Canaux
108470 éléments (108470 non lus) dans 10 canaux
 Actualités
(48730 non lus)
Actualités
(48730 non lus)
 Hoax
(65 non lus)
Hoax
(65 non lus)
 Logiciels
(39066 non lus)
Logiciels
(39066 non lus)
 Sécurité
(1668 non lus)
Sécurité
(1668 non lus)
 Referencement
(18941 non lus)
Referencement
(18941 non lus)
 BetaNews.Com (385 non lus)
BetaNews.Com (385 non lus)
-

Facebook hit with lawsuit over new stock option that gives Zuckerberg a license to print money
Publié: avril 30, 2016, 4:01pm CEST par Mark Wilson
When Facebook announced its first quarter results this week, it also announced that it created a new class of stock. The non-voting Class C stock proposed would enable Mark Zuckerberg and his wife Priscilla Chan to more easily fund their philanthropic ventures, whilst keeping Zuckerberg himself firmly in control of Facebook. In response to this, a lawsuit has been raised that says the proposed deal is unfair. The shareholders raising the class action lawsuit said the deal would grant Zuckerberg even more control and that the board committee didn’t do enough "to obtain anything of meaningful value" in return. The… [Continue Reading] -

Outlinely Express is a powerful free outliner for Mac
Publié: avril 30, 2016, 2:15pm CEST par Mike Williams
Glam Software has released Outlinely Express 2.0, a free version of its popular Mac outliner, Outlinely. The new edition has all the same outlining features as its commercial cousin, with no annoying restrictions or limitations. You don’t get any library management features -- new tools for storing and organizing your outlines -- but the program is very usable without them. (Arguably Outlinely Express 2.0 is better than regular Outlinely 1.x, as it has a much-improved interface and many new shortcuts and productivity tweaks.) If you're new to Outlinely, it's essentially a text editor optimized for outlining. You already know how… [Continue Reading] -

Apple: You're saying it wrong -- iPhones is not a word!
Publié: avril 30, 2016, 12:50pm CEST par Mark Wilson
Apple's marketing chief Phil Schiller has taken to Twitter to set the record straight about the nomenclature of the company's product names. Specifically, he takes umbrage with just sticking an 's' onto the end of product names to pluralize them. Yep -- iPhones is, apparently, not a word. Someone might need to speak with Tim Cook to get him on the same page though, as he doesn't seem to have seen the memo. Schiller goes as far as saying that there is simply no need to ever pluralize the name of any Apple product. If you've been referring to iPhones,… [Continue Reading] -

Twitter's unfair token system gives it far too much control over rival apps
Publié: avril 30, 2016, 11:40am CEST par Mark Wilson
In recent days you probably heard about the demise, and subsequent resurrection, of the Twitter client Fenix. Earlier this week, the app became a victim of its own success, succumbing to what it described as "the infamous Twitter tokens limitation". It's now back in the Google Play Store having carved out some sort of deal with Twitter, but the debacle highlights an important issue. If you want to create a Twitter client -- and why wouldn’t you? -- you'll need access to the Twitter API. This is not something Twitter wants, or permits, to just be a free-for-all, and it… [Continue Reading] -

A company reborn: Intel ditches Atom chips to focus on the cloud, the Internet of Things and 5G
Publié: avril 29, 2016, 11:09pm CEST par Mark Wilson
Big changes are afoot at Intel. A spokeswoman has confirmed that the company is scrapping its Sofia and Broxton mobile Atom chips, and will instead shift focus to more profitable ventures. Having invested billions of dollars in Atom for smartphones and tablets Intel is now switching its attention to the world of connected devices. Giving Atom chips the chop comes just after the company announced 12,000 job cuts and effectively walked away from the PC market. In moving away from mobile devices as well, Intel is undergoing a rebirth. It is looking to focus on key areas of growth, particularly… [Continue Reading] -

Qbot malware resurfaces with renewed powers ready to steal your banking credentials
Publié: avril 29, 2016, 7:32pm CEST par Mark Wilson
Qbot -- also known as Qakbot -- is a form of malware that's been around for a number of years, but security researchers at Cisco Talos have noted that it has returned with a vengeance. Once installed the malware steals sensitive data stored in files and cookies, and also monitors live web sessions to grab login credentials. Detection and immunization is made difficult thanks to the fact that Qbot uses random strings, code blocks, file names and encryption keys to slip under the radar, although it can still be detected by its behavior. Cisco Talos analyzed no fewer than 618… [Continue Reading] -

Microsoft looking into storing data using DNA
Publié: avril 29, 2016, 6:35pm CEST par Anthony Spadafora
Now that users are generating more data than ever before, Microsoft has begun to explore the idea of using DNA molecules to store data. To begin investigating the possibility of accomplishing such a complex task, the company will be purchasing 10 million strands of long oligonucleotides -- or lab made DNA molecules -- from a startup in San Francisco called Twist Bioscience. DNA molecules are an ideal storage solution because they do not degrade in the same way that Blu-Ray discs and other physical media do. Data stored this way could remain intact and still be readable anywhere from 1,000… [Continue Reading] -

What is the most popular Windows Phone?
Publié: avril 29, 2016, 4:37pm CEST par Mihăiță Bamburic
The Windows Phone landscape has evolved at a slow pace in the past three years, and the list of the ten most popular smartphones running the tiled operating system is proof of that. Since July 2013 Lumia 520 has held the top spot in the charts, taking Lumia 920's crown just a few months after being introduced. But, fast forward to today and we finally have a new king. Before you get too excited and think that we finally have some major changes at the top you should know that Windows Phones appeal mainly to folks who shop in the low-end segment of… [Continue Reading] -

Lack of data is a roadblock to account-based marketing
Publié: avril 29, 2016, 4:26pm CEST par Ian Barker
The idea of account-based marketing (ABM), treating B2B customers as individual marketing targets, has been around for a while. Technology has made it more practical approach in recent years, but a new survey reveals there are still factors holding back its use. Business insights specialist Avention has carried out a survey of 100 B2B sales and marketing practitioners about their use of ABM techniques and strategies. While more than 90 percent of those surveyed believe ABM is relevant to their businesses, respondents say that their number one roadblock to starting an ABM program is lack of access to the right… [Continue Reading] -

How to boost your free Microsoft OneDrive storage back up to 15GB
Publié: avril 29, 2016, 2:38pm CEST par Wayne Williams
Last year, Microsoft announced plans to drop the free OneDrive storage amount from 15GB down to 5GB, and also discontinue the 15GB camera roll bonus. Earlier this week we learned that the software giant will be putting this plan into action from July, which means if you’re currently using more than 5GB of storage you will either have to remove some files to get under the new limit, or upgrade to a paid plan. But hold on a minute. Before you do either, there is a third option which you can use to keep your free storage at 15GB. SEE… [Continue Reading] -

Boys aspire to work in IT, girls find it boring
Publié: avril 29, 2016, 2:28pm CEST par Anthony Spadafora
The Internet organization Nominet, best known for running the .uk infrastructure, has compiled new research on the dream jobs of today’s students that shows how male students have begun to aspire for careers in technology while female students find the field less interesting. The top three dream jobs of young boys all pertain to the tech industry, with computer game developers being number one, app developers being number two and website developers being number three. Twenty-four point eight percent of school aged boys would like to develop computer games while 17.2 percent envision themselves developing apps and 15.1 percent hoping… [Continue Reading] -

Microsoft takes just 7 hours to patch colossal Office 365 vulnerability that exposed companies' data
Publié: avril 29, 2016, 1:44pm CEST par Mark Wilson
Companies are often criticized for the length of time it takes them to patch security problems found in software. But this week Microsoft exceled itself, taking just 7 hours to patch a serious security hole in Office 365 that made it possible to gain unrestricted access to businesses' cloud accounts. A problem with the SAML authentication system meant that it was possible to gain access to just about any Office 365 account, including accessing connected services like Outlook, OneDrive and Skype for Business. More than this, the exploit allowed an attacker to infiltrate companies and organizations such as Verizon, Georgia… [Continue Reading] -

Facebook's mobile ads boosting revenue
Publié: avril 29, 2016, 1:41pm CEST par Sam Pudwell
Facebook has put other tech giants to shame by comfortably beating analyst expectations in the last quarter, with revenues over 50 percent up thanks to surging mobile advertising sales. As mobile web browsing continues to grow throughout the world, advertisers are realizing that taking a mobile-first approach has the potential to be extremely lucrative. Facebook has looked to capitalize on this by improving its mobile app and expanding its live video solution, both of which have attracted advertisers. As a result, advertising revenue increased 56.8 percent to $5.20 billion, with mobile ad revenue accounting for approximately 82 percent, up from… [Continue Reading] -

Facebook transparency report shows increase in government data requests, most with gagging orders
Publié: avril 29, 2016, 1:14pm CEST par Mark Wilson
Facebook has published its latest Global Government Requests Report covering the second half of 2015. The transparency report reveals that there has been as 13 percent increase in the number of government requests for data, but it also shows that Facebook is still not able to be as transparent as it might want. For the first time the social network is able to report about the number of data requests that have a non-disclosure order attached to them. More than half of the requests -- 60 percent, in fact -- have gagging orders that prevent Facebook from notifying users about… [Continue Reading] -

Hacker creates reality TV with users' webcams
Publié: avril 29, 2016, 12:47pm CEST par Alan Buckingham
The webcam debuted long ago and has become integrated into many computer systems. People use it for any number of things, and products like Skype utilize this functionality. But the innovation has a darker side. It turns out this little add-on can be hacked, allowing the perpetrator to view the user. A hacker in Russia took this to a higher level by not only accessing people's cameras, but broadcasting the video online, right on YouTube. 2ch's users were hacked and the nation and its media watched it live. As users approached their computers the hacker launched a porn site, in… [Continue Reading] -

85 percent of people won't pay ransoms to recover data
Publié: avril 29, 2016, 12:01pm CEST par Ian Barker
As we've seen in recent reports, ransomware is an increasingly big problem. But how much do people know about it and methods to protect themselves? Security researchers at ESET surveyed over 3,000 people across the US and Canada to gauge their understanding of ransomware and unearthed some interesting findings. One in three of those surveyed say they are unaware of what ransomware is. More worryingly younger people are less likely to understand the concept than older ones. 85 percent say they would prefer to lose their files rather than pay a ransom, while the remaining 15 percent would be willing… [Continue Reading] -

Best Windows apps this week
Publié: avril 29, 2016, 11:27am CEST par Martin Brinkmann
One-hundred and seventy-eight in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days. This week saw the unveiling of the official Facebook app for Windows 10 (now available to anyone), and Messenger, Facebook's chat and messaging service. As always, if I missed an app or game that has been released this week that you believe is particularly good, let me know in the comments below or notify me via email instead. Discounts This Week The following discounts are provided by Red Stripe Deals, a weekly… [Continue Reading] -

Log file reads, writes, creates and deletes with SoftPerfect File Access Monitor
Publié: avril 29, 2016, 11:15am CEST par Mike Williams
Australian developer SoftPerfect has released SoftPerfect File Access Monitor, a smart tool which logs all file create, read, write and delete actions on a PC. If you don’t need every detail then filters enable recording only particular actions, by specified processes, on defined file masks and in your chosen paths. A good range of reporting options start with an Explorer-type view, immediately highlighting folders with recent activity. A separate Chronological view lists file actions by time, and can be filtered by operation, user, process and more. If you’re planning some long-term monitoring then it’s even possible to set up scheduled… [Continue Reading] -

Waze vulnerability allows hackers to track you
Publié: avril 29, 2016, 10:50am CEST par Phoebe Jennelyn Magdirila
Users of Google’s navigation app Waze seem to be at risk of being followed, as a vulnerability in the app could allow hackers to stalk the users of the app in real-time, a group of researchers from the University of California has found. The researchers reverse-engineered Waze’s server code and discovered that thousands of "ghost drivers" could be created on Waze’s systems, which can monitor the real drivers around them. Hackers could even create virtual traffic jams, an exploit to track Waze users in real-time. The hack only works when the app is in the foreground and users can also… [Continue Reading] -

Microsoft pulls another boner -- blocks Chrome and Google from Cortana on Windows 10
Publié: avril 29, 2016, 1:34am CEST par Brian Fagioli
Holy cow, Microsoft makes it really hard to recommend its products lately. Windows 10 was a great way to wash the disgusting Windows 8 taste from consumers' mouths -- initially, at least. Unfortunately, the discovered privacy issues frightened many folks, causing them to delay upgrading. The latest build has a wonderfully refreshed Start Menu, making me think that the company was back on track. Nope; I was wrong. Today, Microsoft announces an anti-competitive bombshell -- it is blocking all third party browsers and search engines from Cortana. Prefer using Chrome and Google? Tough luck. Firefox and Yahoo? Sorry. Microsoft just can't stop pulling… [Continue Reading] -

Developers have a new Windows 10 Anniversary Update SDK Preview to play with
Publié: avril 28, 2016, 9:21pm CEST par Mark Wilson
With the new big update to Windows 10 just around the corner, Microsoft is pulling out all the stops to make sure that developers have access to the tools they need to take advantage of the new features. Windows 10 Anniversary Update is due for release in July and ahead of the big day Microsoft has released a new SDK. Having open-sourced the Xamarin iOS, Android and Mac SDKs, the launch of the Windows 10 Anniversary Update SDK Preview gives developers a chance to make sure their code works ahead of the update rollout. It is compatible with Build 14332… [Continue Reading] -

Quality control and pet monkeys: My search for a decent laptop continues
Publié: avril 28, 2016, 8:21pm CEST par Randall C. Kennedy
What the hell is going on with quality control these days? It seems like every new PC I buy or test has something wrong with it right out of the box. Whether it’s a strange hardware failure, a bizarro software glitch, or something less easily definable, the new machine will undoubtedly go belly up in some fashion within the first six months. Take Dell’s Inspiron 13, for example. In my quest to find a replacement for my HP Envy x2 (abandoned by Microsoft/Intel/HP) and, later, my Surface 3 (destroyed in an incident involving a moving vehicle, alcohol, and an undomesticated… [Continue Reading] -

Human rights group Liberty rips into Snooper's Charter with video highlighting privacy issues
Publié: avril 28, 2016, 8:01pm CEST par Mark Wilson
The Snooper's Charter -- or the Investigatory Powers Bill -- is a highly controversial piece of legislation the UK government is trying to bring into force to allow for the bulk collection of data, NSA-style. Outside of government, it is widely regarded as a massive invasion of privacy, and the human rights group Liberty is just one of the organizations that is very vocally opposed to it. The bill will require ISPs to record customers' browsing histories for an entire year, and will permit the government to remotely hack phones and computers, as well as requiring tech companies to provide… [Continue Reading] -

IT pros feel overworked and underappreciated
Publié: avril 28, 2016, 8:00pm CEST par Anthony Spadafora
A new poll from Kensington, which produces computer accessories, has found that IT professionals feel undervalued and overworked in their organizations. Enterprises are under increasing strain to keep pace with the digital world and 32 percent of the IT decision makers that participated in the poll were frustrated that they were not provided with enough time to increase employee productivity and well-being through the use of technology. Rather, they often felt like firefighters in their organizations as they were constantly drawn away to deal with issues that arose and were rarely ever able to devote the necessary time to provide… [Continue Reading] -

Apple's iPad Pro beats Microsoft's Surface... again
Publié: avril 28, 2016, 7:14pm CEST par Mihăiță Bamburic
The tablet market has seen better days. In the first quarter of 2016 shipments totaled just 39.6 million units, which represents a 14.7 percent decline year-over-year. However, while the market is shrinking there is a category of slates which is gaining more interest from consumers. That category is made up of so-called detachable tablets. Microsoft basically created it with the original Surface and Surface Pro four years ago, but now it is Apple which is reaping the benefits of its rival's efforts with the iPad Pro line. In fact, this is the second straight quarter when iPad Pro obliterates the… [Continue Reading] -

HP Chromebook 13 is a business-focused Chrome OS laptop with USB-C
Publié: avril 28, 2016, 6:41pm CEST par Brian Fagioli
In the grand scheme of things, Chrome OS is hardly a major player from a desktop market share perspective -- for now. With that said, the Linux-based operating system has captured the hearts and minds of many consumers. It has matured quite a bit too, becoming a viable Windows alternative for home users. Actually, it is a great choice for some businesses too -- depending on needs, of course. Today, Google announces the latest business-focused laptop running its desktop operating system -- the HP Chromebook 13. Not only is this Chrome OS laptop powerful, affordable, and beautiful, but very secure too. It… [Continue Reading] -

UK government looking to implement blockchain technology
Publié: avril 28, 2016, 6:38pm CEST par Anthony Spadafora
The UK government is exploring the potential use of blockchain technology to aid it in dealing with the managing and distribution of grants. This technology first gained notoriety through its use in the bitcoin currency. Now many governments and financial institutions are interested in using blockchain as a decentralized ledger which can be verified and shared by a network of computers. It can also be used to store data and can keep track of how assets are exchanged. In a speech at London’s Digital Catapult, Cabinet Office minister Matt Hancock highlighted the ways blockchain technology could be implemented to improve… [Continue Reading] -

Financial services lead the way in BYOD adoption despite security concerns
Publié: avril 28, 2016, 3:04pm CEST par Ian Barker
BYOD is becoming increasingly popular across all industries, but it's the financial sector that's leading the way according to a new report. The findings come from data protection company Bitglass which surveyed more than 800 cybersecurity professionals across five major industries, including financial services, technology, healthcare, government and education. It finds that 72 percent of all organizations support BYOD for all or some employees, but the figure is 74 percent for the financial sector. However, relatively few organizations are able to control access to corporate data, with only 14 percent having successfully deployed mobile application management (MAM) solutions. "The threat of data leakage… [Continue Reading] -

Enterprise Microsoft Azure users get free one-year support
Publié: avril 28, 2016, 3:01pm CEST par Anthony Spadafora
In order to hasten the transition from its traditional retail products to its cloud based products, Microsoft has just announced that it will be offering one year of free technical support to Azure users. From May 1, 2016 through to June 30, 2017 users who purchase Azure Services under an Enterprise Agreement (EA) will receive a year of free support from the company. According to Microsoft: "This upgrade is designed to give you an additional level of support on your journey to the cloud, and it comes at no charge". Customers who are eligible for this offer but choose not… [Continue Reading] -

9 out of 10 office workers suffer technology stress in meetings
Publié: avril 28, 2016, 12:36pm CEST par Ian Barker
A new survey of office workers in the UK shows that a majority suffer stress in meetings when struggling with tasks like sharing screens and finding the right cables in order to give presentations. The study by visualization specialist Barco finds that for 93 percent, this meeting stress has serious knock-on effect on every aspect of their work. Presentations were of a poorer quality, time was wasted, deadlines were missed, and for 12 percent, it even resulted in lost promotions and lost business. People's heart rates reached 179bpm when struggling with technology during a meeting, compared to resting heart rates… [Continue Reading] -

FBI won't tell Apple how it hacked San Bernardino iPhone as it doesn't understand the technique
Publié: avril 28, 2016, 11:43am CEST par Mark Wilson
Apple had been hoping that the FBI would come clean about how it managed to gain access to the San Bernardino iPhone, but that's just not going to happen. The agency managed to crack the iPhone 5C at the center of the case after getting help from a third party rather than Apple. But now the FBI has confirmed that it doesn't really know how the cracking tool works. Or, more precisely, it did not buy the rights to the technical details of the tool. After a very public battle with Apple, the FBI ultimately resorted to getting help from… [Continue Reading] -

Outdated Java, QuickTime installations on the rise in UK
Publié: avril 28, 2016, 11:40am CEST par Sead Fadilpašić
UK’s citizens are getting more diligent when it comes to patching and updating their Windows-operated computers, new survey by Flexera Software’s Secunia Reports team says. QuickTime users, on the other hand, aren't as vigilant. According to the team’s Country Reports, the number of unpatched Microsoft Windows operating systems is on the decline. At the end of the first quarter of 2016, the number sits at 6.1 percent, where last year at this same time, it was at 11.5 percent. QuickTime 7.x users, on the other hand, are lagging behind. The number of users with unpatched software is now at 61 percent,… [Continue Reading] -

Amazon held to account for billing parents for in-app purchases made by their kids
Publié: avril 28, 2016, 11:17am CEST par Mark Wilson
A federal judge has ruled that Amazon is liable for sending out bills to parents of children who made in-app purchases without permission. Amounting to millions of dollars, the bills have now been deemed unauthorized, and Amazon faces having to pay back a large percentage of the money. The case has echoes of similar legal action brought against Google and Apple for purchase made by children in the App Store and Google Play. Amazon, Apple and Google have all implemented system to prevent unauthorized purchases since being investigated by the FTC back in 2014. The FTC is seeking full refunds… [Continue Reading] -

Skype for Business now available on OS X
Publié: avril 28, 2016, 10:27am CEST par Anthony Spadafora
In an attempt to entice enterprise Mac users, Microsoft has just released a preview of its new Skype for Business for OS X. This new version of Skype will be business-focused and is centered around creating an experience tailored to enterprise users. From today, you can request access to the preview from Microsoft. The company will be sending the Skype for Business Mac Preview out to IT administrators in order for them to familiarize themselves with the software before extending the preview to more users. Microsoft’s roll out of the new client will occur in three stages. The first of… [Continue Reading] -

Oculus brings Microsoft's Minecraft to Samsung's Android-powered Gear VR
Publié: avril 28, 2016, 2:46am CEST par Brian Fagioli
Minecraft is a surprisingly popular game. The design pays homage to block-like graphics of games from earlier days -- a time when a large amount of Minecraft fans weren't even born! We have the technology to make more lifelike environments, with curved edges and circles, but that would be blasphemy to the Minecraft community. "What's old is new" as some folks say, I suppose. Today, The Oculus Team announces that it has worked with Microsoft to bring Minecraft to Samsung's smartphone-powered virtual reality platform, the Gear VR. Owners of this solution can now experience a more-immersive Minecraft experience, by leveraging Samsung's heasdset and… [Continue Reading] -

Windows 10 interrupts a live TV broadcast with an unwanted upgrade
Publié: avril 27, 2016, 8:27pm CEST par Wayne Williams
Ever since Microsoft made Windows 10 a recommended update there have been numerous reports of the new operating system installing itself without user consent, and without much warning. Microsoft has always played down this behavior, but an example of how the OS pushes upgrades on unsuspecting users was earlier today shown live on TV during a weather forecast. SEE ALSO: Microsoft reportedly installing Windows 10 without consent -- again If you’re in Iowa you might have seen KCCI 8 News Meteorologist Metinka Slater’s thunderstorm update and warning of 12 hours of heavy rainfall interrupted by an unwelcome upgrade message covering… [Continue Reading] -

Ira Glass arrives on Pandora as This American Life is released on the streaming platform
Publié: avril 27, 2016, 8:25pm CEST par Alan Buckingham
You may well have heard the popular radio show This American Life. It's broadcast out of Chicago, but syndicated around the US, and perhaps has an even greater footprint thanks to its podcast. Host Ira Glass has taken his idea for a little show and turned it into a force in media. Despite the name, the shows are very much international, though they usually involve Americans, even in foreign locations. Glass also covers all sorts of incidents from the financial crisis to crimes. Now the long-running show is coming to Pandora, a platform known for its music streaming system. Pandora… [Continue Reading] -

Malware compromises Swift system -- patch available
Publié: avril 27, 2016, 8:18pm CEST par Anthony Spadafora
The Swift (Society for Worldwide Interbank Financial Telecommunication) system has apparently fallen victim to the same sophisticated hacking scheme that was used to disrupt the Bangladesh central bank last month. The cyberattack in Bangladesh resulted in a loss of $951 million from the central bank's account at the Federal Reserve in New York and it now seems likely, thanks to new research from BAE systems, that Swift was also compromised during the attack. During their investigation of the attack, security researchers at the company found a hidden piece of malware that lead to a loss of $81 million. It was… [Continue Reading] -

Microsoft makes Xamarin SDKs for Android, iOS and Mac open source
Publié: avril 27, 2016, 6:18pm CEST par Mark Wilson
Microsoft's embracing of the open source movement grows ever tighter, and today the company announced that its Xamarin SDKs (available for Android, iOS and Mac) will be open sourced. It's not long since Microsoft bought Xamarin, and just weeks later the SDKs are being opened up. Announced at the Xamarin Evolve 2016 event, the move sees Microsoft trying to encourage mobile developers. The company says it has already made great strides in this area: "we helped nearly 3.5 times more developers get started building great apps with Xamarin than ever in our history as a company". The Xamarin SDK has… [Continue Reading] -

Companies invest more in DDoS protection
Publié: avril 27, 2016, 6:10pm CEST par Sead Fadilpašić
Pretty much every company out there has been, or will be a target of a DDoS attack. A new report by real-time information services provider Neustar, entitled The Threatscape Widens: DDoS Aggression and the Evolution of IoT Risks, released this month, says it’s no longer the question of "if" or "when" a company will be DDoSed -- it’s how often and how long will it last. According to the report, 73 percent of companies were attacked in 2015, with 82 percent of those attacked suffering multiple attacks. Out of that number, 45 percent said they were attacked six times, or… [Continue Reading] -

Google antitrust: Getty Images files complaint against search giant for image scraping and piracy promotion
Publié: avril 27, 2016, 5:30pm CEST par Mark Wilson
Google is already embroiled in one antitrust case in Europe where the company stands accused of abusing Android's dominance. Now photo agency Getty Images is accusing Google of promoting piracy and engaging in anticompetitive behavior by 'scraping' images from third party sites. In a familiar-sounding complaint, Getty Images also says that Google skews search results in favor of its own services -- such as Google Images. The photo agency says that this directly impacts upon rival services, but perhaps the big charge is that a change made to Google Images provided access to copyrighted material and "promoted piracy, resulting in… [Continue Reading] -

Why Microsoft remains 'committed' to Windows 10 Mobile
Publié: avril 27, 2016, 5:06pm CEST par Mihăiță Bamburic
Windows 10 Mobile does not have much of a future. With two very disappointing quarters for Lumia sales, a market share of around one percent, poor vendor support, and no mention of it at Build 2016, this much is clear. You would expect Microsoft to pull the plug any minute now, but the software giant seems to be doing just the opposite. In an internal email, Terry Myerson is encouraging "certain partners" to continue to pour their resources into the platform. Microsoft's EVP of Windows and Devices Group says that the company is still "committed" to Windows 10 Mobile, claiming… [Continue Reading] -

New partnership helps boost eCommerce platform performance
Publié: avril 27, 2016, 2:59pm CEST par Ian Barker
In order to get a competitive advantage, retailers are increasingly looking to deliver a rich, interactive eCommerce experience for their customers. The problem with this is that it can lead to platforms being loaded down with extra functions that result in a drop in performance. Application delivery specialist InstartLogic has announced that it's partnering with IBM to help retail clients accelerate the performance of their eCommerce platforms. Instart Logic's Application Delivery Platform brings a fundamental new approach to website delivery and security to users of the IBM WebSphere Commerce platform and IBM Commerce on Cloud. It uses software and machine… [Continue Reading] -

Win tickets to the Beyoncé Formation World Tour with this Uber promo code
Publié: avril 27, 2016, 2:37pm CEST par Brian Fagioli
Whenever I go to NYC, I have an internal struggle over transportation. Once I arrive in Penn Station by way of the Long Island Railroad, do I choose a yellow cab, or an Uber ride? Many things weigh on my choice, such as the weather, or a very long wait at the cab line in front of Madison Square Garden. Now it seems I have yet another factor in my decision -- Beyoncé. How is the superstar singing sensation impacting my choice between yellow cab and Uber? Well, American Express is now offering a chance to win tickets to her sold-out tour. By using… [Continue Reading] -

Remove CryptXXX ransomware with Kaspersky's free decryption tool
Publié: avril 27, 2016, 2:16pm CEST par Mark Wilson
Security firm Kaspersky has released a tool that can be used to decrypt files on computers hit by the CryptXXX ransomware. Rather than paying the ransom demanded to regain access to files, victims are now able to turn to the free RannohDecryptor utility. CryptXXX had been identified by ProofPoint earlier in the month and described as being closely linked to the Reveton ransomware operation and Angler/Bedep. The ransom of $500 is considered to be quite high, but Kaspersky's free decryption tool means that files can be retrieved without having to part with a cent. CryptXXX uses RSA4096, but Kaspersky's John… [Continue Reading] -

BlackBerry Priv gets Android 6.0 Marshmallow
Publié: avril 27, 2016, 2:12pm CEST par Mihăiță Bamburic
Android 6.0 launched over half a year ago, but even today there are still lots of devices that have yet to receive the software upgrade to Marshmallow. In fact, at the beginning of this month fewer than one in 20 were running Google's latest mobile operating system. For BlackBerry Priv users though things are looking up. The Canadian maker has announced the Marshmallow rollout for its first Android smartphone, introducing improvements to the camera, battery, privacy, security, and more. BlackBerry says that Android 6.0 Marshmallow is available now for smartphones purchased through ShopBlackBerry.com (unlocked models, basically), and will reach carrier-branded… [Continue Reading] -

Can we dispense with the 'Apple is dead' meme -- other CEOs would lose a limb to have a bad quarter like this
Publié: avril 27, 2016, 2:00pm CEST par Joe Wilcox
Listening to Apple's fiscal second quarter 2016 earnings conference call yesterday was like attending a funeral—where the eulogy is for someone whom you know has gone to Hell. There's no way to sugarcoat that the good days are over and an eternity of burning flesh awaits. I kid you not. Haul over to iTunes and download the replay. You'll feel the grim reaper looking over your shoulder while CEO Tim Cook talks as joyfully about Apple's performance as a man granted last words before the gallows. And I wonder why? So what that Apple reported its first revenue decline in… [Continue Reading] -

Free online service helps uncover malicious domains
Publié: avril 27, 2016, 12:29pm CEST par Ian Barker
Phishing sites that use domain names similar to a legitimate company’s, along with cybersquatting are a major problem. Open DNS recently claimed that cyber squatters have become more active during the US election campaign. Web security solutions company High-Tech Bridge is launching a new, free, online service that will allow anyone to instantly detect typosquatted, cybersquatted or phishing domains targeting their domain or brand name. Called Domain Security Radar, the service is simple to use -- just enter a URL and results include details on cybersquatted domains, typosquatted domains and phishing websites. It also shows the latest trends and alerts… [Continue Reading] -

Why ATMs are easy to hack
Publié: avril 27, 2016, 12:24pm CEST par Sead Fadilpašić
Security researchers claim ATM machines are usually not that difficult for hackers to penetrate. Once they’re inside, they can steal money, or banking details from unsuspecting victims. Now, researchers from Kaspersky Lab have investigated what makes ATMs such an easy target for hackers, and came to two conclusions: both software and hardware are easy to access and temper with. According to the researchers, ATMs are usually based on outdated systems (usually Windows XP), which makes them vulnerable to either malware attacks or exploits. In many cases, ATMs communicate with banking infrastructure through an old, unsecure XFS standard. "The problem is… [Continue Reading] -

Feedbro is a one-stop reader for RSS, Twitter, Instagram, YouTube, more
Publié: avril 27, 2016, 11:43am CEST par Mike Williams
Feedbro is a versatile feed reading Chrome extension which keeps you up-to-date with RSS/ Atom/ RDF sources, blogs, Twitter, Instagram and more. The extension is stand-alone, rather than being a front-end for a website, which means there’s no need to sign up, create accounts, log in or anything else. You don’t have to waste time manually transferring feeds from other readers. either. OMPL support means you can have them imported in just a few seconds. In Internet Explorer, for example, click File > Import and Export > Export to a file > select Feeds > Next > Export to save… [Continue Reading] -

Windows 10 Insider Preview Build 14332 for PC and Mobile now available in the Fast ring
Publié: avril 27, 2016, 9:04am CEST par Wayne Williams
The past two Windows 10 Insider Preview releases -- Builds 14316 and 14328 -- have been packed with new features and notable changes. The very latest Fast ring release, Build 14332, marks the start of the Bug Bash, in which Windows Insiders will be set quests to help Microsoft eradicate problems and fix flaws in the OS in preparation for the big Anniversary Update out in July. However, the new build is not only about fixes, there are some new features and improvements too. SEE ALSO: Microsoft's Handoff-like feature makes an appearance in Windows 10 Build 14328 First up, there… [Continue Reading] -

Google Maps Street View sails through the Sydney Opera House
Publié: avril 27, 2016, 6:03am CEST par Brian Fagioli
Believe it or not, I have never been to the opera. Truth be told, I am more of a sports and chicken wings kind of guy, but I am not opposed to more sophisticated things. I've been to my fair share of Broadway shows, and eaten at fancy restaurants with cloth napkins, but the opportunity to attend the opera has never surfaced. Thanks to Google Maps Street View, however, I can now experience the Sydney Opera House, including its famous "sails", from the comfort of my computer. Yes, you can now take a virtual tour as if you are really there! "Perched on… [Continue Reading] -

Satechi unveils Aluminum Mini Docking Station for Windows and Mac
Publié: avril 27, 2016, 5:02am CEST par Brian Fagioli
When it comes to computing, I always prefer a desktop when possible. I like using a big monitor, mechanical keyboard, and mouse. If I am not at a desk in a comfortable chair, my productivity drops. While I do use a laptop when on the go, a trackpad and small screen are pain points for me. Not everyone can afford to have both a desktop and laptop, so luckily, it is easier than ever nowadays to use the latter as a makeshift of the former. Unfortunately, docking stations from laptop manufacturers are often expensive and proprietary. USB variants are sometimes preferable,… [Continue Reading] -

This dude won the Microsoft Open Source Challenge, and you didn't
Publié: avril 27, 2016, 3:43am CEST par Brian Fagioli
The future of computing is open source -- the writing is on the wall. Major companies like Apple, Microsoft, and Google are embracing this software ideology, and more and more consumers are expecting it. Of course, for open source to continue its ascent, we will need students to be knowledgeable about it. Microsoft had this in mind when it announced its Open Source Challenge for students, and now we have four official winners. The top champion is a dude named Akond Rahman -- yeah, that is his smiling face to the right -- and he is now $5,000 richer. Better than the money, he… [Continue Reading] -

Apple fiscal Q2 2016 by the numbers: $50.6B sales, $1.90 EPS
Publié: avril 26, 2016, 10:59pm CEST par Joe Wilcox
The spotlight shines on the world's most-valuable company this fine Tuesday, as Apple revealed results for fiscal second quarter 2016. Wall Street expected the first revenue growth decline in more than a decade and iPhone's first-ever sales retraction . Is the sky finally falling? Eh, not yet. But the sun slowly sets over the vast smartphone empire. Ahead of today's earnings announcement, Wall Street consensus put revenue down 10.4 percent year over year to $51.97 billion, with earnings per share down 14.2 percent to $2. Apple actual: $50.557 billion sales, $10.5 billion net income, and $1.90 EPS. Three months ago, the… [Continue Reading] -

Logi BASE is an elegant iPad Pro charging stand
Publié: avril 26, 2016, 6:53pm CEST par Brian Fagioli
If you are a fan of Apple's iOS, you may be intrigued by the iPad Pro, and rightfully so. Regardless of the screen size you choose, the elegant professional-level tablet is not only great for some business cases, but having fun too. Today, continuing the elegance trend with the iPad Pro, Logi (a Logitech sub-brand) announces BASE. Leveraging the 'Smart Connector' charging pins found on Apple's pro tablets, the stand supplies electricity to the device while both propping it up and proudly displaying the iPad like art. "Logi BASE is the first iPad Pro stand using Apples Smart Connector technology to take charging to a… [Continue Reading] -

Microsoft's Handoff-like feature makes an appearance in Windows 10 Build 14328
Publié: avril 26, 2016, 6:33pm CEST par Wayne Williams
Apple users will be familiar with Handoff. This feature lets you start working on one Apple device -- be it a Mac, iPad or iPhone -- and then pick up where you left off on another, provided the devices are within Bluetooth range of each other. At Build 2016, Microsoft talked about its plans to introduce a Handoff-style feature to Windows 10, codename Project Rome, and the first glimpse of this has appeared in the latest build for Windows Insiders. SEE ALSO: Windows 10 Insider Preview Build 14328 introduces an improved Start menu, and loads of exciting new features If… [Continue Reading] -

Meizu PRO 5 Ubuntu Edition smartphone finally available -- Linux fans, buy it now!
Publié: avril 26, 2016, 6:26pm CEST par Brian Fagioli
Android is a Linux-based operating system, true, but for many, it is sort of a bastardized use of the kernel. Understandably, Nexus devices aside, it can feel very un-Linux-like to have devices with locked bootloaders that cannot be easily updated. Some Linux fans have been clamoring for an alternative. Ubuntu is that alternative. Canonical's operating system can scale well, from desktop to tablet to smartphone. Best of all, you can buy an unlocked device that requires no carrier approval for OS updates. Today, the most exciting phone to run the operating system -- Meizu Pro 5 Ubuntu Edition -- goes on sale.… [Continue Reading] -

New Bamboo Server features help businesses manage growth
Publié: avril 26, 2016, 5:11pm CEST par Ian Barker
Growth is the goal of most businesses, but it can create problems for IT teams as they hit resource limits, lose track of processes, and struggle with inefficient collaboration, security risks and user management problems. Development tools company Atlassian is announcing the release of its latest version of Bamboo Server continuous integration and deployment tool that manages the roll out of automated software builds. Key features of Bamboo 5.11 are an increase in the number of remote agents from 100 to 250, improved diagnostics and better integration. It's now possible to use REST APIs to trigger deployments for continuous delivery.… [Continue Reading] -

Convert cryptic date/time values into something readable
Publié: avril 26, 2016, 4:46pm CEST par Mike Williams
If you regularly investigate raw databases, executables or other binary files then you might sometimes find "dates" that seem to be random numbers, like 12883423549317375. This probably means the date is encoded, but there are many different formats, and no obvious way to detect which one has been used. DateDecoder is a freeware tool for Windows which provides an easy way to solve the problem. Simply paste one or more values into the "Source date/ times" box, click Decode, and the program tries to decipher them using 13 of the most common formats (Ticks, NSDate, Java, HFS, Filetime, AOL, Chrome,… [Continue Reading] -

Cloud native networking helps businesses exploit public clouds
Publié: avril 26, 2016, 3:24pm CEST par Ian Barker
As more businesses turn to the use of public cloud services, they're keen to find ways to gain more visibility into their deployments and make them more secure. Cloud native networking pioneer Aviatrix Systems is addressing this with the launch of its Cloud Native Networking 2.0. The solution combines a software-defined network controller and software gateways to enable businesses using a combination of public, private and hybrid clouds to quickly and easily roll out virtual private clouds. It enables cloud operations teams to set up, securely connect and centrally manage their entire cloud network, connecting users, sites and instances across regions… [Continue Reading] -

Amazon Prime Music debuts on Sonos systems in the UK
Publié: avril 26, 2016, 1:53pm CEST par Alan Buckingham
Amazon Prime has become hugely popular, and it's easy to see why. For $99 per year, customers get free two-day shipping, streaming video, streaming music and Kindle lending library. Sonos is less adopted because of the price, but if you've invested in it then you have a great whole-house audio system. Six months ago, the two came together in the US to add to your musical enjoyment and today Amazon Prime Music will be debuting on Sonos in the UK and filling British homes with tunes. This is full access, meaning over one million songs and numerous playlists. In celebration of… [Continue Reading] -

Free Microsoft OneDrive storage will be slashed to just 5GB in July -- here's what you need to know
Publié: avril 26, 2016, 1:21pm CEST par Wayne Williams
In November last year, Microsoft announced that it would be cutting back on the amount of free storage offered to OneDrive users, taking the base storage figure from 15GB to 5GB, and discontinuing the 15GB camera roll storage bonus. Office 365 Home, Personal, and University users were also informed that they would no longer get unlimited storage, and some paid tiers were to be removed too. After an outcry from outraged OneDrive users, Microsoft backtracked and permitted users with 15GB of OneDrive space to keep their base storage quota and camera roll bonus, even after the changes rolled out, but… [Continue Reading] -

Dropbox previews Project Infinite to blur the boundaries between the cloud and local storage
Publié: avril 26, 2016, 1:20pm CEST par Mark Wilson
At its Dropbox Open in London, Dropbox unveiled a preview of its new Project Infinite technology. At its heart, it's a simple idea. Regardless of whether files have been synced to a device or not, they will show up in Dropbox on the desktop. The aim is to reduce the reliance on browser-based tools which can slow down workflow. It allows for collaborators to gain instant access to files their co-workers have shared with them and allows files stored in the cloud to be treated in the same way as those stored locally. It's being promoted as a useful tool… [Continue Reading] -

Rackspace improves compliance handling for mixed infrastructures
Publié: avril 26, 2016, 1:18pm CEST par Ian Barker
When businesses have specific compliance requirements -- because of the industry they're in for example -- managing them across cloud and hybrid infrastructures can be a tough challenge. Managed services specialist Rackspace is addressing this by adding CloudPassage Halo as the underlying security and compliance platform behind its Rackspace Compliance Assistance service, targeting companies that prefer to outsource the management of their compliance initiatives. "CloudPassage is one of the leading providers in workload-focused security," says Jarret Raim, director, managed security at Rackspace. "Halo has enabled Rackspace to provide a new service to our customers, helping us to define, manage and… [Continue Reading] -

Firefox 46 arrives, security and stability the order of the day for desktop users
Publié: avril 26, 2016, 12:12pm CEST par Nick Peers
Mozilla has released Firefox 46.0 FINAL, a relatively minor refresh of its desktop browser for Windows, Linux and Mac with no standout new features. Also released is Firefox for Android 46.0, which does at least include some noteworthy new features such as the ability to display previously cached pages offline and support for sync via Firefox Accounts. The desktop build contains just two new items, neither of which will set the pulses racing. The JavaScript Just In Time (JIT) compiler has been tweaked to tighten security of JavaScript code on web pages. Now code can be executable or writable, but… [Continue Reading] -

Nokia to splash out $191 million on health and wearables firm Withings
Publié: avril 26, 2016, 11:13am CEST par Mark Wilson
Nokia used to be a name associated with smartphones but now the Finnish company is looking to venture into a different area of the mobile device market. Today the company announced plans to acquire French health, fitness and wearables firm Withings for €170 million ($191 million). Withings will join Nokia Technologies as the former smartphone manufacturer branches out into the Internet of Things and the lucrative health market. The acquisition will be settled in cash, and is expected to be completed by Q3 this year. Ramzi Haidamus, president of Nokia Technologies, said: "Withings shares our vision for the future of… [Continue Reading] -

Disable your keyboard or mouse with BlueLife KeyFreeze
Publié: avril 26, 2016, 10:58am CEST par Mike Williams
BlueLife KeyFreeze is a freeware Windows tool which can selectively lock your mouse and/ or keyboard, without hiding the screen. This is ideal if you’re leaving your toddler to watch a cartoon on your laptop, for example– even if they decide to bash the keyboard or click the mouse, it won’t do any harm. Unzipping the download gets you two executables, 32 and 64-bit, and a ReadMe.txt with instructions. Launch the program and you’ll see a five second countdown. Once this is complete you’ll still be able to see and move the mouse, but clicks no longer work, and keypresses… [Continue Reading] -

EE plans to cover the whole of the UK with 4G
Publié: avril 26, 2016, 10:50am CEST par Sead Fadilpašić
Mobile operator EE said it will cover the entire UK (well, 95 percent of it, at least) with 4G connectivity by 2020. It also said it will shut down its customer call centers in India and create 600 new jobs in the UK and Ireland. The announcement comes after EE landed a contract with the Government, under which it will replace the Airwave radio network and eliminate blinds spots, or 'not-spots' in connectivity, The Telegraph reported recently. Currently, about 60 percent of the country is covered in 4G, with mostly rural areas being in the dark. This must quickly be… [Continue Reading] -

Lionsgate to distribute movies on Valve's Steam platform for Windows, Mac, and Linux
Publié: avril 26, 2016, 3:55am CEST par Brian Fagioli
If you play PC games, you surely know of Steam. If you aren't such a gamer, please know that it is a video game delivery and management platform for Windows, Mac, and Linux. It is a great way to purchase games, and unlike using Microsoft's Windows Store, games can take full advantage of your hardware. Valve is not satisfied with Steam only being for games, you see, and the company is focusing on other media too. Today, Valve announces that Lionsgate movies will be distributed through its delivery solution. More than 100 films, including the wildly popular Hunger Games series, will be available… [Continue Reading] -

Twitter makes it easier to report abusive tweets en masse
Publié: avril 25, 2016, 8:23pm CEST par Mark Wilson
There has been a lot of interest in online abuse in recent months, and social networks are taking steps to weed out the trolls and abusers. Twitter has already introduced a number of measures to help tackle trolls, and today announces the availability of a new reporting tool for users. Now rather than having to report a number of abusive tweets individually, it is possible to report up to five tweets simultaneously. As well as reducing the workload for someone who feels the need to report content, the new tool also makes things easier for Twitter as it allows for… [Continue Reading] -

Microsoft showcases Windows 10, Surface Book, and Surface Pro 4 in new videos
Publié: avril 25, 2016, 7:11pm CEST par Brian Fagioli
Microsoft's Surface line of computers have been rather wonderful, although its latest machines have been plagued with problems. For the most part, issues for both the Surface Book and Surface Pro 4 have been fixed through updates, but like a game of whack-a-mole, more pop up as others are smashed down. Despite these issues, Microsoft is highlighting the good aspects of its latest Surface devices -- plus Windows 10 -- in a series of new video advertisements. Over on YouTube, you can see all eight videos, as seen below. Microsoft has chosen a group of people with very diverse occupations. Doyin… [Continue Reading] -

US cyberbombs ISIS in renewed tech warfare
Publié: avril 25, 2016, 5:55pm CEST par Mark Wilson
ISIS has been able to gain notoriety not only because of the atrocities committed, but through incredibly careful and calculated use of technology in general and the internet specifically. The likes of Twitter and Facebook have been embroiled in an on-going battle against terrorist social media accounts, and now the US military is taking the fight online as well. Cyber Command is waging cyber war on Islamic State, trying to cyberbomb the terrorist organization into submission and prevent it from recruiting or spreading propaganda online. Using information gathered from the NSA, Cyber Command has turned its attention away from its… [Continue Reading] -

Angel investors prefer science and technology startups
Publié: avril 25, 2016, 4:31pm CEST par Ian Barker
It's easy to assume that investors are only interested in making money and adopt a follow-the-leader approach to getting the best returns. However, a new report from online startup investment platform Propel(x) shows that the top reasons for investing are: the management team, cited by 75 percent, ability to understand the technology (52 percent), and the potential return on investment (42 percent). "The results of our survey dispel a common misconception that angel investors are driven by a follow-the-leader mentality," says Swati Chaturvedi, CEO and co-founder of Propel(x). "Our data shows that access to both management and independent industry experts is… [Continue Reading] -

How firms can fight back against ransomware attacks
Publié: avril 25, 2016, 4:30pm CEST par Peter Godden
There is no denying that ransomware attacks are a very real threat for businesses. Given the ever-growing value of data and the importance of business continuity, organizations that have fallen victim to such attacks either face a period of downtime or they pay out in order to retrieve their data to resume business as normal. Headline-grabbing examples, such those affecting the Hollywood Presbyterian Medical Center, or Lincolnshire County Council, are no doubt only the tip of the iceberg. How many others are giving in to ransomware demands without revealing they ever had a problem in the first place? Ransomware attempts… [Continue Reading] -

Windows 10 Anniversary Update is shaping up to be something really special
Publié: avril 24, 2016, 4:22pm CEST par Mark Wilson
Windows 10 has been the subject of a lot of criticism since it launched, including quite a lot from me. But at the same time, Microsoft reports that the latest version of its operating system is installed on a staggering quarter of a billion devices. The company must be doing something right. Where Windows 10 succeeds -- particularly for Windows Insiders -- is that it is constantly evolving. Windows 10 Insider Preview Build 14328 is the latest build out of the door and it shows great signs of improvement. It might be a little early to call it, but if… [Continue Reading] -

Capture, edit and share full web pages with Open Screenshot
Publié: avril 24, 2016, 2:52pm CEST par Mike Williams
Desktop screenshot tools support many capture types, and sometimes this includes taking an image of a full web page, even when it doesn't fit on the screen. Sounds great, but it's extremely difficult for a third-party tool to make this happen consistently with all browsers and web pages, and often it just won’t work. Switching to a browser extension like Chrome's Open Screenshot can be a smarter solution, because it has more access to its host's web content, and doesn't need to try and support everything else. Trying it out is as easy as clicking Open Screenshot's address bar button, selecting… [Continue Reading] -

Microsoft reveals all about Windows 10's Linux subsystem
Publié: avril 24, 2016, 1:49pm CEST par Mark Wilson
The arrival of Bash in Windows 10 took many people by surprise, but it opens up a number of opportunities including the ability to run GUI Linux apps. But it's about much more than just that. Microsoft wants people who are confused about the arrival of (deep breath...) Bash on Ubuntu on Windows to know of the potential, and has produced an explainer about the Windows Subsystem for Linux. Microsoft's Deepu Thomas says that the subsystem was created by the Microsoft Windows Kernel team, and goes on to explain that this is much more than an interpretation layer or virtual… [Continue Reading] -

Hacker finds Facebook backdoor leaking usernames and passwords
Publié: avril 24, 2016, 1:36pm CEST par Mark Wilson
The use of bounty programs to track down security vulnerabilities in websites and software is increasingly common these days, and it's a tactic employed by Facebook. One bounty hunter -- or penetration tester -- hacked his (or her… they are anonymous) way into the social network and made the shocking discovery that someone had already installed a backdoor. Orange Tsai managed to compromise a Linux-based staff server and found there was already a piece of malware in place syphoning off usernames and passwords. These account details were being transmitted to a remote computer, and after revealing this to Facebook, Tsia… [Continue Reading] -

US Justice Department accesses another iPhone without Apple’s help
Publié: avril 23, 2016, 5:05pm CEST par Mark Wilson
When it came to the San Bernardino iPhone, Apple was ready to dig in its heels and refuse to help the FBI to gain access to the encrypted contents. As it turns out, the company needn’t have bothered shouting as a third party helped instead. Now the same thing has happened with another iPhone. This time around, the Justice Department had been looking for help accessing an iPhone at the center of a drugs case in New York. But now federal prosecutors have said they no longer need Apple’s help as they have managed to get by the lockscreen. Unlike… [Continue Reading] -

Apple tells developers watchOS apps must work without an iPhone
Publié: avril 23, 2016, 1:07pm CEST par Mark Wilson
Apple has announced to developers that, starting June 1, all watchOS apps submitted for inclusion in the App Store must be native apps based on watchOS 2 SDK. What this means in practice is that Apple Watch apps must function without an iPhone. This is something that has plagued wearables from other manufacturers -- including Samsung -- and the new rules will almost certainly go down well with consumers. Ultimately this should lead to an improvement in the quality of Apple Watch apps, as developers will be forced to build in more functionality. It's not, however, all good news. The… [Continue Reading] -

SyFy comes to Roku
Publié: avril 23, 2016, 1:55am CEST par Brian Fagioli
There is a common misconception that all computer geeks are rabid science fiction fans. While some of them certainly are, it is definitely just a stereotype. As a self-proclaimed computer geek, I can confirm that I don't enjoy many science fiction films or television shows. Some are good, but a lot of them are just cheesy and lame. Speaking of cheesy, the SyFy network is known for showing low-quality TV movies, like the infamous Sharknado. The network also has some decent original TV shows, however. Today, the TV channel's content comes to Roku with 'SyFy Now'. "Do you have a favorite genre you often flock to? I typically… [Continue Reading] -

12-inch MacBook's three flaws that Apple could've fixed but didn't
Publié: avril 22, 2016, 7:58pm CEST par Joe Wilcox
Earlier this week, Apple finally updated its svelte laptop that launched 13-months ago. I am awe-struck by the company's design-audacity—not for brash innovation but bumbling compromises that make me wonder who needs this thing. The 12-inch MacBook offers much, wth respect to thinness, lightness, and typing experience (the keyboard is clever tech). But baffling is the decision to keep the crappy 480p webcam. These days, not late-1990s state-of-art, 720p is the least a pricey computer should come with, and is it too much to ask for 1080p or 4K when modern smartphones can shoot just that? This shortcoming, and two… [Continue Reading] -

Chip-enabled cards lead to a decrease in fraudulent transactions in US
Publié: avril 22, 2016, 7:30pm CEST par Anthony Spadafora
Credit and debit cards with embedded microchips have finally begun to become widely available in the US and, according to Visa, they have already prevented a great deal of fraud with some large merchants seeing an 18 percent decrease in counterfeit transactions. The company noted that 25 merchants had suffered heavily from fraud in 2014. Five of them decided to begin processing credit and debit cards equipped with EMV (Europay, MasterCard and Visa) technology and this led to an 18.3 percent decrease in fraud. Another five of those merchants did not have the necessary equipment to utilize chip-enabled cards and… [Continue Reading] -

Amazon Fire and Fire Kids Edition tablets get new colors and additional storage options
Publié: avril 22, 2016, 7:09pm CEST par Brian Fagioli
Times are tough for many consumers financially, making new technology purchases a hardship. While a tablet such as the iPad is wonderful, the high starting price makes it unachievable for some. Luckily, thanks to Android, some companies, such as Amazon, have created affordable slabs for the masses. Speaking of Amazon, its 7-inch Fire tablet -- which starts at $49 --is getting a minor refresh. You can now purchase it with a series of new colors and storage options. "Fire will be available in three new colors: magenta, blue, and tangerine, and with either 8 GB of internal storage for $49.99 or with… [Continue Reading] -

Windows 10 Insider Preview Build 14328 introduces an improved Start menu, and loads of exciting new features
Publié: avril 22, 2016, 6:16pm CEST par Wayne Williams
It’s been a couple of weeks since Windows Insiders on the Fast ring got a new build of Windows 10 for PC. A PCI bug prevented a promising build from being released sooner, but the problem has been fixed, and so today Build 14328 arrives for both PC and Mobile. The past few Windows 10 Fast ring releases have debuted some great new features, and Build 14328 is no different, introducing, among other features, Windows Ink, a wealth of Cortana improvements, and a new Start experience. SEE ALSO: Windows 10 Insider Preview Build 14316 arrives on the Fast ring --… [Continue Reading] -

Nearly half of EU businesses don't know where their data's located
Publié: avril 22, 2016, 5:37pm CEST par Anthony Spadafora
According to a survey by the cloud hosting firm UKFast, nearly half of businesses are clueless as to where their data is located. To come to its findings, the company surveyed over 300 IT decision makers in EU businesses, with 47 percent of them unaware of where their personal and company data was hosted. Lawrence Jones, the CEO of UKFast, sees this as a troubling issue for businesses in the UK. Not knowing where their data is stored leaves them unable to reassure their customers of its safety. Also if legal trouble arises, how will these businesses be able to… [Continue Reading] -

Weak Lumia sales prove Microsoft should put an end to Windows 10 Mobile
Publié: avril 22, 2016, 4:21pm CEST par Mihăiță Bamburic
It is hard to take Windows 10 Mobile seriously when Microsoft announces sales of just 2.3 million Lumias in a whole quarter. If you ever thought that the platform can actually be competitive in today's market, now is the time to wake up. This year, smartphones sales are expected to reach 1.5 billion units. If Microsoft manages to move 10 million Lumias in 2016, Windows 10 Mobile's market share would likely be around the one percent mark. Microsoft is not the only Windows Phone/Windows 10 Mobile vendor, but it is the largest by far. It sells about 90 percent of… [Continue Reading] -

Choosing asset management software
Publié: avril 22, 2016, 4:20pm CEST par Ian Barker
Asset management is often seen as something as a chore and something that's relegated to a few hours work with an Excel spreadsheet. But that makes it hard to keep up to date and may not deliver all of the information needed to effectively keep track of equipment and software. Wasp Barcode Technologies has developed its AssetCloud software to give companies a cloud and subscription-based service that helps organizations efficiently track, maintain and collect data on the materials they own. It's also put together an infographic highlighting the features companies need to look for when choosing an asset management system.… [Continue Reading] -

AMD FX 8350 and FX 6350 processors now come with Wraith cooler
Publié: avril 22, 2016, 2:58pm CEST par Brian Fagioli
Many gamers on a budget choose AMD FX processors for their builds. Not only are they affordable, but very capable too. With up to eight cores, and easy overclocking, you can squeeze a lot of performance out of them without breaking the bank. When using an FX processor, it is not uncommon for builders to choose an aftermarket cooler for better cooling or reduced noise. Of course this will add to the overall cost. Today, however, consumers selecting the FX 8350 and FX 6350 may want to forgo the additional cooler purchase. Why? AMD is now bundling its already-legendary Wraith cooler with them.… [Continue Reading] -

Woz: Apple should pay half its income in tax
Publié: avril 22, 2016, 12:52pm CEST par Mark Wilson
The tax arrangements of international technology companies have been in the spotlight for a little while now. Few people disagree with the idea that they should be paying their way when it comes to tax, and one of these people is Steve Wozniak. He thinks Apple should pay tax at a rate of 50 percent -- just like him. Just like Amazon, Facebook and Google, Apple manages to avoid a great deal of tax by channeling money through a subsidiary located in the Republic of Ireland. This reduces its tax bill dramatically by avoiding the UK corporation tax of 20… [Continue Reading] -

Social ad spending rises by 86 percent
Publié: avril 22, 2016, 12:52pm CEST par Ian Barker
Spending on social media advertising has increased by 86 percent in the first quarter of this year compared with the same period in 2015. It's also up eight percent when compared to last year's final holiday shopping quarter. These findings come from agile marketing specialist Kenshoo based on data managed by its platform for over 3,000 advertiser and agency accounts. It attributes the growth to the appeal of new ad types like Facebook Dynamic Product Ads and increased inventory through Instagram. Paid search spend increased by 13 percent year-on-year, buoyed by increased spend on mobile ads (up 77 percent) and product ads… [Continue Reading] -

Best Windows apps this week
Publié: avril 22, 2016, 12:05pm CEST par Martin Brinkmann
One-hundred and seventy-seven in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days. There has been a good selection of newly released applications and games this week. As always, if I missed an app or game that has been released this week that you believe is particularly good, let me know in the comments below or notify me via email instead. Discounts This Week The following discounts are provided by Red Stripe Deals, a weekly changing list of offers, and the Deals Hub application. Here… [Continue Reading] -

Facebook to filter out News Feed crap by timing how long you read articles
Publié: avril 22, 2016, 10:39am CEST par Mark Wilson
Facebook has been going a little crazy with News Feed updates of late, making constant changes in a bid to ensure that people see content they actually want to read. The real motivation may be ad revenue, but it's always pushed as surfacing (ouch... sorry... I slipped into buzzword mode...) more relevant content. The new changes are no different. The most recent update to the feed algorithm will take into account not only which news articles people click on, but how long they spend reading them. This will help Facebook to not only determine what sort of article interest users… [Continue Reading] -

More apps and websites leak credit card data on enterprise handsets
Publié: avril 22, 2016, 10:38am CEST par Anthony Spadafora
In its latest quarterly Mobile Data Report, Wandera has revealed a significant rise in apps leaking credit card data on enterprise mobile devices. The company, which specializes in mobile data security and management, compiled the report by analyzing the data usage trends and traffic patterns across its global network of enterprise mobile devices. Between Q4 2015 and Q1 2016, there has been a 17 percent increase in apps and mobile websites leaking credit card data. The CardCrypt security flaw that was discovered in December of 2015 has played a large roll in the amount of credit card data that has… [Continue Reading] -

Dotcom: If you're still using Mega, back up your cloud-based files right now
Publié: avril 22, 2016, 10:14am CEST par Mark Wilson
It seems that Mega -- the enfant terrible of the cloud storage world -- could be on the brink of closure. Founder of Mega (formerly known as Mega Upload), Kim Dotcom took to Twitter to warn people to back up their files ASAP. Not for the first time, Mega is out of the control of Dotcom, and is currently in the hands of what he refers to as "the fifth most wanted criminal in China". For many people the idea of their cloud storage being in criminal hands would be concerning enough, but Dotcom says that Bill Liu wants to… [Continue Reading] -

Franz: one desktop chat app for 14 messaging services
Publié: avril 22, 2016, 9:44am CEST par Mike Williams
Let’s be frank: there are too many chat services in the world, and it can take a stack of background processes and open browser tabs to manage them all. Franz is a free Windows, Mac and Linux application which makes your life easier by supporting them all. Okay, maybe not "all", but 14 is a good start: Skype, WhatsApp, Steam Chat, Facebook Messenger, Slack, Telegram, HipChat, GroupMe, ChatWork, Grape, Discord, WeChat, Hangouts and Glitter. The underlying technology isn’t anything too surprising. It’s a little like a custom tabbed browser, where each tab represents a particular account and service, and you… [Continue Reading] -

It cost HOW MUCH to crack the San Bernardino iPhone?!
Publié: avril 21, 2016, 9:02pm CEST par Mark Wilson
There are a lot of questions still to be answered about the San Bernardino iPhone that saw the FBI and Apple go head to head. After something of a battle, the FBI found someone to crack the iPhone. But who exactly did it? How did they do it? Will Apple be told how to do it in private? But one question that has also been lurking in the background is just how much it cost to hack into a single iPhone. Now we know the answer. Not precisely, but we have a pretty good idea. Perhaps unsurprisingly, cracking the iPhone… [Continue Reading] -

Evernote 6 for Windows marks evolution rather than revolution
Publié: avril 21, 2016, 8:31pm CEST par Nick Peers
UPDATE: Evernote has unveiled Evernote 6.0.4, a major update of its desktop client for Windows users. The new release sees another user interface revamp, plus focuses on refining existing tools rather than introducing major new features. Version 6.0.4 opens with support for High DPI displays, and rolls out various improvements to the Assisted Search tool. This includes moving the Search bar to the top of the note list, providing more detailed descriptions of the search results and the extension of the tool to cover the user’s entire account, with options for expanding the search to include recently deleted notes as… [Continue Reading] -

Merchants are not security savvy
Publié: avril 21, 2016, 8:29pm CEST par Sead Fadilpašić
More than a third (38.5 percent) of merchants don’t even know what type of risks new technologies such as mCommerce bring. They most likely wouldn’t recognize a fraud threat even if they were right in the middle of it. Those are the conclusions written in the new 2016 Mobile Payments & Fraud Survey, released by Kount. The figures are quite a surprise, knowing that mobile fraud increased by 81 percent between 2011 and 2015. "Despite awareness that the mobile channel poses a greater risk than standard eCommerce, businesses are taking a blanketed approach to their security strategies", said Don Bush,… [Continue Reading] -

SanDisk unveils next-generation iXpand Flash Drive for iPhone, iPad, and iPod touch
Publié: avril 21, 2016, 6:42pm CEST par Brian Fagioli
Storage for iPhone and iPad can be costly. Since you cannot realistically add more inside later, you must decide at purchase how much you will need. Then, each bump up will cost you about $100. This can make an iOS device purchase a very costly affair. As an alternative, however, you can use flash drives on the iPhone, iPod touch and iPad, but there is a catch; you will need to buy a lightning to USB type A cable, or a flash drive with a lightning connector. While not usually an elegant solution, today, SanDisk unveils an intriguing such product -- the next-generation… [Continue Reading] -

Google no longer lists its own site as 'partially dangerous'
Publié: avril 21, 2016, 6:19pm CEST par Anthony Spadafora
According to Google’s online transparency report, Google.com had been considered a "partially dangerous" website. In the report under the Safe Browsing section, the company listed its own website as one that could be dangerous to its visitors followed by a list of site safety details along with testing details. According to these details, Google.com displays some pages that redirect visitors to dangerous websites that install malware on their computers: 7b726aeb-a-62cb3a1a-s-sites.googlegroups.com,polnu4ewtan4iwki.ws, and 40d0dfd9-a-62cb3a1a-s-sites.googlegroups.com. Other dangerous websites that can be reached through the site have sent visitors to: maeaflordapele.com,valeimaginar.blogspot.com, and bou7out.blogspot.com. Under the security and privacy tab on the the transparency report’s… [Continue Reading] -

Even Microsoft's biggest fan doesn't want Windows 10 Mobile
Publié: avril 21, 2016, 6:04pm CEST par Brian Fagioli
Windows Phone has been dead for some time now. I knew it. The world knew it. Dogs knew it. The only people that were seemingly unaware were those that pledged allegiance to Microsoft. You know who they are -- those men and women that some call "fanboys". Even the journalism community has them. Folks like Paul Thurrott and Mary Jo Foley are unapologetic fans of Microsoft. While Thurrott has long since abandoned the horrific Windows Phone platform, Foley has been one of the few holdouts. Today, she announces that she -- Microsoft's biggest fan -- is choosing the Linux-based Android… [Continue Reading] -

Pre-installed Windows 10 apps begging for ratings is wrong
Publié: avril 21, 2016, 5:29pm CEST par Wayne Williams
I don’t use the Windows Calculator very often, but occasionally I need to work something out and so fire it up. Today, upon opening the calculator, I was presented with a message asking me to rate the app in the Windows Store. If I was enjoying it. Which of course I wasn’t. It is a calculator after all, and the only time I’ve ever enjoyed using one of those was as a teenager when I typed in "5318008" and turned it upside down. Even the enjoyment of doing that was very short lived. Now, the Windows 10 calculator begging for… [Continue Reading] -

More than a third of enterprises don't backup business data
Publié: avril 21, 2016, 4:53pm CEST par Ian Barker
The results of a new survey show that many organizations continue to demonstrate a complacent, lax attitude toward backups, leaving them vulnerable to evolving threats. The study from cloud-based backup provider CloudBerry Lab finds that almost half of respondents (49 percent) have only one copy of their business data, which could cause major operational disruption in the event that data becomes inaccessible. Around 36 percent of enterprises backup their business data completely. But while this finding is encouraging, it's offset by the fact that an equal number do no backups at all. Also 27 percent of respondents admit to having lost… [Continue Reading] -

Dell teams with Microsoft and others to launch IoT Partner Solutions Program
Publié: avril 21, 2016, 4:51pm CEST par Alan Buckingham
Yes, the Internet of Things, commonly called the IoT, has been steadily growing and increasingly hard to ignore. It's not all bad, though. In fact, it's great when it works and when it isn't being hacked. Security is obviously the number one concern. Nobody wants a hacker turning off lights, or worse. Now Dell is teaming up with a number of companies for what it calls its "IoT Partner Solutions Program". Those involved, at least initially, are GE, Microsoft, OSIsoft, PTC, SAP and Software AG. "The program builds an ecosystem of partners to help customers navigate the fragmented IoT landscape and… [Continue Reading] -

New technique allows Trojans to remain in memory to evade detection
Publié: avril 21, 2016, 4:19pm CEST par Ian Barker
Remote access Trojans (RATs) have been used for many years to allow attackers to gain access to and take control of user’s systems. Usually RATs are delivered when a user opens an email attachment or downloads a file from a website or peer-to-peer network. This involves direct delivery of the payload which makes detection easier. Researchers at security company SentinelOne have uncovered a more sophisticated delivery technique that ensures that the payload file remains in memory through its execution, never touching the disk in a de-encrypted state. This lets the attack stay hidden from conventional antivirus technologies. Samples analyzed also… [Continue Reading] -

Terminal Wings is a tabbed command line for Windows 10
Publié: avril 21, 2016, 4:17pm CEST par Mike Williams
Windows 10 brought a host of overdue command line improvements -- like selection, resize and copy/ paste tools which actually work as you expect -- but there’s plenty of scope for more. Terminal Wings extends the console further with Chrome-style tabs, new color and wallpaper options, transparency settings, "minimize to tray", and more. The download includes both 32-bit and 64-bit versions, but there’s no installation required -- just run the one you need. Terminal Wings looks like a regular console window, but there’s an extra Chrome-like tab bar. Click its "+" button and you’re able to open new tabs, each… [Continue Reading] -

Taking the pulse of cyber security in healthcare
Publié: avril 21, 2016, 3:34pm CEST par Ian Barker
Large hospitals often have thousands of workstations used by multiple employees to access confidential patient data, so securing them can be a major challenge. Endpoint security specialist Duo Security has compared its customers in healthcare with those in other industries to determine how the sector differs in its security requirements. Among the findings are that healthcare customers are logging into twice as many applications as the average user, widening the attack vector. Twice as many healthcare endpoints have Flash installed and three times as many healthcare customers have Java installed on their devices, again, putting them at greater risk of… [Continue Reading] -

More UK adults taking online courses
Publié: avril 21, 2016, 3:32pm CEST par Anthony Spadafora
Adults in the UK are turning to online learning platforms in order to stay competitive in their fields and to learn new skills, despite their increasingly busy schedules. Coursera, which offers online courses from some of the top universities worldwide, has noticed that the number of new users registering for its educational platform has increased by 50 percent over the course of the past 12 months. In the UK, the company has over half a million users that are registered for a variety of courses. Coursera has noted that of those currently studying, 30 percent are using their smartphones to… [Continue Reading] -

Facebook Messenger adds group calling
Publié: avril 21, 2016, 1:59pm CEST par Mihăiță Bamburic
Facebook Messenger is one of the most popular messaging services today, boasting over 900 million monthly active users. However, since competition in this market is increasingly fierce, to maintain momentum the social network has to keep improving its service. Earlier this month, at its F8 developer conference, Facebook announced support for chat bots with the purpose of enabling businesses to deliver better customer support, and now it is rolling out group calling to Messenger users across the globe. "From any group conversations, just tap on the phone icon to initiate a group call. You can then manage individual participants on… [Continue Reading] -

With security and privacy in mind, will more browsers follow Opera's lead and offer free VPN?
Publié: avril 21, 2016, 12:46pm CEST par Mark Wilson
The modern internet user is somewhat paradoxical -- looking to be more connected and contactable than ever before, whilst simultaneously seeking privacy. Can the two ideas live side by side? It's a tricky balancing act, but many people turn to VPN tools to increase their security and privacy online. Opera is the first web browser to bundle a free VPN tool as standard (with unlimited VPN data, no less), and it's hard to imagine that the competition won’t follow suit. Nothing has yet been announced, but the appearance of versions of Chrome or Firefox with integrated VPN would hardly be… [Continue Reading] -

Oukitel aims to shake up the budget smartphone market with the sub-$50 C3
Publié: avril 21, 2016, 12:02pm CEST par Ian Barker
Not everyone wants or can afford a premium smartphone and Chinese makers have been busy carving out a niche at the lower end of the market with a whole raft of models that provide smartphone features at dumbphone prices. Launching next week the Oukitel C3 is the latest entry into an increasingly crowded market. What makes it stand out is that unlike most cheaper phones which rely on older versions of Android, the C3 runs the latest 6.0 Marshmallow. The phone comes with a 5-inch HD display that has a 720 x 1280 resolution, an MT6580 quad-core chip set, a 1GB… [Continue Reading] -

StableBit CloudDrive is a secure virtual drive for your cloud storage accounts
Publié: avril 21, 2016, 11:46am CEST par Mike Williams
StableBit CloudDrive beta ($34.95) is an interesting tool which creates a secure virtual drive on your PC, and stores the data on your choice of local, network or cloud storage. The program currently supports Amazon S3, Box, Dropbox, Google Cloud Storage, Google Drive, Microsoft Azure, OneDrive and OneDrive for Business accounts. Setup is reasonably easy. Choose a provider, log in, then click Create, optionally tweak a few settings and you’re done. StableBit CloudDrive emulates a real SCSI hard drive, ensuring it shows up in Explorer -- and just about any other software you might install -- as another local drive.… [Continue Reading] -

Free Wi-Fi hotspots are a major security threat for businesses
Publié: avril 21, 2016, 11:27am CEST par Sead Fadilpašić
Free Wi-Fi hotspots are the biggest security threat for mobile workers, according to new reports. The recently released iPass Mobile Security Report says that 62 per cent of organizations are banning their mobile workers from using free Wi-Fi hotspots, with another 20 percent planning on doing the same in the future. For 94 percent of surveyed companies, free and open Wi-Fi hotspots are a "significant mobile security threat". "Wi-Fi is a disruptive technology that has changed the way people work, but in recent times it has also introduced formidable mobile security concerns", said Keith Waldorf, VP Engineering at iPass. "Being… [Continue Reading] -

Digital divide is holding back the UK economy
Publié: avril 21, 2016, 11:21am CEST par Ian Barker
New research by business organization the CBI in conjunction with IBM shows that a digital divide is opening up across the British economy, with just over half (55 percent) of 'pioneer' firms adopting digital technologies and processes, while the remaining 45 percent are falling behind. Despite the UK taking top place globally for e-commerce and fifth place for the availability of technology, it ranks only fourteenth in the world for company-level adoption of digital technology, with many companies struggling to digitize their businesses at the rate of peers in other countries. Reasons for this are given as a lack of… [Continue Reading] -

Deja Vu! Google's antitrust offenses are like Microsoft's (and the defense, too)
Publié: avril 21, 2016, 1:09am CEST par Joe Wilcox
Once again, as it has done in the past, Google makes the classic monopolist defense for its competitive—or anticompetitive, depending on perspective—behavior with respect to Android. Today, the European Union's Competition Commission formerly charged Alphabet and its major subsidiary, which has 12 weeks to provide satisfactory legal response before the Commission issues corrective sanctions. Simply stated, the EC finds that the company abused its dominant position, in part by contracts compelling Android licensees to preload Google apps and related services, including search. Microsoft ran into similar bundling headaches starting in the late 1990s with respect to Windows. Responding today, Kent Walker, Google… [Continue Reading] -

Text an emoji, get free porn
Publié: avril 20, 2016, 9:06pm CEST par Wayne Williams
Want to watch some pornography on your phone but can’t be bothered to actually search for it? From today you can receive links to free adult content just by texting an emoji. Pornhub’s new "Emoji 4 Porn" service offers a selection of 30 public emoji (plus an unspecified number of secret unlisted ones to find) that you can use to request whatever sort of pornography you’re into. Send them a taco emoji, for example, and you’ll receive Latina videos. A camcorder emoji will give you links to amateur content. You can probably work out what sort of videos you’ll get… [Continue Reading] -

AI platform better predicts cyber attacks thanks to human experts
Publié: avril 20, 2016, 9:00pm CEST par Anthony Spadafora
Researchers from MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) have collaborated alongside the machine learning startup PatternEx to demonstrate how an artificial intelligence platform that makes use of continuous input from human experts would be able to predict cyber attacks better than the systems that exist today. CSAIL and PatternEx are calling their new AI platform AI² due to how it combines the intuition of analysts with artificial intelligence. Previously, "analyst-driven solutions" relied on the rules created by security experts which resulted in attacks that did not correspond to their rules slipping through the cracks. The machine learning approach… [Continue Reading] -

New Windows 10 Mobile Preview Build 14327 lets you send and receive texts from a Windows PC
Publié: avril 20, 2016, 7:44pm CEST par Wayne Williams
Microsoft released Windows 10 Mobile Insider Preview Build 14322 less than a week ago, introducing numerous improvements and changes to Action Center, notifications, Cortana, Settings, emoji, Microsoft Edge, lockscreen, and more. Today, the software giant rolls out another new build to the Fast ring, Build 14327, which, as well as fixing various known issues, also introduces a couple of noteworthy additions, including a Messaging Everywhere preview which lets users send and receive text messages from a Windows 10 PC. To use this new feature, you need to be signed in with your Microsoft Account on both your phone and PC.… [Continue Reading] -

Migrating Oracle apps to the cloud
Publié: avril 20, 2016, 7:00pm CEST par Mark Vivian
With companies of all sizes across the globe waking up to the benefits of moving some or all Oracle applications to the cloud, the cloud is rapidly becoming a star in many IT strategies of organizations. The benefits include the reduced need for up-front capital investment in order to accelerate return on investment, as well as gaining greater business insight and an excellent user experience. The reality of today’s cloud technology is now matching -- or even exceeding -- the hype of a few years ago. However, some organizations are still cautious about moving business-critical applications to the cloud, based on perceived… [Continue Reading] -

Google Chrome turns 50
Publié: avril 20, 2016, 7:00pm CEST par Joe Wilcox
Dog years is too slow a measurement when it comes to the Internet, which pace maturing makes Moore's Law look like a skeleton sitting at a feast (it's too feeble a metric). Case in point: Google Chrome 50 officially releases this fine Wednesday, which is a long way from its late-2007 alpha. Whew, where did the years go? Now before you quibble about who's how old when, let's clarify. By my math, and an official blog post, Chrome turned 50 one week ago. Maybe none of us noticed. I write this the afternoon before Big G rolls out the birthday cake,… [Continue Reading] -

Google Inbox makes it easier to manage links, newsletters and calendar events
Publié: avril 20, 2016, 7:00pm CEST par Mark Wilson
When it comes to email, Google is about more than just Gmail. With Inbox, Google has looked to simplify and automate email, and today the company announces three new features that take this further. But Google doesn't think that 'features' is strong enough a word; instead these are 'experiences'. Specifically, there are new experiences that make it easier to keep track of calendar events, manage the links you email to yourself, and view all of the newsletters you subscribe to. Inbox is all about keeping -- or making -- things as simple as possible. This is what the new newsletter… [Continue Reading] -

Canonical releasing Ubuntu Linux 16.04 LTS 'Xenial Xerus' tomorrow -- will you download it?
Publié: avril 20, 2016, 6:12pm CEST par Brian Fagioli
Ubuntu is one of the best -- if not the best -- desktop Linux-based operating systems. Many people, including me, trust it for their computing needs every day. Best of all, Canonical releases special LTS versions every two years, offering a super-long five years of support. Tomorrow, the latest such LTS version, 16.04, will see its official release. I've been running pre-release versions of this operating system for a while now, and it has been brilliantly stable. Tomorrow's release will be the best Ubuntu ever, featuring things like new snap packages, CephFS, and ZFS-on-Linux. "The security mechanisms in snap packages allow for… [Continue Reading] -

ITIF says Europe is 'misguided' in bringing antitrust allegations against Google
Publié: avril 20, 2016, 5:31pm CEST par Mark Wilson
The EU may be bringing an antitrust case against Google in relation to its Android operating system, but the ITIF (Information Technology & Innovation Foundation) thinks that this is 'misguided'. Rather than Google harming customer choice, the institute says that it is the case against Google that should be in the spotlight. Google has made much of the fact that Android is open source, and the ITIF says that "holding 'open' operating systems to higher standard only hurts consumer choice". Vice President Daniel Castro says that the Android ecosystem reduces costs for consumers, increases choice, and complains that the European Commission… [Continue Reading] -

MobileDemand xCase for Microsoft Surface 3 [Review]
Publié: avril 20, 2016, 4:40pm CEST par Mihăiță Bamburic
Microsoft's Surface 3 and Surface Pro 4 are among the best tablets for enterprise use. A full-blown version of Windows, light and sturdy build, adjustable kickstand, good battery life and optional keyboard enables them to work equally well at the desk and on the go. In harsher conditions, however, some extra protection is required. For use in the field, MobileDemand has introduced a rugged case, called xCase. It promises "unparalleled durability and superior protection" for Surface 3 and Surface Pro 4. Offered in two versions, basic and premium, I have tested the latter in a Surface 3 trim -- here… [Continue Reading] -

Bioo charges your phone from a potted plant
Publié: avril 20, 2016, 3:49pm CEST par Wayne Williams
You probably know that you can use a potato as a battery and power clocks and small light bulbs from it. You don’t have to use a potato either -- certain other vegetables and fruits work just as well. Arkyne Technologies claims that plants can also be used as a power source, and has produced a product called Bioo Lite which is able to use leafy green flora to charge devices, like smartphones and tablets. The company is currently seeking finance for its invention on Indiegogo where it has already hit 112 percent of its funding goal with a month… [Continue Reading] -

Frustration with conventional password management leads to risky behavior
Publié: avril 20, 2016, 3:46pm CEST par Ian Barker
One in three Americans indulges in some form of risky password practice, such as writing them down, according to the results of a new survey. The report from access control specialist SecureAuth finds that Americans are exasperated with conventional online password management. It reveals that 74 percent rely on means other than memory to manage their online passwords, 35 percent write passwords down and 25 percent use the same password across several accounts. When asked what they found most frustrating about password management, 29 percent named keeping up with different password requirements across accounts, 18 percent meeting complex password requirements,… [Continue Reading] -

HPE focuses on diversity with 2016 Scholarship for Women Studying Information Security
Publié: avril 20, 2016, 3:31pm CEST par Brian Fagioli
Diversity is a tricky conversation. While everyone should have a fair chance at a job despite skin color, disability, gender, or sexual orientation, you can't force a certain group to enter an industry. In other words, percentages in a diversity report don't really tell the whole story. The best approach to diversity is simply fostering opportunities for those that want it. Scholarships are a great option as it simply opens a door -- the recipient must walk through it. Hewlett Packard Enterprise has been supporting such a thing -- the Scholarship for Women Studying Information Security -- and today, it announces… [Continue Reading] -

Businesses need to use text messages to reach millennials
Publié: avril 20, 2016, 3:09pm CEST par Ian Barker
Millennials have an overwhelming preference for texting according to new research. In fact, when given the choice between only being able to text or call on their mobile phones, 75 percent of millennials would rather lose the ability to talk. Respondents to the survey from enterprise mobile specialist OpenMarket say texts are preferred because they're more convenient and on their own schedule (76 percent), texts are less disruptive than a voice call (63 percent), they prefer to text rather than call in general (53 percent) and because they never check voicemails (19 percent). With millennials making up nearly a quarter… [Continue Reading] -

Microsoft Azure's Container Service now generally available
Publié: avril 20, 2016, 2:50pm CEST par Anthony Spadafora
Microsoft Azure's Container Service in now available to help companies deploy and manage containers using their choice of software. Users of the service will be able to move their container workloads to the cloud easily and can still run their operations using open-source tools. The two most popular tools -- Mesosphere’s Data Centre Operating System (DC/OS) and Docker’s Swarm and Compose -- will be both be supported by Azure Container Service and users will be able to continue running their operations using the one they prefer. Mark Russinovich, Microsoft’s CTO for Azure, sees the support of both platforms as something… [Continue Reading] -

Google denies Android breaches EU antitrust rules
Publié: avril 20, 2016, 2:37pm CEST par Mark Wilson
The European Union has charged Google with anticompetitive behaviour, saying that the company abused the dominance of Android in the mobile marketplace. Regulators have taken exception to Google's requirement on phone manufacturers to install Chrome and Google search, saying that this stifles innovation and limits user choice. Unsurprisingly, Google disagrees and has hit back at the charges saying that "our business model keeps manufacturers' costs low and their flexibility high, while giving consumers unprecedented control of their mobile devices". More than this, Google says it prides itself on having built a sustainable ecosystem built on open source software. It also… [Continue Reading] -

EFF sues Justice Department to discover if secret orders are used to decrypt user data
Publié: avril 20, 2016, 1:55pm CEST par Mark Wilson
EFF (the Electronic Frontier Foundation) has filed a Freedom of Information (FOIA) lawsuit against the Justice Department. The digital rights group wants to learn whether the government has made use of secret court orders to force tech companies to provide access to encrypted user data. After the Apple vs the FBI battle, there has been renewed interest in how companies handle not only encryption, but government requests for access to such data. With services such as WhatsApp enabling end-to-end encryption, attention has now switched to what might be happening in the background without users' knowledge. While Apple very publicly refused… [Continue Reading] -

New analytics platform aims to transform mental healthcare
Publié: avril 20, 2016, 1:03pm CEST par Ian Barker
Healthcare costs for people diagnosed with mental illness and common chronic health conditions are 75 percent higher than for those without a mental health diagnosis according to the Centers for Medicare and Medicaid Services (CMS). This is because there’s often a lack of coordination between multiple care providers, different state policies and diverse payment structures which can result in poor health outcomes and higher costs across health systems. To address the problem behavioral health analytics provider ODH and IBM Watson Health are announcing the launch of Mentrics, a population health management platform designed to help care organizations transform the quality… [Continue Reading] -

Adjust brightness and contrast from software with ClickMonitorDDC
Publié: avril 20, 2016, 11:40am CEST par Mike Williams
ClickMonitorDDC is a tiny free tool which allows adjusting the brightness and contrast of DDC-compatible monitors (and that’s most of them, if you’re unsure). You could do this anyway with the monitor buttons, maybe opening the Display Control Panel applet, but ClickMonitorDDC will often be much more convenient. The program arrives as a single tiny executable, no installation required. Simply run it and an icon appears in your system tray showing the current brightness value. Click the icon and sliders appear for brightness, contrast (on desktops only, not laptops), and there’s a volume slider as a bonus. Clicking and dragging… [Continue Reading] -

Only 23 percent of businesses can effectively respond to cyber attacks
Publié: avril 20, 2016, 11:17am CEST par Sam Pudwell
NTT Com Security today released its annual Global Threat Intelligence Report (GTIR), which examines the threat landscape by analyzing the attacks, threats and trends from the previous year. This year’s report is the most comprehensive to date, featuring key findings from partners including Lockheed Martin and the Center for Internet Security and pulling information from 24 security operations centers, seven R&D centers, 3.5 trillion logs, 6.2 billion attacks and nearly 8,000 security clients across six continents. The report finds that, on average, only 23 percent of organizations are capable of responding effectively to a cyber incident, with 77 percent having… [Continue Reading] -

Win a free Xbox One and custom controller from Microsoft in the comfort of your PJs
Publié: avril 20, 2016, 12:35am CEST par Brian Fagioli
The Xbox One is a marvelous game console and media player. In my living room, it has replaced both my Roku and Blu-ray player, lessening the number of unsightly wires. Best of all, of course, are the high-quality games, providing many hours of entertainment. Understandably, not everyone can afford such a costly piece of tech. If this game console is not in your budget, I have some good news; Microsoft is giving one away at Pax East 2016. As an added bonus, the company is including a custom controller. Don't worry, if you aren't going to Pax, you can participate from… [Continue Reading] -

China wants Apple's source code, but Apple refuses to hand over the goods
Publié: avril 19, 2016, 11:42pm CEST par Mark Wilson
Apple has revealed that Chinese authorities have asked for access to the company's source code in the last couple of years. The revelation was made by Apple general counsel Bruce Sewell as he tried to deflect accusations that have sprung up in the wake of the San Bernardino iPhone case. The battle between Apple and the FBI rumbled on for a while as authorities asked the iPhone manufacturer to crack encryption or provide a backdoor into the phone at the center of the case. Apple refused to help the FBI, leading to accusations that the company was failing to help… [Continue Reading] -

Google's second annual Android security report shows how app and device scanning keep you safe
Publié: avril 19, 2016, 7:27pm CEST par Mark Wilson
As Apple releases its transparency report, Google today releases its second Android Security Annual report. The report covers all things Android, from the security of the operating system itself, to the security of Google Play and the apps it provides access to. Of course, Google is keen to highlight everything it does to improve security for its users. As such, the report shows how the company performs more than 400 million automatic security scans per day on devices with Google Mobile Services. Aided by machine learning, these scans help to home in on what are referred to as Potentially Harmful… [Continue Reading] -

ISPs offer inadequate DDoS protection
Publié: avril 19, 2016, 7:20pm CEST par Anthony Spadafora
A new report from Corero Network Security, which provides security solutions against distributed denial of service (DDoS) attacks, shows that 85 percent of enterprise end users want their Internet Service Providers (ISPs) to offer better protection against DDoS attacks. To compile its research, the security company polled more than 100 ISPs and 75 enterprise customers in regards to their DDoS mitigation strategies. Corero found that a high number of ISPs still rely on outdated technologies to protect their customers from these attacks. Forty-six percent of ISPs divert DDoS traffic to scrubbing centers, which is not only an expensive way to… [Continue Reading] -

Apple transparency report sheds some light on government data requests
Publié: avril 19, 2016, 6:09pm CEST par Mark Wilson
Reinvigorated interest in privacy, security and surveillance means that the transparency reports published by tech companies are always greeted with some enthusiasm. How much data are governments around the world asking for from companies? How much user data are companies handing over to the authorities? Apple's latest transparency report reveals that the iPhone manufacturer has complied with an increased number of requests for data -- including 80 percent of requests in North America, and 97 percent in Latin America. But while the report makes for interesting reading, it also highlights a problem that Microsoft recently sued the Department of Justice… [Continue Reading] -

PC Internet usage is dropping
Publié: avril 19, 2016, 5:38pm CEST par Anthony Spadafora
ComScore, an online measurement specialist, has released new data that shows that less users are using desktop devices to access the Internet and are instead browsing on their smartphones and tablets. The company has noticed a steep decline in the overall time people have spent online in the US using both desktop PCs and laptops. In the past four months, desktop internet usage continued to fall and it has done so on a year over year basis. According to ComScore, it fell 9.3 percent in December of 2015, 7.6 percent in January, two percent in February and six percent in March.… [Continue Reading] -

77 percent of companies don't have the capability to respond to cyber attacks
Publié: avril 19, 2016, 4:18pm CEST par Ian Barker
Only 23 percent of organizations are capable of responding effectively to a cyber incident. This leaves the remaining 77 percent often having to purchase support services after an incident has occurred. This is among the findings of the latest Global Threat Intelligence Report from security company Solutionary. The report is made up of information from 24 security operations centers, seven R&D centers, 3.5 trillion logs, 6.2 billion attacks and nearly 8,000 security clients across six continents. Among other findings are that spear phishing attacks accounted for approximately 17 percent of incident response activities supported in 2015. In many cases, these… [Continue Reading] -

Internet of Things will extend to running shoes
Publié: avril 19, 2016, 4:16pm CEST par Sead Fadilpašić
Your next running shoes will probably be connected to the internet, IoT-style. Footwear branding, labeling and RFID solutions firm Avery Dennison Retail Branding and Information Solutions (RBIS) and IoT firm EVRYTHNG announced today they’re teaming up to give more than 10 billion apparel and footwear products a "unique digital identity". Yes, they’re putting IoT chips into shoes. The products should hit the market within the next three years. The two companies believe this will be the largest number of IoT-connected devices in a single deal, ever. They will be powered by the Janela Smart Products Platform, for digital identity and data management… [Continue Reading] -

Apple's MacBook now offers better performance, longer battery life
Publié: avril 19, 2016, 3:43pm CEST par Mihăiță Bamburic
Apple has announced the first MacBook refresh, a year after the introduction of its thinnest and lightest laptop. The device gets the latest Intel processors, better graphics performance, faster SSD storage and longer battery life. Also new is a rose gold finish, on top of the existing gold, silver and space gray. The 2016 refresh for the 12-inch MacBook brings sixth-generation dual-core Intel Core M processors with speeds of up to 1.3 GHz and Turbo Boost of up to 3.1 GHz, 1866 MHz RAM and HD Graphics 515, which is said to be 25 percent faster than in the original model. There… [Continue Reading] -

US hosts more malicious websites than any other country
Publié: avril 19, 2016, 3:42pm CEST par Ian Barker
According to a new report from German security company G DATA, more malicious websites were hosted in the US in 2015 than in any other country, originating around 57 percent of recorded attacks. China, Hong Kong, Russia and Canada are also major hosts of malware, though Europe is little in evidence, only Germany and Italy making the top seven and accounting for just six percent between them. Overall, the number of websites categorized as being 'evil' has risen by 45 percent, emphasizing how attacks from the web represent one of the biggest and growing threats facing computer users. It also shows… [Continue Reading] -

Viber introduces end to end encryption
Publié: avril 19, 2016, 2:27pm CEST par Mihăiță Bamburic
The major messaging services are now placing a greater emphasis on their users' privacy and security, following the heated encryption debate started by Apple and the FBI. Viber has just announced end-to-end encryption support, making it the second leading player this month to introduce this feature after WhatsApp. Viber has over 700 million users across the globe, but its end to end encryption feature will not be available everywhere right away. The company is focusing on Belarus, Brazil, Israel and Thailand first, with other markets to get the same treatment in the weeks that follow. Viber is also rolling out an option to… [Continue Reading] -

Telegram giving bot developers $1 million
Publié: avril 19, 2016, 2:16pm CEST par Brian Fagioli
If you need a great cross-platform chat solution, Telegram is one of the best. Not only does it work on Windows, iOS, and Android, but Linux-based desktop operating systems too, such as Ubuntu. Not to mention it offers encryption, but not for all messages by default, sadly. Besides being available on many platforms, the company is constantly adding features, always making it better. In fact, Telegram is now putting up a million dollars for developers, in an effort to bolster its bot offerings. After all, bots are all the rage nowadays. "Good news, everyone! This year, Pavel Durov will be… [Continue Reading] -

Hain is a search tool, launcher and desktop assistant for x64 Windows
Publié: avril 19, 2016, 1:59pm CEST par Mike Williams
Hain is an open-source keyboard-oriented launcher, desktop search and productivity tool for 64-bit Windows. The program is convenient to use. Unzip the download, run Hain.exe, it adds an icon to your system tray and pressing Alt+Space (customizable) launches the interface when required. Hain opens with a simple console including a command bar and a list showing the various actions you can take. There’s speedy searching for applications. Enter an executable name, new matches appear as you type, and clicking any item launches it. There’s some tolerance for typos, conveniently: we entered WRD and Microsoft Word still appeared at the top… [Continue Reading] -

How the cyber crime business model is changing
Publié: avril 19, 2016, 12:22pm CEST par Ian Barker
Cyber crime is an increasingly serious business and a new report released today by Trustwave looks at the top trends from the past year based on real-world data from data breach investigations. Key findings from the report include that 97 percent of applications tested by Trustwave in 2015 had at least one vulnerability. In addition 10 percent of the vulnerabilities discovered were rated as critical or high risk. Retail is the industry most commonly targeted by criminals, accounting for 23 percent of Trustwave investigations, followed by hospitality at 14 percent and food and beverage at 10 percent. The findings show… [Continue Reading] -

Google facing antitrust charges in Europe over Android
Publié: avril 19, 2016, 10:50am CEST par Anthony Spadafora
Margrethe Vestager, the European Commission’s antitrust commissioner, is continuing to put pressure on Google in regard to its Android operating system. Vestager gave a speech at a conference in the Netherlands today in which she stressed how her department has now begun a close examination of the contracts Google has with mobile device manufacturers and mobile carriers. The European Commission is objecting to the requirements the company puts on its mobile partners to pre-load Google apps on devices. By making device manufacturers and carriers pre-load the company’s apps, Google is taking away their ability to choose which apps they install… [Continue Reading] -

LaCie unveils '12big' Thunderbolt 3 12-bay desktop RAID unit with up to 96TB capacity
Publié: avril 19, 2016, 2:23am CEST par Brian Fagioli
Nowadays, many computers have paltry amounts of storage. Why? Solid state drives carry a higher cost per gigabyte, meaning these faster SSDs are usually lower-capacity for cost-savings. With the emergence of the cloud, this might be OK for many home and business users. If you need more local storage, an external hard drive is a great way to get it. Not only are these drives convenient, but versatile too. But what if you need a lot of storage -- more than the typical single, double, triple, or even quadruple bay solution? LaCie has you covered. Its all-new '12big' raid unit has… [Continue Reading] -

Pandora generates more than $2 billion in royalties
Publié: avril 18, 2016, 7:24pm CEST par Brian Fagioli
Back in the 90's, buying CDs was a passion of mine. Not only would I be knowledgeable about all of the release dates for my favorite artists, but I would go to midnight store-openings to buy them. Then, alone in my bedroom, I would listen to all of the discs and drift away. Nowadays? Not so much. While I still adore music -- especially hip-hop tunes -- physical media is not part of the equation. Streaming media services are my gateway to music, and it is largely very satisfying. Apparently, I am far from alone in my love for streaming. Today,… [Continue Reading] -

Kaspersky introduces Industrial CyberSecurity solution
Publié: avril 18, 2016, 7:15pm CEST par Sead Fadilpašić
Security firm Kaspersky Lab today announced a new, specialized security solution, aimed at critical infrastructure and industrial facilities. The solution, called Kaspersky Industrial CyberSecurity, is built to protect technological processes in industrial environments from cyber-attacks because, as the company says, these threats now have the potential to cross the realms, from the virtual one into the physical one, threatening not only businesses, but humanity and nature, as well. The solution is aimed for today’s industrial facilities such as nuclear power plants, refineries and assembly lines, facilities which require, as Kaspersky puts it, "faultless continuity and consistency of the technological process".… [Continue Reading] -

SoftMaker FreeOffice 2016 improves performance and interoperability with Microsoft Office
Publié: avril 18, 2016, 7:12pm CEST par Nick Peers
SoftMaker Software has released SoftMaker FreeOffice 2016, a brand new version of its office suite for Windows and Linux that’s free for both personal and commercial use. The new release comes with the promise of improved performance as well as better compatibility with Microsoft Office documents. It also includes a number of new features and tweaks, confined largely to the suite’s presentation and spreadsheet components. FreeOffice 2016 comprises word processor, spreadsheet and presentations tool, and has been built on the back of SoftMaker’s commercial product, SoftMaker Office 2016. One clear performance improvement is support for multi-core processors to render graphics… [Continue Reading] -

Minecraft fans, here's how to score MINECON 2016 tickets
Publié: avril 18, 2016, 6:58pm CEST par Brian Fagioli
Minecraft isn't just a game, it's a phenomenon. When I go shopping at a store like Target, I see toys, clothes, and more featuring things from the game. When Microsoft bought it for $2.5 billion, I thought it was crazy, but between merchandising and other potential revenue generating aspects, it could end up being a bargain. If you are a super-fan of Minecraft, you are no doubt planning to attend MINECON 2016 -- a conference for both players and developers to come together and celebrate the game. Today, Microsoft announces crucial details for scoring tickets, so you need to pay attention. "We… [Continue Reading] -

Microsoft makes Skype free for Ecuador earthquake victims, Canon donates money to Japan
Publié: avril 18, 2016, 6:25pm CEST par Alan Buckingham
In the past week the world has suffered several earthquakes, striking firstly in Japan and then in Ecuador. Both were followed by aftershocks that still continue and each robbed the world of lives. It's a tragedy with broad repercussions, as family members from around the world seek word on their loved ones. Microsoft immediately jumped in to offer free Skype calls to Japan and now the software giant is doing the same for those with family in Ecuador. "In light of the devastating earthquake that has taken place in Ecuador -- and the subsequent impact to the local communications infrastructure… [Continue Reading] -

Windows 10 Mobile to support upcoming Qualcomm Snapdragon 830 processor
Publié: avril 18, 2016, 5:18pm CEST par Mihăiță Bamburic
One of the biggest mistakes that Microsoft has made with Windows Phone is not adding support for the latest hardware in time. For instance, while Android flagships were coming out with quad-core chips and 1080p displays, for a long period of time after smartphones running the tiled operating system still had to make due with puny dual-core chips and lesser 720p screens. Fortunately, this is a mistake that Microsoft will not repeat with Windows 10 Mobile. The company appears to be forward-thinking this time around, as its new smartphone operating system supports all the latest hardware -- including even a… [Continue Reading] -

What the future holds for Wi-Fi
Publié: avril 18, 2016, 5:17pm CEST par William Webb
Throughout its more than 20-year existence, Wi-Fi has evolved to be ever faster. That evolution continues but arguably it has already reached a point where home broadband, device processors and other limitations mean that greater speeds are not of benefit to most. So where next, if anywhere, for Wi-Fi? Of course, the continued success of Wi-Fi is in little doubt. It is in almost every home in the developed world. Wi-Fi chips are embedded in every phone, tablet, laptop and computing device. We send ever-more data each year across WiFi. It has been said that if you want to hold… [Continue Reading] -

Microsoft's Outlook app gains Android Wear support
Publié: avril 18, 2016, 4:59pm CEST par Mihăiță Bamburic
Smartwatches cannot do much on their own, but with some apps they can quickly be turned into useful gadgets. The good news is that major developers are paying attention to this market, slowly adding support for the two main platforms: Apple Watch and Android Wear. In the case of Outlook, Microsoft's popular email client for Android and iOS, support for Apple Watch arrived first, in August of last year, and now it is the turn of Android Wear to receive the same treatment. Here is what you need to know. Android Wear support is introduced through an Outlook for Android… [Continue Reading] -

How to say goodbye to Windows 10 and revert to your previous operating system
Publié: avril 18, 2016, 1:58pm CEST par Wayne Williams
Personally I think Windows 10 is a great operating system. It’s a bit unfinished still, but the Anniversary Update coming in July will fix a lot of the problems, and also introduce additional features. That said, I can fully understand why some people might decide Windows 10 is not for them and opt to roll back to a previous OS. Microsoft allows users to 'undo' an installation directly from within Windows 10, but there is a catch -- you only get 30 days in which you can do this. That’s not the only method of rolling back Windows 10 though,… [Continue Reading] -

Apple could add paid search in App Store
Publié: avril 18, 2016, 1:49pm CEST par Anthony Spadafora
In 2008 Apple debuted its App Store to help its users discover, purchase and download new apps for their iOS devices. While the store has seen many tweaks and upgrades over the years it has yet to have a complete overhaul. Now the company has formed a secret team to explore changes to the store, including a paid search model that could cause quite the stir amongst app developers and the way iPhone and iPad users discover new apps. The secret team consists of 100 employees and is being led by Todd Teresi, who was formerly in charge of iAd.… [Continue Reading] -

Block unauthorized webcam usage with Who Stalks My Cam
Publié: avril 18, 2016, 1:15pm CEST par Mike Williams
Who Stalks My Cam is a free Windows application which alerts you to dubious software attempting to access your webcam. The download unzips to a regular installer, but there’s also a portable version if you just want to take a quick look. Once it’s running, Who Stalks My Cam displays an audio alert and a popup whenever a program tries to access your webcam. You don’t have a webcam-enabled application? Clicking Phrozen > Webcam Testing opens a built-in webcam display. Choose your camera, click Start, you should see a webcam image and get an alert. If the popups are annoying… [Continue Reading] -

UK bosses support a six-hour workday
Publié: avril 18, 2016, 11:20am CEST par Sead Fadilpašić
When workers say they’d love a six-hour workday, no one finds it particularly shocking. Ask them for a two-hour workday and you’ll hear similar responses. But when bosses and HR people also start supporting the idea, that’s when we really start to listen. And believe it or not, a new survey says bosses and HR people really do support the idea. According to a survey commissioned by Crown Workplace Relocations, 75 percent of employees were for a six-hour workday. In London, the figure rose to 78 percent. Among bosses, 60 percent said they’d consider introducing such practice. In London, the… [Continue Reading] -

9.7-inch iPad Pro Preview
Publié: avril 17, 2016, 7:19pm CEST par Joe Wilcox
The more I use Apple's smaller Pro tablet, the less likely I am to reach for the larger one. I have tested the 9.7-inch and 12.9-inch tabs side-by-side since March 31st—and the bigger one is my primary PC (most days). Unquestionably, the behemoth is capable of replacing a laptop, as Apple CEO Tim Cook asserts. The smaller-size model is a fine notebook companion, and certainly can substitute sometimes. But more than two weeks using this surprisingly satisfying kit, I can't yet (and may never) recommend it as your next PC. The 9.7-inch iPad Pro, which screen measures like all its forebears,… [Continue Reading] -

Google refuses to censor search results that identify PJS and YMA
Publié: avril 17, 2016, 2:12pm CEST par Mark Wilson
There's nothing like a good sex scandal to get people talking, and that's certainly what's happened in the case of a celebrity threesome that's currently subject to a superinjunction banning the involved parties from being named. While the identities of the couple cannot be revealed by British newspapers, their names are well-known in other parts of the world, and all over the web. The British press has played ball, agreeing not to name YMA, his husband PJS and the two others, AB and CD with whom a threesome is supposed to have taken place but it is impossible for law… [Continue Reading] -

Kyocera unveils $99 waterproof Hydro REACH Android phone for Boost Mobile and Virgin USA
Publié: avril 17, 2016, 1:56pm CEST par Brian Fagioli
When buying a smartphone, there are many things to consider. Should you get Android or iOS? How much should you spend? Which carrier will you use? It can be very confusing. If you are on a budget, however, Android is the best option -- Apple does not offer truly affordable off-contract phones. Choosing a value-focused, pre-paid carrier -- such as Boost Mobile or Virgin USA -- can be another way to save money. Today, Kyocera announces an affordable waterproof Android handset for those aforementioned carriers. Just how affordable is it? $99! "The Hydro REACH features the Android 5.1 'Lollipop' operating… [Continue Reading] -

Google set to improve transparency and privacy for Chrome extensions
Publié: avril 17, 2016, 1:32pm CEST par Mark Wilson
Google is looking to take steps that will enable Chrome users to make more informed decisions about the extensions they install. Specifically, developers will have to provide more information about data collections in the interests of transparency. In addition, developers will have to produce a privacy policy for their extensions, and must ask for permission before collecting data about users. Google's new User Data Policy introduces these extra requirements in the wake of increased demands from users for more information about what is going on in the background. Google is introducing some restrictions as well as new requirements. If the… [Continue Reading] -

Microsoft helps friends and families of Japanese earthquake victims with free Skype calls [Update: Ecuador too]
Publié: avril 17, 2016, 1:15pm CEST par Brian Fagioli
While many people worry about terrorism as a threat to human lives, and understandably so, mother nature can be quite destructive too. Between natural disasters such as hurricanes, tornadoes, and earthquakes, nature can be downright scary. Speaking of earthquakes, Japan has been dealing with many of them lately in Kyushu, causing death, injuries, and destruction. If you have friends or family in that country, and you are worried about them, Microsoft is here to help. It is currently offering free calls to Japan through its Skype communication service. The Skype Team says the following. Following the devastation and loss of life… [Continue Reading] -

Microsoft helps friends and families of Japanese earthquake victims with free Skype calls
Publié: avril 17, 2016, 1:15pm CEST par Brian Fagioli
While many people worry about terrorism as a threat to human lives, and understandably so, mother nature can be quite destructive too. Between natural disasters such as hurricanes, tornadoes, and earthquakes, nature can be downright scary. Speaking of earthquakes, Japan has been dealing with many of them lately in Kyushu, causing death, injuries, and destruction. If you have friends or family in that country, and you are worried about them, Microsoft is here to help. It is currently offering free calls to Japan through its Skype communication service. The Skype Team says the following. Following the devastation and loss of life… [Continue Reading] -

Identify, monitor and overclock your GPU with NVIDIA Inspector
Publié: avril 16, 2016, 1:25pm CEST par Mike Williams
NVIDIA Inspector is a versatile tool for checking, monitoring and overclocking NVIDIA graphics cards. This can be a complex area, but smart design ensures the program has something to offer every level of user. If you need to identify your hardware, just running the program will display plenty of useful information: name, GPU, BIOS, vendor, memory size, driver version, temperature, voltage, GPU load, and various clock speeds. Maybe you're looking for a hardware monitor? Clicking the tiny graph icon displays real-time graphs for GPU usage, clock, temperature and voltage. A right-click menu enables adding further monitors for VPU and MCU… [Continue Reading] -

Our $27,500 drone. Do you have one, too?
Publié: avril 16, 2016, 9:06am CEST par Robert X. Cringely
This is the kind of thing you find on the bedroom floor of a 14 year-old boy. It’s a gift from last Christmas, still sitting in its box, not yet flown for a reason that often comes down to some variation of "but the batteries need to be charged". I’d forgotten about it totally, which means the little drone missed the FAA’s January 20th registration deadline. Technically, I could be subject to a fine of up to $27,500. If the unregistered drone is used to commit a crime the fine could rise to $250,000 plus three years in prison. Do… [Continue Reading] -

SanDisk unveils 128GB Extreme PLUS microSDXC with gimmicky 'Works with GoPro' scheme
Publié: avril 15, 2016, 7:22pm CEST par Brian Fagioli
Micro SD cards are constantly getting bigger, faster, and more affordable. I purchased a 200GB SanDisk card from Amazon recently for $59.99 -- mind boggling. This will work brilliantly in devices such as the HTC 10, which supports cards up to a theoretical 2TB. Today, SanDisk announces its newest such card, the 128GB Extreme PLUS microSDXC. The card is fast, and should be reliable, as SanDisk says it is "shockproof, temperature-proof, waterproof, and X-ray-proof". The company is quick to tout another aspect of the card, however, but it seems very gimmicky. SanDisk explains that the card is one of the first cards to carry the… [Continue Reading] -

European Parliament approves new general data protection regulations
Publié: avril 15, 2016, 7:13pm CEST par Sam Pudwell
After a whole lot of discussion and debate, new general data protection regulations have been approved by the European Parliament. In what has been described as a watershed moment for enterprise IT, the unification of Europe’s multiple data protection regulations into one common law signals a new beginning for businesses and consumers alike. Although it’s expected that the rules won’t be officially enforced for another two years, organizations will need to start preparing now to ensure compliance, with failure to do so potentially costing up to four percent of annual worldwide turnover. Andrew Dyson, partner and co-chair of DLA Piper’s international… [Continue Reading] -

Microsoft Edge web browser gets plugin-free Skype, and that is great news for Linux users
Publié: avril 15, 2016, 6:41pm CEST par Brian Fagioli
As a Linux user, I have stopped using Skype recently. What was once a great experience on Ubuntu, Fedora, and other such operating systems, has been seemingly abandoned by Microsoft. Skype on Linux is barely usable nowadays, as the client has not seen an update in quite a while. This is rather tragic, as it is otherwise a great service on other platforms, such as Android, iOS, and of course, Windows. Users of Windows 10 that use the Edge web browser are getting a cool update this month, as Microsoft is rolling out plugin-free Skype support. While that is cool, the really… [Continue Reading] -

Microsoft releases Project Madeira public preview
Publié: avril 15, 2016, 5:43pm CEST par Anthony Spadafora
Microsoft has finally released the details regarding "Project Madeira", its enterprise resource planning (ERP) client which many had speculated would be the next version of Dynamics NAV. Dynamics NAV is one of the company’s four different ERP products and it is aimed at small to medium sized businesses. While many thought that Madeira might be the next version of this product, it is actually a separate release. Microsoft has made its new Madeira app available for preview on Windows, iOS and Android over the past few days and it is not a client app for Dynamics NAV but rather a… [Continue Reading] -

Identify the ransomware that's encrypted your data
Publié: avril 15, 2016, 5:27pm CEST par Mike Williams
It’s no secret that the best way to deal with ransomware is to avoid getting infected in the first place, and tools like BDAntiRansomware, Malwarebytes Anti-Ransomware and WinAntiRansom can do a lot to keep you safe. If your defenses are bypassed and some data lost, there may still be hope, as companies and individual researchers are producing recovery tools all the time. There’s just one problem: it’s not always obvious which family of ransomware has attacked your system. And if you don’t know the infection, it’s more difficult to look for a cure. ID Ransomware is an online service which… [Continue Reading] -

UK startups receive less in VC funding
Publié: avril 15, 2016, 5:11pm CEST par Anthony Spadafora
Venture capitalists have scaled back the size and amount of their deals across the world and UK-based startups received less funding during Q1 2016 than in Q4 2015 as a result. A new report from the analytics company CB Insights and the advisory firm KPMG Enterprise has revealed that, between January and March, startups in the UK were able to raise $1.3 billion across 105 deals. Across Europe as a whole venture capitalist (VC) funding totaled $3.5 billion across 338 deals. Thirty-six percent of all VC funding in Europe went to companies in the UK. Tech companies received 77 percent… [Continue Reading] -

Security threat or untapped potential? Dark data and Accounts Payable
Publié: avril 15, 2016, 4:21pm CEST par Stephen Mackey
Data, in whatever format it may take, is a vital part of every business. With phones tracking our every move, all aspects of customer interaction recorded, and new cars generating around of 350MB of data per second, there’s a lot of data to look at. Billions of gigabytes of data are generated across the world every day; so much that it’s almost impossible to quantify. This data poses both a potential problem and a possible reward. With so much information in front of businesses, the vast majority is lost, disappearing into the dark and creating a possible security threat. But… [Continue Reading] -

Stop using shortened URLs to share private content
Publié: avril 15, 2016, 3:58pm CEST par Mihăiță Bamburic
Generating a shortened URL to share content may seem like a good idea, but it may also expose you to unnecessary security risks, a new research paper shows. Titled Gone in Six Characters: Short URLs Considered Harmful for Cloud Services, it explains how short URLs can be used by malicious players to plant malware, copy personal files, and retrieve all sorts of personal information, like your home address, among other things. URL shorteners, as their name suggest, are meant to bring long links, that can contain dozens of characters, usually down to just a few letters and numbers. That has… [Continue Reading] -

Facebook video scam targets Chrome users
Publié: avril 15, 2016, 3:06pm CEST par Ian Barker
Researchers at security company ESET have released details of a new piece of malware that spreads disguised as video posts on Facebook. Malicious links appear as a video post you were tagged in on a timeline, or as a message sent to you via Facebook Messenger by a friend. They use the titles, 'My first video', 'My video', 'Private video' or a string of randomly generated characters. Clicking on the link tells you that a plugin is needed in order to play the video. If this is installed your Facebook wall will be flooded with fake video posts tagging various friends.… [Continue Reading] -

The Commodore 64 returns in computer and handheld versions
Publié: avril 15, 2016, 2:29pm CEST par Wayne Williams
Old computer favorites never die, they just fade away for a bit and then reappear in a new form looking for funding on Indiegogo. The ZX Spectrum was previously resurrected as Vega, and the handheld Vega+, and now there’s a new version of the Commodore 64 looking for funding. Called simply THE 64, this too will be available in desktop and handheld versions. While the Vega/Vega+ is being developed by Sir Clive Sinclair and others responsible for the original ZX Spectrum, THE 64 is being developed by fans of the Commodore classic who have previously had success with other consoles… [Continue Reading] -

Microsoft releases Windows 10 Mobile Insider Preview Build 14322 to Fast Ring -- here's what's new
Publié: avril 15, 2016, 2:19pm CEST par Mihăiță Bamburic
We may not have heard much about Windows 10 Mobile at Build 2016, but Microsoft is actively working on refining its smartphone operating system. Now, we have a new Insider Preview build, introduced to Fast Ring, which adds improvements and changes to Action Center, notifications, Cortana, Settings, emoji, Microsoft Edge, lockscreen, and more. Windows 10 Mobile Insider Preview Build 14322, as it is formally known as, also comes with lots of bug fixes in tow, and a few known issues as well. Here is what you need to know about it. In Action Center Microsoft has modified the way app… [Continue Reading] -

For sufficient data protection, companies must do more than just mirroring
Publié: avril 15, 2016, 1:54pm CEST par Mike Johnson
Many folks question all sorts of things within the IT world, one them being about backup and recovery solutions. Often questions arise that are compelling and need a good answer. One of the more popular queries is why someone would need to install a backup and recovery program when mirroring is already taking place. This is an excellent question, and comes up more often than you may think. Below you will find out why mirroring alone is not enough to ensure total protection regarding your data. Though not entirely crazy, the stance of relying upon mirroring alone for data protection… [Continue Reading] -

Xara Web Designer 365 launches
Publié: avril 15, 2016, 12:55pm CEST par Mike Williams
Xara Group has shipped Xara Web Designer 365, the first release under its new "365 Update Guarantee". Buying a 365 product not only gets you a perpetual license, you’ll also get new features as they’re developed over the 365 days after purchase (no more waiting for the next version), and supporting services such as online hosting are also free over the same period. Sounds good to us, especially as this first release already has a strong set of new features. Animations are a highlight, with new support for parallax scrolling, 30 other scroll animations, and 40 extra "on reveal" animation… [Continue Reading] -

Best Windows apps this week
Publié: avril 15, 2016, 12:44pm CEST par Martin Brinkmann
One-hundred and seventy-six in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days. Microsoft released an online demo for Windows 10 this week which has been designed to persuade users to upgrade to Windows 10. News broke earlier this week that the major Anniversary Update for Windows 10 will likely be released in July. There's no app of the week award this week unfortunately. As always, if I missed an app or game that has been released this week that you believe is particularly… [Continue Reading] -

Chatbots, apps and the path to victory
Publié: avril 15, 2016, 12:38pm CEST par Sameer Singh
This week, Facebook opened up its long awaited bot platform within Messenger following similar moves from LINE, Telegram and Kik. It almost seems as though bots have peaked on the "Hype cycle" in just a few short weeks since they entered mainstream discussion. This isn't a criticism of the concept, but rather of industry discourse. Chatbots certainly have potential, but where that lies is just as important as the eventual scale. Facebook demonstrated quite a few bots during this week's F8 conference. Unfortunately, it appeared as though many of them were just apps built inside a messaging app (a concept… [Continue Reading] -

British workers don't know their privacy rights
Publié: avril 15, 2016, 10:48am CEST par Sead Fadilpašić

British workers are mostly unaware about their privacy rights at work, a new survey suggests. Security firm Comparitech.com has polled 1,000 employees living in the UK, and according to the poll, 53 percent don’t believe bosses should be allowed to read their private communications during working hours.
What’s more, 36 percent said bosses aren’t allowed, legally, to read such emails and texts, while 13 percent said they’d quit their job if they found out their bosses were reading their private communications.
However, Comparitech.com reminds everyone of the January European Court of Human Rights (ECHR) ruling, which said bosses can review any messages sent during working hours.
"Many staff members won’t be clear what the policy is regarding bosses reading their emails unless they’ve read their employment contract in detail -- and by then it may be too late", said Lee Munson, researcher at Comparitech.com.
The company also said every worker should be careful when signing their contracts, and should check to see what the contract says about the use of social media and private communications in general.
"The study proves that people need to be more vigilant in knowing their rights in the workplace by thoroughly checking their contracts for reference to use of social media, personal email and chat at work, especially if they send private messages at work and are concerned about them being read".
Comparitech.com also says if you’re in doubt, assume all emails you send and receive from a corporate email account will be read. If you really must send a private message, make sure to use an encrypted emails service. The best solution would be to use a personal device, with a personal account, through a personal network, and not the corporate Wi-Fi.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Syda Productions / Shutterstock
-

If you have QuickTime for Windows you need to uninstall it NOW
Publié: avril 15, 2016, 9:40am CEST par Wayne Williams

Apple’s QuickTime was popular years ago, particularly for anyone wanting to watch movie trailers on the web, but its time has long since passed. There’s really very little need to have it installed on your system these days.
Because you no longer need it isn’t the only reason to uninstall it through. Trend Micro’s Zero Day Initiative has released two advisories (ZDI-16-241 and ZDI-16-242) which detail new, critical vulnerabilities affecting QuickTime for Windows, and these won’t be patched as Apple has reportedly deprecated the software.
The found vulnerabilities both allow attackers to remotely execute code after users have visited a malicious page or opened malicious files.
Apple hasn’t confirmed the vulnerabilities, nor (at this time) confirmed that it has deprecated QuickTime for Windows, in fact the software was just updated a few months ago in January. However, the latest version of QuickTime for Windows is aimed at users of Windows 7 and Vista, so it’s obviously outdated.
Following Trend Micro’s Zero Day revelations, the Department of Homeland Security's United States Computer Emergency Readiness Team (US-CERT) has advised users to take action and uninstall QuickTime for Windows.
Apple provides information on how to remove the software which you can see here.
Photo credit: Maridav / Shutterstock
-

Mozilla to make internet more inclusive
Publié: avril 15, 2016, 2:36am CEST par Brian Fagioli

Years ago, personal computing and the internet was a hobby reserved for those with a lot of money. Unlike today where you can buy a Chromebook for under $200, a desktop could cost $3,000 or more -- preventing many from participating. In other words, even in many of the richest countries in the world, many people could not afford to surf the web.
Nowadays, however, the number of people owning internet-connected devices has exploded. Heck, many households have multiple such devices and Wi-Fi is ubiquitous. Sadly, not everyone in the world has internet access, and many folks are computer illiterate -- including oppressed women in some countries. Thankfully, Mozilla is looking to change this by making the internet more inclusive.
"Mozilla will launch a public challenge this year to spur innovation and equal-rating solutions for providing affordable access and digital literacy. The goal is to inject practical, action-oriented, new thinking into the current debate on how to connect the unconnected people of the world", says Mozilla.
The Firefox-maker further says, "additionally, Mozilla is building a global hub to help more women learn how to read, write, and participate online. Over the past five years, Mozilla volunteers have started over 100 clubs and run over 5000 local events in 90 countries to teach digital literacy. Building on this model, Mozilla is now working with U.N. Women to set up clubs just for women and girls in Kenya and South Africa. This is the next step towards creating a global hub".
While this initiative sounds great, Mozilla is not exactly a super-wealthy company. I would prefer to see the organization partner with big-name players, such as Google and Microsoft, for a better chance at having the vision realized. In other words, the programs can't be funded by good intentions. But yes, these are very good intentions.
Mark Surman, executive director, Mozilla Foundation says the following:
We must address the breadth but also the depth of digital inclusion. Having access to the Web is essential, but knowing how to read, write and participate in the digital world has become a basic foundational skill next to reading, writing, and arithmetic. At Mozilla we are looking at -- and helping to solve -- both the access and digital literacy elements of inclusion.
What do you think of Mozilla's goals? Tell me in the comments.
Photo credit: one photo / Shutterstock
-

Privacy in the spotlight: Microsoft sues Department of Justice for not allowing transparency about data access requests
Publié: avril 14, 2016, 11:39pm CEST par Mark Wilson

In light of Edward Snowden's surveillance revelations, regular transparency reports from technology companies about the requests they have received from governments about data requests have become very common. But despite the name, transparency reports are not very transparent -- there are great restrictions on what companies like Microsoft are able to report. The company believes this is unconstitutional.
The restrictions are so strict that it is not even possible to precisely report the number of requests for user data that have been received. Instead, this data must be conveyed in bands such as 0-499, 500-999, and so on. Now Microsoft has had enough. There are privacy concerns, of course, but most disturbing is that in half of cases of requests for customer data, Microsoft has been gagged from letting those affected know about the governmental interest. As a result, Microsoft has decided to sue the Department of Justice in a bid to be more transparent.
In its lawsuit, Microsoft harks back to a different era, saying that in the days before the internet "the government had to give notice when it sought private information and communications" that was stored in hard copy or locally. But with Microsoft's -- and other companies' -- predilection for the cloud, it has become far easier for the government to demand instant access to private data that might otherwise have stayed out of sight.
Bringing its case against the Department of Justice, Microsoft says:
Microsoft brings this case because its customers have a right to know when the government obtains a warrant to read their emails, and because Microsoft has a right to tell them. Yet the Electronic Communications Privacy Act (ECPA) allows courts to order Microsoft to keep its customers in the dark when the government seeks their email content or other private information, based solely on a 'reason to believe' that disclosure might hinder an investigation. Nothing in the statute requires that the 'reason to believe' be grounded in the facts of the particular investigation, and the statute contains no limit on the length of time such secrecy orders may be kept in place. 18 U.S.C. § 2705(b). Consequently, as Microsoft's customers increasingly store their most private and sensitive information in the cloud, the government increasingly seeks (and obtains) secrecy orders under Section 2705(b).
More than this, Microsoft accuses the government of taking advantage of the move to the cloud to its own advantage, whilst exploiting tech companies:
The government, however, has exploited the transition to cloud computing as a means of expanding its power to conduct secret investigations. As individuals and business have moved their most sensitive information to the cloud, the government has increasingly adopted the tactic of obtaining the private digital documents of cloud customers not from the customers themselves, but through legal process directed at online cloud providers like Microsoft.
In the space of 18 months, Microsoft says that it received no fewer than 5,624 requests from the US government for access to customer data. Nearly half of these were subject to secrecy orders which prevented Microsoft from informing anyone about the request. In many instances, these secrecy orders had no time limit, meaning that this restriction would never be lifted.
Microsoft says that the First Amendment means that customers should be told when such requests are made and argues that "antiquated laws" are being applied to data in the cloud.
This is an extremely interesting case, and not just because it involves a huge name like Microsoft coming up against the Department of Justice. With Microsoft's contemporaries -- Apple, Google, at al -- all subject to the same restrictions, the outcome of this case could have far-reaching consequences.
Photo credit: Pelykh Konstantin / Shutterstock
-

Demand for web developers rises in UK
Publié: avril 14, 2016, 8:51pm CEST par Anthony Spadafora

New research from the contract recruitment company Sonovate shows that demand for contract web developers in the UK increased by 22 per cent between the last quarter of 2015 and the first quarter of 2016.
The company took a sample of 4289 listings on its job boards to compile its research. Sonovate found that postings for web developers, PHP developers, front end web developers, web application developers, senior web developers and website developers had all risen significantly.
Posts for web application developers were up by 127 percent, posts for senior web developers were up by 84 percent and posts for website developers were up by 206 percent. The increased number of job postings for all of these positions indicate steady and possibly even significant growth.
The Co-CEO of Sonovate, Richard Prime noted that the research clearly showed the increased need for qualified web development contractors across the UK and noted that now would be an excellent time for individuals in the field to enter or even re-enter the job market.
Innovatage was used to source the statistics and it made use of data from IT job postings across more than 180 global job boards and 500,000 employer websites. Currently the highest paid position overall is that of Web Solutions Architect at £650 and Senior Web Developer is the highest paid position by volume with a daily average rate of £389.
Overall Sonovate’s research shows that market for web development contractors is expanding and that their skills are in high demand across the UK.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: alphaspirit / Shutterstock
-

Threat hunting technique helps fend off cyber attacks
Publié: avril 14, 2016, 8:50pm CEST par Ian Barker

With data breaches making the news ever more frequently, businesses are on the look out for new ways to identify and guard against threats.
Cyber threat intelligence company DomainTools has released the results of a new survey conducted by the SANS Institute on the effectiveness of using threat hunting to aggressively track and eliminate cyber adversaries as early as possible.
According to the survey, adopters of this model reported positive results, with 74 percent citing reduced attack surfaces, 59 percent experiencing faster speed and accuracy of responses, and 52 percent finding previously undetected threats in their networks.
"With cyberattacks increasing exponentially each year, it's no surprise enterprises are attracted to threat hunting as a proactive multi-layered approach to discovering and mitigating cyber threats as early as possible," says Tim Chen, CEO of DomainTools. "As the findings note, successful threat hunting isn't necessarily about overhauling an existing cybersecurity program, it's about using the third-party data and technologies that most organizations already possess in order to maximize the chances of proactively finding, attributing and eliminating an adversary before the damage is done".
Though it's a relatively new approach to the early identification of cyber threats, 85 percent of enterprises say they are currently involved with some level of threat hunting. There are barriers to using the technique effectively though, 40 percent cite the need for a formal program and 52 percent a lack of skilled staff.
The top seven data sets that support threat hunting are IP addresses, network artifacts and patterns, DNS activity, host artifacts and patterns, file monitoring, user behavior and analytics, and software baseline monitoring. The most common trigger for launching a hunt is an anomaly or anything that deviates from normal network behavior according to 86 percent of respondents.
However, the survey also reveals that only 23 percent of businesses have hunting processes that are invisible to attackers, meaning that the majority of organizations are at risk from exposing internal hunting procedures in a way that benefits the attacker.
You can learn more in the full report which is available from the DomainTools website.
Image Credit: alphaspirit / Shutterstock
-

IT pros would switch jobs for better training opportunities
Publié: avril 14, 2016, 7:51pm CEST par Sead Fadilpašić

More than a third of IT professionals in the UK (36 percent) haven’t gotten any professional training through their employers in the last three years.
At the same time, pretty much everyone (97 percent of IT pros everywhere) says that knowing the latest skills is essential to them getting their work done. Those are the results of a new survey conducted by the global freelancing site Upwork.
IT managers are also aware of the issues. Ninety-five percent of them know updated skills are essential, but they’re having all kinds of trouble getting there. For 70 percent, technology moves too fast to always keep up with the latest, while for 49 percent, budgets restrictions are holding them back.
What’s more, 44 percent cite time limitations, while 33 percent prioritize other business responsibilities.
But IT managers should really consider investing in trainings and courses, as 89 percent of IT workers said they’d consider leaving their position for better training opportunities elsewhere. This not only means businesses could keep their workers, but they’d also attract new talent, as well.
"IT managers recognize the value in having a well-trained workforce but other business priorities and tight budgets mean training is often neglected", said Rich Pearson, SVP of Marketing at Upwork. "As a result, workers often feel stifled in their jobs, which can have negative effects on performance, morale and loyalty. To alleviate these pressures in-house teams face, businesses shouldn’t be afraid to look beyond their four walls and capitalize on independent professionals with proven expertise in the specific technical skills they need".
"Both training and finding staff with the right skill set is a real challenge for a growing business like ours", said Philip Lilliefelth, Pansofica Founder. "It’s imperative we keep up with evolving skills but upskilling our staff can be expensive and time-consuming, especially given the pace of change. Using freelance specialists who take it upon themselves to stay up-to-date with technical skills solves this problem, we are able to source the desired skill set immediately without major overheads – which in many cases is more suitable for start ups with budget constraints".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Javier Brosch/Shutterstock
-

IT workers will not put up with pirated software
Publié: avril 14, 2016, 6:51pm CEST par Sead Fadilpašić

Workers in the IT and telecoms industry are more prepared to blow the whistle on illegal activities in the office than any others, a new report suggests.
The report, released by BSA | The Software Alliance, looked at unethical and illegal practices in the office, relating mostly to the use of unlicensed and pirated software.
According to the report, 38 percent of UK workers would report their boss for such activities, jumping to 50 percent in the IT and telecoms industry. Out of 2,000 employees questioned, ten percent suspect their boss is up to no good. This figure jumps to 23 percent with workers in the IT and telecoms industry.
"With a third of workers willing to blow the whistle on illegal or unethical IT practices, businesses need to make sure their house is in order before it’s too late", says Sarah Coombes, managing director at BSA EMEA. "Our research shows that employees aren’t willing to put up with any practices that breaks laws or put their ethics into question. As a result we’ve seen a dramatic increase in whistleblower reports we’ve received in the last year".
What’s even more interesting is the fact that 42 percent said they’d do it for moral reasons, while just seven percent said they’d do it for a financial reward.
BSA encourages people to report unlicensed product use, and offers rewards for information which leads to a legal settlement. This year, BSA will launch the 2016 Fact or Fiction campaign, warning UK businesses about the dangers of using unlicensed software.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Marcos Mesa Sam Wordley / Shutterstock
-

HTC 10: All hail the new king of Android smartphones [first impressions review]
Publié: avril 14, 2016, 5:58pm CEST par Brian Fagioli

For the past 6 months or so, I have been using an iPhone 6S Plus. After years of living in an Android world, I decided to give Apple's offering a try. Why? Well, I don't like how some Android manufacturers fail to issue regular updates for their devices. Many people use phones and tablets with known vulnerabilities that will never be patched, and that is not cool. Regardless of your opinion of Apple or iOS, you must admit that the company is timely with updates for all of its currently supported devices.
As a lover of all tech, however, I am still very interested in Android. Google's Linux-based operating system is a very rewarding experience. And so, I found myself extremely intrigued by the HTC 10. That company is known for using premium materials, while also providing a close-to-stock Android experience. More importantly, it historically offers respectable support. Can the 10 live up to my expectations?
Notable specs
- CPU: Qualcomm Snapdragon 820, Quad Core, 64bit, up to 2.2GHz
- RAM: 4GB
- Display: 5.2 inch, Quad HD (2560 x 1440 pixels)
- Storage: 32GB (expandable with micro SD)
- Front camera: 12MP (HTC UltraPixel 2 with 1.55μm pixel)
- Rear camera: 5MP (1.34μm pixels)
- Battery: 3000 mAh (not replaceable)
Unboxing
Impressions
My first time using the HTC 10 was at a launch party in New York City. While listening to trendy music and eating mini-hors d'oeuvres, I got my hands on the newest flagship from the company. To get a fair opinion of the phone, however, it would need to be outside of a controlled environment -- in my home and on the go -- in my daily life.

And so, this is what I have done. Unfortunately, I have not had the device long enough for a proper review, but the HTC 10 has certainly made an impression on me so far, and I would like to share that with you.

After unboxing it, as seen in the above video, I got to work adding my Google credentials and setting things up. Amazingly, even after a 6 month vacation from Android, it was like I never left. Google Now was immediately sharing important information with me, and Google Play had all my apps ready to go.

Once everything was up and running, I decided to set up security with my fingerprint. Yes, the HTC 10 has such a reader on the bottom of its face (which doubles as a capacitive home button), allowing you to easily unlock it. Amazingly, it is very fast -- faster than my iPhone 6S Plus -- at reading my print and allowing me access. As a LastPass user, I found it was compatible with that app too.
Surprisingly, for navigation, HTC has opted for capacitive buttons rather than on-screen variants. While Android purists may pooh-pooh this decision, I like it. It frees up the screen, while reducing the potential of accidentally tapping -- something that I have experienced with on-screen buttons.

The user interface is largely stock Android (6.0.1) out of the box, but with little tweaks that improve the experience, such as the return of the Blinkfeed aggregator.
If you want to customize the UI, HTC offers a brilliant theme engine, allowing you to change the wallpaper, icons, sounds, etc. While themes are not a new concept, the company takes it to another level, offering options that deviate from the typical grid-based positioning of icons. HTC calls this "stickers".

As with most HTC devices, build quality is a large star of the show, and the 10 is no exception. The metal body and chamfered edges make it feel oh-so premium. Quite frankly, this is probably the best build quality of any phone I've ever touched. It is simultaneously artistic and industrial, making you feel confident in your choice.
While Android sometimes is notorious for lag, that is nonexistent here. The quad-core Snapdragon 820 and 4GB of RAM are monsters, making scrolling and navigating the UI extremely fluid. HTC's 'Blink' customization does not noticeably impact performance at all. It is very refreshing.

The 5.2-inch screen is crisp and bright, making colors pop. Pictures and videos look wonderful, rivaling any smartphone before it. The colorful icons and wallpapers when paired with this display create a very inviting and enjoyable experience. Using the phone makes me smile.
I had some worry that the smaller screen found here would be insufficient coming from the larger iPhone 6S Plus. This is a non-issue. Never did I find the screen too small. Actually, the smaller overall size makes it fit in my hand better, while reducing the uncomfortable bulge in my pocket.

HTC 'Boomsound' audio is here, but not front-facing speakers. While music and video audio is not on par with previous HTC handsets, it still sounds great. Hardcore listeners will probably use headphones or a Bluetooth speaker anyway, right? Actually, the USB Type C port can power noise-cancelling headphones as seen above -- very cool.

Battery life -- in my very limited testing -- seems good, but it will require further testing. HTC promises two days, and while I doubt I will ever achieve that, it should absolutely last a full work day, which is more than fine for me as I charge at night while sleeping.
While wireless charging is not included, QuickCharge 3.0 is. Using the included charger and USB Type C cable, you can juice up to 50 percent in 30 minutes. Sweet! Imagine sitting in a Starbucks with a coffee for a half hour, and leaving with your battery half-charged. Very handy.

The rear camera -- with dual-flash, OIS, and laser focus -- takes beautiful pictures, and equally important, it is fast. The HTC One M9 was frustratingly slow at taking pictures, causing me to miss important shots. Thankfully, the company has drastically improved this aspect of its newest flagship.

Ultimately, should you buy the HTC 10? If you want a new Android phone, and the 5.2 screen size meets your needs, absolutely. This smartphone has everything going for it -- great camera, powerful specs, seemingly-long battery life, and of course, legendary HTC build quality.
Please note, I am also testing the Galaxy S7 and LG G5 right now, and while both of those phones have positives (and negatives) the HTC 10 is without a doubt the best of the three. Yes, the 10 is clearly the leader of the current generation of Android flagships. Welcome back, HTC!
-

Video Thumbnails Maker 9.0 adds animated video contact sheets
Publié: avril 14, 2016, 5:56pm CEST par Mike Williams
 SUU Design’s Video Thumbnails Maker 9.0 has shipped with new support for creating animated video thumbnail sheets. You’re able to choose which thumbnail is animated, and the duration of the animation (2-10 seconds).
SUU Design’s Video Thumbnails Maker 9.0 has shipped with new support for creating animated video thumbnail sheets. You’re able to choose which thumbnail is animated, and the duration of the animation (2-10 seconds).The finished results may be saved as WebM or APNG, and a scaled-down version should be embedded here.
Use the embedded video controls to view the example image full-size, and if you don’t see it at all, try again with a browser that isn’t IE.
Elsewhere, "Incremental filenames" and "Save each job into its own folder" settings give you new ways to organize your thumbnail output.
There are also the usual scattering of minor cosmetic changes and bug fixes.
This release is all about the animation, then, and in our first look it worked well and looked great.
If there’s an issue, it’s that there’s no preview, no way to see how your animation is going to look. You have to create it, view the results, and if you’re not happy, tweak your settings and try again.
document.createElement('video');
[softwarecrew.com]Despite that, it’s a good program, with minimal limitations on the free version (one thumbnail shows a splash screen). Take a look.
Video Thumbnails Maker 9.0 is a shareware application for Windows XP and later.
-

Tronsmart's five-port USB charger plays nice with your Quick Charge 3.0 devices [Review]
Publié: avril 14, 2016, 4:50pm CEST par Mihăiță Bamburic

A multiport USB charger is a great tool to have if you need to top up the battery on a couple of devices at the same time. Finding the right one might prove a bit difficult though. There are lots of options available, featuring all sorts of configurations, and with support for different charging standards.
The Chotech six-port USB charger that I reviewed previously is a great all-around option that should keep most people happy for a long time, but for some folks the lack of Quick Charge 3.0 support may be a let down. So, if you have a device that supports Qualcomm's latest fast charging technology you will need to look at a different option, like Tronsmart's latest five-port USB charger which includes a Quick Charge 3.0-ready port.
What's In the Box?
The exact model that I have received for review is known as U5PTA. It is designed to charge up to five devices at the same time, and is fairly compact.
In the box, you will find the charger itself and a cable to connect it to a wall socket. The charger can draw quite a bit of power from the wall socket, so Tronsmart has opted for a beefy cable to handle all the load.

It is longer than the cables typically sold with smartphones, so you should have no issues finding a good place for the charger in your room. The plug that is supplied depends on where you purchase the charger from. My review unit has a European plug, but there are also versions for US and UK.
There are no USB cables in the box, so you will have to use your own. This shouldn't be a problem for most people, as smartphones and tablets are shipped with their own cables anyway. But keep this in mind in case you wish to take it on trips with you.
The Ports
Tronsmart has designed this multiport USB charger with high-end smartphone shoppers in mind. Few devices support Quick Charge 3.0 at this time, with the list including mostly (if not only) the latest Android flagships from the likes of LG, HTC, Samsung and Xiaomi -- basically the handful of smartphones that ship with a Snapdragon 820 processor.
The Quick Charge 3.0 port (the first one to the left in the photo below) is backwards-compatible with previous versions of the technology (like Quick Charge 2.0), meaning that it will work just fine with previous-generation Android devices, like Samsung's Galaxy S6 and Note 5 or LG's G4. I have tested the backwards compatibility using a Xiaomi Mi4c, and I have to say that it works great.
For the Quick Charge 3.0 port, Tronsmart says that it supports charging between 3.6V and 6.5V at 3A, 6.5V and 9V at 2A, and 9V and 12V at 1.5A. The other four ports are limited to 5V and up to 2.4A. The charger will adjust the charging voltage and amperage on its own -- Tronsmart calls this VoltiQ -- so you do not have worry about which port you are plugging your device in. During my testing, I have used all ports without issues using a variety of devices.

Worth pointing out is the fact that if you have more Quick Charge-ready devices you will have to choose which one you want to charge at the fastest-possible rate. As noted in my previous review of the Chotech charger, more Quick Charge ports would not go amiss.
How Much Does It Cost?
Tronsmart sells this USB charger on Amazon for $29.99. It is also available in Europe for roughly £21.99 in UK or €24.90 in France. You can also get it from Geekbuying, where it is priced at $34.99 -- but you get the benefit of being able to choose which plug you get.
Should You Buy It?
There are both cheaper and more expensive chargers around, but as is usually the case with certain configurations you can be hard pressed to find many with a similar port scheme. For the money though, this offers good value and I would recommend it to anyone with a Quick Charge 3.0-ready device as long as they do not mind the fact that there is only one such port available.
Photo Credit: Mihăiță Bamburic
-

UEBA is only one piece of the cyber risk management puzzle
Publié: avril 14, 2016, 4:48pm CEST par Steven Grossman

Just like perimeter protection, intrusion detection and access controls, user and entity behavioral analytics ("UEBA") is one piece of the greater cyber risk management puzzle.
UEBA is a method that identifies potential insider threats by detecting people or devices exhibiting unusual behavior. It is the only way to identify potential threats from insider or compromised accounts using legitimate credentials, but trying to run down every instance of unusual behavior without greater context would be like trying to react to every attempted denial of service attack. Is the perceived attack really an attack or is it a false positive? Is it hitting a valued asset? Is that asset vulnerable to the attack? It is time for cyber risk management to be treated like other enterprise operational risks, and not a collection of fragmented activities occurring on the ground.
Analogous to fighting a war, there needs to be a top down strategic command and control that understands the adversary and directs the individual troops accordingly, across multiple fronts. There also needs to be related "situational awareness" on the ground, so those on the front lines have a complete picture and can prioritize their efforts.
When it comes to cyber risk management, it means knowing your crown jewels and knowing the specific threats to which they are vulnerable. If an information asset is not strategically valuable and does not provide a gateway to anything strategic, it should get a lot less focus than important data and systems. If an important asset has vulnerabilities that are likely to be exploited, they should be remediated before vulnerabilities that are unlikely to be hit. It seems logical, but few large enterprises are organized in a way where they have a comprehensive understanding of their assets, threats and vulnerabilities to prioritize how they apply their protection and remediation resources.
Even "at the front", UEBA is only a threat detection tool. It uncovers individuals or technologies that are exhibiting unusual behavior but it doesn’t take into account greater context like the business context of the user’s activities, associated vulnerabilities, indicators of attack, value of the assets at risk or the probability of an attack. By itself, UEBA output lacks situational awareness, and still leaves SOC analysts with the task of figuring out if the events are truly problematic or not. If the behavior, though unusual, is justified, then it is a false positive. If the threat is to corporate information that wouldn’t impact the business if it were compromised, it’s a real threat, but only worth chasing down after higher priority threats have been mitigated. For example, let’s say through UEBA software, it is identified that an employee on the finance team is logging into a human resources application that he typically would not log into. UEBA is only informing the incident responder of a potential threat. The SOC will have to review the activity, determine if it is legitimate, if not, check if the user has access privileges to access sensitive information in the application, see if their laptop has a compromise that may indicate a compromised account and then make what is at best a not so educated guess that will often result in inaccurate handling. Just as important, the SOC analyst will likely do all of their homework and handle the incident appropriately, but without the right context they may have wasted a lot of time chasing down a threat that of low importance relative to others in the environment.
A true "inside-out" approach to cyber risk management begins with an understanding of the business impact of losing certain information assets. The information assets that, if compromised, would create the most damage are the information CISOs, line-of-business and application owners, SOC investigators, boards of directors and everyone else within the company should focus on protecting the most. They should determine where those assets are located, how they may be attacked, if they are vulnerable to those attacks and the probability of it all happening. Once that contextualized information is determined, everyone within the company can prioritize their efforts to minimize cyber risk.
Photo credit: arda savasciogullari / Shutterstock
 Steven Grossman is Vice President of Program Management, Bay Dynamics. He has over 20 years of management consulting experience working on the right solutions with security and business executives. At Bay Dynamics, Steven is responsible for ensuring our clients are successful in achieving their security and risk management goals. Prior to Bay Dynamics, Steven held senior positions at top consultancies such as PWC and EMC. Steven holds a BA in Economics and Computer Science from Queens College.
Steven Grossman is Vice President of Program Management, Bay Dynamics. He has over 20 years of management consulting experience working on the right solutions with security and business executives. At Bay Dynamics, Steven is responsible for ensuring our clients are successful in achieving their security and risk management goals. Prior to Bay Dynamics, Steven held senior positions at top consultancies such as PWC and EMC. Steven holds a BA in Economics and Computer Science from Queens College. -

Raspberry Pi Zero gains a mysterious new feature, and improved availability
Publié: avril 14, 2016, 3:49pm CEST par Wayne Williams

It’s no surprise that the Raspberry Pi Zero was such a hit. Priced at just $5, the tiny uncased device sold out immediately, and despite occasional reappearances at retailers like The Pi Hut, it’s remained ever-elusive.
If you haven’t yet managed to get your hands on the Pi Zero, the good news is it will soon be back in stock, and in much greater numbers than before. And that’s not the only welcome news. The restocked device will be packing a much requested new feature.
SEE ALSO: How to find and buy the ever-elusive $5 Raspberry Pi Zero
As to what this new feature is, Raspberry Pi Foundation’s CEO Eben Upton isn’t currently saying, but if you’re hoping for the introduction of Wi-Fi he confirms it’s not that, sorry.
The Pi Zero’s production was temporarily halted at the Welsh manufacturing plant when focus switched to producing the Raspberry Pi 3, but from next Monday work will start on cranking out 250,000 new Pi Zeros, and that’s just the start. The plan is to produce at least 50,000 more Pi Zeros a month for the rest of the year.
Expect to see stock in usual Pi Zero stores, including The Pi Hut, Adafruit, Pimoroni and Micro Center, in the next fortnight or so.
What do you think the new feature will be? Leave your thoughts in the comments below.
-

Are old customers more important to online businesses than new ones?
Publié: avril 14, 2016, 2:56pm CEST par Ian Barker

For businesses, particularly online ones, there will always be a mix of new and old customers. But what does the ratio between them tell you about the health of the company?
Cloud marketing company Optimove has studied data from millions of online customers and more than 180 brands to help companies understand if their ratio of new-to-existing customers indicates a state of growth, stagnation or decline.
It finds that online retailers with a new to old customer ratio of 90:10 are unhealthy, with a five-year compound annual growth rate (CAGR) lower than two percent and customer churn rates 100 percent higher than average. These are classed as 'running in place.'
Those with a new-to-existing customer ratio between 70:30 and 40:60 are typically early stage companies (less than seven years old). These are 'rockets' and are growing very fast, with a five-year CAGR over 100 percent and churn rates 50 percent lower than the average.
Businesses with new:existing ratios between 40:60 and 20:80 can be considered as 'healthy grown ups,' as they're typically more than 7 years old and have a five-year CAGR between 20 percent and 60 percent, with the lowest churn rates of any companies in the study.
A ratio of 10:90 or worse is bad news, these businesses, 'old cash cows,' are practically dying, showing declining revenues over the last three to five years.
"Two companies with the same revenue mix may tell very different stories and drive growth in very different ways," says Shauli Rozen, head of professional services at Optimove. "A quick example might be two companies that both derive 75 percent of revenue from existing customers. One might be acquiring many new customers and converting only a small portion of them to active and loyal customers, while the other may choose a more focused acquisition strategy, acquiring a smaller number of new customers, but turning a larger portion of them into loyal, long-time customers".
You can read more about the findings on the Optimove blog.
Photo credit: mtkang / Shutterstock
-

Watch out for phishing as US tax deadline day approaches
Publié: avril 14, 2016, 1:45pm CEST par Ian Barker

As the April 18 deadline for submitting individual and company tax returns in the US approaches, many people will be rushing to submit their information and this makes it a major opportunity for cyber criminals.
The run up to the deadline is likely to see millions of phishing emails sent to consumers and businesses. These will be trying to grab social security numbers, paycheck stubs, bank accounts, passwords, IDs and other key pieces of personal and professional information, using fake web sites and fraudulent emails that masquerade as official government collection agencies.
Fatih Orhan, director of technology for Comodo and the Comodo Threat Research Labs says, "In this age of sharing and collaborating in an online world, being exposed to phishing is an eventuality for virtually every company, well-known or not. It may not be the most groundbreaking attack method cyber criminals use -- but there's no denying that cyber criminals are becoming more clever when crafting their messages. More frequently, they're using well-known applications or social platforms and also action-oriented language in the subject lines to entice recipients to open the emails, click the links or attachments and get the information they want".
Comodo advises users to carefully check the address and domain name of email senders. While it may appear to be official, closer inspection will most likely reveal that the actual address is not linked with the domain name of the company.
In addition check the URL and domain of the website the mail is linking to. Chances are the URL and domain are also not affiliated with the company they’re purporting to represent. It also advises users to check with their IT department before opening or clicking on a link that seems suspicious.
Image Credit: wk1003mike / Shutterstock
-

ORPALIS PDF Reducer cuts document sizes by up to 80 percent
Publié: avril 14, 2016, 1:06pm CEST par Mike Williams

ORPALIS PDF Reducer is an effective tool for optimizing PDF documents, reducing their size by up to 80 percent.
Unlike some of the competition, the program doesn’t just cut your document DPI: it applies multiple techniques to deliver the best results. This starts by checking individual PDF objects. Any which aren’t used are stripped out of the file, and you can optionally remove other items you may not need: annotations, bookmarks, embedded files and more.
If the file contains scanned documents, they’ll all be encoded as full color images. PDF Reducer detects any which are just black and white, then re-encodes them as plain black and white images, often with dramatic savings.
The program applies multiple compression techniques on some images, reducing file size without losing any quality.
If this isn’t enough, you can opt to resample images to a lower DPI.
ORPALIS also claims that the program analyses layout, finds similar bitmaps and uses that information to optimize compression, but we’re not sure how that works or what it can achieve.
All this is extremely easy to set up. At a minimum the program just needs an input and output folder, and you can adjust how it works in a simple Settings dialog (turn off downscaling, maybe, or choose which content to remove).
It also performed well in our tests. As usual, some files barely changed at all, but the program did make its advertised 80 percent reduction in other cases -- more, sometimes -- and without having much effect on quality.
There is one catch. ORPALIS PDF Reducer’s full Professional version is priced at $199, and while there’s a free-for-personal-use build available, it has a nag screen which pops up on launch, and after every five batch-processed files.
The nag screen has a countdown of several seconds (up to 12 in our tests), and can’t be dismissed until then. If you’re hoping to process hundreds of files then you’ll have to sit in front of the PC, wait for the countdown, dismiss the nag screen, then do it again a few seconds later.
While this can be annoying, at least you’re getting the same compression level as the full product, with no watermarks, resolution limits or other hassles. That seems generous to us, and if you’re going to process vast numbers of files then the developer probably deserves some payment.
ORPALIS PDF Reducer is a free-for-personal-use application for Windows XP and later.
-

CyberLink PowerDVD 16 debuts TV Mode, media casting
Publié: avril 14, 2016, 12:18pm CEST par Mike Williams
CyberLink has released PowerDVD 16, the latest edition of its do-everything media player.
New media casting support for ChromeCast, Roku and Apple TV enables streaming audio, video and pictures around your home, with PowerDVD automatically converting files to a format each device can understand.
"TV Mode" is a full-screen interface optimized for large displays, a more capable version of the old Cinema Mode. The program now handles more formats, including MVC and DSD audio.
New batch processing support means you can extract the audio from multiple videos in a single operation.
CyberLink claims the program now makes better use of system resources, improving startup speeds, reducing the impact of background processes, and maybe extending battery life, too.
The PowerDVD Remote app for iOS and Android has been improved.
CyberLink’s Cloud Storage is more generous, too, offering 30GB of storage space for a year (that’s up from 20GB last time).
PowerDVD 16 is available in four editions.
The subscription-based PowerDVD Live offers everything we’ve listed here, as does PowerDVD 16 Ultra.
PowerDVD 16 Pro drops support for 3D, media casting, DLNA, TV Mode, audio batch processing and cloud storage, as well as cutting some audio and social media features.
PowerDVD 16 Standard drops all support for Blu-ray and social media, and further cuts back on audio support (no Dolby TrueHD, DTS-HD, DSD Audio).
PowerDVD 16 is available now for Windows 7 and later.
-

PayPal Credit launches in the UK -- a virtual credit card with an interest-free offer
Publié: avril 14, 2016, 11:44am CEST par Mark Wilson

PayPal is, in many ways, the primary choice for making online payments. The company is keen to build on this and has launched a new product in the UK to widen its appeal. PayPal Credit is a virtual credit card that can be used online, and as an incentive to sign up, there's a four-month interest-free offer.
As this is an online credit card, applying for it takes a matter of moments, and PayPal is quick to point out that there's no hanging around waiting for a card and PIN to arrive. Apply online and you could be approved for a credit extension to your PayPal account.
Just as with any other form of credit card, making an application for PayPal Credit involves a credit check -- something to keep in mind if you're concerned about your credit score. Once signed up, you'll be able to make purchases via PayPal even if you don’t have funds in your linked bank account, or if you just fancy the idea of spreading the cost of a larger purchase.
PayPal describes the new virtual card:
PayPal Credit is like a credit card you can use for your online purchases, it takes minutes to apply and if you’re approved you’ll have a credit limit in your PayPal account right away.
The interest-free offer is... interesting. PayPal bills it as "0% for 4 months to use again and again", going on to explain that "every time you spend £150 or more in one go using PayPal Credit, you’ll get 0% interest for 4 months on that purchase". After four months -- and for purchases under £150 -- the interest rate jumps to a fairly standard 17.9% p.a (variable).
If you want to apply for a virtual card, head over to the PayPal Credit website.
Photo credit: www.BillionPhotos.com / Shutterstock
-

Dell Venue 8 Pro 5855 is an attractive business tablet [Review]
Publié: avril 14, 2016, 11:08am CEST par Ian Barker
The first generation of Dell’s Venue 8 tablet hit the market back in 2013. In January of this year the company launched the updated version that we have here, which comes with a faster Intel Atom X5 processor and 64-bit Windows 10 as standard.
So, how does this latest version measure up, and is it a good option for business users?
In the Box
The Venue 8 Pro is available as Wi-Fi only or you can have a mobile data connection too. It’s powered by a 2.4GHz Intel Atom X5 Z8500 -- the old model had the 1.8GHz Z7340. You get 2GB of DDR3 RAM, a 64GB solid state hard drive and Wi-Fi as standard. Our review unit came with 4GB of RAM and the mobile data option, if you need more space, storage can be further expanded with a microSD card of up to 128GB. It’s worth noting that Dell uses eMMC storage -- which is basically a built-in SD card -- rather than a faster SSD disk.
The tablet measures 130 by 216mm and is only 9.45mm thick. At 377 g it gives an impression of solidity without feeling too weighty to carry around. The tablet has an 8-inch 1280 x 800 screen, a 5MP rear camera and 2MP front. The 5855 supports Miracast so you can wirelessly connect to compatible peripherals like screens and keyboards. The battery is a 19.5 WHr single cell unit.

You get a USB C cable and a mains adaptor in the package and, an attractive feature for business users, Microsoft Office Mobile is included in the price, and you can upgrade to the full version with an Office 365 subscription. Security is taken care of with the Dell Data Protection software.
Business Features
The Dell has a reassuringly solid feel and it should stand up well to the rigours of everyday business life. It comes with the Bamboo Paper digital notebook software that allows you to write and draw on the screen either with your finger or the optional stylus.
The fact that MS Office Mobile is included means you can start work almost as soon as you take it out of the box. You also get Dell’s Data Protection software which offers encryption and anti-malware features to keep your tablet and data secure. The Venue 8 Pro is also compatible with the Dell Client Command Suite, allowing IT departments to centrally manage BIOS and hardware configurations.
In addition you get access to Dell ProSupport Plus as an option, which helps identify and resolve problems and keep your hardware running smoothly. There’s the option of Protected Workspace too, this opens applications likely to be targeted by malware in a sandbox environment to guard against attacks.
There are a number of accessories that will be attractive to business users too, including a docking, station that supports keyboard, mouse and dual displays, a case called "Folio" that converts into a hands free stand, plus an active pen stylus for writing and drawing on the screen. You can also get an adaptor that gives access to HDMI, VGA, Ethernet and USB 3.0 via the USB-C port. Software options include Adobe Create Cloud, Photoshop Elements and Acrobat.
In Use
There’s a power switch on the top along with a headphone socket. The bottom edge has a USB C socket and speaker grille. On the right are the volume control and a hard Windows button plus a slot for SIM and memory cards. Because it’s USB C it’s less fiddly to connect as you don’t have to get the plug the right way around, but you’ll need to get an adaptor if you want to attach a flash drive or other standard USB peripheral.

The back has a ridged finish which makes it pleasant to grip, though it does tend to show finger marks. While the Venue 8 is nicely weighty it isn’t too heavy to hold one-handed. The rear camera is in a slightly raised panel in the centre of the back towards the top. You do tend to place your fingers over this if you’re holding the tablet landscape, so you’ll need to wipe it clean before taking photos. The back of the machine does get warm in use, but not uncomfortably so. The performance of this tablet isn’t going to set the world on fire. but it’s perfectly adequate for everyday tasks.
The screen has quite a wide bezel -- especially on the short edges -- but the viewing area itself is a good size. The screen itself offer 283 ppi pixel density (an improvement on the 189 ppi of the previous generation). What this means in practice is that it has crisp colors, good contrast and delivers smooth video playback. Viewing angles are good too so its possible for two people to watch the screen at the same time. It isn’t quite bright enough to cope with outdoor use on sunny days but that’s a minor quibble. There’s only a single speaker but it delivers decent sound quality.
The number of megapixels doesn’t tell the whole story with the rear camera, as although it’s "only" 5MP it actually delivers pretty impressive results. There’s no flash, but it takes good pictures in both daylight and artificial light. It uses the standard Windows 10 Camera app which is basic but functional. The 2MP front camera is good enough for VoIP calling.
The most disappointing aspect of the Venue 8 Pro is its battery life. Even in relatively light use, like visiting websites or viewing documents you’ll struggle to get more than five or six hours on a charge. Watch videos or play games and you’ll eat through the power reserves much faster.
Conclusion
At £366 for the 64GB version with mobile data as tested -- you can get the 2GB Wi-Fi only version for £259 -- the Venue 8 Pro may seem a little pricey. As a business machine though it looks like an attractive package. It’s solidly constructed, has a good range of practical hardware and software options, and it looks smart in an understated way.
If you can live with the rather disappointing battery life and you value reliability over performance, it’s well worth considering.
Pros
- Impressive display
- USB C
- Good range of business friendly features
Cons
- Disappointing battery life
- Non-SSD storage
- Pricey
ITProPortal Review: 7/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Microsoft releases open source CentOS-based 'Linux Data Science Virtual Machine' for Azure
Publié: avril 14, 2016, 1:01am CEST par Brian Fagioli

Microsoft is both an open source and Linux champion nowadays -- on the surface at least (pun intended). In other words, while it does embrace those things, we may not know the motivation of the Windows-maker regarding them. Regardless, Linux and open source are now important to the Redmond company.
Today, Microsoft announces a CentOS-based VM image for Azure called 'Linux Data Science Virtual Machine'. The VM has pre-installed tools such as Anaconda Python Distribution, Computational Network Toolkit, and Microsoft R Open. It focuses on machine learning and analytics, making it a great choice for data scientists.
"Thanks to Azure's worldwide cloud infrastructure, customers now have on-demand access to a Linux environment to perform a wide range of data science tasks. The VM saves customers the time and effort of having to discover, install, configure and manage these tools individually. Hosting the data science VM on Azure ensures high availability, elastic capacity and a consistent set of tools to foster collaboration across your team", says Gopi Kumar, Senior Program Manager, Microsoft Data Group.
Kumar further says, "in about 15 minutes you can standup your own data science VM within your subscription and you'll be ready to jump right into data exploration and modeling immediately. You have full administrative access to the VM and can install additional software as needed. There’s no separate fee to use the VM image. You only pay for actual hardware compute usage of the virtual machine depending on the size of the VM you're provisioning. You can turn off the VM from Azure portal when it's not in use to avoid being billed for usage. When you restart the VM you can continue your work with all data and files intact. You can further augment your analytics on the data science virtual machine by leveraging services in Microsoft Azure and Cortana Intelligence Suite".
READ MORE: Linux can still beat Windows in the desktop war, and Linus Torvalds is 'working on it'
If you want to try this Linux-based image, you can set it up on Azure here. Keep in mind, unless you are a data scientist or analyst that leverages Azure, this probably is not for you.
Are you impressed by Microsoft's continued embrace of Linux and open source? Tell me in the comments.
Photo credit: Sanit Fuangnakhon / Shutterstock
-

Android N Developer Preview 2 available to download now
Publié: avril 13, 2016, 11:30pm CEST par Mark Wilson

It's only a few weeks since the first developer preview of Android N was released, but now it's time for the second. Google has announced the availability of Android N Developer Preview 2 packed with bug fixes and a raft of new features.
Among the new tools for developers to play with is Vulkan, a new 3D rendering API which Google says provides a big performance boost for certain apps. Other key additions include support for the more human-looking Emoji Unicode 9, and new launcher shortcuts that can be used to quickly jump to specific actions within an app.
Android N Developer Preview 2 also includes API improvements for multi-window support, giving developers the ability to specify height and width for an activity. As before, the preview build is only available for a limited number of devices -- which will hopefully expand over time -- but the range of bug fixes is impressive (although, of course, there are still a number of known issues).
In a blog post, Google explains how to get hold of Android N Developer Preview 2:
The easiest way to get this and later preview updates is by enrolling your devices in the Android Beta Program. Just visit g.co/androidbeta and opt-in your eligible Android phone or tablet -- you’ll soon receive this (and later) preview updates over-the-air. If you’ve already enrolled your device, you’ll receive the update shortly, no action is needed on your part. You can also download and flash this update manually. Developer Preview 2 is intended for developers and not as a daily driver; this build is not yet optimized for performance and battery life.
The N Developer Preview is currently available for Nexus 6, Nexus 5X, Nexus 6P, Nexus 9, and Pixel C devices, as well as General Mobile 4G [Android One] devices. For Nexus Player, the update to Developer Preview 2 will follow the other devices by several days.
To build and test apps with Developer Preview 2, you need to use Android Studio 2.1 -- the same version that was required for Developer Preview 1. You’ll need to check for SDK components updates (including build tools and emulator system images) for Developer Preview 2 -- see here for details.
-

Can Microsoft's online demo persuade you to upgrade to Windows 10?
Publié: avril 13, 2016, 8:52pm CEST par Wayne Williams
Microsoft is doing its best to persuade users of Windows 7 and 8.1 to upgrade to Windows 10. Having seen reasonable -- but not outstanding -- upgrade numbers as a result of aggressively ramming the new OS down users’ throats, the software giant is now trying to sell the benefits of Windows 10 to those customers still on the fence.
An online Windows 10 demo covering PC, Tablet and Phone lets users see the new OS in action, and gives them the opportunity to upgrade if they like what's on offer.
Select a device type at the top, and then pick a category you’re interested in from the list down the left hand side. Options for the PC are:
- Work across my devices
- Meet Cortana
- Get more done
- Stay organized
- Get apps and more
- Personalize my PC
- Keep in touch
- Browse the web
- Manage my photos
- Have more fun
- Find my way with maps
Once you’ve selected one of those you can choose a particular area you’re interested in, and the relevant video will play on the right.
If you want to know how to "get more done", for example, the demo will show you how to mark up and share web pages, work on the go, work hands free, take notes with you, and instantly unlock your PC.
Should the videos do their job of convincing you to upgrade, you can do so by clicking the Shop Now button on the site.
You can try the demo here.
What do you think? Are you tempted to upgrade, and if not, what's holding you back?
-

Cyber-criminals run things like a business
Publié: avril 13, 2016, 8:42pm CEST par Sead Fadilpašić

This cyber-crime thing has gotten to a point where we now really need a digital Batman to fix everything. Security firm Symantec has recently released its Internet Security Threat Report, revealing that cyber-criminals are almost as good as state-sponsored attackers.
They’re highly skilled, well-organized and structured like a business. Here’s what Kevin Haley, director at Symantec Security Response says:
"Advanced criminal attack groups now echo the skill sets of nation-state attackers. They have extensive resources and a highly-skilled technical staff that operate with such efficiency that they maintain normal business hours and even take the weekends and holidays off. We are even seeing low-level criminal attackers create call center operations to increase the impact of their scams". Yeah, I only have Sony Entertainment left to hack this week, then I can go to Bora Bora for a couple of days.
Zero-day vulnerabilities are on the price nowadays. Advanced groups will either take advantage of them, or sell them on the open market. Symantec says that the number of zero-day vulnerabilities discovered in 2015 more than doubled, to 54, breaking records along the way. Compared to a year before, this represents a 124 per cent jump.
The report also sheds some light on data theft, saying that more than half a billion personal information records were either stolen, or lost, last year. Encryption is now used by cyber-crooks to keep data hostage, a practice also known as ransomware. Scam is also making a comeback, with fake tech support centers (a 200 percent increase last year) being the most popular one.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: alphaspirit/Shutterstock
-

Women and black writers are the biggest victims of abusive online comments
Publié: avril 13, 2016, 6:56pm CEST par Mark Wilson

Online abuse is a serious problem. While the likes of Twitter and Facebook are great platforms for trolls to indulge their hobby, it's the good, old-fashioned comments section where you'll find some of the most obvious examples of threats and abuse. The problem is so great that many websites have taken the seemingly drastic step of completely disabling comments on stories, while others do so on an individual basis for articles that could prove controversial.
Clearly this is less than ideal. In many ways it could be viewed as a form of censorship that curtails freedom of speech, and comments can be a valuable way to help a story to evolve. For many sites, comments are a black and white topic; on or off. Moderation -- again, often seen as a type of censorship -- is often employed, but this does little to stop abuse aimed at writers. The Guardian has conducted research into the abuse dealt out via comments on its site, and the findings make for disturbing reading.
It has been argued that the world of tech, and the internet, is dominated by white men and that there is more than a hint of racism and sexism. An article entitled The dark side of Guardian comments bears this out. In depth analysis of more than 70 million comments reveals that when looking at the top 10 'most abused' writers, 80 percent of them are women and 60 percent are black.
As the Guardian notes, the comments section of just about any website is often home to truly hateful abuse:
The Guardian was not the only news site to turn comments on, nor has it been the only one to find that some of what is written 'below the line' is crude, bigoted or just vile. On all news sites where comments appear, too often things are said to journalists and other readers that would be unimaginable face to face -- the Guardian is no exception.
This is not really surprising. The veil of anonymity, and the barrier of distance, that the web affords trolls means people often feel free to unleash torrents of abuse that would be unimaginable in another medium. But it is the breakdown of the most abused writers that is both interesting and disturbing, confirming fears that sexism and racism are rife online.
The Guardian itself points out that the majority of its opinion writers are white men. While many would view this as an issue in itself, these same white men do not find themselves to be on the receiving end of the majority of abuse. Regardless of topic, articles written by women result in more trolling and abuse than those written by men.
The 10 regular writers who got the most abuse were eight women (four white and four non-white) and two black men. Two of the women and one of the men were gay. And of the eight women in the 'top 10', one was Muslim and one Jewish.
And the 10 regular writers who got the least abuse? All men.
What's particularly interesting is that in stereotypically male arenas such as sport and technology, female writers found themselves on the end of more comments deemed blockable by moderators. Some individual topics also attracted more unpleasant comments than others:
We also found that some subjects attracted more abusive or disruptive comments than others. Conversations about crosswords, cricket, horse racing and jazz were respectful; discussions about the Israel/Palestine conflict were not. Articles about feminism attracted very high levels of blocked comments. And so did rape.
The primary focus of the analysis was the different reception men and women enjoyed, but it did reveal more.
We focused on gender in this research partly because we wanted to test the theory that women experience more abuse than men. But both writers and moderators observe that ethnic and religious minorities, and LGBT people also appear to experience a disproportionate amount of abuse.
Running a website means walking a narrow line between saying 'anything goes' and becoming over-enthusiastic with the ban hammer. The Guardian's research throws some interesting light on just how complicated the commenting ecosystem is. Do you give people a free rein to say whatever they want -- risking things going wildly off-topic or getting abusive and personal -- or do you risk accusations of limiting free speech by stepping in as a moderator when things get out of hand?
It's not an easy question to answer, and it's made all the more difficult once gender and race are thrown into the equation.
Photo credit: aastock / Shutterstock
-

ASUS ROG Spatha MMO-focused gaming mouse has 12 programmable buttons, wired or wireless
Publié: avril 13, 2016, 6:48pm CEST par Brian Fagioli

While a talented gamer can get by with any mouse, a gaming device is often preferred. These game-focused mice sometimes feature additional buttons, adjustable weights, and variable DPI. Plus, of course, they often look futuristic and have LED lights, because, you know, all gamers must have such things (sarcasm).
Today, ASUS announces its newest gaming mouse -- the ROG (Republic of Gamers) Spatha. While it looks really cool and is chock full of features, there is one such feature that I really love -- it can be both wired and wireless. If the battery gets low, or depletes entirely, you can connect a cable and continue to game. When you do need to add some juice, the magnetic charger has you covered. That's really cool.
"The Spatha can be a wired mouse and offers wireless freedom as well, featuring an 8200 dpi laser sensor with the ability to track 30g (gravitational) acceleration, 150 ips (inches per second) and at 2000Hz for polling rate (in wired mode, 1000Hz for wireless). The Mayan-patterned grip and ergonomic design make sure you have complete command of the mouse even if you have ginormous hands. The Spatha is perfect for the palm or claw grip", says ASUS.
The company further says, "No matter what games you're into, the 12 programmable buttons including six for the thumb will have you covered - even for MMO (Massively Multiplayer Online) games. The large left and right buttons are separated from the body for responsiveness while different Japanese-made Omron switches offer different tactile-feel, up to 20-million click lifespan, and can be easily swapped out (extra switches come bundled). The Alps encoder scroll wheel provides smooth and accurate movement, vital for when cycling through weapons or the inventory. A 2-level dpi switch with light indicator is perfect for FPS (First Person Shooter) games where you want to zoom in and out instantly to snipe, horizontal (X) and vertical (Y) sensitivity can be customized independently to help keep the crosshair leveled for more headshots".
ASUS shares the following specs and features.
Click to view slideshow.Connectivity
Wireless RF 2.4GHz Wired via USB 2.0
Tracking resolution
8200DPI laser sensor Tracking speed
150 inches per second Tracking acceleration
30g Responsiveness
2000Hz polling rate (in wired mode) 1000 Hz polling rate (in wireless mode)
Switch
OMRON D2FC-F-7N(20M) with 20-million-click lifespan Additional OMRON D2F-01F switches included
Compatible switches:OMRON D2F Series switches: D2F, D2F-F, D2F-01, D2F-01F
OMRON D2FC Series switches: D2FC-3M, D2FC-F-7N, D2FC-F-7N(10M) , D2FC-F-7N(20M)
Cables
2m braided USB cable 1m rubber USB cable
OS compatibility
Windows 10 Windows 8.1
Windows 8
Windows 7
Package contents
1 x wireless receiver/ charging dock 1 x 2-meter braided USB cable
1 x 1-meter regular rubber USB cable
2 x Japanese-made Omron switches
1 x ROG hard carry case
2 x ROG logo stickers
1 x screwdriver
User documentation
Size
137 x 89 x 45mm Weight
175g (without cable) While the mouse should work fine on Linux or OS X, it is designed for Microsoft's operating system. The customization software, which allows you to do things like change the lighting color, or acceleration, is a Windows-only affair. This isn't a huge deal as that operating system is still the choice for PC gamers -- for now.
If you want to buy the ASUS Rog Spatha, I unfortunately do not have any information on pricing or availability. ASUS is remaining quiet on the subject for now. With that said, it will almost certainly be expensive -- over $100 is almost a guarantee.
Do you want it? Tell me in the comments.

-

Meizu Pro 6 is a new flagship Android smartphone with 10-core processor
Publié: avril 13, 2016, 6:32pm CEST par Mihăiță Bamburic

The Android flagships introduced so far this year feature an octa-core processor, typically a Qualcomm Snapdragon 820. Hardly anyone can argue that eight cores are not enough for whatever apps and games users might want to run. Meizu is an exception as with its latest high-end smartphone it is taking things up a notch.
Meizu's new Pro 6 is among the first, if not the first, smartphone to feature a 10-core processor, namely a Helio X25 chip with four Cortex-A53 cores at 1.4 GHz, four Cortex-A53 cores at 2 GHz and two Cortex-A72 cores at 2.5 GHz. On paper it looks much more impressive than a Samsung Galaxy S7 or HTC 10.
The 10-core processor is not the only feature that sets Pro 6 apart from the competition, as the flagship also features 3D Press. That is a Meizu's speak for a pressure-sensitive display, similar to what Apple has introduced in iPhone 6s and iPhone 6s Plus. The Samsung-made AMOLED screen measures 5.2 inches in diagonal, and has a resolution of 1,080 by 1,920. That's a bit low compared to the display on Galaxy S7 and HTC 10, but it's more than enough for the respective size.
The processor is backed by 4 GB of RAM, and there are two storage tiers: 32 GB and 64 GB, both eMMC 5.1 enabled. There is no microSD expansion listed in the specs sheet, so if you are interested in it you might want to opt for the latter version.
In the imaging department, Pro 6 features a 21.16 MP rear-facing camera with an f/2.2 aperture lens. There is phase-detection included, but no optical image stabilization. Focusing time is said to be 0.07s. On paper, it looks like it will struggle to keep up with the competition in low-light conditions. The front camera is a 5 MP unit, with an f/2.0 aperture lens.
There is a fingerprint sensor, called mTouch 2.1, embedded in the home button. Meizu quotes a 0.2s response time; it is designed to store up to five fingerprints.
Pro 6 has a 2,560 mAh battery, which is smaller than what its main competitors offer. That said, it supports quick charging (called mCharge 3.0 in this case), which enables a 24W charging rate. It will charge fully in an hour. Worth pointing out is that there's a USB 3.1 Type-C port at the bottom.
The smartphone measures 147.7 x 70.8 x 7.25 mm and weighs 160 g. The higher weight is likely due to it having a metal body and that 3D Touch-like display.
There is no word on what version of Android underpins Meizu's distribution, called Flyme, but by the looks of it it appears to be 6.0 Marshmallow.
As far as pricing and availability go, Meizu will sell the 32 GB Pro 6 for CNY 2,500 and the 64 GB version for CNY 2,800, starting on April 23. That is about $386 and $433, respectively, which is slightly higher than what Xiaomi asks for its Mi 5, but way below what you can expect to pay for an unlocked Galaxy S7.
-

Crowdsourcing platform creates insights from unstructured data
Publié: avril 13, 2016, 5:54pm CEST par Ian Barker

Getting useful information from unstructured data is a notoriously difficult and time consuming task, but the launch of a new intelligent crowdsourcing platform could be about to change that.
The Spare5 platform uses a known community of specialists to accomplish custom micro-tasks that, filtered for quality, allow product owners to train powerful artificial intelligence models, improve their search and browse experiences, augment their directories and more.
According to IDG, unstructured data is growing at the rate of 62 percent annually and by 2022, 93 percent of all data will be unstructured. The Spare5 platform applies a combination of human insights and machine learning to solve the increasingly complex problem of using unstructured data, including images, video, social media content and text messages. Among the company's first wave of customers are Avvo, Expedia, Getty Images, GoPro, and Sentient Technologies.
"The old adage that a picture is worth a thousand words is true, but it's just the beginning. Spare5 is providing us breakthrough value by delivering nuanced human insights into our photos, at a value and scale that was unthinkable just a year ago," says Steve Heck, CTO of Getty Images.
Recognizing that all people have some expertise, valuable interests and free time, Spare5 has amassed a community of subject matter specialists across a wide range of skills and demographics, and built a library of game-like tasks. This approach enables Spare5 to ensure the right task goes to the right person. In order to continuously improve accuracy its Reputation Engine applies machine learning to rate each individual's performance.
As customers use the platform over time, the process becomes faster, smarter and better. Using a variety of SDKs and APIs, processed data can be easily integrated into existing data workflows and exported to produce top-line business reports.
"Our mission is to tap the world's potential brainpower," says Matt Bencke, founder and CEO of Spare5. "Businesses need specialized human insights to solve complex data problems. It used to be somewhere between impossible and impractical to crowdsource specialized insights at scale, with confidence and speed. Not any more. We love seeing our customers get the help they need to interpret unstructured data, while freeing up their employees to focus on their core competencies. There is a profound difference when the right human intelligence powers machine learning. And we've just begun".
Spare5 uses a subscription model allowing companies to easily make use of the platform. To find out more about it you can take a look at the company's website.
Photo Credit: photobank.kiev.ua/Shutterstock
-

Can you hear me now? 36,000 Verizon workers go on strike
Publié: avril 13, 2016, 5:53pm CEST par Alan Buckingham

Is your phone working? The reason I ask is this morning at 6am EDT 36,000 Verizon workers walked off the job in protest of outsourcing of work to countries such the Philippines, Mexico and the Dominican Republic. The carrier is closing call centers in favor of overseas help. The union also makes accusations of sending workers out of state for extended periods of time.
"Verizon's corporate greed isn't just harming workers' families, it's hurting customers as well," the CWA (Communications Workers of America) says in a statement to CNN.
If you are using Verizon Wireless your mobile will probably be working fine, but if you have one of those old-fashioned landlines then you may experience problems. Likewise with the Fios internet service, though the company promises it's prepared and interruptions should not occur.
Like all situations, there are two sides to this story. While Verizon profits are up, that is the result of the wireless side of the business -- one not served by the CWA. Landlines are in decline and that side of the business is slipping as more and more people find them unnecessary.
While a Verizon spokesman told the New York Times there would be no problems, the union contends that landline service will be degredated and customer service will be less readily available.
Despite the possible problems there is no need to worry about your bill -- it will be unaffected even if your service is having problems.
Image Credit: Ken Wolter / Shutterstock
-

Hackers love Microsoft's PowerShell
Publié: avril 13, 2016, 5:46pm CEST par Sead Fadilpašić
PowerShell, a scripting language inherent to Microsoft operating systems, is largely used to launch cyber-attacks, a new report suggests.
The Unified Threat Research report, released by next-generation endpoint security (NGES) firm Carbon Black, says that 38 percent of incidents reported by Carbon Black partners used PowerShell.
During investigations last year, 68 percent of the company’s responding partners encountered PowerShell, and almost a third (31 percent) reported getting no security alerts before the investigation of incidents related to the scripting language.
The majority of attacks (87 percent) were clic-fraud, fake antivirus programs and ransomware, but social engineering techniques are still the favorite.
"PowerShell is a very powerful tool that offers tremendous benefit for querying systems and executing commands, including on remote machines", said Ben Johnson, Carbon Black’s chief security strategist and cofounder.
"However, more recently we’re seeing bad guys exploiting it for malicious purposes it because it falls under the radar of traditional endpoint security products. This often causes tension between the IT and security professionals. PowerShell gives the bad guys a lot of power because it’s part of the native Windows operating system, which makes it difficult for security teams. On the other hand, PowerShell helps IT guys automate various tasks. The two departments need to come together and strike a balance between IT automation and security".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

New sales platform combines human and machine intelligence
Publié: avril 13, 2016, 4:53pm CEST par Ian Barker

Much of the sales process is about making effective use of information about existing and potential customers. But often that knowledge isn't easily accessible and therefore not used effectively.
A new platform from sales transformation specialist Altify aims to give B2B sales teams real-time visibility into the process based on stored knowledge and its built-in contextual insight engine.
Called Altify Max it monitors what is happening in the opportunity, the account, and the pipeline and forecast, assesses the impact, and notifies the salesperson to act with a suggested measure. Max has 30 years of deep sales knowledge and insights built in to the software, and customers can extend and customize the knowledge with their own insights. This real-time coaching solution is aimed at making the sales team more effective and delivering better results.
"Altify's ongoing mission is to help salespeople provide more value for their customers, and become true business partners," says Donal Daly, CEO of Altify. "We have always embedded knowledge, insight and context into the applications on the Altify Platform, but what makes Max so exciting is that we have poured a lot more knowledge into the system, added contextual notifications, and given our customers the capability to add their own knowledge and insights. This is really augmented intelligence for everyone who uses Salesforce. It is the perfect platform to enable companies to take their sales organizations to a higher level of performance and professionalism".
Benefits of the Max platform include increased engagement and effectiveness, with sales teams able to work more productively. Max can identify warning signs, so salespeople can address risk earlier in the sales process.
Max has been developed using 30 years of sales knowledge and packaged as a set of 'business rules' or insights that can help guide salespeople as they are working their opportunities or accounts. Organizations can personalize Max by customizing or extending the supplied knowledge and by creating insights specific to their own business.
Max will be generally available from next month and you can find out more on the company's website.
Image Credit: Tatiana Shepeleva / Shutterstock
-

Kindle Oasis is Amazon's lightest and brightest e-reader yet
Publié: avril 13, 2016, 4:22pm CEST par Wayne Williams

Tablet manufacturers are forever trying to deliver the lightest and thinnest products, and today Amazon introduces a new Kindle which is designed to feel almost weightless.
The Kindle Oasis isn’t simply light, weighing in at just 131 grams, it’s also very thin, at just 3.4 mm at its slimmest point. That makes it 30 percent thinner on average than any other Kindle. It also offers an ergonomic grip to shift the center of gravity to your palm, making it perfect for reading one handed. The built-in accelerometer automatically detects whether you are reading left or right handed, and rotates the page and page turn buttons accordingly.
The lightness of the new device has been achieved by using a featherweight polymer frame that has been reinforced using structural electroplating, so it shouldn’t be bendy.
"To lean back and read for hours, you need a sanctuary from distraction", said Jeff Bezos, Amazon.com Founder and CEO. "We want Kindle to disappear, and Kindle Oasis is the next big step in that mission. It’s the most advanced Kindle we’ve ever built -- thin and ultra-lightweight, it gets out of the way so you can lose yourself in the author’s world".
The thing about Kindles is they already have an incredibly long battery life, but the Oasis comes with a dual-battery system to expand this even further. There’s a battery in the cover, as well as in the device itself, so you can enjoy months of battery life before needing to charge it, and a new hibernation mode minimizes power consumption when your Kindle is inactive.
The cover is made of high-quality leather and available in black, merlot, or walnut.

The Oasis has the same quality display as the Paperwhite, delivering crisp high-resolution 300 ppi text, and a redesigned front light includes 60 percent more LEDs to make the display as bright as possible.
The new Kindle Oasis is priced at $289.99/£269.99 and will be released on April 27.
-

Your devices will be able to spot bad USB Type-C cables and chargers
Publié: avril 13, 2016, 3:55pm CEST par Mihăiță Bamburic

USB Type-C products that are non standard compliant can be so dangerous that the USB 3.0 Promoter Group has introduced an Authentication protocol, to enable smartphones, laptops and other types of devices to detect out of spec USB Type-C cables and chargers.
The "authenticity" of the cable or charger will be determined "right at the moment a wired connection is made -- before inappropriate power or data can be transferred", so, for instance, there will be no risk of damaging your phone when you plug in a bad cable to charge it.
The USB Type-C Authentication solution is meant to be implemented by OEMs, so its effect will only be seen once major players start adopting it. "In support of the growing USB Type-C ecosystem, we anticipated the need for a solution extending the integrity of the USB interface. The new USB Type-C Authentication protocol equips product OEMs with the proper tools to defend against 'bad' USB cables, devices and non-compliant USB Chargers", says USB 3.0 Promoter Group chairman Brad Saunders.
As noted by the USB 3.0 Promoter Group, the solution offers:
- A standard protocol for authenticating certified USB Type-C Chargers, devices, cables and power sources
- Support for authenticating over either USB data bus or USB Power Delivery communications channels
- Products that use the authentication protocol retain control over the security policies to be implemented and enforced
- Relies on 128-bit security for all cryptographic methods
- Specification references existing internationally-accepted cryptographic methods for certificate format, digital signing, hash and random number generation
Another benefit is that enterprises will be able to enforce a policy that only allows verified USB products to connect to the PCs under its roof. While the vast majority of PCs do not yet offer USB Type-C ports, this will slowly change and this option will no doubt start to get some attention from IT departments.
Of course, none of this helps if you have a USB Type-C device and want to make sure right away whether the cables and chargers that you plan to buy are adequate. So, we advise you to check reviews before purchasing anything, and also check the official list of approved USB Type-C cables and adapters.
Photo Credit: Archiwiz/Shutterstock
-

Employees opt for Apple when given a technology choice
Publié: avril 13, 2016, 3:52pm CEST par Ian Barker

It's becoming increasingly common for companies to offer their employees a choice of technology devices. And according to a new survey when they do have a choice people are more likely to choose Apple devices.
The study by device management company JAMF Software shows that ease of use is the main reason given by people for selecting Mac (75 percent) and iOS (79 percent) as their work device of choice.
The findings also show a generation gap in computer choice. Employees between the ages of 18 and 54 overwhelmingly choose Mac, while those 55 and over are more comfortable using PCs. However, when given a mobile device choice, nearly 80 percent of all age groups select iOS compared to just 18 percent who choose Android. Regardless of age, when staff are given the technology they want, employers are rewarded with more productive and appreciative employees.
"Employees today not only want -- but expect -- the ability to choose the devices they are most comfortable with for work," says Dean Hager, CEO of JAMF Software. "Because Apple builds technology that puts people first, people prefer Apple. When employers combine the freedom of choice with Apple, employees are happier and are empowered to be more productive -- offering a huge business advantage".
Among other findings are that 61 percent of respondents say their company has a choice program and 72 percent claim that the ability to select their device of choice makes them more productive in the workplace. Choice programs are important to the well being of an organization according to 73 percent, and 70 percent of those who currently lack user choice say their organization should give them the right to choose the device that best empowers them to do their job.
More detail is available in the full report which you can find on the JAMF website.
Photo credit: Blablo101 / Shutterstock
-

10 hidden Facebook features you should know about
Publié: avril 13, 2016, 3:22pm CEST par Wayne Williams

I know plenty of people who -- literally -- spend their lives on Facebook, sharing everything they do, and obsessively reading and reacting to every post made by their friends.
But here’s the thing. Despite all of the hours they put into being on the site, they probably only know a fraction of what it has to offer. There are a lot of features tucked away that they -- and you -- might never encounter. Think you know Facebook? Think again...
There’s a Hidden Facebook Inbox
This is something we’ve covered previously, but Facebook occasionally filters messages that have been sent to you into a hidden folder. This secret inbox is essentially a spam folder, but will probably contain messages from people you know or pages you’ve liked. Follow the instructions here to access the folder and see the messages you've been missing.
You Can Still Poke People
You probably haven’t done this in years -- if ever -- but the ability to "poke" people (one of the original Facebook features) still exists, although it’s a little tucked away now.
To Poke someone, go to their profile page and click the ellipses (...) next to the Message tab and select Poke.
There’s a Hidden Chess Game in Messenger
As well as chatting to friends in Facebook Messenger you can challenge them to a nice game of chess.
To start a new game just type @fbchess play during a conversation. A board will appear and your opponent will go first.
The commands you need to play are detailed here.
There’s a Hidden Basketball Game in Messenger
Chess not your thing? Don’t worry, there’s another game you can play in Messenger -- basketball! To activate this, you just need to send a basketball emoji to someone, tap it in the chat window, and the game will start. You’ll find more details on the game here.
You Can Use Dropbox to Share Files
Facebook Messenger has gained Dropbox support this week, so you can now share content through that cloud service. All you have to do is tap the More button in Messenger for iOS or Android, and you'll see Dropbox as an available source. You will need to have Dropbox installed as well though.
You Can Log Out Remotely
Logged into Facebook on a friend’s computer, and forgot to log out again? You know what that means right? They’ll post status updates in your name, and react to posts you would never, ever, normally react to. Fortunately, it’s easy to log out of that location remotely.
Open up Facebook’s web interface, click the down arrow at the top right and select Settings > Security > Where You're Logged In. Find the place(s) you don’t want to be logged in at and click the End activity link.
You Can Secretly Unfriend Someone
Bored by a Facebook acquaintance’s tedious (or odious) postings and comments? You can simply unfriend them but if they find out, they might be annoyed, and that could lead to all sorts of problems.
Thankfully, Facebook lets you unfollow people. This stops them appearing in your timeline, but still lets you see what they’re up to (creep them) if you so wish.
To unfollow someone, hit the Following button on their page and select Unfollow.
You Can Change the Language Settings to Something Amusing
Facebook in English is boring right? Well there are plenty of other languages you can switch to instead. Go to Settings > Language and click on Edit. Obviously, if you don’t speak Mandarin Chinese you might not want to go for that, but you can switch to Pirate or Upside Down English.
View Your Relationship Over the Years
You can see what you’ve got up to with your significant other over the years by going to www.facebook.com/us. This will display all of the shared and tagged content that includes you both.
Save a Post For Viewing Later
Want to read a post on Facebook but don’t have time right now? You can save it for later. Click the down arrow at the top-right of the post and click Save link. This will send the story to your Saved folder which appears in the sidebar on the left.
Photo Credit: Vladimir Gjorgiev/Shutterstock
-

Security is a top priority when installing identity solutions
Publié: avril 13, 2016, 3:10pm CEST par Ian Barker

According to a new survey 78 percent of organizations say that security outweighs cost savings and user experience when choosing identity management solutions.
The survey by access control specialist SecureAuth used responses from over 230 IT security professionals in the US and UK.
When asked why their company has initiated new identity projects in the past, 55 percent of respondents across small, medium and large companies say the deployment of new applications -- including both on-premises and cloud-based -- was the top driver. Board and senior management's drive for increased security is also cited by 50 percent of respondents as a chief reason for new identity project initiation, underscoring that cyber security has become a board-level concern.
Other drivers for installing identity management include compliance and audit requirements at 49 percent, cost savings (44 percent), security breaches at another company (36 percent), increased use of stolen or misused credentials (34 percent) and the company itself experiencing a security breach (25 percent).
"It's no secret that security has become a board room-level imperative," says Craig Lund, CEO of SecureAuth. "A decade ago, it was a nice to have; today, it's a must have. Accordingly, organizations across the globe are abandoning their laissez-faire approaches to cybersecurity and significantly increasing security spending for the coming years. Worthwhile cybersecurity endeavors may require some redirection of budget, but in this day and age, proactivity is just as important as reactivity".
When asked about their plans for identity and access management, 79 percent of respondents say that plans are underway for IAM of externally focused applications, including vendor, partner and customer applications, portals and mobile apps. In addition 47 percent say that IAM investment is a currently funded priority, 32 percent will invest in the next year, and 13 percent will invest in IAM, but don't have a specific time frame.
For more information you can visit the SecureAuth blog.
Photo Credit: Maxx-Studio/Shutterstock
-

Google Calendar now helps you to reach your goals
Publié: avril 13, 2016, 1:53pm CEST par Mark Wilson

It's not long since the Reminders feature arrived in Google Calendar on the web, a few months after it debuted in iOS and Android. Now Google is rolling out another new feature that makes it easier to find time to reach your goals -- whether this is indulging in a hobby a few times a week, or just trying to do some regular exercise.
Goals in Google Calendar is not about ticking items off your bucket list, but automating the process of adding reminders to your calendar without having to manually search high and low for the necessary time. Just indicate what you want to do, and how often, and the rest will be taken care of for you. But it gets better...
Everyone's plans change. Things crop up, schedules alter. Goals in Google Calendar can help. The feature not only finds empty slots in your day to house your run or yoga sessions, but if you later schedule another event that clashes, it will be automatically moved for you. No more excuses for missing out on a session at the gym!
There's an element of learning to Goals as well; the more you use the feature, the better it gets at picking suitable times to schedule events. This is something that is influenced to a certain extent when you elect to manually defer an event. If you keep delaying a reminder first thing in the morning, your calendar will learn that rescheduling later in the day would probably make more sense.
Check out the video below to get an idea of how Goals in Google Calendar works:
For now, Goals in Google Calendar is available to iOS and Android users, so just make sure you have the latest version of the app installed to make us of the feature.
Photo credit: Rawpixel.com / Shutterstock
-

New service helps service providers deliver cloud-based security
Publié: avril 13, 2016, 12:32pm CEST par Ian Barker

Security is a key concern for all enterprises, so it's not surprising that it's something managed service providers are keen to offer their customers in order to add value and differentiate their service.
Network breach detection company Eastwind Networks is launching a Managed Service Provider (MSP) and Managed Security Service Provider (MSSP) program. The new program is designed to help service providers stand out and grow their business with a simple cloud-based breach detection solution that ensures that customer data and assets are secure.
"In today's competitive security industry, MSPs are looking for value-added, easy to deploy and manage solutions that help ensure their customer’s success," says Paul Kraus, president and CEO of Eastwind Networks. "With our new MSP program, we are able to offer our partners services that provide an additional level of security expertise, a strong security platform offering and complete visibility to threats, security gaps, application usage, and overall network awareness".
Available via the Eastwind Cloud or in the customer's private cloud, the platform uses rich data, behavioral analytics, and threat intelligence to pinpoint anomalous behaviors even before they're classified as breaches. It's been designed to catch hackers during the weeks and months that they spend in the network before they take action. Storing and mining more than a year's worth of rich network metadata, Eastwind examines not only current network conditions, but continually analyzes historical data against updated threat sources to find breaches that would have otherwise gone unnoticed.
You can find out more about Eastwind breach detection and the MSP program on the company's website.
Photo credit: allepu / Shutterstock
-

Another quarter, another PC sales drop
Publié: avril 13, 2016, 12:18pm CEST par Anthony Spadafora

The PC market has started off 2016 quite poorly according to both Gartner and the IDC. Worldwide shipments have fallen 9.6 percent to 64.8 million units in the first quarter of the year, according to Garner’s estimates. This makes it the first quarter since 2007 that fewer than 65 million PCs have shipped globally.
Lenovo, HP, Dell, Asus and Apple were the top PC manufacturers in Q1 2016 with only Asus and Apple seeing an increase in the number of units shipped. Lenovo and HP have been hit the hardest this quarter with Lenovo shipments down seven percent and HP’s down nine percent.
The International Data Corporation (IDC) is estimating that the worldwide PC shipments are actually lower than Gartner’s estimate and have dropped 11.5 percent to 60.6 million units during Q1. The company also differs from Gartner in that its results see Lenovo, HP, Dell, Apple and Asus as the top five vendors during the quarter. IDC paints a much gloomier picture of global PC shipments and all of its top PC vendors are in the red, with Asus down eight percent and even Apple down two percent.
The strength of the US dollar is one of the main reasons that PC shipments have continued to decline according to Gartner. The firm also notes that many companies experienced an inventory build up as a result of sales offered during the holidays in the fourth quarter of 2015.
Another big factor in declining PC shipments is enterprise adoption of Windows 10. Many companies have yet to fully embrace the latest iteration of Windows and are merely test driving it to see if it will be a meaningful upgrade for their businesses.
Windows 10 may no longer be offered as a free upgrade come July 29 2016 and this could entice users who have yet to switch to do so albeit through purchasing new hardware. In 2016, we will learn without a doubt how Windows 10 will affect worldwide PC sales.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Mopic/Shutterstock
-

Jewelery meets gadgetry in the Oukitel A8
Publié: avril 13, 2016, 11:44am CEST par Ian Barker

Bluetooth tracking devices to help stop you forgetting your phone have been around for a while, but they've generally been quite functional in design, looking like a remote car key.
Chinese smartphone maker Oukitel is launching its own take on the lost phone finder with a new gadget that looks like a piece of jewelry but also functions as more than just an alarm to tell you you've left your phone behind.
The Oukitel A8 lets you answer and hang up calls so you can appear a bit strange on the train by talking to your pendant -- it could be a good way of getting a seat. It can also control music playback and act as a shutter button to control the phone's camera so it’s handy for taking selfies too.
It has a 280mAh battery which the company says takes only 30 minutes to charge and will give you 15 hours of connected standby or five hours of talk time. It's compatible with both Android and iOS, so it should work with most smartphones on the market and it comes in a choice of blue or black.
Normal price of the A8 is $24.99 but until April 29 it's available for $19.99 from the Tomtop.com site. More details of the gadget are available on the Oukitel website.
-

Take a low-level look at your PC desktop with Window Inspector
Publié: avril 13, 2016, 10:57am CEST par Mike Williams
Binary Fortress Software has released Window Inspector, a free tool for examining the low-level details of any application window.
Move your mouse cursor over any window and a detailed display lists its class, text, icons, owning process, command line, Style and StyleEX flags, and more.
A separate tree lists the hierarchy of all desktop windows, and allows them to be closed individually.
If you’ve not guessed already, Window Inspector is mostly for developers, but it can also be occasionally handy for everyone else.
Suppose a desktop alert appears with a strange error message, for instance, or that you just don’t recognize. Is it malware-related? You’ll want to find the owning process, and Task Manager won’t always tell you.
With Window Inspector, all you have to do is move the mouse cursor over the alert, and you’ll see the process which launched it, along with its path, file name and command line arguments.
The program’s list of open windows can also be a helpful way to find out more about the processes running on your PC.
Expanding a cryptic process name like "avgnt.exe", for example, showed us the text "Avira Free Antivirus -- SysTray": the Avira system tray icon.
You could find similar information in Task Manager, but there’s more. The process also has a window called "Protection Cloud", with prompts like "uploading", "filename" and "please wait while the program started is being analyzed".
Even if you’ve never heard of Avira or Protection Cloud, you can see from this that the process is probably going to look for programs being launched, upload and analyze them somewhere.
This kind of information is only available because the process is going to display it to you anyway, so it won’t help you understand malware, or anything else which is trying to hide a function. But it may still be useful information, and Window Inspector makes it easy to find and explore.
Window Inspector is a freeware tool for Windows XP and later.
-

Box customers can now choose where to store their data
Publié: avril 13, 2016, 10:49am CEST par Sead Fadilpašić

Online file sharing company Box today announced a new service, allowing businesses to store their cloud data across Europe and Asia.
The service, announced at the Box World Tour Europe, is called Box Zones, and it will allow Box customers to choose whether they want to store their data in Germany, Ireland, Singapore or Japan.
"Businesses today are more connected, collaborative and global thanks to the power of the cloud", said Aaron Levie, co-founder and CEO of Box. "Yet for many companies, local laws and regulations have forced them to make technology tradeoffs that limit their success and place a drag on employee productivity and collaboration. Box Zones will help power digital transformation for enterprise customers across Europe and Asia and accelerate our international presence".
The company also said that the new feature will not interfere with any of the existing ones, with features like watermarking, granular permission controls and comments and tasking, staying. Deep integrations with Office 365 and Salesforce are also here to stay.
"Security is the top priority for AWS and our customers. With the recent launch of Box KeySafe running on AWS, Box offers companies of all sizes greater control over their business-critical, sensitive content, and furthers that mission with today’s introduction of Box Zones", said Terry Wise, vice president of Worldwide Partner Ecosystem, Amazon Web Services.
"We believe customers should have the freedom to choose where and how their data is stored. With Box Zones leveraging Amazon Simple Storage Service (Amazon S3), customers can better meet the highest levels of security and regulatory compliance required in their respective geographies".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wavebreakmedia/Shutterstock
-

Software-defined data center adoption will grow in 2016
Publié: avril 12, 2016, 7:15pm CEST par Sead Fadilpašić

Business and IT executives in the UK and the US (62 percent) expect a higher adoption of software-defined data centers (SDDCs) this year, but the projection for faster deployment is slightly higher in the UK (67 percent), compared to the US (64 percent).
Those are the results of a new study conducted by security, compliance and control software company HyTrust, and co-sponsored by Intel. The study takes a look at the issues and trends among businesses migrating to the cloud and software-defined data centre.
There are some sharp differences between businesses in the two countries, regarding SDDC, with 30 percent of UK’s businesses expecting greater tangible benefits and return on investment (ROI), compared to 56 percent in the US.
Adoption for network virtualization is expected among 23 percent in the UK, and at 56 percent in the US, while adoption for storage virtualization is expected among 31 percent in the UK, and 58 percent in the US.
There is also a sharp difference between the two countries in the better alignment of security strategies built to address SDDC -- 14 percent have aligned their strategies in the UK, compared to 48 percent in the US.
Even though security is still the number one issue stopping businesses from deploying all of their apps to the cloud, the report suggests signs of optimism.
When asked if security will be less of an obstacle to greater SDDC adoption by the end of this year, 68 percent in the UK and 69 percent in the US say "Yes".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: sellingpix/Shutterstock
-

'Let's Encrypt' exits beta -- backed by Cisco, Akamai, Mozilla, Google, Facebook, and more
Publié: avril 12, 2016, 6:44pm CEST par Brian Fagioli

Ever since hero Edward Snowden's bombshell document leaks, the technology world has wide eyes for encryption. Sure, it was a topic prior to Snowden, but many failed to give it the focus it deserved. Thankfully, companies are now better implementing encryption, and some of them, such as Apple, are fighting for our rights too.
Today, the encryption initiative, 'Let's Encrypt', finally leaves beta. Josh Aas, ISRG Executive Director says "we set out to encrypt 100 percent of the Web. We're excited to be off to a strong start, and with so much support across the industry". If you are wondering what he means, please know that big players such as Cisco, Akamai, HP, Mozilla, Google, and Facebook are sponsoring it. But what exactly is Let’s Encrypt?
David Bryant, Interim CEO, Mozilla explains it is "a free, automated and open Web certificate authority that helps make it easy for any Web site to turn on encryption. Let's Encrypt uses an open protocol called ACME which is being standardized in the IETF. There are already over 40 independent implementations of ACME. Several web hosting services such as Dreamhost and Automattic, who runs WordPress.com, also use ACME to integrate with Let’s Encrypt and provide security that is on by default".
"In the six months since its beta launch in November 2015, Let’s Encrypt has issued more than 1.7 million certificates for approximately 2.4 million domain names, and is currently issuing more than 20,000 certificates a day. More than 90 percent of Let's Encrypt certificates are protecting web sites that never had security before. In addition, more than 20 other companies have joined Let's Encrypt, making it a true cross-industry effort", says Bryant.
When you see such an initiative, there is a fear that it could be divisive based on who sponsors/backs it. Here, 'Let's Encrypt' has found a very diverse and well-respected group of companies. Best of all? We are all safer and more secure as a result. Three cheers for encryption!
Are you excited that encryption is becoming more widespread? What do you think of Let's Encrypt? Tell me in the comments.
Photo credit: Maksim Kabakou / Shutterstock
-

New platform speeds up development of intelligent search apps
Publié: avril 12, 2016, 6:22pm CEST par Ian Barker

One of the problems with big data is that creating applications to access the information inevitably introduces a time lag and this leads to frustration for the end user.
Search and analytics software company Lucidworks is aiming to cut out this bottleneck with the launch of Lucidworks View, which allows companies to quickly and easily create custom search-driven applications built on Apache Solr and Apache Spark.
"Data lives everywhere, across a growing set of formats and locations. Even the most mature companies struggle to not only wrangle it in high volumes but expose it in a meaningful way," says Will Hayes, CEO of Lucidworks. "We built Lucidworks View to give our users the ability to rapidly create sophisticated applications for customers and, for the first time, truly plug and play with Big Data. Our aim is to eliminate the costly, time consuming complexities usually associated with the front- and back-end development of intelligent apps, moving companies quickly from the question, 'What do I do with my data?' to the statement, 'Data drives every part of the business'".
Lucidworks View lets companies build custom user interfaces that use the power of the popular Apache Solr and Apache Spark database engines. Using the platform can give customers individualized access to essential information while equipping their workforce with the tools they need to make informed business decisions.
Capabilities include simple configuration and workflow so that developers and admins at any level of expertise can start building and deploying intelligent apps with just a few keystrokes and no code. There are out-of-the-box connectors for over 60 systems including MySQL, databases, JIRA, Slack, Logstash, local file systems, and the web.
The product also allows tracking and continual improvement of search results based on user signals like clicks, social, device and geolocation for a contextually relevant data experience powered by machine learning. Developers can easily and quickly customize the interface to meet user expectations and present data in an intuitive, valuable way.
Lucidworks View is available from today and you can find out more on the company's website.
Image credit: Angela Waye/Shutterstock
-

Jaguar Land Rover is building an Uber competitor
Publié: avril 12, 2016, 6:21pm CEST par Sead Fadilpašić

Jaguar Land Rover has announced the launch of a new business, which is basically an Uber competitor. According to the company’s press release, the new technology start-up called InMotion will "build apps and on-demand services to overcome modern travel and transport challenges".
The start-up will soon start testing a couple of different services related to car sharing and car ownership. The testing will take place in North America, Europe and Asia "in the coming months".
InMotion will first conduct a global, in-depth research about the current state of travel and transportation markets, and then will go for closed, real-world experiments. Once it decides on the "most effective" approach to the problem, it will proceed to build and beta test a product.
"With the development of new apps and on-demand services, InMotion provides us with an opportunity to provide engaging and invaluable experiences to both new and existing customers globally", said Adrian Hallmark, group strategy director at Jaguar Land Rover. "As a start-up business, InMotion combines the flexibility and pace needed to compete in the ever-changing mobility sector. It allows us to react quickly to new tech and ever-changing customer demands".
Financial Times says that the new start-up will also build valet parking solutions, as well as insurance products. It has employed former Google employees to make this happen and, according to the report, will throw "hundreds of millions of pounds" if it comes up with technology that demands investment.
The division will be based in London, and will be completely independent from the rest of the company.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Kingston launches new hardware encrypted flash drives
Publié: avril 12, 2016, 5:18pm CEST par Ian Barker

One of the best known names in the flash memory market, Kingston acquired the IronKey brand from Imation in February of this year.
IronKey has long been one of the leading brands in encrypted Flash drives and today we see the first fruits of the new partnership with Kingston's launch of two new managed and 256-bit AES hardware encrypted USB drives.
The DataTraveler 4000G2 with Management (DT4000G2DM) and DataTraveler Vault Privacy 3.0 with Management (DTVP30DM) solve the requirements of organizations that need to meet Federal Information Processing Standards (FIPS) and protect data at the highest level across their mobile workforce. Both devices can be used as a managed solution via the SafeConsole Encryption Management Platform from DataLocker, Kingston's partner for encrypted USB drive management.
Both new drives are 256-bit AES hardware encrypted and FIPS certified (the DT4000G2DM is FIPS 140-2 Level 3 validated; the DTVP30DM is FIPS 197 certified) to ensure maximum corporate and personal data security. Additionally, SafeConsole is the only secure USB management platform for secure USB drives with true password management at both remote and local level. The platform enables secure reset of forgotten passwords, activation of full audit trails, geolocation and geofencing to ensure cross-border compliance, automatic inventory, plus a 'remote kill' feature in the event the device is lost.
"Human error, malicious attacks and technical failures can place employee and corporate data at risk. Companies, agencies and organizations need to implement a security policy well before anything goes wrong as it's critical to prevent non-compliance, fines and even financial loss," says Ken Campbell, Flash business manager, Kingston. "Our latest encrypted managed USB drives, the recent IronKey acquisition and growing DataLocker partnership all demonstrates Kingston's commitment to providing the most secure and largest family of encrypted USB solutions on the market".
The DT4000G2DM and DTVP30DM are available in 4GB, 8GB, 16GB, 32GB and 64GB capacities, and are backed by a five-year warranty and free technical support. More information and details of where to buy can be found on the Kingston website.
-

BlackBerry will release two mid-range Android phones in 2016
Publié: avril 12, 2016, 5:12pm CEST par Anthony Spadafora

BlackBerry will be moving back into the mid-range smartphone market in order to appeal to enterprise customers who were unable to justify the Priv’s $700 retail price.
John Chen, the company’s CEO, has revealed that BlackBerry is planning to release two mid-range Android smartphones during 2016. One will include a physical keyboard to appease fans of the company’s iconic handsets and the other will sport a full touchscreen to appeal towards consumers who have adopted the modern smartphone form factor.
BlackBerry announced last week that it had only sold 600,000 handsets since January which is significantly less than the 850,000 that many analysts had been forecasting. BlackBerry has also yet to release the sales data regarding how many Privs were actually sold since the device’s launch in November of 2015.
Chen regrets that the company’s first Android phone was a flagship device priced out of the reach for many enterprise customers. A $400 Android smartphone from BlackBerry might have made a bigger impact on sales and the company is aiming to recapture that share of the market with the two mid-range devices it releases this year.
BlackBerry was able to take the security features that made its handsets so popular among enterprise users and implement them successfully on the Android platform. Chen believes that his company is the only handset manufacturer that is able to truly make Google’s Android a secure platform.
Hopefully the two mid-range smartphones BlackBerry releases in 2016 will be able to make the company’s top-notch security and devices more accessible for more users.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Pieter Beens / Shutterstock.com
-

Meet HTC 10
Publié: avril 12, 2016, 4:03pm CEST par Mihăiță Bamburic

Despite giving us some of the nicest high-end smartphones, HTC's sales have dropped sharply in the past couple of years. Today, the once-successful company is nothing but a shadow of its former self, posting revenue so low that it makes you wonder how much longer it can keep the lights on. Meanwhile, long time rivals like Apple and Samsung are watching their flagships fly off the shelves.
HTC has clearly made some mistakes, but its latest flagship is proof that things are taking a turn for the better. HTC 10 offers pretty much everything that you could want in a premium smartphone: high-quality build, top level hardware, cutting-edge features, the latest software and a competitive price.
Finally, a Great Camera
The biggest weakness of the One M series has been the camera. For some reason, despite trying some very interesting things, HTC has not managed to deliver a camera that could offer a similar level of performance to the leading players in this segment. It always felt short compared to the equivalent Galaxy S or iPhone.
With HTC 10, things are looking much, much better. The company has opted for a 12 MP UltraPixel shooter on the back, sporting a large, f/1.8 aperture lens that should work great in low-light. The UltraPixel sensor is characterized by having larger pixels, and, in this latest version, optical image stabilization and very fast, laser autofocus too. There's a dual-tone LED flash next to it.

To put things into context, HTC has asked DxOMark to review the smartphone. HTC 10 achieved a score of 88, which puts it at the top of the list, next to Galaxy S7 edge. That is quite a feat. You can read the camera review by hitting the link in this paragraph, but the gist of it is that it's very good.
HTC says that those who want to take RAW (12-bit) photos will be able to do so using Pro Mode, which also exposes some more advanced options. The camera app is claimed to open in 0.6 seconds. Obviously, there is 4K video support.
HTC has opted for optical image stabilization for the front camera too, which will no doubt improve low-light selfies. This shooter has a 5 MP sensor and an f/1.8 lens.
BoomSound Is Here to Stay
HTC has not given up on the audio credentials of the One M series, with its latest flagship featuring 24-bit audio recording when shooting 4K video. There is a headphone amp that is said to deliver twice the power of a conventional one, that can also upscale 16-bit to 24-bit audio. There is also a Personal Audio Profile system, which tunes your profile to match your hearing, and new BoomSound high-fidelity speakers as well.
Competitive Hardware
Those who want the latest and greatest in terms of hardware should be pleased to know that HTC 10 features a 5.2-inch SuperLCD 5 display with a resolution of 1,440 by 2,560. HTC says that it is "30 percent more colorful [and] 50 percent more responsive" than the screen in One M9.
In terms of processing power, there is a Qualcomm Snapdragon 820 processor (up to 2.2 GHz clock speed) with 4GB of RAM, backed by a 3,000 mAh battery. There is Quick Charge 3.0 support, which will charge the battery up to 50 percent in 30 minutes using the provided wall charger. There is no wireless charging here but, other than that, we are looking at very competitive hardware features for this segment.
Worth noting here is that HTC says that there will be two versions of the flagship, each with a different Snapdragon processor. There is no information regarding the other chipset, with the company only saying that Snapdragon 820 will be offered in US.
In terms of storage, HTC has opted for two models. There is a base 32 GB version, which offers 23.1 GB of user-accessible storage, but there is also a 64 GB model, that ups the user-accessible capacity to 52 GB. HTC is, as far as I know, the only major manufacturer which makes the user-accessible storage public, so kudos to it. For expansion, there is a microSD card slot, which can take cards up to 2 TB in size, with support for Android 6.0 Marshmallow's adaptive -- Flex Storage-- storage.
Flex Storage basically lets you expand the so-called "internal" storage using a microSD card. The feature will, more or less, unify the internal chip and microSD card, combining their space to let you install more apps and games as you normally would, without having to worry about moving them on the microSD or whether they support being installed on external storage media. It can be pretty useful. Worth noting is that Galaxy S7 does not support this feature.
In terms of connectivity, HTC 10 offers WI-Fi 802.11 a/b/g/n/ac, Bluetooth 4.2 and NFC. There is also support for Apple's AirPlay, Chromecast and Miracast. HTC opted for USB 3.1 with a Type-C connector.
Refined Design

As far as the design of HTC 10 goes, we are looking at an evolution of the One M series, but with, in my opinion, a notable difference. HTC is no longer wasting the space below the screen by using on-screen buttons, as now there are capacitive keys instead. Between them is a fingerprint sensor that doubles as a home button. This has been my sole complaint regarding the One M series design, and it is nice to see HTC finally making better use of the front panel while keeping the fingerprint sensor in the best-possible place.
The Software
When it comes to the software, HTC has opted for Android 6.0 Marshmallow with its own Sense skin on top. It looks to be fairly light in terms of customizations, which is typical of HTC as of late. You can still expect some features, like Blinkfeed, to be offered though.
Pricing and Availability

Now, let's talk about pricing and availability. HTC 10 will be offered in three colors -- black, silver and gold -- at multiple carriers in US and worldwide. It will cost $699 in the states, and €699 in Europe. Pre-orders for an unlocked version kick off today in US from htc.com, with shipments going out in early May. Other markets will also get HTC 10 in May. There will also be accessories available, like the Ice View cover shown above.
-

Attack by cyber terrorists feared by 63 percent of US security professionals
Publié: avril 12, 2016, 3:17pm CEST par Ian Barker

Key concerns of information security executives include the growing threats of global cyber terrorism, the current state of security within the US and the ability of organizations to prevent such attacks.
These are among the findings of a new study by account management solutions provider Thycotic of more than 200 security industry attendees at RSA.
Cyber terrorism needs to be be taken more seriously as 63 percent of respondents feel terrorists are capable of launching a catastrophic cyber-attack on the US within one year. In addition, 92 percent of respondents believe that a majority of US companies either need more security or are behind the security curve in their ability to defend against cyber terrorism attacks.
"Some may say the whole discussion surrounding the threats associated with cyber terrorism is hyped; however, our findings show that 72 percent actually feel that the topic isn't hyped enough and that more needs to be done to protect companies and country as a whole from these types of vulnerabilities," says Jonathan Cogley, founder and CTO at Thycotic. "Re-examining the type of security technology used to protect both the US government and private sectors is essential to keeping our country safe".
There's a fairly even split on whether public or private sector systems are more at risk, 50 percent of respondents believe US private companies are more vulnerable than government agencies, while 42 percent believe the government is more vulnerable. An overwhelming 89 percent of survey respondents believe that both the military and businesses need to focus more on developing capabilities to defend against terrorist inspired cyber attacks.
You can find out more about the results on the Thycotic blog or register for an upcoming webinar which will discuss the findings.
Photo credit: Kletr / Shutterstock
-

Microsoft adds troubleshooting QR codes to the Windows 10 Blue Screen of Death
Publié: avril 12, 2016, 2:24pm CEST par Wayne Williams
No one enjoys seeing a Blue Screen of Death (BSOD) in Windows. It can be incredibly frustrating, especially if you were right in the middle of something important when it occurred, and you have no idea what caused it.
Armed with the information on the blue screen, and the stop code, you should be able to track down a cause and possible solution on the web, but this does require you to jot down the necessary details. However, that chore is likely to soon be a thing of the past.
Microsoft is tweaking the blue screens in Windows 10 to include a QR code that you can scan with your phone. This will take you to a web page with more information about the problem.
This new addition is to be found in blue screens in the latest Windows 10 preview, Build 14316.
If you experience a BSOD in the new build you'll discover the displayed QR code will currently take you to a page on troubleshooting blue screen errors (try scanning the image above). In future builds, and of course the Anniversary Edition out in July, the codes will redirect you to troubleshooting pages relevant to the problem you encountered.
-

Flexera extends software asset management to the cloud
Publié: avril 12, 2016, 1:46pm CEST par Ian Barker

While it's important for companies to manage their software licensing effectively, with the shift of many systems to the cloud doing so has become more difficult.
Software asset management specialist Flexera is riding to the rescue with the launch of a new solution addressing the management of cloud Infrastructure-as-a-Service.
FlexNet Manager for Cloud Infrastructure gives organizations centralized visibility into their cloud services use and allows them to optimize utilization and control costs. This first release focuses on optimization of Amazon Web Services (AWS) -- the most widely adopted cloud infrastructure service.
"The cloud services industry is growing more than five times faster than other IT categories as organizations shift away from internal hardware to greater use of public cloud infrastructures. This shift in spend means having the ability to track, manage and optimize cloud services usage is essential for responsible governance and cost management," says Jim Ryan, president and CEO of Flexera Software. "With FlexNet Manager for Cloud Infrastructure as part of FlexNet Manager Suite for Enterprises, Flexera Software enables companies to manage and optimize cloud infrastructure services and the software running in the cloud, along with traditional on-premises software".
FlexNet Manager for Cloud Infrastructure can automatically import usage and billing data from multiple accounts to deliver a centralized view of all AWS accounts and instances across the business. A cloud dashboard provides an executive-level view of the organization's use of cloud resources, showing consumption patterns and total spend across all AWS cloud subscriptions.
Cloud usage analysis and reporting enables organizations to eliminate waste and optimize spend. Users can analyze data and view consumption reports and breakdowns based on AWS instance types, both On-demand and Reserved instances, view consumption rates by departments and perform trending analysis.
You can find out more about the product and its features on the Flexera website.
Photo Credit: kentoh/Shutterstock
-

How to run GUI Linux apps from Bash in Windows 10
Publié: avril 12, 2016, 1:04pm CEST par Mark Wilson

Linux apps running in Windows 10? What gives?! As if the arrival of Bash on Ubuntu on Windows 10 wasn't enough, people have been quick to investigate the capabilities and limitation of Microsoft's embracing of the Linux command line.
Some commenters on our how-to guide asked what the point is. How about being able to run Linux apps in Windows without having to resort to using a virtual machine? It can be done. Here's how.
As noted over on Windows Clan, all it takes is a couple of commands to get started. You'll have to begin by making sure you have Bash up and running, and then grab yourself a copy of X Server from SourceForge.
With this done, you can run Firefox, for instance, using the command:
DISPLAY=:0 firefox
Have a play around and see what you can come up with. You might find that performance is a little on the disappointing side, but it's very early days at the moment and this may well improve as Canonical and Microsoft refine things.There's also an active thread over on Reddit where users are sharing tips and ideas -- well worth a look.
Photo credit: Julien Tromeur / Shutterstock
-

Microsoft introduces a new luxury Signature Type Cover for Surface Pro 4
Publié: avril 12, 2016, 12:56pm CEST par Wayne Williams
 Alcantara is a soft, suede-like material made in Italy that’s used in high-end luxury products. It’s often to be found in car, aircraft and yacht interiors because it looks great and gets better with age.
Alcantara is a soft, suede-like material made in Italy that’s used in high-end luxury products. It’s often to be found in car, aircraft and yacht interiors because it looks great and gets better with age.Microsoft has used this proprietary material to create a new Signature Type Cover for Surface Pro 4 and, there's no denying, the end result looks incredibly classy. No longer will you be embarrassed by your Surface Pro 4’s existing scuffed and dirty blue cover as you quaff champagne on a long flight home on your personal Lear Jet, trading amusing stories with BFFs Richard Branson and Elon Musk (I speak from personal experience of course).
The new Signature Type Cover is available in a two-tone gray melange style and will work with both Surface Pro 3 and 4.
It weighs 285 grams, and comes with a 1 year limited hardware warranty.
Naturally, it’s not cheap, but you can’t put a price on style. Unless that price is $159.99.
It’s available to buy now.
If you want to find out more about the Signature Type Cover, Microsoft has put together a video which you can watch below.
-

Legality of UK surveillance laws to be tested by European court
Publié: avril 12, 2016, 12:12pm CEST par Mark Wilson

Laws surrounding online surveillance will always prove controversial, and this is certainly true of the UK's proposed Investigatory Powers Bill -- aka the Snooper's Charter. Currently in draft form, the final content and scope of the bill could be set today as the European Court of Justice rules on a challenge brought against the existing Data Retention and Investigatory Powers Act 2014 (Dripa).
The case has the support of many European states, and the outcome of the case will determine the powers of data collection the UK government is able to exercise. It is expected that the case could be one of the deciding factors in the in-out referendum in June when the UK votes on whether to remain part of Europe or to go it alone.
15 judges in Luxembourg are due to rule on the legality of Dripa which was rushed through parliament; it has already been determined that the Act is at odds with EU law. Specifically, it is said that the Act goes against Article 8 of the European convention on human rights, the right to respect for private and family life, and Articles 7 and 8 of the EU charter of fundamental rights, respect for private and family life and protection of personal data.
The fact that the UK government's proposed gathering of data about all internet users -- not just those under investigation in cases -- is likely to be central to the decision and future direction of surveillance laws. Because rulings by the European Court of Justice must also be applied to UK law. Ultimately it could mean that the Investigatory Powers Bill needs to be rewritten.
Unsurprisingly, privacy groups are far from happy with both Dripa and the Snooper's Charter. Camilla Graham Wood from Privacy International, said:
The UK, in enacting legislation that is almost identical to the European data retention directive which the [ECJ] ruled unlawful, is mandating data retention on a widespread, indiscriminate and untargeted basis.
Such a broad and wholesale retention of communications data is in violation of European law. The effect of Dripa is to use bulk data retention to create a dossier on every person in the UK. It includes every internet and mobile phone transaction you undertake, every location will be filed, every meeting noted, every website indexed and every call marked.
Blanket retention of communications data, without suspicion, creates a honeypot of information for criminals and hackers, and this case will have implications for personal privacy and the security of individual personal data.
Photo credit: nzozo / Shutterstock
-

BBC introduces a family-friendly iPlayer Kids app
Publié: avril 12, 2016, 11:36am CEST par Wayne Williams

Children enjoy watching streaming video, but a lot of content out there really isn’t suitable for them. This is why Google introduced YouTube Kids, a curated, family-friendly version of the video streaming site.
Following in YouTube’s footsteps, the BBC is today rolling out a version of iPlayer aimed at younger viewers which cleverly filters available content based on the age of the child.
Dan Taylor-Watt, Head of iPlayer, BBC Digital, explains:
Rather than create separate BBC iPlayer apps for CBeebies (which is aimed at children aged 0-6) and CBBC (which is aimed at 6-12 year olds), we decided to create a single app that enables kids to tell the app their age and instantly be presented with content curated specially for their age group. So 6 year olds are able to enjoy a mix of CBeebies and CBBC programmes without having to switch between two different apps.
Of course a family might have multiple children of different ages sharing a single device, so the BBC allows support for up to four profiles.
The Shows area offers full A-Z lists of all CBeebies and CBBC shows available to stream, which amounts to over 1,700 episodes. These can all be downloaded for watching offline, thereby making long car journeys a lot more enjoyable for adults.
There’s a search option available for older users that will automatically filter out content for under fives.
The app also offers accessible features, including universal subtitles and the ability to switch between standard and signed and audio described versions.
BBC iPlayer Kids is available to download now for phones and tablets from the Apple, Google Play and Amazon app stores.
-

Porn site xHamster bans North Carolina users in protest against anti-LGBT laws
Publié: avril 12, 2016, 11:06am CEST par Mark Wilson

North Carolina's decision to pass House Bill 2 -- which effectively block measures to protect LGBT people -- means that residents of the state are no longer able to access a popular porn site. Just as Bruce Springsteen decided to show his disgust at the new legislation by cancelling a concert in North Carolina, so xHamster has taken the step of blocking North Carolina porn consumers from accessing the site.
North Carolina's new law prevents local governments from passing anti-discrimination rules to protect lesbian, gay, bisexual and transgender people, and it is sending ripples of disgust through the equal rights movement. With xHamster's involvement, the fight against the legislation has been taken online, hitting state residents where it hurts in a bid to encourage people to sign a petition against the bill.
xHamster has been inaccessible in North Carolina since Monday, and site spokesman Mike Kulich told the Huffington Post that LGBT search terms were very popular in the state. "Back in March, we had 400,000 hits for the term 'Transsexual' from North Carolina alone. People from that state searched 'Gay' 319,907 times".
In a statement the site said that the headline-grabbing ban was about equality:
We have spent the last 50 years fighting for equality for everyone and these laws are discriminatory which xHamster.com does not tolerate. Judging by the stats of what you North Carolinians watch, we feel this punishment is a severe one. We will not standby and pump revenue into a system that promotes this type of garbage. We respect all sexualities and embrace them.
Can porn succeed in helping to overturn the discriminatory law? Only time will tell. In the meantime, expect to see a spike in the use of proxy tools in North Carolina...
Photo credit: KongNoi / Shutterstock
-

SQL Server 2005 support reaches the end
Publié: avril 12, 2016, 11:05am CEST par Ian Barker

We've known for some time that SQL Server 2005 was reaching the end of its extended support period and Microsoft has been busy encouraging users to move to newer software such as SQL Server 2014.
Today is the day when its support finally ends, so users still running the system will no longer receive hotfixes and security updates from Microsoft.
Ali Din, CMO at cloud infrastructure company dinCloud says, "Migrating your infrastructure can seem daunting, but it's imperative for organizations to upgrade to a modern data platform before the support deadline in order to maintain security and compliance. There are a lot of enhancements from SQL Server 2005 to SQL Server 2012, but if you are going to go through an upgrade, I suggest taking advantage of the technology with a proven methodology".
Din recommends that enterprises make the move to the latest version on SQL Server (SQL Server 2014), so that they can take advantage of the latest features and functionality available. In addition they should use an SQL database expert to help with the planning, migration, and optimization of their systems.
The Enterprise edition of SQL Server allows users to take advantage of In-Memory to improve database performance, along with AlwaysOn for high availability. The robust features of SQL Server 2014 should allow companies to save by not having to buy multiple smaller or less feature-rich databases.
More about end of support for SQL Server 2005 and migration options can be found on the Microsoft website and on the dinCloud blog.
Photo credit: 360b / Shutterstock.com
-

Contactless payments market to reach $95 billion by 2018
Publié: avril 12, 2016, 10:41am CEST par Sead Fadilpašić

The global value of contactless payment market will reach almost $100 billion by 2018, a new study by market analysts Juniper Research says.
According to the research, entitled Contactless Payment: NFC Handsets, Wearables & Payment Cards 2016 - 2020, the market will hit $95 billion in two years, up from $35 billion in 2015.
The research says wearable devices, such as smartwatches and smart wristbands will be important for the market, but not crucial. Wearables as a whole would not account for more than two percent of non-card contactless payments by value in 2018.
On the other hand, smartphones will be extremely important. The research says the nine million Apple Watches that were sold in 2015 were "dwarfed" by NFC-capable iPhones. It also said that such devices pose a higher security risk.
With vendors embedding security measures within their devices, the report argues this spells trouble for mobile network operators. Samsung, currently the only Android OEM with its own contactless payment service, is being followed by Xiaomi, ZTE and Lenovo.
"Most operator-led pilots and commercial ventures have now closed down", says research co-author Nitin Bhas. "Apple’s entry into NFC gave the industry a much needed boost, and could well be seen as the tipping point for the technology, but at the same time it sounded the death knell for the mobile operator projects".
The whitepaper, NFC ~ No Contact Required, is available to download from this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: s4svisuals/Shutterstock
-

Facebook Messenger gains integrated Dropbox file sharing on iOS and Android
Publié: avril 12, 2016, 6:16am CEST par Brian Fagioli
There are many cloud storage providers nowadays, but I choose to give Dropbox my money. While there are alternatives that are free, I'd rather spend money on quality, and to support a company that supports Linux. Not to mention, Dropbox is secure, available on many platforms, and the company is constantly introducing new features.
Speaking of new features, today, the company announces that its cloud storage is now officially supported by the wonderful Facebook Messenger. Users of the chat program can now directly share files from Dropbox on both Android and iOS. You must have both the latest version of the Dropbox and Facebook Messenger apps installed for it to work.
"Now, when you tap the More button in Messenger for iOS or Android, you'll see Dropbox as an available source. With the Dropbox app installed on your phone, you can share any file in your Dropbox without having to leave the Messenger app", says DJ Chung, Product Manager, Mobile Platform, Dropbox.
Chung further explains, "videos and images -- including animated GIFs -- will be displayed directly in your chats. For everything else, tapping Open will bring recipients to the Dropbox mobile app, where they can preview and save files. It's a quick, simple way to share vacation snapshots, home movies, and laugh-worthy memes with any of the 900 million people using Messenger -- whether they're Facebook friends or not".
Facebook is already a great way to communicate with friends, and now with Dropbox it becomes even better as a legit collaboration tool. Not only can I see home users using this Dropbox feature to share photos, but businesses employees could potentially use it to share files remotely with each other or with clients.
Will you use this new Dropbox functionality in Facebook Messenger? Tell me in the comments.
-

Master & Dynamic teams with Rolling Stones for 'special edition' MH40 headphones
Publié: avril 12, 2016, 4:12am CEST par Joe Wilcox

If you're headed to London, or live there, the Rolling Stones have a new exhibit (opened last week) at the Saatchi Gallery. Exhibitionism will be there until early September. After which, the gala moves on to 11 other cities, including New York and Paris. Adults can expect to pay £22 (more than US $30, depending on exchange rate that day). VIP tix are £60.
The memorabilia-filled exhibit is meant to be a nostalgic look at the iconic, aging rock band, which youngest member is (cough, cough) 66. But Exhibitionism is as much about selling collectibles, one of which I can't resist calling attention to: "special edition" MH40 headphones. I reviewed the standard set, which sound exactly the same, on March 29th.
The MH40 typically sell for $399. The Stones' Exhibitionism-branded pair cost about $100 more. You wear the tongue! The tongue! Say, shouldn't Mick Jagger and Company update the symbol—give it some modern bling with big piercing? That would be more in tune with younger concert goers; surely the mosh pit isn't filled with the middle-aged and elderly—who might now more than their youth relate to songs like "(I Can't Get No) Satisfaction".
Okay, ribbing agism aside, the MH40 are excellent headphones for listening to the Rolling Stones. During 2016, the band rampaged Central and South America in a tour ending in Cuba last month. The Stones celebrate more than 50 years together, and the Master & Dynamic cans are so retro they could have been used by the rockers a half-decade ago—or by their male relatives flying in World War II bombers.
But audio signature matters more. The MH40 are among the better-balanced headphones for the price. Rather than being bassy, the cans emphasize finer details from the audio source, particularly music engineering during the 1960s, 70s, and 80s.
The MH40 driver is huge—45 mm—with Neodymium transducer. Frequency response is 5Hz to 25kHz, which punches up the midrange, while balancing well against the lows and highs. To repeat: Bass isn’t overbearing but present and clear rather than muddled.

If you're a Rolling Stones fan, the MH40 are great cans. But if you can live without the collector's branding, you could save $100 plus the price of the Exhibitionism ticket.
I'll say this: The MH40 are the tanks of the headphone market. They're sturdy and built to last decades. If you do go for the tongue, the Exhibitionism pair could be an heirloom for your descendants listening to the truly golden oldies in another 50 years. And with the Rolling Stones gone to the afterlife, perhaps your great-grandchild can listen and for a moment feel a little "Sympathy for the Devil".
Photo Credits: Master & Dynamic
-

Google Play and musician Elizabeth Rose create 'Playing With Fire' interactive music video
Publié: avril 12, 2016, 3:26am CEST par Brian Fagioli

As someone born in the 1980's, I grew up with MTV. Quite frankly, before I bought my first cassette or CD, I got my music fix by watching these classic music videos. While MTV has since moved away from music videos, websites like YouTube have stepped in to fill the void.
Even though music videos have evolved with innovative cinematography and cool effects, they are still largely the same old thing -- a mix of audio and video. Today, Google Play announces a collaboration with musician Elizabeth Rose to create something more appropriate for tech-focused millennials -- an interactive music video.
"Aussie artist Elizabeth Rose loves it when fans remix and play with her music. So, to celebrate the launch of her new single 'Playing With Fire', we got together with her to explore 'what if fans could actually play with Playing with Fire, as well?' The idea for a mobile interactive music video was born. The song is about the crazy range of emotions you feel in a relationship. By tapping, swiping and tilting your phone during the video, you can mess with her emotions, make her cry and even slice her in half", says Sophie Hirst, Google Play Marketing Manager, Google Australia.
If you want to try it out, you can do so here. The interactive video will not work on all devices, however. While it worked on an Android smartphone, it failed to work on my iPad. It did, however, work on my Ubuntu laptop running Chromium browser -- nice!
The experience works best with touch and accelerator, as it uses tapping, swiping and rotation. With that said, my laptop does not have a touch screen nor accelerator, so the video let me interact with my mouse -- clicking worked well too.
Regardless of how I interacted, it was a blast. I actually rather like the song, although I doubt I am the target demographic. Hopefully Google does not stop here, and works with more musicians, as interacting with the media definitely enhances it, making it much more fun.
What do you think of this interactive music video? Tell me in the comments.
-

Will robotics bring a new dawn for digital transformation in the UK?
Publié: avril 11, 2016, 6:58pm CEST par Justin Anderson

Digital transformation has become a popular term in IT circles, fast becoming a priority for organizations across the private and public sectors. The UK government’s shift to digital services and departments has been a longstanding goal over the last three years and continues to be a long-term objective, as success across online services has created more efficiency for both workers and UK citizens. It’s surprising therefore that this year’s Budget, as delivered by George Osborne, was a little light on the technology front and neglected the next chapter in the government’s digital story.
IT and technology sectors are considered to be the foundation points for economic growth and needs to continue to be a priority for organizations to get more done. Productivity plays a crucial role in sustaining this growth, but continues to be an area where the UK falls short. Just recently, the Smith Institute found that while UK workers continue to work longer hours, they are less productive. Academics have questioned whether technology has a role in solving this puzzle.
Robotics: The next big thing?
Something that was raised in the Budget was the opportunities that robotics present. The UK will be trialing driverless vehicles to see if they present a viable alternative to resource that can otherwise be used elsewhere. This immediately allows us to think about the opportunities available if we were to raise digital transformation up a notch. It also raises questions as to whether robotic implementation will take over our jobs. Could digital transformation lead to the rise of the machines?
In short -- no. Rather, the introduction of automated machines in organizations is an extension to what is already happening with new technology that is already finding its way into the workplace. Apps, automated machines, smart appliances, smart buildings, all enhance the working environment so that workers can get more done. Robotics will fit in the worker experience in much the same way.
So how can organizations welcome robotics as part of the digital transformation story in a way that will prove positive?
Embracing this new technology, rather than rebelling will be key. It is important to not lose sight of that long term objective and understand that this opportunity creates a wealth of benefits to improve the worker experience. The rise of robotic assistance presents the perfect opportunity to upskill the workforce. Workers now have the freedom to upgrade their skill set, because robotics take the strain on those tasks which were once restrictive or time consuming.
For some industries such as manufacturing, robotic aid has been responsible for simple yet time consuming processes that have taken up valuable resource. Now it can channel this resource into areas of much needed innovation to ensure that this sector is able to grow and thrive.
More time and money can be invested in engaging with the workforce. This in turn creates a strong company culture and keeps retention rates high as workers have more time for themselves -- to learn new things as well counter long hours that prove unproductive.
What this ultimately means is that a better worker experience creates a better customer experience. The two are intrinsically linked. Happy workers mean happy customers. Digital transformation and the prospect of robotics is and will continue to have its role in creating this virtuous cycle.
Photo Credit: Palto/Shutterstock
Justin Anderson VP Sales, CRM and HCM, Appirio
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Google shows love to users with disabilities
Publié: avril 11, 2016, 6:34pm CEST par Brian Fagioli

According to Google, 20 percent of people in the USA will experience a disability at some point in their life. Let's think about this for a moment -- that is one in five people. In other words, people with disabilities are a significant part of the population. While there are many laws on the books protecting the disabled from discrimination, this group of people can still be underrepresented.
Today, the search giant highlights some of the ways it is helping users with disabilities. Google is focusing on multiple platforms, such as Chromebooks, Android, and the web.
"A few weeks ago we announced a preview of Android N for developers. As part of this update we're bringing Vision Settings -- which lets people control settings like magnification, font size, display size and TalkBack -- to the Welcome screen that appears when people activate new Android devices. Putting Vision Settings front and center means someone with a visual impairment can independently set up their own device and activate the features they need, right from the start", says Eve Andersson, Manager, Accessibility Engineering.
Android also received a new feature for those that cannot use a touch screen, called Voice Access Beta. This allows the user to navigate and control their smartphone or tablet using their voice entirely. This would be helpful for someone who cannot use their hands reliably, or at all, to operate their device.
As we reported back in February, Docs for Chrome received a cool update that allowed voice typing and editing. At the time, I expressed that I was dubious that there was value, with the exception of those with a handicap. Google seems to agree, as it is now highlighting it as a tool for those with disabilities.
Regarding Chrome OS, Andersson furthers says, "every Chromebook comes with a built-in screen reader called ChromeVox, which enables people with visual impairments to navigate the screen using text to speech software. Our newest version, ChromeVox Next Beta, includes a simplified keyboard shortcut model, a new caption panel to display speech and Braille output, and a new set of navigation sounds".
One of the real winners, however, is a tool for Android developers that suggests ways to optimize their apps for the disabled. This is particularly intriguing, as it can inform developers that maybe hadn't considered this group of people. This should lead to better apps for disabled folks, and that is always a good thing.
Do you think more companies should follow Google's lead in focusing on users with disabilities? Tell me in the comments.
Photo credit: Voyagerix / Shutterstock
-

The future of developer recruitment [Q&A]
Publié: avril 11, 2016, 6:05pm CEST par Ian Barker

Recruiting developers is often a problem for organizations as the skills required are different from those in other sectors and can be hard to assess. Development often has a great deal in common with more creative fields, where suitability for a job is not so much about qualifications but about what you can do and how you can communicate.
So what can companies do to discover the developer talent they need? We spoke to Mike Bartlett, CEO of developer community site Gitter to get his perspective.
BN: What's wrong with the traditional approach where you simply advertise a job and wait for applications to roll in?
MB: Very seldom is great talent looking for a new job. The best engineers will be highly in demand and can effectively pick and choose where they work and what they work on. If you want the best, as you should, not only do you have to go out and find them, but you're also going to have to convince them why they should be working for you. Higher salaries, better free lunches and more ping-pong tables just won't cut it any more.
You need to start building relationships far in advance of hiring, building trust and an understanding of why working for you is better than working for someone else.
If you're just placing ads on traditional jobs boards or using regular recruiters, you’re probably going to get a large number of CVs through the door and spend a huge amount of time trying to figure out if the candidate is any good. This is hugely time consuming not only for the hiring manager, but will also take time out of your existing development team's schedule as they are generally the ones having to dig into each applicant individually.
BN: Do companies sometimes fail to effectively assess technical skills as part of the recruitment process?
MB: The most common failure is assessing how the candidate works with your particular technology stack, the code you've already written and -- most important -- with the team.
We've seen, and even used, a lot of developer testing techniques. There are particular exercises that will test competency, for example with a particular algorithm and understanding if the candidate truly understands computer science, logic and reasoning and these can weed out some of the obvious bad hires.
What we've found really effective is doing pair programming tests where the applicant will come and spend three or four hours sitting with one of your existing developers and working together on a real problem within your own environment. This will not only test software development skills, but communication skills, team work and a you'll get a really good sense of how that person behaves in real working conditions.
BN: What can businesses do to look for candidates rather than waiting for them to appear?
MB: The whole team should always be hiring. Make sure your developers are always on the look out for great people to hire. This means going to meetups and not just listening to the presentations, but socializing with the other attendees and getting to know one another. It means actively contributing to open source projects and hanging out in the online communities such as our own developer network, Gitter, and building relationships with the people who stand out.
There are great tools such as Workable or Lever where you can give your whole team access and help keep a list of prospective future candidates in a centralized place.
BN: What can developers themselves do to make them more attractive to prospective employers?
MB: Get stuck into the online communities and contribute back to open source projects. Pretty much every technology stack used in software development today is open source; rather than just reporting bugs back to the project maintainers, if you can roll up your sleeves and get stuck into the code, find the bug and send a proposed fix back to the project, you'll immediately gain a lot of credibility and be seen as contributing back to the ecosystem.
BN: Developer recruitment is a bit like online dating really, isn't it?
MB: Oddly enough, I met my wife on Match.com. If she reads me comparing our relationship to hiring developers, I think I might find myself in a lot of trouble!
Photo Credit: sokolovsky/Shutterstock
-

How to run Bash on Ubuntu on Windows 10 Anniversary Update or Preview Build 14316
Publié: avril 11, 2016, 5:24pm CEST par Mark Wilson

Microsoft has been showing Linux a lot of love recently, and at Build 2016 the company announced that the Bash shell was coming to Windows 10. It’s a feature that will make an appearance in the upcoming Windows 10 Anniversary Update (due for release in July), but it's something that Windows Insiders on the Fast Ring already have access to in Build 14316 right now.
If you have installed this build, you'd be forgiven for not being able to find Bash however hard you look; there are hoops you have to jump through. So if you like the idea of accessing the Linux command line in Windows 10, there are a few steps for you to follow, starting off by enabling Developer Mode.
As Microsoft explains: "You can now run Bash scripts, Linux command-line tools like sed, awk, grep, and you can even try Linux-first tools like Ruby, Git, Python, etc. directly on Windows. You can also access your Windows filesystem from within Bash allowing you to work on the same set of files using your preferred Windows tools or Linux command-line tools".
Here are those all-important Bash-enabling steps:
- Open up Settings, click Update & security, and then head to the For developers section. Select the Developer mode option, click Yes to confirm, and then exit Settings.
- Hit the Windows key (or the Start button), type Windows features, and click the Turn Windows Features on or off entry that appears.
- Scroll down to the bottom of the list, check the box next to the Windows Subsystem for Linux (Beta) option, and click OK.
- Wait for a moment while Bash is installed and then click Restart now to restart your computer and complete the process.
- When Windows is back up and running, open a command prompt window, type bash and hit Enter.
- You'll see a message that reads 'This will install Ubuntu on Windows, distributed by Canonical and licensed under its terms'. Press Y followed by Enter to download the software from the Windows Store and complete the installation.
In future, you can access Bash via the Bash on Ubuntu on Windows shortcut in the All Apps section of the Start menu.
Photo credit: charnsitr / Shutterstock
-

Brief WordPress database guide for the absolute beginner
Publié: avril 11, 2016, 4:27pm CEST par Sujain Thomas

WordPress is the finest content management system. Its popularity is proof of that. Websites on WordPress perform great and the platform is easy to use. However, the same cannot be said about managing its database.
If you are a beginner in using this CMS then you might get a migraine or two whenever you try to understand the tons of content available online concerning WordPress databases.
What makes WordPress such a popular platform is the fact that there are so many places where you can access good information about it. Blog posts, articles and even how-to guides plus videos have been created to make usage of WordPress easy. However, for some reason the articles concerning databases just come off as rocket science to some people. There is not a reason why you should struggle though.
Just For the Beginner
One thing that is characteristic of all content management systems, including WordPress and Drupal, is that once you learn how to use them they become so easy. Drupal, for instance, is considered to be the hardest CMS that you could possibly use on this planet, but then it turns out that it is not all that complicated in the first place. You can imagine just how easy it is to use WordPress then. It uses PHP as its scripting language and its database management system is MySQL.
A basic understanding of these two will be very helpful when it comes to troubleshooting problems. It will also help you to understand how WordPress works generally. However, you do not need to go into the details of these technical terms now.
This following section is meant to help you learn how to manage your database using phpMyAdmin, including how you can create database backups. A backup or two will always be good for your database. However, creating the database can be a challenge sometimes, particularly if you have no idea what to look for.
Basics to Get You Started
As mentioned previously, WordPress is written on PHP. This means that the platform uses this programming language to store as well as to retrieve data from the database. The information that is stored in the WordPress database is varied ranging from posts, comments and pages to tags, categories and users.
Once you have installed WordPress it will ask you to provide a database name, username, host and password. This information is usually stored in the configuration file. The information that you provide concerning the database is the one that is going to be used to create tables and also store default installation data in the created tables.
After the installation process is complete, WordPress then runs queries to the database in a bid to dynamically generate HTML pages for the blog or website. It saves you the effort of having to create a .html file for every page that you wish to create.
Creating the Backup Using phpMyAdmin
Photo Credit: Crucial.com.au
To backup your WordPress database from the phpMyAdmin page, click on the WordPress database and on the top menu you will find a tab titled Export -- click on this tab. The newer versions of phpMyAdmin will ask you to select a specific export method that you want to work with. There is the quick method, which will export the database into a .sql file.
There is also the custom method which will provide you with some more options to choose from plus the ability to download the backup in a compressed gzip or zip archive. Using the quick method is tempting and sometimes it is most beneficial if your database does not contain very important things.
The custom method is however, the best for backing up your WordPress database. You should go for the zip compression option though instead of the gzip. This custom method makes it possible for you to exclude all the database tables that you do not want to backup a feature that is lacking in the quick method. For instance, if you have used a plugin which added a table in your database, you can opt to leave out that table from the backup if you do not need it.
When you are done selecting the tables that you want to backup then you can click export to complete. The database file that you exported can be imported into a different database or the same one. All you need to do is going to the Import tab. This is a really good way to protect yourself against disasters of data loss and it is probably the first thing that you need to learn about WordPress databases.
Conclusion
WordPress has really made data management a simple job. Right from the moment that you install it to your site it will create the database automatically for you based on the information that you provide. Creating a backup is important and the process is very simple when you use phpMyAdmin.
Sujain Thomas is a data IT professional who works closely with DBA experts to provide her clients with fantastic DBA services to solve their data problems. If you need data IT solutions, she is the person for the job. She enjoys writing on database administration services and other topics in the IT field.
Photo credit: Ingvar Bjork / Shutterstock
-

SteelSeries APEX M500 is an affordable Cherry MX Red mechanical keyboard for eSports
Publié: avril 11, 2016, 2:58pm CEST par Brian Fagioli

If you are happy with your current keyboard, but it isn't a mechanical variant, you probably could be happier. In other words, you probably don't know what you are missing. Mechanical keyboards offer a very satisfying typing experience, plus potentially better performance when gaming.
Mechanical keyboards are often an expensive affair, however. They are totally worth the investment, but sometimes they have extra features you don't really need or want, which inflates the price. Today, SteelSeries announces the APEX M500 mechanical keyboard with a very reasonable price. It has Cherry MX Red switches, which are ideal for gaming. The eSports-focused keyboard is fairly basic by design, which makes it affordable for many.
"SteelSeries, leader and innovator in gaming peripherals, announces the availability of the SteelSeries Apex M500, a tournament-ready mechanical keyboard outfitted with Cherry MX Red gaming switches and SteelSeries Engine customization software. Available for $99.99 / €119.99, the ultra-durable Apex M500 also features a traditional key layout for universality, Anti-Ghosting technology and blue LED backlighting", says SteelSeries.
The company further explains that the "Apex M500 showcases a smart cable management system with three cable guides that adapts to your keyboard setup to eliminate tangles and interference. It is also armed with 100 percent Anti-Ghosting technology with 104 key rollover to ensure precision no matter how fast you play".
Click to view slideshow.While the SteelSeries APEX M500 is basic and affordable, it is actually quite attractive too. The blue back-lighting contributes just enough to make it exciting, while still maintaining an overall mature look. In other words, it doesn't look like a child's toy -- it means business.
If you are interested purchasing this mechanical keyboard, it will be available later today at Newegg or SteelSeries directly for $99.99. Keep in mind, even though it is designed for eSports, it should work well for everyday computing tasks too.
-

Microsoft throws its support behind EU-US Privacy Shield
Publié: avril 11, 2016, 2:00pm CEST par Mark Wilson

The transfer of data between the US and Europe has been something of a privacy and security nightmare. In an attempt to improve privacy protection, the European Commission established the EU-US Privacy Shield "to restore trust in transatlantic data flows" post-Edward Snowden's NSA surveillance revelations, replacing the controversial Safe Harbor arrangement.
Today Microsoft has announced its support for the principles the framework says that companies will have to abide by. More than this, Vice President for EU Government Affairs at Microsoft, John Frank, says the company will comply with Data Protection Authorities advice in disputes, and cooperate with them on data transfer processes.
Whilst recognizing that "no single legal instrument can address for all time all of the privacy issues on both sides of the Atlantic", Microsoft nonetheless says that Privacy Shield is a good starting pointing. The company says that additional steps will be needed to localize the framework, and praises the European Commission and US Department of Commerce for what it describes as having helped create "stronger and pragmatic privacy protection".
In a blog post, Frank says:
First and foremost, at Microsoft we believe that privacy is a fundamental human right. In a time when business and communications increasingly depend on the transmission of personal data across borders, no one should give up their privacy rights simply because their information is stored in electronic form or their technology service provider transfers it to another country.
We recognize that privacy rights need to have effective remedies. We have reviewed the Privacy Shield documentation in detail, and we believe wholeheartedly that it represents an effective framework and should be approved.
As well as announcing that it will sign up for Privacy Shield, Microsoft also says that it will embrace the dispute resolution process. Specifically, Microsoft will respond to any complaints it receives within 45 days. Having complied with Safe Harbor and cooperated with Data Protection Agencies for nearly 15 years, the company says "we believe it makes the most sense for us to continue with this approach and submit disputes to the DPAs under the Privacy Shield".
The Privacy Shield framework also places transparency obligations on companies, and this is something that Microsoft also embraces:
We also welcome the obligations in the Privacy Shield for transparency about government requests of access to personal information. As a company we have advocated for greater U.S. transparency. In 2013, Microsoft and other U.S. tech companies successfully challenged the U.S. Government over our constitutional right to disclose more detailed information about the Government’s demands for data. And in 2014, we filed suit against the U.S. Government after it attempted to force us to turn over a customer’s email stored in our Irish data center. While we continue to advocate for additional domestic legal steps in the United States, we believe that the European Commission and Department of Commerce have chosen a sensible approach in the Privacy Shield. In this area as in others, we believe the Privacy Shield represents an important step in the right direction.
What needs to happen next is to convince more companies and, importantly, individuals that the Privacy Shield agreement is in their best interests.
Photo credit: StockStudio / Shutterstock
-

Record everything launched on a PC with Process Logger Service
Publié: avril 11, 2016, 1:14pm CEST par Mike Williams
Process Logger Service is a Windows service which logs every process launched on your PC. It’s a useful tool that can help answer a range of questions. Like, did the email you open launched something? What did that installer do? When was a particular program last run? And more.
The service must be set up manually. It’s not a difficult process, but does involve a little more work than we expected.
You must a) unpack the download, b) browse to the 32 or 64-bit ProcLoggerSvc folder, c) copy that to C:\, d) browse to C:\ProcLoggerSvc, and e) run install.bat as an administrator (there’s an uninstall.bat to remove it later).
Once setup is complete, everything else is straightforward. There’s no extra system tray icon, no interface to browse, the program just runs in the background and logs every process launch in the C:\ProcLoggerSvc\Logs folder.
Open that file in Notepad and you’ll see entries like this.
[Process Creation]
11/04/2016 09:46:44
Process: [8496] C:\Windows\System32\notepad.exe
Username/Domain: user/domain
CommandLine: "C:\WINDOWS\system32\NOTEPAD.EXE" C:\ProcLoggerSvc\Logs\MSI\11-04-2016.log
MD5 Hash: 60336413E419C2EA5E215F1A32061E40
Bitness: 64-bit
File Publisher: Microsoft Corporation
File Description: Notepad
File Version: 6.2.10586.0
Integrity Level: Medium
System Process: False
Protected Process: False
Metro Process: False
Parent: [5844] C:\Windows\explorer.exe
Parent CommandLine: C:\WINDOWS\Explorer.EXEThis amount of detail makes for a lengthy log, but fortunately Process Logger Service starts a new log at the beginning of every day, so it remains manageable.
If you still have too much data -- or you don’t have much spare drive space -- then you can just pause logging when you don’t need it by disabling ProcLoggerSvc in the Services applet.
On balance, if you only need to detect process launches briefly then we’d prefer to use Sysinternals’ Process Monitor. It’s more convenient, and records plenty of other process actions, too.
Process Logger Service could be a better choice for longer-term monitoring, though, especially if you’re logging actions on someone else’s PC.
You could even use it to record another user’s actions without their knowledge, although it’s worth remembering that the program doesn’t try to hide itself. If someone notices the extra C:\ folder, or the new Windows service, then your cover will be blown.
Process Logger Service is a free-for-personal-use application for Windows XP and later.
-

New cloud platform streamlines Android app development
Publié: avril 11, 2016, 12:51pm CEST par Ian Barker

Businesses have ever more demand from consumers to deliver services via mobile, so they're looking for ways to produce apps quickly and efficiently.
To address this need, Android solutions provider Genymobile is cloud-based platform that allows enterprises to build, test, show off and service Android applications across the entire application lifecycle while streamlining the development process.
Genymotion Cloud is a cloud-based emulator that combines collaboration and automation features. It enables developers, QA, UI/UX designers, sales and marketing, help desk teams and business decision-makers to easily evaluate apps at any stage of development on more than 3,000 virtual device configurations instantly via any web browser.
"There is mounting pressure for every business to be mobile-powered. It is imperative that mobile development does not become a burden. Our SaaS solution maximizes efficiencies across the whole mobile application value delivery chain," says co-founder and co-CEO of Genymobile, Arnaud Dupuis. "Everyone involved in the project gets the information they need exactly when they need it. This not only means faster time to market. It also means better quality, reliability and improved customer satisfaction".
Collaboration features include the ability to demo the app's functionality on any Android device via any web browser, allowing sales and marketing to gather market feedback before the application is complete. Customized virtual device configurations can be remotely shared, allowing developers working on the same project to share an identical local development environment. The most up-to-date application under-development can also be shared for review, meaning developer teams and UX or UI engineers can collaborate more easily throughout the project. Sales teams can expedite cycles by allowing potential customers to use and test an app under development without requiring additional engineering support.
Genymotion Cloud also offers automation features including continuous integration support, compatible with on-premise CI infrastructures such as Jenkins, Bamboo, Buildbot and TeamCity. Code testing is simplified too with standard HTTPS REST and Java APIs that allows developers to create a testing device, install an application, run and test it against multiple device configurations without leaving the development environment. In addition, it's compatible with industry standard integrated development environments, including Android Studio and Eclipse.
You can find out more about Genymotion Cloud on the company's website.
Image Credit: Alex Mit / Shutterstock
-

How phone agnostic beacon technology will revolutionize mobile payments
Publié: avril 11, 2016, 11:36am CEST par Jonathan Duffy

Mobile payments are gaining momentum in the UK. Apply Pay has an initial monopoly, Google recently announced its UK launch and Samsung is planning to follow suit later this year. Countries across the globe are increasingly moving towards cashless societies thanks to advances in contactless payments. The UK is a leader in contactless payments and, thanks to technology such as Oyster cards, mobile payments are catching on quickly.
Instead of carrying a physical wallet with cash and bank cards, mobile wallets are becoming an increasingly popular method of payment.
The death of the wallet
Mobile payment apps have added a new and convenient way for people to pay for goods and services. The total value of proximity mobile payments is set to see a significant growth of 210 per cent in 2016 and has the power to revolutionize the shopping experience, making payments more convenient and faster. It’s an attractive option for brands and customers alike as it makes the payment journey for the customer much more simple.
As these digital wallets gain market traction, banks could find themselves in trouble. There are more players entering the space. According to Bloomberg News, Walmart, Starbucks and even Chevron petrol stations are working on plans for their own digital wallets.
But the 'walled gardens' of Apple and Samsung Pay make it difficult to implement the systems and add extra costs to the merchants as they are only usable on the phones they manufacture. This significantly limits the systems customers can use. Other limitations include:
- Credit card based systems
- User data owned by Apple et al
- No options for customization
- Added fees
Beacon payment technology gets around these methods using a combination of phone-agnostic beacon technology and a phone app. This method allows banks and payment merchants to regain control through a white-labeled solution that is completely customable.
Banks are leading the charge
Tech-savvy consumers, world-leading smartphone penetration and progressive banks have kept the Nordics ahead of the game with mobile payments. In 2013, Danske Bank launched MobilePay to address the need for very simple money transfers. The ambition was to make transferring money to friends as easy as sending a text message. This app then evolved to a payment system for retailers using beacon technology with the app.
Dankse Bank’s mobile wallet was the third most popular app in Denmark and Norway (after Facebook and Facebook messenger) and over 90 million transactions by 2.8 million individuals were made through MobilePay last year alone.
Danske Bank’s MobilePay payments are now accepted in shops across Scandinavia, including McDonalds and Starbucks outlets, and all that is required of the customer is a free app that is installed on their iOS, Android or Windows Mobile device. Once purchases are scanned at the checkout and payment is requested, the mobile device is waved over the smart beacon with the app running. In response a customer is immediately shown the purchase amount and the app waits for confirmation through a simple pin and swipe gesture. In seconds a purchase is made without having to enter any amount manually or having to use a payment card.
Mobile payments platforms are providing retailers with an intuitive customer experience via inexpensive technology and removes costly merchant fees as the technology takes transactions direct from bank to retailers, changing the value chain.
Directly engaging with customers
By directly engaging their customers, banks can also create additional brand loyalty as well as providing a desirable feature to entice new customers.
The solution does not require technology and equipment that is expensive or difficult to access for retailers and it is intuitive to use and easy to understand for the end users. The payment is so easy and effortless: "They have all been mighty impressed by how easy and fast it is. People get really pleasantly surprised, and sometimes they have to try several times because they have a hard time believing that it really is that easy" says Danish supermarket Rema 1000’s project leader, Steffen Skov Larsen.
This disruptive technology has implications beyond ease of use for the customer and retailer. Because the technology takes transactions direct from bank to retailer, it changes the value chain by removing merchant fees, acquirers and payment service providers from the fee structure and comes with enhanced security so there is less chance of fraud or error.
Millennials opt for mobile first
Beacon technology gives banks and retailers the control to implement their own systems, creating bespoke white-labeled devices to the client’s specification with a custom payment system – outside the expensive walled gardens of Google, Apple and Samsung.
The problem for banks is that millennials who could become their new customers are deciding against conventional banking and choosing instead to bank through the growing number of mobile payment services.
If banks want a fighting chance to catch up with third-party mobile wallets, they’ll need a digital payment technology to do it.
Jonathan Duffy, managing director EMEA, Netclearance
Photo credit: gpointstudio / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The Internet of Things in 2016 -- where is it headed and what are your plans?
Publié: avril 11, 2016, 11:16am CEST par Alan Buckingham
The Internet of Things, more commonly known as IoT and sometimes referred to as a Connected Home or as Home Automation, is one of the biggest trends in technology these days and 2016 doesn't seem to be slowing down as new products continue to pour onto the market while others get updates and increasingly become compatible across platforms.
Product lines abound, from door locks to shades and from lights to crock pots. Manufacturers like Samsung, Insteon, Cree, GE, Nest, Wink, Sensi, Ecobee and many more are out there waiting for your hard earned money.
The writers here at BetaNews have personally used quite a few of these products, myself trying out Nest, GE Link, Cree, Wink and Mivatek. My colleague Brian Fagioli uses WeMo and Wayne Williams has tested Nest and various D-Link Connected Home products.
The market is expected to continue its growth, but it isn't without some pitfalls. There have been security concerns over all of this connectivity.
So where is all of this headed this year and in the longer run?
Richard Gunther, a writer at Digital Media Zone and host of the HomeOn podcast told us "IoT as a market space is growing substantially. More and more devices are connected to the cloud or to each other, in many cases enabling previously unimaginable consumer and business benefits but also introducing new challenges and complexities that we're not yet well equipped to manage. Security and privacy are some obvious issues, but even more subtle concerns arise that can be beyond the means of most consumers to comprehend. It's likely that many if not most of the objects in our daily lives -- homes, appliances, vehicles, clothing, possibly even people -- will in some way be digitally connected in the near future, but the reality is that it will likely get even more complicated and we'll encounter more 'big issues' that we need to solve at both the technical and societal levels before we can all truly benefit from IoT".
That's an optimistic, but realistic, outlook about where we are headed, but there are serious roadbumps along the way. Just last week we saw Nest announce the shutdown of Revolv, and this doesn't just mean the device won't be updated, the company will reach into your home and turn it off.
Ryan Lester of Xively states "Customers of connected products expect constant availability, real-time updates, lifecycle support and anything else that will provide them a truly great customer experience. They may not understand the bits and bytes driving the product, but their biggest concern is that the product is always-on, working and available".
That clearly won't happen in all cases -- companies go out of business and also kill products, though usually not so completely as Nest is doing with Revolv.
In fact, the trend is expected to continue. Pew Research, in a report presented to American Bar Association Section of Science and Technology law on March 30, 2016, states "The vast majority of respondents to the 2014 Future of the Internet canvassing agree that the expanding networking of everything and everyone -- the growth of the Internet of Things and embedded and wearable devices -- will have widespread and beneficial effects by 2025".
So, with that information, both the good and bad, where are you headed in 2016? Are you already connecting your home or do you plan to? Or does all of this make you want to pull out the tinfoil hat and place it squarely on your head? There are many considerations from convenience to security.
Image Credit: Black Jack / Shutterstock
-

Keygen alert: free password generator released for PETYA ransomware
Publié: avril 11, 2016, 12:59am CEST par Mark Wilson

The PETYA ransomware is just one of the recent examples of malware that encrypts victims' hard drives until a fee is paid. The advice from the government is not to pay the ransom -- or at least not expect to get a decryption key if you do -- but a password generator has been created that means you can decrypt your hard drive for free.
While TeslaCrypt 4 boasts 'unbreakable encryption', the same cannot be said of PETYA, although the PETYA ransomware does have the irritating habit of overwriting MBRs. This does mean that there is no way to interact with the drive on the infected computer, but with access to a spare machine to read the drive and access to the online tool created by Leostone, you could have your data back in seconds. As the tool's website proudly proclaims, you can "Get your petya encrypted disk back, WITHOUT paying ransom!!!" -- here's what you need to do.
The process is not something that everyone will be able to follow -- it is a little technical -- but it's worth persevering (hat tip to Bleeping Computer for the heads up!) to avoid coughing up any Bitcoin. You'll need to connect the infected drive to another computer and extract a couple of pieces of data from it, specifically:
- 512 bytes of verification data from sector 55 (0x37) offset 0(0x0) of the disk, converted to Base64
- 8 byte nonce from sector 54 (0x36) offset 33(0x21), also converted to Base64
To help with this, you can use the specially-written Petya Sector Extractor as this will provide you with the data you need.
Fire up your web browser and pay a visit to Leostone's decryption website at [https:] where you'll find two fields into which you can paste the requested data from the infected drive.
With this done, hit Submit and wait for a few seconds while your key is generated. Return the infected drive to its original computer, fire it up, enter the key when prompted, and the drive should be decrypted. For free!
-

Celebrity threesome superinjunction shows disparity between law of the land and law of the web
Publié: avril 10, 2016, 9:50pm CEST par Mark Wilson

The idea of an injunction to prevent newspapers from publishing certain stories are nothing new, far from it. But in recent years, a new breed of superinjunction has been born. These not only prevent the publishing of stories, but can also block the publishing of the names of those involved. Some superinjunctions are such that even reporting the existence of the superinjunction is prohibited.
In recent weeks, a celebrity couple took out a superinjunction to prevent the press from publishing details of an alleged affair (well, a threesome if we cut to the chase). The gagging order prevented news outlets in the UK referring to the couple as anything other than the initials PJS and YMA (not their actual initials, by the way) and the other participants in the alleged ménage à trois as AB and CD. But today a Scottish newspaper took the decision to reveal the names of the couple -- but it could only do so in its print edition, because of the way laws written for the printed press have been awkwardly applied to the web.
The case is something of a legal minefield. Just as the press in England is not able to publish the names of those involved, it is also not permitted to provide clues or hints that could enable readers to determine their identity. This means that British newspapers cannot even name the Scottish newspaper that draws back the curtain. In fact, the newspaper in question is not legally able to publish the same information online as it can in its print edition simply because it could be accessed in England.
If this seems like insanity to you, you are far from being alone. If you're reading this in the States -- or even if you are in the UK -- you are probably already aware of the couple at the center of the case. It has been covered by the National Enquirer (yes, I know...) and there has been intense speculation on Twitter in recent weeks. For the risk of being sued, newspapers reporting the fact that the gagging order has been ignored in some parts of the UK must refer to the publication in question indirectly: 'a Scottish newspaper', very much like referring to 'the Scottish play' instead of risking saying 'Macbeth' in a theater.
It is madness.
The Scottish newspaper's website includes an editorial piece which says:
As our digital content is read in England we cannot reproduce the story online, tell you who they are or even feature the front page.
But their names are already known in the United States where the stories have been published and their identities are all over social media.
Of course, it takes just a few seconds of your time to discover the people involved if you are interested. But something interesting is happening. While Twitter has been abuzz with speculation about who the celebrity couple might be, there is also an element of self-censorship taking place. One user posted a photograph of the newspaper article in which the couple was named, but after taking advice from another news outlet, opted to delete the tweet:
@hex_inc If you don't want to risk getting sued, yes.
— Wings Over Scotland (@WingsScotland) April 10, 2016
But as the newspaper says;
We are publishing the identities today because there is no legal reason not to publish in Scotland what has been banned in England and Wales. Their big secret is no secret at all. America knows. The internet knows. The whole world knows. So now Scotland knows. And so we should.
The paper is quick to point out that the decision was taken as a demonstration of support of freedom of the press:
Just to be clear, we are not naming them because of the story they are trying to suppress. We couldn’t care less. We do, however, care about free speech, a free press and very wealthy people spending huge sums of money stopping stories they do not much like the sound of.
If we did not name them, it would only encourage people -- possibly celebrities, more probably tycoons and politicians -- with something to hide to attempt to hide it behind a court order.
It's crazy to think that the couple involved could possibly have thought that the story could be stopped in its tracks using a court order. If anything it has served only to drag things on for longer than might otherwise have been the case. Left to run its natural course, the story probably would have burned out and been forgotten in a matter of days. As it is, it has been dragged out for weeks, and it has been brought to global attention.
It has also highlighted an important difference between how the law applies to land-based newspapers, and how it applies to the global internet. While newspapers in England may have been effectively censored, the same cannot be said of internet users.
And if you're wondering why we're neither naming the celebrities nor linking to the Scottish newspaper we're taking about, there are a couple of reasons. Firstly, this is not a celebrity gossip site, so this is not the place to discuss A-listers' bedroom antics. But secondly, as stupid as it may be, we're playing it safe. Our pockets simply aren't as deep as those of the couple involved. There is the fact that a) BetaNews is based in the US and, b) I'm writing this from Scotland, but is it worth the risk? Really?
Photo credit: Tashatuvango / Shutterstock
-

Immigration officials allowed to hack phones of refugees and asylum seekers
Publié: avril 10, 2016, 12:52pm CEST par Mark Wilson

The British government secretly rolled out powers that permitted the immigration officials to hack the mobile phones of asylum seekers and refugees, the Observer reveals. The Home Office has confirmed the hacking powers which have sparked outrage from privacy and human rights groups.
Since 2013, immigration officials have not only been permitted to hack into migrants' phones and computers, but also to install surveillance equipment in homes and detention centers. With concern about governmental plans for the snooper's charter and the privacy invasion this entails, claims that the powers are needed to "deal effectively with all immigration crime" are likely to fall on deaf ears.
In a statement about the powers afforded immigration officials, immigration minister James Brokenshire said: "They may only use the power to investigate and prevent serious crime which relates to an immigration or nationality offence, and have done so since 2013".
The revelation has sparked serious concern from campaigners for rape victims; a very large proportion of women in immigration detention centers are survivors of rape. Black Women’s Rape Action Project spokesperson Cristal Amiss says:
These powers are an outrage. People in detention have the right to confidentiality, to speak privately to their lawyer and disclose often very sensitive information such as details of rape, torture, domestic violence and alleged abuse by officials. They have to be able to share private information without their phones being hacked.
The surveillance and hacking powers have been bolted into legislation by amending the Police Act 1997, an act that many argue is completely inappropriate for dealing with technology-related matters. Critics of the power says that the government is targeting and abusing some of the most vulnerable people in society, but the government says that "equipment interference" (read 'hacking' or 'surveillance') has been used to investigate cases of illegal travel documents.
Photo credit: Prazis / Shutterstock
-

Zuckerberg's #BLM rant and the dangers of corporate Thought Police
Publié: avril 10, 2016, 9:48am CEST par Derrick Wlodarz

Corporate leaders, especially those considered thought leaders, have a firm right and assumed expectation to voice their opinion on public policy. As such, I've got no inherent issues with Facebook's founder and chief, Mark Zuckerberg, proclaiming his positions publicly -- even if I happen to blatantly disagree with them.
Mark and other leaders of their respective industries have something very intrinsically unique that most others do not. That comes in the form of the power of the pulpit. It places their opinion in a position which bring inherent weight and reach which many could only dream of. Yet, this advantage comes with a social responsibility so as to not abuse or otherwise misuse the privilege.
There are two subtle, yet very troubling, problems which stem from Zuckerberg's outright (now quite public) shaming of coworkers who disagree with his political viewpoint on Black Lives Matter. And thanks to Gizmodo, where news of this story first broke, the tainted prism with which Zuckerberg's position is being framed says it all:
Mark Zuckerberg Asks Racist Facebook Employees to Stop Crossing Out Black Lives Matter Slogans
The first area of contention I have, which most of the media has either avoided or forgotten to address, is the notion that Zuckerberg's coworkers who don't see eye to eye with him on Black Lives Matter are, as Gizmodo insinuated, racists.
Not only is this characterization blatantly false and self-serving, but it's also an assertion which a majority of America doesn't agree with Zuckerberg on. As public polling data (referenced below) proves, Zuckerberg's narrow views on BLM are in the minority, with most Americans -- and most importantly, even African Americans -- not having a favorable view of the #BLM cause and preferring the All Lives Matter tagline instead.
The bigger issue at play is perhaps how this may be one of the more important recent examples of corporate figures crossing the line from acceptable political advocacy to outright unwanted thought policing of their staff.
As the face of the largest social network in history, Zuckerberg risks taking his personal beliefs beyond corporate policy positions and instilling a culture of zero dissention among the ranks of his workforce. This blurring of the lines between protected free speech and a future potential of say, a Facebook Charter of Acceptable Free Speech, could spell trouble for not only Facebook employees, but set a terrible precedent for workers in other non-IT industries.
It sounds crazy, Orwellian, and perhaps far fetched, but do realize that this barrier is about to be crossed by one of the largest countries in the world: China. It comes in the form of a little-covered initiative, known as the Social Credit System (SCS), that will become mandatory by 2020 for all citizens of the state.
Some parts of the internet took aim at a chilling photo Mark released from his appearance at Mobile World Congress, surprising hundreds of guests while they were entrenched in Gear VR headsets. Possible allusion to a modern, Orwellian future dictated by the whims of our IT industry leaders? That's up for interpretation, but a reality some say may not be far fetched.
Taking its cues from the American credit ratings system, this far-reaching program will not only take into account financial standing, loan history, purchasing history, and related aspects of personal life, but it goes one scary step further.
Relationships, gossip, social media presence, and political dissent will factor into this "rating" that each person gets. Just as the American credit rating system allows for the indirect control of unwanted behavior in financial decisions, China is hoping to keep its citizens' political thoughts and government opinions in check to a T. Yes, thought policing in its most acute and tyrannical form.
This is also the same country which still actively blocks Facebook access to nearly all citizens within its borders. It's not hard to believe that Mark Zuckerberg would love to expand his social empire into this untapped market.
And if that potentially means playing by China's rules, would he oblige? Would the SCS get unfettered Big Data taps into Facebook's never-ending hooks it enjoys in its users' lives?
That's a great question, which makes you wonder. Given Mark's recent propensity towards directing intra-company censure on political issues he deems unworthy, where would the Facebook founder put his foot down?
Data Suggests Zuckerberg's #BLM Stance Doesn't Match America's
That Facebook is made up of employees which, just like the rest of society, represent America at large is something which can't be denied. To me, per media coverage afforded Zuckerberg in blanketing those who disagree with the tagline Black Lives Matter, the assumption is being made that Mark is either in the majority viewpoint or that Facebook's staff exists in a vacuum. Both assertions couldn't be further from the truth.
Hence why publicly available data, which has been widely distributed online, is critical in establishing the argument that these workers weren't "fringe" activists in any way. Judging by polling data released, a wide majority of Americans don't see eye to eye with the name or the motives of Black Lives Matter.
Numbers released by Rasmussen last August stated the mood of America at large when it comes to #BLM. An overwhelming 64 percent of interviewed blacks claimed that, contrary to Zuckerberg's beliefs, All Lives Matter, not Black Lives Matter, was the phrase which more closely associated with their views. This sentiment held true with 76 percent of other non-black minority voters, as well as 81 percent of whites.
Even further, a majority, or 45 percent of all those interviewed, believe that the justice system is fair and equal to black and Hispanic Americans. And perhaps most shocking, a resounding 70 percent of voters believe that crime levels in low income, inner city communities is a far bigger issue than police discrimination of minorities.
It's not surprising that inner city crime is so high on the list of concern for average Americans. These death tolls in the inner cities are shoveled on local news segments daily with such frequency that most people are numb to their dire meaning. And most acutely, much of this crime epidemic comes in the form of "Black on Black" crime, as penned by DeWayne Wickham of USA Today.
Wickham says:
While blacks are just 12.6 percent of the nation's population, they're roughly half of people murdered in this country each year. The vast majority of these killings are at the hands of other blacks.
And DeWayne's questioning of the response at large by the #BLM movement continues, addressing their refusal to discuss black on black crime:
Why such a parsing of contempt? Maybe the people who've taken to the streets to protest [Trayvon] Martin's killing don't care as much about the loss of other black lives because those killings don't register on the racial conflict meter. Or maybe they've been numbed by the persistence of black-on-black carnage.
As such, the credibility of the #BLM movement at large continues to dissipate in the eyes of Americans. A follow-up Rasmussen study of 1000 likely voters, done mid-November 2015, follows the public's dismay with the group's approaches and message.
According to the numbers published, by a 2-to-1 margin, voters don't think #BLM supports reforms to ensure all Americans are treated fairly by law enforcement. A further 22 percent of those surveyed just "aren't sure" whether the group truly supports its stated goals.
And on the question of whether blacks and other minorities receive equal treatment by authorities, this number only went down one percentage point from the August 2015 study, to 44 percent, of those who believe this is a true statement.
A full 30 percent of African American voters said that #BLM doesn't support reforms, with another 19 percent not being sure. A sizable 55 percent of whites said the same about #BLM.
While the racial makeup of Facebook's employee base has been mentioned numerous times in media recently, this has little bearing on the nature of whether there was just cause for Zuckerberg to so publicly throw his staffers' political viewpoints into the spotlight and frame them as malicious or metaphorically, racist.
As the numbers above prove, the overwhelming majority of the American public which includes black Americans, consider themselves better represented by All Lives Matter. Why is Zuckerberg's personal will and viewpoint more important than that of not only his coworkers, but more importantly, that of America's? It's a question I just can't find a reasonable answer for.
Let's make this very clear up front: while Zuckerberg framed his wrath in the prism that coworkers were espousing racist feelings by replacing #BLM markings with the more inclusive #ALM alternative, this mischaracterization of the larger issue shouldn't be mistaken. Mark has a personal, vested interest in pushing his own beliefs on that of Facebook workers. This would have never been such a story if he allowed public discourse to occur on its own, just as it does outside the protected walls of Facebook offices.
While scouring the web to try and make sense of how Zuckerberg's interpretation that Black Lives Matter inherently, actually, really means All Lives Matter, I found numerous discussions online trying to pin justifications for how BLM places an inherent importance on raising black deaths on a pedestal -- while being supposedly careful to stay inclusive, as its supporters duplicitously claim.
This roundabout, purposefully misguided framing of what most of America finds to be a divisive name is what naturally gives rational thinkers like myself cause for alarm. Why would these people, including Zuckerberg based on his wild publicized reaction, not prefer the term which Americans' at large say represents them best -- in All Lives Matter?
Some say actions speak louder than words, and BLM has been doubly guilty of doing many deeds which go counter to their stated goals of equality. Take for example the Nashville chapter of BLM's attempt to take a page out of the segregation era, and try to host a color-only meeting of their members at the Nashville Public Library. Mind you, this happens to be a place that is taxpayer supported and as such, open to the entire public, regardless of color.
The Nashville BLM chapter leader, Josh Crutchfield, didn't deny that their branch has this rule. "Only black people as well as non-black people of color are allowed to attend the gatherings. That means white people are excluded from attending".
The chapter, naturally, claimed that the Library's decision came down to white supremacy in the local government. If that reasoning makes any sense to the average person who may support BLM's objectives, I'd love to hear in what manner. That a taxpayer funded establishment couldn't discriminate entrance based on color in the year 2016 is quite a disappointment for Nashville BLM. I'm perhaps more surprised that the media hasn't picked up on this story to a greater degree.
In a similar display of rash white shaming and public berating of innocents bystanders, BLM protestors decided to hold an impromptu rally inside the Dartmouth College library -- with hooting and chanting in tow.
Protesters were reportedly shouting “F– you, you filthy white f–-” “f– you and your comfort” and “f– you, you racist s–". The college newspaper went into detail about the incident and the kinds of abuse that innocent students who had nothing to do with taking an opposition view had to endure.
Is this the movement and approach that Zuckerberg so proudly decided to stand behind from his pulpit? While the rest of America is judging BLM in a lens of totality that takes into account its actions, Mark is seemingly blinded by the idealism he perhaps wishes to establish as Facebook's public policy stance.
To put a crescendo on the discussion about BLM's shortcomings, I found the words of 1960's civil rights activist Barbara Reynolds to provide quite the clarity on the issues at play. She wrote a lengthy op/ed on how BLM has the right cause but absolutely the wrong approach:
At protests today, it is difficult to distinguish legitimate activists from the mob actors who burn and loot. The demonstrations are peppered with hate speech, profanity, and guys with sagging pants that show their underwear. Even if the BLM activists aren’t the ones participating in the boorish language and dress, neither are they condemning it.
If BLM wants to become a serious patron of bearing the message it is trying to convey, it needs to ditch the white shaming, hate rhetoric, and brazen acts of violence. And most importantly, it needs to distance itself from the distasteful actions taken by decent portions of its base. Sitting by idly without denouncing bad behavior being committed in the name of a movement paints the movement at large. Perhaps, only then, would Zuckerberg have a leg to stand on when it comes to upholding the right and just side of history.
BLM, to its likely dismay, also doesn't care that the only African American formerly in this year's presidential race, Ben Carson, happens to agree that All Lives Matter more accurately reflects the sentiment he holds. "Of course all lives matter -- and all lives includes black lives," Mr. Carson said. "And we have to stop submitting to those who want to divide us into all these special interest groups and start thinking about what works for everybody".
Thought Policing Goes Digital in China: A Model for Zuckerberg?
If you're interested in getting a feel for the direction of an organization, or a country for that matter, just look at the stated motives of those in charge. And in this prism, China's goals for the Social Credit System have some overt overlapping with Facebook's own mission statement.
Per the Facebook Investor Relations website, Zuckerberg's corporate intentions for the company are quite simple:
Founded in 2004, Facebook’s mission is to give people the power to share and make the world more open and connected. People use Facebook to stay connected with friends and family, to discover what’s going on in the world, and to share and express what matters to them.
It's interesting, then, to read the stated intentions behind China's proposed SCS, as put forth by the State Council (per New Yorker):
Its intended goals are "establishing the idea of a sincerity culture, and carrying forward sincerity and traditional virtues," and its primary objectives are to raise "the honest mentality and credit levels of the entire society" as well as "the over-all competitiveness of the country," and "stimulating the development of society and the progress of civilization".
The words chosen for each directive's goals are markedly different, but the intersecting junction of their larger motives are quite the same: making the world more connected and better as a whole.
Yet for the cautious outsider, it's not difficult to see why you may connect some logical future dots between Facebook and a state-imposed SCS like China is rolling out in 2020. Per the New Yorker piece on how one Chinese company is molding its variant of a SCS, "Tencent’s credit system goes further, tapping into users’ social networks and mining data about their contacts, for example, in order to determine their social-credit score".
It's no secret that China employs one of the grandest firewalls in the world, blocking its millions of users from "sensitive" topics deemed unhealthy and politically off-limits by the State. Facebook's website sits on this massive blacklist... so far. A little negotiating between Mark and the Chinese authorities may change matters quickly.
The SCS trials are already live in China, with users having access to mobile apps (one shown above) which gamify the rating process. The various tenets of what makes up one's score -- financial dealings, judicial rulings, mutual contacts, political dissent, and more -- are all built into the algorithms being used. There's no secret in the fact that Facebook APIs feeding this data mining machine would be digital gold to the ruling Communist party in suppressing freedom of thought. (Image Source: ComputerWorld)
Is it far fetched to believe China wouldn't give Zuckerberg passage onto the whitelist if they only agreed to allow the eventual SCS to tap into any data point Mark's datacenters can store and organize?
Let's not forget the lengths to which Mark will go in order to disguise goodwill just to gain a few Facebook users. His company was most recently embarrassed when the Internet Free Basics phone service was barred from India and Egypt because of its hypocritical stance on net neutrality. Zuckerberg's vision of connectivity is firmly seated in an experience that puts Facebook front and center, which Internet Free Basics made no effort to hide.
Mark's critics on Internet Free Basics were so fueled up that they penned enough signatures to send an open letter to Zuckerberg -- spanning support from 65 organizations across 35 countries. The crux of the debate which connects the SCS situation to this latest corporate blunder shines a light on one very critical aspect here: that Mark's company will go to great lengths in order to ensure global penetration.
And having Facebook blocked in China is likely a very troubling, omnipresent problem for the company. Any kind of legalized access for Facebook in the mainland would in some way have to allow for their willingness to oblige in the SCS. It simply defies logic to see this reality end up in any other outcome if the two are to become eventual bedfellows.
The more important moral question here is whether Zuckerberg would have any moral dedication to withholding Facebook from China if SCS penetration is demanded in exchange. It's no secret that Mark's obligation to enhance Facebook's bottom line trumps much of his policy direction.
His company is on the forefront of the H-1B visa debate, arguing that more skilled foreign labor is needed to fill talent shortages here in America -- something, as someone myself who employs those in the IT industry, believes is a big fat falsehood. As others have pointed out, the numbers behind the argument don't add up, and Facebook is just disguising a desire for cheap foreign labor in this newly created false argument.
How dangerous could Facebook's cooperation with the SCS in China be? For average Americans, at least on the short term, quite disinteresting honestly. The dictatorship in China will tweak and hone the SCS, sucking Big Data out of the likes of Facebook for years to further repress its own people who choose to express a free political will. That's always been the big untold agreement in Chinese society; you can have a grand Western-style capitalist economy, but don't dare to import any of those democratic free speech principles.
But the larger moral dilemma at hand is how Zuckerberg would use the experiment in China to encroach on Facebook users, or staff, closer to home. The title of this article alludes to the potential rise of corporate Thought Police. Such a reality doesn't seem as far fetched when the technology is almost there to enable it, and bigwigs like Zuckerberg are showing more willingness to push top-down political agendas.

Zuckerberg isn't shy about the kind of society he wants to foster. Giving us Facebook was the beginning, but what does the next step look like? I believe controlling and censoring the medium may be a logical next step. (Image Source: Yahoo News)
And by all means, I'm not the only one pushing alarm to this possible reality. In the wake of Mark's BLM outburst, piece after piece after scathing piece came out against the notion of a Thought Police encroachment by Mark or other social media behemoths.
Such a reality would likely begin with unpublicized cooperation with the state of China in implementing API hooks between Facebook and their SCS. Naturally, Facebook would then have the technical insight into how China culls and acts on the data gathered, but more importantly, a public precedent for such a civil liberty dystopia.
While there is no automated approach to cleansing Facebook's corporate office whiteboards, lessons learned from a potential SCS implementation with China could very well help enact such technology against its own staff Facebook accounts. Eradicating staff discourse which goes against Mark's agreed upon thought positions would allow for testing broader US-based social media censure, and it could be twisted in such a way to promote adherence to Facebook's corporate mission statement.
If trials went well, could we expect a rollout to all Facebook users? Again, if the dots on the above established logic can be considered viable, this wouldn't be far behind.
It's a dangerous dance to imagine; an ironic reality where the supposed leading platform in internet free speech would become the forefront bastion of political censorship and cleansed open discussion.
Here's hoping such a reality never comes to fruition. But if Mark's now public BLM outburst and subsequent staff shaming is any indication, beware a frightening future of social media that becomes curated by topical whitelists dictated by corporate Thought Police.
Dissenting opinion certainly will need not apply.
Headline Image Source: Cult of Mac
 Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.
Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net. -

'Mumblehard' malware turns thousands of Linux servers into spam botnet -- ESET shuts it down
Publié: avril 10, 2016, 5:02am CEST par Brian Fagioli

Linux-based operating systems are rock solid -- reliable and secure -- but not infallible. The Mumblehard malware, for instance, targets servers running the open source kernel, installing a backdoor, and then turning them into part of a powerful spam-focused botnet. Surprisingly, Mumblehard was rather widespread, infecting 4,000 Linux-powered servers.
Of course, had administrators patched the systems appropriately, there is a good chance that some of them would have avoided infection. I say this, because ESET found that some machines were infected through known exploits, in things like WordPress. Thankfully, ESET successfully terminated the botnet on February 29th, 2016 by taking control of the home IP.
"ESET researchers observed a reaction from the operators of the botnet about a month after we published our paper. In our report we mentioned how we had registered a domain name acting as a C&C server for the backdoor component in order to estimate the botnet size and distribution. The malware authors apparently responded by removing the unnecessary domains and IP addresses from the list of C&C servers included in the malware and keeping only the one that was under their control", says ESET.
The security company further says, "with only one IP address acting as the C&C server for the Mumblehard backdoor and no fallback mechanism, a takeover of that IP address would suffice to stop the malicious activities of this botnet. We decided to take action and contacted the relevant authorities to make things happen".
ESET did not act alone, but rather as a collaboration with both the Cyber Police of Ukraine and a company called CyS Centrum LLC. By taking control of the IP address to which the infected machines would connect, they were able to effectively terminate the botnet. It also allowed them to analyze the data being sent using a "sinkhole".
Slowly but surely, fewer machines are pinging the server as they are probably being patched. With that said, other machines are still infected -- the infection is just benign. In theory, if the criminals were to somehow magically regain control of the IP address -- not likely to happen -- the evil could resume.
If you have a fear that your servers are impacted, you should look into cleaning it ASAP. ESET shares the following GitHub landing to learn more about detection here.
Photo credit: Gunnar Assmy / Shutterstock
-

Draft encryption bill could spell the end of privacy and security as we know it
Publié: avril 10, 2016, 12:01am CEST par Mark Wilson

Apple's battle with the FBI has focused the attention of the technology community on encryption. But while just about all of the big players in the tech world backed Apple's refusal to create a backdoor for the FBI into iOS, Congress has a very different idea about how encryption and governmental access to data should be handled. This is perfectly demonstrated by a new bill.
The draft version of the Compliance with Court Orders Act of 2016 -- penned by Senators Diane Feinstein and Richard Burr -- would essentially force all US companies to decrypt data they may have encrypted, or to provide backdoors when asked. It's a bill described variously as 'dangerous', 'encryption-weakening', and 'anti-security', and it starts off aggressivley in stating that "no person or entity is above the law". In effect, it renders the encryption put in place by the likes of WhatsApp completely pointless as, if the bill is passed, companies would have to decrypt data on demand.
Joseph Lorenzo Hall, chief technologist at the Center for Democracy and Technology says that "it's effectively the most anti-crypto bill of all anti-crypto bills" and that it "basically outlaws end-to-end encryption". What is particularly concerning about the bull is that it would force companies to comply with data requests from any court in the country. The draft says:
Notwithstanding any other provision of law and except as provided in paragraph (2) a covered entity that receives a court order from a government for information or data shall --
(A) provide such information or data to such government in an intelligible format; or
(B) provide such technical assistance as is necessary to obtain such information or data in an intelligible format or to achieve the purpose of the court order.
The mention of encryption comes when the bill says:
A covered entity that receives a court order referred to in paragraph (1) (A) shall be responsible for providing data in an intelligible format if such data has been made unintelligible by a feature, product, or service owned, controlled, created, or provided, by the cover entity or by a third party on behalf of the covered entity.
In other words, if the government wants to gain access to data that is encrypted, the company responsible for the hardware or software must either decrypt the data and hand it over, or help with the decryption process. It renders encryption and security -- and, by extension, privacy -- pointless.
The Information Technology and Innovation Foundation (ITIF) argues that the government should be looking to strengthen, not weaken, cybersecurity, saying that "insisting that the government always have a means to decrypt private data would limit innovation in cybersecurity".
This legislation places an unqualified demand on companies to decrypt their customers’ data upon receiving a court order from law enforcement. While companies should comply with lawful requests, it is simply not possible for a company to do so when the customer controls the only keys used to encrypt the data. For example, the popular messaging app WhatsApp, which provides end-to-end encryption on its platform, would not be able to comply with the legislation, unless it modified its system. Yet, the bill explicitly states that it is not authorizing the government to require or prohibit any specific design changes to software or hardware. In short, this bill sets up a legal paradox that would further muddy the waters about how and when the government can compel the private sector to assist in gaining access to private information.
The draft bill is incredibly one-sided, leaving no wriggle room whatsoever for companies or individuals to appeal against data requests. In its current form, once data has been requested, it is as good as belonging to the government.
Amnesty International argues that encryption is a human rights issue:
In the digital age, access to and use of encryption is an enabler of the right to privacy. Because encryption can protect communications from spying, it can help people share their opinion with others without reprisals, access information on the web and organize with others against injustice. Encryption is therefore also an enabler of the rights to freedom of expression, information and opinion, and also has an impact on the rights to freedom of peaceful assembly, association and other human rights. Encryption is a particularly critical tool for human rights defenders, activists and journalists, all of whom rely on it with increasing frequency to protect their security and that of others against unlawful surveillance.
It's hard to argue with the human rights group's stance, and it's impossible to describe the draft bill as anything other than out of touch and unfit for purpose. It's a serious threat to personal security and privacy, and we can expect to see a huge backlash against it.
Photo credit: wk1003mike / Shutterstock
-

Linux can still beat Windows in the desktop war, and Linus Torvalds is 'working on it'
Publié: avril 9, 2016, 11:12pm CEST par Brian Fagioli

About a year ago, I declared Windows 10 was "the final nail in the coffin for the Linux desktop". What I meant by this was not that Linux on the desktop was really dead, but that the Linux community had failed to capitalize on the negative sentiment towards Windows 8x. What I didn't expect at the time, however, was Microsoft's privacy faux pas with Windows 10. While there are more than a quarter billion installs of the latest operating system, plenty of folks have serious concerns about spying.
Maybe Linux has a chance on the desktop after all. Ubuntu is being integrated into Windows 10, and Android seems to be headed towards the desktop. In other words, Linux is making significant moves. Heck, even Linus Torvalds is prepared to keep fighting the good fight, and he declares that he is still "working on it".
According to CIO, Torvalds gave a comment about Linux on the desktop at the Embedded Linux Conference. You can see his quote below.
The desktop hasn't really taken over the world like Linux has in many other areas, but just looking at my own use, my desktop looks so much better than I ever could have imagined. Despite the fact that I'm known for sometimes not being very polite to some of the desktop UI people, because I want to get my work done. Pretty is not my primary thing.
I actually am very happy with the Linux desktop, and I started the project for my own needs, and my needs are very much fulfilled. That's why, to me, it's not a failure. I would obviously love for Linux to take over that world too, but it turns out it's a really hard area to enter. I'm still working on it. It's been 25 years. I can do this for another 25. I'll wear them down.
While Linux has lost many battles to Microsoft on the desktop, the war is not over. Torvalds pledges to dedicate the next 25 years of his life to usurping Windows. Will the open source kernel prove victorious on the desktop? It is totally possible. After all, time is not finite, and even the Roman Empire fell. If you follow history, nothing lasts forever and that should ring true for Microsoft's stranglehold on the desktop.
Still, let's not forget that the computing landscape is changing. Who knows -- in 25 years, the desktop concept itself could be dead. Linux already owns both the mobile and server markets -- maybe the desktop will prove to be inconsequential in the future.
Is Linus Torvalds delusional, or does Linux really have a chance on the desktop? Tell me in the comments.
Photo credit: 3Dalia / Shutterstock
-

Windows 10 Anniversary Edition is due for release in July
Publié: avril 9, 2016, 6:07pm CEST par Mark Wilson

Microsoft's Windows 10 Roadmap for business users reveals that the eagerly-anticipated Windows 10 Anniversary Edition is due to launch in July this year. At Build 2016 earlier in the month, Microsoft said that the big update was due to launch 'this summer', but did not get any more precise than this for the Redstone branch release.
But digging into roadmap documents, Microsoft makes it clear that it is aiming for a July release. The company has said that the update will bring "significant new features", including taskbar badge notifications and a revamped Start menu, but it is when talking about the new features that are coming to Cortana that the date is revealed.
For Windows Insiders on the Fast Ring, the current build 14316 gives a glimpse of some of the new enhancements -- including the arrival of Bash -- but there's much more on the horizon. One of the new capabilities coming to Cortana is the ability to set reminders via pen, and in selling these digital assistant updates to business users Microsoft lets slip the proposed release date:
Cortana is your truly personal digital assistant who works across all your Windows 10 devices to help you get things done. By learning more about you over time, Cortana becomes more useful every day. Cortana helps you be more productive by handling key tasks like sending emails, scheduling events, and using the power of Bing to quickly search your devices, the cloud, or the web. Cortana is also the best digital assistant at reminders, letting you set them in more ways including by pen, and [coming in July 2016] pulling reminder-relevant info from emails so you have the details at hand. And you can instantly capture your ideas by voice just by telling Cortana to take a note.
We don't yet know a precise date, or even if Microsoft is aiming for the beginning or the end of the month, but the company now has just a few weeks to play with. The launch of Windows 10 was plagued with delays, so it will be interesting to see if this release is more timely.
Photo credit: charnsitr / Shutterstock
-

Thrustmaster announces TMX Force Feedback racing wheel for Xbox One and Windows 10
Publié: avril 9, 2016, 3:37am CEST par Brian Fagioli

Illegal street racing is totally dangerous. Quite frankly, not only can you injure or kill yourself, but even worse, you can impact innocent pedestrians. Luckily, if you have the need for speed, video games can give you your racing fix in a safe environment.
Today, Thrustmaster announces the TMX Force Feedback racing wheel for Xbox One and Windows 10 (plus Vista, 7, and 8x). For under $200, you can take your games to the next level with a feedback-focused racing wheel.
"Equipped with a high-performance force feedback motor offering adjustable intensity and a rotation angle ranging from 270° to 900°, the TMX Force Feedback delivers a realistic and versatile racing experience. The controller’s versatility benefits all players, whether beginners or seasoned pilots, with all types of tracks, cars and races", says Thrustmaster.
The company further says, "another example of this racing wheel's versatility is its force feedback motor, designed by Thrustmaster's development teams to offer performance suited to demanding players, while also remaining accessible to less experienced drivers. The motor features a mixed belt-pulley and gears system with metal ball-bearing axle. The result is a balanced combination of performance, robustness and precision. With 12-bit resolution -- i.e. 4096 values on the wheel's steering axis -- provided by an optical sensor, this racing wheel also offers extreme precision, delivering highly realistic racing sensations".
Click to view slideshow.If you are interested in buying this super-cool steering wheel, you can pick it up next month for $199.99. If you want an even greater immersive experience, it is compatible with some of Thrustmaster's pedals (T3PA and T3PA-Pro) and gear shifter (TH8A) too. Keep in mind, those extra accessories are not required -- the TMX Force Feedback racing wheel can operate on its own.
Will you buy it? Tell me in the comments.
-

If you torrent pirate TV shows, prepare to switch to MKV format
Publié: avril 9, 2016, 1:18am CEST par Mark Wilson

Let's not beat around the bush: we know that a lot of you use the likes of the Pirate Bay, KickAssTorrents and the like to grab copies of movies and TV shows. You're probably aware of a number of release groups on the scene, but you might not know that there are fairly strict rules dictating capturing, formatting and naming releases.
This weekend a major change comes into force. Until now MP4 has been the video format of choice, but the change in standards means that this format is being ousted in favor of MKV. There are astoundingly lengthy standards documents covering standard and high definition releases of TV shows, and while the alterations are touted as bringing things up to date, not everyone is happy.
You can browse through the full scene release rules if you feel so inclined, but TorrentFreak has helpfully hosted the revised standards for HD and SD releases. Although compliance with the standards is described as 'optional' many scene groups have already made the switch ahead of the changeover date. The introduction to the document says:
Since the last revision of this document in 2011, TV-X264 has grown and become a major section that many people contribute to and depend on. This new revision aims to update the standards from 2011 to standards suitable for 2016 and the future. Adding clarity and patching loopholes to once again allow for consistent and quality releases, which was the aim of this standard back in 2011.
Compliance with this document is optional as of its pre date, and mandatory as of 2016-04-10 00:00:00 UTC (1460246400 Unix time).
Not everyone is in agreement that MKV is a superior format to MP4, and many casual torrenters have been confused by a sudden switch in format. MKV has long been used as the format of choice for HD movie releases, applying the standards to TV releases -- included SD versions -- could affect, and bewilder, millions of pirates. Some have complained that their preferred media player doesn’t support MKV.
The rules come into play on Sunday 10 April; you have been warned.
Photo credit: Blablo101 / Shutterstock
-

Microsoft releases Project Centennial Desktop App Converter Preview for Windows 10
Publié: avril 8, 2016, 10:43pm CEST par Mark Wilson
At Build 2016 earlier this month, Microsoft talked about Project Centennial and the Desktop App Converter. Part of the company's app drive, the tool has been designed to make it easier for developers to convert legacy apps into Universal Windows Platform (UWP) apps for Windows 10.
This is Microsoft's attempt to get more apps into the Store, making things as easy as possible for devs. Designed to run on the Enterprise and Pro versions of Windows 10 Anniversary Update build 14316 and newer (Redstone), Desktop App Converter is a free tool that can be used to quickly create apps that will run not only on Windows 10 desktops, laptops and tablet, but also phones, HoloLens and Xbox One, taking full advantage of features such as Live Tiles.
Microsoft's Mark LeBlanc introduces the Desktop App Converter Preview in the Windows Dev Center. He describes the tool as being compatible with "Windows 10 Anniversary Update Enterprise edition preview (Build 10.0.14316.0 and later)", but Paul Thurrott says that Microsoft contacted him to say that this is a typo and the Pro version of Windows 10 is also supported.
LeBlanc's post explains a little about the tool and provides instructions for getting started, along with some examples:
Desktop App Converter is a pre-release tool that enables you to bring your existing desktop apps written for .NET 4.6.1 or Win32 to the Universal Windows Platform (UWP). You can run your desktop installers through the converter in an unattended (silent) mode and obtain an AppX package that you can install by using the Add-AppxPackage PowerShell cmdlet on your development machine.
The converter runs the desktop installer in an isolated Windows environment using a clean base image provided as part of the converter download. It captures any registry and file system I/O made by the desktop installer and packages it as part of the output. The converter outputs an AppX with package identity and the ability to call a vast range of WinRT APIs.
True to recent form for Microsoft, Desktop App Converter has a telemetry element to consider:
Desktop App Converter may collect information about you and your use of the software and send this info to Microsoft. You can learn more about Microsoft's data collection and use in the product documentation and in the Microsoft Privacy Statement. You agree to comply with all applicable provisions of the Microsoft Privacy Statement.
By default, telemetry will be enabled for the Desktop App Converter. Add the following registry key to configure telemetry to a desired setting:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DesktopAppConverter- Add or edit the DisableTelemetry value by using a DWORD set to 1.
- To enable telemetry, remove the key or set the value to 0.
You can grab a copy of Desktop App Converter from Microsoft.
Photo credit: omihay / Shutterstock
-

5 common data migration mistakes
Publié: avril 8, 2016, 10:41pm CEST par Deon Stark

Every once in a while you will have to migrate data from one system to another. This could be for reasons of upgrading your systems or for development of infrastructure. When you want to test your new apps during the development process, you will need to use the data that your business has generated. The test data is really hard to access simply because of the migration work. It is hard for the developers to migrate data from the full sandboxes to the developer sandboxes.
It is only left to the imagination how difficult migrating all of your business’ data can be. There are so many mistakes that you are most likely to make during the data migration process. You should beware of these pitfalls and learn how to avoid them. If you fall into them, you are going to spend a huge amount of money and time repairing the errors that they will cause. Here are some of those challenges.
- Failing to Involve Business Users at the Onset
A majority of companies are all about data warehousing nowadays. This involves a lot of consolidation of multiple systems’ information into one. When you are migrating data from one system to another, you need to involve everyone who might be affected by it. Some people will simply need to be notified about the data migration project that is coming and others will have to take an active part in the planning of the project.
- Poor Legacy Data Quality
The data in the legacy system is the one that is being migrated. If it is of poor quality then even the best data migrator might not help you so much. There are data migration tools which might cover up for some errors, but if you have inconsistencies in the legacy system, you will definitely have a problem with the data migration work.
- Wrong Data Migration Tools
There are so many data loaders and migration tools in the market. It is an assurance that you will be completely spoilt for choice. Flosum, for instance, is one of the best tools for migrating data from Salesforce.
- Failure to Test and Validate Data Migration Process
There is always the temptation to test and validate the process after it has been completed. This is just a recipe for disaster. You should do the testing long before you even begin moving the test data. During the pre-migration stage, you should ask yourself questions like how you are going to test the data and who will do the testing and evaluation.
- Absence of Data Governance Policies
Some companies lack data governance policies and for this reason they are unable to figure out how they are going to use the data or manage it. Who has the right to create, edit, approve and remove data from certain systems? Does the business have a process for managing the data’s lifecycle? These are details that you must consider.
Deon Stark works with one of the best remote database administration companies. He also has experience in data migration processes.
Photo Credit: phoelix/Shutterstock
-

EMC wants to sell Documentum
Publié: avril 8, 2016, 9:09pm CEST par Sead Fadilpašić

The EMC-Dell deal never stops to capture headlines, and today is no different. The media have reported that EMC is looking to sell Documentum, its enterprise content management platform.
Documentum was acquired by EMC in December 2003, when it cashed out $1.7 billion for it. The platform is a part of EMC’s Enterprise Content Division (ECD) business unit.
Bloomberg was the first to start reporting how EMC is looking to sell Documentum, although it failed to mention the price. It did, however, said that the company would be very interested in selling software assets Sonicwall and Quest, all together for a price of about $4 billion.
According to multiple media reports, Documentum has an annual turnover of $600 million, and has a 30 percent profit margin. The sources are, according to Bloomberg, very acquainted with the subject matter, but would like to remain anonymous as the discussions aren’t public.
The Dell-EMC merger was announced on October 12, 2015. Back then, Dell announced it would be acquiring the company in a cash-and-stock deal valued at $67 billion. This is the biggest acquisition to ever happen in the tech industry.
However, such a large acquisition has left Dell is significant debt, which is why it is looking to offload non-core assets to mitigate the cost of the merger. According to The Register, Dell’s services business was sold to NTT Data Corporation in March for $3 billion.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

G.SKILL unveils Trident Z DDR4-3600MHz 16GB (2x8GB) CL15 desktop memory kit
Publié: avril 8, 2016, 6:48pm CEST par Brian Fagioli

If you are a PC builder, you know that we are in the middle of a shift to DDR4. While DDR3 is perfectly fine for now -- and the only option for current AMD builds -- DDR4 is certainly the future. Believe it or not, prices for this newer RAM can sometimes be lower than DDR3 at the same capacity.
If you are planning to do a new Intel build, G.SKILL -- a very well-respected manufacturer -- has a new RAM kit that will certainly interest you. This 16GB DDR4 CL15 kit runs at an insane 3600MHz, making it perfect for things like gaming.
"Utilizing specially selected high performance memory components, G.SKILL has continued to improve upon the specifications of DDR4 to maintain a latency of CL15 at 3600MHz, a high frequency that typically could only be achieved with slower latencies. Designed with XMP 2.0 profiles, achieving a highly efficient system is now easier than ever", says G.SKILL.
The company shares stress test results below (click to enlarge).
While pricing is not yet known, G.SKILL promises that the Trident Z DDR4-3600MHz 16GB CL15 desktop memory kit will be available at the end of April. You can buy it from your favorite retailers, such as Newegg and Amazon.
-

Maktub ransomware phishing scam knows your home address and uses it as leverage
Publié: avril 8, 2016, 5:55pm CEST par Mark Wilson

Ransomware is one of the most prevalent security threats at the moment, and each week there are new examples that up the ante a little more. In recent months we have seen cross-platform ransomware, Tesla 4's unbreakable encryption, and the MBR-overwriting antics of PETYA, but a new phishing scam takes another approach.
In a cleverly orchestrated campaign, a phishing scam is doing the rounds whereby malware meets social engineering in a bid to extract cash from victims. It marries together the file-encrypting Maktub ransomware with a thinly-veiled threat -- home addresses. Quoting victims' home addresses to them serves two purposes: it adds a level of authenticity to the phishing email, but also acts as additional leverage by upping the fear level.
Andrew Brandt from security firm Blue Coat explains that victims receive emails informing them that they owe large sums of money to various businesses. To make the phishing scam seem genuine, victims are advised that hard copies of invoices will be sent to their home address -- which is listed in the email -- but a link purports to provide instant access to the documents. Of course, clicking the link is a mistake.
Speaking to the BBC, Brandt said that the speed with which the ransomware strikes is terrifying:
It's incredibly fast and by the time the warning message had appeared on the screen it had already encrypted everything of value on the hard drive -- it happens in seconds.
There have been suggestions that addresses have been gathered from eBay accounts, but this is something that eBay denies. What is clear however, is that quite some thought has been put into this ransomware campaign which is all about getting people to pay up.
As with other instances of ransomware, pressure is put on victims to pay the ransom to decrypt their files sooner rather than later. Pay within three days, Maktub promises, and the fee is 1.4 Bitcoins (around $588), but leave it a while and this increases to 3.9 Bitcoins (around $1638). The ransomware threatens that if it is ignored for more than two weeks encrypted data could be rendered completely unrecoverable.
Photo credit: zsooofija / Shutterstock
-

Outlook gains Evernote, Facebook and Wunderlist integration on Android and iOS
Publié: avril 8, 2016, 5:45pm CEST par Mihăiță Bamburic

Outlook is without a doubt one of the most powerful email apps available on Android and iOS. It supports all the major email providers, works with popular cloud storage services, gives you access to contacts, and integrates your calendars. On top of all this, Outlook is also optimized for use in the enterprise, so it can be a great app for work too.
Microsoft is now making Outlook even better as it launches Calendar Apps. This is a new feature that is designed to give you access to more calendar sources, with Evernote, Facebook and Wunderlist being the first available services.
Microsoft says that you view the tasks, events and notes that you have in Evernote, Facebook and Wunderlist. The aforementioned accounts will be displayed under Calendars, along with the other services, like Outlook.com and Gmail calendars.
 In the case of Evernote, you can view reminders, to-dos and other things, but also edit content by tapping on the Open with Evernote button under the respective event. The popular service has introduced an add-in for Outlook users, which can be used by Outlook.com and Office 365 users running Outlook 2013, Outlook 2016 or Outlook online, according to Evernote's announcement.
In the case of Evernote, you can view reminders, to-dos and other things, but also edit content by tapping on the Open with Evernote button under the respective event. The popular service has introduced an add-in for Outlook users, which can be used by Outlook.com and Office 365 users running Outlook 2013, Outlook 2016 or Outlook online, according to Evernote's announcement.The Facebook integration adds Facebook Events in your Outlook calendar, which will show events that you have been invited to attend and accepted but also your friends' birthdays. Microsoft says that you can RSVP from within Outlook, and open Facebook when you need more information.
As far as Wunderlist goes, when you add it to Outlook the app will show all of your to-dos. As mentioned in the two cases above, you can also open Wunderlist to edit the entries.
If you want to try the app you can grab the Android version here or the iOS version here.
Photo Credit: 60416644/Shutterstock
-

WhatsApp's end-to-end encryption is not all it's cracked up to be
Publié: avril 8, 2016, 4:53pm CEST par Mark Wilson

Just a few days ago, WhatsApp trumpeted the roll out of end-to-end encryption for its messaging service. The world rejoiced. With events such as the battle between Apple and the FBI turning attention to encryption, the announcement was well-timed to ride the crest of the wave. But it seems that for all of the bluster and bravado, the news about extra protection may not be quite as good as it seems.
Analysis of WhatsApp's privacy documentation reveals that the Facebook-owned company retains a huge amount of data about messages that are sent. If this all sounds familiar, it's because the retention of metadata is precisely what the NSA was (is?) up to, trawling web communications and upsetting Edward Snowden and privacy advocates around the world. WhatsApp's encryption and policies mean that those who are concerned about their privacy should not rest on their laurels.
The end-to-end encryption now employed by WhatsApp may mean that it -- and third parties -- do not have access to the contents of messages that are sent, but it does still know a great deal of potentially privacy-invading information about communication. Included in the data that WhatsApp 'may retain' (which, it's fair to assume, can be read as 'does retain') is information about who has communicated with whom, when this communication took place and the intriguingly worded 'any other information which WhatsApp is legally compelled to collect'.
The privacy section of WhatsApp's Terms of Service says:
WhatsApp may retain date and time stamp information associated with successfully delivered messages and the mobile phone numbers involved in the messages, as well as any other information which WhatsApp is legally compelled to collect. Files that are sent through the WhatsApp Service will reside on our servers after delivery for a short period of time, but are deleted and stripped of any identifiable information within a short period of time in accordance with our general retention policies.
The Apple vs FBI case-that-never-was has highlighted the fact that even when encryption is in place, it is certainly no guarantee that data cannot be accessed by law enforcement agencies. WhatsApp's connection with Facebook -- a social network that gathers huge amounts of information about its users not only in the interests of personalization, but also for ad-tailoring -- coupled with the privacy policy will do little to quell the fears of those concerned about snooping into their correspondence. End-to-end encryption is a step in the right direction, but it is far from being the end of the story when it comes to privacy.
Photo credit: Maksim Kabakou / Shutterstock
-

Consumers do not trust Internet of Things
Publié: avril 8, 2016, 4:50pm CEST par Sead Fadilpašić
Even though consumers see tangible benefits of the Internet of Things (IoT) adoption, many have their doubts regarding security, trust and safety, and that could seriously hurt the adoption of the new technology.
Those are the results of a new study conducted by global mobile trade body Mobile Ecosystem Forum (MEF). The Global Consumer Survey asked 5,000 mobile users in eight markets about the future of the connected world.
Globally, 60 percent of consumers are worried about the new technology, especially in the emerging markets such as Brazil, India and South Africa (66 percent). The biggest concerns are trust (62 percent) and security (54 percent), followed by physical safety (27 percent), and not being able to fix the technology (24 percent).
Ten percent said they couldn’t see the benefits of a world filled with IoT devices.
"Whilst this survey shows that consumers are excited about a future connected world, it also clearly identifies the need for the industry to consider how such technology and services are rolled out when it comes to building a trusted relationship with consumers", said Rimma Perelmuter, CEO of MEF.
"The business opportunities surrounding IoT are clear, but only if industry heeds the lessons of the broader mobile ecosystem when it comes to the paramount importance of building consumer trust at the outset. Our 2016 Global Consumer Trust Report demonstrated the demand for transparency in mobile apps and services with 64 percent saying it’s important to be told when an app is collecting and sharing personal information. This new report reaffirms the need for all stakeholders in the ecosystem to take action now to secure a viable future for such technologies".
The full report detailing how consumers perceive IoT can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Stream torrents before they’re fully downloaded with WebTorrent Desktop
Publié: avril 8, 2016, 3:15pm CEST par Mike Williams
There’s nothing new about the idea of streaming torrents before they’ve finished downloading, but WebTorrent Desktop does a better job than most of making that happen.
It’s open source, and installs on Windows, Linux or Mac with minimal hassle. No adware, no browser extensions, no complicated options to consider: just run the installer and it’s finished within seconds.
The interface is equally straightforward. It’s compact, with jargon and text kept to a minimum. And that’s not because it’s hiding any complexities in a multi-tabbed Settings dialog: there aren’t any.
The functions you do get are easy to discover. Move a mouse over the example tile for the movie "Big Buck Bunny", and familiar Play, Download and Close icons appear.
If you still aren’t sure, hovering a mouse over any of these displays an appropriate tooltip.
We clicked Play, a player window appeared, and the movie began streaming in under 5 seconds.
A progress indicator shows which parts of the movie have downloaded so far. Playback was smooth for us, but if your network or torrent peers aren’t delivering the speed you need, hitting Pause may give them time to catch up (and there’s a Download button for viewing later, if all else fails).
Seeking also worked well. If you seek to a part of the movie which hasn’t downloaded yet, WebTorrent simply reprioritizes to read from that point.
Adding your own torrents is as simple as dragging and dropping a .torrent file, or pasting a magnet link.
Support for tracker servers, DHT, peer exchange and WebTorrent helps the program find and connect to peers.
There’s even support for streaming media to AirPlay, Chromecast, and DLNA, apparently, although we didn’t test this.
Put it all together and WebTorrent is a well-designed package, ideal for torrent novices, and anyone else who’d like to see streaming done properly.
WebTorrent Desktop is an open source application for Windows, Linux and Mac.
-

The Internet of Things gets its own day (and lots more Things)
Publié: avril 8, 2016, 3:11pm CEST par Ian Barker
The idea of connected devices is nothing new, the University of Cambridge had a connected coffee pot, to save on trips down the corridor to see if it had finished brewing, as early as 1991.
But as more and more devices go online we've come up with the idea of the Internet of Things. This, apparently, is such a good idea that it also now has its own day on April 9.
To mark this year's Internet of Things Day, electronics supplier RS Components has produced an infographic looking at how the IoT has developed and what it means for our day-to-day lives.
By 2020 it's reckoned that there will be about 13 billion household Things like toasters, fridges, TVs and thermostats connected to the internet. To put that into perspective in 2016 there are around two billion mobile phones online.
There will also be around 3.5 billion Things in Cars online by 2020, 411 million wearables and 646 million Things in Hospital, like heart monitors and body implants. In addition 9.7 billion Things in the Street like traffic lights, parking meters and buildings will be online too.
You can see more detail in the full graphic below, but just remember, a connected Thing is for life not just April 9.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Facebook encourages conversation with Messenger Links and QR-like Messenger Codes
Publié: avril 8, 2016, 1:48pm CEST par Mark Wilson

WhatsApp may have a billion users, but Facebook Messenger isn't far behind: Mark Zuckerberg says "900 million people now use Messenger every month". Nowadays, Facebook is about much more than people sharing pictures of breakfast and bitching about their friends, it's also a valuable tool for businesses.
With this in mind, Facebook is adding a number of features to Facebook Messenger that it says will make it easier for businesses to connect and converse with their customers. Usernames will make it easier for people to identify businesses, while Messenger Links and Messenger Codes (just think QR codes with a fresh lick of paint) are being rolled out to make it quicker and easier to start conversations.
Messenger Links are fairly self-explanatory affairs: a simple URL that people can click to start a Messenger conversation. The URL takes the form m.me/username, and is really an extension of the idea of vanity URLs. In a very similar vein are Messenger Codes. Like QR codes, these are similar to barcodes and can be scanned with a smartphone camera as a shortcut to starting a messenger conversation.
Zuckerberg himself explains Facebook's spin on QR codes:
Messenger Codes let you just pull out your phone and scan someone else's code -- it's the new circular pattern surrounding their profile photo in Messenger settings. Messenger then starts a conversation with them. No more misspelled names or mistyped phone numbers.
As you can see from the image above, Messenger codes are somewhat more attractive and customizable than QR codes. Facebook says that "businesses can use Messenger Links and Messenger Codes in ads, on their website or in any other marketing channel to prompt people to reach out to them directly".
If you don’t see these new features yet, just sit tight as they're rolling out gradually over the coming weeks.
-

How to access Facebook's secret inbox and view messages you never knew you'd received
Publié: avril 8, 2016, 1:09pm CEST par Wayne Williams

Facebook is a great way to keep in touch with friends both past and present. You can post something on another person’s wall, or spark up a chat through Messenger.
For the most part, holding a conversation on the social network is easy. If someone is a friend they’ll be able to send you a private message, and anyone who isn’t currently connected to you will be able to get in touch by sending a message request. But what you probably don’t know is Facebook has a secret inbox which may well contain messages you never even knew you’d been sent.
Accessing the secret inbox is very straightforward but it will depend on what operating system you’re running and which version.
For the web version of Facebook, click on the Messages button at the top of the page, and then click on Message Requests. Clicking on See filtered requests will reveal the hidden inbox and any messages that were sent to you but automatically filtered out of your main inbox by Facebook. This is essentially a spam folder, but will probably contain messages from people you know or pages you’ve liked.
To get to this folder in iOS or Android, open Messenger and tap Settings at the bottom, then tap on People and Message Requests > See filtered requests.
The process for getting here on Android will vary depending on the version of the OS you’re running, but just find People and go from there.
The messages I had in that folder were all from a couple of years ago, but my wife discovered two messages from last year, including one a friend swore she’d sent, but which my wife had never received -- or so she thought.
Photo credit: serafima / Shutterstock
-

IBM teams up with DocuSign to boost cloud services
Publié: avril 8, 2016, 1:01pm CEST par Phoebe Jennelyn Magdirila

Clients of IBM’s software and services will soon be capable of embedding eSignature and Digital Transaction Management through the IT giant’s new strategic global partnership with DocuSign.
DocuSign is working with IBM Cloud -- with a 47-data center footprint -- to provide customers with access to public, private, and hybrid cloud services. DocuSign’s APIs will also be available through Bluemix, which will be key to embedding eSignature and DTM functionalities within IBM’s Cloud platform.
Many of IBM’s 100 MobileFirst for iOS apps -- such as those for the banking, retail and telco industries -- and users of IBM solutions for human resources and Enterprise Content Management will benefit from the partnership.
IBM also plans to collaborate with DocuSign on a range of Business Process Services solutions aimed to help increase accuracy, speed, and compliance for customers in industries such as home mortgage origination and procurement.
"Cloud offers a way for companies to get started with digital in an agile way, quickly delivering tangible value as they step-up to long-term digital transformation. While companies might be moving assets to the cloud or leveraging near-real time technology to gather insights into what their employees worry about, there is an inherent analog issue when it comes to business processes that require authenticated signatures. This transformation is rapidly changing and through this strategic global partnership, IBM and DocuSign intend to help enterprises accelerate this process", said Inhi Cho Suh, general manager, IBM Collaboration Solutions,
Along with the announcement, DocuSign announced that it has experienced a 125 percent year-over-year customer growth in the DocuSign Global Trust Network, which translates to more than 225,000 companies and more than 85 million users with nearly one million transactions per day.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Best Windows apps this week
Publié: avril 8, 2016, 11:22am CEST par Martin Brinkmann
One-hundred and seventy-five in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days.
This week saw the release of several great applications and games including Quantum Break, a Windows 10 exclusive game (also available on Xbox One).
App of the week is Lego Juniors, a free app for children to use Lego to build and drive vehicles.
As always, if I missed an app or game that has been released this week that you believe is particularly good, let me know in the comments below or notify me via email instead.
Discounts This Week
The following discounts are provided by Red Stripe Deals, a weekly changing list of offers, and the Deals Hub application.
Here is this week's selection:
- Daddy was a thief, an action game for $0.99
- File cards: Modern file manager suite, for $1.49
- Sparkle 2, a Zuma-like puzzle game for $2.99
- Media Player Gold, for $5.99
- Abyss, an exploration game for $1.49
- Doodle Tanks, a puzzle game for $1.49
App of the week

The Lego application introduces children age 4 to 7 to Lego. It is part construction game in which you create drivers and vehicles from Lego pieces, and part (basic) racing game, in which you take your newly created ride for a test drive.
You collect Lego pieces while you ride your vehicle and get access to new pieces once you have collected a certain amount. This can be new car parts or new character outfits that you can use in the construction part of the game.
Additionally, you unlock new scenes at the end of each ride that you may encounter during future rides.
It is refreshing that the app comes without in-app purchases or advertisements.
Other apps
The new UWP application enables you to find hotels, make reservations, and check in or out using the application.
You can create a new account and, once you have done so, check the reservation status, look up support hotlines, or find out more about individual hotels.
You can pin hotels to the Start menu, get a map, and call individual hotels.
This official Microsoft application can be installed already but it may not provide any functionality whatsoever currently (it may display 'Coming soon' on start).
It is a new to-do application for Windows 10 that is simple and easy to use.
This is a Frogger-like game in which you try to cross roads using Disney characters.
You can collect coins scattered around the level and may unlock new characters while you are playing the game.
The game is more advanced than Frogger though, as you will not only encounter obstacles on roads, but also some that advance on you directly.
Suto Stream is a universal unofficial Twitch.tv client. It displays top games on start, and a search to find games or channels not listed on the frontpage.
A click on a channel starts playback right away. The app provides you with options to change the stream quality, and to turn off chat.
The game downloads quite a bit of data on start without revealing how much. If you check later on, you will find out that its total installation size is more than 2.2 Gigabytes.
It is a tactical free to play game set in the Avengers universe. You control up to three characters, including Captain America, Thor, Black Widow or The Hulk against enemy cannon fodder and bosses.
Combat is turn-based, and some actions cost character specific action points, for instance Rage if you control the Hulk or Ammo if guns are used by a character.
Characters level up as you play the game, and you find items and other stuff as well. The game makes heavy use of free to play mechanics such as energy that replenishes over time (you need energy to play the game), premium currency to buy new heroes and abilities, and more.
Bandsaround Concerts ($0.99, free trial available)
This is an unofficial Bandsintown application that provides you with a list of concerts in your local area.
Search for artists and bands, track them, and pin pages to the start menu for quick access.
Tibetan Quest is an adventure game in which you journey to the city of Shangri-La to find your missing niece.
The free version of the game is limited, but you can unlock the full version of the game from within.
The adventure game itself falls into the hidden object type where in which you complete mini games to advance.
Send Anywhere is a cloud-based file transfer service that you can use to send files from one device to another.
Unlike the majority of services out there, it does not require that you create an account first before you can start using the service.
To send files add them using the application. This generates a six digit security key that is valid for 10 minutes or 24 hours. To receive the files, enter the security code using the app and the file download will start immediately thereafter.
Gem Well is a free puzzle game in which you throw coins into a well to gain points. The number of coins you can throw is limited, and you need to get a certain number of points by hitting the right spots in each level to proceed.
Notable updates
- The official Dailymotion application got support for video casting in version 6.1.39.0.
- Fhotoroom, a popular image editor is out of beta and released as a UWP app.
- Todoist application (official) is out of beta.
- Windows Camera support for pause and resume in video mode added.
- Word Mobile supports RTF files with the latest update. Another new feature provides you with options to insert images from the camera directly.
-

Microsoft's Hub Keyboard now available on iPhone, iPad
Publié: avril 8, 2016, 11:22am CEST par Wayne Williams
Microsoft continues to bring out apps for rival mobile operating systems that aren’t available for Windows Phone.
Its Hub Keyboard, which was first released for Android back in February, is now available for iOS and makes it easy to access content from other apps. It also offers Office 365 integration.
Installing Hub Keyboard is the same as installing other keyboards on iOS. Navigate to Settings > General > Keyboards > Add New Keyboard, and select Hub from the list.
Microsoft describes the new app like this:
Isn’t it painful to switch between apps just to complete your routine on-the-go tasks?
Hub Keyboard, a Microsoft Garage project, lets you stay in context by bringing information from different services to your fingertips and help complete your tasks faster. Sign in with your Office 365 work or school account to unlock access to more information.You can use it to access docs and contacts straight from the keyboard, as well as most recently used content. You can also search for what you need.
Hub Keyboard is currently available in English for the US and UK markets but Microsoft is working on adding more languages and countries.
Download Microsoft Hub Keyboard from the App Store for free.
-

Why it's vital for retailers to have a mobile strategy [Q&A]
Publié: avril 8, 2016, 10:57am CEST par Ian Barker

We already know that having a mobile friendly site is important to search rankings, and with Google's announcement in March that it will start to rank mobile-ready sites even higher, companies are likely to focus even more on the mobile experience.
It's particularly important for retailers to connect with millennial shoppers who are more likely to research or buy using their mobile devices. We spoke to Aaron Shook, executive software architect of digital transformation specialist PointSource, to find out why a mobile strategy and good design are key to success.
BN: How important is it for shopping sites to deliver a positive mobile experience?
AKS: Very. Not only does mobile friendliness now affect SEO holistically (desktop included), but it also is a huge driver in determining mobile conversion rate and overall traffic numbers. A poor mobile user experience will send users directly to competitors who offer better experiences on the customer's device.
BN: Does a move towards more mobile friendly sites risk alienating older users?
AKS: No. E-comm sites can be mobile friendly without being flashy. Mobile friendliness simply means that you cater to the device that your user is viewing your page on; older users have a similar need for mobile pages to be easily viewable when using mobile devices. Design differences around flashiness, button sizes, etc. can be driven by analyzing your user demographics, but mobile friendliness is a must regardless of age group.
BN: Are we seeing a trend towards accessing retails sites using apps rather than browsers and what impact does this have?
AKS: For every-day retail shopping, I don't think that retail-branded apps will outpace mobile web in the foreseeable future. When users have simple purchases to make, their go-to is still going to be a web browser rather than downloading a retail-specific app. That said, apps are very valuable because they allow retailers to occupy real estate on users' phones and thus every day lives and continually engage the user. The most loyal customers who are spending the most with your brand are also the ones who will keep brand-specific apps installed, so providing these customers with additional value-adds through an app to reward them for loyalty is definitely a revenue driver. A solid mobile strategy needs to account for both mobile web and apps.
BN: How can mobile be used to enhance the physical in-store experience?
AKS: Newer technologies are making it possible to track user journeys through stores in ways that we couldn't have imagined prior to smartphones. Beacon technologies can allow retailers to track user movements through the store in order to optimize shopping patterns, send promotions, and gain a firm understanding of the user journey in a brick-and-mortar setting.
BN: Surveys have shown that surfers visit fewer pages of a site on mobile devices than they do on desktops. How can retailers adapt to this?
AKS: Our belief is that a big part of the reason for this pattern is twofold, and the reasons are heavily intertwined. Firstly users often pull out mobile phones to research a specific item rather than to browse e-comm storefronts since browsing is easier on a desktop device. Second, user experiences on retail mobile sites are still not up to par with desktop experiences, making it more difficult to shop on the majority of sites. We've seen huge gains in overall traffic, page views per user, average usage time, etc. by designing mobile websites with experiences specifically catering to the needs of mobile users. Designing an experience specifically for your mobile users is a must in order to truly unlock an e-comm mobile site's full potential.
BN: Will we see numbers of mobile shoppers continuing to increase or are we reaching a plateau?
AKS: Numbers continue to rise and don't show signs of stopping any time soon. 2015's holiday period mobile numbers set record numbers for mobile across the board, as did 2014, 2013, and so on. While 2013 and 2014 mobile transaction numbers were still relatively low compared to desktop counterparts, 2015 saw a rise of customers checking out and completing purchases on mobile. According to IBM, more than 36 percent of e-commerce sales during the 2015 holiday period took place on mobile devices, up from 27 percent the year before. The numbers may eventually plateau, but we are not anywhere close to that point yet.
Image Credit: Slavoljub Pantelic / Shutterstock
-

Global IT spending will reach $3.49 trillion in 2016
Publié: avril 8, 2016, 10:33am CEST par Sead Fadilpašić

IT spending, worldwide, will decline 0.5 percent this year, Gartner forecasts. The market analyst firm says this year’s forecast totals $3.49 trillion, down from $3.50 trillion which were spent in 2015. Last quarter’s forecast was 0.5 percent growth, and these new changes are mainly due to currency fluctuations, Gartner says.
"There is an undercurrent of economic uncertainty that is driving organizations to tighten their belts, and IT spending is one of the casualties", said John-David Lovelock, research vice president at Gartner. "Concurrently, the need to invest in IT to support digital business is more urgent than ever. Business leaders know that they need to become digital businesses or face irrelevance in a digital world. To make that happen, leaders are engaging in tough cost optimization efforts in some areas to fund digital business in others".
Device markets (PCs, laptops, ultramobiles, mobile phones, tablets and printers) will continue to shrink, and sales will continue to drop this year. At the same time, the spending on data centers and enterprise software will continue to grow.
The device market is forecast to decline 3.7 percent. "The underlying reasons are a combination of factors and are geography-specific, and the worsening economic conditions in many countries only serve to amplify the impact of these factors", Gartner says in the press release.
Spending on data centers will reach $175 billion in 2016, representing a 2.1 percent increase, compared to a year before. Spending on enterprise software is expected to hit $321 billion globally this year, a 4.2 percent increase from 2015.
The full Gartner report can be found on this link.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: beeboys / Shutterstock
-

Microsoft Translator for iOS gets offline language support and new Safari extension
Publié: avril 8, 2016, 2:52am CEST par Brian Fagioli
While learning a second language is probably very rewarding -- I wouldn't know -- it is becoming less necessary. Thanks to technology, people can easily translate languages while on the go with a smartphone or tablet. The problem? Many translator apps require an internet connection. This is a problem, as many people need these apps when traveling abroad, where they may not have a data connection.
Today, Microsoft updates its Translator app for iPhone, iPad and iPod touch making it infinitely more useful for those traveling without data. In addition, the app is getting a new Safari extension, so users can easily translate webpages when needed.
"Until now, iPhone users needed an Internet connection if they wanted to translate on their mobile devices. Now, by downloading the Microsoft Translator app and the needed offline language packs, iOS users can get near online-quality translations even when they are not connected to the Internet. This means no expensive roaming charges or not being able to communicate when a data connection is spotty or unavailable", says Microsoft.
If you want to take advantage of the offline packs, you can get them for the following languages.
Arabic Greek Romanian Bosnian Hebrew Russian Bulgarian Hindi Serbian Catalan Hungarian Slovak Chinese Simplified Indonesian Slovenian Chinese Traditional Italian Spanish Croatian Japanese Swedish Czech Korean Thai Danish Latvian Turkish Dutch Lithuanian Ukrainian Estonian Malay Urdu Filipino Norwegian Vietnamese Finnish Persian Welsh French Polish German Portuguese The next time you travel to a foreign country, you should download the appropriate language pack in advance. Then, when you go out exploring and sightseeing, you will be prepared to communicate with the locals.
READ MORE: Microsoft releases more details on its Edge Translator extension
When you do have a data connection, and need to translate a webpage, the app is gaining that functionality too. The Windows-maker further says, "in addition to the new downloadable offline language packs, this update to the Microsoft Translator app for iOS includes a new Safari extension which lets users translate web pages within their Safari browser. After you have turned your extension on, whenever you find yourself on a webpage in a language you don't understand, just click on 'Microsoft Translator' from your list of available extensions and it will be translated automatically".
If you want to try the app, you can get it here. If you download it, tell me what you think in the comments.
-

Microsoft bangs another nail in Adobe Flash's coffin with a big change to Edge
Publié: avril 7, 2016, 8:38pm CEST par Wayne Williams

Flash is not as integral to the web as it once was, but it’s still required for some content, despite being a huge security nightmare.
Microsoft, like Google and Mozilla, wants to hasten the transition away from Flash to a more modern, standards based web, and so plans to make a big change to Edge in the forthcoming Anniversary Update to Windows 10.
SEE ALSO: Windows 10 Insider Preview Build 14316 arrives on the Fast ring -- packed with exciting new features
According to John Hazen, Principal Program Manager Lead, Microsoft Edge, the future build of Microsoft’s new browser will "intelligently auto-pause content that is not central to the web page".
Essentially, what this means is any vital Flash content -- like video and games -- will play as normal, but "peripheral content", like Flash animations and ads, will be automatically paused. If you want to activate them you can, but it will be your choice.
Taking this action will, Hazen observes, significantly reduce power consumption and improve performance, while preserving the fidelity of the page.
Pausing non-essential Flash content is just the start for Microsoft. The software giant intends to roll out additional controls in the future, offering users complete control over all Flash content.
"We are planning for and look forward to a future where Flash is no longer necessary as a default experience in Microsoft Edge", says Hazen. And, for most web users, that day couldn’t come soon enough.
Photo credit: WilleeCole Photography / Shutterstock
-

The FBI vs Apple fight is not over
Publié: avril 7, 2016, 8:03pm CEST par Brian Spector

The recent furore between Apple and the FBI over access to the San Bernadino shooter’s iPhone brought privacy debates firmly into the public eye. Despite tech giants, politicians and privacy campaigners explaining the potential ramifications of the case, many people remained on the fence.
A recent survey by the Pew Research Centre found that the majority of Americans sided with the FBI and believe that Apple should have complied with its demands. I find this deeply concerning because it shows how easily our collective privacy could be eroded in the name of national security, and also how little most people seem to understand the encryption technologies which protect us all.
As the UN high commissioner for human rights explained recently, encryption is vital to freedom of expression and opinion, and without it, lives may be endangered. Currently, the only way to communicate securely online is to encrypt everything, so that even if your data were to be accessed by someone else, it would remain private. But any process that weakens the mathematical models used to encrypt data will make the whole system less secure, because it will also weaken the protection.
In the Apple case, the FBI suggested that it could manipulate security in such a way that only it could take advantage of that subversion, but this is wrong. This is why Apple talked of the San Bernadino case setting a dangerous precedent. While it is possible to create an entirely new operating system which undermines the iPhone security features, there is no way to guarantee that this could not one day be used by someone other than the FBI. There is no way to determine when an attacker could discover a vulnerability, and once accessed, exploit it to harm anyone using that connected device, service or system.
The same vulnerabilities used by intelligence agencies to spy on global citizens can also be used by criminals to steal your passwords. We either enable spying -- by either governments or hackers -- or we defend against it. Backdoors will be exploited by anyone, not just the US government.
Just like the Snooper’s Charter proposals in the UK, these demands also force tech companies to make a difficult ethical decision. How can you tell your customers that your products are secure, but also knowingly compromise that security by building backdoors, weakening encryption and storing personal data on a huge scale? Complying with this kind of warrant equates to a catastrophic invasion of customers’ privacy, and has historically required tech companies to collude with the Government and then essentially lie about it to their customers by not disclosing it to them.
The Snowden leaks revealed how the National Security Agency in the United States convinced Microsoft to make changes to security on its Skype program to make it easier for the NSA to eavesdrop on conversations. We also know from the Snowden leaks that the NSA subverted a government standards process to be able to break encryption more easily. Leaked documents revealed that the agency planted vulnerabilities in a cryptographic standard adopted in 2006 -- effectively inserting a backdoor by writing a flaw into a random-number generator which made it easier to unscramble numbers generated by that algorithm and crack technologies using the specification.
These kind of scandals don’t just damage the products and technologies in question, but threaten to damage trust in the Internet entirely. Internet governance was historically left largely to the United States because most people assumed that they were focused on ensuring the security of the Internet, rather than using it as a means of surveillance. The Snowden revelations quashed that belief, and the system is now in turmoil. Some of the potential applications of the Internet that would benefit citizens and entrepreneurs have already been stymied by unresolved trust issues. E-voting has stalled and migration to the cloud is suffering.
For the Internet to continue to grow and flourish, we need to reestablish the foundation for trust, and convince users that the systems they use online are not being used as a means to spy on them. This is no doubt why Apple is planning to hand over iCloud encryption key management to its users. Going a step further, advances in pairing-based cryptography will soon allow a private key to be split into several different parts, eliminating the single point of failure that currently exists. This means that governments wanting to access that key for surveillance purposes would have to fight across multiple different legal jurisdictions in order to gain access.
Even better, individual organizations may soon be able to choose how their root key would be split, empowering them to choose geographies which they feel are least likely to allow Government access. These kind of changes put power back into the hands of the individual and give users valuable new tools in the fight to keep our data secure.
Now that the FBI has dropped its court case against Apple, many will assume that the case is over. But there are no winners here, and a long battle over our collective privacy lies ahead. We all own the Internet, and we need to fix it together.
Brian Spector, CEO, MIRACL
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Junial Enterprises / Shutterstock
-

Pfizer and IBM using Internet of Things for Parkinson's Disease project
Publié: avril 7, 2016, 6:44pm CEST par Brian Fagioli

While life can be a glorious thing, there are many scourges that can make it more difficult. Between things like cancer and heart disease, it can be impossible to get through the minefield of life unscathed. Unfortunately, there are many more health risks out there than just those two aforementioned examples.
One particularly heartbreaking condition is Parkinson's Disease. While many people have the affliction, Michael J. Fox is one person that comes to mind when discussing it. The disease causes him, an others, to lose body control, making day-to-day activities a tiring chore. Today, Pfizer announces that it is partnering with IBM to focus on improving Parkinson's Disease care by using the Internert of Things.
"Parkinson's disease in particular requires ongoing adjustment to medication depending on the progression of the disease and response of the patient. The collaboration seeks to create a holistic view of a patient's well-being by seeking to accurately measure a variety of health indicators, including motor function, dyskinesia, cognition, sleep and daily activities such as grooming, dressing and eating. Insights from these data could help clinicians understand the effect of a patient’s medication as the disease progresses, enabling them to help optimize the patient’s treatment regimen as needed. Data generated through the system could also arm researchers with the insights and real-world evidence needed to help accelerate potential new and better therapies", says Pfizer.
Arvind Krishna, Senior Vice President and Director of IBM Research explains, "with the proliferation of digital health information, one area that remains elusive is the collection of real-time physiological data to support disease management. We are testing ways to create a system that passively collects data with little to no burden on the patient, and to provide doctors and researchers with objective, real-time insights that we believe could fundamentally change the way patients are monitored and treated".
[mms.businesswire.com]While a cure for the disease would be great -- and hopefully discovered one day -- making sure existing sufferers have optimal care is important too. This collaboration could forever change the care that Parkinson's Disease patients receive.
Living with Parkinson's is hard, but these people have friends, family, and lives to live -- the diagnosis is not a death sentence. IBM and Pfizer are using the IoT to potentially provider a better quality of life for existing patients, and future ones too. That is awesome.
Are you excited to see the IoT being used to improve humanity? Tell me in the comments.
-

Apple could soon censor swearing in your music collection
Publié: avril 7, 2016, 6:05pm CEST par Wayne Williams

As the parent of a young child I often have to give some serious thought as to what music I play in the car when she’s with me, in order to avoid accidentally exposing her to a song peppered with swear words.
This problem could soon become a thing of the past however, as Apple has patented a method of using software to automatically censor swearing in music and audio books.
The patent, titled "Management, Replacement and Removal of Explicit Lyrics during Audio Playback" was filed by Apple in September 2014 and granted last week. The system works by identifying offensive words in audio and replacing them with alternative sounds -- bleeps for example -- or silence.
As well as censoring explicit songs and audio books, the technique could also be used in YouTube videos.
iPads are very popular with children and it’s easy to see how teachers and parents could benefit from such a system.
Apple files a lot of patents, many of which never amount to anything, but there’s a good chance we’ll see something that uses this censoring technique in the near future.
-

For $500 you could look through your competitor's email
Publié: avril 7, 2016, 5:37pm CEST par Sead Fadilpašić

So you want to snoop through your competition’s email? Yeah, we can make that happen, but it’ll cost ya! How much? You’d be surprised. Secure Works’ researchers have dug deep into a popular cyber-crime forum to find out how much it costs to hire a hacker to do your dirty work, and the results, somewhat surprising, have been published in the Secure Works report.
Apparently, the luxury of reading your competitor’s email will cost you $500 (£353). To make things even better, the hacker will not change the email’s password or anything, so it will be pretty darn hard for the victim to realize they're being spied upon.
And if you’re interested in someone’s social media account, or private emails such as Gmail, Hotmail, Yahoo!, that’s gonna cost even less -- a stunning $129 (£91).
Despite these surprisingly low prices, and I’ll show you some more below, the researchers say that hackers have also developed a sense of entrepreneurship:
"Prices and goods are not the only way sellers are distinguishing themselves. There also continues to be a focus on salesmanship. Compared to the report last year, our security experts noted this time around that many hackers were expanding their working hours to include weekends and even promising to be available 24 hours a day", the report says.
Credit cards are also quite popular -- American Visa can be bought for $7, while Visa Classic and MasterCard will set you back $15. Asian cards (Visa Classic and MasterCard Standard for Japan and Asia) with Track 1 and Track 2 data cost $50.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: phadventure / Shutterstock
-

Eagle Mode: not your average file manager
Publié: avril 7, 2016, 4:15pm CEST par Mike Williams
Tired of Windows Explorer? There are alternatives around, but most use a very similar core interface with a few extras bolted on.
Eagle Mode is more imaginative. There’s no folder tree, no file pane, in fact it doesn’t look much like a file manager at all. Until you begin to explore…
The program starts by displaying a series of panels. The largest represents your user profile directory, and there are others for each of your drives.
To navigate, all you have to do is move the mouse cursor over a panel, and spin the mouse wheel to zoom in.
If you’re zooming in on drive D, for instance, you’ll see more panels appear representing its folders. To zoom into a folder, move the mouse cursor over it, and spin the mouse wheel again, then repeat the process to get wherever you’re going.
This isn’t just about boxes getting larger or smaller. As you zoom into a folder, any files appear. At first you might just see the name or size, then attributes and owners, and if you zoom on some file types you’ll get a preview (image thumbnails, text). The transitions from one stage to another are all very smooth, even on low-powered machines.
There are lots of actions available for the objects you’re viewing. At its simplest, double-clicking a file launches it or opens it in the default viewer, while double-clicking a folder opens a command window at that location.
The toolbar offers more options, but the default button size is so small that we couldn’t see what they were. But fortunately the zoom interface works here, too: just spin the mouse wheel over the toolbar to zoom in.
File Manager actions available include Copy, Move, Clone, Exchange, Rename, Delete, Pack and Unpack. And you get entirely unrelated extras like an analogue clock and a chess game.
This can feel confusing, at least initially, as it’s so very different to other file managers. Even something simple like panning across our files took time to figure out. Left-click drag, right-click drag, cursor keys, none of those worked: it turns out you have to drag with the mouse button held down.
More seriously, Eagle Mode doesn’t support Explorer’s right-click menu, so there’s no way to use or access whatever shell extensions your other applications have installed.
Would Eagle Mode replace Explorer for us? No. But will we keep it around, use it some of the time? Maybe. The innovative interface looks good, is well-implemented and easy to use, and it’s also surprisingly flexible (be sure to read the help for some tips). Take a look.
Eagle Mode is an open source application for Windows XP+ and Linux.
-

Startup company launches solution to protect connected cars from cyber attacks
Publié: avril 7, 2016, 3:33pm CEST par Ian Barker

In our increasingly connected world it isn't just your computer or smartphone that can fall victim to attack. The Internet of Things is producing a whole new generation of vulnerable devices.
Not least of these are connected cars where attackers can potentially infiltrate and take control over car systems, even killing the engine as you drive.
A new Israeli startup company Karamba Security has produced a purpose-built ECU solution that protects a car's externally connected components. It can identify attack attempts and block exploits from infiltrating the car's network to ensure drivers' safety.
Security detection and enforcement capabilities can be embedded directly on the ECU to ensure only explicitly allowed code and applications can be loaded and run on the controller. Karamba blocks any foreign code, which means the controller is safe from attackers, regardless of how they entered (via the internet, USB drive, service port, etc), with no false alarms.
"Customers have been very excited about our ECU endpoint approach," says Ami Dotan, CEO of Karamba Security. "By stopping attacks at the ECU, attackers can't make it inside the car's network, which means the car's ongoing operations are safe. Our early warning and malware prevention capabilities allow car companies to provide drivers smart vehicles that will get them where they want to go, safely."
The solution can be used to protect existing as well as new cars, manufacturers are able to retro fit protection to older models as part of an ECU software update.
Karamba has received $2.5 million in seed funding from YL Ventures and from the GlenRock private investment company. "We were impressed with Karamba's unique focus on developing an unobtrusive solution to the cybersecurity problems of the automotive industry," says Yoav Leitersdorf, managing partner of YL Ventures. "The experience of the team gave us confidence they could take a unique, shrink wrapped, approach and make it a reality."
You can find out more about the risks and how Karamba's protection works on the company's website.
Photo Credit: ssguy/Shutterstock
-

Reddit launches official Android and iOS apps
Publié: avril 7, 2016, 3:29pm CEST par Mihăiță Bamburic
Reddit has evolved into one of the most popular websites in the world but, despite its success, the self-titled "front page of the Internet" never released an official app. So, over the years, users have turned to third-party clients, one of which -- Alien Blue -- Reddit actually bought two years ago. Now though users are finally getting the real deal.
Reddit has finally launched official apps for Android and iOS. They come with support for inline images and themes, and promise "simpler navigation", and more. Here is what else you can expect.
At first glance, the apps are nicely designed. They appear to offer a similar user experience on Android and iOS, with only a few differences in appearance separating them. Both will let you browse content, upvote, talk to other Redditors, comment, share content, and more.
As far as theme support goes, Reddit offers a dark theme, with more promised to arrive. There are customization options available in the apps, to change how content is displayed, more specifically in a compact or card view.
Worth noting is that the apps may have limited market support at this time. The Android app is listed as being incompatible with all of my devices. I do not have the same problem with the iOS app, though I am using a US account with iTunes whereas my Google Play account is registered with a country on the old continent.
If you want to grab the new Reddit apps, click here for Android and here for iOS.
-

Basic API security measures are often overlooked
Publié: avril 7, 2016, 2:58pm CEST par Ian Barker

APIs are the glue that holds much of the digital world together, connecting systems, apps and data. But a new survey reveals that many organizations are failing to place enough emphasis on API security.
Research company Ovum in partnership with bot detection and mitigation firm Distil Networks, surveyed 100 IT and security professionals. They found that 30 percent of APIs are planned out with no input from the IT security team and 27 percent of APIs proceed through the development stage without the IT security team weighing in.
Other findings include that 87 percent of respondents were running an API management platform, with 63 percent using a platform developed in-house. However, rate limiting, considered to be a basic API security practice, was employed by less than half of respondents.
Of those surveyed 53 percent feel security teams should be responsible for API security, while 47 percent think the developer teams should hold responsibility.
It's clear that APIs have taken hold, with 20 percent of respondents saying they're maintaining, building, or publishing more than 50, while at the other end of the scale, 32 percent are working on between one and 10. The remainder are running somewhere between 11 and 50 APIs, but Ovum expects to see the number grow over the next few years.
A significant proportion are using public APIs that are exposed to developers outside their own companies. 51 percent say that at least part of the rationale for their APIs was to enable an external developer community/ecosystem, while 67 percent say that partner connectivity is a driving factor.
The report's authors note, "Our survey finds that most respondents are at least concerned with the issue of API security, which is as it should be. Furthermore, most of them are using some form of API management platform, and the majority of platforms in use provide some level of security capability. However, there is by no means blanket coverage of all aspects of API security by all platforms."
You can read more about the findings on the Distil Networks site.
Image Credit: Profit_Image / Shutterstock
-

Internet of Things is now mainstream, Verizon says
Publié: avril 7, 2016, 2:56pm CEST par Anthony Spadafora

According to a new report released by Verizon, the Internet of Things is now mainstream. The report, titled State of the Market: Internet of Things (IoT), used the company’s customer usage data, research from Oxford Economics, customer case studies, and third party data to come to its conclusion in regard to the future of IoT.
Verizon’s experts see the combination of five macrotrends as the catalyst behind the IoT finally being embraced by consumers and businesses.
Smartphones have become a staple of modern life and now users are beginning to suspect that their phones are capable of doing a whole lot more. Verizon expects in the next three to five years that a higher level of automation will be present in the lives of all smartphone users. IoT applications and a simplified interface will allow this to take place. Currently, 81 percent of IoT adopters working in the public sector believe that citizens are growing to expect enhanced services and data from the Internet of Things.
The ability to monetize the use of data will be a requirement for businesses going forward. Almost 50 percent of businesses expect to use over 25 percent of their data over the course of the next two to three years. Data analytics will need to evolve to be more predictive in order for companies to gain meaningful insights to benefit their customers. Verizon also sees the regulatory landscape shifting to help establish industry standards at a much quicker pace.
The company’s experts see better network connectivity, low power devices and IoT platforms as a means of democratizing innovation. This will lead to the creation of more tools for developers as well as the creation of an environment that will let business scale the deployments of their IoT solutions from millions to billions of connections in a way that is cost-efficient and facilitates growth.
Growth in the IoT sector is being pushed by IoT startups who are now gaining investments faster than traditional consumer startup companies by 75 percent. Verizon predicts that enterprise IoT startups will be able to raise two to three times more capital than consumer focused IoT startups.
The Internet of Things had a big year in 2015 with new innovations and products dazzling businesses and investors. Perhaps 2016 will be the year that IoT gains the attention of the masses.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

New platform streamlines enterprise software deployment
Publié: avril 7, 2016, 2:00pm CEST par Ian Barker

Modern software is often complex, perhaps running services on multiple machines. This can make deployments complex and prone to errors.
Software deployment specialist Puppet Labs is launching the latest version of its Puppet Enterprise platform which gives development teams control over and insight into the changes they want to push out.
At the same time the company is launching a software operations platform called Blueshift. It engages with products like Docker to give organizations the tools they need to build and operate modern software.
"We're driven by a belief that software can make people more powerful," says Luke Kanies, founder and CEO of Puppet. "To make that a reality, we're focused on building the standard platform for automating delivery and operation of the software that powers everything around us. Puppet gives organizations a common language to deliver and operate modern infrastructure and to adopt whatever comes next -- simply, securely, and consistently".
Puppet makes it possible to push out any change on demand and manage ordered deployments of applications and infrastructure. It's also possible to possible to schedule change in a specific time window, and push change through tools like HipChat, Git, Jenkins or directly with Puppet Enterprise.
Operators gain visibility into deployments and can manage them as required. Thanks to an an interactive dependency graph, teams can visualize dependencies across all the resources they manage with Puppet.
There's also integration with the Splunk operational intelligence platform. This allows users to analyze their infrastructure and get performance metrics for Puppet Enterprise services with data sent direct to Splunk Enterprise.
You can find out more on the Puppet Labs website.
Image Credit: Rafal Olechowski / Shutterstock
-

FBI briefs senator about how it cracked San Bernardino iPhone, but keeps Apple in the dark
Publié: avril 7, 2016, 1:37pm CEST par Mark Wilson

It turned the case of the century in to the case that didn’t really happen. The battle between Apple and the FBI came to a sudden end last month when the US Justice Department said it didn’t need the iPhone manufacturer's help, and then successfully hacked its way into the iPhone in question.
With the San Bernardino shooter's iPhone seemingly successfully cracked, the FBI last night revealed to Senator Dianne Feinstein just how it managed it. There are no current plans to share this information with Apple, but FBI Director James Comey revealed that the tool that was brought in only works on the iPhone 5c.
Apple will almost certainly be disappointed that the FBI is choosing not to share the cracking method, but it's not yet clear whether the company plans to take legal action to obtain this information. The fact that Comey has said the method will not work on the iPhone 5s or iPhone 6 will come as some comfort to those concerned about security and privacy, but Apple will be keen to patch any vulnerabilities exploited by the FBI so that other parties may be prevented from using the same technique to access different iPhone 5c handsets.
As reported by the National Journal, speaking at Kenyon College's Center for the Study of American Democracy last night, Comey said "we just haven't decided yet" in reference to coming clean with Apple. The agency has not said whether or not it managed to garner any useful information from the phone by hacking into it, saying:
We're still working on that, I guess is the answer. It was worth the fight to make sure that we have turned over every rock that we can with respect to the investigation. We owe it to the victims and the families to make sure that we pursue every logical lead.
It's not clear what happens next. There is unspoken, and spoken, pressure on the FBI to reveal all to Apple, and iPhone users will be keen for the company to pursue this in the interests of their security. With the incredible public interest not just in this case specifically, but also privacy, security and encryption more generally, Apple will also be feeling the pressure from its customers, particularly in light of Tim Cook's proclamations of fighting for its user base.
Photo Credit: Shutterstock/ymgerman
-

Nvidia announces Pascal-powered Tesla P100 GPU
Publié: avril 7, 2016, 10:44am CEST par Anthony Spadafora

Nvidia has just announced a new GPU platform called the Tesla P100. However this new GPU is not intended for gamers, but rather for hyperscale datacenter applications.
The Tesla P100 platform will include the company’s Pascal GPU architecture along with the newest memory, semiconductor process and packaging technology to allow for the best graphical and computing experience from such a densely packed card.
Nvidia will be manufacturing the chip using 16nm FinFET manufacturing technology. The Tesla P100’s chip will have over 15 billion transistors and will include 16GB of second generation die stacked High Bandwidth Memory (HBM2). Nvidia has made it easy to link multiple P100 GPUs using its NVLink technology.
The company also unveiled the DGX1 which is a full server appliance platform that combines the power of eight Tesla P100 GPUs with two Intel Xeon Processors in 3U chassis that can easily be mounted in a server rack. The system will require 3500W of power and will cost $129,000 but with the high price tag comes 170 teraflops of performance.
The DGX1 will offer developers and researchers the necessary power to achieve new milestones in the deep learning projects that will pave the way for the future of AI applications. The system will be available directly from Nvidia in May.
Nvidia is widely know as a provider of GPUs for gaming PCs but the announcement of the Tesla P100, the DGX1 and its work in self-driving cars could have a real impact in reshaping what the company is known for.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Newegg bolsters its customer service with Facebook Messenger
Publié: avril 7, 2016, 7:27am CEST par Brian Fagioli
As a PC builder, Newegg is a website on which I spend a lot of time. Not only does this online retailer offer great prices, reliable customer service, and a large amount of available products, but it is a great resource for learning too. Even if you aren't looking to spend money, you can "window shop" at the new offerings, as a way to stay up-to-date on the latest trends and technologies.
Today, Newegg enables a new feature that is really cool and forward-thinking. You can now interact with the retailer's customer service using Facebook Messenger. In other words, the social network's messenger service has value that expands beyond casual chatting -- it is also a legit business tool, dubbed "Messenger for Business".
"Newegg currently offers a breadth of support options via email, SMS text message, phone and chat. Giving customers the ability to engage with Newegg's customer support representatives via Messenger -- one of the most popular apps in the world, with hundreds of millions of users -- is an important asset to add to the company’s mobile strategy", says Newegg.
The online retailer further says, "to reach Newegg's customer support representatives via Messenger, simply visit Newegg's Facebook Page and message the support team. Or, search for Newegg directly from within Messenger to start a conversation. This new service is enabled by In the Chat, whose digital customer service platform brings together contact management capabilities for social media, text, chat, email and messaging apps in a single, convenient contact center solution. During regular business hours, Newegg's customer support representatives will be available to help resolve issues in real-time. Messages sent outside business hours will receive responses the following business day".
If you are the type of person that boycotts Facebook, and other social networks, do not worry -- Newegg will continue to offer more traditional methods of contact, such as phone and email. With that said, I suggest giving Facebook Messenger a try. It is one of the better such offerings, and is available for many platforms -- including the web.
Would you ever utilize Facebook Messenger as a way to interact with a company's customer service? Tell me in the comments.
-

Android gaining ground mainly at Windows Phone's expense
Publié: avril 6, 2016, 8:33pm CEST par Mihăiță Bamburic

Windows Phone sales took a dive in 2015, and it looks like the trend continues in 2016 as well. The platform is losing ground in major markets across the globe, according to a new report by Kantar Worldpanel ComTech. And Android is taking advantage of it.
In the three months ending February 2016, Windows Phone saw its market share drop considerably in five major European markets (France, Germany, Great Britain, Italy and Spain), and US and Australia, with Android adding the percentage points it lost under its belt. Things are looking better in China and Japan, however.
In the five European markets, Windows Phone's market share dropped to just 5.9 percent from 10.1 percent in the three months ending February 2015. That is a loss of 41.58 percent year over year. The biggest loss happened in Spain, where the OS' market share dropped by 68.96 percent. At the opposite end of the spectrum is Great Britain where it posted a 20.51 percent loss in market share.
Android also gained ground at iOS' expense, though Apple's iPhones only lost 8.6 percent of their market share year over year, dropping to 19.1 percent from 20.9 percent a year prior. The platform gained ground only in a single market, namely Spain (it rose by 4.59 percent over last year), while in the other four it lost some of its market share to Android.
"While Android’s share grew steadily in the EU5, performance varied considerably by market, underlining the impact that Huawei and local vendors are making in some markets", notes Katar Wordpanel ComTech Europe business unit director Dominic Sunnebo. "In Great Britain, 42 percent of the smartphone market falls in the premium category, and Huawei’s premium spec devices offering very good value for money have not yet tempted enough of Great Britain’s consumers. Android will be counting on Samsung’s new flagship devices to challenge Apple’s dominance".
Moving over to US, Android saw its market share rise to 58.9 percent, up 5.9 percent from 55.6 percent a year prior. Both iOS and Windows Phone lost market share in the country, with iOS dropping to 38.3 percent from 38.8 percent and Windows Phone sliding to 2.6 percent from 4.8 percent a year prior.
Kantar Worldpanel ComTech mobile analyst Lauren Guenveur believes that the new iPhone SE represents a major opportunity for Apple to claim back some of the lost market share in US. "[At the] $399 price point, [it] will likely appeal to more cost-conscious first-time smartphone buyers who might otherwise be more inclined to pick up an Android smartphone, and to the sizable installed base of iPhone owners who have not yet upgraded".
China is another market where Android has posted better results than last year. Its market share rose to 76.4 percent from 73 percent, while iOS dropped to 22.2 percent from 25.4 percent. Windows Phone remained steady at 0.8 percent market share.
Android's growth is said to come thanks to the strong sales of smartphones running the open source operating system around the Chinese New Year. Meanwhile, this three month period marks the first time when iOS did not rise in urban China since August 2014. The company may recover some of the lost ground thanks to iPhone SE, which may prove to be an attractive option to local shoppers on a budget wanting to join the Apple user ranks.
In Australia, both Android and iOS have grown, though only the former has posted a more significant increase in market share, to 55.1 percent from 51.3 percent a year prior. Apple's iOS rose to 38.2 percent from 37.9 percent. Meanwhile, Windows Phone dropped to 5.8 percent from 9.1 percent.
In Japan, all platforms have gained market share, at the expense of other operating systems. Android rose to 48.2 percent from 47.9 percent, iOS grew to 50.2 percent from 49.8 percent, while Windows Phone saw its market share increase to 0.5 percent from 0.3 percent a year prior.
Photo Credit: Nicholas Piccillo/Shutterstock
-

Windows 10 Insider Preview Build 14316 arrives on the Fast ring -- packed with exciting new features
Publié: avril 6, 2016, 8:20pm CEST par Wayne Williams

Windows 10 Insider Preview builds -- well those on the Fast ring at least -- tend to fall into two camps. There are the exciting releases, like Build 14291, which delivered extensions to Microsoft Edge as well as various other new features, and the duller ones, like Build 14295, which mostly fix bugs and shore up things.
The latest new build for the Fast ring, Build 14316, falls very much into the former camp, with Microsoft introducing lots of new features for Insiders to try, in addition to plenty of welcome improvements across the whole of the OS. Here’s what new.
As announced last week at Build 2016 (that’s the event, not an Insider Preview release!) you can now natively run Bash (a Unix command line tool often used on Linux) in Windows. In order to do this though you’ll firstly need to turn on Developer Mode. Go to Settings > Update & security > For developers and search for Windows Features. Select Turn Windows features on or off and enable Windows Subsystem for Linux (Beta). To install Bash, open a Command Prompt and type bash.
You’ll find more details on the new feature here.
If Bash doesn’t excite you -- and it certainly isn’t for everyone -- the new build also introduces some cross-device features for Cortana. If you have multiple devices running Windows 10, or a smartphone with Cortana installed (Windows 10 Mobile, or Android), these additions will help keep things in sync.
The new features are low battery notifications, find my phone/ring my phone, and the ability to share map directions across devices.
Microsoft has released three videos explaining how these work.
Low Battery Notifications
Find my phone/Ring my phone
Share map directions across devices
Microsoft has also made it easier to set up Cortana and, naturally, there’s a video covering this too, but it’s currently private. We’ll update this article with the embedded video once Microsoft makes it publicly available.
Having released extensions for Edge two builds ago, Microsoft introduces some additional extensions in this build -- Pin It Button and OneNote Clipper. It also updates the first three extensions -- Reddit Enhancement Suite, Mouse Gestures, and Microsoft Translator.
As before, to get these working, click on the ellipses (…) at the top right in Edge, then click Extensions. In the Extensions pane click Get extensions.
In the new build you can now universally toggle between dark and light modes via Settings > Personalization > Colors. This will affect all apps with dark and light themes.
There’s also a new option to show color only on app title bars. Configure this through Settings > Personalization > Colors.
And that’s still not all. There’s a Skype UWP Preview app available to try out, Action Center improvements which include the ability to prioritize app notifications, Virtual Desktop Improvements (you can now pin windows open across desktops) and some updated Emoji.

What, you want more features?
Ok, there’s also a new Update Progress Experience -- you’ll see this when you update your build -- and updated battery settings and battery saving experiences too. Windows Update now lets you tell the OS when you’re at your busiest, so it won’t attempt to install any updates between the specified hours.
Finally commenting in the Feedback Hub has been introduced in this new build too.
As well as all these new features and functionality, the build fixes a bunch of problems including:
- The issue where on some PCs with TPM chips, such as the ASUS Zenbook UX31, you may have experienced glitchy audio and jumpy movement when using the trackpad due to the "tpm-maintenance" task running constantly in the background instead of once per boot-up like it should.
- The issue where if you use Hyper-V and have a Virtual Switch configured for your network adapter, you might see an error indicator (red-colored "X") for your network adapter in the notification area of your taskbar.
- Polished the Wi-Fi flyout UI and fixed an issue where text entry into a Wi-Fi password field was noticeably top-aligned rather than centered.
- Fixed an issue for where when using multiple monitors and full-screen apps like PowerPoint or Remote Desktop would crash Windows Explorer.
- Fixed an issue where Cortana wasn’t showing Settings pages in the search results.
- Updated the Windows Update notification after updates have been installed so now clicking on the notification will take you straight to your update history.
- Fixed an issue where desktop (Win32) apps pinned to the Start menu would sometimes move after updating to a new build.
- Fixed an issue where "Update and Restart" and "Update and Shut Down" wouldn’t start an update.
Naturally, with this being a Fast ring release there are a fair few known problems to be aware of:
- The Visual Studio emulator for Windows 10 Mobile and Hololens will fail with "An authentication error has occurred. The Local Security Authority cannot be contacted". If you are a developer and require the emulator for building apps, we suggesting moving to the Slow ring and skipping this build until we can fix this issue.
- We continue to investigate issues with Narrator and other screen reader apps that make them unable to read selected text in the Feedback Hub, Cortana, and other apps.
- In Microsoft Edge, some large downloads may appear to get stuck at 99% completion. You can work around this issue by renaming the file in your downloads after closing Microsoft Edge. This workaround skips security checks on the file, so it should be used only with files from a trusted source.
- In some cases, attempting to turn on Developer Mode on may crash the Settings app. If this happens, the workaround is to use these steps here to enable Developer Mode.
- Some apps notifications may only show the icon -- however the full text of the notification will be visible within Action Center.
It's clearly full steam ahead as Microsoft prepares for the big Anniversary Update this summer.
Photo credit: charnsitr / Shutterstock
-

Chuwi Hi12 -- a Surface Pro 4 and iPad Pro alternative at a fraction of the cost [Review]
Publié: avril 6, 2016, 8:08pm CEST par Mark Wilson

The number of convertible tablets vying to take on Microsoft's Surface Pro 4 is on the increase. Some are more than reasonable competition while others are little more than cheap knock-offs. The absurdly low price of the Chuwi Hi12 might fool you into thinking that this 12-inch Chinese tablet falls into the latter camp, but you'd be wrong.
Costing an unbelievably low $289.99 (neatly below the promised $300 threshold), the Hi12 is not strictly a direct competitor to the Surface range... it lacks the all-important kickstand. So we're off to a great start with price, and the looks are certainly not to be sniffed at either; it's not a million miles away from iPad territory. But while looks and price are important, it's what's on the inside -- and how it works -- that matters, and the Hi12 does not disappoint.
As you'd guess from the name -- and, indeed, my direct reference to its size -- the Hi12 is a 12-inch tablet. The 3:2 aspect ratio apes the look of an iPad as other features of the tablet do, but the capacitive Windows button is one of the things that reveals the truth. When in landscape mode, this button appears to the right of the screen, just as with modern Surfaces, and stereo speakers appear at the bottom of the unit. This does make for something of a lopsided experience when listening to audio in portrait mode, but the sound is of a decent quality.
The build quality of the Hi12 is generally high, and the all-metal body gives a high-quality feel. The same is true of the optional keyboard. Put the two together, however, and it's not such as happy tale. There is noticeable play in the hinge which, while not concerning enough to completely discourage use, certainly reduces the overall experience. In general usage, the play is not too noticeable -- unless you're typing on your knee and hitting the keys hard enough to cause wobble -- but when you open and close the lid, it's hard to ignore. This is a real shame because it means that the first and final few seconds with the device are disappointing even if the intervening time is perfect.

Like the Surface range, the keyboard (which adds 743g to the overall weight) snaps into place with the help of magnets. It's all pretty secure -- if you hold just the screen, the keyboard isn't going to fall off -- but there isn't the satisfying docking click that the Surface offers. The keyboard not only allows for easy typing by transforming the tablet into a laptop, it also adds a couple of extra USB ports. For a typing session -- even fairly extended one -- the keyboard is a pleasure to use, although backlighting would have been nice. The trackpad is fine, but the clicking action of the integrated left and right mouse buttons is far from perfect. There is something of a cheap feel to clicks that detracts from an otherwise decent piece of hardware. The trackpad is multi-touch friendly though, so you can avoid clicking altogether and just tap instead.

Chuwi claims a battery life of 6-8 hours, and (non-scientific) tests bear this out. This is a machine that could get you through the working day without scrabbling for a power socket every couple of hours. A big bonus is the fact that charging takes place via a microUSB port so you can share a cable with your phone, charge up in the car without the need for an inverter -- it's an all-round neat solution. The Atom processor here may not be a powerhouse, but that's not what the Hi12 is about. This is just about providing a perfectly capable device with above-average performance at a below-average price. On both counts it succeeds admirably.

The screen is of an undeniably high standard, and while the brightness of 400 lumens is not best in class, it's certainly good enough for indoor and outdoor use without problems. There's also a pleasing lack of glare.
Here's a full breakdown of the specs:
- Screen Size: 12.0 Inches
- OS: Windows 10 Home + Android 5.1 (maybe)
- Colors: Champagne Gold; Space Gray
- Screen Resolution: 2160 x 1440 (3:2)
- CPU: Intel X5 Cherry Trail Z8300 1.44GHz (Max up to 1.84GHz), 64-bit quadcore
- GPU: 8th Generation Intel Graphics (up to 500MHz)
- RAM: 4GB DDR3L
- ROM: 64GB
- Extended Storage: Up to an extra 64GB
- Battery: 3.7V / 11000mAh
- Camera: Front - 2MP, Back - 5MP
- Connectivity: Bluetooth 4.0, HDMI, WiDi, 802.11 b/g/n, 1 x USB 2.0, 1 x USB 3.0, 1 x micro USB
- Dimensions: 296.7 x 202.8 x 8.9mm
- Weight: 852g
Is there room for improvement? Sure. A bit more power would be nice, and the wobbly keyboard connection does feel like it lets the side down a little. It would be nice if the keyboard was included as standard, although this would clearly bump up the price, and the choice of going keyboardless is welcome. The keyboard would also benefit from sharing the same material as the Hi12 itself -- simply matching the color isn’t good enough. To be considered a true competitor to the Surface Pro 4 or iPad Pro, a stylus really is needed, but this is something that is just not available for the Hi12, sadly -- not a native peripheral, at least.

If you want to get your hands on the Chuwi Hi12, you can pick one up from Panda Will for just $289.99 -- and that includes free global shipping. A standard US two-pin plug is provided, so bear that in mind if you're in a different part of the world, although any compatible USB charger will do the job. If you like the idea of the keyboard cover, this will set you back a mere $57.99, also from Panda Will. As with the Hi12 itself, the keyboard is available in Champagne Gold or Space Gray (or just Gold and Grey as Panda Will refers to the hues).

If you want to see what you get in the box, check out the unboxing video from Panda Will below:
We had previously -- based on information provided by Chuwi -- referred to the Hi12 as being a dual boot Windows 10 Home / Android 5.1 device. The review sample provided runs only Windows 10 Home, and it is not yet clear whether the Android option is a separate version of the Hi12 or if an update will bring the dual boot feature. We're waiting for clarification from Chuwi, but even if this is just a Windows 10 tablet, it's an incredibly competent and highly recommended one. Android would just be a bonus.
-

Salesforce buys deep learning startup MetaMind
Publié: avril 6, 2016, 8:00pm CEST par Anthony Spadafora

Salesforce has acquired MetaMind and plans on ending the startup’s services on May 4. The deep learning company launched in 2014 with $8 million in initial funding from Salesforce’s cofounder and CEO Marc Benioff and Khosla Ventures.
MetaMind has really set itself apart from its competition through its image recognition capabilities. The site is able to identify the items in images and a demo called MetaMind Food Identification first gave users of the service a taste of what it was capable of.
Salesforce will be integrating MetaMind’s technology into its own platform. Unpaid users of MetaMinds products will be able to make use of them until May 4, when they will be discontinued. Paid users will have an extra month to use their products which will be discontinued on June 4. MetaMind is planning to delete all of the data that both paid and unpaid users have stored on its servers after April 11.
The cofounder and CEO of MetaMind, Richard Socher, published a blog post where he detailed the acquisition of his company by Salesforce. The company will have the opportunity to offer its deep learning technology to even more business users on a much larger scale and he has promised that it will continue its AI research as part of Salesforce.
Salesforce acquired the machine learning startup PredictionIO last month. Also, in May of last year the company purchased Tempo AI for its smart calendar app.
This latest acquisition of MetaMind shows Salesforce’s dedication to scaling both deep learning and machine learning technologies.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Business Intelligence: Reshaping the face of the contact center
Publié: avril 6, 2016, 6:31pm CEST par David Bethers

By now, it’s no secret that business intelligence (BI) software is becoming a widely adopted tool among various industries. The use of BI makes it possible for organizations to gain valuable insight into what areas of the business are thriving and others that might be in need of improvements.
The scenarios where we are starting to see BI becoming most effective are when executives leverage these insights and turn them into actionable data.
So What Is It Anyways?
In its simplest terms, BI technology provides organizations with an integrated tool that presents information in real time -- i.e. agent performance levels, profitability, efficiency numbers, etc. BI makes it possible for organizations, including call centers, to organize large amounts of data into easy-to-understand reports. BI also makes it possible to assess the performance and current success of various departments or employees. And the ability to dissect a business on a much more granular level allows for executive teams to more closely monitor and implement change within certain divisions.
What Does BI Mean for the Contact Center World?
Without insight into the wide range of data that is generated by businesses, call centers are limited in their capabilities. They have no real way of gaging how the call center is performing overall, what employees are excelling or what strategies are making an impact. And without being able to measure these components, call center executives have no true way of implementing change or improving performance levels. Simply put, everything is left to chance.
- Measurement of Agent Performance
Prior to BI, overall performance levels were measured collectively across an entire contact center. Now through the use of BI, it’s become possible to drill down and see individual performance metrics to better evaluate employees on a case-by-case basis.
- Ensure Compliance
As compliance begins to rank higher on a company’s to-do lists, BI is helping play a role in making sure call centers stay up-to-date on all the latest regulations.
- Measure Return on Investment (ROI)
Gone are the days of trying to measure ROI without any concrete metrics. The use of BI makes it possible for call center managers to measure the ROI per agent as well as ROI of the entire operation.
- Focus Managers Time on Growing the Business
Prior to BI, contact center executives oftentimes found the majority of their days spent pulling reports and trying to draw conclusions from the data. Instead, the use of BI makes it possible for managers to be be given the data and performance numbers they need to then make sound business decisions. BI is a significant time saver for senior executives, and makes their role as managers much more streamlined.
When Is It Time to Act?
Once a contact center is able to identify its own internal strengths and weaknesses, BI can play an important role in pinpointing areas that are delivering and those that might be underperforming.
Additionally, BI tools have the ability to report exact gains and/or losses. So, it’s easy to see what’s working versus what isn’t and where call center managers should focus additional attention.
The bottom line -- BI is growing in popularity among contact centers because of the array of benefits it provides. It allows management-level employees to home in on just that -- working to propel the business forward day in and day out rather than getting bogged down by time consuming activities like pulling spreadsheet reports. BI makes it possible for employees to work smarter and for executives to make decisions that help lead to increased efficiency and overall growth.
Photo credit: Maksim Kabakou / Shutterstock
 Dave Bethers is the Vice President of Enterprise Sales for TCN, Inc., provider of the industry-leading, cloud-based call center technology platform for enterprises, contact centers, BPOs, and collection agencies. With more than 9 years of experience in the industry, Dave has been at the forefront of call center technology, spearheading strategic partnerships and assessing client initiatives worldwide
Dave Bethers is the Vice President of Enterprise Sales for TCN, Inc., provider of the industry-leading, cloud-based call center technology platform for enterprises, contact centers, BPOs, and collection agencies. With more than 9 years of experience in the industry, Dave has been at the forefront of call center technology, spearheading strategic partnerships and assessing client initiatives worldwide -

Lian Li PC-J60 is a classy aluminum mid tower ATX case with cable management focus
Publié: avril 6, 2016, 6:30pm CEST par Brian Fagioli

Building a PC can be a really fun project. Not only does it allow you to pick all of the components, but the design of the case/chassis too. Long gone are the days of beige towers. Modern cases come in a multitude of colors, sizes, and shapes. Some even glow thanks to LED lighting.
Unfortunately, many cases have become a bit too liberal with their designs -- they can look like funky spaceships or lava lamps! In other words, sometimes a more mature and reserved chassis would be more appropriate for a build. Today, Lian Li announces the PC-J60 -- an ATX mid tower with a focus on class, maturity, and cable management.
"The PC-J60 makes it easy for builders to have attain the immaculate, organized appearance of popular case builds and mods. A large aluminum cover sheathes the PSU and drive racks along the bottom panel, shrouding them from view in the main compartment so VGA cards and other more glamorous parts can hog the spotlight. Several cable holes with rubber grommets are positioned around the motherboard cut out, along with built-in cable ties, to make organization a breeze", says Lian Li.
The longtime chassis manufacturer further says, "the drive racks are positioned at the bottom of the chassis, making room in the main compartment for the largest VGA cards available on seven expansion slots -- up to 410mm in length. Each drive rack mounts two 3.5 inch or 2.5 inch drives on rubber vibration dampeners. An additional 3.5 inch and 2.5 inch drive can be mounted directly on the motherboard panel for a total of six possible drives. The PC-J60 can mount CPU coolers up to 160mm tall and ATX PSUs 210mm in length".
This case is very intriguing, as it is both beautiful and functional. Its mature design would make it appropriate for an office setting or at a LAN party. If you want to get a little wild, you can opt for the window variant, which also has a pretty red trim. As someone who often builds with AMD, that color interests me very much.
Click to view slideshow.Unfortunately -- for some -- it does not accommodate optical drives. True, fewer folks are using CD, DVD, and Blu-ray nowadays, but some -- like me -- still use media for backup. With that said, from an aesthetic point of view, I'll admit that the front looks better bare. Of course, you can use a USB optical drive with this case if needs be.

Cooling looks to be marvelous, as the cable management should contribute to some great airflow. It uses two 120mm fans for intake, and can accommodate three optional 120mm fans on the top for exhaust. The PSU compartment houses a 140mm fan, however, for additional cooling. Water fans can use a radiator with max dimensions of 430mm length, 160mm width, and 60mm thickness, according to Lian Li.
If you are interested in this case, it will be available on Newegg on April 11. The base model is $189, and the fancier red variant with side-window is $210.
Will you buy it? Check out the specs below, and tell me in the comments.
Model PC-J60 B / WRX Case Type Mid Tower Chassis Dimensions (W)210mm
(H)507mm
(D)489mmColor Black(PC-J60B)
Red(PC-J60WRX)Front bezel Material Aluminum Side Panel Aluminum
PC-J60WRX(Transparent)Body Material Aluminum Net Weight 6.48KG 5.25" drive bay (External) None 3.5" drive bay (External) None HDD bay 3.5" HDD x5
2.5" HDD x1Expansion Slot 7 M/B Type ATX
Micro-ATXSystem Fan (Front) 120mm Fan x2 System Fan (Top) 120mm Fan x3(Optional) System Fan (Bottom) 140mm Fan x1 I/O Ports USB3.0 x 2
HD AudioMaximum Compatibility VGA Card length: 410mm
PSU length: 210mm
CPU cooler height:160mmSpace of Radiator Top: 60 x 430 x 160mm
Front: 120 x 240mmPower Type ATX (Optional) -

Microsoft releases Cloud App Security to protect SaaS apps and data
Publié: avril 6, 2016, 5:56pm CEST par Ian Barker

Back in September of last year we reported that Microsoft had announced its purchase of cloud security firm Adallom to help its customers protect their cloud-based data and applications.
In February it teased that a new Cloud App Security offering based on Adallom's technology would be released in April. Well, today the wait is over and the product becomes generally available as a cloud-delivered service to help IT and security teams gain visibility and control over cloud apps.
Writing on the company's blog back in February, Bret Arsenault, Microsoft's chief information security officer says, "Microsoft Cloud App Security brings the same level of visibility and control that IT departments have in their on-premises network to their SaaS applications including apps like Box, SalesForce, ServiceNow, Ariba, and of course Office 365".
Cloud App Security identifies all cloud applications on a network -- from all devices -- and provides risk scoring and ongoing risk assessment and analytics. It allows admins to set granular controls and policies for data sharing and loss prevention (DLP), leveraging API-based integration. Users can opt to use out-of-the box policies or build and customize their own. Cloud App Security also provides threat protection for cloud applications using user behavioral analytics and anomaly detection.
As a first step network logs are uploaded to the service. These are analyzed and admins can then choose which apps are sanctioned and need to be connected to the service. Once that's done data control policies can be set up and admins start to receive alerts. You can read more about how it works on the Microsoft Cyber Trust Blog.
It's available on a subscription basis at $5 per user per month. If you're interested in finding out more you can visit the Cloud App Security product page to request a trial.
Photo credit: Maksim Kabakou / Shutterstock
-

Huawei's new P9 flagship features dual-lens Leica camera
Publié: avril 6, 2016, 5:40pm CEST par Mihăiță Bamburic

One of the things that separate flagships from the rest of the smartphone crowd is their camera performance. Consumers expect to take great photos and videos with a top of the line handset, so manufacturers tend to use premium sensors and lenses for their best offerings. And, sometimes, they team up with a household name in the field when they really want to woo potential buyers.
For its latest flagship smartphones, called P9 and P9 Plus, Huawei has partnered with famous camera maker Leica. That is not the only thing that's different about its camera, however, as the main highlight is actually its dual-lens setup, which, among other things, enables the device to capture depth information for that lovely bokeh effect.
"Huawei is excited to give P9 users the best smartphone photography experience by leveraging the unrivaled capabilities of Leica, the leader in the world of imaging for more than 100 years", says Huawei Consumer Business Group CEO Richard Yu. "Consumers around the world use their smartphones to take billions of pictures each year, making photography critical to user experience. P9 users can now capture images with unmatched clarity, richness and authenticity, with a masterfully designed and powerful smartphone that looks and feels incredible".
It remains to be seen whether P9 lives up to those claims but, in the meantime, let's take a look at some of its most-important specs, starting with the cameras, of course.
The main thing that you need to know is that the dual-lens setup features two 12 MP, Sony-made, sensors and matching Leica-branded Summarit H lenses with an f/2.2 aperture and an equivalent 27mm focal length. Its field of view is typical of a high-end smartphone, but its low-light performance may to suffer next to, say, Samsung's Galaxy S7 which has a wider-aperture -- f/1.7 -- lens that can transfer much more light to the sensor.
Huawei, however, claims that P9 "truly excels in low-light conditions", though I have a hard time believing that after using a number of devices with a similarly-large lens aperture. There is only so much that you can do with a smartphone sensor these days before running into physical limitations.
Worth noting is that one sensor is RGB, for capturing color, while the other is monochrome, for, Huawei says, capturing better detail. There is Hybrid Focus technology, for super-accurate and fast autofocus. There are also a number of presets to change how images look, which is fairly standard for any smartphone today.
P9 is designed as standard-sized flagship smartphone, so it uses a 5.2-inch display. Where it falls short compared to some its Android-powered rivals is in the resolution department -- its resolution is 1,080 by 1,920. Samsung's Galaxy S7, for instance, has a similarly-sized screen with a resolution of 1,440 by 2,560.
P9 Plus is a larger version of the flagship, featuring a 5.5-inch screen and Press Touch technology. That is Huawei's version of 3D Touch, which debuted on iPhone 6s and iPhone 6s Plus last year.

When it comes to processing power, Huawei has equipped P9 with a homebrew processor, called Kirin 955. Maxim clock speed is 2.5 GHz. There is a 3,000 mAh battery inside, which Huawei claims delivers "outstanding mobility and battery life". There are no estimates offered, however. P9 Plus features a 3,400 mAh battery, and adds dual-IC Rapid Charge, which is similar to Qualcomm's QuickCharge technology -- it is said to add up to six hours of talk time after 10 minutes of charging.
Last, but not least, both devices come with a fingerprint sensor, a feature which is becoming standard on smartphones in this class. It, of course, runs Android, but Huawei does not say which version. Hopefully, that'll be Marshmallow.
Huawei launched P9 in UK, with availability slated for May for both models. P9 will be priced at £449 off-contract, for a 32GB version with 3GB of RAM, while P9 Plus, which features 64 GB of storage and 4GB of RAM, will cost £549. You can check the available color options in the main photo, but you should know that availability will vary.
-

What you need to know about erasing SSDs
Publié: avril 6, 2016, 5:06pm CEST par Pat Clawson

Until recently, hard disk drives prevailed as the dominant storage device on desktop computers, laptops, smartphones, tablets, servers, and data centers. But thanks to the drop in price for solid state drives (SSD), that has changed. SSDs are more popular among both individual users and businesses. But for all of the advantages, they also possess unique traits that present some difficulties in wiping data from them.
Unfortunately, knowledge of the proper solid state drive erasure methods has not been anywhere near as fast or as ubiquitous as the SSD adoption rate. So you will often see methods that are assumed to be reliable -- such as reformatting and factory resets -- being performed on solid state drives. But that doesn’t mean it’s impossible to properly erase data from SSDs -- it just means users need to understand all of the technical features, the key situations when data has to be absolutely erased and the most reliable data removal method that needs to be used.
Know the Basics of How Solid State Drives Work
Solid state drives are simpler than HDDs in that they don’t have moving mechanical parts. They’re also smaller, lighter and less power intensive. But as I said, SSDs are more complicated when it comes to wiping data from them. They apply complex data management schemes to distribute data across their internal memory chips. They also contain a much larger pool of spare memory capacity accessible only by the SSD. In turn, this prolongs the performance and life of the drives. But it also means that certain data on the drive remains hidden from the host.
Proactively Plan to Remove Data in Key Situations
The reality of the world we live in today is that inordinate amounts of information are created, stored, tracked, and transferred within the digital universe. But nothing lasts forever -- that includes SSDs. That means these drives will eventually hit their end of life when a server, storage device or other piece of IT infrastructure is retired, then the drive has to retire along with it. And any data contained on them must be erased too.
Most businesses don’t have the capacity to store all of their data on their own premises -- so they tend to move it from one location to another -- be it to data centers, cloud storage environments or elsewhere. When this data is being moved to its new location, it needs to be wiped clean from its original location. This often gets overlooked -- and it’s something that more companies need to prepare for because of how common it is to move data between locations.
Another situation to be cognizant of -- and plan for -- is data that doesn’t need to live forever. This could be data that was created and stored for a particular time-sensitive project that involves confidential information and parties. When the project ends, the data needs to be erased permanently so that it doesn’t fall into the wrong hands.
Now it’s important to remember the varying types and amounts of corporate data that employees create and store on their laptops, desktop computers, smartphones and tablets. And a growing number of these devices are equipped with solid state drives. But it’s become so rare for employees to stay long periods of time at one company.
So when employees leave the company -- for whatever reason -- all of that data must be erased before they leave. This is extremely important when you consider it’s not just personal information they’re storing on them; it’s often confidential and sensitive company information and files. If that data isn’t erased in the proper manner, it could jeopardize the business in multiple ways.
Following the EU’s passing of the General Data Protection Regulation in December 2015, it’s important to be able to securely, reliably, and verifiably remove data from SSDs when regulation demands that customer data is removed -- or "forgotten". In order to prove compliance with this type of legislation -- and those being imposed by other governing bodies -- simply deleting the data isn’t good enough. It must be completely expunged, forever.
One of the least desirable situations is the time after a major disaster hits, such as an earthquake, a hurricane, or a tsunami. In the same Red Cross and other charitable organizations are dispatched to deploy disaster recovery services. Part of that disaster recovery should include recovery of the data and storage at an offsite location. But once production systems are restored back to normal, any data left on the recovery drives need to be erased.
Know the Most Reliable Way to Erase Data From Solid State Drives
Although upkeep of SSDs can be complicated and difficult, it’s not impossible by any means. It just means users need to use the right data removal method that meets certain criteria. The method should accommodate the functionality differences of SSDs regardless of the manufacturer. Second, it’s critical to use an automated technique to remove system BIOS freeze locks -- that allows users to have better access and control over their internal data erasure processes.
More importantly, users can’t simply assume the method and tool used to remove data from SSDs are reliable. They need to be able to benchmark both the method and tool against industry testing and validation standards. Without this, there is no true way to determine if the method and tool can be trusted. Following this same logic, anyone erasing data from SSDs -- whether it’s an end user or an enterprise user -- should demand physical proof that verifies all data has been completely erased. I often use the filing taxes analogy -- users need to be able to show proof if the IRS comes knocking on their door. The same goes for data removal -- proof will protect you from having data leaked and violating regulatory standards.
Pat Clawson, CEO, Blancco Technology Group
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Imagentle/Shutterstock
-

IObit ships Smart Defrag 5
Publié: avril 6, 2016, 4:31pm CEST par Mike Williams
IObit has shipped Smart Defrag 5, a major update of its freeware disk optimizer. A new defrag engine supports multi-threading for maximum performance.
New defrag types allow users to focus on large files only, or to consolidate free disk space. If you’re unsure which defrag type to use, IOBit’s Smart Defrag/Optimize Technology will intelligently select if for you.
Elsewhere, defrags may now be scheduled to run when you’re not around. And just in case the program still gets in your way, Silent Mode automatically cuts resource use when full-screen tasks or specified processes are running.
The Pro version has gained an option to defragment specified files at boot time.
The interface has been revamped for more intuitive operation. And a new "Readable" skin makes it easier to, well, read.
Smart Defrag 5 is a free tool for Windows 2000 and later.
-

The best mobile apps for business users
Publié: avril 6, 2016, 3:07pm CEST par Ian Barker

Useful apps tend to embed themselves deeply into people's work lives and stay installed on their devices for the long term. As a result it can be hard to get a definitive list of the best apps at any one time.
To try to remedy this, app quality company Applause has produced a report that ranks 130 business apps based on what people feel about them. Categories of apps ranked include communication, organization, work productivity, security and weather.
To qualify for the report, apps needed to have a minimum of 1,000 reviews combined in the Android and iOS app stores. Ranking is based on a sentiment score of 0-100 as determined by Applause's analytics platform for attributes including usability, security, privacy, interoperability and more.
The average score of all 130 apps was 61 out of 100 (the average score of apps across all categories is 67). Organization apps were the highest ranked at an average score of 68/100. Communication and security apps received average scores of 55 and 53, respectively.
In the communication category, Slack (64.5) scored ahead of Google Hangouts (47), HipChat (42.5) and Skype for Business (22). In organization, Box (64.5) scored ahead of Google Drive (61), Dropbox (60) and Microsoft OneDrive (58). Of security apps, Norton Mobile Security (79) scored ahead of Kaspersky Internet Security (77) and Avast Mobile Security (75).
Ten apps earned above average scores based on more than 100,000 reviews. These include ColorNote (93), Duolingo (88.5), CamScanner (85) and Evernote (78). The report's authors note that, "Consumers value apps with elegant user interfaces and simple navigation, accurate information, relevant notifications, quick launch times, fast performance and engaging and fun experiences".
At the other end of the scale the worst scores were received by enterprise mobile management apps such as Good, Mobile Iron and AirWatch, all of which ranked at the bottom with scores under 20.
You can find out more about how Applause measures app sentiment and access the full report on the company's website.
Image Credit: Syda Productions / Shutterstock
-

Facebook boosts live video with new interactive options including Live Reactions and group video
Publié: avril 6, 2016, 3:05pm CEST par Mark Wilson
Facebook Live may have started life as a celebrity-only feature, but it soon spread to all users, giving them the opportunity to share their own live video streams. Today the social network unveils a number of new features with the aim of making it easier to find and share live broadcasts, as well as personalizing and interacting with video.
Live video is all about bringing together a community of people to share an experience, so it's little surprise that the first of today's announcements sees the arrival of Facebook Live to Facebook Groups and Facebook Events. Building on the Reactions feature that rolled out recently, live video now also benefits from Live Reactions. But the laundry list of new features doesn't end there.
To build on the interactivity, Facebook is making more of the ability to comment on live videos. Now when footage is replayed at a later date, comments will also be replayed 'as live'. Personalization is made possible through the addition of Live Filters, and on the horizon is the promise of the ability to doodle on live videos. But bearing in mind the popularity of the standard Reaction, it’s the Live Reactions that will probably go down the best with users. Facebook says:
Facebook Live is interactive and fun: Live reactions, replaying comments made while live and Live filters will make it even more so. Live Reactions makes it easy for your viewers to express their feelings in real time during a live broadcast. Using the same reactions we launched in News Feed, viewers can select Love, Haha, Wow, Sad or Angry, and the reactions animate right on top of the video. Live Reactions appear in real time and disappear quickly so broadcasters and other viewers can get a sense of how people are feeling at different points during the live video -- it’s like hearing the crowd applaud and cheer. When your friend reacts to your video or to a video you are both watching together you’ll see their profile pic and a little starburst before their reaction appears.
Building on the idea of making video viewing a shared experience, Facebook is adding the option to invite friends to watch along with you. There really is a big push of Facebook Live at the moment, and discoverability is the name of the game. On the desktop, today sees the launch of a Facebook Live Map to help people find broadcasts that are taking place at the moment. A similar feature is rolling out to mobile apps which will enable users of the social network to find current, popular and trending videos more easily.
-

Is IBM guilty of age discrimination? -- Part two
Publié: avril 6, 2016, 3:03pm CEST par Robert X. Cringely

This is the promised second part of my attempt to decide if IBM’s recent large U.S. layoff involves age discrimination in violation of federal laws. More than a week into this process I still can’t say for sure whether Big Blue is guilty or not, primarily due to the company’s secrecy. But that very secrecy should give us all pause because IBM certainly appears to be flaunting or in outright violation of several federal reporting requirements.
I will now explain this in numbing detail.
SEE ALSO: Is IBM guilty of age discrimination? -- Part one
Regular readers will remember that last week I suggested laid-off IBMers go to their managers or HR and ask for statistical information they are allowed to gather under two federal laws -- the Age Discrimination in Employment Act of 1967 and the Older Worker Benefit Protection Act of 1990. These links are to the most recent versions of both laws and are well worth reading. I’m trying to include as much supporting material as possible in this column both as a resource for those affected workers and to help anyone who wants to challenge my conclusions. And for exactly that reason I may as well also give you the entire 34-page separation document given last month to thousands of IBMers. It, too, makes for interesting reading.
For companies that aren’t IBM, reporting compliance with these laws is generally handled following something very much like these guidelines from Troutman Sanders, a big law firm from Atlanta. What Troutman Sanders (and the underlying laws) says to do that IBM seems to have not done comes down to informing the affected workers over age 40 of the very information I suggested last week that IBMers request (number of workers affected, their ages, titles, and geographic distribution) plus these older workers have to be encouraged to consult an attorney and they must be told in writing that they have seven days after signing the separation agreement to change their minds. I couldn’t find any of this in the 34-page document linked in the paragraph, above.
Here’s what happened when readers went to their managers of HR asking for the required information. They were either told that IBM no longer gives out that information as part of laying-off workers or they were told nothing at all. HR tends, according to my readers from IBM, not to even respond.
It looks like they are breaking the law, doesn’t it? Apparently that’s not the way IBM sees it. And they’d argue that’s not the way the courts see it, either. IBM is able to do this because of GILMER v. INTERSTATE/JOHNSON LANE CORP. This 1991 federal case held that age discrimination claims can be handled through compulsory arbitration if both parties have so agreed. Compulsory arbitration of claims is part of the IBM separation package. This has so far allowed Big Blue to avoid most of the reporting requirements I’ve mentioned because arbitration is viewed as a comparable but parallel process with its own rules. And under those rules IBM has in the past said it will (if it must) divulge some of the required information, but only to the arbitrator.
I’m far from the first to notice this change, by the way. It is also covered here.
So nobody outside IBM top management really knows how big this layoff is. And nobody can say whether or not age discrimination has been involved. But as I wrote last week all the IBMers who have reported to me so far about their layoff situation are over 55, which seems fishy.
IBM has one of the largest legal departments of any U.S. company, they have another army of private lawyers available on command, they’ve carefully limited access to any useful information about the layoff and will no doubt fight to the finish to keep that secret, so who is going to spend the time and money to prove IBM is breaking the law? Nobody. As it stands they will get away with, well, something -- a something that I suspect is blatant age discrimination.
The issue here in my view is less the precedent set by Gilmer, above, than the simple fact that IBM hasn’t been called on its behavior. They have so far gotten away with it. They are flaunting the law saying arbitration is a completely satisfactory alternative to a public court. Except it isn’t because arbitration isn’t public. It denies the public’s right to know about illegal behavior and denies the IBM workforce knowledge necessary to their being treated fairly under the law. Arbitration decisions also don’t set legal precedents so in every case IBM starts with the same un-level playing field.
So of course I have a plan.
IBM’s decision to use this particular technique for dealing with potential age discrimination claims isn’t without peril for the company. They are using binding arbitration less as a settlement technique than as a way to avoid disclosing information. But by doing so they necessarily bind themselves to keeping age discrimination outside the blanket release employees are required to sign PLUS they have to work within the EEOC system. It’s in that system where opportunity lies.
Two things about IBM’s legal position in this particular area: 1) they arrogantly believe they are hidden from view which probably means their age discrimination has been blatant. Why go to all this trouble and not take it all the way? And 2) They are probably fixated on avoiding employee lawsuits and think that by forestalling those they will have neutralized both affected employees and the EEOC. But that’s not really the case.
If you want to file a lawsuit under EEOC rules the first thing you do is charge your employer. This is an administrative procedure: you file a charge. The charge sets in motion an EEOC investigation, puts the employer on notice that something is coming, and should normally result in the employee being given permission by the EEOC to file a lawsuit. You can’t file a federal age discrimination lawsuit without EEOC permission. IBM is making its employees accept binding arbitration in lieu of lawsuits, so this makes them think they are exempt from this part, BUT THERE IS NOTHING HERE THAT WOULD KEEP AN AFFECTED EMPLOYEE FROM CHARGING IBM. Employees aren’t bound against doing it because age discrimination is deliberately outside the terms of the blanket release.
I recommend that every RA’d IBMer over the age of 40 charge the company with age discrimination at the EEOC. You can learn how to do it here. The grounds are simple: IBM’s secrecy makes charging the company the only way to find out anything. "Their secrecy makes me suspect age discrimination" is enough to justify a successful charge.
What are they going to do, fire you?
IBM will argue that charges aren’t warranted because they normally lead to lawsuits and since lawsuits are precluded here by arbitration there is no point in charging. Except that’s not true. For one thing, charging only gives employees the option to sue. Charging is also the best way for an individual to get the EEOC motivated because every charge creates a paper trail and by law must be answered. You could write a letter to the EEOC and it might go nowhere but if you charge IBM it has to go somewhere. It’s not only not prohibited by the IBM separation agreement, it is specifically allowed by the agreement (page 29). And even if the EEOC ultimately says you can’t sue, a high volume of age discrimination charges will get their attention and create political pressure to investigate.
Charging IBM is it can be done anonymously. And charges can be filed for third parties, so if you think someone else is a victim of age discrimination you can charge IBM on their behalf. This suggests that 100 percent participation is possible.
What will happen if in the next month IBM gets hit with 10,000 age discrimination charges? IBMers are angry.
Given IBM’s glorious past it can be hard to understand how the company could have stooped so low. But this has been coming for a long time. They’ve been bending the rules for over a decade. Remember I started covering this story in 2007. IBM seems to feel entitled. The rules don’t apply to them. THEY make the rules.
Alas, breaking rules and giving people terrible severance packages is probably seen by IBM’s top management as a business necessity. The company’s business forecast for the next several quarters is that bad. What IBM has failed to understand is it was cheating and bending rules that got them into this situation in the first place.
-

Barclays announces Apple Pay support
Publié: avril 6, 2016, 2:50pm CEST par Sead Fadilpašić

Apple Pay is now available to Barclaycard and Barclays customers, the bank has announced. "We are passionate about helping customers access services and carry out their day to day transactions in the way that suits them", said Ashok Vaswani, CEO of Barclays UK.
"As part of this, we have developed a range of digital innovations that allow people to choose how, when and where they bank and make payments. Adding to the existing choice, from today both Barclays debit and Barclaycard credit card customers can use Apple Pay to make payments with their Apple device across the UK".
The new payment method, whose popularity is growing by the second, is supported by these devices: iPhone SE, iPhone 6 and beyond, Apple Watch, iPad Air 2, iPad mini 3, iPad mini 4 and iPad Pro.
According to the press release, there are more than 400,000 contactless locations in the UK, across the London transport network and within participating retailers’ apps.
"Since we introduced contactless to the UK in 2007, it’s changed the way consumers make everyday purchases by cutting out the hassle of handling cash", said Amer Sajed, Interim CEO of Barclaycard. "With Barclaycard and Barclays bringing Apple Pay to our customers, we can now offer the widest choice of ways to make and take payments in a way that’s most convenient for them".
Contactless payment is gaining ground in the UK. According to latest figures by Visa Europe, contactless payments have seen an increase in use of 237 percent year-on-year.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Add style to your photos with ON1 Effects Free
Publié: avril 6, 2016, 1:36pm CEST par Mike Williams
ON1 Effects Free 10 is a collection of professional photo filters and effects which can be used stand-alone, and as Photoshop or Lightroom plugins.
Beginners can use the package much like other apps. Open an image, choose a preset -- Cinematic, Color Grading, Haze Reduction, more -- and just click a thumbnail to apply that effect.
When you need more power, there are ten configurable filters and effects to explore: Adjustable Gradient, Adjustment Brush, Black & White, Borders, Dynamic Contrast, Glow, HDR Look, Texturizer, Vignette and Vintage.
Each of these have plenty of options. Select Vignette, for instance, and you get thumbnails of 12 vignette types, along with tools to adjust brightness, size, roundness, feathering, opacity, effect strength and more.
You’re also able to save custom settings as a preset for easy recall later.
Effects can be applied globally, to a masked area, or painted onto the photo as required.
The developer would like you to upgrade to the $39.99 commercial version, so unsurprisingly the free build has some restrictions to push you in that direction: no Sharpen tool, Blur, Noise Reduction and many other effects.
The Browse module is missing, too, so the only way to find and select your photo is with a standard Open dialog box.
ON1 Effects Free isn’t the best all-round photo optimizer, then, but the effects you do get deliver great results, and are very configurable, and if you just need to enhance a photo or two then it should work very well.
ON1 Effects Free 10 is free application for Windows 7 and later and Mac.
-

Chinese censors spring into action to erase mentions of Panama Papers from the web
Publié: avril 6, 2016, 1:21pm CEST par Mark Wilson

The Panama Papers that leaked following the Mossack Fonseca hack turned the spotlight on the rich and famous seemingly involved in money laundering and tax evasion schemes. High profile names from the world of politics appear in the papers -- including close friends of Russian President Putin and the father of UK Prime Minister David Cameron.
The leaked 11.5 million files, spanning 2.6 TB of data, include references to the relatives of at least eight current or former Chinese officials, says the International Consortium of Investigative Journalists. Chinese censors have now gone into overdrive, working overtime to eliminate all mentions of this from Chinese websites.
An official directive sent to Chinese editors informs them that they are forbidden from writing about the Panama Papers. It's a move that's reminiscent of attempts to erase the Tienanmen protests from the history books. The leaked directive, published by the China Digital Times, issues a stark warning to journalists thinking about covering the topic:
Find and delete reprinted reports on the Panama Papers. Do not follow up on related content, no exceptions. If material from foreign media attacking China is found on any website, it will be dealt with severely.
The Great Firewall of China is famous for limiting the access Chinese citizens have to news from the outside world, and the country's media is very tightly controlled by the communist government. Deviation from directives handed down by the ruling party results in harsh punishment, but the censorship extends beyond the purging of stories from the web.
Free Weibo, a site that monitors the censorship of internet searches in China, reports that the word Panama is the most censored word at the moment, and China Digital Times says that terms such as "Panama + offshore", "offshore + finance", "Panama + Deng Jiagui", and "Panama + Li Xiaolin" are blocked.
Photo credit: Markus Mainka and Ivan Ryabokon / Shutterstock
-

Vivaldi 1.0 arrives, promises uniquely customizable web browser for power users
Publié: avril 6, 2016, 12:50pm CEST par Nick Peers

Vivaldi Technologies has unveiled Vivaldi 1.0 FINAL, the first stable release of a web browser aimed squarely at those who want full control over their web browsing experience.
Vivaldi has been developed by a team led by Jon S von Tetzchner, co-founder of rival Opera, and is available for Windows, Mac and Linux. Vivaldi’s moniker -- "Not for everybody, just for you" -- highlights its different approach to other major web browsers.
This user-focussed approach sees Vivaldi deliberately shy away from the increasingly stripped-down, simplified user interfaces adopted by the likes of Edge, Firefox and Chrome.
Instead, it aims to give as much control to the end user as possible. Vivaldi’s been built using the same Chromium engine that powers Chrome and Opera, which means the underlying browser enjoys decent security and performance while freeing up the developers to focus on the UI.
The final version opens with a first-run wizard, designed to not just give users the opportunity to set up the browser how they want but also to showcase Vivaldi’s flexibility. Users first pick a color scheme (the browser updates accordingly by way of live preview as each is selected in turn) and then choose where tabs will be placed (top, bottom, left or right) before selecting their start page background.
Once complete, users can start exploring Vivaldi’s many unique features: the ability to stack multiple tabs in related groups, which can then be tiled or viewed side-by-side within the browser window for easy switching. A trashcan in the tab bar makes it easy to recover previously deleted tabs.
A collapsible side panel gives users easy access to recent downloads, plus supports bookmark management, the taking of notes and web panels -- these allow users to define web pages that can be displayed alongside the main browser window, such as news feeds, weather forecasts or other web links. Vivaldi also features a Speed Dial function -- just one of many nods to its Opera roots.
Power users are also catered for Quick Commands, which combine keyboard shortcuts with a command-line interface that allows users to access key browser functions through written commands -- just type [F2], start typing and then select from the available commands, with more supported commands being added with each snapshot. Vivaldi also supports mouse gestures for those who prefer it.
Vivaldi’s use of Chrome means it’s capable of running most Chrome extensions -- type vivaldi://extensions into the Address Bar to manage and obtain these via the Google Chrome store.
The browser has evolved rapidly from its first beta release last November, and while most changes have been focused on bug fixes, some new and improved features have slipped through -- Beta 2 introduced a recoverable trash area for deleted bookmarks and notes, for example, while it also added visual notifications (and a mute button) for audio playing on individual tabs, plus made the closing of multiple tabs easier by not resizing remaining tabs until the user had finished.
One minor fly in the ointment with this release is that the program installer continues to claim it’s a beta release -- this is a mistake. So long as the installed version is 1.0.435.38 or later, Vivaldi will be running the stable release.
Vivaldi 1.0 FINAL is available now as a free download for Windows, Mac and Linux. Users can import data from a variety of browsers, including Opera (old and new versions), Edge and Internet Explorer, but not Firefox or Chrome (a HTML option is available instead).
-

The doctor will lose your data now -- 1 in 5 doctors' mobile devices could be at high risk
Publié: avril 6, 2016, 11:35am CEST par Ian Barker

More than 27 million Android devices running medical apps are likely to have high risk malware installed according to a new report.
The Mobile Threat Intelligence report from threat defense company Skycure is focused on healthcare and finds that doctors who use mobile devices to assist their day-to-day practice are exposed to network threats, and that these significantly increase over time.
In a single month, one in five (22 percent) of mobile devices will be at risk of a network attack. This figure nearly doubles to 39 percent after four months. In addition to network threats, mobile devices continue to be plagued by malware. More than four percent of all Android devices were found to be infected with malicious apps. Medical app users need to be particularly wary, as the report shows 27.79 million devices with medical apps installed might also be infected with high-risk malware. The Skycure mobile threat defense platform conducted 51 million network tests in 2015, and detected the installation of nearly 13,000 malicious apps.
"Mobile is a huge attack target for cyber criminals who are after sensitive personal data like patient records," says Adi Sharabani, CEO of Skycure. "Unlike desktop and network security, mobile security is often the weakest link in the security chain. Healthcare is one place where it is clear that one compromised device puts more than just the device owner’s data and identity at risk".
Among other findings are that 80 percent of doctors use their mobile devices to assist in their day-to-day practice and 28 percent store patient data on their mobile device, making their devices prime targets for cyber criminals.
Eleven percent of mobile devices running an outdated operating system with high-severity vulnerabilities might have stored patient data on them. In addition fourteen percent of mobile devices containing patient data likely have no passcode to protect them.
There is some good news, for example, the percentage of devices with passcodes enabled rose slightly to 52 percent in the last quarter of 2015 from 48 percent in Q3 2015. This may be due to the adoption of new devices featuring biometric passcodes. However, it still leaves nearly half of devices completely unprotected.
The report also shows that users of iPhones and iPads are more protected because they are much more likely to have the most current version of their device's operating system. At the end of 2015, 88 percent of iOS users had upgraded iOS 9. By contrast, only three percent of Android users were using Android 6.0, Marshmallow, at the end of the year.
You can find more about the findings by registering for an on-demand webinar, and there's a summary of the findings in infographic form below.
Image Credit: Rob Hyron / Shutterstock
-

Only a third of businesses have proper DDoS protection
Publié: avril 6, 2016, 10:19am CEST par Sead Fadilpašić

Among the biggest cyber-threats to businesses nowadays are phishing, patch exploitation, trojans and DDoS (Distributed Denial of Service), yet new figures show that a quarter of companies don’t have an anti-DDoS protection set up.
Those are the results of a new survey by security firm Kaspersky Lab and B2B International. According to their research, approximately half of businesses surveyed understand the risks cyber-attacks pose, not just to their financials, but also to their reputation. Approximately, the same percentage also thinks being protected from DDoS attacks is an important cybersecurity requirement.
But, there is the 24 percent of companies that don’t use this type of protection, and 41 percent that use it, only partially. "It turns out that just 34 percent of companies are fully protected against this widespread threat", the security firm said.
To make things worse, the majority of companies with no protection fall into the "risk group" -- businesses most frequently attacked. Those include the media (36 percent), healthcare and education, both at 31 per cent.
"It’s important to take DDoS attacks seriously as they can be just as damaging to a business as any other cybercrime, especially if used as part of a bigger targeted attack", said Russ Madley, head of B2B, Kaspersky Lab.
"The ramifications caused by these types of attacks can be far-reaching and very impactful as they’re able to reach deep into a company’s internal systems. Organizations must understand that protection of the IT infrastructure requires a comprehensive approach and continuous monitoring, regardless of the company’s size or sphere of activity".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: sibgat / Shutterstock
-

Google 'Tilt Brush' brings 3D VR painting to HTC Vive
Publié: avril 6, 2016, 2:33am CEST par Brian Fagioli

Quality virtual reality content is starting to come fast and furious. Earlier today, I was was watching an amazing video of YouTube sensation, Barnacules, playing VR horror game, Brookhaven Experiment, with the HTC Vive. The immersive experience made me start to salivate for HTC's VR offering.
Today, Google announces another intriguing program that takes advantage of the Vive. Called "Tilt Brush", the software lets the user virtually "paint" in a 3D environment. While it may seem like nothing more than a cool demo, I see it as much more than that -- the potential future of art.
"With Tilt Brush, you can paint in three-dimensional space. Just select your colors and brushes and get going with a wave of your hand. Your room is a blank slate. You can step around, in and through your drawings as you go. And, because it’s in virtual reality, you can even choose to use otherwise-impossible materials like fire, stars or snowflakes", says Andrey Doronichev, Group Product Manager, Google VR.
Doronichev further says, "one of the best parts about any new medium is just seeing what's possible. So, we brought Tilt Brush to The Lab at Google Cultural Institute -- a space in Paris created to bring tech and creative communities together to discover new ways to experience art. Since then, artists from around the world and from every discipline have come to explore their style in VR for the very first time".
As you can see above, Google put a lot of effort and resources into this project. The breathtaking "Tilt Brush" provides artists with a unique and immersive creation platform. Actually, the platform allows connoisseurs to experience the works of art too. Not only are the digital projects beautiful and three dimensional, but easily transmittable -- there is no "original".
Does Tilt Brush make you want to buy the HTC Vive? Tell me in the comments.
-

Swipebuster: $4.99 is all it costs to see if your partner (or anyone you know) is using Tinder
Publié: avril 6, 2016, 12:18am CEST par Mark Wilson

Its developer -- who wishes to remain anonymous -- says that his website exists to educate people about the importance of privacy. But Swipebuster sells itself as a way for suspicious partners to check upon their other halves if they think they might be making use of Tinder to seek out some 'extracurricular activity'.
Swipebuster taps into the Tinder API to access publicly available data to see if a particular individual appears in the membership database. It’s perfect not only for confirming or denying worst fears, but also a valuable tool for a would-be blackmailer. For just $5, you can conduct three searches to see if people you know are using Tinder.
Talking to Vanity Fair, Swipebuster's developer said that the site is essentially an experiment that highlights the poor privacy practices used by sites and services, as well as the foolhardiness of users. "There is too much data about people that people themselves don't know is available. Not only are people oversharing and putting out a lot of information about themselves, but companies are also not doing enough to let people know they're doing it."
Swipebuster is not quite as scary as it sounds in terms of privacy invasion. Quite. The developer has been fairly careful to provide, and give, just enough information, but not so much as to risk facing lawsuits... probably. To search for a possibleTinder user, you need to provide a first name, age, gender and the location from which you feel they may have been using the dating app. In big cities, it's likely that searches could yield multiple results, but the same cannot be said for people living in more remote areas.
It's fair to say that Swipebuster is morally questionable, but the developer does highlight important privacy issues. This, however, will do little to calm the fears that have been expressed by concerned parties who point out that the site could be used by stalkers and disgruntled exes to gather ammunition. Interestingly, Tinder itself does not seem particularly concerned about the existence of the service. A spokesperson said: "If you want to see who's on Tinder we recommend saving your money and downloading the app for free."
Photo credit: Kaspars Grinvalds / Shutterstock
-

Reminders come to Google Calendar on the web, bringing to-do list support
Publié: avril 5, 2016, 11:21pm CEST par Mark Wilson
A calendar offering reminders might seem like a fairly obvious feature, but here we're talking about Reminders (note the initial cap). Towards the end of last year, Google Calendar on iOS and Android gained support for Reminders -- and, as a result, to-do lists -- and now the same feature is coming to Google Calendar on the web.
Unlike standard calendar appointments, Reminders stick around until you tick them off. There's no need to keep changing the due date on something you don't get round to doing, as it will automatically roll over to the next day and appear on your calendar until you take the appropriate action.
Importantly, Reminders that have been created in mobile apps will sync to the web version of Calendar, but this is not the only place they can be created. Reminders can also be created via Google Now, Keep and Inbox, and these will all be collated together in your calendar. Google says:
Just like on Android and iPhone, you'll get the following:
- Reminders stick around -- If a reminder isn't completed, it will appear at the top of your calendar until you mark it done.
- Reminders work across Google -- Reminders you create in Inbox, Keep, and the Google app will also show in Google Calendar.
- Reminders sync with mobile -- Reminders created in mobile show up on the web and vice versa. So you can stay on track from just about anywhere.
If you don’t see Reminders on the web just yet, you won't have to wait long as the feature is rolling out this week.
-

Full end-to-end encryption shows WhatsApp is serious about privacy
Publié: avril 5, 2016, 10:35pm CEST par Mark Wilson

Encryption has been a hot topic for some time, but the battle between Apple and the FBI really brought it to the fore in recent weeks. In response to the FBI trying -- ultimately successfully -- to crack into the San Bernardino shooter's iPhone, WhatsApp was just one of the companies that promised to increase encryption.
Today the popular chat tool made good on its promise, enabling full end-to-end encryption; this means that calls, messages, photos, videos, files, voice messages, and group chats are all protected with end-to-end encryption. Importantly, this extra layer of security is enabled by default, leading WhatsApp to claim it is "a leader in protecting your private communication".
With more than a billion people making use of WhatsApp, the number of messages that will benefit from encryption is staggering. WhatsApp says that it is one of a small number of communication tools to feature end-to-end encryption by default, and says it hopes it "will ultimately represent the future of personal communication". The company is very blunt about why it feels encryption is so important:
The idea is simple: when you send a message, the only person who can read it is the person or group chat that you send that message to. No one can see inside that message. Not cybercriminals. Not hackers. Not oppressive regimes. Not even us. End-to-end encryption helps make communication via WhatsApp private -- sort of like a face-to-face conversation.
WhatsApp points out that it is easy to check that end-to-end encryption is enabled by simply looking "for the indicator in contact info or group info". The only requirement for end-to-end encryption is that all parties involved need to be using a version of WhatsApp released after March 31, 2016, and the company has provided a white paper that goes into more technical detail about the security used. It starts by saying:
The Signal Protocol, designed by Open Whisper Systems, is the basis for WhatsApp’s end-to-end encryption. This end-to-end encryption protocol is designed to prevent third parties and WhatsApp from having plaintext access to messages or calls. What's more, even if encryption keys from a user’s device are ever physically compromised, they cannot be used to go back in time to decrypt previously transmitted messages.
So to stay secure, just make sure that you have the very latest version of WhatsApp installed, and the rest will be taken care of for you.
Photo Credit: kraphix/Shutterstock
-

HP and Nvidia team up to offer Z Workstations with VR Ready systems
Publié: avril 5, 2016, 7:58pm CEST par Sead Fadilpašić

HP and Nvidia are teaming up to offer developers an easier time building virtual-reality content. The joint effort will see HP’s Z Workstations upgraded with Nvidia's VR Ready systems, equipped with Quadro professional GPUs.
The new systems, which can come with up to two NVIDIA Quadro M6000 24GB cards, support the Scalable Link Interface (SLI), GPU Affinity API and VR Synchronization technologies, doubling the rendering power of even the most demanding VR applications and practically eliminating image tearing.
The two companies are confident the new systems can provide ultra-high frame rates and low latency, even with the most demanding of data sets. Certified configurations include the HP Z240 Workstation with NVIDIA Quadro M5000, HP Z640 Workstation with NVIDIA Quadro M6000 and the HP Z840 Workstation with dual NVIDIA Quadro M6000 graphics.
"We are embarking on a new frontier that will change how content producers and artists develop the most immersive, visually stimulating content available", said Jeff Wood, vice president, Worldwide Product Management, Workstations and Thin Clients, HP Inc. "HP Z desktop workstations with NVIDIA graphics are the ideal combination for this new content creation era".
"VR is expanding beyond gaming to revolutionize fields across everyday life — like medicine, architecture, education, product design and retailing", said Bob Pette, vice president, Professional Visualization, NVIDIA. "Our VR Ready initiative makes it easy for professional users to adopt VR technology to make better, more informed decisions and perform their best work".
Pricing starts at $4,363 (£3,057), the companies added.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Rommel Canlas/Shutterstock
-

Twitter now offers an easier way to share public tweets privately
Publié: avril 5, 2016, 7:08pm CEST par Wayne Williams
While Twitter is designed to provide an open forum for your thoughts, occasionally you might want to have one-to-one discussions in private, and that’s where the Direct Message option comes in.
Today, as part of its quest to make DM conversations "richer", Twitter introduces a feature to make it much easier to share public tweets privately with friends and followers.
Twitter users on iOS and Android will soon start to see a new Message button under tweets that you can tap to quickly share that post in a DM.
Twitter says tweets being shared via DMs is becoming increasingly popular:
Every day, millions of people send Direct Messages to communicate privately with friends, family, experts, brands, and anyone else they find interesting on Twitter. In fact, we’ve seen the number of messages sent grow over 60% in 2015. And the number of Tweets shared privately has grown even faster, at 200% in just the second half of last year.
You’ll need to update your app to see the new button.
-

IT pros have bad security habits
Publié: avril 5, 2016, 5:50pm CEST par Sead Fadilpašić

Double standards, double standards everywhere. Our IT bosses might force us to change our passwords every so often, but they rarely change their own credentials, even though theirs offer administrative privileges.
Those are the results of a new survey conducted by cyber security vendor Lieberman Software. The company had asked 200 IT professionals at RSA Conference 2016 about their password changing habits.
More than half (55 percent) of IT pros force their users to change their passwords more often than they do, and 10 percent of them never change their administrative credentials at all. Seventy-four percent change admin passwords on a monthly or less frequent basis.
"Administrative passwords are the most powerful credentials in an organization -- the keys to the IT kingdom", said Philip Lieberman, president and CEO of Lieberman Software. "The fact that 10 percent of IT professionals admitted that they never change these credentials is astounding. It’s almost like an open invitation to hackers to come in and stay a while. In the meantime, the intruders are nosing their way around the network. They can anonymously help themselves to information and remain undetected until it’s too late".
But that’s not all -- in 36 percent of cases, passwords are shared among the IT staff, and 15 percent of IT pros said that if they are to leave their company now, they would still be able to remotely access it with the same credentials later on.
"Given that insider threats are one of the biggest concerns for CISOs, knowing that more than a third of IT professionals share privileged passwords is ludicrous", Lieberman continued. "The same can be said about so many ex-employees who can still access administrative credentials. Automated privileged access management solutions can prevent these types of cyber threats related to unsecure credentials".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Pixelbliss/Shutterstock
-

Would you pay $3.99 a month for an Outlook.com Premium subscription?
Publié: avril 5, 2016, 5:05pm CEST par Mihăiță Bamburic

Outlook.com offers all the right features that most consumers expect in an email service these days. But, if you are power users, Microsoft believes you may be looking for more, which is why the software giant is now trialling a Premium subscription.
Costing $3.99 a month, this is not the first and only Outlook.com subscription. There already is an Ad-free plan for users who want to get rid of advertisements, that goes for $19.95 a year, however the Premium tier is meant to unlock more extra, pro-level features.
With the Premium subscription, the idea is to offer users a version of Outlook.com that supports up to five custom email accounts, that is also ad-free. The former feature had been offered for free, being embraced by users who own domains, before Microsoft decided to pull the plug -- only those who previously added accounts would get to keep it.
Microsoft does not say if and when it plans to make this subscription available to the public, with a spokesperson saying that "Outlook.com Premium is currently a small pilot program. We’re always investigating new features based on the wants and needs of our customers, and we have nothing more to share at this time". The fact that there is no yearly price is clear evidence of that.
Microsoft's landing page for the subscription does reveal that customers who sign up for it will only be charged after the first year, although this may change with a possible general availability. That said, a one-year trial would be a good play, as the users who Microsoft targets are unlikely to go through the hassle of setting things up again for a short free testing period.
Obviously, because we are only talking about such a small number of custom email accounts, this subscription looks to be designed with a niche crowd in mind, like folks who need a few addresses up and running for their website. Those who purchase an Office 365 subscription may be able to take advantage of it for free, however, and invite up to five users to try it.
The asking price does seem very reasonable considering the number of custom email addresses involved. With Google Apps, for instance, the cost is $5 per user per month, which is higher no matter how you plan on using that Premium subscription with Outlook.com.
-

Open source database targets the big data analytics market
Publié: avril 5, 2016, 4:12pm CEST par Ian Barker

Leader in open source databases MariaDB is announcing the release of its new big data analytics engine, MariaDB ColumnStore.
It unifies transactional and massively parallelized analytic workloads on the same platform. This is made possible because of MariaDB's extensible architecture that allows the simultaneous use of purpose built storage engines for maximum performance, simplification, and cost savings. This approach sets it apart from competitors like Oracle, and removes the need to buy and deploy traditional columnar database appliances.
"I've seen first-hand how traditional columnar appliances arose as reactions to the cost and complexity of Oracle," says Michael Howard, CEO of MariaDB, "But these reactions have only increased complexity and cost further, and most importantly, over-looked critical features. In contrast, MariaDB ColumnStore is ACID compliant, blazingly fast, massively parallelized, and uses a distributed storage engine. What's equally important is its front end -- MariaDB, which provides the same interface, same security, same SQL richness simplifying management, reducing operating costs".
ColumnStore is a columnar storage engine for massively parallel distributed query execution and data loading. It supports a vast spectrum of use cases including real-time, batch, and algorithmic. It can perform complex aggregation, joins, and windowing functions at the data storage level to increase performance. MariaDB ColumnStore is an Open Source GPL2, a fork based on InfiniDB and open source community contributions.
The company is also announcing new data streaming capability in MariaDB MaxScale that will simplify real-time data propagation to external data lakes or data warehouses. This feature allows transactions in MariaDB to be replicated in real time to Hadoop or any other data store. It enables MaxScale and MariaDB to handle replication in mission critical applications without impacting performance. At the same time it includes all necessary metadata so that any program can read it, with no per-value overhead.
MariaDB ColumnStore will be available for beta testers next month, you can sign up for more information on the release on the company's website.
Image Credit: Tashatuvango / Shutterstock
-

Reducing costs is a growing priority for IT departments
Publié: avril 5, 2016, 4:12pm CEST par Sead Fadilpašić

IT departments in businesses across Europe are still focused on saving money, and not on adding value to the company, or innovating to support further growth. Those are the results of a new survey by Vanson Bourne on behalf of Claranet.
Polling 900 European IT leaders, it was unveiled that despite growing IT budgets, these departments are still looking to cut costs and save money. Today, 46 percent said reducing cost was the top priority, compared to 34 percent a year before. For 29 percent, new revenue streams were their core activity, and for 25 percent, that was increasing customer loyalty.
"European IT budgets are growing, which would suggest there’s a recognition within businesses of the importance of IT, however time and resources are still not being spent on more forward-thinking projects that can generate more revenue in the long-term", said Michel Robert, Claranet’s UK managing director.
It is clear from the data that the focus on cost reduction and ‘keeping the lights on’ we witnessed in last year’s report has been maintained and, for many, has actually increased. It goes without saying that costs are important, but it’s critical that IT departments can reposition themselves internally as enablers of business agility and innovation, rather than as cost centers", added Robert.
"Any business looking to digitally transform their processes must have the right partners and suppliers in place to carry out those standard tasks universal to IT departments. By working with a managed service provider, CIOs can effectively outsource this work and spend more time working on strategy and revenue-generating activities", concluded Robert.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: tomertu/Shutterstock
-

Ashampoo releases Photo Optimizer 2016, Backup 2016
Publié: avril 5, 2016, 3:28pm CEST par Mike Williams
Berlin-based developer Ashampoo has released two free programs: Ashampoo Photo Optimizer 2016, and Ashampoo Backup 2016.
Photo Optimizer 2016 is a stripped down version of the company’s commercial photo fixing tool, Ashampoo Photo Optimizer 6. The program can automatically optimize a folder of photos with a click, or you can use manual tools to crop, resize, rotate, sharpen, blur or straighten an image, tweak brightness, contrast or colors, add watermarks and more.
Ashampoo Backup 2016 is a simple tool which backs up your chosen partitions or hard drives.
Options are kept to a minimum -- backup source, destination, frequency, number of backups to keep -- but that does mean it’s very simple to use. You’ll be running your first backup in seconds.
Backups are stored as virtual disks (VMDK format), making them easily accessible in VirtualBox and other tools.
You’re also able to mount the VMDKs to restore selected files or folders, or restore a full backup from Ashampoo Backup 2016 or its bootable recovery disc.
Although the programs are free, you’ll be asked for a licence key during installation. Click "Get free activation key", follow the instructions -- give them your email address, essentially -- and the key is immediately displayed.
Ashampoo Photo Optimizer 2016 is a free application for Windows 7 and later.
Ashampoo Backup 2016 is a free application for Windows XP and later.
-

Behavior ID strengthens mobile and web security
Publié: avril 5, 2016, 3:09pm CEST par Ian Barker

Whether it's down to stolen credentials, weak passwords or bot-based attacks, the threat of an account takeover is one of the major worries for most users.
Mobile identity company TeleSign is launching Behavior ID, a new offering that enables web and mobile applications to measure and analyze a user's behavioral patterns to provide continuous authentication, even after the user has been verified with traditional security measures like passwords.
It provides an additional, transparent layer of security for every type of online account or mobile application, ensuring they are protected them from fraud, without the need for user interaction. Behavior ID delivers a 'similarity score' based on a set of behavioral biometric traits that are collected, analyzed and rated as users go about their everyday tasks, from initial account creation through ongoing access and usage of an account. This profile is then used to calculate a similarity ratio between the user's current behavior and their historical, expected behavior. It can therefore streamline the user experience for known good users, while providing a basis for challenging potentially bad or fraudulent users by asking for re-verification, or two-factor authentication.
No user interaction is required to enroll, enable, and start protecting an account from compromise. Users simply continue to use their web or mobile application as normal with no change to their workflow or behavior.
"With Behavior ID, our customers can immediately increase the level of identity assurance for every user account they have, without adding friction," says Steve Jillings, CEO at TeleSign. "The power of Behavior ID is its ability to adapt to the user, transparently producing a digital fingerprint from a user's behavior to confirm their identity and develop an ongoing authentication without requiring the consumer to do anything. Best of all, these unique biometric patterns are extremely accurate, from the way we move our hand on a mobile device screen or with a mouse, it is virtually impossible to precisely imitate another person's behavior".
Behavior ID SDKs for web and mobile applications are available from today for developers to embed into new or existing web and mobile app platforms. More information can be found on the TeleSign website.
Image Credit: Kirill Wright / Shutterstock
-

iPhone 6s security flaw lets anyone bypass the passcode and access contacts and photos
Publié: avril 5, 2016, 2:22pm CEST par Wayne Williams
It might have taken the FBI quite some time to find a way to unlock a shooter's iPhone 5C, but it turns out to be trivially easy to access contacts and photos stored on the company’s newest flagship, the iPhone 6s.
The trick makes use of Siri and Twitter, and as the owner of a 6s I’ve been able to test this method myself, and can confirm not only that it works, but it’s very simple to implement.
It does require the use of 3D Touch, so if you have an older iPhone you don’t need to worry.
To use the trick, discovered by Jose Rodriguez, you just need to launch Siri from the lockscreen and ask her to search Twitter for an email address. Using a phrase like "Hey, Siri, what's trending on Twitter with an email address?" worked for me. Once one is found, press down hard on the address to call up the 3D Touch context menu from which you can create a new contact or add to an existing contact.
Not only does this give the attacker access to all of your contacts, but if the Contacts app has permission to access the iPhone’s photo library, they can then also explore your snaps by adding a photo to a new or existing contact.
You can watch a video of the trick in action (in Spanish) below.
It’s possible to protect yourself from an attacker viewing your photos by denying Siri and Contacts access to your image library. Go to Settings > Privacy > Photos and disable the option there.
You can also prevent access to Contacts from the lockscreen by going to Settings > Touch ID & Passcode and disabling Siri there.
You could, of course, also just ensure that no one picks up and uses your phone without your knowledge.
-

Use of next generation databases hindered by backup technology
Publié: avril 5, 2016, 2:05pm CEST par Ian Barker

Businesses are showing increased interest in developing their infrastructure to support distributed, scale-out databases and cloud databases, but a lack of robust backup and recovery technologies is hindering adoption.
Backup and recovery is cited by 61 percent of enterprise IT and database professionals as preventing adoption. However, 80 percent believe that deployment of next-generation databases will grow by two times or more by 2018.
These are among the findings of a new report from data protection specialist Datos IO which looks at the concerns of IT leaders and the benefits they cite surrounding the rising demand for distributed applications and adoption of scale-out databases.
Other findings are that 75 percent of respondents predicted that next-generation databases will influence their organizational growth in the coming 24 months. The majority of apps (54 percent) deployed on next-generation databases sit in the analytics category, with business management, IoT and security apps coming close behind.
MongoDB and Cassandra lead the way in distributed database deployment, followed by cloud-native databases from Microsoft and Amazon. Some 89 percent of enterprise IT database professionals say that backup and recovery (as a function of storage) is critical for production applications.
"This survey shows IT application and database professionals clearly understand that for organizations to ride this unprecedented tide of data agility, they also need to innovate data storage, specifically for distributed backup and recovery," says Tarun Thakur, co-founder and CEO of Datos IO. "To deploy and scale next-generation applications, enterprises must be sure that data can be managed and recovered over its lifecycle at scale. To unlock the full potential of data, it is imperative that businesses fill data their protection gaps now".
There's a summary of the findings in infographic form below and you can find out more at the Datos IO site.
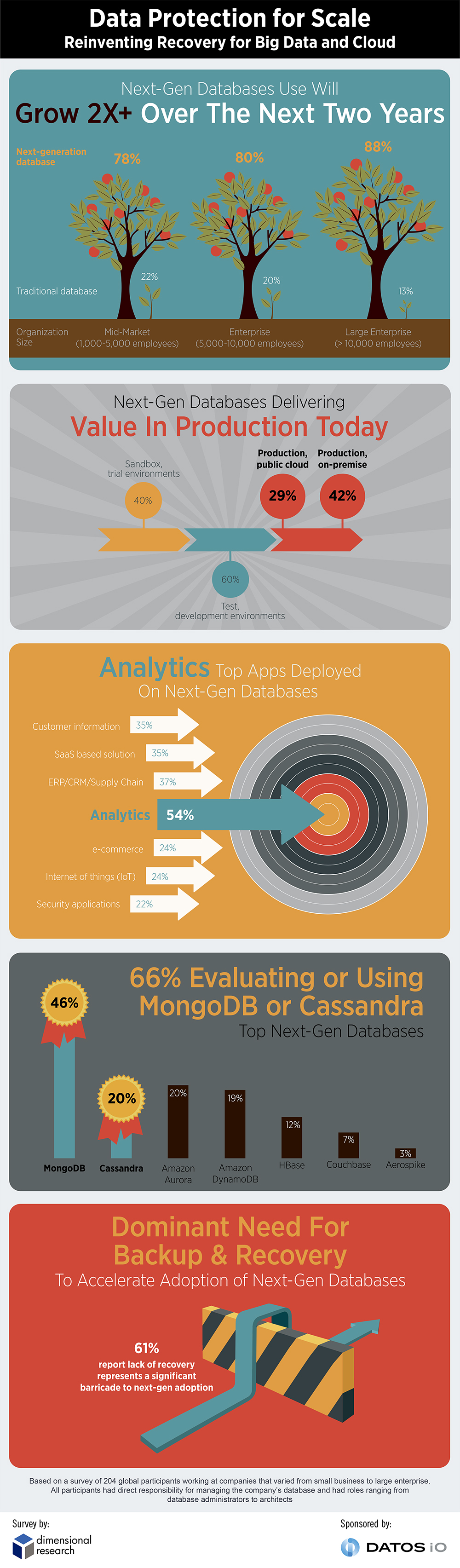
Image Credit: Oleksiy Mark / Shutterstock
-

Why assessing the value of data is vital to your organization
Publié: avril 5, 2016, 12:58pm CEST par Reuben Vandeventer

Based on my experience around data and metadata, I strongly believe that in today’s business environment, understanding the value of data should be a top priority for almost any organization.
Although there are certainly other core elements that help to define organizations, I would say the three most important are people, processes and technology. What each of these elements has in common is its reliance on data -- without which, nearly any organization’s productivity would quickly come to a grinding halt. Of course, most organizational leaders would agree that data is valuable, at least in a general sense. But it takes an additional focus, and deliberate processes, to measure the actual value of data within your organization, and then set up systems that allow you to take advantage of it.
Beware the coming demographic tsunami
Understanding the value of data may seem like an academic question -- but for an increasing number of business leaders, there’s a real sense of urgency to it. This urgency is driven by the fact that workers in the Baby Boom generation are retiring in unprecedented numbers, with major implications for organizations in every sector. This trend has actually led to an entire cottage industry focused on consulting around the complex issue of knowledge transfer from retiring Boomers to their younger colleagues.
This impact of this massive "changing of the guards" is already causing dramatic changes in organizational operations and cultures. But one of the areas of impact that is often ignored until too late is the substantial amount of "tribal knowledge" (that is, metadata) regarding organizational data that retiring employees will take with them, through no fault of their own. Fortunately, forward-looking organizations are taking steps to gather this metadata that not only help to shed light on the value of data, but that can also provide a range of insights into an organization’s people, processes and technology.
Succeeding at this vital effort requires a specialized communication process, that focuses on sustained, face-to-face collaboration among the members of one’s data community -- of all ages. Such a process allows the different groups of stakeholders to collaborate around the data, including those individuals who create, use and modify it. The ultimate goal of this collaboration is to produce the metadata needed to provide context and insights around the organization’s data and its data community -- information that may otherwise be gone forever in a matter of only years.
Other surprising benefits of data valuation
Getting a clear sense of the value of data in an organization can also play a critical role in Mergers & Acquisitions (M&A) activities. Through the application of data valuation and infonomics strategies, an organization can develop a far more accurate assessment of the value of a company it is considering acquiring. This is why any review of a target organization should include a rigorous data certification process that reveals how well the two organizations’ data will mesh.
This is an aspect of mergers that, if ignored or not well understood, can end up having major negative impacts on operational efficiency and ROI. What’s more, as important as it is today, it will very likely become even more important in the near future. Many economists have projected that we are cycling into another broad economic downturn, so effective data valuation can provide organizations with much better insights into which M&A opportunities and other initiatives will best help them manage risk in a turbulent market.
As significant as those types of insights are, an even more essential benefit of understanding the value of data is in helping an organization monetize its data. By finding new ways to safely derive new insights from its operational data, a business can develop entirely new revenue streams, and at the same time, outmaneuver its competition.
My view is that one of the keys to success in any approach to data valuation is to focus on excelling at the functions that only you can do, and at least consider outsourcing the rest. No other organization is more experienced at acquiring and caring for your data than you and your people. But to reach the next level of opportunity -- safely monetizing your data -- you need to develop advanced metadata and algorithms to generate data and insights that are uniquely yours. Depending on your workforce’s current data analytics skill sets, it could be a shrewd investment to outsource that development.
Image Credit: aslysun / Shutterstock
 Reuben Vandeventer is President and Chief Data Strategist at Data Clairvoyance. He has been driving progress and helping to shape the data space for more than a decade, across many industries including Medical Device, Pharmaceutical, Insurance and Asset Management. As the data space has rapidly evolved over the last few years, his background in science, statistics and finance has created a robust foundation to create real economic value for organizations in new and innovative ways.
Reuben Vandeventer is President and Chief Data Strategist at Data Clairvoyance. He has been driving progress and helping to shape the data space for more than a decade, across many industries including Medical Device, Pharmaceutical, Insurance and Asset Management. As the data space has rapidly evolved over the last few years, his background in science, statistics and finance has created a robust foundation to create real economic value for organizations in new and innovative ways. -

Upgrade to Windows 10 Mobile and you can still roll back to Windows Phone 8.1 -- with caveats
Publié: avril 5, 2016, 12:30pm CEST par Mark Wilson

After months of testing, Microsoft has started the process of rolling out Windows 10 Mobile to a selection of Windows Phone 8.1 handsets. Users who have been part of the Insider program will know what to expect, but for others the changes may come as something of a surprise.
In fact, it's entirely possible that you'll upgrade to Windows 10 Mobile and not like what you see. The good news is that Microsoft will allow you to roll back to Windows Phone 8.1, and there's no time limit on doing so.
In many ways, Microsoft is being surprisingly flexible with the Windows 10 Mobile upgrade program -- certainly more so than with Windows 10 on the desktop, many would argue. There is, of course, the fact that not all handsets are in line to get the upgrade, but Microsoft has made it clear that anyone who decides that Windows 10 Mobile is not for them will be able to revert to their previous OS.
But it's not all good news.
There will not be a clean roll back process to follow. In order to revert to Windows Phone 8.1, you'll need to make use of a recovery image as Microsoft confirms on Twitter:
@GabeAul For a Retail user going from 8.1 to 10 who may hit an issue and need to recover, they need an 8.1 image to recover to.
— Jason (@NorthFaceHiker) April 4, 2016
The downside to this is that it wipes the phone, so personal data will have to be backed up first lest it be lost forever. The retention of Windows Phone 8.1 recovery images is great for those of an indecisive nature, but it's also something of a double-edged sword. For Insiders, it means there is no easy way to roll back to a previous build, and Microsoft has no plans to change this:
@zayn_brandon @neil_hedley @windowsinsider @GabeAul No plans for that. Devices that originally had 8.1 will keep those orig recovery images
— Jason (@NorthFaceHiker) April 4, 2016
-

HP ENVY laptops get refresh
Publié: avril 5, 2016, 12:29pm CEST par Brian Fagioli

If you are looking for a quality laptop without breaking the bank, HP's ENVY line is definitely worth a look. The line combines solid performance with attractive designs -- perfect for home, school, or small business.
Today, HP announces a refresh of its popular ENVY line, featuring three distinct models. There is a 360 degree convertible, a 15-inch workhorse and a surprisingly light 17-inch portable workstation.
"Combining power and performance in a new thin profile, the 15.6 inch diagonal HP ENVY x360 is 21 percent thinner with longer battery life compared to the previous generation, weighing just 4.5 pounds and measuring 18.8 mm thin. With a timeless, all metal design, the HP ENVY x360 now offers a higher resolution display option for customers who want to view or edit 4K content", says HP.
The famed company further says, "the new generation of HP ENVY laptops offer sleek, metal designs featuring big power and performance, plus edge-to-edge flush glass displays for beautiful viewing experiences. Both feature three USB 3.0 ports and a USB Type-C that support data transfer to make adding or connecting accessories easy, as well as HP Fast Charge, which allows customers to charge the battery up to 90 percent in just 90 minutes when powered off".
HP shares the following notable features below. As you can see, all three models can be configured with some top notch specs, and all of them have USB Type-C. Only the x360 can be configured with an AMD processor, however -- the other two are Intel-only affairs.
HP ENVY x360 (starting at $679.99)
Click to view slideshow.- Longer battery life with up to 11 hours compared to 8 hours on the previous
generation. - 6th generation Intel Core i5 or i7 processors with optional Intel Iris graphics or 7th generation AMD FX 9800P Quad-Core Processor with Radeon R7 Graphics.
- Full HD display option and clear, premium sound with HP Audio Boost technology with tuning by Bang and Olufsen to extend the entertainment experience.
- Two USB 3.0 Gen 1 ports with one supporting HP USB Boost, one USB Type-C for data transfer, HDMI and SD card reader for maximum productivity.
- Up to 16 GB of system memory and single or dual storage options with up to 2 TB HDD and up to 256 GB PCIe SDD.
HP ENVY 15.6 (starting at $779.99)
Click to view slideshow.- Choice of Intel Core processors up to i7 with option of UMA or Intel Iris
graphics - 16 GB of memory with dual storage options of up to 1 TB HDD and 256 GB PCIe SSD
- Windows Hello support on optional HD IR camera
- 4.4 pounds and 17.95 mm thin
HP ENVY 17.3 ($1,029.99)
Click to view slideshow.- Intel Core i7 processor with NVIDIA GeForce 940MX graphics
- Up to 1 TB HDD (7) or up to 512 GB SATA SSD
- The 17.3” diagonal HP ENVY laptop also comes with an optical disk drive.
- Windows Hello support on optional Intel RealSense camera
- 6.6 pounds with a 25.45 mm profile.
If you are interested in buying one, please know that the availability is a bit confusing. HP shares the details below.
- The 15.6 inch diagonal HP ENVY x360 is planned to be available on HP.com on June 1 and bestbuy.com on May 29 and Best Buy stores on June 12 starting at $679.99.
- The 15.6 inch diagonal HP ENVY laptop is planned to be available on HP.com on May 25 and retailers in June 12 with a starting price at $779.99.
- The 17.3 inch diagonal HP Envy is planned to be available on HP.com on June 1 and bestbuy.com on May 29 and available in Best Buy stores on June 12 with a starting price at $1,029.99.
Which ENVY will you buy? Tell me in the comments.
- Longer battery life with up to 11 hours compared to 8 hours on the previous
-

HP Spectre Notebook is world's thinnest laptop
Publié: avril 5, 2016, 12:28pm CEST par Brian Fagioli

When Apple announced its latest MacBook last year, I was initially in love. After all, who doesn't want a thin laptop with a cutting-edge USB 3.1 Type-C connection? Sadly, that was where the magic ended. The Core M processor was anemic. The USB Type-C connection? The only such port -- making simultaneous charging and use of a USB device impossible without a clunky dongle.
Today, HP announces a laptop that mirrors the beauty of Apple's laptop -- surpassing it, even -- plus destroying it from a performance standpoint by utilizing an Intel Core i5 or i7 processor -- not Core M trash. Called simply the "HP Spectre Notebook", it is as close to portable nirvana as any machine before it. The premium laptop is so special, that it is being used to launch a brand-new HP logo.
HP shares the following features.
- A carbon fiber bottom creates a thin profile that is both durable and lightweight, keeping the total weight of the notebook at just 2.45 pounds
- High gloss copper accents reflect a hand-polished, jewelry-like finish and an innovative hidden piston hinge creates the illusion of a hinge-less design to offer an unmatched premium look-and-feel.
- An innovative hybrid battery split into two thinner pieces delivers the same wattage as a single battery for up to 9 and half hours of battery life while enabling the world’s thinnest laptop.
- Full HD IPS edge-to-edge display featuring Corning Gorilla delivers a superb viewing experience for editing photos, perfecting a presentation, or watching a movie.
- 6th generation Intel Core i5 and i7 processors and a lightning fast PCIe SSD with storage up to 512 GB with up to 8 GB of memory for maximum performance. Integration of Intel hyperbaric cooling system keeps the machine running cool even with powerful processors in a small package.
- Stereo speakers by Bang and Olufsen with HP Audio Boost technology, a combination of hardware and software to give customers the depth they want.
- Three full function USB Type-C connectors, including two of which support Thunderbolt, to provide a fast, versatile I/O connection.

"The HP Spectre is the thinnest notebook in the world, and unlike the majority of other super thin PCs on the market, this laptop doesn’t compromise power or features. A beautiful Full HD edge-to-edge display, Intel Core i processors coupled with Bang and Olufsen sound and a sexy and thin design, HP amazing engineers set a new standard with the all new Spectre", says Kevin Frost, VP and GM, consumer personal systems, HP Inc.

Frost isn't kidding. I recently had the opportunity to try this laptop. Now, I get to see many laptops -- it is not easy to surprise me. HP surprised me. This new Spectre is shockingly thin and beautiful. The moment I saw it, I was speechless -- literally.

Once I composed myself, I giddily put my fingers all over it. Opening the lid, I was amazed at how fluid it moved. The screen is so thin, yet it wasn't fragile nor wobbly. HP has designed a hinge that is both strong and beautiful. The hinge looks non-existent -- it is magic-like.

To get so thin, HP had to drop some features that some people expect from Windows laptops nowadays. The Spectre is not convertible, nor is it touchscreen. If you need a laptop that doubles as a tablet, this is not the machine for you. It is a pure laptop, and I love that.

Unfortunately, you cannot upgrade the Spectre -- it is not designed to be opened. 8GB of RAM is the only configuration. Still, HP had a dissected model to show me. The NVMe SSD was visible -- you will get cutting-edge storage speed. It is amazing how much is crammed into the chassis.

The really impressive aspect, however, is the Core i processors being used. This is something Apple couldn't do -- the MacBook has a weak Core M processor. HP made this happen by utilizing a heat sink-free cooling system -- a hyperbaric cooling system -- that was designed by Intel.

This ultra-thin laptop is powerful enough to double as a desktop. If you were to connect a Thunderbolt dock/hub with Ethernet, video-out, etc., you could power a couple of 4K displays and all of your components using a single cable. In other words, the Spectre Notebook will be brilliant when portable or stationary at home on a desk.

HP shares the following notable specs.
- Operating system: Windows 10 Home
- Processor: 6th generation Intel Core i5-6200U or i7-6500U Processor
- Display: 13.3 inch diagonal FHD IPS UWVA BrightView Corning Gorilla Glass WLED-backlit (1920 x 1080)
- Memory: 8 GB LPDDR3 SDRAM (onboard)
- Solid-State drive: 256 GB PCIe NVMe M.2 Solid State Drive
- Graphics: Intel HD Graphics 520 with up to 4185 MB total graphics memory
- Battery life: Up to 9 hours and 45 minutes
- Product weight: 2.45 lb
- Keyboard: Full-size island-style backlit keyboard

So how much will this cost? You can pre-order it from HP directly, or Best Buy on April 25 with an early-bird starting price of $1,169.99. On May 22 -- the official launch date -- the starting price increases to $1,249.99.

If you really have some money to spend HP will be auctioning off some special artist designed variants of the Spectre as seen below. Tord Boontje designed the ornate midnight blue masterpiece, while Jess Hannah went with an all-gold look. Both are absolutely gorgeous, and feature customized fonts on the keyboard, selected by the artists.
Proceeds of the auction will go to the Nelson Mandela Foundation. HP deserves major kudos for not only designing such a beautiful laptop with the Spectre, but using it to raise money for a worthy cause too.
Click to view slideshow.Will you buy the all-new HP Spectre Notebook? What do you think of the new logo? Tell me in the comments.
-

Mossack Fonseca hack exposes shady financial practices of world's rich and famous
Publié: avril 5, 2016, 10:44am CEST par Sam Pudwell

One of the largest data breaches in history has resulted in the leak of eleven million confidential documents -- around 2.6TB of data -- from financial firm Mossack Fonseca, one of the most secretive companies in the world.
According to the BBC, the leaked documents reveal how "Mossack Fonseca has helped clients launder money, dodge sanctions and evade tax". The client list features some of the world’s richest and most influential people -- including 12 current or former heads of state -- and their irrepressible greed has now been laid out for all to see. The data shows how thousands of off-shore shell companies have been created in order to hide money from the tax man and also reveals "a suspected billion-dollar money laundering ring involving close associates of Russian President Vladimir Putin".
Gerard Ryle, director of the International Consortium of Investigative Journalists (ICIJ), said: "I think the leak will prove to be probably the biggest blow the offshore world has ever taken because of the extent of the documents".
A statement from Mossack Fonseca says: "Your allegations that we provide structures supposedly designed to hide the identity of the real owners, are completely unsupported and false. We do not provide beneficiary services to deceive banks. It is difficult, not to say impossible, not to provide banks with the identity of final beneficiaries and the origin of funds. If we detect suspicious activity or misconduct, we are quick to report it to the authorities. Similarly, when authorities approach us with evidence of possible misconduct, we always co-operate fully with them".
There probably won’t be many times when I’ll get to say this, but nice work hackers, a job well done.
According to IBTimes, international football superstar Lionel Messi is among those detailed in the leaks, along with Michel Platini and several other leading officials, placing the world of football under intense scrutiny.
Luke Brown, VP and GM EMEA, India and Latam at Digital Guardian commented: "Putting aside the fact that the leaked emails and documents appear to include information about illicit operations, for the victims, a data breach of this scale could have life altering or, at the very least, distressing effects. Ultimately, the breach may trigger serious legal repercussions against Mossack Fonseca. Data protection should be of the utmost importance in environments like this and yet we have seen a growing number of data breaches in law firms over the last few months"
"This latest case reinforces the need for 'data aware' security technologies in the legal sector. If Mossack Fonseca had such technologies in place, it could have prevented its most sensitive emails and files from being copied, moved or deleted without approval or permission", added Brown.
"Companies must learn from incidents like this and better protect their IT environment, with the ability to apply security at the data-level being of the utmost importance", further explained Brown.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: igor.stevanovic/Shutterstock
-

Get your Indian Premier League cricket with an ESPN Pass on Roku
Publié: avril 5, 2016, 10:20am CEST par Alan Buckingham

It may not be big in the United States, but cricket equates to baseball in other parts of the world -- a sport with huge crowds and a somewhat similar method of play. The sport is very big in India and the Premier League is what the people want to watch.
Now Roku can bring all of the action to you with ESPN Cricket Pass. The set-top box maker brags that it is the only connected device offering this option for the 2016 season.
"Cricket fans are in luck -- the ESPN Cricket Pass channel is back and streaming all the 2016 VIVO Indian Premiere League (IPL) matches! Roku is proud to be the only connected-TV device that’s featuring this exciting tournament", the device maker states.
This doesn't come particularly cheap -- it's $29.99 for a season pass. However, compared to something such as NFL Sunday Ticket this is a real bargain and you'll get 60 matches for your hard-earned money. It runs from April 9th through May 29th and contains some 200 hours of coverage, all broadcast live.
-

It's lights out as Nest shuts down Revolv
Publié: avril 5, 2016, 6:46am CEST par Alan Buckingham

There have been occasional complaints with the IoT. Things don't always work as planned – lights that fail to come on or go off, a door that won't unlock and other minor annoyances. A bigger concern has been security, as these systems continue to display vulnerability. But, what if a device just suddenly stops working, and not through mechanical error, but because the company just chose to reach into your home and kill it?
Well, that's exactly what's about to happen with Revolv, an IoT hub that was purchased by Nest, which in turn is owned by Google. Officially, Revolv is considered a Nest company, though.
A message on the company website states that the product will be shutting down in favor of other projects with its parent company. The full text can be read below.
Revolv was a great first step into the connected home. It wasn’t perfect, but we worked hard to make something we - and other smart people - could build on. And it worked. In 2014, we were bought by Nest and the technology we made became an integral part of the Works with Nest platform. Now Works with Nest is turning into something more secure, more useful and just flat-out better than anything Revolv created. So we’re pouring all our energy into Works with Nest and are incredibly excited about what we’re making. Unfortunately, that means we can’t allocate resources to Revolv anymore and we have to shut down the service. As of May 15, 2016, your Revolv hub and app will no longer work. Thank you for your support and believing in us. We’re sad for the end of Revolv, but this isn’t the end of the connected home. This is the beginning.
-- Tim & MikeArlo Gilbert at Medium posted a lengthy lament to this death. Revolv controls his home and on May 15th that will cease to happen. While he plans to switch to a different hub, likely SmartThings, he raises some interesting questions about what this move means.
Google has a history of killing products despite consumer outcries -- witness Google Reader. Taken to its next level, this could extend to anything -- Nexus, Chrome OS, you name it. It's a serious worry for consumers. My lights are controlled by Amazon Echo, which thankfully is still being improved and shows no signs of being on the chopping block, but my thermostat is a Nest, which is suddenly worrisome.
Image Credit: kostasgr/Shutterstock
-

There's something you should know about 12.9-inch iPad Pro [seventh in a series]
Publié: avril 5, 2016, 6:43am CEST par Joe Wilcox
April 3, 2016 marks the first day that I truly could use Apple's over-sized tablet to replace my laptop. But I had to spend another $84, before California tax, to do it. Gadget reviewers who say that iPad Pro cannot be your computer are wrong. The apps, performance, and utility are there. Anyone creating content should consider this device as compliment to, or replacement for, an existing PC. The problem with 12.9-inch iPad Pro isn't what it can do but how much it costs to assemble what you need. This kit is far from budget-friendly, which also can be said of Microsoft's competing Surface Pro 4.
I started my iPad Pro sojourn on Groundhog Day, planning to use the device as my primary PC for 30 days. The objective: Apple CEO Tim Cook says the big-ass tablet can replace a personal computer, I want to see if he is right. The experiment isn't my first journey like this. I tried something similar during summer 2011 with one of the first Chromebooks. The path was a dead end. But Spring 2012, when new commercial models released, I started down the path again and never looked back. Google's Chromebook Pixel LS was my main computer before adopting the iPad lifestyle.
Money, Honey
The tablet's biggest foible as laptop replacement isn't apps, hardware, or operating system but the charging system. The 12-watt brick that Apple ships in the box is inadequate. While battery life is excellent, and enough to last a workday for common tasks, recharging takes a long time. More perplexing, you can't really use iPad Pro and charge simultaneously; there isn't enough juice. An Apple Store specialist recently acknowledged the problem, noting that display models often drain the battery even when plugged in.
But there's a fix. Last month, the company released a lightning-to-USB-C adaptor that lets iPad Pro charge using 12-inch MacBook's 29-watt brick, and the changeover makes a huge difference. In my testing, battery recharges in less than half the time—comparable to my experience with MacBook Pro. The tablet also adequately recharges when in use, as you would expect with any laptop. But to get that utility, you pay extra: $49 for the brick, and either $25 or $35 for the cable, depending on length (1 or 2 meters, respectively). Most users will want the longer cord, which is comparable-length to the one they already have.
That extra cost leads into the price equation and where the math adds up for some buyers but not for many others. The overall kit is pricey. The value is there, and on this point I disagree with most other reviewers. That said, price-wary shoppers can get as much, or more, computing benefit elsewhere by spending lots less.
Last month, Apple released a second, iPad Pro that packs same-size screen as the Air 2—9.7 inches. I am testing one of these, too, and with similar objective as the bigger model; seeing what role it can assume alongside, or instead of, a laptop. Preview reaction: Pretty good kit. With the new model's availability, the Pro line now ranges from $599 to $1,229. It's the high-end models that are more suitable for comparing with a laptop; for price and performance.
The 128GB and 256GB WiFi configurations are $949 and $1.099, respectively. Adding cellular radio jumps the prices to $1,079 and $1,229. Pencil and keyboard add $99 and $169 to the kit's cost, and don't forget the 29-watt charger and cable. Add it up and top-of-the-line model runs $1,581, or $1,451 without LTE. For comparison, the 13.3-inch MacBook Pro Retina Display with 256GB storage is $1,499. Display resolution is similar, but there is no touchscreen, cellular radio, or Pencil (e.g. stylus).
Modularity is a benefit, but it comes with a higher price that also applies to Surface Pro 4, which screen is 12.3 inches. From Microsoft Store, 256GB WiFi configuration with i5 processor sells for $1,299 and includes the stylus. Type Cover keyboard adds $129.99 to the price, or $159.99 with fingerprint reader (which is more comparable to iPad Pro). Final cost works out to either $1,428.99 or $1,458.99.
None of these devices is exactly low-cost for the utility given. Microsoft Store sells a broad selection of Windows 10 laptops with touchscreens and 256GB SSDs for under $1,000; many go for less than $800. Selection is broader still from Amazon. While Windows users can choose touchscreen models at most major price points, Mac buyers get nothing. For touch in a laptop-class device, iPad Pro is the only option.
Apples and Oranges
Notice that my comparisons focus on storage, and also screen size and resolution—12.3 inches and 2736 x 1824 resolution for Surface Pro 4; 12.9 inches and 2732 x 2048 for iPad Pro; 13.3 inches and 2560 x 1600 for MBP Retina. Processor and RAM are purposely ignored, because in my testing comparison is meaningless—even using benchmarks. iPad Pro's A9X chip and 4GB RAM deliver subjectively fantastic performance in day-to-day use. There is no perceptible lag compared to my Chromebook LS or MacBook Pro Retina Display, both of which pack i7 processors and 16GB RAM. The larger iPad Pro brings Apple back to the PowerPC era, when comparison to Intel chips quite literally was apples to oranges.
Modular design, powerful performance, and bountiful apps put the iPad Pro in PC replacement territory. But you will pay for the luxury. Whom should that be? Pencil pushers will love the fine control drawing or annotating. I am no artist and yet still see the nuances given; pen-to-paper like. Content creation is sometimes frustrating because of the file system, or lack of meaningful direct access to it. Nevertheless, keys, stylus, and touch open lots of control for editing photos or videos and creating documents, for example.
The keyboard is delightful. That is for me, I can't say for you. As expressed in previous installments in this series, my fingers find the keys by touch typing more accurately than any other keyboard, Responsiveness and travel are excellent. There is only one angle for the screen, when using Apple's keyboard cover, and it's perfect for me. I'm a short guy; 1.68 meters tall (5 feet 6 inches). I sit low enough to the screen without slouching while level enough with the keys to accurately type. But I wonder about taller folks. Then again, Tim Cook is 1.9 meters (6 feet 3 inches) tall. If Apple's CEO doesn't tower over the rig such that the angle is bad, then maybe most anyone can comfortably use the branded kit. Still, a cheap laptop or Surface Pro 4 gives greater flexibility adjusting angle of the screen.
To my surprise, for typing, iPad Pro comfortably sits on my lap, without tipping off. I expected topsy-turvy, which would be a deal breaker for replacing a notebook. I suspect, and someone can correct me, that Apple's single-angle placement in the keyboard as holder maintains balance when the device is used off the desk and on the lap.
In a future installment, I will discuss the app experience and explain why it's surprisingly good enough for most needs, but by no means all. Apple News is a killer content consumption app. Then there is the Pencil and what you do with it.
Returning to the topic of cost, and what you get, I'm aghast that Apple ships such a dinky charging brick with iPad Pro. From about 10 percent level, setting the tablet aside, recharging often takes as long as 6 hours. The MacBook 29-watt brick pulls back the time to under 3 hours, which is good enough. Benefit maybe, but buyers investing so much in the kit shouldn't have to spend another $74 to $84 to get what Cook contends is possible: Tablet that replaces a laptop.
This post is seventh in a series; Parts One, Two, Three, Four, Five and Six.
Photo Credit: Joe Wilcox
-

Google Play goes gaga for triangles with new icons
Publié: avril 5, 2016, 6:08am CEST par Brian Fagioli

While some folks may think icons are nothing more than fluff, they actually have huge significance. Your brain uses them for recall purposes, enabling you to quickly access your favorite apps. This is why I am not a fan of Microsoft's Live Tiles -- they are counter-intuitive, but I digress.
Today, Google announces new icons for all of its Play apps. Curiously, they are all triangular -- somebody in Mountain View, CA suddenly has a huge love for the three-sided shape.
"Whether you like watching Despicable Me on Google Play Movies and TV, streaming 'Sorry' on Play Music, battling your friend in Clash Royale on Play Games or reading John Grisham’s latest on Play Books, Google Play is your home for the best apps, games and digital entertainment. Since launching Google Play four years ago, we've always had dedicated apps in addition to the Google Play store. Today, all our icons are getting an update to provide a consistent look across the entire family of Play apps", says Jonathan Chung, Visual Design Lead, Google Play.
Chung further explains, "you'll start to see the new Google Play icons across devices and online in the coming weeks. We hope you’ll continue enjoying the Play family of products -- now with a new look".
I know what you are thinking -- by using all triangles, won't the app icons get mixed up in users' minds? Yes and no. Actually, the similarity will work in Google's favor. Users will easily recognize a Google Play app, and then differentiate based on color, content and text. The bold design should work well for the search giant.
What do you think of these new Google Play icons? Tell me in the comments.
-

MSI WT72 VR-focused and NVIDIA-powered laptop is Oculus Rift and HTC Vive compatible
Publié: avril 4, 2016, 8:02pm CEST par Brian Fagioli

Virtual reality is definitely a legit thing now. For a while, it felt a bit like a gimmick the tech industry was trying to jam down consumers' throats. While not a new concept, it is finally affordable and offers what should be a satisfying experience. Sure, it is not yet perfect, but devices like the Oculus Rift and HTC Vive are certainly ushering in a new era.
All of this awesome new VR technology requires a powerful Windows PC. Sorry folks, that Chromebook or MacBook you covet is useless here. Heck, even most computers running Microsoft's ubiquitous desktop OS can't handle it. Today, MSI unveils a Quadro M5500-powered laptop that can handle both the Oculus Rift and HTC Vive. The unimaginatively named WT72 mobile workstation is VR-focused and can be configured with top specs. It can even be configured with a Xeon processor! Of course, it is also very expensive.
"Designed for maximum performance, MSI's WT72 is powered by NVIDIA's Quadro M5500 GPU, Intel's 6th generation Core-i7 and Xeon processors, and up to 64GB of DDR4 memory. The latest in professional graphics design technology, the Quadro M5500 is the world's fastest mobile GPU, delivering up to 35 percent performance increase over previous models, with 2,048 cores for optimum speed and power", says MSI.
The company further says, "to enhance the multimedia and user experience, MSI equipped the WT72 with audiophile-grade Dynaudio speakers featuring Nahimic Audio enhancer, True Color Technology screens with Adobe RGB certification for wide viewing angles and the most accurate visuals, and the new SteelSeries backlit keyboard with Silver-Lining Print to eliminate eye strain. The WT72 also comes with Thunderbolt 3 and USB 3.1 connectors, and features a dual fan design for efficient heat dissipation".

Oh my. This beast is drop dead gorgeous, and chock-full of cutting-edge technology. There is no reason not to buy it, right? Well, not so fast -- the price is likely to stop most consumers in their tracks. The starting price is $5,500 -- no, that is not a typo. As you increase the specs, it tops out at $6,900. Jeez, these cost more than my car is worth!
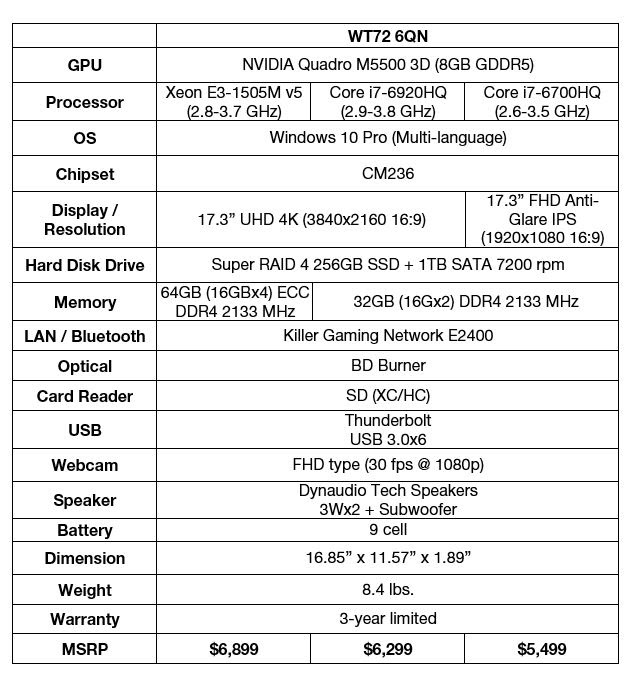
You can see the three configuration options above -- all are available now. While all the models make me want to simultaneously drool and cry tears of joy, none are in my budget, sadly.
Are you willing to spend so much to take advantage of virtual reality with a laptop? Tell me in the comments.
-

The threat of ransomware is so great, the US and Canada issue joint security alert
Publié: avril 4, 2016, 7:30pm CEST par Mark Wilson

Malware is far from being a new problem, but the inexorable rise of ransomware has taken many by surprise. There have been a number of very high profile instances of ransomware such as PETYA, and the threat is perceived as being so high that the US and Canada have taken the unusual step of issuing a joint security alert.
The likes of TeslaCrypt 4 feature 'unbreakable encryption' and use scare-tactics to encourage victims to part with their money. This is what has prompted the joint alert from the US Department of Homeland Security and the Canadian Cyber Incident Response Centre which warns about "destructive ransomware variants such as Locky and Samas". Interestingly, the advisory actively discourages victims from bowing to ransom demands.
The advisory warns that "individuals or organizations are discouraged from paying the ransom, as this does not guarantee files will be released". However, it does recognise that "the authors of ransomware instill fear and panic into their victims, causing them to click on a link or pay a ransom". But this is said to be a bad idea as it could lead to additional malware infection, and could result in the theft of bank details and other data.
The focus is on prevention rather than cure, and US-CERT offers a number of tips aimed at both users and administrators:
- Employ a data backup and recovery plan for all critical information. Perform and test regular backups to limit the impact of data or system loss and to expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Use application whitelisting to help prevent malicious software and unapproved programs from running. Application whitelisting is one of the best security strategies as it allows only specified programs to run, while blocking all others, including malicious software.
- Keep your operating system and software up-to-date with the latest patches. Vulnerable applications and operating systems are the target of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker.
- Maintain up-to-date anti-virus software, and scan all software downloaded from the internet prior to executing.
- Restrict users’ ability (permissions) to install and run unwanted software applications, and apply the principle of "Least Privilege" to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through the network.
- Avoid enabling macros from email attachments. If a user opens the attachment and enables macros, embedded code will execute the malware on the machine. For enterprises or organizations, it may be best to block email messages with attachments from suspicious sources. For information on safely handling email attachments, see Recognizing and Avoiding Email Scams. Follow safe practices when browsing the Web. See Good Security Habits and Safeguarding Your Data for additional details.
- Do not follow unsolicited Web links in emails. Refer to the US-CERT Security Tip on Avoiding Social Engineering and Phishing Attacks for more information.
Photo credit: Borislav Bajkic / Shutterstock
-

Android can't make BlackBerry phones attractive again
Publié: avril 4, 2016, 7:22pm CEST par Mihăiță Bamburic

Realizing that it stands no chance of attracting consumers with BlackBerry 10 OS devices, BlackBerry last year released a smartphone that runs Android. Called Priv, it offers an interesting mix of business and consumer-oriented features that make it a powerful contender in the high-end segment. Many folks seem to like it, but just how much of a success is it?
Priv has what it takes to be a big seller. It has all the right features that consumers say they want in a BlackBerry smartphone: premium build, physical keyboard, large screen, enterprise-friendly apps and, last but not least, Android. You would think that by giving people what they've asked for the company would be struggling to keep up with demand. And yet, in its last fiscal quarter, BlackBerry only sold a very small number of Priv units.
In total, in its Q4 FY2016, which ended February 29, Blackberry sold just 600,000 phones, a number which obviously includes Priv sales. That is not a whole lot of units for a premium vendor, let alone one that also sells more affordable handsets.
BlackBerry is not saying exactly how many Priv devices it sold last quarter, but that number is clearly lower than 600,000. Quite possibly, it may be its biggest seller in the lineup, but that would not be saying much anyway. BlackBerry was expected to sell 850,000 units last quarter, but it missed expectations by 150,000 units.
It would seem that by embracing Android, BlackBerry hasn't managed to turn things around. CEO John Chen wants the company to sell at least three million units this coming year to break even. The way things are going, it may fail to meet that goal, although Chen does say that the "path to profitability looks reasonable".
With a single Android smartphone, BlackBerry cannot realistically expect to impress many consumers. The company is quite possibly looking to expand its Android lineup, and the best way to do that would be to introduce Android on less expensive devices. That said, it might just be best to quit the hardware market altogether.
Looking at BlackBerry's traditional market, businesses have come to realize that it is possible to use Android smartphones and iPhones in enterprise environments. And, at least when it comes to Android, there are lots and lots of options to choose from, many of which can be better suited for employees than Priv or possibly other BlackBerry-made Android devices.
Perhaps BlackBerry should follow in Microsoft's footsteps and reposition itself as a developer in today's mobile market. It would have much more to gain by doing so than selling phones which, as many vendors have come to realize, is a very tough game to win at. Apple and Samsung are the only makers with lots of sales and huge profits, after all. Not to mention that there is very little room to grow, with smartphone sales expected to increase by less than 10 percent this year. So, why bother?
Photo Credit: Minerva Studio/Shutterstock
-

Which is the most complex programming language?
Publié: avril 4, 2016, 6:46pm CEST par Oliver Muhr

JavaScript may be today’s go-to for front-end programming, but in many ways it’s a language that mimics what has come before. Just like COBOL, C, C++, C#, Java and Python, JavaScript is a procedural language. There’s nothing distinctive about JavaScript, with one big exception: JavaScript has a code complexity problem.
How could JavaScript, a language based on the same paradigm as many others, have a complexity problem that is so singular? The answer is temporality. JavaScript sits in a unique spot in software development history, rising squarely in the midst of a shift from mostly back-end to mostly front-end development, which was spurred by the mobile revolution.
Newly popular front-end developers would need to clean up the messy legacy of overtaxed designers, who had played second fiddle and thus rarely received the resources they needed to finish the job. Unfortunately, there wasn’t time for clean-up, or rather, leadership didn’t make time as they continued to ask for more bells and whistles.
This is the conundrum in which JavaScript programmers found themselves in the late 2000s and it’s a story that plays out in the data. Seerene has analyzed more than 400 billion lines of code to identify and visualise the programming languages that create the most headaches for developers.
Take a look at the infographic below to see if your language of choice is among the most complex, confusing or inefficient.

Oliver Muhr, CEO of Seerene.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: alphaspirit / Shutterstock
-

Microsoft and R3 blockchain partnership aims to reduce fraud and costs
Publié: avril 4, 2016, 5:58pm CEST par Mark Wilson

Microsoft has joined forces with a collective of more than 40 financial institutions to help push the development of blockchain technology. Working with the R3 consortium, Microsoft wants to develop and test new technologies to replace and streamline old systems used in banking and enterprise industries.
The announcement comes as the company launches the first Microsoft Envision event with the aims of bringing together business leaders to pool ideas for the digital age. Using Microsoft Azure, the company wants its partners to expand the use of Blockchain-as-a-Service and bring about change faster.
Despite the involvement of financial institutes, and the association with Bitcoin, blockchain is about much more than just moving money from one place to another. Microsoft is looking to create what it describes as an 'enterprise-grade blockchain eco-system' that can also be used in the healthcare industry, digital media and manufacturing.
Announcing the partnership with R3, Microsoft's Executive Vice President of Business Development, Peggy Johnson, says:
Known by many as the backbone of bitcoin, blockchain offers a secure and transparent way to digitally track the ownership of assets. Simply put, it promises to revolutionize the way financial institutions conduct transactions. Blockchain modernizes legacy financial processes, so trades of assets like stocks and bonds can be finalized in minutes, not days. And by enabling a more direct transfer of ownership, it eliminates the need for middlemen like clearing houses, both cutting costs and greatly reducing the risk of fraud.
With that in mind, I’m thrilled to announce a strategic partnership with R3, a consortium of leading banking institutions, to help move blockchain technology from hype to reality for the financial services industry. Together, we will help R3’s over 40 member banks develop, test and deploy blockchain technologies to modernize decades-old processes and streamline operations, potentially saving billions of dollars from back-office operations.
Check out the video below in which Microsoft explains its vision a little:
Photo credit: Olga Donskaya / Shutterstock
-

93% of UK mobile users have their location tracked every day
Publié: avril 4, 2016, 5:39pm CEST par Mark Wilson

Awareness of the privacy issues involved in using various devices and software has grown dramatically in recent years -- there can be few readers who do not know about the telemetry and privacy concerns surround Windows 10, for instance. But a new campaign by privacy-focused advocacy group Krowdthink aims to raise aware of the privacy implication of owning a mobile phone in the UK.
The 'Opt me out of Location' campaign aims to highlight the fact that nearly every single mobile phone owner in the UK (93 percent) has unwittingly signed up for a contract that permits their location to be tracked. More than this, the data collected allows providers to build up highly detailed customer profiles which Krowdthink warns leaves millions of users just one serious data breach away from having private data exposed to and abused by criminals.
Krowdthink says that "the big location data breach has yet to occur", but there is great concern around the fact that most people are simply unaware that their location is being almost constantly -- and very precisely -- monitored. All the more worrying is the selling on of this data, opening up even more opportunities for data to be hacked, leaked, or breached. The group says that education is important, saying "we need to exercise our rights to opt out and ideally seek an explicit opt-in from those tracking us".
Geoff Revill, the founder of Krowdthink, cautions:
The fact of the matter is your mobile and Wi-Fi service providers know -- without you knowing -- where you are, how you got there and can figure out where you are going.
It's not just mobile phone providers that are cause for concern; Krowdthink says that public Wi-Fi service providers are also concerning sources of location data. Pete Woodward from security company Securious says: "location tracking data would be gold dust for the criminal fraternity and would be very saleable on the black market".
Research by Krowdthink says that while most mobile users are suspicious of apps that make use of GPS, few people think about the fact that their location is highly trackable when they connect to cell towers. By gathering data about location and movement, it is possible to build up detailed user profiles that could be valuable to criminals. Burglars, for instance, would be able to quickly determine when particular houses were usually empty, but there is also scope for data that's gathered to be used for blackmail: "… identifying any cases of infidelity -- including when, where and how long for. [Location data also] identifies your sex, probable sexual orientation, your religion and many other personal preference".
Similar research has been carried out by the Open Rights Group, with the findings suggesting that consumers are simply not being given enough information to make properly informed decisions about how their data is used.
You can find out more about the Opt Me Out Of Location at the campaign website, where you'll also find out how to manually opt out of location tracking with a number of mobile providers.
Photo credit: Georgejmclittle / Shutterstock
-

The monitoring problems of IT pros
Publié: avril 4, 2016, 5:35pm CEST par Kent Row

Recently an IT friend of mine told me that for the past five years he has been longing for a tool which could alert him when non-routable interfaces went down. To be perfectly honestly my heart went out to the guy -- that’s such a basic monitoring request, why hasn’t it been fulfilled I thought. But when I thought about other monitoring requests I’ve heard over the years it made me realize there is a major contradiction when it comes to IT pros and monitoring.
On the surface no IT professional will accept sub-optimal performance or functionality for any technology. IT pros overlock their systems, exploit back doors, root phones to get the latest (or un-supported) version, memorize complex key combinations to access god-mode -- we won’t settle for anything but the best and do our upmost to support it.
However when it comes to monitoring this is not the case. I’m constantly meeting network engineers and sysadmins who install monitoring functions which completely fail to do the job required. What is more upsetting is how so many IT pro’s accept this as de rigueur -- there is no sense of urgency to demand more sufficient monitoring tools.
I’ve therefore decided to tackle this problem myself in this two part series to help identify why IT pros are putting themselves through this.
Home-Grown vs Corporate Monitoring Solutions
One of the first issues behind monitoring stems from how the tool is implemented in an organization. The two most popular ways are via a home-grown solution or a corporate project. Both of which have benefits, but which also won’t always offer the best results.
Home-grown monitoring solutions are often created on the side and on the cheap with a "that will do for now" mind-set. On the plus side, the price is right and the solution will do exactly what the user needs (give or take, depending on their skill). On the down side, these types of solutions won’t grow or improve without a crisis.
The person that created it will rarely touch it again unless it’s broken because, well frankly, they have more important things to do than spend their time adapting a so-so monitoring solution. This ethos immediately gets the organization stuck with an average monitoring tool that can more-or-less do the job at hand, but to no exceptional standard.
On the flip side there are corporate-sponsored projects to implement an enterprise-wide monitoring solution. These are usually sponsored by executives who, following a fancy presentation from a vendor complete with numbers and buzzwords, believe they have The Solution and any naysaying on the part of staff is just resistance to change.
And what I’ve learned over the years is often when a sales guy comes and says "ROI", "efficient" and "speed" multiple times to an executive, it’s hard for them not to fall in love with whatever product they are selling. The knock on effect of this is that the tool then becomes associated as that executive’s metric for success.
And so, since these solutions are typically not cheap, there is a huge push to not only get it implemented (come hell or high water) but also get it working everywhere with everything. Because gosh darn it we need to get our money’s worth out of this thing! Subsequently the tool, whatever its strengths may be, gets shoehorned into various situations it was never meant for.
In this instance you’re left with a great tool that isn’t being used in the way it was meant for and is being owned by teams who have no vested interest in it. Thus much of the potential this monitoring tool could offer to an organization goes to waste.
Do Monitoring Professionals Even Exist?
Another challenge in the monitoring "space" is that it’s difficult to get specialists from all of the relevant teams; network, systems, virtualization, storage etc. to agree on a set of metrics for monitoring. As difficult as that is, it’s even trickier to find a monitoring professional who is familiar with all the different areas and has the knowledge to confidently mediate between the different teams to find a solution that works for all. To be quite frank it can be difficult to even find a monitoring professional at all.
Most organizations make do with a consultant who is an expert in a particular toolset. With larger solutions even this becomes a challenging proposition as experts sub-specialize in various aspects of the tool. If the expert is keen on code, every problem looks like a scripting solution. Protocol centric pros will leverage SNMP, WMI, or the like. And so on.
The net effect is that monitoring options offered to technicians may be feature sparse (if the software is home grown); or undertaking the wrong tasks, or undertake them the wrong way (if it’s a corporate sponsored solution).
Thus implementing a monitoring solution that is robust enough to deal with the challenges and demands of multiple teams within a business is, and this is a gross understatement, hard.
The Path to the Promised Land
Implementing a monitoring system that covers all the bases and provides teams and organizations with the information and responses needed to be valuable requires several things: it requires multiple tools, often from multiple vendors (though few vendors will admit this). It requires technical leadership who can get the right teams into the room, start the right conversations, and help them to answer the right questions. And it requires organizations to commit to the level of expertise both during the implementation phase and the subsequent usage to make any set of solutions truly effective.
Clearly it’s harder to do this than people realized as, based on discussions with my colleagues, customers, and coworkers, it looks like many IT pros have given up on it altogether. In the face of this kind of challenge, many just accept the status quo of monitoring because they feel too many variables are out of their hands.
However, my view is this is categorically unacceptable for any organization, any budget, any industry and any size. When monitoring is done right it can be a powerful force within an organization, enabling not just the remediation of downtime, but the avoidance of it; it drives performance improvement rather than just tracking degradation; it helps organizations avoid un-necessary spending rather than just being a sunk cost; as well as being a morale boost to engineers who know they can rely on something besides their own eyes and gut to tell them that everything is sufficient, and to quickly and accurately lead them to the root cause of a problem when it’s not.
This Promised Land I am describing does exist "out there" and can exist in your company, and I’ll tell you how to get there in my next post.
Kent Row, IT admin and superhero, SolarWinds.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: auremar/Shutterstock
-

New capabilities help drive application release automation
Publié: avril 4, 2016, 5:00pm CEST par Ian Barker

Digital transformation strategies are often held back by complex IT systems that have been built over the years and represent significant investment. This may lead to departments seeking their own solutions, placing yet more pressure on back office systems.
Business automation specialist Automic is launching new capabilities to its DevOps release automation product, Automic Release Automation, to allow companies to deliver greater agility, scalability, and speed in order to drive competitive advantage.
"We are simplifying how our customers execute on their DevOps journey by specifically targeting all of the applications across an enterprise with the goal of driving the digital transformation required by our clients", says Chris Boorman, chief marketing officer at Automic. "Our experience in automation, expertise in production IT environments, and industry recognized technology are key differentiators that position us and our clients for success. The Automic Blueprint for Continuous Delivery provides a practical approach that an enterprise can employ to scale continuous delivery across both back-office applications and the new digital front-office. This blueprint provides a clear and structured approach for all enterprises to use in driving their digital transformation".
Features include a new cloud-based sandbox, and visualization of the delivery pipeline of all applications to better understand the impact and time implications of multiple concurrent releases throughout the organization.
Automic Release Automation enables enterprises and service providers to serve multiple departments and clients in isolation from each other on a single shared platform, simplifying operations and maintenance, and making scaling easier.
It also integrates with the Automic marketplace allowing developers to contribute and utilize new content seamlessly. There's a new online assessment service too that will benchmark an enterprise against key indicators of maturity. By answering a set of simple questions, enterprises can benchmark themselves against the Automic standard, against their peers, their industry or their region.
You can find out more about Automic Release Automation, which is available now, on the company's website.
Image Credit: Stokkete / Shutterstock
-

Biometric Authentication: Making mobile devices and apps safer
Publié: avril 4, 2016, 3:29pm CEST par Kevin Curran

According to comScore, from September 2010 to September 2014, smartphone usage increased by 394 percent, while tablet usage rose by an astronomical 1,721 percent in the United States. So it’s certainly no surprise that mobile payments are predicted to skyrocket over the next five years. mobilThis shows that the global mobile payment volume in 2015 was 450 billion U.S. dollars, and projects that number to surpass 1 trillion U.S. dollars in 2019.
With the growing interest in and use of mobile devices and payments, users are rightfully concerned with cybersecurity threats. To combat these threats, there has been a surge in using biometric technologies for user authentication.
What are biometric solutions and how can they increase safe authentication?
Biometric solutions measure specific characteristics of a person, including: voice, handwriting, fingerprint(s), face, retina or iris of the eye, gait, vein infrared thermogram, hand geometry and palm print or from a combination of all these identifiers termed multimodal-biometrics -- essentially, "something about you" that is practically impossible to copy, steal or reproduce. Biometric-based authentication provides a robust alternative to using passwords and pins. It validates the identity of a user by measuring unique physiological and behavioral characteristics of an individual. Such a measure maximizes between-person random variations (e.g. someone else putting in your password,) while at the same time minimizes within-person variability. In contrast with passwords and pins, a biometric identifier cannot be lost, forgotten or shared.
Mobile payments and biometric verification
MasterCard has been working to announce its "selfie" pay, which allows users to approve online purchases by taking a picture of themselves (facial recognition) for verification, users can also opt for authenticating their purchase through a fingerprint. The accuracy of facial recognition systems can vary greatly due to factors like lighting, camera angle, sensitivity and more. Likewise, fingerprint readers are affected by temperature, position and other factors.
Yes, it is feasible that biometric authentication can become an actual form of providing credentials (although it should be combined with multi-factor methods). Hardware devices do potentially offer ideal security but often the problem is the need to carry such a device on the person. Hence the move towards making our mobile phones the actual hardware device. One popular hardware approach for authentication is smart cards. Smart card technology provides an excellent medium for storing biometrics. A smart card can provide a strong authentication platform in our pocket. Mobile phones and smart cards can be used for both physical and logical access authentication.
Making Biometrics effective
Fingerprint scanners have been manufactured in masses for mobile phones due to Apple’s Touch ID system, but have of course been integrated on laptops for years, yet are hardly used. The Touch ID system from Apple is quite impressive from a security perspective, however fingerprint scanners are not the be-all, end-all solution for identity theft and cybersecurity prevention as we leave fingerprints on every surface we touch. There have been many examples of Apple's Touch ID being bypassed through the use of scanners, latex and patience.
The most current widespread authentication approach employs solely using passwords. Deployment of proper biometric solutions should significantly reduce identity thefts, with great benefits for the economy by eliminating the use of just passwords from the equation in place of more reliable solutions. The most successful way to use biometrics for security is to incorporate multi-factor authentication which would reduce risk by involving separate types of factors that would require an attacker to use different methods of attack, thus making a breach more difficult.
Multi-factor authentication combines at least two of the following methods to strongly authenticate a user. Therefore a PIN plus a password is not actually multi-factor, since both items are something you know. Full three-factor authentication, when combined with a device ID, allows enterprises to easily combine "what we have" and "what we know" with the all-important "who we are". Thereby integrating a core benefit to future security systems, including;
- Something you know (typically a password/PIN)
- Something you have (a trusted device identifier that is not easily duplicated, e.g. location)
- Something you are (a unique biometric)
Widespread Adoption and Concerns
Trust is particularly important for consumers when it comes to using biometrics for financial institutions and merchant purchases, including identify theft, account blocking inconvenience, etc. We can expect the first true full-scale biometrics deployment will involve mobile payments and other financial organizations.
It’s estimated that online "direct" fraud is costing the global economy around £60bn a year. The associated indirect costs of identity theft and recovery have not been fully quantified but it’s possibly 10 times the actual direct costs. Large e-commerce merchants believe that fraud is inevitable but understand that their prevention efforts will result in more positive customer relationships and ensuring the proper security measures are in place will help that.
In order to make biometric authentication successful, companies need to introduce multi-factor authentication and be sure that users are educated on how and why they are using biometrics.
Photo credit: ra2studio / Shutterstock
 Kevin Curran is IEEE Senior Member and Faculty of Computing and Engineering, University of Ulster. His achievements include winning and managing UK & European Framework projects and Technology Transfer Schemes. Dr Curran has made significant contributions to advancing the knowledge and understanding of computer networking and systems, evidenced by over 700 published research papers.
Kevin Curran is IEEE Senior Member and Faculty of Computing and Engineering, University of Ulster. His achievements include winning and managing UK & European Framework projects and Technology Transfer Schemes. Dr Curran has made significant contributions to advancing the knowledge and understanding of computer networking and systems, evidenced by over 700 published research papers. -

Work-life balance gains importance as tech worker salary expectations fall
Publié: avril 4, 2016, 3:24pm CEST par Ian Barker

What are the trends driving the careers of tech professionals? A new report based on information gathered from the Woo platform, which allows workers to find jobs with companies that offer the things they really want, reveals what has changed in the first quarter of 2016.
The Woondex (Woo Index) shows there has been a 12.6 percent drop in salary expectations compared to the final quarter of last year. However, there's an 8.2 percent increase in the number of workers looking for a better work-life balance over the same period.
The San Francisco Bay Area is still the most popular location for tech workers in the US, but its appeal could be waning as there's a 6.9 percent increase in the number of Bay Area workers who say they are willing to relocate. The most popular choice for those who want to move on is New York, followed by Seattle.
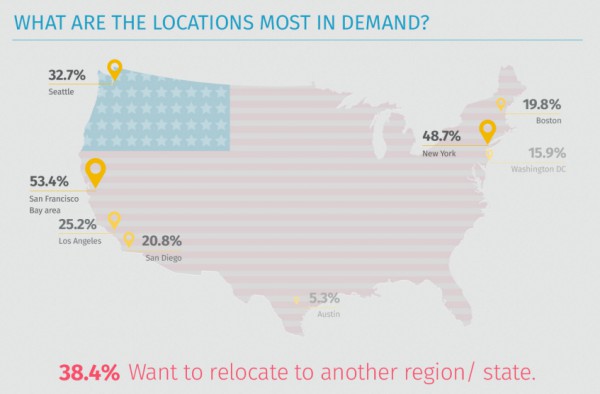
It seems that size matters too, at least for businesses, with 82.6 percent wanting to work at larger companies compared to only 76.5 percent willing to work at startups.
The most in demand technologies are Java (18.2 percent), NodeJS (15.2 percent) and AngularJS (14 percent). When it comes to sectors big data/cloud is still most popular, followed by health and finance.
You can find out more about how Woo helps gauge their worth and find fulfilling roles on the company's website.
Photo Credit: wavebreakmedia/Shutterstock
-

Get the lowdown on your PCs storage devices with Diskovery
Publié: avril 4, 2016, 3:23pm CEST par Mike Williams
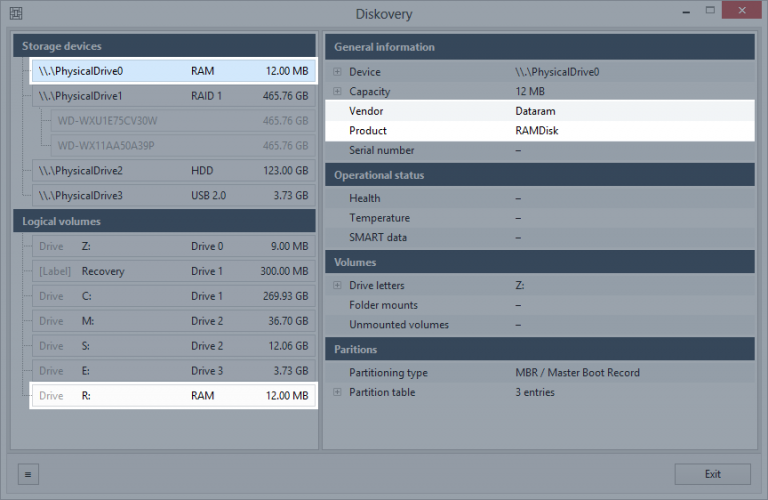
Bvckup 2 developer Pipemetrics has released the first beta of Diskovery, a free system information tool which reveals all about your PC’s storage devices.
It’s a familiar idea, but Diskovery stands out for its thoroughness, using multiple technologies to discover and talk to drives.
Direct ATA queries, ATA pass-through queries, SCSI pass-through queries, Common Storage Management Interface, the Virtual Disk Service and Windows API are all involved, allowing the program to uncover much more data than some similar tools.
You can expect details on local drives, external USB disks, RAID setups (hardware and software) and more, even RAM disks and -- maybe -- encrypted volumes.
The report includes device product ID, manufacturer, volume/ PNP ID, volume type, partition types, capacity, used space, file system, SMART data, supported features, USB type of a drive enclosure, RAID type/ status/ composition, and more.
What you don’t seem to get, unfortunately, is any way to save this information as a report, a problem if you were hoping to analyze it later.
Diskovery is still a beta, of course, so this might arrive in a future release. And if you’re interested, we’d say take a look anyway: it’s only a 226KB download, a single executable, no installation or other hassles involved.
Diskovery is a freeware tool for Windows Vista and later.
-

New Start Menu features on the way in Windows 10 Anniversary Update
Publié: avril 4, 2016, 2:34pm CEST par Mark Wilson
Windows Insiders will soon be able to try out a new Start Menu when preview builds of Windows 10 Anniversary Update begin to roll out. We already know some of what to expect from this big update to Windows 10 -- such as badge notifications in the taskbar for UWP apps -- and now we can see what the updated Start menu looks like too.
The same Microsoft software engineer who shared details of badge notifications -- Jen Gentleman -- has posted an animated GIF to Twitter that shows the Start Menu in action. There are a few notable changes in the updated version, including a nested hamburger menu.
As the new Start Menu is only currently being tested internally at Microsoft and is yet to roll out even to Windows Insiders on the Fast ring, it's entirely possible that things will change over the coming weeks. That said, the animation does give an intriguing insight into the ideas that Microsoft is playing with.
Ms Gentleman's tweet may only be a few seconds long, but it has generated a good deal of interest:
By popular request, to ease some concerns, and because @ZacB_ asked nicely, here's the new start menu in action!
 pic.twitter.com/MiIPO8Epuf
pic.twitter.com/MiIPO8Epuf— Jen Gentleman (@JenMsft) April 4, 2016
The hamburger menu is used to house the icons that currently appear in both the All Apps and 'Most used' sections. The redesign also helps to provide easy access to system folders such as Music and Documents. There are also changes on the cards for the Start screen as the Feedback Hub reveals:
Start menu: This view is predominantly designed for PC. We've heard your feedback, and we’ve focused on consistency, efficiency, simplicity, and making better use of the space.
The All apps list is essential to understanding which apps you have on your device. We’ve elevated this list to the top level of the UI to reduce clicking & scrolling. This makes it easier to access apps in the All Apps list. It also reinforces the consistent Start experience across form factors.
Start screen: This view is predominantly designed for tablet. We've heard from Insiders that they feel Windows 8.1 start screen delivered a better tablet experience than what we have in Windows 10 today. We are addressing that and are looking to make the All apps list more usable in two ways:
- Full-screen All apps list in tablet mode. We heard your feedback that the All apps list should be full-screen in tablet mode and explored several designs that aid efficiency while taking advantage of the additional real estate when Start is full screen. Specifically, we’re striking a balance between density and "scan-ability" (i.e. how easy it is to scan the list to find the app you want).
- A combined "Most used" and "All apps" list view. With this approach, we hope to address the confusion that many users felt with the two very similar list views ("Most Used" and "All apps").
As part of this improvement, we’ve also made it easier and more clear how to switch between the "Pinned Tiles" and "All apps" views by adopting the navigation pane pattern used throughout Windows.
Microsoft is looking for feedback about this change just as it has done with other new features of Windows 10, and you can provide your thoughts via the Feedback Hub and find out more on Sway.
-

How to stay safe using public Wi-Fi hotspots
Publié: avril 4, 2016, 2:17pm CEST par Joey Tominna

One of the most convenient things about connecting to the Internet through your computer, tablet, or smartphone is being able to tap into public Wi-Fi from pretty much anywhere. These days, there are hotspots available all across the country, so you’re practically never without Internet access. However, it’s a smart move to be cautious when it comes to connecting to public Wi-Fi.
When you’re tapping in to an unfamiliar hotspot, you could potentially be putting your personal data -- and the security of things like your bank accounts, your passwords, and your identity -- at risk. Even if a public WiFi hotspot looks secure, you might still miss the small red flags that signal trouble. Let’s take a look at how public WiFi works to connect you to the Internet, some risks that come with it, and how to ensure you’re keeping your data safe while you’re on a hotspot.
The Reward and Risk of Public Wi-Fi
It’s hard to imagine being out and about without access to the Internet, and for people looking to connect while outside of the house, utilizing the nearest Wi-Fi is a good solution. Public Wi-Fi works much the same as your own Wi-Fi does at home, except on a larger scale, and it is open to pretty much anybody. Once you’ve opened up the Wi-Fi connectivity options on your laptop or phone’s settings, you can search through which networks are available to use, and the ones that aren’t locked for private use are generally available for access.
Those who regulate the servers for public WiFi are generally businesses who charge patrons for access to their hotspots, or community places like libraries, airports, and hotels that may offer their Wi-Fi free of charge. In some cases, entire swathes of cities (like Tel Aviv, Helsinki, and Hong Kong) are equipped with free municipal Wi-Fi that anyone can use -- from places like city parks to even underground subways.
While this is definitely convenient -- and, if you’re using your smartphone, it can save you from using your own data plan -- it’s not as secure as using your own home WiFi network, or your smartphone data, where you have control over the security. And unlike when you’re at home, you probably won’t know everybody who’s on the network with you. Although it’s true that people with malicious intent won’t be creeping around on every single network, it’s always better to be safe rather than sorry -- even if that means going the extra mile to make sure that you’re properly protected.
"Just because most wireless routers have a firewall to protect you from the Internet doesn’t mean you’re protected from others connected to the same network", says Lifehacker ."It’s remarkably easy to steal someone’s username and password, or see what they’re doing just by being on the same network".
You can’t be too careful when it comes to the safety of your data when you’re connecting to public Wi-Fi, particularly when you’re accessing a hotspot that doesn’t require a password. The fact that there’s no password involved allows your data to pass through unencrypted, which makes it easy for anyone in range of the network to see what you’re doing and which websites you’re browsing.
According to How-To Geek, using a WiFi hotspot without a password means that "people can see what unencrypted web pages you’re visiting, what you’re typing into unencrypted web forms, and even see which encrypted websites you’re connected to". This means that other users can snoop in on your Internet session and even possibly hack in to your data.
Ill-intentioned individuals can use trickery to work their way into your device once you’re connected to an unencrypted hotspot. The Houston Chronicle explains how hackers are able to set up an "evil twin" with the same name as a legitimate hotspot, and when people accidentally use the evil twin, they’ve fallen for the trap. So even if you might think you’re logged on safely, you could inadvertently be providing hackers with data and information that can be used to compromise bank accounts, commit identity theft, and more.
How to Connect Safely
The good news is that you don’t need to avoid public WiFi altogether -- you just need to make sure you’re using it in a smart and safe way. Here are a few tips for ensuring that your public WiFi experience isn’t putting your personal data at risk:
Always Look For HTTPS
This means that the website you’re browsing is encrypted and your data can’t be snooped by others. As Lifehacker states: "Many sites -- including Facebook, Gmail, and others -- will [use HTTPS] automatically, but keep an eye on the address bar and make sure the 's' in 'https' is always there when you’re exchanging sensitive information. If it disappears, you should log out immediately. Other sites will default to HTTP connections, but support HTTPS if you manually type it in".
One caveat: Even though you’ll find HTTPS on banking websites and other places that deal in financial transactions, try to avoid doing any banking or exchanging financial data over public Wi-Fi. Unless it’s absolutely an emergency, wait until you get home and have secure home WiFi to do anything that involves the input of your financial information -- just to be extra safe.
Keep the Wi-Fi Setting on Your Phone Turned Pff When You’re Not Using It
This will help prevent your phone from automatically logging in to any networks that you may have previously accessed. If you’re ever not sure about a public hotspot that you’ve connected to, be sure to log out and use your phone commands to forget the network. That way you won’t accidentally end up hopping back on it if you’ve left your WiFi setting turned on. (As McAfee reminds us, "some of your mobile applications such as Skype, Twitter and instant messaging apps may be using local hotspots without you realizing it" -- better to be completely logged out!)
Make Sure Your Software Is Up to Date and You Have All Current Security Patches Installed
If your software requires an update, don’t put it off, especially if you’re a user of public WiFi -- some updates contain patches to help avoid potential security threats, and can help keep unwanted guests from snooping into your phone or laptop. Another setting to look into is the firewall; be sure that your computer’s firewall settings are enabled for an extra layer of protection from the other users on the network.
Use Public Wi-Fi Safely
Public WiFi is indeed helpful and convenient when you’re out and about with your phone (or laptop) in hand -- but it’s always good to remember that when you connect to the public network, it’s not just you who could have access to your files, but everyone else on the network as well. Instead, be sure to look for extra security from both your device’s settings and the Internet browser, and be cautious with where you click to. Having safety in mind can make all the difference for the protection of your data.
Joey Tominna, president of Rushstar Wireless
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Sidarta / Shutterstock
-

MacClean promises to improve security and privacy as well as clean your Mac
Publié: avril 4, 2016, 12:41pm CEST par Nick Peers
iMobie has released MacClean 3.0.5, a brand new version of its freeware Mac cleanup tool. The app, which boasts a large number of cleaning tools, returns with a new security bolt-on and completely redesigned user interface.
Version 3.0.5’s major new feature is the implementation of new privacy and security tools, the latter based around the open-source ClamAV malware scanning engine.
The new security tool requires a separate download and installation -- it’s packaged as 'Security Engine and Database', but is actually the open-source ClamAV tool, which is used to scan for threats on demand. Any detected threats then find themselves placed in the program’s new Quarantine section for further review and action – if required.
MacClean 3 also unveils a new Privacy Issue scan, which allows users to review recent app usage, opened documents and even 'private' app histories. Once done, users are invited to review what’s been found before cleaning.
A third tool -- Malicious Cookies -- scours the caches of popular browsers (including Safari, Firefox, Chrome and Opera) for cookies known to steal personal data and compromise security in other ways.
The app also unveils a complete redesign, showcasing a more minimalist user interface that sits in nicely with the latest OS X look and feel. The app also reorganizes its tools into two sections, with the scanning tools listed under Cleanup and other tools found under Utilities.
These additional tools -- some of which are used by the program’s scanning components -- are split into two sections: Cleanup Tools include a duplicates finder and 'old and large files' tool for rooting out potentially redundant space hoggers. There’s also a secure file eraser and tools for thoroughly cleaning apps and getting rid of unused language files.
Optimization Tools features an iPhoto cleaner, extension manager, secure trash sweep and 'binary' junk remover that attempts to streamline individual app sizes by removing what it terms 'redundant binary junk'.
MacClean 3.0.5 is available now as a freeware download for Macs running OS X 10.7 (Lion) or later.
-

The cloud revolution you probably haven't heard about yet
Publié: avril 4, 2016, 12:39pm CEST par Chris McNabb

Like the PC, World Wide Web, and virtualization, the cloud is considered a revolutionary technology because it completely changes business processes, cost structures, and time to value. Volumes of information have been written about the benefits of the cloud, with most stories focusing on low-cost storage, reducing hardware costs, anywhere access to applications, and relocating and scaling compute resources.
But another cloud benefit, a cloud-based application integration framework, is just beginning to resonate in many c-suites. This framework has the potential to completely transform application economics by dramatically simplifying business processes, reducing costs and accelerating time to value. Best of all, this particular cloud revolution can be introduced into an organization incrementally, leveraging existing investments.
Businesses today fully understand traditional application integration using middleware. And they understand the need to connect new cloud applications with their existing systems using APIs or custom coding. But what most companies still don’t understand is what’s required to achieve what Gartner calls a "postmodern ERP" environment. They need an architectural framework that allows them to easily combine best-of-breed cloud and on-premises business process applications into a single environment, painlessly create end-to-end business processes across these applications, and control and interact with the entire environment as if it were built by a single vendor.
Today’s agile businesses increasingly rely on cloud-based services like Salesforce.com, Workday and NetSuite, but the value of these solutions is far less than optimal if they just become another silo in the organization. Most companies want to integrate these applications with their legacy on-premises CRM and ERP solutions. They also likely see the benefit of integrating these solutions with other cloud solutions.
Until a few years ago, the only way to achieve this integration was with a typical middleware project involving lengthy customer coding and testing. Such projects were a struggle since middleware solutions were not designed to work with cloud environments. In addition, each time one of the integrated components was upgraded, another expensive custom-coding project ensued, erasing much of the cost benefits of having moved to a cloud solution in the first place.
Today, companies have the option of coding application integrations using application programming interfaces (APIs). Vendors increasingly publish APIs for their solutions, and developers can use these APIs to integrate cloud-to-cloud and cloud-to-on-premises solutions. Of course, this is still a custom-coding project and requires maintenance and re-coding as the software solutions evolve.
Enter integration platform as a service (iPaaS). According to Gartner, Integration Platform as a Service (iPaaS) "is a suite of cloud services enabling development, execution and governance of integration flows connecting any combination of on-premises and cloud-based processes, services, applications and data within individual or across multiple organizations".
The revolutionary aspect of iPaaS is that it typically eliminates the need for some or all custom coding, which shortens development time, reduces errors, and makes maintenance far easier. iPaaS unifies the creation of all the types of integrations that enterprises actually need today: cloud-to-cloud, cloud-to-on-premises, on-premises-to-on-premises, B2B, EDI and mobile. A well-designed iPaaS solution also provides a single, centralized visual design and management interface to enable citizen developers and business users to create and maintain integrations, along with prebuilt connectors between common applications to make creating many types of integrations almost instantaneous. Offered as a service, iPaaS can be introduced into an organization incrementally, for example, a single integration, then a single workflow, then a complete business process.
iPaaS takes the existing benefits of SaaS -- such as no hardware to deploy, maintain or upgrade -- and elevates those benefits infinitely. When you introduce an iPaaS to enable organizations to integrate and monitor the interactions of these best-of-breed solutions from a single management console, you reap the compounded as-a-service benefits. For example, a business may need 10 integrations between Salesforce and NetSuite. Or it may need thousands of integration combinations between dozens of SaaS solutions. With iPaaS, organizations can extend the value and effectiveness of their business processes by combining best-of-breed solutions with simple, ongoing management and fast, cost-effective change management.
It is essential that enterprises adopt iPaaS technology to integrate cloud and on-premises applications, quickly create new end-to-end business processes, and adapt those processes to changing business needs. With a single, cloud-based platform, the business has the power to develop, manage and rapidly deploy the necessary integration flows that are critical to digital transformation.
Image Credit: leolintang/Shutterstock
 Chris McNabb is the General Manager of Dell Boomi where he is responsible for all operations and strategic direction. Chris brings over 20 years of software development and line of business experience from a diverse set of prior roles that include software development, professional services, LOB leader and consulting. In his role at Dell Boomi, Chris is constantly engaged with customers and partners to ensure alignment between business needs and Dell Boomi’s strategy and operations. Chris joined the Dell Boomi team in 2011 following a 12 year career with SunGard Higher Education. In his prior roles, Chris was SVP of worldwide software development and had responsibility for all software execution, delivery and quality to over 1600 customers. Chris spent two years as a management consultant at a subsidiary of Pennsylvania Blue Shield advising on project management and quality assurance initiatives to improve development execution.
Chris McNabb is the General Manager of Dell Boomi where he is responsible for all operations and strategic direction. Chris brings over 20 years of software development and line of business experience from a diverse set of prior roles that include software development, professional services, LOB leader and consulting. In his role at Dell Boomi, Chris is constantly engaged with customers and partners to ensure alignment between business needs and Dell Boomi’s strategy and operations. Chris joined the Dell Boomi team in 2011 following a 12 year career with SunGard Higher Education. In his prior roles, Chris was SVP of worldwide software development and had responsibility for all software execution, delivery and quality to over 1600 customers. Chris spent two years as a management consultant at a subsidiary of Pennsylvania Blue Shield advising on project management and quality assurance initiatives to improve development execution.
-

Consumers would trust PIN authentication for online transactions
Publié: avril 4, 2016, 10:35am CEST par Sead Fadilpašić

Nine in ten (90 percent) of frequent online shoppers are confident that PIN is a good authentication method for mobile commerce transactions. Those are the results of a recent survey by myPINpad, provider of multi-factor authentication technology for touchscreen devices.
Following the survey, the company has released a new report, entitled PIN: From Brick to Click, which takes a closer look at the PIN, and if consumers are ready to use it on their smart devices the same way they use it, for example, at ATM machines.
The short answer is -- yes, they are. The report also says more than 40 percent of all e-commerce in the UK is now carried out on a mobile phone, or a tablet.
"Banks’ ability to invest in innovation is in many cases inhibited by the need to maintain legacy systems, and by the overhead of regulatory compliance", said myPINpad CEO, Phil King. "But, for over 30 years, PIN had been used at ATMs and consumers are familiar with entering a four-digit code to access their bank account. Its introduction in the UK reduced face-to-face fraud by 69 percent. We are now firmly embedded in the age of digital commerce. Having taken the PIN from ATM to the store, consumers are now ready to take the PIN into the digital age".
Security compliance now requires an effective authentication system, especially with financial institutions involved in payment transactions. Their duty is to have a quality system in order to prevent money laundering and reduce fraud.
"They must now balance all of this with not just maintaining but improving the consumers’ experience", the company says.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: mtkang / Shutterstock
-

Pedants revolt -- the Internet is dead, long live the internet
Publié: avril 3, 2016, 8:02pm CEST par Mark Wilson

In a move that's likely to prove somewhat divisive -- old-fashioned stick-in-the-muds on one side, sensible people on the other -- the Associated Press is dropping the capitalized Internet from its widely-adopted style guide.
For what seems like far, far too long, the internet has been treated by the AP and countless websites, magazines and newspapers as a proper noun, driving those of a sensible bent mad. But now it's only a matter of weeks before Internet is consigned to history and 'internet' will become the norm.
There will almost certainly be a few stalwarts who hang on doggedly to the old, capitalized spelling, but the power of the AP style guide is such that 'internet' should start to become even more prevalent than it currently is. If you are likely to see Internet used anywhere, it will be in the same places where you'll see Email or e-mail used with gay abandon.
The style guide is due to be updated in just a couple of months, as the AP revealed via Twitter:
We will lowercase internet effective June 1, when the 2016 Stylebook launches. #ACES2016 pic.twitter.com/vv53323GL6
— AP Stylebook (@APStylebook) April 2, 2016
Which side of the fence do you fall on? Will the capital I have to be wrestled from your cold, dead hands?
Photo credit: dizain / Shutterstock
-

Windows 10 Anniversary Update to bring badge notifications to the taskbar
Publié: avril 3, 2016, 7:13pm CEST par Mark Wilson
The idea of badges is a very familiar concept on mobile phones. A little numerical overlay on app icons provides at-a-glance info about the number of notifications there are to look at for different apps and services. Now Microsoft has revealed that the same feature is coming to the desktop.
Among the changes in Windows 10 Anniversary Update are taskbar badge notification for Universal Windows Platform apps. This new style of notification joins improved toast notifications and changes to the Action Center. Developers will be able to try out the feature soon, and we've got a sneaky glimpse of how things will look.
As with so many of the announcements to come out of Build 2016, Microsoft has not said exactly when this feature will actually see the light of day. Of course, it's Windows Insiders who will be able to try badges in action first, and with Windows 10 Anniversary Update pegged for a late summer release, it shouldn’t be long before we get to see a preview.
In the meantime, we can content ourselves with an image shared on Twitter by Microsoft software engineer Jen Gentleman:
Favourite announcement at #Build2016? Hard call - there were so many good ones.. Hope you didn't miss this, though
 pic.twitter.com/hraHxz1X39
pic.twitter.com/hraHxz1X39— Jen Gentleman (@JenMsft) April 2, 2016
It's a feature that has been a very long time coming. It's worth noting that taskbar icons have long been updatable to indicate the number if notifications that are pending, but the new system for UWP apps should make the process simpler and more widespread.
Photo credit: Jen Gentleman
-

SmartThings brings new Belkin WeMo devices to the UK family, certifies Harmony
Publié: avril 3, 2016, 1:44pm CEST par Alan Buckingham

There's no shortage of connected devices on the market these days and more seem to come along almost daily. The problem, to an extent, is interoperability. That's improving somewhat as devices are starting to play nice with other systems.
Now SmartThings, one of the more popular offerings on the market, is introducing new products to its UK line. Both are from Belkin, which makes the WeMo line.
There is the Belkin WeMo LED bulb and Belkin WeMo Switch Outlet. Both devices will be fully controllable through the SmartThings app. "Using SmartThings, the WeMo LED bulb can be paired directly to SmartThings without the need for a WeMo Link (available with the WeMo LED lighting starter set), and also comes with a dimming/brightening capability", the company announces.
In addition, the company has certified both the Logitech Harmony remote and the Aeotec Siren (Gen 5). The latter is also known as the Aeon Labs Siren and it works as a home security device.
You can find the full list of compatible SmartThings devices for the UK here.
-

Turn your PC into a wifi hotspot with NirSoft’s HostedNetworkStarter
Publié: avril 3, 2016, 1:05am CEST par Mike Williams
NirSoft has released HostedNetworkStarter, a free tool which turns your wifi-enabled PC or laptop into a wireless
 hotspot.
hotspot.There's no installation required, no network drivers or anything else involved: the program is just a simple front-end for the standard Windows wifi hosted network feature.
Getting started can be as easy as entering a network name and key.
Optional settings include choosing an internet connection to share, and setting the maximum number of clients that you'll accept.
While this works much like many other tools, HostedNetworkStarter stands out for the details it displays about your hotspot.
A table lists your network GUID, name, connection name, MAC address, channel number, link speeds, sent and received packet totals, and -- useful for troubleshooting -- any error messages or codes returned by Windows when setting up your hotspot.
Everything is displayed in the usual NirSoft way, which means you can sort the table by any field, and save the details on demand as a text or HTML report.
HostedNetworkStarter is a freeware tool for Windows 7 and later.
-

10 'ARGH!' moments every computer user experiences
Publié: avril 2, 2016, 3:56pm CEST par Mark Wilson

Computers make life easier, right? Computers are fun, valuable tools, yeah? True, but they can also be such utterly infuriately pieces of tech that they seem to serve no purpose other than to raise our blood pressure and drive us mad.
I'm not talking about when Windows crashes, when an app hangs, or the internet slows to a crawl. I'm talking about those 'ARGH!' moments we've all experienced where there's no one to blame but ourselves. When things go wrong because of 'user error' it doesn't make them any less infuriating; in fact, the opposite is often the case. Here are ten of the most frustrating scenarios that just about every computer user has encountered at some point.
1. Trying to interact with a non-touchscreen monitor
We've all done it. It's easy to get used to working with your phone or tablet and not transition smoothly to your regular desktop or laptop. How many of us have jabbed pointless at an icon to try to open a file, or needlessly swiped a finger across the lock screen to access the password entry screen? You'd think we'd learn, but no...
2. Accidentally hitting a link in bookmarks bar
Filed under 'Almost, but not quite', we've all missed our intended target in a web browser. Positioning the bookmark toolbar beneath the Back and Refresh buttons was clearly asking for trouble, and it's all too easy to be whisked away from what you were looking at to some completely unrelated website. The distance of just a few pixels between the different hot-zones is clearly to blame, but it never gets any less infuriating.
3. Accidentally deleting files / emails
A close relative of 'accidentally hitting a link in bookmarks bar' is the accidentally deleted file or email. A poorly judged mouse click or key press is all it takes to send a missive or document into oblivion. Seriously, who at Google though that it was a good idea to put the Delete button smack in between Spam and Mark As Read? It's asking for trouble! The same goes for the Delete option in context menus -- one slip of the finger and that file is history. It's easy to feel that the Recycle Bin and email trash are just for idiots who can’t use computers properly, but we've all gone scurry there, shame-faced, looking to retrieve that important message or file.
4. Downloading files to the wrong folder and then not knowing where the f@$! they are
You might be one of those people who always download files to the Downloads folder, or maybe the desktop is your preferred destination. But even if you are regimented in your download location, there will always be the odd occasion when an alternative folder is used. Select folder, hit Save. Open folder... no file! Which damned folder did I just select? It sure as hell wasn't the one I intended to use! [Fires up a file search...]
5. Forgetting the volume is up über high
This YouTube video is a bit on the quiet side. I'll just crack up the volume.
Time passes. Forget about increased voume. Decide to put on some Nine Inch Nails
Argh! Jeezo!
Ears bleed
6. Trying to select a bunch of files, but moving them instead
If you're a fan of holding down the Shift key while selecting a series of files, you've probably never experienced the bewilderment that accidentally relocating documents. If, however, you like to draw a selection box around files, you've almost certainly flung the first file you were trying to select into a random folder. Obviously happens when you're in a rush... without fail!
7. Having pen selected instead of crop tool
Rightio... time to get to work on those holiday snaps; there are a few photos that would benefit from a little reframing courtesy of the crop tool. Well, you thought you had the crop tool selected -- but, no, it your image editor has default back to the pen so you've scrawled a diagonal line from one corner to another. Goddamit!
8. Accidentally opting to always open a certain file type with a particular app
Easily done on both a phone or a computer. You might have installed a new app and no have multiple apps that are capable of opening images or some other file type. Of course, you'll be presented with a list to choose from, as well as the option of always using a certain app. It goes without saying that you had the wrong app selected before okaying the change in defaults. Gnnnrrrr!
9. Having caps lock enabled when typing without looking
There's a danger in being able to touch type coupled with a habit of watching TV whilst working. It's something I'm guilty of, and it means I frequently type away without looking at either my keyboard or screen. When my attention is guided back to concentrating fully on what I'm doing, there have been numerous occasions when I find I've been typing away with Caps Lock on. Gah! If you're in Word, there's the handy keyboard shortcut Shift + F3 to change the case of selected text, but there are far too many applications (and, obviously, web sites) on which this doesn't work. Maddening.
10. Not being able to get the cursor into diagonal-double-headed-arrow mode to resize a window and trying to hit the target for hours on end
The title says it all, really. It's something that should take a second or less -- quickly resizing a window to a different size or shape. But can you get your mouse positioned over the corner pixel (and it does seem to be an area no bigger than a single pixel) to be able to resize horizontally and vertically at the same time? Can you flip! There it is... oh, missed it! There! No! Quick! Click and drag! Oh, forget it...
Anything you would add to the list? What makes you want to punch your monitor in inexpressible rage.
Photo credit: Ollyy / Shutterstock
-

Tidal: one year and 3M subscribers later
Publié: avril 2, 2016, 7:26am CEST par Joe Wilcox
April 1st marks my first-year anniversary subscribing to Tidal, which relaunched the same day last year, under new ownership of Jay Z. I love and loathe the music streaming service, which I cancelled at least five times and always renewed—typically before the billing cycle ticked over. But checking archived emails, I see that my sub completely expired thrice but not since July.
Gotta ask: What fool starts a business on April Fools, and what does the day foreshadow; if anything? Apple did it, 40 years ago today. Many commentators have called Jay Z the fool for buying Tidal, which competes against established players like Spotify and newcomer Apple Music. The service claimed to have 540,000 subscribers when acquired last year. This week, Tidal revealed globally there are now 3 million subscribers. Someone correct my math—456 percent increase, right? If Jay Z's the fool, gimme some of that foolishness.
Still, Tidal trails rivals. As of February 2016, Apple Music topped 10 million subscribers; Spotify reached 30 million last month. Both figures come from publicly released data.
Origin Story
In January 2015, Jay Z and his investment partners paid $56.2 million for Tidal, which history goes back to February 2010, when Aspire Group and Platekompaniet debuted the WiMP music service in Norway. The subscription streamer aggressively expanded to other European countries, and among portable and music devices, before adding lossless, CD-quality music under the WiMP HiFi brand on Oct. 1, 2013. A year later, the rebranded Tidal opened for business in the United Kingdom and the United States, focused on higher-fidelity encoding and streaming.
By March 2015, before relaunch under new management, Tidal was also available in Austria, Belgium, Canada, Cyprus, Czech Republic, Denmark, Estonia, Finland, France, Greece, Hungary, Ireland, Italy, Latvia, Lithuania, Luxembourg, Malta, the Netherlands, Norway, Portugal, Romania, Singapore, Slovakia, Slovenia, Spain, South Africa, Sweden, Switzerland, and Turkey.
Unlike some other streamers, Tidal does not offer a free option; elsewhere, freemium means advertisements. You pay to play—$9.99 per month for 320kbps compressed MP3s. Big spenders, those plunking down $19.99, get big sound. HiFi.
Music Lesson
Tidal's appeal is twofold: HiFi encoding and artist exclusives, of which there are many. Competing stores or services claiming CD-quality usually deliver bitrate of 320kbps. They lie about what that is. The compressed files aren’t even close to the source material. Using the Free Lossless Audio Codec, Tidal promises the real thing: 44 kHz, 16 bit, and 1411kbps bitrate. I listen with higher fidelity headphones—Grado Labs RS1e and Master & Dynamic MW60, which I bought with birthday and Christmas money, respectively, in 2014 and last year.
I hear the difference, and you may not, between the lossless and compressed AACs or MP3s tracks—even from Tidal. Detail is finer, overall ambiance is brighter (e.g. less muddy), vocals are crisper but also flatter, and bass is more natural rather than pounding. Because I can hear the difference, and really like it, Tidal pulls me back every time I try to cancel. I'm committed now; stopped trying to quit months ago.
Here and Nowhere Else
Exclusives are the other selling point. Among them, as I write: TWENTY88, a collaboration between Big Sean and Jhene Aiko; Edward Sharpe & The Magnetic Zeros' single "Perfect Time"; and exclusive playlists compiled by artists, including Gwen Stefani and Jay Z. Kanye West's album "The Life of Pablo" debuted on Tidal, exclusively during February, generating 250 million streams over 10 days. Exclusivity ended yesterday.
The sound should be a big draw, but there is the price as barrier. According to Tidal, only 45 percent of the 3 million subscribers pay for pricier HiFi. Too bad, because lossless listening is the service's distinctive feature, and it's one sure to be obscured. I expect Apple Music to offer something similar sometime this year.
Likes and Gripes
My major problem with Tidal: Justify spending the $19.99 monthly fee; I have too many different monthly services, and some competing streamers offer family plans for $5.00 less than Tidal's single-subscriber price. So, for example, six people can share the same Apple Music account for $14.99 monthly. Tidal does cut the price for additional users by half. Primary subscriber plus one other would be $29.98 per month, with both getting HiFi. The service does offer select discounts. Student: $4.99 for compressed and $9.99 for lossless. Military: $5.99 and $11.99. Available only to new, standard subscribers: First six months (after 30-day trial) discounted when paid as one sum. That averages out to either $8.49 or $16.99 monthly, depending on encoding.
Besides price, some of my other gripes:
- The web player requires Adobe Flash.
- The music catalog isn't as extensive as Apple Music.
- The default playback setting on mobile apps is Normal not HiFi.
- Music playback doesn't sync across devices; you can't stop listening on one and resume on another.
What makes me a Tidal subscriber:
- HiFi is just that.
- Playlists are superbly curated.
- The video collection is superb, as is playback.
- Tidal feels like an artist showcase, not record labels'.
- Exclusive content is plentiful and frequently updated.
- Tidal X live concerts connect artists and fans—fidelity rocks!
- Many albums are available in U.S. and/or international versions.
Listen Up
Tidal claims its music library tops 40 million tracks, while there also are 130,000 music videos. The user experience is excellent across interfaces. I have used the Android and iOS apps, as well as the website. Features are comparable to Apple Music and other competitors, which makes Tidal's apps immediately usable.
Wrapping up, exclusives are fine, but any service can offer them. Audio encoding sets apart Tidal—for now—from major competitors. Wanna hear? I suggest testing Tidal by streaming The Beatles catalog from there and somewhere else. Vocals aren't as crisp, bass is punchier, and high notes are more muted on Apple Music, for example. The questions: Can you hear the difference? If so, do you like it, and would you say twice as much for the pleasure?
Photo Credit: Joe Wilcox
-

Brits would share their data with tech companies for financial gain
Publié: avril 1, 2016, 9:24pm CEST par Sead Fadilpašić

Brits would love to share personal data with companies, for the promise of monetary gain. Not only that, but they’d give companies access to their connected home habits, if that means they’d get paid for it.
Those are the results of The Global Internet of Things Smart Home Survey. Sixty-three percent would share data about their daily habits, 61 percent would give companies access to their connected home devices, and 77 percent would do it to get bonus tax credits.
At the same time, they’re quite worried about the security implications smart homes bring. Ninety-one percent fear hackers taking control of home devices and using those devices against them.
The "virtual babysitter" device is something the majority doesn’t want in their home. Also, three quarters are anxious about the number of passwords required to keep a smart home safe.
"Smart homes produce a wealth of data about the way we live and by leveraging this data, companies have the potential to improve how we go about our daily lives", said Simon Hunt at Intel Security. "People are aware of how valuable this data is for third party companies, but this data is not just valuable for these companies it’s also like gold dust for hackers. In the rise of the Internet of Things, security has to be addressed from the outset to prevent the smart home hackers. When done right, security can unlock the benefits IoT promises to deliver".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Lucia Pitter/Shutterstock
-

Get loads more free space on your Apple iPhone with this one weird trick (seriously)
Publié: avril 1, 2016, 8:02pm CEST par Wayne Williams

I have to apologize upfront for employing such a well-known clickbait-style headline, but I’m genuinely about to show you how to immediately reclaim a lot of free space on a nearly full Apple iPhone using a weird trick. It’s not an April Fool’s either.
If you have an iPhone that’s close to running out of space, you can use this method to free up a sizable amount of storage. On my iPhone, which was filled to bursting with vacation photos, music and apps I managed to claw back a couple of gigabytes, which is some going.
The trick only works on an iPhone that’s very low on space. What you need to do is note how much storage you have remaining by going to Settings > General > Usage, and then try to rent a movie from iTunes that is larger than the storage you have available. If you have 500MB free, for example, you could try and rent Bridge of Spies, which is a 5.79GB download.
You have to try to rent the film through the iTunes app on your phone, not through iTunes on your PC or Mac. Unless you actually want to watch the film that is.
When you click Rent, a loading symbol will appear but then you’ll receive a message informing you that "there is not enough available storage" to download the film, and you’ll be given the option of managing your storage in Settings.
Tap the Settings button, and -- ta-da! -- you should see the amount of free storage you now have is much greater than before. Repeating the process will free up even more space.
According to this Reddit post, it seems what the device is doing is deleting unnecessary files from installed apps in an effort to free up the room you need to install the movie.
Don’t worry though, even if you do manage to free up enough space for the film in question, it won’t be installed. Unless you click on Rent again that is...
Photo credit: Ollyy / Shutterstock
-

Egypt bans Facebook Free Basics for NOT spying on users
Publié: avril 1, 2016, 7:40pm CEST par Mark Wilson

In another blow for Mark Zuckerberg's free internet service, Facebook Free Basics has been banned in Egypt. The Egyptian government made the decision after Facebook refused to allow it to use the service to spy on users.
The shutdown comes just five months after Facebook Free Basics launched in Egypt, having proved controversial in other countries for contravening net neutrality rules. But Facebook's refusal to permit government surveillance of users means that the service has been banned this time for political reasons.
The decision is not completely unexpected. The Egyptian government suspended Facebook Free Basics at the end of December because, as Reuters reports, the initial permit to operate was only temporary.
Egypt's Ministry of Communication implies that the ban comes as a result of anti-competitive behaviour, with spokesman Mohamed Hanafi saying:
The service was offered free of charge to the consumer, and the national telecommunication regulator saw the service as harmful to companies and their competitors.
While details are thin on the ground, Reuters cites 'two sources with direct knowledge of discussions between Facebook and the Egyptian government'. Whatever the thinking behind the ban is, it is unlikely to prove popular with Egyptians looking for a free way to gain access to the internet. Facebook had said at the time of the Free Basics suspension that it hoped to resolve the situation, but it has not commented on the current ban.
Photo credit: tulpahn / Shutterstock
-

Windows 10 is now on nearly one in four Windows PCs and tablets, according to Microsoft
Publié: avril 1, 2016, 7:28pm CEST par Wayne Williams

NetMarketShare today released its latest desktop OS usage figures, and they reveal a steady increase for Windows 10. According to the web analytics firm, the new OS currently has 14.15 percent usage share. However, Microsoft has updated its own market share figures and they paint a very different picture, showing the OS to be a much, much bigger hit.
According to the recently updated Windows and Store trends page, as of February, Windows 10 is on 24 percent of PC and tablet devices running Windows, growing at a pace of around 2 percent a month. And not only that, the new OS is also a huge hit with gamers, with Microsoft claiming Windows 10 is on 35 percent of their devices. So how come Microsoft’s figures differ so significantly from NetMarketShare’s? There are a couple of reasons.
SEE ALSO: Windows 10 continues its slow march to desktop domination
Firstly, NetMarketShare records all operating system usage figures -- not just how many people are using the various flavors of Windows, but also Mac and Linux. Microsoft however, measures Windows market share -- how many people have installed its OS.
Additionally, NetMarketShare focuses on the desktop side of things in its figures, while Microsoft also factors in tablets.
That alone doesn’t explain the gulf -- Microsoft is claiming Windows 10 is on 10 percent more devices than NetMarketShare has recorded -- but the answer for the difference is a simple one. The software giant only includes Windows 10, 8, 8.1 and 7 in its charts -- ignoring XP and Vista as it no longer considers those versions relevant.
If we strip out those two aging Windows editions and all non-Windows systems from NetMarketShare's figures, the result is pretty close to those numbers reported by Microsoft for February.
Microsoft’s share breakdown has Windows 10 on 24 percent, Windows 8.1 on 18 percent, Windows 8 on 3 percent, and Windows 7 on 55 percent.
As Microsoft has claimed Windows 10 is now on 270 million devices, we can use the new percentages to roughly size the market, which suggests there are over 618 million Windows 7 users and 236.25 million Windows 8.x users out there for Microsoft to try to persuade to upgrade to its new OS. Factor in those Windows XP and Vista stragglers, and new PCs and tablets, and getting Windows 10 on one billion devices within the next couple of years might just be possible.
Photo credit: Brian A Jackson / Shutterstock
-

Get a Red Hat Enterprise Linux license totally free -- here's how
Publié: avril 1, 2016, 7:24pm CEST par Brian Fagioli

While many people use the old cliché that nothing in life is free, that isn't always true. Are there often strings attached? Absolutely. With Gmail, Google combs through your communications for targeted advertising. Microsoft's Windows 10 is a free upgrade for many, but it has more strings than a gross of violins -- from a privacy standpoint, that is.
In the world of open source, however, free sometimes really means free. Today, Red Hat -- fresh from celebrating a historic $2 billion in annual revenue -- releases a developer-focused gift to the world. The Red Hat Enterprise Linux Developer Suite is totally free, including a RHEL license and valuable developer tools, like the JBoss Middleware portfolio. This is through the Red Hat Developer Program.
"Offered as a self-supported, non-production developer subscription, the Red Hat Enterprise Linux Developer Suite provides developers with a more stable development platform for building enterprise-grade applications and enables a clear pathway to supported, mission-critical deployments across cloud, physical, virtual and container-centric infrastructures", explains Red Hat.
The popular open source company further explains, "with the Red Hat Enterprise Linux Developer Suite, developers have access to a broad and up-to-date set of development tools, in addition to the latest version of Red Hat Enterprise Linux Server, enabling the creation of modern applications for deployment across the hybrid cloud. In addition, enterprise IT teams who are embarking on modern application development, through DevOps, CI/CD or other practices, can now have a more simple and efficient environment with platform compatibility across development and deployment".
Red Hat shares the following components of the free program.
- Red Hat Enterprise Linux Server -- An application development entitlement to the world’s leading enterprise Linux platform.
- Development tools with long-term support -- Each major Red Hat Enterprise Linux release includes a broad set of base tools that, like the operating system, are supported for 10 years; including Python, PHP, Ruby, OpenJDK 7 (1.7), OpenJDK 8 (1.8) and many more.
- Development tools with frequent updates - Multiple open source programming languages, databases, web servers, and development tools are updated yearly with the most recent, stable versions, and are packaged via Red Hat Software Collections and Red Hat Developer Toolset.
If you want to take advantage of this amazing offer, you can sign up here. If you aren't a developer, however, you shouldn't waste your time. If you are merely interested in the RHEL license (which is self-supported anyway), and are a desktop Linux user, it would be wiser to target the always-free Fedora or CentOS instead.
If you are a developer, you should definitely take advantage of developing on the platform. Red Hat is a leader in open source technologies, and it is smart to leverage this generous offering.
Photo credit: Aha-Soft / Shutterstock
-

Windows 10 will soon show you notifications from your Android phone
Publié: avril 1, 2016, 6:53pm CEST par Mark Wilson

The Notification Center in Windows 10 is a great idea but, many would argue, one that is both limited and poorly implemented. For anyone with a Windows 10 Mobile phone it is marginally more useful thanks to notification sharing, and this feature is due to expand to Android users as well.
At Build, Microsoft revealed that the Notification Center is in line for a major overhaul that will not only bring Cortana-power notification mirroring to Android users, but will also bring a richer, more image-heavy notification experience. The news isn’t so great for iPhone users as the more tightly controlled nature of iOS means Microsoft has a harder task on its hands.
It doesn’t end there. Also on the cards is a 'universal dismiss' option that will make it possible to kill a notification on one device and have it wiped from others at the same time. But it is almost certainly notification mirroring that will generate the most interest. It means that you will be able to see notifications from your Windows 10 computer on your Android phone, or phone notifications on your computer.
In addition to being able to see from your computer that a message has come through on your phone, you'll also be able to dismiss notifications, and even reply to messages without having to switch devices. For anyone who spends their days sitting at a computer and switching between PC and phone for different tasks, this could be a real productivity boost.
Developers will need to enable support for notification mirroring in their apps, and users will be free to enable and disable the feature for individual apps -- handy to ensure that you don’t get overwhelmed with messages.
Microsoft has not said when we'll be able to try out the feature for ourselves, but it's likely that it will make an appearance in the Insider builds that precede the upcoming Windows 10 Anniversary Update.
Photo credit: tanuha2001 / Shutterstock
-

Windows 10 Insider Preview Build 14295 ISOs now available for download
Publié: avril 1, 2016, 5:58pm CEST par Wayne Williams

A week ago, Microsoft released a new Windows 10 Insider Preview build for PC and Mobile. While Build 14295 isn’t the most exciting of releases, it does include a lot of notable bug fixes and Microsoft deems it stable enough for the Slow ring which is welcome news for any Insiders not on the cutting edge.
There’s also good news for anyone struggling to update their existing Insider Preview build through Windows Update (or for anyone wanting to do a fresh install or try out the new build in a virtualized environment) as Microsoft has just made Build 14295 available for download in ISO format.
It’s important to remember, that while Build 14295 is mostly just bug fixes, it follows on from Build 14291 which delivered extensions to Microsoft Edge, as well as pinned tabs and other Edge enhancements. There was an updated Maps app, and a wealth of other changes (including the introduction of a new Feedback Hub) in that build too.
If you’re not currently running Build 14295 you can download the ISOs for it from this link. You’ll need to be a Windows Insider, but you can join the program if you’re not already part of it.
Once you’ve downloaded the ISO you can burn it to DVD or write it to a USB flash drive, and install it.
Photo credit: charnsitr / Shutterstock
-

Facebook Messenger now lets you manage your KLM flights
Publié: avril 1, 2016, 5:40pm CEST par Anthony Spadafora
Facebook Messenger is used by 800 million people globally and now KLM Dutch Airlines will be the first airline to allow its customers to check in, receive flight updates and change their travel itineraries right from within the app.
Facebook believes that customer service can easily be handled and even improved through its Messenger app. The company was inspired by popular messaging services in Asia such as WeChat, Line and KakaoTalk that give their users the ability to schedule many of their day to day activities right from within their apps including hailing taxis, making reservations at restaurants, shopping for shoes, playing games and sending gifts such as coupons for meals and coffee.
Last year Facebook launched Messenger for Business to begin exploring the idea of "conversational commerce" with companies which are interested in adopting the site’s messaging platform to communicate with customers. Walmart, Everlane and even the hotel chain Hyatt have all tried out the service as a new way to interact with their customers.
Messaging has quickly gained in popularity and analysts predict that it could one day overtake social media as the main way consumers spend their time online. Two and a half billion people have registered for at least one messaging app and it is estimated that this number could reach 3.6 billion by 2018.
In the past, companies scrambled to quickly develop and deliver their own apps to consumers with the advent of smartphones and app stores. Now they have come to realize that most people only use a few app throughout the day. By interacting with customers through Facebook Messenger it will be easier to reach their clients who are now no longer burdened with installing a separate app for every company they have interactions with.
Facebook is eventually planning to sell its own services to customers through mobile, but the company sees Messenger for Business and companies such as KLM adopting Messenger as a cautious way to capitalize on the success and widespread use of its messaging service.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Losing selfies is a major concern for the majority of smartphone users
Publié: avril 1, 2016, 3:48pm CEST par Sead Fadilpašić

Mobile memory experts Leef quizzed the UK population to see just how important smartphones are for them, and how often they back such devices up. It turns out, not so frequently. As a matter of fact, some people don’t even know what backing up actually means.
So here’s the thing. The quiz polled 1,000 smartphone users across the country, and more than half would be terrified of losing their smartphone, mostly because of "their selfies and other irreplaceable photos from their smartphone", the Leef report says.
The percentage jumps even higher, to 62 percent, among the younger population, aged 16 - 24. The older generation has more fears of losing their contacts, and still rarely backs up their devices. On top of it all, five percent don’t know what "backing up" means.
"Increasingly often people are having great moments and photo opps blighted by the ‘memory full’ pop up on their phone. As we rely on our phones more and more, backing them up is vital!",said David Smurthwaite, partner at Leef. "If you don’t back your phone up because you are worried the cloud in unsafe, or you can’t be bothered with a clumsy web of cables -- search for a better solution! You don’t want to be left kicking yourself because you’ve lost years’ of precious content...".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Vladimir Gjorgiev / Shutterstock
-

FCC cannot investigate Netflix for throttling its own customers
Publié: avril 1, 2016, 2:46pm CEST par Mihăiță Bamburic

Netflix last week revealed that it has throttled the video streams of customers who have been accessing its service from AT&T's and Verizon's networks, after the two carriers were believed to be at fault. The company says that this has been done to keep those users from exceeding their monthly data plans, but some believe the video streaming service has taken things too far, right into the net neutrality danger zone.
Despite offering what looks to be a good reason for the throttling, Netflix is still in the wrong. Customers were not informed of the company's decision before it went into effect more than five years ago. There is no way of turning the "feature" off, at least not until a data saver option is introduced in May. And the focus of the throttling has been rather limited, with this move not extending to other carriers in US, like Sprint and T-Mobile. So, obviously, affected customers have very good reasons to complain.
The customers who Netflix targeted have been limited to 600 Kbps video streams, which is well below the capabilities of modern, 4G LTE cellular networks. The obvious advantage to doing this is a decrease in traffic, which could mean lower costs for Netflix. Although AT&T and Verizon also stand to benefit for the same reason, the former carrier, at least, says that it is "outraged" by Netflix's actions.
Naturally, some Netflix users feel the same, going as far as to suggest that Netflix may have broken the net neutrality rules by throttling their connections. As you may know, the Federal Communications Commission, lead by Tom Wheeler, is responsible for enforcing net neutrality rules, so if there's an agency that can do something about FCC should be it.
However, according to Wheeler, what Netflix is doing is actually outside of FCC's jurisdiction. The agency cannot investigate what so called "edge providers" or websites are doing, as those entities are "outside the open Internet" order, according to statements given to Reuters earlier this week.
That may be disappointing to hear but, as you may know, the net neutrality rules are designed with the idea of protecting customers from having their Internet connections throttled by ISPs. Since Netflix is not the company offering Internet service, it can apparently throttle its own customers at will with no repercussions from the FCC.
So what can you do about it? Well, it looks like, if Netflix throttles you, you will have to wait until it enables the data saver mode that it promised last week, so that you can unleash the full potential of your cellular connection while streaming video.
Photo Credit: JStaley401/Shutterstock
-

Google fails Gmail users with misguided 'Mic Drop' April Fool's prank
Publié: avril 1, 2016, 2:02pm CEST par Brian Fagioli

As a tech enthusiast, I dread the stupid April Fool's Day every year. What should probably be a fun day for children to pull safe and respectful pranks, has evolved into a day when companies announce fake products. Is it all in good fun? Yes, but some of these companies are publicly traded and worth billions of dollars. It's time to grow up. Some of us are interested in legit news.
One such company, Google, provides services to billions of people -- including some for business use. And so it has a responsibility to its users, and shareholders, to not cause harm with goofy jokes. Today, the search giant does exactly that, however, with a prank called "Mic Drop". In fact, the prank was so misguided, that Google has since pulled it.
"Today, Gmail is making it easier to have the last word on any email with Mic Drop. Simply reply to any email using the new 'Send + Mic Drop' button. Everyone will get your message, but that's the last you'll ever hear about it. Yes, even if folks try to respond, you won't see it", says Victor-bogdan Anchidin, Software Engineer. Clicking the button sends a GIF of a Minion dropping a microphone before shutting down the email thread.
Really, Google? Placing a fake send button next to the real one? I am not sure who is in charge of the asylum over there in Mountain View, but people use your email service for serious things. Such a blatant disregard of respect could have dire results for people both personally and professionally.
Over on Business Insider, they share some examples of how things have gone wrong for some users -- if the users are to believed. Trolling or not, the potential for these things are all too real. As someone who planned a family funeral earlier this year, and utilized Gmail to do so, the last thing I would want is an April Fool's prank sabotaging it.
Those that use Gmail for business, could end up losing their jobs, or potentially embarrassing themselves in front of coworkers or clients. While you may think this is overkill, I am honestly rethinking my use of Gmail going forward.
I covered similar nonsense in a 2014 article called "Hey Google, grow up -- enough with the April Fool pranks already". In it, I wrote the following regarding a "Shelfie" prank.
It set my theme as a picture of Katy Perry -- While seemingly harmless, I was checking my email in public. I like to get respect from people I work and meet with. The picture makes me look goofy. I actually like Ms. Perry, but not when I am trying to make a certain impression. Some may say that I could have just closed the window. However, the pop-up says "Not sure? Use the Top Trending Shelfies". I wasn't sure, so that's what I did.
Enough, Google. You have been doing this for far too long. Luckily, with the "Mic Drop" prank, Google got the message and pulled it. Anchidin writes the following.
Well, it looks like we pranked ourselves this year.
 Due to a bug, the Mic Drop feature inadvertently caused more headaches than laughs. We’re truly sorry. The feature has been turned off. If you are still seeing it, please reload your Gmail page.
Due to a bug, the Mic Drop feature inadvertently caused more headaches than laughs. We’re truly sorry. The feature has been turned off. If you are still seeing it, please reload your Gmail page.Calling this a bug is disingenuous, adding more fuel to the fire. Either way, it can't harm anyone else today.
Do you think it is time for Google to drop the April Fool's Day shtick? Tell me in the comments.
UPDATE: Google apologizes a second time.
We heard feedback that some of you were negatively impacted by this feature, so we quickly turned it off late last night. In addition, we are working to bring back Mic-Dropped messages that had subsequent replies to your inbox, so you can read those.
We realize many of you use Gmail for very important messages, and we are sorry if Mic Drop was in any way harmful to you. Note that if you’re a Google Apps business, education or government user this feature was never turned on.
At Google we have a culture of sharing what we learned when things go wrong, and we want to share these learnings with you:- We should have asked you before turning on the feature, and it should have included a confirmation before sending.
- We didn't anticipate accidental clicks: "Send + Mic Drop" was too close to other send buttons ("Send" as well as "Send & Archive"), which caused confusion.
- And yes there was a bug. It was rare, but possible to press the regular "Send" button and still Mic Drop if you did the following:
- Opened a new compose window
- Pressed the “Send & Mic Drop” button with no recipients and saw error message
- Edited the message by adding message recipient(s)
- Pressed the regular send button.
Again, sorry. We love April Fools jokes at Google, and we regret that this joke missed the mark and disappointed you.
Photo credit: Rawpixel.com / Shutterstock
-

Windows 10 continues its slow march to desktop domination
Publié: avril 1, 2016, 12:52pm CEST par Wayne Williams

At Build 2016 Microsoft revealed that Windows 10 is now on 270 million devices. By switching the new operating system to a recommended update, the software giant has managed to add 70 million devices to its tally in just under 3 months. An achievement somewhat tainted by the fact that not every upgrade was actually wanted nor knowingly actioned, but that’s still a very respectable number to crow about.
With it being the first of the month, NetMarketShare has released its latest usage figures for the various flavors of Windows and, as you’d expect, Windows 10 shows the most growth.
The new OS had 12.82 percent of the desktop market in February, but gained 1.33 percentage points in March, and now stands on 14.15 percent.
That places it well ahead of its predecessor. Windows 8.1 lost 0.27 percent and now stands on 9.56 percent. Windows 8 actually gained 0.02 percentage points, to put it on 2.45 percent. Combined, the tiled OS dropped 0.25 percentage points and now sits on 12.01 percent, Just over two percent behind Windows 10.
Windows 7 shed 0.45 percentage points, but remains the dominant OS with 51.89 percent. If Windows 10 continues to grow at the same rate it posted in March, and Windows 7 declines by the same percentage, the new OS will overtake the old one in around two years' time.
Of course there are a lot of factors that might influence that including Microsoft finding new and even more aggressive ways to get Windows 10 on to systems, and we still don’t know what the software giant is planning to do regarding pricing once the free upgrade period ends in the summer.
Photo credit: Tamisclao / Shutterstock
-

Best Windows apps this week
Publié: avril 1, 2016, 12:42pm CEST par Martin Brinkmann
One-hundred and seventy-four in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days.
Microsoft's Build 2016 conference is still underway, and if you are interested in what is coming to Windows 10 later this year, I suggest you check out our coverage here on BetaNews.
This week saw the release of exciting apps and games, and an increase in Xbox game conversions. Game of the week is Killer Instinct which you can download and play for free in a base version.
As always, if I missed an app or game that has been released this week that you believe is particularly good, let me know in the comments below or notify me via email instead.
Discounts This Week
The following discounts are provided by Red Stripe Deals, a weekly changing list of offers, and the Deals Hub application.
The following is this week's selection:
- Pin More, pin custom tiles for $1.49
- Vampire Legends: The True Story of Kisilova, an adventure game for $3.49
- Runtastic PushUps PRO, push-up training app for $0.99
- Space Marshals, tactical top-down shooter for $2.49
- Doodle God: 8-Bit Mania, a puzzle game for $0.99
- Sago Mini Superhero, a game for children for $0.99
- Total Manager Pro, a file manager for $4.99
- IP Cameras Online, access public IP cameras worldwide, for $2.99
App of the week

Killer Instinct is a 2D fighting game that was originally released for the Xbox One in 2013.
This version, dubbed Season 3, is available for Xbox One and Windows 10, and like other games released by Microsoft recently, features cross-buy, -play and -save functionality.
The base game can be downloaded for free on Windows 10, but you will have to pay for the full experience.
The game features single- and multiplayer modes, supports controllers (recommended), and Xbox Live features such as leaderboards, achievements or Game DVR.
It is highly recommended to check the minimum and recommended PC specifications before you download the game.
Other applications
The Australian Football League application features everything fans could ask for. From live scores and team/player stats to video highlights, interviews and press conference footage.
You get player profiles and information, as well as ladder and fixture information on top of that.
Some features that the app provides require an AFL Live subscription. With it, you can watch live video streams of games, watch on-demand full replays and gain access to the AFL TV channel.
Audiotica is a music player and downloader that is now also available for Windows 10.
The player supports local music that you can add to it, and several online streaming services such as Spotify, SoundCloud, Deezer and Last.fm.
According to its devs, it is faster and saves 70 percent on battery life when compared to Spotify or Xbox Music.
The official HoloLens application from Microsoft provides you with options to pair your HoloLens device with the app to gain access to features such as starting and stopping applications, capturing "mixed reality" photos and videos, and viewing a live stream from the device's point of view.
The game plays a bit like the classic swashbuckling game Pirates. You start as a captain of a Sloop and work your way up the foot chain by fighting other ships, increasing your fleet, upgrading ship and captain skills, and more.
The game features a story driven campaign, different types of sea battles and -- for a Windows 10 game -- fine visuals.
Join by joaoapps ($1.49, free trial available)
The app brings Android device notifications to the Windows Notification Center.
Options to react on notifications are provided as well, you can reply to messages directly from the Windows device for instance.
The official Air Asia application for Windows 10 features a flight search, and flight status checks.
You can use it to check-in or print your boarding pass, and manage things such as in-flight meals, seat reservations and more.
Notable updates
AccuWeather -- Weather for Life updated with Cortana support, videos, new playlists and more.
Mail and Calendar updated. Add holidays to your calendar, view an entire year in year view, move messages to folders of your choice, and add attachments by pasting them into the message body.
Monster Buster: World Invasion with support for Windows 10 desktop and mobile.
Playcast, the casting app, has been updated. The update brings Chromecast bug fixes, crash fixes, and better DLNA server handling.
-

Adjust PDF brightness, contrast and gamma with YACReader
Publié: avril 1, 2016, 12:36pm CEST par Mike Williams
Text-based PDFs are generally easy to read, with high contrast, crisp fonts, and a zoom tool if you need to check the small print.
PDFs of scanned images can be very different, especially if they’re old documents, maybe handwritten, and have faded over the years.
Open these images in a graphics editor and you’d be able to tweak brightness, contrast and whatever else you need, but unfortunately most specialist PDF viewers have no equivalent options at all.
YACReader is a comic (and PDF) reader which has been designed to handle images, and supports the image adjustment tools you need.
The interface isn’t as polished as the big name PDF readers -- just a tiny toolbar -- but initially it works just like everything else: hit Open or Ctrl+O, choose a document, and use the back/ forward buttons or left/ right keys to step through the pages.
If you’re struggling to read a faded page, click Options (the gear icon, top right) > Image Adjustment and you’re able to tweak brightness, contrast and gamma, which immediately made a huge difference to our test documents.
Hiding these settings away in a separate dialog makes them less convenient to access, and could be a problem if you want to tweak your settings from page to page.
Despite that, just having any adjustment options at all is a major improvement on most PDF viewers, and -- if this is a regular issue for you -- probably justifies the download all on its own.
YACReader is a free application for Windows, Mac and Linux.
-

How UK tech companies could comply with Snoopers Charter
Publié: avril 1, 2016, 10:48am CEST par Jonathan Parker-Bray

It would be hugely ironic if the UK government’s plans to help it seize back control of the digital age actually pushed technology firms even further down the path of encryption.
The second version of the Investigatory Powers Bill -- or Snoopers Charter, as it has been colloquially dubbed -- was published by the Home Office on March 1. This came in light of criticism of the first version -- published in December -- from three parliamentary joint committees: the Science and Technology Committee, the Intelligence and Security Committee, and the Joint Committee for the bill itself -- which made some 86 recommendations alone.
The revised version aimed to appease demands for change, but has failed to pour water on the fears that ignited huge debate over public concerns around encryption, hacking and mass data theft.
Indeed, Dr Gus Hosein, executive director of Privacy International, said of the revised bill: "It would be shameful to even consider this change cosmetic... The continued inclusion of powers for bulk interception and bulk equipment interference -- hacking by any other name -- leaves the right to privacy dangerously undermined and the security of our infrastructure at risk".
What’s So Wrong With the Bill?
Summarizing the bill in general, NSA whistleblower Edward Snowden tweeted: "By my read, #SnoopersCharter legitimizes mass surveillance. It is the most intrusive and least accountable surveillance regime in the West".
A key issue with the proposed bill is the requirement for service providers to keep an itemized list of users’ browsing histories in the last 12 months on file for access by the police and authorities. This has drawn understandable concerns over whether this data would remain secure, especially in the wake of the recent TalkTalk customer data hack.
The bill would also give security services greater power to acquire bulk collections of data -- NHS health records, for example -- and be legalized to bug computers and phones with an approved warrant -- which companies would legally have to assist them with.
The government’s outlined take on encryption is also extremely controversial. Companies have voiced their concerns that this could give security services the power to eavesdrop on messages whenever they liked. But the revised bill clarified the government’s encryption standpoint, making it clear that companies can only be asked to remove encryption that they themselves have applied, and only where it is "practicable" for them to do so.
Take a Positive Mentality
The implications of the Snoopers Charter may sound all doom and gloom for the technology and communications industries and the British public, but there is a glimmer of light for technology companies that choose to build a positive response to the language being used.
When it comes to encryption, the vagueness of the government’s use of the word "practicable" has the potential to be extremely broad, potentially encompassing anything that fits "when the government has a warrant and the technology company has the power to do it". It would therefore not be surprising if security companies took steps to make it impracticable for them to decrypt their solutions, in response to the government’s demands.
For example, in the current Apple/San Bernardino case in the US, the steps that the FBI is asking for, such as updating the iPhone with a new version of iOS that disables brute force attack protections, are entirely practicable. The FBI has a court order and Apple can do it, but are arguing that they shouldn’t. However, Apple itself has said it is currently working on solutions that will prevent it having to take this action with future devices, which is precisely what could turn laws like this into a positive driver for the security industry.
To protect themselves against the burden of the new legislation, UK companies may have to go a step further and ensure their products are secure, even from themselves. The only way businesses can protect their users’ data fully is by ensuring that they cannot access it, even upon request.
There are a few methods that could be taken to achieve this, such as making a device or software platform verify and reject updates that lower security standards. The goal then becomes developing security solutions that are more intelligent and resilient, and more capable of protecting businesses from outside threats and forced internal actions.
Another reading of the Investigatory Powers Bill was announced on March 15, with a final vote on its introduction likely before the end of April.
Jonathan Parker-Bray, CEO and founder of Pryvate.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Maxx-Studio / Shutterstock
-

Many Brits now do not trust online banking
Publié: avril 1, 2016, 6:51am CEST par Sead Fadilpašić

Almost half of people living in the UK (48 percent) fear either their identities, or their banking data will be stolen. Those are the results of a new survey from financial technology company Intelligent Environments. According to the report, the fear is well founded, with 20 percent of Britons being victims to some type of cyber-crime, either identity theft or bank details theft.
The report reveals a cybersecurity map of Britain. In it, it says that Birmingham is most concerned with cybersecurity, with 57 percent fearing banking information theft, and 59 percent identity theft. Birmingham is followed by Newcastle and Cardiff.
But perhaps the most important revelation of the report is that people are refraining from using online banking in the first place, thanks to security threats. Twenty-two percent don’t trust digital banking apps, and 12 percent don’t trust online banking. Another seven percent have given up on online banking having been victims to an attack.
"People are more on edge these days, and with good reason", says managing director of Intelligent Environments, David Webber. "High profile hacking attacks on organizations like Ashley Madison, Bitdefender and TalkTalk as recently as six months ago have put the issues at the top of people’s minds, and as a result they are rightfully concerned about their security online. Of course, banking data is always going to be a primary concern as it’s particularly attractive to hackers. We’re therefore calling on banks to play a more active role in educating customers on how best to keep themselves and their financial information safe while they’re online".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: mama_mia / Shutterstock
-

An Apple 40th birthday reflection
Publié: avril 1, 2016, 6:12am CEST par Joe Wilcox
Summer 1984, Chapel Hill, N.C., I learned something about prejudice and discrimination in America and saw my first Macintosh. Strangely, looking back at Apple, which celebrates its 40th birthday today, the two things connect.
As I reflected in Jan. 18, 2004, personal post: "Racism and Naiveté", I never thought much about skin color growing up in a region of America where most everyone is Caucasian. Northern Maine is a white wonderland for more than abundant snowfall. Strangely, though, my best friends had last names like Chung and Zivic. The local Air Force base, Loring, added color to the populace, and when it came to people I was decidedly colorblind.
Because I witnessed so little racism, or discrimination, firsthand, I had no context to understand -- even when learning about slavery or the Civil Rights Act of 1964 in school. Twenty years after that landmark legislation came to be, I watched the film “From Montgomery to Memphis“, and it changed my perspective. First, there was the shock about black and white buses, then black and white waiting rooms at bus stations, and segregated bathrooms. Separate water fountains!
The same afternoon I watched the film, I wandered around the University of North Carolina campus contemplating the documentary. I ambled into the college bookstore, where placed prominently for anyone and everyone to see was Macintosh. I knew nothing about Apple, nor should I have not being a computer geek -- then or even now. But I nevertheless marveled at the graphic display. I had seen movie "WarGames" a few months earlier and recognized the dramatic differences between this machine and the one used by actor Matthew Broderick. (Hehe, Loring Air Force Base plays a role in one of the climactic scenes.)
The next year, I moved to predominately black Washington, D.C. for work, coincidentally. You don’t grow up white and male and suddenly have a feeling for what it’s like to be a minority or female of any race. One movie wouldn't change that, nor my long-time living in the D.C. metro area.
Hello, Mac
While residing there, I bought my first computer -- January 1994 -- months after reading a compelling story in Washington Journalism Review about the coming era of online publishing. I made a career change from general-interest magazine editor to tech-industry reporter. Except for a brief flirtation with IBM OS/2, I exclusively used Windows until December 1998, when I hauled a Bondi Blue iMac out of the local CompUSA. Curiosity -- and interest in expanding tech reporting beats -- prompted the impulsive purchase.
I came to love the fruit-logo company's products, while as a tech journalist developing a reputation for being anti-Apple -- which I am not. Several Apple fanboy bloggers fan the flames of hate through their criticism, sarcasm, and witlessness; they are defenders of the forbidden fruit and tolerate little real or perceived criticism.
I am not much bothered, as I don't typically read their posts or those from their accolades commenting on my stories (and other writers'). I abide by the "be hardest on those whom you love most" principle and therefore understand (and excuse) the misplaced "anti-" accusations. Few of my stories are kind, I concede.
I am not then, nor at anytime, have been a fanboy of Apple or any other tech company. The products are all just tools to me, and I use what makes sense at the time. Google gives greater contextual utility that matters to most everyone, but Apple does deliver things that make people happy to hold, look at, and use in a more human-like, responsive, and immersive way.
Apple Activism
In the nearly 18 years since I booted my first Mac much has changed. Apple has gone from being the little company that could to the behemoth that couldn't -- my first iMac is example of the one and the March 21st "Are you in the Loop?" event as metaphor for the other. CEO Tim Cook's innovation focus is customer retention rather than expansion, and maybe in the end that will prove to be the "can do" strategy.
Apple's empire is built on iPhone, which accounted for 67.4 percent of revenues during fiscal Q1 2016. Yesterday, Gartner warned that global smartphone sales would be flat in the two largest markets -- China and the United States. Existing iPhone owners in those countries could become larger customers, if Cook and Company deftly execute.
During this decade, Apple is also an activist, aggressively and vocally taking positions on real and perceived discrimination, equality, gender bias, and human rights issues, particularly in the United States. That includes the recent ruckus with the FBI about iPhone encryption. By contrast, the company showed little public social activism under Steve Jobs' leadership.
So the two threads tie together from that afternoon in 1984, when I saw America's bad past behavior magnified and a glimmer of the future displayed from a beige box. Prejudice and discrimination aren't easily swept away, and the United States still grapples with both. Eliminating either enables huge portions of our population.
Technology enables everyone, if iPhone's success means anything. No matter what Apple's future, over 40 years the company has succeeded to humanize technology and diminish the complexity using it. Nokia invented the smartphone two decades before Apple brought to market iPhone, which fundamentally changed the cellular handset market -- directly and by way of derivative, imitative devices released by other vendors.
Happy Birthday, Apple.
Photo Credit: Shutterstock/Sean Locke Photography
-

The right PC can improve job satisfaction
Publié: avril 1, 2016, 4:53am CEST par Sead Fadilpašić

Do you want satisfied workers? Give them a well-designed PC, a good and secure mobile device, and let them work when they want to, where they want to. Those are, in a nutshell, the results of a new research by Redshift Research, which had polled 1,016 people, across France, Germany, the UK, Italy, Netherlands, Spain and Switzerland.
For 90 percent of IT decision makers, device security is a current concern, because in the last 12 months, a quarter of Europe’s businesses have been breached. That has resulted in less than a third (32 percent) being completely confident in the level of security offered by their current devices.
The report also says that PC design is important -- for 69 per cent of IT decision makers it must allow for mobility, and 77 percent believe it can improve job satisfaction.
"The way that we’re seeing our customers use their business devices is continuing to evolve and is resulting in greater collaboration, mobility and productivity for users", said John O’Reilly, director of Corporate, Enterprise & Public Sector and Personal Systems at HP. "However, this new way of working also presents a real challenge for IT decision makers in ensuring that their devices remain secure whilst being able to provide beautiful, stylish products that match the productivity and design demands from their employees".
In case you were wondering what might be wrong with their current PC setup, that’s mostly unattractive design (27 percent), and short battery life (25 percent).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Zurijeta / Shutterstock
-

Investigate your PC’s RAM use with ATM
Publié: avril 1, 2016, 3:13am CEST par Mike Williams
ATM is a portable tool which gives an in-depth, low-level look at your PC's system memory use.
Forget the usual Task Manager clones, this is more about memory standby lists, the system file cache, Superfetch performance, page file effectiveness, even (on Windows 10) memory compression.
The program is designed for IT professionals, so there’s no hand-holding, no Help file, no attempt to hide complex details. Every figure is displayed in a huge block of text, which updates in real time.
Once you're past the initial shock, it’s not really so bad. At least all the data is displayed up-front, without you having to click on various tabs to find whatever you need. And there's useful information to explore here, too.
One example. We recently wrote about "Empty Standby List", a console program which could free up RAM by flushing the contents of various Windows standby memory lists. But which lists are best to empty on your system, and how much RAM are they using?
ATM gives you all this information, including the individual lists by priority, and the overall total, typically around 50% of the RAM on our test PC.
Would clearing these lists help? There are buttons to do it, or flush the file cache, process working sets and more.
The problem with this kind of memory "optimisation" is your system may have to reload data from disk, but ATM has that covered, too, with tools to assess your system file cache and page file effectiveness.
That works for us, but if you find yourself getting lost, just look to the right, where a colorful chart gives a simpler real-time view on how your RAM is being used.
ATM is a free and portable application which runs on anything from Windows 2000 up.
-

Acer unveils 'Chromebase for meetings' all-in-one with videoconferencing focus
Publié: avril 1, 2016, 1:22am CEST par Brian Fagioli
While many people view Chrome OS as nothing more than a basic operating system for home users, it is actually much more. In fact, the Linux-based machines can work beautifully for businesses too -- depending on needs, of course. As more and more solutions become web-based, a traditional Windows/Office solution from Microsoft becomes less of a necessity.
One way that Chrome OS shines in business environments, is videoconferencing and collaboration with Hangouts. Google's 'Chromebox for meetings' has proven to be a great option in this regard for some companies, thanks to low cost and ease of use. Today, business decision-makers that prefer all-in-one solutions to diminutive desktops gain a new option -- Acer's Chromebase for meetings. With an integrated display, this all-in-one is inexpensive, attractive, and extremely easy to setup and deploy.
"Designed for videoconferencing, Acer's Chromebase for meetings features the largest screen of all Chrome OS devices on the market, a 24-inch Full HD (1920 x 1080) display with IPS technology, reproducing consistent and accurate colors at up to 178-degree wide viewing angles. An array of four microphones and two speakers ensure that participants can hear and be heard clearly, while an adjustable HD webcam and a chassis that easily tilts from - 5° to 30° allows them to be framed perfectly on the call", says Acer.
Google explains, "so now, you can collaborate and meet over video from a dedicated device at home, your desk at work or a phone room. And since meeting in smaller spaces creates additional opportunity to work together across larger groups, we've also recently expanded the number of meeting participants to 25 people for Google Apps customers".
Click to view slideshow.Acer shares the following specs.
- CPU: CELERON-3215U
- Ram: 4 GB
- Storage: 16 GB
- Screen Size: 23.88 inch
- Form Factor: all-in-one
- Touchscreen: Yes
I know what you are thinking -- what if a business sometimes needs a larger than 24 inch screen? No worries -- the Chromebase for meetings features HDMI out, so you can connect to a larger display, television, or projector if needed. Of course, if you have no need for the integrated display, a Chromebox could be a smarter buy.
It also features gigabit Ethernet, three USB 3.0 ports, a single USB 2.0 port, 3.5mm audio jack and an SD card reader. Of course, Wi-Fi and Bluetooth are included too.
This $549 computer will be available imminently at various retailers. In the interim, you can pre-order now here.