Canaux
108470 éléments (108470 non lus) dans 10 canaux
 Actualités
(48730 non lus)
Actualités
(48730 non lus)
 Hoax
(65 non lus)
Hoax
(65 non lus)
 Logiciels
(39066 non lus)
Logiciels
(39066 non lus)
 Sécurité
(1668 non lus)
Sécurité
(1668 non lus)
 Referencement
(18941 non lus)
Referencement
(18941 non lus)
éléments par Sam Pudwell
BetaNews.Com
-

The 'age of automation' can benefit the security landscape
Publié: novembre 30, 2016, 7:12pm CET par Sam Pudwell
Artificial intelligence (AI), machine learning and automation are technology trends dominating discussions in many different industries at the moment and cyber security is no exception. As cyber criminals become more advanced and the threat landscape continues to develop, businesses are looking to new technologies that can help secure their organization in a more proactive way. According to Dave Palmer, director of technology at Darktrace, this move to the so-called "age of automation" is an inevitable and much needed one: "When you think about networks getting faster and big data, it’s been just as useful for the bad guys as it… [Continue Reading] -

Oracle buys DNS provider Dyn
Publié: novembre 23, 2016, 3:24pm CET par Sam Pudwell
Oracle is showing no desire to slow down it's spending spree after announcing the acquisition of DNS provider Dyn for an undisclosed sum. The timing of the deal has raised a few eyebrows as, although Dyn powers some of the biggest sites in the world such as Netflix, Twitter and Spotify, in October it was hit by a DDoS attack which took several of its big-name clients offline. But it appears that this has not discouraged Oracle, with TechCrunch reporting that the enterprise services giant plans to integrate Dyn's DNS solution into its cloud platform to add to its IaaS… [Continue Reading] -

Bitcoin price surges after Trump's victory
Publié: novembre 10, 2016, 10:11am CET par Sam Pudwell
The world is still reeling from the outcome of the US elections, where Donald Trump came out on top against Hillary Clinton to become the 45th President of America. Financial markets around the world have been affected by the shocking and unexpected news and the notoriously unpredictable digital currency Bitcoin is no exception, with prices close to hitting a 35-month high against the pound amidst investor uncertainty. Against the dollar, the price of Bitcoin rose by up to 4.6 percent to reach a high of $738 on Wednesday, before settling at the $726 mark. This is approximately a three percent rise… [Continue Reading] -

What you need to know about enterprise resource planning
Publié: novembre 1, 2016, 8:24pm CET par Sam Pudwell, Ian Barker
We’ve already covered what businesses need to know about enterprise content management (ECM), so now it’s time to move on to another popular business tool: enterprise resource planning (ERP). ERP is business process management software -- typically consisting of a suite of integrated applications -- that allows an organization to manage its entire business and automate many back-office functions. It is designed to be used by larger enterprises -- often requiring dedicated teams to customize and analyze the data -- and integrates various facets of an operation, including sales and marketing, product planning, manufacturing and inventory management, making sure everything… [Continue Reading] -

What you need to know about enterprise content management
Publié: octobre 28, 2016, 8:00pm CEST par Sam Pudwell, Ian Barker
Thanks to the likes of smartphones, the internet and big data, we now have access to more information in various shapes and sizes than ever before. In most cases, having more information is a good thing for businesses, but there comes a point where there is simply too much to keep track of. This is especially true in large enterprises, where invoices, word documents, receipts and purchase orders are in abundance and could be needed by anyone at any time. Keeping on top of all of this would be a challenge for even the most organized individuals, so that’s where… [Continue Reading] -

Flash storage adoption is on the rise in UK
Publié: octobre 26, 2016, 10:32am CEST par Sam Pudwell
A new survey carried out by data management company NetApp reveals the trends in flash storage adoption throughout various industries in the UK. The legal industry is currently leading the way, with (50 percent) of respondents having already adopted it. This is followed by finance and manufacturing (both at 46 percent), education (42 percent) and IT and telecommunications (40 percent). At the other end of the spectrum is healthcare, where nearly half (45 percent) of decision makers said they have no plans to invest in flash storage in the next 12 months. This was a view shared by 40 percent of retail… [Continue Reading] -

What you need to know about DevOps
Publié: octobre 20, 2016, 8:18pm CEST par Sam Pudwell, Ian Barker
The term DevOps is being thrown around a lot in the IT industry at the moment, but what exactly does it mean and, more importantly, how can it help an enterprise? As a combination of developer and operations, DevOps looks to bring these two different areas of digital business together to provide the perfect combination of innovation and user-focused processes during software development. Continuous deployment and continuous delivery are both important aspects of this and, when adopting DevOps, it is vitally important that businesses assess which one is right for them. It also looks towards the automation of delivering changes to… [Continue Reading] -

Microsoft Surface Book: Not the ultimate laptop, but close [Review]
Publié: octobre 3, 2016, 10:54am CEST par Sam Pudwell
The developing digital landscape has changed the way people interact with hardware. We are now more device-agnostic than ever -- both in our personal and professional lives -- meaning we are often carrying around two, sometimes three, devices to complete different tasks. The 2-in-1 (or hybrid) market has looked to address this by merging the power and performance of a laptop with the flexibility and mobility of a tablet. For the most part, Microsoft has led the way in this area with its Surface and Surface Pro devices, but is now being pushed hard by the likes of Apple and Huawei.… [Continue Reading] -

The growing security risks in enterprise Windows environments [Q&A]
Publié: septembre 12, 2016, 7:28pm CEST par Sam Pudwell
ManageEngine recently announced the results of its global Active Directory and Windows Server Security -- Trends and Practices Survey for 2016, which found that 70 percent of IT administrators across the globe agree that their Windows environments are not immune to malicious attacks. To delve a bit deeper, we spoke to Derek Melber, a technical evangelist for ManageEngine. ITPP: Is the actual level of risk growing, or are IT admins simply becoming more aware of threats that have always existed? The level of risk is growing daily. However, regardless of the level of risk or risks, at the time of… [Continue Reading] -

Growing number of cyber attacks suggests no one is safe
Publié: septembre 7, 2016, 3:53pm CEST par Sam Pudwell
I've been at CloudSec 2016 in London, listening to various security professionals from the likes of Trend Micro and Microsoft talk about the challenges businesses face in securing their data in the cloud. As you could probably have guessed, talks have centered around the ever-expanding threat landscape, the continued industrialization of cybercrime through various underground marketplaces around the world and general cyber security trends. But what's been really catching my attention throughout the day -- rather appropriately, seeing as I'm at a security conference -- has been the stream of data breach notices and press releases that have been appearing in my… [Continue Reading] -

Cyber criminals using insiders to carry out telecommunications attacks
Publié: août 25, 2016, 10:34pm CEST par Sam Pudwell
Cyber criminals are frequently turning to insiders to gain access to telecommunications networks and subscriber data, according to a new report from Kaspersky Lab. According to the report, 28 percent of all cyber-attacks and 38 percent of targeted attacks now involve malicious activity by insiders. Telco providers are some of the top targets for cyber-attacks due to the vast amount of confidential data they collect, so criminals are recruiting employees through underground channels or blackmailing staff with compromising information to carry out their attacks. The blackmailing approach in particular has grown in popularity as a result of breaches that have… [Continue Reading] -

Cisco will cut 5,500 jobs
Publié: août 18, 2016, 8:45pm CEST par Sam Pudwell
According to reports, Cisco Systems is planning a mass jobs cull with 5,500 jobs in danger -- or around seven percent of its global workforce. Cisco, the world’s biggest networking equipment company, is expected to announce more details of any potential cuts in the next few weeks a part of an ongoing transition to a more software and cloud-orientated strategy. As of 30 April, Cisco had around 70,000 employees globally and less than a year ago opened new offices in London, bringing its UK employee headcount up to around 7,000. Following a decrease in spending by telecom carriers and enterprises… [Continue Reading] -

Failing to attract security experts may prove costly for businesses
Publié: août 17, 2016, 6:05pm CEST par Sam Pudwell
A new report from Kaspersky Lab has found that large businesses that struggle to attract sufficiently skilled security experts end up paying up to three times more to recover from a cyber security incident. The much talked-about skills gap in the security industry continues to cause problems for businesses, as increasing wages, a general shortage of expert availability and the need for more specialists are all prevalent. This skills shortage is being brought about by today’s rapidly expanding threat landscape, with businesses highly motivated to grow their security intelligence to help guard against costly security incidents. In fact, the improvement of… [Continue Reading] -

Russia fines Google over breaking antitrust rules with Android
Publié: août 12, 2016, 11:03am CEST par Sam Pudwell
Google has been fined 438 million rubles ($6.75 million) by the Russian antitrust authority for abusing its market position following a complaint by Yandex, Russia’s biggest search engine. Google has been found guilty of forcing Android smartphone makers to install its search engine on their devices, which has been seen to breach "protecting competition" laws. Yelena Zayeva, the head of the Federal Antimonopoly Service’s (FAS) department for regulating communications and IT says that the ruling "will allow the development of competition on the mobile software market in Russia, which will have a positive effect for consumers". In response, Google says: "We have received notice… [Continue Reading] -

Salesforce buys Quip for $582 million
Publié: août 4, 2016, 5:47am CEST par Sam Pudwell
Salesforce is taking the fight to Alphabet and Microsoft with the $582 million acquisition of Quip, a document collaboration firm that competes with Alphabet’s Google Docs and Microsoft’s Office products. The deal will be completed entirely in stock options and is Salesforce’ third acquisition in the last few months, following the £2.8 billion purchase of enterprise cloud commerce solutions provider Demandware and the acquisition of deep learning company MetaMind. The deal enables Salesforce to boost its document creation and collaboration offering, as well as taking advantage of Quip’s mobile platform. Quip said in a statement: "Salesforce and Quip share the same philosophy about software: it should be in… [Continue Reading] -

Most enterprises lag behind in mobile security
Publié: août 3, 2016, 11:21am CEST par Sam Pudwell
Enterprises are still not doing enough to protect corporate data on their employee’s mobile apps and devices from cyber threats, according to a new report from MobileIron. According to the Mobile Security and Risk Review report for Q2 2016, less than five percent of enterprises are using mobile threat detection software and only eight percent have an enforced operating system update policy in place. Furthermore, 40 percent of enterprises experienced missing devices (a seven percent increase from Q4 2015) and 27 percent had out of date policies (up from 20 percent in Q4 2015). These are surprising and alarming statistics in equal… [Continue Reading] -

Uber China will merge with Digi Chuxing
Publié: août 2, 2016, 1:55pm CEST par Sam Pudwell
Uber CEO Travis Kalanick announced via a blog post that Uber China -- a subsidiary of the taxi-hailing app -- will merge with its biggest competitor in the region -- Didi Chuxing -- in a whopping $35 billion deal. The blog post has recently been doing the rounds on Chinese social media, with the deal effectively signalling the end of a hard-fought market share battle in China in which both companies have invested huge amounts of money without really getting anywhere. According to Business Insider, the terms of the deal state that Didi will invest $1 billion in Uber Global at a $68 billion valuation, leaving Uber… [Continue Reading] -

BQ's Aquaris M10 Ubuntu Edition is an underwhelming tablet [Review]
Publié: août 1, 2016, 2:39pm CEST par Sam Pudwell
As employees have become more and more flexible in recent years thanks to the power and performance of mobile devices, the way we work has changed dramatically. We frequently chop and change between smartphones, tablets and laptops for different tasks, which has led to the growth of the hybrid market -- devices such as Microsoft’s Surface Pro 3 and Apple’s iPad Pro -- that provide the power and functionality of a laptop with the mobility and convenience of a tablet. The latest company to try and tempt users onto one device that covers all eventualities is BQ, a Spanish firm… [Continue Reading] -

Apple revenue and iPhone sales are down
Publié: juillet 27, 2016, 5:39am CEST par Sam Pudwell
Apple today announced its financial report for Q3 FY2016 (Q2 CY2016), revealing a drop in revenue and falling iPhone sales compared to both the previous quarter and this time last year. Apple posted quarterly revenue of $42.4 billion and a net income of $7.8 billion, with the bulk (nearly $18 billion) coming from the Americas. This revenue is compared to $50.5 billion in Q2 FY2016 and $49.6 billion in Q3 FY2015, drops of 16 percent and 15 percent respectively. The iPhone sales slump is also continuing, with 40,399 units sold in Q3 FY2016 compared to 51,193 in the previous quarter… [Continue Reading] -

Euro 2016 app leaking private user data
Publié: juin 30, 2016, 5:47pm CEST par Sam Pudwell
I’ve been trying not to think about Euro 2016 after England’s whimpering exit on Monday night, but new research from mobile security and management firm Wandera has grabbed my attention. According to analysis of data traffic patterns from enterprise mobile devices, the official UEFA Euro 2016 Fan Guide App is leaking user’s personal information -- including usernames, passwords, addresses and phone numbers -- over unsecure internet connections. This means the app, which has been downloaded over 100,000 times, could provide an access point for hackers to access, and potentially steal, valuable user data. And, with modern employees frequently using the same devices for work… [Continue Reading] -

Customers penalize businesses with a bad mobile experience
Publié: juin 24, 2016, 7:29pm CEST par Sam Pudwell
Think mobile experience isn’t important to the success of your business? Think again. A massive 85 percent of people are unlikely to do business with a company following a bad mobile experience, according to the results of a new study from LogMeIn and research firm Vanson Bourne. The study also revealed that businesses are currently falling short in delivering satisfying mobile experiences for their customers, with the number of respondents happy with their last mobile engagement with a business dropping from 59 percent in 2015 to 52 percent in 2016. Although it should come as no great surprise, mobile continues… [Continue Reading] -

Salesforce buys cloud commerce solutions provider Demandware
Publié: juin 2, 2016, 1:48pm CEST par Sam Pudwell
Salesforce has announced that it has agreed to purchase enterprise cloud commerce solutions provider Demandware in a $2.8 billion cash deal. Salesforce will commence a tender offer for all outstanding shares of Demandware -- which boasts the likes of L’Oreal and Marks & Spencer as customers -- for $75.00 a share, with the transaction expected to close at the end of July 2016. Marc Benioff, chairman and CEO of Salesforce said: "Demandware is an amazing company -- the global cloud leader in the multi-billion dollar digital commerce market. With Demandware, Salesforce will be well positioned to deliver the future of… [Continue Reading] -

Tech leaders are not satisfied with IT departments
Publié: mai 3, 2016, 6:39pm CEST par Sam Pudwell
The pace of change within IT has accelerated rapidly in recent years and, according to new research from IT resourcing firm Experis, many organizations now believe they have fallen behind the competition. The report found that tech leaders believe their departments are a whole four years behind their most innovative competitors, whilst also believing that 29 percent of their teams need to be changed in order to drive digital transformation. IT leaders identify a lack of skills as being a primary factor. Organizations want their teams to deliver more cloud services (61 percent), more mobile apps (53 percent) and turn… [Continue Reading] -

Facebook's mobile ads boosting revenue
Publié: avril 29, 2016, 1:41pm CEST par Sam Pudwell
Facebook has put other tech giants to shame by comfortably beating analyst expectations in the last quarter, with revenues over 50 percent up thanks to surging mobile advertising sales. As mobile web browsing continues to grow throughout the world, advertisers are realizing that taking a mobile-first approach has the potential to be extremely lucrative. Facebook has looked to capitalize on this by improving its mobile app and expanding its live video solution, both of which have attracted advertisers. As a result, advertising revenue increased 56.8 percent to $5.20 billion, with mobile ad revenue accounting for approximately 82 percent, up from… [Continue Reading] -

Only 23 percent of businesses can effectively respond to cyber attacks
Publié: avril 20, 2016, 11:17am CEST par Sam Pudwell
NTT Com Security today released its annual Global Threat Intelligence Report (GTIR), which examines the threat landscape by analyzing the attacks, threats and trends from the previous year. This year’s report is the most comprehensive to date, featuring key findings from partners including Lockheed Martin and the Center for Internet Security and pulling information from 24 security operations centers, seven R&D centers, 3.5 trillion logs, 6.2 billion attacks and nearly 8,000 security clients across six continents. The report finds that, on average, only 23 percent of organizations are capable of responding effectively to a cyber incident, with 77 percent having… [Continue Reading] -

European Parliament approves new general data protection regulations
Publié: avril 15, 2016, 7:13pm CEST par Sam Pudwell
After a whole lot of discussion and debate, new general data protection regulations have been approved by the European Parliament. In what has been described as a watershed moment for enterprise IT, the unification of Europe’s multiple data protection regulations into one common law signals a new beginning for businesses and consumers alike. Although it’s expected that the rules won’t be officially enforced for another two years, organizations will need to start preparing now to ensure compliance, with failure to do so potentially costing up to four percent of annual worldwide turnover. Andrew Dyson, partner and co-chair of DLA Piper’s international… [Continue Reading] -

Mossack Fonseca hack exposes shady financial practices of world's rich and famous
Publié: avril 5, 2016, 10:44am CEST par Sam Pudwell

One of the largest data breaches in history has resulted in the leak of eleven million confidential documents -- around 2.6TB of data -- from financial firm Mossack Fonseca, one of the most secretive companies in the world.
According to the BBC, the leaked documents reveal how "Mossack Fonseca has helped clients launder money, dodge sanctions and evade tax". The client list features some of the world’s richest and most influential people -- including 12 current or former heads of state -- and their irrepressible greed has now been laid out for all to see. The data shows how thousands of off-shore shell companies have been created in order to hide money from the tax man and also reveals "a suspected billion-dollar money laundering ring involving close associates of Russian President Vladimir Putin".
Gerard Ryle, director of the International Consortium of Investigative Journalists (ICIJ), said: "I think the leak will prove to be probably the biggest blow the offshore world has ever taken because of the extent of the documents".
A statement from Mossack Fonseca says: "Your allegations that we provide structures supposedly designed to hide the identity of the real owners, are completely unsupported and false. We do not provide beneficiary services to deceive banks. It is difficult, not to say impossible, not to provide banks with the identity of final beneficiaries and the origin of funds. If we detect suspicious activity or misconduct, we are quick to report it to the authorities. Similarly, when authorities approach us with evidence of possible misconduct, we always co-operate fully with them".
There probably won’t be many times when I’ll get to say this, but nice work hackers, a job well done.
According to IBTimes, international football superstar Lionel Messi is among those detailed in the leaks, along with Michel Platini and several other leading officials, placing the world of football under intense scrutiny.
Luke Brown, VP and GM EMEA, India and Latam at Digital Guardian commented: "Putting aside the fact that the leaked emails and documents appear to include information about illicit operations, for the victims, a data breach of this scale could have life altering or, at the very least, distressing effects. Ultimately, the breach may trigger serious legal repercussions against Mossack Fonseca. Data protection should be of the utmost importance in environments like this and yet we have seen a growing number of data breaches in law firms over the last few months"
"This latest case reinforces the need for 'data aware' security technologies in the legal sector. If Mossack Fonseca had such technologies in place, it could have prevented its most sensitive emails and files from being copied, moved or deleted without approval or permission", added Brown.
"Companies must learn from incidents like this and better protect their IT environment, with the ability to apply security at the data-level being of the utmost importance", further explained Brown.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: igor.stevanovic/Shutterstock
-

Enterprises should prioritize availability, not backups
Publié: mars 31, 2016, 6:15pm CEST par Sam Pudwell

With today being World Backup Day 2016, many companies are rightly preaching the importance of regular backups. However, Veeam is bucking the trend by saying that -- in the enterprise space -- just backing up is no longer enough.
The company thinks that the most important question for enterprises now should be "are we always available?" and has thus declared today as "World Availability Day". The argument is that for consumers, just having backups in place is sufficient, but enterprises are expected to be up and running 24/7 and downtime is no longer tolerated in today’s fast-paced world.
According to a recent survey conducted by Veeam, 84 percent of CIOs are unable to meet the expectations of constant availability and admit that it is costing them up to $16 million a year. Downtime actually increased in 2015, with companies experiencing an average of 15 unplanned downtime events, compared to 13 events in 2014.
Richard Agnew, VP NW EMEA, Veeam, explains: "Driving backup awareness amongst consumers is still important, but for today’s enterprises, backup alone is no longer relevant, or enough. Organizations have discovered that the question is no longer, "Are we backed up?" but instead, "Are we available?" Backup as it is traditionally known is being replaced by a new category: Availability.
"We’re seeing an 'Availability Gap' (the gulf between what IT can deliver and what users demand) in today’s organizations characterized by data loss, long recovery times, lack of visibility, and unreliable data protection. Fifty-nine percent of businesses in our research reveal that they experience unplanned downtime caused by IT failures, external forces, or other factors up to ten times a year at the cost of up to $100,266 per hour. It’s clear that this is hitting the bottom line, not to mention leaving a lasting impact on customer confidence (68 percent) and damage to brand integrity (62 percent)".
"Businesses should be putting availability and enabling an Always-On Enterprise on the boardroom agenda, to meet the demands of their employees who expect access to applications and data at any time, from any place, and from any device. No employee or customer will accept being without access to a critical application for even a few hours. While it’s good that backup solutions exist, if an employee has to retrieve the tape from the depths of a warehouse across town before a restore can even begin, the problem is far from solved, and downtime will not be tolerated".
"Advancements in technologies such as storage snapshots and virtualization have made it feasible for organizations to backup as often as every 15 minutes, and recover anything in the same amount of time".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit scyther5 / Shutterstock
-

Would you like a digital passport on your smartphone?
Publié: mars 31, 2016, 6:37am CEST par Sam Pudwell

I’m sure most of you will be familiar with the frantic scrabble to find the correct documents at the airport, resulting in a mild heart attack when your passport isn’t where you thought it was. FYI, it’s probably in your back pocket.
Well, this could soon be a thing of the past thanks to a company called De La Rue, which is working on creating digital passports on your smartphone that can be used at airport immigration, making travel an entirely paperless experience.
Of course, the biggest challenge for De La Rue will be creating a solution that is acceptable for governments around the world, as significant security and anti-counterfeit measures will be required.
De La Rue chief executive Martin Sutherland told The Times that the project is a long-term one, but the company has already started working on removing the need for a physical passport.
Despite the excitement that may be felt by consumers, security professionals have been quick to warn of the potential dangers: "Most European countries have been using digital chips embedded in traditional passports for ten years with little or no impact to security, but with the introduction of a passport being associated with an internet connected device, the threat model changes significantly", said Gavin Millard, technical director with Tenable Network Security, speaking to MailOnline.
"With the recent launch of Apple Pay and Google Wallet, proving that mobile devices can be used securely for transactions though, the obvious next step in the evolution of everything digital is the paperless passport. If introduced, many will err on the side of caution and not enable this capability on their devices, but for frequent travelers convenience will probably trump security concerns".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Laborant/Shutterstock
-

MWC 2016: The most important products announced so far
Publié: février 25, 2016, 8:34pm CET par Sam Pudwell

We are just past the half way point at Mobile World Congress 2016, which has so far given us smartphones, tablets and Internet of Things solutions in abundance from some of the industries biggest players.
If you haven’t been paying attention for the last couple of days, here’s a quick round up of some of the big stories you might have missed.
Tablets
There’s been an emergence of business-focused 2-in-1 tablets at this year’s MWC, with the likes of Fujitsu, Lenovo and Huawei all getting in on the act.
Microsoft first led the way in this category with its Surface Pro devices, followed by Apple which released the iPad Pro last year. Aimed at the modern mobile worker, these hybrid devices aim to provide the mobility of a tablet with the power and performance of a laptop, thus enabling employees to work anywhere.
Huawei held a press conference in Barcelona on Sunday to launch the MateBook, its own 2-in-1 effort which it hopes will "redesign the new style of business". Running Windows 10 and powered by an Intel 6th Generation Core m-series processor, the MateBook certainly looks well places to disrupt the market. I got my hands on the device and it is an impressive piece of kit, starting at $699 for the cheapest option.
Lenovo has also targeted professionals with the TAB3 10 Business, an Android tablet that offering full support for Android for Work and featuring a range of security and encryption options to ensure work-related data remains secure. Starting at just $199, it is a much cheaper option than the Huawei MateBook and will be available from June this year.
Not wanting to be left out, Fujitsu has focused on security with the STYLISTIC Q736. Powered by the 6th Generation Intel Core i7 vPro processor, the Q736 features Fujitsu’s unique PalmSecure technology which scans the veins in your palm to provide a more secure biometric reading.
Smartphones
On to smartphones now, which of course are a prime focus at MWC. HP kicked things off with the Elite x3, which is actually more than just a smartphone -- it’s a mobility ecosystem designed to drive the next generation of mobile computing. The Elite x3 bridges phablet, laptop and desktop use cases through a single device -- a phablet with a 6-inch display, the latest Qualcomm 820 processor and a massive 4,150 mAh battery.
As with the Huawei MateBook, the Elite x3 is a slick looking device and its versatility could make it very popular with today’s mobile workforce that needs to be able to switch between smartphone and laptop.
From a more consumer point of view, Samsung and LG have also both launched new flagships at MWC. The Samsung Circus rolled into town on Sunday evening to announce the Galaxy S7 and Galaxy S7 Edge, both of which have made steps forward from their predecessors. A surprise appearance from Mark Zuckerberg added to the excitement at an event where virtual reality was also heavily featured.
LG added the G5 to its mobile portfolio, doing away with the leather casing of its predecessor for an all-metal finish which, although not quite as polished as the Galaxy S7, is still a marked improvement on the G4. Add Qualcomm’s Snapdragon 820 processor and 4GB of RAM into the mix and you’ve got yourself a top-quality smartphone.
Other
MWC isn’t all about hardware and there have been a few other interesting stories to emerge over the last couple of days. Probably the most notable is Samsung’s semiconductor arm positioning itself as an advocate for a cashless society, with its NFC and digital payments solution ready to take on the burden of our spending habits.
Moving on to cars, Ford has announced that its automotive connectivity technology SYNC 3 is coming to Europe and that it is working on autonomous and semi-autonomous vehicles.
There’s still one more day to go at MWC 2016, so be sure to check back for more news and updates from the biggest mobile show on earth.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Enterprises have no protection against mobile malware
Publié: février 24, 2016, 3:20pm CET par Sam Pudwell

Mobile enterprise security firm MobileIron has released its Q4 2015 Mobile Security and Risk Review, discussing the threats and risks that enterprises face in their mobile deployments.
The report reveals the worrying find that more than 50 percent of enterprises have at least one non-compliant device, creating a broader attack surface for malware and data theft.
"Mobile threats, both internal and external, are on the rise and the enterprise security chain is only as strong as its weakest link", said Michael Raggo, director, MobileIron Security Labs. "A single, compromised device can introduce malware into the corporate network or enable the theft of sensitive corporate data that resides behind the firewall".
"The real risk is that enterprises will underestimate the seriousness of the problem", Raggo continued. "A single compromised device that goes undetected constitutes a breach. Whether a company loses millions of records or just one record it’s still a breach. For all companies, but particularly ones in highly regulated industries, this is a huge problem".
The incidence of compromised devices -- i.e. a jailbroken or rooted device -- rose significantly during the quarter by 42 percent and less than 10 percent of enterprises are enforcing patching, thus leaving the device vulnerable to data loss.
Other key findings are that a massive 95 percent of enterprises have no protection against mobile malware and 22 percent had users who had removed the PIN from their mobile device which eliminates the first line of defense.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: LoveFreedom / Shutterstock
-

Are you ready to cut the cash?
Publié: février 23, 2016, 9:56am CET par Sam Pudwell

One of the big debates happening at the moment is when -- and indeed, whether -- we will see the emergence of a cashless society where digital payments rule the roost.
We are already seeing it happening. Last year, cashless payments overtook physical currency in the UK and the release of services such as Apple Pay has helped propel mobile payments into the mainstream.
The debate will certainly rage on for some time, but one company ready to embrace a cashless society and help drive it forward is Samsung. At MWC I have met two executives from Samsung’s semiconductor arm -- Joerg Suchy and Thomas Arenz -- both advocates of getting rid of cash once and for all.
And the reason is NFC. Samsung has been working with a company called SmartLink to create something called the Contactless Companion Platform (CCF), a customizable NFC payments service for mobile and wearable devices that allows users to pay for items their way, using their preferred form factor.
The platform can store any kind of payment card as well as things like transport tickets or hotel room keys, with the phone being "the host to transfer NFC services to any form factor".
As Thomas delicately pointed out, "for many people NFC translates into No F***ing Clue", but Samsung is hoping the CCF will change that. Picture the scenario: Your son wants to go out to the cinema with his friends, so instead of giving him cash which can easily be lost of stolen, you distribute £20 to a wearable device. You then set a timeframe in which the money has to be used by and send him on his way. If the wearable gets lost of stolen, it can be disabled from the smartphone so only the wearable is lost, not the money.
The aim, Thomas explained, is to "replace inherently insecure things like cash and tickets and use the mobile phone to manage the distribution onto a form factor of your choice", whether this be a wearable, smartwatch, ring of piece of clothing.
And when you think about it, the use cases are easy to imagine. Your ski jacket could have a sensor in the sleeve so you can get access to ski lifts or pay for food and drink without having to spend ages removing clothing and digging around in your pocket for money. When you go for a run or a bike ride, instead of having to take your wallet or cash with you, you strap on a wristband with as much money as you need.
Now, people will argue that removing cash altogether would be quite a drastic move, especially when dealing with larger sums. But moving mountains isn’t the idea. Joerg thinks things need to stay as "close to cash" as possible in the early stages to ease security worries. We’re talking about those small payments that we all make every day, where convenience is the top priority.
So, Samsung's semiconductor arm is very much looking ahead to a world of digital payments. The only question is, will the public be ready and willing to cut the cash?
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: s4svisuals/Shutterstock
-

Lenovo unveils TAB3 10 Business tablet
Publié: février 22, 2016, 12:57pm CET par Sam Pudwell

As the BYOD trend continues to grow throughout SMBs and enterprises alike, more and more mobile devices such as tablets and smartphones are being introduced into the workplace.
With this in mind, Lenovo has unveiled the TAB3 10 Business at MWC 2016, an Android powered tablet designed to combine the power and versatility of Android 6.0 with the service capabilities that matter most to business users.
The TAB3 10 Business is optimized for professional use, offering full support for Android for Work and featuring a range of security and encryption options -- such as persistent endpoint protection and geo-technology to enable businesses to track devices -- to ensure work-related data remains safe and secure.
The tablet comes pre-loaded with Android for Work apps, Google Play for Work and supports industry solutions in areas such as classroom, point-of-sale and eHealth management. Wear and tear isn’t an issue, as the TAB3 10 Business boasts IP52 certification for dust- and splash-proofing and shielding through scratch-resistant Gorilla Glass 3 panels to deal with the toughest working environments.
Multi-tasking and multi-window support is provided by the 1.3GHz Quad-core processor and the 12-hour battery life means employees can stay mobile throughout the day without having to stop and recharge.
As business-specific use cases range from digital displays to conference calls, a 10-inch full-HD IPS display with Gorilla Glass 3 and dual speakers boosted by Dolby Atmos cinematic movie audio are also packed in, with an 8MP auto-focus rear camera and 5MP fixed-focus front camera produce quality pictures with high-resolution clarity.
The TAB3 10 Business will be available from June 2016, retailing at $199 for the Wi-Fi only option, $249 for 2GB and LTE and $299 for 3GB and LTE.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Huawei MateBook first-impressions review
Publié: février 22, 2016, 10:32am CET par Sam Pudwell

At MWC 2016, Huawei has announced the MateBook 2-in-1 tablet, entering an ever-growing market already populated by the likes of Apple’s iPad Pro and Microsoft’s Surface Pro devices.
Aimed at business users, the Intel-powered MateBook provides the mobility of a smartphone with the power and performance of a laptop, enabling the modern mobile workforce to work anytime, anywhere.
We got up close and personal with the new device today and, I’ve got to say, I was impressed. Firstly, it looks good, which is now an important factor in the business world as today’s customers want style as much as substance. The MateBook has a crisp, clean-cut design with sharp lines and just the right amount of bezel.
It’s also thin (just 6.9mm, which is the same as the iPad Pro) and light (weighing 640 grams) so holding it in one hand for short periods of time is relatively comfortable. From a style point of view it ticks all the boxes both up close and from further away and is every bit as good as Apple and Microsoft’s efforts.

Although I didn’t get a chance to really test out the performance, the MatePad worked as smoothly as you would expect during a quick fiddle. Apps loaded quickly and smoothly -- even when multiple were open at once -- with Microsoft’s Windows 10 operating system driving proceedings nicely. You’d have to be able to use the device for a few days to really test its limits, but seeing as it’s being pitched a productivity tool, you would expect pretty smooth sailing in most situations.

Let’s move on to the stylus. The MatePen costs an extra $59 and having spent a bit of time playing with it, I’m inclined to say that it’s worth the extra outlay. First and foremost, it’s comfortable to hold with a ridged section in the middle so it wouldn’t easily slip out of your hand. That’s one box ticked.
Secondly, it looks good -- very sleek and professional looking -- and fits well with the MateBook when placed together. That’s another tick. But as well as all that, it also has some nifty features -- namely the laser pointer and slide-show navigation buttons -- that would make it hard to say no too.

Using the MatePen is also a delight. It glides smoothly over the display and is very sensitive to changes in pressure and direction. The harder you press, the thicker the line you’re drawing gets and even my useless art skills were made to look adequate. Another clever touch is that you can rest your writing hand on the display as you’re using the pen without affecting the output, providing a perfectly natural writing position.
All in all, I believe Huawei has got a serious device on its hands that has the potential to be a serious thorn in the sides of Apple and Microsoft. It is due to launch in Asia, Europe and North America within the next few months, with prices starting at $699.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The majority of IT pros view email as a major security threat
Publié: février 18, 2016, 9:17pm CET par Sam Pudwell

Sixty-five percent of IT professionals don’t feel equipped to defend against email-based cyber attacks, according to the findings of a report carried out by email security and archiving company Mimecast.
The global study of 600 IT security professionals -- Mimecast Business Email Threat Report 2016, Email Security Uncovered -- also found that 64 percent of respondents regard email as a major security threat and one third believe email is more vulnerable today than it was five years ago.
"Our cyber-security is under attack and we depend on technology, and email in particular, in all aspects of business. So it’s very disconcerting to see that while we might appreciate the danger, many companies are still taking too few measures to defend themselves against email-based threats in particular", said Peter Bauer, chief executive officer, Mimecast.
"As the cyber threat becomes more grave, email attacks will only become more common and more damaging. It’s essential that executives, the C-suite in particular, realize that they may not be as safe as they think and take action. Our research shows there is work still to be done to be safe and we can learn a lot from the experience of those that have learnt the hard way", adds Bauer.
Mimecast categorized respondents into five distinct "personas" based on their perceptions of data breach confidence. They are: The Vigilant, Equipped Veterans, Apprehensive, Nervous and Battle-Scarred. The breakdown and explanations are shown in the image below.
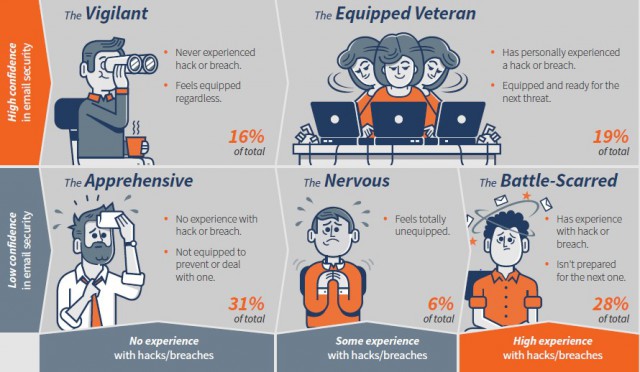
The biggest gaps between the most and least prepared respondents were found in budgets and C-suite involvement. Out of the IT security manager polled, only 15 percent say their C-suite is extremely engaged in email security, while 44 percent say their C-suite is only somewhat engaged, not very engaged, or not engaged at all.
Unsurprisingly, those respondents that felt more prepared have larger budgets allocated to email security. Specifically, 50 percent more than IT managers who were less confident in their readiness to defend against an attack.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Pavel Ignatov/ Shutterstock
-

Snooper's Charter is vague and confusing
Publié: février 2, 2016, 3:25pm CET par Sam Pudwell

A group of MPs has criticized plans put forward in the Draft Investigatoy Powers Bill after consulting with several top technology firms, including the likes of Apple, Facebook and Google.
The Science and Technology committee has slammed the bill as being vague and confusing, issuing a 43-page report outlining its views on key issues such as encryption and data collection.
The committee’s chairwoman, Nicola Blackwood MP, said: "The current lack of clarity in the Draft Investigatory Powers Bill is causing concern among businesses. There are widespread doubts over the definition, not to mention the definability, of a number of the terms used in the draft bill. The government must urgently review the legislation so that the obligations on the industry are clear and proportionate".
One of the most contentious aspects of the bill is encryption, with some firms worried that they will have to adopt weaker encryption standards and build backdoors into their products so that data can be accessed. This is especially relevant for companies that use end-to-end encryption, with Apple’s iMessage communication being a prime example.
On this area, the report says: "There is some confusion about how the draft bill would affect end-to-end encrypted communications, where decryption might not be possible by a communications provider that had not added the original encryption. The government should clarify and state clearly in the Codes of Practice that it will not seek unencrypted content in such cases, in line with the way existing legislation is currently applied".
Bulk data collection is also raising some serious concerns. Communications providers such as BT and Sky are worried about the prospect of having to keep records on all customers for 12 months, something which raises both ethical and security issues.
"Given the volume of data involved in the retention of ICRs and the security and cost implications associated with their collection and retention [...] it is essential that the government is more explicit about the obligations it will and will not place on the industry as a result of this legislation", the report says.
Antony Walker, deputy CEO of techUK comments: "There are several important recommendations in this report that we urge the Home Office to take on board. In particular we need more clarity on fundamental issues, such as core definitions, encryption and equipment interference. These are all issues that we highlighted to the Committee and can be addressed both in the Bill and in the Codes of Practice which we believe must be published alongside the Bill, and regularly updated, as recommended by the Committee. Without that additional detail, too much of the Bill will be open to interpretation, which undermines trust in both the legislation and the reputation of companies that have to comply with it".
"The draft Bill presents an opportunity for the UK government to develop a world leading legal framework that balances the security needs with democratic values and protects the health of our growing digital economy. But we have to get the details right", adds Walker.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Creativa Images / Shutterstock
-

Businesses need to place higher priority on cyber security
Publié: janvier 20, 2016, 8:12pm CET par Sam Pudwell

Only 45 percent of worldwide organizations are confident in their ability to fend off today’s sophisticated cyber attacks. This is one of the key findings from Cisco’s 2016 Annual Security Report, which was released today.
With the rate of digital transformation continuing to increase, business leaders are increasing measures to secure their organizations’ future, with 92 percent agreeing that regulators and investors will expect them to manage cyber security risk.
John N. Stewart, senior vice president, chief security and trust officer, Cisco said: "Security is resiliency by design, privacy in mind, and trust transparently seen. With IoT and digitisation taking hold in every business, technology capability must be built, bought, and operated with each of these elements in mind. We cannot create more technical debt. Instead, we must meet the challenge head on today".
Other key findings include:
- Aging infrastructure: 92 percent of Internet devices are running known vulnerabilities and 31 percent of all devices analyzed in the survey are no longer supported or maintained by the vendor.
- The SMB weak link: From 2014 to 2015, the number of SMBs using web security dropped by more than 10 percent.
- DNS blind spot: Nearly 92 percent of "known bad" malware was found to use DNS as a key capability. This is frequently a security "blind spot" as security teams and DNS experts typically work in different IT groups within a company.
- Shifting server activity: Cyber criminals are changing their approach to target compromised servers to support their attacks. WordPress is a prime example, as the number of attackers using WordPress domains grew by a whopping 221 percent between February and October 2015.
Cisco also sounds a global call-to-arms in the study, calling for greater collaboration and investment in the processes, technologies and people to help protect against cyber criminals.
Industry Reaction
Stephen Love, Security Practice Lead for EMEA, Insight:
As cyber-attacks are becoming increasingly sophisticated, businesses are realizing the ever-growing need to protect their data assets, but are unclear as to how. Couple this with a growing expectation for full transparency of cyber security risks, organizations begin to lose confidence in their abilities to detect, moderate and recuperate from an attack.
It is time to face the inevitable situation; businesses are highly likely to face a data breach in the near future. Every organization -- no matter how large or small -- must have a robust security approach to its data management. It is crucial then that businesses assess just what portion of their data is most valuable and needs closer security attention.
Not all data in an organization would be deemed sensitive. By carrying out a thorough assessment as to what data is uniquely distinct to the organization, then discovering in what ways this data is at risk, and putting in place security measures accordingly, every organization can feel confident that they have the best defensive measures possible in place.
David Kennerley, Threat Research Manager, Webroot:
For too long have smaller companies adopted the attitude that they are too small or too low value to be targeted, and for too long has cyber-security taken a back seat. As this research shows, the outsourced approach is increasingly a viable alternative to the "go at it alone" status quo. It opens the door to a world of experienced MSPs, the best of which offer comprehensive, lightweight security solutions that are affordable, easy-to-install and provide real-time protection against modern threats.
These small businesses are often targeted by advanced and persistent threats because of their partnerships with bigger fish. Without addressing these security capabilities SMBs will find it increasingly difficult to work with larger enterprises. It’s encouraging, however, that SMBs are broadly conscious of their cybersecurity failings. Our research shows that, overall, 81 percent of SMBs plan on increasing their annual IT security budget for 2016, by an average of 22 percent.
Darren Anstee, Chief Security Technologist, Arbor Networks:
This report serves as yet another confirmation that attackers are becoming ever more sophisticated and, as a result, it is becoming ever more difficult to identify and stop their activities before they reach their goal. Although detection technologies, threat intelligence sharing and IR processes are improving in many cases, many businesses are still not able to prevent a breach, something that can have huge legal and financial consequences, as well as a significant loss of customer trust, especially if disclosure is not handled well.
Fundamentally, attackers are moving more quickly than the technologies that we deploy to counter them. Further improvements in intelligence sharing, and better resourcing of IR teams will help but we need to make sure we are focusing our resources on the attacks that have the highest risk -- and this isn’t necessarily just those that pop up as "red" in our SIEM. To do this our incident responders need to spend more of their time in the right parts of the IR process, and we can drive this by giving them the right tools.
If we can speed up the triage and investigative aspects of IR then we can obviously respond more quickly, but we can also free resources for more proactive exploration of suspicious activities that may otherwise have gone un-investigated.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: jijomathaidesigners / Shutterstock
-

Intel Security and AirWatch team up to boost mobile protection
Publié: janvier 7, 2016, 8:00pm CET par Sam Pudwell

Intel Security has expanded its partnership with VMWare’s enterprise mobility subsidiary AirWatch, placing a greater emphasis on mobile security initiatives.
The two companies aim to help organizations cope with the numerous security issues posed by mobile devices, as well as integrating enterprise protection across PCs, operating systems, networks and the cloud.
Data protection, threat detection and prevention and security management will be the three key areas of focus, with a key aspect of the partnership being to correlate threat event information in order to improve incident visibility and faster response times in the enterprise environment.
Noah Wasmer, vice president of mobile engineering and product management for end-user computing at VMWare said: "To drive mobile business transformation, organizations need the foundational security elements they already leverage across their enterprise to work seamlessly across their mobility assets".
As part of the extended partnership, Intel Security and AirWatch have joined each other’s respective mobile security initiatives, the Intel Security Innovation Alliance and the AirWatch Mobile Security Alliance.
D.J. Long, head of the Intel Security Innovation Alliance, commented: "The VMware and Intel Security partnership is an integral part of our mobile security strategy and is an important step toward improving our mutual customers’ threat defense lifecycle and providing better data protection, regardless of where that data resides or travels".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Basar / Shutterstock
-

IPv6 adoption nearly doubles in a year
Publié: janvier 5, 2016, 8:08pm CET par Sam Pudwell
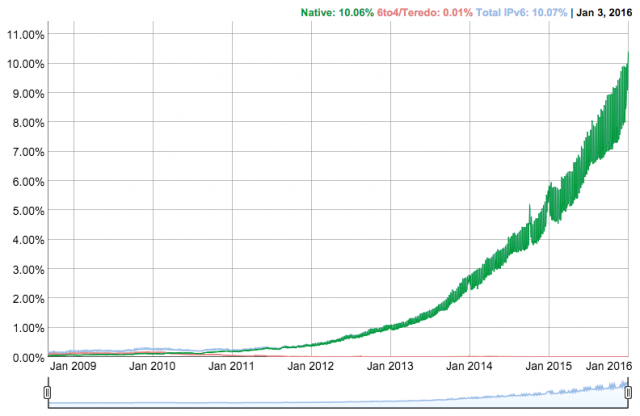
New data released by Google has shown that the uptake of IPv6 -- the most recent version of the internet communications protocol -- has grown considerably in the last 12 months.
Google revealed that 10.09 percent of all traffic to its websites was made of IPv6 connections as of January 2 2016, nearly double that from the same time last year when the number was 5.47 percent.
In terms of the number of IPv6 connections made per country, Belgium is currently leading the way with 44.32 percent, followed by Switzerland with 30.89 percent and the US with 25.63 percent.
As things stand the UK is a long way behind, with IPv6 connections to Google sites taking place just 2.95 percent of the time. That’s pretty disappointing seeing as the UK is supposed to be one of the great pioneering countries in technology, but this figure will no doubt improve as the need to switch becomes more pressing in 2016.
Last year the American Registry of Internet Numbers (ARIN) urged companies to consider IPv6, saying: "ARIN encourages customers to seriously undertake a review of what they will need to make the switch to IPv6", the organization said. "The internet is evolving and, as it changes and expands into new territories like the IoT, IPv6 will play a critical role".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The bad security habits enterprise IT needs to leave behind in 2016
Publié: décembre 31, 2015, 4:13am CET par Sam Pudwell
 2015 has played host to some significant cyber breaches. Experian, TalkTalk and Ashley Madison all fell foul of malicious attacks, and they weren’t the only ones. In 2016, businesses need to resolve to do better -- but the question is, how?
2015 has played host to some significant cyber breaches. Experian, TalkTalk and Ashley Madison all fell foul of malicious attacks, and they weren’t the only ones. In 2016, businesses need to resolve to do better -- but the question is, how?What bad security habits need to be given up to ensure a safer, more secure experience next year? What lengths could, and indeed should have businesses gone to this year in order to prevent some of the data breaches that occurred?
Industry experts elaborate on what they believe needs to be done better in 2016, and how to leave those bad habits behind.
Jeremiah Grossman, Founder of WhiteHat Security:
2016 is the year companies must resolve to get better at Web security. A lot better. Let’s look at just one of the past year’s major breaches -- TalkTalk. TalkTalk, a major UK telecoms operation, was arguably one of the most widely reported breaches of the year with reputable media reports suggesting the attack was carried out through SQL injection. SQLi gives a remote attacker the ability to run commands against the backend database, including potentially stealing all the data contained in it. This sounds bad because it is.
The more we learn about incidents like TalkTalk, the more we see that these breaches are preventable. We know how to write code that’s attack-resilient and we know multiple methods for fixing vulnerabilities and defending against incoming attacks. All it takes to stop these breaches from happening is doing the things we already know how to do. Doing the things we already know work. Let’s make 2016 the year we take web security seriously.
Perry Correll, Principal Technologist, Xirrus Networks:
Xirrus recently polled Wi-Fi users and found that 76 percent connect to Wi-Fi outside of their home. Public Wi-Fi offers the convenience of accessibility, but typically doesn’t encrypt data, which leaves passwords exposed and sensitive data vulnerable to the possibility of capture by those with malicious intentions.
It’s bad enough worrying that while sipping a latte, cyber criminals might be trying to steal your credit card data and bank account numbers, but even more daunting to know that corporate espionage is on the rise. Hotel Wi-Fi networks, which are notoriously easy to breach, offer hackers little challenge when it comes to intercepting private or classified information accessed by executives who stay in hotels on business. Now more than ever, large and small enterprises -- from coffee houses to airports and hotels -- must upgrade their networks to provide better security for their customers.
David Juitt, Chief Security Architect, Ipswitch:
Given we’re spending a whopping $70 billion on security per year, it’s not surprising it ranks high among IT concerns. The harsh reality is we are not doing a good enough job keeping pace with the adversaries. Despite the high levels of security investment, we can’t say with any degree of certainty whether we are safer than we were a year ago or five years ago.
Accepting some level of risk is part of doing business. Managing that risk in 2016 by recognizing and shoring up points of vulnerability is the difference between using data as a competitive advantage and being the victim of a catastrophic data loss.
Wieland Alge, VP & GM EMEA, Barracuda:
All IT Security experts should try to give up SEP -- the concept of Somebody Else’s Problem. As The Hitchhiker’s Guide to the Galaxy’s Ford Prefect described it: 'An SEP is something we can’t see, or don’t see, or our brain doesn’t let us see, because we think that it’s somebody else’s problem'.
SEP behavior exists right across the IT security community because we’ve often been treated as nerds, techies and obstacles to business.
If the Business IT team move some web applications into the Cloud without telling the IT Security team, then -- despite it being Business IT’s problem -- we know that the apps no longer have the protection of a proper Firewall/WAF and we should really help resolve it. Likewise, we can’t continue to say 'Cool, no attacks coming!' whenever the Internet goes down.
A good New Year’s Resolution would be to actively search for SEPs and fix them.
Mark Edge, UK Country Manager, Brainloop:
The General Data Protection Regulation (GDPR) arrives in 2017, so CISOs should spend this year resolving bad data protection practices.
The regulation will address the changing way businesses operate in the modern world, with a focus on protecting data stored and transferred in and out of Europe. It may be surprising to hear that malicious, or, more likely, careless employee behaviour is the number one threat to data security. Email, especially personal email, is simply not secure enough to communicate highly sensitive information, whilst consumer-grade file sharing solutions have little in-built security and no audit trail. USB drives, Instant Messaging and hard copies of confidential documentation also present a clear data protection problem.
CISOs must break bad habits with a positive change, so instead of placing cumbersome restrictions upon employees, they should implement intuitive and highly-secure collaboration tools that form positive habits and an easy transition ahead of the GDPR.
Thomas Fischer, Principal Threat Researcher, Digital Guardian:
Hundreds of thousands of customer details were leaked as a result of corporate data breaches in 2015. This data is most valuable to hackers before the leak is discovered and made public, as it then becomes much harder to sell off or act without attracting attention. However, even after the breach is discovered this information is still out there, still accessible, and is often used in a second wave of attacks targeting the victims themselves many months later.
Hackers will often bombard breached email addresses with phishing attacks in an attempt to gain access to more of their victims’ details. By impersonating banks, retail companies and government agencies the attacker will try to trick users into sending them money or personal information. These imitations are becoming more convincing, with hackers explaining to users that they are vulnerable to an attack and must change their details immediately by handing them over in some way.
Businesses shouldn’t be fooled twice, 2016 must be the year organizations combat phishing attacks. Educate your employees on social engineering, including how to identify suspicious messages and phishing sites, outline a clear policy on emails that seem out of place and ensure that everyone remains vigilant with regular security awareness training.
Chris Hurst, Director UK Sales, RedSocks:
There is no doubt that cyber security attacks will continue in terms of frequency and severity. Too many organizations rely on traditional security protection such as anti-virus, endpoint protection and firewalls, which is clearly not enough.
As cyber security threats become more sophisticated, measures to detect intrusions that we know will inevitably make their way onto a company’s network are as important as those designed to prevent them. 2016 should be the year in which companies resolve to monitor traffic as it leaves the network.
This will enable suspicious behaviors and destinations to be identified and will help ensure that any incidents can be assessed and remediated in as timely a manner as possible.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Javier Brosch/Shutterstock
-

Microsoft has a bright future, says Goldman Sachs
Publié: décembre 21, 2015, 10:19am CET par Sam Pudwell

Goldman Sachs thinks Microsoft is making a comeback. The investment banking firm has produced a 22-page document -- titled Righting a Wrong -- looking at Microsoft’s current business, the recent changes it has made and it’s future opportunities.
The research analyzes Microsoft’s core businesses of Azure, Windows and Office and believes that the future looks bright for the company, going as far as to change its stock rating from Sell to Neutral.
Goldman highlights the transition Microsoft is making to cloud computing through its Office 365 platform and also praises the work of CEO Satya Nadella and CFO Amy Hood: "The company’s ongoing transition to the cloud [has] been very well executed by new senior leadership, most notably Satya Nadella and Amy Hood".
In terms of Microsoft’s three core businesses, Goldman is very much looking at the positives. In terms of Office, the report highlights the potential opportunities for expansion in areas such as mobile devices and emerging markets and praises the move to increase prices for Office E5 (aimed at businesses) which Nadella believes could generate as much as $50 billion (£33 billion) in revenue.
Moving on to Azure, the report recognizes the value that it brings to Microsoft -- especially seeing as Nadella and co. have not bowed to pressure from the likes of Google and Amazon to lower prices -- and also notes that moving to a more service-based business model by giving away Windows 10 for free is a positive step for the company.
As a result of the research, Goldman has increased its price target for Microsoft stock from $45 to $57.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: alphaspirit/Shutterstock
-

Apple and IBM partnership reaches 100 enterprise apps milestone
Publié: décembre 17, 2015, 7:50pm CET par Sam Pudwell

Apple and IBM today announced that they have reached the 100-app milestone in their mobile partnership, covering 60 professional roles across 14 different industries including government, transportation, healthcare and telecommunications.
Maribel Lopez, principal at Lopez Research said: "I think [Apple] brings the concept of simplicity (direct to task) and beauty to enterprise apps. IBM on the other hand understands business workflow, what generates productivity and back-end integration".
"Partnerships like this help companies create apps that were better than their PC predecessors because they can use more functions of the device -- camera, voice, messaging, location -- and they can do it anywhere since it’s [portable]".
Each app designed in this partnership is unique as development is undertaken in close collaboration with the people who will actually be using the app. Mobile development principles are applied after a specific problem and the nature of the workflow have been identified, with the ultimate goal being simplicity.
Speaking to TechCrunch, Katharyn White, vice president of IBM and Apple Partnership for IBM Global Business Services, highlighted a desire to change the way people work: "My motivation is to change the lives of people at work. The sub-benefit is that we are also changing the way we sell and changing our company".
Many of the apps work with back-end systems such as ERP and CRM, and IBM’s enterprise experience is vital in helping companies connect the apps to these systems. IBM also has plans to make use of its cognitive intelligence platform Watson, which could generate some exciting results.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Minerva Studio/Shutterstock
-

Understanding the basics of quantum computing [Q&A]
Publié: décembre 14, 2015, 9:03pm CET par Sam Pudwell

Computers have been growing more and more powerful for some time now and, as processors become faster and memory more plentiful, we’re reaching the limits of current technology.
Quantum computers are the next step in this evolution and more and more companies are investing in this area. Intel recently announced it will be putting over £30 million towards the technology and just this week Google boasted that its quantum computer is 100 million times faster than a regular PC. For a deeper insight into this growing area, we spoke to Mike Mayberry, corporate vice president and managing director of Intel Labs. The full interview can be found below.
ITPP: As a taster, how does quantum computing differ from traditional binary-based computing?
Quantum computing uses physical principles to do calculations. Simplistically you prepare a quantum system with the equivalent of many possible answers and then apply operations to encourage the system to evolve towards the right answer. It is by nature a probability calculus and only a subset of problems are considered appropriate for QC.
ITPP: Can you give us some concrete examples of where quantum computers could excel compared to current technologies?
Simulating the properties or shape of a molecule is, by nature, a quantum calculation. We can emulate that calculation with traditional binary computing, but QC could do the calculation natively. There are other hard mathematical problems where QC could find a likely answer quicker than sorting through all of them sequentially.
ITPP: Would they still be built on silicon? What would a quantum chip physically look like?
There are about a dozen technologies under investigation, all of which use conventional electronics to control and manipulate the properties but they look very different for the quantum elements. One of the choices that looks more scalable is quantum dots which then look much like a conventional silicon chip. If you saw a QC system most of what you’d see is cooling and control electronics.
ITPP: How would Intel-based QC offerings be different from products currently on the market (D-Wave Systems)?
The D-Wave system is a quantum annealer, not a general purpose QC. We would pursue the more general computing model. It is too early to say what our commercial offerings might look like as we are over 10 years away.
ITPP: A couple of months ago, Intel announced a significant investment in a Dutch university. What prompted the company to choose that particular organization? What do they have that Intel couldn’t either acquire or replicate in-house?
Delft has a broad expertise in the physics and control systems. Intel can provide value with fabrication and integration of complex systems. We think that by working together we can go faster than either working alone.
ITPP: Will Quantum Computing be where storage and computing will be unified?
No. It is likely that you are thinking of neuromorphic computing, which operates more like how our brains work.
ITPP: Will QC extend Moore’s law (which is based on transistor count) or will it make it redundant?
The opposite is true. Advances in Moore’s Law had led to more sophisticated electronics which allows more precise control of the physics and allows more complex operations. If/when QC is a reality, it will supplement conventional computing, not replace it.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: kentoh / Shutterstock
-

What's the most popular IT asset management software?
Publié: décembre 7, 2015, 7:05pm CET par Sam Pudwell

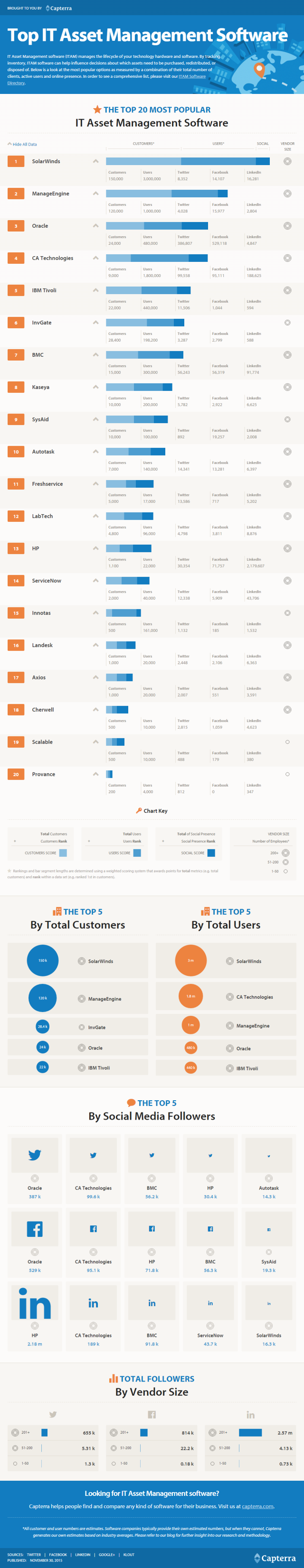
IT asset management (ITAM) software manages the lifecycle of hardware and software. It can help influence decisions about which assets need to be purchased, redistributed, or disposed of.
There is a lot of choice in the market when it comes to picking the right ITAM software for your company, but Camterra has made it easy by rating the top 20 IT asset management software solutions as measured by total customers, users, social presence and vendor size.
Of the 20 reviewed, SolarWinds has come out on top, with ManageEngine and Oracle completing the top three. SolarWinds boasts the highest number of total customers (150,000) and total users (3 million). CA Technologies is its closest competitor for users with 1.8 million -- still some way off the top spot.
The number of social media followers for each vendor also makes for interesting reading. Oracle has the most Twitter followers (387,000) and Facebook followers (529,000) and HP can claim to rule LinkedIn with 2.18 million followers.
Provance completes the list of 20, with 200 customers, 4,000 users, 812 Twitter followers and 347 LinkedIn followers.
All of this information and more has been collated into a handy infographic, which can be found below.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: gguy/Shutterstock
-

Hackers hide malware inside Dropbox accounts to target media organizations
Publié: décembre 4, 2015, 7:46pm CET par Sam Pudwell

A new form of malware that targets mass media agencies has been discovered by researchers at the US-based security firm FireEye. The malware was detected in Hong Kong where it was being used to target a small number of media agencies with the initial targets of the attack being newspapers, radio stations and television studios.
The malware leaves a user vulnerable by offering a backdoor to their system. The way in which this is achieved is unique because its command and control or C&C server is hidden inside Dropbox accounts. FireEye was able to trace the malware back to a group of hackers by the name admin@338, who is believed to have ties with the Chinese government.
This group has previously targeted international organizations from the financial, economic and trade policy sectors. In the past, amdin@338 has employed spear phishing campaigns to infect users with Remote Access Trojans (RATs) such as Poison Ivy. In this latest string of attacks the scope has been narrowed possibly to target media agencies who supported last year’s protests in Hong Kong.
The group often includes booby-trapped word documents in emails sent to victims with information about anti-Chinese and pro-democracy topics. The word documents contain the CVE-2012-0158 Microsoft Office vulnerability which allows the hackers to install the LOWBALL malware onto the PC’s of unsuspecting users.
This recent attack was particularly unique because the C&C server was located inside of a Dropbox account as opposed to somewhere else online. FireEye worked alongside Dropbox to halt the initial campaign that occurred in August but now both companies have become aware of a new series of ongoing attacks.
Currently the security firm has identified over 50 machines that are being targeted by these attacks.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: igor.stevanovic/Shutterstock
-

SecuSUITE for Enterprise enables secure calling and messaging
Publié: novembre 16, 2015, 8:04pm CET par Sam Pudwell

BlackBerry and its subsidiary Secusmart have announced the release of SecuSUITE for Enterprise, a new voice encryption solution that protects mobile calls on the Android, iOS and BlackBerry operating systems.
By using the VoIP, software-based, cloud-hosted solution, employees will be able to conduct secure conversations worldwide and be able to send encrypted text messages of any length.
Voice and text messages are encrypted with 128-bit Advanced Encryption Standard (AES) on the individual device level, meaning messages are stored on the receiver’s smartphone and only sent to the recipient when they are available to receive them.
Dr Hans-Christoph Quelle, CEO of Secusmart, said: "With SecuSUITE for Enterprise, we are adding a user-friendly and completely independent solution to our portfolio. Thanks to the globally secure BlackBerry infrastructure, governments -- and now, companies -- around the world can protect themselves from the threat of corporate espionage using flexible and extremely effective encryption technology".
SecuSUITE for Enterprise comes with a user-friendly, cloud-based admin portal that enables administrators to enroll or deactivate users and adjust settings. More than 15 governments have so far placed their trust in Secusmart’s security technology using the current SecuSUITE for BlackBerry 10 solution.
The solution will be available through an annual license and the app will be available later this month for Android, BlackBerry 10 and iOS smartphones.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Markus Mainka / Shutterstock
-

Priv is BlackBerry's last hope -- can it woo consumers and business users?
Publié: novembre 16, 2015, 11:05am CET par Sam Pudwell

It’s fair to say that BlackBerry has been struggling a bit in recent times. After initially being a leading light in the smartphone arena last decade, it has since seen its main competitors go on to take control of the market.
The likes of Apple and Samsung are selling more phones than ever and are now -- and have been for some time -- the dominant forces in a world that BlackBerry is struggling to still be a part of. A report from earlier in the year said that Apple now enjoys a 34.1 percent share of the UK smartphone market, with Android leading the way 53.2 percent and BlackBerry bringing up the rear with 1.2 percent.
But don’t give up all hope just yet. The Canada-based company has finally decided to do away with its own beleaguered OS and has created an Android device in the shape of the BlackBerry Priv. The questions is, is it all too little too late?
Initial Reactions
When the BlackBerry Priv was first announced by CEO John Chen (at the same time as the company revealed disappointing financial results for Q2 2015 which included a £44 million loss) many people were happy to hear that BlackBerry had finally seen sense and jumped into bed with Android.
Then, when the first pictures were released a few days later, it actually looked pretty good. It appeared relatively thin and had kept hold of the traditional hardware keyboard that distinguishes BlackBerry from other smartphone makers. Some of this early optimism was negated somewhat when Chen gave a rather awkward and bumbling demo of the device, but we’ll put that down to him just having a bad day.
In terms of specs, the BlackBerry Priv features a 5.4-inch display with a 1,440 x 2,560 pixel resolution, a quad-core Qualcomm Snapdragon 808 processor, 3GB of RAM, an 18-megapixel rear camera and a 3,410 mAh battery. Now, that all seems fine on the face of things, but when you add in the £580 price tag it’s clear that despite the improvements, this device is still going to struggle against many of the other smartphones available.
Why Priv?
The main aspects of the Priv that BlackBerry is touting are privacy and security (Priv apparently stands for privacy). At the initial announcement of the device, Chen said: "Priv combines the best of BlackBerry security and productivity with the expansive mobile application ecosystem available on the Android platform".
A blog post further highlighted the emphasis on privacy and security, saying: "Because it’s Powered By Android, Priv will also deliver the largest choice in apps and the most secure experience possible to the widest audience. Priv users will enjoy choice, innovation, security, privacy AND productivity. In other words, no compromises".

From an enterprise point of view, this is exactly what CEOs will want to hear as the issues of user privacy and securing confidential company data continue to dominate conversations. BlackBerry has always placed a high priority on privacy and security -- as shown by its recent £280 million acquisition of Good Technology -- and the Priv certainly takes things to another level.
In a blog post, director of BlackBerry Security Alex Manea explained what makes the Priv so secure. He wrote about BlackBerry’s "Hardware Root of Trust" which refers to the introduction of cryptographic keys to the device hardware at a fundamental level, the presence of Verified Boot and Secure Bootchain technology and the new DTEK application which performs tasks such as app monitoring and provides recommendations on how to improve privacy levels.
Realistically, the BlackBerry Priv is probably the company’s last chance in the smartphone market and it could be the case that its security credentials is what gives the company its last shot at regaining some of its former glory.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

You can now buy Microsoft's Surface Pro 4 in UK
Publié: novembre 13, 2015, 10:46am CET par Sam Pudwell

Microsoft’s Surface Pro 4 tablet is now available to buy in the UK through the Microsoft Store, as well as Amazon, Argos, Dixons Travel, John Lewis, Harrods, PC World / Currys, Selfridges, Staples and Very.co.uk.
The Surface Pro 4 has packed more power and performance into the thinnest Surface yet, featuring Intel Core i5 or Core i7 processors, up to 1TB of storage and a 12.3-inch PixelSense display with a 2,736 x 1,824 pixel resolution.
Speaking of performance, Microsoft claims that the Pro 4 is a third faster than its predecessor and a whopping 50 percent faster than a MacBook Air, making this device a serious force.
A 9-hour battery life will allow users to enjoy a full day of work on a single charge and the 5-megapixel front-facing and 8-megapixel rear-facing cameras enable video conferencing with colleagues from around the world.
It also comes with various accessories. A redesigned Surface Pen offers 1,024 levels of pressure sensitivity, an "all year" battery life and can be magnetically attached to the tablet, In addition, a new Type Cover comes with redesigned back-lit keys and a 40 percent bigger trackpad enabling users to instantly switch to a highly versatile laptop.
Prices for the Surface Pro 4 start at £749 (including the Surface Pen) or £859 (including the Surface Pen and Type Cover).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

What you need to know about Disaster Recovery as a Service
Publié: novembre 11, 2015, 5:58pm CET par Sam Pudwell

Cloud adoption is continuing to grow amongst enterprises and small businesses alike and, as competition in the technology industry becomes ever-more intense, it has never been more important to be able to respond to network outages and unplanned downtime.
This is where Disaster Recovery as a Service (DRaaS) comes in, providing a failsafe in the event of man-made or natural catastrophes through the replication and hosting of physical or virtual servers by a third-party.
Various studies have highlighted the importance of Disaster Recovery (DR). ComputerWeekly.com found that DR has been a top priority this year for 45 percent of UK IT departments but, in a study from Timico, only five percent of respondents were confident that their DR plan was adequate.
Read on for everything you need to know about Disaster Recovery as a Service, including tips on how to prepare your IT department and how to deal with unplanned downtime.
DRaaS in the Enterprise
Disaster Recovery as a Service is expected to grow at an unprecedented rate over the next few years, with spending predicted to rise to $1.2 billion (£766 million) by 2017. Furthermore, Gartner predicts that the market could be worth $5.7 billion (£3.4 billion) by 2018, which again illustrates its potential.
This growth is primarily being driven by cost-saving demands but is also being forced through by the multiple business benefits that DRaaS offers. Enterprises and CIOs are being drawn to the speed, scalability and security of disaster recovery solutions, with another key advantage being that it reduces operational complexity.
However, as with any modern technology, not everyone is convinced with DRaaS. For example, many IT professionals cite fears such as losing control and visibility, trusting cloud infrastructure and uncontrollable costs, all of which can be overcome with the right DRaaS solution.
Preparing Your Company
Having an effective disaster recovery plan in place is vital for companies of all shapes and sizes but many organizations -- particularly smaller companies, of which only 30 percent have a business continuity plan in place -- still aren’t preparing themselves well enough for when disaster strikes.
Although each business will have slightly different requirements, but there are some general steps that can be taken to prepare for unexpected downtime. As with all new technologies, planning and testing are vital to ensure everything is up to date and working as it should.
Enterprises implementing a DRaaS plan should also be focusing on areas such as storage, security and planned downtime, as well as making sure that critical systems are prioritized and that there is a plan in place for employees during an emergency situation.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Olivier Le Moal/Shutterstock
-

Most IT pros are against UK's Investigatory Powers bill
Publié: novembre 9, 2015, 10:51am CET par Sam Pudwell

Late last week, the UK government introduced a new Investigatory Powers bill, which requires Internet service providers to keep a record of the Internet activity of everyone in Britain, as well as cracking down on encryption and increasing government surveillance.
The initial reaction from industry professionals was mixed, but a new survey from Swiss data bank Artmotion has found that a massive 87 percent of IT leaders disagree with the government’s plan to reduce the strength of data encryption.
The research, which questioned 500 IT decision makers across the UK, also found that only 13 percent believe the government’s plans are "sensible" and 60 percent claimed that they would not trust the government with the security of their private information.
Interestingly, one in five respondents would not support any reduction in encryption technology, even for the sake of national security.
Mateo Meier, CEO of Artmotion said, "Our research highlights a growing unease amongst the IT community that the UK government is placing unspecified threats to national security ahead of the genuine risk of cyber attacks. While it’s good to see that the government has dropped its ill-conceived plans to ban encryption entirely, this updated 'Snoopers’ Charter' does little to reassure the tech community".
"We live in an age where teenagers are capable of bringing down established brand names with nothing more than a laptop, and yet the government continues to release ham-fisted legislation that will do little more than drive businesses away from the UK while simultaneously opening the nation to further potential cyber attacks", added Meier.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Maksim Kabakou / Shutterstock
-

Apple Pay in UK: The story so far
Publié: novembre 3, 2015, 3:43pm CET par Sam Pudwell
On 14 July 2015, Apple’s mobile payments system Apple Pay was finally launched in the UK after a huge amount of build-up and excitement. At the time of launch, Apple Pay was supported by several of the UK’s biggest financial institutions -- including Royal Bank of Scotland, Santander, Natwest and Nationwide -- along with thousands of supermarkets, restaurants, hotels and retailers.
Initial reviews were largely positive and industry professionals were understandably excited about Apple Pay’s potential as it rode the crest of a growing mobile payments wave. Mix this in with Apple’s loyal fan base and its power in the consumer market and it’s easy to see why its competitors might struggle to keep up.
The system was initially launched in the US the previous October and, although there were some initial concerns around identity theft, it enjoyed a strong start to life in the States as the likes of Disney, McDonald's and Subway jumped on-board early.
Mobile Payments -- The Story So Far
In the months since its launch, Apple Pay has continued to grow. Lloyds Bank, Halifax and HSBC have all signed up for the service -- along with thousands more UK retailers and the limit has risen from £20 to £30.
Its early success has been helped by the growth of the mobile payments industry, both in the UK and abroad. According to a survey published in July by nVest Ventures, millennials are driving the trend, with 26 percent saying paying with cash was inconvenient, 41 percent saying they are interested in using mobile payments and 58 percent expressing a desire for a mobile service that shows their spending habits.
This has led to fierce debate as to whether mobile solutions such as Apple Pay really will trigger the start of a cashless society. Jeremy Nicholds, executive director of mobile at Visa Europe claimed that we are approaching a "seismic shift from plastic to digital" and others have gone so far as to suggest that Apple can rule the sector through in-app payments.
Although it won’t happen overnight, current trends certainly point towards cash being on the way out. Non-cash payments have already overtaken cash payments in the UK and, unless its rivals catch up fast, it’s looking likely that Apple will be at the forefront of the cashless revolution
Benefits For Businesses
Of course, it’s not just consumers that are able to enjoy the benefits of digital payments. There are also some serious advantages for businesses, from small startups all the way up to large enterprises.
US business owners that have embraced mobile payments are growing three times faster than the national average and it’s in the retail sector where going contactless can have a real effect.
For example, the time-consuming transactions of old involving digging through a wallet to find the right card or correct amount of cash will be a thing of the past, so those retailers that experience a regular lunchtime rush will be able to get through significantly more customers in a shorter period of time.
Furthermore, Apple Pay also provides a fresh tool for digital marketers, enabling them to collect customer data to build detailed purchasing habits, engage with customers through personalized promotional content and reach more potential customers through in-app purchases.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

15 year-old suspected of TalkTalk cyber-attack
Publié: octobre 27, 2015, 6:33pm CET par Sam Pudwell

The Metropolitan Police have released a statement saying that a 15-year-old boy has been arrested in County Antrim, Northern Ireland, in relation to the recent TalkTalk cyber attack.
He has been arrested on suspicion of Computer Misuse Act offenses and is currently being questioned by detectives from the Police Service of Northern Ireland (PSNI).
According to the statement released earlier today, this is a joint investigation between the PSNI and the Metropolitan Police Cyber Crime Unit (MPCCU), with a search of the boy’s house still ongoing.
The attack on TalkTalk was described by the company as "significant and sustained" and involved the potential theft of personal data from the broadband supplier’s four million UK customers.
The industry has not reacted well to news of the breach -- TalkTalk’s third in the past 12 months -- with various business leaders calling for action to tackle cyber crime and MPs vowing to launch an inquiry into the attack.
But the bad news doesn’t end there for TalkTalk, as it is now facing a huge compensation bill which could be steep enough to put it out of business. According to a recent report in The Daily Star, customers affected could be in line for a payout up to £1,000.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: arda savasciogullari / Shutterstock
-

What's the most-destructive PC virus?
Publié: octobre 26, 2015, 5:14pm CET par Sam Pudwell

Cyber security is at the forefront of people’s minds in the technology industry at the moment, with a plethora of high-profile breaches pushing the subject into the mainstream.
The likes of Sony, Ashley Madison and T-Mobile have all been hacked within the last 12 months and developing trends such as cloud computing and Bring Your Own Device (BYOD) have made security a hot topic for discussion.
There are several different ways in which breaches can occur, but one of the most prevalent is the computer virus. To delve a bit deeper into this area, SupremeSystems has created an infographic looking at the most destructive computer viruses of all time.
According to its findings, approximately 33 percent of the world’s computers have been affected by some kind of malicious software, with viruses accounting for 57 percent. The countries most affected are China (56 percent), South Korea (51 percent) and Taiwan (44 percent).
But which viruses have been the most destructive? In terms of the number of computers affected, the Storm Worm Trojan, which was transmitted via email and affected Microsoft users, hit around 10 million computers to claim top spot.
The reported damages for Storm Worm are unknown, so the clear winner in this category is My Doom, with reported damages of $38 billion (£24.5 billion).
The full infographic can be found below.
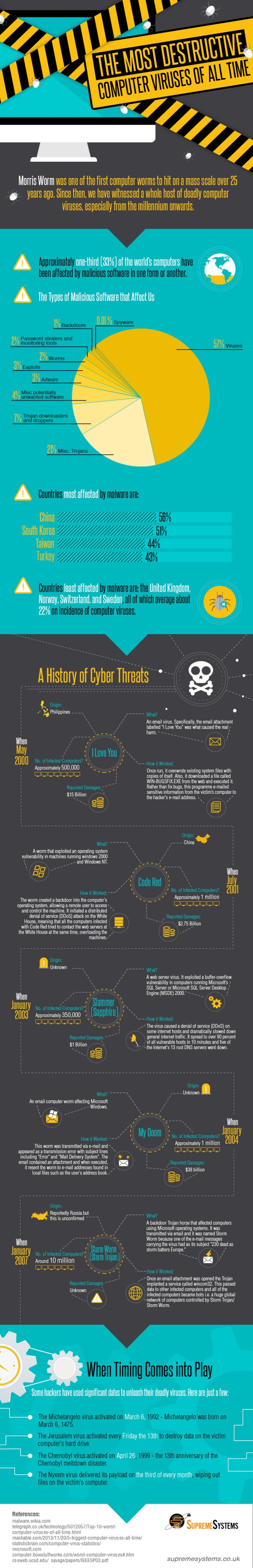
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credits: maraga/Shutterstock
-

EMC and VMware spin-off Virtustream cloud services business
Publié: octobre 22, 2015, 4:19pm CEST par Sam Pudwell

EMC Corporation and VMware have announced plans to combine their respective cloud capabilities into a new cloud services business.
The new business will incorporate existing Virtustream cloud offerings and will be marketed under the Virtustream brand, which will be jointly owned by VMware and EMC and led by Virtustream CEO Rodney Rogers.
EMC Corporation Chairman and CEO Joe Tucci said: "Through Virtustream, we are addressing the changes in buying patterns and IT cloud operation models that we are seeing in the market. Our customers consistently tell us that they are focused on their IT transformations and journeys to the hybrid cloud. The EMC Federation is now positioned as a complete provider of hybrid cloud offerings".
Virtustream will focus on providing enterprise-centric cloud services, providing a complete spectrum of managed services for on-premises infrastructure and its enterprise-class Infrastructure-as-a-Service platform. According to the press release, the plan is to grow into a multi-billion dollar business "over the next several years".
The new business will incorporate and align the cloud capabilities of EMC Information Infrastructure, VCE, Virtustream and VMware to provide the complete spectrum of on- and off-premises offerings including: VMware vCloud Air, VCE Cloud Managed Services, Virtustream’s Infrastructure-as-a-Service, and EMC’s Storage Managed Services and Object Storage Services offerings.
Pat Gelsinger, CEO of VMware, said: "The new Virtustream business will feature the industry’s broadest portfolio of hybrid cloud offerings, enabling customers to move all their applications to cloud-based IT environments and seamlessly manage their on-premises and off-premises environments".
|We see tremendous growth opportunities for VMware and EMC with the new Virtustream business, building on the strong momentum of vCloud Air".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Lightspring / Shutterstock
-

Large number of businesses use Windows 10, claims security firm
Publié: octobre 21, 2015, 5:19pm CEST par Sam Pudwell

New research from end-point security software firm Avecto, conducted at this year's IP EXPO Europe event in London, has found that 54 percent of enterprises are already using Windows 10.
Microsoft’s latest and arguably greatest operating system has enjoyed a strong start to life, especially in the business environment where it is already making more headway than its predecessor Windows 8.
Looking at the bigger picture, a recent study by Spiceworks found that 40 percent of businesses intent to upgrade to Windows 10 within a year and that the current penetration rate for businesses with 1,000 employees or more is 22.7 percent.
Mark Austin, co-founder and CEO at Avecto said: "With Microsoft setting a target of 1 billion devices to be migrated by 2017, it’s clear that Windows 10 will be a dominant force in the years to come. With an increasing number of organizations contemplating a move to Windows 10, we’ve experienced an uplift in the number of customers asking us to support them in their migration. The addition of Windows 10 support to Defendpoint provides a consistent approach to managing privileges and applications across all Windows endpoints, while sandboxing all web based threats".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: rvlsoft / Shutterstock
-

Apple's aggressive recruitment allegedly drives motorcycle startup to bankruptcy
Publié: octobre 20, 2015, 6:17pm CEST par Sam Pudwell

Although Apple has never publicly confirmed that it is developing an electric car, the company has been aggressively hiring auto experts from the likes of Tesla, Ford and Mercedes-Benz.
Now, this strong-arm recruitment has resulted in a startup specializing in electric motorcycles having to close its doors for good due to losing all of its top talent to the iPhone-maker.
The startup in question, Mission Motors, ceased operations in May and filed for bankruptcy in September after multiple staff were tempted to join Apple’s forces, no doubt with increased salaries and benefits. When you consider that Mission Motors only had 35 employees at the time, it’s easy to see how a few key losses could seriously harm the startup.
Former Chief Executive Derek Kaufman said: "Mission had a great group of engineers, specifically electric drive expertize. Apple knew that -- they wanted it, and they went and got it".
The timing of Apple’s approach also worked against Mission, as efforts to raise funding were seriously undermined which resulted in potential investors backing out.
This is not the first time a smaller company has come out second best in a fight against the juggernaut that is Apple. Elon Musk has publicly trolled the Cupertino-based company for hiring its engineers and electric-car battery maker A123 Systems sued Apple earlier in the year for alleged employee poaching.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: TK Kurikawa / Shutterstock
-

Twitter accused of eavesdropping on Direct Messages
Publié: septembre 17, 2015, 1:57pm CEST par Sam Pudwell

Social network Twitter is facing a potential lawsuit after allegedly spying on users’ Direct Messages, a popular feature where people can talk privately without anyone else seeing.
A court case has been filed in San Francisco by Wilford Raney, in which it accuses Twitter of using algorithms to "surreptitiously" eavesdrop on users.
The secret surveillance supposedly takes place whenever a user includes a hyperlink in their message. The lawsuit claims that Twitter’s algorithms replace any hyperlinks with its own custom links, meaning the person clicking on the link has to go through Twitter’s servers to get to the website.
Using the New York Times as an example, the lawsuit says: "For example, Twitter changes links like 'www.nytimes.com' to links like 'http:/t.co/CL2SKBxr1s' (while still displaying the text 'www.nytimes.com' to its users). Should someone click on this new link (http:/t.co/CL2SKBxr1s), they would first be taken to Twitter’s 't.co' website and then forwarded to the original 'www.nytimes.com' website".
According to the lawsuit, this allows Twitter to track links for advertisers and be be identifies as a source of traffic for potential partners, thereby allowing the social network to negotiate improved advertising rates.
The company does admit to tracking user links in its Privacy Policy, saying: "We do this to help improve our Services, to provide more relevant advertising, and to be able to share aggregate click statistics such as how many times a particular link was clicked on".
The Direct Message feature recently received an update, allowing users to use up to 10,000 characters and removing the original 140-character limit.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credits: Brian A Jackson/Shutterstock
-

Microsoft Excel: 7 top tricks that you should know [Infographic]
Publié: septembre 14, 2015, 5:46pm CEST par Sam Pudwell
Microsoft Excel has been around for 30 years, it’s one of the most popular programs in the world and it’s likely that most of us at some point or other have used spreadsheets at work.
Recent reports show that, 78 percent of middle-skill jobs require digital literacy and 67 percent of office roles require expertise in Microsoft Excel. So sharpening up your Excel skills really can help improve pay and job prospects.
But is your knowledge up to scratch? Luckily, Best STL has created an infographic to help you become and Excel master, with all the key bases covered.
The guide covers Charting (data presentation), Conditional Formatting (highlighting points of interest within datasets), Quick Analysis (easier when working with small datasets), Autofill (follows patterns to fill in rows or columns automatically), Power View (data exploration and visualization), Pivot Tables (to quickly summarize large sets of data) and Vlookup (collating data from different sheets).
The full infographic can be found below. Go forth and become and Excel master.
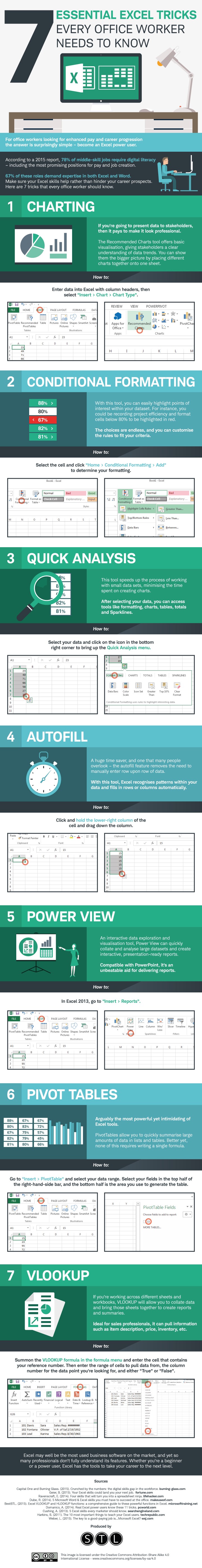
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The rise of telecommuting: 45 percent of US employees work from home
Publié: septembre 11, 2015, 9:07pm CEST par Sam Pudwell

The traditional 9-5 working day of driving to an office, sitting in a cubicle for hours and then forgetting all about work at the end of the day is all but extinct.
Thanks to telecommuting and the rise of millennials on the workplace, employees are now able to work from pretty much anywhere at any time of day, with little or no disruption or sacrifice in productivity.
The New Jersey Institute of Technology’s Online MBA program has created the infographic below to take a closer look at the rise of telecommuting and how management styles are evolving as a result.
According to the report, 45 percent of US employees work from home and 53 million people work as freelancers, contributing $715 billion (£464 billion) annually to the American economy. Of these freelancers, 40 percent are independent contractors, 27 percent are moonlighters, 18 percent are diversified workers, 10 percent are temporary workers and five percent are freelance business owners.
But just which companies are hiring these remote workers? Well, Teletech comes out in first place and the likes of Amazon, IBM and SAP all feature in the top ten.
The infographic also offers advice on how to manage your virtual team, with tips for hiring freelancers -- such as picking a dedicated freelance site and checking for positive reviews -- and some of the top collaboration and communication packages on offer.
The full infographic can be found below.

Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Vasiliy Koval/Shutterstock
-

Apple Watch vs Android Wear: Which has the biggest effect?
Publié: septembre 8, 2015, 7:55pm CEST par Sam Pudwell

The rise of wearables has led to the biggest technology companies in the world developing smartwatches and other wearable devices.
Two of the most prominent are, of course, Apple and Google, with the Apple Watch dominating headlines since its release in May and Google’s Android Wear platform being used by a number of hardware vendors.
But how do the two compare? As part of its State of Wearables Report, Crittercism took a deep dive into how Apple and Google are doing in the OS-stability department.
In terms of adoption, Apple’s iOS 8 reached 81 percent by the end of April 2015, propelled by the earlier release of the Apple Watch, leaving iOS 7 behind on 17.5 percent. For Google, Jelly Bean leads the way on 44.5 percent, followed by KitKat on 39.8 percent.
The subject of compatibility also throws up some interesting statistics, with Apple’s OS becoming compatible with more devices (including the Apple Watch) faster than Android’s OS with Android Wear.
The final area is stability, with iOS 8 showing 1.99 crashes per device, slightly better than Android 4.2 which shows 2.2 crashes per device.
The full infographic can be found below and more information can be found at the Crittercism website.
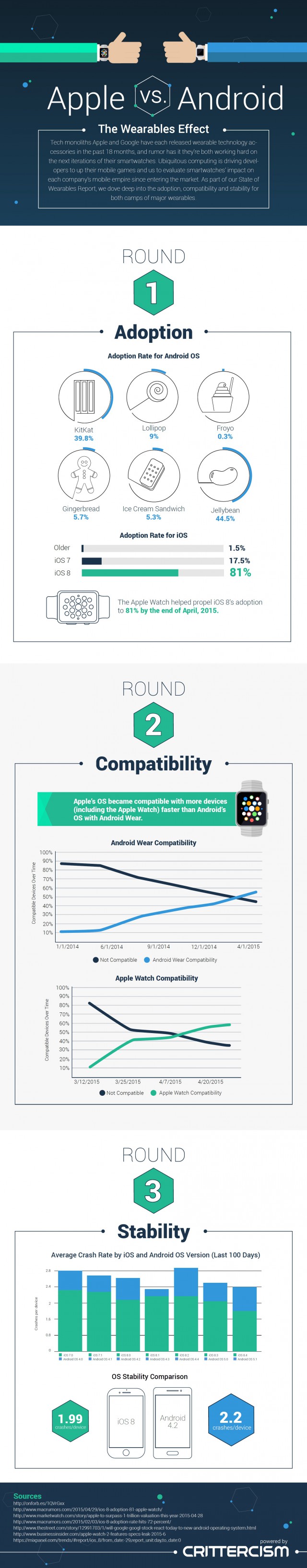
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Blablo101/Shutterstock
-

What you need to know about cybersquatting [Infographic]
Publié: septembre 1, 2015, 1:45am CEST par Sam Pudwell

As the internet has expanded in recent years to become a vital part of practically everything, companies have been scrambling to get their hands on the best domains in order to leverage their business potential to the maximum.
But, this has been made tricky by a growing phenomenon known as cybersquatting, which is where companies of individuals register a particular domain with the sole intention of selling it on at a later date.
The domains usually contain a brand of company name, meaning the owners can charge astronomical amounts when the respective brand comes calling.
Cybersquatting really came into prominence in 2011 when the organization in charge of top-level domains (ICAAN) expanded the number of domains available. Over 500 have since been approved with a further 837 under process.
The US is currently the country filing the most domain name cases, with the top five industries consisting of retail (13 percent), banking and finance (11 percent), fashion (10.3 percent), internet and IT (7 percent) and heavy industry and machinery (6.3 percent)
To delve a little deeper into the cybersquatting phenomenon, mobile app development firm IrishApps has created an infographic, which can be found below.
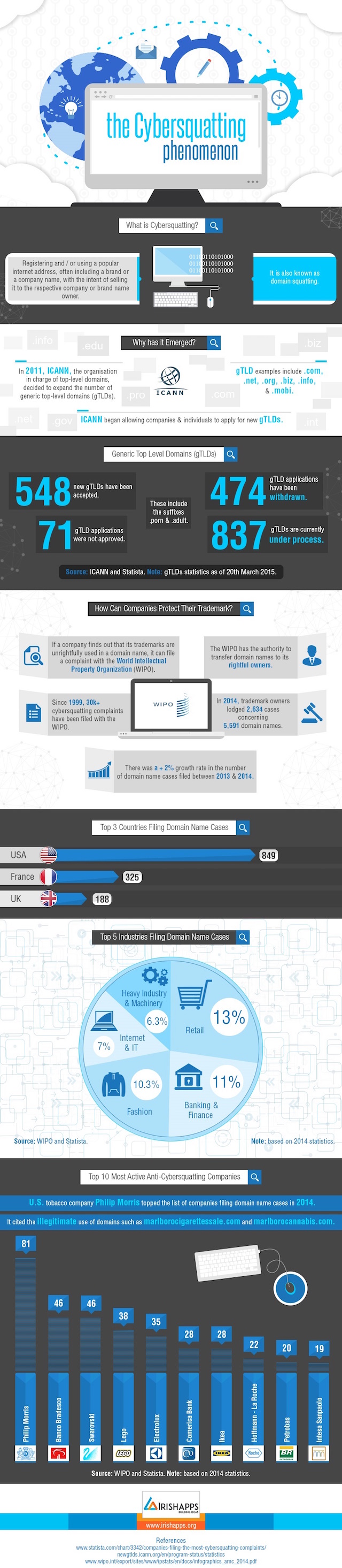
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Tomislav Pinter / Shutterstock
-

The best enterprise firewalls based on user reviews [Infographic]
Publié: août 24, 2015, 11:22am CEST par Sam Pudwell

A good firewall will keep your company’s and customers’ private information secure in order to prevent issues such as identity theft, hackers and viruses by shutting off access to your network where necessary.
With recent data breaches like that of the U.S. Office of Personnel Management and at Harvard, firewalls are gaining increasing importance in business.
IT Central Station, a crowdsourced platform for unbiased enterprise tech reviews, recently announced its top ten enterprise firewalls based on data from over 85,000 views from 2014 to Q1 2015. IT Central Station is a trusted vendor neutral site that helps keep users informed in order to help them make the best buying decisions for their company.
They additionally use a triple verification process including community policing, interviews, and LinkedIn to promote transparency and ensure the validity of reviews. Currently, there are 252 postings on firewalls on the site, with 1,546 followers, and so far this month, FireEye has been trending up based on member views.
In the below infographic, users on the site distinguished Fortinet FortiGate as the best overall firewall, followed by Cisco ASA and pfSense. Others in the top ten include Cyberoam UTM, FireEye, WatchGuard XTM, and Sophos UTM, as well as Check Point VSX, Juniper SRX, and Cisco Sourcefire Firewalls. Even though FireEye came in fifth, it was given a 9.8 ranking by users, making it the highest rated firewall.
FireEye is followed by Cyberoam and ptSense, rated 9.2 and 8.8 respectively. Meanwhile, WatchGuard has the most active customers, receiving 18 reviews, and is followed by Cisco, with 16 reviews. Meanwhile, Fortinet far outstripped its competitors in terms of views, with 23,615 page views, well over 1.5 times its nearest competitor, Cisco.
Fortinet and Cisco again lead the way in terms of followers, but Palo Alto Networks WildFire comes in as a close second, with 726 followers.
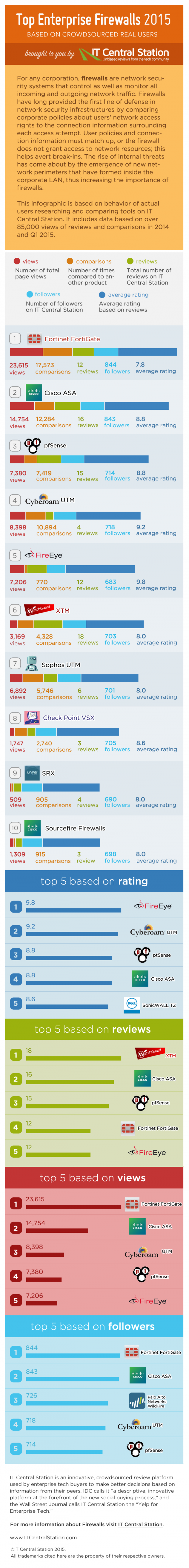
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: wk1003mike/Shutterstock
-

How connectivity affects hardware design [Infographic]
Publié: août 17, 2015, 5:28pm CEST par Sam Pudwell

Connectivity has changed dramatically over the last 30 years or so, as devices have become smaller and more powerful and we as a species have become more mobile.
To chart this change, Bluepost Digital has created an infographic of the devices we used to know and love, starting all the way back in the 1980s. At this time, Floppy Disks were used to store files, computer screens were introduced by IBM and an external CD ROM drive cost around $1,000 (£6420.
This era of the tower computer quickly gave way to the laptop in the 1990s and 2000s. Bluetooth was introduced in 1994 and is now a standard connectivity option and USBs came about in 1996, now being able to reach speeds of up to 4Gbps.
Perhaps most importantly, cloud computing started to become popular around 2006 -- championed by the likes of Google and Amazon -- and is now a multi-billion pound industry (and still growing).
Moving up to the present day, we have entered an era of single-port devices as slimmer, lightweight devices are favored.
Apple's iPads, for example, have only a single port for both charging and connectivity and USB-C has eliminated the need for multiple ports, meaning there is just one size for computers and smartphones.
The full infographic on the history of connectivity can be found below.
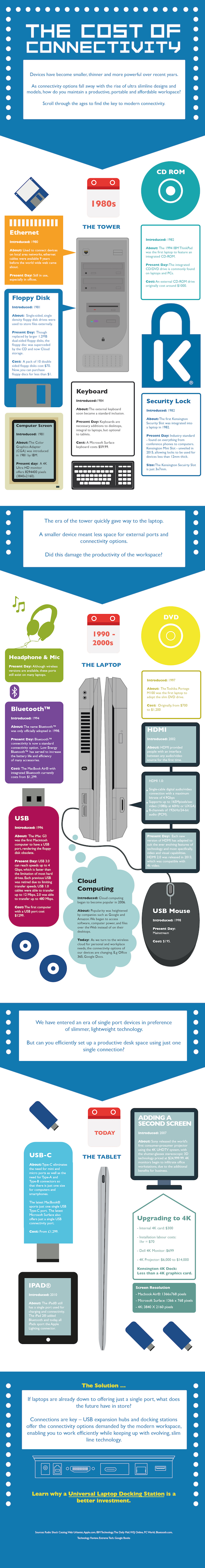
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Mario Lopes/Shutterstock
-

Choosing the right software for your startup [Infographic]
Publié: août 3, 2015, 5:30pm CEST par Sam Pudwell

So, you’ve perfected the business plan, moved into a brand new office and hired your first employees to get things started.
But, there’s one area of your startup that you probably haven’t thought about as much: the software. The efficiency and effectiveness of your startup will be impacted depending on the software you choose, so getting it right is vital.
To help any new startups out there, QuickBooks has created an infographic highlighting some of the key things to think about.
Like with email, for example. Do you go for a web client which can be accessed by any device and stores all data in the cloud, or a desktop client which requires local storage and allows better offline access?
Settling on an email solution is an important decision for any company -- as much as 13 hours of the average work week is taken up by email management according to software firm Contatta -- but its not the only one. There’s also Customer Relationship Management (CRM) software, accounting software and security software which all needs to be chosen to best suit the needs of the startup.
Check out the full infographic below for a run-through of the key software areas that any startup needs to consider and the important questions that should be asked along the way.

Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Eugenio Marongiu/Shutterstock
-

Facebook dominates social website logins [Infographic]
Publié: juillet 29, 2015, 6:11pm CEST par Sam Pudwell

Customer identity management firm Gigya has released its Q2 "landscape of customer identity" figures, showing how consumers are using third party identity providers such as Facebook and Google+ to log into other websites.
Facebook continued its dominance, now controlling two-thirds of all social logins, followed by Google+ (20 percent), Twitter (six percent) and Yahoo (four percent).
In terms of global preferences, the pattern remains fairly similar. Facebook commands a 65 percent dominance in North America, 74 percent in Europe, 79 percent in Central and South America, 63 percent in Africa and 79 percent in Asia.
Richard Lack, director of Northern Europe at Gigya commented: "In the second quarter of 2015, Facebook continued its steady dominance as a third-party identity provider (IdP), with the business now controlling an astounding two-thirds of all social logins across the globe. The company’s share on mobile devices stood at 77 per cent -- significantly higher than all other IdPs in Q2 of 2015".
"However, Facebook’s share of logins on eCommerce properties fell by two percent, with payment providers Amazon and PayPal continuing to build momentum. Consumers appear to be taking advantage of being able to log in and pay for items on websites using the same identity for one seamless interaction".
"Social login is an effective mechanism for brands to identify site visitors at the point of entry, allowing marketers to tie demographic, interest and behavioral data to individual user identities. This unification of data enables brands to personalize user experiences on an individual level -- even as users move across channels and device".
"What’s more, identity data is permission-based and captured directly from consumers, resulting in more accurate and complete information that leads to more effective segmentation", adds Lack.
The full infographic can be found below.
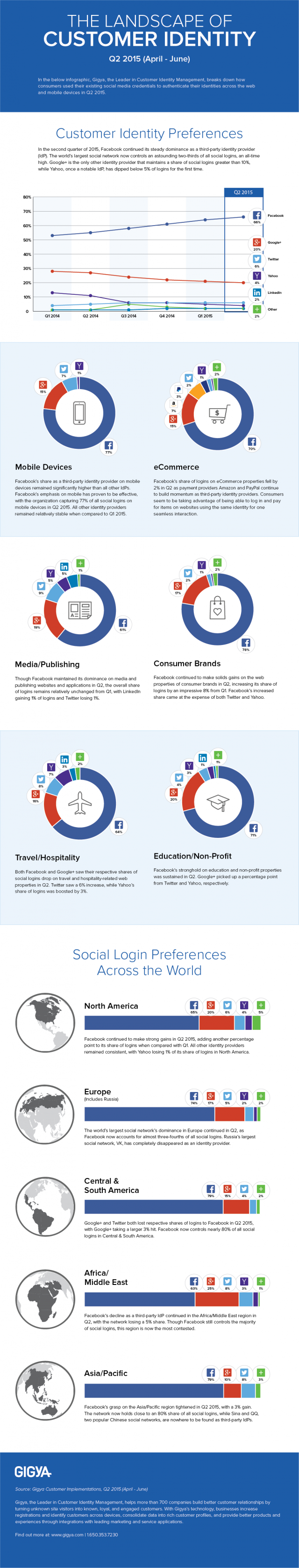
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Twin Design / Shutterstock
-

30 essential free iPhone apps
Publié: juillet 29, 2015, 4:53pm CEST par Sam Pudwell

If you’re the same as me, you’ll resent the idea of having to pay for apps. Fortunately, there are plenty of free gems out there and, since these freebies are available in pretty much every category you could think of, the likelihood is you’ll be able to find exactly what you’re looking for without having to spend a penny.
That’s not to say that they’re all good apps. A lot of them are duds that won’t be worth your while, but there’s no fool-proof way of knowing that until you actually test them. Alternatively, you can just have a look through a list that sifts out the best from the rest. Wouldn’t that be convenient?
With the rising popularity of the iPhone 6 and iPhone 6 Plus, we thought that this would be the ideal time to update our list of the top free iPhone apps, and that’s exactly what we’ve done. Just to be clear, these aren’t the official top-selling iPhone apps or anything like that, just 30 top-notch apps that we think should be on everyone’s iPhone 6 download list.
If you think we’ve missed anything out, feel free to let us know in the comments section below. Get your thumbs ready.
The BBC’s has one of the best interfaces of all news apps -- it’s clean, with relevant headlines, good photos and, perhaps best of all, no advertisements. The Beeb has correspondents in every corner of the globe, and covers a huge variety of topics. Another perk is that you can elect to view some news in other languages, such as Urdu, Arabic, Russian and so many more.
I’m sorry people, I just couldn’t resist sticking this one in. This hugely popular and addictive game has to feature in the list, mainly because you get so much game time for a free app. I’ve had a minor (okay, major) addiction to this for the last few months now, but I know I’m not the only one. There are two different modes you can play in and once you really get going the levels are tough enough to keep things interesting. Warning: prepare to be hooked like never before.

Citymapper is one of the best transit apps on the market, coming runner-up in Apple’s App of the Year awards in 2013. Available in a host of major cities including London, Paris, Barcelona, New York and San Francisco, the app displays virtually all of a city’s transit options, as well as showing estimated costs and travel times. Simply a must-have for any frequent travelers.
In today’s mobile world, where we use multiple computers and devices on a daily basis, having a means of accessing your files from wherever you are is an absolute must. Whether it’s your office computer, home desktop, laptop or smartphone, the Dropbox app for iOS allows you to access files from wherever you have a decent connection. Documents are stored in the cloud and a straightforward interface enables easy uploading and downloading.
The eBay iPhone app makes the buying and selling processes quick and easy with a fluid search tool, large, high-resolution images and an easy-to-navigate interface. The app will notify you when auctions are about to end, has a barcode scanner feature for comparing prices and a local shopping feature so you can pick up your items from a nearby retailer.
Without the Evernote app for iPhone, I’d be a lot less productive while I’m away from my desk. This free, straightforward, note-making app outperforms most competitors thanks to its strong search capabilities and effortless organization. But the real key to its success and popularity is that Evernote synchronizes all your files by saving them to the cloud, meaning anything you create or alter from your iPhone will be there waiting for you when you log into any other version of Evernote. A must-have for anyone who finds themselves constantly on the move.
Social networks thrive with a mobile app -- you’ve got to be social on the go, of course -- and Facebook for iPhone is solid. Despite occasional crashes, Facebook loads pretty quickly and has a slick interface for viewing updates and photos. The design is easy to navigate, too.
The Find My iPhone app from Apple helps you locate a lost or stolen iPhone. You can use your Apple login details to find the geo-location of any of your devices, as long as they are connected to Wi-Fi or 3G/4G. You can also remotely make your phone blare out a loud noise, even if it’s in silent mode, if you think it’s still within earshot. You can also remotely send a message to your phone’s screen if you think someone trustworthy has it in their possession, and you want them to be able to contact you.
Speed, improved search functionality and color-coded threading make the standalone Gmail iPhone app superior to the built-in Mail app (where you can access Gmail). It allows iPhone users to decide what they value in an email app. Do you prefer search capability to text displayed at readable sizes? Is it more important for your various email accounts to be managed in one app, as Mail arranges them, or would you rather have a dedicated app just for Gmail that looks more like Gmail on the web? The Gmail app searches your entire email in slicker and quicker fashion than the pre-installed Mail app.
As far as I’m concerned, Google Maps is the best navigation tool out there by a long way and should be one of the first apps you download on your new iPhone 6. You can view search results in a list or on the map itself, the app is generally familiar and smooth, it has great graphics and allows you to save your favorite destinations. An absolute steal.
Search giant Google has many excellent free apps (several are on this very list), but its search app is the one closest to its founding business and is thus bursting with some pretty smart features. You can search for stuff by typing keywords, speaking or even snapping a photo, as there’s a toggle for Google Goggles (in the settings area), which lets you take photos of books, landmarks, logos, artwork and so forth to find out more about them. You can also save pictures you take, and the app will scan and read any text that appears on them too. The Google Search app does a lot more than just trawl the Internet, making it well worth the free download.

Now owned by Facebook after a cool $1bn (around £620 million) acquisition in 2012, Instagram is the hugely popular picture-sharing app that allows you to spice up your photos through a range of different filters and then share your creations through Facebook and Twitter. You can also tag your friends, "Like" other people's photos, add comments and follow your favorite celebrities. Be prepared for a barrage of selfies, as well as snaps of food and exotic holiday destinations.
In this fast-paced, high-pressure world where business mixes with your personal life all too often, an app like LinkedIn’s turns out to be a pretty useful one to have at your fingertips. If you’ve ever found yourself wanting to suggest a potential new connection to a colleague or connect with someone whilst at an event, the LinkedIn app is the one you want. It’s the central place where you can find all those “loose ties”, the acquaintances that often turn out to be the most valuable in terms of career advancement and overall success.
Match.com is one of the UK’s top-rated dating websites and now it has a sleek, easy-to-use app so you can manage your private life on the go. It has taken cues from Tinder and carried out a recent overhaul to make the mobile experience more enjoyable. Browse other member profiles, search for singles near you, send winks and chat in real time with potential dates, all for free on your phone.
The free fitness app, MyFitnessPal, is one of the best all-in-one calorie counter and exercise trackers for the iPhone. A simple design and interface ensure the app is quick and easy to use, although its biggest selling point is the app’s exhaustive food and nutrition database, which trounces every competitor’s that we’ve seen.
PayPal is one of the most accepted payment services in the world so is a logical inclusion in this list. The app uses your location to find any merchants around you that accept PayPal and to pay, all you have to do is enter your mobile number and PIN into the app at the checkout. It’s a quick and easy way to pay without cash and the app itself is clearly laid-out and easy to use.
Pinterest is a virtual pin-board that lets you organize and share pictures of anything you find online or photograph in your life. With the app on your iPhone, it’s easy to snap photos in the real world and upload them to your boards. You can watch what others are pinning and sometimes the items are for sale and can be purchased by following a link out to the retailer’s site. It’s a great tool for collecting and browsing images of things you like or that inspire you.
I’m sure we’re all familiar with the situation; you’re browsing the web and you see a great article. You don’t have time to read it, for whatever reason, but you’re pretty sure you can remember it for later on, only to draw a total blank when you do get a free moment. Well, this is now a thing of the past thanks to Pocket, an offline reading tool that allows you to save articles, pictures and even videos for later viewing. You can also sync the app across devices and platforms, meaning you’ll never miss out on that trending article again.
For all you exercise fanatics out there, this is a great app that uses GPS to track activities such as running and cycling, providing you with information regarding pace, distance and calories burned, as well as several other metrics. You can also monitor your progress over time and sync the app with other devices to keep track of all your exercise sessions.
Skype is one of the best free communication tools for the iPhone, enabling you to call phone numbers or other Skype accounts, make high-quality video calls as well as featuring an instant messaging tool. All the features work on either Wi-Fi or 3G/4G and you can have up to four people in a video chat at any one time. An intuitive interface makes the app easy to navigate and interact with.
The Spotify Music app has all the features you would expect it to have; search through a seemingly-infinite database of tracks, artists and albums, create and share playlists and discover new tunes with the personal recommendations tool. The recently added Your Music feature also allows you to collect your favorite music in one place and sync that list across all devices for that extra personal touch.
Ah Tinder, the mobile dating app everyone loves to hate. This is a bit of a tongue in cheek inclusion but, despite the criticism it has received, the app has enjoyed incredible success since its launch. For those of you who don’t know, the app presents you with a picture of someone near to your location and you either swipe right if you like them or left if you don’t. If both people swipe right, it’s a match and you can start a conversation. It’s very much a light-hearted approach to online dating and is great if you don’t take yourself, or the dating process, too seriously.

Whatever your taste, you’ll find it on this app. TuneIn boasts the world’s largest collection of sports, news, music and talk stations, with access to over 100,000 radio stations and four million podcasts at the touch of a button. It also possesses a clean and easy-to-use interface, making it the first choice app for all you radio fans.
Twitter has had its own app for a while now, having previously left the job to third-party developers. For those of you who prefer to express yourself in 140 characters or less, Twitter’s quick, responsive and easy-to-use app is the one for you. The Discover and Activity tabs allow you to delve into the world of Twitter more than ever before, so if you don’t tweet and have been on the fence about joining the masses, the iPhone app makes it easy and convenient to get on board.
Viber is a fast-growing communications app that is giving Skype some fierce competition, having already attracted over 400 million users worldwide. It allows you to make video calls, texts and send photo messages to any other Viber user for free, whether on Android or iOS. The app syncs with your contact list to automatically detect which of your contacts also have the Viber app.
This is a hugely popular instant messaging app that Facebook believed to be worth an eye-watering $19bn (£11.39bm) when it acquired the start-up in February of this year. The app automatically syncs to your phone’s contacts and enables you to send text, photos, voice notes or video messages. A word of warning though, although the app is free to download, after the first year it’ll cost you $0.99 (£0.60) per year, but this minimal expense is definitely worth it.
If you’re constantly dealing with different currencies, then you need an app that will display live, up-to-date currency rates in a way that’s easy to understand. That’s exactly what XE Currency does. Rates are updated every minute, which you can choose to change if you wish, and recent rates are stored on your phone so you can still get access to the information even without a Wi-Fi connection.
Unlike many other weather apps, Yahoo Weather strikes the perfect balance between looks and content, displaying a comprehensive amount of information on a visually appealing interface. The app will tell you basic information such as temperature and a short-term forecast, as well as including more advanced data like wind speed and barometric pressure. It may not be quite as powerful as some other weather apps, but you’ll find all the information you need to plan your day around the temperamental British weather.
This one doesn’t need much explanation as everyone knows about the power of YouTube by now. From hilarious cat videos, to tutorials, to music videos, its got the lot. Whatever you need, there’s probably a video of it on YouTube, so for that reason alone it definitely deserves a place on this list.
Dull evenings stuck at home in front of the telly are a thing of the past thanks to YPlan, the event discovery app that is a fantastic source of tickets and attractions for spontaneous nights out. The app recommends a range of events such as gigs, film screenings and experiences that are personalised to your taste. It currently covers London, Edinburgh, New York, San Francisco and Las Vegas but more cities have been promised soon.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit: Bloomua / Shutterstock
-

Dmail brings self-destructing emails to Gmail
Publié: juillet 29, 2015, 1:51pm CEST par Sam Pudwell

Following the release of the Undo Send option last month, Gmail users can now also delete sent emails.
Through a new Chrome extension called Dmail, users will be able to use a self-destruct option, which deletes sent mails after a stipulated period of time.
By installing the Chrome extension, users will be able to set automated timers to destroy a sent mail. This also means that after doing so, the recipients’ access to the email will be revoked and they will receive an email saying that the message will self destruct, also stipulating the time set by the sender.
This service, however, does not physically delete emails on the recipient’s side. Users who send emails via Dmail will have their messages encrypted and then decrypted on the recipient’s side. However, if a sender wants to revoke access to a sent email at a later time, the email gets encrypted by a 256-bit encryption algorithm and the recipient gets a "message unavailable" prompt.
"Neither Gmail nor Dmail servers ever receive both the decryption key and encrypted message. Only the recipient and sender can read the email legibly", Dmail product lead Eric Kuhn said.
Dmail is created by engineers from bookmarking web service Delicious.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: iQoncept / Shutterstock
-

What are the perks that employees want the most?
Publié: juillet 20, 2015, 5:21pm CEST par Sam Pudwell

It’s a question that CEOs and managers around the world are asking: "How can I keep my employees loyal?".
In the modern working world, staff loyalty is almost a thing of the past. Whereas employees used to stay at the same company for most, if not all, of their career, jumping from one job to another in quick succession has become the norm.
To investigate the impact of staff perks on employee loyalty, Towergate Insurance has created an infographic which contains some interesting statistics.
For example, 40 percent of employees think that compensation is the benefit that would increase engagement and loyalty the most, followed by better benefits (36 percent), career advancement opportunities (34 percent) and training or education (31 percent).
Fifty-one percent of respondents identify flexible schedules as something that would make them want to stay at their job and 39 percent of working adults have actually left a job or considered leaving because it wasn’t flexible enough.
In terms of perks, 20 percent of UK employees want a pension, 19 percent want an increase in basic salary and 11 percent want financial benefits during long-term injury or illness.
The study also identifies some of the more unusual perks on offer at various companies around the world, such as Microsoft’s on-site shopping center exclusively for staff, Google’s free haircuts and Airbnb’s themed Formal Fridays.
The full infographic can be found below.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Goodluz/Shutterstock
-

In-depth analysis of Apple Pay in UK
Publié: juillet 15, 2015, 1:08pm CEST par Sam Pudwell

There’s no possible way it could have happened (unless you have been living under a rock) but if you have missed the news that Apple Pay was just launched in the UK, don’t panic, we can help.
This article provides the ultimate Apple Pay analysis from industry professionals, giving you a comprehensive overview of Apple’s attempts to rule the digital payments industry.
Missing the Point About Apple Pay? It’s All About In-App, Not In-Store -- James Allgrove, Stripe:
It’s bizarre that the most transformative feature about Apple Pay -- in-app payments -- is being overlooked. The simplicity of buying things with a fingerprint means mobile conversion rates in apps are generally twice as high. This will power huge growth for mobile-first start-ups such as Bloom & Wild and Dice.fm which are revolutionizing the way we buy everything from flowers to gig tickets.
Mobile is bringing the internet to everyone, everywhere, but the legacy financial infrastructure just hasn’t kept up with the internet economy. This has left us with a situation where only 2 percent of global consumer spending happens online, despite the web being 25 years old. Fixing this and enabling more transactions on mobile is a challenge rooted in code and design, not finance.
If it would be of interest, we could also potentially connect you with some businesses in the UK -- including Lush, Bloom&Wild and Dice.FM -- that will be using Apple Pay to ramp up in-app sales.
Apple Pay and Security -- Liam Lannon, Payments Transformation Consultant, Sopra Steria:
It’s fairly safe to say that the Apple Pay Secure Element is as secure as the chip in the chip and PIN cards in your pocket, purse or wallet. Consider that the underlying architecture and standards which define what a Secure Element is, what it does and how it protects sensitive data, also cover the security hardware which we see every day in our chip and PIN cards.
In fact, in many cases, exactly the same hardware as is used in our EMV-compliant chip and PIN cards will be integrated into handsets like the iPhone 6 as the Secure Element.
Not only is the hardware basically the same, the microcontroller which is at the heart of chip and PIN cards and Secure Elements will have been subject to rigorous security testing to ensure that it is fit for purpose i.e. able to withstand external attacks and to employ tamper-resistant techniques to ensure that information is wiped should a hardware attack be detected.
A Massive Boost for Mobile Payments -- Ian Hermon Mobile Payments Specialist at Thales e-Security:
The launch of Apple Pay has caused a real shift in the payments landscape -- its UK debut will be exciting news for consumers, offering access to a slick and quick payment option with a brand they love, and carry around with them 24/7. What these consumers won’t see, however, is the significant rearrangement behind the scenes as card schemes and issuing banks grapple to establish new relationships, security approaches and commercial models.
The launch will cause further momentum in an already extensive contactless NFC terminal infrastructure in the UK -- a further endorsement of the established payment rails and EMV infrastructure. This will likely lead to an uptick in adoption of mobile payment technology, and consequently, Apple will find itself in a constant battle to balance user convenience with ensuring security is factored in from the start.
This simply has to be a number one priority if consumers are going to put their trust in mobile payments. With that in mind, it is encouraging to see tokenisation at the heart of the security agenda, which will help issuers with payment channel separation and also protect the merchant in the event of a data breach.
Alarm Bells for HSBC -- Pinar Ozcan, Assistant Professor of Strategic Management, at Warwick Business School:
Apple Pay’s launch is certainly good news for the UK, taking the country to the era of digital payments using the NFC technology.
What has always been a struggle is for Apple Pay and the competitors to build a large enough ecosystem of merchants and bank partners in order to enable immediate adoption.
While it is not clear why HSBC has decided not to support Apple Pay’s UK launch, it certainly rings alarm bells as consumers often have a now or never approach to new technologies, easily deciding not to adopt for a long time if it is cumbersome to do so at the beginning.
A Game-Changer, or Just a Lot of Noise? -- Jens Bader, Secure Trading Chief Commercial Officer:
The first thing to remember when it comes to Apple Pay is that contactless payment is by no means new, or unique to Apple. The use of Near Field Communication (NFC) technology for payment is well established. Contactless cards have already been successfully trialled, adopted by card issuers, and embraced by UK consumers.
Apple is simply trying to brand the NFC technology. No doubt, Apple is imagining customers will walk into a shop and ask the question 'Do you accept Apple Pay here?' which, in my opinion, is an unlikely future. With so many competitors adopting contactless (from card companies, to other tech schemes such as Android Pay), 'contactless accepted here' is the sign I expect to see on shop-fronts.
While the combination of contactless with mobile technology will promise increased functionality, such as the ability to see your balance on your phone screen as you pay, or receive an instant e-receipt, whether these features will be enough to completely alter the payments industry is a different story. I think it is definitely premature to say that Apple Pay will be the death of cash and cards. While the omnipotence of smartphones for the younger generation may make contactless mobile payment desirable for some in that demographic, the vast majority of the population will stick to what they know.
Working in the payment industry you sometimes forget that there are still people uncomfortable with mobile technology, or even paying on their computers, but the reality is that this is the case -- so Apple Pay is a far stretch for this demographic.
Cash is by far and away the most inclusive payment method (used internationally and across all sectors of society) and therefore will remain safely unchallenged as the most successful payment method.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The history of Windows
Publié: juillet 10, 2015, 11:41am CEST par Sam Pudwell
Windows 10 is just around the corner, with Microsoft confirming a 29 July release date for its new operating system.
The general opinion appears to be positive for Windows 10, with 73 percent of IT pros saying they will deploy it within the first two years, despite there still being a few kinks to sort out.
And this will definitely be a relief to Microsoft after the decidedly mixed reactions that its predecessor received when it was released in 2012.
So, Windows 10 is Microsoft’s newest OS, but where did it all begin? The answer, of course, is Windows 1, which was first released all the way back in 1985.
From there we travel up through the numbers, with Windows NT in 1993, XP in 2001 and Vista in 2008 being the only variations.
To take us through this journey, Microsoft Training has created an infographic mapping all the variations over the last 30 years, which can be found below.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Wozniak: Robots will rule, treat us as their pets
Publié: juin 29, 2015, 6:34pm CEST par Sam Pudwell

Speaking at the Freescale Technology Forum about the growth of artificial intelligence, Apple co-founder Steve Wozniak has claimed that one day robots will be in charge and will treat humans as their pets.
After previously warning about the dangers of AI, "the woz" now believes that the robots we create will learn to protect and nurture us in much the same way that we look after dogs today.
"They’re going to be smarter than us and if they’re smarter than us then they’ll realize they need us", he said. "We want to be the family pet and be taken care of all the time. I got this idea a few years ago and so I started feeding my dog fillet steak and chicken every night because 'do unto others'".
Wozniak’s acceptance seems to go against the general feeling that AI is something to be feared rather than promoted.
SpaceX and Tesla founder Elon Musk recently went so far as to say that we are "summoning the demon" with regards to robots and AI, voicing fears that Google boss Larry Page could accidentally create humanity-destroying machines.
And he’s not alone, as Microsoft founder Bill Gates and Professor Stephen Hawking have also confessed to having concerns about the rise of AI, prompting a widespread debate as to whether we should fear artificial intelligence.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Ed Schipul
-

Box and IBM team up for cloud collaboration
Publié: juin 25, 2015, 9:58am CEST par Sam Pudwell

IBM and Box have announced a global partnership that aims to transform work in the cloud by integrating existing products and services to develop new solutions for a range of industries and professions.
Box will combine its collaboration platform with IBM’s extensive portfolio of solutions in security, analytics, content management and social capabilities to partner in three key areas:
- Transformation of Enterprise Work
- International Reach and Security
- New Content Rich Apps and Solutions
Aaron Levie, co-founder and CEO of Box said: "Today’s digital enterprises demand world-class technologies that transform how their organizations operate both internally and externally".
"This extensive alliance between Box and IBM opens up an exciting opportunity for both companies to reach new markets and deliver unified solutions and services that can redefine industries, advance secure collaboration and revolutionize enterprise mobility".
The two companies also plan to help leading retailers manage their omni-channel experiences in areas sucha as advertising, promotional materials, pricing and packaging.
Bob Picciano, senior vice president of IBM Analytics commented: "This partnership will transform the way work is done in industries and professions that shape our experience every day. The impact will be felt by experts and professionals in industries such as healthcare, financial services, law, and engineering who are overwhelmed by today’s digital data and seek better solutions to manage large volumes of information more intelligently and securely".
"The integration of IBM and Box technologies, combined with our global cloud capabilities and the ability to enrich content with analytics, will help unlock actionable insights for use across the enterprise".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple iPhone 6 Plus vs Smart Ultra 6: Which is best for you?
Publié: juin 23, 2015, 5:50pm CEST par Sam Pudwell

Vodafone recently decided to get involved with the phablet hype by launching its own 4G device: the Smart Ultra 6.
Despite being positioned at the budget end of the scale with a cheerful £125 price tag when purchased on a pay-as-you-go plan, it still boasts an impressive set of specifications. But, how does it compare to Apple’s most recent flagship smartphone, the Apple iPhone 6 Plus? We took a closer look to find out.
Design
On first glance, the two devices look very similar. Both feature similar rounded edges with the top bezel holding the front camera and speaker looking virtually identical.
The bottom bezel is slightly different, with Vodafone plumping for three different buttons similar to that of the Sony Xperia devices rather than Apple’s traditional single home button.
The Ultra 6 is slightly chunkier in all areas than the iPhone 6 Plus, measuring 154 x 77 x 8.35mm compared to 158.1 x 77.8 x 7.1mm. But apart from that, the two smartphones are rather similar... at a distance that is.
When you look a big closer you see that the Ultra 6 does have more of a budget look and feel about it, but that is to be expected.
Display
Both phablets feature 5.5-inch displays, so Vodafone has clearly followed the trend for big screens with this device. I must admit I prefer a slightly smaller screen, but that’s a bit of a moot point seeing I’m comparing phablets, so let’s move on.
The Ultra 6 also has a foot-up on the competition with the display, being 1080p when most other devices in the price range are 720p. So kudos to Vodafone for not allowing any compromise on the display.
Apple’s iPhone 6 Plus display has a 1,920 x 1,080 pixel resolution with a 401ppi, which doesn’t match other top-of-the-range devices such as the Nexus 6, but is still a quality screen.
Camera
Surprisingly, the Ultra 6 has outdone the iPhone 6 Plus on both the front and back cameras. The Ultra 6 boasts a 13-megapixel rear camera and a 5-megapixel front camera, whereas the iPhone 6 Plus users can only make use of an 8-megapixel rear camera and a lowly 1.2-megapixel selfie snapper.
This camera combination also beats Google’s Nexus 6 (13-megapixel and 2-megapixel) so Vodafone can be very proud of its efforts.
Under the hood
While Apple (somewhat surprisingly) opted for a dual-core Apple A8 processor with a clock speed of 1.4GHz in the iPhone 6 Plus, Vodafone more than matched this with a 1.5 GHz octa-core Qualcomm Snapdragon processor.
The Ultra 6 also comes out on top with a 3,000 mAh battery and 2GB of RAM compared to a 2,915 mAh battery and just 1GB of RAM in the iPhone 6 Plus.
The final difference is that the Ultra 6 runs Android Lollipop 5.1, whereas the iPhone 6 Plus of course runs Apple’s iOS 8 operating system.
Verdict
For a budget phone, Vodafone has done exceptionally well to create a device with serious substance, although it does let itself down somewhat in the style department when compared to the high-end iPhone 6 Plus.
Having said that, if it’s budget you’re after the design probably isn’t all that important, making the Ultra 6 an extremely viable option.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Robots might take over 35 percent of UK jobs [Infographic]
Publié: juin 22, 2015, 5:46pm CEST par Sam Pudwell
In the industry we’re in you’ll be hard pressed to find someone who is anything but positive about the development of technology. Thanks to technological advancements, we can carry whole computers in our pockets, travel to anywhere in the world without having to leave our living room through devices such as Oculus Rift and 3D print body parts to save lives.
But there is one area where people aren’t quite so enthusiastic and that is in employment, where jobs in a variety of industries are under threat from automation.
According to Deloitte, 35 percent of UK jobs are at "high risk" of being made redundant by technology and/or robotics in the next two decades and Big Think expert Andrew McAfee recently said that he thinks white-collar jobs are in danger as much as their blue-collar colleagues.
ebuyer.com has recently published an infographic on the subject, suggesting that only 40 percent of jobs are considered low or no risk and that 10 million jobs could be lost by 2034.
The full infographic can be found below.

Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Ociacia / Shutterstock
-

Using technology to understand what makes bike riders so fast
Publié: juin 15, 2015, 2:01pm CEST par Sam Pudwell

The blurring of technology and sport is something that I have written about several times before and now have another perfect example to add to the list, this time in motorbike racing.
To celebrate the final day of the Isle of Man TT races, EMC Corporation is announcing the results of a data analysis competition designed to reveal exactly what makes one of the riders so fast.
The subject was John McGuinness, also known as The Morecambe Missile. John is a legend in the motorcycle racing world, with a distinguished 25-year history in motorcycle racing and a 23-time winner of the Isle of Man TT races.
It all started at the Circuit Monteblanco in Spain, where EMC used sensors fitted onto the racing suits of John and Adam Child -- a control subject who is a senior road tester with Motor Cycle News -- to capture over 700,000 rows of performance, biometric and mechanical data.
This data was then released to the data science community in the form of an open competition where entrants were tasked with uncovering the most compelling insights.
One of the winners was Stefan Jol, who split up each element of the track for analysis and identified which parts had the greatest impact on overall performance.
The other winner was Charlotte Wickham, assistant Professor of Statistics at Oregon State University, who claimed the visualization prize by tracking each riders’ racing line and displaying this on a map of the track, thus providing a visual representation of each lap.
Mike Foley, Director of data science at EMC said, "Stefan was the only entrant who looked at how performance in one area of the track impacted performance in the other, which was ultimately why we awarded him the first place. We wanted the community to think differently when approaching this challenge to draw out new insights into why John is so fast, and Stefan did just that. Similarly, from a visualization perspective, Charlotte presented the data in an engaging way which made the differences in the riders clear to those outside of the data field".
The findings inspired EMC to repeat the experiment at the Isle of Man TT with a more elaborate array of sensors which will be able to capture significantly more data and more definitively answer the question: What makes John McGuinness so fast?
Ahead of the races this week, John said: "I’ve been racing since I was 18 and I don’t really know why I’m so good at what I do. I thought it was interesting to see just how both the speed and positioning in the corners made the difference, from the test in Spain. I’m really looking forward to what can come out of the data from the TT and hope that some of information can be used to help make me an even better rider and the sport safer in the future".
Jonathan Martin, CMO of EMC said: "We were really excited to see how big data can provide revealing new insights about someone like John McGuinness, and have been thrilled with the interest shown in this project from the data science and motorcycling communities around the world. A project like this has never been undertaken before, and is already proving some interesting and significant observations. We are gaining a better understanding of what makes extreme athletes like John perform at such a superior level, but also through big data analytics we are gaining deep insights into how we can make the sport of motorcycle racing safer.
"We’re looking forward sharing this story with the world in the second half of 2015 through our documentary The Math Behind The Morecambe Missile which chronicles our journey with John and team", adds Martin.
This kind of research obviously has huge potential benefits for riders and their teams and might be worth considering for some of John’s competitors, seeing as The Morecambe Missile won this years race by 14 seconds, securing a new lap record in the process.
The project has also been documented in a film, the trailer of which can be found here.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: kqlsm/Shutterstock
-

How to minimize your company's driving costs
Publié: juin 2, 2015, 1:18pm CEST par Sam Pudwell

Tracking business costs can be a murky job, especially when it comes to driving. With so many variables and potential accidents on and off the road, it is hard to see where and how money can be saved.
A recent study by Nestle highlights this. The chocolate maker calculated that it needed to sell 235 million KitKats just to cover the costs incurred through road accidents across Europe.
Driving for Better Business, a Government-backed campaign working with Volvo Car UK and Fleet21 to help businesses understand the costs associated with poor driver management, has some suggestions to save money on driving costs, namely by looking at the smaller issues instead of the main factors like insurance and car replacements/repair.
One of the best ways to find what is hurting your business is to audit all drivers’ risk management, insurance, car type and create a policy for safe driving (in and out of work) and of leasing cars to employees, create a "choose-your-own" system for picking the car.
This way, employees know the risks when it comes to driving dangerously even outside of work. Having a choose-your-own system also allows the business to make informed decisions on the safest cars with the latest safety technology installed, alongside low insurance rates and low/zero emissions.
Having a policy and regular employee audits is crucial and could save the company thousands in insurance and accident costs. Also, picking the cars for employees makes the business risk portfolio drop, meaning insurance companies are likely to offer better rates to the whole company.
The policy must extend to higher-ups in the business, meaning executives have to choose a car with similar safety features and not get involved in accidents outside of work. Setting an example is crucial for large companies, who follow the leader’s image.
Even though companies with an already poor reputation might struggle to save money, new businesses that want to be efficient with savings should set up audits and company policies immediately for driving, in order to minimize the amount spent on company cars and insurance.
Volvo’s Co-Pilot scheme offers small-to-medium sized enterprises (SMEs) a safety and risk management program to reduce the risk of road accidents.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: ssguy/Shutterstock
-

Internet of Things can help keep the elderly safe at home
Publié: mai 27, 2015, 10:00am CEST par Sam Pudwell

A major challenge for society in the near future will be meeting the needs of an aging population, set to rise by 23 percent from 2010 to 2018, with the 65+ UK population expected to reach 16.9 million by 2035.
The combined pressures of this demographic change, reduced health and social care budgets and the desire of individuals to lead independent lives for longer will drive the need for more personalized health programs based on home-centric care.
IoT will have a big part to play in this movement says Mark Lee, Chief Commercial Officer at Intamac, an IoT enabler and innovator, with over a decade of experience in the IoT sector: "This is exemplified in the tragedy of preventable deaths of elderly people at home every winter due to cold homes. In the UK alone, the death of up-to 30,000 people each year has been attributed to cold homes, with those over the age of 75 accounting for the majority of these deaths".
"While energy efficiency programs such as Green Deal and Energy Company Obligations aim to help, many elderly people living in fuel poverty, those living on their own are often missed by these schemes. Many of these deaths, and other health related issues, could be prevented by simply installing an IoT connected sensor in the homes of vulnerable and elderly people", adds Lee.
IoT technology can securely collect, analyze and automate appropriate responses and actions to real-time data drawn from sensors and other devices within homes or other properties. The technology can identify and send alerts on acute emergencies requiring urgent intervention as well as identifying, tracking and monitoring trends and patterns over time that may be indicative of health or other problems.
This information can be accessed securely and remotely, by people such as family members, emergency services or healthcare professionals.
This concept has already been successfully piloted in a trial involving Humberside Fire and Rescue, KC, Intamac and Sprue Aegis (Fireangel), the leading safety sensor manufacturer. The pilot ran through the coldest period of the 2014/2015 winter, ensured the safety and wellbeing of a group of elderly and vulnerable householders by measuring the air temperature and other key indicators within their homes.
This information was shared with emergency services and healthcare providers, who could intervene in the event of an emergency, such as the temperature falling below a safe threshold. Analysis of the pilot event records has shown there is strong evidence to suggest, for at least two elderly people, the system averted a potentially life threatening situation where their home was dangerously cold.
This is one of many examples where intelligent IoT solutions can be integrated with people based services to deliver improved outcomes at a greatly reduced cost.
In Intamac’s experience, often the biggest demand for this technology comes from concerned family members, who are increasingly living far away from their elderly relatives.
Mark comments the applications of IoT in this sector offer a great reassurance to these people: "Remote diagnostics and monitoring offer a discreet way for those with vulnerable family members to have peace of mind. Our intelligent technology is non-intrusive, but offers a way to identify changes in normal domestic behavior that might suggest a problem. For example just monitoring when hot water is used in the home will generate a behavior profile. Any variation to this behavior can then be identified and an alert triggered to check everything is ok".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Goodluz/Shutterstock
-

Wear Your Own Device is coming to the workplace, and enterprises need to start preparing today
Publié: mars 23, 2015, 8:23am CET par Sam Pudwell

Anyone interested in technology will know that the mobile boom has brought with it new considerations for businesses in the form or BYOD (Bring Your Own Device). Despite still being a concept that many companies are yet to fully grasp, it is about to be overtaken by a new mobile trend.
WYOD (Wear Your Own Device) is hot on its heels, as wearables and smartwatches continue to gain traction. To shed some light on the growth of WYOD and what businesses need to do to stay ahead of the curve, I spoke to Paula Skokowski from mobile file sharing provider Accellion.
Overview of Paula’s background
Paula Skokowski has worked at the forefront of the Internet of Things and is an expert on intelligent devices.
Paula began her career as a robotics engineer working on vision guided high-speed robot applications for companies including Ford and Motorola.
An expert on intelligent devices and mobile security, her work at Accellion is focused on securing enterprise content across smartphones, tablets and the latest generation of intelligent devices like wearables.
BYOD and WYOD: Are they one and the same or should they be considered separately?
Employees bringing their own smartphones into the workplace started the BYOD trend requiring enterprises to deal with the serious security implications that come from these devices.
The decision for employees to wear their own device (WYOD) poses similar problems for IT departments, as employees use these devices, sometimes discretely, to access and share business content.
This puts corporate data at risk, and reinforces the need for IT managers to focus on securing the content, rather than the device that’s in use. Wearable devices simply add another level of access and security concern to what we’ve already seen with the BYOD trend.
What are the key risks of WYOD?
As with all security risks, being prepared for the unpredictable is vital in minimizing threats to IT.
We’re expecting a surge in demand from workers wishing to use wearables in the workplace, but a recent study that Accellion undertook with researchers Vanson Bourne revealed that enterprises aren’t ready to tackle the security risks of WYOD.
In questioning decision makers from organizations with more than 1,000 employees, 77 percent of them didn’t include wearable technology as part of their broader mobile security strategic planning. Wearables are coming to the workplace, and enterprises need to start preparing today so they are not caught off-guard.
How can WYOD help businesses?
Utilizing mobile devices, including wearables enhances productivity in a variety of industries -- from the surgeon using Google Glass to access a patient’s vital information, to the worker navigating a vast warehouse using a head display to indicate what items to pick out.
The convenience and usability of wearable technology allows quicker response time and empowers mobile workers in any industry to access the content they need, in real-time, wherever their location.
What issues do businesses run into when trying to develop BYOD policies?
Businesses are struggling to deliver the flexibility and speed necessary to keep up with BYOD trends.
A lot has been made of the devices, be it tablets or smartphones, but focusing on the device neglects what’s really important; the content. In most instances businesses don’t own the device, and security breaches occur when sensitive content falls into the wrong hands.
Securing content through a private cloud means data is protected, no matter if an employee laptop is left on the train, or phone or tablet is misplaced.
In a BYOD world, the cost to business is not a lost device, since the device is owned by the employee, the true cost to business is loss of enterprise content, and this is often overlooked by BYOD policies.
What type of devices do you think will become most useful to businesses? Smart glasses/smart watches/trackers?
Watches, trackers and smart glasses all have their place in different environments across industries. While Google Glass is perhaps best suited to workers who need to work hands-free such as healthcare workers, smart watches have real potential to make a broad impact for remote workers.
Being able to receive notifications, share and sign off documents and communicate with colleagues all by using a watch can transform business productivity.
We’re also seeing navigational trackers helping warehouse workers navigate vast environments -- helping to drive efficiency and save time in locating goods and services.
Many businesses are still struggling to come to terms with BYOD, is it too soon to be talking about WYOD?
IT teams always need to be one step ahead of the trends. While this doesn’t mean that IT needs to camp out overnight at the Apple store to be the first to get their hands on the latest devices, it does mean that IT needs to anticipate what devices will be coming into the workplace and how to keep enterprise security intact.
According to a global forecast by CCS Insight, wearable device shipments are expected to grow to 135 million in 2018. The age of WYOD is here, and IT needs to include these devices into their current security strategies to make sure that any corporate data accessed on these devices is secure.
Wearable devices are promising users easy access and connectivity to applications and data on smartphones, which could include enterprise information.
Does anyone stand a chance against the Apple Watch?
The iPad kick-started mass demand for tablets both in the home and in the workplace, and next month’s anticipated arrival of the Apple Watch has the potential to do the same.
Going back only 10 years, personal technology lagged behind office IT, in terms of purchasing power. Now with the consumerization of IT, employees prefer to purchase and use their own devices, due in part to an emotional attachment that we have with our products, and also because today personal technology can often exceed corporate IT’s capabilities.
It will be interesting to witness the public demand for the Apple Watch, and how the growing smart watch market reacts.
What do you think the future holds for Google Glass?
Google Glass is a revolutionary technology that is perhaps best suited for the enterprise, rather than for consumer use.
For example, healthcare organizations welcome the ability that doctors now can view patient information, read scans and examine patients without stopping to check a screen or manually search through notes.
Public consumer adoption of Google Glass has hit well-documented stumbling blocks, with concerns over the fact that it’s physically obtrusive and potentially invasive of personal privacy, but the enterprise is where Glass can excel.
With the investment that Google is putting behind the project, Google Glass and other competitive head displays could someday make tablets and smartphones redundant for medical and remote field workers, fundamentally changing the way we interact with technology in the workplace.
What future trends can we expect to see in the BYOD/WYOD space?
Wearable devices are both input and output devices that can not only display information to the user but also have the potential to capture vast amounts of data that the user maybe unaware of including location, video, images and temperatures.
This could lead to organizations being able to infer information about employees, which would make businesses very nervous about the security of the data being collected via wearable devices.
These are issues that go beyond phones and tablets. By 2018 a high percentage of wearable devices are going to be inconspicuous, and it won’t be obvious what data is being captured or displayed on this new class of devices.
This is why focusing on the security of content remains key for enterprises. As organizations work to embrace the devices that employees wish to use, it’s more important than ever for IT to make enterprise content secure and available via the cloud.
Private cloud solutions that enable organizations to own the encryption keys, and track all content access and sharing are essential and enable IT managers to sleep a little easier, knowing that measures are in place to protect and assure the security of corporate content.
Image Credit: JMicic/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Brits are ready to be 'digital by default'
Publié: janvier 20, 2015, 9:42am CET par Sam Pudwell

A new study from Fujitsu has revealed that UK consumers are ready for a nation that is digital by default.
Over a fifth of us will always opt for a digital-first approach, when a digital service is offered. Driven by a desire to speed up (66 percent) and simplify (62 percent) everyday processes, the results show a digitally confident nation, one that is seeking to move faster towards a digital future (39 percent) and that would vote for a political party if it focused on digital policies (20 percent).
Financial services was the standout sector when it came to digital services currently offered, topping the table in terms of importance of (62 percent) and satisfaction with (64 percent) according to consumers.
This was followed by retail where satisfaction in the services offered is 60 percent. When examining individual digital services used in our everyday lives, online banking and online shopping reign supreme as the most used (67 percent and 66 percent respectively) and valued (63 percent) across the nation; but also in the importance placed on them by consumers.
The research suggests a burgeoning confidence amongst Brits getting to grips with digital services, with nearly two-thirds (63 percent) commenting that they were comfortable with the digital services offered to them by organizations overall.
"We are speeding towards a digital-first Britain. From click and collect through to renewing our road tax online, the wealth of digital services available has driven great behavioral change in the UK," said Michael Keegan, Chief Executive Officer UK & Ireland, Fujitsu.
"We are now more confident in our ability to use the services offered, we understand the benefits and as such, it is consumers themselves pushing organizations to create a digital future".
There are, however, still many barriers which are preventing the UK becoming a truly digital-first nation. Brits were quick to point out those they would like to see further improvement in, with both Local (24 percent) and, to a lesser extent, Central Government (20 percent) named as the two key sectors that must improve quickly to remain relevant.
While vertical sectors have work to do on their digital offerings, talking to those who never use digital services (12 percent) a myriad of issues blocking a digital future appear. Over a third (37 percent) simply prefer human interaction, while one in five had concerns about security and 15 percent felt they were too complicated and didn’t know how to use them.
"While Britain is on the right path for digital greatness, the message here is clear -- education is essential. For Britain to become truly ‘digital by default’ organizations from the Government to private organization bodies, must work together to ensure digital inclusion is a reality for all", said Neil Crockett, CEO, Digital Catapult.
"Only by collaborating and facing this issue head-on can we ensure Britain becomes a digital-first nation, taking its place on the world stage as a leader in digital services and an example to the rest of the world".
Education is key to ensuring the future of digital is secure in the UK, and for many, is something that is currently lacking.
Only a quarter (26 percent) felt that enough was being done across the UK to educate citizens on digital services, while 54 percent said they would like to see the Government do more to prepare us for a digital future.
A third of respondents said they believe the organization providing the service should be the one to educate them.
"The UK’s digital future is, in some ways, just beginning. For it to continue at this pace, organizations have a responsibility to continue creating digital services that simplify the customer experience", continued Keegan.
"At the same time, there is little evidence to suggest that the UK will become a digital-only nation; instead, citizens have shown a desire for access to a wealth of services, across all channels, enabling them to make their own decisions on the digital services they adopt and when they chose to do so".
Photo Credit: ra2studio / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Cloud adoption set to rocket in 2015
Publié: novembre 20, 2014, 9:04am CET par Sam Pudwell

A global survey carried out by Equinix has found that, over the next 12 months, the majority of business applications will be deployed to not just one, but multiple clouds across several geographies.
Of the 659 respondents, 77 percent said they planned to deploy to multiple clouds in the next 12 months and 74 percent expected cloud services to command a larger budget in 2015.
Globally, 38 percent of companies plan to deploy between three and five cloud services over the next year, with 11 percent planning on more than 10.
Interestingly, these figures are lower for North America, coming in at 6 percent and 30 percent respectively.
Furthermore, 74 percent of respondents said they plan to deploy cloud services in multiple countries as opposed to a single location.
Ihab Tarazi, Equinix CTO, said: "What surprised us about this survey is how quickly multi-cloud strategies are becoming the norm worldwide. Businesses have discovered that colocation provides a meaningful ROI for WAN optimisation, and it is clear that multi cloud deployment will improve the ROI even more".
IT executives and IT managers made up the bulk of the respondents at 44 percent and 54 percent respectively, with IT service providers comprising the final 2 percent.
Photo Credit: Fun Way Illustration/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Phil Neville reveals how big data is now essential in professional soccer
Publié: novembre 13, 2014, 2:20pm CET par Sam Pudwell

With high-tech player tracking and analysis systems gaining serious traction in the world of professional sport, data can now be used to instantly analyze player and team performance like never before.
But this hasn’t always been the case, as we found out from former Manchester United player and coach Phil Neville, who helped to shed some light on the role of big data in professional football and how it has changed throughout his career.
He started off by taking us back to Manchester United’s famous 1999 Champions League final win against Bayern Munich. As surprising as it might sound, he said that there was no data used at all back then.
The team just watched a video of one of Bayern’s previous matches, pointed out a few tactical areas that could be exploited and that was it.
Fast-forward fifteen years and things are very different. Today’s top clubs employ people specifically to analyze data collected on their own players and opposition teams and Neville went so far as to say that these days, "data analysts are almost as crucial as the manager".
Data is collected on everything: Match performance, training performance, blood tests, heart rates, sleep patterns and much more. But, as Neville rightly pointed out, "the key is knowing how to use the data".
If handled correctly, this information can be used to create individualized training programs, plan recovery and, perhaps most importantly, predict injury and illness.
There are several examples of players competing at the top level well into their 30’s (Ryan Giggs, Frank Lampard and Neville himself are prime examples) and this increased longevity is largely down to the role data analysis has played.
But it’s not only the players and coaches that are benefiting from big data. It’s also improving the fan experience, as it "helps the football world get clarity on situations", which greatly increases the appeal for spectators.
Neville finished by saying, "I can’t see a negative in this system" and, as coaches and managers continue to gain more and more insight into their players’ performances, you’ll be hard-pressed to find anyone who disagrees.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How to play music directly from Gmail
Publié: novembre 12, 2014, 3:49pm CET par Sam Pudwell
For anyone who has ever been sent MP3 songs or YouTube videos via Email, you may be interested to hear that you can actually play these straight from your Gmail inbox.
It’s also possible to compile all the songs and videos that you’ve ever received into a playlist, meaning you can listen to all your favorite music without having to open another tab or program. Here's how it’s done.
First, you’ll need to open your web browser of choice, be that Chrome, Firefox, Safari, or any other, this should work fine with all of them.
Next, download Play My Inbox, a free app that collates all the music files and music video links from your Gmail account.
After you’ve done that, just click the "Play My Inbox" button whilst still in the app and log in using your Gmail information.
The app will then populate your playlist with songs and music videos from your inbox, meaning all you have to do is click on the song you want to listen to and use the standard playlist controls such as "previous", "next" and "shuffle" to navigate your playlist.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Majority of UK businesses still not ready for cloud migration
Publié: novembre 12, 2014, 1:55pm CET par Sam Pudwell

New research commissioned by technology services firm Reconnix has found that 82 percent of UK IT leaders do not believe they are fully ready to make the move to Infrastructure-as-a-service (IaaS) providers, due to a shortage of in-house skills.
Only 10 percent of the 100 IT decision makers involved believed they were ready, whilst a further 8 percent had already migrated or were in the process of migration.
Just seven percent of respondents were confident of having an in-house team capable of managing an IaaS environment, compared to 36 percent who believed they had most skills in-house and 59 percent believed they had some of the skills required or did not know.
Steve Nice, CTO at Reconnix, said: "There’s a very clear desire for businesses to move applications away from traditional environments and towards Infrastructure-as-a-Service providers, however a lack of adequate skills seem to be holding back many IT departments from making this move. It’s natural for businesses to err on the side of caution, but this conservative approach can mean that many are missing out on the transformative benefits of the cloud".
In terms of providers, Microsoft Azure was acknowledged as the most trusted, being chosen by 36 percent of respondents. IBM’s SmartCloud came second with 22 percent, followed by Amazon Web Services and Rackspace, both with 14 percent.
"The prominence of Azure and IBM in IT buyers minds is surprising, especially considering how far ahead AWS is, both technically and in terms of market share," explained Nice. "IT departments not used to buying cloud services can sometimes not be aware of the difference in levels of performance between IaaS providers and it can be tempting to choose a trusted name".
Cost was also identified as a key factor, cited as both the biggest motivator (32 percent) and the biggest barrier (30 percent) to migration. Other motivators included flexibility (30 percent) and increased computer power (18 percent).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How technology can empower patients with Chronic Heart Failure
Publié: novembre 4, 2014, 2:07pm CET par Sam Pudwell

Chronic Heart Failure (CHF) affects approximately 5.1 million people in the US and 900,000 people in the UK each year, costing an estimated $32billion. The demand for care is expected to rise dramatically over the next few years, along with healthcare costs, but the amount of caregivers available is unlikely to be able to keep up.
In order to deal with this discrepancy, e-health applications are starting to play a more prominent role and at JiveWorld 2014 we heard from Dr Folkert Asselbergs, consultant cardiologist at University Medical Centre Utrecht, about how his smart health application is being used to monitor and empower patients in their battle against the disease.
Dr Asselbergs is the co-founder of EMPOWER, a patient-led telemedicine platform that aims to improve external engagement by "establishing a partnership with the patient and increasing awareness through education and feedback".
Partnered with 24care, the platform promotes the idea of self-management, helping patients to "take control of their disease" by integrating several engaging and collaborative functions.
As strange as it might sound, Dr Asselbergs believes that gamification could be a key ingredient. Compliance with long-term treatment for chronic condition is currently only around 50 percent due to factors such as the patient's perceptions of the treatment benefits, poor patient-physician communication and a lack of social support.
To deal with this, Dr Asselbergs explained that "patients have to be stimulated," so by offering rewards for things like taking medicines and attending check-ups, it is hoped patients will be more likely to stay on top of their treatment.
The platform also offers video consulting and messaging options, which enables communication between the patient and physician to take place at any time. This is an important element, as sufferers of chronic heart disease are "mostly older people who are less mobile and therefore rely on others to bring them to the clinic".
It also provides a range of contact numbers, forums and online questionnaires and all information is shared with the patient's physician, meaning both parties can keep track of his or her progress.
The platform's infrastructure is being delivered by Jive Software, a provider of communication and collaboration solutions that is involved with several other healthcare applications. Although currently being piloted, there are plans to roll EMPOWER out officially to four or five hospitals next year.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Tesco Hudl 2: A fantastic value-for-money family tablet [Review]
Publié: octobre 31, 2014, 8:18am CET par Sam Pudwell

Following on from the success of Tesco's first generation budget tablet, it was only a matter of time until its successor was released.
Tesco sold 35,000 units of the Hudl in the first few days after it was launched last year and ended up shifting over 750,000, placing this endeavor firmly into the 'success' category for the supermarket giant. The Hudl 2 was recently released and we were given the chance to take it for a test spin to find out if Tesco has got another bargain success story on its shelves.
Design
This device is never going to win any design awards but, being aimed at the money-conscious consumer, that's obviously not the point. If a top-of-the-range design is a key priority, then you're better off shelling out a bit more (ok, a lot more), on an iPad.
Personally, I like the look of the Hudl2. It's simple, clean-cut and much sleeker looking than its predecessor, although it does have a somewhat budget feel to it with a rubberized casing. Having said that, the rubber does make it comfortable to hold. If I'm being picky I would have preferred slightly larger bezels on the top and bottom but that's a minor complaint.
The jump up from 7 inches to 8.3 inches is a significant improvement on the Hudl and at 9.3mm thick it's still thin enough to fit in with today's skinny models.
It's heavier than the first model, jumping up to 410g from 370g, which does make it a bit weighty to hold in one hand and may be tiring for younger users. But the curved edges give it a nice, rounded look and it certainly feels like a durable piece of kit.
Display
When buying a budget tablet, one of the areas you might expect to be slightly compromised is the display quality, but Tesco has left me pleasantly surprised with the Hudl 2. The 8.3-inch HD display has a resolution of 1920 x 1200 megapixels, a substantial improvement from the Hudl's 1440 x 900 megapixels, and a pixel density of 265ppi.
Sure, the screen isn't doesn't match up to some of the higher-end tablets out there, but for the amount you're paying, the colors are bright and the images are sharp enough for all your viewing needs.
Performance
The Hudl 2 packs 2GB of RAM and an Intel Atom, quad-core processor with a speed of 1.8 GHz which, although not massively fast, is plenty good enough to browse the web, use apps and navigate around the home screen without any problems.
Some slight issues start to occur when multiple programs are running at once, resulting in some lag when switching between apps and moving graphical effects can get a bit jerky. In general, it runs well and will comfortably play basic 2D games as well as more complicated 3D ones.
Another problem that came up during our review was the battery life. The advertised 8-hour battery life is average and the Hudl 2 also seems to lose its charge very quickly when on stand-by mode, which can be very frustrating.
Camera
Unfortunately, this is an area where the Hudl 2 doesn't exactly cover itself in glory. With just a 5-megapixel rear camera and 1.2-megapixel front camera, you're never going to get great photos, but the rear camera is improved from the 3-megapixel snapper on the original Hudl. Most of the images come out quite grainy, especially if you're not in the best lighting, but for casual family usage it's probably good enough to do the job.
Extras
This is where the Hudl 2 is really impressive. Dolby-optimized stereo speakers give the sound quality a real punch which wouldn't be out of place on a more expensive tablet and a microSD slot gives you the option of upgrading the storage from 16GB to 48GB.
One of the main features that Tesco is pushing with this device is personalization and the Hudl 2 has achieved this extremely well. It comes in a range of bright colors, including blue, orange, black and red and the Android 4.4.2 KitKat operating system puts over a million apps at your fingertips.
Finally, there is a micro-HDMI slot to connect the tablet to your TV and the pre-loaded "pioneering parental control app," which allows parents to set up profiles that can be tailored according to age and suitability. A time limit can be set to restrict the amount of time children spend on the tablet and certain apps and websites can be blocked.
Verdict
When talking about the Hudl 2, it’s important to remember who it's aimed at. If it's a high-end tablet you're after then look elsewhere, but if you're on a budget or are looking for a second tablet for the family, then this really is the one for you. It's solid enough to be able to deal with rowdy children, has a good display to watch videos or play games and the parental control features mean usage can be kept under control.
The only things that slightly let it down are the camera and the battery life but if you're willing to compromise on those areas, this is a tablet that will keep both kids and parents entertained whilst offering fantastic value for money.
Good Points
- Good HD display
- Brilliant value for money
- Parental control features
- Plenty of personalization
Bad Points
- Average battery life
- Poor camera quality
Manufacturer and model Tesco Hudl 2 Processor 1.83 GHz Intel Atom quad-core Operating system Android 4.4.2 KitKat RAM 2GB Memory 16GB Memory expansion MicroSD up to 48GB Display 8.3-inch, 1,920 x 1,200 full HD Connectors Micro HDMI, micro USB, 3.5mm headphone jack Rear camera 5-megapixels Front camera 1.2-megapixels Wi-Fi Wi-Fi a/b/g/n Battery 4,900 mAH Dimensions 224 x 128 x 9mm Weight 410g Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Pavlok wristband motivates wearers with an electric shock
Publié: octobre 2, 2014, 5:15pm CEST par Sam Pudwell

Have you ever needed a helping hand to break a bad habit? Maybe you want to stop hitting that ever-tempting snooze button on the alarm, or have finally convinced yourself that now would be the right time to give up fast food.
Or, you might have set yourself the target of going to the gym every day and just need a little bit of extra motivation every now and then.
Well, the solution to all these problems has now arrived in the shape of a wearable wristband that can be programmed to give the user a quick zap of electricity whenever he or she does something they shouldn't be doing.
The band, called Pavlok, is now up on crowdfunding site Indiegogo and has already raised 125 percent of its $50,000 target with nearly a whole month to go.
According to its website, "Pavlok offers a simple, wearable device that helps consumers form better habits. Using psychologically proven and user-tested algorithms, the Pavlok wristband enforces users' commitments to fitness, productivity and more -- even if that means 'sparking' their commitment by delivering a mild (but jolting) electric shock".
The strength of the electric jolt can be set to anything from 17 to 340 volts and, according to creator Maneesh Sethi, work is being done to open up the platform to developers so that accompanying apps can be made by anyone.
The habit-forming/habit-breaking devices are available for $125 via Indiegogo, with shipments expected to begin in April 2015.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Hand over your child and get free Wi-Fi
Publié: octobre 2, 2014, 11:02am CEST par Sam Pudwell

A handful of London residents unwittingly agreed to give up their first-born child when signing in to a public Wi-Fi hot spot as part of an experiment carried out by the Cyber Security Research Institute.
A "Herod clause" was included in the T's and C's, which promised free Wi-Fi if "the recipient agreed to assign their first born child to us for the duration of eternity".
Luckily for the six people who failed to read the small print, security firm F-Secure, who sponsored the experiment, assured everyone that the clause wouldn't be enforced.
In a rather tongue in cheek statement, the Finnish company said, "We have yet to enforce our rights under the terms and conditions but, as this is an experiment, we will be returning the children to their parents. Our legal adviser Mark Deem points out that, while terms and conditions are legally binding, it is contrary to public policy to sell children in return for free services, so the clause would not be enforceable in a court of law".
This experiment does of course carry a serious message regarding the dangers of using public Wi-Fi, as outlined by Troels Oerting, assistant director at Europol, "We have found that the security on many Wi-Fi hotspots is rather low. So because they are not set up in the proper way, the criminals don't even need to set up their own service. They can simply look into the service that is providing the Wi-Fi to get what they want".
The research demonstrates that, along with obviously not reading the terms and conditions, many members of the public simply aren't aware of the security issues that accompany public Wi-Fi. So, although the chances of having to hand over your children are relatively low, you might be giving away your personal information without even realizing.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The Ryder Cup is the most technologically advanced golf event ever
Publié: septembre 26, 2014, 9:02am CEST par Sam Pudwell

This year's Ryder Cup in Scotland is one of the most technologically advanced golfing events, thanks to the introduction of Radio Frequency Identification Technology (RFIT).
Spectators receive a special wristband with their tickets which allows them to take part in various activities around the course, such as the BMW car display, the Ryder Cup Experience with Standard Life Investments and the 'Walk the Course' competition from Active Scotland.
Fans are be able to share their experiences on social media, touch the wristband on several points throughout the course to register on a supporters' leaderboard and show support for their team in the form of a virtual 'high five'.
The bands can also be used as a method of cashless payment at certain locations around the famous Gleneagles course.
Antonia Beggs, operations director for the 2014 Ryder Cup, said, "Ryder Cup Europe and the key stakeholders wanted to deliver the best possible spectator experience. As social media, smartphones and mobile internet have become a part of everyday life, the RFID technology seemed a natural choice to lift the event beyond the standard set previously".
The radio technology embedded in the wristband contains information about the wearer which can be uploaded to the tournament website when the ticketholder registers their band.
"Our RFID wristbands will mark The 2014 Ryder Cup out as something completely different to what has gone before in terms of interaction with spectators, media and indeed anyone visiting the course," said Serge Grimaux of Intellitix, the firm providing the wristbands.
"The technology is totally secure and has been proven at a number of large scale events across the world".
Team Europe are looking to defend their crown at this year’s competition, having narrowly beaten team America thanks to a dramatic late comeback at the 2012 Ryder Cup in Illinois.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

eBay heavily criticized for leaving user data exposed
Publié: septembre 25, 2014, 12:42pm CEST par Sam Pudwell

eBay is being put under intense pressure by leading security researchers to take action over the dangerous listings that are tricking customers into giving away their personal data.
The vulnerability relates to user's ability to insert custom JavaScript and Flash content into their listing pages, which significantly raises the likelihood of malicious code being included through a technique known as cross-site scripting (XSS).
The compromised pages appear as legitimate listings, but when clicked upon the user is automatically re-directed to a malicious website designed to steal personal information such as credit card details.
James Lyne, from security firm Sophos, said, "The summary is that it is exceptionally dodgy and redirecting the user to a nasty web page with some really suspect scripts.
"At present we can't get our hands on the end payload, so can't be sure of the attackers' complete motive, but it is clear there are still nasty malicious redirects on the eBay site".
It is unclear exactly how long this has been an issue on the site, with some experts saying that the problem has been present for over a year.
"Many of our sellers use active content like JavaScript and Flash to make their eBay listings perform better," eBay said in a statement.
"We have no current plans to remove active content from eBay. However, we will continue to review all site features and content in the context of the benefit they bring our customers as well as overall site security".
This stance has been heavily criticized by several industry professionals, including Mikko Hypponen from security firm F-Secure, "It's not OK for eBay to have cross-site scripting vulnerabilities on its website.
"If they can't make it work without the risk of exposing users to cross-site scripting, they shouldn't allow it".
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The lights that guided Lewis Hamilton to victory at the Singapore Grand Prix
Publié: septembre 23, 2014, 12:51pm CEST par Sam Pudwell

For those of you who tuned in to the Formula One Singapore Grand Prix on Sunday, you would have undoubtedly been delighted to see Lewis Hamilton storming to a first place finish and leapfrogging teammate and arch-rival Nico Rosberg in the drivers' Championship standings.
What you may not have noticed, however, was the flag signal system that was in place.
Singapore made history back in 2008 by becoming Formula One's first-ever night race and with this came the obvious issue of how the drivers would see the flags traditionally used by marshals to communicate with the drivers.
To solve this, the race organizers incorporated electronic flag displays similar to those used to guide pilots at major airports, which supplemented the manual flag-waving of the marshals.
The system was developed by lighting consultant firm Valerio Maioli Spa and went through vigorous testing at the Barcelona, Imola and Monza racing circuits before meeting the FIA's stringent requirements.
A total of 35 displays were placed around the track, each controlled by a hand-held panel and connected to a central monitor that provides the race director with an overview of the warnings being displayed around the circuit.
The displays have so far proven to be a great success and, along with an abundance of floodlights and projectors, have helped to turn the Marina Bay Street Circuit into a truly spectacular venue.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Smartphone users sticking with the same apps rather than downloading new ones
Publié: septembre 18, 2014, 10:42am CEST par Sam Pudwell

Research has shown that smartphone users are spending more time on their favorite apps rather than downloading new ones, illustrating how difficult it is for new apps and developers to break into the industry.
The study, carried out by Boston-based firm Localytics, also found that consumers are now using apps 21 percent more than they did last year. This rise is apparently down to users opening applications more often, rather than simply spending longer within them. App session length stayed constant at 5.7 minutes, whereas the average amount of app openings increased by 22 percent from 9.4 to 11.5 times a month.
In what is an extremely saturated market, the largest growth has come from music, health and fitness, and social networking apps, all of which have a largely personal focus, whether this be through choosing your perfect playlist or recording personal health measurements.
However, despite these increases, a worrying sign for the app industry is that fewer applications are being downloaded each month, with users tending to stick with their favorites rather than experimenting with new ones.
As well as developers, this also gives the likes of Google and Apple cause for concern, as the app ecosystem remains an important part of their overall strategies.
But with the abundance of apps on offer and the fact that fewer apps are being installed, it's hard to see how new apps will ever get any traction, let alone become commercially viable.
Image Credit: logolord / Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Tag Heuer wants to get in on the smartwatch action
Publié: septembre 18, 2014, 1:30am CEST par Sam Pudwell

Luxury watch brand Tag Heuer has announced plans to follow the likes of Apple and Samsung into the smartwatch industry.
The Swiss watchmaker, now part of French luxury goods group LVMH, recently lost its vice president of global sales, Patrick Pruniaux to Apple and is seeking revenge by going into direct competition with the tech giant.
Jean-Claude Biver, Tag Heuer's head of watchmaking, told a local Swiss newspaper: "We want to launch a smartwatch at TAG Heuer, but it must not copy the Apple Watch".
Earlier in the year, CEO Stephane Linder launched a scathing attack on the smartwatch efforts of Samsung, Sony, Qualcomm and Pebble, describing them as "cheap, plastic-designed watches".
He went on to say: "In the luxury category, we work on every detail for crafted value. When I see the smartwatch, it's interesting, but in terms of design, it looks like a cheap wrist computer. There's not one that makes a great connection."
Tag Heuer isn't completely new to the smartwatch industry, having produced 50 limited edition watches for the Oracle USA World Cup sailing team in 2013. The Aquaracer AC72 model featured a monochrome display to report various sailing metrics such as wind direction and intensity, as opposed to traditional moving hands.
However, despite this move away from the company's traditional roots, luxury is still the priority for Linder: "I don't see us taking a big risk, unless we find a way to make luxury watches looking like real luxury watches that provide very easy-to-use, smart information that isn't complicated -- and don't just replicate the mobile phone", he said.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Apple takes the lead in the health and fitness race
Publié: septembre 12, 2014, 7:36pm CEST par Sam Pudwell

The health and fitness industry is one that Apple has been involved in for a while now. Its partnership with Nike has seen a bunch of dedicated apps appear on several previous iPhone and iPod models. Apple's latest batch of products is no exception. In fact, the fruit-themed company has made the iPhone 6, iPhone 6 Plus and Apple Watch much more fitness-focused than any of its previous products, which clearly suggests that the company sees this area as a potentially lucrative one.
The first illustration of this comes through the iOS 8 operating system, which will be available as a free upgrade from 17 September. iOS 8 will be released with a health app, as well as a tool for developers called 'HealthKit,' which will bring information from a potentially unlimited amount of health apps straight to your fingertips.
According to Apple, "The new Health app gives you an easy-to-read dashboard of your health and fitness data. And we've created a new tool for developers called HealthKit, which allows all the incredible health and fitness apps to work together, and work harder, for you. It just might be the beginning of a health revolution".
The tech giant has demonstrated some of the possibilities that the app offers through its recent 'Strength' advert, which shows a host of athletes using various pieces of software to track their exercise progress, monitor weight loss, analyze golf swing technique and even trace the trajectory of a football. Although the ad specifically looks like it is targeting iPhone 5S users, the campaign is clearly also directed at the iPhone 6 and 6 Plus, and showcases apps that will appeal to the whole range of potential users, from the part-time runner to the professional sportsman.
Then we move on to the Apple Watch, which I believe shows more potential as a fitness tool than any other smartwatch currently on the market. Apple says that the watch, "Unites the capabilities of an all-day fitness tracker and a highly advanced sports watch in one device," and you know what -- it's not lying.
Firstly, it features an accelerometer to measure movement, as well as a built-in heart rate monitor to measure the intensity of your exercise, immediately providing competition to traditional fitness-tracking wearables from the likes of Fitbit and Garmin.
Next up is the Activity app, which has three different modes to measure your daily exercise. The 'Move' mode shows you how many calories you've burned and suggests daily goals based on your history, the 'Exercise' mode monitors the amount of more intense exercise that you do each day and the 'Stand' mode tracks how often you stand up during the day and provides reminders if you've been sitting down for too long.
Add to this the dedicated Workout app that provides real-time statistics, such as distance travelled and calories burned, allows you to set goals, gives you updates of any milestones you've reached and tracks your achievements, and you've got a pretty comprehensive exercise tool on your hands. Or should I say, wrist.
But I know what you're thinking. There are plenty of wearables out there that do similar things and are probably a fair bit cheaper. The difference with Apple, I think, is threefold. Firstly, there's the sheer amount of information at your disposal, which is more comprehensive than in any other device.

Secondly, the HealthKit platform means that there is no limit to the apps that could sync to the Watch and thirdly, the partnership that Apple has with Mayo Clinic and Epic Systems, the electrical health records vendor, means that all of this information can connect to health institutions and actually be put to good use.
So, although I'm willing to admit that Apple's latest batch of products may not immediately revolutionize how we keep track of our exercise and fitness, they are certainly leading the race so far.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

85% of Android and iOS apps are failing on privacy
Publié: septembre 12, 2014, 9:24am CEST par Sam Pudwell

A report carried out by the Global Privacy Enforcement Network (GPEN) has revealed that the majority of apps are failing when it comes to user privacy.
Of the 1,211 apps examined, the study found that 85 percent didn't clearly explain what data was being collected and nearly one in three requested an excessive amount of personal information.
Simon Rice, the group manager for technology at the UK's Information Commissioner's Office (ICO), said, "Today's results show that many app developers are still failing to provide this information in a way that is clear and understandable to the average consumer. The ICO and the other GPEN members will be writing to those developers where there is clear room for improvement. We will also be publishing guidance to explain the steps people can take to help protect their information when using mobile apps".
Dr Stephen Murdoch, a researcher at University College London, believes that the use of third-party advertising platforms should take some of the blame. "Often privacy leaks from mobile apps don't come from the app itself, but from the advertisements which are added. Quite frequently the people who are writing the application don't understand themselves what they advertisement code is doing. If you couple it with the fact that the money for these apps are made almost purely through ads - developers don't want to ask too many questions".
The report was collated from research carried out by various data watchdogs in nearly 40 countries, including the ICO who examined 50 of the most popular UK apps on the Android and iOS platforms.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Has the bubble burst for Apple?
Publié: septembre 9, 2014, 9:21am CEST par Sam Pudwell

After months of rumors, leaks and even more rumors, the iPhone 6 is set to be unveiled by Apple in California today. As is the norm with Apple launches, the announcement has garnered a lot of excitement, with people going so far as to queue up outside Apple stores weeks in advance of the actual release.
However, despite these crazy levels of attention and raging anticipation, Apple is still having some rather serious questions asked of it. This one in particular: does the Apple brand still have the X-factor it once boasted?
Going back to when Steve Jobs announced the first iPhone all those years ago, there was no doubt that Apple was the undisputed the king of mobile. The iPhones looked and performed better than all others on the market so, naturally, everybody wanted one.
The company became well-known for both starting and leading trends -- defining the market, rather than reacting to it -- meaning its main competitors struggled to keep up as the Cupertino-based company went from strength to strength.
Now, however, it seems that other companies have caught up and, in some cases, might have even overtaken Apple. It's no longer a question of "when" you're going to go out and buy the new iPad or iPhone, but "if". Apple's rivals have innovated well, advertised aggressively and created products that excite consumers in the same way that Apple used to.
The Sony Xperia Z3 and the Galaxy Note 4 are both perfect examples of this. Both of these phones, unveiled at IFA last week, are high-end models with impressive features and, with the announcements coming within a week of the iPhone 6 launch, have served to rain on Apple's parade somewhat. One specific trend that Apple has seriously lagged behind in is size. At last, the iPhone 6 or rumored iPhone Air is set to follow in the footsteps of its rivals' models. So much for trend-setting.
Furthermore, Apple seems to have lost some of the startup-esque imagination it used to be celebrated for. Since the iPhone 4S was released (about a week after Steve Jobs' passing), we've seen little more than incremental upgrades. Where previously this wasn't an issue -- why mess with a proven formula? -- there is now a large range of other handsets available that are much more interesting, more affordable, while offering similar or greater levels of functionality. This is illustrated by the fact that, according to a recent comScore report, the Android operating system now enjoys a significantly greater market share than iOS.
I wouldn't go so far as to say that the bubble has totally burst for Apple, but there's no arguing with the fact that it is no longer the all-conquering force it once was. Its once-humble rivals have caught up and the now constant churn of top-end, Android-powered smartphones shows just how much the gap has closed.
Obviously a powerhouse like Apple isn't going to disappear overnight. It still makes eye-wateringly large profits on a yearly basis but, unless the batch of products we see this week is seriously impressive, we might just witness a spectacular fall from grace.
Image Credit: klublu/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

IBM: Watson, go help those nice scientists with their research
Publié: août 30, 2014, 2:00am CEST par Sam Pudwell

IBM's Watson supercomputer is set to tackle scientific research head-on after being re-programmed to analyze big data in the cloud.
Currently, the testing of scientific hypotheses and theories often takes days or months of arduous work, but with Watson's Discovery Advisor program, this can now be carried out at a significantly faster rate.
So far, the future does indeed look bright for the industry after initial tests involving research into p53, a protein related to several cancers, have yielded extremely encouraging results.
Dr Oliver Lichtarge, the principal investigator and professor of molecular and human genetics, biochemistry and molecular biology at Baylor College of Medicine, said, "On average, a scientist might read between one and five research papers on a good day".
"To put this into perspective with p53, there are over 70,000 papers published on this protein. Even if I'm reading five papers a day, it could take me nearly 38 years to completely understand all of the research already available today on this protein.
"Watson has demonstrated the potential to accelerate the rate and the quality of breakthrough discoveries".
Mike Rhodin, the senior vice president of IBM's Watson Group, also hailed the machine's new abilities. "We're empowering researchers with a powerful tool which will help increase the impact of investments organizations make in R&D, leading to significant breakthroughs".
The supercomputer previously shot to fame in 2011 with a dominating performance on American quiz show Jeopardy, comfortably beating two of the show's most successful contestants.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo Credit: Sunny studio/Shutterstock
-

The technology behind the Commonwealth Games 2014
Publié: juillet 23, 2014, 9:21am CEST par Sam Pudwell

As the 20th Commonwealth Games kicks off in Glasgow, most of the attention will be focused on the athletes attempting to turn years of hard work into gold medals. However, there is another less public, yet still hugely important, side of the games that we think also deserves some attention.
Behind the scenes in Scotland, computer giant Dell will have an integral role in providing the IT infrastructure that will help meet the demands of the 71 participating federations and ensure that the entire event runs as smoothly as possible.
A statement on the Dell's website reads, "Our IT solutions will provide the reliability and support needed to ensure that everyone involved -- the fans, volunteers, athletes and officials will have the best experience possible".
It will deploy what it describes as a large-scale, end-to-end infrastructure designed to support business critical functions and connect athletes, volunteers and officials on a global scale, through the provision of 1,500 desktops, 200 laptops and 60 servers and storage solutions.
The setup will connect across all 40 competition and supporting venues, including the Technology Operations Center, Media Center and Athletes' Village.
The Technology Operations Center will act as the central hub, where Dell will monitor, operate and manage the games using PowerEdge servers equipped with Intel Xeon processors and Dell EqualLogic and PowerVault storage, as well as providing a helpdesk for any technology queries.
Its equipment will be used at the Media Center to efficiently deliver results to the press, and in a logistical capacity at the Athletes' Village, covering tasks such as ordering food, coordinating laundry services for all 6,762 beds and ensuring that all athletes make it to their events on time.
The importance of IT in the running of the games was highlighted by Brian Nourse, the chief technology officer for Glasgow 2014. "Technology underpins everything at the Commonwealth Games and we have multiple sites across Glasgow that require a fit-for-purpose technology solution. Dell's role is crucial in ensuring that we have a robust, flexible infrastructure in place that can guarantee everything runs flawlessly – both in the planning and staging of the Games, and during the 11 days of competition".
Tim Griffin, the vice president and managing director of Dell UK, said, "Technology is often the unsung hero of the sporting world. Nearly everything, from coverage of the events and ticketing, to how athletes perform and results are reported, requires a high level of technology support".
This is not the first time Dell has delivered technology for a global sporting event. In 2006 it was the official hardware provider for the Melbourne Commonwealth Games, supplying desktops, servers and storage technology.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Google bans porn ads from search results
Publié: juillet 4, 2014, 11:22am CEST par Sam Pudwell
 Google has made changes to its ad network by banning the promotion of pornographic websites.
Google has made changes to its ad network by banning the promotion of pornographic websites.The ban specifically concerns sites that feature "graphic sexual acts with intent to arouse including sex acts such as masturbation."
A Google spokesperson said that the company has had restrictions on its adult category for some time, but not all industry experts agree.
Theo Sapoutzis, the chairman and CEO of AVN Media Network said, "I was caught by surprise. I was one of the very first advertisers for AdWords back in 2002. It's something that's been [untouched] for 12 years, so you don't expect change is going to start happening."
Adult industry insiders say that the impact of this ban won't be clear for some time, as many adult sites are found through word of mouth and by natural search results.
"There are many people who say the biggest losers are the ones who play by the rules," says Tom Hymes, senior editor at industry trade publication AVN. "The winners are the huge properties with a lot of free content and frequent updates — the type of actions the Google algorithms really like.
"But at the end of the day, there are some people out there who have been abiding by every [rule] that Google sets and they're getting cut off at the knees now."
"Porn" is one of the most common Google searches and, according to Google AdWords Keyword Planner, related keyword searches almost hit the 351 million mark in May 2014.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Image Credit: Aquir/Shutterstock
-

Office 365 prices to rise for enterprise customers
Publié: juillet 4, 2014, 8:30am CEST par Sam Pudwell

Microsoft's August price list has revealed increases of up to 15 percent for Office 365 enterprise customers.
Those without a software assurance plan will be hit with the largest hikes, whereas those who do will have their prices frozen until the end of their contract.
It's not all bad news though. Existing customers will not experience any price increases when renewing their contracts and anyone who bought Office 365 from Microsoft or through its open licensing program won't be affected.
"The vast majority of our customers will not see an increase in the cost of Office 365," said a Microsoft spokesperson. "All existing Office 365 EA customers are guaranteed prices will not change for the duration of their agreement.
"New Office 365 EA customers who don't have a previous investment in our products will see an increase to align our pricing to our other channels. We are always evaluating our pricing to maximize the value to our customers as we continue to add more features and benefits to Office 365".
In an effort to counter this price increase, greater discounts will be offered for Office 365 E1, E3 and E4 subscriptions, which will be priced at $8, $20 and $22, respectively.
Office 365 is currently enjoying successful adoption rates across the board and reportedly generates $2.5 billion in annual revenue.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Samsung not concerned about the prospect of an Apple smartwatch
Publié: juin 30, 2014, 7:27pm CEST par Sam Pudwell

Speaking at a press event as part of Samsung's Business Discovery Day, Jae Shin, the vice president of Samsung's Knox mobile security business group, said that wearable devices will take off with or without Apple's help.
Historically, the hype surrounding the launch of a new Apple product has provided the kick-start for interest in a new type of technology. This has previously been the case for smartphones and tablet computers, thanks to the iPhone and iPad, respectively.
However, when asked whether Samsung was worried about losing its early lead in the wearables market when Apple eventually releases its much-rumored iWatch, Shin argued that consumers have "the know-how and the resources to make a smart decision".
He went on to say that Apple isn't the only company that can generate excitement in its products anymore and that other firms can get in on the action.
"Consumers are lot smarter these days and there's a lot for information available to them," he continued.
"At Samsung, we provide a lot of technical support and SDKs to developers so that they actually create innovation solutions and applications and user experiences that provide what the consumer wants; transparent technology. They want to be able to use it for a purpose they're going to benefit from".
Apple's iWatch will inevitably attract a lot of hype and publicity when it does arrive, but until that time comes, Samsung won't be wasting any time worrying about it.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Harley-Davidson unveils its first electric motorcycle
Publié: juin 20, 2014, 4:12pm CEST par Sam Pudwell

Legendary motorbike manufacturer Harley-Davidson has invited members of the public to test its first electric motorbike. Instead of the bike going on general sale, US customers will be invited to take it out for a spin and provide feedback.
The bike, labelled project LiveWire, will visit over 30 Harley-Davidson dealerships between now and the end of the year by travelling down the US' iconic Route 66.
"Project LiveWire is more like the first electric guitar - not an electric car", said the senior vice president at Harley-Davidson Motor Company, Mark-Hans Richer. "It's an expression of individuality and iconic style that just happens to be electric. Project LiveWire is a bold statement for us as a company and a brand".
Fans have, so far, offered mixed reactions, with members from the Harley-Davidson Riders Club of Great Britain displaying some early scepticism.
Dave Scott said, "It looks OK but I'd need a real engine in it", whilst others questioned its safety. "For an electric bike it has a good look, but I can't help think a silent bike is a recipe for disaster on our ever increasingly busy roads".
A teaser video released by the company shows the motorcycle travelling down Route 66 in almost complete silence.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The moon now has faster broadband than some parts of the UK
Publié: mai 29, 2014, 9:13am CEST par Sam Pudwell

Thanks to work carried out by MIT and NASA, the moon now has faster broadband than some parts of the UK, after registering speeds of just under 20mbps.
According to Wired, the Earth's satellite is now able to receive large amounts of data, with video and audio streaming possible as a result of new, record-breaking broadband transmission speeds.
A laser-powered communication uplink was used to achieve a top download speed of 19.44mbps. To give this some perspective, a recent report carried out by Ofcom revealed the average UK broadband speed to be 17.8mbps, whilst average speeds in rural areas came in at 11.3mbps.
If you can't quite get your head around that, think of it this way: it is now potentially possible for bored astronauts to catch up on their favorite "Breaking Bad" episodes whilst being almost 300,000km away from our planet's safe ground.
The signal also registered an upload speed of 622mbps, 4,800 times faster than the previous record.
There are, obviously, some connection issues, as outlined by Mark Stevens of MIT Lincoln, who told Wired, "Communicating at high data rates from Earth to the moon with laser beams is challenging because of the 400,000-kilometre distance spreading out the light beam. It's doubly difficult going through the atmosphere, because turbulence can bend light-causing rapid fading or dropouts of the signal at the receiver".
So there we have it, the Internet is now available on the moon. Good luck getting someone out to fix your connection though (especially as Ofcom recently had to warn BT about its slow response times).
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.