".
"The latest results measured in our data centre at Wallotstraße in Dresden undercut the energy values of the most modern and efficient server facilities significantly. Also, those of Google and Facebook", says Nicolas Röhrs, CEO of Cloud&Heat.
Reference values of the measurement methods are the Power Usage Effectiveness value, PUE, and the Energy Reuse Effectiveness value, ERE. "We have achieved a sensational PUE of 1.01* and a ERE of 0.62**, with regard to a year. This is the lowest measured value worldwide. We have not reached this value in cool Scandinavia or Alaska but in our data centre in Dresden, Germany, with a current expansion stage of 60 percent", says Röhrs
This latest server generation will be presented, exclusively, during the CeBIT, March 14 - 18. There, the Dresden, Germany-based start-up will demonstrate a continuous live-measurements of its power usage effectiveness (PUE).
"We verifiably operate the energy- and cost-efficient data centre in the world. Two years ago, nobody has trusted us to achieve this", says founder and physicist Dr. Jens Struckmeier.
The company compares its datacenter with Google’s and Facebook’s: "Our values undercut Google’s PUE about four percent and the ERE about 42 percent. For a company like Google, these four percent already mean an energy saving in the double-digit million".
"With this technology, the carbon dioxide emission could be reduced by several thousand tons -- even without considering reusing the heat. Our system meets all requirements of a sustainable IT landscape and fulfil the standards of data security made in Germany", explains Röhrs.
"The high efficiency can mainly be justified by the used water cooling and the waiver of any cooling systems. Furthermore, the air is pre-cooled according to the needs over an existing underground car park, so that a cooling can take place all year", concludes Röhrs.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: potowizard / Shutterstock
-

One in three laptops will ship with an SSD in 2016
Publié: mars 4, 2016, 9:45am CET par Sead Fadilpašić

The average contract price of mainstream PC-Client OEM SSDs in Q1 of 2016 has dropped, a new report by TrendForce’s DRAMeXchange suggests.
MLC-based SSDs, as well as their TLC-based counterparts have seen their prices drop 10-12 percent, and seven-12 percent respectively.
The TLC ones are doing slightly better because most SSD makers are just starting to ship the products, the report suggests. That is mostly because the first quarter is traditionally slow season for notebooks.
The price change between different disks will also shrink, the report says. The difference between 128GB SSDs and 500GB HDDs will shrink to less than $3 (£2.13) this year, and the difference between 256GB SSDs and 1TB HDDs will shrink to less than $7 (£4.98).
Overall, this is expected to be a good year for the SSD, as its adoption in notebooks will reach 30 per cent.
Samsung will still be the number one player in the game, however it might focus more on migrating to 3D NAND-Flash products, in order to cut costs. Other SSD manufacturers will play the catch-up game, as they step up shipments of 15nm/16nm TLC products with higher margins.
The overall amount of shipments of Client-SSDs for Q1 of 2016 is expected to drop anywhere between four and six percent, compared to Q4 2015. Notebook shipments, on the other hand, will drop somewhat more.
Senior manager at DRAMeXchange, Alan Chen, said that by taking retail SSD sales into account, the total Client-SSD shipments for Q4 2015 were 22.6 million.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Imagentle/Shutterstock
-

Unified communication tools boost productivity and satisfaction for remote workers
Publié: mars 2, 2016, 8:19pm CET par Sead Fadilpašić

Cloud unified communications specialist Outsourcery says that the full potential of remote working can only be achieved if strong UC tools are in place. Skype for Business, Slack or Trello, just to name a few, are proven to boost productivity and the possibility of working from virtually anywhere, anytime, has great effects on employee satisfaction.
There have been numerous studies about the benefits of remote working, and all of them came to the same conclusion -- this is something all of us should be implementing. One of those studies was recently published by Lancaster University’s Work Foundation, which suggests that by 2017, more than half of all UK businesses will have employed flexible working at some parts of their organization.
Jon Seddon, Head of Product at Outsourcery, commented: "As this survey found, businesses who enable their employees to work from multiple locations experience great benefits to their efficiency, employee satisfaction and industry reputation as positive places to work. With the rise of millennials in the workplace, remote working and flexible hours are becoming more commonplace and suitable systems need to be implemented in order to ensure the benefits are realized".
One of the main concerns executives have, regarding remote working, is the lack of supervision. Some of them believe people would work less, if they’re not being monitored. Seddon believes otherwise.
"The effective collaboration and teamwork between employees working remotely is one that an integrated UC tool can greatly benefit. With voice and video calls, instant messaging and conferencing all enabled in a UC solution, workers are contactable regardless of their location, ensuring the business still runs efficiently. The ease of contact that a UC solution brings can also address the concerns of some managers who would prefer their people to be in the office. Team collaboration can be maximized with easy conference call set up across video, voice and mobile devices with powerful screen and document sharing built in".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: olly/Shutterstock
-

Malvertising campaigns now use fingerprinting techniques
Publié: mars 2, 2016, 12:29pm CET par Sead Fadilpašić

Cyber-criminals are now using fingerprinting techniques in their malvertising campaigns, researchers from security firms Malwarebytes and GeoEdge have reported.
Fingerprinting is an evasion technique in which crooks, through snippets of code, check if the targeted machine is a honeypot set up by malware researchers or an actual machine belonging to a potential victim.
"For many years, threat actors have leveraged the ad industry to deliver malicious payloads in very efficient ways. However, most malvertising attacks usually tend to be discovered early on and thwarted, therefore increasing the amount of work required to set up new ones constantly", said Jérôme Segura, senior security researcher at Malwarebytes.
So far, this technique was only spotted at the exploit kit level, mostly with Angler, but has now moved "up the chain", as the researchers say, reaching the malvertising phase, thanks to online ads.
"This flaw allows attackers to enumerate the local file system and look for the presence of certain clues that might identify a machine belonging to a security researcher or acting as a honeypot", researchers Jerome Segura from Malwarebytes, and Eugene Aseev from GeoEdge write in their report entitled Operation Fingerprint. Now, bogus advertisers are analyzing potential victims.
There are four types of possible campaigns, the report suggests, including the 'Fake company' campaign (attackers use stolen websites, slightly rebranded to appear legitimate), the Custom SSL campaign (leverages the CloudFare infrastructure to hide the malicious server’s IP), the Custom URL shortener campaign (hiding the fingerprint payload within a GIF image served over HTTPS), and the DoubleClick Open Referrer campaign (the code is still hidden within a GIF, but is now encoded with a special key, only provided once per IP address).
"Borrowing techniques from exploit kits makers, rogue advertisers are prescreening potential victims via an Internet Explorer information disclosure vulnerability that lets them check for the presence of certain files on disk that belong to security software, network traffic tools, and Virtual Machines. This is done simply by inserting a hidden piece of code in the last place one would expect, within an innocuous GIF pixel tracker typically used by the ad industry", Segura added.
The vulnerability seems to be targeting Internet Explorer 10 users, the researchers have said. They also gave advice how to keep safe from potential threats:
To defend against malvertising, users should keep their computers up to date and uninstall any piece of software they no longer or rarely use in order to reduce the surface of attack. For example, browser plugins such as Flash or Silverlight have been heavily exploited in recent months and users are advised to consider disabling or removing them all together.
Since the best security posture is one that has layers, it is also good practice to run additional tools that fend off attacks at different levels. When it comes to drive-by download attacks such as malvertising, exploit mitigation software is particularly effective, as well as other programs that restrict JavaScript or ad banners with the ability for the user to opt-in.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: lolloj/Shutterstock
-

Cloud solutions offer intangible benefits to businesses and customers
Publié: mars 1, 2016, 8:54pm CET par Sead Fadilpašić

There are ways cloud-based solutions are improving businesses that are easy to spot and monitor, such as faster and more flexible access to technology, as well as less spending, but it’s the changes that you can’t see, or measure, that are transforming businesses, eg solutions says.
The Cloud Industry Forum has done the research, and here’s what cloud-based solutions can do to your business that’s basically intangible: 60 percent have reported improvements to both customer and employee propositions, and 29 percent have reported improvements in customer service.
Moreover, 26 percent say customer satisfaction also improved. If that wasn’t enough to convince you to go Cloud, here’s more: 45 percent said it was crucial to enabling innovation, while 31 percent said it was a major initiative to improve customer service and support.
Elizabeth Gooch, CEO, eg solutions, stated: "The way in which forward-thinking organizations transact and interact with both their customers and employees today has fundamentally changed. There are opportunities for businesses of all sizes to embrace digital technologies as a means to disrupt traditional industries and secure competitive advantage".
"The imperative for change, as seen in this research and indeed our own research findings, are many. But chief amongst them are the mounting demands of the consumer and the increasingly blurred line between our personal and working lives. This is the beginning of the era of the 'Always-On' Enterprise and those businesses that can adapt to the changes in the way that we as consumers interact are the ones that will flourish", added Gooch.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: phloxii/Shutterstock
-

Some smartphone users would not be 'upset' by data theft
Publié: mars 1, 2016, 3:51pm CET par Sead Fadilpašić

There are two kinds of people in this world, and I don’t mean those who can read binary and those that cannot. I’m thinking about those who are aware of the security risks smartphones pose, and those who aren’t.
And according to a new survey by security firm Norton, the world is literally split in half over this -- 56 percent of those surveyed say the prospect of the financial and banking information stored on their phone being hacked is "upsetting". Meaning, for the remaining 44 percent it’s not upsetting.
Not only is it not upsetting, but they "either do not care about their information being hacked or they are less concerned about financial hacks than other information being compromised", Norton says in its report.
For almost 10 percent, out of more than 5,000 surveyed in US, UK, Canada, Australia and Japan, there’s not a single thing a hacker could take from their phone that would upset them. That doesn’t mean it’s necessarily true -- that just means they feel that way. "They don’t think anything bad could happen on a smartphone", Norton comments.
It’s the same with IoT -- globally, users feel more comfortable using banking and financial apps than home IoT devices. Despite the fact that we’ve seen countless examples of IoT devices getting hacked, people would still feel secure.
The point is not to panic, or to stop using IoT devices, Norton says. Instead, the point is to educate everyone that using these devices comes with great responsibility. "We want the people who are not concerned about hacking to understand the risk", Norton says.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: View Apart/Shutterstock
-

Your business doesn't have a website? A DDoS attack can still happen
Publié: mars 1, 2016, 2:46pm CET par Sead Fadilpašić

Just because your business doesn’t have a website, that doesn’t mean it can’t be a victim of a DDoS (distributed denial of service) attack. This sentence might not make much sense at this point, but keep reading.
Security firm Kaspersky Lab and researchers B2B International looked at what cyber-crooks go for when attacking businesses and enterprises, and here’s what they came up with:
Last year, 16 percent of companies (globally), were victims of a DDoS attack. Among enterprises, the percentage jumps up to 24. For most, external activities, such as websites, were targeted. Among half, websites had been hit, logins and portals were attacked in 38 percent of cases, while communications services were attacked 37 percent of times. Transactional systems had been affected in 25 percent of cases.
But also, in 25 percent of cases, file servers had been hit, and 15 percent said their operational systems were targeted. Another 15 percent said a DDoS attack hit their ISP network connectivity.
"It’s important to take a DDoS attack seriously. It’s a relatively easy crime to perpetrate, but the effect on business continuity can be far-reaching. Our study found that alongside the well-publicized impact of an attack, such as website downtime, reputational damage and unhappy customers, DDoS hits can reach deep into a company’s internal systems. It doesn’t matter how small the company is, or whether or not it has a website; if you’re online, you’re a potential target. Unprotected operational systems are just as vulnerable to a DDoS attack as the external website, and any disruption can stop a business in its tracks", said Evgeny Vigovsky, head of Kaspersky DDoS Protection, Kaspersky Lab.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Duc Dao / Shutterstock
-

More than half of UK businesses will embrace flexible and remote working in 2017
Publié: février 29, 2016, 9:08pm CET par Sead Fadilpašić

Next year will be the tipping point for flexible and remote working in the UK, with more than 50 percent of businesses adopting it by the end of next year. That number will grow even more, to 70 percent, by the time we get to 2020.
Those are the results of a new survey produced by Lancaster University’s Work Foundation, and commissioned by Citrix. The survey, entitled Working anywhere: A winning formula for good work?, asked 500 employees at a managerial level about the pros and cons of flexible working.
So what are the pros? The study highlights four reasons why companies should implement flexible working: increased productivity, improved employee wellbeing, talent attraction and retention and reduction in accommodation costs.
So why is flexible working, if it’s so good, not yet already at 90 percent, at least? The report says there are cultural barriers that need addressing: 37 percent of managers believe this means longer hours, while 22 percent say they feel disconnected from the team. An additional 28 percent felt it blocked them from overseeing other people’s work. A quarter (24 percent) also said all work is carried out in company premises.
That’s not all, though -- 75 percent believe this will put more strain on the HR department, 84 percent say it will require changes to performance management, and 82 percent think this will require changes to employment terms and conditions.
The study says implementing flexible working requires three key commitments: careful planning, leadership and a new approach.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shutterstock/Rawpixel
-

Ransomware is the biggest threat to Android users in UK
Publié: février 29, 2016, 8:36pm CET par Sead Fadilpašić

Ransomware was the biggest threat to Android users in the UK last year, a new report by security company Bitdefender says.
Even though it’s not as dangerous or prolific as its Windows counterpart, ransomware still played a major role in the overall mobile security landscape for last year.
Here are the numbers: In Q3 2015, ransomware on Android accounted for 28 percent of all malware. For Q4, that number was at 19 percent. Compared to other types of malware, ransomware was 14 percent more frequent in Q3 and seven percent in Q4.
Android.Trojan.Slocker accounted for 22 percent of Android malware threats in the UK in the latter half of the year, the report says, topping the charts in the UK, Germany and Australia.
"Due to the popularity of Android devices, malware developers will continue to write code specifically targeting them. Android malware is not only a lucrative business for hackers but also a gateway for other malicious actions", states Catalin Cosoi, chief security strategist at Bitdefender.
"Users must avoid installing applications from unofficial vendors, instead only using those found on trusted marketplaces. Non-reputable apps have a high chance of containing malware such as ransomware or data-stealing Trojans, resulting in significant financial or data loss".
Looking at the global scale, ransomware is not that big of a threat on Android -- it’s much more dangerous on Windows. On Android, it accounts for four percent of all malware reported in the second half of the year.
Bitdefender suggests that the UK is a big target as ransomware seems to have a high success rate on the Island -- 44 percent have apparently paid to get their devices unlocked.
The report doesn’t say how much money victims have to pay, but previous reports on ransomware suggest it’s anywhere between $12 and $300, usually paid in Bitcoin.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Ton Snoei / Shutterstock
-

Most consumers don't like to be tracked, but few are doing something about it
Publié: février 29, 2016, 5:07pm CET par Sead Fadilpašić

Most users know their online activity is being tracked. They’re not OK with it, yet most of them do nothing about it. Those are the general conclusions of a new quiz entitled Are you cyber savvy?, made by Kaspersky Lab.
The security firm says consumers don’t know how to protect their privacy online.
The majority of users (79 percent) don’t like being tracked, but 41 percent do nothing about it. Nine percent didn’t even know they were being tracked.
Twenty-seven percent use their browser’s privacy mode, and 11 percent use a special plug in, Kaspersky Lab says, before giving tips on how to stay safe online:
- Disable auto add-on installation. Block suspicious websites and pop-ups, make SSL certificate checks compulsory and block third party cookies.
- A lot of software (especially freeware) come bundled with other software. That other software is sometimes called bloatware and basically installs toolbars, plugins and extensions that often collect user data.
- Use HTTPS sites whenever you can. Dedicate a specific browser for primary online services.
- Use VPN traffic encryption
- Use private features offered in various security programs and browsers.
David Emm, principal security researcher at Kaspersky Lab says, "Consumers are uncomfortable with the fact that their online activities are being tracked. And who can blame them? With tracking data, it’s possible for advertisers, or even malicious third parties, to peer into the life of a person -- from where they go, to the sites they browse. However, the crux of the problem is that many users simply aren’t cyber-savvy enough when it comes to protecting themselves from online tracking. They may be concerned, but do nothing about it. Even worse, they may not understand that they are putting their privacy at risk at all".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Roobcio / Shutterstock
-

Malware spreading through cloud apps
Publié: février 29, 2016, 3:00pm CET par Sead Fadilpašić

There’s a good chance the cloud apps you use at work are laced with malware. Those are the findings of the latest report by cloud access security broker Netskope. In its February 2016 Netskope Cloud Report, the company says the usage of cloud apps in enterprises has never been this high -- ever.
In Q4 of 2015, employees used on average 769 different cloud apps, representing a 26.5 percent increase from the previous report. But (there’s always a but) -- 4.1 percent of enterprises have sanctioned malware-infected cloud apps.
"Considering that unsanctioned apps represent the majority of an enterprise’s total cloud app footprint (at 95 percent), report findings indicate IT may have an even larger scope of cloud app-based malware in enterprises than initially realized", it says in the report.
Employees can spread malware through sync and share mechanisms, without actually knowing. As many people use different cloud apps to collaborate and work, malware can rapidly spread throughout an organization.
"Employees are adopting cloud apps at an unprecedented rate, and organizations must prepare for the increasing security risks and challenges associated with the changing workplace", said Sanjay Beri, co-founder and CEO, Netskope. "Now more than ever, it’s imperative that organizations have complete visibility into and real-time actionable control over their cloud app usage to better monitor and understand trends and vulnerabilities. It’s only with this knowledge that IT can begin to protect against threats lurking in cloud apps, such as malware".
The report also suggests that Microsoft’s cloud apps are eclipsing those of Google, as well as that enterprise cloud apps aren’t prepared for the EU GDPR (general data protection regulation), something we’ve covered before.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Blue Island/Shutterstock
-

Dragon Anywhere dictation app now available on Android, iOS
Publié: février 26, 2016, 7:33pm CET par Sead Fadilpašić

Dragon Professional, the dictation program from Nuance Communications, is now available on mobile platforms, both Android and the iOS.
The mobile dictation app, called Dragon Anywhere, is available in UK English for mobile phones and tablets, and it’s powered by the cloud.
It offers continuous dictation (no time or length limits), voice formatting, editing, as well as rich customization features. All dictated notes can be synchronized across devices, both mobile and static.
Besides being able to share files via Dropbox, mail, Evernote or the clipboard, Dragon Anywhere files can also be shared cross-platform, to Mac computers and PCs operating the Dragon Professional Individual or Dragon for Mac.
"We designed Dragon Anywhere for today’s professionals who spend more of their time in the field or traveling but are still tasked with documentation demands that lengthen the work day and cut into other important tasks", said Peter Mahoney, senior vice president and general manager of Dragon. "With Dragon Anywhere, professionals can complete, edit, and share important documents and reports in real-time, simplifying the paperwork process, saving time, and improving productivity".
You can get Dragon Anywhere, on UK English, as a subscription service via the Nuance online store. It has a couple of subscription options, including a one-week free trial.
Subscriptions start at £14.99 a month with the annual package costing £149.99.
Besides buying it on the Nuance online store, the app can also be found on Google Play and the App Store. It requires iOS 8.1 or Android 4.4 or higher.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Major cities to become 'smart' by 2020
Publié: février 26, 2016, 3:51pm CET par Sead Fadilpašić
Within the next four years, a bunch of cities around the world will be transformed into smart cities, technology research firm IHS Technology suggests.
By becoming smart, they will offer operators $25 billion (£17.96bn) in opportunities.
According to IHS Technology, Los Angeles, San Francisco, Chicago and New York, London, Amsterdam, Seoul, Hong Kong, Tokyo and Singapore are most likely to become "smart" before 2020.
Currently, there are 423 smart city projects, including safety and security, energy and resource efficiency, mobility and transport, physical infrastructure, governance and healthcare.
The biggest effort is in the mobility and transport industry, which currently has 110 projects, IHS Technology says.
Physical infrastructure industry sits on number two with 107 projects, while there are 104 energy and resource efficiency projects. The least amount of projects are in the healthcare industry, a total of 13.
Companies looking for places to kickstart their smart city initiatives should go either to the United States or the Asia Pacific region, the company suggests.
The United States is the country with the highest number of smart city projects (91), while the Asia-Pacific region is a key market for smart city development. This is due to accelerated urbanism and economic growth in the region.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Kaspersky declares war on Lazarus hacking group
Publié: février 26, 2016, 10:19am CET par Sead Fadilpašić

Oooohhh, things are about to get really interesting in the cyber-security world. Kaspersky Lab has just declared war on the infamous hacking collective Lazarus Group, and it’s bringing its friends to the fight.
Together with Novetta and "other industry partners", Kaspersky Lab has announced the formation of Operation Blockbuster targeted at disrupting the activity of the Lazarus Group.
For those unfamiliar with the name, Lazarus Group is believed to be responsible for the 2014 attack on Sony Pictures Entertainment, as well as the 2013 Operation DarkSeoul, which targeted media and financial institutions.
Kaspersky Lab, Novetta and AlienVault have analyzed samples of malware spotted on different incidents and have managed to link a number of high-profile attacks to the group. Prior to the revelation, those attacks were attributed to an "unknown attacker".
The security researchers said they found a couple of interesting things that linked various attacks to the same group. First, it was discovered that they were recycling code, borrowing fragments from one malicious program to use in another. They also spotted similarities in the way the group works: the droppers (files used to install malware) all kept their payloads within a password-protected ZIP archive.
"The password protection was implemented in order to prevent automated systems from extracting and analyzing the payload, but in reality it just helped researchers to identify the group".
Eventually, tens of different targeted attacks were linked to a single actor. The group says the first attack might have occurred in 2009, five years before the Sony incident. It seems as the group is working in the GMT+8 and GMT+9 time zones.
"As we predicted, the number of wiper attacks grows steadily. This kind of malware proves to be a highly effective type of cyber-weapon. The power to wipe thousands of computers at the push of a button represents a significant bounty to a Computer Network Exploitation team tasked with disinformation and the disruption of a target enterprise. Its value as part of hybrid warfare, where wiper attacks are coupled with kinetic attacks to paralyse a country’s infrastructure remains an interesting thought experiment closer to reality than we can be comfortable with. Together with our industry partners, we are proud to put a dent in the operations of an unscrupulous actor willing to leverage these devastating techniques", said Juan Guerrero, senior security researcher at Kaspersky Lab.
"This actor has the necessary skills and determination to perform cyber-espionage operations with the purpose of stealing data or causing damage. Combining that with the use of disinformation and deception techniques, the attackers have been able to successfully launch several operations over the last few years", said Jaime Blasco, chief scientist, AlienVault. "Operation Blockbuster is an example of how industry-wide information sharing and collaboration can set the bar higher and prevent this actor from continuing its operations".
"Through Operation Blockbuster, Novetta, Kaspersky Lab and our partners have continued efforts to establish a methodology for disrupting the operations of globally significant attack groups and attempting to mitigate their efforts to inflict further harm", said Andre Ludwig, senior technical director, Novetta Threat Research and Interdiction Group. "The level of in-depth technical analysis conducted in Operation Blockbuster is rare, and sharing our findings with industry partners so we all benefit from increased understanding is even rarer".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Sangoiri / Shutterstock
-

Spotify moves to Google's cloud
Publié: février 25, 2016, 8:57pm CET par Sead Fadilpašić

Swedish music streaming service Spotify has decided to transport its entire product onto Google’s cloud. The news was confirmed on the Spotify blog.
In the blog post, written by the company's vice-president of engineering and infrastructure, Nicholas Harteau, it was explained how Spotify decided for the move as it could no longer scale fast enough to meet the demand.
"But in a business growing quickly in users, markets and features, keeping pace with scaling demands requires ever increasing amounts of focus and effort. Like good, lazy engineers, we occasionally asked ourselves: do we really need to do all this stuff?", Harteau wrote.
He also said that Spotify thought about the idea of migrating to a cloud platform for a long time, but the terms of business were simply not good enough before. We can thank the fierce competition between Google and Amazon for the drop in prices and the availability of cloud services we have today.
Amazon is the oldest player in the game, and the usual number one choice, with Google being the top alternative. Harteau said Spotify decided to go for the latter as it had better tools.
"What really tipped the scales towards Google for us, however, has been our experience with Google’s data platform and tools. Good infrastructure isn’t just about keeping things up and running, it’s about making all of our teams more efficient and more effective, and Google’s data stack does that for us in spades", explained Harteau.
Wired reports that the company has so far shifted about 250,000 user accounts, out of 20 million subscribers and about 55 million additional users. The migration is planned to last 18 months.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: 360b / Shutterstock
-

Baidu's browser leaks sensitive information
Publié: février 25, 2016, 5:20pm CET par Sead Fadilpašić

The browser provided by Baidu (China's answer to Google), leaks all kinds of personal data. Researchers at Canada’s Citizen Lab tested the browser and concluded it "collects and transmits a lot of personal user data back to Baidu servers that we believe goes far beyond what should be collected, and it does so either without encryption, or with easily decryptable encryption".
The Android version of the browser is even worse: "Data collected and transmitted in the Android version without any encryption includes a user’s GPS coordinates, search terms, and URLs visited. The user’s IMEI and nearby wireless networks are sent with easily decryptable encryption".
The Windows version leaks search terms, hard drive serial number, network MAC address, as well as the title of all visited webpages. GPU model number is also transmitted.
At this point, things just become ridiculous. Neither the Windows nor Android versions of the browser protect their software updates with code signatures. That means a hacker could, quite easily, make the app download and execute malicious code.
But it’s not just the Chinese whose data could be leaking here. The researchers believe pretty much everyone could be at risk here, as the Baidu Browser’s software development kit is "repurposed and employed in thousands of other applications developed by Baidu and third parties, affecting potentially hundreds of millions of users".
"Thousands of other applications, many of them available on the Google Play Store outside of China, and some of which have been installed hundreds of millions of times, contain the same flaws, and are sending back the same detailed information, to Baidu servers", Citizen Lab concludes.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Jamie Wilson / Shutterstock
-

ASUS' routers will be audited for 20 years
Publié: février 25, 2016, 10:19am CET par Sead Fadilpašić

Taiwanese hardware manufacturer Asus has agreed to settle Federal Trade Commission charges, the agency reported on Tuesday. Back in 2014, it was discovered that Asus’ routers had poor security protocols, putting hundreds of thousands of users’ data at risk.
Under the settlement, Asus will have to establish and maintain a comprehensive security program, subject to independent audits for the next 20 years. The FTC said the vulnerabilities allowed attackers to gain access to at least 12,900 routers.
"The Internet of Things is growing by leaps and bounds, with millions of consumers connecting smart devices to their home networks", Jessica Rich, director of the FTC’s Bureau of Consumer Protection said in a written statement. "Routers play a key role in securing those home networks, so it’s critical that companies like ASUS put reasonable security in place to protect consumers and their personal information".
Back in 2014, thousands of Asus routers were compromised, and whoever did it, left a text file on the device, explaining what happened.
"Your Asus router (and your documents) can be accessed by anyone in the world with an Internet connection", the good Samaritan hacker told the owners.
The complaint said that Asus password protection was often too easy to bypass, using a couple of techniques, including the specially crafted URL that was supposed to be accessed only after logging in, or by exploiting cross-site request forgery, to name a few.
The agency alleges that ASUS did not address these security flaws on time, and failed to notify its users about the risks these vulnerable routers pose.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: ollyy/Shutterstock
-

Majority of data breaches occur in US
Publié: février 24, 2016, 8:41pm CET par Sead Fadilpašić

There have been 1,673 data breaches last year. They have led to 707 million data records being compromised. Those are the results of a new report by digital security firm Gemalto, entitled Breach Level Index.
The Breach Level Index tracks all data breaches worldwide, looking at their size, severity, as well as the number of records compromised.
Since the company began tracking data breaches in 2013, more than 3.6 billion data records have been exposed, Gemalto said. Last year, malicious outsiders were the number one source of these breaches, accounting for 58 percent. Accidental loss accounted for 36 percent, state-sponsored attacks two percent, and malicious insiders accounted for 14 percent.
Looking at compromised records, malicious outsiders accounted for 38 percent, state-sponsored attacks for 15 percent and malicious insiders 7 percent.
The majority of breaches (77 percent) occurred in North America, with 59 percent of those being in the United States.
Europe accounted for 12 percent, and Asia Pacific for eight percent.
"In 2014, consumers may have been concerned about having their credit card numbers stolen, but there are built-in protections to limit the financial risks", said Jason Hart, vice president and chief technology officer for data protection at Gemalto.
"However, in 2015 criminals shifted to attacks on personal information and identity theft, which are much harder to remediate once they are stolen. As companies and devices collect ever-increasing amounts of customer information and as consumers’ online digital activities become more diverse and prolific, more data about what they do, who they are and what they like is at risk to be stolen from the companies that store their data. If consumers’ entire personal data and identities are being co-opted again and again by cyber thieves, trust will increasingly become the centerpiece in the calculus of which companies they do business with", added Hart.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: elwynn/Shutterstock
-

Former employees are a major security threat
Publié: février 24, 2016, 6:59pm CET par Sead Fadilpašić

If you’re a business owner in the UK, chances are a good portion of your workers are looking for the first opportunity to ditch you.
According to a new report by Ilex International, the identity and access management firm, 59 percent of workers are looking for a new job in 2016. Two reasons are behind this: first that the majority feels underpaid, and the second is that the economy is improving and better prospects are out there.
But that’s not the issue Ilex is tackling -- it’s saying that people leaving work are a security threat for the company staying behind. That’s why the company is urging businesses to put strict security controls in place.
According to Ilex’s report, entitled Staff migration: The security impact to business, 39 percent of large businesses take up to a month to close dormant accounts, leaving a lot of room for opportunistic hackers and disgruntled workers to strike.
Large businesses are doing somewhat better -- 58 percent remove access to data on the day, or even a day before departure.
The company urges businesses to shut down inactive accounts fast, to focus on protecting key data, to track and audit data access and implement a strong identity and access management solution.
"Disgruntled employees or partners are unlikely to wait until a month after leaving to access confidential company information. Access is likely to be sought in a matter of days", warned Thierry Bettini, director of international strategy at Ilex International. "The findings highlight the importance of having a system in place that helps close inactive accounts immediately".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Olivier Le Moal / Shutterstock
-

Ford announces new Kuga at MWC 2016
Publié: février 23, 2016, 5:26pm CET par Sead Fadilpašić

Ford has announced today that it will unveil the new Ford Kuga SUV during the Mobile World Congress taking place in Barcelona this week.
If you were wondering what the hell is a car doing on a fair for mobile things, keep on reading.
Besides the new SUV, Ford is also announcing that its connectivity technology SYNC 3 is coming to Europe. Moreover, it will expand its Ford Smart Mobility plan by tripling the investment.
Ford’s plan is to transition from a carmaker, to an auto and a mobility company. Basically, it’s building autonomous and semi-autonomous cars, too.
The company said it is taking two different paths to autonomous vehicles -- on one side there’s a dedicated team developing autonomous tech, while on the other is the Pre-Collision Assist with Pedestrian Detection – a couple of radars and cameras scanning the road around the car, detecting people and other cars.
To make all of that happen, it needs a customer experience platform, which is why it’s debuting FordPass in Europe this year. Its partners will be BP and Mobile City. FordPass also will integrate Ford Carsharing, run with Germany’s Flinkster Carsharing.
"As we look to the future, it is clear we are on the cusp of a revolution in mobility -- from car sharing to autonomous driving to the customer experience", said Ford CEO Mark Fields. "Technology and innovation provide us with the opportunity to address these trends and to make people’s lives better by changing the way the world moves".
"The use of semi-autonomous functions such as Traffic Jam Assist and Fully Active Park Assist make driving easier and more enjoyable for our customers", said Ken Washington, vice president, Ford Research and Advanced Engineering.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Android Pay's security to be put to the test in 2016
Publié: février 23, 2016, 4:00pm CET par Sead Fadilpašić

Dell has released its Security Annual Threat Report, taking a detailed look into the IT security landscape of 2015, as well as predicting a few trends for the ongoing year.
The report is based on "Dell SonicWALL Global Response Intelligence Defense (GRID) network with daily feeds from more than one million firewalls and tens of millions of connected endpoints, Dell SonicWALL network traffic and other industry sources".
Looking back at 2015, exploit kits were on the rise, with Angler, Nuclear, Magnitude and Rig being the most popular ones. Adobe Flash, Adobe Reader and Microsoft Silverlight were the most popular targets.
Cyber-criminals are improving their techniques and becoming harder to detect, the report says, as they’re using "anti-forensic mechanisms; URL pattern changes; steganography which is concealing the file, message, image, or video within another file, message, image, or video; and modifications in landing page entrapment techniques".
Looking forward into 2016, some things will change, while others are expected to stay the same.
Android will continue to be a prime target, especially Android Pay, as uptake continues. Adobe’s Flash could get some breathing space, as the loss of major browsers support will make them less interesting for attackers.
Android Pay will be a target through the vulnerabilities in Near Field Communications (NFC), which can target point-of-sale terminals. Attacks against Android Auto can also be expected, the report suggests.
"The threat vectors for malware distribution are almost unlimited, ranging from classic tactics like email spam to newer technologies including wearable cameras, electric cars, and Internet of Things (IoT) devices", said Patrick Sweeney, vice president of Product Management and Marketing, Dell Security. "In today’s connected world, it’s vital to maintain 360 degrees of vigilance, from your own software and systems, to your employees’ training and access, to everyone who comes in contact with your network and data".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Majority of UK businesses want to move their IT infrastructure to the cloud
Publié: février 19, 2016, 6:40pm CET par Sead Fadilpašić

A significant portion of UK businesses, 63 percent of them, plan to move their entire IT infrastructure to the cloud in the near future, according to a new report by the Cloud Industry Forum (CIF).
The adoption rate of the Cloud among UK’s businesses currently sits at 78 percent, the same as a year before, but "substantially higher" than when the research was first conducted back in 2011, the report says. The report also says that the adoption is likely to increase to 85 percent in the next two years.
More than three quarters (77 percent) of the businesses using Cloud use at least two services, while one in eight (12 percent) use five or more.
Webhosting (57 percent), email (56 percent), eCommerce (53 percent) and collaboration services (52 percent) are the applications most likely to be hosted in the Cloud, the report adds.
When asked why they decided to go for the cloud, flexibility is the number one reason for 77 percent of those surveyed, followed by scalability (76 percent) and 24/7 service dependence (74 percent). Furthermore, 45 percent said they decided to invest in the cloud as it enables innovation, their business objective, followed by improving customer service (31 percent) and enhanced business continuity (37 percent).
"This is the sixth major body of research we have conducted into the UK end user community, and while we are continuing to analyze and report on trends and adoption rates within the UK, we also wanted to explore the issue of digital transformation and how Cloud computing is facilitating business change", stated Alex Hilton, CEO of CIF.
"It should come as no surprise that digital transformation is creeping up businesses’ agendas as they seek to stay ahead of the competition. Cloud is very much part of the digital transformation agenda, and it is clear from this research that those companies with plans to digitally transform, struggle to do so without the delivery model", added Hilton.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Chaiyapop Bhumiwat / Shutterstock
-

Mendix products now available on Microsoft Azure
Publié: février 19, 2016, 10:18am CET par Sead Fadilpašić

Platform-as-a-service provider Mendix and Microsoft today announced a partnership which will bring Mendix services on the Azure cloud platform.
Mendix says the new partnership will allow Azure customers to seamlessly access Mendix’s rapid application development capabilities, adding that two versions are available -- free and commercial.
The Free Edition features a full-production platform that allows building unlimited apps, with up to 10 users each. Exact pricing for the Pro Edition was not disclosed, as it depends on the number of application users and "other factors".
"The apps of the future cannot be built with the tools of the past", said Derek Roos, CEO and co-founder of Mendix. "By working together, Mendix and Microsoft are providing a comprehensive cloud stack to power the digital enterprise of the future and unleash a tidal wave of digital innovation".
"Microsoft Azure is committed to offering best-in-class tools for every developer, so that IT teams can better respond to growing business demands", said John Gossman, architect, Microsoft Azure. "We are excited that the Mendix platform is now available in Microsoft Azure Marketplace. The combination of Mendix’s rapid application development capabilities and Microsoft Azure’s public cloud services enables digital innovation at astonishing speed and scale".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wongwean/Shutterstock
-

Automation will take away more than 100,000 jobs within 20 years in the UK
Publié: février 18, 2016, 9:34pm CET par Sead Fadilpašić

You shouldn’t fear immigrants taking your job, you should fear robots. A new study by jobs search engine Adzuna suggests that more than 100,000 of current job vacancies will be fully automated within the next 20 years.
The results are based on the study of Oxford University researchers, looking at which jobs would basically be given to robots before 2035.
Adzuna looked at 1.2 million job adverts across the country, and came to the conclusion that almost 10 percent (1 in 11 vacancies) have more than 75 percent chance to be given to robots.
Machine operators and plant managers are most at risk, together with admin and secretarial roles.
Looking at where you’d want to live in the next 20 years, London seems to be the best place, while you’d want to get away from Exeter, Norwich and Plymouth. Researchers believe almost nine percent of all ads for jobs in the Devon city will be given to robots. In London, Reading and Edinburgh, 1 in 20 vacancies could face a similar fate.
"We’ve heard that more than a third of current British jobs may be lost to automation, but our new analysis of the job market suggests that a high proportion of advertised vacancies are still for roles that are at high risk of being performed by robots in the not too distant future", said Adzuna co-founder Doug Monro.
"The risk of a robot invasion on the Devon coast might sound fanciful, but there’s a serious message for younger workers, whether they’re looking for their first job, or are comfortably in a career: if you want to remain relevant in the workplace, you need to develop skills that cannot be easily automated".
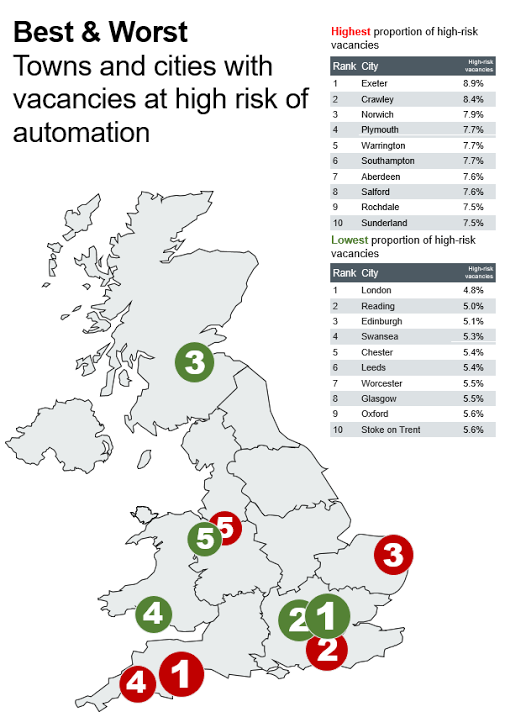
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: bogdanhoda / Shutterstock
-

IBM introduces Blockchain-as-a-service
Publié: février 18, 2016, 5:38pm CET par Sead Fadilpašić

IBM is looking to move blockchain technology beyond Bitcoin and money transfer as it announced Blockchain-as-a-service on Tuesday.
Blockchain-as-a-service allows developers to "create digital assets and accompanying business logic to more securely and privately transfer assets among members of a permissioned blockchain test network".
The best part of it all is that it’s free -- 44,000 lines of code are available on GitHub to developers everywhere. Blockchain technology is an online public ledger where you can log pretty much any kind of transaction. Being decentralized, and allowing all parties to double-check the transfers, in theory it could reduce errors or misuse.
"London Stock Exchange Group is directly engaged in the development of the open blockchain technologies with IBM and we are excited to help enable the creation of solutions that will help manage risk and bring additional transparency to global financial markets", said Moiz Kohari, EVP, group head of technology innovation, London Stock Exchange Group. "We believe this technology has the potential to drive change across the industry but will need to be developed in partnership with customers and industry participants under an open source approach".
In order to speed things up, IBM has opened up what it calls IBM Garages -- places where developers and IBM experts can collaborate on the design and implementation of blockchain for business. The IBM Garages will open up in London, New York, Singapore and Tokyo.
"In just a few short months, IBM’s vision for making blockchain a powerful new business solution across multiple industries is becoming a reality as our clients begin piloting innovative new code, services and z Systems optimized for distributed ledgers", said Arvind Krishna, Senior Vice President, IBM Research. "These advancements are making it easier for developers to move from understanding the potential of blockchain, to actually using it to change their business processes in powerful new ways".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Cisco announces Firepower Next-Generation Firewall
Publié: février 18, 2016, 9:47am CET par Sead Fadilpašić

Cisco has released a new firewall solution which aims to completely change how security services tackle cyber-threats.
The new product, Cisco Firepower Next-Generation Firewall (NGFW), is built to detect threats on a system, and not keep the system on a lockdown. Here’s how Cisco explains the new product
"Think of it as legacy NGFWs protecting 'homes' by securing windows and doors, whereas Cisco’s approach is to identify, detect and protect against would-be burglars no matter how they try to gain access to a property", Cisco says NGFW is the first product in the industry to link contextual information about the usage of apps with threat intelligence.
To complement the firewall, the company has also unveiled the new Cisco Firepower 4100 Series appliances, for high-performing business apps. These dense, compact units are capable of 40GbE network connectivity. They will be managed through the Cisco Firepower Management Center, also a new Cisco product. The Center will serve as a 'nerve center', providing a rich, unified management console.
"Attackers are getting bolder and coordinating their efforts. The industrialization of hacking is putting businesses on the defensive against a growing group of adversaries that steal information for profit", said David Goeckeler, senior vice president and general manager at Security Business Group, Cisco.
"In the last three years, Cisco has spent billions in strategic cybersecurity acquisitions and internal innovations to help stay ahead of the world’s most malicious attacks that threaten organizations. For businesses to get real value and manage risk as they implement digital operational models, their security platforms need to integrate into the business and support growth opportunities. This means taking a threat-centric approach, with protection from the mobile endpoint to the cloud", added Goeckeler.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Katherine Welles / Shutterstock
-

The role of collaboration in GDPR compliance
Publié: février 17, 2016, 9:02pm CET par Sead Fadilpašić

As the European Union reaches an agreement on the General Data Protection Regulation (GDPR), which will require companies to comply with state-of-the-art cybersecurity requirements, security firm Palo Alto Networks has surveyed businesses to see how much they know about cyber-security and where the responsibility lies.
The survey suggests much work still needs to be done, particularly in areas of collaboration and responsibility sharing.
The key takeaway from the survey is that a significant amount of accountability is placed solely in the IT. Forty-eight per cent of managers, and 57 percent of IT departments agree IT has sole domain over a company’s security.
The lack of consensus over where the duty lies could come from the lack of basic understanding what cyber-security is, at a leadership level, Palo Alto Networks suggests.
Thirteen per cent of C-Level executives could "kind of" understand what defines an online security risk to a business and "still have to use Google to help explain it". On the other hand, 10 percent of employees don’t believe executives understand current cybersecurity issues.
Here’s what Palo Alto Networks suggests:
- Create a strategy focusing on preventing cyber-attacks. Make sure you include every step of the attack, and take employee awareness and accountability into consideration
- Use automated security technology
- Educate your employees on their role in preventing cyber-attacks
"The new EU regulations will require businesses to step up their cybersecurity practices, and this can be an opportunity or a risk, depending on how these businesses choose to approach it", said Greg Day, vice president and regional chief security officer, EMEA, Palo Alto Networks. "Ultimately, it is critical that managers recognize that, when it comes to cybersecurity, the onus is on everyone -- it’s no longer a dark art but an everyday business practice that must pervade every level of the organization".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Lightspring / Shutterstock
-

Your VoIP phone could be used to spy on you
Publié: février 17, 2016, 5:44pm CET par Sead Fadilpašić

You should be careful when running voice-over-IP (VoIP) phones, as weak passwords could turn your device into a covert spying tool.
Security consultant Paul Moore says he has discovered how default and weak passwords on enterprise-grade Snom VoIP phones could allow attackers to make their own calls using your service, or listen to your conversations.
In a report on the issue, The Register says it was confirmed that this was, in fact, a beta version of Snom VoIP firmware, even though it was marked as the latest version. Moore had done quite a thorough investigation and a proof of concept, saying he will now redo the tests with the new firmware version.
His tests have shown that the device’s setup console had no authentication protocols, meaning you could be exploited by simply visiting a site with a hostile JavaScript payload.
Together with a pair of colleagues, he made a proof of concept:
"Unbeknownst to me, Per has forced my VoIP phone to call his premium rate number and disabled the speaker, so unless I’m looking at the phone, I wouldn’t know it’s dialing", Moore says.
"What can the attacker do? Make calls, receive calls, transfer calls (even before it rings), play recordings, upload new firmware and crucially... use the device for covert surveillance. If you install, use or just find yourself sat next to one of these devices, just remember... it’s basically a PC, with all the security vulnerabilities associated with them", adds More.
"Don’t assume it’s safe because it’s running as the manufacturer intended; seek professional advice", concludes More.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Everett Collection / Shutterstock
-

Ransomware is lucrative -- almost half of all victims pay
Publié: février 16, 2016, 10:06am CET par Sead Fadilpašić

I recently covered a story in which security firm Imperva said Cryptowall 3.0 was the most successful ransomware of all time, earning its creators $325 million (£225.7m) so far. Now another story about ransomware emerges, and this one comes from another major security firm, Bitdefender.
In its report, the company says almost half (44 percent) of all ransomware victims have paid to get their data back, with 39 percent saying they expect to be attacked again, in the future.
Ransomware is a type of malware which encrypts all the data on the victim’s computer and demands money in Bitcoin to release the data. If no payment is made in a specific timeframe, the documents are lost.
Victims are willing to pay up to £400 for their data, the company says. The survey also shows that most respondents know exactly what ransomware is and how a computer gets infected with it.
Ransomware is expected to grow and become even more present in 2016.
Catalin Cosoi, chief security strategist at Bitdefender said: "The ransomware phenomenon has been hitting internet users and generating huge profit for cybercriminals for years. While victims are usually inclined to pay the ransom, we encourage them not to engage in such actions as it only serves to financially support the malware’s developers. Instead, coupling a security solution with minimum online vigilance could help prevent any unwanted ransomware infection".
Bitdefender says it has already developed anti-ransomware technology, protecting documents, video and photos from being encrypted by ransomware.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Ton Snoei / Shutterstock
-

IT security experts are confident they can spot a data breach
Publié: février 15, 2016, 8:13pm CET par Sead Fadilpašić

A new study by security firm Tripwire says IT security experts are very confident they can detect a breach, and that they can detect it quite fast. For automated tools, they do not share the same levels of confidence.
The survey questioned 763 IT professionals in various verticals, including retail, energy, financial services and public sector organizations in the US, about the seven key security controls that need to be in place in order to quickly spot an ongoing hack attack.
The seven key controls, which are required by security regulators, are PCI DSS, SOX, NERC CIP, MAS TRM, NIST 800-53 and IRS 1075. These controls also align with US-CERT recommendations and international guidance such as the Australian Signals Directorate’s Strategies to Mitigate Targeted Cyber Intrusions.
The company said the majority of respondents answered with confidence, saying they could detect a data breach. However, they weren’t sure how long it would take automated tools to discover some of the key indicators.
The key question revolved around the detection of unauthorized configuration changes, as that is, according to Tripwire, the "hallmark of malicious covert activity".
When asked how long it would take automated tools to detect unauthorized configuration changes to an endpoint on the organization’s network, 67 percent could not be precise or did not use such tools at all. Still, 71 percent said it would take minutes, or hours at worst, to detect a configuration change to an endpoint on the organization’s network.
"All of these results fall into the 'we can do that, but I’m not sure how long it takes' category", said Tim Erlin, director of IT security and risk strategy for Tripwire. "It’s good news that most organizations are investing in basic security controls; however, IT managers and executives, who don’t have visibility into the time it takes to identify unauthorized changes and devices, are missing key information that’s necessary to defend themselves against cyber-attacks".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: elwynn/Shutterstock
-

Electronic toys maker wants to blame parents for data breaches
Publié: février 12, 2016, 4:07pm CET par Sead Fadilpašić

Electronic toys maker VTech has recently been a victim of a cyber-attack, which has seen the data of more than 6.3 million children exposed. The hackers got access to chat logs and photos.
Following the breach, VTech has updated its End User License Agreement, saying the company can’t provide a 100 percent guarantee that it won’t be hacked. It also shifts the responsibility back to the parents:
You acknowledge and agree that you assume full responsibility for your use of the site and any software or firmware downloaded.
You acknowledge and agree that any information you send or receive during your use of the site may not be secure and may be intercepted or later acquired by unauthorized parties.
You acknowledge and agree that your use of the site and any software or firmware downloaded there from is at your own risk.
Commenting on the move, security expert Jonathan Lieberman, VP of Product Strategy at Lieberman Software says:
It’s only a matter of time before every online business has T&Cs attempting to limit their liability in the case of cybercrime. This kind of avoidance language is all around us. When you park your car in the city, there’s a sign saying they aren’t responsible if someone steals something. When you leave your valuables in a gym locker, there is a notice that it’s at your own risk. It’s natural that when you put your information into a website or data in the cloud that they will hang up a sign telling you criminals may attempt -- and succeed -- to take it.
As the money associated with online crime grows both in the form of rewards criminals can reap and premiums insurance firms insuring against those losses, you will see lawyers crafting ever more creative and complex terms to protect their clients from liability associated with data breach. The key is how well they will work to protect you while you use their online service and how well you will protect yourself.
He advises parents to read the terms and conditions carefully, and see if the company is taking reasonable measures to protect the data. If you can’t sit through countless pages of legal language, limit the exposure of your information.
Mark James, Security Specialist at ESET said:
Every company has a responsibility to protect the data they harvest while you use their products. I agree with VTech that no company can protect 100 percent against the possibility of being hacked, but taking sufficient precautions and ensuring a good level of security is maintained should be the fundamentals of any policy where user’s private data is being held.
To shift ownership over to the users is bad enough in itself, but to make it known through walls of text in T&Cs or EULAs is a bad way to do it, no one honestly reads it, especially a parent trying to setup something for their children. Can you imagine telling your three year-old that they need to wait a little longer while you read, digest and decide if you want to keep the toy based on the terms and conditions?
Our minors’ data should be ultra-important for any organization and protecting that should be their number one priority. If voting with your feet is the best way to make them understand then maybe that’s the right thing to do. It’s our data, but more importantly it’s the data of our possible future leaders that’s at stake here, we must take it very seriously indeed.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: M. Dykstra/Shutterstock
-

What makes Cryptowall 3.0 the most successful ransomware?
Publié: février 12, 2016, 10:43am CET par Sead Fadilpašić

Cryptowall 3.0 is the most successful ransomware of all time, a new report by security firm Imperva says. Ransomware is a type of malware which, once active on a device, encrypts all the data and demands payment from the victim, typically through Bitcoin.
In its report on the dangers of ransomware, and the impotent attitude of the FBI, which usually advises victims to pay the ransom, Imperva says Cryptowall 3.0 has caused $325 million (£225.7m) in damages so far.
Commenting on the news, Jonathan Sander, VP of product strategy at security firm Lieberman Software says it’s not that the police isn’t doing anything -- it’s that they can’t do much in the first place:
"It’s not that local law enforcement doesn’t want to help with Cryptowall, they can’t. A friend works with cybercrime efforts of local police here in the States, and recently told me that since Cryptowall most often crosses international boundaries there’s not much the police can do. They know this already. So when they are told about it they mostly give condolences and move on to investigations where they can have an impact".
Sander also said Cryptowall is easily avoided with a good backup policy: "The other problem is that reporting Cryptowall issues to more savvy law enforcement sounds like reporting your bike was stolen when you didn’t bother to lock it up. Since a good back up strategy can be almost 100 percent effective to combat Cryptowall, police may simply feel the real crime was your own lack of preventative measures".
Even though the advice to back up a computer sounds simple, many companies don’t do it. Sander compares it to the health and fitness advice we hear all the time.
"So much good security advice sounds like health advice. Everyone knows they should eat right and exercise, but so many simply shrug at this advice as they return to chips in front of the television. Every organization knows they need to back up, monitor file activity, protect admin privileges, and run basic perimeter defenses like antivirus and firewalls. Since none of that security seems to contribute to the bottom line and takes a modicum of effort, people’s laziness kicks in and they skip the basics".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Robynrg/Shutterstock
-

More consumers now care about how businesses handle their data
Publié: février 11, 2016, 2:55pm CET par Sead Fadilpašić

Nearly three million Brits have decided to leave a service provider that got hacked, a new research by security firm Privitar reveals. The report shows that 23 per cent of Brits have been affected by a security breach at some point, and 24 per cent of these reacted by switching providers.
The company says consumers now pay attention to how well a company handles data, when making choices. Even though data handling has become one of the key selling points for many companies, 52 per cent of consumers say it’s difficult to find any information on how companies store and use their personal information.
Consumers are not ones to stick around, though -- 83 per cent have said they’d gladly switch to another service, if they believed it could manage their private data better.
"High profile breaches such as those at TalkTalk and Ashley Madison mean that the issues of privacy and data protection have entered mainstream consumer consciousness", said Privitar CEO Jason du Preez.
"People are taking a more active interest in how their data is used day-to-day. Organizations have two years to comply with GDPR, but those that are proactive can gain competitive advantage by winning customer trust. Organizations should look to adopt leading technology solutions to add privacy protections, particularly as part of big data analytics infrastructure and clearly communicate with their customers as to how they are protecting and using their data".
The GDPR (General Data Protection Regulation) is expected to become law by May, and it will force companies to adopt Privacy-by-design in new information architectures.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Johavel / Shutterstock
-

Windows 10 hits 18 percent usage share in the enterprise
Publié: février 5, 2016, 3:12pm CET par Sead Fadilpašić

Windows 10 is doing great. Despite various problems, security and privacy issues people have had with its virtual assistant Cortana, the adoption rate of Microsoft’s latest operating system has been quite impressive.
According to the latest studies done by Spiceworks, 18 percent of businesses are currently using Windows 10. The predictions are saying that 40 percent of businesses are expected to upgrade by July this year, when Windows 10 celebrates its first birthday. The operating system seems to be on good course, as the penetration has increased seven percent since October last year.
Besides doing great on its own, Windows is also doing much better than its predecessors, the report suggests. Windows 10 took half a year to reach 200 million devices. Windows 7 took a full year, while Windows 8 needed more than 15 months to reach the same goal.
In terms of the penetration rate in the enterprise, Spiceworks has compared Windows 10 to Windows 8. Windows 8 had a 9.3 percent penetration rate, six months after the launch, while Windows 10 has double the rate.
As one might expect, the best penetration rate is in North America, where Windows 10 is "well above" the worldwide baseline of 18 percent, Spiceworks says.
The Europe, Middle East and Africa (EMEA) region falls in line with the overall average, while Latin America and Asia-Pacific regions "significantly" lag behind.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Anton Watman / Shutterstock
-

Why the Internet of Things is a security nightmare
Publié: février 4, 2016, 9:19pm CET par Sead Fadilpašić

The good guys over at Context Information Security have cracked Motorola’s outdoor security camera just to point out how the Internet of Things is still a completely unsecure industry that needs serious work.
The camera that got cracked was the Motorola Focus 73, and not only did the researchers manage to get inside, but they also managed to obtain the home network’s Wi-Fi password, take full control of the camera’s movement and even redirect the video feed.
The exploit was fixed in the meantime, and the update to the firmware released without the end user having to do anything. So basically, if you have one of those cameras, there’s no need to panic, any more.
The process of cracking the camera was, according to the researchers, a piece of cake: "During set up, the private Wi-Fi security key is transmitted unencrypted over an open network, using only basic HTTP Authentication with username 'camera' and password '000000', while a number of legacy webpages on the camera revealed that the device is based on the same hardware as a legacy baby monitor product", the company said.
After some more investigation, the researchers managed to get root access to the camera. The root password was easy to crack as it was '123456' -- one of those passwords you should never set up. The home network’s Wi-Fi password was sitting there in plaintext, as well as factory wireless credentials for secure test networks.
What’s even more worrying, is that the credentials for the developers’ Gmail, Dropbox and FTP accounts were also there. For the icing on the cake, the researchers managed to install their own firmware and it wasn’t checked for validity.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Lighthunter/Shutterstock
-

Brits say their smartphone data is worth £6,504
Publié: février 4, 2016, 6:42pm CET par Sead Fadilpašić

Choosing between the wallet and the smartphone, the majority of Brits would rather have their wallet stolen, a new research by the Ponemon Institute and Lookout has found.
But that’s not because of the smartphone’s quality, value or price. It’s what’s inside that counts.
A lot of Brits use their smartphones to access corporate email and corporate data in general, and they’re aware that such information is valuable, not only to themselves and their company, but to hackers, as well.
They’ve also said that the photos and videos stored there are priceless -- 38 percent have said that they could never replace the content on their phone.
Nearly half (45 percent) have said that the amount of confidential data stored on their phones has increased significantly in the past 24 hours. That trend is set to continue, the report adds.
In total, individuals value the data in their devices at £6,504, the report adds.
But even though Brits are aware of the value of the data in the device, almost half don’t think data protection features are an important thing to have on a smartphone.
"Despite the growing amount of lucrative data and consumers’ growing concern about getting hacked, almost half of Brits (47 percent) don’t see data protection features as important when purchasing a mobile device", the report concludes. "Unless we start to safeguard our personal data as much as we do our physical belongings, we are liable to lose our priceless content and memories through a breach or hack".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: D. Hammonds/Shutterstock
-

Jaguar Land Rover wants autonomous cars to emulate human drivers
Publié: février 3, 2016, 7:46pm CET par Sead Fadilpašić

Jaguar Land Rover wants to make autonomous vehicles behave more like humans, and less like robots.
The company is looking into how humans behave in specific situations, like slow-moving traffic, roadworks and busy junctions.
I’m not entirely sure why anyone would want to build a robot car that’s going to honk maniacally every time someone slows down for no apparent reason, and would love to know if the car is going to cuss at jaywalking people, or will that be left to the "real" humans.
Jokes aside, Jaguar Land Rover says it’s important to know how humans behave behind the wheel and try to emulate that behavior, in order to make humans feel more relaxed around autonomous cars. Bosch and Direct Line Group are also partners in the project.
"To successfully introduce autonomous cars, we actually need to focus more on the driver than ever before", said Dr Wolfgang Epple, director of research and technology at Jaguar Land Rover.
"Understanding how drivers react to a range of very dynamic and random situations in the real world is essential if we want drivers to embrace autonomous cars in the future. By understanding and measuring positive driving behaviors we can ensure that an autonomous Jaguar or Land Rover of the future will not simply perform a robotic function", Epple added.
The research is a part of a £5.5 million project, with a goal of developing specialist insurance for autonomous vehicles. The MOVE-UK initiative was announced yesterday by Sajid Javid MP, Secretary of State for Business, Innovation and Skills, alongside a £2.75 million grant from Innovate UK to help fund the research.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: RioPatuca/Shutterstock
-

More students taking up computing courses
Publié: février 3, 2016, 2:52pm CET par Sead Fadilpašić

There is a resurgence of interest in computing courses, the Higher Education Statistics Agency (HESA) claims. According to the agency’s latest report, there has been an increase of 5 percent in the number of students starting an undergraduate computing course in 2014/15.
A total of 24,900 students signed up. The computing courses significantly outperform undergraduate enrollments as a whole, the agency continues, saying that in the same period, it rose by only 2 percent.
The rise comes after a few years of decline, suggesting a resurgence of interest, but some problems are still present, including a fairly high percentage of dropouts, as well as a low percentage of females.
Just 15 percent of those signing up for computer courses are female -- while out of all undergraduate students, 55 percent are female.
The dropout rate is also fairly high, and goes up to 20 percent, which is another reason to be worried. Only 19,480 achieved a qualification in 2014/15, which represents a fall of 3 percent on the previous year, and the third consecutive year of decline since 2010/11.
What’s also interesting, and quite unbelievable, is that 10 percent of computing graduates have been unemployed for six months after graduating in 2014. Unbelievable, knowing how severe the lack of IT staff is.
The report claims this is the highest level compared to any other subject grouping, which is why it is the topic of investigation by Sir Nigel Shadbolt, principal of Jesus College, Oxford.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Goodluz/Shutterstock
-

How much do UK businesses spend on mobile devices per year?
Publié: février 3, 2016, 9:46am CET par Sead Fadilpašić

An average business in the UK spends approximately £1,272 every year on a mobile device and all the expenses that come with owning one.
Those are the results of a new survey by mobile data security firm Wandera. Surveying 500 UK IT decision makers, Wandera’s survey has shown the true cost of ownership (TCO) of mobile devices for UK enterprise.
Here’s how the expenses are split: carrier charges take up 36 percent of cost, hardware 21 percent, bill shock 14 percent, security 11 percent, IT resource 10 percent and additional services 8 percent.
There are two particularly interesting things about this report: one is that bill shock (additional unexpected charges for exceeding carrier plans or roaming charges), that takes up 14 percent of TCO, can jump up to 21.9 percent for the largest companies.
Larger companies, per annum, can pay up to £279 per device for bill shock.
Another important discovery is that more than half (58 percent) of TCO is controllable. "Costs can be reduced through improved mobile data management, policy setting and security threat prevention", the company said in a press release, adding that using these measures usually removes about 28 percent of the total TCO.
"For years, most enterprises have considered TCO to be simply made up of the cost of the device plus the carrier charges", comments Eldar Tuvey, CEO of Wandera. "But this is frankly a naive view. In fact, the 'real' TCO is twice as much as commonly expected. In the UK, approximately £644 per device of annual costs for services, security and IT are not being taken into account when calculating the TCO of enterprise mobility".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Syda Productions / Shutterstock
-

NSA's lead hacker offers security tips
Publié: février 2, 2016, 8:00pm CET par Sead Fadilpašić

An interesting talk happened recently during the Usenix Enigma security conference in San Francisco. It was held by Rob Joyce, basically the number one hacker of the US. He is the head of NSA's Tailored Access Operations, or TAO. That's pretty much the government's hacking team, tasked with breaking and entering into the systems of its enemies. Or allies, if need be.
This man, who assumed the position of hacker-in-chief just a few months before Edward Snowden blew the whistle on the whole ordeal, spoke about a lot of things which Wired summed up in one smart sentence -- he explained how to keep people like him out of your systems.
Although everyone agrees that he probably didn’t say anything about TAO's classified operations, he did say a couple of interesting things.
1. NSA Hunts Sysadmins
The NSA will always look for the credentials of network admins and pretty much anyone with high levels of access. It will also look for hardcoded passwords in legacy protocols.
2. No Crack Is Too Small
If your system has a crack and NSA can find it, it will use it. No matter how small and insignificant it might be. Do not underestimate what even the tiniest of cracks can do to your system.
3. BYOD Is Dangerous
If you use your own device to connect to your company’s network, make sure to keep it safe, use it only for work and don’t give it to your kids. Joyce said that Steam, the Internet-based digital distribution platform for games, is a huge security threat.
So basically, if you want to stay safe, limit access privileges for important systems and segment the networks. Patch up your systems and remove any legacy protocols. And remove hardcoded passwords.
A more detailed overview of the conference can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: igor.stevanovic/Shutterstock
-

Risk of malware infection growing in UK
Publié: février 2, 2016, 5:53pm CET par Sead Fadilpašić

UK's businesses have had a bigger chance of being attacked by a malware than those in the US or the Republic of Ireland in December 2015, a new report by security researchers suggest.
According to a report by Check Point, in December 2015, UK was the 99th most attacked country globally, surpassing the US (122nd) and the Republic of Ireland (116th).
The risk of malware infection in the UK increased 17 percent, the company concludes, with the number of active malware families increasing by 25 percent. The company says more than 1,500 different active malware families were identified in December, up from 1,200 in November.
The most popular malware was (and remains) Conficker, accounting for 25 percent of all known attacks in the period. Its popularity is seen even better once it’s compared to second-placed Sality, which accounted for 9 percent of attacks.
Conficker works by disabling security services, rendering the machine vulnerable to DDoS and similar attacks.
Nathan Shuchami, head of Threat Prevention at Check Point said: "The increase in active malware during December highlights the severity of the threat posed to organizations' networks and sensitive data. As a result, organizations should be pushing cyber-security to the top of their agendas for 2016, as cyber-criminals continually find new ways to attack networks, so that they can be equally relentless in robustly securing their networks".
The top three malware variants used to attack UK networks during November were Conficker, Kelihos and HackerDefender.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Balefire / Shutterstock
-

Cloud email adoption is low in the enterprise
Publié: février 2, 2016, 9:09am CET par Sead Fadilpašić

Cloud email services are still not as big as you’d expect in the enterprise, but they are growing stronger. Those are the results of an automated survey by market analyst Gartner.
According to the survey, 8.5 percent of public companies use cloud email service from Microsoft’s Office 365, while 4.7 percent use Google Apps for Work.
The rest, 87 percent, use either on-premises, hybrid, hosted or private cloud email, managed by smaller companies.
The automated report looked at a large number of publicly available email routing records, Gartner said. By using the email server addresses in the domain records of some 40,000 public companies worldwide, Gartner was able to pinpoint which of those use cloud email from Google or Microsoft.
"Although it is still early days for cloud email adoption, both Microsoft and Google have achieved significant traction among enterprises of different sizes, industries and geographies", said Nikos Drakos, research vice president at Gartner. "Companies considering cloud email should question assumptions that public cloud email is not appropriate in their region, size or industry. Our findings suggest that many varied organizations are already using cloud email, and the number is growing rapidly".
Microsoft dominates, especially in industries such as utilities, energy and aerospace, while Google is more present in software publishing, retail, media, food and beverage or education.
"Among public companies using cloud-based email, Microsoft is more popular with larger organizations and has more than an 80 percent share of companies using cloud email with revenue above $10 billion", said Jeffrey Mann, research vice president at Gartner. "Google’s popularity is better among smaller companies, approaching a 50 percent share of companies with revenue less than $50 million".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: 2jenn/Shutterstock
-

Majority of UK shoppers prefer mobile devices
Publié: février 1, 2016, 7:22pm CET par Sead Fadilpašić

Shopping via mobile phones is now the default in the UK, a new research by market intelligence company SimilarWeb suggests.
According to the research, 64.54 percent of all website visits, by UK shoppers to retailers, was made via a mobile device this year. With these figures, the UK has now surpassed the US (55 percent), Germany (43 percent) and France (35 percent). It is still, however, lagging behind India, a country with 65 percent of mobile shoppers.
A total of 35.46 percent of people visited shopping sites from a desktop computer, but that’s not the only metric analyzed. The number of pages visited, as well as the time spent on each is different, as well. On smartphones, people visited, in average, 7.3 pages per session. On desktops, that figure stands at 12.4 percent.
Mobile shoppers also take less time to do their shopping, spending an average of 5:50 minutes. On desktop, they usually take 7:21 minutes.
All of the most popular 10 UK retail sites, including Amazon, eBay and Argos, registered a bigger share of visits from mobile, compared to desktop visits.
Pavel Tuchinsky, SimilarWeb Digital Insights Manager, said: “Shopping via mobile is now the default, with all leading retailers experiencing a majority of visits to their sites via smartphones. The UK is now a European leader in mobile shopping, far ahead of France, and Germany.
"However engagement and time on site has not been maintained in the transition towards mobile shopping. Retailers must continue to embrace the rapid change towards mobile, including better checkout flows, and integrations between desktop and mobile sites".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: D. Hammonds/Shutterstock
-

DDoS attacks are now more sophisticated
Publié: février 1, 2016, 5:46pm CET par Sead Fadilpašić

Kaspersky Lab has released its report into DDoS attacks for the fourth quarter of 2015, and it claims that the global reach of attacks shrunk, but the sophistication of those attacks grew.
According to the report, in the fourth quarter of 2015, resources in a total of 69 countries were attacked. In the previous quarter, that number stood at 79. Similar to the previous quarter, in the last three months of 2015 the majority of attacks (94.9 percent) took place in just ten countries, with the US, China and South Korea being the most affected of the bunch.
A marathon DDoS attack was also noticed in Q4, one which lasted 15.5 days, or 371 hours. Linux bots are also on the rise, from 45.6 percent to 54.8 percent.
"We can see that the complexity and the power of DDoS attacks have not diminished with time, even if the number of attacked resources has fallen. Unfortunately, DDoS remains a convenient and affordable tool for online crime because there are still software vulnerabilities that attackers can use to penetrate servers", said Evgeny Vigovsky, head of Kaspersky DDoS Protection at Kaspersky Lab. "There are also users who fail to protect their devices, increasing the chances of those devices being infected by bots. For our part, we are committed to providing businesses with information about the DDoS threat and promoting the fight against it, because DDoS is a threat that can and should be combated".
The full Kaspersky Lab report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Duc Dao / Shutterstock
-

Bull's Bullion S server sets performance record
Publié: janvier 29, 2016, 2:06pm CET par Sead Fadilpašić

Bullion, high-end servers from Atos' technology brand Bull, has set a new global record in performance, the company has announced.
The record was set in accordance with the Standard Performance Evaluation Corporation.
The server was equipped with a 16-socket configuration. The bullion S has 288 cores on 16 Intel Xeon E7 v3 processors, and comes with 4TB of RAM. According to the press release following the announcement, it achieved a peak performance of 11600 -- 11100 Base -- according to SPECInt_rate2006 benchmark.
"This recognition is paramount to Atos strategic commitment to develop -- through its Bull brand -- innovative systems for high performance computing to process large volumes of data -- exactly what is needed to overcome the challenges of the 21st century", said Arnaud Bertrand, group SVP, head of Big Data & HPC at Atos.
"Bullion is the most powerful server in the world and thus a real pride for the Group. Bull’s technological expertise in the field of infrastructure is again welcomed. The power demonstrated by bullion, coupled with its exceptional memory capacity, makes it the benchmark of servers chosen for its memory capacity and supports our ambition to become a world leader in Big Data".
Bullion x86 can come with up to 24 TB of RAM, allowing it to run big data applications such as the SAP HANA. It also offers TCO reduction (total cost of ownership) of virtualization clusters, as well as the virtualization of critical applications.
Full results of the bullion benchmark can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

IT security professionals are looking for a challenge
Publié: janvier 29, 2016, 10:22am CET par Sead Fadilpašić

The notion that IT security professionals are mercenaries when it comes to work and would most likely move if given an opportunity to earn more is, by a large margin, incorrect.
That’s basically what a new report by AlienVault says. The report, entitled Blood on HR's floor -- The Challenge of Retaining IT Security Skills, has a couple of interesting points.
The first one, and arguably the most important one, is that people IT security professionals change jobs when they’re looking for something more challenging and interesting. Of the 132 people surveyed, 33.9 percent confirmed that they would move to a more exciting assignment.
Money and flexible working hours were ranked second (23 percent) and third (17 percent).
A similar pattern can be noticed with IT security professionals who are staying at their current job -- 65 percent do so because they are happy and content, not because of how much money they’re earning. The report says that 19 percent stay because of convenience, and 13 percent because of money.
What was also interesting to notice is that IT security professionals don’t usually leave jobs -- they leave bosses.
"Being unhappy with the boss or company culture was an underlying theme across the survey", says Javvad Malik, security advocate at AlienVault. "Yet, several participants, particularly those in larger organizations, felt a distinction should be made between the company culture and team culture. Noting that one can be very satisfied with ones colleagues and boss but dissatisfied with the company culture".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Syda Productions / Shutterstock
-

Is your business wasting the software budget?
Publié: janvier 28, 2016, 5:41pm CET par Sead Fadilpašić

No matter how much money your company spends on software, it’s likely to spend less if your boss reads this article.
A new survey by American software company Flexera Software suggests that most companies are wasting their software budget, and the software they buy is often either underused or overused.
According to the report entitled The State of the (Software) Estate: Waste Is Running Rampant in Enterprises, most companies are wasting money on something called shelfware, which is unused or underused software, and are simultaneously out of compliance with their software contracts.
That leads to many companies being audited by software vendors, some even multiple times a year.
The report says 75 percent of businesses claim at least some of their software is overused, while 65 percent of them were audited by software vendors (23 percent three times, or even more).
It also says that basically all key players in the software industry, including Microsoft, Oracle, Adobe, to name a few, are reviewing license keys for a number of businesses, while 44 percent of enterprises paid $100,000 (£70,000) or more in true-up costs to their software vendors as a result of noncompliant software use.
The software license landscape is complex due to the sheer number of contracts to manage, the different types of licenses that must be administered, the different rules adopted by different vendors, and the fact that many organizations track their licensing information manually.
"We believe that as much as 33 percent of the software budget is being wasted due to insufficient software license management", said R “Ray” Wang, principal analyst and founder at Constellation Research. "Organizations should focus on continual software license compliance to reduce software audit risk, and on fully utilizing the product use rights they’ve negotiated in their contracts to reduce shelfware".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Jean Lee / Shutterstock
-

Tablet shipments see double digit drop in 2015
Publié: janvier 28, 2016, 10:48am CET par Sead Fadilpašić

The demise of the tablet seems inevitable, as shipments percentage dropped in double digits for the first time ever. Market intelligence provider TrendForce reported that in 2015 a total of 168.5 million units were shipped, representing a 12.2 percent drop year-over-year.
Notebook analyst for TrendForce, Anita Wang, confirmed what we all already knew -- smartphones, phablets and two-in-one devices were interfering too much with the tablet market, and with the devices having a somewhat longer lifespan, the results are a decrease in new shipments.
"The saturation of the tablet market, the long life cycles of tablets themselves and the abundance of substitute devices were major factors that contributed to the large shipment decline", said Anita Wang. "Tablets were challenged by many large and small devices during 2015, from smartphones sized 5-inches and above to two-in-one PCs. Their demand diminished as a result".
Looking at the top players in the tablet industry, not much has changed -- Apple is still the number one brand, with its iPad series. But those who fly high are the ones to hit the ground hardest, and Apple has felt it with a drop in shipments of 22 percent, from 63.4 million units in 2014 to 49.6 million in 2015.
Samsung’s tablet shipments fell 18 percent annually to 33.5 million units, and its market share fell by just 1.5 percent over the year to 19.9 percent.
Even though it failed to make the top five, Microsoft is an honorable mention -- its tablet shipments grew 50 percent annually, thanks to its Surface Pro 4 tablet.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Onypix / Shutterstock
-

One in three home routers will double as a public hotspot by 2017
Publié: janvier 27, 2016, 5:54pm CET par Sead Fadilpašić

Would you be willing to share your Wi-Fi router so that everyone around you could use it as a public hotspot? Your Internet connection would stay secured behind a firewall.
This is actually not a rhetorical question, but an inevitability, according to a recent Juniper Research report. According to the market analysts, by 2017, one in three home routers will be used as a public Wi-Fi hotspot, and by 2020 there will be a total of 366 million of these units worldwide.
The report, entitled Wi-Fi Hotspots: Deployment Strategies & Forecasts 2016-2020, says that home routers will slowly be transformed into "homespots", and they will offer two networks: one for your personal use, and the other one as a public Wi-Fi hotspot.
Why do we need this, you ask? Juniper Research claims big broadband operators, including BT, UPC and Virgin Media, Comcast and Cablevision are using this approach as a fast and low-cost way to expand their domestic Wi-Fi coverage.
The research also suggests this trend will lead to a rising number of global Wi-Fi aggregators such as iPass that lease its network on a wholesale basis to such as telcos, cable operators and corporate customers.
The report also suggests this trend isn’t transparent enough and that people are not quite aware their routers were being used to support the public Wi-Fi initiative.
"While most operators now allow consumers to opt-out, if they so wish, most consumers simply have no idea that their routers are being used in this way", said research author Gareth Owen. "Given the current concerns around privacy and data security, the realization that home routers can be accessed by complete strangers is unlikely to be viewed in a positive light".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Kitto Studio / Shutterstock
-

Millennials make purchases based on social media recommendations
Publié: janvier 26, 2016, 8:57pm CET par Sead Fadilpašić

Recommendations that millennials see on social media are their primary shopping driver, a new survey by Demandware says.
The enterprise cloud commerce solutions provider released a global research of 7,000 consumers aged 18-34, with 1,000 being from the UK. The results say that 77 per cent of respondents have bought something after seeing it favorited or shared on some of the social media.
The type of social media is also important here. Facebook and YouTube dominate, with 59 percent and 41 percent of respondents acting on recommendations on each respective network. Twitter follows with 29 percent, then Instagram (25 percent) and the communications app WhatsApp (20 percent).
Google Plus (15 percent), Pinterest (14 percent) and SnapChat (12 percent) also have a noticeable share. When looking at an even younger audience, Tumblr, Snapchat and Vine dominate.
"In total, Tumblr and Vine have influenced purchases in three times as many 16-19s as they have 30-34 year-olds. Snapchat in nearly twice as many", the company said in a press release following the announcement.
The trend is set to grow, as well. The younger the audience, the higher the chance of it acting on recommendations, the survey says. Between 16 and 19 years of age, 84 percent have acted on recommendations, and between 20 and 24 – 81 percent.
"Clearly, today’s millennials are subject to an incredibly diverse range of influences when it comes to making a buying decision but friends and peers are valued over professional reviewers and celebrities", said Sharon Forder, senior director marketing, EMEA at Demandware. "The next generation of shoppers will be more adept at navigating the vast choices in front of them and adopting those technologies that give them the greatest advantage. Our research shows that retailers will need the agility to market products quicker and at a lower price to achieve growth".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Jason Howie/Flickr
-

Enterprise apps will drive augmented reality adoption
Publié: janvier 25, 2016, 6:40pm CET par Sead Fadilpašić

We might look at augmented reality (AR) as another means of entertainment, but it is its business applications that will fuel growth for the next five years, a new report suggests.
Beecham Research's Augmented Reality and Wearable Technology -- an operational tool for the enterprise report suggests that different markets such as manufacturing, healthcare and retail, areas where AR offers a new way for people to interact with information without the use of hands, is where this technology is expected to shine in the next five years.
"It is clear that the overall status of the enterprise market for AR and wearable technology is at a tipping point, moving from trials and testbed projects to real commercial deployments", says Matthew Duke-Woolley, market analyst at Beecham Research and author of the report. "While it is still questionable to provide a firm forecast, if this speed of transition accelerates as companies quickly recognize the benefits and return on investment, we believe the market can reach just under $800 million by 2020".
The report sees heads-up displays in manufacturing, remote assistance of specialist distant engineers and technicians, as well as medical systems which enable surgeons to access crucial data without distractions, key drivers of growth in the coming period.
"Current human-computer interfaces in mobile computing are primarily based around touchscreens, but AR along with WT offers a hands-free computing environment enabling greater interaction with information and the user’s surroundings", said Saverio Romeo, principal analyst at Beecham Research. "We expect to see rapid evolution of smart glasses with more miniaturization, better field of view and battery life, while there will also be increasing attention on the convergence with virtual reality (VR) technology and the Internet of Things to deliver competitive advantage. Collaboration with AR/VR and IoT players will be crucial".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Ahmet Misirligul/Shutterstock
-

AppRiver reveals the malware and spam trends in 2015
Publié: janvier 22, 2016, 8:41pm CET par Sead Fadilpašić

American email and web security firm AppRiver has released its end-of-the-year report, where it showcased a detailed analysis of malware and spam trends in 2015.
The report, entitled Global Security Report, says that the number of email messages containing malware doubled, year-on-year. From January to November, AppRiver quarantined 944 million messages, and in December alone, another 705 million.
The security firm also said its spam filters stopped 26 million spam messages last year.
AppRiver says 2015 was a busy year, with attacks on Anthem, Premera, LastPass, Ashley Madison and the Office of Personnel Management (OPM) grabbing the limelight. The OPM breach alone saw the data of 18 million of current and former government employees compromised.
In terms of the types of attacks which were most prevalent in the past year, AppRiver singles out malware, macros, ransomware, wire transfer fraud and Javascript obfuscation.
"The Protecting Cyber Networks and National Cybersecurity Protection Advancement Acts will incentivize companies to share cyber threat information with US government agencies", says co-author and manager of security research, Troy Gill. "The goal is to prevent future attacks by sharing threat intelligence through joint efforts of government agencies and companies".
Report co-author, Jon French, adds, "This year featured personal attacks on consumers, as cybercriminals favored personal data, such as health insurance records, online dating profiles, and HR files over financial information, such as credit card accounts and routing numbers. Cybercriminals are likely using this information to form detailed consumer profiles on the Dark Web for future attacks, like spear phishing and blackmail".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: wk1003mike / Shutterstock
-

PC users, get rid of Adobe Flash end of life versions
Publié: janvier 22, 2016, 7:01pm CET par Sead Fadilpašić

Secunia Research at Flexera Software has published a report covering the fourth quarter of 2015 for 14 countries, regarding vulnerable software, applications and PCs.
Turns out we’re not really good at keeping our computers safe, and our software up to date.
The key finding of the UK Country Report says that 78 percent of users have Adobe Flash Player 19 installed. This is an end-of-life version of Flash, one which no longer receives updates from Adobe.
Secunia links this to the vulnerability discovered in Flash on December 28 2015, which was rated ‘Extremely Critical’, as it can be triggered from remote and can execute arbitrary code.
Vulnerabilities in newer versions can be (and probably are, often) used to exploit these older versions, which is why Secunia Research urges everybody to patch their Flash Player immediately, and remove any end-of-life products they might have.
"The vulnerability discovered in Adobe Flash Player/ AIR 20 in December makes it even more important than usual to keep Adobe Flash Player up to date and get rid of end-of-life versions", said Kasper Lindgaard, director of Secunia Research at Flexera Software. "Adobe Flash is the most popular application within exploit kits, because it is so widely used and can therefore be used to leverage access to different platforms and both private and corporate users. While security-aware organizations know not to allow Adobe Flash Player anywhere near their business critical systems, private PC users tend not to be quite so mindful".
Other programs are also rarely patched, the report suggest, saying that non-Microsoft software is usually critical. It says that 11.4 percent of non-Microsoft programs on private PCs were unpatched in Q4, while only 4.1 percent of Microsoft programs were unpatched.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: zwola fasola/Shutterstock
-

Majority of consumers expect their data to be compromised in 2016
Publié: janvier 22, 2016, 4:41pm CET par Sead Fadilpašić

The series of high-profile data breaches we witnessed last year has left a mark on the way consumers perceive online business, a new research from NCC Group and IDG Research Services shows.
According to the research, entitled Trust in the Internet 2016, 63 percent of consumers expect their data to be compromised this year, and 60 percent are now worried, more than ever, about protecting their data on the Internet.
The poll questioned 10,000 consumers in the UK and the US about online habits and security.
Rob Cotton, CEO at NCC Group says this is a wake-up call for global business, as consumers have lost faith on businesses’ ability to keep their data safe. "This should set alarm bells ringing not just in the IT and marketing departments, but in the boardroom too as it is ultimately the responsibility of a company’s executives", he said.
"In the years to come the fight for customer trust is going to be won by brands that clearly show that the security of customer data is of paramount importance. It’s one of the many ways that cyber security can have a genuine impact on a company’s bottom line. It’s up to the board to decide whether they want that impact to be positive or negative".
The survey also suggests a few interesting solutions: 87 percent of respondents said a secure community of safe internet websites is needed, and exactly half said they’d feel better if a business communicated what it does to keep the data safe.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Di Studio / Shutterstock
-

Businesses believe compliance is effective at stopping data breaches
Publié: janvier 22, 2016, 9:53am CET par Sead Fadilpašić

Companies are approaching the data safety issue the wrong way, according to Vormetric's 2016 Data Threat Report, which was issued in conjunction with analyst firm 451 Research. The two companies polled 1,100 senior IT security executives from large businesses worldwide.
Key findings suggest that the rate of breaches is up, with 61 percent experiencing one in the past. From that number, 22 percent happened in 2015, and 39 percent in the year prior.
Another key finding is that a vast majority (64 percent) are confident compliance is extremely effective at preventing cyber-breaches. This is an increase, as 58 percent thought the same thing last year. Senior analyst at 451 Security, and the report’s author, Garrett Bekker, thinks otherwise.
"Compliance does not ensure security", he says. "As we learned from data theft incidents at companies that had reportedly met compliance mandates (such as Anthem, Home Depot and others), being compliant doesn’t necessarily mean you won’t be breached and have your sensitive data stolen. But we found that organizations don’t seem to have gotten the message, with nearly two thirds (64 percent) rating compliance as very or extremely effective at stopping data breaches".
Compliance was also the number one spot for IT spend for 46 percent of senior IT security executives polled.
"Organizations are also spending ineffectively to prevent data breaches, with spending increases focused on network and endpoint security technologies that offer little help in defending against multi-stage attacks", added Bekker. "It’s no longer enough to just secure our networks and endpoints".
IT security investments seem to be misplaced, as the majority of enterprises focus on perimeter defenses that keep on failing.
The full 2016 Vormetric Data Threat Report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Franck Boston/Shutterstock
-

2016 is the year when SSDs will truly take off
Publié: janvier 21, 2016, 4:27pm CET par Sead Fadilpašić

It seems as 2016 will be the year of the SSD (solid-state drive), with more and more IT decision makers saying they’re looking to use the advanced storage technology within their organizations.
This is according to a Spiceworks Voice of IT survey, done by Crucial, which asked 306 IT decision-makers in Europe and North America about their storage plans.
Even though hard-disk drives (HDD) are still the most commonly used type of drive, with an adoption rate of 91 percent, SSD disks are gaining popularity. It currently sits at 58 percent, with 18 percent more planning to deploy the technology this year.
SSD doesn’t seem to have a single defining factor why decision-makers are using it. Instead, it’s a combination of energy efficiency (39 percent), data case management (35 percent) and data center expansion (33 percent). Reliability, price and performance were key consideration points.
It’s no wonder, really, that organizations are looking to switch to SSD drives, as they’re said to be able to perform everyday tasks six times faster than traditional hard drives. By employing SSDs, businesses can work faster and more efficiently.
Jonathan Weech, Crucial SSD senior product line manager, said: "How much more productive could your business be if everyone on the team was able to work faster? While it’s widely known that SSDs are significantly faster than hard drives, it’s been difficult to quantify the net impact on organizational productivity -- until now".
Stephane Rizzetto, Crucial product marketing manager EMEA, added "SSDs transform the pace of business. On an individual level, SSDs allow you to get things done instead of waiting on your computer to load. When you can do more, you can serve more customers, ship more orders, crunch more data, and finish digital tasks faster. On an organizational level, SSDs take this a step further. When everyone is working faster, the business as a whole can move faster, serve customers more efficiently, and outwork the competition".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Hadrian/Shutterstock
-

When it comes to storage, reliability trumps price
Publié: janvier 21, 2016, 2:36pm CET par Sead Fadilpašić

When it comes to storage, saving money is no longer the number one priority for businesses, a new survey by Western Digital Corporation says.
According to the storage maker’s second annual global survey of CIOs and IT decision-makers, businesses have recognized the positive impact data can have on their bottom line.
Almost three quarters are growing their storage and archiving capacities, while more than 80 percent are investing in data analytics. Budgets are increasing, as well as build-out initiatives, in order to better store and access data gathered.
More than half of all businesses surveyed are still not storing all the data they need, and 60 percent are saying that the biggest challenge is being able to quickly access and process data collected.
"The findings of our survey underscore the increasing value of data, where dependable access through reliable storage systems and devices, is more critical than ever before", said Dave Tang, senior vice president at Western Digital Corporation.
"As data-driven organizations strive to extract more value from their operational and historical data, advanced architectures like Active Archiving enable data to be accessed easily and cost-effectively to transform data into a competitive advantage. With a reputation for quality and reliability, our storage solutions and devices will play a critical role in the infrastructure build out in 2016 and beyond".
Cloud is trending, the survey suggests, with decision-makers watching it closely, and identifying it as the leading growth area in terms of budget. The Internet of Things is another big trend, with decision-makers saying it’s driving change within data centers, and saying its impact is biggest in energy, finance, IT/telecom, and manufacturing sectors.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: hadescom / Shutterstock
-

Intel introduces 6th generation Core vPro processor family for office PCs
Publié: janvier 21, 2016, 12:58pm CET par Sead Fadilpašić

Intel has just announced new processors for office computers. The 6th Generation Intel Core vPro processor family is designed "for the modern workforce" and comes with a few innovations to keep office life tolerable.
Intel says the new processor offers "2.5 times the performance and a 30-times increase in graphics performance over a 5-year-old device", providing users with much more productive and powerful business tools.
In terms of safety, there’s the nifty little feature Intel calls the Intel Authenticate Solution – "a hardware-enhanced multi-factor authentication solution that strengthens identity protection". There are three stages of authentications users need to pass in order to confirm their identity -- something they know (a password), something they have (a smartphone or a tablet) and something they are (highly in debt... I mean, a fingerprint scanner!).
IT can choose from these authentication protocols according to the company policy. The Intel Authenticate Solution is available on Windows 7, Windows 8, Windows 8.1 and Windows 10. A preview version is also available.
"With incredible, new, eye-catching designs, added performance, and longer battery life, the 6th Gen Intel Core and Intel Core vPro processors are setting a new standard for business computing", said Tom Garrison, vice president and general manager for the Intel Business Client division. "By also adding enhanced security capabilities in the hardware, Intel has helped to make these newest PCs an integral part of a business’s overall security solution, making users more secure and productive than ever before".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Rose Carson/Shutterstock
-

Barclays introduces virtual credit card replacement
Publié: janvier 20, 2016, 5:47pm CET par Sead Fadilpašić

All those who have a habit of losing their credit cards, only to end up somewhere without a means to pay, rejoice!
Barclaycard has announced a new service, UK’s first, which allows for the instant replacement of a lost credit card -- first virtually, followed by a real card replacement.
The service works by calling the contract center for free from the Barclaycard app. After that, the virtual replacement card will be instantly downloaded to the smartphone, allowing the customer to pay straight away.
That way, those red-faced situations in which people realize they have no means to pay until it’s too late, can be avoided. A physical card replacement follows soon after. Besides being able to pay for transactions of up to £30 using contactless, customers with Android Contactless Mobile can enter their PIN and pay for transactions of up to £100 using the touch and go technology.
"With cards increasingly being used to pay for everything from the morning coffee to an evening meal, going about your life while your card is somewhere else can lead to potentially awkward situations", says Tami Hargreaves, commercial director of digital consumer payments at Barclaycard. "With contactless spending now over a billion pounds a month, we may even be witnessing the beginning of the end for the bar tab as we currently know it".
It makes sense. Barclaycard’s recent research has shown that almost a sixth of 21-55 year olds questioned reported that they have forgotten their credit or debit card behind the bar, with nearly half only realizing later, when they tried to pay for something else.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: 3Dstock / Shutterstock
-

Many UK SMEs aren't paying attention to physical security
Publié: janvier 20, 2016, 1:40pm CET par Sead Fadilpašić

There are many ways a data breach can occur, with via internet being just one of them. However, companies don’t really pay that much attention to their physical security, a new research suggests.
According to a research by access control and smart card specialists Digital ID, 59 percent of SMEs in the UK mostly go for locks and security lights and nothing more. Even then, nearly two thirds said the security was not operational during working hours.
Digital ID says this is not enough and puts businesses at serious risk of a security breach.
The research says that 23 percent have very little visitor security, while 36 percent have no visitor security installed at all.
Forty-one percent had a more complex security measure in place: ID cards and restrictive access gates are the most popular ones.
Adam Bennett, digital marketing manager at Digital ID, said: "At the very least, small businesses should have cyber security in place, but construction sites or building firms for example, should make sure there’s a level of access control in areas where items or equipment could be stolen. It’s surprising how much we hear of this kind of security breach, with a lot of it happening in broad daylight".
"It’s not just equipment that can be lost too, but important data, such as payment details and intellectual property, costing a business its reputation as well as money. Although every business has different needs, it’s still unfortunate to see so many businesses with little to no security, yet more than two thirds said they would be prepared to invest up to £10,000 in building security", added Bennett.
Digital ID says cyber security, access control and staff ID and visitor ID cards were the most important security processes SMEs should have in place.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: hxdbzxy/Shutterstock
-

Internet of Things' rising popularity will increase security risks, business costs
Publié: janvier 19, 2016, 4:41pm CET par Sead Fadilpašić

We all know that the Internet of Things is growing, and more and more firms are using the new technology to take their businesses to the next level, but just how big is IoT now, and how much will it grow?
Gartner has given a few interesting predictions, including one which says that more than half of all new business processes and systems will use some form of IoT by 2020.
As the production price of IoT continues to drop, so will its adoption grow.
"Uses of the IoT that were previously impractical will increasingly become practical", said W. Roy Schulte, vice president and distinguished analyst at Gartner. "The IoT is relevant in virtually every industry, although not in every application. There will be no purely IoT applications. Rather, there will be many applications that leverage the IoT in some small or large aspect of their work. As a result, business analysts and developers of information-centric processes need to have the expertise and the tools to implement IoT aspects that play a role in their systems".
But it’s not all butterflies and rainbows for businesses implementing IoT -- Gartner predicts 75 percent of all IoT projects will face schedule extensions of up to 100 percent, and firms will have to pay the price.
Hackers will also get in on the action, with a predicted black market for IoT devices selling fake sensors allowing data theft. The black market is expected to be worth $5 billion. Keeping your IoT devices safe means bigger spending for businesses, too. Annual security budgets will have to be increased at least 20 percent because of new IoT elements.
"Major cybersecurity vendors and service providers are already delivering roadmaps and architecture of IoT security, in anticipation of market opportunity", said Earl Perkins, research vice president at Gartner. "Small startups delivering niche IoT security in areas such as network segmentation, device-to-device authentication and simple data encryption are offering first-generation products and services, including cloud-based solutions where applicable. Large security vendors have already begun acquiring some of these IoT startups to support their early roadmaps and fill niches in their portfolios".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Young people find traditional education inadequate
Publié: janvier 19, 2016, 10:25am CET par Sead Fadilpašić

Today’s youth has a positive view about the future and their role in it. However, many young people believe that traditional education doesn’t do enough to prepare them for their professional life.
These are the results of a recent poll commissioned by consulting firm Infosys.
The report, entitled Amplifying Human Potential: Education and Skills for the Fourth Industrial Revolution, was conducted by independent research agency Future Foundation and has polled 1,000 young people, aged 16 to 25, across Australia, Brazil, China, France, Germany, India, South Africa, United Kingdom and United States.
In all of the countries, youngsters acknowledged the importance of technology skills in finding a good career opportunity; in both developing and developed countries, computer sciences subjects were key education tools for them.
However, traditional education does not provide enough, the report suggests, adding that young people had to seek additional knowledge in order to do their jobs.
"In the US, 45 percent of those polled considered their academic education to be very or quite old-fashioned, and that it failed to support career goals, compared to 37 percent in China", the report says.
Seventy-seven percent of polled youngsters in UK and Australia had to learn new skills, and in India that percentage was at 66.
"Young people around the world can see that new technologies, such as artificial intelligence and machine learning, will enable them to reimagine the possibilities of human creativity, innovation and productivity", said Dr. Vishal Sikka, CEO and managing director, Infosys.
"To empower these young people to thrive in this great digital transformation, our education systems must bring more focus to lifelong learning, experimentation and exploration -- in addition to bringing computer science and technology more fundamentally into the curriculum", added Sikka.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Asier Romero/Shutterstock
-

Big Data EMEA revenue to reach $2.7bn by 2019
Publié: janvier 18, 2016, 9:11pm CET par Sead Fadilpašić

Big Data, and its infrastructure is expected to grow significantly in the next four years, a new study by the International Data Corporation (IDC) shows.
IDC has done an in-depth market sizing of the Big Data infrastructure in Europe, Middle East and Africa, including servers and storage, as well as cloud resources, and here are the results:
Big Data-related server shipments will jump from six percent this year to 16 percent by 2019. The business is currently valued at $1 billion (£700m), but will be worth $2.7bn (£1.88bn) by the same year.
The storage capacity will reach 20 exabytes. If you’re not sure how much that is, here’s a Wikipedia article.
The analysis also says 134,000 server units got shipped in 2015 for Big Data, as well as 764 petabytes of storage capacity. Most of the storage was external, it adds.
Compliance is the main reason why most of the data, especially sensitive one, will remain in companies’ own datacenters, although analytics workloads will be moved to the public cloud.
Public cloud infrastructure share of Big Data workloads is expected to jump from 19 percent to 34 percent by 2019, and storage capacity on public clouds will also rise, from 25 percent to 55 percent by 2019.
"Big Data and analytics have risen to the top of executives’ and developers’ agendas as the technology has evolved and mindsets are starting to change in organizations in EMEA", said Andreas Olah, senior research analyst, European Datacenters and Big Data, IDC. "The main challenge is not the data or its volume, but the ability to generate value from it"
"Many customers are still at the beginning of their journey and still don’t know where to start. Others have high ambitions and clear ideas but are slowed down by increasing complexities and the lack of highly skilled data scientists and developers", adds Olah.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Tashatuvango / Shutterstock
-

Seagate introduces 10TB enterprise HDD for data centers
Publié: janvier 15, 2016, 8:08pm CET par Sead Fadilpašić

Seagate is looking to increase its presence in the data center market as it unveils a new hard disk drive.
The Seagate Enterprise 3.5 Capacity HDD offers 10 TB of storage and, according to the company’s press release following the announcement, the disk is quiet and energy-efficient.
It uses the 3.5-inch CRM design, and incorporates seven platters and 14 heads. The drive is sealed in helium which, as the company says, creates a turbulence-free environment, "decreasing both friction and resistance on the platters and delivering the industry’s lowest power/TB ratio and weight specifications for a 10TB HDD".
The disk also offers 25 percent more density, the company said, which helps increase petabytes per rack.
"More and more data centers are being put into operation as a result of data growing at an exponential rate. With this in mind, we are laser focused on lowering our TCO and confident the new Seagate Enterprise Capacity 3.5 HDD can help us with this endeavor", said Li Shu, senior expert technical support for storage and research and development, at Alibaba. "We value the drives winning combination of higher storage capacities, increased performance and low power consumption— making it a win-win for both us and our customers".
Next to IoT and wearables, Cloud has become one of the most important business opportunities in the past couple of years, to the point where it can make or break a business.
As Jonathan Bridges recently wrote here, IT will no longer be seen as a catalogue of services but as a collection of application environments that are monitored for usage and broken down by departments within the business.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

IT workers want an early retirement
Publié: janvier 15, 2016, 2:44pm CET par Sead Fadilpašić

It seems as nobody wants to work, and that’s a real bummer. Everyone wants to retire early, but that’s a particularly important problem in the tech industry, as it is already lacking staff, and people leaving early will only cause even more trouble.
According to a new report by Randstad Technologies, almost half (49 percent) of all tech workers want to retire before state pension age. In other industries, that percentage is at 35.
A report by Ros Altmann, the UK Pensions Minister has some nasty predictions: by 2022, the number of people aged 50 to state pension will jump to 13.8 million, up from the current 3.7m. At the same time, the amount of workers 16-49 will drop by 700,000. Once these seniors leave, someone in the tech sector is going to get a headache.
The reasons behind such thinking are also interesting. Apparently, 78 percent of tech workers believe they will basically be obsolete when they reach a certain age. The remaining 12 percent are worried about age discrimination.
"The Tech industry is facing an expansive experience exodus. The early retirement of the baby-boomers generation could lead to a serious skill shortage in the sector", said Ruth Jacobs, managing director of Randstad Technologies. "This generation helped build the technology sector in the 1980s with pioneers like Steve Jobs and Bill Gates leading the way. Companies need this experience if the sector is going to continue to expand. There’s already fierce fighting for talent as it is, and early retirements will make it even harder to find the right people for the right jobs".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Ditty_about_summer/Shutterstock
-

Security vulnerabilities, exploits are on the rise
Publié: janvier 15, 2016, 11:35am CET par Sead Fadilpašić

It’s been a busy year for security firms everywhere -- cyber-attacks, malware, ransomware and other malicious online behavior reached new heights in 2015.
Those are the results of a report by Bromium, a company which deals in threat isolation in service of data breach prevention. Its report, entitled Endpoint Exploitation Trends 2015 analyzed the security risks of popular websites and software.
Here’s what the report suggests: vulnerabilities and exploits, targeting popular software such as Firefox or Adobe Flash have spiked significantly; vulnerabilities jumped 60 percent, and exploits jumped 40 percent. Unsurprisingly, Adobe Flash exploits increased 200 per cent.
Malvertising was also persistent; out of the top 1000 Alexa sites, 27 percent had malicious advertising on them. To make things worse, 2015 has seen the return of Macro malware, malicious code pretending to be legitimate Microsoft Office documents. Angler Exploit Kit remained the most popular choice for attackers, and on top of it all ransomware doubled.
Since 2013, a type of attack in which crooks are demanding ransom in order to either decrypt disks which were previously taken over, or in order to stop a DDoS attack, has become one of the most common attack trends. The number of ransomware families increased 600 percent in the past two years.
"Attackers focus on high value targets with the path of least resistance, which means that attack vectors may shift as previously vulnerable software implements new security to mitigate attacks", said Rahul Kashyap, EVP, Chief Security Architect. "We have seen Microsoft take great steps to improve the security of Internet Explorer and Windows, which has forced attackers to focus on Flash exploits, malvertising and macro malware delivered through phishing emails".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: wk1003mike / Shutterstock
-

Qualcomm and TDK announce joint venture valued at $3bn
Publié: janvier 14, 2016, 5:53pm CET par Sead Fadilpašić

Qualcomm and Japanese tech firm TDK Corporation have announced a joint venture, valued by Reuters at approximately $3 billion (£2bn).
The new company, named RF360 Holdings, will be building modules needed to communicate wirelessly with mobile devices and IoT devices. Those modules include the RF front-end (RFFE) and RF filters, the two companies said in a press release.
The agreement is subject to receipt of regulatory approvals and other closing conditions and is expected to close by early 2017.
The two companies have also said that the new joint venture should provide an answer to the ever-growing problem of connectivity. With different modules, such as 2G, 3G, 4G, Bluetooth, satellite navigation and wireless LAN, a new level of miniaturization is needed, and that’s what RF360 Holdings should do.
Qualcomm will own 51 percent of the new company, while the rest will go to EPCOS AG, a subsidiary of TDK.
"TDK is a leading electronic components manufacturer with cutting-edge expertise in RF filters and modules, and we are looking forward to deepening our collaboration and together accelerating innovation and better serving the ecosystem for next-generation mobile communications", said Steve Mollenkopf, CEO of Qualcomm Incorporated.
"The joint venture’s RF filters will bolster Qualcomm RF360™ front-end solutions to enable Qualcomm Technologies, Inc. (QTI) to deliver a truly complete solution to the ecosystem. This will enable us to expand our growth opportunity by allowing us to accelerate our strategy to provide OEMs across our business segments with fully integrated systems that will enable them to deliver at scale and on an accelerated timeframe".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: EDHAR/Shutterstock
-

The first MIPS processor celebrates 30th birthday
Publié: janvier 14, 2016, 4:53pm CET par Sead Fadilpašić
Here’s something to make you feel really, really old. The first commercially available microprocessor chip was created in January 1986 -- exactly 30 years ago.
Back then, a team of Stanford University researchers and Silicon Valley veterans joined forces and created something that completely changed the way we see computers today. If it weren’t for these guys, who knows what modern computers would have looked like today.
Those people were current-day Stanford University president John L. Hennessy, Skip Stritter from Motorola and John Moussouris from IBM. They formed a small start-up company named MIPS Computer Systems Inc. In January 1986, the team unveiled R2000 CPU, a 32-bit processor which had 110,000 transistors.
According to a follow-up press release, the MIPS CPU units have been at the heart of "most exciting" and "most iconic" consumer products, including the original Sony PlayStation and Nintendo 64 consoles, but all the way to today’s IoT devices and TVs.
Today, 32-bit and 64-bit MIPS CPUs are used in autonomous vehicles, wearables, Internet of Things devices and many, many others.
British-based tech R&D company Imagination Technologies used the opportunity to write a blog post remembering the story of the first microprocessor. It describes its inception and the stiff competition the product faced back then in Motorola 68000 and Intel 80386 microprocessors.
The first processor had speeds of up to a stunning 15 MHz!
"To put that into perspective, a MIPS-based CPU manufactured in 2015 using a 28nm process can include 24 to 48 high-frequency, superscalar cores running at up to 2.5 GHz, large and highly-associative L1 and L2 caches, and enormous DRAM bandwidth, representing an incredible increase in frequency speed and a remarkable shrinkage in semiconductor manufacturing processes", says Imagination’s blog.
You can read more about the revolutionary product at this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft rebrands Revolution R Open, will keep it free and open-source
Publié: janvier 14, 2016, 12:29pm CET par Sead Fadilpašić

Microsoft has announced new offerings regarding the recently acquired Revolution Analytics and its R language for statistical computing and predictive analytics.
Most importantly, its Revolution R Open is now called Microsoft R Open and will remain open-source and free for download.
You can download Microsoft R Open here.
The company has made four other important announcements. Revolution R Enterprise for Hadoop, Linux and Teradata was renamed to Microsoft R Server, while the Microsoft R Server Developer Edition is now a freeware, with all the features of the commercial version.
From now on, Microsoft Data Science Virtual Machine will come with a prepared Microsoft R Server Developer Edition.
On top of it all, Microsoft R Server will be available for students through its Microsoft DreamSpark program.
"Advanced and predictive analytics is about developing and testing new models. But it’s also about their incorporation by developers into production deployments of decision support and automation solutions that can benefit the whole organization. With its new offerings for the R ecosystem, Microsoft is playing an important role in bringing analyst modelling and productivity tools as well as deployment tools to a broader audience", said Dan Vesset, program VP, Business Analytics and Information Management at IDC.
Microsoft closed the announcement by stressing how committed it is to helping everyone build advanced analytics platforms -- both in and out of the cloud.
"These announcements reinforce our commitment to making it easy for enterprises, R developers and data scientists to cost-effectively build applications and advanced analytics solutions at scale, both on-premises and in the cloud".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: rvlsoft/Shutterstock
-

Employees don't want a paperless office
Publié: janvier 13, 2016, 7:30pm CET par Sead Fadilpašić

The paperless office isn’t happening, people. We can blame lousy tablets or whatever we want, but research is clear: people still believe they’re more productive with the old fashioned pen and paper.
Epson Europe has conducted a research and surveyed more than 3,600 European employees, and here’s what they say: 64 percent said they’d rather read reports and brochures on a hard copy, as it’s easier to share (53 percent), easier to read (44 percent) and easier to edit (41 percent).
A majority (63 percent) also said errors are less likely on paper than in the digital form. In total, 83 percent believe ‘paperless office is unrealistic’.
With that in mind 86 percent of UK workers said banning paper would limit their productivity. Rob Clark, senior vice president of Epson Europe, states "it is clear from our research that -- despite digital advances -- people still like to work with paper, preferring print rather than working on-screen for certain tasks".
Clark continues: "The reality is organizations need printing, not only to help employees work more effectively but reap wider productivity. People collaborate effectively for many tasks digitally; for many others, a printed page is key, or an interactive whiteboard, an augmented reality headset or an in-person huddle. Businesses need to provide their employees with the options to use the best technology and processes for each task in each circumstance, from the humble printed page to the more sophisticated digital collaboration tools".
Even though digital documents might limit productivity, paper has its downsides too. Apparently, the average distance to a printer in the UK is 13 meters, marching 110 kilometers every year, and spending 19 hours a year walking to and from a printer.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: urfin/Shutterstock
-

US is spying on its allies for 'national security' purposes
Publié: décembre 31, 2015, 11:11am CET par Sead Fadilpašić

Even though US president Barack Obama promised to end the eavesdropping on highly-positioned officials among US allies, which was revealed during the Edward Snowden events, it seems that some officials are still under close watch by the NSA.
Among those is the prime minister of one of US' biggest allies -- Israel. According to a Wall Street Journal report, the White House decided to keep certain high-ranking officials under close watch, including Netanyahu and Recep Tayyip Erdogan, president of Turkey.
Wall Street Journal quoted a senior US official: "Going dark on Bibi? Of course we wouldn’t do that", a senior US official said, using Mr. Netanyahu’s nickname.
The spying on Netanyahu ruined the relations between the two countries to some extent, after it was uncovered that Netanyahu tried to sabotage the nuclear arms agreement the US was trying to achieve with Iran.
"The US, pursuing a nuclear arms agreement with Iran at the time, captured communications between Mr. Netanyahu and his aides that inflamed mistrust between the two countries and planted a political minefield at home when Mr. Netanyahu later took his campaign against the deal to Capitol Hill".
The eavesdropping revealed how Netanyahu and his advisers had leaked details of the US - Iran negotiations to undermine the talks; coordinated talking points with Jewish-American groups against the deal; and asked undecided lawmakers what it would take to win their votes.
Current and former US officials agree -- Obama kept monitoring Netanyahu because it served a "compelling national security purpose".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Brian A Jackson/Shutterstock
-

Adobe Flash gets the final security patch of 2015
Publié: décembre 31, 2015, 5:03am CET par Sead Fadilpašić
 There’s nothing quite like kicking a dead corpse, and that’s basically what Adobe is doing with its once powerful product Flash.
There’s nothing quite like kicking a dead corpse, and that’s basically what Adobe is doing with its once powerful product Flash.Adobe has issued a security update for Flash, one which, according to it, addresses "critical vulnerabilities that could potentially allow an attacker to take control of the affected system".
"Adobe is aware of a report that an exploit for CVE-2015-8651 is being used in limited, targeted attacks", the company said in the patch’s description. "Adobe recommends users update their product installations to the latest version using the instructions referenced in the security bulletin".
This has been a horrible year for Flash -- used countless times by hackers to take control of a victim’s computer, the developers have tried to patch vulnerability after vulnerability, but to no avail.
316 Flash bugs have been discovered this year -- meaning Sunday was likely the only day of the week which was free of new Flash vulnerabilities.
The vulnerabilities -- most of them quite dangerous -- have prompted big tech companies and services to switch to alternatives.
In January, YouTube dropped the bug-ridden software in favor of HTML5 to handle its video, and in July, Facebook’s chief security officer asked for an "end-of-life date for Flash". That same month, Mozilla partially blocked the once-ubiquitous plugin in its Firefox browser.
But perhaps the worst hit Flash could get happened in December, when Flash developer Adobe started distancing itself from its creation, saying that it will now "encourage content creators to build with new web standards".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: 360b/Shutterstock
-

Intel unveils 8 new Broadwell and Skylake processors
Publié: décembre 30, 2015, 2:37pm CET par Sead Fadilpašić

US chip maker Intel has recently announced eight new processors, as it expands its Broadwell and Skylake families. The chips will be available for both desktop and mobile CPUs, the company added.
The new processors announced today include the Celeron 3855U, Celeron 3955U, Core i3-6098P, Core i5-6402P, Core i5-5200DU, Core i5-6198DU, Core i5-5500DU, and the Core i7-6498DU. Out of these, the two new desktop CPUs are the Core i3-6098P and the Core i5-6402P. Like previous processors with a "P" prefix, it is likely that these processors do not come with an integrated GPU. They have been priced at $117 (£79) and $182 (£122), respectively.
The four new mobile CPUs -- Core i5-5200DU, Core i5-6198DU, Core i7-5500DU, and the Core i7-6498DU are dual-core SKUs with four threads. The D in the name is still a mystery.
According to CPU World, the Celeron 3855U and 3955U are both ULV dual-core processors and come with an integrated Intel HD 510 graphics and 2MB of L3 cache.
The company announced new processors the same day it announced the completion of the acquisition of Altera. According to the company’s press release, the acquisition will enable new classes of products in the IoT and datacenter businesses.
"Altera is now part of Intel, and together we will make the next generation of semiconductors not only better but able to do more", said Brian Krzanich, Intel CEO. "We will apply Moore’s Law to grow today’s FPGA business, and we’ll invent new products that make amazing experiences of the future possible -- experiences like autonomous driving and machine learning".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Rose Carson/Shutterstock
-

Seagate will introduce larger HAMR-based HDDs in 2018
Publié: décembre 29, 2015, 3:35pm CET par Sead Fadilpašić

The first HAMR hard disk drives are set to appear on the market in early 2018. The disks, which will be built by storage company Seagate, will be given to select customers and used as testing devices in late 2016 or early 2017, before shipping out to other consumers a year later.
The HAMR technology, (heat-assisted magnetic recording) promises to increase capacities of HDDs significantly in the coming years. You might wonder why HDD is still a thing when SSD is doing such a good job, but HDD is still used by millions of people and across virtually all data centers worldwide.
"As for new generation technologies, HAMR or TAMR, the start of mass production will be [slightly] delayed to 2018", Anandtech cites Hideo Ichikawa, president of Showa Denko. The official mid-term business plan of the company reads that the new-generation media "will be launched in or after 2018".
Storage has been a significant battlefield in 2015, and all clues are pointing towards an even bigger battle next year. Internet of things, big data, user-generated content, enterprise storage, those are all the main drivers in the ever-growing need for additional storage.
Samsung Electronics believes that the NAND flash industry will produce 253EB of flash memory in 2020, up from 84EB in 2015, and analysts from International Data Corp. and Western Digital Corp. estimate that data storage capacity shipped by the industry in 2020 will total approximately 2900 exabytes (1EB = 1 million TB), up from around 1000EB in 2015.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Piotr Tomicki/Shutterstock
-

Microsoft CMO hints at 'breakthrough' Surface phone
Publié: décembre 29, 2015, 10:38am CET par Sead Fadilpašić

Microsoft is doing something about its smartphones business and according to the company’s CMO, it is something revolutionary, shocking, breathtaking.
I’m not being cynical here, I’m just reporting -- that’s the best part.
During the most recent Windows Weekly -- a popular show with Mary Jo Foley -- chief marketing officer of Microsoft, Chris Capossela, dropped some hints that sent ripples through the internet.
"We need some sort of spiritual equivalent on the phone side that doesn’t just feel like it’s a phone for people who love Windows", he said in that interview. "It’s got to be a phone where it’s like, 'Wow, that’s a real shock or that’s a real breakthrough, and that’s going to make me (as a hypothetical Apple fan) pause before I buy my 17th iPhone'. And we need time to actually go build that".
So no, he didn’t exactly say what the company is building, or how long it is going to take it to build whatever it is that it’s building, but it’s going to be a "real breakthrough". That is something Microsoft really needs at this moment. No one said it better than Mary Jo Foley, who asked Capossela to "give me something to hope for in the new year as a Windows Phone fan, Chris, because I’m abandoning hope".
That 'something breathtaking' just might be the Surface Phone, and 2016 just might be a big year for Microsoft -- if a revolutionary Windows 10 Mobile phone gets released, and Windows 10 continues on its path of success.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: PathDoc / Shutterstock
-

UK's average Internet speed grows by 10 percent in 2015
Publié: décembre 29, 2015, 3:23am CET par Sead Fadilpašić

All European countries surveyed recently, experienced a quarterly increase in average connection speeds, with double digit gains being posted by Norway (15 percent) and the UK (10 percent). Year-over-year it was up by 21 percent in the United Kingdom. Those are the results of a new report by Akamai, the content delivery network.
Global average connection speed has increased slightly (0.2 percent) to 5.1 Mbps from the second quarter, accounting for a 14 percent increase year-over-year, the report said.
The Akamai’s Third Quarter, 2015 State of the Internet Report, based on data gathered from the Akamai Intelligent Platform, provides insight into key global statistics such as connection speeds, broadband adoption metrics, notable Internet disruptions, IPv4 exhaustion and IPv6 implementation.
Besides the global average connection speed increase, the report also says that 2015 saw the Regional Internet Registry (RIR) for North America completely exhaust its available inventory of IPv4 address space.
"The continued depletion of IPv4 space, in both North America and around the world, should further spur organizations to expand or accelerate their own IPv6 adoption, particularly as the cost of obtaining IPv4 address space may rise as scarcity increases", said David Belson, editor of the State of the Internet Report.
South Korea had the top average connection speed at 20.5 Mbps, followed by Sweden (17.4 Mbps), Norway (16.4 Mbps) and Switzerland (16.2 Mbps). European countries dominate the global top 10 country/region listing for 25 Mbps adoption, and also lead the world in IPv6 adoption.
The full Akamai report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Dudarev Mikhail/Shutterstock
-

UK sees 5.2 percent growth in IT jobs this year
Publié: décembre 28, 2015, 7:50pm CET par Sead Fadilpašić

The growth of the IT sector in the UK has accelerated to its fastest rate since the end of the recession, according to an analysis by Nixon Williams.
Nixon Williams analyzed data obtained from a variety of recent reports published by the Office of National Statistics, which show that there are currently 154,765 active IT enterprises in the UK, a 7.9 percent increase on the previous year when there were 143,450 active IT enterprises. The rate of new business creation in the IT sector is at its highest level since before the start of recession in 2008.
The number of active enterprises in the IT sector fell by 0.3 percent, from 123,065 to 122,685 between 2008 and 2009, and has increased at an annual rate of 6.3 percent between 2009 and 2013, before surging by 7.9 percent over the past year.
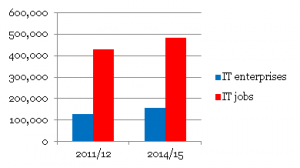 At the same time, demand for IT skills is accelerating. The total size of the IT workforce is also increasing at its fastest rate since the end of the recession. A further 24,000 IT jobs were added over the past year, an increase of 5.2 percent on the previous year. By comparison, the number of financial service sector jobs -- which often competes with tech companies for the best talent -- declined from 1,178,000 in 2009 to 929,000 in 2015, a fall of 21 percent.
At the same time, demand for IT skills is accelerating. The total size of the IT workforce is also increasing at its fastest rate since the end of the recession. A further 24,000 IT jobs were added over the past year, an increase of 5.2 percent on the previous year. By comparison, the number of financial service sector jobs -- which often competes with tech companies for the best talent -- declined from 1,178,000 in 2009 to 929,000 in 2015, a fall of 21 percent.According to Nixon Williams, demand for IT contractors with specific skills sets is growing strongly, particularly among start-ups, which are often hesitant to commit to hiring full-time employees.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: suphakit73/Shutterstock
-

Samsung Pay will have 50 percent market share in Asia
Publié: décembre 28, 2015, 12:46pm CET par Sead Fadilpašić

Maybe Samsung isn’t doing all that great in the smartphones department, but it has high expectations from its mobile payment service that will be introduced in China early next year.
So high, in fact, that Hyundai Securities is predicting a 50 percent market share in China, and a significant share globally, too. The news was first reported on by ETNews.
Samsung is expected to achieve this goal with the help of UnionPay and Alibaba. According to SamMobile, UnionPay controls 73 percent of the Asian markets, and all the debit and credit cards issued by the company can be used in 150 countries and at 26 million affiliated stores.
Alibaba, on the other hand, controls 75 percent of the Chinese e-commerce market.
Hyundai Securities estimates that some 200 million Samsung smartphones will come with Samsung Pay preloaded next year.
"Because Samsung Pay has quickly settled itself in South Korea, it is expected that it will expand towards Chinese and the U.S. markets", said Kim Chul-young who is a researcher for Hyundai Securities Co., Ltd. "Cellphone payment service businesses and module businesses will also benefit from this".
This year, Samsung Pay was available on just four models: Galaxy S6, Galaxy S6 edge, Galaxy S6 edge Plus, and Galaxy Note 5. However Samsung Electronics is planning to apply Samsung Pay to inexpensive models too next year to quickly expand influence of Samsung Pay.
Those will include the Galaxy A5 (2016), and the Galaxy A7 (2016).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Oracle agrees to warn Java users of malware risk
Publié: décembre 23, 2015, 6:48pm CET par Sead Fadilpašić

Oracle is about to issue a warning that Java users could be exposed to malware, the media have reported on Tuesday.
The exposure is the result of a flaw that existed in Java’s software update tool. After an investigation conducted by the US Federal Trade Commission, Oracle (Java’s distributor) has agreed to issue a warning over its social media channels and on its website, otherwise it would have been fined.
According to a BBC report, Oracle has admitted no wrongdoing. All of this seems like a bunch of (un)necessary formalities.
According to the FTC’s complaint, Oracle was aware of security issues in the Java SE (standard edition) plug-in when it bought the technology’s creator, Sun, in 2010.
"The security issues allowed hackers to craft malware that could allow access to consumers’ usernames and passwords for financial accounts, and allow hackers to acquire other sensitive information", the FTC said.
The point is -- Oracle promised its users that updating Java would ensure their PCs would remain "safe and secure", but never mentioned that any risk remained -- even though it did remain.
This was because Sun’s original update process did not delete earlier versions of its software, which hackers could exploit to carry out their attacks. The problem was resolved in August 2014.
Oracle could not plead ignorance because the FTC had obtained internal documents dated from 2011 that stated “[the] Java update mechanism is not aggressive enough or simply not working”.
The plug-in is installed on many PCs to let them to run small programs written in the Java programming language.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: bahri altay/Shutterstock
-

Here are the system requirements for Microsoft Azure Stack
Publié: décembre 23, 2015, 3:47pm CET par Sead Fadilpašić

Microsoft has announced the hardware requirements needed to run its Azure Stack – the upcoming on-premise hybrid version of the Azure cloud.
The Azure Stack first gets installed on a server and delivers Azure services in a customer’s datacentre, enabling developers and IT professionals to build, deploy and operate cloud applications using consistent tools, processes and artifacts.
Here’s what it’s comprised of:
- Cloud-inspired infrastructure, which includes: Software-defined infrastructure platform -- SDS | SDN | Compute, Software-Defined Security and Infrastructure management -- Provisioning and Operations
- Azure portal
- Azure-based IaaS services
- Azure-based PaaS services
- Azure Resource Manager -- a declarative, template-based approach that helps specify and configure applications for automated deployment
The focus of the product will be on enterprise applications like SQL Server, Exchange and SharePoint.
Basically, it’s something of a private cloud -- it simplifies the app scaling process across current data centers, but if need be, extra resources can be pulled from the cloud.
Here’s how it will work: Users will need a single server (Microsoft says Hewlett-Packard’s Enterprise DL 360 Gen 9 would be the best choice. Or a Dell R630) with at least 96GB of RAM and 12 cores -- 128GB of RAM and 16 cores are recommended.
It needs at least Hyper-V Enabled (with SLAT support), Windows Server 2012 R2, and an OS disk with minimum of 200 GB available for system partition (SSD or HDD). Concerning disk drivers, Microsoft says four disks with a minimum of 140GB of capacity is needed, while 250GB is recommended.
Full specifications can be found on this link.
Through Azure Stack, Microsoft is trying to be more competitive in regards to Amazon Web Services and Google’s clouds. SiliconAngle has noticed how none of the two provide options for hosting your own service.
The Azure Stack is similar to the hybrid cloud angle VMware has been chasing since 2013, when it launched its vCloud Hybrid Service, promising a virtual extension of customers' on-premise environments to the cloud.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: drserg / Shutterstock
-

Windows 10 patch messing with your Office 2016 templates? Here's how you can get them back
Publié: décembre 23, 2015, 2:13pm CET par Sead Fadilpašić

A cumulative Windows 10 patch has had some Word 2016 users cringing in despair. The patch, titled Cumulative Update KB3124200, is causing the Word 2016 template file Normal.dotm to be renamed.
Then, once the text processing program is restarted, it sees the file missing and creates a new one, basically restoring it to factory settings, which is a bummer. The Normal.dotm file is where Word stores all the custom macros, custom spellcheck and auto-correct features.
The update, which was released next week, has made some users hit the forums for complaints.
The good news is that the old Normal.dotm does not get deleted after the patch -- it just gets renamed to Normal.dotm.old, so in order to restore all your settings, all you need to do is replace the new file with the old one.
A member of Microsoft’s product team, going by the name Rob L, gave instructions in the forum post how to restore the settings:
1. Close Microsoft Word.
2. Press Windows + R and type in %appdata%\Microsoft\Templates and press Enter.You are now looking at the Templates that Word (and other Office apps) use. (Note that if you have "file extensions" turned on, then you may see slightly different names). You should see a file named "Normal" of type "Microsoft Word Macro Enabled Template". This is your current Normal template (which is missing the data you want).
Let’s save a backup of this normal template just in case.
3. Rename the "Normal.dotm" file to "NormalBeforeRestore.dotm". You can rename the file by right-clicking it, selecting "Rename", and typing in the new name.
Now we have to determine which file to restore. The issue we identified typically results in a file called "Normal.dotm.old", but under some circumstances, there could be other saved versions of your Normal template in that directory as well.
You should see at least one of the following: "Normal.dotm.old", "NormalPre", "NormalPre15", "NormalOld", or "OldNormal". If you see more than one of these files, then you will need to choose the correct file to restore; this is likely the file with the most recent "Date modified" value, which should be "Normal.dotm.old". Don’t worry if you choose the wrong one, you can repeat steps 4-6 as many times as necessary to find the right file.
4. Select the file you want to restore. Right click and select "Copy".
5. Now create the copy of the file by clicking the Home tab and choosing "Paste". (or press Ctrl + V)
6. Now select the new file you just created and rename it. Right-Click and select "Rename".- If you have file extensions turned on, or if the file you are renaming is called "Normal.dotm.old" or "Copy of Normal.dotm.old", then you will need to rename the file to "normal.dotm". You may be warned about changing the file extension -- this is OK.
- If you do not have file extensions turned on and the file is not called "Normal.dotm.old" or "Copy of normal.dotm.old", then rename the file to "Normal".
7. Close File Explorer and launch Word. Your AutoText blocks, Styles, Macros, etc. will now be available for use in your documents.
8. If you still cannot find your content, and there were other templates in your Templates folder to choose from, then shut down Word, go back to your templates folder, delete Normal and go back to step 4. (we are only making copies in step 5, so you won’t be losing anything when you delete Normal here.)That's it.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: fotoscool/Shutterstock
-

DDoS attacks rise by 180 percent in 2015
Publié: décembre 22, 2015, 8:54pm CET par Sead Fadilpašić

To some this will come as a surprise, to others not as much, but the Distributed Denial of Service, also known as DDoS -- was the most popular type of cyber-attack in the past year.
According to a report by security firm Akamai, there has been a jump of 180 percent in the number of DDoS attacks in 2015. The ending year also saw records broken in the size of the attacks, as well.
The DDoS is a type of attack where a large number of infected machines are ordered to try and access a particular website. With millions of computers trying to open the same site, it eventually crumbles under pressure, bringing the site down.
This can lead to losses in both reputation and finance -- with damages going up into millions.
According to Akamai State of the Internet Security report, this year saw a number of attacks that were so large they could bring down a "tier one router" -- the kind of router employed by our internet service providers.
A few weeks ago someone tried a large attack against one of the servers underpinning the internet. Luckily, its army of infected devices -- its botnet -- wasn’t big enough.
When looking at countries most responsible for attacks, two stand out -- USA and China. USA accounted for almost 400 attacks in the last 24 hours, and China for 360.
The US also holds the all-time ranking for botnet attacks -- at over seven million, where China had 6.3 million.
Among the most notable DDoS attacks in 2015 were the TalkTalk incident, as well as a Dota 2 tournament worth $18 million.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

Toshiba will cut 6,800 jobs
Publié: décembre 22, 2015, 11:33am CET par Sead Fadilpašić

Japanese tech giant Toshiba is forced to restructure itself following enormous losses, and now it is known that some 6,800 people will lose their jobs.
The company is into many businesses, from laptop building, television to nuclear energy. The people losing their jobs work in the electronic devices department. The plans to restructure the company were unveiled after Toshiba overestimated its profit expectancies for a six-year period.
The scandal, which escalated when it was unveiled that certain subordinates faked financial results to show more profit, has led to the resignation of the company’s president.
Toshiba plans to sell its TV production plant, as well as its washing machine plant -- located in Indonesia. A Hong Kong-based company Skyworth will allegedly buy the plants. The company is also looking for investors for its health-related business.
Among those 6,800 workers, some will retire early.
Toshiba was formed in 1875, and in 1985 it has built its first laptop. Currently it employs almost 200,000 people. The company’s shares have dropped 40 percent since April 2015.
The cause of many problems also lies in the tsunami which hit Japan in 2011, and which led to the disaster in the Fukushima power plant. Toshiba was in charge of the plant.
Toshiba said it had not yet fully calculated the impact of the nuclear disaster on its books.
The latest earnings projection means Toshiba is sinking into its second straight year of red ink, after racking up a nearly 38 billion yen (£209 million) loss for the fiscal year that ended in March.
Senior market analyst at Spreadex, Connor Campbell, has compared Toshiba to Tesco, another company that was in a similar position. Looking at how Tesco managed its problems, Campbell does not see a bright future in front of Toshiba. "It’s a situation remarkably similar to Tesco’s; both companies hit by huge accounting scandal, both in sectors hurt by price-wars, both with an arduous and costly path ahead", he says. "Not that that will be much comfort to Toshiba given how poorly Tesco has performed in the aftermath of its own issues".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Anton Watman/Shutterstock
-

Microsoft will offer custom Windows 10 to the Chinese government
Publié: décembre 18, 2015, 7:12pm CET par Sead Fadilpašić

Microsoft has signed an important deal with the Chinese government, one which will see the American company deploy its latest operating system directly to the government agencies.
The Verge has reported how the Redmond-based software company will deploy a customized version of Windows 10 to the Chinese government through a newly-formed company called C&M Technologies.
The company is still subject to regulatory approval.
Microsoft said the joint venture will license, deploy, manage and optimize a custom version of the operating system for government agencies. In addition to government agencies, it will serve "state-owned enterprises in key infrastructure fields such as energy, telecommunications, and transportation".
All the necessary support, patches and updates will be handled by C&M Technologies, as the exclusive licensor of the custom Windows 10. It will also take feedback on exactly what future versions of the operating system will need. Microsoft, on the other hand, gets an important foothold in one of the biggest markets in the world. Prior to the agreement, Microsoft has already made deals with other Chinese companies such as Lenovo, Tencent and Xiaomi.
"We will maintain ownership of the core Windows 10 technology while working, as we’ve always done, to allow customers and partners to build components that plug into our platform", Microsoft’s Yusuf Mehdi wrote in a blog post announcing the deal. "We’ll continue to keep Windows 10 secure and sustain our strong privacy standards, while recognizing that public sector solutions may differ from technology offered to private sector enterprises and consumers around the world".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: rvlsoft / Shutterstock
-

Security researcher finds 685TB of unprotected MongoDB data
Publié: décembre 18, 2015, 11:24am CET par Sead Fadilpašić

There is roughly 685TB of private data from MongoDB instances sitting online, without any protection, researchers have uncovered.
Following the recent discovery by security researcher Chris Vickery, who saw the data of more than 13 million MacKeeper users exposed, another researcher ventured even deeper and found even more unprotected data.
A developer at online devices search engine Shodan, John Matherly, investigated the publicly accessible mongoDB databases in July and found 595.2TB of data there. After the MacKeeper discovery he ventured back, and saw that the database grew by another 90TB and that no security measures are in place.
In his new investigation, which he describes on his blog, Matherly found that the number of publicly available, unauthenticated instances of MongoDB running on the internet had increased by 5,000. According to the blog post, these are hosted mostly on Amazon, Digital Ocean and Alibaba’s cloud computing service Aliyun.
This is something of a surprise though, as new versions of NoSQL are secure by default -- which means users are changing the default setup to something less secure. They aren’t enabling firewalls for protection, either.
"In the previous article it looked like the misconfiguration problem might solve itself due to the new defaults that MongoDB started shipping with; that doesn’t appear to be the case based on the new information. It could be that users are upgrading their instances but using their existing, insecure configuration files", said Matherly.
"Finally, I can’t stress enough that this problem is not unique to MongoDB: Redis, CouchDB, Cassandra and Riak are equally impacted by these sorts of misconfigurations", he added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: liuwenhua / Shutterstock
-

Slack announces App Directory store
Publié: décembre 17, 2015, 4:35pm CET par Sead Fadilpašić

The business communication tool Slack is trying to end the year on a high note, and looking at what the company announced yesterday, it seems to be on the right track.
The team-communication app, which now has two million daily users and 570,000 paying customers has announced three things -- an app store which will offer other productivity tools (like Trello, for example) to integrate with Slack, an $80 million fund to help developers create more apps for the store, and a new framework called Botkit which should simplify the process of creating apps.
The Slack App Directory, available on this link, currently offers 160 apps sorted into different lists: by category, popularity, staff favorites.
"Installation is easy -- you’ll be using these new apps inside your Slack team after just a few clicks", the company said in a blog post announcing the novelties.
The fund, aimed at motivating developers to take part, is backed by Slack and six of its investors: Accel, Andreessen-Horowitz, Index Ventures, KPCB, Spark, and Social+Capital.
"If you’re a developer or small company deciding whether to make a bet on the Slack platform, the Slack Fund is a new source of support to help you get started building apps", Slack says.
The Slack Fund will fund both "Slack-first" apps as well as B2B and enterprise tools that make Slack integrations a core part of their offering.
Botkit, which was developed by Howdy, "greatly simplifies the creation of apps (especially bots) with a flexible codebase that handles things like authenticating apps to a team and the sending, receiving, and processing of messages with our API".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Most Android devices run an outdated OS version
Publié: décembre 17, 2015, 2:43pm CET par Sead Fadilpašić

More than 80 percent of Android devices are running an outdated version of the operating system. Those are the results of an inquiry among users of G DATA security solutions for Android.
G DATA believes the lag in the adoption of new versions lies in the long delays before manufacturers roll out updates to their devices, as well as the fact that some devices simply don’t support the latest version of Android.
The full report can be found on this link (PDF). It was done during the third quarter of 2015 and does not include Android 6.0 Marshmallow.
Android Jelly Bean (4.1 - 4.3) is still the most popular version of Google’s operating system, with the market share of 36.93 percent. KitKat came in second, with 20.29 percent, while Ice Cream Sandwich has a 10.66 per cent market share.
By the end of the third quarter of 2015, G DATA analysts had already counted more Android malware instances (1,575,644) than in the whole of 2014 (1,548,129). 574,706 different Android malware strains were found in the third quarter alone. This represents an increase of 50 percent compared to the same period last year.
The report also says hackers are targeting Android on the IoT, as well as there are more smartphones with pre-installed malware.
G DATA security experts expect to see an increase in complex malware that combines Windows and Android attack campaigns on online banking customers. The criminals’ aim is to manipulate banking transactions on the Internet.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Joe Wilcox
-

13 million MacKeeper accounts leak online
Publié: décembre 16, 2015, 8:40pm CET par Sead Fadilpašić

The anti-virus software for Apple’s OS X, MacKeeper, kept the user data of more than 13 million of its customers online without much protection, and someone eventually stumbled upon it.
Yes, stumbled is the perfect word in this instance, as the data was accessed through an IP address, no username or password required.
The data was uncovered by security researcher Chris Vickery, who was browsing the net through Shodan -- a specialized search engine that looks for and indexes virtually anything that gets connected to the Internet.
He said he uncovered four IP addresses that took him straight to a MongoDB database, containing a range of personal information, including names, email addresses, usernames, password hashes, phone numbers, IP addresses, system information, as well as software licenses and activation codes.
Vickery contacted MacKeeper, which reacted quickly, patching up the holes and thanking him for what he has done.
"Some 13 million customer records leaked from is aware of a potential vulnerability in access to our data storage system and we are grateful to the security researcher Chris Vickery who identified this issue without disclosing any technical details for public use", the company said in a statement published on its site. "We fixed this error within hours of the discovery. Analysis of our data storage system shows only one individual gained access performed by the security researcher himself. We have been in communication with Chris and he has not shared or used the data inappropriately".
The users’ financial information is safe, though, and it said it will reset all passwords.
"Billing information is not transmitted or stored on any of our servers. We do not collect any sensitive personal information of our customers", the statement continues.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: wk1003mike / Shutterstock
-

VMware backs out of Virtustream venture, leaving EMC on its own
Publié: décembre 16, 2015, 6:43pm CET par Sead Fadilpašić

VMware, the US cloud software company, said it will not participate in the joint venture cloud services Virtustream with its parent company EMC.
The announcement was made in a recent regulatory filling, which you can read here.
"VMware announced that it will not be participating in the formation of the Virtustream Cloud Services Business previously announced by EMC and VMware on October 20, 2015", it says in the filing.
The pull-out is most likely linked with the recent acquisition deal under which Dell would buy EMC for $67 billion, thus gaining control over VMWare’s shares. As part of the deal, a VMware tracking stock is being constructed and Dell would offer up to 50 percent of Dell’s shares on the stock market. VMware investors were unhappy with all this and the stock price has fallen.
Eight days after that deal was announced, EMC and VMware announced plans to create Virtustream as a 50-50 venture, Re/Code said in a report, adding that the Virtustream has been blamed for contributing to a 25 percent decline in the value of VMware shares during the last two months.
Virtustream was expected to record a $200 million to $300 million loss in 2016, The Register reported.
"Virtustream was going to result in a, roughly, $200M to $300M non-GAAP hit to the bottom line for VMware in 2016, and this remains one of the more “head scratching” moves we have seen recently across the tech space", Daniel Ives with FBR & Co told the Barron’s blog.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Creativa Images / Shutterstock
-

Most enterprises use hybrid clouds
Publié: décembre 14, 2015, 3:39pm CET par Sead Fadilpašić

Canopy, the Atos Cloud, in collaboration with EMC commissioned a study about hybrid cloud adoption, conducted by Forrester Consulting. Surveying over 150 companies with revenues of $1 billion+ across multiple countries, the findings show an increased adoption of hybrid cloud services with 58 percent of the respondents saying they already have some form of hybrid cloud environment.
Organizations using hybrid cloud define it as a "cloud spread across multiple deployment models" with 40 percent of respondents seeing it as a combination of private and public cloud usage.
Fifty-one percent of respondents consider that the hybrid cloud has the potential to allow the consolidation of the management of all cloud services.
Further to that, respondents said that when deploying a hybrid cloud solution, the most important factors to be considered are the ability to monitor and optimize cloud costs (55 percent) and performance (49 percent).
In response to the potential risks represented by shadow IT, bring-your-own device and cloud, the survey shows that recognition is high amongst IT professionals for the need of improved management and better governance.
This brings orchestration and service brokering to the heart of the IT strategy, with service management taking centre stage in IT organizations which are rapidly shifting to a role of providers and brokers of business services.
Forty-six percent of respondents identified the rewriting of applications to scale as a deployment scenario for Hybrid Cloud, and 33 percent stated that they have already built some service templates across hybrid clouds.
When asked what to watch for when deploying a hybrid cloud, 47 percent of respondents said that it was important to ease the ability to port applications across different clouds.
This response indicates that the cloud has become a target platform for many applications, not only for cloud-native applications but also for many enterprise applications which are becoming candidates for cloud deployment.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wavebreakmedia/Shutterstock
-

Most consumers like the idea of a single-brand ecosystem
Publié: décembre 14, 2015, 10:34am CET par Sead Fadilpašić

A new Xerox report, The State of Customer Service 2015, reveals that more than half (51 percent) of consumers are comfortable with the idea of buying into a single brand ecosystem for all their technology, communications and media needs.
By 2025, 37 percent believe a single supplier will manage their home.
Technology consumers -- who cited 166 different brands for five different devices -- are already buying into one-brand ecosystems with 40 percent having at least two devices from the same brand. Furthermore, nearly half (43 percent) of those willing to buy into a single brand would like their chosen technology brand to be their sole supplier for telecoms and media too.
The Xerox study, which surveyed 6,000 consumers across the media, telecoms, and technology sectors in the United States, United Kingdom, Germany, France and the Netherlands, about their attitudes to customer care, found that technology consumers are the most satisfied, with the lowest risk of churn.
When compared to customer satisfaction in telecommunications (34 percent) and media (41 percent), more consumers are highly satisfied with technology brands (48 percent).
Other trends revealed by the report include:
- It’s still bricks and mortar when buying new technology: Over a third (35 percent) of all purchases still take place in-store; 26 percent of Gen Z consumers (those aged 16 to 20) prefer to shop in-store. Despite technology users’ embrace of the store however, 26 percent of complaints to technology brands went through the call centre. Overall, the retail store is still the channel of choice for consumers contacting technology brands in France (25 percent), Germany (28 percent), the Netherlands (25 percent), and the United Kingdom (25 percent). In the United States, the call center is the channel of choice (32 percent), with 21 percent preferring the retail store.
- The privacy vs personalization challenge: Only one in five are comfortable with brands using their personal data. At the same time, 68 percent of consumers expect at least basic personalization of communications and services from their technology brands, with only 10 percent of consumers feeling that technology brands fully understand them.
- Consumers demand omni-channel contact: Nearly half (48 percent) of consumers were unable to contact technology brands via their preferred channels over the last 12 months. When consumers were unable to use their preferred digital channels, 60 percent stayed within the digital landscape, but one in five fell back to the call center.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: CLIPAREA l Custom media/Shutterstock
-

The struggle to keep up with private cloud workload demands
Publié: décembre 11, 2015, 8:10pm CET par Sead Fadilpašić

Organizations are struggling with the ability to deliver infrastructure to end users to enable the demands of a DevOps environment.
Those are the results of a new global survey conducted by Qualisystems, provider of private/hybrid cloud orchestration software for DevOps and cloud sandboxing.
The Qualisystems survey queried nearly 650 architects, engineers, system administrators, IT managers, directors, VPs and C-level executives from the US and Europe at VMWorld in October.
The survey results revealed most organizations take over one week to deliver infrastructure to end users. Seventy-five percent cannot deliver infrastructure within a typical workday.
In addition, the number of applications with workloads that have a high mix of physical and virtual infrastructure requirements is projected to grow. Right now, 40 percent of application environments have a high mix of physical and virtual requirements, and 34 percent are network heavy.
The private cloud is gaining traction with 30 percent of application workloads currently running in the private cloud, and 40 percent of application workloads expected to run in the private cloud within 24 months, a projected growth rate of 10 percent.
"We see the demand on enterprises and service providers to deliver more complex applications and software-defined services as a major driver in the growth of private clouds, especially in devtest labs and DevOps oriented data centers", said Joan Wrabetz the CTO of Qualisystems. "This emphasizes the need to provide development, test and QA teams with Sandboxes that allow them to mimic complex private cloud infrastructure from development all the way to production".
In January, Qualisystems will debut its CloudShell 6.4 product along with its strategy for launching an open community for users and developers of its CloudShell platform.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ferbies / Shutterstock
-

Data security is key for customer retention
Publié: décembre 11, 2015, 6:03pm CET par Sead Fadilpašić

Nearly two-thirds (64 percent) of consumers worldwide say they are unlikely to shop or do business again with a company that had experienced a breach where financial information was stolen, and almost half (49 percent) had the same opinion when it came to data breaches where personal information was stolen.
This is according to a recent global survey by Gemalto, titled Broken Trust: 'Tis the Season to Be Wary, which surveyed 5,750 consumers in Australia, Brazil, France, Germany, Japan, United Kingdom and United States.
Six in ten people (59 percent) believe that threats to their personal information increases during the festive season, and two in ten (18 percent) believe that they are likely to be a victim of a breach during the holiday season.
Only a quarter (25 percent) of all respondents feel that companies take the protection and security of customer data very seriously. More than twice as many respondents feel that the responsibility of protecting and securing customer data falls on the company (69 percent) versus the customer (31 percent). Of the employed respondents, only around two fifths (38 percent) feel that their employer takes the protection and security of employee data very seriously.
The survey revealed that 31 percent of consumers have already been affected by a data breach in the past. Around four in ten state the most likely causes for being a victim of a breach are visiting a fraudulent website (42 percent), phishing attacks (40 percent) or clicking a fraudulent web link (37 percent). The emotional impact of data breaches has also created apprehensive feelings towards businesses with nearly one fifth (19 percent) feeling they are likely to be a victim of one within twelve months to three years.
Ninety percent of surveyed consumers feel that there are apps and websites that pose significant risks to the protection and security of their personal information. Fifty-five percent believe that social media sites expose them to the greatest risk, and around two in five consumers believe adult content and torrent apps/websites carry the greatest risk to the security of personal information.
Around a quarter (23 percent) of respondents who have been a victim of a data breach, either have, or would, consider taking legal action against the breached company involved in exposing their personal information. Almost half (49 percent) of respondents said they would take or would consider taking legal action against any of the parties involved in exposing their personal information.
However, the consumer is not completely absolved of responsibility. Despite the many risks involved, the survey also found that a majority (54 percent) of respondents are using the same password for all or some of their online accounts. Of the respondents who actively use social media accounts, only a quarter (25 percent) use two-factor authentication to secure all of their social media accounts.
Of the respondents who actively use online/mobile banking, around three fifths (58 percent) say that all of their banks use two-factor authentication to secure their internet banking. This isn’t as widespread amongst retailers, however.
Of the respondents who actively use online retail accounts, one in four (25 percent) state that all of the online retail apps/websites they use, require two-factor authentication to secure online transactions.
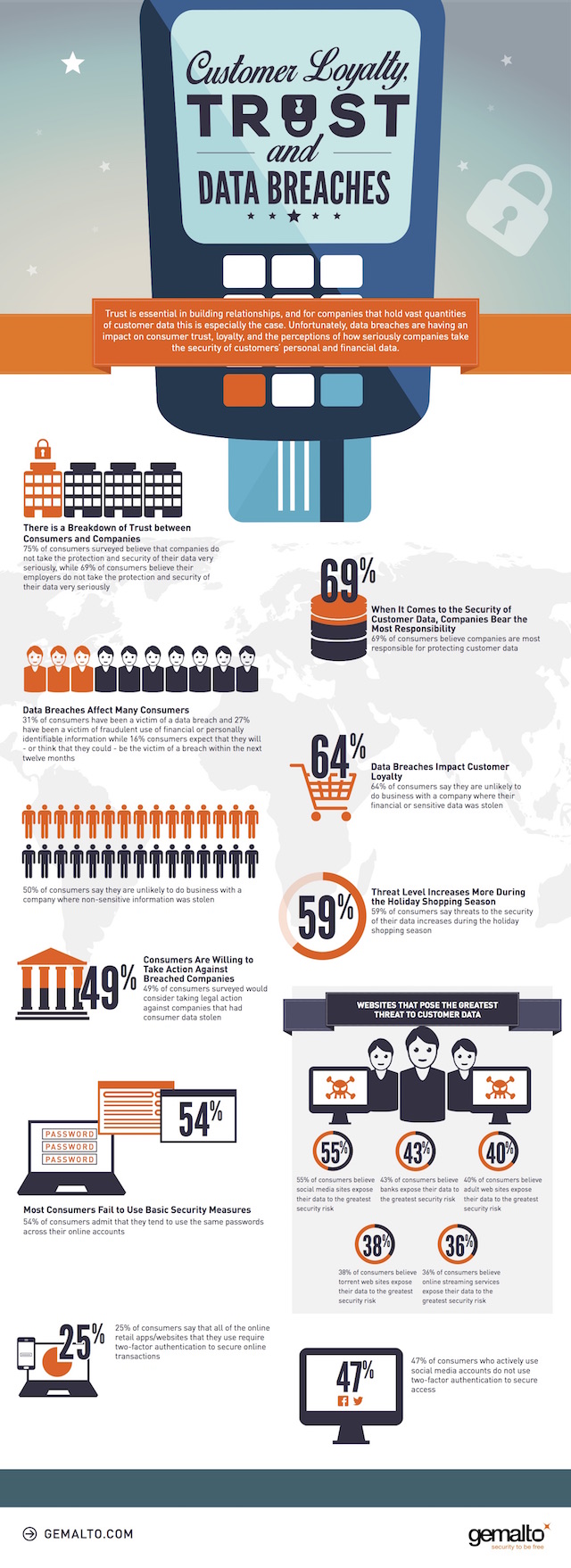
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: wk1003mike / Shutterstock
-

EU signs its first cyber-security rules
Publié: décembre 10, 2015, 5:01am CET par Sead Fadilpašić

European legislators have reached an important agreement, as they sign first cyber-security rules for the Union.
The rules, comprised in the Network and Information Security Directive have, among other things, asked tech giants such as Google and Amazon to be more open and transparent about their security, as that will help protect EU’s essential infrastructure, such as air and road traffic control systems and the electricity grid, from cyberattacks.
"Today, a milestone has been achieved: we have agreed on the first ever EU-wide cyber-security rules, which the Parliament has advocated for years", said a clearly delighted Parliament rapporteur Andreas Schwab.
"Parliament has pushed hard for a harmonized identification of critical operators in energy, transport, health or banking fields, which will have to fulfill security measures and notify significant cyber incidents. Member states will have to cooperate more on cybersecurity -- which is even more important in light of the current security situation in Europe".
According to a report by The Inquirer, the European Parliament has long pressed for cloud services to be included in the legislation. "Moreover, this directive marks the beginning of platform regulation", Schwab said.
"Whilst the Commission’s consultation on online platforms is still on-going, the new rules already foresee concrete definitions -- a request that Parliament had made since the beginning in order to give its consent to the inclusion of digital services".
The directive cannot be forced upon EU member states, though -- they will need to pass new or amended legislation in their individual parliaments.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Sergei Gontsarov / Shutterstock
-

McAfee's enterprise security software can be bypassed with a 'specially crafted username'
Publié: décembre 9, 2015, 1:37pm CET par Sead Fadilpašić

A kind word will open any door, but a special kind word will open all doors to an otherwise safe computer system, a McAfee advisory says.
The advisory has said that "a specially crafted username" can get past the Security Information & Event Management logins without authentication, and without a password, "if the ESM is configured to use Active Directory or LDAP".
What does that mean, exactly? It means a potential attacker can get access to NGCP (the default username created at first installation).
"A specially crafted username can bypass SIEM ESM authentication (password is not validated) if the ESM is configured to use Active Directory or LDAP authentication sources. This can result in the attacker gaining NGCP (master user) access to the ESM", the advisory says.
Designated CVE-2015-8024, the bug covers "McAfee Enterprise Security Manager (ESM), Enterprise Security Manager/Log Manager (ESMLM), and Enterprise Security Manager/Receiver (ESMREC) 9.3.x before 9.3.2MR19, 9.4.x before 9.4.2MR9, and 9.5.x before 9.5.0MR8, when configured to use Active Directory or LDAP authentication sources, allow remote attackers to bypass authentication by logging in with the username 'NGCP|NGCP|NGCP;' and any password", the advisory states.
There are, however, ways to protect yourselves. The best solution would be to update the software immediately, but in case you’re not able to do so -- don’t worry. For now, disabling all Active Directory and LDAP authentication sources in the Enterprise Security Manager will suffice.
The update link for the software is in the advisory.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Sergey Nivens / Shutterstock
-

A third of businesses use mobile banking to make payments
Publié: décembre 4, 2015, 9:05pm CET par Sead Fadilpašić

Not only does every other top manager make payments from corporate accounts via mobile banking, but it was also discovered that over 30 percent of companies use mobile devices to access corporate bank accounts and to make financial transactions.
Those are the result of a recent joint survey conducted by Kaspersky Lab and B2B International.
The survey concluded that business representatives were increasingly making financial transactions with the help of mobile devices. In particular, 28 percent of small and medium companies, and 34 percent of enterprises, conducted financial transactions via mobile devices.
And it is not just those in financial departments (63 percent) but also top managers (54 percent) and even ordinary employees (eight percent) that freely make corporate financial transactions via mobile apps.
Hackers also know this, and are increasingly targeting mobile platforms. In fact, in the third quarter of 2015, Kaspersky Lab products for mobile devices detected more than 300,000 new malicious programs.
Of these, the highest growth rates were demonstrated by a Trojan-Banker designed to steal credentials to Internet banking and e-payment systems, as well as credit or debit card data. The share of this type of malware increased from 0.6 percent (630 programs) in the second quarter to 1.5 percent (2500 programs) in the third quarter.
"The trend shows a continual increase in mobile banking usage by corporate banking clients. This trend is certain to continue as corporate and consumer banking clients alike migrate to the convenience of mobile banking. This creates an operational imperative for banks to very carefully consider the security and fraud prevention approaches they need to take in order to adequately ensure secure mobile banking applications, protect confidential customer data, and guard high-value corporate customer transactions", says Ross Hogan, head of SafeMoney Business Development, Kaspersky Fraud Prevention, Kaspersky Lab.
"All users of mobile banking services, corporate and consumer, must also be vigilant about their own security and behavior while also questioning their bank about the measures taken to ensure their safety", adds Hogan.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: mama_mia / Shutterstock
-

Patent troll claims HTTPS ownership, lawsuits ensue
Publié: décembre 3, 2015, 9:24pm CET par Sead Fadilpašić

Ah, don’t you love the smell of patent trolls in the morning?
In the latest news regarding these wonderful creatures, it was unveiled this week that a Texas company called CryptoPeak Solutions has sued basically everyone, everywhere, for using the HTTPS protocol.
Yes, they’re claiming ownership of HTTPS. The patent, called "Auto-escrowable and auto-certifiable cryptosystems", reads as follows:
A method is provided for an escrow cryptosystem that is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The key generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public/private key pair, and a certificate of proof that the key was generated according to the algorithm. Each generated public/private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual’s private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The cryptosystem is overhead free since there is no additional protocol interaction between the user who generates his or her own key, and the certification authority or the escrow authorities, in comparison to what is required to submit the public key itself in regular certified public key systems. Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware.
According to Ars Technica, AT&T, Costo, Expedia, GoPro, GroupOn, Netflix, Pinterest, Target and Yahoo are just some of the companies being sued for patent infringement. All lawsuits include almost identical language: "Defendant has committed direct infringement by its actions that comprise using one or more websites that utilize Elliptic Curve Cryptography ('ECC') Cipher Suites for the Transport Layer Security ('TLS') protocol (the 'Accused Instrumentalities')".
Some companies are willing to fight the lawsuit, while others have decided to settle it outside the courthouse.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit:Nixx Photography/Shutterstock
-

Tablets are doing worse than laptops
Publié: décembre 3, 2015, 8:27pm CET par Sead Fadilpašić

Notebooks still have a straw to hold on to, while tablets seem to have broken theirs and continue to sink, according to a forecast by global market research firm TrendForce.
TrendForce says total notebook shipments will drop 6.4 per cent for 2015, to about 164.4 million units. The company’s analyst Anita Wang believes shipments will recover in 2016, mostly because of branded vendors, such as Xiaomi and Huawei entering the market.
"We estimate that total notebook shipments for 2016 will increase a little by one percent year on year to 165 million units", she said.
On the other hand, tablets continue to sink. The devices which are still limited to browsing and entertainment, have very little to offer in terms of functionality, and are thus being replaced by smartphones, which grow in size with each passing year.
TrendForce has lowered its tablet shipment forecast for 2015 to 163.4 million units, representing a year-on-year decline of 14.9 percent. "Our estimation indicates that a total of 153.4 million tablets will be shipped in 2016, down 6.1 percent year on year".
The share of 7-inch models in the global tablet market has contracted from 57 percent in 2014 to the estimated 50 percent this year. With large smartphones moving into their territory, tablet vendors in response have rolled out products of even larger sizes with the intention of expanding into the notebook market.
TrendForce projects that tablets sized 10-inches and above will account for almost 30 percent of the global tablet market in 2016, a significant increase from the estimated 18 per cent of this year. The two things driving most of the sales will be narrow bezel design and a full-HD resolution.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: CLIPAREA l Custom media/Shutterstock
-

Server shipments, vendor revenue go up in Q3 2015
Publié: décembre 3, 2015, 7:46pm CET par Sead Fadilpašić

In the third quarter of 2015, worldwide server shipments grew 9.2 percent from the third quarter of 2014, while vendor revenue increased 7.5 percent year over year, Gartner has reported.
From the regional standpoint, Asia/Pacific grew the most in shipments, with a 23.8 percent increase. The region also posted the highest vendor revenue growth at 25.4 percent for the period.
HP continued to lead the worldwide server market based on revenue. The company posted just over $3.7 billion in server vendor revenue for a total market share of 27.3 percent for the third quarter of 2015.
All of the top five global vendors had revenue increases for the third quarter of 2015, except for IBM with a decline of 42.8 percent. IBM’s decline is due primarily to its sale of its x86 server business to Lenovo.
Beyond that, IBM’s server revenue fell 3.1 percent for the RISC segment, but grew 15 percent for mainframes to post a 5.1 percent total growth in the third quarter for the server businesses that it retained.
In server shipments, HP remained the worldwide leader in the third quarter of 2015 with a year-over-year shipment increase of 7.7 percent. HP’s worldwide server shipment market share was 22.2 percent, virtually the same share as in the third quarter of 2014.
All of the top five vendors in server shipments worldwide produced shipment increases in the third quarter of 2015, with Lenovo recording the largest growth of 183.2 percent.
In EMEA, server shipments totaled 533 million units and grew 1.4 percent (see Table 4) in the third quarter of 2015. Server revenue totaled $3.0 billion, an increase of 3.7 percent (see Table 3).
In shipment terms, HP saw its share increase in the third quarter of 2015 and managed to maintain first place. Dell held second place as its share of shipments also increased year over year thanks to executing well as a privately held company.
HP, Dell and Cisco have all benefitted from Lenovo taking over IBM’s x86 server business. Lenovo moved to third place, but its market share remained below that of IBM’s x86 business of a year ago.
In revenue terms, HP and IBM were the only top five server vendors to exhibit a decline in the third quarter of 2015. IBM lost two positions year over year, while Cisco narrowly moved ahead of IBM. Cisco benefitted from continued demand for blade servers, while IBM’s mainframe refresh slowed during the quarter.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: lucadp/Shutterstock
-

Hackers make DDoS threats to extort Greek banks
Publié: décembre 2, 2015, 8:58pm CET par Sead Fadilpašić

A group of hackers is trying to extort money from three Greek banks and is threatening the financial institutions with DDoS attacks unless they comply.
The group, which goes by the name Armada Collective, has asked the three banks which weren’t named, to pay a ransom in Bitcoin or face a distributed denial of service attack.
They had sent websites of all three banks offline briefly, just to show they mean business. At the same time, law enforcement agencies and telecoms have stepped in to help, according to local media, with a number of service providers increasing capacity for the banks to handle traffic, while law enforcement have created a special taskforce to deal with the attack.
The taskforce made up of the Greek National Intelligence Service, Financial Crimes Squad and Bank of Greece.
The banks said that online banking is interrupted, but the banks’ financial transaction systems are unaffected.
According to Greek financial journalist Yannis Koutsomitis, evne the FBI is involved.
The attack comes less than a week after a similar thing happened to UAE-based bank, when a hacker going by the name Hacker Buba, blackmailed the bank and asked for $3 million.
In that case, however, there were no DDoS threats, but instead the hacker threatened to release the bank’s customers’ account statements.
Customers include government entities, private companies and individuals. As it turned out, the bank refused to pay and the hacker kept his word to start doxing confidential bank statements via Twitter.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: HomeArt/Shutterstock
-

Accidental DDoS takes down Google's European cloud
Publié: décembre 2, 2015, 6:42pm CET par Sead Fadilpašić

Google got accidentally DDoSed by an unnamed European network carrier, sending its cloud service offline on the old continent for about an hour.
The incident occurred last Monday, but it is only now that Google has decided to explain exactly what happened.
According to a Google blog post, the accidental denial of service happened in Google’s Europe1-West region, sending it offline for around 70 minutes. The blog post says that Google’s engineers activated an additional link with an unnamed network carrier with whom the company already shares many peering links globally.
The majority of the addresses affected by the error were located in eastern Europe and the Middle East, and Google saw its traffic decline 13 percent during that time.
As the link was activated, the peer’s network signalled that it could route traffic to many more destinations than Google engineers had anticipated, and more than the link had capacity for, the blog post reads.
"Google’s network responded accordingly by routing a large volume of traffic to the link. At 11:55, the link saturated and began dropping the majority of its traffic".
This would not have happened if automation was operational, Google says, adding that it usually is.
"In normal operation, peering links are activated by automation whose safety checks would have detected and rectified this condition. In this case, the automation was not operational due to an unrelated failure, and the link was brought online manually, so the automation’s safety checks did not occur".
To stop this issue from flaring up again, Google’s network engineers have taken steps to disallow manual link activation.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

Security is a major concern for cloud migrations
Publié: décembre 2, 2015, 4:58pm CET par Sead Fadilpašić

When it comes to migrating to the cloud, 65 percent of companies are concerned with security, a new survey by Netwrix has unveiled.
Moreover, 40 percent worry about the loss of physical control over data in the cloud. In particular, 69 percent of companies fear migration will increase the risk of unauthorized access, while 43 percent worry about account hijacking.
In particular, 69 per cent of companies are afraid that migration to the cloud will increase the risks of unauthorized access, while 43 percent worry about account hijacking.
Netwrix surveyed more than 600 IT professionals worldwide, representing technology, manufacturing, government, healthcare, finance, education and other industries, to answer questions about cloud security, expectations from providers and measures being taken to ensure data security. The full survey can be found on this link.
Other key survey findings show that:
A hybrid cloud deployment model is preferred by 44 percent of respondents as they transition from an on-premise infrastructure to a cloud-based model. Private clouds attract 37 percent of organizations prepared to invest in additional security.
Companies that are migrating, plan to enforce internal security policies: 56 percent plan to improve identity and authentication management; 51 per cent will utilize encryption; and around 45 percent of medium and large enterprises plan to establish auditing of changes and user activity.
Overall, 13 percent of organizations reject the idea of adopting the technology in the near future. However, 30 percent of them are ready to reconsider their decision as soon as cloud security mechanisms are improved.
Some 30 percent of organizations already take advantage of improved cloud security, while more than 40 percent of organizations are ready to invest in additional security guarantees, if offered.
Overall, 71 percent of enterprises perceive continuous auditing of cloud infrastructure as a very important part of security guarantees to ensure data integrity in the cloud.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Chaiyapop Bhumiwat / Shutterstock
-

Some VPN services might expose your IP address
Publié: décembre 1, 2015, 6:53pm CET par Sead Fadilpašić

Just because you’re hiding behind a VPN (virtual private network), it doesn’t mean your real IP address cannot be traced. Those are the results summarised in a report by security firm Perfect Privacy, which says that it has found a vulnerability "in a number of providers".
The flaw, described as "port fail", affects virtual private network providers which offer port forwarding and do not have appropriate protection against the vulnerability.
"This IP leak affects all users: The victim does not need to use port forwarding, only the attacker has to set it up", it says in the report. After that, the attacker has to connect to the same server as the victim and have it click a link to a site which is under the attacker’s control.
Not an easy task, truth be told.
But if the attacker pulls this off, he can find out the victim’s true IP address.This affects all VPN protocols across all operating systems, Perfect Privacy says. The security firm has also given ways to mitigate the problem. Affected VPN providers should implement one of the following:
- Have multiple IP addresses, allow incoming connections to ip1, exit connections through ip2-ipx, have port forwardings on ip2-ipx
- On Client connect set server side firewall rule to block access from Client real IP to port forwardings that are not his own.
The vulnerability has sparked conversations over the (ab)use of the flaw. According to Tech Radar, speculations are already running rampant whether movie and music industry trade bodies could have been using this vulnerability to track down the IP addresses of pirates.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: dizain/Shutterstock
-

Raspberry Pi generates predictable SSH keys
Publié: décembre 1, 2015, 11:27am CET par Sead Fadilpašić
The ultra-cheap Raspberry Pi computers have a security flaw which results in the devices generating a weak and predictable SSH key, new research suggests. The researchers say the computer’s operating system, Raspbian, should be patched to avoid the flaw.
"As soon as the systems start up systemd-random-seed tries to seed /dev/urandom, but /var/lib/systemd/random-seed is missing, because it hasn’t been created yet", explains the developer oittaa.
"/etc/rc2.d/S01regenerate_ssh_host_keys is executed, but /dev/urandom pool doesn’t have that much entropy at this point and predictable SSH host keys will be created", he continues.
According to the report, there are two ways developers can create random numbers, through /dev/random and /dev/urandom functions.
The /dev/random one is better, as it requires user-generated input such as mouse movements, keyboard input or various hardware-generated activities to create numbers. However, the function will freeze the system until it has enough data to generate strong random numbers, which is why developers opt for /dev/urandom instead.
This function generates random numbers based on a PRNG (Pseudo-Random Numbers Generator) algorithm, regardless of the user entropy data it has at its disposal.
In Raspbian’s case, because of an incorrect boot sequence, there is not enough data, not even in the /dev/urandom function, and if the OS is set to generate SSH host keys right at startup, it will put together predictable values that are far less secure than what it would generally be needed for SSH data.
The Raspbian and Raspberry Pi projects have worked together to put out a fix.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Security breaches don't lead to a change in IT policy
Publié: novembre 28, 2015, 9:07am CET par Sead Fadilpašić

A survey conducted by training company QA, reveals that eight out of ten (81 percent) UK IT decision makers experienced some sort of data or cyber security breach in their organization in 2015. Sixty-six percent said that the breach had led to a loss of data, 45 percent said that it had resulted in a loss of revenue, and 42 percent said that it had resulted in a PR nightmare for the business.
Despite this, however, less than a third (27 percent) plan to invest in cyber security technologies next year. It would also appear that not all organizations have learnt from their experience, with less than half (43 percent) of IT decision makers saying that the breach had not resulted in a change of policy and procedure.
Perhaps it’s not surprising that 40 percent said they didn’t feel confident they had the right balance of cyber security skills in their organization to protect it from threats in 2016.
The Biggest Threats to Corporate Security in 2016
- Organized/automated cyber-attack (54 percent)
- Compromise through employees e.g. social engineering (11 percent)
- Lack of encrypted data (10 percent)
- Employee negligence e.g. lost laptops or other mobile devices (eight percent)
- Not having or enforcing security policies and procedures (six percent)
- Human error is the second largest concern (19 percent) for IT decision makers, with both "compromise through employees" and "employee negligence" both featuring in the top five threats.
When asked about key areas for investment to protect the organization from cyber threats in 2016, over two thirds (70 percent) of IT decision makers said they plan to invest in hiring qualified cyber security professionals in the coming year. Seventy-eight percent said that they also expected budgets for hiring to increase next year. However, hiring isn’t a quick and easy solution.
Over eight out of ten (84 percent) respondents said that it took on average up to three months to fill a cyber security skilled role on their team. To help address this, 45 percent say they plan to invest in further training for existing cyber security staff and 34 percent of IT decision makers said they planned to cross-skill/train other IT staff in cyber security specialism.
When asked which organizations they would go to for advice on increasing capabilities around cyber security, the findings show respondents would predominantly turn to the IT sector. An overwhelming 92 percent said they would turn to their IT/technology services partner and almost half (45 percent) would seek advice from IT vendors.
Top 10 places for advice on increasing capabilities around cyber security:
- IT/technology services partner (92 percent)
- IT vendors (45 percent)
- Security consultant/consultancy (25 percent)
- Government bodies (20 percent)
- Training organizations (17 percent)
- The Information Commissioner (ICO) (16 percent)
- Accrediting body (14 percent)
- Peers (14 percent)
- Trade & Industry associations (14 percent)
- Colleagues (nine percent)
A large majority of high profile breaches, comprise a mix of technological know-how and human error.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: ra2studio/Shutterstock
-

Lenovo fixes two security vulnerabilities in its preloaded Windows tools
Publié: novembre 27, 2015, 5:30pm CET par Sead Fadilpašić

Lenovo has issued a patch which fixes vulnerabilities located in the software which comes preloaded with some of the laptops it sells.
The company recently released version 5.07.0019 of Lenovo System Update. This tool is made to keep the BIOS and drivers updated, previously called ThinkVantage System Update.
The patch "provides a direct connection to Lenovo Service and Support for ThinkPad and ThinkCentre drivers, software and BIOS updates", and "helps maximize your system performance and minimize security vulnerability", Lenovo said.
The vulnerabilities this patch fixes were spotted by researchers at IOACtive.
One of the vulnerabilities allowed users to start an Internet Explorer with administrator privileges, even though they weren’t on the administrator account.
That was possible as Lenovo System Update itself runs under a temporary administrator account that the application creates when installed, so any process it spawns will run under the same account.
"From there, an unprivileged attacker has many ways to exploit the web browser instance running under Administrator privileges to elevate his or her own privileges to Administrator or SYSTEM", IOActive security researcher Sofiane Talmat said.
The second vulnerability is related to the way usernames and passwords are generated. Even though the passwords were randomly generated, the script was built in a predictable way.
"It is possible for an attacker to regenerate the same username based on the time the account was created", Talmat said.
"This means an attacker could under certain circumstances predict both the username and password and use them to elevate his or her privileges to Administrator on the machine".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: m00osfoto / Shutterstock
-

Post Deletion Stress Disorder: Is it real?
Publié: novembre 26, 2015, 8:56pm CET par Sead Fadilpašić

A recent study, which asked 1,000 UK consumers about their digital device habits, has revealed that more than half of them (56 percent) delete things from their devices to make room for something else, and then regret doing so.
The move is called Post Deletion Stress Disorder and, according to a press release from the study’s maker WD, is only set to continue.
WD, a Western Digital company, found that seven percent of people surveyed are running out of storage on their mobile devices on a daily basis, while 16 percent are reaching full capacity at least weekly.
One in three (31 percent) run out of storage capacity at least monthly.
We obviously need more selfie space.
WD says that when given a choice, consumers generally prefer to own content outright, rather than rent it. As a result, storage allocations on devices are being pushed with 77 percent downloading an app to a mobile device at least monthly, and around one third (33 percent) downloading a feature film to a mobile device this often.
Photographs were found to take up the most storage capacity across a range of consumer devices, (29 percent within smartphones), while 44 percent admit they don’t know what content is taking up storage capacity on their devices.
Forty-four per cent said they were trying to make things work on a total of 64GB of storage. Despite 31 percent saying their device reaches full capacity at some point only a third (33 percent) of those with personal storage/back up technology, have invested in an external hard drive, connected via a cable.
Moreover, two percent of those surveyed are using a paid cloud storage solution, and less than a fifth (16 percent) are taking advantage of a free cloud storage service.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Kirill__M /Shutterstock
-

UK banking customers believe PIN will soon be obsolete
Publié: novembre 26, 2015, 6:17pm CET par Sead Fadilpašić

A grim future awaits the PIN code, if Brits are to be believed. According to a recent survey, a majority of Brits believe PIN will be a thing of the past, and soon.
In a survey of 2,000 UK banking customers, financial technology company Intelligent Environments has found that two thirds of Brits (67 percent) believe the PIN will soon be obsolete. When those respondents were asked to predict how quickly this might happen, the average response was just under five years.
On the other hand, 32 percent believe the PIN will never die out.
The research also indicates that for most UK banking customers, the PIN may be outdated -- almost a third (32 percent) said they had never changed their PIN, while 37 percent said they are the only ones that know their PIN.
Intelligent Environments has called on banks to start innovating.
David Webber, managing director of Intelligent Environments, says: "The research indicates that banking customers may be losing faith in the PIN. As criminals continue to adopt new methods to commit fraud, people clearly don’t have confidence that the PIN is strong enough to protect what’s most important. In addition, many customers’ failure to observe basic PIN security measures demonstrates a dangerous ambivalence, which could be putting them at risk".
"Innovative alternatives to the PIN are not only possible, they’re preferable, since they not only make accounts more secure, but they enhance the banking experience for the customer. Whether or not Brits are right about the PIN being dead within five years, it’s clear that banks need to act now to change the current security landscape".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Tomislav Pinter / Shutterstock
-

Security tips for Black Friday shoppers
Publié: novembre 26, 2015, 4:20pm CET par Sead Fadilpašić

More than a quarter of UK and US-based online shoppers would proceed with a bargain purchase without first checking if the website is secure, a new survey has shown.
Moreover, shoppers in the US are more likely to put themselves at risk than those in the UK, with more than a third of US-based respondents admitting that they wouldn’t check the website’s security before purchasing. This is particularly worrying given that more than half of shoppers are expecting to use their credit or debit card to purchase goods this Black Friday weekend.
These are the results of a survey conducted by Opinion Matters on behalf of WhiteHat Security. The survey also found that a third of UK and US-based shoppers are not sure, or definitely do not know how to identify if a website is secure.
The retailers have a big part to play in website security. WhiteHat Security analysed retail websites between July and September 2015 and found that they are more likely to exhibit serious vulnerabilities compared to other industries. The most commonly occurring critical vulnerability classes for the retail industry were:
- Insufficient Transport Layer Protection (with 64 percent likelihood): When applications do not take measures to authenticate, encrypt, and protect sensitive network traffic, data such as payment card details and personal information can be left exposed and attackers may intercept and view the information.
- Cross Site Scripting (with 57 percent likelihood): Attackers can use a vulnerable website as a vehicle to deliver malicious instructions to a victim’s browser. This can lead to further attacks such as keylogging, impersonating the user, phishing and identity theft.
- Information Leakage (with 54 percent likelihood): Insecure applications may reveal sensitive data that can be used by an attacker to exploit the target web application, its hosting network, or its users.
- Brute Force (with 38 percent likelihood): Most commonly targeting log-in credentials, brute force attacks can also be used to retrieve the session identifier of another user, enabling the attacker to retrieve personal information and perform actions on behalf of the user.
- Cross Site Request Forgery (with 29 percent likelihood): Using social engineering (such as sending a link via email or chat), attackers can trick users into submitting a request, such as transferring funds or changing their email address or password.
According to Jeremiah Grossman, founder at WhiteHat Security, there are a few simple tricks that can help shoppers stay safe online over the next few days:
- Look out for HTTPS when browsing: HTTP -- the letters that show up in front of the URL when browsing online -- indicates that the web page is using a non-secure way of transmitting data. Data can be intercepted and read at any point between the computer and the website. HTTPS on the other hand means that all the data being transmitted is encrypted. Look out for the HTTPS coloured in either green or red and a lock icon.
- Install a modern web browser and keep it up to date: Most people are already using one of the well-known web browsers, but it is also very important that they are kept up to date with the latest security patches.
- Be wary of public Wi-Fi: While connecting to free Wi-Fi networks seems like a good idea, it can be extremely dangerous as it has become relatively easy for attackers to set up Wi-Fi hotspots to spy on traffic going back and forth between users and websites. Never trust a WiFi network and avoid banking, purchasing or sensitive transactions while connected to public Wi-Fi.
- Go direct to the website: There will be plenty of big discount emails around over the next few days that will entice shoppers to websites for bargain purchases. Shoppers should make sure that they go direct to the site from their web browser, rather than clicking through the email.
- Make your passwords hard to guess: Most people wouldn’t have the same key for their car, home, office etc., and for the same reason, it makes sense to have hard-to-guess, unique passwords for online accounts.
- Install ad blocking extensions: Malicious software often infects computers through viewing or clicking on online advertisements, so it is not a bad idea to install an ad blocking extension that either allows users to surf the web without ads, or completely blocks the invisible trackers that ads use to build profiles of online habits.
- Stick to the apps you trust: When making purchases on a smartphone, shoppers are much better off sticking to apps from companies they know and trust, rather than relying on mobile browsers and email.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Christos Georghiou / Shutterstock
-

HP unveils Elite x2 Windows 10 hybrid for enterprise customers
Publié: novembre 23, 2015, 12:32pm CET par Sead Fadilpašić

HP today announced the HP Elite x2 -- a hybrid it says is perfectly designed for the mobile professional.
According to HP, it is an "incredibly versatile" device that offers the "productivity of a full notebook with the convenience of a tablet".
The 12-inch tablet is made out of milled CNC aluminum and weighs less than two pounds (one kg). In terms of performance, it comes with a sixth generation Intel Core M vPro processor, storage starting at 128GB and maxing out at 512GB, and from 4 up to 8 GB of RAM. It has a detachable keyboard and a stylus.
There are two types of keyboards buyers can choose from; keyboards are leveraged from the HP EliteBook Folio 1020 and layered in a stiff aluminum base. The stylus has integrated pressure sensors to help control the width of lines when writing or drawing onscreen. The pen also includes App Launch, a programmable Bluetooth application launch button to quickly launch OneNote, or a favorite Windows application.
The device is powered by Windows 10, and HP says it has "long battery life", although it fails to elaborate just how long that is.
The Elite x2 is designed with the ports commercial users need by including both Thunderbolt 3 and USB-A ports. The device also incorporates an optional, built-in 4G LTE modem offering the convenience of connectivity virtually anywhere without the need for tethering.
Based on industry-leading technology provided by Qualcomm Technologies, the Qualcomm Snapdragon X5 LTE modem provides fast and reliable connectivity and supports all major 3G/4G networks.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Banking trojan Dyreza goes after Windows 10, Microsoft Edge users
Publié: novembre 20, 2015, 9:08pm CET par Sead Fadilpašić

The Dyreza banking trojan has (unfortunately) been updated, and now can target users sporting Windows 10 and its internet browser, Microsoft Edge.
The new version of the banking trojan was spotted and analyzed by EU-based security firm Heimdal Security, which claims that Dyreza will now also seek and find security products, terminating their underlying OS processes.
This new feature works regardless of the PC’s underlying architecture, 32-bit or 64-bit, and affects all operating systems, not just Windows 10.
"By adding support for Windows 10, Dyreza malware creators have cleared their way to growing the number of infected PCs in their botnet", Heimdal writes in a blog post. |This financial Trojan doesn’t only drain the infected computers of valuable data -- it also binds them into botnets".
According to the report, 80.000 machines are already infected with Dyreza worldwide and the number is expected to increase.
The banking trojan is delivered via the Upatre malware downloader, and all infected machines are also added to a worldwide botnet. When Upatre runs, it scans the target and downloads Dyreza if it finds the target suitable. After that the malware looks for any financial details it can find, in banking apps or by hooking into the browser. Once data is found, it is packed into an HTTP request, and sent to a remote C&C server in the control of the attacker.
The timing also couldn’t be better. The malware is spreading just before the holiday season, at the time of the year when everyone’s online shopping activity is at its utmost peak.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: lolloj/Shutterstock
-

Zerodium reveals price list for zero-day exploits
Publié: novembre 20, 2015, 3:44pm CET par Sead Fadilpašić
Exploit acquisition platform Zerodium has just published a price chart for different classes of digital intrusion techniques and software targets that it buys from hackers and later resells in a subscription service to its clients.
This is important as it is the first time someone has publically put a price tag on hacking.
Consequently, it has gained a lot of attention and while some praise the move, others are disgusted.
Hacking a WordPress-based website and remotely executing code is fairly cheap – it can be done for $5,000 (£3,200). But doing same on Flash Player can cost you up to $50,000 (£32,000). Remote exploits that entirely defeat the security of an Android or Windows Phone device go for as much as $100,000. And an iOS attack can earn a hacker half a million dollars, by far the highest price on the list.
Wired, which broke the story, says the move "could actually encourage more hackers to sell the intrusion methods they create; Independent security researchers have long complained that the lack of public pricing in the zero-day trade makes it difficult for them to get a 'fair' price".
But there are other opinions, as well. Publicly trading in secret intrusion techniques has made Zerodium CEO Chaouki Bekrar a target for criticism from both the privacy community and the software companies whose hackable flaws he exploits for a profit. Google security staffer Justin Schuh once called him an "ethically challenged opportunist". ACLU lead technologist Chris Soghoian has labelled Bekrar’s Vupen a "modern-day merchant of death", selling "the bullets for cyberwar".
The full pricelist can be found on Zerodium’s website.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Anonymous releases guides to help anyone hack Islamic State
Publié: novembre 20, 2015, 1:53pm CET par Sead Fadilpašić

Hacktivist group Anonymous, which has recently declared "war" on ISIS, has released a guide on how to find and take out ISIS-related websites and social media accounts.
The group posted three different guides, to be used within #OpParis, the online campaign against the Middle-Eastern militants.
SEE ALSO: Anonymous aims to delete the Islamic State 'virus' from the web, and wants your help
According to the International Business Times, their instructions included a "NoobGuide" for those who want to learn how to hack, a "Reporter" guide explaining the process of setting up bot accounts as well as a "Searcher" to find ISIS websites.
"Instead of sitting idle in the [chat] channel or lurking around and doing nothing, you can benefit greatly from the different tools and guides that have been provided to you", a member of Anonymous reportedly wrote.
"Your contribution means a lot and we encourage you to partake in all of the Op’s activities if you can, the more the merrier".
ISIS has called Anonymous "idiots" and shrugged off their threats as pointless. "The #Anonymous hackers threatened in new video release that they will carry out a major hack operation on the Islamic state (idiots)", the message says, according to Business Insider, which obtained a copy of it. "What they gonna hack?"
The terrorist organization has, however, also issued a guide advising its members on how to protect themselves from the hackers.
The extent damage #OpParis will do to ISIS' online presence is still unclear, but analysts say Anonymous will go after online personas, ISIS websites and social media accounts, making the information publicly available.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Lucky Team Studio / Shutterstock
-

LG announces its own mobile payments service
Publié: novembre 20, 2015, 11:07am CET par Sead Fadilpašić

Korean tech giant LG has announced it will soon be launching its own mobile payment service. The service, which will be a direct competitor to Apple Pay, Samsung Pay, Android Pay and other mobile payment systems, will be available in South Korea and the US, for starters.
According to IB Times, LG has registered the trademark LG Pay in South Korea and United States, so it’s very likely that will be the service’s name.
"We will sign a deal with some of the country’s major card companies before officially launching our mobile payment platform", said an LG official to the Korean Times. South Korea’s two biggest credit card companies that expected to sign a deal with LG are Shinhan Card and KB Kookmin Card.
LG first announced its plans for a mobile payment system back when it released its latest flagship smartphone, the LG V10. The V10 is a fairly large smartphone, sporting a 5.7-inch screen, and a fingerprint sensor embedded on the backside of the device.
The backside itself is made of durable materials, making the phone more resilient to punishment than what you’re usually used to. It also features a secondary screen, placed right above the main one, which serves as a sort of a ticker where you can add specific shortcuts and various buttons.
The LG Pay system will have a tough competition to face in both Apple Pay and Samsung Pay, services which have gotten some traction lately, especially with the aggressive marketing campaigns both companies employ.
-

iPhones generate 94 percent of global smartphone profits
Publié: novembre 18, 2015, 9:14am CET par Sead Fadilpašić

If you ever needed evidence that the iPhone is a huge money maker, it’s safe to say that we now finally have it. On paper, in black and white.
According to a recently published Canaccord Genuity report, Apple has made 94 percent of global smartphone profits during the third quarter of the year, even though it had sold 14.5 percent of all smartphones in the quarter.
How is that possible, you might ask? Well, because Apple’s devices are expensive, and the company’s operating margins (how much money the company makes on each iPhone) are at 37 percent.
To put things into perspective, Samsung achieved 24.5 percent of global sales during the same period, yet took just an 11 percent share of profits. Its operating margins are at 10 percent.
You also might have noticed how Samsung and Apple combined make up more than a 100 per cent of the market share, which definitely can’t make sense, but it actually does. Sony, HTC and other smartphone makers actually posted a negative operating income.
Such high figures, especially knowing that Apple has made 85 percent global smartphone profits this time last year, have prompted some analysts to say that Apple has nowhere to go but down.
Apple CEO Tim Cook disagrees, recently saying that the demand for the iPhone exceeded supply.
"We believe that iPhone will grow in Q1, and we base that on what we’re seeing from a switcher point of view", Cook said. "We recorded the highest rate on record for Android switchers last quarter at 30 percent. We also look at the number of people that have upgraded, that were in the install base prior to iPhone 6 and 6 Plus, and that number is in the low 30 percentages, so we feel like we have a very open field in front of us".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Wayne Williams
-

Tim Cook: Apple won't weaken encryption, but is willing to cooperate with UK government
Publié: novembre 17, 2015, 4:55pm CET par Sead Fadilpašić

In a recent interview with the Irish Independent, CEO Tim Cook has once again said Apple will not weaken the encryption it uses in its mobile communication devices.
He did, however, say that the company he runs will work closely with the UK government to help create a quality legislation.
Tech companies have been going head to head with the UK and the US governments over encryption issues. While governments say it’s vital for law enforcement agencies to have a backdoor entrance into people’s devices so that crucial evidence related to possible criminal activity wouldn’t be left in the dark, tech companies aren’t keen on doing so.
By strengthening the encryption, they want to show that not only they’re not working with (for) the government, but also that they listen to what the consumers are saying. And the consumers are saying they want more encryption, and don’t want anyone, especially not the government, accessing their communications devices.
"The UK government has been clear publicly that they are not seeking to weaken encryption", says Cook. "And so I take them at their word that they would not do that. And at the moment as you know, we encrypt iMessage end-to-end and we have no backdoor. And we have no intention of changing that. Any change made would contradict the UK government’s view that they would not weaken encryption".
"I think that we’ll work closely with them. And I have every faith that through this process of the next year, give or take a year, that the bill will become very clear".
The full interview can be found on The Independent’s website.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple might offer peer to peer money transfers
Publié: novembre 16, 2015, 6:54pm CET par Sead Fadilpašić

Apple is looking to add peer-to-peer money transfer to its Apple Pay service and hopes it might help it take off.
According to a recent report by The Wall Street Journal, Apple believes adding the peer-to-peer money transfer would interest millennials, and it’s been talking to a number of banks about it.
The American tech giant has been looking into the money transfer idea for a year now, and has been discussing it with JPMorgan Chase, US Bancorp, Wells Fargo and Citi.
The reason why Apple has decided to partner up with banks instead of building its own system is to avoid filing for money transmitter licenses, people with knowledge of the program told Quartz.
By sidestepping such licenses -- which PayPal, Venmo, Facebook, and even AirBnb have -- Apple can focus on the consumer side and avoid scrutiny from regulators.
Quartz also says Apple might use its messaging app -- iMessage -- to get the service across.
"It’s already one of the most used default apps on iPhones and is especially popular with the younger crowd -- a survey by messaging service Jott found that 60 percent of teens say that it’s their preferred messaging app", QZ says in its report.
The idea is far from being new or revolutionary -- Alibaba’s AliPay and messaging app WeChat are tied, and Facebook uses its Messenger for a similar service.
The social media giant has released its payment service through Messenger back in June for the US market, allowing person-to-person payments.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Aysezgicmeli / Shutterstock
-

Microsoft's Project Oxford can detect human emotions
Publié: novembre 14, 2015, 12:15pm CET par Sead Fadilpašić

In a scene in the 2014 sci-fi movie Robocop, the namesake main character analyzes his enemy’s emotional condition and concludes that violence is imminent.
You can say he successfully detected emotions. For a living person, that isn’t really a big deal, but for a computer, that’s science fiction. Or, to be precise, that was science fiction. Not any more.
Microsoft has announced plans to release public beta versions of new tools in its Project Oxford, one which can help developers create smarter apps, including those that can recognize emotion.
Project Oxford includes four main components -- face recognition, speech processing, visual tools, and language understanding intelligent service (LUIS).
The new tools are ideal for those who are not really experts in artificial intelligence, but would still love to use AI capabilities in their apps.
The emotion tool can be used to create systems that recognize eight core emotional states -- anger, contempt, fear, disgust, happiness, neutral, sadness or surprise -- based on universal facial expressions that reflect those feelings. The tool is available to developers as a public beta.
"Developers might want to use these tools to create systems that marketers can use to gauge people’s reaction to a store display, movie or food. Or, they might find them valuable for creating a consumer tool, such as a messaging app, that offers up different options based on what emotion it recognizes in a photo", Ryan Galgon, a senior program manager within Microsoft’s Technology and Research group said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: kaczor58/Shutterstock
-

There will be 20.8 billion Internet of Things devices by 2020
Publié: novembre 12, 2015, 5:50pm CET par Sead Fadilpašić

It is being predicted that the ever-growing market of the Internet of Things will support total services spending of $235 billion (£155bn) in 2016. At the same time, the number of connected devices will grow 30 percent year-on-year, reaching 6.4 billion units globally.
But the growth won’t stop there. As a matter of fact, it will speed up, reaching 20.8 billion units by 2020. According to a Gartner report, the professional category will dominate. In it, businesses contract with external providers in order to design, install and operate IoT systems.
Still, consumer and connectivity services will grow at a higher pace.
"IoT services are the real driver of value in IoT, and increasing attention is being focused on new services by end-user organizations and vendors", said Jim Tully, vice president and distinguished analyst at Gartner.
"Aside from connected cars, consumer uses will continue to account for the greatest number of connected things, while enterprise will account for the largest spending", Tully said, pointing out that Gartner estimates that four billion connected things will be in use in the consumer sector in 2016, and will reach 13.5 billion in 2020.
In terms of hardware spending, according to Gartner, consumer applications will amount to $546 billion (£360bn) in 2016, while the use of connected things in the enterprise will drive $868 billion (£572bn) in 2016.
When it comes to enterprise, Gartner looks at two classes: generic / cross-industry devices used in multiple industries and vertical-specific devices, seen in particular industries.
"Connected things for specialized use are currently the largest category, however, this is quickly changing with the increased use of generic devices", Tully says. "By 2020, cross-industry devices will dominate the number of connected things used in the enterprise".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Microsoft and ConsenSys will offer blockchain technology to financial institutions
Publié: novembre 12, 2015, 11:24am CET par Sead Fadilpašić

Microsoft has partnered up with Brooklyn-based blockchain start-up ConsenSys to bring the technology to financial institutions.
Blockchain is the technology that underpins Bitcoin. It is essentially a vast, decentralized ledger that registers every transaction anonymously, and because the ledger is public, it makes blockchain tamper-proof and ideal for financial clients.
Blockchain could also underpin other data exchanges and some companies are building personal blockchains that extend the functionality beyond Bitcoin, UK’s Business Insider says in a report.
Other companies are now building their own blockchains that provide additional features to the original bitcoin one, including Ethereum who’s built a fully programmable blockchain, now used by Microsoft for the blockchain platform launched Tuesday.
The platform will be available to banks and insurance companies that are already using Microsoft’s cloud-based Azure platform. Microsoft said four large global financial institutions had already signed up to the service.
"Working with our customers that wanted to start playing around with blockchain technology, the major pain point that we kept hearing from them was that it was just too hard to get started, and too expensive", Microsoft’s director of tech strategy for financial services, Marley Gray, told Reuters on the sidelines of Ethereum’s "DevCon" conference in London.
Gray described the platform as providing a "fail fast, fail cheap" model for firms: they can experiment with the cloud-based technology using templates provided by Microsoft without having to build their own systems.
"We bet the entire farm on the cloud, pretty much", said Gray.
This seems to be a pretty logical move, knowing Microsoft CEO Satya Nadella’s plan to shift the company towards the cloud.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Lightboxx / Shutterstock
-

Adobe announces private data marketplace
Publié: novembre 11, 2015, 8:57pm CET par Sead Fadilpašić

Adobe today announced Audience Marketplace, a new data exchange in Adobe Audience Manager, the company’s data management platform (DMP).
Audience Marketplace is a private data marketplace that connects advertisers and content publishers to buy and sell second and third-party data faster and with more simplicity. The data exchange also enables companies to scale their high-value audience segments for personalized and targeted content across marketing channels.
Adobe says that through Audience Marketplace, customers will benefit from integrations with leading data providers, while Adobe will make sure they are adhering to standard data privacy and security policies. The network will be able to offer "large volumes of high-value audience data for more accurate and valuable insights".
Moreover, first-party, second-party and third-party data can now be merged, Adobe says: "For example, companies with look-alike audiences, such as an airline and a hotel, can exchange data since both audiences have similar consumer profiles associated with travel".
"Audience Marketplace redefines how marketers manage, activate and monetize audiences across marketing channels", said Amit Ahuja, general manager of Data Management, Adobe. "Unlike other companies, Adobe simply wants to connect customers with data providers without trying to monetize any of the data in the exchange itself".
Samsung was quick to praise Adobe’s new service: "Samsung is focused on delivering a cohesive, personalized customer experience across all digital touchpoints, and Adobe Audience Manager plays a critical role in our cross-channel data ecosystem", said Jesse Laskaris, senior product manager of Personalization at Samsung Electronics America. "With Audience Manager, we can aggregate our first, second and third-party data, and then build high-value audience segments to more effectively understand and engage with customers through programmatic buying, site personalization and other channel-specific tactics".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Marynchenko Oleksandr / Shutterstock
-

GCHQ finds major cyber-attacks against UK doubling in 2015
Publié: novembre 11, 2015, 6:35pm CET par Sead Fadilpašić

The number of "serious" cyber-attacks against the UK has doubled in just a year, BizTek Mojo reported on Tuesday, saying the company responded by forming a cyber-security academy to tackle the issue.
According to the report, GCHQ says there are, in average, seven serious threats faced by the country each day, and just last month it recorded 200 attacks, including state-sponsored assaults.
These "serious" attacks don’t include cyber-attacks on civilian home computers, but instead only track bank attacks, nuclear establishment attacks and attacks against power plants. Organized crime and state-sponsored attacks are also considered "serious".
"The GCHQ did not mention any state or nation that they had caught snooping around in the UK’s network", the report claims.
The UK responded to the increased threat by launching a cyber-academy. The University of Southampton is launching the Cyber Security Academy to aid average consumers, both big and small businesses, and government to be more prepared and protected against malicious attackers.
The Academy was announced on November 9 during an IAI5 event in London. Graduates from the CSA will be trained under industry-relevant CPD programs. It will also be responsible for hosting enterprise, consultancy and research regarding the field.
Roke Managing Director David Cole said: "In order to meet the demands of an increasing cyber security threat, the UK needs a continual flow of high quality engineers and consultants to protect our critical infrastructure and enterprises, and to protect personal data. The Cyber Security Academy partners will work together to drive forward the UK’s cyber capability and talent -- attracting and developing world class experts into the cyber security industry, facilitating technology innovation, creating new opportunities and driving UK productivity".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: arda savasciogullari / Shutterstock
-

Intel adds new products to the Xeon D-1500 line
Publié: novembre 11, 2015, 11:18am CET par Sead Fadilpašić

Intel has announced new products in the Xeon processor family, in a move which seeks to boost the Internet of Things industry.
The new products and collaborations will "accelerate the move toward more agile and cloud-ready communications networks that can address today’s demand for new telecommunications, cloud and data centre services and handle tomorrow’s devices and services", the company said.
Specifically, Intel announced new offerings in the Intel Xeon processor D-1500 product family, which will "provide a foundation for extending intelligence from the network core to the edge for improved performance and lower latency".
The eight new processors offer high-performance, low-power and twice the maximum memory of previous generations in an integrated system-on-chip, making them well-suited for various networking, cloud storage, enterprise storage and IoT applications that operate in dense, rugged environments.
There’s also the new Intel Ethernet Controller X550 family -- a low-power, cost-effective 10 Gigabit Ethernet connectivity solution. The company also announced that it was selected to be a technology consultant for América Móvil, a mobile network operator in Latin America, and that its Intel Network Builders program is now available in more than 180 companies.
To top things off, Red Hat is now the first ISV to actively contribute to all key focus areas of the Intel Network Builders Fast Track.
"Networks are facing extraordinary demands as more devices become connected and new digital services are offered", said Sandra Rivera, vice president, Data Center Group and general manager, Network Platforms Group, Intel. "Building intelligence throughout the communications infrastructure and using a standards-based approach offers service providers the foundation to build agile, cloud-ready networks that allow them to expand their services capabilities".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Rose Carson/Shutterstock
-

Smartphone theft affects most organizations
Publié: novembre 10, 2015, 5:39pm CET par Sead Fadilpašić

Did you ever consider that keeping sensitive business files on your mobile device could be risky, as your device could be lost or stolen? Did you consider protecting those files, or the mobile device in general, with a password?
A new research by Imation looked into this idea and the results are quite disappointing. According to the study, 44 percent of organizations believe a member of their senior management has lost a mobile device in the last year, whilst 39 percent say senior management had a device stolen.
The numbers are no better among non-executives: 54 percent of organizations say a non-senior management employee lost a device, while 49 percent reported a device stolen within the past year.
Vanson Bourne conducted the survey of 500 IT decision makers in the UK and Germany.
A vast majority (93 percent) of these devices contained work related data, including confidential emails (49 percent), confidential files or documents (38 percent), customer data (24 percent) and financial data (15 percent), yet basic security rules are not being implemented.
Nearly a third (32 percent) of organizations do not specify that devices taken outside the office must be protected with either encryption or passwords, and a quarter (25 percent) does not specify that digital files taken outside the office must be protected with either encryption or passwords.
Companies are failing to control how data leaves the office, with nearly half (48 percent) admitting that they cannot keep track of how employees take data with them, and 54 percent saying that data could be more adequately secured.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Antonio Guillem/Shutterstock
-

A quarter of all websites run WordPress
Publié: novembre 10, 2015, 11:53am CET par Sead Fadilpašić

Out of all websites on the entire internet that have any sort of content management system (CMS), WordPress powers more than half.
Considering the fact that half of the internet doesn’t use any recognizable CMS system, it brings us to the conclusion that WordPress, the open-source content management platform, powers 25 percent of the entire Internet
Let that sink in for a moment.
The information was brought by W3Techs, a company that measures both usage and market share: "WordPress is used by 58.7 percent of all the websites whose content management system we know. This is 25.0 percent of all websites". While these numbers naturally fluctuate over the course of the month, the general trend for WordPress has been slow but steady growth.
"We should be comfortably past 25 percent by the end of the year", Automattic founder Matt Mullenweg declared. "The big opportunity is still the 57 percent of websites that don’t use any identifiable CMS yet, and that’s where I think there is still a ton of growth for us (and I’m also rooting for all the other open source CMSes)".
Even though the figures are impressive, there’s still half of the entire internet to conquer, so there’s room for growth.
However, the methodology used by W3Techs is also worth mentioning. It examines websites and not individual pages, but if a technology is on any of a website’s pages, it is considered to be used by the website.
Also, the company doesn’t scan the entire WWW, but the top 10 million websites, based on Alexa’s ratings. It also excludes subdomains and redirected domains, so the actual number is somewhat fewer than 10 million.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Ingvar Bjork / Shutterstock
-

US has three months to come up with an agreeable Safe Harbor 2.0 deal
Publié: novembre 9, 2015, 6:00pm CET par Sead Fadilpašić

Exactly a month after the Safe Harbor agreement was struck down by the EU Court of Justice, the EU has called for the US to make the next move in the creation of an alternative solution.
The Safe Harbor Agreement, which is now defunct, represented a legal framework within which US companies could extract data of EU citizens. It was ruled invalid for not providing sufficient legal safeguards.
"We need a new transatlantic framework for data transfers", said Vĕra Jourová, the European Commissioner for Justice and Consumers, emphasizing the urgency of the situation. However, she said at a news conference in Brussels on Friday, "It is now for the U.S. to come back with their answers", PC World cites Jourová.
According to TechCrunch, the Commission has given a three-month timetable to create a new deal, dubbed Safe Harbor 2.0.
The Commission released a new guide to help businesses legally extract personal data to the US on Friday. The guide, however, doesn’t help the businesses much, as it repeats the advice the Commission gave on the day of the ruling: "Until such time as the renewed transatlantic framework is in place, companies need to rely on the alternative transfer tools available", the guide says.
Jourová recognized that won’t always be easy: "Companies face some limitations when relying on alternative tools". She is due to travel to Washington DC shortly to meet her U.S. counterparts for continued discussions.
She said the measures currently undertaken by the US means the country is moving in the right direction, but still far away from where they want to be.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Kuzma/Shutterstock
-

What's the real cost of the UK's Investigatory Powers law?
Publié: novembre 9, 2015, 3:09pm CET par Sead Fadilpašić

The Home Office has issued an Impact Assessment, looking into the price of the proposed Investigatory Powers law, which would allow government agencies to intercept digital communications.
Secretary of State Theresa May’s department estimates a price of some £247m over a 10-year-period to cover the costs of the spy law, but according to The Register, which calls upon industry sources, little to no consultation has taken place so far. The true price of the bill can be significantly larger and can go up to £2 billion, with the bulk of finances going to telecom firms to cover the costs of storage.
In another scenario, the telecoms could be forced to suck up any hidden costs, which could in the end mean higher prices for customers.
The £2 billion estimate is made taking into account Labour’s Interception Modernization Program which carried a £2bn price tag, and May’s Communications Data Bill which would have cost an estimated £1.8bn.
"The current £247m does not take into account the potential costs for interception of bulk personal data and hacking into computer systems. Costs associated with those 'policy provisions' are marked as 'N/K' – not known", The Register writes in the report.
Still, the compensation costs of some £859m to be paid to telecoms over the course of 10 years were mostly dismissed by the industry, saying the estimates were too speculative.
May’s department said in its latest Impact Assessment that: "There would be minimal increases above existing baseline costs for interception, equipment interference, and bulk personal data".
The Home Office said in its assessment of the spy law: "The costs of the Bill are primarily in relation to increased cost of establishing a new oversight body (led by the Investigatory Powers Commissioner), including accommodation, overheads, running costs, and the administration of a new warranty process".
"The provisions in the Bill in relation to internet connection records and the request filter for communications data have associated costs to business, which are reimbursed by government", added the Home Office.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Roobcio/Shutterstock
-

Major tech companies don't care much about your privacy
Publié: novembre 7, 2015, 12:44am CET par Sead Fadilpašić

Sixteen of the biggest tech companies out there, eight internet firms and eight telecoms, were analyzed in terms of how much they allow their users to express themselves, and how much they protect their users’ privacy.
None passed the analysis with flying colors.
The study, first of its kind from a new outfit, is titled 2015 Ranking Digital Rights Corporate Accountability Index, and assesses the companies on 31 points and judges in terms of modern day privacy conventions. The points include questions on whether firms have an overseer for privacy practices.
Google came out on top, scoring 65 percent. Just six companies scored at least 50 percent, and the worst performers were Russian mail provider Mail.ru and UAE-based service provider Etisalat.
Over half the companies scored under 25 percent, showing a "serious deficit of respect for users’ freedom of expression and privacy".
"The 2015 Index shines a needed spotlight on corporate practices around freedom of expression and privacy. We found that many of the world’s most powerful internet and telecoms companies fail to disclose key information about practices affecting users’ rights", said Rebecca MacKinnon, director of the Ranking Digital Rights project.
"Even the companies that ranked highest are missing the mark in some ways, and improvements are needed across the board to demonstrate a greater commitment to users’ freedom of expression and privacy".
"When we put the rankings in perspective, it’s clear there are no winners. Our hope is that the Index will lead to greater corporate transparency, which can empower users to make more informed decisions about how they use technology", said MacKinnon.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Ivelin Radkov / Shutterstock
-

People care more about hacker attacks than break-ins
Publié: novembre 6, 2015, 10:38pm CET par Sead Fadilpašić

People feel more violated when someone hacks into their computer, than when someone breaks into their house, a new research has shown.
The research, done by American multinational software Citrix, polled 2,000 full-time workers in the UK about hacking and private files they keep on their computers. The poll shows that 48 percent of young people, aged 16 to 24 have more than one private file on their computers which they want to remain secret.
Almost half (45 percent) would feel more violated by the thought of someone hacking in and stealing their personal information and files than a stranger breaking into their home.
"The fact that younger generations are willing to store a large amount of personal, and often secret, data online could cause severe security concerns around sensitive corporate data as this age group enters the workplace over the coming years", the follow-up press release states.
Older users are not so keen on putting sensitive data online -- among those aged 55 and above, only 16 percent would do so.
The increasing awareness around the risks and consequences of data theft is more acute in London than any other region, with more Londoners (49 percent) finding data theft a more serious concern than somebody breaking into their home (44 percent).
The research also revealed that one in four (25 percent) of 16 to 24-year-olds keep all of their passwords in one file on their computer or mobile device. As a result, just one instance of data theft could in fact make all of their accounts and folders vulnerable to attackers.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
credit: Blazej Lyjak/Shutterstock
-

How many users are actually paying for Dropbox?
Publié: novembre 6, 2015, 6:31pm CET par Sead Fadilpašić

Stat attack: Dropbox has more than 400 million users worldwide. Out of that number, some 8 million are business users.
From those 8 million, there are more than 150,000 paying ones. Those are the numbers given by the company’s chief executive officer Drew Houston, during the Dropbox Open conference, held in San Francisco yesterday.
The company had 130,000 paying customers just a few months ago.
"We have added 50,000 paying business customers in the past 10 months", Houston said.
He also discussed the competition, without actually saying the company’s name. "We’ve added more paying business customers than they have in their lifetime, think about that", Houston said. VentureBeat believes he was actually talking about the publicly traded Box.
Dropbox’s unnamed "competitor" is facing a "challenge", Houston said, because it doesn’t "have that kind of bottoms-up adoption. It’s a lot harder for them to get customers".
During the conference Dropbox also announced the launch of Dropbox Enterprise, a tier of service that builds on Dropbox Business and is leaning toward the biggest businesses.
Dropbox Enterprise provides the same core security features, admin capabilities, and modern collaboration tools as Dropbox Business -- plus new deployment tools, advanced controls, and services and support designed specifically for large organizations.
With Dropbox Enterprise, IT can give employees the Dropbox they love while getting the advanced capabilities they need to effectively manage tens of thousands of users, protect company data, and get the most from the investment.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Kaspersky Lab discovers 320 hour long DDoS attack
Publié: novembre 5, 2015, 4:57pm CET par Sead Fadilpašić

Kaspersky Lab has released a new report on the evolution of distributed denial of service (DDoS) and it shows some interesting figures, including the fact that a server was targeted for 320 hours straight.
The Kaspersky DDoS Intelligence Report Q3 2015 is based on the constant monitoring of botnets and observing new techniques utilized by cybercriminals. It shows that DDoS attacks remain highly localized, with 91.6 percent of the victims’ resources located in only ten countries around the world, although Kaspersky Lab has recorded DDoS attacks targeting servers in 79 countries total.
DDoS attacks are very likely to originate from the same countries, the security firm understands, adding that China, USA and South Korea are the highest rating countries in both sources of attack and sources of targets.
According to the report, more than 90 percent of all attacks observed in the third quarter lasted less than 24 hours, but the number of attacks lasting over 150 hours has grown significantly. At the same time, there was this one server that was hit extremely hard -- 22 times. It is located in The Netherlands.
Kaspersky says that even cyber-crooks go on vacation, after realizing that August is the quietest month of the quarter. Linux-based botnets are significant, and account for up to 45.6 percent of all attacks recorded by Kaspersky Lab. The main reasons for this include poor protection and higher bandwidth capacity.
Looking at who the most frequent victims are, banks stand out the most, being frequent targets for complex attacks and ransom demands.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

Banks don't want you to share Apple Pay-enabled iPhones, iPads
Publié: novembre 4, 2015, 5:50pm CET par Sead Fadilpašić

Banks are warning iPhone users that if they store more than one set fingerprints on the device, they will treat them as if they had failed to keep their personal data safe. They are equalizing multiple fingerprint storing to sharing a PIN code.
Apple’s iPhone device allows up to ten fingerprints to be stored. The company designed it so to make it easier for multiple family members to use the Apple Pay service for contactless payments.
However, The Telegraph reports that banks are warning their customers about possible issues. They’re basically ridding themselves of any responsibility in the case of any possible problems when multiple fingerprints have been stored.
The terms and conditions applying to Lloyds customers read in full: "If Touch ID is available on your device, you must ensure you only register your own fingerprints (and not anyone else’s)". This basically means that the banks are telling their customers that all other fingerprints should be deleted from their device.
When asked about the wording of its Apple Pay warning, HSBC told Telegraph Money: "Our customers’ financial safety and security is of the utmost importance to us, as such we advise all our customers to keep their details as secure as possible. This means not sharing their Pin or in the case of Apple Pay not letting others access their phone".
But the bank added: "We will always endeavor to help our customers should they become a victim of fraud".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: bahri altay/Shutterstock
-

Major IT vendors are clueless about blockchain technology
Publié: novembre 3, 2015, 9:15pm CET par Sead Fadilpašić

Major global IT vendors -- including leading hardware, systems software, eCommerce, big data, cloud, network, telco and systems integrator companies -- have little wisdom, advice or vision to offer their customers and prospects when it comes to blockchain technology.
This is the result of a survey entitled Searching in Vain for The Block Chain, conducted by enterprise IT specialist consulting firm Lighthouse Partners. It is also the main reason this company decided to start offering consulting services on the topic.
The company’s principal Peter Harris surveyed 100 "major global IT vendors", searching each company’s website for the term "block chain". According to Harris, 77 percent had no mention of the technology, a figure that rose to 85 percent when management consultancies and IT analysts were removed from the results.
The interest in this technology is growing, Lighthouse says, mostly because it promises to simplify the technology infrastructure needed to run financial services, healthcare, legal services and government.
"Around 100 start-ups are developing block chain-based applications and nearly $1 billion of venture capital has been invested to date (a figure similar to investment in the internet in its early years)", the company said in a press release.
"Despite all that it has going for it, blockchain technology won’t hit mainstream acceptance without the participation of major global IT vendors", said Harris. "History shows that enterprise users partner with major global IT vendors to craft their emerging technology strategies. That has been the case with innovations including big data, cloud computing, mobile commerce and open source, and it’s what block chain needs in order to succeed. For their part, the major global IT vendors need to work with the start-ups innovating in this space to create their own product and service offerings".
In order to address the lack of understanding and initiatives relating to block chain by the major IT global vendors, Lighthouse Partners has begun to offer its expertise to them in order to accelerate their endeavors.
The company also announced The Block Chain Conference, set to take place in San Francisco on February 10, 2016. A major goal of the conference is to encourage the necessary dialog and engagement the enterprise IT ecosystem -- both vendors and users -- and the start-ups innovating in the blockchain space.
The complete survey can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: PathDoc/Shutterstock
-

Trust is key in mitigating IT risks, say most CIOs
Publié: novembre 3, 2015, 7:15pm CET par Sead Fadilpašić

Over three-quarters (76 percent) of senior IT leaders in the UK, France and Germany feel more personal risk when making decisions than they did five years ago because of IT’s increasingly central role in businesses, a study commissioned by Colt reveals.
At the same time, 77 percent of chief information officers (CIOs) say that pivotal moments in a business calendar define their career trajectories, and not day-to-day performance. This is compounding the sense of vulnerability felt during key decision-making moments, as highlighted in Colt’s recent ‘Moments that Matter’ study.
The study, which covered 301 European senior technology decision makers, reveals a discrepancy in CIOs’ perceptions of personal/career and company risk. The areas where this is seen are:
- Creating the business case for change is more important for the company than the career of the CIO -- 35 percent ‘company’ risk against 28 percent ‘personal’ risk.
- Selecting the right team and skills is considered key to personal success -- 39 percent ‘company’ risk against 48 percent ‘personal’ risk.
- Communicating with internal and external stakeholders is undervalued -- 27 percent ‘company’ risk against 19 percent ‘personal’ risk.
The study, surveyed businesses whose revenues spanned from 10M to 5BN euros, also shows that the majority (73 percent) of CIOs believe the personal risk they experience is mitigated when working with a team they trust.
Trust is also very important when dealing with external teams, as the majority of respondents (85 percent) believe technology issues are sometimes inevitable. A partner proves its value when things go wrong, they understand the impact of service interruption and act accordingly.
The research was conducted by Loudhouse, an independent research agency based in London.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: liuwenhua / Shutterstock
-

Ericsson, Intel and Nokia backing new IoT standard
Publié: novembre 3, 2015, 12:00pm CET par Sead Fadilpašić
Internet of things devices need a communication standard, a universal type of communication which would allow these devices to communicate, no matter who the maker is. The standard is now also a subject of debate, as US and European makers are backing one type, while Huawei and other vendors are backing another one.
As Lightreading writes in a report, Intel, Ericsson and Nokia are backing Narrow-Band Long-Term Evolution (NB-LTE). At the same time, Huawei is more leaned towards the existing Narrowband Cellular IoT (CIoT) proposal.
As the report states, timing is crucial here, as the third Generation Partnership Project (3GPP) Radio Access Network (RAN) group will meet in Phoenix next week to vote on the proposed LTE specs.
"The 3GPP group’s decision will be key, as narrowband LTE specifications are going to play a crucial role in the development of the IoT market", the report says.
A spokesperson from Intel explained in an email why it is backing NB-LTE over other proposals for narrowband 4G:
The key difference is that the NB-LTE technology allows a high re-use of already existing LTE network technology for both infrastructure and chipset. This will favor a fast adoption and maximize economies of scale. Clean Slate requires dedicated investments for network infrastructure and chipsets, as well as the creation of a new ecosystem. We believe NB-LTE will provide superior technology that leverages existing investments and an existing ecosystem, which we believe will be the key prerequisite for enabling the future of the cellular IoT.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Tashatuvango/Shutterstock
-

Symantec unveils new unified business services security solution
Publié: novembre 2, 2015, 4:35pm CET par Sead Fadilpašić

Symantec has released a new solution promising to unify corporate security, something that’s becoming increasingly harder to control.
The Symantec Advanced Threat Protection (ATP) is, according to the press release, "the first solution that can detect and remediate advanced threats across control points, from a single console with just a click, all with no new endpoint agents to deploy".
The problem with today’s security measures, according to Symantec, is that with all the different types of malware, security professionals can no longer rely on using individual point products at each control point to stop them. Also, the process of uncovering threat data across endpoint, network and email gateways is manual and time-consuming, which gives attackers an edge.
The Symantec ATP can correlate suspicious activities across all control points, which is its main selling point.
The ATP will allow security experts to uncover a full range of threats, prioritize what matters most by correlating the threat intelligence from across local control points with all that Symantec sees globally through its telemetry, remediate the threats fast through containment of endpoints and blocking new instances across control points and leverage existing investments in Symantec Endpoint Security and Email Security.cloud, without deploying any new endpoint agents.
The ATP solution will be available before 2015 ends, the company said, adding that it will cost $40 (£26), $60 (£39) and $70 (£45) per user annually to secure one, two or three control points, respectively.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Gil C / Shutterstock
-

HP details new Helion OpenStack cloud platform
Publié: novembre 2, 2015, 12:36pm CET par Sead Fadilpašić

Hewlett-Packard recently announced HP Helion OpenStack 2.0, the second iteration of the company’s customized version of OpenStack. During the OpenStack Summit Tokyo 2015, HP announced the "production ready, open source based cloud platform designed to meet enterprise requirements".
HP Helion OpenStack 2.0 offers an enterprise grade cloud platform, the company said in a press release, adding that it now offers new features to address organizations’ lifecycle management and security challenges.
Among the new features are the easy provisioning of new infrastructure and the ability to repurpose existing infrastructure to meet scalability needs without impacting availability, rolling upgrades which facilitate entire cloud environment software upgrades without requiring planned or unplanned downtime, as well as continuous patch management allowing security patches and updates without application interruption.
The company said Helion OpenStack 2.0 has an easy to use administrator interface, centralized logging and monitoring at scale across a cloud environment, network configuration flexibility to enable connectivity with existing IT environments and strict OpenStack API adherence which enables cross-cloud compatibility and ability to leverage the upstream ecosystem of third party plug-ins.
"Enterprises want to benefit from the powerful capabilities of OpenStack technology, but they must have the enterprise-grade capabilities required to support their businesses", said Bill Hilf, senior vice president and general manager for HP Cloud.
"The configuration, security and scalability advances in HP Helion OpenStack 2.0 enable organizations to deploy OpenStack technology into production with the confidence that they are backed by the experience and support of a trusted end-to-end technology partner".
Helion OpenStack 2.0 is now available worldwide, and pricing varies by configuration and individual customer requirements, the company said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Dragan Jovanovic/Shutterstock
-

Businesses store a lot of irrelevant data in the cloud
Publié: octobre 30, 2015, 10:32am CET par Sead Fadilpašić

Businesses are spending tons of money to keep their data in the cloud, but only a small portion of that data is actually business-critical. The rest is completely redundant, increasing their costs and putting their cyber-security at risk.
These are some of the conclusions seen in a new report by Veritas Technologies, backup and recovery solutions firm. The report, entitled Databerg report 2015, looked at how European organizations across the public and private sector manage their data.
Among the bigger issues are the fact that employees use corporate IT systems as their personal infrastructure, as well as the fact that businesses rely on the cloud all too much -- creating a higher risk of data loss.
According to the Databerg Report 2015, 59 percent of data stored and processed by UK organizations would be invisible and could contain everything from cat videos to adult material, creating a high risk of non-compliance.
The Databerg report also estimates the average mid-sized UK organization holding 1000 Terabytes of information is spending £435k annually on Redundant, Obsolete or Trivial data, which is known to be useless. This means just 12 percent of the cost of data storage is known to be business-critical one of the lowest clean data scores in the study.
The survey provides insights on how 1,475 respondents (including 200 in the UK) in 14 different countries across the EMEA region are dealing with the challenges surrounding turning data into valued business information.
The full report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wavebreakmedia/Shutterstock
-

Apple Pay to arrive in Australia, Canada this year
Publié: octobre 29, 2015, 6:01pm CET par Sead Fadilpašić

Apple Pay is set to expand beyond the US and the UK, and before the end of 2015. The news was confirmed during the presentation of Apple’s fiscal results, by the company’s CEO, Tim Cook.
However you’ll need a particular card in order for the service to work.
Apple's contactless payment service is coming to Australia and Canada by the end of 2015, while Hong Kong, Singapore and Spain will get it in early 2016. You’ll need an American Express card.
"With our global reach, we are able to bring Apple Pay to Card Members quickly in these important countries", said Tony Prentice, vice president, mobile products and payments, American Express. "We believe it is critical to be on the forefront of seamless and innovative payment solutions for our Card Members and we are pleased to be able to deliver on that with Apple Pay".
"Our customers love their experience with Apple Pay and we want to bring it to as many of our users worldwide as possible", said Jennifer Bailey, vice president of Apple Pay. "With a global issuer like American Express, we are thrilled to seamlessly bring our easy, secure and private way to pay to more customers internationally".
However, if you’re not a big fan of American Express, don’t despair. Rumor has it that other providers will jump in on the action quite soon. TD Canada recently added Apple Pay to its list of services by mistake, and was quick to remove it.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Oracle intros new IaaS products
Publié: octobre 29, 2015, 3:57pm CET par Sead Fadilpašić

Oracle announced a new set of Infrastructure as a Service (IaaS) products earlier this week, going head to head with the likes of Amazon with its Web Services.
Among the new sets are the Oracle Elastic Compute Cloud, two new Storage Cloud services, as well as a number of technology stacks on the Oracle Cloud.
The new services were introduced by Thomas Kurian, Oracle’s president of product development, at its OpenWorld show in San Francisco.
The Oracle Elastic Compute Cloud allows customers to chose between elastic and dedicated compute options. While Elastic allows the user to run any workload in the cloud in a shared compute zone, the dedicated adds capabilities such as CPU pinning and complete network isolation, PCWorld writes in a report.
The new Storage Cloud offers two types of storage -- an archive option and a File Storage service, which offers file-based NFS v4 network protocol access to both Object Storage and Archive Storage tiers in Oracle Storage Cloud Service.
The technology stacks on the Oracle Cloud are available in a standard service catalog to simplify deployment.
The new offerings "really help round out Oracle’s IaaS solutions portfolio", said Charles King, principal analyst with Pund-IT.
At the same time, though, "Oracle is also making good on delivering key parts of its application portfolio via the cloud, including the eBusiness Suite, PeopleSoft and JD Edwards solutions", he pointed out. "That should stir the particular interest of existing Oracle customers, and could also tempt businesses already considering deployment of those solutions", King said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: 360b/Shutterstock
-

IBM goes into the weather business -- no, really
Publié: octobre 29, 2015, 2:11pm CET par Sead Fadilpašić

IBM’s artificial intelligence computer Watson is expanding into the weather forecast territory. According to the company, it is buying The Weather Company’s B2B, mobile and cloud-based web properties, including WSI, weather.com, Weather Underground and The Weather Company brand.
The TV segment -- The Weather Channel -- will not be acquired by IBM, but will license weather forecast data and analytics from IBM under a long-term contract, the company added.
All of abovementioned acquired technology will be used to power the new Watson Internet of Things unit.
Even though weather seems to be in the focus here, it’s actually about data -- and large quantities of it. "The planned acquisition would bring together IBM’s powerful cognitive and analytics platform and The Weather Company’s dynamic cloud data platform, which powers the fourth most-used mobile app daily in the United States and handles 26 billion inquiries to its cloud-based services each day".
"The Weather Company’s extremely high-volume data platform, coupled with IBM’s global cloud and the advanced cognitive computing capabilities of Watson, will be unsurpassed in the Internet of Things, providing our clients significant competitive advantage as they link their business and sensor data with weather and other pertinent information in real time", said John Kelly, senior vice president, IBM Solutions Portfolio and Research.
"This powerful cloud platform will position IBM to arm entire industries with deep multimodal insights that will help enterprises gain clarity and take action from the oceans of data being generated around them".
The acquisition will help IBM offer weather data insights, but the goal is to help businesses operate more efficiently.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Comcast to launch MVNO using Verizon's network
Publié: octobre 29, 2015, 11:28am CET par Sead Fadilpašić

Comcast has just invoked a three years old agreement with Verizon which allows it to use its network. According to Comcast’s Chief Executive Officer Brian Roberts, the network will be used to test a wireless service.
Roberts said during the earnings call on Tuesday that his company plans to "trial and test some things".
Comcast has had to wait six months before activating the Verizon agreement. It is left unclear if that waiting time is over and if not -- when it will be.
According to media reports, the company will use more than 11 million of its Wi-Fi hotspots to go after the big phone companies, thus trying to earn more money for itself. "It’s an opportunity to take the network and the investments that we have made and see if we can continue relationships", Roberts said.
Of course, it’s all about the Benjamins. The third-quarter earnings for the company have been in line with what analysts had expected. The shares fell one percent to $61.54 (£40.14) at the close in New York. They have gained 6.1 percent this year.
In terms of cable TV subscribers, the company has shown good stats, best in nine years. It has lost 48,000 subscribers in the quarter. According to Bloomberg, analyst had projected an average drop of 66,000 last quarter.
At the same time, the company is looking to sell some TV station airwaves to wireless carriers. The auction is set to take place in March next year.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: watcharakun / Shutterstock
-

Millennials don't want a job in cyber-security
Publié: octobre 28, 2015, 8:14pm CET par Sead Fadilpašić

Those 800,000 IT experts Europe will be missing by 2020 won’t be that easy to find, as the new study suggests that Millennials are not really crazy about a career in cyber-security.
These are the results of the annual study of millennials entitled Securing Our Future: Closing The Cyber Talent Gap. According to the study, young adults are not really interested in cybersecurity, but what’s even worse -- the number of young women in the US interested in a cyber-career is five times smaller.
Mike Daly, cyber chief technology officer (CTO) at Raytheon, told SCMagazine.com it is a cultural thing: "It seems it has to do a bit with culture. When asked whether they had been made aware of cyber opportunities [by educators and other adults], 47 percent of men said they had been made aware and only 33 percent of women said they had".
"Cyber more than any other industry is dependent on diversity to find solutions", Daly adds. "Without diversity you can’t possibly find solutions for all the different people and the ways they use and store data".
If you thought it couldn’t possibly get worse -- you were wrong. These young adults haven’t heard of a single cyber-attack in the last year. They haven’t heard of the TalkTalk event, the Anthem breach or even the American Airlines assault.
"One the things that jumped out was that 67 percent of young adults haven’t heard any cyber attacks in the last year", said Daly.
The report was conducted by Zogby Analytics and has surveyed approximately 4,000 adults aged 18.26, in four global regions.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wk1003mike/Shutterstock
-

Chase Pay mobile payments service arriving in 2016
Publié: octobre 28, 2015, 6:50pm CET par Sead Fadilpašić

JP Morgan Chase announced its own smartphone payment platform on Tuesday, called Chase Pay. The platform, due to make its debut mid-2016, will be a direct competitor to the likes of Apple, Google and Samsung.
Chase Pay is built upon the Current C, a retailer-led mobile payment system that has largely been written off by Silicon Valley techies for its reliance on barcodes rather than the more sophisticated NFC (near-field communications) technology adopted by its competitors.
"Chase customers will be able to use Chase Pay wherever CurrentC is accepted -- either directly, or through the CurrentC app. Chase is also partnering with 17 technology vendors so that merchants who are not Chase Commerce Solutions clients can also participate in Chase Pay", it says.
Chase Pay works by displaying a barcode on the customer’s smartphone. The retailer then scans the barcode and completes the payment. There’s also a version that works online.
Chase Pay uses somewhat simpler solution (unlike its competitors going for the near-field communication (NFC) technology), which means it will be available to a much wider array of devices. The Chase Pay platform will roll out to Chase’s 94-million credit, debit and pre-paid card account holders, and will also tie-in with retailer loyalty cards.
"Our partnership links Chase and its customer base with CurrentC’s extensive network of leading retailers, restaurants, grocery stores and fueling stations, which process over a trillion dollars in transactions annually at more than 100,000 U.S. locations. This is a significant milestone, not just for MCX and Chase, but for mobile payments overall as the industry continues to take shape. Everywhere CurrentC is accepted, Chase Pay will be accepted", said Brian Mooney, CEO of MCX.
-

EU Antitrust Commission might still investigate Google
Publié: octobre 28, 2015, 5:37pm CET par Sead Fadilpašić

Google might have changed its name to Alphabet, but the stand-off it has with the European Union’s Antitrust Commission won’t go away.
In an extensive interview for The Wall Street Journal, European Commissioner for Competition Margrethe Vestager explains she still has the company in her sights.
"The important thing is that people can understand what is going on. The Google case is about misuse of a dominant position, to promote yourself in a neighboring market not on your merits but because you can. And no matter the course of the case, there should be a takeaway which can be understood", she says.
The Commission has a few ongoing cases against Google. One is the comparison shopping case where, after a couple of complaints, charges have been filed against Google, accusing it of illegally favoring its own Google Shopping service over the rivals in the search results.
Another case is the Android -- which Vestager opened herself. The case argues that Android should not come bundled with proprietary Google services for mapping, search, and others.
The Advertising case sees the Commission investigating the effect of exclusivity deals with publishers, and restrictions in Google’s standard contracts preventing advertisers from moving their online campaigns to rival platforms.
There’s also an investigation on Google scraping copyright information from other websites.
Google still has a long way to go before it brings closure to all the cases it has with the European Union’s Antitrust Commission. Looking at the Wall Street Journal interview, it’s safe to assume that we’re looking at a long, long wait.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: photogearch / Shutterstock
-

Anonymous threatens to reveal identities of 1,000 Ferguson KKK members
Publié: octobre 28, 2015, 11:14am CET par Sead Fadilpašić

One thing no one seems to understand is that you don’t mess with Anonymous. Not unless you want all your dirty laundry publicly exposed on the plains of the digital world.
This time around, Anonymous has set its crosshairs at the KKK, or to be more specific, the Traditionalist American Knights of the Ku Klux Klan (TAKKKK) of Ferguson. It plans on revealing the identities of 1,000 of its members.
During last year’s protests in Ferguson, following the announcement that the police officer Darren Wilson won’t be indicted for killing of unarmed black teenager Mike Brown, the TAKKKK warned the protesters that "lethal force" will be used against them.
This prompted global hacktivists group Anonymous to react, taking control of KKK’s main Twitter account, and through it, gaining information regarding some alleged members of the TAKKKK. The amorphous group also alleged that it had evidence of a connection between the Ferguson police department and the TAKKKK, IBTimes wrote in a report.
"We are not attacking you because of what you believe in as we fight for freedom of speech", Anonymous said in a statement released last week. "We are attacking you because of what you do to our brothers and sisters".
"Due to your actions we will be rearranging Operation KKK. We’ve gained access to yet another one of your KKK Twitter account. Using the info obtained, we will be revealing about 1000 of your klan member identities. The aim of the operation is nothing more than cyber Warfare. Anything you upload will be taken down, anything you use to promote the KKK will be shut down".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Vincent Diamante
-

Facebook at Work signs up 100,000 RBS workers
Publié: octobre 27, 2015, 7:19pm CET par Sead Fadilpašić

Facebook at Work, the social network’s business version, has signed an agreement with the Royal Bank of Scotland (RBS), bringing the service to 100,000 of its staff.
The deal, dubbed "ground breaking partnership" by RBS will "allow employees to communicate faster and more efficiently", the bank said.
|As well as using it on their desktop computers, employees will also be able to download it to their phones and tablets so that they can keep track of work when they are on the move".
According to the press release, the bank’s employees have already tested the network and the results have shown it to be a success. The staff were |able to work much more efficiently together, answer customer questions faster, update other colleagues on their work in a much more engaging way and source a far wider range of ideas for on-going projects", it says.
"I’ve already been using Facebook At Work while we test it and it’s been so useful -- allowing me to exchange information and ideas quickly and securely with all my team on a wide range of projects", said Simon McNamara, RBS chief administrative officer. "I’m excited about how bringing people together from all across the bank through Facebook At Work can help our employees do their job better -- whether it’s being able to find answers to customer queries much faster or helping us come up with bright new ideas".
No financial details have been released, nor has RBS outlined how Facebook at Work will operate in terms of compliance within the regulatory framework.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Tesla's Autopilot rolling out across the globe
Publié: octobre 27, 2015, 10:56am CET par Sead Fadilpašić

A few days after it was released in the United States, the Autopilot feature for certain Tesla Model S cars is rolling out across most supported markets
Japan is the only market where Teslas can be bought but can’t use the Autopilot service, as the country is still reviewing the necessary regulations.
Tesla CEO Elon Musk confirmed the news via Twitter: "Regulatory approvals received, so Autopilot rolling out to all countries! (Excluding Japan, which is still under review)", he wrote.
The update is made over-the-air, meaning the car doesn’t need to be taken to a shop for the update. However, not all cars can have it. When asked if Autopilot hardware could be installed in older Model S vehicles, Musk said the amount of physical change needed was "enormous -- like a spinal cord transplant, would cost less and work better with a new car", IBTimes wrote in a report.
Ten days ago, Tesla brought the Autopilot feature to its cars. The company stressed that the feature is still in beta, and that the drivers should keep their hands on the steering wheel at all times.
"The whole Tesla fleet acts like a network. When one car learns something they all learn it", Tesla CEO Elon Musk said. "As ... more people enable autopilot, the information about how to drive is uploaded to the network. Each driver is effectively an expert trainer in how the autopilot should work".
In a follow-up tweet, Musk said an update, called Autopilot 1.01, would be coming soon and include "curve speed adaption [sic], controller smoothness, better lane holding on poor roads, improved fleet learning".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Alphabet prepares for $5 billion stock buyback
Publié: octobre 26, 2015, 7:18pm CET par Sead Fadilpašić

With all this cash lying around, Alphabet is planning on buying back shares of its own stock, The Economic Times has reported.
According to the report, high profit which the company had in the third quarter of this year, has prompted it to announce it would give investors some of the money.
"They’re growing up", The Economic Times cites Colin Gillis, an analyst with BGC Financial.
One of the bigger issues with Google is the fact that it has a lot of companies and firms that are completely unrelated to its core business, like self-driving cars, pharmaceutical companies and whatnot.
Those firms, also called "Larry Page’s moonshots", have had investors questioning how profitable they are and how much the company is really spending on risky business ideas. With Google getting a parent company, and leaving only the core business to itself, the financial results will be clearer.
"Products like Search, Android, Maps, Chrome and YouTube each have over a billion users already, and Google Play crossed that milestone this quarter as well", said Sundar Pichai, Google’s new chief executive. |But what’s most exciting is that we’re just beginning to scratch the surface".
|This is the appetizer, and the main meal comes next quarter when they report the new corporate structure", said Ben Schachter, an analyst with Macquarie Securities.
Typical of a company filled with engineers, the buyback was encased in a riddle, with an exact value of $5,099,019,513.59 -- which mirrors the square root of 26, as in the 26 letters of the alphabet.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Filipchuk Oleg/Shutterstock
-

Tech specialists make 35 percent more money than other employees
Publié: octobre 23, 2015, 7:05pm CEST par Sead Fadilpašić

If you want to earn more money than your friends, consider a career in tech. Median gross annual earnings for tech specialists in 2014 were £36,600, new figures published this week by Tech Partnership show.
This is more than one third (35 percent) higher than the level for all full-time employees, a follow-up press release reads.
In the three out of the four broad occupational groups into which they fall, tech specialists earn more than their non-tech counterparts, the figures, based on analysis of Office of National Statistics data show.
"This is particularly marked in more senior occupations", the release adds. "Tech specialists operating at Manager, Director and Senior Official level earn 60 per cent more than non-tech specialists at an equivalent level".
There are also discrepancies in terms of location and gender -- one in four tech businesses are located in London, and almost half in London and the South East. There, tech specialists out-earn their equivalents elsewhere by 19 percent.
While salaries for tech specialists are generally higher in the tech industry itself -- a premium of six percent across the UK as a whole -- non-tech firms in London and the North East are paying more highly than tech firms.
In terms of the gender gap -- 17 percent of people employed in tech specialist roles are women. Even though women in tech earn more than women doing other jobs, they take home 15 percent less than their male counterparts (£32,000 median annual earnings vs £37,700 for men).
Finally, tech specialists who make a career in the discipline can expect to see their earnings rise with age. Those under 24 earn £20,700, but peak salaries are taken home by those aged 45 - 54: £42,200.
The full bulletin is available for download on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Artem Samokhvalov/Shutterstock
-

UK and China sign cyber-attack agreement -- but will it be honored?
Publié: octobre 23, 2015, 6:49pm CEST par Sead Fadilpašić

Chinese president Xi Jinping, and the British prime minister David Cameron, signed an agreement saying the two countries won’t hack and steal each other’s secrets.
A similar agreement was signed between China and the US, just a day before a Chinese cyber-attack against the States.
The agreement was signed during Jinping’s visit to Britain, as the Chinese president tries to fix the country’s reputation of being the world’s biggest hacking menace and the biggest distributor of malware, right after that "hottest chick nearby" ad. "It sets out very clearly what they agree they will not do", a Downing Street spokeswoman said.
In an effort to repair the country’s image, in August the state announced the arrests of 15,000 people suspected of internet security crimes. Pretty much every time a cyber-attack on a state institution, or particular industry is unveiled, the finger is pointed at China.
In one of recent such attacks, which China obviously denied having anything to do with, the Office of Personnel Management (OPM) was attacked.
The breach affected OPM’s IT systems and its data stored at the Department of the Interior’s data centre, which is a shared service centre for federal agencies, a DHS official said on condition of anonymity. The official would not comment on whether other agencies’ data had been affected.
It is also being reported that the Chinese are using "Great Cannon" to launch DDoS attacks.
Researchers at the University of Toronto have discovered the Great Cannon after coding site GitHub was grounded by a distributed denial of service attack (DDoS). The attack particularly focused on users of the site with a history of trying to circumvent China’s censorship programs: The New York Times’ Chinese mirror and GreatFire.org.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Basar / Shutterstock
-

HP to 'sunset' Helion Public Cloud in 2016
Publié: octobre 23, 2015, 11:37am CEST par Sead Fadilpašić

HP is going to shut down its cloud business, and this time it means it. Seriously. The company’s executive, Bill Hilf, wrote a post on the HP blog, where he announced that the Helion service will be put out of its misery next year.
"We will sunset our HP Helion Public Cloud offering on January 31, 2016", he writes. Instead, the company will focus on turning its hardware gear into the building blocks for private enterprise clouds.
"As we have before, we will help our customers design, build and run the best cloud environments suited to their needs -- based on their workloads and their business and industry requirements", he adds.
"To support this new model, we will continue to aggressively grow our partner ecosystem and integrate different public cloud environments. To enable this flexibility, we are helping customers build cloud-portable applications based on HP Helion OpenStack® and the HP Helion Development Platform".
According to the blog post, Hewlett-Packard will expand its support for Amazon AWS and Microsoft Azure -- two clouds that have run the IT titan out of town.
"We also support our PaaS customers wherever they want to run our Cloud Foundry platform -- in their own private clouds, in our managed cloud, or in a large-scale public cloud such as AWS or Azure".
"All of these are key elements in helping our customers transform into a hybrid, multi-cloud IT world", Hilf boldly states.
"We will continue to innovate and grow in our areas of strength, we will continue to help our partners and to help develop the broader open cloud ecosystem, and we will continue to listen to our customers to understand how we can help them with their entire end-to-end IT strategies".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Saikom/Shutterstock
-

IT pros take more security risks than the average office worker
Publié: octobre 22, 2015, 8:48pm CEST par Sead Fadilpašić

A whopping 93 percent of office workers engage in some form of unsafe online habits that could jeopardize their employer or their customers, a new report has shown.
The report, entitled 2015 Insider Risk Report, was done by Intermedia and it exposes the online security habits of more than 2,000 office workers in both the U.K. and the U.S.
There’s a sense of irony in the report, which says that IT experts, those who know the most and those who are tasked with keeping the company secure -- they are much more likely to engage in risky behaviors than your average company Joe.
The report says that 32 percent of IT professionals have given out their login/password credentials to other employees (compared to 19 percent across all respondents), while 28 percent of IT pros said they have accessed systems belonging to previous employers after they left the job (compared to only 13 percent among all respondents)
Furthermore, 31 percent of IT pros said they would take data from their company if it would positively benefit them -- nearly three times the rate of general business professionals
"These kinds of practices create risks that include lost data, regulatory compliance failures, data breaches, eDiscovery complications, ex-employee access, and even out-and-out sabotage by a disgruntled current or former employee", Intermedia says in a follow-up press release.
Intermedia’s report also includes data across a range of industries, such as healthcare, finance and legal services, as well as across job functions. Additionally, it examines security habits across age group, company size and job tenure.
The full 2015 Insider Risk Report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Olivier Le Moal / Shutterstock
-

Western Digital acquires SanDisk in $19 billion deal
Publié: octobre 22, 2015, 11:25am CEST par Sead Fadilpašić

Data storage company Western Digital is acquiring another data storage company, SanDisk, thus creating a true behemoth in the industry.
According to Western Digital, it has to shell out $19 billion (£12.3bn) for the acquisition, which means SanDisk’s stock is worth $86.50 per share (£55.9).
Western Digital is an American data storage company creating non-volatile memory (NVM), with the focus on hard-disk drives (HHD). SanDisk, on the other hand, focuses on flash memory, something we’ve seen grow in popularity over the past few years, especially with the increased availability of the fast solid-state drives (SSD).
"This transformational acquisition aligns with our long-term strategy to be an innovative leader in the storage industry by providing compelling, high-quality products with leading technology", said Steve Milligan, chief executive officer of Western Digital. "The combined company will be ideally positioned to capture the growth opportunities created by the rapidly evolving storage industry. I’m excited to welcome the SanDisk team as we look to create additional value for all of our stakeholders, including our customers, shareholders and employees".
Steve Milligan will continue to serve as chief executive officer of the combined company, and the company will remain headquartered in Irvine, California. Upon closing, Sanjay Mehrotra is expected to join the Western Digital Board of Directors, the company stated in the press release.
The transaction will be financed by a mix of cash, new debt financing and Western Digital stock. In connection with the transaction, Western Digital expects to enter into new debt facilities totaling $18.4 billion (£11.9bn).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: EDHAR/Shutterstock
-

Tim Cook: We shouldn't have to choose between privacy and security
Publié: octobre 21, 2015, 12:16pm CEST par Sead Fadilpašić

In a debate held on Monday, Apple’s CEO Tim Cook argued with government agencies over privacy and backdoor issues once again, stressing that a backdoor is not a good solution.
According to a Bloomberg report, he squared off with NSA Director Admiral Michael Rogers at the Wall Street Journal Digital Live technology conference in Laguna Beach, California.
Rogers kicked things off by saying that it’s just a matter of time before someone abuses the strong encryption US tech companies offer. He did say, however, that "strong encryption is in our nation’s best interest", but when asked about impenetrable encryption, he said no.
"That’s not what I said", he answered. "Strong encryption is in our nation’s best interests".
"Security, encryption: good. The ability to generate insights as to criminal behavior and threats to our nation’s security, also good", he added. "It’s only a matter of time I believe until someone does something destructive", Rogers said.
Tim Cook, on the other hand, defended the privacy stance, saying the issue will only become more important in the future.
"It will become increasingly more important to more and more people over time as they realize that intimate parts of their lives are in the open and being used for all sorts of things", Cook said.
But he also said that the US should not be forced to choose between privacy and security.
"Nobody should have to decide privacy and security. We should be smart enough to do both", Cook told the conference, calling any compromise a "cop-out".
"Both of these things were essential parts of our Constitution. It didn’t say prioritize this one above all of these", he said. "I mean, these guys were really smart folks and they held all of these things and said all of these are what it means to be an American".
But the backdoor is a big no-no: "You can’t have a back door in the software because you can’t have a back door that’s only for the good guys", Cook said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

China attacks US after signing cybertheft agreement
Publié: octobre 20, 2015, 7:44pm CEST par Sead Fadilpašić

Hackers associated with the Chinese government attacked a handful of American companies just a day after the two countries agreed not to cyber-attack one another.
According to CrowdStrike, a prominent American security firm, the attacks against seven American companies started on September 26. On September 25, President Barack Obama said he and Chinese President Xi Jinping agreed that neither government would knowingly support cyber theft of corporate secrets to support domestic businesses.
However, the agreement didn’t restrict spying for government secrets.
Dimitri Alperovitch, CrowdStrike’s co-founder, said he believed the hackers were affiliated with the Chinese government based on the servers and the software they had used for the attack.
According to UK’s Business Insider, the software used is called Derusbi, and has previously turned up in attacks on Virginia defence contractor VAE Inc and health insurer Anthem Inc.
The "primary benefits of the intrusion seems clearly aligned to facilitate theft of intellectual property and trade secrets, rather than to conduct traditional, national-security-related intelligence collection", CrowdStrike said in a blog post to be published on Monday.
There was no immediate comment from China’s Foreign Ministry.
The White House acknowledged CrodwStrike’s findings, but declined to address the company’s conclusions.
"As we move forward, we will monitor China’s cyber activities closely and press China to abide by all of its commitments", said the official who did not want to be identified by name.
The names of the seven companies in question were not revealed, but CrowdStrike did say that the attacks were rebuffed.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Jirsak/Shutterstock
-

IBM allows China to take a look at its source code
Publié: octobre 20, 2015, 12:31pm CEST par Sead Fadilpašić

IBM has allowed China to review the source code for some of its programs, The Wall Street Journal reported on Monday, but the details are scarce.
According to the media report, the deal between IBM and the Chinese government is a completely new practice, which was implemented recently. It allows the Chinese government to take a closer look at the source code behind some of IBM’s software, but does not allow for the code to be copied or tampered with in any way.
It is also unknown how much time ministry officials have to look at the code.
"Strict procedures are in place within these technology demonstration centres to ensure that no software source code is released, copied or altered in any way", IBM said in a statement.
According to the report, Chinese authorities have been pressing US companies looking to expand into China to give them the source code for review, in order to confirm that there are no security risks.
According to The Register, this turn of events coincides with IBM’s recent announcement that it struck a deal with 21Vianet Group -- one of China’s data centre service providers. The deal will allow IBM to place its Bluemix cloud computing platform into China.
China has become a very important market for American companies. Aside from IBM, both Apple and Uber are fighting hard battles to gain ground in the most populated country in the world. Apple is doing a good job, with its iPhone smartphones achieving quite a notable success.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Tomasz Bidermann/Shutterstock
-

Security is the top challenge for IT pros
Publié: octobre 16, 2015, 6:01pm CEST par Sead Fadilpašić

Security is the biggest challenge among IT professionals across the globe, trying to keep their company’s business running, a new survey suggests.
A report titled "The 8 Issues Derailing IT Team Innovation", was created by Ipswitch who tried to uncover the biggest issues IT departments are facing as 2016 approaches.
After surveying 2,685 IT professionals across the globe, security stood out as the biggest challenge for 25 percent of them.
IT infrastructure and application performance monitoring was second with 19 percent, while new technology, updates and development was on third place with 14 percent of answers.
The biggest focus was on North America, with 61 percent of answers coming from the continent, while Europe gave 24 percent. Asia-Pacific assisted with 12 percent of answers, while Latin America gave three percent.
"Behind every business-critical application that serves as the lifeblood of modern commerce, companies rely on IT teams to keep them up and running 24/7", said Jeff Loeb, CMO at Ipswitch. "This survey identifies the key challenges facing IT organizations heading into 2016, and highlights how IT teams are coping with increasing complexity and security threats".
Ipswitch split the challenges into eight distinct categories:
- Security (25 percent)
- IT Infrastructure and Application Performance Monitoring (19 percent)
- New Technology, Updates and Deployment (14 percent)
- Time, Budget and Resource Constraints (10 percent)
- Business Issues (seven percent)
- Data Management and Storage (six percent)
- Device Management and End User Issues (five percent)
- Automation and Reporting (four percent)
The findings of the report are available here and the major themes will be discussed during the Ipswitch Innovate 2015 Summit, a two-day virtual conference on October 21 and 22.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Manczurov / Shutterstock
-

Flash isn't dead yet, but it might as well be
Publié: octobre 16, 2015, 4:58pm CEST par Sead Fadilpašić

After being hit by another malware attack this week, Adobe issued a batch of 69 patches for Flash, but also for its other products, including Reader and Acrobat.
This is yet another in Adobe’s many attempts to try and save its (in)famous product, that’s been like a punching bag for hackers lately, exposing many of the plugin’s vulnerabilities. However, the frequent patches and quick responses from Adobe don’t seem to be helping the plugin much, as both Google Chrome and Mozilla Firefox have both blocked it.
Commenting on the latest attack on the barely living Flash, BUFFERZONE CEO, Israel Levy, explains how is it possible that Flash still has unpatched holes, after so many interventions.
"Vulnerabilities are inherent in the many layers of technology that are used to build a modern software application. Adversaries will continue to uncover these vulnerabilities whenever the price is right", Levy told IT Pro Portal via email. "There’s a 'supply chain' of hackers that uncover vulnerabilities and sell them on the dark net, hackers that create exploit kits, and criminal organizations. And the only way to break is to either:
- Fix every bug in every application -- which is simply not an achievable goal
- Isolating the flash session in a virtual container, so that the cost of breaking into the organization is high enough to make the return on investment for the exploit unattractive".
The biggest winner of the assault on Flash is JavaScript, says Levy, adding that even though it’s inferior to Flash, it now has close to 90 percent of penetration.
"The trend in Flash usage is showing a sharp and swift decline losing over 2.5 percent market share in the past year. JavaScript is already the king of the castle on the client side with close to 90 percent penetration and although some areas (such as 3D) may be inferior, overall, it’s a winner".
Levy doesn’t, however, see the light at the end of the tunnel for Flash. Asked if he can see Flash ever returning to its former glory, his answer is simple: "NO".
In capital letters.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: IkeHayden / Shutterstock
-

India wants to regulate ride-sharing apps
Publié: octobre 15, 2015, 7:24pm CEST par Sead Fadilpašić

India has proposed a set of rules aimed at regulating ridesharing apps such as Uber. The rules will see the tech companies operate more like traditional taxi fleets, a move which will probably please other taxi companies in the country.
India’s Ministry of Road Transport and Highways released the guidelines proposal, which suggests all cars run by these companies should have an emergency button and an in-app feature to call the police.
The companies are also advised to conduct in-depth criminal background checks on all potential drivers, and form 24/7 call centres. They should also have branded vehicles, as well as a meter to track the distance travelled and the passenger fee.
Ridesharing company Ola commented on the proposal: "We welcome the advisory from the Ministry of Road Transport and we believe this is a major step towards positively impacting the ecosystem and its stakeholders, that technology platforms like ours have created. We will continue to work with the government, under the aegis of this progressive directive, offering our complete support and commitment towards building mobility for a billion people".
Uber is yet to make a comment.
The American ride-sharing company has had a rough ride in India. After the rape of a female passenger by an Uber driver, the company implemented privacy and in-app safety measures, but it still faces backlashes in form of police investigations and bans.
Both Uber and Ola have had their applications for radio taxi licences rejected, TechCrunch says, but they’ve been able to work around these roadblocks.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: STILLFX / Shutterstock
-

US government to invest $20 million to drive fuel cell development
Publié: octobre 15, 2015, 2:49pm CEST par Sead Fadilpašić

The U.S. Energy Department has announced it will invest more than $20 million (£12.9m) in the fuel cell and hydrogen technologies industries, following the revelation that the industry is basically exploding.
A total of 10 projects will be funded, aiming to advance fuel cell and hydrogen technologies and to enable early adoption of fuel cell applications such as light-duty fuel cell electric vehicles (FCEV).
The end goal is, according to Energy.gov, to accelerate American innovation in clean energy technologies and reduce the nation’s dependence on foreign oil. Cutting carbon emissions was also mentioned as an important goal.
"These projects announced today will continue to make advances in our rapidly-expanding portfolio of hydrogen and fuel cell technologies", said Assistant Secretary for Energy Efficiency and Renewable Energy David Danielson. "Energy Department-supported projects have helped reduce the modelled cost of transportation fuel cells by 50 percent since 2006, and more than double durability and reduce the amount of platinum necessary by a factor of five. We are pleased to support the recognition of the first-ever National Hydrogen and Fuel Cell Day on October 8, aptly chosen to represent the atomic weight of hydrogen (1.008)".
The investment follows a report by the Energy Department, which shows that the fuel cell industry is growing at an amazing rate. It totalled more than $2.2 billion (£1.43bn) in sales last year. That means the industry grew by almost $1 billion (£650m) in a year -- back in 2013 it was worth $1.3bn (£840m).
In addition, the city of Ithaca, New York has proposed to become home to one of the first commercial hydrogen-electrolyser fuelling stations in the north-eastern United States and to ramp up outreach through the use of FCEVs.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Adobe and Dropbox team up for easier PDF management
Publié: octobre 14, 2015, 6:01pm CEST par Sead Fadilpašić

Adobe and Dropbox have announced a partnership, bringing stronger integration between the two products which will surely be beneficial for users on both sides.
The new partnership means people using Adobe products will be able to save files directly to their Dropbox folders, while those going into their cloud locker first will be able to edit PFF files directly in the cloud.
The integration might not mean much for the desktop user who already has it the easy way, but iOS and Android users will have reasons to feel jolly.
"As the inventor of PDF, Adobe brings over 20 years of experience with secure digital documents", said Kevin M. Lynch, senior vice president and general manager of Adobe Document Cloud at Adobe. "The requirements of our customers have constantly evolved over time; today, mobile has become the rule and people expect to complete work quickly and simply wherever and whenever they need. Our work with Dropbox, as our first file sync and share partner, will help Adobe Document Cloud customers and people around the world be more productive with the documents at the center of their daily lives".
Users anywhere in the world can take advantage of the new feature starting today, adding their Dropbox account in Acrobat DC or Acrobat Reader on desktop.
The iOS integrations between Acrobat Reader and Dropbox will be available in the coming months, Adobe says, with Android and web integrations to follow sometime next year, in 2016.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Facebook pays less in taxes than the average UK worker
Publié: octobre 13, 2015, 1:21pm CEST par Sead Fadilpašić
The numbers showing just how much Facebook has paid Britain in taxes has some people outraged and others utterly confused, but the problem seems to be in the legislation, and not in the companies themselves.
The biggest social media site in the world, Facebook, has paid £4,327 to the British government last year. At the same time, the company earned more than £100m from advertising and other forms of revenue.
How did it manage to get away with this? It was able to cut its tax bill by reporting an accounting loss of £28.5million, having handed out £35.4million to its workers through a share bonus scheme.
Facebook commented on the news, saying it has done nothing wrong. A company’s spokesperson says: "We are compliant with UK tax law and in fact all countries where we have employees and offices. We continue to grow our business activities in the UK".
So how much money does an average tax payer in Britain give to the state? £5,500 in tax -- over £1,000 more than Facebook was forced to pay. According to the Mirror, an average salary in the UK is £26,500.
Facebook’s 362 UK staff earned an average of £210,000 in pay and bonuses last year.
John Christensen, the director of campaign group the Tax Justice Network, said: "it’s very likely they’re using all the usual techniques to shift profits around".
George Osborne, the chancellor, has pledged to crack down on tax avoidance by global firms by swiftly legislating to enact a new set of rules drafted by the Paris-based Organization for Economic Co-operation and Development (OECD), which has become a hub for global tax reform in recent years, The Guardian wrote in a report.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

EE: UK will need more than 2 million IT workers by 2020
Publié: octobre 12, 2015, 6:58pm CEST par Sead Fadilpašić

If you thought the story about Europe needing 800,000 workers in the IT security industry by 2020 was insane, you’ll be blown away with what O2 claims.
According to its research, the UK alone will need 2.3 million workers with IT skills by the same time. The research also predicts 766,000 new jobs will be created over the next five years, with London and the south-east being the main targets.
This poses somewhat of a problem, with the north-west and east of England expected to create just eight percent of digital jobs.
As a result, O2 has launched a Digital Communities pilot in St. Helens, in Merseyside, to encourage young people to pursue IT careers outside London.
"It’s promising to see so many jobs will be required to fulfil the UK’s digital potential. But we can’t get complacent -- these figures highlight that the economy is nowhere near digital maturity and -- worryingly -- the opportunities that are being created, are predominantly in the south", O2 business director, Ben Dowd, said.
"We’re committed to playing our part -- which is why we’ve launched an ambitious partnership with St Helens Council to show other communities what’s possible when they put connectivity at their heart".
The general idea is to create a "blueprint", which could serve as a road sign, showing other areas in the country all the benefits of connectivity and the benefits of going digital.
Dowd said he will encourage other countries to do the same, so that "the entire nation can feel the benefits of the UK’s growing digital economy".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: dotshock/Shutterstock
-

Uber blames Lyft CTO for data theft
Publié: octobre 9, 2015, 6:34pm CEST par Sead Fadilpašić

Uber is laying blame for the February 2015 hack and data theft on none other than its main competitor -- Lyft.
Back in February 2015, someone broke into Uber’s servers and stole data of more than 50,000 its drivers, and now Uber claims the thief’s IP address points to Lyft’s chief of technology Chris Lambert.
Uber filed a lawsuit in San Francisco federal court and, according to the company’s court papers, an unidentified person using a Comcast IP address had access to a security key used in the breach.
According to a Reuters report, two sources say the address was assigned to Lambert.
The court papers draw no direct connection between the Comcast IP address and the hacker. In fact, the IP address was not the one from which the data breach was launched. But, US Magistrate Judge Laurel Beeler ruled that the information sought by Uber in a subpoena of Comcast's records was "reasonably likely" to help reveal the "bad actor" responsible for the hack.
On Monday, Lyft spokesman Brandon McCormick said the company had investigated the matter "long ago" and concluded "there is no evidence that any Lyft employee, including Chris, downloaded the Uber driver information or database, or had anything to do with Uber’s May 2014 data breach", Reuters wrote in a report.
McCormick declined to comment on whether the Comcast IP address belongs to Lambert. He also declined to describe the scope of Lyft’s internal investigation or say who directed it.
Lambert declined to comment in person or over email.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: M. Dykstra/Shutterstock
-

US businesses fear Safe Harbor dismissal will affect European operations
Publié: octobre 9, 2015, 5:05pm CEST par Sead Fadilpašić

Small and medium-sized enterprises (SME) in the US are saying that the suspension of the Safe Harbor law might mean end of overseas operations for them, Reuters reported on Thursday.
The Safe Harbor law allowed companies in the United States to transport data regarding its European users to the States. It was struck down recently, by the European Court of Justice.
In a victory for privacy advocates, the European Court of Justice ruled that national regulators in the EU can override the 15-year-old Safe Harbor pact used by about 4,500 companies, including Apple and Alphabet’s Google, because it violates the privacy rights of Europeans by exposing them to allegedly indiscriminate surveillance by the US government.
Now, some US companies fear they will be locked out of the European market.
"The biggest fear is they’ll lose the opportunity to provide data services in Europe", said Emery Simon, counsellor to BSA, The Software Alliance.
"Any U.S. company with employees or customers in Europe is potentially impacted by this ruling", RetailMeNot spokesman Brian Hoyt told Reuters by email. "We also believe it may also create challenges for data sharing necessary to rapidly provide data analysis for business operations".
Adobe said it was |evaluating options| to transfer personal data between continents and Autodesk also said it was evaluating the decision, while Symantec said it has other mechanisms in place to legally protect data transfers, but the uncertainty following the ruling has made it difficult for such companies to determine their next steps and how much business might be lost.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Grigory Galkin/Shutterstock
-

Porsche believes Android Auto collects too much data, opts for CarPlay
Publié: octobre 8, 2015, 6:58pm CEST par Sead Fadilpašić

Porsche won’t install Google’s Android Auto system in its future 911 models because the American tech giant is asking for too much personal (or should I say, mechanical) information about the vehicles.
Instead, it will go for Apple’s CarPlay system.
According to a report by MotorTrend, Porsche has opted for Apple’s rival CarPlay system over Android Auto due to privacy concerns.
"There’s no technological reason the 991/2 doesn’t have Android Auto playing through its massively upgraded PCM system. Why doesn’t it have it? As part of the agreement an automaker would have to enter with Google, Porsche said certain pieces of data must be collected and transmitted back to Mountain View, California", the report notes.
Those "certain" pieces are vehicle speed, throttle position, coolant and oil temp, engine revs. "Basically Google wants a complete OBD2 [on-board diagnostic] dump whenever someone activates Android Auto".
"Porsche feels info like that is the secret sauce that makes its cars special. Moreover, giving such data to a multibillion-dollar corporation that’s actively building a car, well, that ain’t good, either".
It seems as Porsche is afraid of a little competition.
Google’s spokesperson Liz Markman commented, basically saying the information is needed to make the driving experience as good as possible. In a statement, Markman said Google does not collect some of the data listed by Porsche, such as throttle position and coolant temp, although she declined to provide a full list of data collected.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Caracarafoto/Shutterstock
-

Technology affects our long-term memory
Publié: octobre 8, 2015, 3:50pm CEST par Sead Fadilpašić

Technology is making us forget things, and now we’ve got a Kaspersky Lab research to prove it.
According to a study by security firm Kaspersky Lab, when asked a question, 57 percent will try to remember the answer themselves, but 36 percent won’t even think about it -- they’ll just pull up their phone and head for Google.
That 36 percent is out of 6,000 people surveyed, and among those older than 45, that percentage rises to 40. "These consumers seem to be reluctant to spend time trying to recall something from memory or possibly doubt the accuracy of those memories", the press release following the survey reads.
What’s even worse, a quarter of those respondents (24 percent), admit they forget the answer as soon as they had used it. Similar to the previous discovery, the percentage in this case also rises to 27 percent among the older population. This is called Digital Amnesia.
Some 12 percent assume the information will always be available somewhere online.
The experts who advised on the Digital Amnesia report highlight how a failure to make use of the information stored in our memories -- for example by preferring to search online -- can ultimately result in the dilution or disappearance of those memories.
"Our brain appears to strengthen a memory each time we recall it, and at the same time forget irrelevant memories that are distracting us. Past research[ii] has repeatedly demonstrated that actively recalling information is a very efficient way to create a permanent memory. In contrast, passively repeating information (e.g. by repeatedly looking it up on the internet) does not create a solid, lasting memory trace in the same way. Based on this research, it can be argued that the trend to look up information before even trying to recall it prevents the build-up of long-term memories", explains Dr Maria Wimber, lecturer, School of Psychology, University of Birmingham.
The security can be an early casualty of our impatience to access information online. Kaspersky Lab has found that just under a fifth (18 per cent) of consumers -- 22 percent of those aged up to 24 -- will opt for speed over protection when downloading files. This leaves the door wide open for malicious software intent on stealing personal data and compromising the device and any other devices connected to it.
If consumers haven’t protected their data, their online accounts and devices with strong passwords and data back-ups, the memories and information these hold could be lost or damaged forever.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: PathDoc / Shutterstock
-

Malwarebytes: There's no WinRAR vulnerability, we're sorry!
Publié: octobre 8, 2015, 10:43am CEST par Sead Fadilpašić

Security firm Malwarebytes recently unveiled a vulnerability in WinRAR, the popular compression program which, according to the firm, has put millions of its users at risk.
The program’s developers, RARLab, shrugged it off saying it’s not really a vulnerability. It turns out they were right, and Malwarebytes has apologized for its mistake.
As it turns out this vulnerability is more an attack vector that only works with the user's cooperation, Malwarebytes wrote. "The vulnerability was fixed by Microsoft in November of 2014".
RARLab’s response to the matter was that without this patch, every software utilizing MS Internet Explorer components including Internet Explorer itself can be vulnerable.
"The entire attack is based on vulnerabilities in Windows OLE MS14-064 patched in November 2014. System installed the patch are safe. System without patch must install it. Without this patch every software utilizing MS Internet Explorer components including Internet Explorer itself can be vulnerable to specially crafted HTML page allowing code execution. WinRAR SFX module displays HTML in start dialog, so it is affected too, but components of Internet Explorer are used in a huge number of different tools, not just in WinRAR SFX archives", it wrote.
Malwarebytes apologized for its mistakes, saying that it takes too much user cooperation to be considered a vulnerability.
"I would like to apologize to WinRar as this is not a vulnerability in their software. It takes too much user cooperation and even then it does not run the resulting code in an elevated manner", adds Malwarebytes.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: mtkang/Shutterstock
-

Malware targeting Microsoft Outlook Web App is after your password
Publié: octobre 7, 2015, 8:32pm CEST par Sead Fadilpašić

A newly discovered malware targets Microsoft’s Outlook Web App, the company’s web-based email client. The news was unveiled by security firm Cybereason, which said the advanced persistent threat (APT) can enable patient attackers to steal an organization’s email passwords over time.
By using this approach, the hackers managed to collect and retain ownership over a large set of credentials, allowing them to maintain persistent control over the organization’s environment, Cybereason says.
The company found the malware after an organization’s IT team spotted "behavioral abnormalities" in its email servers.
The security firm goes on explaining the malware: "The Cybereason platform found a suspicious DLL loaded into the Outlook Web App (OWA) server (a webmail component of Microsoft Exchange Server), with several interesting characteristics. Although it had the same name as another benign DLL, the suspicious DLL went unsigned and was loaded from a different directory. Since OWA servers typically load only legitimately signed DLLs, the Cybereason behavioural engine immediately elevated this event to a suspicion".
Cybereason says the attack is important, as whoever has access to the OWA server, owns the organization’s domain credentials:
"The attack on OWA is significant", claims Cybereason, because OWA authentication is based on domain credentials. "Whoever gains access to the OWA server becomes the owner of the entire organisation’s domain credentials", it says.
"The hackers installed a back-doored malicious OWAAUTH.DLL which was used by OWA as part of the authentication mechanism, and was responsible for authenticating users against the Active Directory (A/D) server used in the environment. In addition, the malicious OWAAUTH.DLL also installed an ISAPI filter into the IIS server, and was filtering HTTP requests".
"This enabled the hackers to get all requests in cleartext after SSL/TLS decryption. The malware replaced the OWAAUTH by installing an IIS filter in the registry, which enabled the malware to automatically load and persist on every subsequent server restart", adds Cybereason.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Jirsak/Shutterstock
-

People rating app Peeple disappears
Publié: octobre 7, 2015, 4:55pm CEST par Sead Fadilpašić

The, uhm, app for people rating, has disappeared from the web. This is news because, as you might imagine, it is very hard for something to completely disappear from the internet.
The app, called Peeple, gained a lot of media attention recently, as it was dubbed "Yelp for People". Yelp is an app where people can rate restaurants, hotels and stuff like that. A lot of feedback was negative and threatening, as the app was seen as a huge platform for online bullying.
Now, the complete business has disappeared. The website is offline, and the app’s Facebook and Twitter pages seem to have been removed.
Few people who have been able to connect to the website have been met with a landing page that reads "Join the positive revolution #oct12", which hints the app could make a return, IB Times wrote in a report.
One of the app’s founders wrote a blog post a few days back, trying to defend the app against the raging mob also known as everyone, everywhere.
"Since the interview with The Washington Post, I’ve received death threats and extremely insulting comments aimed at me, my investors, and my family on almost every social media tool possible", said Julia Cordray in her blog post. "I hope now if nothing else by watching me you can clearly see why the world needs more love and positivity".
Cordray said Peeple would work on a 100 percent opt-in system, with no one being put on the platform without their permission and that there would be no 48-hour waiting period to remove negative comments.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

WinRAR will not get 'useless' security patch to fix 'vulnerability'
Publié: octobre 5, 2015, 5:17pm CEST par Sead Fadilpašić

Usually when a security firm finds a vulnerability in an app or a program, and notifies the developers, a patch is issued in a matter days, sometimes even hours.
Not when it comes to WinRAR. The guys over at RARLab have been reached out to by both Vulnerability Lab and Malwarebytes about a vulnerability which, they say, on a danger scale of 1 to 10 is a 9.2.
RARLab doesn’t really buy the whole "vulnerability" story.
According to Vulnerability Lab and Malwarebytes, a victim could be infected by simply unzipping (or unrarring, I guess) a file. With people downloading a lot of compressed stuff every day, the two security firms agreed that more than 500 million users are at risk here.
Security researcher Mohammad Reza Espargham, who posted the proof-of-concept (PoC) and the manual steps needed to reproduce the attack, explained, "The code execution vulnerability can be exploited by remote attackers without privilege system user account or user interaction".
RARLab renders all of this "useless":
A "malicious hacker can take any executable, prepend it to archive and distribute to users. This fact alone makes discussing vulnerabilities in SFX archives useless", RARLab wrote. "It is useless to search for supposed vulnerabilities in SFX module or to fix such vulnerabilities, because as any exe file, SFX archive is potentially dangerous for user’s computer by design. As for any exe file, users must run SFX archives only if they are sure that such archive is received from a trustworthy source. SFX archive can silently run any exe file contained in archive and this is the official feature needed for software installers".
What they’re basically saying is that any program can be created and compressed in a way that it installs automatically upon decompression.
"Limiting SFX module HTML functionality would hurt only those legitimate users, who need all HTML features, making absolutely no problem for a malicious person, who can use previous version SFX modules, custom modules built from UnRAR source code, their own code or archived executables for their purpose. We can only remind users once again to run exe files, either SFX archives or not, only if they are received from a trustworthy source".
It doesn’t seem like we’re getting a patch.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Ozgur Coskun / Shutterstock
-

New London transport rules could spell trouble for Uber
Publié: octobre 1, 2015, 6:38pm CEST par Sead Fadilpašić

Transport for London will propose a new set of rules which are designed to address the cabs vs Uber struggle. The way rules are set, it seems as Uber is in for a bumpy ride.
Documents seen by the Telegraph reveal that London’s transport body is due to consult on new proposals for private hire companies that would ban some of Uber’s key features.
The proposals include a minimal five minute wait between ordering a ride and it actually getting there, as well as a ban for operators on showing cars for hire within a smartphone app – a key Uber feature.
TfL also proposes a limitation on ride-sharing, which is a direct hit against Uber’s UberPool service.
“These bureaucratic new rules will not improve your ride,” said Jo Bertram, Uber’s general manager for the UK, Ireland and Nordics. “They’re designed to address the concerns of black cab drivers, who feel under pressure from increased competition.”
“But the answer is to reduce the onerous regulations cabbies face today – not increase them for everyone else.”
According to a report by The Telegraph, Transport for London is planning to launch a September consultation on the matter “in the interests of public safety and an effective and up to date regulatory system”.
TfL is consulting on the following proposals that could affect Uber:
- Operators "must provide booking confirmation details to the passenger at least five minutes prior to the journey commencing". Uber matches potential passengers with the nearest riders, meaning they are picked up in, on average, three minutes after requesting a car.
- Companies "must not show vehicles being available for immediate hire either visibly or virtually via an app". One of Uber’s key features is a map of available drivers in the area around the passenger.
- Operators "must offer a facility to pre-book up to seven days in advance", an option that would create major headaches for Uber, since it does not allow passengers to pre-book rides.
- Drivers may only work for one operator at a time. Uber says many of its drivers are part-time workers whose main employer is a traditional minicab firm.
- There should be "controls on ridesharing in public vehicles". Uber’s chief executive Travis Kalanick has said he wants to bring the UberPool service, which allows several customers to share a car, to London.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

YouTube will show more relevant ads in videos
Publié: octobre 1, 2015, 5:03pm CEST par Sead Fadilpašić

YouTube has announced it’s adding new capabilities to the advertising on the site. Yay, more ads on our YouTube videos, who wouldn’t be happy?
Anyway, long story short -- marketers will be able to buy ads which will be displayed during product-focused videos, such as game reviews, unboxings, product reviews and how-to videos.
Google explained how the new system will work in a blog post published on the AdWords blog:
"These will let you show a click-to-buy ad within partner videos on YouTube, going beyond your own videos to transform any relevant video into your digital storefront. Similar to Shopping ads on Google, you only pay when a user clicks on your ad", it says in the blog post.
It seems as users are increasingly turning to YouTube for instructional and informational videos, especially when they’re researching something they’re planning on buying. Google has noticed this trend and is investing in new ways in order to increase shopping-related activities on YouTube.
According to a report by IOL, the new YouTube offering is being announced as part of Advertising Week, an annual event in New York focused on the latest trends and products in the advertising industry.
"YouTube will roll out the click-to-buy service in the coming months, following similar moves by parent Google and social networks such as Facebook Inc.’s Instagram and Pinterest Inc. to make it easier to shop via their sites", it says.
"YouTube has become the place the world comes to watch, share and engage with video", the company said in the post. "And we want to keep creating even better experiences for the viewers, advertisers and creators who turn to YouTube every day".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Don't expect a major increase in IT budgets for 2016
Publié: octobre 1, 2015, 12:50pm CEST par Sead Fadilpašić

Bad news for IT experts in the West. According to a survey, IT budgets are expected to increase by only one percent in 2016. On top of that, the IT headcount is expected to stay pretty much the same.
All of that, despite the fact that the demand for IT experts has exploded, and that Europe will need 800,000 IT security experts by 2020.
The 2016 State of IT report done by Spiceworks says 67 percent of the IT professionals surveyed cite technology end-of-life (EOL) as a driving force behind new hardware, software and services investments in 2016.
For example, some 66 percent of companies are still running Windows XP and 60 percent are running Windows Server 2003, both operating systems which have reached EOL.
"Among those planning operating system refreshes in 2016, 47 percent said they planned to invest in Windows 10 and 32 percent said they planned a Windows Server 2003 migration", it says in the follow-up press release. "Additionally, 12 percent said they’re planning a Microsoft SQL Server 2005 migration, a database application that reaches end-of-life on April 12, 2016".
The spending on security hardware, software and services will also remain pretty much the same, but companies do plan on allocating six percent of their total IT budget to security.
However, 59 percent of respondents don’t feel their organization is adequately investing in security and 48 percent don’t feel their company data is adequately protected. Additionally, only 26 percent of respondents said recent high-profile security incidents have led their organization to change its security practices.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
credit: Gunnar Pippel/Shutterstock
-

Tens of thousands of medical devices are exposed to hackers
Publié: septembre 30, 2015, 7:21pm CEST par Sead Fadilpašić

Thousands of critical medical systems such as MRI machines, completely out in the open and vulnerable to a hacker’s attack, have been exposed online, the media reported on Tuesday.
According to a report by The Register, more than 68,000 medical systems from a "very large" unnamed US organization have been exposed. That institution has some 12,000 staff and 3,000 physicians, it says in the report.
"Exposed were 21 anaesthesia, 488 cardiology, 67 nuclear medical, and 133 infusion systems, 31 pacemakers, 97 MRI scanners, and 323 picture archiving and communications gear".
This was all made possible through Shodan, a search engine for devices connected to the public Internet. Security researchers Scott Erven and Mark Collao found the machines by using Shodan to target medical institutions.
"Once we start changing [Shodan search terms] to target speciality clinics like radiology or podiatry or paediatrics, we ended up with thousands with misconfiguration and direct attack vectors", Erven said. "Not only could your data get stolen but there are profound impacts to patient privacy".
Collao said that the vulnerabilities could be used to steal patient data and build up detailed intelligence on healthcare organizations, including the floors in which certain medical devices are housed.
"You can easily craft an email and send it to the guy who has access to that [medical] device with a payload that will run on the (medical) machine", Collao said. "[Medical devices] are all running Windows XP or XP service pack two... and probably don’t have antivirus because they are critical systems".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
credit: vision001/Shutterstock
-

Yahoo wants to spin off Alibaba stake, risking billions in taxes
Publié: septembre 30, 2015, 5:23pm CEST par Sead Fadilpašić

Yahoo is moving forward with its plan to spin off its Alibaba shares, even though it risks a tax bill of a couple of billion dollars.
In a filing posted with the US Securities and Exchange Commission earlier this week, Yahoo said that the company’s board authorized it to continue with the proposed spinoff. Yahoo added that it’s hoping the process will go without any hiccups.
But the stakes are high -- the transaction could carry up to $9 billion (£5.9bn) in taxes. The transaction is expected to be complete in the fourth quarter this year.
The value of the Alibaba stake is now worth significantly less than when Mayer initially unveiled her spinoff plans. When she announced the plans, they were worth $40 billion (£26.33bn). Now, they’re worth about $22 billion (£13.16bn)
Yahoo CEO Marissa Mayer has, since January, talking about an elaborate restructuring plan that would see Yahoo offload its stake in Alibaba, without incurring taxes, all by transferring them to a new entity.
However, in the first week of September, the US Internal Revenue Service (IRS) declined to issue a private-letter ruling regarding the plan. A week later, the IRS issued guidance, which does not specifically mention Yahoo, expressing concerns of spinoffs that consist largely of investment assets and minimal operating businesses.
Yahoo will also transfer to Aabaco services for small businesses that it hosts in its Internet cloud.
The company bought a 40 percent stake in the Chinese company in 2005 for $1 billion (£660m).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Ken Wolter / Shutterstock.com
-

Elon Musk expects EVs will have 1000km range by 2017
Publié: septembre 29, 2015, 6:53pm CEST par Sead Fadilpašić

I love Elon Musk’s predictions, they’re always so optimistic about the future of the world. The latest such statement regards electric autonomous vehicles, when we might expect them to become more of a mainstream thing, and just how good they will be.
During an interview with a Dutch publication, he said that we can expect electric cars to go 1,000 kilometers (621 miles) or more by 2017 on a single charge. That’s more than double of what such cars achieve today.
He also said that this progress depends mostly on battery technology, which he expects to constantly improve, meaning we can see an increase in the car’s range from 5 to 10 percent every year.
"My guess is that we could probably break 1,000km within a year or two. I’d say 2017 for sure... in 2020 I guess we could probably make a car go 1,200km. I think maybe 5-10 percent a year [improvement], something like that", he said.
To top things off, he said that by 2035 all new cars will not require a driver, and that the technology will roll out very soon, but the regulators around the world need to work faster.
The AutoPilot self-driving feature currently being beta tested by Tesla will be rolled-out to all compatible Model S vehicles by the end of October. "My guess for when we’ll have full autonomy is about three years, approximately three years".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Google Nexus 6P: Official specs and images leak
Publié: septembre 29, 2015, 5:20pm CEST par Sead Fadilpašić

Hardware specs for the upcoming Nexus phone have been leaked, and it seems Apple will have a tough battle on its hands this time.
Android Police has released what seem to be a couple of slides made for retail employees, with hardware specifications and images of the new phone.
The Huawei-made Nexus 6P, the larger of the two new devices, is expected to be unveiled on September 29 (today).
Hardware-wise, the Nexus 6P attacks the Apple iPhone 6s Plus, as the two are somewhat similar. The Nexus 6P comes with a 5.7-inch display, while the iPhone 6s Plus has a 5.5-inch one. However, the Nexus 6P comes at a much higher resolution: 2560 × 1440 pixels, while the iPhone 6s Plus has 1920×1080.
Nexus 6P also beats Apple in terms of battery, although that’s still a long shot. The Nexus 6P will come with a 3,450mAh battery, while the 6S Plus has a 2,915mAh one. However, Apple’s devices are known for good optimization and low energy consumption, so it’s still too early to say if the Nexus 6P will outperform the iPhone 6s Plus.
The Nexus 6P will have a fingerprint sensor located at the back, and will come in a metal unibody which could give the device a premium feel.
It will also be somewhat lighter -- weighing just 178 grams, it will be lighter than the iPhone 6s Plus, which weighs 192 grams. Still, we’re talking 14 grams here, and I’m pretty sure no one would notice the difference.
The Nexus 6P comes in four colours: aluminum (grey), graphite (black), frost (white), and gold which will only be available in Japan "for now".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

You're not alone in abandoning that shopping cart
Publié: septembre 29, 2015, 3:58pm CEST par Sead Fadilpašić

If you have a habit of abandoning your virtual shopping cart before actually purchasing anything, you’re not alone. In fact, four out of ten UK shoppers do this, 50 percent of the time.
This is the result of a new research by Talend, global big data integration software provider, polling the views of online consumers across the UK.
"This represents hundreds of billions in merchandise and a significant loss of potential revenue for retailers", it says in the report, adding that as much as 40 percent of this revenue could be recovered with the timely delivery of special offers.
The research also revealed a significant gap between the proportion of consumers who say it is always their intention to buy the goods they put in their online cart (42 percent) and the four percent of all customers, who always proceed to purchase the items in their cart.
It was revealed that the shopping cart is used as the part of the browsing process, as 58 percent of consumers said they use it as a way to generate a wish list or calculate costs.
But 90 percent of respondents said they would either complete a purchase or return to an abandoned cart, if they were offered free delivery on that cart, while 85 percent said they would take one of these two options if they were offered a real-time discount or bundled offer on their cart.
Further underlining the power of harnessing analytics driven, real-time insight to drive sales, 36 percent of the sample said they would take one of the two options provided, if the retailer could inform them what the products in their shopping cart cost at other online websites.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: mtkang/Shutterstock
-

Microsoft working on Google Cardboard-like virtual reality headset
Publié: septembre 29, 2015, 12:54pm CEST par Sead Fadilpašić
It seems as Microsoft is working on a virtual reality device that bears huge resemblance to Google’s Cardboard project. The Microsoft VR kit will be given to developers attending a hackaton which will take place on October 17.
The kit works the same way Google Cardboard works -- it’s a generic headset with a slot for a Lumia phone.
Microsoft wants the developers to use the kit and create apps in three categories: games, education and corporate. After evaluating the creations, it will award the best apps in all categories, and the team behind it will be given the VR kit to continue development.
This is not Microsoft’s first entry into the virtual reality space. It already has HoloLens, a promising technology which mixes the real world with the digital one.
Microsoft announced Windows Holographic at its "Windows 10: The Next Chapter" press event on January 21, 2015. It is set to be introduced as part of the general rollout of Windows 10, through the smart glasses headset Microsoft HoloLens.
The Windows 10 launch began July 29, 2015 with release of the PC version, with HoloLens to be released within the next year. Microsoft HoloLens is a smart-glasses headset that is a cordless, self-contained Windows 10 computer.
It uses advanced sensors, a high-definition stereoscopic 3D optical head-mounted display, and spatial sound to allow for augmented reality applications, with a natural user interface that the user interacts with through gaze, voice, and hand gestures.
If you are interested in participating in the event, you can sign up on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Fake Apple Stores sell real Apple products in China
Publié: septembre 25, 2015, 5:19pm CEST par Sead Fadilpašić

Fake Apple stores selling genuine Apple products are popping up around China like mushrooms after the rain.
According to a Reuters report, Apple only has one official store in Shenzhen and five authorized dealers in the area, but China’s southern boomtown has more than 30 stores selling these products.
"Many of the stores look just like Apple’s signature outlets, right down to the sales staff kitted out in blue T-shirts bearing the company’s white logo and the sample iPads and iWatches [Apple Watches] displayed on sleek wooden tables", it says in the report.
The company commented, suggesting anyone interested in buying an Apple product to do so online via their site, but this turn of events just goes to show how popular Apple is in the world’s most populated country.
"There are many Apple fans in China", said a clerk surnamed Zhao at one of the unauthorized dealers that opened just two weeks ago. "There are many silly people in China who are willing to pay extra money just to get a new iPhone ahead of everyone else".
Hilariously, the fake stores are also taking pre-orders for new devices.
What’s even more hilarious about the whole story is that there are actually shops there selling logos, display shelves and shopping bags needed to make an unauthorised outlet feel like a genuine Apple store. There’s actually a store where you go to buy an Apple store.
It is no wonder that Apple considers China a very important market and that it’s looking to expand the number of stores from the current 22 to at least 40.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Stuart Miles / Shutterstock
-

Children increasingly prefer mobile devices to PCs, consoles for gaming
Publié: septembre 25, 2015, 4:08pm CEST par Sead Fadilpašić

Perhaps Konami wasn’t that insane when it announced it’s almost entirely switching to the mobile platform, and Nintendo also might be onto something with its announcement that it’s creating a couple of mobile games.
According to a report by the NPD Group, mobile is the number one platform for gaming, overpassing even the PC. The report called Kids and Gaming 2015 offered insights into what platforms children ages 2-17 play the most.
I didn’t even know two-year-olds played video games in the first place. Turns out they do, and they are the ones that made all the difference.
Now, 63 percent of children reported they play games regularly on mobile devices. By comparison, 45 percent of children ages 2-17 reported that they play on a home computer, which is down 22 percent from 2013.
This decline is seen within the entire age group, but is "most pronounced" for those ages 2-5, NPD said.
It’s not just the PC who’s seeing a decline. Console gaming, even mobile consoles such as PS Vita or Nintendo 3DS are suffering. A specific percentage decrease figure was not shared, though the NPD said it was nowhere near the drop reported for PC gaming.
"The largest and most surprising shift in the 2015 gaming ecosystem was kids’ move away from the computer", NPD Group analyst Liam Callahan said in a statement. "In the past, the computer was considered the entry point for gaming for most kids, but the game has changed now that mobile has moved into that position. This may be related to a change in the behavior of parents that are likely utilizing mobile devices for tasks that were once reserved for computers".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shkljoc/Shutterstock
-

Facebook flips the switch on 360 degree videos
Publié: septembre 25, 2015, 11:47am CEST par Sead Fadilpašić

Facebook has joined YouTube and implemented a feature which allows users to view 360-degree videos.
As of Wednesday, September 23, users on PCs and smartphones can view 360-degree videos, and to mark the new feature, Facebook has released a couple of cool videos.
Those include a Star Wars clip, one which lets you look around the desolate, war-torn wasteland of a far-off planet, a Saturday Night Live video, which has you join the live audience during its 40th anniversary show, and a GoPro clip which brings you along for a dirt bike ride in the Idaho desert.
The clips work in the same way as they do on YouTube: once the video starts rolling, you can press and hold the left mouse button on the screen to "grab" it, and then move in any direction you want.
On smartphones, you can tilt the device to rotate the image, but panning with your finger also works.
On his Facebook page, Facebook’s top product executive, Chris Cox, called it "a really cool experience that takes you somewhere else". Cox said anyone will be able to upload 360 Video "very soon".
"It’s an open-ended format, so we’re really excited to see what creators around the world come up with as they get their hands on it", Cox wrote.
It’s a great feature, one which most certainly brings us a step closer to virtual reality, but it still doesn’t come cheap. A camera capable of recording 360-degree video will set you back at least $400 (£260).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
//
Photo credit: dolphfyn / Shutterstock
-

Europe wants to change data sharing deal with US
Publié: septembre 24, 2015, 7:26pm CEST par Sead Fadilpašić

A comment by the European Court of Justice’s Advocate General about data transfer between European Union and the United States has sent ripples through the tech world, as it might completely change the way EU and the US companies do digital business.
"The Commission decision is invalid", Reuters quotes Advocate General Yves Bot saying, referring to the Safe Harbour framework enabling data transfers to the United States.
He basically suggests that national authorities should be able to stop data on EU citizens being transferred overseas, if it’s going to be used in a way which violates EU rights.
This could also mean a step away from the "Safe Harbour" data sharing agreement between the European Commission, US and Switzerland reached back in 2000.
According to a report by the Financial Times, tech groups reacted with dismay: "We are concerned about the potential disruption to international data flows if the court follows today’s opinion", said John Higgins of DigitalEurope, a European trade association.
Austrian law student Max Schrems had challenged Facebook’s data collection practices in Europe, after revelations of mass U.S. surveillance programs, Reuters adds.
"*YAY* AG at the #CJEU: #SafeHarbor is invalid. Irish #DPC has a duty to investigate. Further details as soon as we get the written version", Schrems wrote on Twitter.
*YAY* AG at the #CJEU: #SafeHarbor is invalid. Irish #DPC has a duty to investigate. Further details as soon as we get the written version.
— Max Schrems (@maxschrems) September 23, 2015
The ECJ can be expected to make a final decision in a few months’ time. If it agrees with the Advocate General, it could have widespread consequences for how data is collected and used by American technology companies. The Telegraph says that in practice, the Advocate-General is rarely overruled by the court.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Lightspring / Shutterstock
-

The PC market's decline continues, despite Windows 10's release
Publié: septembre 24, 2015, 11:45am CEST par Sead Fadilpašić

The PC market is in a decline, and there’s nothing new about it. We reported earlier how the upgrade cycle for the PC won’t be complete before 2017, when people are mostly expected to upgrade their machines.
However, much was expected from the recent release of Microsoft’s latest operating system, Windows 10. To be more precise, the OS was expected to boost PC sales before 2017. That, according to a Gartner report, didn’t happen.
Instead, sales are set to plummet 7.3 percent year on year, slightly less than the 9.8 percent dip the firm recorded in the second quarter. PC shipments are expected to total 291 million units in 2015.
Ranjit Atwal, research director at Gartner, said: "Until the end of 2015, currency devaluation and subsequent price increases will continue to restrain the replacement of ultramobiles and notebooks by businesses in particular".
"In 2016, we expect currency impacts will negate and while Windows 10 products on the Intel Skylake platform will increase in volumes throughout the year, Windows 10 adoption among businesses will ramp sharply in 2017, where we expect the PC market to return to a 4 percent growth", added Atwal.
But it’s not just the PC market that’s experiencing a solid hit. Tablets are not looking fly, either.
"The tablet market is coming under increasing pressure", said Annette Zimmermann, research director at Gartner. "Users of tablets with a screen size between 7 and 8 inches are increasingly not replacing their devices".
The smartphones category, meanwhile, is the only one showing growth. Likely fueled by the imminent release of the iPhone 6s, Gartner predicts a 14 percent rise in smartphone sales this year, The Inquirer wrote in a report.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Mopic/Shutterstock
-

We're one step closer to VR movies
Publié: septembre 23, 2015, 8:21pm CEST par Sead Fadilpašić

A company creating cameras and software capable of filming 360-degree videos has just gotten a significant money boost, which signals that the era of virtual reality movies is almost upon us.
The company, called Jaunt, has received $65 million (£42m) in series C round of funding. In investment was led by The Walt Disney Company, together with Evolution Media Partners -- a partnership of CAA-backed Evolution Media Capital, TPG Growth and Participant Media; and China-based China Media Capital (CMC).
The company, which makes hardware and software for virtual reality, has now raised more than $100 million (£64.6m) since it was founded two years ago. It says it will use the money to "greatly increase production" and advance its camera hardware and software tools, the company said in a press release.
"This round further illustrates our commitment and dedication to advancing the scope of cinematic VR -- for filmmakers, storytellers, and audiences alike", said Jens Christensen, CEO and co-founder of Jaunt. "With the support of these world-class companies, we will explore new avenues, building on our leadership position to deliver amazing VR experiences using best-in-class tools, technology, and creative teams".
"We have been closely monitoring the evolution of video technology on the global horizon, and are excited about the potential for VR. It is having implications in areas such as film, television, games, sports, mobile, as well as other entertainment content and experiences where CMC has a profound connection and substantial engagement", said Ruigang Li, chairman of China Media Capital. "Jaunt will be an important step in CMC’s foray into this global entertainment technology revolution".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Belgium believes Facebook is as bad as the NSA for spying
Publié: septembre 23, 2015, 4:14pm CEST par Sead Fadilpašić

Belgian Privacy Commission (BPC) said during a court hearing earlier this week that Facebook is spying on its users in Europe. The American social media company is allegedly violating privacy laws, monitors information of non-users and logged-out users, all for the purpose of placing ads, IB Times just wrote in a report.
This is a developing story which started in April this year, when the Centre of Interdisciplinary Law and ICT at the University of Leuven in Belgium claimed the social network’s privacy policy violates European Union laws.
Facebook was quick to respond, saying the part about tracking people who weren’t members of Facebook was a bug and they fixed it. It has also called the BPC report false and has maintained that its practices are in compliance with European Union law.
Still, it didn’t stop the Belgian privacy commission from taking the social media giant to court.
"When it became known that the NSA was spying on people all around the world, everybody was upset. Facebook is doing the very same thing", said Frederic Debussere, representing the BPC.
"We will show the court how this technology protects people from spam, malware, and other attacks, that our practices are consistent with EU law and with those of the most popular Belgian websites", the Facebook spokesperson was quoted as saying by the Guardian.
Currently, Facebook is facing a plethora of charges and changes to how it deals with Europeans information. Several other US corporations including Google, Yahoo and Microsoft are also being investigated by different courts in Europe.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: dolphfyn / Shutterstock
-

People trust governments with their data, but not private companies
Publié: septembre 23, 2015, 11:39am CEST par Sead Fadilpašić

Here’s a plot twist: despite everything that’s been going on with governments spying on other governments and people, despite countries looking to ban encrypted communications apps and generally fighting against encrypted communications, people still trust the government with their data more than private service providers.
Those are the results of a survey made by secure Swiss-based data center provider Artmotion. It surveyed more than 1000 citizens in the US, Europe, Russia and Australia.
"When provided with the choice, consumers consistently agreed that government systems -- such as tax and medical databases -- were more secure than data held by the likes of Facebook, Amazon, Google, Apple and Microsoft", it says in the press release.
Germans are the most trusting of the bunch, with 82 percent trusting public sector systems more than services like email providers.
On the bottom of the list were US consumers. They were most trusting of commercial services, with 69 percent still considered government systems to be the most secure.
In the U.S. email accounts were widely considered the least secure communication channel, while the UK was less trusting of social media sites such as Facebook and Twitter.
Commenting on these findings, Mateo Meier, CEO of Artmotion said: "Data privacy is essential for the safe development and evolution of business. With ever more data being inputted and uploaded by individuals, ensuring the safety of sensitive personal data can often be paramount to a business' success".
"While there is still significant room for improvement by governments the world over when it comes to data security sector, these results highlight just how low some of the world’s biggest internet companies are regarded when it comes to data privacy", added Meier. "Between Ashley Madison, Apple’s iCloud, Amazon Twitch and the attack on Sony Pictures, is it any wonder that customers have lost faith in the ability of Facebook, Google and the other key digital players to protect their data?".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: phloxii/Shutterstock
-

Skype calls will work in Microsoft Edge without a plugin
Publié: septembre 22, 2015, 5:39pm CEST par Sead Fadilpašić

Skype has announced that Microsoft’s new web browser, Edge, will soon support Skype voice and video calls without the need for a plugin.
This will work for new versions of both Skype for Web and Skype for Outlook.com, and should be implemented "later this year". Considering that this year has just over three months to go, it’s safe to assume it will come pretty fast.
"Starting later this year, Skype users will be able to make voice and video calls without needing to install a plug-in on Microsoft Edge and we are working on bringing the same seamless experience to Skype for Business", it says on the Skype blog.
How is this possible, you might ask? Microsoft has recently released Windows 10 preview build 10547, which features a lot of tweaks and improvements, but also a preview of the Object RTC (ORTC) APIs for Microsoft Edge.
Object RTC is a collection of tools which will make it easier for developers to build audio and video calling into Web apps without the need for a browser plugin. However, ORTC is not Microsoft’s technology, PC World explains, but rather a broader effort of which Microsoft is part.
"We’re thrilled about the exciting scenarios that ORTC APIs enable and we are proud to be one of the first to use these ORTC APIs in the Edge Browser", Skype says in the blog post.
"The ORTC APIs will enable us to develop advanced real-time communications scenarios -- like group video calls with participants all on different browsers and operating systems -- using features like Simulcast and Scalable Video Coding (SVC), all while preserving the ability to easily interop with existing telephony networks".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Australia's primary schools to teach coding
Publié: septembre 22, 2015, 5:01pm CEST par Sead Fadilpašić

Australia is preparing for the jobs of the future by having children learn coding and programming at a very young age.
According to a report by Mashable, 21st century computer coding will be taught in primary schools from Year 5, and programming will be taught from Year 7. The curriculum was approved by Education Minister Christopher Pyne in one of his last acts before being sworn in as Minister for Industry, Innovation and Science.
The Department of Education and Training recently announced it will be pumping AUD$12 million (£5.54m) into four different science, technology, engineering, and maths (STEM) education initiatives as part of the Industry, Innovation and Competitiveness Agenda.
Those initiatives are the development of innovative mathematics curriculum resources, supporting the introduction of computer coding across different year levels, establishing a P-TECH-style school pilot site, and funding summer schools for STEM students from underrepresented groups.
"We’re making great progress, including the recent release of two new science units under our Science by Doing initiative, as well as professional development workshops for primary school teachers under the Primary Connections programme", Mr Pyne said. "We are restoring the focus on STEM subjects in schools and making sure our teachers get more instruction on STEM during initial teacher training".
"I’m pleased the Education Council has united to boost STEM study, with members from all levels of government in Australia, as well as New Zealand Ministers responsible for school education, early childhood development and youth affairs", added Pyne.
Opposition Leader Bill Shorten signalled his support for coding in schools earlier this year but then Prime Minister Tony Abbott opposed the idea.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: spaxiax / Shutterstock
-

This is BlackBerry's first Android smartphone
Publié: septembre 22, 2015, 10:52am CEST par Sead Fadilpašić

If you were wondering how BlackBerry’s first Android phone, Venice, will behave in action, wonder no more.
First video footage of the smartphone has been released online, and on it we can see its sliding QWERTY keyboard in action. The keyboard can also be used as a touchpad by sliding your fingers across the keys. This interesting feature is not unique though, it was already seen on the BlackBerry Passport.
What’s also interesting to notice is that the device runs something of a stock Android, with services such as Google Now and BlackBerry Hub pre-installed.
The device’s specs are still somewhat of a mystery, but PhoneArena claims it knows what the phone will bring.
It will reportedly arrive with a QHD display, 3 GB of RAM, 18 MP main camera and at least a 3,000 mAh battery. Phone Arena’s source also told it that, in true BlackBerry tradition, the Venice’s security would be "second to none". Other rumours for the BlackBerry Venice suggest it will have a 5 MP front-facing camera and a 1.8 GHz Hexa-core Snapdragon 808 processor. The display size is said to be 5.4 inches.
As for the release date, the exact date is unknown, but we do know (or, should I say, we suspect) it will be released in November 2015.
BlackBerry is a phone maker which was once considered one of the best but has, similar to Nokia, been defeated by Samsung and Apple, companies that now dominate the smartphone market. With Venice, however, the company just might make a big comeback.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Samsung Pay hits the 500,000 users mark
Publié: septembre 18, 2015, 7:09pm CEST par Sead Fadilpašić

Samsung’s mobile payment system Samsung Pay has hit the ground running in South Korea and the results show a lot of promise as the company prepares to launch the service in the United States.
Only last Wednesday did the media report that Samsung Pay has 25,000 subscribers but now -- less than a week after -- Business Korea reports 500,000 users.
The service has been active in the country for less than a month now. "If this trend continues, it seems to be only a matter of time to surpass 1 million subscribers in 1 to 2 months", it says in the report.
It’s no wonder that the company is looking to expand its service to other countries. China, The United States, Spain and the United Kingdom are all on Samsung’s expansion list.
Samsung has already secured distribution networks by forging partnerships with major financial companies overseas. In the US, the tech firm is a partner company of Bank of America, US Bank, Visa, and MasterCard. In China, Samsung is finalizing its partnership with China UnionPay, the largest card issuer in China.
Things get better, though. Samsung’s recently announced smartwatch, Gear S2, is said to support Samsung Pay starting with November.
Samsung Pay is a mobile payments service developed from the intellectual property of LoopPay, a crowdfunded start-up company that Samsung acquired in February 2015.
SamsungPay incorporates technology by LoopPay known as MST -- Magnetic Secure Transmission. It transmits card data to the pay terminal’s swipe slot using an electromagnetic field, causing the terminal to register it as if it were a normally swiped card.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Germany changes stance on Wi-Fi rules to boost hotspot availability
Publié: septembre 18, 2015, 2:27pm CEST par Sead Fadilpašić

If you’ve ever been to Germany, you know it’s more likely you’ll stumble upon the World Cup trophy somewhere along the way, than to find a Wi-Fi internet connection in a cafe or a hotel somewhere.
Germany has very strict rules regarding internet piracy and has, until recently, held the providers of the Wi-Fi network responsible for any illegal activity such as piracy conducted on the network.
Basically, you could go to a local café and download the entire internet, and the café would have to take the blame.
Obviously, this forced restaurants, hotels, cafes and others in the service industry to abandon the Wi-Fi altogether. Many would argue that’s no big deal, knowing how Germany is well-covered with mobile networks, but the country wants to be up to date with the latest trends, obviously.
That’s why it has introduced a new bill, which removes hotspot-operators’ liabilities for any wrongdoings of whoever uses the network.
"The amendment clarifies that these service providers can rely on the so-called liability privilege", Die Bundesregierung writes in a report.
"It causes these service providers for violations are others not liable for damages and not be liable to prosecution. The liability privilege is an essential part of the European Directive on electronic commerce".
However, don’t think this will turn Germany into a piracy-friendly country. Organizations whose main business is copyright infringement won’t be excused liability.
The new bill should, however, make things a little easier for travellers waiting for Europe’s mobile new low-price roaming regulations to kick in during 2017.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shutter_M / Shutterstock
-

MyFord Mobile app gains Android Wear, Apple Watch support
Publié: septembre 18, 2015, 1:02pm CEST par Sead Fadilpašić

Ford has updated its MyFord Mobile app and gave it support for both the Apple Watch and Android-powered smartwatches.
According to a report by T3, the app doesn’t actually let you drive the car with your watch, but instead offers a handful of nifty features to make your driving experience more enjoyable.
So for example, the app allows you to precondition the car from the outside before travelling, to display a detailed summary of mileage, show the last trip the car made and supply various pieces of data concerning the car.
The app also grades your driving in a gaming kind of way, giving you scores in the shape of green leaves, to tell you how efficiently you’re driving. That way, the app is trying to make drivers more responsible.
But perhaps the best thing this app has to offer is a navigation of its own -- it can help you locate your car if you’ve left it somewhere and have no idea how to get back to it (or maybe if it gets stolen? I don’t know). It works for both walking to the car, and driving to it -- in case you really messed something up.
Included with the update is incorporation of Google Maps in the MyFord Mobile app, which is used to show nearby electric car charging stations. The Android Wear and Apple Watch apps are available right now and you can start playing around with the features as long as you own a Ford C-MAX Energi, Ford Focus Electric or Ford Fusion Energi.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Russia opens antitrust investigation against Google
Publié: septembre 16, 2015, 6:29pm CEST par Sead Fadilpašić

Google has been hit by anti-monopoly lawsuits all over the world. The Americas, Europe, India, China, have all had (or currently have) some sort of lawsuit against the search giant, claiming the American company abuses its dominant position in the search engine market.
Now, Russia is jumping on the bandwagon, with its anti-monopoly agency saying Google is using Android to promote its other services.
According to a Reuters report, the FAS anti-monopoly body said Google had violated the law by pre-installing certain applications on mobile devices.
The company "could face penalties totaling up to 15 percent of its 2014 revenue in this part of the Russian market", it says in the report.
The exact price of the fine is unknown, and FAS said it would make that decision after September 28. It added Google must then pay and change its ways, or risk more fines if violations continue.
Google Russia said it would analyze the decision and declined further comment until then.
A Russian search engine and Google’s biggest competitor in the market, Yandex, welcomed the decision.
"We believe the FAS decision will serve to restore competition on the market", the company said. It filed a complaint against Google with FAS in February, saying it bundled applications from the Google Mobile Services with the Google Play store.
That would require pre-installation of the Google search engine as the default one, and give Google application icons preferential placement on the screen of mobile devices.
"In addition, the investigation confirmed the existence of agreements on prohibition of pre-installation of competitors’ apps", Yandex said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft to announce new Windows 10 devices at October event
Publié: septembre 16, 2015, 5:17pm CEST par Sead Fadilpašić

We knew that Microsoft won’t be making any announcements related to its newly released operating system during the IFA 2015 fair, but now we have more details.
Microsoft has taken to Twitter to announce it is holding a separate event on October 6 at 10 am EDT (3 pm London time) in New York.
"We have some exciting news to share about Windows 10 devices", the announcement says, without going into much detail. We do know that you will be able to livestream the event on this link.
According to IB Times, it’s widely expected that the Redmond-based software giant will introduce multiple devices including the flagship Windows 10 Mobile phones Lumia Talkman (Lumia 950) and Cityman (Lumia 950 XL), Surface Pro 4 and Microsoft Band 2.
Talkman should come with a 5.2-inch display, and a Qualcomm Snapdragon hexa-core 808 processor, together with 3GB of RAM.
Cityman will be somewhat bigger (5.7-inch), will have a more powerful octa-core Snapdragon 810 and 3GB of RAM. Both devices will have a 20-MP PureView camera.
The upcoming Surface Pro 4 tablet is expected to be very thin and offer a large display, similar to older models. "Rumor further suggests the use of a new Skylake processor and Windows 10 operating system", IB Times says in a report.
According to a report by The Verge, rumors have suggested Microsoft is planning Windows Hello support for the Surface Pro 4, but it’s unlikely the company will fit an Intel RealSense camera into the thin device. Instead, a fingerprint scanner on an updated and refined Surface keyboard sounds more likely.
Watch it live on October 6. #Windows10devices [t.co] pic.twitter.com/H1QKMB42La
— Microsoft (@Microsoft) September 14, 2015
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

IT security professionals are well paid and in high demand
Publié: septembre 15, 2015, 3:45pm CEST par Sead Fadilpašić

If you’re young and want to earn well, I suggest you take up IT as a profession. Salaries in the industry are soaring, according to multiple reports.
Global professional services consultancy Procorre says nearly one sixth (15 percent) of cyber security professionals are paid at least £100,000 a year. The reason behind such a large increase in pay is high demand -- new cyber security roles are making up 14 percent of all new UK-based IT roles. Procorre found that out of 10,210 IT vacancies in the UK, 1,420 are in cyber security.
British universities responded to the increased demand for cyber security experts, with 42 universities offering specialist degrees related to cyber security at an undergraduate level, and more than 700 cyber security related degrees available at postgraduate level.
Now, Oxford University, Royal Holloway, University College London and Warwick University offer Master of Science degrees in areas such as cyber security management, software and systems security, and information security.
Computing.co.uk has done a similar survey and has come to the same conclusion -- IT security is a profession where salaries are growing, fast.
According to Wiktor Podgorski, contracts and HR manager at Procorre, companies are spending time working on strengthening firewalls in-house.
"Many of the businesses that have been hacked over the past few years have lost very sensitive information. Even if the information lost does not put them at personal risk of financial loss, customers lose faith in companies that are unable to keep information secure, so data losses can have a significant long-term impact on sales and revenue", said Podgorski.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Syda Productions / Shutterstock
-

Health insurer discovers hack half a year too late
Publié: septembre 11, 2015, 6:43pm CEST par Sead Fadilpašić

A health insurer in upstate New York was hacked, and more than 10 million of its members might have had their data stolen, Reuters reported on Thursday.
The Rochester-based insurer Excellus BlueCross BlueShield said it and its affiliates had been the target of a sophisticated cyberattack. It is offering free identity theft protection services to the affected.
According to a Reuters report, Excellus said it learned of the cyberattack on August 5 from experts it had hired to perform a forensic assessment of its computer systems.
The assessment was done after other health insurers were attacked. A subsequent investigation found that the initial hack occurred in December of 2013.
Attackers may have gained access to members’ information, including names, date of birth, Social Security number, mailing address, telephone number, member identification number, financial account information and claims information, the company said.
"We are taking additional actions to strengthen and enhance the security of our IT systems moving forward", the company said in a notice posted on its website.
"The investigation has not determined that any such data was removed from our systems and there is no evidence to date that any data has been used inappropriately", Excellus spokesman Jim Redmond said.
"The FBI is investigating a cyber intrusion involving Lifetime Healthcare Companies, which include Excellus BlueCross BlueShield, and will work with the firms to determine the nature and scope of the matter", the FBI confirmed in an emailed statement.
"Individuals contacted by the companies should take steps to monitor and safeguard their personally identifiable information and report any suspected instances of identity theft to the FBI’s Internet Crime Complaint Center", it added.
Bryan Lillie, Chief Technology Officer, Cyber Security at QinetiQ has commented: "This hack identifies the importance of regular monitoring for intrusions. This hack was going on for over a year and half before it was found which is a long time".
"While current reports haven’t found evidence of data theft or misuse, a year and a half gives a party with an ulterior motive a huge amount of time with which to adversely impact a company’s IT systems. To prevent this kind of intrusion, protective monitoring is a must; this will spot unusual activity and move security from a background function to a proactive, key part of the business".
"Often people deploy security in wrong way. They install a software package or appliance but don’t think about how it works. Few people change their password regularly let alone modify their firewall or check logs to see if there is anything odd going across boundary, or something has been trying to get in. If you’re not looking, you’re not going to find it".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Lighthunter/Shutterstock
-

Apple's shares expectedly drop after 'Hey Siri' event
Publié: septembre 11, 2015, 4:18pm CEST par Sead Fadilpašić

Apple’s shares went down some two percent following Wednesday's event which saw the unveiling of a couple of new products.
Apple unveiled the iPhone 6s and the iPhone 6s Plus, as well as the new iPad Pro, Apple TV and a couple of new features for the Watch.
SEE ALSO: Apple takes the wraps off iPhone 6s, iPhone 6s Plus
Cynics will say investors were not pleased with what Apple had to offer which is why shares slid 1.92 percent to close at $110 (£71.5), however The Independent says investors tend to be cautious in the immediate aftermath of an Apple product launch.
"We believe that Apple has plenty of additional growth drivers which can propel earnings ahead of 2016 street estimates", analysts at JPMorgan said in a note to investors.
Shares were trading around $111 in the run up to the launch, down on the previous day. Apple’s new iPhone features a reinforced casing to prevent any possible #Bendgate problems, and a new 3D Force Touch technology which allows the user to interact with the device in new ways.
The Apple TV product has been built from the ground up with the latest hardware and will feature Siri, the digital assistant, as well as apps for the TV.
"We view this next generation Apple TV as the tip of the iceberg", said David H Ives, analyst at FBR. Apple TV is a “core foundation” for the future of Apple content. The introduction of TV streaming services, expected in early 2016, will clear the path for a lucrative content business in the future, he said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: TK Kurikawa / Shutterstock
-

Intel wants you to forget what it's like to use a password
Publié: septembre 11, 2015, 11:18am CEST par Sead Fadilpašić

Intel wants you to buy new PCs and laptops based on its latest, 6th generation Core processors. They were released last week, and power some of the latest Windows 10 devices.
Intel’s selling point? With the new processors, you can forget about passwords and use facial recognition software and other methods for logging in because hey, no one likes passwords any more.
"We want to eliminate all passwords from computing", Kirk Skaugen, Senior VP and general manager of Intel’s Client Computing Group said at the Citi Global Technology Conference held on Tuesday. "I can confidently say today, you can eliminate all your passwords today, if you buy a 6th Generation Core system".
For example, Microsoft’s latest operating system features Windows Hello -- facial recognition software. To enjoy the full functionality of Windows Hello, you also need Intel’s RealSense 3D Camera, which looks at multiple angles to detect the photo’s depth and heat to determine the user’s identity.
"You can do everything from measure blood pressure, blink detection, all these kinds of things... In fact, in Berlin, one of my funniest demos in my 23 years at Intel is when I brought two identical twins out on stage and I mixed them up and only one could log in with the PC, and it actually worked", he said.
Intel has become a strong advocate of the password elimination initiative, and this is not the first time it spoke openly about their abolishing.
Last year, the company acquired a startup called PasswordBox that makes it easy for users to log-in to websites and apps without having to type in passwords, and after that it released an app called True Key, which lets the user log in to multiple apps using biometric features.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: shutteratakan / Shutterstock
-

Adblock Browser arrives on Android, iOS
Publié: septembre 10, 2015, 7:05pm CEST par Sead Fadilpašić

After some time in the beta stage, Adblock web browser for iOS and Android is as of today officially available in version 1.0.
"Adblock Browser for Android was in an open beta for a while now, and thanks to the amazing feedback we received there, we were able to evolve it into something we’re proud to release", it says in the official news post following the release.
"On iOS, we took a different route: We went with a closed, invite-only beta and usability testing. We’re definitely happy with what we’ve built here, but still quite eager to get more user feedback now. So please try it, and tell us what you think!".
Adblock Browser will enable users to surf the web without having to look at various ads, and it is compatible with Android 2.3 and newer devices. The installation will require 24MB of storage, 384MB of RAM and a display of at least 320×240 pixels.
On the other hand, if you want to use the Adblock Browser on the iOS, you’ll need an iOS device with iOS 8 or newer.
The Android version of the browser can be found on this link, and the iOS version on this link.
The AdBlock Browser claims to only remove intrusive ads by default, but according to a report by Expertreviews.co.uk, it removes pretty much everything.
"Banner ads, pre-roll videos, overlays and ad-sponsored 'related' stories were all removed from the sites we visited", it says in the report.
Google previously barred an Adblock Plus app from the Google Play store because the service "interfered with or accessed another service or product in an unauthorized manner". This app, however, is listed on the Google Play Store.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Quka/Shutterstock
-

Apple and Microsoft are winning the PR game against the US government
Publié: septembre 10, 2015, 5:15am CEST par Sead Fadilpašić

Microsoft and Apple are battling the US government over the right to keep their users’ data safe, and according to a report by The New York Times, the American tech companies are winning.
At least they’re winning in the public relations game, as the general notion today is that those companies are doing everything they can to protect their users’ privacy.
The US government, on the other hand, argues that having strong encryption, the one we see in Apple’s and Google’s products (the iOS and Android) increase the risk to national security, as they cannot monitor potential threats.
The Microsoft vs USA case is particularly interesting. The US government took Microsoft to court, asking the company to hand over data about a suspected criminal -- data it stores on its servers in Dublin, Ireland.
If Microsoft loses this battle, it could mean that other foreign countries, such as China or Russia, could get their hands on data about US citizens, stored in servers in the States.
"Clearly, if the U.S. government wins, the door is open for other governments to reach into data centers in the US", Brad Smith, Microsoft’s general counsel, said in a recent interview. Companies and civil liberties groups have been sending in briefs of their own, largely opposing the government’s surveillance powers.
Chinese firms already have plans to build facilities on American soil that would store electronic communications, so the question may be more than hypothetical, New York Times writes. Microsoft argues that Congress will ultimately have to weigh in on the issue, since it is as much a political matter as a legal one.
Microsoft and the US government are set to argue it out this week when both parties appear in a federal appeals court on Wednesday.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: maraga/Shutterstock
-

Our smartphone addiction, by the numbers
Publié: septembre 9, 2015, 1:41pm CEST par Sead Fadilpašić

One in ten smartphone owners in Britain checks the device the moment they wake up. Sky News, reporting on Deloitte’s research of the matter, calls it an addiction. (I thought everyone checks their smartphone the moment they wake up, but I guess I was wrong.)
Deloitte’s research on how much Britons use smartphones has shown some crazy statistics: a third of smartphone owners look at their device more than 25 times a day. Even worse, a sixth check it more than 50 times each day.
Which means, if an average person sleeps an average of eight hours, he’s awake the other 16. That amounts to 960 minutes every day. Divided by 50, it turns out some people check their smartphone every 20 minutes.
Hey, that’s not so bad, especially with all the notifications ringing and vibrating all the time, right? But don’t let me make any conclusions, let’s stick to news reporting here.
Deloitte, which carried out the research, says the extent of smartphone usage shows that it is one of the best-value devices that people can own.
The firm’s head of technology, Paul Lee, said: "The modern, touchscreen-based smartphone is less than a decade old, but it is more intertwined with our lives than ever. Constant technological improvements are allowing us to delegate more and more tasks to our phones, from ordering taxis to browsing catalogues and paying for a meal".
“The frequency of consumers glancing at their smartphones arguably makes it one of the best value devices available. For the sixth of smartphone owners who look at their devices 50 times or more a day, the cost per glance is less than two pence a day for a £700 handset kept for two years. And that’s before allowing for trade-in value", adds Lee.
The usage intensity is higher for the younger population -- 80 percent of young people use their devices on public transport and 43 percent while eating at a restaurant.
A fifth of 18 to 24 year-olds admit to checking their phones when crossing the road.
They also check their phones around 52 times each day, compared to 12 times a day for those aged over 55.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Syda Productions / Shutterstock
-

Messaging slowly replacing phone calls for smartphone users
Publié: septembre 9, 2015, 12:00pm CEST par Sead Fadilpašić

Smartphones are a great way to communicate with people, but according to some new research, our communication is switching from voice to other means.
Talking over the phone is actually dropping in popularity. The number of people making a phone call once a week went from 96 percent to 75 percent over the past three years, according to research carried out by Ipsos Mori for Deloitte, The Guardian reports.
People are using alternative methods -- older users go for text messaging, and younger ones for instant messaging. The amount of time a typical UK smartphone user spends on non-voice activities has almost trebled since 2012 to reach 90 minutes a day.
Text messaging, instant messaging and communicating through images and video is very convenient, believes Paul Lee, head of technology, media and telecommunications research at Deloitte.
"There has been a proliferation of tools on the market which allow you to talk without speaking. The main alternative in terms of usage is text messaging for older people and IM for younger people but there are lots of other variants", Lee explained.
"If you wanted to order a minicab beforehand, you would have to call and book. Now you can do all of that without talking. There are more and more processes where the need to talk is being shifted onto a smartphone user interface. For those who don’t want the talk the ability to avoid it is getting easier", Lee said.
"If you imagine your boiler is not working and you call up the plumbers, you can either try and describe what’s wrong or you can show the flashing light. It creates a much more value-added experience when you can start showing things rather than just describe them in words", Lee added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: View Apart/Shutterstock
-

BlackBerry buys mobile security company Good Technology
Publié: septembre 8, 2015, 5:52pm CEST par Sead Fadilpašić

BlackBerry has announced its purchase of Good Technology, a mobile security company. The deal was sealed with $425 million (£280 million) heading Good’s way. The Good Dynamics platform provides encryption, advanced data loss prevention and secure communication between applications.
But BlackBerry is already good at that, isn’t it? It is one of the safest, if not the safest smartphone out there, so what good can Good do (pun definitely intended)?
Good Technologies helps corporate clients to manage smartphones running on different operating systems. In particular, around 64 percent of active Good devices run iOS.
"The acquisition of Good is aligned with BlackBerry’s strategy to offer customers the most complete, end-to-end solution that secures the entire mobile enterprise, across all platforms", reads the company’s official statement.
The company hopes that it will be able to |provide customers with increased choice for securely deploying any leading operating system in their organization".
"By acquiring Good, BlackBerry will better solve one of the biggest struggles for CIOs today, especially those in regulated industries: securely managing devices across any platform", said BlackBerry CEO John Chen. |By providing even stronger cross-platform capabilities our customers will not have to compromise on their choice of operating systems, deployment models or any level of privacy and security".
BlackBerry expects the acquisition to be completed |toward the end of the company’s 2016 fiscal third quarter", subject to usual approval.
The company anticipates the acquisition to be accretive to earnings and cash flow within the first year after closing. BlackBerry also expects to realize approximately $160 million (£104m) in GAAP revenue from Good in the first year.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How to disable OK Google voice search on Android
Publié: septembre 4, 2015, 5:00am CEST par Sead Fadilpašić

Google voice search is a powerful feature of the Android-powered smartphone. By simply talking to your phone, you can do internet searches, call contacts, take photos, set an alarm, create a calendar event, make a note, the list goes on.
However, not everyone wants to use the voice-controlled feature for various reasons. Some don’t like the idea of their smartphone listening to them, while others don’t speak English that well and don’t see the benefits of keeping the feature turned on.
Whatever the reason may be, here is a simple tutorial on how you can turn the feature off on your Android device. The process is very simple and only takes a couple of seconds to complete.
- Navigate to Settings
- Tap the General tab
- Under "Personal" find "Language and Input"
- Find "Google voice typing" and tap the Settings button (cog icon)
- Tap "Ok Google" Detection
- Under the "From the Google app" option, move the slider to the left.
That’s it, you have successfully turned OK Google off.
In case you can’t find the settings, there is another way:
- Open the Google app
- In the top left corner of the page, touch the Menu icon
- Tap Settings > Voice > "OK Google" Detection
- From here, you can choose when you want your phone to listen when you say "OK Google".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Brian Fagioli
-

Apply Magic Sauce uses Facebook likes to determine your personality
Publié: septembre 3, 2015, 4:00pm CEST par Sead Fadilpašić
We all know that Facebook has a lot of information about us, but what exactly can it learn from all that data?
Aside from the most obvious -- the things you give it, such as gender, date of birth, place of living, education, work, your favorite sports clubs, music and movies -- it can also conclude a lot of things on its own.
Those include your Big Five personality traits (openness, conscientiousness, extraversion, agreeableness, neuroticism), intelligence, life satisfaction, sexual preference, political orientation, relationship status and education -- all based solely and exclusively by what you liked on the site.
How do I know all that? Because researchers at the University of Cambridge’s Psychometrics Centre have built a tool that uses your likes, and no other data, to build up a picture of your personality.
The tool, called Apply Magic Sauce, uses your Facebook likes to estimate the things I have listed above.
You can also follow links to take further personality tests on the University of Cambridge website.
This is not Facebook’s tool, but rather a tool of the researchers, but it shows the picture of you that the social network can build just based on your activity. In reality, likes are only a fraction of the information Facebook has on you.
Visit the Apply Special Sauce website here and select "Try it Out".
You’ll be asked to log in via Facebook. The website says it only collects your profile’s LikeIDs, but will not store any of your information once the test is complete.
I have tried it out myself and it’s pretty accurate.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

GRIP platform lets you sue Google more easily
Publié: septembre 3, 2015, 5:59am CEST par Sead Fadilpašić

You know things are getting out of hand when people start making platforms to sue you more easily. That’s what’s currently going on with Google in Europe, as a new platform called GRIP is launched.
GRIP, standing for Google Redress & Integrity Platform is created for those who believe to be affected by Google’s alleged anti-competitive behavior in Europe. According to a Reuters report, it was created by U.S. law firm and class action specialist Hausfeld.
It said the platform would build on the European Commission’s April charge sheet, which accuses Google of unfairly promoting its own shopping service to the disadvantage of rivals.
"GRIP offers corporations, consumers and other entities harmed by Google’s anti-competitive business practices in Europe a mechanism to evaluate their potential claims", Michael Hausfeld, chairman of Hausfeld, said in a statement.
Google declined to comment.
Public affairs consultancy Avisa Partners, which is helping French Internet search firm 1plusV in its EU complaint against Google, will jointly manage the platform.
Google is currently fighting the same battle on multiple fronts, where various companies and state institutions claim the search engine giant is abusing its dominant position in the search engine market to promote its own services, at the expense of the competition.
European Commission is currently looking into the matter on the Old Continent, while Google claims the accusations are incorrect and unfounded. The same issue is currently unfolding in India.
Antitrust regulators in the US wrapped up a probe into Google’s practices in 2013 without requiring that the company make any major changes to how it ranks websites.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Women largely prefer Pinterest, while men are most likely to use Twitter
Publié: septembre 3, 2015, 2:16am CEST par Sead Fadilpašić

There is no connection between levels of education and whether or not someone uses social media because, as it turns out, everyone uses social media.
However, there is a correlation between a person’s education, income and gender and which social media it uses. According to a fairly extensive research paper by the Business Insider, women are more likely to use Pinterest, while men are more likely to use Twitter.
In terms of age, the younger audience is more inclined to Tumblr and Snapchat, and when it comes to income, higher-paying adults seem to visit LinkedIn the most.
Here are a few of the key takeaways from the BI Intelligence report.
Among US female internet users, 42 percent reported being on Pinterest in Pew’s late-2014 survey, compared to only 13 percent of men.
Thirty-two per cent of US teenagers cited it as their most important social network in Piper Jaffray’s twice-annual teen survey, compared to only 14 percent saying that of Facebook.
Forty-five per cent of Snapchat’s adult users are between 18 and 24, followed by Vine (28 percent) and Tumblr (28 percent), according to comScore.
LinkedIn is used by 44 percent of Americans with income of $75,000 (£48,000) or more, according to Pew.
Seven percent of all people in the US aged 12 and older use WhatsApp, according to the Edison Research and Triton Digital survey.
Less than two-fifths of Facebook’s adult user base in the US is aged 18 to 34, according to comScore.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Rawpixel / Shutterstock
-

Apple's iPhones and iPads will work better with Cisco enterprise networks
Publié: septembre 2, 2015, 10:15am CEST par Sead Fadilpašić

Apple and Cisco have, through a joint statement, announced a partnership which will see Apple’s apps and devices become more productive in enterprise networks.
The goal of the partnership is to optimize Cisco’s networks for iOS devices and apps and integrate the iPhone with Cisco enterprise environments. That will create a "fast lane" for iOS business users, Apple has said in a press release.
Cisco will provide services specially optimized for iOS devices across mobile, cloud, and on premises-based collaboration tools such as Cisco Spark, Cisco Telepresence and Cisco WebEx.
"iOS is the world’s best mobile platform, and nearly every Fortune 500 and Global 500 company today has put iOS at the centre of their mobile strategy", said Tim Cook, Apple’s CEO. "iPhone and iPad have become essential tools for the modern workforce and are changing the way work gets done. Together with Cisco, we believe we can give businesses the tools to maximize the potential of iOS and help employees become even more productive using the devices they already love".
Apple and Cisco are also working together to make iPhone an even better business collaboration tool in Cisco voice and video environments, with the goal of providing employees with a seamless experience between iPhone and their desk phone.
"Ninety-five percent of companies in the Fortune 500 count on Cisco Collaboration and Cisco networks to help their teams be more productive", said Cisco Executive Chairman John Chambers. "Through this engineering and go-to-market partnership, we’re offering our joint customers the ability to seamlessly extend that awesome Cisco environment to their favorite iOS devices. Together, we’re going to help teams achieve higher levels of productivity and effectiveness".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Guenter Albers / Shutterstock
-

Are consumers starting to lose interest in wearables?
Publié: août 31, 2015, 3:08pm CEST par Sead Fadilpašić

The wearables market in the US from 2014 through the first half of 2015 has shown fast growth in year-over-year volume of consumer feedback, however after peaking post-holidays in January 2015, demand growth has slowed significantly, according to a new report from Argus Insights.
Over the last 18 months, the wearables market has started to mature and has grown considerably with new players entering the market with numerous products such as fitness bands, smartwatches, smart glasses, and other sensor-enabled devices.
Using data compiled from approximately 328,000 consumer reviews since January 2014, the report reveals that after the holiday season of 2013, consumers briefly lost interest in wearables before steadily increasing demand reached its high point in January of this year where it was four times the level of a year earlier. Since then demand has slowed.
According to the report, the Apple Watch stole consumer interest from Fitbit and other wearables at the time of its announcement in September 2014, as potential buyers waited to determine whether they wanted the Apple Watch. Interest in Fitbit devices resumed and grew once the Apple Watch details were announced, as Fitbit and other wearable manufacturers saw a strong 2014 holiday period. Since its IPO, Fitbit has continued to gain mindshare with consumers.
Consumer delight, measured from the volume and the content of consumer reviews, showed that Fitbit was achieving a very high level of buzz, though the satisfaction of their consumers is dropping while Apple is quickly gaining in delight. Other surprising insights include high consumer delight scores for smartwatch manufacturers Motorola and LG, as consumers are reporting more satisfaction from smartwatches than from fitness bands.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: JMicic/Shutterstock
-

These are Microsoft's Windows 10 Mobile flagships
Publié: août 28, 2015, 4:55pm CEST par Sead Fadilpašić

Known tech leaker Evan Blass has posted a couple of pictures on his Twitter profile which seem to be press renders of the upcoming Lumia phones.
According to the tweets, the two phones are Microsoft Lumia 950 and Lumia 950XL, codenamed Talkman and Cityman, respectively.
It was rumored that Microsoft is planning to unveil a couple of smartphones in October, and those should run Windows 10 Mobile. Both devices have distinctive design features that we’ve seen on previous Nokia handsets, such as the camera bulge.
The two devices are very similar in design and differentiate only in screen size: the 950XL has a 5.7-inch display (slightly larger than an iPhone 6 Plus) while the 950 sits at 5.2-inches. Both phones have identical chipsets, cameras (20MP PureView lenses), RAM and support USB Type-C.
.@bdsams I see your Cityman, and raise you a Talkman (top to bottom) pic.twitter.com/u9rACR4CeX
— Evan Blass (@evleaks) August 27, 2015
In April 2014, Microsoft has acquired Nokia, the Finnish mobile phone manufacturer. Nokia failed to compete with Samsung and Apple mostly because it failed to adapt to the Android/iOS transition and held on to the dying Symbian OS.
Microsoft, on the other hand, needed a smartphone manufacturer to push its operating system into the mobile waters and to compete with both Google and Apple for the market.
Even though Windows Phone doesn’t take up much of the smartphone market share (Android and iOS combined make up 6.8 percent, while Microsoft’s Windows Phone is at 2.5 percent), the American software company is going all in on the smartphone market, hoping that the newly released Windows 10 will spark the interest in their devices.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Former Apple CEO's company unveils two affordable smartphones
Publié: août 28, 2015, 4:16pm CEST par Sead Fadilpašić
Former Apple CEO John Sculley announced two new smartphones from his Obi Worldphone brand, built to target the developing world.
The devices, powered by Android, will apparently cost less than £160, and are built for the Asian, African and the Middle Eastern markets, Cnet says in a report.
Sculley described the SF1 and SJ1.5 in a statement as "two high-quality, premium-designed smartphones priced at an exceptional value to attracting discerning young people in fast-growth markets in Asia, Africa and the Middle East".
The SF1, named after San Francisco, is a 4G/LTE smartphone equipped with a 5-inch, 1,920×1,080-resolution Gorilla Glass 4 display, a metal and fibreglass body, dual SIM card slots, a Snapdragon 615 processor and a 13-megapixel rear camera.
It will come in two variations; a $199 (£128) model with 2GB of RAM and 16GB of internal storage and a $249 (£160) model decked out with 3GB of RAM and 32GB of storage.
Meanwhile, the 3G SJ1.5, a homage to San Jose, features more budget specs. It’s powered by a MediaTek MT6580 Quad-Core processor and has a 5-inch HD Gorilla Glass 3 display, dual SIM slots and 16GB of internal storage with expandable memory.
The devices are similar to one another and can be differentiated by the rubber detailing on the bottom of the SJ1.5.
Sculley is a 76-year-old American businessman, perhaps best known for firing Steve Jobs from Apple in 1985, eight years before he himself was sacked as CEO. Since then, he has been active in the tech world.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple prepares huge event for iPhone 6s unveiling
Publié: août 28, 2015, 10:56am CEST par Sead Fadilpašić

As Apple’s September event draws close, new information appear, but it doesn’t tell much -- it only fuels the speculation fire to the point where we all might burn out in its flames.
According to the latest reports coming from the Apple Insider, the Cupertino company is preparing a huge event for the unveiling of the iPhone 6s -- much larger than what the iPhone 6 and the iPhone 6 Plus got.
Starting with the venue, Apple has apparently rented out the large Bill Graham Civic Auditorium in San Francisco from September 4 to September 13.
The venue can hold up to 7,000 people, which means Apple is expecting quite the crowd. To put things into perspective, last year when it unveiled the iPhone 6 and its big sister, it used the Flint Center in Cupertino, which can hold 2,400 people.
But it gets weirder. Not only did Apple rent the place for nine days, giving itself enough time to set up and dismantle a large press event, it also managed to get the surrounding streets blocked.
According to Hoodline, there will be multiple street closures in the area surrounding the Bill Graham Civic Auditorium on Wednesday September 9 from 4am to 12pm -- with some streets apparently closing as early as 6pm on Tuesday September 8.
Here’s where people get really wild with their speculations. Some believe Apple is expecting so many people it has to close a couple of streets down, but others think it might be used to showcase the autonomous car the company’s been developing.
Even though the latter seems highly unlikely, it would definitely be cool.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shutterstock/Andrey Bayda
-

Enterprises should block Tor to protect data, says IBM
Publié: août 27, 2015, 4:32pm CEST par Sead Fadilpašić

Cyber crooks looking to hold your data hostage and extort money use the Tor network, and enterprises should block it if they value their data, a new report says.
The IBM X-Force Threat Intelligence Quarterly 3Q 2015 paper says hundreds of thousands of malicious events have originated from Tor in the US so far this year.
"This latest report reveals that more than 150,000 malicious events have originated from Tor in the US alone thus far in 2015", the report said.
"Tor has also played a role in the growing ransomware attack trend. Attackers have evolved the use of encryption to hold data hostage and demand payment/ransom for the decryption code", adds the report.
The paper says people are fooled by false advertising, frequently installing malware while they think they’re installing an antivirus.
"A surprising number of users are fooled by fake/rogue antivirus [AV] messages that are nothing more than animated web ads that look like actual products. The fake AV scam tricks users into installing or updating an AV product they may never have had", it explains, adding that in some cases people pay the money without thinking. "Afterward, the fake AV keeps popping up fake malware detection notices until the user pays some amount of money, typically something in the range of what an AV product would cost".
IBM said SQL injection attacks are the most common Tor-led threat to come at its customers. The dark web is a truly dark place to visit, and IBM says your safest bet would be to, first, back-up your data and, second, block Tor and move on.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: 75tiks / Shutterstock
-

Turn your smartphone's camera into a 3D scanner with Microsoft's Mobile Fusion app
Publié: août 27, 2015, 11:14am CEST par Sead Fadilpašić
Microsoft has been really busy lately, and now it has shown one of the things it has been working on -- a 3D scanner inside a regular smartphone.
The app, called MobileFusion, turns your average smartphone camera into a high-tech 3D scanner, allowing you to scan objects and turn them into 3D models for viewing, sharing and 3D printing, right in front of your very eyes.
A promotional video was created to showcase the technology.
"This allows the user to capture a full 3D model of an arbitrary object in seconds. The computation happens purely on the phone and the final 3D models are detailed enough for 3D printing, use in augmented reality games and for instant 3D capture for sharing with friends and colleague", it says in the video.
"Under the hood, the system first densely tracks the device in 3D by comparing the live RGB data with the previous frames. It will take the current live frame and perform efficient stereo-matching to compute a depth map. These stereo depth maps are then merged into a single 3D model", adds Microsoft
The software then creates the model right there, on the spot.
"The 3D model is built live in front of the user’s eyes, which allows user to instantaneously see how complete the scan is and whether the critical parts are missing. As the object is captured from all angles, the 3D model gets refined and completed. Once satisfied with the scan, the user can view, share or print the 3D model instantaneously", Microsoft further explains.
This research project can allow any mobile device to turn into a real-time 3D scanner.
The team says it hopes to introduce the software to the general public at some point but, at present, there is no release date scheduled.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple: iPhones thriving in China
Publié: août 26, 2015, 7:50pm CEST par Sead Fadilpašić

Even though China’s smartphone market is saturated, and now relies only on people replacing their devices instead of buying their first one, Apple still bets a lot on that market.
In its third quarter earnings the iPhone business grew by more than half, to $31bn (£19.64bn) on 47.5 million shipments. According to a report by the IB Times, sales in China more than doubled to $13bn (£8.24bn), over a quarter of Apple’s revenue. The company did not say exactly how many iPhones it sold in China last quarter, but it was an 87 percent increase on a year earlier.
Cook told Jim Cramer of the Street in an email exchange, "I can tell you that we have continued to experience strong growth for our business in China through July and August".
"Growth in iPhone activations has actually accelerated over the past few weeks, and we have had the best performance of the year for the App Store in China during the last 2 weeks", Cook added. "Obviously I can’t predict the future, but our performance so far this quarter is reassuring".
"Additionally, I continue to believe that China represents an unprecedented opportunity over the long term as LTE [4G] penetration is very low and most importantly the growth of the middle class over the next several years will be huge", concludes Cook.
Not only does Apple have to battle in a saturated market, it also needs to battle Android, as well as cheap Chinese phones, which are a powerful force in the country.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Shutterstock/Andrey Bayda
-

Most developers don't build mobile apps
Publié: août 26, 2015, 4:02pm CEST par Sead Fadilpašić

Even though the world is increasingly mobile, more than half of developers have never built a mobile app, a new survey, called Telerik State of Mobile Development, shows.
Telerik, the company who conducted the survey, asked 3,000 IT professionals about mobile development. Among the biggest issues developers have with building mobile apps is the fact that a lot of them are still new to mobile development or have never built a mobile app (57 percent), while others develop just one functional mobile app a year (47 percent).
Constraints and constantly changing development practices and technology is an issue for 16 percent of developers, while others struggle with the lack of time (19 percent) and the lack of tools (15 percent).
Among the key reasons for building a mobile app was improved operational efficiency, new revenue opportunities (39 percent), increased employee productivity (38 percent), improved customer service (35 percent) and the possibility to engage customers in a more meaningful way (34 percent).
User experience is the most important element to consider when building these apps. Forty-four percent of those surveyed said user experience is the most important, followed by ease of maintenance (24 percent), performance (15 percent) and security (11 percent).
"The most poignant finding of the survey is that 57 percent of developers have never built a mobile app, indicating that mobile app development remains highly specialized", said Karen Tegan Padir, president, Application Development and Deployment, Progress. "It’s clear that the developer community as a whole needs easy-to-use tools and processes to move forward with their mobile app development efforts in a more substantial way".
The full report can be found at this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Rafal Olechowski / Shutterstock
-

Samsung smart fridge might leak your Gmail credentials
Publié: août 25, 2015, 8:54pm CEST par Sead Fadilpašić

Your smart fridge might be good for storing cold beer, but it definitely isn’t good for storing your Gmail credentials, as those can be easily stolen. During the recent DEF CON hacking conference, the vulnerability was unveiled at the IoT hacking challenge run by Samsung.
The fridge that got owned was the RF28HMELBSR smart fridge. It downloads Gmail Calendar information and displays it on an on-screen display. The device does implement SSL, but it fails to validate SSL certificates, thereby enabling man-in-the-middle attacks against most connections.
According to a report by The Register, hackers from the Pen Test Partners that managed to get into the local network are able to grab the Gmail credentials through the fridge.
"The internet-connected fridge is designed to display Gmail Calendar information on its display", explained Ken Munro, a security researcher at Pen Test Partners. |It appears to work the same way that any device running a Gmail calendar does. A logged-in user/owner of the calendar makes updates and those changes are then seen on any device that a user can view the calendar on".
"While SSL is in place, the fridge fails to validate the certificate. Hence, hackers who manage to access the network that the fridge is on (perhaps through a de-authentication and fake Wi-Fi access point attack) can Man-In-The-Middle the fridge calendar client and steal Google login credentials from their neighbors, for example".
Pen Test Partners’ Pedro Venda added: "We wanted to pull the terminal unit out of the fridge to get physical access to things like a USB port and serial or JTAG interfaces, but ran out of time. However, we still found some interesting bugs that definitely merit further investigation. The MiTM alone is enough to expose a user’s Gmail creds".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Bloomua/Shutterstock
-

Most Android lock patterns are easy to guess
Publié: août 25, 2015, 10:29am CEST par Sead Fadilpašić
Your Android lock screen patterns are so predictable, it almost makes no difference if you use one or not.
According to a study by a woman named Marte Løge, a graduate of Norwegian University of Science and Technology, a vast majority of Android users use lock patterns which are easy to guess.
The study looked at 4000 patterns created, and discovered that 77 percent of the patterns started from one of the four corners. Forty four percent of the patterns created began from the top left corner.
More than 10 percent of the ones she collected were fashioned after an alphabetic letter, which often corresponded to the first initial of the subject or of a spouse, child, or other person close to the subject.
The average number of nodes used in the study was five, meaning the average lock screen selection was one in 7152 possibilities.
A large number of users selected four nodes, which means their pattern was one in 1624 possibilities.
As a comparison, those who used eight or nine modes had a pattern that was one in over 140,000 possible combinations.
"Humans are predictable", Løge told Ars last week at the PasswordsCon conference in Las Vegas, where she presented a talk titled Tell Me Who You Are, and I Will Tell You Your Lock Pattern. "We’re seeing the same aspects used when creating a pattern locks [as are used in] pin codes and alphanumeric passwords".
Løge says that to create a successful lock pattern, use a high number of nodes, make the pattern complex with crossovers, and turn off the "make pattern visible" option so that someone can’t look over your shoulder to discover your lock pattern.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Sony unveils SmartBand 2 fitness tracker
Publié: août 21, 2015, 6:43pm CEST par Sead Fadilpašić

Sony has unveiled a new fitness wearable called SmartBand 2. The device is a successor to the first SmartBand, and its key feature is an advanced heart rate sensor.
Even though it is a common feature on most fitness wearables today, the heart sensor was absent from the first SmartBand. This time around, Sony has upped the game. It also features a smart notification system, which works through a set of vibrations and colored LEDs.
That means you can use the band to keep track of calls, messages, e-mails, and general social notifications. The device is paired with Sony’s Lifelog app, where you can track all the usual stuff like calories burned and distance covered.
Trusted Reviews quoted Sony Mobile’s senior VP of creative design, who said the device is there to bring meaningful data.
"We set out to create the most advanced wearable at this section of the market -- SmartBand 2 has the capability to deliver, and make biometric data meaningful for users within Lifelog", he said.
Tajima adds: "Not only does it represent a powerful vision of how consumers can learn more about themselves -- it allows us to explore exciting new opportunities with development partners".
Its biggest minus will most likely be the battery, which can last approximately two days on a charge. That is fairly low, considering that the device doesn’t have a display.
Its retail price in Europe is €119 (£85), but the official price for UK is yet to be confirmed. It is safe to assume it won’t differ much from the European price.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Your Uber driver might be a convicted felon
Publié: août 21, 2015, 5:31pm CEST par Sead Fadilpašić

Even though Uber prides itself on the extensive background-checking of its drivers, it is now being accused that some of its drivers are convicted felons.
According to a report by Sky News, a complaint was filed by the San Francisco district attorney’s office, in which it was said that one of the drivers is a convicted murderer who spent 26 years in prison before being released on parole in 2008.
He allegedly joined Uber in 2014 under a fake name and gave 1,168 rides before being discovered.
Another driver had a conviction for "committing lewd or lascivious acts against a child under 14" which did not appear in a background check. According to the filing, he gave close to 6,000 rides, unaccompanied children included.
One driver was convicted of kidnapping for ransom with a firearm, cocaine selling and drunk driving.
San Francisco district attorney wants Uber to use a fingerprint-based system called Livescan to identify its drivers, but Uber is rejecting it, saying Livescan is no better than their own background-checking system.
In a statement Uber said: "While we agree with the district attorneys that safety is a priority, we disagree that the Livescan process used by taxi companies is an inherently better system for screening drivers than our background checks".
"The reality is that neither is 100 percent foolproof -- as we discovered last year when putting hundreds of people through our checks who identified themselves as taxi drivers", added Uber. "That process uncovered convictions for DUI, rape, attempted murder, child abuse and violence".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: 360b / Shutterstock.com
-

With Marshmallow, Google is hoping Android can catch up with iOS
Publié: août 20, 2015, 6:39pm CEST par Sead Fadilpašić

Google might have a greater market share when it comes to mobile operating systems, but it is behind Apple on some of the essentials, and it shows.
That is the opinion of Wall Street Journal’s Dan Gallagher, who reflected on the Google vs Apple, Android vs iOS battle, as Google prepares the launch of Android 6.0, named Marshmallow.
Marshmallow is set to be released in the fall, and a full-blown tool kit is available for developers.
Google might have a greater market share (Android accounted for about 83 percent of smartphones sold in the second quarter according to IDC, where Apple’s iOS had about 14 percent share in the period), but the majority of that share goes on older versions of Android:
"Barely 18 percent of current Android devices are using the most-current version of the software, launched last year. Nearly three-quarters of Android’s user base are on the KitKat and Jelly Bean versions launched two and three years ago, respectively", he says.
And that’s where the problem lies for Android.
"By contrast, 86 percent of iOS users are on the most current version of the software. That has helped Apple build up a lucrative content ecosystem that is expected to generate nearly $20 billion in revenue this year".
"Apple also paid out more than $10 billion to developers last year compared with Google’s $7 billion, another indication that market share isn’t everything. Looked at that way, Android hasn’t taken over the world".
That’s why he feels Marshmallow’s actual task is to catch up with Apple, even though Android dominates the market.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Lenovo issues BIOS updates to fix security vulnerability
Publié: août 19, 2015, 4:58pm CEST par Sead Fadilpašić

Lenovo has issued a BIOS fix for some of its machines, thus preventing a vulnerability which could allow potential hackers to gain control of a desktop or a laptop computer from the manufacturer.
In a press release published on the Lenovo website, the company has urged consumers to manually update their BIOS. Newer machines will have the fix by default.
The vulnerability was linked to the way Lenovo utilized a Microsoft Windows mechanism in a feature found in its BIOS firmware called Lenovo Service Engine (LSE) that was installed in some Lenovo consumer PCs. It was first spotted by an independent security researcher, Roel Schouwenberg.
Together with Schouwenberg, Lenovo and Microsoft have discovered possible ways this program could be exploited in the Lenovo Notebook implementation by an attacker, including "a buffer overflow attack and an attempted connection to a Lenovo test server".
As a result of these findings, Microsoft recently released updated security guidelines (see page 10 of this linked PDF) on how to best implement this Windows BIOS feature, it says in the release.
"Lenovo’s use of LSE was not consistent with these new guidelines. As a result, LSE is no longer being installed on Lenovo systems. It is strongly recommended that customers update their systems with the new BIOS firmware which disables and or removes this feature".
Depending on the configuration of your BIOS, Lenovo has also put up instructions to help you install the update on your machine. The full list of all affected machines can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Maksim Kabakou/Shutterstock
-

Only a quarter of businesses feel confident about stopping data breaches
Publié: août 18, 2015, 7:29pm CEST par Sead Fadilpašić

Only a quarter of U.K. businesses believe their organization could detect a data breach at any time, a survey by software provider Informatica has shown.
The survey further shows that 33 percent say their organization is very good to excellent at detecting and containing breaches.
Meanwhile, nearly half (49 percent) of respondents admit to having experienced a breach in the past 12 months and believe it could have been avoided if certain processes and intelligent technologies had been in place.
Fifty-six percent of responding businesses say securing and protecting data is a high priority for them. In total, 59 percent say that they worry about mistakes from a temporary worker or contractor, up from 53 percent in 2014. Additionally, 52 percent fear third party or outsourcers’ management of data.
An overwhelming majority (61 percent) of businesses listed customer data as the information most at risk, followed by business intelligence (32 percent) and the data contained within emails or attachments (29 percent).
According to the survey, top data security solutions in place today include data classification, monitoring and discovery tools, with respondents believing that compliance and security could be improved through intelligent solutions, such as automated user access history with real-time monitoring (74 percent), policy workflow automation (74 percent) and automated data discovery/risk assessment (69 percent).
"As the gap between believing in data security intelligence solutions and actually possessing them diminishes, so inevitably will the risk of data breaches", said Dr. Larry Ponemon, chairman and founder, Ponemon Institute. "Given the growing business and societal costs of breaches, and the runaway proliferation of sensitive data, organizations need to seriously consider adopting a data-centric security stance without delay. To do otherwise may soon be construed as negligence".
The survey of 118 U.K. IT and IT security professionals with responsibility for data protection was completed by the Ponemon Institute as part of the annual 2015 State of Data Security Intelligence study sponsored by Informatica.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: AlexandreNunes/Shutterstock
-

Is this the new Google Nexus 5?
Publié: août 18, 2015, 4:11pm CEST par Sead Fadilpašić

It looks like the first photo of the next Google Nexus phone leaked online, and it shows some interesting details.
According to the Irish Examiner, which says the photo was "posted online", the Nexus 5 phone is on course for a refresh.
The back of the alleged Nexus 5 phone was photographed, and it has a couple of interesting features. First, it’s white in color and has a protruding camera sensor. We can also see a circular fingerprint scanner, as well as a large "not for sale" sticker.
The back also features a large Nexus logo, as well as a sticker with the LG logo.
According to the Irish Examiner, this photo features some of the elements that were showcased in recent renders. "These renders were apparently based on detailed factory schematics sent out to third-party accessory makers", it says in the report.
Rumors indicate that the device will be available in 5.2-inch and 5.7-inch variants. The smaller will be made by LG, while Huawei will handle the larger model.
According to a report by Engadget, the device could be somewhat cheaper because of its plastic casing.
"It could mean that Google will take the Nexus back to its lower priced roots -- LG’s original Nexus 5 was $349 (£223), while the Motorola Nexus 6 was $649 (£415)", it says.
Previous rumors have been saying that Google was actually collaborating with both Huawei and LG for their upcoming Nexus phone, but it seems as it is only LG who will be making the new device.
Apparently this is the new Nexus. Looks fine from this angle. Give us more, Mr Blurricam! pic.twitter.com/qmmvDDCZyY
— Marques Brownlee (@MKBHD) August 17, 2015
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Hello, walking billboards -- wearable displays are coming
Publié: août 14, 2015, 7:21pm CEST par Sead Fadilpašić
Researchers at the Korea Advanced Institute of Science and Technology (KAIST) have created a fiber-like LED that can be directly woven to create wearable fabric.
In plain terms, Korean scientists have created bendable wearable displays.
"Our research will become a core technology in developing light emitting diodes on fibres, which are fundamental elements of fabrics,” said Professor Choi, head of the research team at the School of Electrical Engineering at KAIST. “We hope we can lower the barrier of wearable displays entering the market".
The process of making this fabric involves a lot of dipping and drying and is, as researchers claim, a much more efficient way of applying LED materials to small cylindrical structures than any heat-treating method.
Gizmag has the details: "The scientists start with a fiber of polyethylene terephthalate, which they then dip several times into a solution of PEDOT:PSS (poly(3,4-ethylenedioxythiophene) polystyrene sulfonate) and then dry at 130° C (266° F) for 30 minutes to ready it for layering with organic materials. Once dried, the dipped fiber is then re-dipped in a bath of super-yellow (poly-(p-phenylenevinylene) polymer organic LED (OLED)) solution, dried again in an oven, and finally coated with a Lithium Fluoride/Aluminum (LiF/Al) compound".
The researchers believe this will speed up the process of creating wearable displays as this process is simple, cheap and effective. LED fibers could be mass-produced as easily as nylon or polyethylene fiber is produced today.
"This technology will eventually allow the production of wearable displays to be as easy as making clothes", said Seon-Il Kwon, a member of the KAIST Electrical Engineering team.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

BBC iPlayer Radio hits one million downloads
Publié: août 12, 2015, 9:12am CEST par Sead Fadilpašić
People still want downloadable music and radio programs, despite the surge in popularity of streaming services, as the BBC has found out. Its iPlayer Radio service has just reached the milestone of one million program downloads.
"We knew from the success of our Podcast service that there was a demand to download BBC radio and music content to listen to whenever they wanted," Andrew Scott of BBC Digital told Digital Spy. The download functionality was added to the on-demand service less than a month before the figures were compiled.
"But hitting one million downloads across the whole of BBC radio and music has far surpassed our expectations. We’re looking forward to bringing audiences even more features like this over the coming months", Scott added.
Among the most popular iPlayer Radio downloads was BBC Radio 4 Drama, which includes programming such as Diamonds Are Forever and Silk: The Clerks’ Room, as well as Benedict Cumberbatch’s Rumpole.
BBC Radio 1’s Summer Mixes, The Archers, I’m Sorry I Haven’t a Clue, and Book at Bedtime made up the remainder of the top five.
The BBC reports that Sunday at around 10pm is its busiest download period, as users load content onto their devices for the week ahead.
BBC iPlayer downloads are available on iOS, Android and Kindle devices. On Android, it has an average score of 3.5, and somewhere between 10 and 50 million downloads. For the iOS, the current version has 376 ratings, and a total of two stars.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Big data being used in the war against Islamic State
Publié: août 10, 2015, 7:47pm CEST par Sead Fadilpašić

ISIS might be a formidable force, but you know who they can’t defeat? Robots.
Yes, that’s right, artificial intelligence is getting the better of ISIS, and according to a BBC report, researchers have used it to better understand the group’s tactics.
The digital brain analysed 2,200 recorded ISIS events since the second half of 2014, and the findings will be presented in a conference this week.
The analysis shows how different strategies the group uses relate to certain events on the battlefield, as well as worldwide. So, for example, it was noticed that the group switches from large infantry-style attacks to improvised explosive devices (IED) when facing air strikes.
Paulo Shakarian at Arizona State University, one of the co-authors of the paper and a former US army officer who served in Iraq in 2006, told the BBC: "When they experience a lot of air strikes against them they shift away from a large infantry-style operation and use IEDs".
Researchers also discovered that the use of vehicle-borne bombs increased prior to large infantry operations by the militants. One example of this occurred in Iraq.
"We believe this relationship is because they want to prevent reinforcements from the Iraqi army getting out of Baghdad", explained Dr Shakarian.
Elizabeth Quintana, director of military sciences at the Royal United Services Institute (Rusi), said forces targeting Islamic State were likely to find research like this useful.
"The military has access to a lot of information", she said, "They need a way to bring it down to a digestible format. Analytics is definitely the way to do that".
ISIS, sometimes referred to as ISIL (Islamic State of Iraq and Syria, or Iraq and the Levant) is a rebel group which currently controls large areas of Syria and Iraq. The group has used the security vacuum which was created after the US withdrew from Iraq, the Arabic Spring events and the civil war in Syria, to seize control of large parts of the two countries.
It aims to create a "Caliphate" state, and is known for filming war atrocities, such as burning and drowning its prisoners of war.
Image Credit: Mopic / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft doubles budget for bug bounty program
Publié: août 7, 2015, 12:15pm CEST par Sead Fadilpašić

You might think you have the best programmers in the world, but chances are there’s a kid in his parents’ basement somewhere who’s smarter than all your engineers combined.
That’s why bounty hunting for bugs has become hugely popular among software makers, employing pretty much every hacker worldwide in their search for overlooked bugs. Microsoft is one of such companies, and it’s using the Black Hat conference to promote its new bug bounty program, which sees the bounty doubled.
According to a post by Jason Shirk, security architect at Microsoft, there will be a couple of changes to the company’s bug bounty program.
Rewards for the Bounty for Defense, a reward for defensive ideas that accompany a qualifying Mitigation Bypass submission have been raised from $50,000 (£32,200) to $100,000 (£64,400).
Microsoft says this alteration "brings defense up on part with offense", of which the tech giant already offers the lure of up to $100,000 for "truly novel" exploits against the Windows operating system.
"Learning about new exploitation techniques earlier helps Microsoft improve security by leaps, instead of capturing one vulnerability at a time as a traditional bug bounty alone would", Microsoft says.
Microsoft Service Account and Azure Active Directory authentication vulnerabilities discovered within the two-month period can pay up to $30,000 (£19,330), rather than Microsoft’s standard $500 to $15,000 reward (£9,600).
On July 29, Microsoft has released its newest operating system Windows 10, and is now turning to all hackers worldwide to help it in its search for overlooked and leftover bugs.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: wk1003mike/Shutterstock
-

Hackers can steal fingerprints from Android phones
Publié: août 7, 2015, 11:21am CEST par Sead Fadilpašić

Hackers can steal fingerprint data on a large scale through insecure Android phones, researchers claim, saying that vendors that ship with fingerprint sensors don’t lock them down well enough.
FireEye researchers Tao Wei and Yulong Zhang are singling out Samsung Galaxy S5 and HTC One Max as the most vulnerable examples, and are set to announce new research during the Black Hat conference in Las Vegas on Wednesday.
They have also added other smartphones from Huawei and HTC to the list, and have stressed that even though it might not be a big issue today, in five years’ time, it will be.
By 2019, it is believed that at least half of all smartphone shipments will have a fingerprint sensor, which is where the real issue lies.
Of the four attacks outlined by the researchers, one in particular -- dubbed the "fingerprint sensor spying attack" -- can "remotely harvest fingerprints in a large scale", Zhang told ZDNet by email.
"In this attack, victims’ fingerprint data directly fall into attacker’s hand. For the rest of the victim’s life, the attacker can keep using the fingerprint data to do other malicious things", Zhang said
Affected vendors have since provided patches after being alerted by the researchers.
Zhang failed to say which vendor was least secure, but he did say that Apple is "quite secure", as it encrypts fingerprint data from the scanner.
"Even if the attacker can directly read the sensor, without obtaining the crypto key, [the attacker] still cannot get the fingerprint image", he said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft: Windows 10 collects users' private information, but not for ads
Publié: août 6, 2015, 3:37pm CEST par Sead Fadilpašić

It’s been a week since Windows 10 was released, and the biggest issue about Microsoft’s latest OS seems to be in the nature and the amount of private data it collects.
We recently wrote about Cortana, the digital assistant, and how much it collects, and now Microsoft has updated its terms of service agreement to better clarify what it collects and how it uses such data.
According to the agreement, the OS will save your Bing searches, private email content and the apps you access, as well as "your typed and handwritten words".
Microsoft says the data is being collected to personalize the OS.
"We will access, disclose and preserve personal data, including your content (such as the content of your emails, other private communications or files in private folders), when we have a good faith that doing so is necessary to protect our customers or enforce the terms governing the use of the services", Microsoft said in its recently updated new terms of services agreement.
"Windows does not collect personal information without your consent. To effectively provide Windows as a service, Microsoft gathers some performance, diagnostic and usage information that helps keep Windows and apps running properly. Microsoft uses this information to identify problems and develop fixes".
It also added that the data is not being collected to serve ads.
"However, we do not use what you say in email, chat, video calls or voice mail, or your documents, photos or other personal files to target ads to you", Microsoft’s privacy statement reads.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Anton Watman / Shutterstock
-

Ransomware targets prospective Windows 10 users
Publié: août 5, 2015, 6:25pm CEST par Sead Fadilpašić

If you’re still waiting for your free update to Windows 10, be careful, as there’s serious malware circulating around the net. As usual, cyber crooks are fast to react to a trending topic and will try to take advantage of it to place malware on unsuspecting victims.
This time, they are tapping into the Windows 10 upgrade trend and are trying to sneak malicious code to people who think they’re getting their copy of the latest Microsoft OS. According to a report by Cisco’s security group Talos, someone is "impersonating Microsoft in an attempt to exploit their user base for monetary gain".
"The fact that users have to virtually wait in line to receive this update, makes them even more likely to fall victim to this campaign", it adds.
The gig is simple -- someone is sending people emails which seem to be, by all means, sent by Microsoft itself. The email, designed and formatted to replicate real emails coming from Microsoft, even down to using the same color scheme as the software giant, will offer the unsuspecting victim a download link.
The email subject is "Windows 10 Free Update". The "from" field features the email address update@microsoft.com, but according to Talos, it is coming from Thailand.
The software downloaded is not Windows 10, but ransomware instead, which will see your files locked and if you don’t pay, you will lose them all.
The particular ransomware variant in this case is CTB-locker and like all ransomware it encrypts the files on your computer and demands a ransom be paid in a given period of time or risk losing the files forever. In this case the window for payment is just 96 hours which is much shorter than most ransomware demands.
The criminals are asking for payment in Bitcoin and are using the Tor network to remain anonymous.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Carlos Amarillo / Shutterstock
-

Why killing Flash may be a huge mistake
Publié: août 3, 2015, 1:29pm CEST par Sead Fadilpašić

Flash might be a buggy program with multiple holes in its system. Flash might also be extremely vulnerable and a potential risk to millions of users out there.
But Flash should not be discarded, believes Cisco security veteran John Stewart, saying it might in fact be the lesser of two evils.
Facebook’s CSO Alex Stamos has called for the death of Flash, and Mozilla was one of the companies to follow that trend, labelling Flash a threat, and later dumping it from its Firefox browser.
TrendMicro also labelled Flash a threat. However, Stewart believes Flash should not be discarded easily as whatever replaces it might be worse.
"I have a lot of sympathy for the (Adobe) teams. They need to weather the storm", Stewart told The Register in a media call on Friday. "Adobe is zeroing in on ensuring security testing happens across their portfolio in a big way".
"If anyone thinks something is better than Flash then they need to consider what that alternative is against doubling-down security efforts on what we already have", added Stewart
The number of malware attacks through Flash rose 317 percent in the first quarter of 2015.
The McAfee Labs Threats Report May 2015 paper (PDF) says that the number of recorded Flash malware instances was almost 200,000 in Q1 2015, compared with 47,000 in Q4 2014.
Flash has been drawing a lot of attention to itself with the frequent attacks on unsuspecting browsers done through the platform.
For example, back in February this year, one of the most popular websites in the United States, Forbes, was used for a similar attack.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: bahri altay/Shutterstock
-

Uber shows phantom cabs on taxi map
Publié: juillet 30, 2015, 11:14am CEST par Sead Fadilpašić

You know all those little car icons you see when you open up your Uber app? All those little cabs in close proximity, just waiting to pick you up?
Well, they might be fake. Researchers from think-tank Data & Society said the cars shown to be very close to you could be fake, but the arrival times are still accurate.
According to LBC, employees of think-tank Data & Society wrote: "The presence of those virtual cars on the passenger’s screen does not necessarily reflect an accurate number of drivers who are physically present or their precise locations".
Why would Uber do such a thing in the first place? Apparently so you could better visualize how close the cars really are.
"Instead, these phantom cars are part of a 'visual effect' that Uber uses to emphasize the proximity of drivers to passengers. Not surprisingly, the visual effect shows cars nearby, even when they might not actually exist".
Uber claims that it aims to be as accurate as possible, LBC says, although it’s not always technically possible, while it also wants to protect the safety of the drivers by not revealing their location until a taxi is booked.
A UK spokesman for Uber told Independent: "This is simply not true. The cars you see in the app are the cars on the road".
Alex Rosenblat, a New York-based data researcher who studied how Uber drivers interact with the Uber app, alleges that Uber customers are manipulated by the symbols on their screens, Independent says.
|If a potential passenger opened up the app and saw no cars around, she might take another cab service. But if she saw a cluster of cars seemingly milling around on the same street, she’s more likely to request a ride", wrote Mr Rosenblat, whose research -- funded by Microsoft -- is published on Vice magazine’s Motherboard blog.
"What the passenger app shows can be deceptive", writes Mr Rosenblat, who found that Uber drivers "across multiple forums discuss the fake cars they see on their own residential streets".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: 360b / Shutterstock.com
-

Microsoft should quit making hardware
Publié: juillet 27, 2015, 5:10pm CEST par Sead Fadilpašić

Microsoft is good at making software and it should stick to it, analysts say, adding that exiting the hardware business could see the company’s share soar.
According to a recently published report by Reuters, Microsoft’s hardware division, comprising of mostly Xbox and Surface tablets, is showing great sales. However, they contribute less than a 10th of the company’s revenue and they’re barely profitable.
"Unless Microsoft can get to hardware break-even within two years or demonstrate sufficient offsetting value elsewhere in the portfolio, we think the company should exit the hardware business", RBC Capital Markets analysts said in a client note.
Exiting hardware could add up to $4 per share to Microsoft’s market value, they said.
Under the new CEO Satya Nadella, Microsoft has shifted its attention to cloud business and corporate software, but it said it would pump ensuing savings into its hardware division, as well.
Analysts agree that investing in cloud and Windows 10 makes strategic sense, but some say the rationale behind pouring more money into hardware is less clear.
"Hardware remains a more commoditized piece across tech", said FBR Capital Markets analyst Daniel Ives, who thinks all of Microsoft’s resources should be going into software. "Hardware is not what got Microsoft here -- software did".
Even so, Nadella said he remained committed to making phones to attract Windows users.
"We believe redeploying funds into [...] hardware is a mistake given that business’s lack of margin and strategic importance to Microsoft", Jefferies & Co analyst John DiFucci told Reuters.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Franck Boston/Shutterstock
-

BT will start testing 500Mbps broadband service
Publié: juillet 22, 2015, 5:15pm CEST par Sead Fadilpašić

It’s a big week for BT. After rolling out the first ultra high-definition entertainment bundle, the UK telecommunications company now getting ready to start testing 500Mbps broadband next month.
The broadband technology is called G.fast, and around 2,000 participants are expected to be involved.
BT Openreach told ISPreview that the trial would begin in August and take place in Huntingdon, Cambridgeshire, Gosforth in the Northeast of England, and Swansea. Various ISPs will be invited to participate.
"As you’d expect the purpose of the first trial is simply to test the deployment processes and the technology itself, as well as the speeds and experiences it delivers for customers", ISPreview says, adding that it’s unlikely to see any preliminary pricing details or results until well after the summer.
According to Stuff.tv, the installation of the new technology also means setting up more street cabinets: "G.fast works in much the same way as Openreach’s current 80Mbps capable FTTC service, but requires more radio spectrum and therefore needs to work over shorter runs of copper cable -- apparently 350m is the ideal limit", it says in the report.
We won’t see the commercial rollout of the new technology before 2016, and even when we get to that point, the speeds will probably be capped at about 300Mbps, at least at start.
BT’s eventual aim is to make 500Mbps broadband available to "most homes" in the UK. At present, the fastest consumer broadband available in the UK is Virgin’s 152Mbps service, followed by BT Infinity and Plusnet’s 76Mbps services.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Dudarev Mikhail/Shutterstock
-

Apple Watch user satisfaction tops iPhone, iPad
Publié: juillet 22, 2015, 1:38pm CEST par Sead Fadilpašić

People are more satisfied with the Apple Watch than they were when they first bought the iPhone and the iPad, a new survey shows.
The report by Apple Watch research platform Wristly, published on 19 July 2015, found that three months after the launch of the smartwatch, overall customer satisfaction is at 97 percent.
To put things into perspective, the first iPhone, released back in 2007, had a customer satisfaction of 92 percent, while the iPad, launched in 2010, had scored 91 percent.
"The customer satisfaction rating places it ahead of both of these beloved Apple 'v1.0' products", the report says. "Only time will tell if the sales results also play out accordingly, but for now this is a very strong early indicator of Apple’s product execution for its first wearable product".
Within the wearables themselves, the classic Watch scores somewhat better than the sports version.
Wristly’s research found that the perceived value of the Apple Watch was considered good or very good by the majority of wearers: "When asking our members for their perceived value of the Watch, the very large majority stated that considering its cost, the Watch was a good (73 percent), or even very good (14 percent) value. Only 12 percent of you thought that the Watch was of poor value relative to cost", the report says.
Battery life has once again proven as the weakest point of the device, with 12 percent reporting that they were either somewhat dissatisfied or very dissatisfied. According to Wristly, even these figures were not as bad as previous reports have suggested.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The cost of the Ashley Madison hack: $200 million
Publié: juillet 22, 2015, 10:30am CEST par Sead Fadilpašić

The Ashley Madison hack has once again shown how serious and just how devastating cyberattacks can be. According to a report by Business Insider, the attack against the infidelity site could cost it $200 million (£128m).
According to the report, the site planned on launching a $200 million initial public offering in London later this year.
Business Insider later reported that the company was close to canceling its plans in favor of privately paying its shareholders dividends. The data breach all but rules the IPO out completely.
"It is likely to heavily shake customer confidence (and hence the company’s financial performance) as well as investors’ perception of the company, two important factors in any IPO", Business Insider wrote in a report today. "ALM declined Business Insider’s request for comment on how the attack would affect its plans".
AshleyMadison is a site where married people come to look for an affair. It offered its users the option to completely delete their profile for £15 in the UK and $19 in the US. But a team of hackers going by the name The Impact Team hacked the site and stole the information of its 37 million users.
The group claims the site lied to its users and does not completely wipe the information. AshleyMadison denied these accusations.
Impact Team threatened to release the information, including full names and addresses of its users to the internet, unless AshleyMadison.com is taken offline.
"Avid Life Media has been instructed to take Ashley Madison and Established Men offline permanently in all forms, or we will release all customer records, including profiles with all the customers’ secret sexual fantasies and matching credit-card transactions, real names and addresses, and employee documents and emails", the hacker’s manifesto read, according to Krebs Security. "The other websites may stay online".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Nomad_Soul/Shutterstock
-

Google does not like it when employees know each other's salaries
Publié: juillet 21, 2015, 8:27pm CEST par Sead Fadilpašić

An ex Google employee says her bonuses were blocked by management because she created a crowd-sourced spreadsheet which revealed inequality in pays.
Erica Baker worked at Google for nine years before switching to Slack. She recently took to Twitter to explain what she did. On a boring Sunday afternoon at work, Baker and a couple of colleagues created a spreadsheet that would list everybody’s salaries as an experiment in radical transparency.
It was shared on Google’s internal social network and soon "took off like wildfire" and "got re-shared all over the place".
"I was invited to talk to my manager", Baker says. "Higher up people weren’t happy. [My manager] wasn’t happy. Why did I do it?".
Google has $150 (£96) bonuses which the staff can give each other for good work, and she found out hers were not getting through.
She was getting the bonuses from employees that managed to get salary increases thanks to the spreadsheet.
"Peer bonuses are rewarded at managers' discretion. My manager was rejecting all of them... once a PB is rejected, that can’t be undone", she tweeted, claiming a male colleague who worked on the spreadsheet was still receiving his bonuses.
Baker concluded her Twitter monologue: "Fighting for justice and fairness inside Google doesn’t go over well. Salary sharing is only one example... guaranteed that if Ida Wells were alive and working at Google today, there’s be many private calendar meetings focused on 'her future' there... the sharing of one doodle does not a bastion of support for justice and civil disobedience make".
Google has been contacted for comment.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: albund / Shutterstock
-

Samsung's Galaxy S6 is secure-enough for UK government
Publié: juillet 21, 2015, 11:26am CEST par Sead Fadilpašić

If you’re a government employee in the UK, looking for a device secure enough for you to use, you can go for the Samsung Galaxy S6 and the Galaxy S6 Edge.
The Communications and Electronics Security Group (CESG) has said that the duo of handsets meet the compliance standards for its Commercial Product Assurance requirements.
This has made the two devices the first two smartphones to get such approval in the country.
Samsung can credit its onboard software Knox for this, as the firm said it allows employees to securely connect to work files and email "with just a few taps".
Graham Long, vice president of Samsung’s Enterprise Business Team, said: "Mobile security and data confidentiality is of paramount importance to Samsung, and we are delighted that the Galaxy S6 and S6 Edge have been recognized as the most secure devices for use by the UK government".
"CESG’s acknowledgment of Samsung Knox is testament to the high standard of security offered by the Samsung Android platform, and once again reinforces our leading position in area, helping to provide secure mobile technology to government organizations and businesses throughout the UK", adds Long.
This information could help Samsung boost its market share in the government sector, and in the smartphone business in general.
Security has become the number one priorty around the world, especially after the Snowden revelations.
Apple currently dominates the business world, with 72 percent share in the first quarter of this year. It owes most of its popularity to the newest iPhone 6.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Google blames other driver for latest self-driving car accident
Publié: juillet 20, 2015, 6:50pm CEST par Sead Fadilpašić

Google’s self-driving car has been involved in yet another accident and the company has said it wasn’t the autonomous vehicle’s fault.
The car was rear-ended at a crossroads, and the company laid the blame on the human driver behind it.
On Thursday, Google revealed that three of its employees, who had been riding in one of its driverless Lexus cars, were taken to hospital with minor whiplash after a car rear-ended it at traffic lights in Mountain View, California earlier this month,The Telegraph reports.
Chris Urmson, who leads the company’s driverless car project, said not a single accident had been caused by Google’s cars. However, the vehicles have been involved in 14 accidents in six years and almost two million miles of testing.
"Our self-driving cars are being hit surprisingly often by other drivers who are distracted and not paying attention to the road. That’s a big motivator for us" he wrote in a blog post. "The most recent collision... is a perfect example".
The company even released a video showing how the crash appeared to the driverless car, which uses multiple sensors to scan the environment.
Urmson said the statistics were starting to show that Google’s cars were significantly safer than human drivers. In the most recent collision, the car had failed to break at traffic lights, and had hit the back of the Google vehicle at 17 miles per hour.
"Other drivers have hit us 14 times since the start of our project in 2009 (including 11 rear-enders), and not once has the self-driving car been the cause of the collision", Urmson wrote.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Here is Marshall's first smartphone
Publié: juillet 20, 2015, 12:40pm CEST par Sead Fadilpašić

For those unaware of what Marshall is – it’s one of the world’s best guitar amplifier maker. That is a fact at least for the author of this article who has, in his lifetime, tried at least 30 different amplifiers.
The lovable guitar amp maker has surprised the entire world when it unveiled its first Android smartphone and, you guessed it right, this one is all about music.
Named London, Marshall’s smartphone is said to be designed specifically for music lovers. Some of the unique features of this strange phone include twin stereo jacks, allowing two people to plug in and listen to music, dual speakers which should provide us with quality audio if we have no headphones around, as well as the scroll wheel which gives you quick access to volume control with tactile precision.
It also has a dedicated music button, called the M-Button. "Thanks to this ingenious bit of engineering, you can control your music on top of whatever else you happen to have on your screen", Marshall says.
Marshall claims to provide the best in class audio quality with the Wolfson WM8281 Audio Hub processor embedded inside the London. The company will also give you customized headphones from its own stock.
Even if you’re not a huge music fan, this phone will work just fine. Its hardware is similar to most popular mid-range phones.
It features Android Lollipop, has a 4.7 inch display with a resolution of 1280 by 720 pixels, a Snapdragon 410 processor, a 2GB RAM, 16GB of internal storage and a 2,500 mAh battery.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

If iOS crashes, don't pay these scammers to get it fixed
Publié: juillet 17, 2015, 5:23pm CEST par Sead Fadilpašić

There’s a new-old elaborate scheme going around the English-speaking world, and this one targets Apple users and their wallets.
According to a report by The Telegraph, iPhone and iPad users in the US and the UK have started getting pop-ups on their devices, telling them the iOS had crashed and that they need to call support in order to fix the problem.
Of course, the pop-up offers the phone number which needs to be dialed which is, as you might imagine, not the real Apple support phone line.
Scammers have targeted Safari, the default web browser for iOS devices, telling users in the US to ring the helpline and pay between $19 (£12) and $80 (£51) to fix it.
Users in the UK have also reported the issue, with one saying they had been asked for £20 to fix the crash, The Telegraph says.
When browsing Safari, users receive a notification saying: "Warning!! iOS Crash Report!!. Due to a third party application in your device, iOS is crashed. Contact Support for Immediate Fix".
Some users said the pop-up had frozen activity on their browser.
They are given one of a series of numbers to dial -- including 0800 279 6211, 0800 652 4895 and 0800 310 1061 in the UK. Users of the Apple support forum said that on dialling the numbers, they were told that a third party app was stealing their data, and demanded credit card details in order to fix it.
The scam was first reported in the US in November last year but is still being used and has spread to the United Kingdom.
In order to fix and block these crash reports, Apple says users should:
- Switch to Airplane Mode.
- Delete Safari Data: Settings > Safari > Clear History and Website Data.
- Exit Airplane Mode.
This is obviously a scam and users are advised not to dial the given number, and not to give the iCloud username and password, or bank details to anyone over the phone.
If you have been a victim of this scam you should report it to Action Fraud on 0300 123 2040 or online www.actionfraud.police.uk.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Banning encrypted messaging apps is a stupid idea
Publié: juillet 16, 2015, 3:40pm CEST par Sead Fadilpašić

In light of the recent news that the UK government is pushing harder for a legislation which would allow it to monitor all digital communications, and ban those apps that use encryption, a huge debate has sparked on whether the government should be allowed to do this or not.
Professor of Law at the London School of Economics, Andrew Murray, has had his say on the matter in a Huffington Post article, arguing that banning communications apps to curb the work of terrorist groups would be similar to banning cars in order to stop terrorists from using them.
"There is a risk that a terrorist cell may use WhatsApp to organize a terrorist attack, but equally there is a risk they will use a family car to carry a car bomb or public transport to get to their target. Are we also going to ban public transport and family cars unless the security services have the ability to monitor everyone who makes use of them? What about the sale of knives or even petrol? The infinitesimal risk that Snapchat or WhatsApp could be used in this manner needs to be set against the much greater risk that data security breaches will see our bank or credit card details revealed or our personal communications compromised", he writes.
There are many arguments against government communications surveillance, which is why the Minister of State for Security has pledged that "new legislation will be published for pre-legislative scrutiny later this year and we do intend this to be a very consultative process, subject to full parliamentary scrutiny".
"This is to be welcomed", professor concludes. "There has been for too long an overwhelming democratic deficit in the scrutiny and review of UK surveillance powers: at times to make sense of them has felt like trying to do a jigsaw in the dark and with some of the pieces hidden from us. We will hold the Minister to his pledge. It is time for a full public and parliamentary review of the law".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: kraphix/Shutterstock
-

Young people are all for equality in games
Publié: juillet 10, 2015, 7:00pm CEST par Sead Fadilpašić

If game designers opt for a male protagonist thinking it would make it easier to tap into the predominantly male gaming audience, then they’re in for a nasty surprise.
A recent study conducted by Time has shown that most boys don’t really care which gender the main character is, as well as that they’re aware that women are underrepresented in video games.
The survey was conducted to examine issues of sexism in video games and asked over 1,400 students about their feelings surrounding how women are depicted in the medium. Here are the results: 70 percent of girls surveyed said that the gender of a protagonist doesn’t factor into them playing a game. The same thing was said by 78 percent of boys.
And 58 percent of boys who identified as gamers think there should be more female heroes in games, such as Lara Croft from The Tomb Raider (see picture), or Bayonetta, even.
Also, 47 percent of middle-school and 61 percent of high-school-aged boys believe that female characters in video games are too often treated as sex objects. It’s interesting to add that "very few" of those questioned knew what Gamergate was.
"This all matters because gaming has become an important part of our culture, and it’s sending the wrong message onto our boys’ and girls’ screens", Time writes in a report. "Our kids deserve better. And it’s what they want".
The survey does a great job at dispelling the myth that all gamers are just horny boys.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Phoenixns/Shutterstock
-

Being proactive about security is the best defense against cyber attacks
Publié: juillet 10, 2015, 2:41pm CEST par Sead Fadilpašić
 Edinburgh council was the target of a cyberattack this week, and the details of more than 13,000 email addresses were stolen. The council was quick to issue a warning to all those who have an account with the authority, saying they might experience an increase in spam and phishing.
Edinburgh council was the target of a cyberattack this week, and the details of more than 13,000 email addresses were stolen. The council was quick to issue a warning to all those who have an account with the authority, saying they might experience an increase in spam and phishing.It said: "We are taking this incident very seriously. We have made sure that our service providers have reinforced the security of our website and we will continue to monitor security regularly".
"Vulnerabilities in websites are incredibly common, even amongst the largest brands, and cyber-attacks like these have become an everyday occurrence. Many businesses are still unaware of online business risks, or have delayed taking appropriate action, which is unfortunate for them and their users", said Matt Johansen, director Security Services and Research at WhiteHat Security.
"According to our 2015 website security statistics report 86 percent of 30,000 websites have at least one serious vulnerability where an attacker could compromise the system and cause serious commercial or reputation damage. And to add insult to injury, it takes an average of 193 days to remediate the vulnerabilities that are fixed not to mention the 39 percent of flaws that are never closed".
The best way to protect yourself against hackers is to be proactive about your website’s security, he concludes:
"It’s vital that businesses understand their own true security posture better than the cyber-criminals. The best way to do that is constantly check for and report website vulnerabilities proactively before disaster strikes".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Vladru/Shutterstock
-

Swiss Post testing drone deliveries
Publié: juillet 9, 2015, 9:24pm CEST par Sead Fadilpašić

Switzerland’s postal service started testing drone parcel deliveries, the company said in a statement on Tuesday.
The testing, done together with Swiss WorldCargo and Matternet, will investigate the technology and determine the cost-effectiveness of such a business idea, although flying postmen are not expected to be widely used for the next five years.
Postal service executives showed off the drones for the first time on Tuesday, The Telegraph says, and said initial tests of the machines’ post-delivery abilities would run until the end of July.
The snow-white drones are made of four branches with propellers on the end. The drone’s body is a hollow ring, designed to fit a yellow box bearing the postal service logo.
"The drone has an extremely light construction and is capable of transporting loads of up to one kilogram (2.2 pounds) over more than 10 kilometers (6.2 miles) with a single battery charge", Swiss Post said in a statement.
The drone "flies autonomously, following clearly defined, secure flight paths, which are drawn up by cloud software developed by Matternet (the drone’s US manufacturer)", Swiss Post added.
Swiss Post said that the technology, and the practice would be thoroughly tested before being put into any wide-scale use.
"Until the time of their realistic commercial use in around five years, there are various requirements which need to be clarified. This includes the regulatory framework. In addition, there are technical restrictions with the drones of today, such as limited battery life".
"The focus is primarily on their use in exceptional cases or the transport of special items".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Linus Torvals says we shouldn't fear AI
Publié: juillet 9, 2015, 12:38am CEST par Sead Fadilpašić

Linux founder Linus Torvalds doesn’t understand the fear Tesla CEO Elon Musk, Professor Stephen Hawking and Apple co-founder Steve Wozniak share about artificial intelligence.
Musk said creating artificial intelligence would be equal to “summoning a demon”, and has even donated millions to protect humans from the impending doom. Torvalds, on the other hand, describes such fears as "bad" science fiction, during a Q&A session with Slashdot users.
"We’ll get AI, and it will almost certainly be through something very much like recurrent neural networks", he said in response to one user’s question. "And the thing is, since that kind of AI will need training, it won’t be 'reliable' in the traditional computer sense. It’s not the old rule-based prolog days, when people thought they’d 'understand' what the actual decisions were in an AI".
"And that all makes it very interesting, of course, but it also makes it hard to productize. Which will very much limit where you’ll actually find those neural networks, and what kinds of network sizes and inputs and outputs they’ll have".
"So I’d expect just more of (and much fancier) rather targeted AI, rather than anything human-like at all. Language recognition, pattern recognition, things like that. I just don’t see the situation where you suddenly have some existential crisis because your dishwasher is starting to discuss Sartre with you".
"The whole 'Singularity' kind of event? Yeah, it’s science fiction, and not very good Sci-Fi at that, in my opinion. Unending exponential growth? What drugs are those people on? I mean, really", adds Torvals
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Linus Torvalds says we shouldn't fear AI
Publié: juillet 9, 2015, 12:38am CEST par Sead Fadilpašić

Linux founder Linus Torvalds doesn’t understand the fear Tesla CEO Elon Musk, Professor Stephen Hawking and Apple co-founder Steve Wozniak share about artificial intelligence.
Musk said creating artificial intelligence would be equal to “summoning a demon”, and has even donated millions to protect humans from the impending doom. Torvalds, on the other hand, describes such fears as "bad" science fiction, during a Q&A session with Slashdot users.
"We’ll get AI, and it will almost certainly be through something very much like recurrent neural networks", he said in response to one user’s question. "And the thing is, since that kind of AI will need training, it won’t be 'reliable' in the traditional computer sense. It’s not the old rule-based prolog days, when people thought they’d 'understand' what the actual decisions were in an AI".
"And that all makes it very interesting, of course, but it also makes it hard to productize. Which will very much limit where you’ll actually find those neural networks, and what kinds of network sizes and inputs and outputs they’ll have".
"So I’d expect just more of (and much fancier) rather targeted AI, rather than anything human-like at all. Language recognition, pattern recognition, things like that. I just don’t see the situation where you suddenly have some existential crisis because your dishwasher is starting to discuss Sartre with you".
"The whole 'Singularity' kind of event? Yeah, it’s science fiction, and not very good Sci-Fi at that, in my opinion. Unending exponential growth? What drugs are those people on? I mean, really", adds Torvals
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Bitcoin prices rise after Greece referendum
Publié: juillet 7, 2015, 6:25pm CEST par Sead Fadilpašić

A crisis to some is an opportunity to others, and Bitcoin seems to be taking full advantage of Greece’s current situation.
IBTimes reported on Monday how the price of Bitcoin rose to a four-month high this past Sunday. The price rose after Greece voted "No" in a referendum regarding the international bailout.
According to Coindesk’s Bitcoin Price Index, the cryptocurrency reached a peak of $273 (£175) at around 6pm GMT on Sunday. At the same time, reports started coming in on the Greek referendum results.
Greece was offered financial bailout, but would have to make painful reforms and pays and pensions cuts in return. About 60 percent of Greeks voted to reject Eurozone cash-for-reform proposals, an outcome that several European leaders warned will result in the country leaving the Eurozone -- also referred to as Grexit.
It wasn’t only Bitcoin that increased its value after the events in Greece. Often referred to as the silver to bitcoin’s gold, Litecoin rose in price by 17 percent over the last 24 hours.
And while those who supported saying no to austerity measures celebrated at the Sintagma square in Athens, Europe didn’t even try to hide its disappointment. German vice-chancellor and chief to the ruling social democrats, Sigmar Gabriel, had said that the negotiations about a new financial aid program are hard to imagine, following the results of the referendum.
He says that Alexis Tsipras and his government are pushing Greeks along the path of bitter renunciation and hopelessness.
Sigmar Gabriel told the Tagesspiegel newspaper: "With the rejection of the rules of the eurozone.. negotiations about a program worth billions are barely conceivable".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Lightboxx/Shutterstock
-

Google discounts Nexus 6
Publié: juillet 6, 2015, 7:37am CEST par Sead Fadilpašić

Google has decided to significantly reduce the price of its Nexus 6 models in the UK. The devices are now available on Google Store for as low as £399.
The 32GB model of the Motorola-made handset comes in at that price, while the 64GB version is down to £479. The devices' initial prices were £479 and £549 respectively.
The Nexus 6 has been given temporary price cuts through various channels before, and the latest reduction is temporary.
The Nexus 6 device is a 159.26 x 82.98 x 10.06 mm Android phone. It has a 6-inch AMOLED display with the resolution of 1440 x 2560. It packs a 2.7GHz Qualcomm Snapdragon 805 quad core processor, and 3GB of RAM.
The battery is 3,220 mAh, and it’s said that it has 24 hours of talk time, and 330 hours of stand-by time. It comes in two variants, the 32GB and the 64GB.
It was released in October 2014, but this April, Google admitted the interest in the brand has "declined" since the release of the Nexus 6 and Nexus 9.
"Other revenues grew 23 percent year-over-year to $1.8 billion (£1.15bn), but were down 2 percent quarter-over-quarter, driven really by year-over-year growth in the Play Store, offset by decline in Nexus, and the currency fluctuations", said Google in a statement back then. "Year-over-year it hasn’t been as strong given the strength of the Nexus 7 last year".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Joe Wilcox
-

UK businesses risk data loss with BYOD policies
Publié: juillet 4, 2015, 4:31pm CEST par Sead Fadilpašić

By allowing you to bring your own, unprotected mobile devices to work (BYOD), UK businesses risk losing data, a new research report suggests.
Forty percent of UK businesses have no security or policies in place to prevent unauthorised employees from accessing what they shouldn't, the research by Arlington Research and Acronis found.
The research, done in May, also says there are no policies to prevent sharing sensitive company information using personal phones and devices like iPads, Android devices and others.
Forty percent of respondents also admitted to having no policy in place to specify how employees should use their own personal devices in work.
One in five UK employees admit to losing a personal device, which had sensitive company data on it, research suggests.
The number of people using their personal devices for work is not negligible -- 60 percent of the UK population are using their personal devices for work. This highlights a "staggering gap in data protection and lack of control by UK businesses – especially for the rising population of mobile workers", Acronis says in a press release.
"It also confirms how the average UK employee can easily access sensitive company and customer information, using it for their own benefit".
The study also discovered 40 per cent of businesses have an opportunity to better train their employees to understand the risks involved in mobile privacy and protection. To help protect against data loss due to mobile device use, Acronis has created five top tips for UK businesses to consider:
- Create a mobile security policy -- Creating a mobile device security policy doesn’t have to be complicated, but it needs to encompass devices, data and files. The simplest place to start is to ensure employees use a device key-lock and password protection. Whether you opt for VPN security, key locks, Active Directory Monitoring or endpoint security, the choice is yours. But it is time to make a policy -- and stand by it.
- Stop making exceptions to your policy -- We all know that rules are not meant to be broken; so why aren't businesses taking their own IT policies seriously? Don’t make any exceptions, especially to senior personal. Those with access to presumably the most sensitive data in the organisation are usually allowed to break the rules. Does your CEO know his tablet could take down the business?
- Make data protection everyone’s responsibility – Many businesses allow employees to bring smartphones, tablets and even their own Macs or PCs into the office. Although this improves productivity and increases collaboration, a little education is needed to prevent the risks. If everyone understands the privacy risks involved with their own devices, your data could be safer and you would feel more comfortable loosening the reigns.
- Don't underestimate the dangers of public clouds -- When it comes to data protection, you have to worry about more than just devices. Everyone, at some point, has been guilty of saving corporate presentations or other files and documents in free public clouds, like Dropbox and Google Drive. It’s convenient instant access, but public clouds are not secure, and leave data constantly vulnerable in the digital ether, so be careful.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: baranq/Shutterstock
-

Minecraft sales exceed 20 million copies
Publié: juillet 2, 2015, 8:46pm CEST par Sead Fadilpašić

The extremely popular sandbox game Minecraft has now sold more than 20 million copies on PC and Mac.
According to the statistics on the official Minecraft page, at the time of writing, 20,007,577 people have bought the PC/Mac version of the game.
In the last 24 hours alone, 10,429 people bought the game. Mojang’s Owen Hill announced the big figure on Twitter, capturing the moment five sales on from the 20 million.
Zoik! 20 million! pic.twitter.com/d5vH270PbU
— Owen Hill (@Bopogamel) June 30, 2015
Seventeen hours after the screenshot was taken, another 7,572 copies were sold.
Years after the game was initially released, it still sells in five figures daily.
Back in September 2014, Minecraft was acquired by Microsoft for the sum of $2.5 billion (£1.60bn). At the moment no one knew exactly what Microsoft would do with such a game, but later it turned out the game was perfect for its HoloLens project.
The HoloLens is an augmented reality headset developed by Microsoft, and the company recently showcased how the game looks while the player is wearing the device. Gizmodo’s Sean Hollister has had a chance to try out the game with the headset, and according to him, it was "pretty awesome".
"When Microsoft said you’d be able to make Minecraft worlds appear in your living room with its new HoloLens headset, perhaps you squealed in glee. Or perhaps you wrote it off as smoke and mirrors—not reality. Guess what? I just played it. Everything you saw on stage is real", he said.
I’m not sure if Minecraft is still selling good because of HoloLens, or if HoloLens will sell good thanks to the popularity of Minecraft. Whatever happens, Mojang wins.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Smartphone porn consumption will explode
Publié: juillet 2, 2015, 4:34pm CEST par Sead Fadilpašić

A wise man once said our phones started getting bigger when we realized we could watch porn on them. If you had the slightest doubt in your mind about these wise words, then the latest research from Juniper should put it to rest.
According to that research, each "each smartphone user (who access adult content) is expected to watch an average of 348 videos this year". That means, more than 136 billion porn videos will be watched this year alone. But don’t worry, it will grow. By 2020, estimates say that number will hit 193 billion, which is a growth of almost 55 percent.
The report, Digital Adult Content: Market Trends, Forecasts & Revenue Opportunities 2015-2020, says both net growth and usage levels will see an increase: "Net growth will be greatest in the US, with other mature markets -- such as Western Europe, seeing a more modest increase".
In developing countries, the growth will follow the increasing availability of 4G and Wi-Fi networks, as well as the growth in smartphone and tablet ownership.
"3G, 4G and Wi-Fi have changed the nature of video-based services, as they make the streaming of high quality video quicker and more readily available to users 'on the go'", the report says.
In contrast, revenue growth in the porn segment will be steady and nothing spectacular for the next five years. Video chat and web-cam offerings will benefit the most, while adult SMS markets will basically plummet.
It’s estimated the global porn industry is worth about $97 billion (£61.8bn) annually.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Pavel Ignatov / Shutterstock
-

Kaspersky scanning your PC when visiting Facebook
Publié: juin 29, 2015, 10:18am CEST par Sead Fadilpašić

Facebook has added security firm Kaspersky Lab to its roster of antivirus companies protecting its users from malicious software, the social media site has announced.
In a blog post by Facebook Security, the company said it is keeping users’ computers safe just by using Facebook, in the way that Kaspersky Lab, together with the likes of ESET, F-Secure and Trend Micro, runs a clean-up tool in the background while you use the social network.
If a person logs on to Facebook via an infected machine, it gets scanned and the user gets notified once the scan is complete to see what it found.
"In the past three months, Kaspersky Lab helped us protect more than 260,000 people accessing Facebook from malware", Facebook said.
Facebook says that in the past three months, thanks to the collaboration of these companies, it has helped clean up more than two million people’s computers that it detected were infected with malware. It says it avoids the "whack-a-mole" approach and instead systematically combats malicious activity and does away with whole clusters of bad links at a time.
"This strategy works well, but to make an even greater impact, we begin a few steps earlier and help fix compromised computers when they connect to Facebook", it says in the blog post. "We use a combination of signals to help find infections and get the malware off of your computer for good, even if the malware isn’t actively spreading spam or harmful links".
Being used by more than a billion people worldwide, Facebook is among the top targets of hackers wanting to spread malware.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Gil C / Shutterstock
-

Most IT pros will deploy Windows 10 in the next two years
Publié: juin 26, 2015, 2:41pm CEST par Sead Fadilpašić

A total of 73 percent of IT professionals will deploy Windows 10 within the first two years, a new report by Spiceworks shows.
The report, called Windows 10: Will it Soar? found that 96 percent of IT decision-makers are interested in Windows 10, and 60 percent of IT departments have tested or are actively testing the new operating system. The survey also found that 40 percent of companies plan to begin rolling out Windows 10 within the first year and an additional 33 percent expect to begin deploying Windows 10 within two years.
Even though Windows 10 offers new features, such as Cortana or the new Edge browser, IT professionals are mostly interested in the system’s stability and simplification of everyday tasks.
Sixty-four percent of IT professionals said they were most interested in the return of the Start button, 55 percent cited the free upgrade from Windows 7 and 8/8.1, and 51 percent referenced enhanced security. Only eight percent of respondents said they were interested in the touch-optimized interface, six percent cited Cortana, and five percent were interested in Hello.
When it comes to Edge, they don’t seem to be all that much interested, with nearly half saying they didn’t know enough about the new browser to have formed an opinion. Twenty-five percent said they were somewhat to very positive, 23 percent said they were neutral, and four percent were somewhat to very negative
IT professionals’ emphasis on stability was clear when asked about any concerns they may have as they adopt Windows 10. Seventy-nine percent cited hardware/software compatibility as their biggest concern followed by early release bugs, user training, lack of third party support, and the time it would take to complete the upgrade process.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Android is the biggest target for mobile malware
Publié: juin 26, 2015, 10:51am CEST par Sead Fadilpašić

Most of the malicious software for mobile devices targets Google’s Android operating system, a new report by Pulse Secure says.
Last year, almost one million individual malicious apps for Android were released, according to Pulse Secure’s Mobile Threat Report. That means the number of threats quadrupled in comparison to the year before.
The report is based on data pooled from more than 2.5 million mobile applications, Pulse Secure says.
"There was significant growth in Android malware, which currently consists of 97 percent of all mobile malware developed. In 2014 alone, there were 1,268 known families of Android malware, which is an increase of 464 from 2013 and 1,030 from 2012", it said.
Apple’s iOS, on the other hand, went through last year basically unscratched. The report said that there were just four iOS targeted attacks in 2014, and the majority of those were designed to infiltrate jailbroken devices.
Pulse said these numbers should serve as a warning to all enterprises, to think long and hard before allowing the bring-your-own-device (BYOD) policy, while those who already have a BYOD scheme should regularly review their security.
"Enterprise networks, while continually hardened at the perimeter, need to apply similar mobile security controls to appropriately deal with the ever increasing BYOD push coming from employees", said Troy Vennon, director of the Pulse Secure mobile threat centre.
"The focus on Android and jailbroken iOS devices by mobile malware developers illustrates that they are actively attempting to exploit mobile devices as the weak link in enterprise security", Vennon added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: style-photography.de/Shutterstock
-

Businesses struggle mining big data archives
Publié: juin 25, 2015, 9:17pm CEST par Sead Fadilpašić

While some businesses saw an increase in revenue of more than £6 million, others struggle mining big data archives, a new study has shown.
The landmark study Mining for Insight: Rediscovering the Data Archive is an IDC white paper, just announced and published by Iron Mountain.
It shows that some organizations of all sizes and across various industries are drowning in data, unable to effectively mine their data archives for key insights that could ultimately improve business outcomes.
The research reveals that organizations with a well-defined data archive process stand to realize value from two potential avenues: cost savings and added revenue from monetizing archives.
More than half of the organizations polled saved more than £640,000 over the past year, with the top 21 percent saving more than £6.4 million, the study shows. That’s not all, 44 percent of organizations saved more than £640,000 by reducing operational or capital costs.
New revenue streams have also been noticed. While 39 percent of companies surveyed benefitted from an additional $1M (£640,000) or more in revenue, the top 15 gained more than $10 million (£6.4 million). On average, companies polled saw an additional $7.5 million (£4.8 million) in new revenue streams from their data archive.
Despite leaving money on the table, the majority of organizations -- 76 percent -- believe they are already maximizing the value of their archives, making data archiving a real blind spot for business leaders.
With only 38 percent of companies using archives for business analysis, a critical process to drive additional revenue by better understanding markets, improving products and service delivery and better serving customers, it’s clear that the majority of respondents are not truly leveraging the power of their archive.
Of the 24 percent of businesses that acknowledge they could be leveraging their archives more effectively, nearly three quarters believe they could be extracting two times or more value than they realize today, with more than a quarter believing they could gain five times or more value.
To help organizations bridge the disconnect between perception and reality, Iron Mountain and IDC recommend organizations implement the following processes:
- Hire a chief data officer to oversee and derive value from the data archive, while working closely with the chief operating and chief information officers to set long-term business and data strategies.
- Develop information maps of all data sources and repositories (and their value) across the organization.
- Implement a holistic, consistent archiving strategy that addresses data retention schedules, use cases, the value of data, necessary accessibility and archive costs.
- Consider working with a third party vendor with specific expertise to help optimize your archiving solution while freeing up internal IT resources to focus on more strategic and innovative work.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Marynchenko Oleksandr / Shutterstock
-

How to encrypt your emails
Publié: juin 25, 2015, 5:11pm CEST par Sead Fadilpašić

If there’s one thing that Edward Snowden left us with, it’s the notion that our digital data isn’t all that safe and that the government knows what we did last summer. But in essence, that only applies to that data being created and used using standard tools -- emails, browsers, etc.
However, if you really want to keep your data private, including browsing history and email, there are ways to do it. They’re simple to use, accessible and close to impossible to crack.
When it comes to browsing, using TOR (The Onion Router) is a safe bet. But email is not that straightforward. What you want to do with your emails is encrypt them.
What Is Encryption?
PGP (Pretty Good Privacy), also called data encryption is a process in which your email is scrambled, from basic letters and sentences into huge walls of symbols which, on first sight, make no sense whatsoever. In order to read the message, the recipient must have the encryption key, which will transform the mumbo-jumbo back into readable content.
That way, whoever intercepts your message won’t be able to read it. Can it be cracked? Basically, no.
How to Encrypt Emails
Encrypting can be done with a number of different tools. Some are websites, others are add-ons for your favourite browsers, but all of them are useful.
SecureGmail
Gmail being one of the most popular email clients in the world, I’ll start with this one. SecureGmail is a free extension for Chrome, which encrypts and decrypts messages within the browser, and keeps messages encrypted in both the sender’s and the receiver’s inbox. The messages also expire after a set amount of time.
Sendinc
Sendinc is a web service that makes sending an email safe and secure. You and your recipients can use Sendinc for free, and no software is required. Sendinc secures your message by ensuring that your data remains encrypted from the time it leaves your computer through the time your recipients retrieve it.
CryptoAnywhere
This is one of my favourite programs as it’s small enough to fit on a USB drive. If you don’t have your computer with you but still need to send that touchy email, make sure you have your CryptoAnywhere with you. With CryptoAnywhere you can send and receive secure email to and from anyone with an email account -- the recipients do not have to have Crypto Anywhere themselves.
Crypto Anywhere is free for personal and corporate use.
These are just some of the programs you can find out there, with lots popping up every day, thanks to Edward Snowden. However, keep in mind that many email programs and clients have an auto-save option, which save drafts before you send the message. Always make sure you write an email offline in a word processing app before sending the email.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: faithie / Shutterstock
-

Enterprise mobile apps to be in very high demand
Publié: juin 25, 2015, 11:48am CEST par Sead Fadilpašić

The demand for new enterprise mobile applications is about to rapidly increase, a new research shows.
Sponsored by Kony, the new 451 Research global survey of IT management, IT development and line of business professionals found that more than half of the 480 respondents, from North America, Europe and Australia, plan to deploy 10 or more enterprise mobile apps during the next two years.
However, it also revealed that IT departments are ill-equipped to meet the demand for mobile apps due to budget and resourcing limitations, skills gap, legacy infrastructure, overall technology fragmentation and immature lifecycle workflows.
That’s why many businesses look to outsourcing to meet the demands.
According to the study, the types of apps in highest demand by enterprises in all industries including, healthcare, financial services, insurance and retail, are customer relationship management apps for sales, marketing and services, customer engagement and general employee productivity apps.
A growing proportion of companies will look to IT for the bulk of their internal apps development. However, the mix of development diversifies beyond just IT, with 42 percent of mobile app development work being done outside of IT.
"The global market for enterprise mobility is expected to grow from $72 billion (£45.7bn) to $284 billion (£180bn) by 2019, nearly quadrupling in size", said Dave Shirk, president of Products and Marketing, Kony, Inc.
"Companies need to be prepared to meet this demand for mobile apps with proper alignment between lines of business, IT developers and IT management, to effectively manage and lead enterprise mobility projects. As the largest independent provider of enterprise mobility application solutions, Kony has successfully helped the world’s leading enterprises to effectively use mobility as a catalyst for business innovation", added Shirk.
The full report findings can be found on this link (PDF).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Maksim Kabakou/Shutterstock
-

5G networks will be ready in five years
Publié: juin 23, 2015, 9:53am CEST par Sead Fadilpašić

The International Telecommunication Union (ITU) has defined the fifth generation networks (5G) and decided to commercialize that technology by the year 2020.
ITU-R Working Party 5D of the UN’s telco arm finalized its 5G vision and rubber-stamped it as IMT-2020 at a meeting in San Diego, California last week, Total Telecom reported.
The union defined 5G as the network capable of speeds up to 20gbps (gigabits per second), and said the first demonstration of the new technology will come in 2018.
The 5G network will also have a capacity to provide more than 100 megabits-per-second average data transmission to over one million Internet of Things devices within one square kilometer. Video content services, including ones that use holography technology, will also be available thanks to the expanded data transmit capacity, the ministry said.
The ITU has determined the name of the 5G network as IMT-2020, following the IMT-2000 for the third-generation network and the IMT-Advanced for the fourth-generation one.
In a statement on Friday, the ITU said the next step is to establish detailed technical performance requirements for the radio systems to support 5G, taking into account a wide portfolio of future scenarios and use cases.
"The buzz in the industry on future steps in mobile technology -- 5G -- has seen a sharp increase, with attention now focused on enabling a seamlessly connected society in the 2020 timeframe and beyond that brings together people along with things, data, applications, transport systems and cities in a smart networked communications environment", said ITU secretary general Houlin Zhao.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Grey Carnation / Shutterstock
-

BitTorrent Shoot is a cross-platform photo sharing app
Publié: juin 18, 2015, 1:12pm CEST par Sead Fadilpašić

If you’re afraid of sending your photos to anyone over the internet, as all data is stored on some servers somewhere, you might like the new photo sharing app from BitTorrent.
The company best known for its torrent client and the BitTorrent Sync is offering an app called Shoot.
Shoot is available on Android, iOS and Windows Phone platforms, and it’s essentially a photo sharing app which uses QR codes for authentication and avoids the cloud.
With this app you can share your photos with your friends regardless of whether they’re using an iPhone, an Android device, or a Windows Phone device, but you need to be in close proximity to the recipient, as the app uses QR codes.
If you’re the sender, you choose the files you want to transfer and then your phone will display a QR code; the receiver scans it with their camera and the files move on over. The app uses BitTorrent Sync technology, meaning nothing goes up into the cloud.
Cross-platform image sharing is no big deal, as there are tons of apps out there which do the same thing, including Facebook’s Messenger, Viber, WhatsApp, as well as the good old MMS.
If you want to give it a shot, the app is available for $1.99 (£1.27). You can install the app for free to try it out -- you can send three photos, after which you’ll be prompted to pay to unlock the app.
QR codes have never really picked up and I’m quite interested to see how it works for BitTorrent.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

People are more interested in the iPod than the Apple Watch
Publié: juin 18, 2015, 10:09am CEST par Sead Fadilpašić
So apparently, people are more interested in dead things than the Apple Watch, and it’s a devastating statistic.
According to a chart for Apple, from Pacific Crest analyst Andy Hargreaves, people are more interested in the iPod than the Apple Watch. No, that was not a typo, I wasn’t trying to say iPad. I meant -- iPod, the thing that’s basically been dead for years now.
The interest was measured by Google Trends, back from mid-March to last week.
The Apple Watch was the company’s first new product since the launch of the iPad back in 2010. Even though the initial demand was strong, and the watch selling out basically everywhere, Hargreaves thinks the company probably won’t achieve its goals for this year.
"After strong initial demand, follow-on interest in Apple Watch appears mediocre", he says.
As Business Insider writes in a report, he believes Apple will ship some 11 million units by September, which is still pretty good. However, his view is "confidence" in the product is in a decline.
He thinks Apple could whiff on his estimate of Apple selling 24 million watches in fiscal year 2016.
Apple has done a great job marketing the new product, with demands running so high that it’s only been today since the watch could actually be bought in a store.
However, with critics saying the apps are slow and almost useless, and the watch itself not enhancing the phone in a way everyone expected, we could see the Watch ending up as complete failure.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

3D printing robots will build a bridge
Publié: juin 16, 2015, 5:30pm CEST par Sead Fadilpašić

Here is the craziest news of the day: robots will build a bridge over a canal in Amsterdam by 3D printing it in mid-air.
They will need no supporting structures. Dutch 3D printing R&D start-up MX3D has invented a 3D printing technique whereby multi-axis industrial robots are able to print strong, complex structures anywhere without needing a print bed, IB Times writes in a report.
The material used is a metal that melts and then solidifies within seconds, fast enough for it not to fall down into the water.
Aided by the geometry of the overall bridge design, the material is able to print horizontally without bending.
"We start with a piece of metal attached to the canal bank. The robots start from one side of the canal, they print their own support structure, so essentially it prints its own bridge. It stands on the floor of the bridge, 3D prints out more and keeps moving", MX3D’s CTO Tim Geurtjens told IB Times.
"We have the same physics as everyone else, but it looks like it’s gravity-defying. We put a drop of metal, drop by drop at a time and it solidifies. But you could also print tubes, and then print layer over layer of tubes", adds Geurtjens.
The 3D printed bridge project is a collaboration between MX3D, designer Joris Laarman, Autodesk, construction firm Heijmans and several other partners, including French welding specialists Air Liquide.
Geurtjens says MX3D's software could change the future of robotics. He said: "Our software translates CAD model software into welding strategies, and then translates that into the Rapid software used by ABB to tell the robot how to move".
Full report can be found over at the IB Times website.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Airbus demos its electric airplane
Publié: juin 16, 2015, 8:33am CEST par Sead Fadilpašić

If you thought cars were the only means of transport being pressed hard by the "green" idea of lowering CO2 emissions, you were terribly wrong.
Even though they’re not exactly the center of attention, airplane makers are also looking for ways to switch to electric-powered engines, and now Airbus has unveiled an interesting two-seater.
During the Paris Air Show, it unveiled the E-Fan 2.0 prototype aircraft. The all-electric vehicle claiming to be a "plug-in" plane that has a wingspan of 31 feet. In those wings lie 120 lithium-ion polymer batteries, powering twin 30kw engines that are capable of flight speeds up to 136 miles per hour.
The plane is crafted from carbon fiber composite materials, keeping the aircraft’s weight at an incredible 1100 lbs when empty.
The two-seater plane is nearly silent and has zero Co2 emissions, but is only able to stay up in the air for about an hour.
Even though this is not a commercial plane that could take you anywhere serious, it clearly shows Airbus' intent on completely switching to renewable energy.
The company says it wants to have a 100-seat electric passenger plane by 2050, and the E-Fan technology is currently being used by Airbus to build electric aircraft training models for flight schools.
A four-seater E-Fan 4.0 is also in the works and it scheduled for production by 2019.
Airbus introduced the first E-Fan with a YouTube video in April 2014 (which can be seen above), describing the training aircraft as a "highly innovative technology experimental demonstrator based on an all-composite construction".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

This is how you downgrade back to iOS 8.3 from iOS 9 beta
Publié: juin 11, 2015, 2:00pm CEST par Sead Fadilpašić
After Apple released the beta version of its latest operating system, iOS 9, many users wanted to see what the new release of their favorite OS brings.
However, as with any other beta version of any program out there, iOS 9 comes with untested bugs and broken features, making it unviable for daily use.
f you are among the curious bunch that tried iOS 9, and now want to go back to the tried and tested iOS 8.3 (the latest-available stable version at the time of writing this article), here’s how you do it:
Warning: Before proceeding, make sure you backup whatever information you have on your device. You never know when things can go haywire, and you don’t want to lose all those cat photos you’ve been saving for years on your iPhone.
- Download the latest version of iOS 8 for your device. All firmware can be found on this iClarified site.
- Launch iTunes on your Mac or Windows PC
- Boot your device into DFU mode (press and hold the Home button and the Sleep/Wake button at the same time).
- Wait for 10 seconds, then release the Sleep/Wake button. Continue holding the Home button until your device gets detected in recovery mode in iTunes.
- Press and hold the Alt/Option key (Shift in Windows) and then hit the Restore iPhone/iPad button.
- Choose the firmware file you downloaded earlier from the pop-up window.
- Click Restore button once again to confirm and continue with the restore process.
-

iOS Mail vulnerability lets hackers steal your passwords
Publié: juin 11, 2015, 8:43am CEST par Sead Fadilpašić

Users of iOS, beware. An unfixed vulnerability has been found in the Mail app, which allows hackers to steal passwords by sending an email.
The flaw was first noticed by Ernst and Young forensic bod Jan Soucek. He has created a tool capable of generating slick iCloud password phishing emails he says exploits an unpatched bug.
He has even recorded a proof-of-concept video.
He made an iOS 8.3 Mail.app inject kit. It exploits a bug in the native email app and can produce a realistic pop-up. Soucek explained that he first told Apple about the bug in January, but that the company had not responded or fixed the problem.
Now he has opted for a more extreme approach. The complete kit is available on Github.
"Back in January 2015 I stumbled upon a bug in iOS' mail client, resulting in HTML tags in email messages not being ignored", Soucek said.
"This bug allows remote HTML content to be loaded, replacing the content of the original email message. JavaScript is disabled in this UIWebView, but it is still possible to build a functional password 'collector' using simple HTML and CSS", Soucek added.
"It was filed under Radar #19479280 back in January, but the fix was not delivered in any of the iOS updates following 8.1.2", Soucek explains.
Hackers can now use the free tools to customize them and attack whichever iOS credentials they wanted. Unsuspecting Apple users would only get a security pop-up no different from the regular iCloud identification process.
Apple is yet to comment on the issue.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: D. Hammonds/Shutterstock
-

Future cars to be seen as 'a big moving mobile device'
Publié: juin 10, 2015, 7:33pm CEST par Sead Fadilpašić

As smart cars enter the mainstream, carmakers will have to work out a way to properly collaborate with start-ups, which means they have to start thinking like one.
That was the general conclusion of a TechCrunch/TechNode Shanghai panel when Juergen Bauer, who manages the Audi-Tongji Joint Lab in Shanghai, asked a panel of representatives from car companies about how the auto industry can handle the transition.
This could trigger a "fight of the titans", Tech Crunch writes in a report, as automakers and tech giants like Apple, Google, and Samsung negotiate for control over what goes into vehicles.
First step would be to find a way to integrate autonomous features into cars that won’t confuse drivers.
"Of course in the car, we have lots of opportunities to build things which you can integrate into the whole design and interior of cars. One thing is a very nice heads up display, which you can’t really reproduce in other ways now", said Carsten Isert, the head of BMW Technology Office China.
"On the other hand, we want customers to have the latest software and functionality, which you get from the big IT companies and start-ups, so again, we have to think about safety, which is a critical issue especially since many severe accidents are caused by using phones or texting while driving".
Drivers that spend a lot of time behind the wheel are perfect users for tech companies, but they must tread carefully when choosing what to put in a smart car.
This means that automakers can’t see the car as a vehicle anymore, but as a big moving mobile device", said Francis Man, the head of Interior Electronics Solutions in China for Continental Automotive.
The full report from panel, with quotes from PSA Peugeot Citroen’s David Allard and Carsten Isert, the head of BMW Technology Office China can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: RioPatuca/Shutterstock
-

Apple Music's killer feature is its price
Publié: juin 10, 2015, 1:19pm CEST par Sead Fadilpašić

As with all things Apple, there’s been a lot of talk about its new music streaming service, ingeniously named Apple Music.
After it got officially unveiled and showcased during this year’s annual Apple Worldwide Developers Conference (WWDC), the initial amazement was quickly replaced by a profound feeling of meh. Onstage the company said it would transform the listening experience for fans, and the creative act for artists, but once the hype died down it became obvious -- it’s not really offering features you can’t find elsewhere in the market. And then it hits you -- the price!
Apple offers a family plan that can be shared by up to six people for $14.99 (£9.89). Spotify and Rdio also offer family plans, but those cost $14.99 for two people and $29.99 (£19.60) for five.
The price triggered alarms in the heads of competitors. Apple’s biggest competitor hopes to match its offer. Speaking to The Verge, Spotify’s global head of communications and public policy, Jonathan Price confirmed the move.
"We already have similar family pricing in some markets and we expect to offer competitive pricing everywhere in the near future", he said.
He pointed out that in Sweden, Spotify already charges roughly $20 (£13) a month for a family of five.
This draws us to an interesting conclusion: either Apple has managed to negotiate an incredibly cheap deal with music labels worldwide, or it decided to hit at their savings to subsidize a very generous offer as means of killing the competition.
Either way, Apple forcing its competitors to further trim their already very thin margins.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Future cars will be able to detect your alcohol levels
Publié: juin 9, 2015, 4:50pm CEST par Sead Fadilpašić

In the future, your car might decide if you’re capable of driving, or drunk out of your mind and unable to drive 200 metres without looking like a GTA character.
The National Highway Traffic Safety Administration (NHTSA) revealed an alcohol-detection technology that it wants to implement in future vehicles. If the technology detects you’ve been drinking, it can decide not to start the car at all.
Named DADSS (Driver Alcohol Detection System for Safety), the program can detect if the person behind the wheel is intoxicated beyond legal limit in two ways. One is a breathalyzer attached to the steering wheel that analyses the driver’s breath. The other is a sensor on the ignition button that will similarly detect BAC levels using infrared light to scan the finger. In both cases, the car’s engines are locked down if the driver is found to be alcohol impaired.
Alcohol-impaired driving crashes kill nearly 10,000 people annually, NHTSA says in a press release, adding that this alcohol-detection vehicle technology could potentially save thousands of lives each year.
"This is a perfect example of why we at DOT are bullish on technology", said U.S. Transportation Secretary Anthony Foxx. |Education, awareness and enforcement have succeeded in dramatically reducing drunk driving fatalities, but the advanced technology of DADSS brings enormous potential to save even more lives".
The NHTSA isn’t looking to make this technology mandatory. Still, it’s already being opposed by those concerned with the reliability of simply measuring BAC levels without context. Each person processes alcohol differently, so an outright reading of DADSS might not be accurate.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

EU pushes forward with net neutrality plan, removal of roaming fees
Publié: juin 9, 2015, 1:28pm CEST par Sead Fadilpašić

European Commissioner for Digital Economy and Society, Günther Hermann Oettinger, is set to meet with national ministers next Friday to try and end the deadlock between national ministers and MEPs on the subject of net neutrality.
Negotiations on the so-called Telco Package had ground to a halt on Tuesday night when national representatives from the Council and those from the European Parliament failed to compromise on net neutrality or roaming charges, The Register writes in a report.
"The law has been so mangled by various revisions that these two elements are all that’s really left of a raft of legislative proposals. With so many aspects chipped away, the Commission now plans to launch a separate policy initiative in 2016", it says.
"Commissioner Oettinger and Latvian Minister Matiss have invited telecoms ministers for an informal breakfast on Friday to discuss the situation and to make further progress", said Nathalie Vandystadt, spokeswoman for the Commission. "The European Commission continues supporting the most ambitious approach: we need to end roaming charges and get strong net neutrality rules as soon as possible. We should not disappoint Europeans, who are waiting for the end of roaming charges as soon as possible. They also want their access to the open internet to be ensured. This is why we need strong net neutrality rules".
Civil liberties groups have congratulated MEPs for taking a firm stance on the net neutrality issue:
"MEPs have clearly affirmed that they will not accept the least common denominator proposed by EU member states on roaming and net neutrality. This is an important decision -- and OFE congratulates the Parliament for its firm stance -- but one that brings policy debates to a dangerous deadlock", said Graham Taylor, CEO of OpenForum Europe.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: mindscanner / Shutterstock
-

Adware spreading through Skype links
Publié: juin 8, 2015, 8:21am CEST par Sead Fadilpašić

Skype users, beware. There are nefarious links being spread around through Skype, and if you click them you will be presented with a lot of adware. However, there are good news, and bad news here.
Researchers at the security behavior management company PhishMe have identified a campaign in which Skype was used to distribute adware, SC Magazine reported on Wednesday.
The threat was first discovered when one PhishMe user received a message over Skype, where the other party tried several times to contact him.
The attacker was trying to call with a username that also contains a link to a domain, www.viewror[d]com. Once clicked, a voice directs the user to click the download link and install a "proprietary" video player in order to play the video.
"This download is part of an affiliate program where the attacker is probably getting money on a per-install or per-download basis", it says on the PhishMe website.
Once the executable is opened, it asks to run as administrator. The user is presented with a screen to install different aspects of the program, all of which are pieces of adware, PhishMe says.
Those were the bad news, and now for the good ones: The researchers contacted Microsoft as well as Amazon, which was hosting some of the domains where the attacks and spam were coming from.
Together, the two companies are disrupting this scheme by nuking the Skype accounts involved and going after the IP addresses used.
As usual, most security breaches start with a phishing attempt, where an unsuspecting victim clicks and instals malicious software. Be careful and double-check anything you receive in mail, over Skype or any messenger service, before installing.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

20,000 London police officers will wear body cameras
Publié: juin 5, 2015, 2:22pm CEST par Sead Fadilpašić

Police in London are about to be equipped with 20,000 cameras on their bodies, together with tablet computers, improved computer systems and 999 text messages.
No, of course a single police officer won’t be wearing all 20,000 of them.
London’s mayor, Boris Johnson, announced the plans following a successful testing phase, in which 1,000 officers were equipped with chest and head-mounted cameras.
Johnson claimed that the cameras have shown their potential to reduce complaints and increase the number of early guilty pleas, helping to speed up the justice process.
"This is exciting technology that will build trust, help the police do their jobs, and allow the public to hold officers more accountable", he said. "Our plans for the rollout of body-worn video will make the technology available to more officers in a single city than anywhere else in the world, and is a giant step towards a truly 21st century police force for London".
“For too long our equipment has lagged behind the technology almost everyone has in their pockets to capture events as they unfold", explains Johnson. "Soon, more of our officers will be able to make a record of the very challenging circumstances they are asked to deal with on a daily basis and then demonstrate, more effectively, the reality of policing our capital".
"It will also improve public scrutiny of how we carry out our role. That is a vital part of being an accountable police officer. It is also an essential tool in gathering evidence of offenses", adds Johnson.
The project, part of a technology strategy overhaul, is worth £200 million.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Dutourdumonde Photography/Shutterstock
-

The cost of cyber attacks is rising dramatically
Publié: juin 4, 2015, 2:13pm CEST par Sead Fadilpašić

The cost of a cyberattacks to businesses has more than doubled in the past year, a new report by PWC says.
The Department for Business, Innovation and Skills (BIS) commissioned the survey which has shown that not only has the cost doubled, but the number of security breaches has increased.
To make things even worse, 11 per cent of respondents changed the nature of their business as a result of their worst breach.
The average starting costs for a major security breach at large organizations rose to an average £1.46 million, up from £600,000 last year. Smaller firms were no less immune to the financial drain caused by a cyberattack. The minimum they could expect to pay last year for the most extreme breaches jumped to £310,000 from £115,000 in 2014.
The costs include covering business disruption, lost sales, recovery of assets, fines and compensation.
Speaking to The Telegraph as the report was launched, Ed Vaizey, Digital Economy Minister, said: "The UK’s digital economy is strong and growing, which is why British businesses remain an attractive target for cyberattack and the cost is rising dramatically. Businesses that take this threat seriously are not only protecting themselves and their customers’ data but securing a competitive advantage".
The survey also found that 90 percent of large organizations suffered a cyberattack over the year, a rise of nine percentage points. For small businesses the figure was 74 percent, up from 60 percent a year ago.
Among the greatest areas of vulnerability are our growing dependence on mobile devices, as well as human error.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: arda savasciogullari / Shutterstock
-

Microdia unveils 512GB microSD card, might cost $1000
Publié: juin 4, 2015, 11:42am CEST par Sead Fadilpašić

Only day has passed since I wrote a story about SanDisk squeezing an impressive 128GB into a USB drive the size of a penny, and now Microdia has to come to steal the limelight.
Cnet visited the Computex event in Taipei and came across the Microdia stand. There it saw a microSD card "that stuffs 512GB worth of storage space into a piece of plastic smaller than your fingernail".
Of course, the card of such capacity won’t come cheap -- Microdia says it estimates the Xtra Elite will cost around $1,000 -- which converts to around £655 -- when it goes on sale in July, though that’s not the final retail price.
The Xtra Elite will use version 4.0 of the Secure Digital standard, and feature an Ultra High Speed (UHS) bus with data transfer rates of up to 300MBps.
Using SD 4.0 means the card will feature an additional row of pins below the standard ones.
However, even though you might like what you see and don’t mind whipping out the thousand, if you’re not a professional photographer, Microdia is not targeting you with this product.
As Cnet writes, Microdia expects the card to be mostly used by professional photographers who will appreciate the fast transfer speeds. Because of its diminutive size, you’ll want to be extra careful it doesn’t go missing.
A few days ago SanDisk unveiled its dime-sized drive capable of storing 128GB of data (the same as the latest MacBook Air or a top-end iPhone). The SanDisk Ultra Fit costs $120 (£78).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

SanDisk's dime-sized Ultra Fit drive now available with 128GB option
Publié: juin 3, 2015, 12:00pm CEST par Sead Fadilpašić

When it comes to squeezing megabytes into a tiny space, SanDisk takes the crown, as it managed to fit 128GB of storage into a dime-sized drive.
Just look at the photo above -- these two items are placed next to each other. However, the SanDisk Ultra Fit is something we’ve seen before, but never capacities this big. We’ve seen 16GB, 32GB and 64GB variants.
But this time SanDisk made a 128GB version, enough to fit 16 hours of full HD video or 18,000 standard MP3s. Lets not forget that MacBook Air offers 128GB of storage, as well as the top-end iPhone.
According to SanDisk’s director of product marketing Phillippe Williams, the trick is to take the full advantage of the device’s height, as well as its length.
"Using proprietary technologies, our memory die are vertically stacked—each of which is shaved to be thinner than a strand of hair", Williams explained to Wired over email. "Fitting more memory into the same form factors is one of our in-house skill sets... While Moore’s Law allows us to regularly increase capacity, the work we do on packaging and product design accelerates this".
The Ultra Fit is intended as a "plug-and-stay" device, acting as an ever-present storage boost rather than a portable solution.
"You could see this as being particularly attractive in emerging markets, where price is an even more important consideration", says Williams.
Stepping up from 128GB to 256GB on otherwise identical MacBook Airs costs $200, a full $80 more than just buying the base model and augmenting with an Ultra Fit.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Self-driving cars are vulnerable to hacker attacks
Publié: juin 2, 2015, 11:07am CEST par Sead Fadilpašić

Here’s an interesting prospect: You’re sitting comfortably in your autonomous vehicle, minding your own business, reading your favorite news site on your fancy new tablet, when all of a sudden -- your car hits a wall and you end up in intensive care for the rest of the month.
Cause? A hacker broke into your car and made it accelerate instead of brake, when it encountered an obstacle on the road.
Even though unlikely, especially as these cars won’t hit the streets for the next five years, this scenario is a possibility, security experts have warned.
US security firms Mission Secure Inc (MSi) and Perrone Robotics Inc say the new self-driving technology elements (cameras, a radar, sonar, LiDAR and everything else a driverless car needs) which were meant to make the cars safe and reliable, could end up leaving them vulnerable to hacker strikes.
The two security companies, working with the University of Virginia and the Pentagon, have run tests that have shown they believe it is possible to hack into and disrupt the multi-sensor system, Business Insider writes.
One trial was to change how the car responded when it encountered an obstacle.
"One attack scenario forces the car to accelerate, rather than brake, even though the obstacle avoidance system (using LiDAR) detects an object in front of the car. Rather than slowing down, the car hits the object... at high speed, causing damage to the car and potential threat to the life and safety of the passengers in the car under attack and in the car being struck", according to the report available on MSi’s website.
"If an attack were carried out successfully, automobile manufacturers have no means of quickly gathering information for forensic analysis or to rapidly deploy additional protections to cars in response to new and evolving attacks", the report warns.
Car makers are well aware of this issue and are working hard to make sure cars stay safe. For example, Google has a team of top programmers tasked with only trying to hack into the car’s software.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: RioPatuca/Shutterstock
-

IRS hack exposes personal data of more than 104,000 taxpayers
Publié: mai 28, 2015, 6:11pm CEST par Sead Fadilpašić

Hackers stole personal information from more than 104,000 taxpayers this spring, the International Revenue Service (IRS) just revealed.
Commissioner John Koskinen said in a press conference that the information included several years' worth of returns and other tax information filed with the IRS, and explained exactly what happened.
The thieves hacked into a system called "Get Transcript", clearing a security screen that requires users to know the taxpayer’s Social Security number, date of birth, address and tax filing status.
They tried to access information from 200,000 taxpayers, and successfully got information on 104,000 of them.
Those who successfully downloaded the transcripts gained access to information from prior years' tax returns that could be used to file fraudulent tax returns that more closely resemble those of legitimate taxpayers, officials said.
The system, which is now shut down, was targeted from February to May. While the system is shut down, taxpayers can apply for transcripts, sometimes needed for tax returns and mortgage applications, by mail.
"To get these, our criminals already had to have personal identifiers available and personal information for each taxpayer", Koskinen said, adding that whoever’s behind this is definitely not an amateur.
"We’re confident that these are not amateurs but organized crime syndicates that not only we, but others in the financial industry are dealing with", he said.
The criminals were able to use the information to submit fraudulent tax returns, he said, adding that the IRS is notifying taxpayers whose information was accessed, and providing them with credit monitoring services.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Mark Van Scyoc/Shutterstock
-

Strange things happening during Lyft, Uber rides
Publié: mai 28, 2015, 4:32pm CEST par Sead Fadilpašić

An average Lyft or Uber passenger can come across some really strange and hilariously twisted things, and for some of us reading these experiences is quite entertaining.
That’s why I would like to personally thank Hilary Mason for creating Twitter bots that retweet when someone includes the words "my uber driver" or "my lyft driver".
The two bots that can be found at these two links retweet some extremely hilarious content, like this guy asking around for orgies, this middle-aged man listening to Hannah Montana, or this generous individual who gave weed to her passenger.
And those are just things happening on Uber rides. Lyft has its share of dubious content.
"Why did my lyft driver try to convince me to let him do hypnotherapy on me last night?", asks one user, while another one was worried about what his driver was doing.
"Lol ok my @lyft driver today has a breathalyzer machine in his car that he had to blow in while driving. This company is a joke", he tweeted.
Mason, the founder of Fast Forward Labs, created two twitter bots for fun, Business Insider quotes her saying. "It’s really simple. It was just a fun, frivolous project".
"The particular demographic of people who use these services are going to say funny things", Mason said. "We all have our own experiences, but here’s a little taste of what the world sees".
Uber did not respond with comment, while a Lyft spokesperson said that "Our social support team actively monitors all mentions of Lyft on social media and immediately follows up with both drivers and passengers to answer questions and resolve any issues".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Elon Musk is afraid Larry Page might end up destroying the world
Publié: mai 26, 2015, 4:05pm CEST par Sead Fadilpašić

When SpaceX and Tesla founder Elon Musk recently said that with artificial intelligence we’re "summoning the demon", he wasn’t joking.
He was genuinely concerned about artificial intelligence turning against humanity, and according to a new book by Ashlee Vance, he still is.
In his new book, Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic Future, Bloomberg reporter Ashlee Vance recalls a dinner conversation he had with Musk, and here’s what he wrote:
He opened up about the major fear keeping him up at night: namely that Google’s cofounder and CEO Larry Page might well have been building a fleet of artificial intelligence-enhanced robots capable of destroying mankind.
“I’m really worried about this,” Musk said. It didn’t make Musk feel any better that he and Page were very close friends and that he felt Page was fundamentally a well-intentioned person and not Dr. Evil. In fact, that was sort of the problem. Page’s nice-guy nature left him assuming that the machines would forever do our bidding. "I’m not as optimistic", Musk said. "He could produce something evil by accident".
Vance said Musk was always keeping an eye on artificial intelligence. On the other hand, Google’s CEO Larry Page has a different perspective on the whole AI thing.
Truth be told, artificial intelligence in some form already exists -- there are dozens of programs learning how to manipulate big data every day, and turn it into meaningful insights. The problem lies in that artificial intelligence being implemented in robots capable of movement.
Musk isn’t the only figure in science and technology that feels strongly about the idea that artificial intelligence should be approached with caution. Microsoft co-founder Bill Gates and Stephen Hawking have both voiced similar opinions.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Daimler and Qualcomm to introduce wireless charging in cars
Publié: mai 26, 2015, 1:09pm CEST par Sead Fadilpašić

Car maker Daimler has announced that it’s partnering up with mobile tech company Qualcomm to bring wireless charging to mobile phones in cars, as well wireless charging to the vehicles themselves.
The move comes in time of increased pressure towards carmakers to downsize their engines due to tightening emission rules, Reuters writes in a report.
In a joint statement, Daimler and Qualcomm said they were assessing the application of wireless technology to charge their electric vehicles (EV) and plug-in hybrid EVs without ever having to plug them in.
The companies also said they were exploring ways to wirelessly charge other devices, such as smartphones and tablets inside the vehicle, as well as ways to enhance in-car experience through high-speed 3G/4G connectivity.
"It’s important that we remain on the cutting edge of technology and continue to deliver unparalleled experiences to our customers", Daimler’s board member for research and development Thomas Weber, says.
"With this in mind, we are eager to jointly explore possible fields of future cooperation with an internationally leading tech firm like Qualcomm", Weber says in a statement.
"The automobile has become a mobile platform and an extension of always-on connectivity", says Qualcomm president Derek Aberle in a statement announcing the deal.
Back in 2010, Qualcomm acquired WiPower, a technology for wireless in-car device charging.
As green and renewable energy sources move higher into the mainstream, the automobile industry is looking increasingly at risk of falling behind. However, with electric cars, autonomous vehicles and wireless charging, cars most likely won’t stay behind for long.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Bocman1973/Shutterstock
-

How to back up all your Gmail emails
Publié: mai 22, 2015, 9:17pm CEST par Sead Fadilpašić

Gmail might be the most popular email service in the world, but even the biggest players fall sometimes, and once that happens, the little guys will be there to cheer.
Server outages and crashes have happened before, and even though Gmail is generally seen as a solid, well-built and stable product, it too can crash, leaving you without all those precious emails you’ve been saving.
If you’re keeping some really important stuff on your Gmail account (and I’m guessing a lot of you are, as 425 million of you are using the service), you might want to consider backing that mail up every once in a while, just in case.
There are a couple of ways to back up your emails, and the easiest one would be to use an email client, be it Microsoft Outlook, Mozilla Thunderbird or any other. The other way is to download a third-party email backup app to do the bidding for you.
So without further ado, let’s get down to it:
Back Up Using Desktop Email Clients
If you’re using Microsoft Windows, you probably have Outlook installed. Outlook is an email client with the very useful feature of downloading all your mails to your hard drive. All you need to do is link it up with your Gmail account in a few quick steps and you’re safe. Here’s what you need to do:
- Open your Gmail account in the browser
- Press Settings (the gear icon) and navigate to Settings
- Go to Forwarding and POP/IMAP tab and press Enable IMAP
- Save changes
- Open Outlook
- File > Info > Add Account
- Add your Gmail account: Select the bubble directly left of the e-mail account option and enter your name, Gmail address, and password.
- Press Next, Finish.
Now all you need to do is occasionally run Outlook so that it downloads your emails.
On a Mac
OS X works on a principle similar to Windows:
- Launch the Mail app
- Mail > Preferences > Accounts
- Select Google from the list of available mail accounts, and enter your name, Gmail address, and password before clicking the Set Up button in the bottom right-corner of the window.
Done. Now you should occasionally open the app to download your mails.
The other way to back up your emails is to use third-party software such as Gmail Backup, Fetchmail, Backupify or Gmvault Gmail Backup.
All of these apps work in a similar fashion to your email clients and require your account’s credentials in order to work.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Bloomua/Shutterstock
-

SURE turns your Android device into a universal remote
Publié: mai 21, 2015, 5:56pm CEST par Sead Fadilpašić
You can turn your tablet or smartphone into a remote and control every smart device in your home, thanks to a new app available worldwide now.
Tekoia, the provider of smart universal remote solutions for digital media, smart appliances and the Internet of Things, has announced it launched SURE globally.
SURE is an Android-only app which enables users to control all smart house appliances such as TVs and sound systems.
Using IR and WiFi technology, SURE can control smart TVs such as LG and streaming products such as Roku. Users can control their Roku 3 through WiFi and stream pictures, videos and music from their phone to their TV. This basically means users can achieve advanced smart TV functionality with Roku and SURE even if they don’t have a smart TV.
SURE can also be used as a keyboard when supporting the Roku service to simplify searching. For LG smart TVs, SURE can also serve as a mouse, allowing for games to be played with a wave of the hand using the user’s smartphone.
SUREs biggest advantage is the fact it can replace many remotes that come with various devices. With SURE you no longer need dedicated remotes for different devices. The app is, as the official press release puts it, "simple-to-use, slick and intuitive". It is available for Android-powered devices for free, and can be found at this link.
"The remote control like many products before it is outdated and it became apparent to us that the smartphone is becoming much more augmented with every new model, so why not have it replace our remote controls as well?", says Viktor Ariel, CEO, Tekoia.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Facebook could allow businesses to contact you through WhatsApp
Publié: mai 20, 2015, 3:32pm CEST par Sead Fadilpašić

Facebook said it might allow businesses to contact users through their chat app WhatsApp, Bloomberg said in a report on Tuesday.
This might be the first hint on how the social media giant plans on making money off the app that it bought for $22 billion (£14 billion).
Facebook is currently testing some features in its standalone messaging app Messenger, and one of the features is business-to-consumer interaction which marketers can pay for. These features could find their way to WhatsApp, as well.
"We think that enabling that business to consumer messaging has good business potential for us", Wehner said at the JPMorgan technology conference in Boston earlier this week. "As we learn those things, I think there’s going to be opportunities to bring some of those things to WhatsApp, but that’s more longer-term than the near-term".
WhatsApp currently sits with 800 million users, but Mark Zuckerberg said it needed at least a billion to be a "meaningful business". However, the business is growing rapidly (the app had 600 million users last August), so it’s fairly realistic to expect WhatsApp hitting one billion users before the end of the year.
In October, Facebook for the first time disclosed financial information for the messaging service, revealing, for example, that WhatsApp made nearly $16 million in revenues during the first half of 2014 but lost $232 million (£149.5 million) during the same period, mostly from stock-related expenses, Mashable says in a report.
The situation looked pretty similar for 2013, when the company generated $10.2 million (£6.5 million) in revenues for the year but likewise hemorrhaged $138 million (£88 million), also from stock-related expenses.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: kraphix/Shutterstock
-

10 things you don't know about Facebook
Publié: mai 18, 2015, 2:07pm CEST par Sead Fadilpašić

For a site like Facebook, which has become sort of a synonym for the Internet itself, it’s hard to say there are things we still don’t know about it. Everything’s already been said, everything’s been discovered and the site is as transparent as it gets.
But there are still things we (or at least some of us) still don’t know about it, and those include some awesome, but long lost and forgotten options the site has to offer, like:
1. Facebook Used to Be College Only
You may have known that Facebook was built by then-college student Mark Zuckerberg in his dorm room, but what you may have not known is that he built it to connect with his college friends first, then it was expanded to other colleges before becoming available to all.
2. Get Paid to Find Bugs
The company takes security very seriously, but even with thousands of employees and some of the best software engineers working there, there is always a possibility of a breach. That’s why Facebook offers anyone (and everyone) a solid reward for finding a bug in their system.
3. The Pirate Option
Newer users might not know this, and older may have never seen the feature in action, but you could switch Facebook’s language to Pirate. Yes, the site has numerous language options, including English (Pirate), in which a simple Yes would be transformed into Aye, if memory serves me well. Arrrr.
4. The Facebook Guy Is Actually Al Pacino
Remember The Facebook Guy? The original image of anyone freshly registered to the network was an image of a male, slightly hidden behind a wall of binary code. While everyone thought it was Mark Zuckerberg on the photo, it was actually Al Pacino in his early days.
5. Zuck’s Page Shortcut
A couple of years ago, Facebook enabled its pages to get custom shortcuts, so instead of having to type in www.facebook.com/pages/01234549134 or whatever, you could have named your page something more meaningful. The company’s founder Mark Zuckerberg also gave his page a custom link (of course), which is facebook.com/zuck. However, you can also access it via facebook.com/4, and no one knows why the number 4 was used -- and not 1 -- or any other number for that matter.
6. Teens Ran Away…
With Facebook being increasingly used by older people (in older I mean those with kids), teens started moving from the network to other ones, not used by their parents and grandparents, in an attempt to avoid embarrassing comments by family members on their half-naked bathroom selfies.
The results of a survey conducted by Piper Jaffray that were released in April of 2015 stated that only 14 percent of teenagers polled claimed that Facebook was the "most important" social network. That number was 33 percent in 2013.
7. ...But Teens Are Still Here
However, although it might not be the most important network for them, 71 percent of teens still use it, according to a 2015 Pew survey.
8. MySpace Could Have Bought Facebook
Remember MySpace? Of course you don’t, it’s as old as the Old Testament, but that used to be the social network before Facebook was cool. Back in the day, Zuckerberg offered TheFacebook to MySpace for a measly $75 million (£47 million), but its CEO Chris DeWolfe turned the offer down.
9) There’s a Facebook Graveyard
People die every day, and with more than a billion of us using Facebook, its users also die every day. But what happens to a Facebook profile after you’ve gone? The company offers two choices: one is to turn the site into a page, a memorial of sorts, where people can leave wall posts and post pictures. The other choice is to delete the profile completely, but in order to do so, Facebook will need proof the person is actually dead.
10) Like Was Almost Awesome
One of the biggest features Facebook has today is the Like button. When the company first thought about implementing a feature where people could acknowledge someone’s post without actually leaving a comment, they thought about the word Awesome. Zuckerberg didn’t like idea. See what I did there?
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: JuliusKielaitis / Shutterstock
-

Alibaba has to expand globally, or it 'won't be able to last'
Publié: mai 15, 2015, 6:25pm CEST par Sead Fadilpašić

Even though it reigns supreme in one of the world’s largest markets, China, Alibaba wants to expand globally. If it fails to do so, it might not survive, the company’s new CEO said recently.
In a speech given to employees on Wednesday, the new Alibaba CEO Daniel Zhang said Alibaba will heavily invest in "new and existing overseas operations".
In his speech, Zhang said he wants to recruit talent from other countries and adopt "global thinking". If the company can’t globalize, then Alibaba won’t last, he said. "We need to have global talent", he said.
"'We must absolutely globalize and it must be a successful effort -- if not Alibaba won’t be able to last' for more than 100 years, one of Alibaba Executive Chairman Jack Ma’s loftiest corporate goals".
Alibaba is mostly focused on the Chinese market, where it operates two online retail sites, Tmall.com and Taobao Marketplace. The company has slowly been expanding into other markets, where it will eventually have to clash with the likes of eBay and Amazon.
It already has its AliExpress site, an English-language e-commerce platform that sells Chinese-made goods to international customers. And it has been courting foreign brands to sell through its Tmall site.
The company is also making a strong push into cloud computing. It already provides cloud and big-data analytics services to 1.4 million customers in China, and Aliyun, the company’s cloud-computing arm, recently opened a data center in Silicon Valley and this week announced a technology joint venture in Dubai.
"This year, I think it’s very important that cloud computing keeps growing its number of customers, the quality, efficiency", Zhang said. "Cloud computing is taking off, I have confidence that (it) can become as important as e-commerce and finance because big data is our basic, fundamental, important platform".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Nonnakrit/Shutterstock
-

Our attention span is shorter than that of goldfish
Publié: mai 15, 2015, 4:45pm CEST par Sead Fadilpašić

The results of a recently conducted study have shown that our attention span is... oh wait, I lost you.
That’s right. Our attention span has dropped from 12 seconds back in 2000, to an alarming eight seconds today. To put things into perspective, a goldfish’s attention span is nine seconds. So yes, a goldfish can read this article longer than you do without getting bored to death and opening Facebook.
These are the results of a study recently conducted by Microsoft. The company surveyed 2,000 people and used electroencephalograms (EEGs) to monitor the brain activity of another 112 in the study, which sought to determine the impact that pocket-sized devices and the increased availability of digital media and information have had on our daily lives, The Independent writes.
You guessed it, smartphones and tablets and other gadgets are to blame.
"Canadians [who were tested] with more digital lifestyles (those who consume more media, are multi-screeners, social media enthusiasts, or earlier adopters of technology) struggle to focus in environments where prolonged attention is needed", the study reads.
"While digital lifestyles decrease sustained attention overall, it’s only true in the long-term. Early adopters and heavy social media users front load their attention and have more intermittent bursts of high attention. They’re better at identifying what they want/don’t want to engage with and need less to process and commit things to memory", it says in the report.
On the bright side of things, our ability to multi-task has drastically improved in the information age.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Volt Collection/Shutterstock
-

Worried about damaging your Apple Watch? Get a case for it!
Publié: mai 14, 2015, 10:20am CEST par Sead Fadilpašić

Our smartphones might need protection, as their displays can be scratched by keys in our bags and pockets. We might also drop them in a moment of inadvertency, or we might slip whilst texting and go down, bringing the expensive device down with us.
But what about a smartwatch? Does the smart wearable device which has no contact with car keys and has close to zero chance of falling to the ground need protection?
Well, case maker Speck thinks it does, and has created a case for the Apple Watch.
The case is the CandyShell Fit, and the design incorporates several of the elements which make Speck’s iPhone CandyShell cases stand out.
The shell is made from hard polycarbonate and acts like a bumper for the body. It has a raised 1.5mm lip surrounding the Watch’s display, to make sure we don’t scratch it.
However, it doesn’t cover the Digital Crown, the screen, or the heart rate sensor on the rear, ensuring the Watch can be operated as normal.
Speck has made sure the case is easy to put on and take off and once released, the case will be available for both the 38mm and the 42mm Apple Watch, and it will be suitable for the Watch, Watch Sport, and the Watch Edition.
The release date hasn’t been confirmed, but you can expect it sometime before the end of May, for the price of $30 (£19).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Vatican believes that open source is the way to preserve history
Publié: mai 9, 2015, 8:42am CEST par Sead Fadilpašić

Vatican wants to save the human history in a digital form, and the best way to do so is to use open-source, non-proprietary software that will still be easily accessible and usable in 50 years, it says.
During the EMC World conference in Las Vegas, Vatican Library CIO Luciano Ammenti argued his case. A total of 82,000 manuscripts were digitized, as there was never enough room in the reading rooms.
"The Vatican Library is a conservation library. We try to preserve our history. We tried to expand the number of reading rooms available for people that want to use our library", The Inquirer quotes him saying. "But we realized that reading rooms will never be enough. We have 82,000 manuscripts in total, and at any one time only 20 percent of them can be read in the library. To get round this over the last few years we’ve had a focus on conservation of the manuscripts in digital form".
"The main question at the start of our project was which format to save the texts. We needed to make sure people could still read the digital files in 50 years’ time".
So they chose to go for images, as images can always be looked at.
"We save it as a picture as it’s longer life than a file. You don’t rely on PowerPoint or Word. In 50 years they can still just look at it,"he said.
"Normally people try to use the TIFF format when archiving. This has several problems. It’s not open source and it doesn’t update. The last time was in 1998. On top of this it’s 32-bit and not ready for 3D imaging, which limits the information it can preserve -- what the script’s made of etc. So instead we use the FITTS format. FITTS is open source, 64-bit, 3D ready and updated regularly. It gives all the information you need on the image".
Image Credit: cesc_assawin / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Tesla Powerwall already sold out for 2015
Publié: mai 8, 2015, 8:34am CEST par Sead Fadilpašić

Just a few days after it was announced, the Tesla Powerwall battery has already been sold-out for the next year. Now that’s what I call a good business deal.
The company received more than 38,000 reservations for the Powerwall, said Tesla’s CEO Elon Musk during its first quarter earnings call. The reservations include some 2,800 businesses looking to buy the Powerpack, which is a commercial version of the battery.
"The volume of demand here has just been staggering", The Verge quoted Musk saying. "It really feels like, man, the stationary storage demand is just nutty. Like, worldwide, it’s just crazy".
Musk said he expected the product to appeal more to industrial companies rather than individual companies. "We expect most of our stationary storage sales to be at the utility or industrial scale," he said.
Tesla Powerwall is a battery which stores excess energy created from solar panels and wind turbines during peak hours. That energy can later be consumed at the time when the production is at a low, during dusk, dawn or night. "As most of you probably know, the sun doesn’t shine during the night, and it’s a problem we should address", said Musk during the Powerwall introduction.
The strength of the Tesla product and its extremely competitive price have been making headlines ever since it was introduced last Friday.
The company says its Powerwall home battery system can untether your home from the power grid for a few hours, which might not sound like much, but could have huge implications for the way we power our lives.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Majority of UK companies will miss the Windows Server 2003 deadline
Publié: mai 1, 2015, 5:31pm CEST par Sead Fadilpašić
Two thirds of UK companies will continue running Windows Server 2003, after Microsoft cuts the support for the service on 14 July, a recent report has shown.
The continued use of a program with no developer support leaves the user open to many risks, it says in the report called Windows Server 2003 (WS2K3) End-of-Life Survey, conducted by endpoint security specialist Bit9 + Carbon Black.
A total of 153 UK organizations were surveyed. Out of that total, more than two-thirds of those organizations running Windows Server 2003 today will still be using it after the end of support deadline, and of those that are planning to upgrade, more than a third will miss the deadline by the time their project has been completed.
Just under a quarter of those still running WS2K3 after the end of support deadline have no plans to put any compensating controls in place -- leaving them at serious risk of a security breach.
Servers, including domain controllers and web servers, are where most organizations’ critical information resides. So if organizations continue to run Windows Server 2003 without implementing appropriate compensating controls -- such as application whitelisting -- they will put customer records, trade secrets, and other highly valuable data at risk. Cyber criminals, hacktivists and nation-states prey on unprotected servers, leaving enterprises exposed to potentially catastrophic breaches that can lead to lawsuits, regulatory fines and loss of customer trust.
The worst part of it all is that once an exploit has been found, hackers can keep using it as no patch is being prepared, ever.
If these companies wish to keep their businesses up and successfully running, there are some things they can do.
For enterprises looking to address Windows Server 2003 end of life without upgrading, they should consider compensating controls to keep their systems secure and compliant after Microsoft support ends.
Effective compensating controls for organizations without an upgrade plan include: network isolation, application whitelisting, and continuous server monitoring.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Android Wear: How to set up your smartwatch
Publié: mai 1, 2015, 1:03am CEST par Sead Fadilpašić

So you’re thinking about getting yourself an Android Wear smartwatch, but you're not sure if it’s too complicated to set up?
The truth is it’s a very simple device and setting up is no different than, say, setting up an app on your smartphone.
Anyone who tried out a Galaxy Gear from Samsung last year is familiar about how this goes.
- Before anything, make sure that your smartphone is compatible with the Android Wear watch.
- You’ll then need the companion app and the new version of Google Play Services. The latter should install itself automatically once you’ve begun.
- The former can be downloaded using this link. The download and installation process is no different from any other app out there.
- During the installation process, you’ll need to give permission for the app to do things like recognize your contacts or track your position; they are necessary in order for the app to work properly.
- Once you have installed the app, turn on Bluetooth on both of your devices.
- You should see your Android Wear smartwatch listed as an available device, and you might see other devices nearby.
- Choose the Android Wear smartwatch, and you’re automatically connected to your smartphone through the device’s Bluetooth connection.
- One more thing you should do is go through the notifications tutorial, to see how to enable notifications on your smartwatch.
After that, you’re directed to look at your watch and to familiarize yourself with the various settings and functions.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Joe Wilcox
-

LG G4 vs Samsung Galaxy S6: Which flagship has the better camera?
Publié: avril 30, 2015, 8:53pm CEST par Sead Fadilpašić

Samsung’s Galaxy S6 is a great device, no doubt about it. It has all the elements needed for a great smartphone: a large, high quality display, powerful processor, a great operating system with countless features, and two amazing cameras.
However, the competition out there is merciless. Apple has hit the South Korean giants hard with the iPhone 6 and 6 Plus models, and now the LG G4 seems to be out for blood, as well.
The G4 hasn’t even been properly unveiled yet, and Forbes has already made a detailed comparison of the cameras on the two smartphone heavyweights, and even though LG has some hardware advantages over the Galaxy S6, the question remains whether or not is it worth extra $$$.
"One aspect of which the company is most proud is the G4’s main lens. Its f/1.8 aperture is currently the brightest on any smartphone and is a massive improvement on the f/2.4 lens found on the current G3 model. Perhaps more importantly it just pips Samsung’s excellent f/1.9 Galaxy S6 camera at the post", says Forbes, later adding that the 0.1 difference might not be "incredibly important", as LG likes to put it.
Manual control over shutter speed, ISO and white balance are also big advantages for the G4.
Still, the automatic snapshots are what will ultimately determine the better camera for most owners. Both Apple and Samsung are extremely good at that, and we will still have to wait and see just how LG’s flagship G4 can compete with the duo.
Startup time, handling of the phone while taking pictures, megapixels; those are all elements making the difference between a good camera and a great camera.
"These early details look very promising, but the Galaxy S6 is a very tough act to follow and it will definitely take more than just an f/1.8 lens to pull it off", Forbes concludes.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

What Google's looking for in a manager
Publié: avril 30, 2015, 8:09pm CEST par Sead Fadilpašić

Being a manager at a company is a difficult task. You need to help people, motivate them to work, plan their projects, and make decisions. Even though a lot of people dream of becoming a manager, or any sort of boss at a company, not everyone is fit for that kind of pressure and expectation.
But when it comes to Google, being a manager is a completely different experience. The reason? It’s kinda hard to manage people that are most likely a lot smarter than you.
Google’s head of human resources, Laszlo Bock spoke to Quartz’s Max Nisen recently, on the subject of employing and managing people, and he says managing Googlers is a vastly different experience.
Bock says that in most companies you get rewarded and promoted for having better insights than the people you’re surrounded with, as well as being able to play the game of politics. "Everything you experience teaches you that you need to be assertive, and out in front, and making all of the decisions".
At Google, managing doesn’t mean making decisions -- it means getting the maximum out of the team.
"You realize that you have a lot less levers, control and power than you do at a lot of other companies. You don’t decide who to hire, or how big a bonus somebody gets, you don’t decide who gets promoted".
You need to motivate them without the leverage of power.
"You’re forced to figure out how to add value without relying on power, and you do that by influencing, by giving people the opportunity to learn, and giving people more freedom".
Master this skill, and you will be a great Google manager.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How small businesses can boost Facebook engagement
Publié: avril 28, 2015, 1:13pm CEST par Sead Fadilpašić

If you have a small business, and that business doesn’t have its own Facebook page, then you’re doing your business wrong.
Come on, people’s pets have Facebook fan pages, and your business doesn’t. Many will agree that having a fan page is essential to your business, but with basically everyone on there, the rules have changed.
Various companies and their lousy social media strategies have forced Facebook to start prioritizing posts made by 'generic' users, and to push posts made by pages below in the news feed.
Facebook has also drastically reduced the reach of a page’s post, forcing businesses to buy sponsored posts in order to get more visibility.
But it’s not all so grim news, as there are still ways for your business to take full advantage of Facebook without having to spend hundreds (or thousands) of pounds to promote your deals and new offers.
Social Media Examiner has written a guide with 11 ways to boost Facebook engagement for small businesses, but in reality, those 11 ways all boil down to just one -- being creative.
The Keep it Short and Simple (KISS) principle works a bit different on Facebook -- it should be Keep it Short and Shareable, as shareable content is king for businesses.
Images, statuses, contests and giveaways -- they won’t matter unless people want to share what you post. With sharing come likes and comments, and those three things combined will make your page a success, and will definitely help your business.
As it can be seen in the guide, being creative and having a sense of humor are the two most important aspects in getting engagement on your posts. Sharing funny pictures, jokes and being generally laid-back on Facebook brings likes and comments. Showing personality is also a big bonus.
Most of the examples illustrate what’s working for small businesses in their Facebook updates.
"For your business, focus your energy on getting into the news feed", it says in the guide.
Here are some key takeaways from these examples:
- Use visual content, including good images and interesting videos.
- Add a personal touch, which can help differentiate you from other small businesses.
- Incorporate humor and have fun -- that always gets engagement.
Photo credit: JuliusKielaitis / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The Top 15 Apple Watch apps -- according to Apple
Publié: avril 27, 2015, 8:24am CEST par Sead Fadilpašić

When the Apple Watch hit the stores last Friday, the Watch App Store opened its virtual doors to everyone in possession of the fabled wearable device.
The store already has some 3,000 apps available for download, but the Cupertino company narrowed the choice down to a handful of apps it believes are a must-have at this point.
BuzzFeed News published the list just as the Apple Watch App Store opened for the first time. As you will see in the list below, many of the apps are popular social media apps we already use, while others are fitness-oriented, taking advantage of the Watch’s health-tracking features.
So, without further ado, here’s what Apple thinks you should have:
1. Target
The Target app allows you to create a shopping list on your wrist.

2. Instagram
Browse your favorite vintage-looking cat pics right from your watch.
3. Twitter
Read all the irrelevant Twitter posts faster than ever before.
4. Citymapper
If you want to go from point A to point B and do it fast, Citymapper is for you.

5. Strava
Strava is an app for all the sport freaks out there.
6. Dark Sky
Why look at the sky to check the weather when you can look at your fancy new phone?
7. NY Times
Read the latest on ISIS, Ukraine, North Korea and other things you really don’t want to know.
8. Pacemaker DJ
It’s like an auto song-mixer which mixes and plays songs from your iPad.
9. Lifesum
An app which sends you reminders when you should eat and drink. I didn’t know I needed this.
10. Mint Personal Finance
Let Apple handle your finances when you’re not able to control your impulse buying.
11. Elevate
An app to help you train your focus, memory, speaking abilities and stuff like that. Fairly useful.
12. Fitstar Yoga
Control your yoga sessions from your wrist.
13. Golfshot
It’s a golf course management app. You know, for when you play golf. You don’t play golf? Oh, my!
14. Centered
An app to help you schedule your meditation sessions.
15. Yelp
Find the closest (and best) restaurants.

Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Samsung Galaxy S5 could be leaking your fingerprints
Publié: avril 24, 2015, 12:05pm CEST par Sead Fadilpašić

I’m usually not the paranoid one in a relationship, but the fingerprint scanner on smartphones always used to freak me out.
And now, a pair of researchers from security firm FireEye breathes new life into my paranoia, as they claim hackers can steal your fingerprint data before it gets encrypted in the device. One of the potentially dangerous devices, ‘leaking’ fingerprints is the Samsung Galaxy S5.
The security researchers have found a way to intercept a person’s biometric data after it is captured by the built-in scanner, but before it becomes encrypted.
Tao Wei and Yulong Zhang from FireEye are will discuss their findings at this week’s RSA conference in San Francisco. However, the flaw is only present in the older version of the Android operating system, 4.4 KitKat and earlier, so those using Android 5.0 should be safe.
That’s why the duo advises anyone having an older version of Android and a fingerprint scanner on the same device to update as soon as possible, before it’s too late.
The vulnerability means that a hacker can access the kernel, or core, of the Android operating system.
Once inside they can monitor all data sent to and from the phone, as well as data recorded by the handset’s built-in sensors, including the fingerprint scanner.
"If the attacker can break the kernel [the core of the Android operating system], although he cannot access the fingerprint data stored in the trusted zone, he can directly read the fingerprint sensor at any time. Every time you touch the fingerprint sensor, the attacker can steal your fingerprint", Zhang told Forbes. "You can get the data and from the data you can generate the image of your fingerprint. After that you can do whatever you want".
Tom Armstrong, UK Manager at Dashlane, offered the following comment: "On paper, biometrics seems like a great way to secure a device because there’s the assumption that fingerprints can’t be stolen. The Samsung Galaxy S5 leak is case and point that this is not true. It can be hacked and the issue is there is no going back -- you can’t replace your stolen iris, or in this case, fingerprint. The lesson we can learn from this is that biometric authentication, alone, is not fool proof. It should be used as an additional authentication layer, alongside strong or randomly generated passwords that can be changed very quickly in the event of a breach".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple releases first iOS 8.4 beta with new Music app in tow
Publié: avril 15, 2015, 6:06pm CEST par Sead Fadilpašić

Apple has released the iOS 8.4 beta and with it, the upcoming revamped Music app.
The new music app features a stylish design (as we would expect from Apple), and a well thought-through interface, which includes a mini-player that remains visible while you’re looking around the app.
As Neowin reports, the new-look app is expected to integrate later this year with Apple’s new music streaming service, effectively a relaunch of its Beats Music acquisition from last year.
Apple is expected to announce the service at its Worldwide Developer Conference (WWDC) in June.
Here are the release notes from Apple for the new app:
All-New Design. Music app has a beautiful new design that makes exploring your music collection easier and more fun. Personalize playlists by adding your own image and description. Enjoy stunning pictures of your favorite artists in the Artists view. Start playing an album right from the album list. The music you love is never more than a tap away.
Recently Added. Albums and playlists you’ve recently added are now at the top of your library, making it effortless to find something new to play. Simply tap play on the artwork to listen.
Streamlined iTunes Radio. Discovering music with iTunes Radio is easier than ever. You can now quickly return to your favorite stations in Recently Played. Choose from a selection of hand-curated stations in Featured Stations, or start a new one from your favorite artist or song.
New MiniPlayer. With the new MiniPlayer, you can see what’s playing and control playback while browsing your music collection. To open Now Playing, just tap on the MiniPlayer.
Improved Now Playing. Now Playing has a stunning new design that showcases your album artwork the way it was meant to be. In addition, you can begin wirelessly streaming your music using AirPlay without leaving Now Playing.
Up Next. It’s now simple to find out which songs from your library will play next -- just tap the Up Next icon in Now Playing. You can even reorder, add, or skip songs whenever you like.
Global Search. You can now search from anywhere in the Music app — just tap the magnifying glass. Search results are conveniently organized to help you quickly find that perfect song. You can even start an iTunes Radio station right from Search.
Screenshots of these new features can be found in a photo gallery, over at 9to5Mac.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Bloomua / Shutterstock
-

Europe faces shortage of 800,000 IT workers by 2020
Publié: avril 15, 2015, 3:53pm CEST par Sead Fadilpašić

New trends such as machine-to-machine communications and cloud computing are opening great new opportunities, and Europe is in serious danger of missing out if it doesn’t produce enough experts in the field.
During a speech in Belgium, European Commission (EC) Digital Single Market chief Andrus Ansip said Europe might face a huge deficit in skilled ICT workers, V3 reports.
"Despite rapid growth in the ICT sector, creating some 120,000 new jobs a year, Europe could face a shortage of more than 800,000 skilled ICT workers by 2020", he said. "We still see big differences in skills levels between EU countries, and different implementation of national skills programmes designed to minimize Europe’s digital divide".
Ansip said this could prove to be a huge problem, as these jobs can only be filled by tech-savvy workers.
"Global big data technology and services are set to grow from €3 billion ($3.17 billion) in 2010 to €16 billion ($16.9 billion) this year, seven times more quickly than the overall IT market", he said. "To me, that is the kind of rapid growth that means hundreds of thousands of new jobs across Europe in the coming years".
He also emphasized the expected expansion of cloud computing: "But is Europe ready for the advent of big data? Perhaps not yet: 29 percent of larger EU companies see themselves as ready, but more than 50 percent say they are not".
"By 2020, cloud computing is due to expand to almost five times its market size in 2013, meaning more value to the economy, more jobs, more innovation", he said. "Since much more data is likely to be stored in the cloud in the years ahead, it is vital to address issues like data storage, ownership and management sooner rather than later".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Krasimira Nevenova/Shutterstock
-

The majority of Brits are worried about online security
Publié: avril 10, 2015, 8:37am CEST par Sead Fadilpašić

For every ten British adults, seven are seriously concerned about the privacy of their online data and fear it might get stolen by hackers, a new study has revealed.
The study, conducted by international internet-based market research firm YouGov, surveyed more than 2,000 British adults and found that 72 percent are concerned about their private online information, while 32 percent are willing to pay someone to keep their data safe.
Also, 29 percent thought it was their responsibility to safeguard their online information.
"Gone are the days when consumers took a back seat in protecting their data online", The Guardian quotes chief executive of security firm CloudMask, Wael Aggan. "High-profile data breaches, including celebrities’ nude photographs being pasted over the internet, credit card details being hacked and governments gaining permission to access Google and Microsoft customer data is forcing consumers to take more control of their privacy".
YouGov’s survey also found that 70 percent of people signing up for different online services give away information like address and date of birth, which are often considered part of the secret personal information used to verify a person’s identity for banking and other secure services.
Still, more than half of those surveyed said that they wouldn’t pay to be protected, and 61 percent believe whoever they’re signing up to should keep their data safe.
"Consumers are becoming much more aware of the need to protect their personal data online and even though this survey shows they might be prepared to pay to do that, it is still ultimately the responsibility of the businesses who hold that data to make sure they follow the laws around data protection", said Garreth Cameron from the information commissioner’s office.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The Internet of Things will aid criminals and burglars
Publié: avril 9, 2015, 9:06am CEST par Sead Fadilpašić

The billions of interconnected devices, which are expected by 2020, could be an invaluable tool in the hands of ‘offline’ criminals, a new study suggests.
The main reason behind this claim is the fact that these devices are not designed with privacy or data security in mind.
A new report by application security company Veracode suggests that the combination of connected devices, the IoT and cloud software services leads to vulnerabilities that can help crooks in both cyber and physical crimes.
"Businesses are increasingly being breached by attackers via vulnerable web-facing assets; what is there to keep the same from happening to consumers? The short answer is nothing", claimed the Veracode paper, entitled Internet of Things: Security Research Study.
"Already, broad-reaching hacks of connected devices have been recorded and will continue to happen if manufacturers do not bolster their security efforts now", it added.
One of the examples mentioned was when Russians enabled people to watch CCTV cameras, live streams from insecure cameras and baby monitors. Last time people were just watching, but there’s really nothing stopping individuals from using that information for theft. If they know when someone’s not home, they know when they can break inside and take whatever they want.
Microphones can also be used to steal private information and use it for blackmailing.
"It’s hard to not be excited about what the Internet of Things has enabled and will bring in the future, although that doesn’t mean cyber security should be sacrificed in the process", said Brandon Creighton, Veracode security research architect.
If they want to make IoT a success, developers need to focus on security and data privacy.
![Veracode-Infographic-v7[1]](http://betanews.com/wp-content/uploads/2015/04/Veracode-Infographic-v71.jpg)
Photo Credit: Bartlomiej K. Kwieciszewski/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Twitter rolls out 'retweet with comment' feature
Publié: avril 8, 2015, 12:49pm CEST par Sead Fadilpašić

Twitter has rolled out a revamped retweet feature, allowing users to post comments on other people’s tweets without having to shorten the original post.
If the above statement is a bit confusing, that’s because I tried, and most likely failed, to explain a somewhat complex feature with a single sentence.
So let’s break it down: Twitter only allows 140 characters per post. If someone wanted to retweet another person’s post and leave their own comment or opinion of it, they had to shorten the original post as much as possible to make room for their own words.
Or they could post a link to the original comment, but even that wasn’t a quality solution.
For Twitter, that was obviously the problem, because shortening someone’s original statement means risking changing its entire context, and people were struggling, going out of their way to do something as simple as posting a comment on someone’s tweet. It simply wasn’t seamless enough.
That’s why the company started testing a "retweet with comment" feature last summer, which would help solve this problem, without abandoning the 140 character limit.
Now it’s live, and it works very simple: the original comment gets embedded and isn’t even recognized as text, leaving the commenter the full 140 characters to say whatever he or she wants to say.
The feature is now available on Twitter’s site and iPhone app and will be available on its Android app soon.
Some people think the feature is great, others that it’s ugly, but nevertheless, it will most definitely be useful.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Facebook usage linked to depression
Publié: avril 8, 2015, 9:27am CEST par Sead Fadilpašić

If you’re feeling a bit depressed lately, try logging off Facebook. No, seriously, get off Facebook.
According to a recent study, there is a link between people becoming depressed, and them scrolling through Facebook all day. It’s not the social media itself which causes depression though, it’s a bit more complicated than that.
It is in everyone’s subconscious to compare themselves to others, and having a pretty good insight into other people’s lives, Facebook offers a good platform for people to compare themselves to their friends.
However, people only post the good and interesting things from their lives, filtering out the boring parts (obviously, no one wants to see you calculating your bills, even though it might sound interesting to some), and when others only see the fun stuff, they start believing their lives are boring and -- ta da! Depression!
A research called 'Seeing Everyone Else’s Highlight Reels: How Facebook Usage is Linked to Depressive Symptoms' published in the Journal of Social and Clinical Psychology, University of Houston researcher Mai-Ly Steers expands on previous studies about the detrimental effects of Facebook, particularly with regards to the unrealistic expectations of quality of life it creates, The Independent reports.
"Although social comparison processes have been examined at length in traditional contexts, the literature is only beginning to explore social comparisons in online social networking settings", Steers said.
"It doesn’t mean Facebook causes depression, but that depressed feelings and lots of time on Facebook and comparing oneself to others tend to go hand in hand", Steers explained.
"One danger is that Facebook often gives us information about our friends that we are not normally privy to, which gives us even more opportunities to socially compare".
There you have it, folks. Stop comparing yourselves to other people, and if you can’t help it -- log off.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Smart homes: Consumers are ready to start living like the Jetsons
Publié: avril 1, 2015, 11:34am CEST par Sead Fadilpašić

Consumers clearly see the benefits offered by home automation but they also have very specific requirements that need to be met before they’d consider investing, a new survey has shown.
The survey, which asked US, UK and German consumers their attitudes towards the smart home, showed that almost half (46 percent) of consumers think smart home devices will become mainstream within five years and revealed a strong preference for smart home solutions that offer tangible benefits.
The new research from the Bluetooth Special Interest Group released today shows that most appealing smart home gadgets are those that allow consumers to control their environment, such as smart heating/thermostats, smart lighting and smart security/monitoring devices.
But consumers know exactly what their devices should be like: 54 percent said a device should be straightforward to use, and 41 percent believe it should be easy to set up.
Price and security also figured prominently, with 42 percent of consumers feel that both keeping their data secure and offering products at competitive price points will make smart home devices much more desirable.
Currently, 67 percent of consumers are concerned that some smart home devices would make their data vulnerable.
"This study confirms consumers are looking for smart home products that 'just work'," said Mark Powell, executive director of the Bluetooth SIG. "It’s evident demand for smart home devices is ramping up and consumers are keen to live in the scenarios conjured up by the Jetsons over 60 years ago. Smart home manufacturers need to deliver products that are simple, cost-effective and secure for this segment to become mainstream".
Here are the survey’s key stats at a glance
- 6 percent think smart home devices are already mainstream i.e. most people own a smart home device or consider it normal to do so
- 46 percent think smart home devices will be mainstream within the next five years
- 66 percent think smart home devices will be mainstream within the next 10 years
The top five most important factors when deciding which smart home device to purchase are:
- It should be simple to use -- 54 percent
- It should be competitively priced -- 42 percent
- It should keep data secure -- 42 percent
- It should be easy to set up -- 41 percent
- It should connect easily and quickly with a smartphone, tablet or PC -- 28 percent
- 73 percent would be frustrated if it took too long to set up a smart home device
- 67 percent are concerned some smart home devices wouldn’t keep their data secure
The top three types of devices consumers find most appealing are:
- Smart home heating/thermostat -- 45 percent
- Smart lighting/light bulbs -- 34 percent
- Smart security and monitoring devices -- 33 percent
- 66 percent would like to be able to program their home system to perform automatic actions, such as lights turning off when exiting a room or heating turning on when returning home from work
- 73 percent would like to receive smartphone notifications from their home security system if it detects a threat
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

British Airways frequent flyer Executive Club accounts compromised
Publié: mars 31, 2015, 11:30am CEST par Sead Fadilpašić

Tens of thousands of British Airways frequent flyer accounts have been compromised in a cyberattack, forcing the company to freeze the accounts and issue an apology, the media have reported.
British Airways sporadically responded to tweets from concerned customers, The Register reports. In one such exchange it said:
"We’re sorry for any concern. We’ve become aware of some unauthorized activity in relation to your account and have frozen your Avios as a precaution. We’ll be sending you more details via an email".
The company said only a small portion of its millions of customers were affected, and that personal information, such as names, credit card information addresses was not stolen in the attack.
However they won’t be able to use their accumulated flight time for some time now.
The company, which has millions of customers, expects to resolve the problem in a few days.
"British Airways has become aware of some unauthorized activity in relation to a small number of frequent flyer Executive Club accounts", a company spokesman said in a statement sent to IB Times UK.
"We would like to reassure customers that, at this stage we are not aware of any access to any subsequent information pages within accounts, including travel histories or payment card details".
"We are sorry for the concern and inconvenience this matter has caused, and would like to reassure customers that we are taking this incident seriously and have taken a number of steps to lock down accounts so they can no longer be accessed", the spokesman added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Sony's PlayStation 4 goes on sale in China
Publié: mars 23, 2015, 1:15pm CET par Sead Fadilpašić

The hugely popular Sony PlayStation 4 gaming console has finally arrived to China, but the Chinese still have very little reason to rejoice.
There are a total of six games which can, at this moment, be played in China, and those are Knack, Dynasty Warriors 8, Trials Fusion, Rayman Legends, King of WuShu and Mr. Pumpkin’s Adventure.
That's right. No GTA, no Final Fantasy, and most importantly -- no FIFA. Well, maybe the Chinese are not so crazy about football, but it’s still an issue.
Sony said it hopes to quickly expand its game library in China. A spokesperson said the company was working to produce Chinese language versions and secure approval from authorities, CNN reports.
However, getting approval for the games and passing strict censorship rules will be a hard task. China holds a firm grip on the gaming console industry, and has only recently lifted its 14-year-old ban on game consoles back in January 2014.
The now lifted ban, which was imposed in 2000 over fears of violent content and the potential for moral decay, is a huge opportunity for Sony, Microsoft and Nintendo to expand their gaming market.
Microsoft was the fastest to react, offering the Xbox One console to the Chinese market back in September.The ban didn’t stop the black market from offering the console though, so pirated versions of the PlayStation 4 were widely available at electronics markets in China, and lax enforcement allowed them to be sold in the open.
Controversial game titles could also be purchased.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

TAG Heuer teams up with Intel and Google to take on Apple Watch
Publié: mars 20, 2015, 9:07am CET par Sead Fadilpašić

Not only has Apple made Samsung and other smartphone manufacturers hang their heads in despair, it has had a similar effect on watch makers around the globe too.
Not too long ago, right after the Apple Watch was unveiled, Swiss watch maker Swatch announced it’s working on a smartwatch of its own, and it’s not the only company doing so.
Tag Heuer plans to unveil a smartwatch, as luxury watchmakers fight back against Apple.
As industry sources have said, Tag Heuer won’t be alone in this fight -- it has Intel and Google by its side.
Next autumn, the company will launch a smartwatch version of its Carrera model that will offer many of the same functions as the Apple Watch such as geolocation, distance walked and altitude.
The major difference is that the watch will be a digital replica of the original Tag Heuer black Carrera, known for its bulky, sporty allure, and will look like the original.
“People will have the impression that they are wearing a normal watch,” Tag Heuer Chief Executive Jean-Claude Biver told Reuters in an interview at Baselworld, the industry’s biggest fair where retailers place their orders for the year.
Biver agreed with Swatch Group Chief Executive Nick Hayek who said the smartwatch “would increase the cake” for the industry as a whole, but still referred to the Apple Watch as not a real watch.
“Apple will get young people used to wearing a watch and later maybe they will want to buy themselves a real watch,” Biver said.
Watch Tag Heuer's announcement below.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

LG: Apple has it right -- smartwatches should be a fashion item first, gadget second
Publié: mars 12, 2015, 6:30pm CET par Sead Fadilpašić

During the Wearable Technology Show in London, LG’s head of business development Justin Jungsup Lee spoke about smartwatches, early adopters and sales.
Speaking in front of a packed out room in the LG keynote, Lee said that smartwatches should be more of a fashion item, and less of a gadget. And least of all, a smartphone accessory.
"It’s a mindset change, making the watch a fashion item, rather than a gadget", Lee explained. "The challenge is to align the smart devices with the watch world. When you switch from a functional device to a fashion device, it becomes very different. When you position the smartwatch as fashion, the marketing message becomes very easy".
He continued, commending Apple’s new device and hinting that LG will use a similar marketing strategy for their upcoming LG Watch Urbane.
"Apple’s on the right path on with its marketing, using Vogue and making it a fashion item", he said, "which is in line with our own strategy".
He also said that new developers will face flat sales and lots of problems in the first few years.
"Not that many wearable devices have been sold. 20 million devices -- that’s just 0.04 percent penetration, and just 1 percent of the innovator segment. Crossing the chasm is the next step", said Lee. "There are lots of technical barriers. Battery life is still close to smartphones, and the screen size is too small. Input is near impossible other than the voice, and it’s still seen as an accessory to the smartphone," Lee added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Nest looking to make a move into home audio
Publié: mars 12, 2015, 6:16pm CET par Sead Fadilpašić

Nest, the home automation company that designs and manufactures sensor-driven, Wi-Fi-enabled, self-learning, programmable thermostats and smoke detectors, is making a move into home audio.
A recruitment add appeared on the Nest website, seeking a "highly technical Head of Audio to lead the development of Nest Audio across hardware and software, present and future".
Whoever gets the job, will have to "lead the Nest Audio team, including acoustics, audio electronics, audio software, audio test and validation for all Nest Products, build a world class audio team through hiring and mentoring and develop an audio roadmap for Nest products, including hardware and software, that can support delightful user experiences and innovative features".
The founder and CEO of Nest is Tony Fadell -- a man very familiar with the music industry. He is the former Apple executive behind the iPod (he was also nicknamed "The father of the iPod").
The media speculate on what the software part of the work will include. While some believe it might mean the development of a brand new streaming service, others think it will more likely mean the creation of a music controlling app, considering that Google has two: Google Play All Access and YouTube Music Key.
Nest was bought by Google for $3.2 billion back in January 2014.
The Guardian says Sonos will most likely to be the main rival to Nest: "That company is expected to record $1 billion in sales of its connected audio hardware in 2015, and recently raised $130 million of funding to continue growing. Google’s deep pockets could make Nest a formidable competitor".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Driverless car tech could lead to better robots
Publié: mars 9, 2015, 12:12pm CET par Sead Fadilpašić

We’re only a few steps away from real-life Transformers. Or Terminators. Or both.
A recent report from the consulting firm McKinsey says the technology used to build the self-driving cars could end up in robots, benefiting the human race in many ways.
Robots could be built using the same technologies currently being developed for autonomous cars, such as GPS, image recognition, or artificial intelligence.
Some of that hardware used in self-driving cars could find its way into robots, lowering production costs and the price for consumers. More importantly, common parts could help mechanics fix broken robots and broken cars, and the machine-to-machine communication could also be shared.
Autonomous vehicles have become increasingly popular among car manufacturers and other forward thinking companies. Google, Audi, BMW, even Apple apparently, those are the companies building their own driverless vehicles.
Intel, Sony, Honda and Toyota, together with Google, are building robots, too.
The report said that the companies will outline their plans for driverless cars within the next few years. Trucks will be the first vehicles to lose their drivers. This makes sense because truck drivers often have to drive for days, putting themselves in danger. However, this also means truck drivers should soon start looking for a new career path.
Insurers will end up covering manufacturers for technical failures, McKinsey said.
Autonomous cars won’t appear in critical mass on public roads before 2040, but when they do, they will give people an extra 50 minutes in their day, which is usually spent on driving to and from work.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

China drops leading western tech brands for state purchases
Publié: février 26, 2015, 9:37am CET par Sead Fadilpašić

China has decided to remove some of the world’s leading technology brands from its state approved purchase lists and replace them with thousands of locally built products.
Some say this move comes as a response to revelations of widespread cyber-surveillance conducted by the West, while others believe this is more of a way for China to protect domestic technology industry from fierce competition.
The biggest casualty of the new lists is the US network equipment maker Cisco Systems, which in 2012 had 60 products on the Central Government Procurement Center’s (CGPC) list, but by late 2014 had none.
Apple, Intel and McAfee all joined Cisco and were removed from the purchase lists.
The number of products on the list, which covers regular spending by central ministries, jumped by more than 2,000 in two years to just under 5,000, but the increase is almost entirely due to local makers.
An official at the procurement agency said there were many reasons why local makers might be preferred, including sheer weight of numbers and the fact that domestic security technology firms offered more product guarantees than overseas rivals.
"The Snowden incident, it’s become a real concern, especially for top leaders", said Tu Xinquan, Associate Director of the China Institute of WTO Studies at the University of International Business and Economics in Beijing. "In some sense the American government has some responsibility for that; (China’s) concerns have some legitimacy".
China’s change of tack coincided with leaks by former US National Security Agency (NSA) contractor Edward Snowden in mid-2013 that exposed several global surveillance programs.
Image Credit: Tang Yan Song / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft releases the first major Band update
Publié: février 25, 2015, 7:16pm CET par Sead Fadilpašić

Microsoft Band, the wearable fitness tracker, and its accompanying Health app have received their first major update, some four months after the initial release.
With the latest update, the band is getting some new features -- enabling it to monitor biking (yes, even stationary biking), a quick read feature for notifications and -- (you’re not going to believe this) -- an on-screen keyboard.
One can’t but wonder how in God’s name can anyone type anything on a 1.4-inch touchscreen, but Microsoft is betting a lot on its Word Flow technology to ease the typing process.
The company says its Word Flow technology will allow you to type "with minimal errors", and has also included a voice dictation feature.
It has also released a web portal for a more detailed look at your daily activities’ statistics, and will allow MapMyFitness users to sync with the service.
The Bike Tile can track both outdoor and indoor bikes, optimizes the heart rate monitor and activates elevation tracking.
What’s really nice for the stationary bikes is that it can track the speed, and how long it will take you to recover from the workout.
The Health web portal has also been revamped, giving access to all of the information available in the mobile apps, including both sleep and workouts.
My fav feature in the Feb update is the Virtual keyboard...replying to texts from my #MicrosoftBand for WP 8.1. pic.twitter.com/aFIQMjO3AW
— Paul Britton (@paulstorms) February 23, 2015
Microsoft has also introduced an SDK for the Band to allow third-party apps on the fitness tracker.
It is still in developer preview, but the SDK will allow developers to get data directly from the Band’s sensors.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

A third of Brits embarrassed by wearables
Publié: février 24, 2015, 11:11am CET par Sead Fadilpašić

Over a third of the people in the UK would feel embarrassed or self-conscious if they wore wearable tech as it currently appears, new research has found. As a result, businesses and app developers are being urged to do more if they want to improve uptake
The study was conducted by the UK mobile app developer Apadmi to form part of its new report looking into the public’s view of wearable technology, such as smart glasses, watches and fitness trackers.
Among other things, consumers were asked questions about currently available wearable tech and 35 percent said they would feel embarrassed or self-conscious if they wore it.
Some 34 percent thought it made people look like show-offs and 32 percent claimed that wearable technology makes people look ridiculous.
In addition, 17 percent said it makes people look unattractive when they wear it.
On the other hand, 20 percent said the wearable tech makes people look intelligent and successful, 10 percent would feel cool wearing it, and 8 percent believe it makes people look attractive.
Apadmi’s director says the developers must do much more to make wearables a long-term prospect.
"These findings illustrate that more can be done to make wearable tech desirable. Wearables are entering the market thick and fast but we’re already seeing early adopters abandoning them. This is down to many of the reasons highlighted in our research but also because the app experience is not satisfying users," said Howard Simms, co-founder and director at Apadmi.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Demand for Linux developers on the rise
Publié: février 20, 2015, 7:33pm CET par Sead Fadilpašić

The demand for Linux developers has jumped seven percent in comparison to last year, a study has shown.
The 2014 Linux Jobs Report shows that hiring managers at tech-powered companies are focusing more attention on Linux talent, and that’s reverberating in the market, with stronger than average salary increases to those working with the OS.
Dice and The Linux Foundation surveyed both hiring managers and Linux talent to gain a 360-degree view of the thriving jobs landscape, and here’s what they found:
Some 77 percent of hiring managers have "hiring Linux talent" on their list of priorities for 2014, up from 70 percent a year ago. With these strategic priorities set, more than nine in ten hiring managers plan to hire a Linux professional in the next six months.
Almost half of hiring managers (46 percent) are beefing up their plans for recruiting Linux talent over the next six months, a three-point increase over last year, and 86 percent of Linux professionals report that knowing the OS has given them more career opportunities.
Another 64 percent say they chose to work with Linux because of its pervasiveness in modern-day technology infrastructure.
This year’s survey includes responses from more than 1,100 hiring managers at corporations, small and medium businesses (SMBs), government organizations, and staffing agencies across the globe -- as well as responses from more than 4,000 Linux professionals worldwide.
The OS has always had a strong presence in the technology world, but these numbers show that the open-source software is really picking up steam.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Neptune Duo turns the smartphone/smartwatch relationship on its head
Publié: février 20, 2015, 2:32pm CET par Sead Fadilpašić

Neptune Duo is an interesting smartwatch/smartphone concept that flips our traditional view of the wearable tech on its head. Ask yourself: What’s a smartphone, and what’s a smartwatch?
Most of us (I dare say almost everyone) thinks of a smartphone as a mobile computer, small enough to fit in your pocket, but large enough to watch videos, even movies on it, write emails, chat, talk to your friends, all that jazz.
Smartwatches on the other hand (no pun intended) are nothing more than a watch with a display, capable of reading out notifications without the need to pull the phone out of your pocket, and stuff like that.
Well, Neptune thinks otherwise. The company believes it’s the watches that should be 'smarter' than the phones, so it built the Neptune Duo -- a duo in which the smartwatch rules, and the smartphone is basically nothing more than a monitor, capable of doing a thing or two.
I find it to be a very interesting concept, one that just might prove revolutionary -- the display and the processor are the two biggest power consumers on the device, and if you split them up on two devices, you just might get a smart 'hub' where the battery can last for a few days, and still be as powerful as any device, and have a pumped up display.
The wrist wearable packs a quad-core CPU, 64GB of storage, 4G, Wi-Fi, NFC, Bluetooth and a raft of sensors all hidden behind its 2.4-inch capacitive display, while the phone gets a 5-inch 720HD display, a duo of cameras (8MP and 2MP) and -- 2,800 mA/h battery. The makers say the duo can last "a few days" of "normal usage" on a single charge.
The devices cost $798, or you can pledge $199 right now and pay $399 at shipping.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Uber bringing food delivery to Barcelona
Publié: février 20, 2015, 11:21am CET par Sead Fadilpašić

Uber, the taxi-hailing company from Los Angeles, has announced a food delivery service for Barcelona.
The same service is already available in Los Angeles under the name UberFresh, while in Barcelona it’s called UberEats.
Even though the company is present globally, this is the first time its food delivery service has been presented outside the United States.
The new service comes to Barcelona in cooperation with Plateselector, a Barcelona food guide website, and its menu will be regularly updated with new selections, it says in an Uber blog post.
Uber claims that lunch and dinner menus can reach their customer in less than ten minutes.
"In the same time it takes you to walk up Las Ramblas you can open up your Uber app, choose your meal and get it delivered to an address of your choice", it says on the blog.
Plateselector co-founder Johann Wald said his company is "excited to be a part of this collaboration with Uber, an internationally renowned brand", adding how they’re fans of the Uber app.
Uber has faced numerous controversies, and was even banned in a couple of countries including Spain, although temporarily, when a judge ruled that it posed unfair competition to existing taxi services.
The company has also faced problems in India, where an Indian woman was allegedly raped by an Uber taxi driver.
Last month, Times of India reported that the woman hired a top American trial lawyer to sue the Los Angeles company.
"I can confirm that I have been retained by the young lady who was raped by an Uber driver in Delhi, India, last December", Wigdor told ToI.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

IBM launches new storage software portfolio
Publié: février 18, 2015, 10:20am CET par Sead Fadilpašić

Tech giant IBM unveils IBM Spectrum Storage, a new storage software portfolio designed to address data storage inefficiencies. The portfolio is aimed to change the economics of storage with a "layer of intelligent software".
The software creates a "data footprint", which stores data at the optimal cost, thus maximizing performance and security. The Spectrum Storage incorporates more than 700 patents to help users move massive amounts of data fast and easy, from a single dashboard.
According to IBM: "The software helps clients move data to the right location, at the right time, from flash storage for fast access to tape and cloud for the lowest cost".
Aside from the new software portfolio, IBM also announced it will be investing more than $1 billion in its storage software portfolio over the next five years.
The investment will focus on R&D of new cloud storage software, object storage and open standard technologies including OpenStack.
"A new approach is needed to help clients address the cost and complexity driven by tremendous data growth. Traditional storage is inefficient in today’s world where the value of each piece of data is changing all the time", said Tom Rosamilia, senior vice president, IBM Systems. "IBM is revolutionizing storage with our Spectrum Storage software that helps clients to more efficiently leverage their hardware investments to extract the full business value of data".
IBM’s Spectrum Storage portfolio can centrally manage more than 300 different storage devices and yottabytes of data. This device interoperability is the broadest in the industry -- incorporating both IBM and non-IBM hardware and tape systems.
IBM Spectrum Storage can help reduce storage costs up to 90 percent in certain environments by automatically moving data onto the most economical storage device -- either from IBM or non-IBM flash, disk and tape systems.
In addition to Spectrum Accelerate, IBM Spectrum Storage portfolio includes key storage software such as Spectrum Virtualize, Spectrum Scale, Spectrum Control, Spectrum Protect and Spectrum Archive.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Is Apple really worth $1,300,000,000,000? Activist investor Carl Icahn believes so
Publié: février 14, 2015, 5:28am CET par Sead Fadilpašić

A major Apple shareholder and activist investor, Carl Icahn, believes Apple is worth much more than it is currently valued.
He believes the American company’s stock should be valued at $216 (£140), which is far more than the current price of $124.92 (£81.32). At $216, the company would be worth $1.3 trillion (£845 billion), which is about the size of South Korea’s gross domestic product, Reuters writes.
Even without these crazy numbers, Apple is still the most valuable company in the world, worth $700 billion (£455.5 billion).
"This is why we continue to own approximately 53 million shares worth $6.5 billion [£4.23b], and why we have not sold a single share", Icahn said in a letter to his Twitter followers.
"Also, to the extent Apple introduces a TV in FY 2016 or FY 2017, we believe this 20X multiple is conservative", he wrote.
Carl Icahn is one of Apple’s top investors, and has predicted a 100 percent increase in share value back in October 2014. Apple’s shares were worth $100 (£65) back then.
He urged the company to use its cash and buy back more shares.
"[...] We look forward to the capital return program update in April, anticipating it will include a large increase to share repurchases", Icahn wrote.
Apple had cash reserves of about $178 billion (£115.82 billion) as of December 27, enough to buy IBM.
However, the company said it would give back more than $130 billion (£84.59 billion) to shareholders by the end of 2015.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: FooTToo / Shutterstock
-

Facebook now lets you buy and sell stuff in Groups
Publié: février 13, 2015, 9:05pm CET par Sead Fadilpašić

Step aside, eBay, Facebook is here. The social media giant announced it’s rolling out new features for Groups, allowing users to buy and sell stuff using Facebook.
People posting in groups on Facebook will now have the option to add whether they're buying or selling a certain item, and include prices and shipping methods.
Groups is a very popular feature on the social network, with groups where people buy and sell goods being among the most popular ones.
Now all users and admins of such groups will have a much easier time doing business.
Currently, members in those groups usually post photos of items for sale and add details in the description.
With the new feature, each profile will have a list of previous items bought and sold.
Facebook however, emphasises that it’s simply giving users a new option and is in no way affiliated or responsible for the business done.
The new feature was spotted in December when it was still in testing phase, after which the company confirmed it was working on it.
Now, the feature is rolling out globally to more Groups on the web, Android and iOS.
"We will continue to introduce new features in the coming months to help people in the For Sale Group community easily connect, browse and search", says Facebook in a blog post.
"These new features will roll out to all Facebook For Sale Groups in the coming months across iOS, Android and web", adds the company.
Facebook Group admins who would like to participate now can nominate their Group on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Twin Design / Shutterstock
-

US likely responsible for Iran's cyber warfare know-how
Publié: février 13, 2015, 12:26pm CET par Sead Fadilpašić

Iran might have learned advanced cyber warfare from the US, recently revealed government documents have shown.
Leaked National Security Agency (NSA) documents published by The Intercept show fears that the American cyberattacks on Iran might have helped that country develop sophisticated cyber tactics and strategies.
The document was created before a meeting before NSA and its British counterpart, the Government Communications Headquarters (GCHQ), called because of Iran’s cyberattacks against some financial institutions in the US.
Iran’s nuclear and oil facilities have been targeted numerous times and the US and Israel are thought to be behind them.
"Iran’s destructive cyber attack against Saudi Aramco in August 2012, during which data was destroyed on tens of thousands of computers was the first such attack NSA has observed from this adversary", it says in the report.
"Iran, having been a victim of a similar cyber attack against its own oil industry in April 2012, has demonstrated a clear ability to learn from the capabilities and actions of others", the report says.
However, the document says Iran has had no plans on targeting the UK or the US at the time, but NSA cannot rule out that possibility.
"While the NSA has no indications at this time that Iran plans to conduct such an attack against a U.S. or UK target, we cannot rule out the possibility of such an attack, especially in the face of increased international pressure on the regime", adds the report.
Iran has been under a lot of pressure, including international sanctions, because of its nuclear program.
The West fears Iran uses its nuclear facilities to create an atomic bomb, while Iran says it has no such plans and wants to use the nuclear facilities for peaceful purposes.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Jirsak/Shutterstock
-

The kill switch works! Smartphone theft drops in major US, UK cities
Publié: février 12, 2015, 11:43am CET par Sead Fadilpašić

Smartphone theft in some of the major cities in the US and the UK has declined dramatically, so say the authorities.
But it's not because of improved law enforcement, it's actually down to manufacturers implementing a kill switch option, allowing smartphones to be deactivated remotely.
London saw a drop in smartphone thefts by 50 percent, San Francisco by 40 percent, and New York by 25 percent, said authorities on Tuesday.
"We have made real progress in tackling the smartphone theft epidemic that was affecting many major cities just two years ago", said London Mayor Boris Johnson.
Senior politicians of these cities started a joint campaign back in 2013, asking manufacturers to introduce a kill switch to their devices, saying that tens of thousands of devices are being stolen every month.
Only in London, as the mayor said, 10,000 handsets are stolen every month.
Apple was the first to react, adding a "lock phone" feature to its Find my iPhone app in 2013, followed by Microsoft and Google, who had announced, in July 2014, a similar feature.
California is about to implement a new law that would force manufacturers to implement a kill switch feature. The initiative has gotten wide support from California prosecutors and law enforcement agencies.
"The wireless industry continues to roll out sophisticated new features, but preventing their own customers from being the target of a violent crime is the coolest technology they can bring to market", said San Francisco District Attorney George Gascon.
Photo Credit: The To/Shutterstock
-

All smart home security systems are insecure
Publié: février 12, 2015, 12:35am CET par Sead Fadilpašić

Every "smart" security device in your home is vulnerable, a new study suggests.
Results of a security testing study conducted by tech giant HP show that 100 percent of the studied devices used in home security contain significant vulnerabilities, including password security, encryption and authentication issues.
Home security systems, such as video cameras and motion detectors, have gained popularity as they have joined the booming Internet of Things (IoT) market and have grown in convenience.
Manufacturers are quickly bringing to market connected security systems that deliver remote monitoring capabilities. The network connectivity and access necessary for remote monitoring presents new security concerns that did not exist for the previous generation of systems that have no internet connectivity.
The most common and easily addressable security issues reported include insufficient authorization, insecure interfaces, privacy concerns and a lack of transport encryption.
The study questions whether the devices make our homes safer, or more vulnerable.
"As we continue to embrace the convenience and availability of connected devices, we must understand how vulnerable they could make our homes and families", said HP’s Jason Schmitt.
"With ten of the top security systems lacking fundamental security features, consumers must be diligent about adopting simple and practical security measures when they're available, and device manufacturers must take ownership in building security into their products to avoid exposing their customers unknowingly to serious threats", adds Schmitt.
As companies push to incorporate much needed security measures, consumers are advised to be extra vigilant when deciding to go for a smart security system for their home.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: bahri altay/Shutterstock
-

Facebook's real name policy now causing issues for Native Americans
Publié: février 11, 2015, 7:59pm CET par Sead Fadilpašić

You might poke some innocent fun at your Native American friend Sitting Bull while he's on the toilet, but if you're that Native American, you wouldn’t want to be trolled by, let's say, Facebook.
That's exactly what happened to Shane Creepingbear, a Native American who, Facebook thinks, is using a fake name.
Through the social media's fake name policy, Facebook forces people to use their "real" names (those in their identification documents). This policy has been criticized before, mostly by members of the LGBT community who, wanting to protect themselves in not so LGBT-friendly environments, used fake names.
Facebook was forced to apologize and promised to create a way for people to identify themselves using "legitimate pseudonyms".
As you can see from the Twitter post below, Shane Creepingbear wasn't best pleased.
Hey yall today I was kicked off of Facebook for having a fake name. Happy Columbus Day great job #facebook #goodtiming #racist #ColumbusDay
— Shane Creepingbear (@Creepingbear) October 14, 2014
But he isn't the only person with this issue. According to the Last Real Indians blog, a person named Oglala Lakota Lance Brown Eyes had his account suspended and, after wrestling with Facebook's administration, got his profile back under the name Lance Brown.
Only after threatening with a lawsuit, was he able to get his full name back.
There are many examples of Native Americans struggling with Facebook. The social network wants people to use real names and, if the person gets suspended, he or she must provide a scanned copy of a legal document such as a passport or a driver’s licence, to confirm his or her identity.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Most mobile email users prefer iOS over Android
Publié: février 11, 2015, 10:54am CET par Sead Fadilpašić

People in the UK really love Apple products. OK, to be more precise, people in the UK with email accounts love Apple products.
More than half of all email in the UK (54 percent) is opened on an Apple device, says SendGrid, an email delivery platform. The total number of opened emails on iPads and iPhones has increased by 18 percent and five percent respectively.
Android devices, on the other hand, have dropped 30 per cent year-over-year, down to a total of eight percent this year.
According to SendGrid, it's not Nokia who stole Android's market share. Nokia also lost market share showing a drop of 68 percent in the number of emails opened on its phones compared to the same period in 2014.
Blackberry showed a steady increase of 20 per cent year-on-year, which SendGrid suggests might be due to the company's renewed interest in privacy.
SendGrid analyzed millions of emails opened in a 10-day period at the start of 2015 and compared it to the same period in 2014.
Email users in the rest of western Europe seem to favour Apple products as well, with the exception of Italy. In France, 47 percent of all email are opened on an Apple device, exactly the same as in Spain, while in Germany it's 46 percent.
Italy, however, saw a decrease of 44 per cent year-over-year in the use of Apple products to read emails.
Aaron Beach, Senior Data Scientist of SendGrid, believes Android's problem lies in its handset makers: "The variety of devices people use for email tells us a lot about how different platforms are performing across the UK. While people might own a number of devices it seems that Apple is still the firm favorite, as their recent results show. Android was the surprise this year showing a marked drop on 2014, perhaps reflecting the problems of handset makers such as Samsung".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Manchester City Football Club scores its own wearables app
Publié: février 10, 2015, 11:17am CET par Sead Fadilpašić

Manchester City has claimed the title of the world’s first football club to create an app for Android Wear smart watches.
The app is called CityMatchday Wear, and it can be downloaded for free from the Google Play store. It offers club related news, goal alerts and notifications for different events, such as yellow and red cards, penalties, team sheets, match details and substitutions.
The app also provides a textual commentary on the games, as well as a compilation of best tweets from Manchester City fans around the world.
"CityMatchday Wear is another example of how we are constantly exploring and adopting new technology with the ultimate goal of improving the fan experience and strengthening fans’ engagement with the Club", said Diego Gigliani, director of Media and Fan Relationship Management. "We recognize the smart watch market is still in its early stages but its popularity is projected to increase rapidly as new players come into the market. We’re thrilled to get in early and start discovering ways to tap into the devices’ potential".
Manchester City is currently in second spot in the Barclays Premier League, lagging seven points behind leaders Chelsea.
City have failed to win in their last four Premier League games, drawing with Hull City, Chelsea and Everton, and losing to Arsenal, showing how important Yaya Toure is to the team.
In the past month, the midfielder has been participating in the African Cup of Nations, where he played for his home country, Ivory Coast.
On Sunday night, Ivory Coast defeated Ghana on penalties and were crowned champions of the African Cup of Nations 2015.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Gartner: Businesses are not prepared for the Internet of Things
Publié: février 6, 2015, 4:12pm CET par Sead Fadilpašić

Even though most IT and business leaders are certain that their business will benefit from smart devices in the next three to five years, very few organizations actually have a clear strategy on how to take advantage of the new market. That’s the result of a survey conducted by Gartner. The company surveyed almost 500 IT and business leaders and found that 40 percent believe the Internet of Things will benefit their business in the next three years, while the other 60 percent believe it will happen in the next five years.
However, basically nobody has thought of a clear and concise strategy on how to take advantage of the emerging market.
"The survey confirmed that the IoT is very immature, and many organizations have only just started experimenting with it", said Nick Jones, vice president at Gartner. "Only a small minority have deployed solutions in a production environment. However, the falling costs of networking and processing mean that there are few economic inhibitors to adding sensing and communications to products costing as little as a few tens of dollars", Computing quotes Jones.
"The real challenge of the IoT is less in making products 'smart' and more in understanding the business opportunities enabled by smart products and new ecosystems".
Gartner said that senior leaders still don’t have a full understanding of the IoT’s potential, and has singled out banking, education and insurance as areas where even the highest executives know next to nothing about the meaning of IoT for their business.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How to remove embarrassing photos from social networks
Publié: janvier 26, 2015, 1:21pm CET par Sead Fadilpašić

Sharing photos and videos online has never been easier. Internet access is available practically anywhere and everywhere, and interconnected wearable and portable devices with photo and video recording options are omnipresent.
In such a world, getting the wrong material posted online can become a huge problem, especially for teenagers unaware of the consequences.
So how big of a problem is it?
In a recent study conducted by Northwestern University, 29 percent of surveyed Facebook users reported losing face from embarrassing content posted online.
And teenagers have been victimized by others, posting unflattering pictures online without their consent. Some even go to the extent of posting "revenge porn" -- posting explicit images and videos of people without their consent.
One in ten former partners have threatened to post such materials online, and according to a McAfee study, 60 percent of those threats have been carried out.
Images posted online are very hard, maybe even impossible, to remove. Embarrassing photos can lead to humiliation, dismissal from work, and loss of self-esteem, among other things.
How to remove your embarrassing photos from Facebook
There are six different options when it comes to removing photos from Facebook.
- Once the image is opened, press 'Options' and then either 'Report Photo' or 'Remove Tag'.
- Ask the friend who uploaded the photo to remove it.
- Send an email to info@support.facebook.com asking for the photo to be removed.
- File a complaint using the Facebook Intellectual Property Infringement Form.
- Post in the Help community to receive advice from other users and Facebook staff.
- File a complaint using the Facebook Terms Violation Reporting Form.
How to remove your embarrassing photos from Instagram
To remove images from Instagram, take one of these three options:
- To de-tag, select 'Hide from my profile'.
- Click on 'More options' and choose 'Remove me from photo'.
- Report the photo as inappropriate
How to remove your embarrassing photos from Twitter
To remove photos from Twitter, visit [https:], select the relevant option and send the report.
For more information on the subject, have a look at the infographic created by WhoIsHostingThis?
Photo Credit: eurobanks/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How to monitor your home using an Android Wear smartwatch
Publié: décembre 19, 2014, 12:07pm CET par Fadil Pašić

Anyone using an Android powered smartwatch no longer needs to worry about actually having to pick up their smartphone in order to see what’s going on back home, or in the office while they’re gone.
Now they can do it through the smartwatch.
What am I talking about? The Android app IP Cam Viewer of course, an application that lets users remotely access their video camera, digital video recorder, network recorder and webcam, now supports Android Wear.
IP Cam Viewer is reportedly one of the best IP camera apps on Android, and this functionality only makes it better.
The updated version also added drivers for more cameras, support for Chromecast, added Dropbox support for imports and exports and fixed a few known bugs for some existing drivers.
The app has a built-in web server that enables remote control of the app to change the record mode settings away from home or for use as a video wall, or function as a transcoder to fetch frames from devices with proprietary protocols.
It has a built in motion detection, that works with all cameras and plays a sound when motion is detected.
The app has various uses. It can be used as a security camera for homes, garages and cars, as well as a baby monitor.
It also includes various video formats and features like matrix view, pan, tilt and zoom.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

OnePlus is the latest firm to be banned in India
Publié: décembre 18, 2014, 8:52am CET par Fadil Pašić

The High Court in Delhi has temporarily banned the sales of smartphones built by Chinese smartphone maker OnePlus.
The ban comes after Micromax, an Indian consumer electronics company, filed a lawsuit alleging OnePlus violated an exclusivity agreement it signed with Cyanogen.
Cyanogen is an open source operating system for smartphones and tablet computers, based on the Android mobile platform. It is developed as free and open source software based on the official releases of Android by Google, with added original and third-party code.
The Delhi High Court issued a temporary order that restricts OnePlus from importing, marketing and selling Cyanogen-based handsets in India, effective immediately, Live Mint reports.
Micromax was given an exclusive license to integrate and distribute Cyanogen’s technology as a part of its devices in India through an "ambient services and application distributions agreement", which is why it complained that, by launching its phones on 2 December, OnePlus had infringed its exclusive rights.
Micromax claimed that it had "incurred major expenses for creation of a brand exclusivity for providing to Indian customers mobile phones with Cyanogen operating systems" and "it would suffer irreparable harm and loss if the defendants (OnePlus) are permitted to continue with their illegal acts in violation of the agreement between Micromax and Cyanogen".
On the other hand, OnePlus says it had a collaboration agreement and trademark license agreement with Cyanogen since February, and that it got terminated a fortnight before its launch in India.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

OnePlus is the latest smartphone maker to be banned in India
Publié: décembre 18, 2014, 8:52am CET par Fadil Pašić

The High Court in Delhi has temporarily banned the sales of smartphones built by Chinese smartphone maker OnePlus.
The ban comes after Micromax, an Indian consumer electronics company, filed a lawsuit alleging OnePlus violated an exclusivity agreement it signed with Cyanogen.
Cyanogen is an open source operating system for smartphones and tablet computers, based on the Android mobile platform. It is developed as free and open source software based on the official releases of Android by Google, with added original and third-party code.
The Delhi High Court issued a temporary order that restricts OnePlus from importing, marketing and selling Cyanogen-based handsets in India, effective immediately, Live Mint reports.
Micromax was given an exclusive license to integrate and distribute Cyanogen’s technology as a part of its devices in India through an "ambient services and application distributions agreement", which is why it complained that, by launching its phones on 2 December, OnePlus had infringed its exclusive rights.
Micromax claimed that it had "incurred major expenses for creation of a brand exclusivity for providing to Indian customers mobile phones with Cyanogen operating systems" and "it would suffer irreparable harm and loss if the defendants (OnePlus) are permitted to continue with their illegal acts in violation of the agreement between Micromax and Cyanogen".
On the other hand, OnePlus says it had a collaboration agreement and trademark license agreement with Cyanogen since February, and that it got terminated a fortnight before its launch in India.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple Pay gaining momentum as more companies sign up
Publié: décembre 17, 2014, 2:08pm CET par Fadil Pašić

Apple has announced that its mobile payment service Apple Pay has received even more support -- now 90 percent of all credit purchases by volume in the United States can be achieved by using Apple Pay.
SunTrust, Barclaycard, USAA, and dozens of other companies have joined the likes of Citibank and Chase in the last weeks and agreed to work with Apple, so that customers can buy things with little more than a wave on their iPhone, The New York Times reports.
Ten more banks, including TD Bank North America and Commerce Bank, will back the new form of payment on Tuesday.
Aside from the banks, 1,400 Staples' locations now accept Apple Pay as a means of payment. Winn-Dixie, Albertsons, Amway Centre, just some of the other leading names that now use Apple’s mobile payment service.
New additions suggest that Apple Pay has generated more traffic than its competitors from the likes of Google, Verizon and AT&T.
"Retailers and payment companies see Apple Pay as the implementation that has the best chance at mass consumer adoption, which has eluded prior attempts," said Patrick Moorhead, president of research firm Moor Insights & Strategy. "They believe it will solve many of the problems they had before with electronic payments".
Forrester Research has recently published a paper saying mobile payments volume in the United States will reach $142 billion by 2019.
Denée Carrington, a Forrester analyst, believes Apple Pay will be among the biggest "culprits" for the huge boom in mobile payments in the US. It certainly seems to be gaining traction fast and doesn’t look like slowing down any time soon.
But what do you think? Let us know in the comments section.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Ad blockers under threat from Google, Microsoft and others
Publié: décembre 10, 2014, 11:37am CET par Fadil Pašić
Several internet giants and media publishers, (Google, Microsoft and Le Figaro newspaper included), are threatening legal actions against the developers of software that blocks ads from reaching consumers.
This is, obviously, a problem for websites that rely on advertising as the web becomes more and more popular.
Japan Today writes that a quarter of the $545 billion spent on global advertising this year went on digital ads, however, with digital ads being present everywhere, the popularity of ad blocking software has grown substantially.
In the beginning, apps like these were unknown to the general public, and were used only by a handful of tech-savvy individuals.
Now, it’s a different story.
Adblock Plus, the most popular ad blocking browser add-on, has nearly five million active users in France, two million in the United Kingdom and 1.5 million in Spain.
According to a September report from Adobe software developer, Adblock boasts 144 million active users worldwide, up 69 percent in a year.
The publishers, whose revenue depends mostly on digital ads, find these results alarming, and are considering legal actions.
"This is no small matter; it affects all publishers. Our members have lost an estimated 20 to 40 percent of their advertising revenue", said Laure de Lataillade, CEO of GESTE, an association of web publishers in gaming, media, music and other domains.
Sean Blanchfield, CEO of PageFair, compared the campaign against ad blockers to Napster’s demise: "They should instead learn from the Napster story that the users will ultimately get what they want", said Blanchfield.
The problem has encouraged Google to launch an alternative to web advertising, called Google Contributor. It charges users between $1 and $3 a month to be spared ads, with the fee going to the affected websites. The idea is currently being tested on sites like Mashable, The Onion and Science Daily.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple vs Samsung: Still no end in sight for the patent war
Publié: décembre 10, 2014, 8:48am CET par Fadil Pašić

It seems as though the Apple vs Samsung patent wars will never end. Samsung has asked the US court to toss the $930 million lawsuit that Apple won, claiming that it didn’t plagiarize the iPhone and that the compensation was too high.
Samsung’s lawyer Kathleen Sullivan, argued that the lower court made an error and that the phones have separate distinct features, such as Samsung’s phones not having a 'home' button.
Apple was awarded Samsung’s total profits on those phones, which was described as "absurd", arguing that it was akin to awarding entire profits on a car because of an infringing cup holder.
Apple’s lawyer William Lee says the $930 million decision was the right one.
"This is not the cup holder", he said. "After two years, their market share was plummeting. In three months, they came up with something that was identical to the iPhone".
In April of 2012, a jury awarded Apple $1 billion in damages after Samsung was found guilty of infringing upon many of Apple’s patents. The compensation was lowered to $930 million after Samsung’s appeal.
Of this total, $399 million was for the copying of three patent designs for the shape, corners, translucent screen and colorful icon, $382 million was for the trademarked look and another $149 million for infringing on three other patents.
Apple and Samsung have been going back and forth with different lawsuits and fighting over various patents for a long time now and it is unlikely that this latest round will end any time soon.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Windows Phone has a massive apps problem
Publié: décembre 8, 2014, 7:14pm CET par Fadil Pašić

If Microsoft wants Windows Phones to have a higher market share than the current 2.8 percent, it needs to step up its applications game.
The current state of affairs is simple: There are just not enough apps. Some apps have hundreds of fakes and rip-offs in the store, some available for Android or iOS are simply missing for Windows Phone and arrive half a year late.
Last week, Jackdaw Research published a 30-page report highlighting how bad the situation with Windows Phone actually is.
Business Insider detailed a few examples from the report: "A search for 'YouTube' on the Windows Phone returns dozens of obvious fake YouTube apps".
"A search for ‘Swing Copters, a game for iOS and Android created by the maker of 'Flappy Bird', returns more than 25 fake apps with 'Swing Copters' in their title. In fact, the app isn’t available for Windows Phone".
And those are just some of the examples.
Microsoft might never be able to escape the death spiral: the lack of apps drives people to other platforms, which then keeps the popularity of Windows Phones low, which is why developers don’t want to build apps for that platform.
According to IDC, Windows Phone’s market share peaked at 3.4 percent in the last quarter of 2013, and has since fallen to 2.8 percent.
Jackdaw suggests Windows should build an awesome flagship phone, and somehow convince developers that they can make money by building apps for that platform. What actually happens remains to be seen.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple's new patent aims to limit the damage caused by dropping your phone
Publié: décembre 4, 2014, 12:22pm CET par Fadil Pašić

You know how a slice of bread always falls on the buttered side? Or how a cat, when dropped onto its back, always somehow manages to turn around mid-air and land on its feet?
Well, basically, Apple has been awarded a patent that does just that -- makes sure its products, when dropped, land exactly how they want them to land. Of course, this desired landing will be one that is the least likely to damage crucial components.
On Monday, U.S. Patent 8,903,509: "Protective mechanism for an electronic device", was awarded to Apple’s Nicholas King and Fletcher Rothkopf.
The patent covers a device that can use its motion sensors to detect when a device is in free fall, calculate how much time it needs to hit the ground and then act accordingly to make sure no components (or no important components) are damaged in the fall.
There are a number of different methods listed in the patent, including a weight inside the device that can move and turn it around, motors like the one used for vibrations, or even including wings to reduce the impact velocity.
Also, listed are some amazing suggestions, like the device grabbing onto a headphones cable when it detects a fall, or the use of little gas cylinders to produce thrust and change angles, Ender’s Game style.
Of course, this is all hypothetical at the moment, but it could potentially mean we’ll be seeing some kind of cat-like technology implemented in the iPhone 7.
Patent wars between tech giants have been going on for years -- entire companies are being bought because of them -- so it could also be interesting to see if Apple faces any disputes from this one. Your move Samsung.
Photo Credit: Bloomua / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Sony hack leads to unreleased movies leaking online
Publié: décembre 2, 2014, 11:07am CET par Fadil Pašić

A number of unreleased movies, as well as some confidential data, has been leaked online following a massive hack at Sony Pictures that happened last week.
In the Reddit thread covering the issue it says that, movies aside, confidential data including visa and passport information of cast and crew members working on different Sony projects, email inboxes and other important documents were leaked.
Among the movies that leaked online was Fury, starring Brad Pitt, currently the third most downloaded video in the past 48 hours on The Pirate Bay website.
Other movies included DVD screen copies of Still Alice, Mr Turner and Annie, none of which have officially been released yet.
Re/Code reported that Sony Pictures Entertainment is investigating the matter, claiming that there is a possibility that hackers working on behalf of North Korea, perhaps operating out of China, may be behind a devastating attack that brought the studio’s network to a screeching halt earlier this week.
Sony has threatened with a "merciless retaliation" if the movie The Interview gets released.
The film, starring Seth Rogen and James Franco, tells the story of two journalists, tapped by the CIA, who are sent to North Korea to assassinate Kim Jong-Un, the country’s leader.
North Korea called this movie an "act of war".
A group that calls themselves #GOP hacked Sony Pictures offices last week, paralyzing the outfit, and threatening the following:
"We already warned you, and this is just a beginning. We continue till our request be met. We’ve obtained all of your internal data including your secrets and top secrets. If you don’t obey us, we’ll release the data shown below to the world".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Wearhaus unveils 'social headphones'
Publié: novembre 18, 2014, 9:01am CET par Fadil Pašić

If you’ve ever been to a silent disco, you’ll know that listening to music through a pair of headphones doesn’t necessarily mean that you have to shut out everyone around you.
Sharing music with friends that all wear headphones has traditionally been reserved for these kinds of parties, which is something the boys and girls from Wearhaus are trying to change.
The Wearhaus Arc, described by the company as "social headphones", is designed to wirelessly synchronize multiple headphones using Bluetooth technology and thus share music with other people nearby.
Accompanied by a smartphone app, the headphones can be used to either tune in to whatever someone else is listening to, or to share and broadcast your own playlist.
The Wearhaus Arc also has a built-in LED light that, as they say, is designed to help you "express yourself through color".
The app isn’t only used for broadcasting or finding different people or playlists. It can also be used as a chat service, so that you can talk to other people without having to put the headphones down or scream over the music in your ears.
The headphones have simple, smartphone-like controls, with commands like tap (on the outside of the headphone ear) to play or pause, double tap to share, tap and hold to sync, swipe left or right to change the song, or swipe up or down to control the volume.
The headphones have a range of 65 feet indoors and 100 feet outdoors and the first batch is expected to ship in January 2015.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Facebook explains why it split Messenger from main mobile app
Publié: novembre 10, 2014, 8:37am CET par Fadil Pašić

Facebook CEO Mark Zuckerberg has finally explained the reason behind the company's decision to split Facebook and Facebook Messenger into two different mobile apps.
He said that the Facebook app was weighing down on messaging, making communication more difficult and slower.
Changing things is never easy. It's a truth that people will always complain about changes -- especially abrupt ones.
Facebook recently decided to free Messenger, a communication app, from the main Facebook app, to users accessing the site on mobile devices. Even though the majority didn't quite welcome the change, and even publicly cried out against it, Facebook stuck to its guns, and Zuckerberg has finally spoken of the reasons behind this decision.
He explained how the Facebook app's primary goal was the news feed, and how sending messages was something that just kept growing.
"Messaging was this behavior people were doing more and more," Zuckerberg explained. "10 billion messages are sent per day, but in order to get to it you had to wait for the app to load and go to a separate tab. Because Messenger is faster and more focused, if you're using it, you respond to messages faster, we've found".
He added that exchanging messages has become more popular than actually using the social network's primary features and that, in some countries, 85 percent of people use Facebook, while 95 percent communicate via SMS or messaging.
"Asking everyone in our community to install a new app is a big ask," added Zuckerberg. "On mobile, each app can only focus on doing one thing well, we think".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

British police using data to predict crime before it happens
Publié: novembre 4, 2014, 10:57am CET par Sead Fadilpašić
 Gang members that apparently have the highest chance of committing a crime can now reportedly be identified using a special product.
Gang members that apparently have the highest chance of committing a crime can now reportedly be identified using a special product.Accenture's new software, resembling that seen in the Minority Report movie, relies on data that has been collected over four years.
London Metropolitan police has ordered the software with the goal of trying to predict when people will commit crimes. The software passed a 20-week-long trial, and has used different statistics and social networks as sources of information.
"What this does is tell you who are the highest risk individuals that you should target your limited resources against," Muz Janoowalla, the head of public safety analytics at Accenture, told the BBC.
The test compared four years of data with events of the coming year. In that way, the police tried to retroactively test the program's capability and accuracy.
Police unfortunately wouldn't go into details of the test, or the criteria used when generating conclusions.
"For example, if an individual had posted inflammatory material on the Internet and it was known about to the Met -- one gang might say something [negative] about another gang member's partner or something like that -- it would be recorded in the Met's intelligence system," explained Janoowalla.
Heads of Big Brother Watch, a British civil liberties and privacy pressure group, have asked the police to reveal more information.
"The police need to be very careful about how they use this kind of technology," said research director Daniel Nesbitt.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.