 In what can be called nothing less than a clever use of well-planted deflection, the head of the NSA, General Keith Alexander, recently let loose that the NSA relies heavily on Microsoft SharePoint for its data sharing needs. Or, more accurately, he decided to namedrop on SharePoint to allude to a mistaken notion that the inherent use of SharePoint was the reason why the NSA got breached by Edward Snowden recently.
In what can be called nothing less than a clever use of well-planted deflection, the head of the NSA, General Keith Alexander, recently let loose that the NSA relies heavily on Microsoft SharePoint for its data sharing needs. Or, more accurately, he decided to namedrop on SharePoint to allude to a mistaken notion that the inherent use of SharePoint was the reason why the NSA got breached by Edward Snowden recently.
The information was first picked up by The Register after the General was caught making the admission at a recently broadcast cyber security forum (which can be viewed on YouTube in its entirety). He described of Snowden: "This leaker was a sysadmin who was trusted with moving the information to actually make sure that the right information was on the SharePoint servers that NSA Hawaii needed".
Further in, Gen Alexander went on to say how sysadmins have a "need" to use removable media for their day to day jobs. He also touched on the fact that there was a "break in trust and confidence" due to the Snowden incident, and the NSA is purportedly picking up the pieces and fixing the broken links in its internal security procedures.
The funny part about this entire charade is that this isn't the first major SharePoint incident the government has dealt with. Remember Bradley Manning and his massive document dump a few years back? His recent acquittal of the most damaging charges against him have him back in the news, but Wired Magazine reported back in 2011 that Manning used similar scraping scripts to rob the US Military of a comparable treasure trove of confidential information off SharePoint backbones.
An easy cop out is to point the finger at SharePoint for these breaches. But the problem is, SharePoint itself -- neither its mechanisms for handling security, nor the code that controls the platform's workings -- had nothing to do with how these two individuals made out like bandits. The Register pointed to a group of researchers that was set to present its findings on holes in SharePoint at DEFCON this year, but again, none of these supposed bugs was used in any way by Manning or Snowden. It's like blaming the manufacturer of the deadbolt to your front door for a criminal entering your home using a spare key. The US government has fallen victim to threats from within in every possible way.
If we're to use these as examples for how enterprise security, especially in government, needs fixing, then we need to pinpoint our efforts at the people and protocols behind how these 'big data' systems are employed.
'Best Practices' Documentation on SharePoint is Prevalent
If the NSA and its fellow government IT administrators are anything like the corporate world, their approach to security regarding IT infrastructure (especially SharePoint) is probably way too laid back for its own good. This lax attitude towards securing data sharing platforms has proven to be an issue time and time again. Most recently, InfoSecurity magazine released a (not-so) shocking study that claims only about one-third of businesses using SharePoint have proper security policies in place detailing usage and access of the leak-prone platform.
The same study found that 65% of respondents admitted their organizations are not marking data into categories or sensitivity levels in any way. And again, while the study has no representation of US government branches, it wouldn't be surprising to see government IT admins following similar laziness as the corporate sector. Judging from the Manning and Snowden incidents hitting the US government in a span of only three years apart, it seems that the curator of some of the biggest secrets of the free world still can't get it right.

The NSA doesn't seem to be alone in its sub-par security practices surrounding SharePoint. A recent study by Emedia, covered in full by InfoSecurity magazine in February 2013, found that only about one-third of organizations with 25-5000 users employing SharePoint have security policies covering the platform. Even worse, just over one-fifth, or 22%, admitted that they don't have one and won't be making one. Security complacency seems to be an industry wide problem. (Image courtesy: Boldon James)
Call it poor planning, lack of oversight -- whatever you wish. It's not like the documentation isn't out there for how to properly implement SharePoint environments for highly secretive and confidential scenarios. A simple Google search yielded hundreds of helpful results, and I'm as far from a SharePoint administrator as could be. For example, Microsoft has this publicly available document on "Governance 101: Best practices for creating and managing team sites" with basic steps on how permissions should be doled out in SharePoint environments.
Even further, Microsoft has a "Plan your permissions strategy" article posted that goes into detail about the various aspects that help restrict data access in SharePoint. And finally, they published an in-depth TechNet wiki on security planning techniques that go deeply into best practices surrounding proper preparations for sites and content in SharePoint.
Not enough reading material for a head sysadmin? Just Google "security planning for sharepoint" and there are over 7 million results culled. To say that one would be hard pressed to have an easy set of resources in properly planning and executing a confidential SharePoint environment is nothing short of lying through one's teeth.
Lessons for the Enterprise: How to Prevent Your Own Data Leak Disaster
Even though my company primarily consults smaller organizations ('50 and unders' you can call them) on their IT needs, this doesn't mean that the same security protocols don't apply. Basic principles like leveraging security groups and using the concept of "least privilege" in assigning rights are common sense scruples that any sysadmin worth his weight in salt should know. I don't actively manage any SharePoint servers in my day to day work, but perhaps some outsider knowledge wouldn't be bad for those in charge of our nation's most sensitive SharePoint systems.
If you're tasked with protecting a SharePoint ecosystem, or other valuable data-rich infrastructures, here are some key steps that should be considered. A few items are really only practical for government implementation, but I'm going to mention them anyway (since our fine gov sysadmins could clearly learn a thing or two from the Manning-Snowden double header by now):
- Configure and leverage auditing when possible. It boggles my mind that the US government wouldn't be taking advantage of SharePoint's built-in auditing capabilities to have higher level managers keeping track of both what is going on and by who. Seeing that Windows Servers are likely being used, other overlapping layers of auditing can be enabled and deployed for nearly any action done on systems being touched by sysadmins. The bread crumbs could have easily been picked up by Snowden's bosses -- if they knew where to look.
- Front-access USB ports should be disabled on high-value systems. The "what if I need it" excuse is complete malarkey. Any tool that a sysadmin may need that can go on a flash drive can just as easily fit on burned CDs as well. Having a policy against any type of removable media in the server room not only lessens the risk of malware entering the data center, but also takes the risk of data leakage down considerably. Burn-once CDs and DVDs have much less risk of carrying malware, and can just as easily replicate the same kinds of tools a sysadmin would need. And if USB drive usage is a necessity, this brings up my next point....
- Incorporate the concept of "working in pairs". One sysadmin gone bad is always possible, but two at the same time? The risk gets cut considerably. And if these sysadmins answer to different managers? You've effectively trimmed this risk of co-conspirators down to negligible levels. Introducing duplicity in layers, along with inherent gravitation towards transparency, leads to less risk of data being shuffled out by one bad apple.
- Least privilege is king when it comes to permissions. This applies to SharePoint environments, Active Directory user membership, and any other IT platform where division of access is necessary. Don't fall victim to assigning custom rights for each user. Stick to leveraging security groups which can pass down permissions to members on the fly -- and have permissions revoked just as quickly. The more stragglers that exist with customized permissions, the more likely data access oversights will come into play.
- One managing IT administrator is never enough. Division of duties works wonders for many other aspects in various industries -- so how come IT doesn't leverage this same policy for dealing with troves of sensitive data? Naming one senior sysadmin as the sole curator of large caches of data is like placing all your eggs in a single basket. Two or more sysadmins should be given authority over separate sets of data to ensure that one person doesn't have the kill switch across the entire data set. This reduces risk for widespread leaks, and increases transparency.
- Patching on a regular schedule is a necessity. Whether it be SharePoint, or SQL Server, or any other facet of a modern IT infrastructure, it needs to be patched regularly. There is no such thing as a bulletproof platform this day in age. Outside threats are perusing new vulnerabilities on a daily basis, and every day that systems are left unpatched is an extra day that hackers get to consider your environment a playground for their exploits.
- If you're harboring large sensitive data sets, encryption should be part of your gameplan. Most aspects of a modern SharePoint environment can be encrypted in one way or another. The SQL server database(s) for SharePoint support native encryption through TDE, for example, and Windows Server has supported full disk encryption through BitLocker since version 2008. Even traffic between different SharePoint servers can be configured for encrypted transmission. There is no excuse for not being able to have a rock-solid, secured backbone when dealing with such ecosystems in 2013.
Can organizations of all sizes learn from the mishaps of the NSA and US Military? Surely. Common sense, back to basics security principles don't take a genius to figure out. The unfortunate truth of the matter is that most system administrators think that these kinds of incidents won't happen to them, or that security planning can be put off until later down the road. This kind of flawed thinking is what leads to oversight and downright fumbling when it comes to critical data breaches.
Remember: the Snowden and Manning incidents weren't examples of external threats. These leaks happened directly from within, behind closed doors which provided the false sense of security which ultimately, and ironically, represented the largest data breaches known to the United States. It's time we stop blindly blaming the software developers behind the products we employ, and start looking inwards towards those in charge of the keys to the information.
Photo Credit: Picsfive/Shutterstock
 Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over 8+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.
Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over 8+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.



 The standard Windows "uninstall a program" applet may not exactly be packed with features, but it’s fine for occasional use. Find and select your program, click Uninstall, and follow the instructions -- it’s all very straightforward.
The standard Windows "uninstall a program" applet may not exactly be packed with features, but it’s fine for occasional use. Find and select your program, click Uninstall, and follow the instructions -- it’s all very straightforward.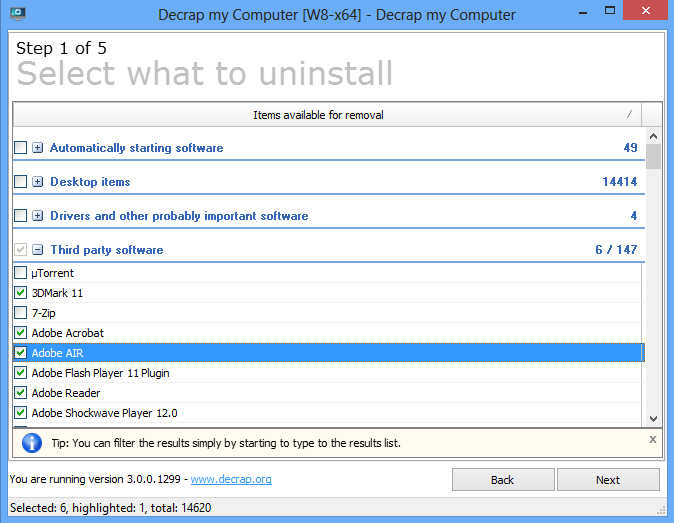


 When I built my newest computer, I was excited to get a motherboard with native USB 3.0 ports -- I was finally at the forefront of USB speed. I bought a USB 3.0 flash drive, hard drive enclosure and hub. All the devices worked great and life was good.
When I built my newest computer, I was excited to get a motherboard with native USB 3.0 ports -- I was finally at the forefront of USB speed. I bought a USB 3.0 flash drive, hard drive enclosure and hub. All the devices worked great and life was good. It is the same old story in households consisting of more than one member. The Netflix account is a family thing, but not all members have the same tastes and can sometimes post vastly different reviews of the same flick. This is what Netflix describes as "Honey, you ruined my Netflix". Now the company aims to right this problem.
It is the same old story in households consisting of more than one member. The Netflix account is a family thing, but not all members have the same tastes and can sometimes post vastly different reviews of the same flick. This is what Netflix describes as "Honey, you ruined my Netflix". Now the company aims to right this problem.

 I use Soluto to manage my PCs and iOS devices, as well as hardware belonging to a select group of less technically literate friends and family. It’s a handy service that makes it easy to view hardware details of the devices you’re monitoring, as well as cut boot times, manage and update apps, remove unwanted browser extensions, and more.
I use Soluto to manage my PCs and iOS devices, as well as hardware belonging to a select group of less technically literate friends and family. It’s a handy service that makes it easy to view hardware details of the devices you’re monitoring, as well as cut boot times, manage and update apps, remove unwanted browser extensions, and more. The rapid growth in usage of tablets and smartphones is turning us into a nation of multi-taskers according to a report by the UK telecoms regulator
The rapid growth in usage of tablets and smartphones is turning us into a nation of multi-taskers according to a report by the UK telecoms regulator  In what can be called nothing less than a clever use of well-planted deflection, the head of the NSA, General
In what can be called nothing less than a clever use of well-planted deflection, the head of the NSA, General 
 Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company
Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company  Internet Explorer is an integral part of Microsoft's tiled operating system, and the software giant has endeavoured to improve the way it handles touch in Windows 8.1, adding new touch elements and improving existing ones.
Internet Explorer is an integral part of Microsoft's tiled operating system, and the software giant has endeavoured to improve the way it handles touch in Windows 8.1, adding new touch elements and improving existing ones. Smartphones and tablets are no longer just electronic devices -- they are fashion statements. It is becoming increasingly rare to find someone using one naked (without a case or cover). At some point, our iPhone-culture started to demand that our devices remain in flawless condition; this birthed an entire industry of fashion-based device protection. Yes, there were leather pouches and cases for old Palm Pilots and flip-phones, but a scuff or scratch on those devices was inconsequential.
Smartphones and tablets are no longer just electronic devices -- they are fashion statements. It is becoming increasingly rare to find someone using one naked (without a case or cover). At some point, our iPhone-culture started to demand that our devices remain in flawless condition; this birthed an entire industry of fashion-based device protection. Yes, there were leather pouches and cases for old Palm Pilots and flip-phones, but a scuff or scratch on those devices was inconsequential.