When Active Directory first hit the enterprise computing scene over a decade ago, the tech pundits dismissed AD as just another Microsoft sideshow. Something that would never see any widescale adoption in the face of NetWare and other heavy hitters in the LDAP arena. Even longtime Microsoft watcher Paul Thurrott got it wrong and doubted success. Thirteen years later and organizations small and large live and die by their Active Directory domains.
When Active Directory first hit the enterprise computing scene over a decade ago, the tech pundits dismissed AD as just another Microsoft sideshow. Something that would never see any widescale adoption in the face of NetWare and other heavy hitters in the LDAP arena. Even longtime Microsoft watcher Paul Thurrott got it wrong and doubted success. Thirteen years later and organizations small and large live and die by their Active Directory domains.
It's funny, then, that AD is the sole dinosaur running atop on-premise servers at corporations worldwide which supposedly "can't" be moved to the cloud. Microsoft has been busily converting its on-premise products into cloud platforms with relatively good results over the last 3-4 years. While Microsoft surely doesn't want to become a has-been within the physical server arena for organizations hesitant to move to the cloud, it no doubt has been playing two face when it comes to on-prem vs cloud-hosted solutions.
For the uninitiated, Active Directory is the de-facto LDAP (Lightweight Directory Access Protocol) platform for most organizations 25 users or larger today. The service is a critical component to companies and entities that have sprawling corporate networks because it allows user accounts, network resources, computers and file shares to be managed quite harmoniously. Rights are easily controlled from a sysadmin's chair through the standardized concept of least-privilege. The form of AD found in traditional on-premise server scenarios is called Active Directory Domain Services (ADDS) and it has been around since Windows 2000 transformed the corporate networking scene.
So with seemingly all other core Windows Server offerings being transformed and re-envisioned for the cloud age, what's keeping Active Directory back? Why can organizations run their email, SharePoint, file shares, SQL instances, etc in the cloud today, but Active Directory stays stuck in a virtual purgatory? As an IT consultant by day that is trying to answer this very question for customers of mine, I decided to do some digging.
The short answer? Active Directory is well on its way to shedding the on-premise dependencies it has today. The writing is clearly on the wall if you know how to read Microsoft's bread crumbs. Microsoft is publicly keeping mum on the matter, but its intentions are speaking for themselves.
Windows Azure Already Has AD, Right?
A common point of confusion among fellow IT pros and customers is: doesn't Azure already have Active Directory capability? Yes -- and no. I was originally under the assumption that cloud-hosted Active Directory being offered through Azure was meant to be the replacement for its on-premise cousin. After some fact finding, I found out that this just wasn't the case. Microsoft evangelist Chris Avis penned an excellent article about how Windows Azure Active Directory (WAAD) is not the same beast as Active Directory Domain Services (ADDS) we have befriended. How Microsoft fooled me.
For those organizations thinking that they can shimmy their Active Directory domains right up into the Azure cloud as WAAD domains, this simply won't work. For one, Azure Active Directory is a service offering that (in its current form) only allows for identity authentication across cloud services like Office 365, for example. It definitely is possible to sync up with your on-premise servers, but this doesn't reduce your on-premise physical footprint in any way. Companies trying to hit the magic number of zero servers onsite won't accomplish this goal through WAAD. Yet.
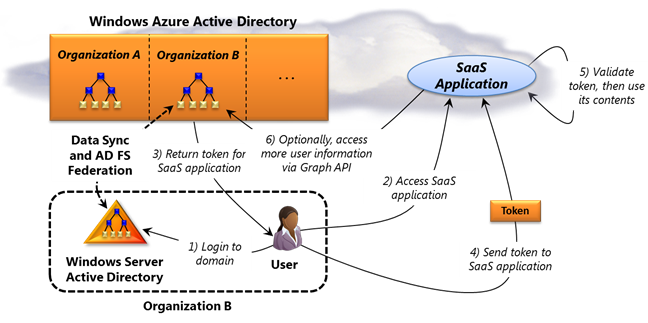
Windows Azure Active Directory (WAAD) is a great solution to solving the single sign on dilemma for the plethora of cloud services necessitating otherwise separate logins. But it does nothing to rid us of the on-prem AD server controlling users, computers, etc at our offices. Those looking for a server-less office solution should steer clear. (Image source: Microsoft.com)
Second, the Azure Active Directory service has no way of communicating with your physical computers at the office on its own. Not only that, the problem is compounded by the fact that WAAD only works with User objects; that is, traditional user logins that merely provide authentication capabilities and single sign on for access to cloud services. This is a problem because for WAAD to behave like traditional ADDS for company computers and resources, it has to provide native support for these other types of objects. Whether Microsoft is working to introduce this is anyone's guess.
In its current form, I find WAAD to be an extremely stripped back version of AD that is only beneficial for organizations looking to leverage SSO (single sign on) for cloud software like Office 365, SharePoint Online, etc. For the rest of us looking for truly cloud-hosted AD, we must look elsewhere in Microsoft's portfolio.
Server 2012 Domain Controllers, DirectAcces on Azure
If there's one thing that Azure does darn well, it's hosting virtual machines in the cloud. My previous review on Azure highlighted its winning aspects in full detail. I've tried quite a few different vendors in the cloud VM space including big players like Rackspace, Amazon EC2, and SoftSys, among others. The pricing and excellent interface of the Azure platform keep making it an easy recommendation for my customers. And knowing how determined Microsoft is to make Azure a bona fide staple in the marketplace, its dedication to innovation is clearly evident based on the numerous enhancements hitting near monthly now it seems.
In the hunt to find a better alternative to WAAD, I stumbled upon numerous online postings from individuals who have actually moved their Domain Controllers up to the Azure cloud. Not as a part of WAAD, but as fully distinct instances running in private Server 2008 R2 or Server 2012 VMs. In fact, Microsoft's own support pages even passively-condone the practice of setting up Windows Server Domain Controllers (using standard ADDS) in the cloud. Going a step further, Microsoft even advertises how you can leverage an Azure Virtual Network to connect your physical office(s) to Azure hosted domain controllers over VPN for seamless integration. Could this be it?
For workers who happen to be situated at single locations and don't need to work from home, this is great. It actually does replicate the same functionality as we know and love from physical Active Directory servers located onsite. However, the number of routers and firewall devices that Microsoft has stamped with approval for working with this functionality is far and few between. Cisco ASAs, Juniper boxes -- expensive gear that the smallest of small businesses just can't afford to purchase or maintain.
Fellow industry colleague Brian Lewis wrote about how Azure now allows for neat Point to Site VPN capability, but even this functionality is not a fool proof solution because of the complexity of the setup. Point to Site VPNs are a way for single computers to connect to Azure Networks remotely (anywhere) for secure access to an Azure fabric.
This can be used, for example, to also have direct Remote Desktop access to Azure boxes without exposing the usual RDP port to the entire world openly. For the small organizations looking to offset their IT infrastructure to the cloud, who likely don't have dedicated IT people, this is a lofty proposal for offloading Active Directory easily.
I ran across another possibility: DirectAccess. This excellent alternative to traditional VPN configurations has been around since Server 2008 R2 but it used to be a royal pain in the rear to configure and meet minimum requirements for. Server 2012 has simplified DirectAccess considerably, rendering many of the arcane requirements of the Server 2008 R2 iteration as no longer needed.
Two problems with this approach exist as well. One the one hand, Microsoft doesn't consider Azure-hosted DirectAccess as officially supported. It's interesting, however, because numerous blogs have outlined how they have gotten the functionality working already. And more importantly, perhaps the biggest downer, is that only Windows 8 Enterprise has DirectAccess baked in.
Extremely disappointing -- seeing that this could have been an easy way to leverage cloud-hosted AD on Azure with minimal effort. Enterprise edition is usually only accessible to companies or organizations with an Enterprise Agreement with Microsoft. Small businesses need not apply.
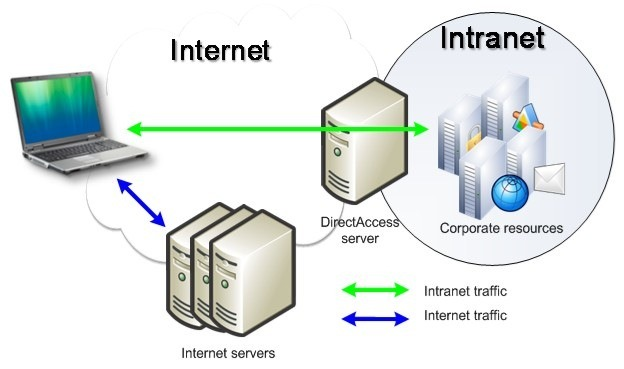
DirectAccess could be a core component of any future Active Directory Domain Services alternative introduced as an offering in Azure. This relatively recent technology eschews (sometimes complex) VPN setups for a directly-brokered tie to client computers, making connections to the corporate network seamless and automatic for the user. Just what cloud-hosted AD needs. (Image source: Microsoft.com)
In the end, there is no great "short" answer which meets the goals of ridding the office of the AD server in exchange for an Azure alternative. While Microsoft is being complacent in allowing customers to host Active Directory Domain Services on Server 2012 and 2008 R2 boxes in Azure, their usefulness is only as good as the VPN connectivity you can muster for your staff. DirectAccess, while a very promising technology, has its hands tied due to its own unfortunate limitations.
Perhaps 'Project Mohoro' Can Answer Some Questions
I've touched on this still (relatively) secretive initiative gaining steam within Microsoft a few times in the past. While Mohoro happens to double as lovely town in the Comoros Islands, Microsoft has supposedly tagged the moniker to a clandestine project team within the company dedicated to bringing a first-party VDI solution to the masses. While VDI (virtual desktop infrastructure) has the aim of simplifying delivery and management of application catalogs, it has been marred with notoriously tough deployment routines and extremely hefty costs up front.
More specifically, Mohoro is aiming at giving Microsoft a way to deliver a cloud-hosted version of an extension of the existing Remote Desktop Services (RDS) function known as RemoteApp. Why is this important? Because if Mohoro sees the light of day, this "RemoteApp-as-a-Service" offering could completely render cloud-hosted Active Directory unnecessary. Knowing Microsoft's hardened direction in moving swiftly to the cloud, they could see this as a clear cut for organizations looking to take their physical systems up to the interwebs completely. Since the applications are deployed through RDS, and there is an underlying assumption of AD connected on the backside, having the need for clients to directly speak with an AD controller on Azure becomes a non-issue.
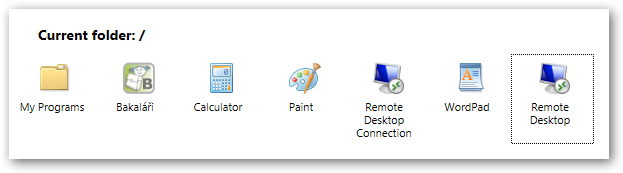
RemoteApp (above) already exists in Server 2012, and allows applications to be delivered via a public web page accessible anywhere internet is available. Is Microsoft expecting this feature to go mainstream? If Mohoro delivers a cloud version of RemoteApp as rumored, and Intune matures into a true AD counterpart, then this powerful duo may represent the future of BYOD corporate computing. (Image source: Microsoft.com)
Besides, there's a powerful AD arch-enemy already rearing its head in Microsoft's cloud. It's called Windows Intune and its been a hot topic from Redmond for a few years now. Intune is basically a poor-man's Active Directory in the cloud that focuses less on granular policy enforcement and more-so on device oversight, security, and tracking targeted towards mobile workforces. The service recently entered into its Wave D release which continues the platform's transition from a mainly Exchange ActiveSync (EAS) powered entity, to that of one utilizing native MDM functionality more akin to what Windows Phone 8 and iPhone support out of the box. This translates into extremely powerful management capabilities that can be deeply tied into the core backbones of any connected devices.
Windows Intune is the most compelling alternative to full blown Active Directory not only because of its extreme ease of use, but also due to its very cost effective price point. The service is now only a mere $6/user per month. And the best part is that this cost doesn't cover just a single device -- but you can have up to five devices enrolled per user. The service supports nearly every ecosystem including Android, Mac OS, Windows, Windows Phone, Windows RT, and iOS. It's only missing BlackBerry 10 support it seems. Blackberry Server 10 is relatively powerful in its own right, but it lacks any control over Windows devices; a big knock for Windows-first shops.
The biggest roadblock to most small businesses that have wanted to roll out AD is the heavy cost involved with not only planning and implementing the technology, but also maintaining it. It's no secret that consultants like myself charge a pretty penny to keep these expansive systems humming.
And a lot of small customers of ours right now are not interested in upgrading their aging 2003 domains to 2012 for these reasons. They want to move into a cloud-powered, server-less future. Workers can enroll all of their devices into Intune and receive integrated patch management, tracking, remote access, security software, and more. Intune is looking a lot more attractive then the thousands of dollars it takes to deploy or upgrade an AD backbone on-premise.
What's The Future of AD Looking Like? A Bit Of Everything
I wish I knew exactly where Microsoft was heading with its endeavors. What I was hoping to be a simple, clear answer for how to deploy cloud-hosted Active Directory led me to numerous meandering options which may eventually careen back towards a single path. Microsoft has been busting its rear end in taking popular on-premise technologies like Exchange and Lync and moving them to the cloud (leading to Exchange Online and Lync Online, respectively) and the end results have been generally quite commendable.
It's not hard to connect the dots on Microsoft's intended future for enterprise computing, and it's got cloud written all over it. Intune, RemoteApp, and Azure are all taking slightly different paths towards a likely common end goal of bringing the power of corporate AD into the friendly ecosystem of the cloud. With remote workers spending more time either on the road or at home, the assumption that a corporate VPN connection is always plausible is becoming a thing of the past.
Mohoro is scheduled to launch sometime in the second part of 2014, so it will be interesting to see what direction it takes -- and if it even sees the light of day. My money's on the former if I'm calling Microsoft's next move correctly. They already took a portion of their staple Windows Server line to the slaughterhouse last year, and I wouldn't be shocked in the least to see traditional AD see the same fate.
Photo Credit: 2jenn/Shutterstock
 Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over 8+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.
Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over 8+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.



 While the jury remains in deliberation over Windows 8, and its upcoming successor, Office is still a workhorse in the Microsoft stable of software. Even the attempt to turn it into a subscription model did little to phase customers. Businesses on the other hand are even more acceptable to these options and now Microsoft has announced expanded markets for its latest Office 365.
While the jury remains in deliberation over Windows 8, and its upcoming successor, Office is still a workhorse in the Microsoft stable of software. Even the attempt to turn it into a subscription model did little to phase customers. Businesses on the other hand are even more acceptable to these options and now Microsoft has announced expanded markets for its latest Office 365.


 This is my first Samsung Android device so it also is my first experience with TouchWiz -- Samsung’s custom UI and launcher. As an Android purist, I always tried to buy Nexus devices and use stock launchers. However, TouchWiz is far more intuitive and beautiful than stock Android. The animations, wallpapers, sounds, launcher and app drawer are all delightful. I even found a setting to take screenshots by sliding my hand across the screen. Though there are many modifications, the underlying operating system is the very modern Android 4.2.2.
This is my first Samsung Android device so it also is my first experience with TouchWiz -- Samsung’s custom UI and launcher. As an Android purist, I always tried to buy Nexus devices and use stock launchers. However, TouchWiz is far more intuitive and beautiful than stock Android. The animations, wallpapers, sounds, launcher and app drawer are all delightful. I even found a setting to take screenshots by sliding my hand across the screen. Though there are many modifications, the underlying operating system is the very modern Android 4.2.2. Get out your wallet and prepare your foreign investment portfolio because, just as Jimmy Buffet tells us it is always five o'clock somewhere, the market is also always open somewhere. Google Finance today grows a bit fatter, adding even more of those exchanges to its reporting.
Get out your wallet and prepare your foreign investment portfolio because, just as Jimmy Buffet tells us it is always five o'clock somewhere, the market is also always open somewhere. Google Finance today grows a bit fatter, adding even more of those exchanges to its reporting.
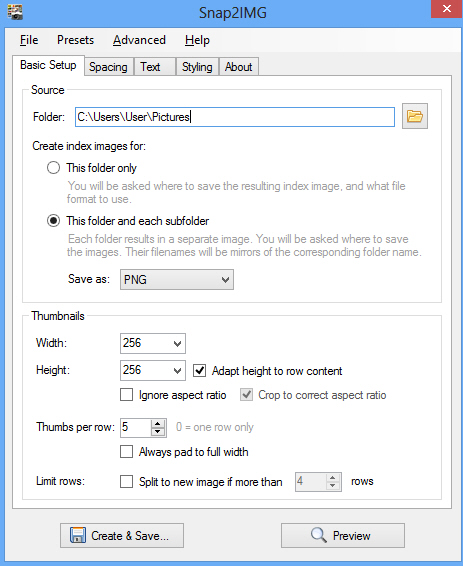 Understanding how your digital photo collection is laid out normally requires just a few moments of thumbnail browsing. Click a folder here, another over there, and you’ll quickly be able to locate the pictures you need.
Understanding how your digital photo collection is laid out normally requires just a few moments of thumbnail browsing. Click a folder here, another over there, and you’ll quickly be able to locate the pictures you need.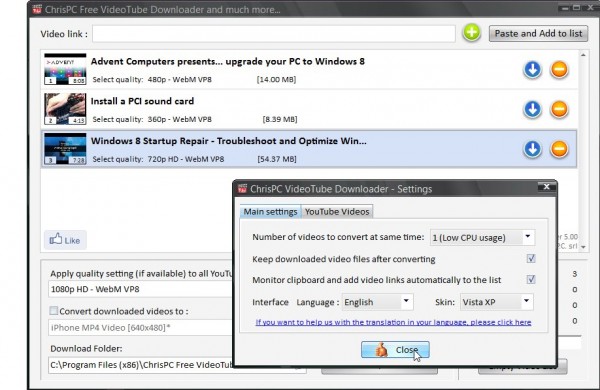


 Explore any Windows application and you might find some content you’d like to use elsewhere: the soundtrack in a game, an introductory video somewhere, maybe a few embedded images or icons. Sometimes these might be available as separate files in the program’s folders, but often they’ll come packaged in a DLL or some other library format which can’t be accessed as easily.
Explore any Windows application and you might find some content you’d like to use elsewhere: the soundtrack in a game, an introductory video somewhere, maybe a few embedded images or icons. Sometimes these might be available as separate files in the program’s folders, but often they’ll come packaged in a DLL or some other library format which can’t be accessed as easily.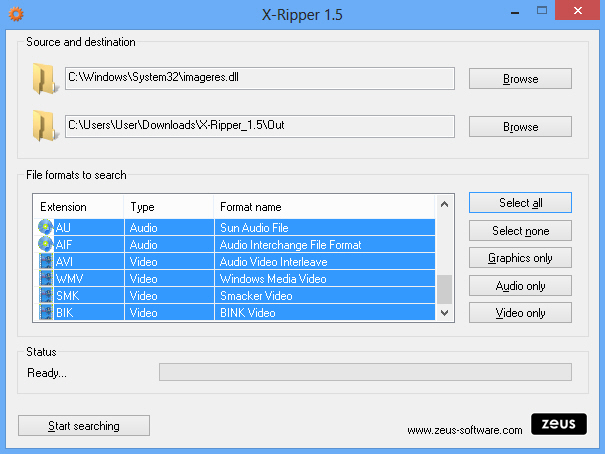
 When Active Directory first hit the enterprise computing scene over a decade ago, the tech pundits dismissed AD as just another Microsoft sideshow. Something that would never see any widescale adoption in the face of NetWare and other heavy hitters in the LDAP arena. Even longtime Microsoft watcher Paul Thurrott got it wrong and
When Active Directory first hit the enterprise computing scene over a decade ago, the tech pundits dismissed AD as just another Microsoft sideshow. Something that would never see any widescale adoption in the face of NetWare and other heavy hitters in the LDAP arena. Even longtime Microsoft watcher Paul Thurrott got it wrong and 


 Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company
Derrick Wlodarz is an IT Specialist that owns Park Ridge, IL (USA) based technology consulting & service company  Rumors that Microsoft was planning to cut the price of Surface RT have been swirling for a couple of days, and yesterday they came true. Staples in the US is currently
Rumors that Microsoft was planning to cut the price of Surface RT have been swirling for a couple of days, and yesterday they came true. Staples in the US is currently